From c957271453558716e71aeba32e357199bc9f921e Mon Sep 17 00:00:00 2001
From: Swissky <12152583+swisskyrepo@users.noreply.github.com>
Date: Wed, 8 Sep 2021 12:49:32 +0200
Subject: [PATCH] SSRF PDF PhantomJS
---
Server Side Request Forgery/README.md | 14 +++++++++++++-
1 file changed, 13 insertions(+), 1 deletion(-)
diff --git a/Server Side Request Forgery/README.md b/Server Side Request Forgery/README.md
index 485ee53..f522a74 100644
--- a/Server Side Request Forgery/README.md
+++ b/Server Side Request Forgery/README.md
@@ -450,7 +450,7 @@ gopher://127.0.0.1:6379/_save
## SSRF exploiting PDF file
-
+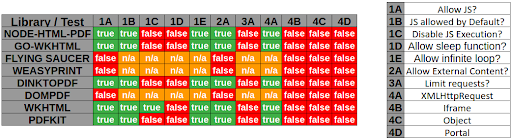
Example with [WeasyPrint by @nahamsec](https://www.youtube.com/watch?v=t5fB6OZsR6c&feature=emb_title)
@@ -458,6 +458,18 @@ Example with [WeasyPrint by @nahamsec](https://www.youtube.com/watch?v=t5fB6OZsR
```
+Example with PhantomJS
+
+```js
+
+```
+
## Blind SSRF
> When exploiting server-side request forgery, we can often find ourselves in a position where the response cannot be read.