mirror of
https://github.com/carlospolop/hacktricks
synced 2024-12-22 11:03:24 +00:00
155 lines
9 KiB
Markdown
155 lines
9 KiB
Markdown
|
|
# 135, 593 - Pentesting MSRPC
|
||
|
|
|
||
|
|
{% hint style="success" %}
|
||
|
|
Learn & practice AWS Hacking:<img src="../.gitbook/assets/arte.png" alt="" data-size="line">[**HackTricks Training AWS Red Team Expert (ARTE)**](https://training.hacktricks.xyz/courses/arte)<img src="../.gitbook/assets/arte.png" alt="" data-size="line">\
|
||
|
|
Learn & practice GCP Hacking: <img src="../.gitbook/assets/grte.png" alt="" data-size="line">[**HackTricks Training GCP Red Team Expert (GRTE)**<img src="../.gitbook/assets/grte.png" alt="" data-size="line">](https://training.hacktricks.xyz/courses/grte)
|
||
|
|
|
||
|
|
<details>
|
||
|
|
|
||
|
|
<summary>Support HackTricks</summary>
|
||
|
|
|
||
|
|
* Check the [**subscription plans**](https://github.com/sponsors/carlospolop)!
|
||
|
|
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks\_live**](https://twitter.com/hacktricks_live)**.**
|
||
|
|
* **Share hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||
|
|
|
||
|
|
</details>
|
||
|
|
{% endhint %}
|
||
|
|
|
||
|
|
<figure><img src="../.gitbook/assets/image (3).png" alt=""><figcaption></figcaption></figure>
|
||
|
|
|
||
|
|
Join [**HackenProof Discord**](https://discord.com/invite/N3FrSbmwdy) server to communicate with experienced hackers and bug bounty hunters!
|
||
|
|
|
||
|
|
**Hacking Insights**\
|
||
|
|
Engage with content that delves into the thrill and challenges of hacking
|
||
|
|
|
||
|
|
**Real-Time Hack News**\
|
||
|
|
Keep up-to-date with fast-paced hacking world through real-time news and insights
|
||
|
|
|
||
|
|
**Latest Announcements**\
|
||
|
|
Stay informed with the newest bug bounties launching and crucial platform updates
|
||
|
|
|
||
|
|
**Join us on** [**Discord**](https://discord.com/invite/N3FrSbmwdy) and start collaborating with top hackers today!
|
||
|
|
|
||
|
|
## Basic Information
|
||
|
|
|
||
|
|
The Microsoft Remote Procedure Call (MSRPC) protocol, a client-server model enabling a program to request a service from a program located on another computer without understanding the network's specifics, was initially derived from open-source software and later developed and copyrighted by Microsoft.
|
||
|
|
|
||
|
|
The RPC endpoint mapper can be accessed via TCP and UDP port 135, SMB on TCP 139 and 445 (with a null or authenticated session), and as a web service on TCP port 593.
|
||
|
|
|
||
|
|
```
|
||
|
|
135/tcp open msrpc Microsoft Windows RPC
|
||
|
|
```
|
||
|
|
|
||
|
|
## How does MSRPC work?
|
||
|
|
|
||
|
|
Initiated by the client application, the MSRPC process involves calling a local stub procedure that then interacts with the client runtime library to prepare and transmit the request to the server. This includes converting parameters into a standard Network Data Representation format. The choice of transport protocol is determined by the runtime library if the server is remote, ensuring the RPC is delivered through the network stack.
|
||
|
|
|
||
|
|
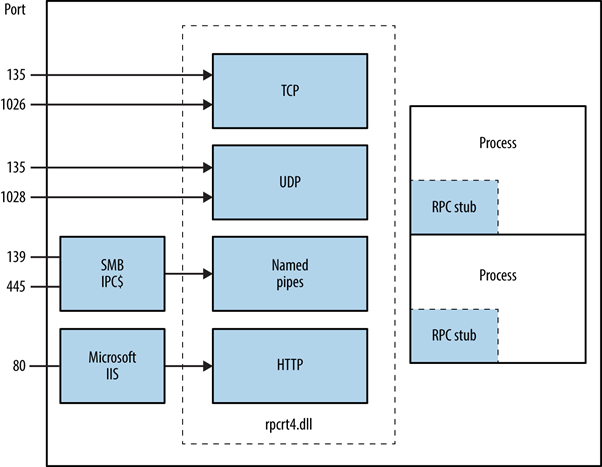
|
||
|
|
|
||
|
|
## **Identifying Exposed RPC Services**
|
||
|
|
|
||
|
|
Exposure of RPC services across TCP, UDP, HTTP, and SMB can be determined by querying the RPC locator service and individual endpoints. Tools such as rpcdump facilitate the identification of unique RPC services, denoted by **IFID** values, revealing service details and communication bindings:
|
||
|
|
|
||
|
|
```
|
||
|
|
D:\rpctools> rpcdump [-p port] <IP>
|
||
|
|
**IFID**: 5a7b91f8-ff00-11d0-a9b2-00c04fb6e6fc version 1.0
|
||
|
|
Annotation: Messenger Service
|
||
|
|
UUID: 00000000-0000-0000-0000-000000000000
|
||
|
|
Binding: ncadg_ip_udp:<IP>[1028]
|
||
|
|
```
|
||
|
|
|
||
|
|
Access to the RPC locator service is enabled through specific protocols: ncacn\_ip\_tcp and ncadg\_ip\_udp for accessing via port 135, ncacn\_np for SMB connections, and ncacn\_http for web-based RPC communication. The following commands exemplify the utilization of Metasploit modules to audit and interact with MSRPC services, primarily focusing on port 135:
|
||
|
|
|
||
|
|
```bash
|
||
|
|
use auxiliary/scanner/dcerpc/endpoint_mapper
|
||
|
|
use auxiliary/scanner/dcerpc/hidden
|
||
|
|
use auxiliary/scanner/dcerpc/management
|
||
|
|
use auxiliary/scanner/dcerpc/tcp_dcerpc_auditor
|
||
|
|
rpcdump.py <IP> -p 135
|
||
|
|
```
|
||
|
|
|
||
|
|
All options except `tcp_dcerpc_auditor` are specifically designed for targeting MSRPC on port 135.
|
||
|
|
|
||
|
|
#### Notable RPC interfaces
|
||
|
|
|
||
|
|
* **IFID**: 12345778-1234-abcd-ef00-0123456789ab
|
||
|
|
* **Named Pipe**: `\pipe\lsarpc`
|
||
|
|
* **Description**: LSA interface, used to enumerate users.
|
||
|
|
* **IFID**: 3919286a-b10c-11d0-9ba8-00c04fd92ef5
|
||
|
|
* **Named Pipe**: `\pipe\lsarpc`
|
||
|
|
* **Description**: LSA Directory Services (DS) interface, used to enumerate domains and trust relationships.
|
||
|
|
* **IFID**: 12345778-1234-abcd-ef00-0123456789ac
|
||
|
|
* **Named Pipe**: `\pipe\samr`
|
||
|
|
* **Description**: LSA SAMR interface, used to access public SAM database elements (e.g., usernames) and brute-force user passwords regardless of account lockout policy.
|
||
|
|
* **IFID**: 1ff70682-0a51-30e8-076d-740be8cee98b
|
||
|
|
* **Named Pipe**: `\pipe\atsvc`
|
||
|
|
* **Description**: Task scheduler, used to remotely execute commands.
|
||
|
|
* **IFID**: 338cd001-2244-31f1-aaaa-900038001003
|
||
|
|
* **Named Pipe**: `\pipe\winreg`
|
||
|
|
* **Description**: Remote registry service, used to access and modify the system registry.
|
||
|
|
* **IFID**: 367abb81-9844-35f1-ad32-98f038001003
|
||
|
|
* **Named Pipe**: `\pipe\svcctl`
|
||
|
|
* **Description**: Service control manager and server services, used to remotely start and stop services and execute commands.
|
||
|
|
* **IFID**: 4b324fc8-1670-01d3-1278-5a47bf6ee188
|
||
|
|
* **Named Pipe**: `\pipe\srvsvc`
|
||
|
|
* **Description**: Service control manager and server services, used to remotely start and stop services and execute commands.
|
||
|
|
* **IFID**: 4d9f4ab8-7d1c-11cf-861e-0020af6e7c57
|
||
|
|
* **Named Pipe**: `\pipe\epmapper`
|
||
|
|
* **Description**: DCOM interface, used for brute-force password grinding and information gathering via WM.
|
||
|
|
|
||
|
|
### Identifying IP addresses
|
||
|
|
|
||
|
|
Using [https://github.com/mubix/IOXIDResolver](https://github.com/mubix/IOXIDResolver), comes from [Airbus research](https://www.cyber.airbus.com/the-oxid-resolver-part-1-remote-enumeration-of-network-interfaces-without-any-authentication/) is possible to abuse the _**ServerAlive2**_ method inside the _**IOXIDResolver**_ interface.
|
||
|
|
|
||
|
|
This method has been used to get interface information as **IPv6** address from the HTB box _APT_. See [here](https://0xdf.gitlab.io/2021/04/10/htb-apt.html) for 0xdf APT writeup, it includes an alternative method using rpcmap.py from [Impacket](https://github.com/SecureAuthCorp/impacket/) with _stringbinding_ (see above).
|
||
|
|
|
||
|
|
### Executing a RCE with valid credentials
|
||
|
|
|
||
|
|
It is possible to execute remote code on a machine, if the credentials of a valid user are available using [dcomexec.py](https://github.com/fortra/impacket/blob/master/examples/dcomexec.py) from impacket framework.
|
||
|
|
|
||
|
|
**Remember to try with the different objects available**
|
||
|
|
|
||
|
|
* ShellWindows
|
||
|
|
* ShellBrowserWindow
|
||
|
|
* MMC20
|
||
|
|
|
||
|
|
## Port 593
|
||
|
|
|
||
|
|
The **rpcdump.exe** from [rpctools](https://resources.oreilly.com/examples/9780596510305/tree/master/tools/rpctools) can interact with this port.
|
||
|
|
|
||
|
|
## References
|
||
|
|
|
||
|
|
* [https://www.cyber.airbus.com/the-oxid-resolver-part-1-remote-enumeration-of-network-interfaces-without-any-authentication/](https://www.cyber.airbus.com/the-oxid-resolver-part-1-remote-enumeration-of-network-interfaces-without-any-authentication/)
|
||
|
|
* [https://www.cyber.airbus.com/the-oxid-resolver-part-2-accessing-a-remote-object-inside-dcom/](https://www.cyber.airbus.com/the-oxid-resolver-part-2-accessing-a-remote-object-inside-dcom/)
|
||
|
|
* [https://0xffsec.com/handbook/services/msrpc/](https://0xffsec.com/handbook/services/msrpc/)
|
||
|
|
|
||
|
|
<figure><img src="../.gitbook/assets/image (3).png" alt=""><figcaption></figcaption></figure>
|
||
|
|
|
||
|
|
Join [**HackenProof Discord**](https://discord.com/invite/N3FrSbmwdy) server to communicate with experienced hackers and bug bounty hunters!
|
||
|
|
|
||
|
|
**Hacking Insights**\
|
||
|
|
Engage with content that delves into the thrill and challenges of hacking
|
||
|
|
|
||
|
|
**Real-Time Hack News**\
|
||
|
|
Keep up-to-date with fast-paced hacking world through real-time news and insights
|
||
|
|
|
||
|
|
**Latest Announcements**\
|
||
|
|
Stay informed with the newest bug bounties launching and crucial platform updates
|
||
|
|
|
||
|
|
**Join us on** [**Discord**](https://discord.com/invite/N3FrSbmwdy) and start collaborating with top hackers today!
|
||
|
|
|
||
|
|
{% hint style="success" %}
|
||
|
|
Learn & practice AWS Hacking:<img src="../.gitbook/assets/arte.png" alt="" data-size="line">[**HackTricks Training AWS Red Team Expert (ARTE)**](https://training.hacktricks.xyz/courses/arte)<img src="../.gitbook/assets/arte.png" alt="" data-size="line">\
|
||
|
|
Learn & practice GCP Hacking: <img src="../.gitbook/assets/grte.png" alt="" data-size="line">[**HackTricks Training GCP Red Team Expert (GRTE)**<img src="../.gitbook/assets/grte.png" alt="" data-size="line">](https://training.hacktricks.xyz/courses/grte)
|
||
|
|
|
||
|
|
<details>
|
||
|
|
|
||
|
|
<summary>Support HackTricks</summary>
|
||
|
|
|
||
|
|
* Check the [**subscription plans**](https://github.com/sponsors/carlospolop)!
|
||
|
|
* **Join the** 💬 [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** us on **Twitter** 🐦 [**@hacktricks\_live**](https://twitter.com/hacktricks_live)**.**
|
||
|
|
* **Share hacking tricks by submitting PRs to the** [**HackTricks**](https://github.com/carlospolop/hacktricks) and [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
|
||
|
|
|
||
|
|
</details>
|
||
|
|
{% endhint %}
|