mirror of
https://github.com/EdOverflow/bugbounty-cheatsheet.git
synced 2024-11-24 20:13:06 +00:00
Add CSP bypass via JSONP endpoints section.
This commit is contained in:
parent
8ca83f2dee
commit
a201142cb5
1 changed files with 18 additions and 0 deletions
|
|
@ -311,3 +311,21 @@ __ javascript:alert(document.domain)
|
||||||
```js
|
```js
|
||||||
{{constructor.constructor('alert(1)')()}}
|
{{constructor.constructor('alert(1)')()}}
|
||||||
```
|
```
|
||||||
|
|
||||||
|
**Content Security Policy (CSP) bypass via JSONP endpoints**
|
||||||
|
|
||||||
|
Grab the target's CSP:
|
||||||
|
|
||||||
|
```
|
||||||
|
curl -I http://example.com | grep 'Content-Security-Policy'
|
||||||
|
```
|
||||||
|
|
||||||
|
Either paste the CSP into https://csp-evaluator.withgoogle.com/ or just submit the target's address into the "Content Security Policy" field. The CSP Evaluator will notify you if one of the whitelisted domains has JSONP endpoints.
|
||||||
|
|
||||||
|
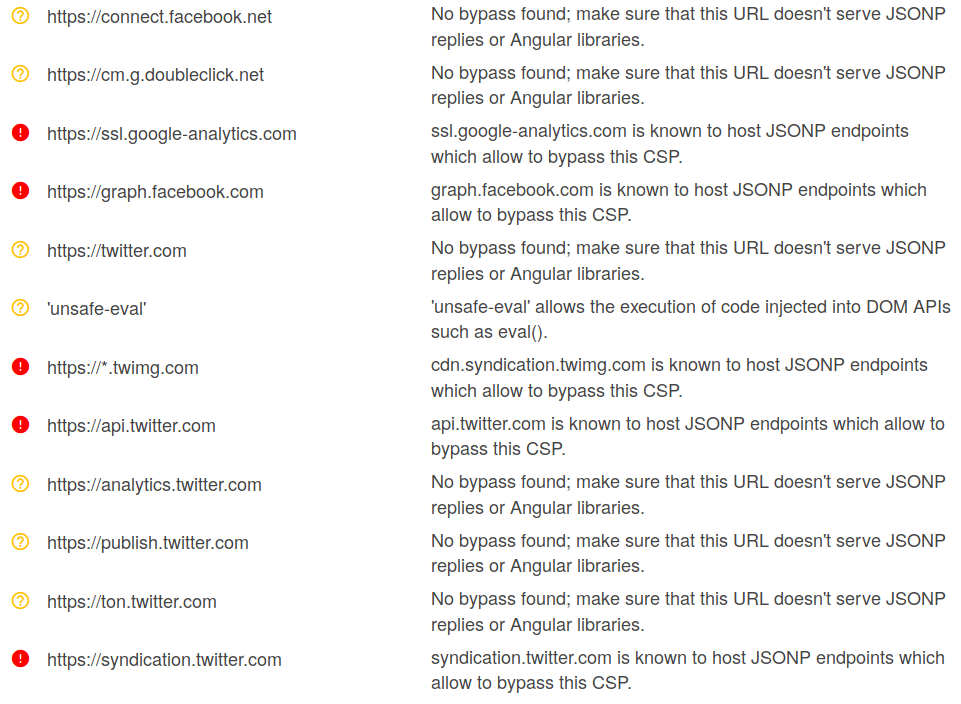
|
||||||
|
|
||||||
|
Now we can use a Google dork to find some JSONP endpoints on the domains listed above.
|
||||||
|
|
||||||
|
```
|
||||||
|
site:example.com inurl:callback
|
||||||
|
```
|
||||||
|
|
|
||||||
Loading…
Reference in a new issue