mirror of
https://github.com/swisskyrepo/PayloadsAllTheThings.git
synced 2024-11-10 07:04:22 +00:00
Fix changed urls
This commit is contained in:
parent
2d4b98b9c2
commit
0913e8c3bd
5 changed files with 11 additions and 11 deletions
|
|
@ -10,7 +10,7 @@
|
||||||
|
|
||||||
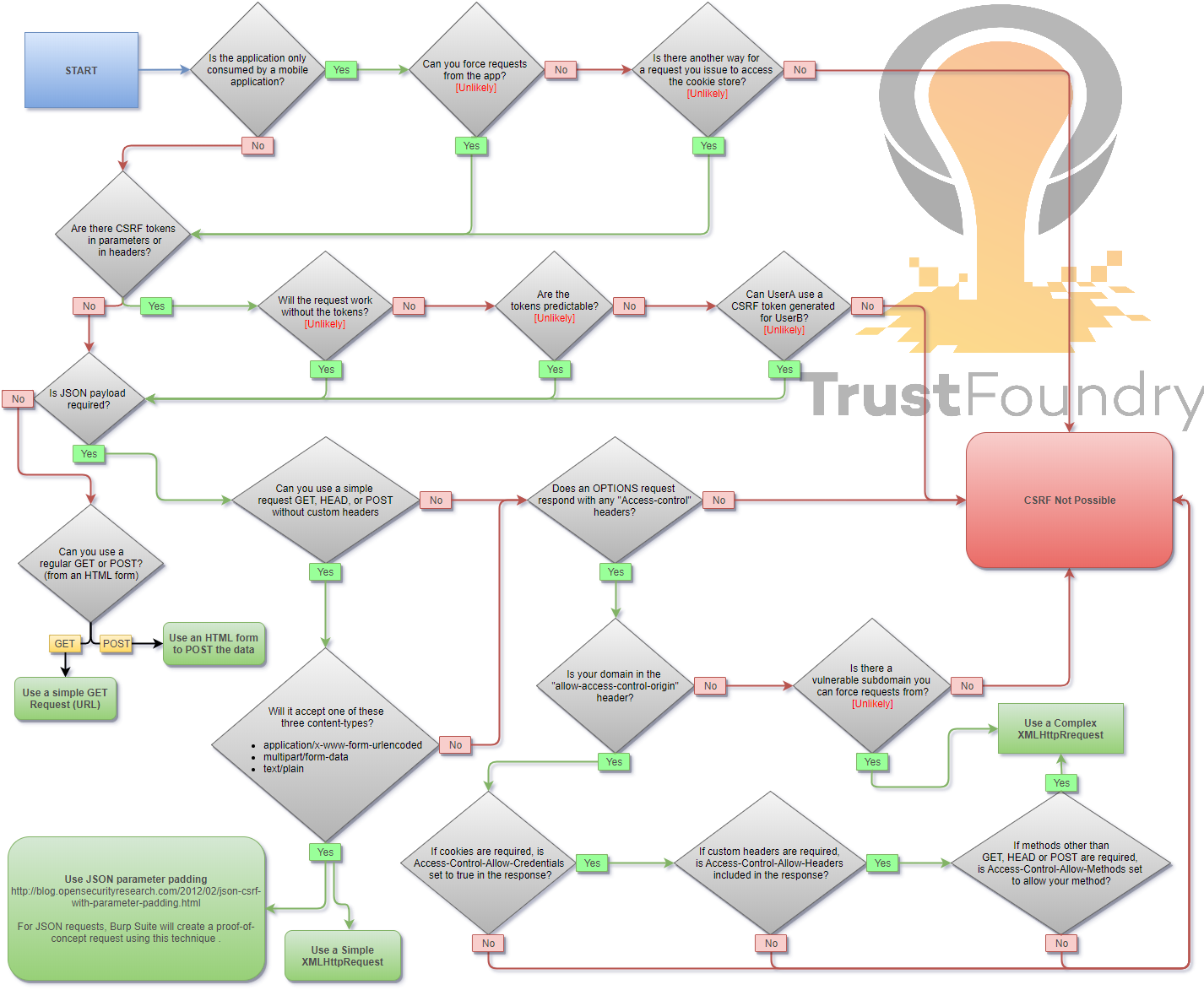
## Methodology
|
## Methodology
|
||||||
|
|
||||||

|
|
||||||
|
|
||||||
## Payloads
|
## Payloads
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -8,7 +8,7 @@ The following magic methods will help you for a PHP Object injection
|
||||||
* __destruct() when an object is deleted.
|
* __destruct() when an object is deleted.
|
||||||
* __toString() when an object is converted to a string.
|
* __toString() when an object is converted to a string.
|
||||||
|
|
||||||
Also you should check the `Wrapper Phar://` in [File Inclusion - Path Traversal](https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/File%20Inclusion%20-%20Path%20Traversal#wrapper-phar) which use a PHP object injection.
|
Also you should check the `Wrapper Phar://` in [File Inclusion](https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/File%20Inclusion#wrapper-phar) which use a PHP object injection.
|
||||||
|
|
||||||
## __wakeup in the unserialize function
|
## __wakeup in the unserialize function
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -10,12 +10,12 @@ Attempting to manipulate SQL queries may have goals including:
|
||||||
|
|
||||||
## Summary
|
## Summary
|
||||||
|
|
||||||
* [CheatSheet MSSQL Injection](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/SQL%20injection/MSSQL%20Injection.md)
|
* [CheatSheet MSSQL Injection](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/SQL%20Injection/MSSQL%20Injection.md)
|
||||||
* [CheatSheet MySQL Injection](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/SQL%20injection/MySQL%20Injection.md)
|
* [CheatSheet MySQL Injection](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/SQL%20Injection/MySQL%20Injection.md)
|
||||||
* [CheatSheet OracleSQL Injection](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/SQL%20injection/OracleSQL%20Injection.md)
|
* [CheatSheet OracleSQL Injection](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/SQL%20Injection/OracleSQL%20Injection.md)
|
||||||
* [CheatSheet PostgreSQL Injection](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/SQL%20injection/PostgreSQL%20Injection.md)
|
* [CheatSheet PostgreSQL Injection](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/SQL%20Injection/PostgreSQL%20Injection.md)
|
||||||
* [CheatSheet SQLite Injection](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/SQL%20injection/SQLite%20Injection.md)
|
* [CheatSheet SQLite Injection](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/SQL%20Injection/SQLite%20Injection.md)
|
||||||
* [CheatSheet Cassandra Injection](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/SQL%20injection/Cassandra%20Injection.md)
|
* [CheatSheet Cassandra Injection](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/SQL%20Injection/Cassandra%20Injection.md)
|
||||||
* [Entry point detection](#entry-point-detection)
|
* [Entry point detection](#entry-point-detection)
|
||||||
* [DBMS Identification](#dbms-identification)
|
* [DBMS Identification](#dbms-identification)
|
||||||
* [SQL injection using SQLmap](#sql-injection-using-sqlmap)
|
* [SQL injection using SQLmap](#sql-injection-using-sqlmap)
|
||||||
|
|
|
||||||
|
|
@ -176,7 +176,7 @@ http://127.1.1.1:80:\@@127.2.2.2:80/
|
||||||
http://127.1.1.1:80#\@127.2.2.2:80/
|
http://127.1.1.1:80#\@127.2.2.2:80/
|
||||||
```
|
```
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
|
|
||||||
## SSRF exploitation via URL Scheme
|
## SSRF exploitation via URL Scheme
|
||||||
|
|
@ -198,7 +198,7 @@ ssrf.php?url=http://127.0.0.1:80
|
||||||
ssrf.php?url=http://127.0.0.1:443
|
ssrf.php?url=http://127.0.0.1:443
|
||||||
```
|
```
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
The following URL scheme can be used to probe the network
|
The following URL scheme can be used to probe the network
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -49,7 +49,7 @@ python2.7 ./tplmap.py -u "http://192.168.56.101:3000/ti?user=InjectHere*&comment
|
||||||
|
|
||||||
## Methodology
|
## Methodology
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
## Ruby
|
## Ruby
|
||||||
|
|
||||||
|
|
|
||||||
Loading…
Reference in a new issue