mirror of
https://github.com/carlospolop/hacktricks
synced 2024-11-22 04:33:28 +00:00
GitBook: [master] 6 pages and one asset modified
This commit is contained in:
parent
420adf74af
commit
bae851e425
7 changed files with 247 additions and 14 deletions
BIN
.gitbook/assets/image (562).png
Normal file
BIN
.gitbook/assets/image (562).png
Normal file
Binary file not shown.
|
After Width: | Height: | Size: 1.8 MiB |
|
|
@ -56,8 +56,9 @@
|
|||
## MacOS
|
||||
|
||||
* [MacOS Security & Privilege Escalation](macos/macos-security-and-privilege-escalation/README.md)
|
||||
* [MacOS Red Teaming](macos/macos-security-and-privilege-escalation/macos-red-teaming.md)
|
||||
* [Mac OS Protocols](macos/macos-security-and-privilege-escalation/mac-os-protocols.md)
|
||||
* [Inspecting and debugging Mac OS Sotware](macos/macos-security-and-privilege-escalation/inspecting-and-debugging-mac-os-apps.md)
|
||||
* [Inspecting, debugging and Fuzzing Mac OS Software](macos/macos-security-and-privilege-escalation/inspecting-and-debugging-mac-os-apps.md)
|
||||
* [Mac OS Serial Number](macos/macos-security-and-privilege-escalation/macos-serial-number.md)
|
||||
* [Mac OS Architecture](macos/macos-security-and-privilege-escalation/mac-os-architecture.md)
|
||||
|
||||
|
|
@ -564,4 +565,5 @@
|
|||
* [1911 - Pentesting fox](1911-pentesting-fox.md)
|
||||
* [Online Platforms with API](online-platforms-with-api.md)
|
||||
* [Stealing Sensitive Information Disclosure from a Web](stealing-sensitive-information-disclosure-from-a-web.md)
|
||||
* [Post Exploitation](post-exploitation.md)
|
||||
|
||||
|
|
|
|||
|
|
@ -4,23 +4,21 @@ First of all, please note that **most of the tricks about privilege escalation a
|
|||
|
||||
{% page-ref page="../../linux-unix/privilege-escalation/" %}
|
||||
|
||||
## Security Restrictions
|
||||
## MacOS Security Mechanisms
|
||||
|
||||
### Gatekeeper, Notarizing, and File Quarantine
|
||||
### Gatekeeper
|
||||
|
||||
\*\*\*\*[**In this talk**](https://www.youtube.com/watch?v=T5xfL9tEg44) Jeremy Brown talks about this protections and a bug that allowed to bypass them.
|
||||
|
||||
#### Gatekeeper
|
||||
[**In this talk**](https://www.youtube.com/watch?v=T5xfL9tEg44) Jeremy Brown talks about this protections and a bug that allowed to bypass them.
|
||||
|
||||
_**Gatekeeper**_ is designed to ensure that, by default, **only trusted software runs on a user’s Mac**. Gatekeeper is used when a user **downloads** and **opens** an app, a plug-in or an installer package from outside the App Store. Gatekeeper verifies that the software is **signed by** an **identified developer**, is **notarised** by Apple to be **free of known malicious content**, and **hasn’t been altered**. Gatekeeper also **requests user approval** before opening downloaded software for the first time to make sure the user hasn’t been tricked into running executable code they believed to simply be a data file.
|
||||
|
||||
#### Notarizing
|
||||
### Notarizing
|
||||
|
||||
In order for an **app to be notarised by Apple**, the developer needs to send the app for review. Notarization is **not App Review**. The Apple notary service is an **automated system** that **scans your software for malicious content**, checks for code-signing issues, and returns the results to you quickly. If there are no issues, the notary service generates a ticket for you to staple to your software; the notary service also **publishes that ticket online where Gatekeeper can find it**.
|
||||
|
||||
When the user first installs or runs your software, the presence of a ticket \(either online or attached to the executable\) **tells Gatekeeper that Apple notarized the software**. **Gatekeeper then places descriptive information in the initial launch dialog** indicating that Apple has already checked for malicious content.
|
||||
|
||||
#### File Quarantine
|
||||
### File Quarantine
|
||||
|
||||
Gatekeeper builds upon **File Quarantine.**
|
||||
Upon download of an application, a particular **extended file attribute** \("quarantine flag"\) can be **added** to the **downloaded** **file**. This attribute **is added by the application that downloads the file**, such as a **web** **browser** or email client, but is not usually added by others like common BitTorrent client software.
|
||||
|
|
@ -75,21 +73,59 @@ find / -exec ls -ld {} \; 2>/dev/null | grep -E "[x\-]@ " | awk '{printf $9; pri
|
|||
|
||||
### XProtect
|
||||
|
||||
**X-Protect is Apple’s built in malware scanner.** It keeps track of known malware hashes and patterns.
|
||||
**X-Protect** is also part of Gatekeeper. **It's Apple’s built in malware scanner.** It keeps track of known malware hashes and patterns.
|
||||
You can get information about the latest XProtect update running:
|
||||
|
||||
```bash
|
||||
system_profiler SPInstallHistoryDataType 2>/dev/null | grep -A 4 "XProtectPlistConfigData" | tail -n 5
|
||||
```
|
||||
|
||||
## Sandbox
|
||||
### MRT: Malware Removal Tool
|
||||
|
||||
Should malware make its way onto a Mac, macOS also includes technology to remediate infections. The _Malware Removal Tool \(MRT\)_ is an engine in macOS that remediates infections based on updates automatically delivered from Apple \(as part of automatic updates of system data files and security updates\). **MRT removes malware upon receiving updated information** and it continues to check for infections on restart and login. MRT doesn’t automatically reboot the Mac. \(From [here](https://support.apple.com/en-gb/guide/security/sec469d47bd8/web#:~:text=The%20Malware%20Removal%20Tool%20%28MRT,data%20files%20and%20security%20updates%29.)\)
|
||||
|
||||
### Automatic Security Updates
|
||||
|
||||
Apple issues the **updates for XProtect and MRT automatically** based on the latest threat intelligence available. By default, macOS checks for these updates **daily**. Notarisation updates are distributed using CloudKit sync and are much more frequent.
|
||||
|
||||
### TCC
|
||||
|
||||
**TCC \(Transparency, Consent, and Control\)** is a mechanism in macOS to **limit and control application access to certain features**, usually from a privacy perspective. This can include things such as location services, contacts, photos, microphone, camera, accessibility, full disk access, and a bunch more.
|
||||
|
||||
From a user’s perspective, they see TCC in action **when an application wants access to one of the features protected by TCC**. When this happens the user is prompted with a dialog asking them whether they want to allow access or not. This response is then stored in the TCC database.
|
||||
|
||||
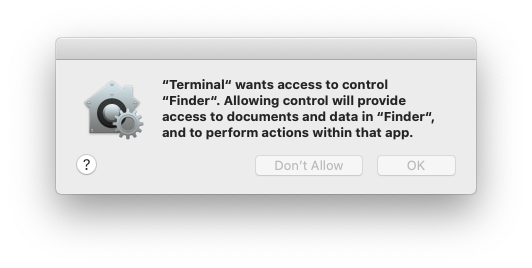
|
||||
|
||||
Check some of the **already given permissions** to apps in `System Preferences --> Security & Privacy --> Privacy --> Files and Folders`.
|
||||
|
||||
The TCC database is just a **sqlite3 database**, which makes the task of investigating it much simpler. There are two different databases, a global one in `/Library/Application Support/com.apple.TCC/TCC.db` and a per-user one located in `/Users/<username>/Library/Application Support/com.apple.TCC/TCC.db`. The first database is **protected from editing with SIP**\(System Integrity Protection\), but you can read them by granting terminal\(or your editor\) full disk access.
|
||||
|
||||
This information was [taken from here](https://rainforest.engineering/2021-02-09-macos-tcc/) \(read the **original source for more information**\).
|
||||
|
||||
Some protected directories:
|
||||
|
||||
* $HOME/Desktop
|
||||
* $HOME/Documents
|
||||
* $HOME/Downloads
|
||||
* iCloud Drive
|
||||
* ...
|
||||
|
||||
Unprotected directories:
|
||||
|
||||
* $HOME \(itself\)
|
||||
* $HOME/.ssh, $HOME/.aws, etc
|
||||
* /tmp
|
||||
|
||||
Here you can find examples of how **malware has been able to bypass this protection**:
|
||||
|
||||
* [https://www.jamf.com/blog/zero-day-tcc-bypass-discovered-in-xcsset-malware/](https://www.jamf.com/blog/zero-day-tcc-bypass-discovered-in-xcsset-malware/)
|
||||
|
||||
### Seatbelt Sandbox
|
||||
|
||||
MacOS Sandbox works with the kernel extension Seatbelt. It makes applications run inside the sandbox **need to request access to resources outside of the limited sandbox**. This helps to ensure that **the application will be accessing only expected resources** and if it wants to access anything else it will need to ask for permissions to the user.
|
||||
|
||||
Important **system services** also run inside their own custom **sandbox** such as the mdnsresponder service. You can view these custom **sandbox profiles** inside the **`/usr/share/sandbox`** directory. Other sandbox profiles can be checked in [https://github.com/s7ephen/OSX-Sandbox--Seatbelt--Profiles](https://github.com/s7ephen/OSX-Sandbox--Seatbelt--Profiles).
|
||||
|
||||
Check some of the **already given permissions** to apps in `System Preferences --> Security & Privacy --> Privacy --> Files and Folders`.
|
||||
|
||||
To start an application with a sandbox config you can use:
|
||||
|
||||
```bash
|
||||
|
|
@ -100,6 +136,11 @@ sandbox-exec -f example.sb /Path/To/The/Application
|
|||
Note that the **Apple-authored** **software** that runs on **Windows** **doesn’t have additional security precautions**, such as application sandboxing.
|
||||
{% endhint %}
|
||||
|
||||
Bypasses examples:
|
||||
|
||||
* [https://lapcatsoftware.com/articles/sandbox-escape.html](https://lapcatsoftware.com/articles/sandbox-escape.html)
|
||||
* [https://desi-jarvis.medium.com/office365-macos-sandbox-escape-fcce4fa4123c](https://desi-jarvis.medium.com/office365-macos-sandbox-escape-fcce4fa4123c) \(they are able to write files outside the sandbox whose name starts with `~$`\).
|
||||
|
||||
### SIP - System Integrity Protection
|
||||
|
||||
This protection was enabled to **help keep root level malware from taking over certain parts** of the operating system. Although this means **applying limitations to the root user** many find it to be worthwhile trade off.
|
||||
|
|
@ -549,6 +590,11 @@ RunService ()
|
|||
}
|
||||
```
|
||||
|
||||
### Other persistence techniques and tools
|
||||
|
||||
* [https://github.com/cedowens/Persistent-Swift](https://github.com/cedowens/Persistent-Swift)
|
||||
* [https://github.com/D00MFist/PersistentJXA](https://github.com/D00MFist/PersistentJXA)
|
||||
|
||||
## Memory Artifacts
|
||||
|
||||
### Swap Files
|
||||
|
|
@ -638,6 +684,23 @@ security dump-keychain | grep -A 5 "keychain" | grep -v "version" #List keychain
|
|||
security dump-keychain -d #Dump all the info, included secrets (the user will be asked for his password, even if root)
|
||||
```
|
||||
|
||||
### chainbreaker
|
||||
|
||||
\*\*\*\*[**Chainbreaker**](https://github.com/n0fate/chainbreaker) can be used to extract the following types of information from an OSX keychain in a forensically sound manner:
|
||||
|
||||
* Hashed Keychain password, suitable for cracking with [hashcat](https://hashcat.net/hashcat/) or [John the Ripper](https://www.openwall.com/john/)
|
||||
* Internet Passwords
|
||||
* Generic Passwords
|
||||
* Private Keys
|
||||
* Public Keys
|
||||
* X509 Certificates
|
||||
* Secure Notes
|
||||
* Appleshare Passwords
|
||||
|
||||
Given the keychain unlock password, a master key obtained using [volafox](https://github.com/n0fate/volafox) or [volatility](https://github.com/volatilityfoundation/volatility), or an unlock file such as SystemKey, Chainbreaker will also provide plaintext passwords.
|
||||
|
||||
Without one of these methods of unlocking the Keychain, Chainbreaker will display all other available information.
|
||||
|
||||
### kcpassword
|
||||
|
||||
The **kcpassword** file is a file that holds the **user’s login password**, but only if the system owner has **enabled automatic login**. Therefore, the user will be automatically logged in without being asked for a password \(which isn't very secure\).
|
||||
|
|
@ -699,7 +762,14 @@ The following line can be useful to find the applications that can open files de
|
|||
/System/Library/Frameworks/CoreServices.framework/Versions/A/Frameworks/LaunchServices.framework/Versions/A/Support/lsregister -dump | grep -E "path:|bindings:|name:"
|
||||
```
|
||||
|
||||
Or use something like [https://github.com/Lord-Kamina/SwiftDefaultApps](https://github.com/Lord-Kamina/SwiftDefaultApps).
|
||||
Or use something like [SwiftDefaultApps](https://github.com/Lord-Kamina/SwiftDefaultApps):
|
||||
|
||||
```bash
|
||||
./swda getSchemes #Get all the available schemes
|
||||
./swda getApps #Get all the apps declared
|
||||
./swda getUTIs #Get all the UTIs
|
||||
./swda getHandler --URL ftp #Get ftp handler
|
||||
```
|
||||
|
||||
You can also check the extensions supported by an application doing:
|
||||
|
||||
|
|
@ -790,6 +860,15 @@ codesign --verify --verbose /Applications/Safari.app
|
|||
spctl --assess --verbose /Applications/Safari.app
|
||||
```
|
||||
|
||||
## Remote Access Services
|
||||
|
||||
You can enable/disable these services in "System Preferences" --> Sharing
|
||||
|
||||
* **VNC**, known as “Screen Sharing”
|
||||
* **SSH**, called “Remote Login”
|
||||
* **Apple Remote Desktop** \(ARD\), or “Remote Management”
|
||||
* **AppleEvent**, known as “Remote Apple Event”
|
||||
|
||||
## Specific MacOS Enumeration
|
||||
|
||||
```bash
|
||||
|
|
|
|||
|
|
@ -1,4 +1,4 @@
|
|||
# Inspecting and debugging Mac OS Sotware
|
||||
# Inspecting, debugging and Fuzzing Mac OS Software
|
||||
|
||||
## Static Analysis
|
||||
|
||||
|
|
@ -149,3 +149,65 @@ fs_usage -w -f filesys ls #This tracks filesystem actions of proccess names cont
|
|||
fs_usage -w -f network curl #This tracks network actions
|
||||
```
|
||||
|
||||
## Fuzzing
|
||||
|
||||
### [ReportCrash](https://ss64.com/osx/reportcrash.html#:~:text=ReportCrash%20analyzes%20crashing%20processes%20and%20saves%20a%20crash%20report%20to%20disk.&text=ReportCrash%20also%20records%20the%20identity,when%20a%20crash%20is%20detected.)
|
||||
|
||||
ReportCrash **analyzes crashing processes and saves a crash report to disk**. A crash report contains information that can **help a developer diagnose** the cause of a crash.
|
||||
For applications and other processes **running in the per-user launchd context**, ReportCrash runs as a LaunchAgent and saves crash reports in the user's `~/Library/Logs/DiagnosticReports/`
|
||||
For daemons, other processes **running in the system launchd context** and other privileged processes, ReportCrash runs as a LaunchDaemon and saves crash reports in the system's `/Library/Logs/DiagnosticReports`
|
||||
|
||||
If you are worried about crash reports **being sent to Apple** you can disable them. If not, crash reports can be useful to **figure out how a server crashed**.
|
||||
|
||||
```bash
|
||||
#To disable crash reporting:
|
||||
launchctl unload -w /System/Library/LaunchAgents/com.apple.ReportCrash.plist
|
||||
sudo launchctl unload -w /System/Library/LaunchDaemons/com.apple.ReportCrash.Root.plist
|
||||
|
||||
#To re-enable crash reporting:
|
||||
launchctl load -w /System/Library/LaunchAgents/com.apple.ReportCrash.plist
|
||||
sudo launchctl load -w /System/Library/LaunchDaemons/com.apple.ReportCrash.Root.plist
|
||||
```
|
||||
|
||||
### Sleep
|
||||
|
||||
While fuzzing in a MacOS it's important to not allow the Mac to sleep:
|
||||
|
||||
* systemsetup -setsleep Never
|
||||
* pmset, System Preferences
|
||||
* [KeepingYouAwake](https://github.com/newmarcel/KeepingYouAwake)
|
||||
|
||||
#### SSH Disconnect
|
||||
|
||||
If you are fuzzing via a SSH connection it's important to make sure the session isn't going to day. So change the sshd\_config file with:
|
||||
|
||||
* TCPKeepAlive Yes
|
||||
* ClientAliveInterval 0
|
||||
* ClientAliveCountMax 0
|
||||
|
||||
```bash
|
||||
sudo launchctl unload /System/Library/LaunchDaemons/ssh.plist
|
||||
sudo launchctl load -w /System/Library/LaunchDaemons/ssh.plist
|
||||
```
|
||||
|
||||
### Internal Handlers
|
||||
|
||||
[**Checkout this section**](./#file-extensions-apps) ****to find out how you can find which app is responsible of **handling the specified scheme or protocol**.
|
||||
|
||||
### Enumerating Network Processes
|
||||
|
||||
This interesting to find processes that are managing network data:
|
||||
|
||||
```bash
|
||||
dtrace -n 'syscall::recv*:entry { printf("-> %s (pid=%d)", execname, pid); }' >> recv.log
|
||||
#wait some time
|
||||
sort -u recv.log > procs.txt
|
||||
cat procs.txt
|
||||
```
|
||||
|
||||
Or use `netstat` or `lsof`
|
||||
|
||||
## References
|
||||
|
||||
* [https://www.youtube.com/watch?v=T5xfL9tEg44](https://www.youtube.com/watch?v=T5xfL9tEg44)
|
||||
*
|
||||
|
|
|
|||
|
|
@ -0,0 +1,66 @@
|
|||
# MacOS Red Teaming
|
||||
|
||||
## Common management methods
|
||||
|
||||
* JAMF Pro: `jamf checkJSSConnection`
|
||||
* Kandji
|
||||
|
||||
If you manage to **compromise admin credentials** to access the management platform, you can **potentially compromise all the computers** by distributing your malware in the machines.
|
||||
|
||||
## Active Directory
|
||||
|
||||
In some occasions you will find that the **MacOS computer is connected to an AD**. In this scenario you should try to **enumerate** the active directory as you are use to it. Find some **help** in the following pages:
|
||||
|
||||
{% page-ref page="../../pentesting/pentesting-ldap.md" %}
|
||||
|
||||
{% page-ref page="../../windows/active-directory-methodology/" %}
|
||||
|
||||
{% page-ref page="../../pentesting/pentesting-kerberos-88/" %}
|
||||
|
||||
Some **local MacOS tool** that may also help you is `dscl`:
|
||||
|
||||
```bash
|
||||
dscl "/Active Directory/[Domain]/All Domains" ls /
|
||||
```
|
||||
|
||||
Also there are some tools prepared for MacOS to automatically enumerate the AD and play with kerberos:
|
||||
|
||||
* [**Machound**](https://github.com/XMCyber/MacHound): MacHound is an extension to the Bloodhound audting tool allowing collecting and ingesting of Active Directory relationships on MacOS hosts.
|
||||
* \*\*\*\*[**Bifrost**](https://github.com/its-a-feature/bifrost): Bifrost is an Objective-C project designed to interact with the Heimdal krb5 APIs on macOS. The goal of the project is to enable better security testing around Kerberos on macOS devices using native APIs without requiring any other framework or packages on the target.
|
||||
|
||||
### Domain Information
|
||||
|
||||
```text
|
||||
echo show com.apple.opendirectoryd.ActiveDirectory | scutil
|
||||
```
|
||||
|
||||
### Users
|
||||
|
||||
The three types of MacOS users are:
|
||||
|
||||
* **Local Users** — Managed by the local OpenDirectory service, they aren’t connected in any way to the Active Directory.
|
||||
* **Network Users** — Volatile Active Directory users who require a connection to the DC server to authenticate.
|
||||
* **Mobile Users** — Active Directory users with a local backup for their credentials and files.
|
||||
|
||||
The local information about users and groups is stored in in the folder _/var/db/dslocal/nodes/Default._
|
||||
For example, the info about user called _mark_ is stored in _/var/db/dslocal/nodes/Default/users/mark.plist_ and the info about the group _admin_ is in _/var/db/dslocal/nodes/Default/groups/admin.plist_.
|
||||
|
||||
In addition to using the HasSession and AdminTo edges, **MacHound adds three new edges** to the Bloodhound database:
|
||||
|
||||
* **CanSSH** - entity allowed to SSH to host
|
||||
* **CanVNC** - entity allowed to VNC to host
|
||||
* **CanAE** - entity allowed to execute AppleEvent scripts on host
|
||||
|
||||
## External Services
|
||||
|
||||
MacOS Red Teaming is different from a regular Windows Red Teaming as usually **MacOS is integrated with several external platforms directly**. A common configuration of MacOS is to access to the computer using **OneLogin synchronised credentials, and accessing several external services** \(like github, aws...\) via OneLogin:
|
||||
|
||||

|
||||
|
||||
###
|
||||
|
||||
## References
|
||||
|
||||
* [https://www.youtube.com/watch?v=IiMladUbL6E](https://www.youtube.com/watch?v=IiMladUbL6E)
|
||||
* [https://medium.com/xm-cyber/introducing-machound-a-solution-to-macos-active-directory-based-attacks-2a425f0a22b6](https://medium.com/xm-cyber/introducing-machound-a-solution-to-macos-active-directory-based-attacks-2a425f0a22b6)
|
||||
|
||||
|
|
@ -38,3 +38,10 @@ The more common they are, the more probable the AV will detect it.
|
|||
* AutoOpen\(\)
|
||||
* Document\_Open\(\)
|
||||
|
||||
## Malicious Macros Generators
|
||||
|
||||
### MacOS
|
||||
|
||||
* \*\*\*\*[**macphish**](https://github.com/cldrn/macphish)\*\*\*\*
|
||||
* \*\*\*\*[**Mythic Macro Generator**](https://github.com/cedowens/Mythic-Macro-Generator)\*\*\*\*
|
||||
|
||||
|
|
|
|||
17
post-exploitation.md
Normal file
17
post-exploitation.md
Normal file
|
|
@ -0,0 +1,17 @@
|
|||
# Post Exploitation
|
||||
|
||||
### **Local l00t**
|
||||
|
||||
* \*\*\*\*[**PEASS-ng**](https://github.com/carlospolop/PEASS-ng): These scripts, apart for looking for PE vectors, will look for sensitive information inside the filesystem.
|
||||
* \*\*\*\*[**LaZagne**](https://github.com/AlessandroZ/LaZagne): The **LaZagne project** is an open source application used to **retrieve lots of passwords** stored on a local computer. Each software stores its passwords using different techniques \(plaintext, APIs, custom algorithms, databases, etc.\). This tool has been developed for the purpose of finding these passwords for the most commonly-used software.
|
||||
|
||||
### **External Services**
|
||||
|
||||
* \*\*\*\*[**Conf-Thief**](https://github.com/antman1p/Conf-Thief): This Module will connect to Confluence's API using an access token, export to PDF, and download the Confluence documents that the target has access to.
|
||||
* \*\*\*\*[**GD-Thief**](https://github.com/antman1p/GD-Thief): Red Team tool for exfiltrating files from a target's Google Drive that you\(the attacker\) has access to, via the Google Drive API. This includes includes all shared files, all files from shared drives, and all files from domain drives that the target has access to.
|
||||
* \*\*\*\*[**GDir-Thief**](https://github.com/antman1p/GDir-Thief): Red Team tool for exfiltrating the target organization's Google People Directory that you have access to, via Google's People API.
|
||||
* \*\*\*\*[**SlackPirate**](https://github.com/emtunc/SlackPirate)**:** This is a tool developed in Python which uses the native Slack APIs to extract 'interesting' information from a Slack workspace given an access token.
|
||||
* \*\*\*\*[**Slackhound**](https://github.com/BojackThePillager/Slackhound): Slackhound is a command line tool for red and blue teams to quickly perform reconnaissance of a Slack workspace/organization. Slackhound makes collection of an organization's users, files, messages, etc. quickly searchable and large objects are written to CSV for offline review.
|
||||
|
||||
|
||||
|
||||
Loading…
Reference in a new issue