mirror of
https://github.com/carlospolop/hacktricks
synced 2024-11-26 22:52:06 +00:00
58 lines
3.7 KiB
Markdown
58 lines
3.7 KiB
Markdown
|
|
# Parameter Pollution
|
|||
|
|
|
|||
|
|
**Copied from** [**https://medium.com/@shahjerry33/http-parameter-pollution-its-contaminated-85edc0805654**](https://medium.com/@shahjerry33/http-parameter-pollution-its-contaminated-85edc0805654)\*\*\*\*
|
|||
|
|
|
|||
|
|
**Summary :**
|
|||
|
|
|
|||
|
|
HTTP Parameter Pollution \(HPP\) means to pollute the HTTP parameters of a web application for achieving a specific malicious task. It refers to manipulating how a website treats parameters it receives during HTTP requests. It changes a website’s behaviour from its intended one. HTTP
|
|||
|
|
parameter pollution is a simple kind of attack but it is an effective one.
|
|||
|
|
|
|||
|
|
When you pollute any parameter the code runs only on the server-side which is invisible to use, but we can see the results on our screen. The process in between is a black box.
|
|||
|
|
|
|||
|
|
For example, there is a URL https://www.anybank.com/send which has three parameters :
|
|||
|
|
|
|||
|
|
1. from :
|
|||
|
|
2. to :
|
|||
|
|
3. amount :
|
|||
|
|
|
|||
|
|
**URL : https://www.anybank.com/send/?from=accountA&to=accountB&amount=10000**
|
|||
|
|
|
|||
|
|
Now this is a normal URL which will proceed a transaction of 10000 from accountA to accountB but what if we add another same parameter **“from :”**
|
|||
|
|
|
|||
|
|
So the URL will be like **https://www.anybank.com/send/?from=accountA&to=accountB&amount=10000&from=accountC**
|
|||
|
|
|
|||
|
|
When this URL will be proceed a transaction of 10000 it will be deducted from accountC rather than accountA. This is how you manipulate the parameters in **HTTP Parameter Pollution** attack. Although the scope of this vulnerability is not limited only to **GET** request you can also perform this attack on a **POST** based request. You can try this vulnerability on many places like password change, 2FA, comments, profile photo upload, on a parameter where API key is passed, OTP etc.
|
|||
|
|
|
|||
|
|
When you manipulate any parameter, it’s manipulation depends on how each web technology is parsing their parameters. You can identify web technologies using “[Wappalyzer](https://addons.mozilla.org/en-US/firefox/addon/wappalyzer/)”. Below is the screenshot of some technologies and their parameter parsing.Technologies and their parameter parsing
|
|||
|
|
|
|||
|
|
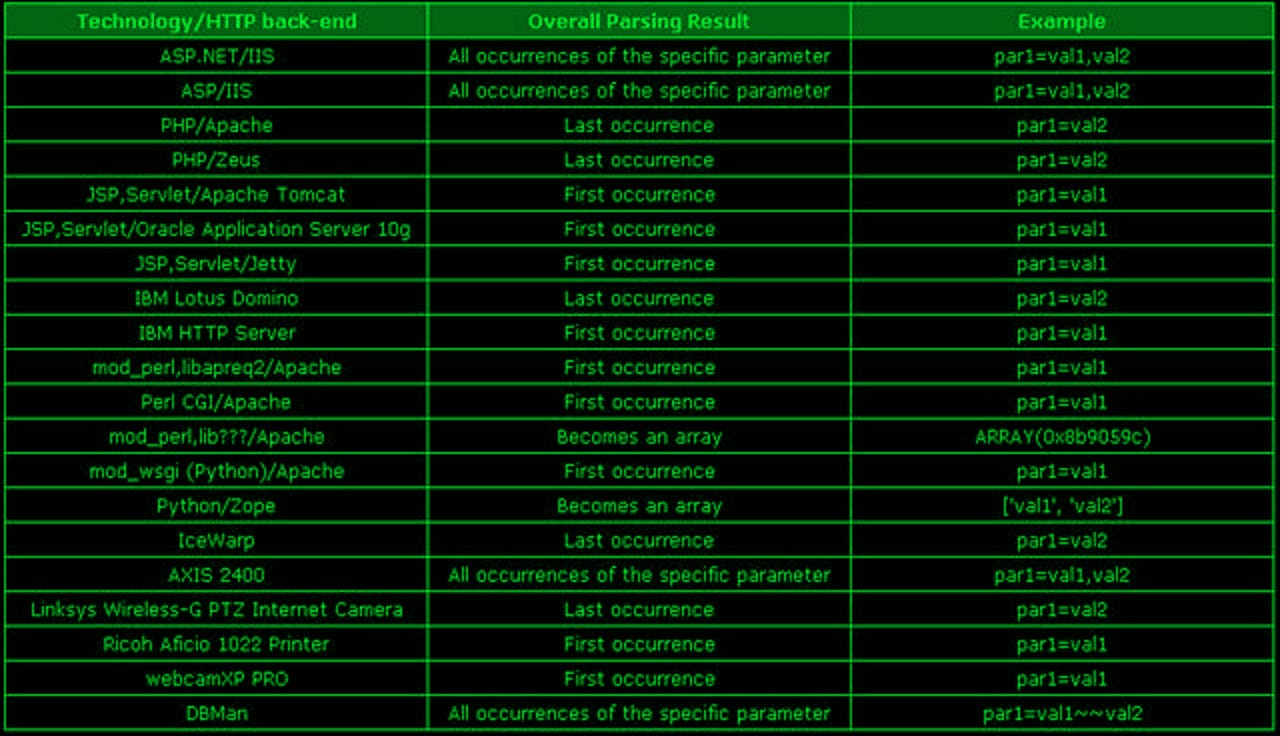
|
|||
|
|
|
|||
|
|
I would like to share one of my finding of HPP where I was able to take over an account using this vulnerability.
|
|||
|
|
|
|||
|
|
**How I find this vulnerability ?**
|
|||
|
|
|
|||
|
|
1. I went to a login page of that program, it asked for an OTP for login
|
|||
|
|
|
|||
|
|
Send OTP
|
|||
|
|
|
|||
|
|
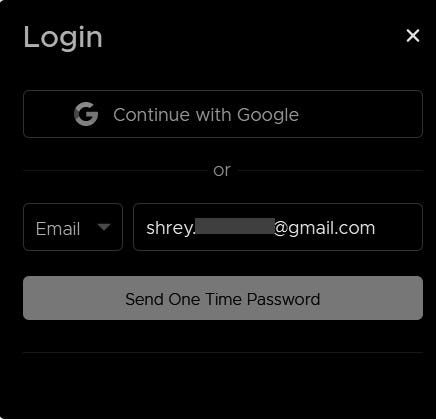
|
|||
|
|
|
|||
|
|
2. I typed an email and clicked on “Send One Time Password”
|
|||
|
|
|
|||
|
|
3. I intercepted the request using burp suite and added another email by using same parameter \(I created two emails for testing purpose\)Burp Request
|
|||
|
|
|
|||
|
|
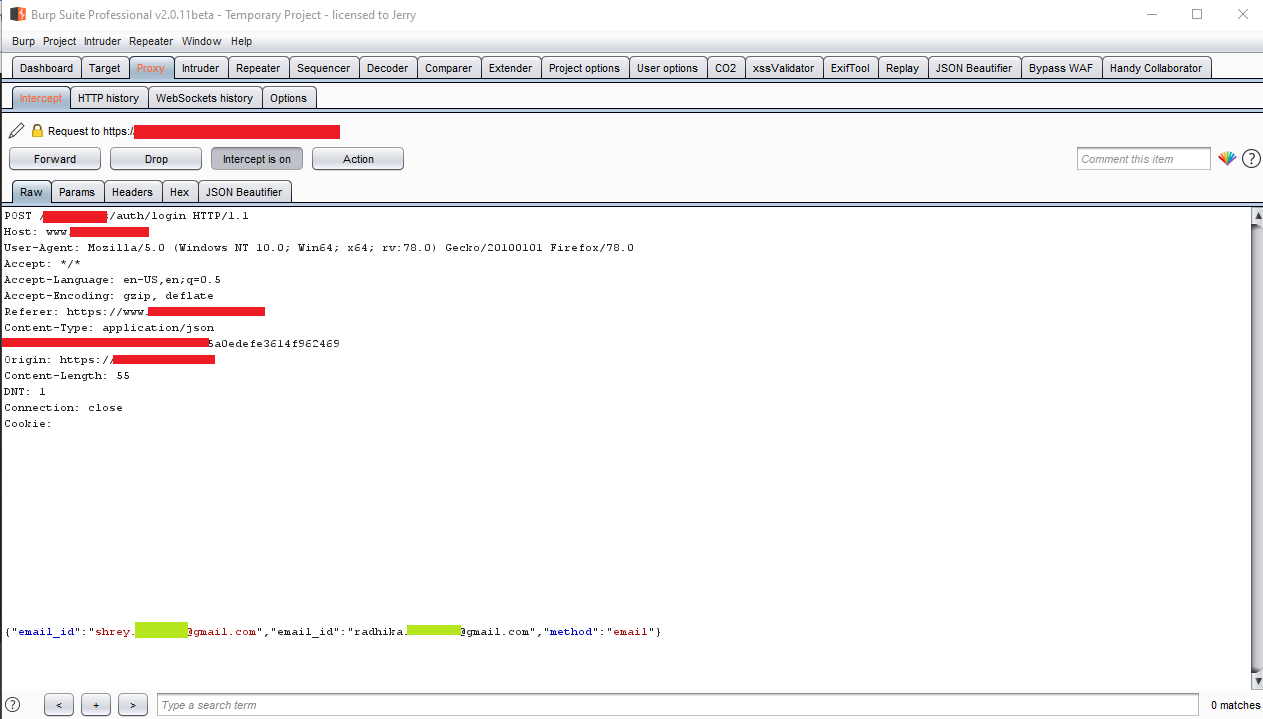
|
|||
|
|
|
|||
|
|
4. I received an OTP of shrey……@gmail.com to my another account radhika…..@gmail.com OTP
|
|||
|
|
|
|||
|
|
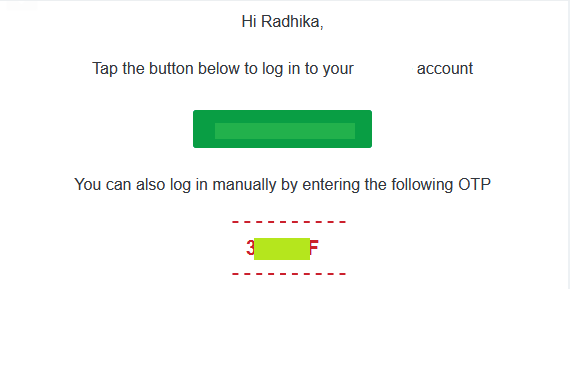
|
|||
|
|
|
|||
|
|
5. I copied the OTP and went to shrey….@gmail.com on that program’s login screen, I entered this OTP and I was in the account.Account Take Over
|
|||
|
|
|
|||
|
|
|
|||
|
|
|
|||
|
|
So what happened here is the back-end application took the value of first “**email**” parameter to generate an OTP and used the value of second “**email**” parameter to supply the value, which means an OTP of shrey….@gmail.com was sent to radhika….@gmail.com.
|
|||
|
|
|
|||
|
|
**NOTE :** Here in an image on 4th step where I received an OTP to radhika….@gmail.com I was confused because the message said Hi Radhika, so I thought that the parameter is not polluted and the OTP was for radhika….@gmail.com but when I tried the OTP on shrey….@gmail.com it worked.
|
|||
|
|
|