7.5 KiB
Wireshark tricks
Wireshark tricks
Support HackTricks and get benefits!
- Do you work in a cybersecurity company? Do you want to see your company advertised in HackTricks? or do you want to have access to the latest version of the PEASS or download HackTricks in PDF? Check the SUBSCRIPTION PLANS!
- Discover The PEASS Family, our collection of exclusive NFTs
- Get the official PEASS & HackTricks swag
- Join the 💬 Discord group or the telegram group or follow me on Twitter 🐦@carlospolopm.
- Share your hacking tricks by submitting PRs to the hacktricks github repo.
Improve your Wireshark skills
Tutorials
The following tutorials are amazing to learn some cool basic tricks:
- https://unit42.paloaltonetworks.com/unit42-customizing-wireshark-changing-column-display/
- https://unit42.paloaltonetworks.com/using-wireshark-display-filter-expressions/
- https://unit42.paloaltonetworks.com/using-wireshark-identifying-hosts-and-users/
- https://unit42.paloaltonetworks.com/using-wireshark-exporting-objects-from-a-pcap/
Analysed Information
Expert Information
Clicking on Analyze --> Expert Information you will have an overview of what is happening in the packets analised:
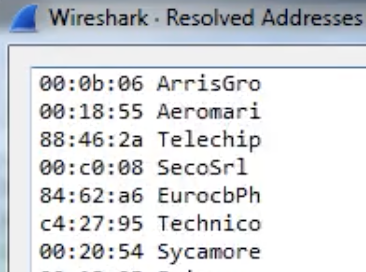
Resolved Addresses
Under Statistics --> Resolved Addresses you can find several information that was "resolved" by wireshark like port/transport to protocol, mac to manufacturer...
This is interesting to know what is implicated in the communication.
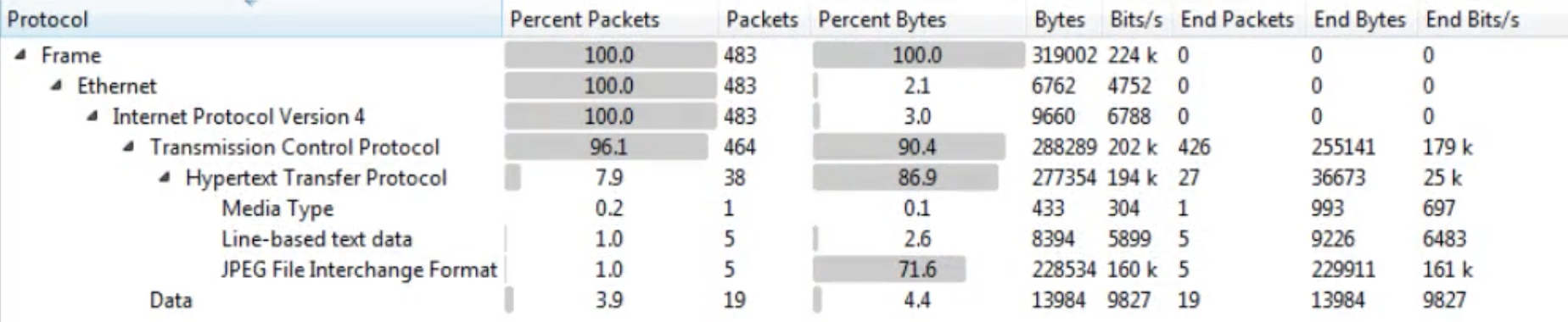
Protocol Hierarchy
Under Statistics --> Protocol Hierarchy you can find the protocols involved in the communication and data about them.
Conversations
Under Statistics --> Conversations you can find a summary of the conversations in the communication and data about them.
Endpoints
Under Statistics --> Endpoints you can find a summary of the endpoints in the communication and data about each of them.
DNS info
Under Statistics --> DNS you can find statistics about the DNS request captured.
I/O Graph
Under Statistics --> I/O Graph you can find a graph of the communication.
Filters
Here you can find wireshark filter depending on the protocol: https://www.wireshark.org/docs/dfref/
Other interesting filters:
(http.request or ssl.handshake.type == 1) and !(udp.port eq 1900)- HTTP and initial HTTPS traffic
(http.request or ssl.handshake.type == 1 or tcp.flags eq 0x0002) and !(udp.port eq 1900)- HTTP and initial HTTPS traffic + TCP SYN
(http.request or ssl.handshake.type == 1 or tcp.flags eq 0x0002 or dns) and !(udp.port eq 1900)- HTTP and initial HTTPS traffic + TCP SYN + DNS requests
Search
If you want to search for content inside the packets of the sessions press CTRL+f
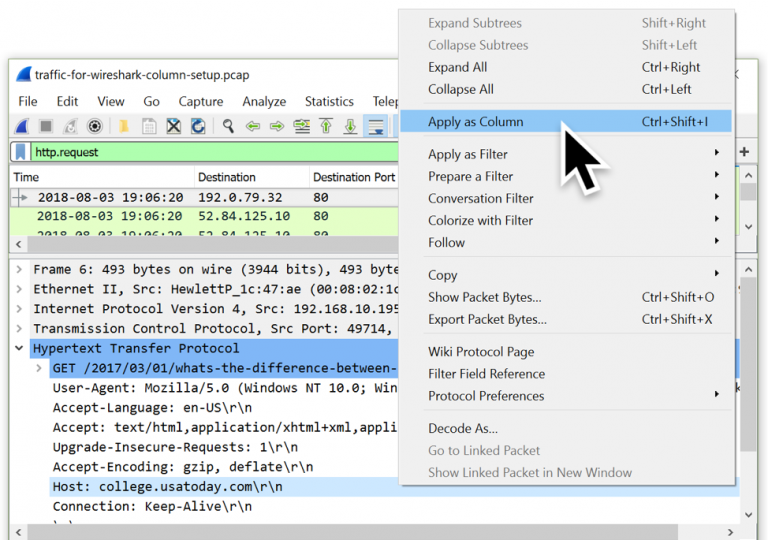
__You can add new layers to the main information bar (No., Time, Source...) pressing right bottom and Edit Column
Practice: https://www.malware-traffic-analysis.net/
Identifying Domains
You can add a column that show the Host HTTP header:
And a column that add the Server name from an initiating HTTPS connection (ssl.handshake.type == 1):
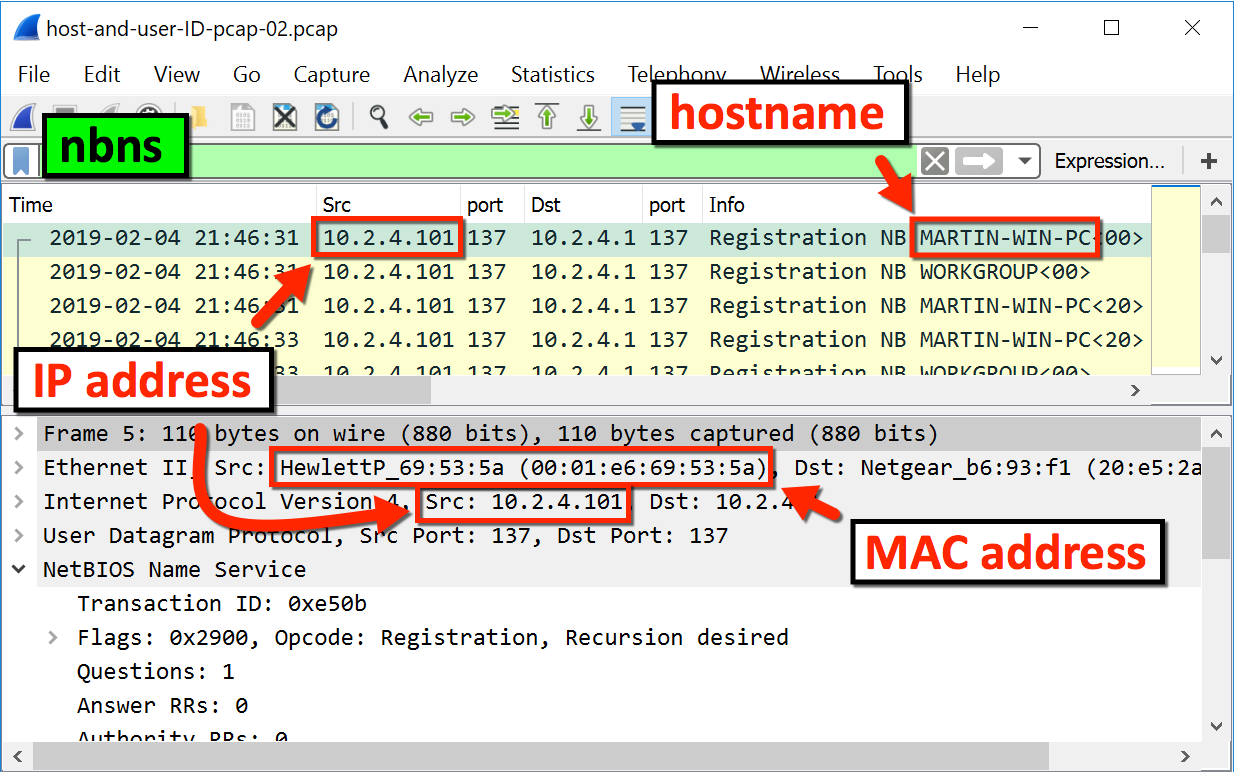
Identifying local hostnames
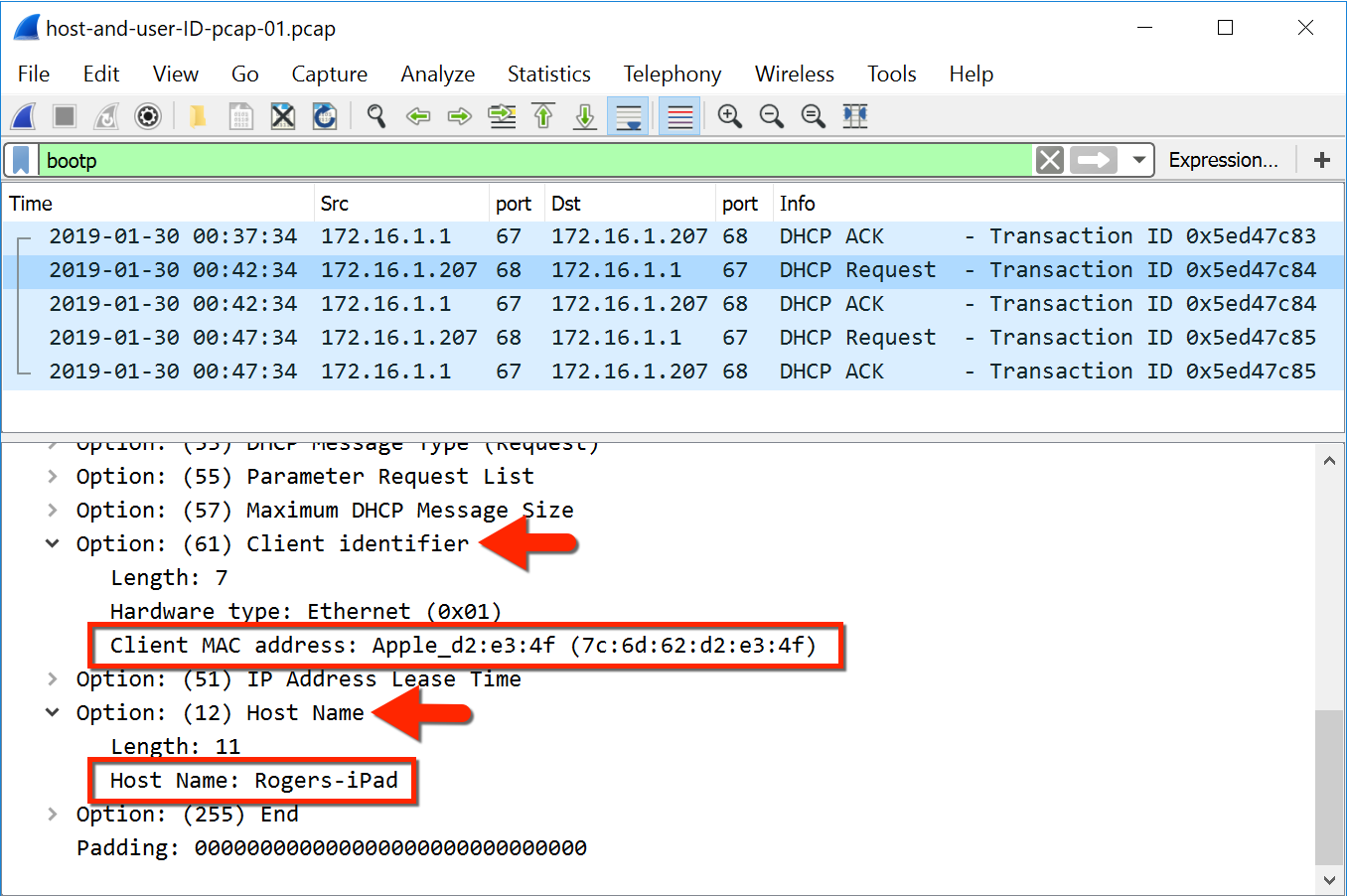
From DHCP
In current Wireshark instead of bootp you need to search for DHCP
From NBNS
Decrypting TLS
Decrypting https traffic with server private key
edit>preference>protocol>ssl>
Press Edit and add all the data of the server and the private key (IP, Port, Protocol, Key file and password)
Decrypting https traffic with symmetric session keys
It turns out that Firefox and Chrome both support logging the symmetric session key used to encrypt TLS traffic to a file. You can then point Wireshark at said file and presto! decrypted TLS traffic. More in: https://redflagsecurity.net/2019/03/10/decrypting-tls-wireshark/
To detect this search inside the environment for to variable SSLKEYLOGFILE
A file of shared keys will looks like this:
To import this in wireshark go to edit>preference>protocol>ssl> and import it in (Pre)-Master-Secret log filename:
ADB communication
Extract an APK from an ADB communication where the APK was sent:
from scapy.all import *
pcap = rdpcap("final2.pcapng")
def rm_data(data):
splitted = data.split(b"DATA")
if len(splitted) == 1:
return data
else:
return splitted[0]+splitted[1][4:]
all_bytes = b""
for pkt in pcap:
if Raw in pkt:
a = pkt[Raw]
if b"WRTE" == bytes(a)[:4]:
all_bytes += rm_data(bytes(a)[24:])
else:
all_bytes += rm_data(bytes(a))
print(all_bytes)
f = open('all_bytes.data', 'w+b')
f.write(all_bytes)
f.close()
Support HackTricks and get benefits!
- Do you work in a cybersecurity company? Do you want to see your company advertised in HackTricks? or do you want to have access to the latest version of the PEASS or download HackTricks in PDF? Check the SUBSCRIPTION PLANS!
- Discover The PEASS Family, our collection of exclusive NFTs
- Get the official PEASS & HackTricks swag
- Join the 💬 Discord group or the telegram group or follow me on Twitter 🐦@carlospolopm.
- Share your hacking tricks by submitting PRs to the hacktricks github repo.