mirror of
https://github.com/anchore/grype
synced 2024-11-10 06:34:13 +00:00
Update README.md to highlight supported distros and languages (#135)
* Update README.md to highlight supported distros and languages Same content, just bullet points instead of a single item for each type. Just visually easier to identify if you're looking for this info. Signed-off-by: Zach Hill <zach@anchore.com> * incorporated README feature comments Signed-off-by: Alex Goodman <alex.goodman@anchore.com> Co-authored-by: Alex Goodman <alex.goodman@anchore.com>
This commit is contained in:
parent
8757b470cc
commit
be6a7ea4f5
1 changed files with 22 additions and 4 deletions
26
README.md
26
README.md
|
|
@ -10,15 +10,27 @@ A vulnerability scanner for container images and filesystems. [Easily install th
|
|||
|
||||
|
||||
**Features**
|
||||
|
||||
- Scan the contents of a container image or filesystem to find known vulnerabilities.
|
||||
- Find vulnerabilities for major operating system packages across Alpine, BusyBox, CentOS / Red Hat, and Debian / Ubuntu flavored distributions
|
||||
- Find vulnerabilities for Ruby (Bundler), Java, JavaScript (npm/yarn), Python (Egg/Wheel) packages, and Python Pip/requirements.txt listings
|
||||
- Find vulnerabilities for major operating system packages
|
||||
- Alpine
|
||||
- BusyBox
|
||||
- CentOS / Red Hat
|
||||
- Debian
|
||||
- Ubuntu
|
||||
- Find vulnerabilities for language-specific packages
|
||||
- Ruby (Bundler)
|
||||
- Java (JARs, etc)
|
||||
- JavaScript (NPM/Yarn)
|
||||
- Python (Egg/Wheel)
|
||||
- Python pip/requirements.txt/setup.py listings
|
||||
|
||||
> :warning: **This is pre-release software** and it may not work as expected. If you encounter an issue, please [let us know using the issue tracker](https://github.com/anchore/grype/issues).
|
||||
|
||||
## Getting started
|
||||
|
||||
[Install the binary](#installation), and make sure that `grype` is available in your path. To scan for vulnerabilities in an image:
|
||||
|
||||
```
|
||||
grype <image>
|
||||
```
|
||||
|
|
@ -31,6 +43,7 @@ grype <image> --scope all-layers
|
|||
```
|
||||
|
||||
Grype can scan a variety of sources beyond those found in Docker.
|
||||
|
||||
```
|
||||
# scan a docker image tar (from the result of "docker image save ... -o image.tar" command)
|
||||
grype docker-archive://path/to/image.tar
|
||||
|
|
@ -40,11 +53,13 @@ grype dir://path/to/dir
|
|||
```
|
||||
|
||||
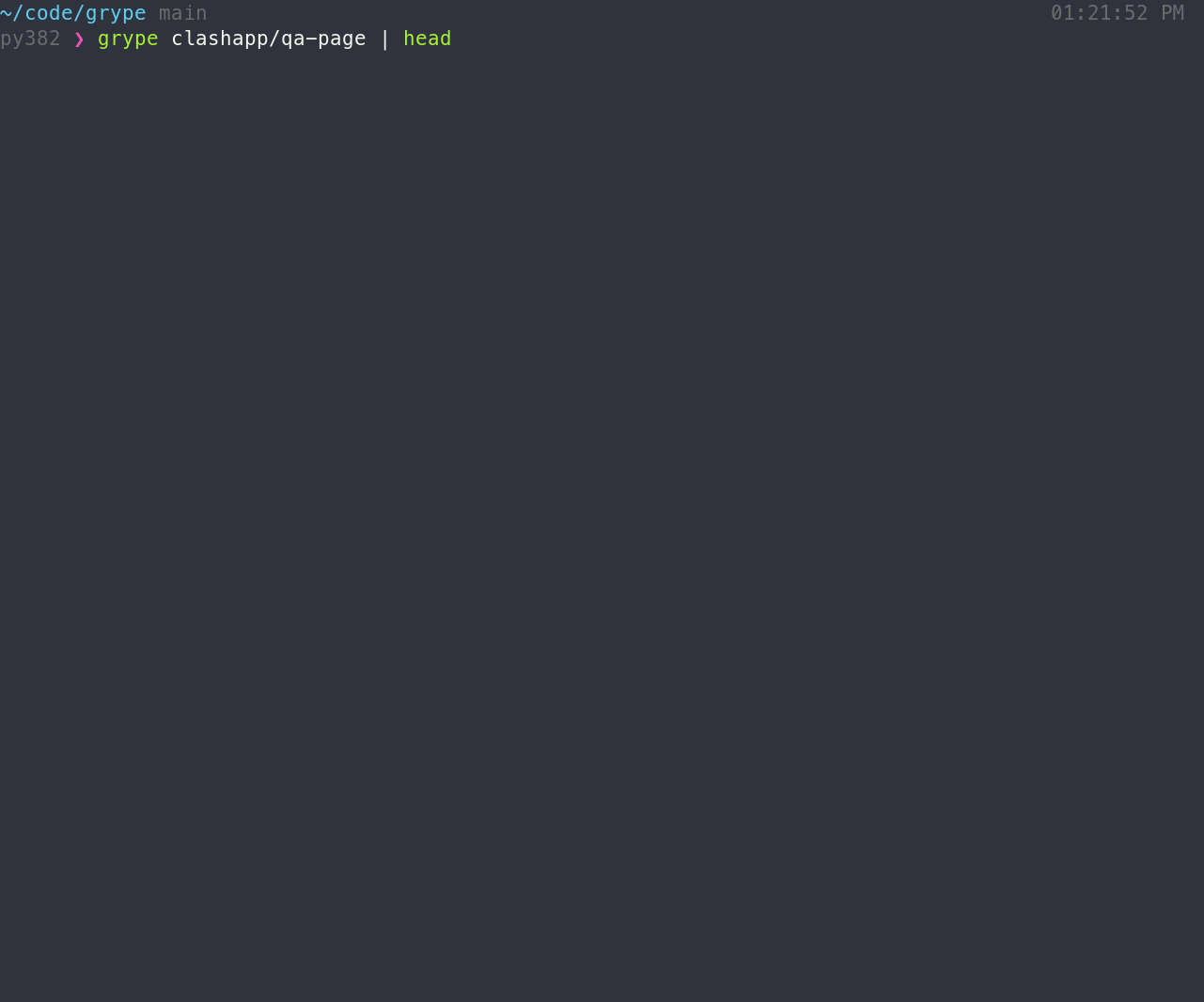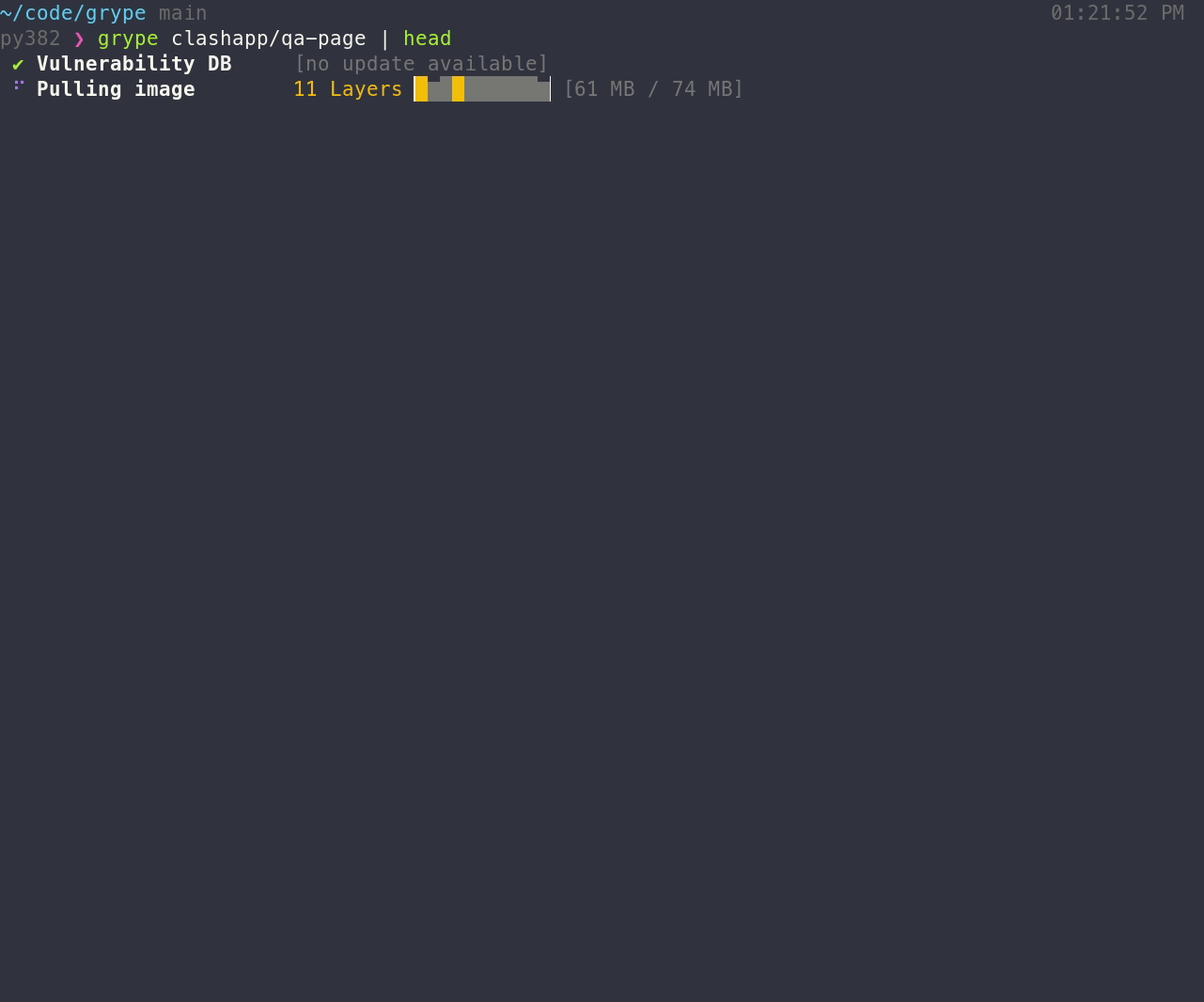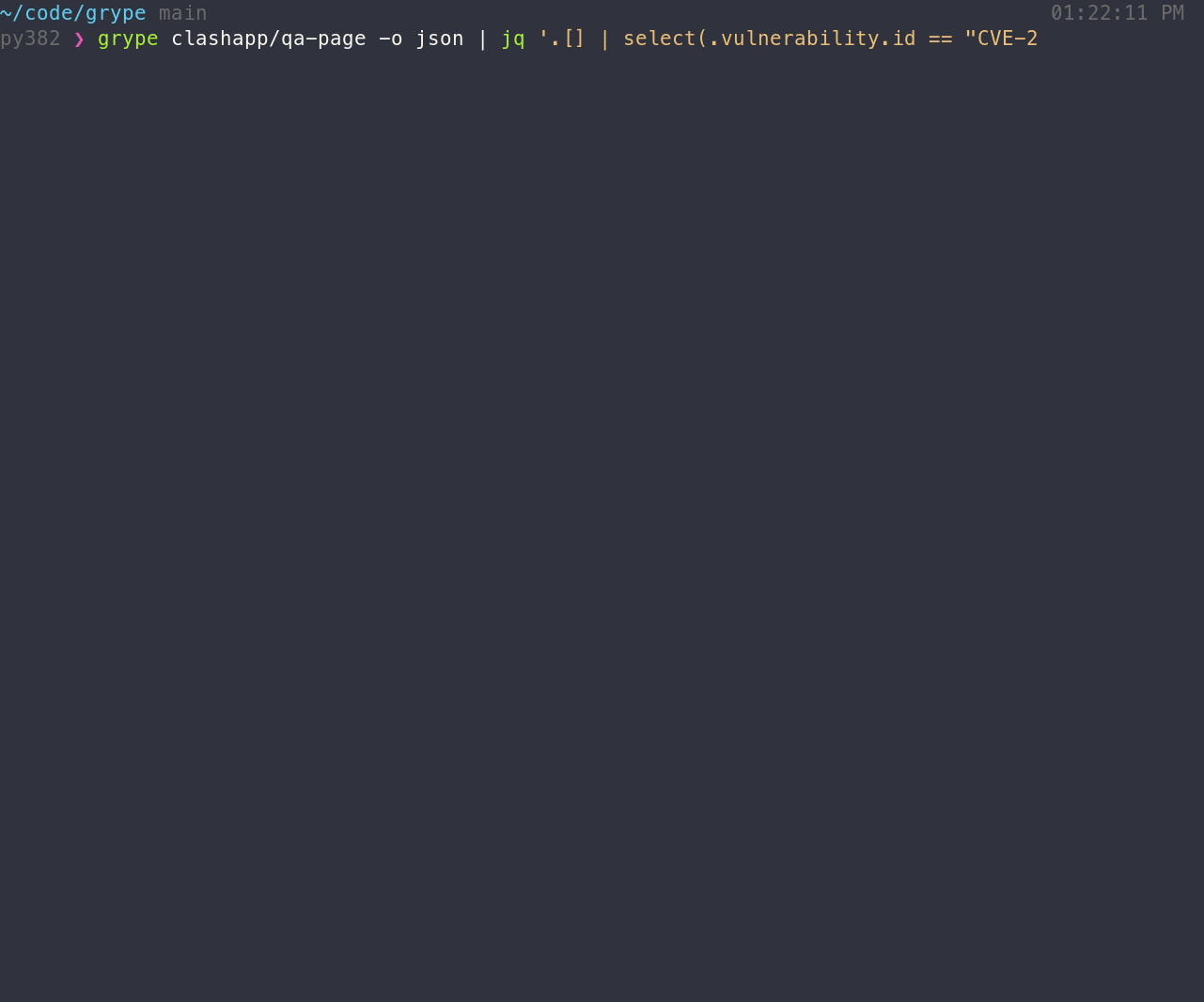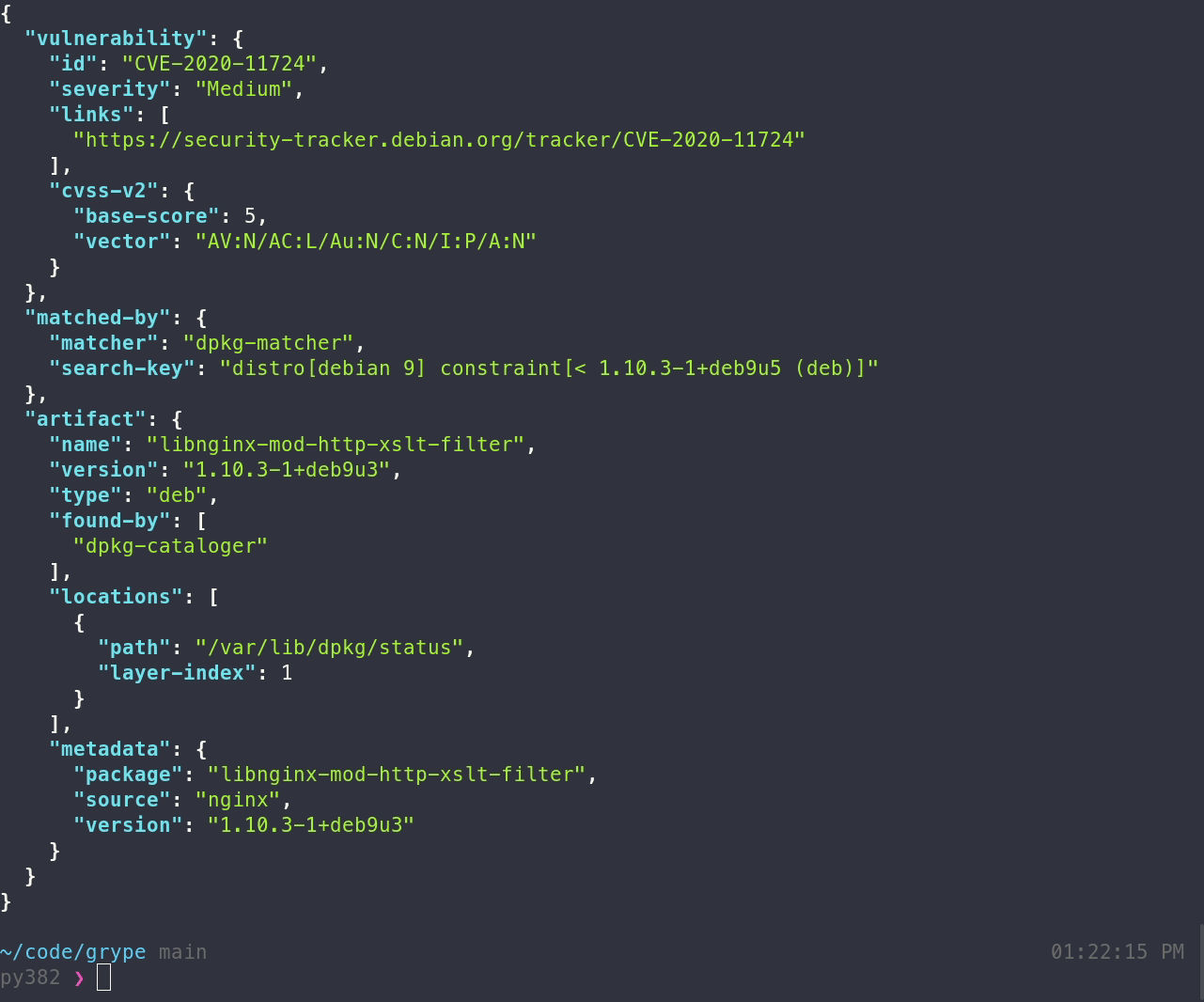
By default Grype shows a summary table, however, a more detailed `json` format is also available.
|
||||
|
||||
```
|
||||
grype <image> -o json
|
||||
```
|
||||
|
||||
Grype pulls a database of vulnerabilities derived from the publicly available [Anchore Feed Service](https://ancho.re/v1/service/feeds). This database is updated at the beginning of each scan, but an update can also be triggered manually.
|
||||
|
||||
```
|
||||
grype db update
|
||||
```
|
||||
|
|
@ -52,6 +67,7 @@ grype db update
|
|||
## Installation
|
||||
|
||||
**Recommended**
|
||||
|
||||
```bash
|
||||
# install the latest version to /usr/local/bin
|
||||
curl -sSfL https://raw.githubusercontent.com/anchore/grype/main/install.sh | sh -s -- -b /usr/local/bin
|
||||
|
|
@ -61,14 +77,16 @@ curl -sSfL https://raw.githubusercontent.com/anchore/grype/main/install.sh | sh
|
|||
```
|
||||
|
||||
**macOS**
|
||||
|
||||
```bash
|
||||
brew tap anchore/grype
|
||||
brew install grype
|
||||
```
|
||||
|
||||
You may experience a "macOS cannot verify app is free from malware" error upon running Grype because it is not yet signed and notarized. You can override this using `xattr`.
|
||||
|
||||
```bash
|
||||
xattr -rd com.apple.quarantine grype
|
||||
xattr -rd com.apple.quarantine grype
|
||||
```
|
||||
|
||||
## Configuration
|
||||
|
|
@ -120,7 +138,6 @@ db:
|
|||
|
||||
There are a few useful things to know before diving into the codebase. This project depends on a few things being available like a vulnerability database, which you might want to create manually instead of retrieving a released version.
|
||||
|
||||
|
||||
### Inspecting the database
|
||||
|
||||
The currently supported database provider is Sqlite3. Install `sqlite3` in your system and ensure that the `sqlite3` executable is available in your path. Ask `grype` about the location of the database, which will be different depending on the operating system:
|
||||
|
|
@ -177,6 +194,7 @@ CVE-2006-2450 libvncserver nvd = 0.7.1 unkn
|
|||
## Future plans
|
||||
|
||||
The following areas of potential development are currently being investigated:
|
||||
|
||||
- Add CycloneDX to list of output formats
|
||||
- Support for allowlist, package mapping
|
||||
- Establish a stable interchange format w/Syft
|
||||
|
|
|
|||
Loading…
Reference in a new issue