{% hint style="success" %}
Learn & practice AWS Hacking: [**HackTricks Training AWS Red Team Expert (ARTE)**](https://training.hacktricks.xyz/courses/arte)
[**HackTricks Training AWS Red Team Expert (ARTE)**](https://training.hacktricks.xyz/courses/arte) \
Learn & practice GCP Hacking:
\
Learn & practice GCP Hacking:  [**HackTricks Training GCP Red Team Expert (GRTE)**
[**HackTricks Training GCP Red Team Expert (GRTE)** ](https://training.hacktricks.xyz/courses/grte)
](https://training.hacktricks.xyz/courses/grte)
Support HackTricks
* Check the [**subscription plans**](https://github.com/sponsors/carlospolop)!
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks\_live**](https://twitter.com/hacktricks\_live)**.**
* **Share hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
{% endhint %}
Some applications don't like user downloaded certificates, so in order to inspect web traffic for some apps we actually have to decompile the application & add a few things & recompile it.
# Automatic
The tool [**https://github.com/shroudedcode/apk-mitm**](https://github.com/shroudedcode/apk-mitm) will **automatically** make the necessary changes to the application to start capturing the requests and will also disable certificate pinning (if any).
# Manual
First we decompile the app: `apktool d *file-name*.apk`
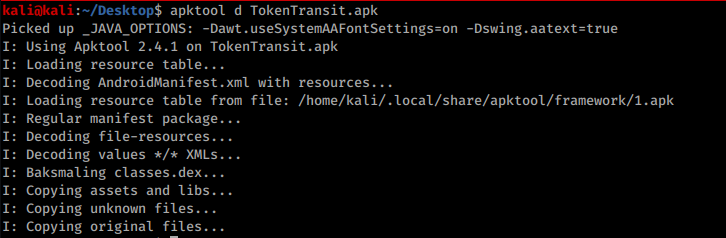
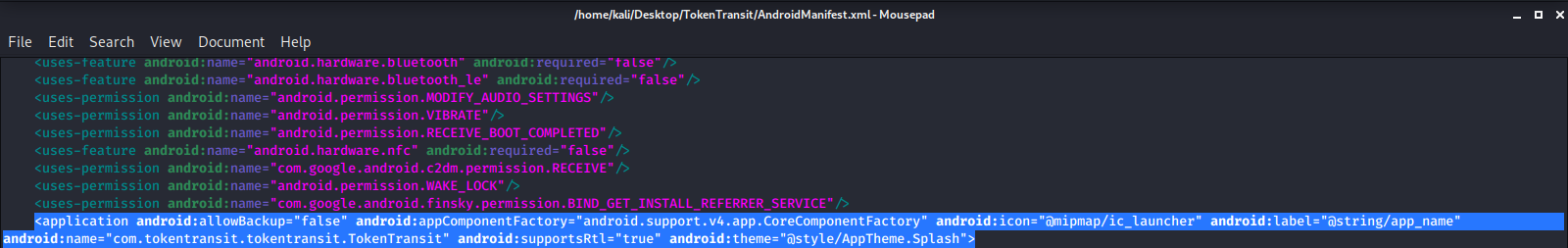
Then we go into the **Manifest.xml** file & scroll down to the `<\application android>` tag & we are going to add the following line if it isn't already there:
`android:networkSecurityConfig="@xml/network_security_config"`
Before adding:
After adding:
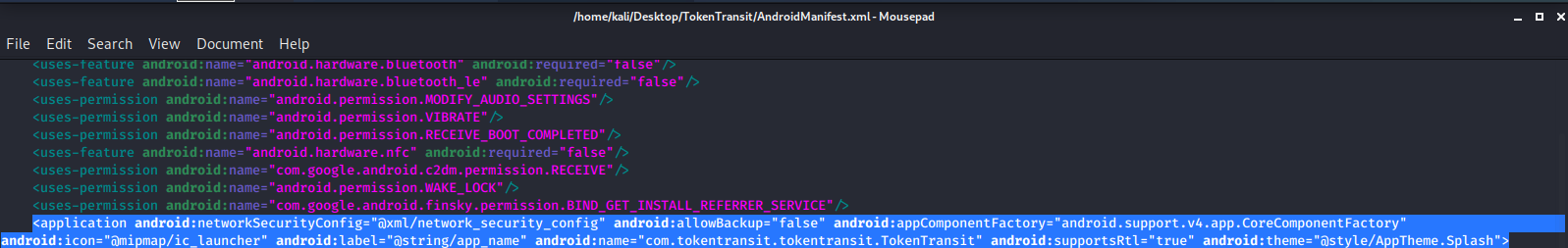
Now go into the **res/xml** folder & create/modify a file named network\_security\_config.xml with the following contents:
```markup
```
Then save the file & back out of all the directories & rebuild the apk with the following command: `apktool b *folder-name/* -o *output-file.apk*`
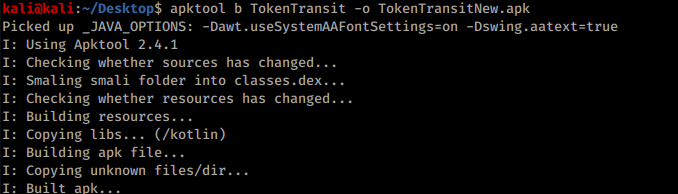
Finally, you need just to **sign the new application**. [Read this section of the page Smali - Decompiling/\[Modifying\]/Compiling to learn how to sign it](smali-changes.md#sing-the-new-apk).
{% hint style="success" %}
Learn & practice AWS Hacking: [**HackTricks Training AWS Red Team Expert (ARTE)**](https://training.hacktricks.xyz/courses/arte)
[**HackTricks Training AWS Red Team Expert (ARTE)**](https://training.hacktricks.xyz/courses/arte) \
Learn & practice GCP Hacking:
\
Learn & practice GCP Hacking:  [**HackTricks Training GCP Red Team Expert (GRTE)**
[**HackTricks Training GCP Red Team Expert (GRTE)** ](https://training.hacktricks.xyz/courses/grte)
](https://training.hacktricks.xyz/courses/grte)
Support HackTricks
* Check the [**subscription plans**](https://github.com/sponsors/carlospolop)!
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks\_live**](https://twitter.com/hacktricks\_live)**.**
* **Share hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
{% endhint %}
 [**HackTricks Training AWS Red Team Expert (ARTE)**](https://training.hacktricks.xyz/courses/arte)
[**HackTricks Training AWS Red Team Expert (ARTE)**](https://training.hacktricks.xyz/courses/arte) \
Learn & practice GCP Hacking:
\
Learn & practice GCP Hacking:  [**HackTricks Training GCP Red Team Expert (GRTE)**
[**HackTricks Training GCP Red Team Expert (GRTE)** ](https://training.hacktricks.xyz/courses/grte)
](https://training.hacktricks.xyz/courses/grte)
 [**HackTricks Training AWS Red Team Expert (ARTE)**](https://training.hacktricks.xyz/courses/arte)
[**HackTricks Training AWS Red Team Expert (ARTE)**](https://training.hacktricks.xyz/courses/arte) \
Learn & practice GCP Hacking:
\
Learn & practice GCP Hacking:  [**HackTricks Training GCP Red Team Expert (GRTE)**
[**HackTricks Training GCP Red Team Expert (GRTE)** ](https://training.hacktricks.xyz/courses/grte)
](https://training.hacktricks.xyz/courses/grte)