mirror of
https://github.com/carlospolop/hacktricks
synced 2025-01-06 10:18:55 +00:00
79 lines
2.9 KiB
Markdown
79 lines
2.9 KiB
Markdown
|
|
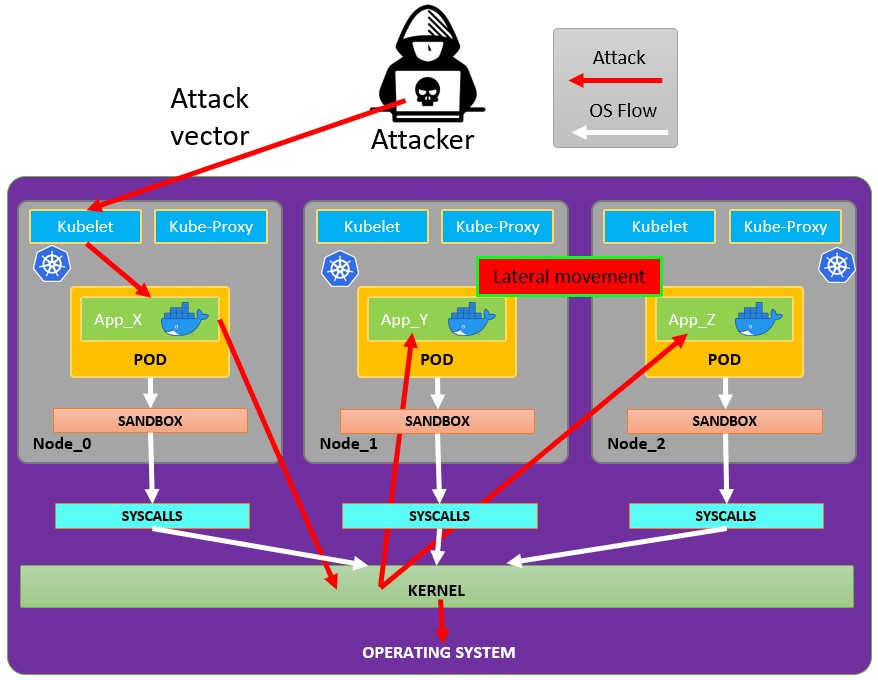
# Attacking Kubernetes from inside a Pod
|
||
|
|
|
||
|
|
## **Pod Breakout**
|
||
|
|
|
||
|
|
**If you are lucky enough you may be able to escape from it to the node:**
|
||
|
|
|
||
|
|
|
||
|
|
|
||
|
|
### Escaping from the pod
|
||
|
|
|
||
|
|
In order to try to escape from the pos you might need to **escalate privileges** first, some techniques to do it:
|
||
|
|
|
||
|
|
{% content-ref url="../../linux-unix/privilege-escalation/" %}
|
||
|
|
[privilege-escalation](../../linux-unix/privilege-escalation/)
|
||
|
|
{% endcontent-ref %}
|
||
|
|
|
||
|
|
You can check this **docker breakouts to try to escape** from a pod you have compromised:
|
||
|
|
|
||
|
|
{% content-ref url="../../linux-unix/privilege-escalation/docker-breakout/" %}
|
||
|
|
[docker-breakout](../../linux-unix/privilege-escalation/docker-breakout/)
|
||
|
|
{% endcontent-ref %}
|
||
|
|
|
||
|
|
### Abusing Kubernetes Privileges
|
||
|
|
|
||
|
|
As explained in the section about **kubernetes enumeration**:
|
||
|
|
|
||
|
|
{% content-ref url="enumeration-from-a-pod.md" %}
|
||
|
|
[enumeration-from-a-pod.md](enumeration-from-a-pod.md)
|
||
|
|
{% endcontent-ref %}
|
||
|
|
|
||
|
|
Usually the pods are run with a **service account token** inside of them. This service account may have some **privileges attached to it** that you could **abuse** to **move** to other pods or even to **escape** to the nodes configured inside the cluster. Check how in:
|
||
|
|
|
||
|
|
{% content-ref url="hardening-roles-clusterroles.md" %}
|
||
|
|
[hardening-roles-clusterroles.md](hardening-roles-clusterroles.md)
|
||
|
|
{% endcontent-ref %}
|
||
|
|
|
||
|
|
### Abusing Cloud Privileges
|
||
|
|
|
||
|
|
If the pod is run inside a **cloud environment** you might be able to l**eak a token from the metadata endpoint** and escalate privileges using it.
|
||
|
|
|
||
|
|
## Search vulnerable network services
|
||
|
|
|
||
|
|
As you are inside the Kubernetes environment, if you cannot escalate privileges abusing the current pods privileges and you cannot escape from the container, you should **search potential vulnerable services.**
|
||
|
|
|
||
|
|
### Services
|
||
|
|
|
||
|
|
**For this purpose, you can try to get all the services of the kubernetes environment:**
|
||
|
|
|
||
|
|
```
|
||
|
|
kubectl get svc --all-namespaces
|
||
|
|
```
|
||
|
|
|
||
|
|
### Scanning
|
||
|
|
|
||
|
|
The following Bash script (taken from a [Kubernetes workshop](https://github.com/calinah/learn-by-hacking-kccn/blob/master/k8s\_cheatsheet.md)) will install and scan the IP ranges of the kubernetes cluster:
|
||
|
|
|
||
|
|
```bash
|
||
|
|
sudo apt-get update
|
||
|
|
sudo apt-get install nmap
|
||
|
|
nmap-kube ()
|
||
|
|
{
|
||
|
|
nmap --open -T4 -A -v -Pn -p 80,443,2379,8080,9090,9100,9093,4001,6782-6784,6443,8443,9099,10250,10255,10256 "${@}"
|
||
|
|
}
|
||
|
|
|
||
|
|
nmap-kube-discover () {
|
||
|
|
local LOCAL_RANGE=$(ip a | awk '/eth0$/{print $2}' | sed 's,[0-9][0-9]*/.*,*,');
|
||
|
|
local SERVER_RANGES=" ";
|
||
|
|
SERVER_RANGES+="10.0.0.1 ";
|
||
|
|
SERVER_RANGES+="10.0.1.* ";
|
||
|
|
SERVER_RANGES+="10.*.0-1.* ";
|
||
|
|
nmap-kube ${SERVER_RANGES} "${LOCAL_RANGE}"
|
||
|
|
}
|
||
|
|
nmap-kube-discover
|
||
|
|
```
|
||
|
|
|
||
|
|
### Sniffing
|
||
|
|
|
||
|
|
In case the **compromised pod is running some sensitive service** where other pods need to authenticate you might be able to obtain the credentials send from the other pods.
|